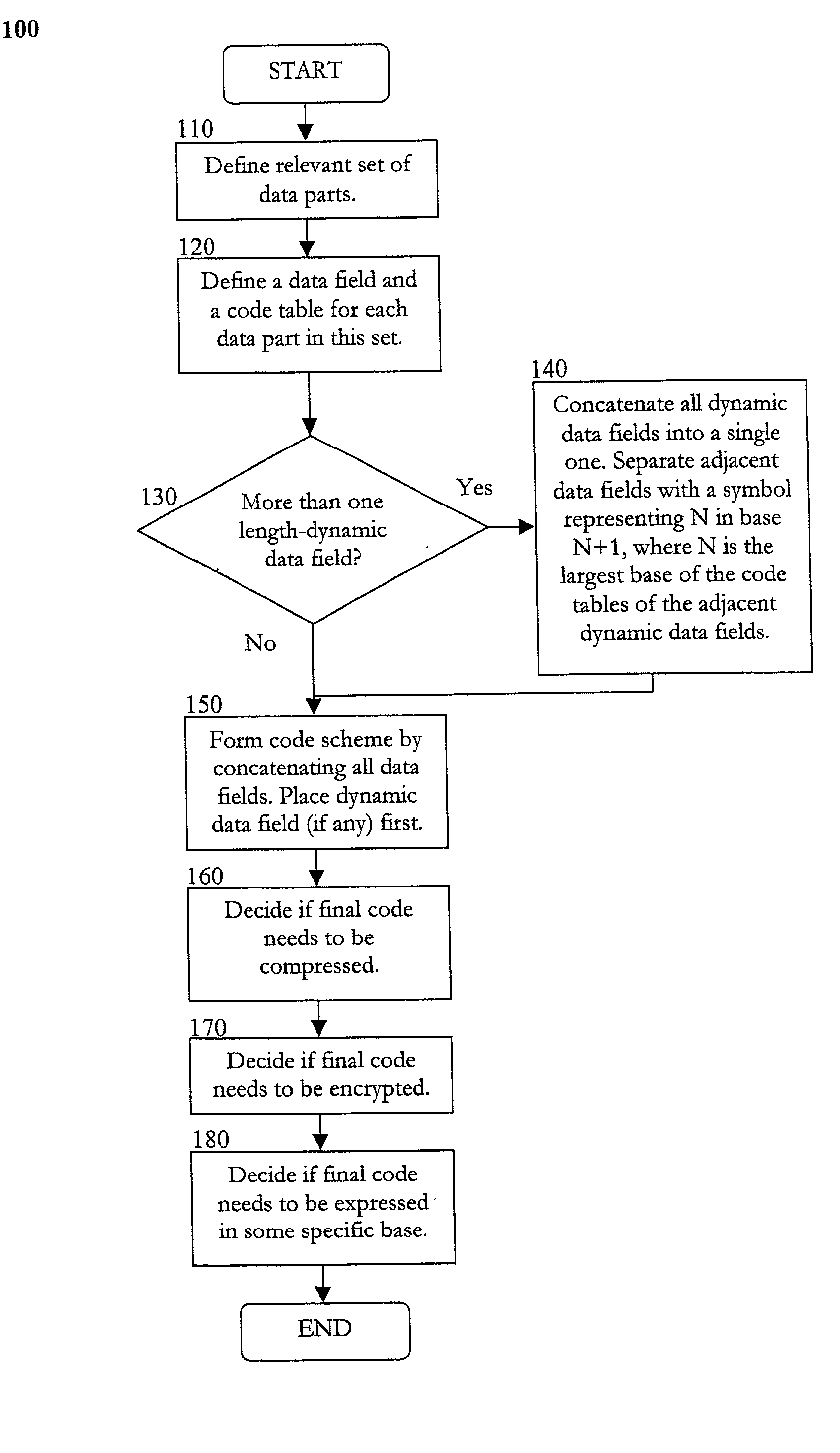
Patents
Literature
33 results about "Number series" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
True random number generator
InactiveCN101515228AImprove design efficiencySimple structureRandom number generatorsNumber seriesData signal
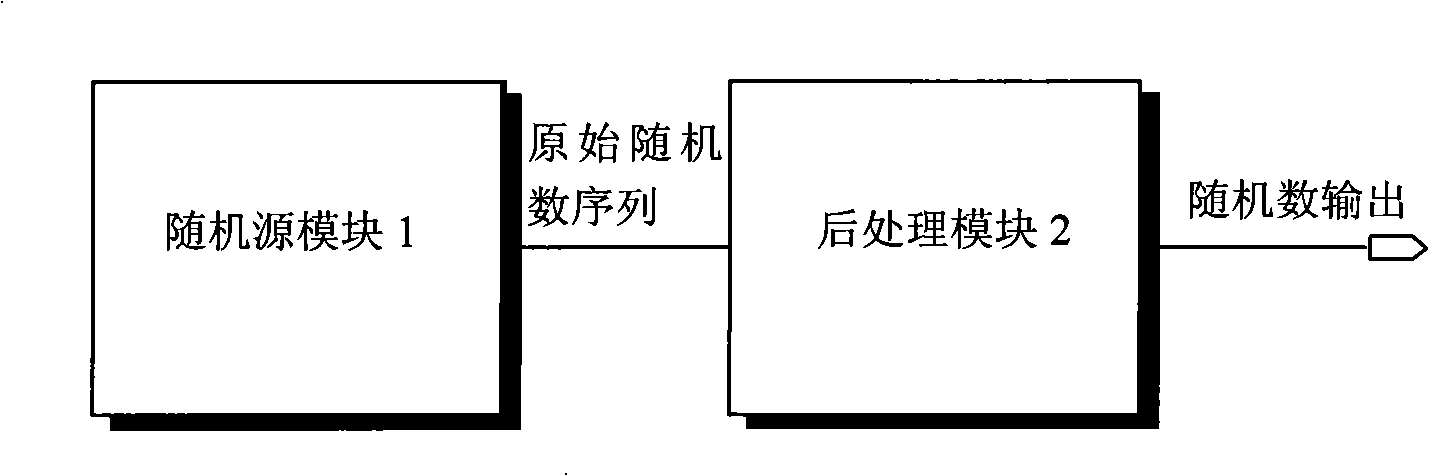
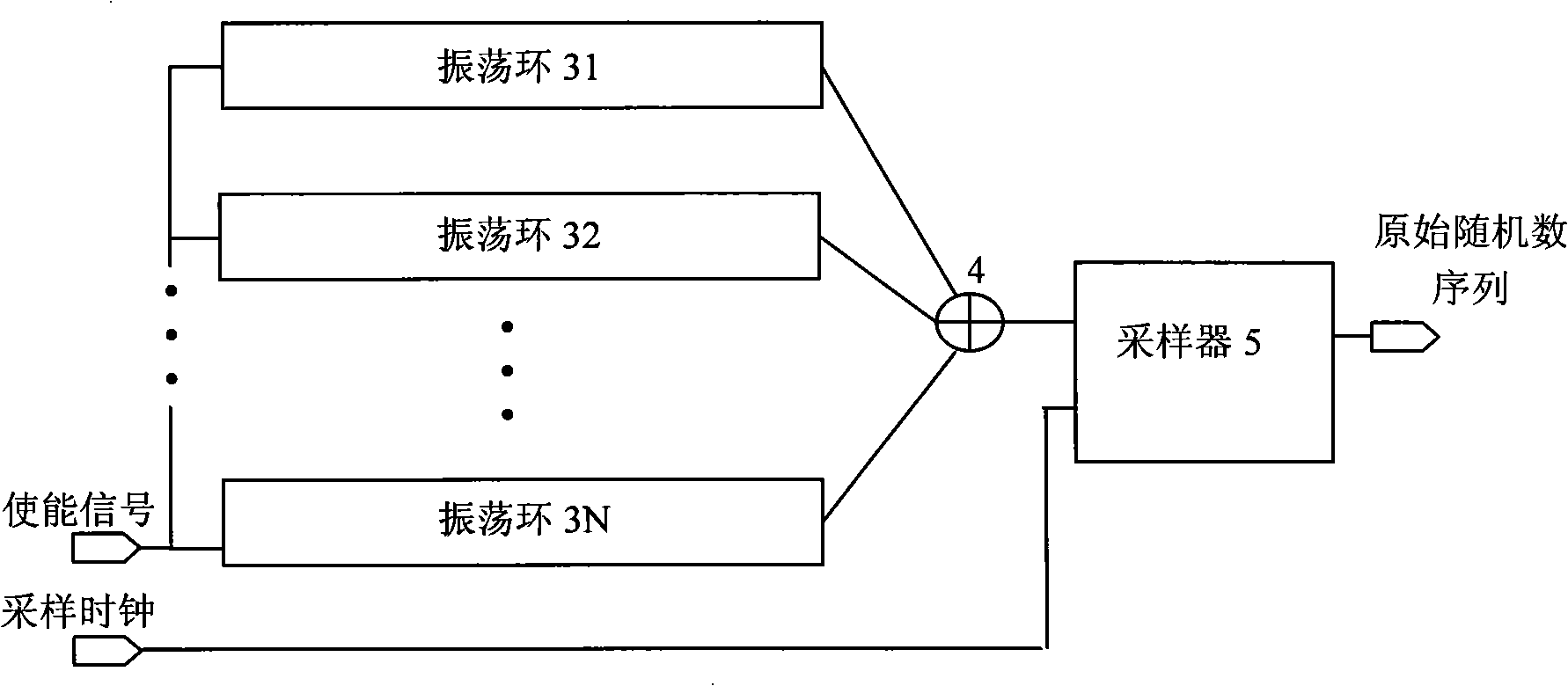
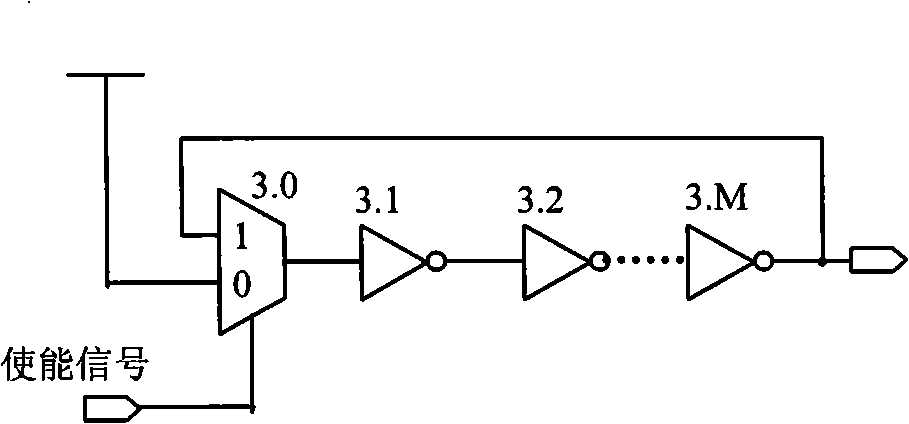
The invention discloses a true random number generator, comprising a stochastic source module and a post-processing module. The stochastic source module is used for generating digital signals having random characteristics and providing the digital signals for the post-processing module; the post-processing module carries out post-processing for the digital signals by using a loop code error-correcting method, thereby eliminating bias of data signals to obtain random number series. The stochastic source module can be composed of a plurality of sets of inverter oscillating rings, and the post-processing module is realized by a linear feedback shift register (LFSR). The TRNG (True Random Number Generator) has simple structure and only general digital logic devices are used, so the true random number generator has good technology weak correlation and can be rapidly transplanted in an integrated circuit design flow after prototype verification is carried out, thereby improving the efficiency of module design and reducing the development risk.
Owner:HUAZHONG UNIV OF SCI & TECH
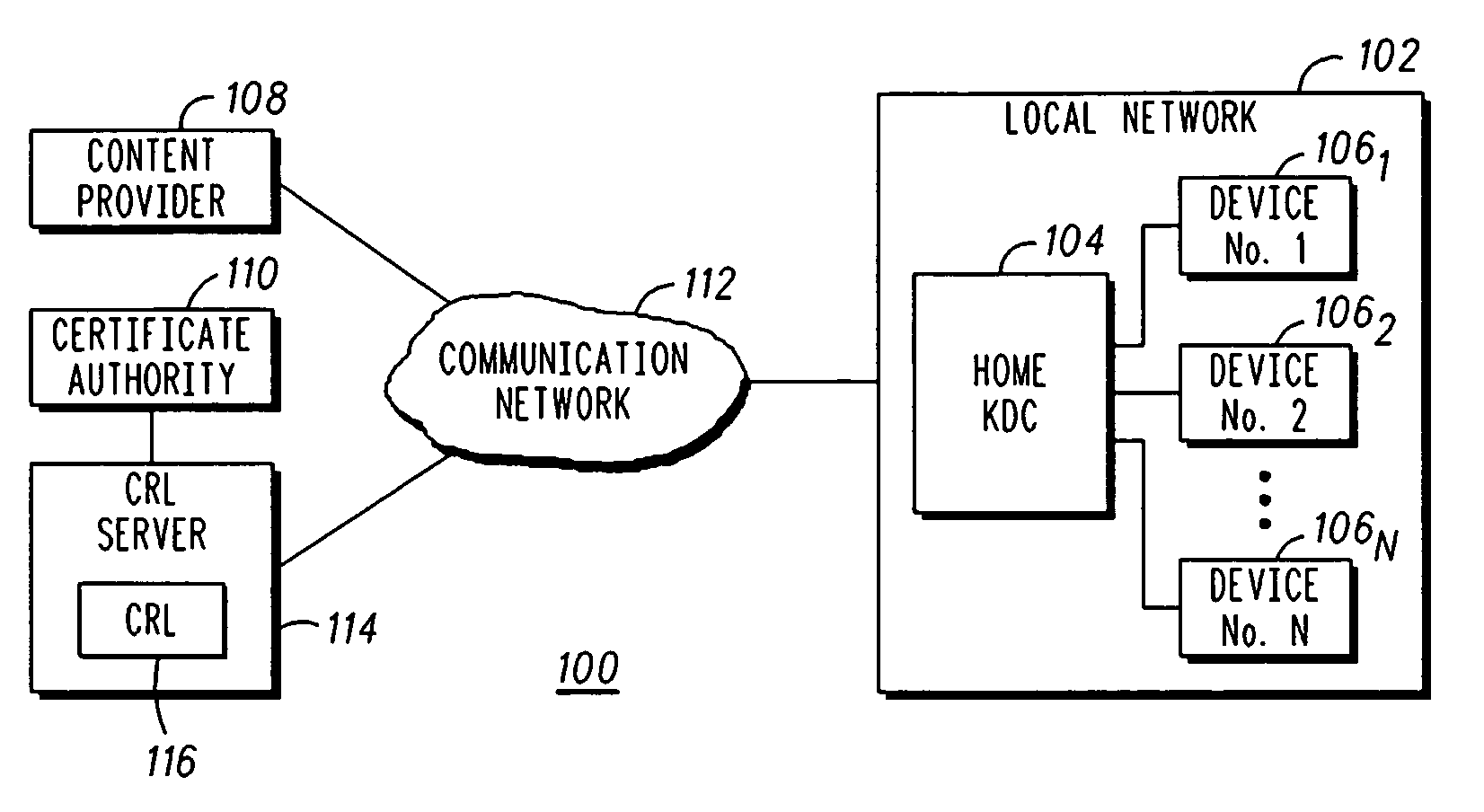
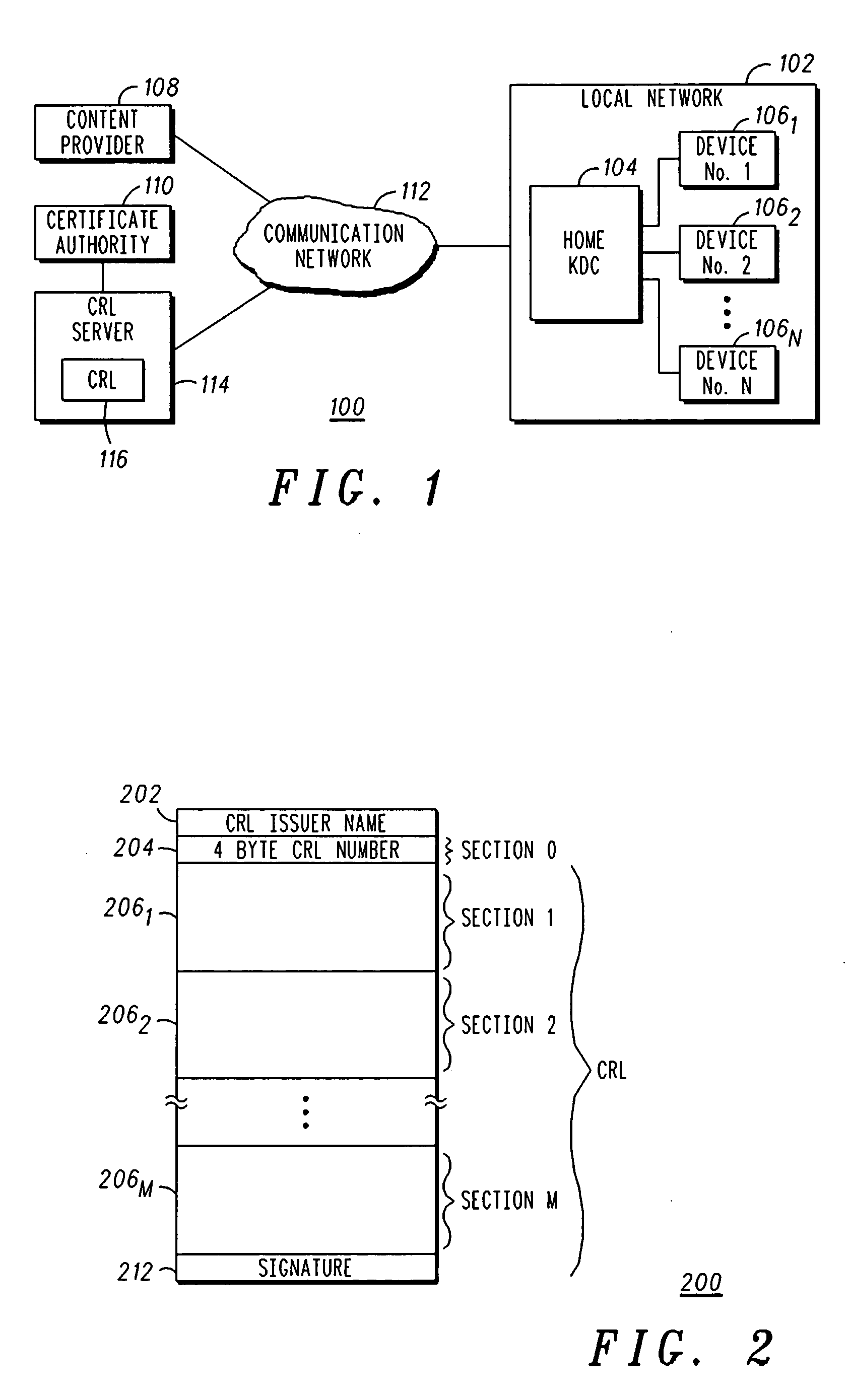
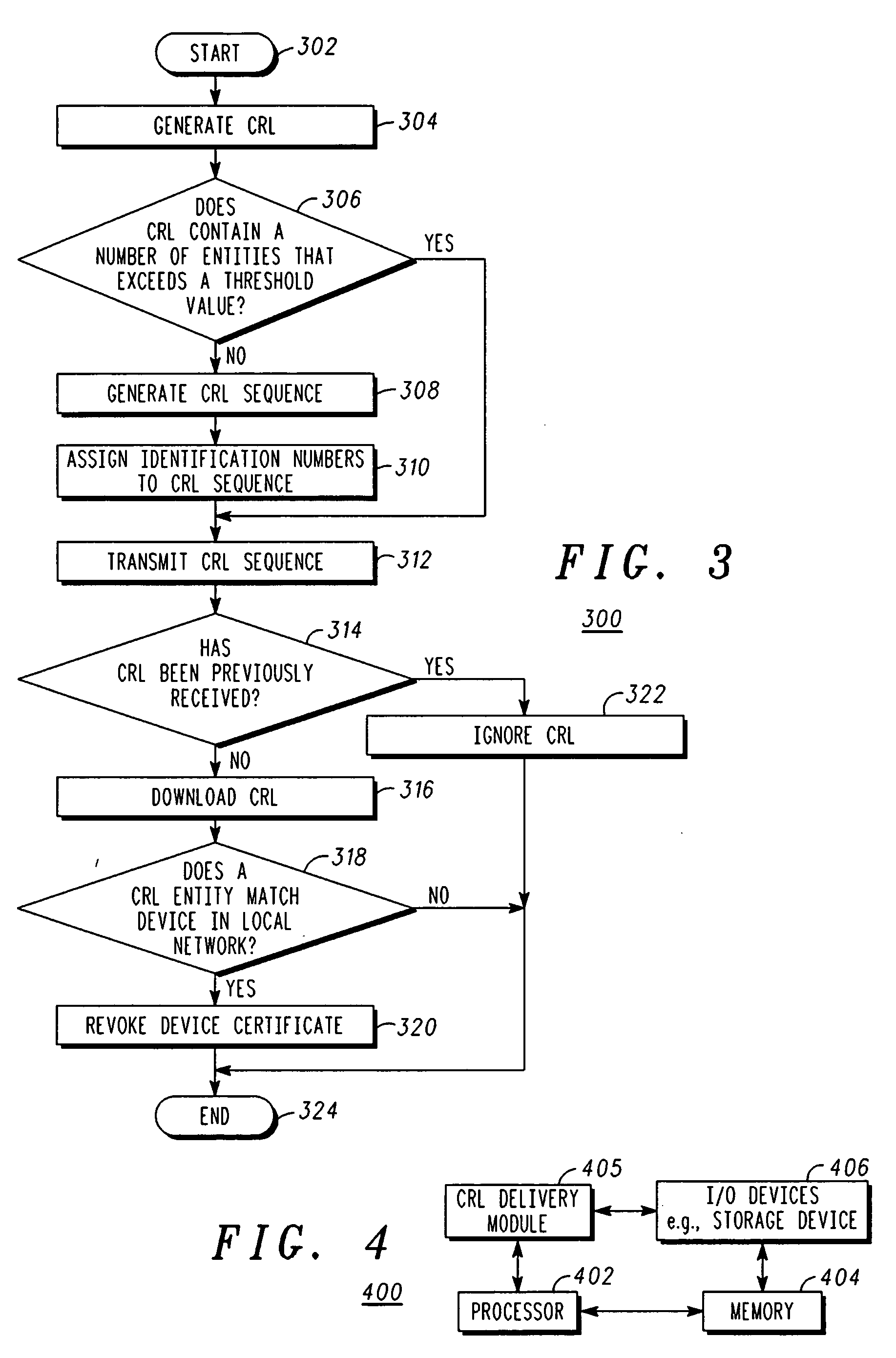
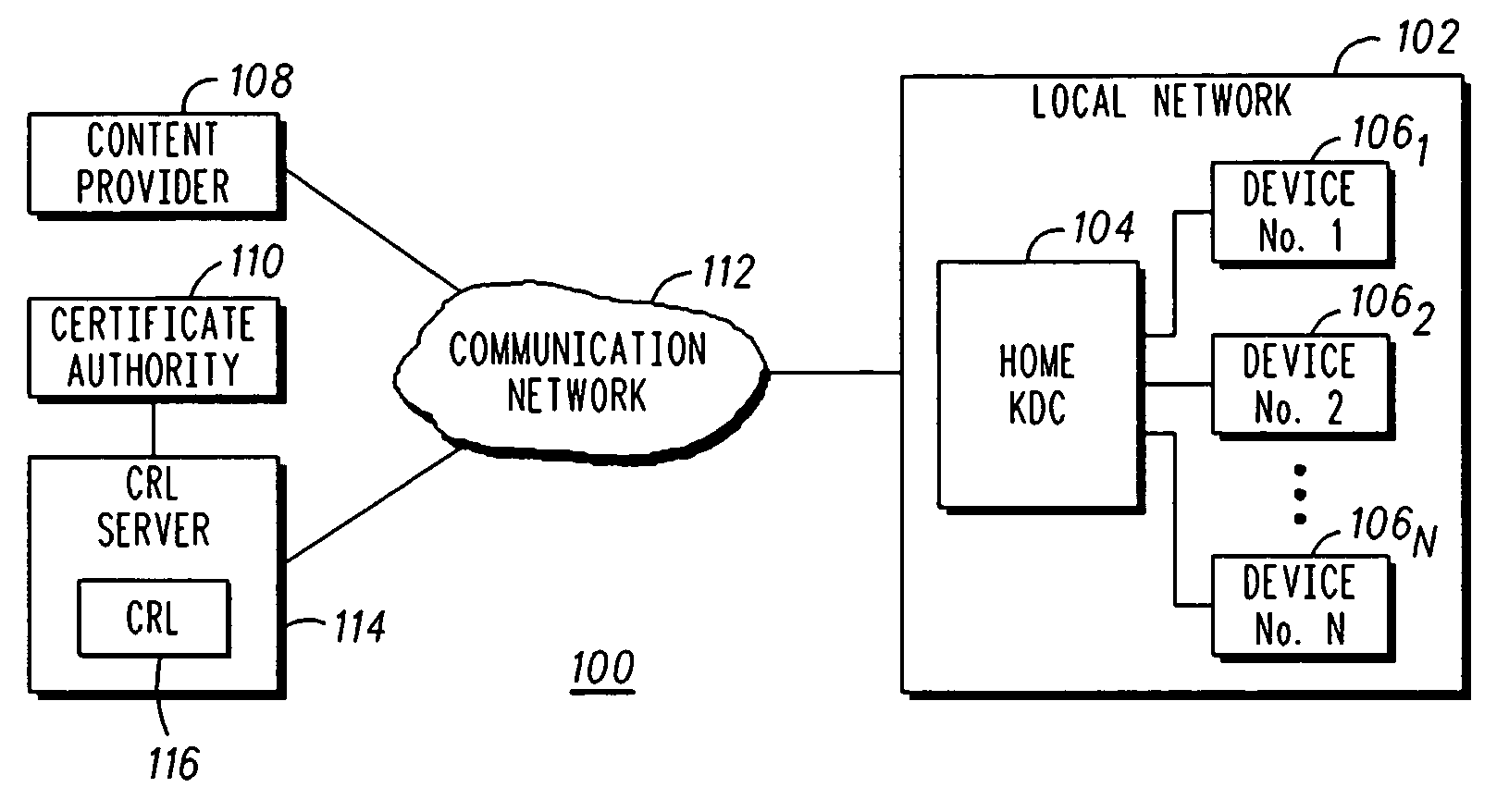
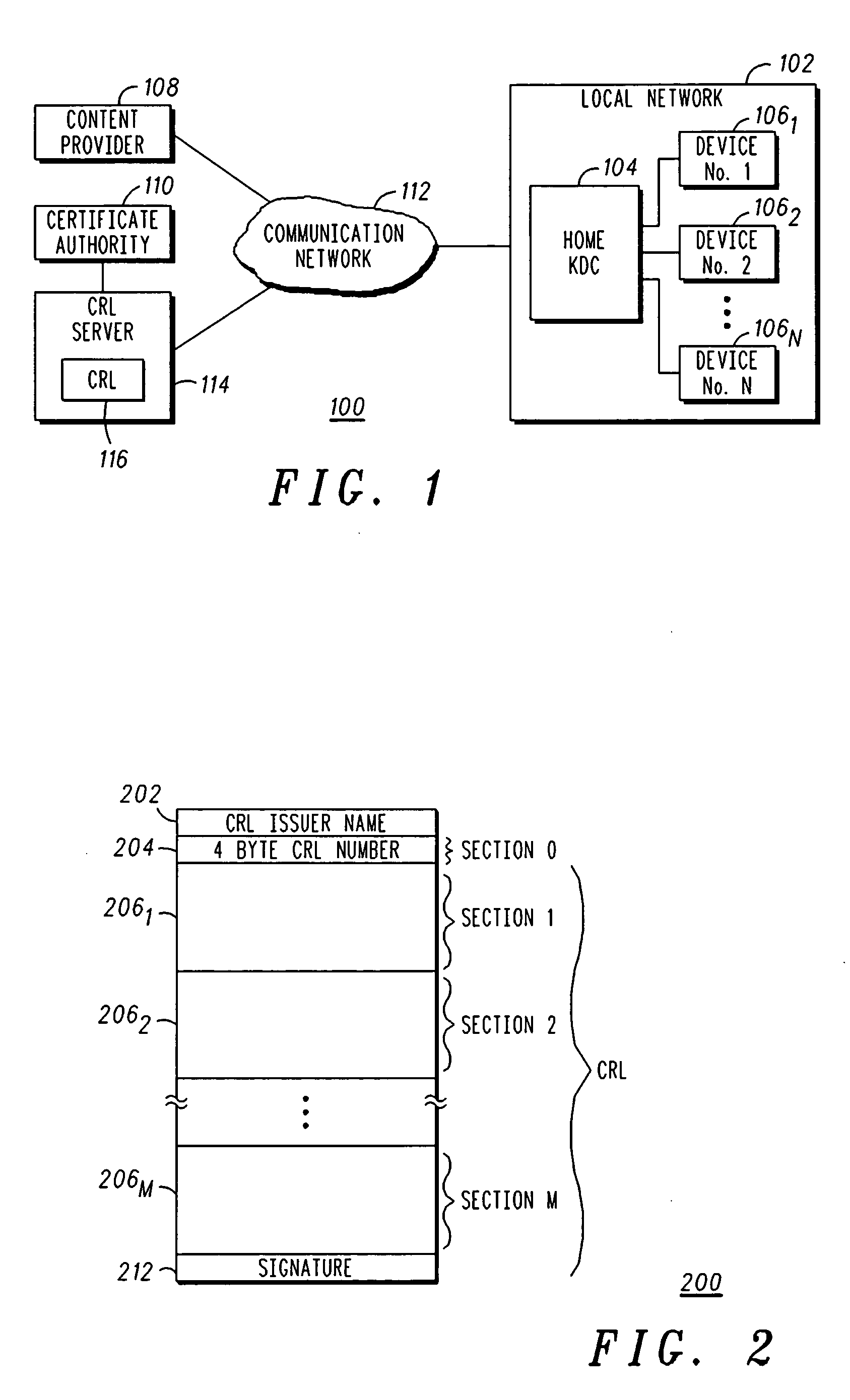
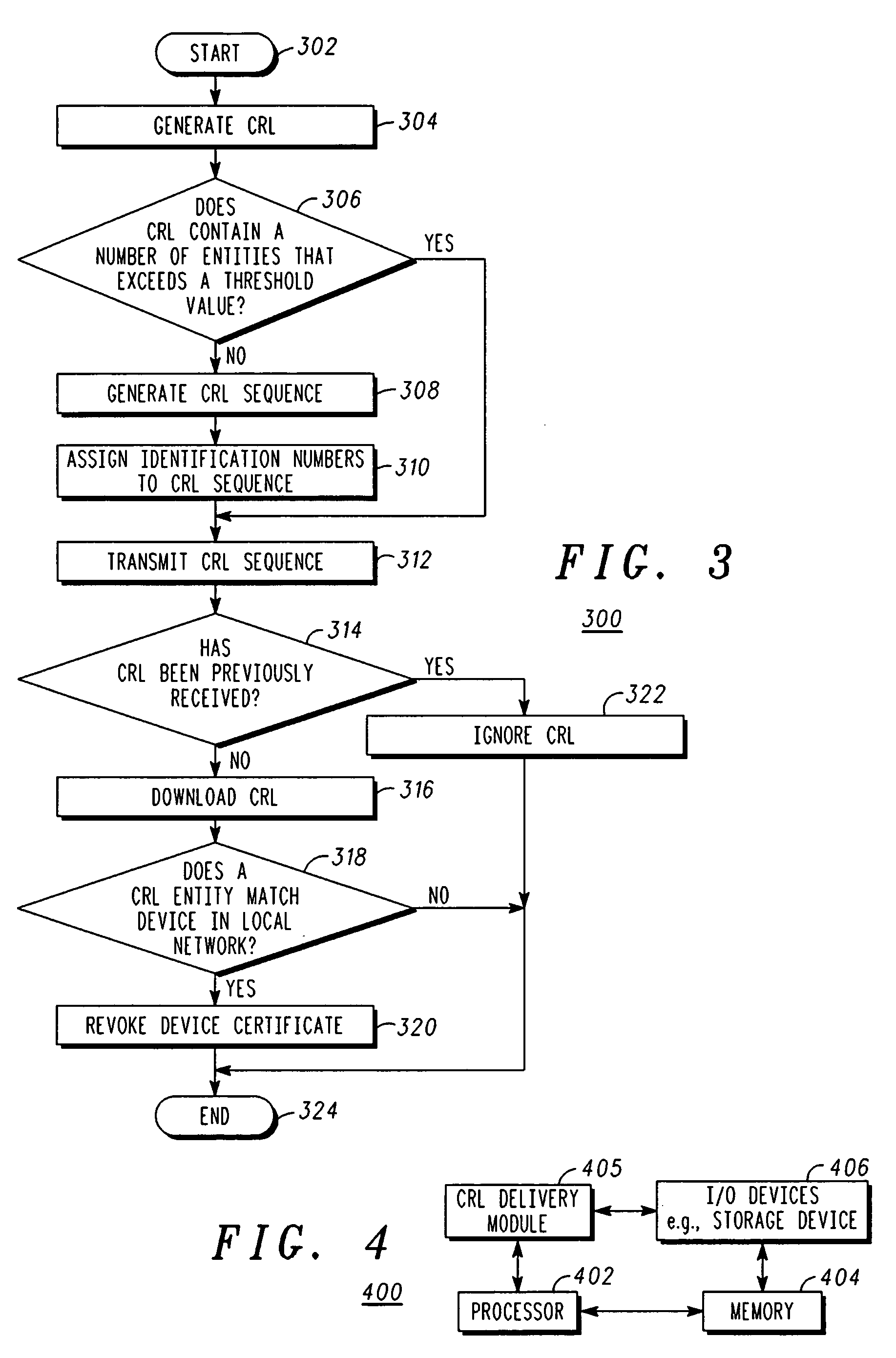
Method and apparatus for delivering certificate revocation lists
The present invention discloses an apparatus and method for delivering a revocation list over a one-way broadcast network to receivers with limited memory capabilities. In one example, the revocation list is partitioned to form a first certificate revocation list (CRL) sequence if the number of entries in the revocation list exceeds a predetermined value. Individual identification numbers belonging to a first identification number series are subsequently assigned to partitions of the first CRL sequence. Afterwards, the first CRL sequence is interleaved into a first content transport stream.
