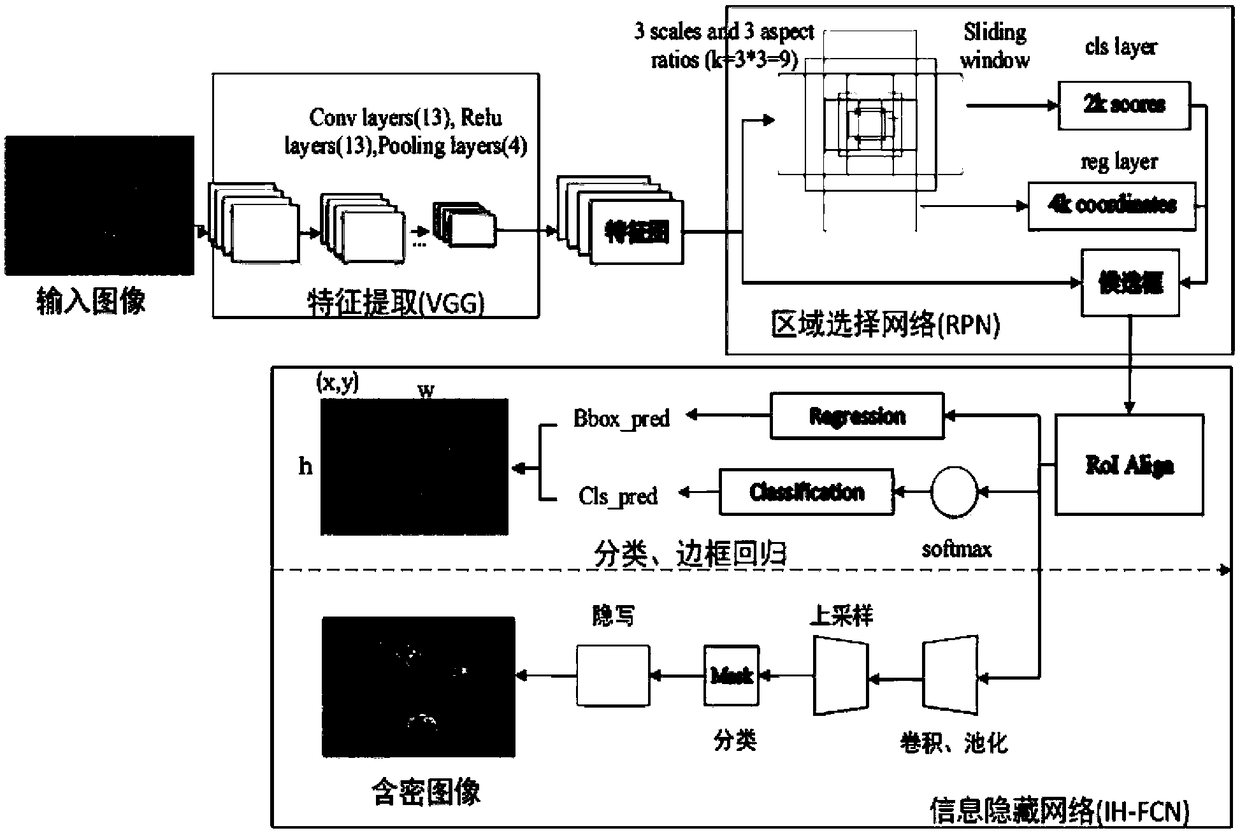
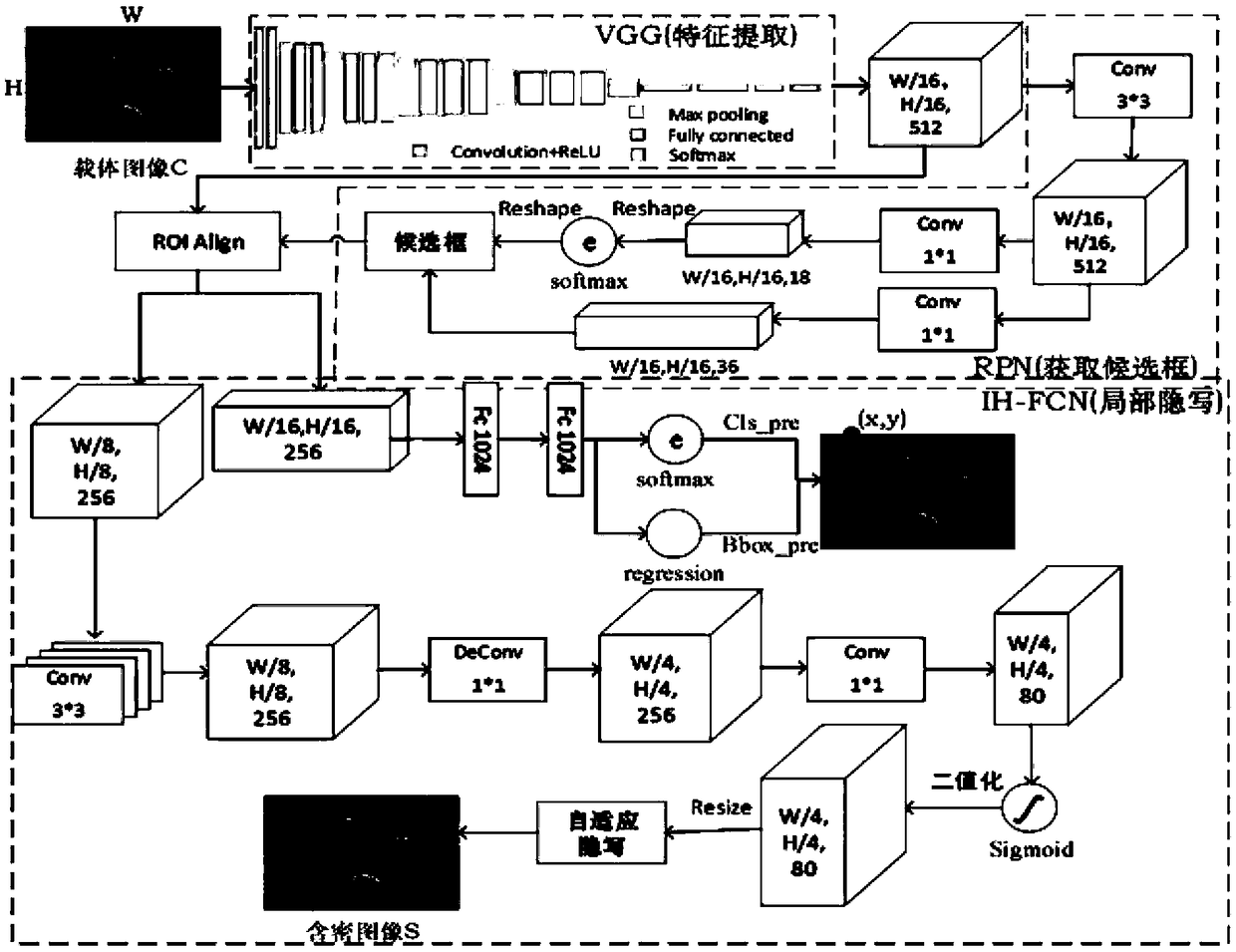
Patents
Literature
398 results about "Steganography" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
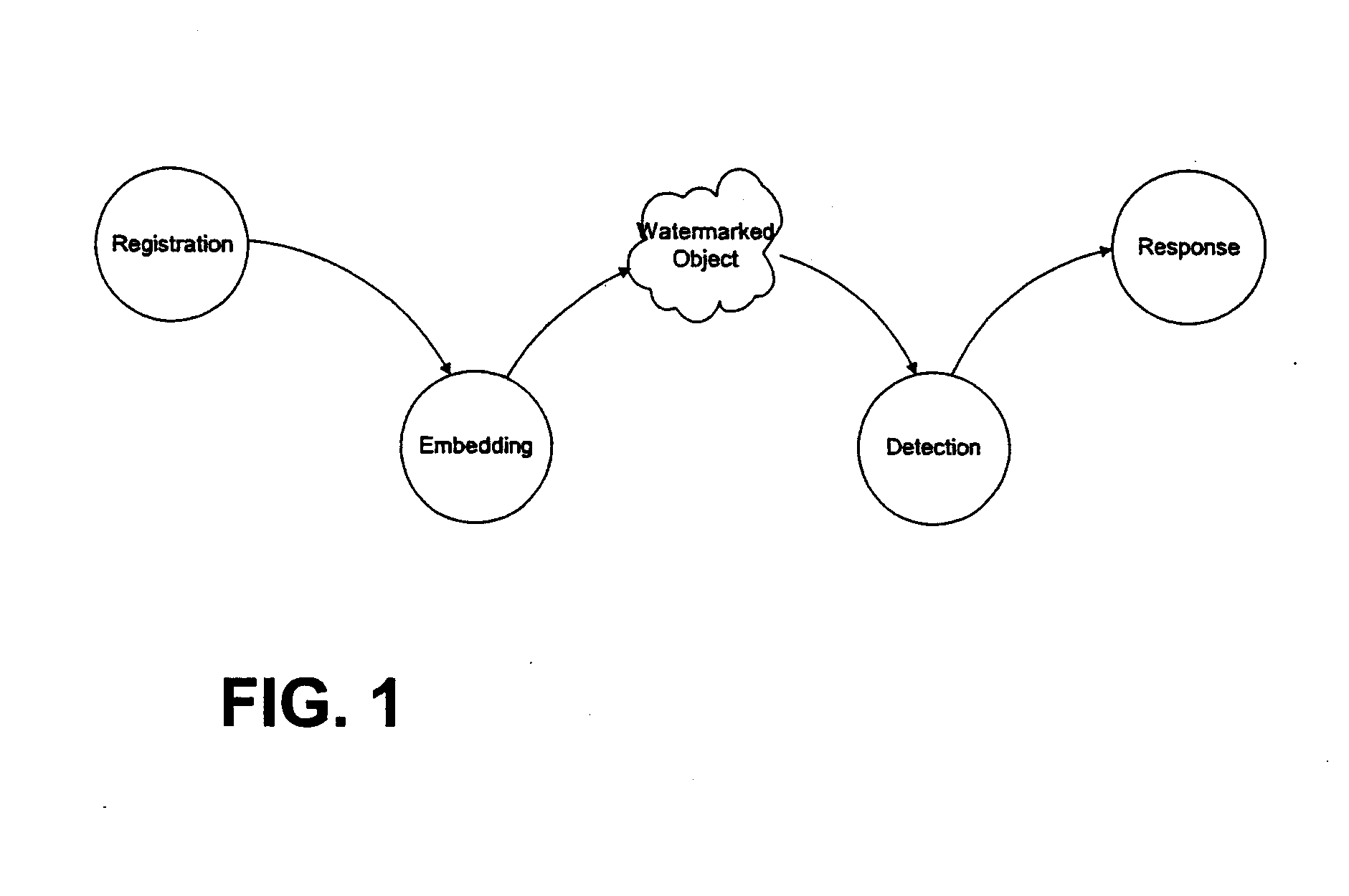
Steganography (/ˌstɛɡəˈnɒɡrəfi/ STEG-ə-NOG-rə-fee) is the practice of concealing a file, message, image, or video within another file, message, image, or video. The word steganography combines the Greek words steganos (στεγᾰνός), meaning "covered or concealed", and graphe (γραφή) meaning "writing".
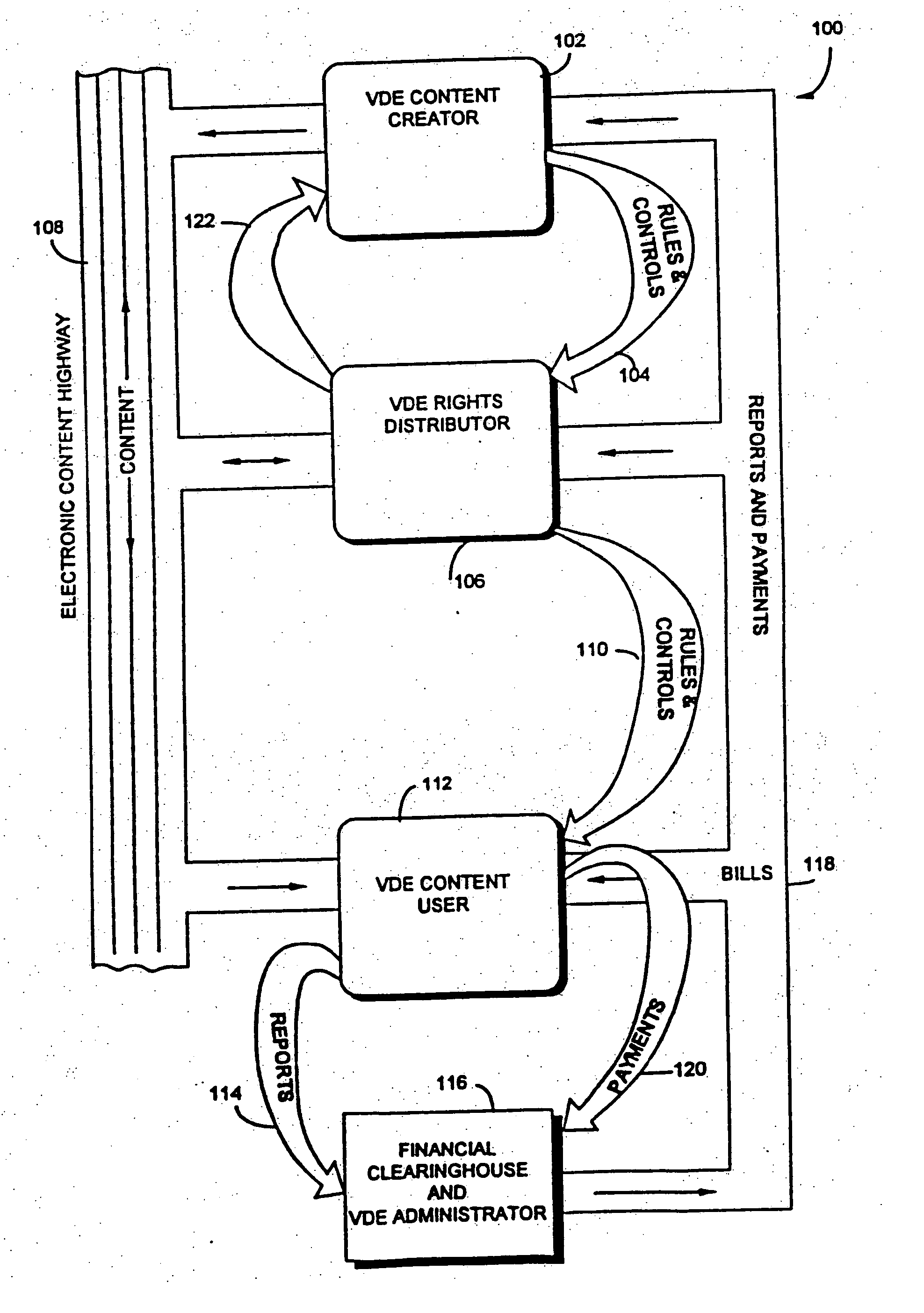
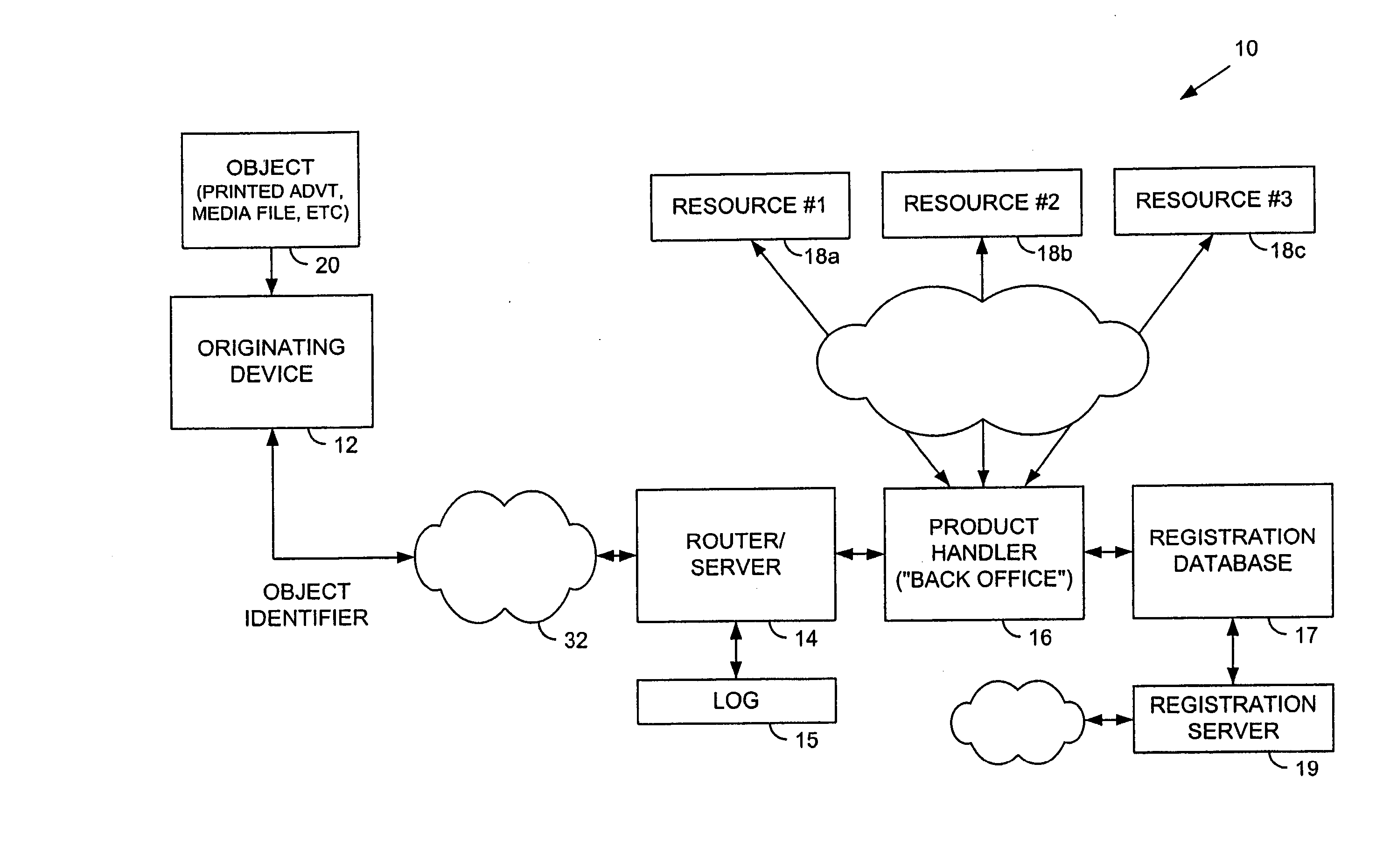
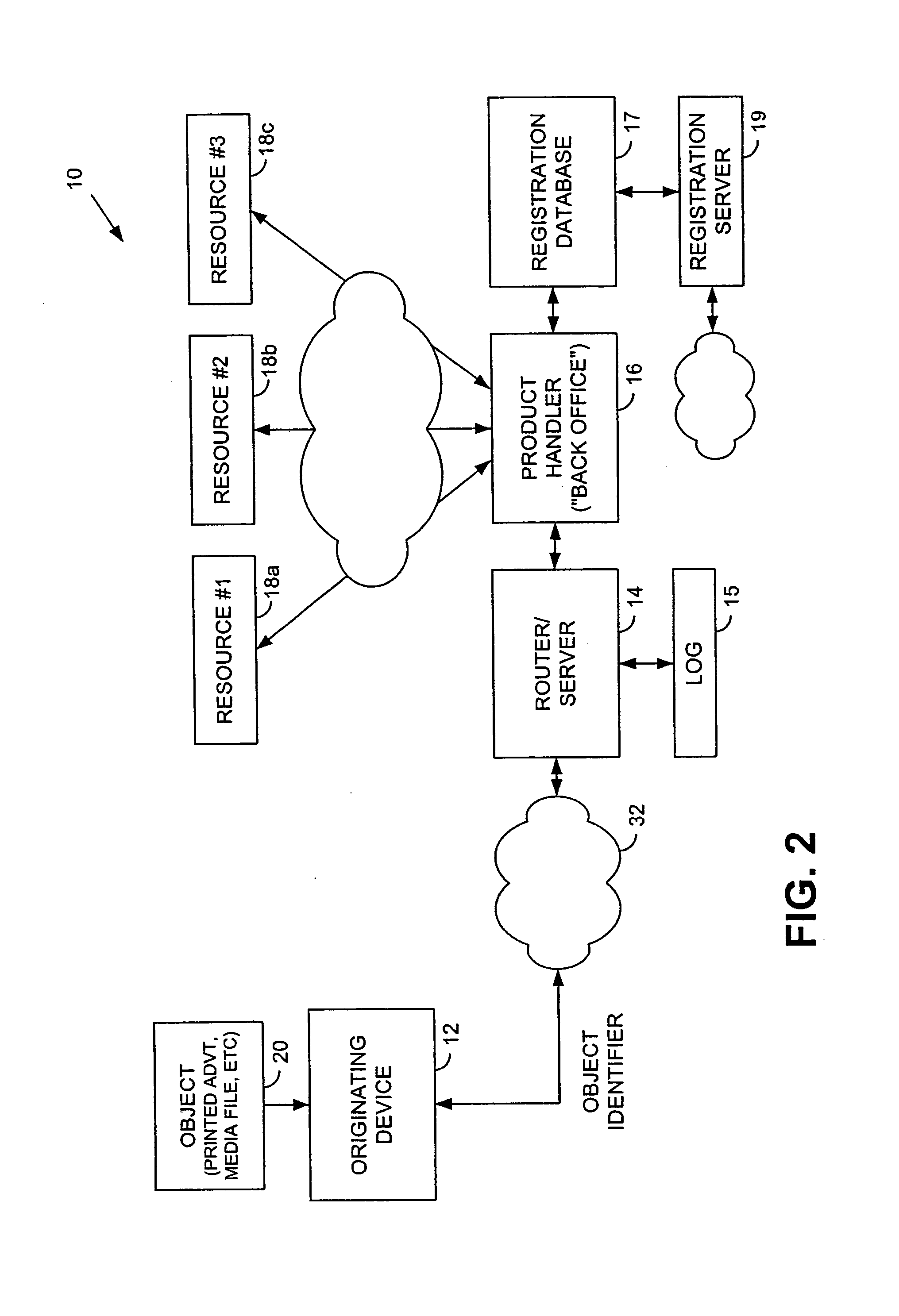
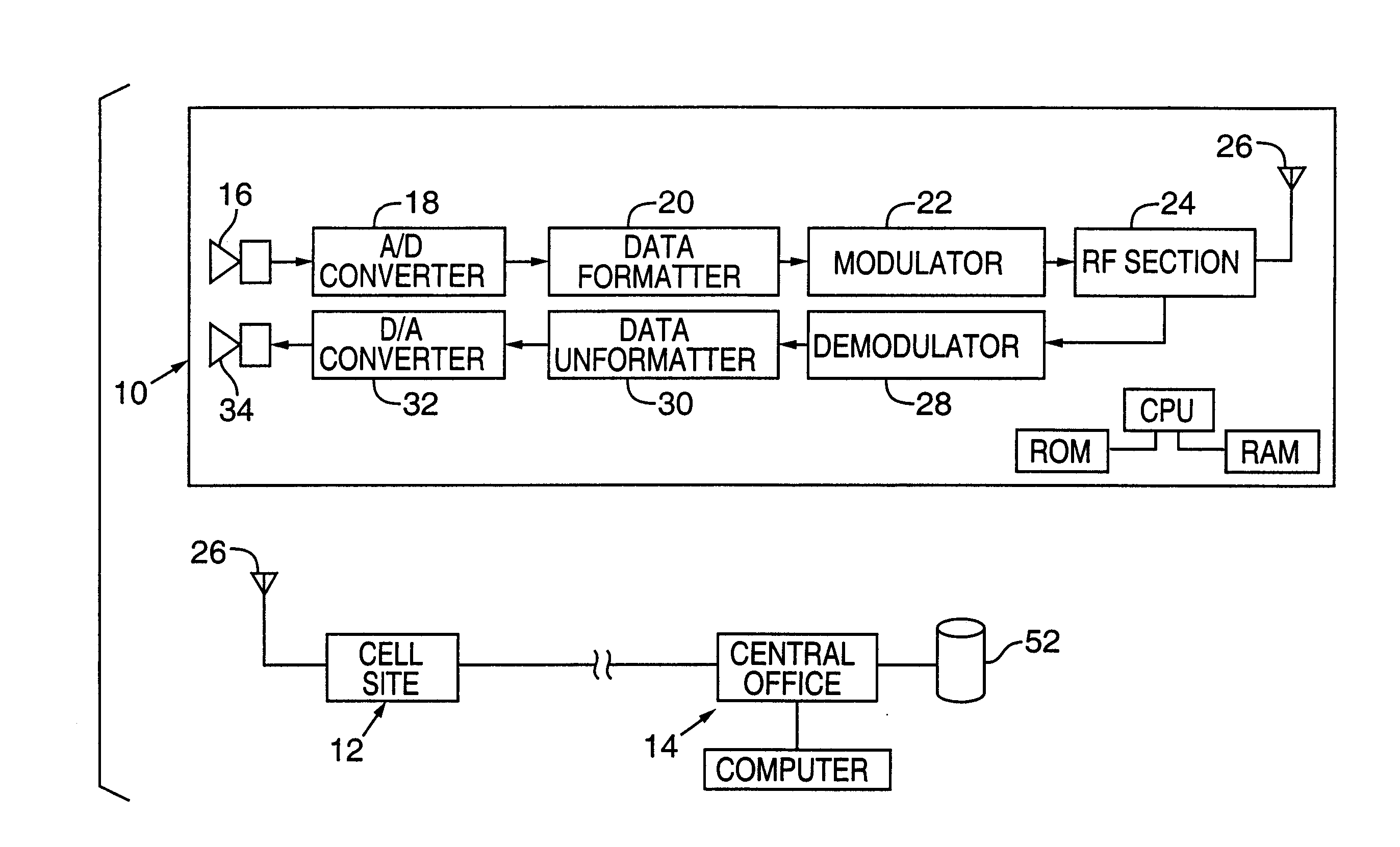
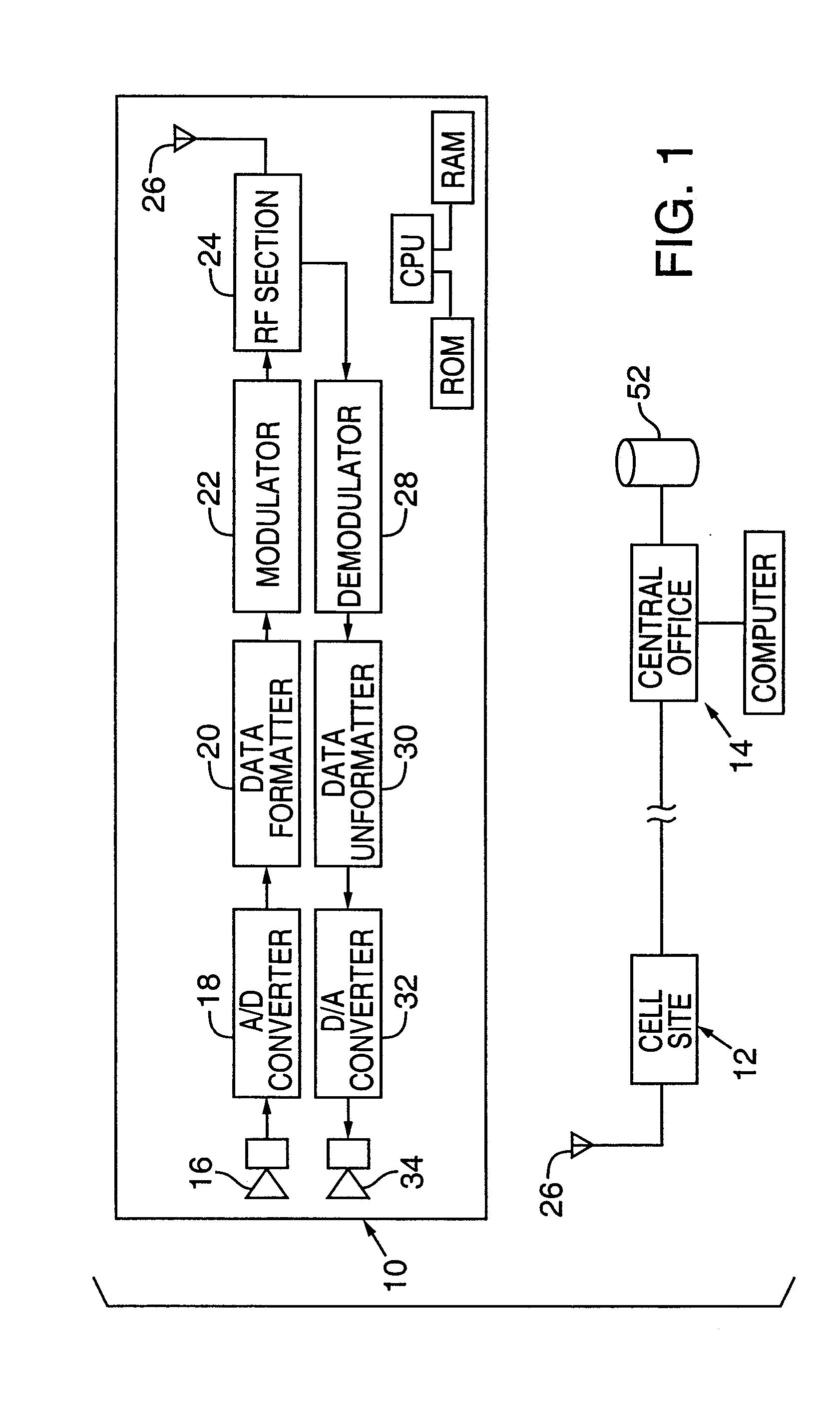
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
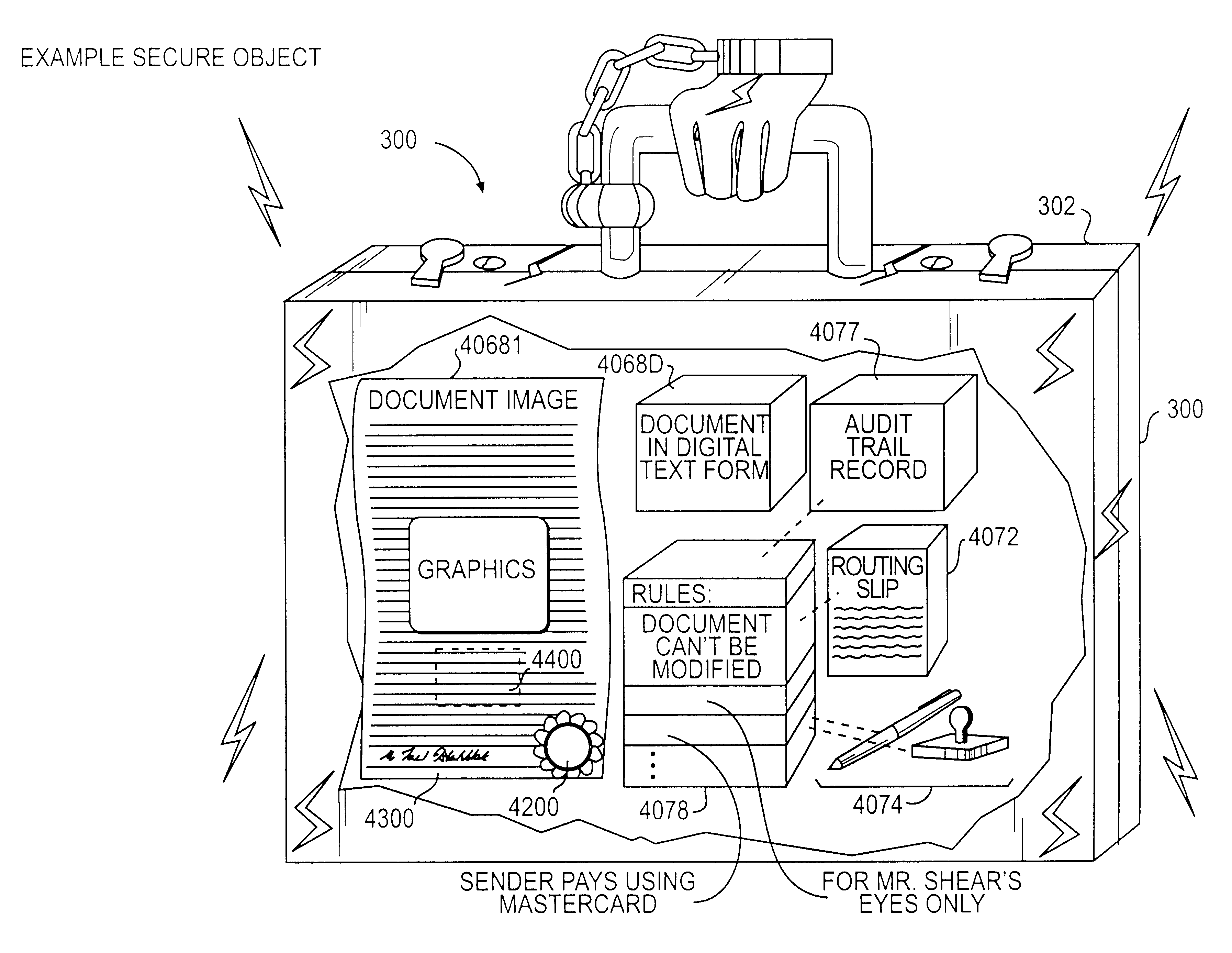
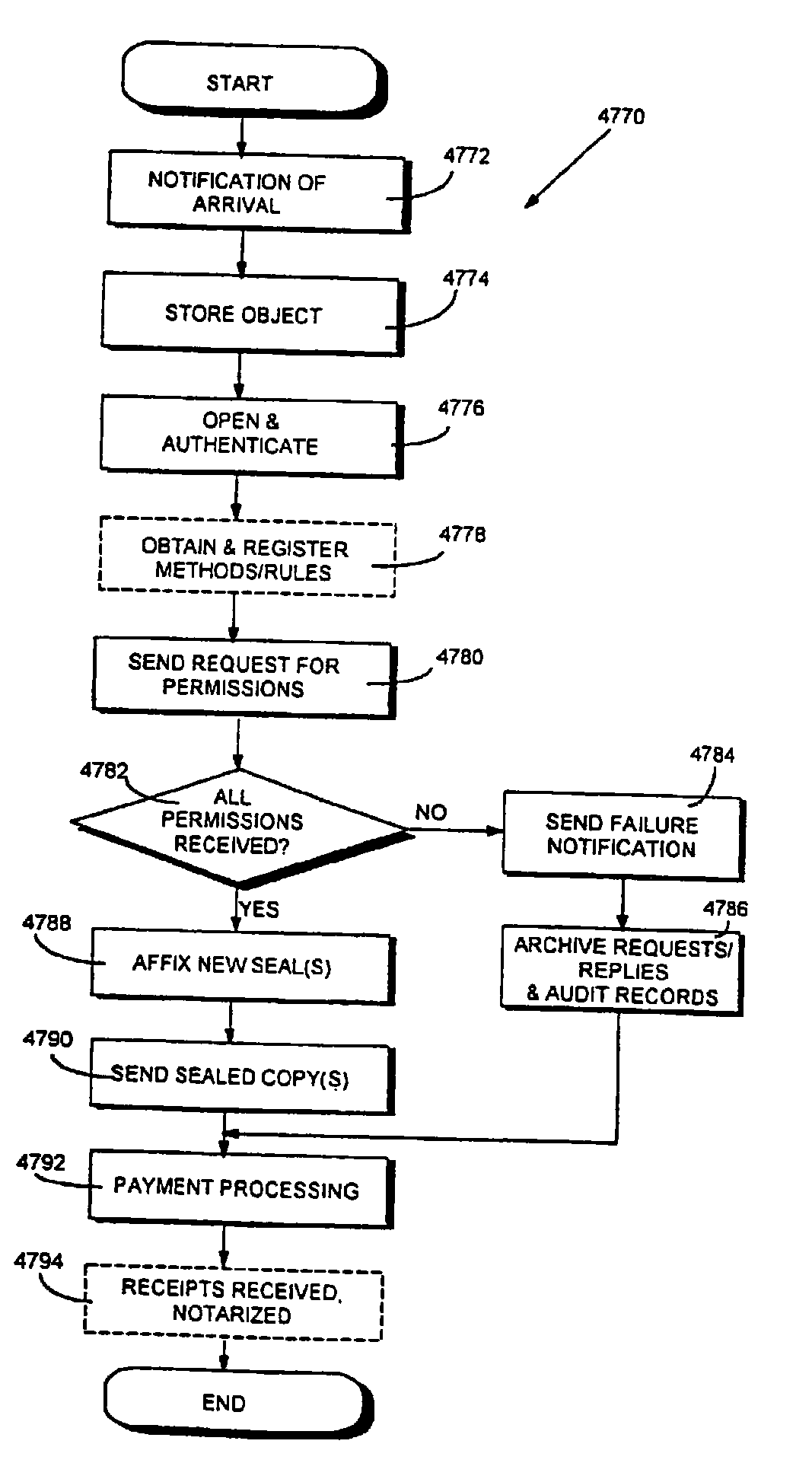
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
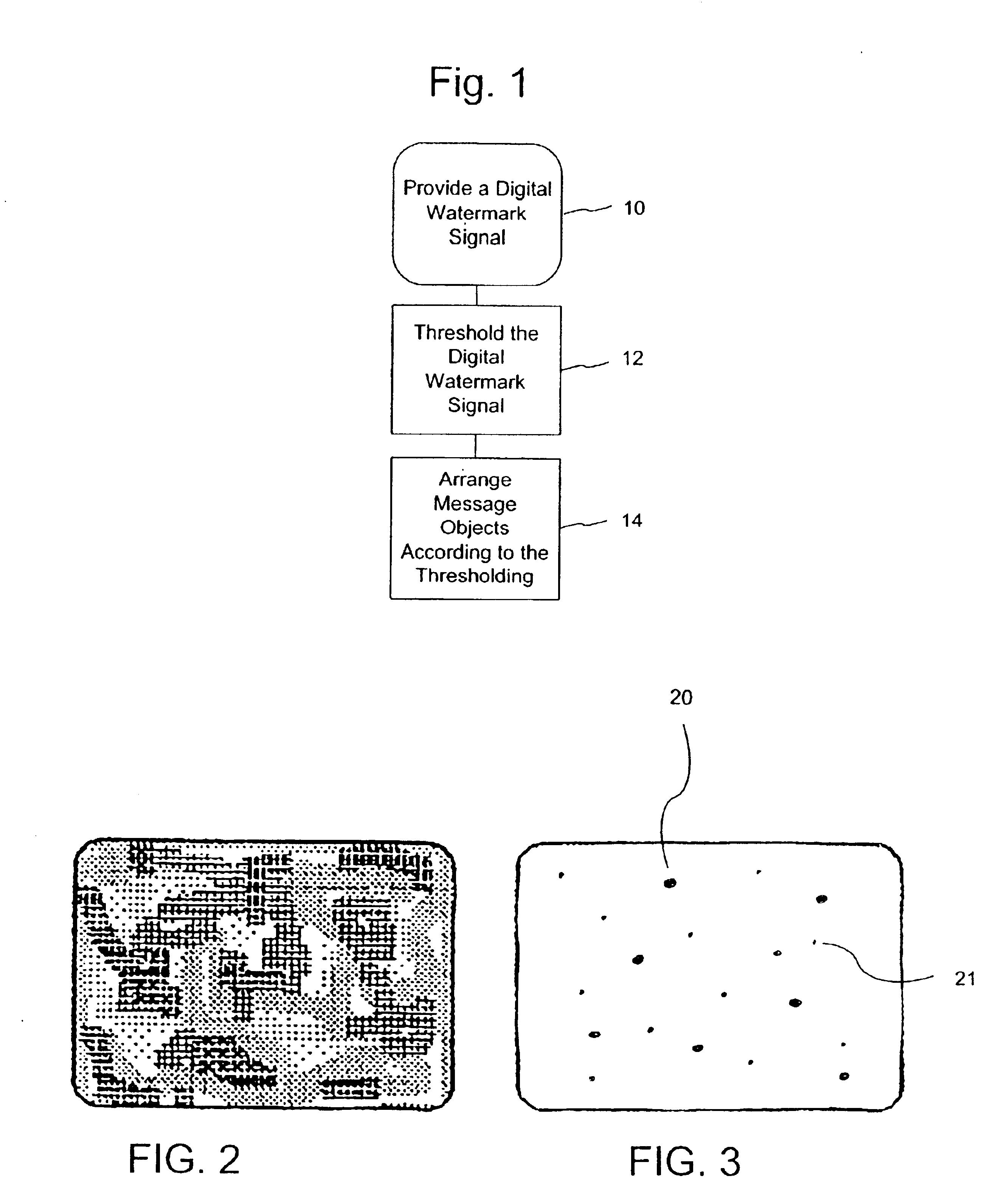
Hiding geo-location data through arrangement of objects
InactiveUS6993152B2Television system detailsUser identity/authority verificationGeolocationDigital watermarking
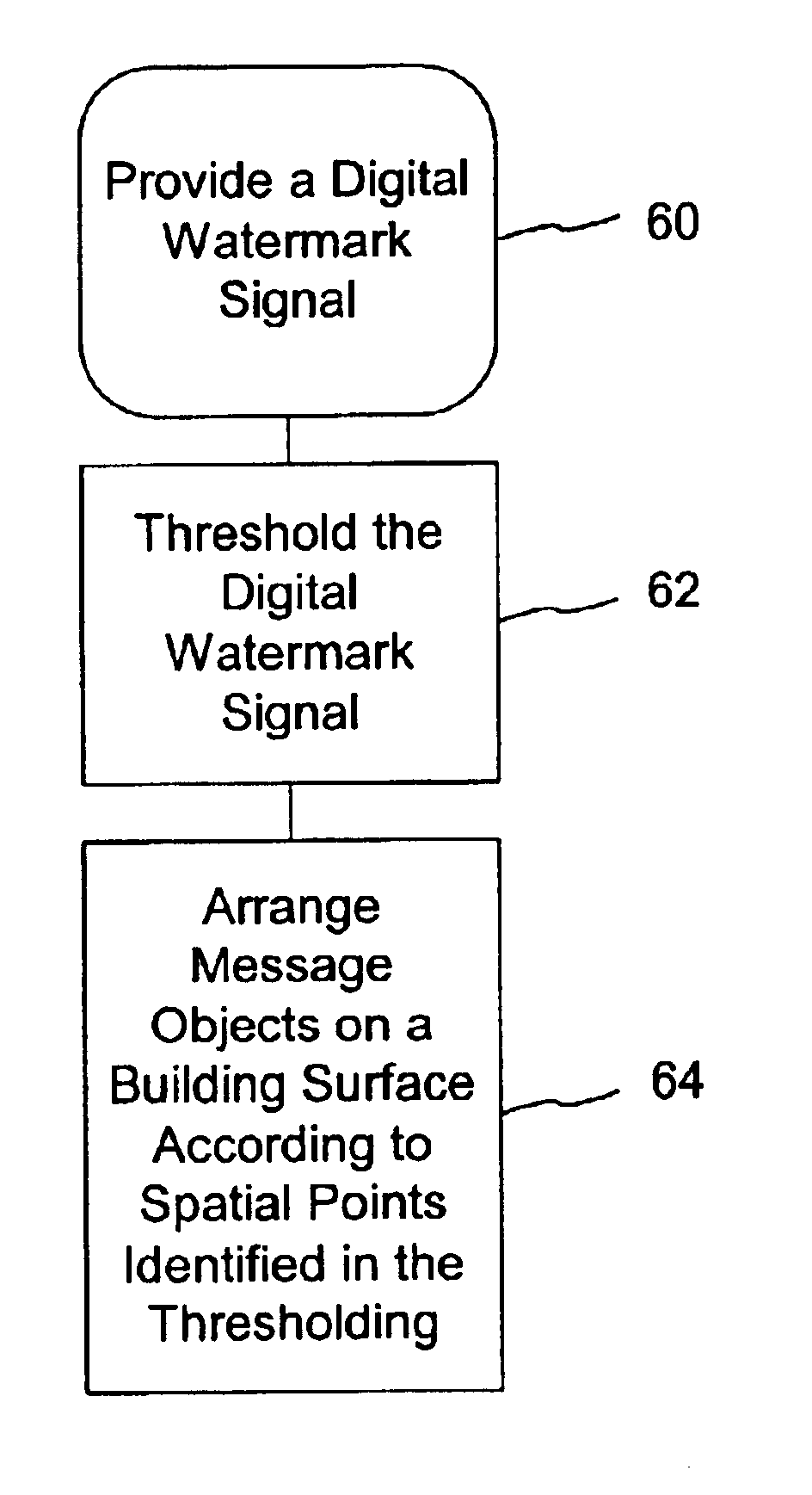
