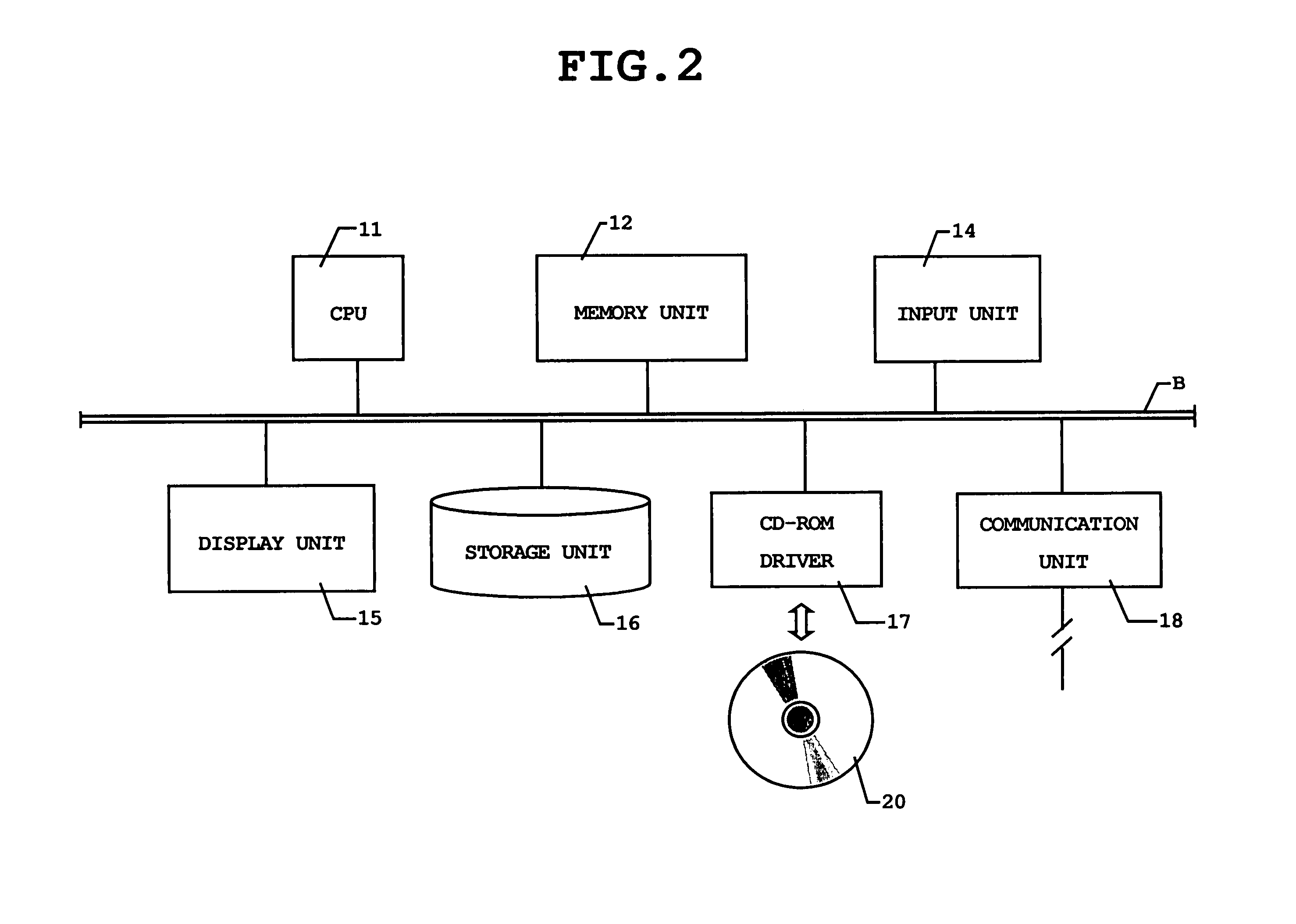
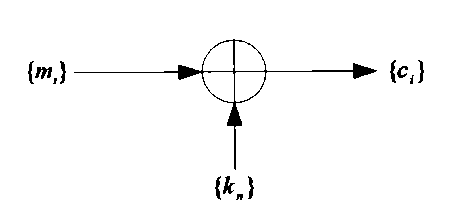
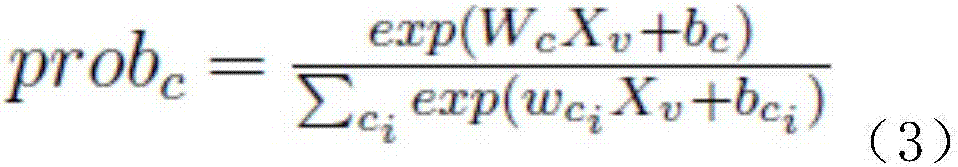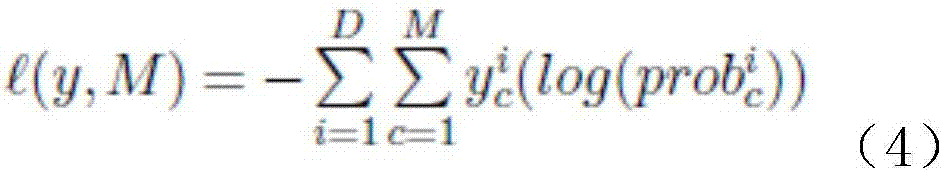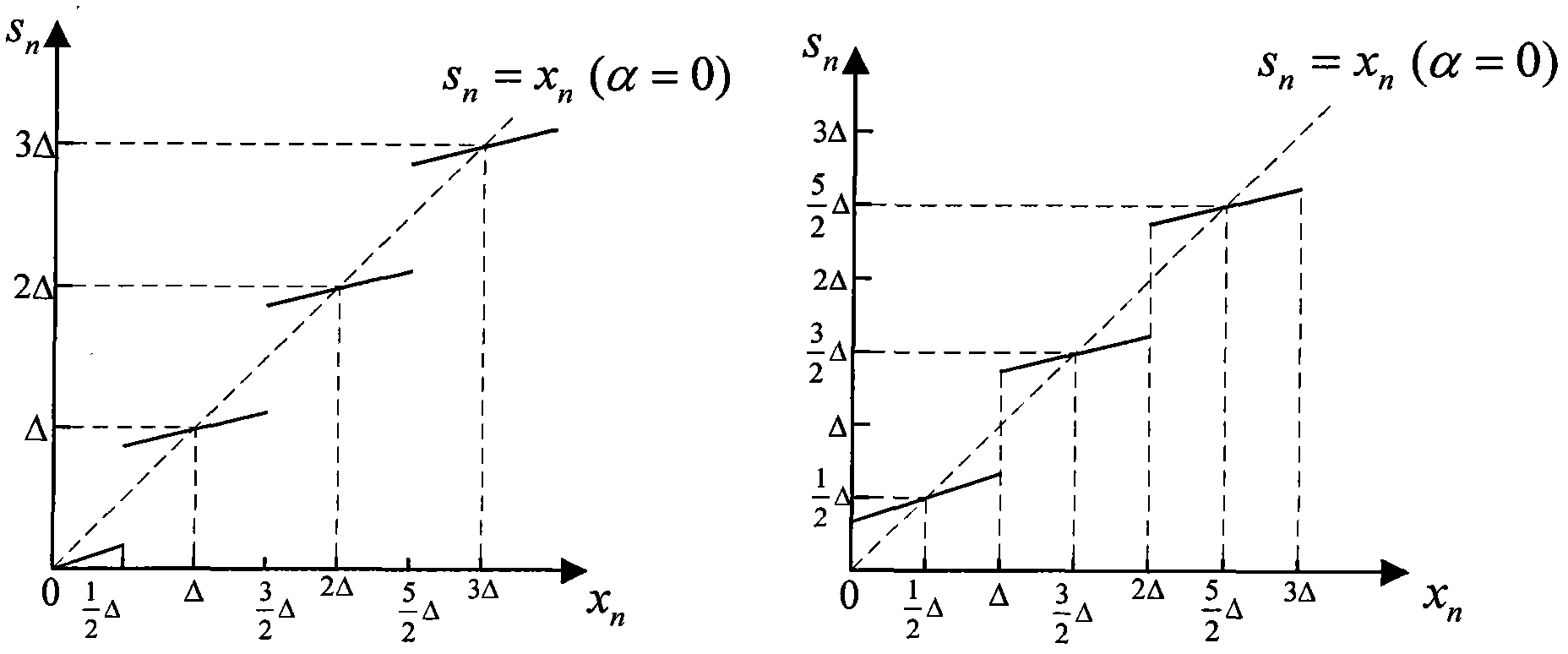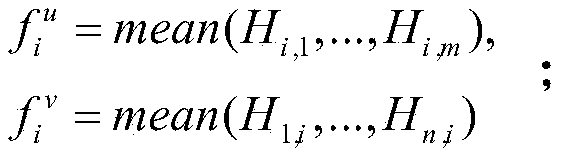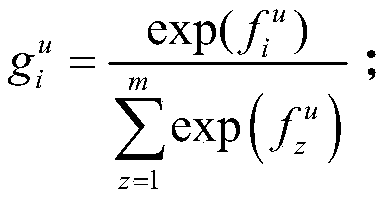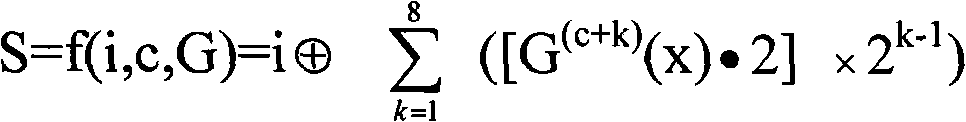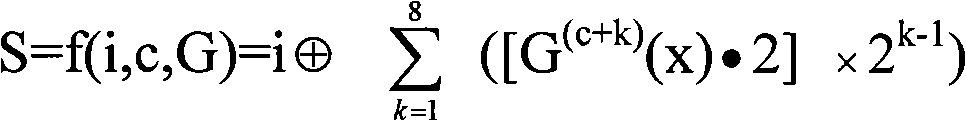Patents
Literature
651 results about "Information embedding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
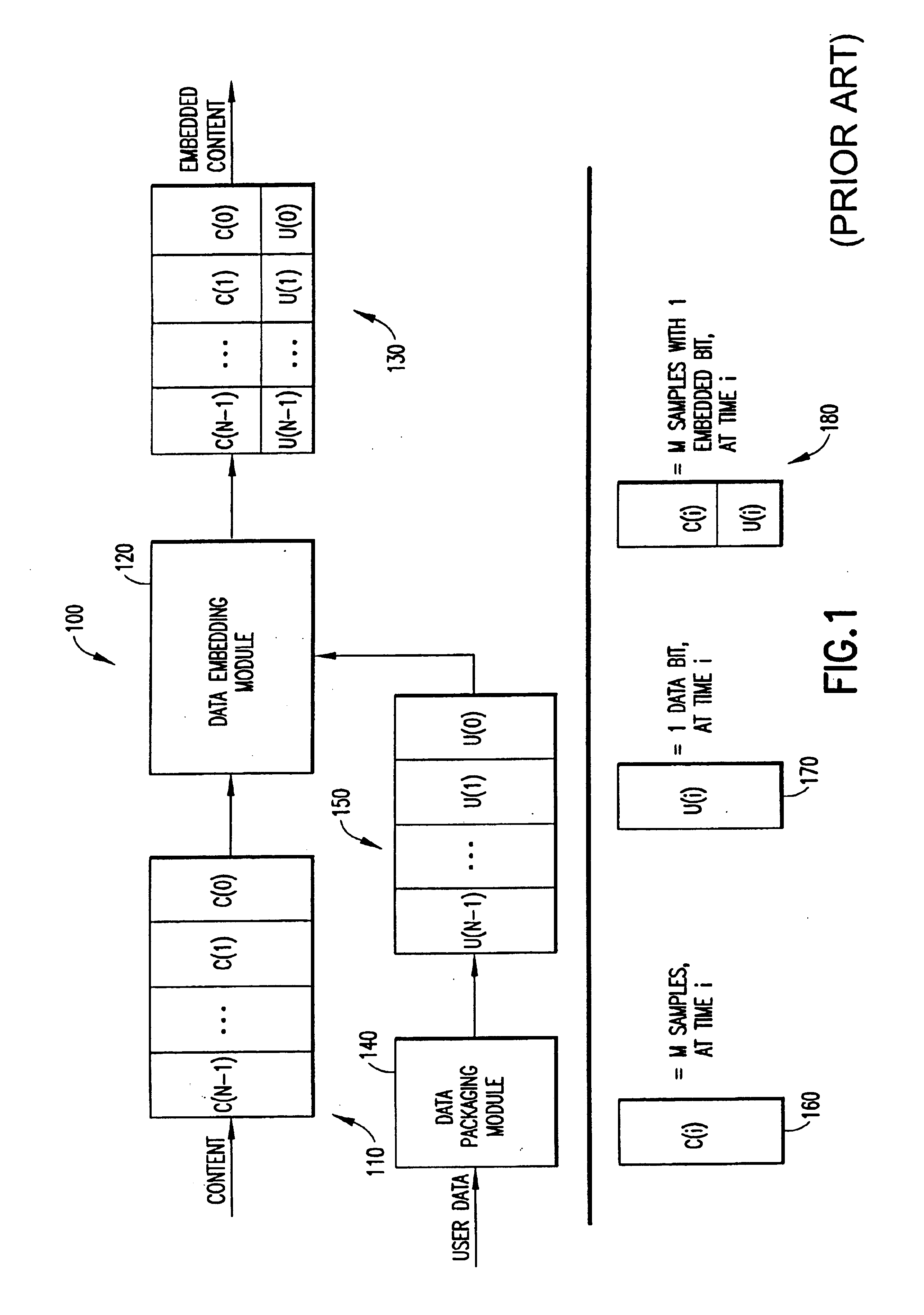
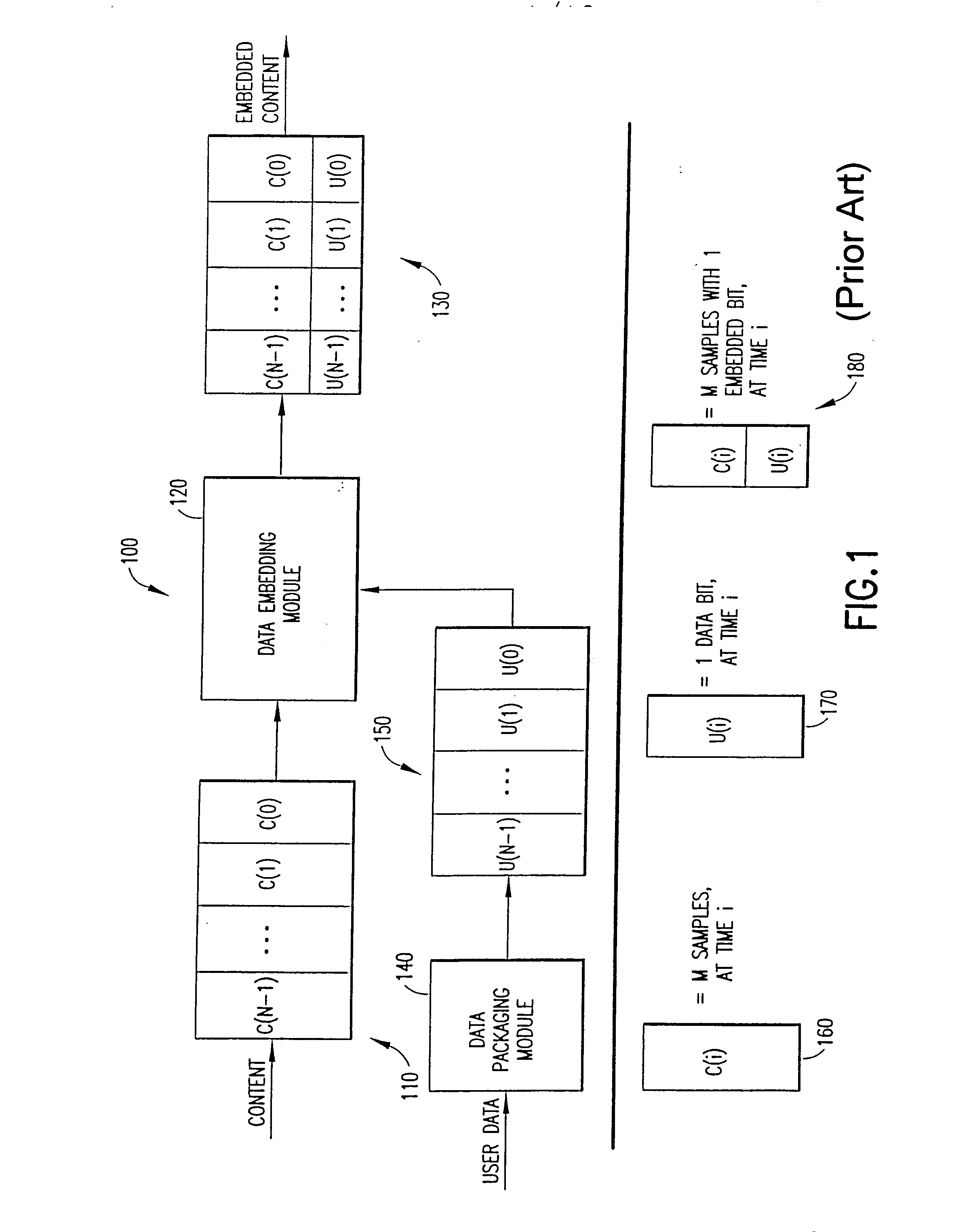
Method for embedding and reading watermark-information in digital form, and apparatus thereof
InactiveUS6185312B1Information can be droppedOther printing matterCharacter and pattern recognitionInformation embeddingOrthogonal transformation
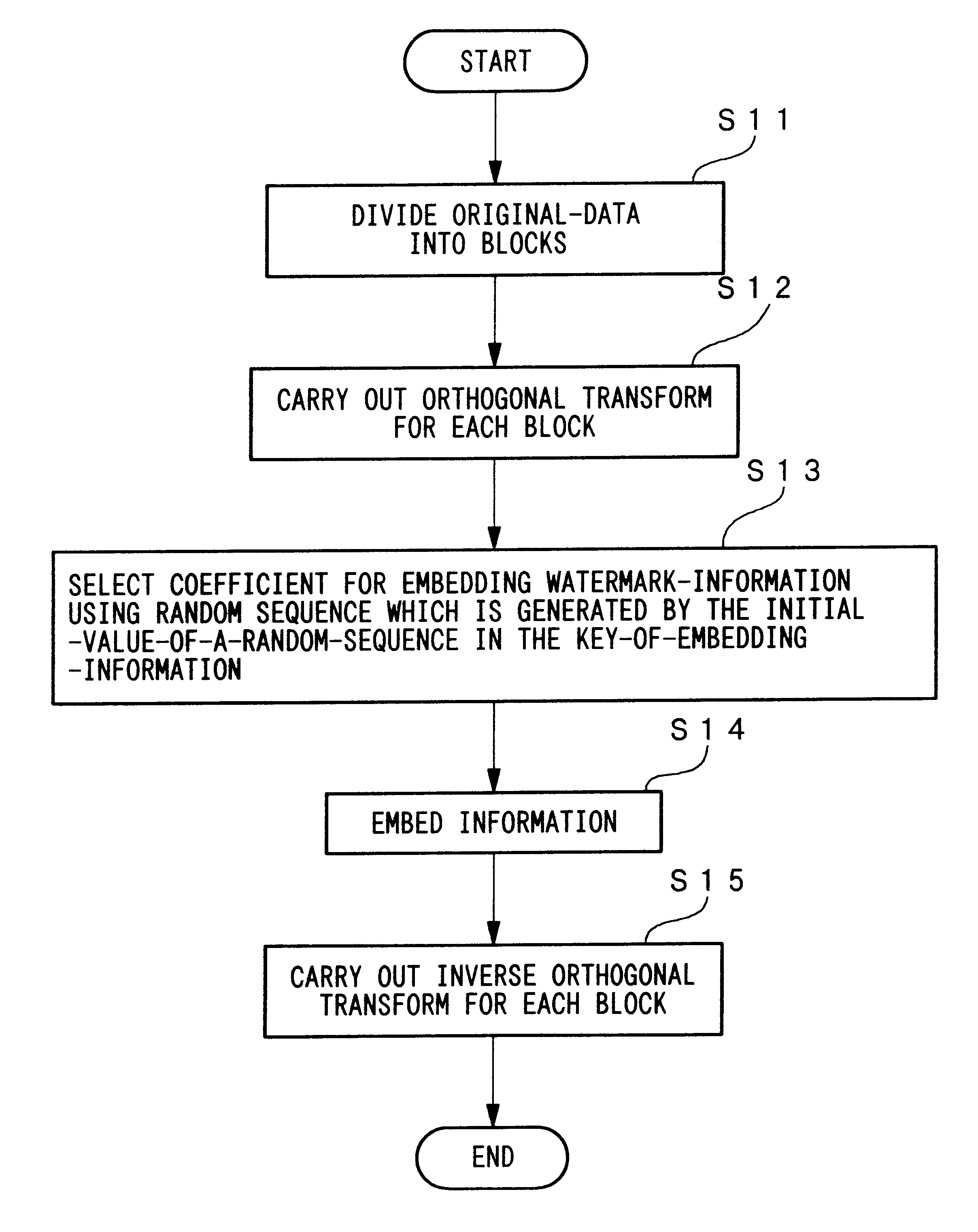
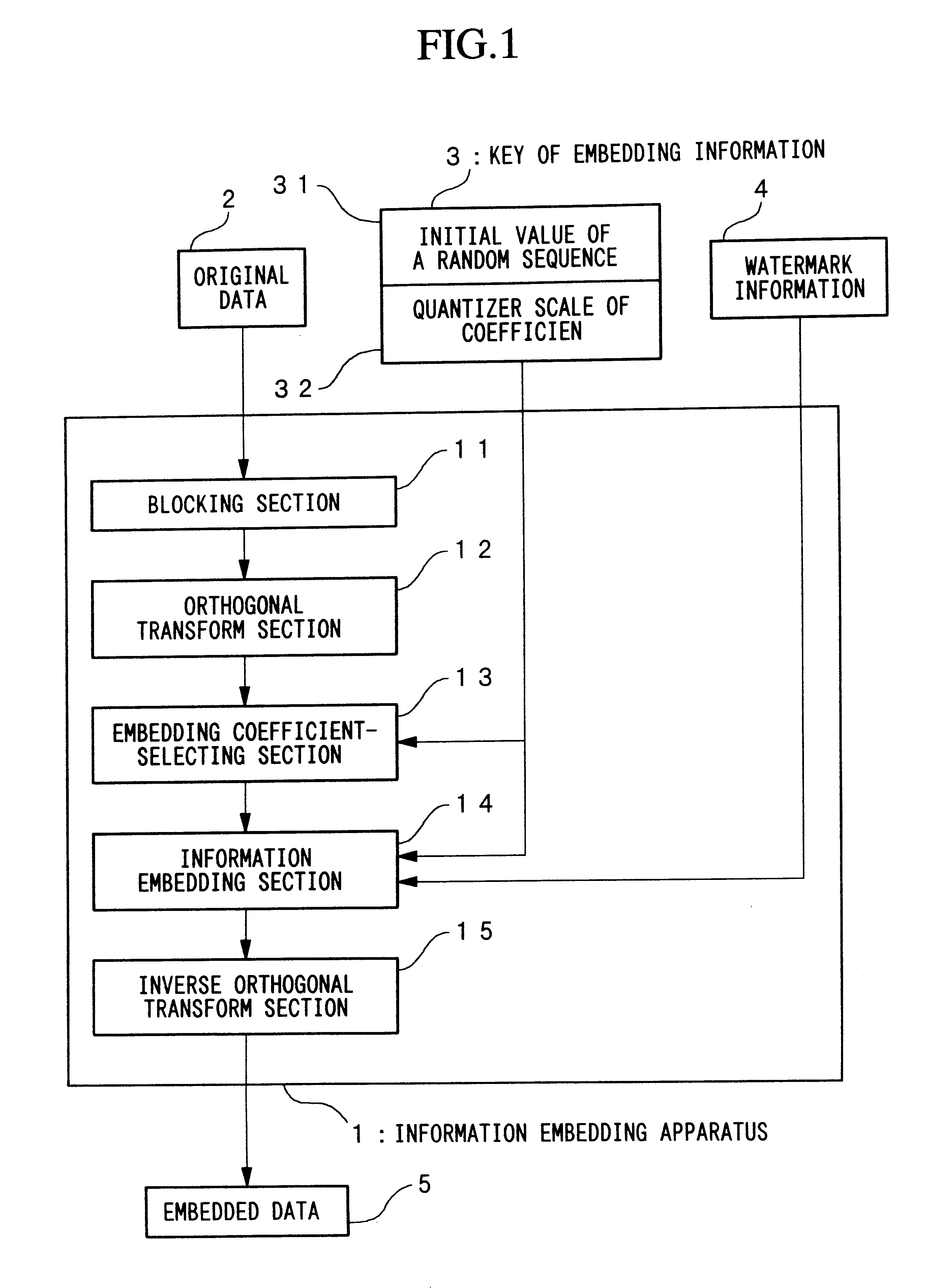
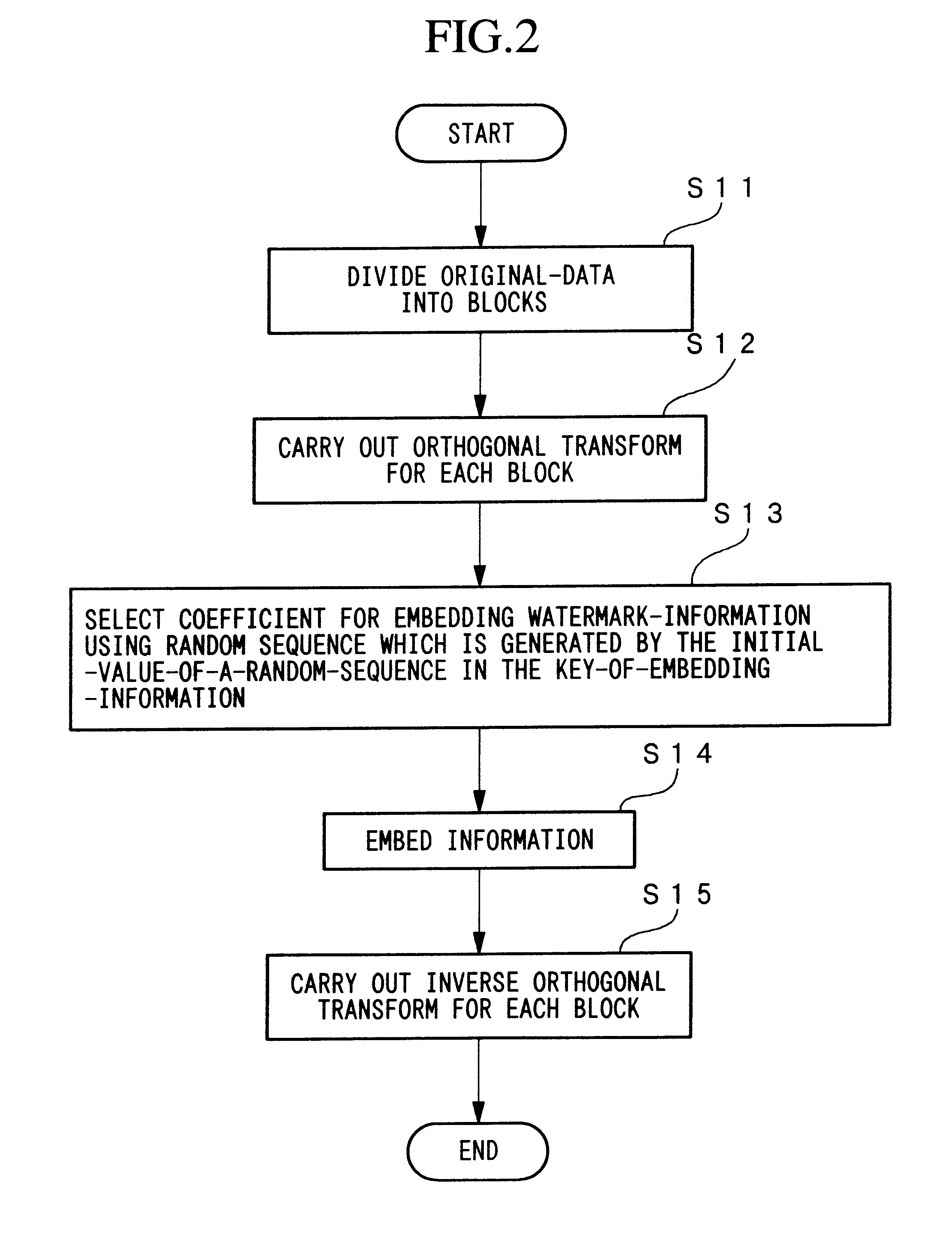
An apparatus for embedding information comprises: a blocking step for dividing data to be processed into blocks; an orthogonal transform step for obtaining coefficients by carrying out orthogonal transformation for each block; an embedding coefficient selecting step for determining coefficients in which the watermark-information will be embedded by using a random sequence which is generated by initial value; an information embedding step for sequentially embedding the watermark-information, which has arbitrary length of bits, by quantizing value of said coefficients using a predetermined value for quantization; and an inverse orthogonal transform step for carrying out inverse orthogonal transformation for modified coefficients to form block in which the watermark-information is embedded, as well as combining the divided blocks and reconstructing the original form.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
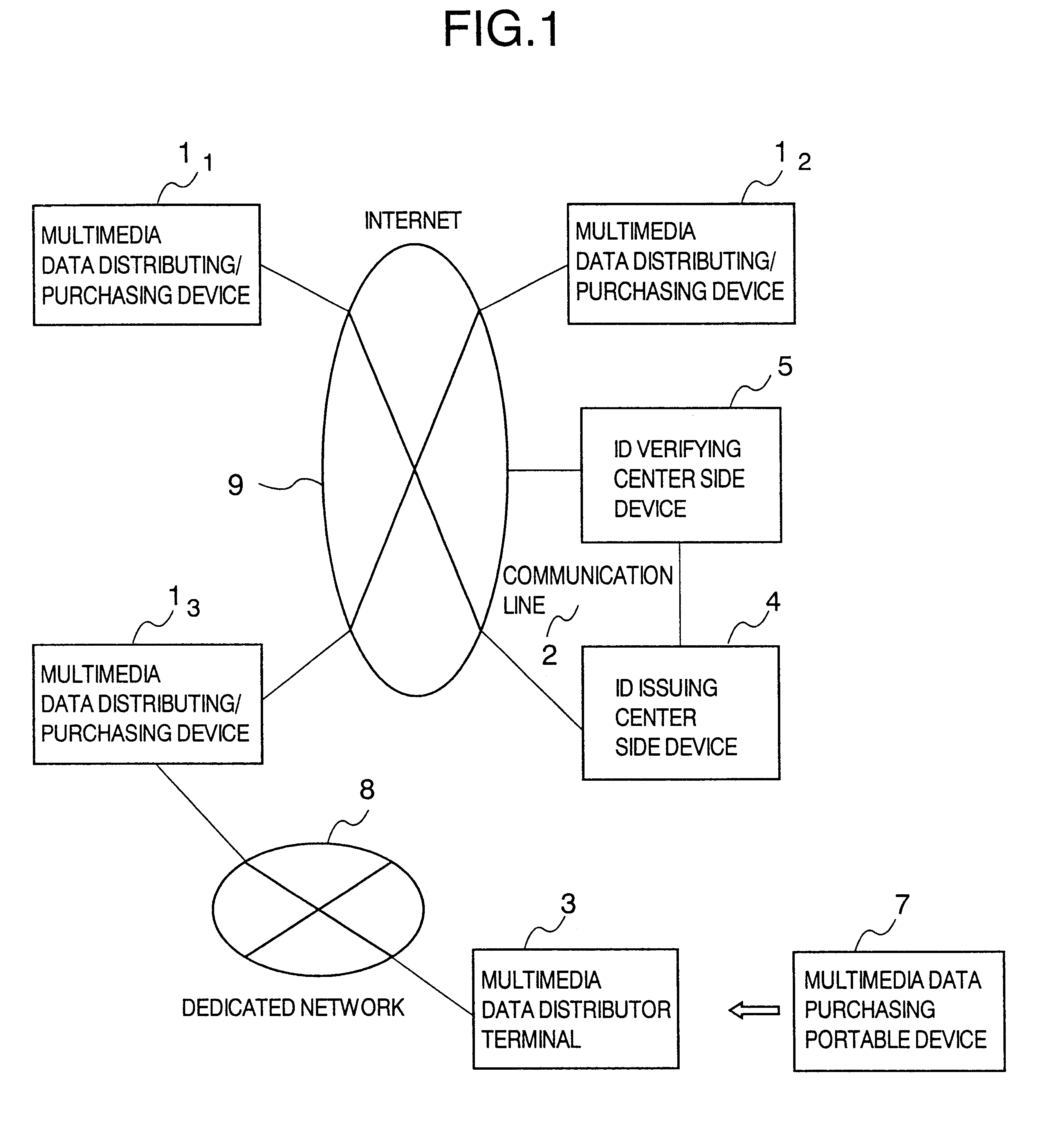
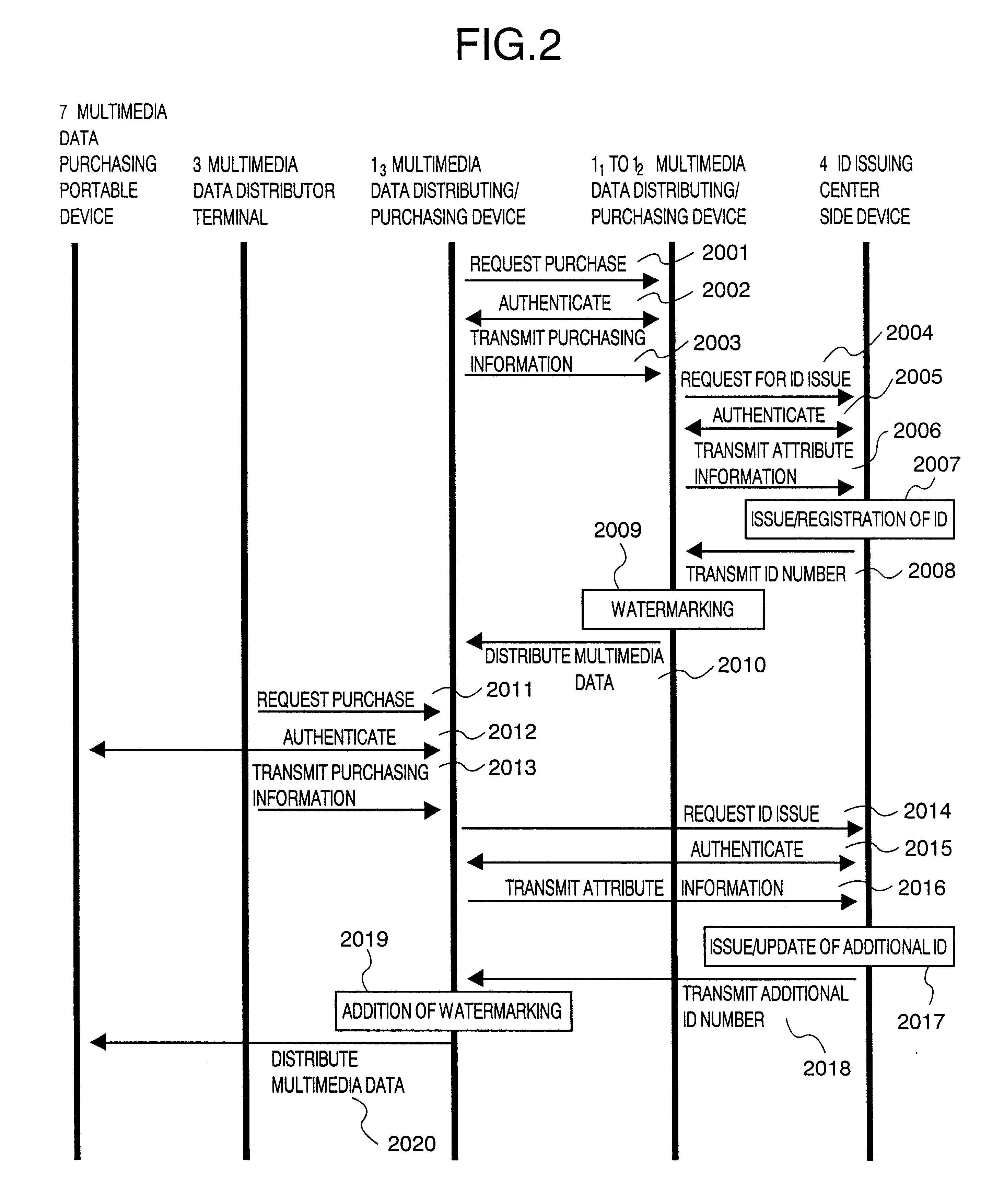
Method and system for distributing multimedia data with management information
InactiveUS6889211B1Data processing applicationsDigital data protectionInformation embeddingManagement information systems
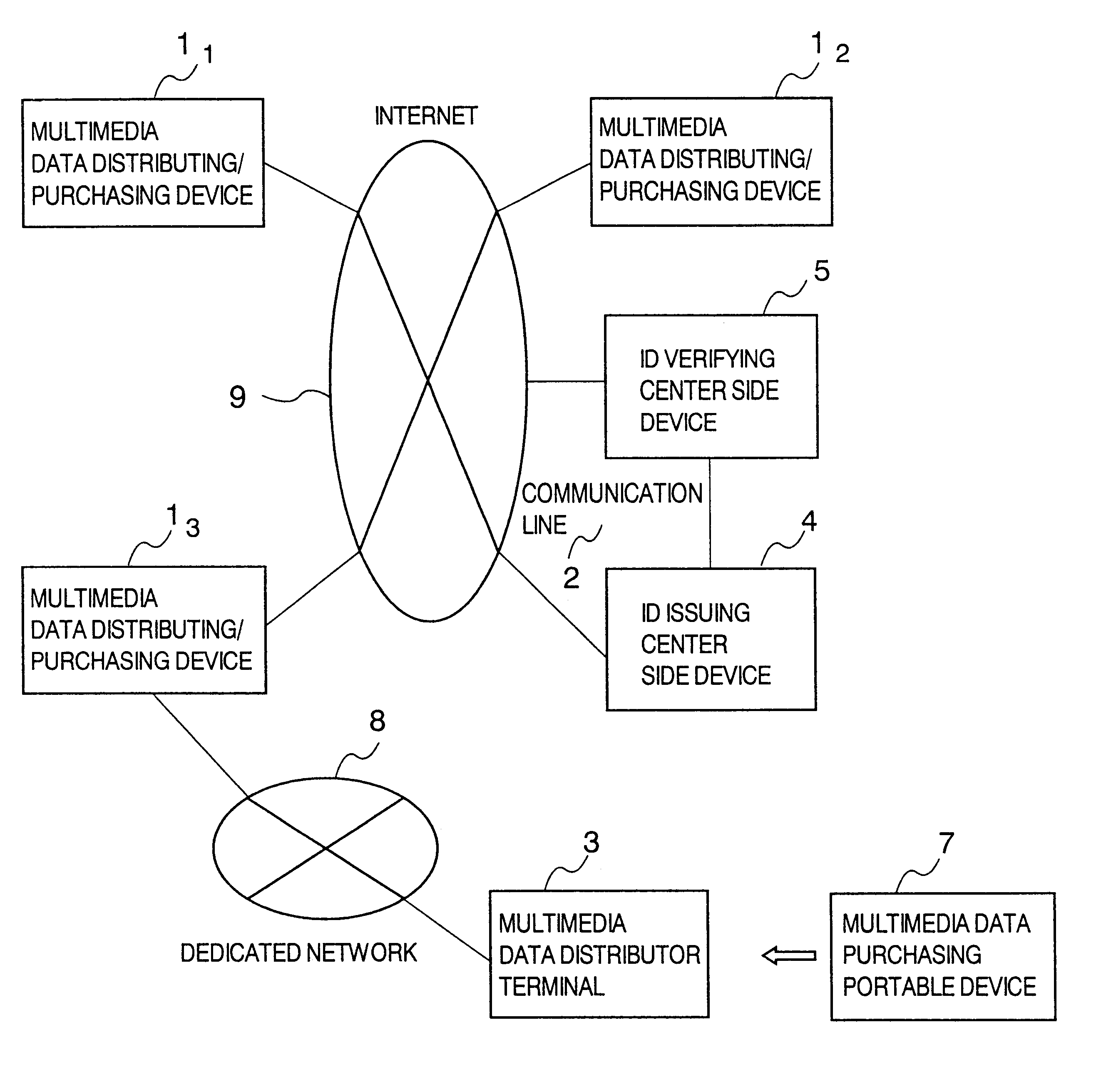
A multimedia data distributing system comprising an ID issuing center side device and a multimedia data distributor side device for distributing multimedia data as electronic data to a purchaser of the multimedia data. The multimedia data distributor device includes: an attribute information transmitting unit that transmits attribute information of the electronic data indicating the multimedia data to be distributed, to the ID issuing center side device; a watermark information embedding unit that embeds information specifying the ID number transmitted from the ID issuing center side device in response to the attribute information transmitted to the attribute information