Owner:GOOGLE TECH HLDG LLC
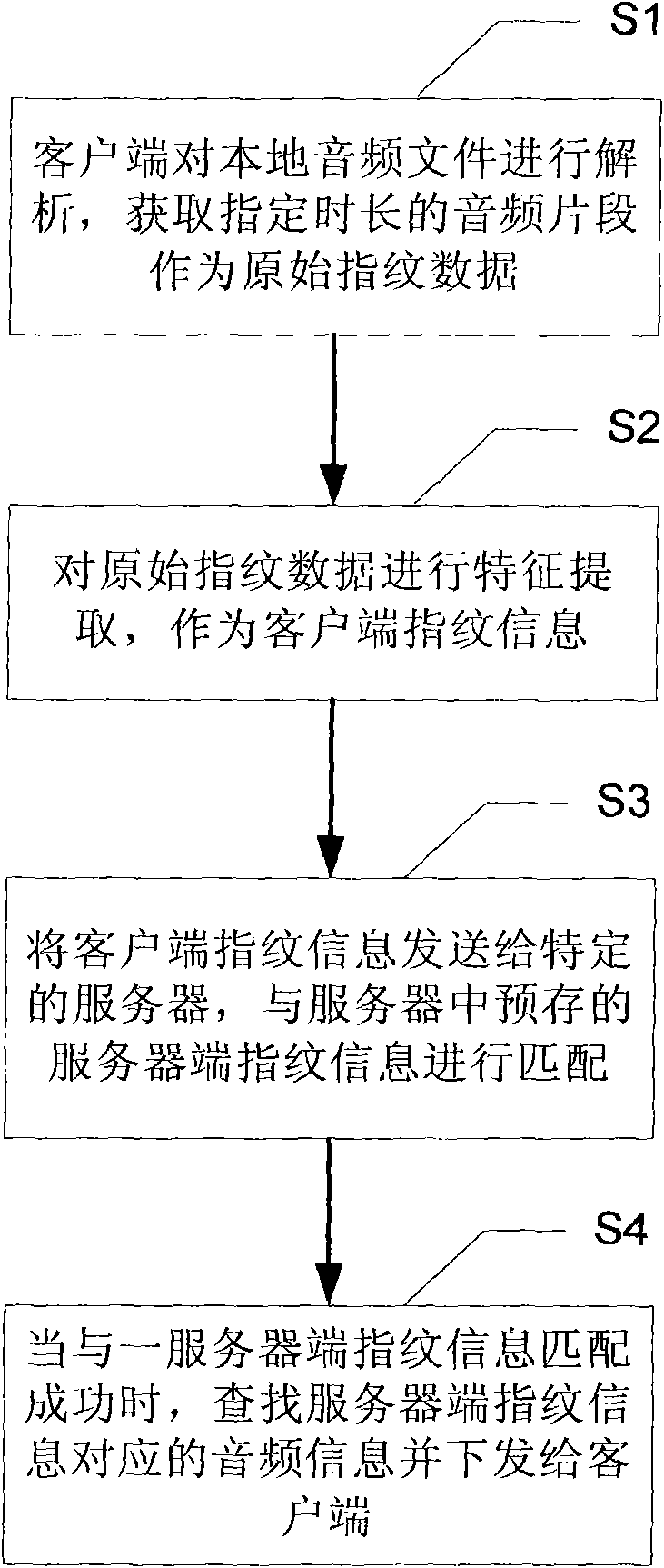
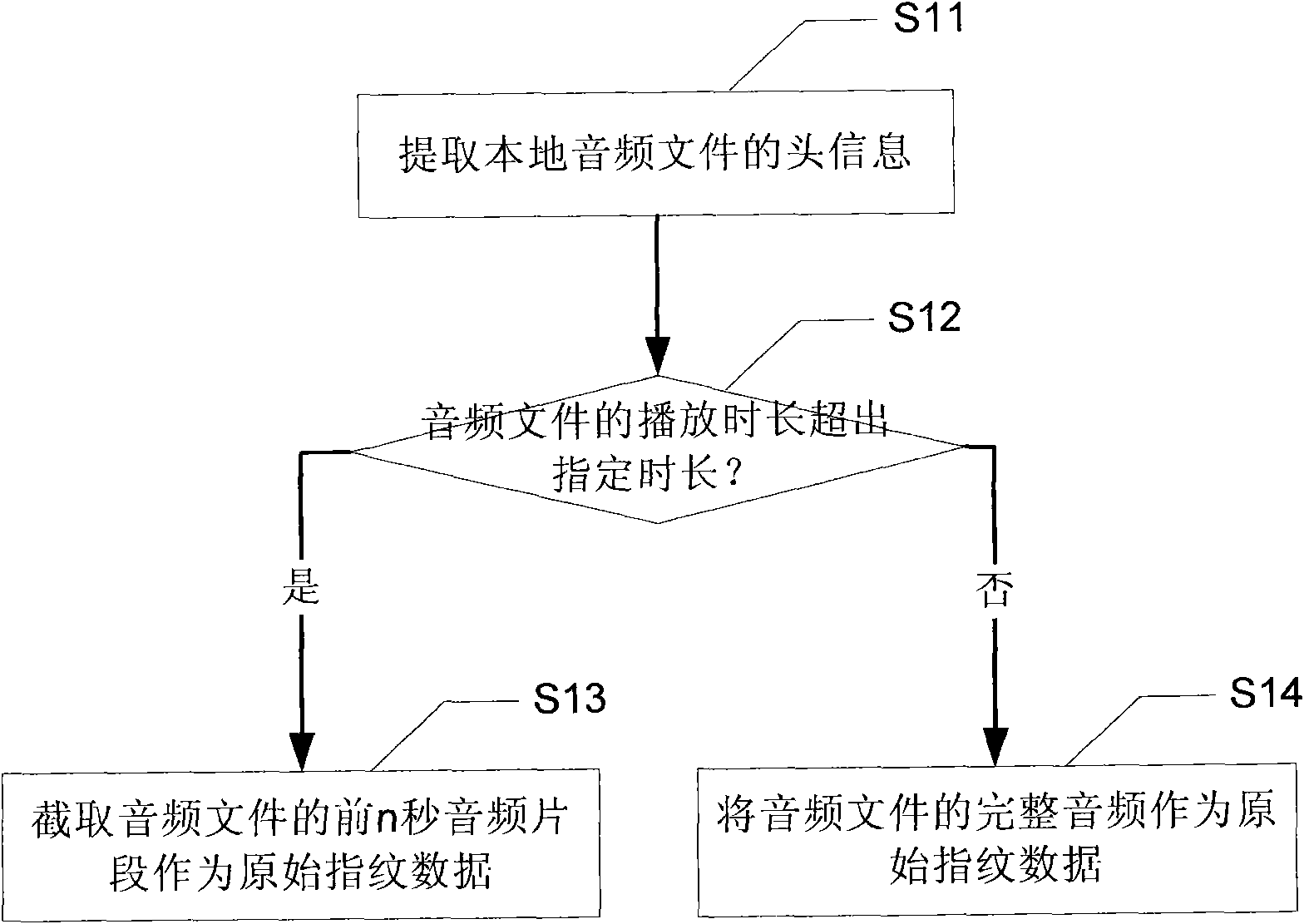
Method, system, client and server for providing related audio information
InactiveCN101651694AEasy to useTransmissionSpecial data processing applicationsComputer hardwareFast Fourier transform
The invention discloses a method, a system, a client and a server for providing related audio information. The method comprises the following steps: a client resolves local audio files and acquires audio segments with a set duration as original fingerprint data; frames of the original fingerprint data are segmented, and fast Fourier transform (FFT) is carried out to each frame so that the originalfingerprint data are transformed into a set of number series as the fingerprint information of the client; the fingerprint information of the client is sent to a special server to match fingerprint information prestored in the server; and when the fingerprint information of the client is successfully matched with one fingerprint information of the server, audio information corresponding to the fingerprint information of the server is searched and submitted to the client. The invention ensures that the local audio files of the client has integral and uniform audio information and improves theuse experience of a user.
Owner:北京亮点时间科技有限公司
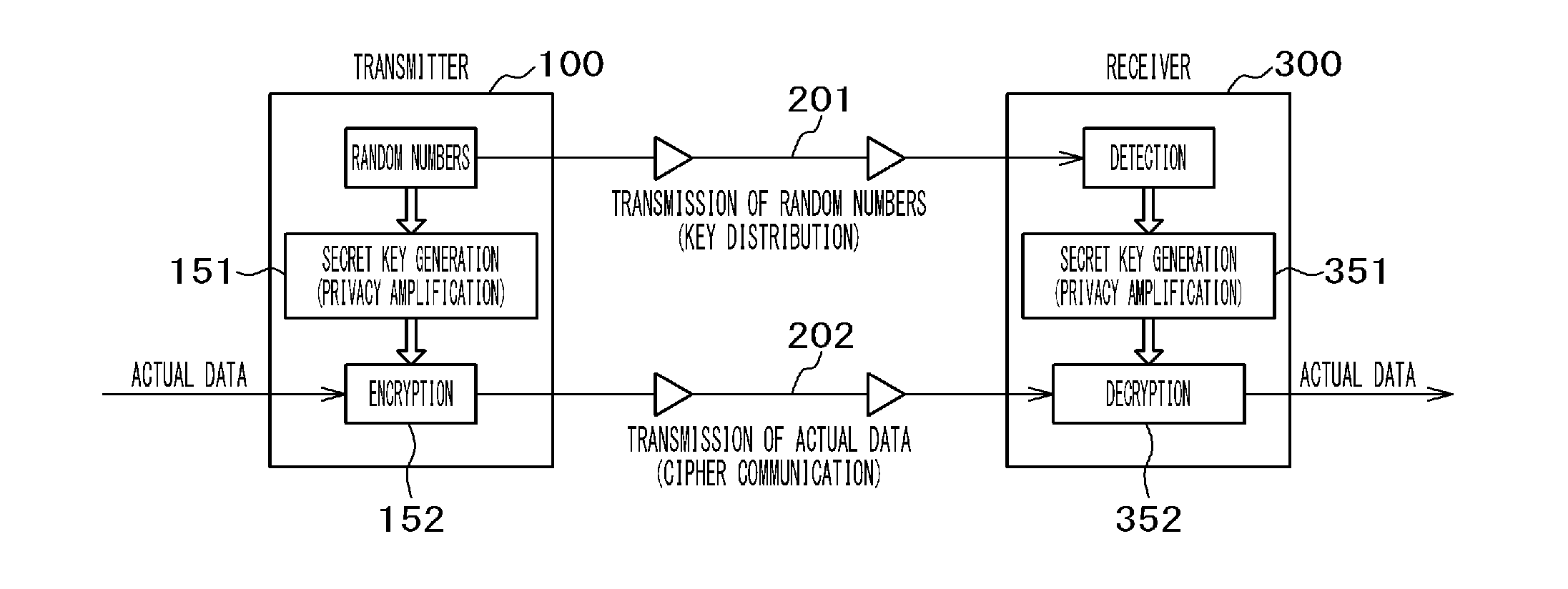
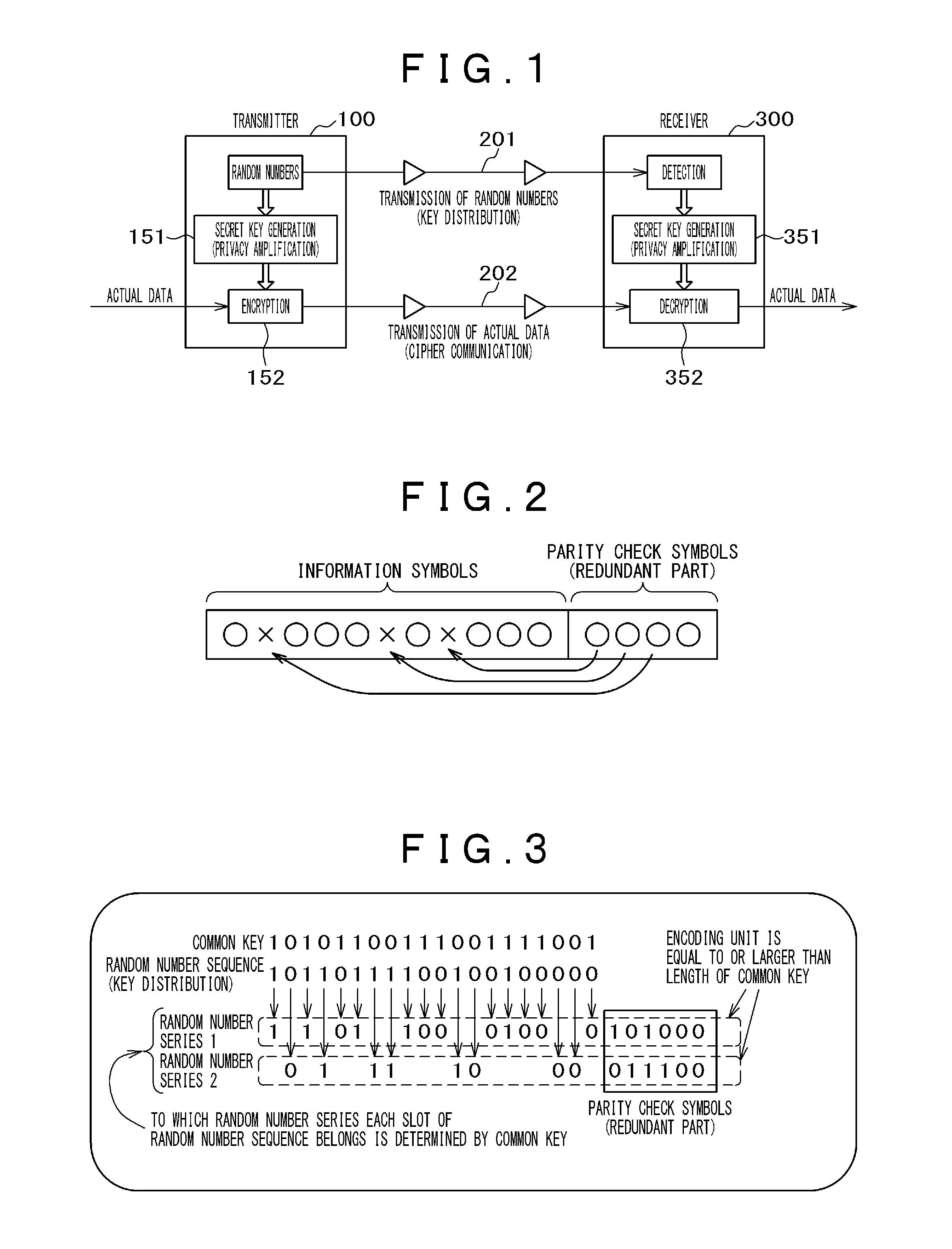
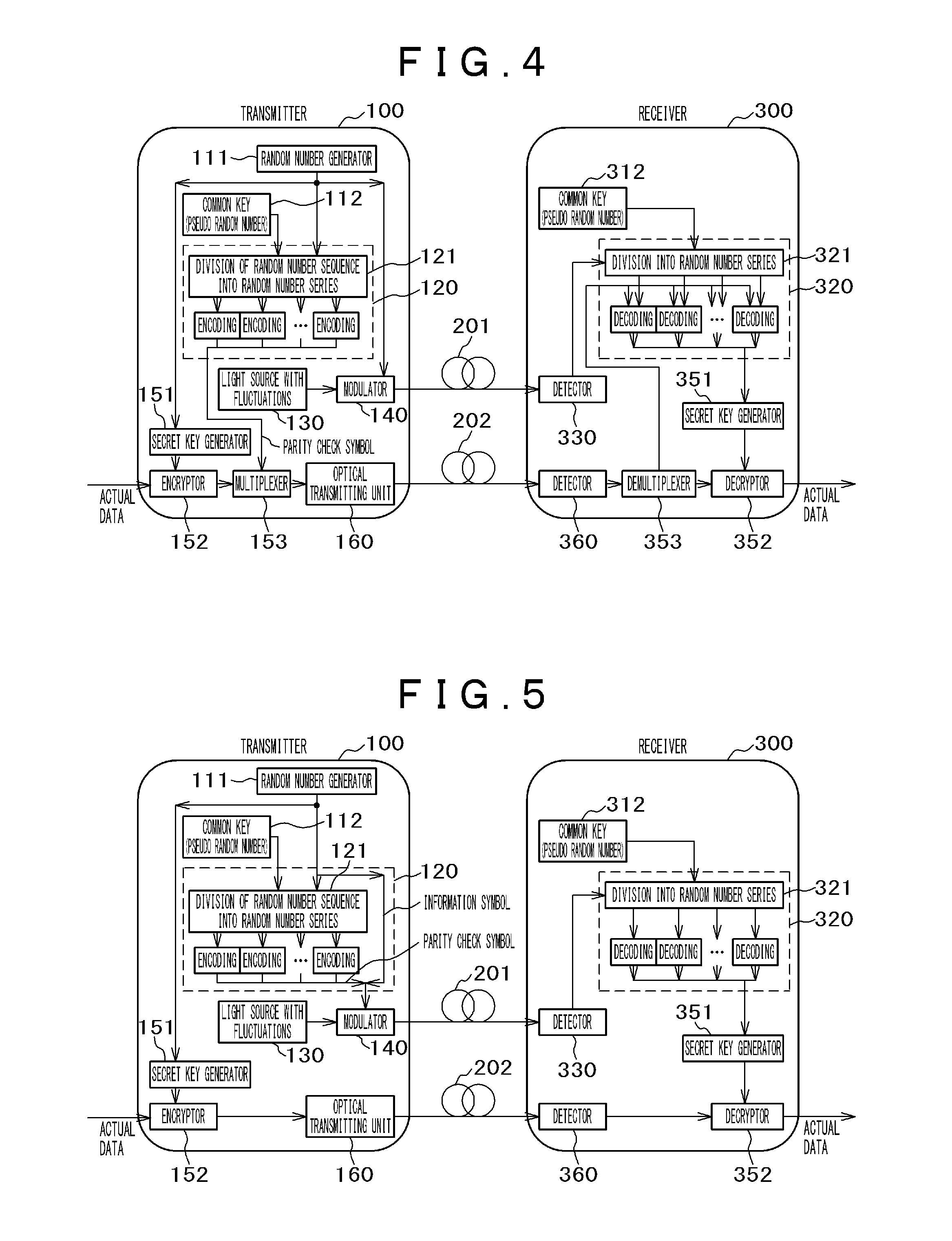
High-Security Communication System, and Transmitter and Receiver Both Used Therein
ActiveUS20160112189A1Correction errorEasily corrects bit errorsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCommunications systemTransmission channel
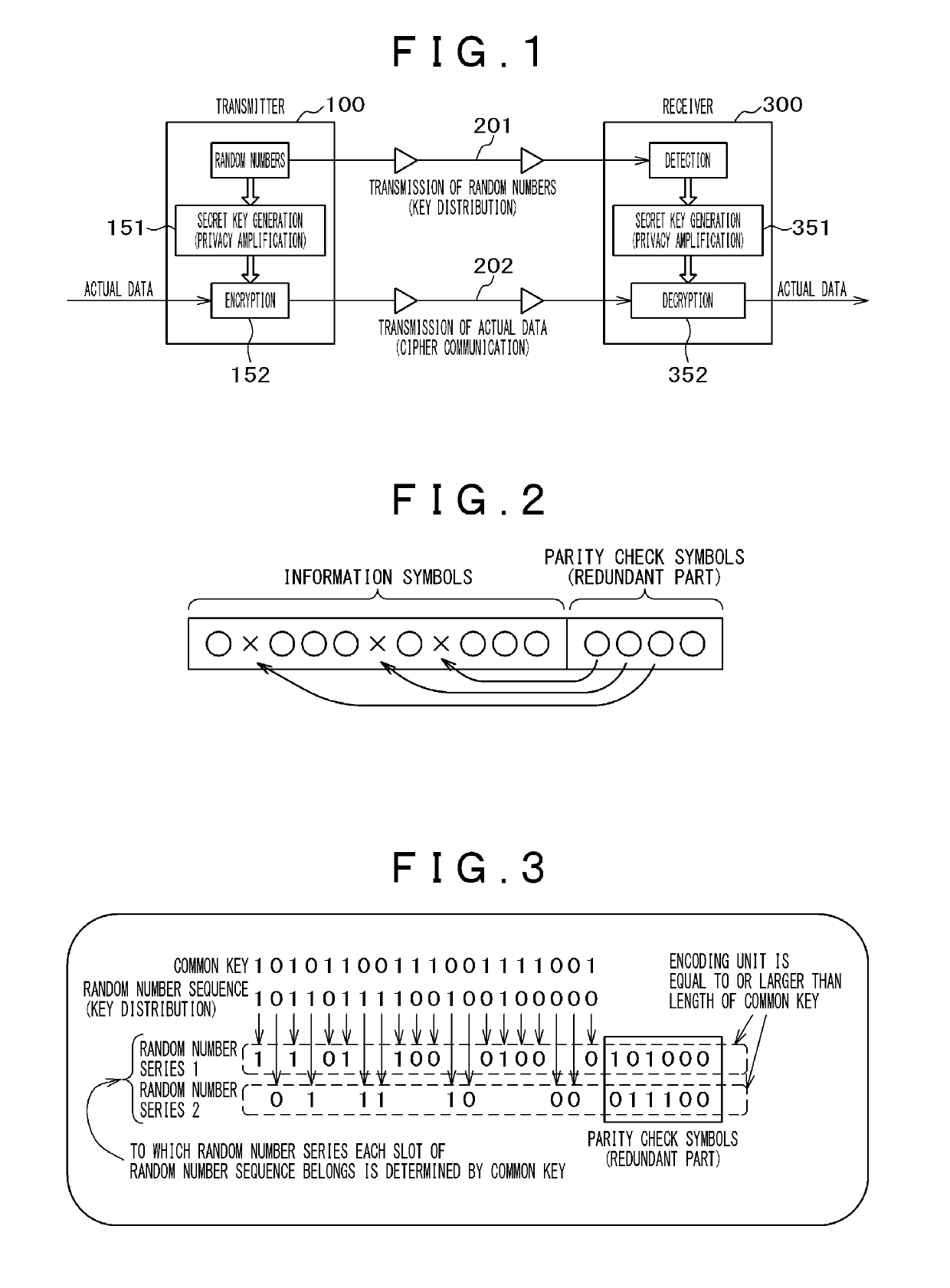
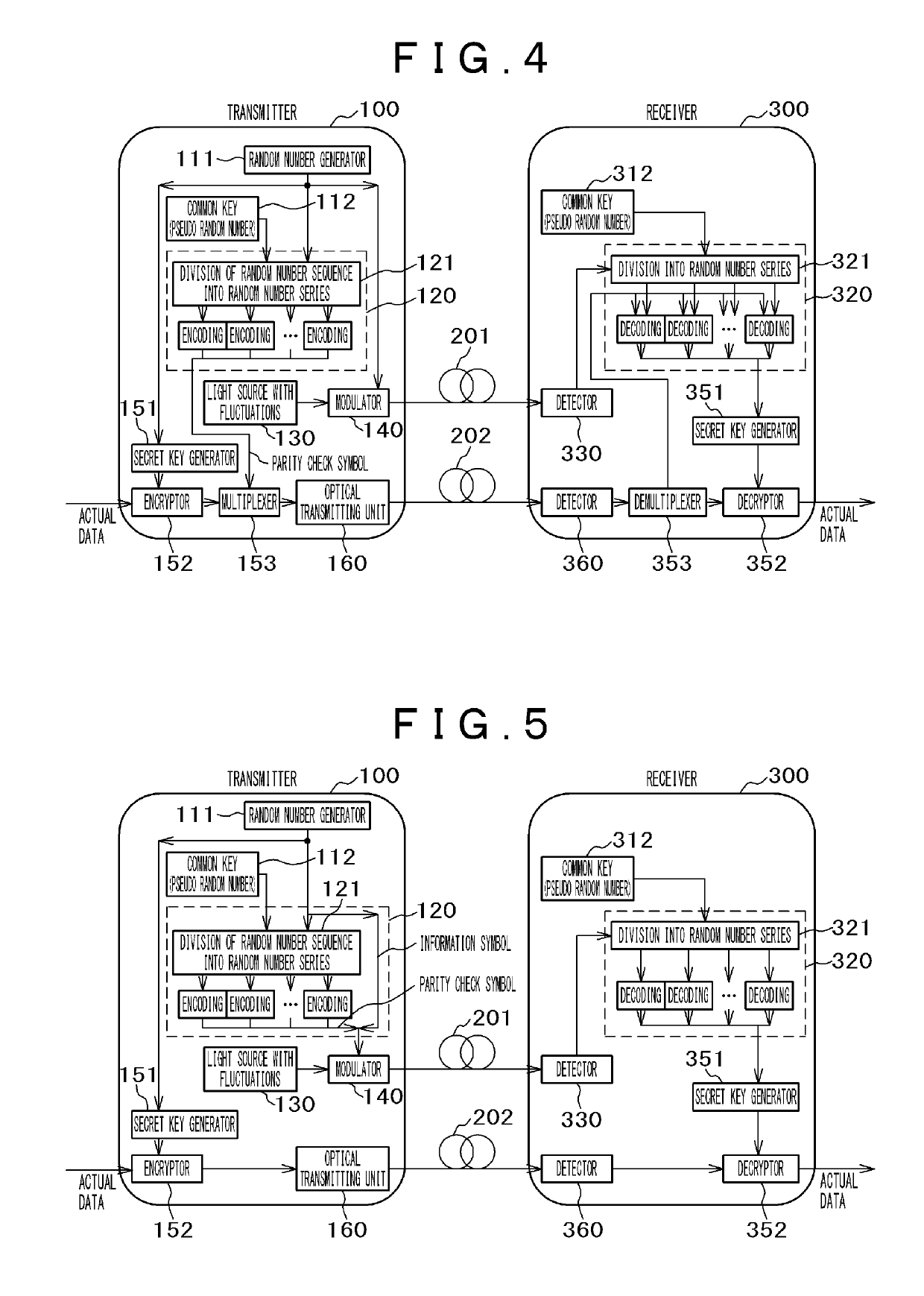
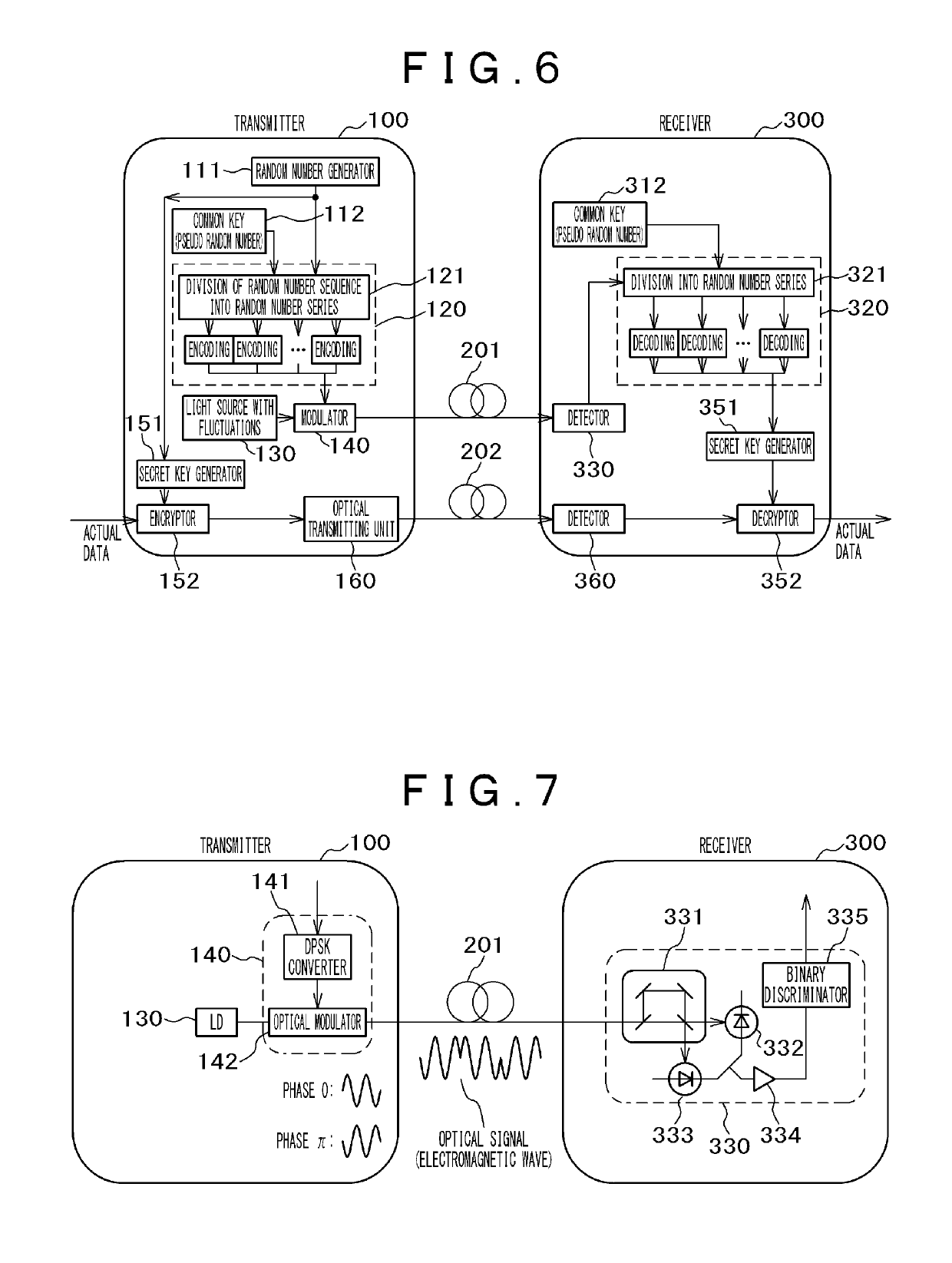
The objective of the invention is to provide an encoding method and a communication method wherein bit-error correction is easy for a authorized recipient but difficult for an unauthorized recipient. A transmission channel in which bit errors are moderately controlled is used to transmit / receive a random number sequence. A common key is shared between a transmitter and a receiver in advance; each bit value of the common key is connected with each slot of the random number sequence; the common key is used to divide the random number sequence into two or more random number series in accordance with the connection; and each random number series is independently encoded and parity check symbols are generated. The unit of the encoding is equal to or greater than the length of the common key so as to make a partial analysis by an unauthorized recipient impossible.