The present invention provides steganographic-embedding techniques. In one implementation a digital watermark signal is mapped to a set of spatial positions. Physical message objects are positioned according to the set of spatial positions. The signal is provided on a physical structure such as a building or road. The signal may include geo-location information. The geo-location information identifies the location of the physical structure. In other cases the signal includes a marker or identifier. The marker or identifier provides a reference point for images depicting the physical structure.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
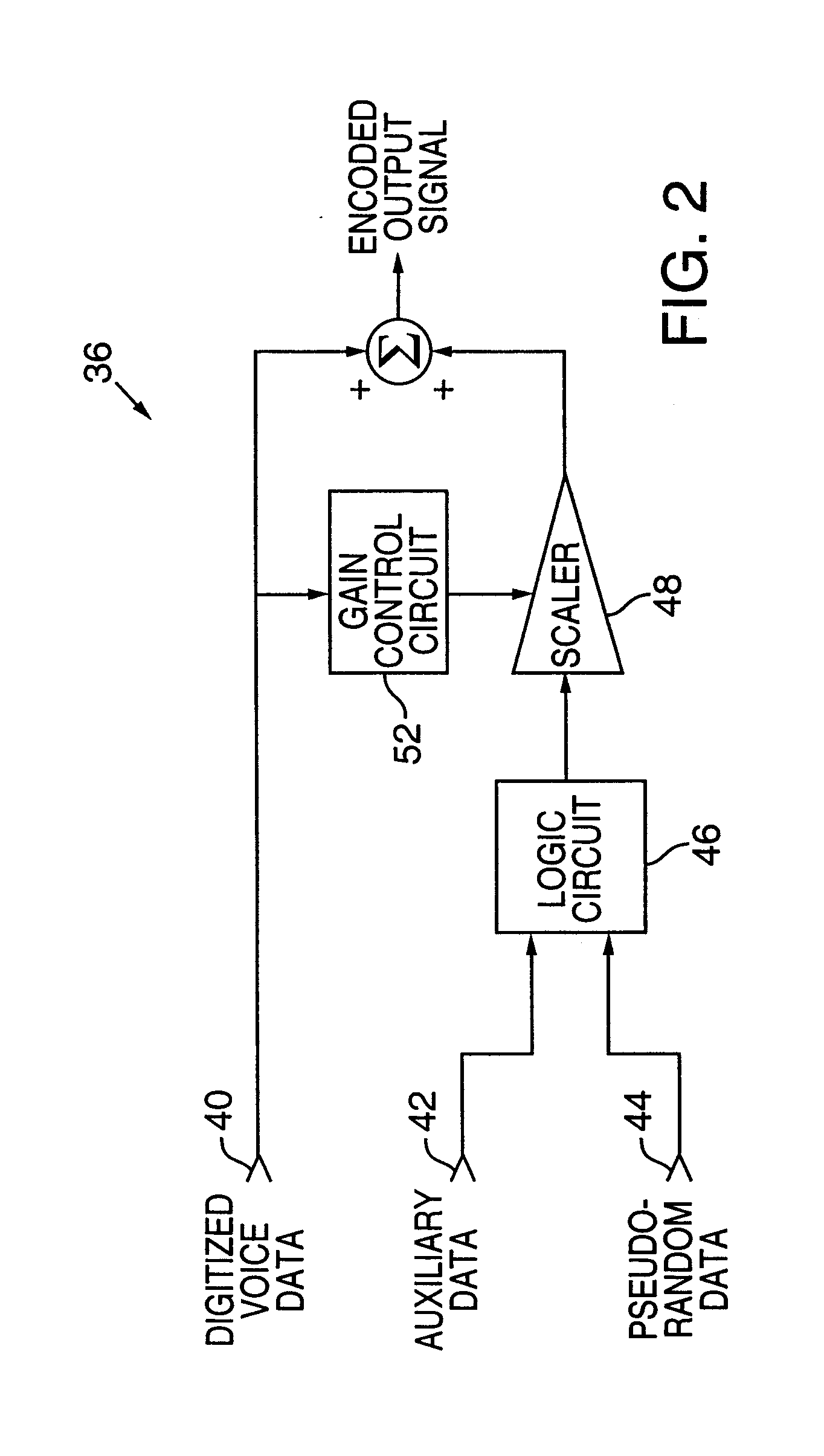
Color adaptive watermarking
InactiveUS7391880B2Effectively create and manipulateReduce the amount requiredAnalogue secracy/subscription systemsCharacter and pattern recognitionData encodingFeature selection
The presently claimed invention relates generally to data encoding and steganography. One combination recites a method of encoding data representing color imagery with an auxiliary signal. The method includes: providing a set of encoding values for a data sample; determining a color characteristic associated the data sample based on associated color values; and selectively scaling color values in the data sample based on the color characteristic to encode at least a portion of the auxiliary signal in the data representing color imagery. Of course, other combinations are provided as well.