transmitting unit, as an watermark information in the electronic data indicating the multimedia data to be distributed; and a distribution unit that distributes the electronic data indicating the multimedia data, in which the information specifying the ID number is embedded as the watermark information by the watermark information embedding unit, to the purchaser of the multimedia data. The ID issuing center side device includes: an ID number generating unit that generates a unique ID number and registering the generated ID number in a database in a manner to correspond to the attribute information transmitted by the distributor of the multimedia data; and an ID number transmitting unit that transmits the information specifying the generated ID number to the multimedia data distributor device.
Owner:HITACHI LTD
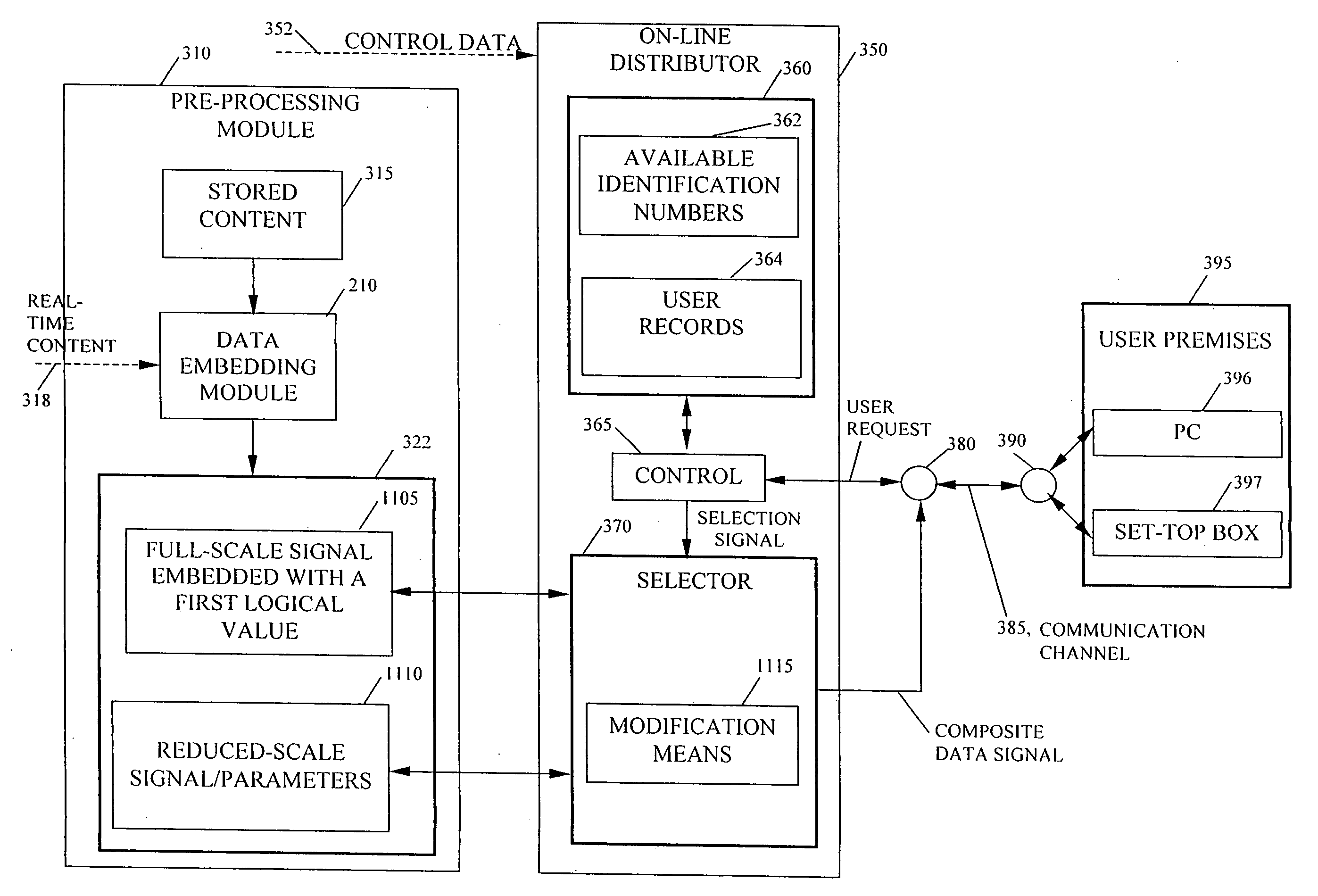
Pre-processed information embedding system
InactiveUS20060005029A1Reduce the possibilityReduce distractionsTelevision system detailsUser identity/authority verificationComputer hardwareComputation complexity
Methods are provided for embedding auxiliary information in a host content signal which reduce the memory, bandwidth and computational complexity of the embedding and transmission systems. In one embodiment, a first reduced-scale signal is produced which corresponds to the host content embedded with a first logical value and producing a second reduced-scale signal corresponding to the host content embedded with a second logical value. A first set of segments from the first reduced-scale signal may be combined with a second set of segments from the second reduced-scale signal in a pre-defined manner to produce a composite embedded host content. Thus the storage and transmission requirements of the watermarking system are reduced to having to deal with only the original content plus two reduced-scale signals.
Owner:VOBILE
System and method for presenting and inputting information on a mobile device
InactiveUS20070250711A1Perceived latencyProviding user controlUser identity/authority verificationInformation formatSession managementWeb service
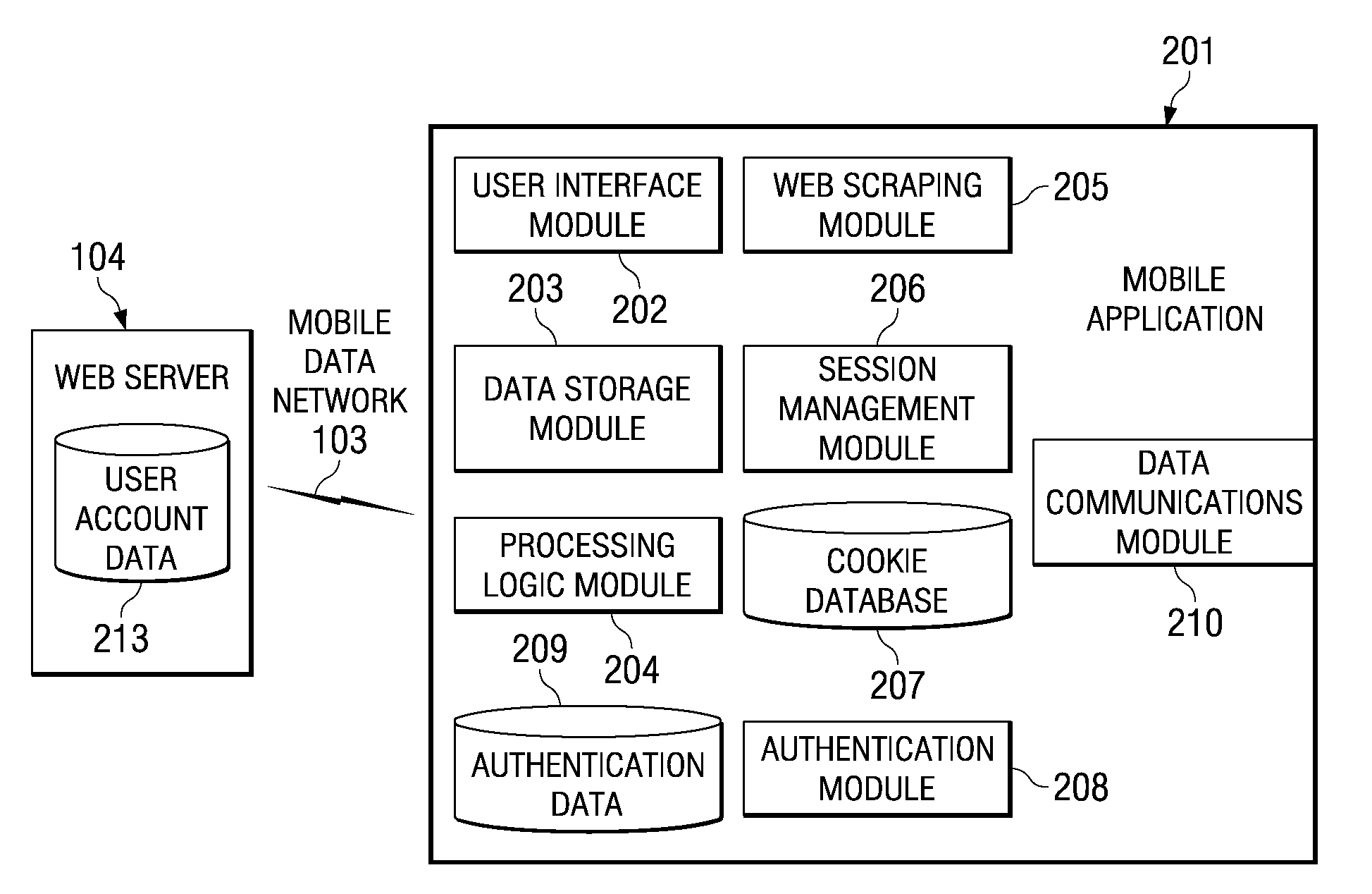
Disclosed are combinations of authentication, session management and web scraping implemented on a mobile device to support a rich mobile application using secure connections to existing websites to access data sources. The mobile application presents information in logical units rather than screen by screen, and fetches data in the background for low perceived delay. The mobile application provides consistent navigation using the 12-key or QWERTY keypad. The mobile application maintains a history of screens, allowing the user to easily return to a prior screen. A web server allows phrases to be configured on-line by an individual user and downloaded to that user's mobile device to simplify data entry on the mobile device. A method of embedding user profile information in a signed application executable file that allows applications to be pre-configured per user. A licensing mechanism that supports multiple distribution channels.