Owner:HITACHI LTD
Deterministic random number generator for cryptography and digital watermarking
ActiveUS20090193065A1Performs betterRandom number generatorsDigital computer detailsNumber seriesNumber generator
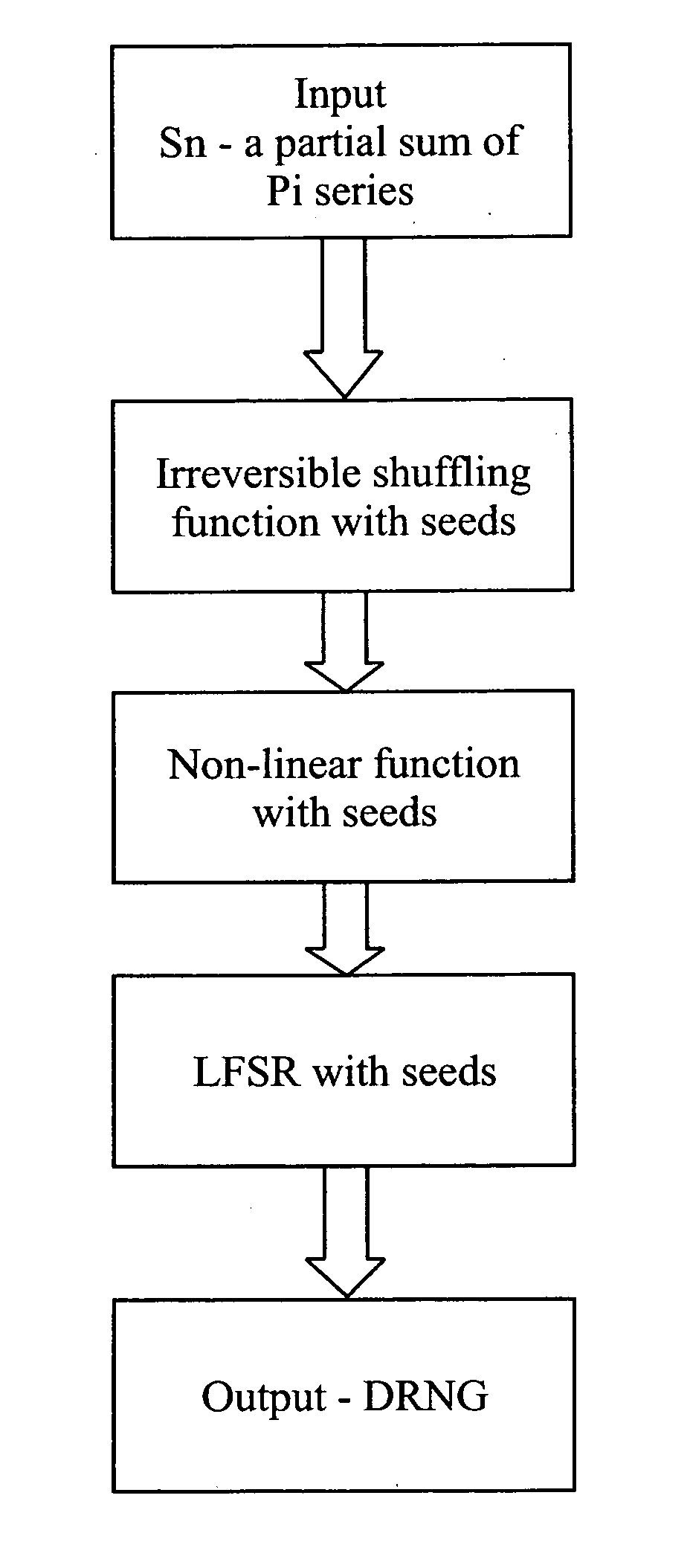
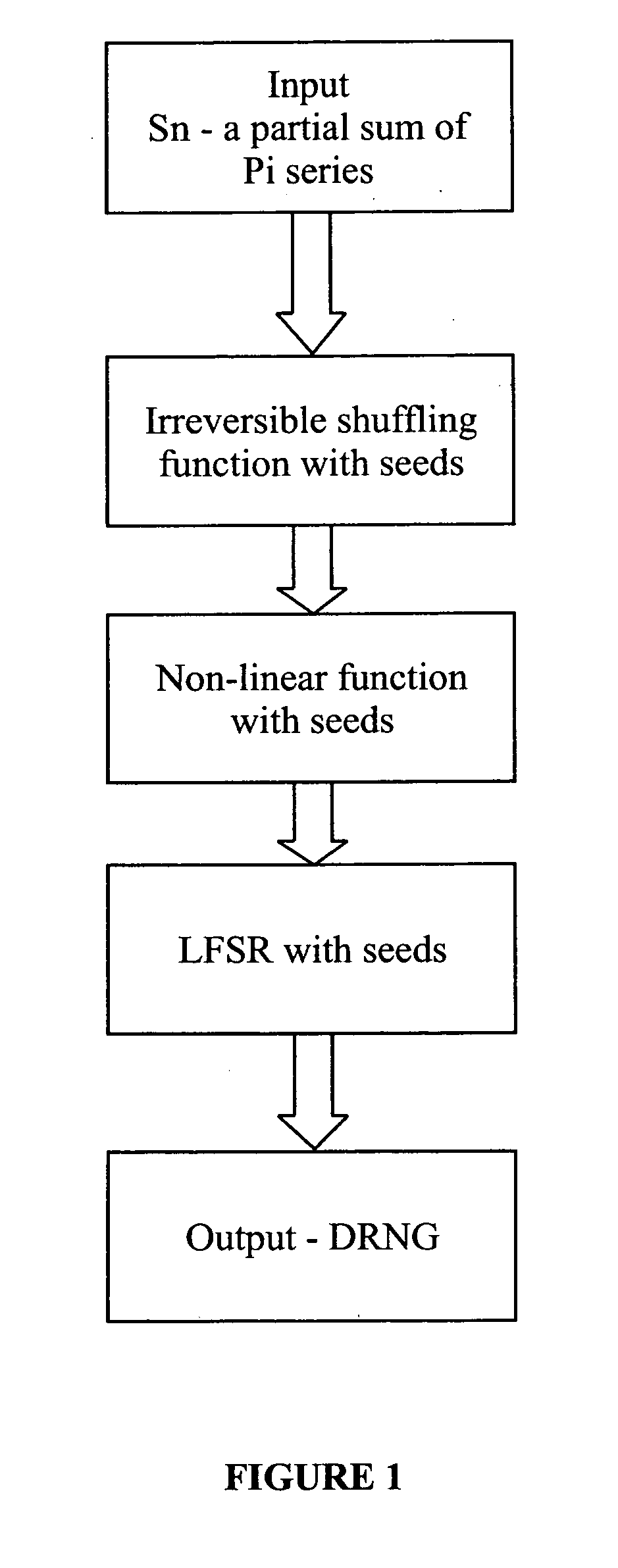
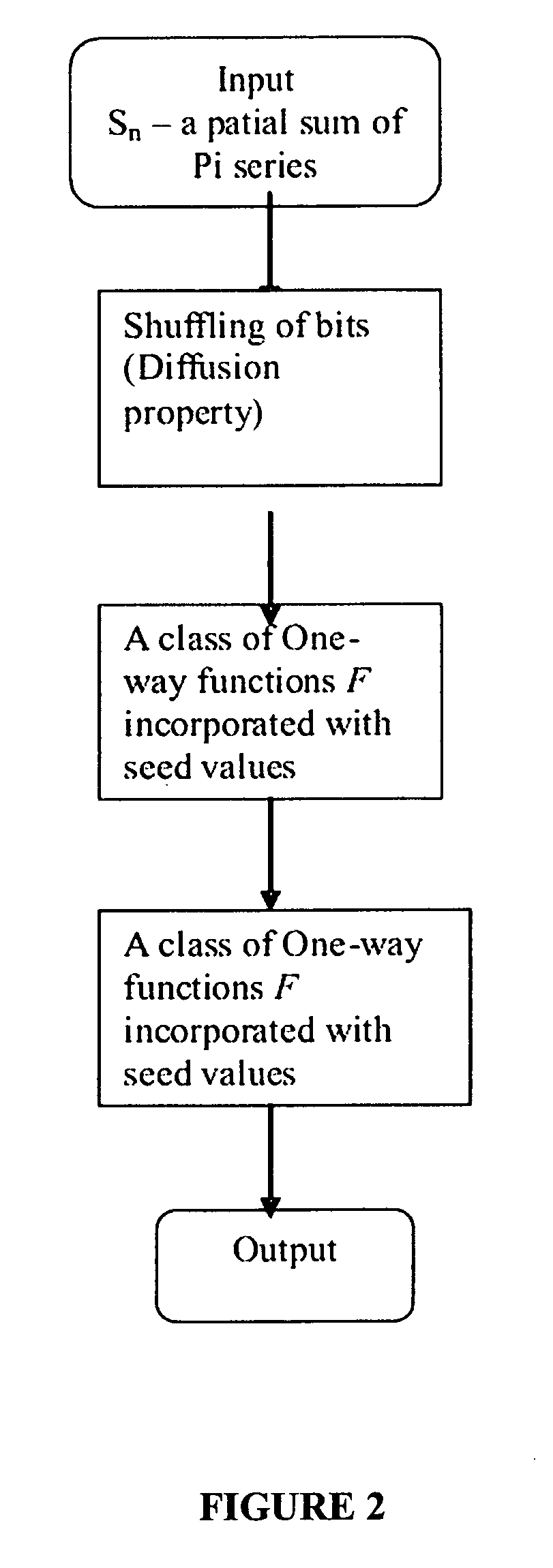
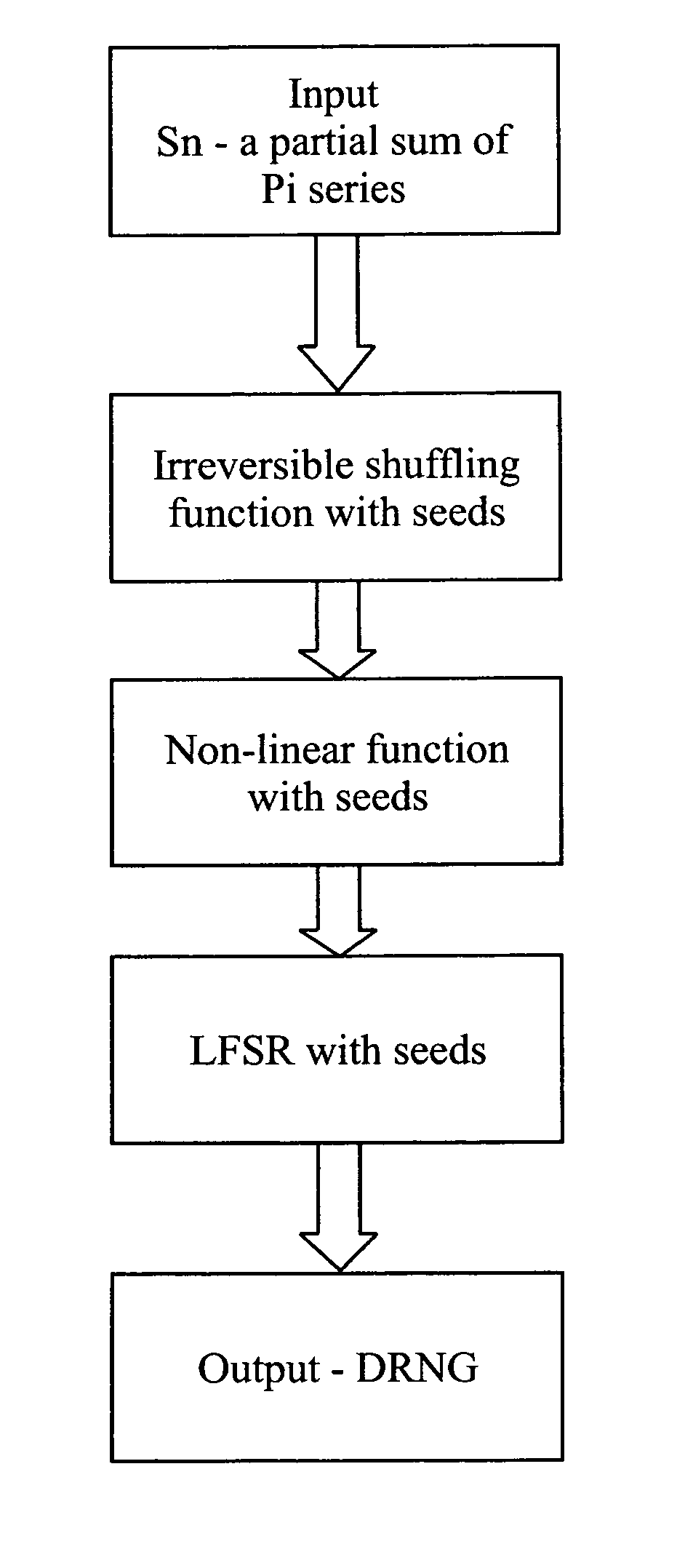
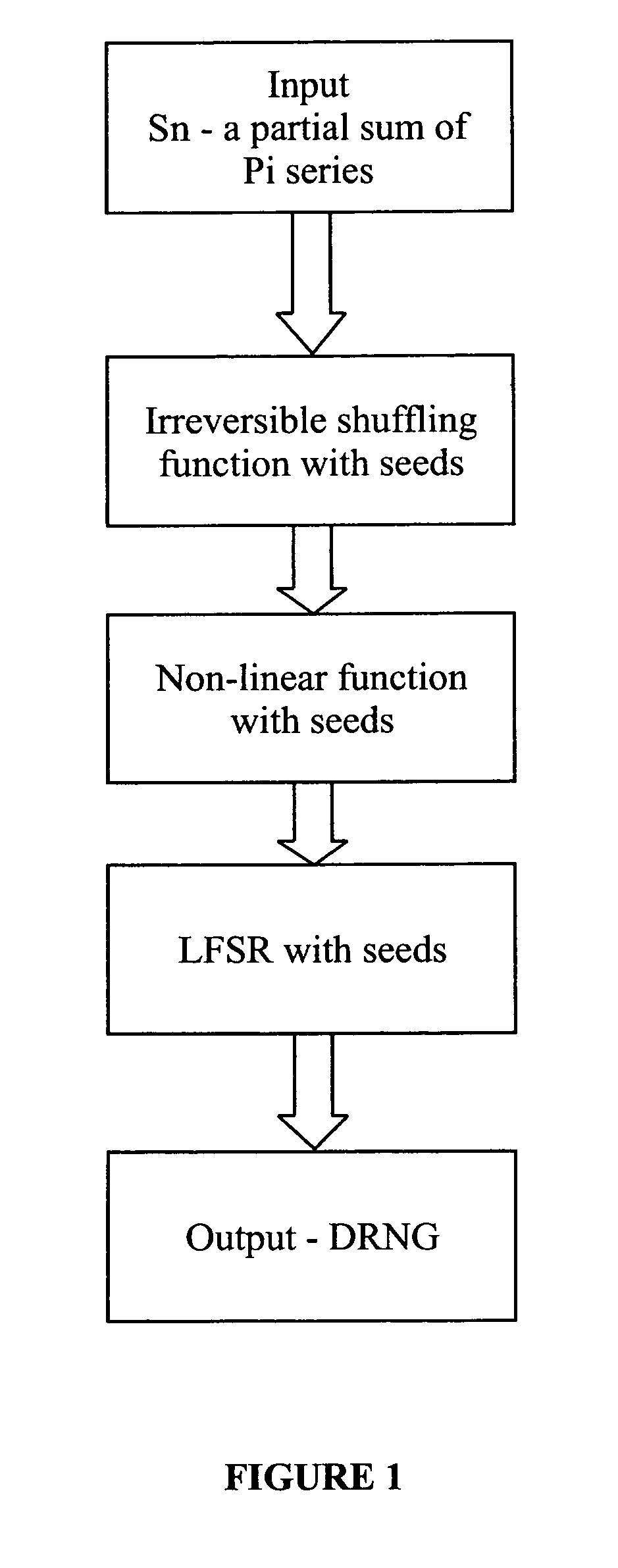
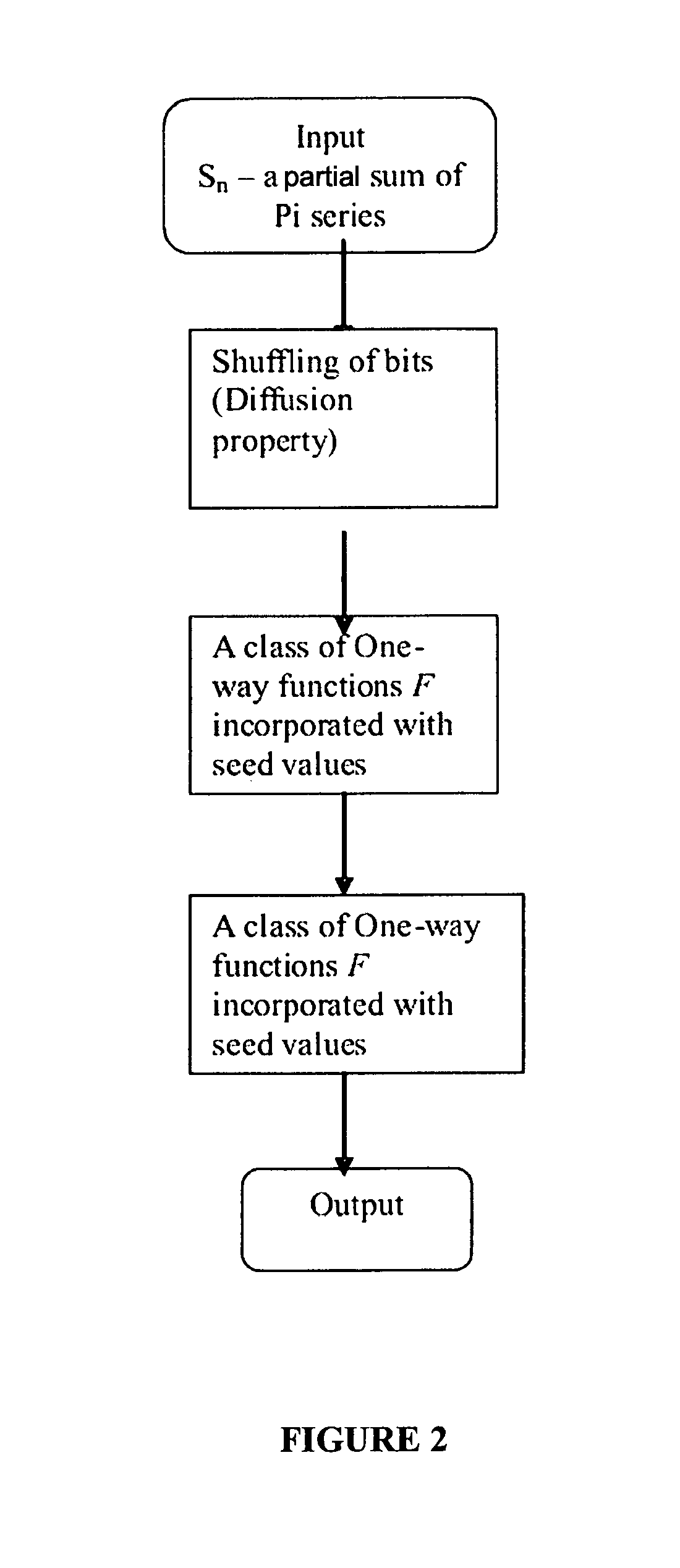
A deterministic random number generator comprising:number series generator adapted to generate an infinite Pi series;summation means adapted to generate a partial sum of said infinite Pi series;computation means adapted to compute a finite sequence from said partial sum of infinite Pi series;shuffling means adapted to shuffle said computed finite sequence to obtain a shuffled sequence;masking means adapted to mask said shuffled sequence to obtain a masked sequence;non-linear function means adapted to process said masked sequence to obtain a non-linear processed sequence; andlinear feedback shift register means adapted to receive and shift bits of said non-linear processed sequence in a pre-determined manner to obtain a deterministic random number and a method for generating a deterministic random number for cryptography and watermarking.
