Patents
Literature
30results about How to "Ensure system security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Remote intelligent evidence obtaining system and method based on mobile Internet
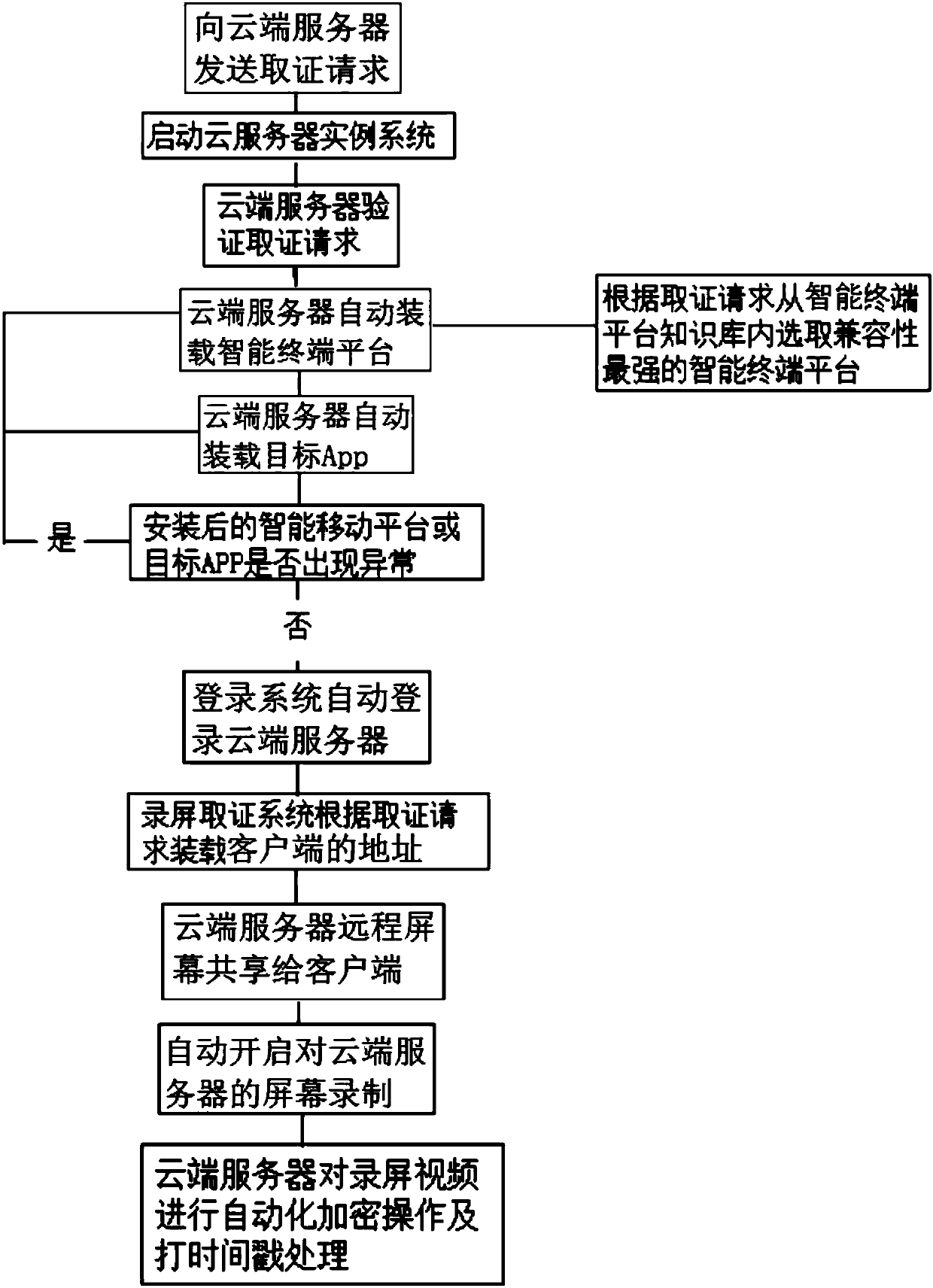
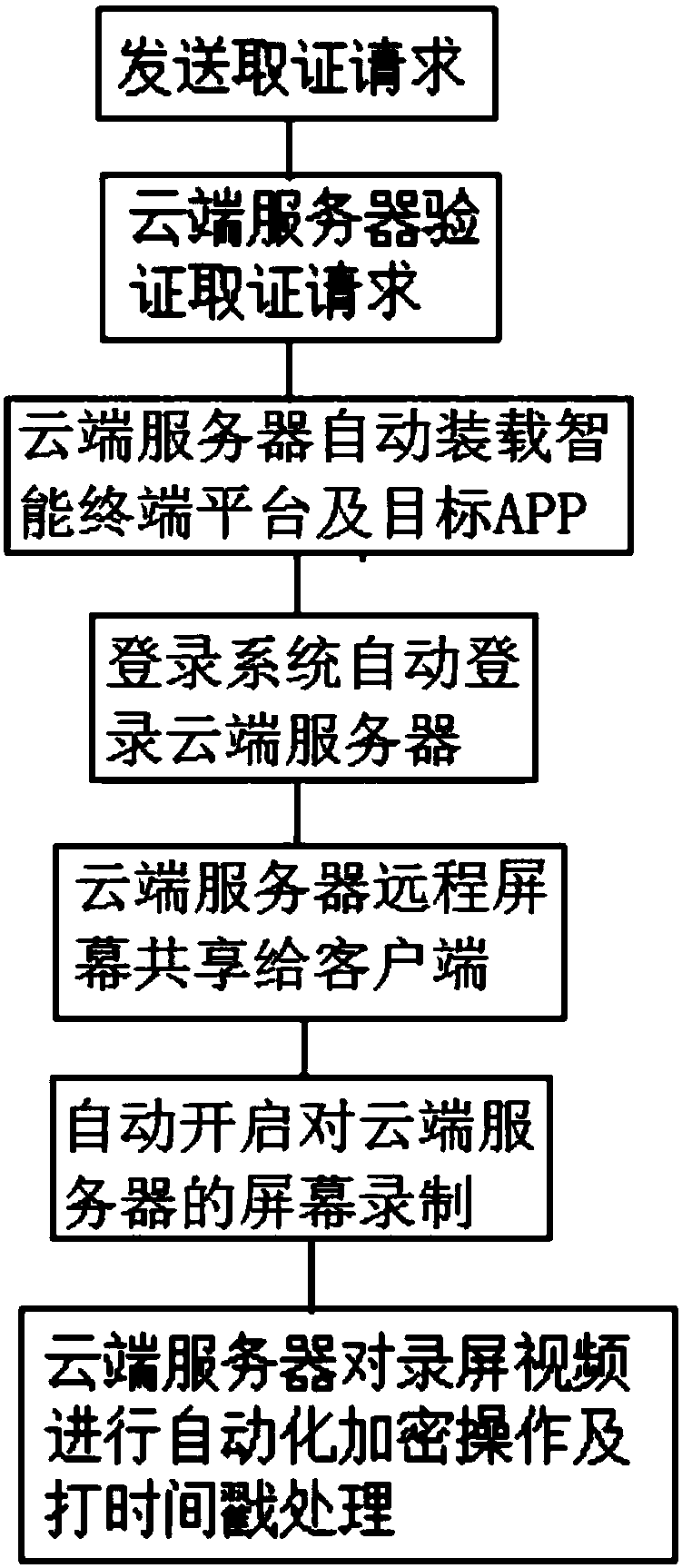
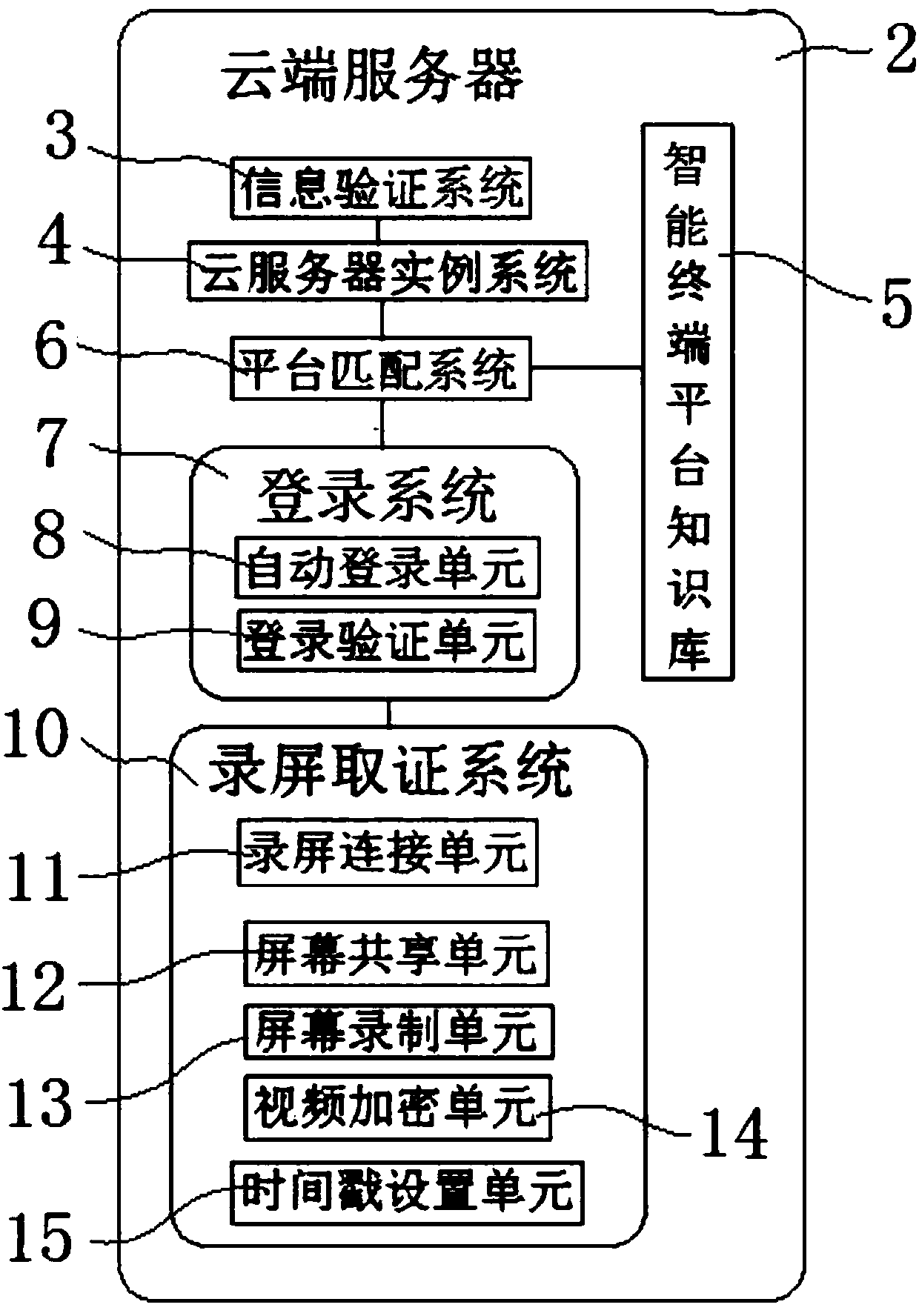
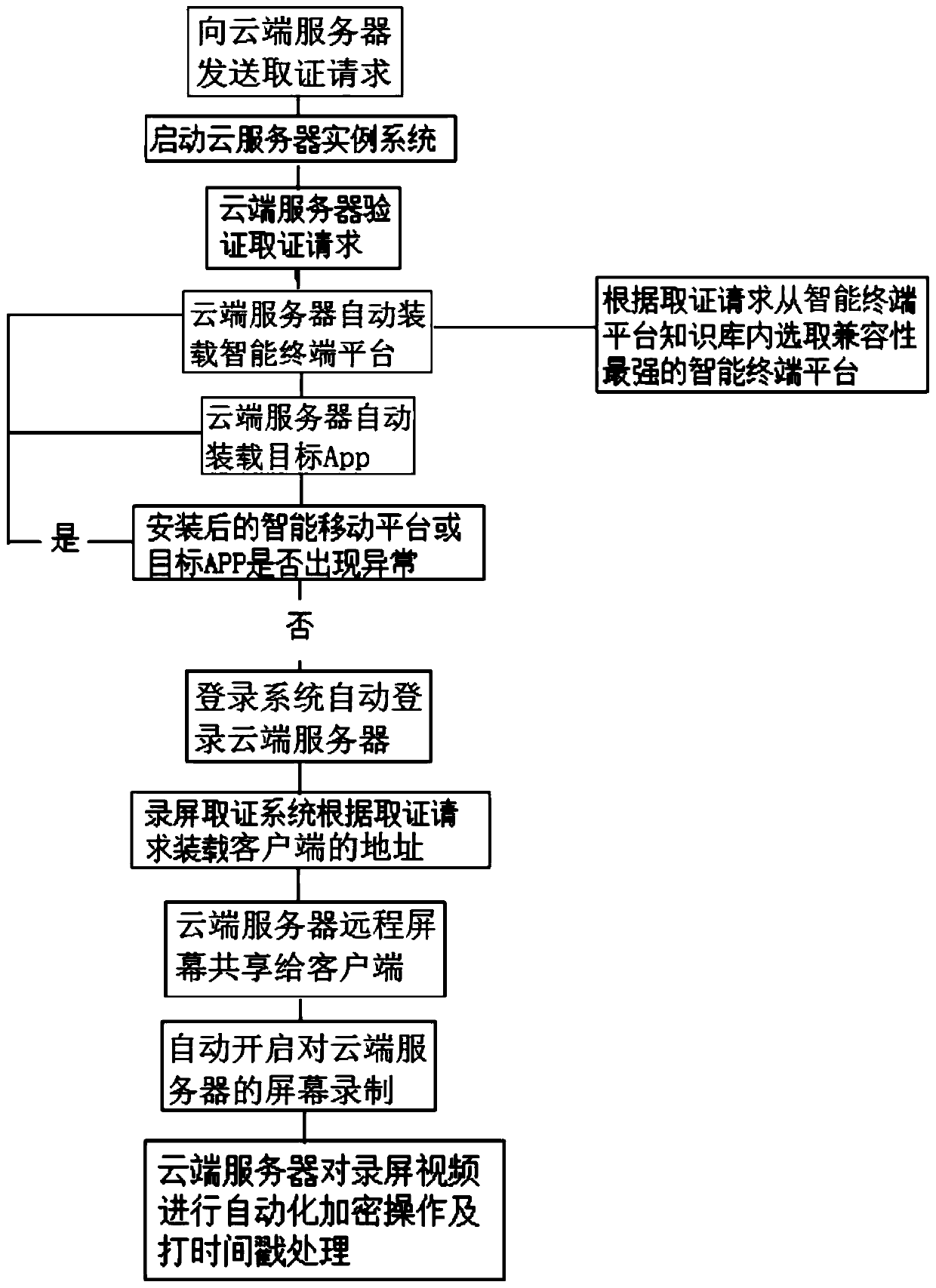
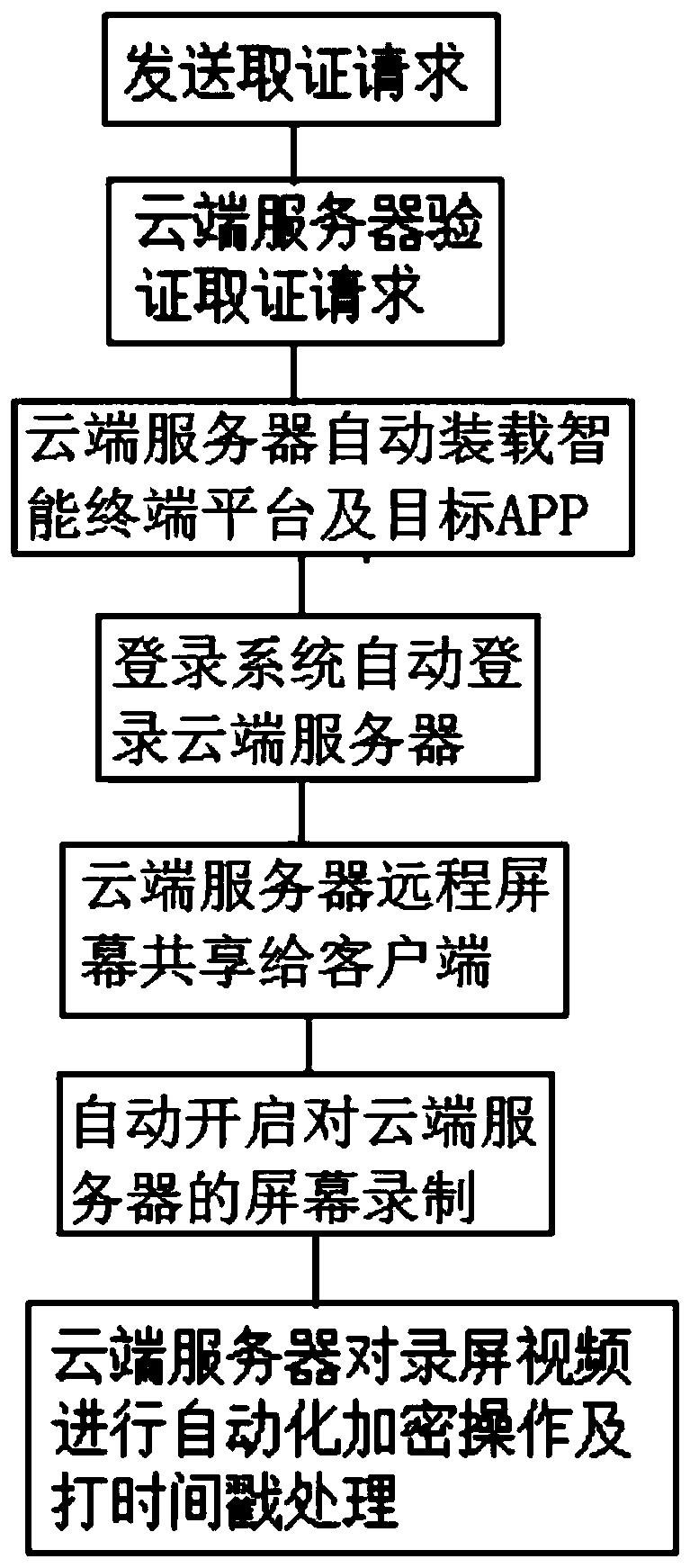
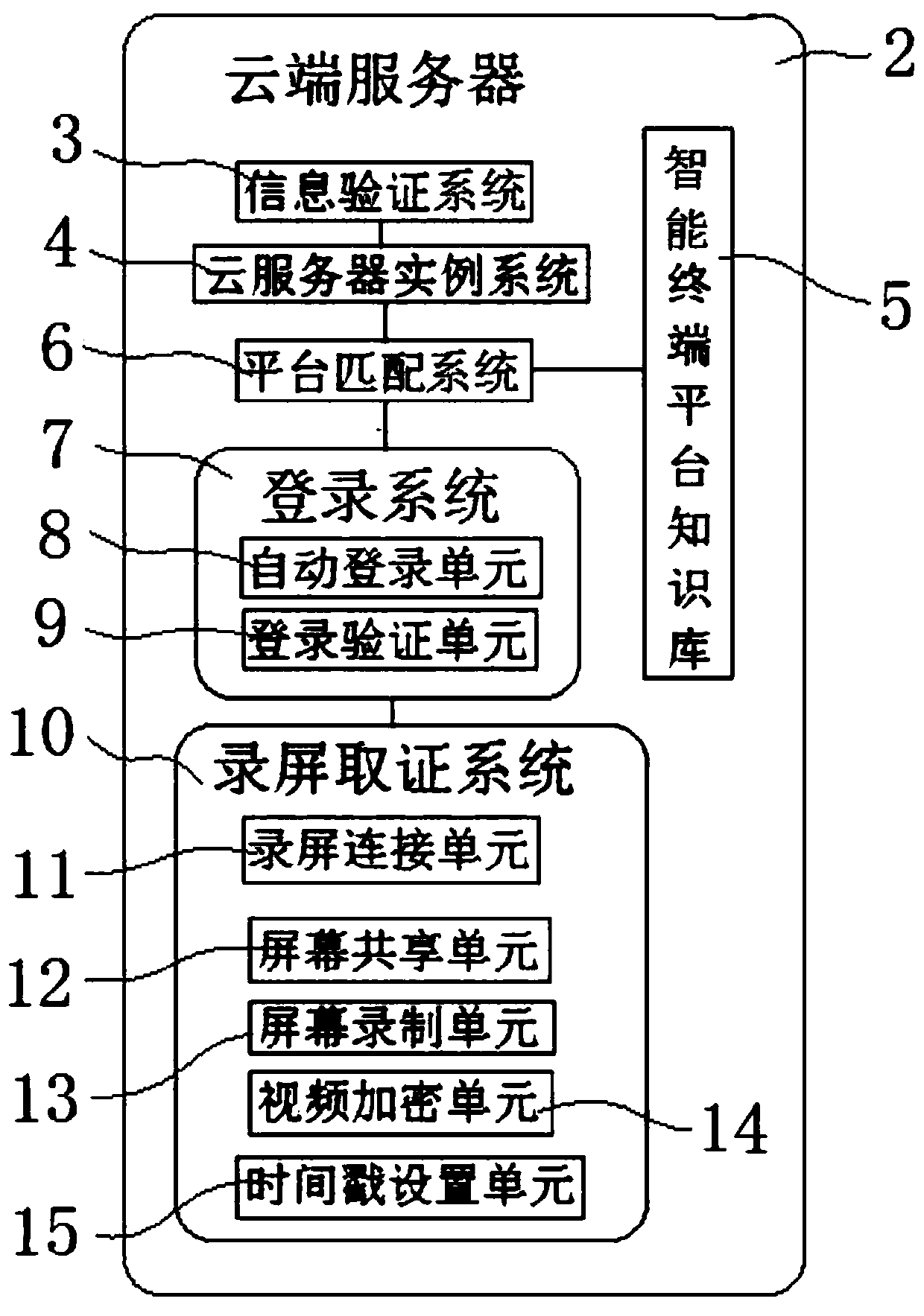
The invention relates to a cloud intelligent evidence obtaining system of a mobile Internet. The system comprises a client installing an evidence-obtaining App and used for sending an evidence-obtaining request to the evidence-obtaining App, a cloud server for verifying the evidence-obtaining request and automatically loading a corresponding intelligent terminal platform and a target App accordingto the evidence-obtaining request after passing of the verification, a login system for detecting the fact that the intelligent terminal platform and the target App are installed and automatically log in the cloud server according to the evidence-obtaining request, and a screen-recording evidence-obtaining system for controlling the cloud server to share the screen thereof to the client installing the target App after successful login and starting screen recording of the cloud server after screen sharing; and the cloud server automatically performs encryption operation and time stamping processing on screen-recorded videos after finishing of screen recording. According to the system, the whole-evidence obtaining process and stored content are both stored in the cloud server, and the cleanness and the system security of the whole evidence-obtaining process are guaranteed.
