Patents
Literature
1171 results about "Random sequence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The concept of a random sequence is essential in probability theory and statistics. The concept generally relies on the notion of a sequence of random variables and many statistical discussions begin with the words "let X₁,...,Xₙ be independent random variables...". Yet as D. H. Lehmer stated in 1951: "A random sequence is a vague notion... in which each term is unpredictable to the uninitiated and whose digits pass a certain number of tests traditional with statisticians".
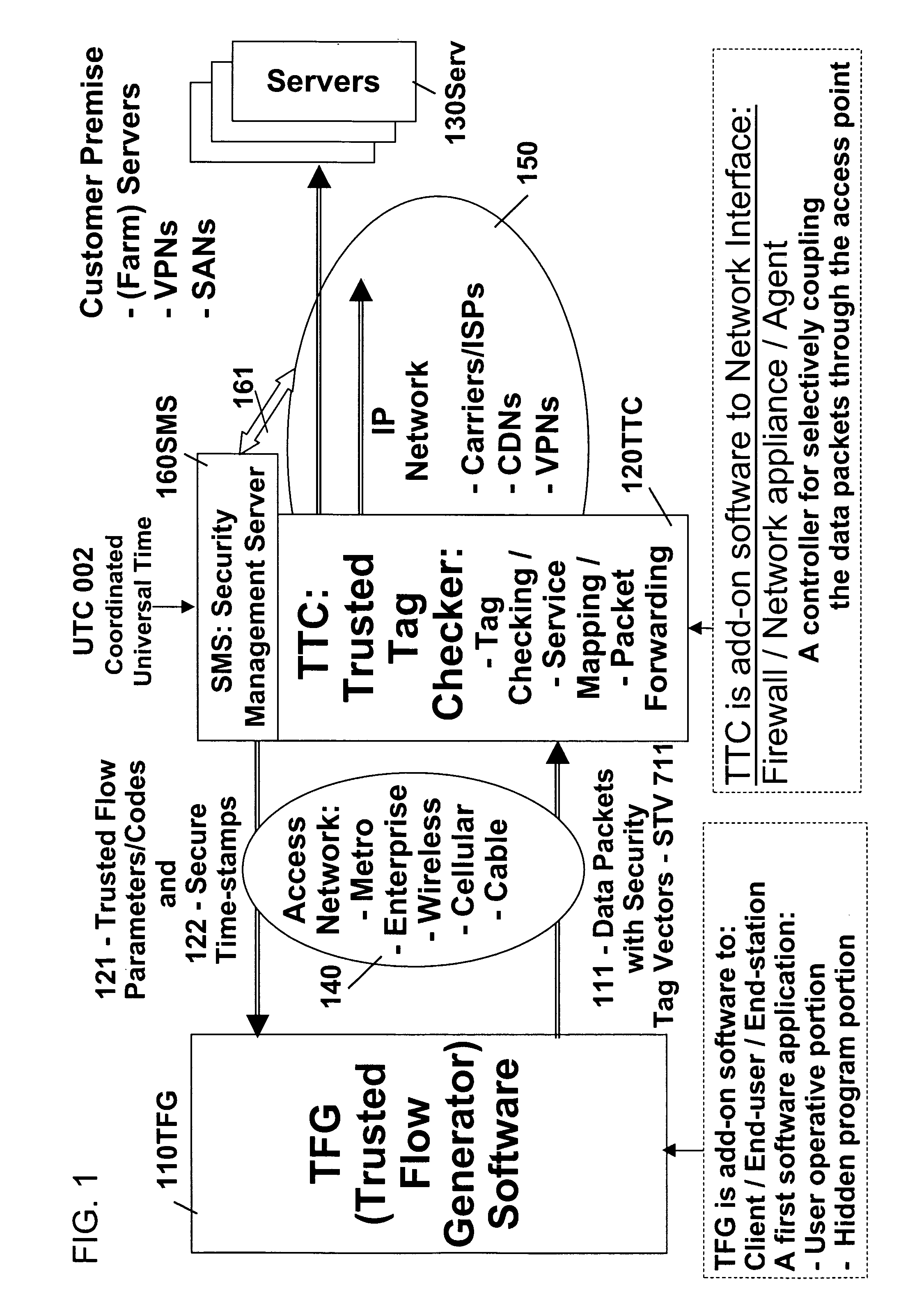
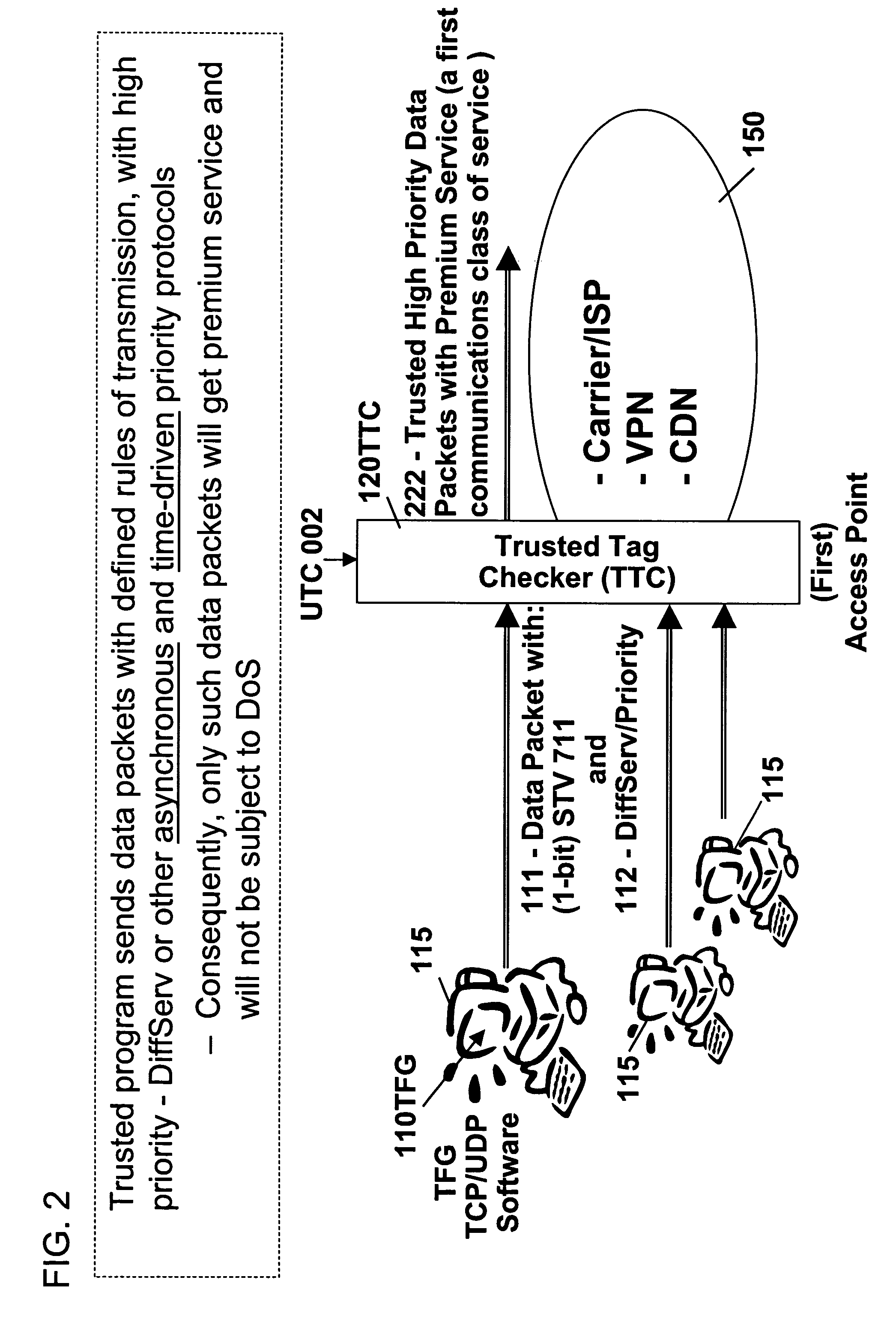
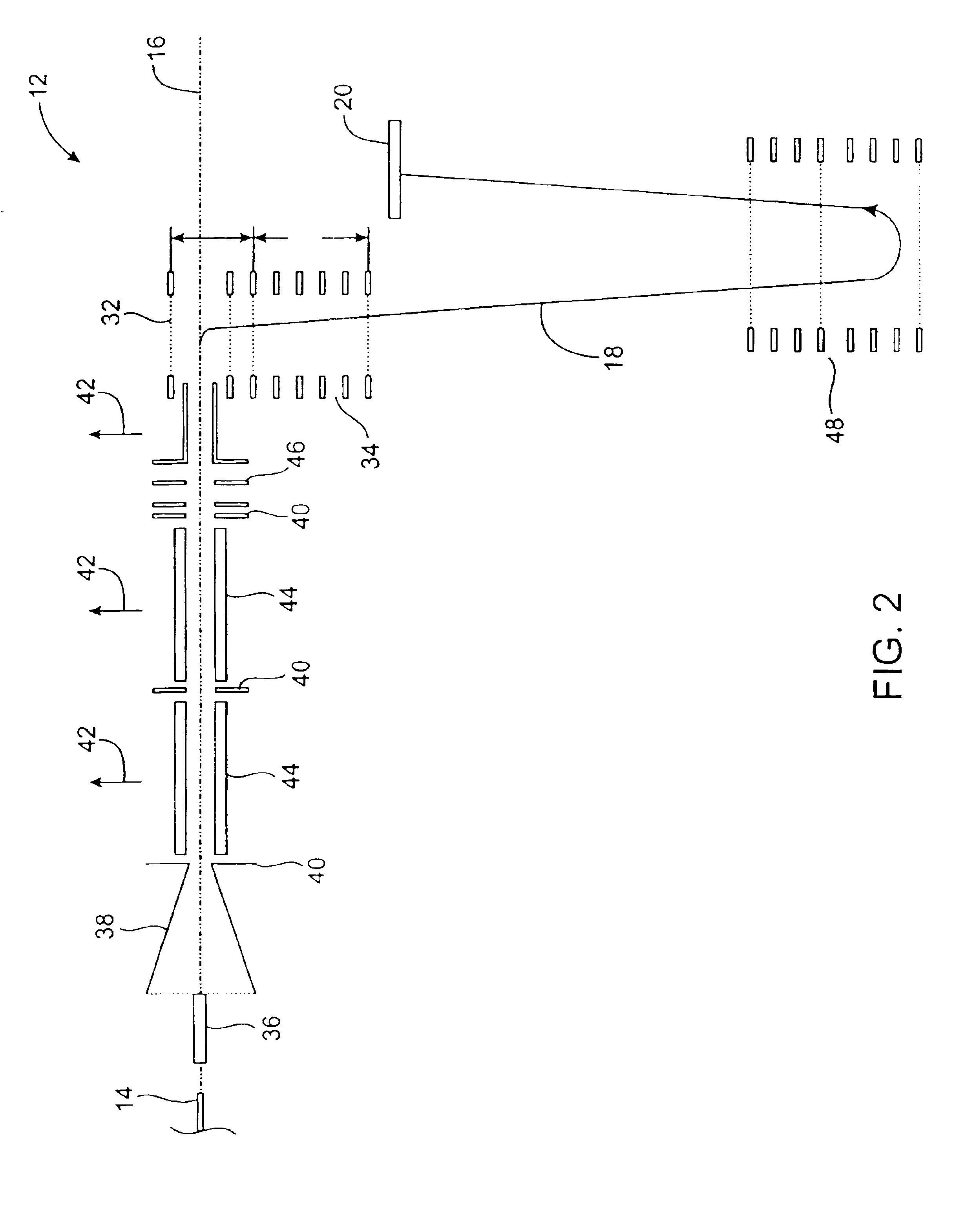
Method for embedding and reading watermark-information in digital form, and apparatus thereof
InactiveUS6185312B1Information can be droppedOther printing matterCharacter and pattern recognitionInformation embeddingOrthogonal transformation
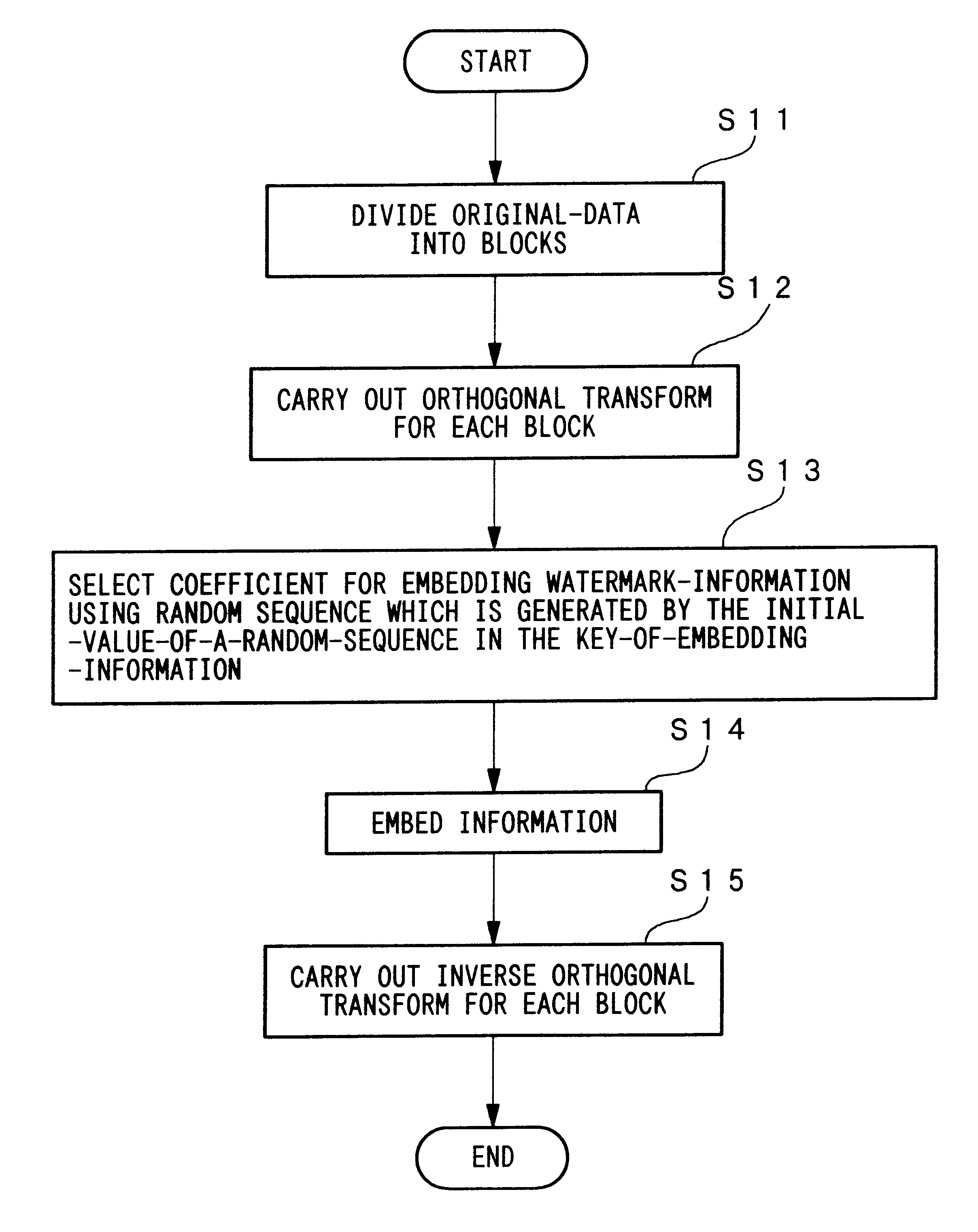
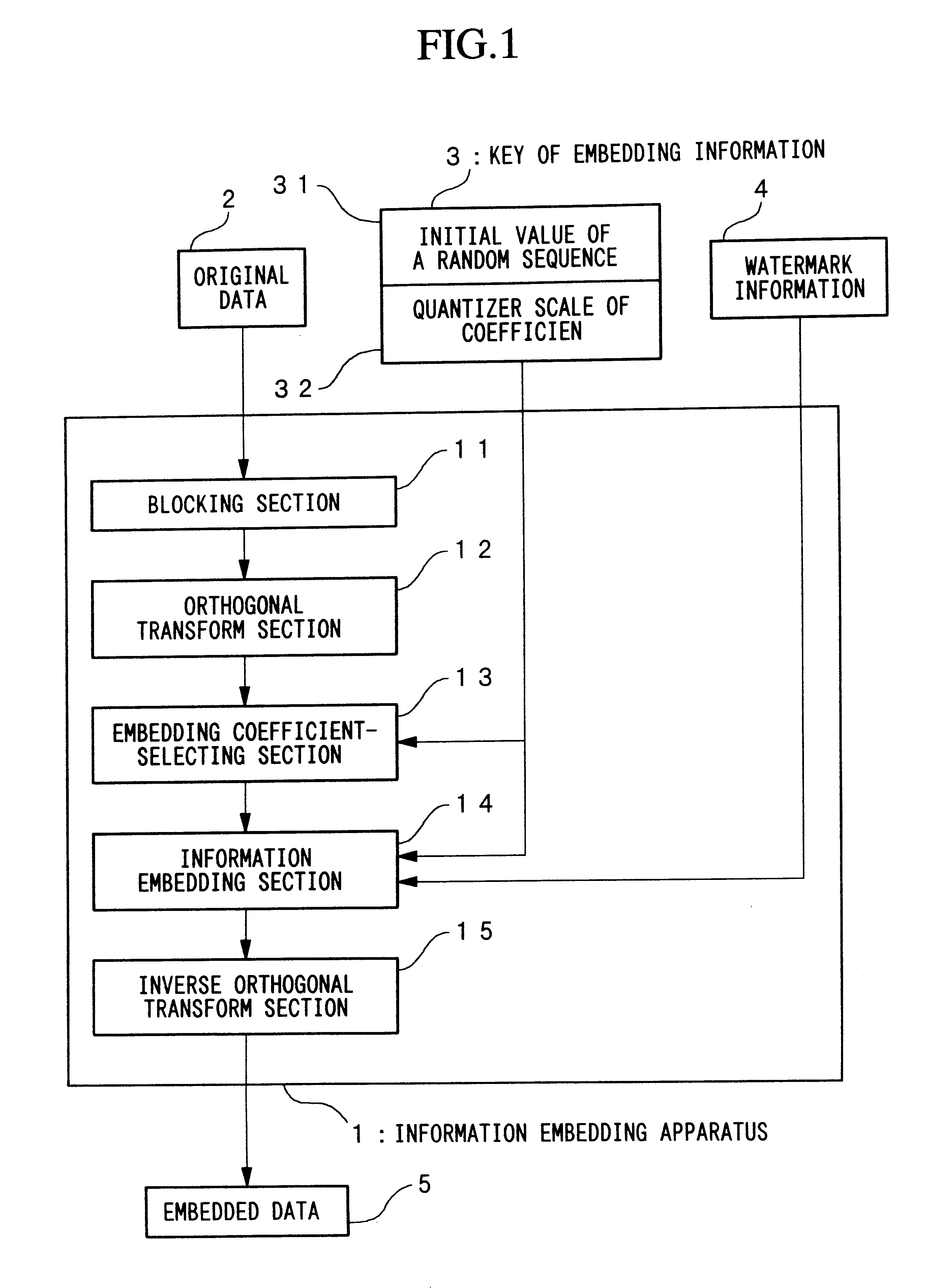
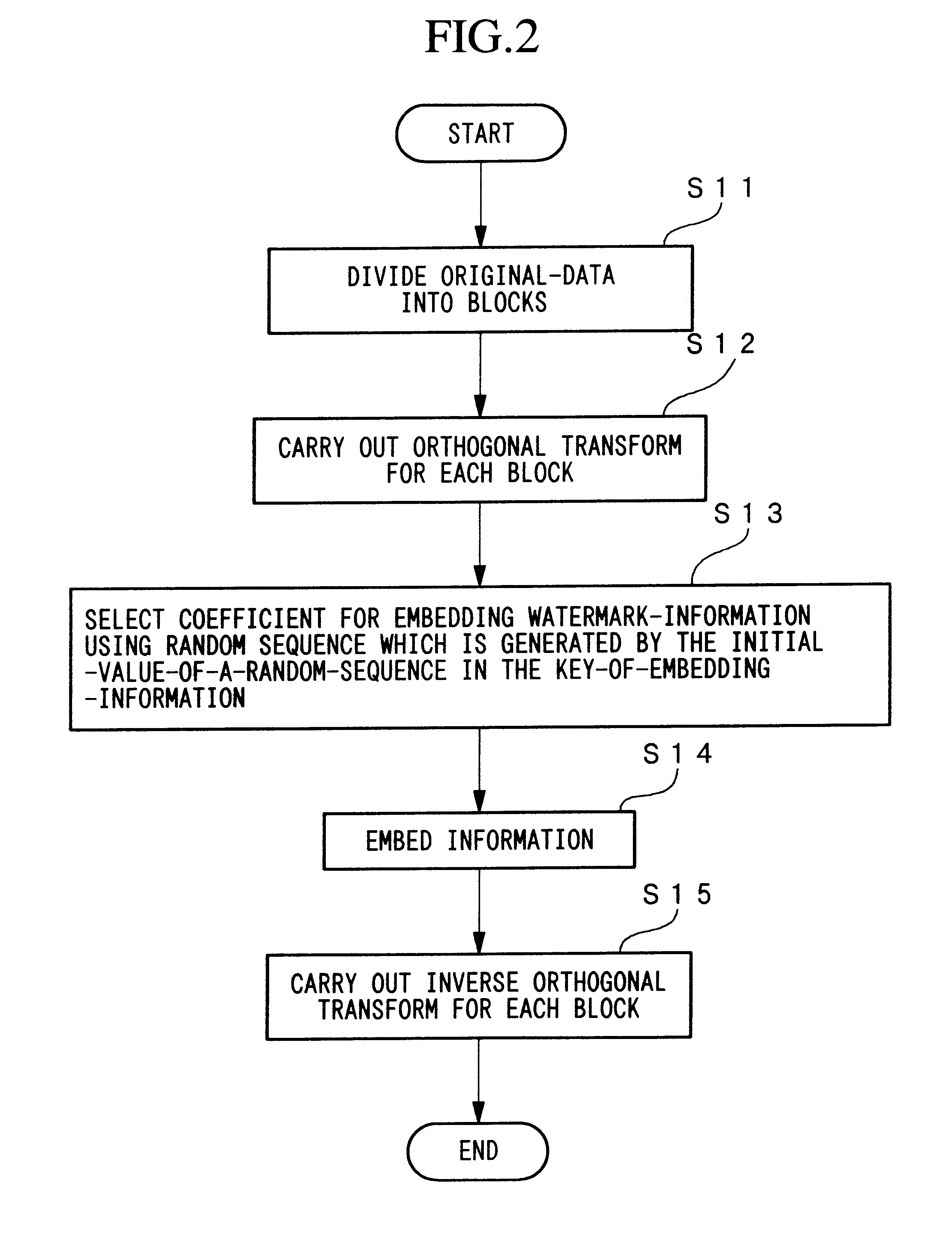
An apparatus for embedding information comprises: a blocking step for dividing data to be processed into blocks; an orthogonal transform step for obtaining coefficients by carrying out orthogonal transformation for each block; an embedding coefficient selecting step for determining coefficients in which the watermark-information will be embedded by using a random sequence which is generated by initial value; an information embedding step for sequentially embedding the watermark-information, which has arbitrary length of bits, by quantizing value of said coefficients using a predetermined value for quantization; and an inverse orthogonal transform step for carrying out inverse orthogonal transformation for modified coefficients to form block in which the watermark-information is embedded, as well as combining the divided blocks and reconstructing the original form.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Remotely authenticated operation method
InactiveUS7509687B2Improvement effortsEfficient use ofDigital data processing detailsUser identity/authority verificationTrusted ComputingMedia server
The objective of this invention is to provide continuous remote authenticated operations for ensuring proper content processing and management in remote untrusted computing environment. The method is based on using a program that was hidden within the content protection program at the remote untrusted computing environment, e.g., an end station. The hidden program can be updated dynamically and it includes an inseparable and interlocked functionality for generating a pseudo random sequence of security signals. Only the media server that sends the content knows how the pseudo-random sequence of security signals were generated; therefore, the media server is able to check the validity of the security signals, and thereby, verify the authenticity of the programs used to process content at the remote untrusted computing environment. If the verification operation fails, the media server will stop the transmission of content to the remote untrusted computing environment.
