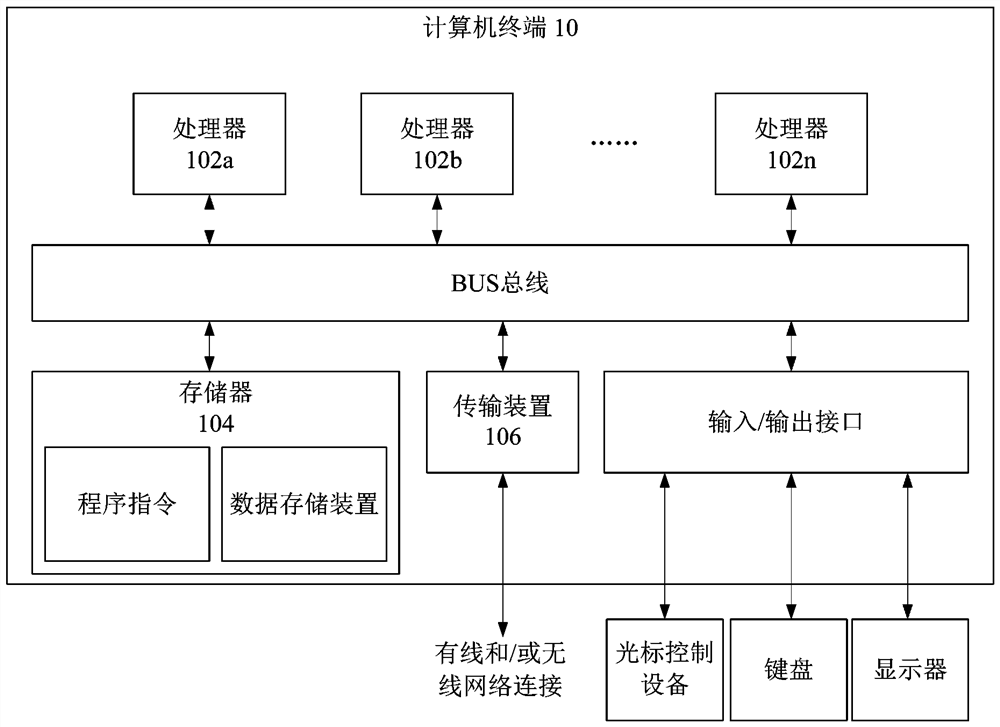
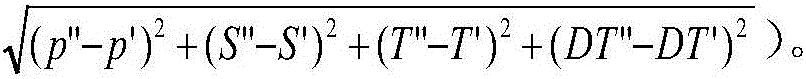Patents
Literature
30results about How to "Improve authentication strength" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
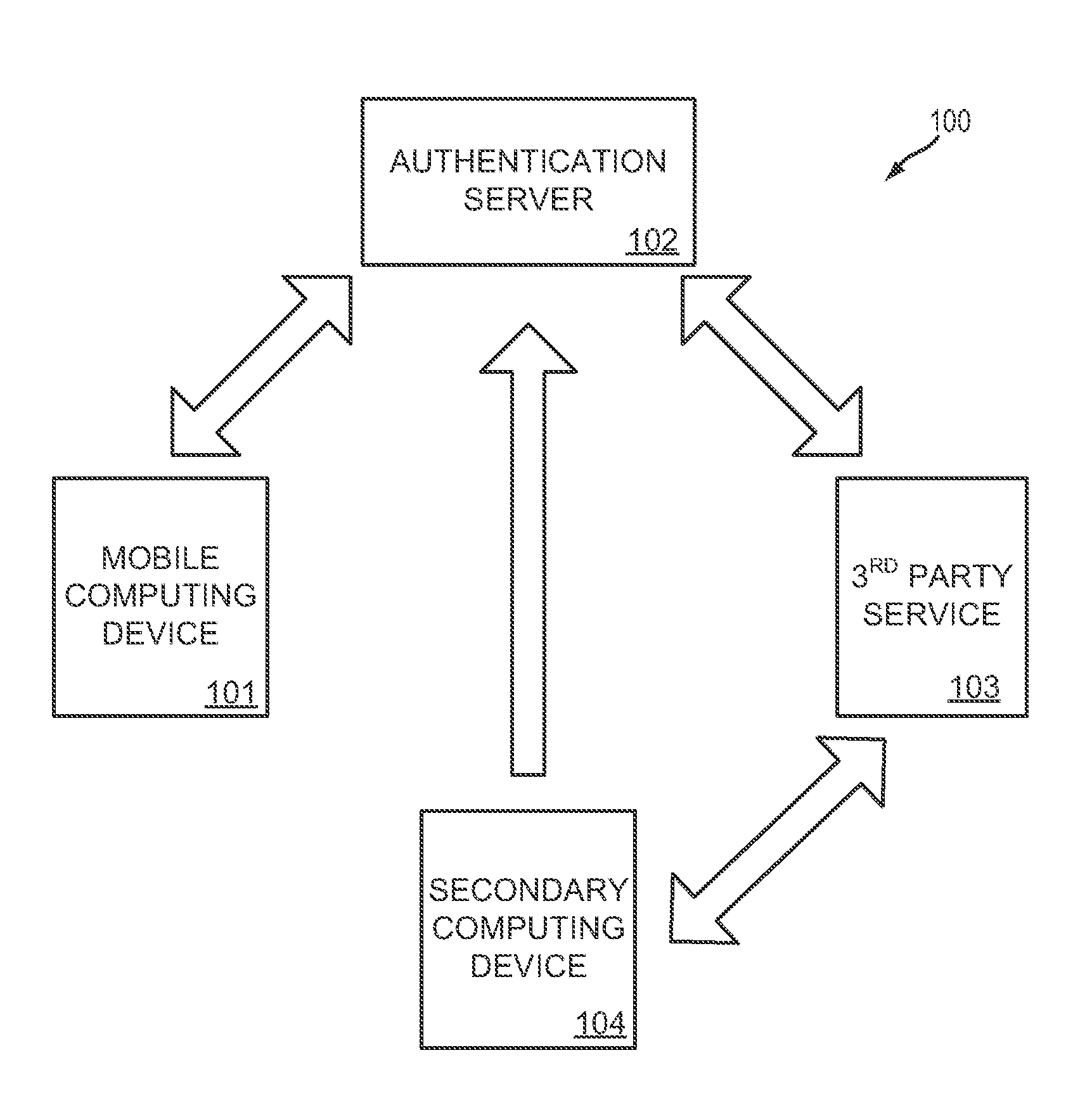
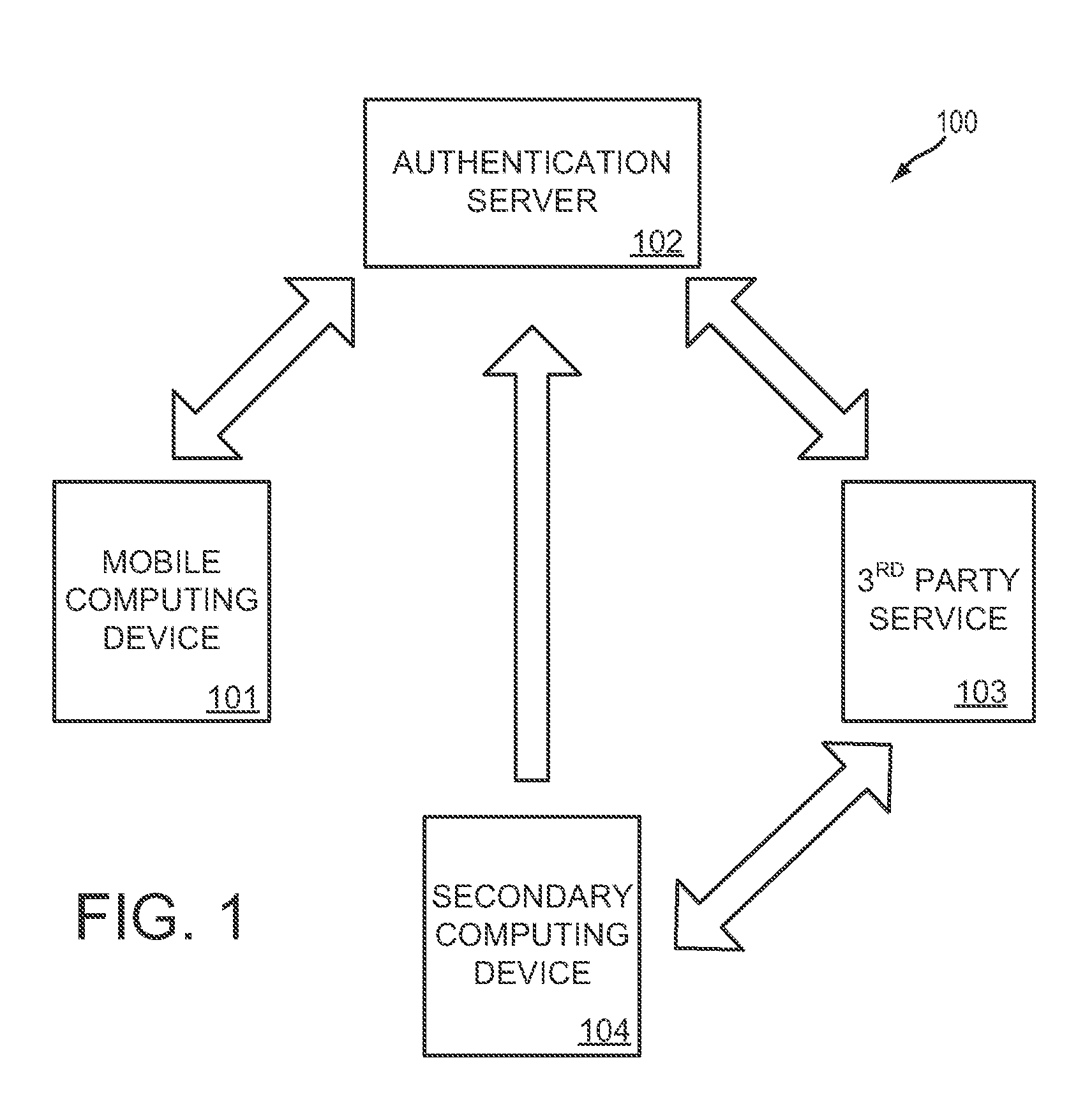
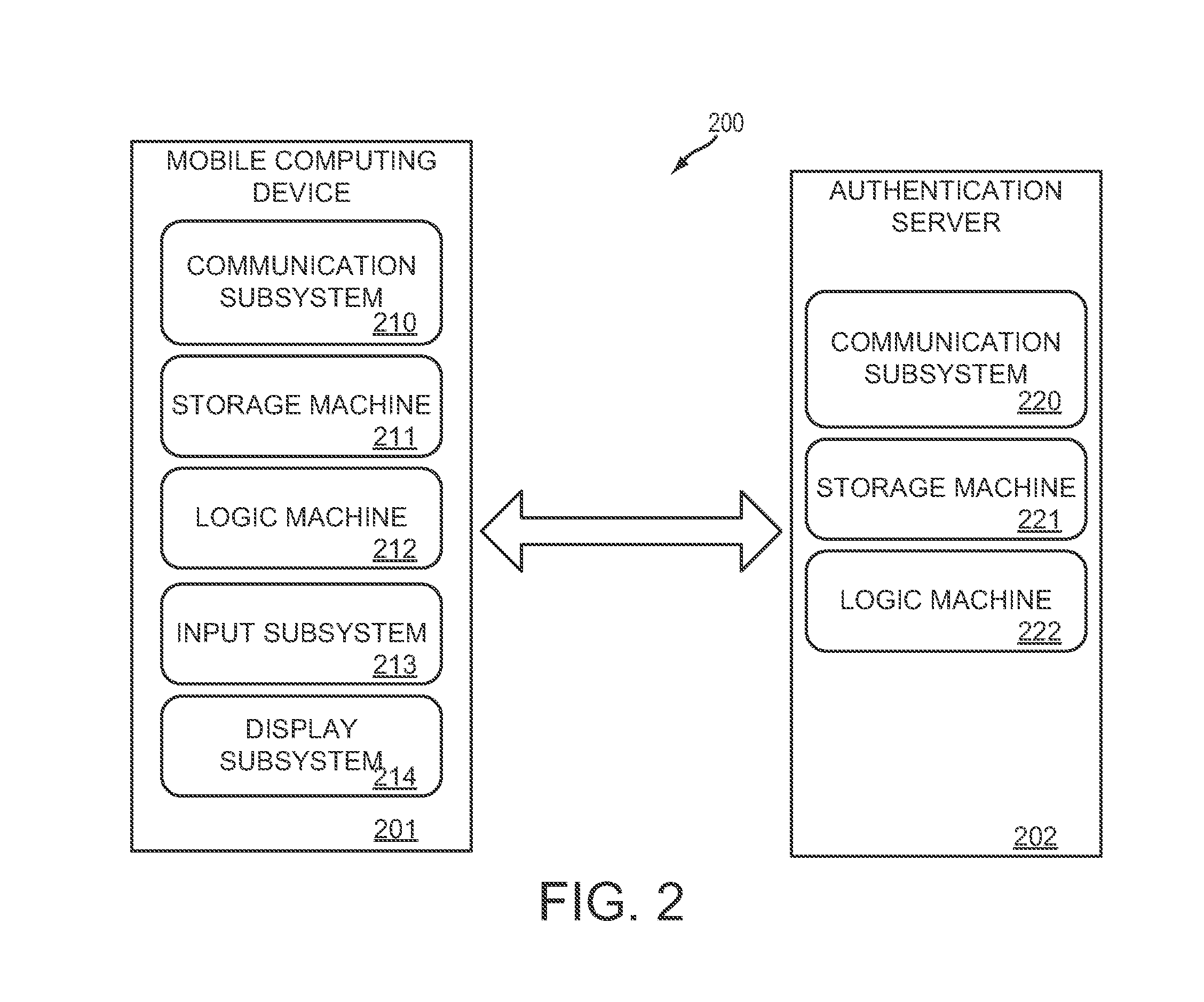
System and methods for one-time password generation on a mobile computing device
InactiveUS20140365780A1Increase the number ofImprove authentication strengthService provisioningDigital data processing detailsAuthentication serverOne-time password
A method for a mobile computing device comprises downloading a one-time password initializer from an authentication server, the one-time password initializer configured to generate a device-specific signature for the mobile computing device; uploading a device-specific signature to the authentication server; and downloading a device-specific configuration and one-time password generator from the authentication server. In this way, both the mobile computing device and authentication server may independently generate equivalent one-time passwords based on unique information associated with the mobile computing device.
Owner:MOVASSAGHI SAFA
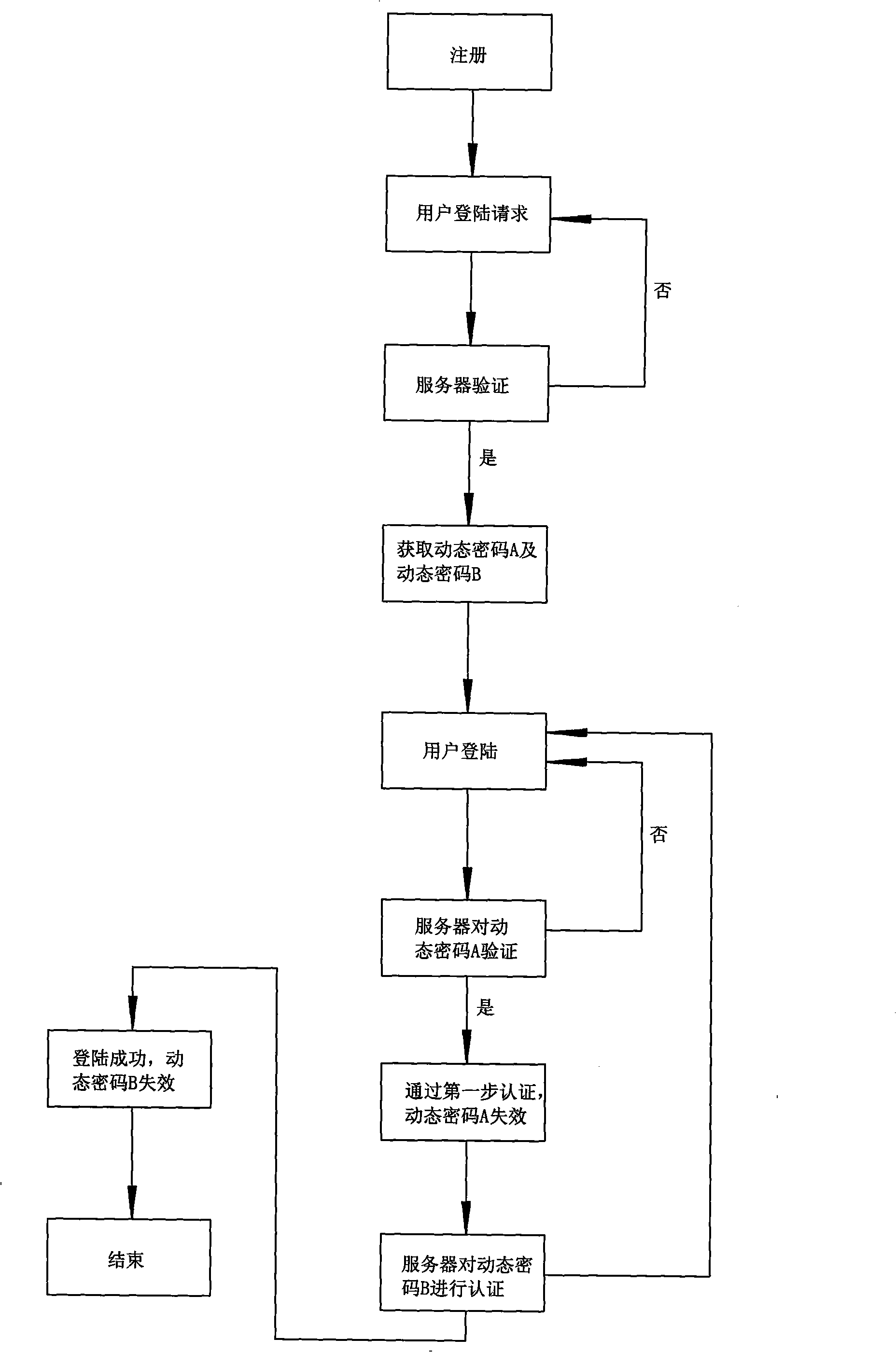
Method for protecting account number safety
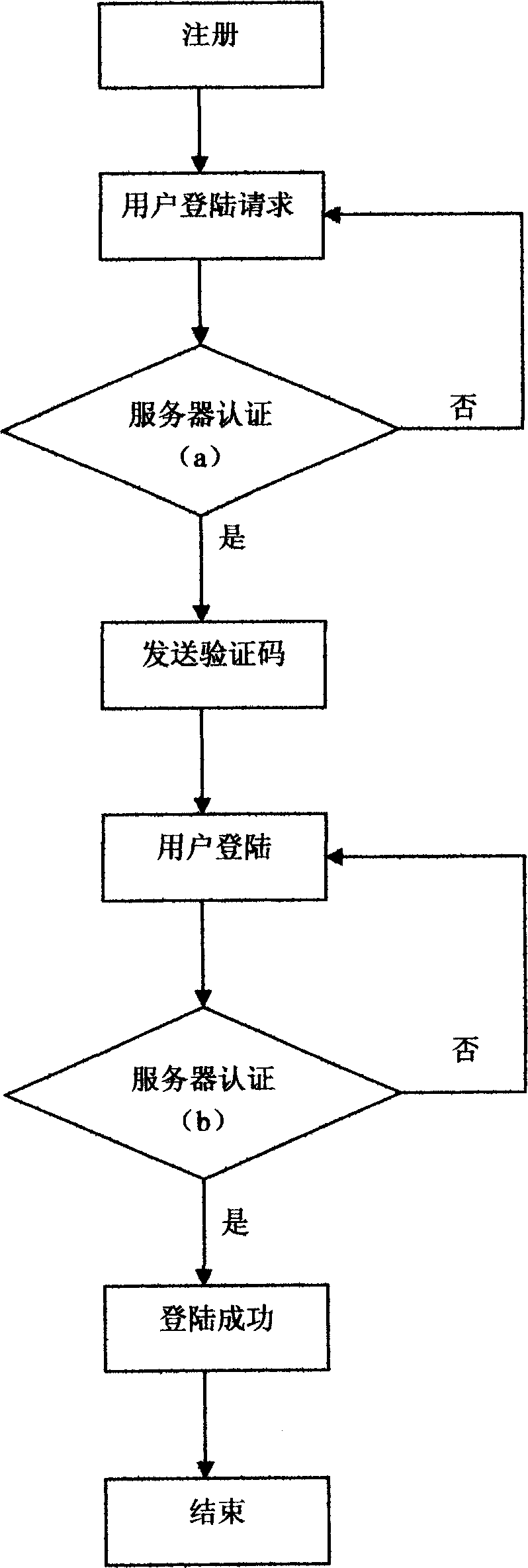
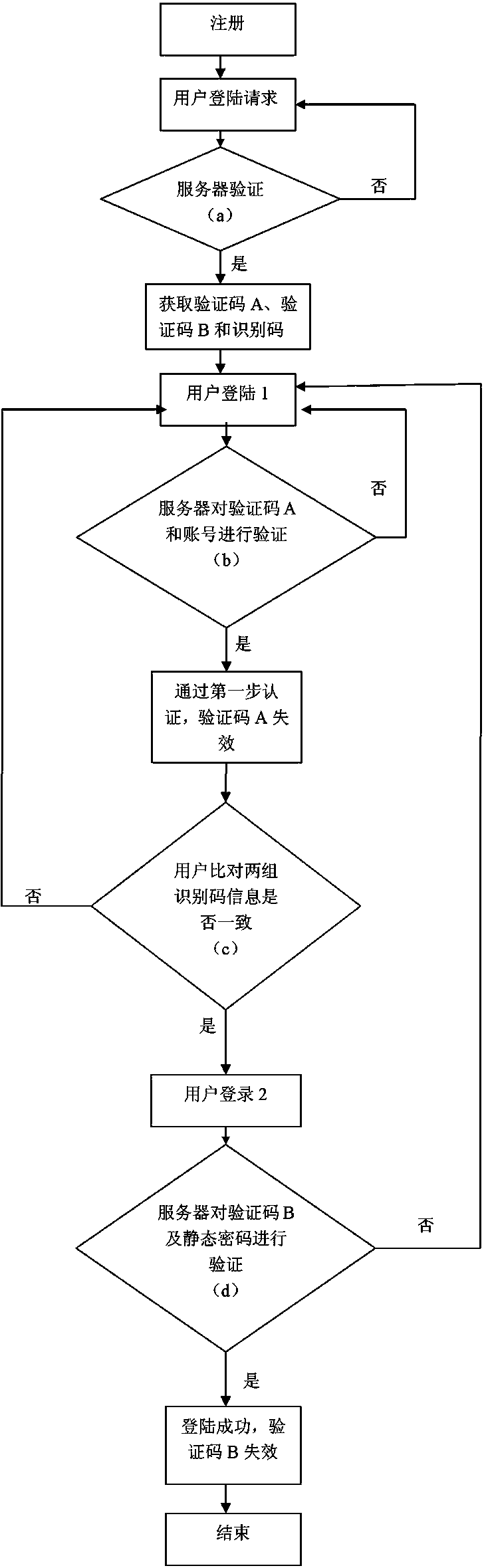
InactiveCN101257489AEnhanced authentication strengthImprove reliabilityUser identity/authority verificationRadio/inductive link selection arrangementsServer authenticationCipher
The invention provides a method for protecting the account number cryptographic security, wherein the system reliability is high, the transferring secret degree of the dynamic cipher information is high, which is not afraid of declassification and watching stealthily, meanwhile can effectively keep away the attack of cockhorse viral with low cost. The method includes the following steps: (1) registering; (2) entry request; (3) sever authentication; (4) transmitting the dynamic cipher; (5) user's entry; (6) sever authentication, which is characterized in that the steps of (5) and (6) need to be executed for two times respectively, and the ciphers for entry for two times are both dynamic ciphers. The account number and the dynamic cipher A are input in the first entry, the dynamic cipher A is out of work immediately after passing by the authentication, then the dynamic cipher B is input for the next entry, the dynamic cipher B is out of work immediately after the successful entry.