Owner:DIGIMARC CORP
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS20080141033A1Highly cost-effectiveHigh of confidenceDigital data processing detailsUser identity/authority verificationDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, “trusted” virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS20050182956A1Highly cost-effectiveHigh of confidenceDigital data processing detailsAnalogue secracy/subscription systemsDocument preparationDocumentation
Owner:INTERTRUST TECH CORP
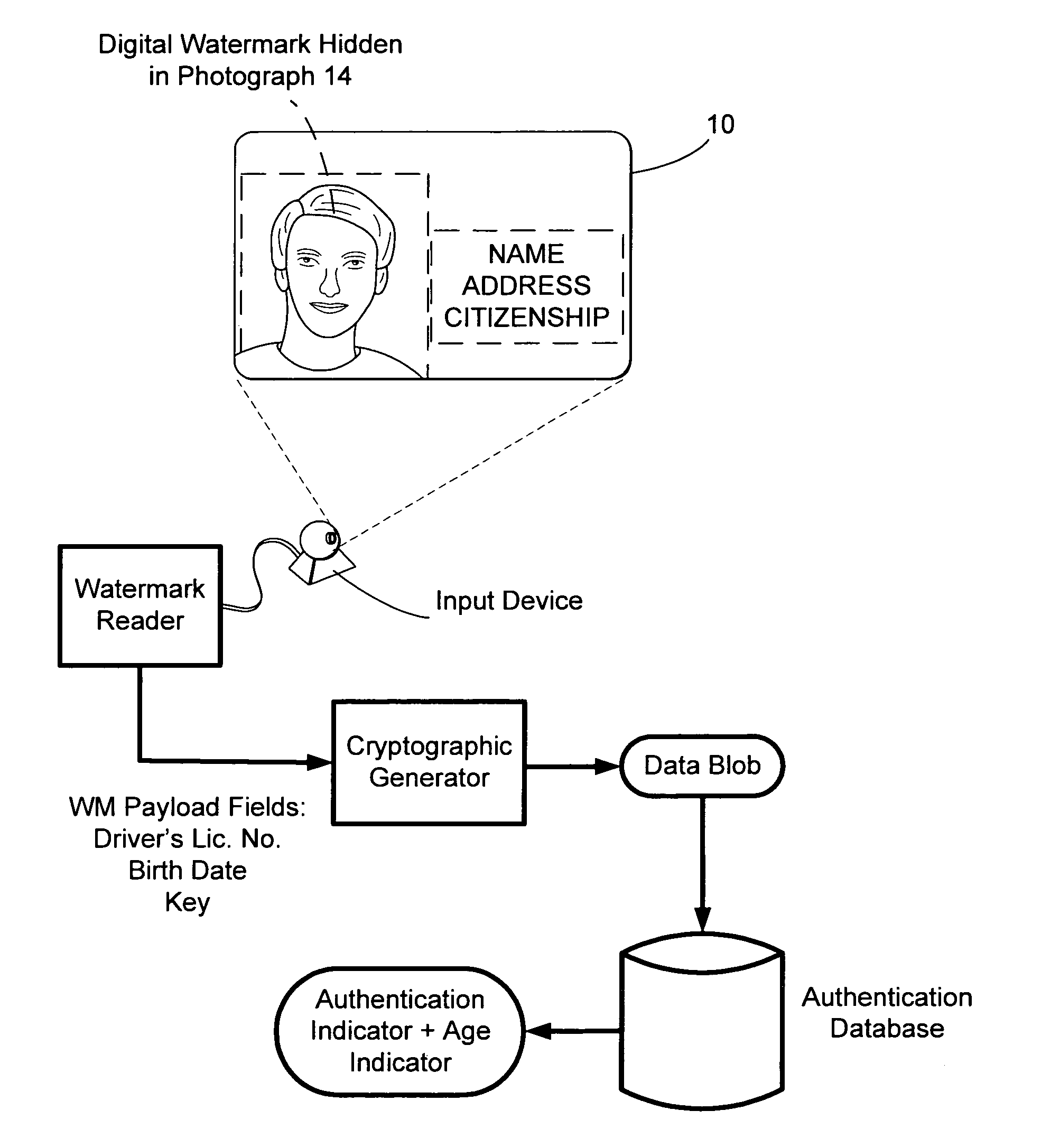
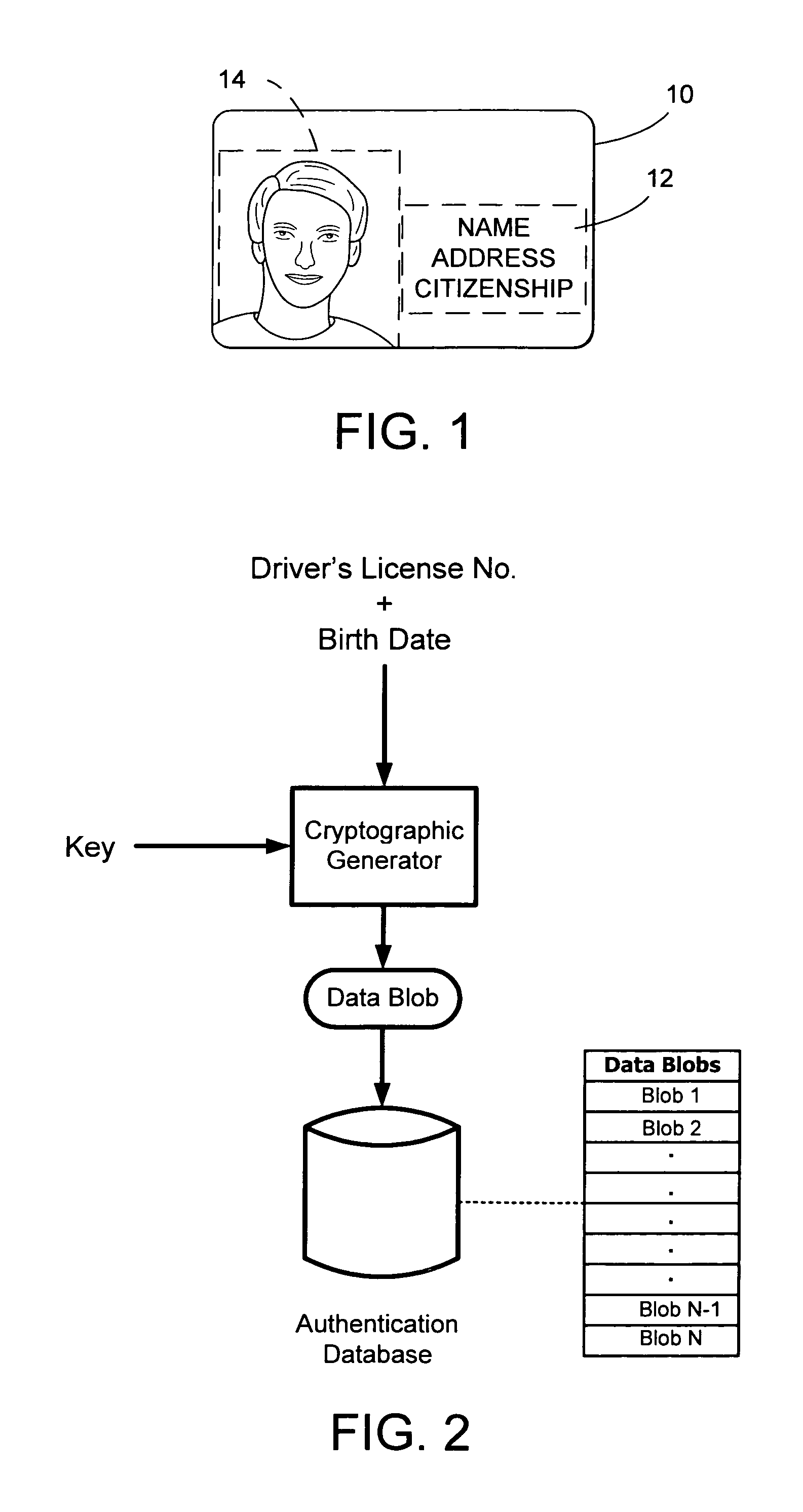
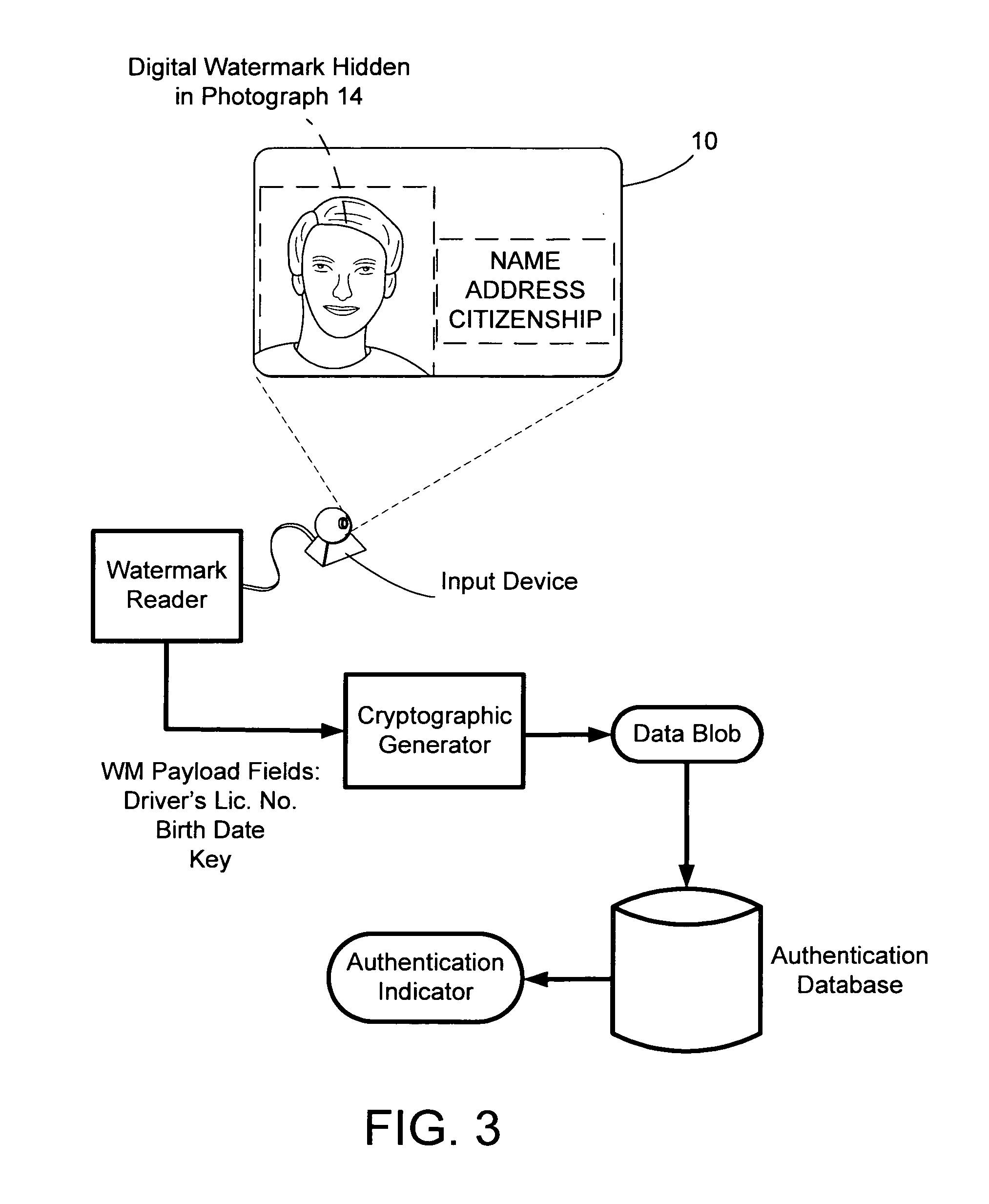
Safeguarding private information through digital watermarking
InactiveUS20070204162A1User identity/authority verificationSecret communicationData matchingInternet privacy
The present invention relates generally to digital watermarking and steganography. In one implementation, a method includes receiving permuted or encrypted data generated at a remote computing device, wherein the received data is encrypted or permuted according to a key carried by a digital watermark embedded in a security document; determining whether the received data matches or corresponds to data stored in a data repository, where the data repository indexes data stored therein without associating indexed data to a particular person or to an issued security document; and communicating an authentication indication to the remote computing device in accordance with a result of the act of determining.
Owner:DIGIMARC CORP
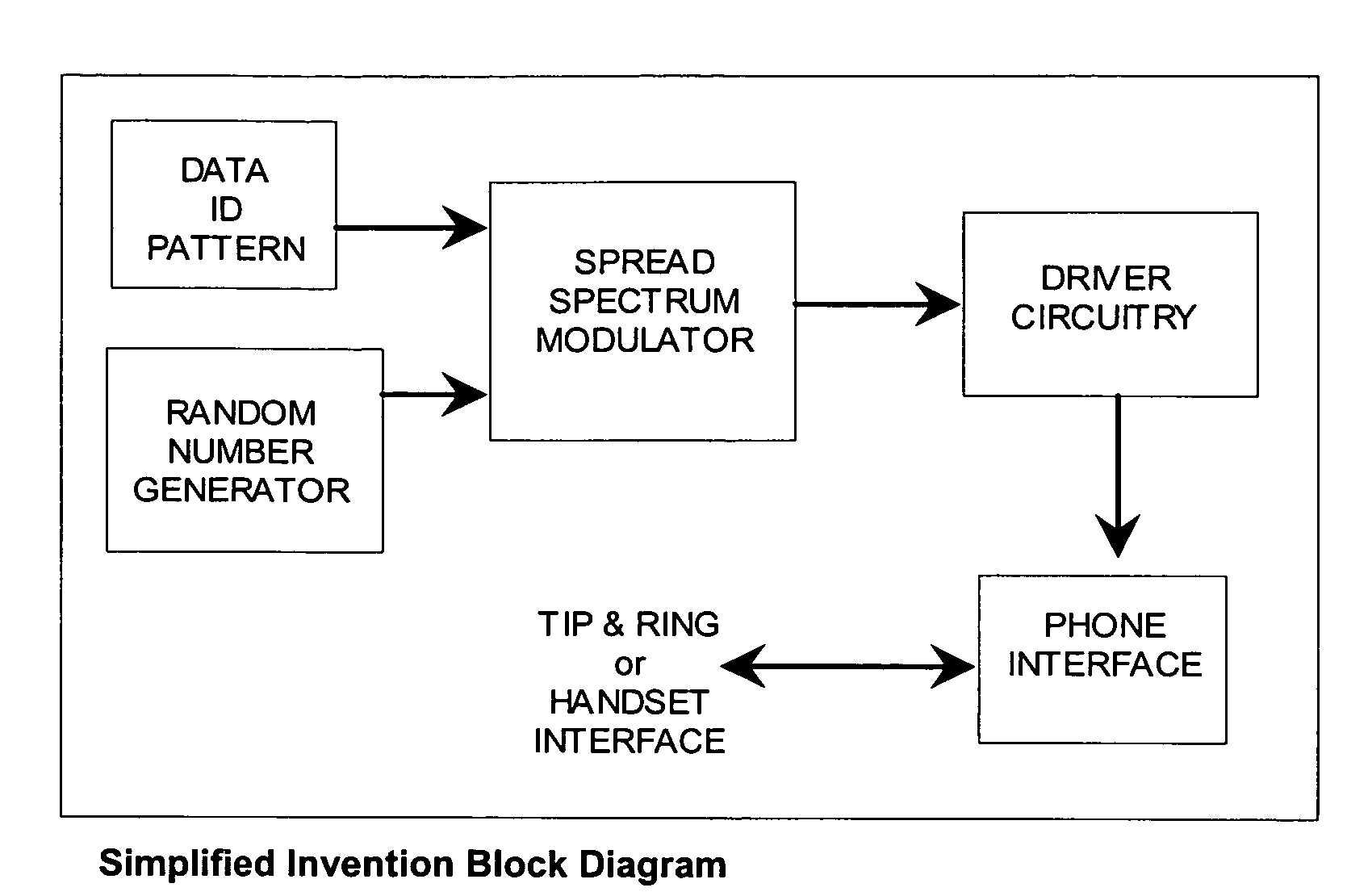
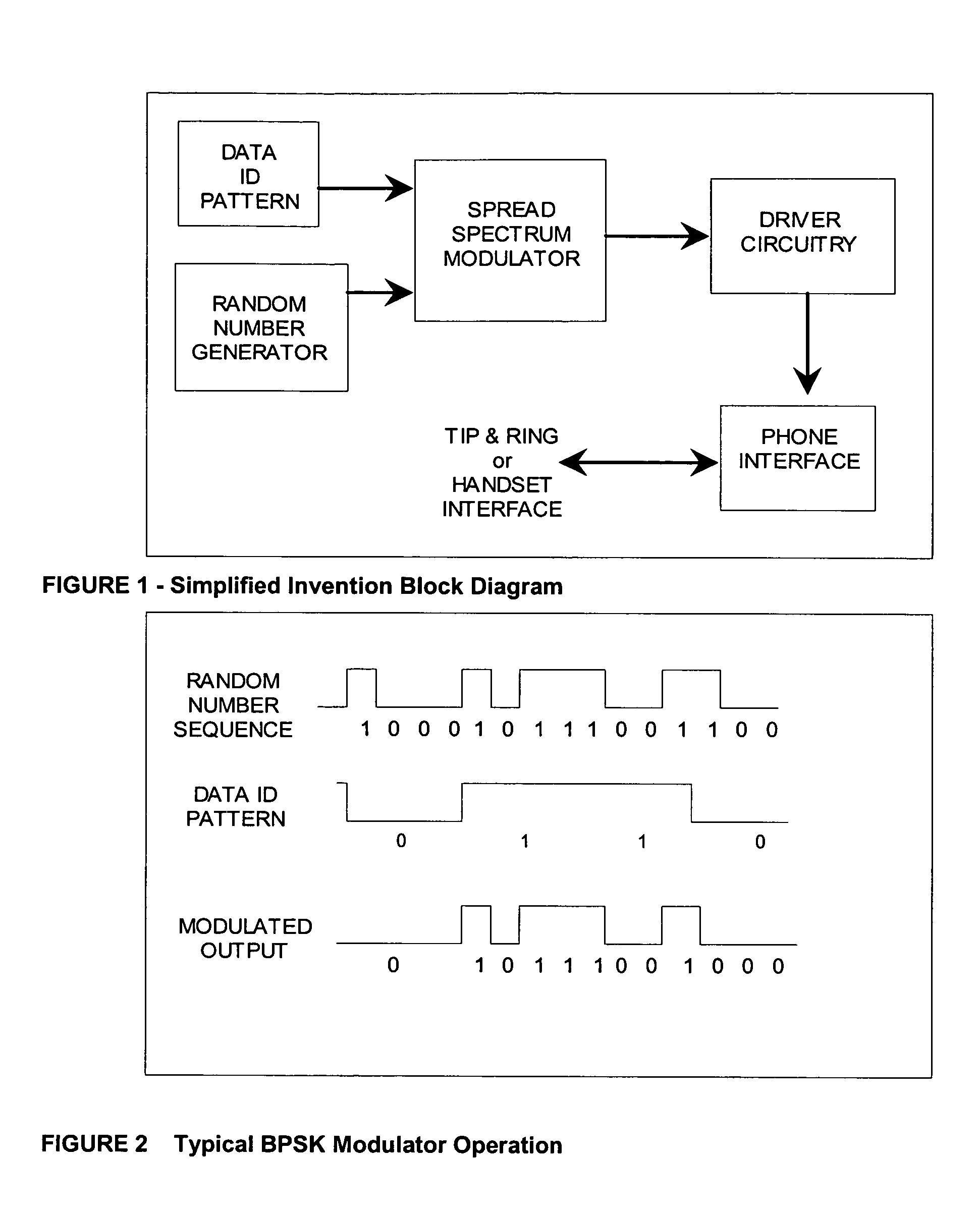
Three-way call detection using steganography
ActiveUS7248685B2Improve reliabilityAccurate and reliable processSpecial service for subscribersSupervisory/monitoring/testing arrangementsSignal onCarrier signal
Owner:DSI ITI INC
Using steganography to perform payment transactions through insecure channels
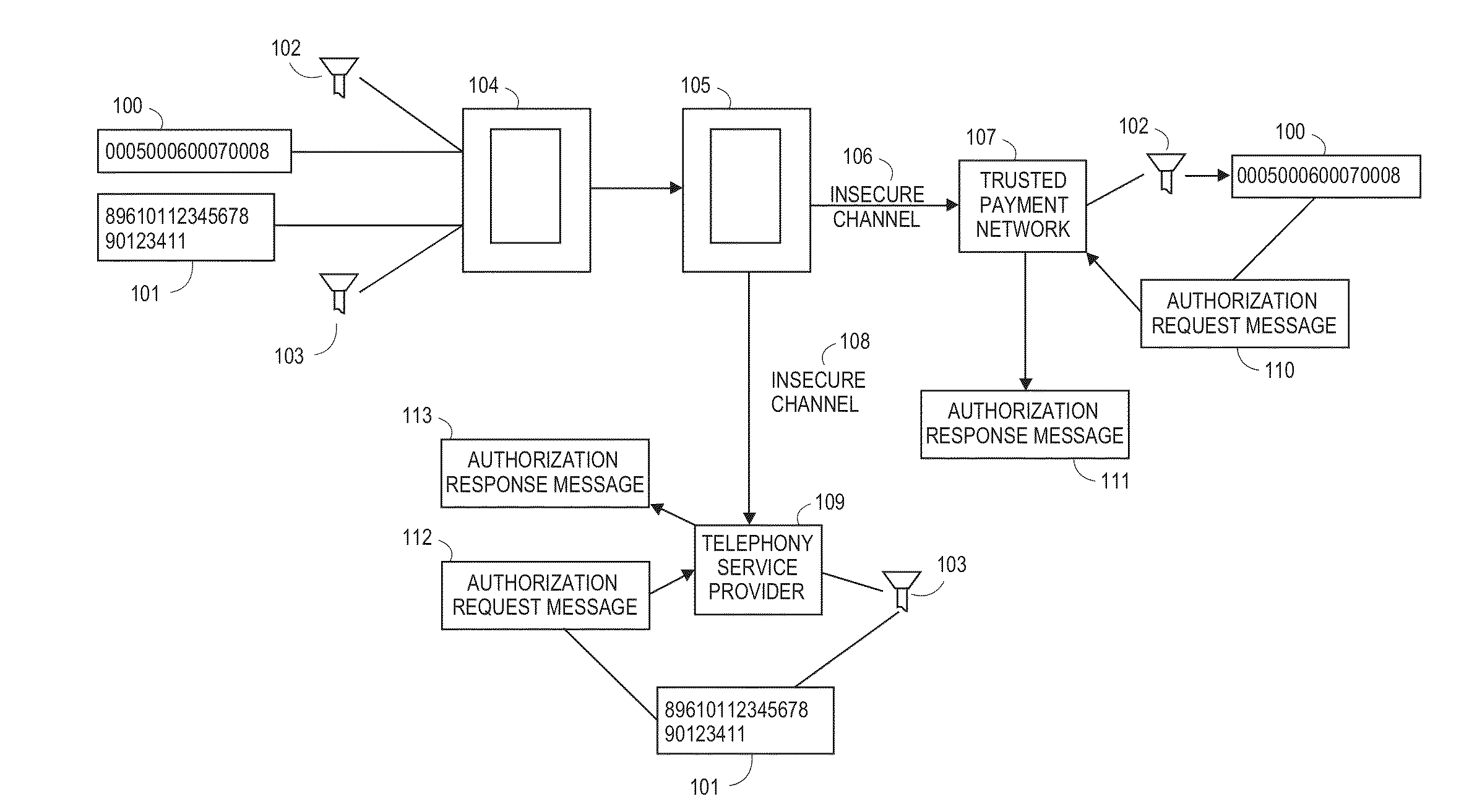
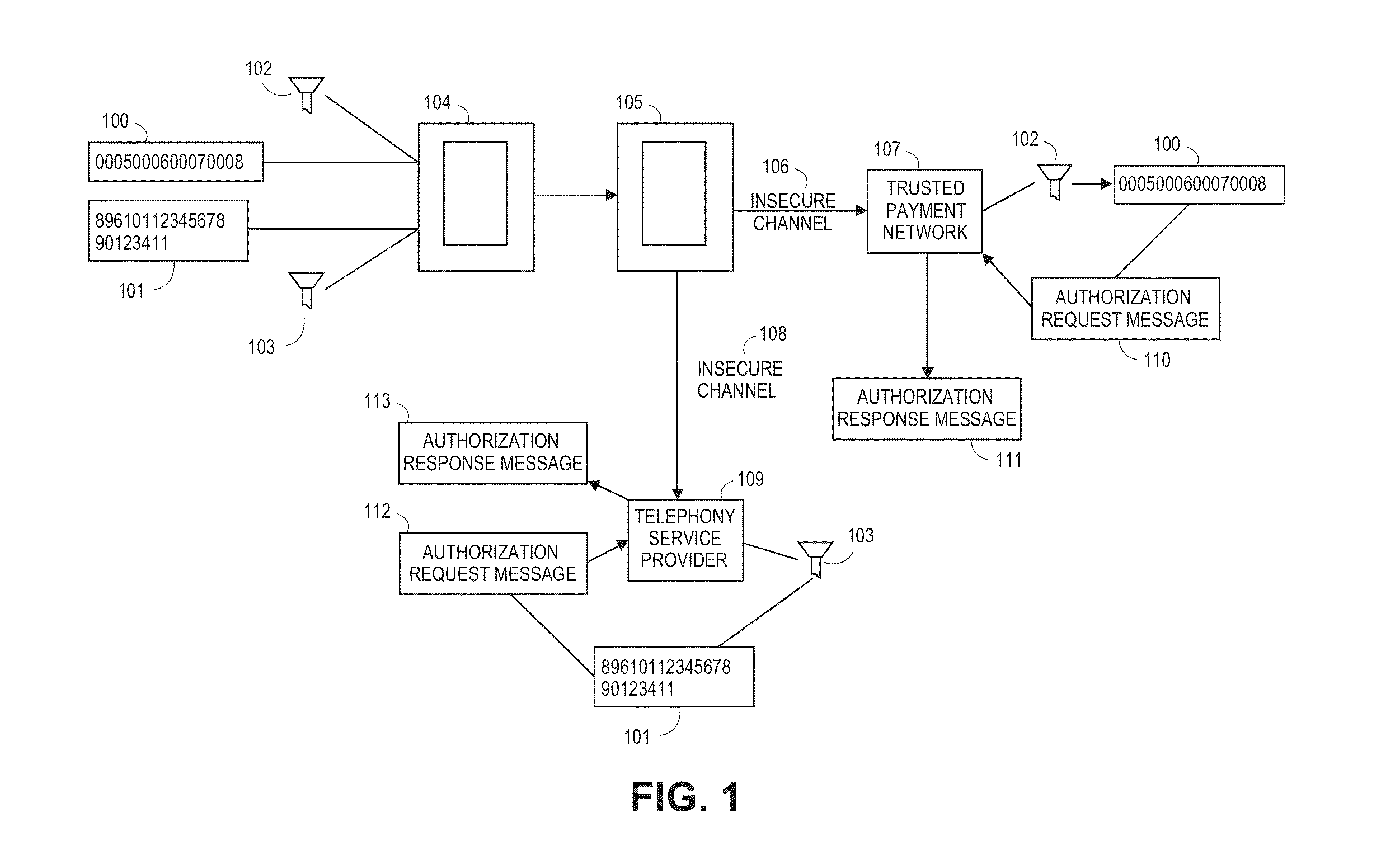
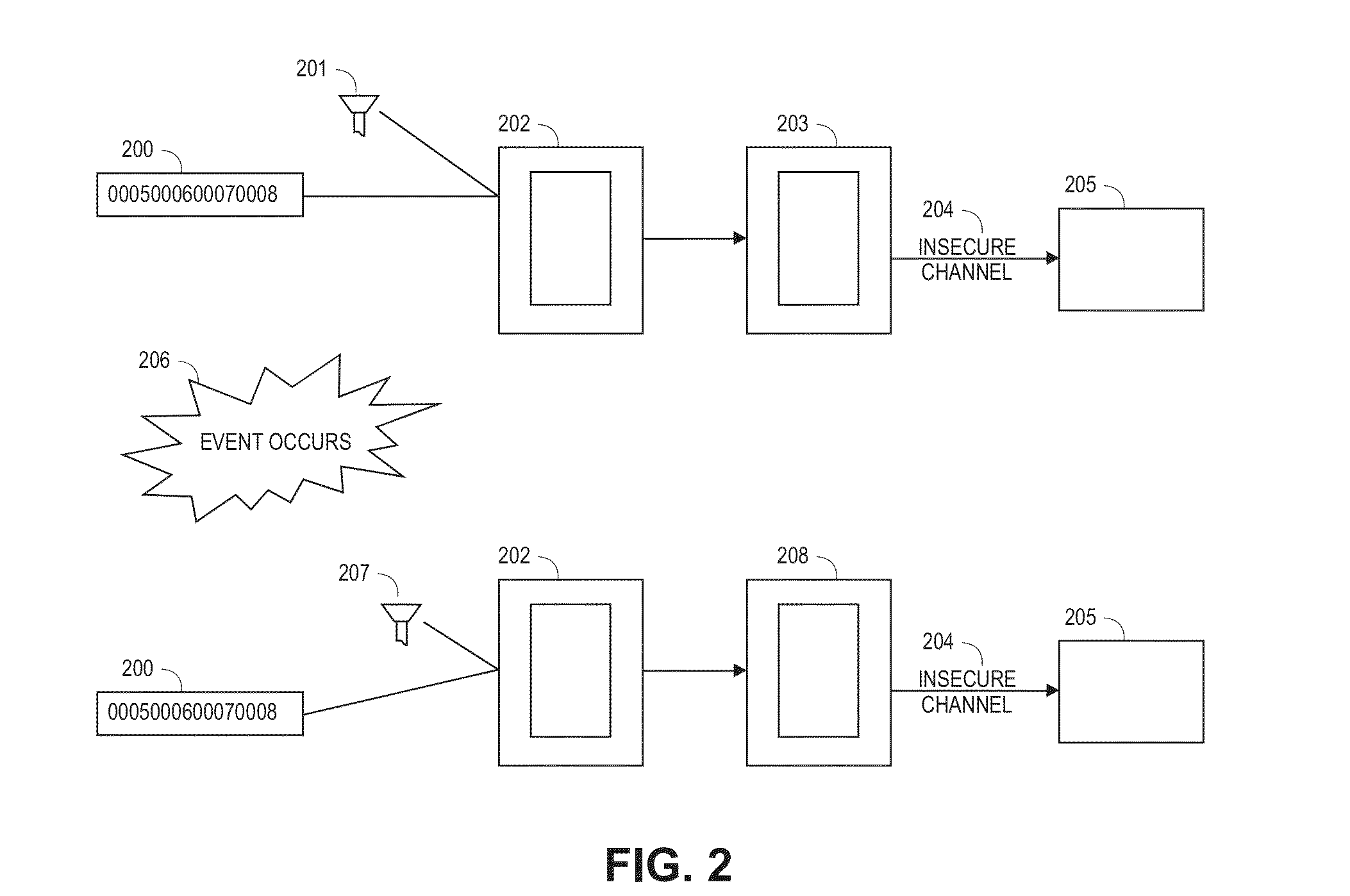
InactiveUS20150006390A1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningPayment transactionTelephone network
Steganographic techniques are used to embed financial information or authentication information within an image, audio, or video file using a quantization table and / or other filter. The file is then transmitted over an insecure network, such as a GSM cell phone network, and a server extracts the information from the image, audio, or video using the same quantization table and / or filter. Multiple sets of information, such as telephone numbers and / or payment account numbers, are extracted from the same image by those entities possessing the appropriate keys. The filters and tables used to embed financial information can be updated periodically or according to events. A video of images, some with embedded information, some with ‘dummy’ data, can be used to hide information over insecure networks for payment transactions.
