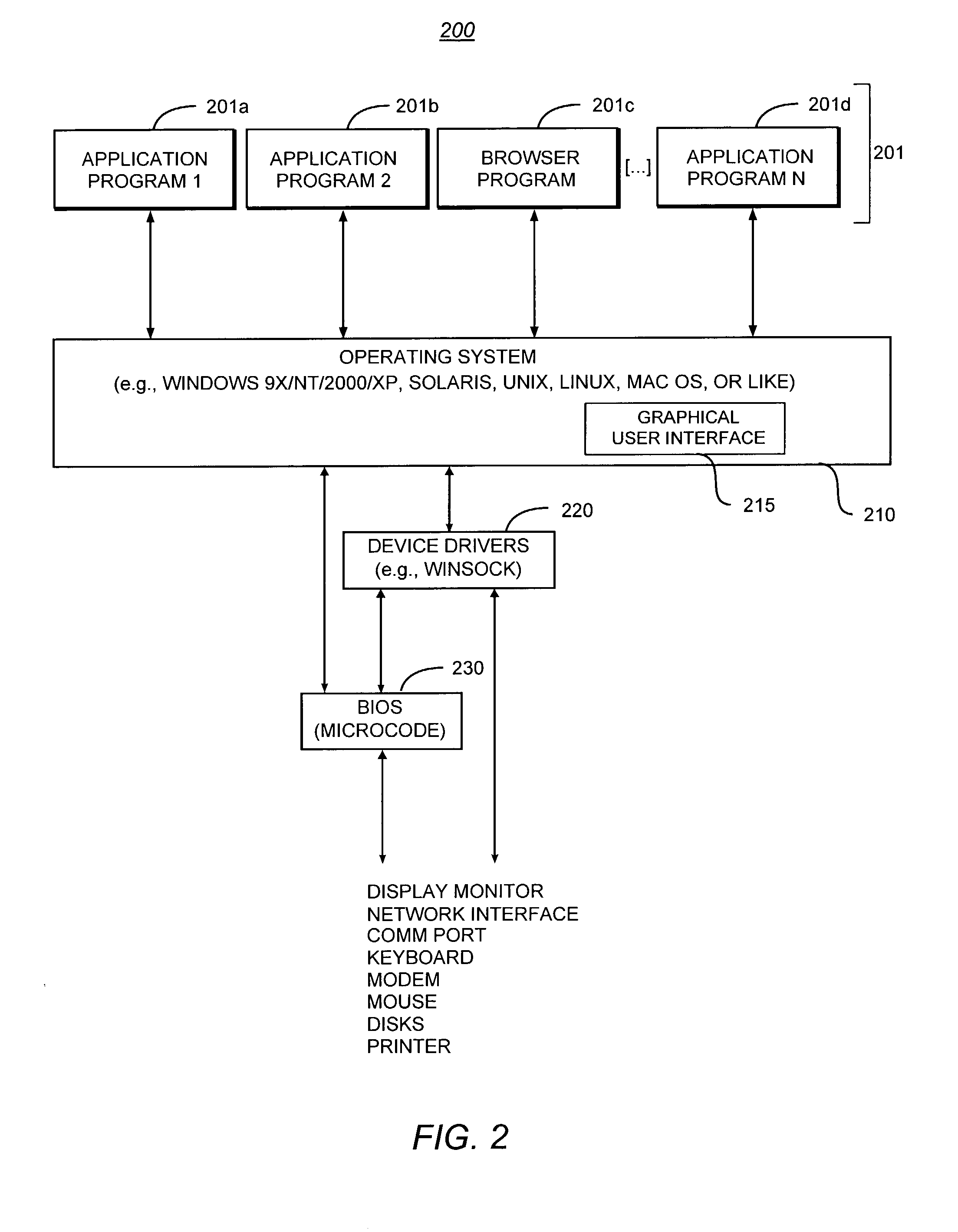
Patents
Literature
43549 results about "Computer security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer security, cybersecurity or information technology security (IT security) is the protection of computer systems from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.
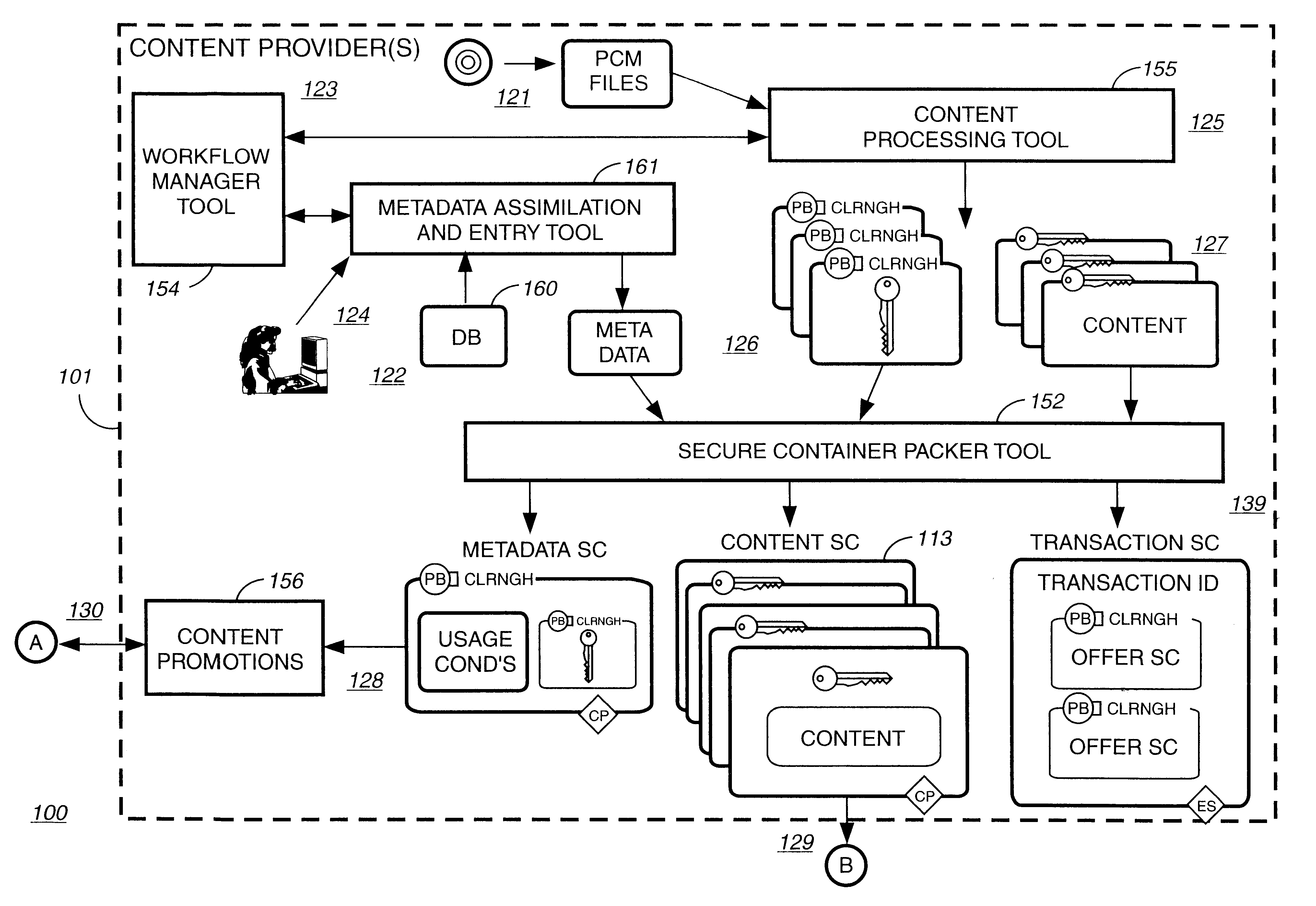
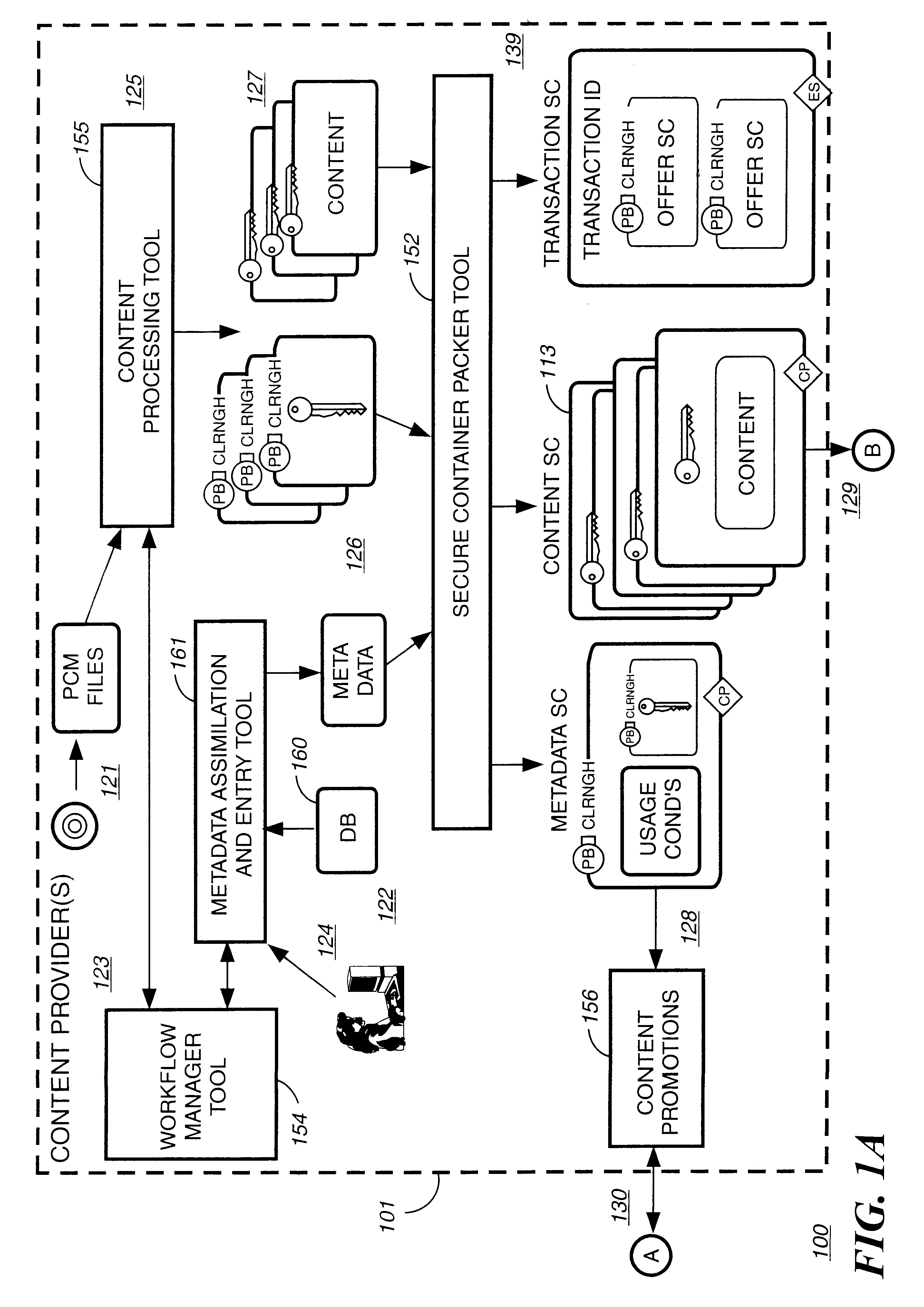
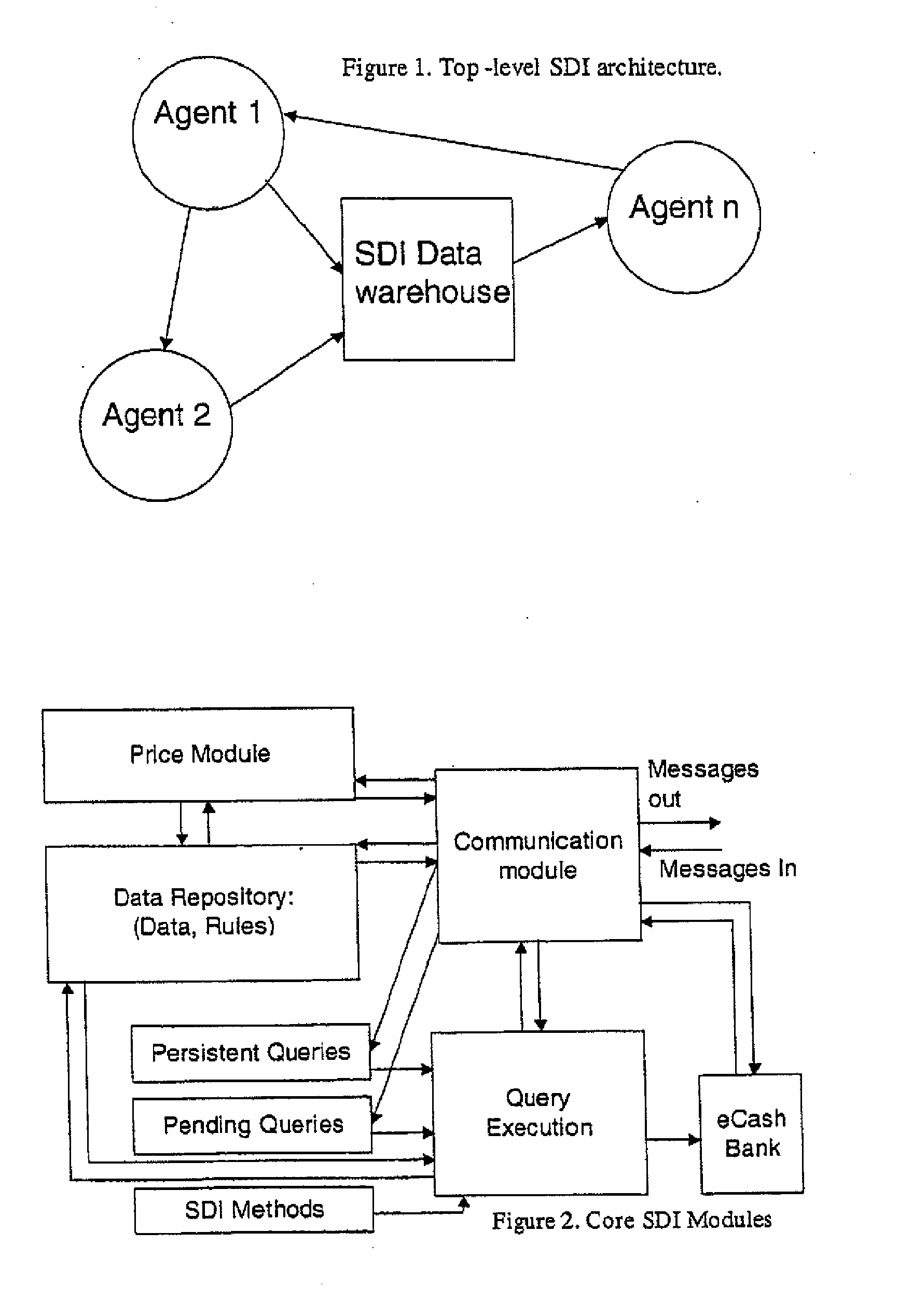
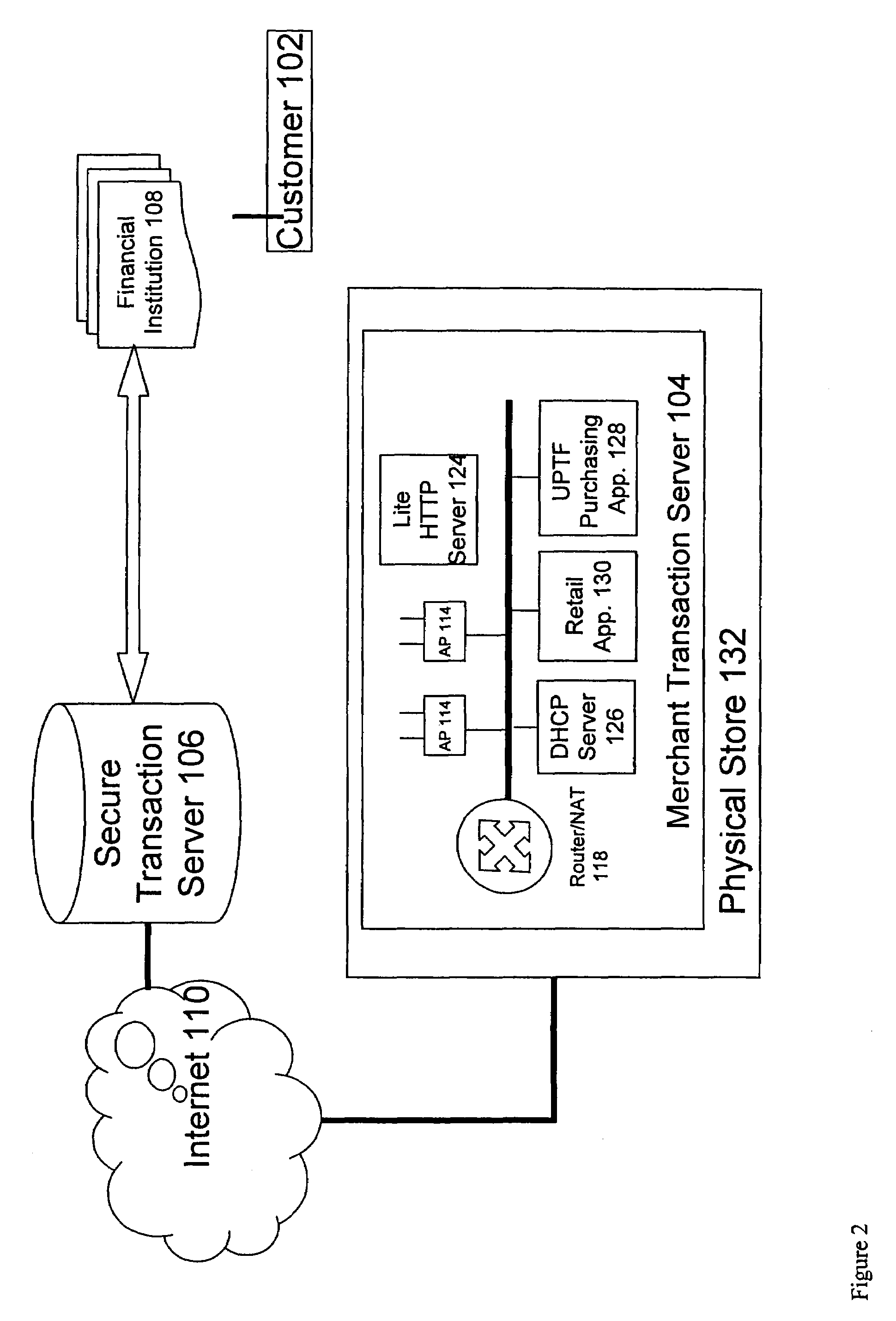
Electronic content delivery system
InactiveUS6226618B1Key distribution for secure communicationDigital data processing detailsDelivery systemSystem safety
Disclosed is a method and apparatus of securely providing data to a user's system. The data is encrypted so as to only be decryptable by a data decrypting key, the data decrypting key being encrypted using a first public key, and the encrypted data being accessible to the user's system, the method comprising the steps of: transferring the encrypted data decrypting key to a clearing house that possesses a first private key, which corresponds to the first public key; decrypting the data decrypting key using the first private key; re-encrypting the data decrypting key using a second public key; transferring the re-encrypted data decrypting key to the user's system, the user's system possessing a second private key, which corresponds to the second public key; and decrypting the re-encrypted data decrypting key using the second private key.
Owner:LEVEL 3 COMM LLC
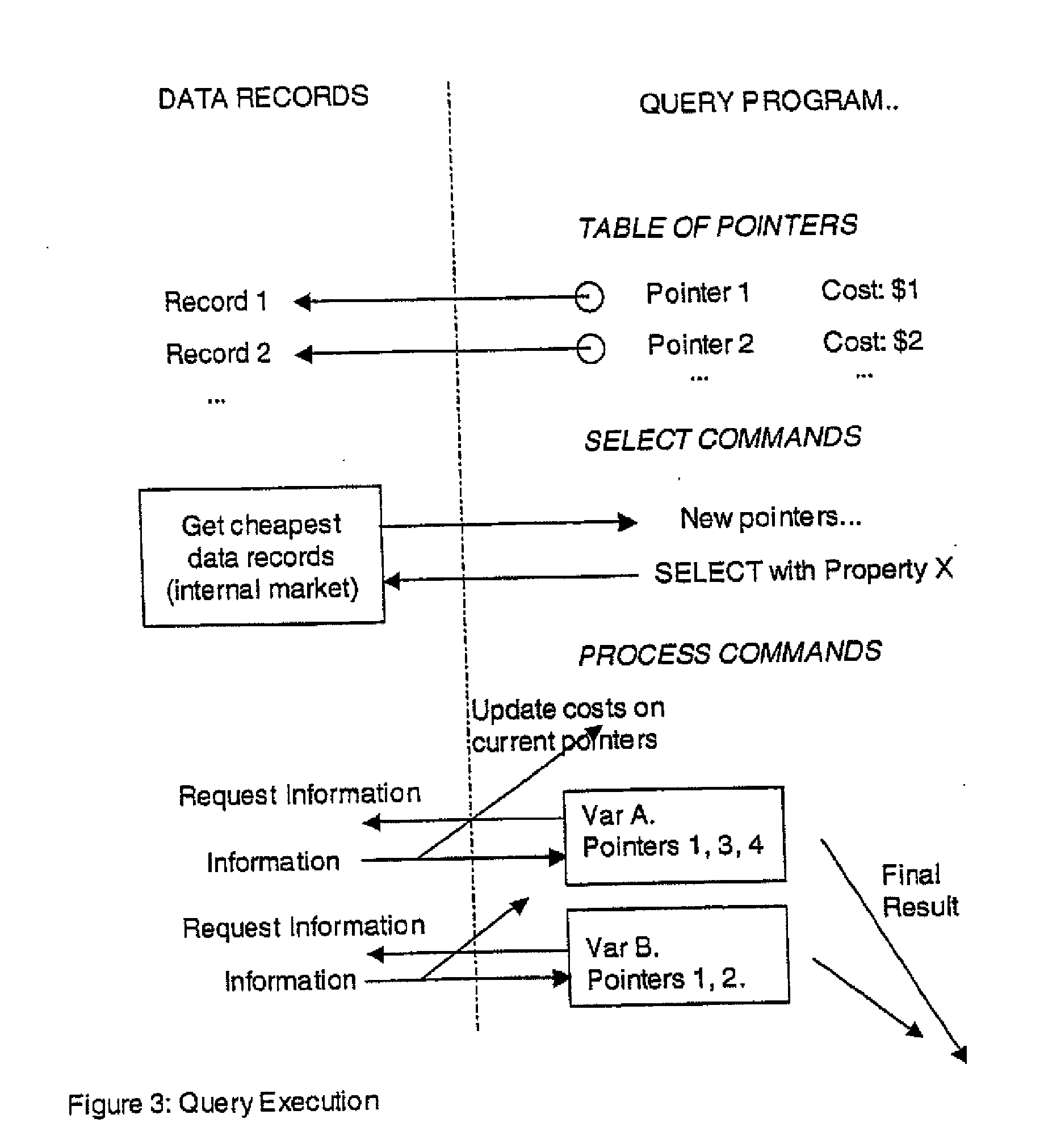
Secure data interchange
InactiveUS20090254971A1Improve privacyLimited accessDigital data processing detailsAnalogue secracy/subscription systemsInformation accessData interchange
A secure data interchange system enables information about bilateral and multilateral interactions between multiple persistent parties to be exchanged and leveraged within an environment that uses a combination of techniques to control access to information, release of information, and matching of information back to parties. Access to data records can be controlled using an associated price rule. A data owner can specify a price for different types and amounts of information access.