Owner:陈珂
Method for protecting safety of account number cipher
InactiveCN1832401AImprove authentication strengthResistance to attacksMultiple keys/algorithms usageUser identity/authority verificationMobile Telephone NumberAuthentication server
This invention relates to a method for protecting safety of codes of account numbers including the following steps: a user should submit the account number name and its cell phone number to a registration certification server system, which binds the name and the number, logs on the request, then the server certifies and sends it the verification code, the user logs on then the server certifies it.
Owner:陈珂
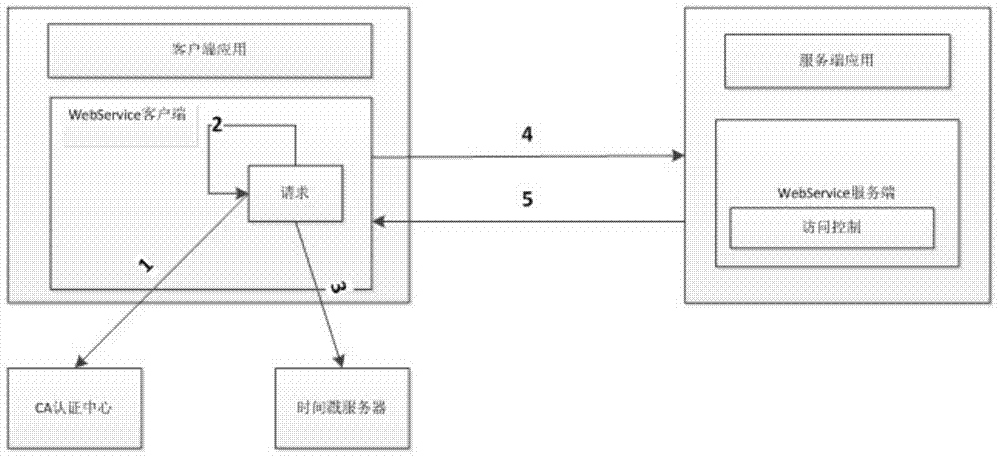
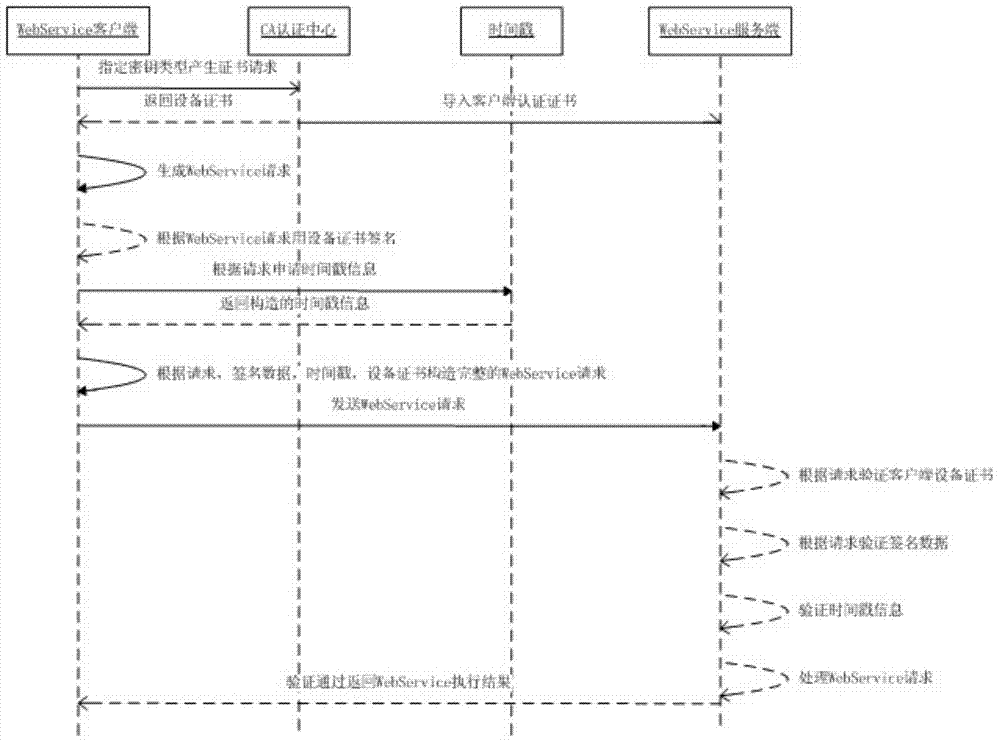
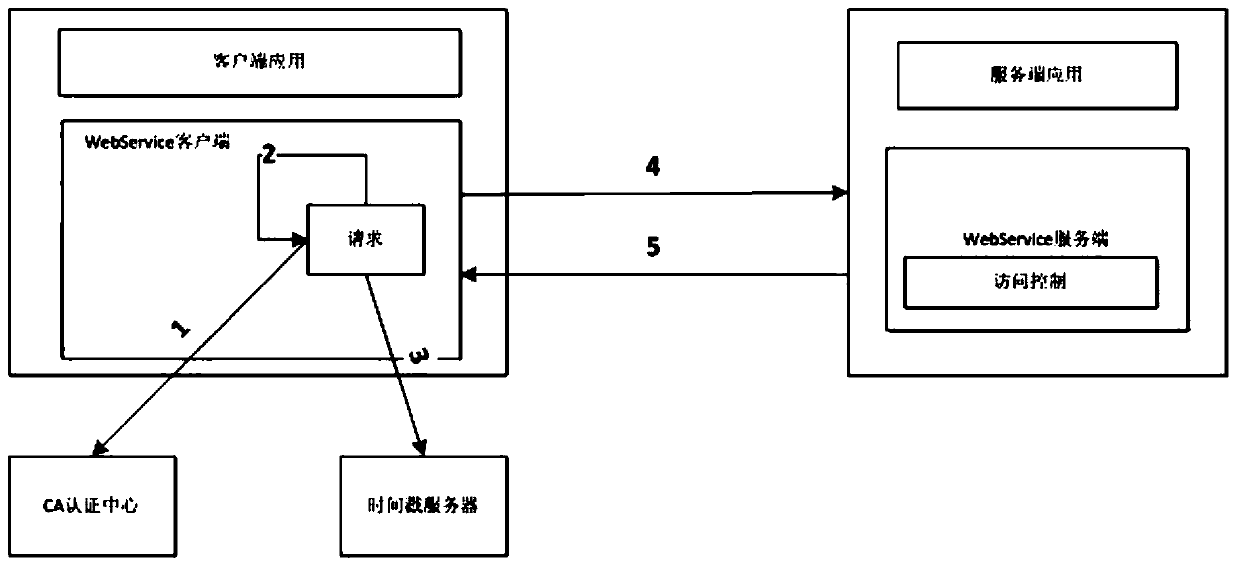
WebService security certification access control method based on software digital certificate and timestamp
ActiveCN104753881AGuarantee the correctness of accessTight control over securityUser identity/authority verificationTimestampAccess time
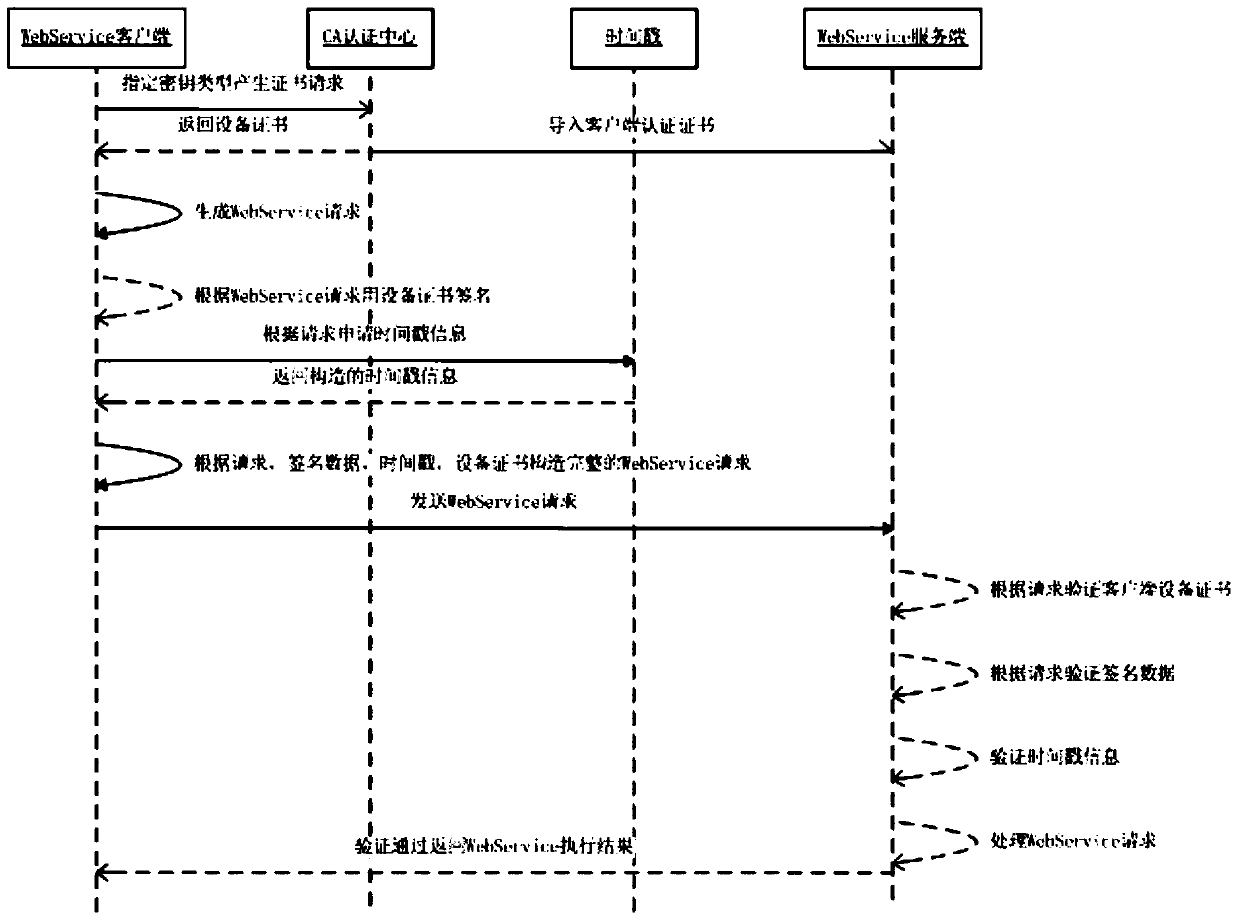
The invention discloses a WebService security certification access control method based on a software digital certificate and a timestamp. The method specifically comprises the steps of (1) generating a client credit certificate through a WebService client; (2) creating a WebService request through the client, and signing the WebService request data through a device certificate; (3) calling the timestamp through the client, acquiring stand time from a time source through a timestamp server, and signing and issuing the timestamp to the WebService data through a timestamp server private key; (4) sending the original request text, the device certificate of the WebService client, a signature message and the timestamp information to the server side by the client through a WebService interface after packaging; (5) receiving the WebService request through the server side, sequentially verifying the client device certificate, the digital signature data and the timestamp information, then processing the WebService request, and returning the processing result to the WebService client. With the adoption of the method, the credible access control certification can be performed for all WebService services; in addition, the validity of the request can be determined through the time, and the time can be accessed.
Owner:KOAL SOFTWARE CO LTD
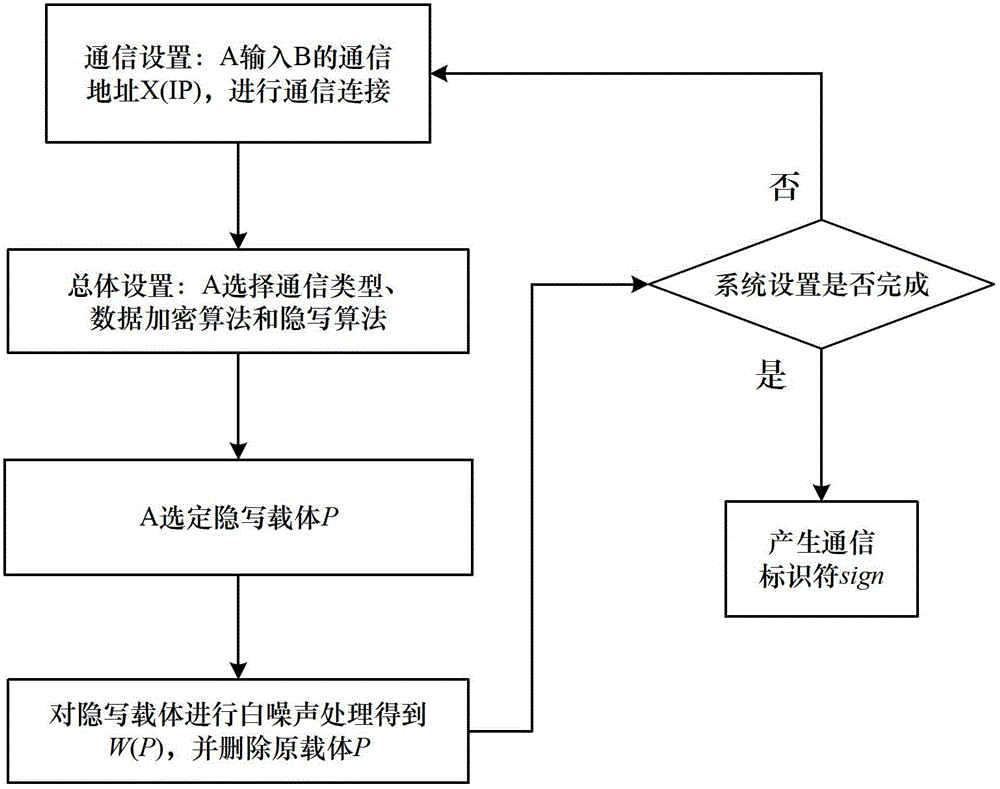
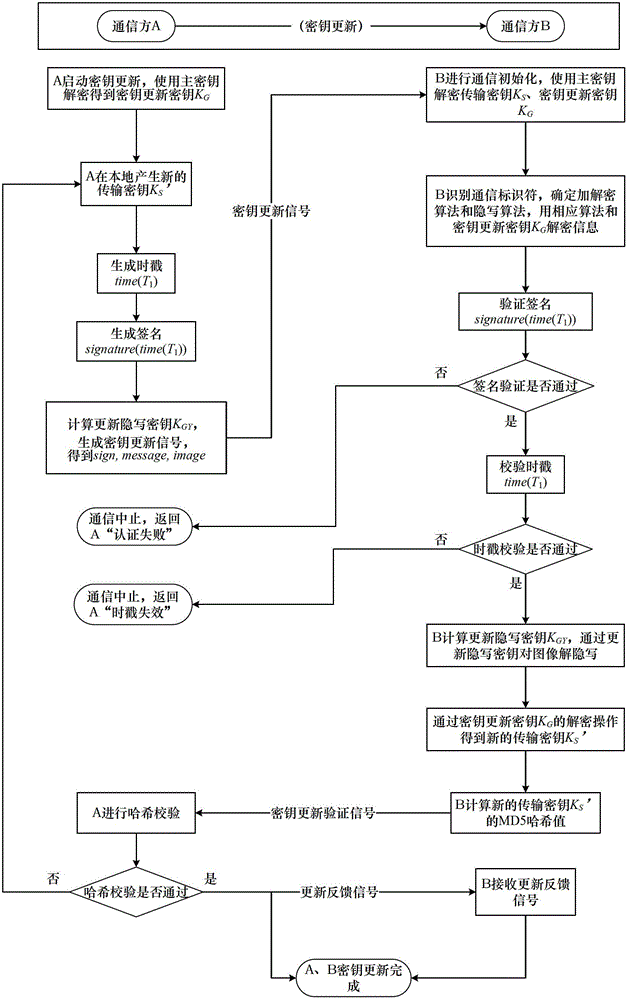
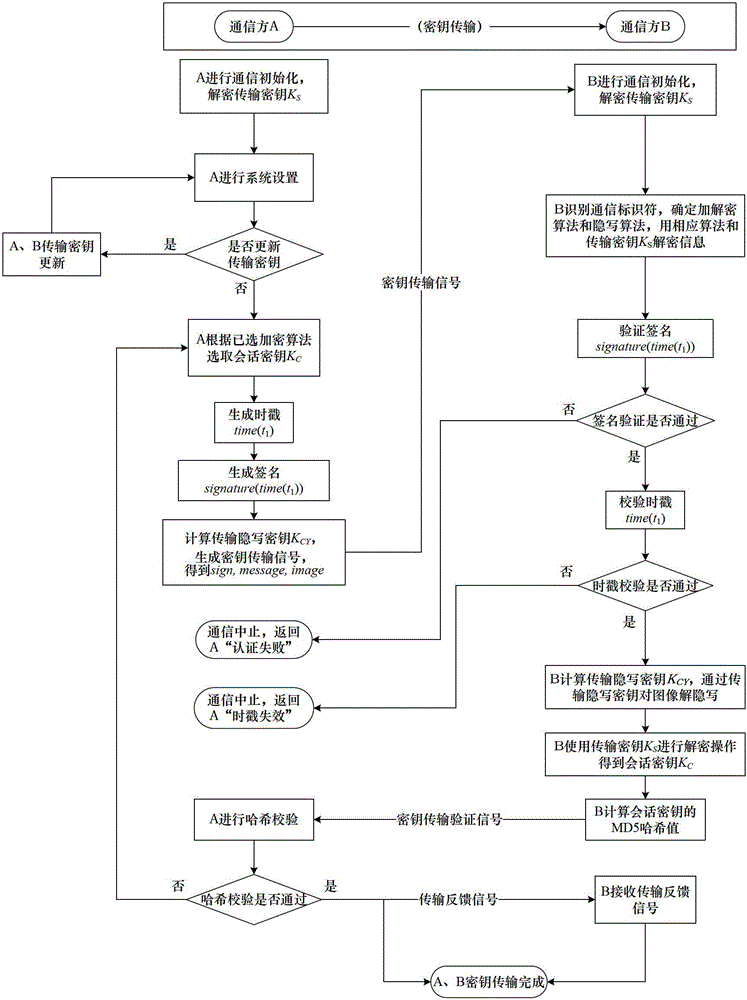
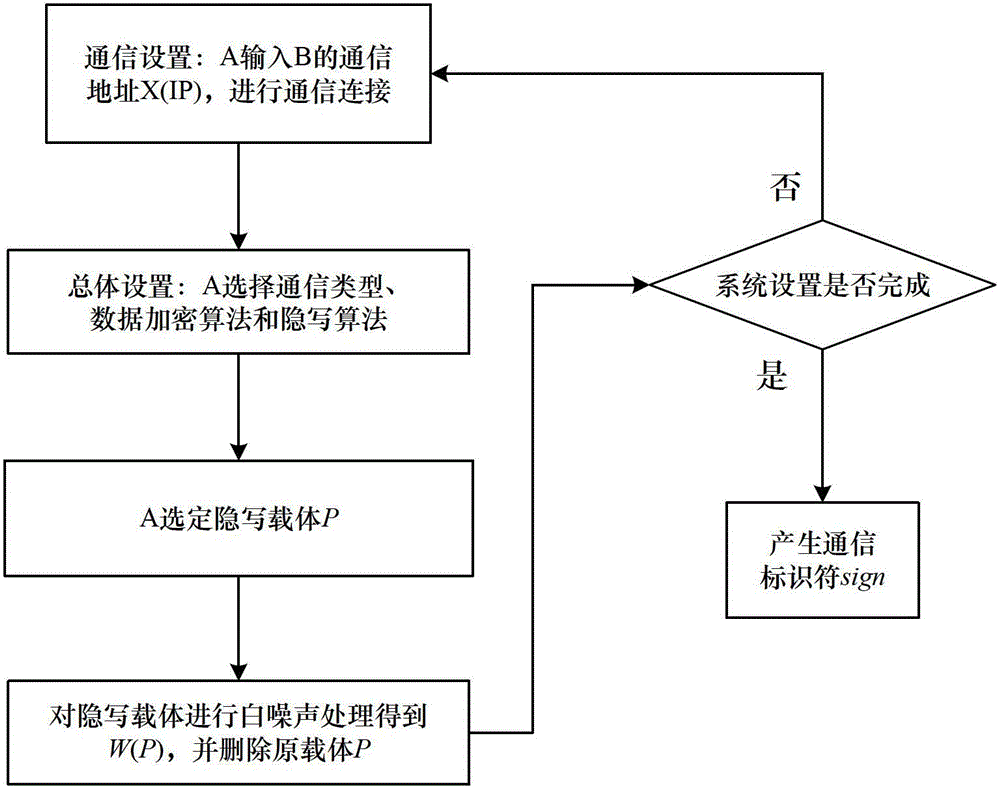
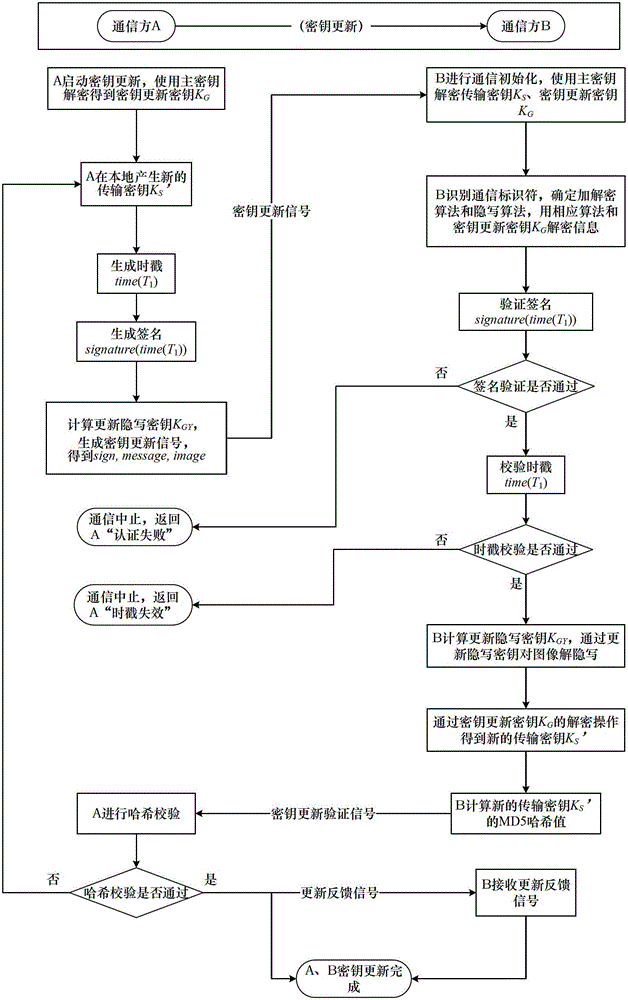
Steganography-based key transmission and key updating method
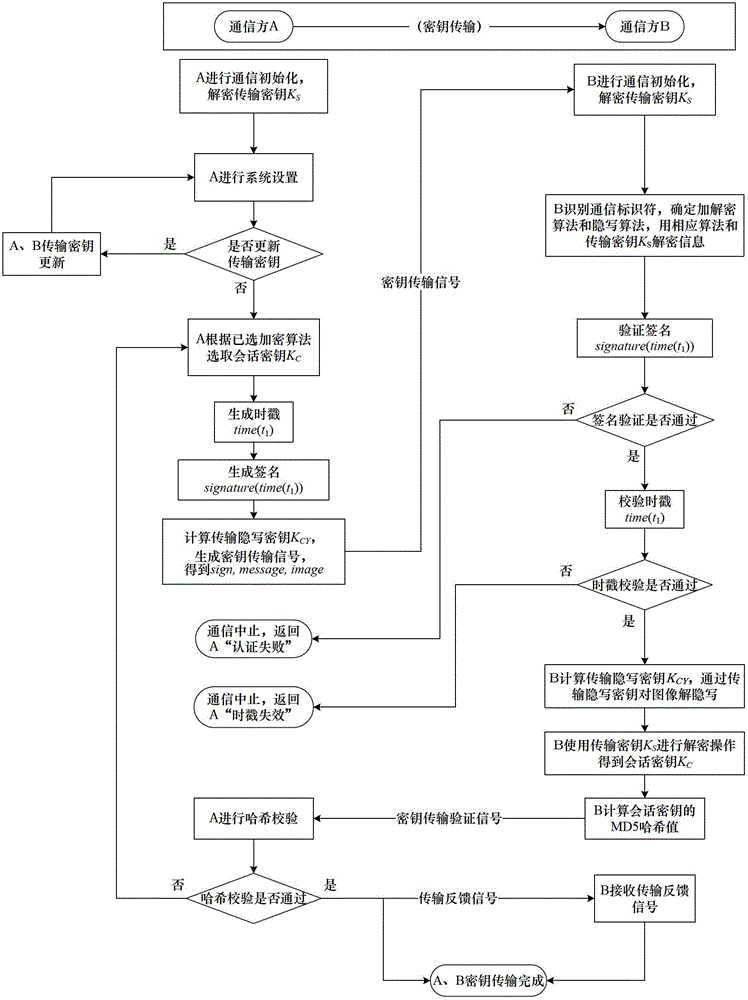
ActiveCN102724041AEffective verification of identity informationImprove authentication strengthEncryption apparatus with shift registers/memoriesUser identity/authority verificationMultiple encryptionCiphertext
The invention provides a steganography-based key transmission and key updating method, which is applied to the field of information safety. The method comprises the steps that a communication party A sets a communication type, an encryption algorithm an steganography algorithm, selects a steganography carrier and generates a communication identifier and then performs the updating of a transmission key or the transmission process of a conversion key; a new transmission key is selected when in updating, a time stamp and a signature are generated to encrypt and steganograph the transmission key, the key updating information is generated to be transmitted to a communication party B, and the communication party B performs the verification, de-staganography and deciphering to obtain the transmission key; and the conversion key is selected in transmission to generate a time stamp and a signature so as to encrypt and steganograph the conversion key, the key transmission information is generated to be transmitted to the communication party B, and the communication party B performs the verification, de-steganography and deciphering to obtain the conversation key. The key is concealed by utilizing the steganography, so that an encrypted data format in the key transmission process and the key updating process can be effectively protected, and the safety transmission of multiple encryption and decryption algorithm conversation keys can be realized.
