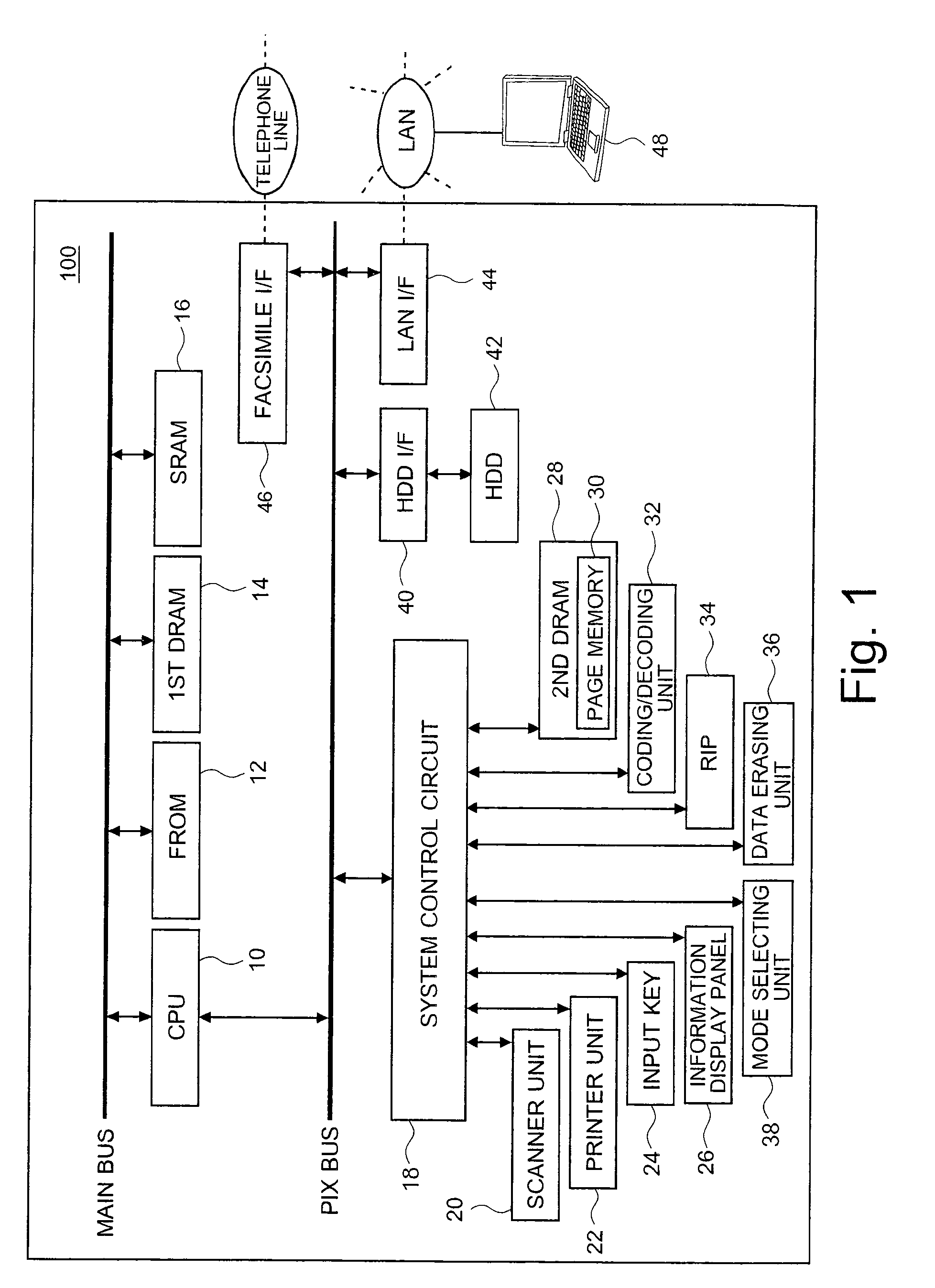
Patents
Literature
227results about How to "Avoid data breaches" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
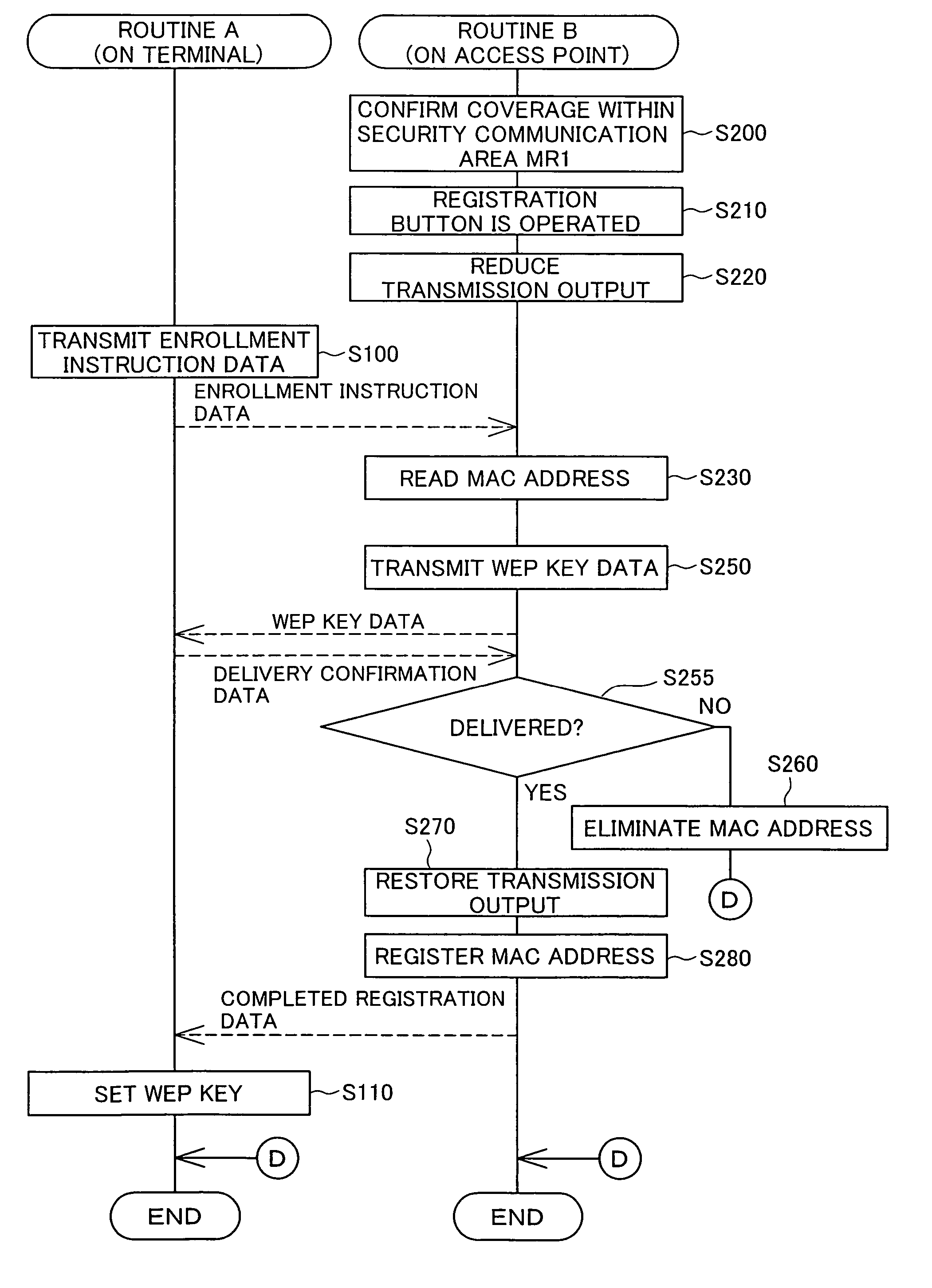
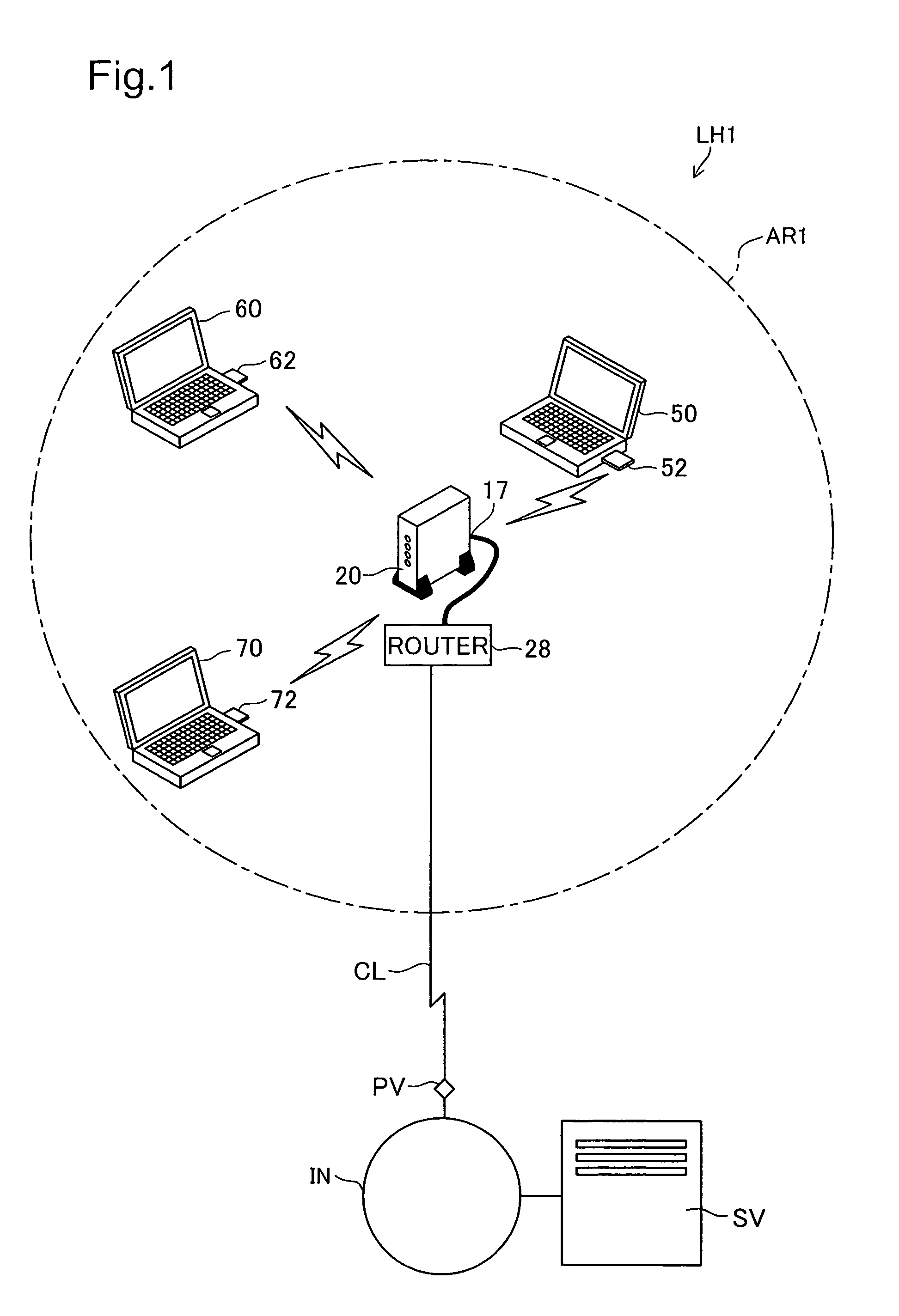
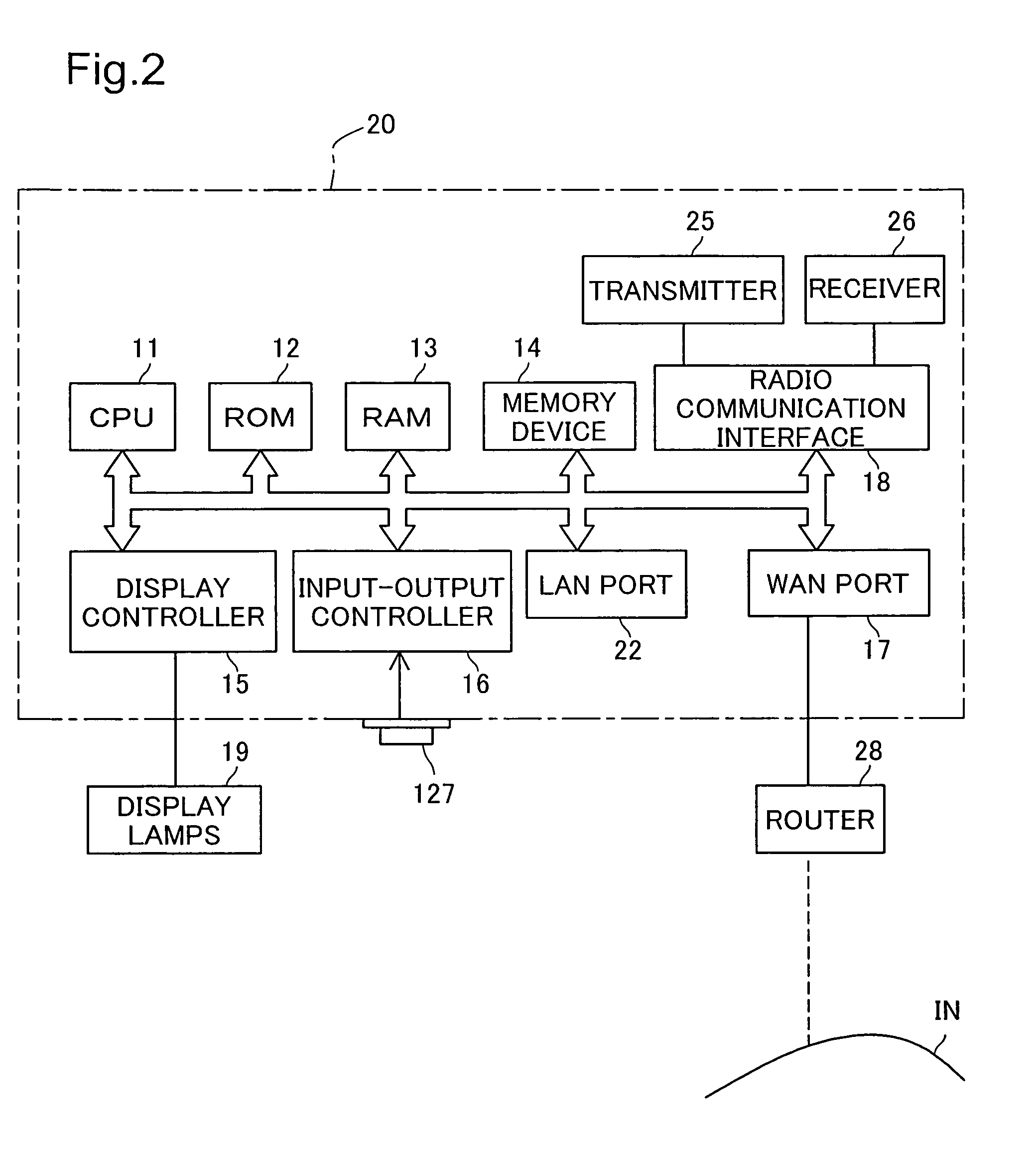
Encryption key setting system, access point, encryption key setting method, and authentication code setting system
ActiveUS7289631B2Avoid data breachesEnergy efficient ICTUser identity/authority verificationSecure communicationWireless lan
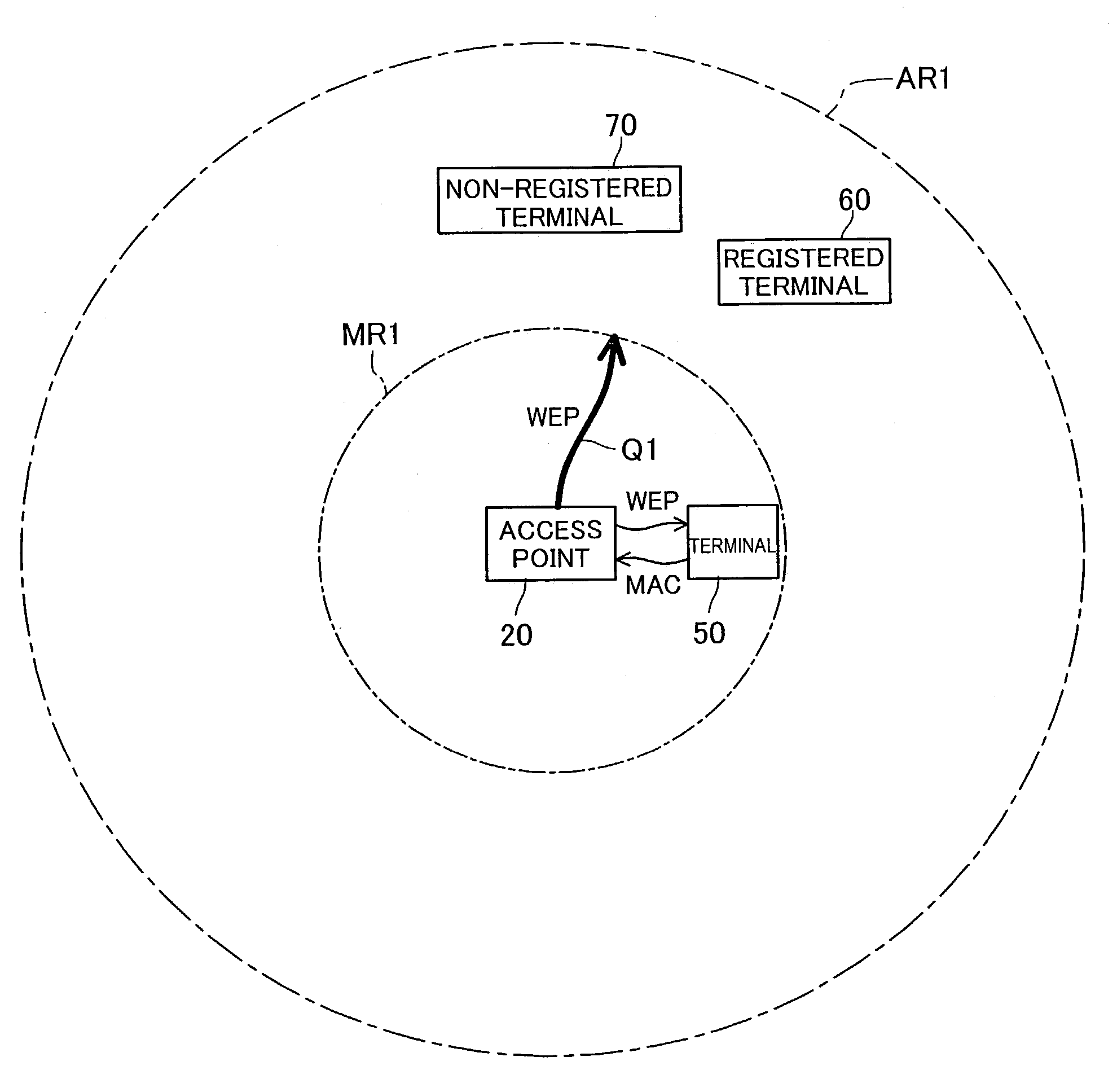
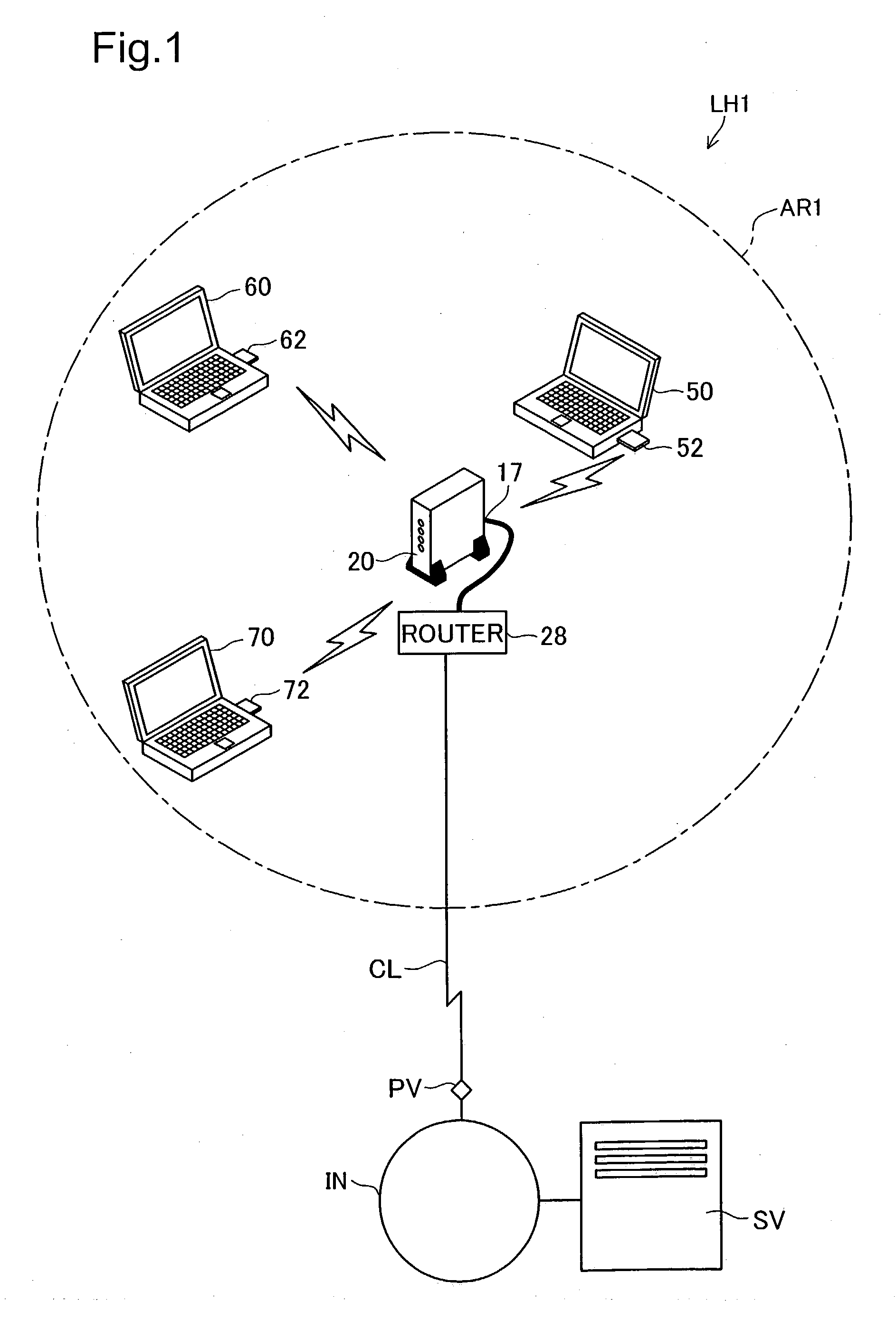
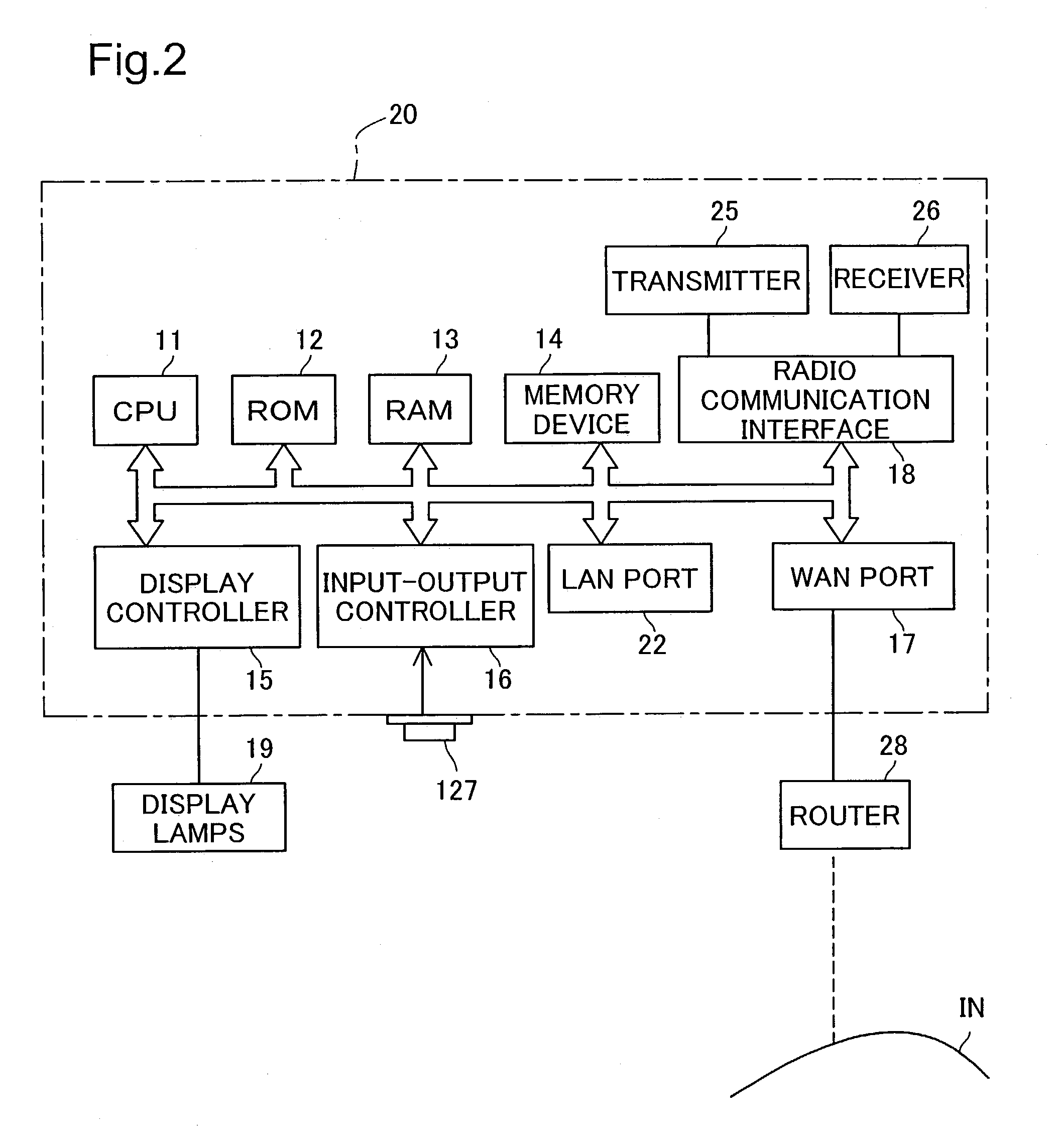
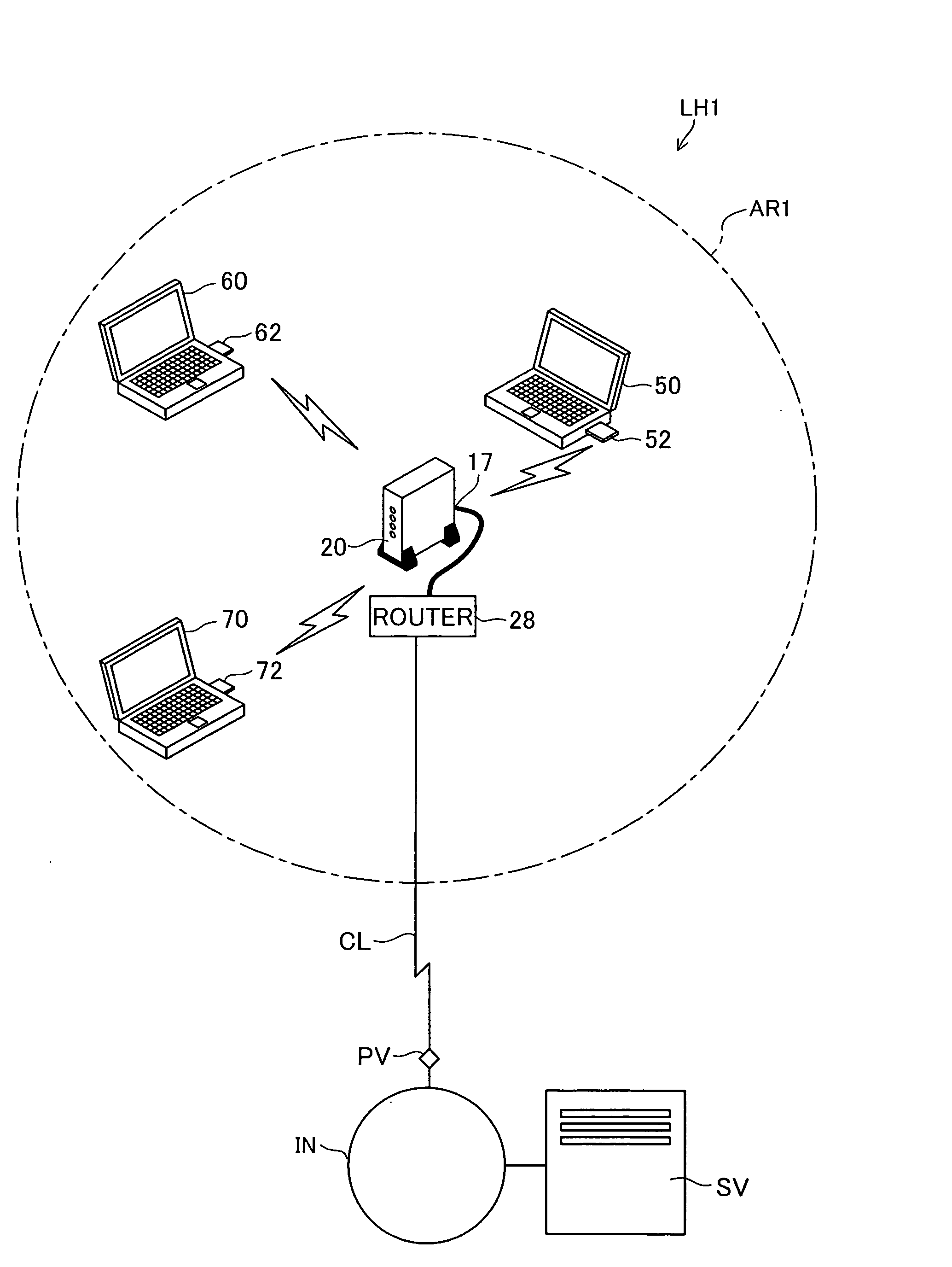
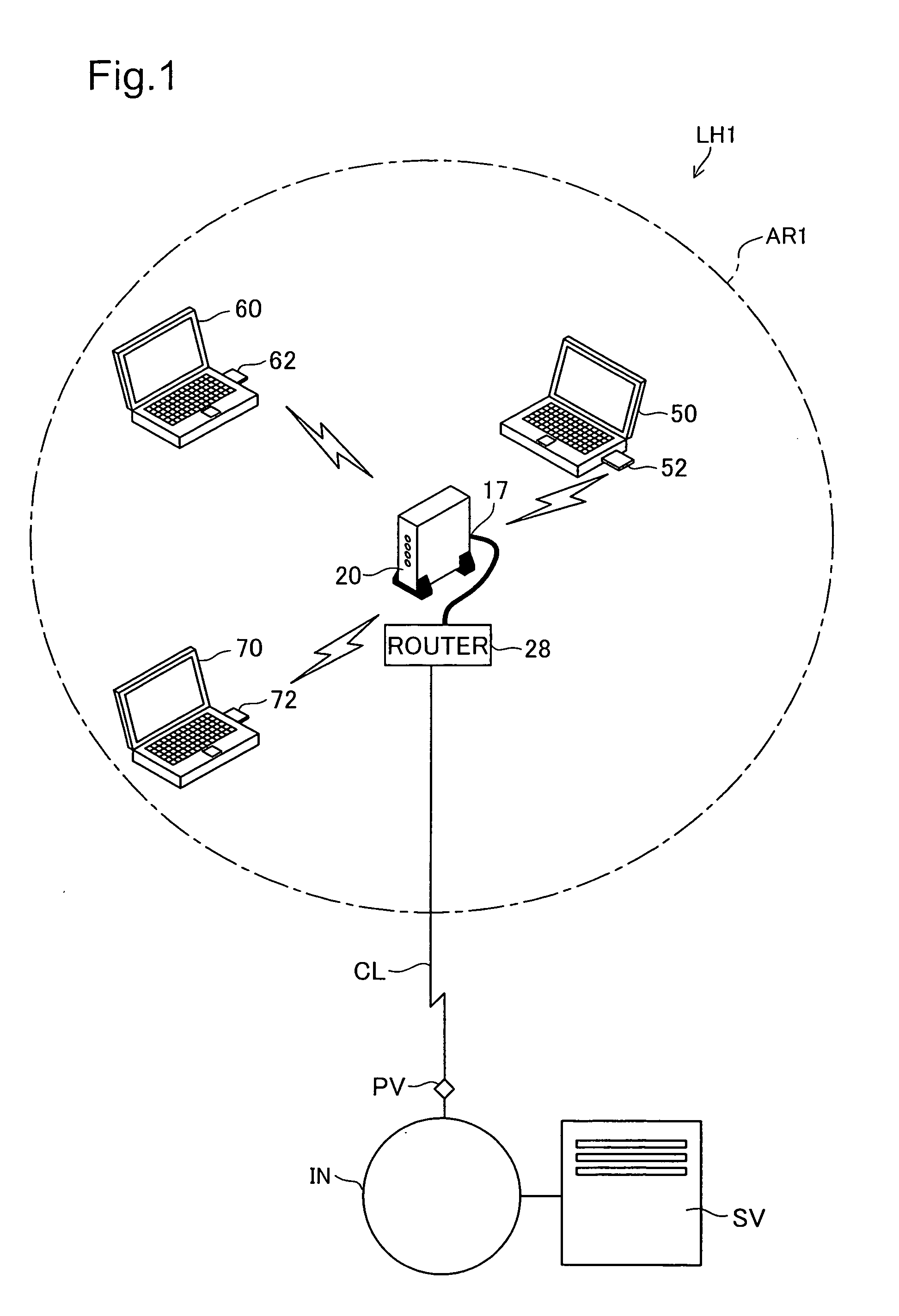
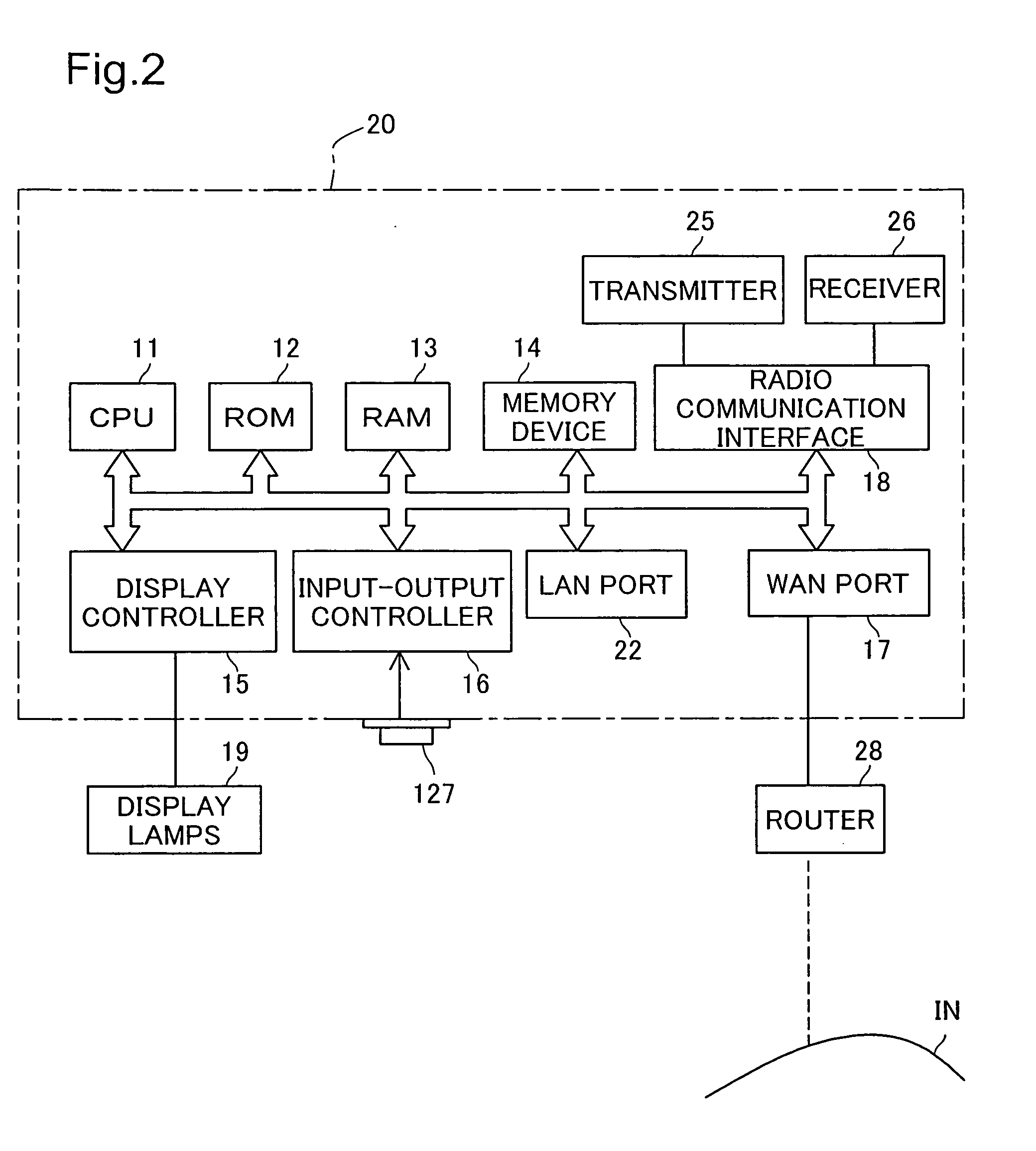
In an encryption key setting system of the present invention, in response to an operation of a registration button 127, an access point 20 restricts the coverage of radio wave transmitted from the access point 20 from a general radio communication area AR1 to a narrower security communication area MR1. The access point 20 subsequently delivers a WEP key to a terminal 50, confirms the successful delivery, and registers a MAC address of the terminal 50. The terminal 50 sets the delivered WEP key in itself. This arrangement desirably allows for new enrollment of a terminal for a wireless LAN by a simple method, while effectively preventing leakage of data representing an encryption key.