Owner:PHONIFIED
Information-embedding apparatus, encoder, tamper-detecting apparatus, information-embedding method, tamper-detecting method, and recording medium having program recorded therein for executing both of the methods
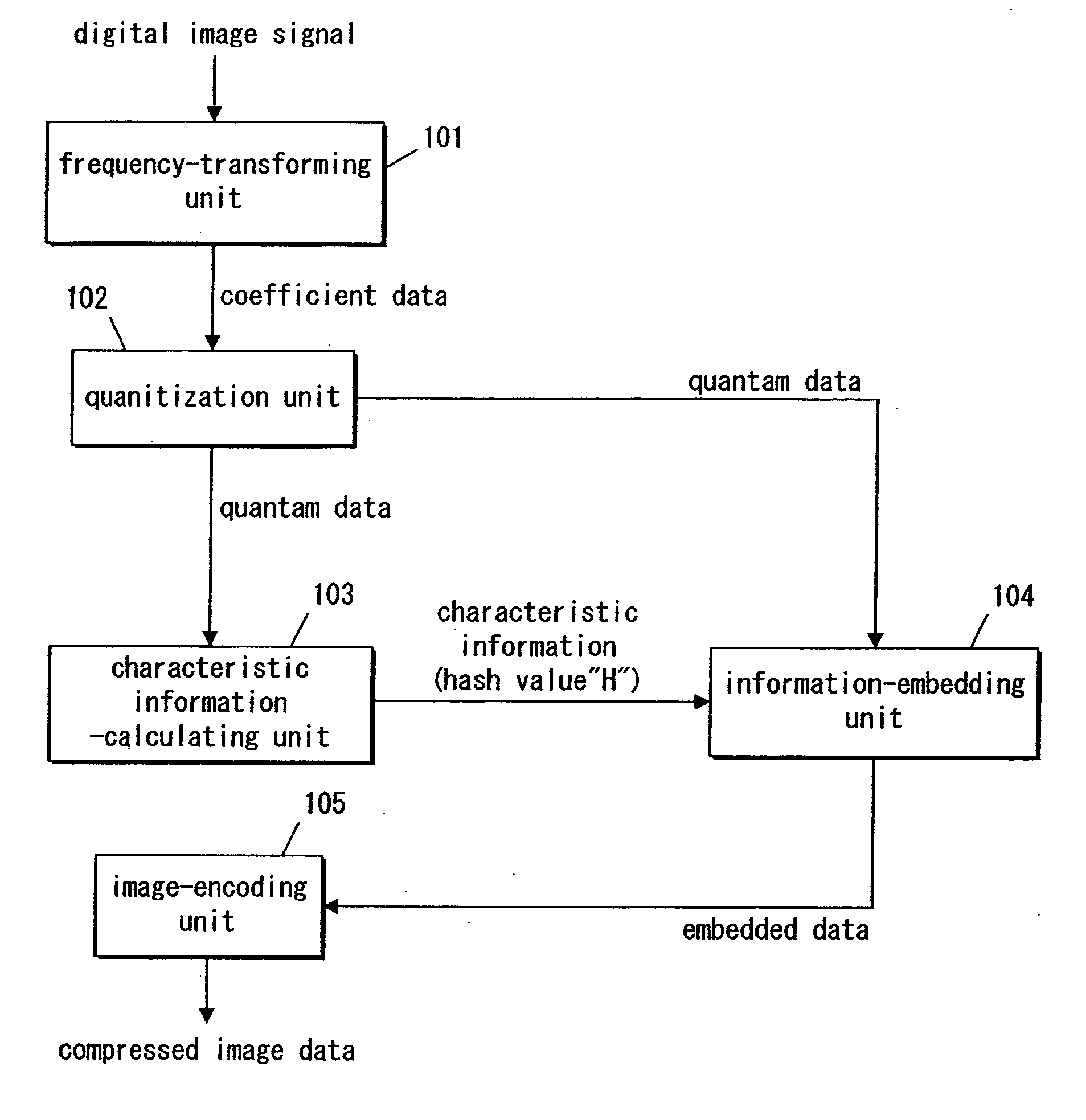
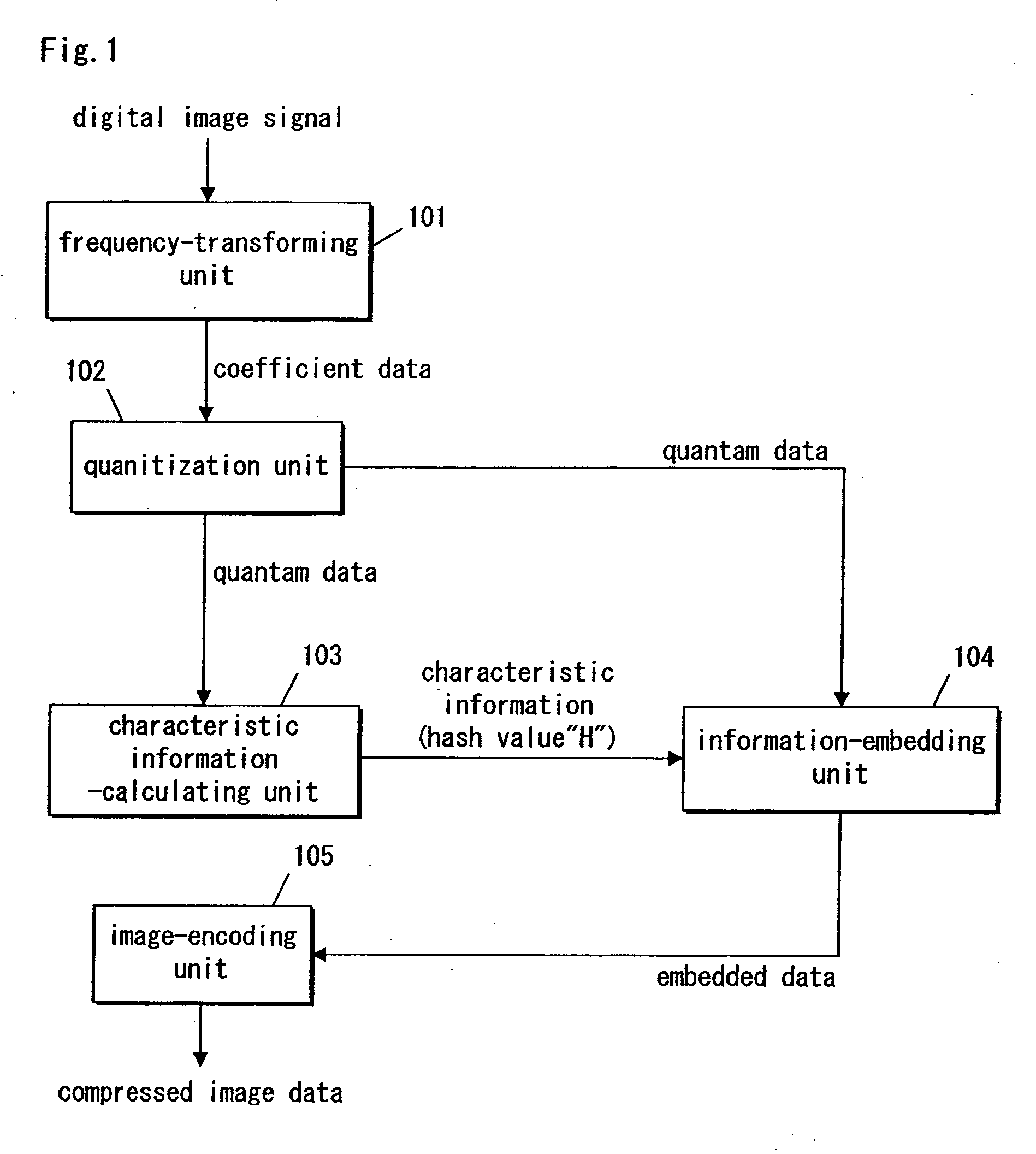
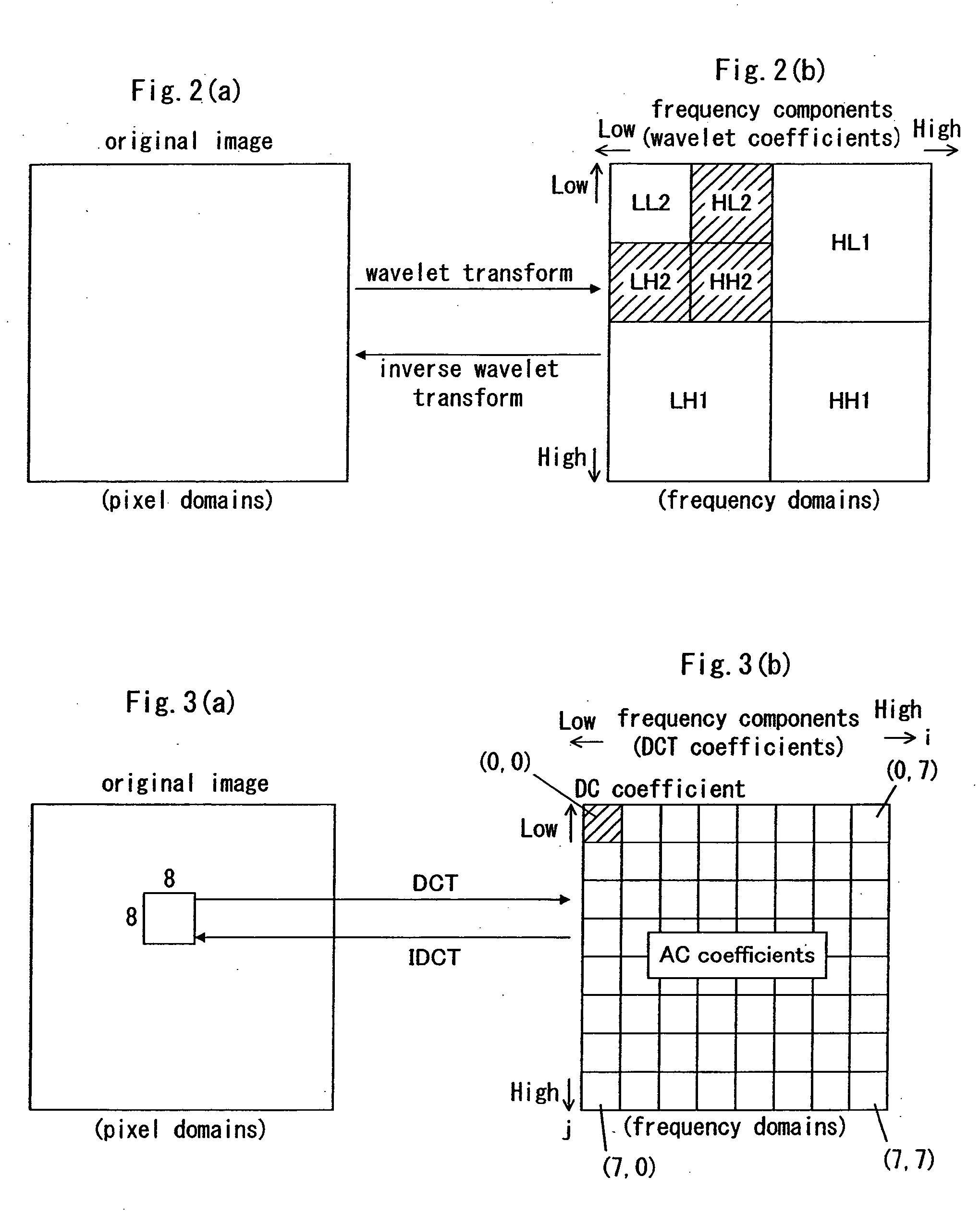
InactiveUS20060013488A1Possible to detectEliminate needCharacter and pattern recognitionImage watermarkingInformation embeddingDigital image
A digital image signal is transformed in frequency, thereby providing partitioned frequency components. Characteristic information is calculated in accordance with a coefficient at a first frequency domain that is selected from among the partitioned frequency components. A coefficient at a second frequency domain is handled in accordance with predetermined rules, thereby embedding the characteristic information into the coefficient at the second frequency domain. The second frequency domain is selected from among areas that differ from the first frequency domain. The frequency coefficients that exhibit several frequency components are encoded in a predetermined manner, thereby producing compressed image data.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
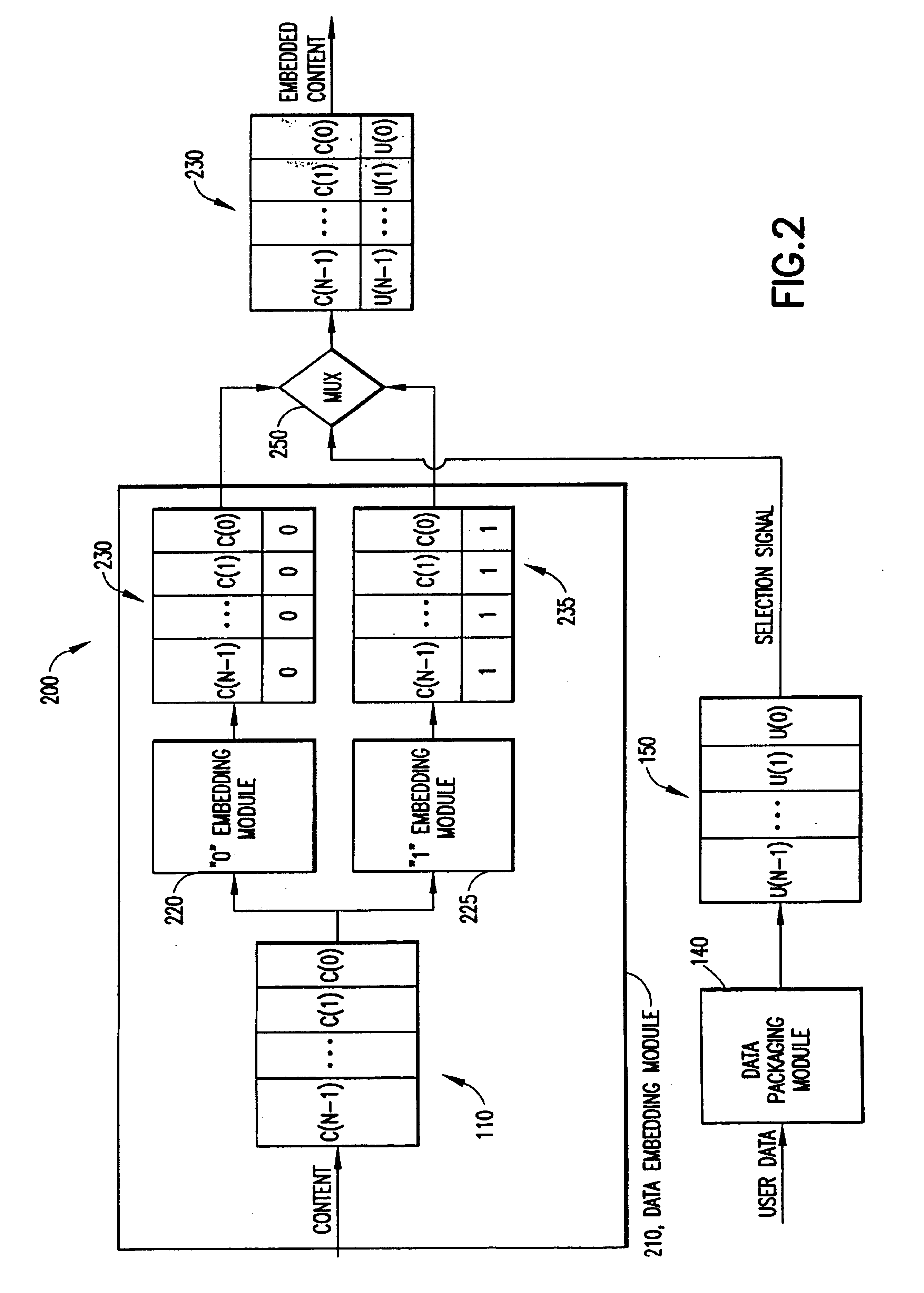
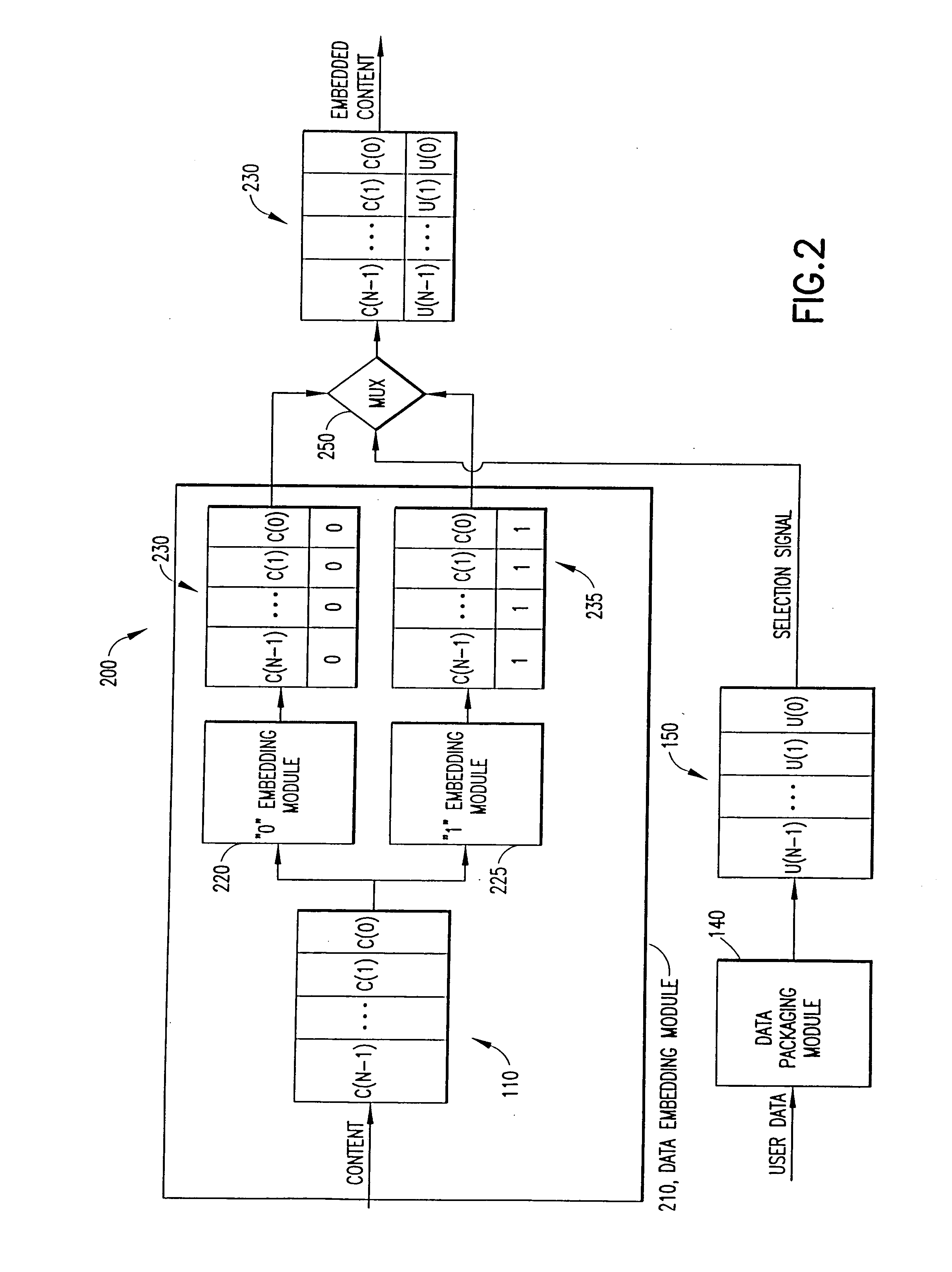
Pre-processed information embedding system
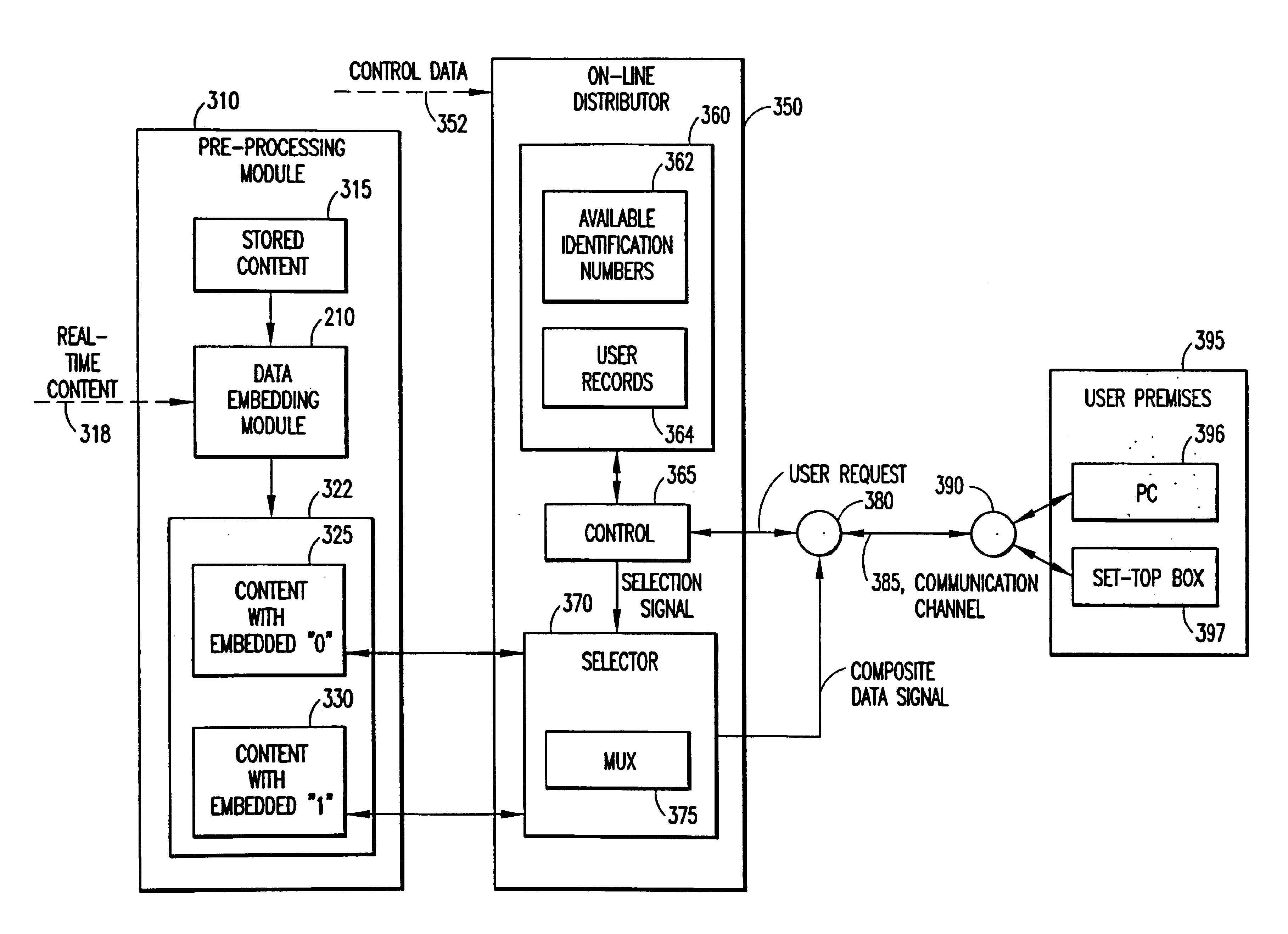
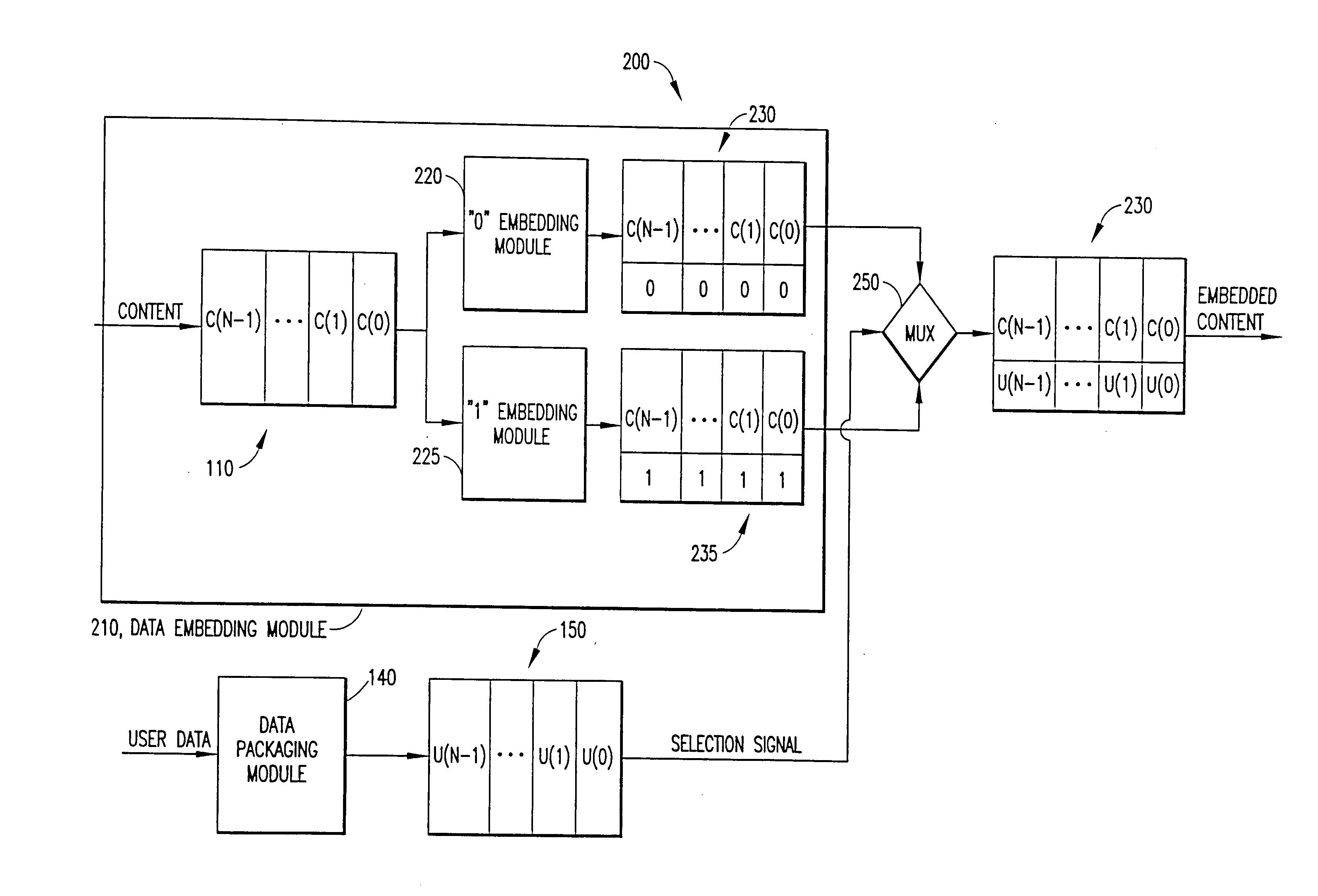
InactiveUS6912315B1Reduce the possibilityLower requirementColor signal processing circuitsDigital data processing detailsInformation embeddingThe Internet
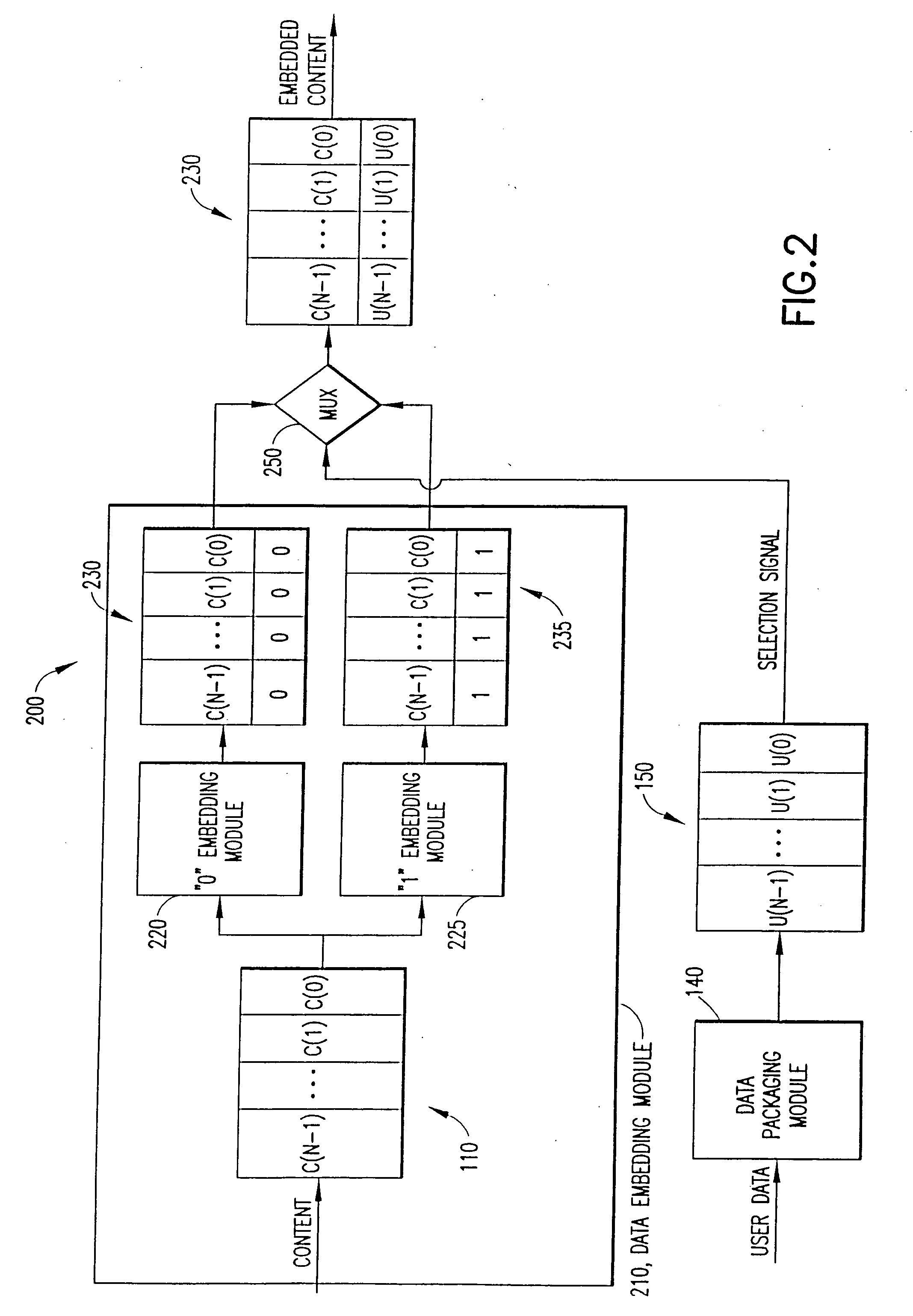
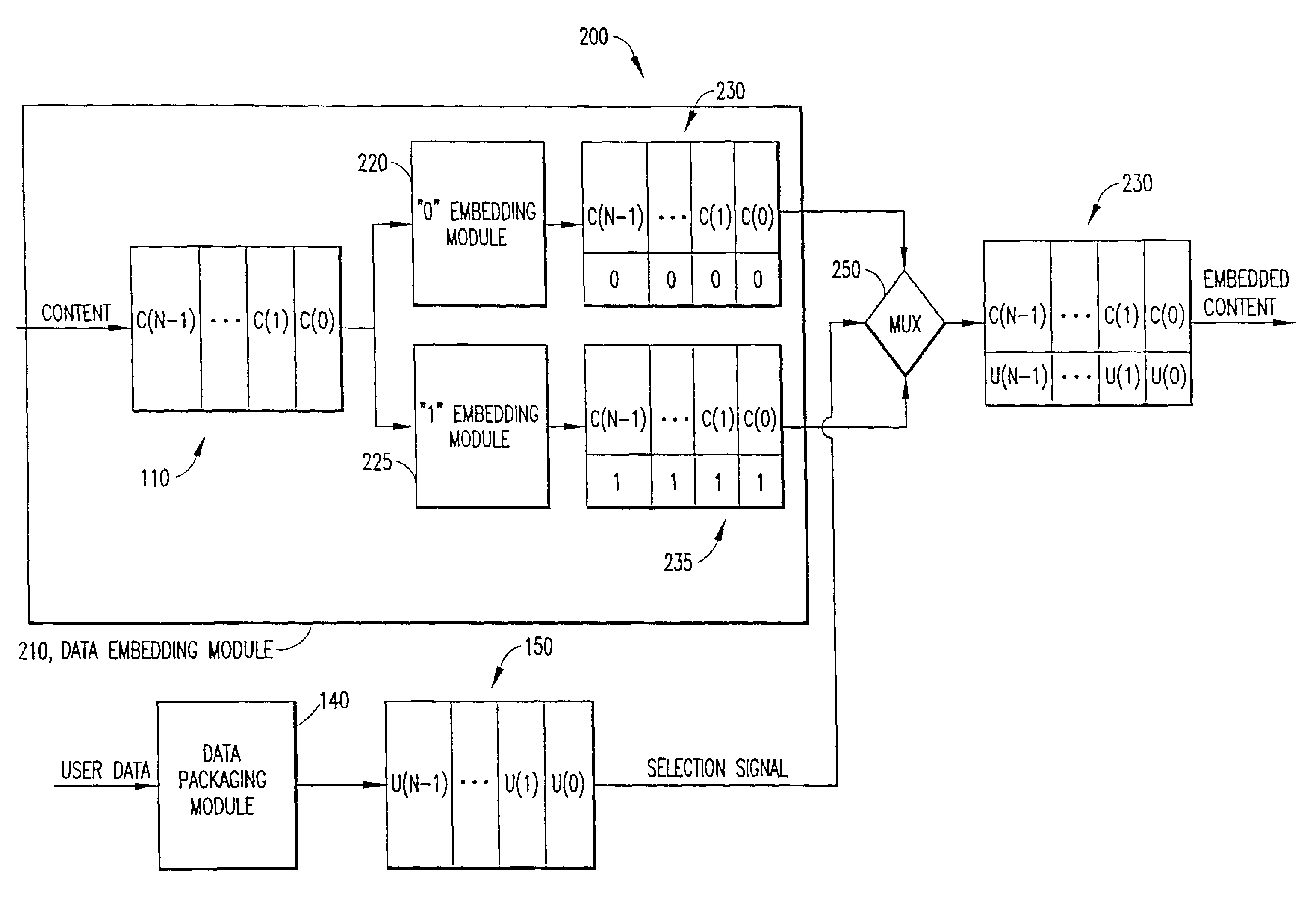
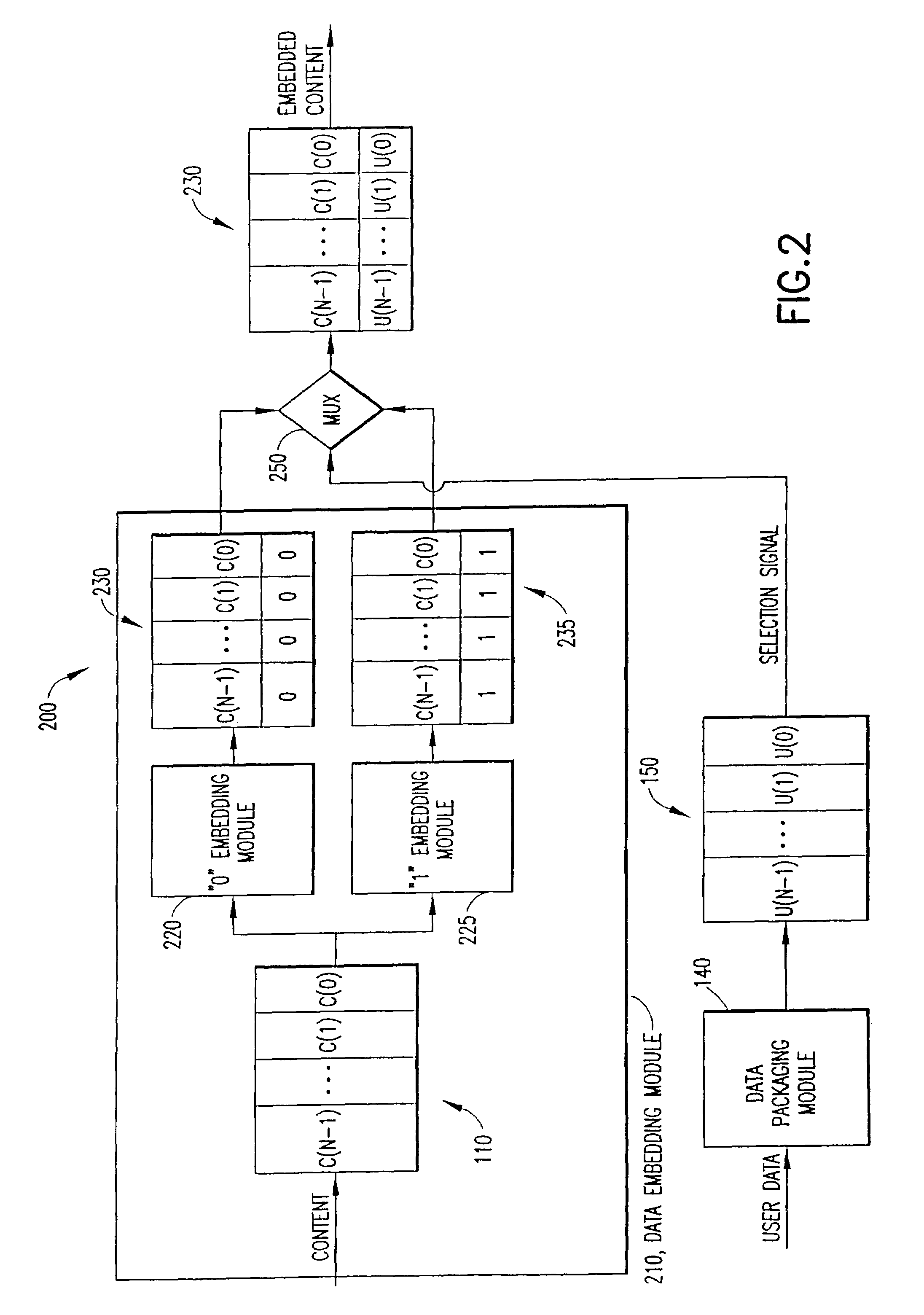
Auxiliary information (150) representing binary or multi-level (M≧2) logical values is embedded into successive segments (110) of an audio, video or other data signal in response to a user request to download the data signal via an on-line distributor (350) on a computer network such as the Internet. To avoid unnecessary delays in providing the data signal to the user, the data signal is pre-processed to provide two sets or copies of data (230, 235). One set (230) of the data contains segments with an embedded binary “0”, while the other set (235) contains corresponding segments with an embedded binary “1”. Successive segments are selected from one of the two sets to provide a time-multiplexed composite data signal (230) that has the desired content, but with an embedded binary data sequence that identifies the user.