Owner:BEIHANG UNIV
Electronic storage apparatus, authentication apparatus and authentication method
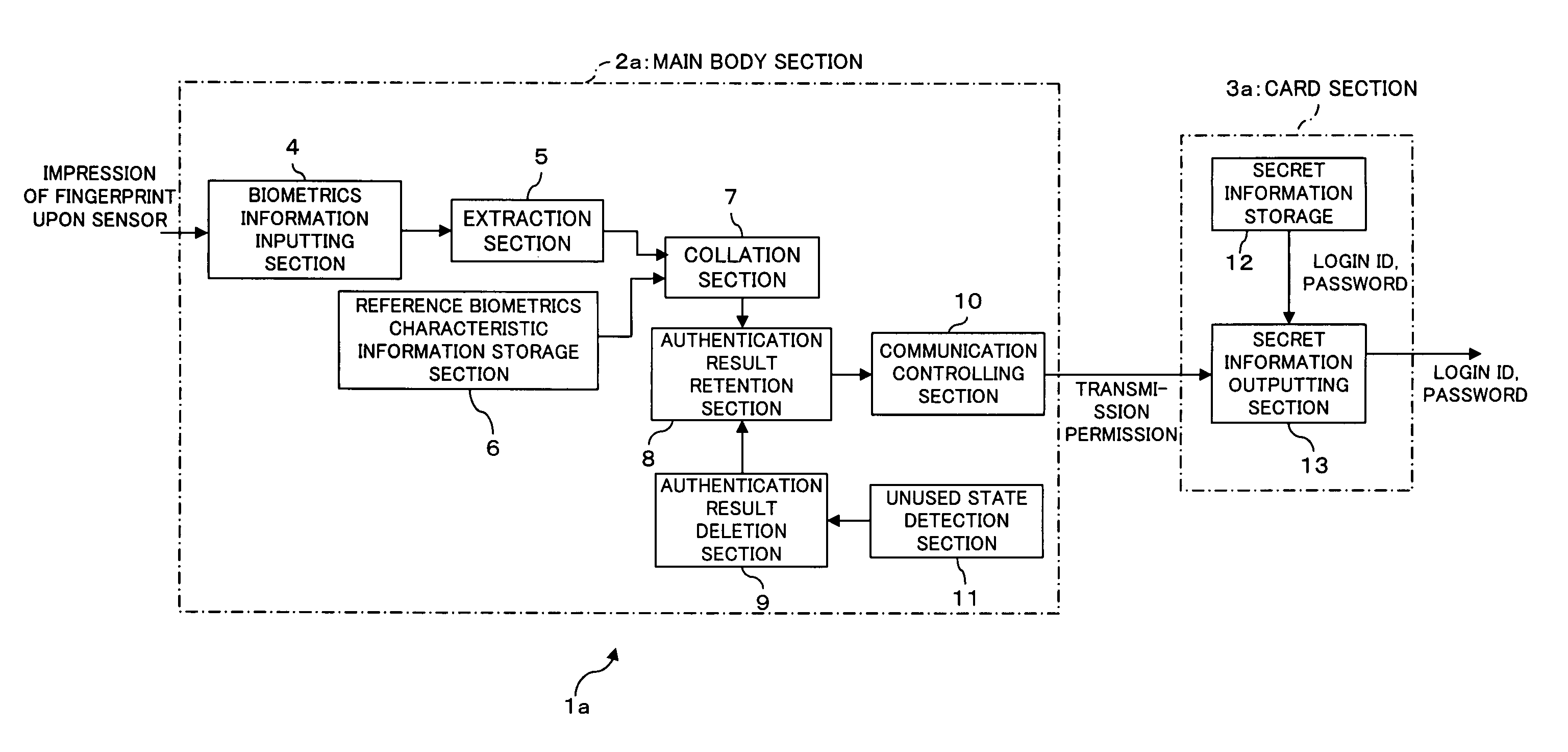
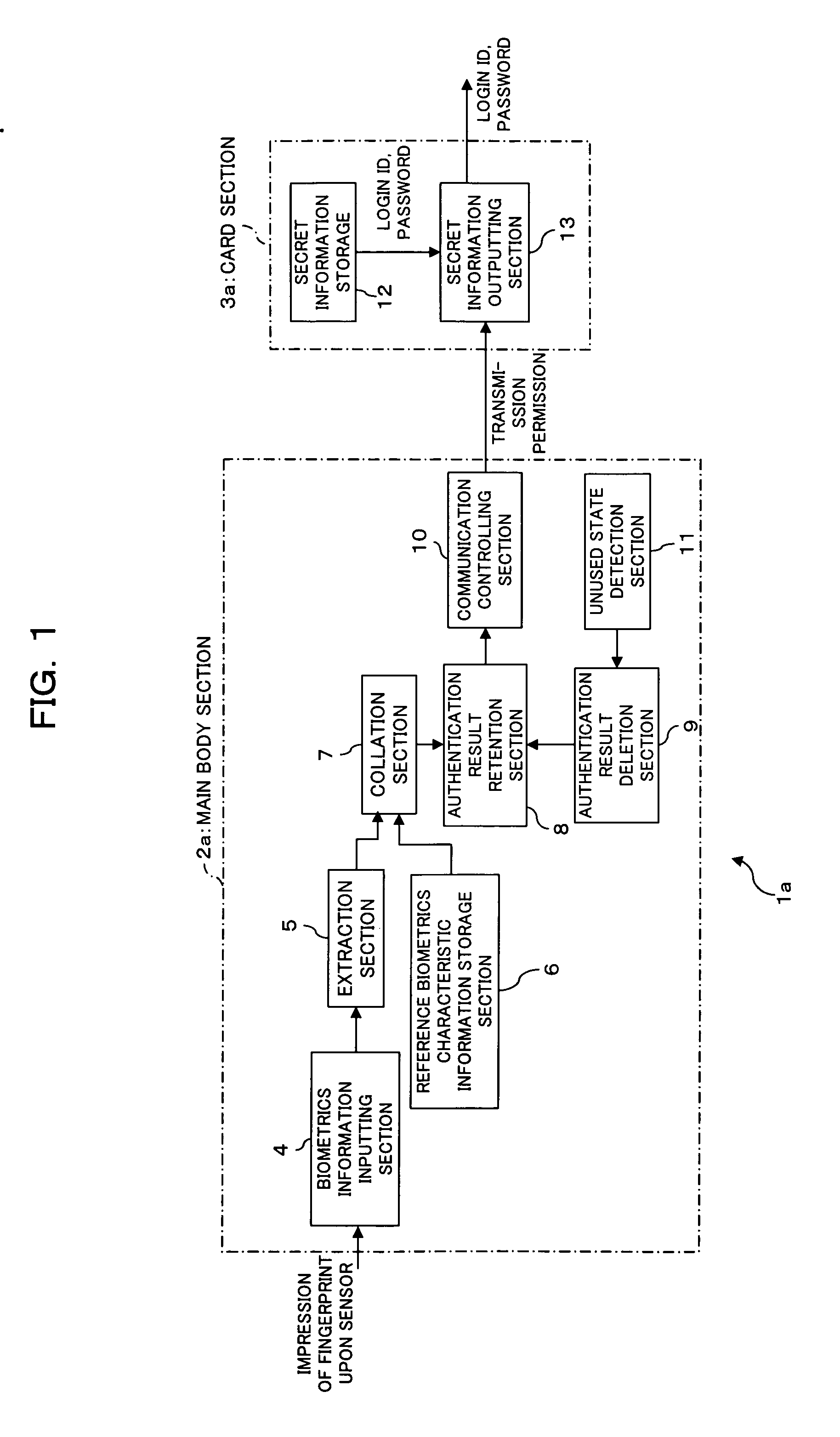
InactiveUS20050144354A1Simple configurationImprove authentication strengthDigital data processing detailsUser identity/authority verificationBiometricsCollation
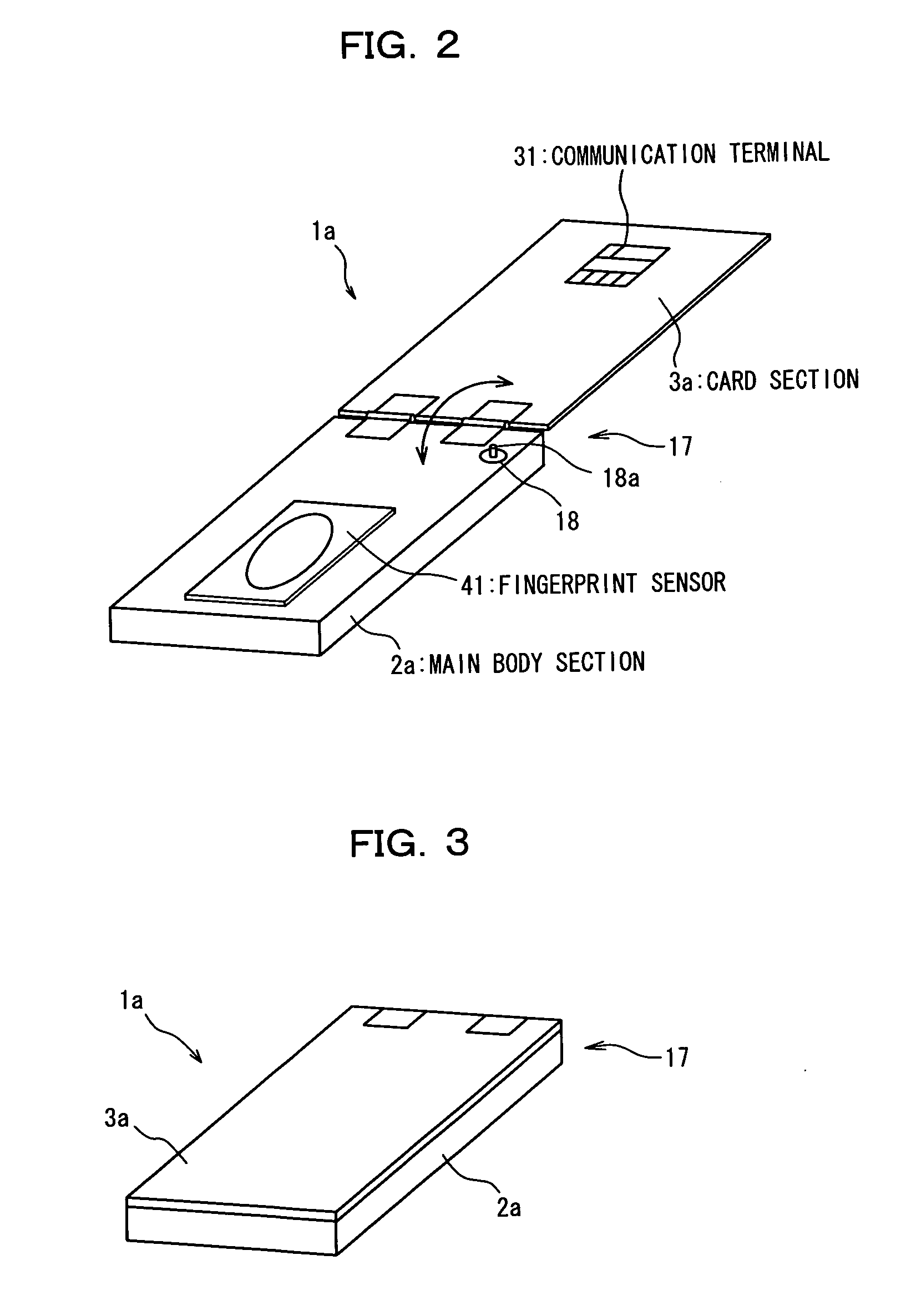
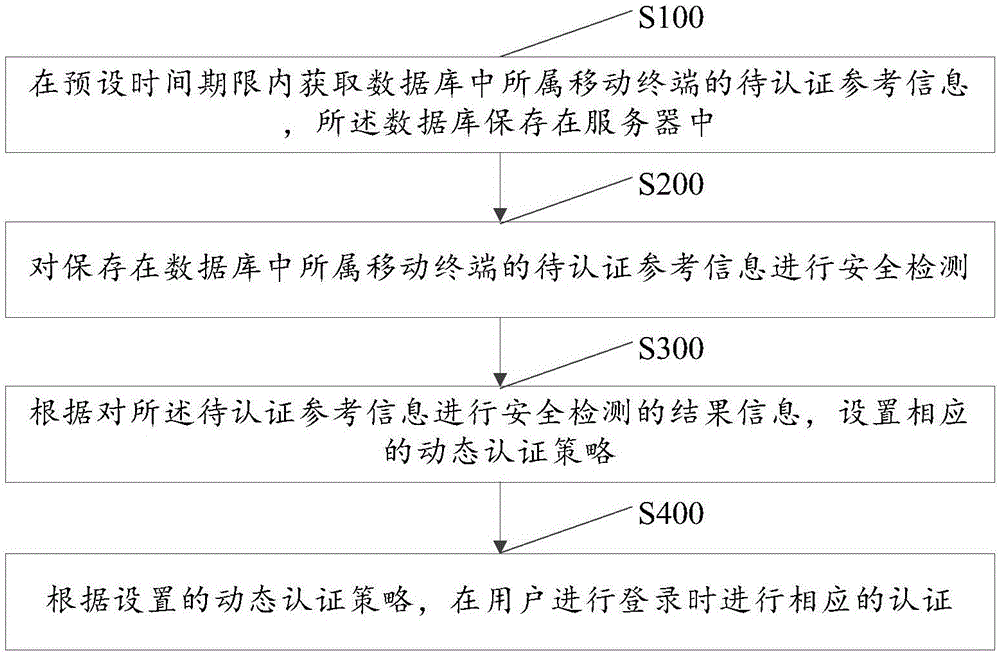
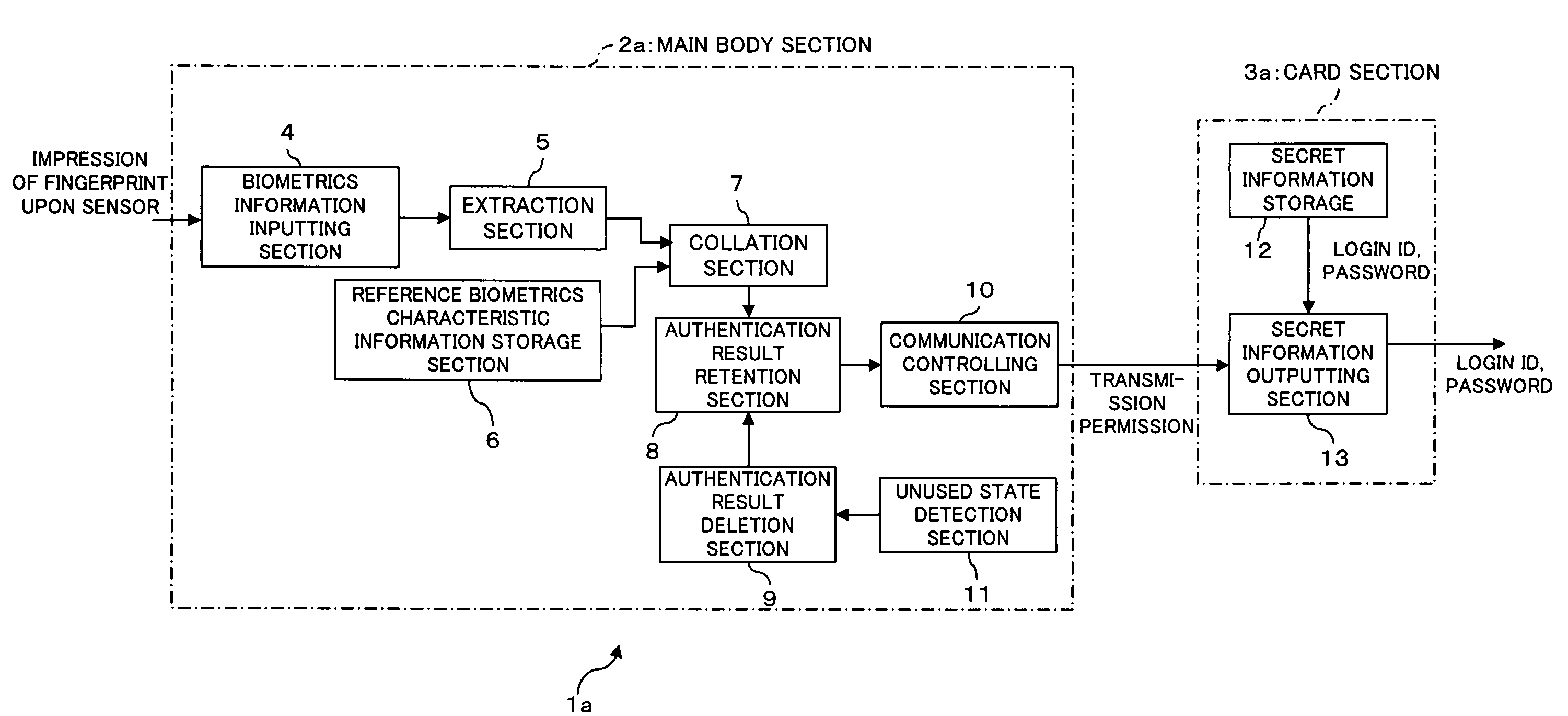
An electronic storage apparatus comprises a biometrics information inputting section, a collation section for comparing and collating collation biometrics characteristic information and reference biometrics characteristic information with each other, an authentication result retention section for retaining, where it is recognized that the collation biometrics characteristic information is that of an owner, the result of the authentication, a secret information outputting section capable of outputting secret information of the owner stored in a secret information storage section to the outside, and an authentication result deletion section for deleting, when an unused state detection section detect that the secret information outputting section is in an unused state, the result of authentication retained by the authentication result retention section, whereby the security strength of a card type storage medium is raised and the electronic storage apparatus can be used more easily by a user.
Owner:FUJITSU LTD
Safety proxy method
ActiveCN1558584AImprove authentication strengthImprove securitySecuring communicationStructure of Management InformationRights management
The invention discloses a safety proxy method for realizing port based safety proxy mode through employing an identification mode integrating digital certificate and electronic key and authority control combining digital certificate, wherein no amendment on the existing applied system for hardware and software is required to improve the identification intensity of the existing applied systems.