Owner:BUFFALO CORP LTD
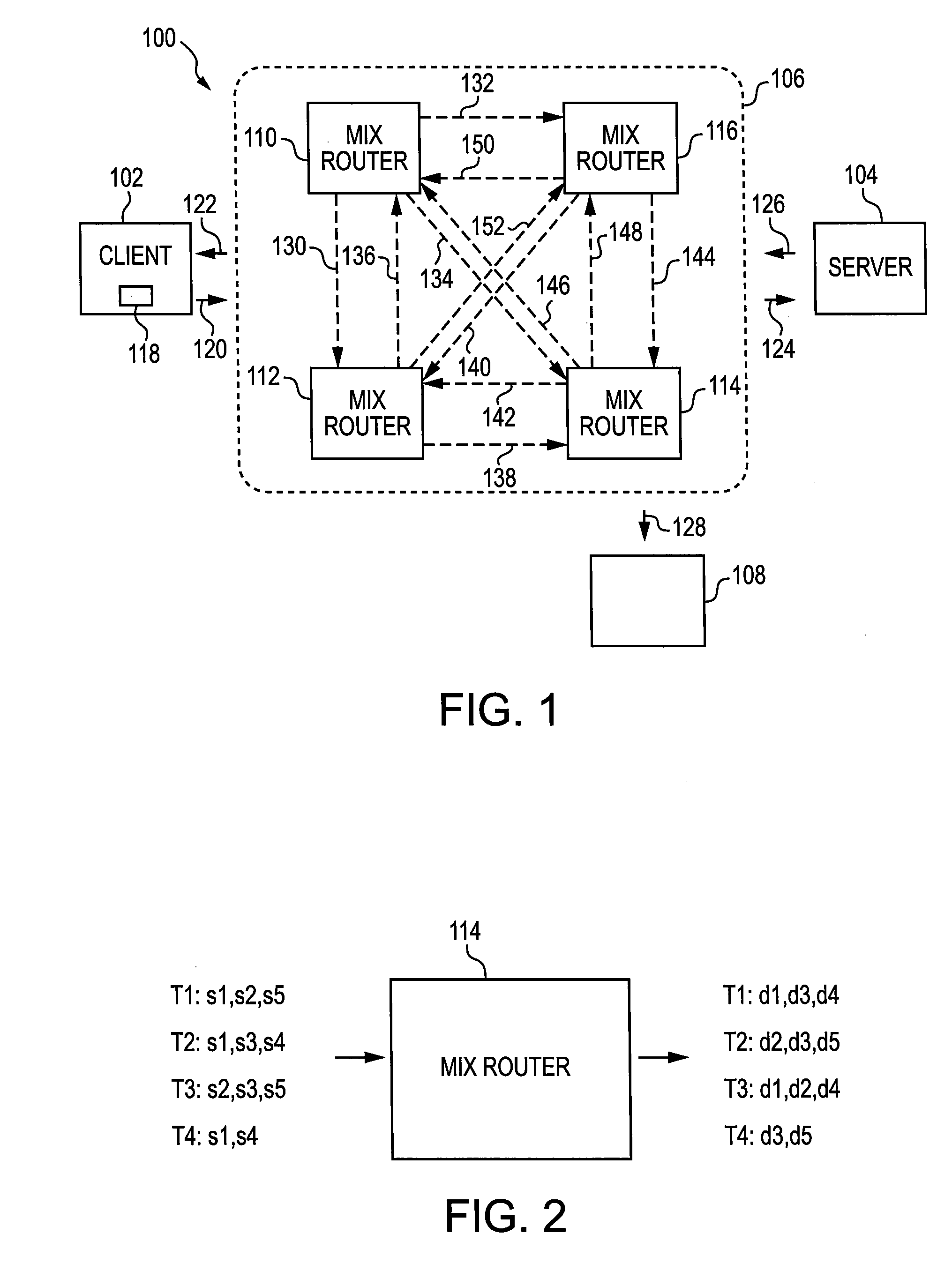
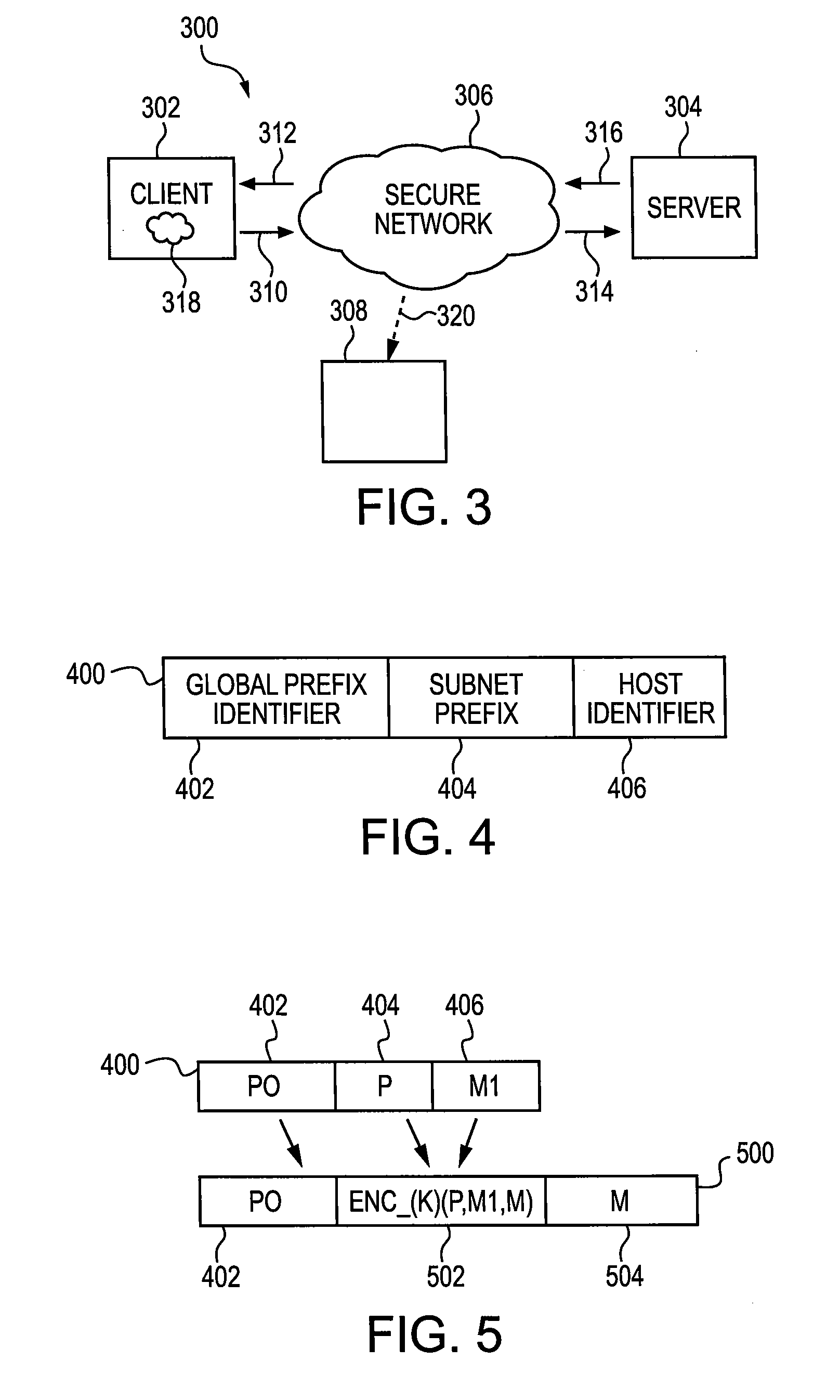
System and Method of Encrypting Network Address for Anonymity and Preventing Data Exfiltration
ActiveUS20090228708A1Avoid data breachesEnsure normal communicationDigital data processing detailsUser identity/authority verificationNetwork packetNetwork addressing
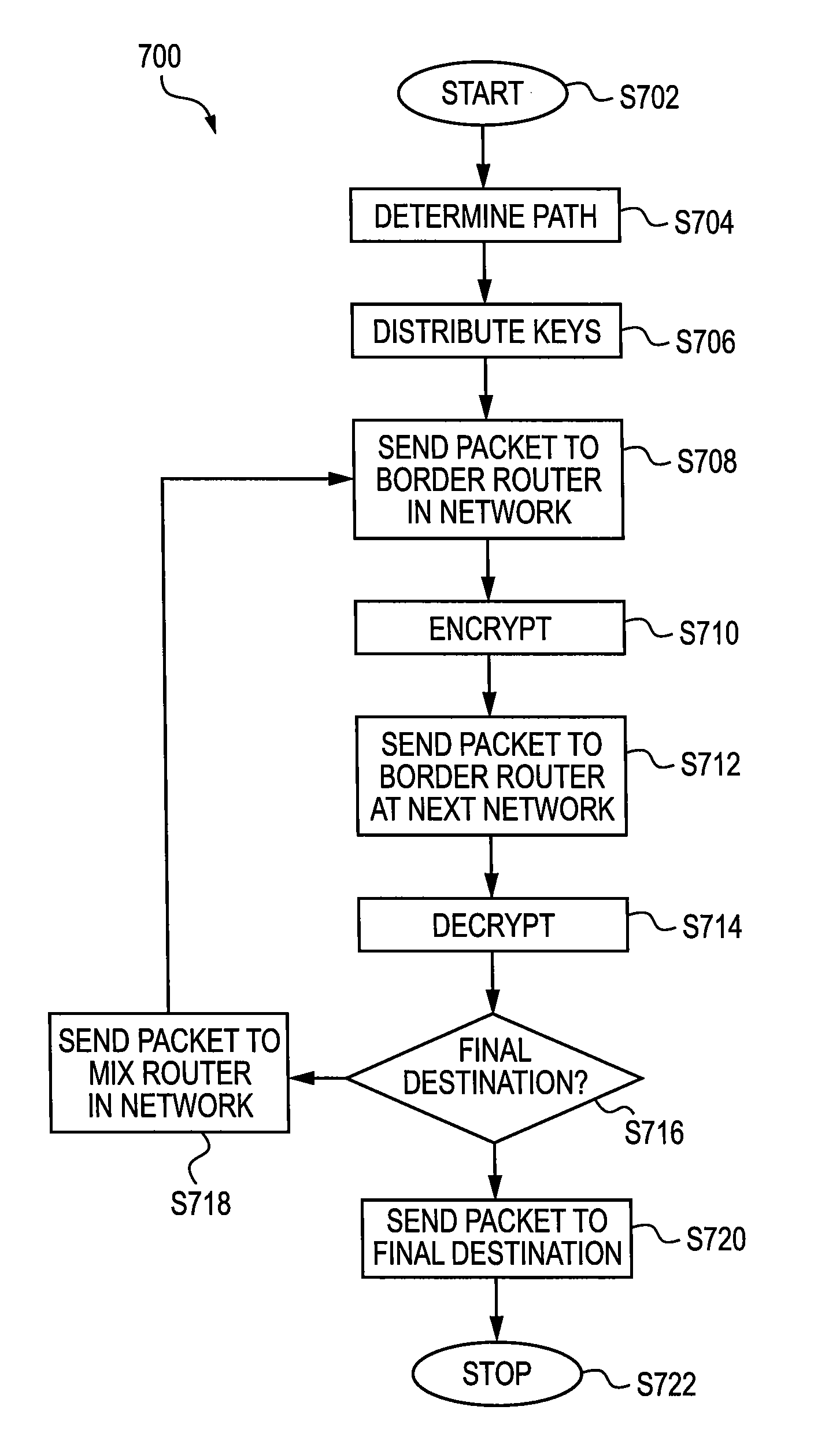
A method is provided for sending a data packet from a client through a network and to a server. The data packet is a data structure having an originating address portion and destination address portion. The network includes a first mix router and a second mix router. The client has a client address, whereas the first mix router has a first mix router address, the second mix router has a second mix router address and the server has a server address. The method includes encrypting the originating address portion of the data packet and encrypting the destination portion of the data packet, transmitting the encrypted data packet, decrypting the originating address portion of the encrypted data packet and the destination portion of the encrypted data packet, providing a first data packet and providing a second data packet. Specifically, the encrypting the originating address portion of the data packet is based on the client address and the encrypting the destination portion of the data packet is based on one of the first mix router address and the second mix router address. The encrypting generates an encrypted data packet. The encrypted data packet is transmitted to the one of the first mix router and the second mix router, wherein it is decrypted to generate a decrypted data packet. The first data packet is based on the decrypted data packet and is provided to the other of the first mix router and the second mix router. The second data packet is provided to the server.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
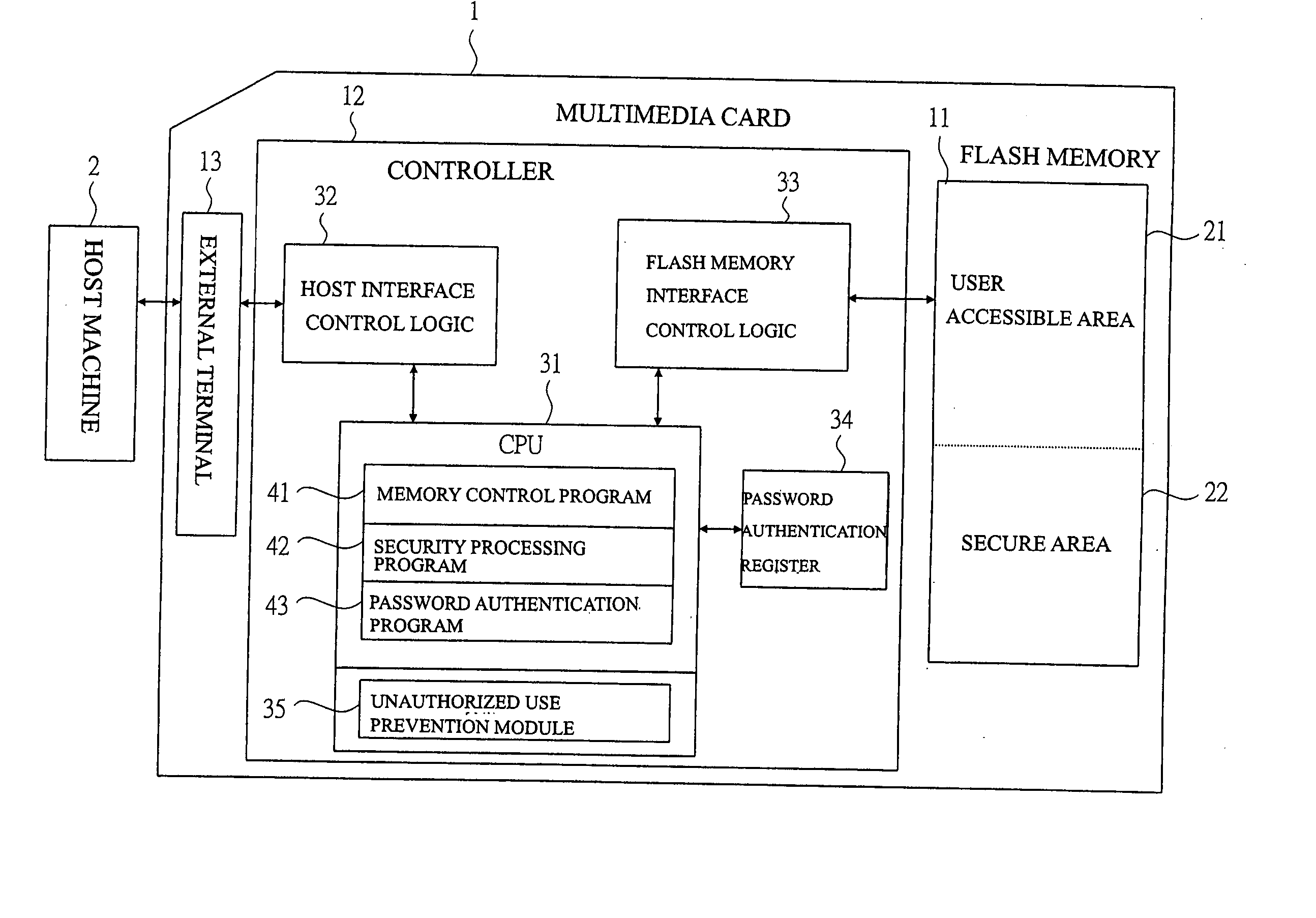
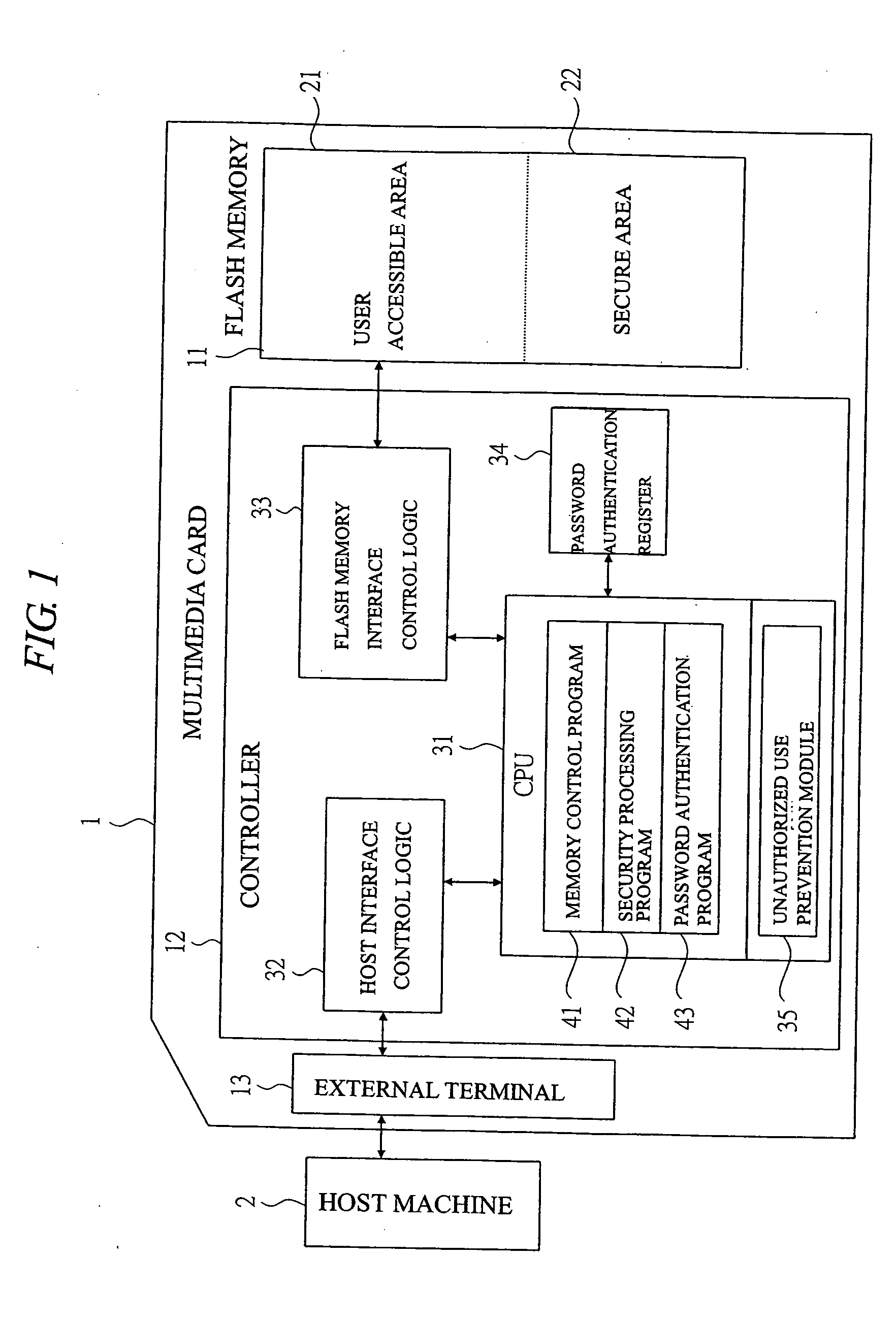
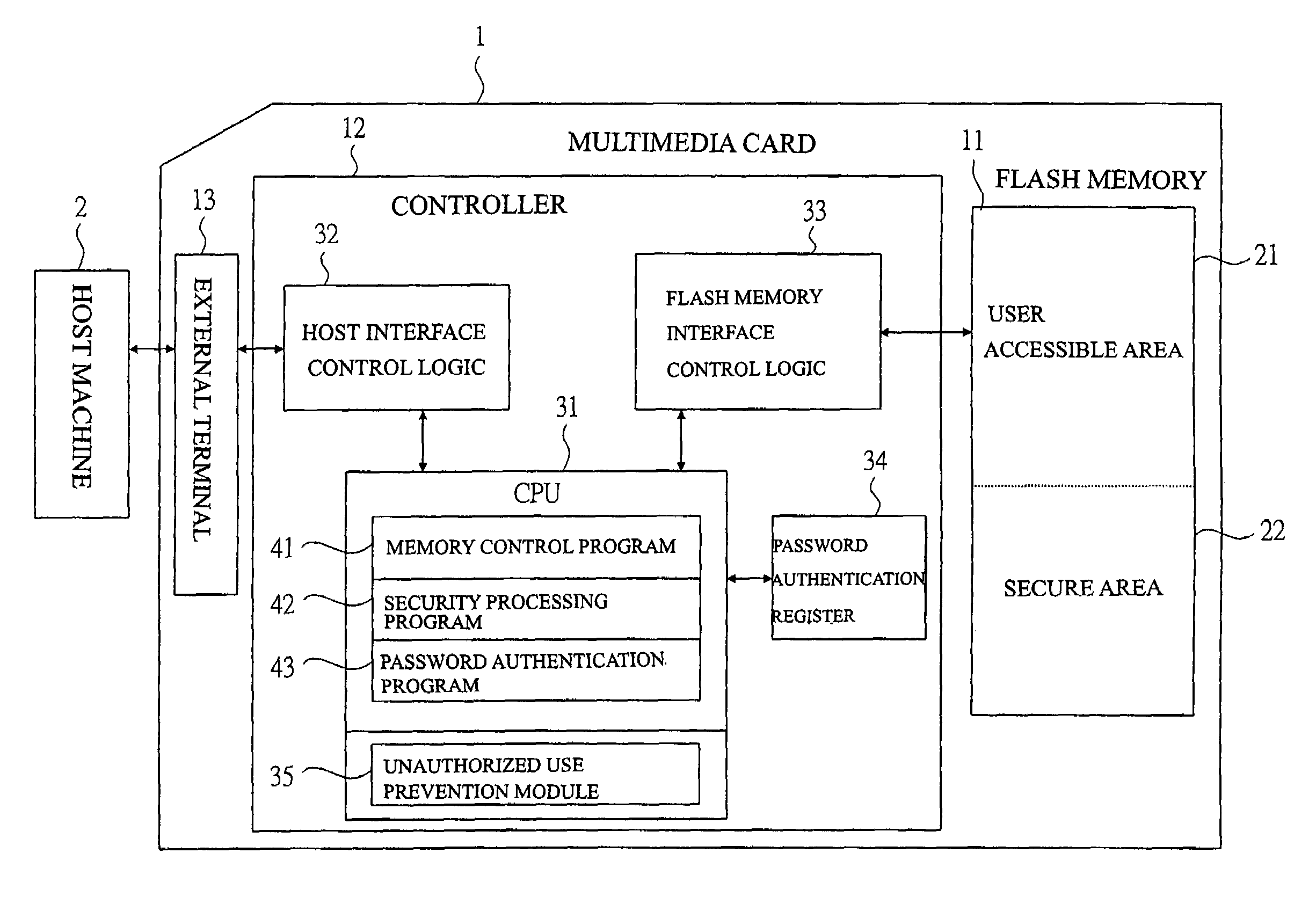
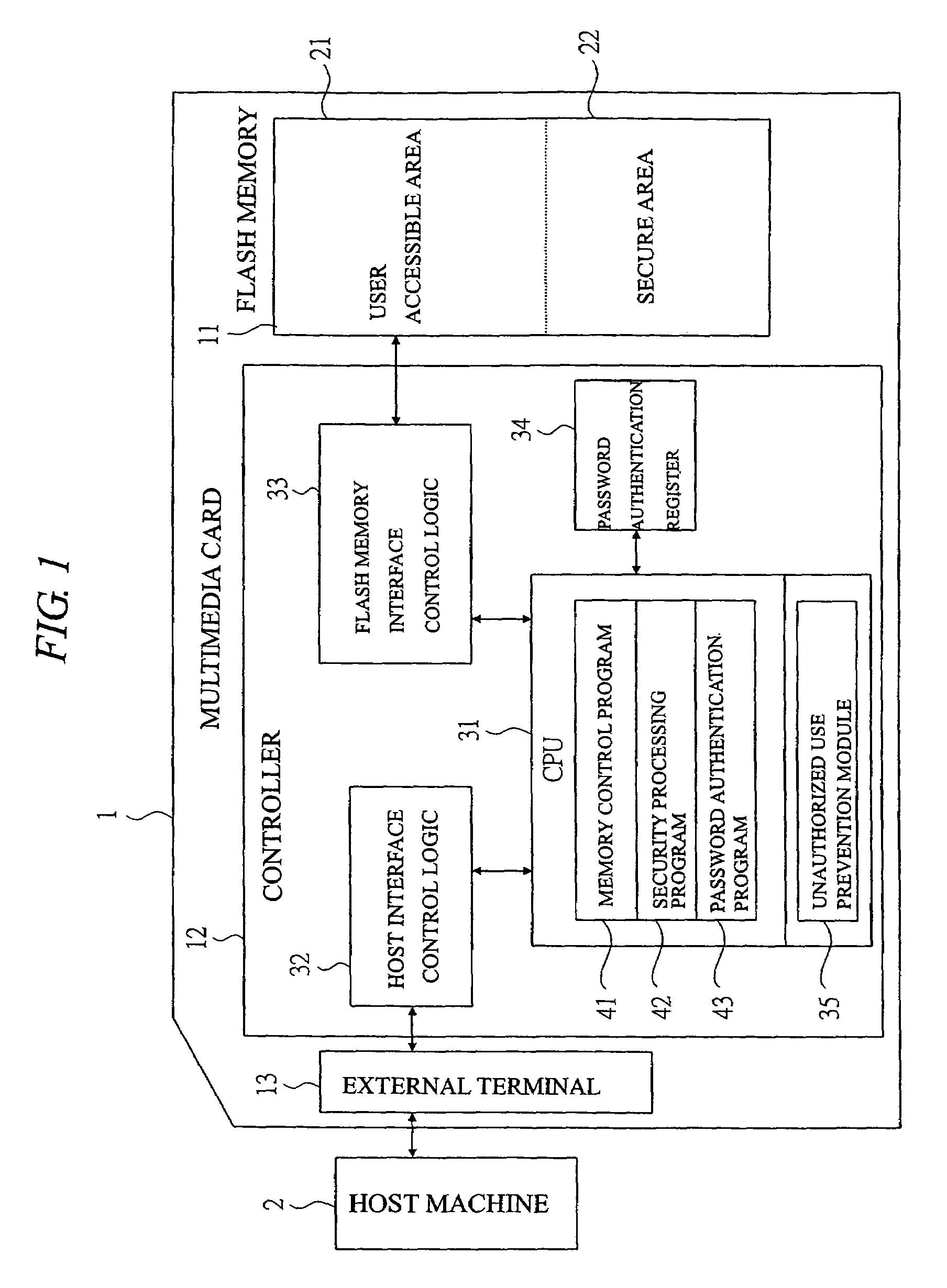
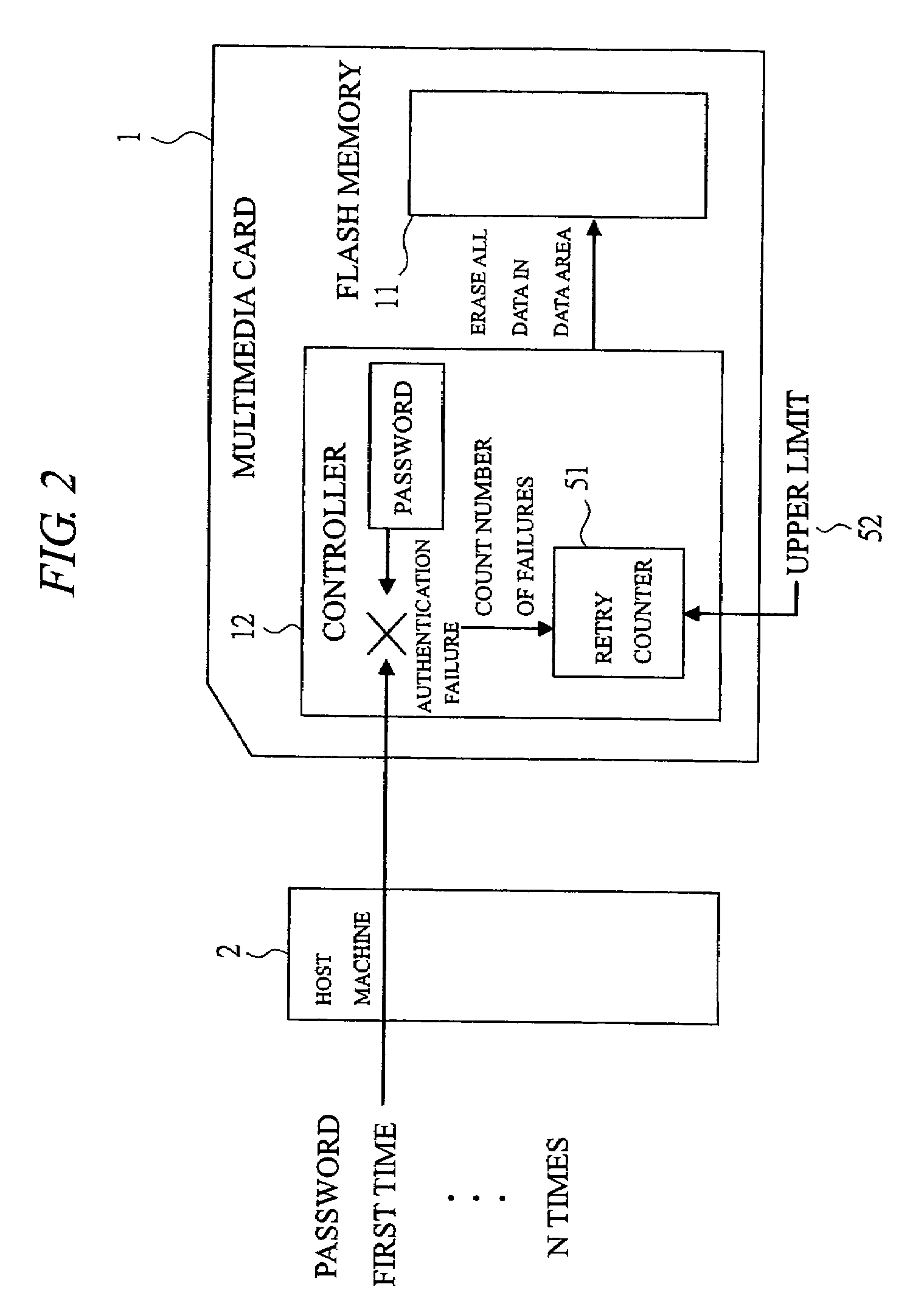
Memory card
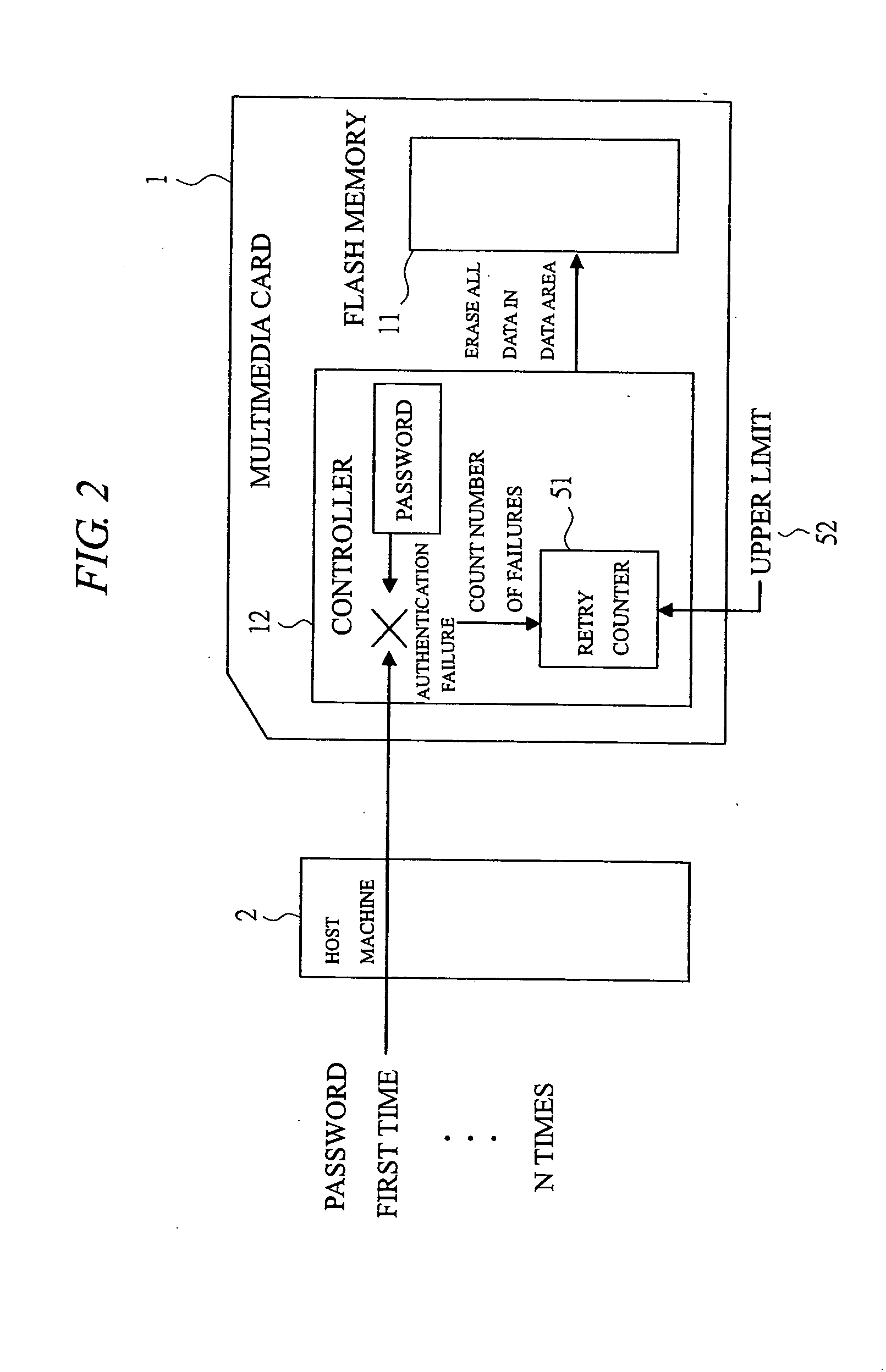
InactiveUS20050005131A1Easy to disconnectPrevent leakageUnauthorized memory use protectionHardware monitoringElectricityThird party
In order to protect the user security data, provided is a memory card capable of preventing the data leakage to a third party not having the access authority by imposing the limitation on the number of password authentications and automatically erasing the data. In a system comprised of a multimedia card and a host machine electrically connected to the multimedia card and controlling the operations of the multimedia card, a retry counter for storing the number of password authentication failures is provided and the upper limit of the number of failures is registered in a register. When passwords are repeatedly entered once, twice, . . . and n times and the retry counter which counts the entries reaches the upper limit of the number of failures, the data is automatically erased so as not to leave the data in the flash memory.