Owner:真相网络科技(北京)有限公司 +1
Linux system repairing method
InactiveCN103207816AFix bugsShorten recovery timeDigital data protectionPlatform integrity maintainanceGNU/LinuxUsability
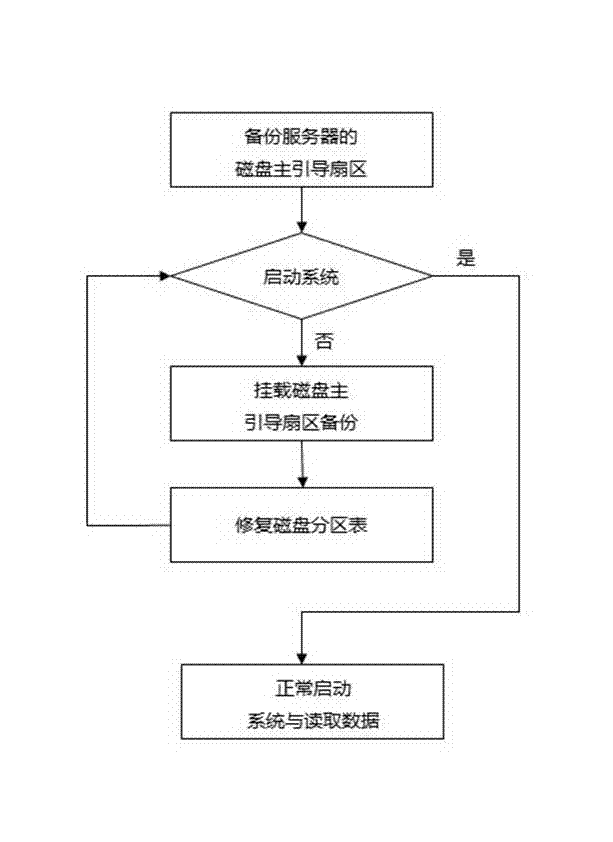
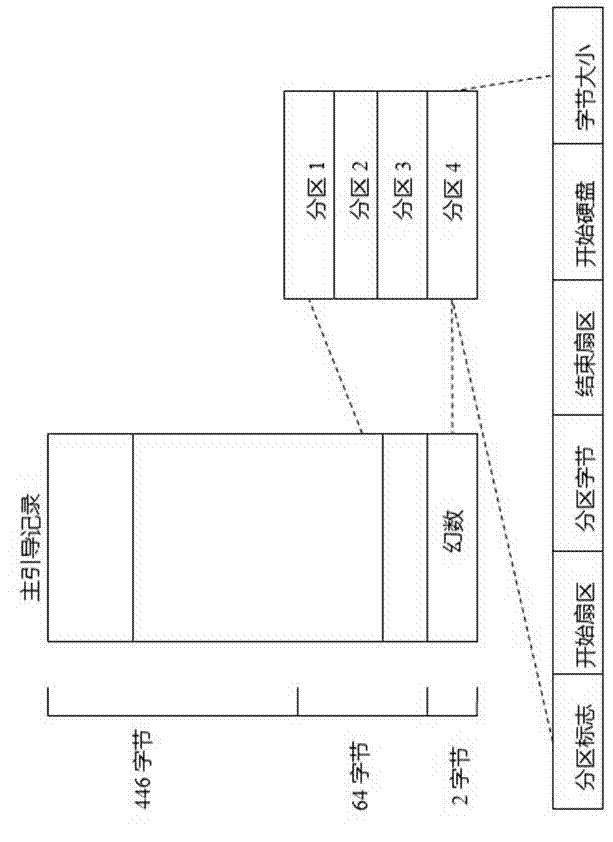
The invention discloses a Linum system repairing method. The method includes following steps: A, providing a physical server and installing a Linum system, backing up a master boot sector related information onto other systems or equipment; B, zero-setting a partition table of a system disc to simulate a scene where a Linux server in a production environment may damage the partition table duo to virus or accidental shutdown of the system; and C, restoring an operation system and disc data by repairing the partition table of the system disc. By the Linux system repairing method, failure of the Linux system can be effectively repaired, so that system safety and data safety of the Linux server are guaranteed, restoring time of the Linux system is shortened, and usability of the Linux system is improved. The Linum system repairing method is suitable for Linux systems such as RedHat, Debian, SUSE and Gentoo.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Method and device for acquiring GPU temperature through server BMC
InactiveCN108196999AEasy to monitorEnsure system securityHardware monitoringTechnical supportSystem safety
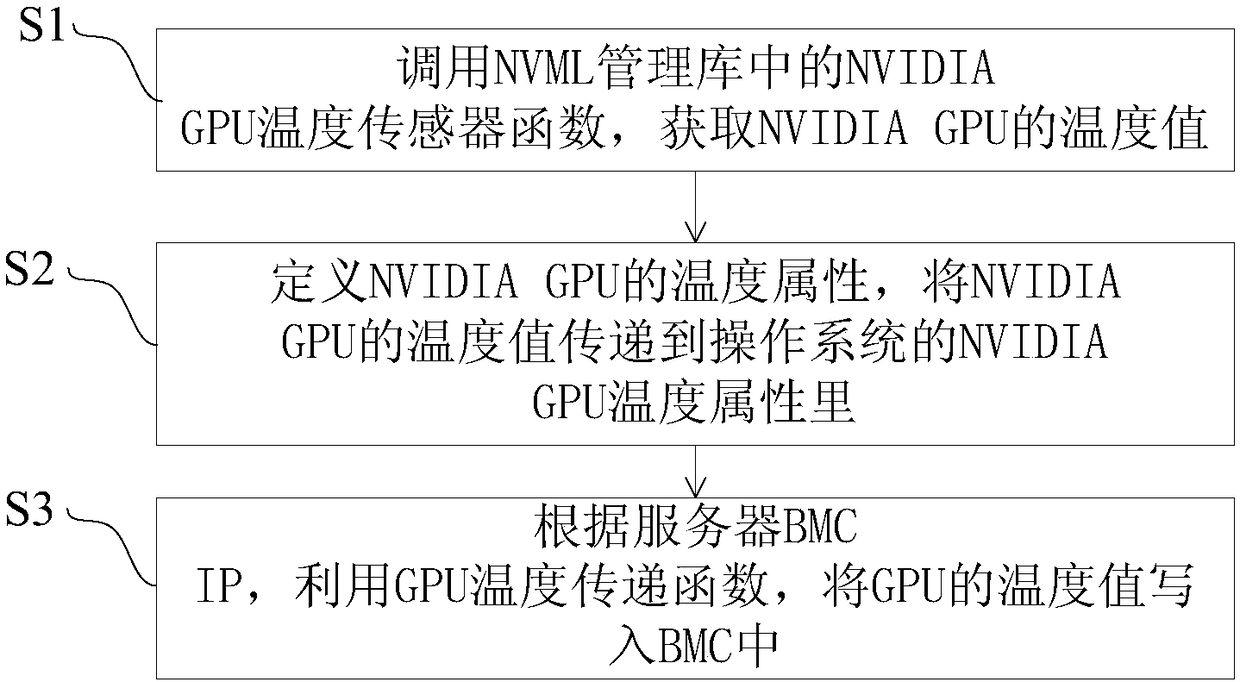
The embodiment of the invention discloses a method and device for acquiring the GPU temperature through a server BMC. The method comprises the steps that an NVIDIA GPU temperature sensor function in an NVML management library is called, and a temperature value of an NVIDIA GPU is acquired; a temperature attribute of the NVIDIA GPU is defined, and the temperature value of the NVIDIA GPU is transmitted to the temperature attribute of the NVIDIA GPU of an operation system; according to the server BMC IP, by using a GPU temperature transmission function, the temperature value of the GPU is writteninto the BMC. According to the method, the problems are solved that an NVIDIA manufacturer cannot provide technical support and accordingly the GPU temperature cannot be acquired, the server can acquire the GPU temperature, the GPU temperature is conveniently monitored, and the system safety is guaranteed.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
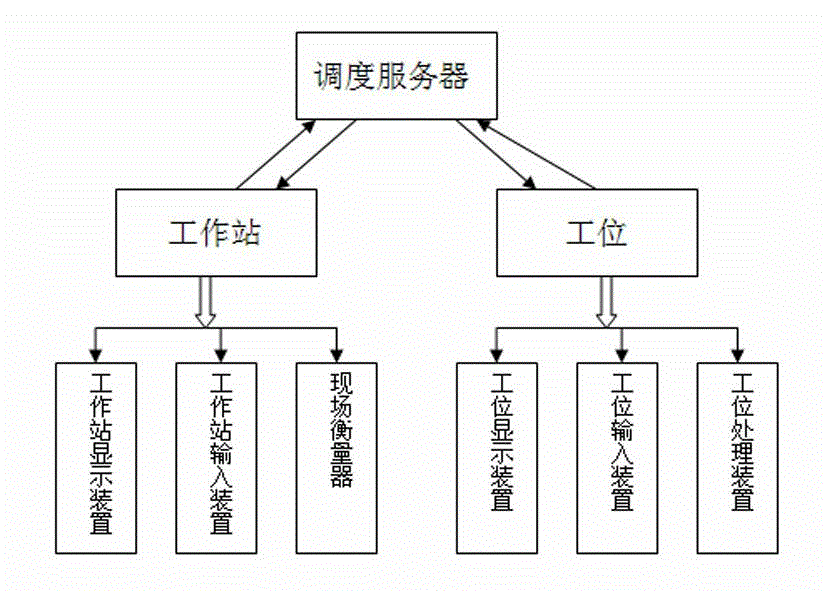
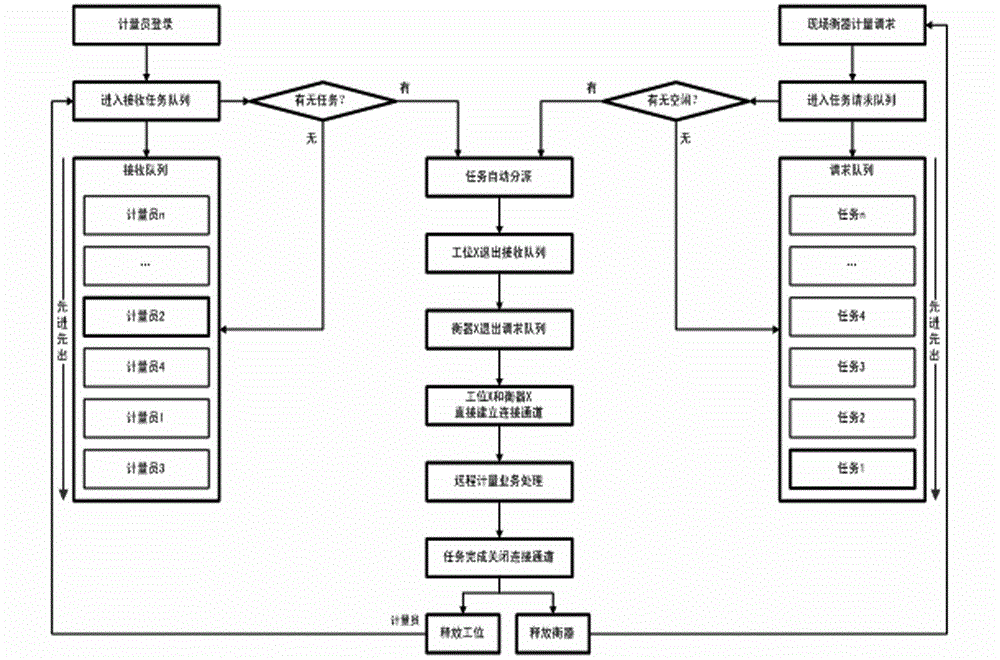
Centralized scheduling method based on distributed terminal
InactiveCN103337003AImprove the level of controlEnsure system securityResourcesTransmissionWork statusReal-time computing
The invention relates to a measuring system, in particular to a centralized scheduling method based on a distributed terminal to the measuring system. A remote gauger in a workstation inputs an on-site measuring device idle status to a workstation input device; a worker in the workstation inputs information requiring measuring to a station input device; a scheduling server processes workstation and station information obtained in a real-time manner via a communication network; based on a computing power of the workstation and a "first-in first-out" principle, the information requiring metering of each station is assigned to each station in the idle state, and assignment information is simultaneously transmitted to a station display device; the remote gauger in the workstation obtains a work task through the workstation display device, inputs a message that the on-site measuring device is in a working state into the workstation input device, and begins to measure the work task through the on-site measuring device; the remote gauger in the workstation, after completing a metering work, inputs a measuring result and a message that the on-site measuring device is in an idle state to the workstation input device; and the scheduling server receives measuring results of all workstations and the workstation on-site measuring device statuses, transmits the measuring results to a corresponding station completing the measuring task, and assigns a new measuring task to an idle station.
Owner:SHANXI TAIGANG STAINLESS STEEL CO LTD
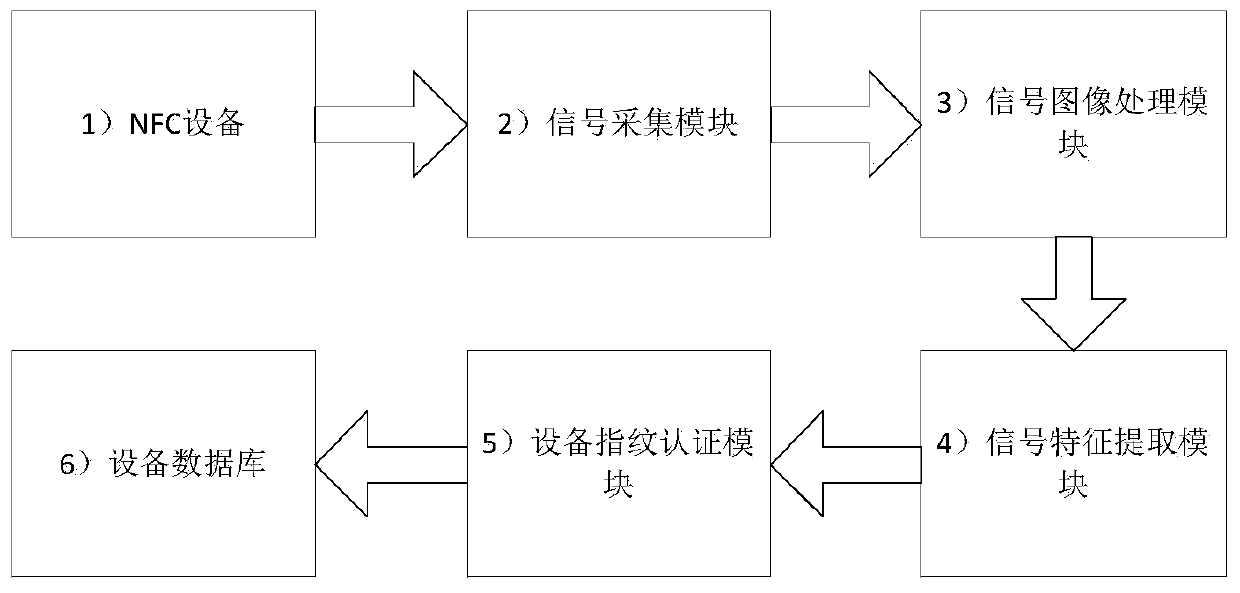
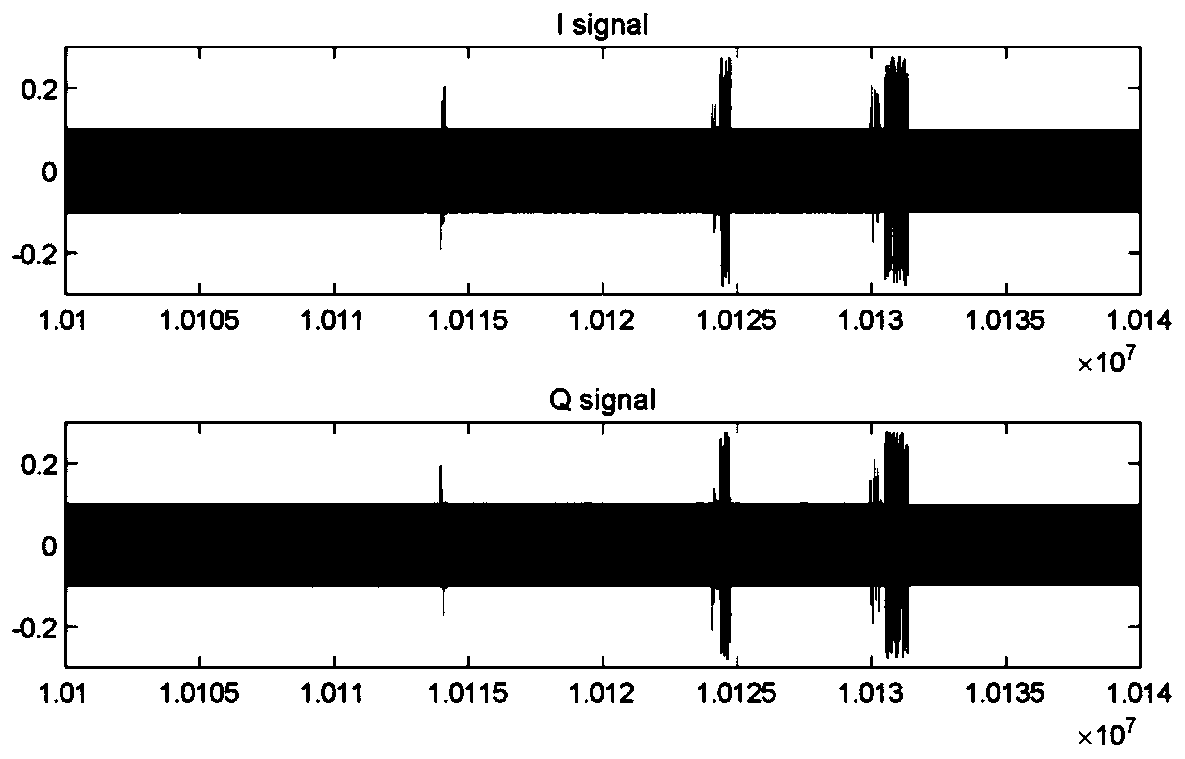
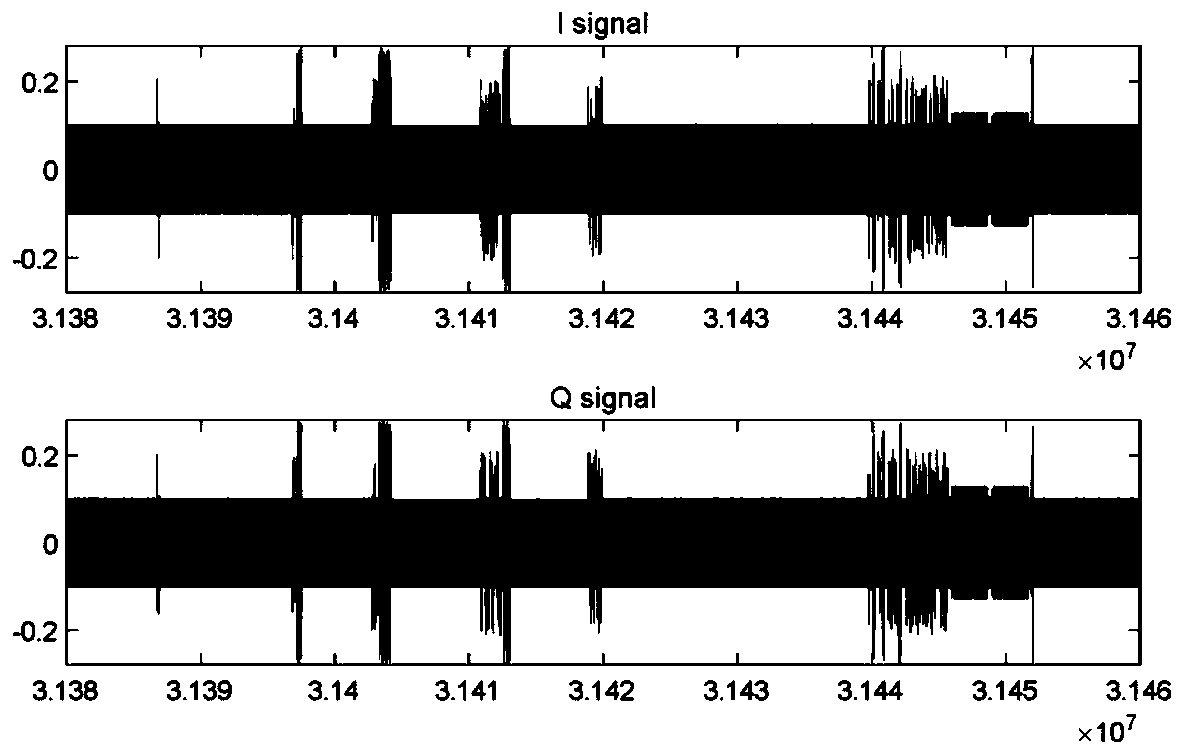
NFC device fingerprint authentication method and system based on CNN image recognition
ActiveCN111160424AEnsure system securityImprove securityStill image data indexingCharacter and pattern recognitionData transmissionPower grid
The invention discloses a power grid NFC device fingerprint authentication method and system based on CNN image recognition. The method comprises the following steps: preprocessing an analog signal during data transmission of the safety NFC equipment, drawing an image by using MATLAB software, extracting features through a convolutional neural network (CNN), and establishing a model library of a positive sample, thereby realizing non-contact safety monitoring of an NFC equipment access system. Through analog signal acquisition, image data preprocessing and image feature extraction, a correct equipment model library is established, and safety monitoring of the NFC equipment of the power grid is realized. According to the invention, access safety monitoring of the NFC equipment of the powergrid can be realized, and the safety and reliability of an electric power Internet of Things system are improved.