Owner:ATTESTWAVE LLC
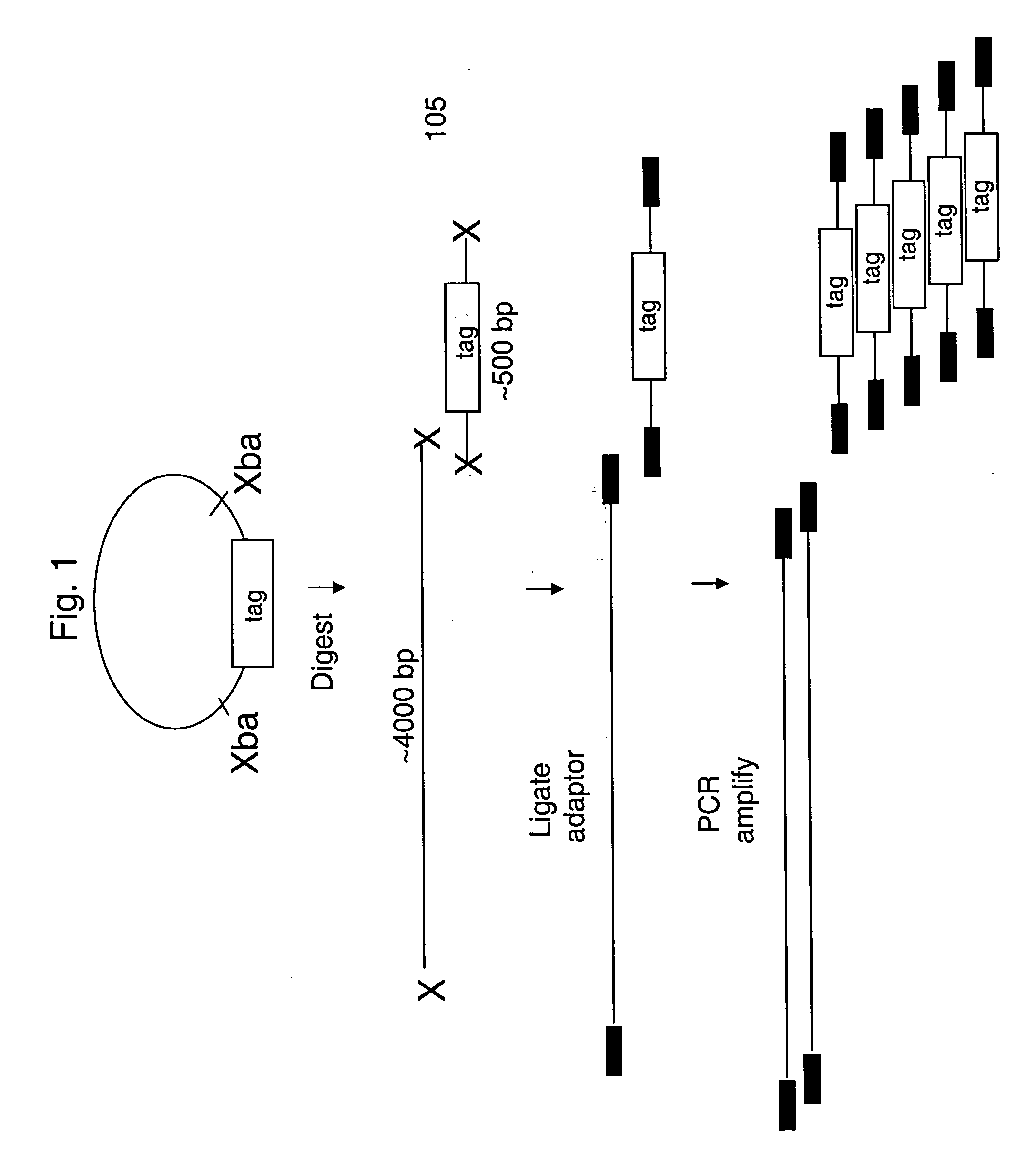
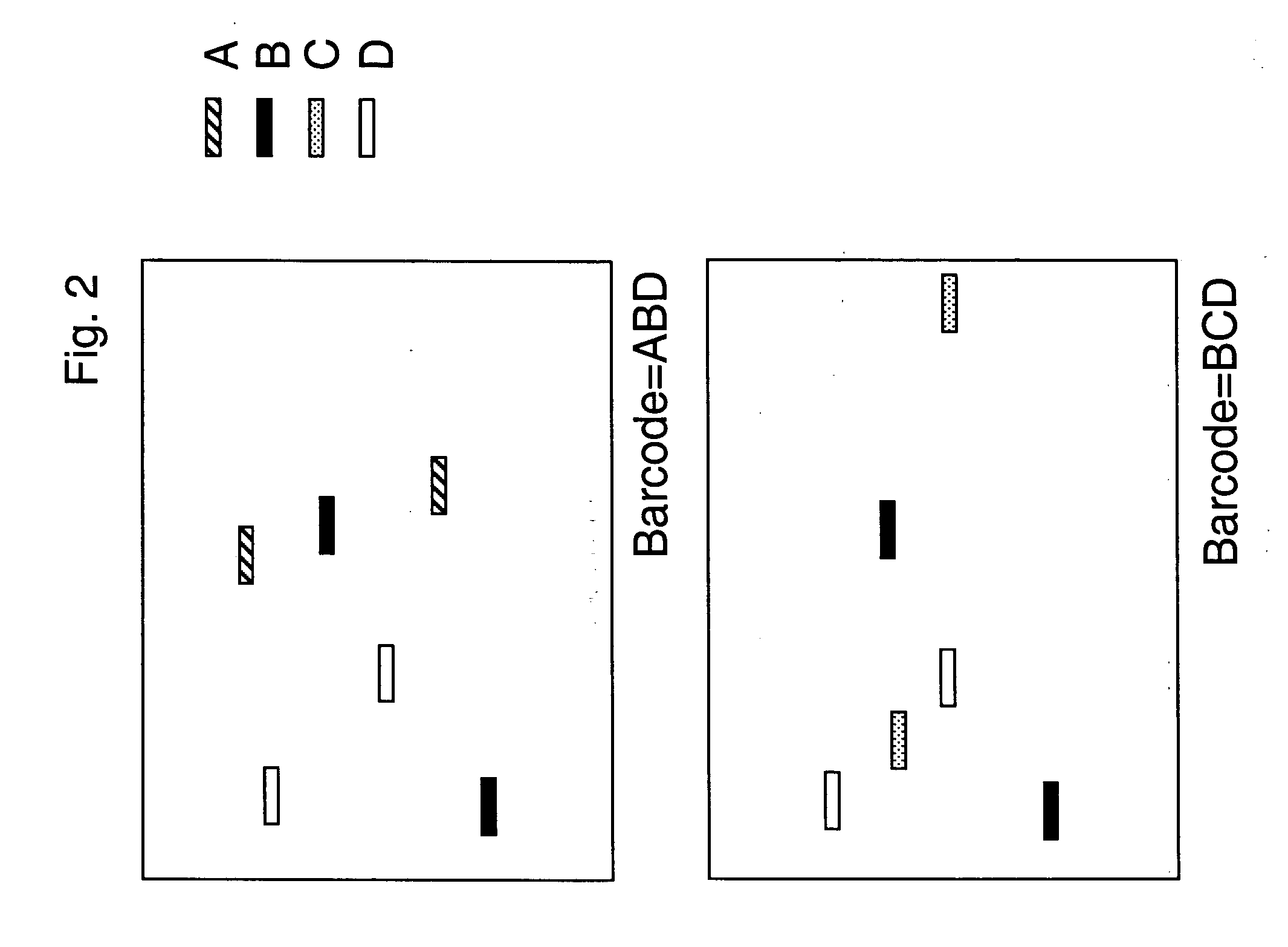
Methods for identifying biological samples
InactiveUS20060073506A1Efficient amplificationSugar derivativesMicrobiological testing/measurementNucleic acid sequencingCross hybridization
The present invention provides methods for marking nucleic acid samples with detectable markers by adding different combinations of marker molecules to each sample. Each sample may be marked with a different combination of two or more marker molecules each carrying a different tag nucleic acid sequences. The tag nucleic acid sequences may be random sequences that are not naturally occurring in the nucleic acid sample and do not cross hybridize to sequences naturally occurring in the nucleic acid sample. Methods of detecting the combination of tag sequences present in a sample, in parallel with methods of genetic analysis of the sample are disclosed. Kits containing marker molecules suitable for generating barcoded samples by mixing different combinations of marker molecules into each sample are also disclosed.
Owner:AFFYMETRIX INC
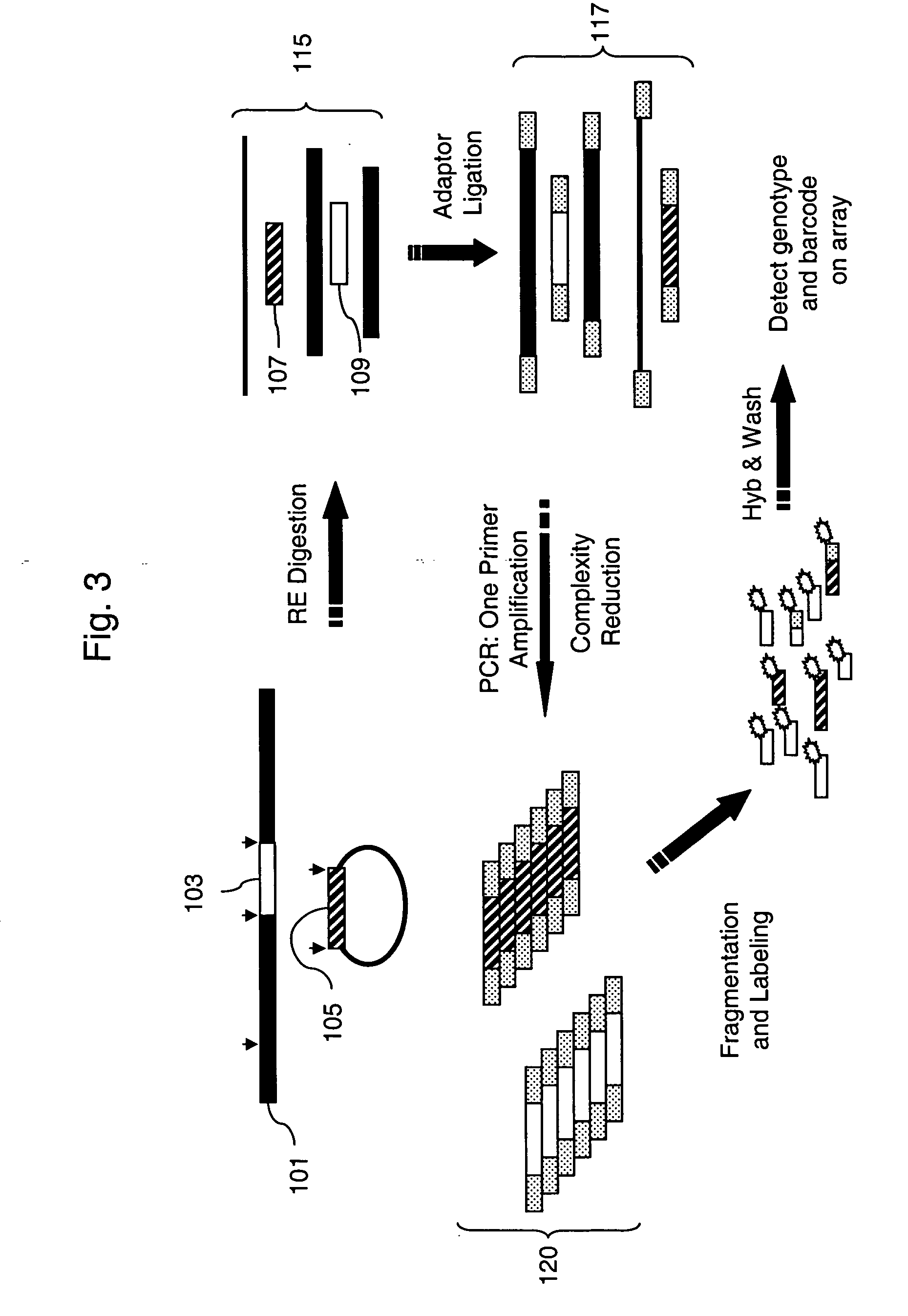
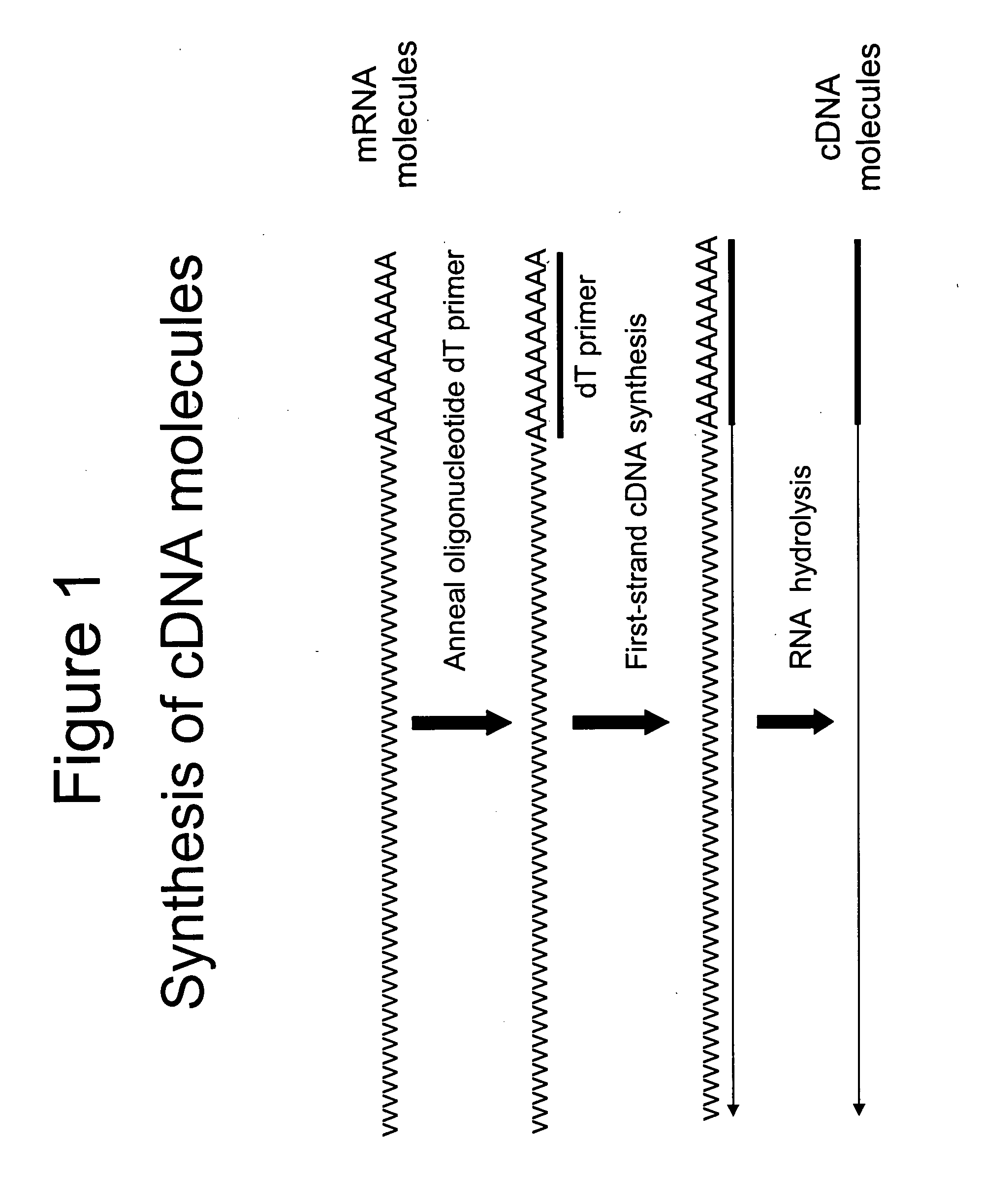
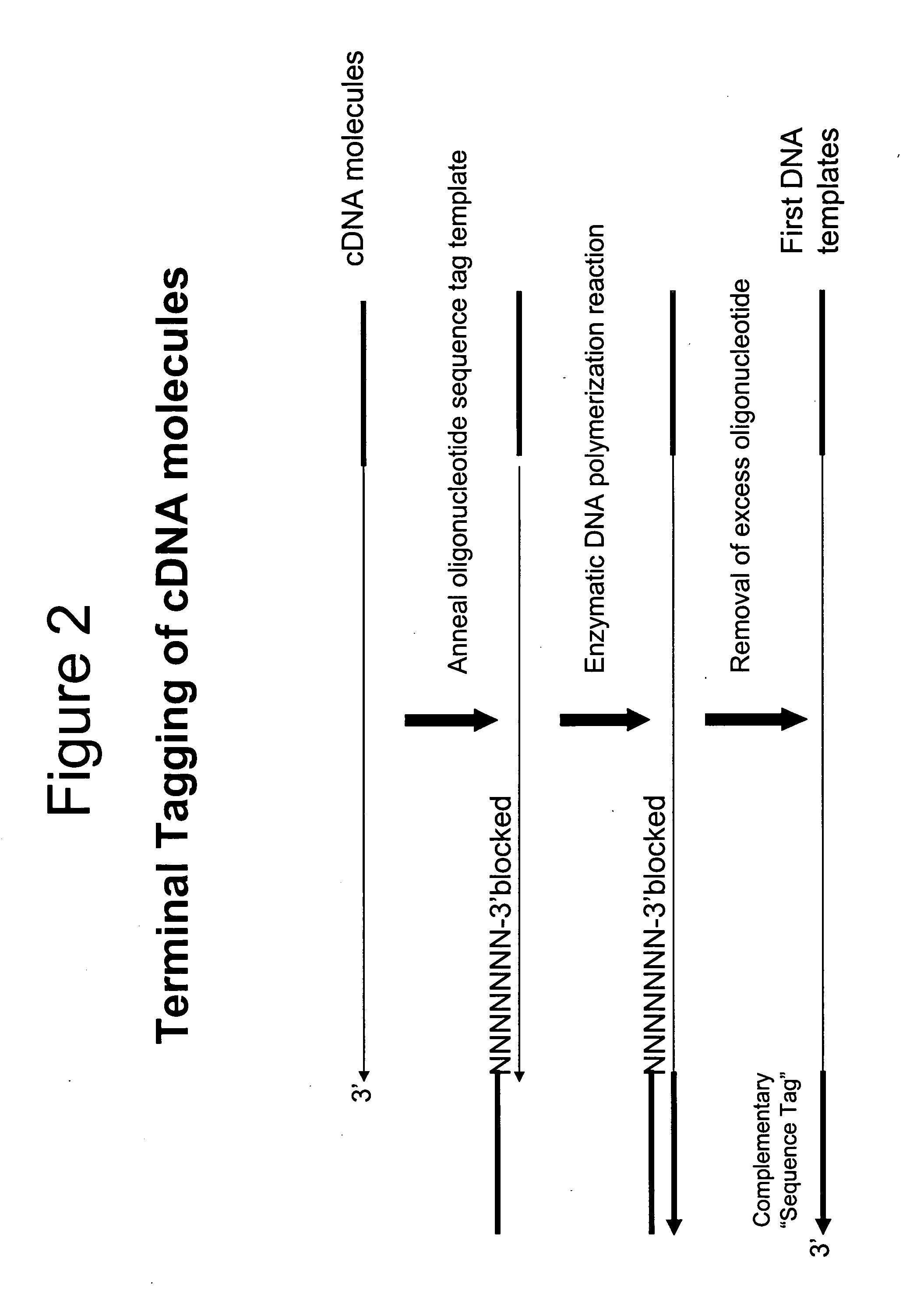
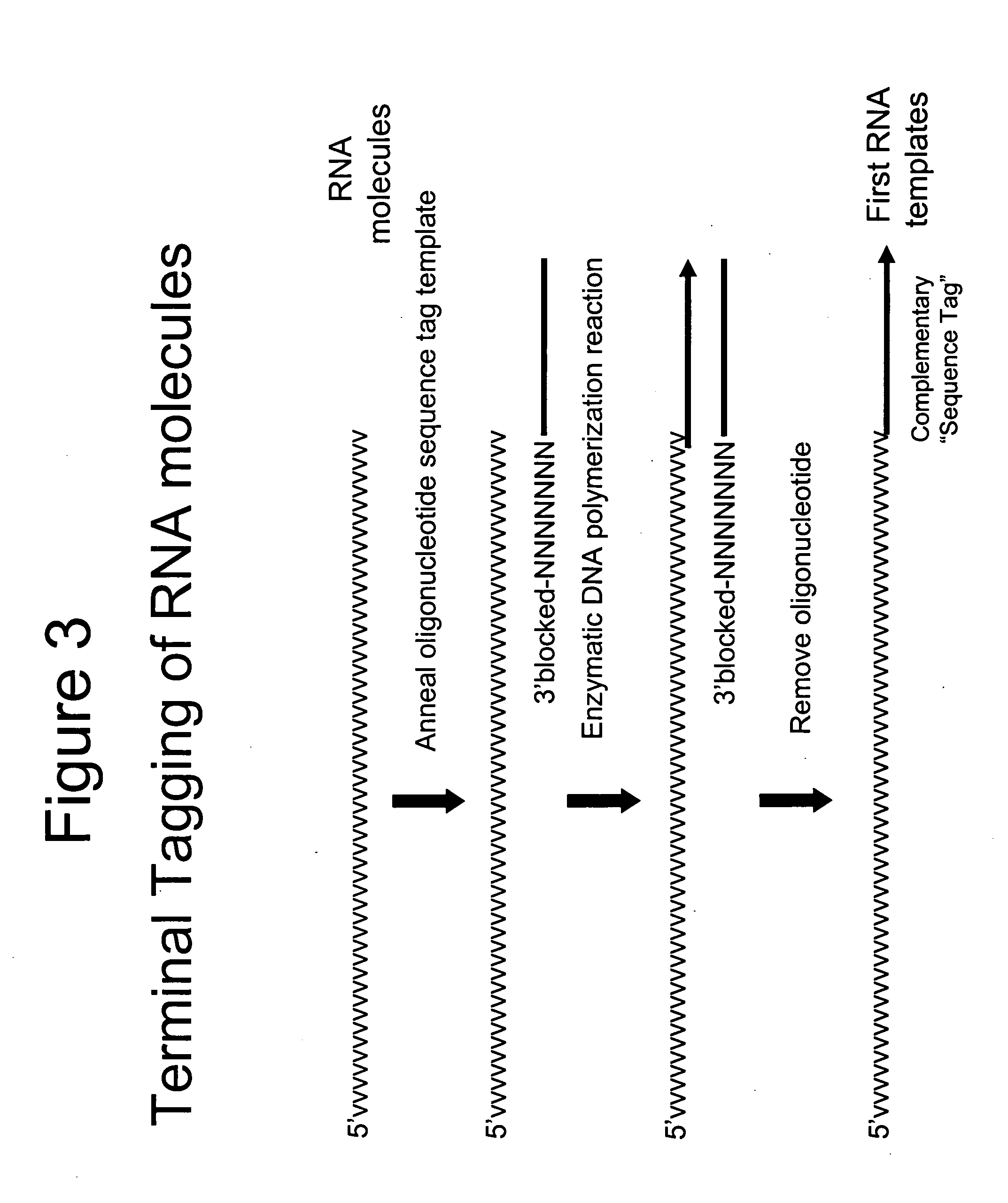
Selective terminal tagging of nucleic acids
InactiveUS20050153333A1Microbiological testing/measurementFermentationDna amplificationDouble stranded
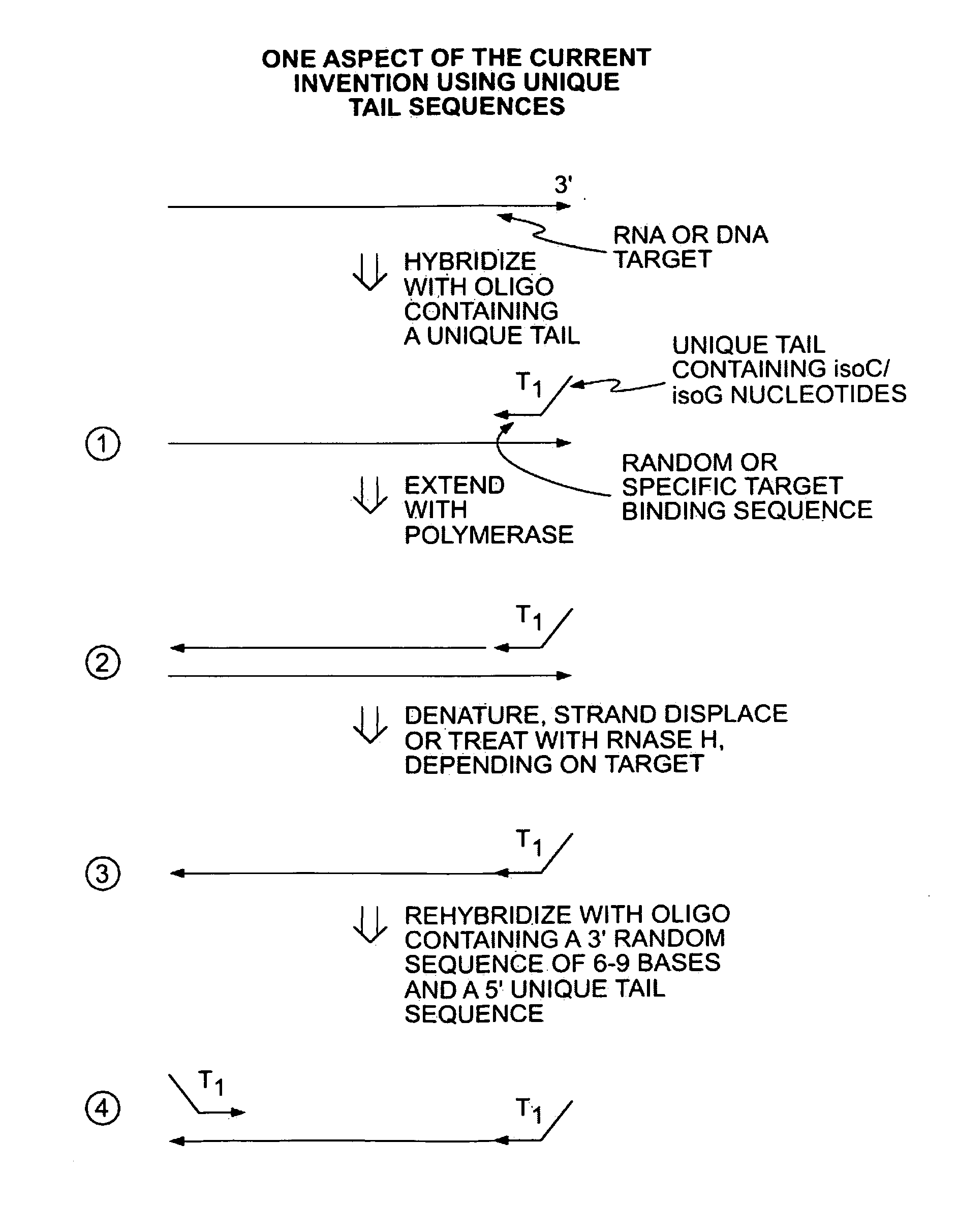
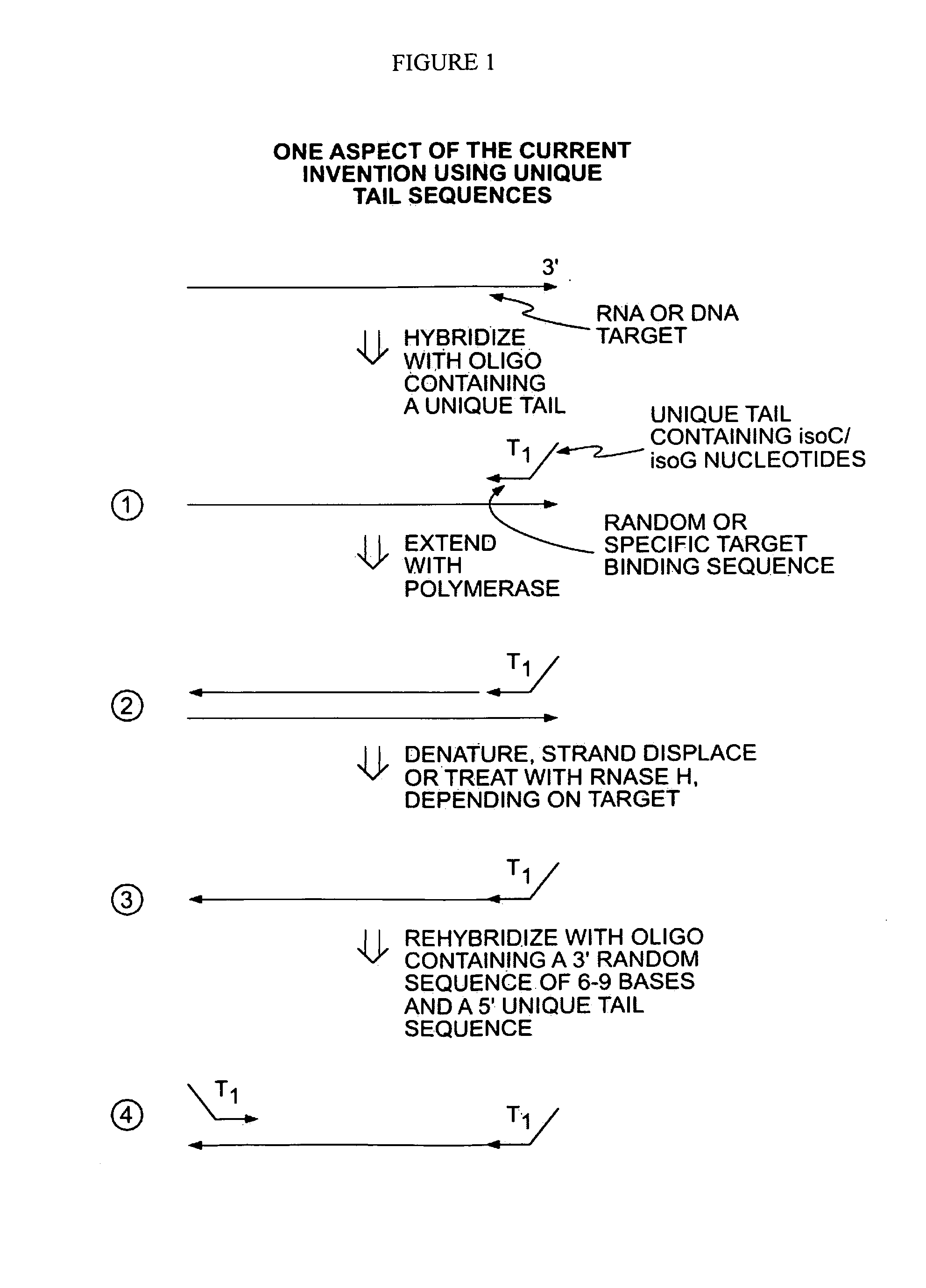
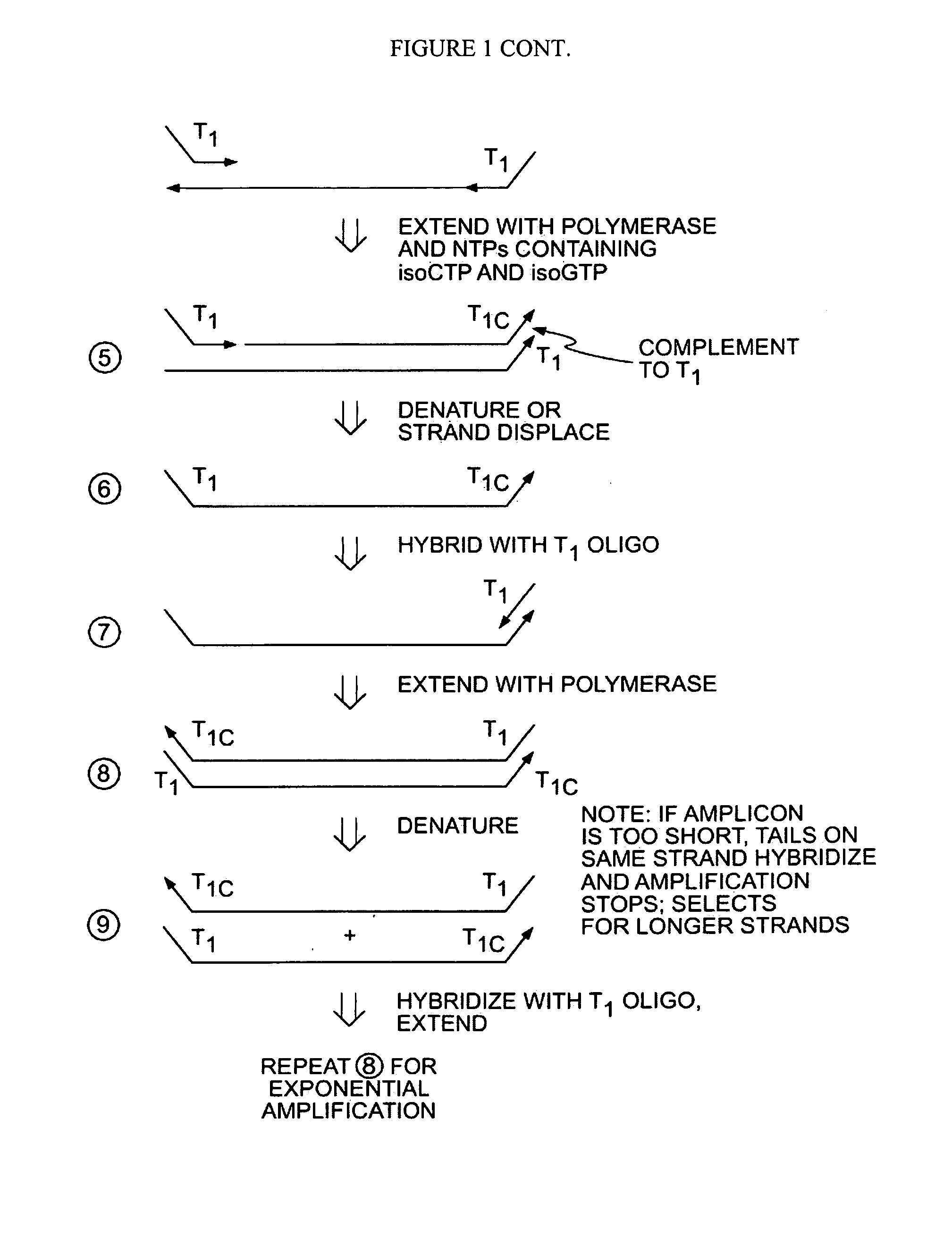
A method is provided for adding a terminal sequence tag to nucleic acid molecules for use in RNA or DNA amplification. The method involves contacting with a mixture of oligonucleotides, each having a sequence tag template, a random sequence and a blocked 3′ terminus, under conditions such that, the random sequence anneals with the nucleic acid molecules and the nucleic acid molecules are extended using the sequence tag template as template. For synthesis of RNA from DNA molecules having terminal sequence tags, the method