Owner:RENESAS ELECTRONICS CORP
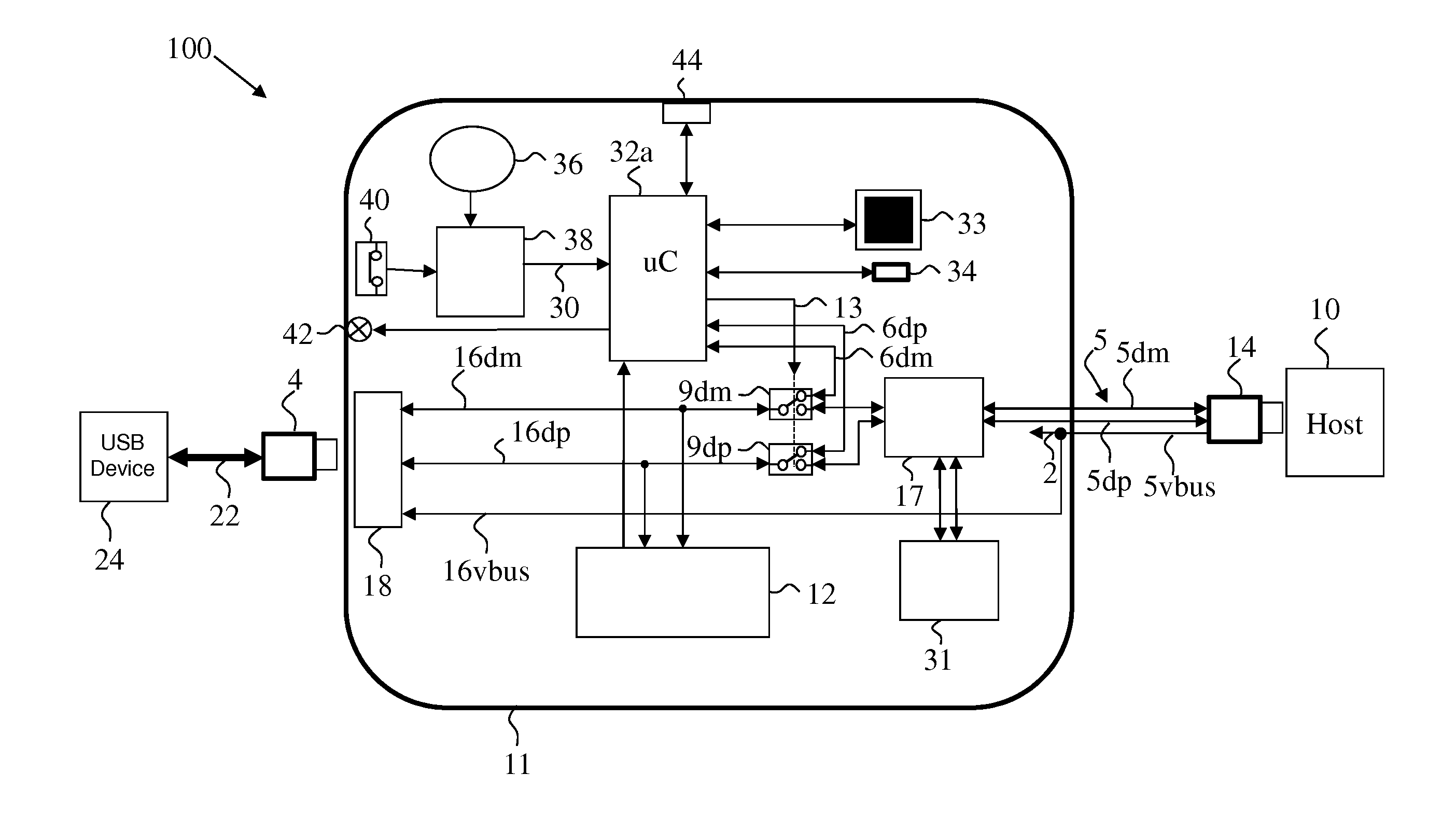
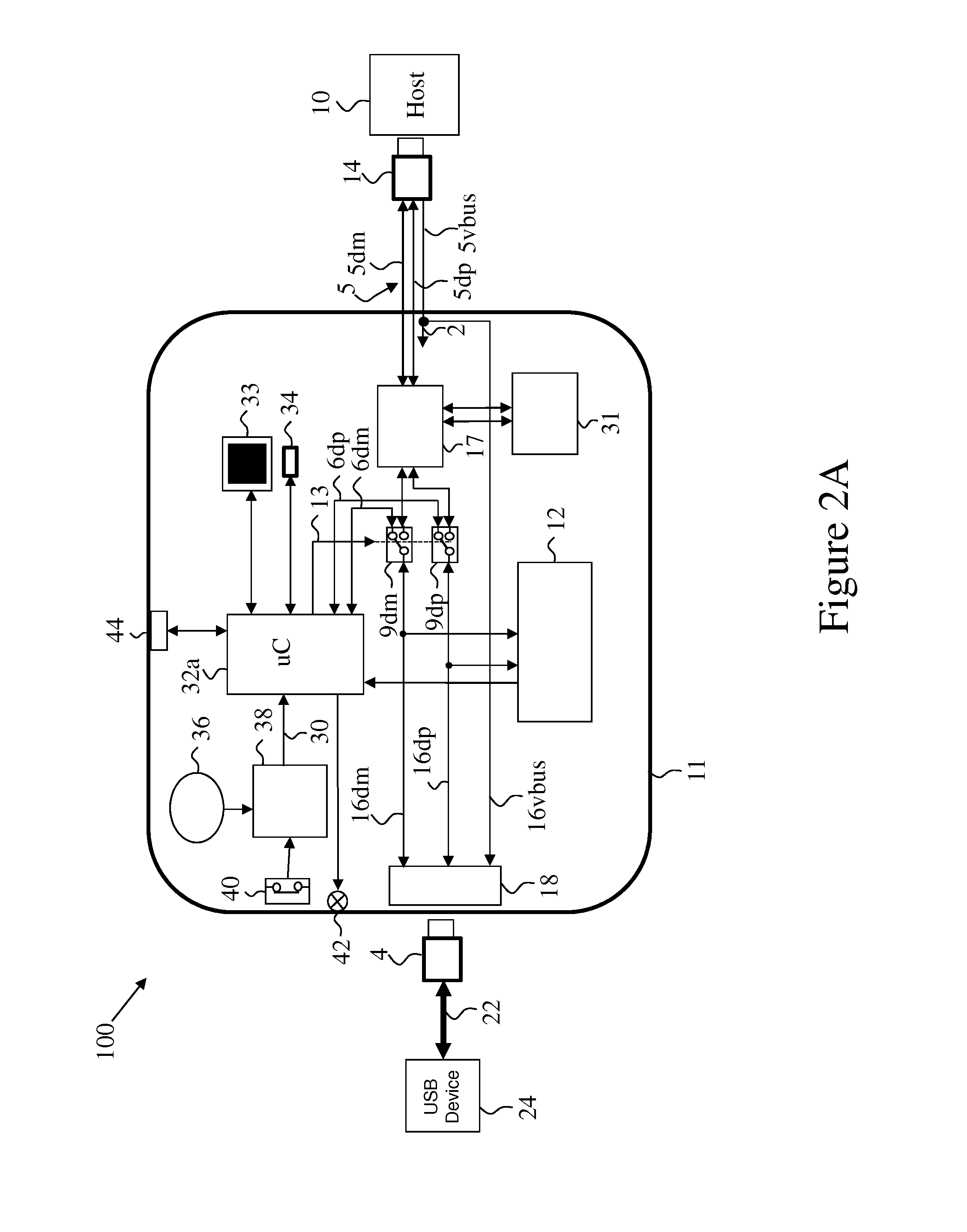
USB security gateway
InactiveUS20150365237A1Function increaseAvoid data breachesDigital data processing detailsUser identity/authority verificationMode selectionUSB
A USB gateway connected to a plurality of host computers having a USB device port connect to a peripheral device; and a security circuitry. The security circuitry comprises: a pre-qualification microcontroller; a mode select switch connected to the peripheral device port and selectively connecting it to one of: the pre-qualification microcontroller; or to a host selector switch that switches among the plurality of connected host computes. An enumeration and reset detector is connected to the USB peripheral device port to monitor that port and casing the mode select switch to switch back to the pre-qualification microcontroller when the peripheral device is disconnected or reset. The pre-qualification microcontroller is capable of enumerating a connected peripheral device and controlling the gateway according to a table containing lists of: device qualifications, indication of which device can connect to each host, and direction of data flow between host and device. The table of peripheral device qualifications may be field re-programmed.
Owner:HIGH SEC LABS LTD
Encryption key setting system, access point, encryption key setting method, and authentication code setting system
ActiveUS20050201557A1Prevent leakageAvoid data breachesUser identity/authority verificationNetwork topologiesNormal rangeComputer hardware
Access point 20 starts the WEP key setting process by working registration button 127A of remote controller 30. The range reached by the electric waves transmitted from access point 20 is changed from wireless communication area AR1 which is the normal range to security communication area MR1 which is a narrower range. After that, access point 20 delivers the used WEP key to terminal 50, and after confirming delivery, registers the MAC address of terminal 50. Terminal 50 sets the delivered WEP key itself. As a result, it is possible to realize with a simple method the new addition of terminals used for a wireless LAN while preventing leaking of data that represents the encryption key.
Owner:BUFFALO CORP LTD
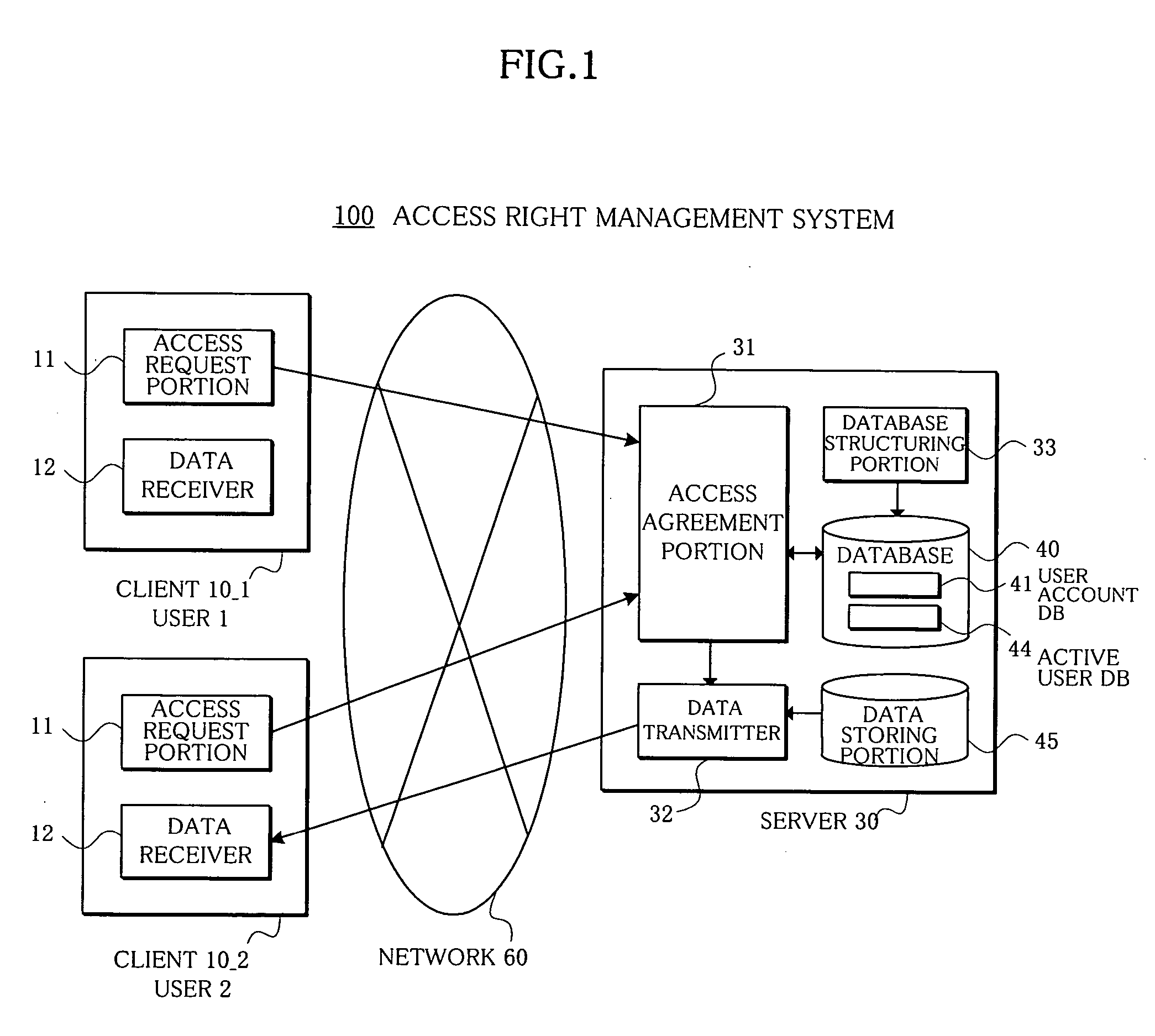
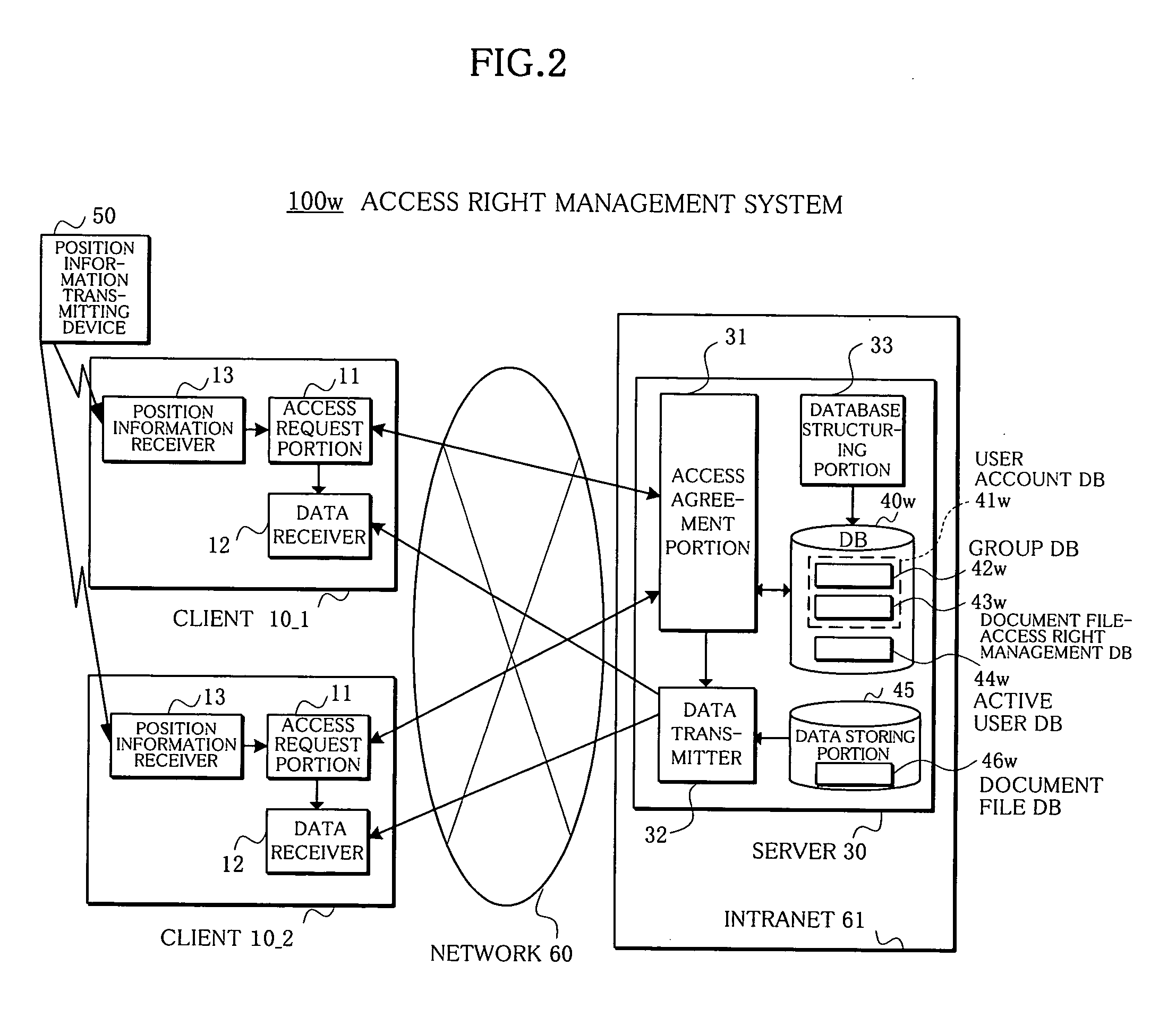
Access right management system and method
InactiveUS20050223008A1Avoid data breachesDigital computer detailsUnauthorized memory use protectionData accessRights management
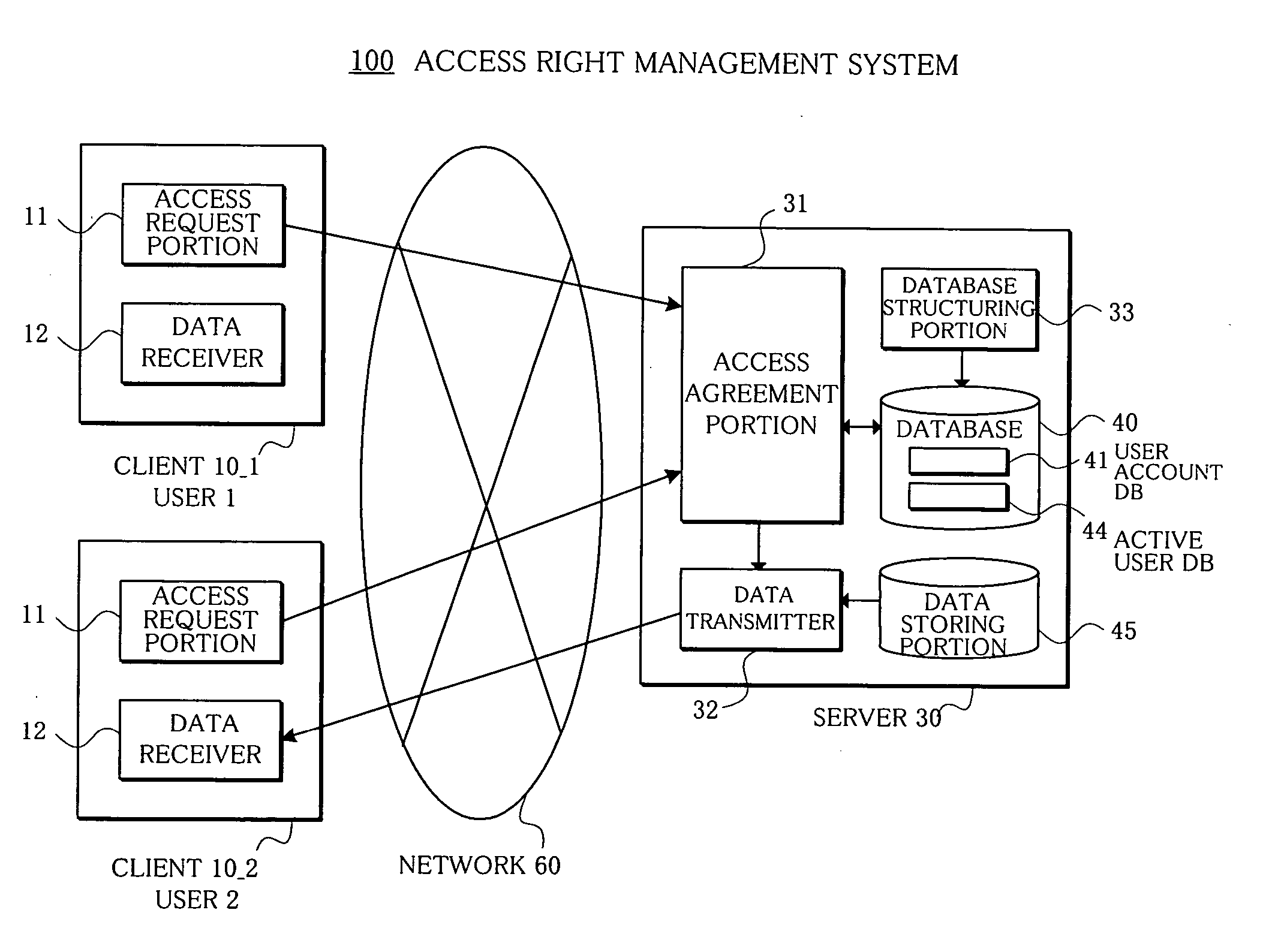
In an access right management system and method which manage access to data and prevent the data from leaking, a plurality of associated users who possess access rights to data are registered in a user account database, users who agree to the access to the data at present among the access right possessing users are registered in an active user database, and an access agreement portion agrees, only when a present number of access right possessing users having agreed and registered in the active user database is plural, to the access to the data with access right possessing users who have requested the access to the data.
Owner:FUJITSU LTD
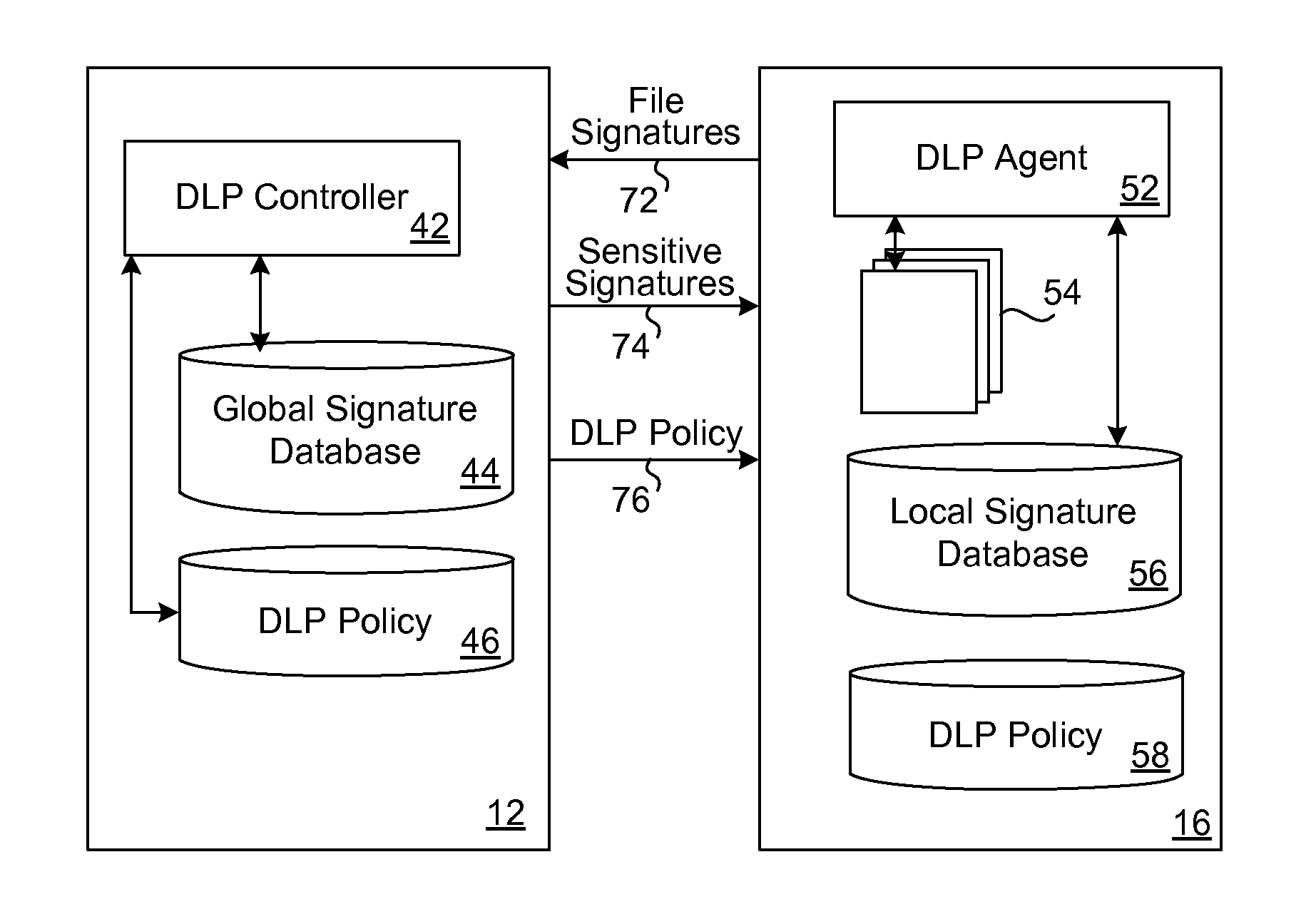
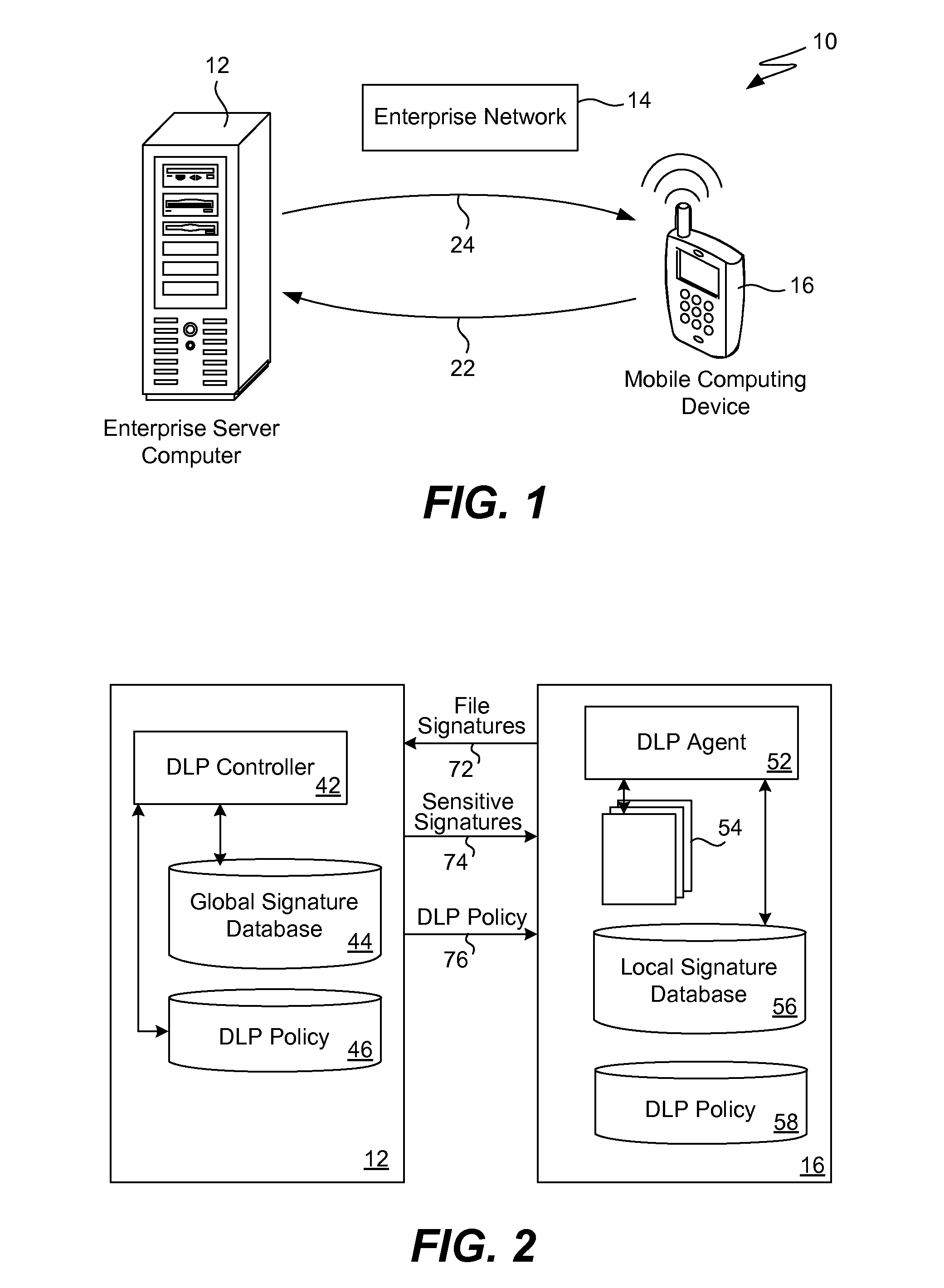
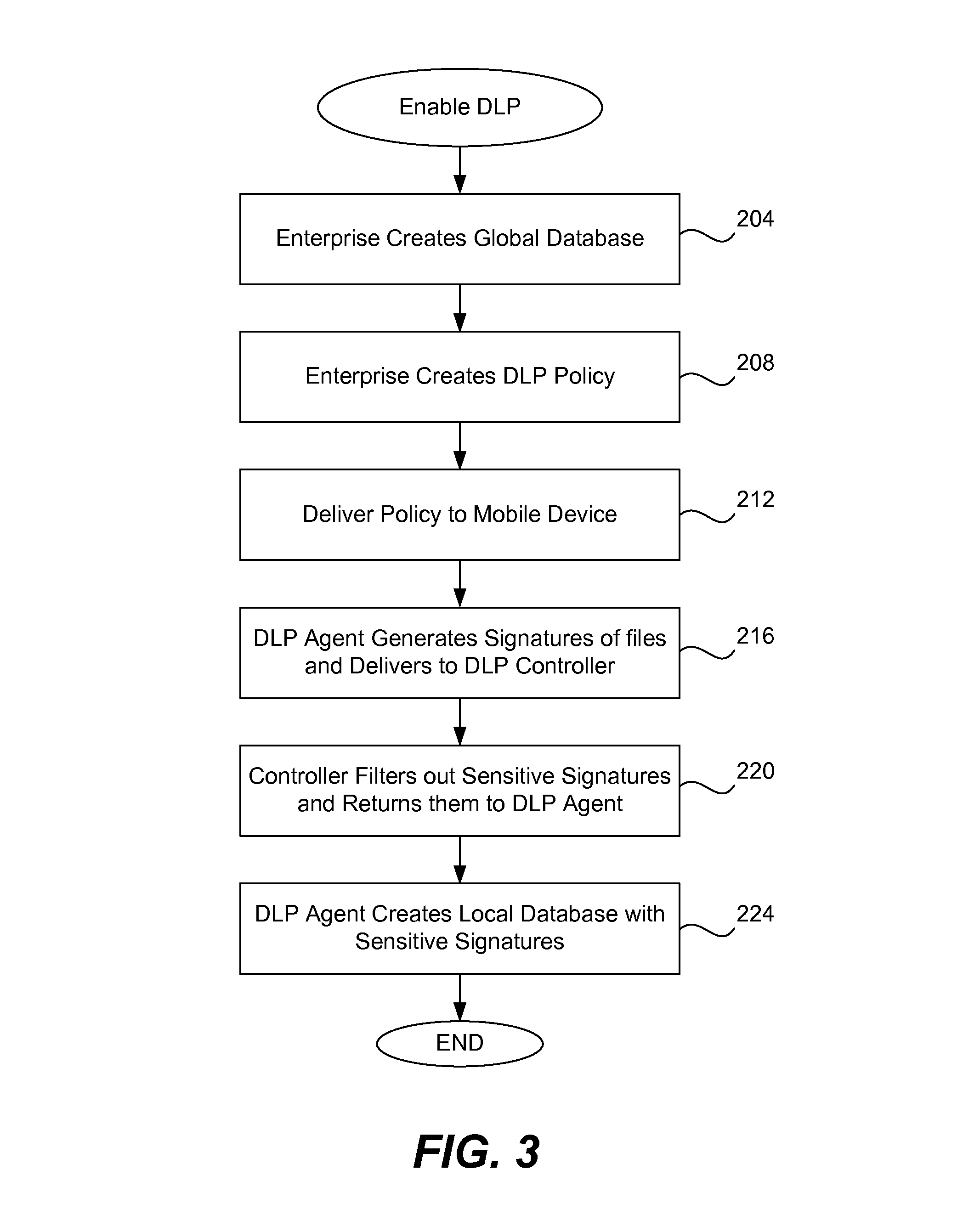
Data leakage prevention for resource limited device
ActiveUS8286253B1Efficient and effectiveSimple to executeDigital data processing detailsDatabase distribution/replicationDigital signatureMobile telephony
When a resource-limited device (such as a mobile telephone) joins a network associated with an enterprise, the agent in the device generates digital signatures for all the files in the device and sends them to an enterprise controller. The controller compares them to the global signature database; it filters out the sensitive digital signatures and feeds them back to the agent in the device. The agent receives the feedback of digital signatures and consolidates them into its own local signature database. The agent analyzes each file that is attempting to be output from the device according to the local signature database and DLP policy. If the signature of the file is present in the local database then the action to output file is blocked. If a new file is created on the device, the agent generates and sends its digital signature to the controller for inspection. If the signature is sensitive, this new digital signature will be placed into the local signature database. If the DLP controller updates the global signature database, the device will send its signatures once again for comparison.