Owner:VISA INT SERVICE ASSOC
Methods and devices employing optical sensors and/or steganography
InactiveUS20070274561A1Digital data information retrievalCharacter and pattern recognitionBarcodeOptical transducers
A wireless phone is equipped with a 2D optical sensor, enabling a variety of applications. For example, such a phone may also be provided with a digital watermark decoder, permitting decoding of steganographic data on imaged objects. Movement of a phone may be inferred by sensing movement of an imaged pattern across the optical sensor's field of view, allowing use of the phone as a gestural input device through which a user can signal instructions to a computer-based process. A variety of other arrangements by which electronic devices can interact with the physical world are also detailed, e.g., involving sensing and responding to digital watermarks, bar codes, RFIDs, etc. Other novel arrangements are also detailed.
Owner:DIGIMARC CORP
Methods Utilizing Steganography
InactiveUS20070180251A1The process is convenient and fastEver-increasing affordabilityUser identity/authority verificationCharacter and pattern recognitionData profilingComputer science
The present invention relates generally to steganography, digital watermarking and data hiding. In one embodiment a method is provided including: processing data representing content; analyzing the data to determine whether a plural-bit identifier is steganographically encoded therein, the plural-bit identifier encoded in the data through modifications to the data, the modifications steganographically hiding the presence of the plural-bit identifier; and upon detection of the plural-bit identifier, redundantly carrying out an action while attempting to conceal the action from one or more users of the content. Of course, other embodiments are described and claimed as well.
Owner:DIGIMARC CORP
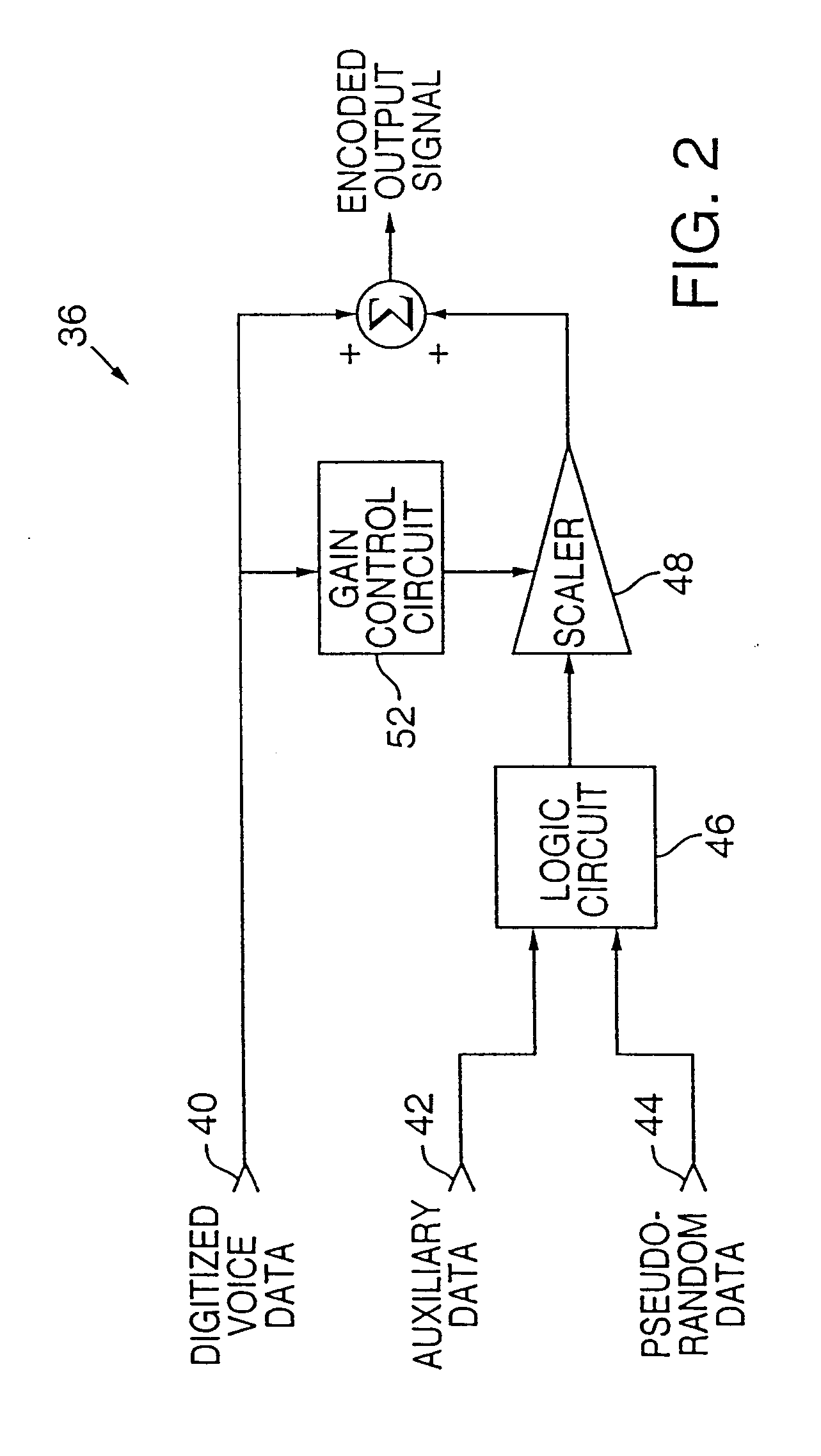
Data hiding via phase manipulation of audio signals
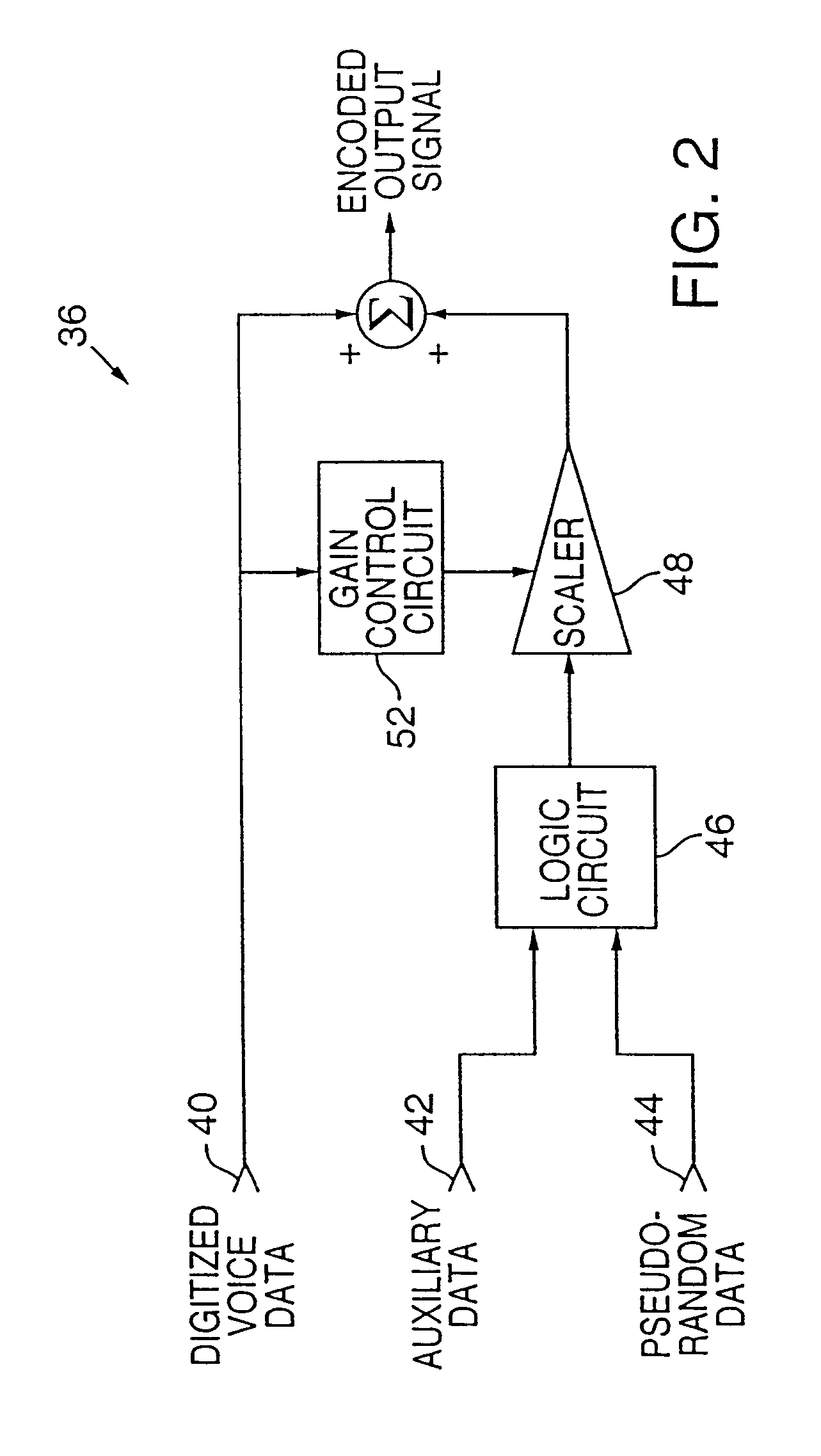
ActiveUS20050033579A1Preventing further illegal distributionImprove robustnessSpeech recognitionRelative phaseAudio signal flow
Data are embedded in an audio signal for watermarking, steganography, or other purposes. The audio signal is divided into time frames. In each time frame, the relative phases of one or more frequency bands are shifted to represent the data to be embedded. In one embodiment, two frequency bands are selected according to a pseudo-random sequence, and their relative phase is shifted. In another embodiment, the phases of one or more overtones relative to the fundamental tone are quantized.
Owner:MZ AUDIO SCI LLC
Methods and tangible objects employing machine readable data in photo-reactive materials
InactiveUS7313253B2Television system detailsSemiconductor/solid-state device detailsTangible objectMachine-readable data
The present invention relates generally to steganography and data hiding. In one implementation we provide a method including: obtaining auxiliary data; providing a mask for a photo-reactive material, the mask corresponding at least in part to the auxiliary data; and exposing the material through the mask to steganographically impart the auxiliary data in the photo-reactive material. The auxiliary data is machine-readable from the exposed material. In another implementation the material is exposed through photolithographic illumination. Of course, other implementations are described and claimed as well.