includes forming DNA templates having a double stranded promoter sequence and synthesizing RNA from the DNA templates. For amplification of sequences from DNA molecules having terminal sequence tags, the method includes forming DNA templates by extension of one primer having a sequence that is complementary to the terminal sequence tag and another primer having a sequence that is derived form one of the DNA molecules.
Owner:EPICENT BIOTECH
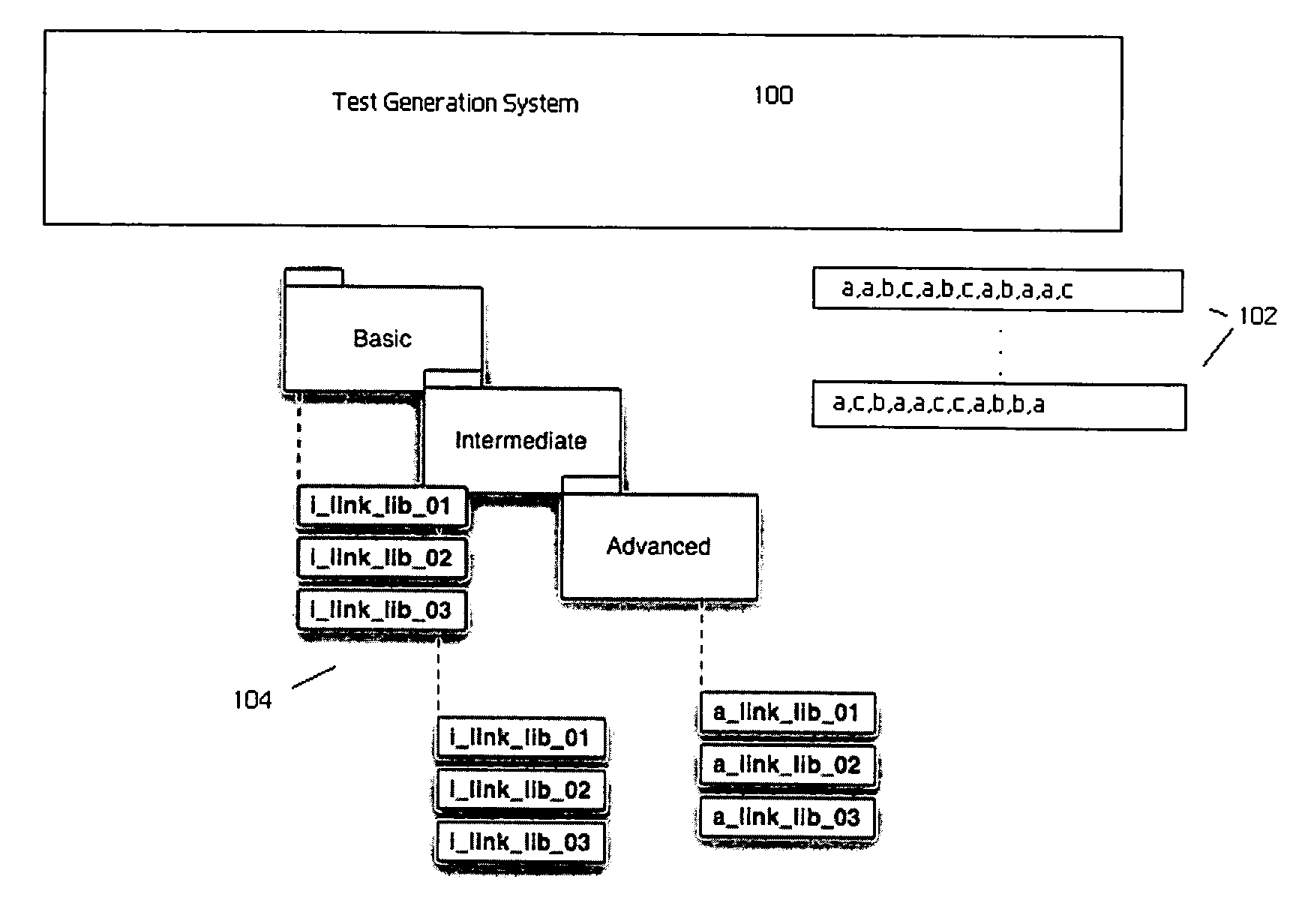
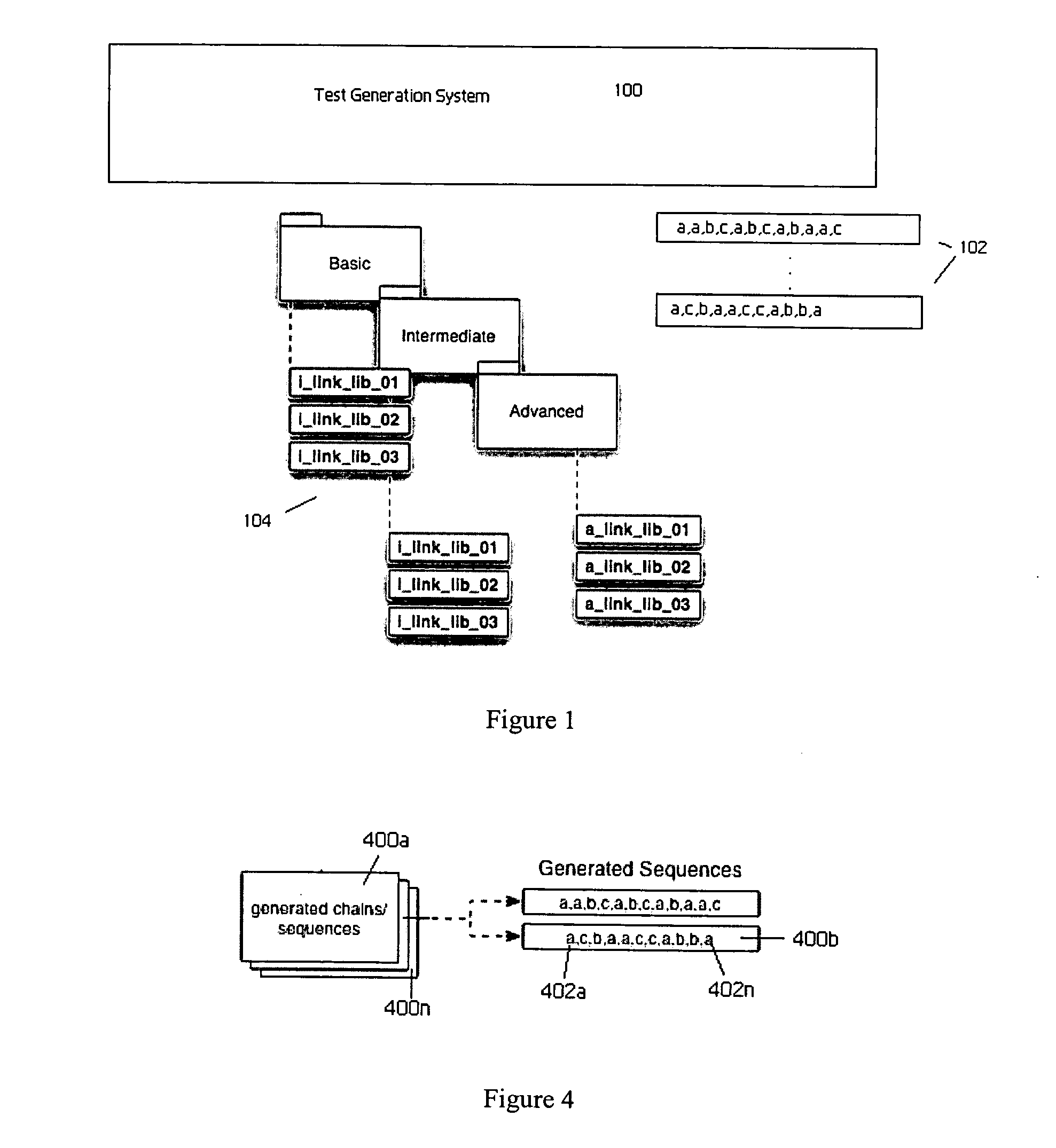
Method of and system for dynamic automated test case generation and execution
InactiveUS20070162894A1Easily reproducibleImprove abilitiesError detection/correctionSpecific program execution arrangementsExploratory testingSystem under test
An automated system that randomly generates test cases for use in hardware or software quality assurance testing, wherein a given test case comprises a sequence (or “chain”) of discrete, atomic steps (or “building blocks”). A particular test case (i.e., a given sequence) has a variable number of building blocks. The system takes a set of test actions (or even test cases) and links them together in a relevant and useful manner to create a much larger library of test cases or “chains.” The chains comprise a large number of random sequence tests that facilitate “chaos-like” or exploratory testing of the overall system under test. Upon execution in the system under test, the test case is considered successful (i.e., a pass) if each building block in the chain executes successfully; if any building block fails, the test case, in its entirety, is considered a failure. The system adapts and dynamically generates new test cases as underlying data changes (e.g., a building block is added, deleted, modified) or new test cases themselves are generated. The system also is tunable to generate test sequences that have a given (e.g., higher) likelihood of finding bugs or generating errors from which the testing entity can then assess the system operation. Generated chains can be replayed easily to provide test reproducibility.