Owner:TREND MICRO INC
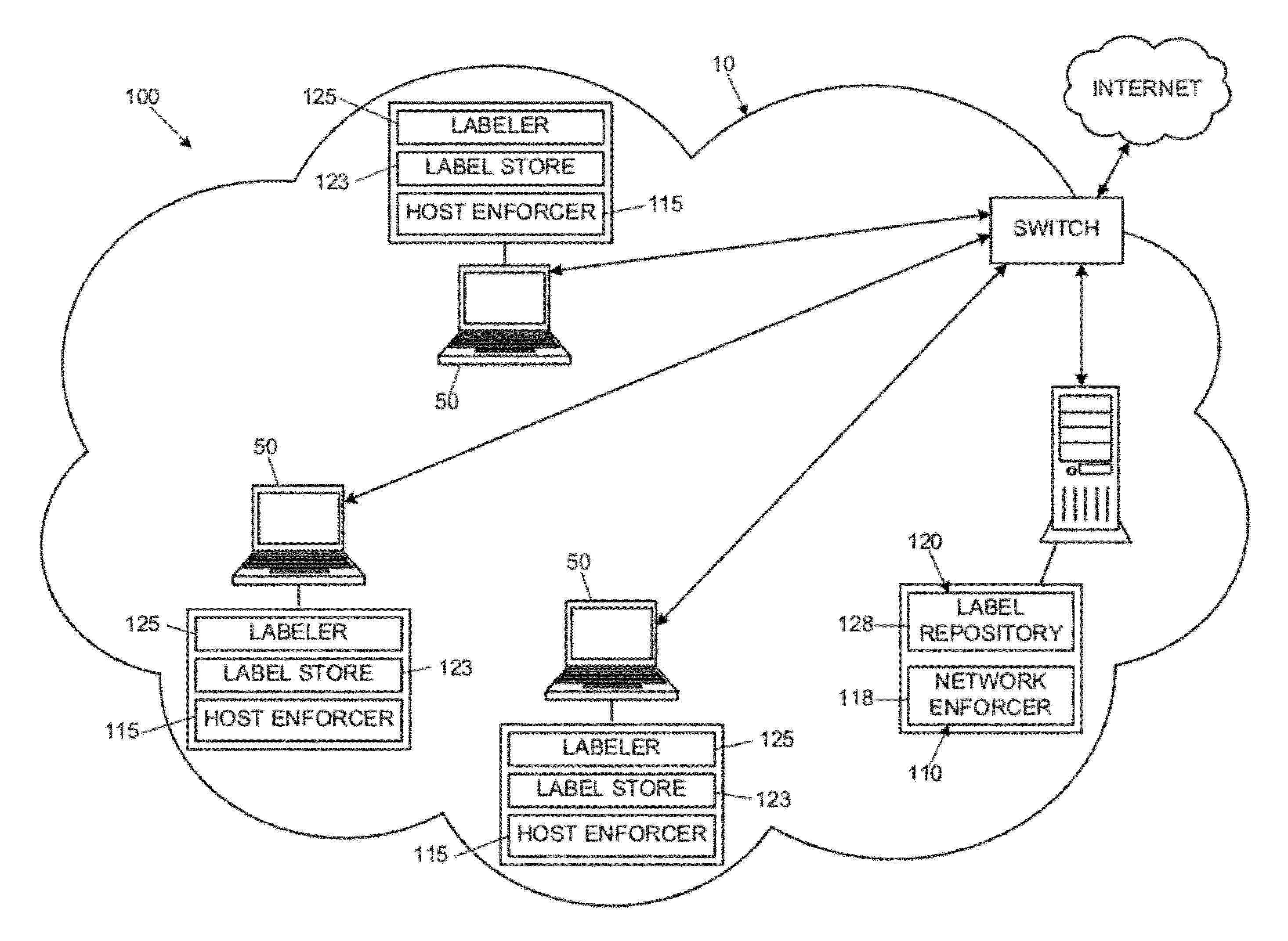
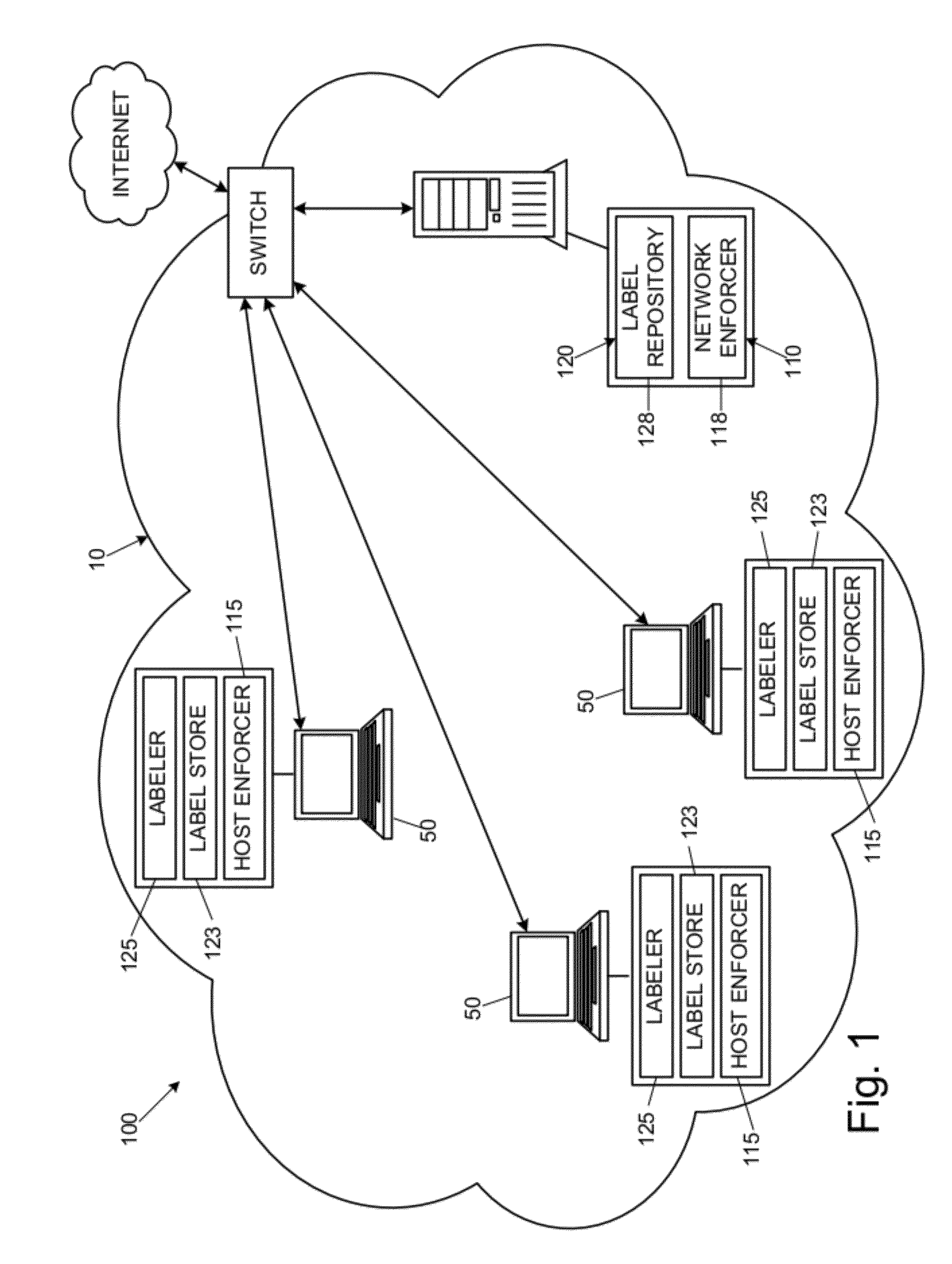
Security systems and methods to reduce data leaks in enterprise networks
InactiveUS20120137375A1Harder to evadeSolve excessive overheadDigital data processing detailsAnalogue secracy/subscription systemsSecurity systemDistributed computing
Disclosed are embodiments of a security system for reducing data leaks by checking information flows between resources of a network. When an information flow is attempted between a sending resource, which can be anywhere in the network, and a receiving resource residing at a specific host within the network, a host labeler can determine whether information is allowed to flow from the sending resource to the receiving resource. The sending resource and the receiving resource can each have an applicable label, and each label can comprise zero, one, or more taints. For each taint having an active secrecy characteristic in a label of the sending resource, the host labeler can require that there be a matching taint with active secrecy characteristic in the receiving resource. If this condition is not met, the security system can block the information flow between the sending and receiving resources.
Owner:GEORGIA TECH RES CORP
Information processing device, information processing method, and program distribution system
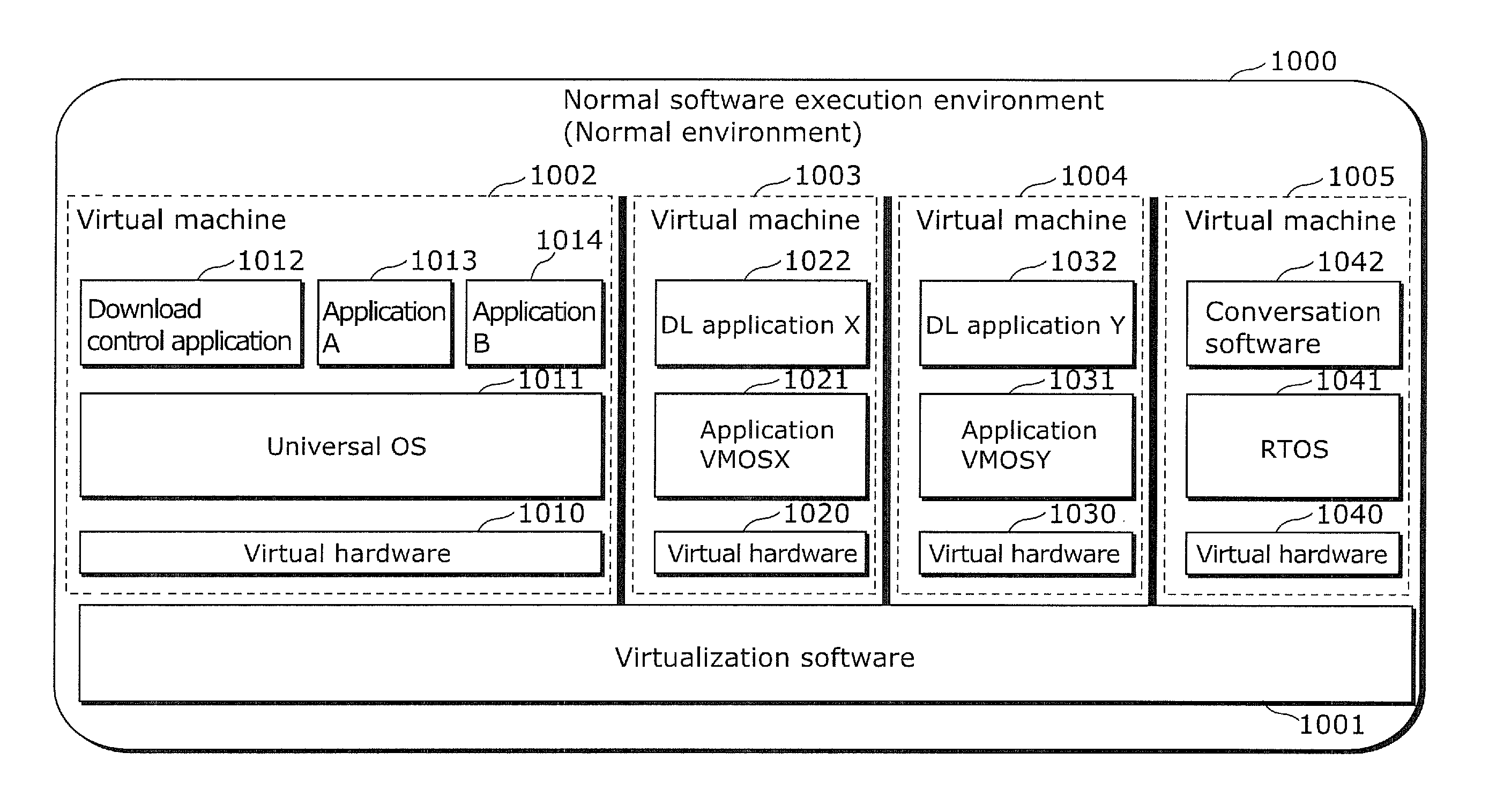
InactiveUS20120117566A1Avoid data breachesPlatform integrity maintainanceSoftware simulation/interpretation/emulationInformation processingData transport
Provided is an information processing device which is capable of preventing data leakage caused by a malicious application or malicious device driver and of allowing cooperation among virtual machines. The information processing device (110) includes: an external connection unit (1309) which connects to an external device; and a communication control unit which obtains data from a first virtual machine (1002), transmits the data to a second virtual machine (1003), and transmits, to the external connection unit, transmission completion information indicating that the data is already transmitted to the second virtual machine, wherein the external connection unit (i) determines, based on the transmission completion information, whether or not a virtual machine is the second virtual machine to which the data is already transmitted, when the external connection unit receives, from the virtual machine, a request for a connection to the external device, and (ii) permit a connection between the virtual machine and the external device, when the external connection unit determines that the virtual machine is not the second virtual machine to which the data is already transmitted.
Owner:SOVEREIGN PEAK VENTURES LLC
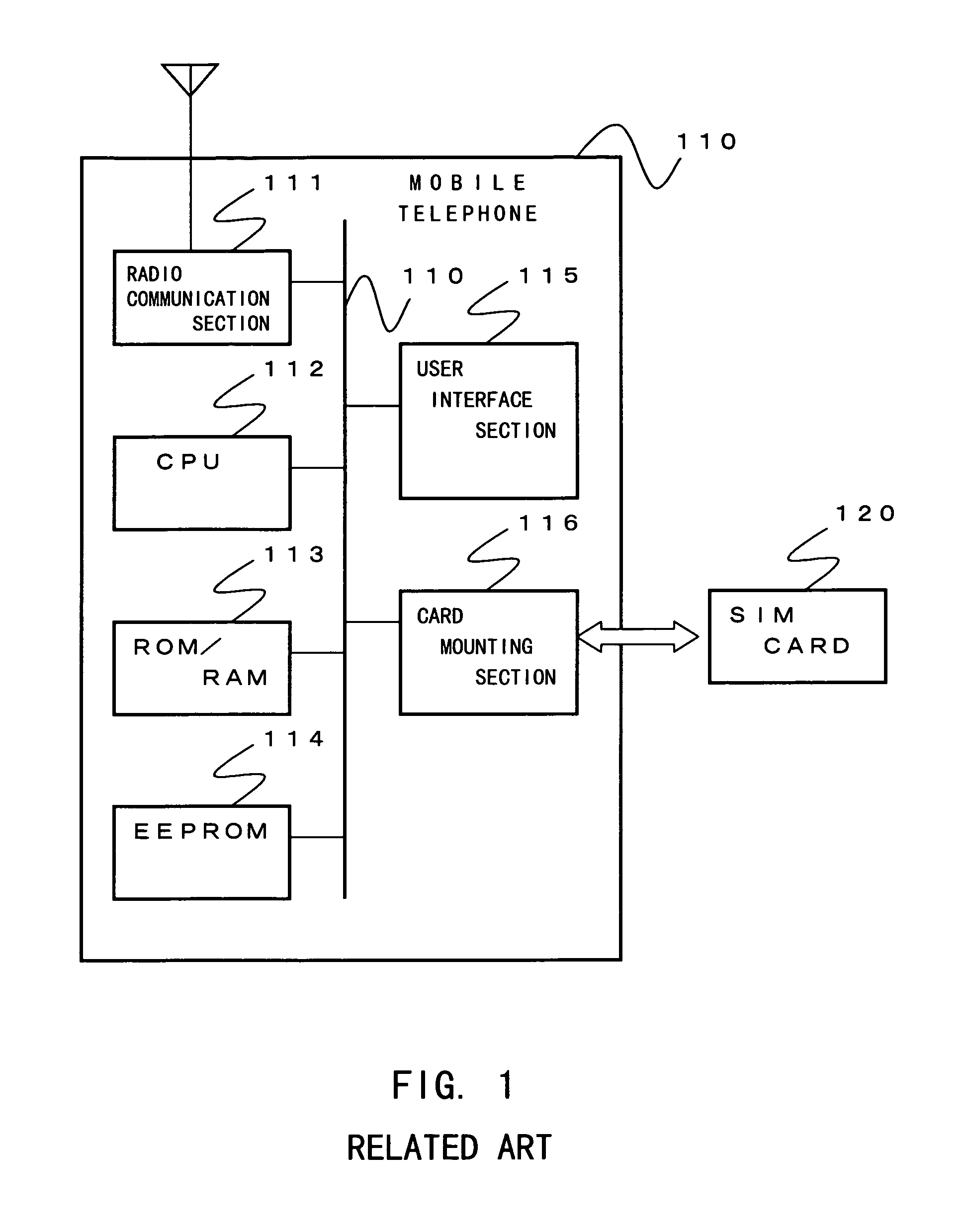
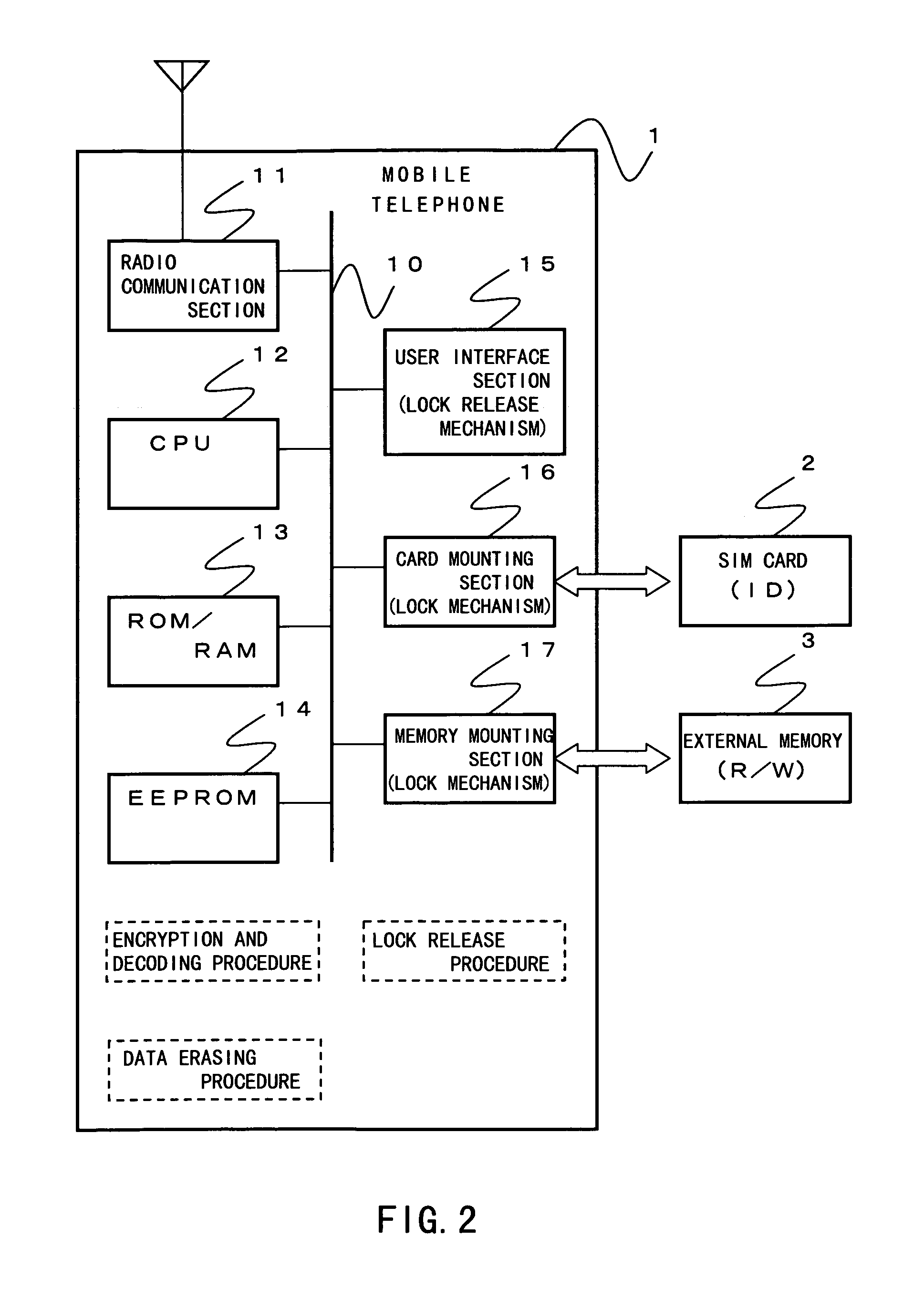
Mobile telephone using subscriber card
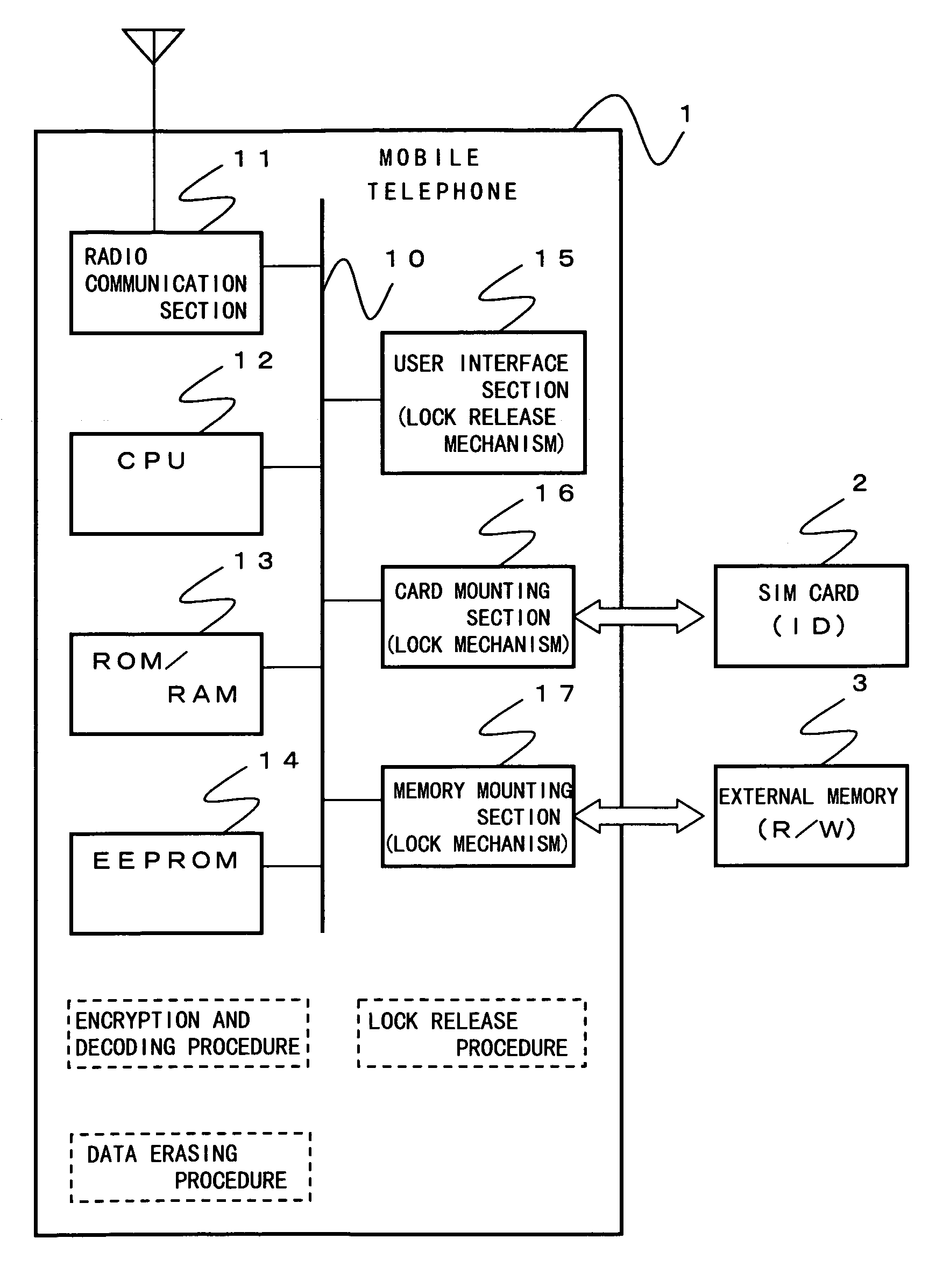
InactiveUS7151922B2Prevent leakageAvoid dataEngagement/disengagement of coupling partsCalling susbscriber number recording/indicationExternal storageLocking mechanism
Private data in an EEPROM (14) is erased in a data erasing procedure when pulling out an SIM card (2) from a mobile telephone (1). Before being erased, the private data is encrypted in an encryption procedure and it is transferred and recorded to an external memory (3). The private data encrypted and recorded to the external memory can be reused when the SIM card is used in another mobile telephone. Furthermore, it is possible to prevent the external memory from being left behind when the SIM card is pulled out by interfacing a lock mechanism of a card mounting section (16) with that of a memory mounting section (17).
Owner:NEC CORP
Encryption key setting system, access point, encryption key setting method, and authentication code setting system
ActiveUS7522729B2Avoid data breachesPrevent leakageUser identity/authority verificationNetwork topologiesNarrow rangeSecure communication
Owner:BUFFALO CORP LTD
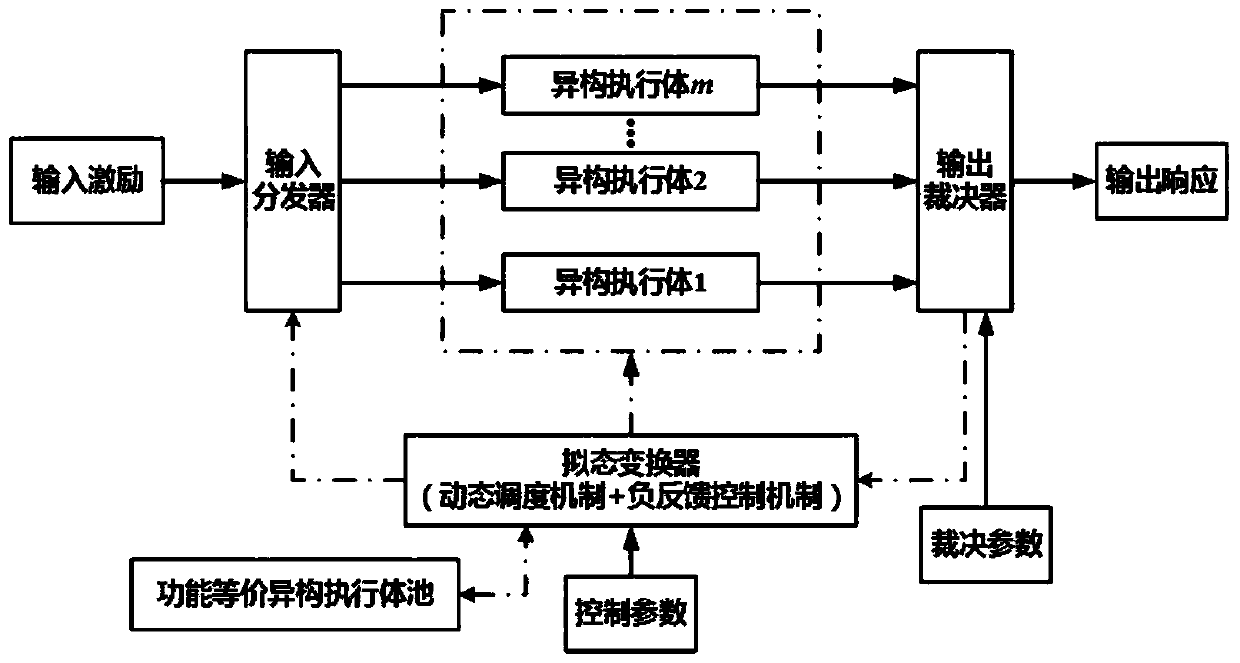
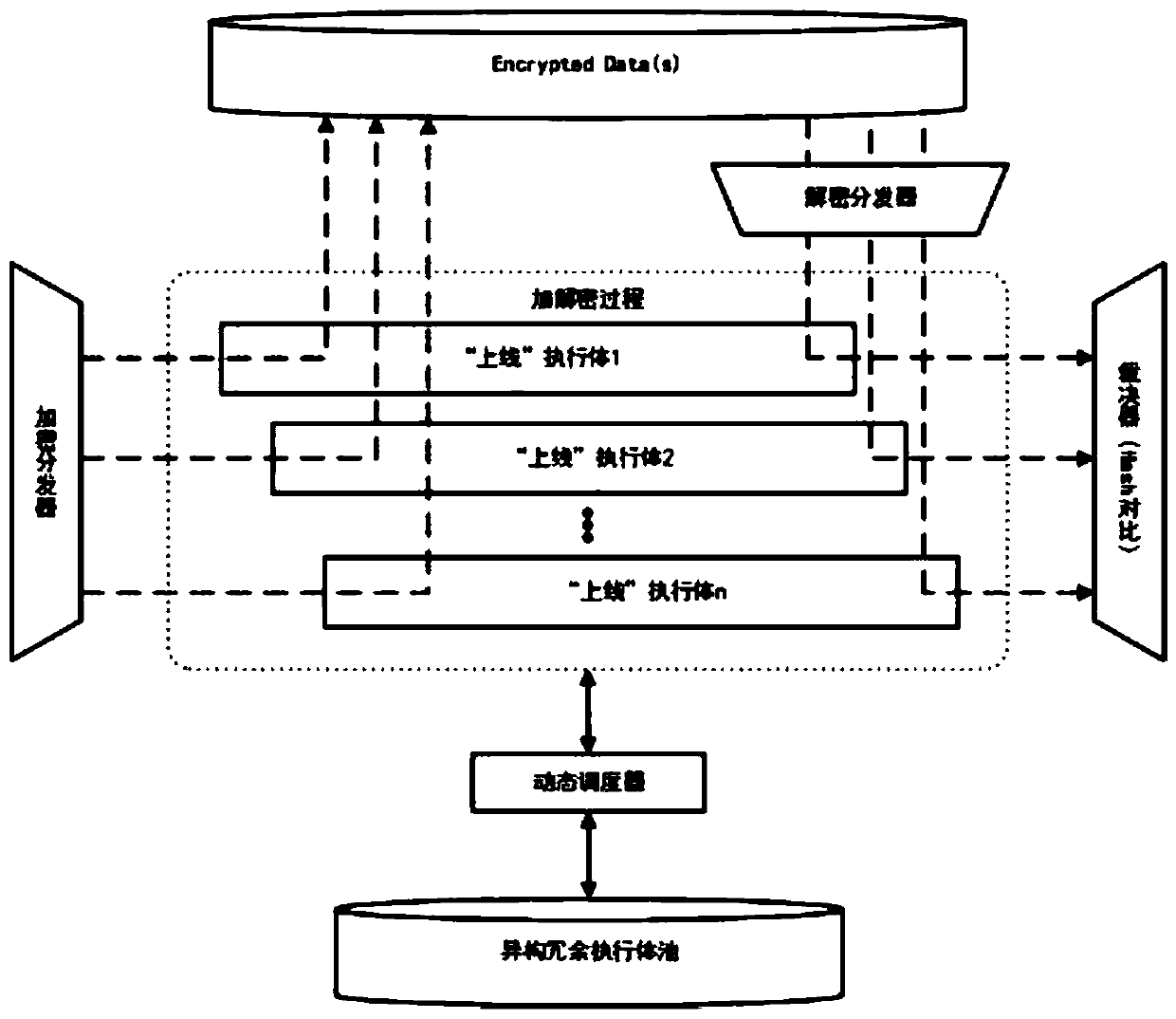
Architecture for protecting key data based on mimicry defense
ActiveCN110750802AAvoid data breachesGuaranteed normal outputDigital data protectionEmbedded systemNegative feedback
The invention discloses a framework for protecting key data based on mimicry defense. The framework comprises a heterogeneous redundant execution body, a dispatcher, a decision device and a mimicry converter, excitation is input from the dispatcher and then enters the heterogeneous redundant executor, and the mimicry converter is connected with the dispatcher, the adjustor and the mimicry converter and carries out mimicry conversion through dynamic scheduling and negative feedback control. The heterogeneous redundant executor processes the input excitation of the distributor and then outputs the processed input excitation to a decision device, and the decision device outputs a response; according to the technical scheme, the architecture is applied to data protection, so that the difficulty of stealing and tampering protected data can be greatly improved, and key data can be better protected.