Owner:CHINA SOUTH POWER GRID ELECTRIC POWER RES INST +1
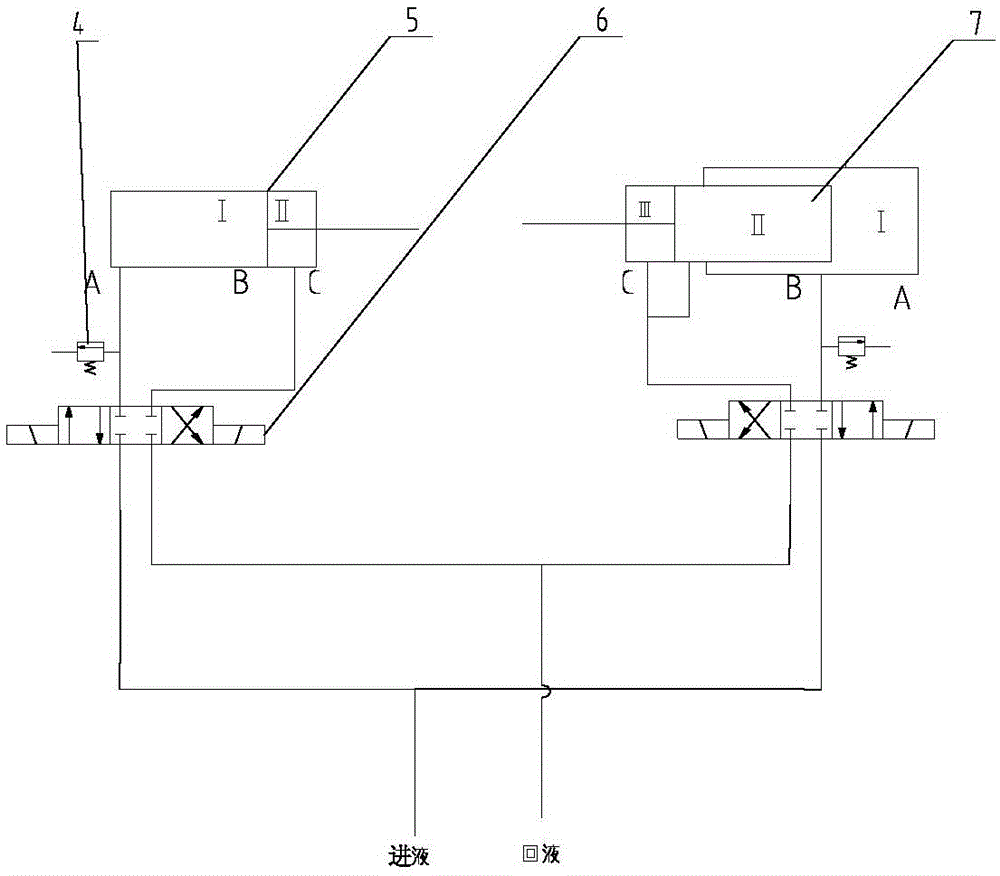
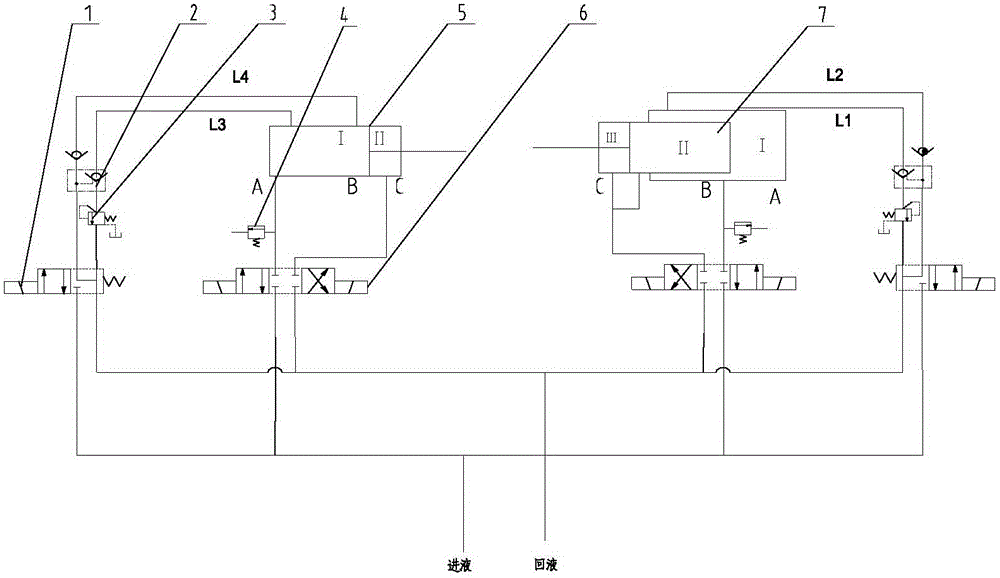
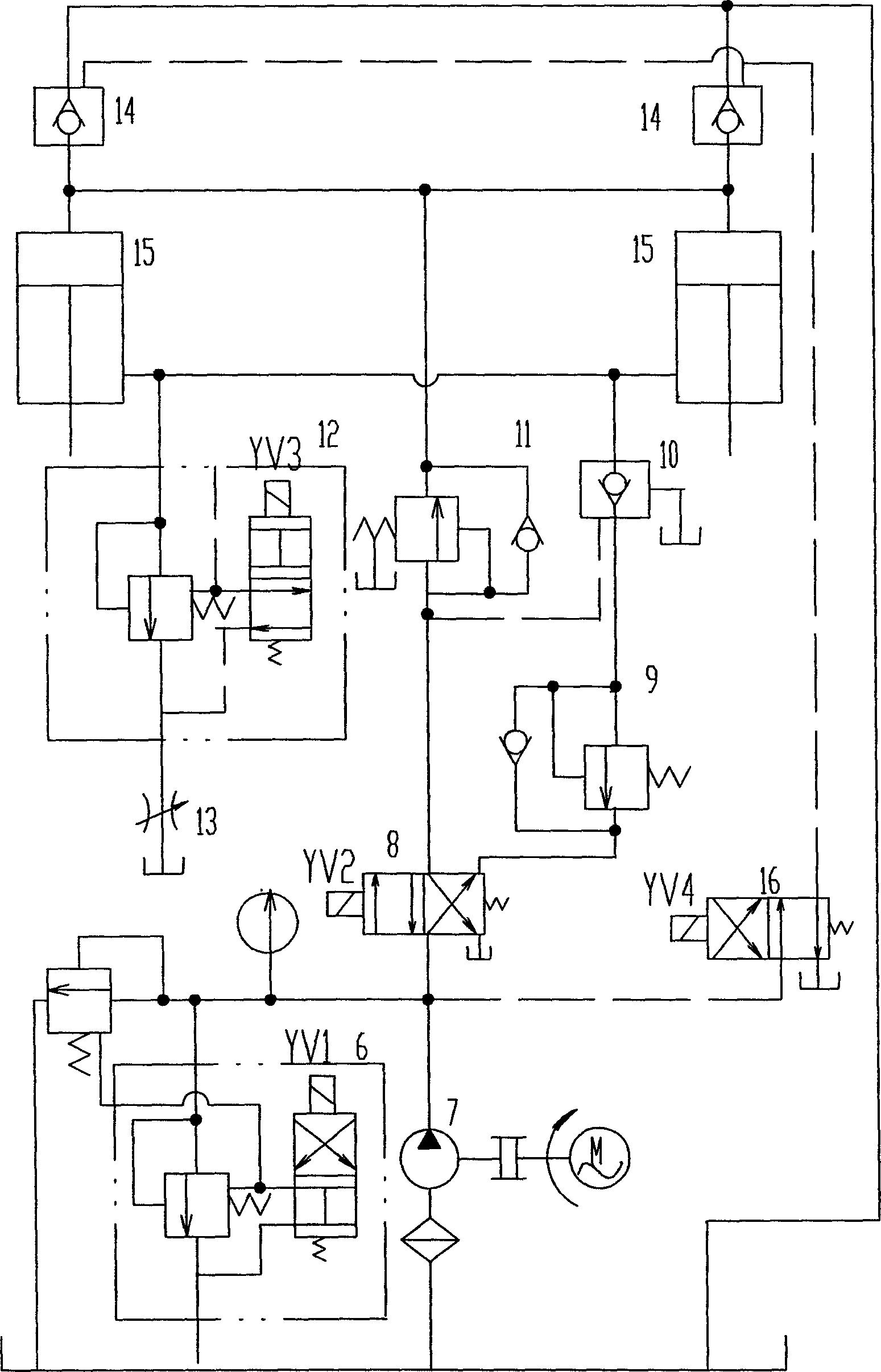
Mining hydraulic support for replacing hydraulic media under pressure
InactiveCN105041362APrevent spoilageEnsure system securityMine roof supportsProps/chocksCorrosionEngineering
The invention relates to a mining hydraulic support for replacing hydraulic media under pressure. The hydraulic support comprises a balanced oil cylinder (5), a safety valve (4), a three-position four-way reversing valve (6), a stand column oil cylinder (7), a connecting pipeline, a liquid inlet pipeline and a liquid return pipeline. The hydraulic support is further provided with a first auxiliary pipeline (L1), a second auxiliary pipeline (L2), a third auxiliary pipeline (L3) and a fourth auxiliary pipeline (L4). The auxiliary pipelines are communicated with the oil cylinder (7) through an opening in the cylinder wall of the oil cylinder, and then are communicated with the liquid return pipeline or the liquid inlet pipeline to form a complete hydraulic loop after being sequentially connected with a one-way valve (2), a sequence valve (3) and a two-position four-way reversing valve (1). According to the scheme, liquid inside the oil cylinders can be replaced under the condition that the oil cylinders are not telescoped; meanwhile, the supporting force and drawing force of the oil cylinders are unchanged when the liquid is replaced; besides, oil cylinder corrosion is reduced by replacing 'dead water' in the oil cylinders.
Owner:SANY HEAVY EQUIP +1
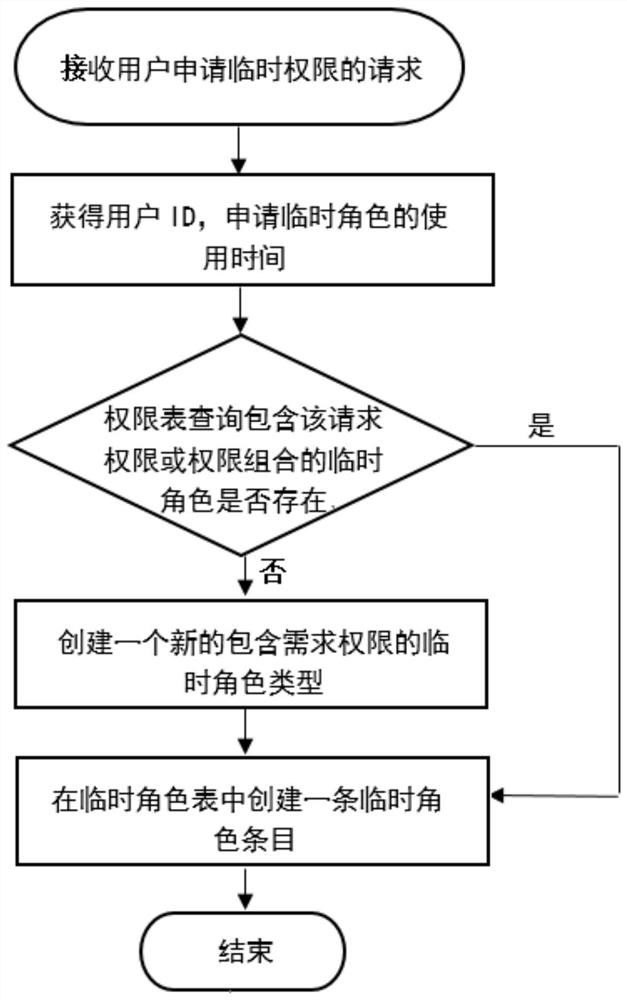
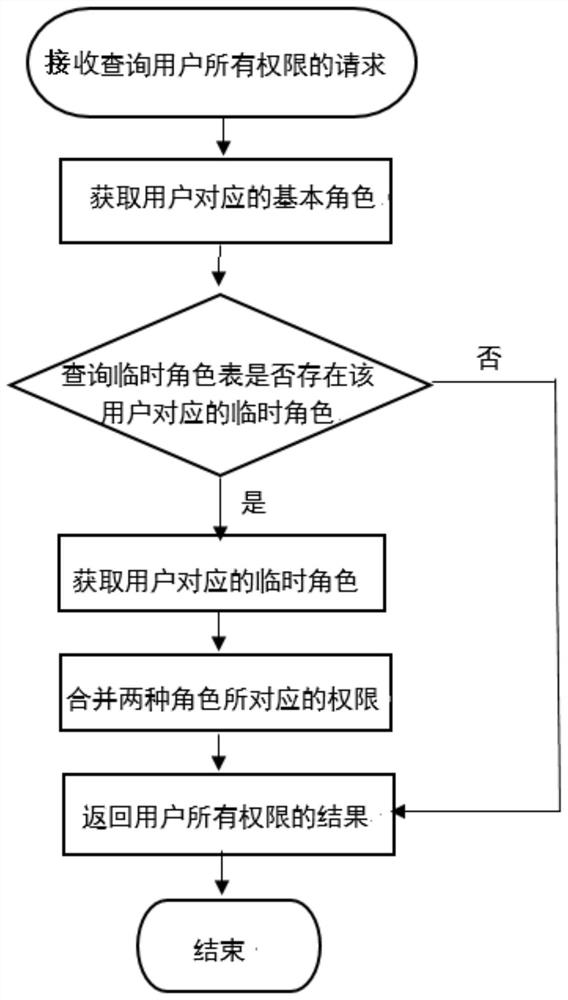
Time-limited user temporary role management method and device
ActiveCN111737711AEnsure system securityReliable design principleDigital data protectionComputer securityInternet privacy
The invention provides a time-limited user temporary role management method and device, and the method comprises the following steps: 1, receiving and processing a request of a user for requesting temporary permission, specifically including the steps: receiving the request of the user for applying for the temporary permission, after a request of a user for applying for the temporary permission isreceived, obtaining a user ID and use time for applying for the temporary permission; 2, when the survival time of the temporary role of the user expires, deleting the expired temporary role entry from the temporary role table. According to the invention, the survival time attribute of the temporary role can realize a mechanism of automatically deleting the expired temporary role, so the automation of temporary role management is achieved. Meanwhile, after the temporary role is expired, the user does not continue to have additional temporary permission, so the system security is ensured.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Herbage bale drying system
ActiveCN113639535ASolve drying problemsPrevent mildewAgriculture tools and machinesGrass dryingThermodynamicsProcess engineering
The invention belongs to the technical field of herbage machinery, particularly relates to a bale drying system, and aims to solve the problems that herbage bales are difficult to dry and a herbage bale drying system is not intelligent in the prior art. According to the herbage bale drying system, air supply needles can be inserted into the herbage bales, high-pressure hot air is blown into the herbage bales through an air supply device, drying is carried out on the herbage bales, and therefore the herbage bale drying problem is solved, the herbage bales can be dried to be below the storage safety moisture by utilizing the system, and mildewing is avoided. According to the system, automatic control is adopted, the temperature and humidity in the herbage bales are collected through the Internet of Things, the drying time and the drying temperature are intelligently analyzed and adjusted, filling, feeding, drying, cooling and unloading are automatically achieved, in addition, the herbage bales can be dehumidified again during cooling, and a guide mechanism is arranged, so that an upper hollow air needle assembly and a lower hollow air needle assembly rise and fall stably, and the drying efficiency and the system safety are guaranteed.