Owner:STRIPE INC
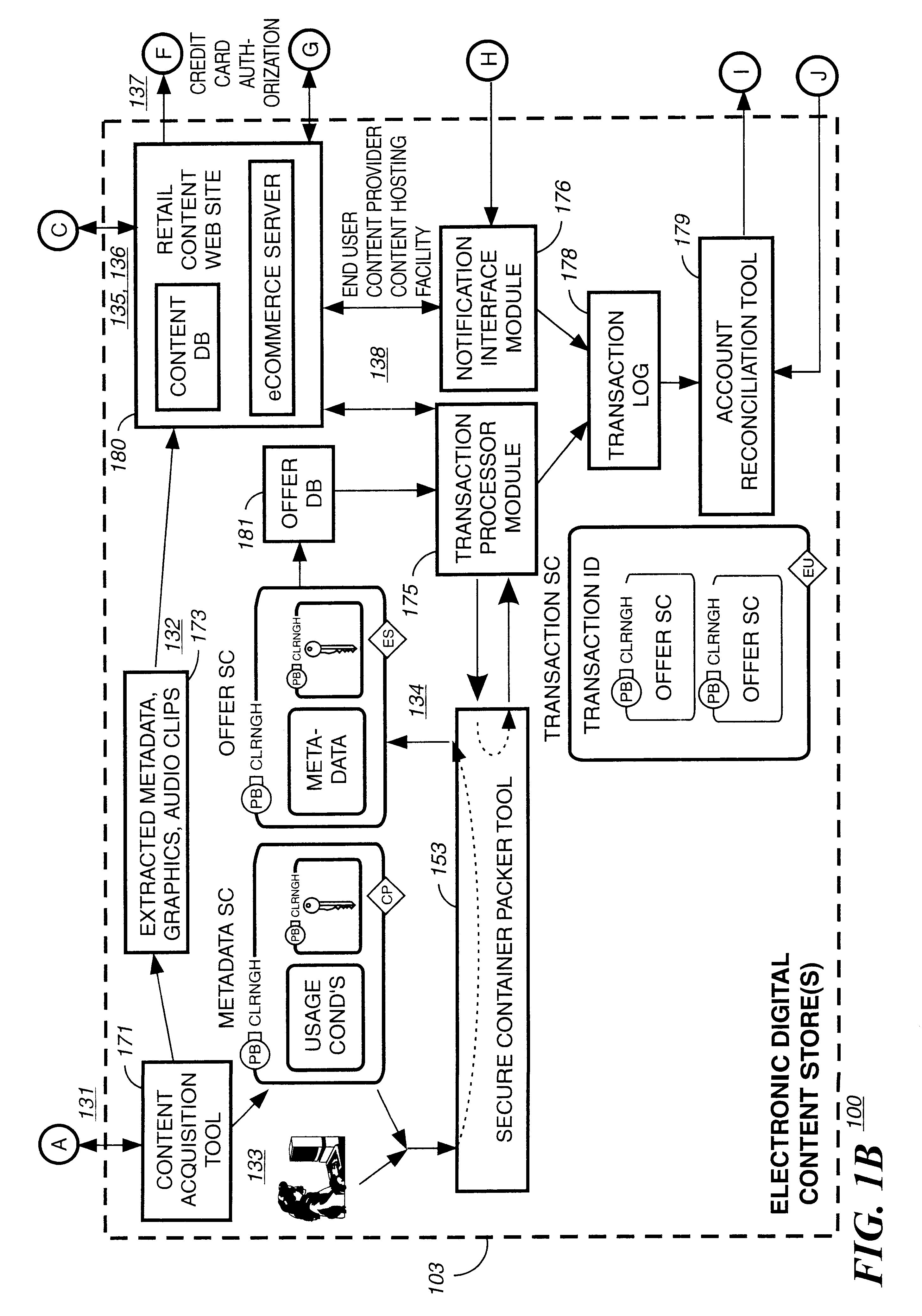
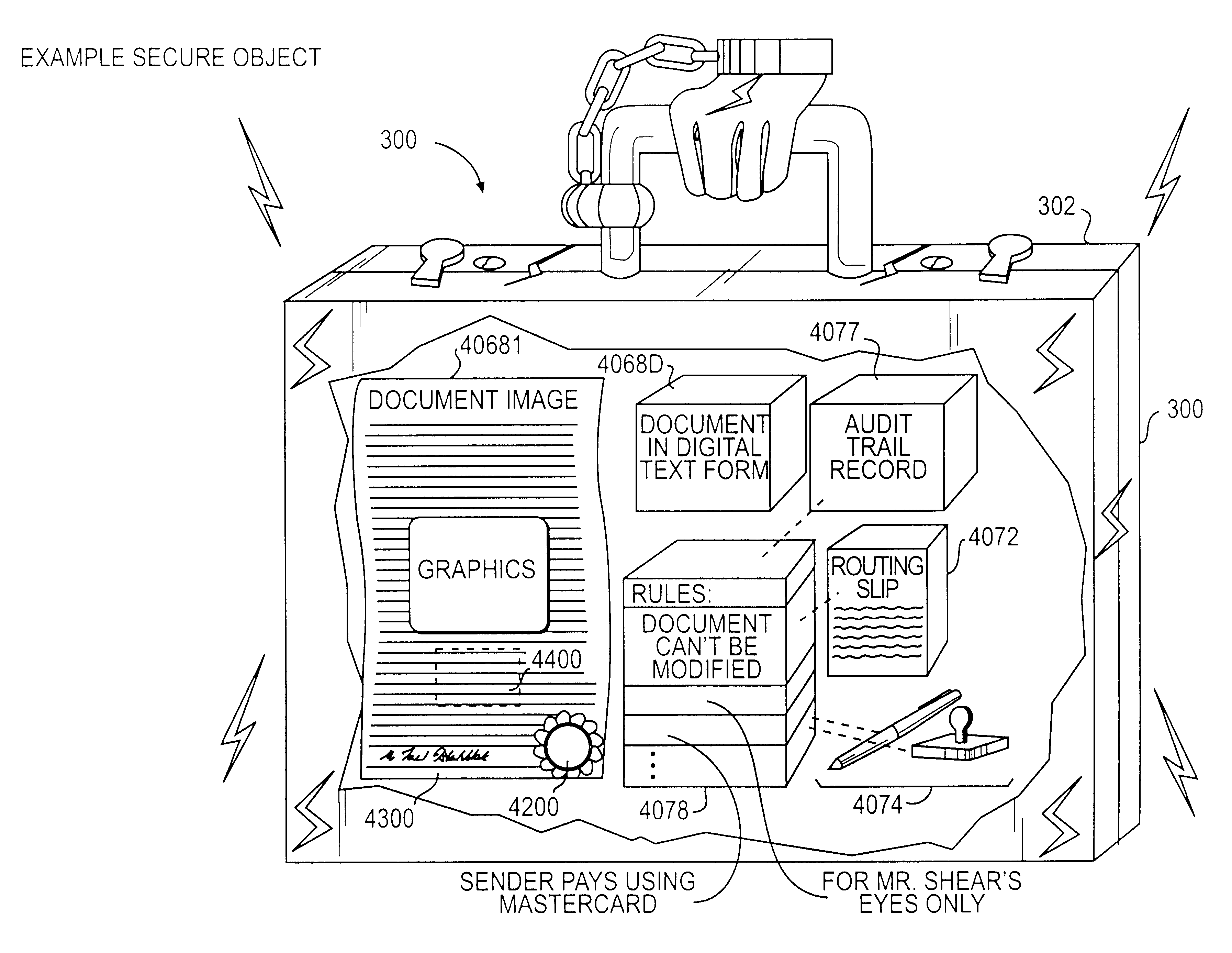
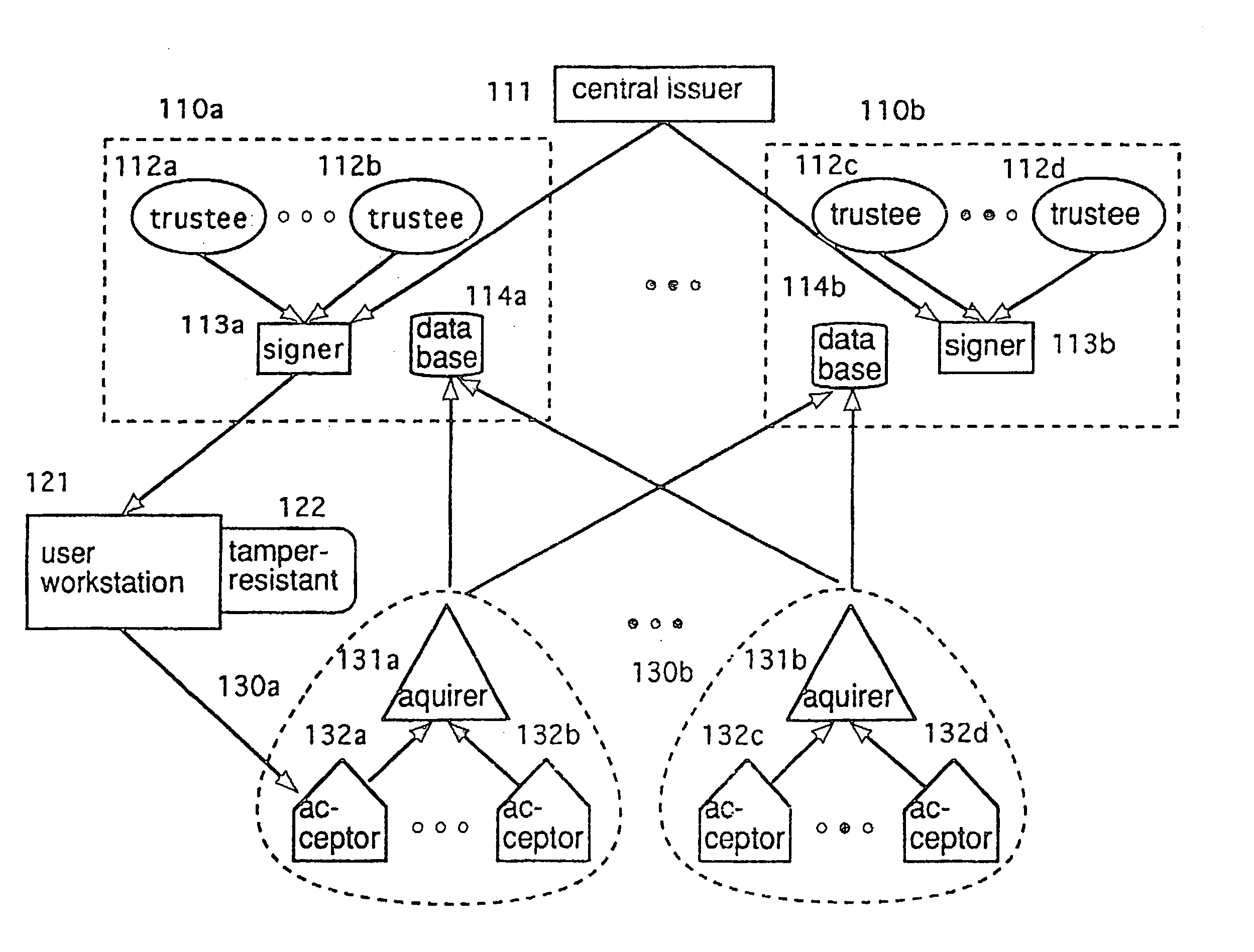
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
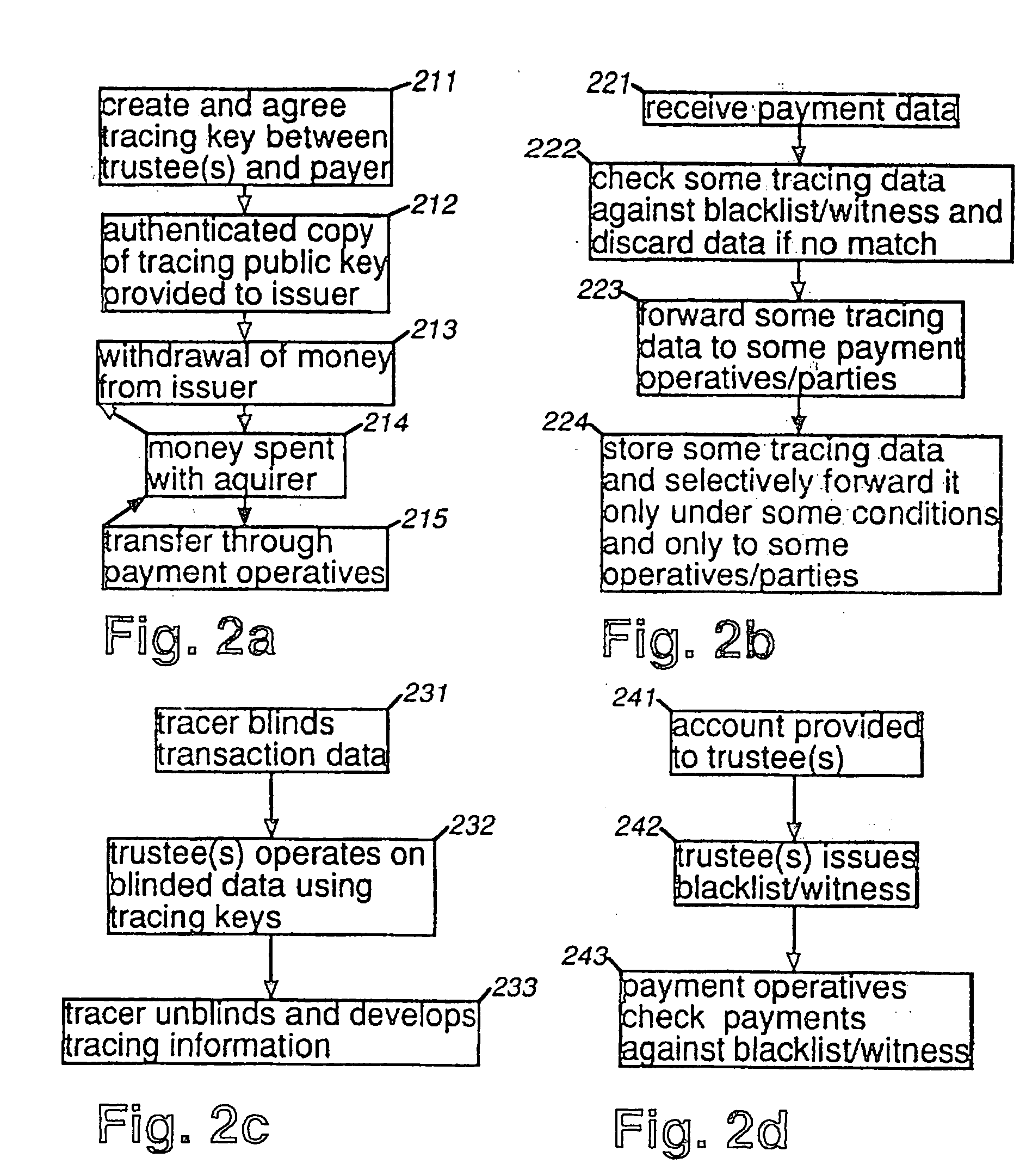
RFID mutual authentication verification session
ActiveUS7450010B1Privacy can be assuredElectric signal transmission systemsDigital data processing detailsMutual authenticationComputer security
Owner:AMTECH SYST
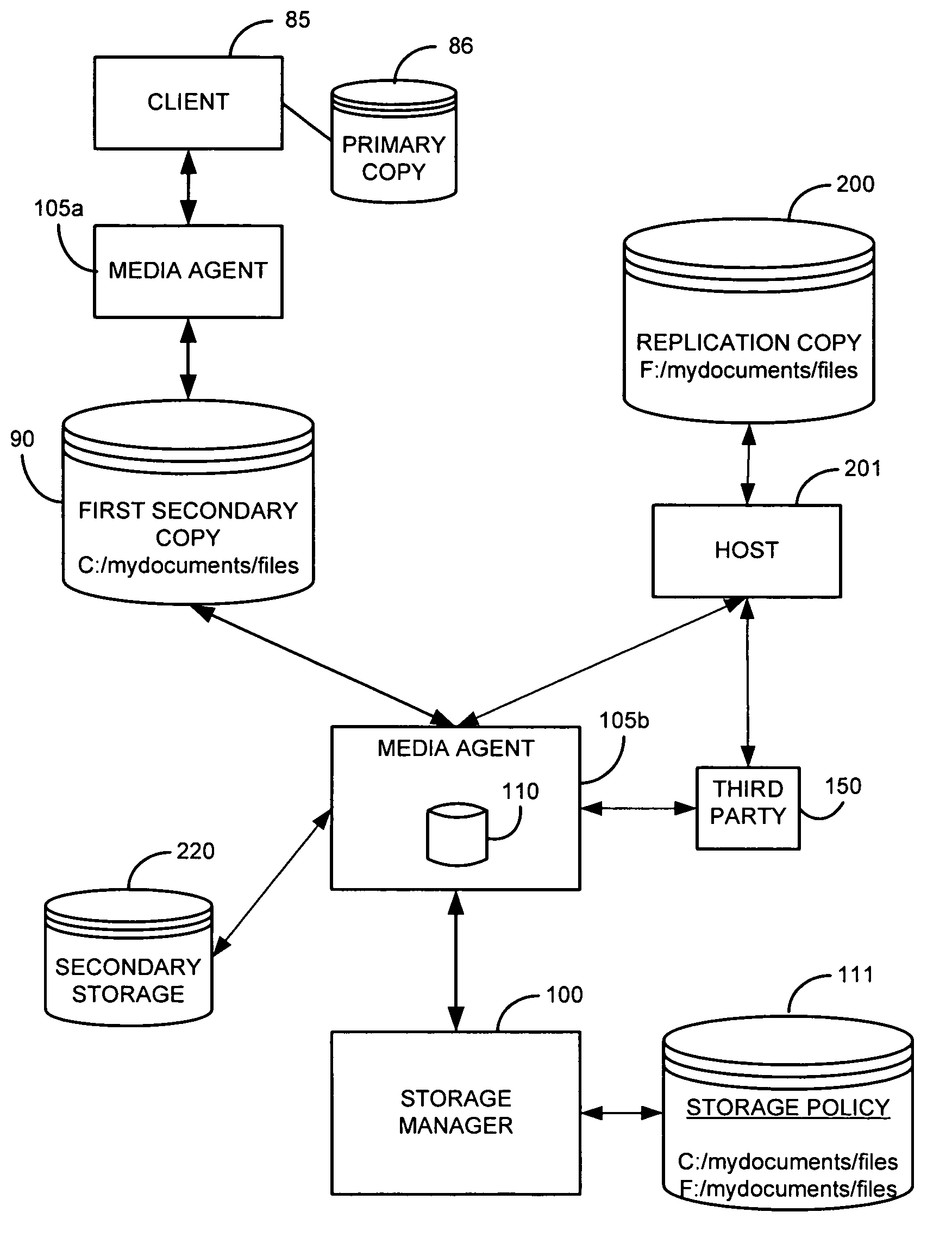
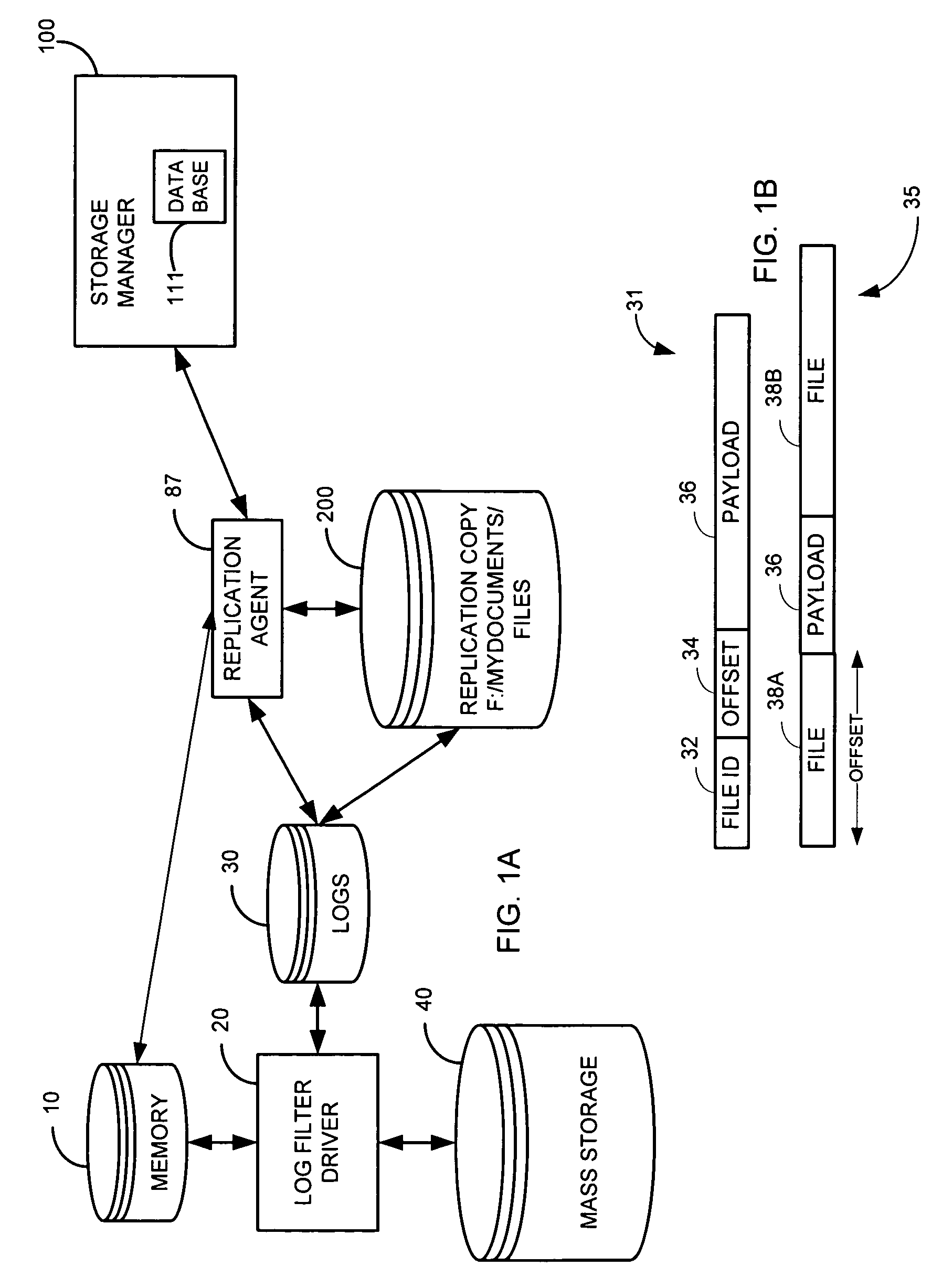
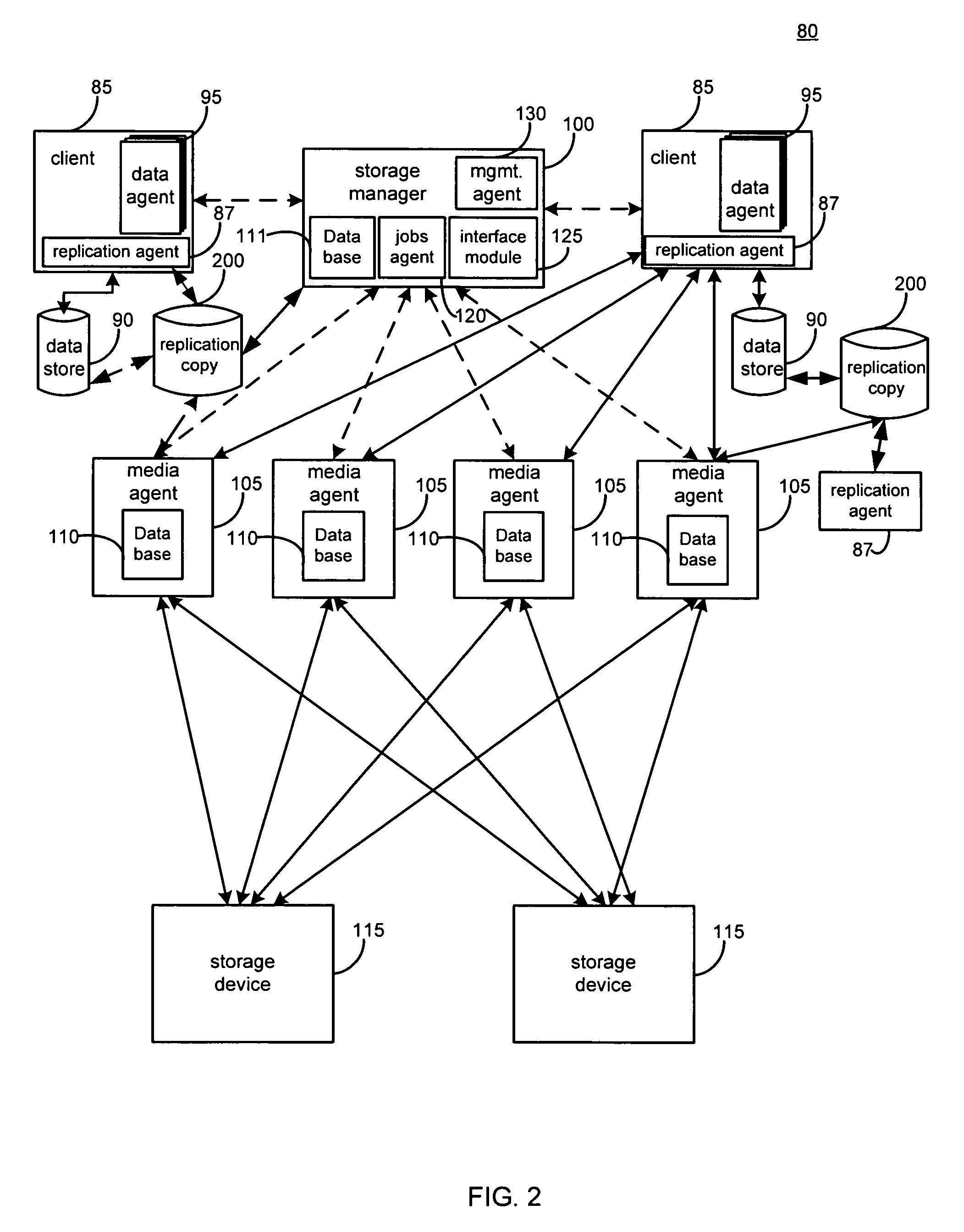
System and method for performing replication copy storage operations
InactiveUS7606844B2Data processing applicationsDatabase distribution/replicationThird partyEngineering
A system and method are provided for performing storage operations relating to a first secondary copy of electronic data. A storage policy or storage preferences may dictate that a replication copy should be used in storage operations performed to a particular client, sub-client, data, media or other item. Based on the storage policy, when a new client, sub-client, data, media or other item is received, a media agent determines whether there is a replication copy of the item. In the absence of a replication copy, one may be created. The replication copy may be provided by a third party application, or created by the client or a storage management system component. Information regarding the replication copy and its corresponding first secondary copy may be stored in a database. To optimize use of system resources, storage operations relating to the first secondary copy may be performed using the replication copy instead of the first secondary copy.
Owner:COMMVAULT SYST INC
Methods and systems for sharing risk responses between collections of mobile communications devices
Methods are provided for determining an enterprise risk level, for sharing security risk information between enterprises by identifying a security response by a first enterprise and then sharing the security response to a second enterprise when a relationship database profile for the first collection indicates the security response may be shared. Methods are also provided for determining whether to allow a request from an originating device where the request may have been initiated by a remote device.
Owner:LOOKOUT MOBILE SECURITY
System and method for policy management
InactiveUS20070180490A1Computer security arrangementsSpecial data processing applicationsStrategy makingComputer security
The invention provides a system and method for providing policy-based protection services. As a new threat is understood, one or more protection techniques are considered for protecting the asset, the organization assigns responsibilities to carry out or protect the asset, and a policy is constructed. After the policy is developed a plan is put into action to protect the asset, and a policy implementer is developed and / or purchased, distributed, configured, and managed. Finally, the policy, its enforcement, and its effectiveness, are reviewed to determine any changes needed, and new requirements are discovered, closing the lifecycle.
Owner:ALLEGENT TECH GROUP
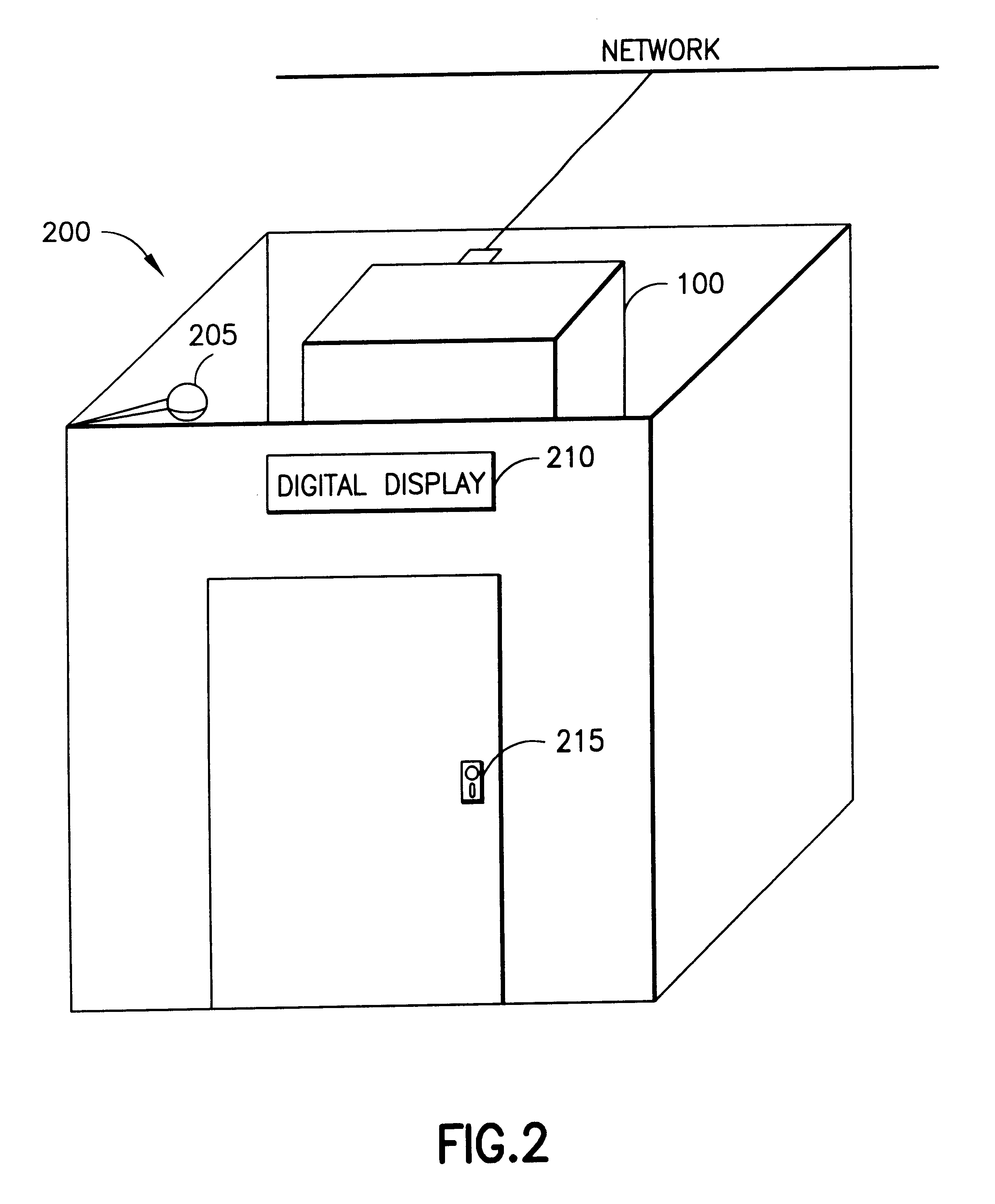
Method and apparatus for registering a mobile device with a gaming machine
InactiveUS20060189382A1User identity/authority verificationCard gamesComputer hardwareCommunications system
Disclosed are methods, apparatus, and systems, including computer program products, implementing techniques for securing a gaming machine for a player of the gaming machine using a mobile device such as a cell phone associated with the player. A player input requests securing of the gaming machine. Responsive to the player input, an access code and a security code are retrieved. The access code defines an access point of a communication system. The security code is specific to a game play session for the player at the gaming machine. The retrieved access code and security code are provided for the player. When the mobile device accesses the communications system and submits the security code, a secure signal is sent to the gaming machine, instructing the gaming machine to enter a remote game play state. The gaming machine can be released from the remote game play state responsive to a releasing event. In one implementation, a wireless interface enables communication between the mobile device and gaming machine according to a wireless protocol such as Bluetooth.