Owner:ZTE CORP
Dynamic authentication method and system based on mobile terminal
ActiveCN106453422ASmart experienceReasonable experienceTransmissionSecurity arrangementTime limitDatabase preservation
The invention discloses a dynamic authentication method and system based on a mobile terminal. The dynamic authentication method based on the mobile terminal comprises the steps of: S100, acquiring to-be-authenticated reference information of a subordinate mobile terminal in a database in a preset time limit, and storing the database in a server; S200, carrying out safety detection on the to-be-authenticated reference information of the subordinate mobile terminal in the database; S300, according to result information obtained after carrying out safety detection on the to-be-authenticated reference information in the step S200, setting a corresponding dynamic authentication strategy; and S400, according to the dynamic authentication strategy set in the step S300, carrying out corresponding authentication when a user logs in. In the invention, according to detection on a safety state of the mobile terminal, when the safety state is good, a low-level authentication strategy is used, and when the safety state is poor, authentication strength is automatically strengthened; and user experience is more intelligent, and authentication strength is more reasonable and safer.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Electronic storage apparatus, authentication apparatus and authentication method
InactiveUS7404081B2Improve authentication strengthImprove security strengthDigital data processing detailsUser identity/authority verificationComputer hardwareBiometrics
Owner:FUJITSU LTD
Identity recognition method based on keystroke characteristics
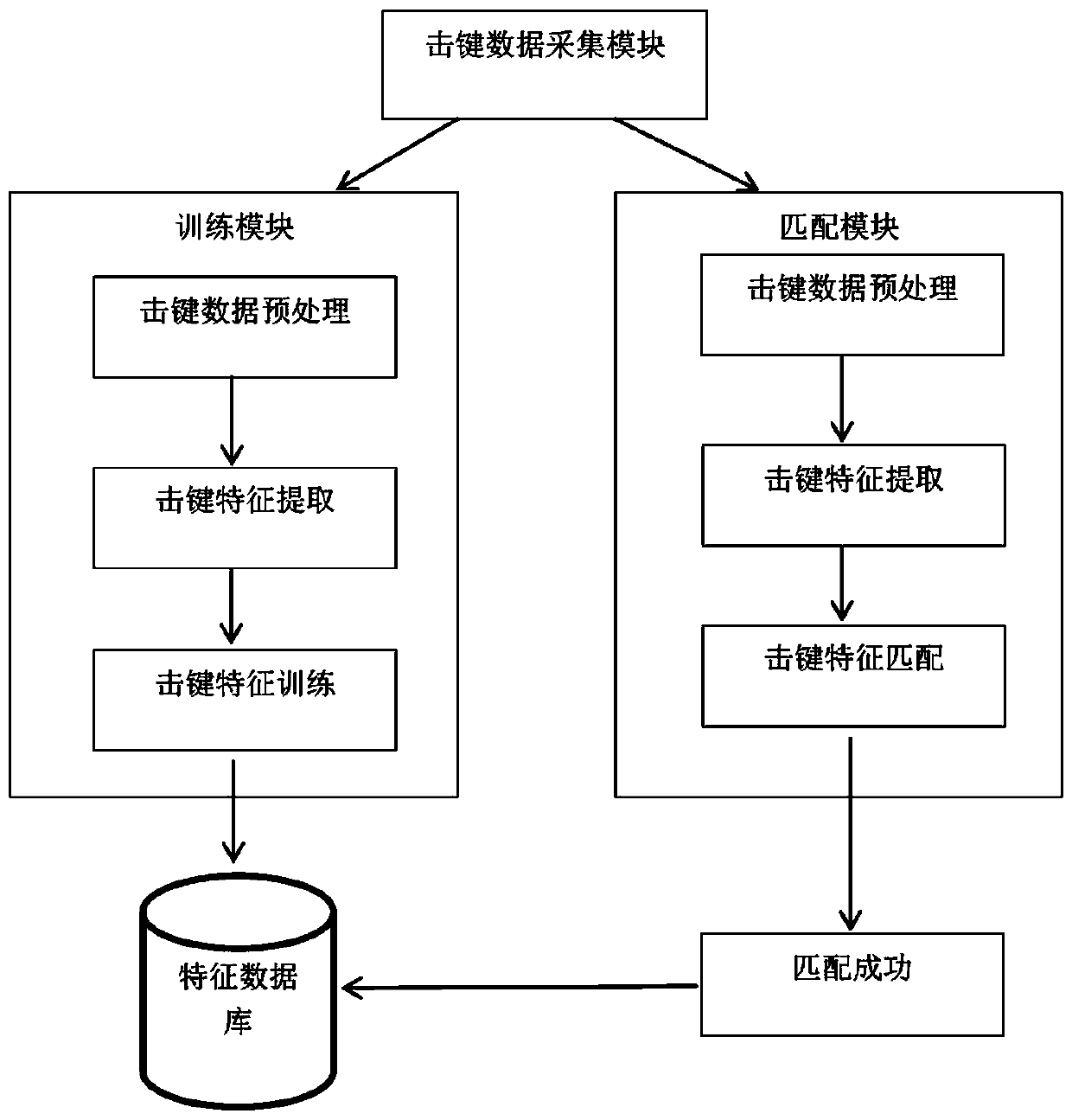
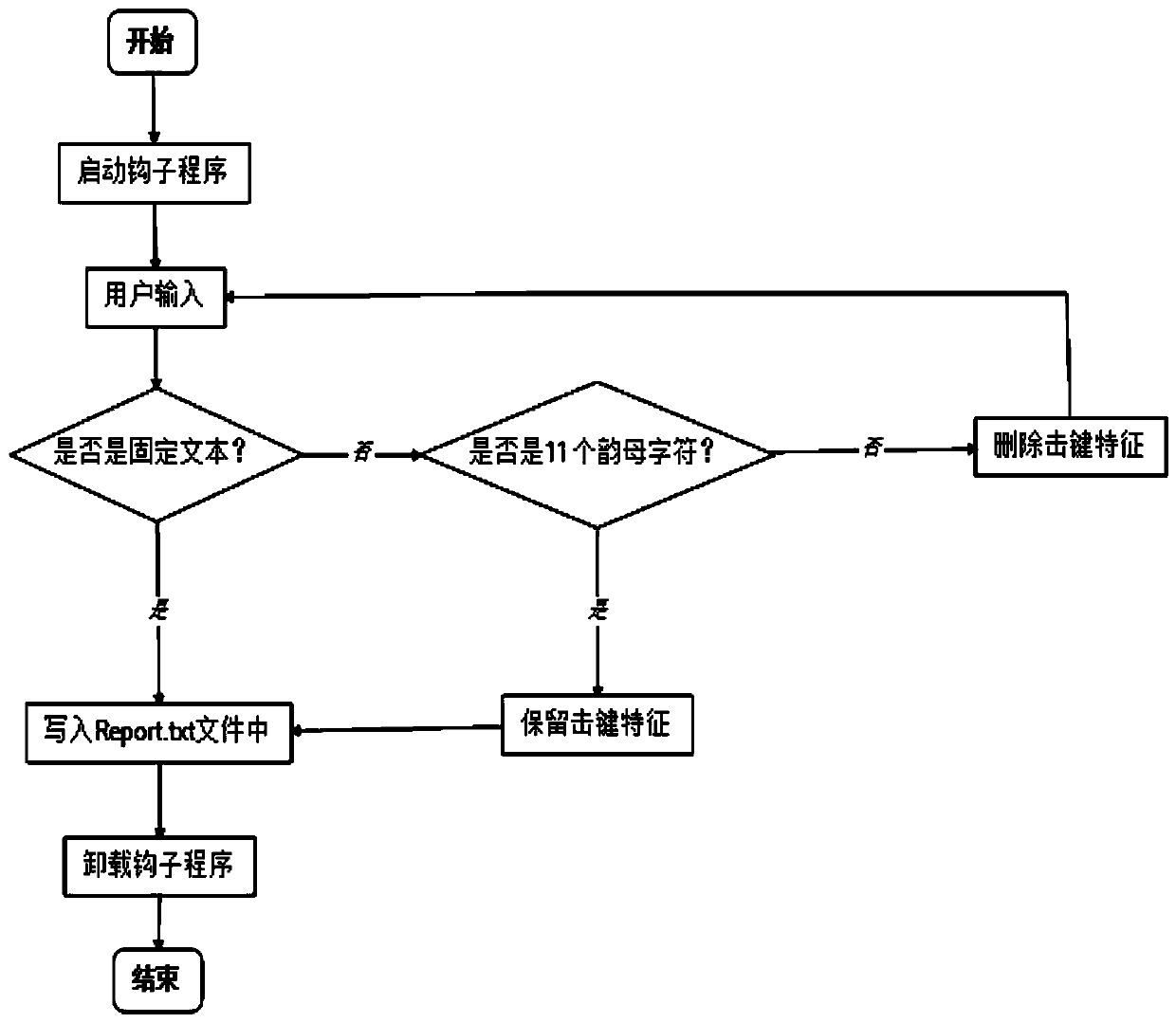
InactiveCN110443012AEasy data collectionMonitor keystrokesCharacter and pattern recognitionDigital data authenticationFeature extractionIdentity recognition
The invention belongs to the field of network security identity recognition methods, and particularly relates to an identity recognition method based on keystroke characteristics, which comprises a keystroke data acquisition module, a training module and a matching module. The keystroke data acquisition module is mainly used for collecting keystroke data generated by a user to obtain original datawhen the user performs a keystroke behavior. The training module is used for completing extraction and separation of keystroke feature data; carrying out keystroke data preprocessing and keystroke feature extraction on sample keystroke information input by a user from a keyboard, and finishing user sample data training classification to generate a feature database. The matching module is used forjudging whether the keystroke characteristics of the user are matched. The method has the advantages of high correct recognition rate, no need of specific physical hardware, hardware installation andpopularization and low cost.
Owner:CHINA CRIMINAL POLICE UNIV
Boot file credible verify based on mobile TPM
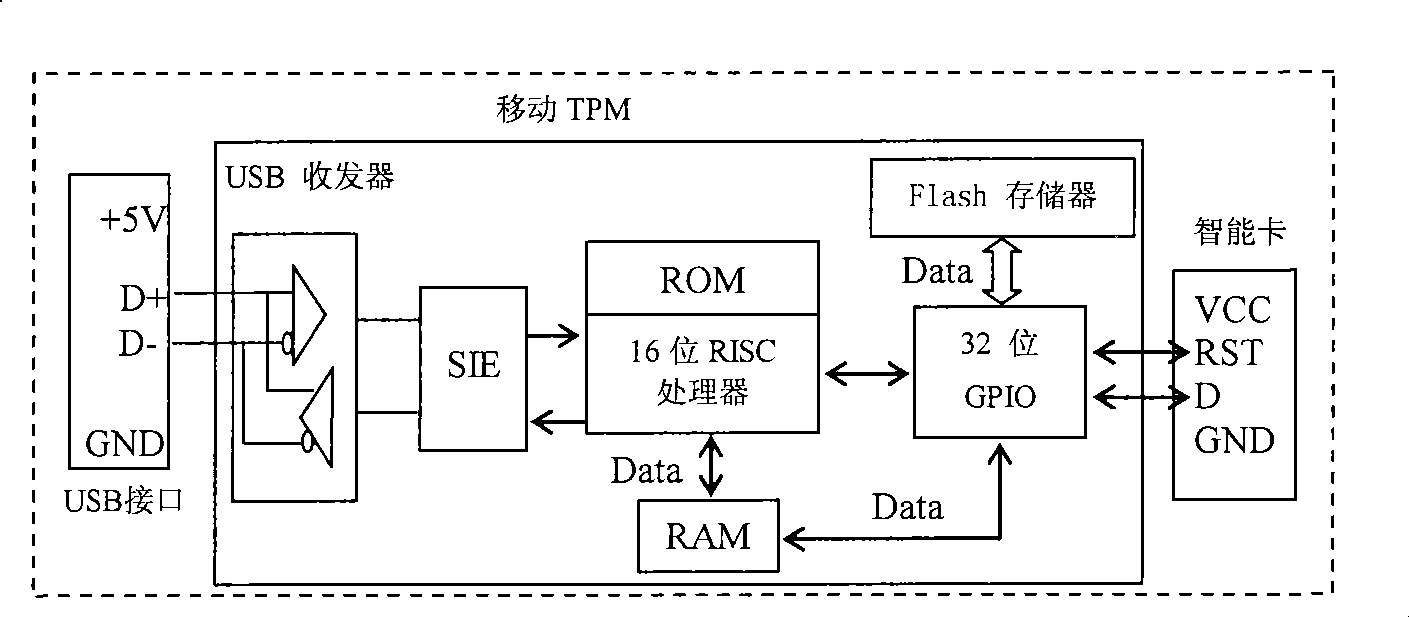
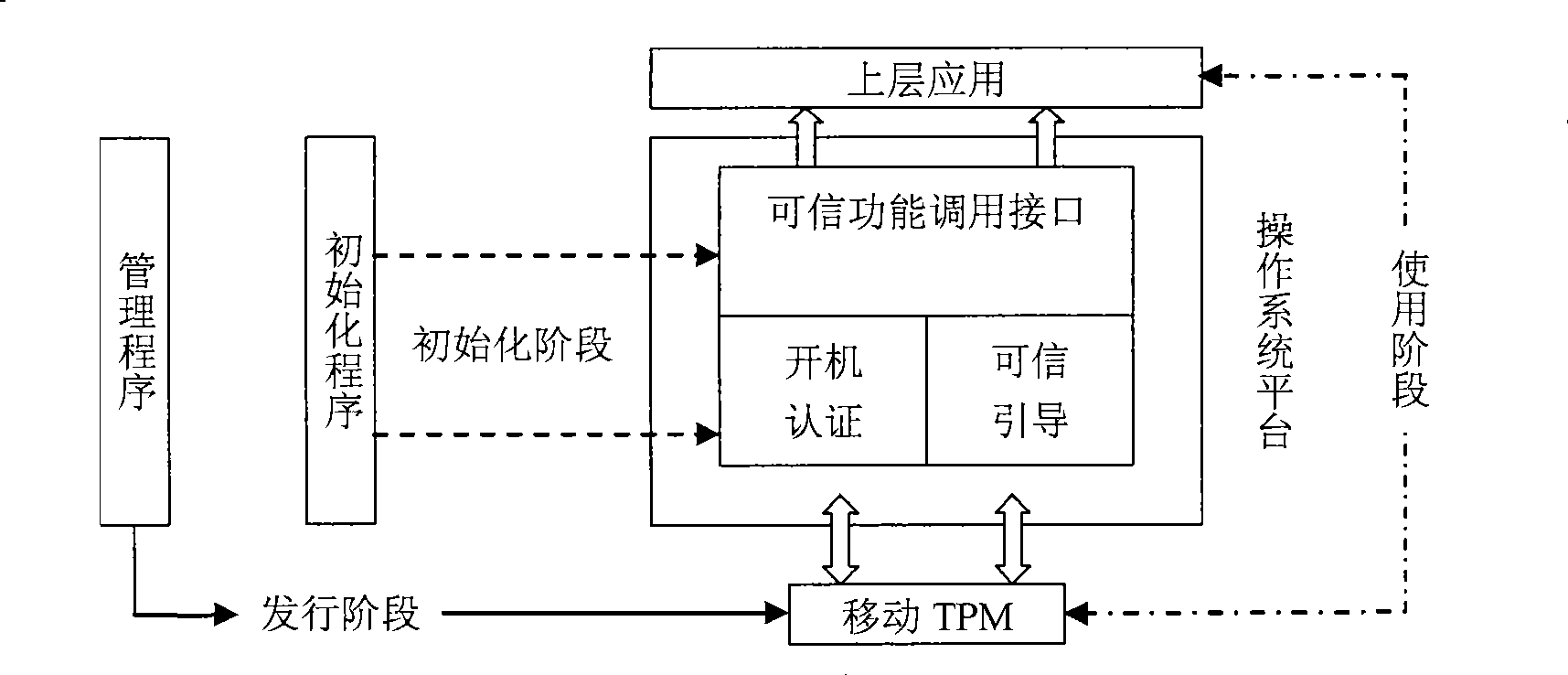
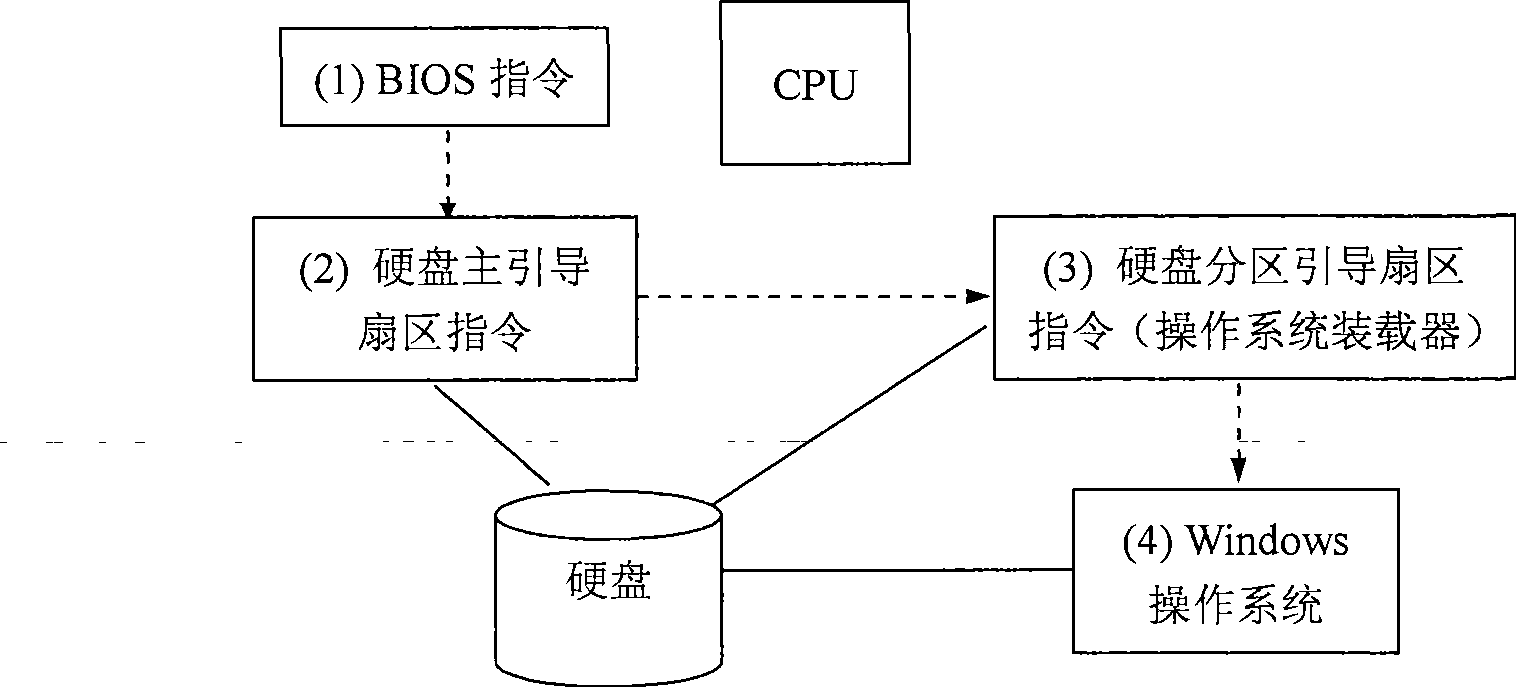
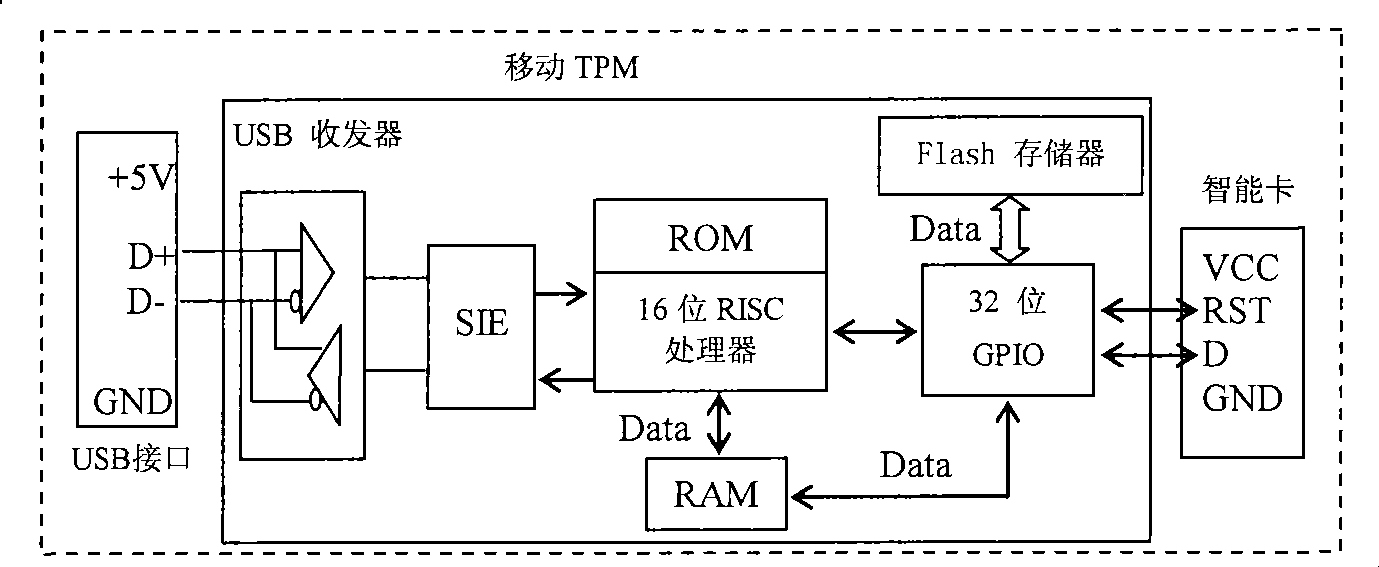
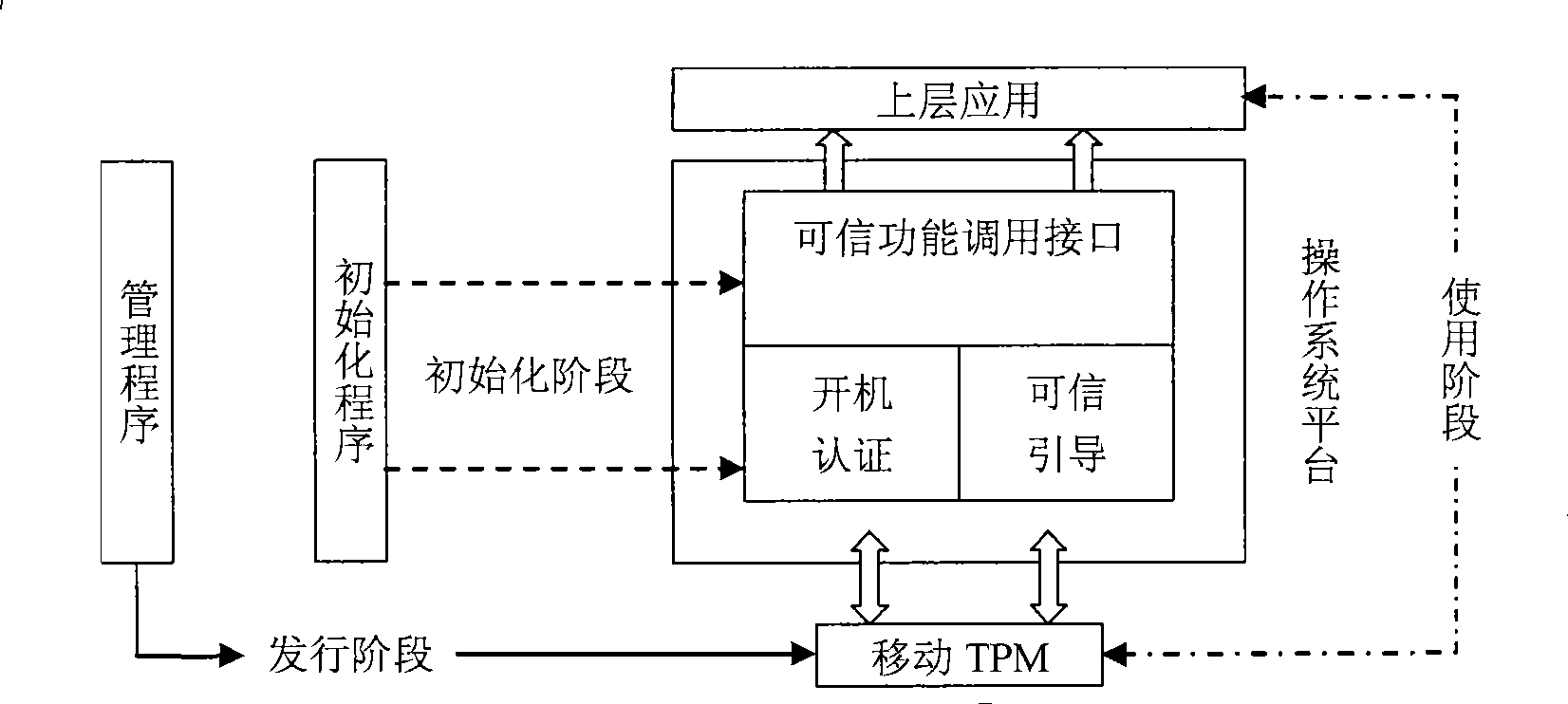
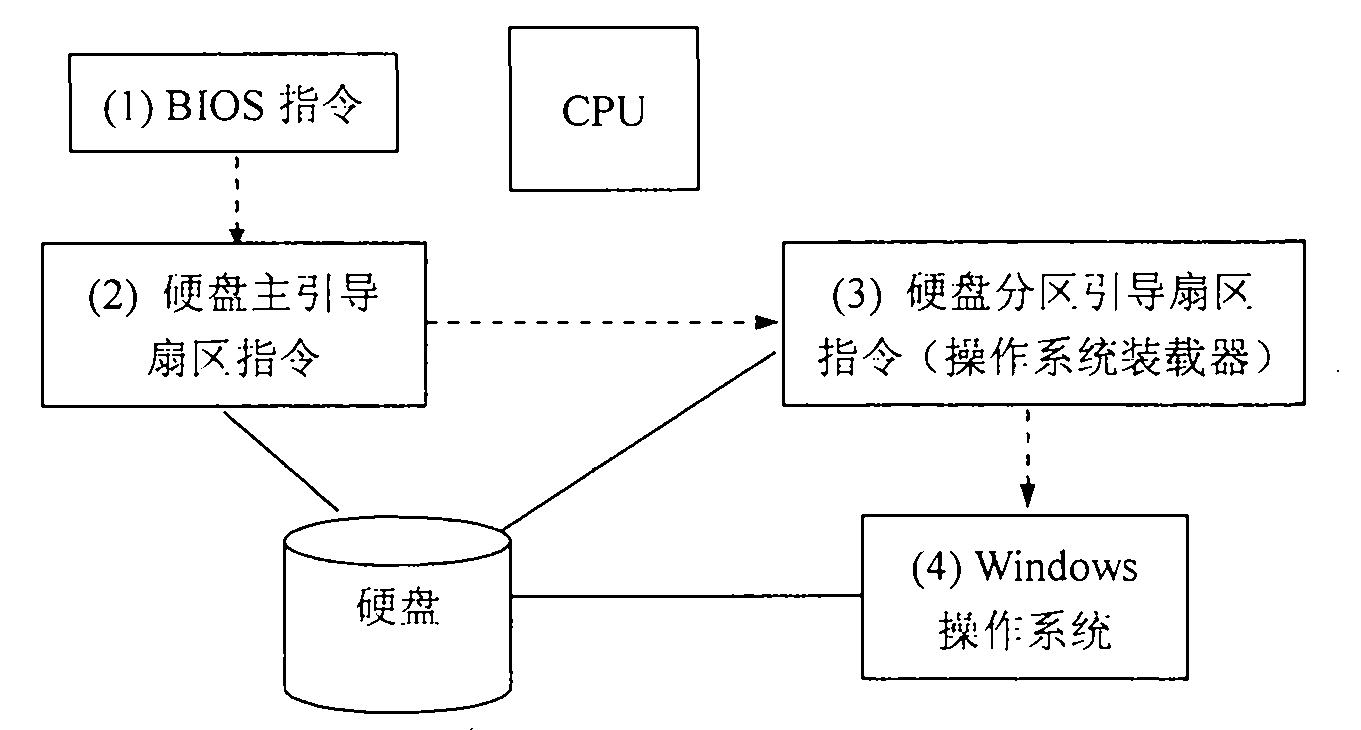
InactiveCN101419654ARetain investmentImprove versatilityPlatform integrity maintainanceSpecial data processing applicationsOperational systemFile system
The invention relates to a guide file credible check based on mobile TPM. The check comprises the following steps: the mobile TPM is initialized; relevant authentication information and check information in a guide process are set; a driving module for the mobile TPM before the start of an operating system at the guide stage is designed and implemented; the driving module is tested according to the operating environment of a DOS operating system; a Part 1 code is arranged at the 0 sector position of a hard disk; an original MBR of the system is moved to a second sector of the hard disk; a Part2 code is arranged at a third sector of the hard disk and a subsequent position thereof; the Part2 code comprises the driving module and a calling interface of the mobile TPM; the credible check is implemented on the reading function of an NEFS file system and files to be read; after the file check is succeeded, the execution is changed from Part2 to an original MBR code. An original process of the system is started for the operation. And the Windows system is ensured to be clean and credible.
Owner:BEIJING JIAOTONG UNIV
