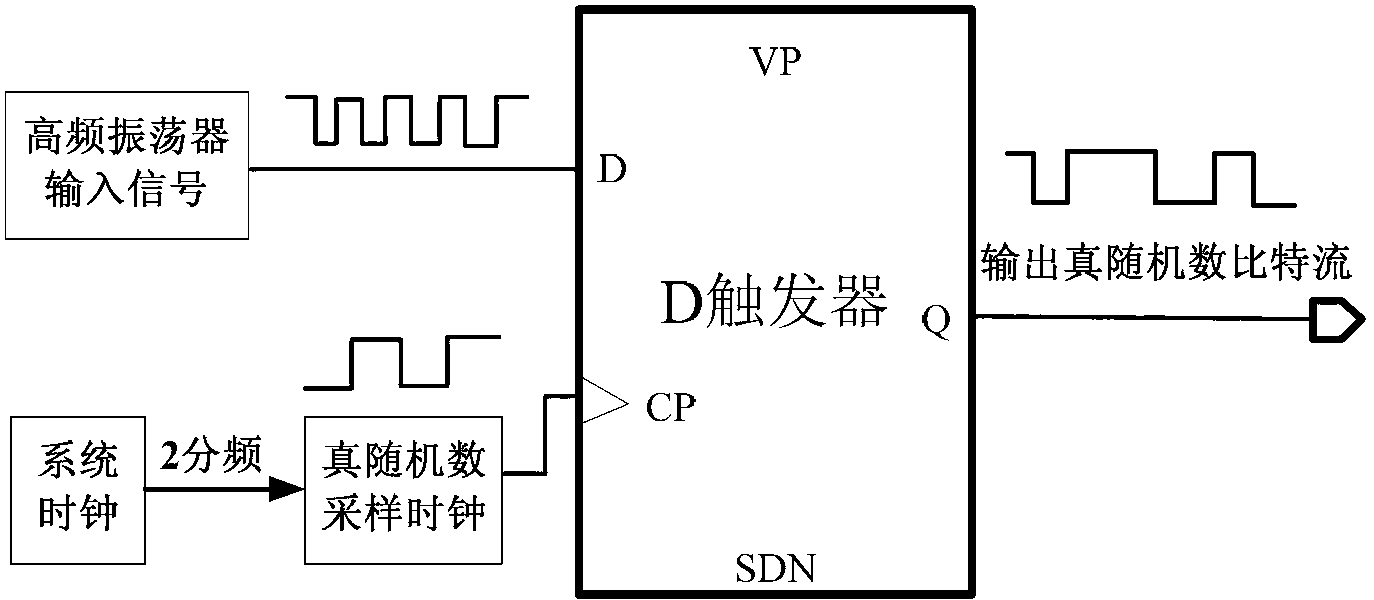
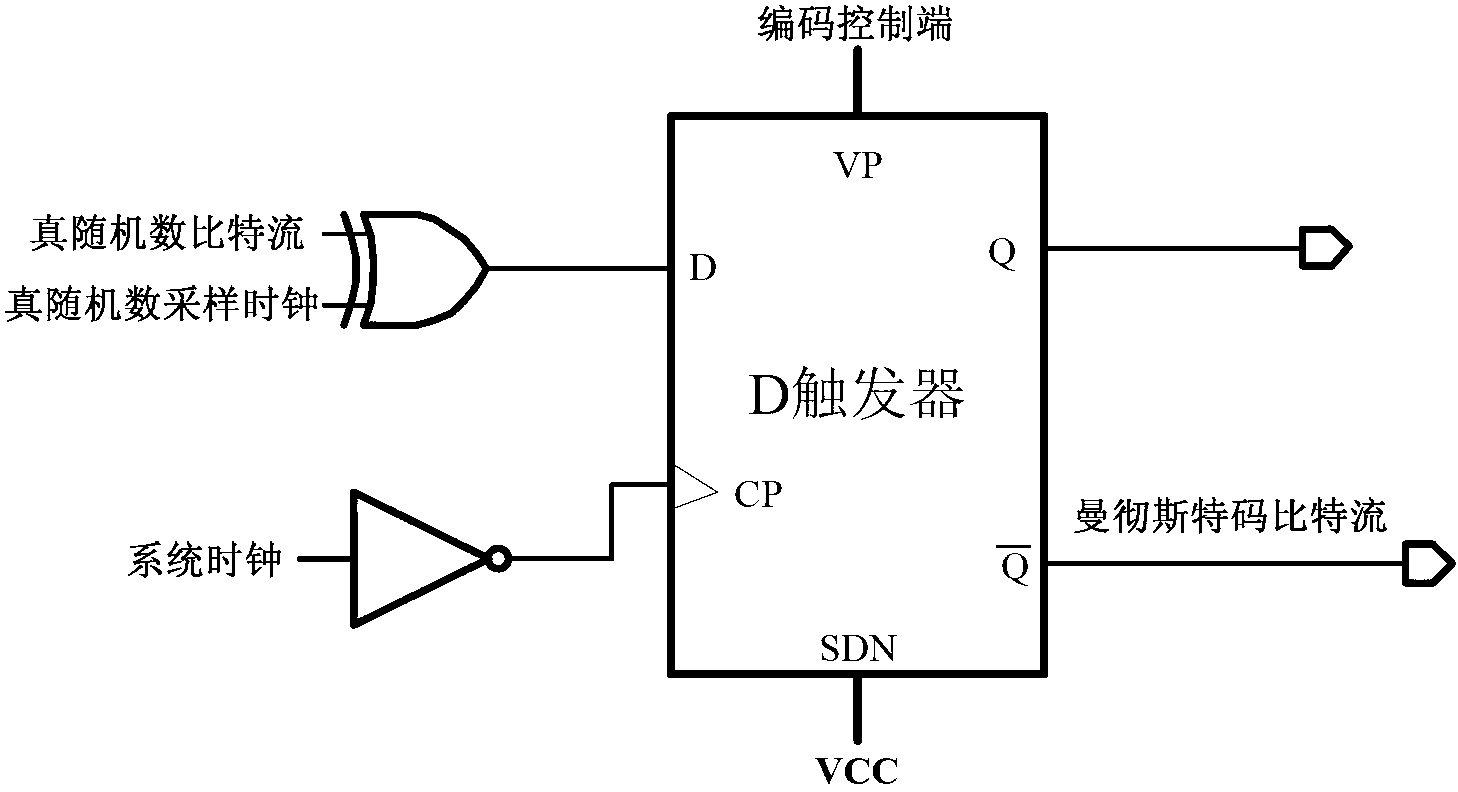
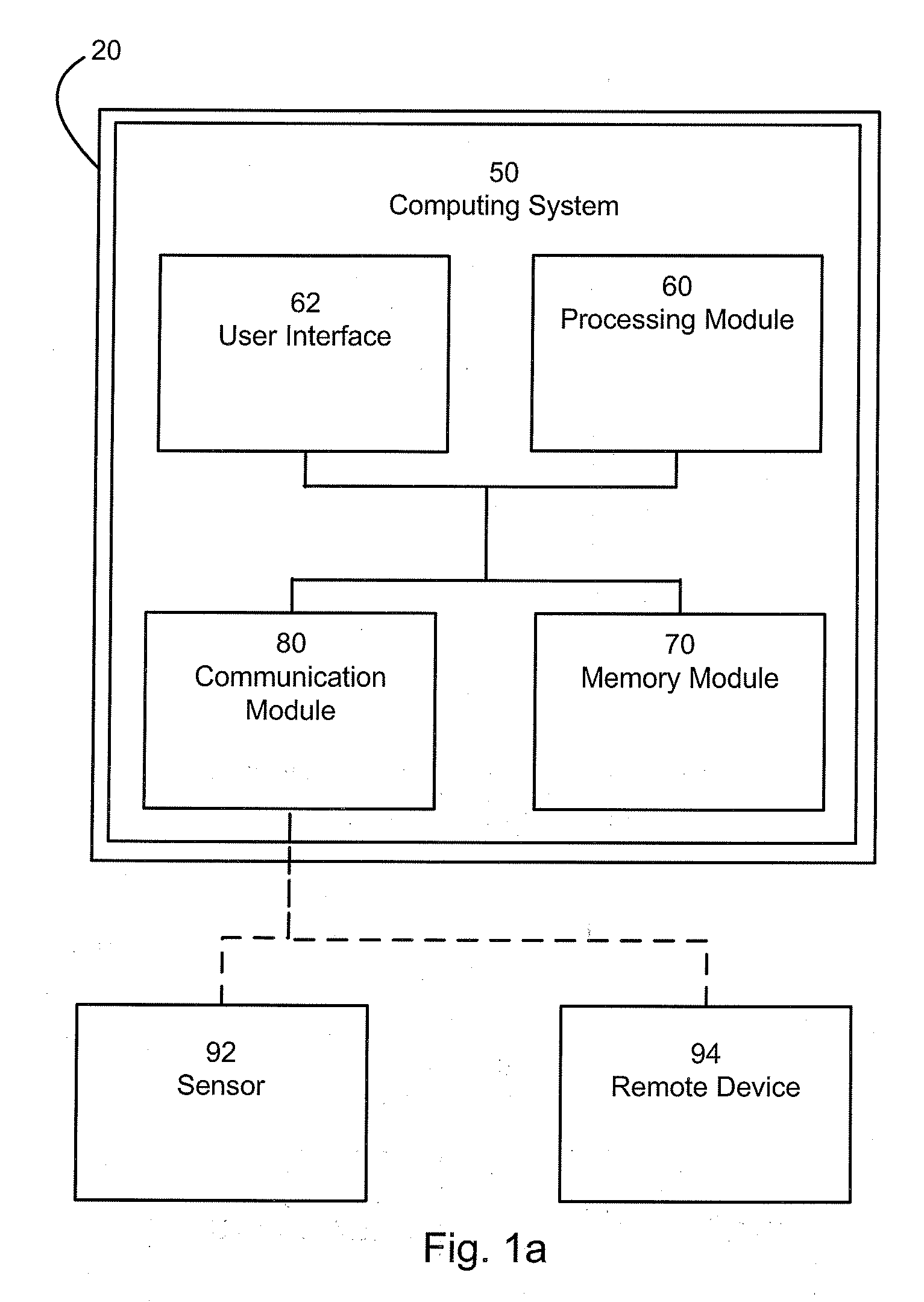
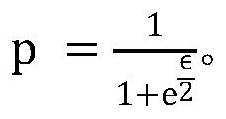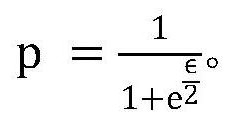Patents
Literature
157 results about "Pseudo random number generation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
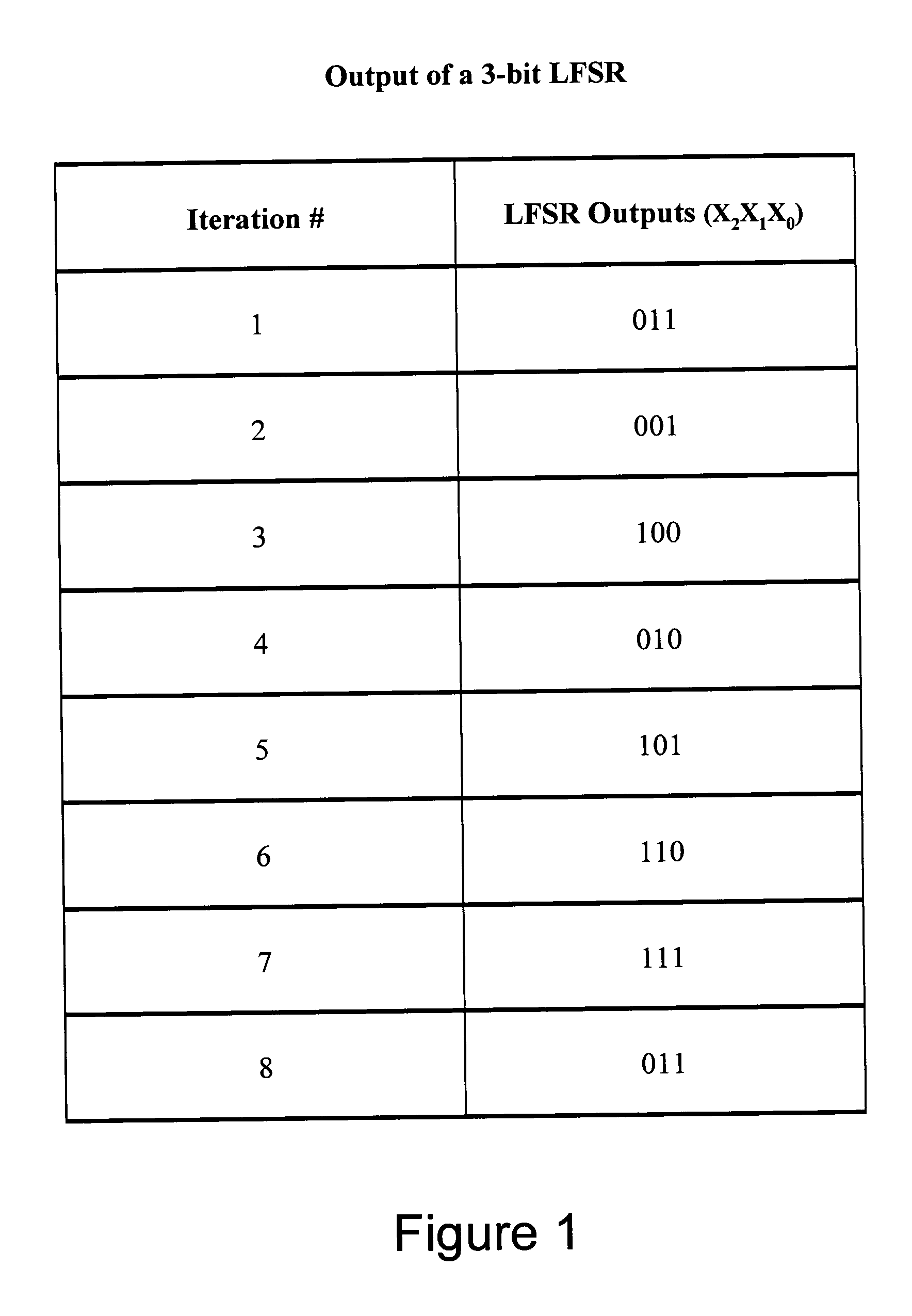
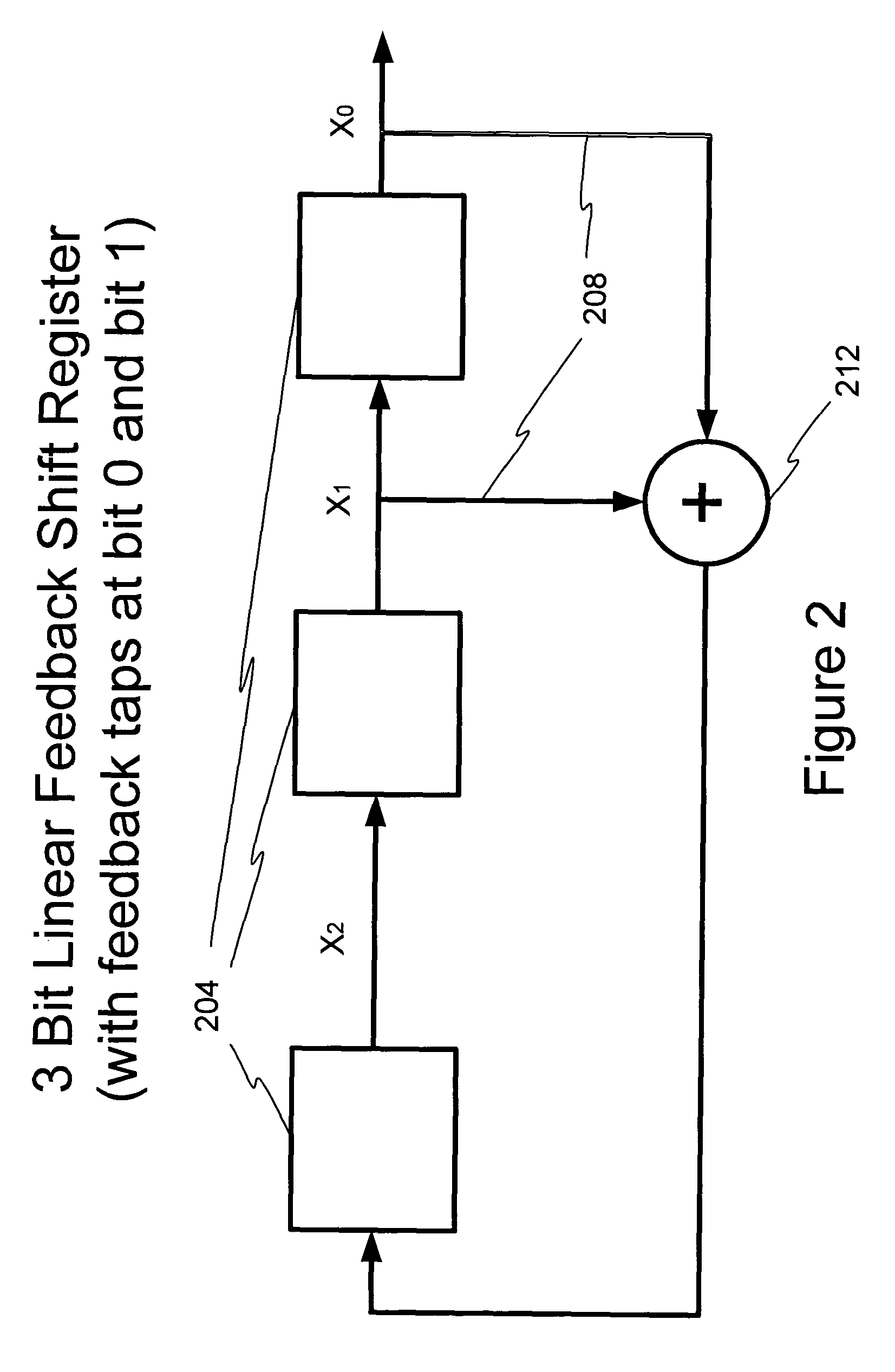
A pseudo random number generator (PRNG) refers to an algorithm that uses mathematical formulas to produce sequences of random numbers. PRNGs generate a sequence of numbers approximating the properties of random numbers. This is determined by a small group of initial values.
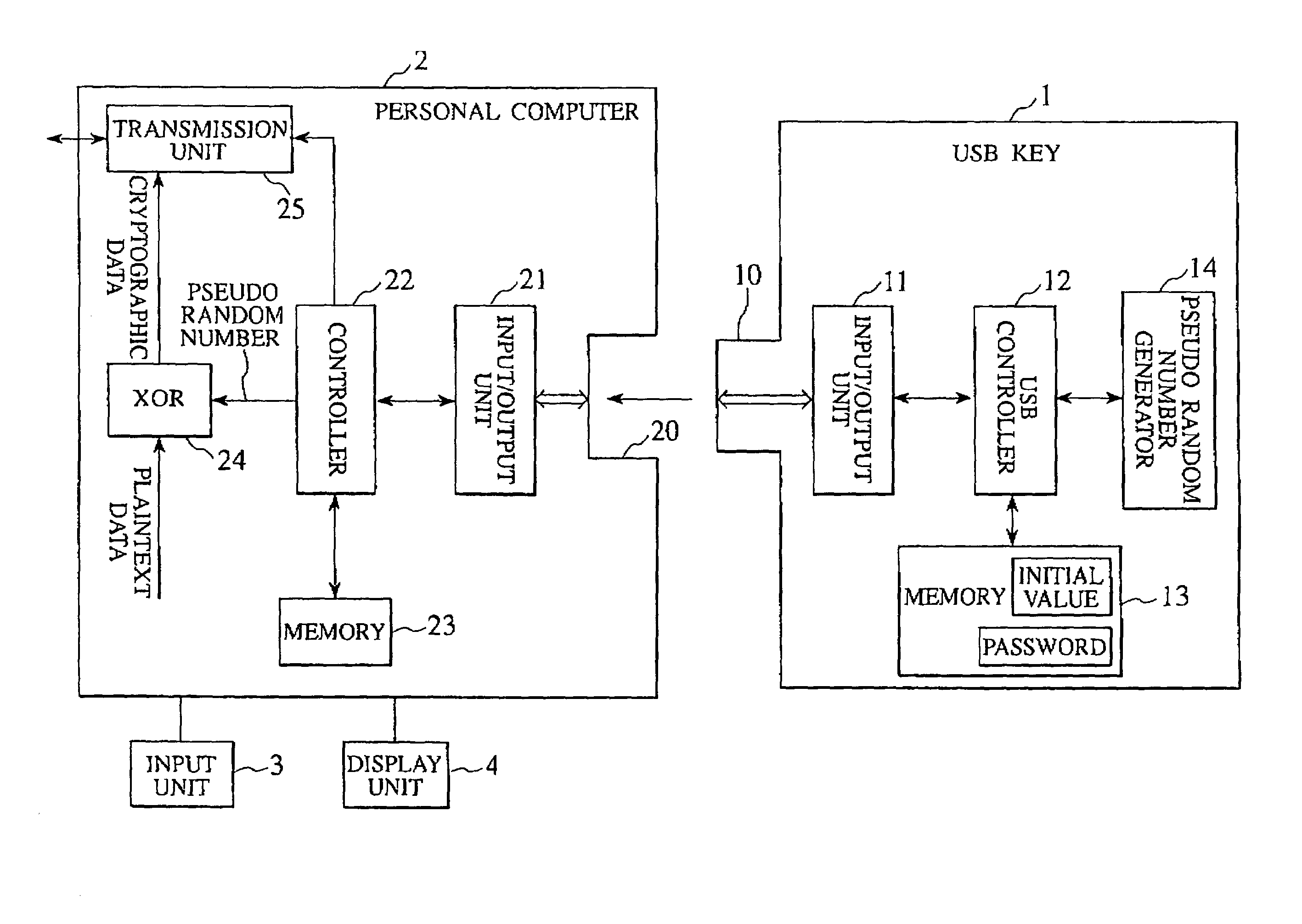
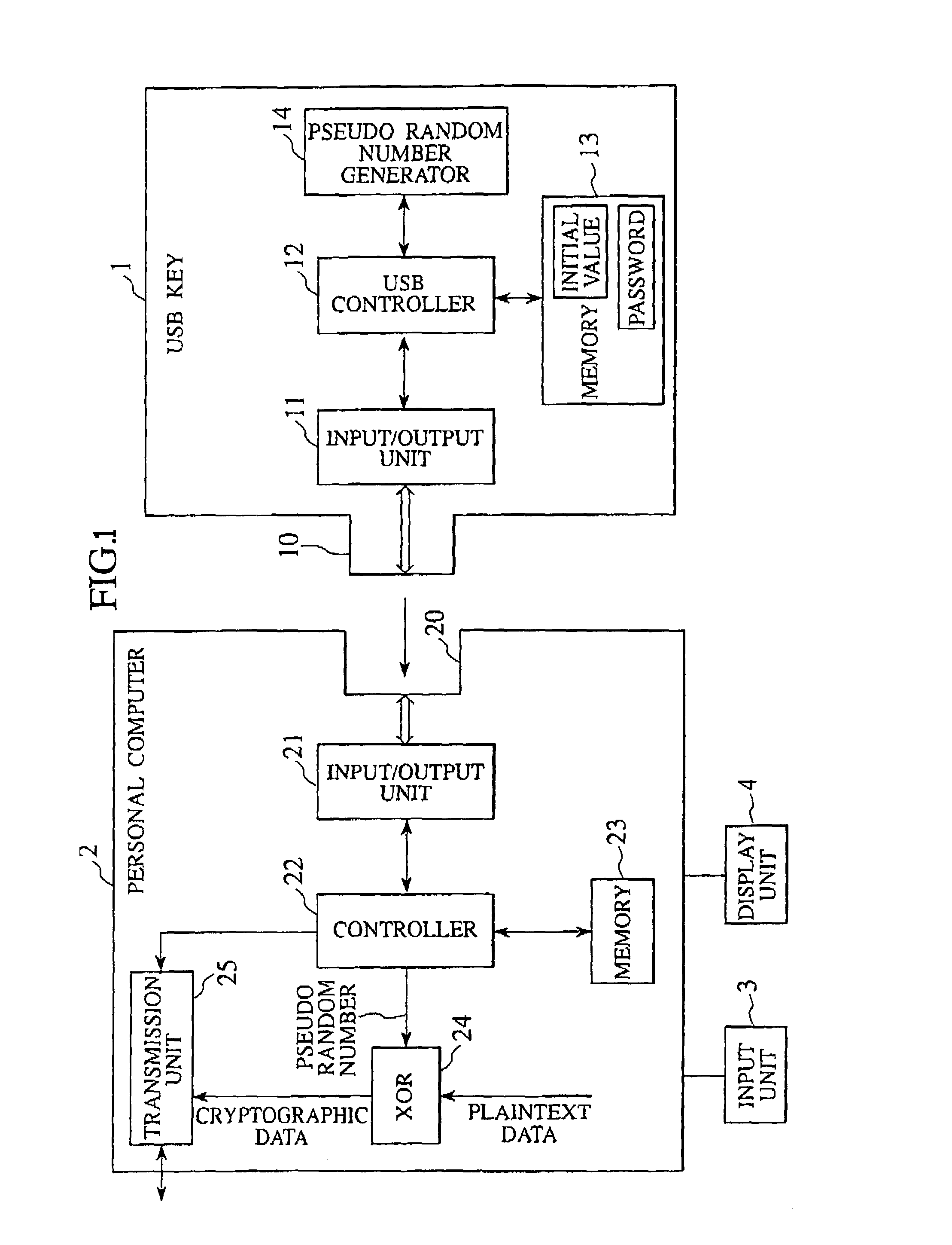
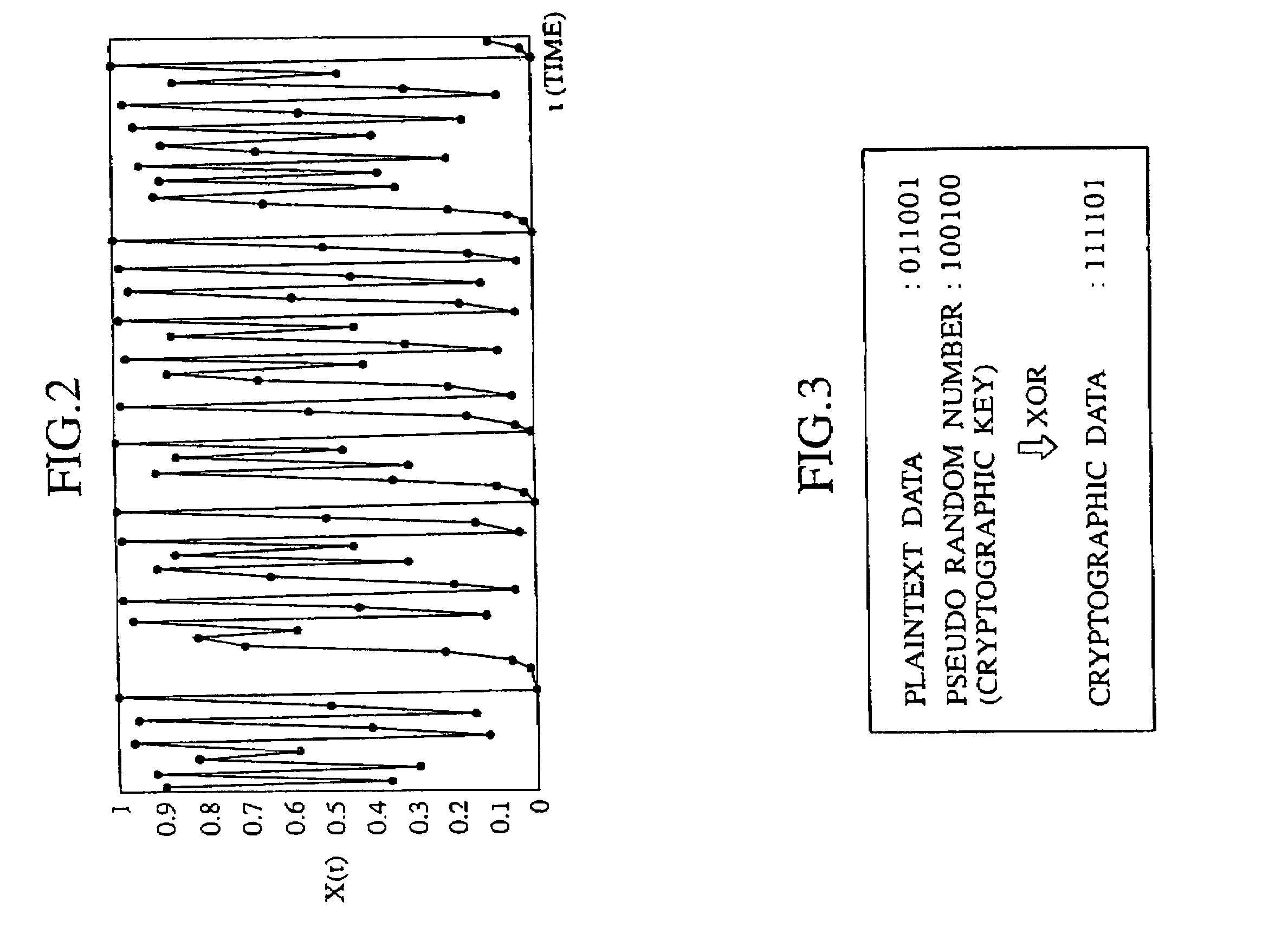
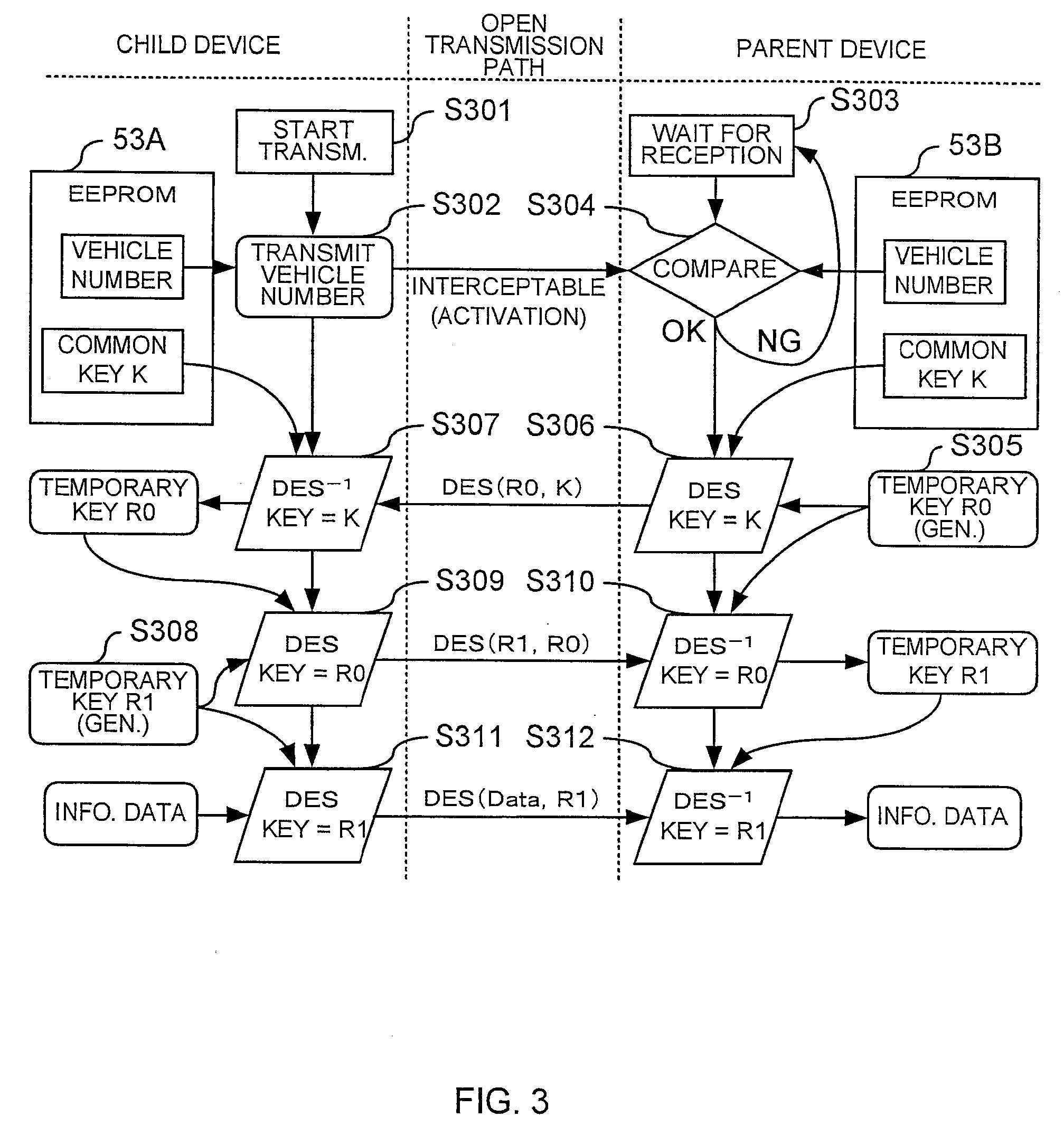
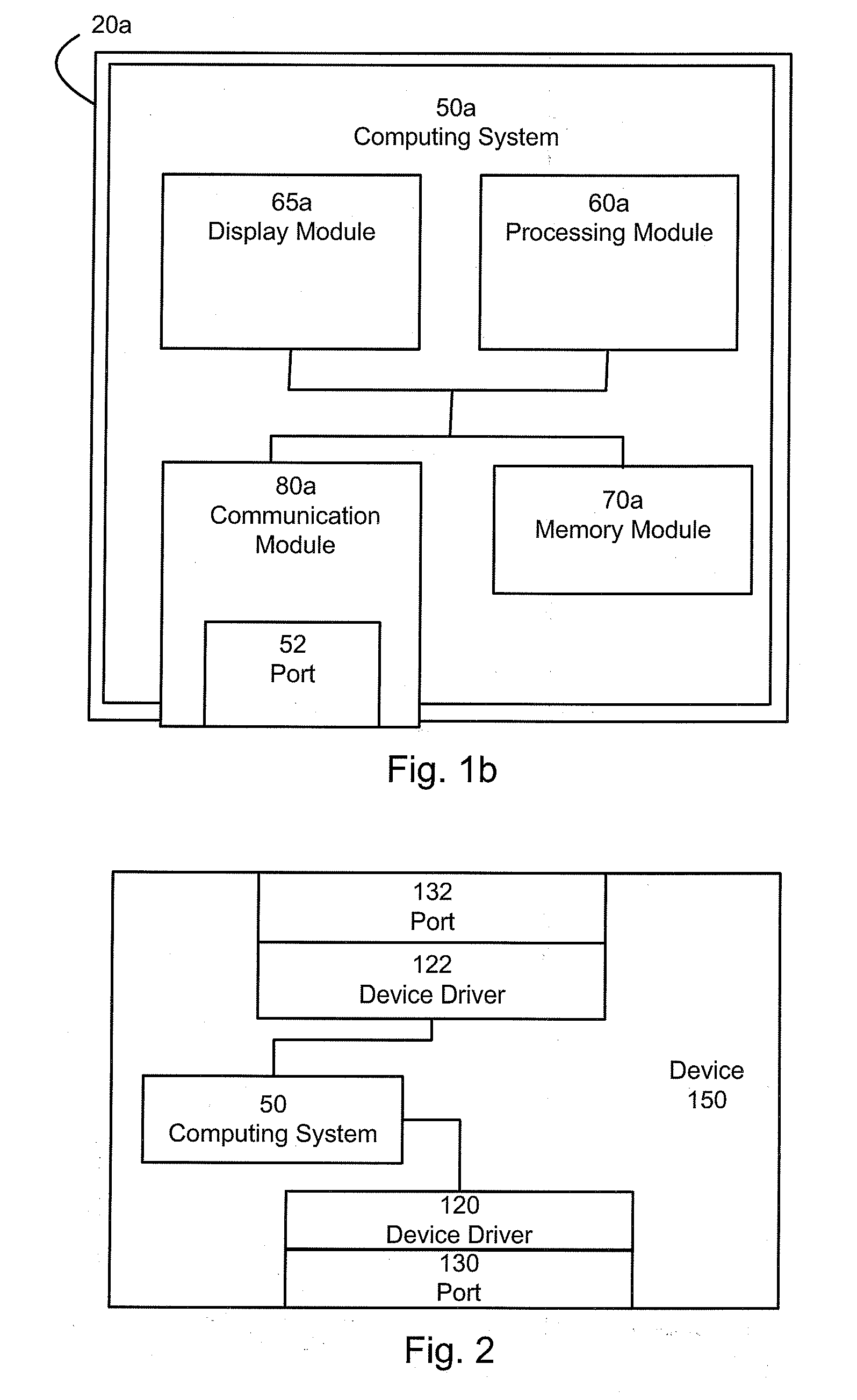
Cryptographic key, encryption device, encryption/decryption device, cryptographic key management device, and decryption device
ActiveUS7269258B2Random number generatorsSecuring communication by chaotic signalsComputer hardwareCryptographic nonce
Owner:YAZAKI CORP
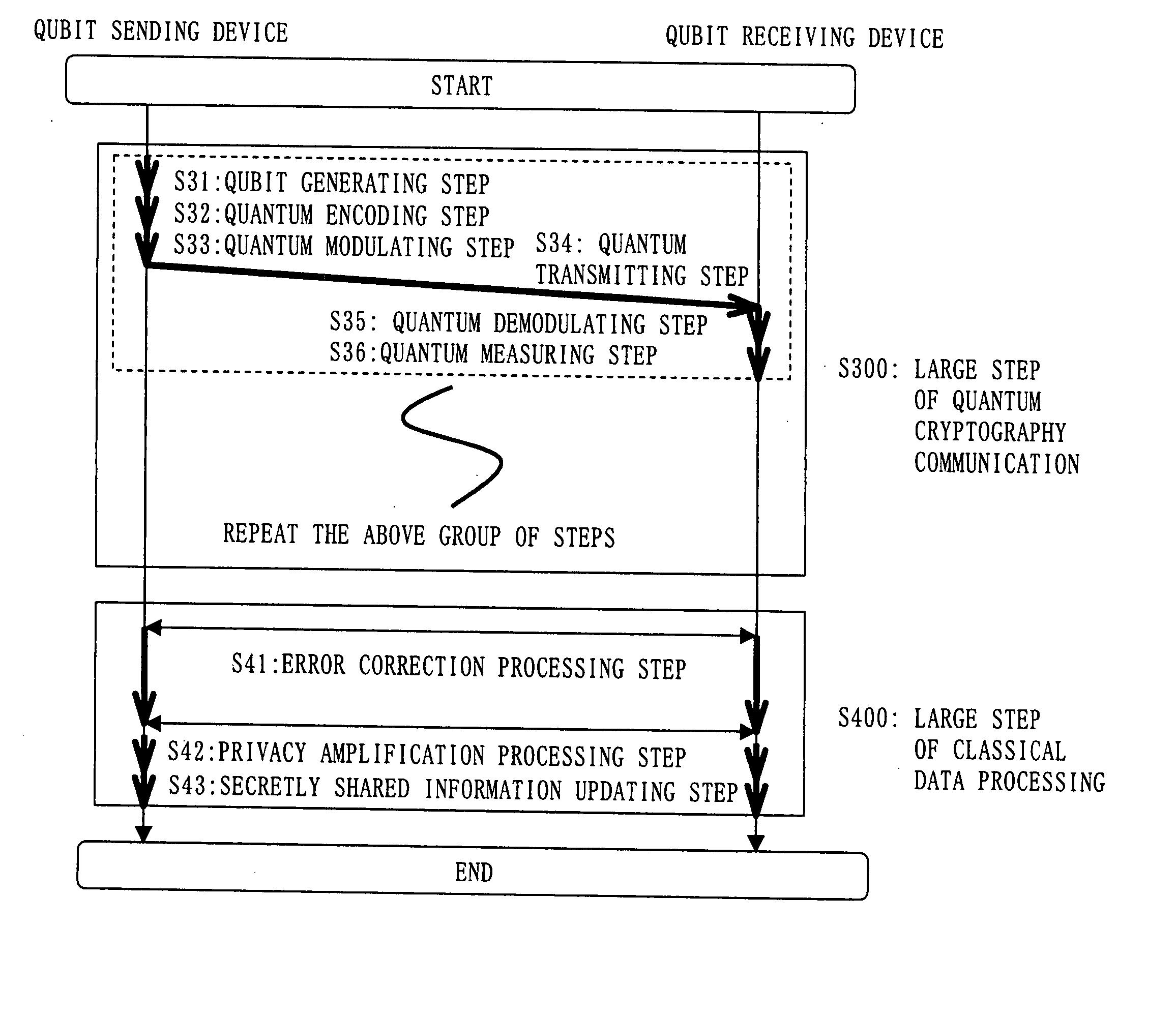
Crytographic communication apparatus
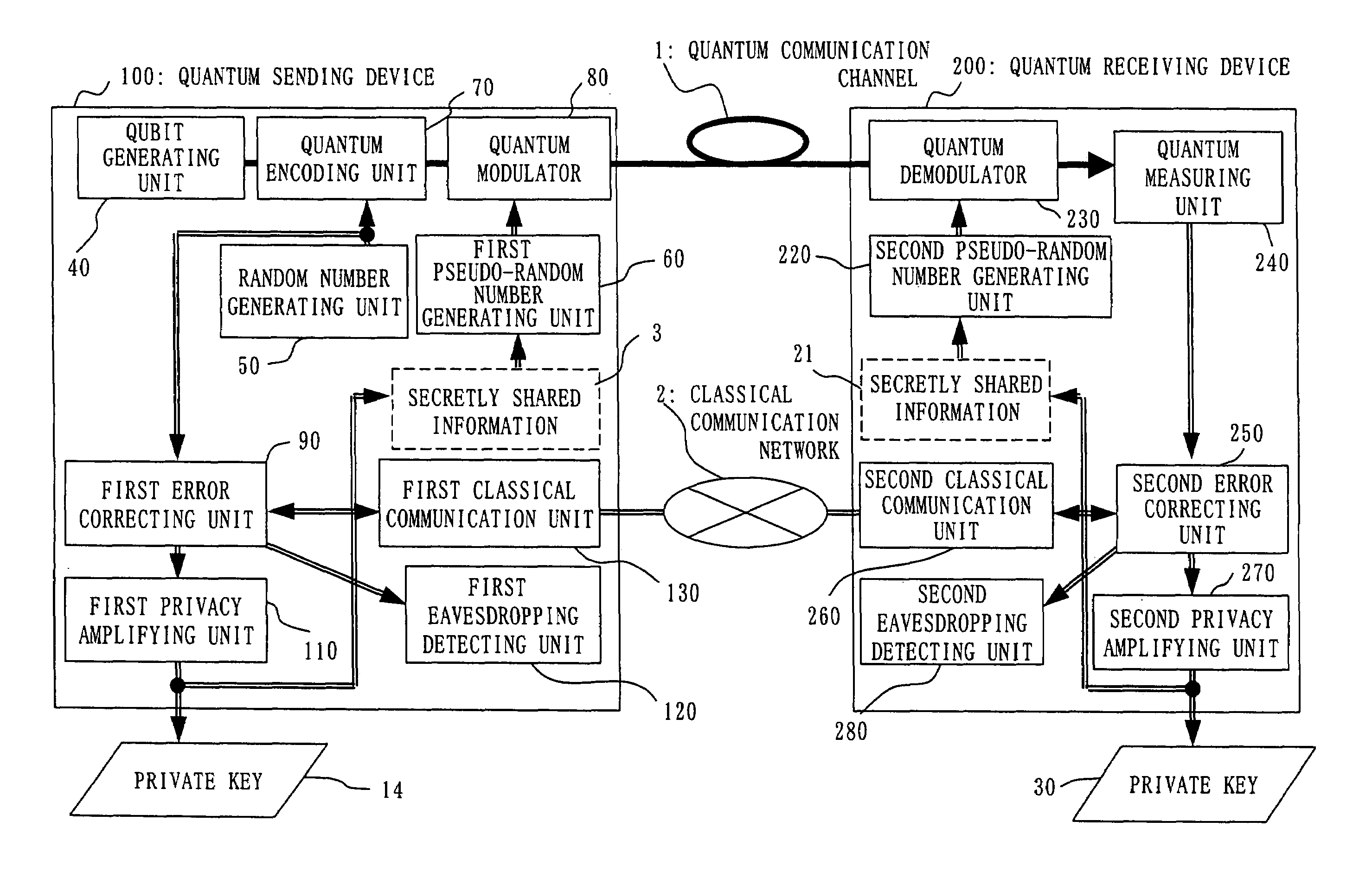
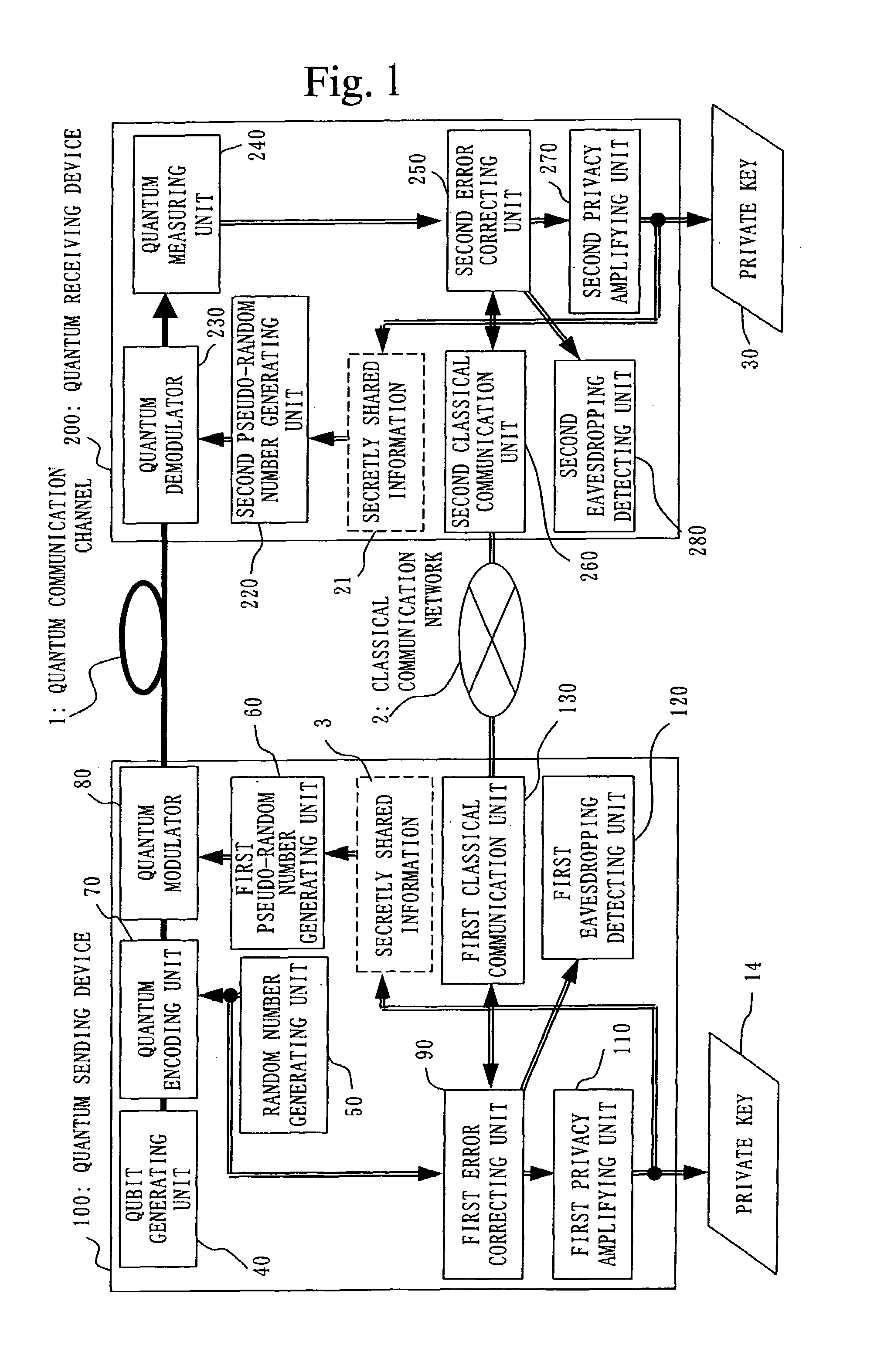
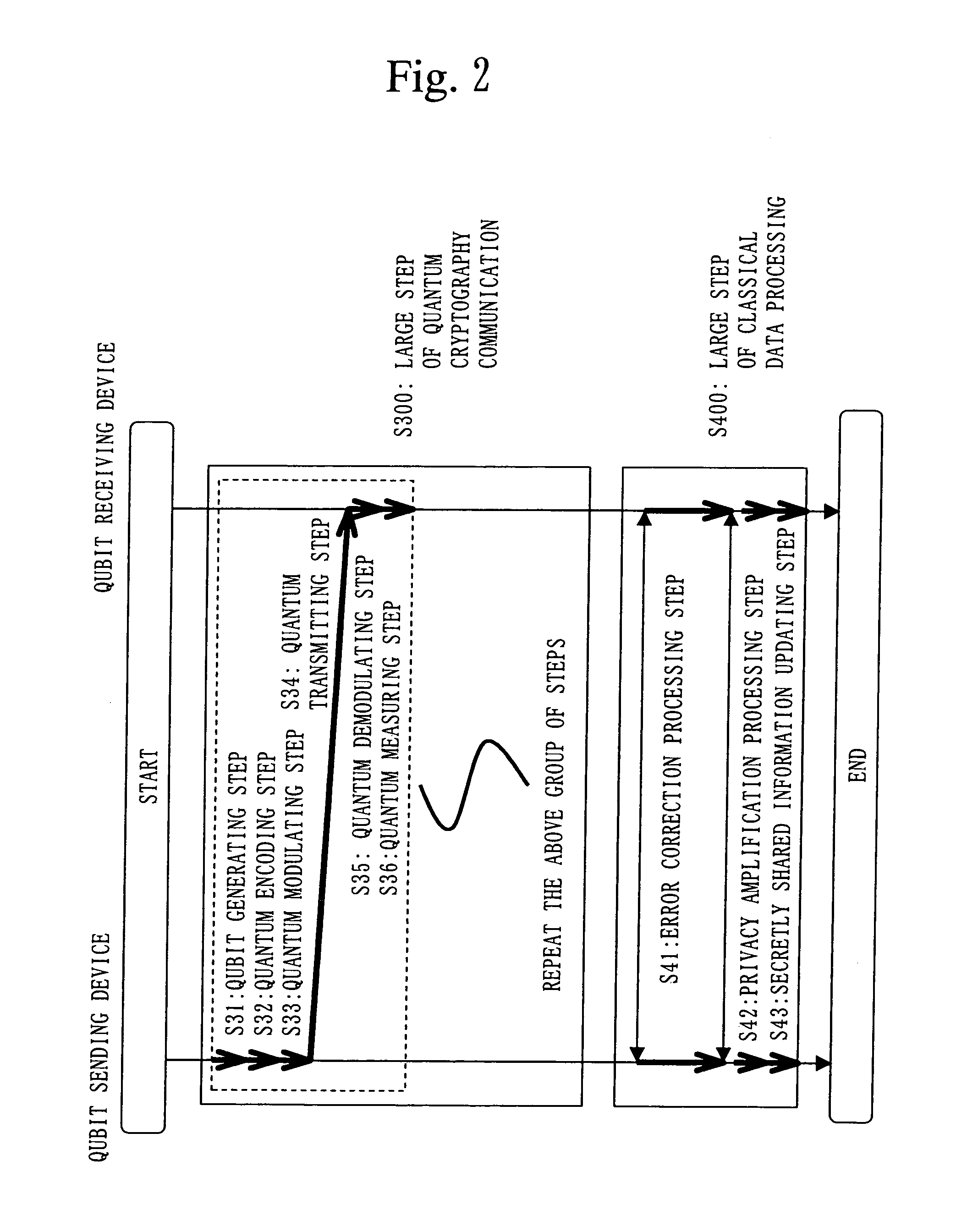
InactiveUS20050157875A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesPseudo random number generationQuantum electrodynamics
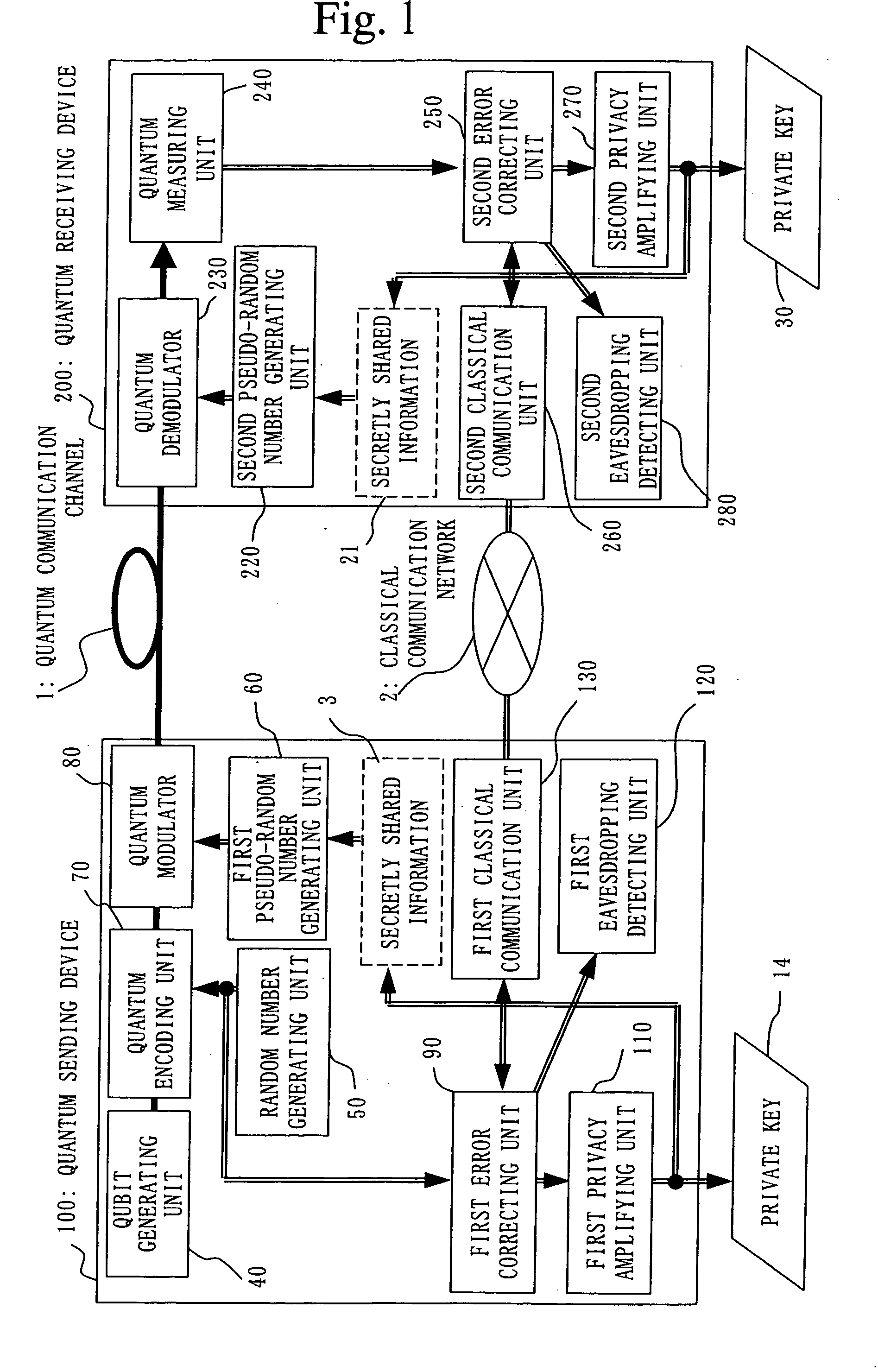
A qubit generating unit 40 generates a qubit having a predetermined quantum state. A qubit encoding unit 70 performs quantum encoding of the generated qubit. A first pseudo-random number generating unit 60 generates a first pseudo-random number from secretly shared information 3 which has been secretly shared with the quantum receiving device 200 in advance. A quantum modulator 80 performs quantum modulation of the qubit on which quantum encoding has been performed based on the first pseudo-random number and sends the modulated qubit to the quantum receiving