Owner:IGT
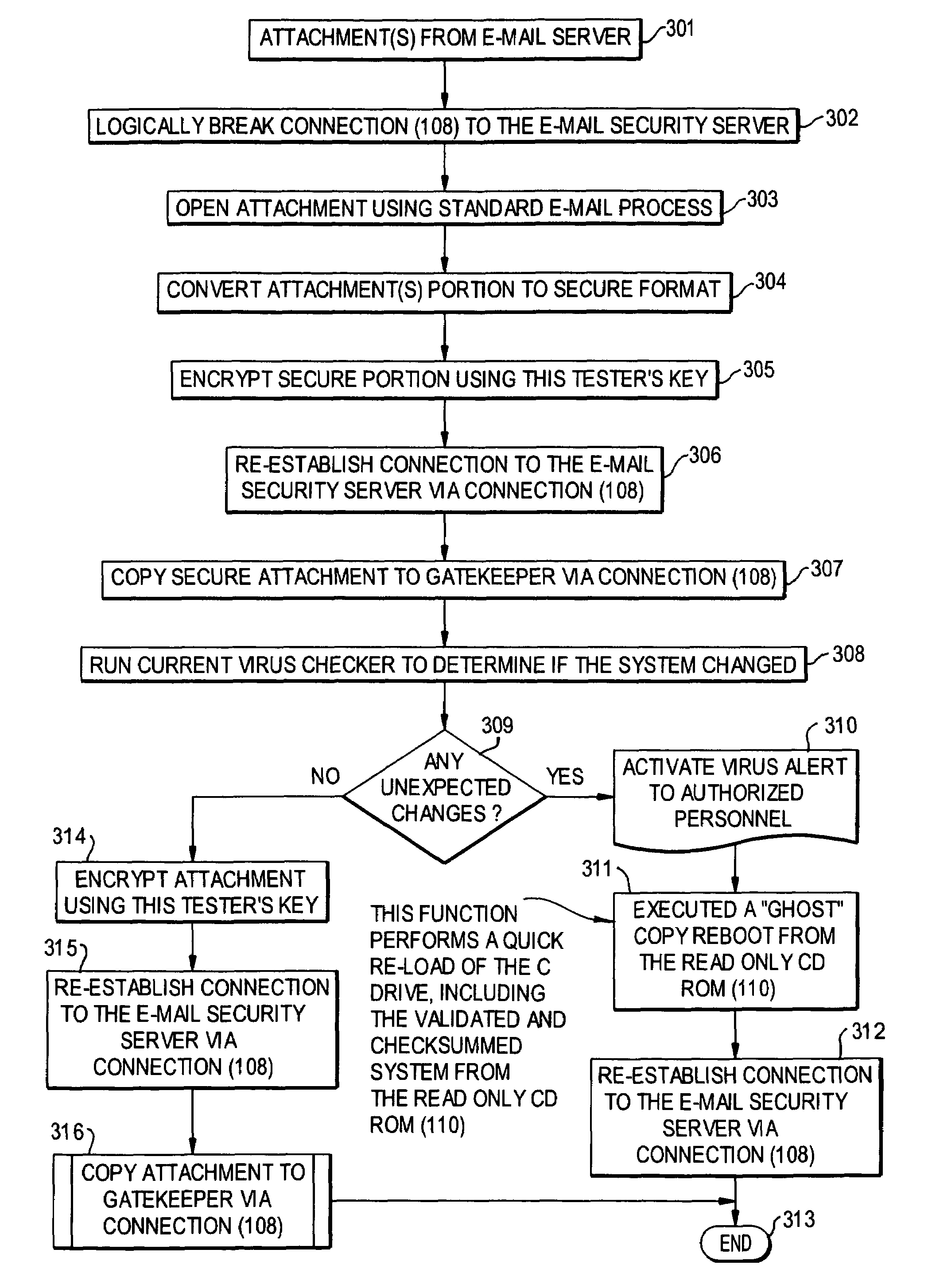
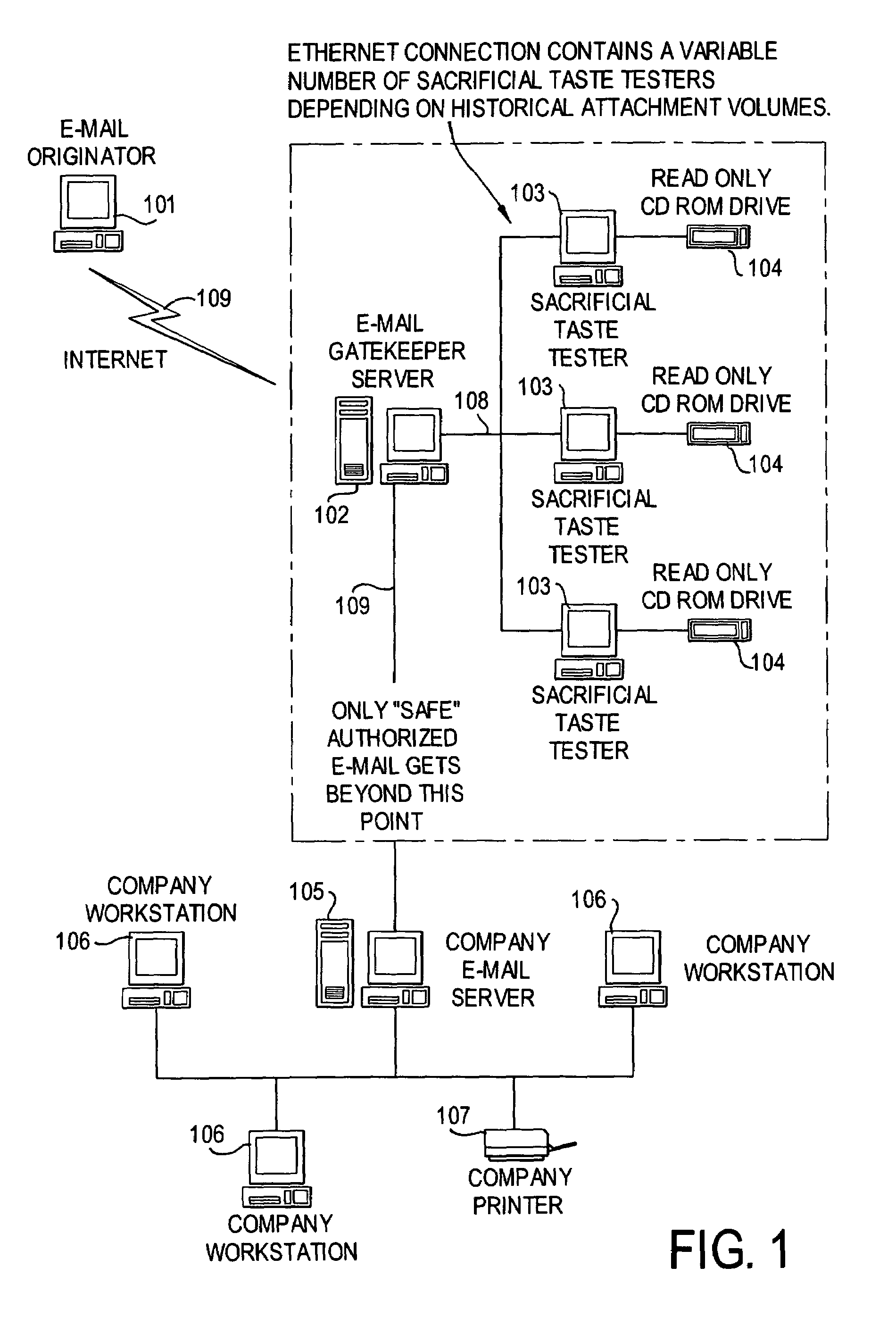
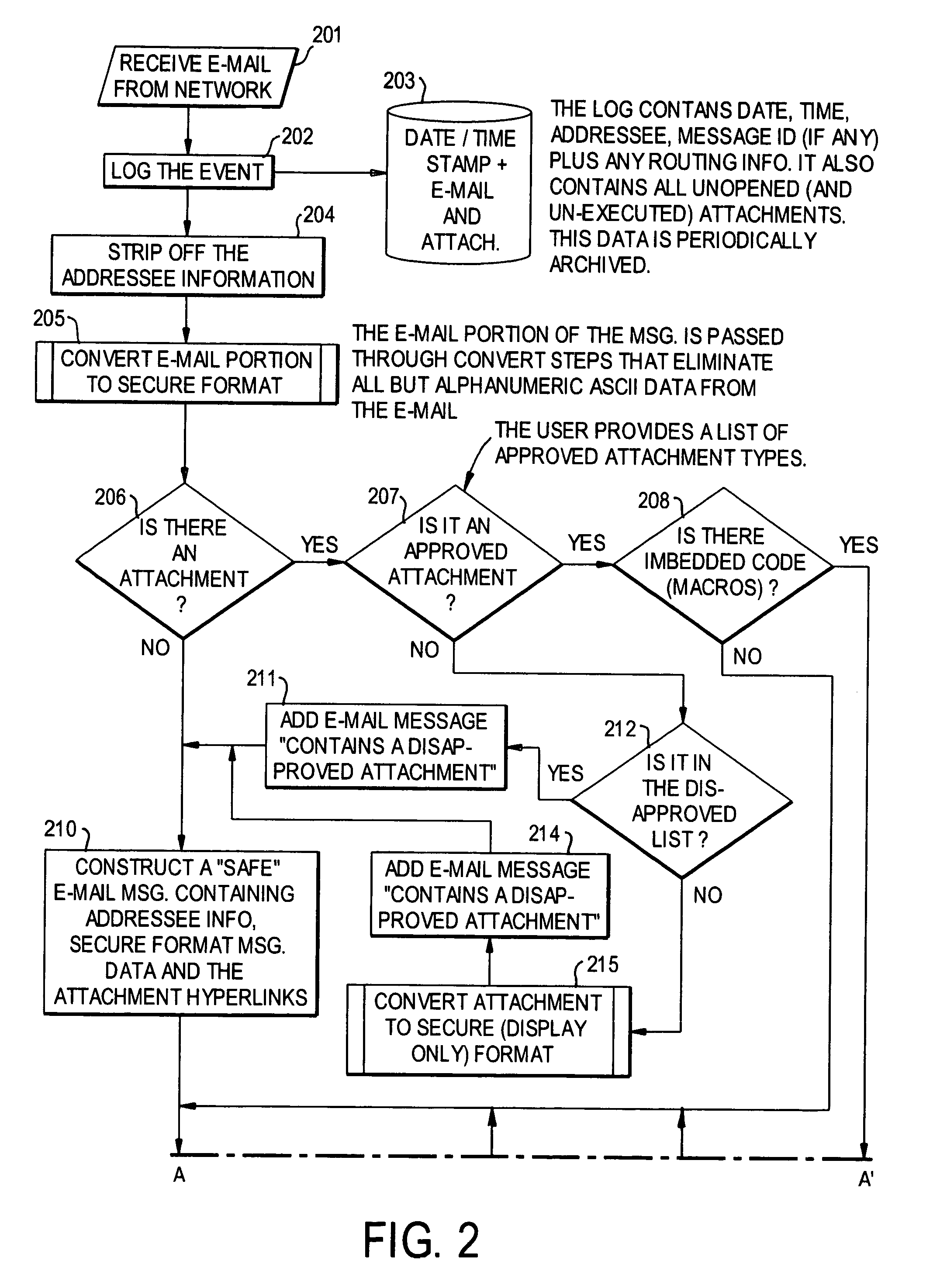
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
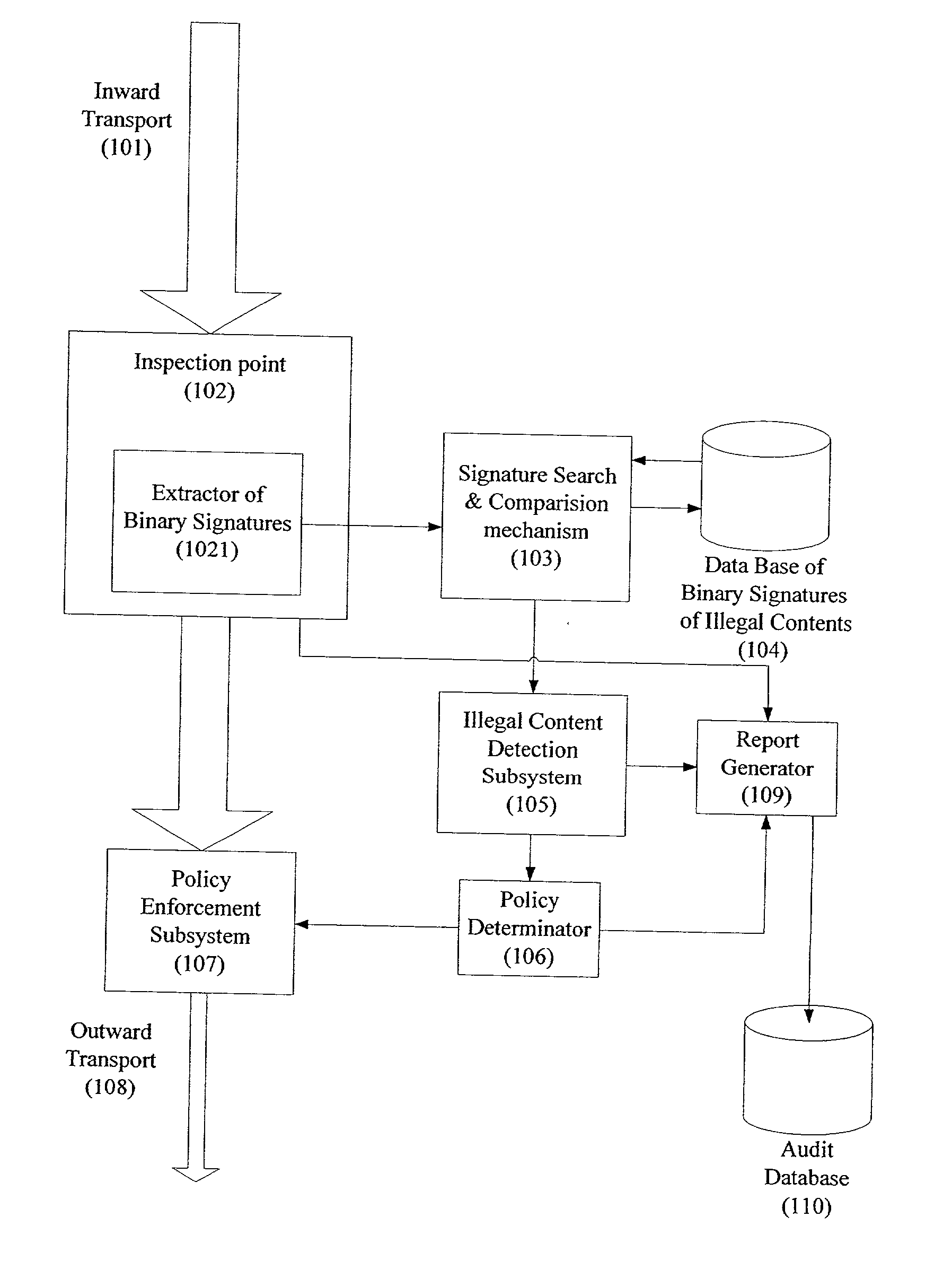
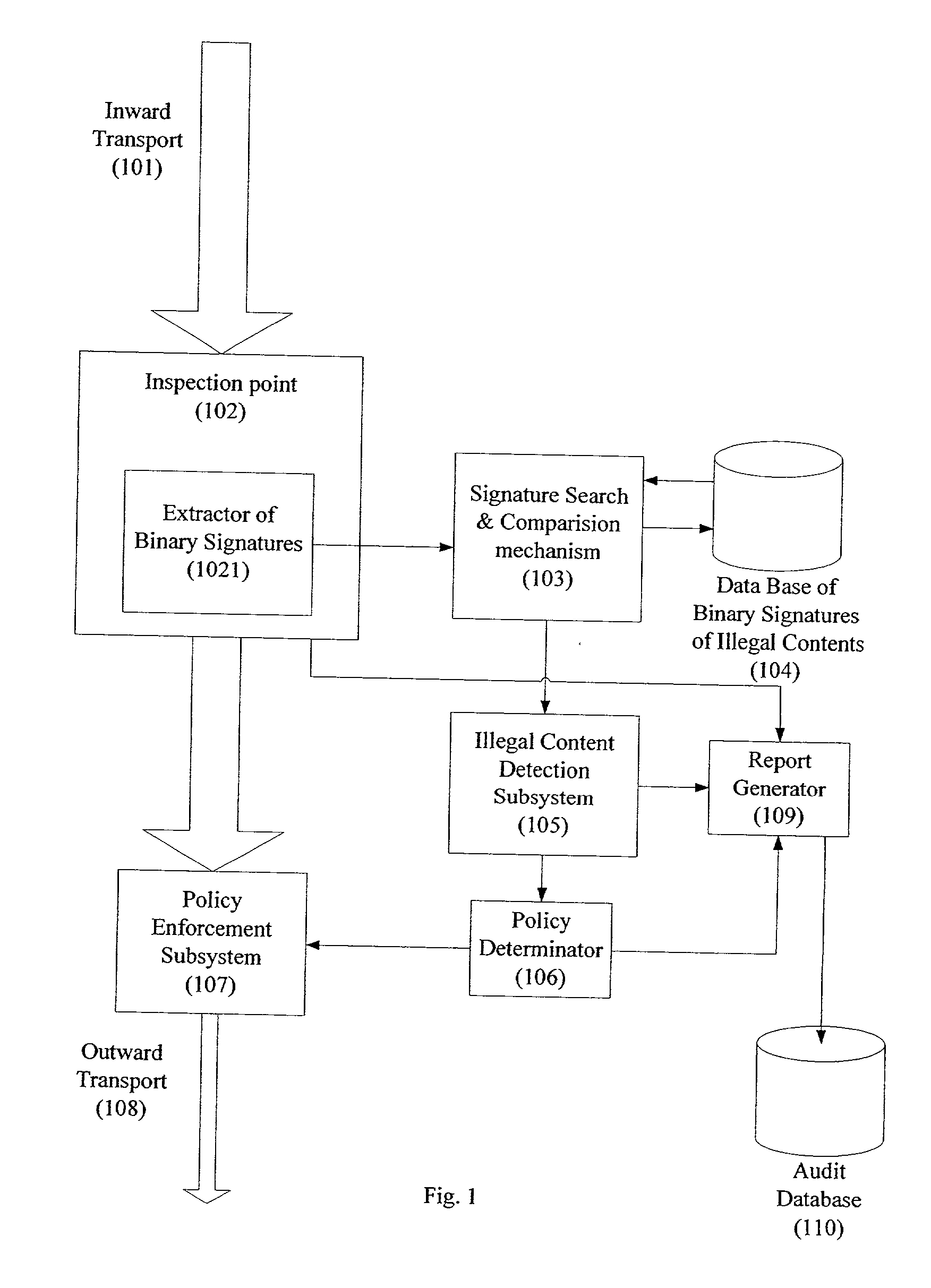
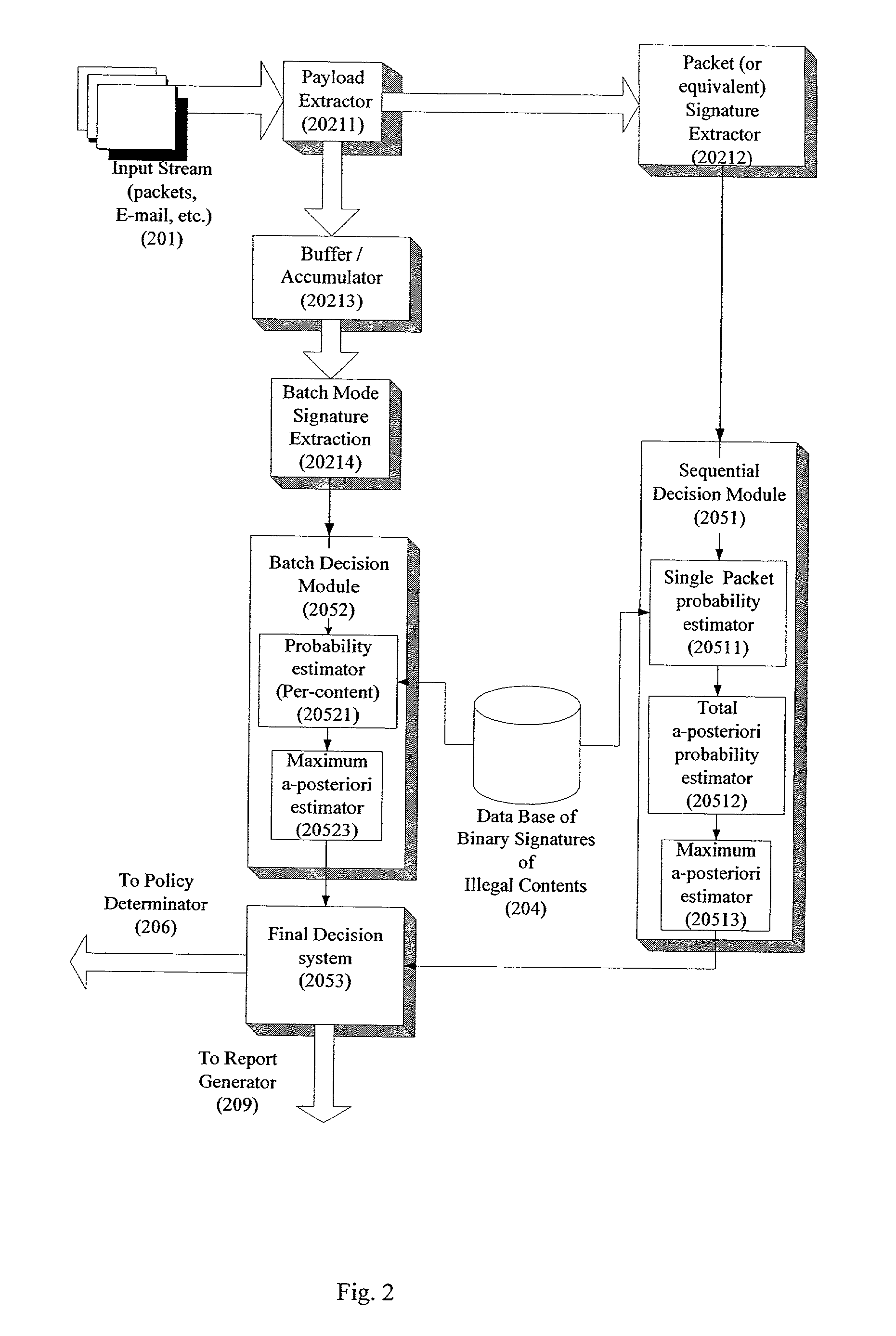
System and method for monitoring unauthorized transport of digital content
ActiveUS20020129140A1Reduce decreaseAttenuation bandwidthMemory loss protectionError detection/correctionDigital contentNumber content
A system for network content monitoring and control, comprising: a transport data monitor, connectable to a point in a network, for monitoring data being transported past said point, a signature extractor, associated with said transport data monitor, for extracting a derivation of said data, said derivation being indicative of content of said payload, a database of preobtained signatures of content whose movements it is desired to monitor, and a comparator for comparing said derivation with said preobtained signatures, thereby to determine whether said payload comprises any of said content whose movements it is desired to monitor. The monitoring result may be used in bandwidth control on the network to restrict transport of the content it is desired to control.
Owner:FORCEPOINT LLC
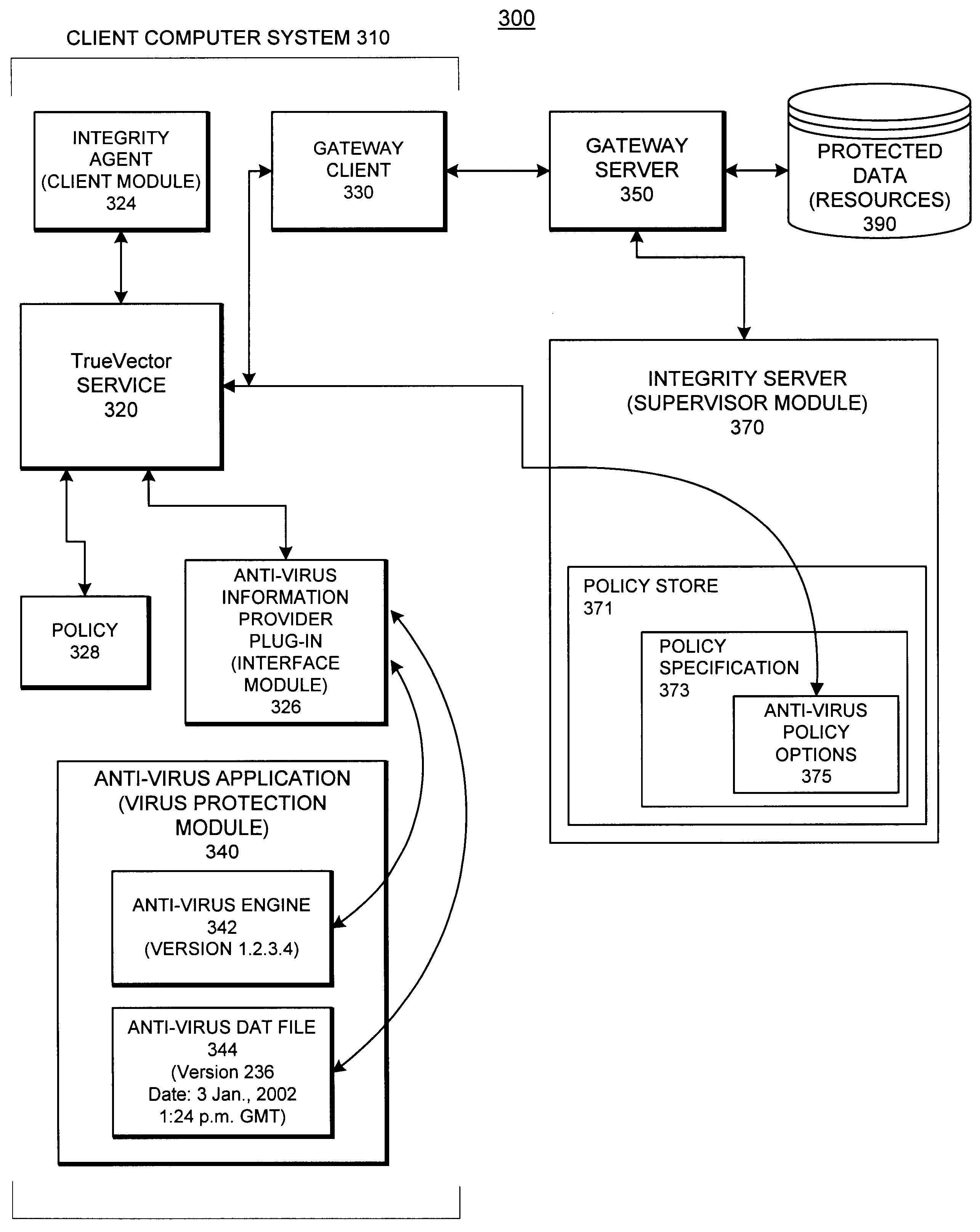
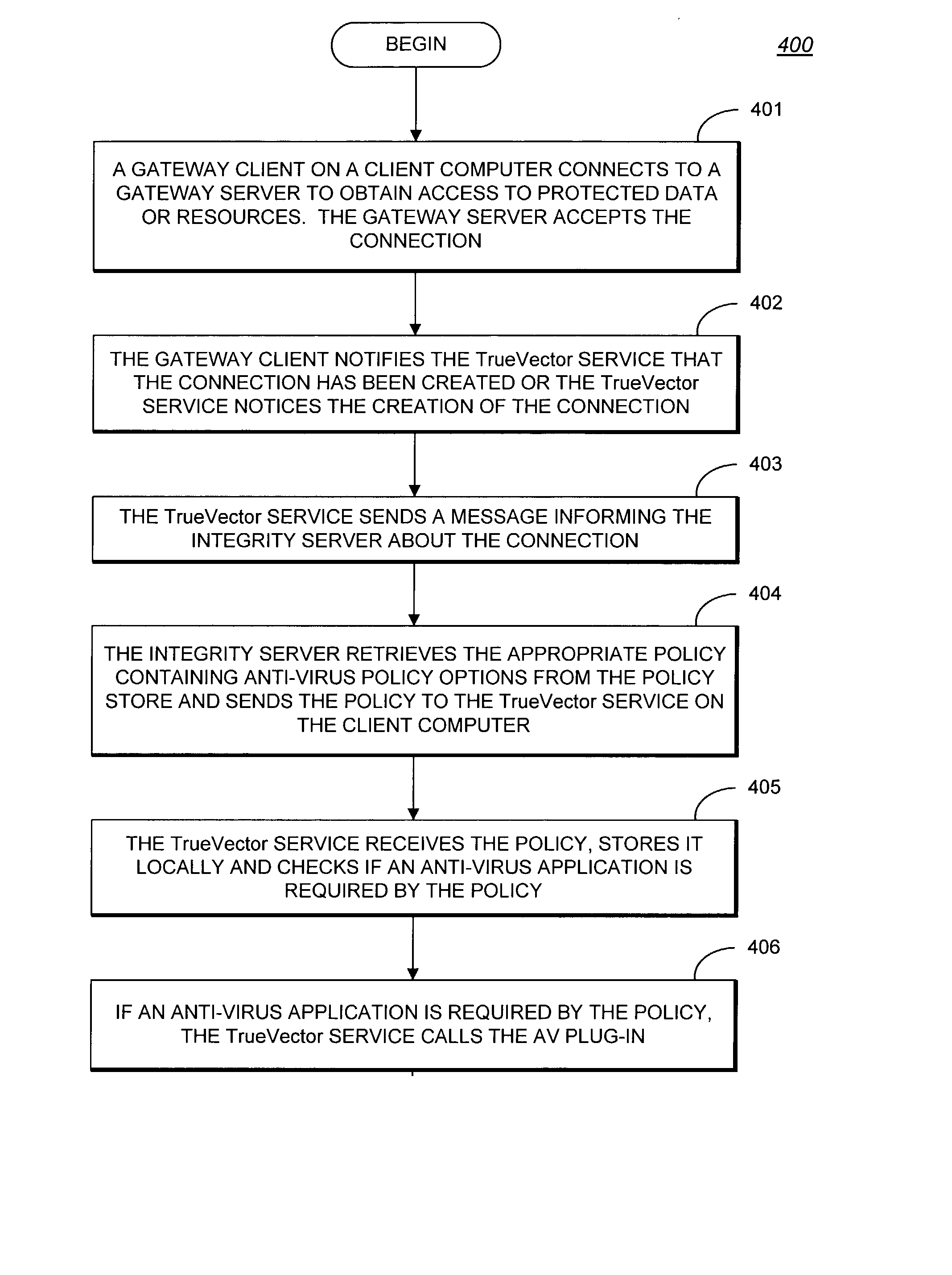
System and methods providing anti-virus cooperative enforcement
InactiveUS6873988B2Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
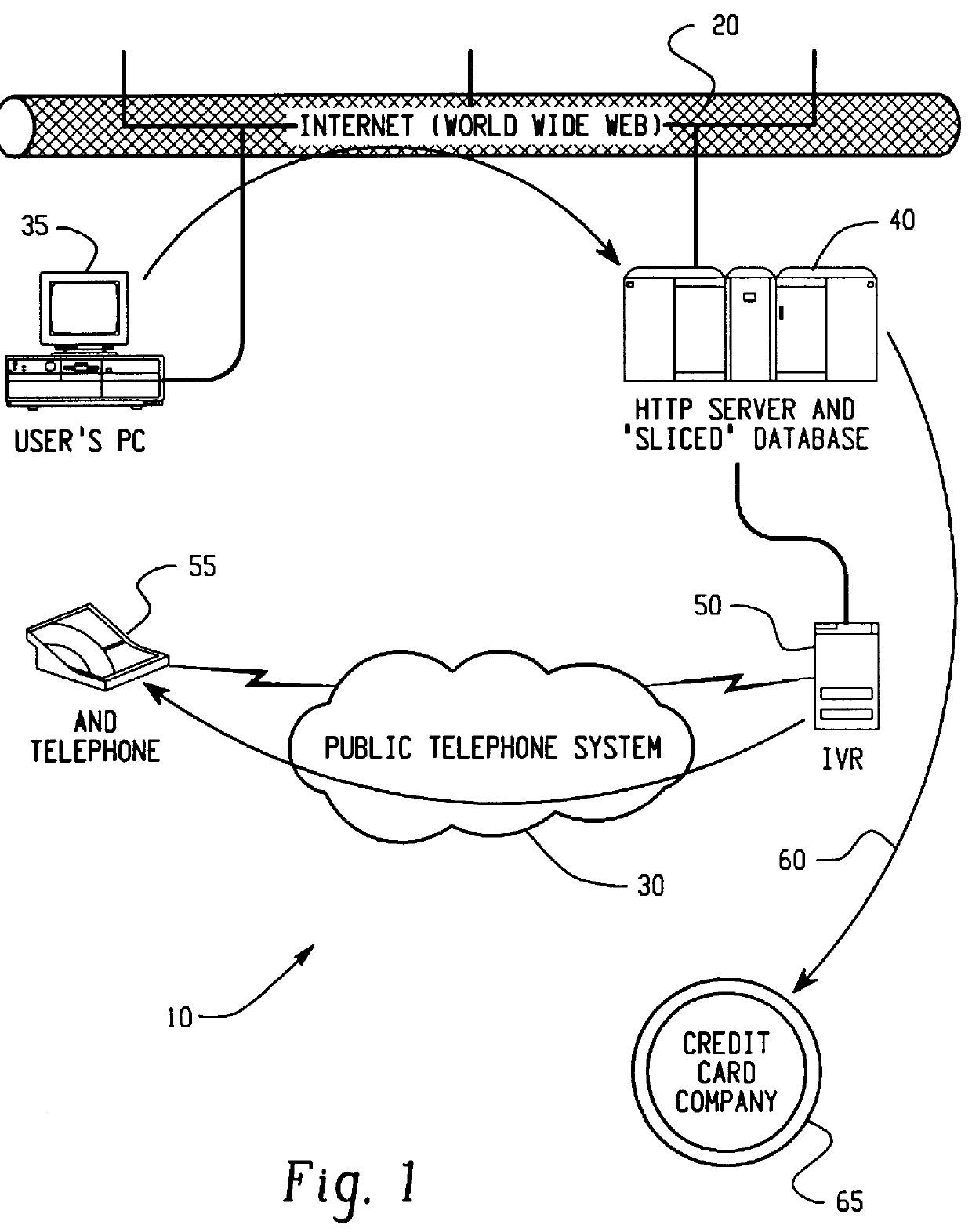
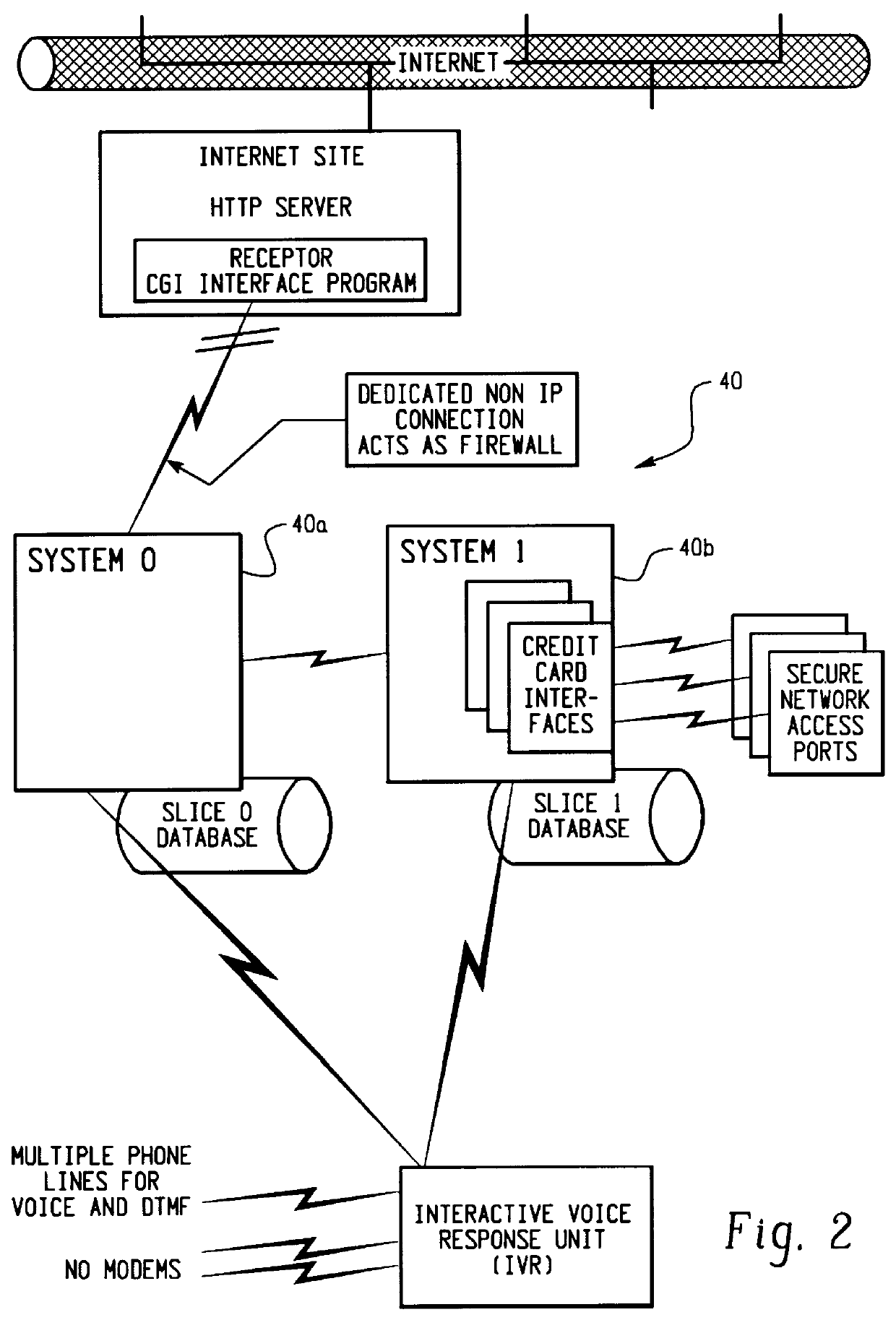
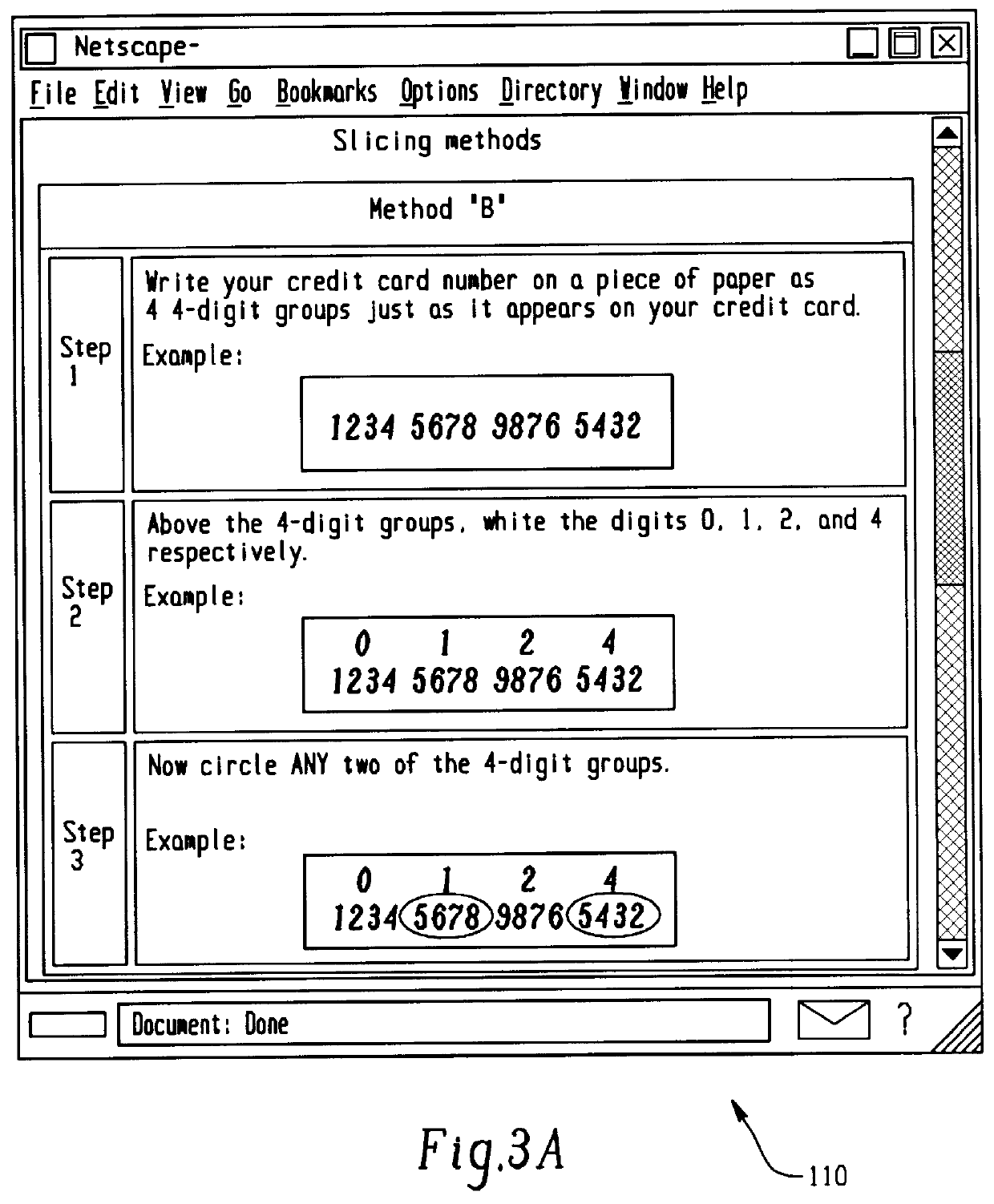
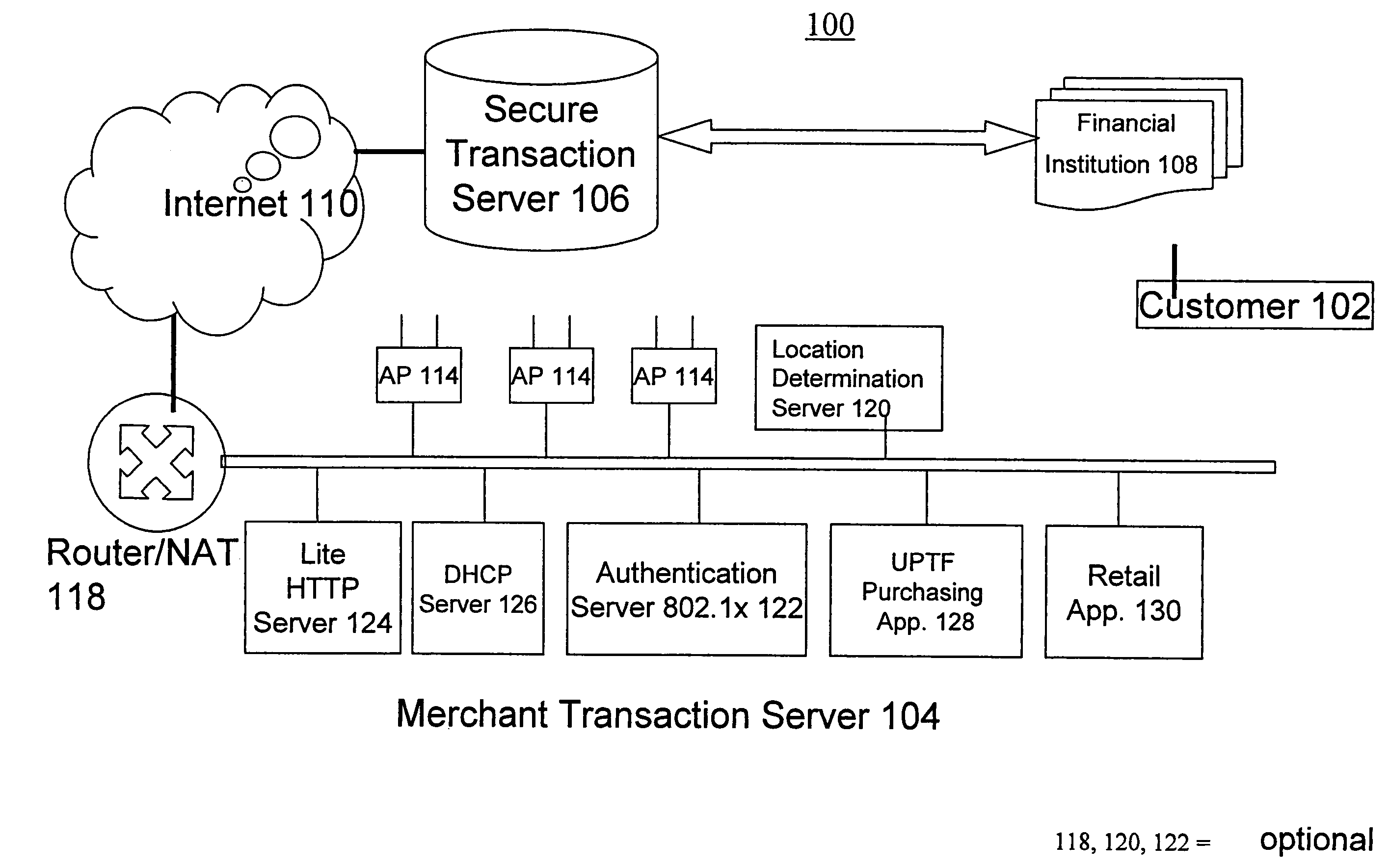
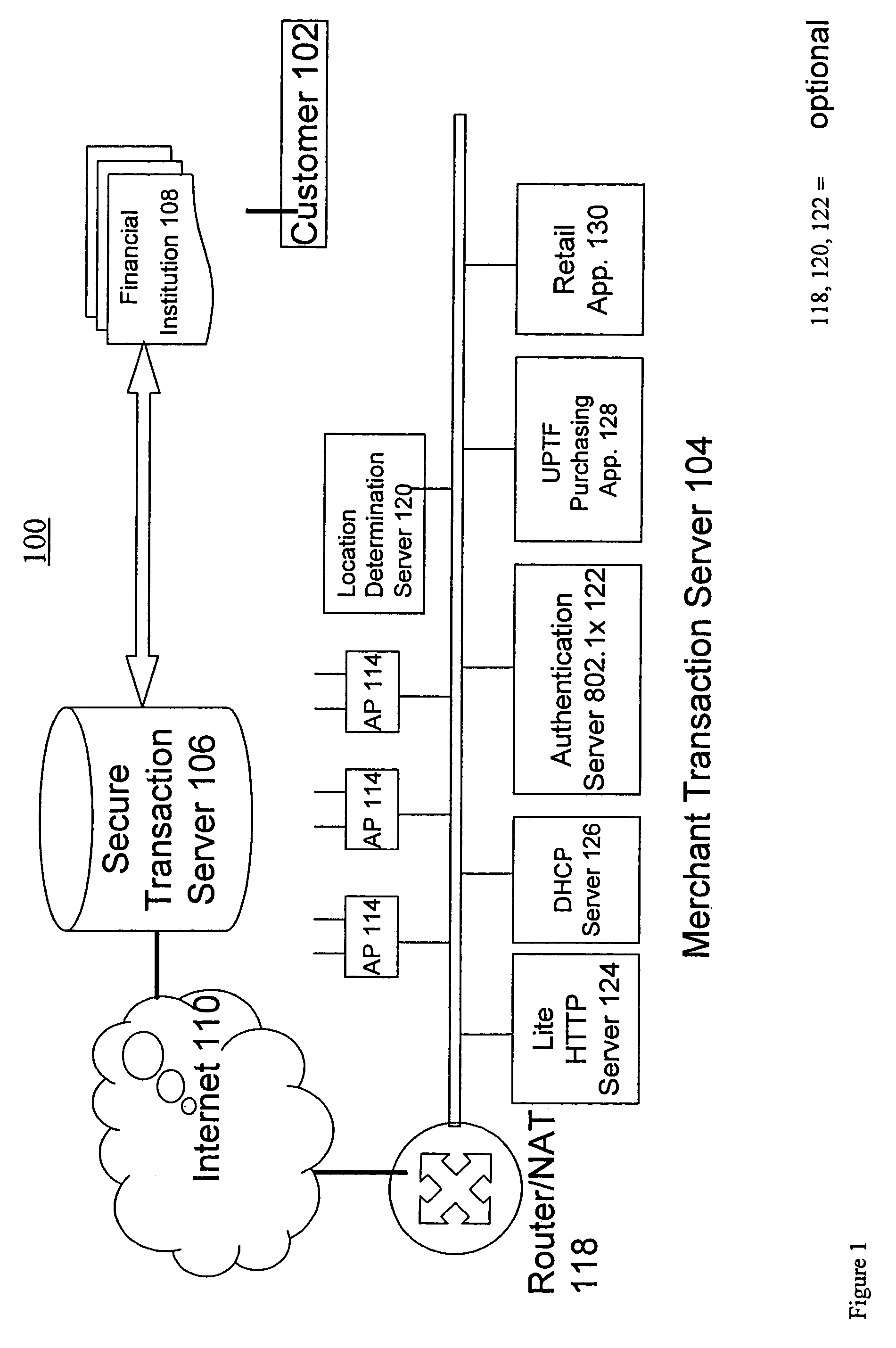
Transaction security method and apparatus
A method for performing secure transactions, such as credit card purchases, using two or more non-secure networks (such as the Internet and the public telephone system) in such a way that security is insured. A person wishing to initiate a secure transaction sends a message over one of the non-secure networks to a computer. That computer automatically uses the second non-secure network to contact the person back to verify the transaction. The call-back mechanism employs a method to authenticate the identity or authority of the person initiating the transaction. No single wire-tapping or network snooping device sees the entire transaction. No single database contains the entire set of information.