Owner:DIGIMARC CORP
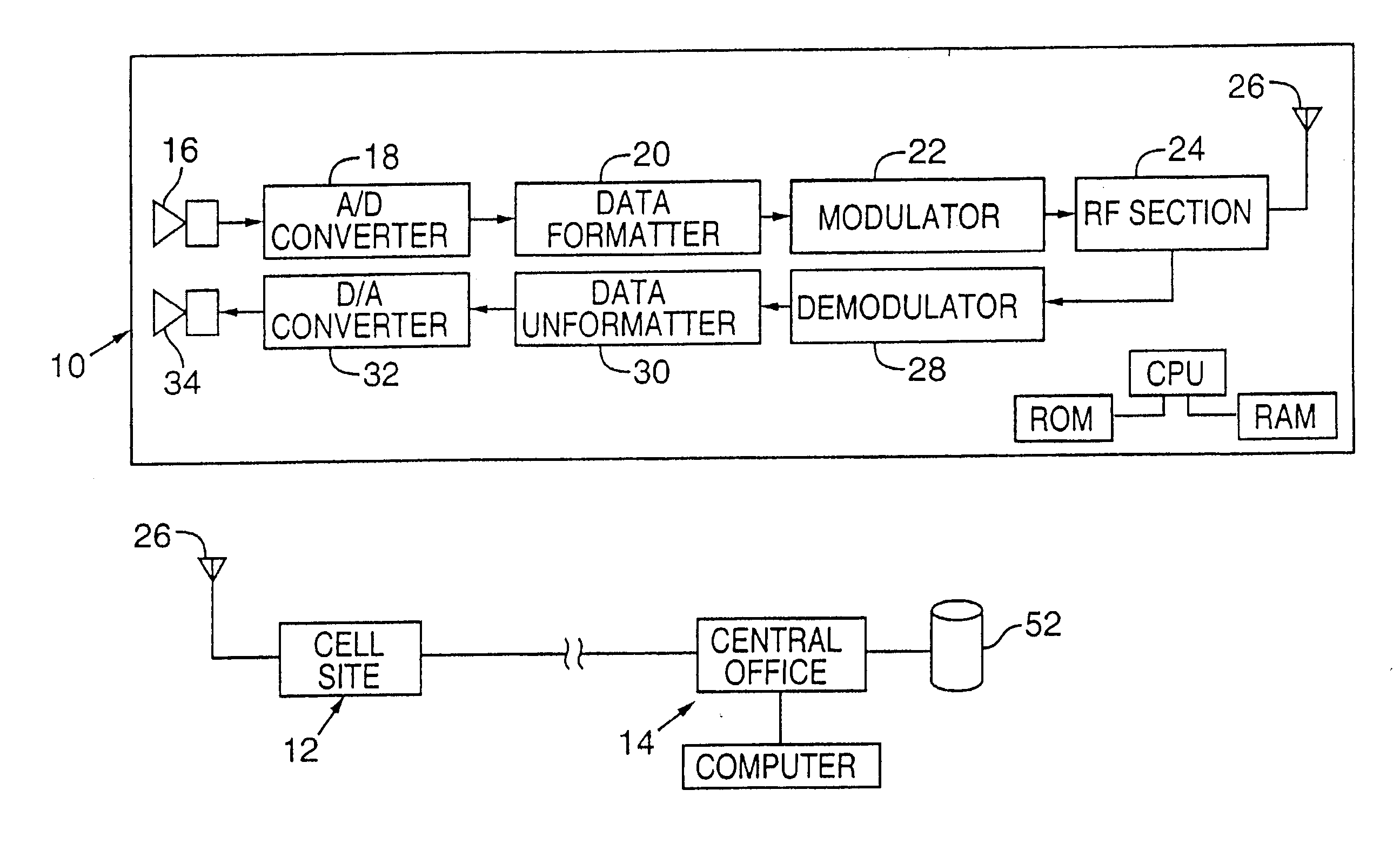
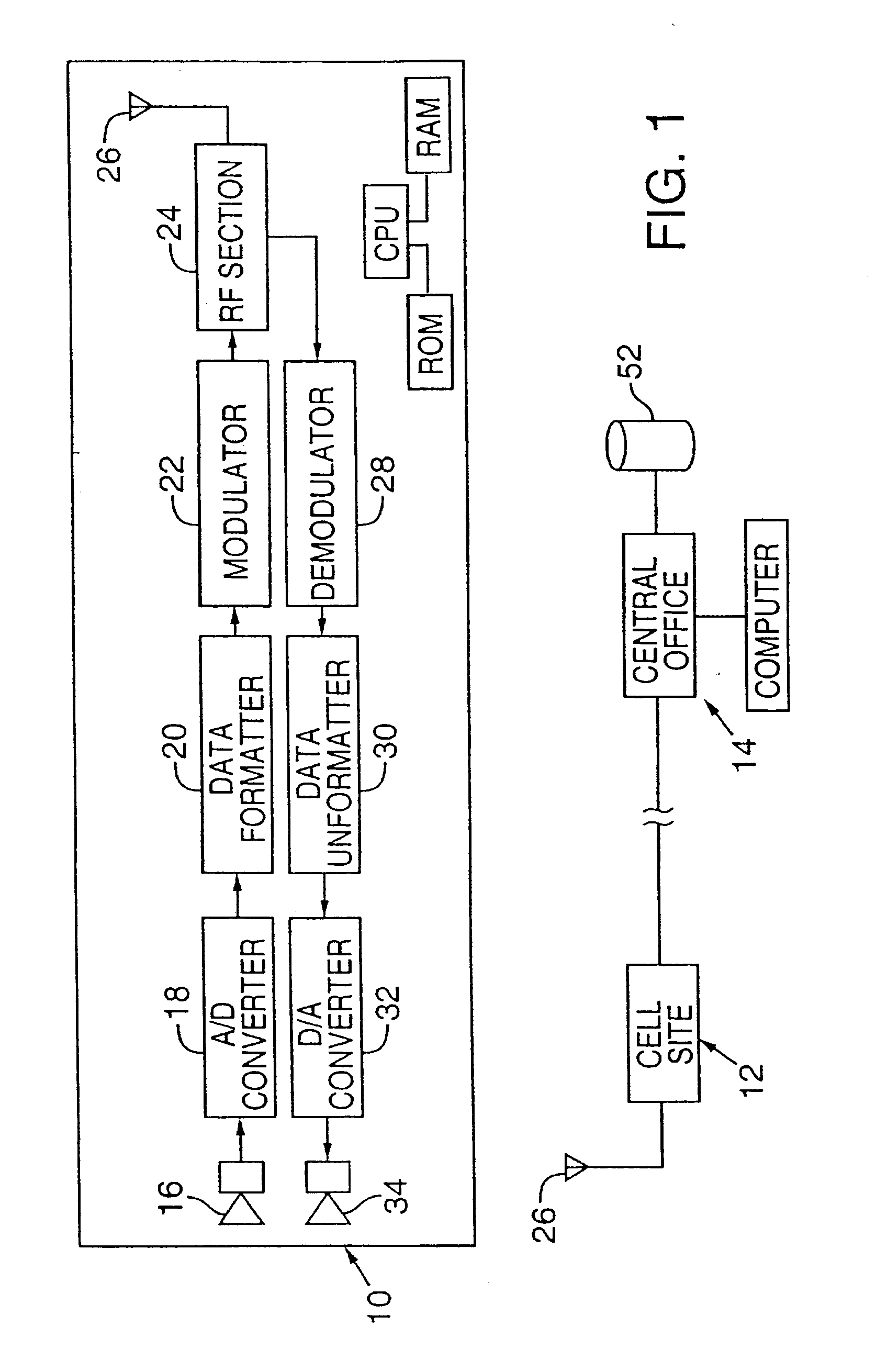
Wireless methods and devices employing steganography
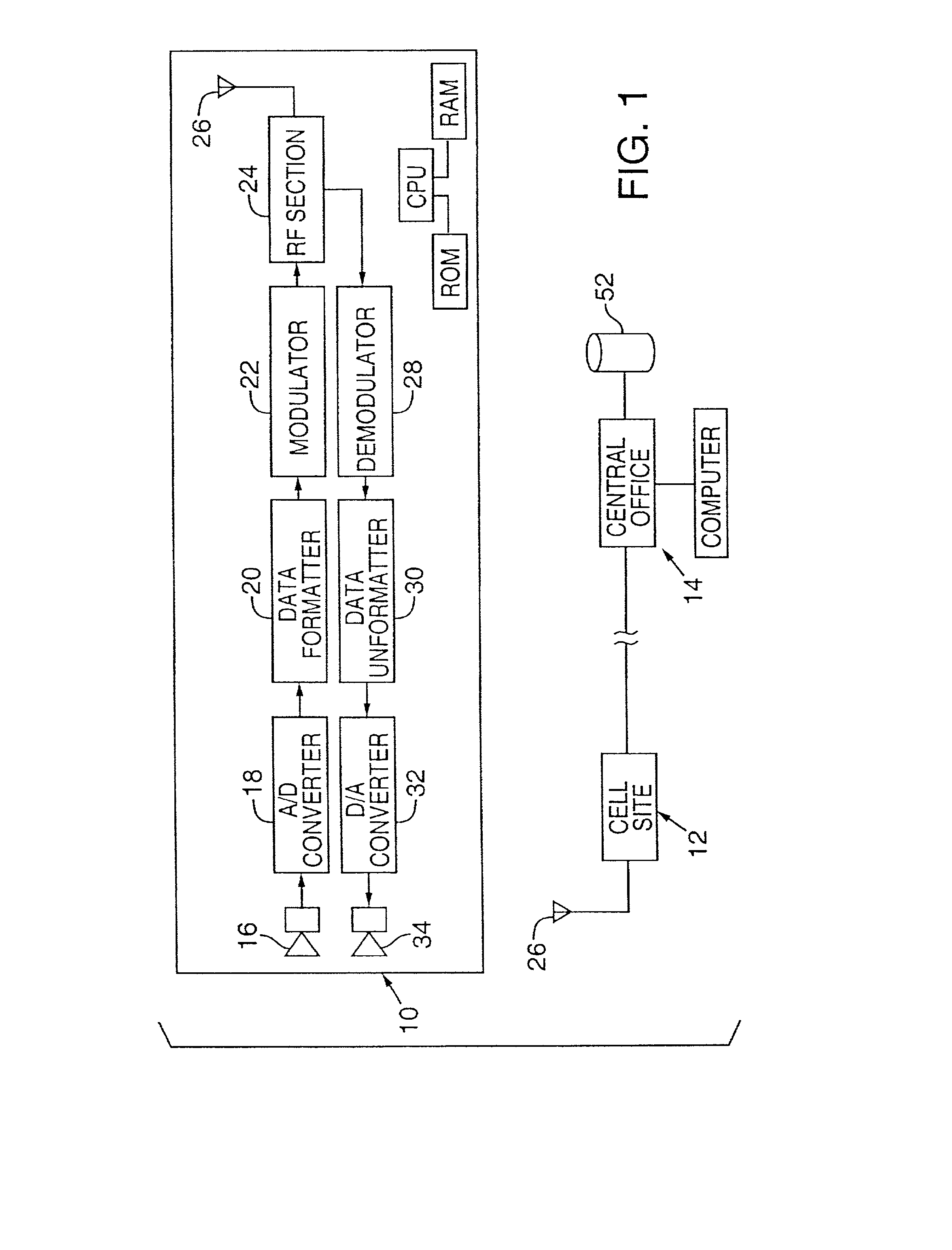
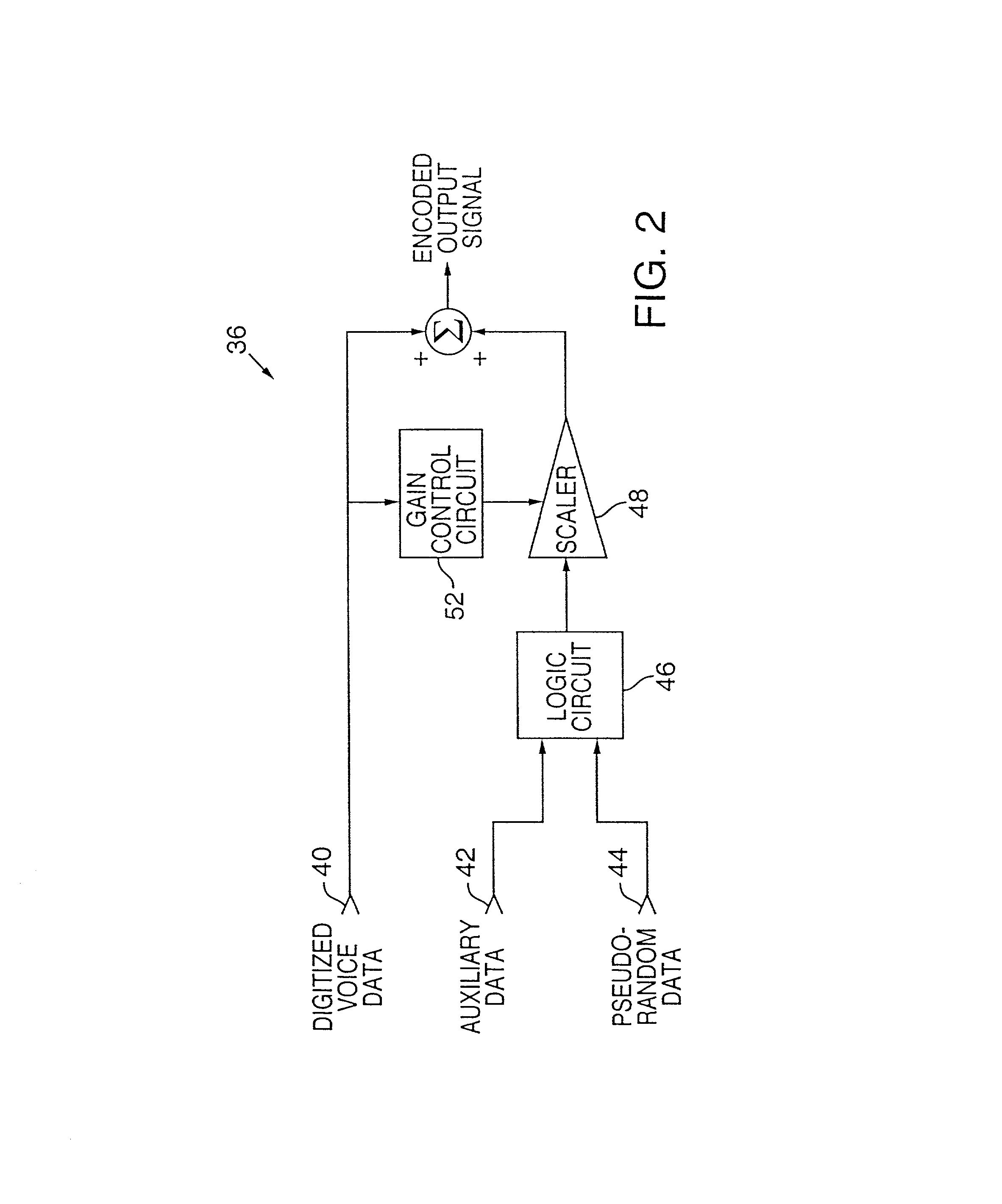
InactiveUS7362781B2Improve concealmentUnauthorised/fraudulent call preventionCoin-freed apparatusSystems managementLoudspeaker
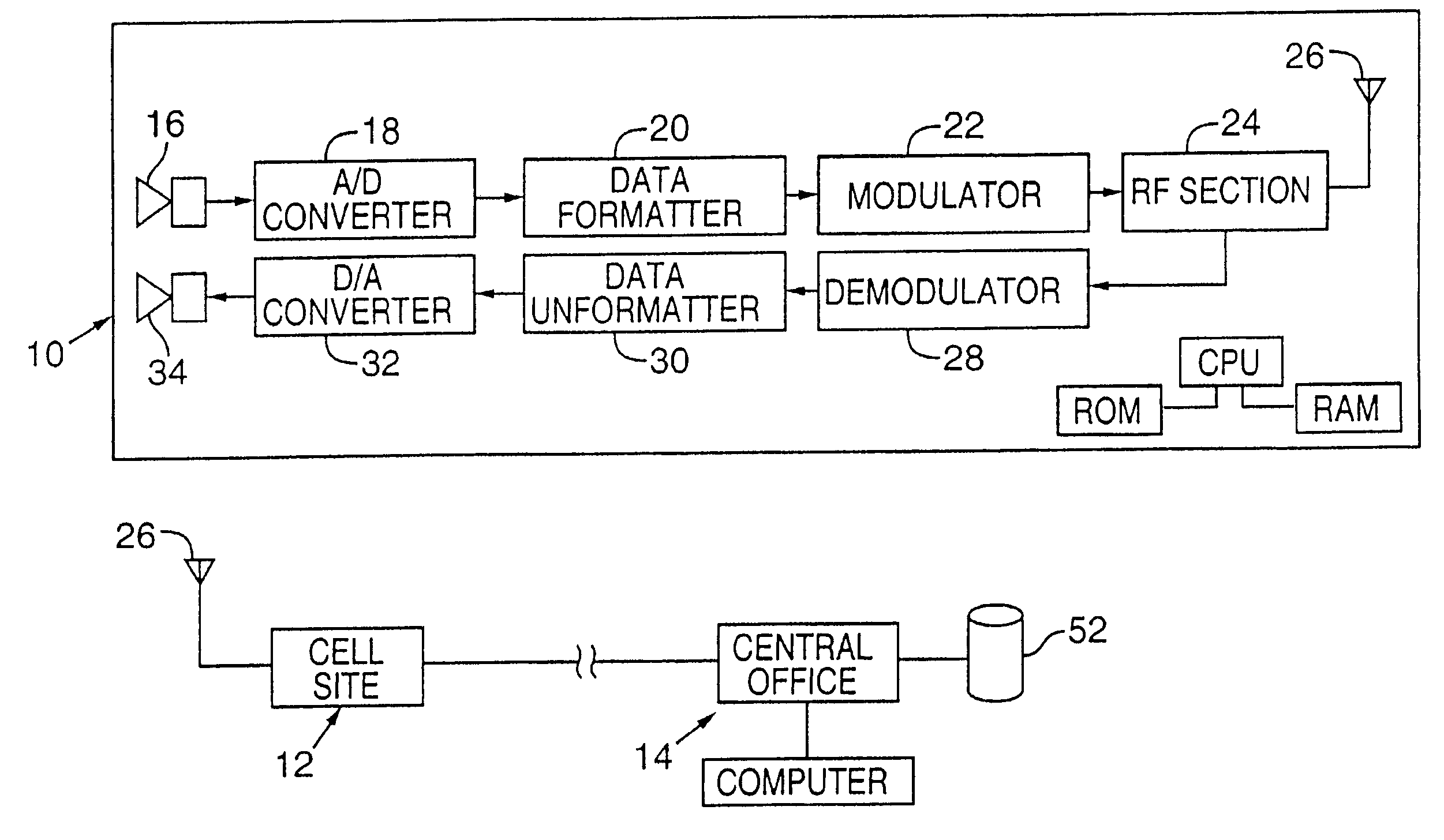
Wireless devices and methods employ steganography to convey auxiliary data in addition to audio information. An exemplary application is a battery-powered cell phone, having, e.g., a microphone, a speaker, a modulator, an antenna, and an RF amplifier. The steganographically-encoded auxiliary data can be sent to, and / or sent from, such a device, and used for purposes including authentication, system administration, etc.
Owner:DIGIMARC CORP
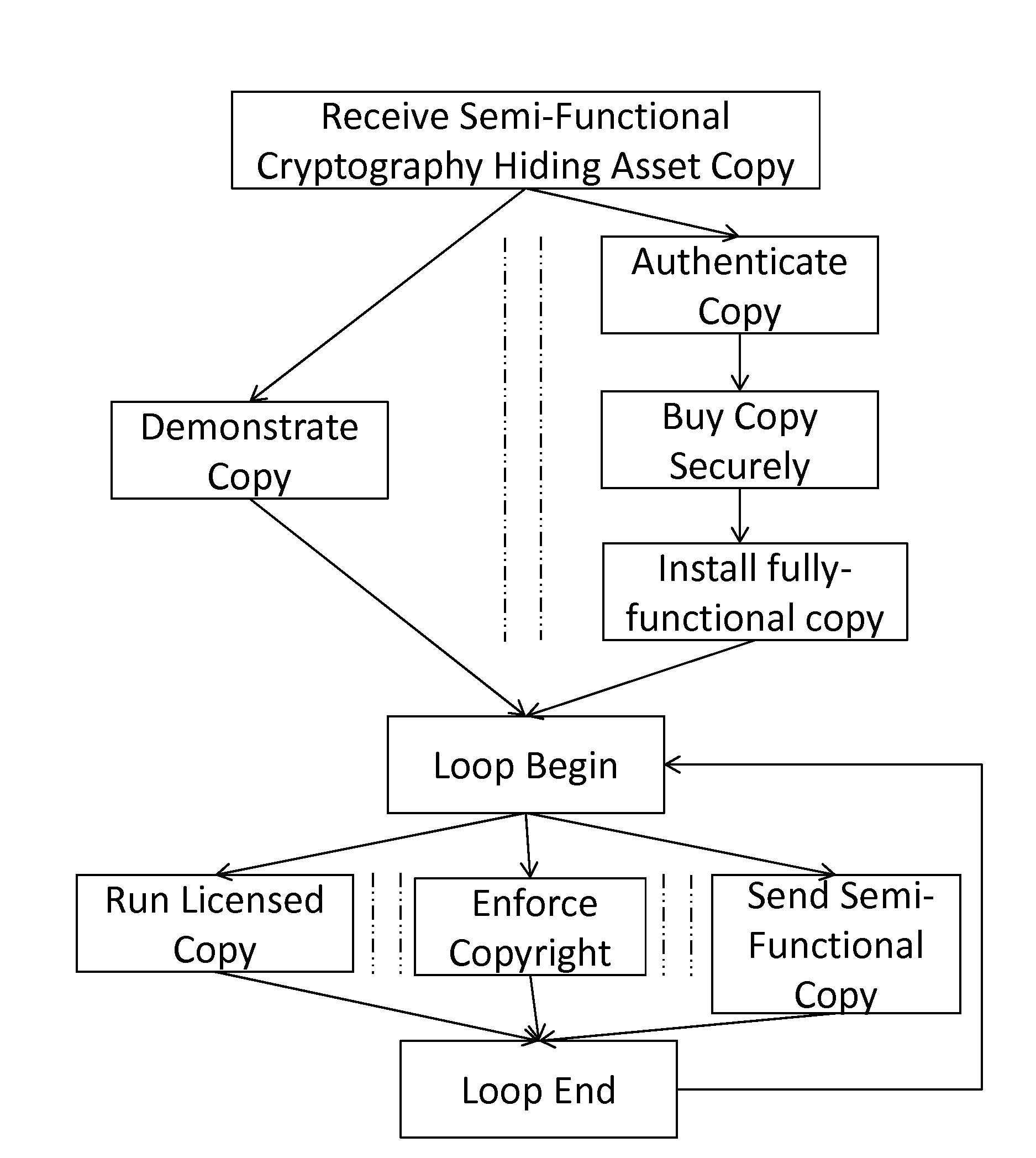
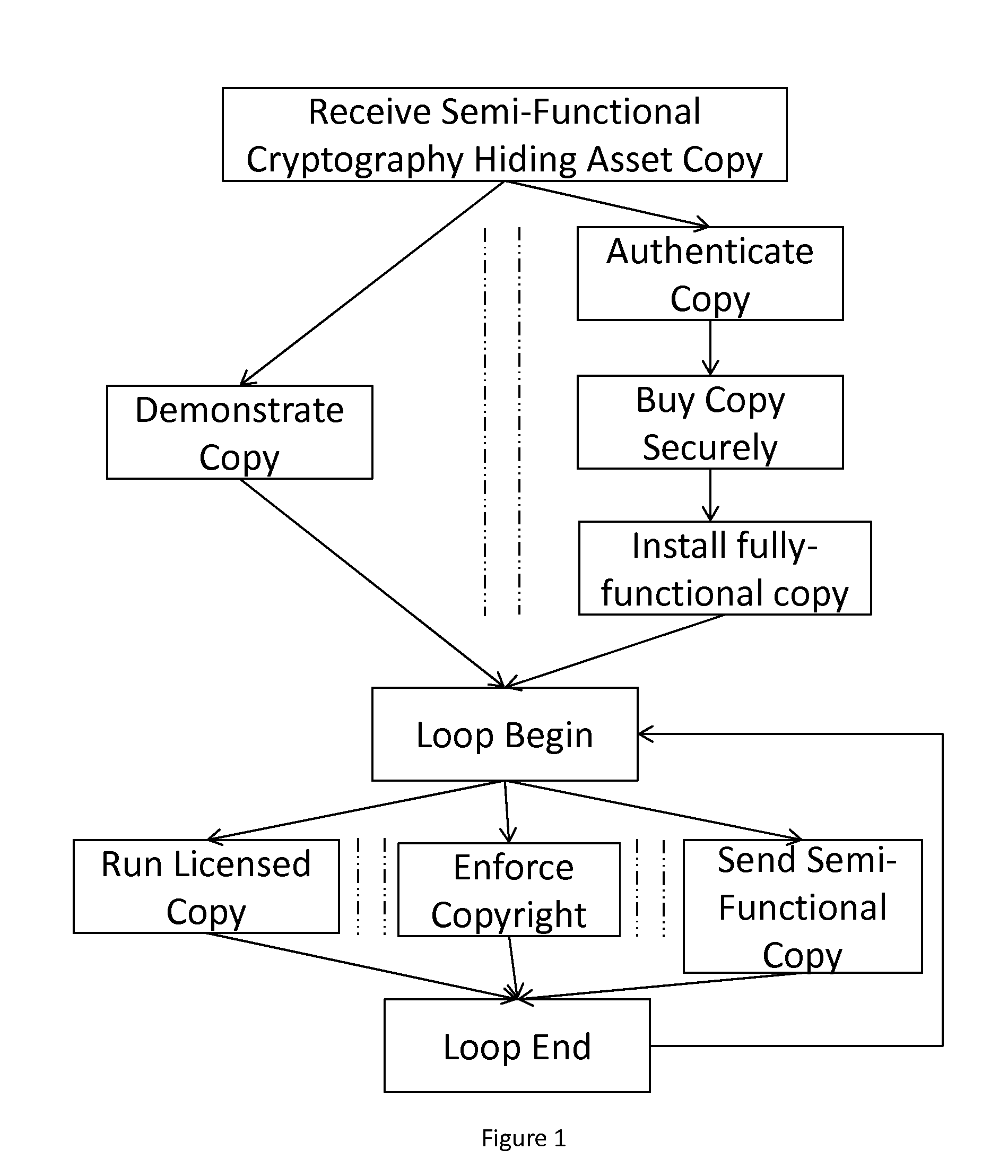
Potentate: A Cryptography-Obfuscating, Self-Policing, Pervasive Distribution System For Digital Content
InactiveUS20160364707A1Cryptography processingDigital data protectionSource transformationViral marketing
A system and method for self-policed, authenticated, offline / online, viral marketing and distribution of content such as software, text, and multimedia with effective copyright and license enforcement and secure selling. The system is based on key and cryptography hiding techniques, using source-to-source transformation for efficient, holistic steganography that systematically inflates and hides critical code by: computation interleaving; flattening procedure calls and obfuscating stack by de-stacking arguments; obfuscating memory management; and encoding scalars as pointers to managed structures that may be distributed and migrated all over the heap using garbage collection. Multimedia / text content may be partitioned and sold with expiry dates for protection and updates for long life. Authenticity of software installed on a machine may be monitored and ensured, supporting even authentic software deployment in an unknown environment. The system can be implemented with commonplace networking or browser software, commonplace hardware and content provision over a secure website (https standard).
Owner:VARMA PRADEEP
Enhanced electronic mail security system and method
InactiveUS20050268327A1Data switching networksSpecial data processing applicationsPatent searchClient-side
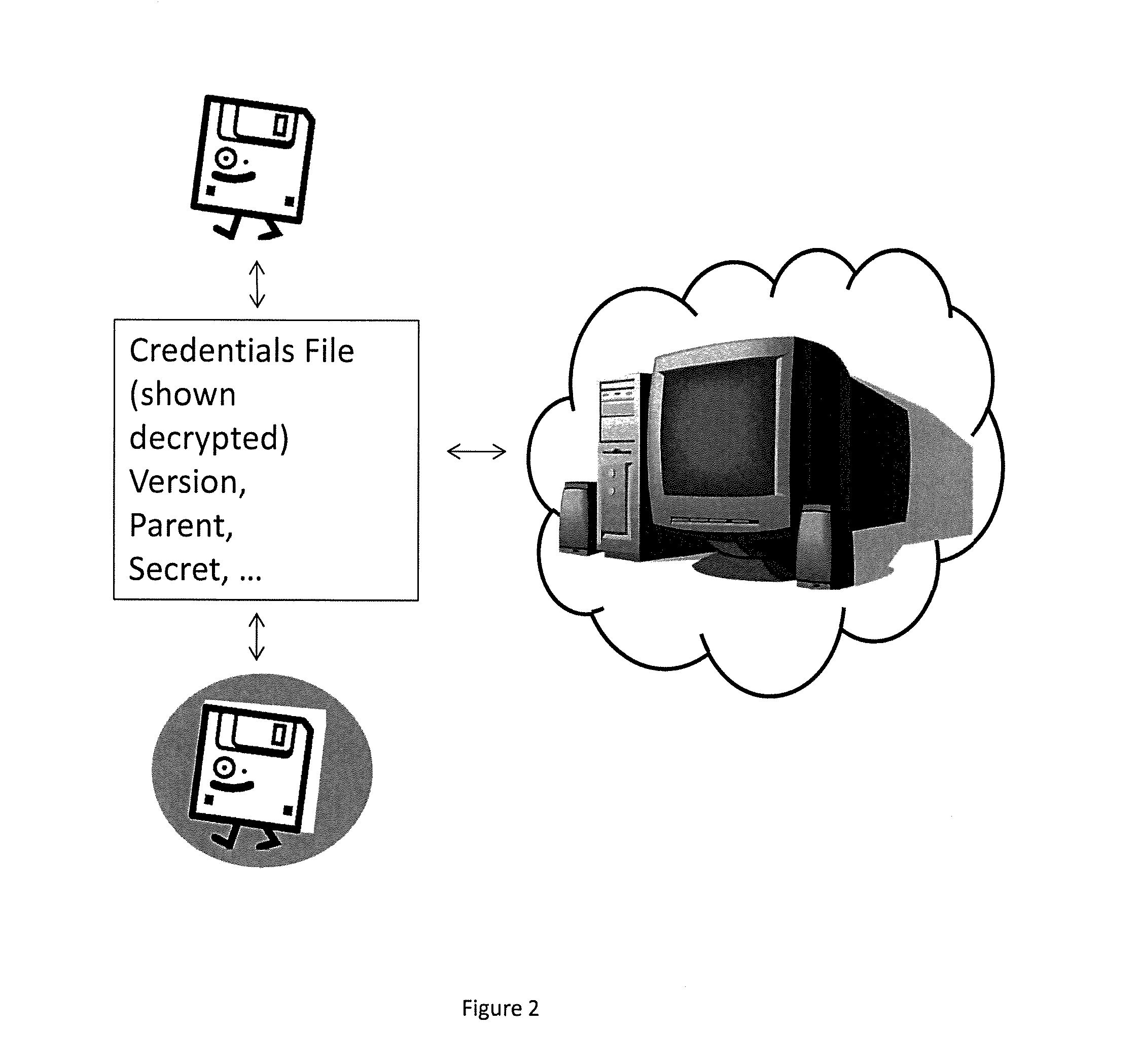
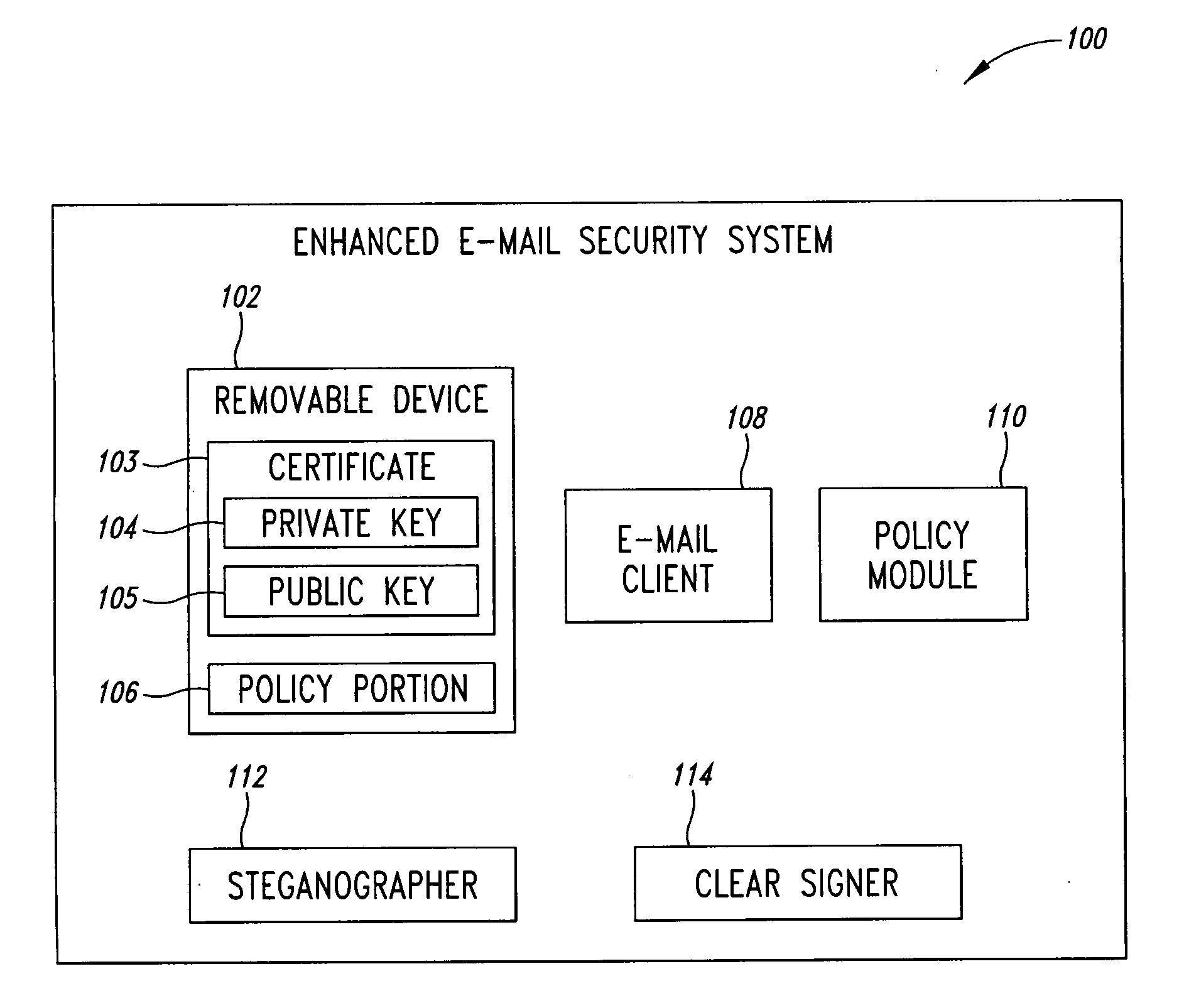
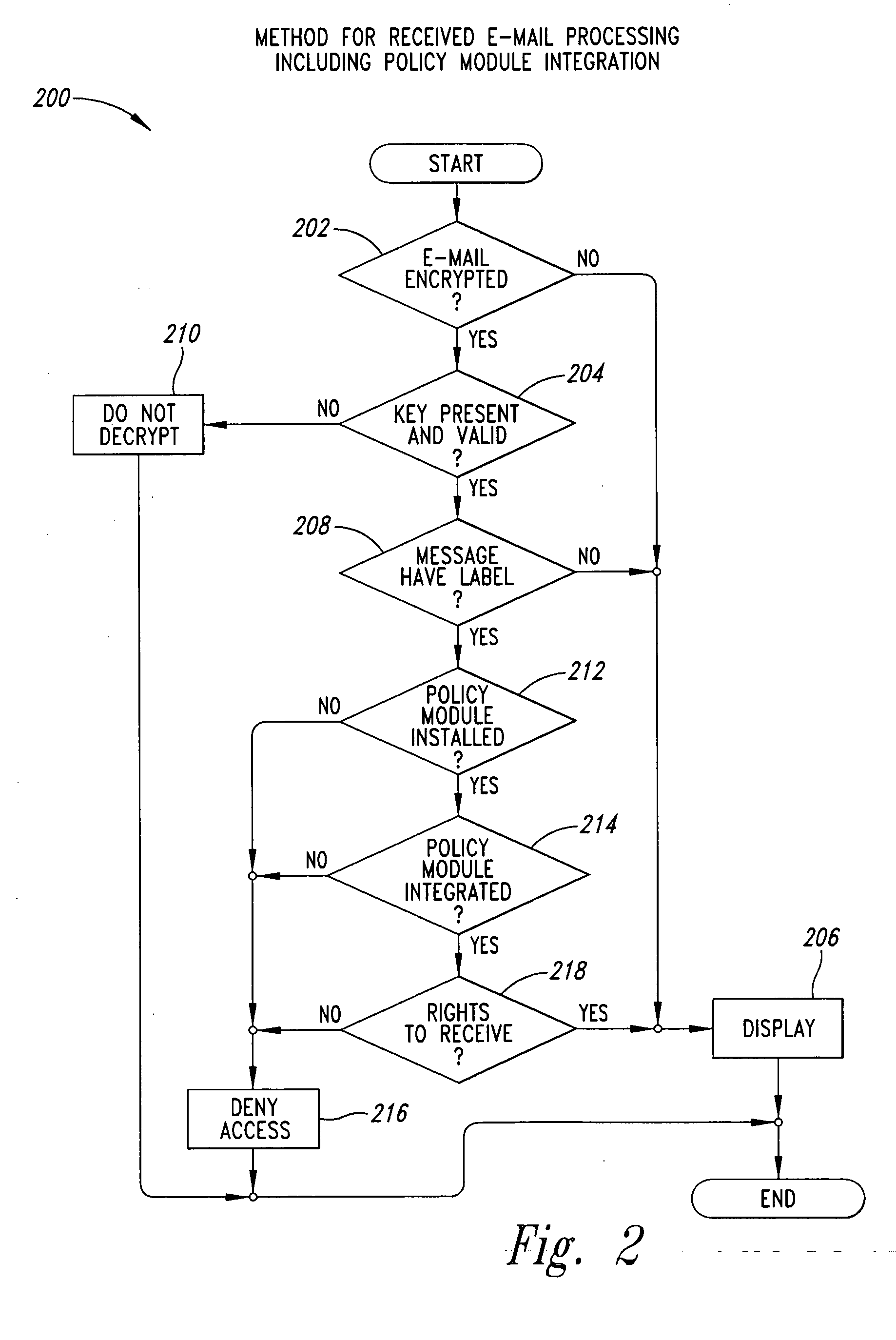
For purposes of patent searching the following description involves an enhanced system that has an e-mail client, policy module, a clear signer and a steganographer. A removable device includes a public key, a private key, and a policy portion. The policy module requires the policy portion for operation such as in decrypting e-mails. The e-mail client encrypts using the private key in conjunction with clear signing with the public key and / or using steganography to mask e-mails. Other validation features are described that can be used before decryption of e-mails occurs.