Owner:创元网络技术股份有限公司
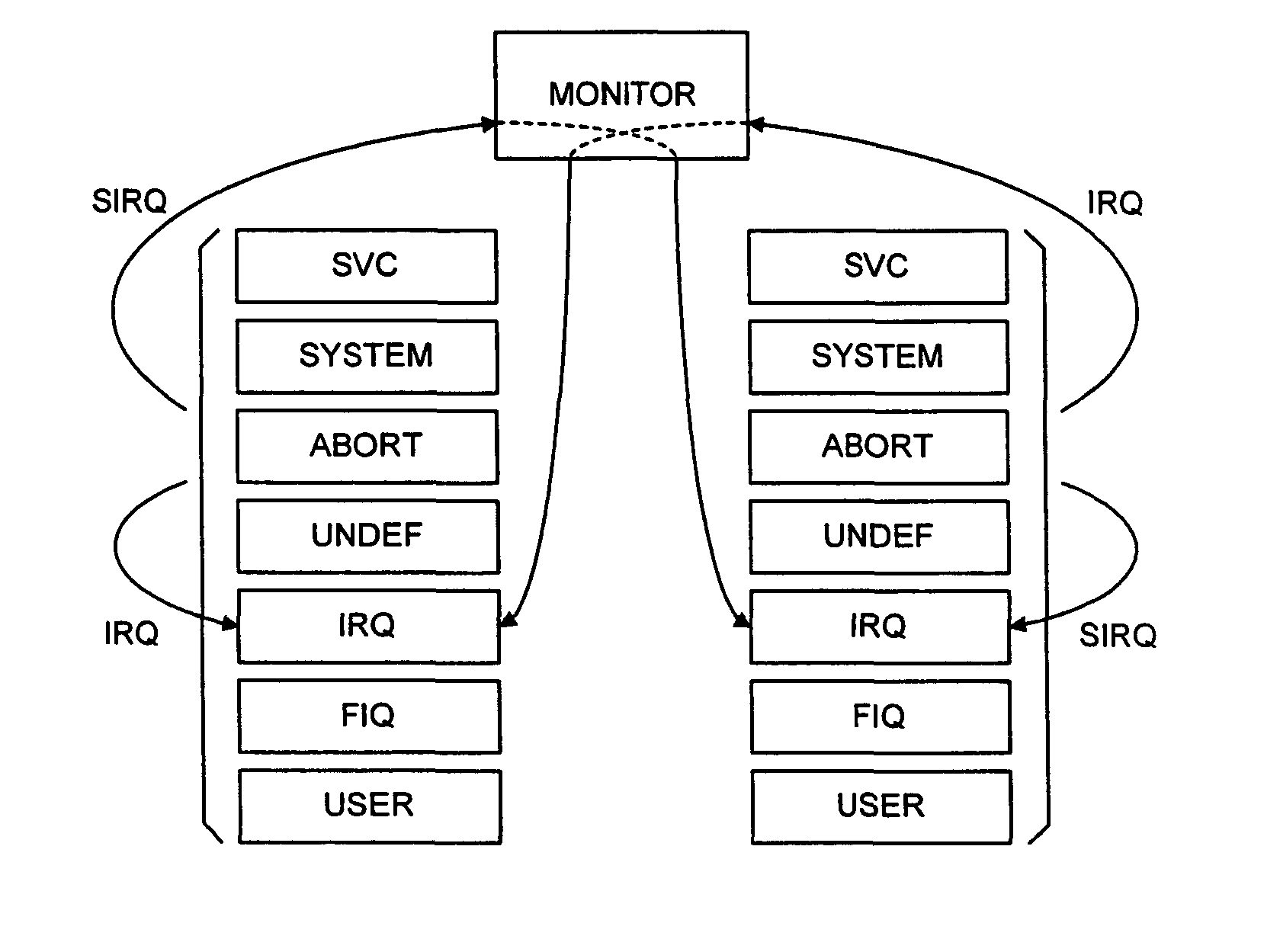
Monitoring control for monitoring at least two domains of multi-domain processors
ActiveUS7849296B2Improve securityRisk of leakageHardware monitoringGeneral purpose stored program computerMulti domainMonitor function
There is provided a method of controlling a monitoring function of a processor, the processor being operable in at least two domains, comprising a first domain and a second domain, the first and second domains each comprising at least one mode, the method comprising the steps of: setting at least one control value, the at least one control value relating to a condition and being indicative of whether the monitoring function is allowable in the first domain; and only allowing initiation of the monitoring function in the first domain when the condition is present if its related control value indicates that the monitoring function is allowable. In some embodiments the first domain is a secure domain and the monitoring function is a debug or trace function.
Owner:ARM LTD
Memory card
InactiveUS7418602B2Easy to disconnectAvoid data breachesUnauthorized memory use protectionHardware monitoringThird partyElectricity
In order to protect the user security data, provided is a memory card capable of preventing the data leakage to a third party not having the access authority by imposing the limitation on the number of password authentications and automatically erasing the data. In a system comprised of a multimedia card and a host machine electrically connected to the multimedia card and controlling the operations of the multimedia card, a retry counter for storing the number of password authentication failures is provided and the upper limit of the number of failures is registered in a register. When passwords are repeatedly entered once, twice, . . . and n times and the retry counter which counts the entries reaches the upper limit of the number of failures, the data is automatically erased so as not to leave the data in the flash memory.
Owner:RENESAS ELECTRONICS CORP
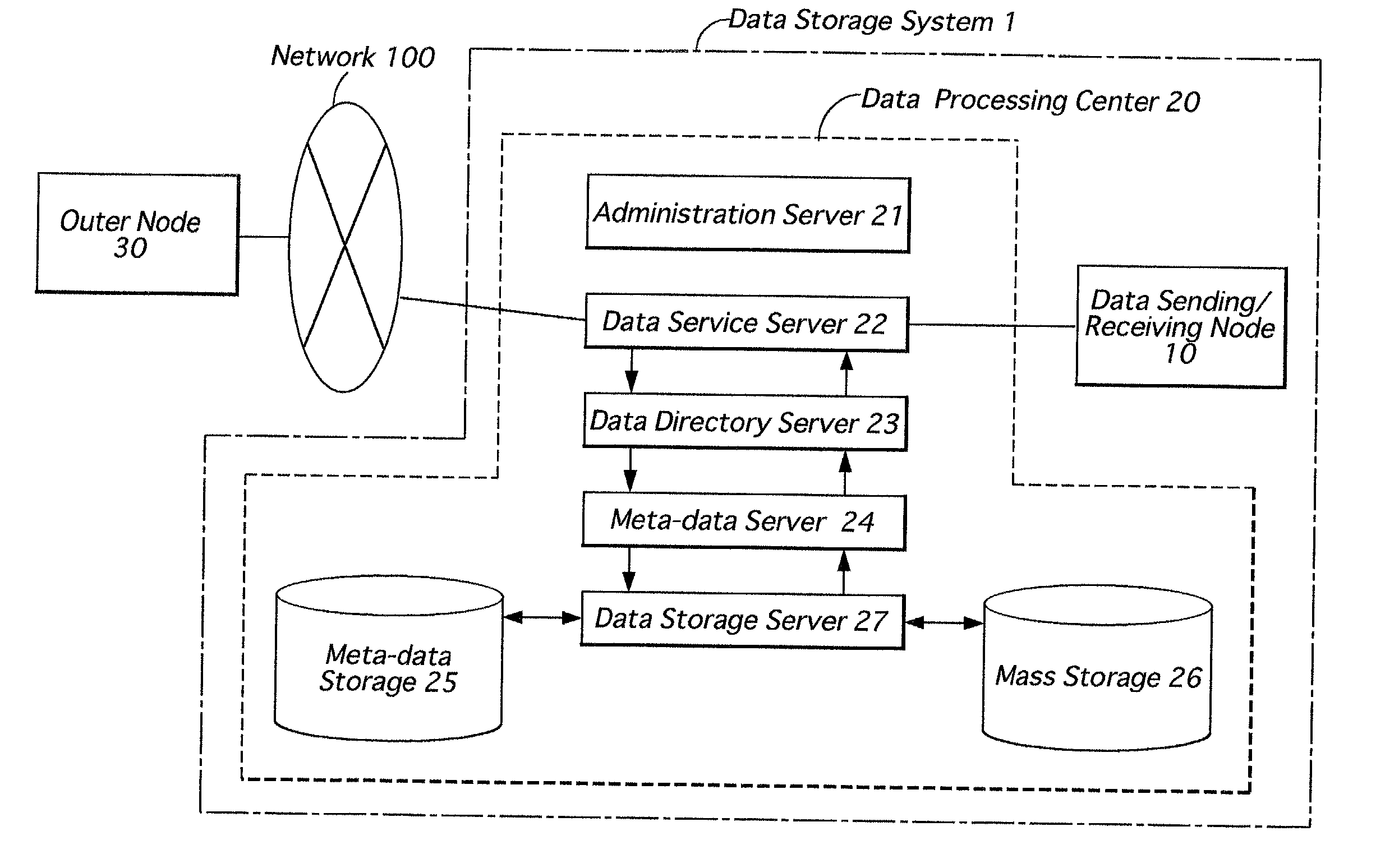
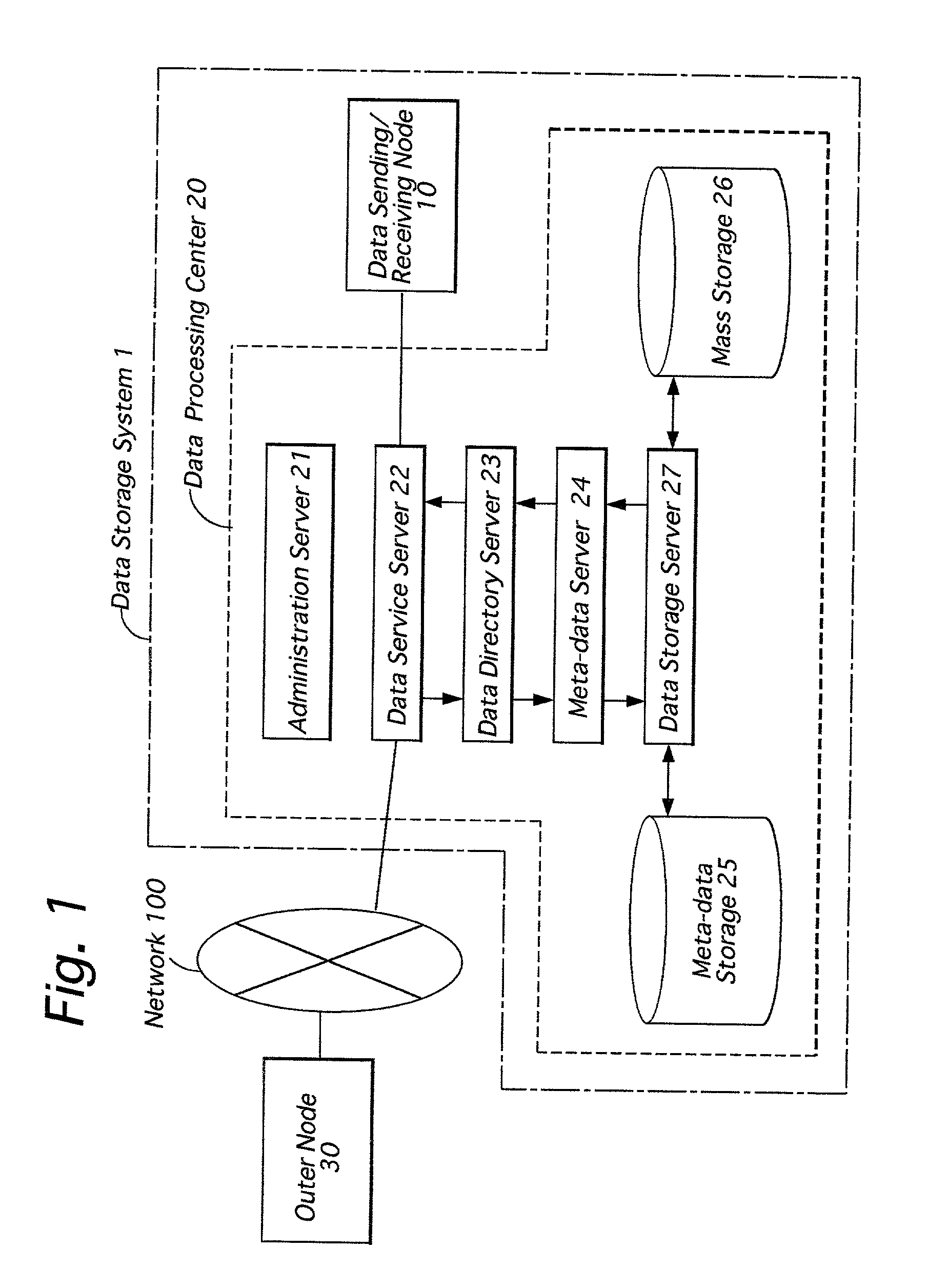
Data storage system
InactiveUS20020059444A1Reduce the burden onEasy transferUnauthorized memory use protectionHardware monitoringTrunkingEngineering
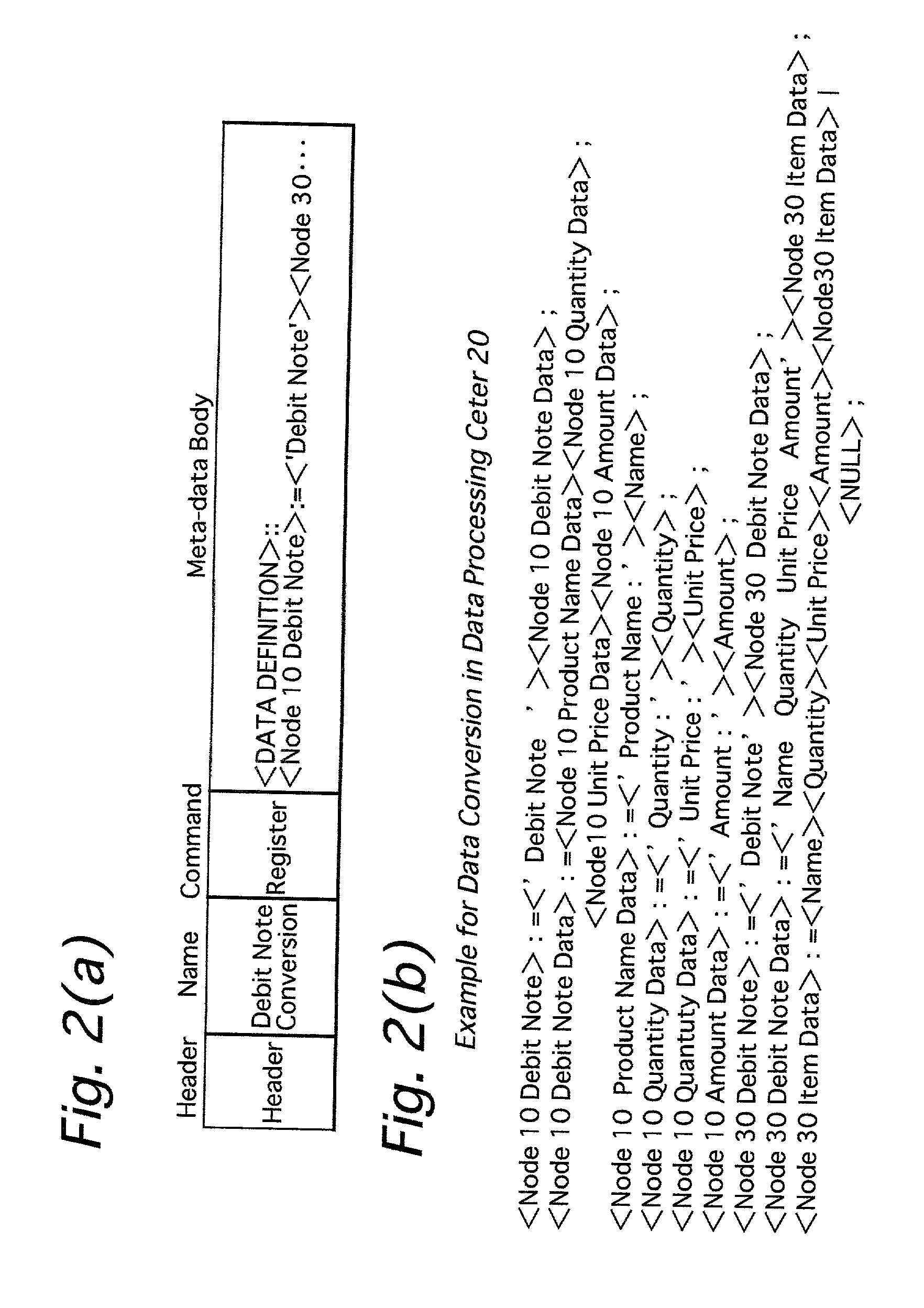
A data storage system including data sending / receiving nodes and a relay node, which is provided between the data sending / receiving nodes and a network, for relaying data between said data sending / receiving nodes and said network. The relay node has a meta-data memory for registering data processes which should be conducted in the relay node as meta-data, and a data processor for conducting data process in accordance with the processes defined by the meta-data registered in said meta-data registering memory. In the relay node, meta-data designated by said data sending / receiving node is selected from the meta-data registering memory, and data sent from said data sending / receiving node or data received by said data sending / receiving node is processed in accordance with the processes defined by the selected meta-data.
Owner:CEC
Cloud storage-based data security protection system and method
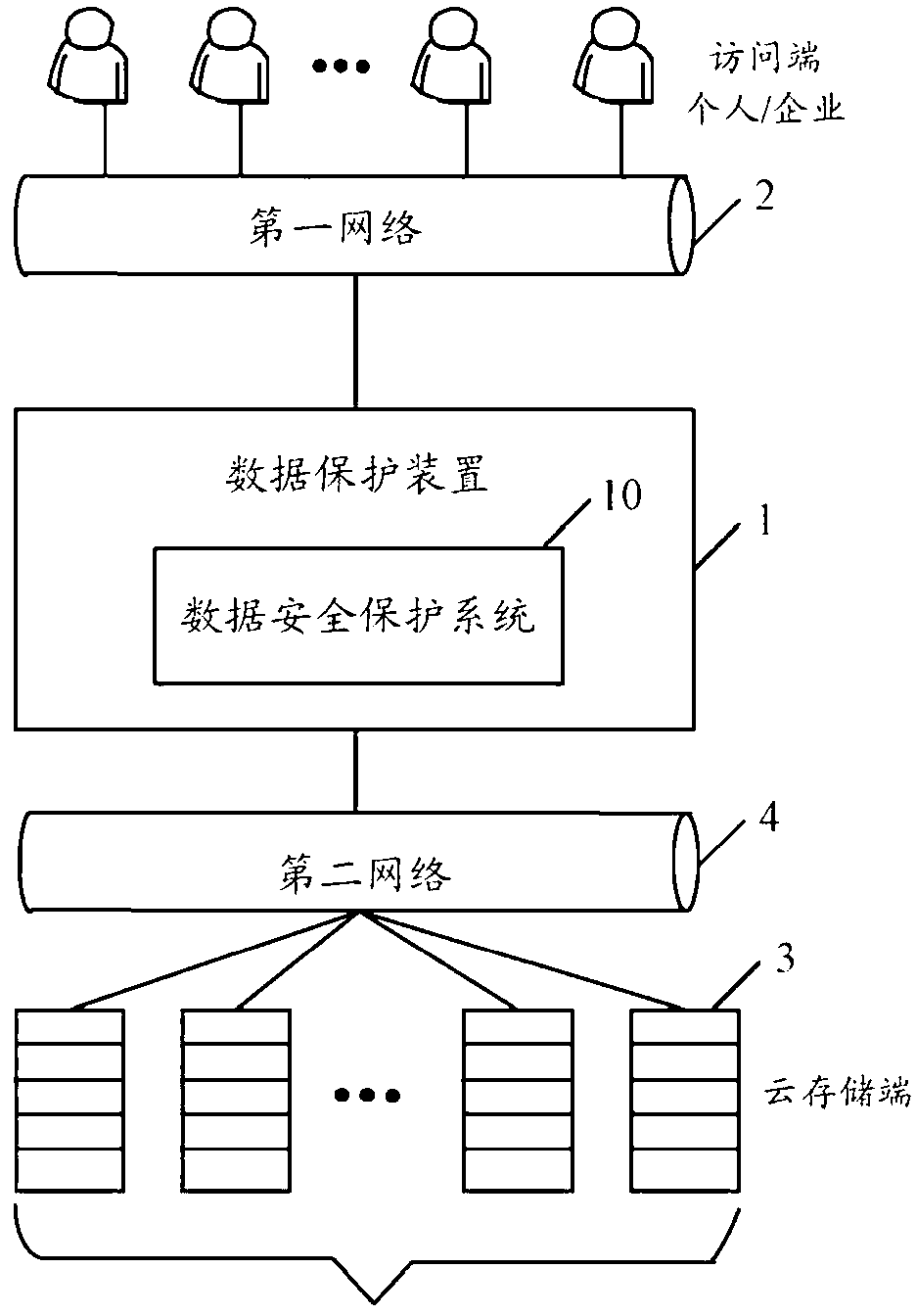
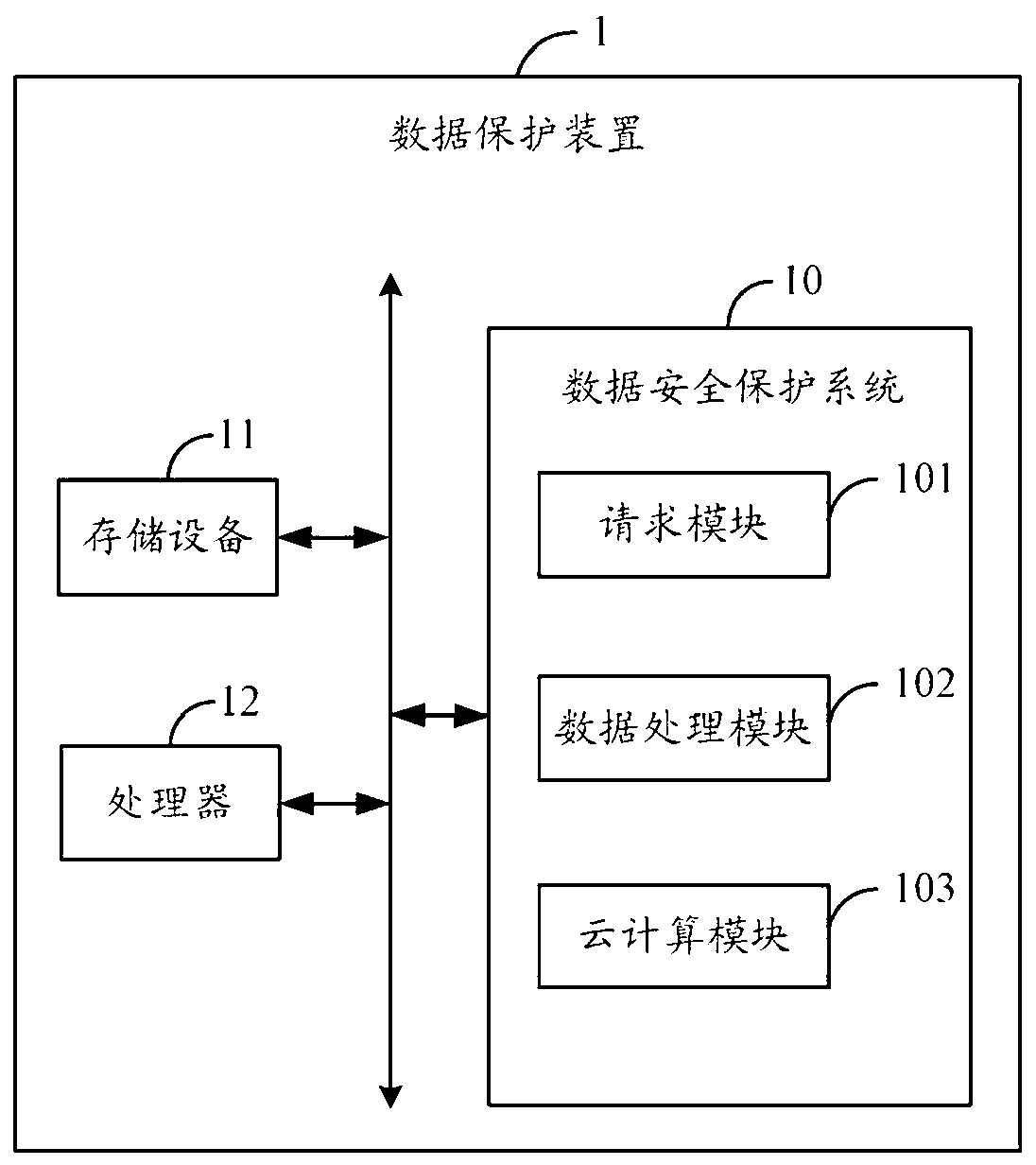
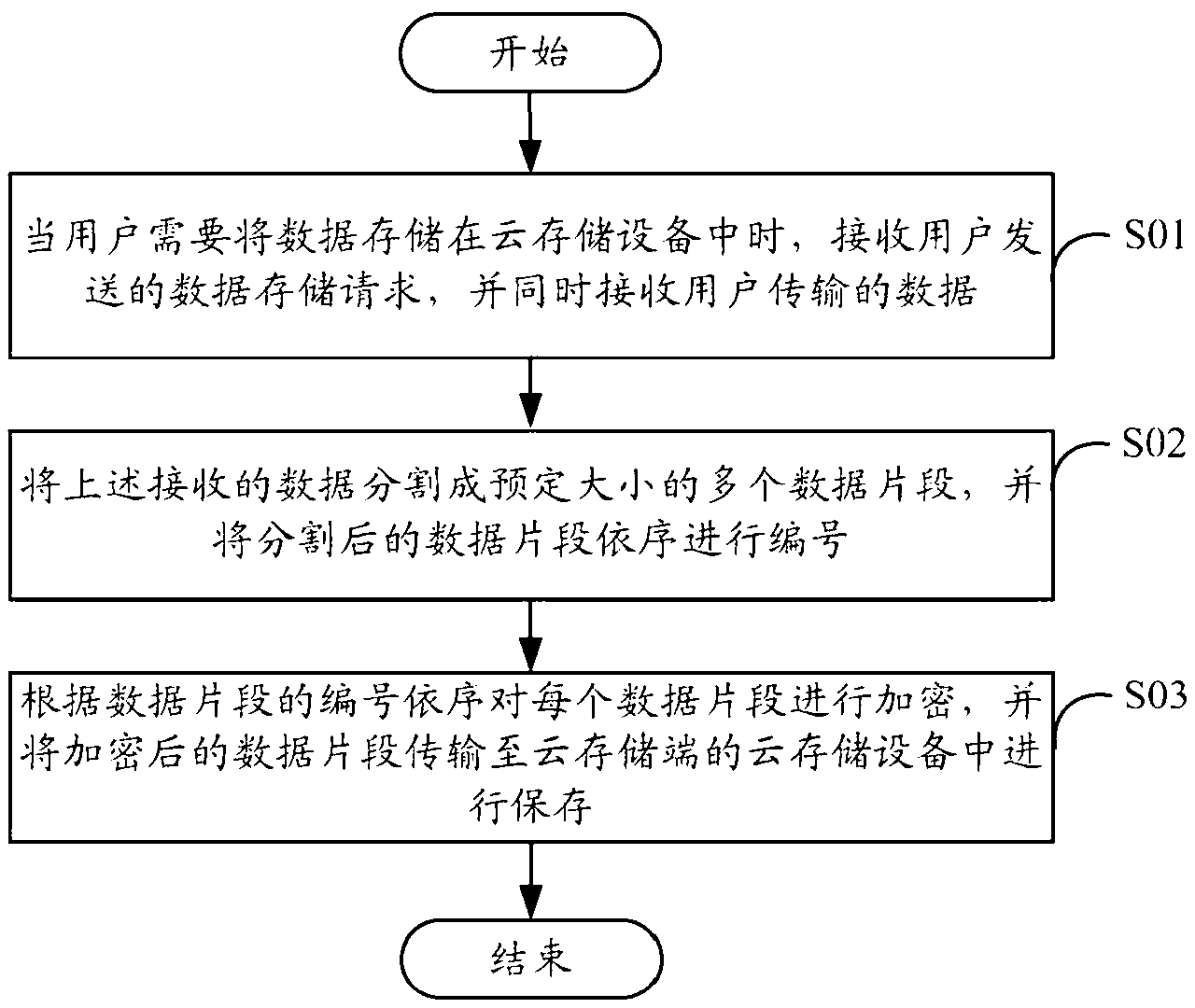
InactiveCN103207971AImprove data securityAvoid data breachesDigital data protectionTransmissionUser needsData segment
The invention discloses a cloud storage-based data security protection system, which is applied to a data protection device. When a user needs to store data in cloud storage equipment, data transmitted by the user is segmented into a plurality of data segments of a predetermined size by the system; and then each data segment is encrypted by the system, and each encrypted data segment is transmitted to the cloud storage equipment at the cloud storage side for storage. The invention also provides a cloud storage-based data security protection method. By implementing the system and the method, the data security of cloud storage can be improved.