Owner:呼伦贝尔菁华草业科技发展有限公司
Thermal treatment method for preventing stainless steel from being sensitized in water chamber of high-pressure heater
ActiveCN103361473AEnsure system securityGuaranteed performanceFurnace typesHeat treatment furnacesThermal insulationExpansion factor
The invention relates to the technical field of heat treatment, in particular relates to a thermal treatment method for preventing stainless steel from being sensitized in a water chamber of a high-pressure heater, and aims at solving the problems that the stainless steel is sensitized and the expanding quality is bad caused by the large difference of linear expansion factors since materials of a pipe are different during the heat treatment after the girth welding of the water chamber of the high-pressure heater. The thermal treatment method is characterized in that the thermal treatment method is carried out on an outer housing, a thick pipe plate and a U-shaped pipe of the high-pressure heater, a welding line and a heat affected zone of the water chamber are annealed by the local heat treatment, and a thermal insulation carpet is arranged at the welding line side of the stainless steel to prevent heat energy to be directly radiated to a stainless steel part, so that the temperature of the stainless steel part can not be risen to the sensitization temperature. The temperature of the stainless steel part can not be risen to the sensitization temperature, the anti-scouring function of the U-shaped pipe can be improved, the pipe exposure accident rate of the equipment can be reduced, and the service life of the equipment can be prolonged.
Owner:HANGZHOU BOILER GRP CO LTD
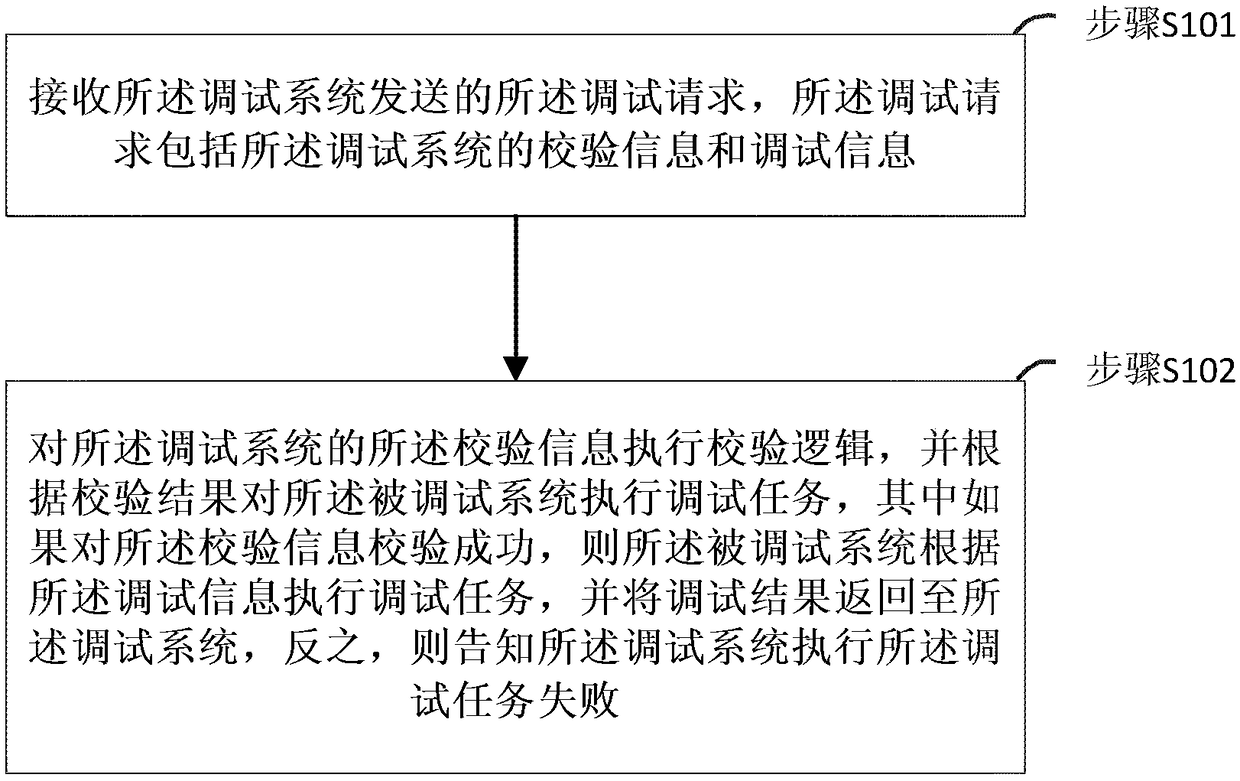
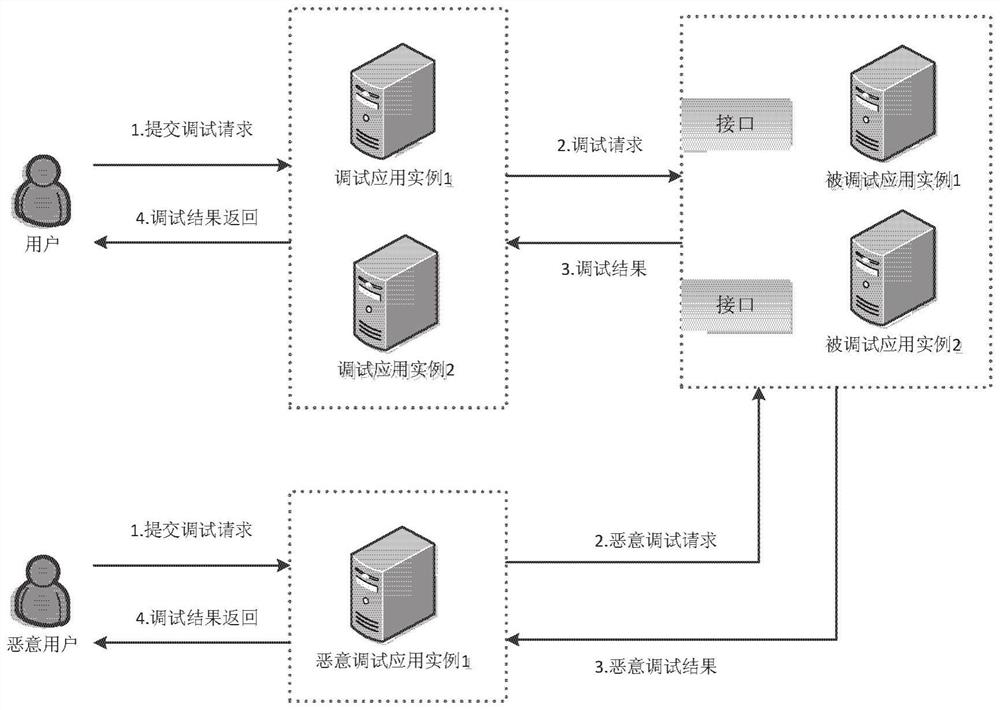
Method and system for realizing secure interaction between systems
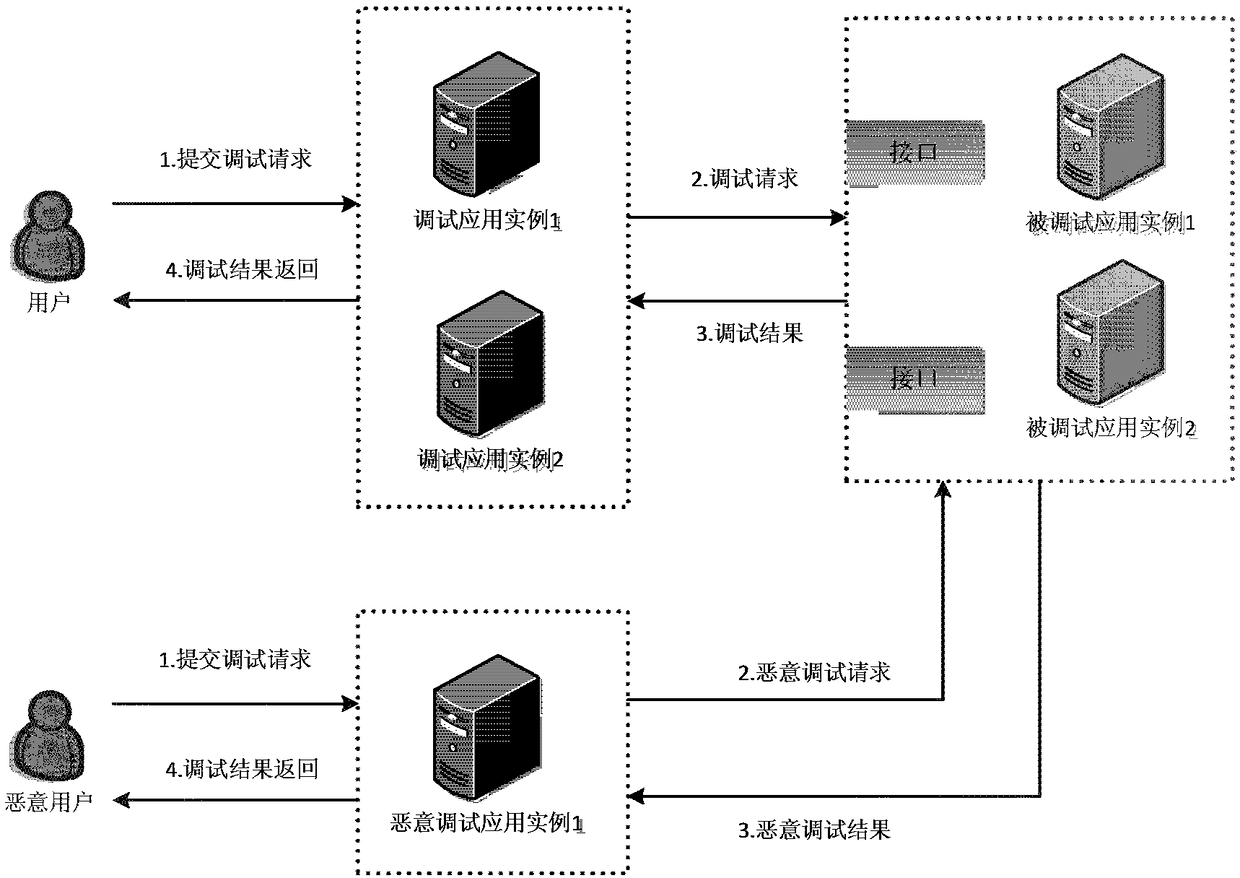
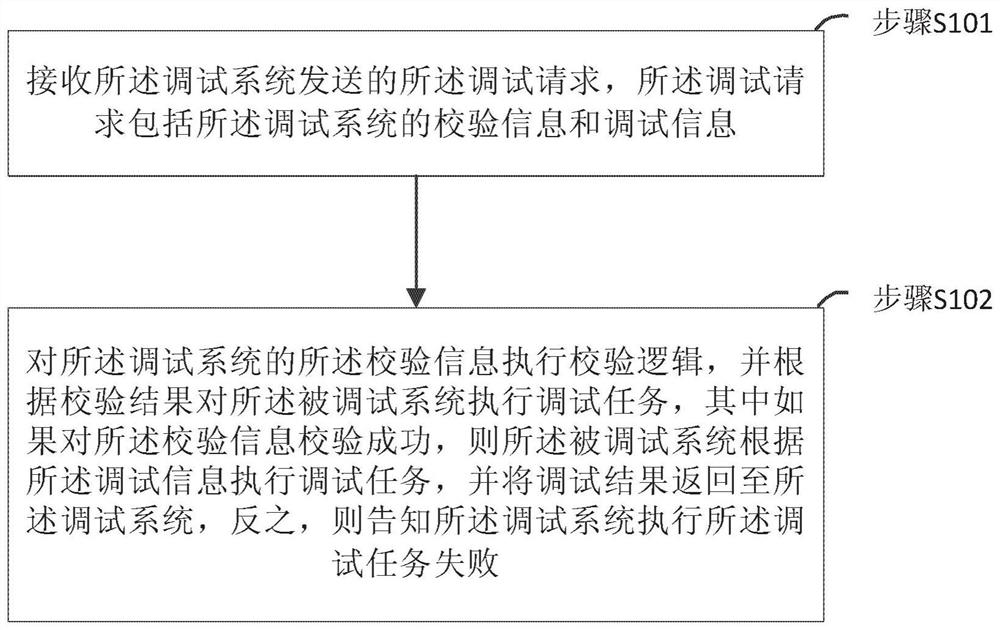
ActiveCN108734033AAvoid security issuesImprove scalabilityInterprogram communicationInternal/peripheral component protectionExtensibilityComputer hardware
The invention provides a method and system for realizing secure interaction between systems. After a debugging request is sent to a debugged system by a debugging system, the method comprises the following steps of: receiving the debugging request sent by the debugging system by the debugged system, wherein the debugging request comprises verification information and debugging information of the debugging system; and executing verification logic for the verification information of the debugging system, executing a debugging task for the debugged system according to the verification result, ifthe verification information is successfully verified, executing the debugging task by the debugged system according to the debugging information and returning a debugging result to the debugging system, and otherwise, informing the debugging system that the debugging task fails. According to the method and system, the security problem of debugging interfaces between debugging systems and debuggedsystems in the prior art is solved. Moreover, verification manners can be dynamically extended, so that extensibility of system debugging interfaces is improved under the premise of ensuring the system security and data security of business systems.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Penetration test method in allusion to mobile geographic information security of underground pipelines
InactiveCN105631342AAvoid data breachesEnsure system securityPlatform integrity maintainanceUnderground pipelineVulnerability scanning
The invention discloses a penetration test method in allusion to mobile geographic information security of underground pipelines. The method comprises the following steps: changing the suffix of an APK file into zip and decompressing the compressed file to obtain a class.dex file therein; copying the class.dex file into a catalogue to which a dex2jar.bat file belongs, executing a dex2jar class.dex command under a command line, and generating a class-dex2jar.jar file under the current catalogue; opening a jd-gui code check tool, importing the class-dex2jar.jar file and checking a reversed application source code; setting the address of a test machine and collecting a server-side interface list by utilizing the test machine; and carrying out vulnerability scanning on a server by using a burp suit tool through the server-side interface list, outputting a vulnerability analysis statement to the test machine, and carrying out sql injection test on a server side by utilizing a sqlmap tool so as to detect the sql injection vulnerabilities. The penetration test method is capable of finding the vulnerabilities of the application service programs on the underground pipeline map servers in allusion to the mobile GIS applications which carry underground pipeline route data, so as to prevent the data leakage of the underground pipelines.