Owner:SECURE COMM TECH
Wireless methods and devices employing plural-bit data derived from audio information
Wireless devices and methods employ steganography for a variety of purposes. An exemplary application is a battery-powered cell phone, having, e.g., a microphone, a speaker, a modulator, an antenna, and an RF amplifier. In such application, steganographic techniques can be employed to encode, or decode, signals processed by the phone. Some embodiments use an image sensor to capture watermarked image data. The phone can respond to detection of such marked imagery by overlaying distinctive graphics on a cell phone display screen. Such graphics may be positioned within the display, and affine-warped, in registered relationship with the position of the watermarked object, and its affine distortion, as depicted in the image data.
Owner:DIGIMARC CORP
Big data image protection method and system based on a security area
ActiveCN109492416AAchieve hiddenImplement image protectionCharacter and pattern recognitionDigital data protectionColor imagePattern recognition
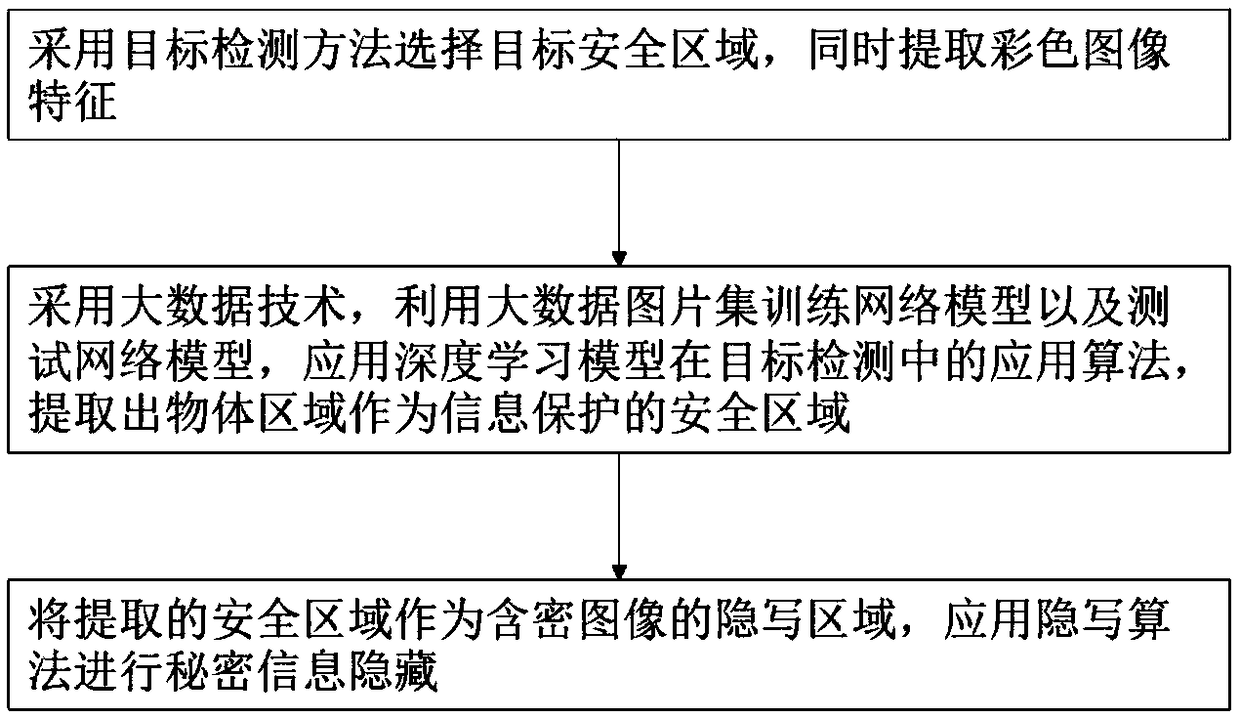
The invention provides a big data image protection method based on a security area, and the method comprises the steps: S1, selecting a target security area through employing a target detection method, and extracting color image features; s2, a big data technology is adopted, a big data picture set is utilized to train a network model and a test network model, an application algorithm of a deep learning model in target detection is applied, and an object area is extracted to serve as a safety area of information protection; and S3, taking the extracted security area as a steganography area ofthe encrypted image, and carrying out secret information hiding by applying a steganography algorithm. According to the invention, the application algorithm of the deep learning model is applied in the target detection, that is, the Mask R-CNN instance segmentation method, and select the region with complex texture noise in the image, an area with complex texture noise in the image, namely a foreground part, is selected, secret information is accurately hidden in a foreground object, and therefore the purpose of more secret image secret information hiding protection is achieved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
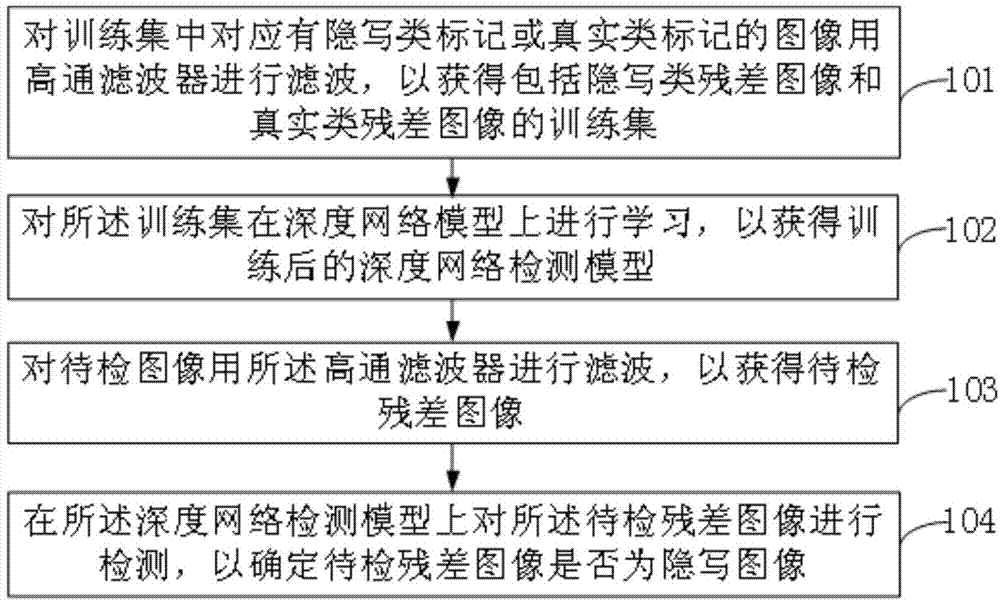
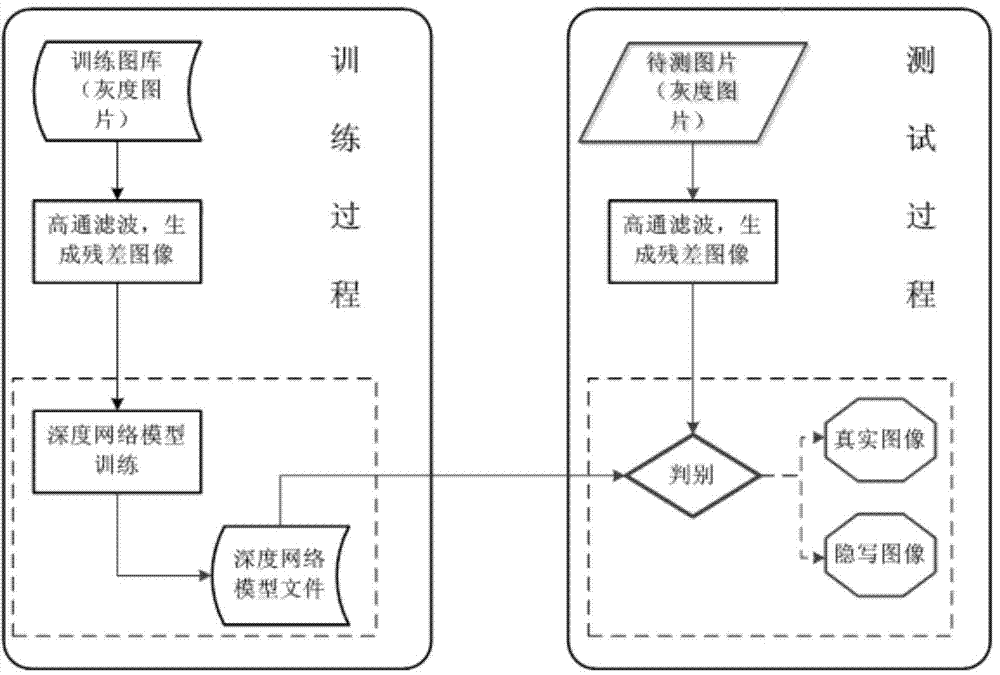
Image stego-detection method on basis of deep learning
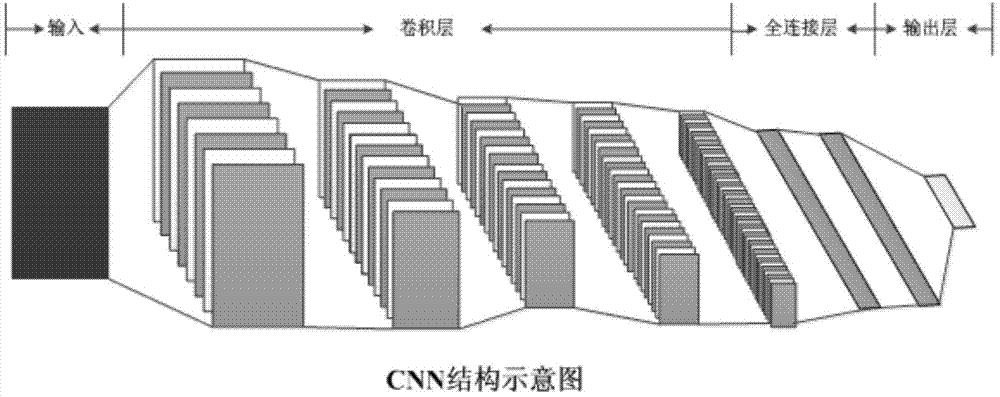
InactiveCN104778702AImprove versatilityAccurate identificationImage analysisNetwork modelAutomatic learning
The invention provides an image stego-detection method on the basis of deep learning, which comprises the following steps: filtering images which are correspondingly provided with steganography marks or reality marks in a training set by a high-pass filter so as to obtain a training set comprising steganography residue images and reality residue images; carrying out learning on the training set on a deep network model so as to obtain the trained deep network detection model; filtering an image to be detected by the high-pass filter so as to obtain a residue image to be detected; detecting the residue image to be detected on the deep network detection model so as to determine whether the residue image to be detected is a steganography image. The image stego-detection method provided by the invention can realize creation of a blind-detection model by automatic learning and can accurately identify the steganography image.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Wireless Methods And Devices Employing Steganography
InactiveUS20070189533A1Improve concealmentRecord information storagePayment architectureGraphicsAudio power amplifier
Wireless devices and methods employ steganography for a variety of purposes. An exemplary application is a battery-powered cell phone, having, e.g., a microphone, a speaker, a modulator, an antenna, and an RF amplifier. In such application, steganographic techniques can be employed to encode, or decode, signals processed by the phone. Some embodiments use an image sensor to capture watermarked image data. The phone can respond to detection of such marked imagery by overlaying distinctive graphics on a cell phone display screen. Such graphics may be positioned within the display, and affine-warped, in registered relationship with the position of the watermarked object, and its affine distortion, as depicted in the image data.
Owner:DIGIMARC CORP
Wireless Methods and Devices Employing Steganography
InactiveUS20080125083A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareSpeech sound
A wireless device includes a data capture system, a radiant-energy data transmission system, and a steganographic encoder that hides a plural-bit auxiliary code within data captured by the data capture system prior to its transmission by the data transmission system. An illustrative system, operable with audio input data, is a cell phone that steganographically encodes a user's voice. In some arrangements the steganographic encoding depends on data wirelessly received from a remote location. A variety of other arrangements and systems are also detailed.
Owner:DIGIMARC CORP
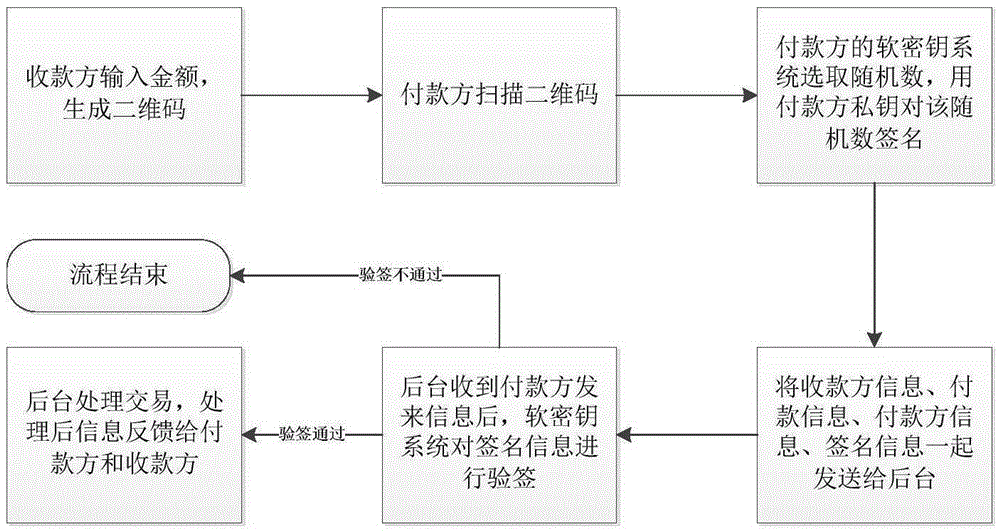
Novel terminal safety soft secret key management method
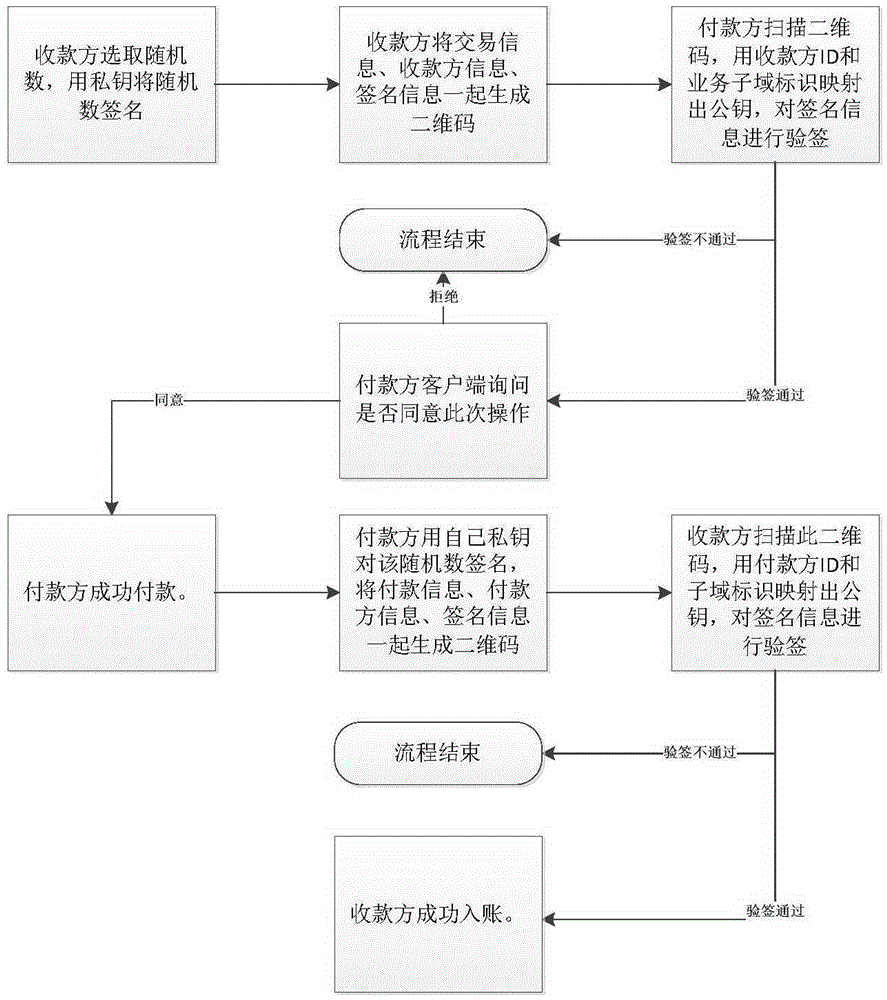
InactiveCN105407079AConvenient payment operationImprove securityKey distribution for secure communicationPayment protocolsComputer terminalDimensional modeling
The invention discloses a novel terminal safety soft secret key management method. According to the method, information of two transaction parties are selected by a soft secret key system as identification ID, public and private key pairs are formed through mapping on the basis of business subdomain identification; for online payment, a two-dimensional code is generated at a receiving party; after the two-dimensional code is scanned by a payment party, signature is carried out by utilizing a private key pair randomized number, and information is sent to a background management system; signature verification is realized by the background management system through utilizing public key pair signature information; if signature verification succeeds, transaction is processed; for offline payment, signature is carried out by the receiving party through utilizing the private key pair randomized number, and a two-dimensional code is generated; the two-dimensional code is scanned by the payment party, and signature verification is realized through public key pair signature information; if signature verification succeeds, payment is carried out by the payment party according to transaction information; signature is carried out by the payment party through utilizing the private key pair randomized number, a two-dimensional code is generated; the two-dimensional code is scanned by the receiving party, and signature verification is realized through public key pair signature information; if signature verification succeeds, payment is successfully realized for the receiving party. Through the method, system safety is not only improved, system disposition cost is further reduced, transaction validness is fully guaranteed, and invalid information tampering and information steganography can be avoided.
Owner:CHINA SMARTCITY TECH
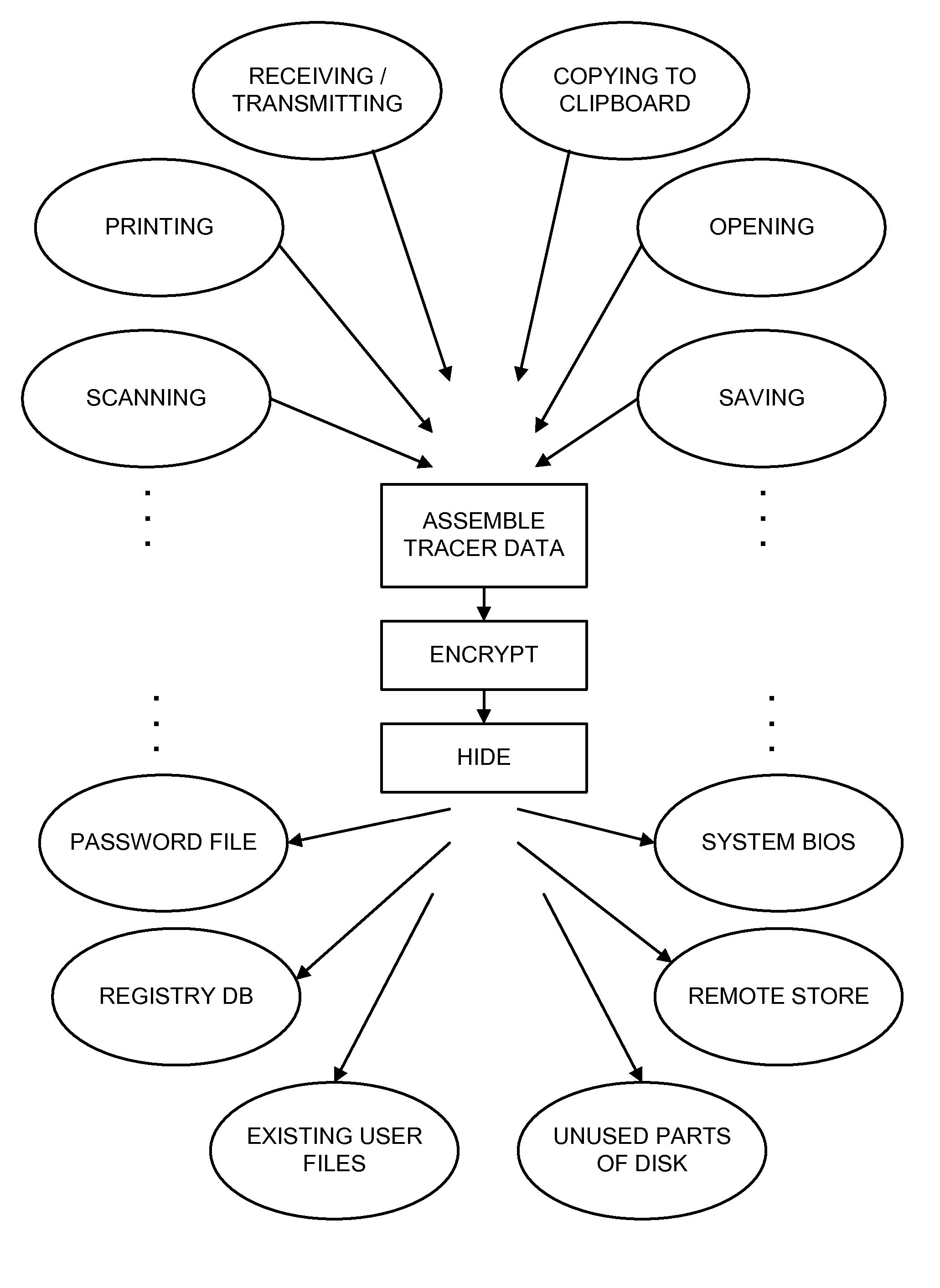
Hiding ciphertext using a linguistics algorithm with dictionaries
Encrypted communications is made to appear to be normal text so as to avoid undue attention to either the sender or recipient. Information can be hidden or embedded in innocuous documents using steganography wherein the information is masked within a larger document. Other approaches would translate the ciphertext into a form of normal looking text that would in effect be gibberish but would use normal words in at least one native language. There are many tradeoffs and benefits to be considered when attempting any form of encrypted communications.
Owner:GLOBAL INTEGRITY INC
Method for authenticating a clent mobile terminal with a remote server
InactiveUS20100293376A1Not easy to detectKey distribution for secure communicationUser identity/authority verificationServer authenticationClient-side
The disclosure relates to a method and a device for authenticating a client mobile terminal on a remote server of said terminal, with said server sending a challenge to said mobile terminal in advance, said mobile terminal having to respond to the challenge, to authenticate at the same time, by transmitting a response consisting in encoding said challenge combined with a secret key known to said terminal and the same time to the server, wherein the secret key is hidden in a media file recorded in the mobile terminal using steganography.