device 200. A second pseudo-random number generating unit 220 generates a second pseudo-random number from secretly shared information 21 which has been secretly shared with the above quantum sending device 100 in advance synchronously with generation of the above first pseudo-random number. A qubit demodulator 230 performs quantum demodulation of the qubit which has been received from the quantum demodulator 80 based on the second pseudo-random number.
Owner:MITSUBISHI ELECTRIC CORP
Method and apparatus for improved pseudo-random number generation
InactiveUS7007050B2Improve securityRandom number generatorsSecuring communicationSecure communicationMobile Telephone Service
A pseudo-random number generator (PRNG) for a cryptographic processing system is disclosed in which the PRNG is reseeded at each instance of input entropy and in which a standard timestamp variable used in determining random sequence outputs is replaced with a running counter. The method employed by the PRNG demonstrates increased resistance to iterative-guessing attacks and chosen-input attacks than those of previous technologies. The PRNG is suitable for use in, for example, a mobile telephone system for accomplishing secure communications.
Owner:WSOU INVESTMENTS LLC
Pseudo-random number generation method and pseudo-random number generator
InactiveUS20060039558A1Easy to changeHigh encryption strengthRandom number generatorsCoding/ciphering apparatusLinearityNumber generator
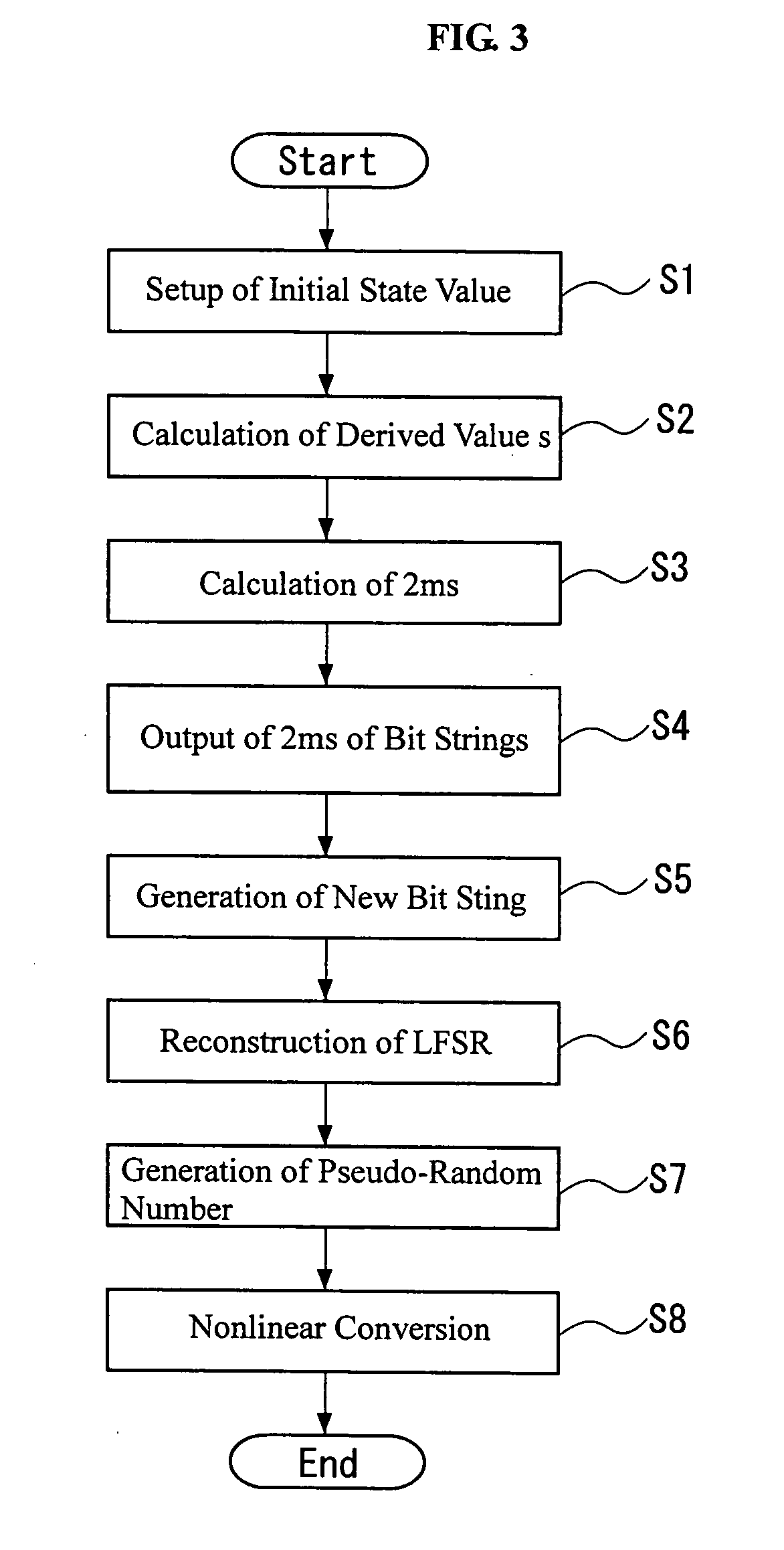
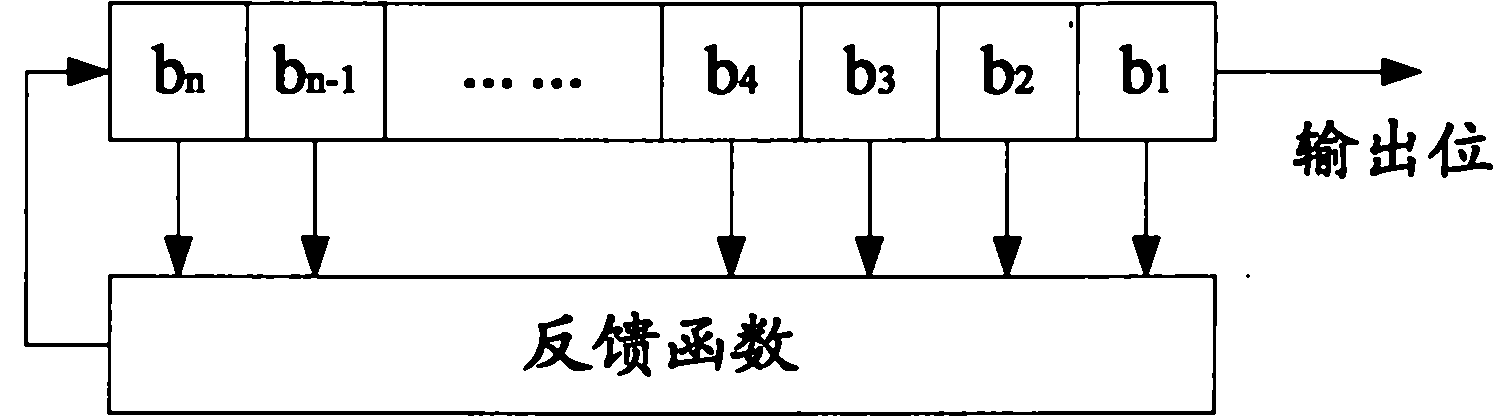
A bit string obtained by sampling, every the number s, bits of a bit string whose output sequence is M sequence, when the bit number per one cycle of the M sequence is prime to the derived value, constitutes M sequence of a linear feedback shift register having other construction. Further, the linear feedback shift register can be determined from bits corresponding to at least two cycles by Berlekamp-Massay algorithm, whereby the linear feedback shift register 11 can be easily and dynamically reconstructed based on the initial state value.