Owner:HITACHI VANTARA LLC
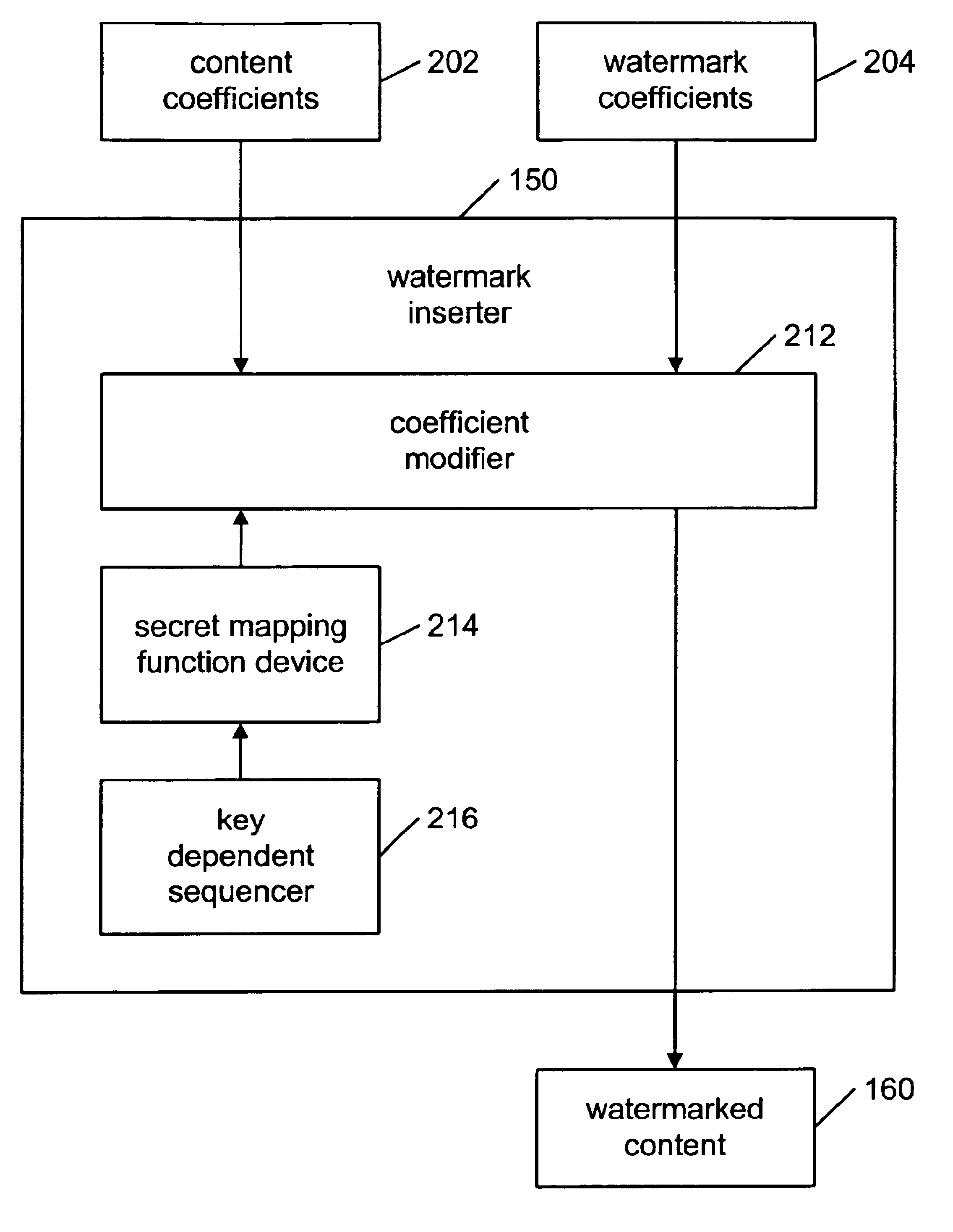
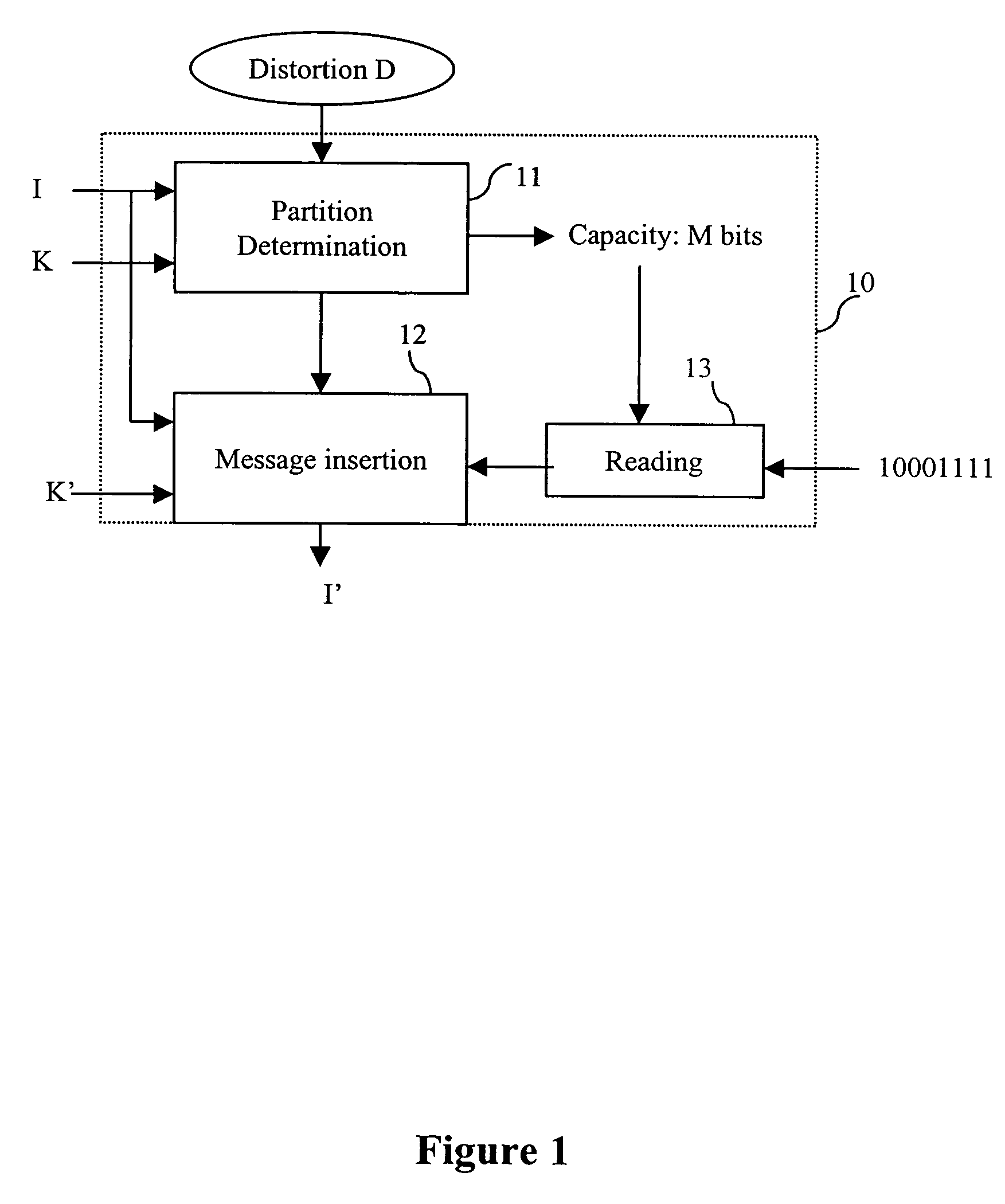
Secure oblivious watermarking using key-dependent mapping functions
InactiveUS6901514B1Protects watermarkReduce distractionsUser identity/authority verificationSecret communicationComputer hardwareDistortion
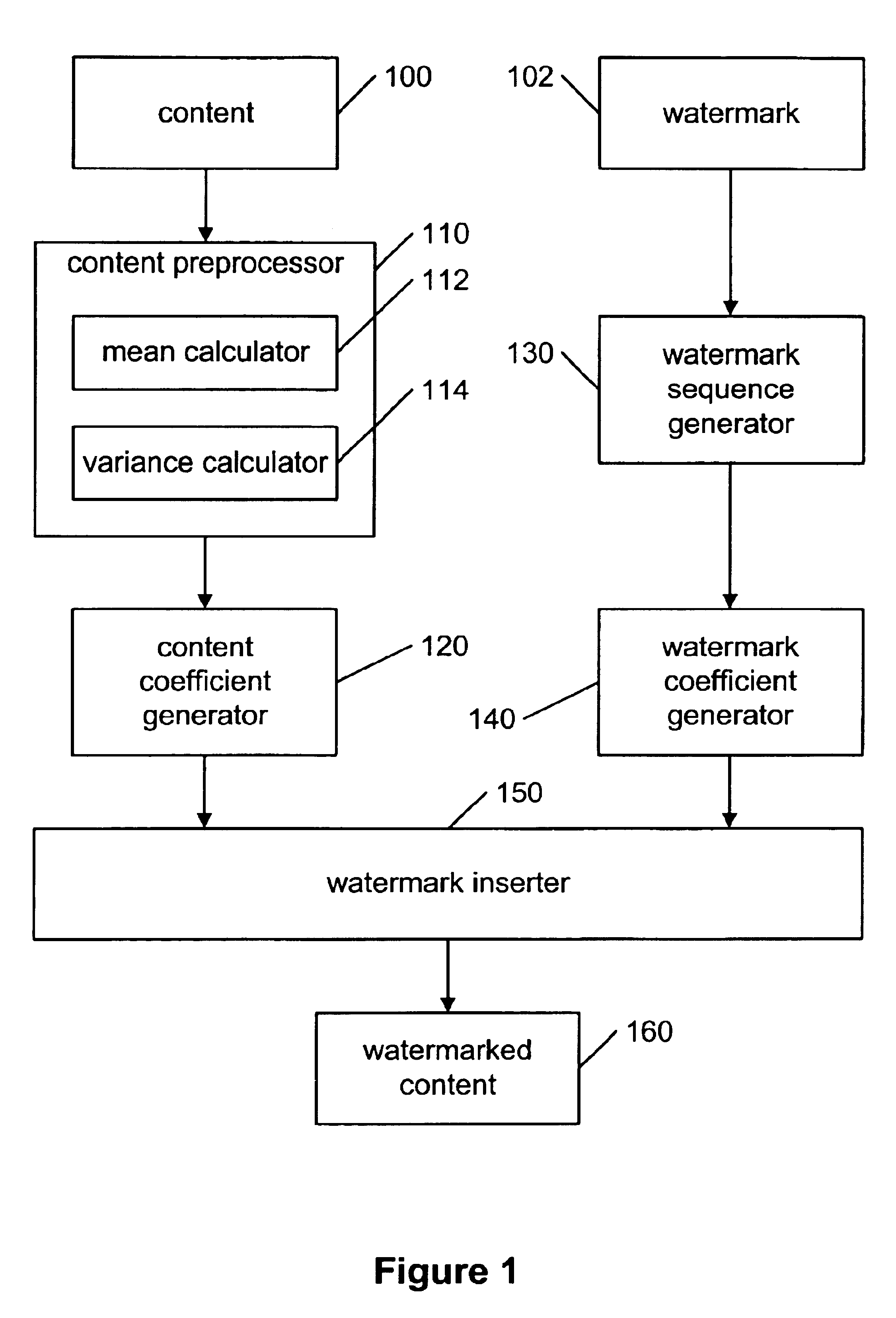
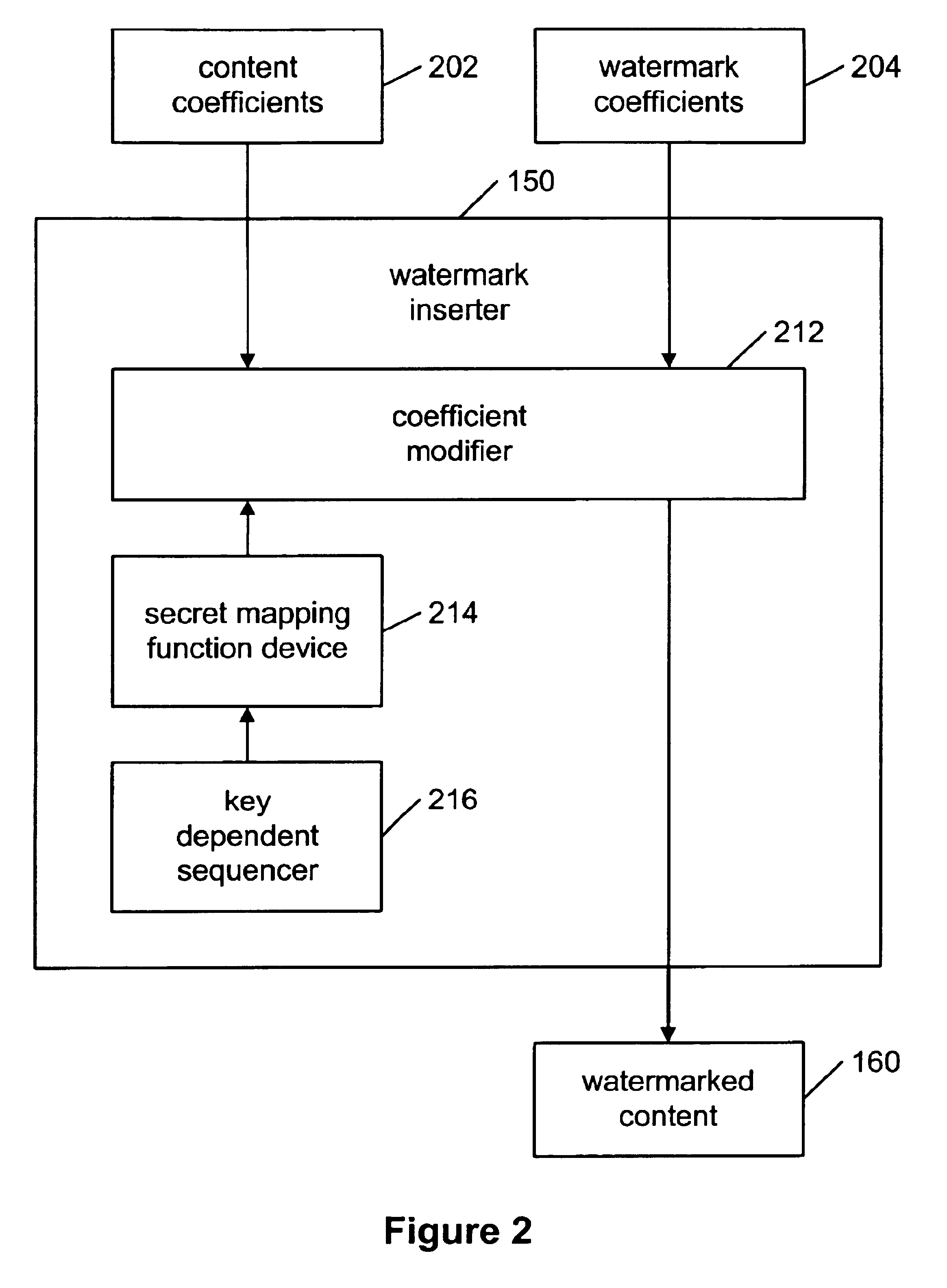
A method for embedding a watermark into content is disclosed. The content contains content samples. The method including the steps of: receiving the content, creating a continuous watermark sequence from the watermark, and for each content sample in a first predetermined order: calculating a sample mean, calculating a sample variance, and normalizing the content. Further steps include generating a set of content coefficients from the content, generating a set of watermark coefficients from the watermark sequence, embedding the watermark in the content by adjusting the amplitude of the watermark coefficients so that the distortion between the content coefficients and the associated watermark coefficients are minimized using a secret mapping function, and outputting the content. The mapping functions may be controlled by a key-dependent random sequence to protect the watermarks.
Owner:GOOGLE LLC
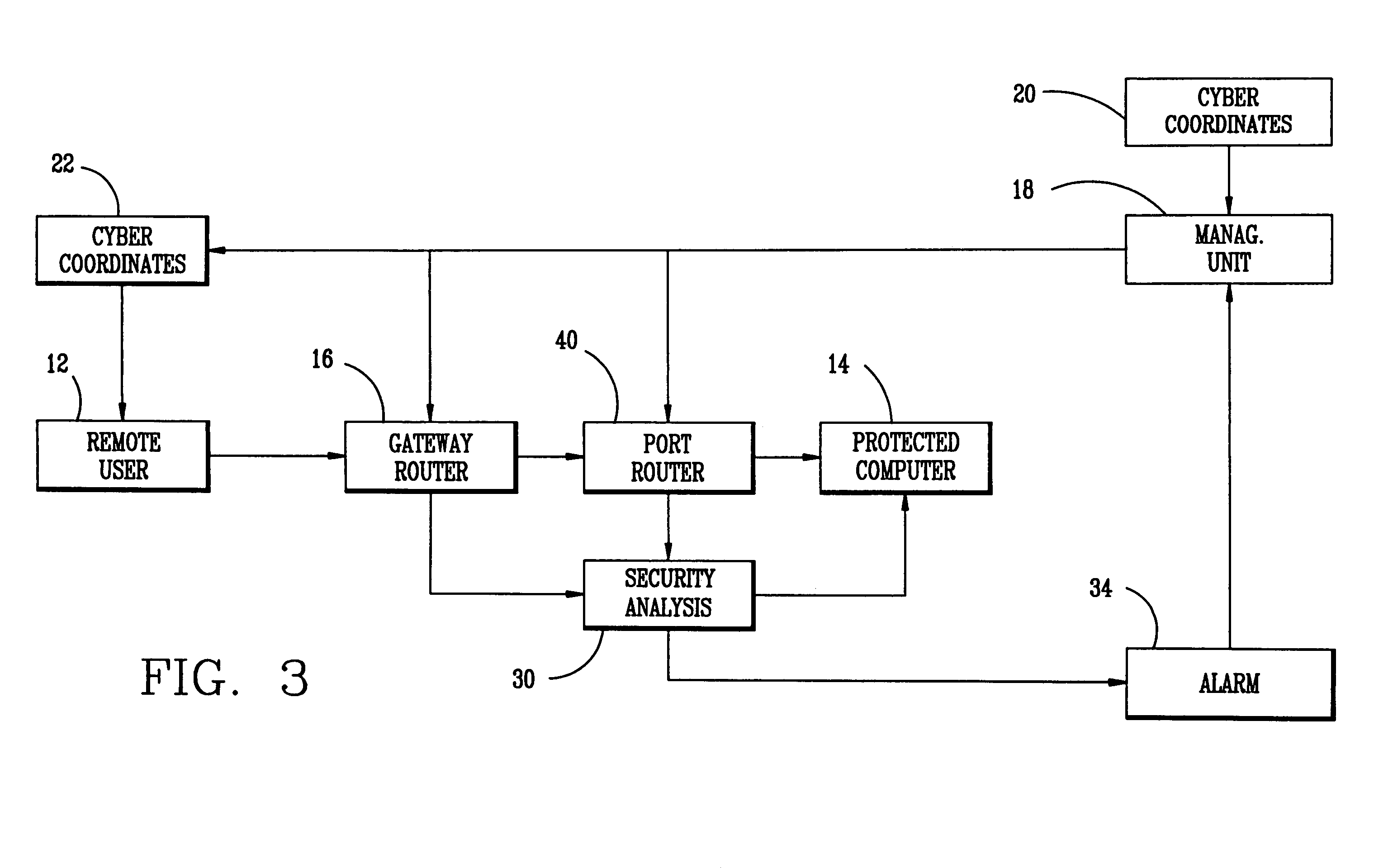
Method of communications and communication network intrusion protection methods and intrusion attempt detection system
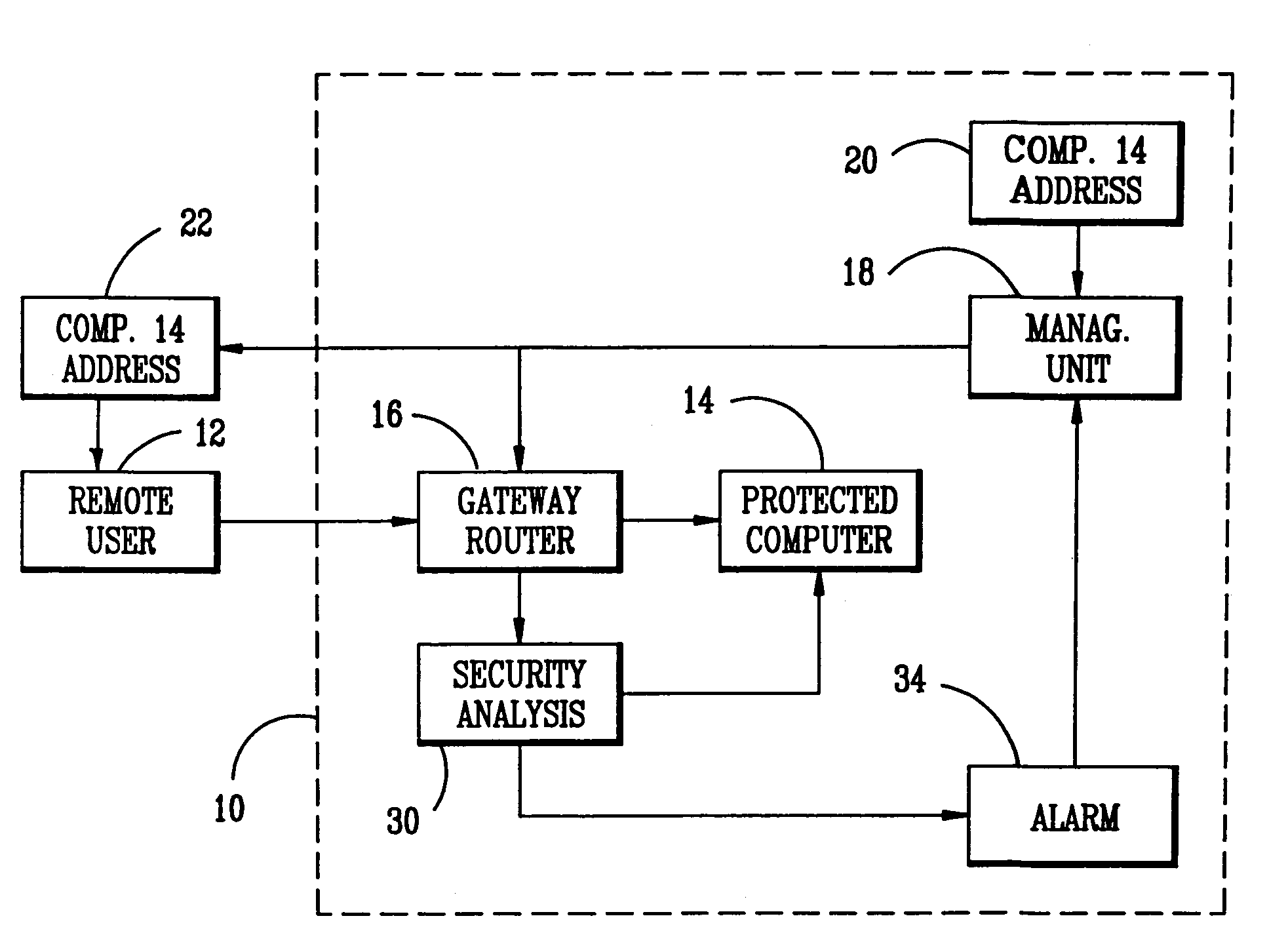
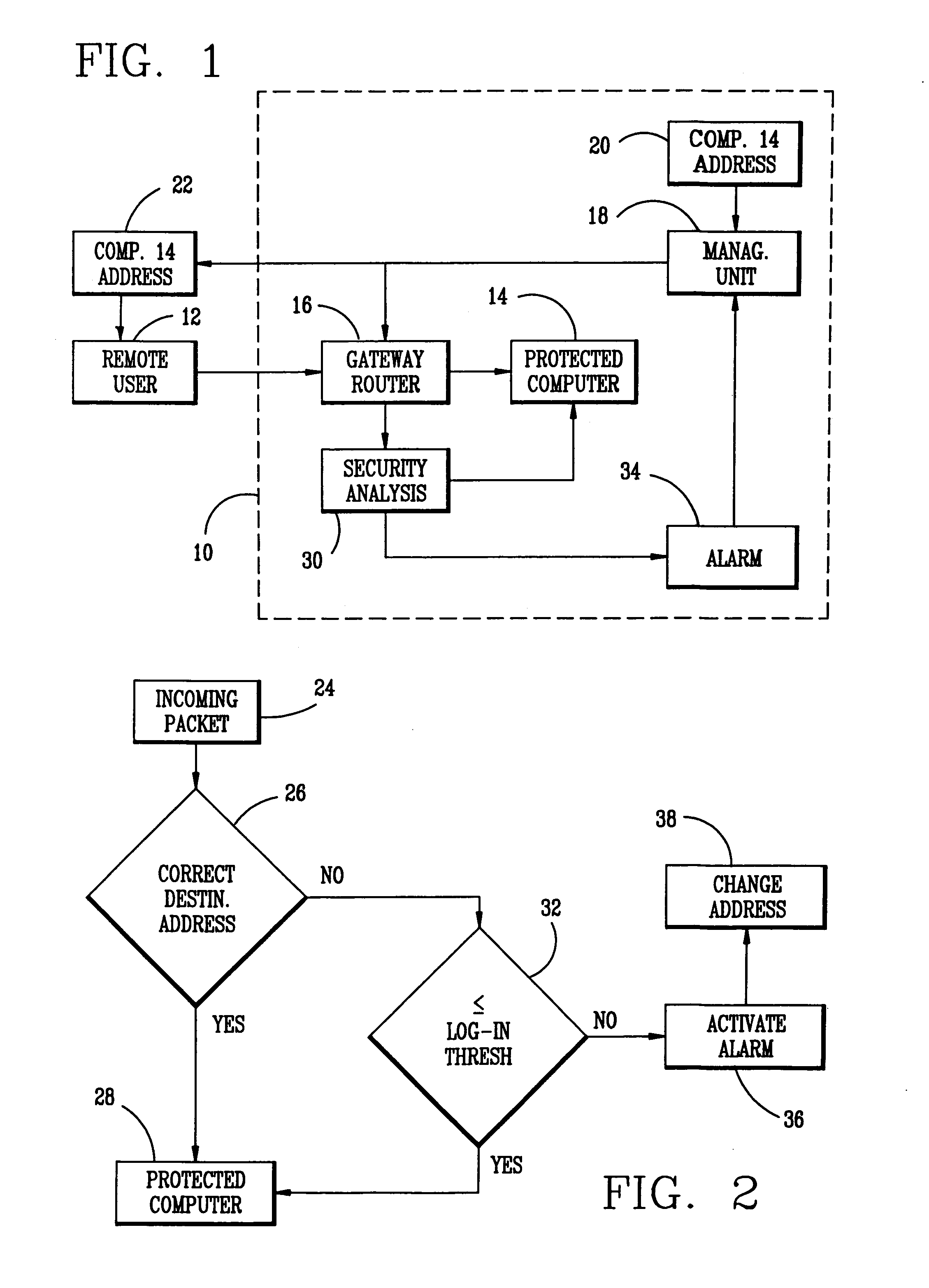
The intrusion protection method and system for a communications network provides address agility wherein the cyber coordinates of a target host are changed both on a determined time schedule and when an intrusion attempt is detected. The system includes a management unit which generates a random sequence of cyber coordinates and maintains a series of tables containing the current and next set of cyber coordinates. These cyber coordinates are distributed to authorized users under an encryption process to prevent unauthorized access.