Intelligent glasses device and implicit authentication method thereof
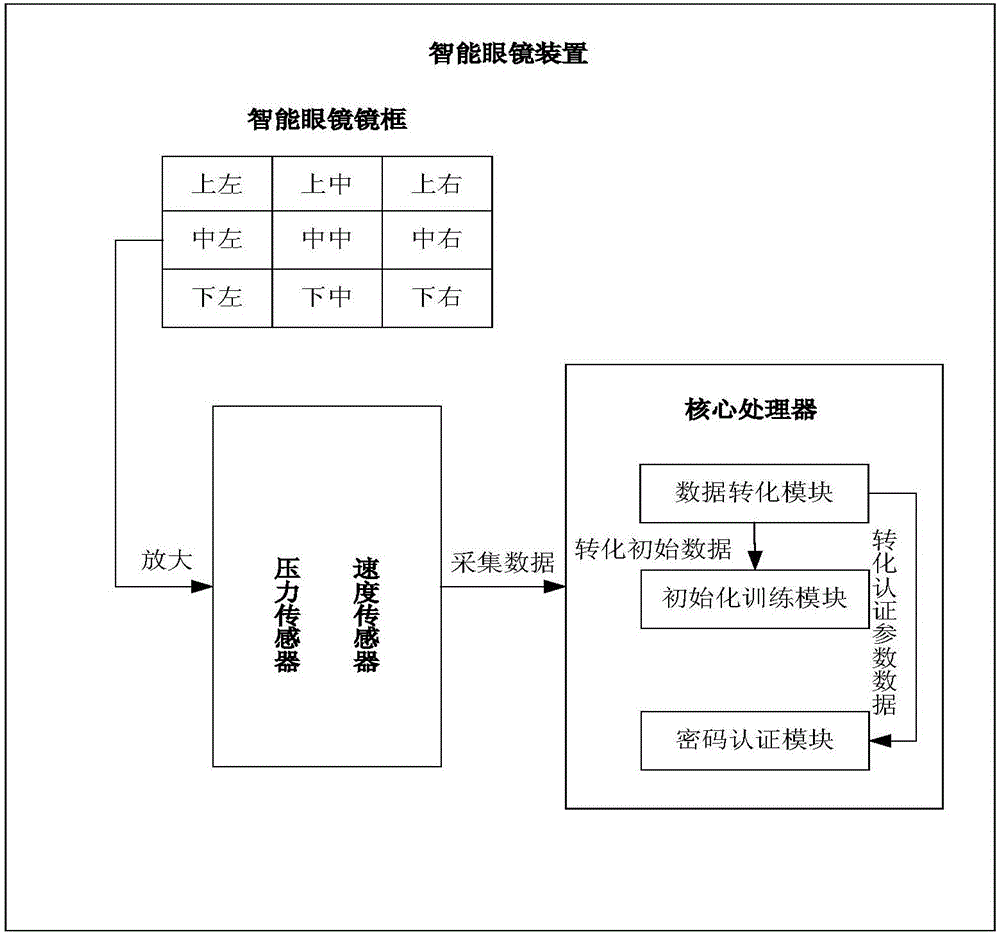
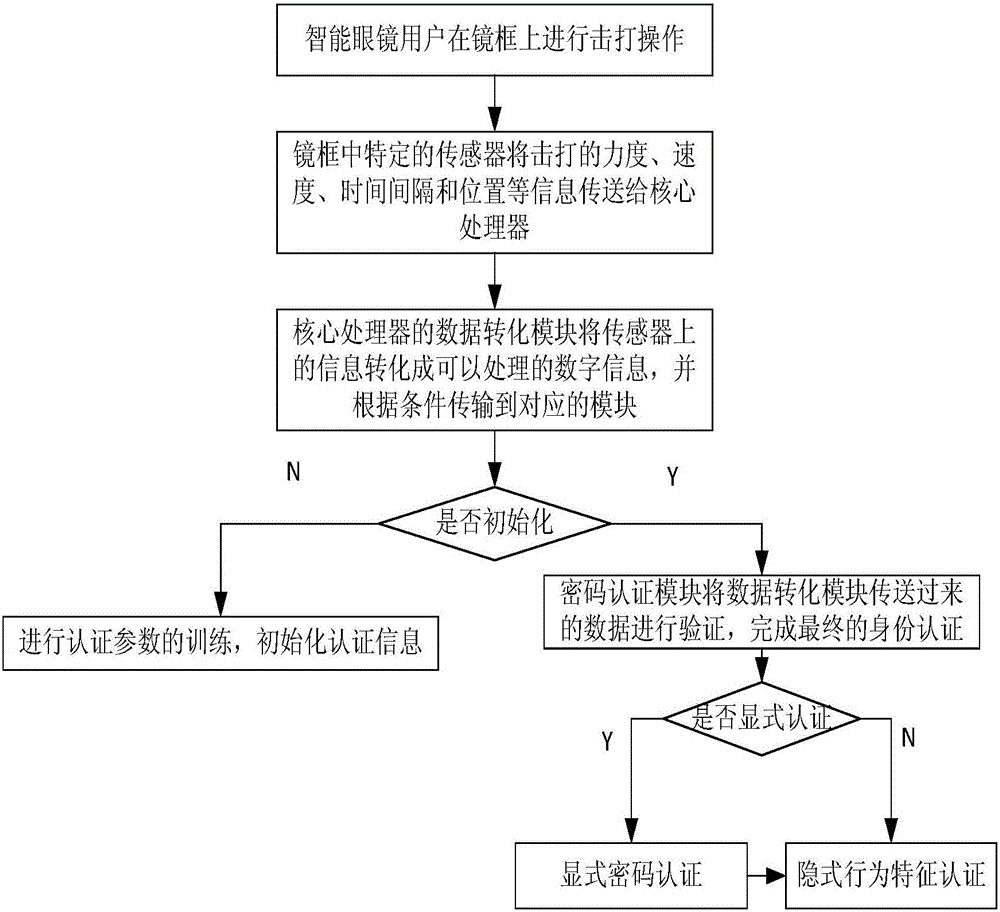
PendingCN106599638AGuarantee data privacy and securityHigh strengthNon-optical adjunctsDigital data protectionData conversionMulti-core processor
The invention discloses an intelligent glasses device and an implicit authentication method thereof. The device comprises a spectacle frame and a core processor, wherein the spectacle frame is divided into a plurality of positions, a pressure sensor and a speed sensor are embedded into each position, click operation and double-click operation can be performed at each position, the pressure sensors and the speed sensors in the spectacle frame are connected with the core processor through a circuit, tapping pressure, speed and time intervals are sensed through a built-in piezoelectric element, and a time threshold value is set inside the core processor to distinguish the click operation from the double-click operation; the core processor comprises a data conversion module, an initialization training module and a password authentication module. The implicit authentication method of the intelligent glasses device is also included. By the adoption of a tapping authentication mode, inconvenience brought by a pair of intelligent glasses based on a traditional keyboard and voice authentication is overcome. A click mode and a double-click mode are available, so that explicit password authentication strength is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Radio frequency identification authentication system and method based on quantum cryptography network
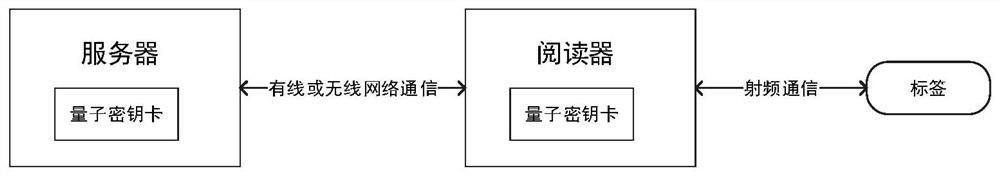
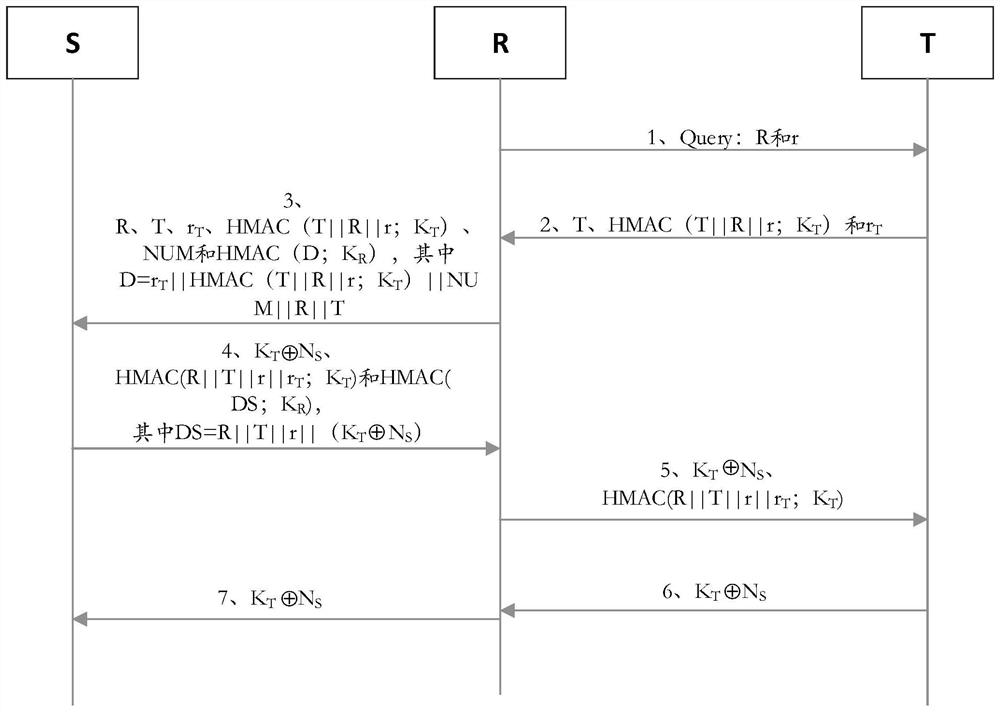
PendingCN114666040AImprove security strengthImplement updateKey distribution for secure communicationRf fieldKey (cryptography)
The invention belongs to the field of encryption communication of a quantum cryptography network, and provides a radio frequency identification authentication system and method based on the quantum cryptography network. The radio frequency identification authentication system based on the quantum cryptography network comprises a server, a reader, a quantum key card and a label, the ID of the reader and the corresponding authentication key thereof, and the ID of the tag and the corresponding authentication key thereof are stored in a database of the server; the server and the reader are respectively and correspondingly connected with the quantum key card, so that the server and the reader are subjected to identity bidirectional authentication through a quantum encryption channel; the reader and the tag communicate with each other through a radio frequency field, the server and the tag also adopt a bidirectional authentication mode to authenticate the identity, and when the bidirectional authentication of the identity between the reader and the server and the identity between the server and the tag succeeds, the radio frequency identification authentication succeeds.
Owner:QUANTUMCTEK +1
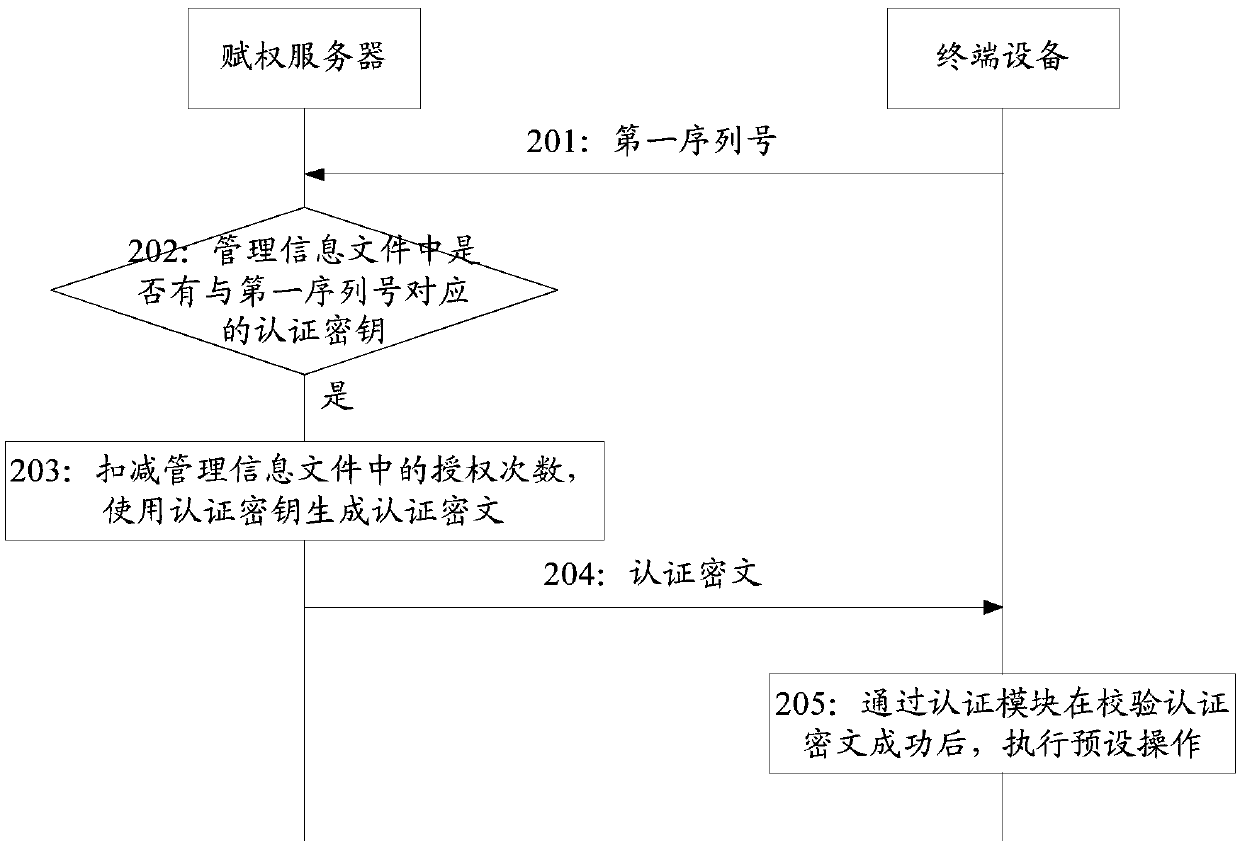
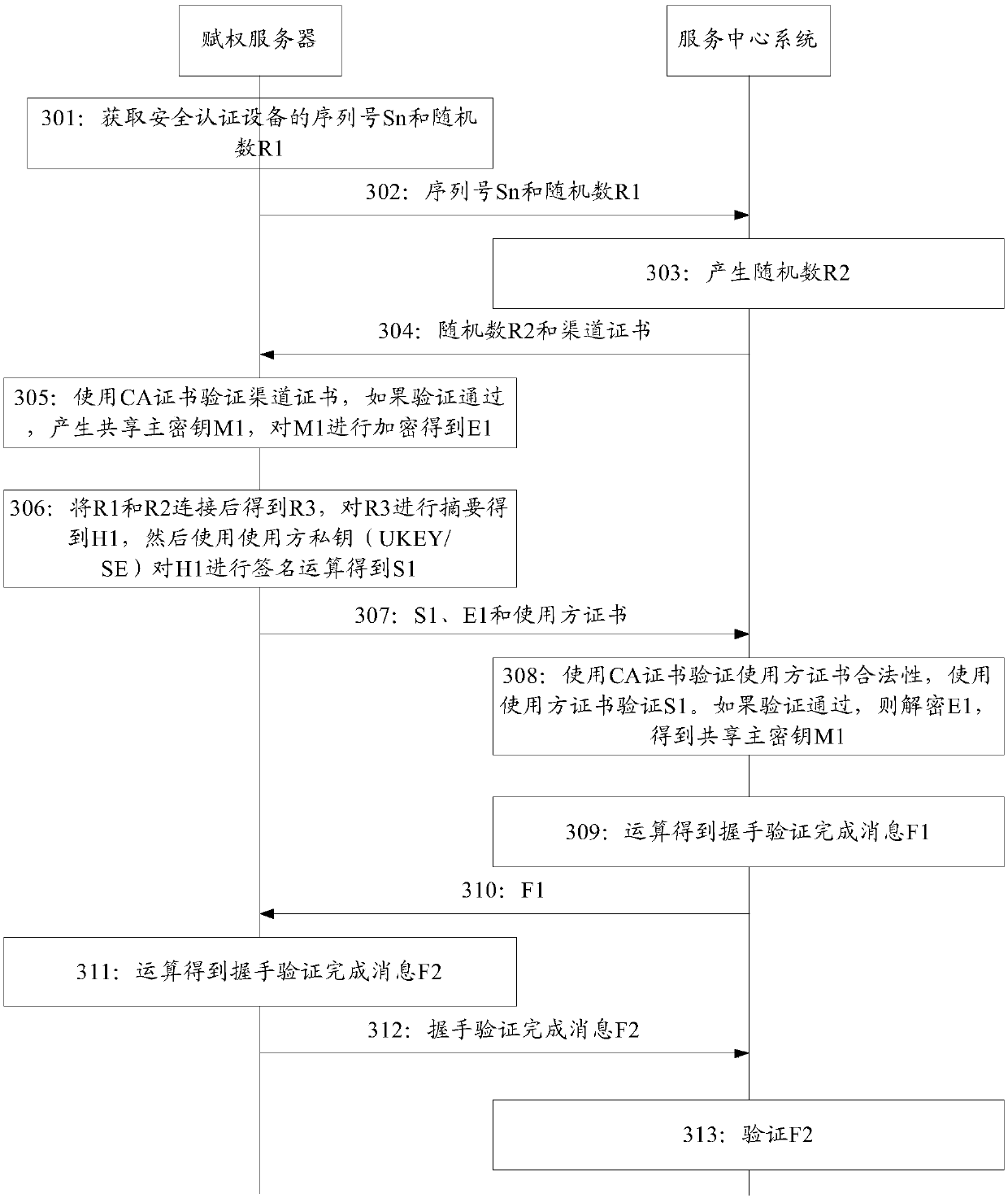
Authentication management method and related equipment
ActiveCN110401613AStrengthen authentication strengthImprove securityUser identity/authority verificationAuthorizationManagement system
The invention relates to an authentication management method, an empowerment server, a terminal device and an authentication management system, and belongs to the field of data processing. The methodcomprises: an empowerment server obtaining a first serial number sent by a terminal device, and the first serial number being identification information of an authentication module on the terminal device; the empowerment server judging whether an authentication key corresponding to the first serial number exists in a pre-stored management information file or not, wherein the management informationfile comprises a corresponding relationship between the serial number and the authentication key; if an authentication key corresponding to the first serial number exists in the management information file, deducting the authorization frequency in the management information file by the authorization server, and generating an authentication ciphertext by using the authentication key; and the empowerment server sending the authentication ciphertext to the terminal device, so that the terminal device executes a preset operation after successfully verifying the authentication ciphertext through the authentication module. By adopting the method provided by the invention, the security of authentication management can be improved.