Owner:TATA CONSULTANCY SERVICES LTD
Crystal display device and driving method thereof
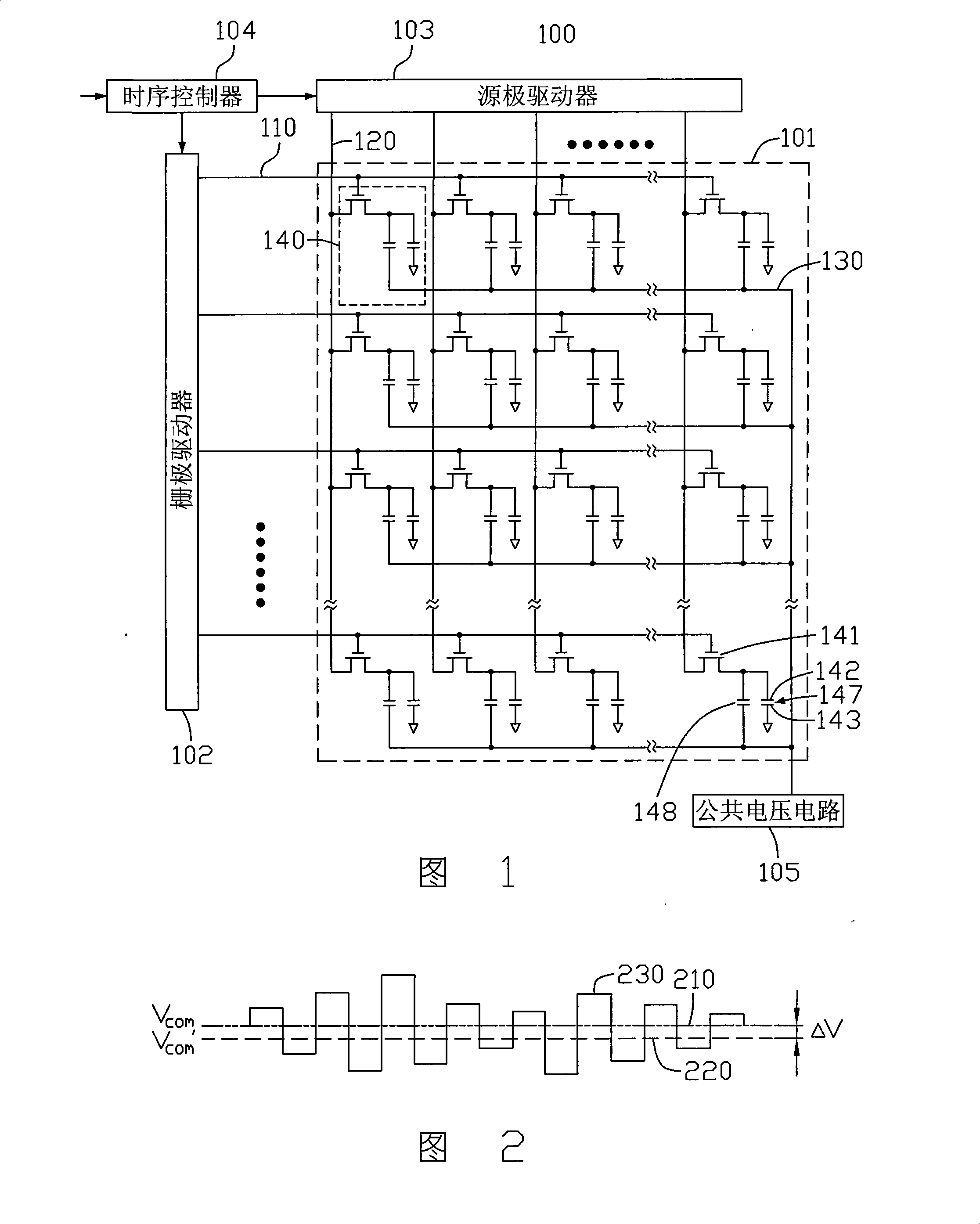
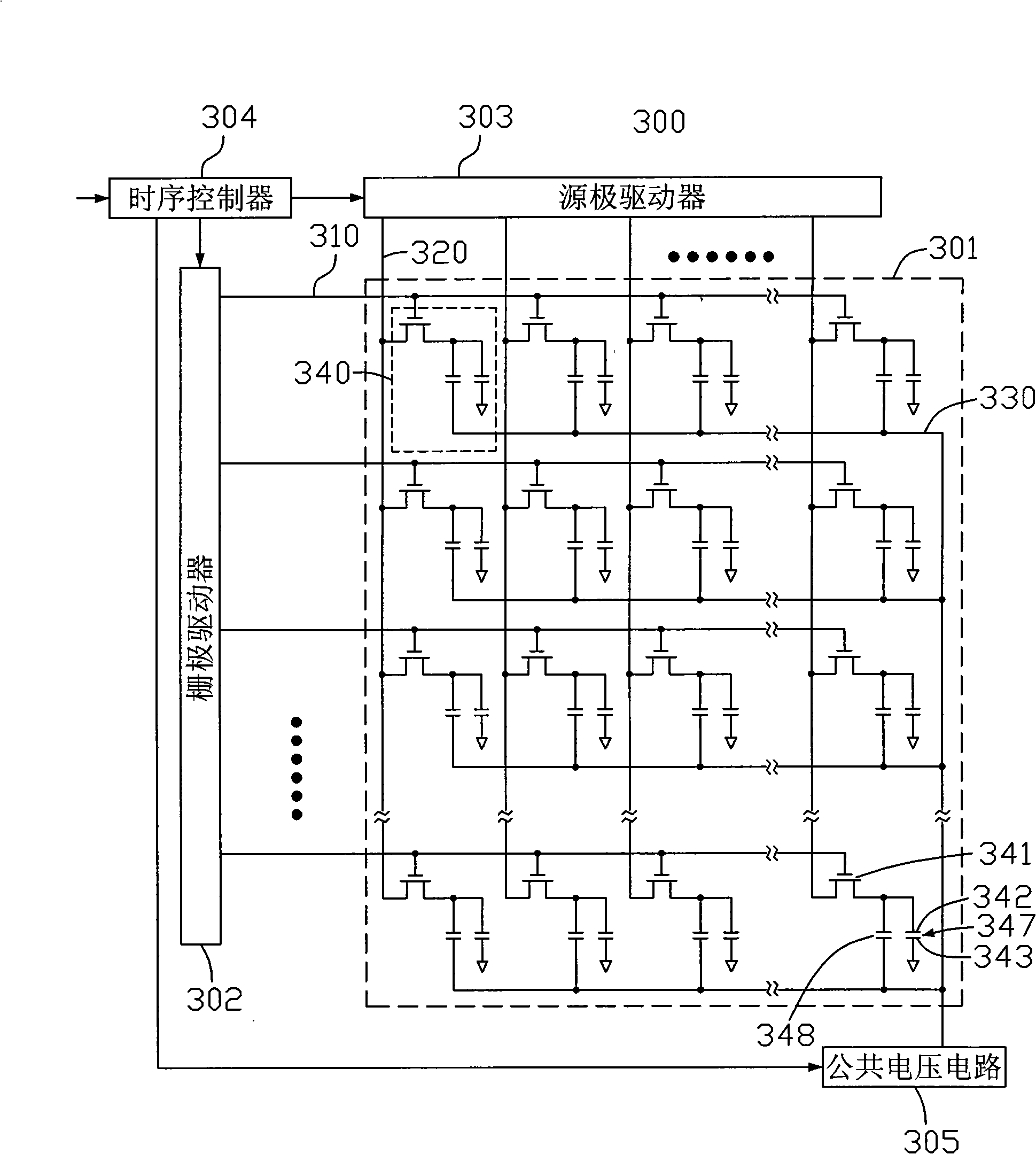
InactiveCN101295110AReduce color castReduce crosstalkStatic indicating devicesNon-linear opticsNumber seriesLiquid crystal
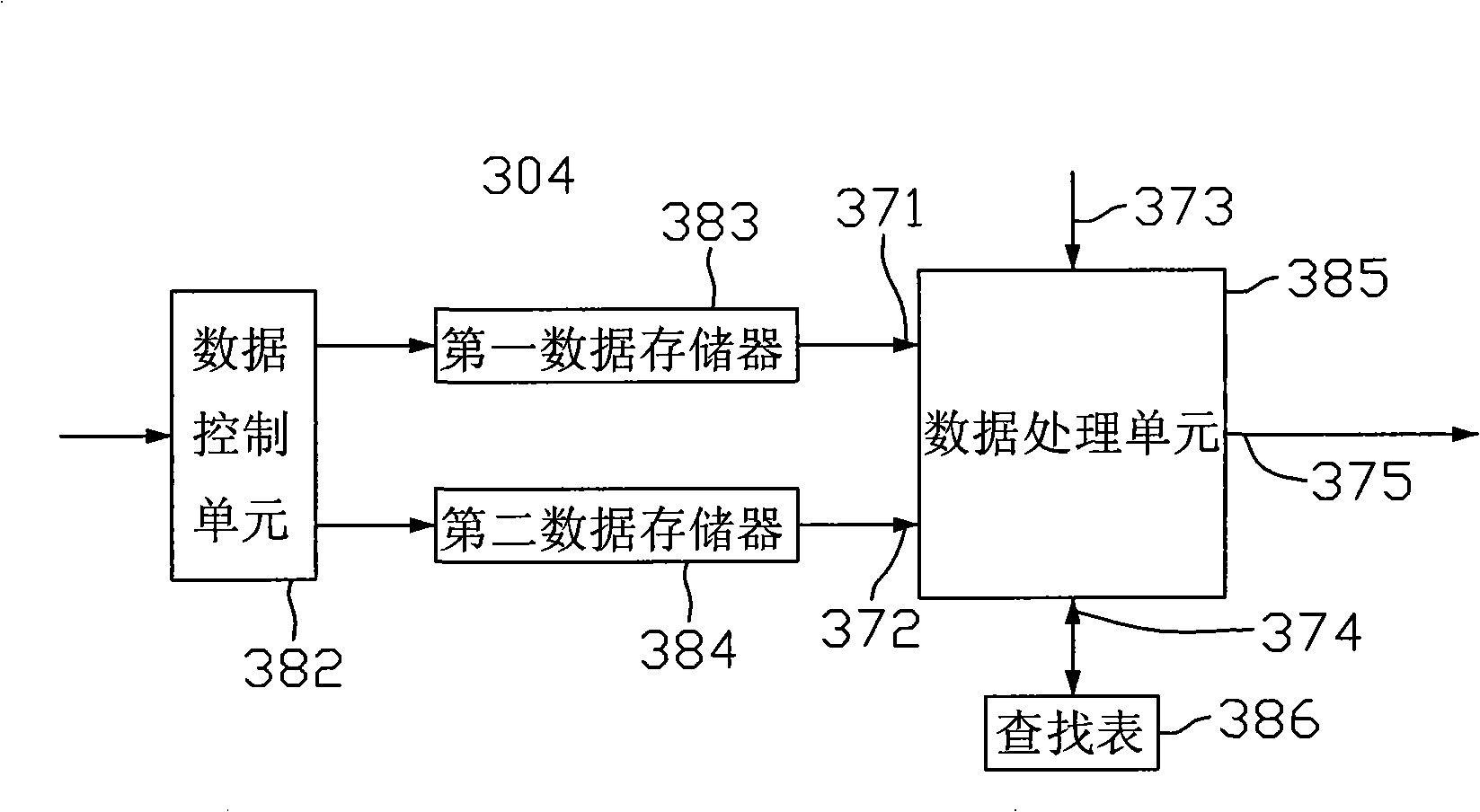
The invention provides a liquid crystal display device which comprises a liquid crystal panel, a data processing unit and a common voltage circuit, wherein, the data processing unit respectively receives the display signals of odd number series and the display signals of even number series, and carries out comparative analysis to the display signals of the odd number series and the display signals of the even number series; the common voltage circuit adjusts the common voltage according to analysis results, and outputs the adjusted common voltage to the liquid crystal panel. The invention also provides a driving method of the liquid crystal display device at the same time.
Owner:INNOCOM TECH (SHENZHEN) CO LTD +1
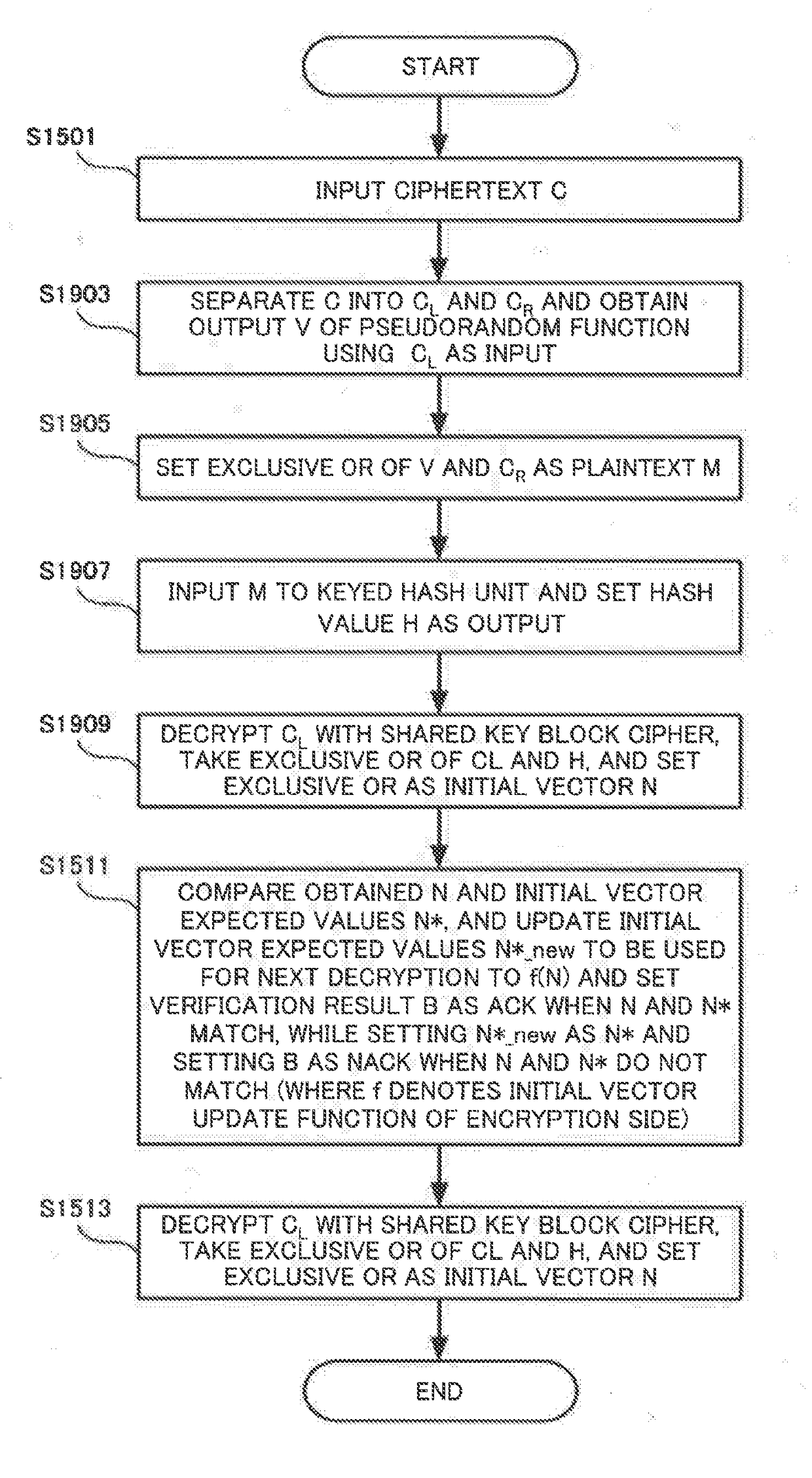
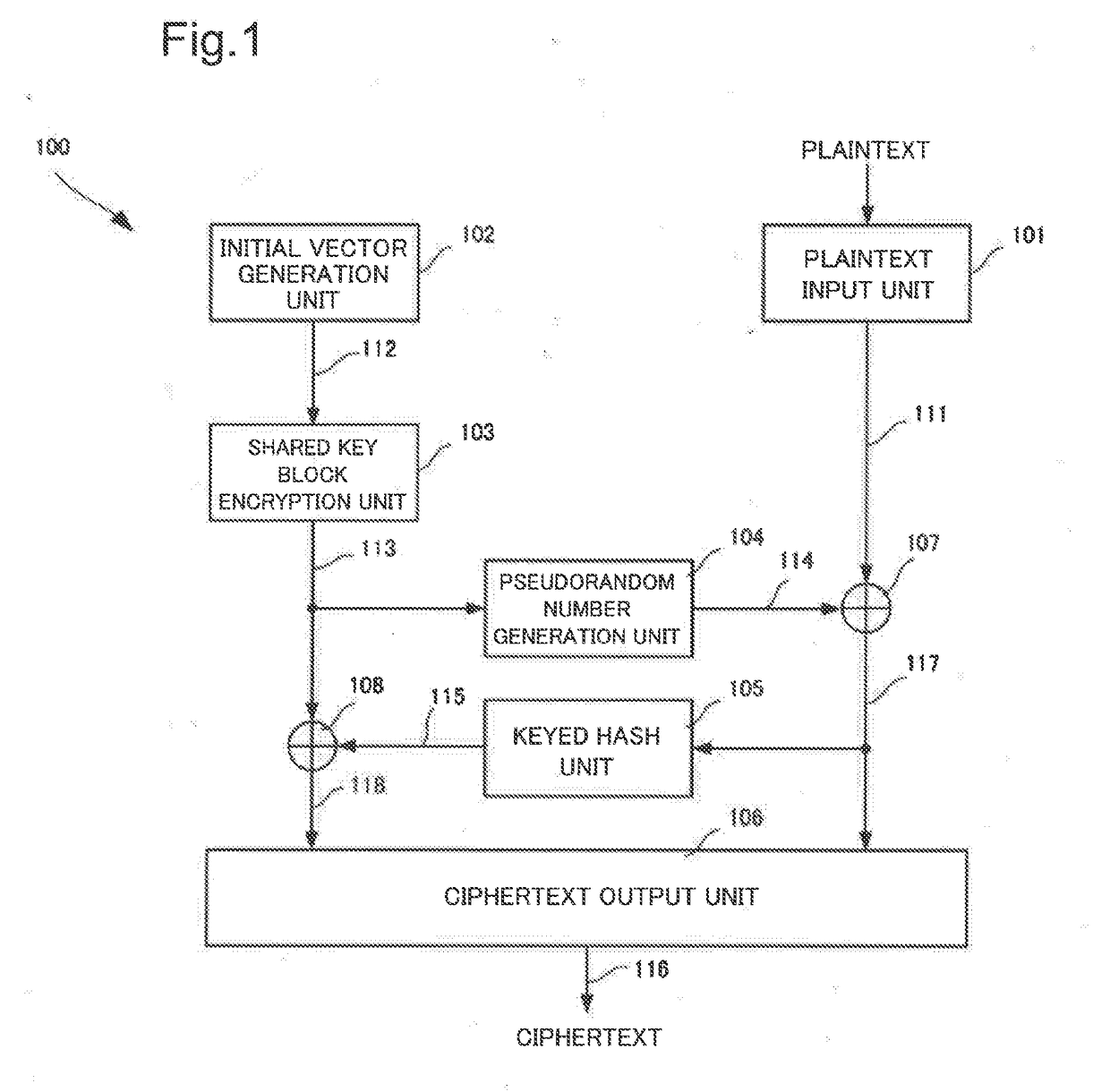
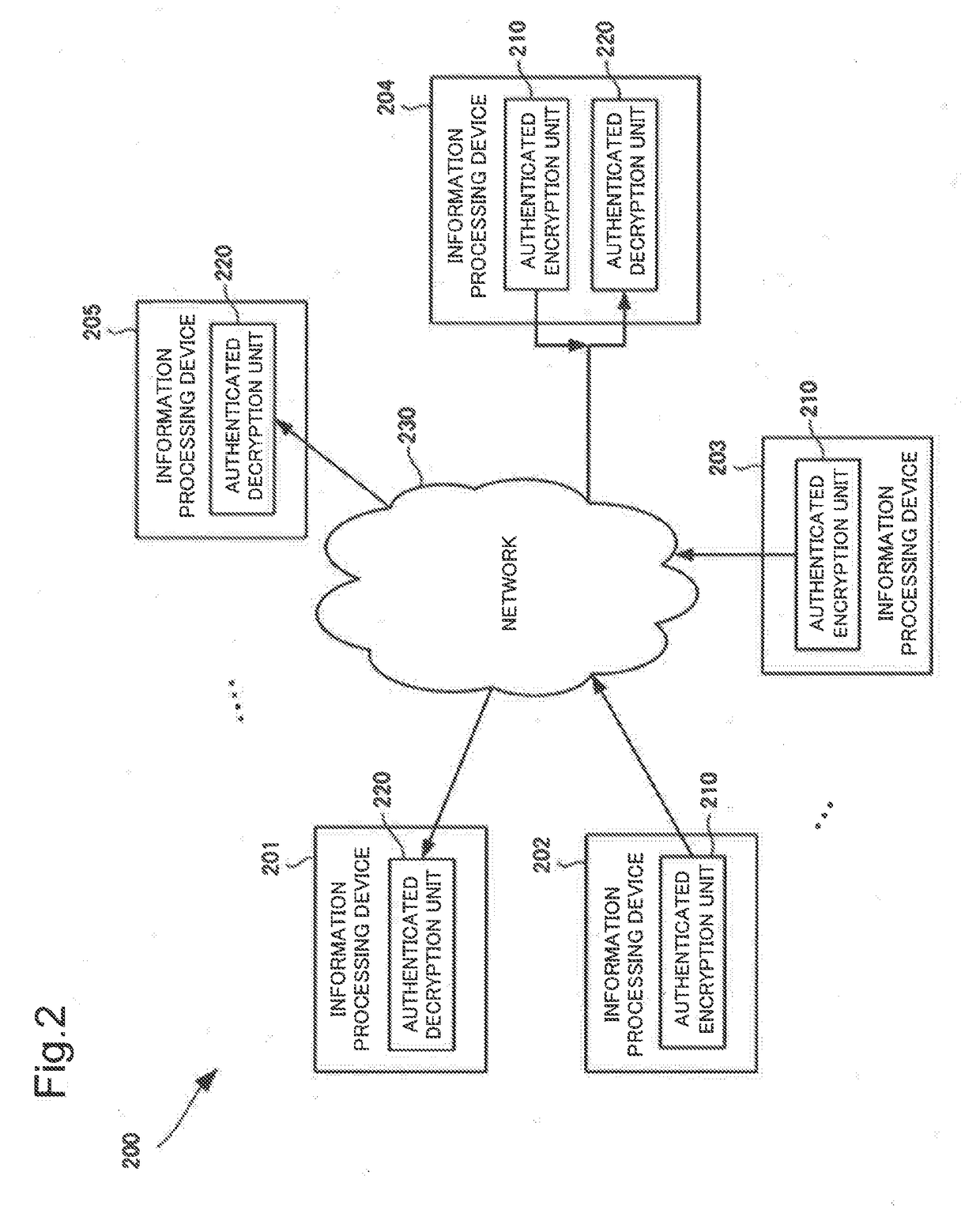
Authentication encryption method, authentication decryption method, and information-processing device
ActiveUS20170272239A1Efficiently enableSmall increase of band (length) of ciphertextEncryption apparatus with shift registers/memoriesComputer hardwareInformation processing
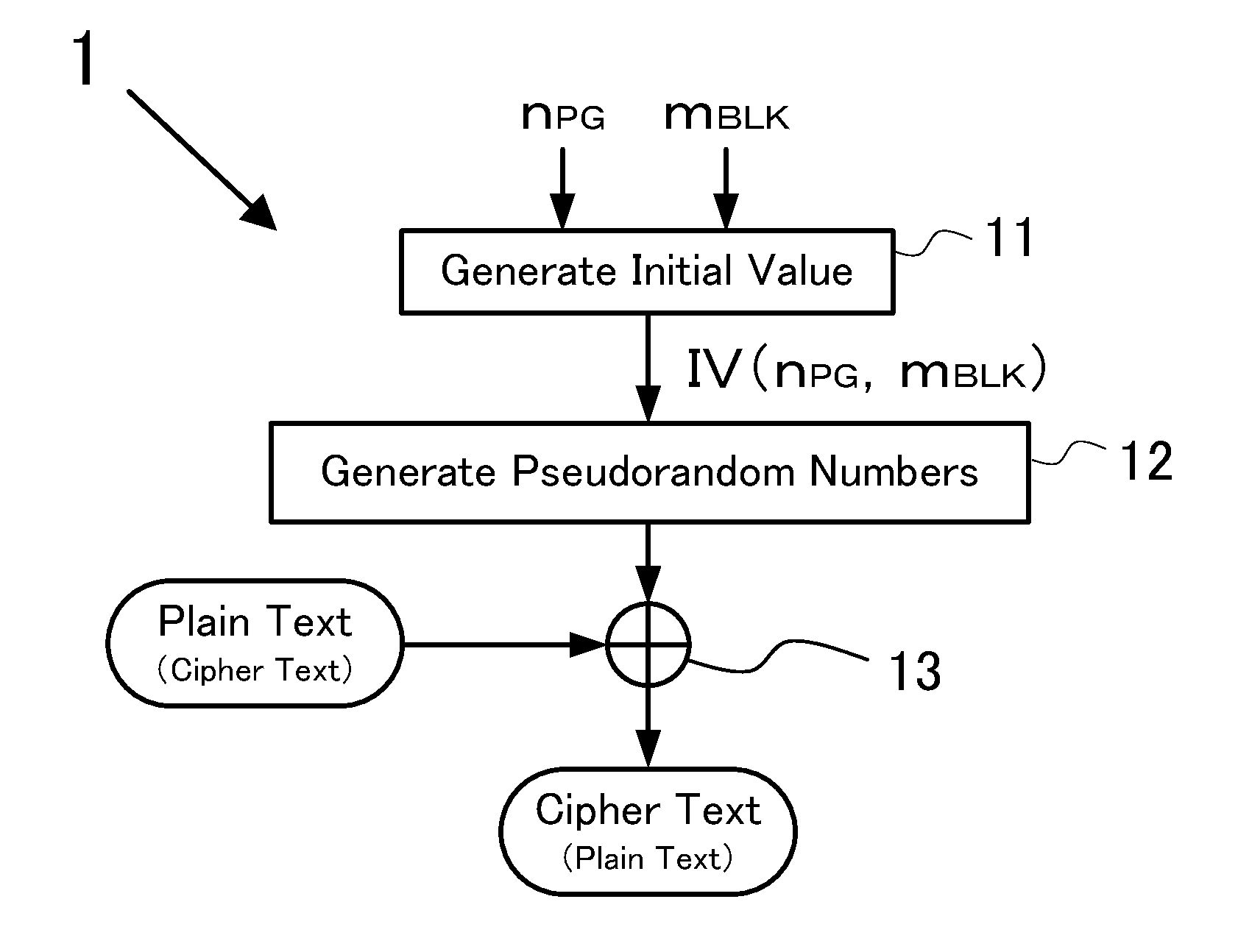
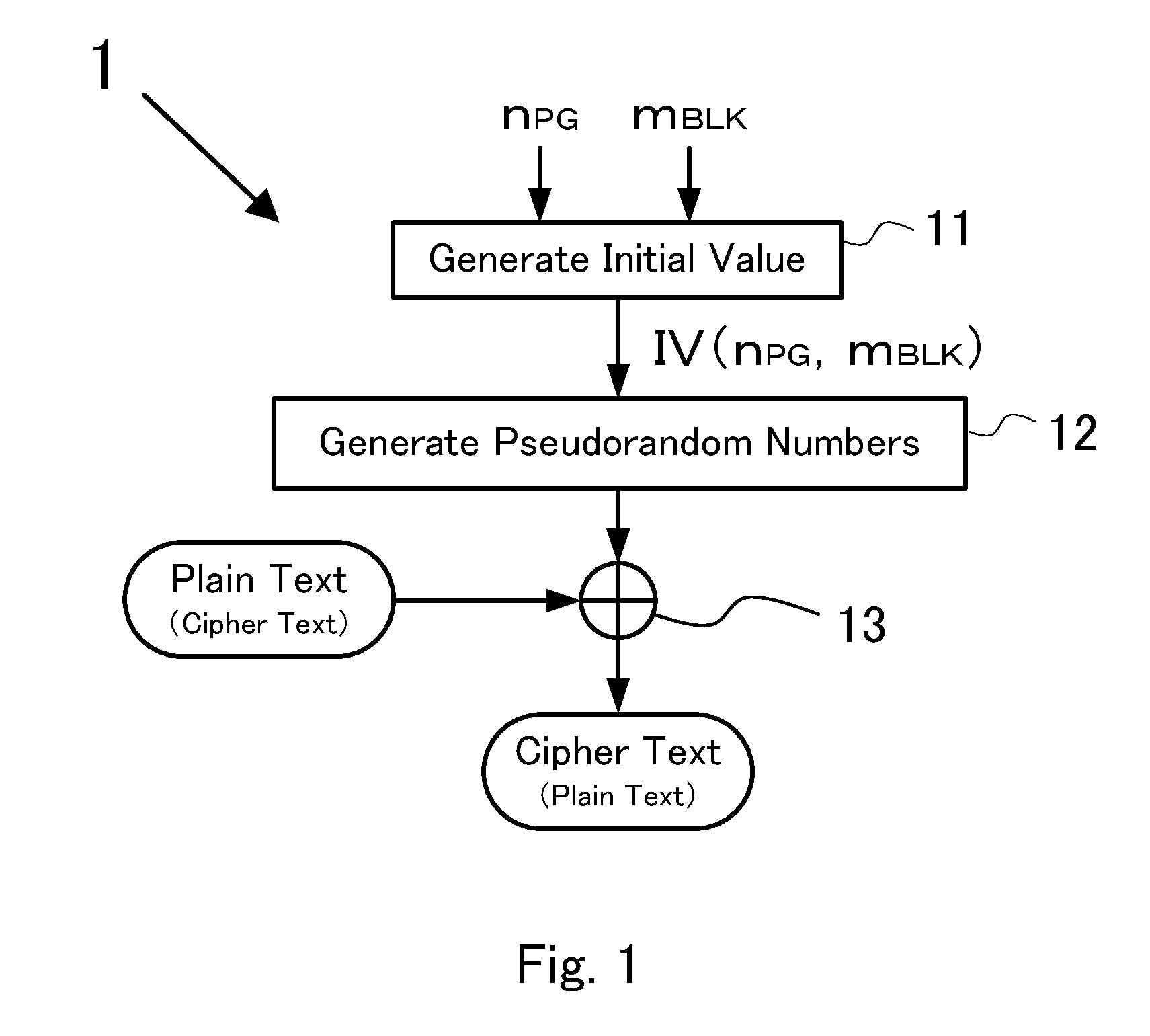
An information-processing device is provided with: a plaintext input unit for inputting plaintext; an initial vector generation unit for generating an initial vector; a common key block encryption unit for performing common key block encryption on the initial vector and generating an encrypted initial vector; a pseudorandom number generation unit which, accepting the encrypted initial vector as input, generates a pseudorandom number series in the same length as the plaintext; a keyed hash unit which, accepting the first portion of a ciphertext in which the pseudorandom number series and the plaintext are exclusive-OR'ed as input, generates a hash value; and a ciphertext output unit for concatenating the second and first portions of a ciphertext in which the hash value and the encrypted initial vector are exclusive-OR'ed and outputting the concatenated portions as a ciphertext.