Owner:BEIJING INST OF RADIO METROLOGY & MEASUREMENT
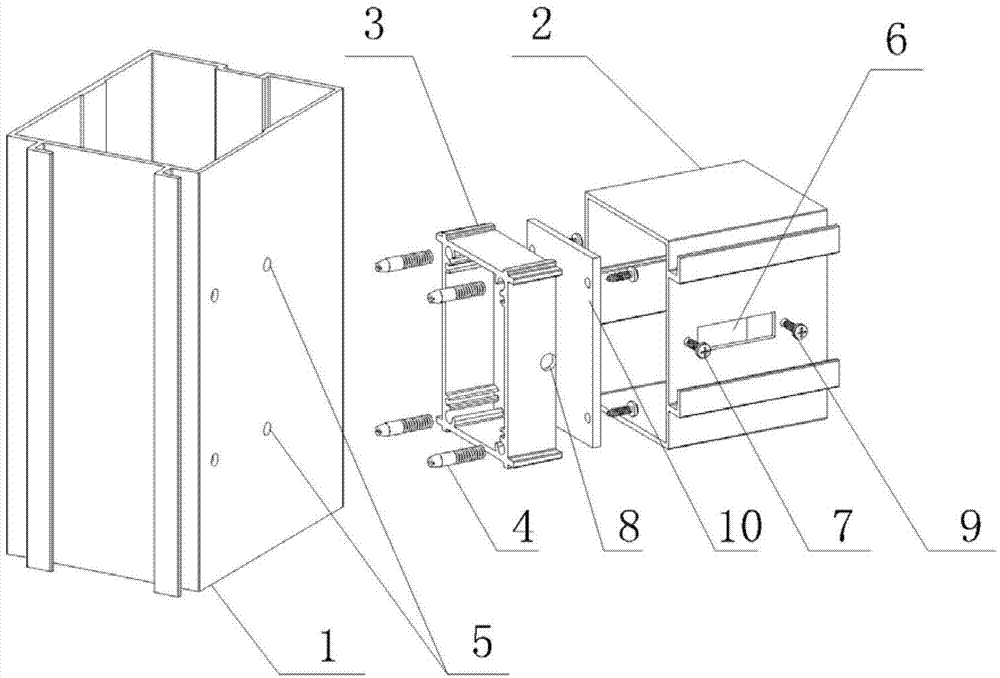
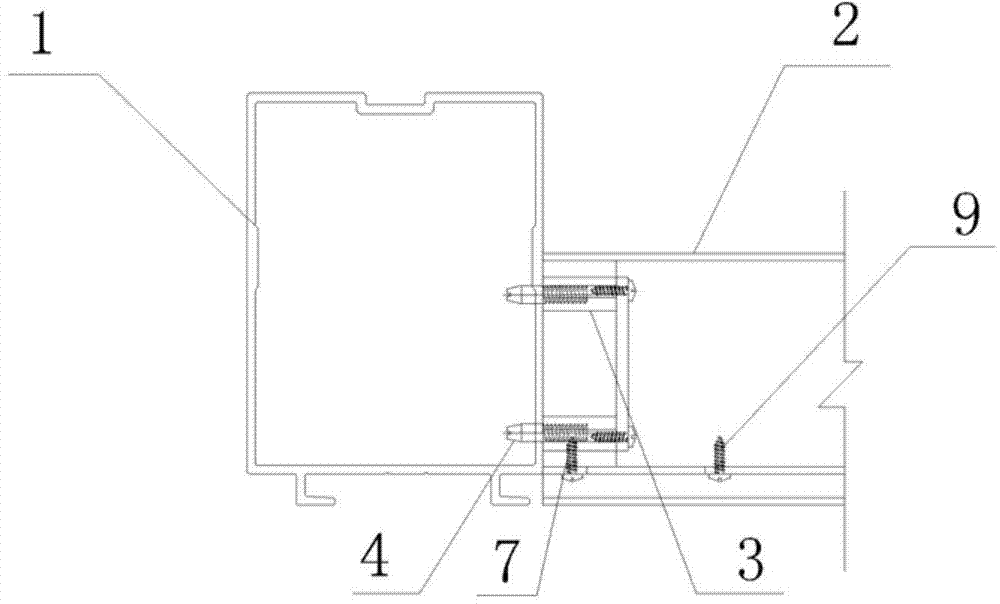
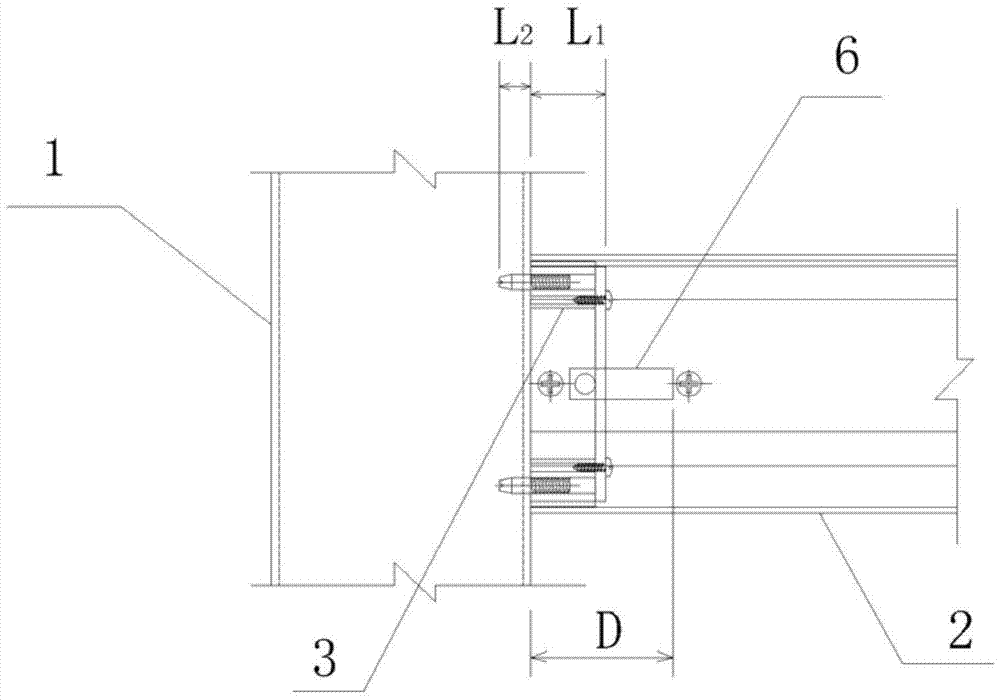
Cross beam and stand column connecting structure
ActiveCN103774756AEasy to installEnsure system securityBuilding constructionsStructural engineeringEngineering
Owner:杜军桦
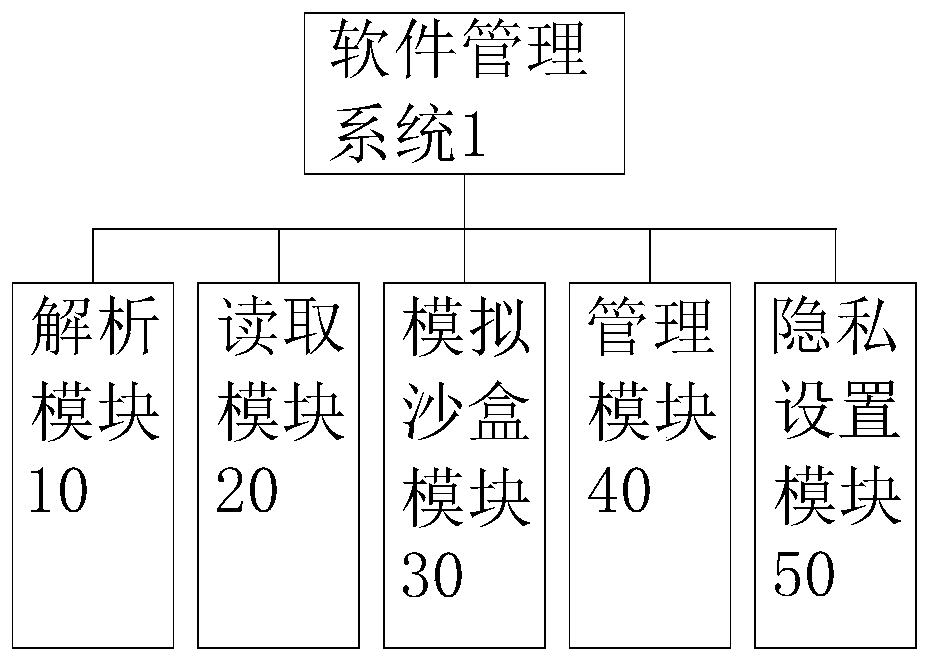
Software management system and software protection method thereof
InactiveCN110543760AExpand the scope of managementProtect personal information and account securityDigital data protectionPlatform integrity maintainanceManagement systemManagement effects
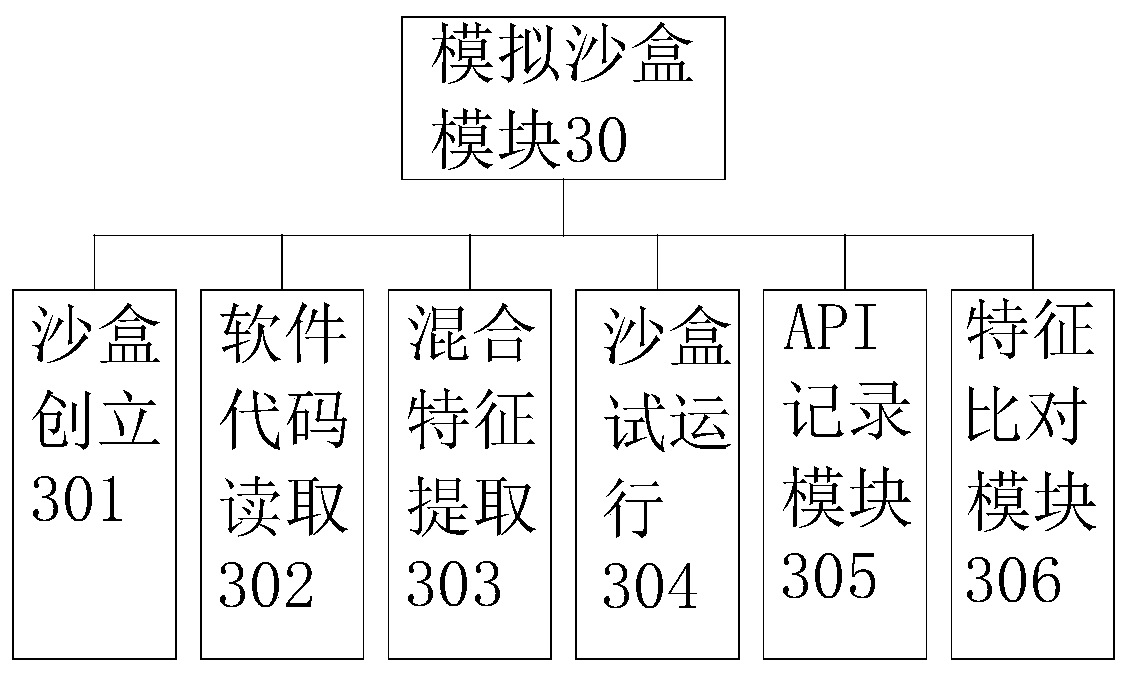
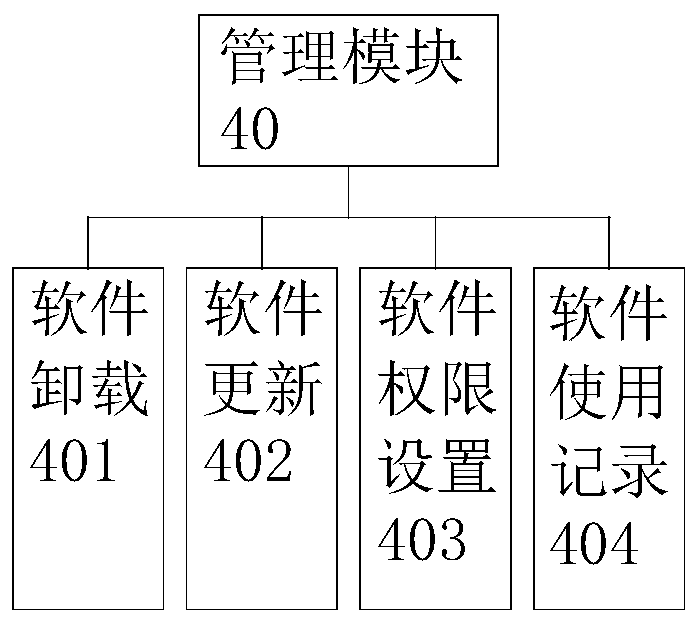
The invention discloses a software management system and a software protection method thereof. The software management system comprises an analysis module, a reading module, a simulation sandbox module and a management module; the analysis module is used for analyzing a software installation package, therefore the size and brief introduction information of software is obtained; the reading moduleis used for reading the analyzed software installation package and obtaining configuration information of software; the simulation sandbox module is a created sandbox model completely isolated from the main system, and virus Trojan and the like carried in software can be prevented from invading the main system while the software is started; and the management module is used for performing operations such as unloading and updating on the installed software, thereby facilitating centralized management. According to the method and the system, the privacy setting module is added on the basis of existing software unloading updating and permission setting, and advanced permissions such as hiding, opening and rewriting of the software are set by logging in an account, so that the management rangeof the software is widened, the management effect of the software is improved, and meanwhile, personal privacy is protected.
Owner:NANJING CHENXIAO SOFTWARE TECH CO LTD
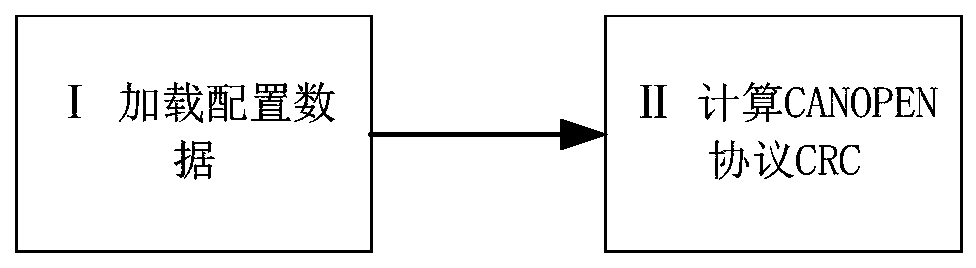
Method for calculating CANOPEN protocol CRC through redundant code words
ActiveCN111130695ALow costEnsure system securityForward error control useProtocol for Carrying Authentication for Network AccessEngineering
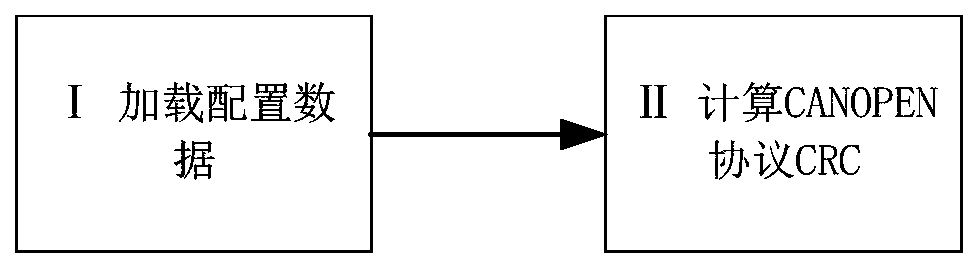
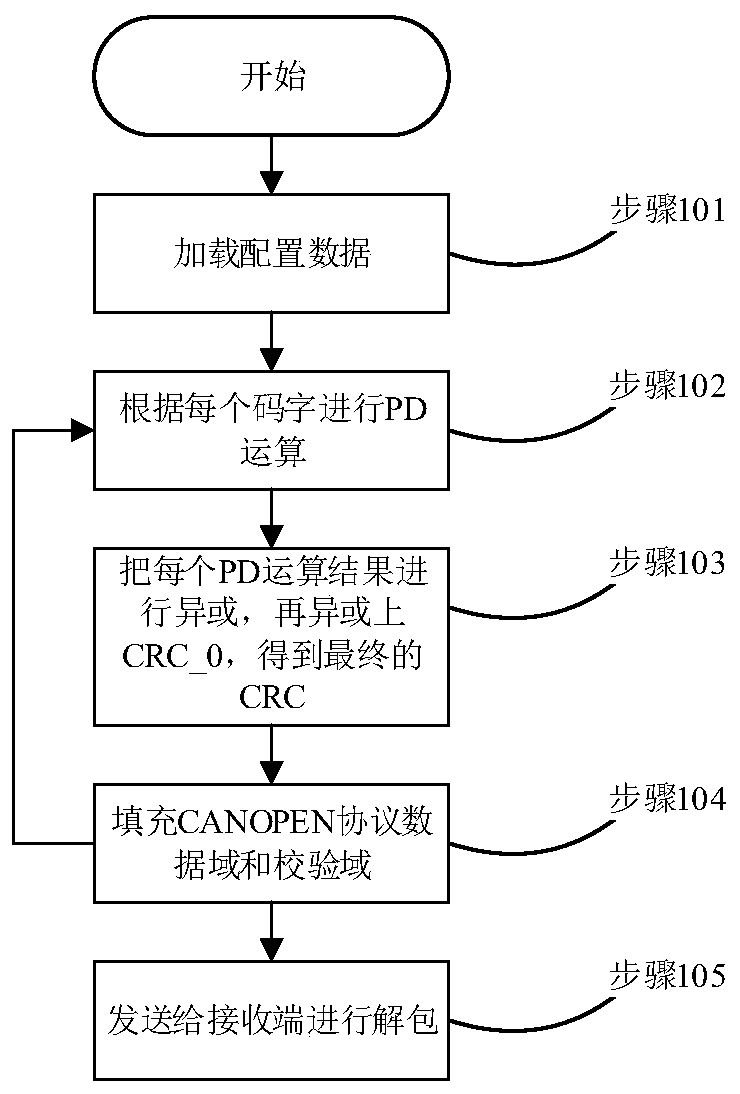
The invention relates to a method for calculating CANOPEN protocol CRC (cyclic redundancy check) through redundant code words. In the method, 32-bit code words are used to calculate CRC to ensure thecorrectness of calculation processes, a data domain of a protocol to be sent out is filled with state data corresponding to the code words, and the state data corresponding to the code words is 0 or 1. Compared with technologies of the prior art, the method is advantageous in that effective communication is established among the modules adopting different technologies on the premise of ensuring safety.
Owner:CASCO SIGNAL
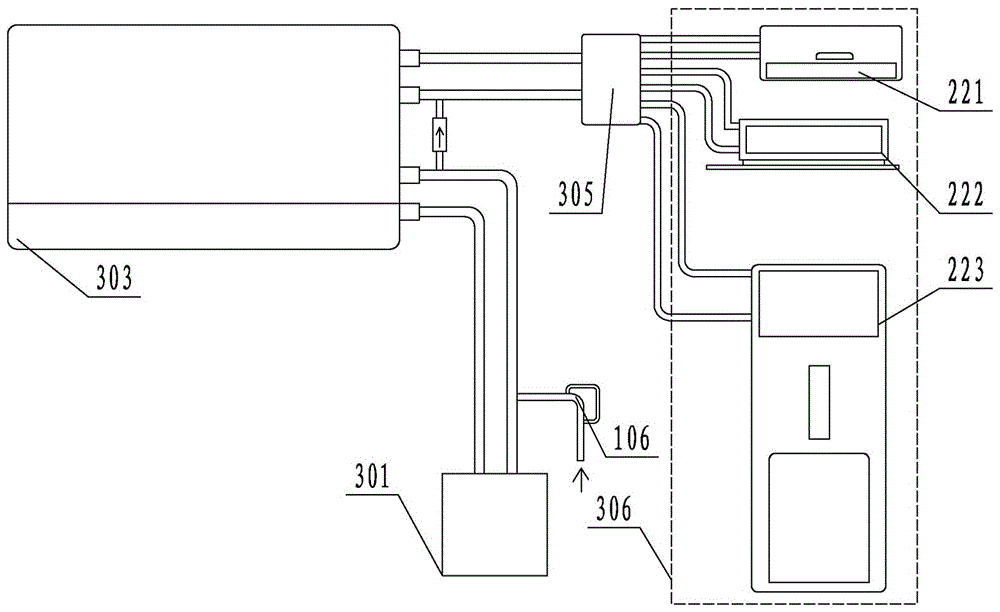
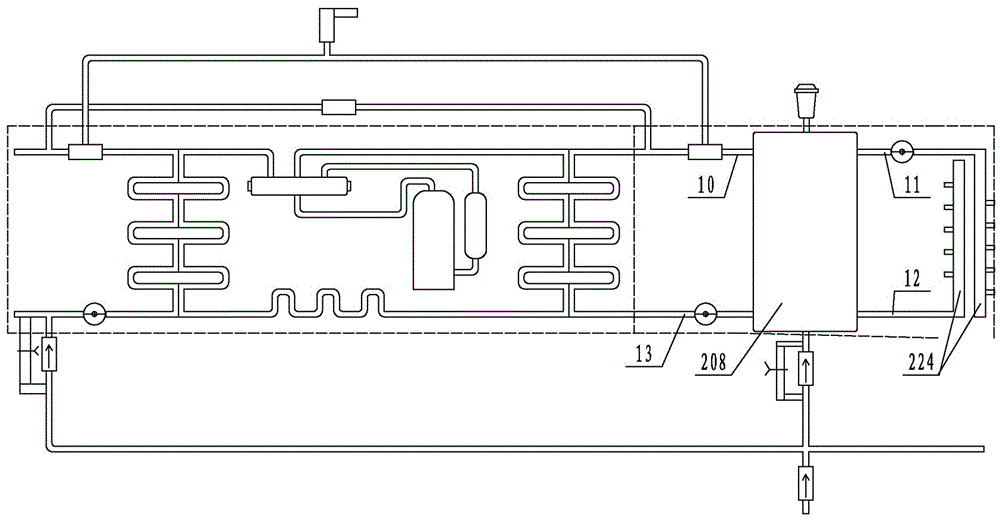
Household ground energy water machine central air conditioning system for buildings
ActiveCN106091174BExtended service lifeReduce the number of starts and stopsMechanical apparatusLighting and heating apparatusHome useArchitectural engineering
The invention relates to a central air-conditioning system for buildings with household ground energy water machines, which includes an outdoor device and an indoor unit. The outdoor device includes an outdoor geothermal circulation well group with a unit building as a unit and a supervisor connected with the outdoor geothermal circulation well group; the indoor unit It includes the main unit of the ground energy water machine of the resident unit of the unit building, the branch pipes connected in parallel on the main pipe, the centralized distributor and the end; the main machine of the ground energy water machine is respectively connected with the corresponding branch pipes; the invention makes the household central air conditioning system move towards A new stage, flexible and intelligent use features, simple and economical modular installation and the use of environmentally friendly materials have added new vitality to the revolution of household air conditioners.