Owner:INVICTA NETWORKS INC
Cryptographic system configured for extending a repetition period of a random sequence
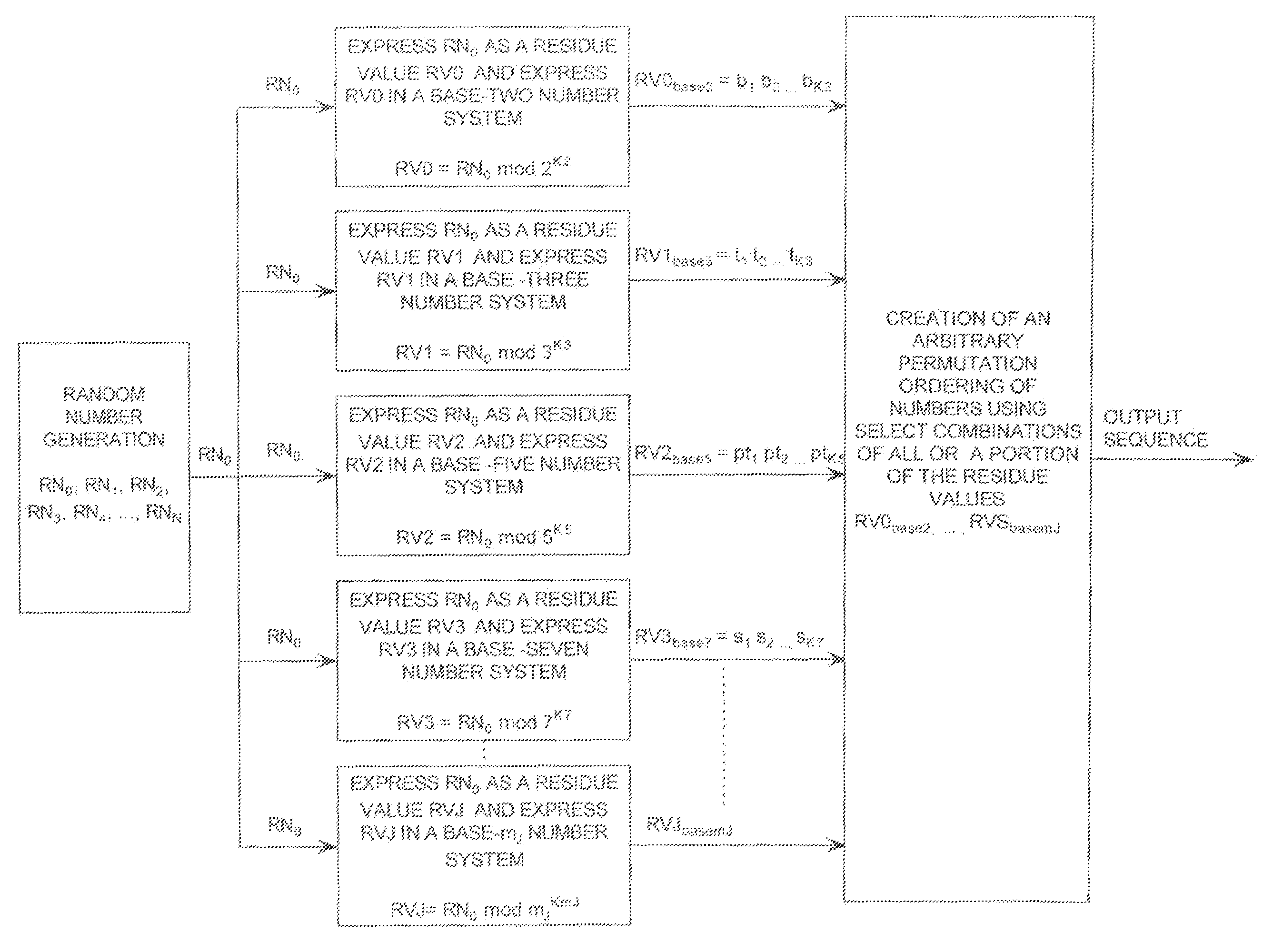
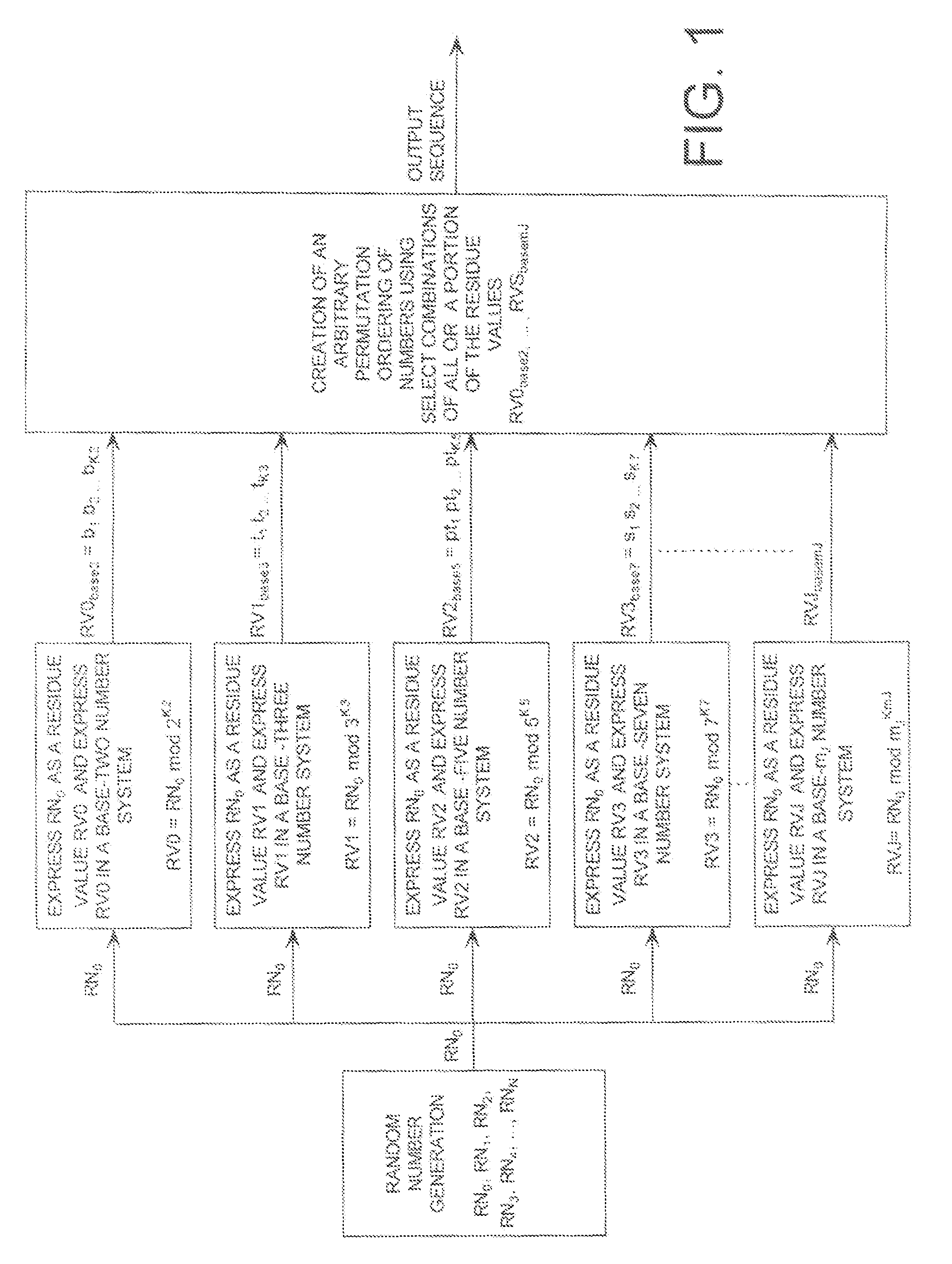
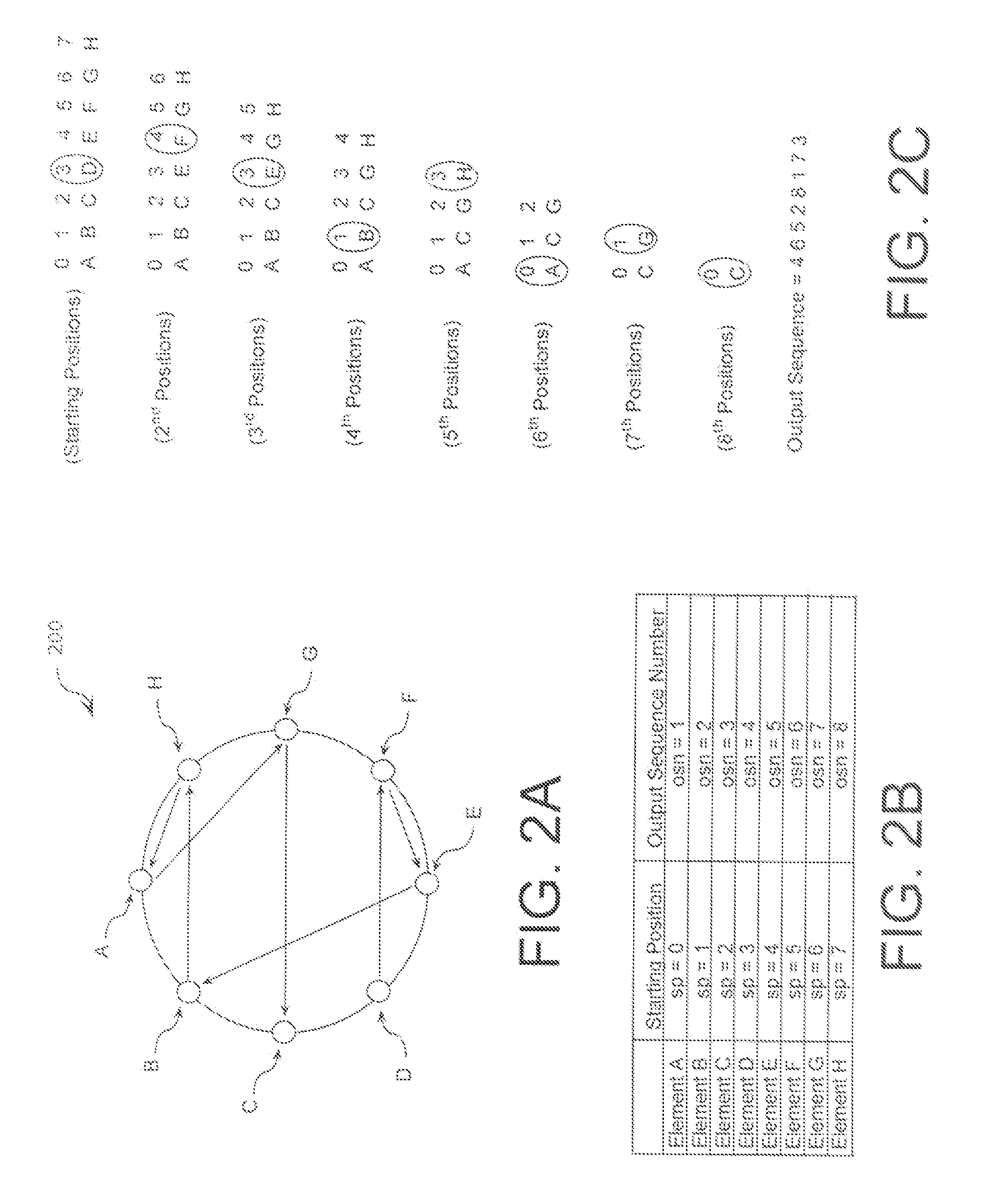
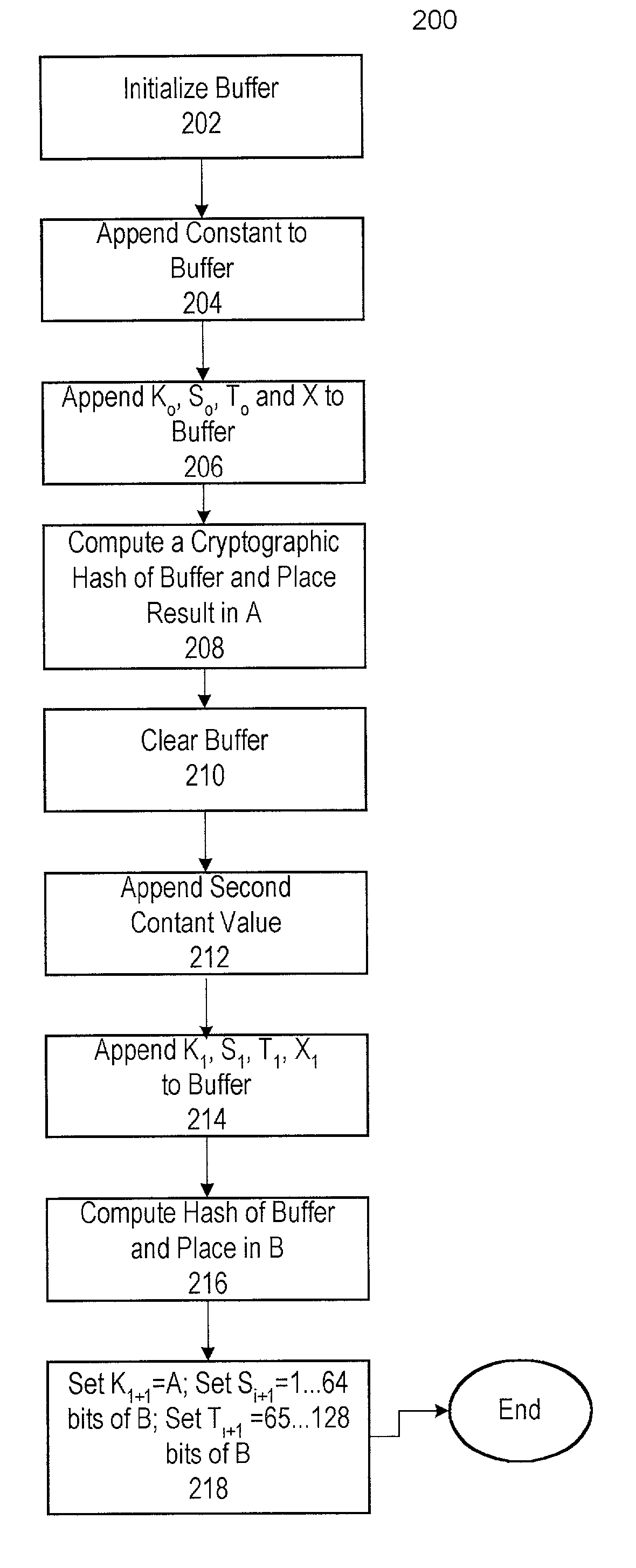
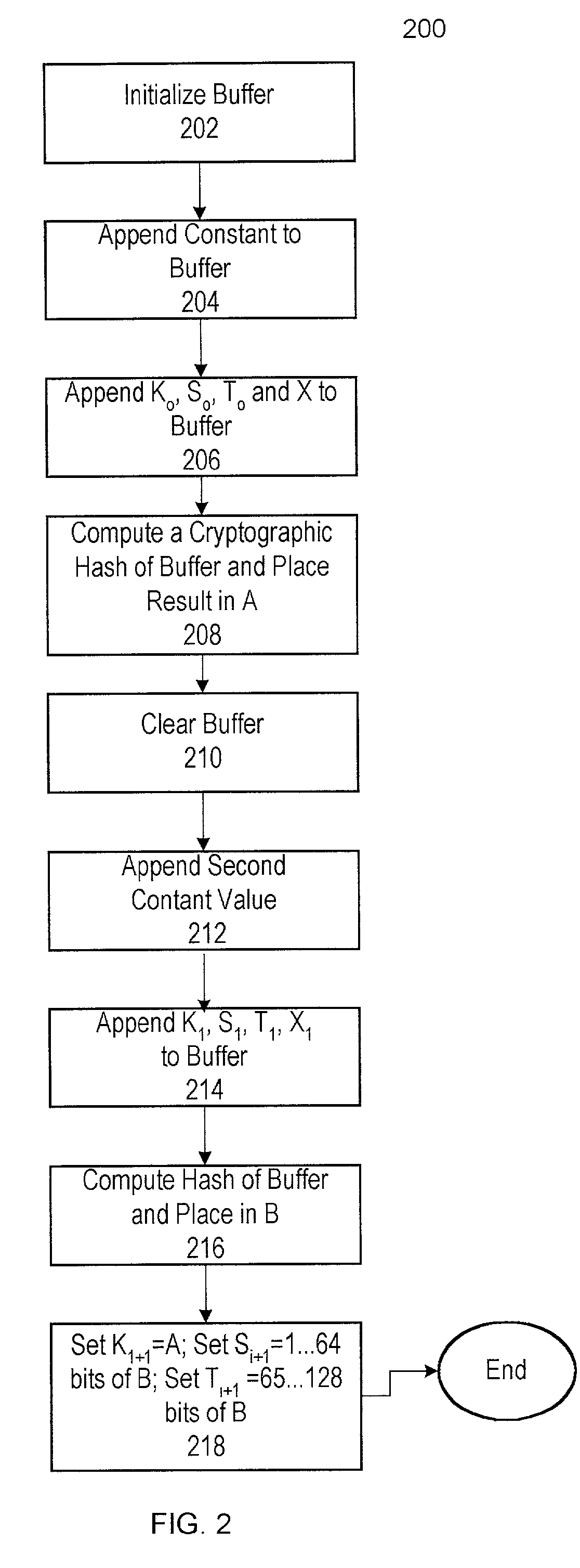
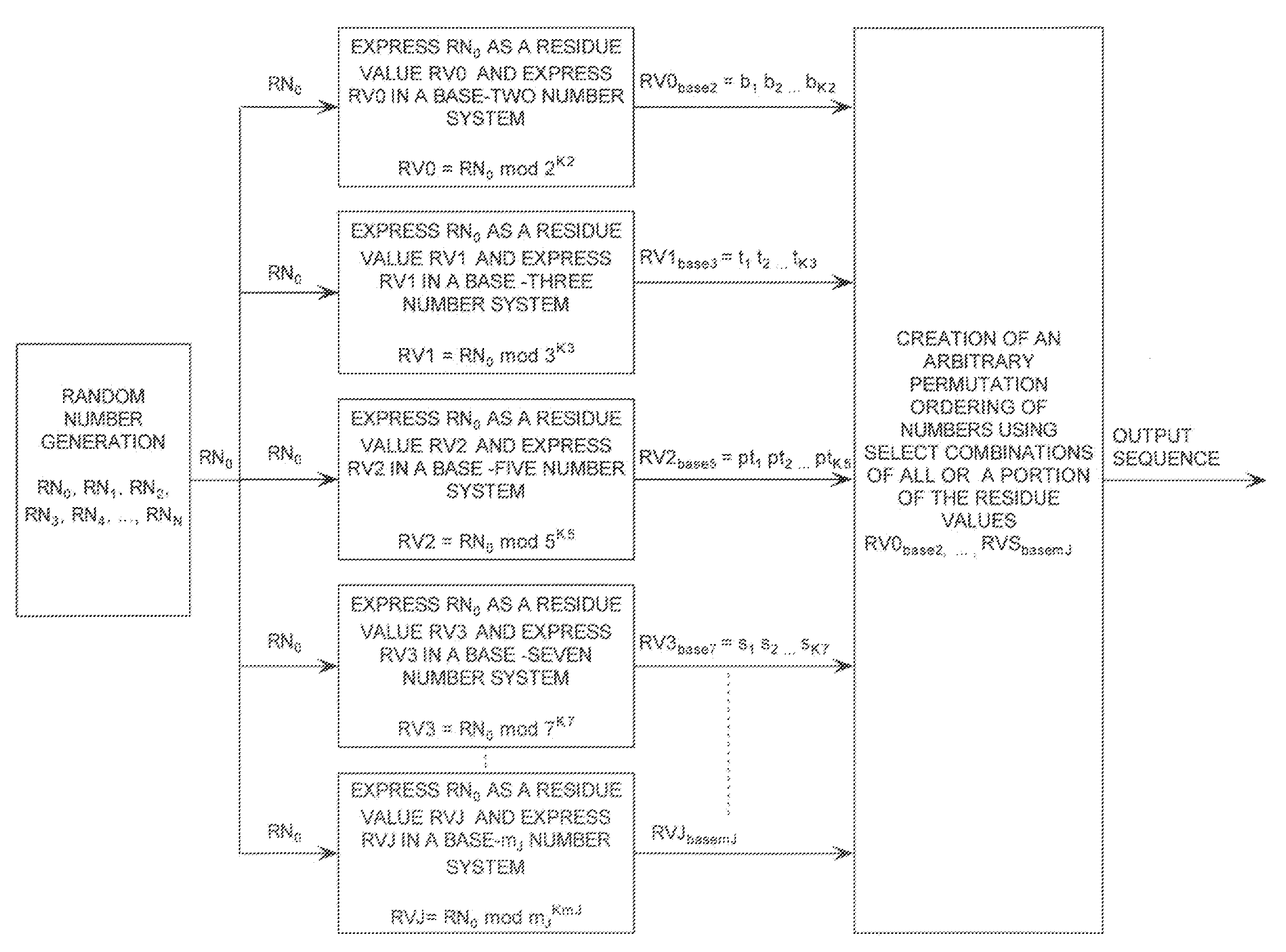
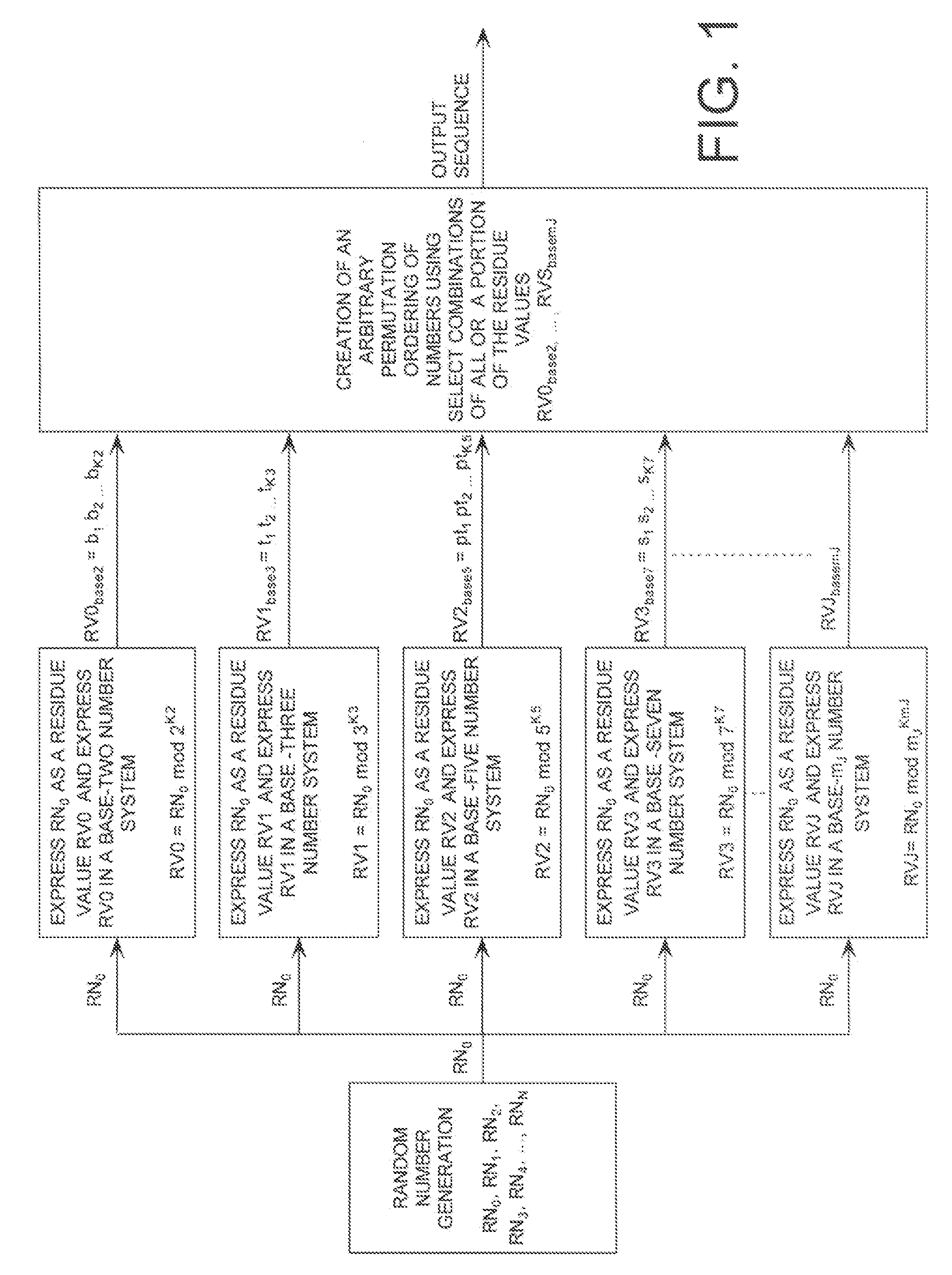
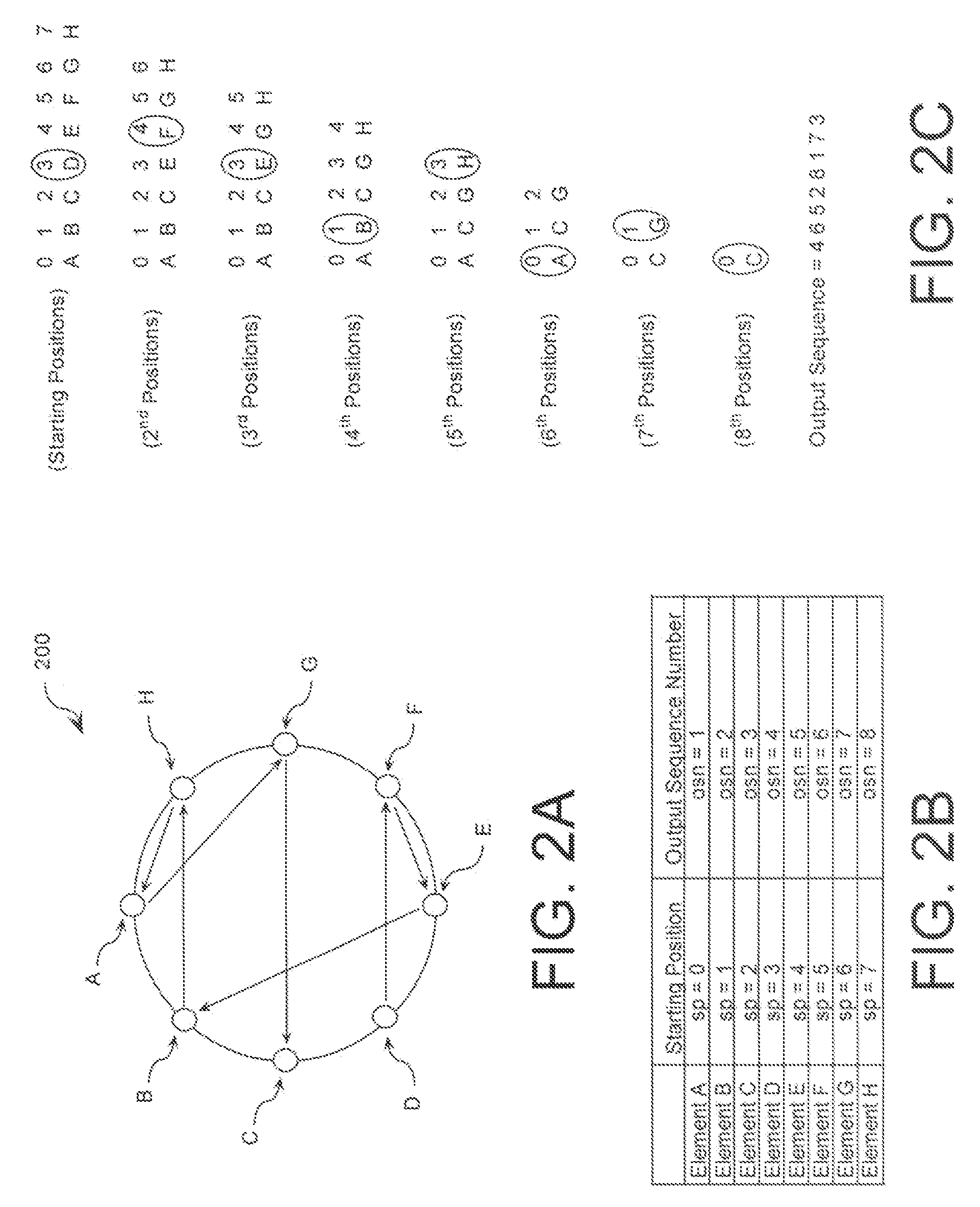
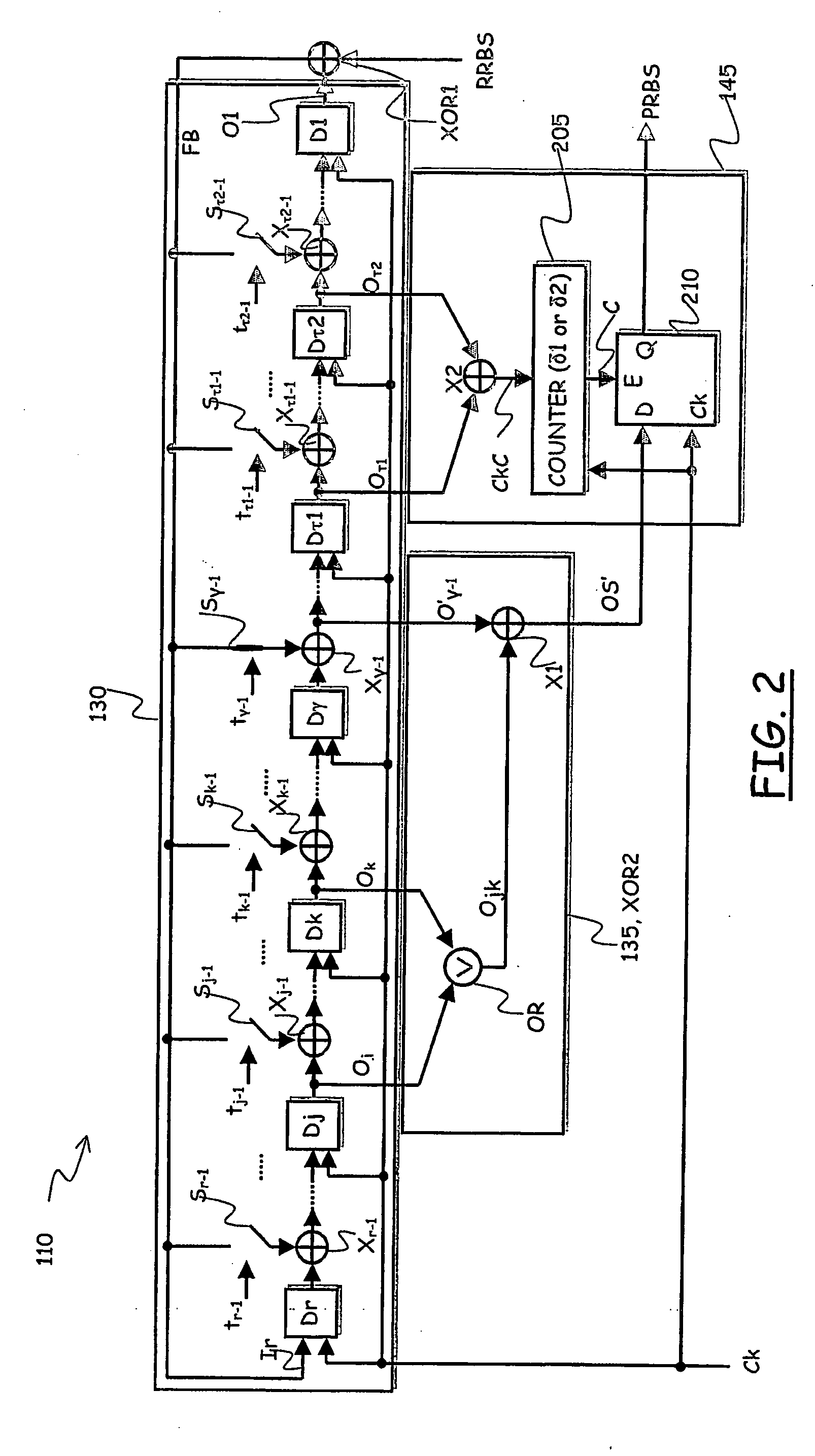
ActiveUS20090110197A1Data stream serial/continuous modificationDigital data processing detailsData streamNumbering system
A cryptographic system (CS) is provided. The CS (500) is comprised of a data stream receiving means (DSRM), a ring generator (RG) and an encryptor. The DSRM (602) provides a data stream (DS). The RG (400) includes a computing (404-408), converting (404-408) and permutation (410) means. The computing means is configured to perform RNS arithmetic operations to express a random number in a random number sequence as RNS residue values (RNSRV). The converting means is configured to convert each RNSRV to a relatively prime number system so that each RNSRV includes at least one digit. The permutation means is configured to generate an arbitrary permutation ordering of output sequence numbers (OSNs) using a select combination of digits associated with each RNSRV. The arbitrary permutation ordering is determined using a cyclic structure. The encryptor is configured to generate a modified data stream by combining the OSNs and DS.
Owner:HARRIS CORP
Mosaic tags for labeling templates in large-scale amplifications