Owner:KOBAYASHI AKIRA +1
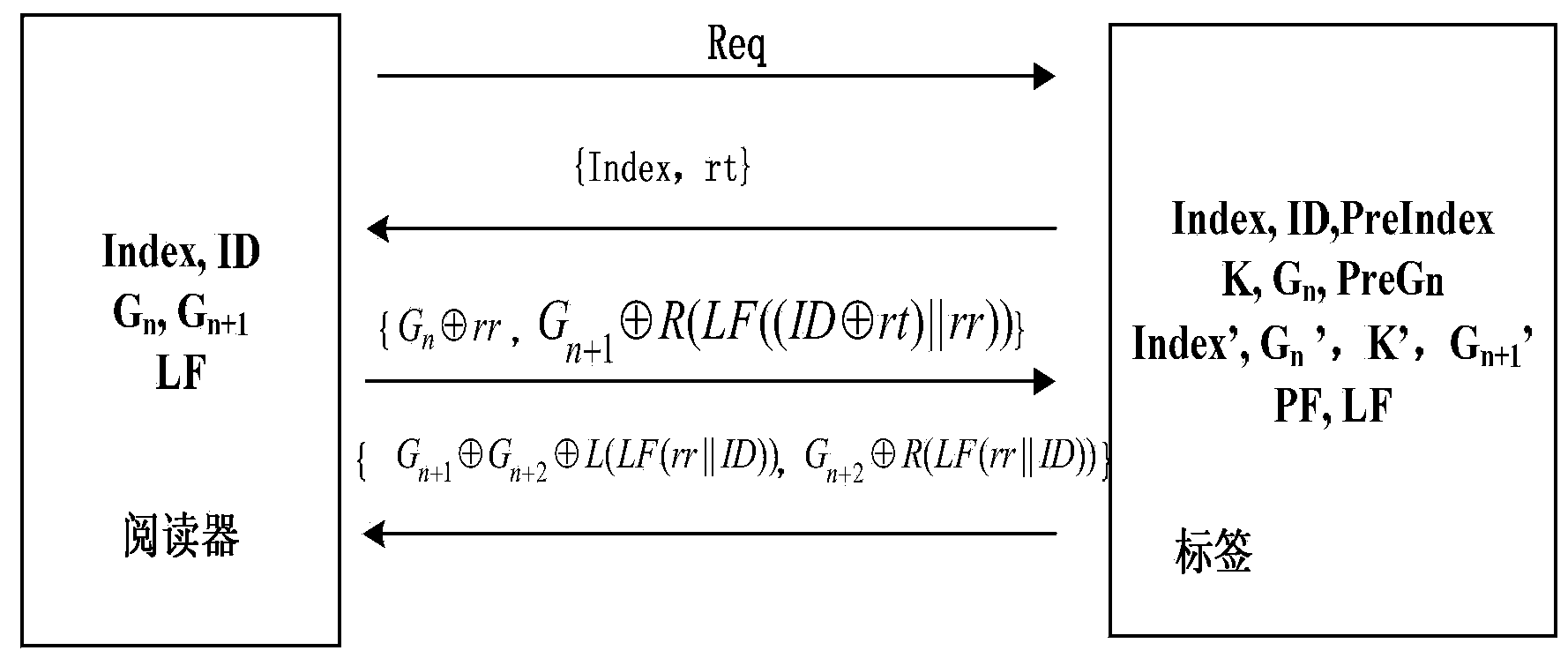
RFID lightweight class bidirectional authentication method based on PUF
InactiveCN103905202AReduce complexityLow costUser identity/authority verificationCo-operative working arrangementsAttackThe Internet
The invention discloses an RFID lightweight class bidirectional authentication method based on a PUF. Information encryption and pseudo random number generation are carried out through a linear feedback shift register protected through a secret key seed, counterfeit attack can be resisted, a pseudo random number generator does not need to be additionally integrated, and complexity and cost of a label are reduced; in the communication process, all communication information is effectively utilized to carry out authentication, the problem of desynchronization attack of out-of-step information between a reader and the label can be effectively solved through falsification and other means, and security is higher. The method can be widely applied to the internet of things and information security authentication fields.
Owner:GUANGDONG UNIV OF TECH
Cryptographic communication apparatus
InactiveUS7649996B2Key distribution for secure communicationSynchronising transmission/receiving encryption devicesQuantum gatePseudo random number generation
Owner:MITSUBISHI ELECTRIC CORP
Method and apparatus for identifying and verifying RFID privacy protection
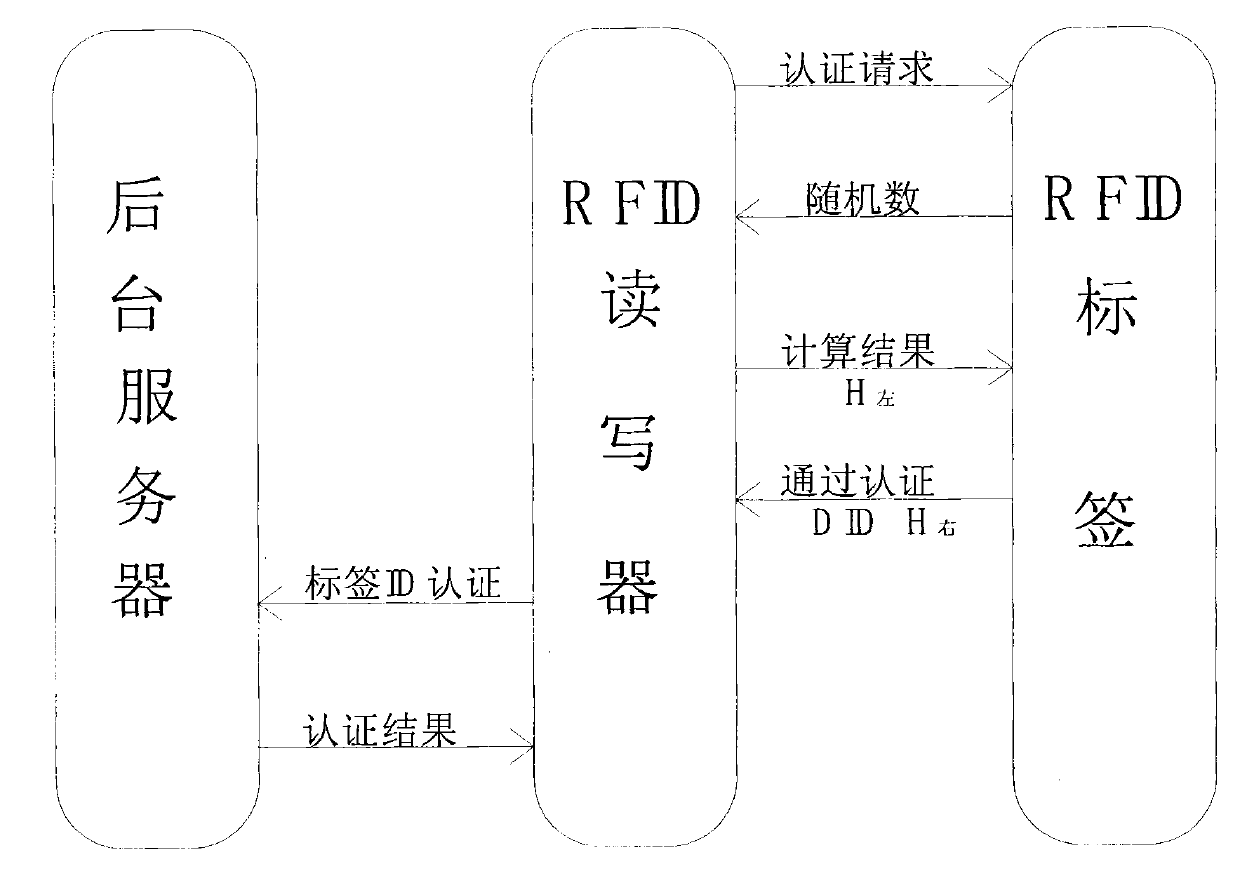
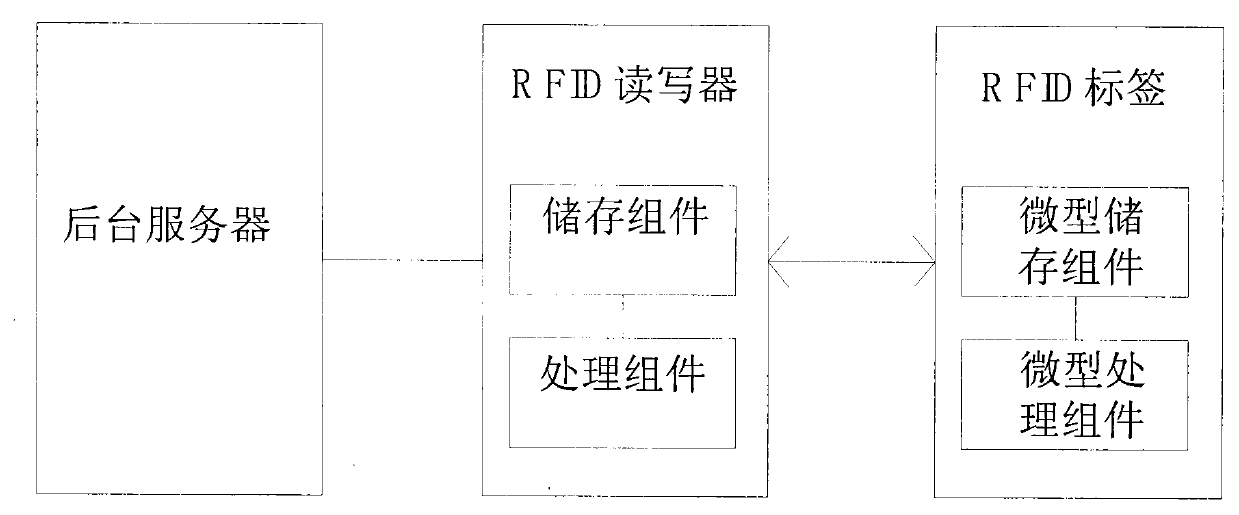
InactiveCN102737260ARealize two-way two-level authenticationReduce security threatsCo-operative working arrangementsTransmissionHash functionCiphertext
The invention discloses a method and an apparatus for identifying and verifying RFID privacy protection. Attacks of illegal reader scanning and position tracking are resisted by mutual authentication between an RFID tag and an RFID reader, and one-way hash function H(x) and exclusive-or operation are introduced in the authentication of the RFID tag and the RFID reader; a pseudo-random number generating module and a one-way hash function module are introduced in the RFID tag, the pseudo-random number generating module and the one-way hash function module are also introduced in the RFID reader, a background server stores an ID of the RFID tag, and a shared ciphertext Kr is also stored in the RFID tag and the RFID reader. According to the invention, the tag, the reader and a background database carry out mutual authentication successively and independently, which not only realizes a bidirectional authentication, but also realizes a two-level authentication carried out by the reader and the background database on the tag. A bidirectional two-level authentication between the tag and the reader in an RFID system is realized; various security threats faced by the RFID system can be comprehensively and effectively prevented or reduced, and especially attacks such as illegal reader scanning, position tracking and the like are comprehensively resisted.
Owner:深联致远(北京)科技有限公司
Random Number Generating Circuit
InactiveUS20070067374A1Difficult to predictRandom number generatorsEncryption apparatus with shift registers/memoriesPseudo random number generationComputer science
Owner:SANYO ELECTRIC CO LTD
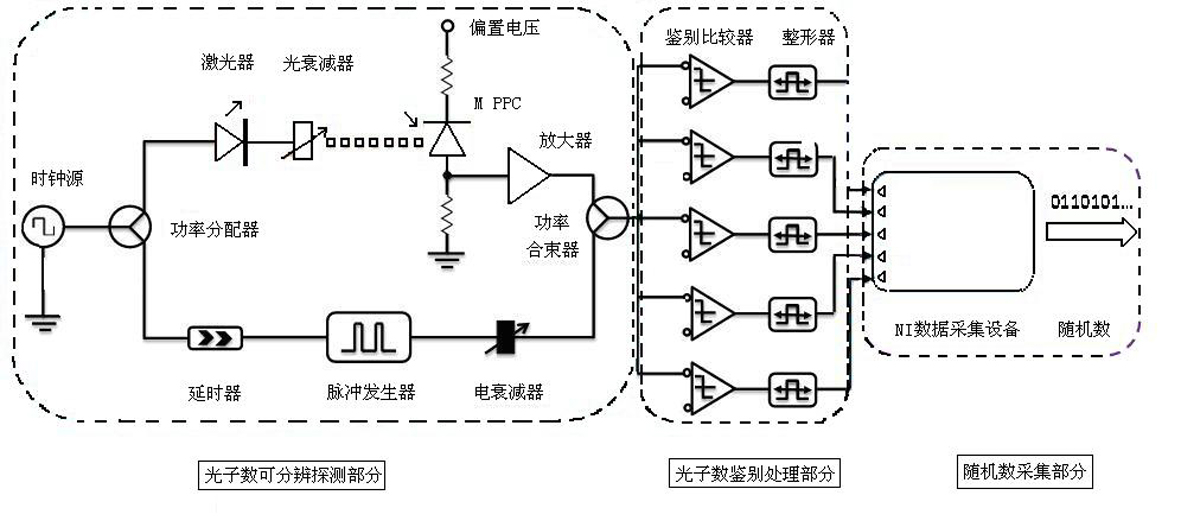
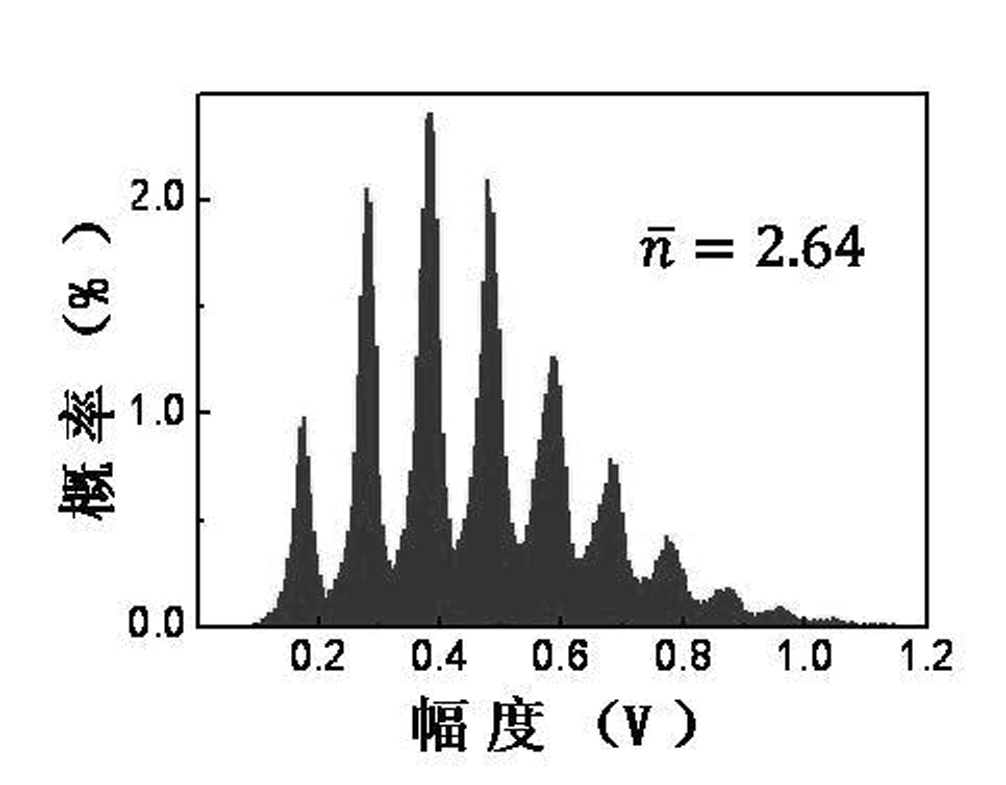
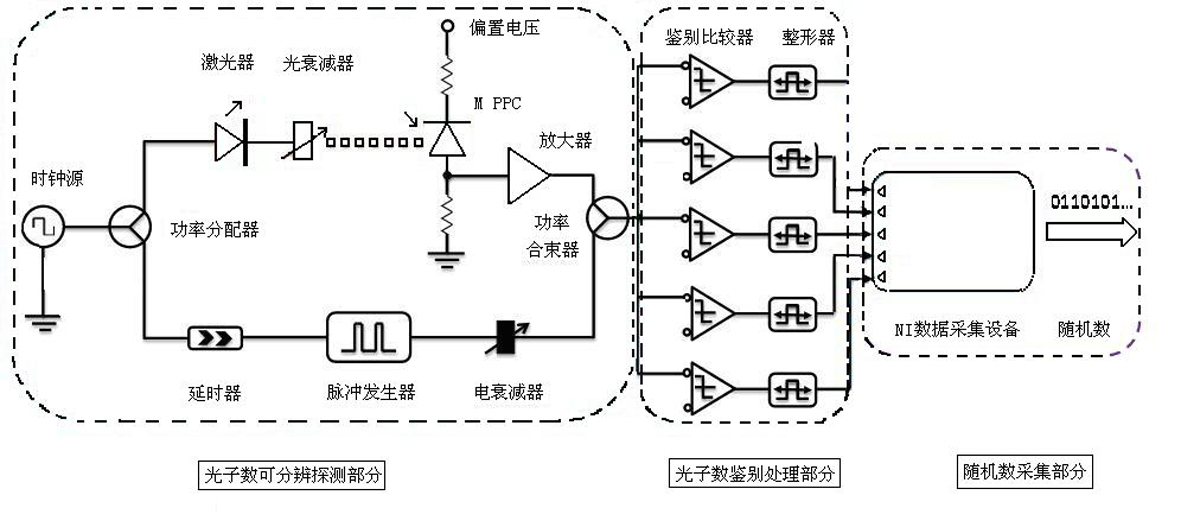
Photon-number distinguishable detection-based true random number generator
InactiveCN101980146ANo complex post-processing requiredRandom number generatorsSecure communicationProcess module
The invention discloses a photon-number distinguishable detection-based true random number generator and belongs to the class of quantum secure communication. Different photon-number incident events are combined into a 2-bit random number sequence according to the uncertainty principle of poisson distribution by using the characteristics of a photon-number distinguishable detector capable of distinguishing incident photon numbers. The true random number generator mainly comprises a photon-number distinguishable detection module, a photon-number identifying and processing module and a random number acquisition module and can generate high-speed random secret keys needed in the quantum secure communication. The true random number generator has stable and reliable random sources; the generated true random number cannot be repeated or deciphered by the random characteristics of light quanta; a complex post-processing procedure is not needed; and the true random number generator is convenient to use.
Owner:EAST CHINA NORMAL UNIV
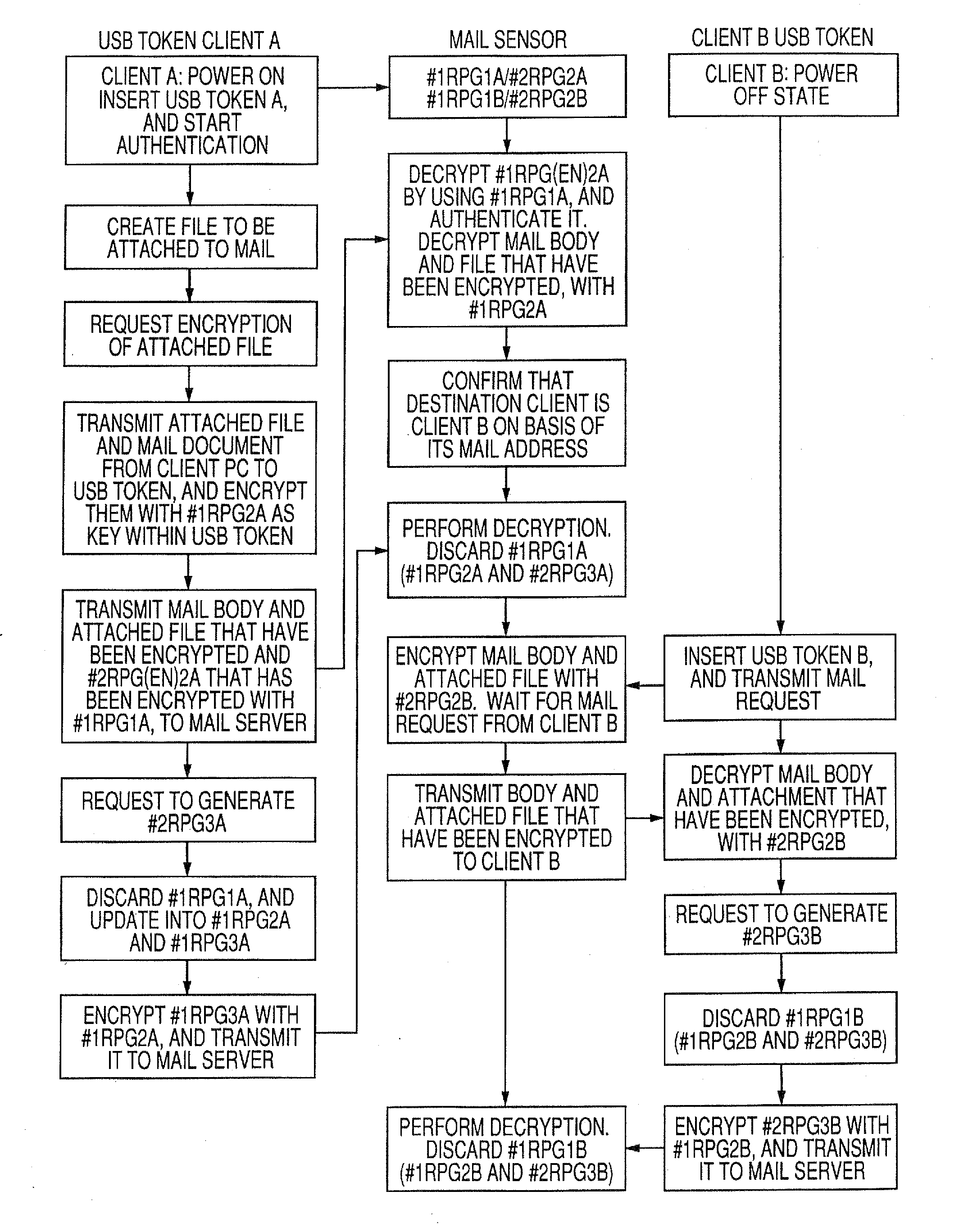
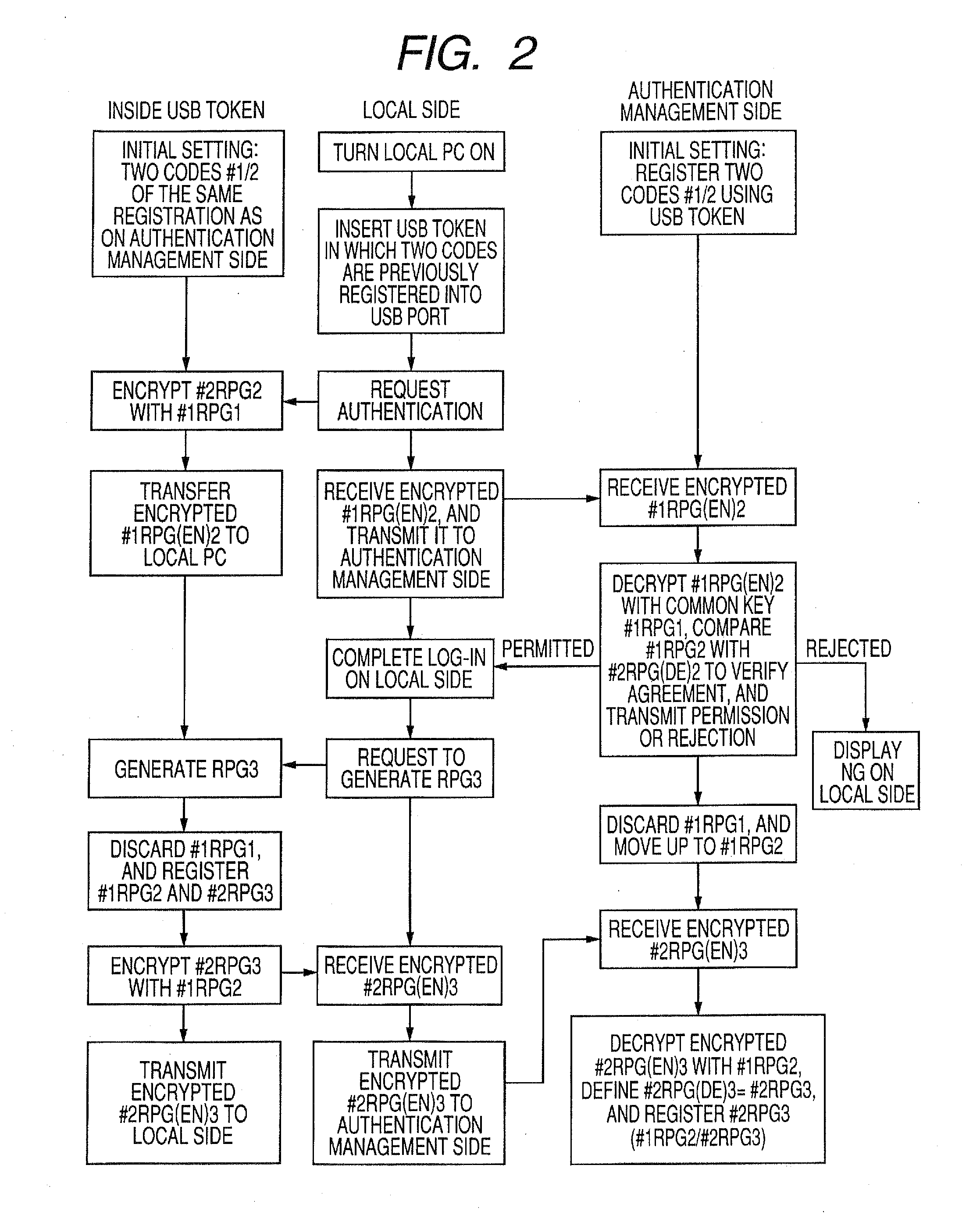
Authentication device using true random number generating element or pseudo-random number generating element, authentication apparatus, and authentication method
InactiveUS20120210127A1Limiting the number of usersUser identity/authority verificationUnauthorized memory use protectionUSBAuthentication system
Provided are an authentication device using a true random number generating element or a pseudo-random number generating element, for example, a USB token, an authentication apparatus using the same, an authentication method, an authentication system and the like. In the authentication system, the authentication device is prepared on a user side, and one code generated in the authentication device is used to encrypt another code. The authentication apparatus registers the codes and decrypts the encrypted code sent from the authentication device by using the registered codes to perform an authentication.
Owner:KAMEDA OSAMU +1
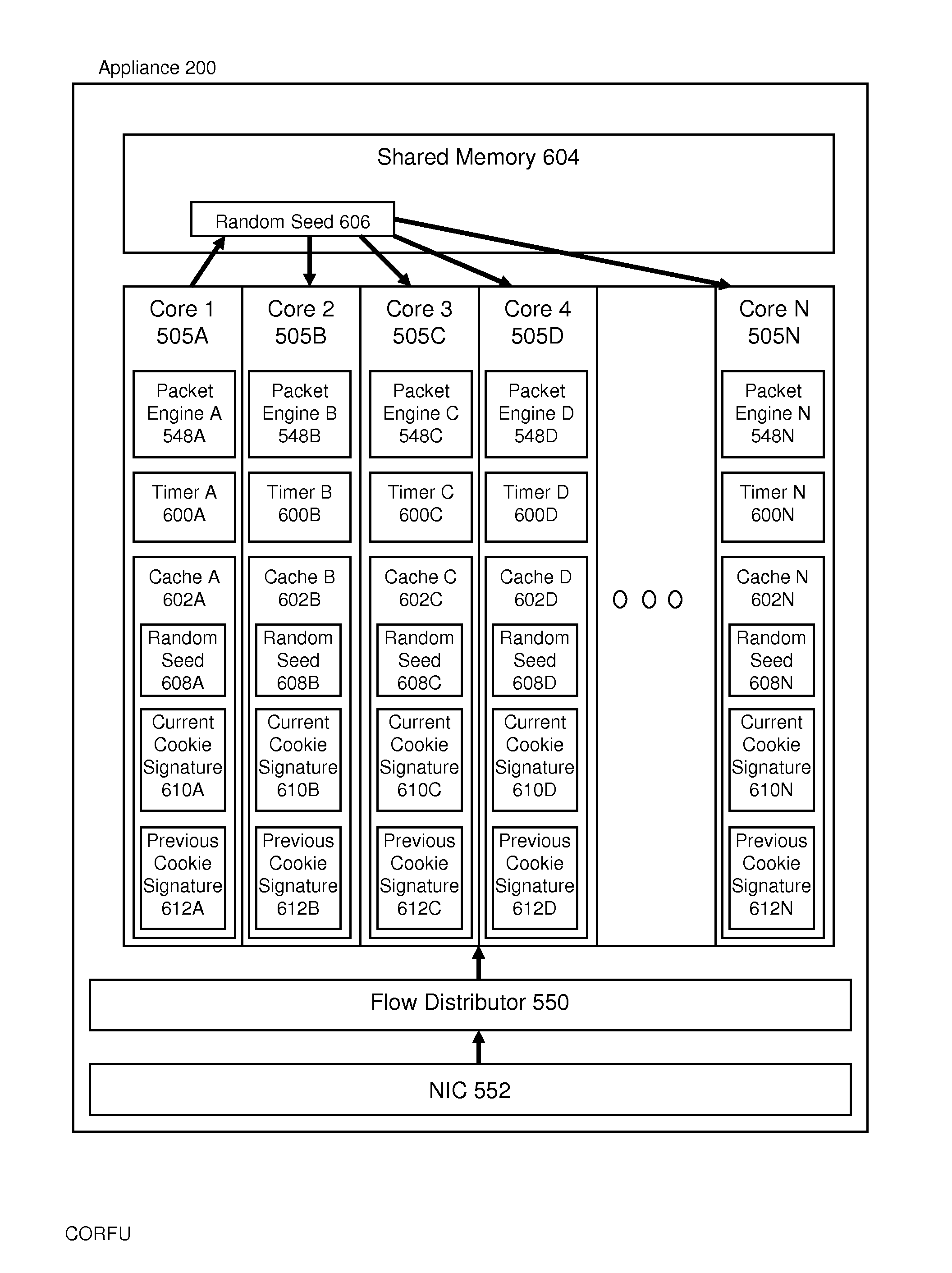
Systems and methods for generating and managing cookie signatures for prevention of HTTP denial of service in multi-core system
The present application is directed towards systems and methods for generating and maintaining cookie consistency for security protection across a plurality of cores in a multi-core system. A packet processing engine executing on one core designated as a primary packet processing engine generates and maintains a global random seed. The global random seed may be used as an initial seed for creation of cookie signatures by each of a plurality of packet processing engines executing on a plurality of cores of the multi-core system using a deterministic pseudo-random number generation function such that each core creates an identical set of cookie signatures.