Owner:河北华威新能源科技有限公司
Polarization coding quantum key distribution system encoder
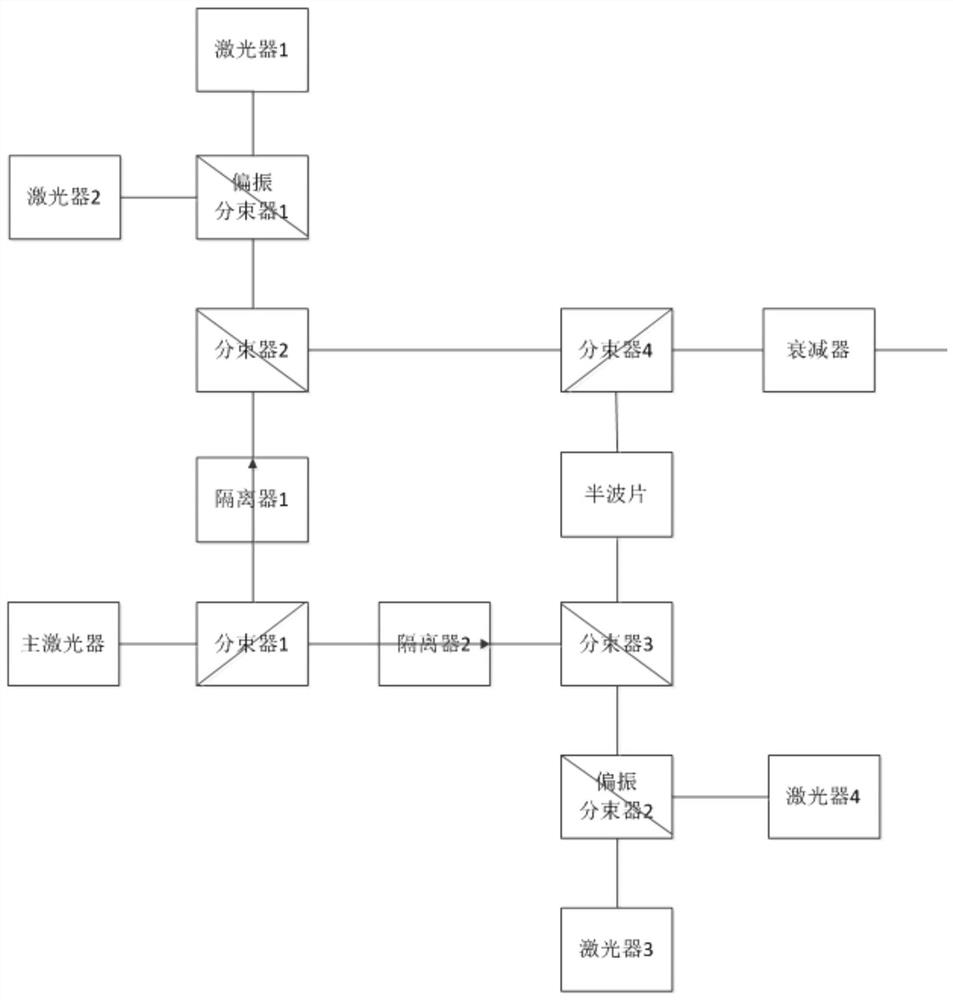
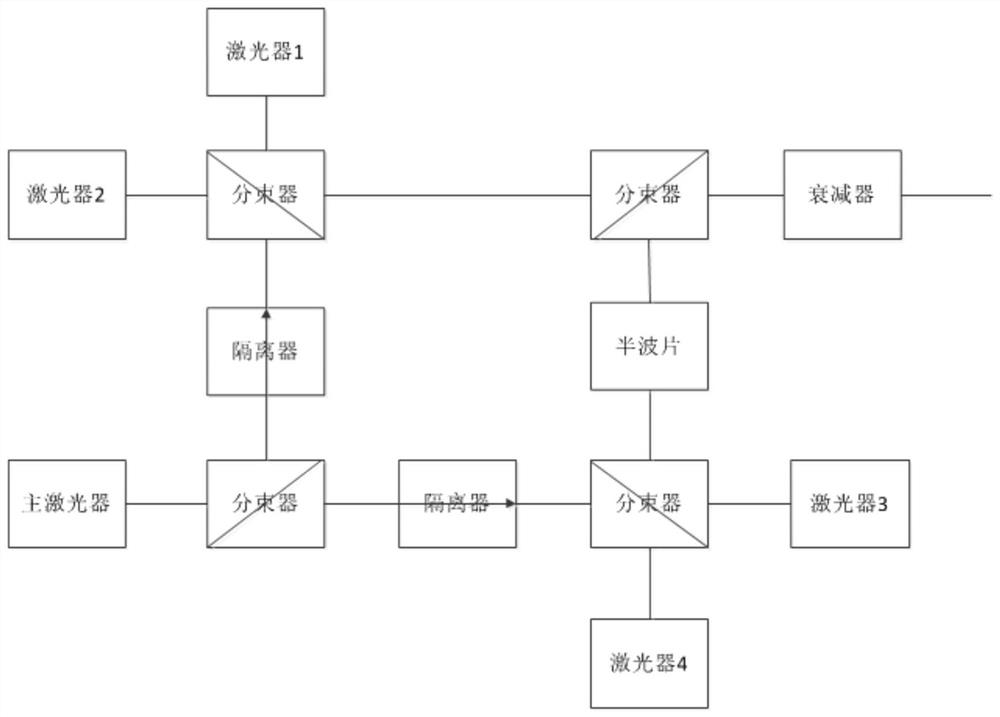
PendingCN113259090AGuaranteed feasibilityEnsure system securityKey distribution for secure communicationPhotonic quantum communicationBeam splitterWavelength
The invention discloses a polarization coding quantum key distribution system encoder. A main laser device emits 45-degree linearly polarized light pulse laser signals, the 45-degree linearly polarized light pulse laser signals are divided into horizontal linearly polarized light and vertical linearly polarized light through a beam splitter and a polarization beam splitter, and the horizontal linearly polarized light and the vertical linearly polarized light are injected into a laser device 1, a laser device 2, a laser device 3 and a laser device 4 respectively, and the emergent polarized light and the injected polarized light of different lasers are consistent, and finally, single photon transmission is attenuated through beam combination. According to the encoder, the frequency domain consistency among multiple lasers can be realized under the condition that the lasers are adopted at the transmitting end of the polarization encoding quantum key transmitting system, so that the engineering implementation feasibility is ensured, and the system safety is also ensured.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
A communication device for the internal and external units of an air conditioner, and a communication method for the air conditioner and its internal and external units
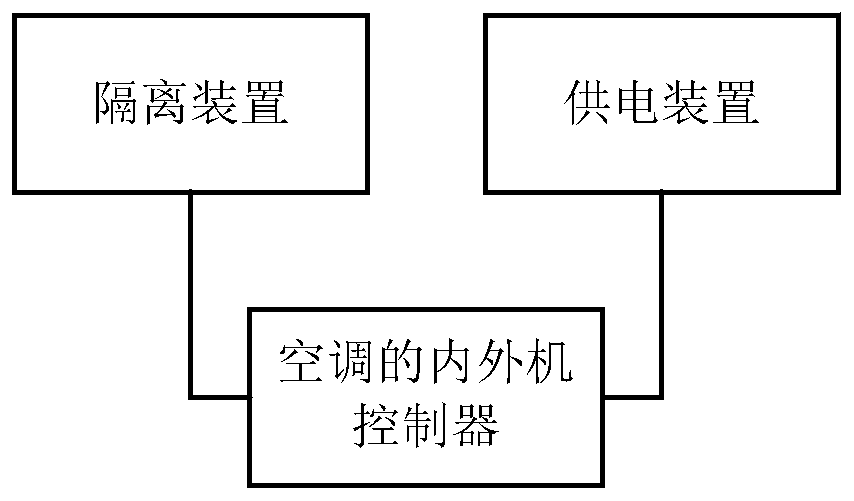
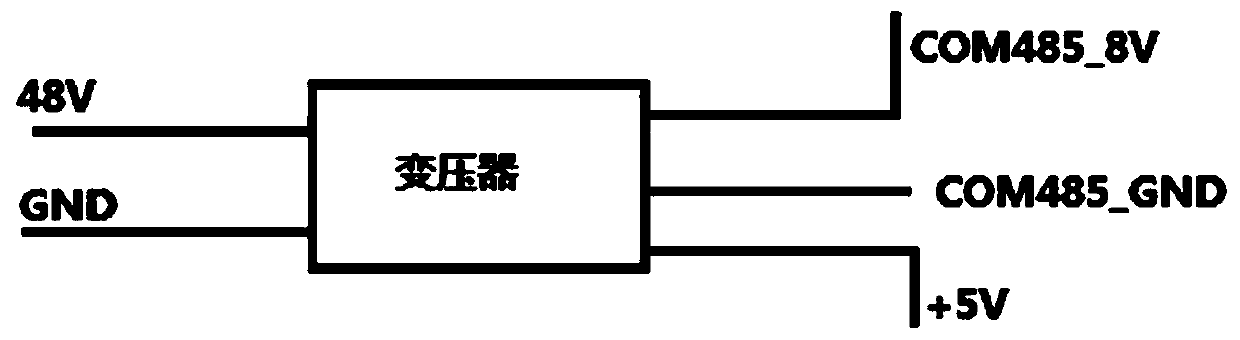
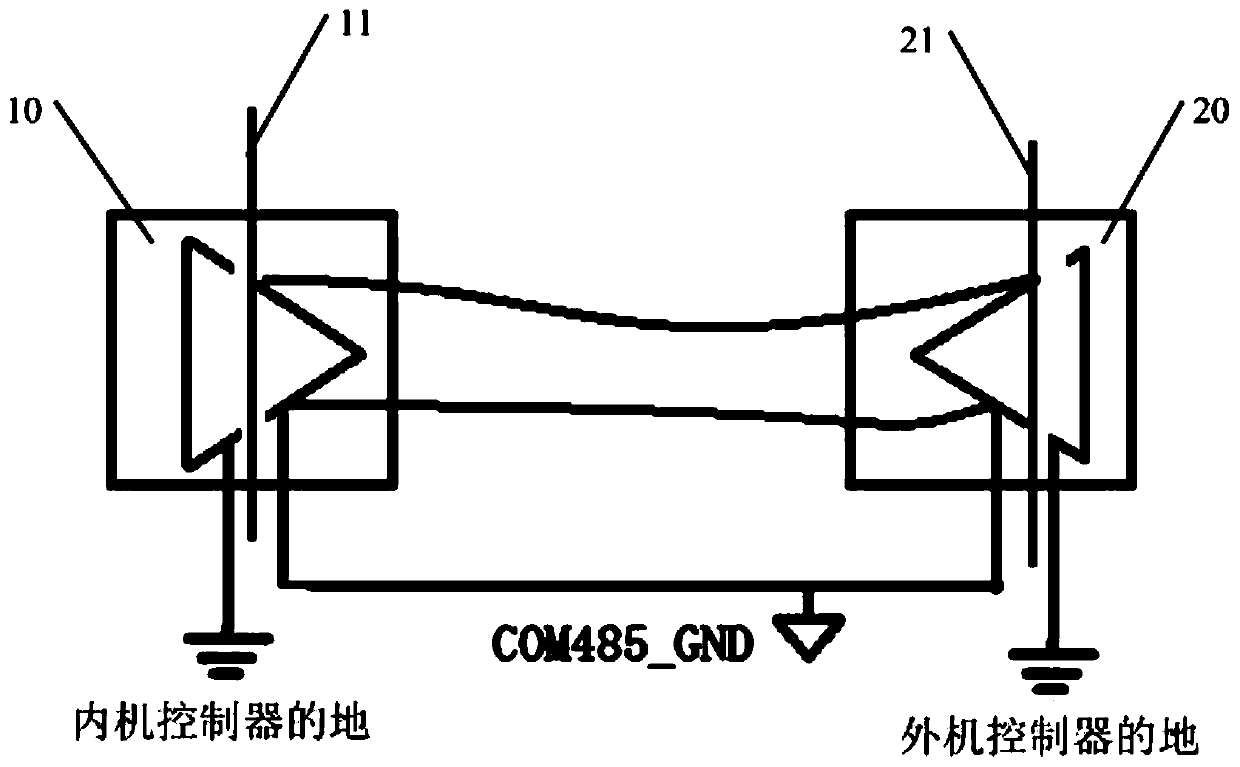
ActiveCN109140700BEnsure personal safetyEnsure system securityMechanical apparatusSpace heating and ventilation safety systemsEngineeringControl circuit
The invention discloses a communication device of an indoor unit and an outdoor unit of an air conditioner, the air conditioner and a communication method of the indoor unit and the outdoor unit of the air conditioner. The communication device comprises an isolation device and a power supply device, wherein the isolation device is used for isolating a communication circuit from a control circuit of an indoor unit and outdoor unit controller of the air conditioner; and the power supply device is used for supplying power to the communication circuit and the control circuit of the indoor unit andoutdoor unit controller under the situation that the communication circuit and the control circuit of the indoor unit and outdoor unit controller are isolated. According to the scheme, the problem that in the prior art, communication nodes of the indoor unit and the outdoor unit of the air conditioner are connected to respective local ground, and communication safety is poor can be solved, and the effect of improving the communication safety is achieved.
Owner:GREE ELECTRIC APPLIANCES INC
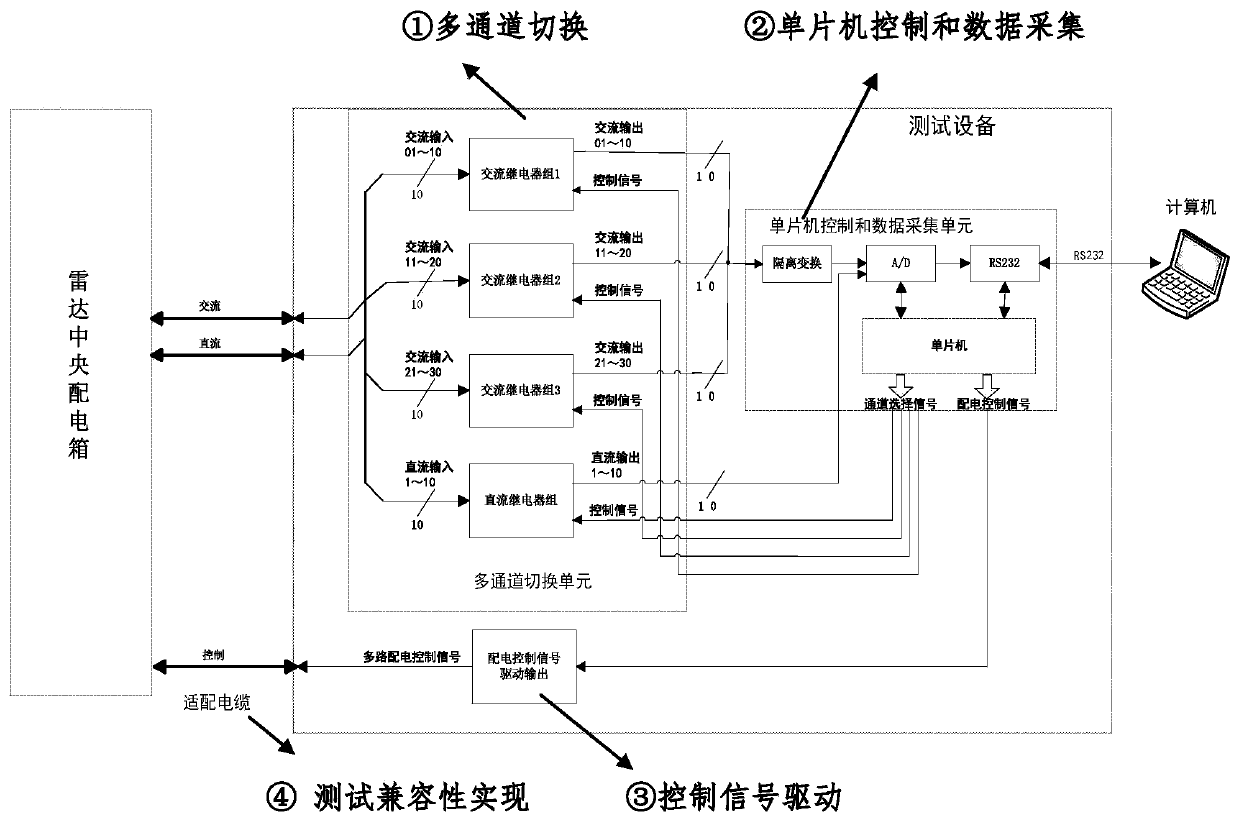
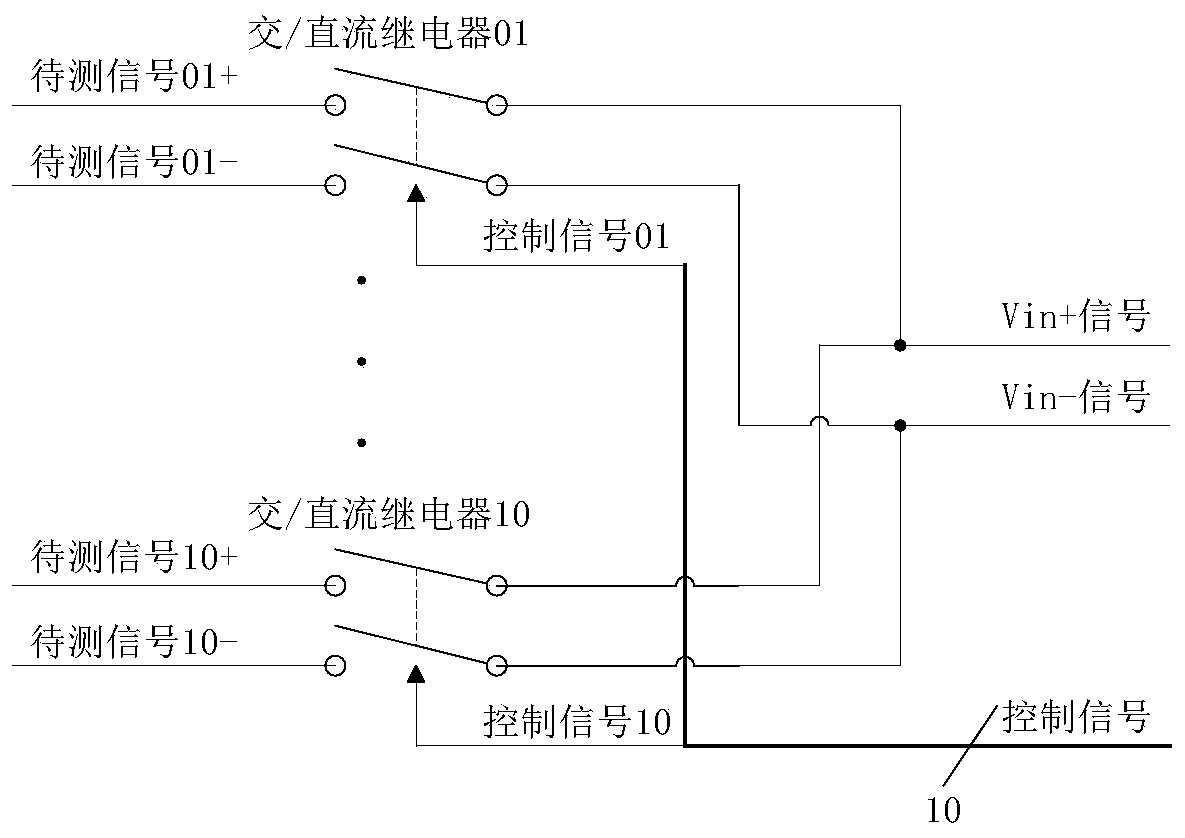
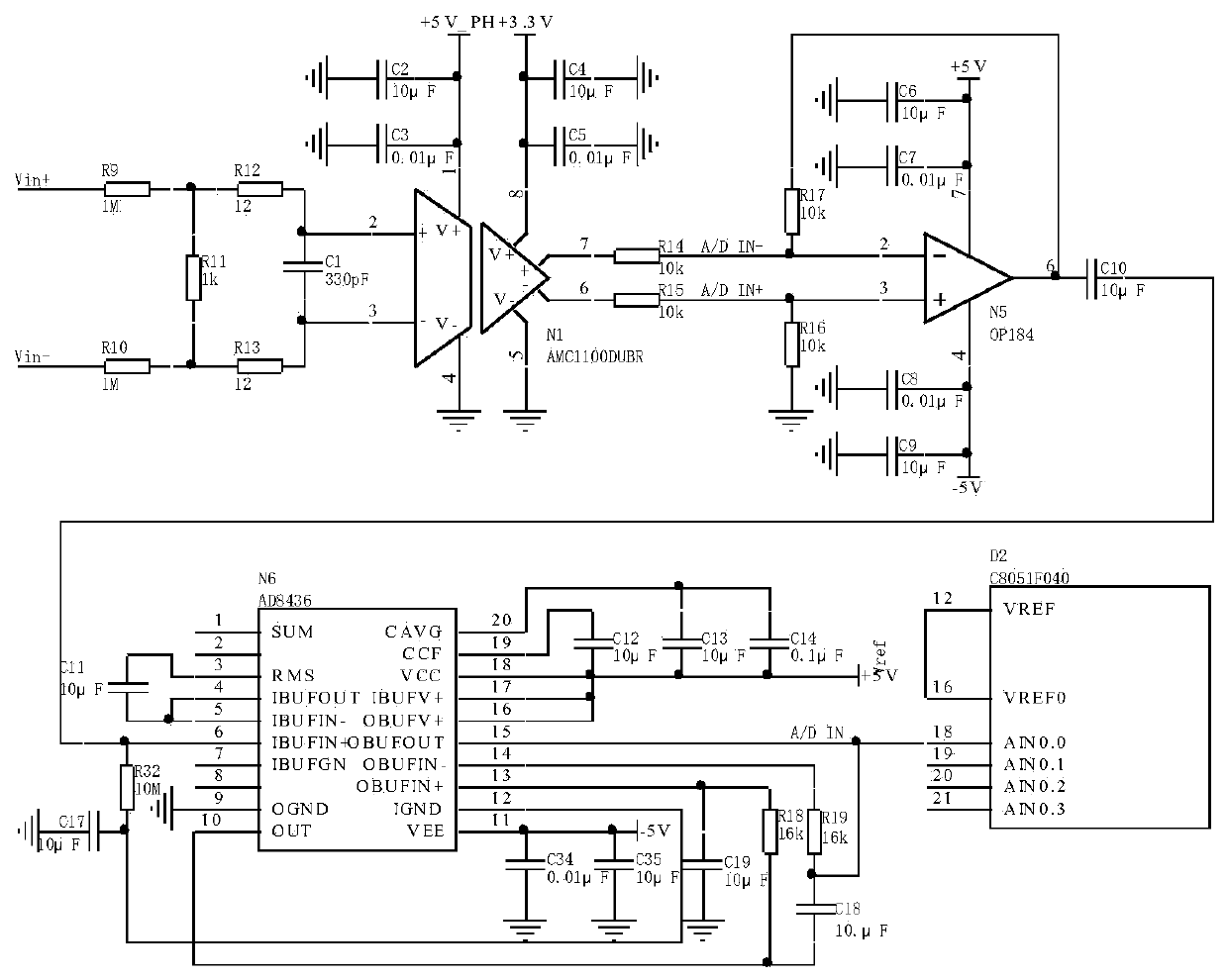
Radar center power distribution box offline automatic detection system and method
ActiveCN110542890AImprove securityImprove convenienceWave based measurement systemsPower supply testingTest efficiencyNumerical control
The invention relates to a radar center power distribution box offline automatic detection system and method. The system comprises a multi-channel switching unit, a single-chip microcomputer control and numerical control collection unit, and a power distribution control signal driving output module. Through the single-chip microcomputer control and numerical control collection unit, the power distribution control signal driving output module is controlled to control on or off of the multi-channel switching unit for a power distribution work state of each circuit required for a radar center power distribution box, so as to collect a detected signal. The radar center power distribution box offline automatic detection system and method greatly improve security, convenience, compatibility andtraceability of system test while greatly enhancing test efficiency.