The invention relates to methods of labeling nucleic acids, such as fragments of genomic DNA, with unique sequence it referred to herein as “mosaic tag,” prior to amplification and / or sequencing. Such sequence tags are useful for identifying amplification and sequencing errors. Mosaic tags minimize sequencing and amplification artifacts due to inappropriate annealing priming, hairpin formation, or the like, that may occur with completely random sequence tags of the prior art. In one aspect, mosaic tags are sequence tags that comprise alternating constant regions and variable regions, wherein each constant region has it position in the mosaic tag and comprises a predetermined sequence of nucleotides and each variable region has a position in the mosaic tag and comprises a predetermined number of randomly selected nucleotides.
Owner:ADAPTIVE BIOTECH
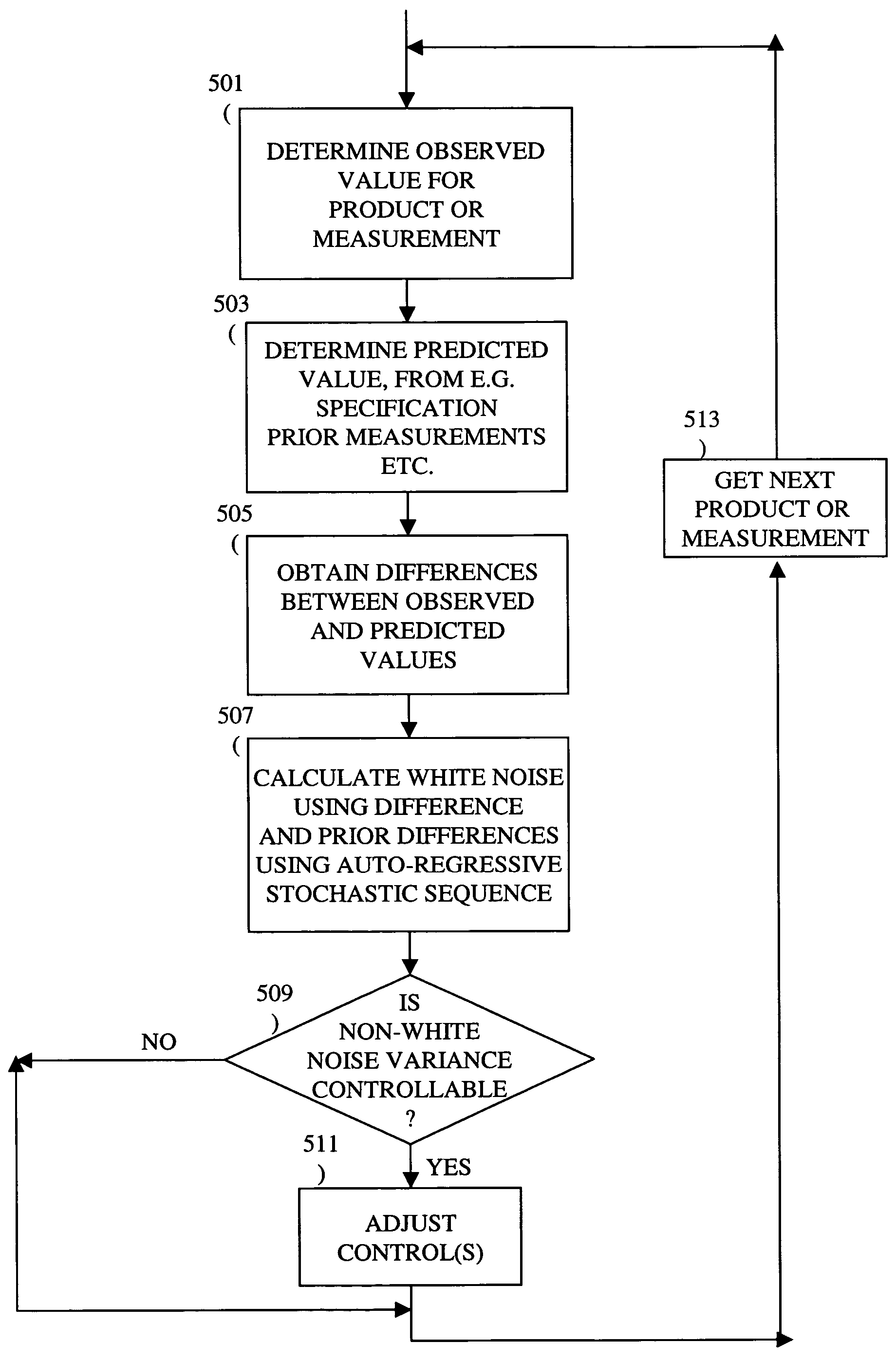
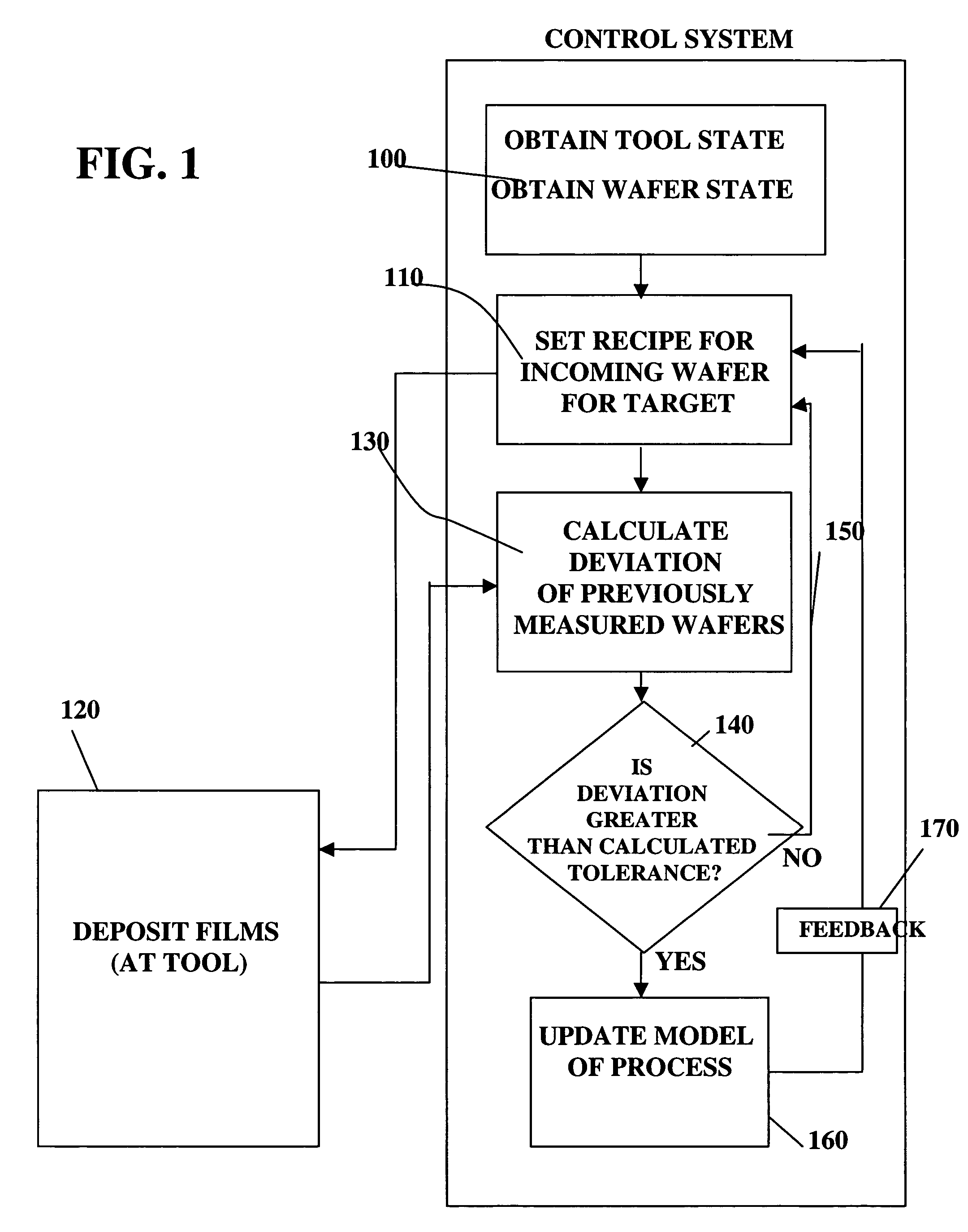
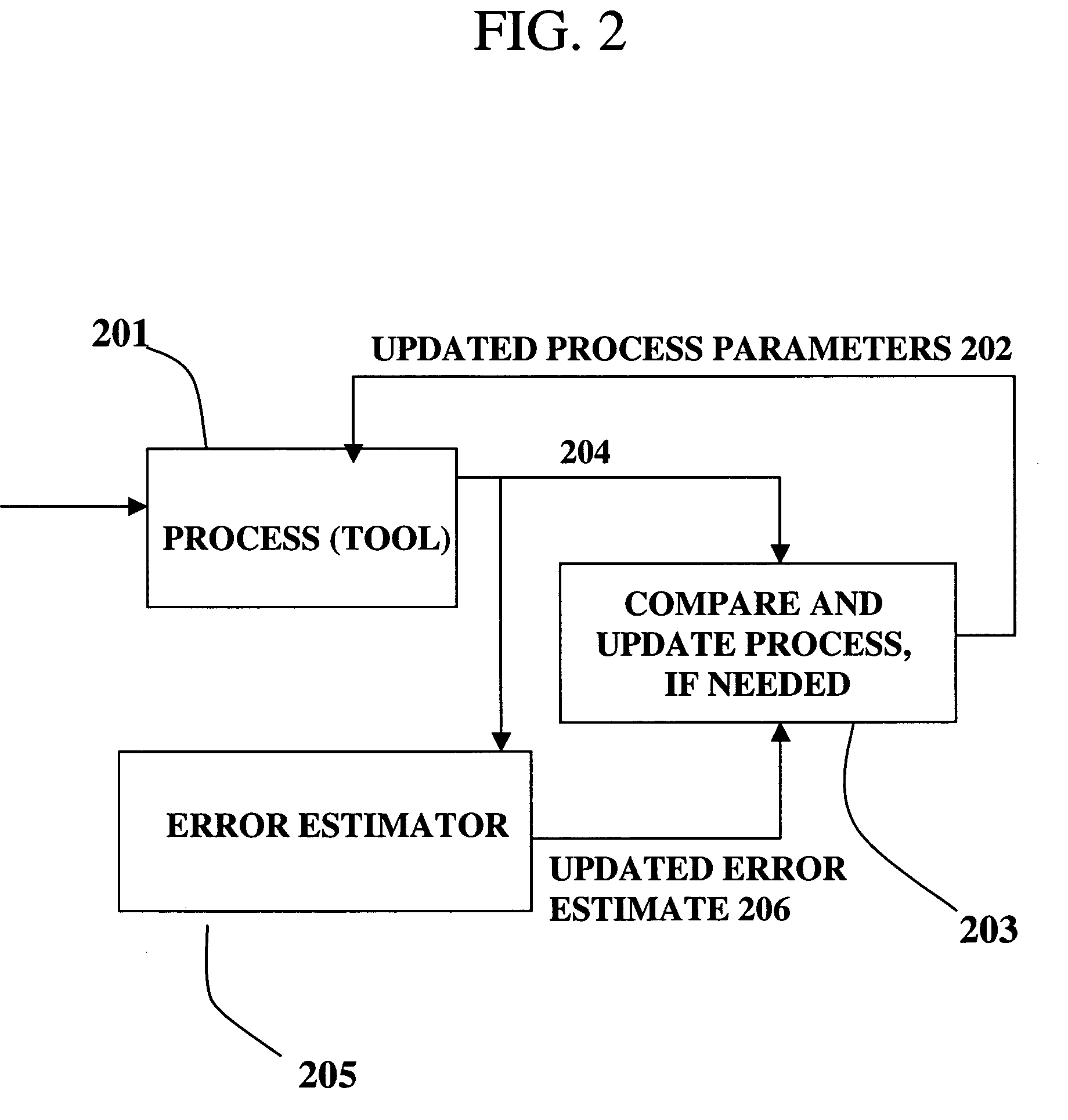
Adjusting manufacturing process control parameter using updated process threshold derived from uncontrollable error
InactiveUS7349753B2Strict controlNon-controllableTotal factory controlSpecial data processing applicationsSemiconductor chipRandom noise
Owner:APPLIED MATERIALS INC
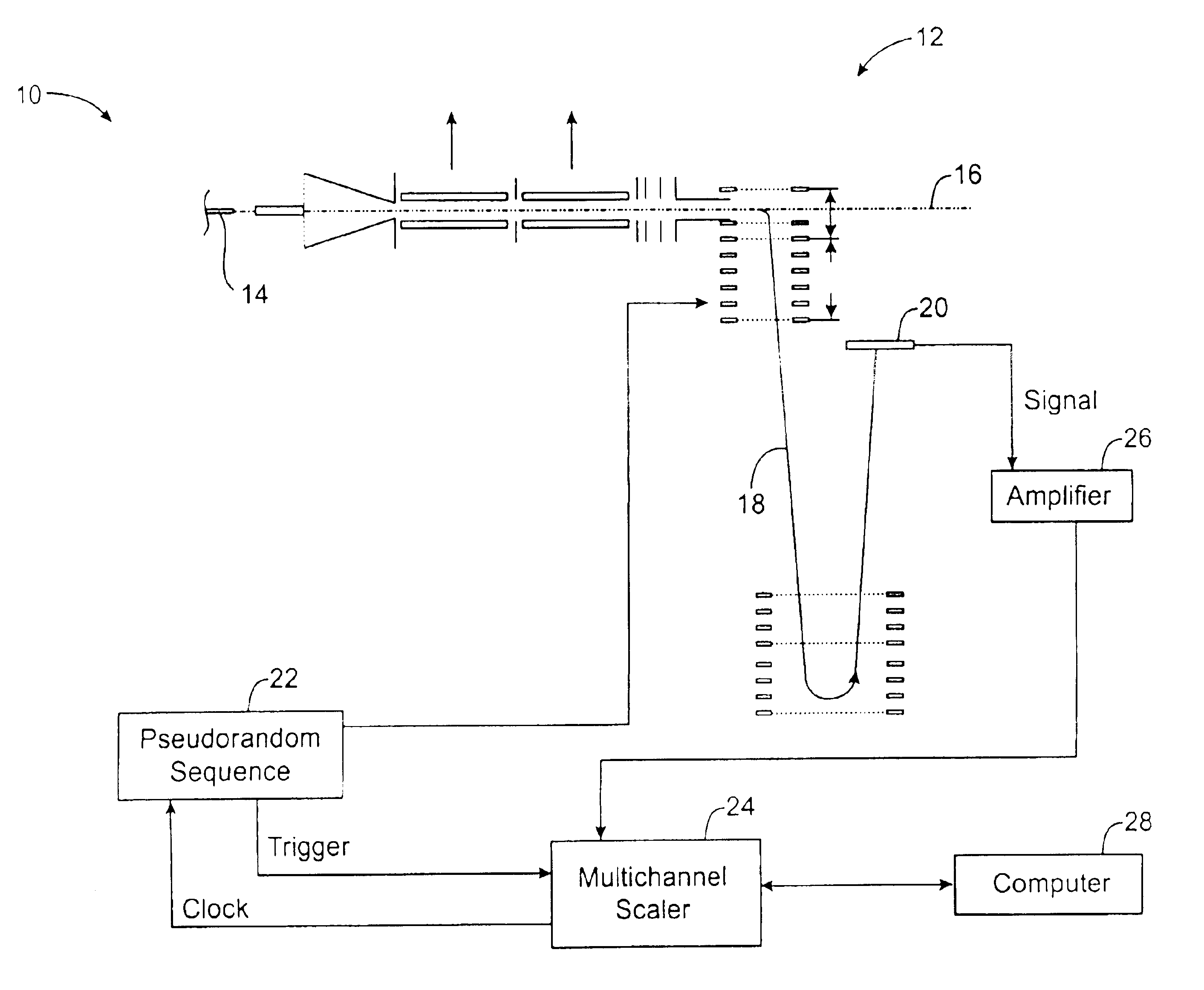
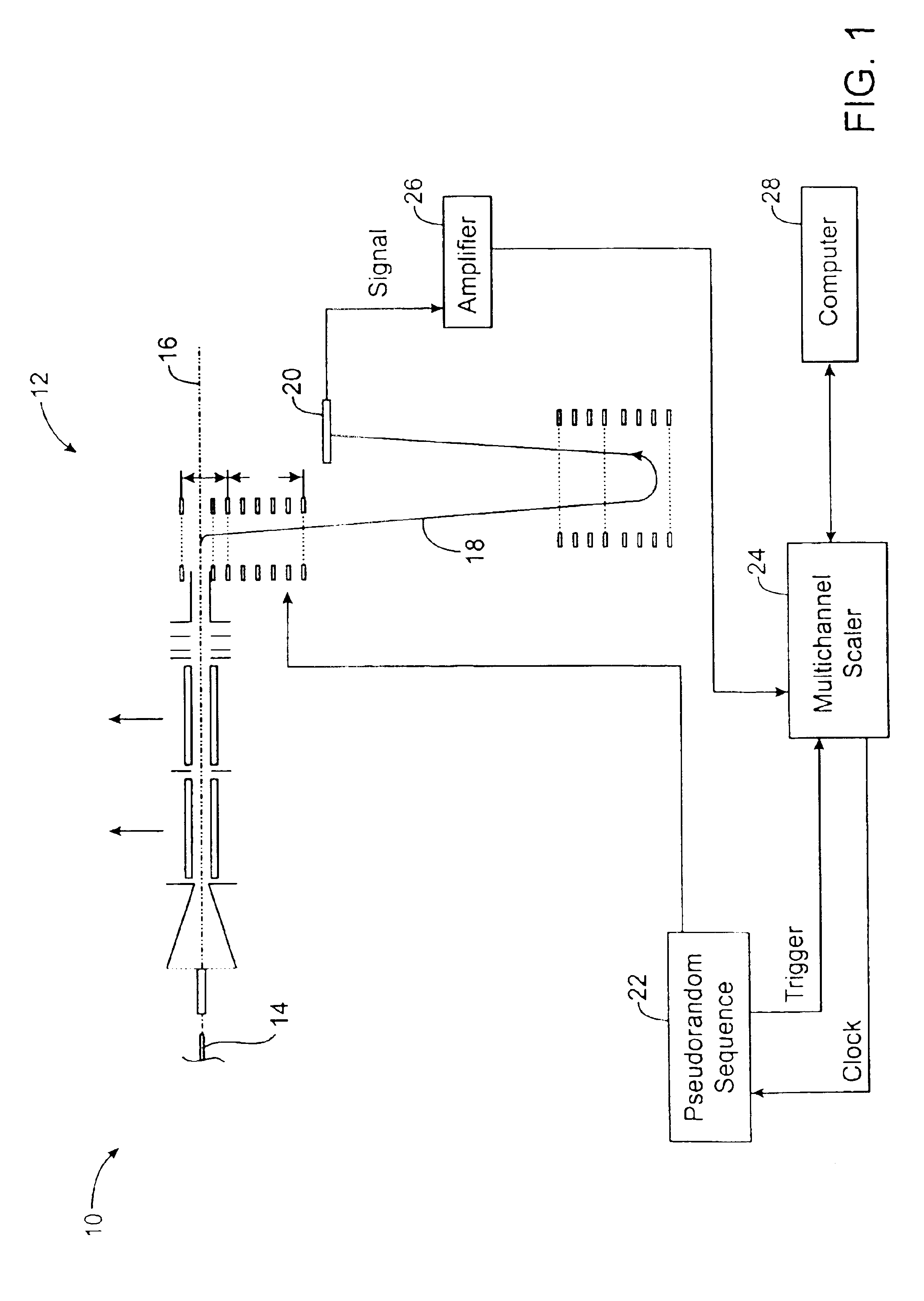
Multiplexed orthogonal time-of-flight mass spectrometer
InactiveUS6900431B2Time-of-flight spectrometersParticle spectrometer methodsHadamard transformTime-of-flight mass spectrometry
A mass spectrometer and associated methods analyze an ion beam by accumulating ions for a sequence of time periods, and driving the accumulated ions in pulses. Differing quantities of ions can be accumulated in the sequential pulses according to a psuedo-random sequence, and the slower ions are overtaken by the faster ions of a subsequent pulse. A mass spectrum may be reconstructed from an overlapping ion detector signal using an inverse of a weighted simplex matrix or inverse Hadamard transform techniques.