Owner:CITRIX SYST INC
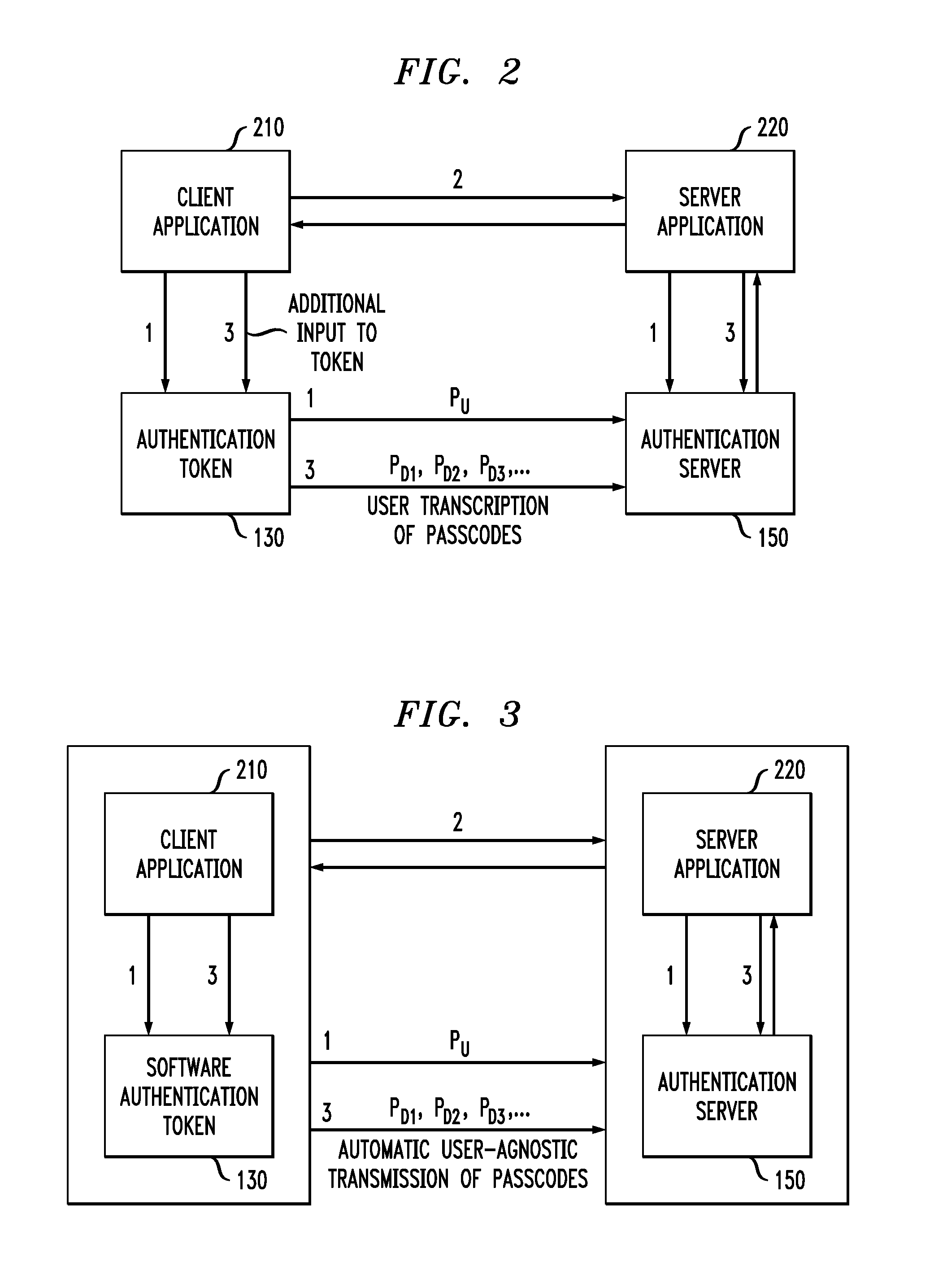
Event-based data signing via time-based one-time authentication passcodes
ActiveUS9225717B1Readily apparentEncryption apparatus with shift registers/memoriesDigital data processing detailsUser authenticationPseudo random number generation
Methods and apparatus are provided for signing data transactions using one-time authentication passcodes. User authentication passcodes are generated by generating a time-based user authentication passcode based on a forward-secure pseudorandom number, wherein the generated time-based user authentication passcode is used for authentication of the user; and generating an event-based user authentication passcode based on a forward-secure pseudorandom number, wherein the generated event-based user authentication passcode is used to sign one or more data transactions. The generation of an event-based user authentication passcode can be performed on-demand. The generation of the event-based user authentication passcode can optionally be performed substantially simultaneously with the generation of the time-based user authentication passcode.
Owner:EMC IP HLDG CO LLC
Cascaded stream cipher
ActiveUS20020054679A1Random number generatorsSecret communicationNumber generatorPseudo random number generation
A pseudo-random number generating circuit and method, comprising: a plurality of pseudo-random number generator (PRNG) units combined in a cascade structure of several layers to produce a pseudo-random output stream, the PRNG units of any given layer running more slowly than those PRNG units of more downstream layers of the cascade structure and running more quickly than those PRNG units of more upstream layers of the cascade structure, the PRNG units including a relatively slow but cryptographically very secure PRNG unit feeding the most upstream layer of the cascade structure, and very fast, but possibly cryptographically insecure PRNG unit at the most downstream layer.
Owner:VESELY IVAN
Cascaded stream cipher
InactiveUS6961426B2Random number generatorsSecret communicationPseudo random number generationNumber generator
Owner:VESELY IVAN
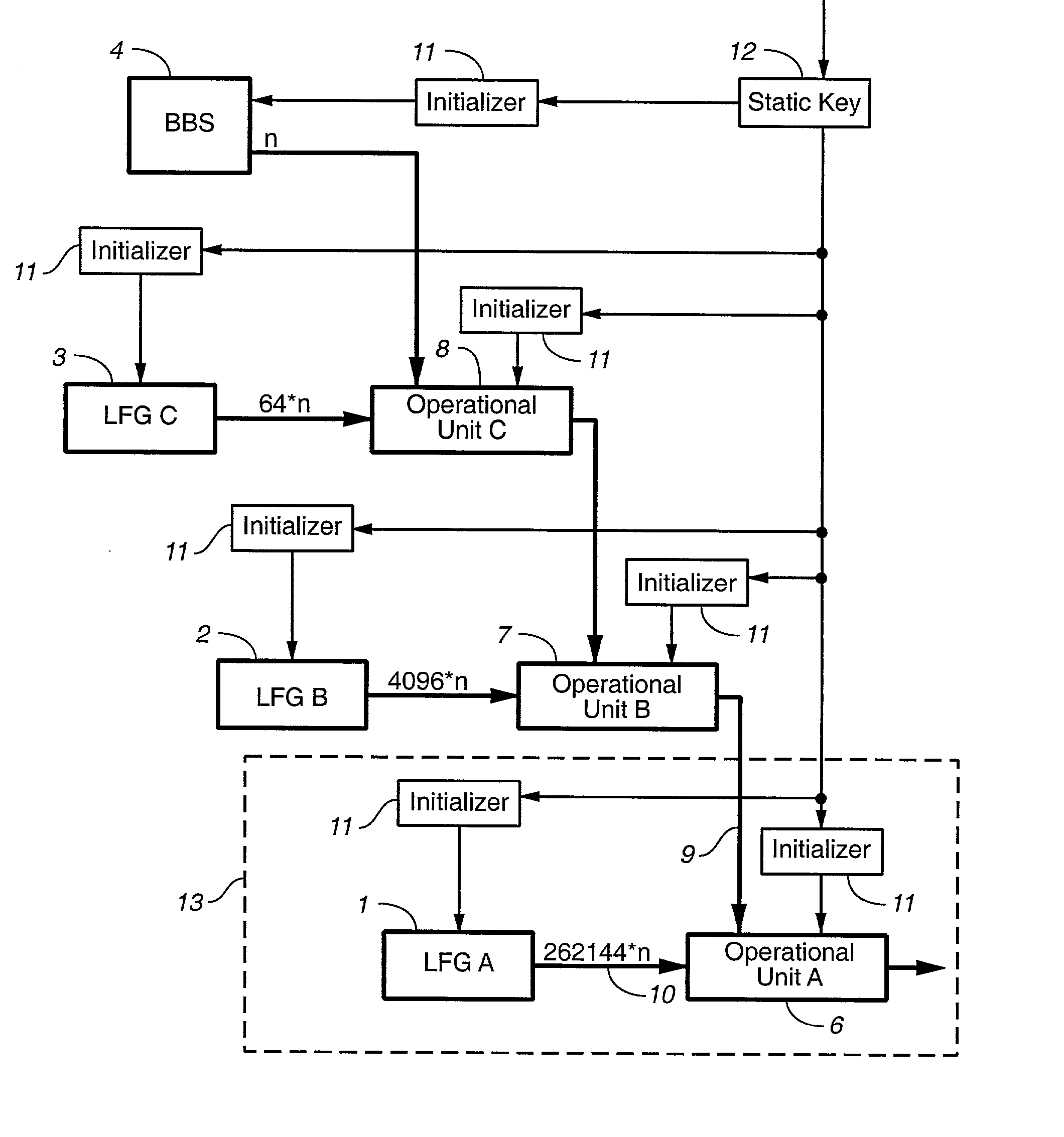
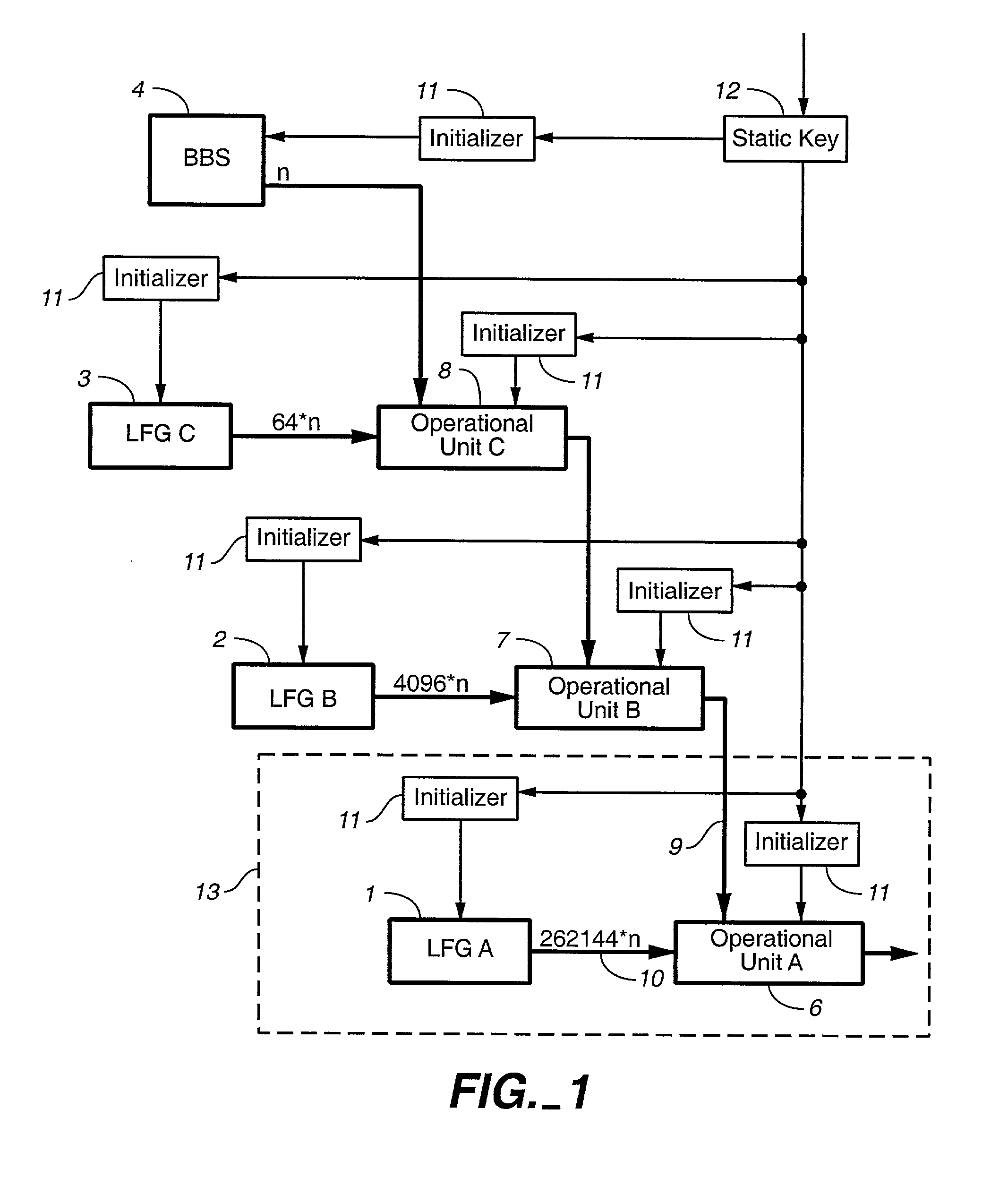
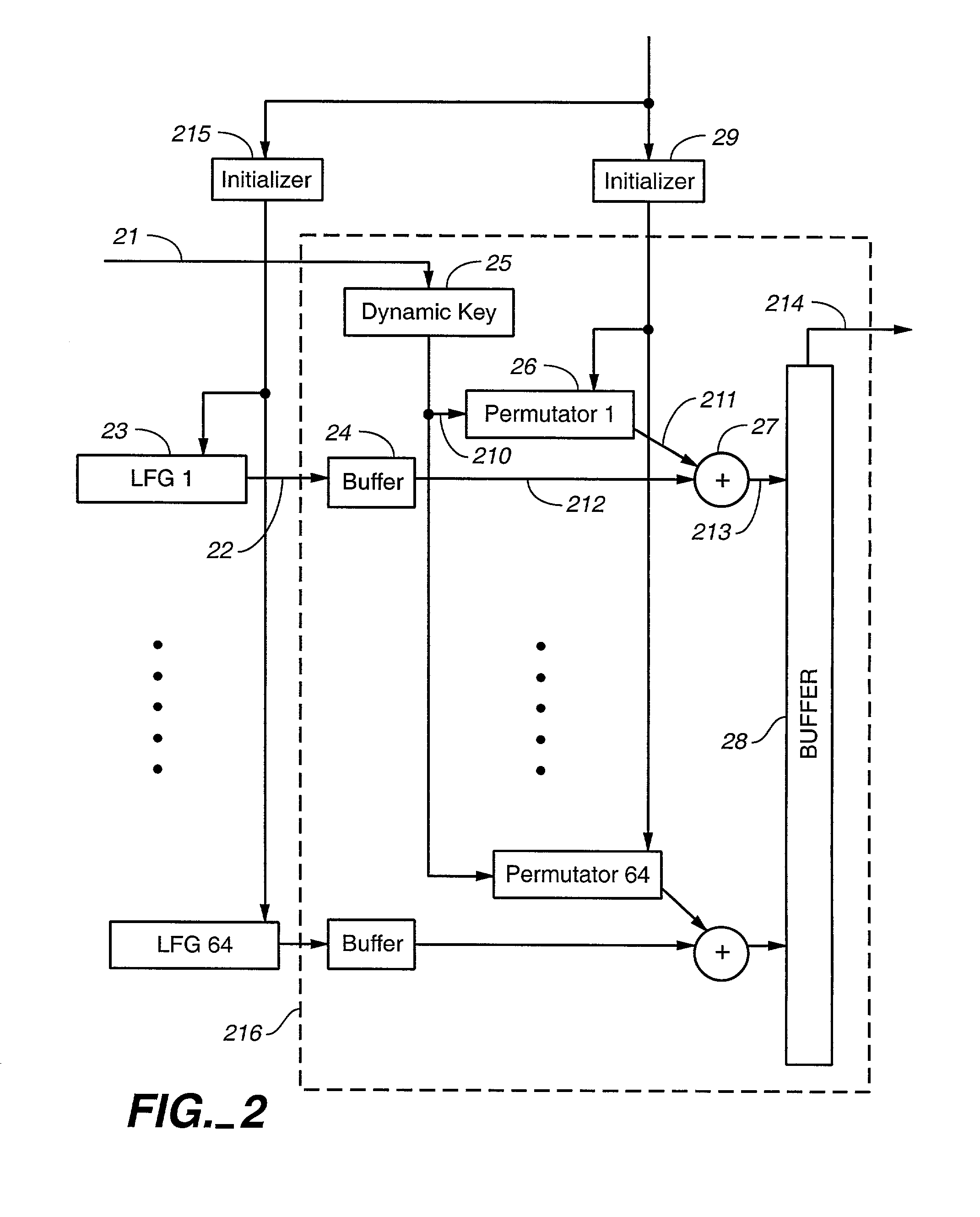
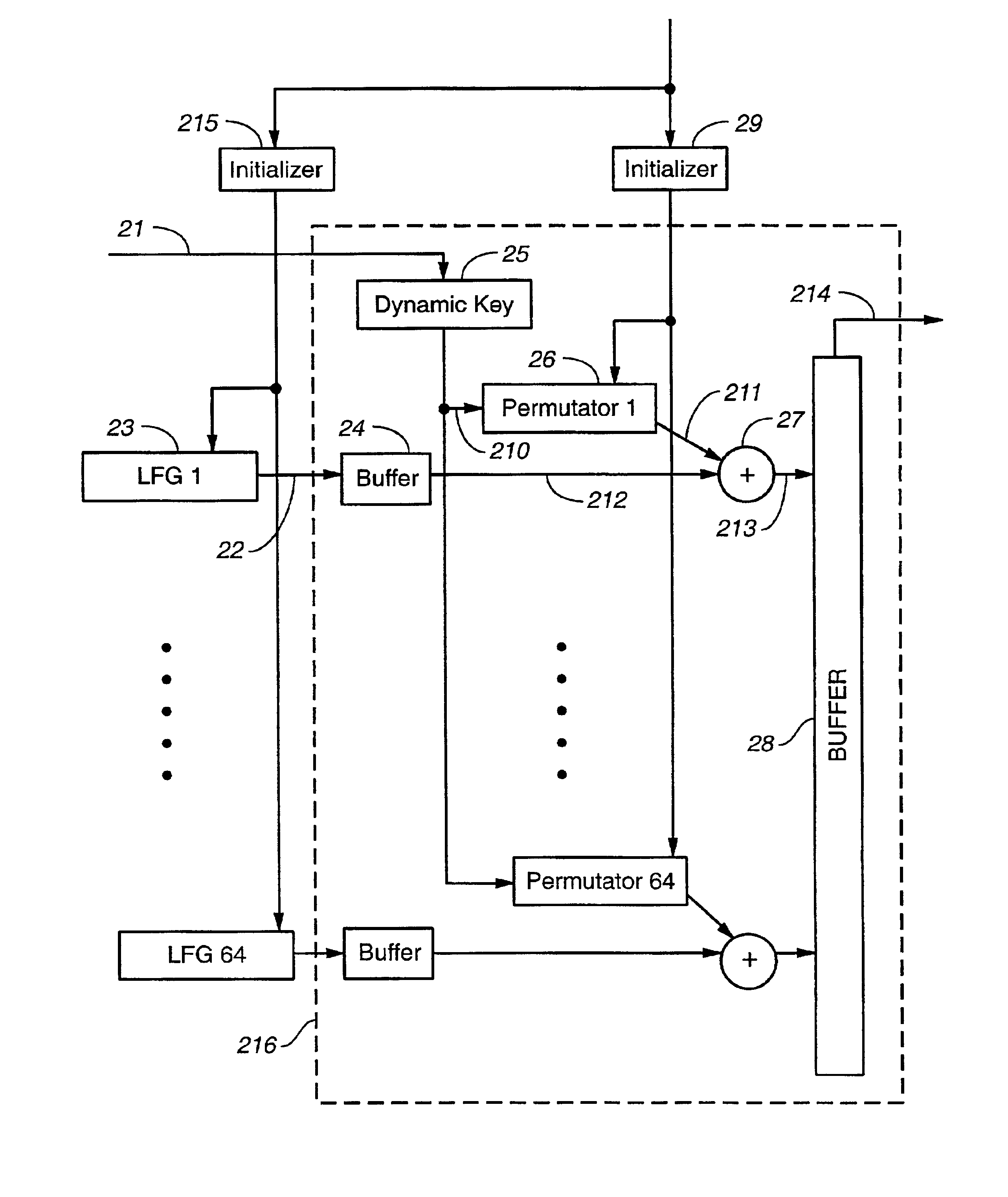
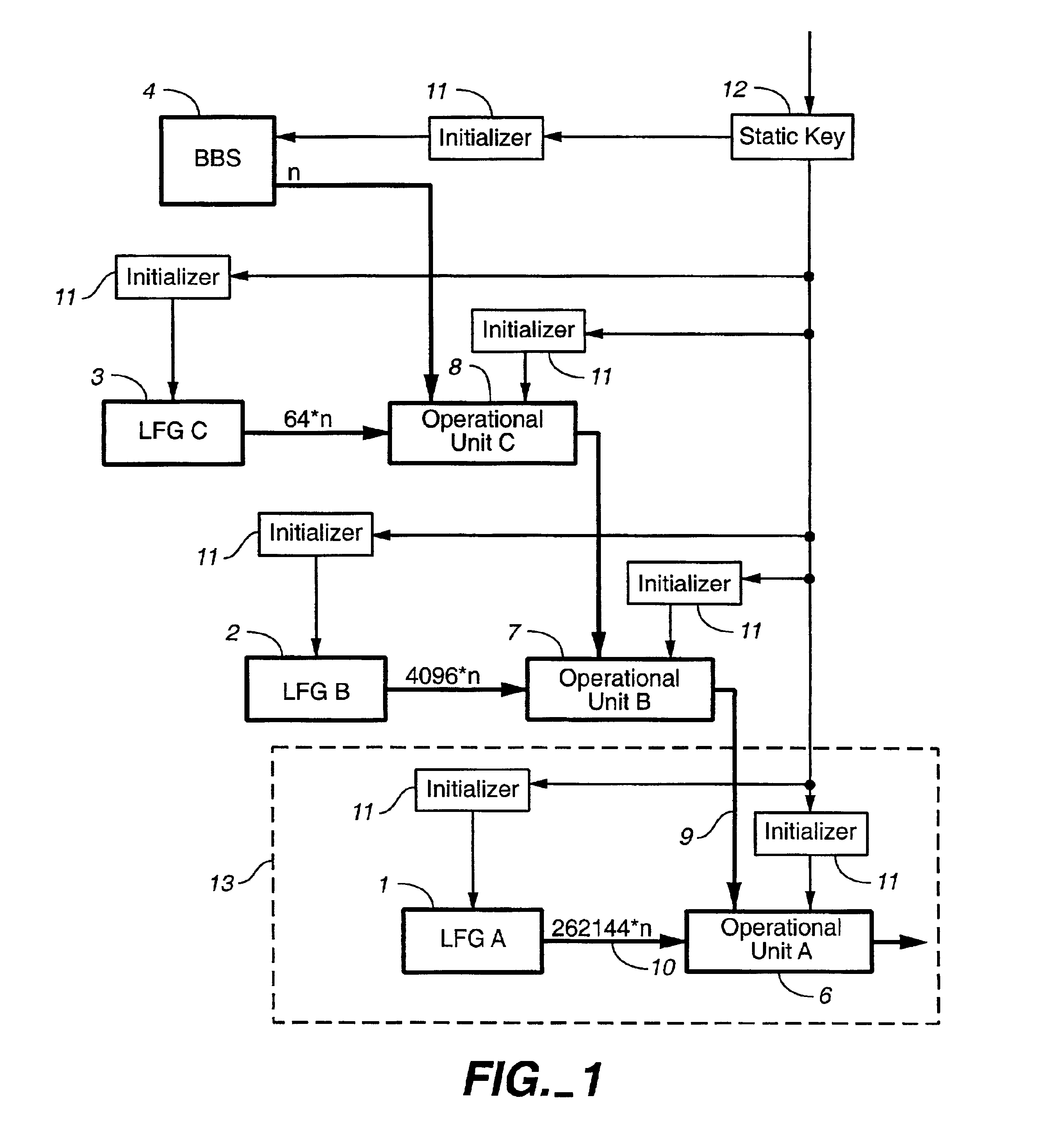
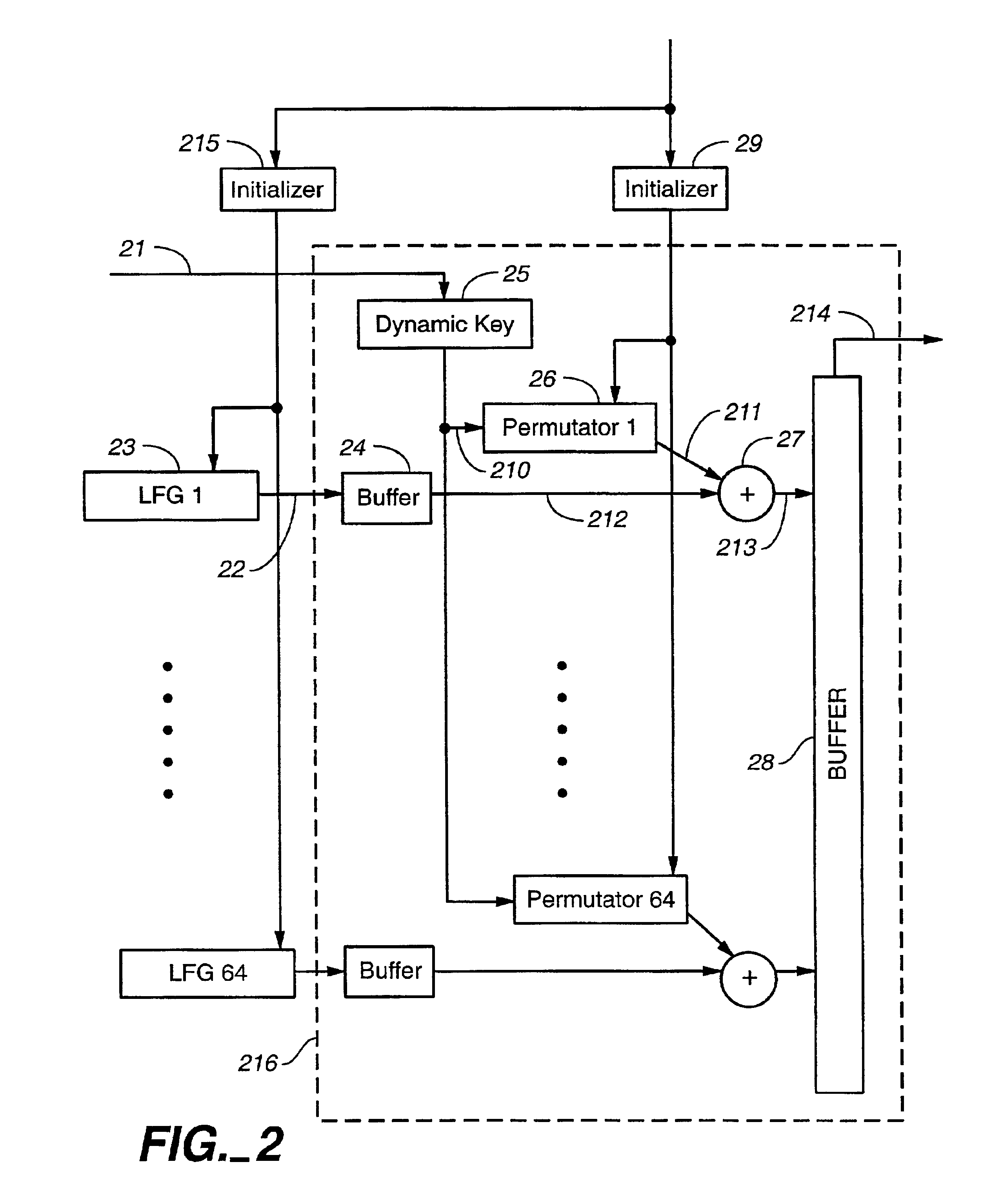
Pseudo-random number generation based on periodic sampling of one or more linear feedback shift registers
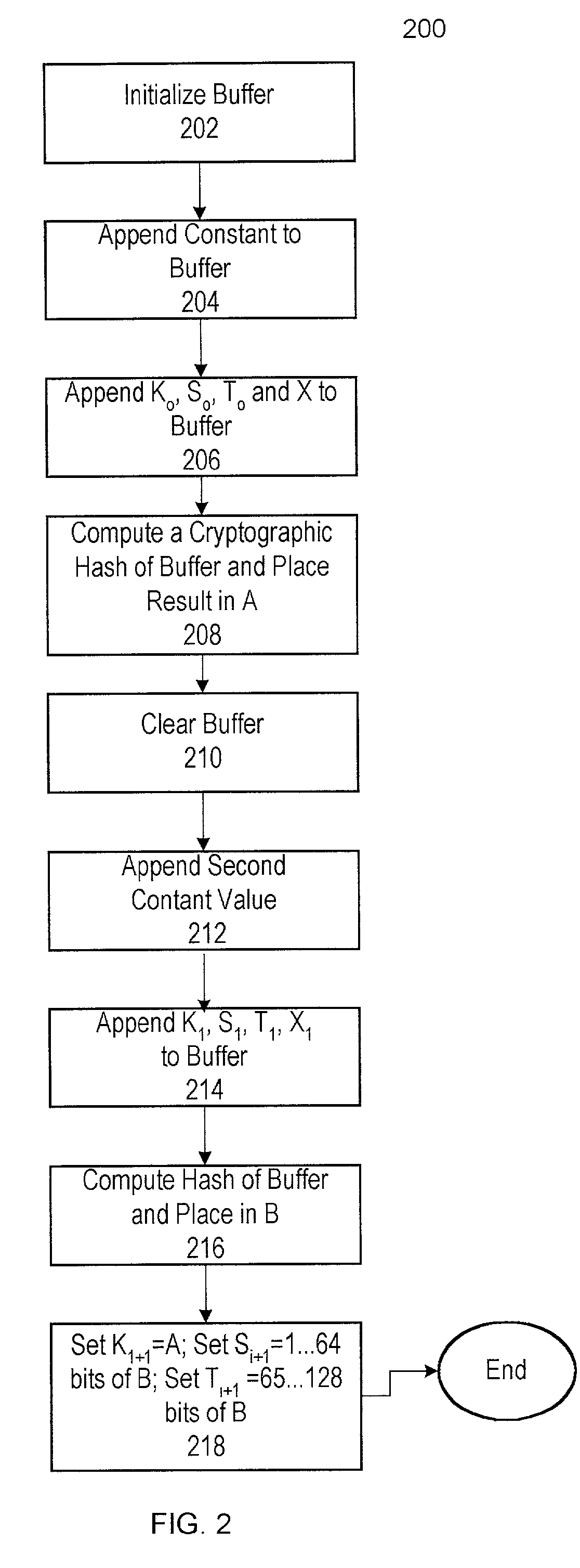
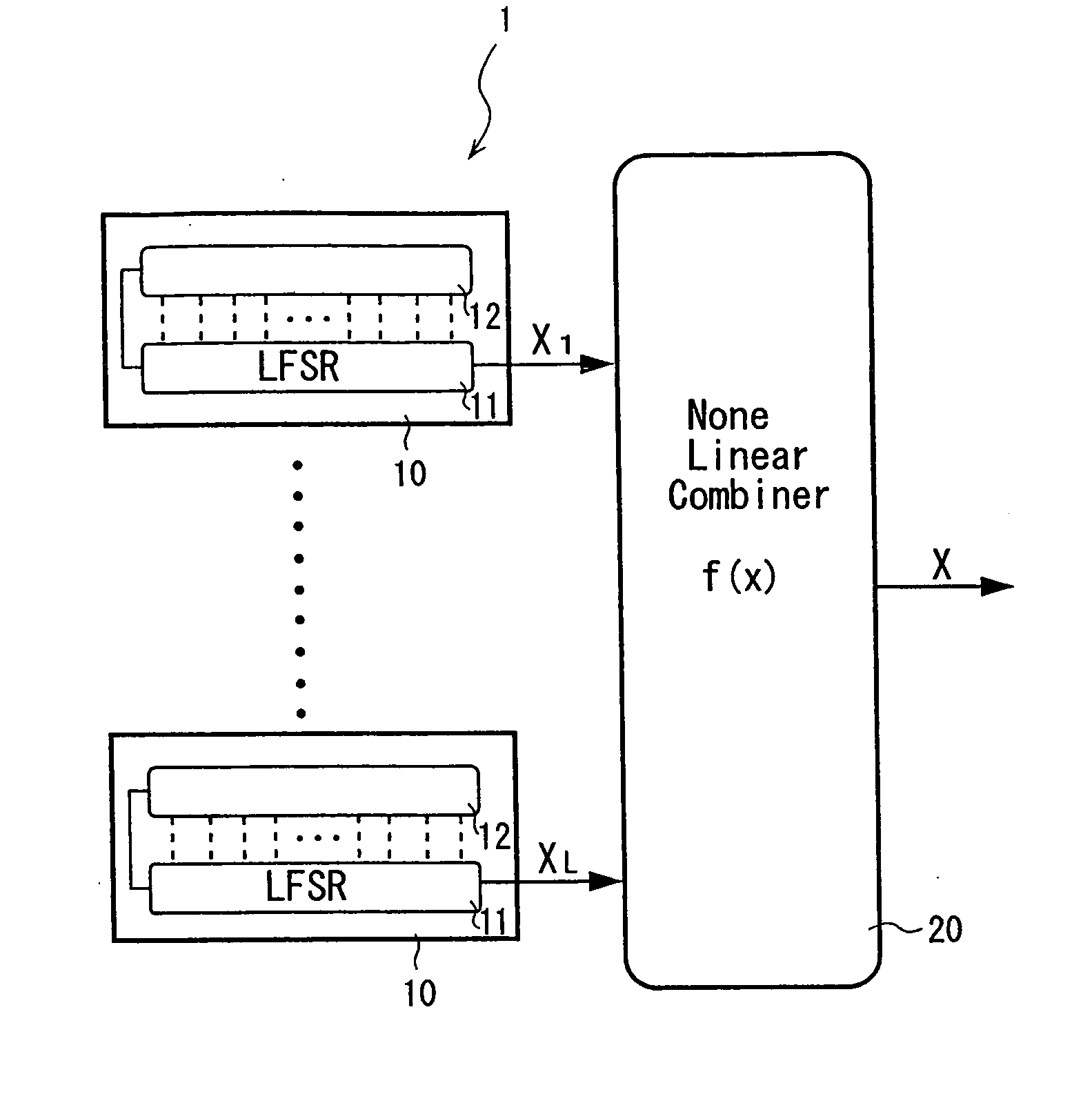
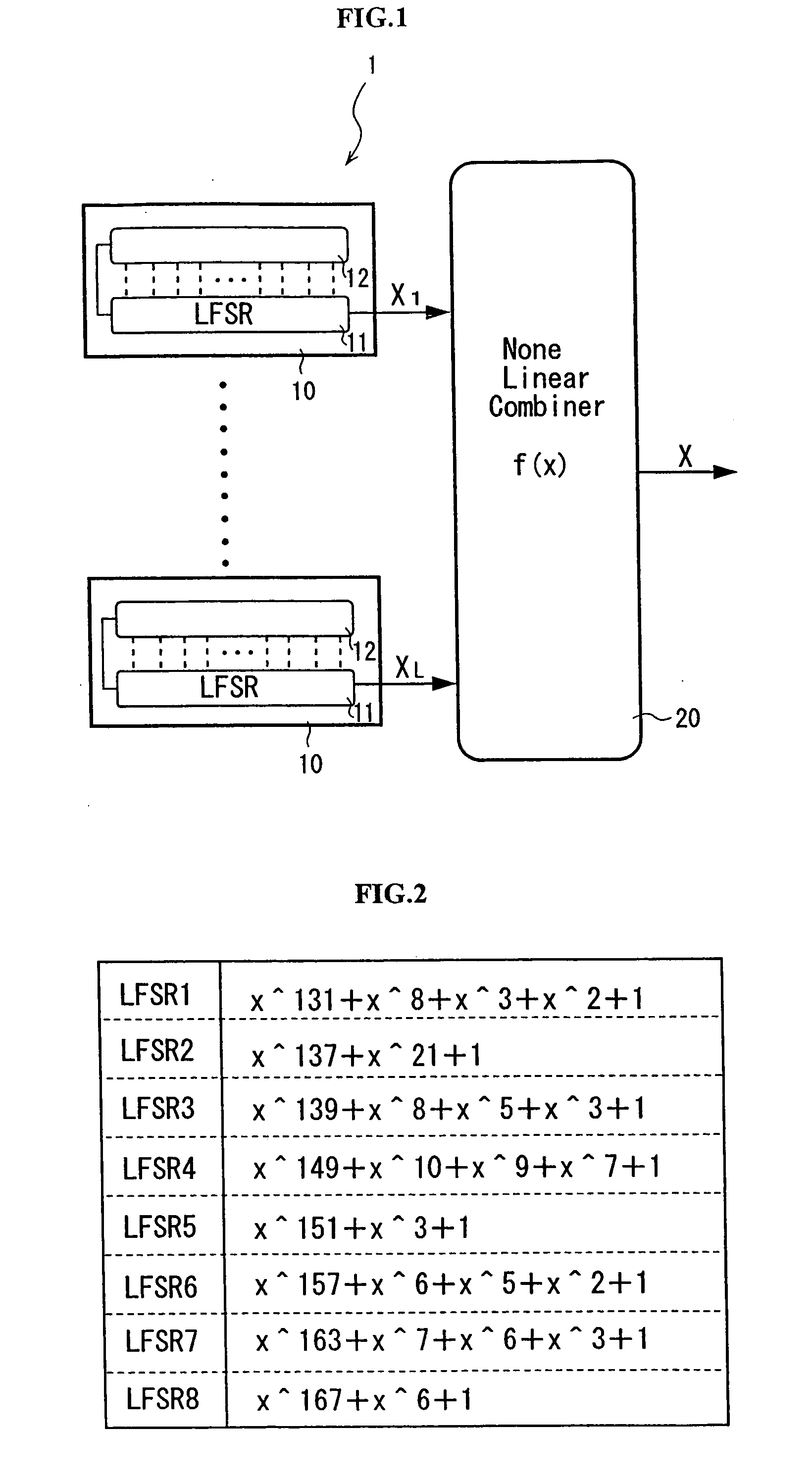