Owner:PICKETT THOMAS E
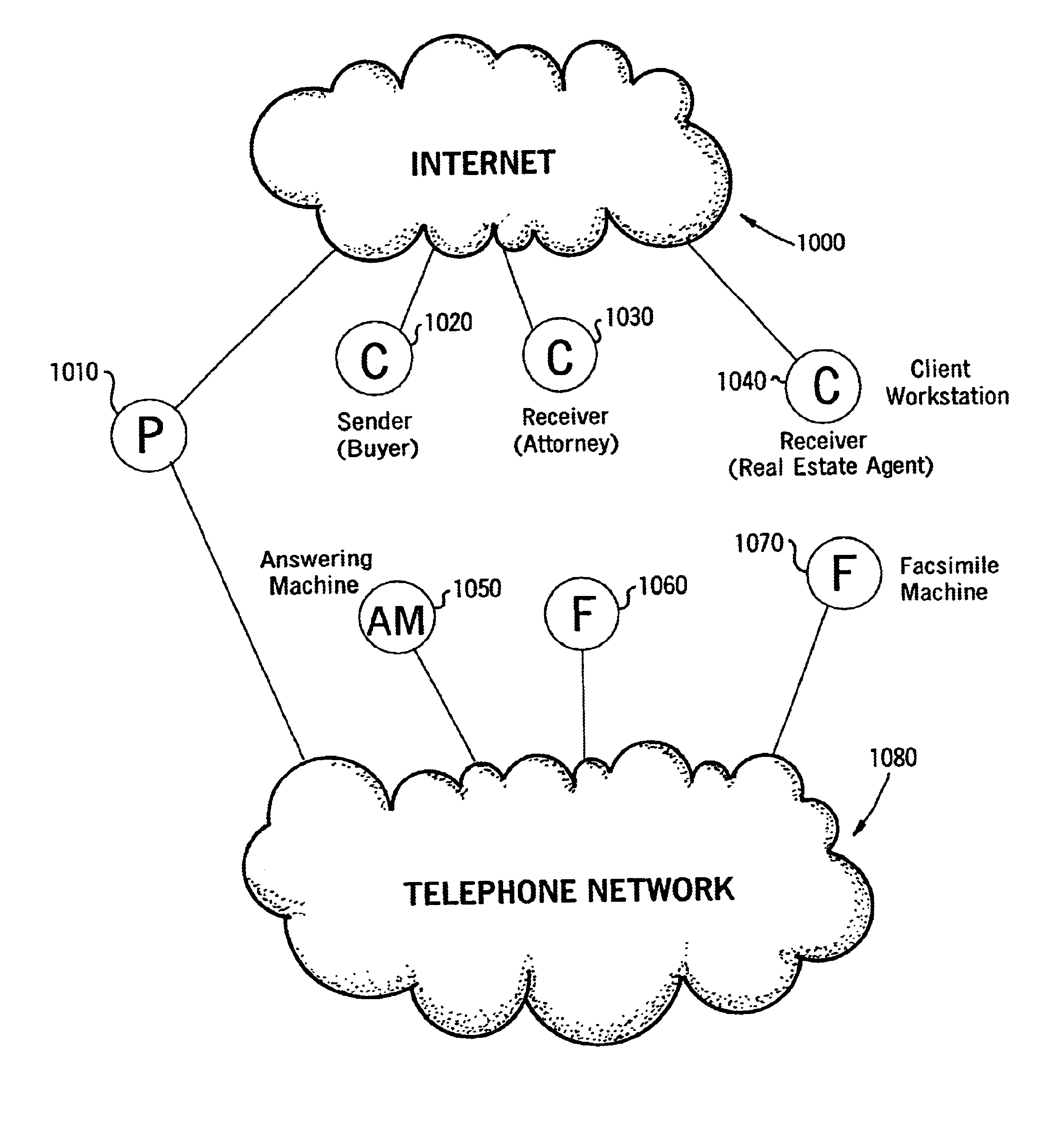
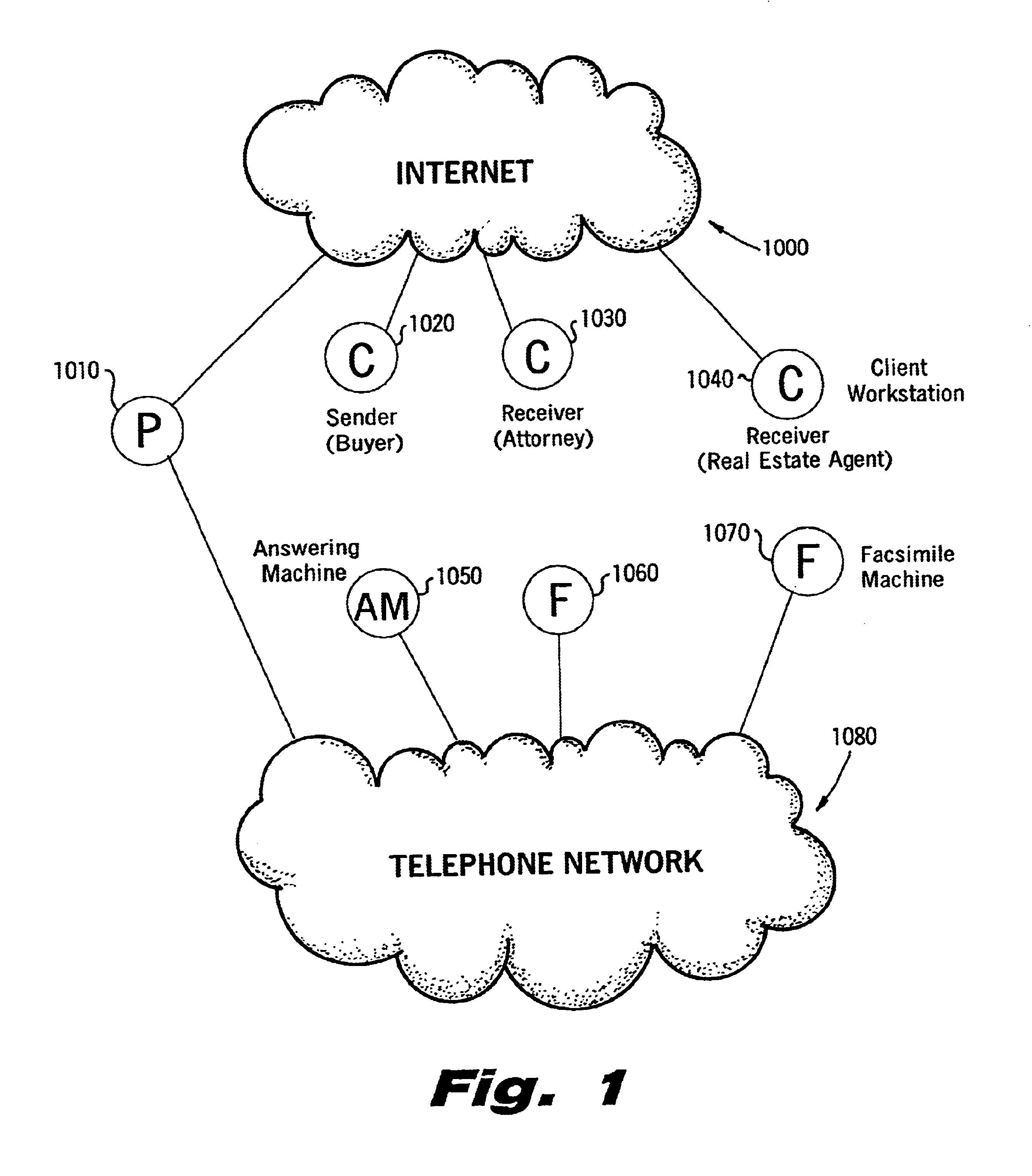
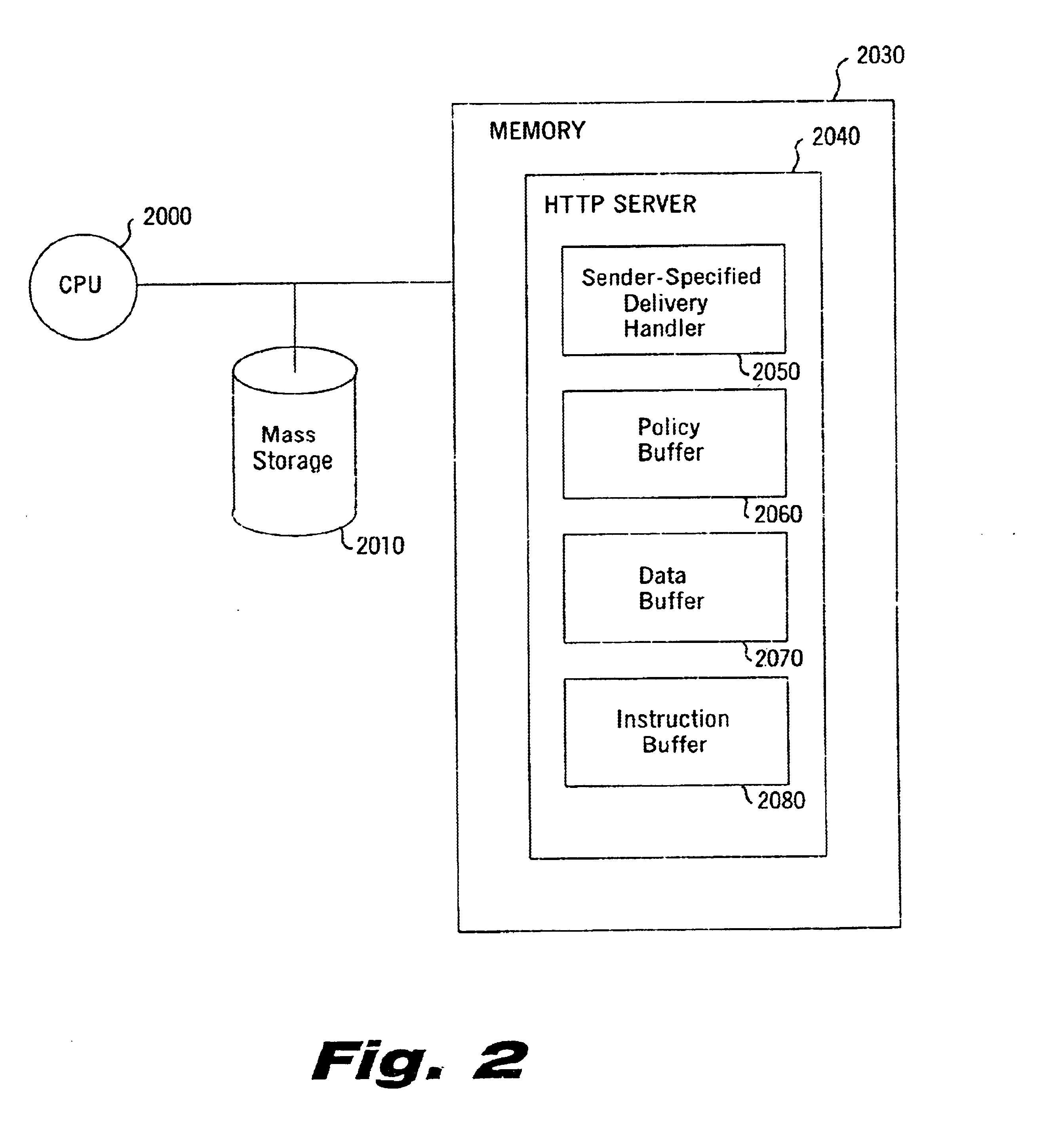
Sender- specified delivery customization
InactiveUS6643684B1Telephonic communicationMultiple digital computer combinationsSecure transmissionFacsimile
A system and method that enables a given sending user to specify a set of delivery policies and have them used for the electronic delivery of a given message, the message potentially having several heterogeneous parts (e.g., text and pictures) each of which is handled differently, and delivered to multiple heterogeneous devices (e.g., PCs, Smartphones, fax machines), and possibly to several distinct recipients. The factors with which a sender can qualify their delivery policies include: time / date, transmission cost; whether the transmission can be forwarded; receiving device capability; and network reliability, speed, and security transmission. Methods are also provided enabling a sender to specify that particular transmissions be redirected or copied, e.g., "send fax copy to my broker and my accountant." In one embodiment, the delivery policies may be specified using PICS.
Owner:SNAP INC
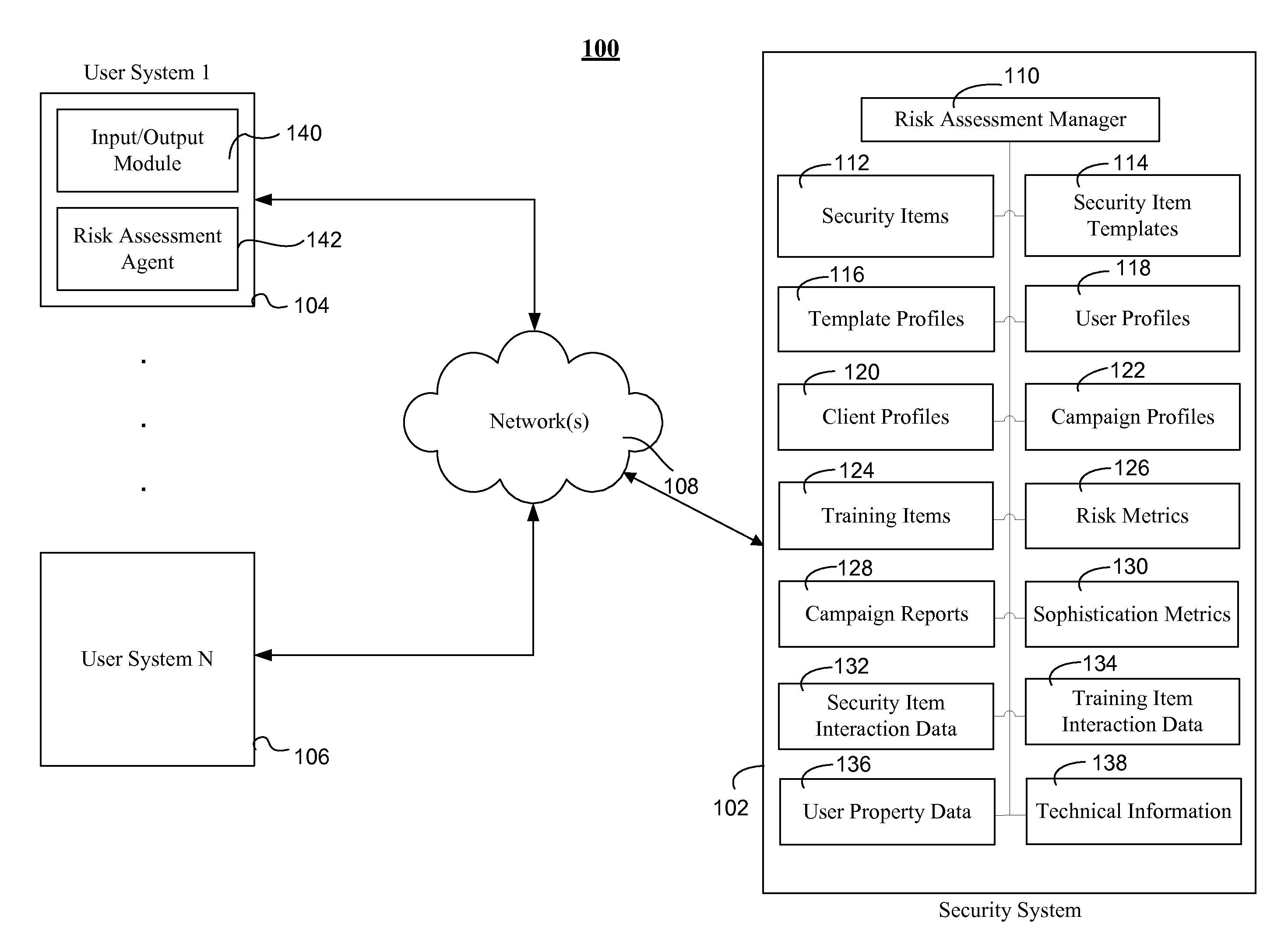
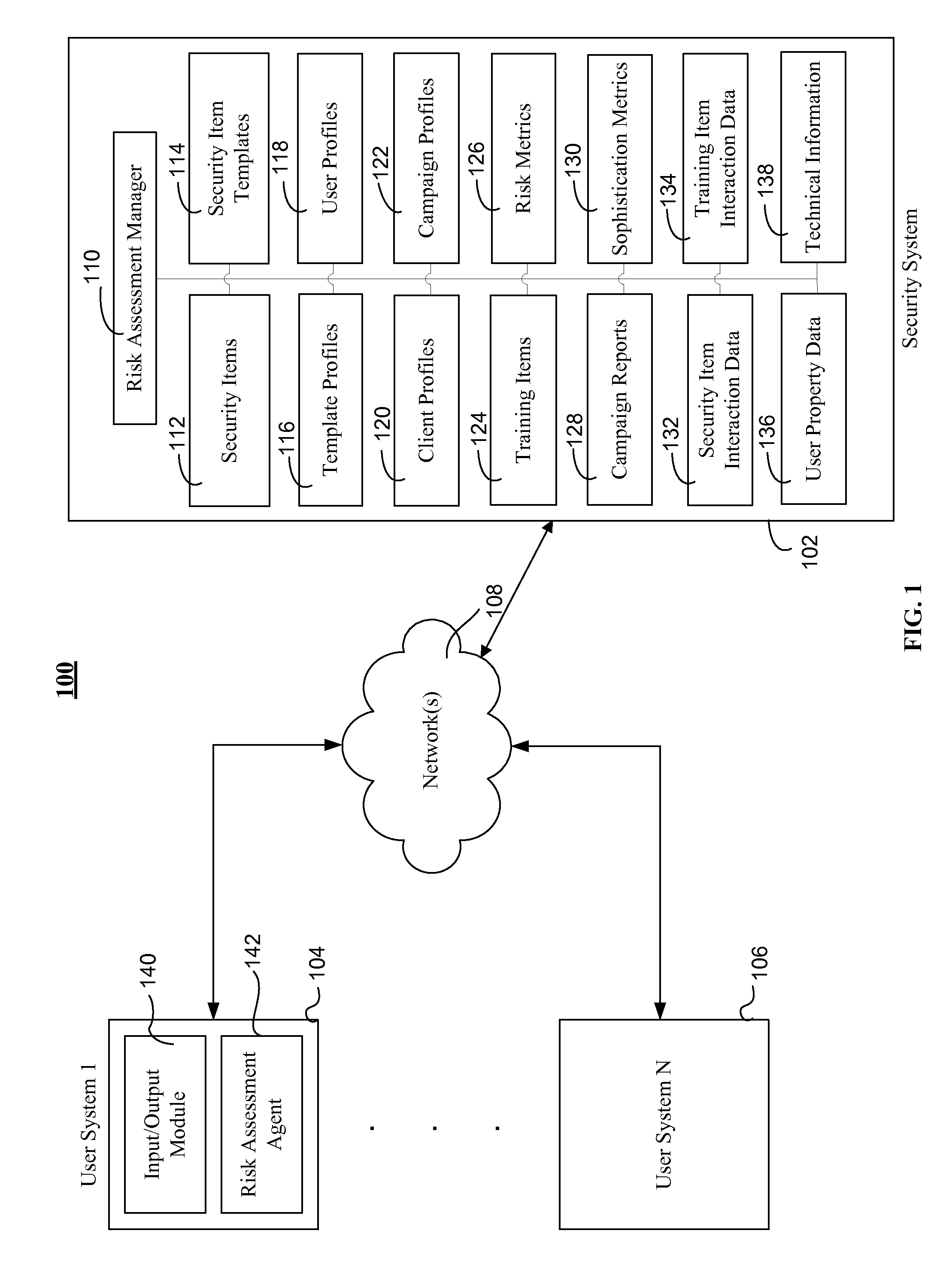
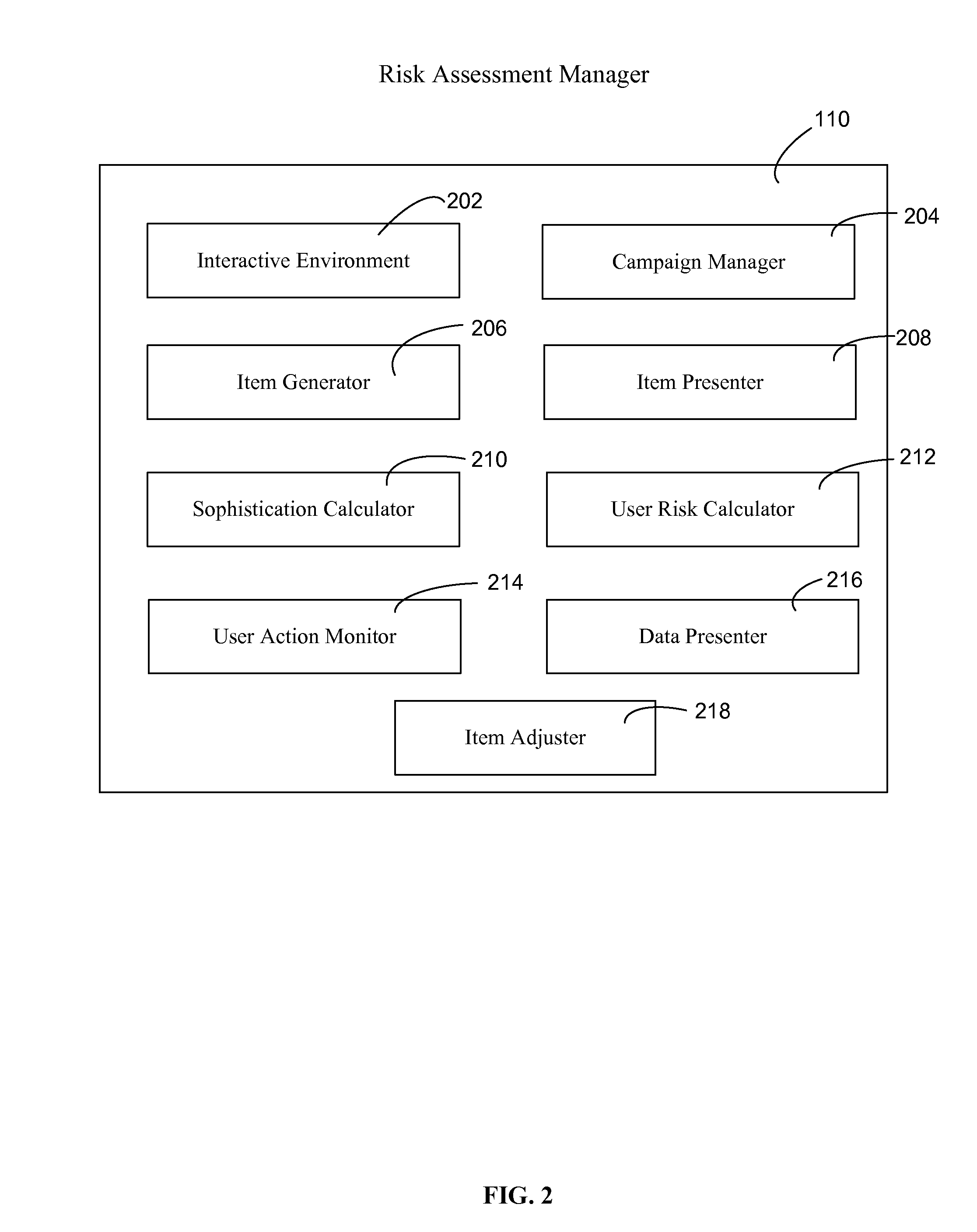
Assessing security risks of users in a computing network
InactiveUS20150229664A1Memory loss protectionError detection/correctionTechnical informationComputer security
Various embodiments assess security risks of users in computing networks. In one embodiment, a set of input data is obtained. The set of input data comprises at least one of security item interaction data, training interaction data, and technical information for each of a set of users in a plurality of users associated with an entity. The security item interaction data comprises at least one action performed by each of the set of users with respect to at least one computing network-based security item presented to each of the set of users. The set of input data to is compared to a plurality of security risk scoring metrics. Based on this comparison, a security risk score for each of the set of users with respect to a computing network is calculated.