Owner:NEC CORP
Method of gaining access to a device
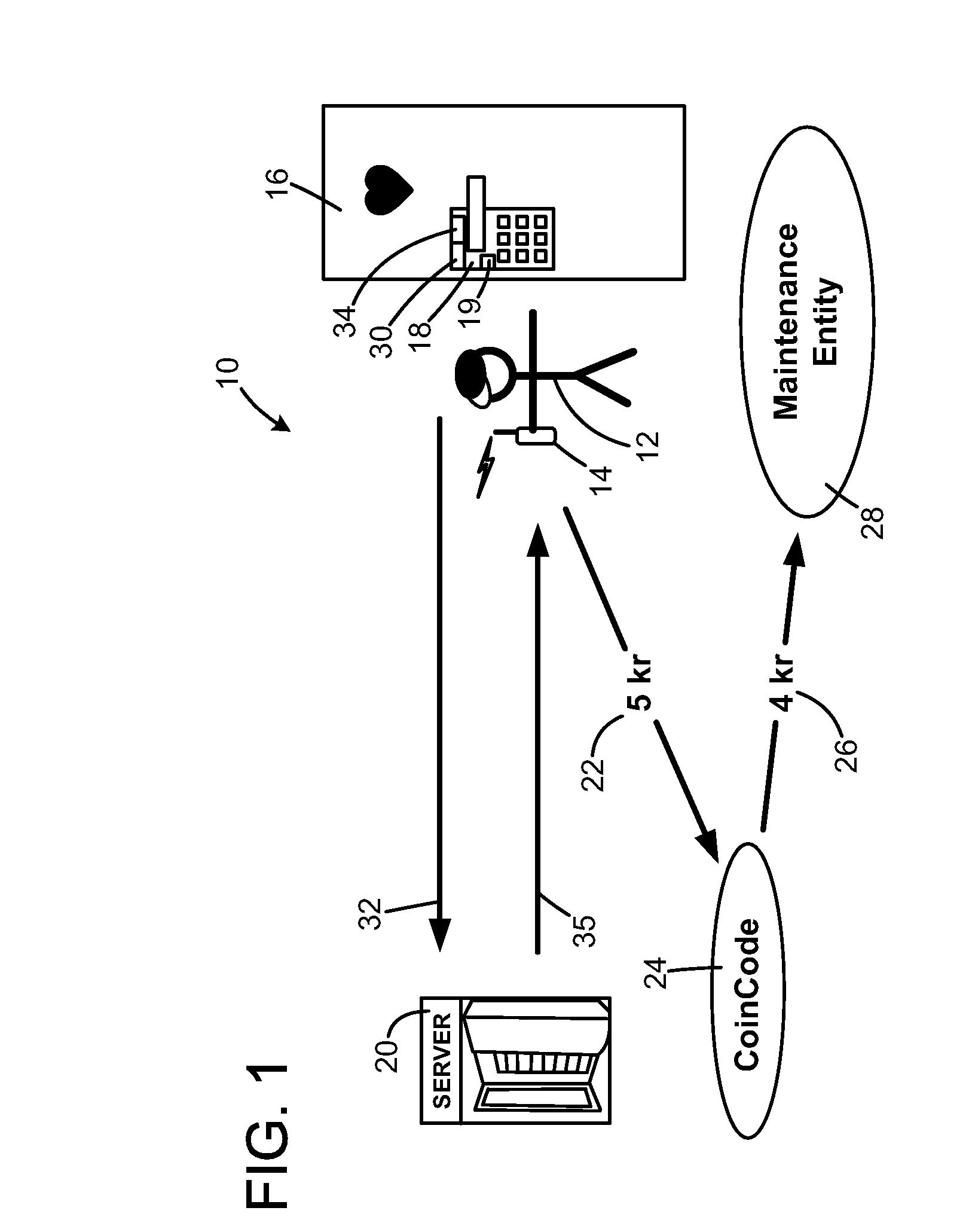
ActiveUS20080162676A1Digital computer detailsIndividual entry/exit registersComputer hardwareNumber series
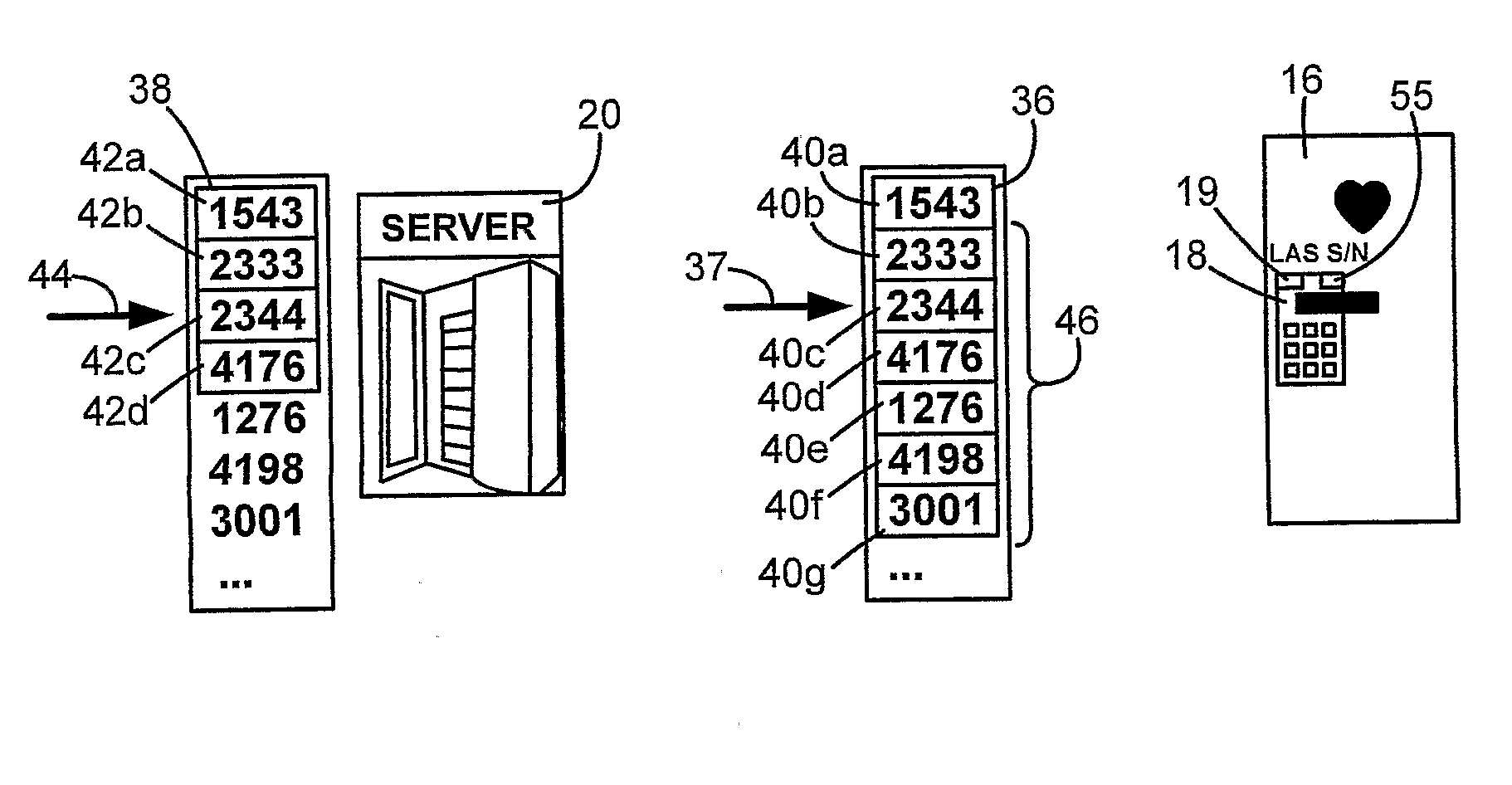
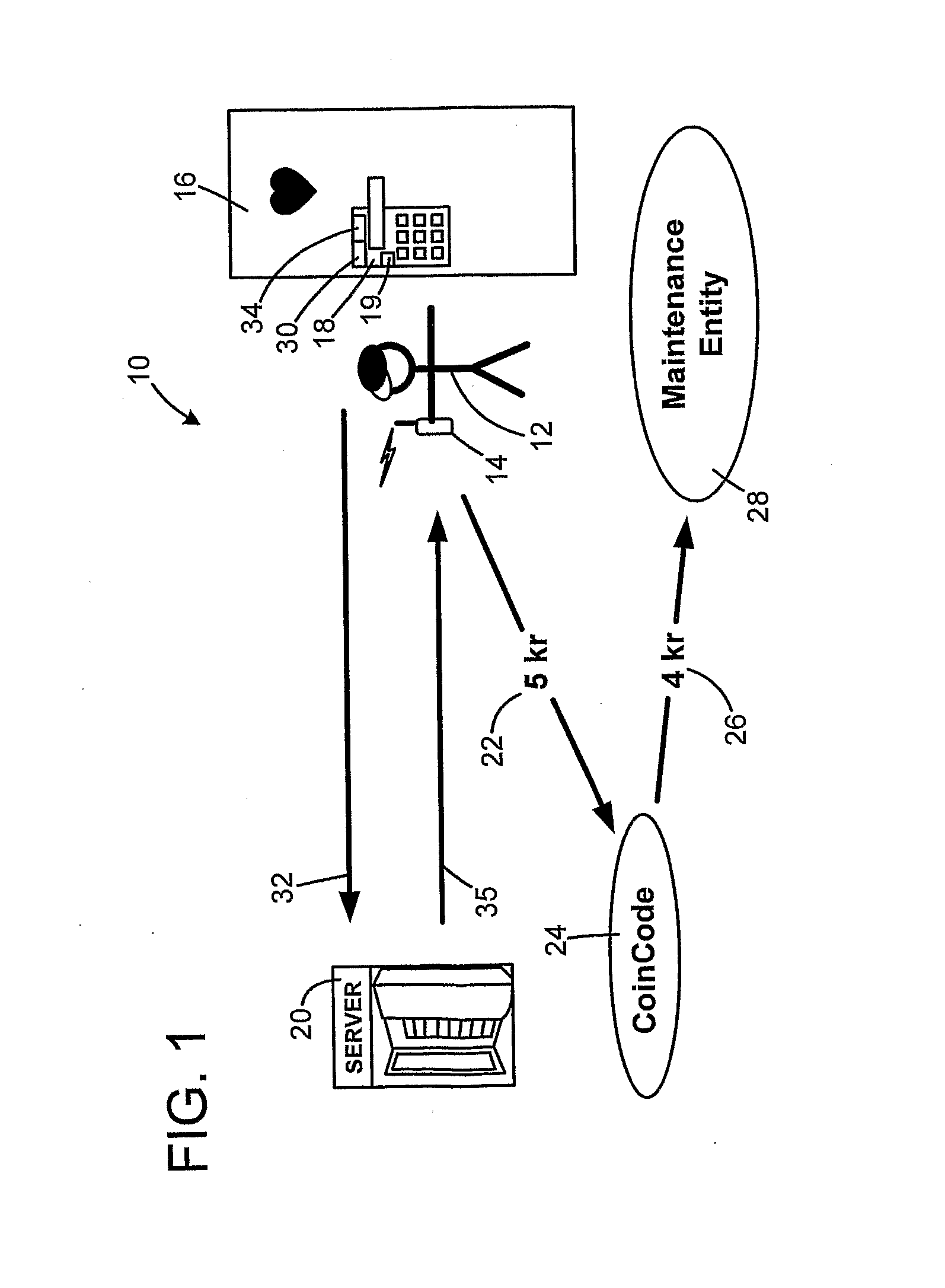
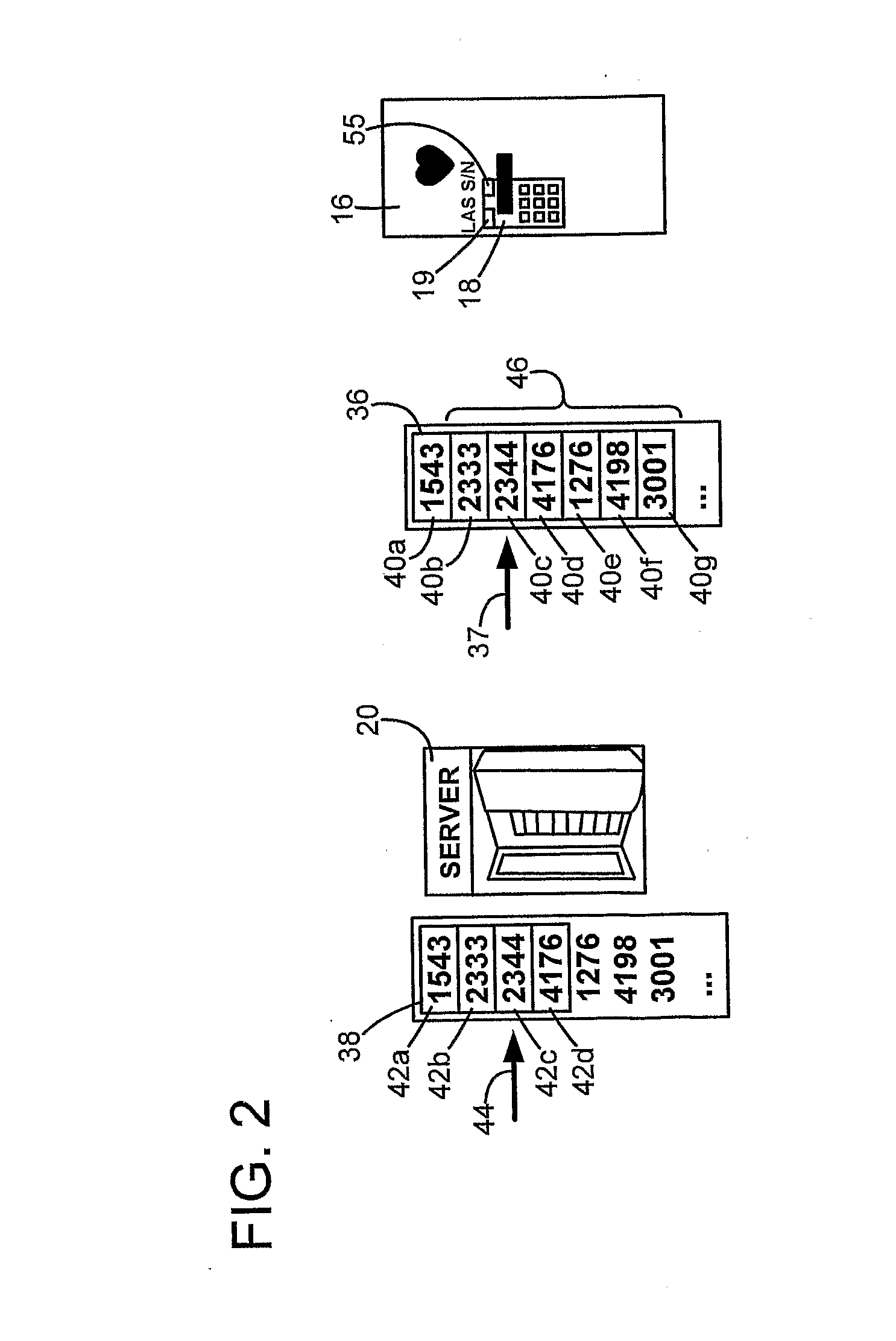
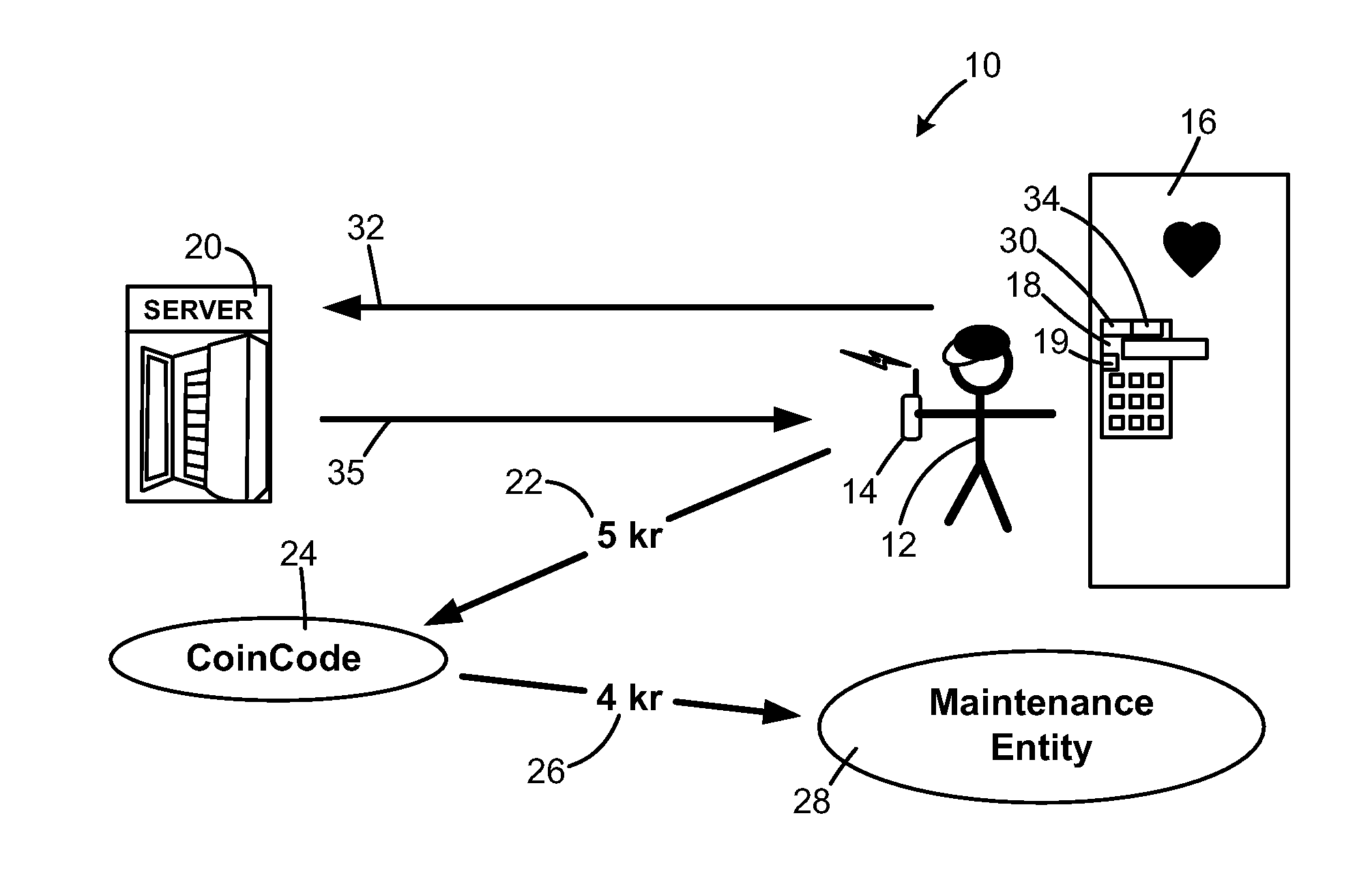
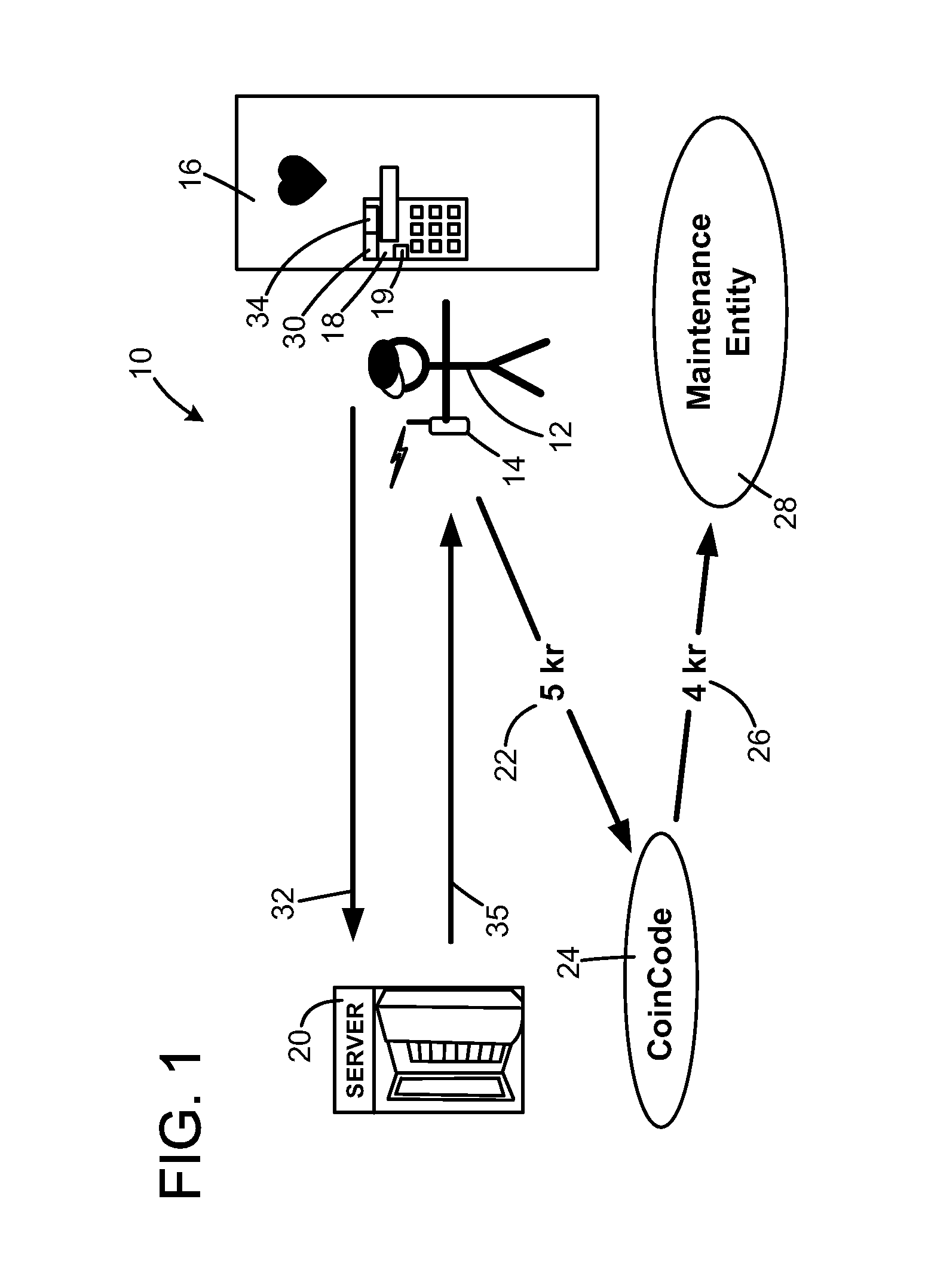
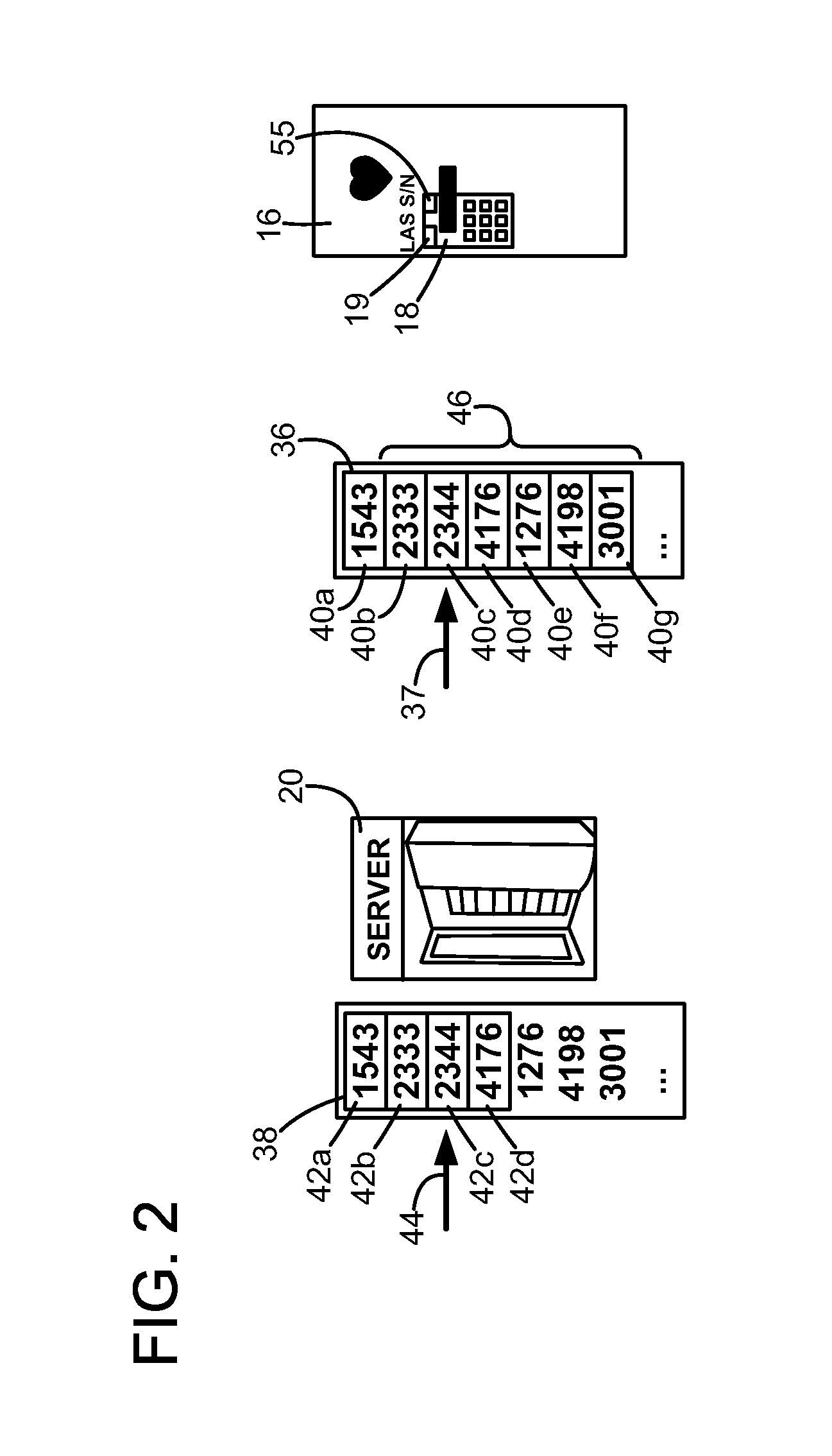
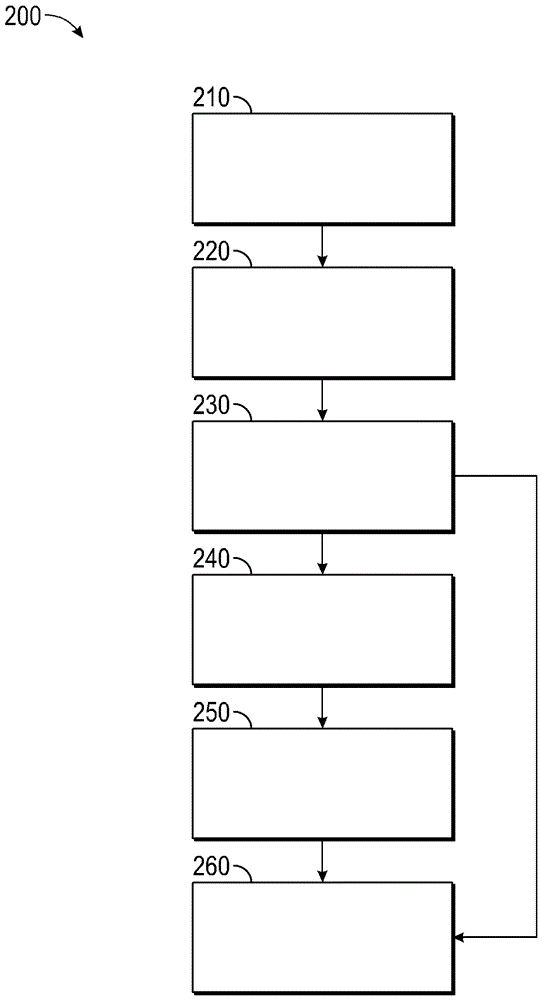
The method is for activating a device. A communication device (14) is provided that is in communication with a server unit (20) that has a processor for generating a number series (38). An application device (16) has a processor (19) for generating a number series (36). The communication device (14) is not communicating directly with the application device (16). The user sends a message (32) including the identification number (30) to the server (20). The server (20) identifies a code number pointed at by a pointer (44) and sends back the code number. The pointer (44) steps forward in the number series (38) at predetermined time intervals. The user enters the code number into the application device (16). The processor (19) compares the code number with a number pointed at by a pointer (37) and sends an activation signal to an activation device (16) to activate the application device.