Owner:WATCHDATA SYST
Method for quickly verifying vehicle frame
InactiveCN109282974AImprove authentication strengthShorten the lifetime verification cycleMachine part testingVehicle suspension/damping testingVehicle frameRoad surface
The invention relates to a method for quickly verifying a vehicle frame so that problems of high cost and long cycle of verification of a vehicle frame in the prior art can be solved. A pit and / or protrusion that are / is used for simulating an impact work condition on a real road surface are / is arranged on a proving road; and a stress peak of the impact work condition is tested to realize quick verification of the vehicle frame. When a vehicle frame needs to be verified and tested, simulation of the serious impact work condition of the vehicle on the real road surface is realized by the pit orprotrusion, so that the verification result is close the rear situation. Meanwhile, because of the simulation of the serious impact work condition of the vehicle frame, the verification strength of the vehicle frame is improved equivalently, so that the full-life verification cycle is reduced. When the vehicle frame has a local defect, only verification of the serious impact work condition needs to be carried out on the local defect of the vehicle frame by the pit and the protrusion on the proving road to realize the full-life verification effect instead of full-life verification testing, so that the cost is saved and the verification cycle is reduced.
Owner:ZHENGZHOU YUTONG BUS CO LTD
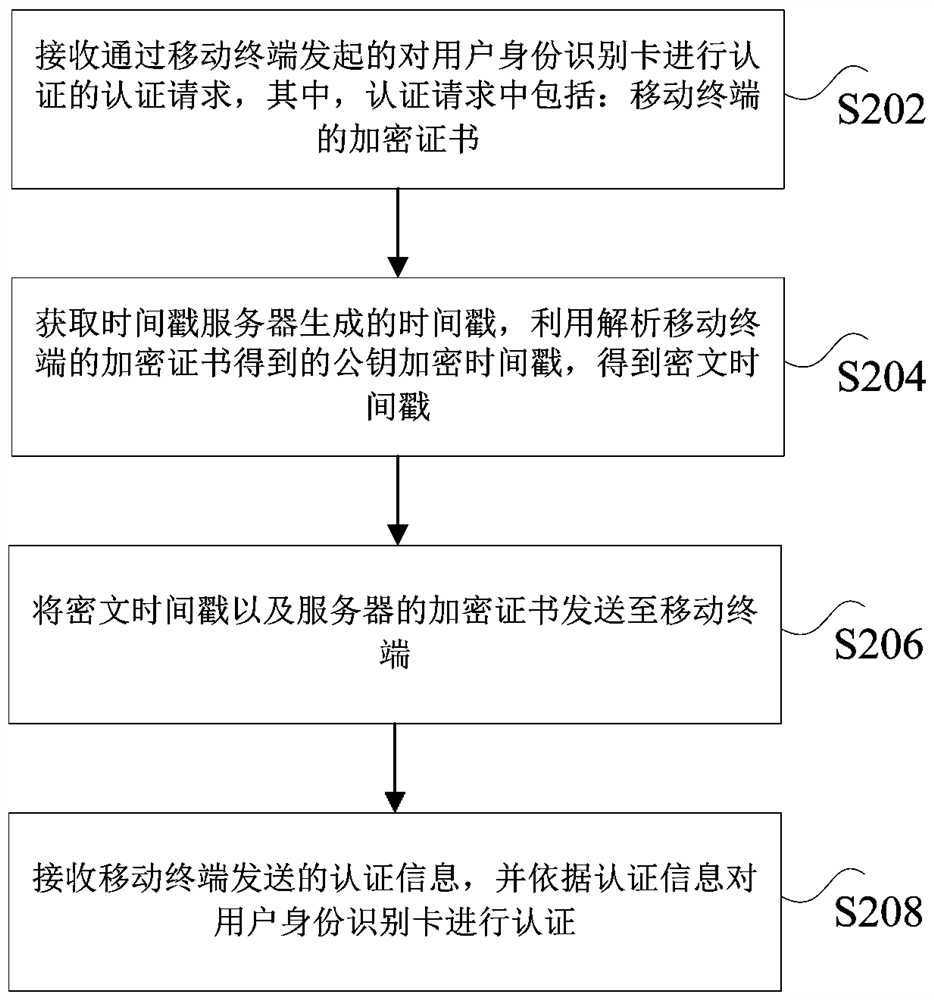
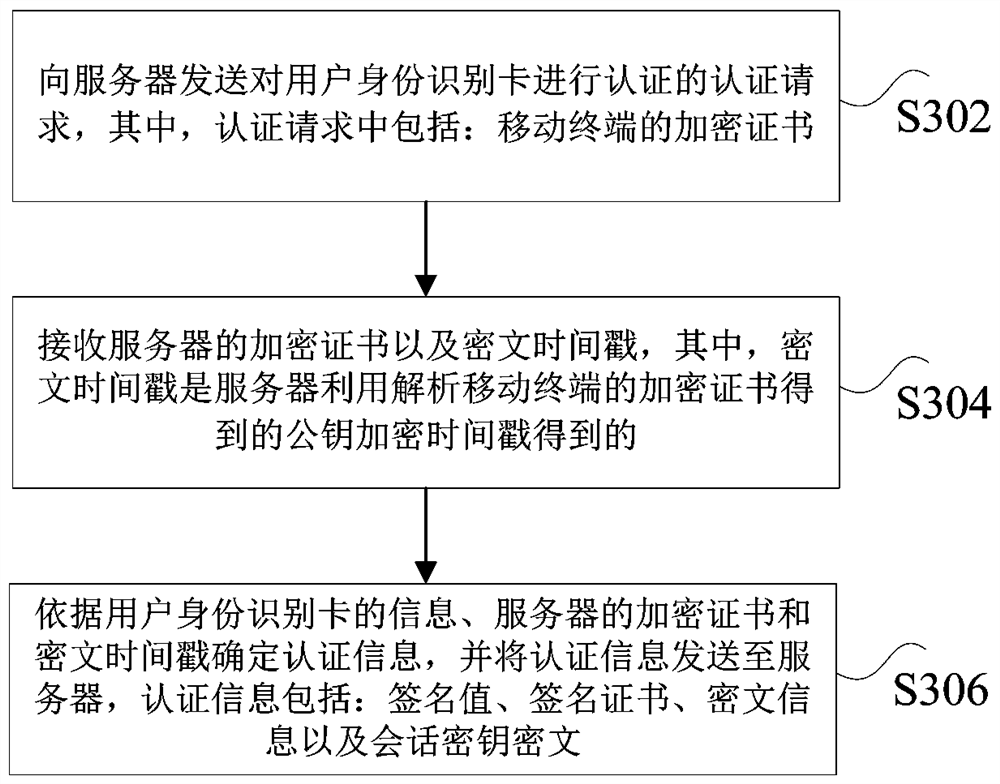
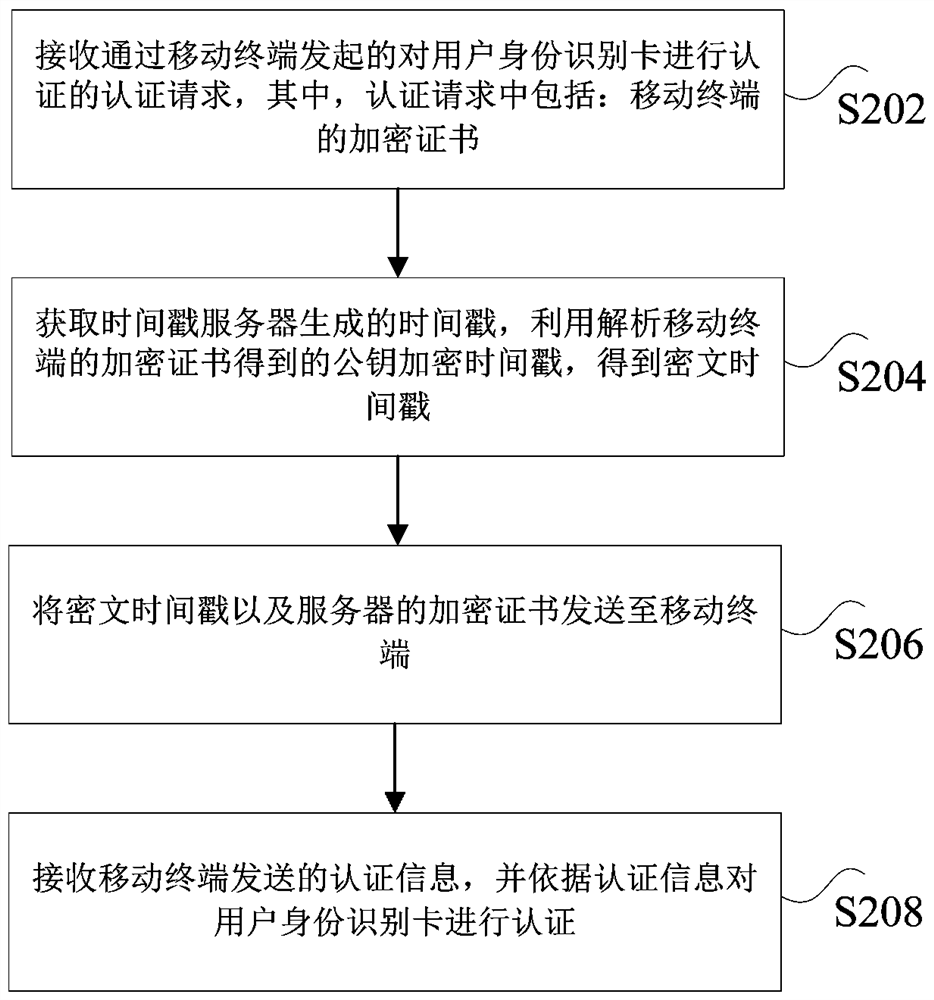
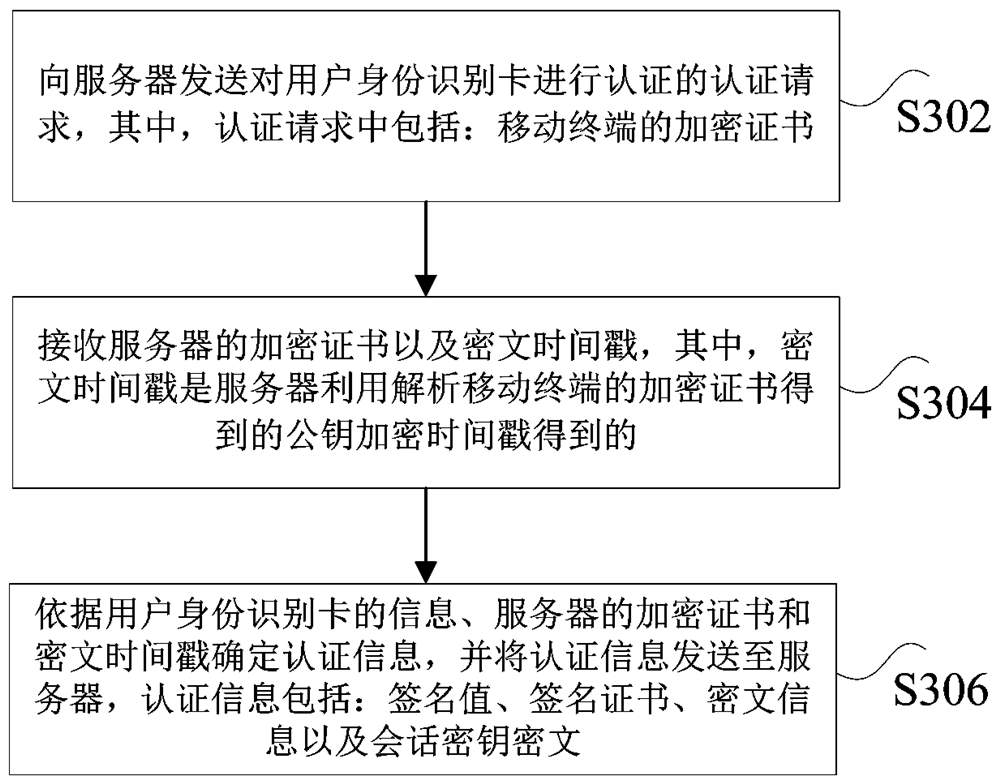
Authentication method and device of subscriber identity module card and nonvolatile storage medium
ActiveCN114520976AImprove authentication strengthImprove securityUser identity/authority verificationSecurity arrangementTimestampEngineering
The invention discloses an authentication method and device of a subscriber identity module card and a nonvolatile storage medium. The method comprises the following steps: receiving an authentication request which is initiated by a mobile terminal and is used for authenticating a subscriber identity module card, and the authentication request comprises an encryption certificate of the mobile terminal; obtaining a timestamp generated by the timestamp server, and encrypting the timestamp by using a public key obtained by analyzing the encryption certificate of the mobile terminal to obtain a ciphertext timestamp; sending the ciphertext timestamp and an encryption certificate of the server to the mobile terminal; authentication information sent by the mobile terminal is received, the user identity identification card is authenticated according to the authentication information, and the authentication information is obtained by the mobile terminal based on the information of the user identity identification card, the encryption certificate of the server and the ciphertext timestamp. The technical problems of low verification intensity and low safety coefficient of the existing SIM card authentication technology are solved.