Owner:FU TAI HUA IND SHENZHEN +1
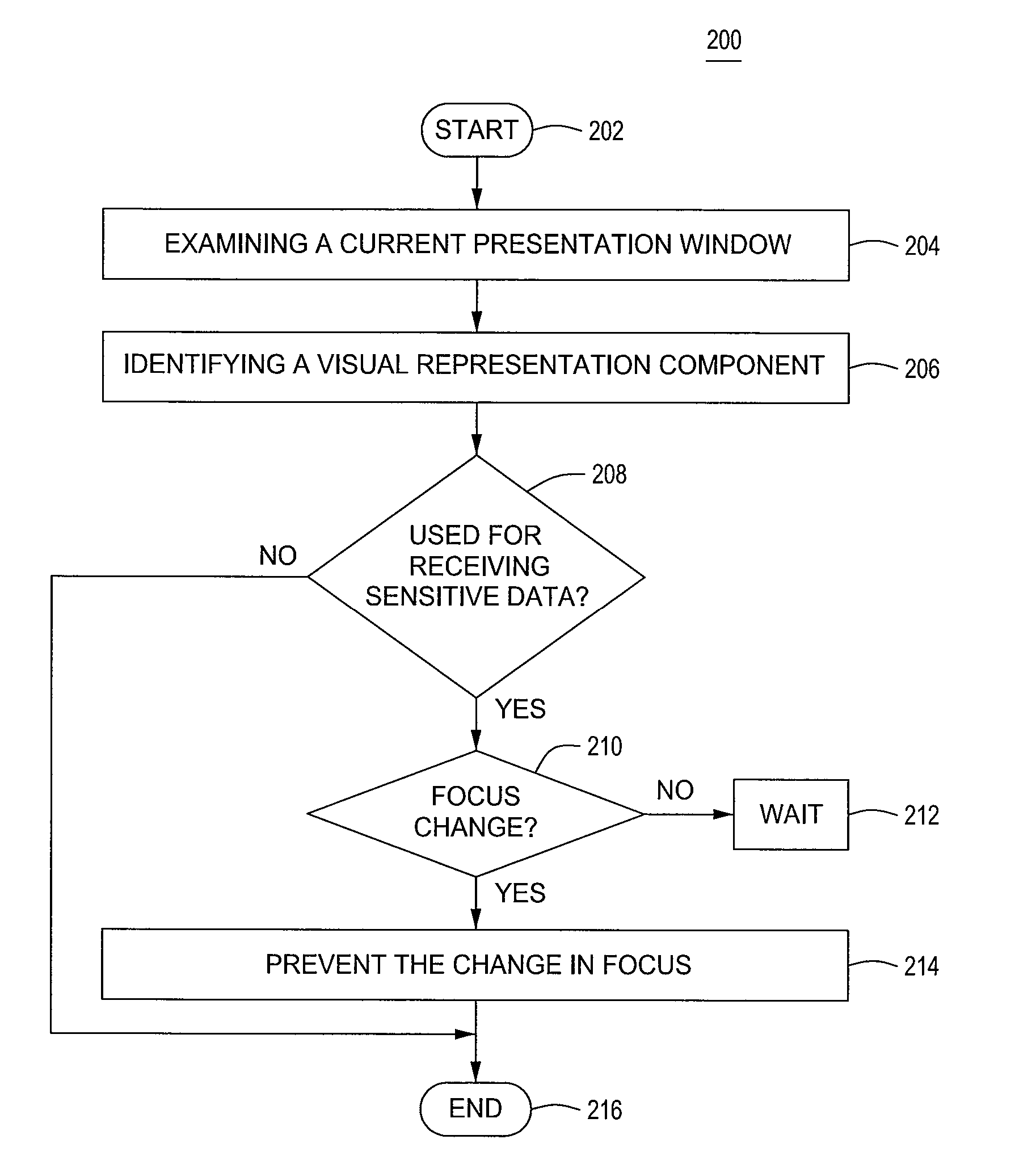
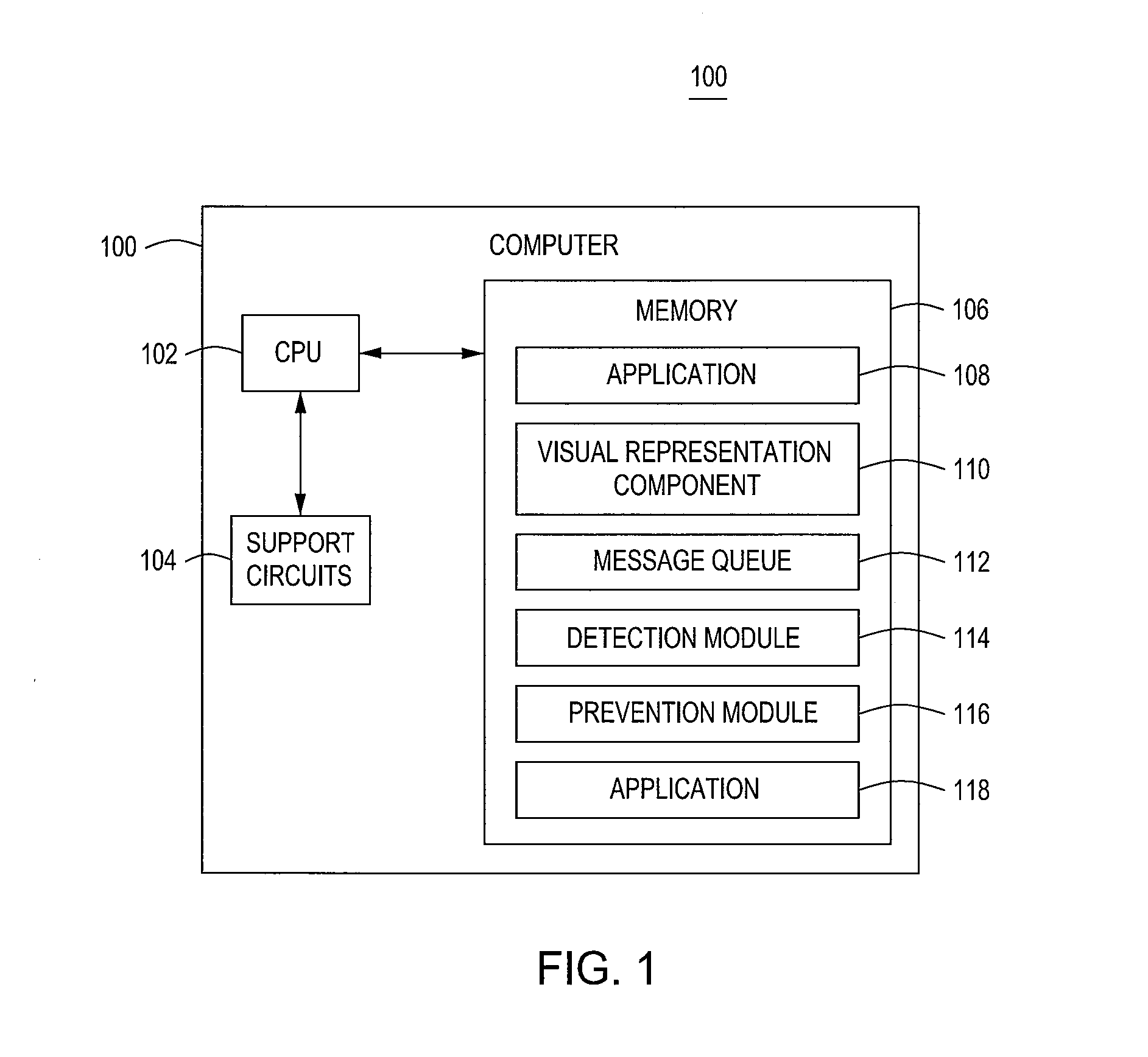
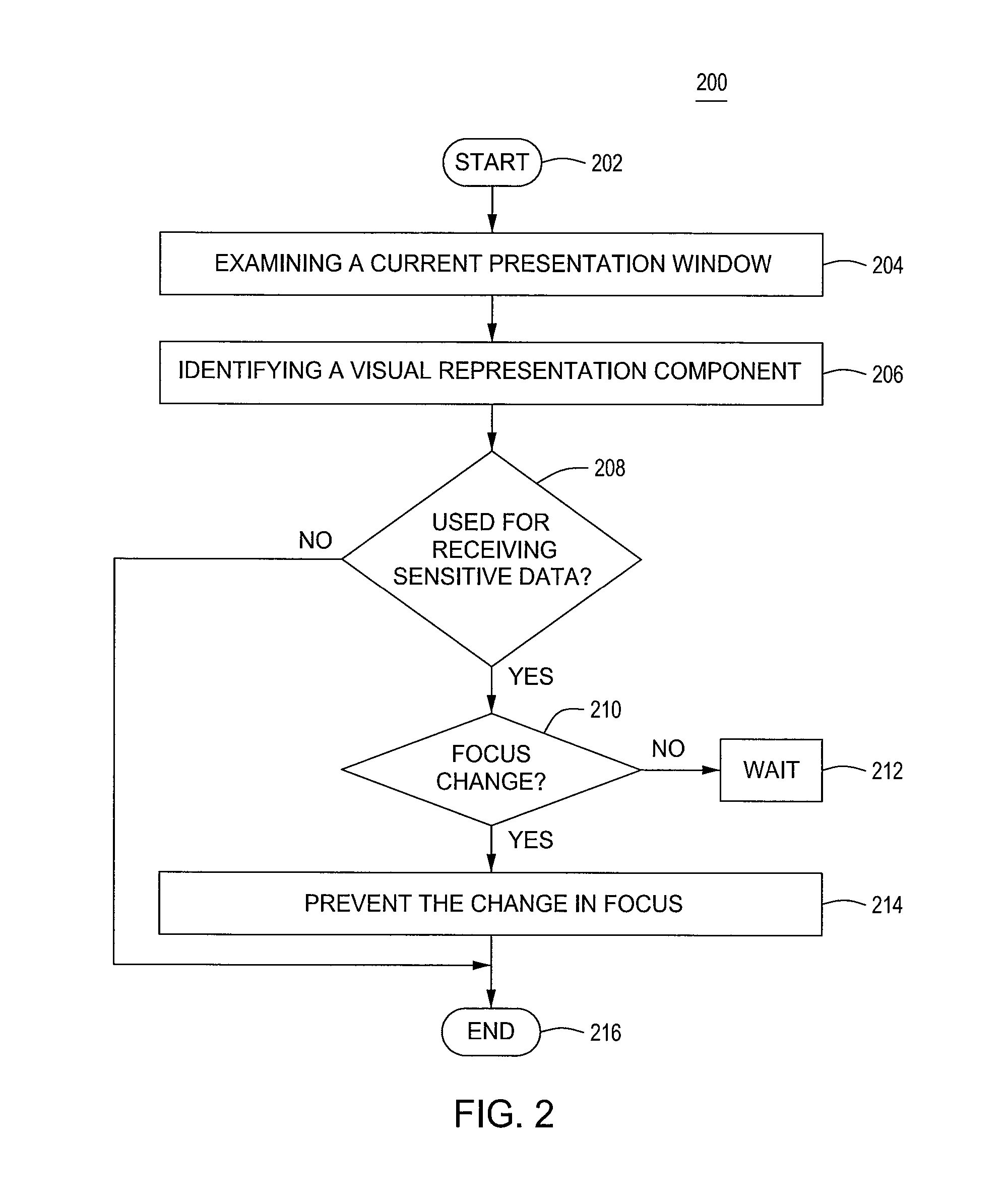
Method and apparatus for preventing sensitive data leakage due to input focus misappropriation
ActiveUS8392992B1Prevent Sensitive Data LeakageAvoid changeMemory loss protectionError detection/correctionRepresentation ComponentVisual perception
Owner:SYMANTEC CORP
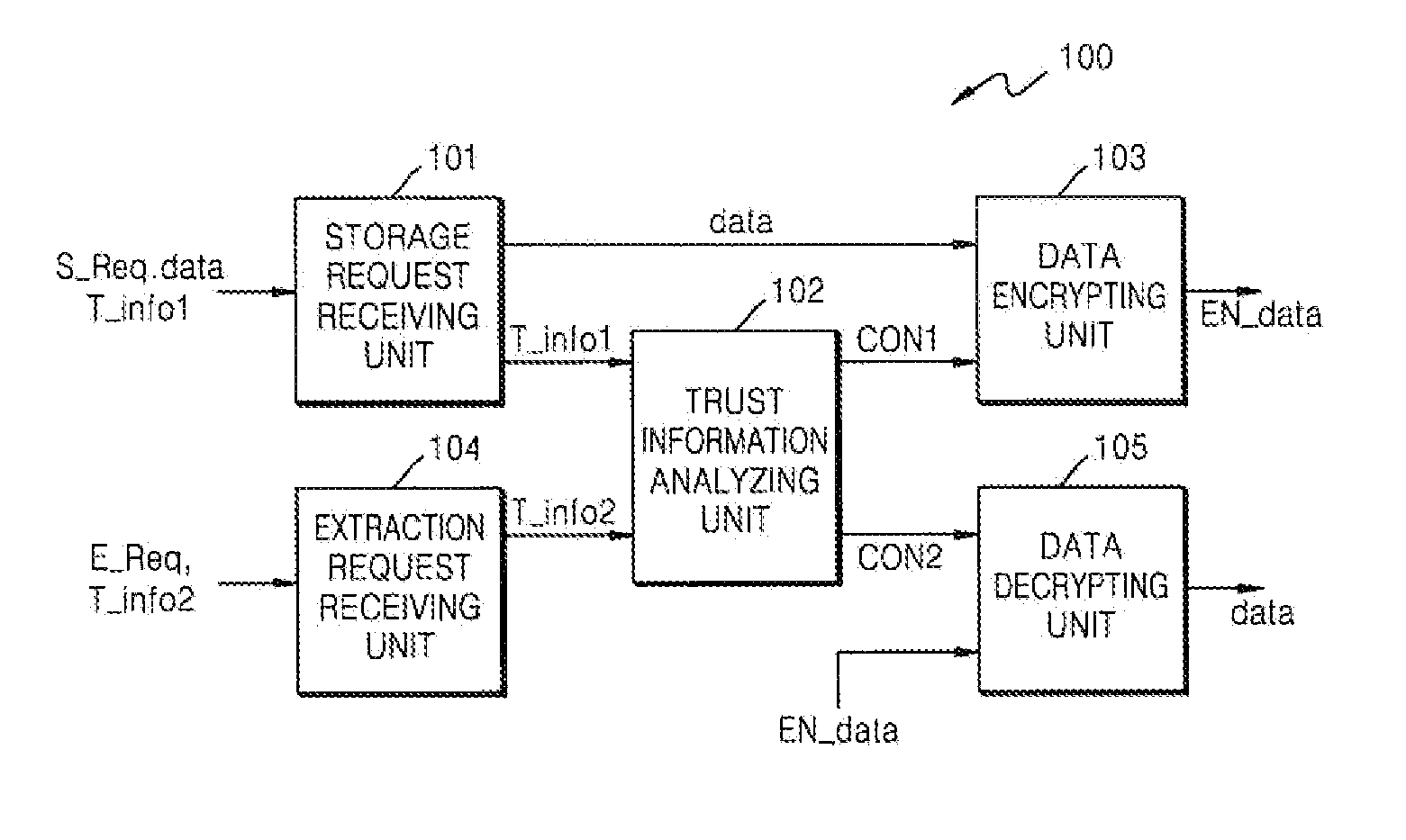
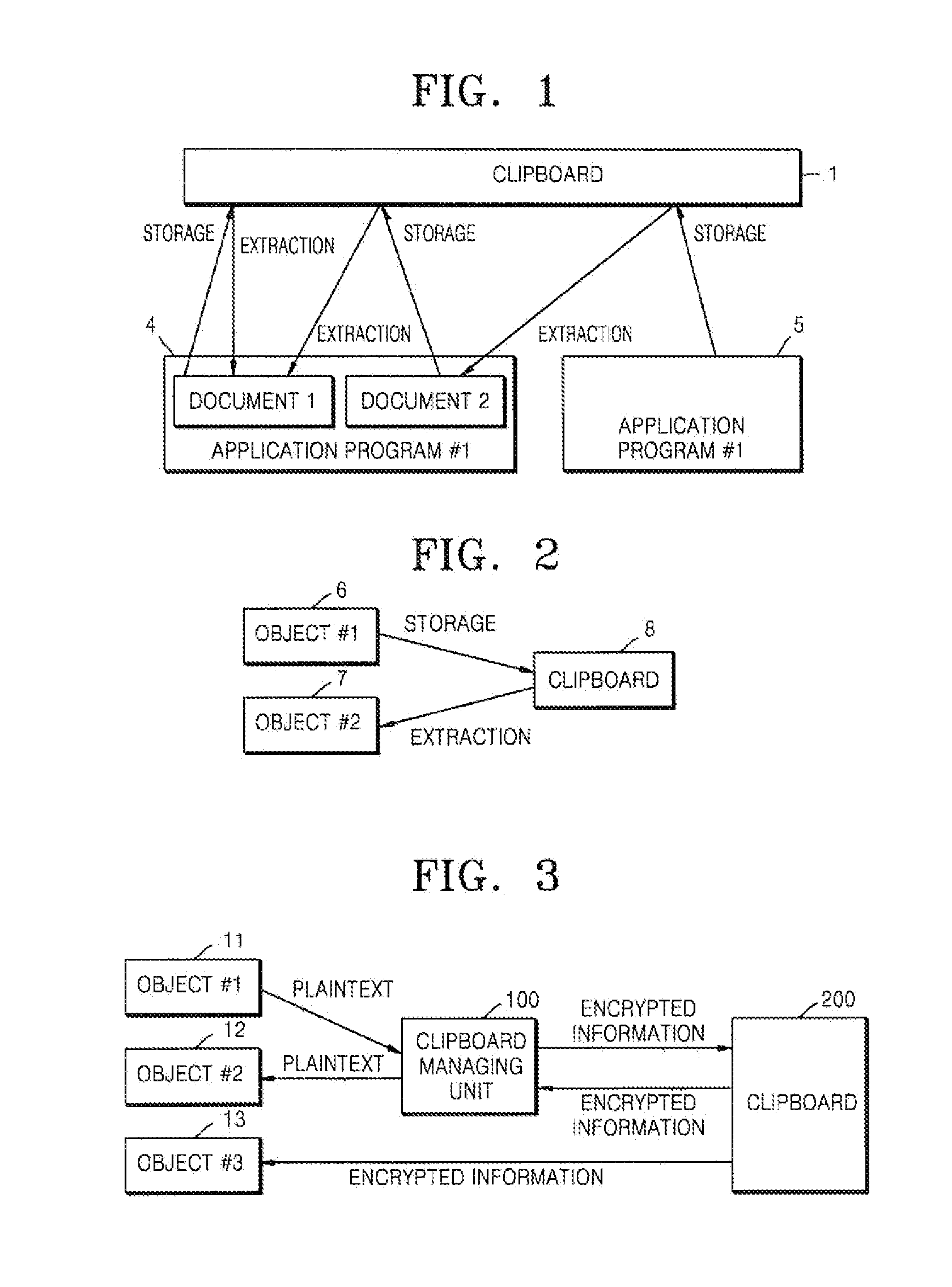
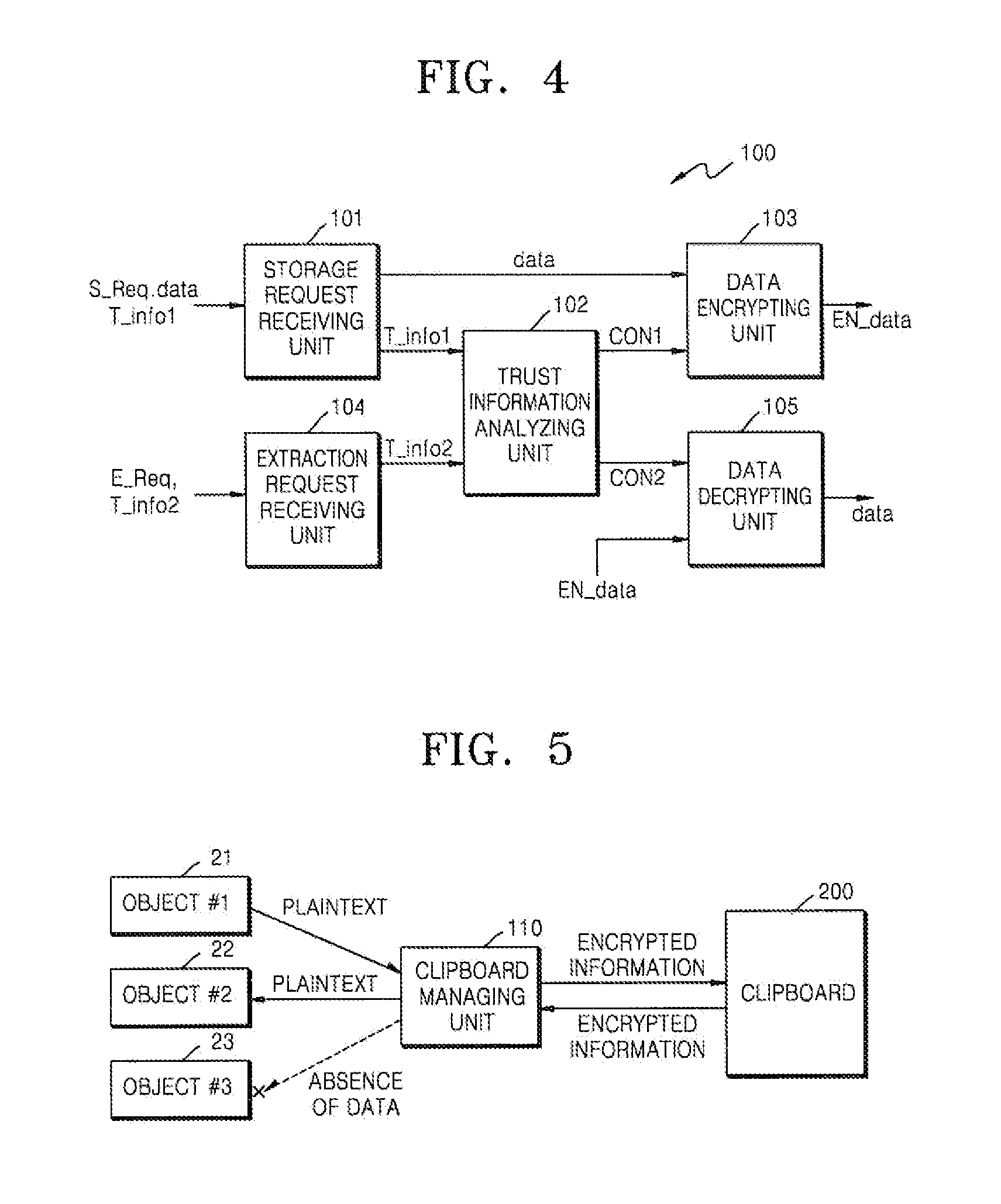
System and method for clipboard security
ActiveUS20120226913A1Prevent leakageEffective maintenanceUnauthorized memory use protectionHardware monitoringTrust relationshipData storing
Provided is a clipboard security system and method for improving security of data transmission made through a clipboard which is frequently used in utilization of a computer. An example of the clipboard security system includes a clipboard managing unit for storing data in a clipboard or extracting data from the clipboard in response to a request from one or more objects, in which the clipboard managing unit includes a data encrypting unit for encrypting the data for which storage is requested according to a trust relationship of an object which desires to store the data in the clipboard and a data decrypting unit for decrypting the encrypted data according to a trust relationship of an object which desires to extract the encrypted data stored in the clipboard.
Owner:FASOO
Data protection method and user terminal
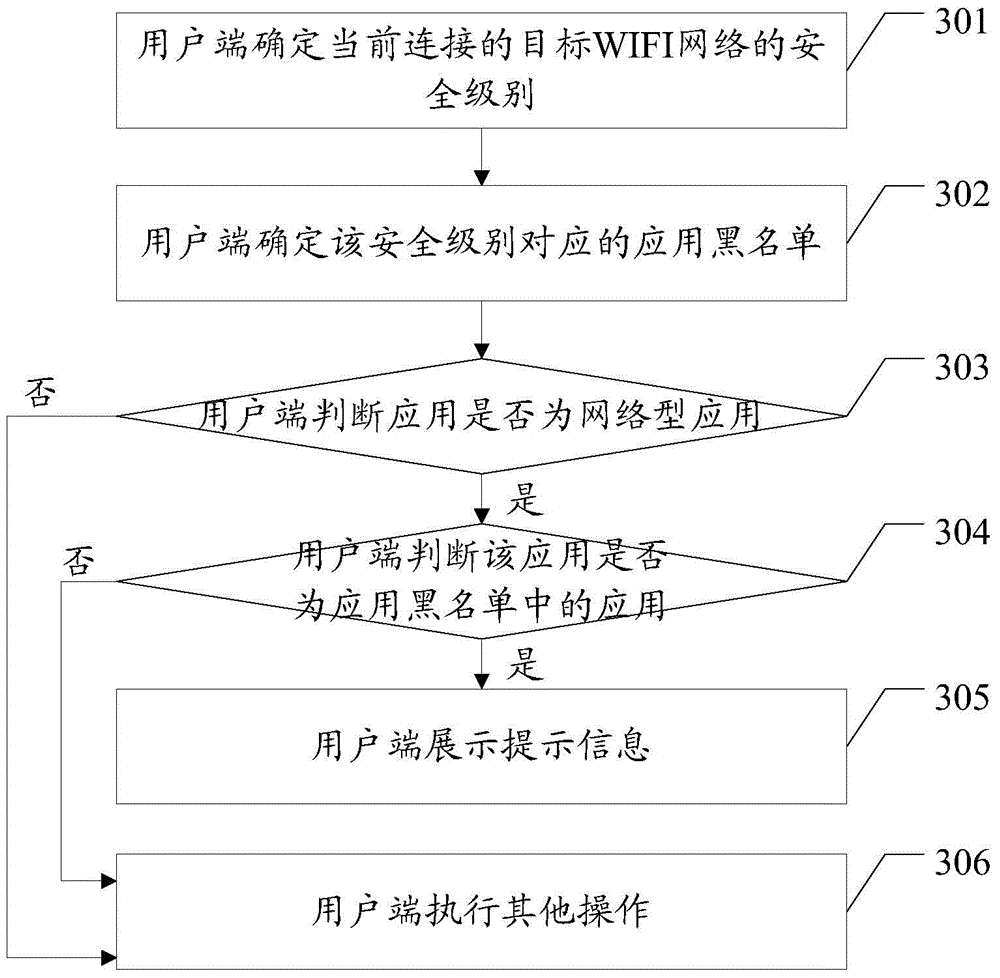
An embodiment of the invention discloses a data protection method used for monitoring management of applications on a user terminal according to an application black list corresponding to a safety level of a target network to which the user terminal is currently connected. The method includes that the user terminal determines the safety level of the currently connected target WIFI network; the user terminal determines the application black list corresponding to the safety level; the user terminal performs monitoring management on the applications of the user terminal. According to the invention, the user terminal can obtain the safety level of the current connected WIFI network and determines different application black lists according to the safety level. The user terminal can perform monitoring management on the applications on the user terminal according to the application black list. Namely, the user terminal can perform monitoring on the applications on the user terminal by adopting different monitoring strategies according to different network safety levels, so that data leakage when the user terminal runs safe applications due to unsafe network connection is avoided.
Owner:深圳市立鳌科技有限公司
Information processing apparatus having illegal access prevention function and illegal access prevention method
ActiveUS20060278701A1Prevent unauthorized accessImprove securityFinanceDigital data processing detailsComputer hardwareInformation processing
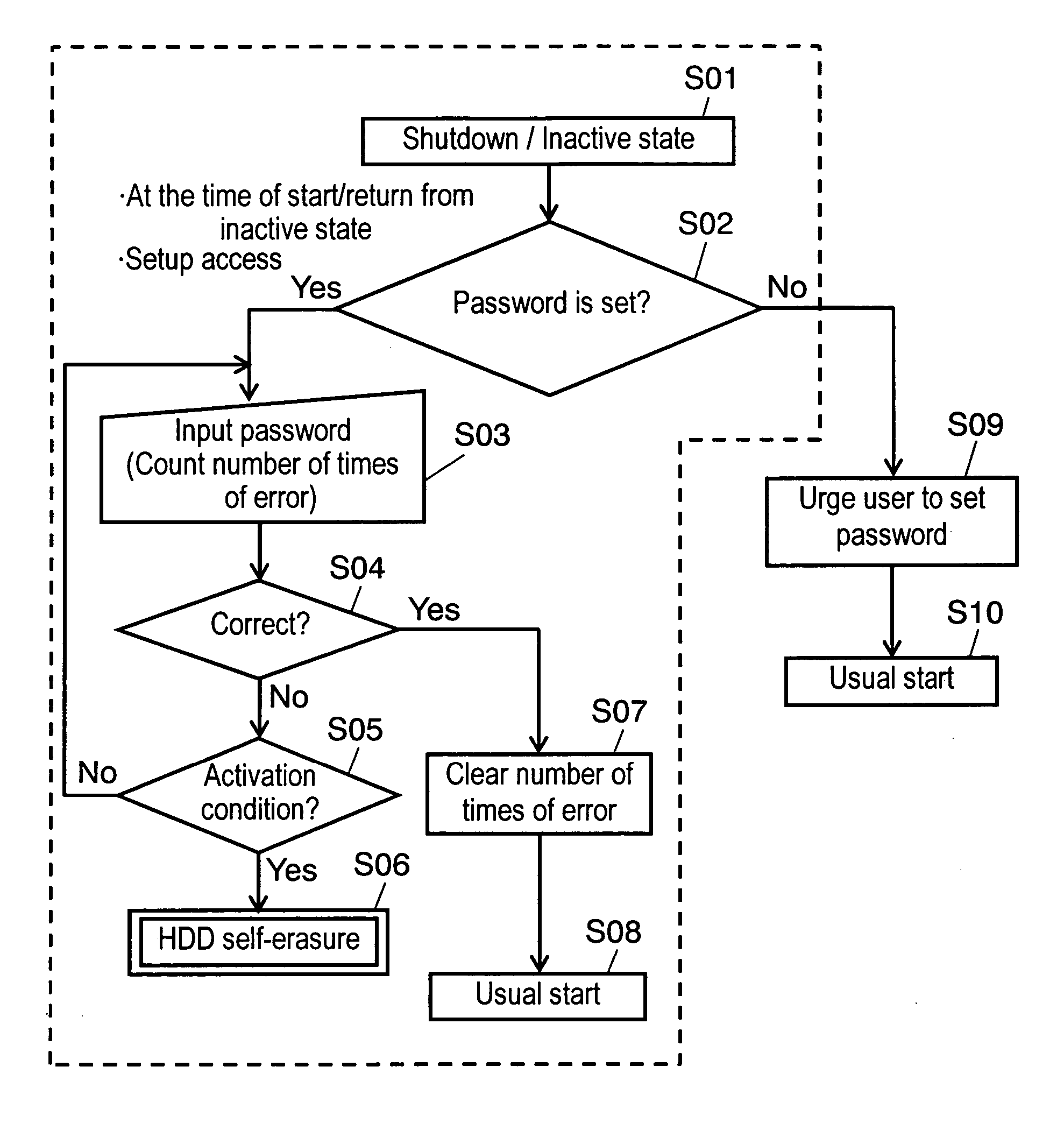
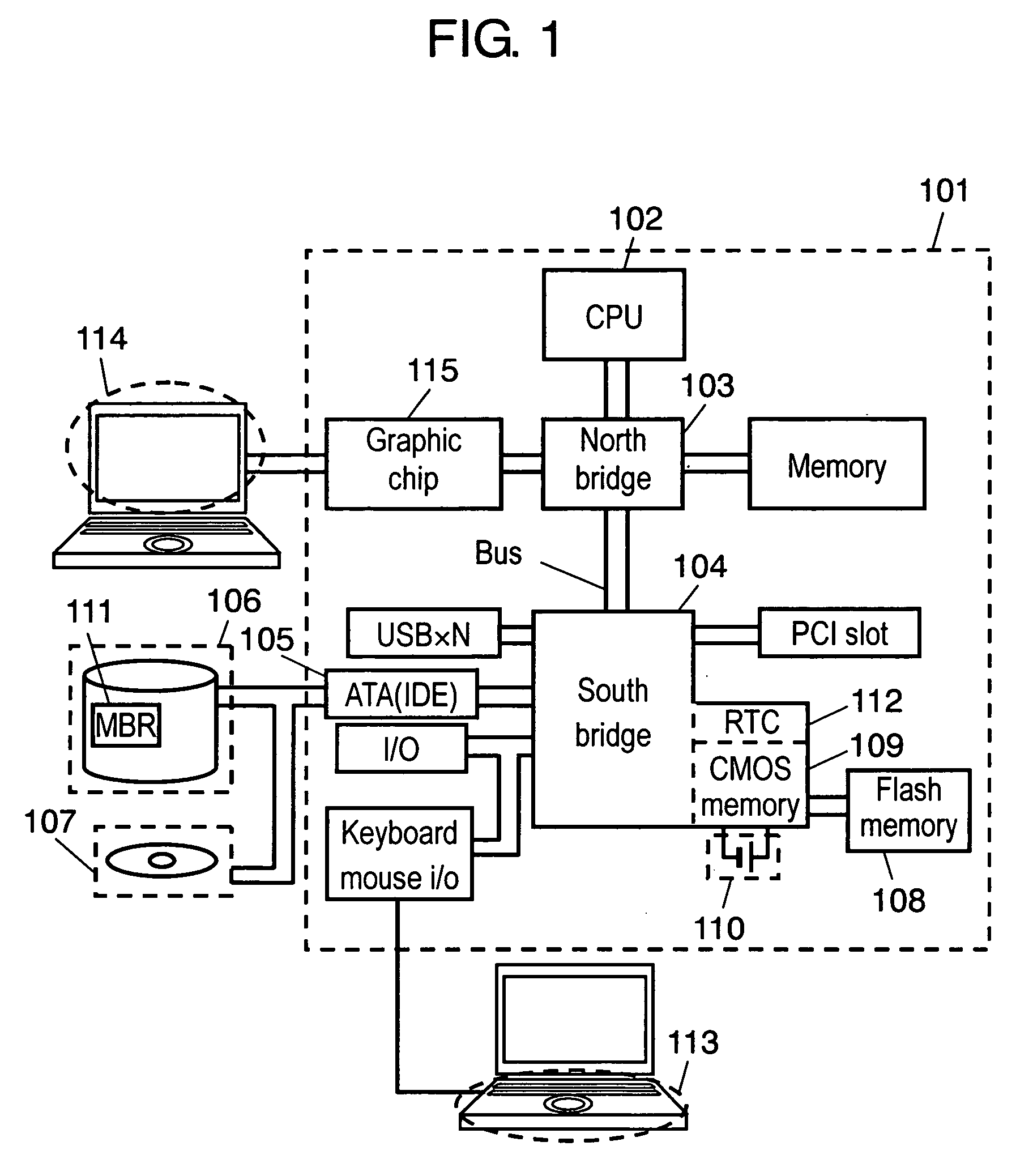
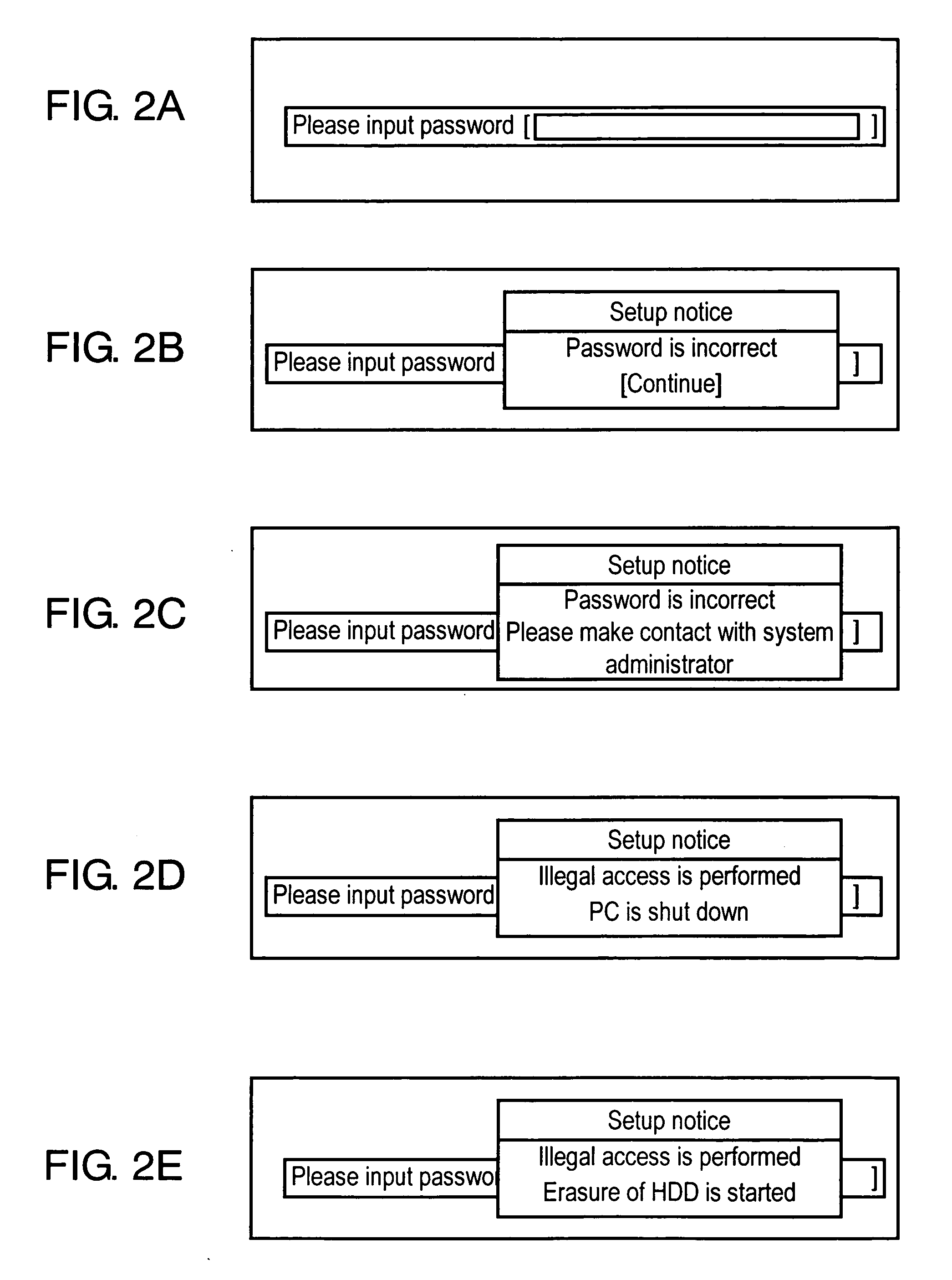
An information processing apparatus includes a first recording medium, a password input unit, a password judging unit, and a condition judging unit. The first recording medium is capable of recording programs and data. The password input unit requests a user to input a password. The password judging unit judges whether a password inputted to the password input unit and a password stored in advance coincide with each other. The condition judging unit judges, when the apparatus is started, whether a condition set in advance is satisfied. When the condition set in advance is satisfied, the information processing apparatus sets a self-erasing program in the first recording medium. The first recording medium self-erases programs and data recorded in the first recording medium according to the self-erasing program.