Owner:TELKEY SOLUTIONS AB
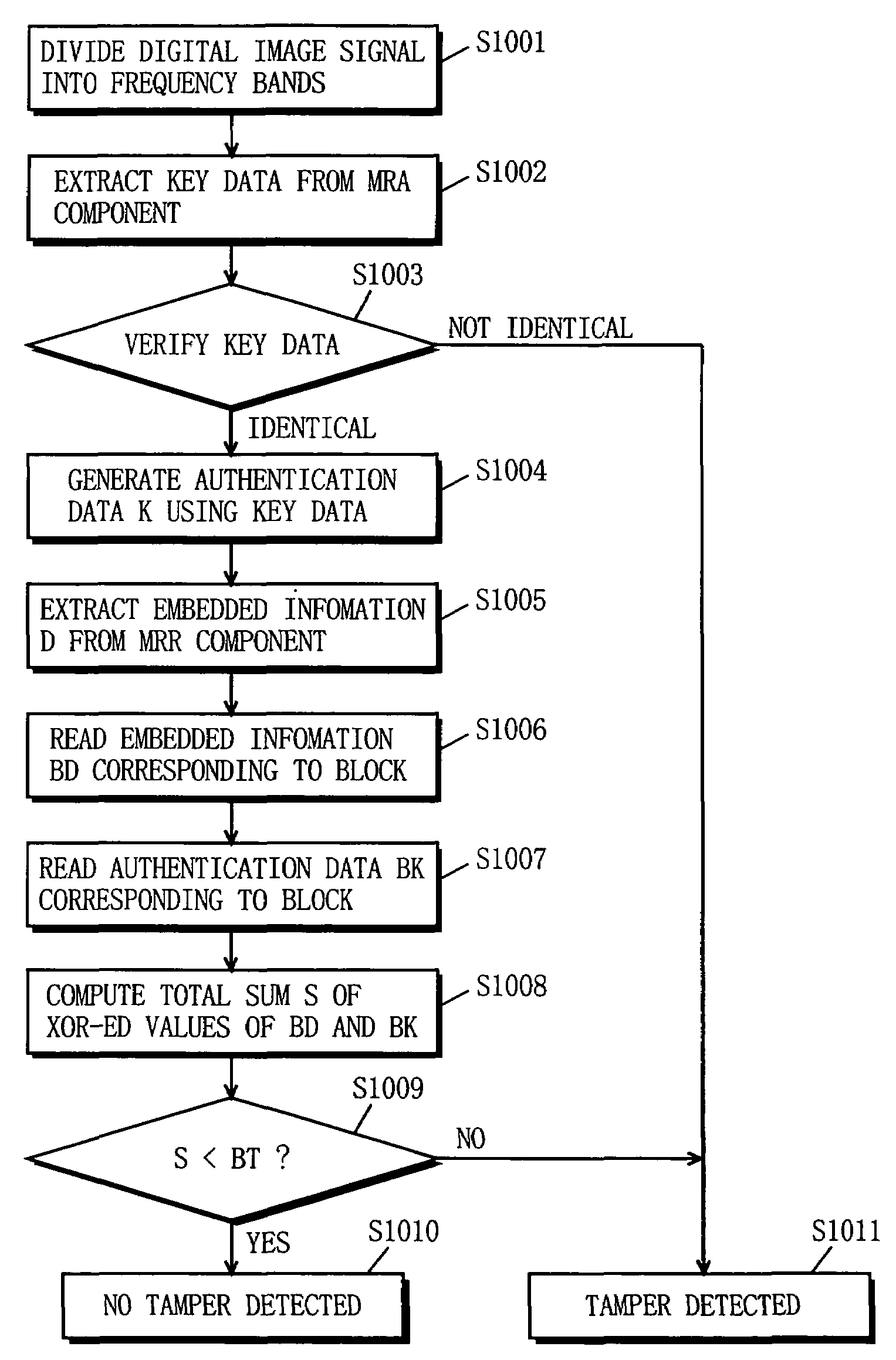
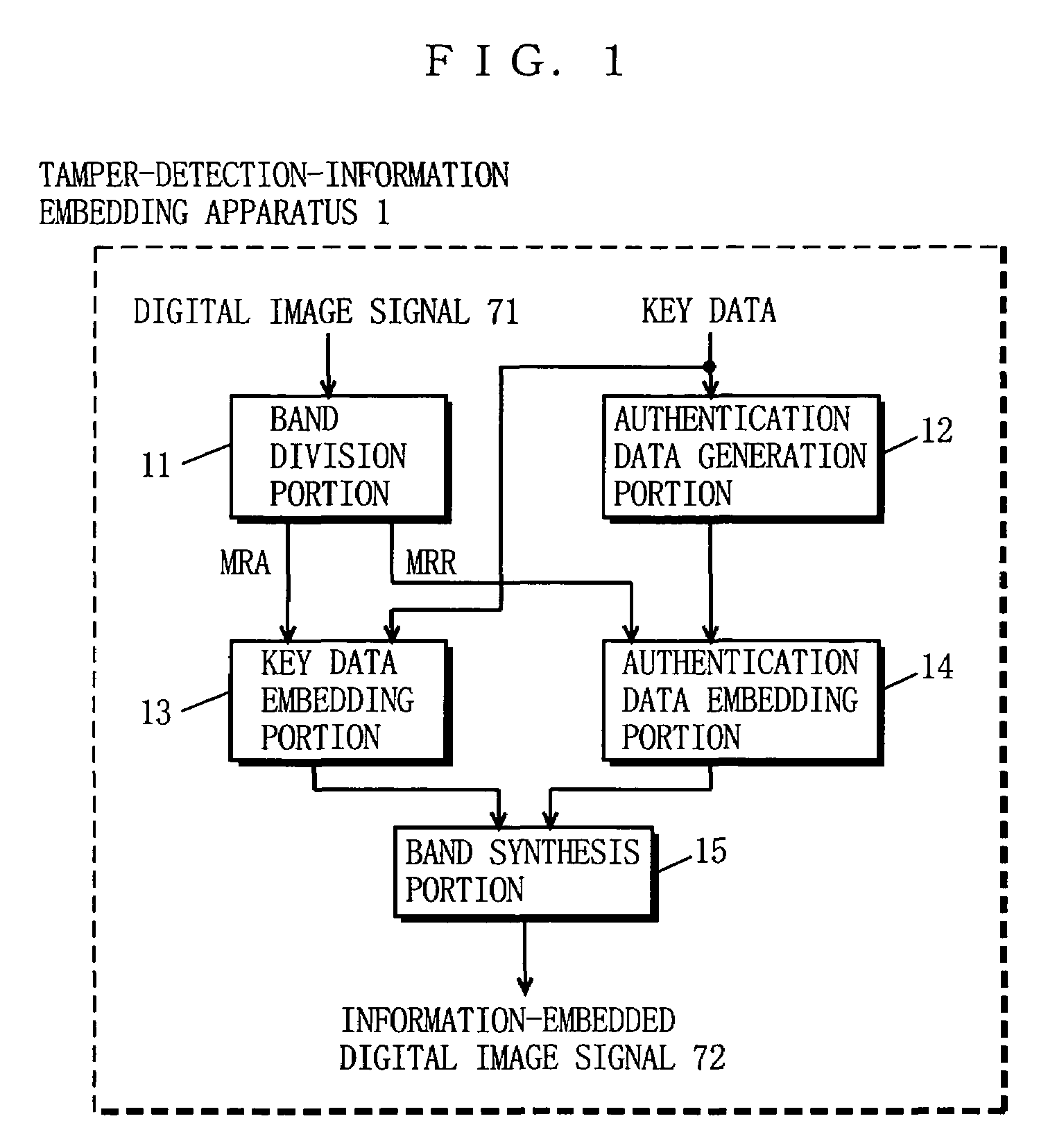
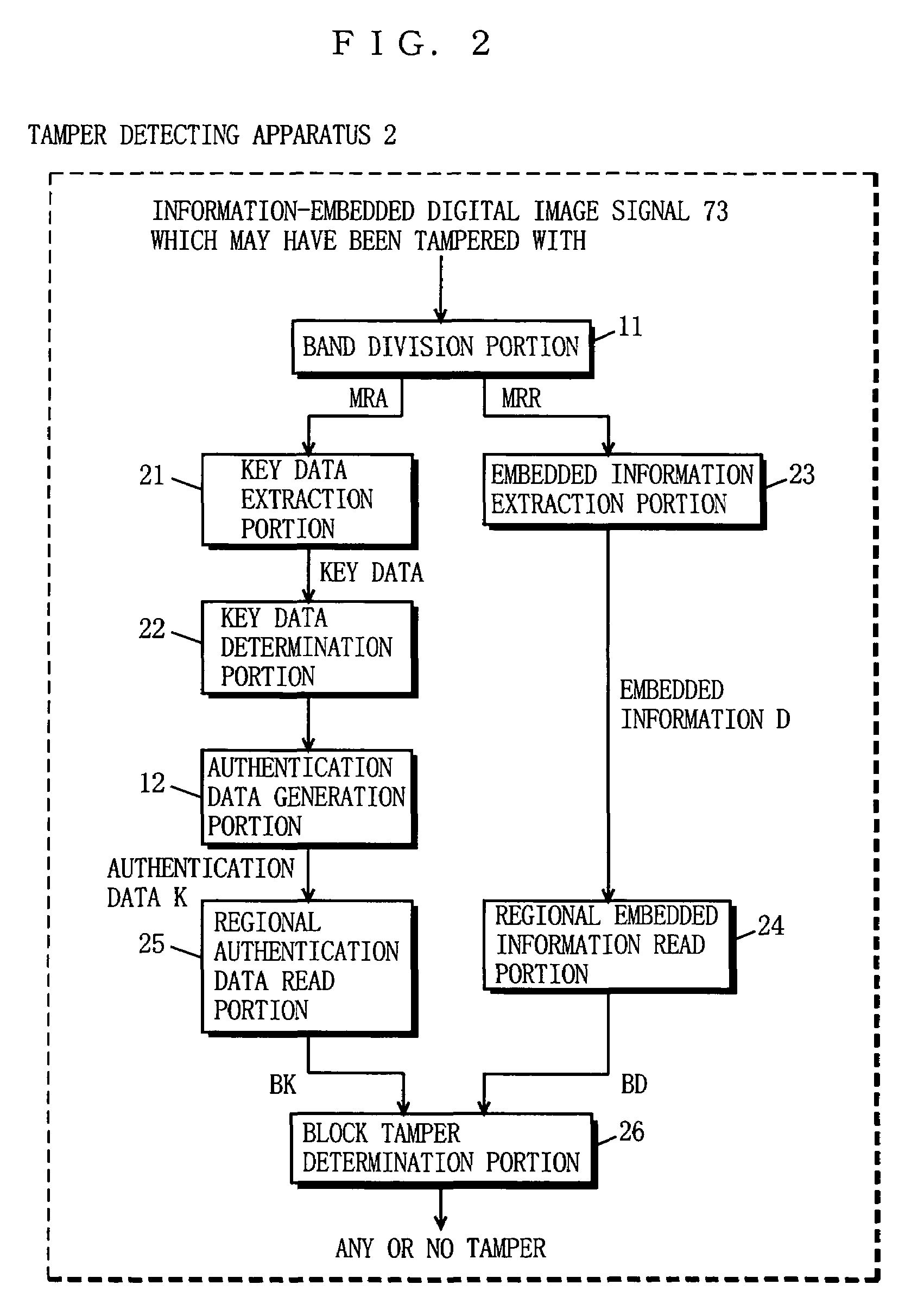
Apparatus and method for embedding information for tamper detection and detecting tamper and recording medium having program for carrying out the method recorded thereon
InactiveUS7003666B1Preventing overwriting and replacementAuthentication smallUser identity/authority verificationUnauthorized memory use protectionData seriesPattern recognition
An object of the present invention is to provide an information embedding / tamper detecting apparatus and method capable of distinguishing between changes caused by image processing and intentional image tampering, and further capable of localizing, on a regional basis, a tampered position on an image. A tamper-detection-information embedding apparatus 1 divides the image into a plurality of frequency bands to obtain transform coefficients, and then generates a pseudo-random number series by using key data, and further generates authentication data. The key data and the authentication data are embedded in the transform coefficients of MRA and MRR, respectively. the image in which the information is embedded is reconstructed by using MRA and MRR. A tamper-detecting apparatus 2 extracts the key data from MRA obtained by dividing the image into frequency bands and generates the authentication data assumed to have been embedded, and further extracts the embedded information from MRR. The image is divided in to a plurality of blocks composed of a predetermined number of pixels. For each block, an information series embedded in the transform coefficients of MRR representing the same spatial region as the unit block is compared, for verification, with the corresponding authentication data series so that the tamper is determined on a regional basis.
Owner:SOVEREIGN PEAK VENTURES LLC
Position determination II - calculation
InactiveUS20050104861A9Input/output for user-computer interactionDigitally marking record carriersNumber seriesComputer science
Owner:ANOTO IP LIC
Data encryption device and memory card
InactiveUS20120191984A1Improve securityHigh speed accessUnauthorized memory use protectionHardware monitoringNumber seriesComputer science
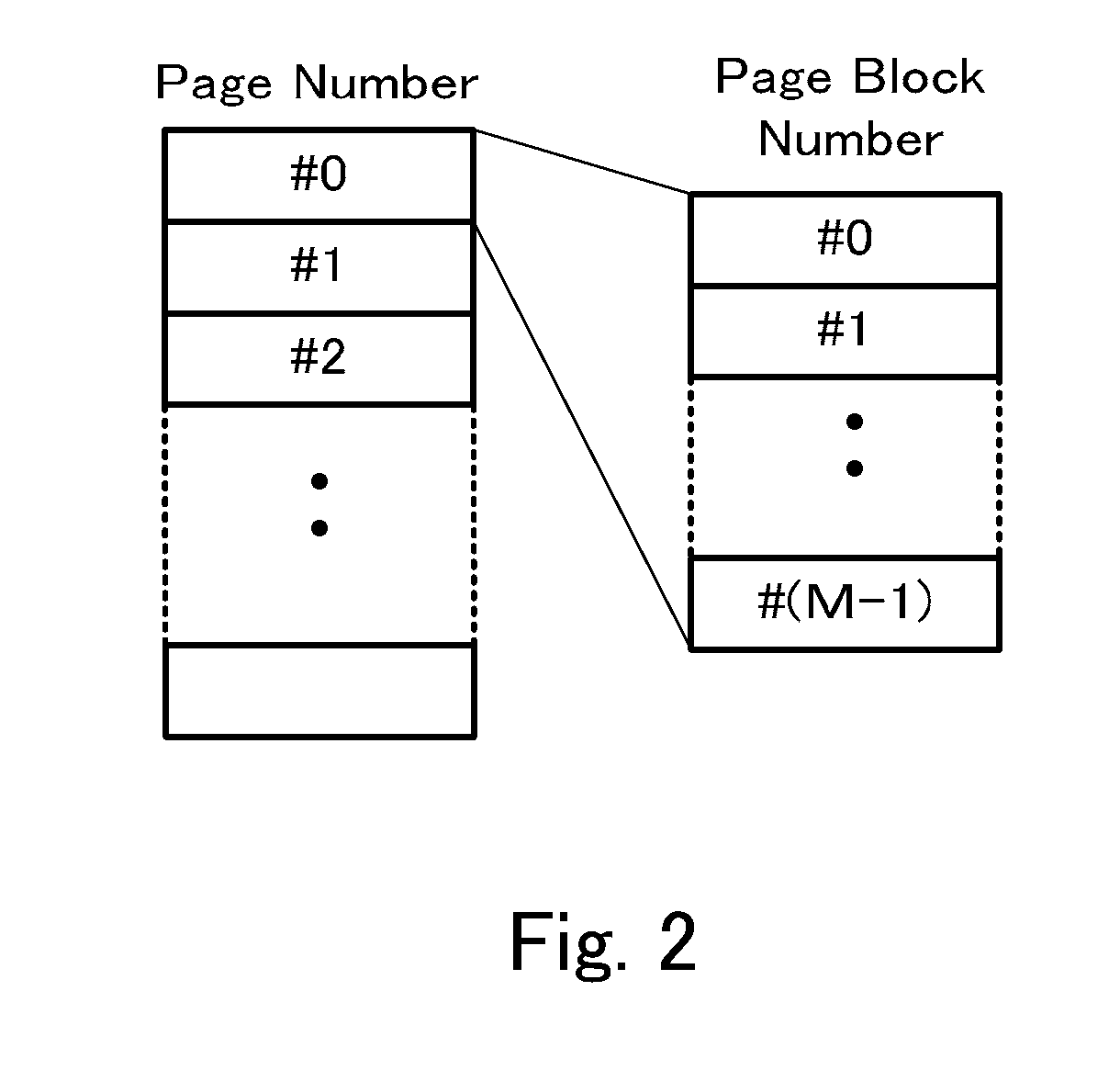
The invention provides a data encryption device that can perform high-speed access to an arbitrary page when encrypting data and writing it to a storage device that can be accessed in a page unit or reading data therefrom and decrypting it. The device: encrypts data and writes it to the storage device or reads data from the storage device and decrypts it by a stream cipher; uses a counter mode of a block cipher to generate pseudorandom number series; specifies a data position in the storage device based on a page number and a page block number, by dividing one page into plural page blocks having a block length of the block cipher; and uses a value determined by a function of the page number, the page block number, and an arbitrary offset value, as an initial value of a pseudorandom number to be used in the counter mode.
Owner:SHARP KK
Date display assembly for an electronic device
InactiveUS20060285445A1Less rotationMinimizing energyVisual indicationElectric indicationNumber seriesEngineering
A date display assembly for displaying the day of the month in an electronic device, the assembly comprising a units ring and a tens disc, the units ring comprising at least one series of numerals from 0 to 9 and the tens disc comprising a series of numerals from at least 1 to 3 and optionally the numeral 0; wherein the units ring and the tens disc being positioned relative to each other so as to display in the space of a window two numerals side by side, one of which is carried by the units ring and the other of which is carried by the tens disc, wherein the units ring is divided into ten sectors or a multiple of ten sectors each separating the numerals 0 to 9, the one sector separating the numerals 9-0 having an angular extent equal to ¾ of the angular extent of the sectors separating the other numerals. In the preferred embodiment, the device is a timepiece and a wristwatch in particular.
Owner:TIMEX GROUP
A verification code generation method based on hidden graphics
InactiveCN109299602AResolve identifiabilitySolve the problem of convenient user inputDigital data authenticationProgram/content distribution protectionGraphicsUser input
The invention relates to a verification code generation method based on hidden graphics, which comprises the following steps: S1, presetting M large graphics, each containing N sub-graphics; 2, extract n sub-graphics from N sub-graphics of each large graphics, and preprocess that n sub-graphics; 3, randomly selecte J graphics and correspond pre-processed K sub-graphics from that large graphics; 4,randomly selecte k sub-graphics as a verification code accord to that K sub-graphics obtained after the pre-processing at random; S5: setting the obtained k subgraph number series to S0; S6: outputting the selected k verification codes to the front end, and simultaneously recording the output sequence S1 of the k verification codes; S7: outputting J large graphics to the front end S8: setting a rule for selecting an implied sub-graphics; S9, recording the input and the clicking sequence of the authentication code clicked by the user, and generating the input series S0 'and the sequence sequence S1'; S10, respectively comparing the values of S0 and S0 'and the values of S1 and S1', and judging whether the authentication code input by the user is correct or not.
Owner:XIAMEN UNIV TAN KAH KEE COLLEGE
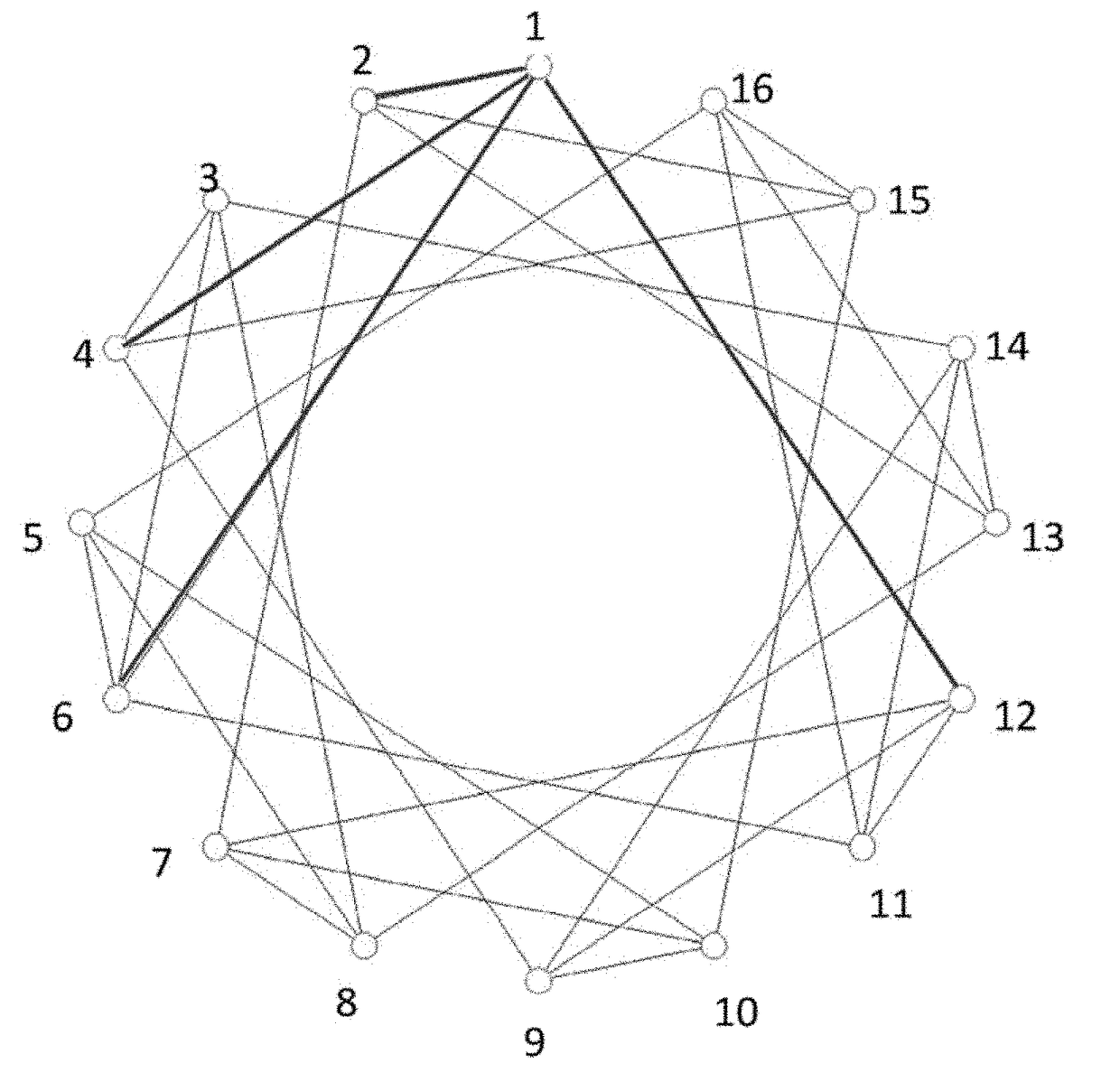
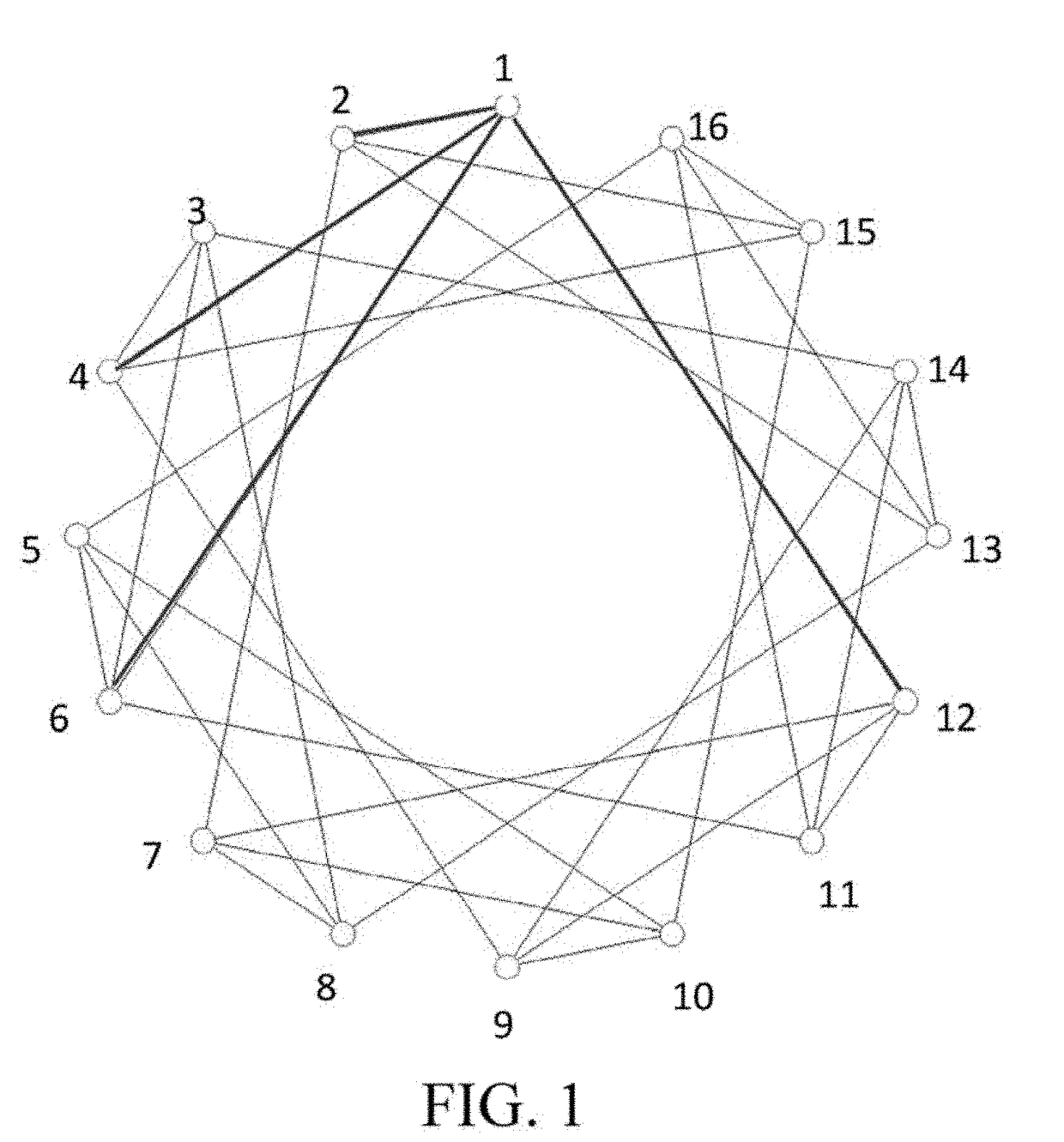
Network topology system and method
ActiveUS20170272327A1Simple network structureReduce networking costsMultiplex system selection arrangementsDigital computer detailsNumber seriesComputer science
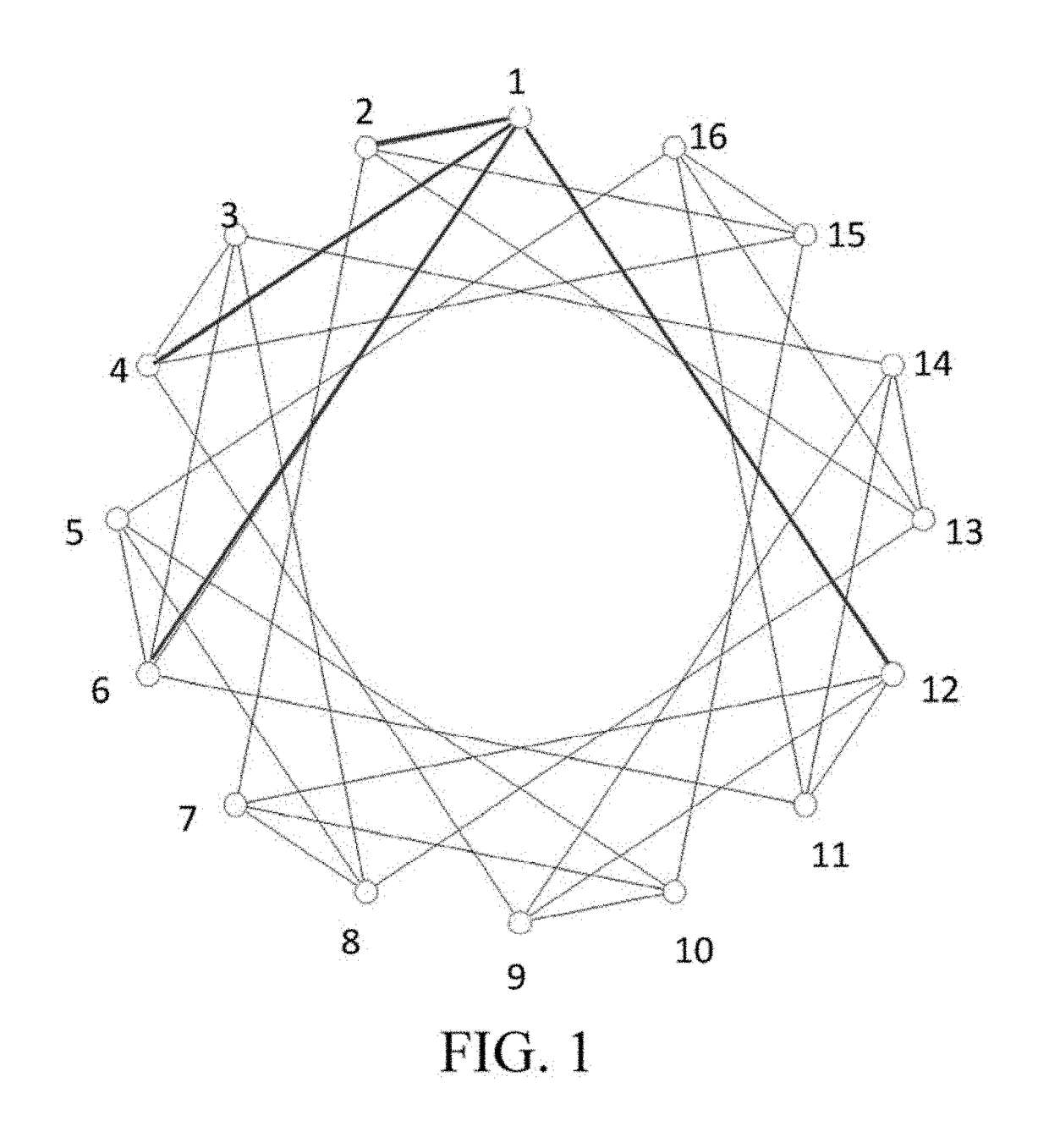
A network topology system comprises a plurality of nodes, each of the plurality of nodes having a set of connection rules which is built by the steps of: generating a series of prime number differences; generating a series of communication strategy numbers; extracting as many terms as the number of connecting nodes from a recursive sequences to serve as an index series; generating a series of connection strategy numbers by extracting the Nth terms from the series of communication strategy numbers, wherein N stands for each number of the index series; and generating a series of connecting nodes numbers by calculating the sum of each odd number and each term of the series of connection strategy numbers so as to build the connection rules for each odd-numbered node to connect the nodes numbered in corresponding with the numbers of the connecting nodes number series.