Owner:WOMBAT SECURITY TECH
Methods for purchasing of goods and services
InactiveUS7349871B2Risk minimizationReducing credit card fraudPayment circuitsElectronic credentialsThird partyPurchasing
Owner:PCMS HOLDINGS INC
Parimutuel wagering system with opaque transactions
InactiveUS20050096124A1Apparatus for meter-controlled dispensingBuying/selling/leasing transactionsDeposit accountCredit union
A seamless ledger-based wagering system is provided wherein a secure, flexible and automated database method and apparatus is used for retrieving information and accounting for wagers in an electronic wagering format. The accounting system can be a ledger wherein funds are accounted for by a financial structure (e.g., financial institution such as a bank, credit union, savings and loan, deposit account, and the like) so that funds may be transferred through an intermediate transaction (e.g., the electronic wager entered onto the account) on the ledger and committed to payment at the ultimate target of the transfer (e.g., the pari-mutuel site, and ancillary recipients of wagering monies, such as horseman's associations, totalisator companies, automated machine lessors, track association, governmental agencies and the like). As the financial records from the financial structure never ‘sees’ the wagering facility in the transaction, transferring funds or guaranteeing funds to the intermediate transaction on a ledger, the entire transaction is in compliance with state and national regulations prohibiting or limiting or rendering illegal the availability of funds in the wagering transaction or transferring funds into a wagering account.
Owner:ASIP HLDG INC
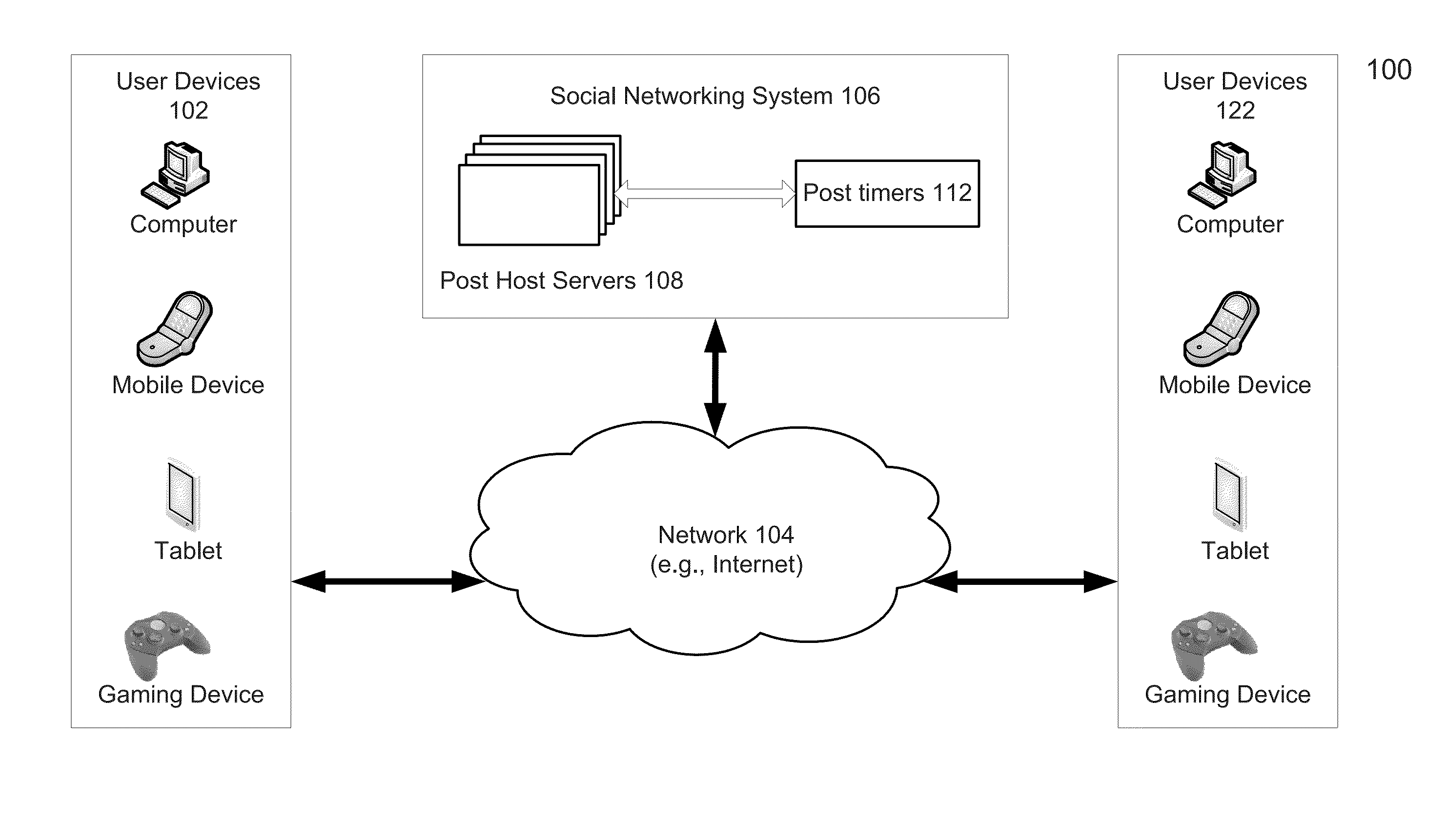
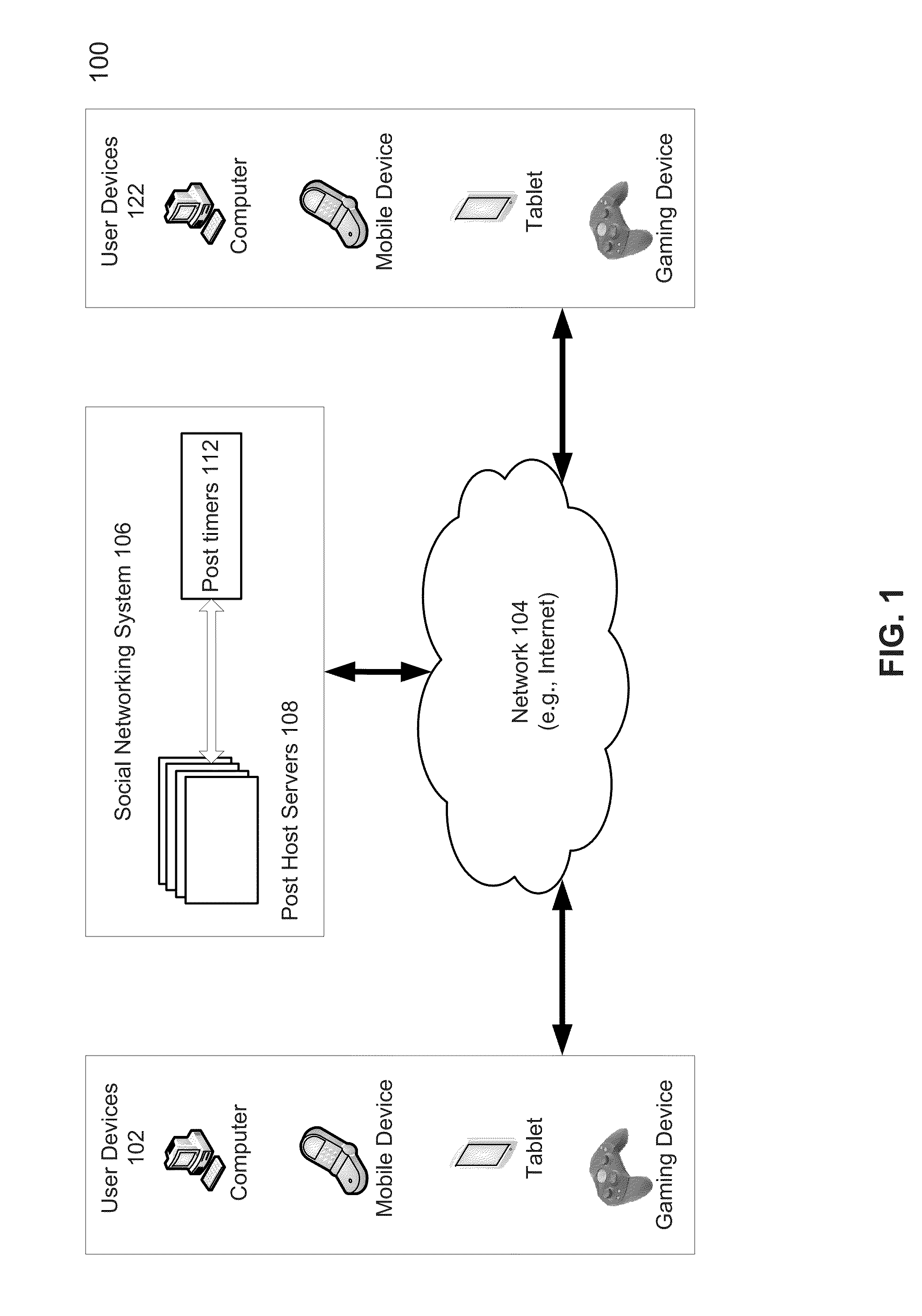
Method and system of managing ephemeral post in a social networking system
A method of posting ephemeral posts is disclosed. The method starts with receiving, from a user of a social network, a request to post an ephemeral post, the request including an ephemeral variable associated with a threshold event. The ephemeral post is posted on behalf of the user. Then an occurrence of the threshold event is monitored. When the threshold event has not occurred, the post is allowed to be accessible to at least one viewer other than the user. When the threshold event has occurred, the post is blocked from being accessible by the at least one view other than the user.
Owner:META PLATFORMS INC
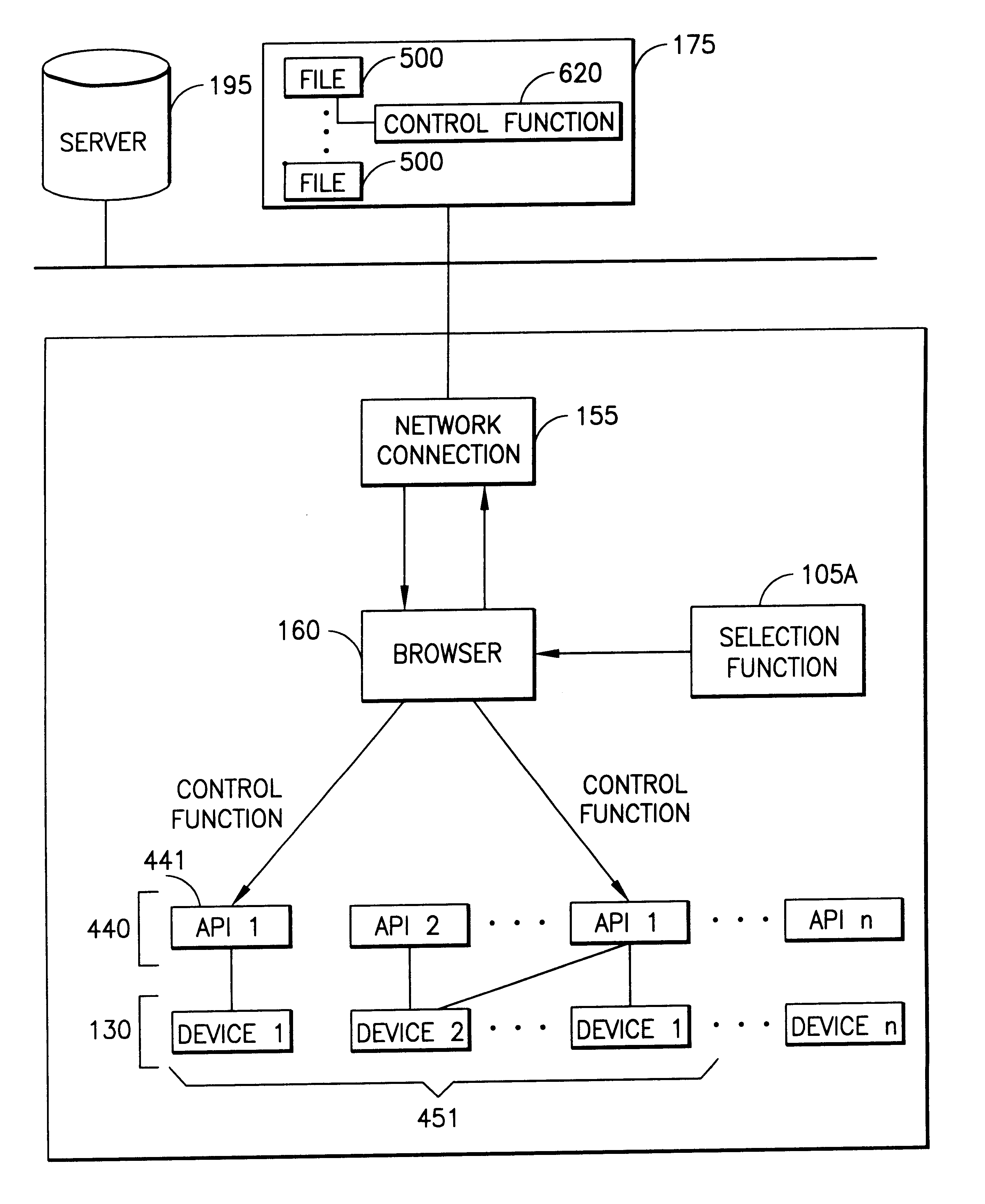
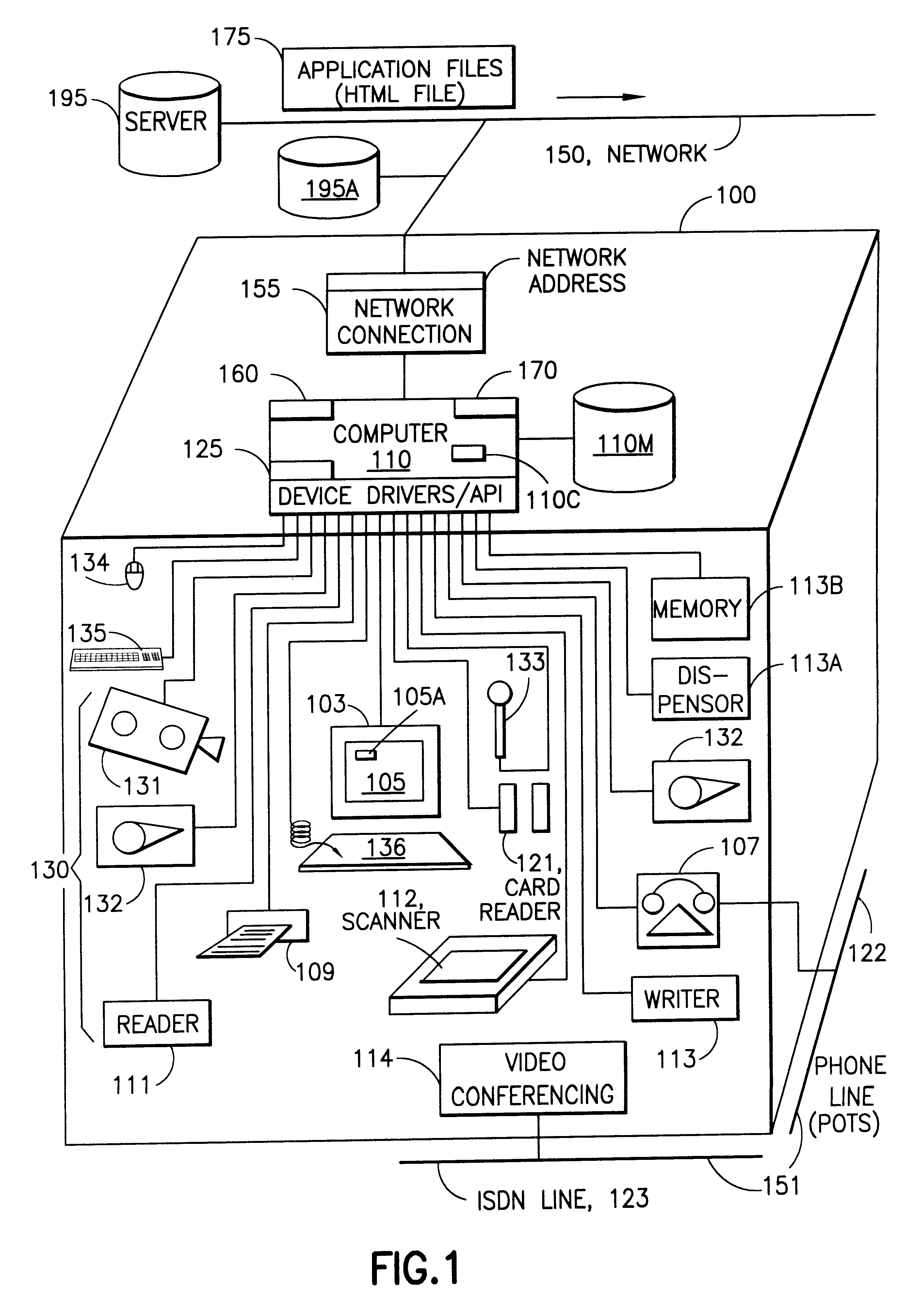
Server for reconfiguring control of a subset of devices on one or more kiosks
InactiveUS6195694B1Faster and reliable accessLow costAcutation objectsData switching by path configurationM-governmentComputer terminal
A server system that is connected to one or more networks, e.g., the Internet, corporate or government intranets, extranets, etc. The server has one or more application files or configuration sets that the server serves to from one or more kiosks on the network. The configuration sets are application specific. (An application is a use for which the kiosks are configured or reconfigured.) One or more of the files in the configuration sets include one or more embedded (control) programs that are used to control the local APIs of one or more of the devices on the kiosk. In this way, the devices are controlled to configure the kiosk to perform the application.
Owner:IBM CORP
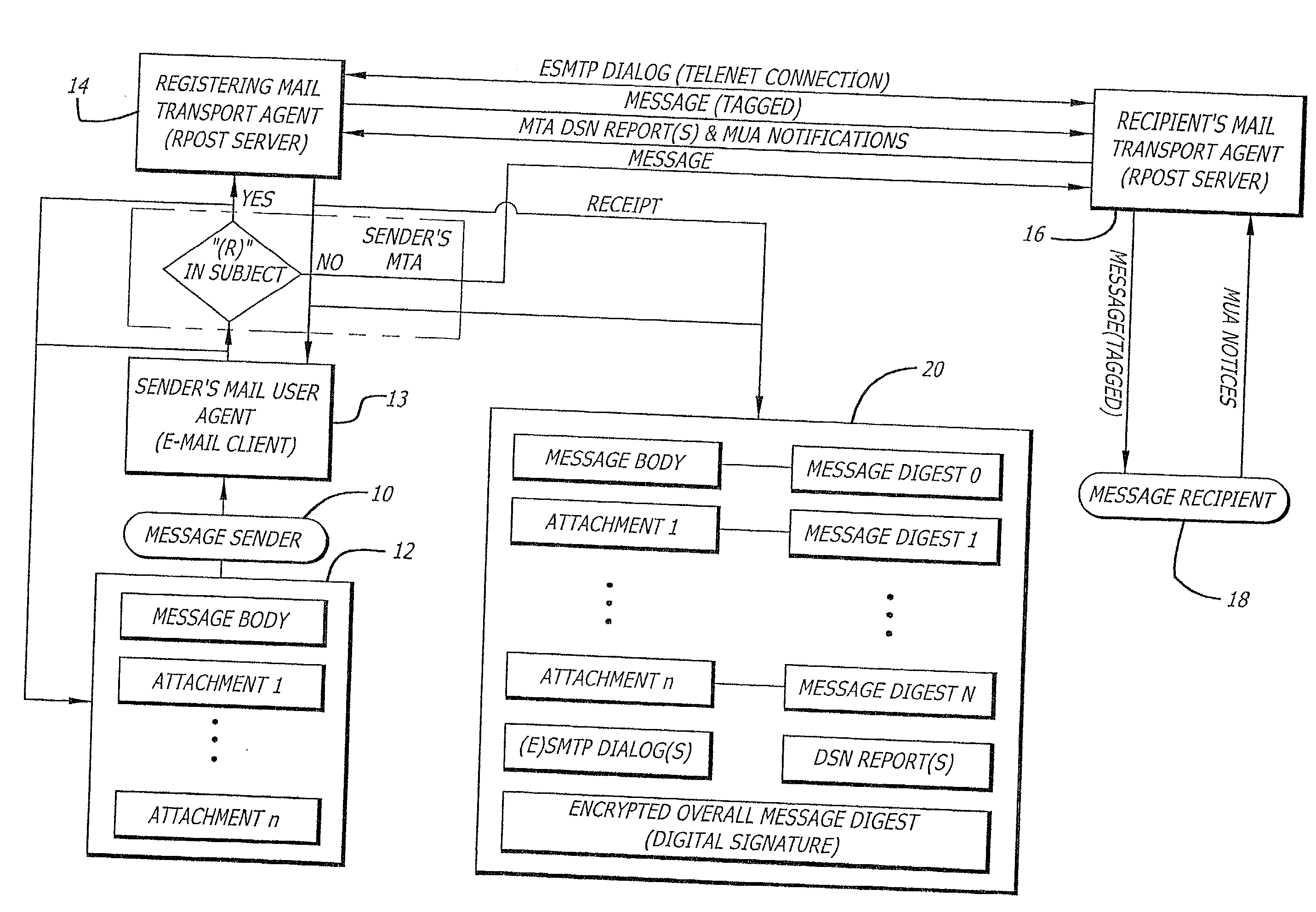
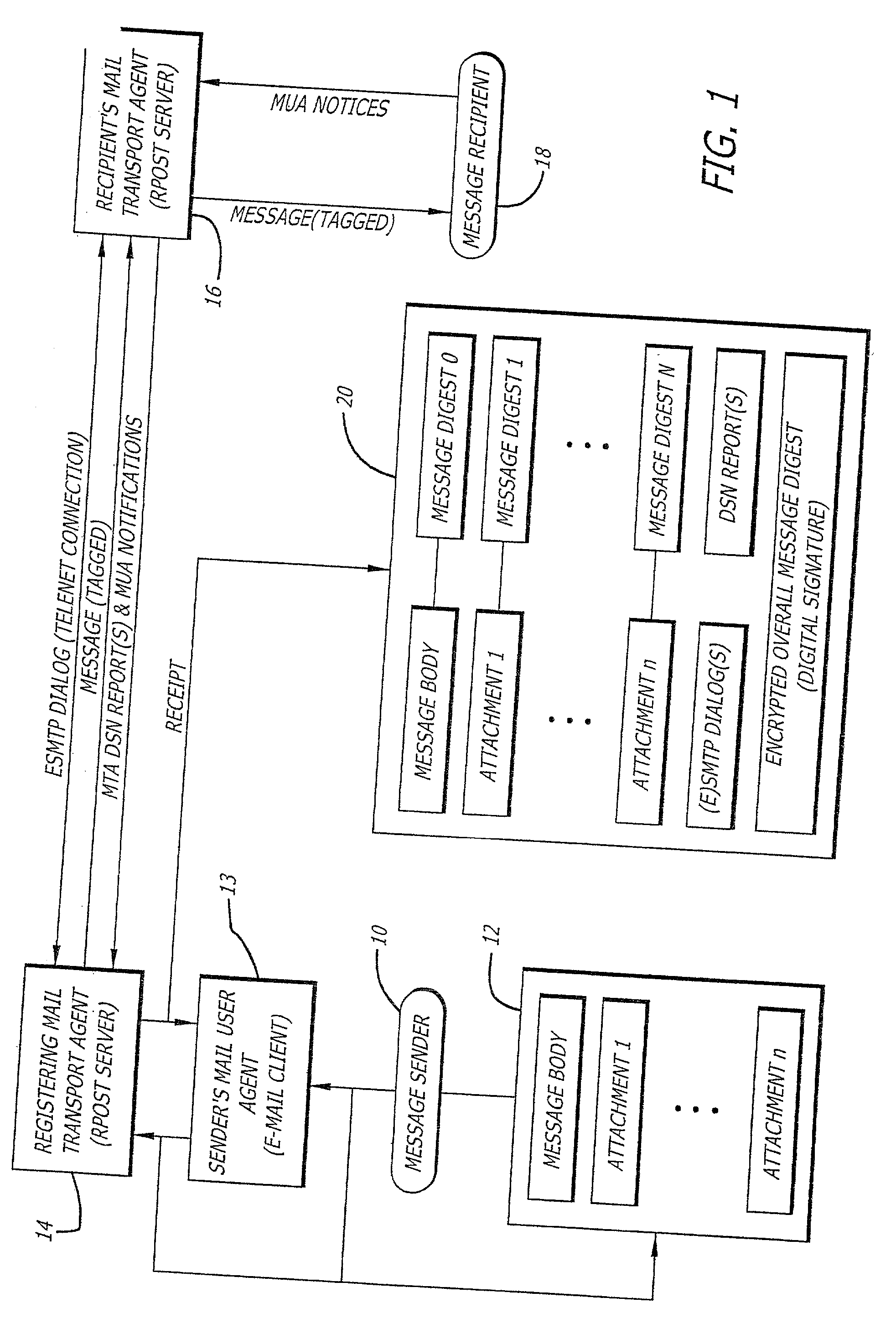
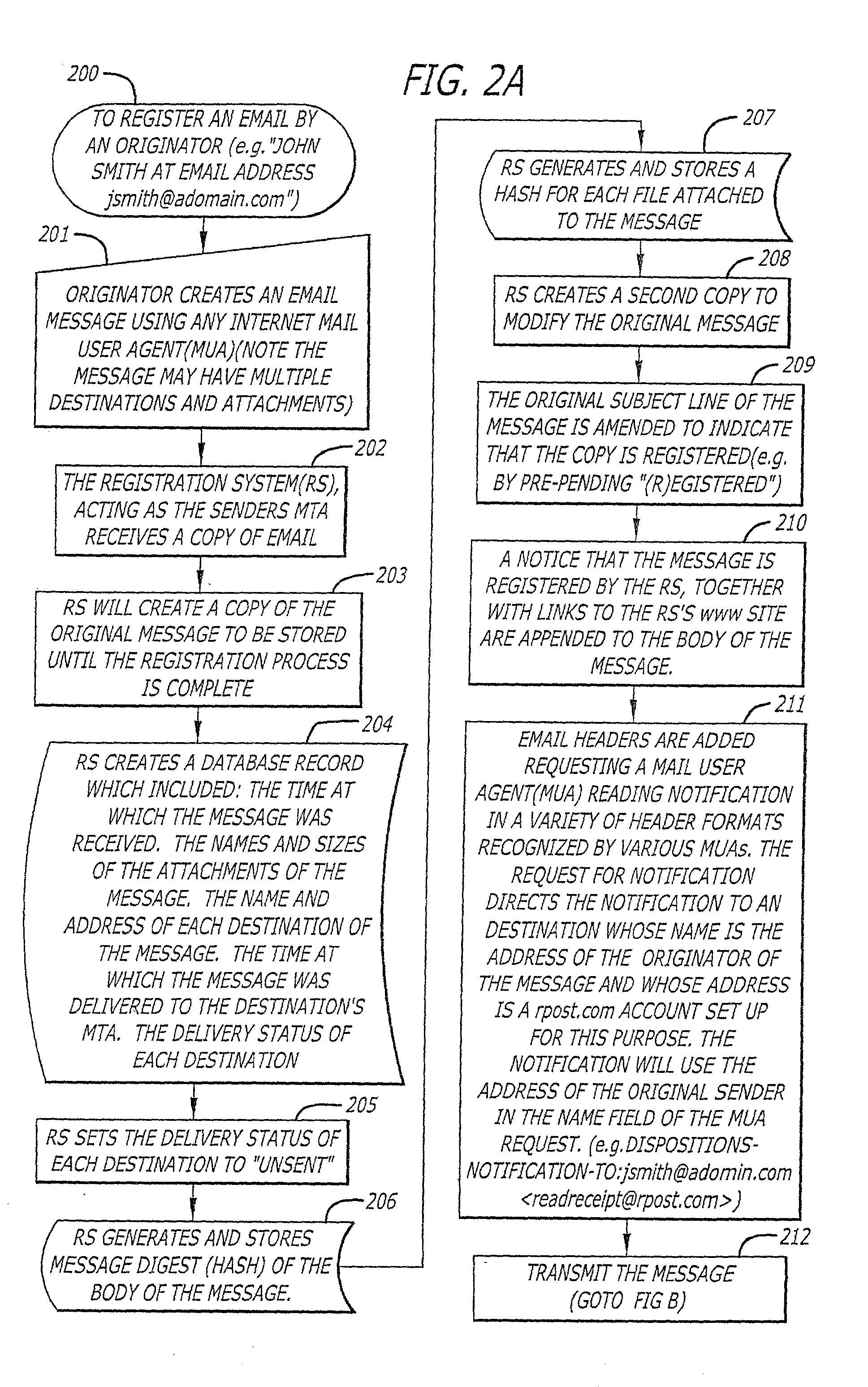
System and method for verifying delivery and integrity of electronic messages
InactiveUS20020144154A1Key distribution for secure communicationDigital data processing detailsDigital signatureThe Internet
A server receives a message from a sender and transmits the message through the Internet to a recipient. The server normally transmits the message in a first path through the Internet to the recipient. When the sender indicates at a particular position in the message that the message is registered, the server transmits the message in a second path through the Internet to the recipient. The sender can also provide additional indications in the message to have the server handle the message in other special ways not normally provided by the server. After learning from the receipt or the recipient's agent through the Internet that the message was successfully received, the server creates, and forwards to the sender, an electronic receipt. The receipt includes at least one, and preferably all: the message and any attachments, a delivery success / failure table listing the receipts, and the receipt times, of the message by the recipient's specific agents, and the failure of other agents of the recipient to receive the message and a digital signature of the message and attachments subsequently. By verifying that the digital signature on the sender's receipt matches the digital receipt at the server, the server can verify, without retaining the message, that the receipt is genuine and that the message is accurate.