Owner:VOBILE
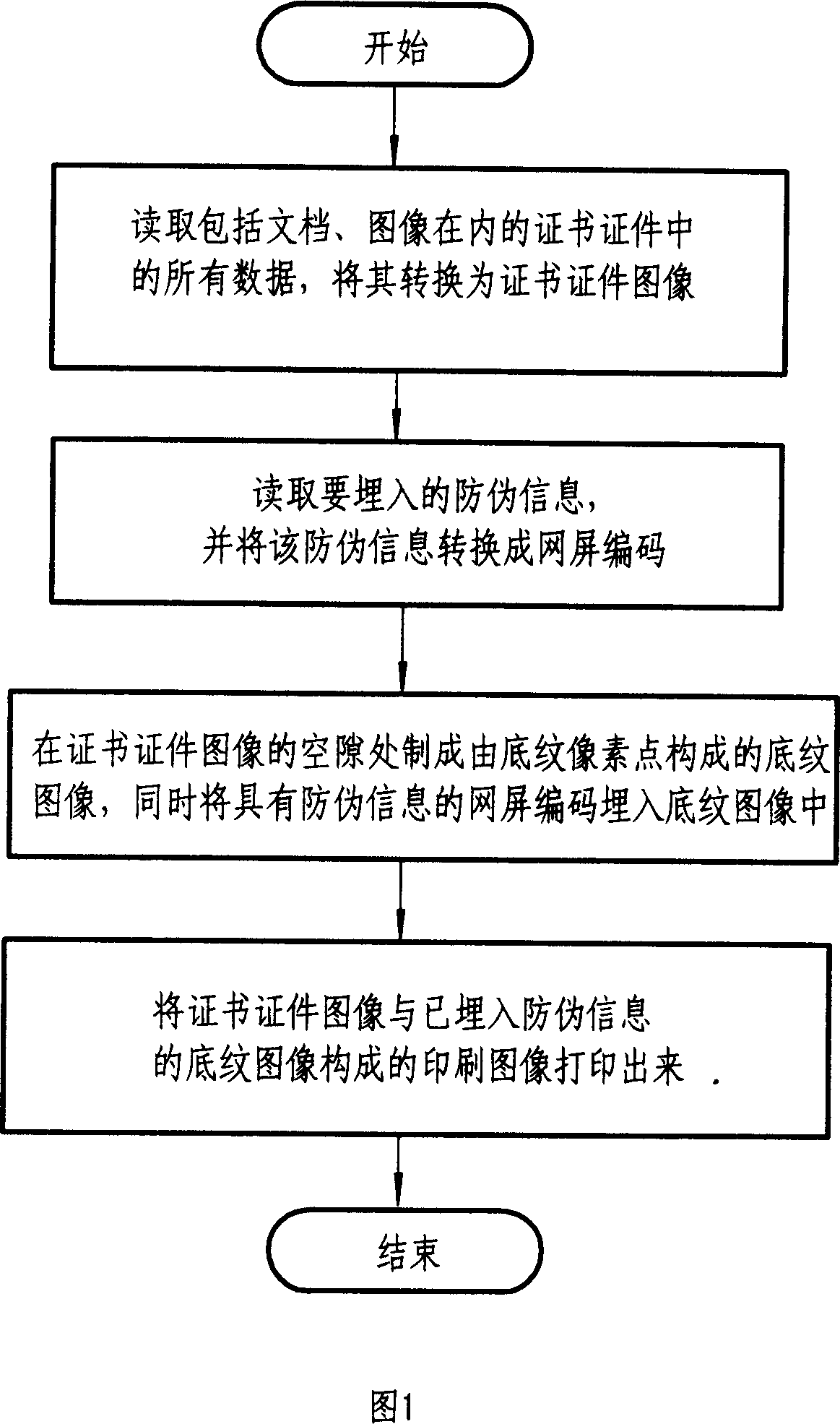
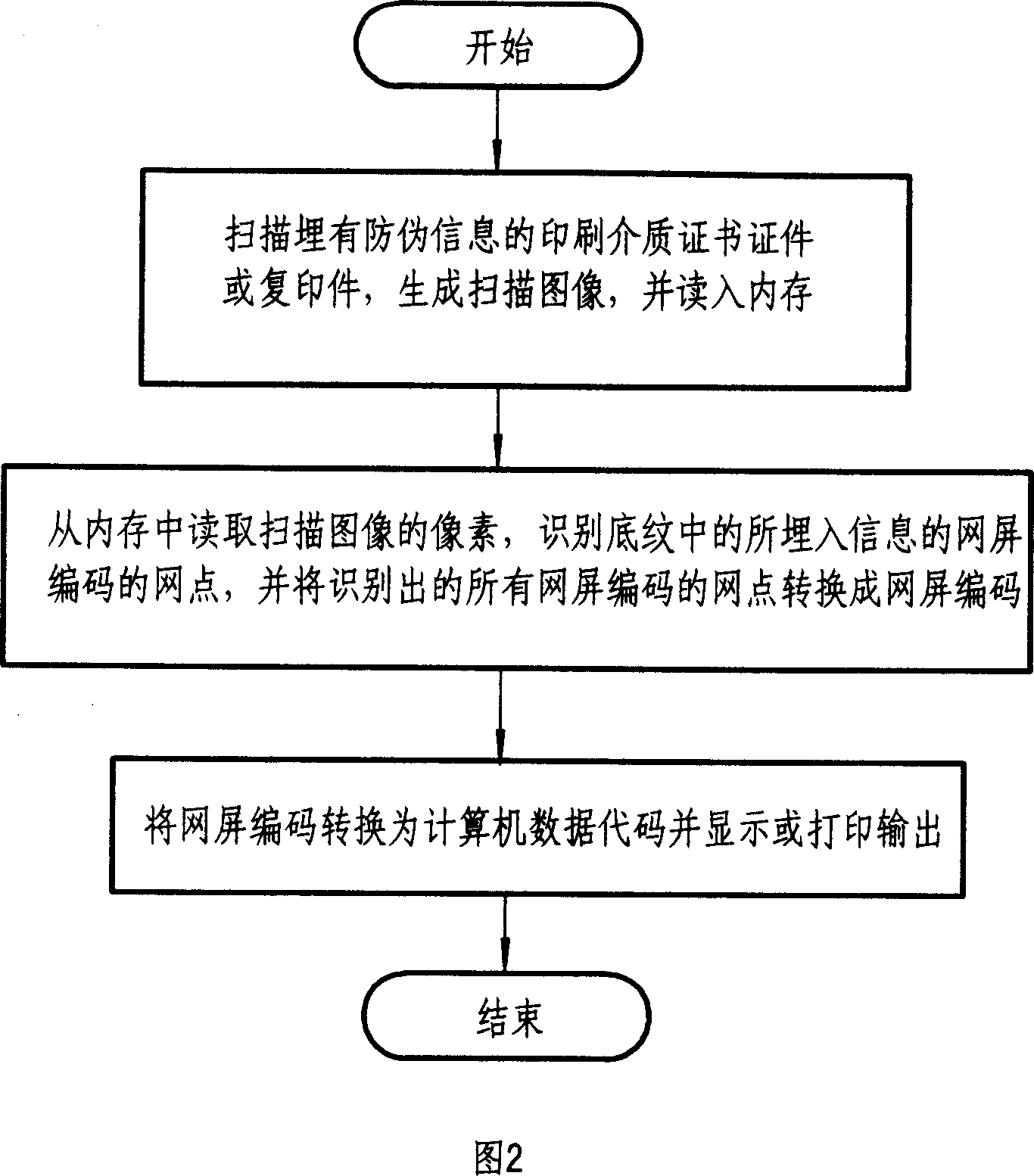
Printing medium certificate documents and false proof handling method of copy thereof
ActiveCN1928916ARealize anti-counterfeiting and anti-tampering processing methodVisual presentation using printersImage data processing detailsPrint mediaInformation embedding
The related false proof information embedding method for print-media certificate comprises: printing the false proof shading image in certificate content gap, and embedding the false proof information of screen code on the shading without changing shading pixel feature. The corresponding recognition method comprises: scanning the print media to recognize the false proof information, and comparing both the false proof information and certificate or copy together. This invention can also recognize the copy, needs low cost, and benefit to spread.
Owner:顾泽苍
License management system, license management device, relay device and terminal device
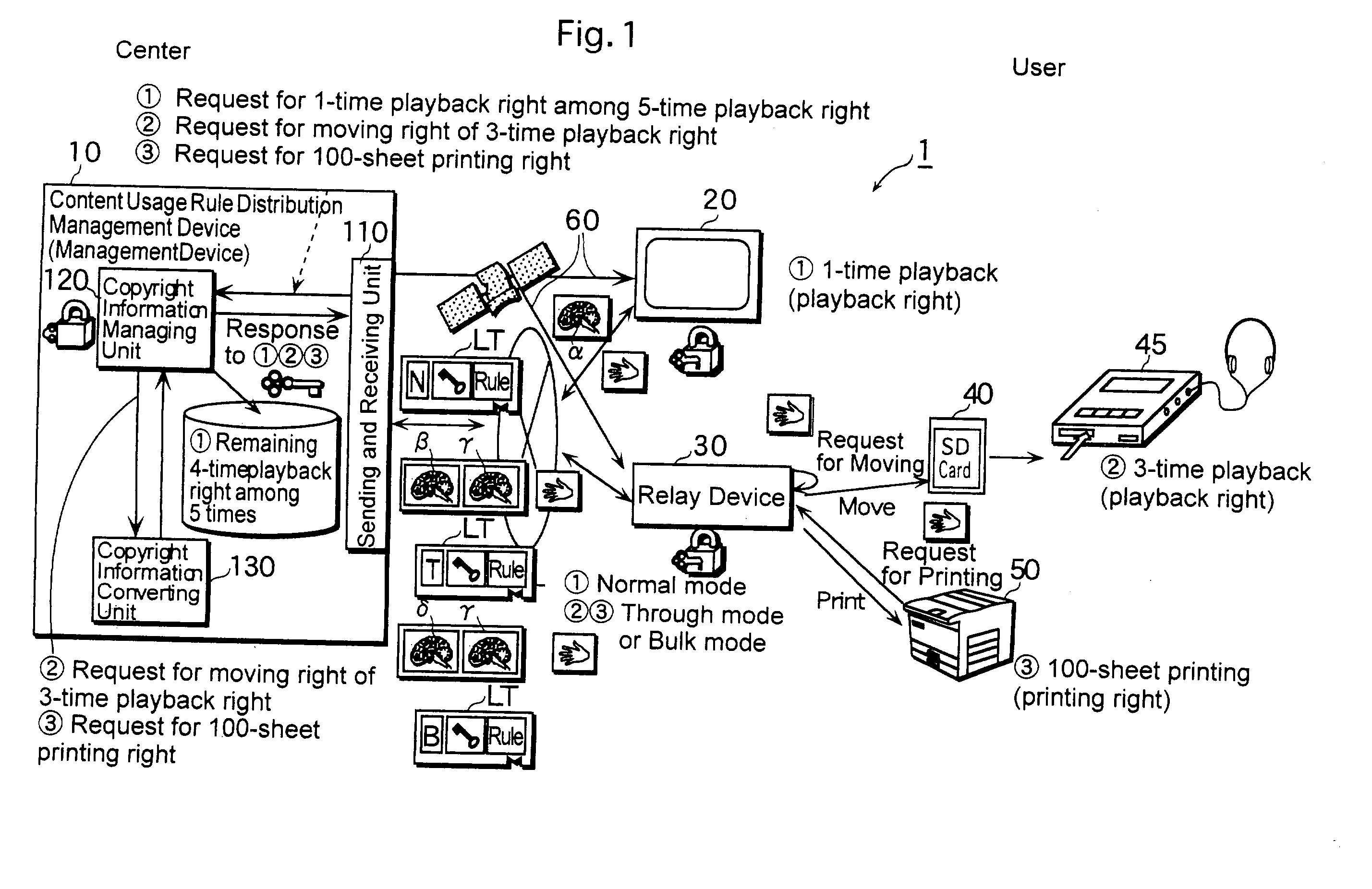
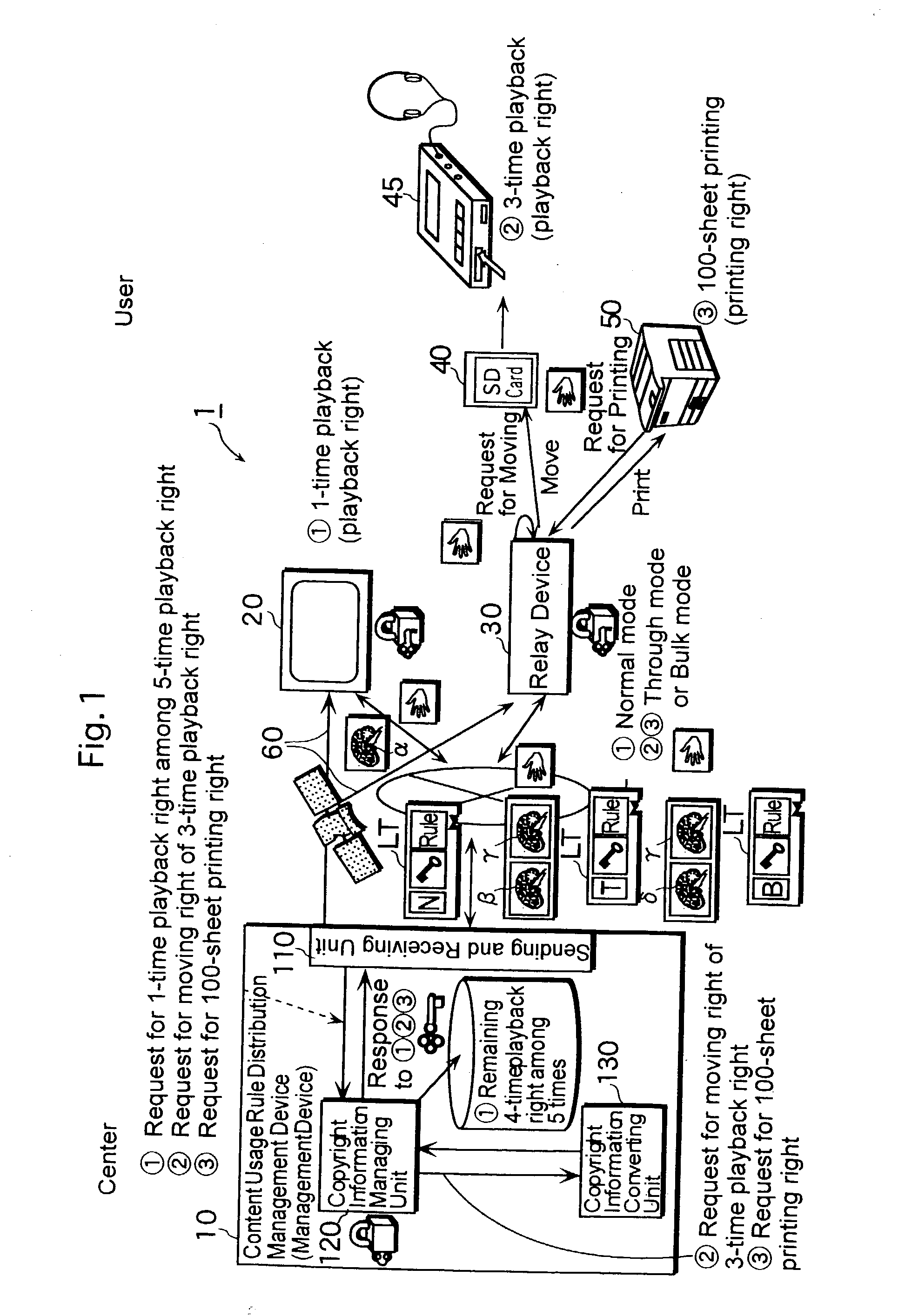
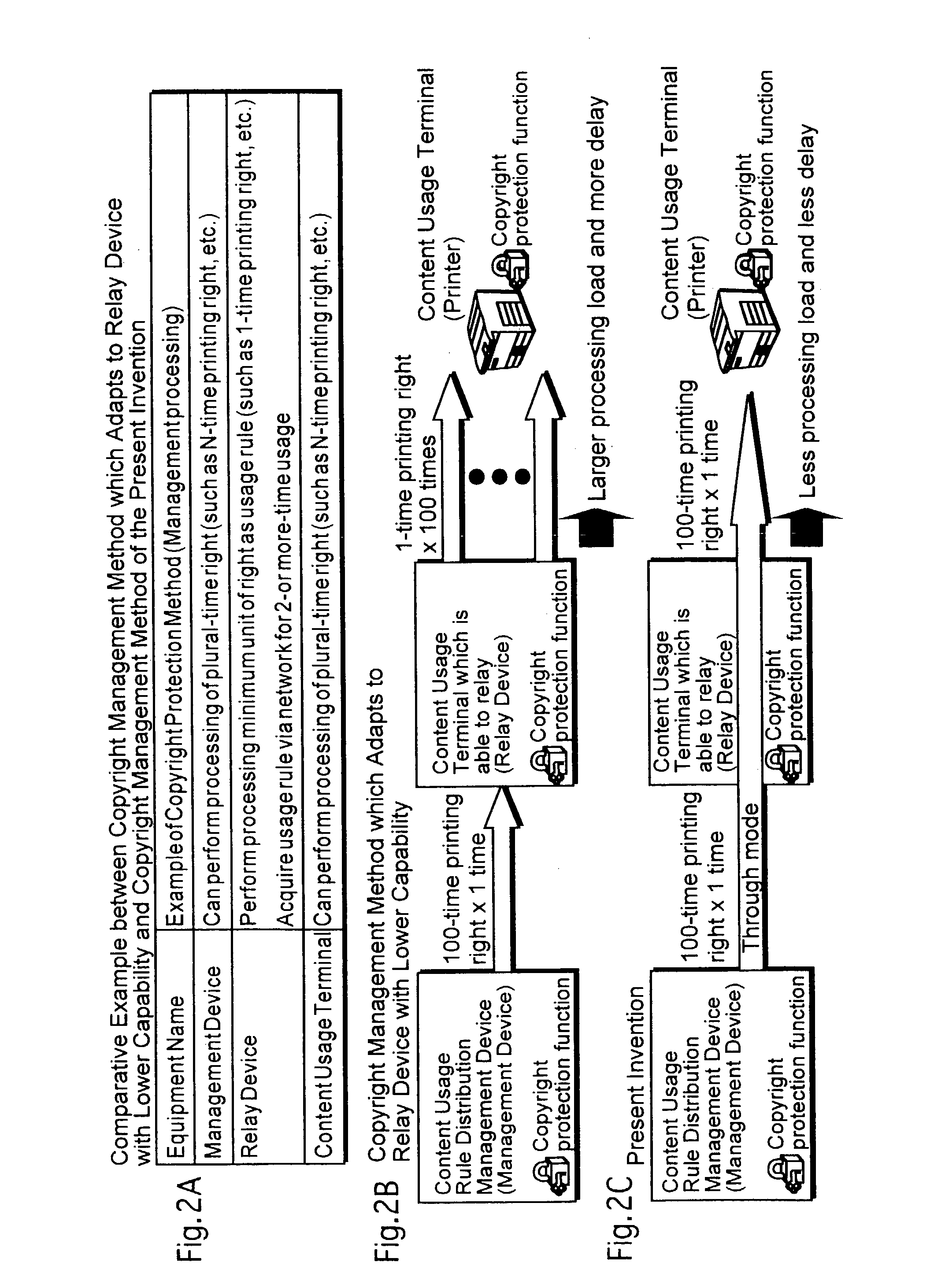
ActiveUS20030140009A1Possible to useCopyright protection function which is inherent in the terminal device is exerted effectivelyTelevision system detailsVolume/mass flow measurementTerminal equipmentManagement system
A management device 10 of a license management system 1 acquires a usage request of a content from an SD card 40 or a printer 50 via a relay device 30, analyzes the acquired usage request, acquires usage environment information of the SD card 40 or the printer 50 from the relay device 30, analyzes the acquired usage environment information, generates license information including a usage rule corresponding to the analysis results of the usage request and the usage environment information, generates instruction information indicating how to handle the license information in the relay device based on the analysis result of the usage environment information, embeds the generated instruction information in the license information, and sends the license information to the relay device 30. The relay device 30 receives the license information in which the instruction information is embedded, and transfers the received license information to the SD card 40 or the printer 50 according to the instruction information which is embedded in the license information with performing certain processing or without performing any processing to the license information.
Owner:LILLY PATHWAY LLC
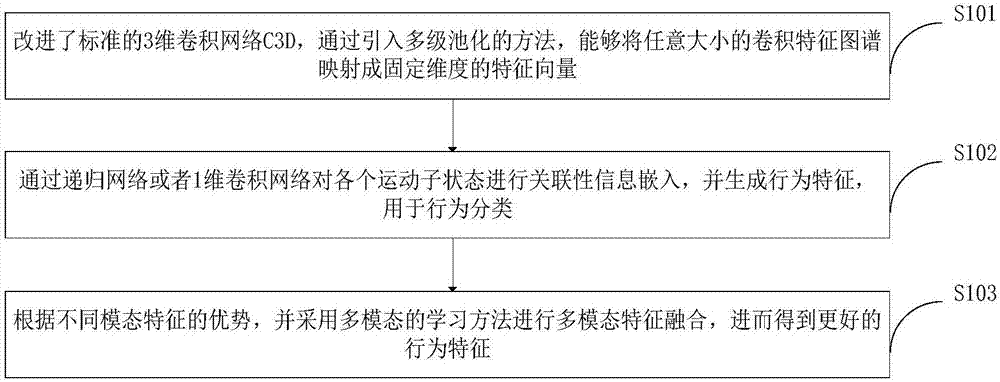
Human behavior identification method based on 3D deep convolutional network
ActiveCN107506712AImprove robustnessScale upCharacter and pattern recognitionNeural architecturesHuman behaviorFeature extraction
The invention belongs to the field of computer vision video motion identification, and discloses a human behavior identification method based on a 3D deep convolutional network. The human behavior identification method comprises the steps of: firstly, dividing a video into a series of consecutive video segments; then, inputting the consecutive video segments into a 3D neural network formed by a convolutional computation layer and a space-time pyramid pooling layer to obtain features of the consecutive video segments; and then calculating global video features by means of a long and short memory model, and regarding the global video features as a behavior pattern. The human behavior identification method has obvious advantages, can perform feature extraction on video segments of arbitrary resolution and time length by improving a standard 3D convolutional network C3D and introducing multistage pooling, improves the great robustness of the model to behavior change, is conductive to increasing video training data scale while maintaining video quality, and improves the integrity of behavior information through carrying out correlation information embedding according to motion sub-states.
Owner:CHENGDU KOALA URAN TECH CO LTD
Pre-processed information embedding system
InactiveUS20050196051A1Reduce the possibilityDigital data processing detailsCharacter and pattern recognitionInformation embeddingThe Internet
Auxiliary information (150) representing binary or multi-level (M≧2) logical values is embedded into successive segments (110) of an audio, video or other data signal in response to a user request to download the data signal via an on-line distributor (350) on a computer network such as the Internet. To avoid unnecessary delays in providing the data signal to the user, the data signal is pre-processed to provide two sets or copies of data (230, 235). One set (230) of the data contains segments with an embedded binary “0”, while the other set (235) contains corresponding segments with an embedded binary “1”. Successive segments are selected from one of the two sets to provide a time-multiplexed composite data signal (230) that has the desired content, but with an embedded binary data sequence that identifies the user.
Owner:VERANCE
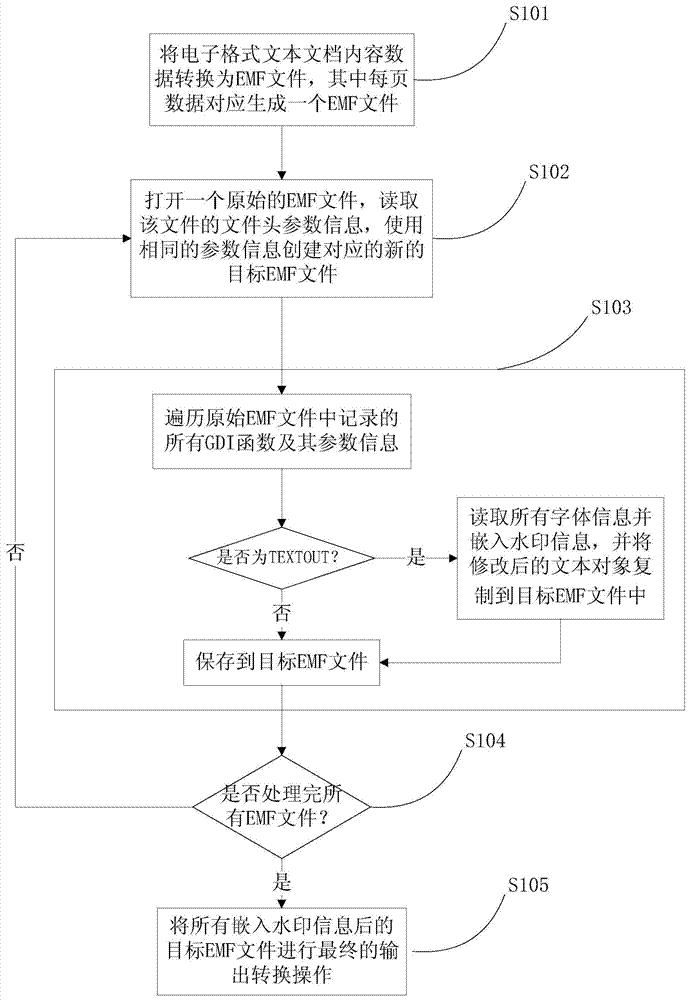
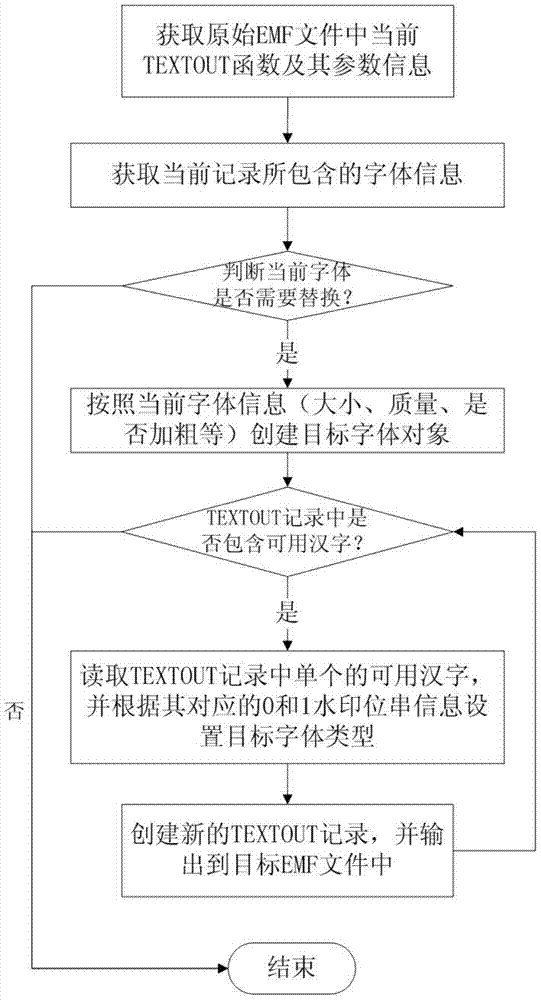
Inlaying method and device of digital watermarks in text documents
ActiveCN103500296ARealize security prevention and controlRealize traceabilityImage data processing detailsProgram/content distribution protectionElectronic formInformation embedding
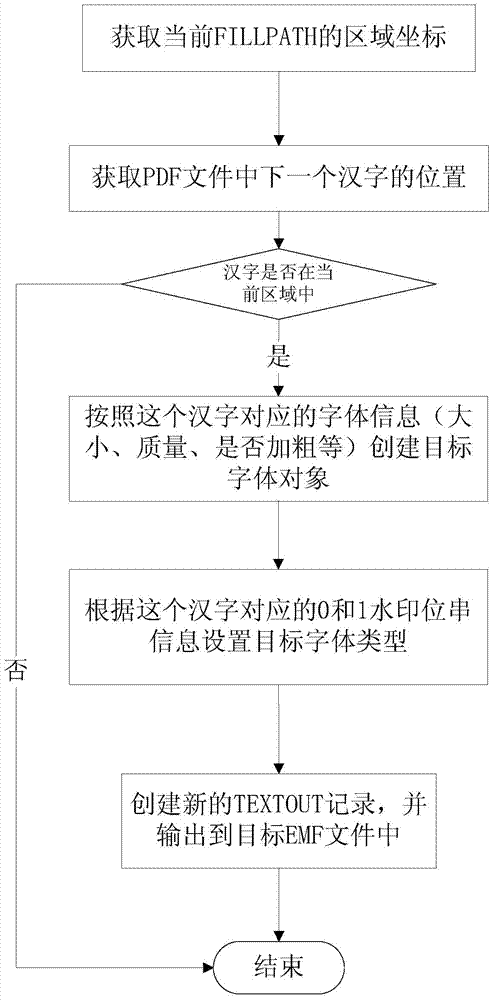
The invention relates to an inlaying method and device of digital watermarks in text documents. The method comprises the steps that electronic form text documents are converted to EMF documents, the converted initial EMF documents are opened, document header parameter information is used for setting up corresponding target EMF documents, all GDI functions and parameter information of the GDI functions in the initial EMF documents are all searched, whether the DGI functions are TEXTOUT is judged, if yes, all font information is read and watermark information is inlaid, and then the GDI functions are copied to the target EMF documents, if not, the DGI functions are directly copied to the target EMF documents, and after all the initial EMF documents are processed, all target EMF documents inlaid with the watermark information are subjected to the final output conversion operation. According to the method and device, the problem of watermark information inlaying of various electronic form text documents and paper text documents is solved, and safety monitoring and controlling, source tracing and content protection of important text documents are achieved.