One or more methods and systems of generating pseudo-random numbers that are used as encryption keys in cryptographic applications are presented. In one embodiment, a method of generating pseudo-random numbers is performed by sampling output sequences of a linear feedback shift register with a specified periodicity. In one embodiment, the generating of pseudo-random numbers using linear feedback shift registers is accomplished by periodically switching between iterative outputs generated by multiple linear feedback shift registers. In one embodiment, a method of encrypting a pseudo-random number generated by a linear feedback shift register comprises using a nonlinear operator. In one embodiment, a method of further encrypting a pseudo-random number is accomplished by using a hashing function whose initial value varies over time by way of a function operating on one or more variables. In one embodiment, an apparatus for generating pseudo-random numbers using linear feedback shift registers comprises a digital hardware.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
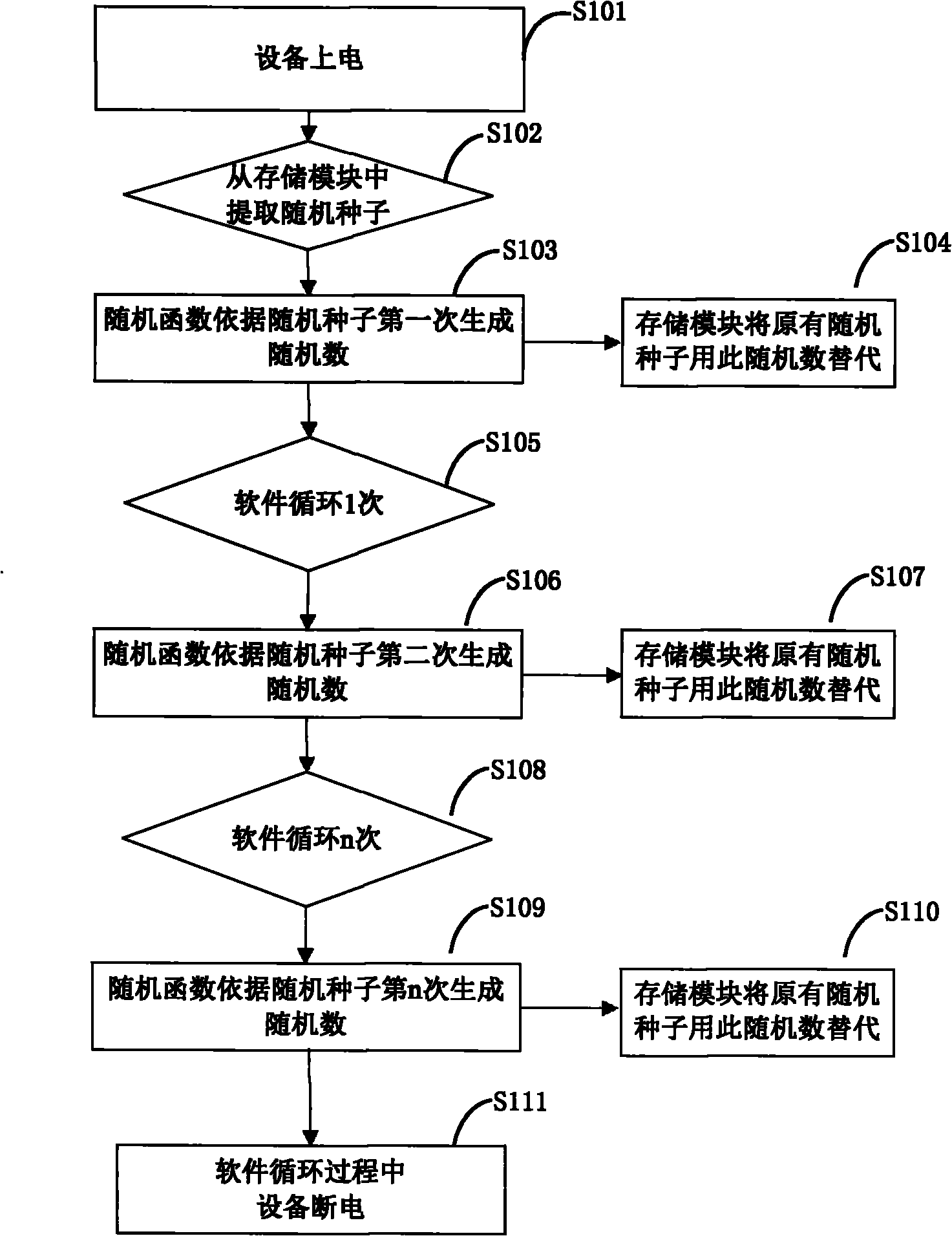
True random number generation method implemented by software
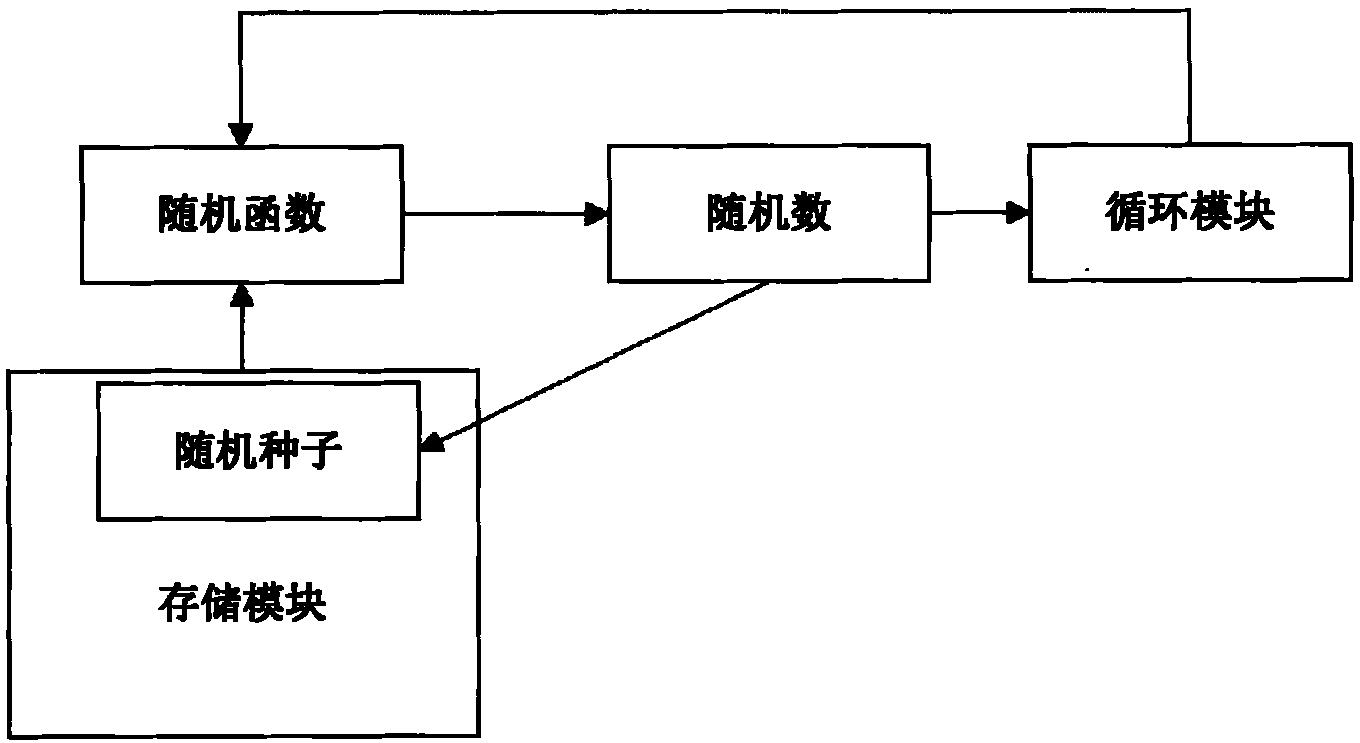
InactiveCN102063285ASolve the problem that only pseudo-random numbers can be generatedRandom number generatorsElectricityRandom seed
The invention discloses a true random number generation method implemented by software. The method comprises a pseudo random number generation module, a circulation module and a storage module. The pseudo random number module generates a pseudo random number according to a random seed stored in the storage module; the circulation module uninterruptedly generates new pseudo random numbers with the pseudo number through software circulation; and the storage module is used for storing the random numbers generated by the circulation module at fixed period. Due to uncertainty of power-on time of electronic equipment in final detection and using process of users, the true random number can be generated after the equipment is used for multiple times.
Owner:倍奥锐(北京)科技有限公司
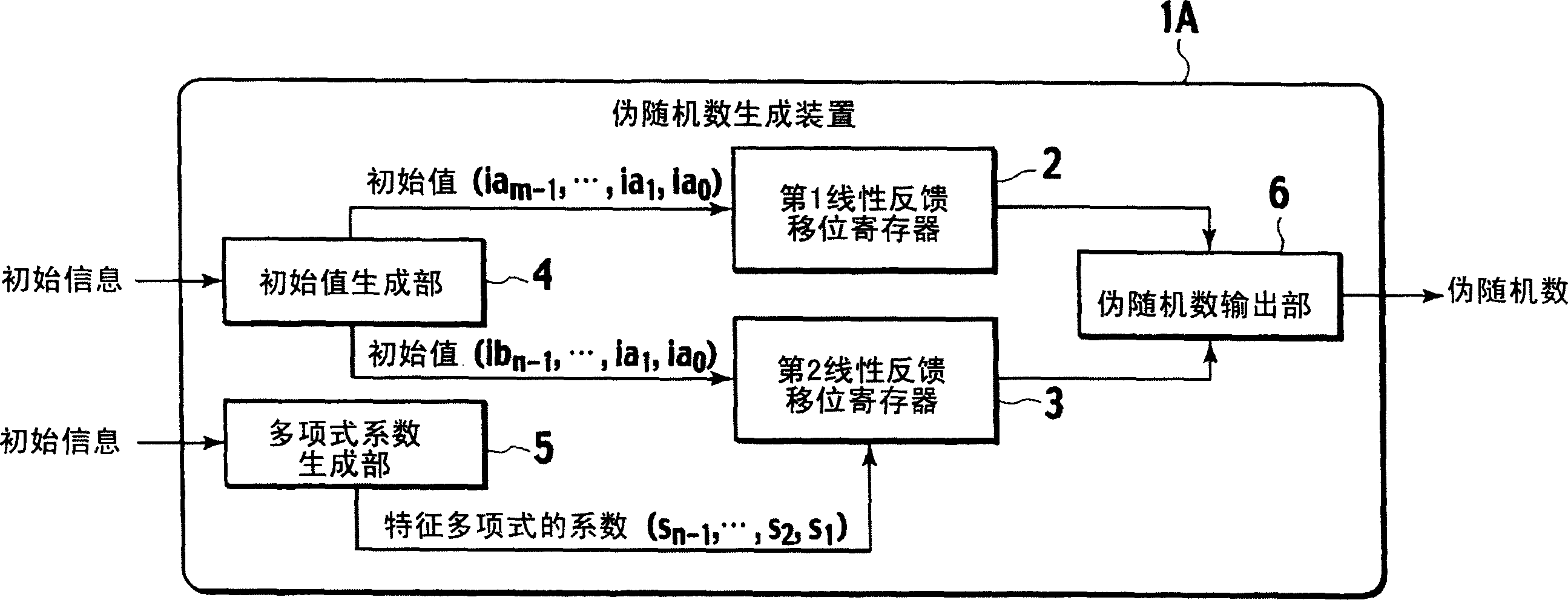
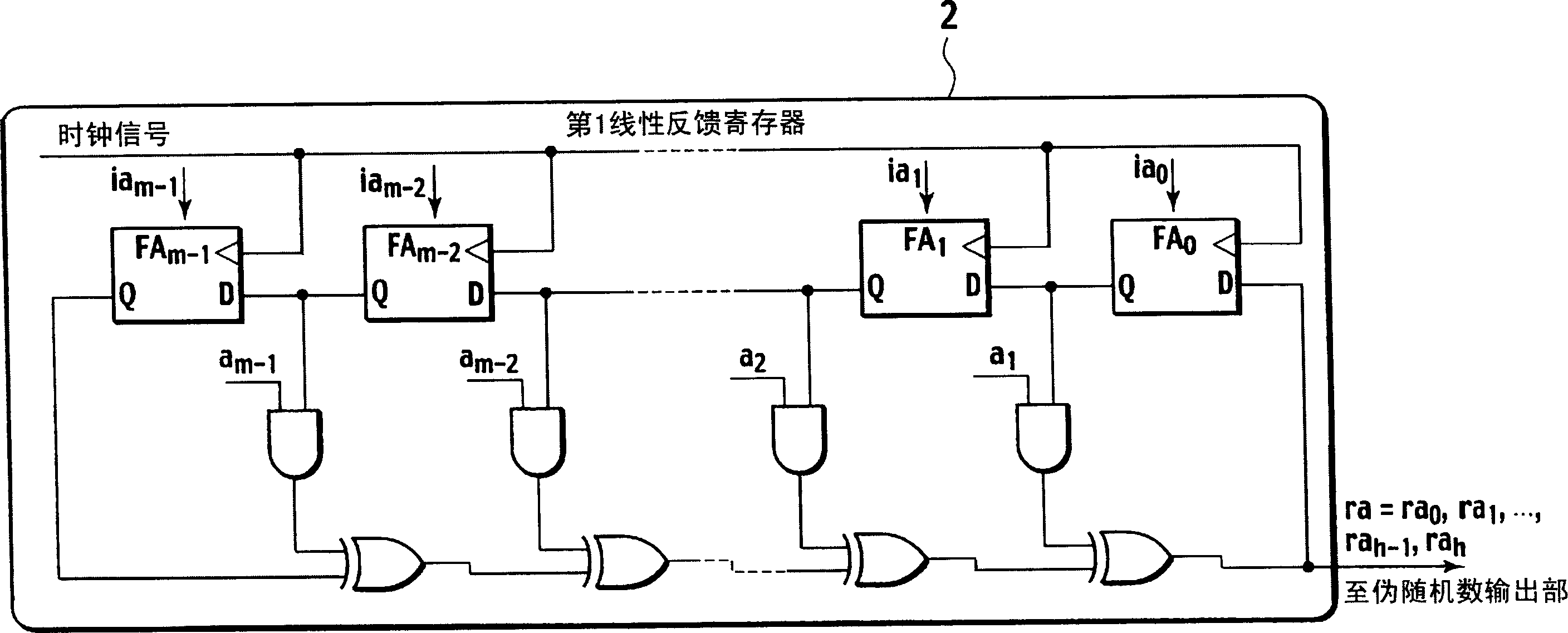
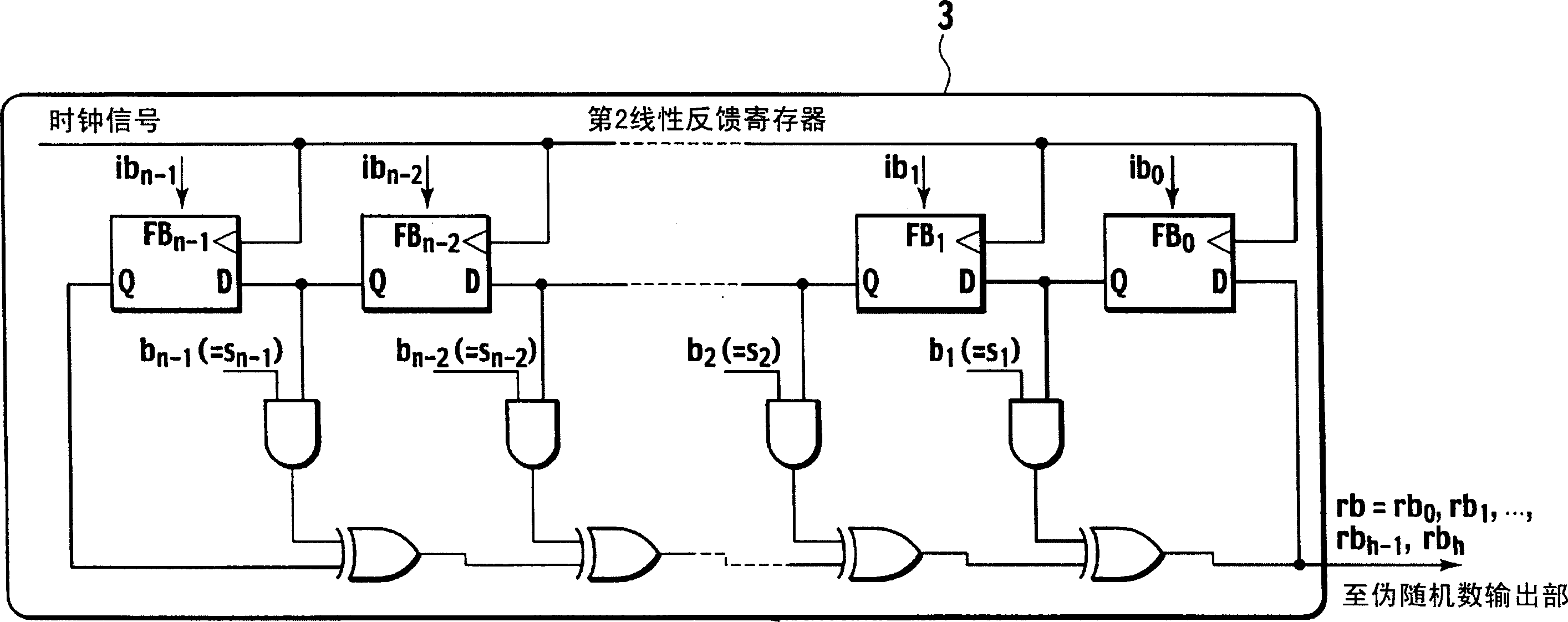
Pseudo random number generation device and pseudo random number generation program
InactiveCN1914590ARandom number generatorsPulse generation with predetermined statistical distributionNonlinear feedback shift registerExclusive or
A pseudo random number generation device(1) includes a first linear feedback shift register(2), a second linear feedback shift register(3), an initial value generation unit(4), a polynomial coefficient generation unit(5), and a pseudo random number output unit(6). The initial value generation unit(4) generates an initial value and supplies it to the first linear feedback shift register(2) and the second linear feedback shift register(3). The polynomial coefficient generation unit(5) generates a characteristic polynomial coefficient and supplies it to the second feedback shift register(3). The pseudo random number output unit(6) generates a pseudo random number from the exclusive OR of each bit according to the bit string successively output from the first linear feedback shift register(2) and the second linear feedback shift register(3) and outputs it.