Owner:NAT CHENG KUNG UNIV
Method and apparatus for delivering certificate revocation lists
ActiveUS9054879B2User identity/authority verificationSelective content distributionNumber seriesBroadcasting
The present invention discloses an apparatus and method for delivering a revocation list over a one-way broadcast network to receivers with limited memory capabilities. In one example, the revocation list is partitioned to form a first certificate revocation list (CRL) sequence if the number of entries in the revocation list exceeds a predetermined value. Individual identification numbers belonging to a first identification number series are subsequently assigned to partitions of the first CRL sequence. Afterwards, the first CRL sequence is interleaved into a first content transport stream.
Owner:GOOGLE TECH HLDG LLC
LED chip thermal vibration accelerated life prediction method based on gray system theory
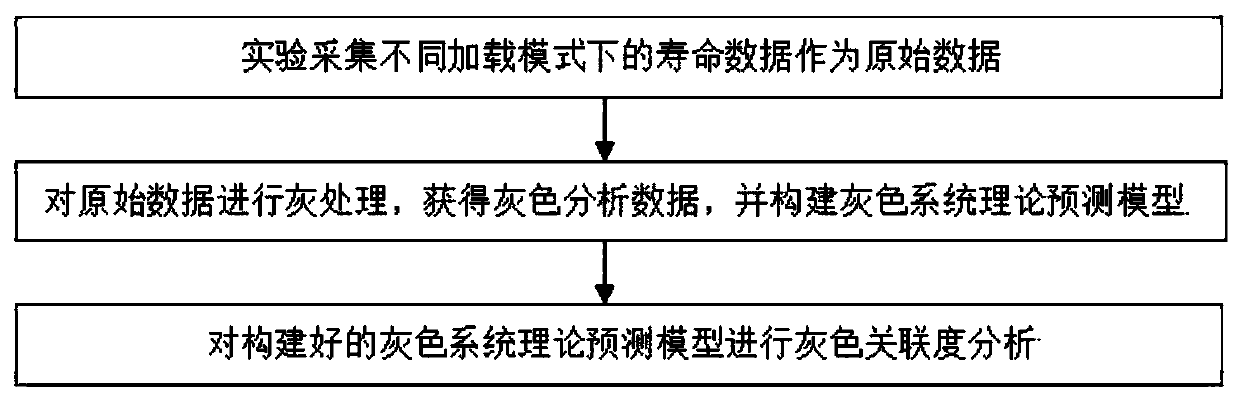
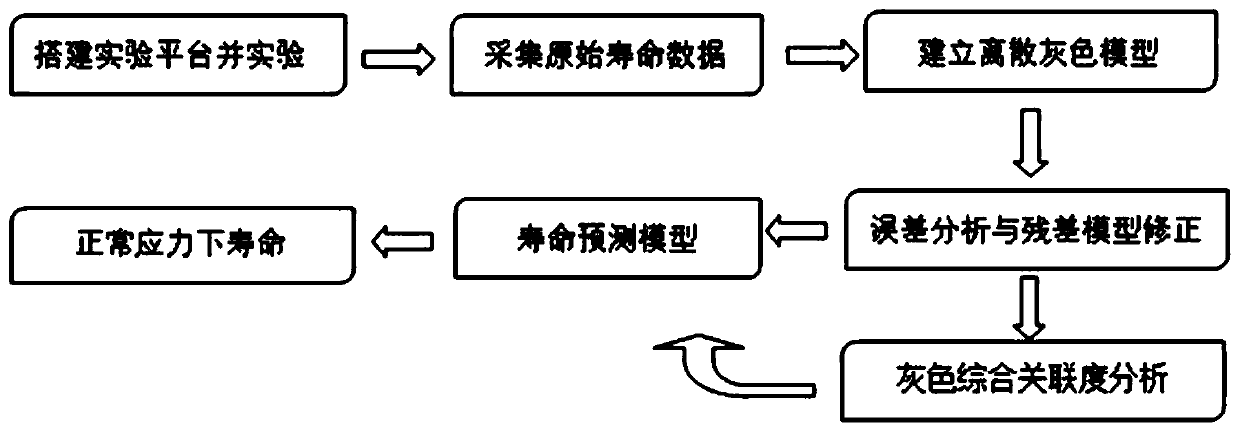
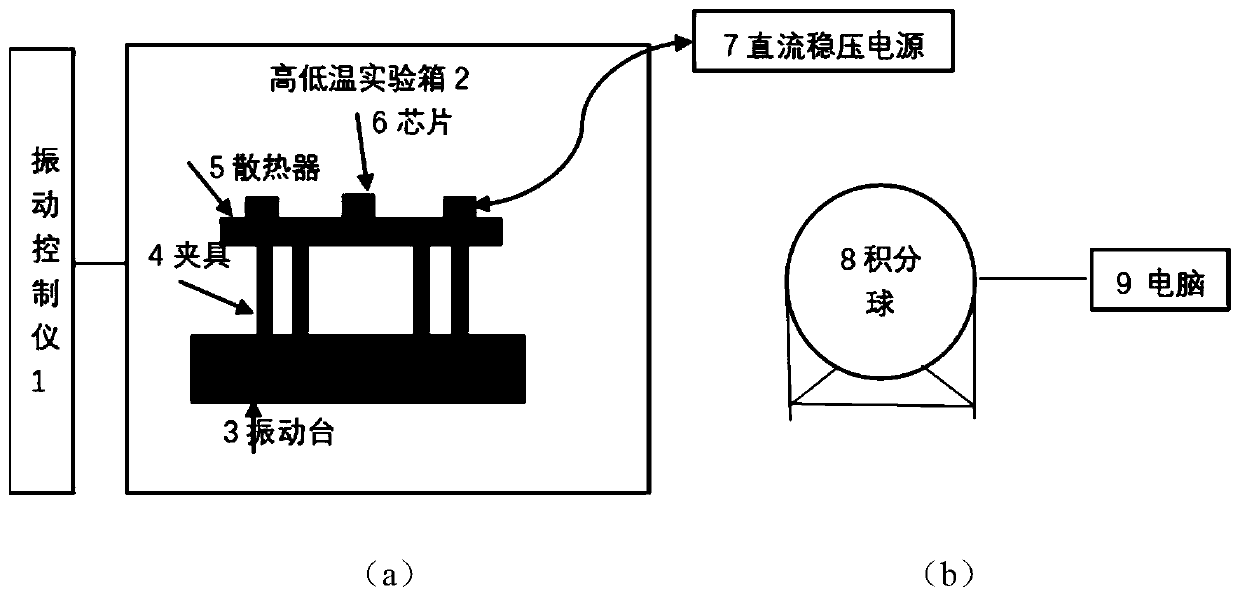
InactiveCN110045257AAccurate and Effective PredictionSemiconductor operation lifetime testingComplex mathematical operationsAnalysis dataOriginal data
The invention discloses a LED chip thermal vibration accelerated life prediction method based on gray system theory, which comprises the following steps: firstly, applying acceleration stress under different loading modes to an LED chip, and acquiring life experiment original data under different acceleration stress; then, carrying out grey processing on the experiment original data by using a grey system theory to obtain grey analysis data, and constructing a grey system theory prediction model; and finally, carrying out grey correlation degree analysis on the constructed grey system theory model. Compared with the prior art, the grey system prediction model does not need to consider a temperature-vibration interaction relationship and a statistical model related to a physical failure rule, and can obtain efficient and accurate prediction and evaluation. According to the method, the service life of the LED chip under the thermal and vibration double stress in normal work can be estimated through the original service life data under the acceleration stress and the number series prediction of the gray system theory, the prediction result is closer to the engineering practice, and ascientific data theory reference basis can be provided for designing and producing the LED chip with high performance and high stability.
Owner:JIANGSU UNIV
Chinese intelligent telephone capable of batch updating push-to-talk service
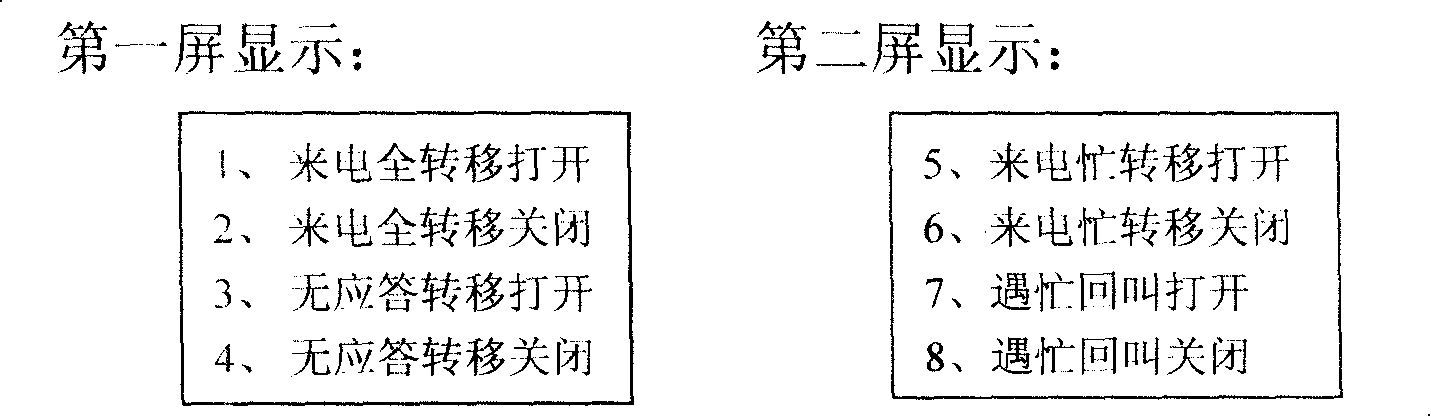
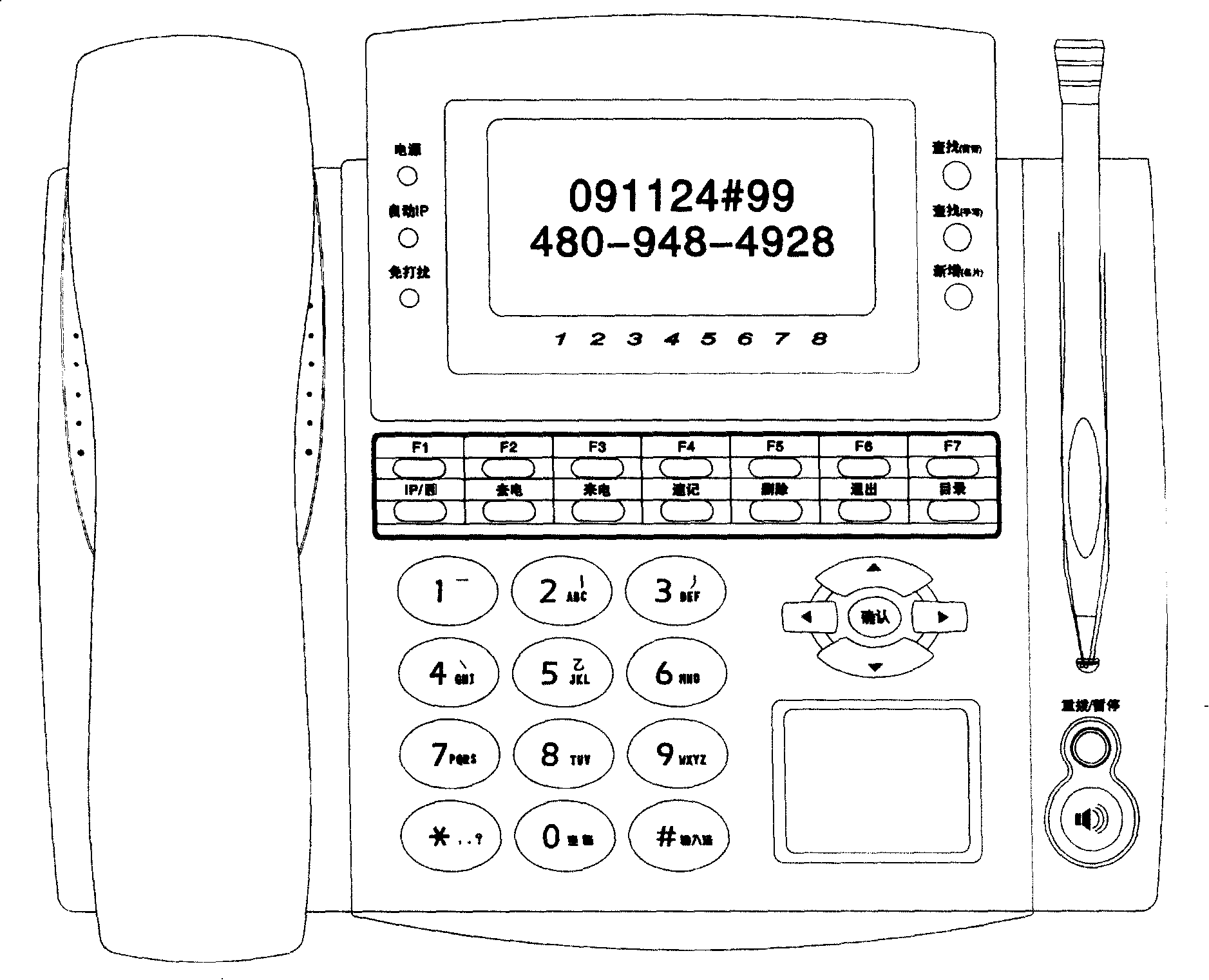
InactiveCN101222528APerfect push-to-talk functionSpecial service for subscribersSubscriber signalling identity devicesScreen printingNumber series
The invention provides a one-key-is-enough service Chinese intelligent telephone which can be mass-refreshed, belonging to the communication filed and aiming at overcoming the defects that the one-key-is-enough function of the common PSTN telephone lacks of flexibility and can not be mass-upgraded and the Chinese intelligent telephone is low in popularizing rate, wherein a PSTN network based Chinese intelligent telephone panel is additionally provided with more than one one-key-is-enough service grouping keys, each of which is responsible for C to 9 one-key-is-enough services, thereby when a grouping key is pressed, the one-key-is-enough service list which includes service names and service number series corresponding to the number key of 0 to 9 is displayed; when a corresponding number key is pressed, the one-key-is-enough service dial can be directly realized; the names and the short code dialing contents in the one-key-is-enough service list can be modified and refreshed by the PC communication or a built-in intellect SIM card read-write device; the grouping key can also be renamed by silk-screen printing again or using the self-adhesive tapes with printing types; the invention can meet the requirements of the telecommunication voice added value and the flexible customization of the industry VIP clients.
Owner:北京益通利智能通讯技术有限公司
Mapping program including a map, process and system for precisely representing or determining a location on the map and an electronic device and a storage medium therefor
InactiveUS7382290B2Intuitive informationPrecise positioningInstruments for road network navigationRoad vehicles traffic controlNumber seriesLongitude
A mapping program includes an overlay grid of intersecting lines represented by two series of numbers. An origin is defined and an area of interest is defined. The origin corresponds to a location on a map. One series of numbers relates to longitude; while the other series of numbers relates to latitude. Each series of numbers are represented by two or more digits. Each digit represents up to 35 different numerals or letters. When two digits are used to represent a location, the combined number of lines for each series of number may comprise up to 1225 lines. Thus, the total number of lines represented by each series of number corresponds to a power of the base number of possibilities up to 35; the power being represented by the number of digits used in each series of numbers. These numbers are overlaid onto a map having points corresponding to actual longitudinal and latitudinal locations. A device for converting between the latitude and longitude is provided. A storage medium is also provided for storing a series of steps to perform the operations.
Owner:BOWLING SHANNON
Multi-speed ring oscillator
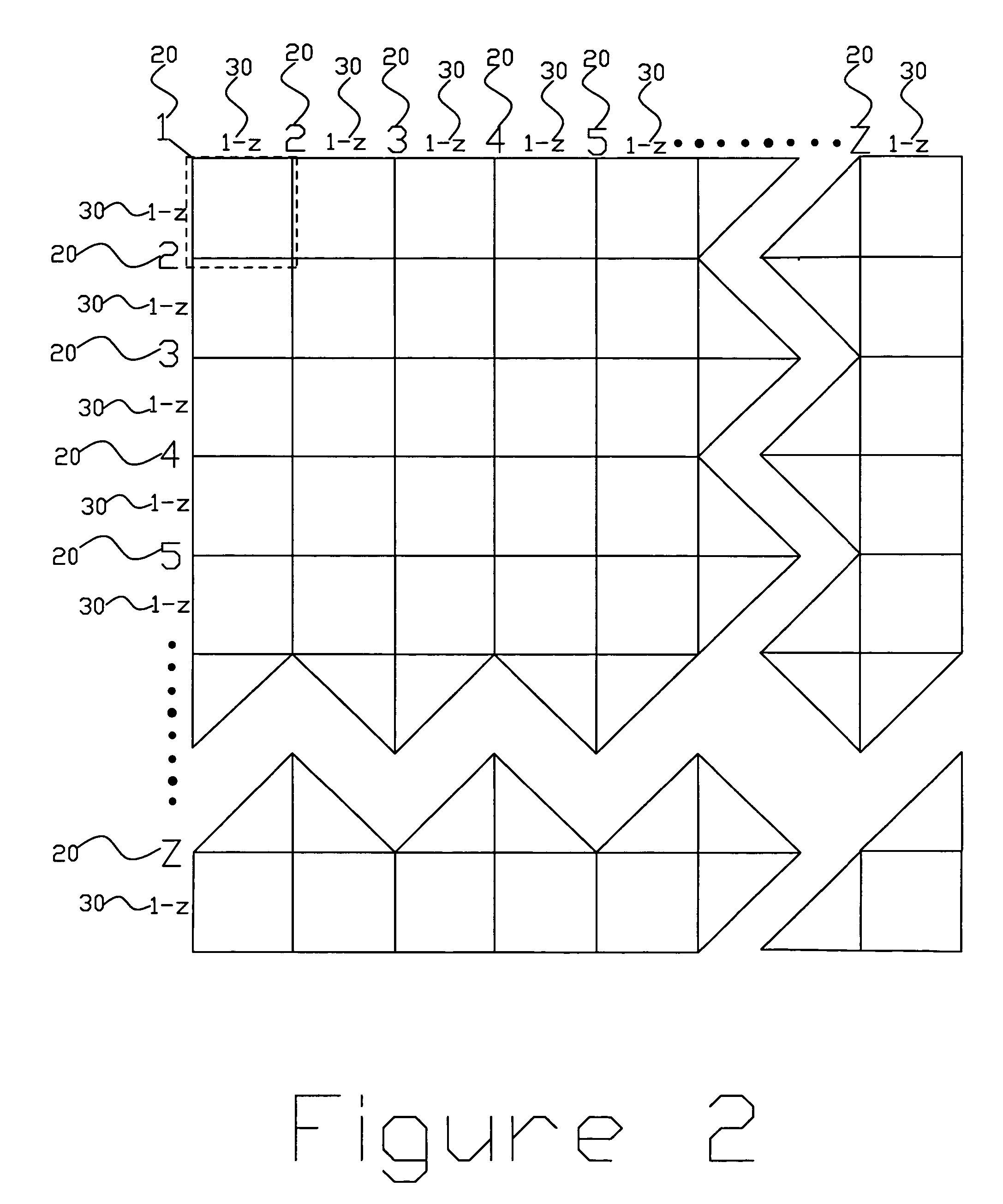
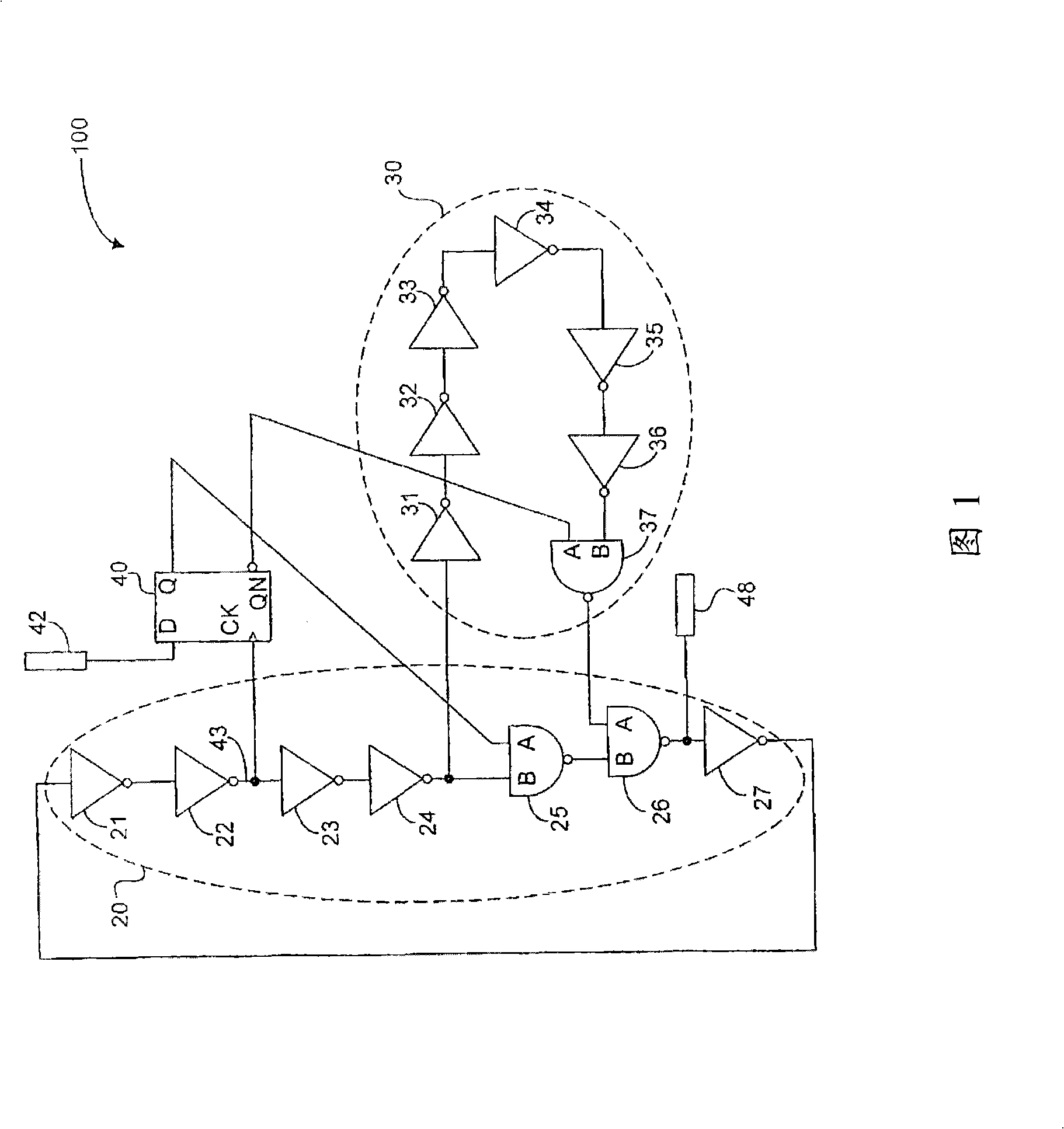
An annular oscillator comprises a control circuit for receiving the frequency selecting signal; the frequency selecting signal can be operated as processing the selection in at least two different annular oscillator frequencies; the control circuit uses the control signal to generate a first control signal and a second control signal; a main chain with the odd number series-connecting connections, the main chain comprises a main switch non-gate; the main switch non-gate is responding to the first control signal which can be operated as implementing the logical non-function or ignoring function for the first oscillating inputting signal to output the first outputting signal; and a slave chain series-connecting non-gate; the slave chain is collaterally connected to the main switch non-gate of the main china at least; the slave chain comprises a slave switch non-gate; the slave switch non-gate is responding to the second control signal which can be operated as implementing the logical non-function or ignoring function for the second oscillating inputting signal to output the second outputting signal.
Owner:TECH PROPERTIES
Hollow thin electric conduction link
InactiveCN106129757ARealize the application of continuous rotary functionRotary current collectorSlip ringNumber series
The invention relates to the technical field of electrical apparatuses and particularly provides a hollow thin electric conduction link. The traditional electric conduction link mostly has a solid shaft, collector rings and electric brushes are arranged in an axial overlapped mode, no channel for adding of wires exists in the axis direction, line connection between certain execution devices in need of serial connection and with relative rotary motion relies on external open wires, playing of the continuous rotary function of devices is limited, and the devices can only rotate within 360 DEG. In order to solve the problem of wire number application expansion of the electric conduction link, the invention provides a hollow and thin electric conduction link, and a certain number of wires can pass through the hollow channel. With a middle piece associated with a fixing ring and a moving ring, radial and axial constraints on the moving ring by the fixing ring are formed, an electric conduction link structure with the fixing ring and the moving ring capable of rotating relatively combined into a whole is formed, a hollow hole in the moving ring becomes the channel for expanding the wires, and the purpose of wire number series expansion can be realized.
Owner:沈阳凤天机器人科技有限公司
Deterministic random number generator for cryptography and digital watermarking
A deterministic random number generator includes a number series generator adapted to generate an infinite Pi series, a summation generator adapted to generate a partial sum of said infinite Pi series, a computer adapted to compute a finite sequence from said partial sum of infinite Pi series, a shuffler adapted to shuffle said computed finite sequence to obtain a shuffled sequence, a masker adapted to mask said shuffled sequence to obtain a masked sequence, a non-linear function processor adapted to process said masked sequence to obtain a non-linear processed sequence, and a linear feedback shift register adapted to receive and shift bits of said non-linear processed sequence in a pre-determined manner to obtain a deterministic random number and a method for generating a deterministic random number for cryptography and watermarking.
Owner:TATA CONSULTANCY SERVICES LTD
A code bearer
InactiveUS20030189102A1Easy to handleImprove security levelFinanceRecord carriers used with machinesDigital dataData field
The present invention relates to a code bearer, a data-coding device and a method for coding data onto a bearer, provided for manual reading of a first code followed by an input of the first code to a machine, said bearer comprising at least one numerical data field comprising the first code as a series of multiple figures. A second code is generically provided specifying the numerical data field with the first code through modulo arithmetic with a predetermined base, represented by at least one symbol accomplished through compressing each series of multiple figures in the at least one data field. The symbols are concatenated in a predetermined pattern for entering into the machine, wherein enhanced readability of the first code through the symbol pattern applied for the first code is accomplished, thus providing an aid for facilitated, protected and error-minimized input of data belonging to the first code into the machine / apparatus.