Owner:RPOST COMM
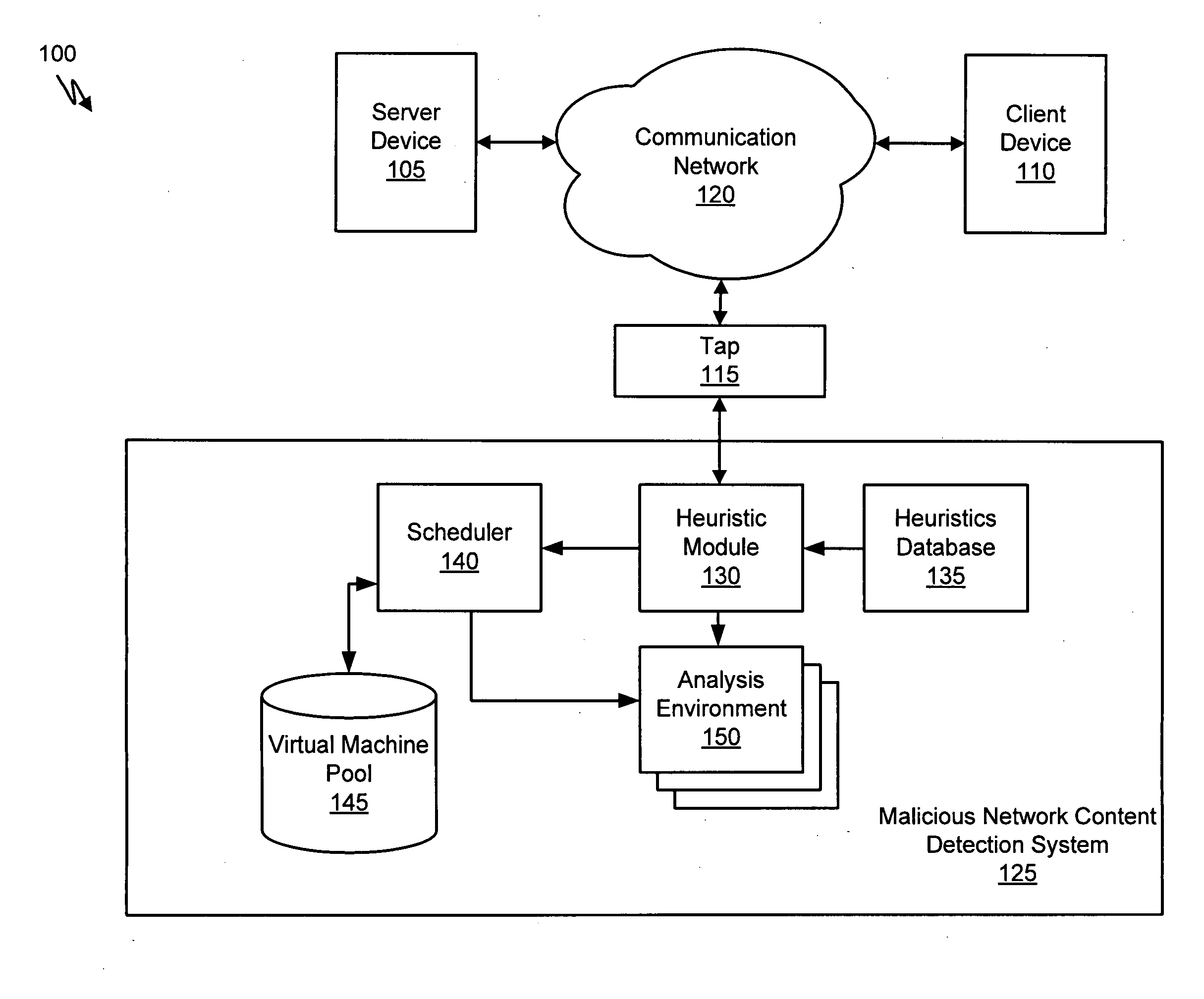
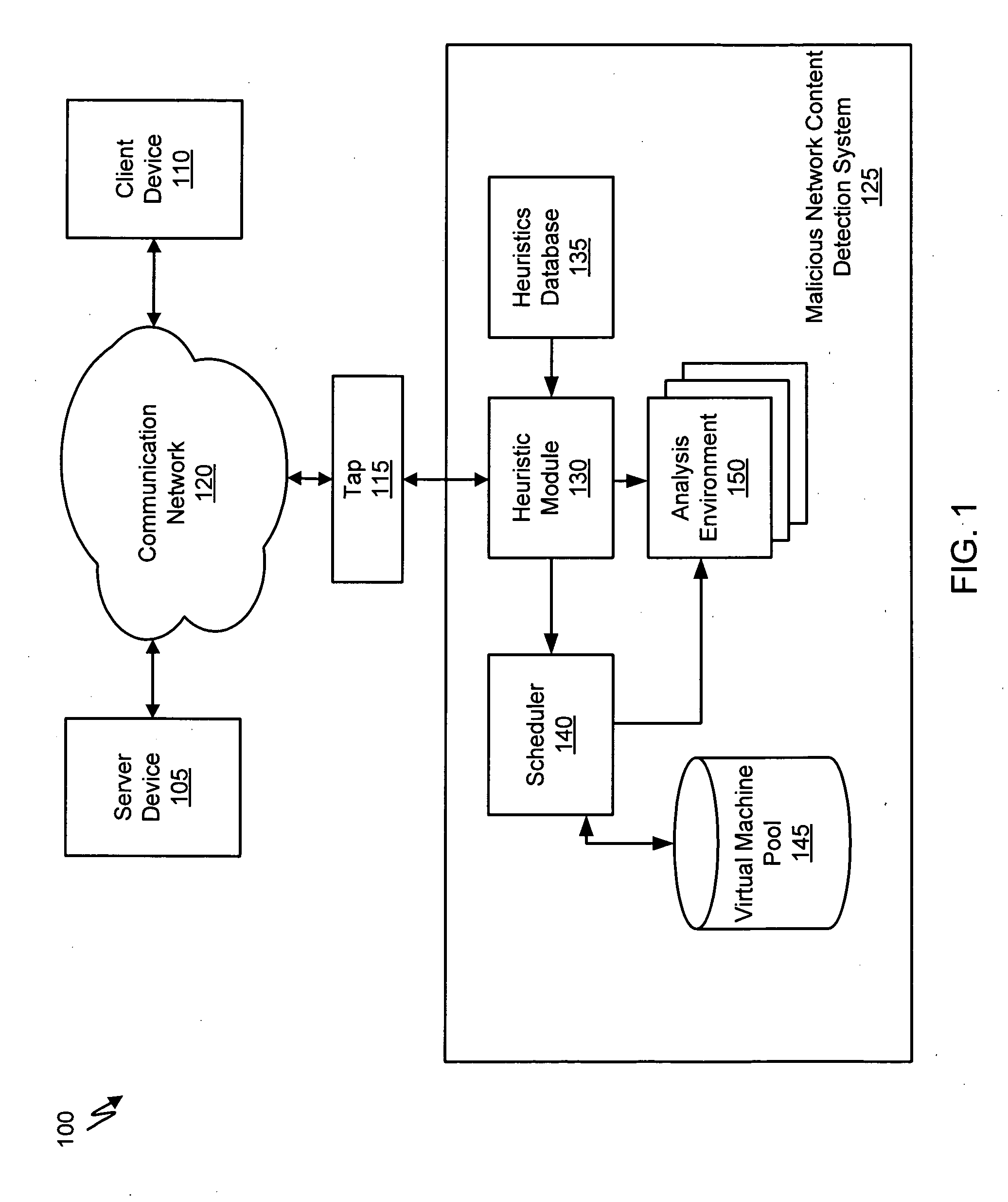
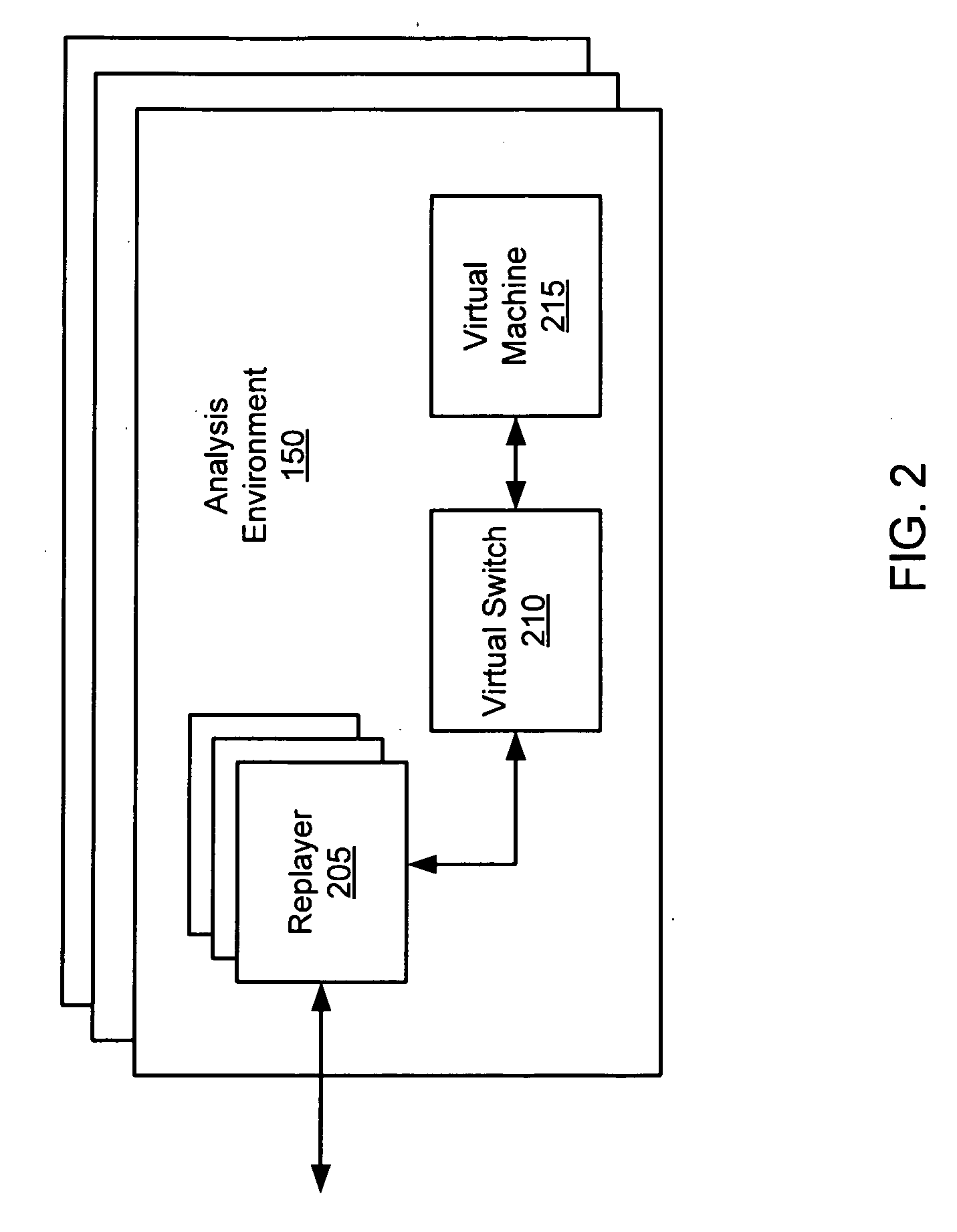
Systems and Methods for Detecting Malicious Network Content
A method for detecting malicious network content comprises inspecting one or more packets of network content, identifying a suspicious characteristic of the network content, determining a score related to a probability that the network content includes malicious network content based on at least the suspicious characteristic, identifying the network content as suspicious if the score satisfies a threshold value, executing a virtual machine to process the suspicious network content, and analyzing a response of the virtual machine to detect malicious network content.
Owner:FIREEYE SECURITY HLDG US LLC
Secure Dynamic Communication Network And Protocol
ActiveUS20160219024A1Increase the difficultyUsefulness of their knowledge would be short-livedMultiple keys/algorithms usageData taking preventionDigital dataData segment
In a secure cloud for transmitting packets of digital data, the packets may be repeatedly scrambled (i.e., their data segments reordered) and then unscrambled, split and then mixed, and / or encrypted and then decrypted as they pass through media nodes in the cloud. The methods used to scramble, split, mix and encrypt the packets may be varied in accordance with a state such as time, thereby making the task of a hacker virtually impossible inasmuch as he or she may be viewing only a fragment of a packet and the methods used to disguise the data are constantly changing.
Owner:LISTAT LTD
System and methods providing anti-virus cooperative enforcement
InactiveUS20030055994A1Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
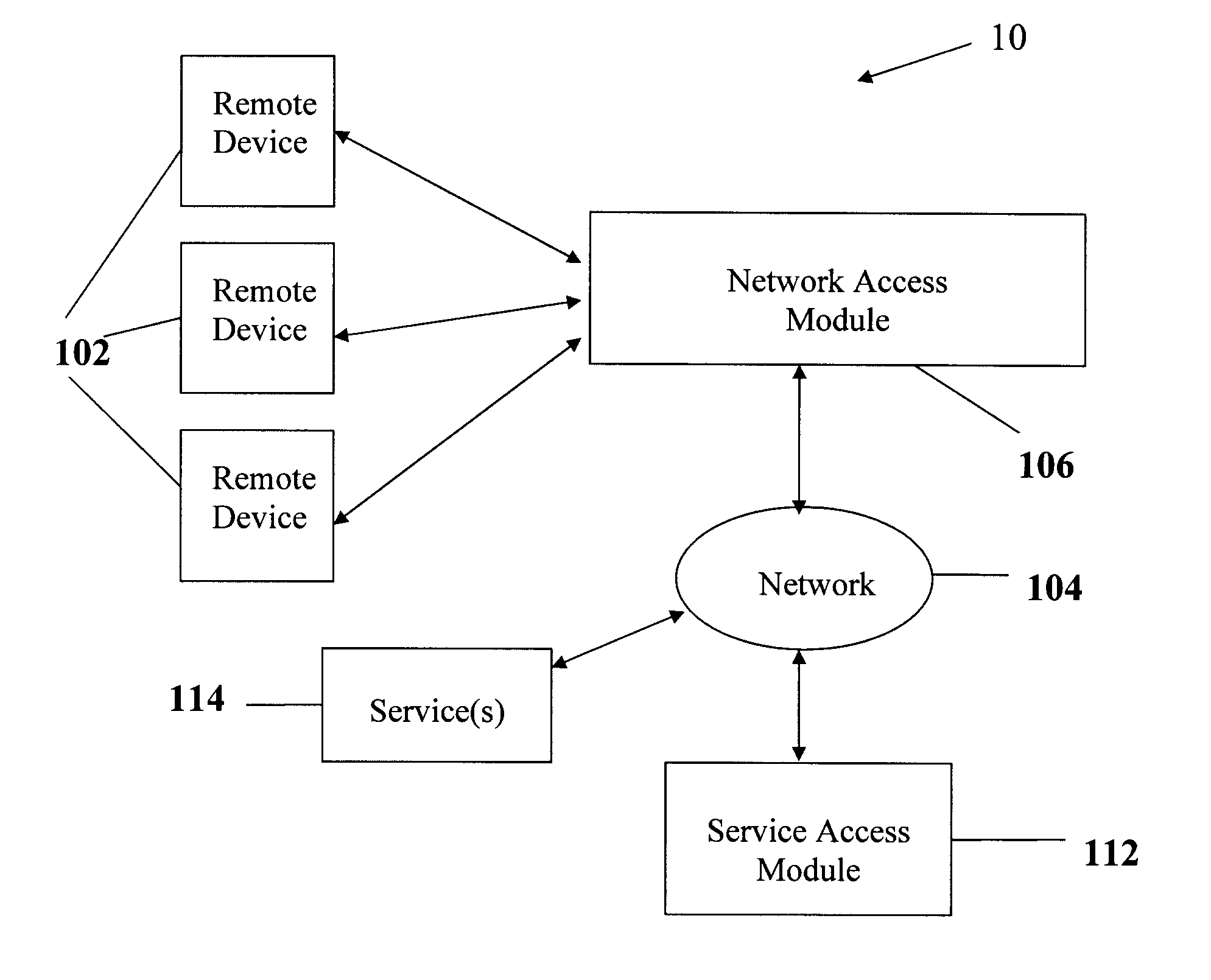
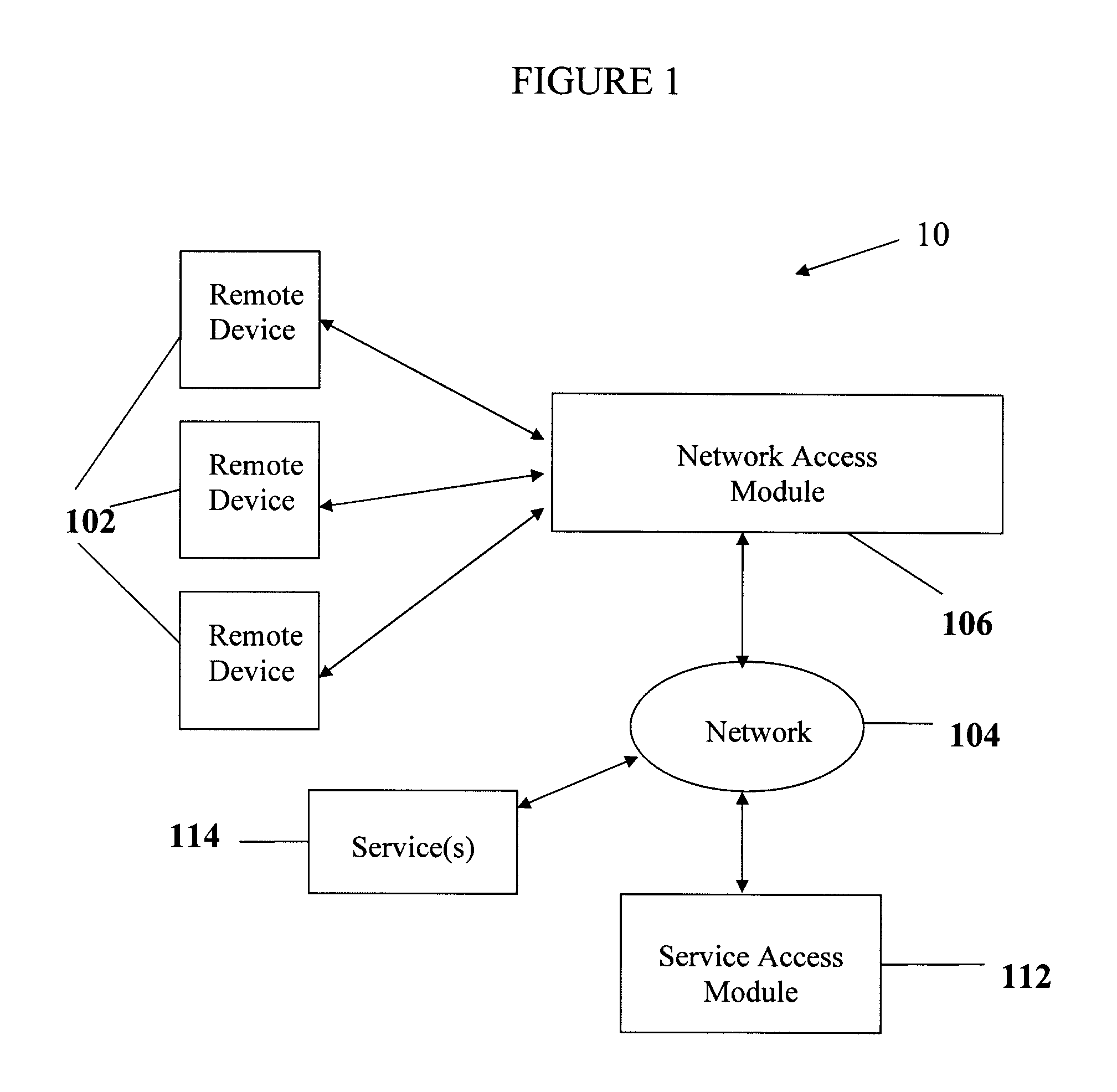
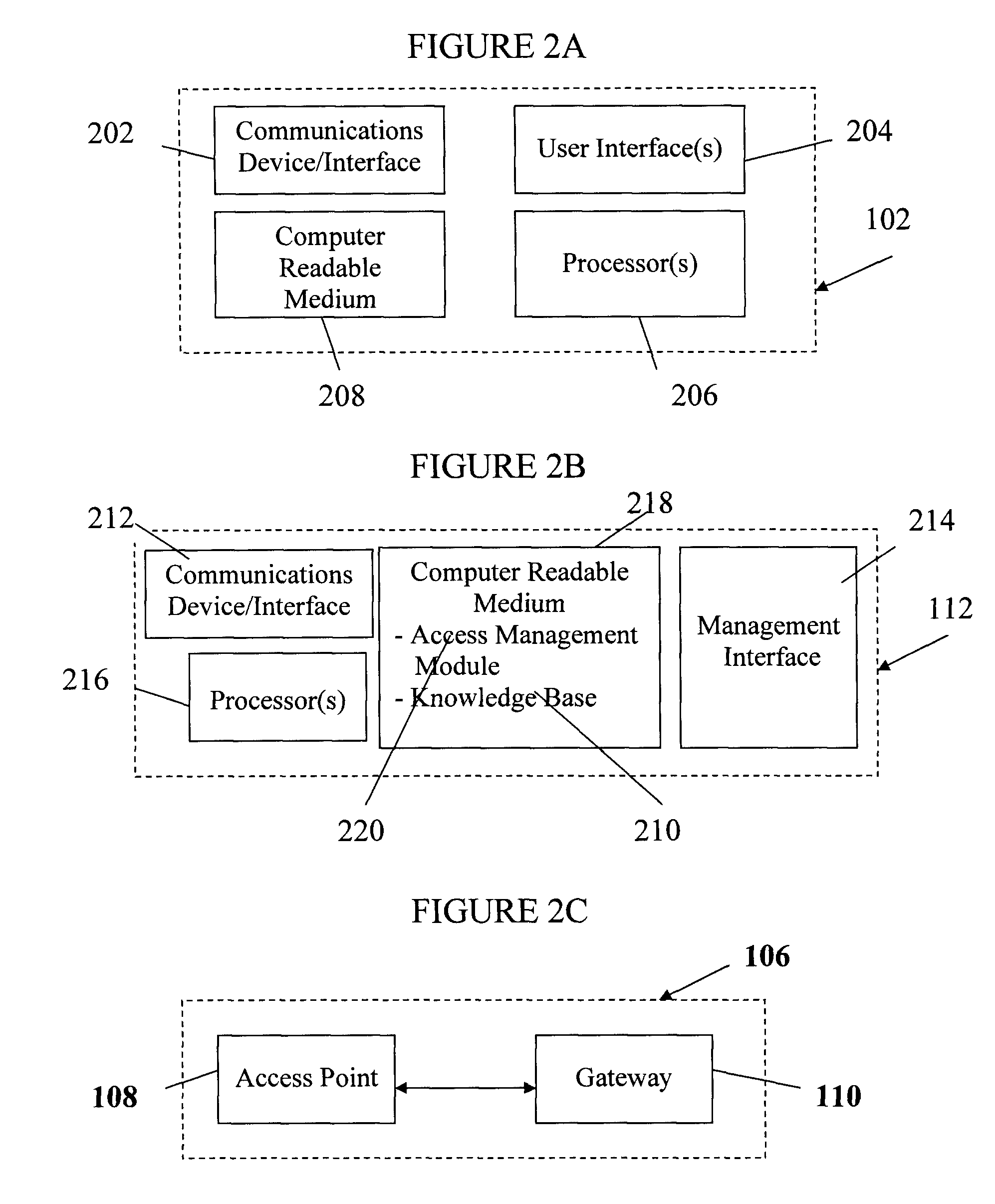
Remote service access system and method
InactiveUS20100107225A1Limited accessDigital data processing detailsMultiple digital computer combinationsData validationComputer network
A wireless service access system and method are disclosed. One aspect of the disclosed system provides a remote device wireless access to one or more services over a communication network, the system comprising a network access module adapted for communicating wirelessly with the remote device and for receiving therefrom identifying data; and a service access module, communicatively linked to the network access module, for authenticating the remote device based on the identifying data and authorizing access to the one or more services thereto via the network access module.
Owner:DATAVALET TECH
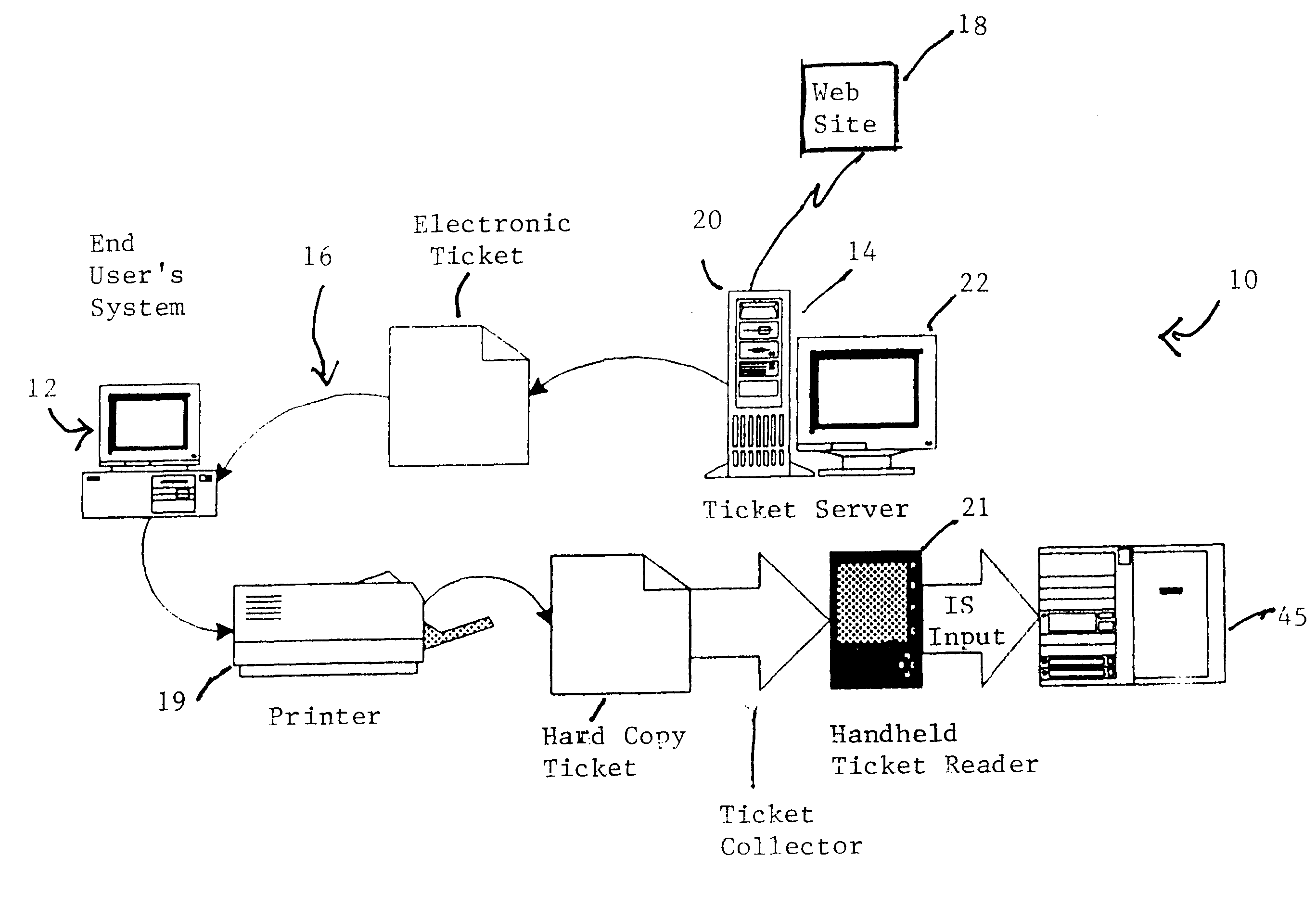
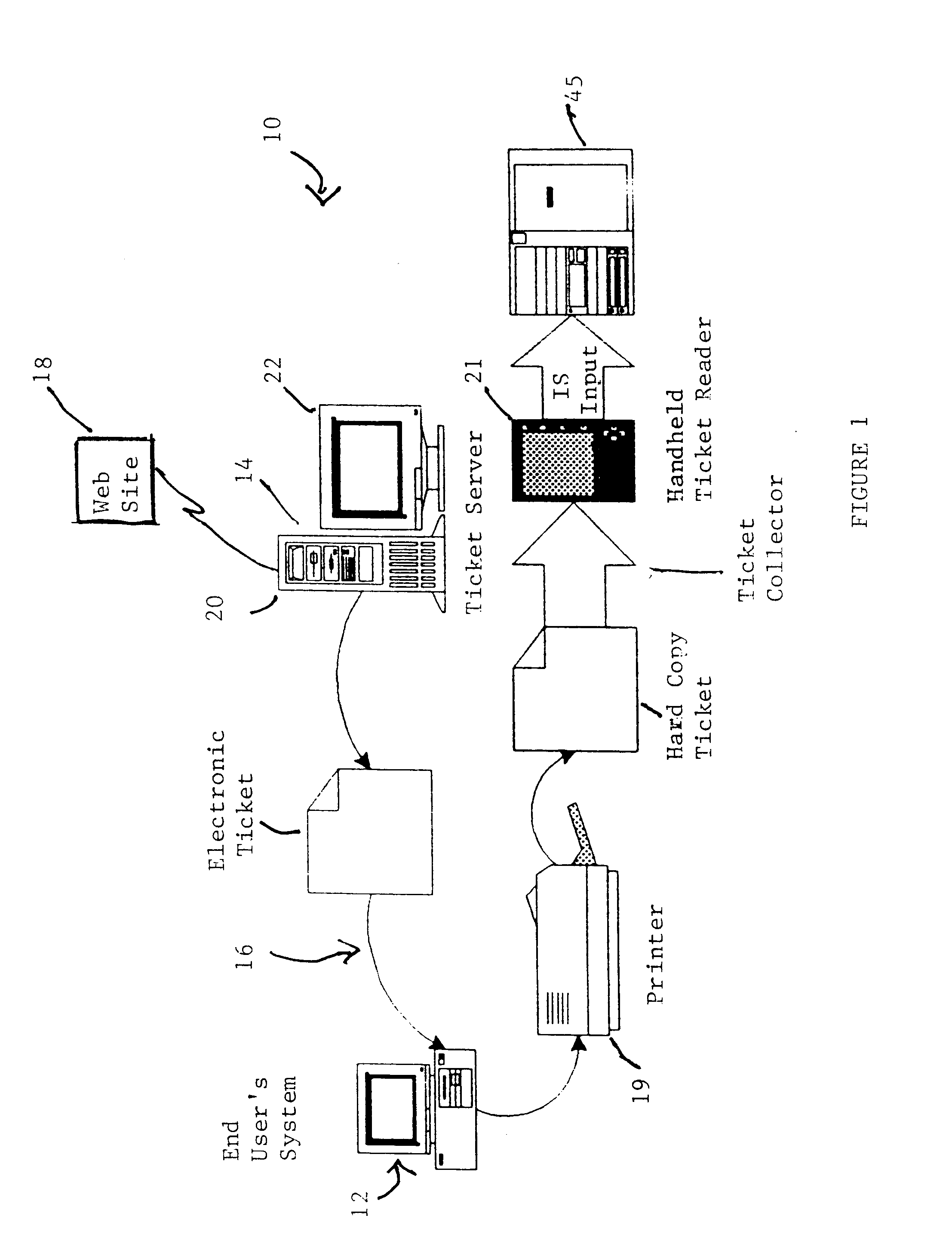
Cryptographic encoded ticket issuing and collection system for remote purchasers
InactiveUS6223166B1Prevent ticket fraudTicket-issuing apparatusElectrical apparatusCollection systemInformation networks
A cryptographic encoded, ticket issuing and collection system for real-time purchase of tickets by purchasers at remote user stations in an information network that includes a plurality of remote user stations coupled to a server in an information network, e.g., the Internet, for purchase of services, products, or tickets to an event. An operator of the remote user station selects a ticket for purchase to an event using standard protocols of information network. An electronic ticket is transmitted to the operator and includes a cypher code created using a public key cryptography system. The operator displays the electronic ticket for verification purposes and proceeds to print out the ticket at the station. The ticket is presented to a ticket collector whereupon the ticket is scanned by a portable terminal for decoding the cypher code using a public key reloaded into the terminal by the producers of the event. The decoded cypher code is compared against the event description stored in the portable terminal and if equal, the ticket is accepted for admission to the event. The ticket information is stored in the portable terminal and subsequently uploaded to the information system to check for duplicate tickets.