Owner:VICTOR CO OF JAPAN LTD
Linear feedback shift register (LFSR)-based random test device for external storage interface
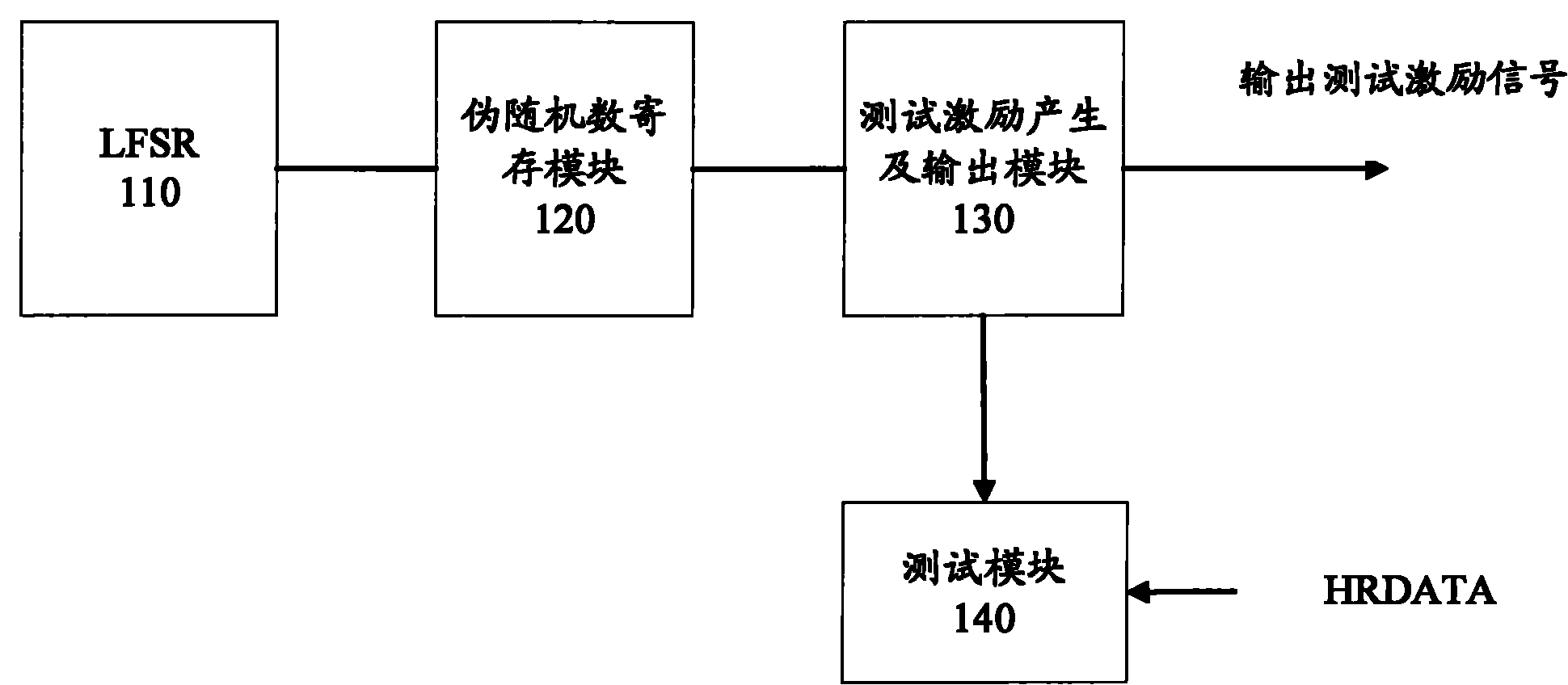
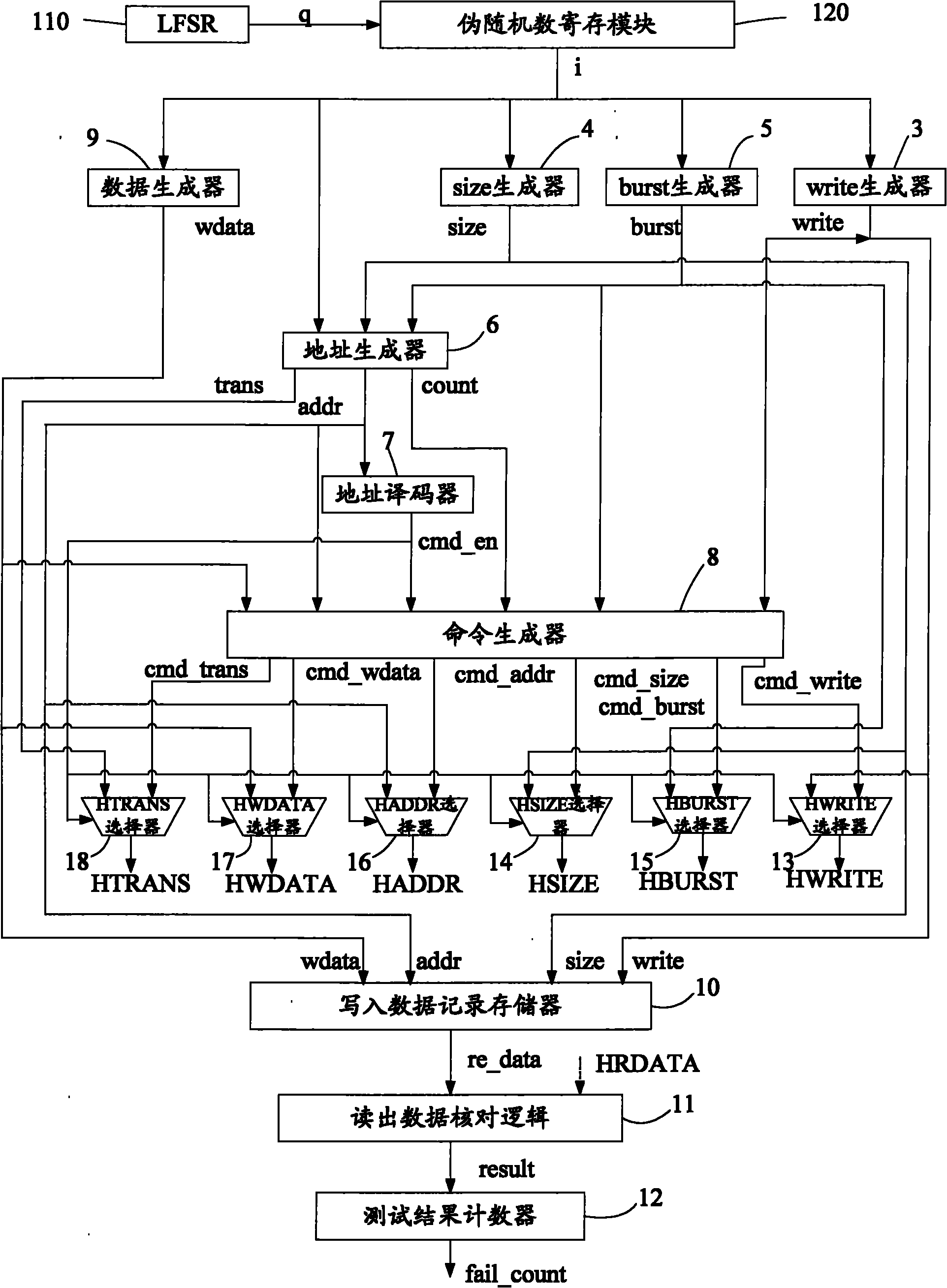
The invention provides a linear feedback shift register (LFSR)-based random test device for an external storage interface. The device comprises a pseudo random number generating module for generating a pseudo random number, a pseudo random number register module for storing the pseudo random number, a test actuation producing and outputting module for generating a random test actuating signal according to the pseudo random number and a test module for comparing a read data signal with data written in the same address of an external storage and counting total failure times. The LFSR-based random test device for the external storage interface of the invention takes the LFSR as a pseudo random number generator and converts the produced pseudo random number into random test actuation, which is accordant with an advanced high-performance bus (AHB) protocol, of the external storage interface so that the random test of the external storage interface is realized.
Owner:TSINGHUA UNIV
True random number generator with digital post-processing circuit
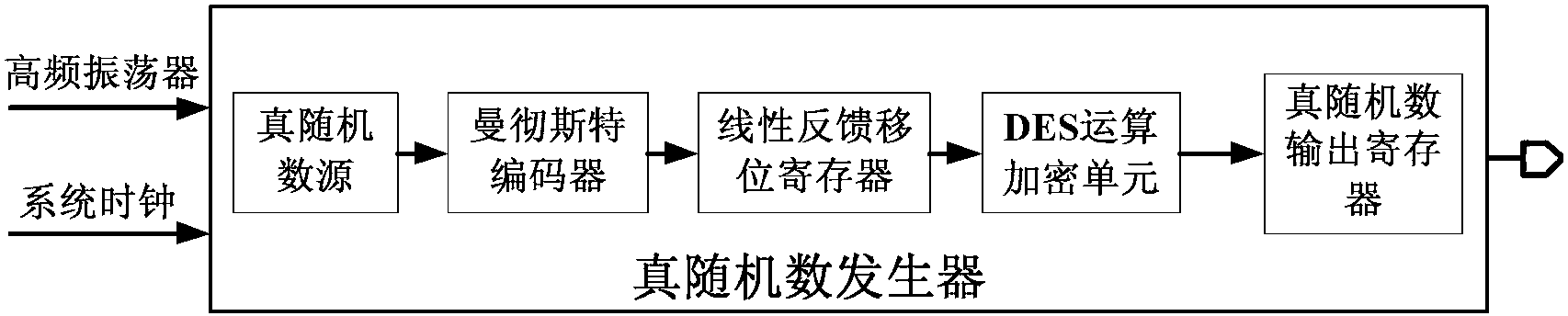
InactiveCN103019648AQuality improvementImprove securityRandom number generatorsManchester codeProcessor register
The invention discloses a true random number generator with a digital post-processing circuit, which comprises a true random number source and a true random number output register. The true random number generator is characterized in that the digital post-processing circuit is connected between the true random number source and the true random number output register, wherein the digital post-processing circuit comprises a Manchester encoder, a linear feedback shift register and a DES (data encryption standard) encryption unit which are connected from the true random number source to the true random number output register; the true random number output register is used for latching the ciphertext output by the DES encryption unit; and finally, the true random number is output to a chip by the true random number output register. The true random number generator improves the quality of random number sequences generated by the true random number source; the finally output random number sequences have the characteristics of good uniformity and high independence; the security for information storage of the cryptographic chip is improved; and the true random number generator has higher actual application value in the aspects of cryptographic chip, information security and the like.
Owner:TIANJIN UNIV
Random dormancy scheduling routing method for wireless sensor network
InactiveCN102083163AReduce and balance energy consumptionPower managementNetwork topologiesNetworking protocolWireless sensor networking
The invention discloses a random dormancy scheduling routing method for a wireless sensor network, belonging to wireless network protocol. The method is specifically characterized in that each node maintains one pseudo-random number sequence. The number sequences are generated from seeds, randomly generated by nodes, by the same pseudo-random number generation algorithm. Then, each node determines own random dormancy time sequence arrangement in the network operation cycle according to the random number sequence. By broadcasting own seed during network initiation, the node and a hop neighbor thereof can acquire both pseudo-random number sequences through calculation so as to acquire both dormancy and awake time. When needing to send data, the node sends a data packet to the first awake node by calculating the awake time of own neighbor. The mechanism achieves the alternative working of the nodes through a random dormancy scheduling mechanism in order to reach the purpose of reducing and equalizing the energy consumption of the entire network.
Owner:江苏中科泛联物联网科技股份有限公司
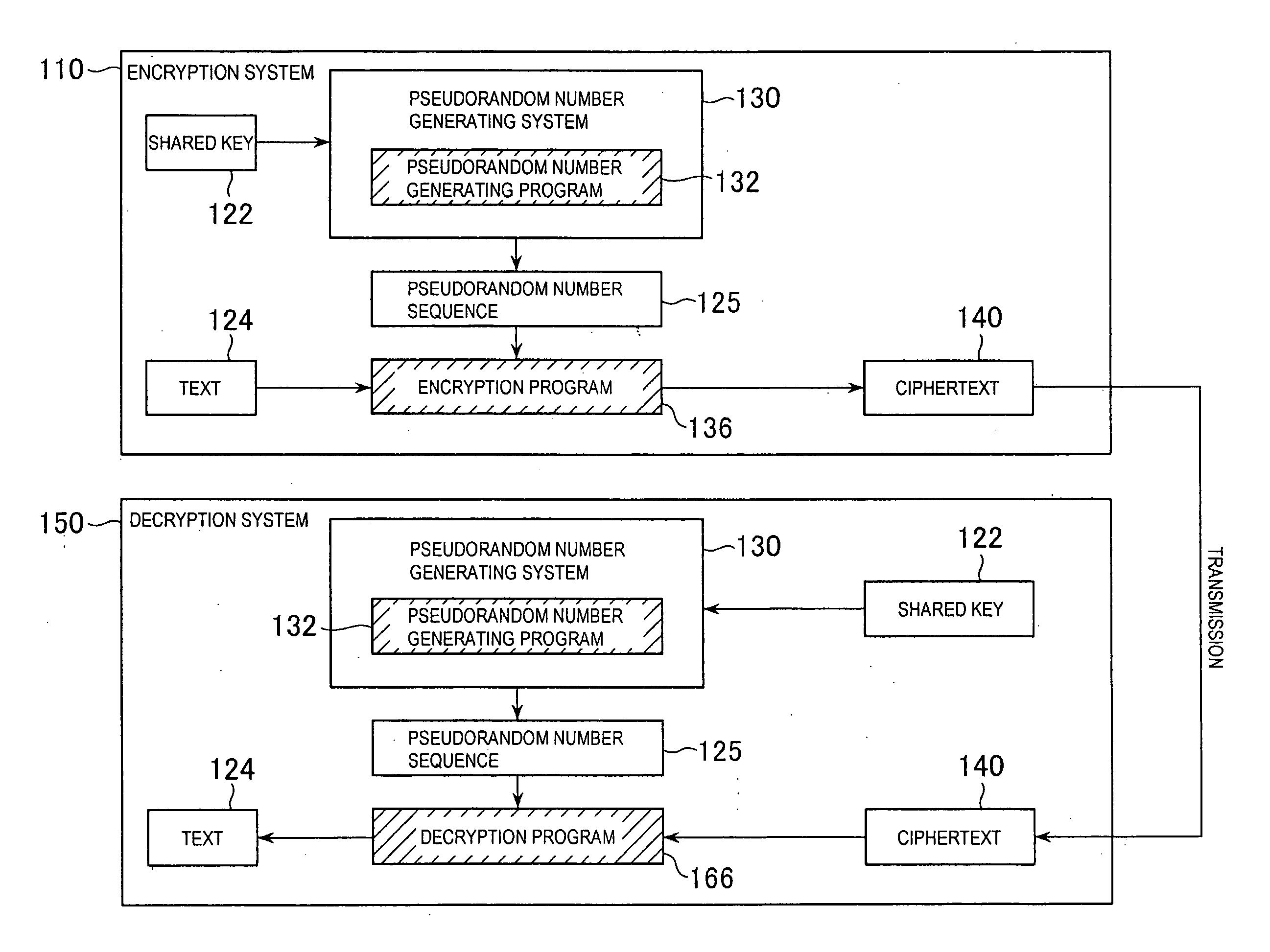
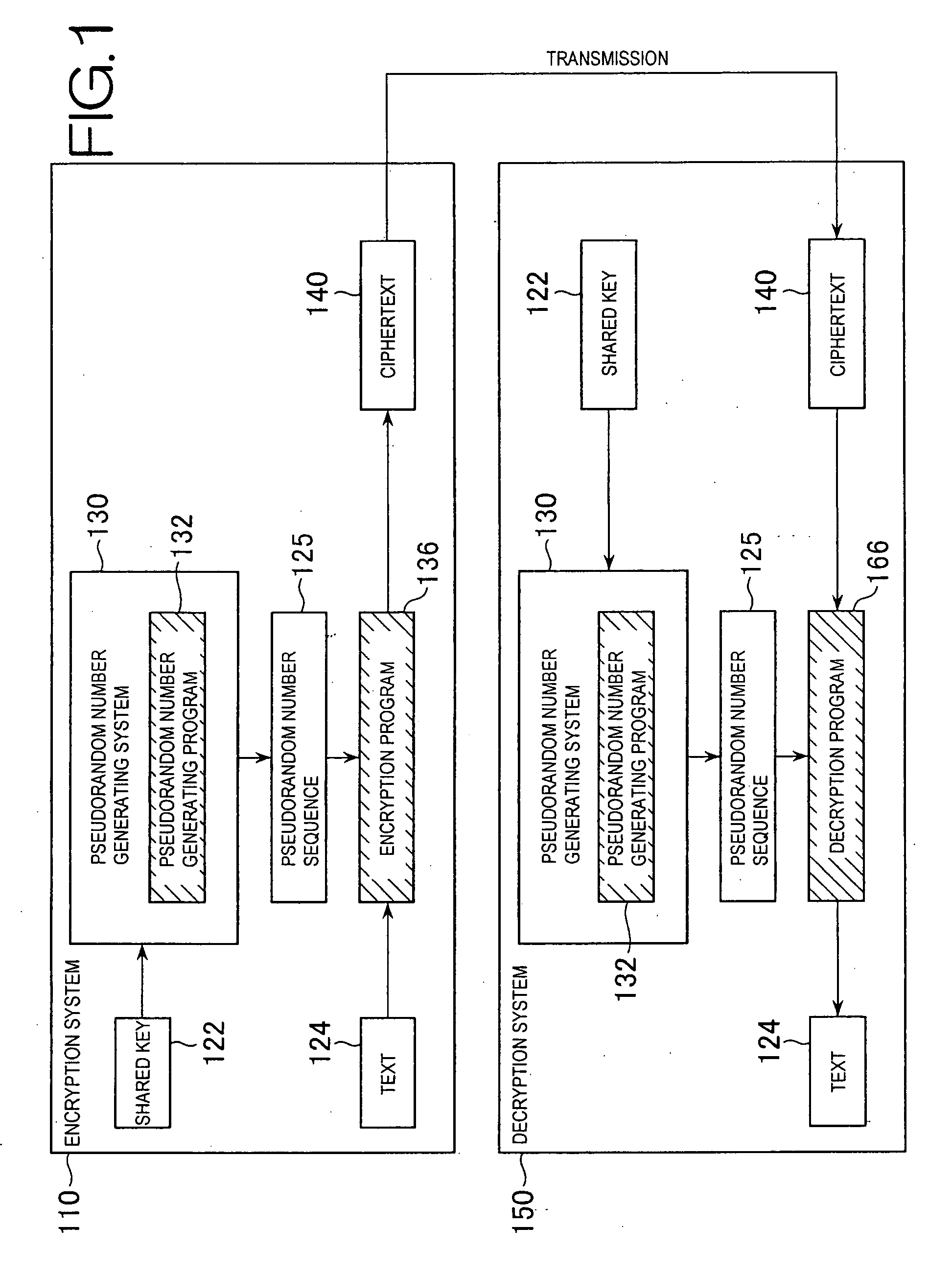
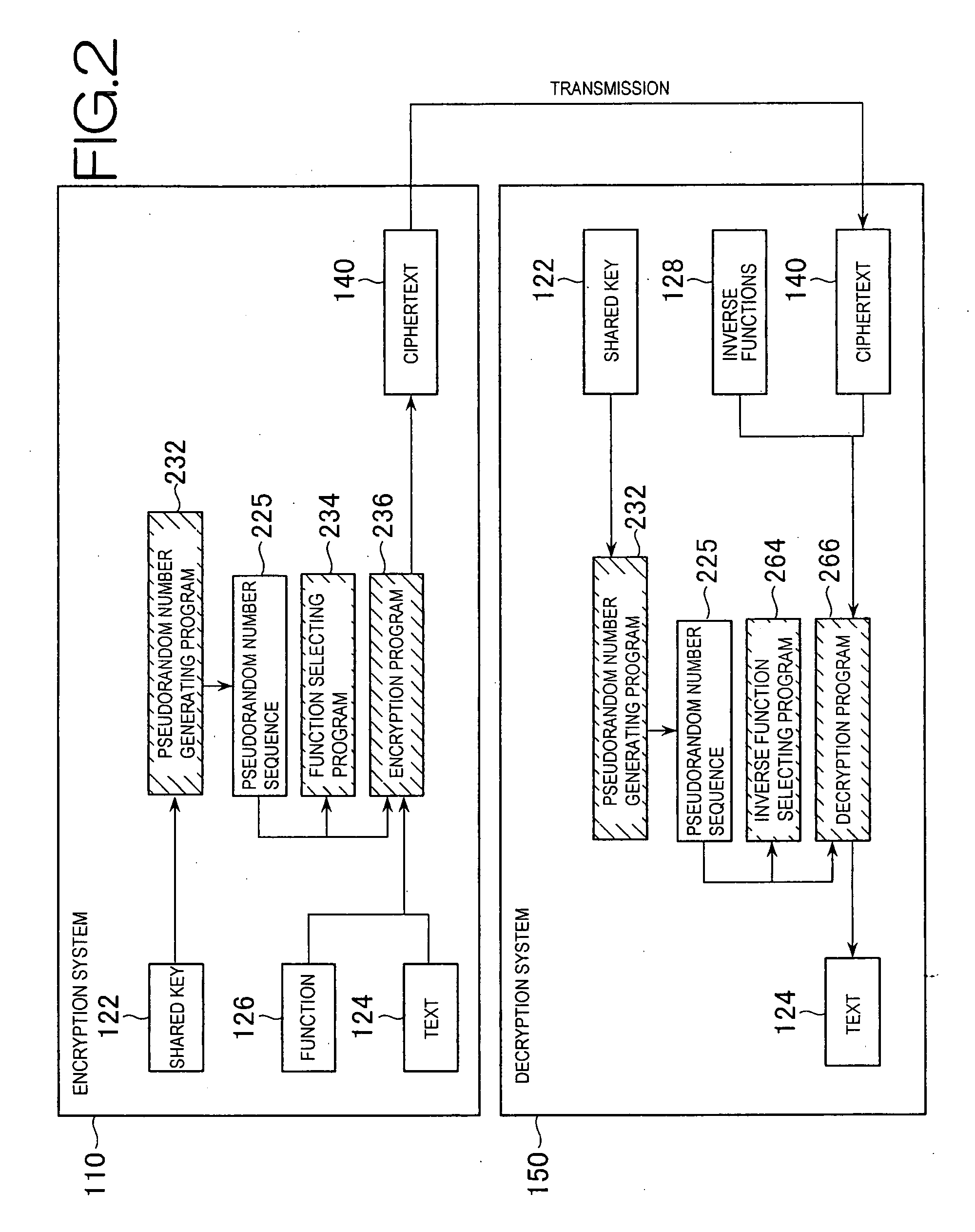
Pseudorandom number generating system, encryption system, and decryption system
InactiveUS20090296928A1Raise security concernsKeep for a long timeRandom number generatorsUser identity/authority verificationEncrypted functionPseudo random number generation
The present invention provides a pseudorandom number generating system, an encryption system, and a decryption system. The pseudorandom number generating system of the present invention repeatedly performs simple transformation of a non-secure pseudorandom number sequence that may be generated quickly, and thus may quickly generate a highly secure pseudorandom number sequence having a long period. In addition, the encryption system and the decryption system of the present invention do not generate a large encryption function difficult to be deciphered based on a shared key 122, but prepare multiple functions 126, which perform fast, different types of transformation, and select a combination of functions determined based on information of the shared key 122, and make the selected functions transform a text multiple times, thereby encrypt the text. Each of the functions is basically fast, and thus transformation by the entire combination is also fast. Furthermore, since the combination of functions and repetitive count for them can be changed, future improvement in specification is easy. Moreover, security is high since which functions are applied in what order is unknown.
Owner:OCHANOMIZU UNIVERSITY +1
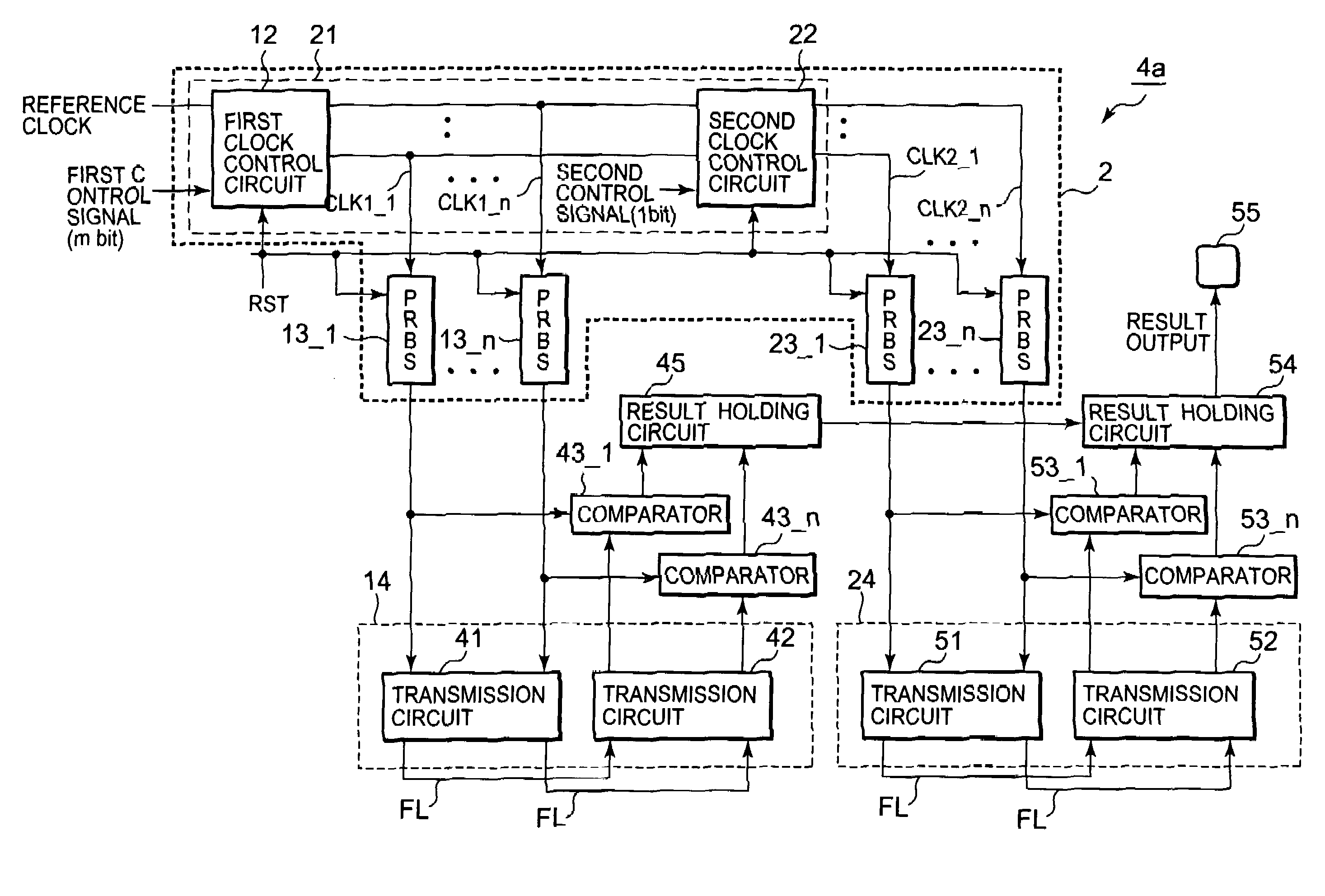
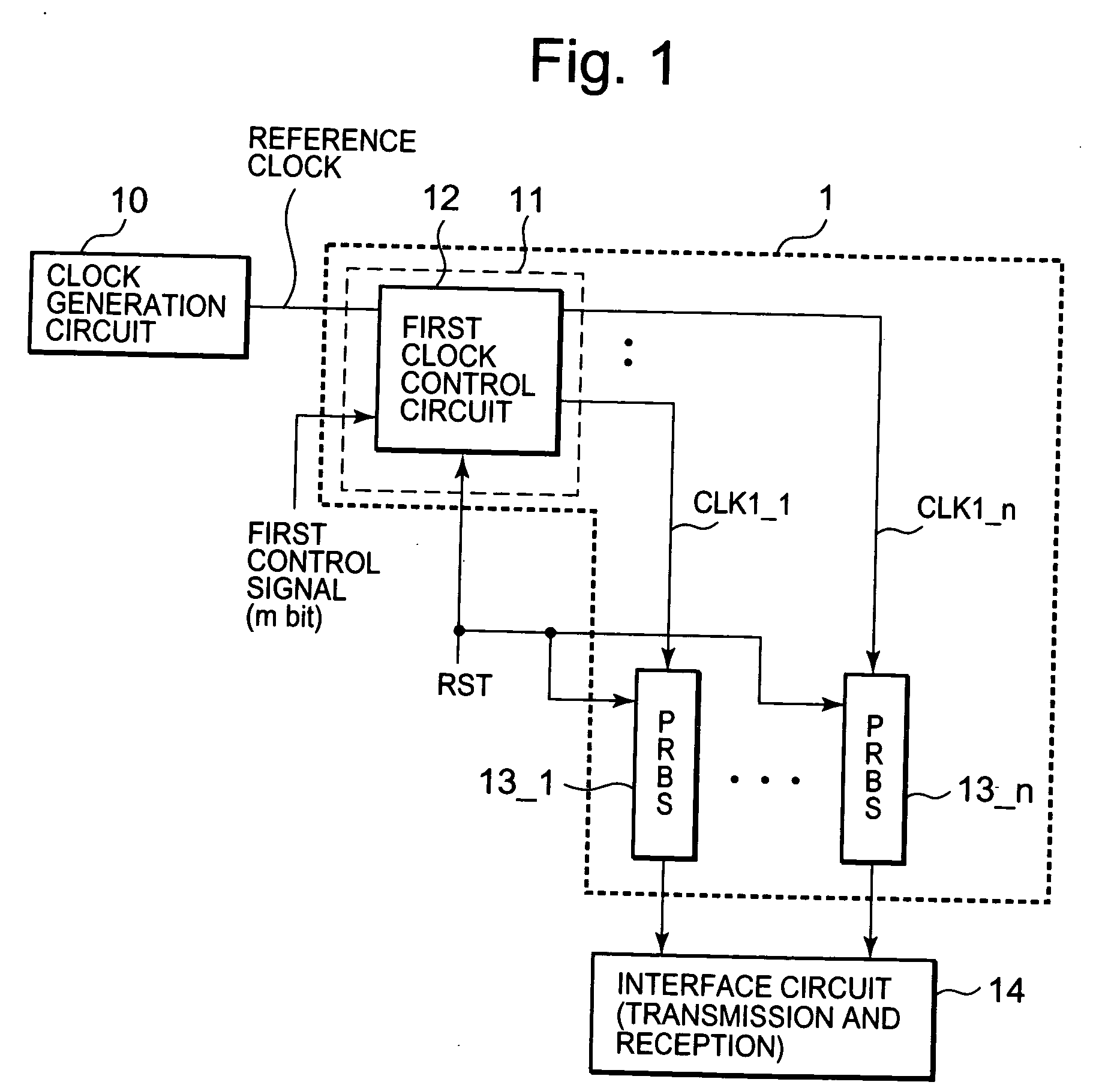
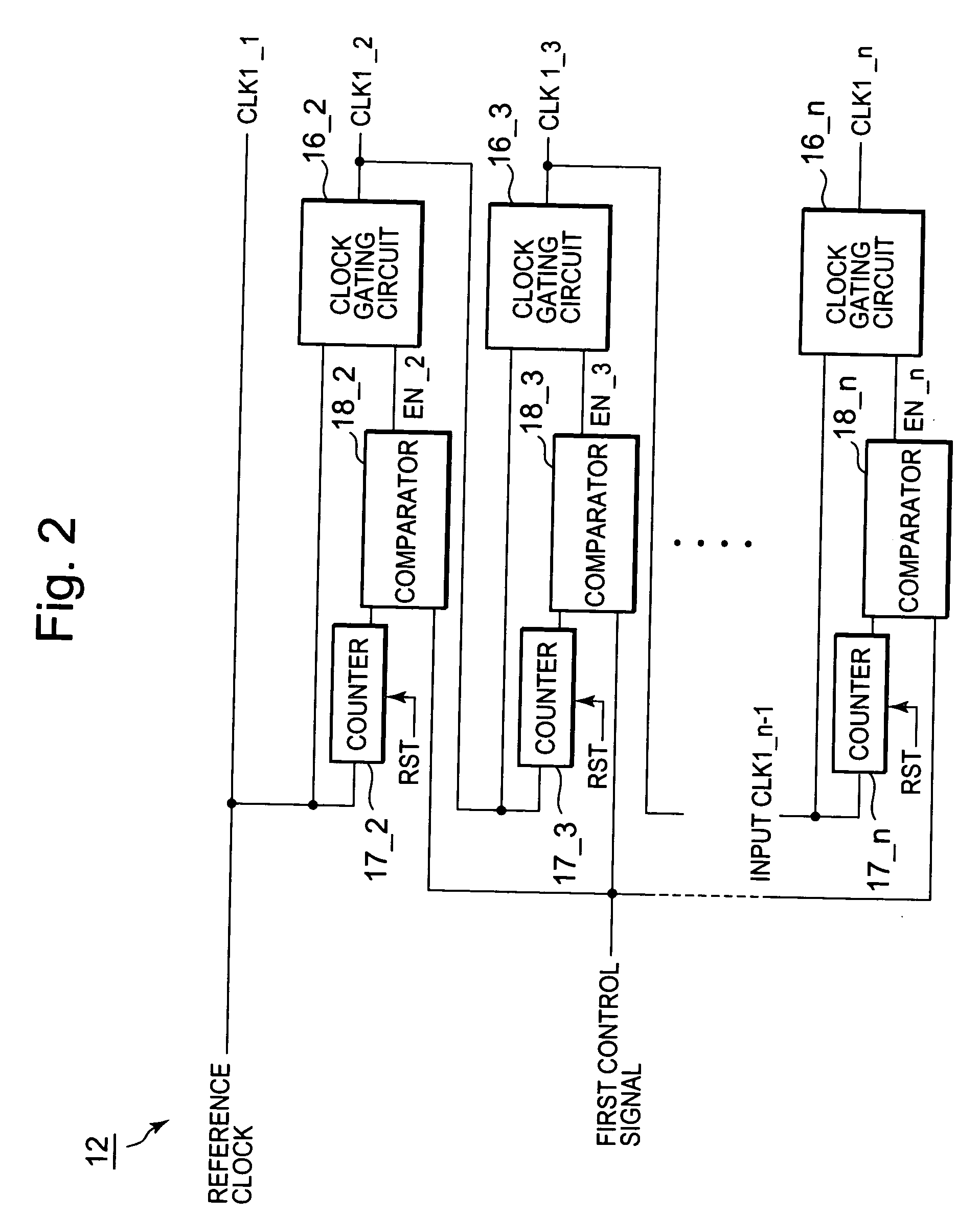
Test pattern generation circuit having plural pseudo random number generation circuits supplied with clock signals at different timing respectively
InactiveUS20080178055A1Improve test coverageData augmentationElectronic circuit testingError detection/correctionControl signalPattern generation
A test pattern generation circuit has multiple pseudo random number generation circuits and a clock control circuit. The pseudo random number generation circuits are provided corresponding to the respective signal lines in a bus wiring, and have predetermined first initial values, which take the same value. In response to first clock signals, the pseudo random number generation circuits generate pseudo random numbers including the first initial values as starting values. According to the value of a control signal, the clock control circuit determines the output-start timings of the first clock signals to be respectively provided to the multiple pseudo random number generation circuits.