Owner:PANASONIC CORP
Image processing system
ActiveUS20050275887A1Avoid data breachesEffectively prevents data leakageDigital computer detailsPictoral communicationComputer hardwareImaging processing
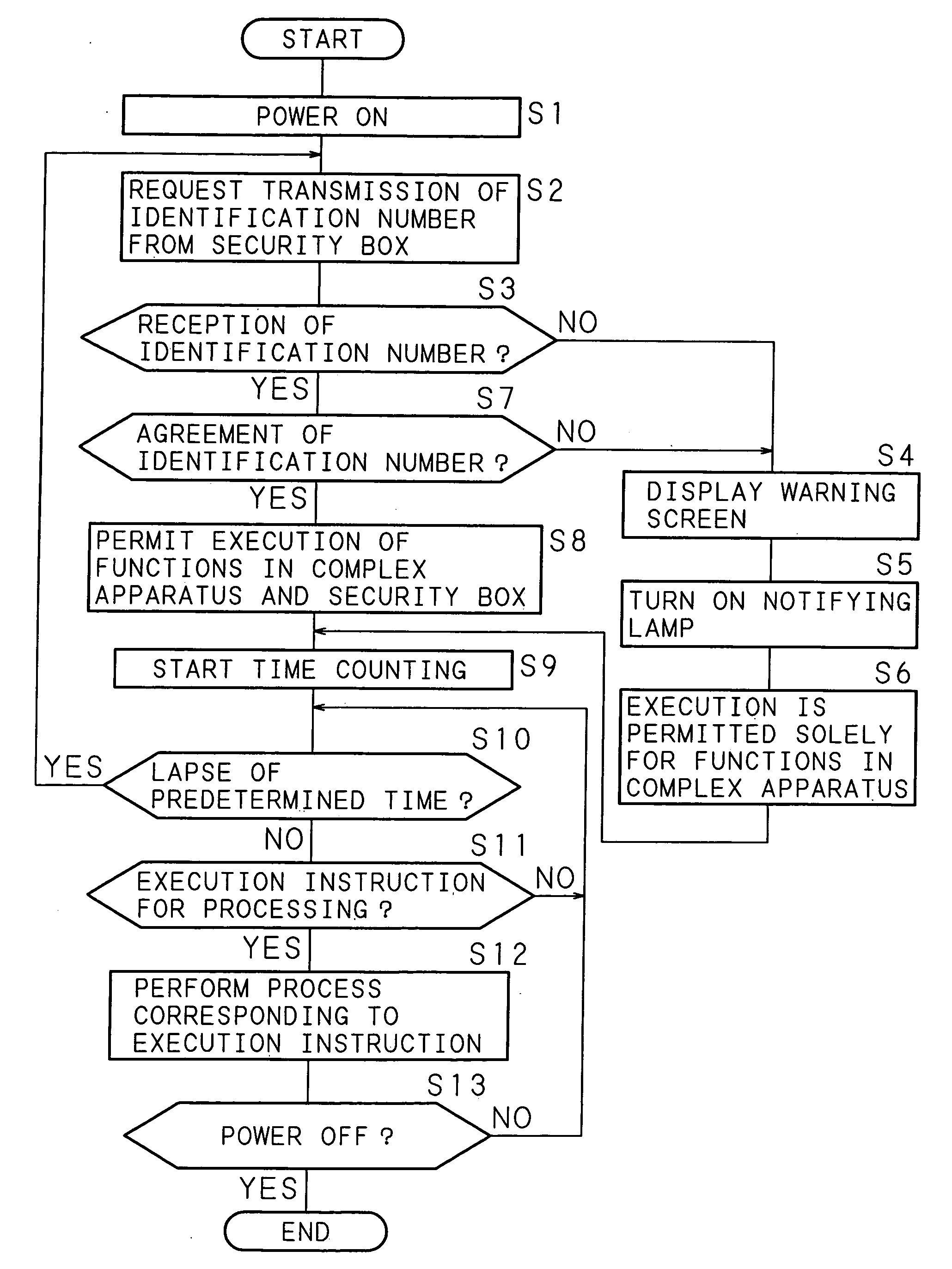
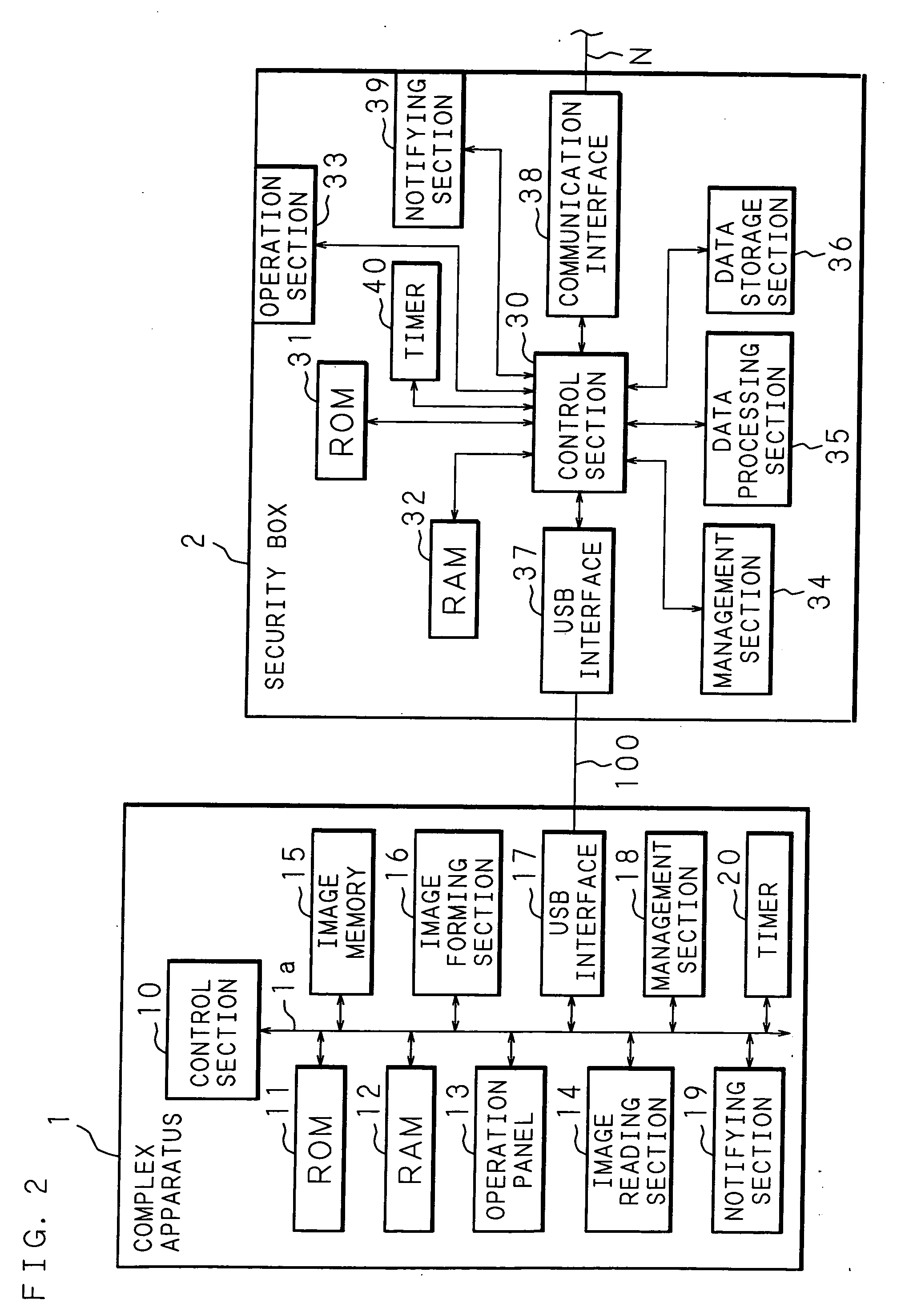
A complex apparatus (image processing apparatus) requests the transmission of an identification number from a security box (data processing apparatus). The security box transmits the stored own identification number to the complex apparatus. When no response is received within a predetermined time after the request of transmission of the identification number, or alternatively when the identification number transmitted from the security box differs from the identification number of a security box stored in advance, the complex apparatus displays a warning screen indicating that the appropriate security box has been removed, on the displaying section of the operation panel, and then turns ON a notifying lamp.
Owner:SHARP KK
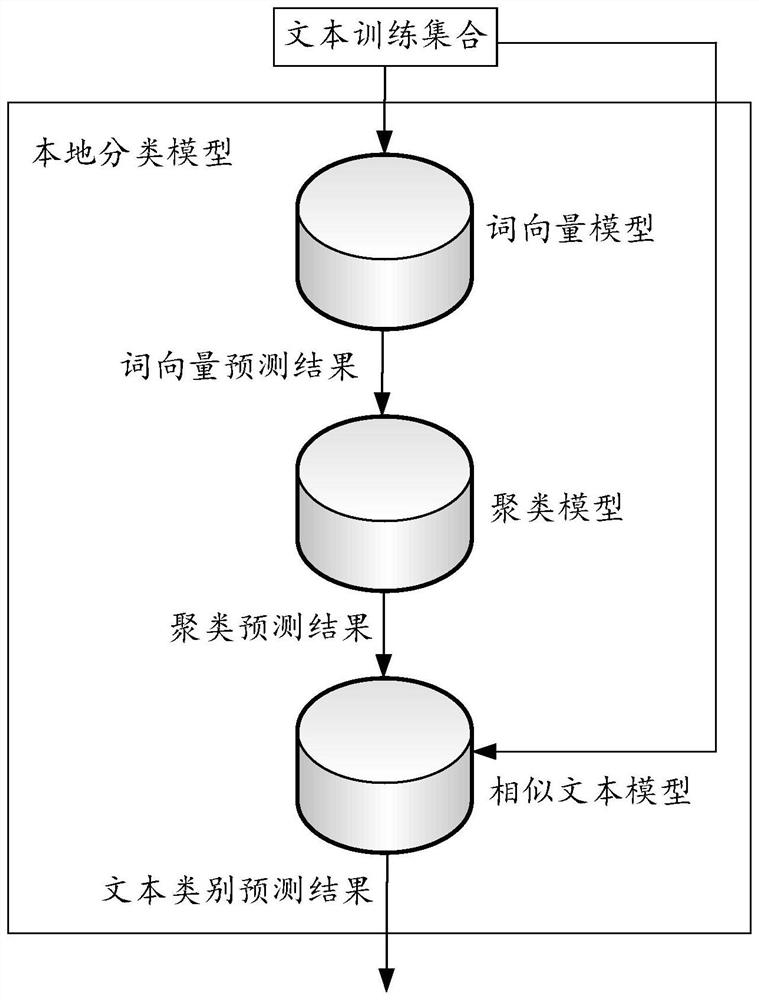
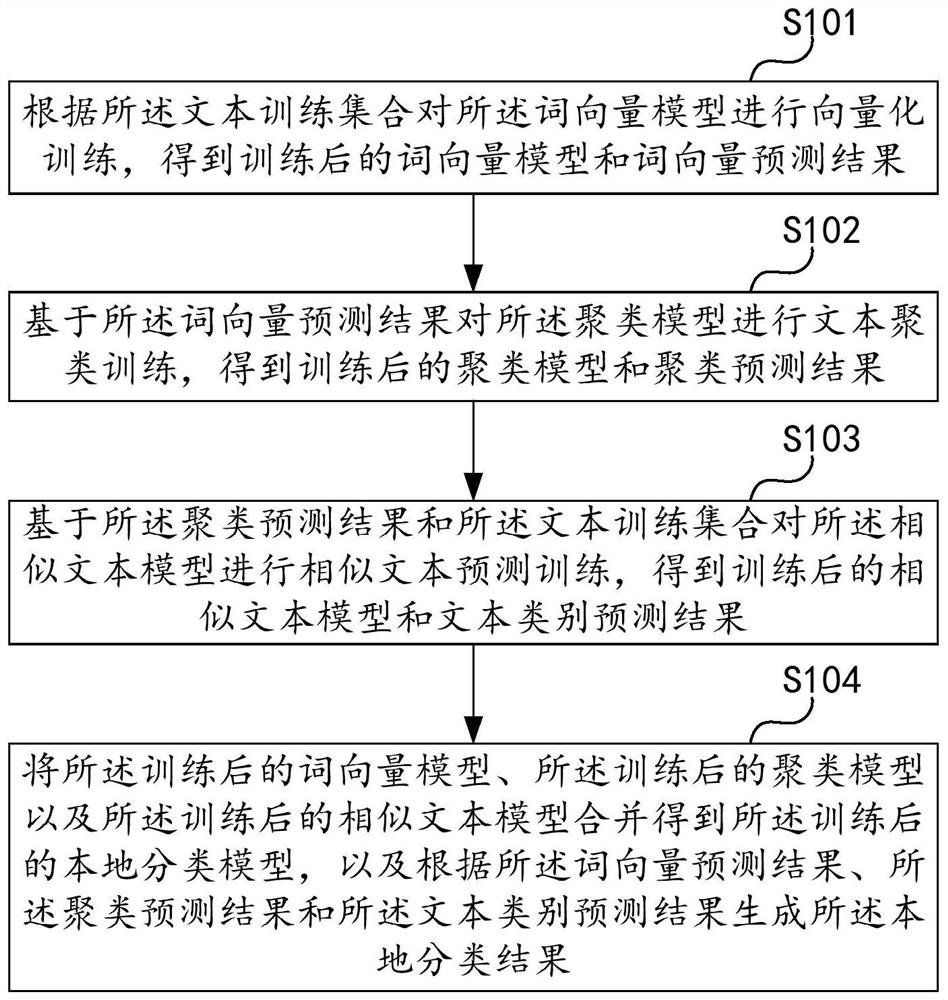
Model training method and device, text classification method, computer equipment and medium
PendingCN112256874AImprove accuracyAvoid data breachesEnsemble learningCharacter and pattern recognitionMachine learningFederated learning
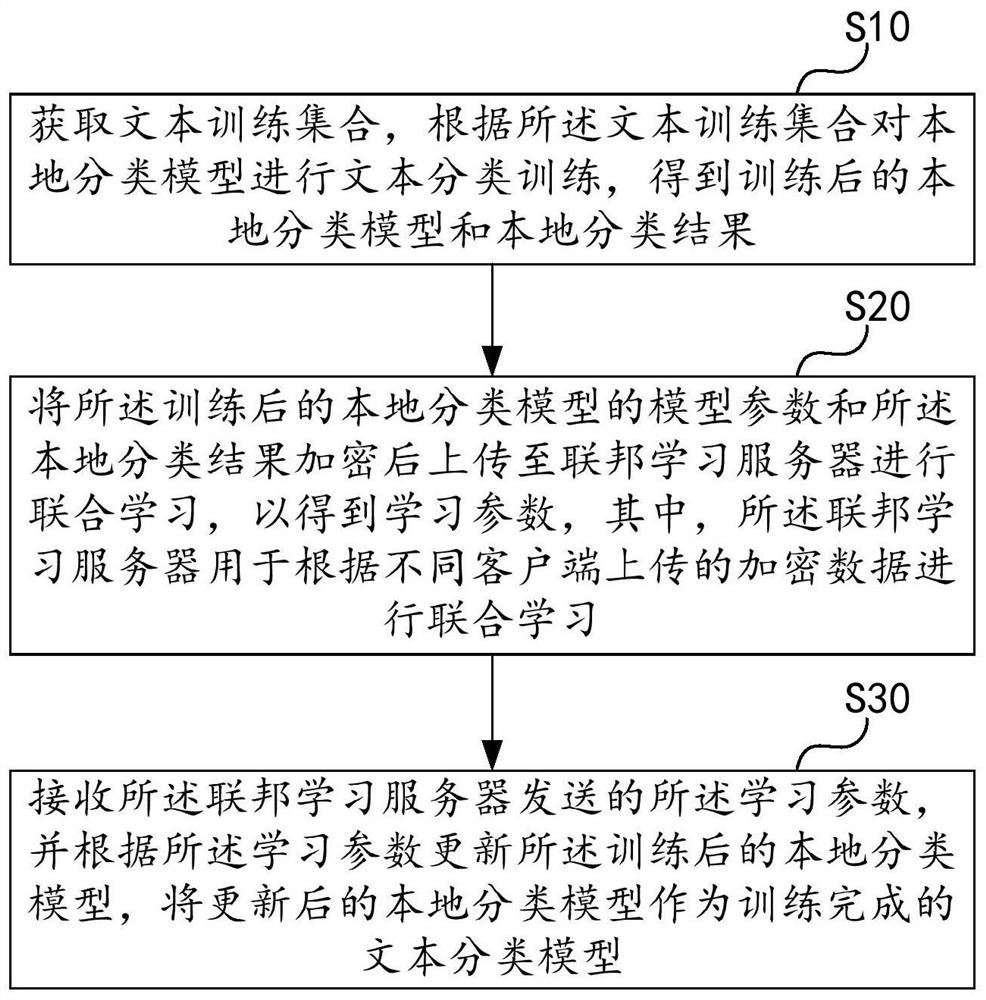
The invention relates to the field of artificial intelligence and model construction, and by uploading model parameters of a local classification model and a local classification result to a federatedlearning server for joint learning, the security of text data in a model training process can be improved. The invention relates to a text classification model training method and device, a text classification method, computer equipment and a medium, and the training method comprises the steps: obtaining a text training set, and carrying out text classification training on a local classificationmodel according to the text training set; encrypting the model parameters of the trained local classification model and the local classification result, and uploading the encrypted model parameters and local classification result to a federated learning server for joint learning to obtain learning parameters; and receiving the learning parameters sent by the federated learning server, updating thetrained local classification model according to the learning parameters, and taking the updated local classification model as a trained text classification model. In addition, the invention also relates to a blockchain technology, and the text training set can be stored in the blockchain.
Owner:PING AN TECH (SHENZHEN) CO LTD
Gateway-based audit log and method for prevention of data leakage
ActiveUS9313227B2Avoid data breachesDigital data protectionInternal/peripheral component protectionSecure transmissionComputer security
A system and method for prevention of data leakage, the system comprising: a server configured to receive and transmit user activity commands; a protection module configured to validate and reconstruct commands received from the server and to transmit the validated reconstructed commands, the protection module further configured to create a security image associated with a specific user; and a secured transmission module configured to transmit the security image to the server while ensuring that the security image is sent securely to the associated user, wherein the server is further configured to receive the security image via the secured transmission module and to present the security image to the associated user.
Owner:CA TECH INC
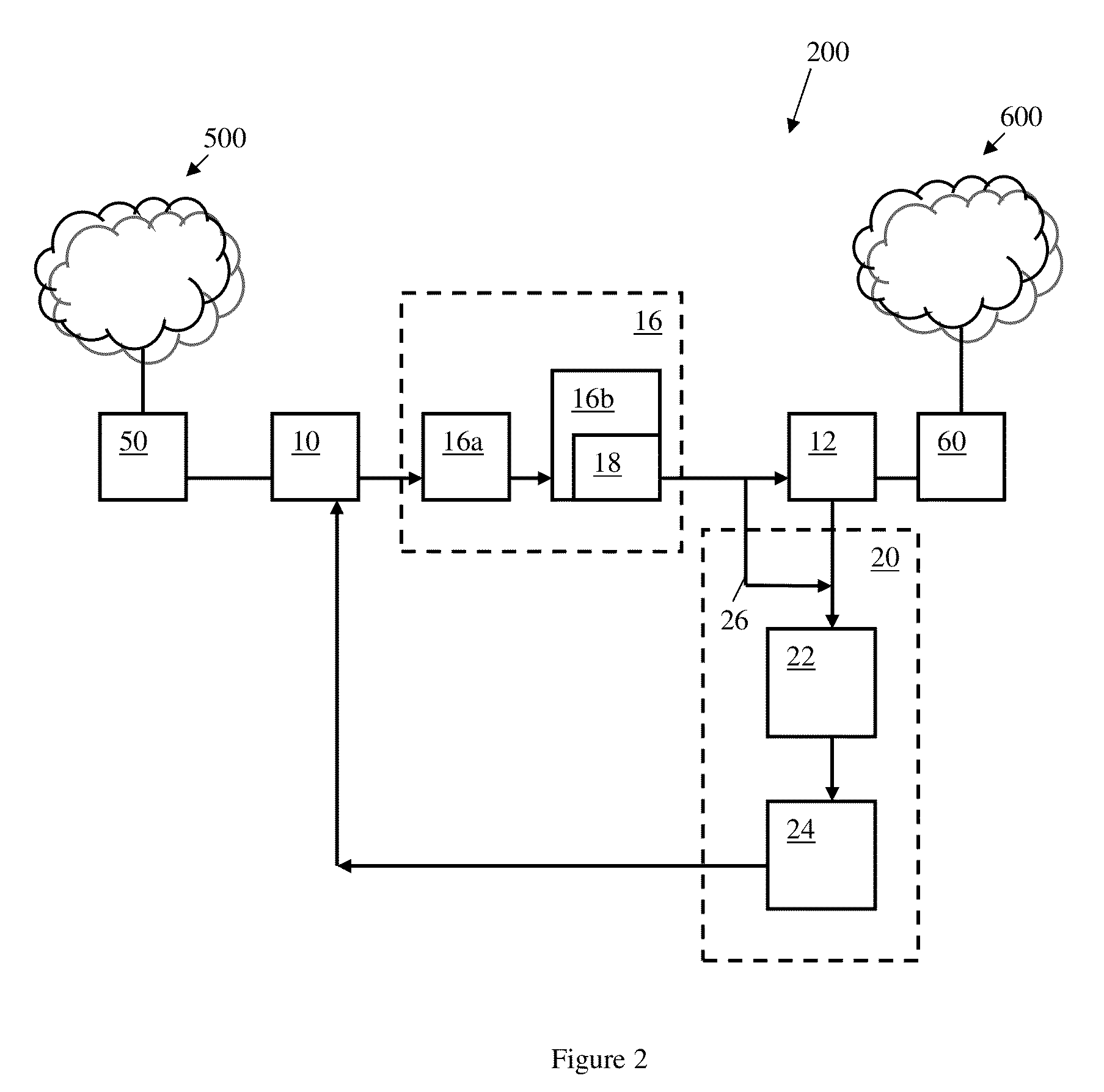
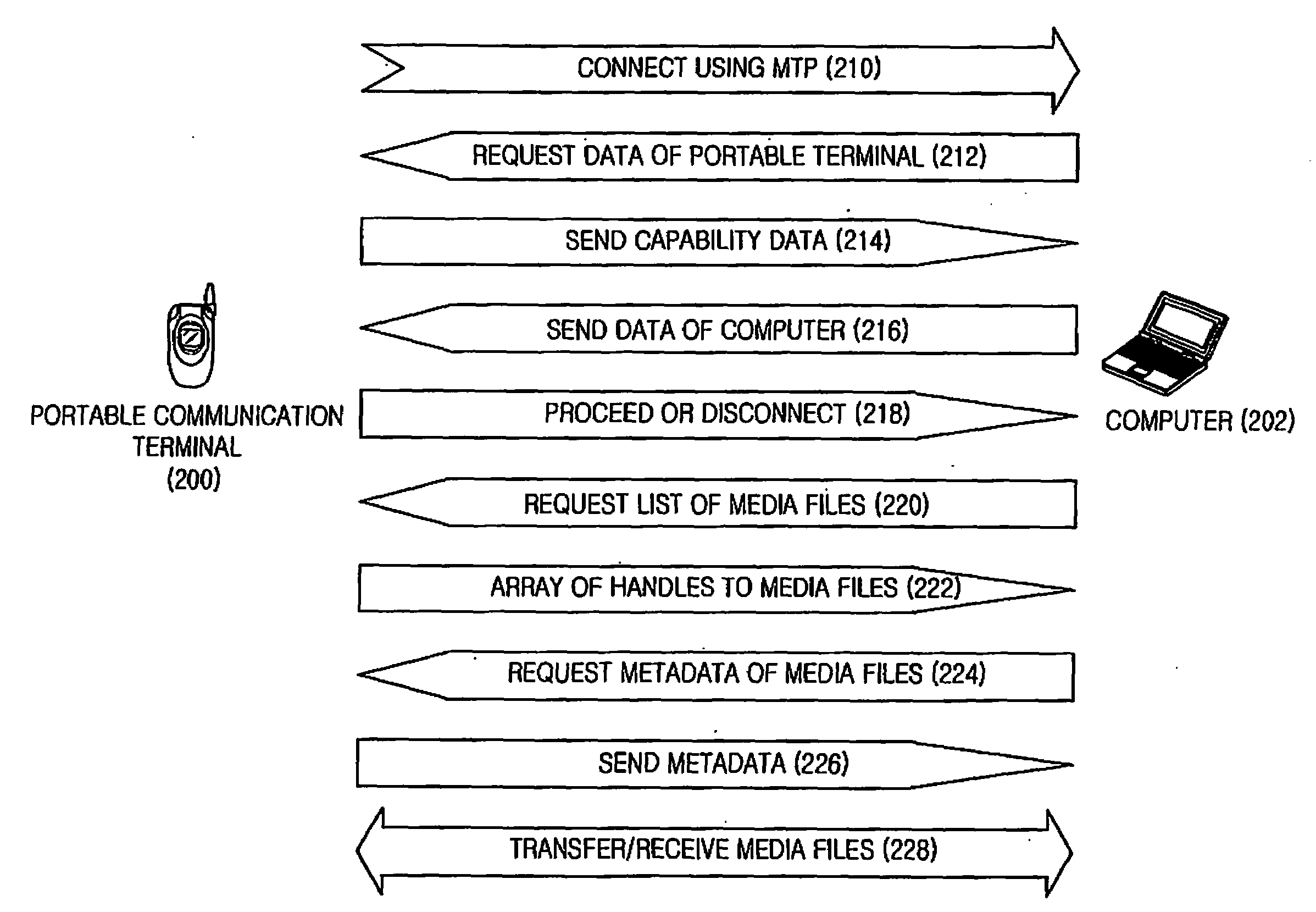
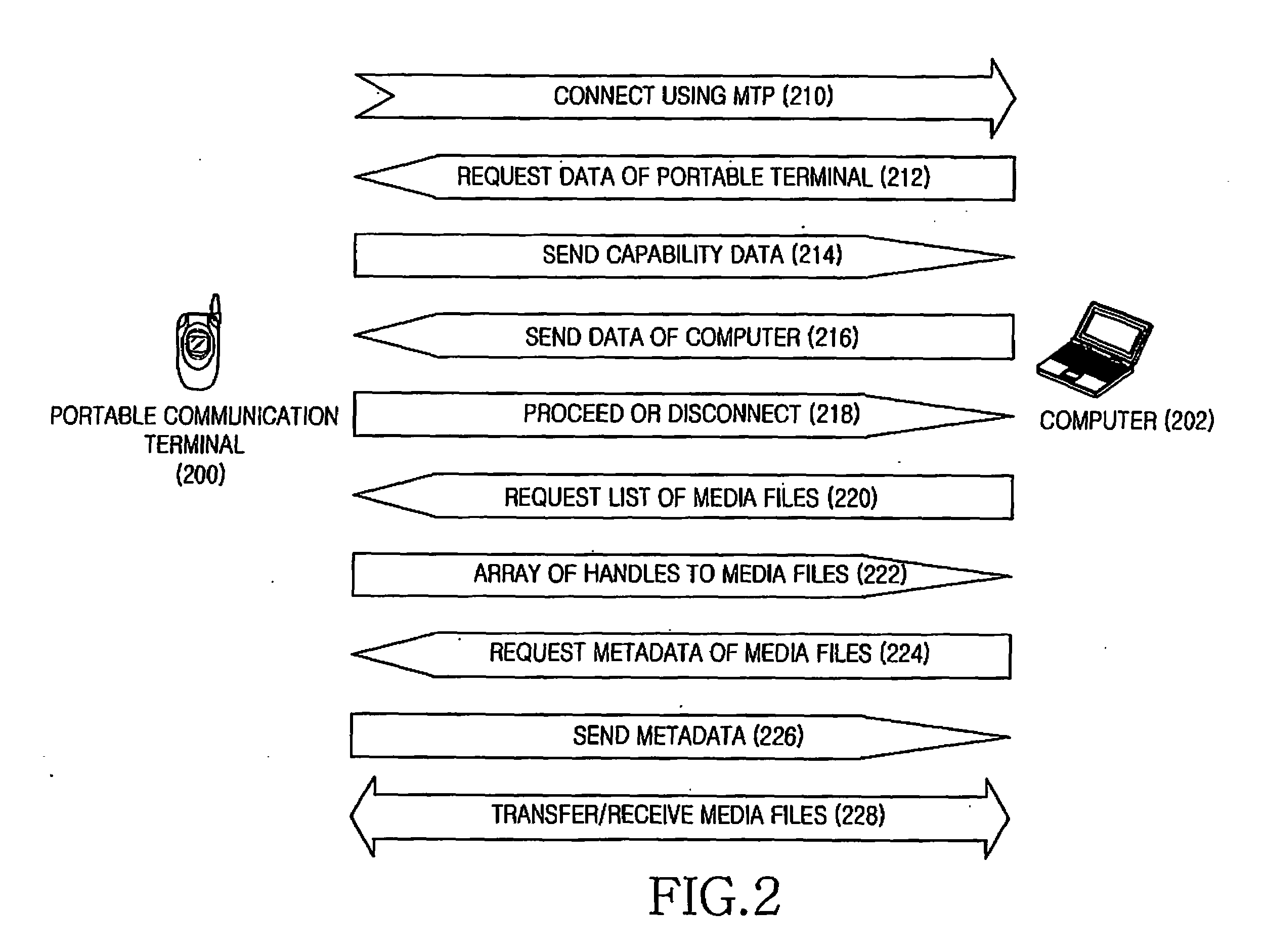
Method and apparatus for preventing data leakage in portable terminal
InactiveUS20080016228A1Avoid data breachesComputer security arrangementsMultiple digital computer combinationsMedia transfer protocolAuthentication
Provided are a method of preventing data leakage from a portable terminal and an apparatus employing the method. The method includes checking whether computer identification (ID) data from a computer is received when the portable terminal is connected to the computer using a media transfer protocol (MTP). A computer authentication using the computer ID data is performed when the computer ID data is received.
Owner:SAMSUNG ELECTRONICS CO LTD
Privacy protection multi-side diagnostic model fusion method and system, and cloud server
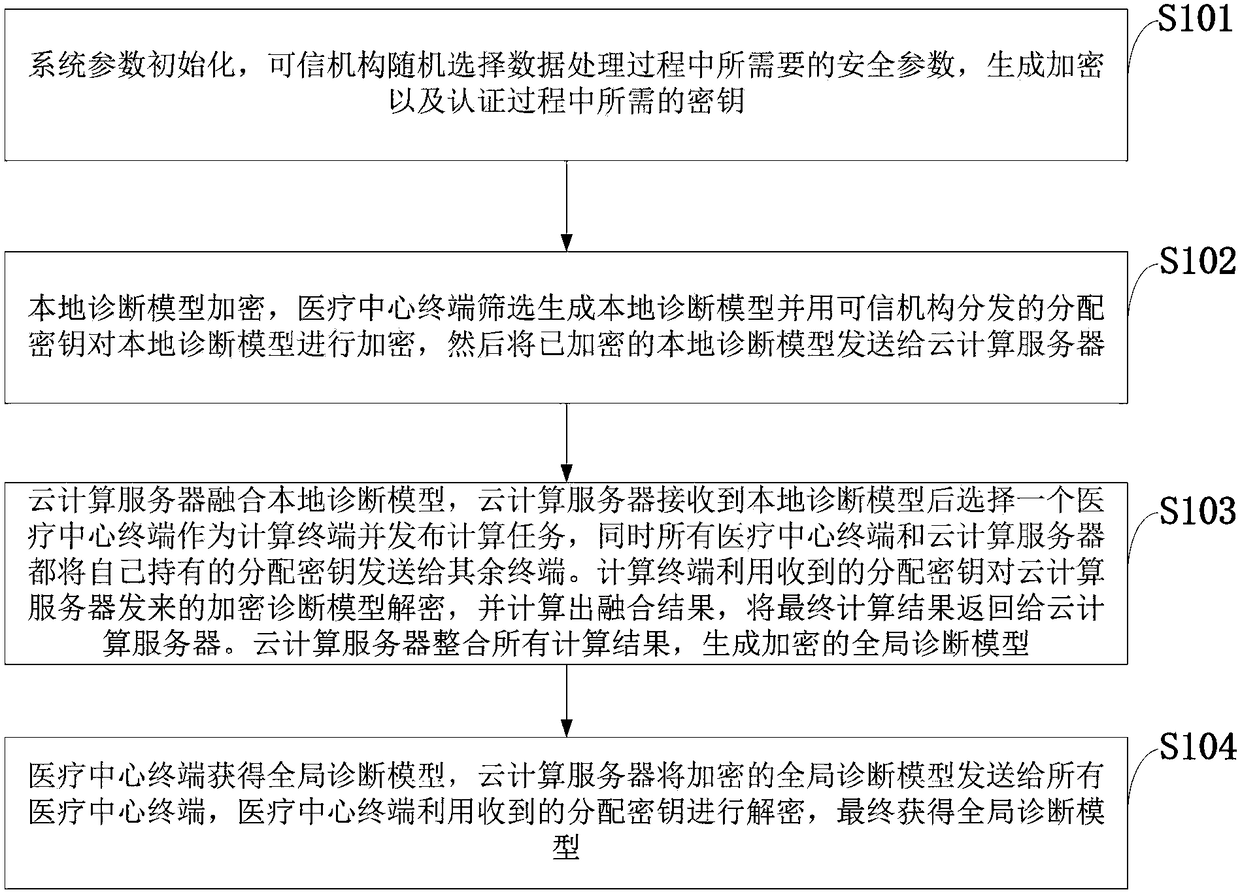
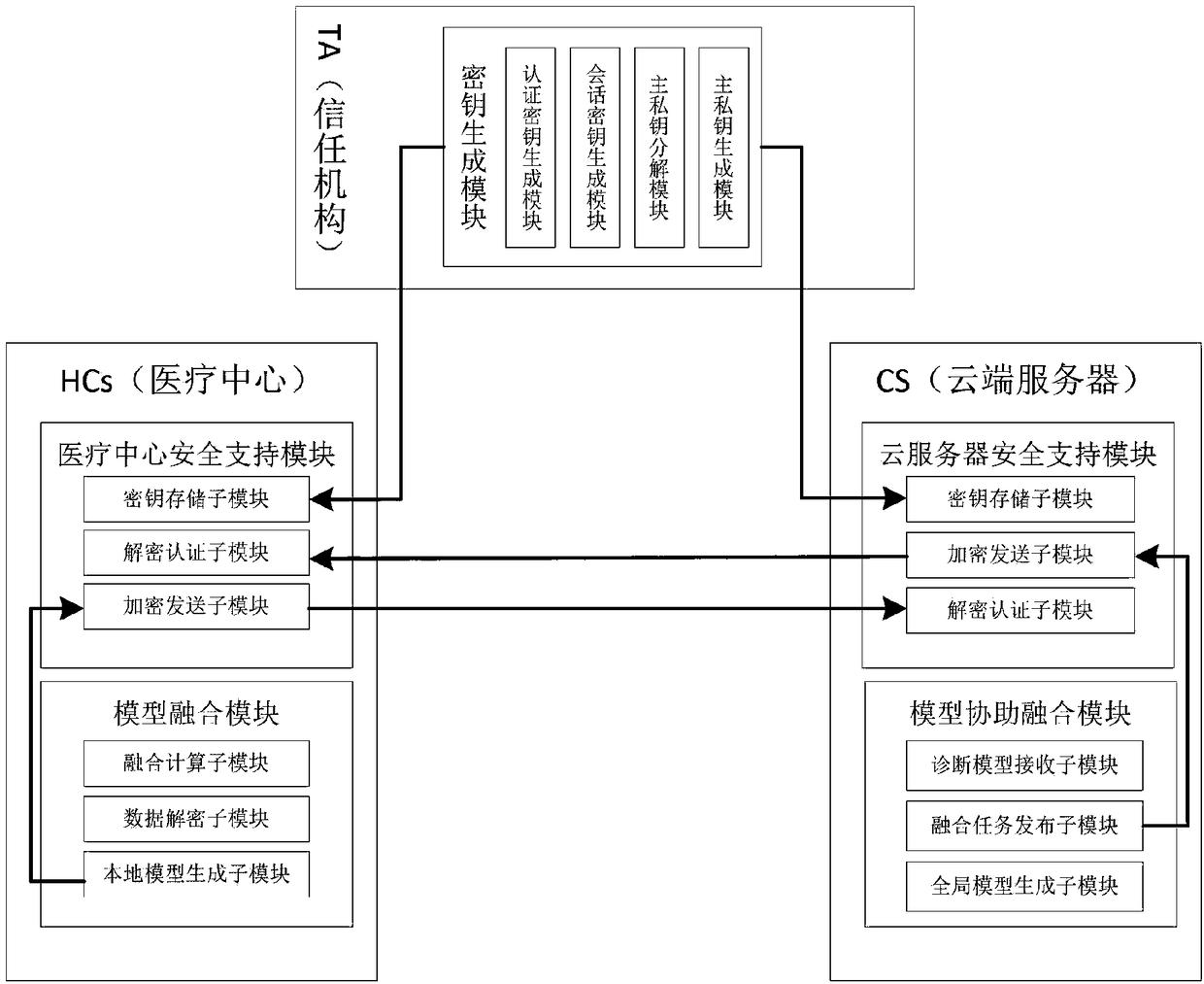
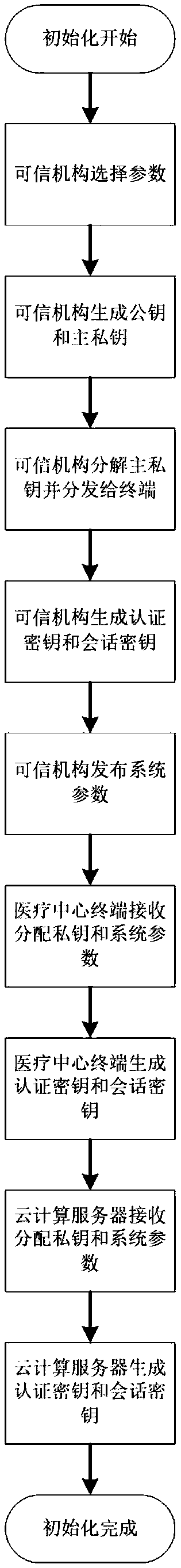
ActiveCN109194523ARealize privacy protectionImprove privacyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPrivacy protectionDiagnostic model
The present invention belongs to the technical field of information safety, and discloses a privacy protection multi-side diagnostic model fusion method and system, and a cloud server. The system comprises a credible mechanism, a cloud server and a medical center terminal. The credible mechanism completes system initialization to provide system parameters and secret key distribution for the medical center terminal and the cloud computing server, the cloud computing server stores encrypted data resources and fuse local diagnostic models to generate a global diagnostic model, the medical centerterminal generates the local diagnostic models, sends the local diagnostic models through encryption to the cloud computing server and is used for fusion computing task published by the cloud computing server, and the medical center terminal and the cloud computing server can perform bidirectional authentication in the service. The privacy protection multi-side diagnostic model fusion method and system, and the cloud server can achieve privacy protection of the local diagnostic models and case data resources of the medical center, can improve the system efficiency and can be used to provide convenient and private online medical service for users in the real life.