Owner:SYNCHRONOSS TECH FRANCE
Compressive sensing-based adaptive video information hiding method
InactiveCN102917227AOrnamental effectSmall amount of calculationTelevision systemsDigital video signal modificationPattern recognitionKey frame
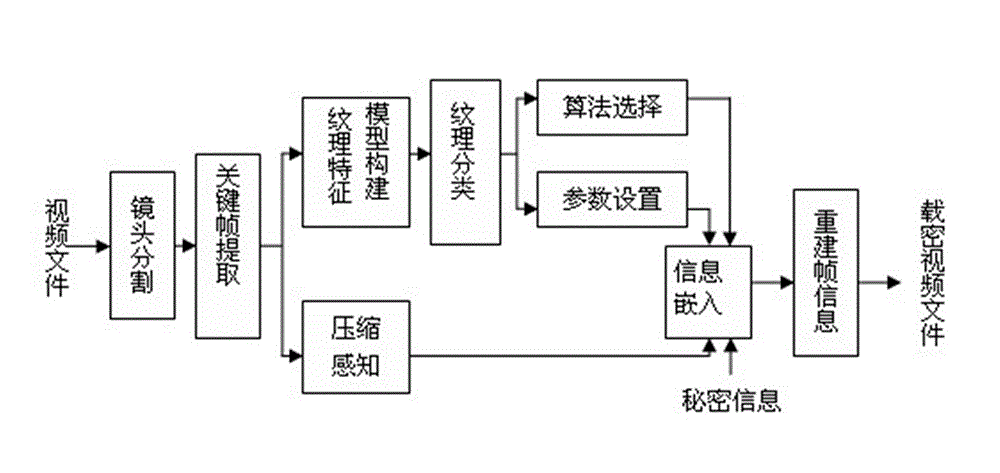
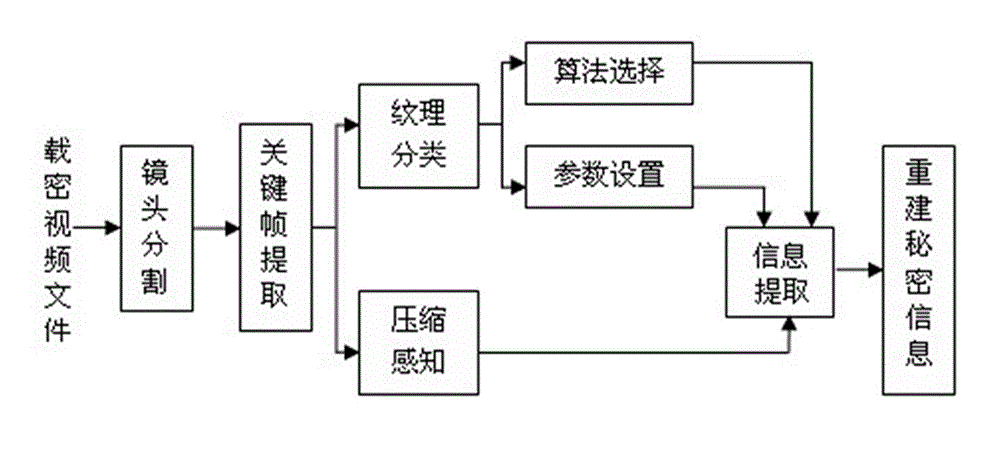
The invention discloses a compressive sensing-based adaptive video information hiding method, which is characterized by comprising the following steps of: a, framing a video file by using shot as a unit; b, taking the first frame of each shot as a key frame; c, establishing an image texture classification model to obtain a texture classification model mark of each key frame; d, determining a texture category of each key frame and determining whether the key frame is a texture region, or a smooth region or between the texture region and the smooth region; e, selecting an algorithm and determining insert depth; f, inserting secret information, i.e., inserting the secret information in a coefficient matrix; and g, synthesizing a video file. According to the video information hiding method, the secret information can be adaptively inserted under the condition that the entire video file is not required to be decompressed, so that the ornamental value of the video is not affected, and the method has the advantages of small amount of calculation, high information steganography efficiency, small influence on the video and good secret information safety. The method can be widely applied to various fields such as copyright authentication, pirate tracking and secure communication.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
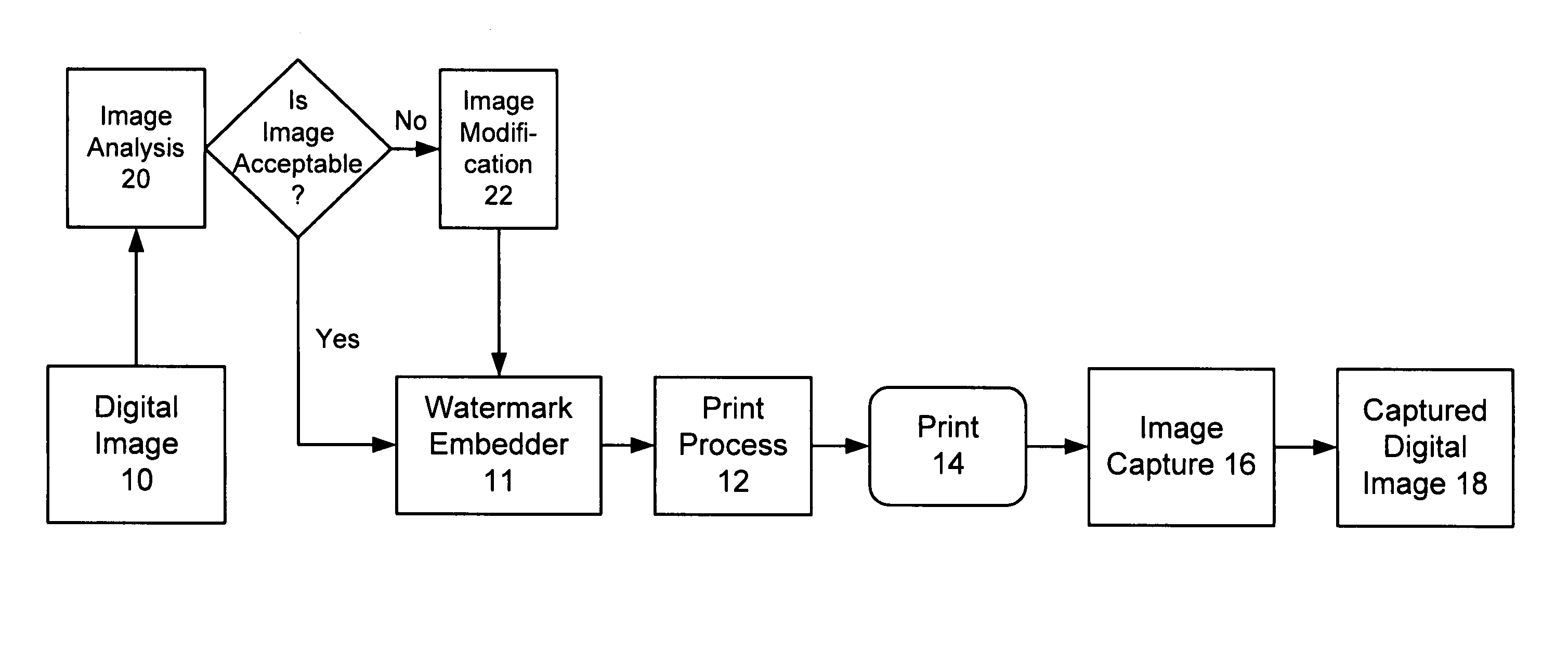
Conditioning imagery to better receive steganographic encoding
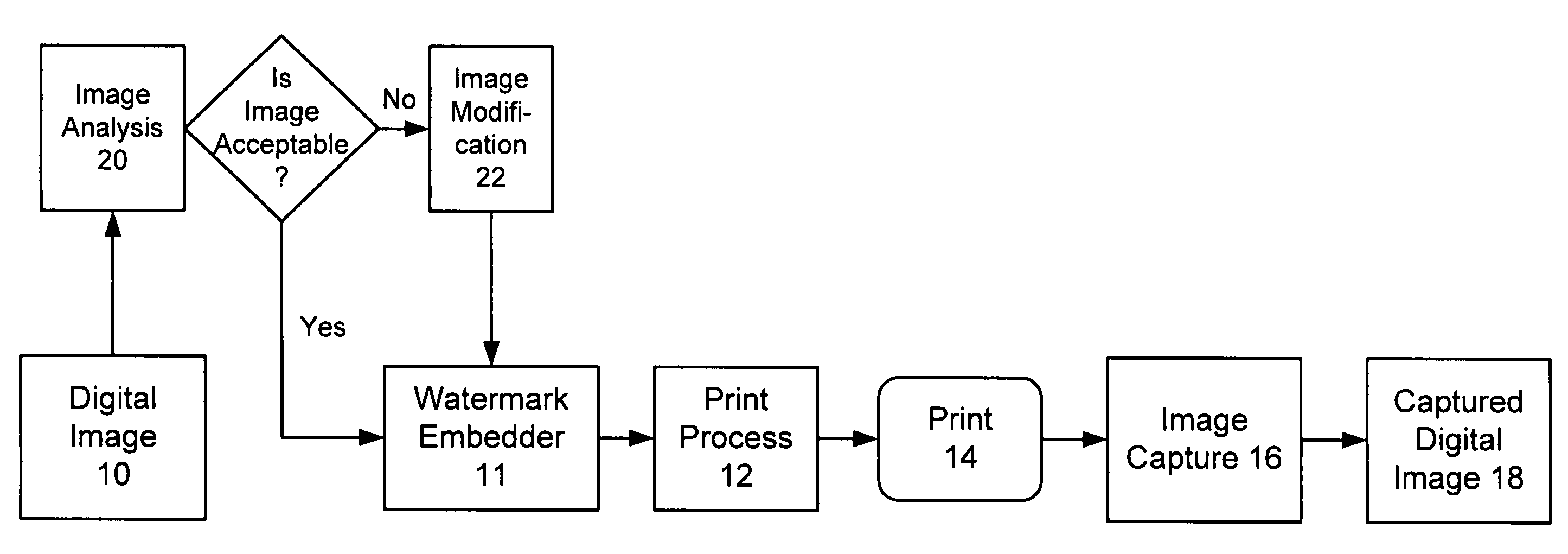
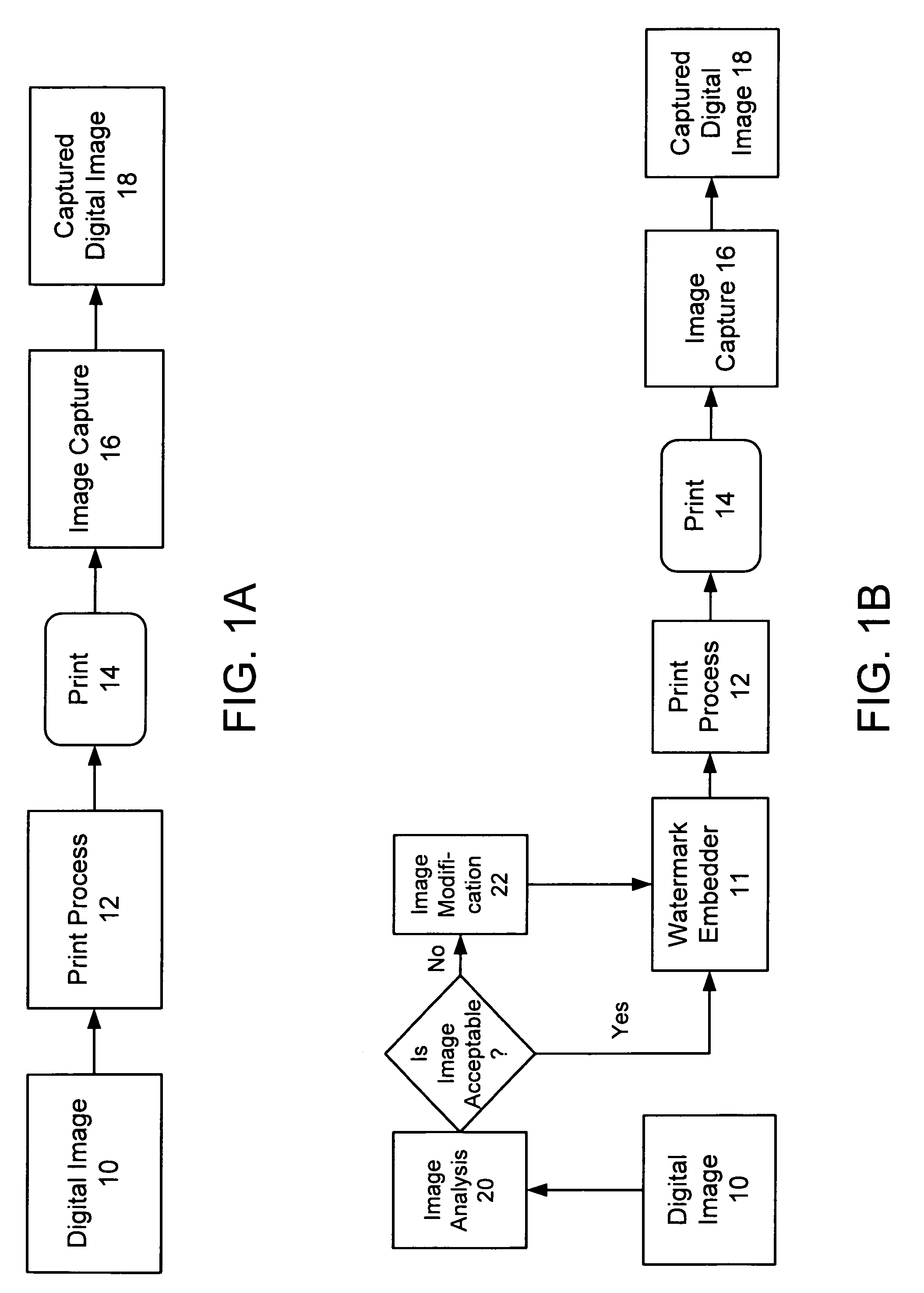
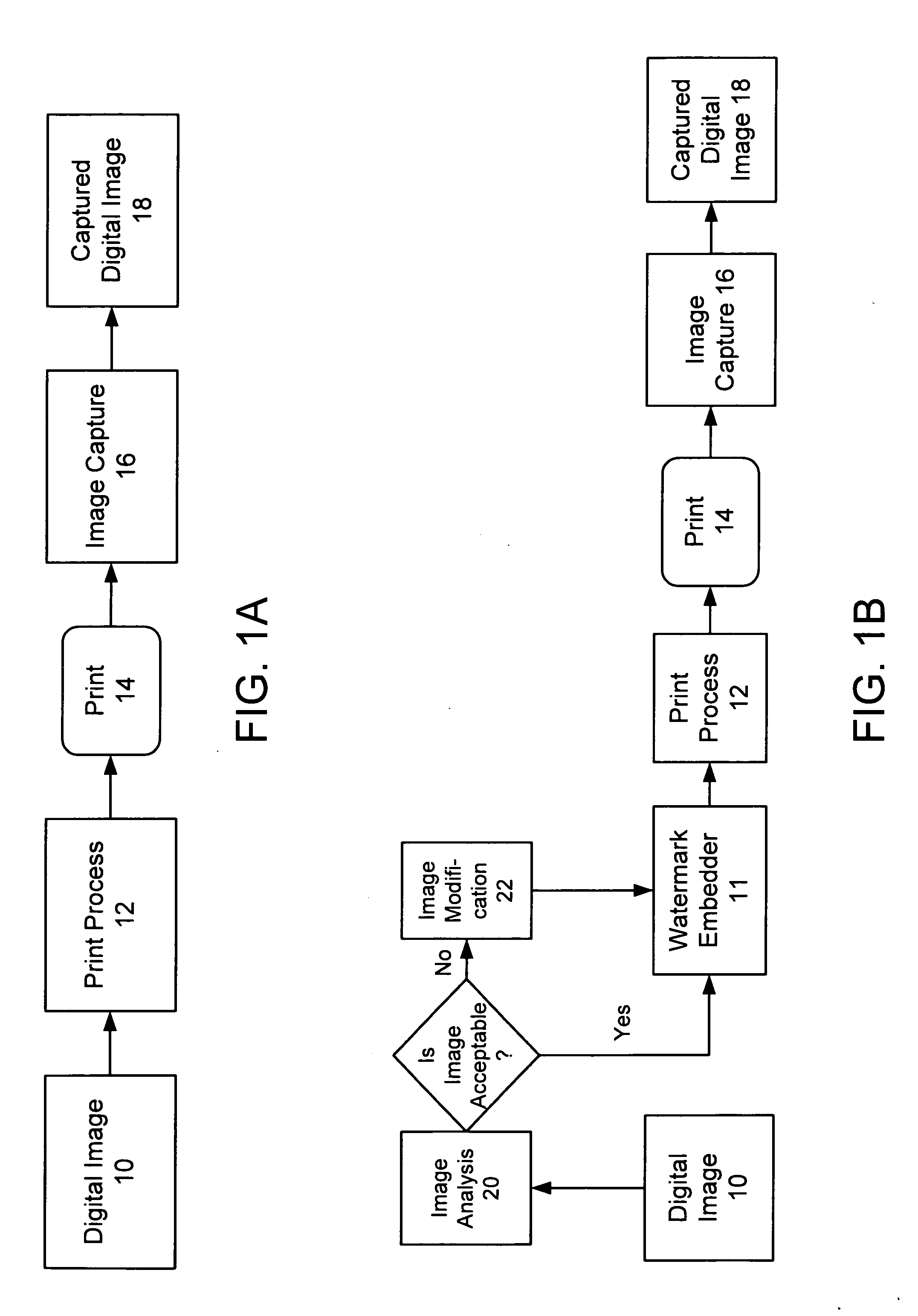
The present invention relates to steganography and digital watermarking. In one implementation, we provide a method to analyze a digital image to determine whether the digital image will be a suitable host to receive steganographic encoding or digital watermarking. Suitability is determined, at least in part, by analyzing the digital image relative to an expected workflow process through which a watermarked version of the digital image is expected to flow through. Our methods and systems determine whether the digital image forms a suitable host to receive digital watermarking relative to the expected workflow process. If the digital image is not suitable, the digital image is modified to better receive digital watermarking in anticipation of the expected workflow process.
Owner:DIGIMARC CORP
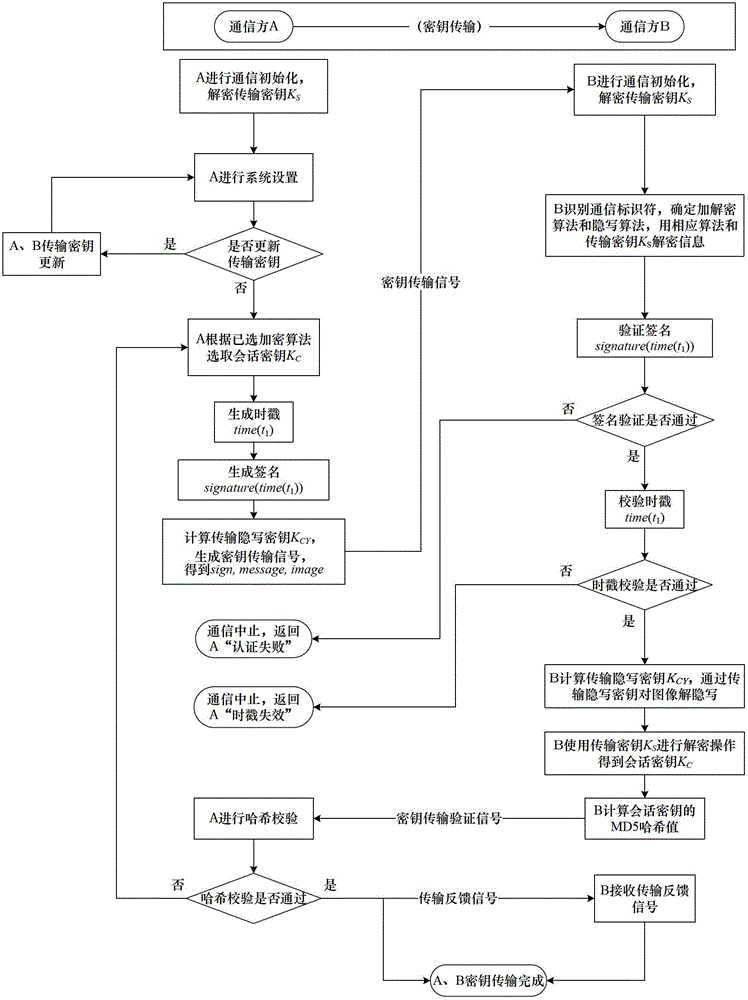
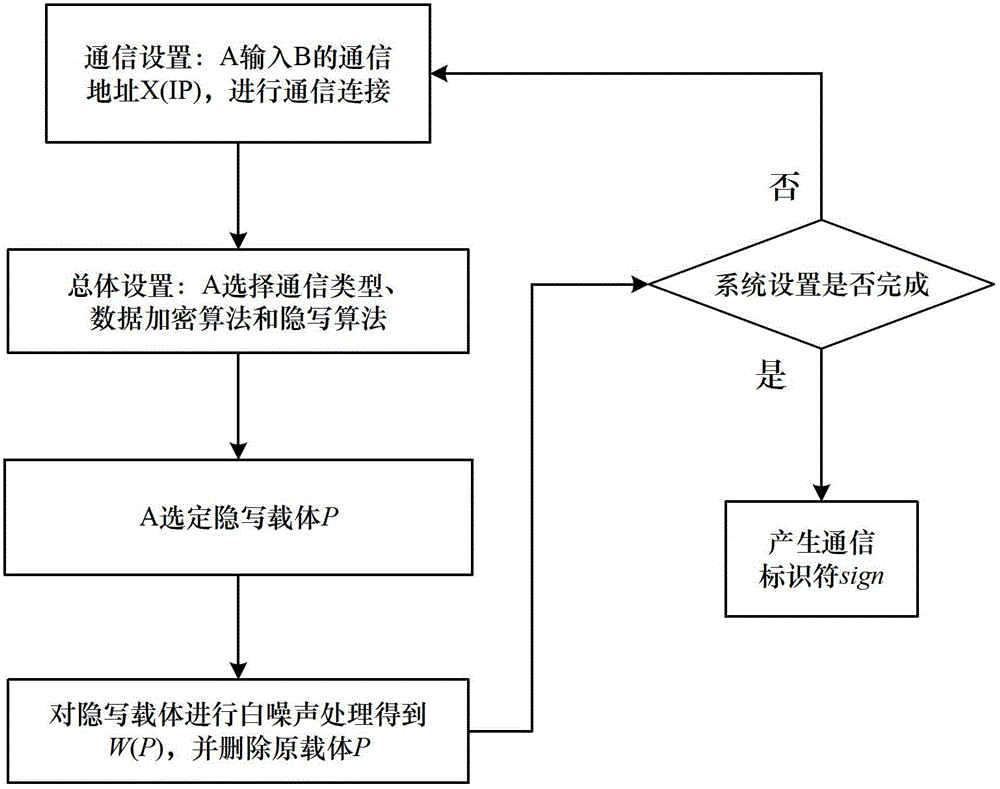
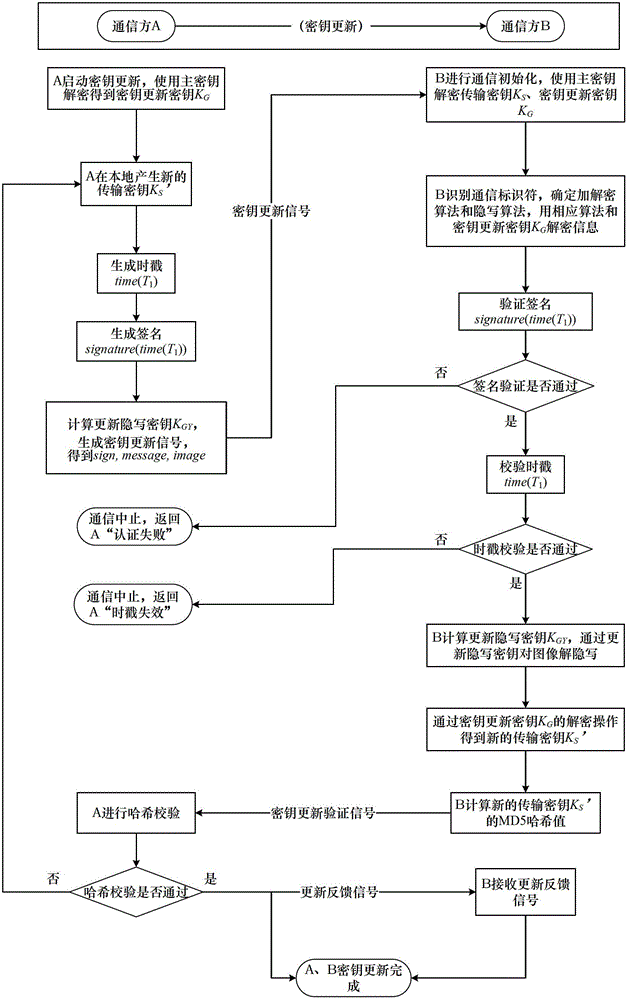
Steganography-based key transmission and key updating method
ActiveCN102724041AEffective verification of identity informationImprove authentication strengthEncryption apparatus with shift registers/memoriesUser identity/authority verificationMultiple encryptionCiphertext
The invention provides a steganography-based key transmission and key updating method, which is applied to the field of information safety. The method comprises the steps that a communication party A sets a communication type, an encryption algorithm an steganography algorithm, selects a steganography carrier and generates a communication identifier and then performs the updating of a transmission key or the transmission process of a conversion key; a new transmission key is selected when in updating, a time stamp and a signature are generated to encrypt and steganograph the transmission key, the key updating information is generated to be transmitted to a communication party B, and the communication party B performs the verification, de-staganography and deciphering to obtain the transmission key; and the conversion key is selected in transmission to generate a time stamp and a signature so as to encrypt and steganograph the conversion key, the key transmission information is generated to be transmitted to the communication party B, and the communication party B performs the verification, de-steganography and deciphering to obtain the conversation key. The key is concealed by utilizing the steganography, so that an encrypted data format in the key transmission process and the key updating process can be effectively protected, and the safety transmission of multiple encryption and decryption algorithm conversation keys can be realized.