Owner:IBM CORP
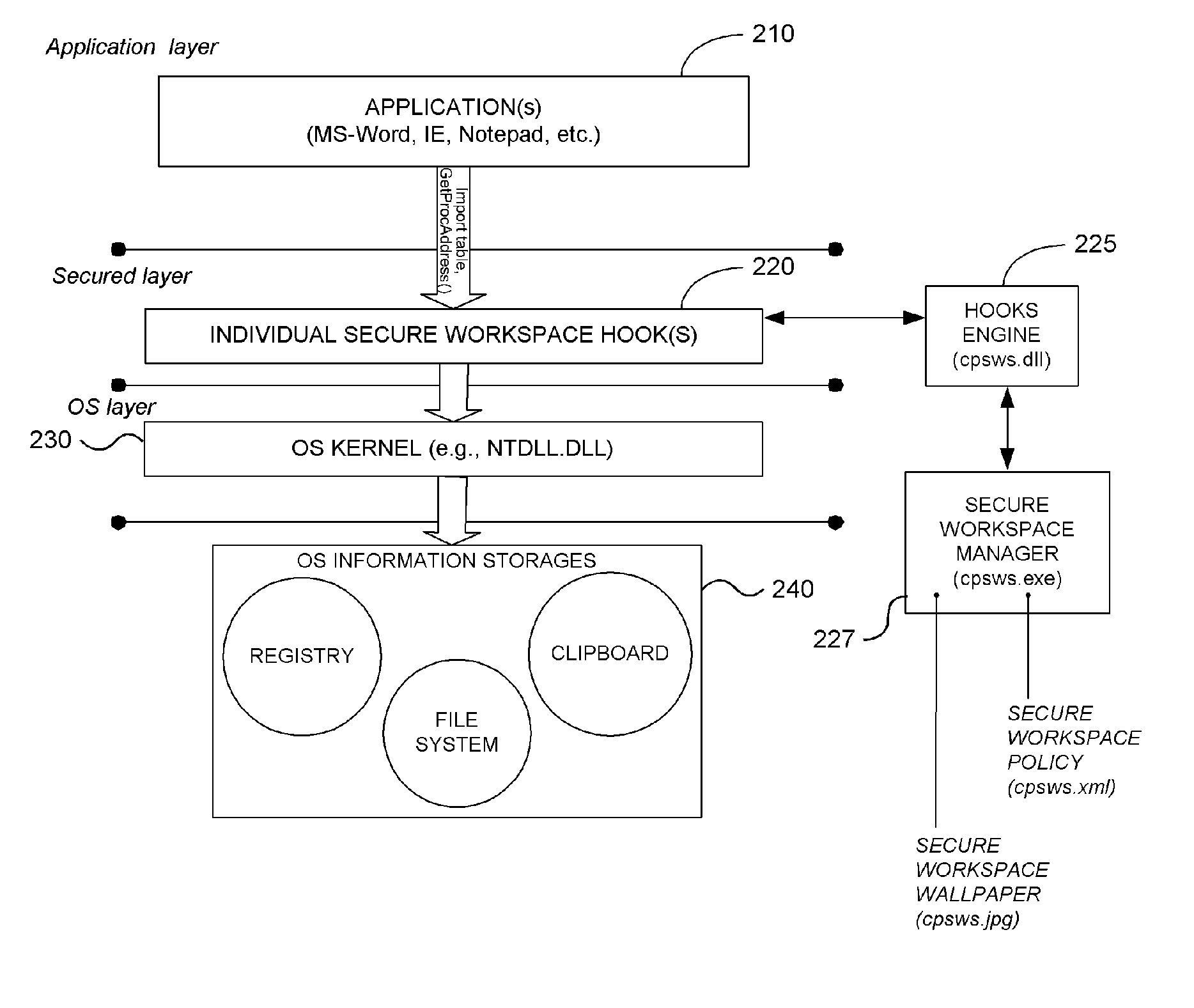
System and Methodology Providing Secure Workspace Environment
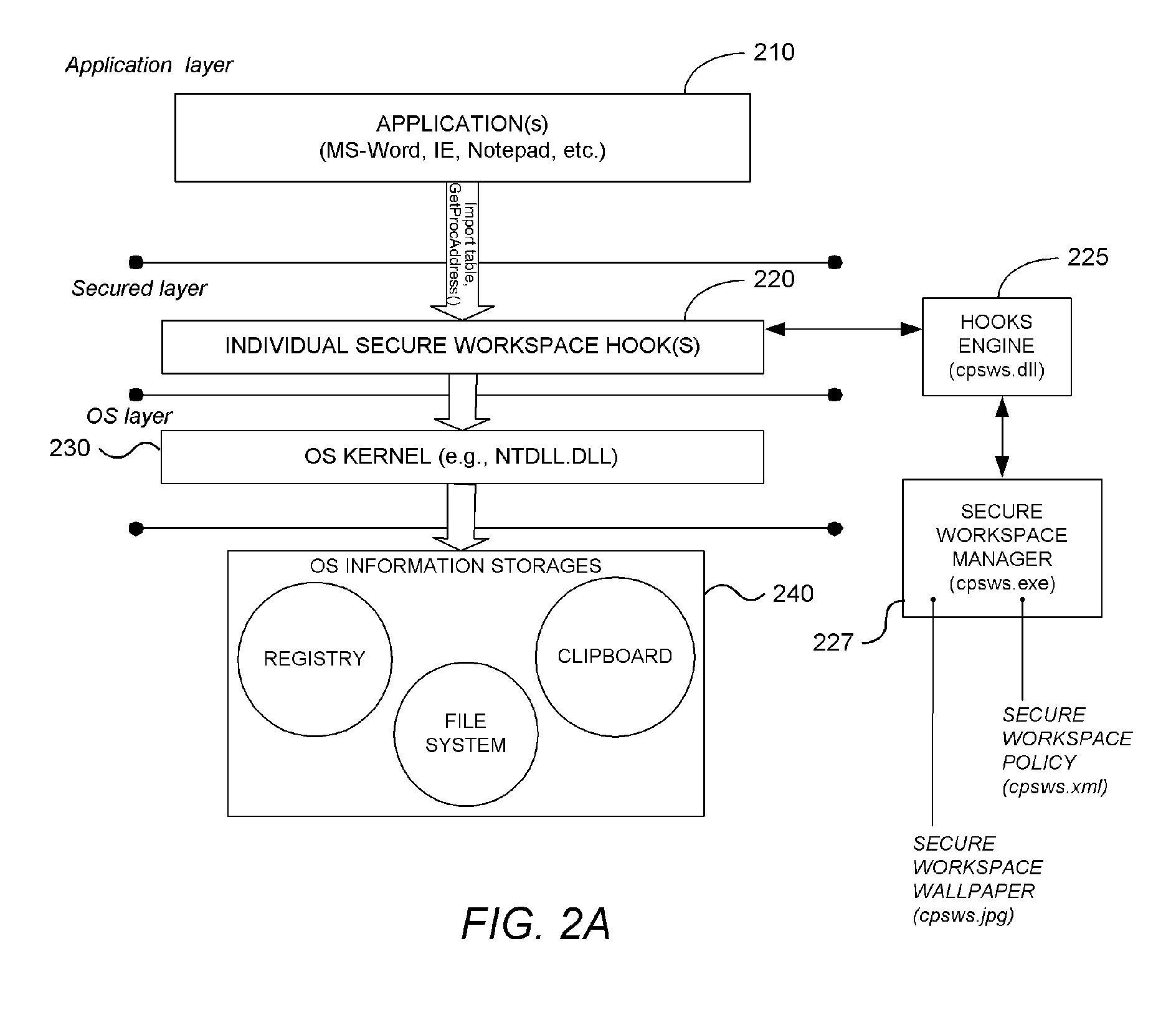
ActiveUS20070101435A1Avoid violationsUser identity/authority verificationAnalogue secracy/subscription systemsOperational systemWorkspace
System and methodology providing a secure workspace environment is described. In one embodiment, for example, in a computer system, a method is described for creating a secured workspace within an existing operating system for allowing users to run applications in a secured manner, the method comprises steps of: creating a policy for configuring the secured workspace, the policy specifying how information created during operation of the applications may be accessed; hooking particular functions of the operating system in order to obtain control over the information created during operation of the applications; during operation of the applications, encrypting the information to prevent unauthorized access; in response to a request for access to the information, determining whether the request complies with the policy; and if the request complies with the policy, satisfying the request by providing access to a decrypted copy of the information.
Owner:CHECK POINT SOFTWARE TECH INC
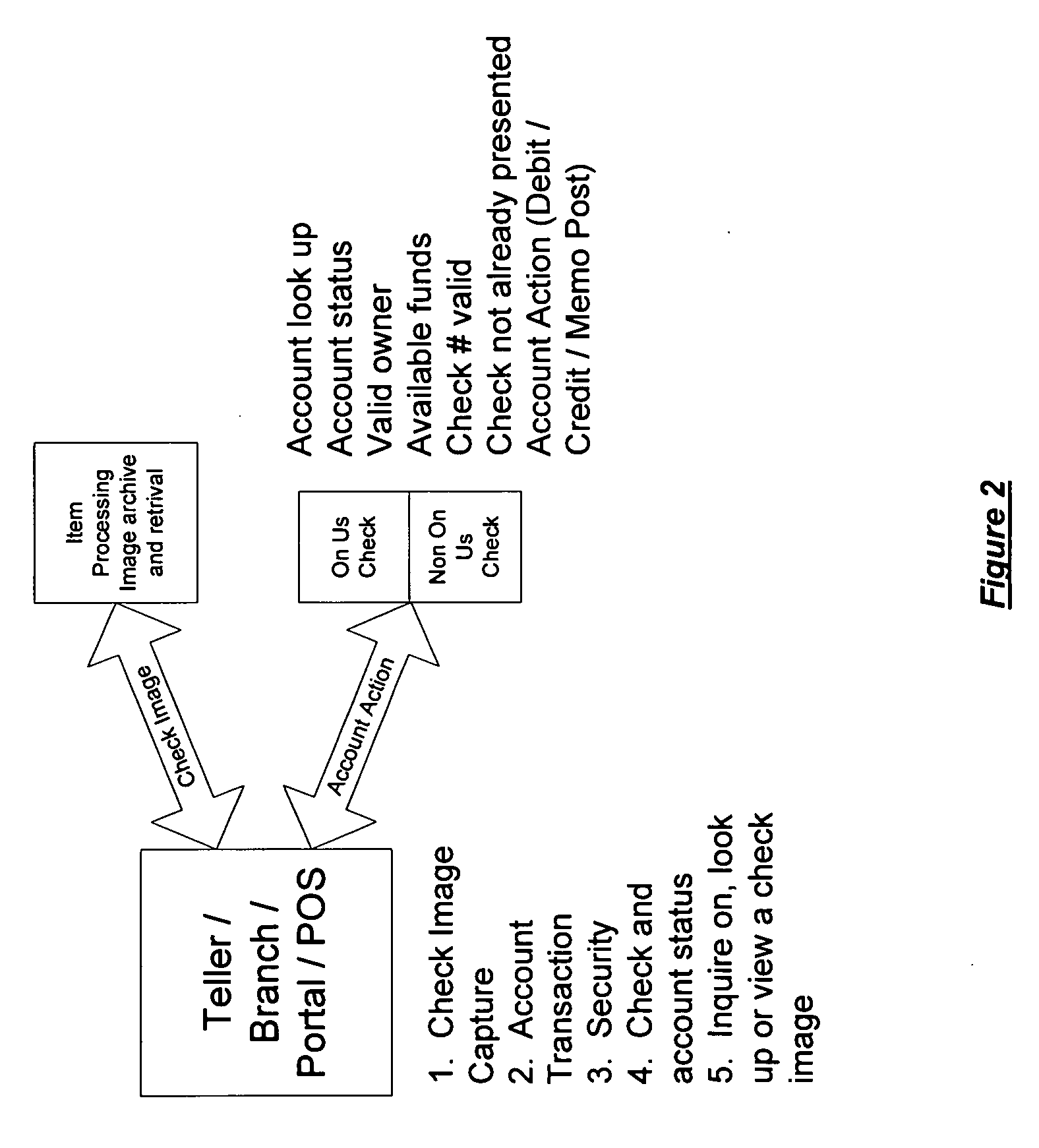
Quality assured secure and coordinated transmission of separate image and data records representing a transaction
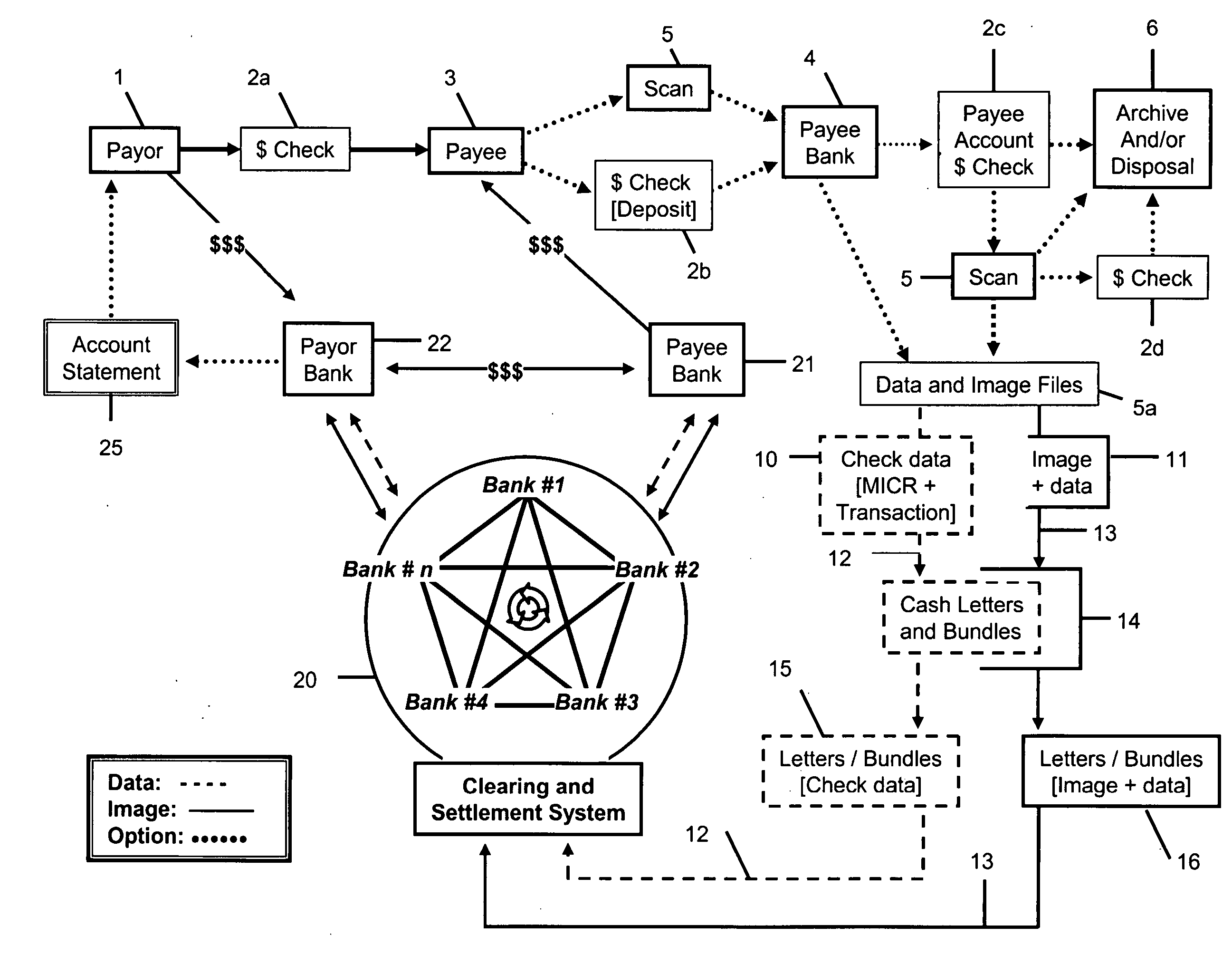
InactiveUS20050071283A1Reduces network impactOptimize network bandwidth utilizationFinanceBilling/invoicingQuality assuranceDocument preparation
A system and method of securely processing an electronic transaction in which an image and data associated with the transaction are separately processed and 1) a legally acceptable substitute record of the transaction may be recreated at any step in processing, 2) unauthorized access to the image, data and or substitute document is detectable, 3) quality assurance of the image and data is provided, and 4) participants in a network may create additional security for the transactions.
Owner:WMR E PIN
Biometric authentication of mobile financial transactions by trusted service managers
ActiveUS20090307139A1Digital data processing detailsUser identity/authority verificationUser inputFinancial transaction
A method for authenticating a financial transaction at a point of sale (POS) includes storing an application program in a first secure element of a mobile phone. The application is configured to generate instruction codes to effect the financial transaction upon verification of a user's identity. The user's credentials are stored in a second SE of the phone, which is operable to verify the user's identity from a biometric trait of the user input to the phone and to generate data authenticating the financial transaction in response to the verification of the user's identity. At the POS, the user invokes the application and then inputs a biometric trait to the phone. The second SE verifies the user's identity, and upon verification, generates data authenticating the transaction. The financial transaction data, including the instruction codes and the authenticating data, are then transmitted from the phone to the POS.
Owner:PAYPAL INC
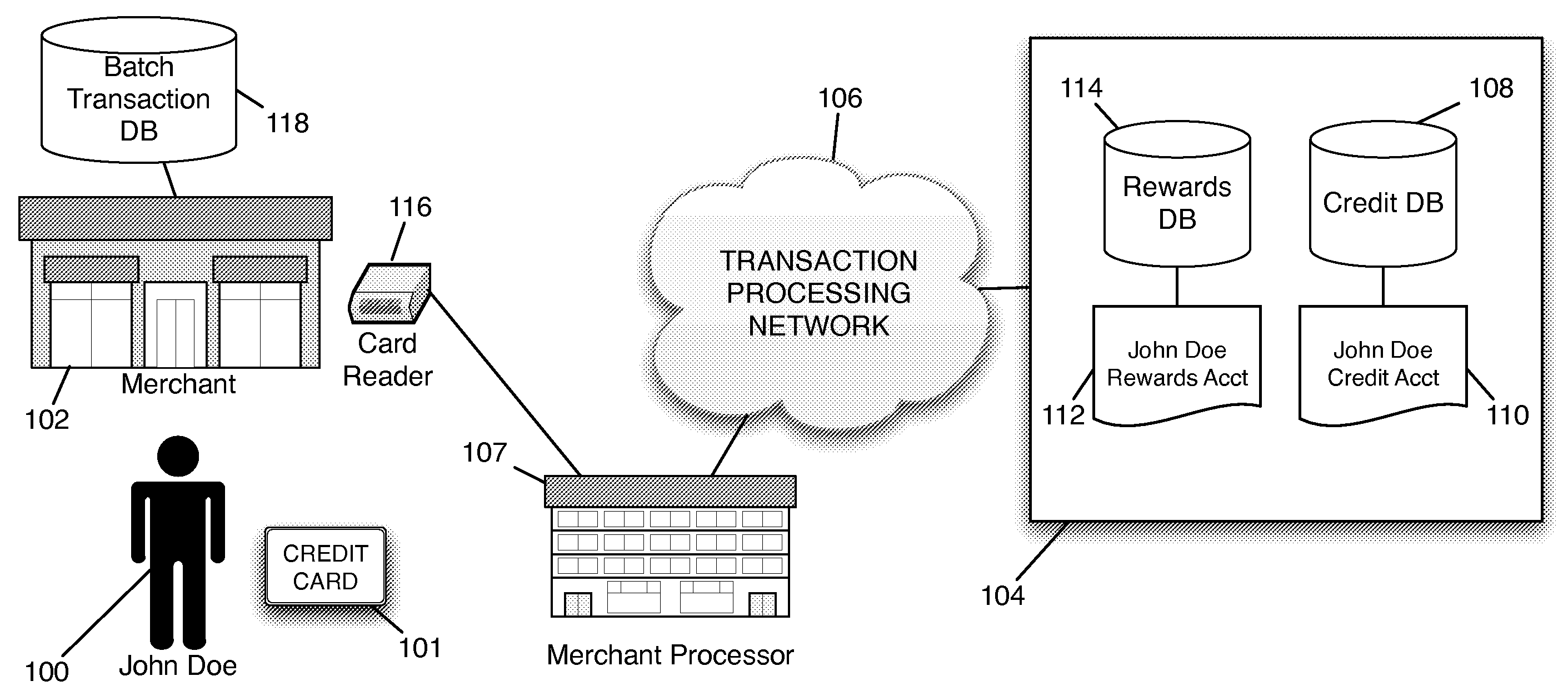
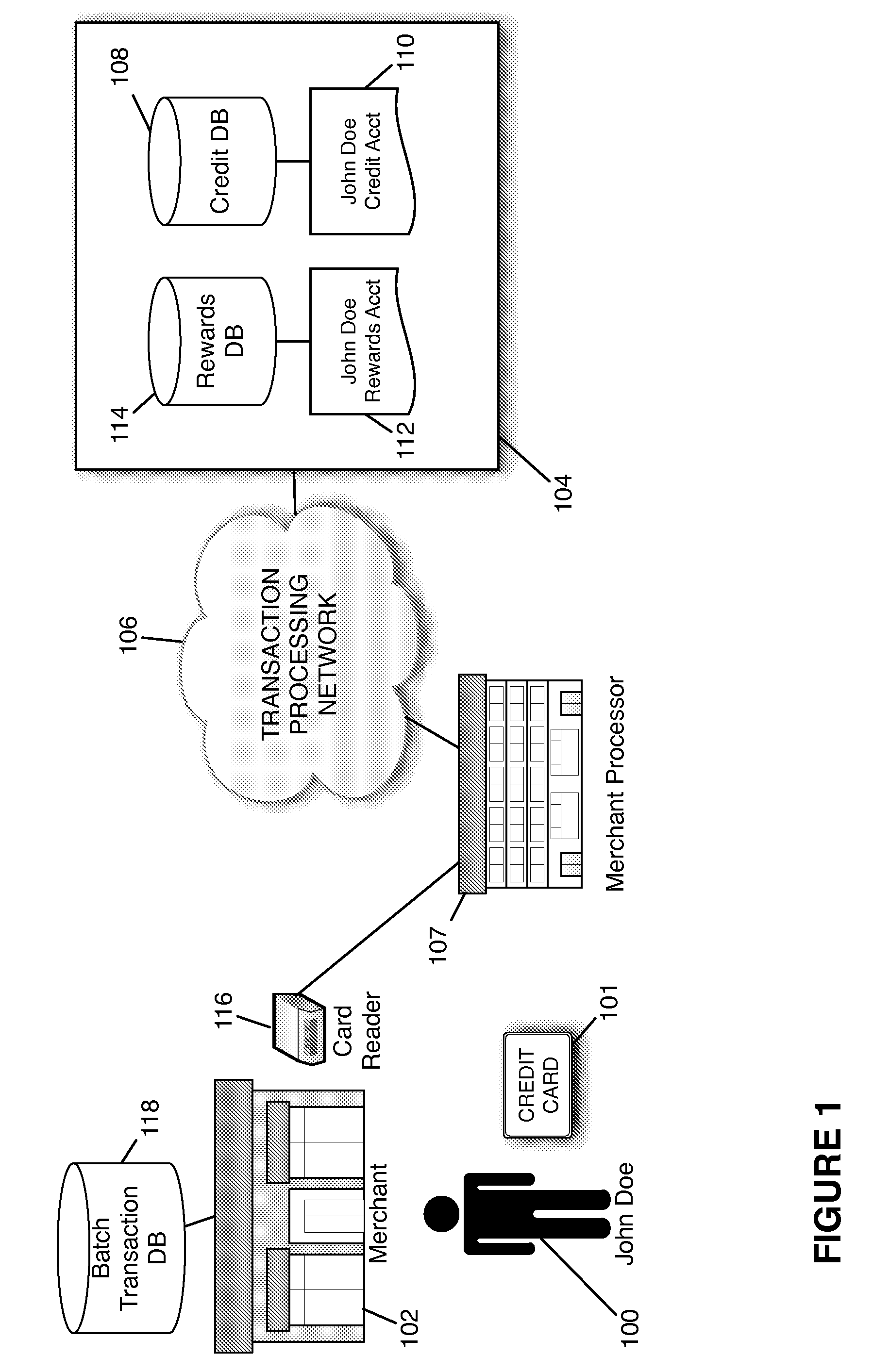
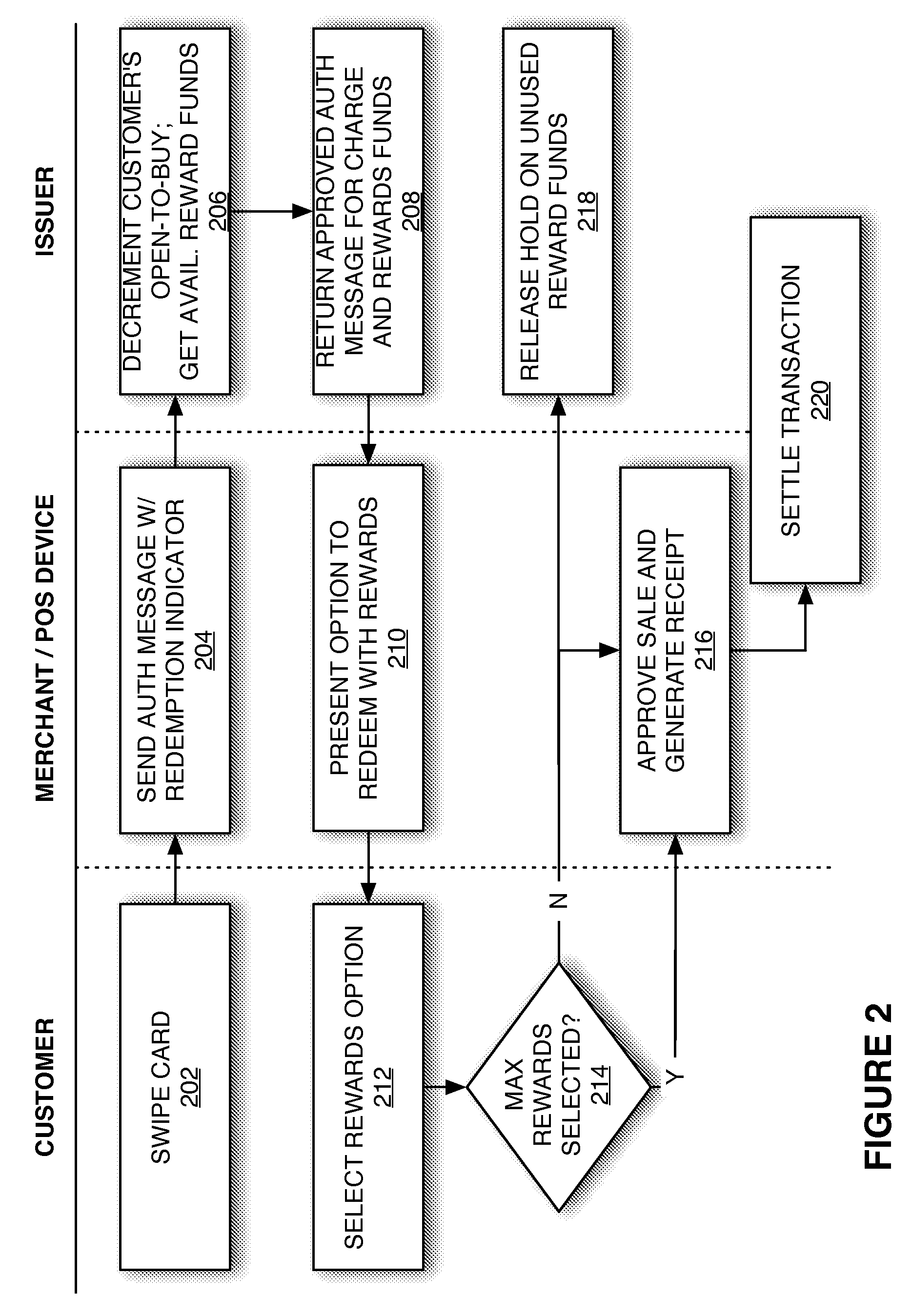
Redemption of Credit Card Rewards at a Point of Sale
Systems and methods are described for redeeming rewards at a merchant's point-of-sale. The reward redemption takes place in real time and can be accomplished without the active participation of the merchant. A single credit card with no additional information may be used with a single swipe from the consumer to access both credit and rewards accounts, such that a single authorization request is made to encompass both rewards and credit. Merchants can be fully compensated for transactions by the issuer despite the customer's choice to redeem rewards.