Owner:北京时代亿信科技股份有限公司
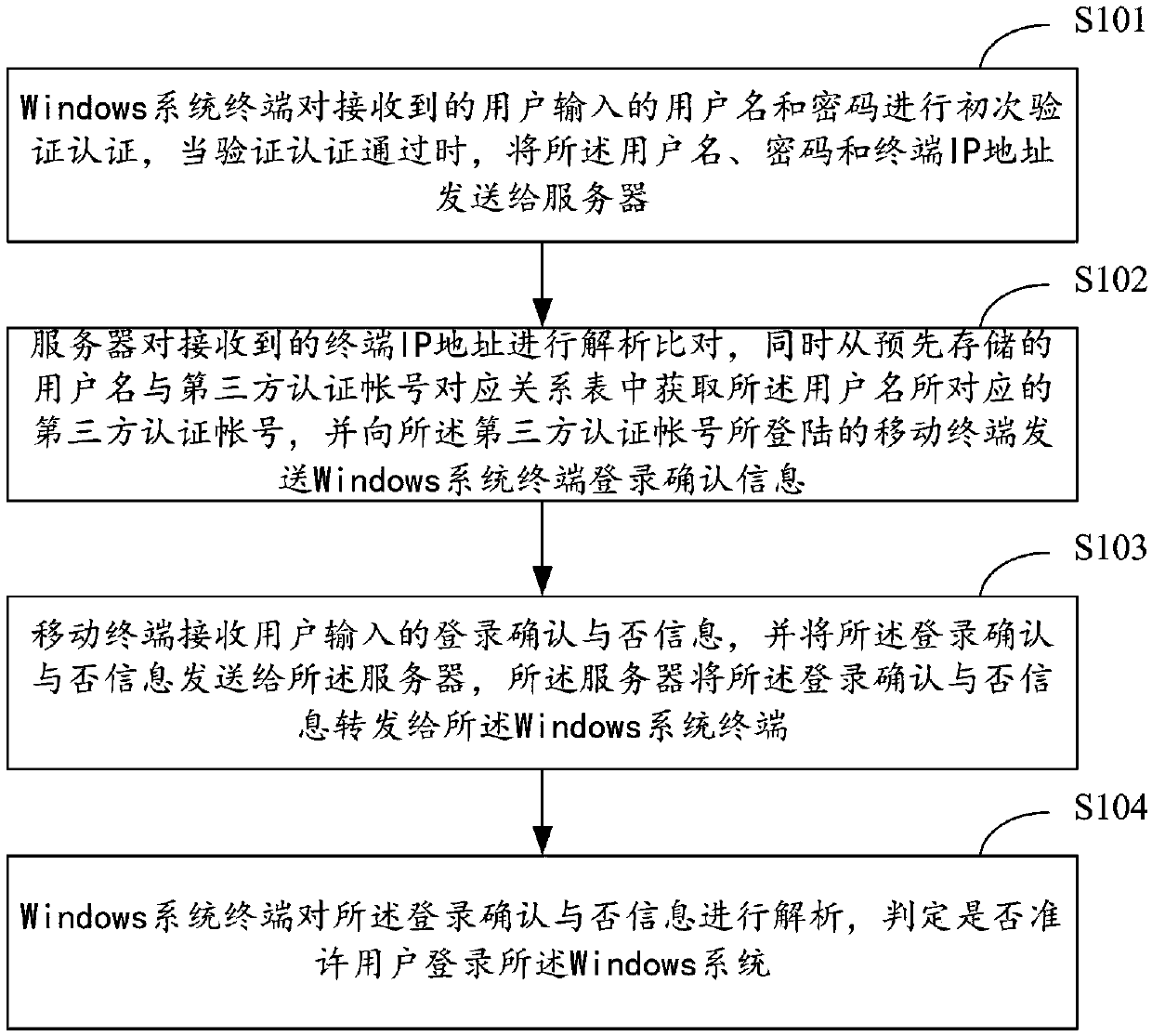
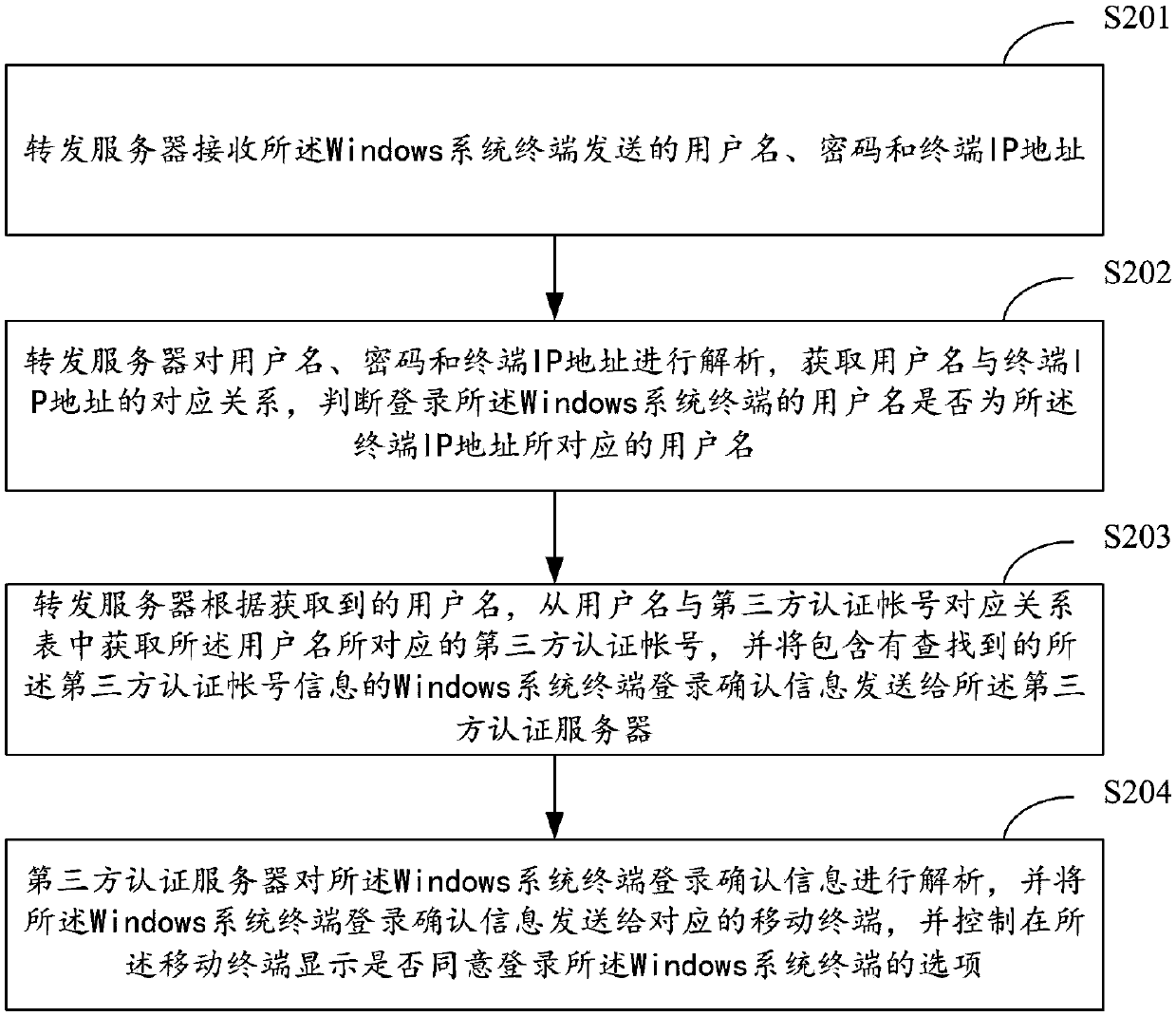
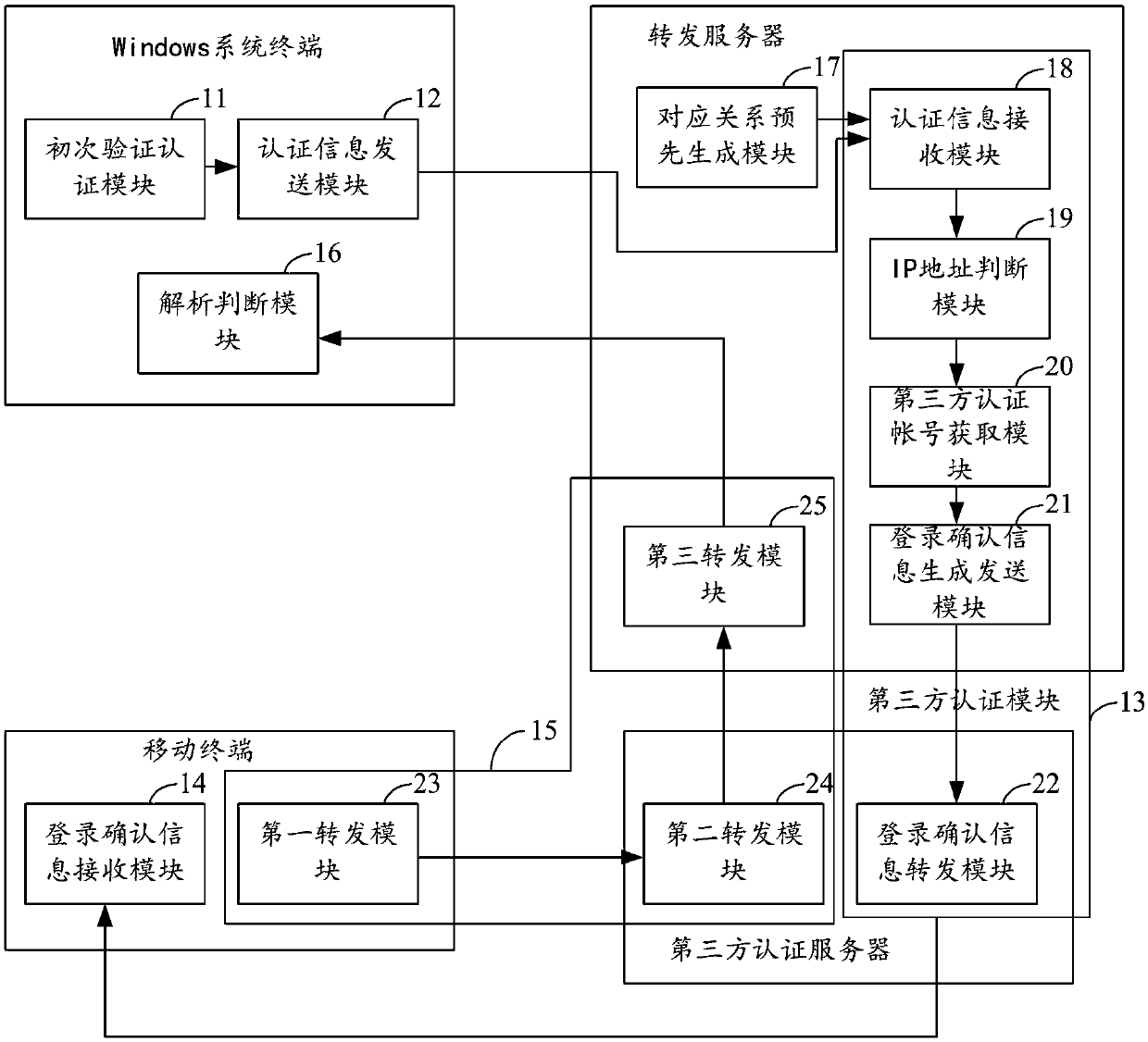
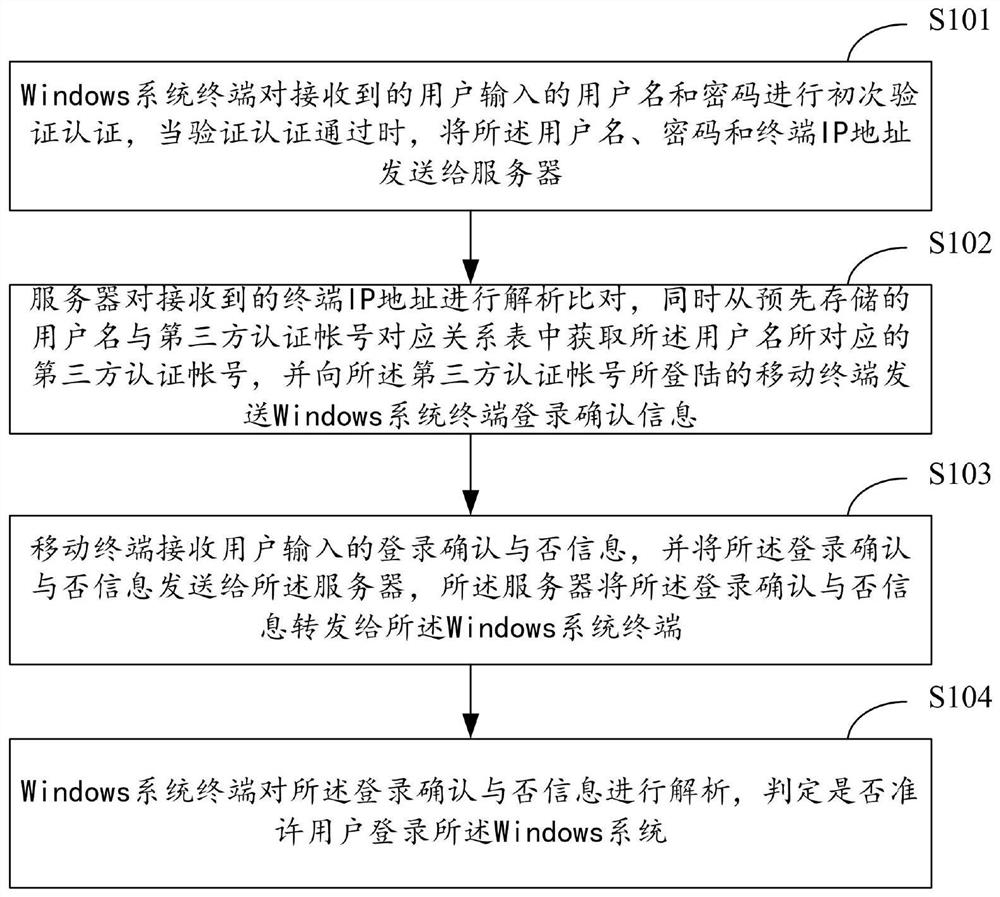
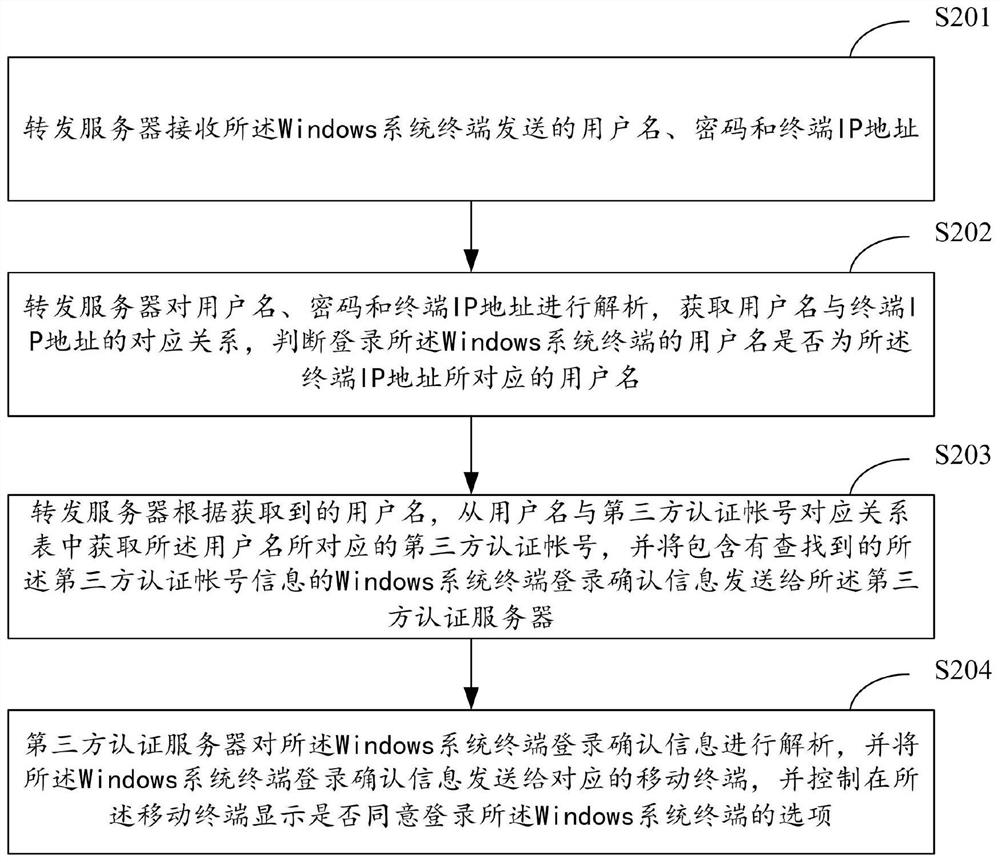
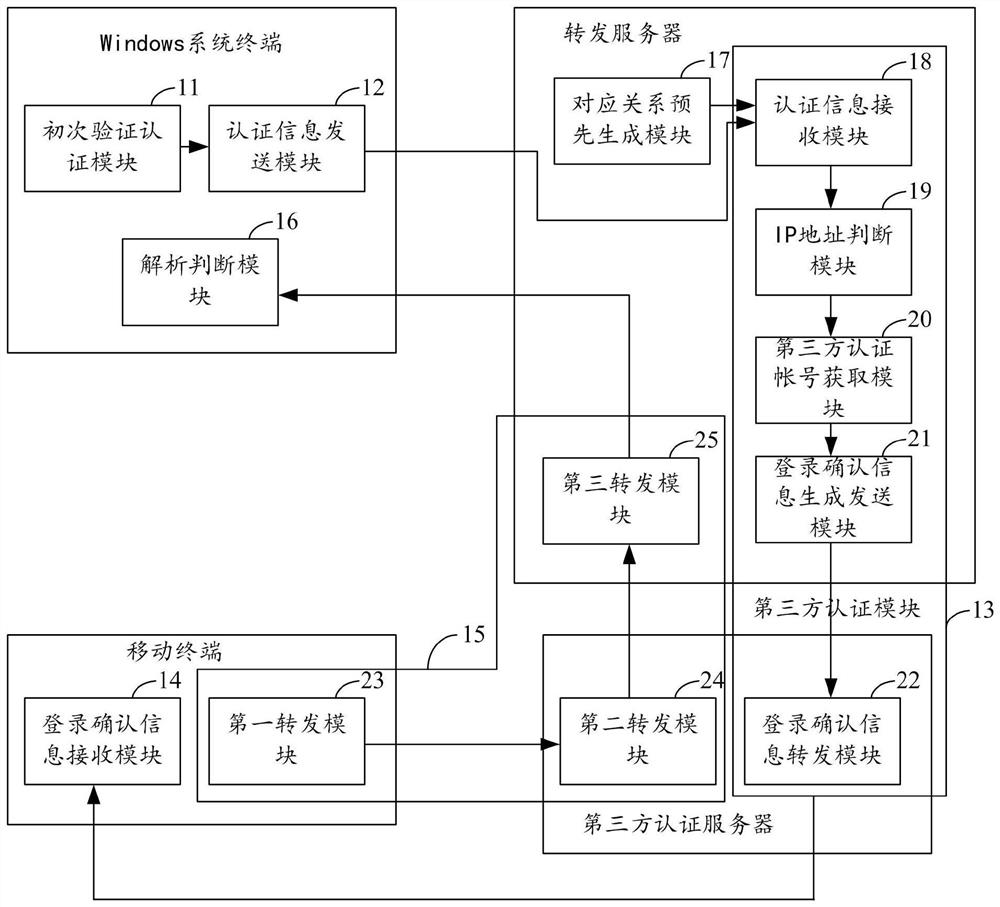
Windows system login authentication method and system
ActiveCN107612902ARealize unified managementImprove authentication strengthUser identity/authority verificationDigital data authenticationThird partyPassword
The invention relates to the technical field of security authentication, and provides a Windows system login authentication method and system. The method comprises the following steps that: a Windowssystem terminal performs first verification authentication on a user name and a password, and transmits the user name, the password and a terminal IP (Internet Protocol) address to a server when the verification authentication is passed; the server acquires a third-party authentication account, and transmits Windows system terminal login confirmation information to a mobile terminal in which the third-party authentication account logs; the mobile terminal transmits information indicating whether login confirmation is performed or not to the server, and the server forwards the information indicating whether login confirmation is performed or not to the Windows system terminal; and the Windows system terminal resolves the information indicating whether login confirmation is performed or not,and determines whether a user is allowed to log into a Windows system or not. Through adoption of the Windows system login authentication method and system, combination of dual authentication of theWindows system is realized; the authentication strength is enhanced; the security is improved; and unified management of a system account is realized.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
A Windows system login authentication method and system
ActiveCN107612902BRealize unified managementImprove authentication strengthUser identity/authority verificationDigital data authenticationThird partyPassword
The invention relates to the technical field of security authentication, and provides a Windows system login authentication method and system. The method comprises the following steps that: a Windowssystem terminal performs first verification authentication on a user name and a password, and transmits the user name, the password and a terminal IP (Internet Protocol) address to a server when the verification authentication is passed; the server acquires a third-party authentication account, and transmits Windows system terminal login confirmation information to a mobile terminal in which the third-party authentication account logs; the mobile terminal transmits information indicating whether login confirmation is performed or not to the server, and the server forwards the information indicating whether login confirmation is performed or not to the Windows system terminal; and the Windows system terminal resolves the information indicating whether login confirmation is performed or not,and determines whether a user is allowed to log into a Windows system or not. Through adoption of the Windows system login authentication method and system, combination of dual authentication of theWindows system is realized; the authentication strength is enhanced; the security is improved; and unified management of a system account is realized.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
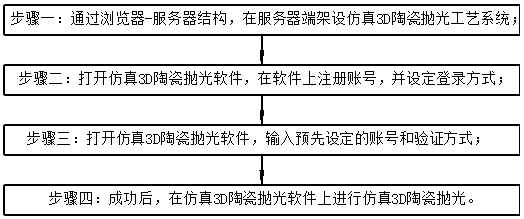
Simulated 3D ceramic polishing process
PendingCN111507022AImprove operational efficiencyImprove authentication strengthDigital data authenticationDesign optimisation/simulationProcess engineeringBrowser service
The invention discloses a simulated 3D ceramic polishing process which comprises the following steps of: erecting a simulated 3D ceramic polishing process system at a server side through a browser-server structure; opening simulated 3D ceramic polishing software, registering an account on the software, and setting a login mode; opening the simulated 3D ceramic polishing software, and inputting thepreset account and a verification mode; and after successful login, performing simulated 3D ceramic polishing on the simulated 3D ceramic polishing software. The simulated 3D ceramic polishing process has the beneficial effects that the polishing process is simulated on a simulated scene, and the simulation process is in one-to-one correspondence with the actual polishing process, so that a usercan grasp the polishing process more firmly, the user can apply the theory to the reality conveniently, and the operation efficiency is improved; and the verification mode is one or more of password verification, fingerprint verification and iris verification, so that the verification intensity is improved, and the risk that the account is stolen is reduced.
Owner:陕西励峰德精密陶瓷科技有限公司
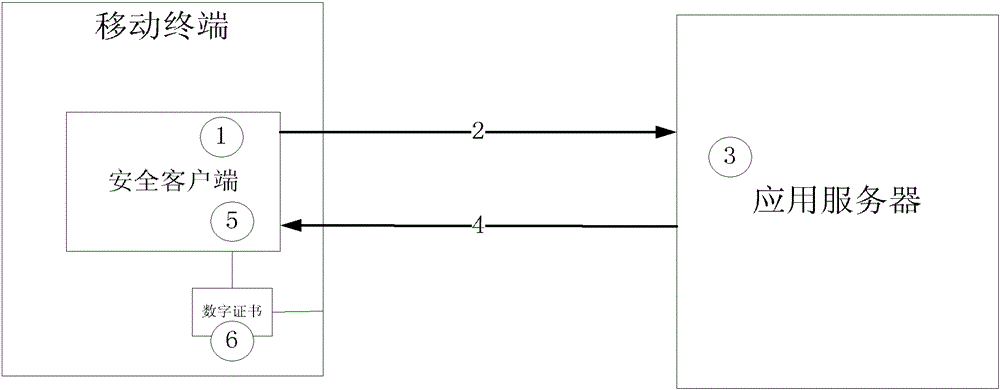
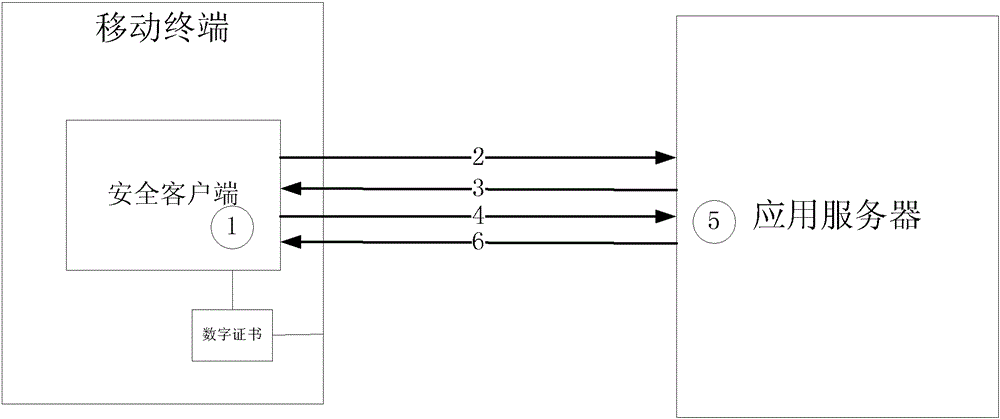
A mobile terminal unique authentication method based on software digital certificate
ActiveCN103167491BImprove authentication strengthNot afraid to stealUser identity/authority verificationSecurity arrangementApplication serverEngineering
The invention discloses a mobile terminal uniqueness authentication method based on a software digital certificate, which belongs to the technical field of computer and information security, and is specifically as follows: (1) The mobile terminal installs a security client, generates a certificate request associated with device information, and sends a request to the server register. The server issues a digital certificate to the mobile terminal to realize the association between the digital certificate and the device. (2) When in use, the server sends random information to the mobile terminal, the security client receives the information, uses the private key of the digital certificate of the machine to sign the random information, and sends the signed data to the server. The application server uses the digital certificate public key to verify the signature and confirm the identity of the communication peer. The invention can well verify the mobile terminal, and enhances the strength of the verification without adding hardware verification devices.
Owner:KOAL SOFTWARE CO LTD
Method and arrangement for protecting a charging station against improper use
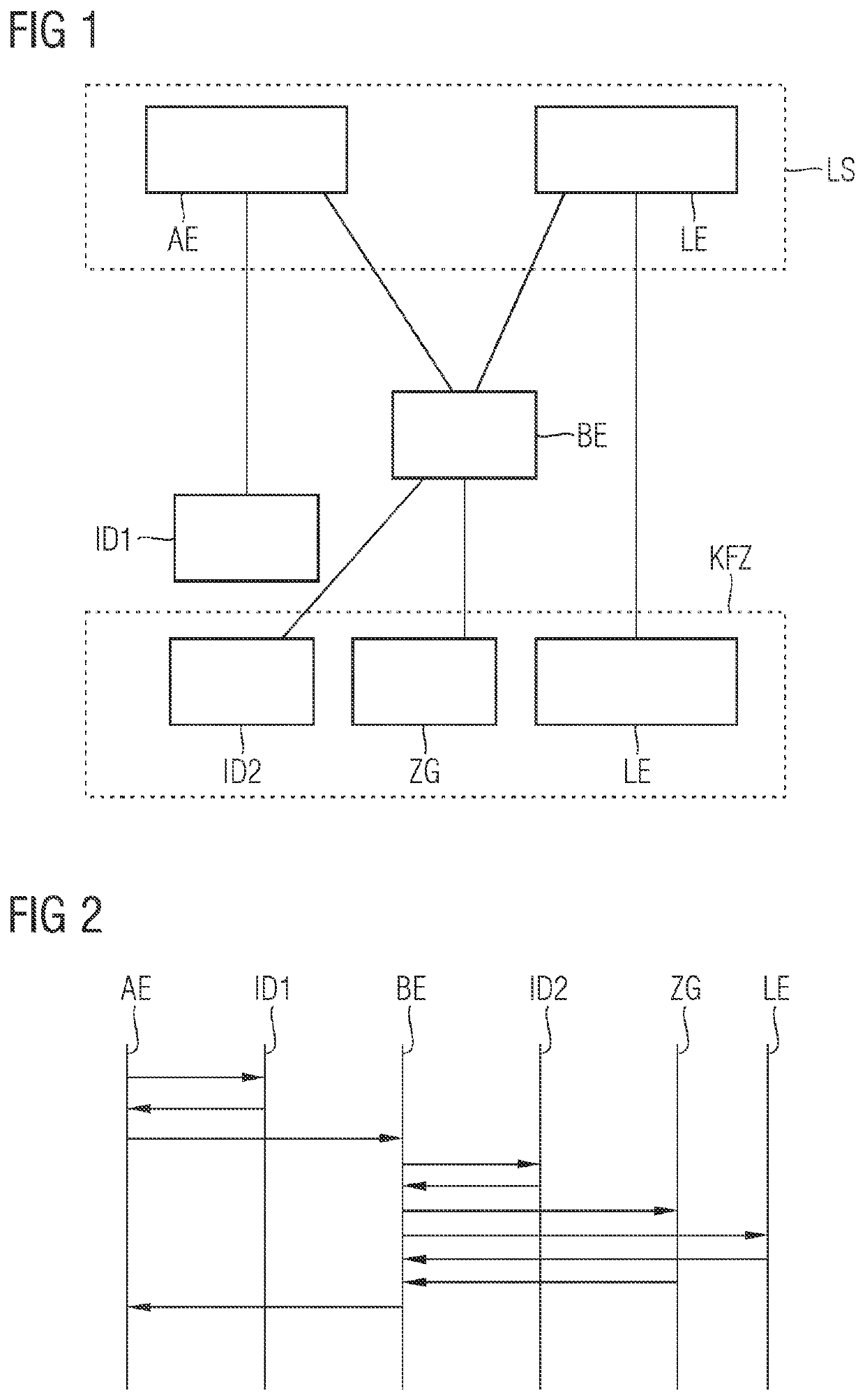
PendingUS20220134898A1Great expenseLow thresholdCharging stationsPayment architectureCharging stationAuthorization
To protect a charging station LS against improper use, a second identification feature ID2 is also checked in addition to a first identification feature ID 1. The charging process is only authorized or continued if the check of the second identification feature ID2 was also successful. The authentication or authorization is thus implemented in a low-threshold manner by means of an additional authentication, in which a weak identification is supplemented by one or more further automatic identifications, which can also be checked continuously. This means that an authorized and genuine user does not incur any additional expense, while at the same time any damage caused by behavior in breach of contract by authorized users can be greatly reduced. Related system and methods for protecting against unauthorized use are also disclosed.