Owner:李晓妮
Watermark information embedding device and watermark information detection device
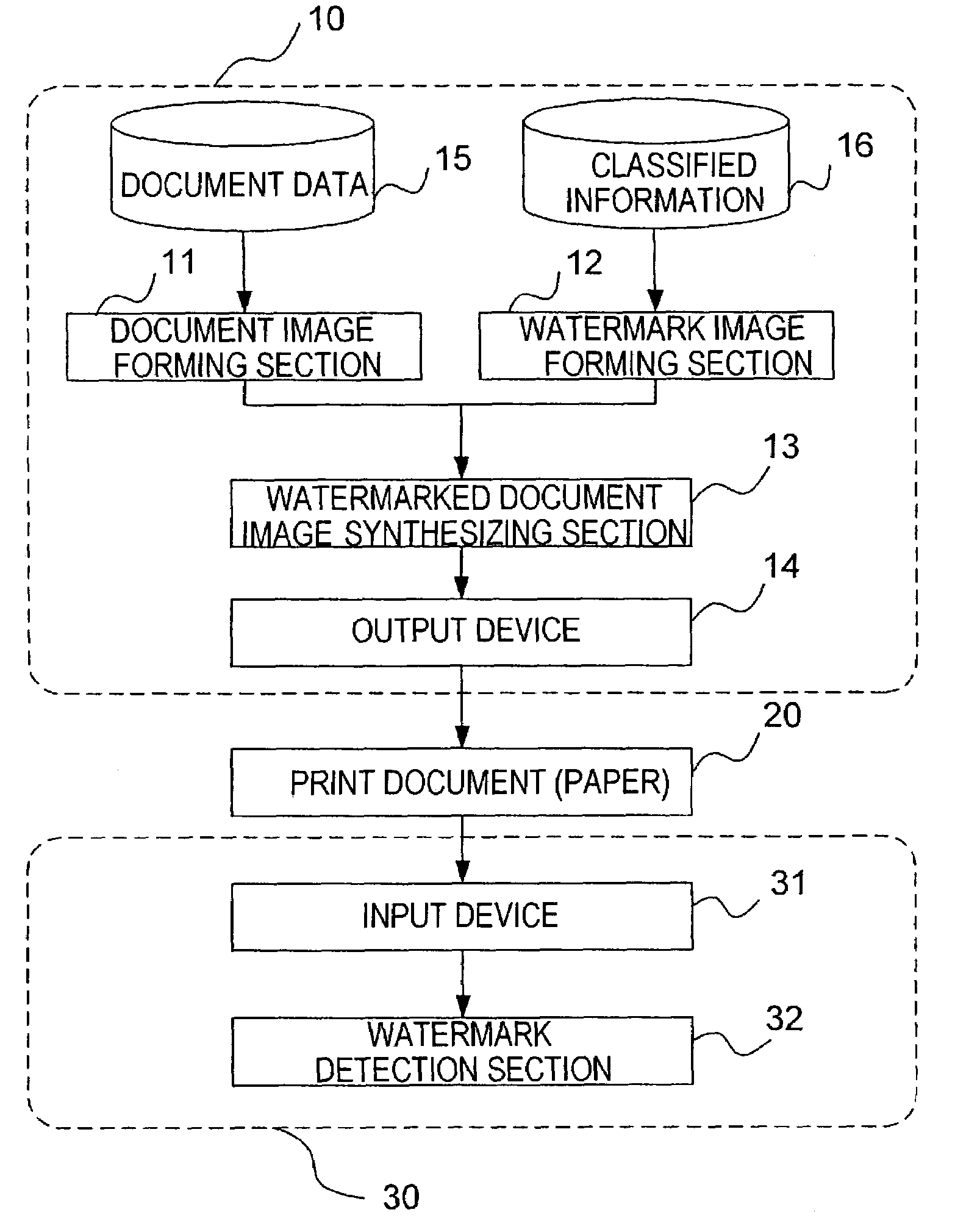
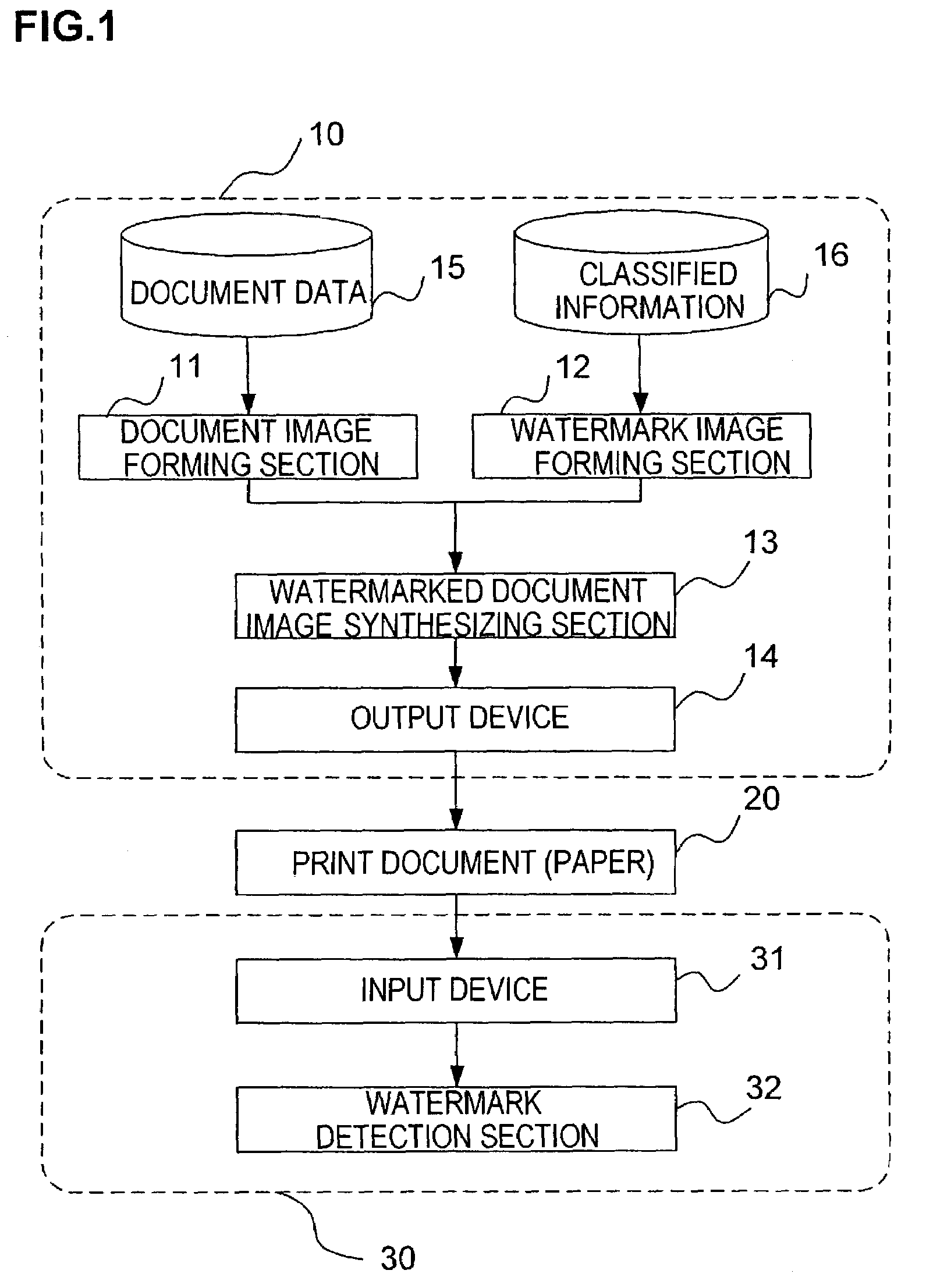
ActiveUS7085399B2Accurate extractionImprove detection efficiencyCharacter and pattern recognitionVisual presentationClassified informationInformation embedding
There are provided a watermark information embedding device and a watermark information detection device which can correctly extract classified information. In the watermark information embedding device, a plurality of dot patterns the wave directions and / or wavelengths of which are changed depending on dot arrangements are prepared, one symbol is given to one of the dot patterns, and the dot patterns are combined and arranged, so that the classified information is given. The watermark information detection device includes two-dimensional wavelet filters the number of which is equal to the number of dot patterns and which have the same wave directions and the same wavelengths as those of the dot patterns. Convolutions between an arbitrary region in a watermarked image and the plurality of two-dimensional wavelet filters are calculated, and it is determined that the dot pattern corresponding to the two-dimensional wavelet filter having the maximum convolution is embedded in the region.
Owner:OKI ELECTRIC IND CO LTD
Electronic watermark embedding apparatus and electronic watermark detection apparatus
InactiveUS20080080009A1Accurate detectionTelevision system detailsVisual presentationInformation embeddingComputer vision
An embedding area in which a background pattern can be embedded from the color document image is extracted. At least one of a color and a shape of a background pattern appropriate for the embedding area is determined depending on an area color of the embedding area. A background pattern image is generated by embedding watermark information in the embedding area using the determined background pattern.
Owner:FUJITSU LTD
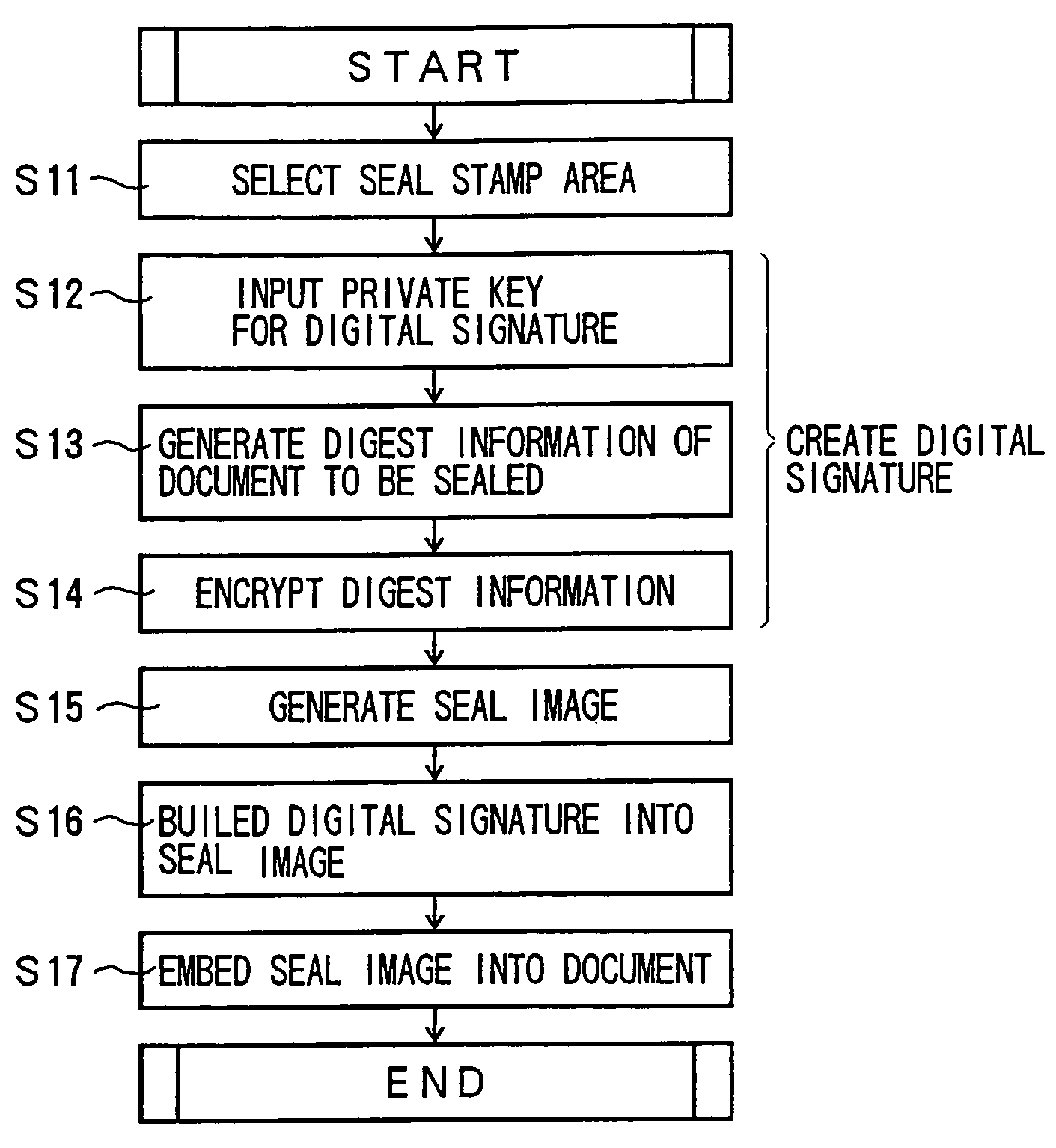
Apparatus and method for authenticating digital signatures and computer-readable recording medium thereof
InactiveUS7024558B1User identity/authority verificationCharacter and pattern recognitionDigital signatureDocumentation
In an apparatus for authenticating a digital signature, a signature generating part encrypts a digital document by using a private key defined by a signer and digest information for checking whether the digital document has been tampered with, and generates a digital signature. A signature synthesizing part creates image information by synthesizing the digital signature and a predetermined mark. And an image embedding part embeds the image information created by said signature synthesizing part into an indicated position in the digital document.
Owner:FUJITSU LTD
Digital hidden data transport (DHDT)
InactiveUS7460667B2Manipulation can be minimizedReliable dataSpeech analysisRecord information storageHidden dataNoise level
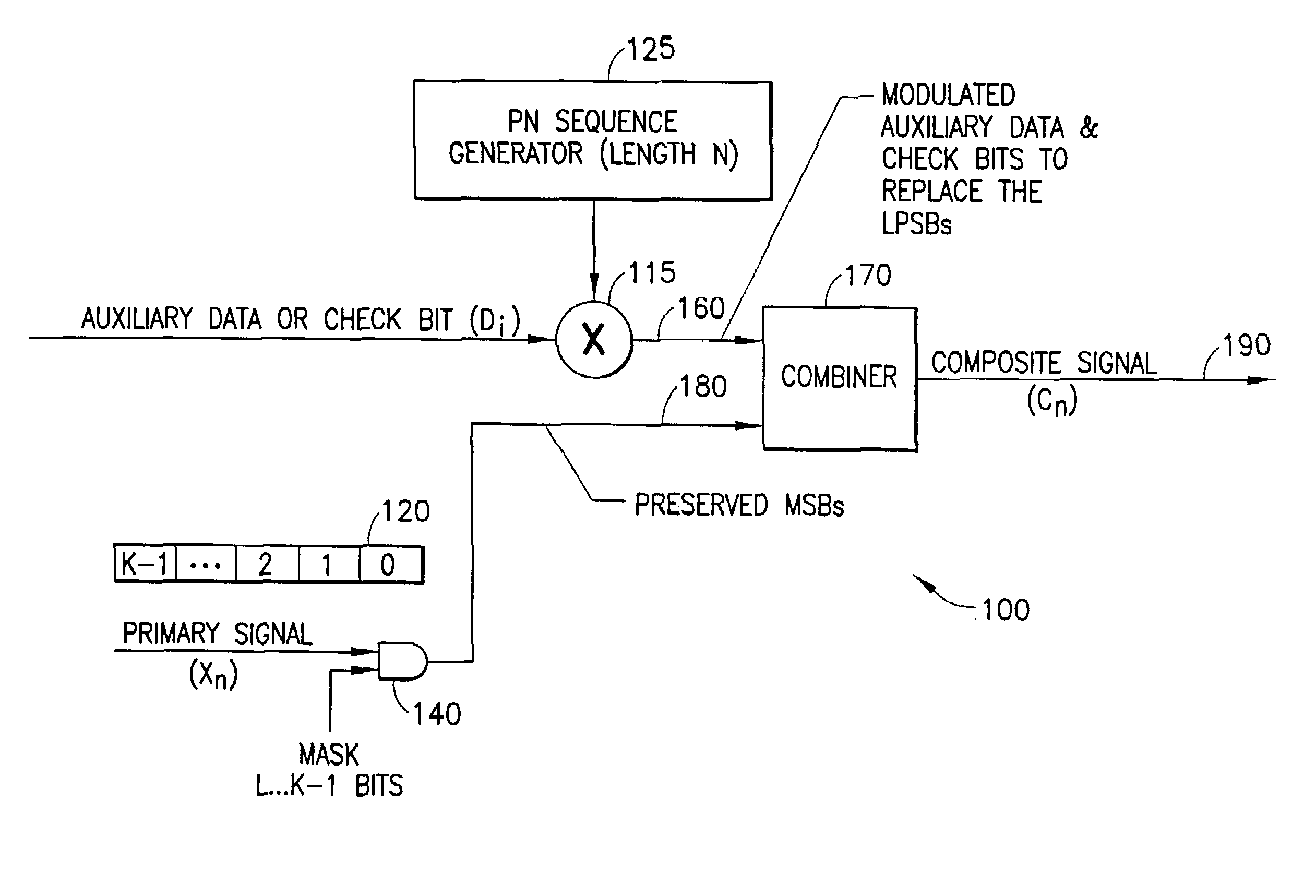
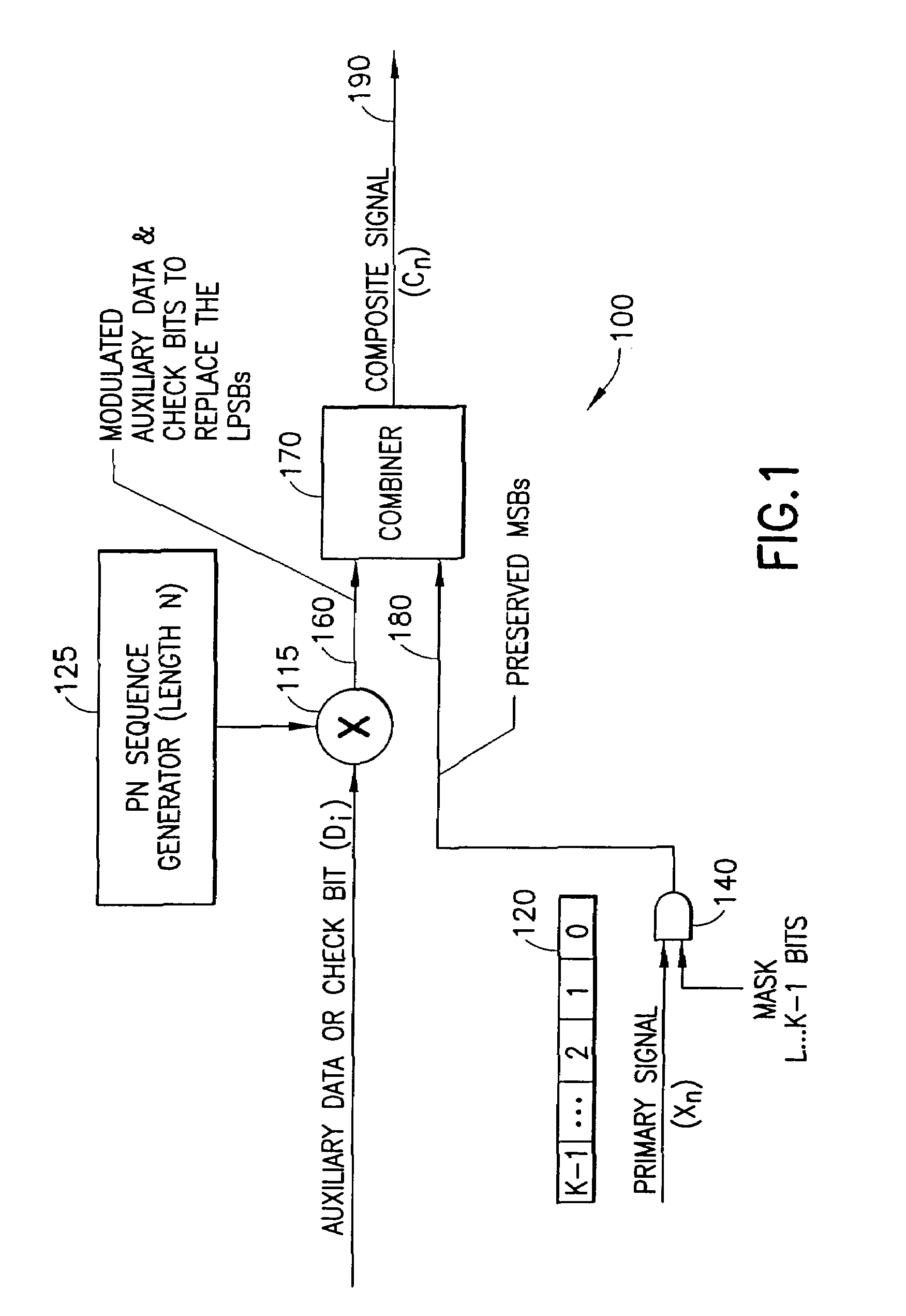
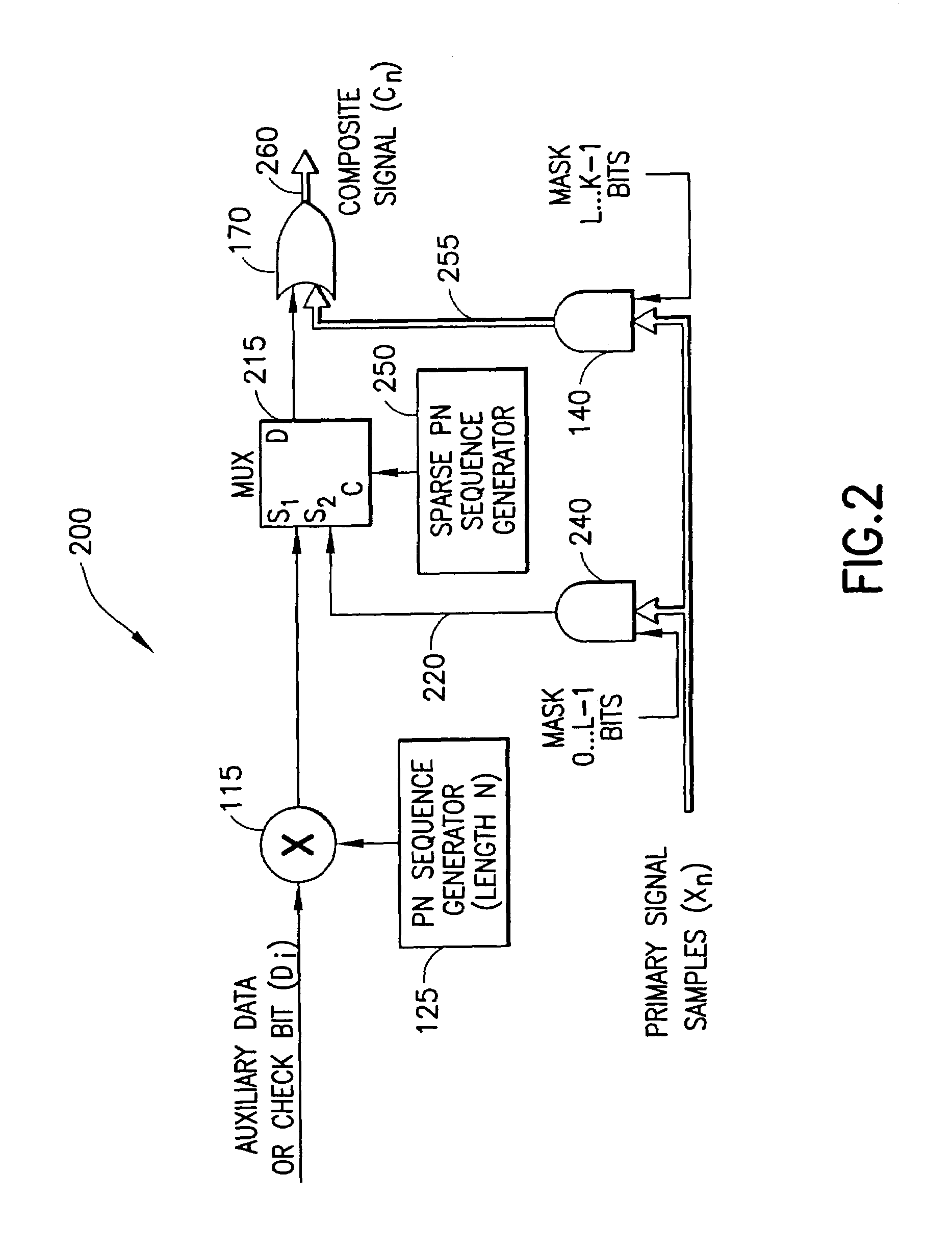
A system for embedding auxiliary digital information into a primary digital signal to form a composite digital signal. Auxiliary data bits modulate a pseudo-random (e.g., PN) sequence to provide an auxiliary data sequence used to modify the Least Perceptually Significant Bits (LPSBs) of successive multi-bit samples of the primary signal. In a cross-term compensation embodiment, a correlation between the PN sequence and the sample bits is determined, and compared to the auxiliary data bits to determine whether there is a desired correspondence. The LPSBs in the samples are toggled, if necessary, to provide the desired correspondence. The selection of LPSBs to modify accounts for a desired noise level of the auxiliary data in the primary signal. LPSBs may be modified based on a sparse PN sequence to achieve the desired noise level and conceal the presence of the auxiliary data.
Owner:VERANCE
Pre-processed information embedding system
InactiveUS7644282B2Reduce the possibilityReduce distractionsTelevision system detailsUser identity/authority verificationComputer hardwareInformation embedding
Methods are provided for embedding auxiliary information in a host content signal which reduce the memory, bandwidth and computational complexity of the embedding and transmission systems. In one embodiment, a first reduced-scale signal is produced which corresponds to the host content embedded with a first logical value and producing a second reduced-scale signal corresponding to the host content embedded with a second logical value. A first set of segments from the first reduced-scale signal may be combined with a second set of segments from the second reduced-scale signal in a pre-defined manner to produce a composite embedded host content. Thus the storage and transmission requirements of the watermarking system are reduced to having to deal with only the original content plus two reduced-scale signals.
Owner:VOBILE INC
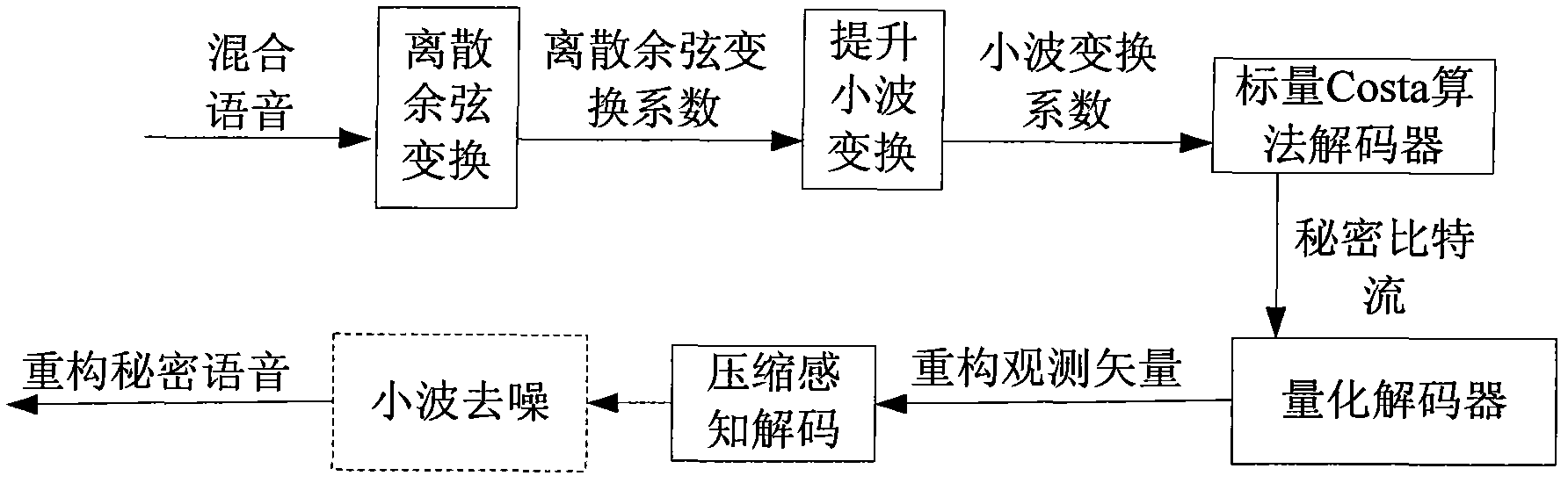
Voice secret communication system design method based on compressive sensing and information hiding
ActiveCN102034478AQuality improvementImprove sparsitySpeech analysisSecret communicationWavelet denoisingVoice communication
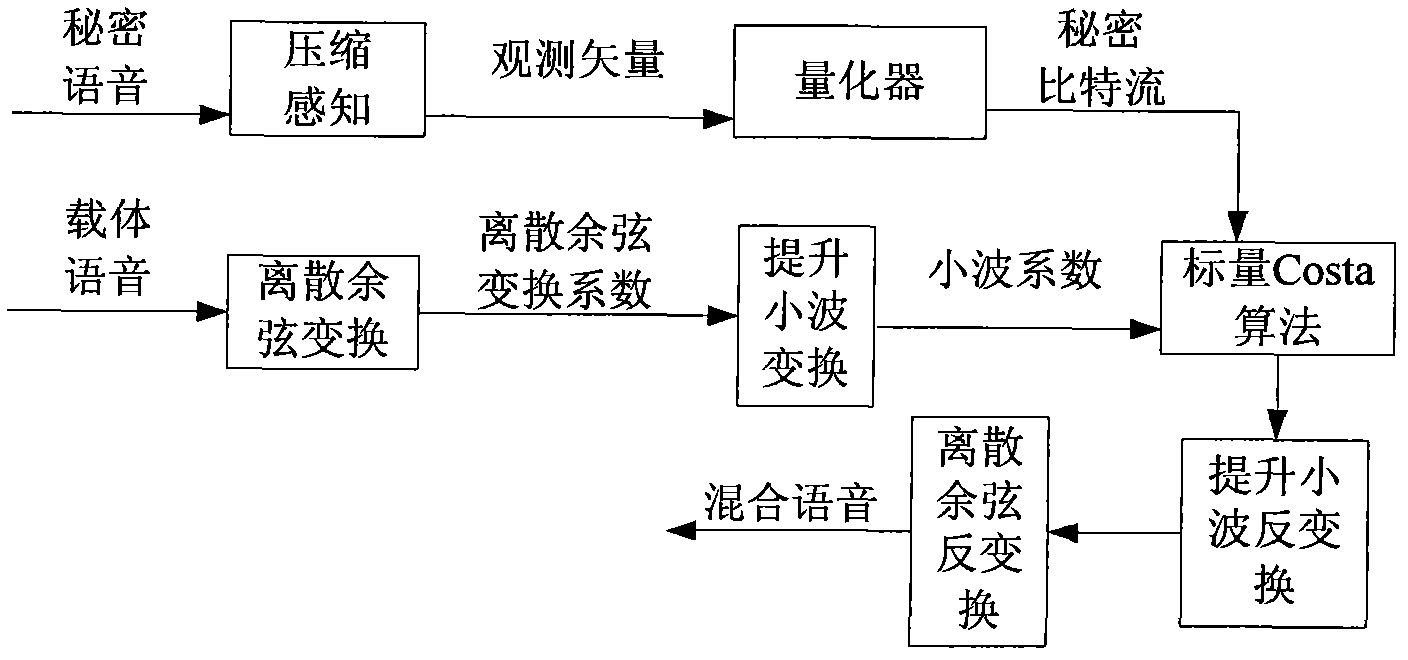
The invention discloses a voice secret communication system design method based on compressive sensing and information hiding, comprising the following steps: embedding secret voice into carrier voice by an embedded system to obtain mixed voice; designing a compressive sensing overcomplete dictionary aiming at the voice signal; sampling the secret voice by a compressive sensing self-adaption observation matrix to obtain a observation vector for reducing dimensions; quantizing the observation vector by an LBG (Linde-Buzo-Gray algorithm) vector, taking the quantized observation vector to serve as secret information to embed into the carrier voice, and carrying out two-stage transform on the carrier voice to obtain mixed voice; extracting the secret voice from the mixed voice by an extraction system; carrying out discrete cosine transform on mixed voice, and improving wavelet transform two-stage transform to obtain a wavelet transform coefficient; obtaining a secret bit stream by a scalar Costa decoding algorithm; obtaining a reconstructing observation vector by an LBG vector quantization decoder; reconstructing the secret voice by a compressive sensing orthogonal matching pursuit algorithm; and improving the quality of the reconstructed secret voice with a wavelet denoising method.
Owner:NANJING UNIV OF POSTS & TELECOMM
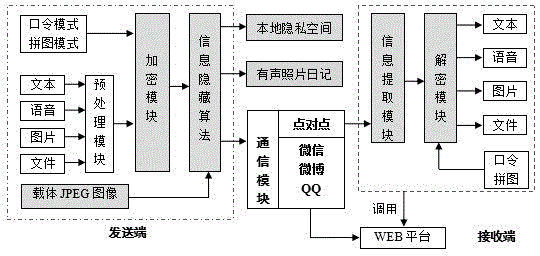
JPEG image information hiding based private information communication method and system
ActiveCN105426709AHidden efficientLarge capacityImage data processing detailsProgram/content distribution protectionUser inputInformation embedding
The invention relates to a JPEG image information hiding based private information communication method and system. The system comprises a preprocessing module used for converting to-be-transmitted information into binary data, an encryption / decryption module used for generating an information hiding key by a password input by a user, an information hiding module used for embedding the converted binary data into a carrier JPEG image, a transmission module for transmitting and sharing the JPEG image embedded with the binary data information, and an information extraction module used for extracting the binary data in the image embedded with the binary data information, wherein the information hiding module comprises an entropy decoding module, an information embedding module and an entropy encryption module. The invention provides a complete multi-morphological information hiding core algorithm taking an image as a medium and a communication solution. The private information communication method and system have important theoretical and application values.