Owner:RENESAS ELECTRONICS CORP
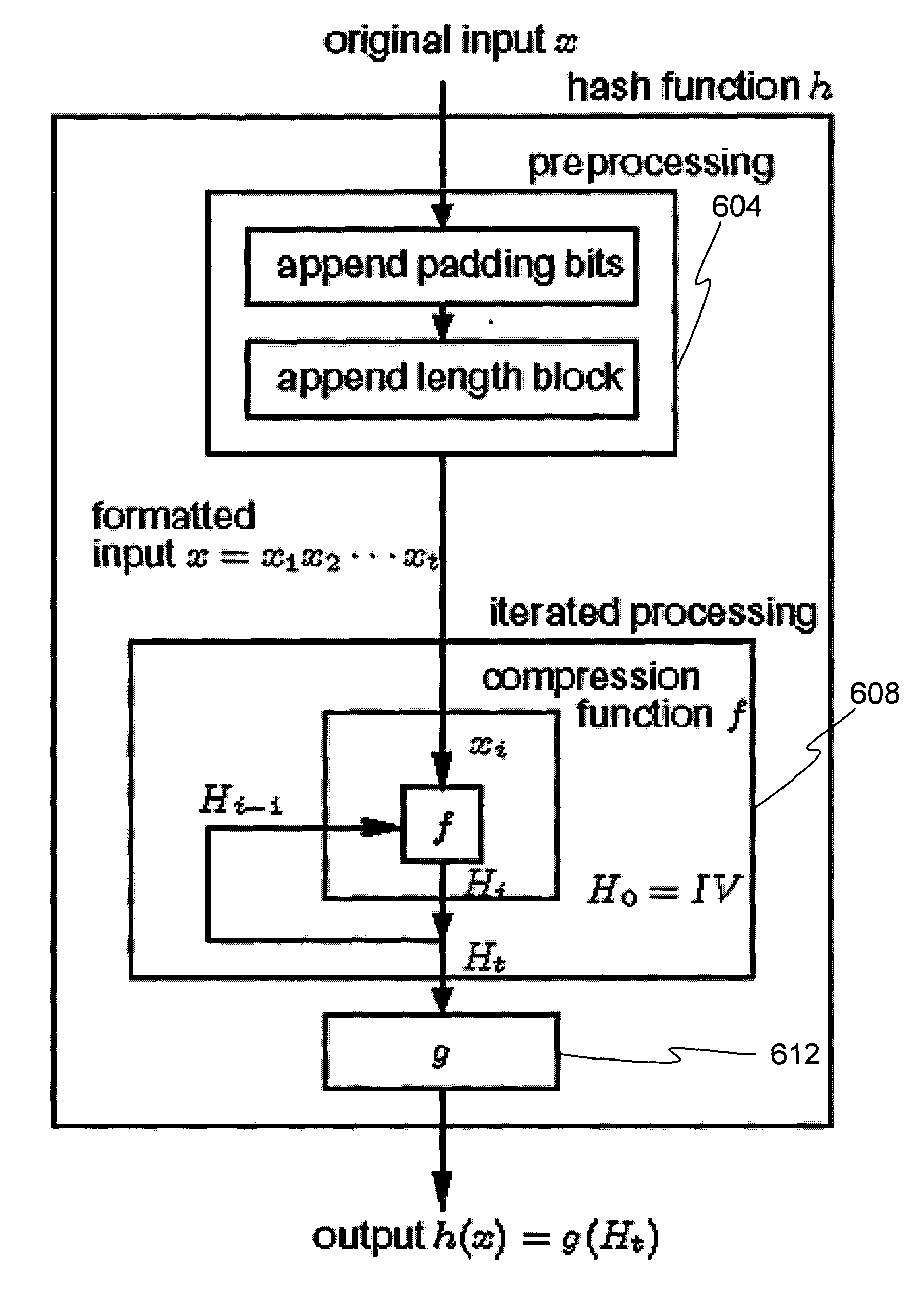
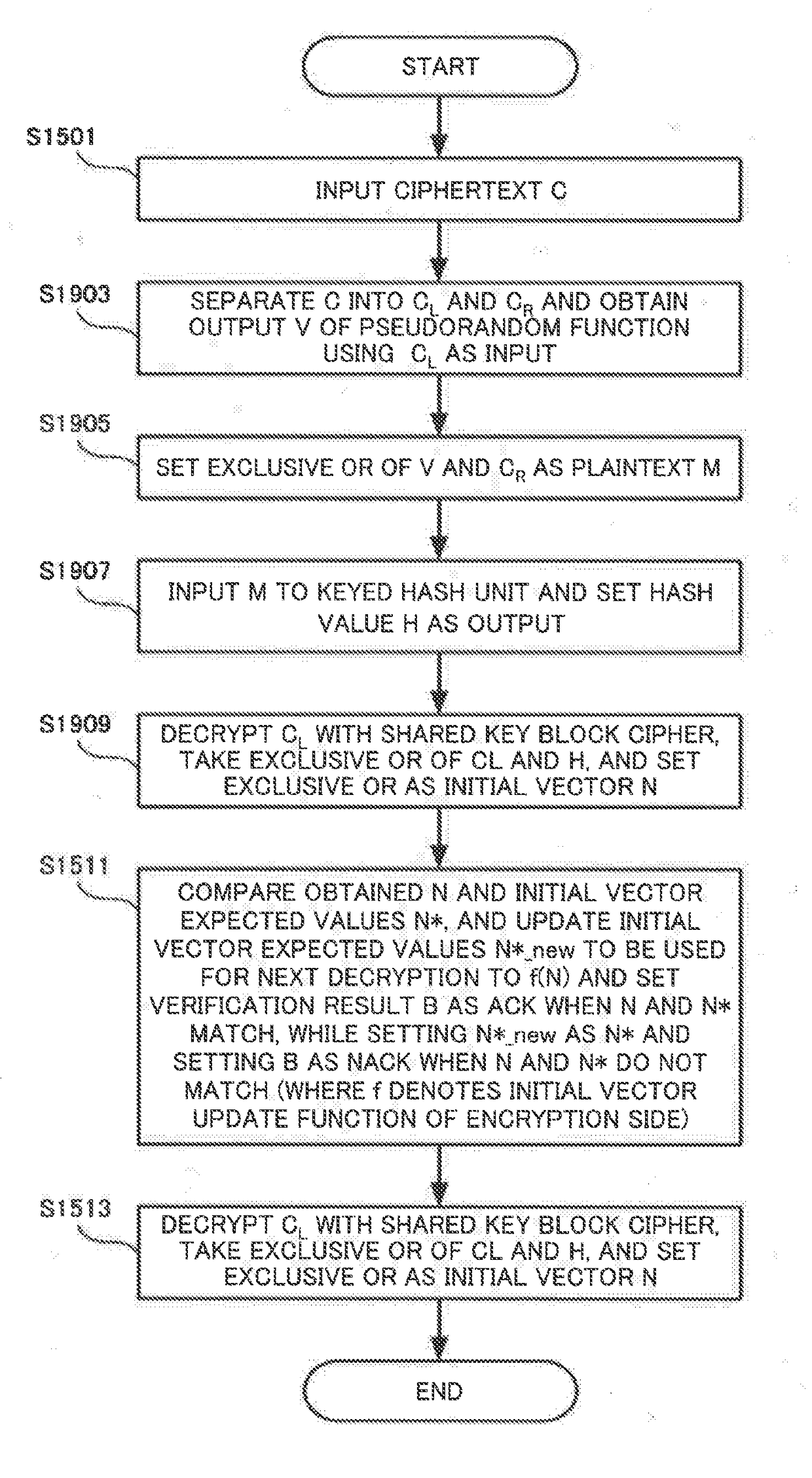
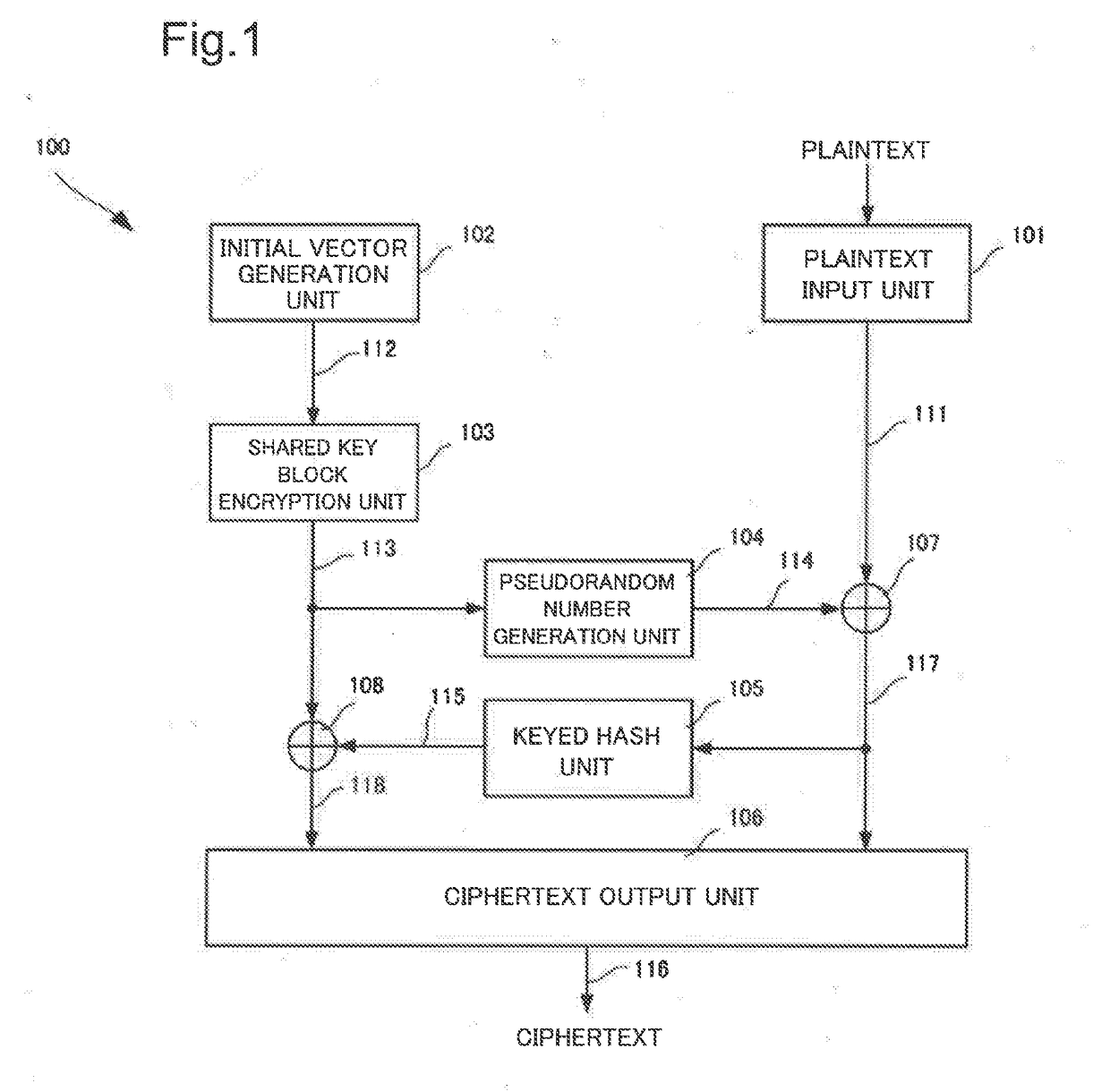
Authentication encryption method, authentication decryption method, and information-processing device
ActiveUS20170272239A1Efficiently enableSmall increase of band (length) of ciphertextEncryption apparatus with shift registers/memoriesComputer hardwareInformation processing
An information-processing device is provided with: a plaintext input unit for inputting plaintext; an initial vector generation unit for generating an initial vector; a common key block encryption unit for performing common key block encryption on the initial vector and generating an encrypted initial vector; a pseudorandom number generation unit which, accepting the encrypted initial vector as input, generates a pseudorandom number series in the same length as the plaintext; a keyed hash unit which, accepting the first portion of a ciphertext in which the pseudorandom number series and the plaintext are exclusive-OR'ed as input, generates a hash value; and a ciphertext output unit for concatenating the second and first portions of a ciphertext in which the hash value and the encrypted initial vector are exclusive-OR'ed and outputting the concatenated portions as a ciphertext.
Owner:NEC CORP
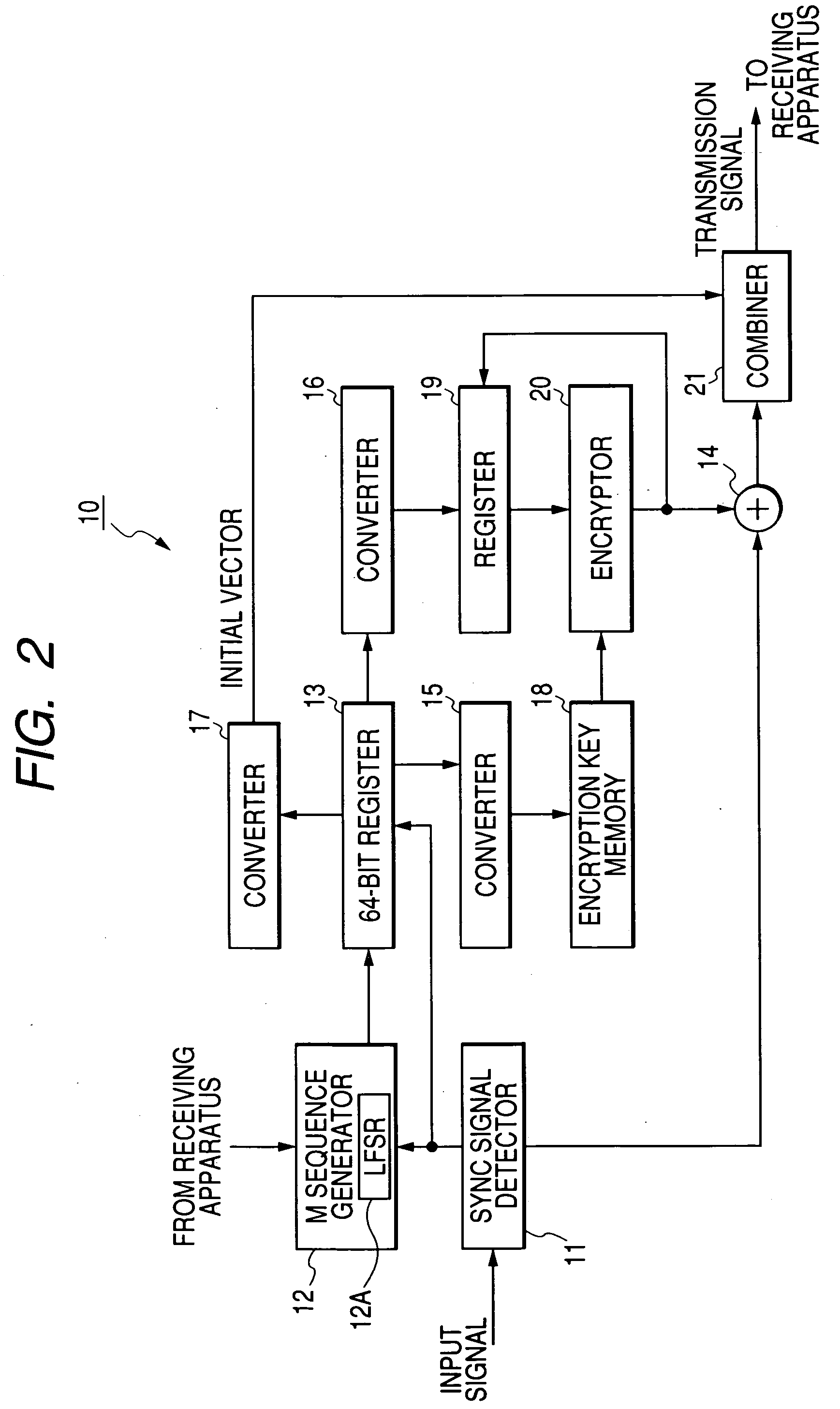
Information transmission system
ActiveUS20050058293A1Accurate timingSimple structureSynchronising transmission/receiving encryption devicesPulse modulation television signal transmissionComputer hardwareInformation transmission
A sending apparatus generates a first initial vector, a second initial vector, and an encryption key in response to a pseudo random number. Original information is encrypted into cipher information in response to the encryption key and the second initial vector. The cipher information and the first initial vector are transmitted from the sending apparatus to a receiving apparatus. The receiving apparatus generates a first initial vector, a second initial vector, and an encryption key in response to a pseudo random number equal to that in the sending apparatus. The cipher information is decrypted back to the original information in response to the generated encryption key and the generated second initial vector. The receiving apparatus compares the received first initial vector and the generated first initial vector to check whether or not encryption / decryption-related synchronization between the sending apparatus and the receiving apparatus is normally maintained.
Owner:RAKUTEN GRP INC
Common-Key Block Encryption Device Common-Key Block Encryption Method, and Common-Key Block Encryption Program
InactiveUS20080253561A1Reduce the amount of solutionIncrease volumeEncryption apparatus with shift registers/memoriesSecret communicationPlaintextComputer hardware
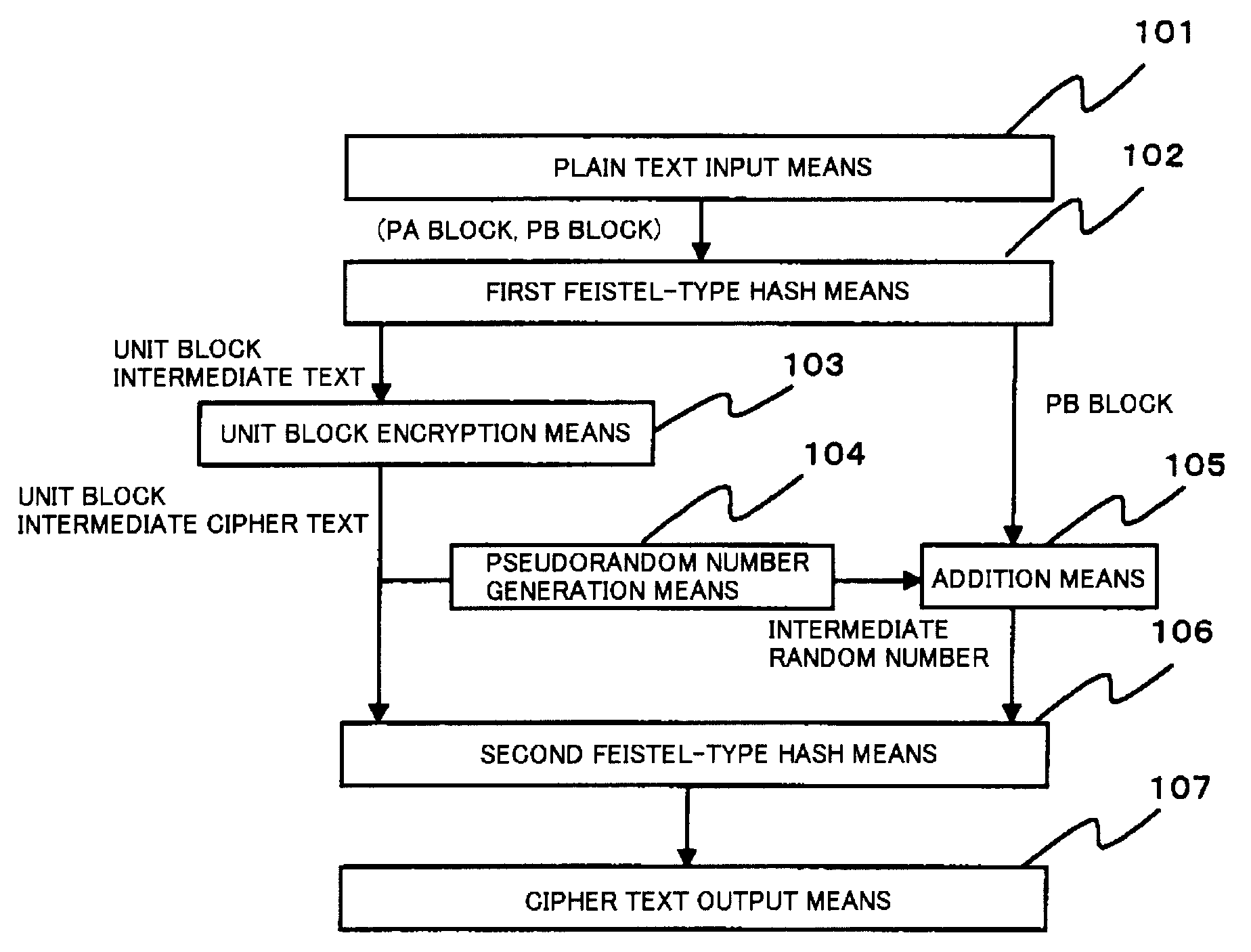
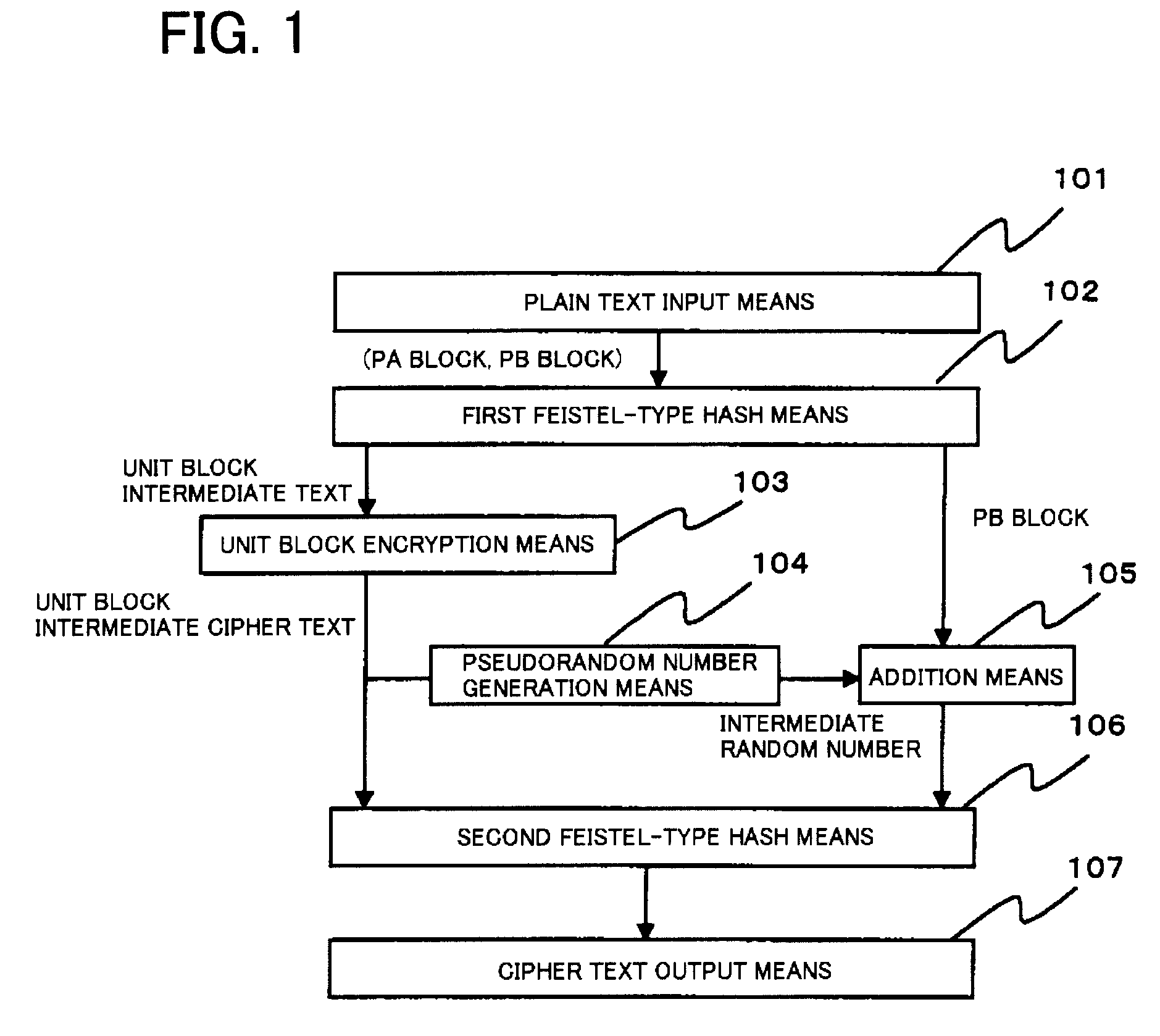
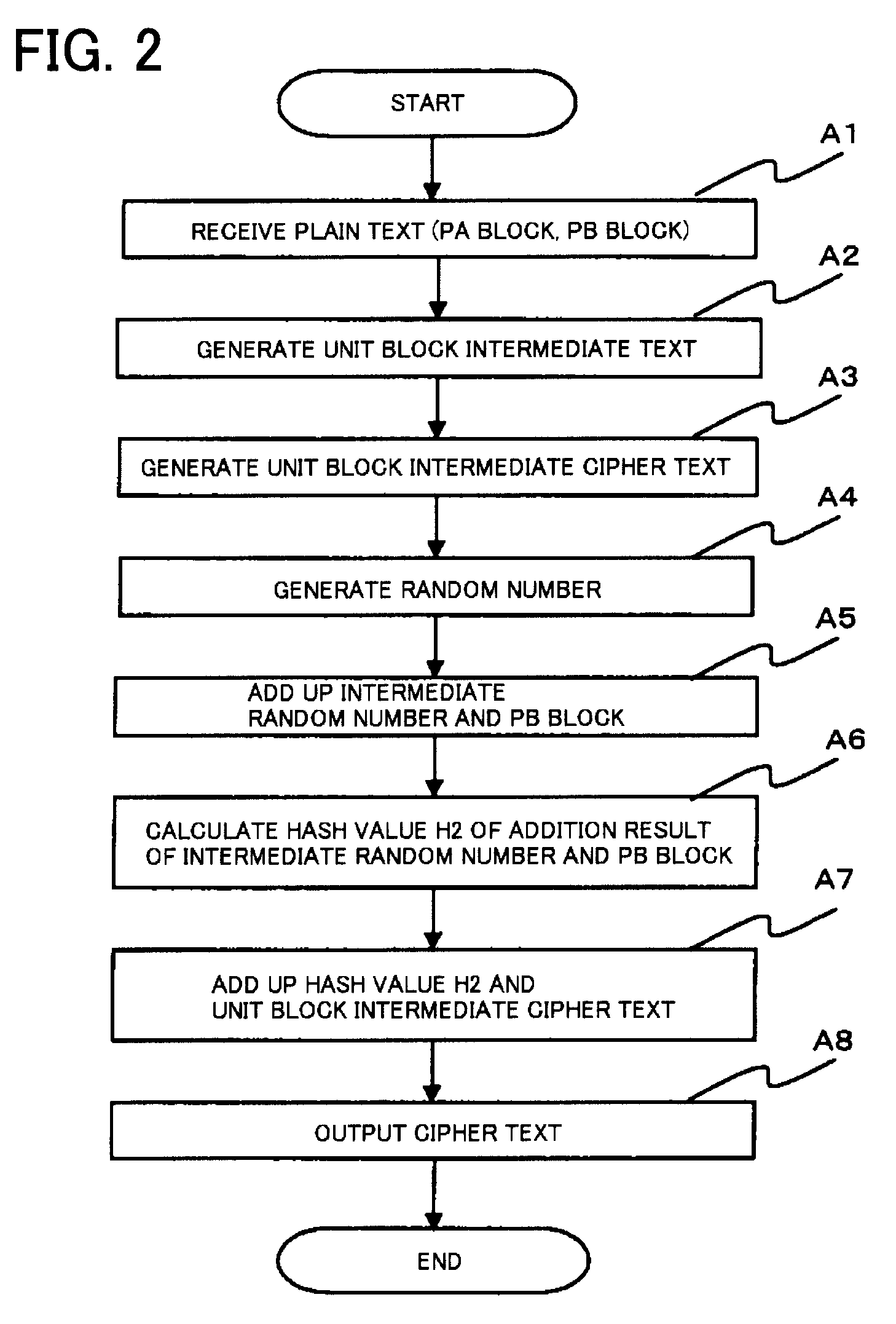
Disclosed is a common-key block encryption device including first Feistel-type hash means that divides a plain text into a PA block and a PB block and adds the PB block, which is compressed by a hash function, and the PA block to generate a unit block intermediate text; unit block encryption means that encrypts the unit block intermediate text to generate a unit block intermediate cipher text; pseudorandom number generation means that generates an intermediate random number based on the unit block intermediate cipher text; addition means that adds the intermediate random number and the PB block and outputs an addition result; second Feistel-type hash means that outputs a result that is a combination of a second addition result, generated based on the addition result compressed by a hash function and the unit block intermediate cipher text, and the addition result; and cipher text output means that outputs the output result as a cipher text.