Owner:SIEMENS AG
Safety proxy method
ActiveCN1314221CImprove authentication strengthImprove securitySecuring communicationStructure of Management InformationRights management
The invention discloses a safety proxy method for realizing port based safety proxy mode through employing an identification mode integrating digital certificate and electronic key and authority control combining digital certificate, wherein no amendment on the existing applied system for hardware and software is required to improve the identification intensity of the existing applied systems.
Owner:ZTE CORP
Unified security management system and identity authentication method
ActiveCN113114464AReduce the probability of being attackedReduce leakageUser identity/authority verificationInternet privacySafety management systems
The invention discloses a unified security management system and an identity authentication method. The system comprises a security management portal and a security management center, the security management center further comprises a centralized authentication service, a remote user dialing authentication service, a program account interface and a one-time password service; the remote user dialing authentication service is used for forwarding an authentication request of a host to the centralized authentication service for centralized authentication; and the program account interface and the one-time password service are used for distributing one-time access passwords for the application programs when the application programs log in the host, and the one-time password service is further used for providing the one-time access passwords for the centralized authentication service for identity authentication. Therefore, according to the scheme of the invention, based on the transformed 4A system, the security of the host can be improved, the software complexity is reduced, the user information leakage is effectively prevented, and the possibility that a password is cracked is avoided.
Owner:中国移动通信集团重庆有限公司 +1
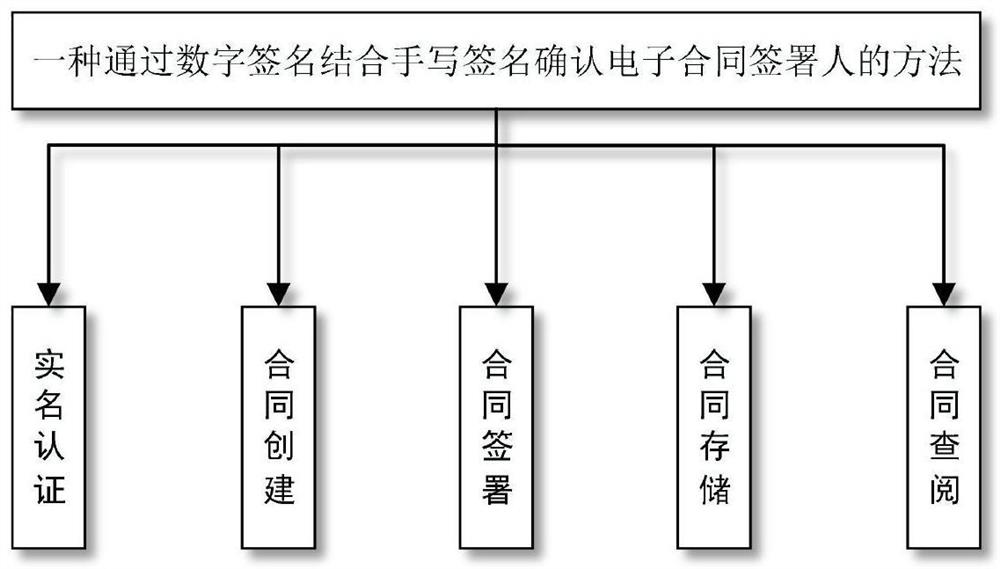
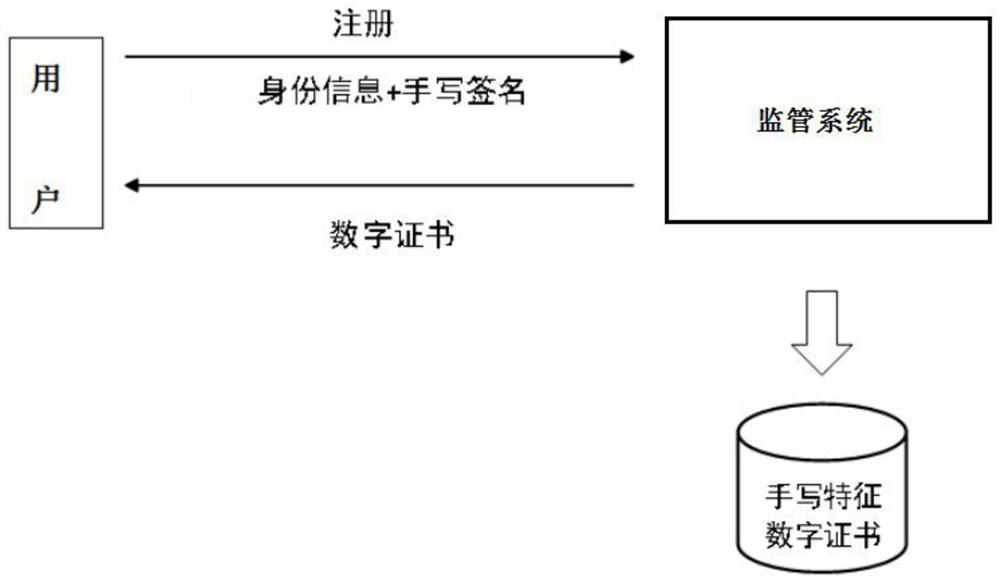
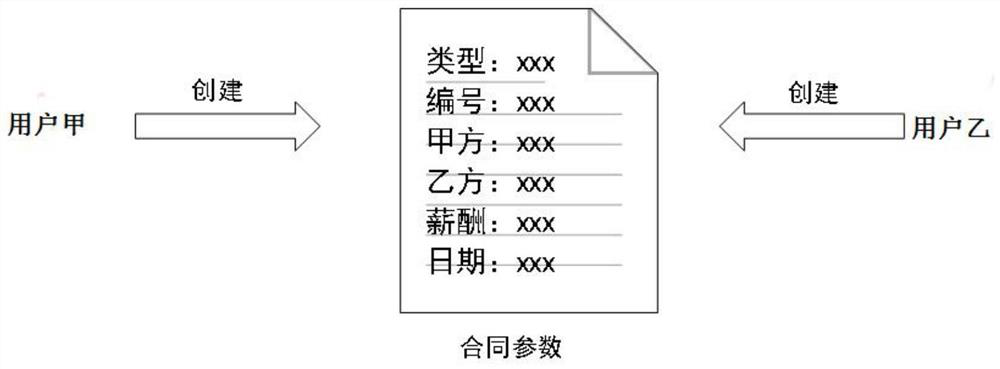
A method for confirming the signer of an electronic contract by combining a digital signature with a handwritten signature
ActiveCN110674523BAdd handwritten signature featureImprove authentication strengthUser identity/authority verificationDigital data protectionElectronic contractsDigital signature
The invention provides a method for confirming a signer of an electronic contract with a digital signature combined with a handwritten signature. The method firstly performs real-name authentication and contract creation, and secondly, both parties sign the contract to sign the contract, and generate a contract signature feature and a digital signature, and then The supervision system verifies the contract signature features and digital signatures, and then performs special processing on the verified contracts, and finally puts the specially processed contracts on the blockchain for on-chain storage, and both parties to the contract can check the contract parameters by decrypting them. Contract, on the basis of confirming the identity of the contract signer through the traditional digital signature, the present invention increases the user's handwritten signature feature, enhances the identity authentication strength of the contract signer, increases the difficulty of contract forgery, and combines new blockchain technology as a contract. The storage platform ensures that the contract cannot be tampered with, forged and denied.
Owner:民生科技有限责任公司
Authentication method and device for user identification card, and non-volatile storage medium
ActiveCN114520976BImprove authentication strengthImprove securityUser identity/authority verificationSecurity arrangementTimestampCiphertext
The present application discloses a user identity card authentication method and device, and a non-volatile storage medium. The method includes: receiving an authentication request initiated by a mobile terminal to authenticate a user identity card, wherein the authentication request includes: an encryption certificate of the mobile terminal; obtaining a timestamp generated by a timestamp server, and analyzing the mobile terminal's The public key encryption time stamp obtained by the encryption certificate is obtained, and the ciphertext time stamp is obtained; the ciphertext time stamp and the server's encryption certificate are sent to the mobile terminal; the authentication information sent by the mobile terminal is received, and the user identity card is authenticated according to the authentication information. , wherein the authentication information is obtained by the mobile terminal based on the information of the user identity card, the encryption certificate of the server and the ciphertext timestamp. The present application solves the technical problems of low verification intensity and low safety factor in the existing SIM card authentication technology.
Owner:北京时代亿信科技股份有限公司
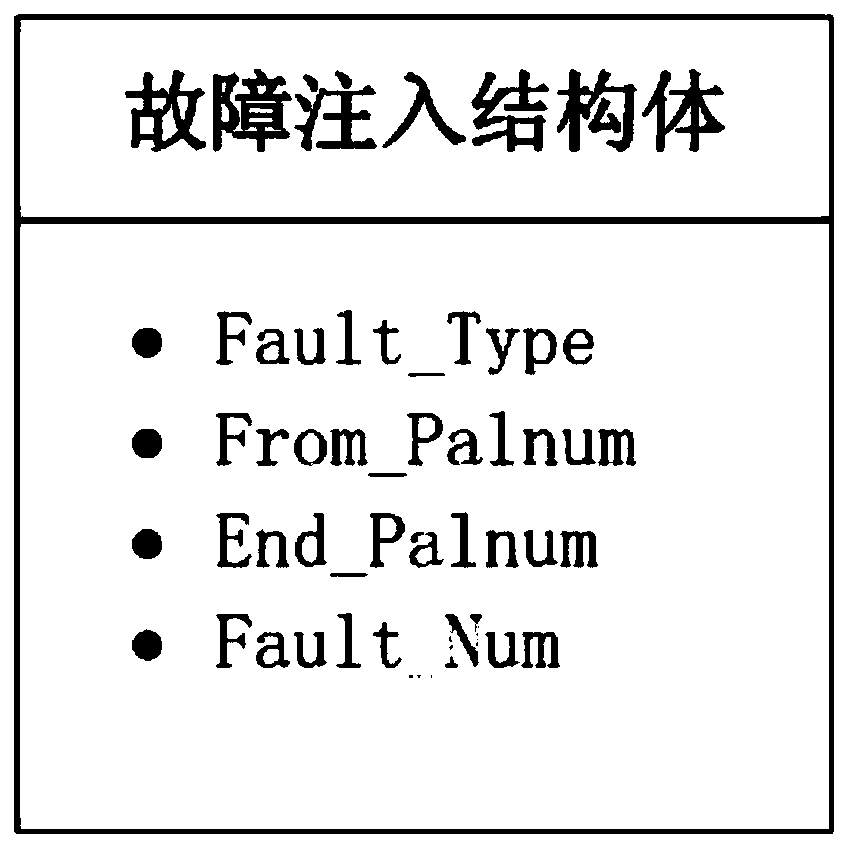
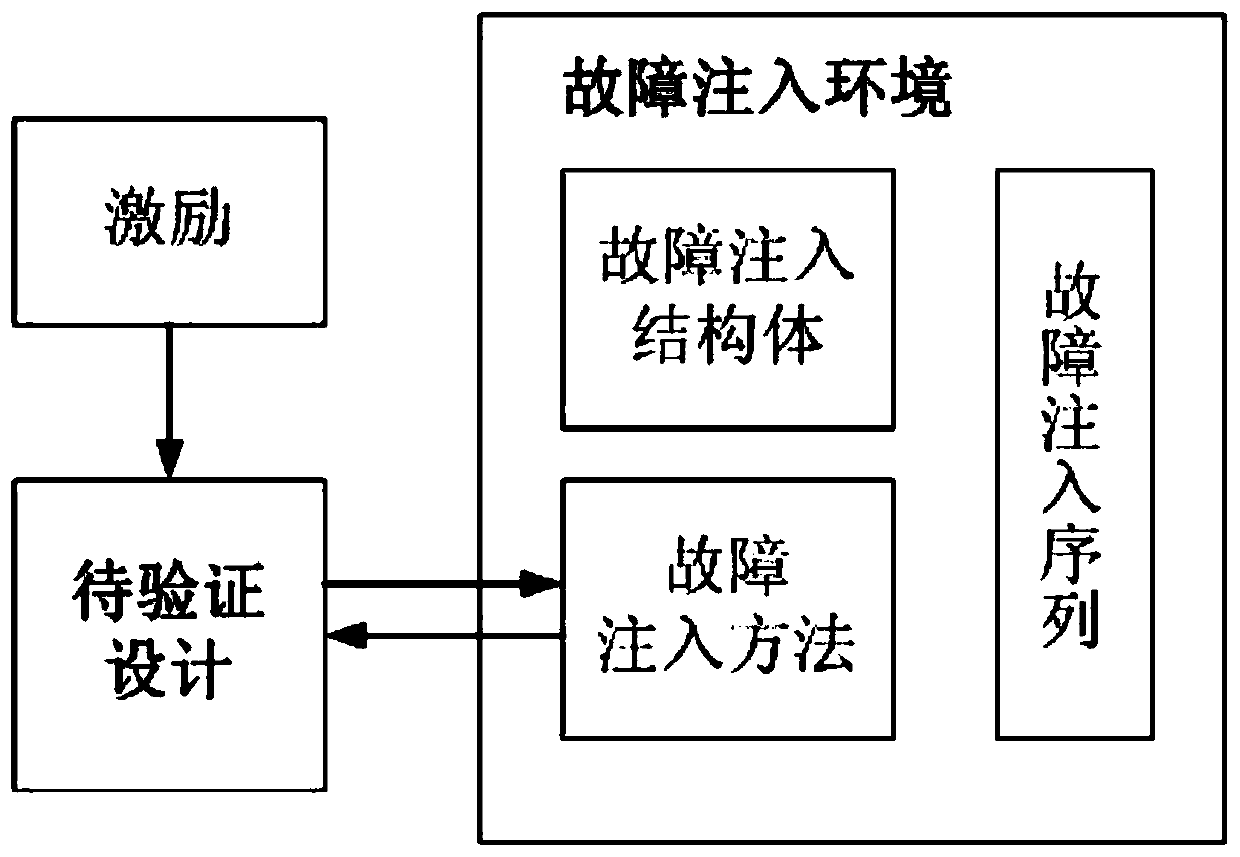
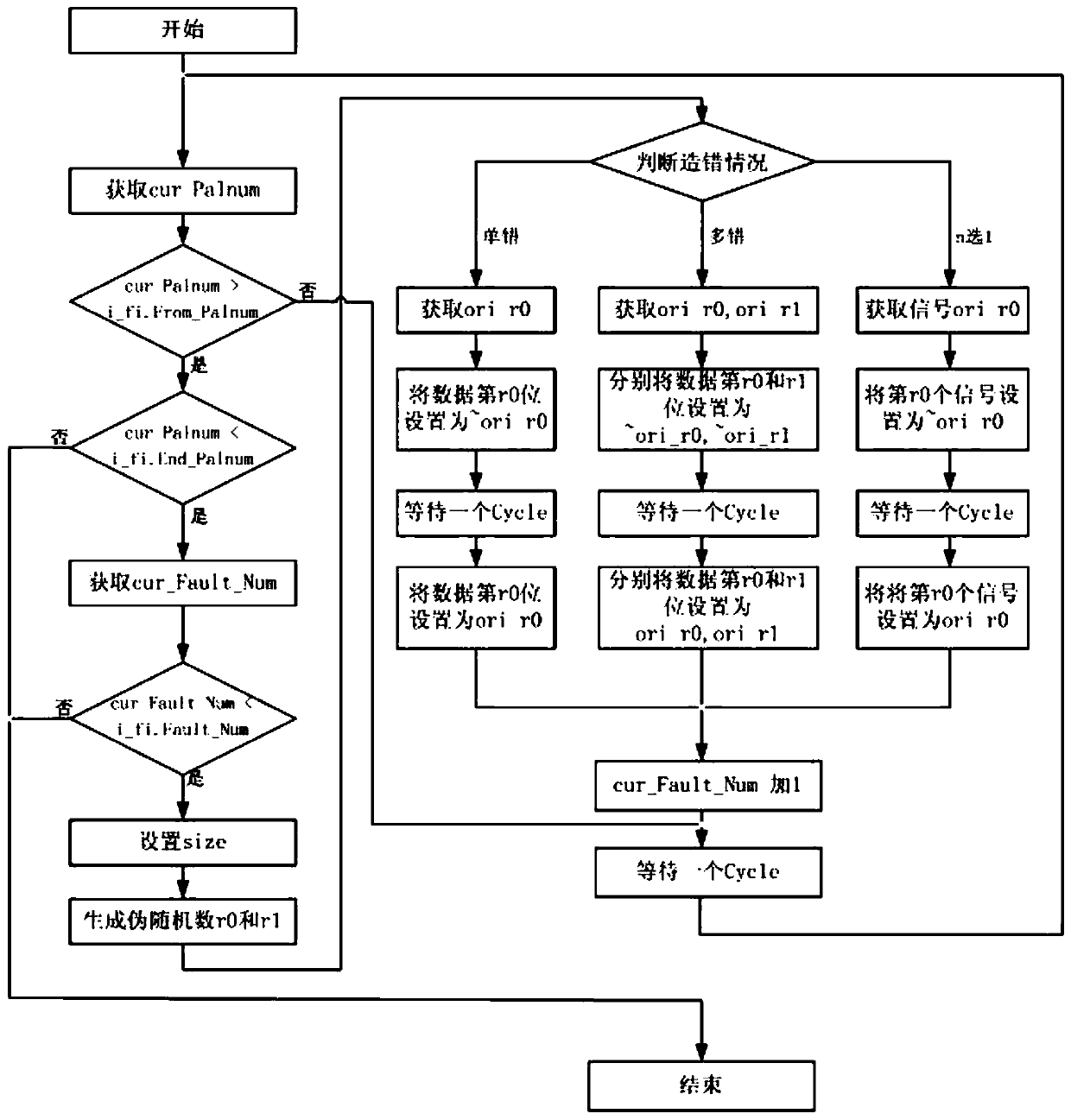
Controllable random fault injection method applied to simulation verification of processor chip
ActiveCN110688271AImprove authentication strengthImprove controllabilityRandom number generatorsFunctional testingAlgorithmParallel computing
The invention relates to a controllable random fault injection method applied to simulation verification of a processor chip. The controllable random fault injection method comprises the following steps of defining a fault injection structure body; finding a design signal path and a name of fault injection according to a design scheme and a design code of the chip, and associating the design signal path and the name with variables in a fault injection environment through a binding mode supported by a simulator; monitoring and acquiring a current exit instruction number, and acquiring a recorded current fault injection number when the exit instruction number is in the fault injection instruction number interval; obtaining a data bit width size, obtaining two different random numbers r0 andr1 by using a pseudo random number generation method, wherein the value ranges of the random numbers r0 and r1 are between 0 and size-1; and selecting a data bit or a signal bit for fault injection byadopting random numbers r0 and r1 according to different error generation conditions. According to the invention, the controllability, randomness and expandability of fault processing flow verification are enhanced.
Owner:上海高性能集成电路设计中心
Steganography-based key transmission and key updating method
ActiveCN102724041BEffective verification of identity informationImprove authentication strengthEncryption apparatus with shift registers/memoriesUser identity/authority verificationMultiple encryptionCiphertext
The invention provides a steganography-based key transmission and key updating method, which is applied to the field of information safety. The method comprises the steps that a communication party A sets a communication type, an encryption algorithm an steganography algorithm, selects a steganography carrier and generates a communication identifier and then performs the updating of a transmission key or the transmission process of a conversion key; a new transmission key is selected when in updating, a time stamp and a signature are generated to encrypt and steganograph the transmission key, the key updating information is generated to be transmitted to a communication party B, and the communication party B performs the verification, de-staganography and deciphering to obtain the transmission key; and the conversion key is selected in transmission to generate a time stamp and a signature so as to encrypt and steganograph the conversion key, the key transmission information is generated to be transmitted to the communication party B, and the communication party B performs the verification, de-steganography and deciphering to obtain the conversation key. The key is concealed by utilizing the steganography, so that an encrypted data format in the key transmission process and the key updating process can be effectively protected, and the safety transmission of multiple encryption and decryption algorithm conversation keys can be realized.
Owner:BEIHANG UNIV
A webservice security authentication access control method based on software digital certificate and time stamp
ActiveCN104753881BGuarantee the correctness of accessTight control over securityUser identity/authority verificationAccess timeDigital signature
Owner:KOAL SOFTWARE CO LTD
Boot file credible verify based on mobile TPM
InactiveCN101419654BRetain investmentImprove versatilityPlatform integrity maintainanceSpecial data processing applicationsOperational systemFile system
The invention relates to a guide file credible check based on mobile TPM. The check comprises the following steps: the mobile TPM is initialized; relevant authentication information and check information in a guide process are set; a driving module for the mobile TPM before the start of an operating system at the guide stage is designed and implemented; the driving module is tested according to the operating environment of a DOS operating system; a Part 1 code is arranged at the 0 sector position of a hard disk; an original MBR of the system is moved to a second sector of the hard disk; a Part2 code is arranged at a third sector of the hard disk and a subsequent position thereof; the Part2 code comprises the driving module and a calling interface of the mobile TPM; the credible check is implemented on the reading function of an NEFS file system and files to be read; after the file check is succeeded, the execution is changed from Part2 to an original MBR code. An original process of the system is started for the operation. And the Windows system is ensured to be clean and credible.
Owner:BEIJING JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com