Owner:FUJIAN NORCA TECH
Digital waterprint imbedding and extracting method based on remainder image
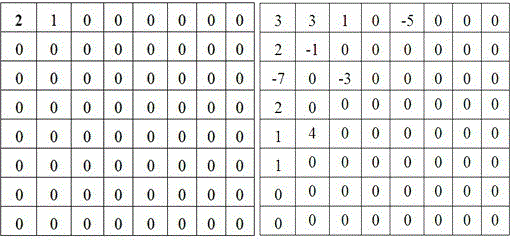
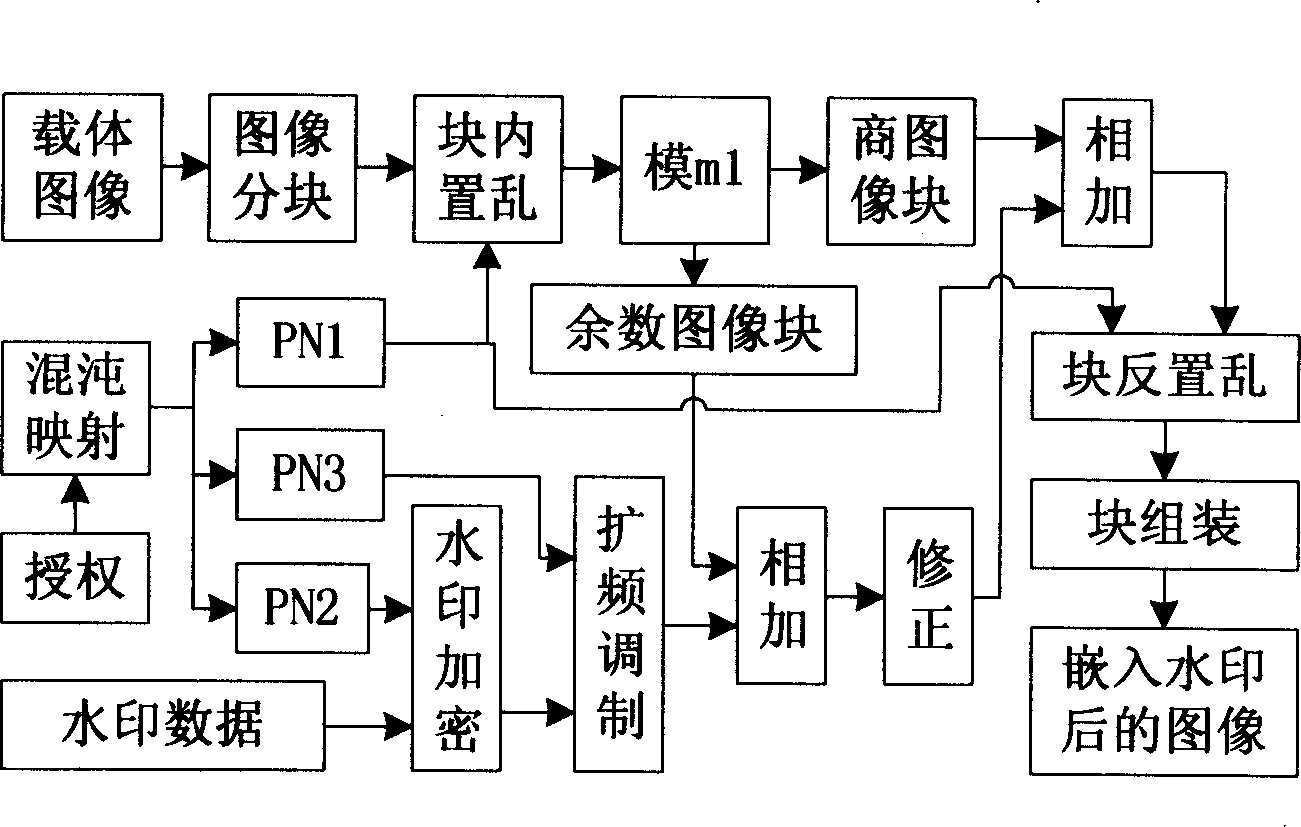
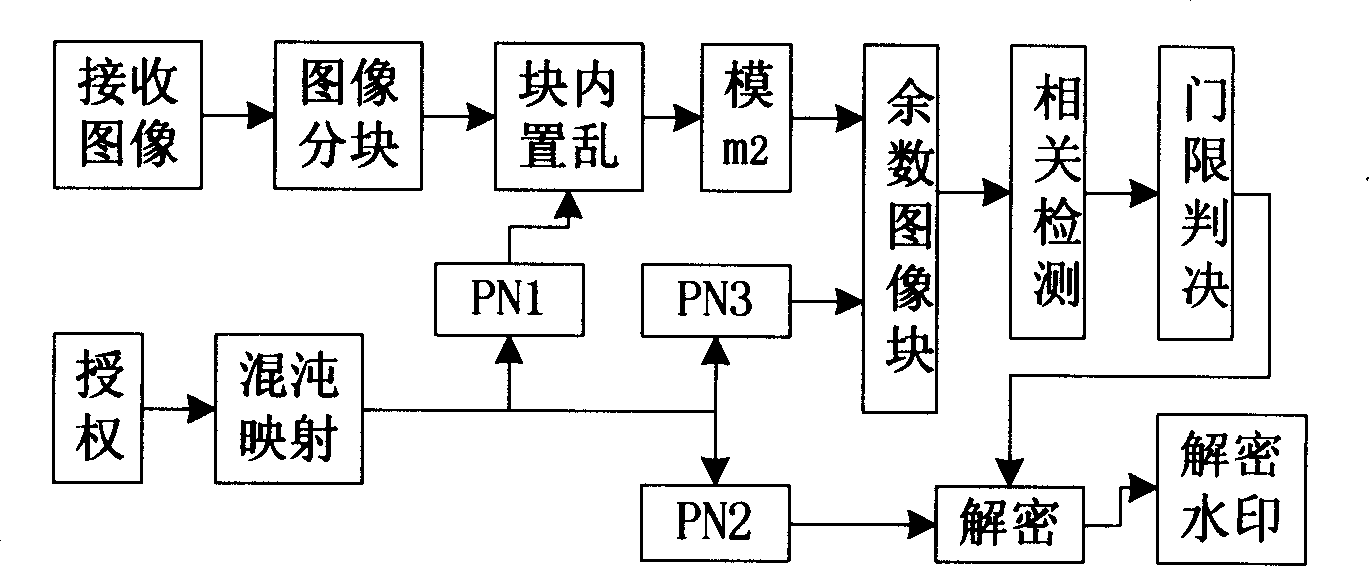
InactiveCN1471019AImprove distributionEasy to manageImage enhancementTelevision system detailsInformation embeddingComputer graphics (images)
The image partitioned to small pieces in space domain and each small pieces scrambled by using chaos mapping are carried out. Carrier image data in each piece is decomposed into 'residual image block' and 'quotient image block'. Watermark information is encrypted and carried out direct sequence spread spectrum by using chaos sequence. The processed watermark information is embedded to the 'residual image block'. After processing the data of crossing the border, each 'residual image block' and corresponding 'quotient image block' is assembled. The image with the watermark embedded is obtained by assembling each anti-scrambled block with chaos mapping. When picking-up watermark, the cryptic watermark information is recovered after operations of scrambling, demodulating and threshold decision are carried out.
Owner:SHANGHAI JIAO TONG UNIV
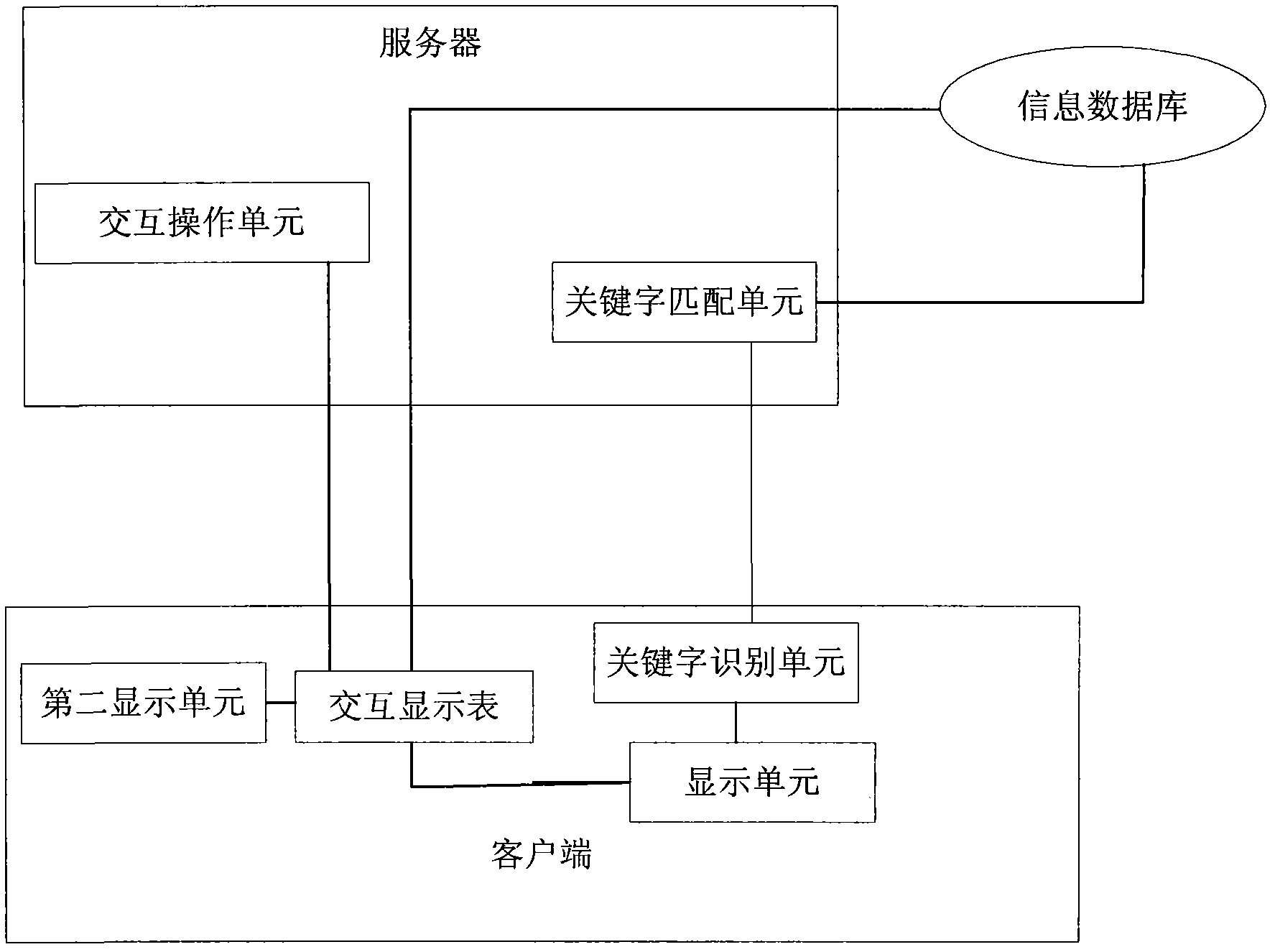
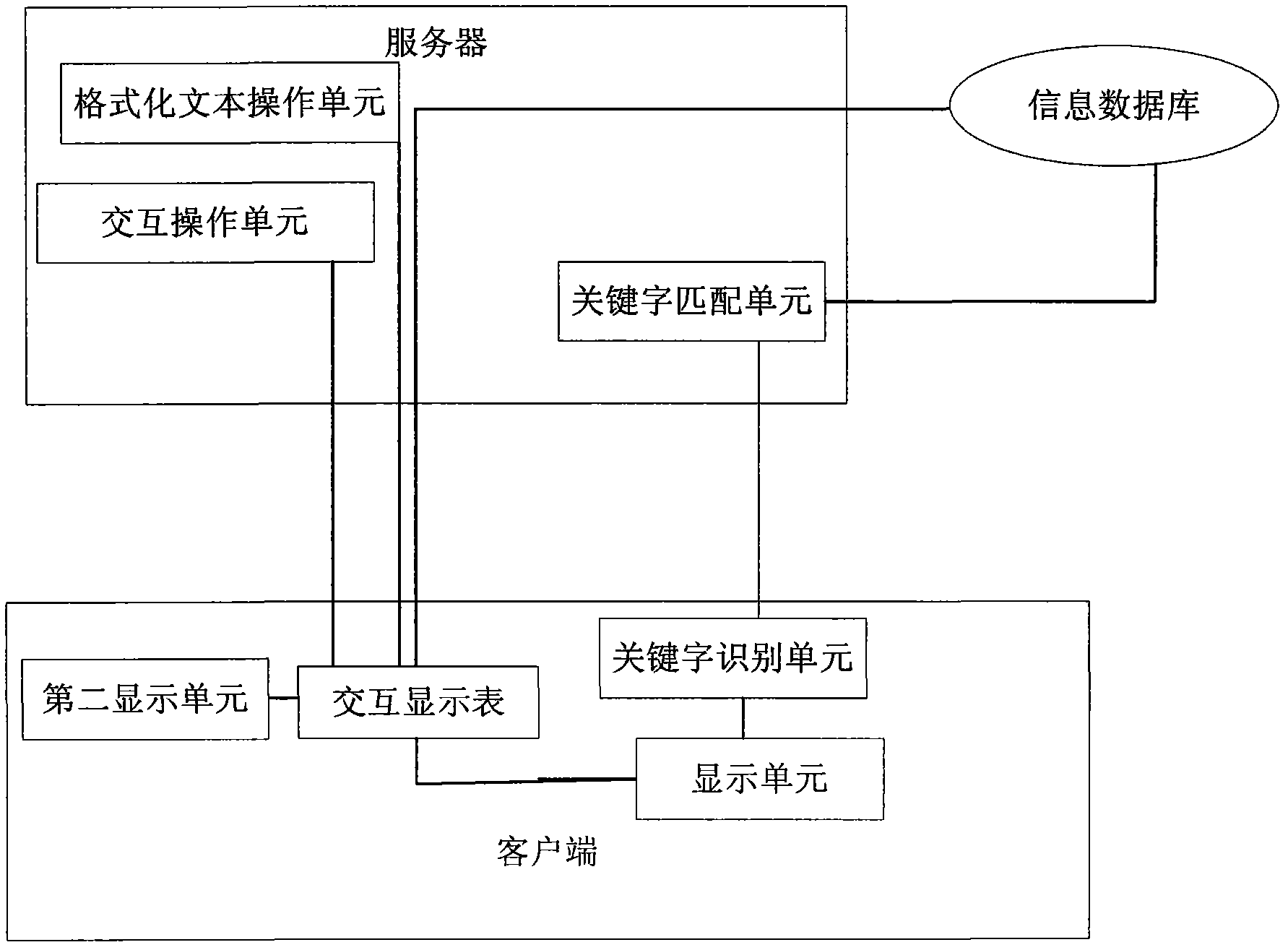
Information embedding and interaction system facing real-time communication and method
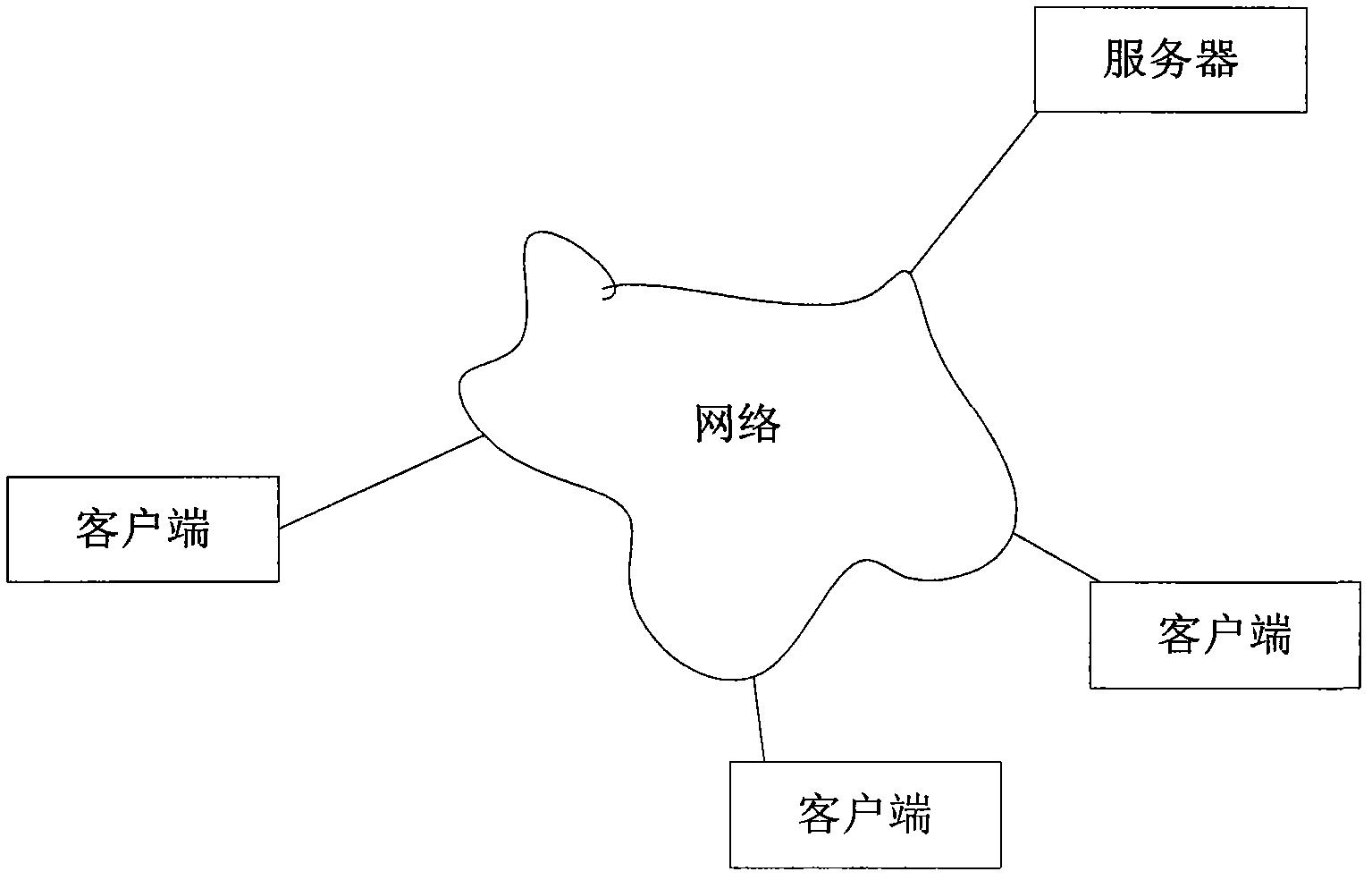
InactiveCN102323933AImprove experienceImprove user experienceData switching networksSpecial data processing applicationsInteraction systemsInformation embedding
The invention relates to an information embedding and interaction system facing real-time communication and a method. The system at least comprises a client end, a server and an information database, wherein the client end comprises a keyword identification unit, a display unit and an interaction display meter; the server comprises a keyword matching unit for keyword matching and an interaction operational unit; and the information database is used for storing a large amount of data information. The system is designed to better provide services for real-time chatting users and information and overcome defects of the existing information embedding technique. Information of the services can be stored in the information database through keywords, accurate search can be achieved through matching of the keywords with the information stored in the information database, and thus cluttered information can be avoided.
Owner:张潇
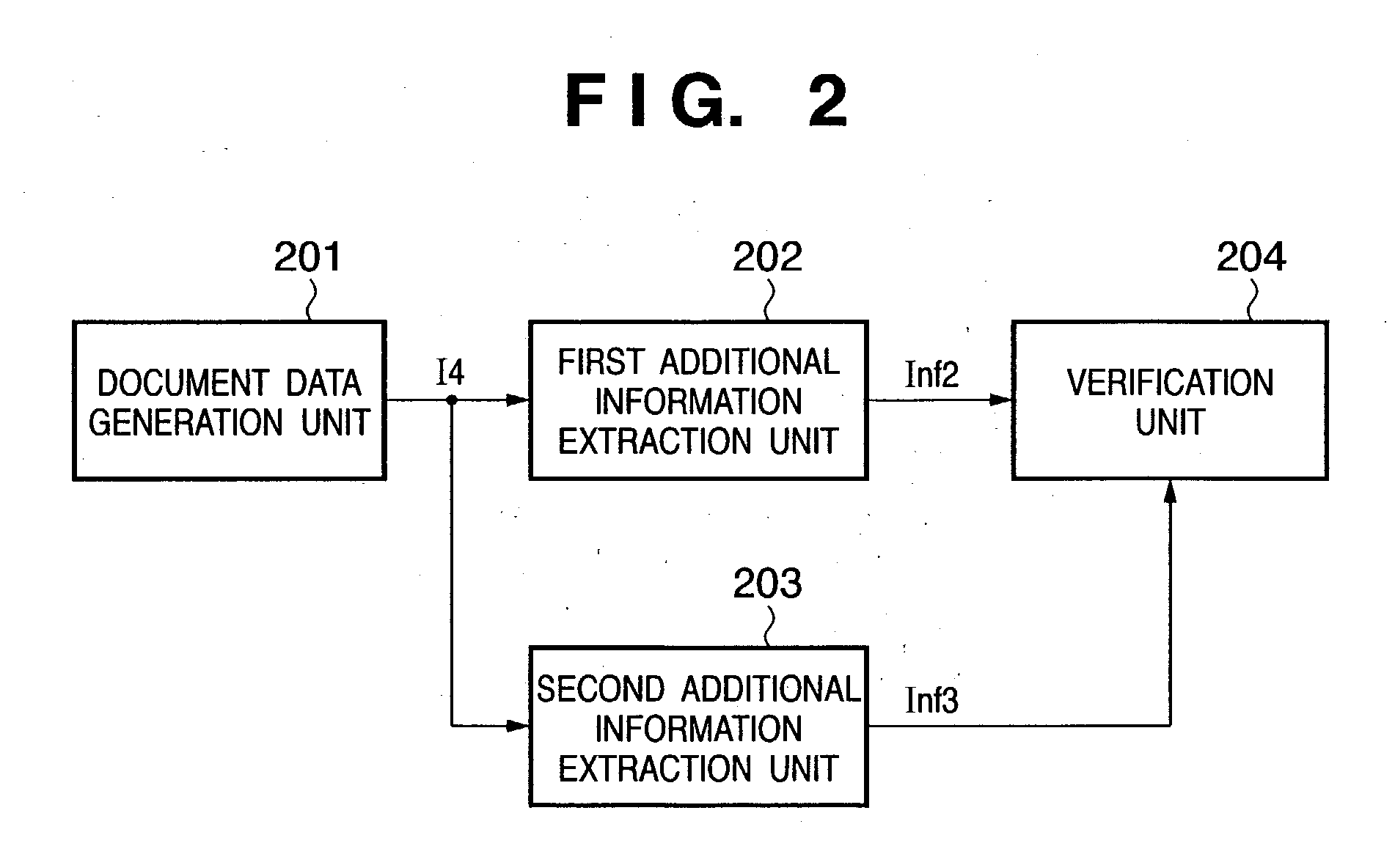
Information processing method and apparatus, and computer program and computer-readable storage medium
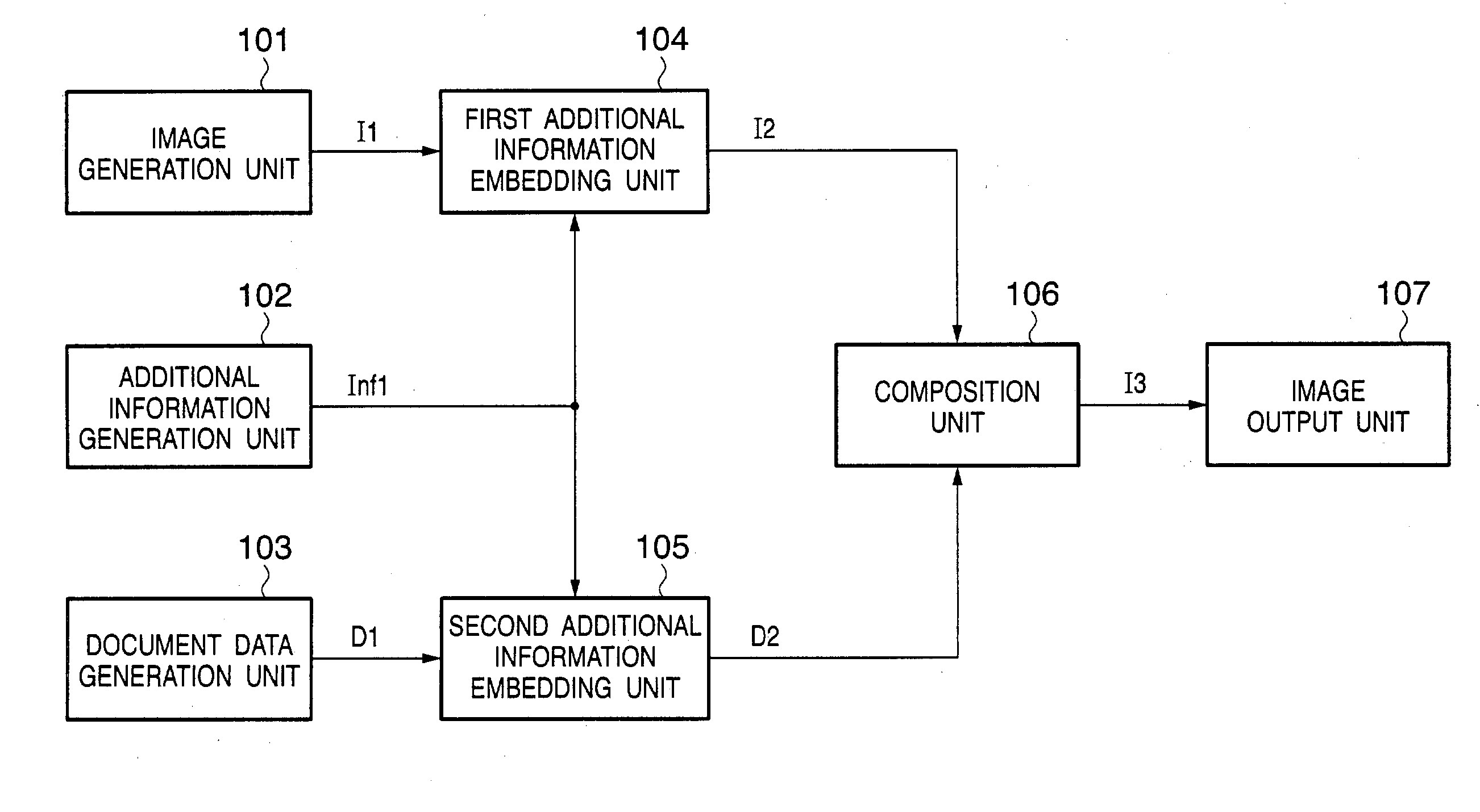
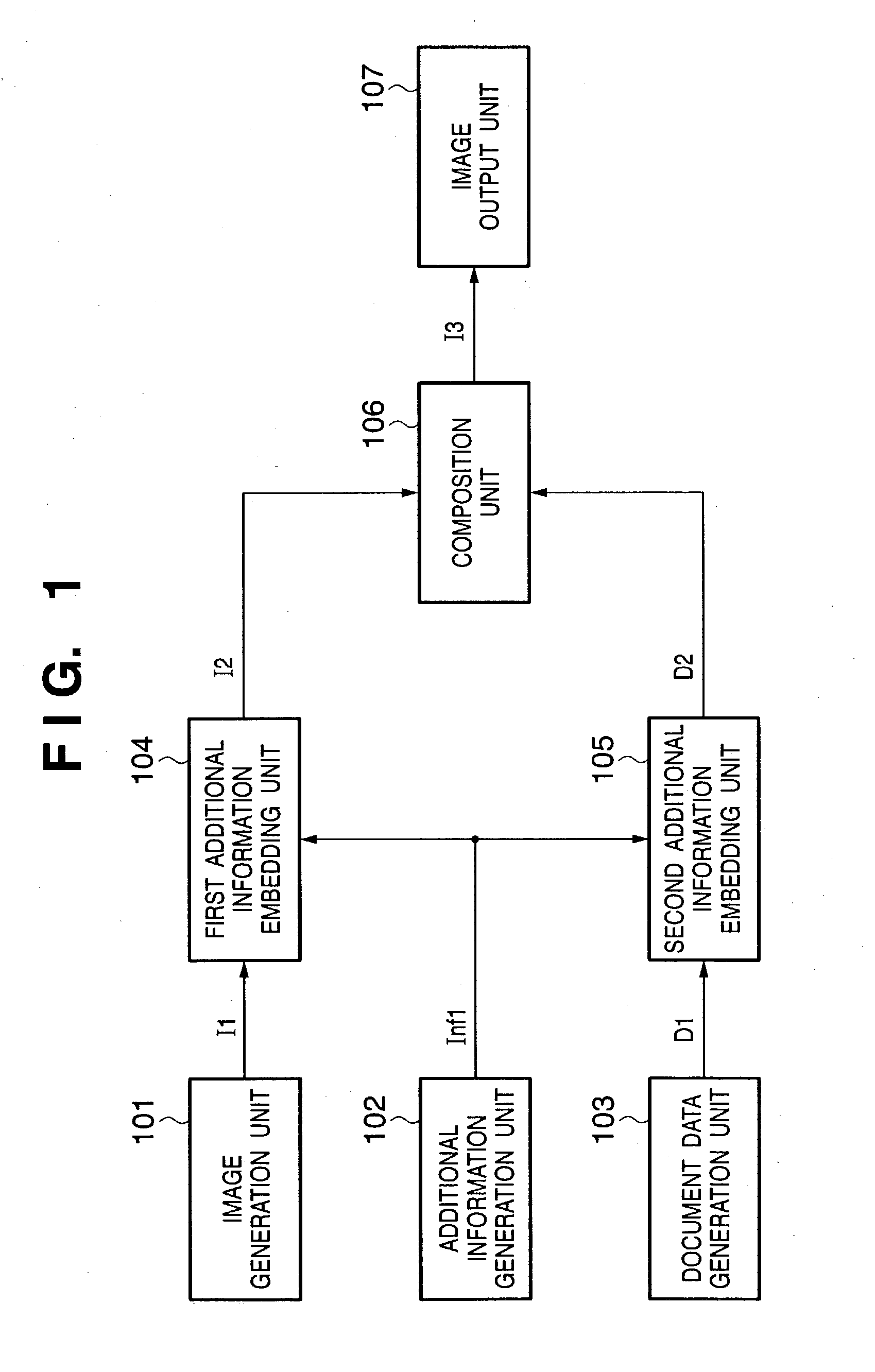
InactiveUS20030204812A1Digital data processing detailsUser identity/authority verificationInformation processingInformation embedding
This invention has as its object to embed information in a document by a plurality of different methods, and verify the information embedded by the respective methods to determine the relationship with a master. To this end, a method of this invention includes an image data input step of inputting image data, a document data input step of inputting document data, an additional information input step of inputting additional information, a determination step of determining whether or not the additional information can be embedded in the document data, a region segmentation step of segmenting the image data into first and second regions in accordance with the determination result of the determination step, a first additional information embedding step of embedding the additional information in the first region, a second additional information embedding step of embedding the additional information in the second region, a composition step of compositing the image data and document data embedded with the additional information, and an image output step of outputting the image data composited in the composition step.