Owner:NORVIEL VERN
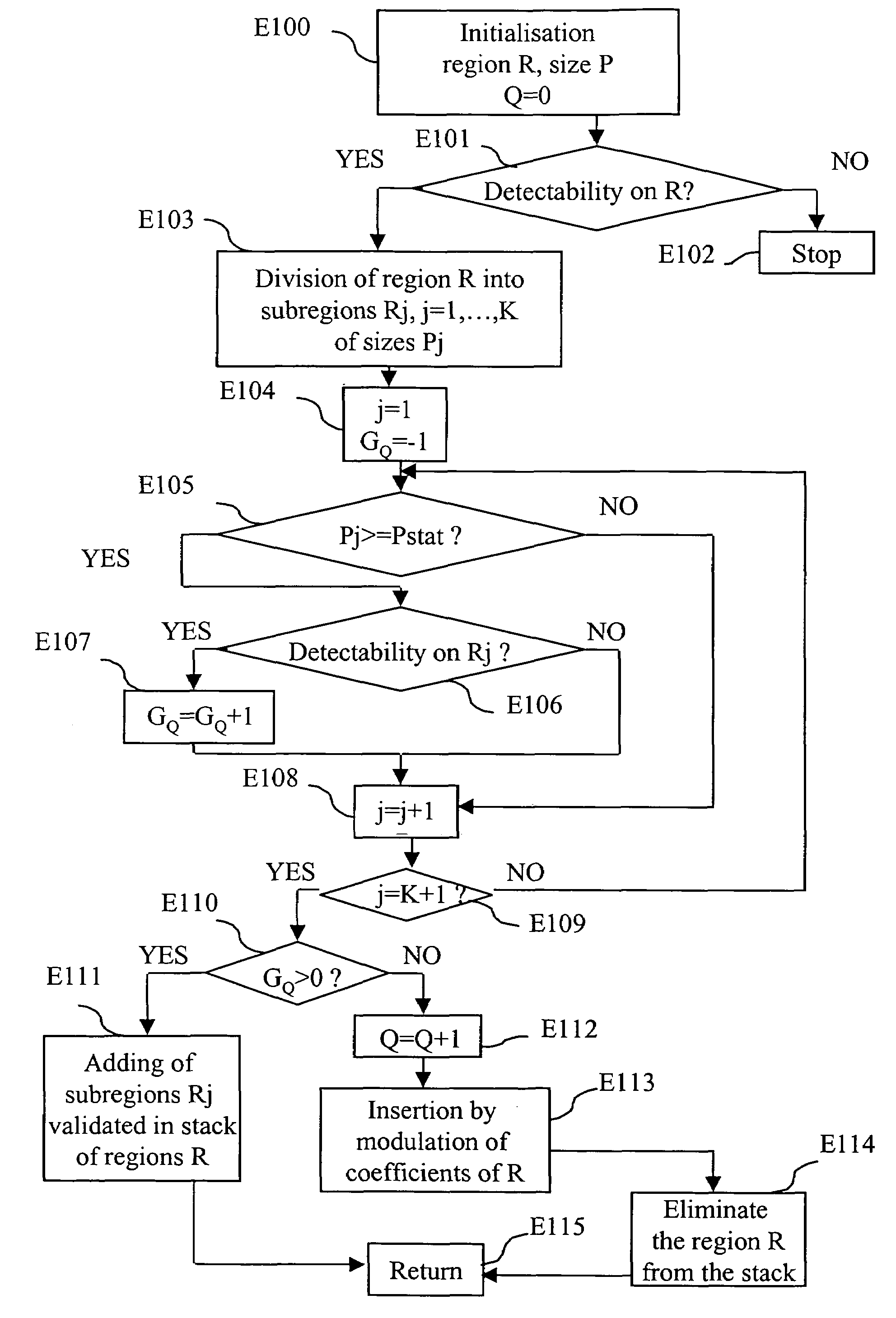
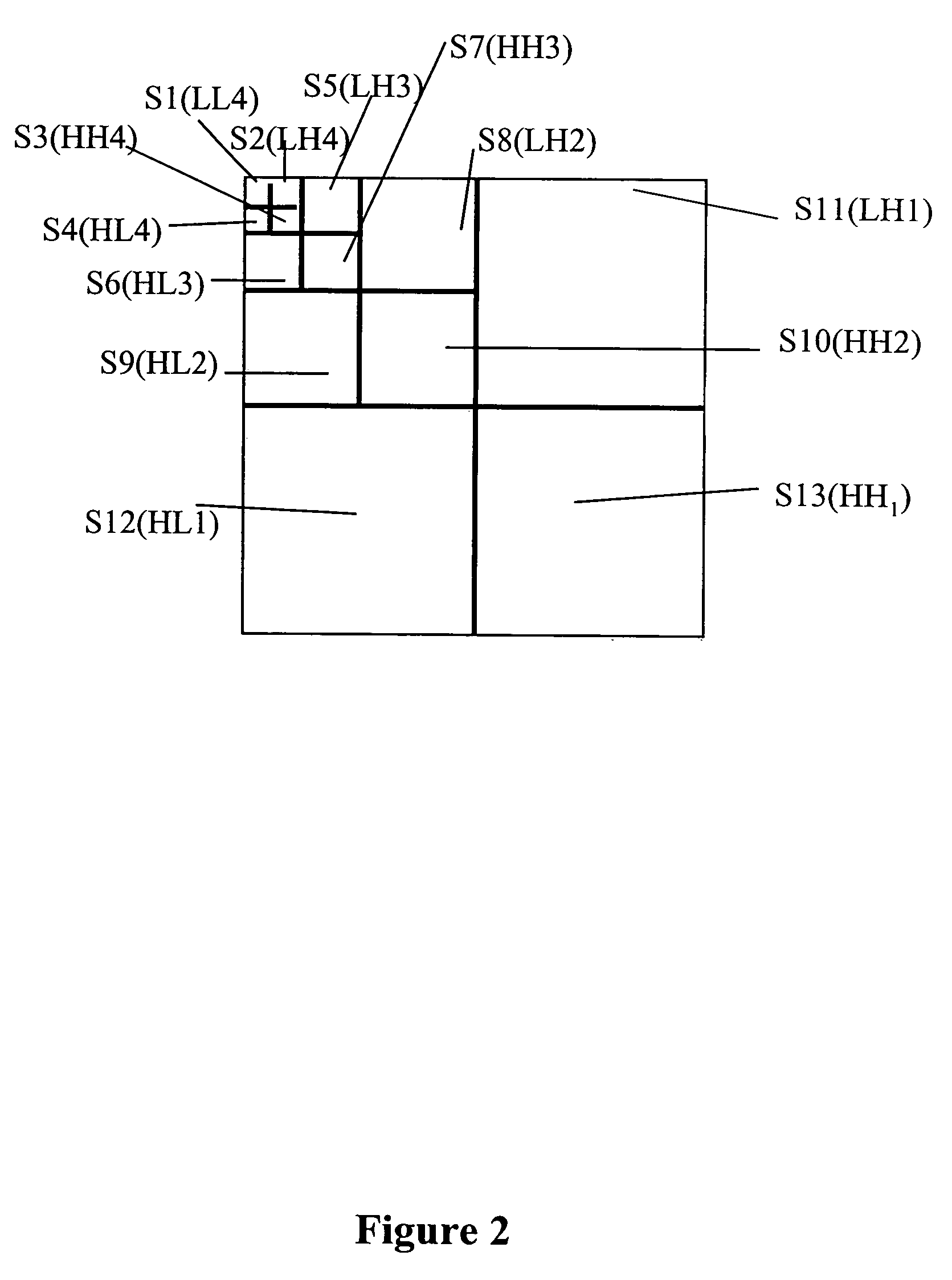
Method for determining a partition in order to insert a watermark, and associated insertion and decoding methods
InactiveUS7031491B1Guaranteed detection effectEnsuring imperceptibilityUser identity/authority verificationCharacter and pattern recognitionPseudo random sequenceDecoding methods
A method of determining a partition into distinct regions of a set of coefficients representative of at least a part of an image in order to insert a watermark comprises the following steps:generation (E501) of a centred pseudo-random sequence (w) equal in size to the cardinal number (N) of the said set of coefficients, formed from centred pseudo-random sub-sequences;modulation (E502) of the said set of coefficients by the said centred pseudo-random sequence (w) in order to insert the same information bit on the said set of coefficients; andchecking (E504–E508), over each region, of a criterion of detectability of the information bit inserted by modulation.Use especially for determining an adaptative partition as a function of a criterion of detectability of an information bit inserted on each region.
Owner:CANON KK
Methods for Amplifying a Complete Genome or Transcriptome
InactiveUS20140274811A1Eliminates misprimingReduces misprimingLibrary creationDNA preparationNucleotidePolymerase L
The present invention provides methods for amplifying a complete genome or transcriptome. The genome or transcriptome is prepared as a set of target nucleic acids and mixed with a first primer. The first primer comprises a target-binding region having a first random sequence of about 6 to about 9 nucleotides and a tag sequence that contains one or more non-natural nucleotides. The first primer is annealed to the target nucleic acids and extended by polymerase to produce a first duplex nucleic acid. The target nucleic acid is removed from the first nucleic acid. A second primer is annealed to the first nucleic acid having a second random sequence of about 6 to about 9 nucleotides and a tag sequence that contains one or more non-natural nucleotides. The second primer is extended by polymerase to produce a second duplex nucleic acid. The second nucleic acid contains a tag sequence on one terminus and a complement of the tag sequence on the other. The first nucleic acid is removed from the second nucleic acid. A third primer is annealed to the second nucleic acid having the same sequence as the tag sequence or a portion thereof and at least one of the non-natural nucleotides of the tag sequence. The third primer is extended by polymerase to produce a third duplex nucleic acid. The second nucleic acid is removed from the third nucleic acid. The third primer is annealed to the second nucleic acid and the third nucleic acid. The third primer is extended by polymerase. Repeating these last three steps thereby results in amplification of the genome or transcriptome.
Owner:AEGEA BIOTECH
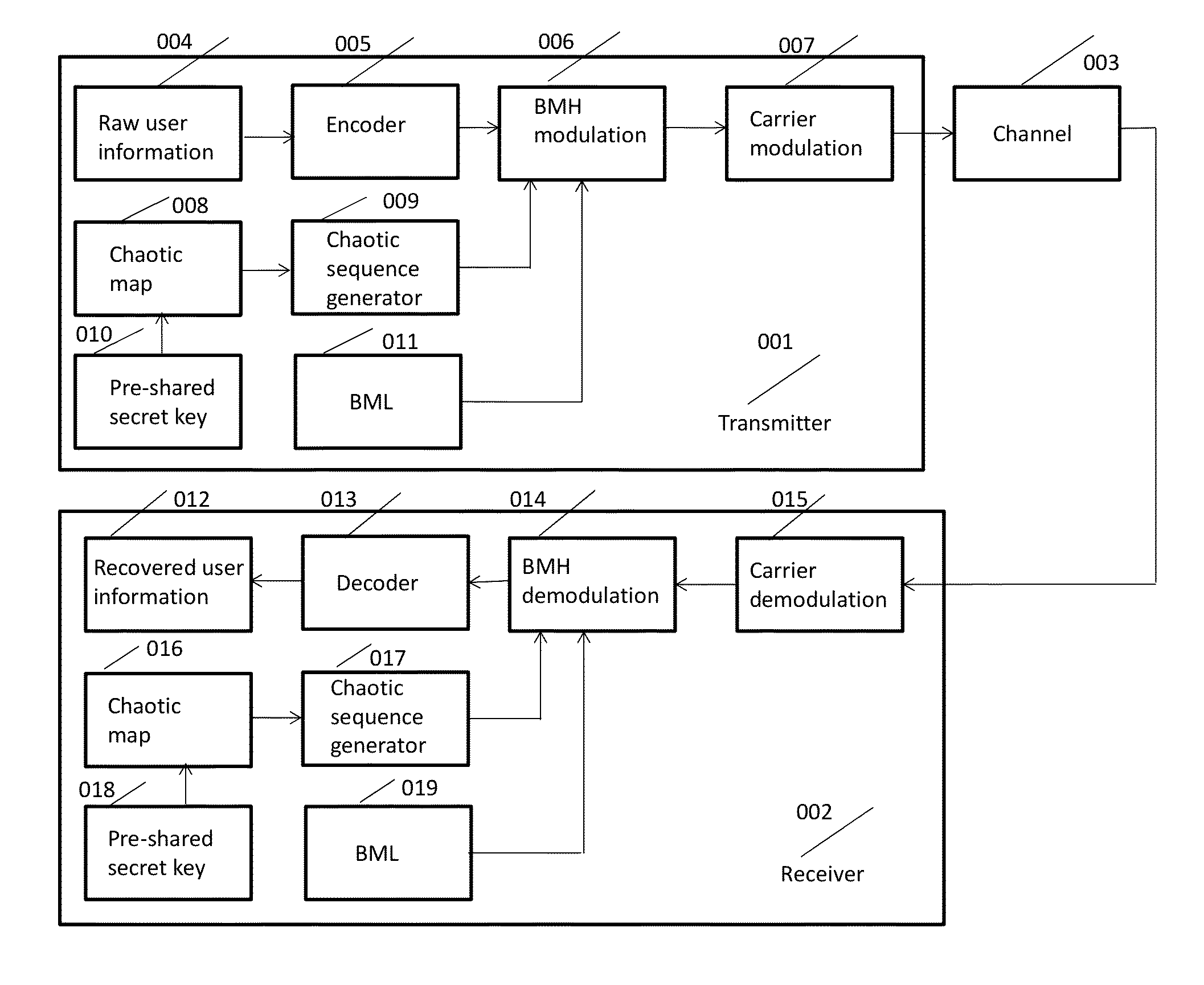
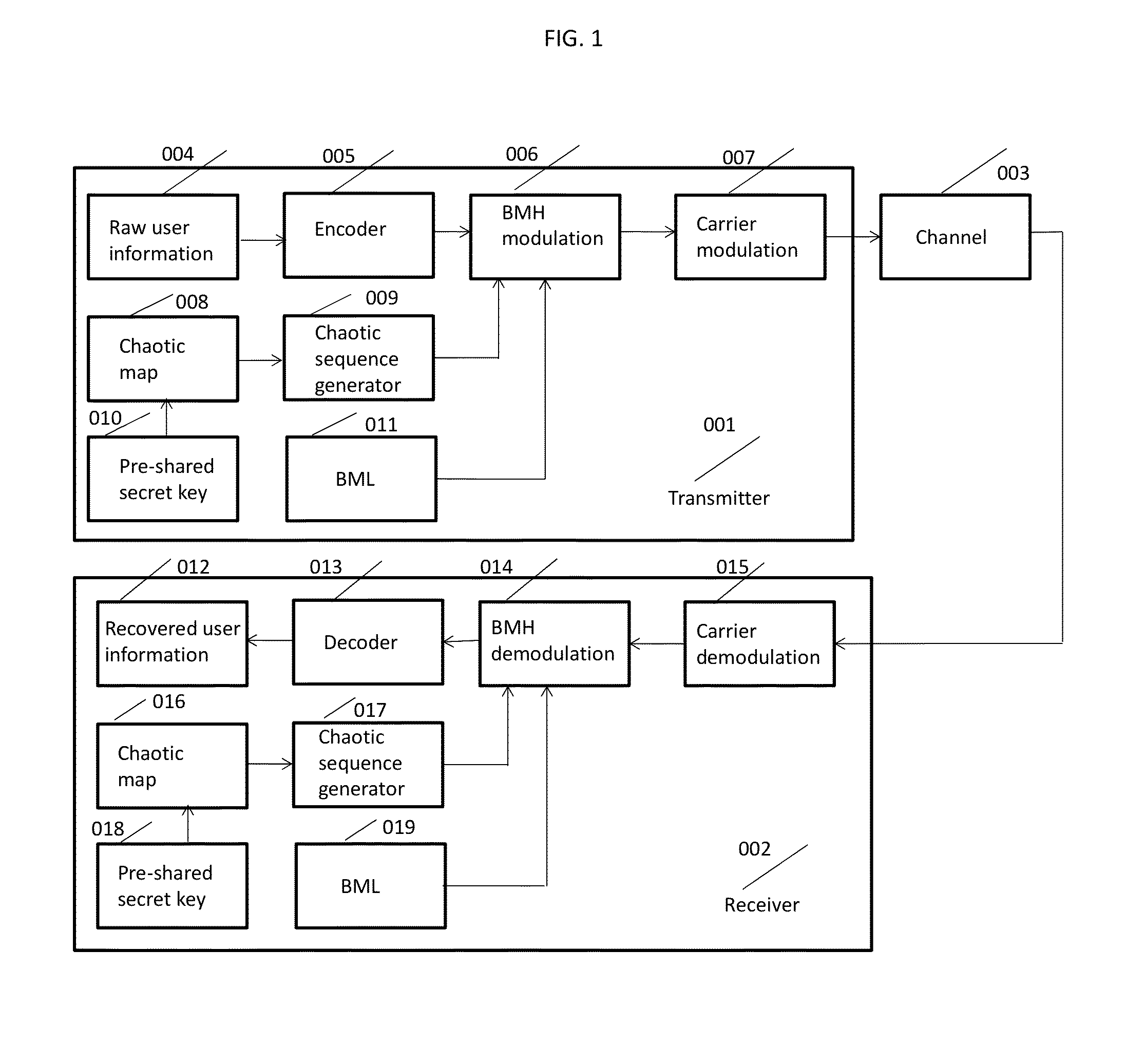
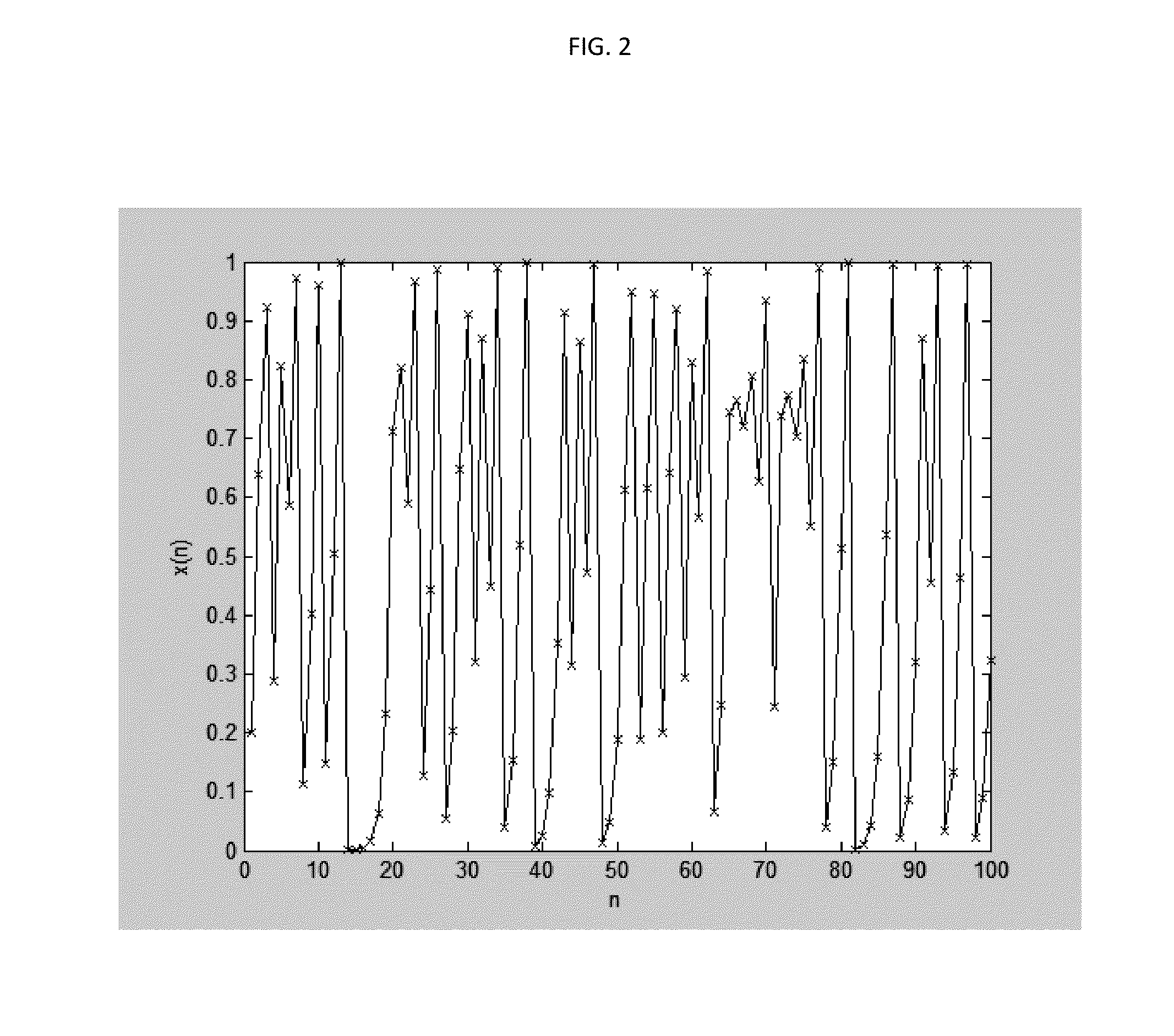
Chaotic Baseband Modulation Hopping Based Post-Quantum Physical-Layer Encryption
A post-quantum physical-layer encryption / decryption system based on chaotic Baseband Modulation Hopping (BMH). The baseband constellation, mapping, power level, and phase will vary symbol-by-symbol according to assigned random sequences. Pre-shared secret keys are used as the chaotic system parameters, initialization, and quantization parameters to generate the BMH codes. The BMH physical-layer encryption / decryption system can be combined with digital-domain based encryption algorithms such as AES, code-based post-quantum cryptography, and other physical-layer secure communication techniques such as Frequency Hopping (FH) and Direct Sequence Spread Spectrum (DSSS). It can also be combined with Quantum Key Distribution (QKD) to provide mutual authenticated key distribution. This invention can be applied to all kinds of communication systems including wireless (radio frequency, optical, quantum channel, sonar) and wire (optical fiber, power-line, telephone line, wire quantum channel, etc.), single carrier and multi-carrier, OFDM, MIMO channels.