Owner:CNGC INST NO 206 OF CHINA ARMS IND GRP
Special individual household central air conditioning system with geothermal-energy water machine for storied building
ActiveCN106091174AExtended service lifeReduce the number of starts and stopsMechanical apparatusSpace heating and ventilation safety systemsDistributorAutomotive engineering
The invention relates to a special individual household central air conditioning system with a geothermal-energy water machine for a storied building. The special individual household central air conditioning system with the geothermal-energy water machine for the storied building comprises an outdoor device and an indoor machine, wherein the outdoor device comprises an outdoor geothermal circulating well cluster which uses a cell building as a unit and a main pipe connected with the outdoor geothermal circulating well cluster; the indoor machine comprises a geothermal-energy water machine main body which uses each inhabitant of the cell building as a unit, and branching pipes, centralized distributors and tail ends, which are connected onto the main pipe in parallel; the geothermal-energy water machine main body is communicated with the corresponding branching pipes. By using the special individual household central air conditioning system with the geothermal-energy water machine for the storied building, a domestic central air conditioning system is enabled to march toward a new stage; new vitality is added to the revolution of a domestic air conditioner by flexible and intelligent usage characteristics, concise and economic modular mounting and the usage of environment-friendly materials.
Owner:河北华威新能源科技有限公司
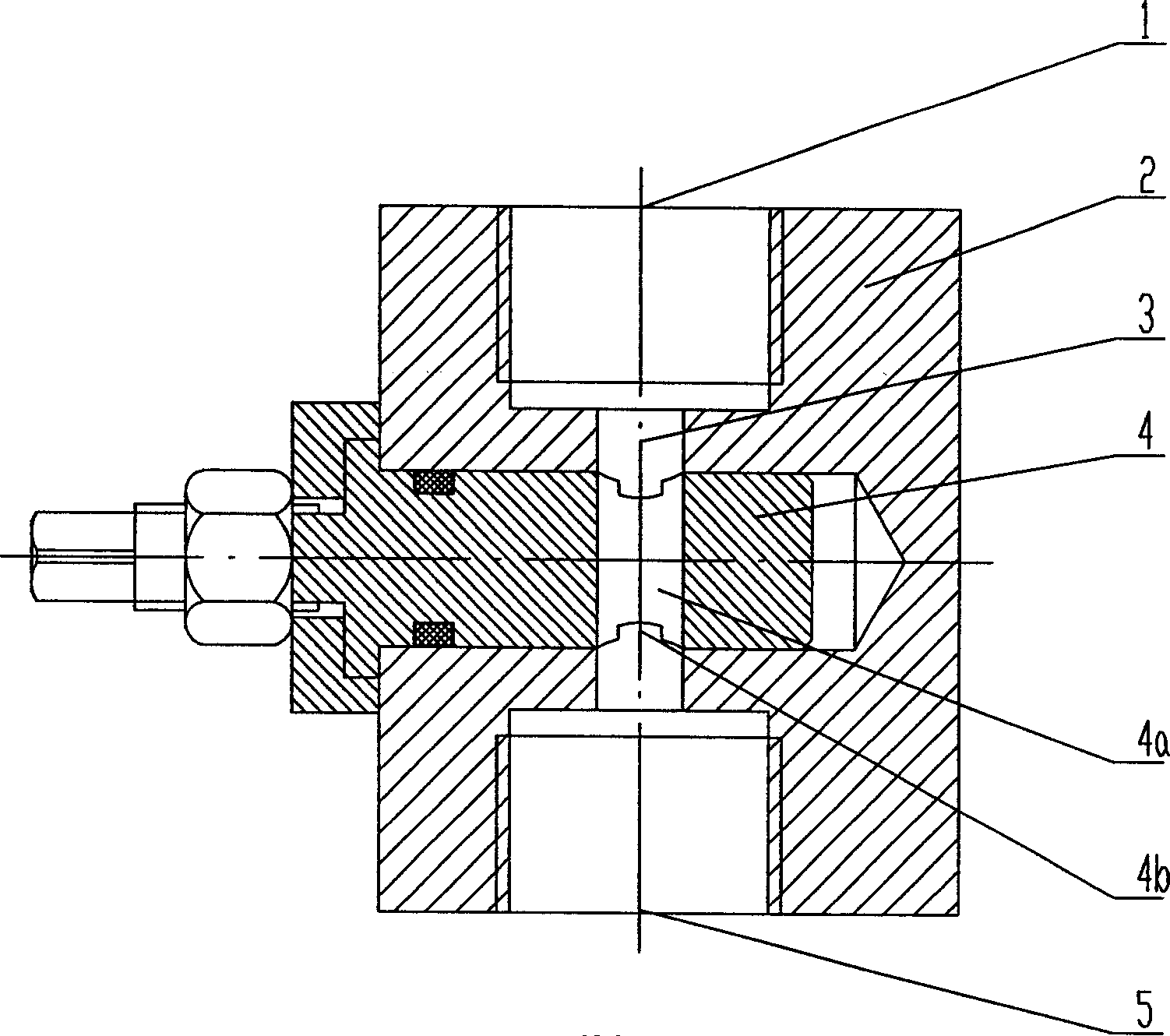
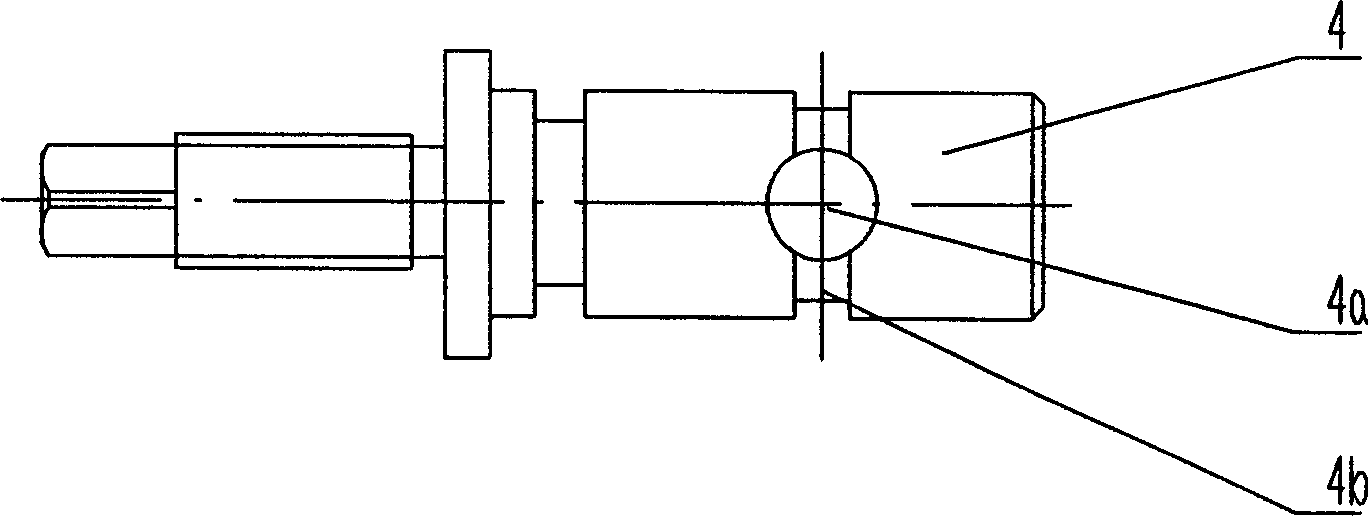
Safety throttle valve
The invention discloses safe throttle which belongs to throttle technical field. It includes valve body and core. The valve body is set oil inlet and outlet which are connected. And it is also set blind hole. The valve core is set in the blind hole. And its outer surface is set round oil groove. While running, the valve core can change flow area; the round oil groove can not make throttle switch off fully; and it can avoid kong bursting while setting between safety valve outlet and oil case in forcing press. The invention can adjust flow speed and keep system safe by setting appropriate round oil groove area.
Owner:JIANGSU GUOLI FORGING MACHINE TOOL
A method and device for implementing secure interaction between systems
ActiveCN108734033BAvoid security issuesImprove scalabilityInterprogram communicationInternal/peripheral component protectionSoftware engineeringVerification
The invention provides a method and system for realizing secure interaction between systems. After a debugging request is sent to a debugged system by a debugging system, the method comprises the following steps of: receiving the debugging request sent by the debugging system by the debugged system, wherein the debugging request comprises verification information and debugging information of the debugging system; and executing verification logic for the verification information of the debugging system, executing a debugging task for the debugged system according to the verification result, ifthe verification information is successfully verified, executing the debugging task by the debugged system according to the debugging information and returning a debugging result to the debugging system, and otherwise, informing the debugging system that the debugging task fails. According to the method and system, the security problem of debugging interfaces between debugging systems and debuggedsystems in the prior art is solved. Moreover, verification manners can be dynamically extended, so that extensibility of system debugging interfaces is improved under the premise of ensuring the system security and data security of business systems.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Remote control distribution box with auxiliary power supply
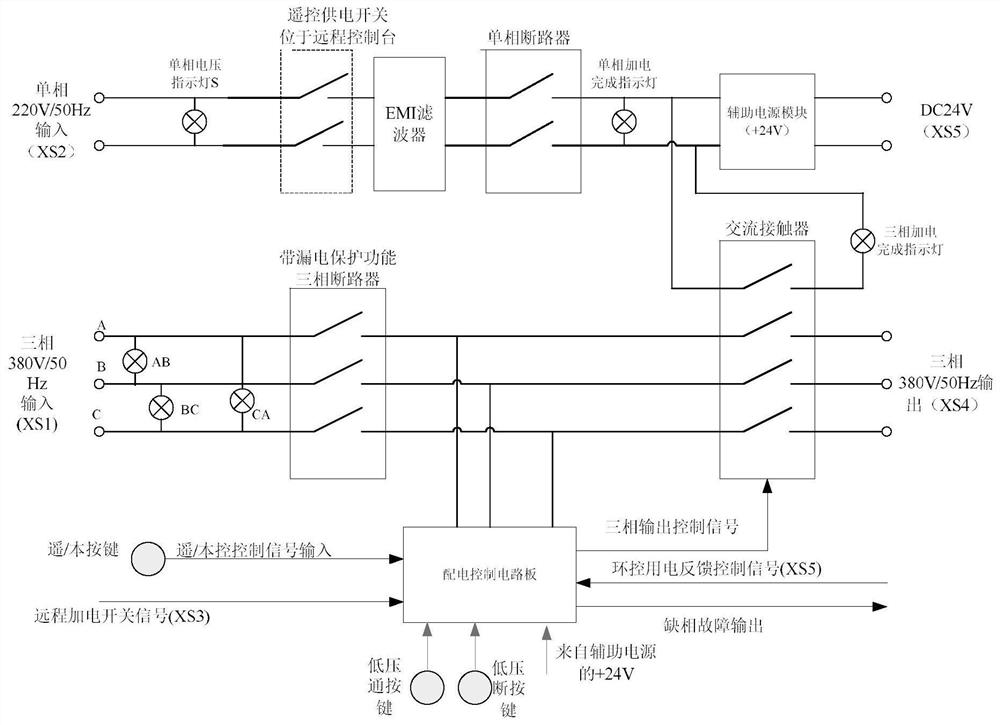
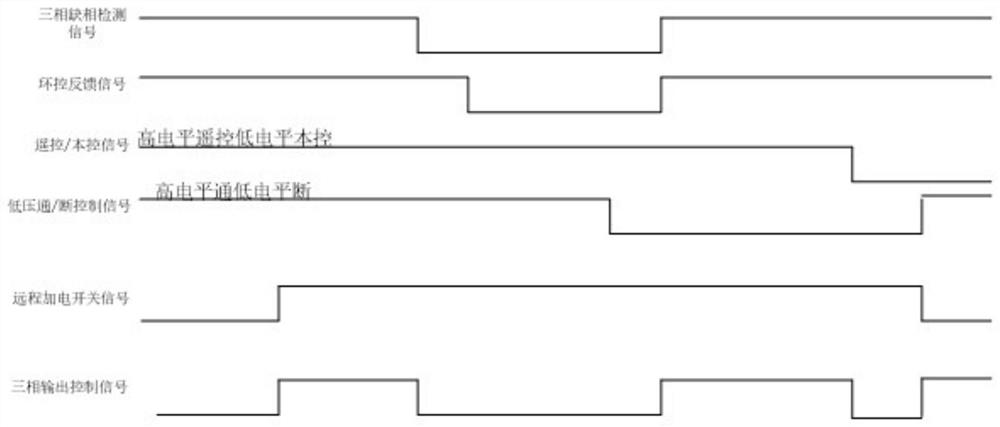
ActiveCN113644556AImprove powerEnsure personal safetyBoards/switchyards circuit arrangementsArrangements responsive to underloadDistribution controlRemote control
The invention discloses a remote control distribution box with an auxiliary power supply. The remote control distribution box comprises a distribution box body, a single-phase circuit breaker, a three-phase circuit breaker, an auxiliary power supply module, a distribution control circuit board, an alternating current contactor, a remote control power supply switch and an EMI filter. When the single-phase circuit breaker is in a closed state, AC220V input by the power supply equipment is converted into auxiliary power supply DC24V to be output, and when the three-phase circuit breaker is in a closed state, the power distribution control circuit board controls whether AC380V input by the power supply equipment is output or not according to a remote / local control state and a power-up signal state fed back by the environment control equipment. The remote control distribution box has a remote control state and a local control state, and can output DC24V when not outputting AC380V, so that the safety and convenience in use are improved.
Owner:中国船舶重工集团公司第七二三研究所
A sequence-controllable energy storage device and method
ActiveCN107045896AReduce power consumptionEnsure system securityNuclear energy generationNuclear reaction controlSystem safetyEngineering
A sequence-controllable energy storage device and method are provided. For each circuit breaker, a second time relay II, a third time relay III and a fourth time relay IV are switched on through an action of a first time relay I after a remote opening pulse signal is received by the first time relay I; a second control loop is connected to the second time relay II, the third time relay III and the fourth time relay IV which are in parallel connection; the inside of the third time relay III is provided with opening time; a normally open contact of the third time relay III is closed to perform opening in the opening time, and is disconnected in other time; the inside of the fourth time relay IV is provided with energy storage time; the inside of the second time relay II is provided with closing time; and the closing time and the energy storage time do not overlap. Opening and energy storage signals of shutdown circuit breakers are separated, and different pulse contacts of the time relays are utilized to control opening and energy storage respectively, thus reducing power consumption of a power supply and ensuring system safety.
Owner:713 RES INST OF CHINA SHIPBUILDING IND CORP
Highly-integrated low-temperature stop valve with overflowing function
PendingCN112524257AEnsure system securityIncrease internal diameterOperating means/releasing devices for valvesEqualizing valvesPhysicsEngineering
A highly-integrated low-temperature stop valve with an overflowing function comprises an overflowing valve assembly, a connecting tube, a valve body, a valve cover and a hand wheel, wherein the overflowing valve assembly is connected to the valve body in an embedded mode through straight threads, so that a gas cylinder connecting pipeline is minimized, and the diameter of a valve passage is maximized; one end of the connecting tube is welded to the valve body, and the other end of the connecting tube is welded with a boosting liquid outlet of the gas cylinder; the hand wheel is in threaded connection to the valve body, and the valve body between the valve body and the overflow valve assembly is of a structure inclining outwards by 45 degrees, so that the hand wheel achieves the outward inclination angle of 135 degrees to the maximum degree.