Owner:CANON KK
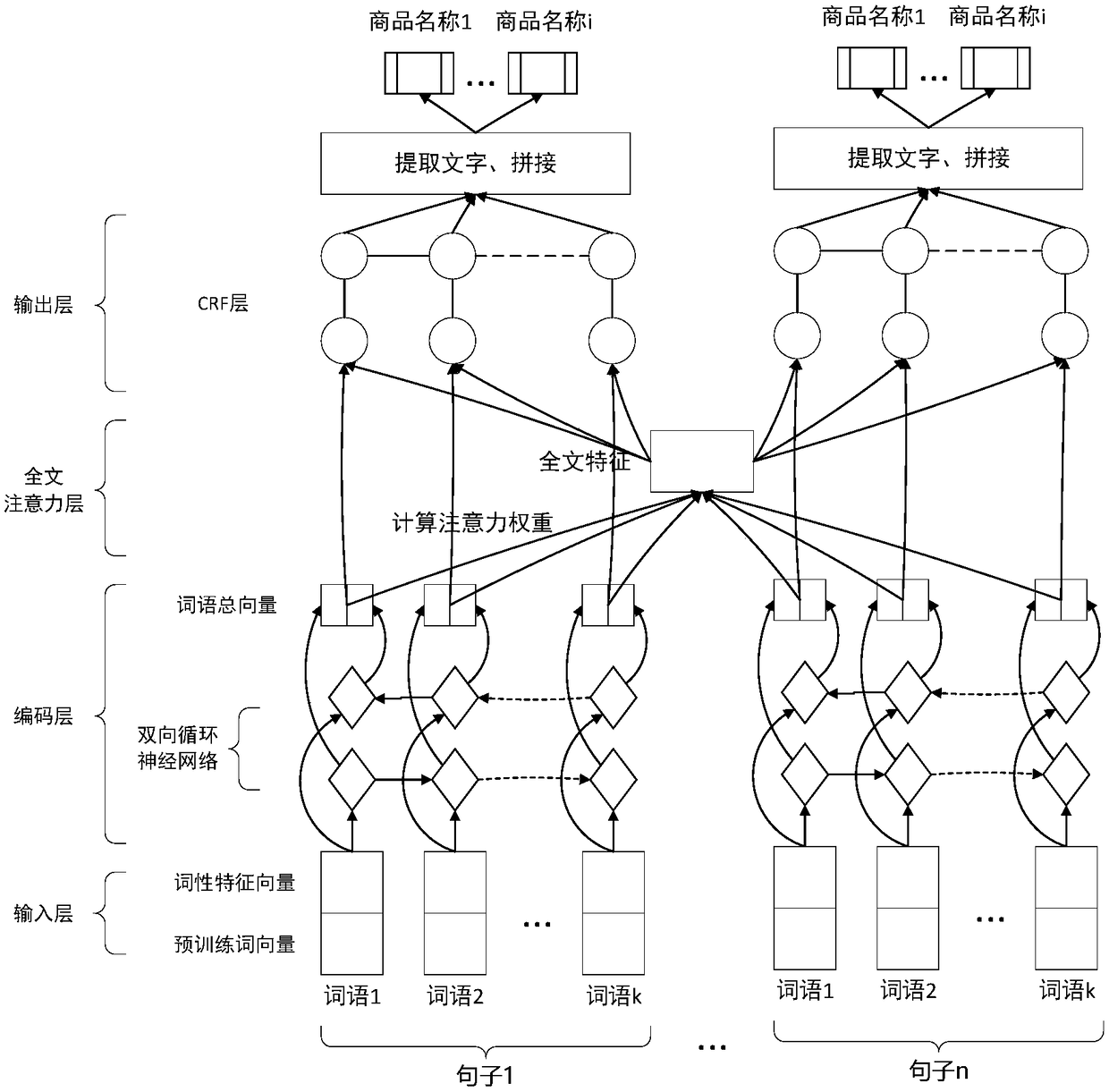
Trade name recognition method based on full-text attention mechanism
ActiveCN109062893AEfficient extractionSolve the problem of identifying inconsistenciesNatural language data processingNeural learning methodsAlgorithmInformation embedding
The invention discloses a commodity name recognition method based on a full-text attention mechanism. The method comprises the following steps: establishing a depth neural network model with a full-text attention mechanism; adding a full-text attention layer into the depth neural network model; in the full-text attention layer, the full-text information being represented by a method of embedding aword into a vector; the full-text attention layer being represented by a full-text information embedding vector. Then, for each word to be annotated, the similarity between them and the full-text attention-level word vector is calculated, so that the word can obtain the 'attention weight' of the full-text, that is, the word can focus on the context information of the document, and the additionalfeatures of each word can be calculated by using the sum of the attention-level weight, so as to identify the trade name. The method of the invention can effectively extract commodity names from irregular texts, solves the problem of inconsistent identification of the same commodity in context, and improves the accuracy of identification.
Owner:SOUTH CHINA UNIV OF TECH
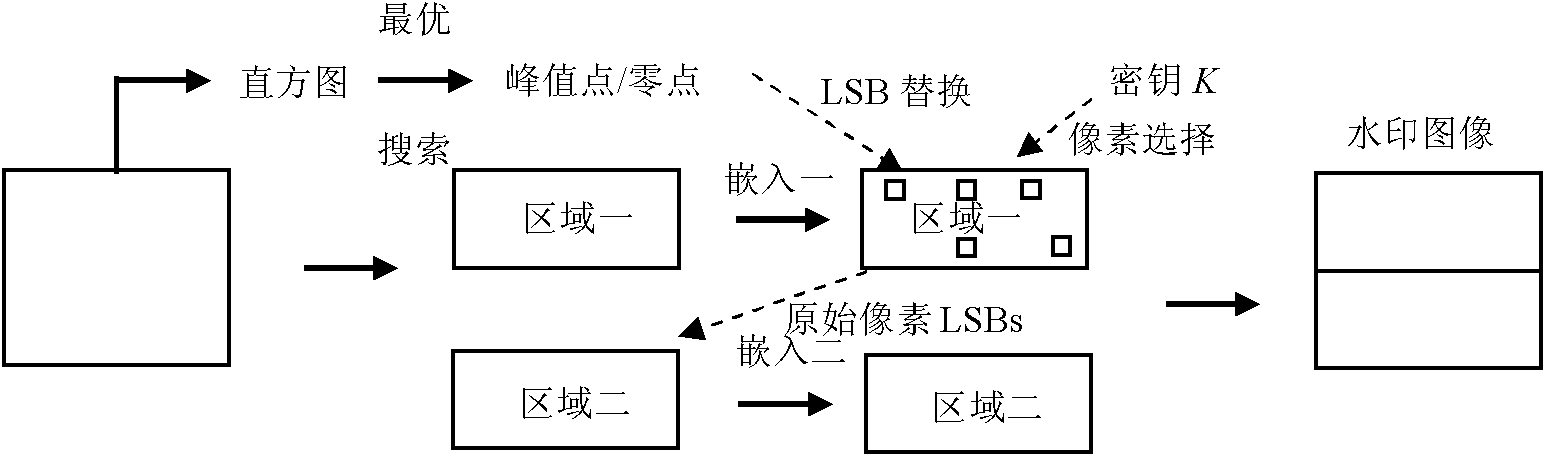
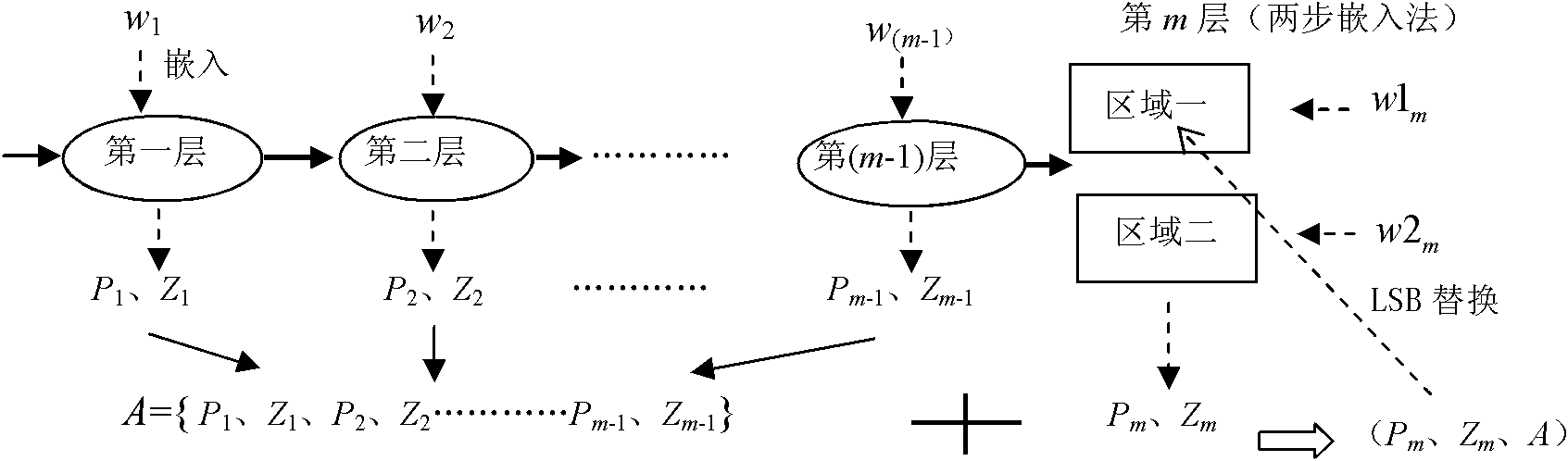
Reversible watermark method utilizing histogram shifting
InactiveCN102567942AReduce sizeEasy to compressImage data processing detailsProgram/content distribution protectionBit blitGeneration process
The invention provides a reversible watermark method based on histogram shifting and has significant practical values for protecting multimedia copyrights. By means of the reversible watermark method, traditional histogram shifting algorithms are improved in two aspects, firstly, 1 and 0 in a bite map are more imbalanced by arranging a generation process of the bit map on watermark embedding rather than in a non-pretreatment stage, so that compression is easier, and embedding capacity is improved; and secondly, the reversible watermark method is a two-step embedding method. The watermark blind extraction is achieved and troubles that the histogram shifting method needs extra side information transmitting are solved by dividing an image into an upper large area and a lower large area, subjecting the upper area to the watermark embedding, embedding the generated side information into the lowest significant bit containing watermark pixels in the area, and embedding the left watermark information and the replaced lowest significant information into the lower area.
Owner:SUN YAT SEN UNIV
Document watermark copyright information protection device based on Opentype vector outline fonts
InactiveCN102495833AImprove robustnessEasy to operateProgram/content distribution protectionSpecial data processing applicationsInformation embeddingDocumentation
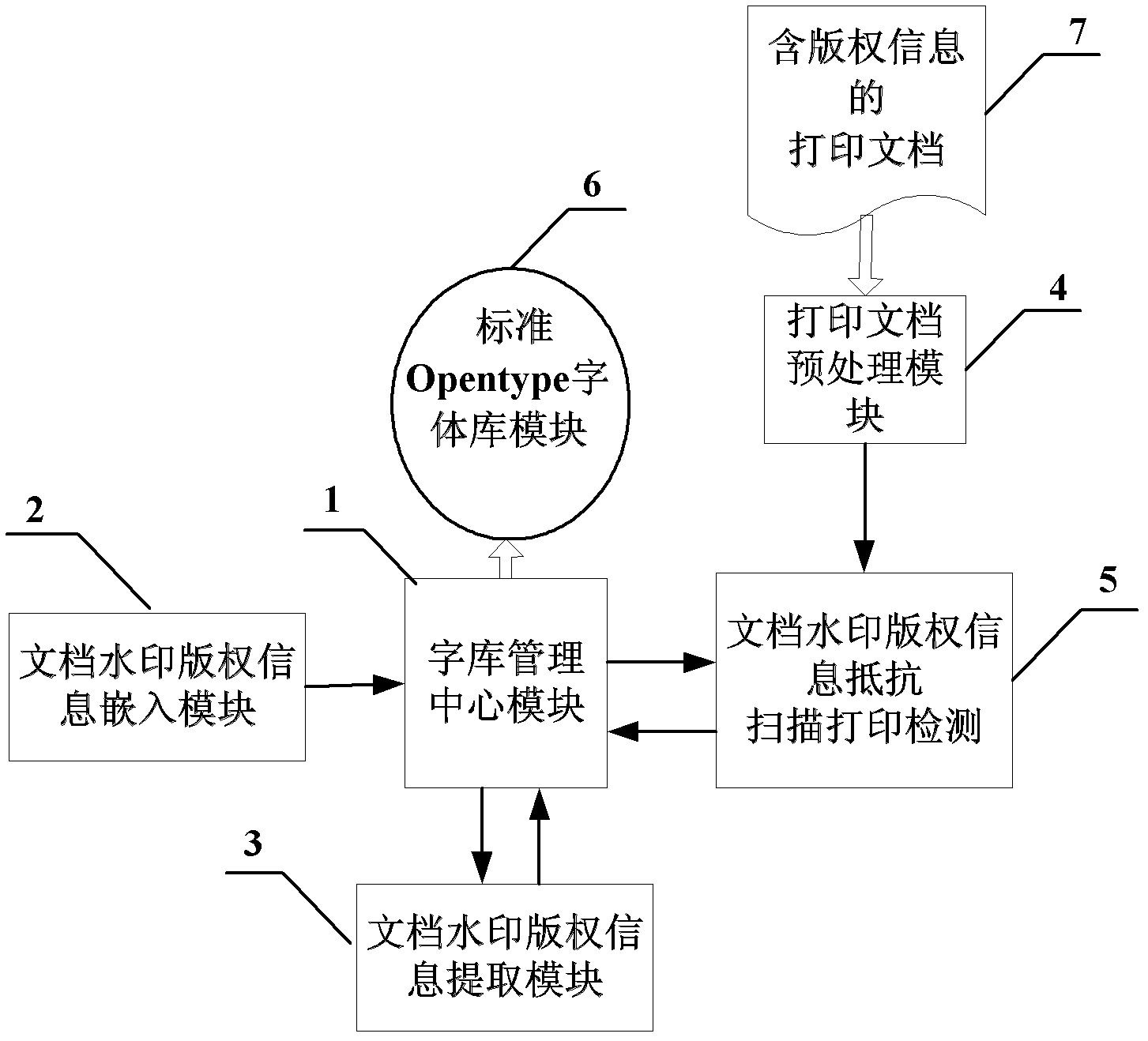
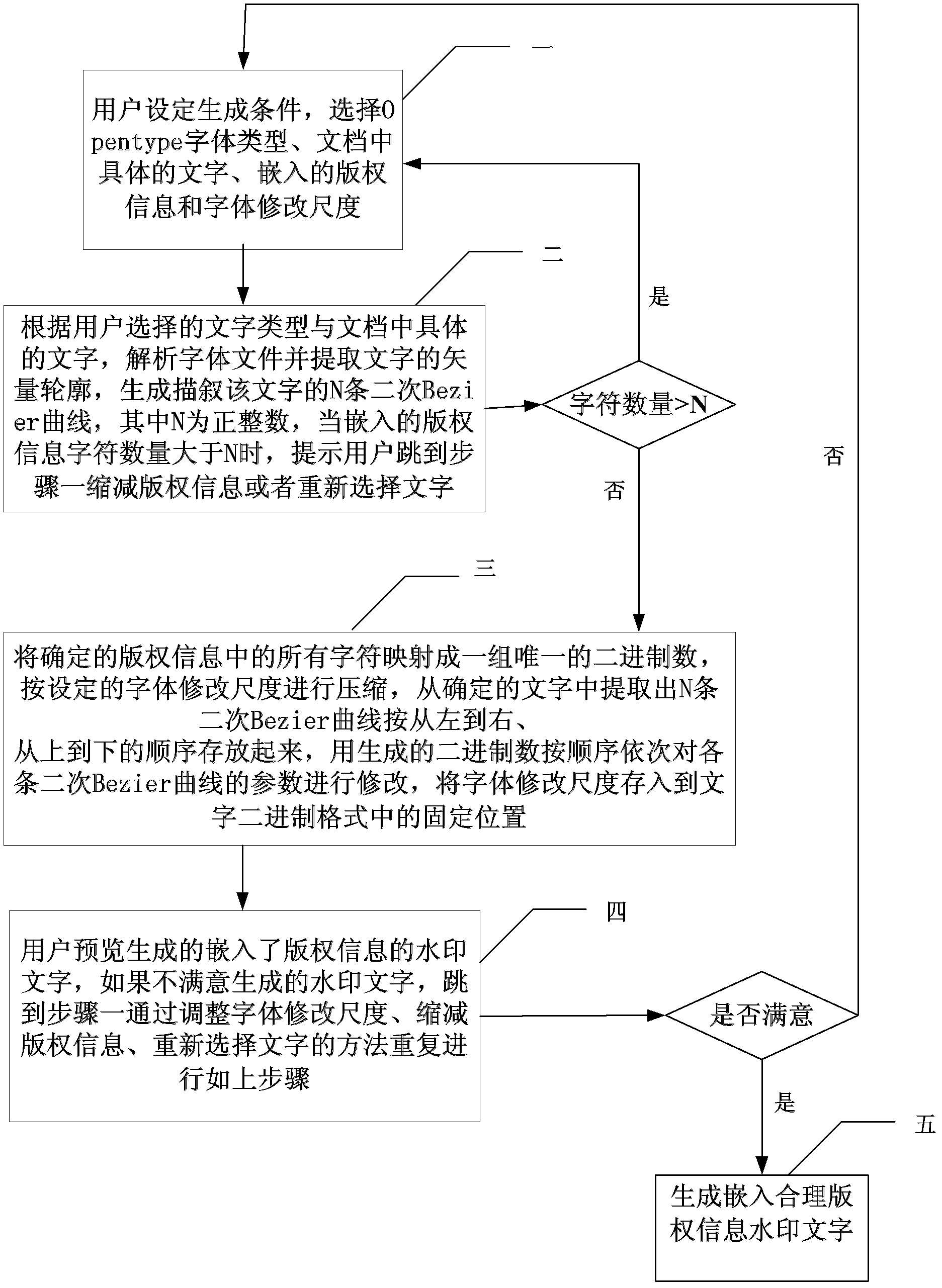
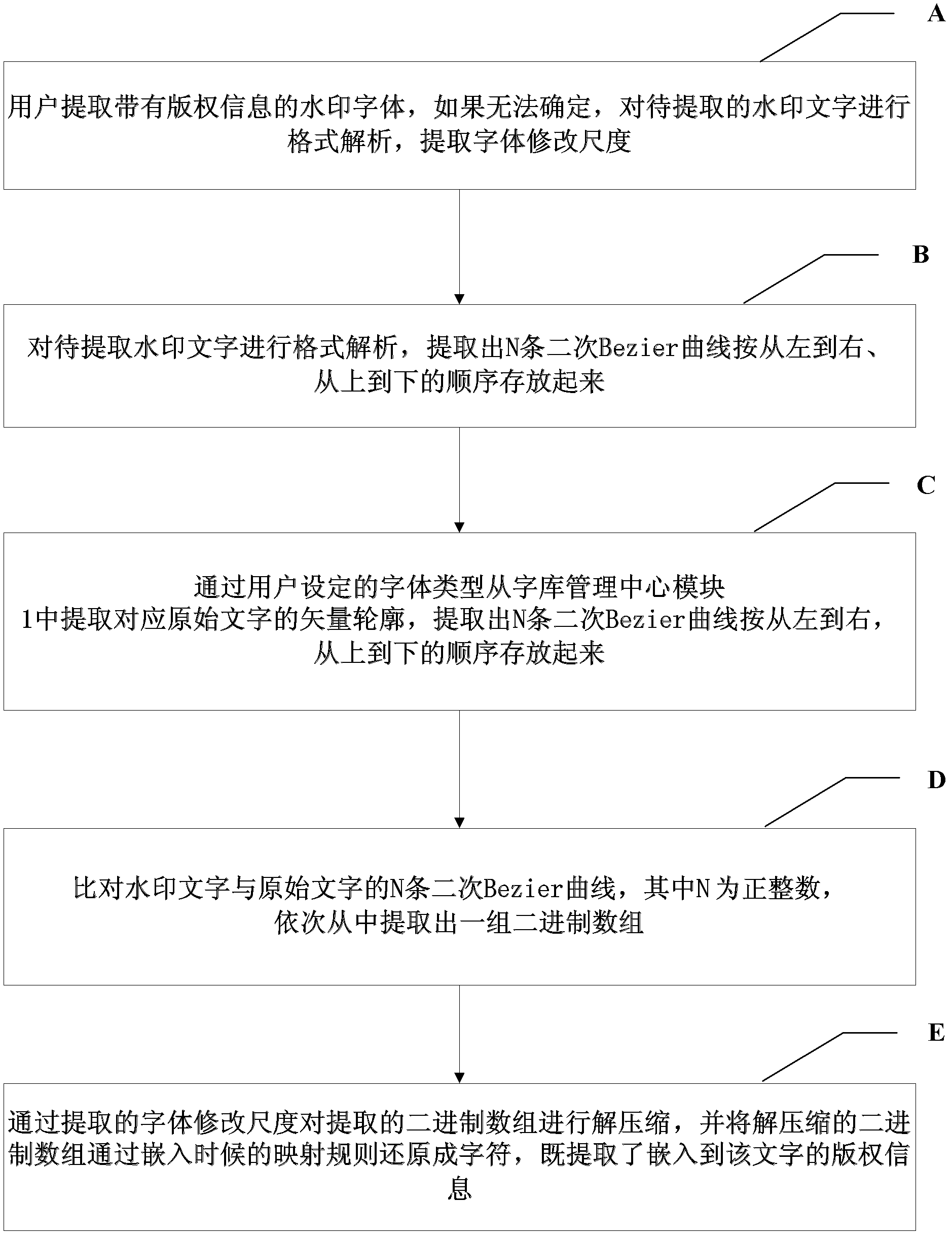
The invention discloses a document watermark copyright information protection device based on Opentype vector outline fonts, belongs to the fields of digital watermark technologies and document information protection in information safety, and aims to solve the problems of low robustness and complexity in operation of the conventional document watermark technology caused by conversion of a document into an image before a watermark is embedded. A font library management center module manages original standard font library information in which watermark information is not embedded, and provides comparison information; a document watermark copyright information embedding module generates specific watermark characters through selected Opentype fonts and embedded copyright information; a document watermark copyright information extraction module extracts the copyright information according to comparison parameters; a printed document pre-processing module scans a printed document, and performs image binarization, de-noising, positioning and refining to form continuous single-pixel curves; and a document watermark copyright information anti-scanning printing detection module extracts stroke parameters. The document watermark copyright information protection device based on the Opentype vector outline fonts is applicable to protection of document watermark copyright information.
Owner:HARBIN INST OF TECH
Link prediction method based on network structure and text information
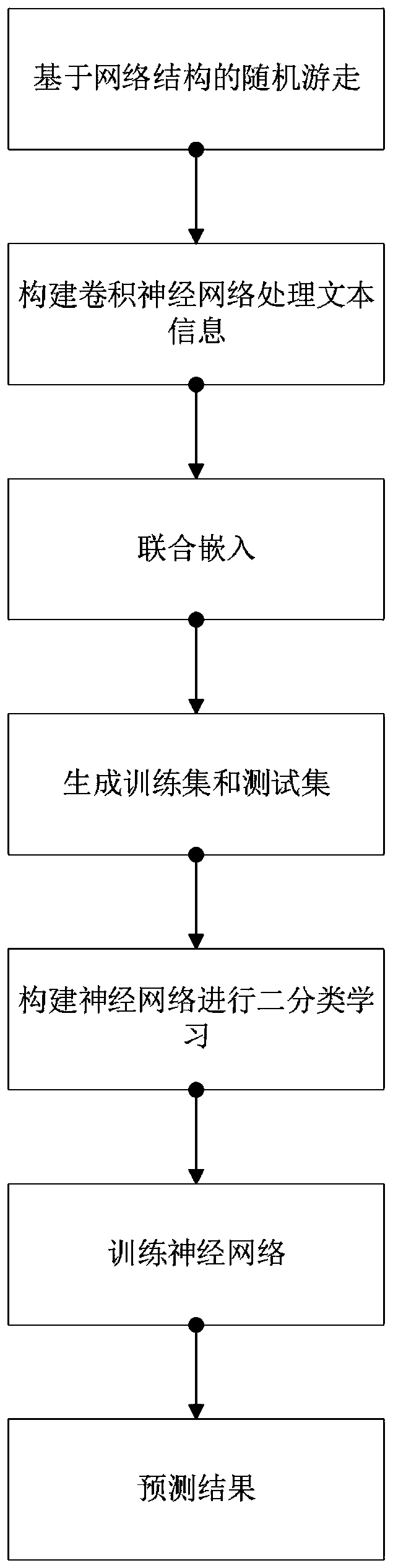
ActiveCN111368074AAvoid missingExcellent predictive experimentData processing applicationsNeural architecturesInformation embeddingComputer network technology
The invention relates to the technical field of computer networks, and discloses a link prediction method based on a network structure and text information, and the method comprises the steps: S1, obtaining a structure embedding vector of a node based on a random walk node in the network structure; s2, constructing a convolutional neural network to process the text information of the nodes to obtain text information embedding vectors of the nodes; s3, performing joint embedding on the structure embedding vector and the text information embedding vector of the node; s4, generating a training set and a test set; s5, constructing a neural network for binary classification learning; s6, training a neural network; and S7, result prediction: the link prediction method based on the network structure and the text information is simple in calculation process, small in error and high in prediction accuracy.