Owner:XIDIAN UNIV
Trusted computing-based dynamic management service system and method
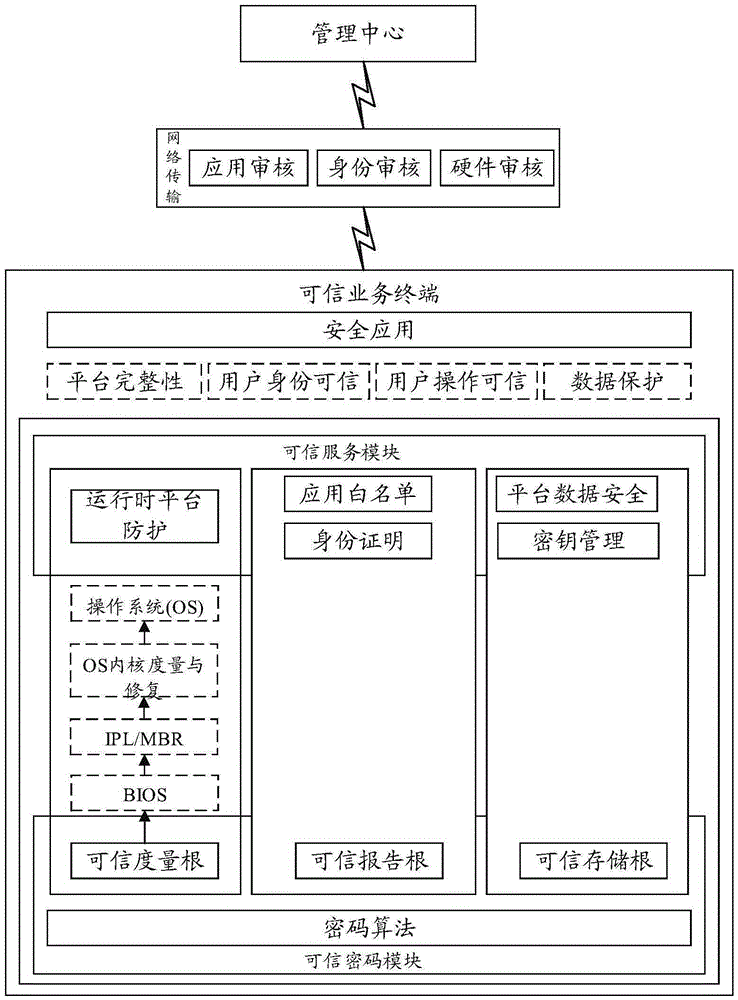
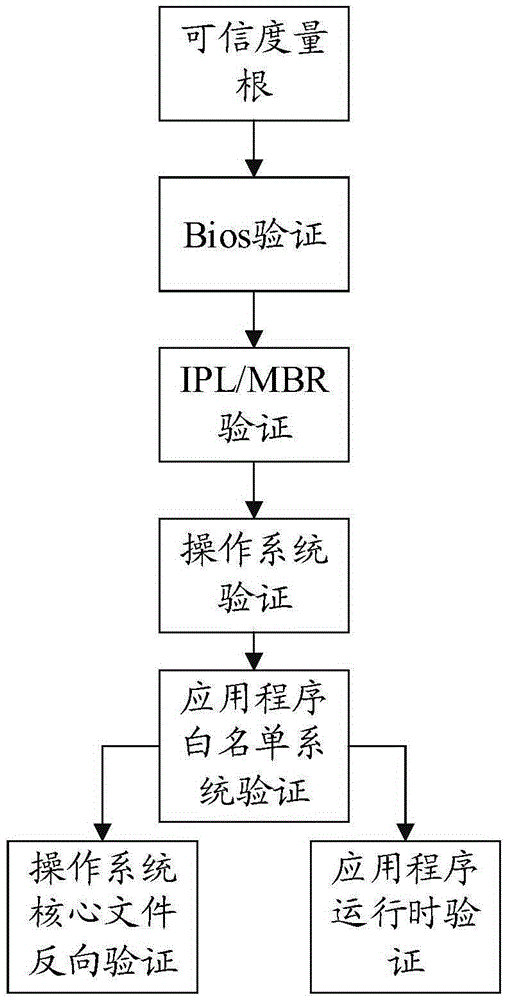
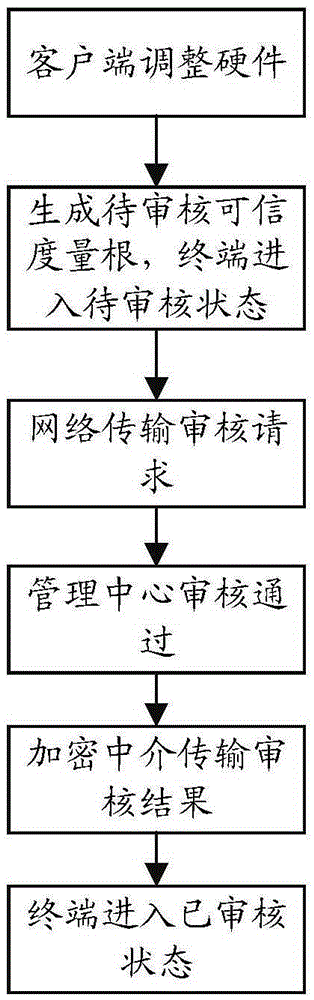
InactiveCN105429808AIntegrity guaranteedAvoid data breachesInternal/peripheral component protectionProgram loading/initiatingOperational systemIdentity recognition
The invention relates to a trusted computing-based dynamic management service system and method. The system comprises a trusted service terminal and a management center; the trusted service terminal comprises a trusted cryptography module for providing a trust measurement root, a trust storage root and a trust report root and realizing a trusted mechanism, and a trusted service module used for providing trusted services; and the management center is used for communicating with the trusted service terminal and verifying the hardware credibility, application credibility and user credibility of the trusted service terminal. With the trusted computing-based dynamic management service system and method adopted, the integrity of hardware and an operating system can be ensured, data leakage and system tampering can be prevented; a trusted identity recognition system is established to identify fake platforms; and a centralized management system is established, so that the configuration performance of clients can be improved.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Safety control system and method
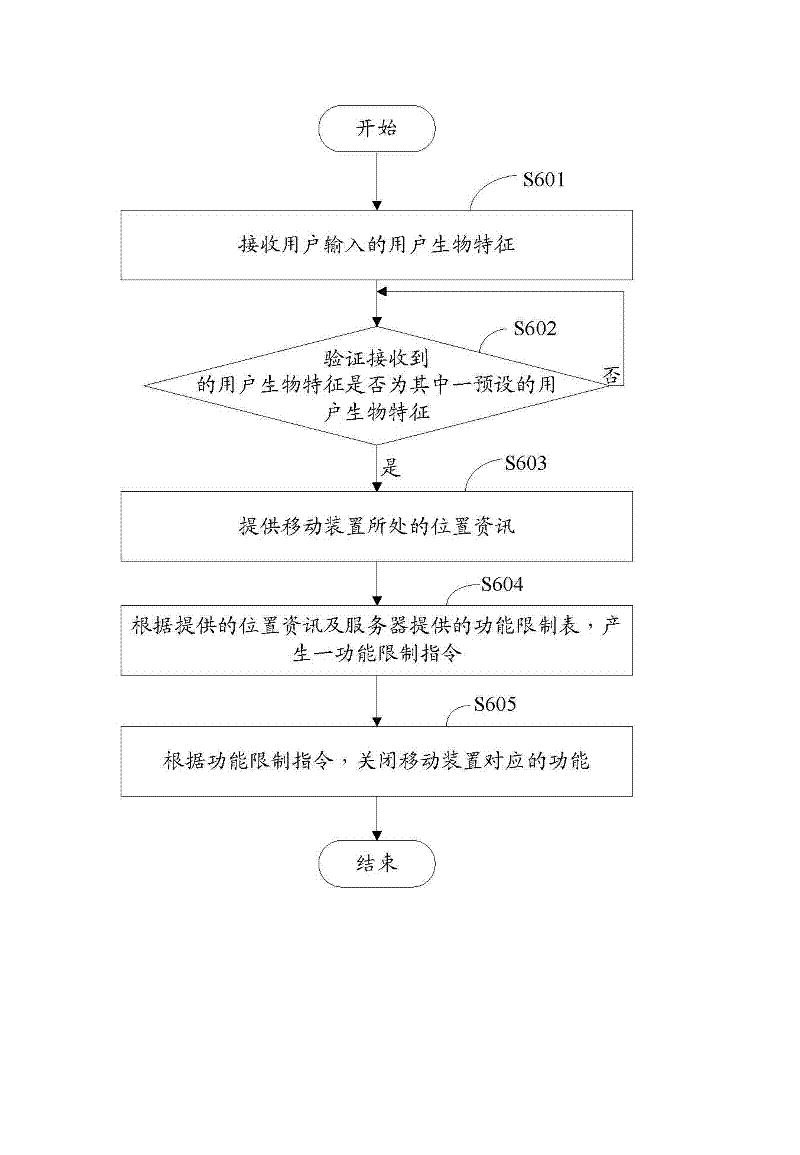
InactiveCN102404686AAvoid data breachesImprove securityLocation information based serviceSecurity arrangementComputer moduleMobile device
The invention provides a safety control system and method. The safety control system is applied between a mobile device and a server, wherein a function limit table is stored in the server, and functions to be closed, corresponding to different position information of the mobile device, are recorded in the function limit table. The safety control system comprises an information offering module, a function limiting module and a function closing module, wherein the information offering module is used for offering the position information of the mobile device; the function limiting module is used for generating a function limit instruction according to the position information offered by the information offering module and the function limit table provided by the server; and the function closing module is used for closing the corresponding functions of the mobile device according to the function limit instruction of the function limit module. By adoption of the safety control system disclosed by the invention, the data safety can be protected.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
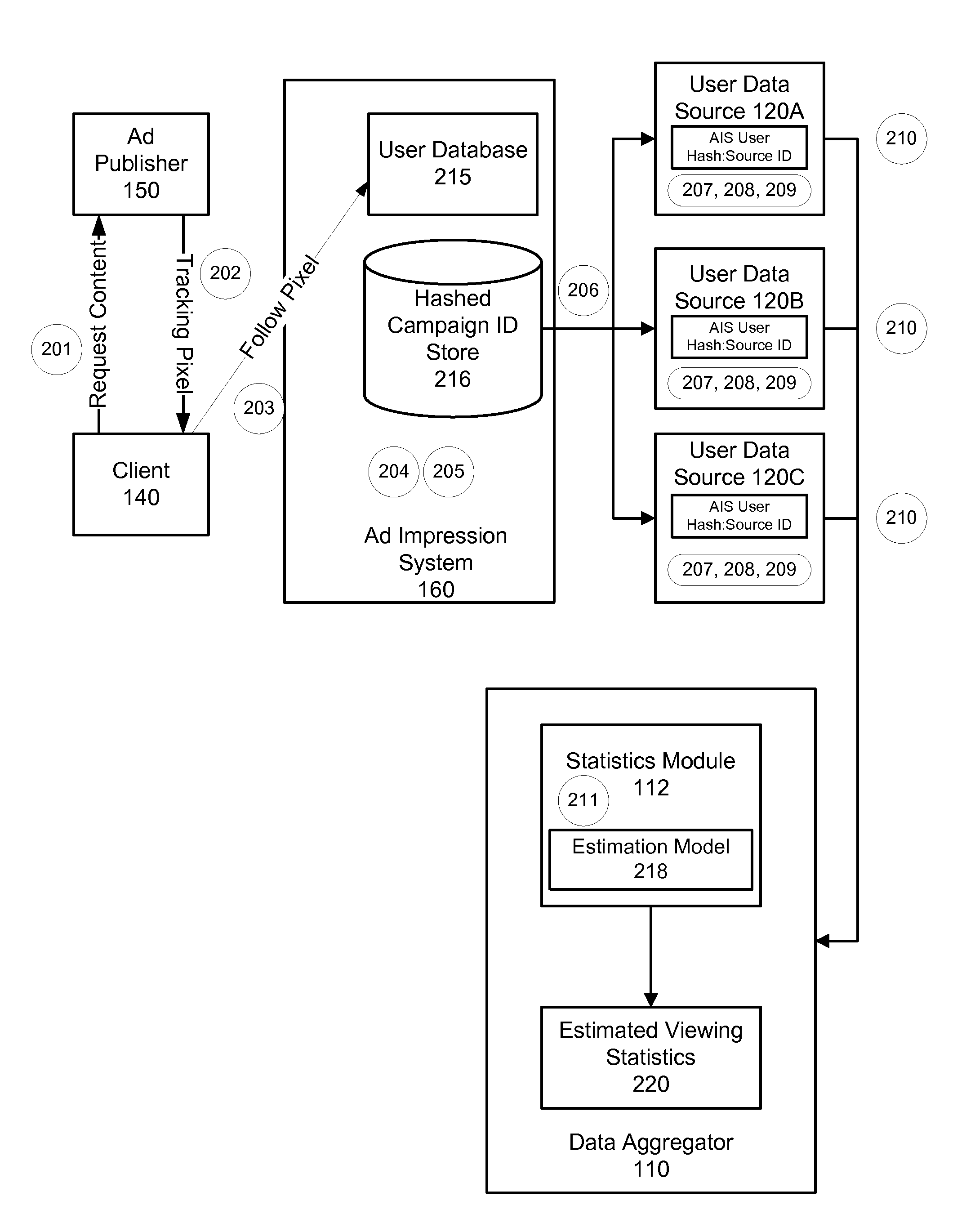
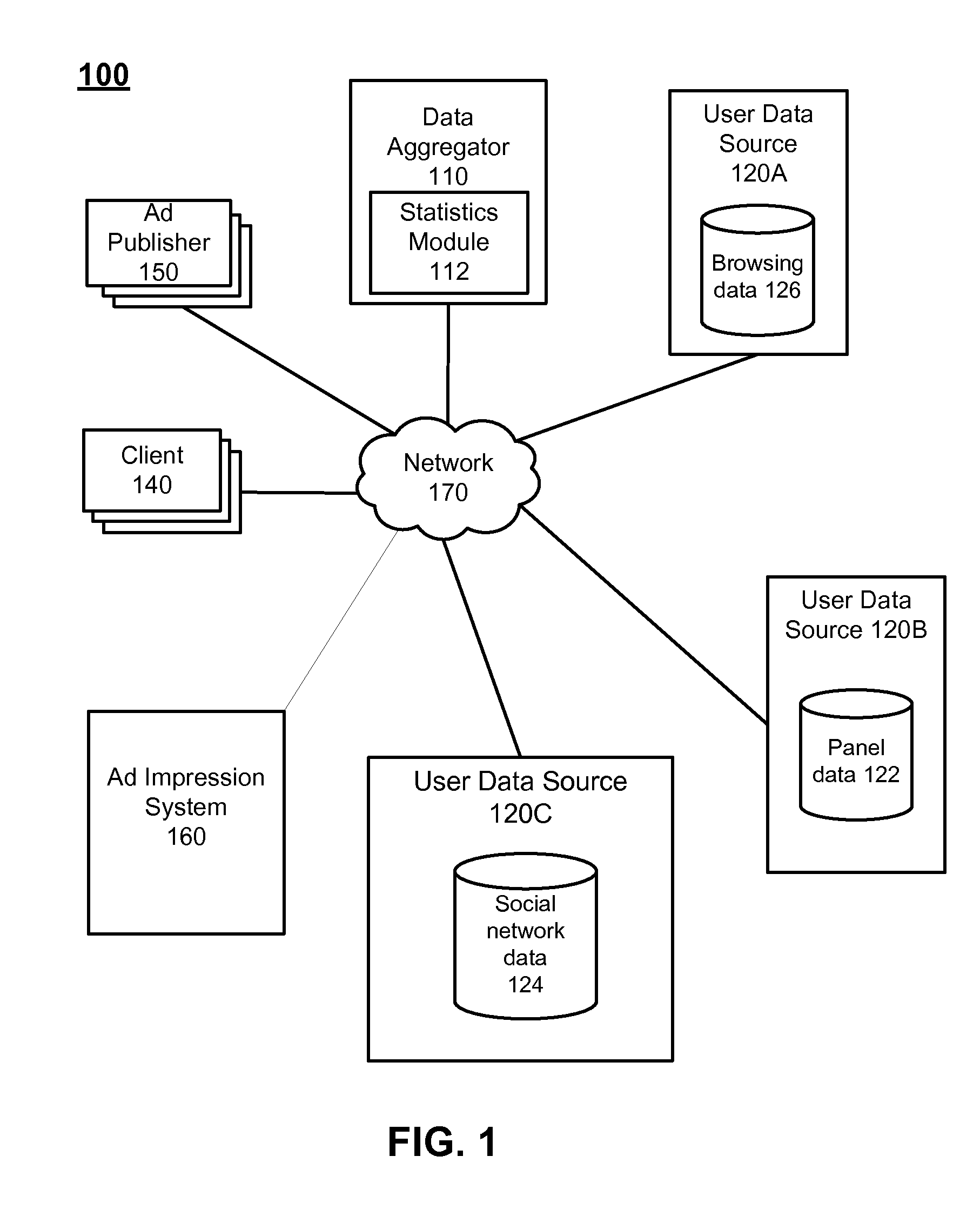
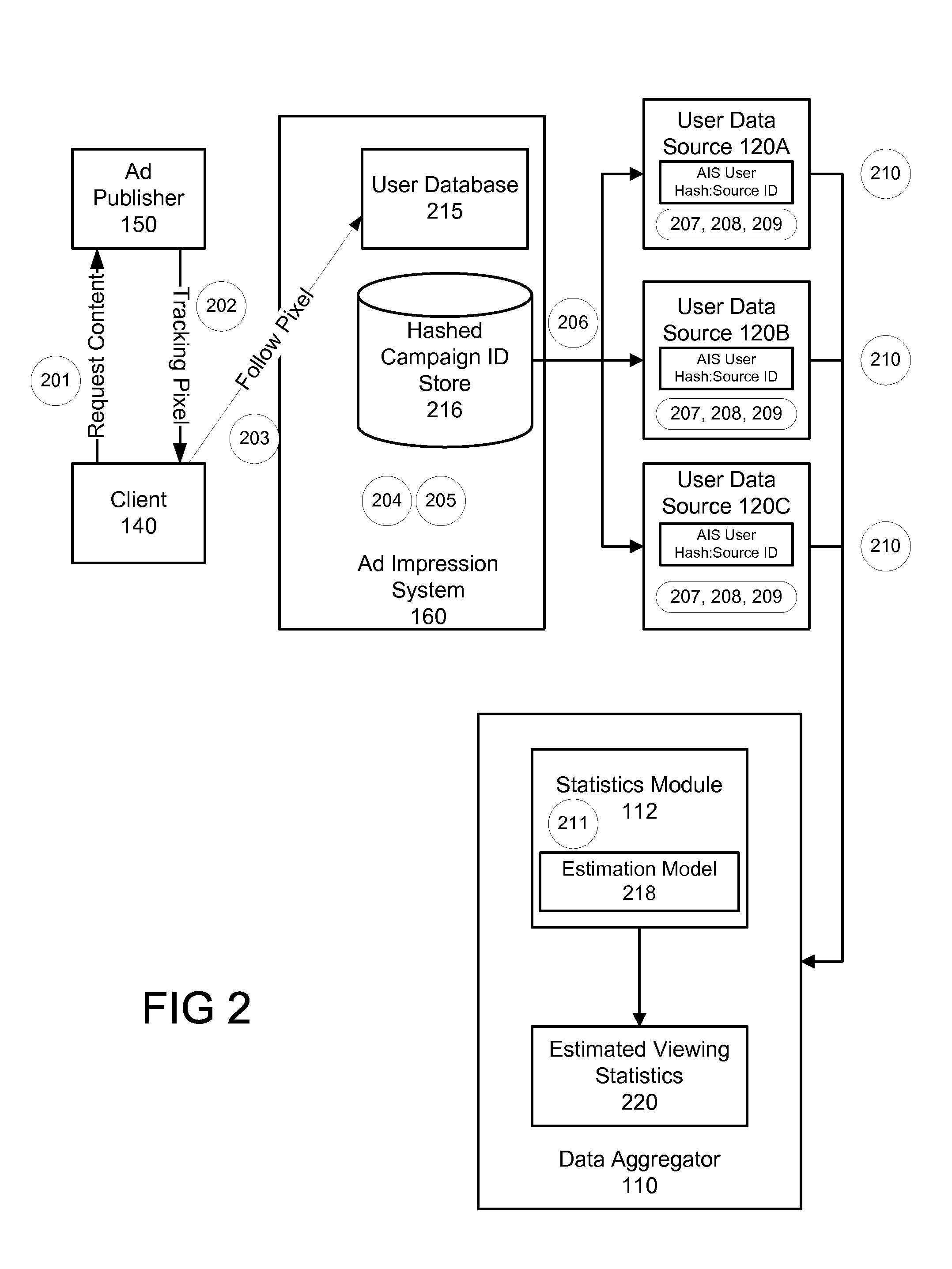
Obtaining Metrics for Online Advertising Using Multiple Sources of User Data
A system for obtaining metrics for online advertising uses multiple sources of user data, including panel data, social networking system data, and user data from other online service providers. An advertising impression system notifies each data source when an advertising impression occurs for an advertising campaign. The user data sources identify users corresponding to the impression by referencing a look-up table that matches a user ID at the advertising impression system with the user ID of users at the user data source. Each user data source generates a demographics report based on the user data known to that user data source. The user data sources transmit the demographics reports to a data aggregator, which determines estimated viewing statistics based on the various user data sources without revealing personally identifiable information from the user data sources.
Owner:META PLATFORMS INC
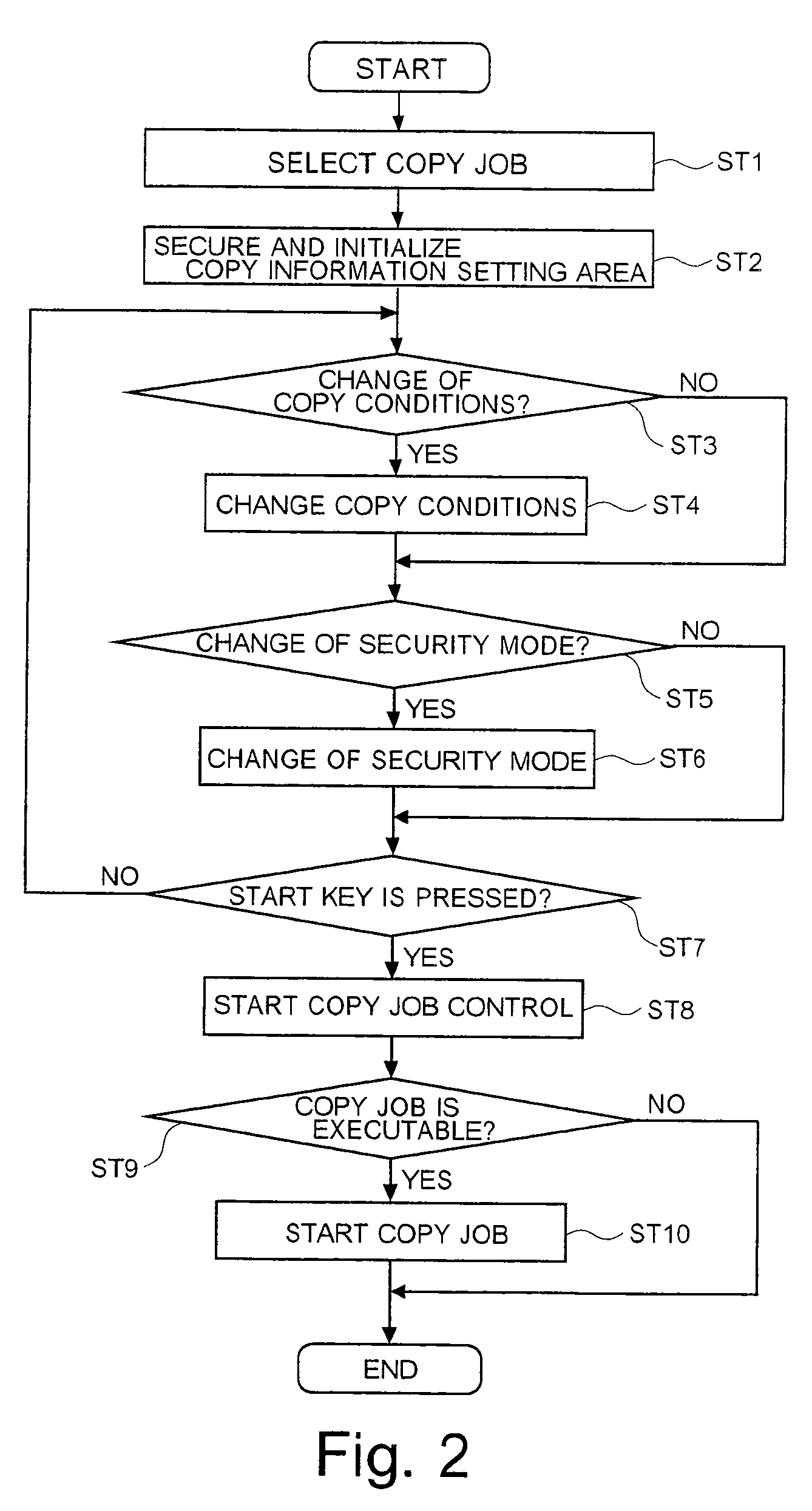
Image Forming Apparatus and Image Forming Method
InactiveUS20070296932A1Prevent leakageAvoid data breachesDigital data protectionPhotographic printingHard disc driveData input
An image forming apparatus includes an image data input unit configured to take in image data, an image data storing unit having a hard disk drive and a volatile memory for saving the image data inputted from the image data input unit, a mode selecting unit configured for a user to select one of a normal security mode and a high security mode as a security mode for the image data, and an image data output unit configured to output the image data saved in the image data storing unit, in a predetermined format. If the normal security mode is selected by the mode selecting unit, the image data is saved in the hard disk drive, and if the high security mode is selected, the image data is saved in the volatile memory.
Owner:KK TOSHIBA +1
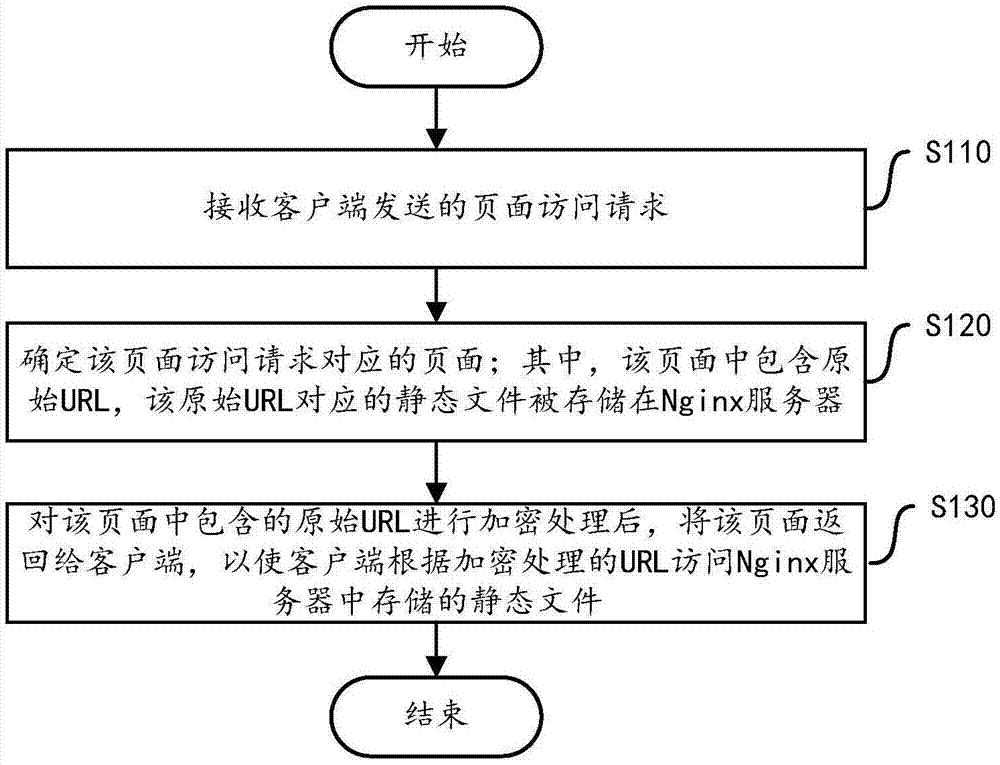
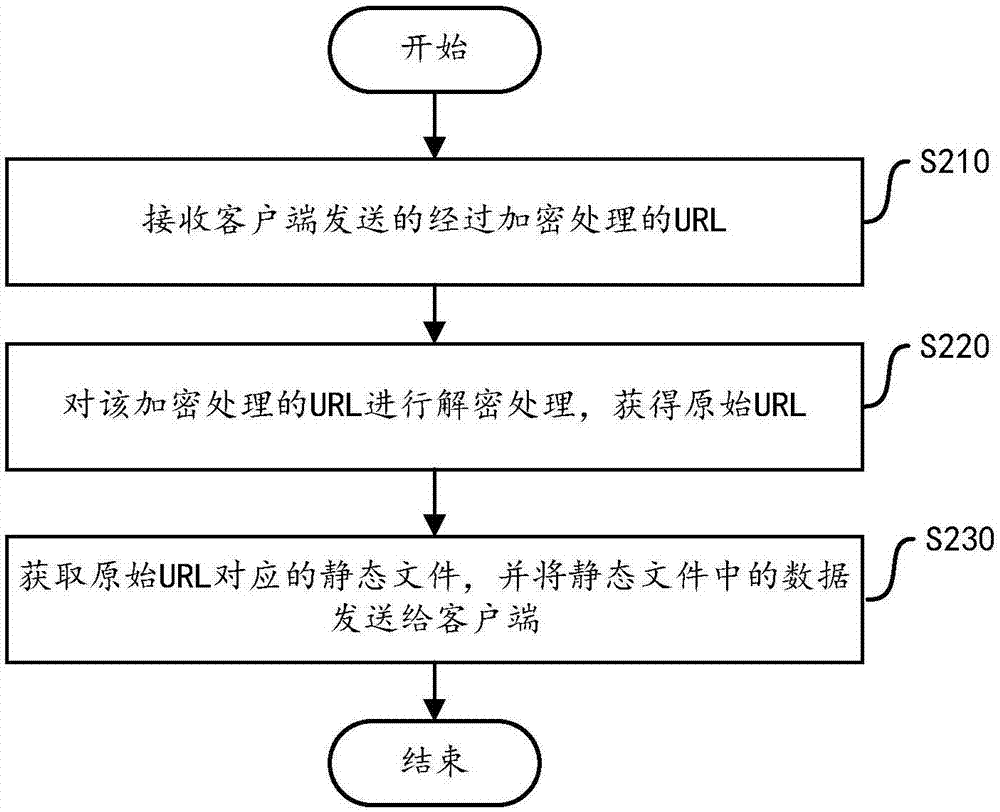
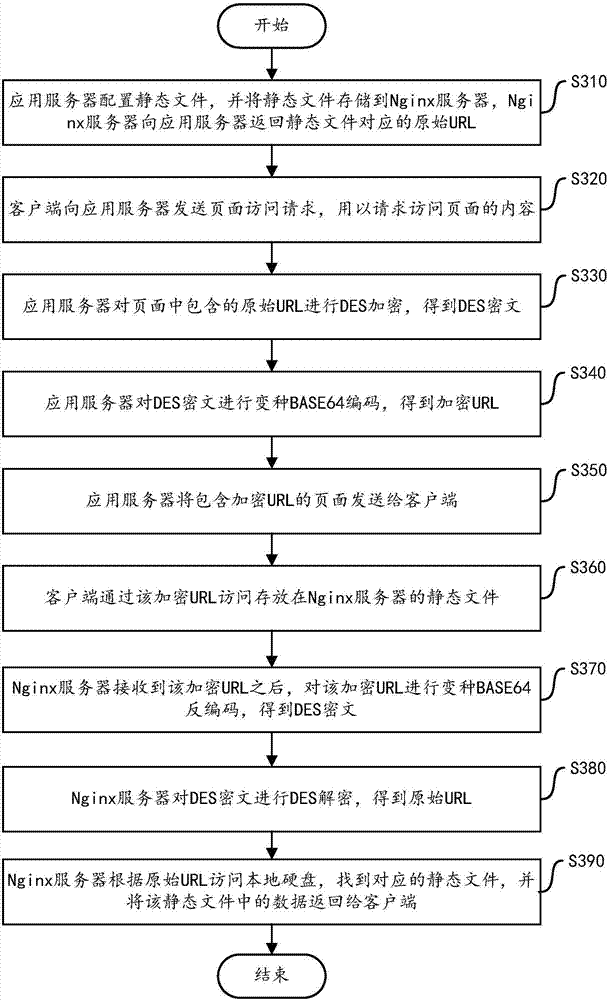
Static file access method and device based on Nginx
The invention discloses a static file access method and device based on Nginx. The method comprises the following steps executed at an application server side: receiving a page access request sent bya client; determining a page corresponding to a page access request, wherein the page contains the original URL; and returning the page to a client after performing the encryption processing in the original URL included in the page. The method comprises the following steps executed at a Nginx server side: receiving the encrypted URL sent by the client; and decrypting the encrypted URL to acquire the original URL; acquiring a static file corresponding to the original URL, and sending the data in the static file to the client. The application server provided by the invention encrypts the staticfile in a saving path in the Nginx server, and sends the URL in a ciphertext way to the client, thereby enabling the client to access the static file in the Nginx server according to the URL in the ciphertext way, and then the problem of data leakage caused by intercepting the URL is avoided, and the security of the Nginx server is improved.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com