Owner:NEC CORP
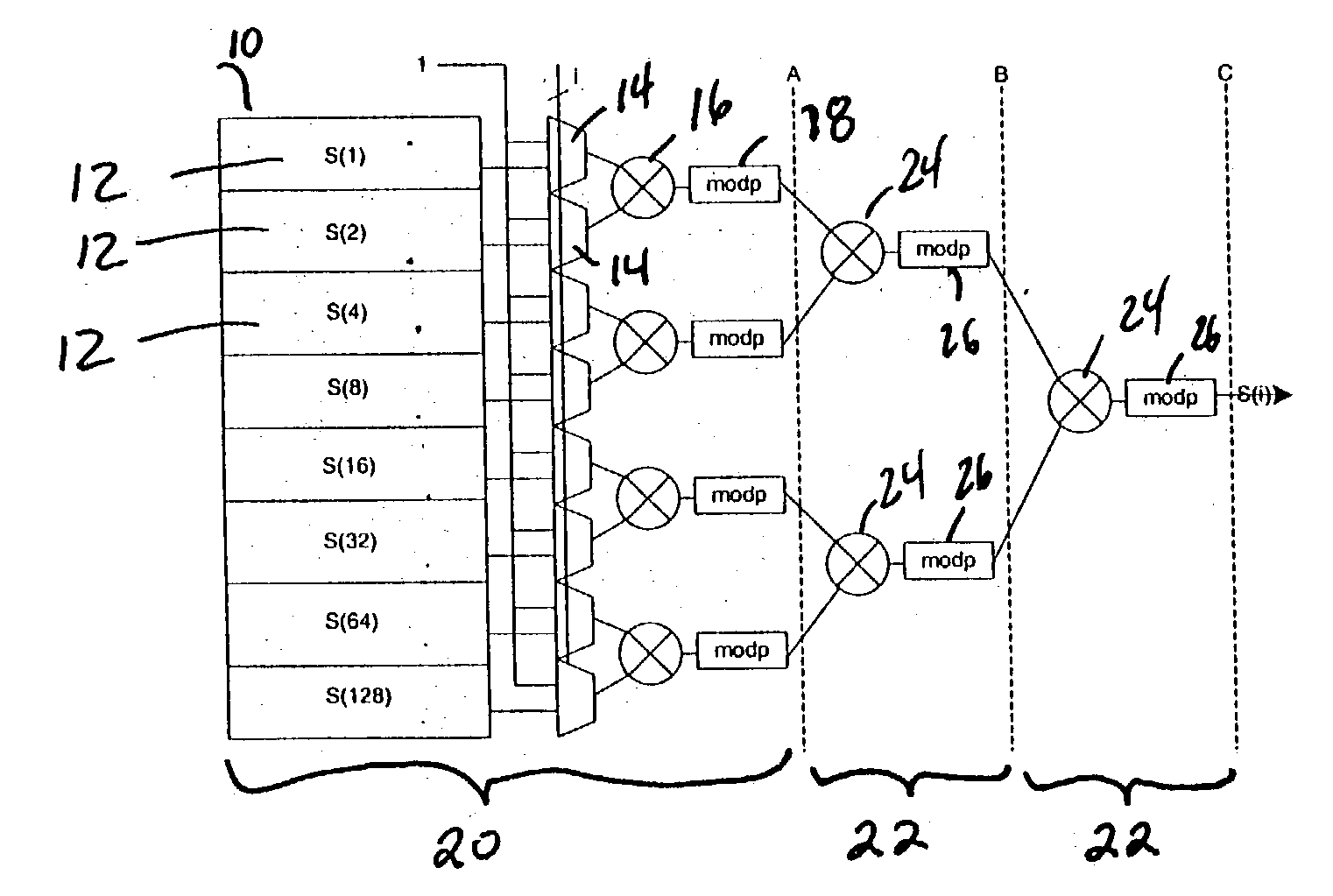
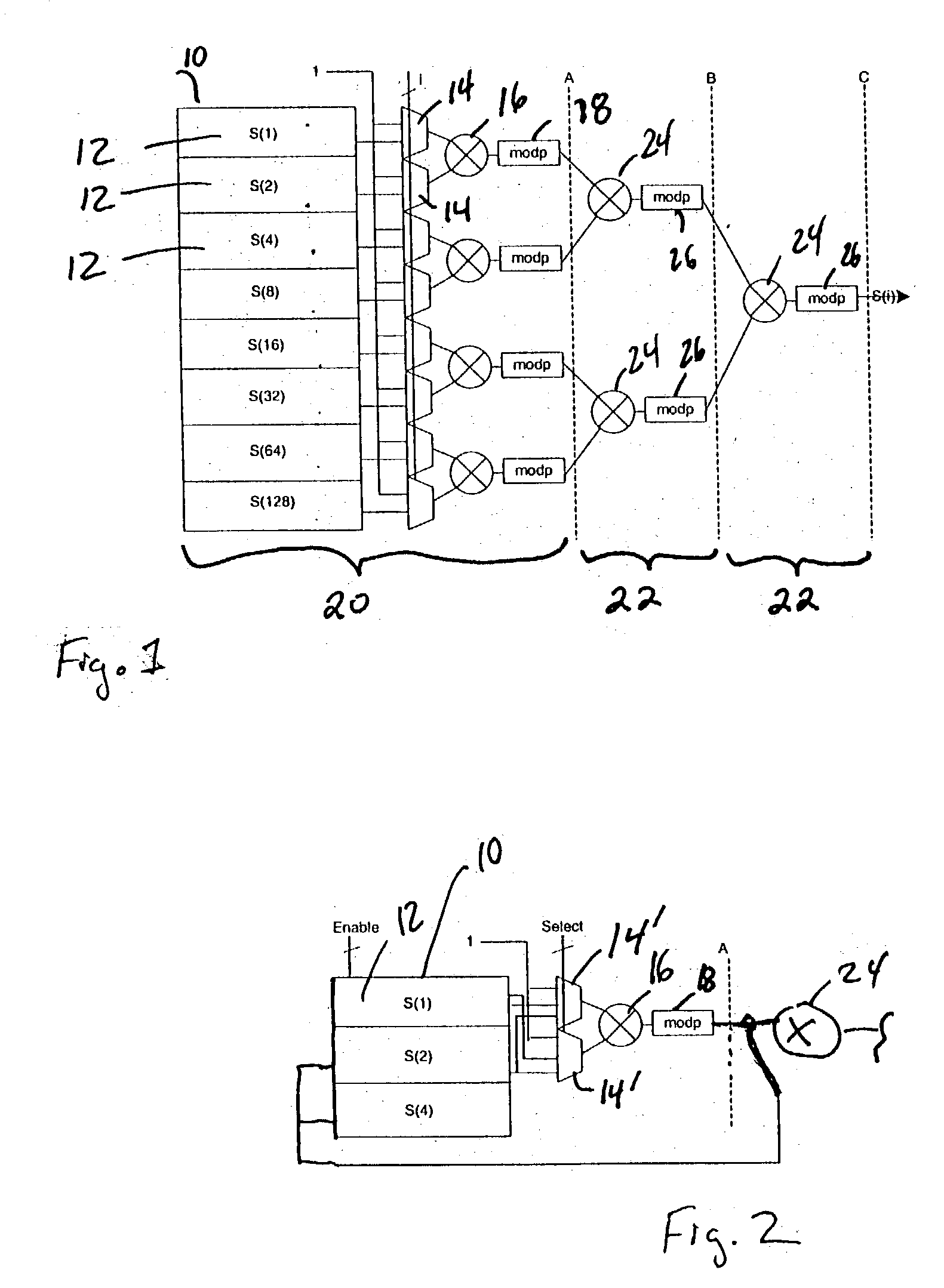
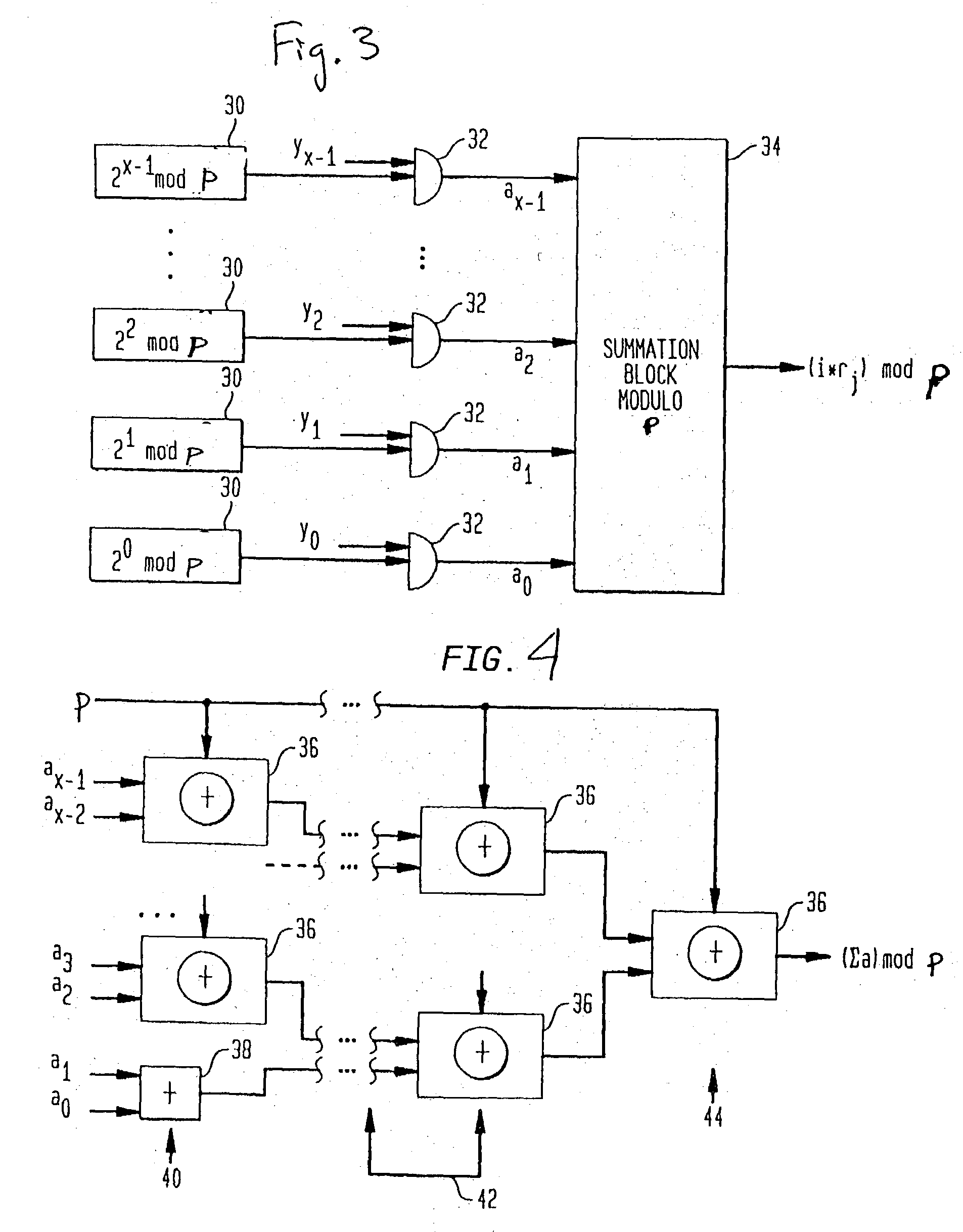
Method and apparatus for generating a pseudo random number
ActiveUS20040162863A1Random number generatorsDigital function generatorsPseudo random number generationComputer science
In the method of generating a pseudo random number, pseudo random numbers equal to pseudo random numbers generated from a pseudo random number generation function indexed by orders of two are stored. Then, a pseudo random number is generated based on the stored pseudo random numbers.
Owner:ALCATEL-LUCENT USA INC
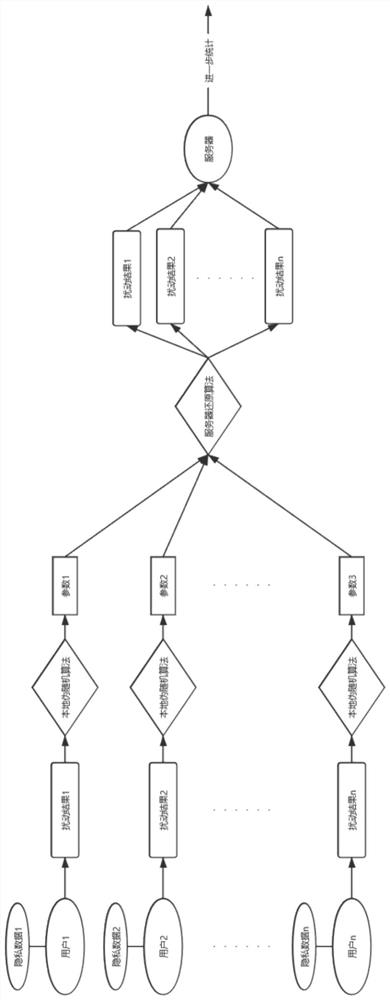
Localized differential private data exchange method and storage medium
ActiveCN111669366AReduce overheadHigh transmission accuracyKey distribution for secure communicationOriginal dataDifferential privacy
The invention discloses a localized differential privacy data exchange method. The method comprises the following steps of firstly, defining a pseudo random number generation algorithm G, a differential privacy budget parameter epsilon and a data range L, enabling the client to disturb the one-hot vector V of the original data x according to the differential privacy budget parameter epsilon, recording the bit index with the value of 1 in V as Info, and recording the bit with the value of 1 after disturbance as N, selecting N different random numbers which are uniformly distributed from the L pieces of data by utilizing the algorithm G to obtain an array Indexes, adding random numbers offset which are uniformly distributed on [0, L-1] to each element to obtain a disturbance sequence, and sending a triple (seed, N, offset) to a server, and enabling the server to access a pseudo-random number generator G(seed) and restoring the disturbance vector according to an algorithm. The invention further discloses a computer storage medium based on the method. According to the method, the transmission and operation expenditure is greatly reduced while the privacy data transmission precision isguaranteed.
Owner:NANJING UNIV
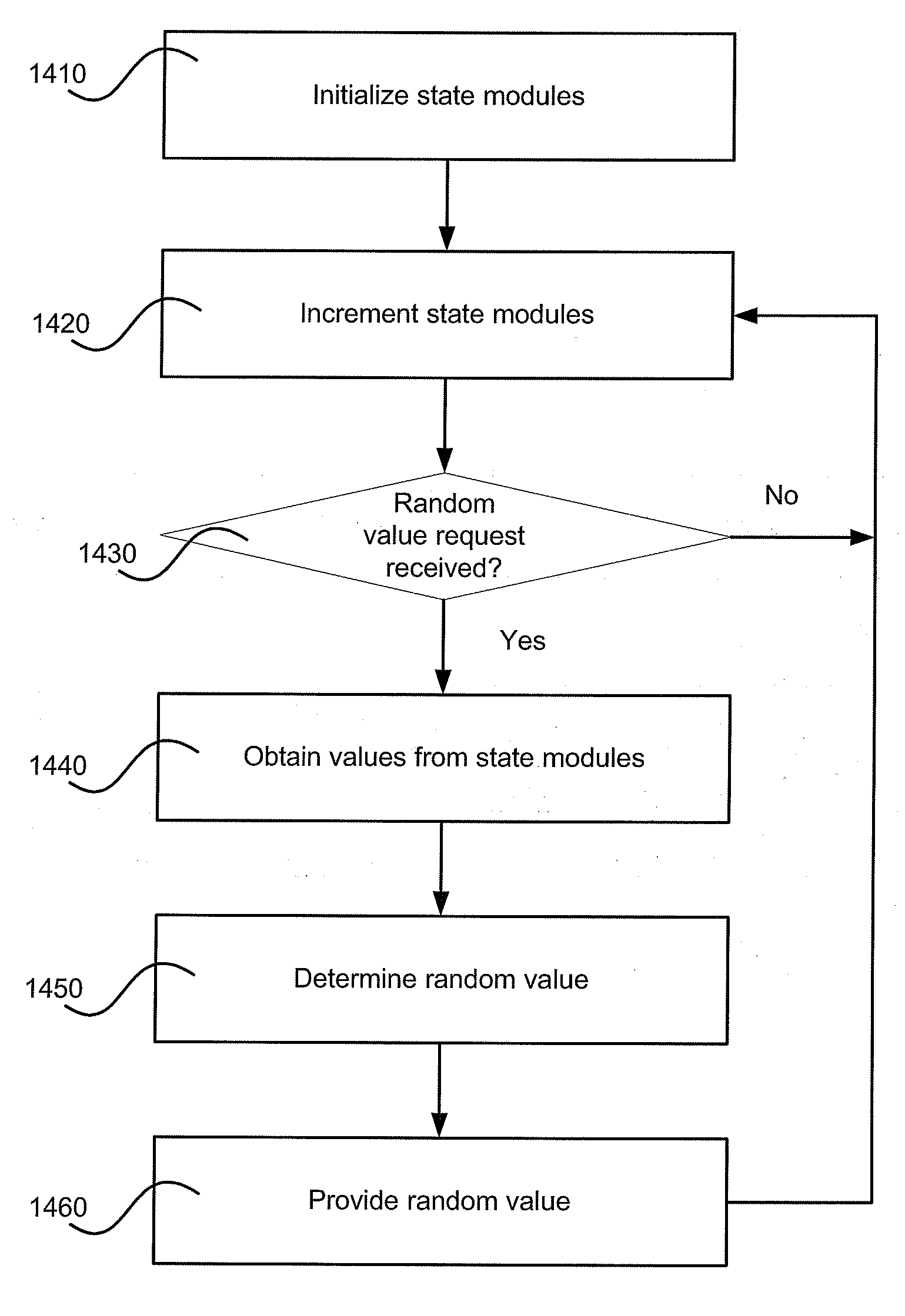
Pseudorandom Number Generation
ActiveUS20090106338A1Well formedRandom number generatorsSecuring communicationTheoretical computer scienceLimit value
A system and method of for obtaining a pseudorandom number generator are disclosed. A set of state modules, each with a limit value, may be provided. In an embodiment, each of the limit values may be relatively prime to the other limit values. In response to one or more events, the values of the state modules are incremented. At some frequency that may be statistically independent from the occurrence of the one or more events, the values of the state modules are obtained and combined to form a random number. The values may be combined as desired and, if desired, may be combined modulo 2w, where 2w represents the number of possible random values.
Owner:SCHNEIDER ELECTRIC USA INC
True random number generation method and system
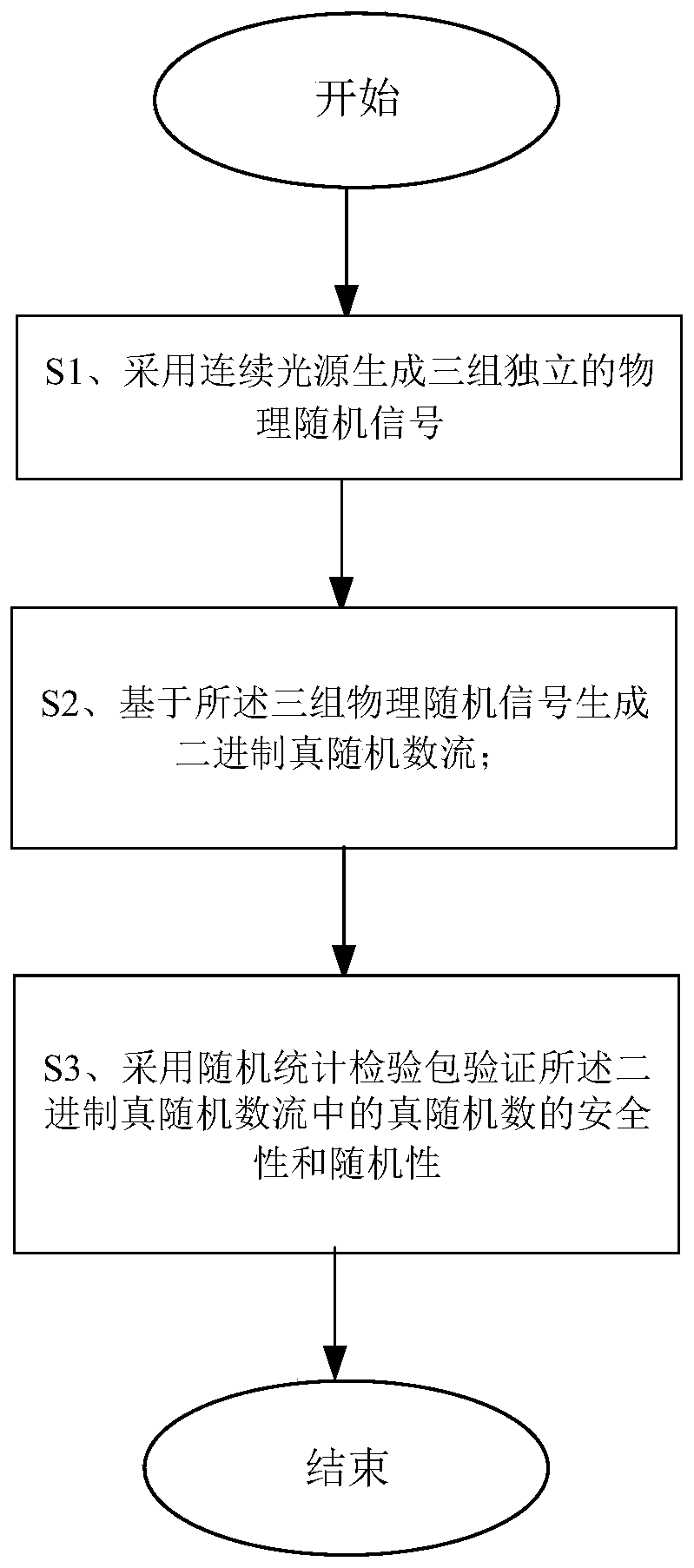
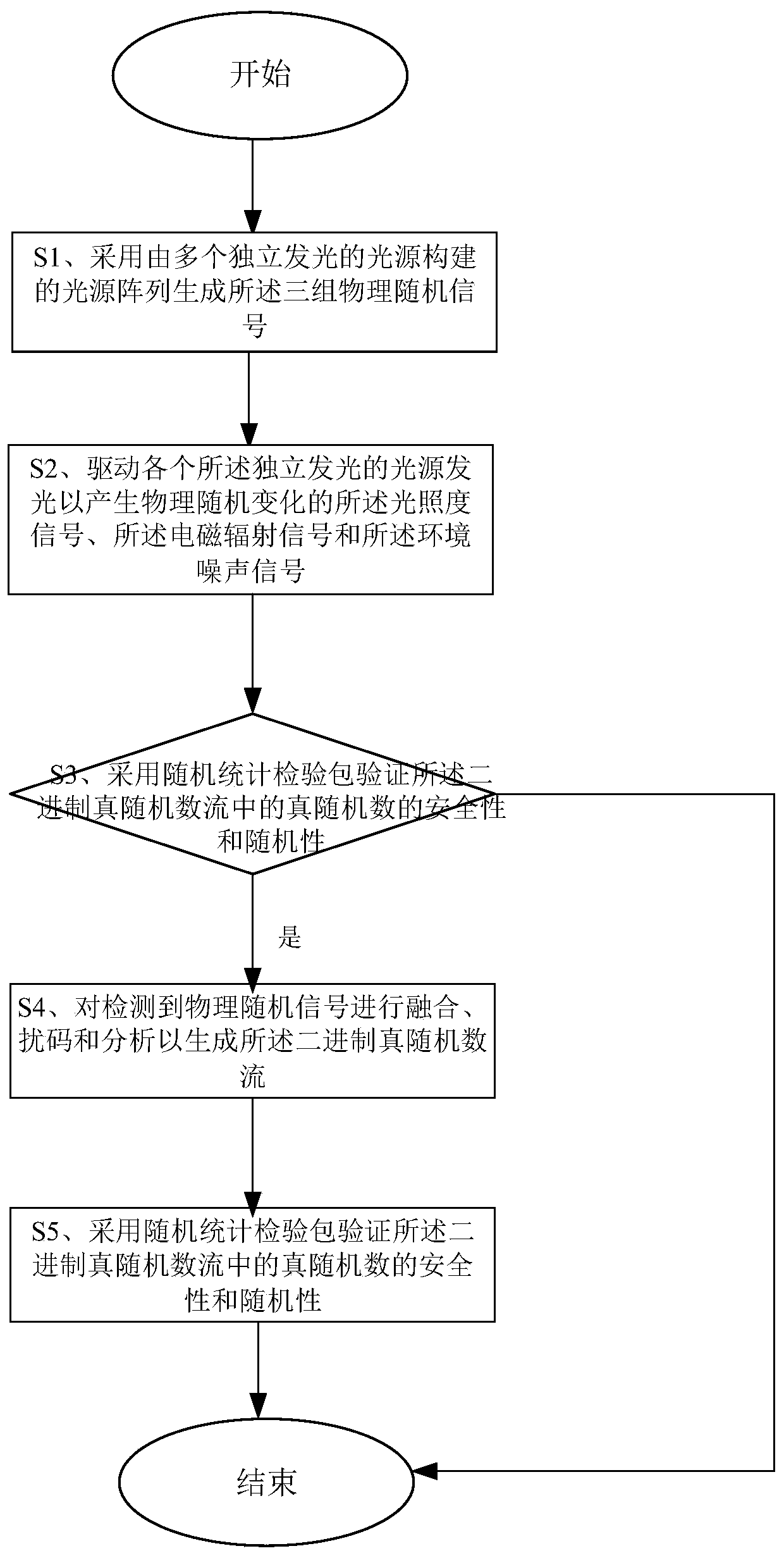
ActiveCN110333842AQuality improvementHigh speedRandom number generatorsContinuous lightPseudo random number generation
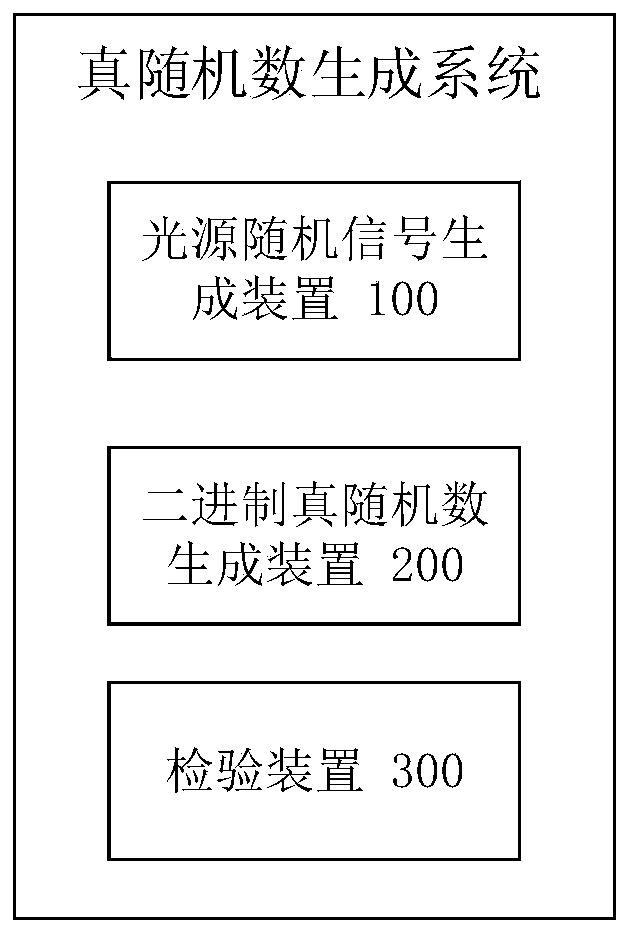
The invention relates to a true random number generation method. The method comprises the following steps: S1, generating three groups of independent physical random signals by adopting a continuous light source; s2, generating a binary true random number stream based on the three groups of physical random signals; and S3, verifying the security and randomness of the true random number in the binary true random number stream by adopting a random statistical test packet. The invention further relates to a true random number generation system, which comprises: a light source random signal generation device for generating three groups of independent physical random signals; a binary true random number generation device which is used for generating a binary true random number stream based on the three groups of physical random signals; and a verification device which is used for verifying the safety and randomness of the true random numbers in the binary true random number flow by adoptinga random statistical test packet. By implementing the true random number generation method and system provided by the invention, the high-quality random number with unpredictability and irreversibility can be simply generated at a high speed by adopting a common physical random signal source.
Owner:SHENZHEN Y& D ELECTRONICS CO LTD
Uniform random number generation method for encoding deep-space communication protocol
InactiveCN103197912AIncrease randomnessMeet the requirements of variable bit widthRandom number generatorsCommunications systemTheoretical computer science
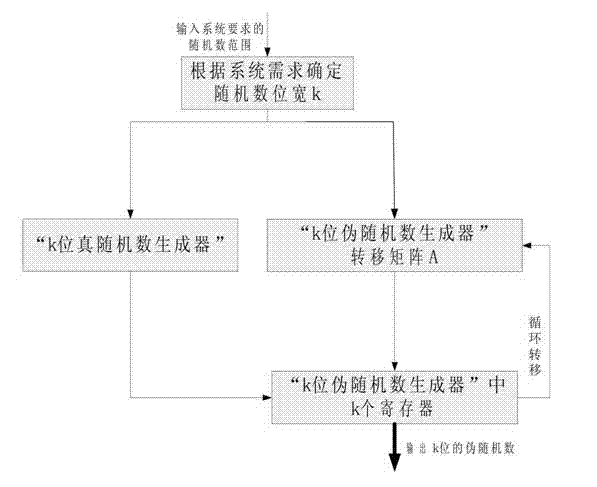
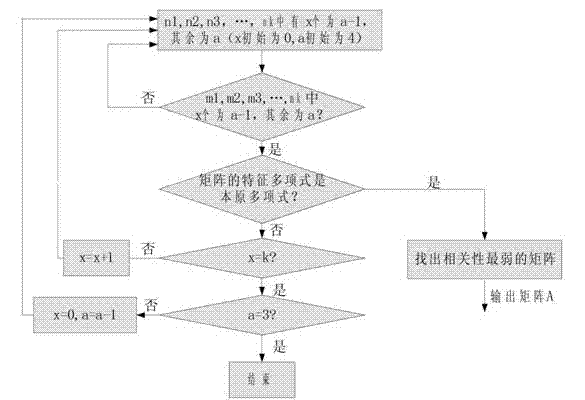
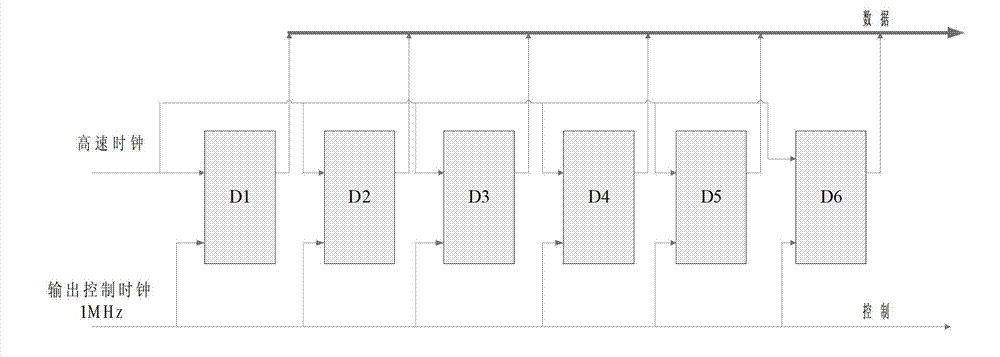
The invention relates to a uniform random number generation method for encoding a deep-space communication protocol, belonging to the technical field of deep-space communication and communication signal processing. According to the invention, a k*k dimension pseudo-random number generation matrix is designed, so that the generated pseudo-random number reaches the maximum period and the random performance of the random number is improved; and the bit width of the generated random number is k, and thus the requirement that the bit width is variable is met when the deep-space communication protocol is realized. In addition, a true random number is generated as a seed of a pseudo-random number generator, and thus a true random number which is not limited by the period is obtained and better output random characteristics of the random number are obtained.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com