Owner:KOZICA MARCUS +1
Method of Gaining Access to a Device
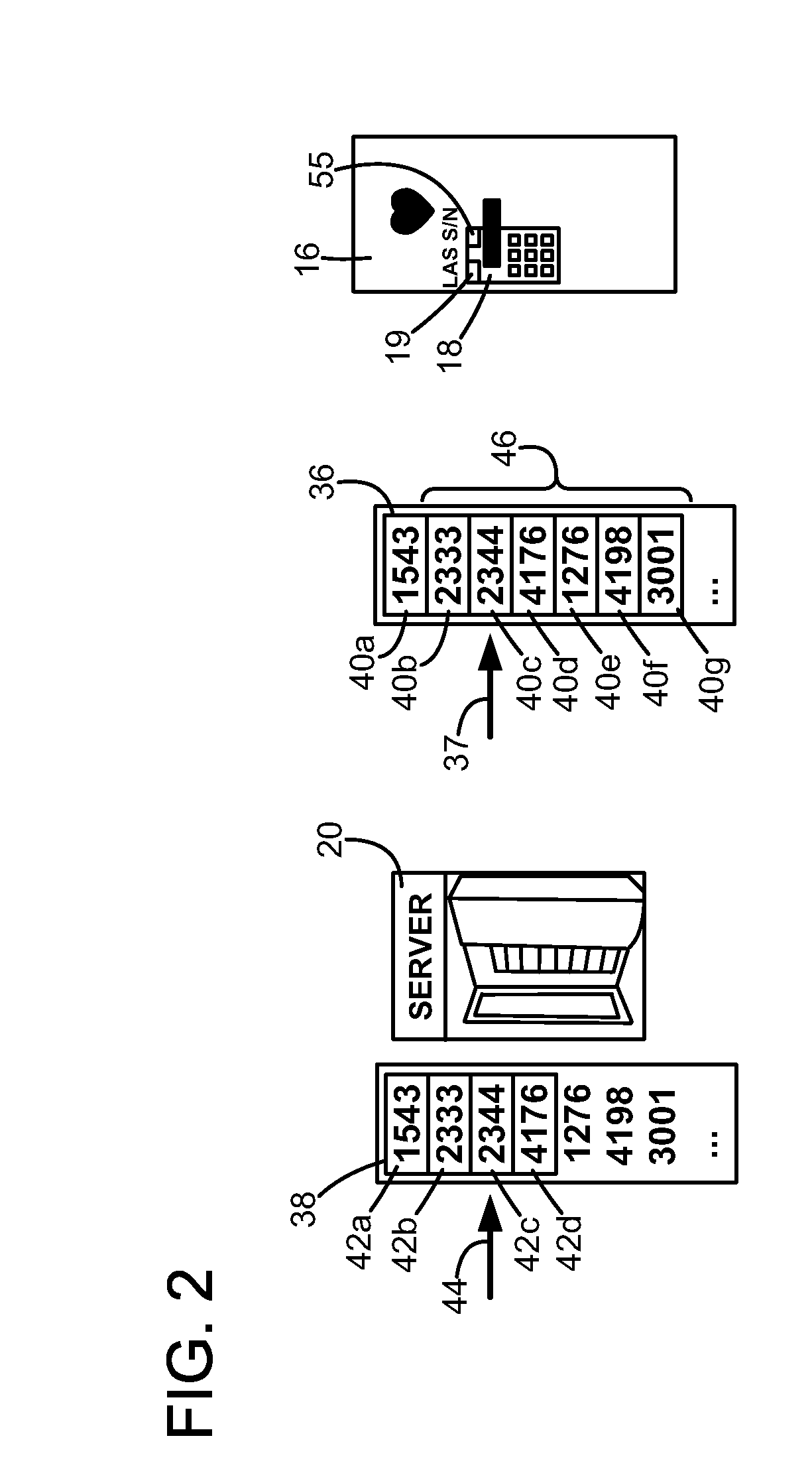
InactiveUS20090320112A1Complete banking machinesTicket-issuing apparatusComputer hardwareNumber series
The method is for activating a device. A communication device (14) is provided that is in communication with a server unit (20) that has a processor for generating a number series (38). An application device (16) has a processor (19) for generating a number series (36). The communication device (14) is not communicating directly with the application device (16). The user reads an identification number (30) and sends a message (32) including the identification number (30) to the server (20). The server (20) identifies a code number (42c) pointed at by a pointer (44) and sends back the code number (42c). The user enters the code number (42c) into the application device (16). The processor (19) compares the code number (42c) with a number (40c) pointed at by a pointer (37) and sends an activation signal to an activation device (18) to activate the application device.
Owner:MAGNUSSON NIKLAS +1
Network topology system and method
ActiveUS10193757B2Simple network structureNo power consumption of the switchMultiplex system selection arrangementsData switching networksNumber seriesNetwork topology
A network topology system comprises a plurality of nodes, each of the plurality of nodes having a set of connection rules which is built by the steps of: generating a series of prime number differences; generating a series of communication strategy numbers; extracting as many terms as the number of connecting nodes from a recursive sequences to serve as an index series; generating a series of connection strategy numbers by extracting the Nth terms from the series of communication strategy numbers, wherein N stands for each number of the index series; and generating a series of connecting nodes numbers by calculating the sum of each odd number and each term of the series of connection strategy numbers so as to build the connection rules for each odd-numbered node to connect the nodes numbered in corresponding with the numbers of the connecting nodes number series.
Owner:NAT CHENG KUNG UNIV
A Communication Method of Distributed Dispatch System Based on Local Area Network Multicast Group
The invention relates to a communication method of a distributed scheduling system based on a local area network multicast group. Since the IP addresses in the same network segment must be different in the method, the random number sequences must be incongruent, and an arbitration result must be obtained. Since multiple robots use exactly the same algorithm, the results of their respective arbitration pairs are also exactly the same. Accordingly, after a conflict occurs, the arbitration can be completed without any communication between the conflicting robots. That is, arbitration does not consume any bandwidth at all, except for the necessary information such as robot position, direction, and resource application that need to be transmitted during scheduling. Logging in and out also only results in very small data transfers at boot time. This method enables multiple robots moving indoors to share scheduling information with the minimum network bandwidth, and supports adding new robots at any time without any configuration.
Owner:SHENZHEN PUDU TECH CO LTD
Method for storing character string matching rule and character string matching by storing rule
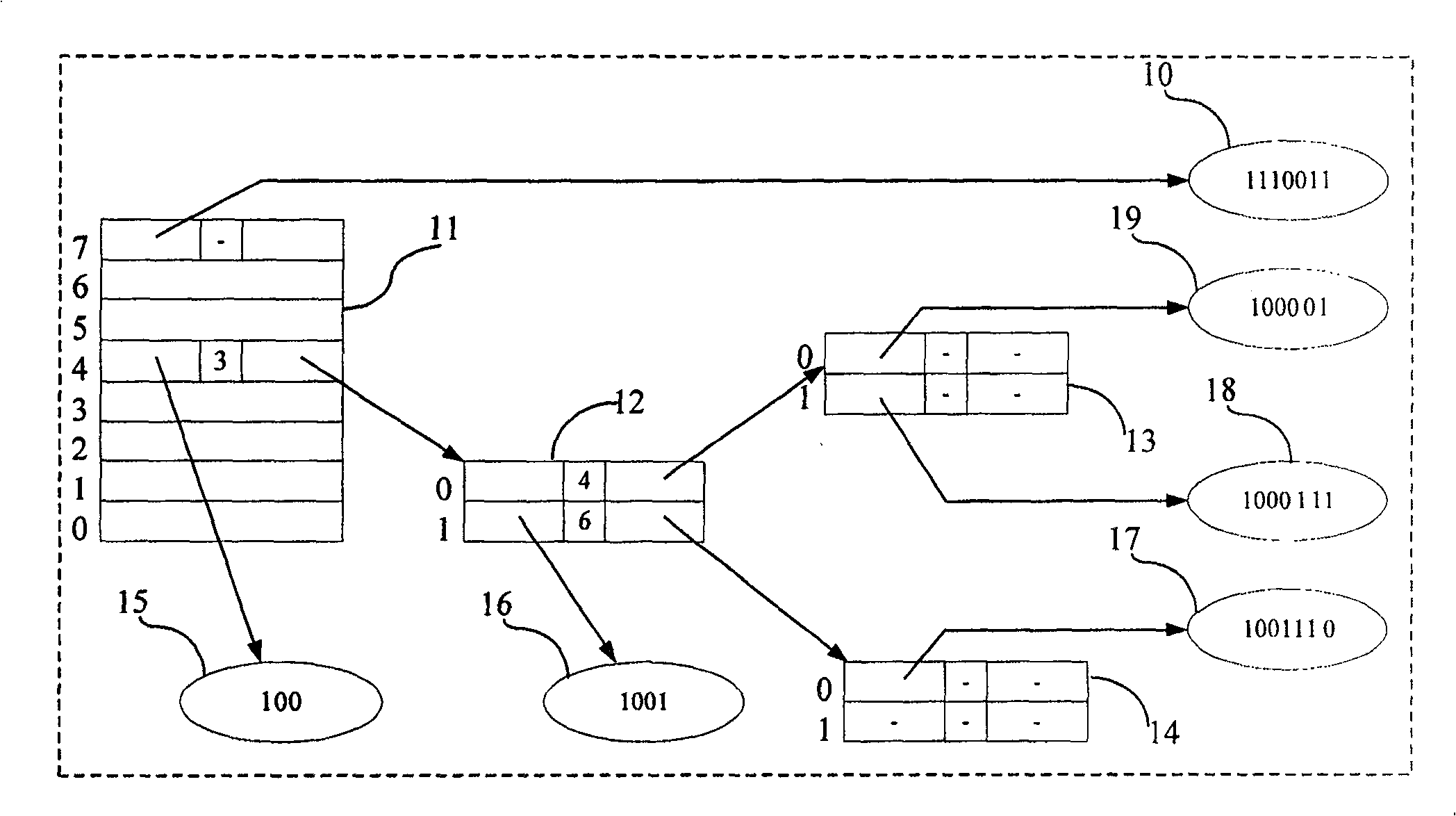
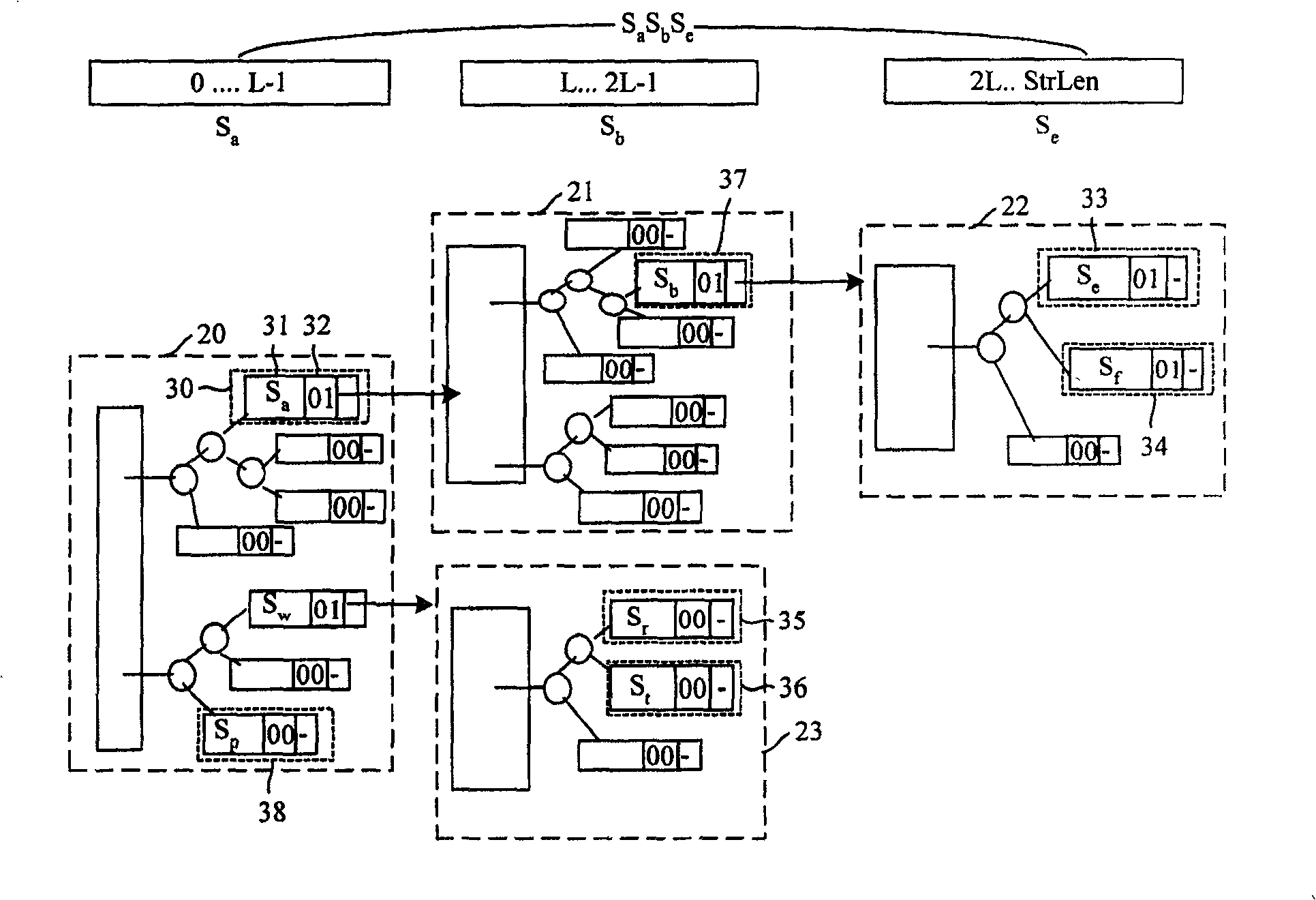
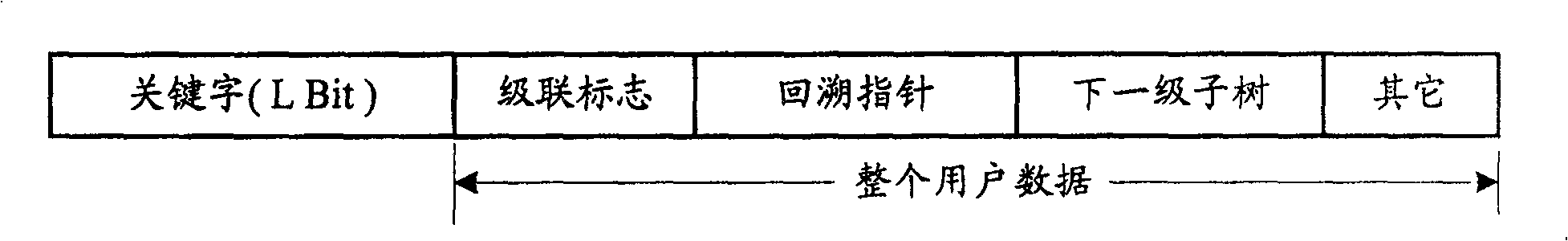
InactiveCN100531179CAchieve matchingReduce in quantityTransmissionTheoretical computer scienceNumber series
The invention discloses a method for storing character string matching rules. The method divides the keywords of the rules to be saved into several sub-keywords, each sub-keyword is connected in series with the corresponding leaf number to form a string, and then the Word strings are used as keywords to construct leaves in the rule tree, so that the keyword of the rule and the data part of the rule are inserted into the rule tree to save; the invention also discloses a method for string matching using the rule tree, which will be The matching string is divided into several sub-keywords, each sub-keyword is concatenated with the corresponding leaf number to form a string, and the longest prefix match of these strings is found in the above rule tree, so as to realize the string matching process. The method can save long character string matching rules, and because no subtree is needed when using the rule tree to save the rules, it can reduce the occupation of hardware resources and improve the processing capacity.
Owner:HUAWEI TECH CO LTD
Management of calling name delivery in telephone networks providing for telephone number portability
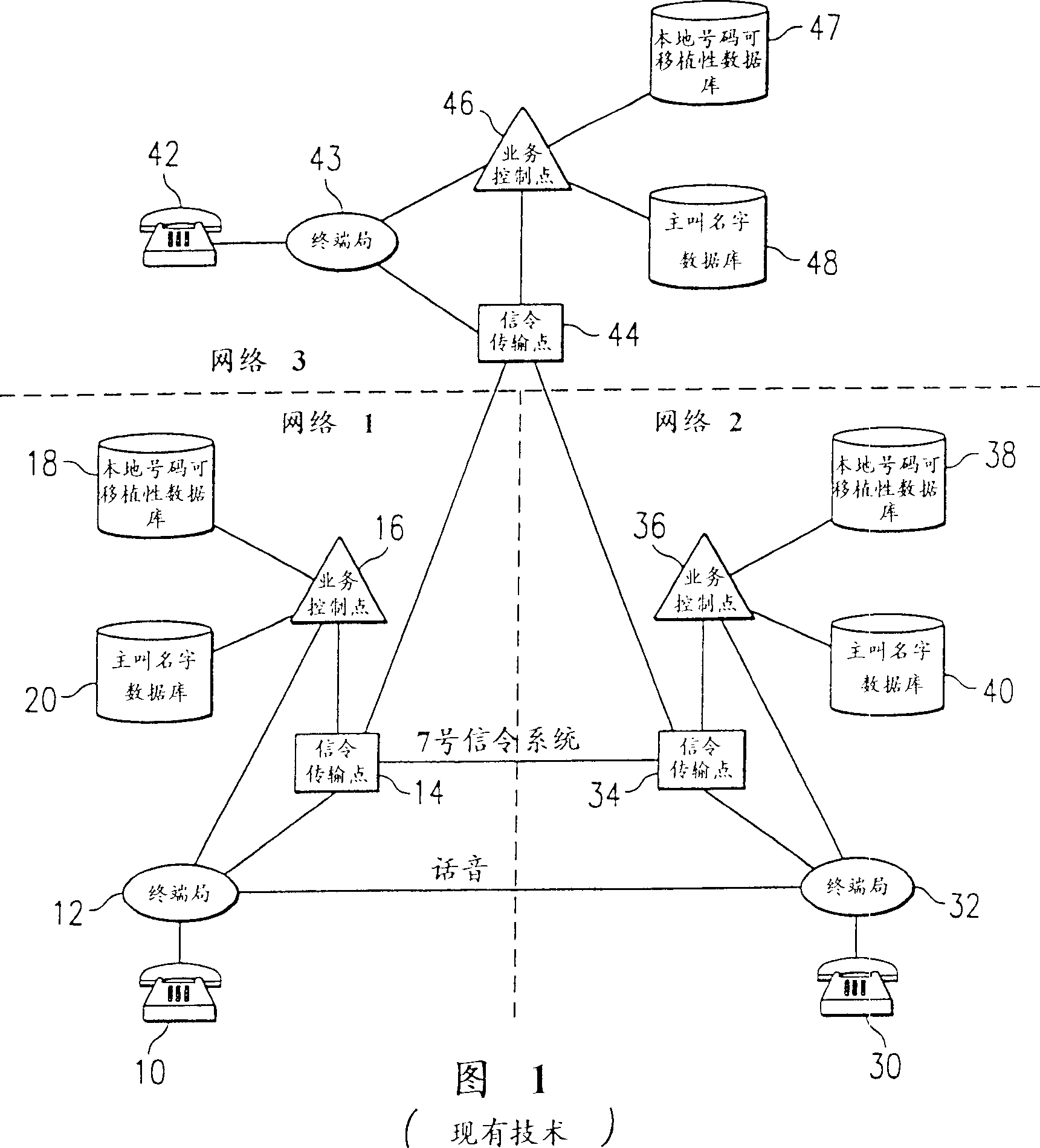
InactiveCN1108707CMultiplex system selection arrangementsSpecial service for subscribersNetwork connectionNumber series
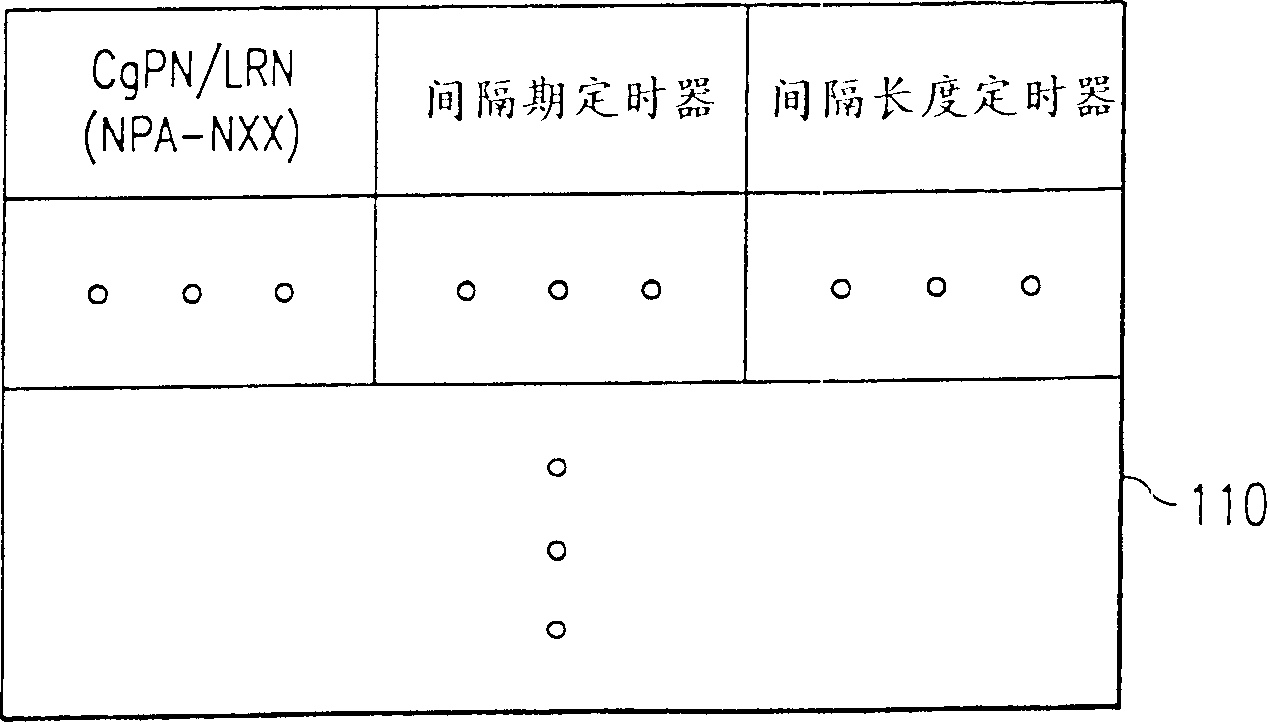
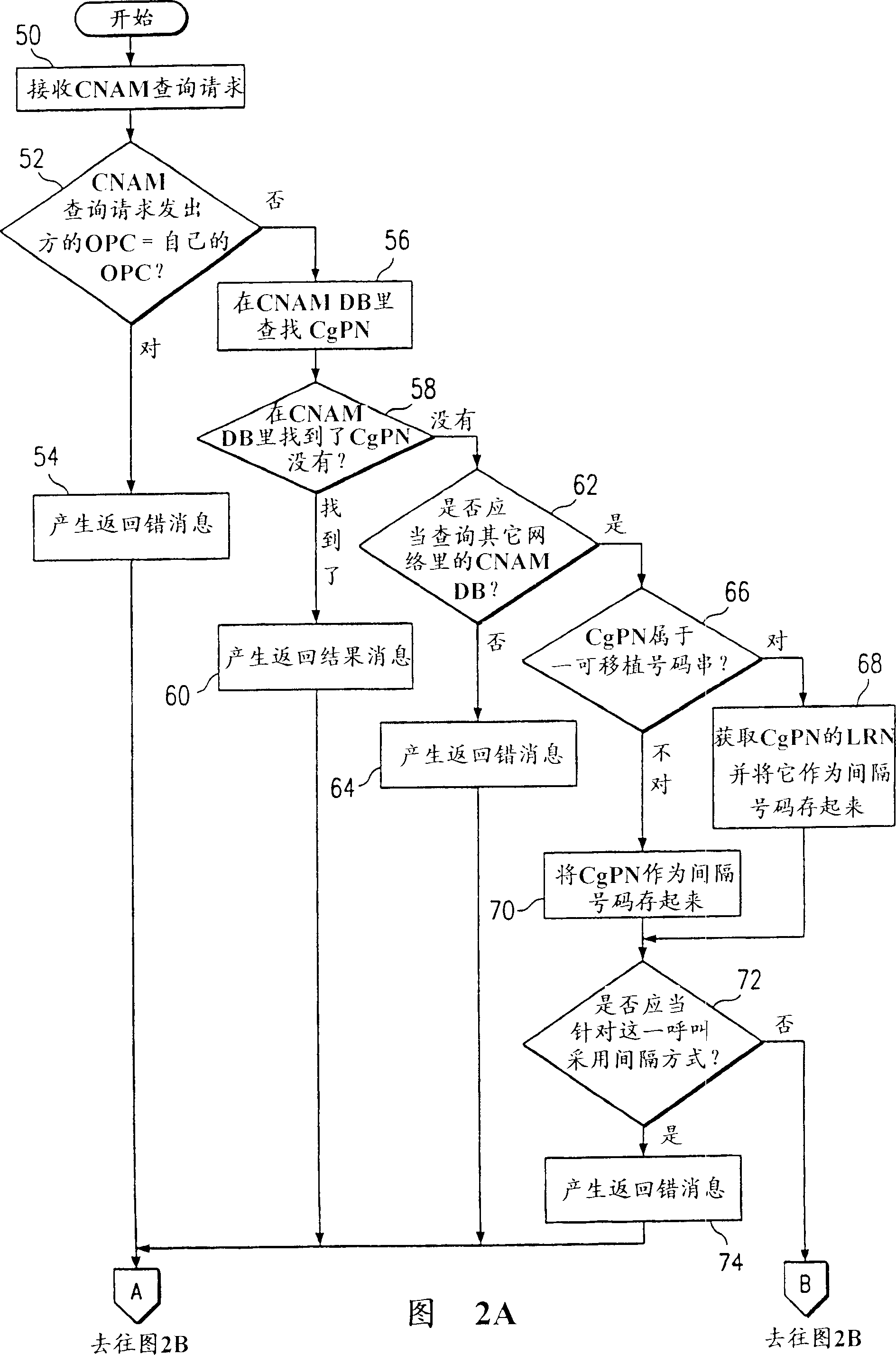
A system and a method for managing calling name (CNAM) queries in a plurality of telephone networks (1-3) including a plurality of subscribers (10, 30, 50) each assigned a telephone number in a predetermined number series associated with a particular switch (12, 32, 52) in one of the telephone networks, wherein at least one of the number series is a portable number series including telephone numbers assigned by one network but connected to another network. According to the present invention (FIGs. 2A-B), if the calling party number (CgPN) belongs to a portable number series, gapping will be applied to CNAM queries containing either portable telephone numbers associated with a location routing number (LRN) identifying the switch and network to which the CgPN is connected, or non-portable telephone numbers belonging to the same number series as the LRN. On the other hand, if the CgPN does not belong to a portable number series, gapping will be applied to CNAM queries containing telephone numbers belonging to the same number series as the CgPN.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method of gaining access to a device
ActiveUS8931072B2Digital data processing detailsMultiple digital computer combinationsComputer hardwareNumber series
The method is for activating a device. A communication device is provided that is in communication with a server unit that has a processor for generating a number series. An application device has a processor for generating a number series. The communication device is not communicating directly with the application device. The user sends a message including the identification number to the server. The server identifies a code number pointed at by a pointer and sends back the code number. The pointer steps forward in the number series at predetermined time intervals. The user enters the code number into the application device. The processor compares the code number with a number pointed at by a pointer and sends an activation signal to an activation device to activate the application device.
Owner:TELKEY SOLUTIONS AB
High-security communication system, and transmitter and receiver both used therein
ActiveUS10305681B2Easily corrects bit errorsCorrection errorKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCommunications systemNumber series
The objective of the invention is to provide an encoding method and a communication method wherein bit-error correction is easy for a authorized recipient but difficult for an unauthorized recipient. A transmission channel in which bit errors are moderately controlled is used to transmit / receive a random number sequence. A common key is shared between a transmitter and a receiver in advance; each bit value of the common key is connected with each slot of the random number sequence; the common key is used to divide the random number sequence into two or more random number series in accordance with the connection; and each random number series is independently encoded and parity check symbols are generated. The unit of the encoding is equal to or greater than the length of the common key so as to make a partial analysis by an unauthorized recipient impossible.
Owner:HITACHI LTD
Vehicle anti-theft system and method
The invention relates to an anti-attack anti-theft system. Systems and methods for anti-theft of vehicles are provided. Each of the two or more locking point devices generates a random number and broadcasts it to all other locking point devices. Each of the lockpoint devices retains its own local copy of the nonce and concatenates its own local copy of the nonce to the other of the two or more lockpoint devices from the bus A random number for the device. From the nonce broadcast on the bus all nonces are concatenated in a predetermined sequence to form a single challenge, which is sent to the remote transponder. Each locking point device then compares the individual response from the transponder with its local concatenation. When a specific portion of the response from the transponder matches the local series, the function of the locking point device is enabled.
Owner:GM GLOBAL TECH OPERATIONS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com