Owner:DFS SERVICES
Notification systems and methods with user-definable notifications based upon occurance of events
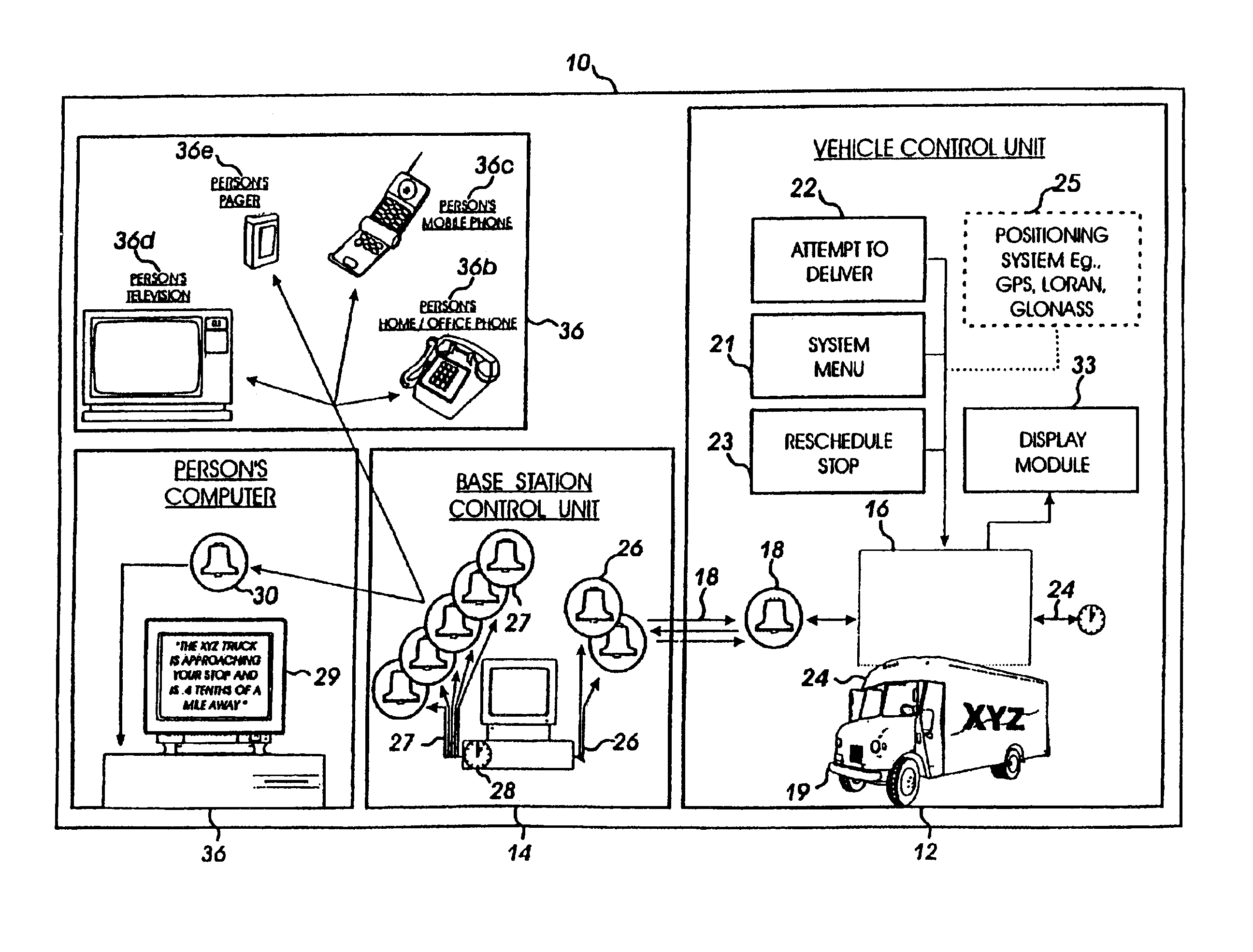
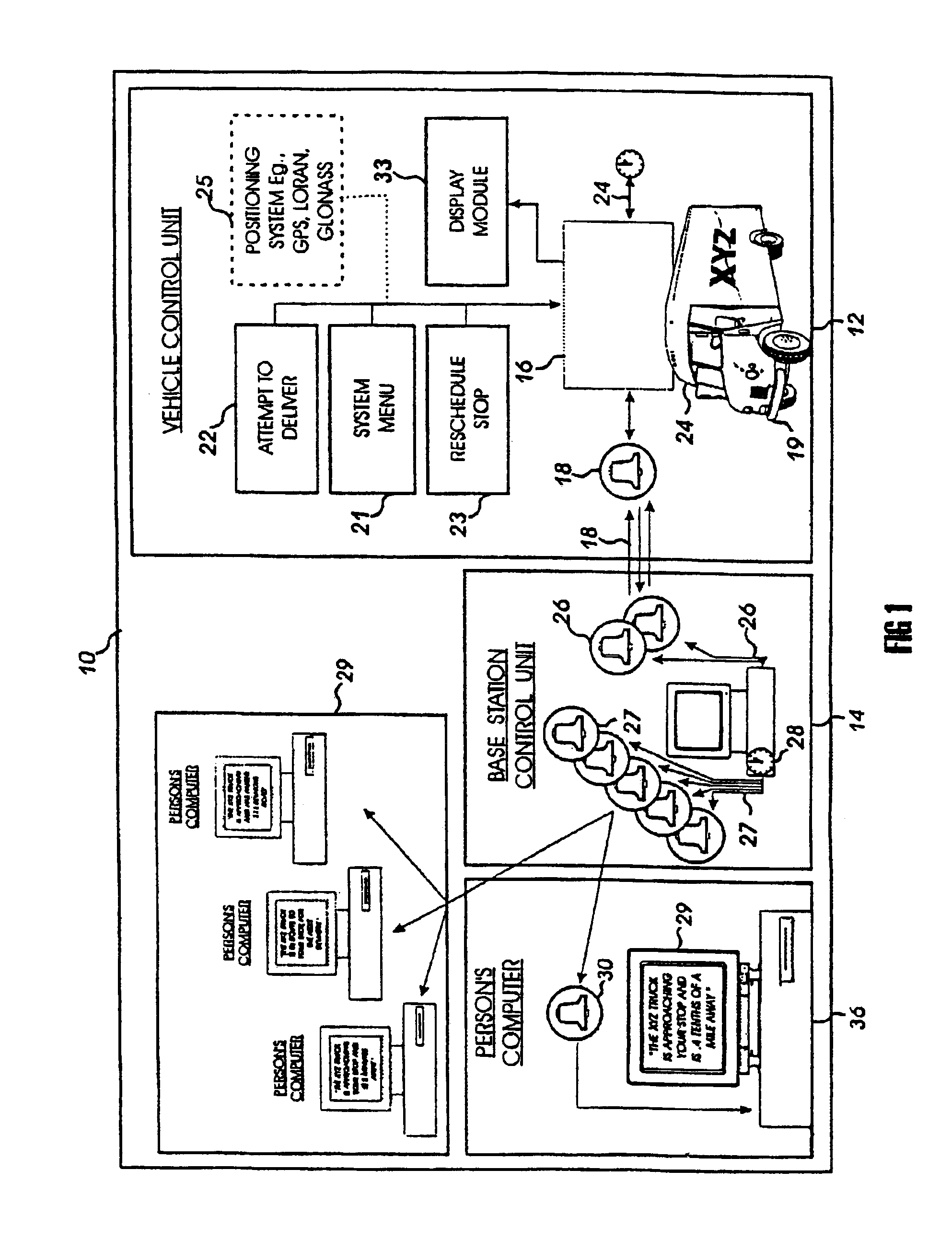
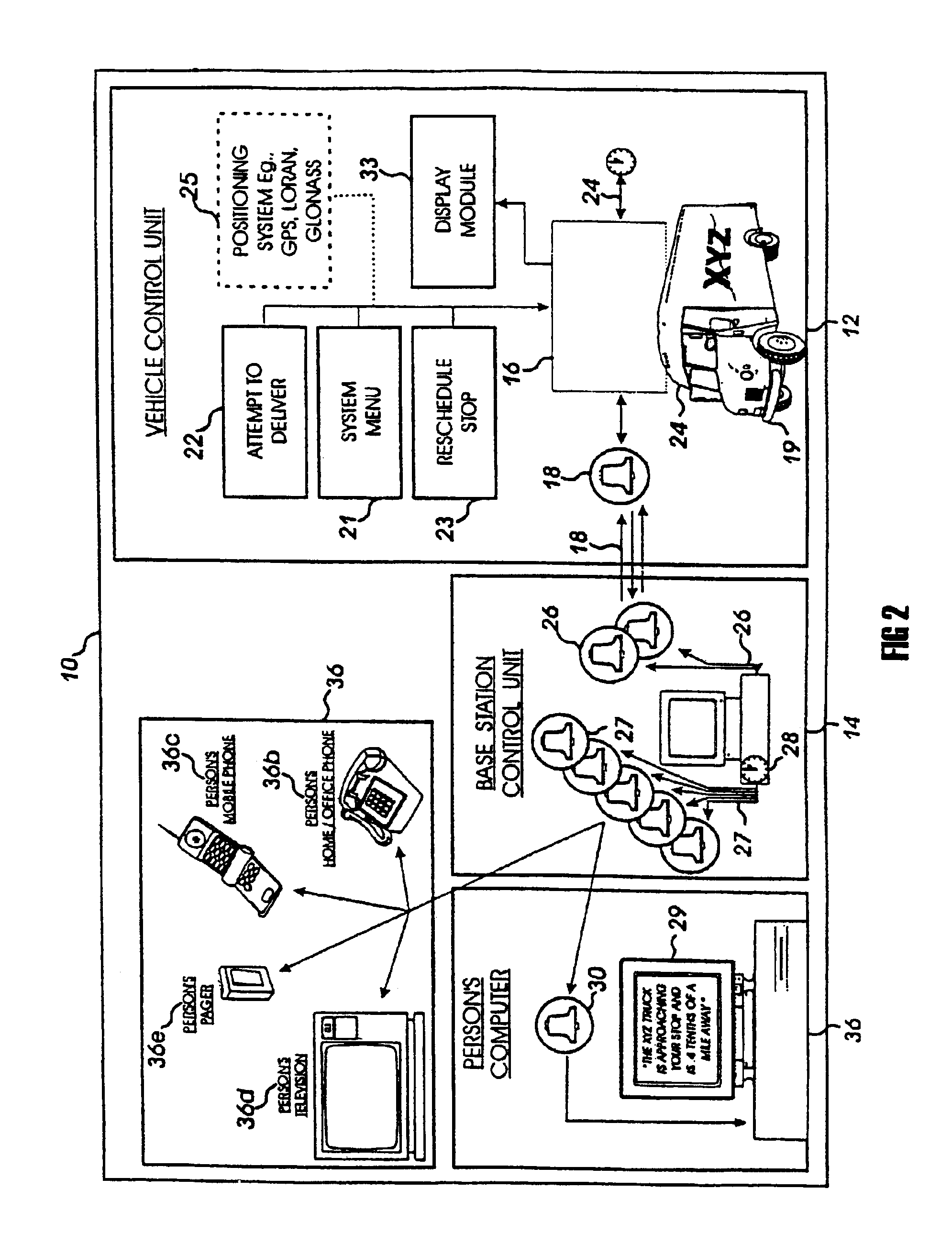
InactiveUS6904359B2Instruments for road network navigationRoad vehicles traffic controlMobile vehicleTelecommunications link
Methods and systems are disclosed for a vehicle status reporting system for allowing a user to define when a user will receive a vehicle status report about the status of a mobile vehicle, in relation to a location, for establishing a communication link between the system and the user, and for delivering the status report during the communication link, the status report indicating occurrence of one or more events.
Owner:SHIPPING & TRANSIT
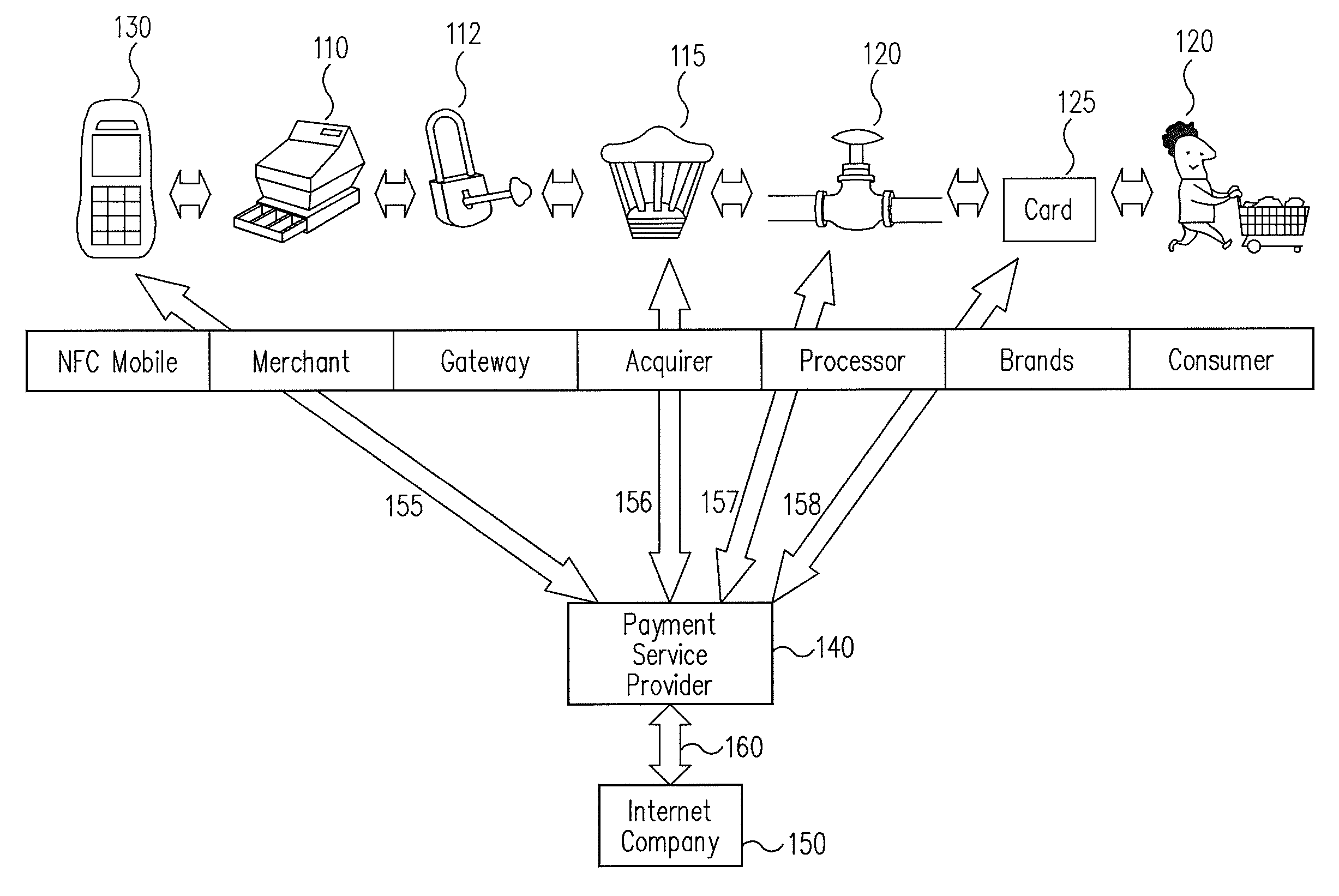
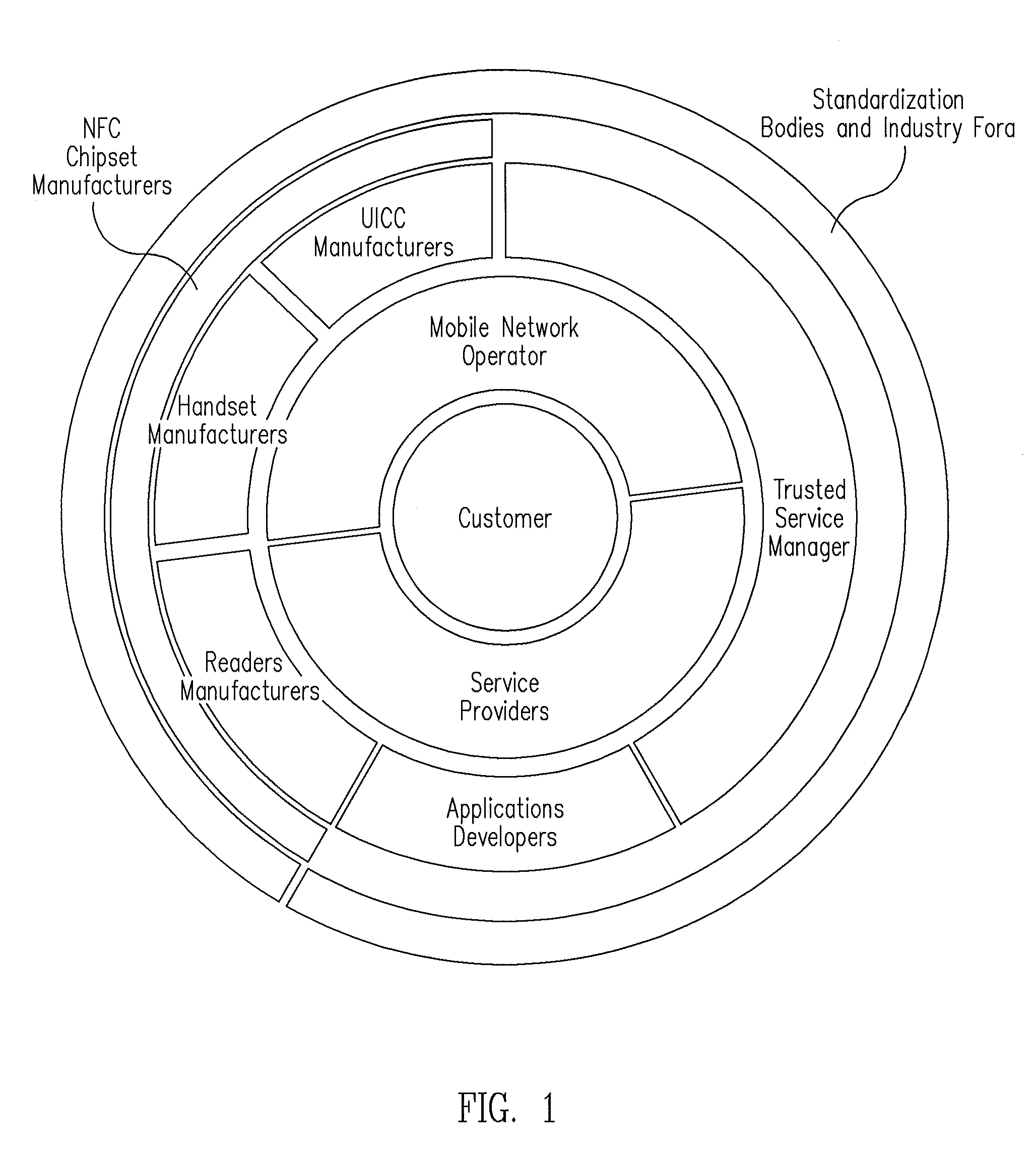
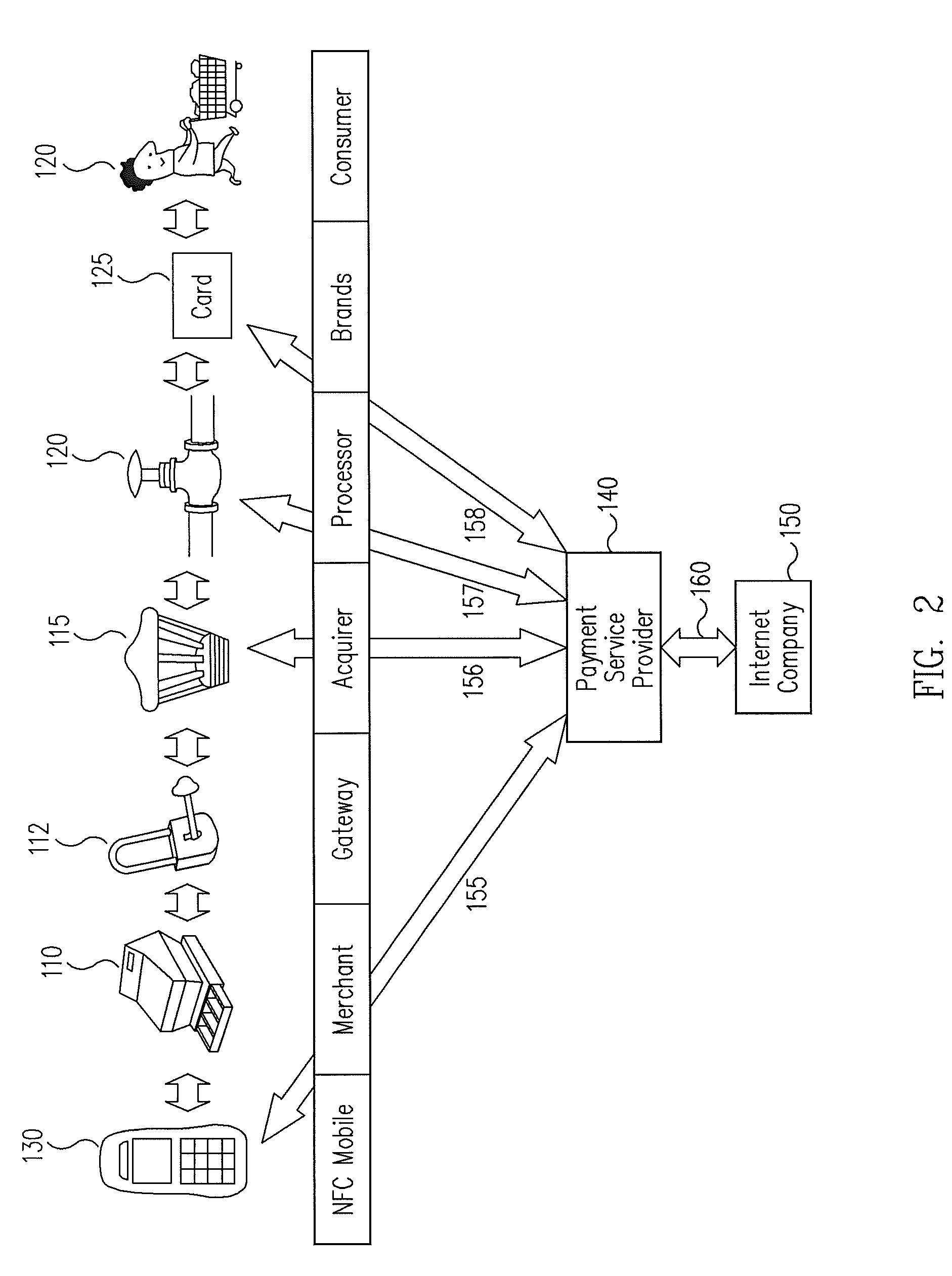
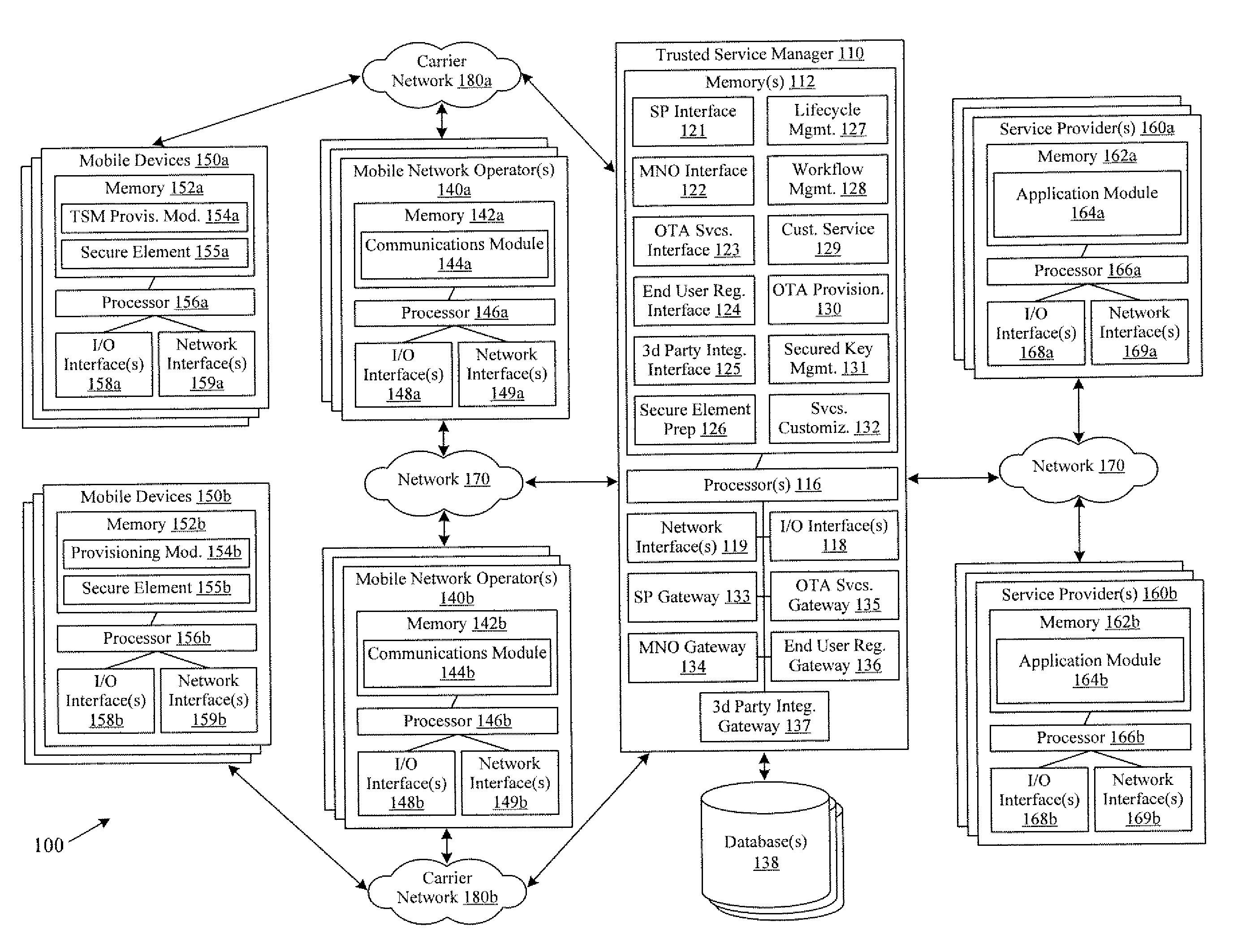
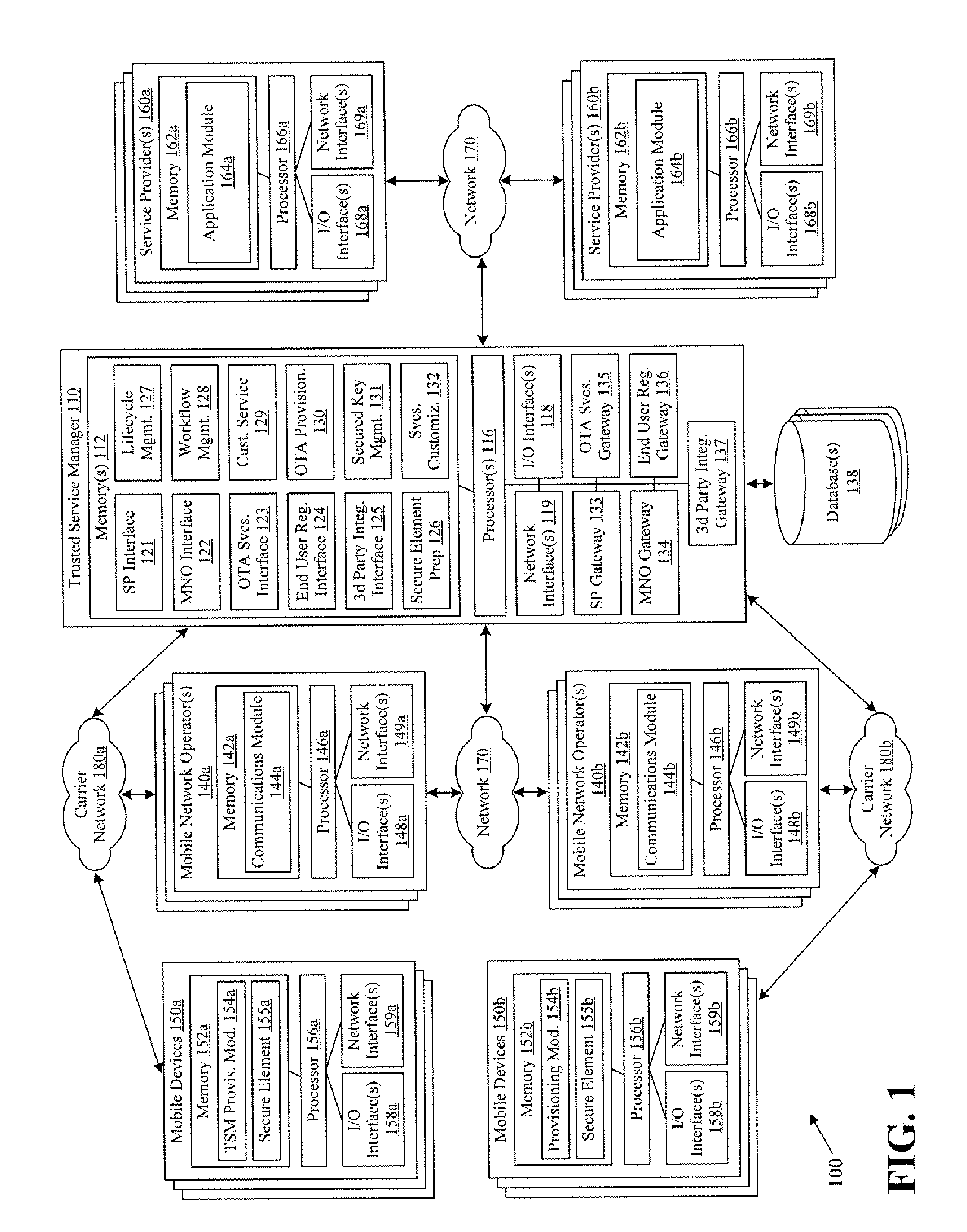
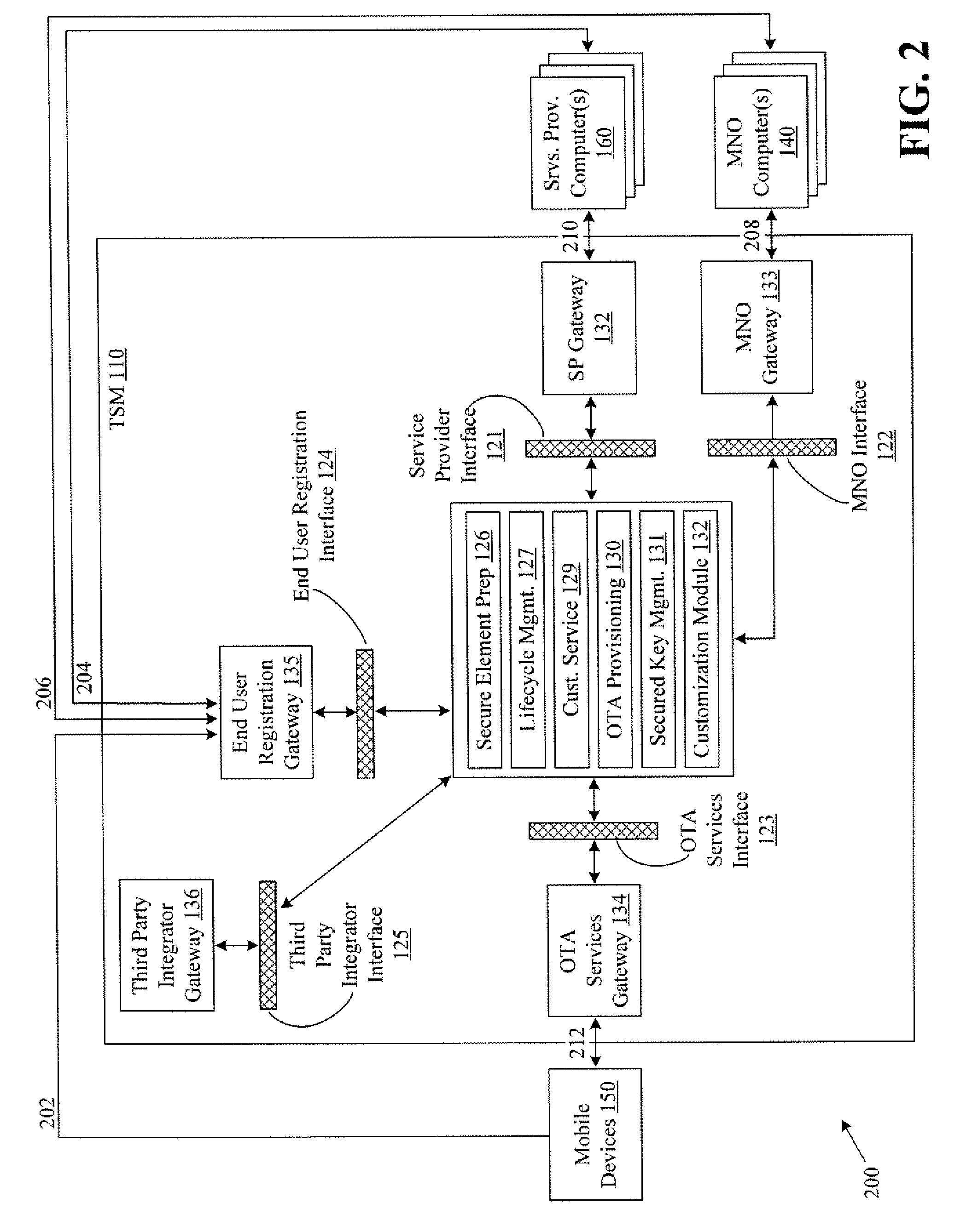
Systems and methods for providing trusted service management services
InactiveUS20100291904A1Easy maintenanceOptimize networkService provisioningSpecial service for subscribersService provisionMobile device
Embodiments of the invention provide systems and methods for providing trusted service management services. According to one embodiment, a system can include at least one service provider gateway operable to receive and transmit messages with multiple service providers; at least one mobile network operator gateway operable to receive and transmit messages with multiple mobile network operators; at least one provisioning gateway operable to transmit mobile device application data with multiple mobile devices and to receive messages from the plurality of mobile devices. The system can further include a processor operable to execute computer-executable instructions to: facilitate service provider communications by providing a common service provider interface for the service providers; facilitate mobile network operator communications by providing a common mobile network operator interface for the mobile network operators; facilitate provisioning multiple mobile device applications with the mobile devices; and facilitate communications with the mobile devices.
Owner:FIRST DATA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com