Owner:XIDIAN UNIV
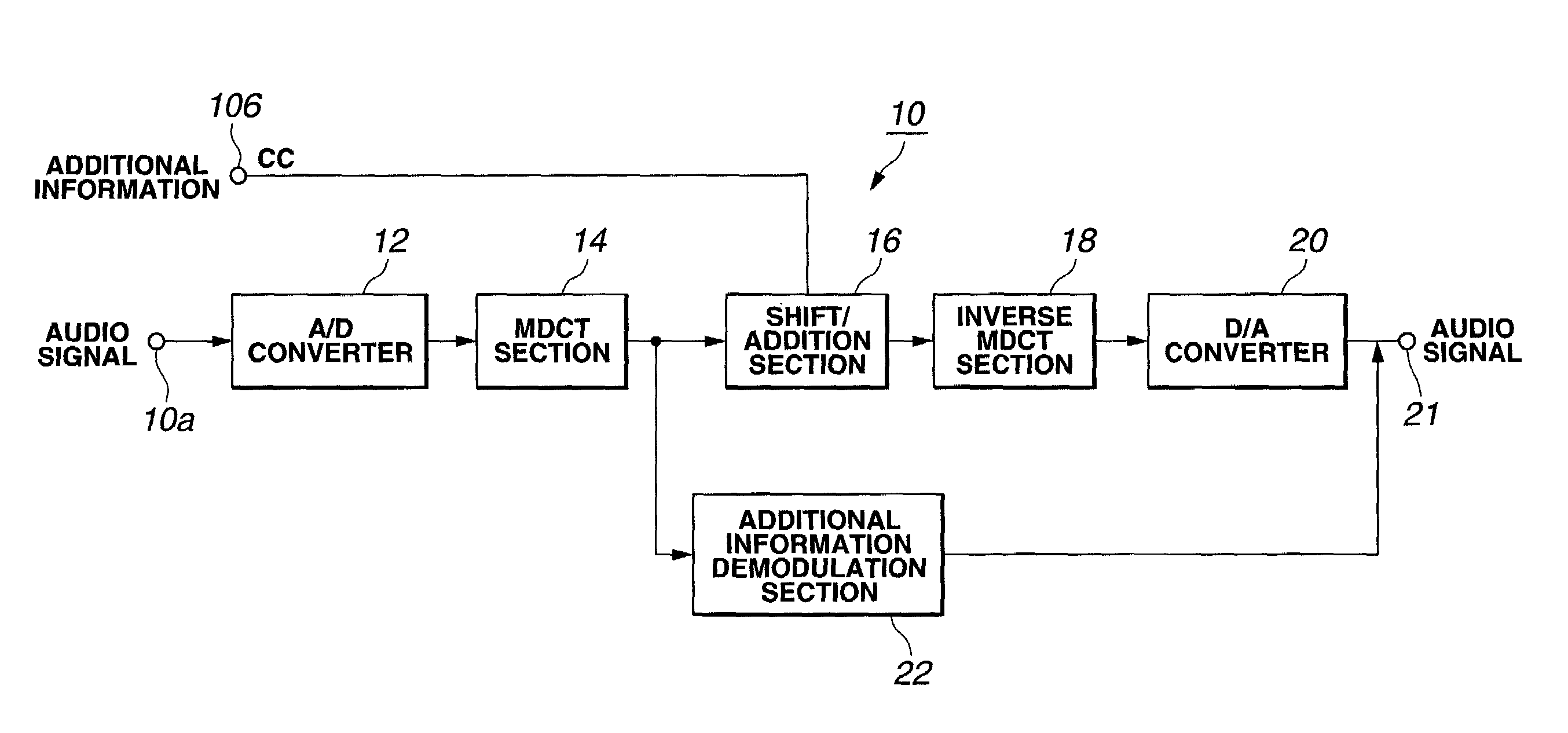
Additional information embedding method and it's device, and additional information decoding method and its decoding device
InactiveUS7299189B1Deteriorating quality of reproduced soundQuality improvementUsing non-detectable carrier informationRecord information storageDecoding methodsInformation embedding
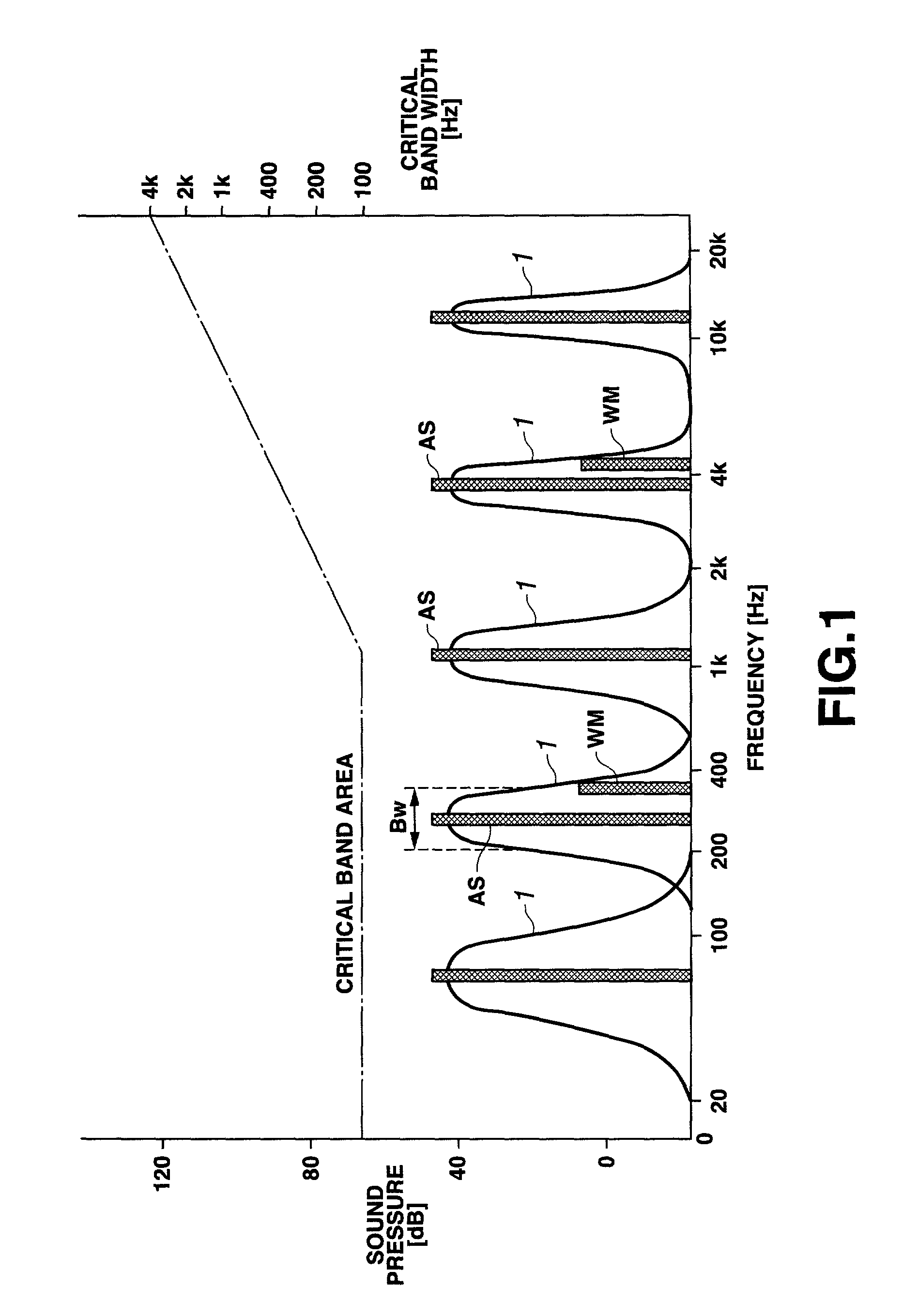
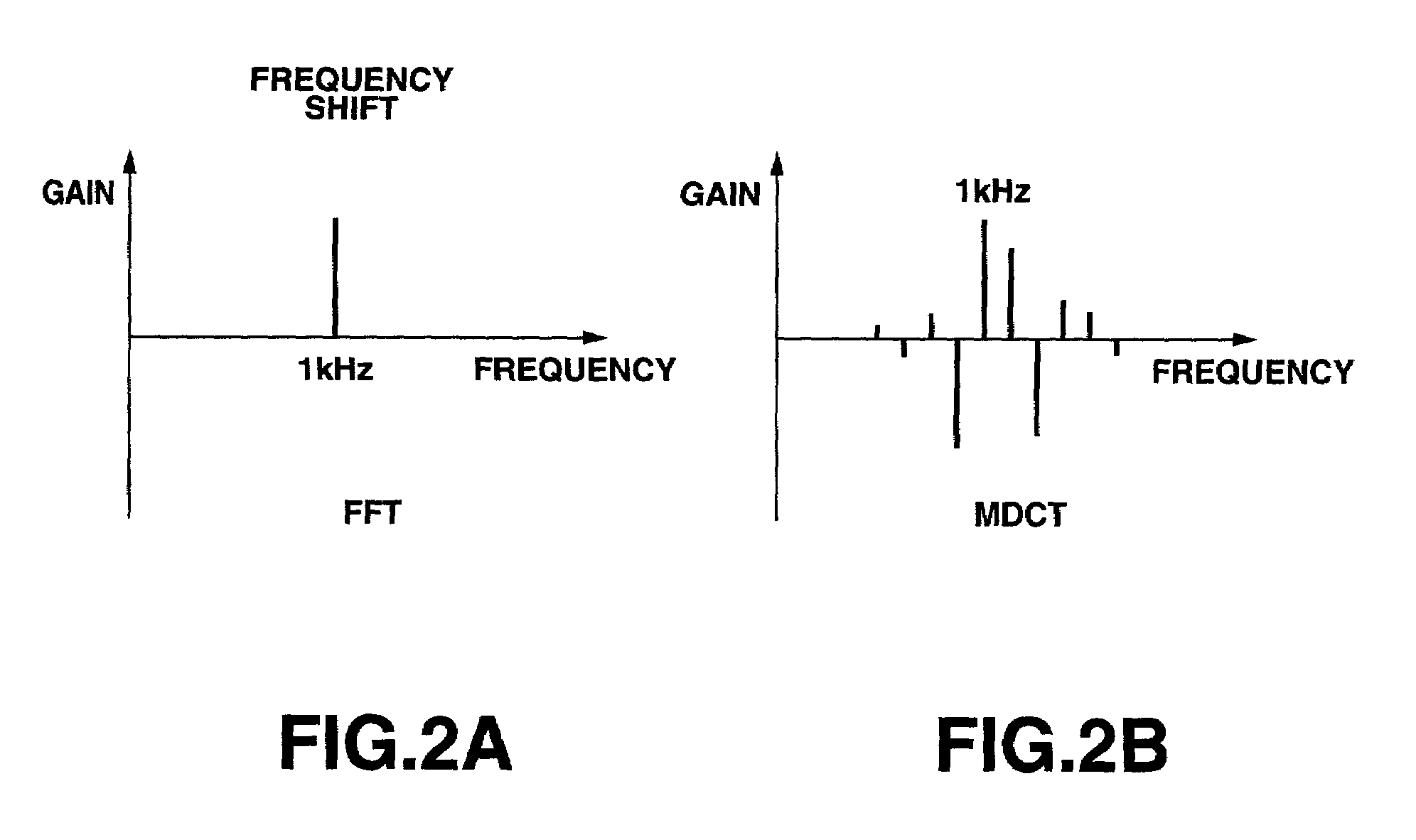
The present invention relates to an additional information embedding method for embedding additional information into an audio signal, in which the audio signal is MDCT-transformed to calculate an MDCT coefficient and the calculated MDCT coefficient is damped, shifted in the direction of the frequency axis and added to the original MDCT coefficient, thereby embedding the additional information as a watermark into the audio signal.
Owner:SONY CORP
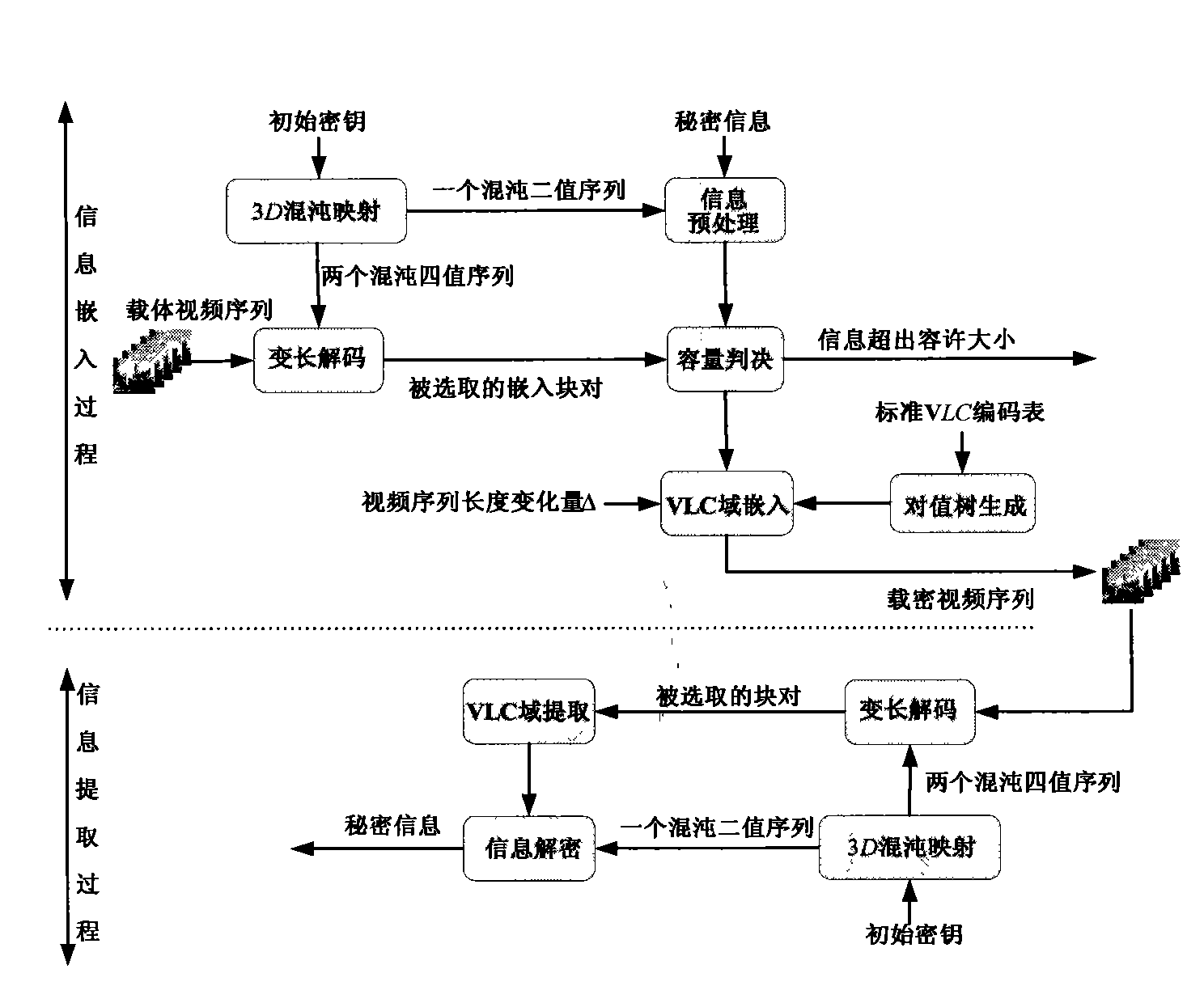
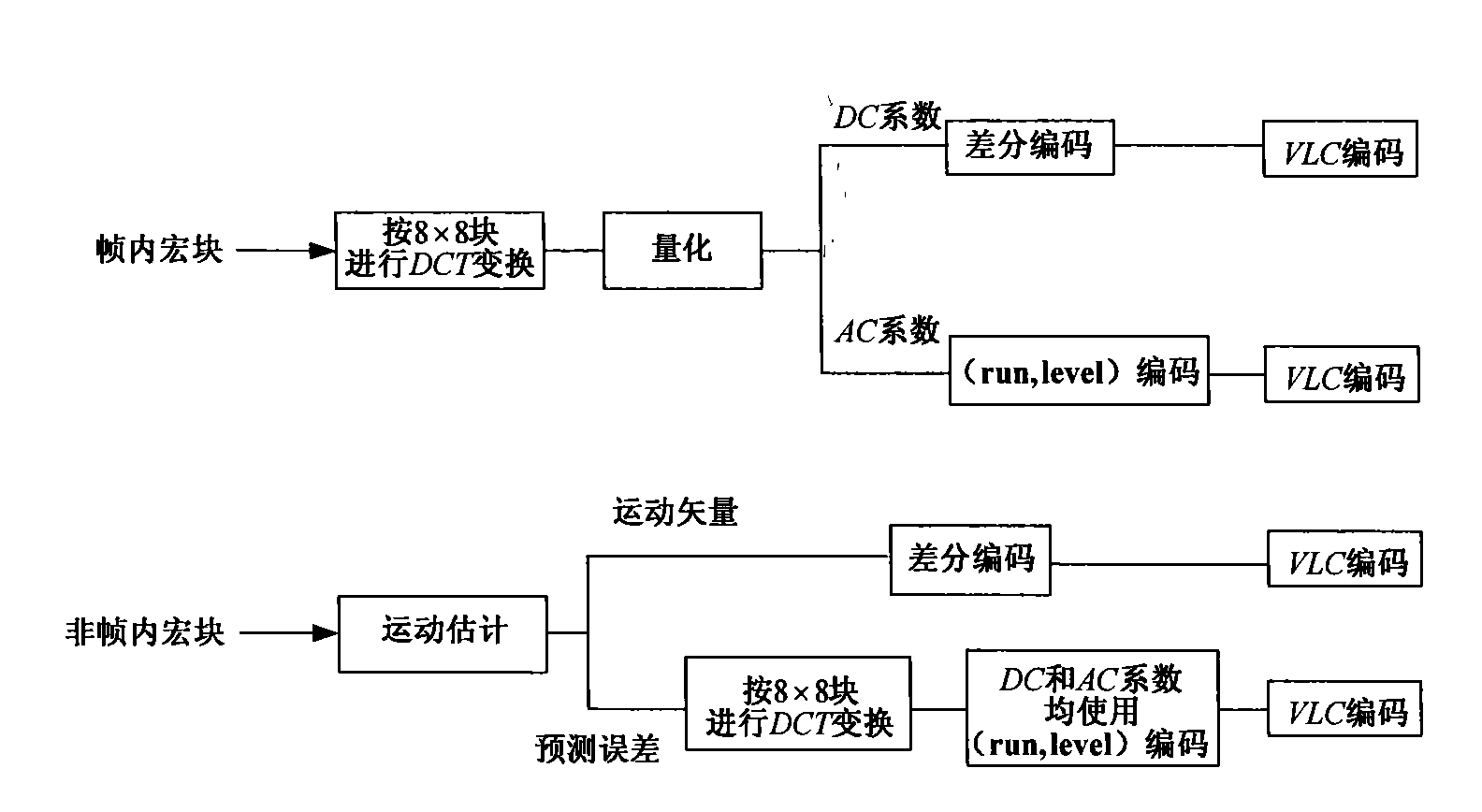
Information steganography method by taking compressed video as carrier
InactiveCN101610405AMeet real-time requirementsPulse modulation television signal transmissionDigital video signal modificationInformation embeddingValue tree
The invention belongs to an information steganography method by taking compressed video as a carrier in the field of communication and information security. The method is characterized by using VLC encoding list in ISO / IEC 13818-2 standard in the realization process to preconstruct a group of increase / decrease pair value tree AST, selecting a certain leaf node of AST in information steganography to automatically guide the operation of an embedding method, thus the size of a compressed video file does not change remarkably before and after information embedding, and the transparency of a video steganography method is ensured. The information embedding and extraction operations of the method are performed completely in VLC domain, thereby avoiding decoding and recoding processes aiming at compressed video stream and meeting the real-time requirement of the video steganography method.
Owner:刘镔
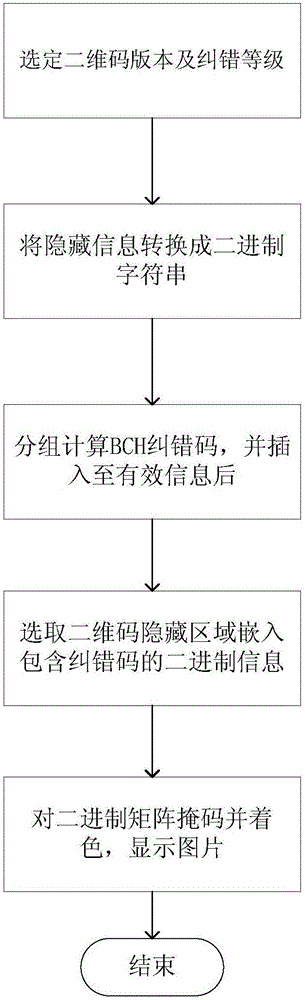
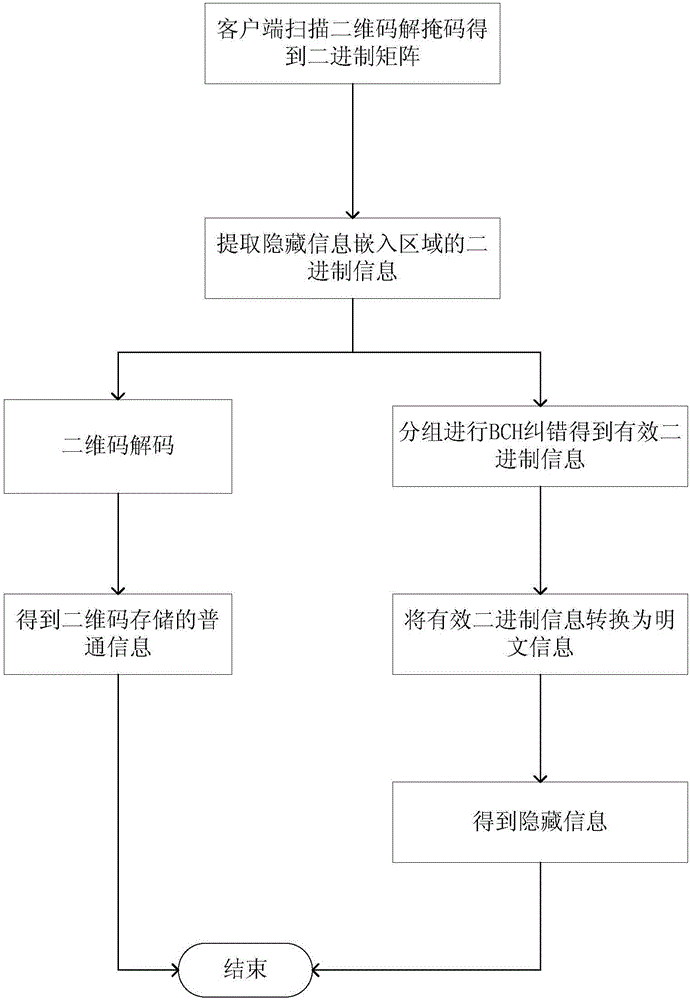
Two-dimensional code-based information hiding method
InactiveCN106815544ARecord carriers used with machinesSensing by electromagnetic radiationInformation embeddingOriginal data
The present invention relates to a two-dimensional code-based information hiding method. The method is characterized by embedding the information needing to be hidden in the coding in a manner based on bits and providing the BCH error correction based on the error correction performance of the QR codes to the coded original data, then adopting an extraction method corresponding to the hiding information embedding to extract the hidden information, thereby achieving the purpose of transferring the hidden information. The present invention aims to provide the method having the following advantages that the information hiding and the two dimensional codes are combined, the two dimensional codes are used as the carriers of the information hiding, and the characteristics of a coding mechanism are utilized to write the hidden information directly; by using different decoders to read, the general decoders only can read the general information in the two dimensional codes but can not read the unexpected hidden information in the two dimensional codes, and only by utilizing the decoders designed by a special algorithm provided by the present invention, the hidden information in the two dimensional codes can be decoded.
Owner:WUHAN UNIV
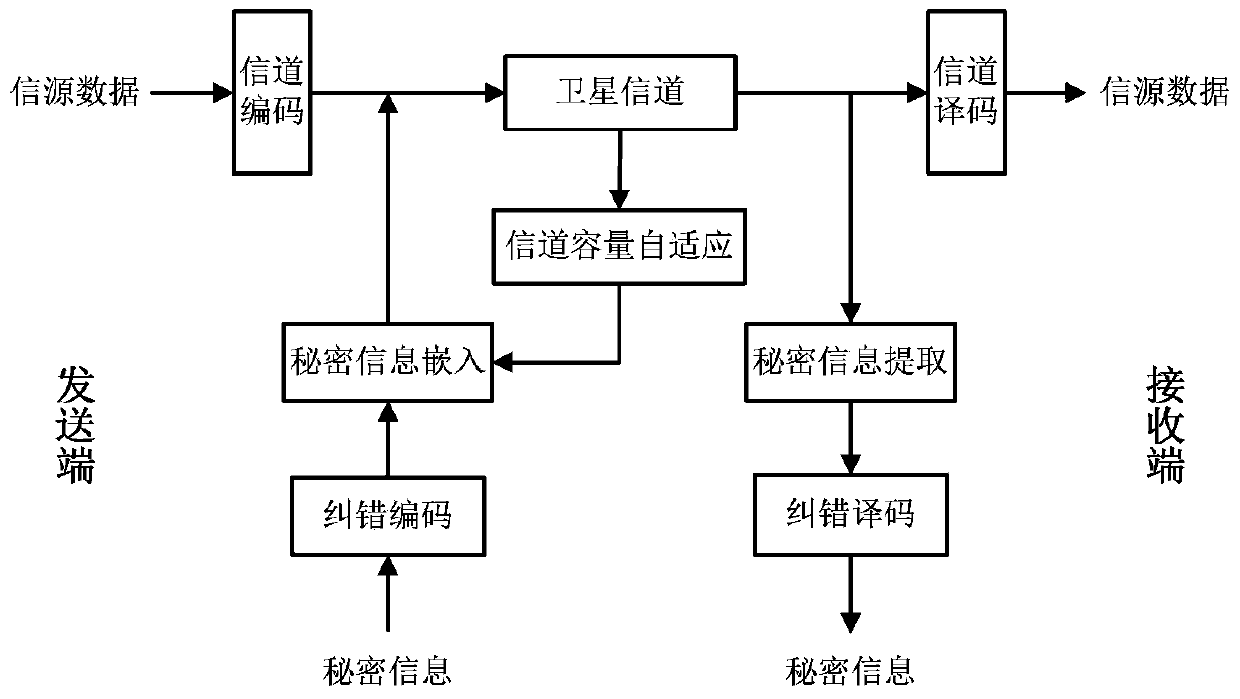
Self-adaption covert communication method based on satellite channel coding
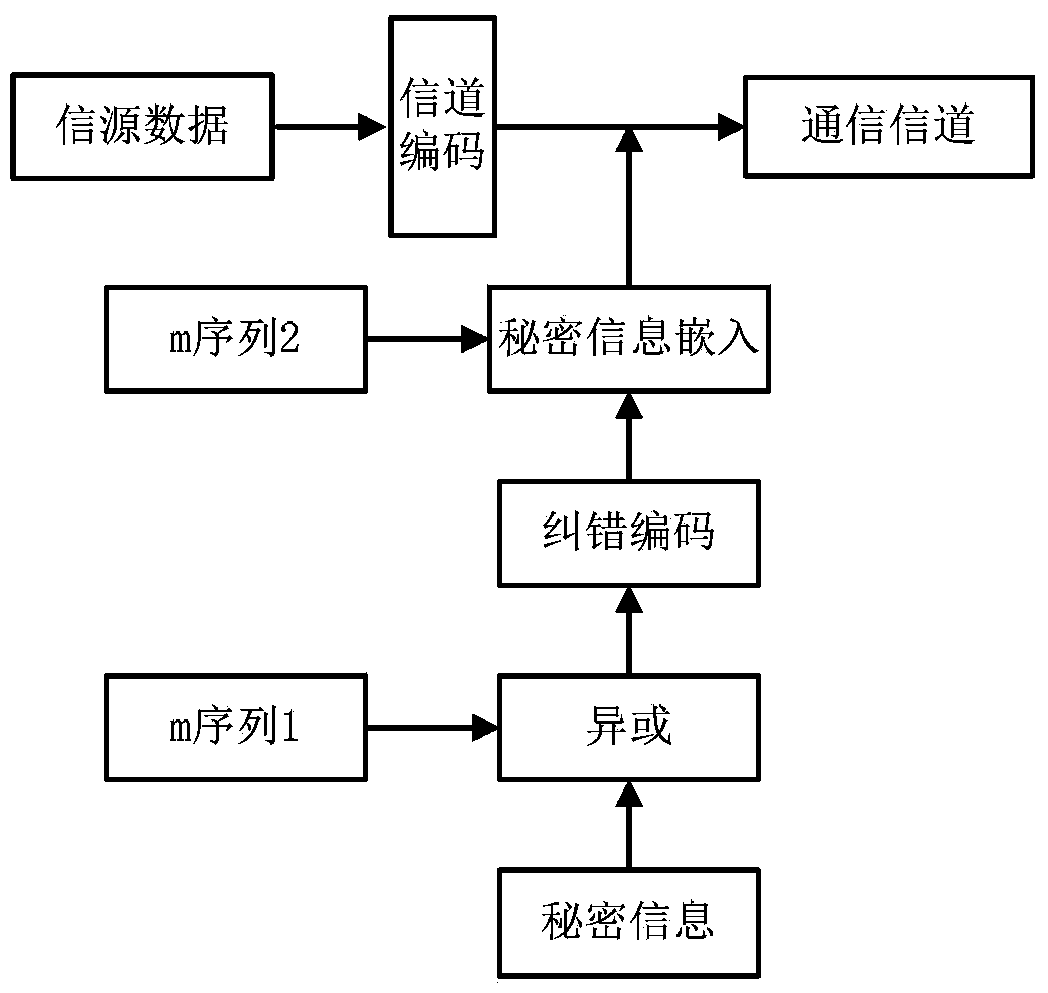
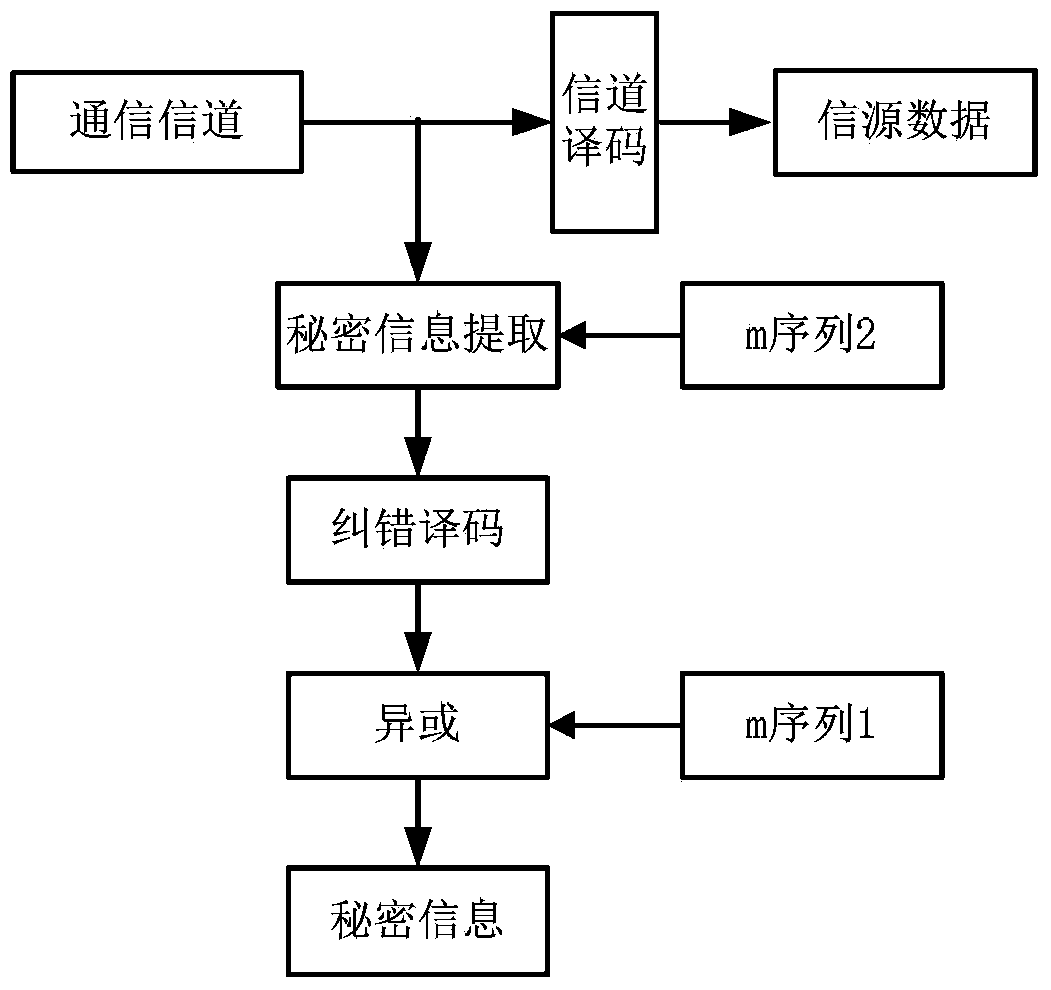
InactiveCN103476026AAvoid bit errorsImprove securityError preventionSecurity arrangementBlock codeCovert communication
The invention provides a self-adaption covert communication method based on satellite channel coding, and directing at different channel encoding algorithms of block codes, RS codes, convolutional codes, serial concatenated code and the like, provides a capacity self-adaption method for secrete information embedding; further provides a channel encoding information embedding and extracting algorithm based on m sequences. By the utilization of the self-adaption covert communication method, the capacity of covert channels can be determined in a self-adaption mode according to different used channel encoding algorithms and different used communication environments; normal use of carriers containing secretes is not influenced, and main steganalysis attacks such as chi-square analysis attacks and RS analysis attacks can be resisted; under the condition that the satellite channel bit error rate is 10-3-10-5, quasi error-free transmission of secrete information can be realized.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Method and device for embedding and detecting watermark in document by using computer system
InactiveCN101957810AControl illegal transmissionImprove robustnessSpecial data processing applicationsDistribution controlSoftware engineering
The invention relates to method and device for embedding and detecting a watermark in a document by using a computer system, in particular to method and device for loading a document watermark to an electronic text document by using a computer program so as to protect the electronic text document, belonging to the technical field of document protection. The computer program at least comprises the generation of the electronic text watermark, the loading and embedding of the watermark and the detection of the watermark. The method comprises the following steps of: firstly, generating watermark information from copyright information prepared to be added into the electronic document by using a watermark generating module; then, reasonably optimizing the analysis of a watermark carrier medium, the preprocessing of embedded information, the selection of an information embedding point, the design of an embedding mode and the control of embedding modulation by using a watermark loading and embedding module; and equivalently transforming set natural language semantics to embed the watermark through reasonably selecting a secret key. If a copyright dispute happens, a watermark detection module designed in the invention can be used for detecting and extracting the document watermark of the electronic document by using the preset secret key, and the result shows that the document watermark embedded in advance can provide an identification basis for solving the electronic document copyright dispute. Thus, the invention can be widely applied to document protection encryption, tracking, illegal distribution control and technical protection of copyrights.
Owner:XIAN TENGWEI SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com