Owner:BEIHANG UNIV
Method of generating secure tokens and transmission based on (TRNG) generated tokens and split into shares and the system thereof
ActiveUS20140341374A1Key distribution for secure communicationRandom number generatorsTest suiteNumber generator
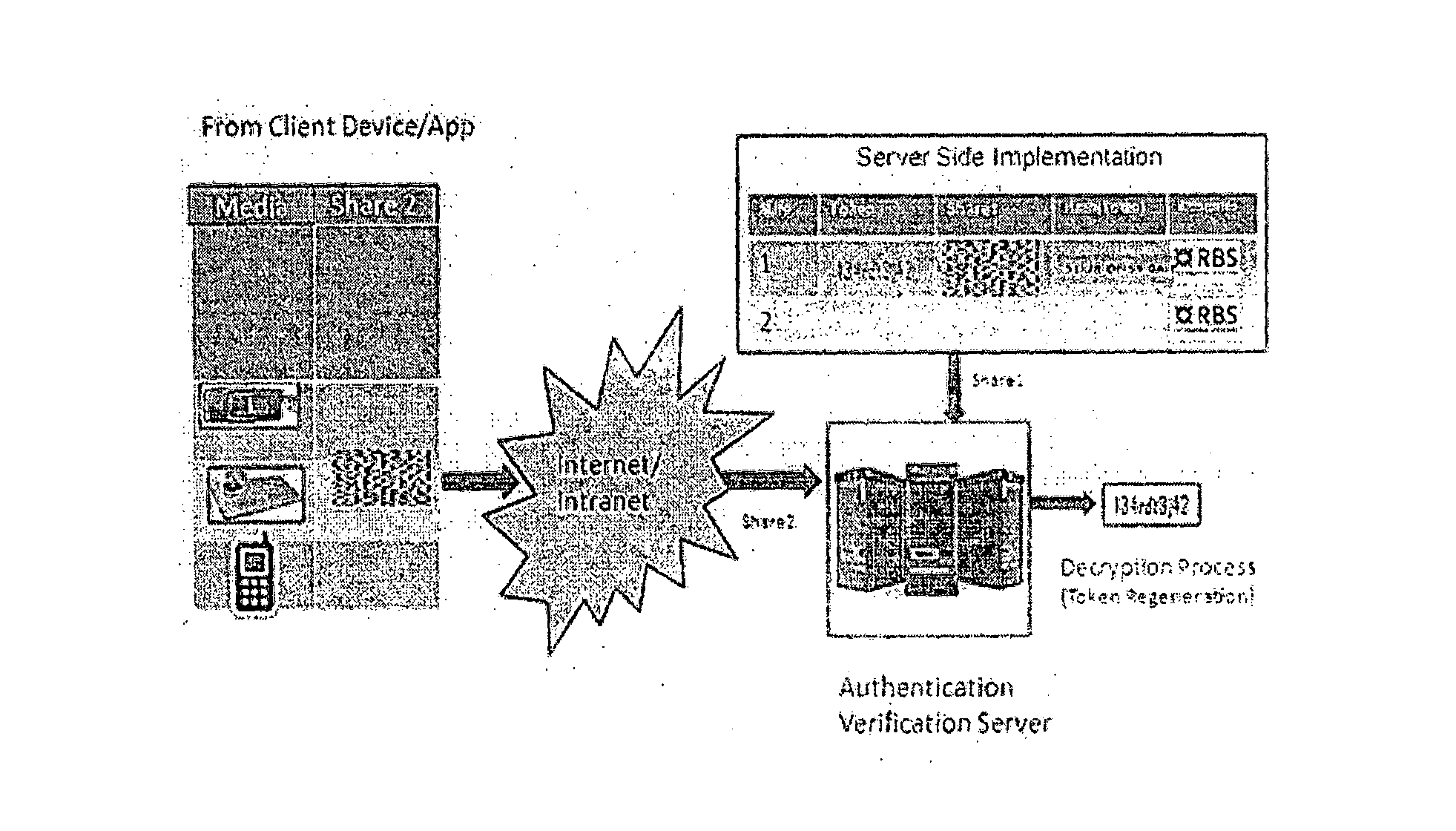
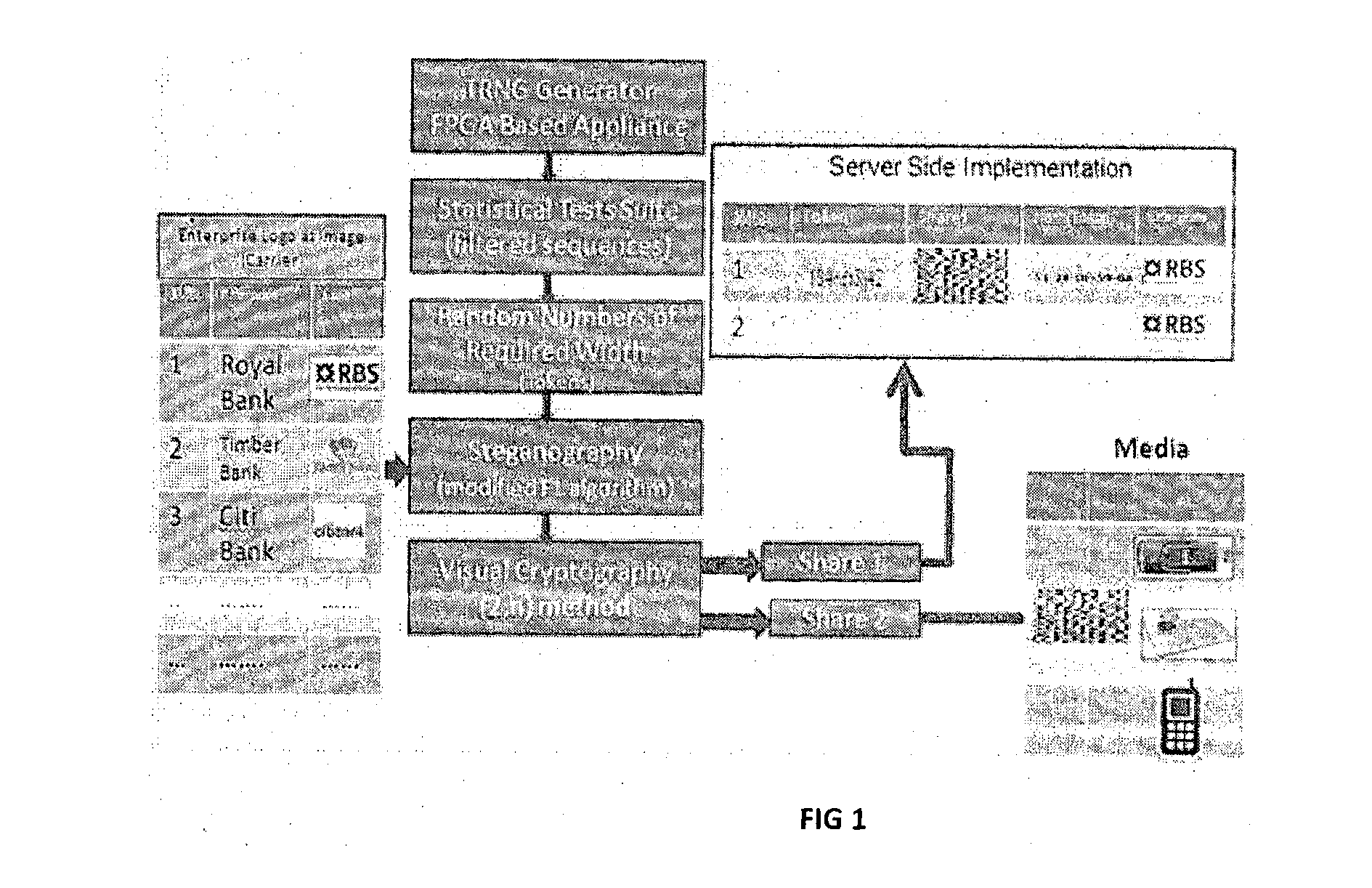
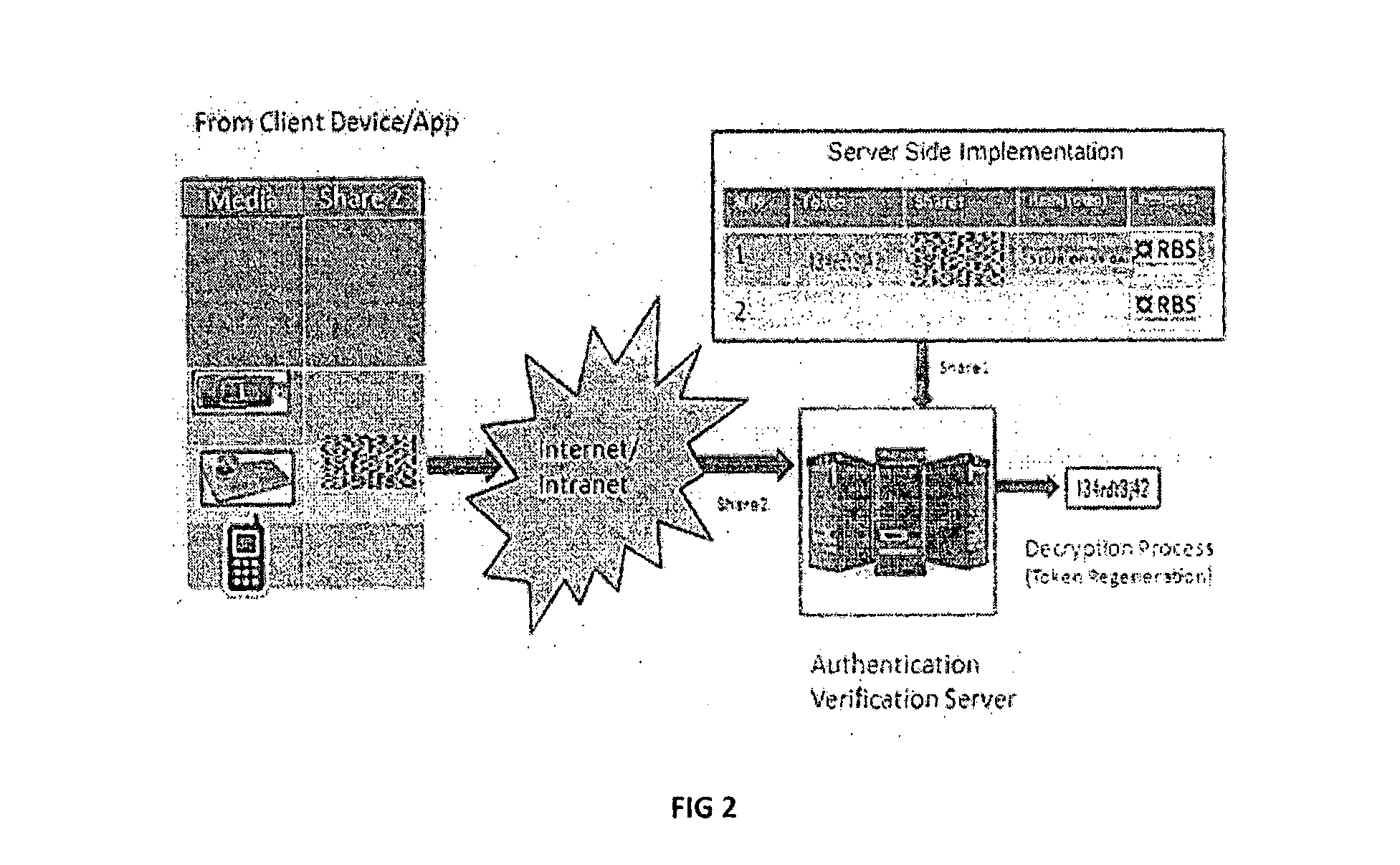
A method of generating secure tokens and transmission based on (TRNG) generated tokens and split into shares, the method comprising steps of generating the keys by a hardware based True Random number Generator (TRNG); sieving / filtering the generated keys using statistical tests suite and are orthogonal amongst the created; selecting the random numbers of required width as tokens; applying number to image transformation for the said tokens; applying steganography methods of injecting into image carrier to the selected tokens; and splitting the steganographic contents into at least two shares using Share Generation Appliance (SGA), which is based on visual cryptographic methods.
Owner:INTEGRITA COMPUTING SYST INDIA
Conditioning imagery to better receive steganographic encoding
ActiveUS20060002583A1Easy to receiveHigh saturationImage enhancementTexturing/coloringDigital imageDigital watermarking
THE present invention relates to steganography and digital watermarking. In one implementation, we provide a method to analyze a digital image to determine whether the digital image will be a suitable host to receive steganographic encoding or digital watermarking. Suitability is determined, at least in part, by analyzing the digital image relative to an expected workflow process through which a watermarked version of the digital image is expected to flow through. Our methods and systems determine whether the digital image forms a suitable host to receive digital watermarking relative to the expected workflow process. If the digital image is not suitable, the digital image is modified to better receive digital watermarking in anticipation of the expected workflow process.
Owner:DIGIMARC CORP
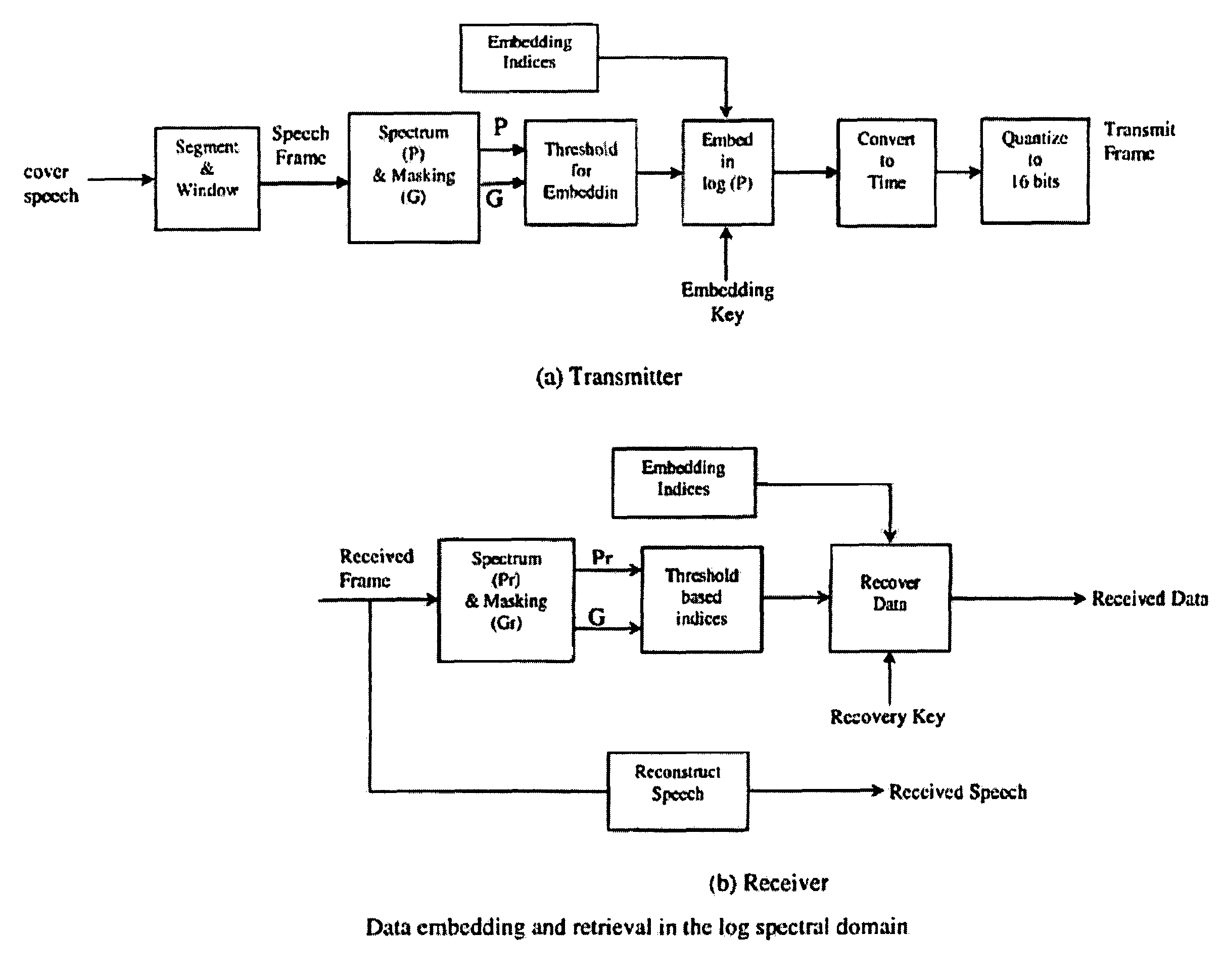
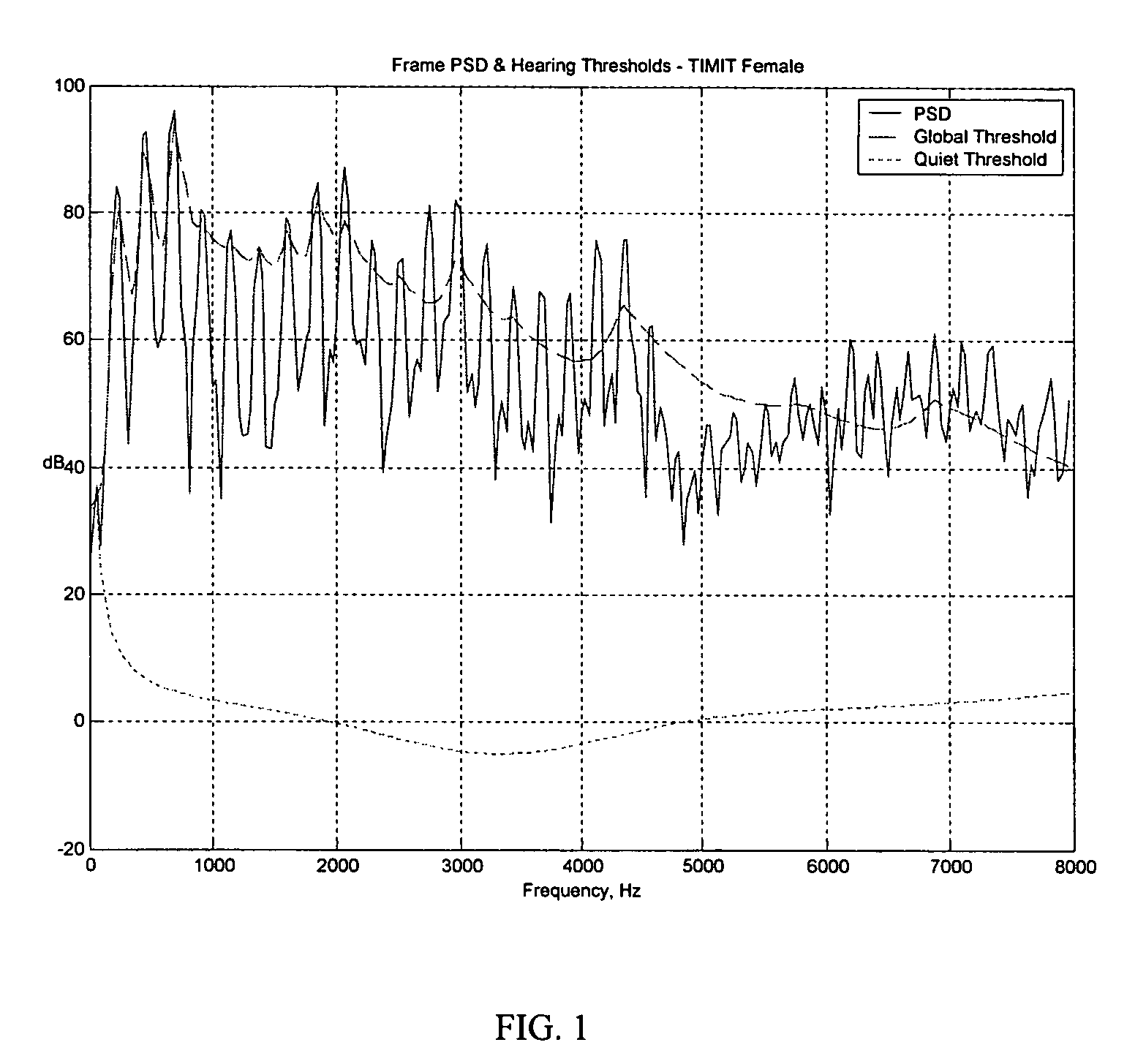
Audio steganography method and apparatus using cepstrum modification
Audio steganography methods and apparatus using cepstral domain techniques to make embedded data in audio signals less perceivable. One approach defines a set of frames for a host audio signal, and, for each frame, determines a plurality of masked frequencies as spectral points with power level below a masking threshold for the frame. The two most commonly occurring masked frequencies f1 and f2 in the set of frames are selected, and a cepstrum of each frame is modified to produce complementary changes of the spectrum at f1 and f2 to correspond to a desired bit value. Another aspect of the invention involves determining a masking threshold for a frame, determining masked frequencies within the frame having a power level below threshold, obtaining a cepstrum of a sinusoid at a selected masked frequency, and modifying the frame by an offset to correspond to an embedded data value, the offset derived from the cepstrum.
Owner:PURDUE RES FOUND INC
Information steganography method by taking compressed video as carrier
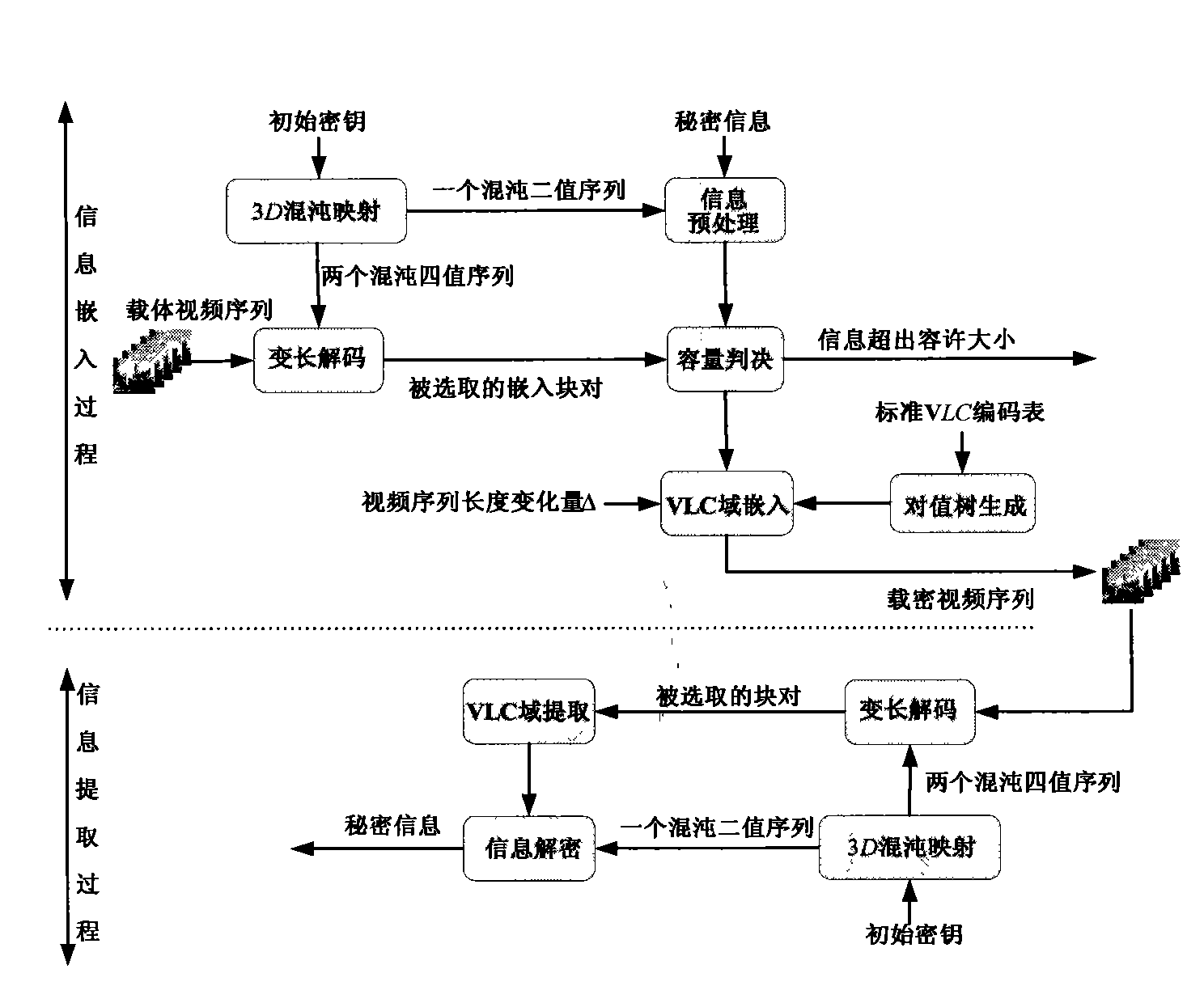
InactiveCN101610405AMeet real-time requirementsPulse modulation television signal transmissionDigital video signal modificationInformation embeddingValue tree
The invention belongs to an information steganography method by taking compressed video as a carrier in the field of communication and information security. The method is characterized by using VLC encoding list in ISO / IEC 13818-2 standard in the realization process to preconstruct a group of increase / decrease pair value tree AST, selecting a certain leaf node of AST in information steganography to automatically guide the operation of an embedding method, thus the size of a compressed video file does not change remarkably before and after information embedding, and the transparency of a video steganography method is ensured. The information embedding and extraction operations of the method are performed completely in VLC domain, thereby avoiding decoding and recoding processes aiming at compressed video stream and meeting the real-time requirement of the video steganography method.
Owner:刘镔
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com