Owner:欧阳国法
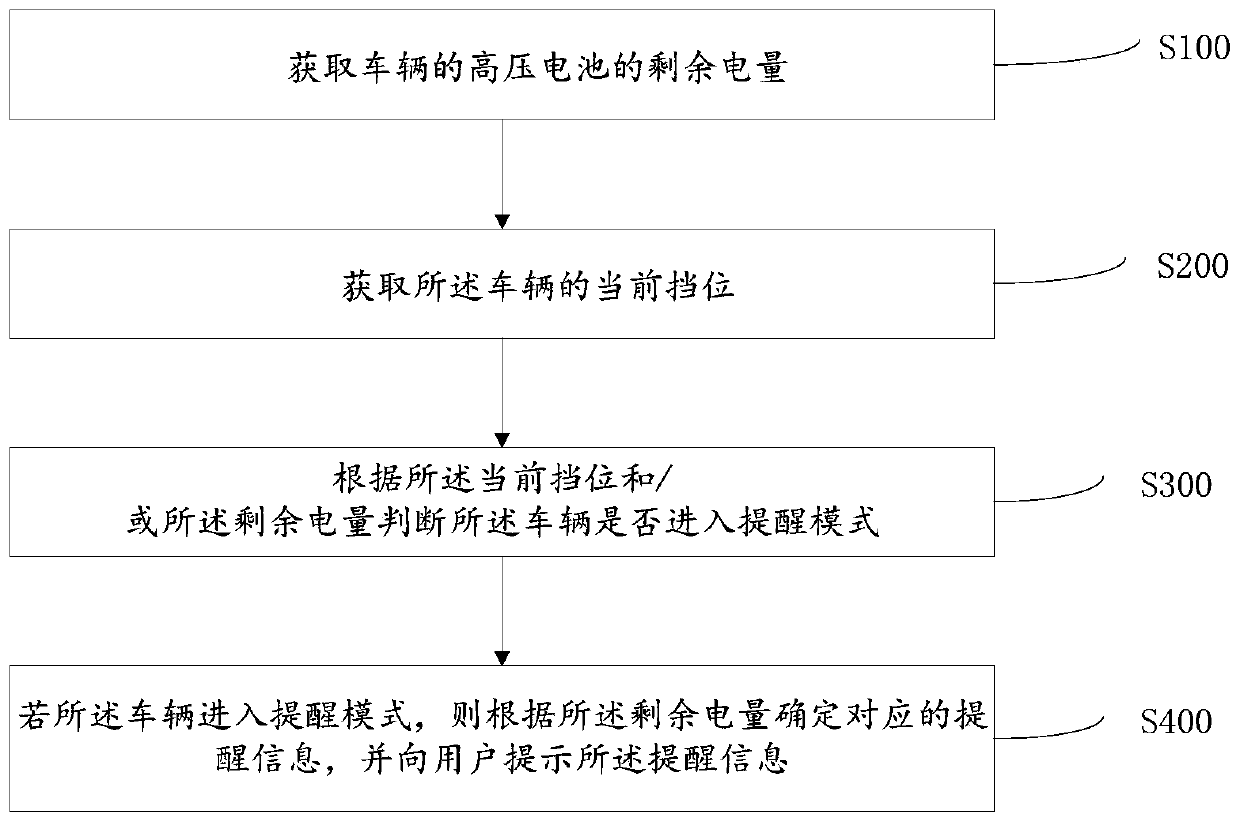
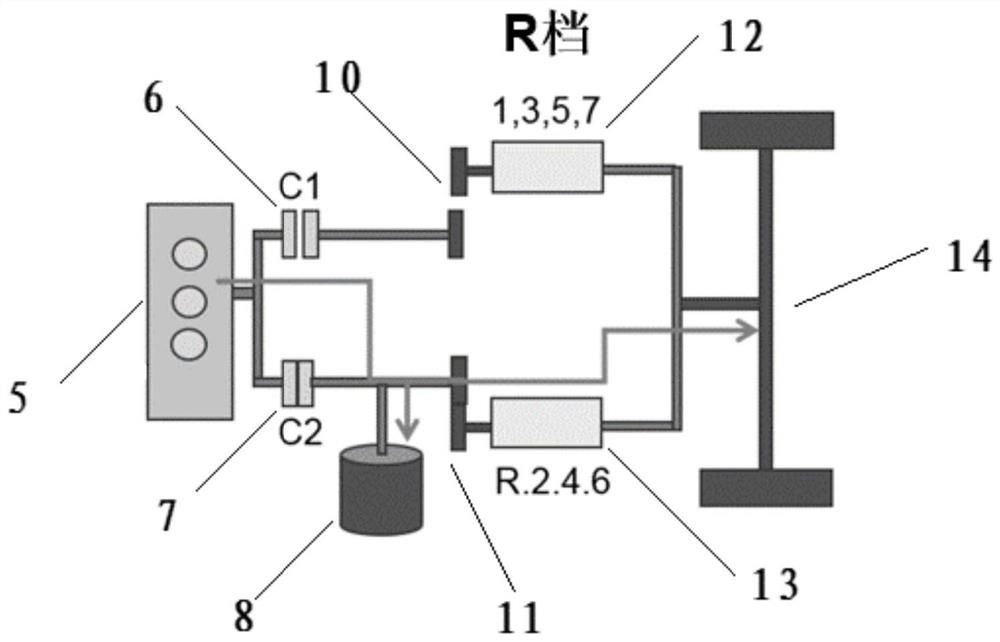
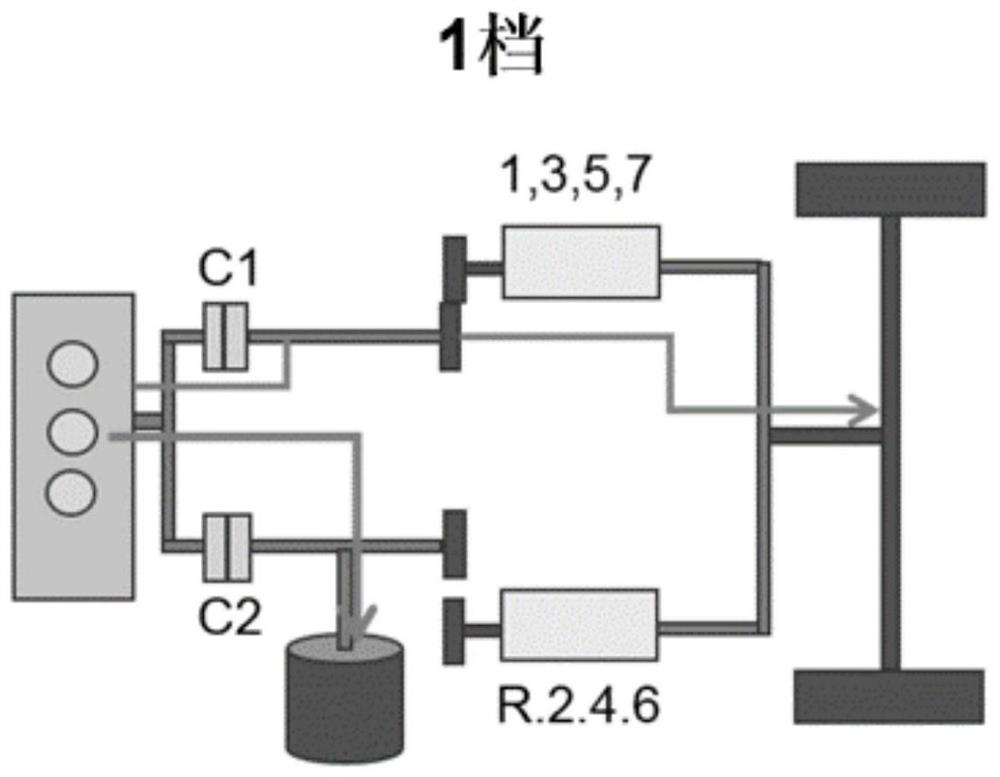
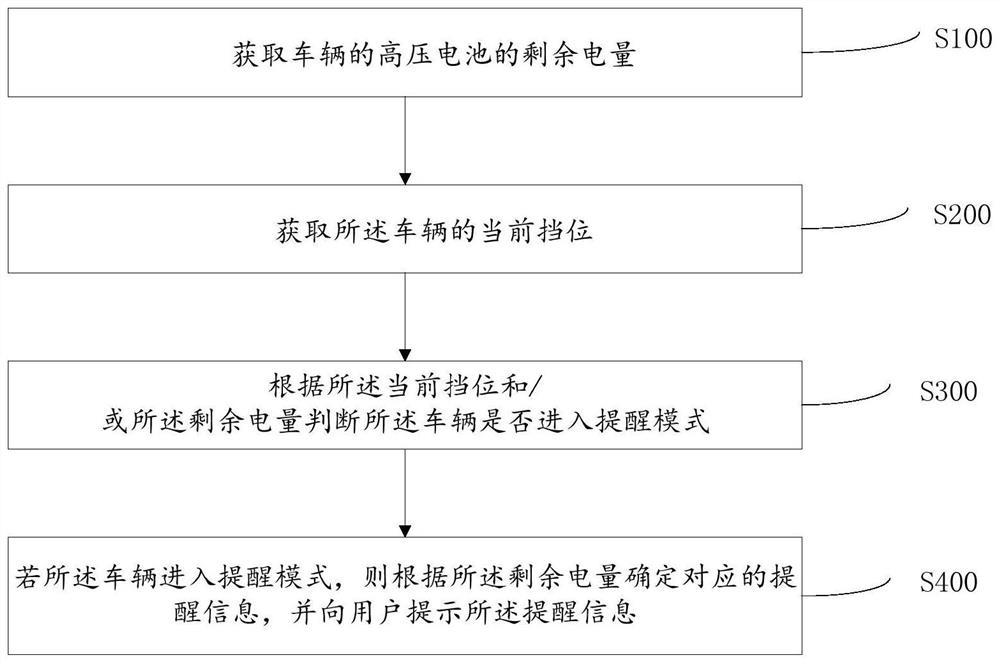
Reverse reminding method, reminding device, vehicle and terminal
ActiveCN110293907AEliminate potential safety hazardsEnsure driving safetySignalling/lighting devicesVehicular energy storageComputer terminalSystem safety
The invention discloses a reverse reminding method. The reverse reminding method includes the steps of obtaining the residual power of a high-tension battery of a vehicle; obtaining the current gear of the vehicle; judging whether the vehicle enters the reminding mode or not according to the current gear and / or the residual power; determining corresponding reminding information according to theresidual power and prompting the reminding information to a user if the vehicle enters the reminding mode. The invention further discloses a reverse reminding device, the vehicle and a terminal. The reverse reminding method, the reverse reminding device, the vehicle and the terminal have the advantages that when the vehicle is in the reverse gear, different reminding information can be sent to a driver according to the residual power of the high-tension battery, the potential safety hazard is eliminated, and normal driving and system safety are guaranteed.
Owner:ZHEJIANG GEELY HLDG GRP CO LTD +1
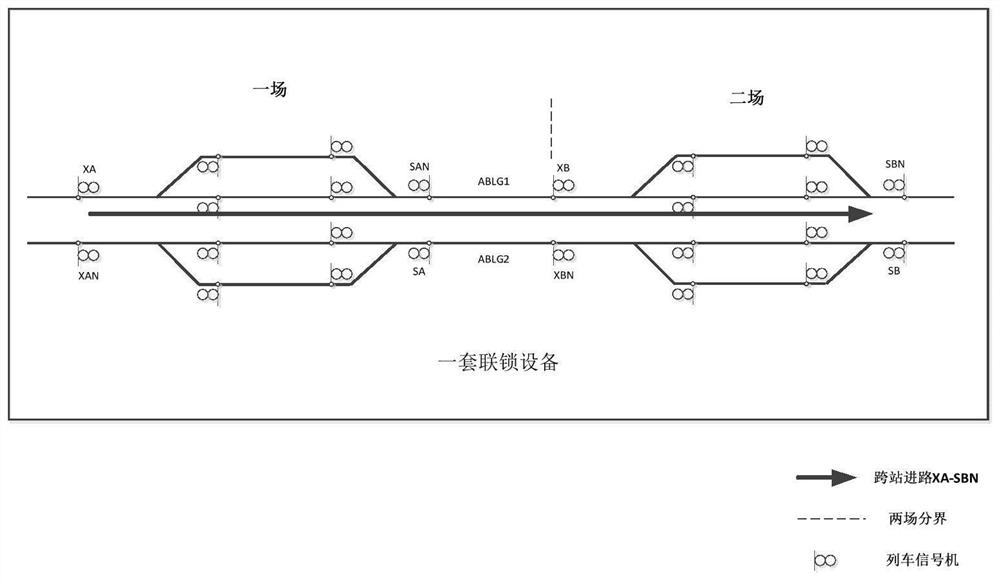
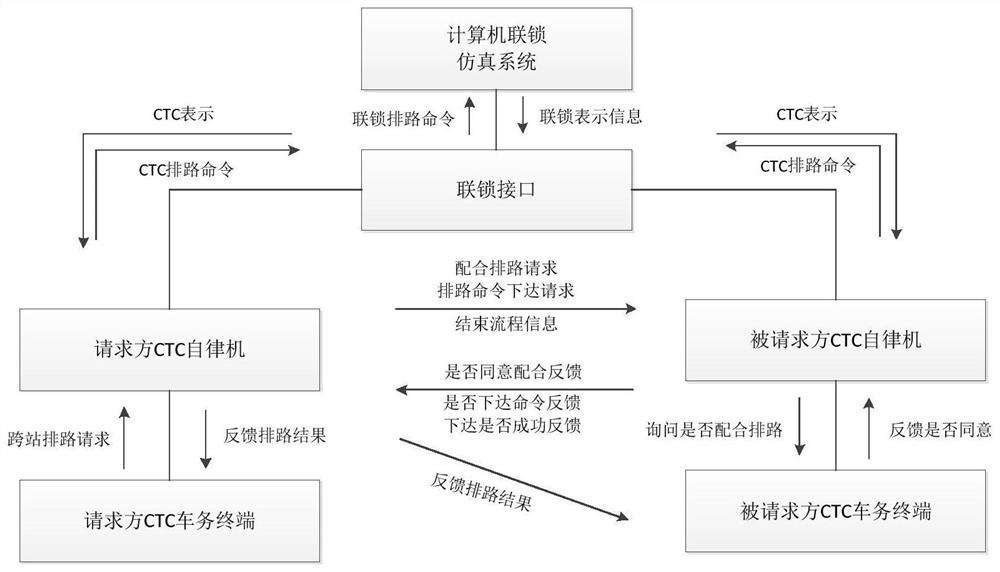
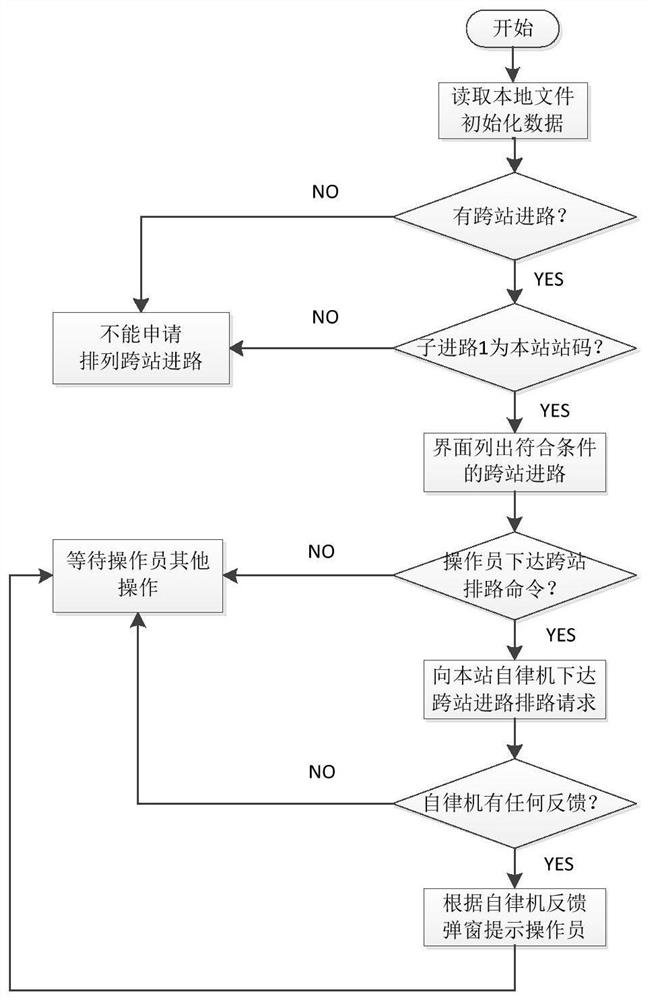
A method and system for cross-station routing of decentralized autonomous dispatching and centralized stations
ActiveCN112172876BConvenience guaranteedGuaranteed completenessRailway traffic control systemsSignal boxes station blockingStationOperation mode
The invention discloses a method and system for cross-station routing of decentralized self-discipline dispatching and centralized stations. Compared with the existing operation mode, the cross-station routing method proposed by the invention maintains the convenience characteristics of the CTC system, and the operation is simple and intuitive. You only need to apply, agree or reject, and the rest of the complex logic judgments are completed by the self-discipline machine in the background; each station independently controls its own station, and when it is necessary to arrange cross-station routes, the system will automatically apply to other relevant stations; this method does not violate the dispatching centralized system The principle that each station can only control its own station does not affect the existing routing logic of the system, and through the perfect communication process, the completeness of routing inspection and system security are guaranteed, which can well solve the problems that cannot be solved in current applications. Solve the problem of cross-station routing.
Owner:SIGNAL & COMM RES INST OF CHINA ACAD OF RAILWAY SCI +3
A system for ensuring normal shutdown and blowing of sulfur during sulfur recovery
InactiveCN104909342BEnsure system securityLow costSulfur preparation/purificationFlareProcess engineering
The invention provides a system for guaranteeing normal shut-down sulfur blow in a sulfur recovery process. The system comprises a natural gas output pipeline, a balance pipeline connected with the natural gas output pipeline in parallel, a balance valve arranged on the balance pipeline, a fuel gas pipeline and a release flare pipeline, and also comprises a first pipeline and a control valve group, wherein the first pipeline is arranged in the flow direction of a gas in the fuel gas pipeline, one end of the first pipeline is arranged behind the balance valve, the other end is arranged on the fuel gas pipeline, the first pipeline connects the balance pipeline with the fuel gas pipeline, and the control valve group is arranged on the first pipeline, and is used for controlling the pressure of a gas in the first pipeline. The system can effectively meet fuel gas required by emergency shut-down of a sulfur recovery workshop section, is safe and reliable, and can reduce the investment of enterprises and increase the economic benefit.
Owner:内蒙古大唐国际克什克腾煤制天然气有限责任公司
Reverse gear reminder method, reminder device, vehicle and terminal
ActiveCN110293907BEliminate potential safety hazardsEnsure driving safetySignalling/lighting devicesVehicular energy storageDriver/operatorHigh voltage battery
Owner:ZHEJIANG GEELY HLDG GRP CO LTD +1
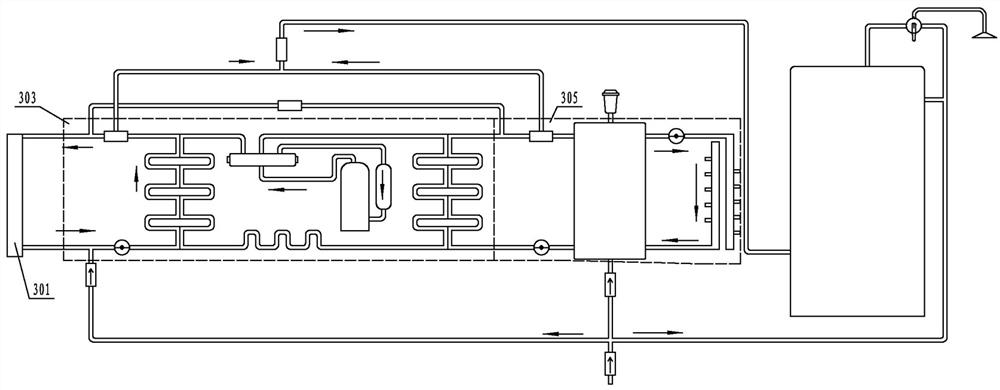
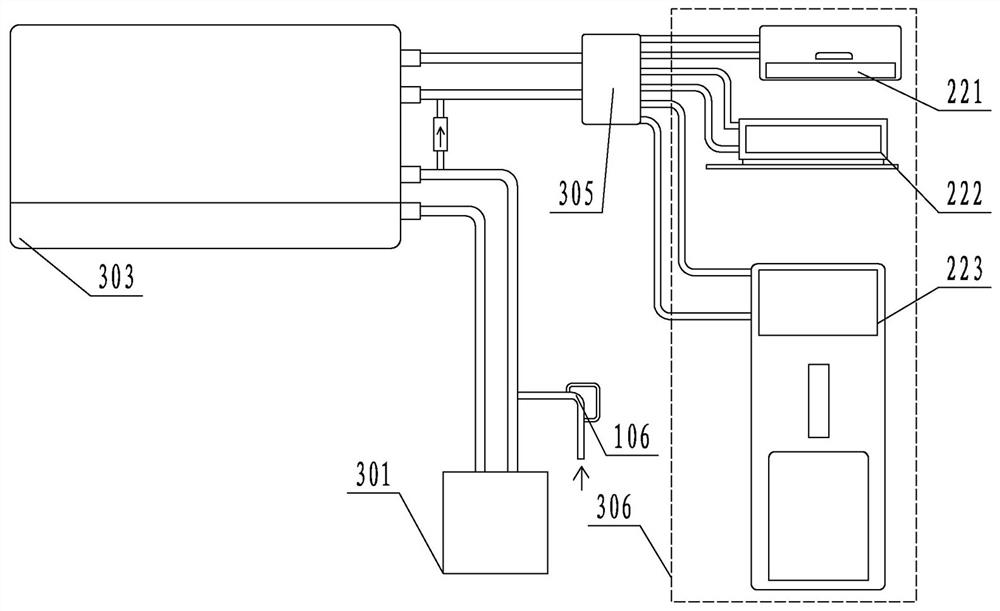
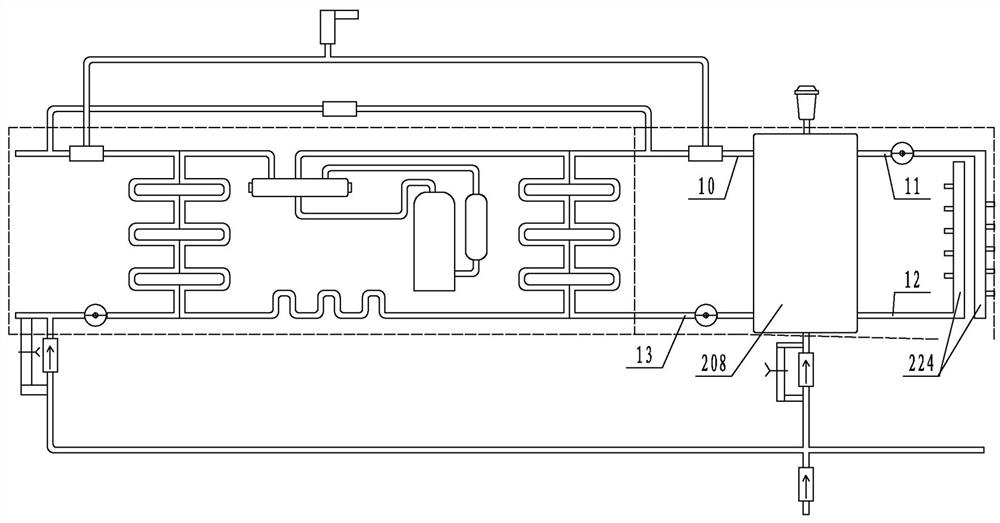
Remote intelligent forensics system and method based on mobile Internet
ActiveCN107666460BGuaranteed cleanlinessEnsure system securityTransmissionScreen sharingSoftware engineering
Owner:真相网络科技(北京)有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com