Owner:LI WENHUA +1
Antiviral oligonucleotides
ActiveUS20050176661A1Easy to adaptOrganic active ingredientsNervous disorderMode of actionAntiviral drug
Owner:REPLICOR INC
Outer loop transmission power control method and radio communication device
InactiveUS20050186981A1Power managementTransmission control/equalisingCommunications systemDummy data
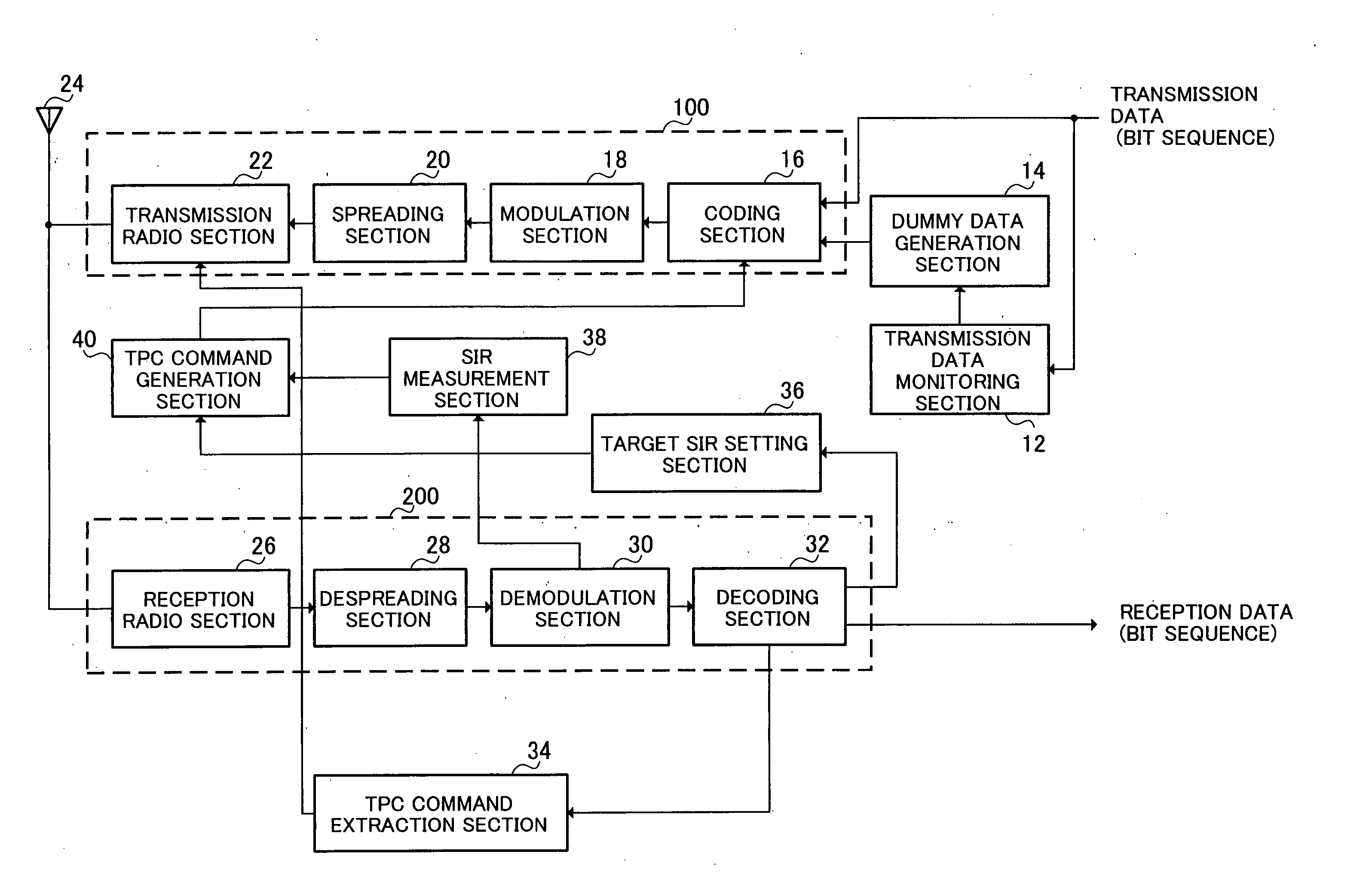
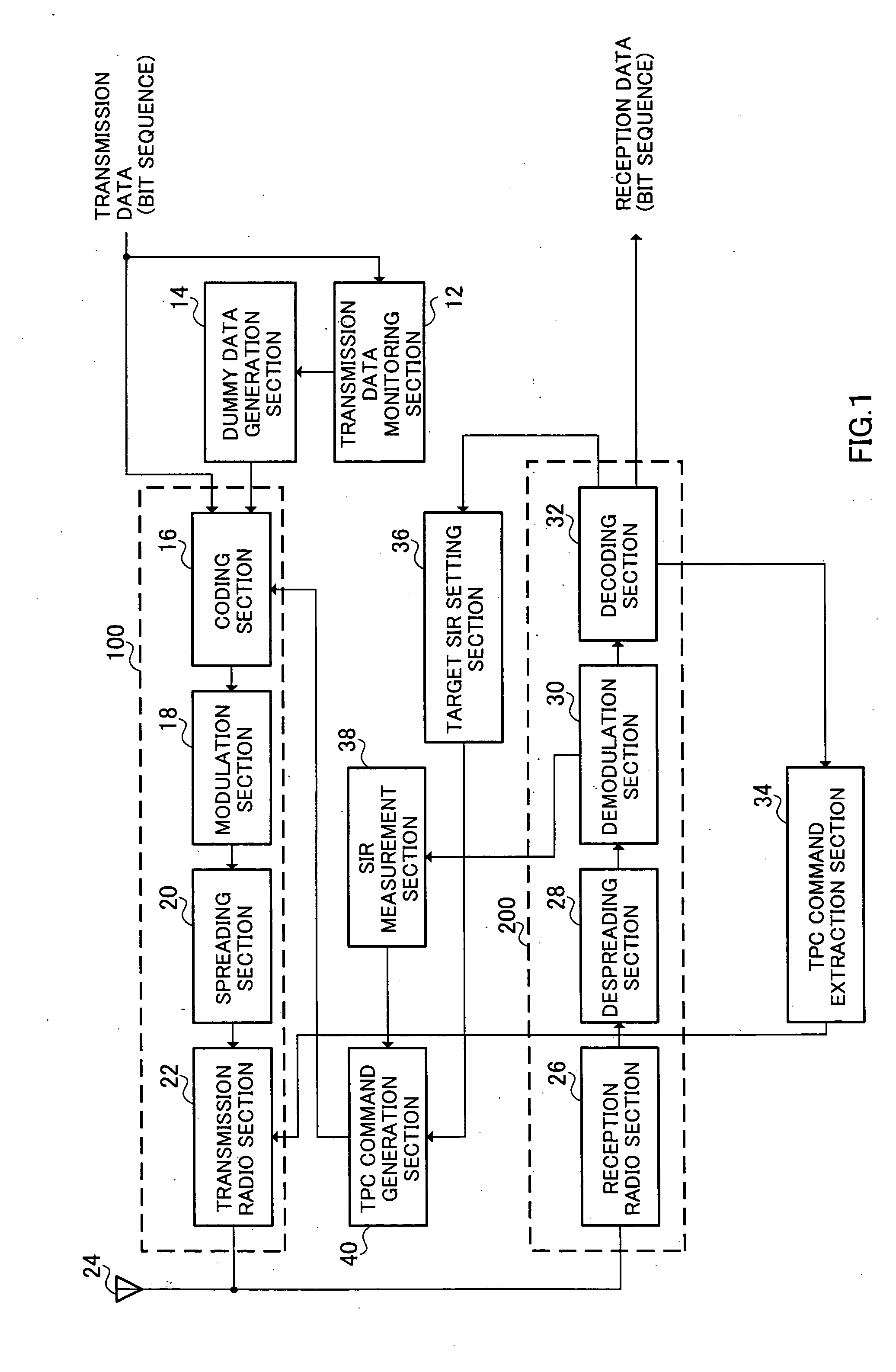
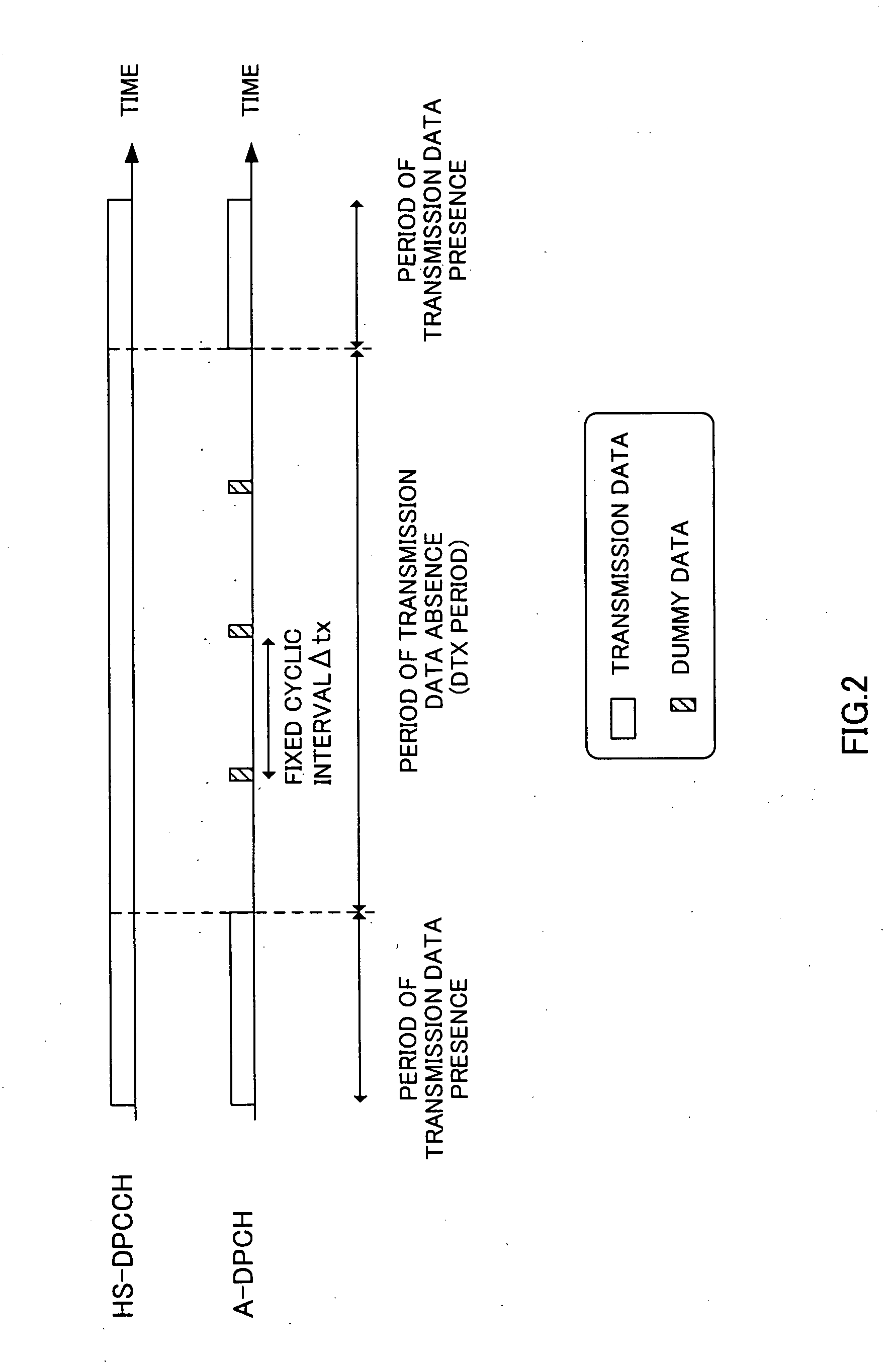
In a wireless communication system in which A-DPCH (Associated-Dedicated Physical CHannel) and HS-DPCCH (High Speed-Dedicated Physical Control CHannel) exist, for the purpose of performing an appropriate outer loop transmission power control for HS-DPCCH even during an A-DPCH DTX (Discontinuous Transmission) period, transmission data monitoring section 12 monitors whether a bit sequence transmitted via A-DPCH is present or not, and dummy data generation section 14 generates a random sequence used for outer loop transmission power control of HS-DPCCH during a DTX period in which a bit sequence is absent, and coding section 16 performs CRC coding on the generated random sequence, and transmission radio section 22 then transmits the CRC-coded random sequence via A-DPCH.
Owner:PANASONIC CORP
Method and apparatus for improved pseudo-random number generation
InactiveUS7007050B2Improve securityRandom number generatorsSecuring communicationSecure communicationMobile Telephone Service
A pseudo-random number generator (PRNG) for a cryptographic processing system is disclosed in which the PRNG is reseeded at each instance of input entropy and in which a standard timestamp variable used in determining random sequence outputs is replaced with a running counter. The method employed by the PRNG demonstrates increased resistance to iterative-guessing attacks and chosen-input attacks than those of previous technologies. The PRNG is suitable for use in, for example, a mobile telephone system for accomplishing secure communications.
Owner:WSOU INVESTMENTS LLC
Apparatus and methods for detection of objects using broadband signals
ActiveUS20170023661A1Electromagnetic wave reradiationRadio wave reradiation/reflectionTime lagBroadband transmission
Broadband signal transmissions may be used for object detection and / or ranging. Broadband transmissions may comprise a pseudo-random bit sequence or a bit sequence produced using, a random process. The sequence may be used to modulate transmissions of a given wave type. Various types of waves may be utilized, pressure, light, and radio waves. Waves reflected by objects within the sensing volume may be sampled. The received signal may be convolved with a time-reversed copy of the transmitted random sequence to produce a correlogram. The correlogram may be analyzed to determine range to objects. The analysis may comprise determination of one or more peaks / troughs in the correlogram. Range to an object may be determines based on a time lag of a respective peak.
Owner:BRAIN CORP
Extending a Repetition Period of a Random Sequence
ActiveUS20080294710A1Extended maintenance periodRandom number generatorsHandling data according to predetermined rulesNumber generatorComputer science
A method is provided for extending a sequence repetition period of a random number generator in systems based on the availability of random sequences. The method includes performing RNS arithmetic operations to express a random number in a sequence as RNS residue values. Each generated random number has a value between zero and n!−1. The method also includes converting each of the RNS residue values to a relatively prime base number system so that each of the RNS residue values includes at least one digit. The method further includes generating an arbitrary permutation ordering of output sequence numbers using a select combination of digits associated with each of the RNS residue values. The arbitrary permutation ordering is applied to a cyclic structure having n elements. Each of the n elements has an associated output sequence number.
Owner:HARRIS CORP
Protecting images with an image watermark
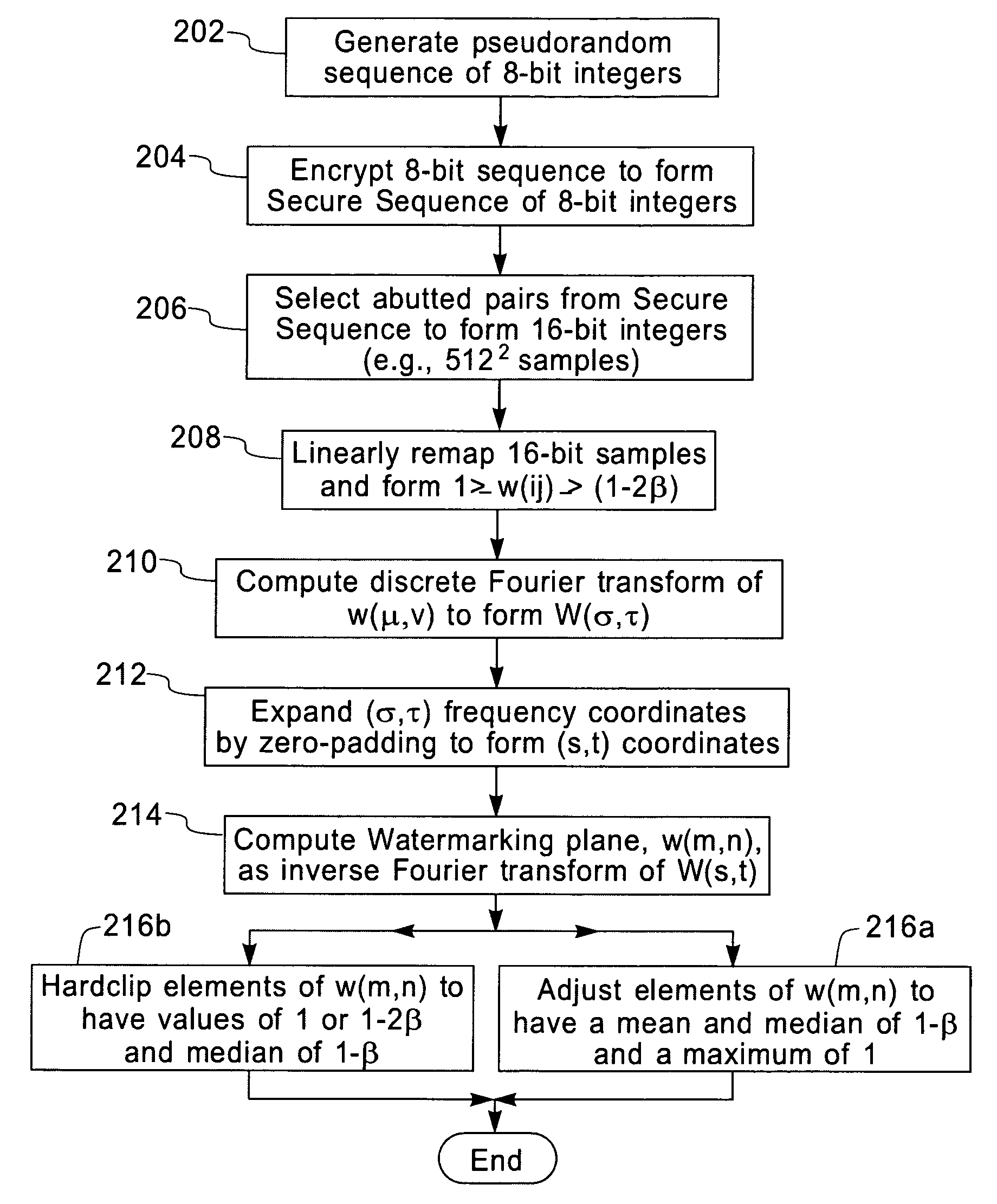
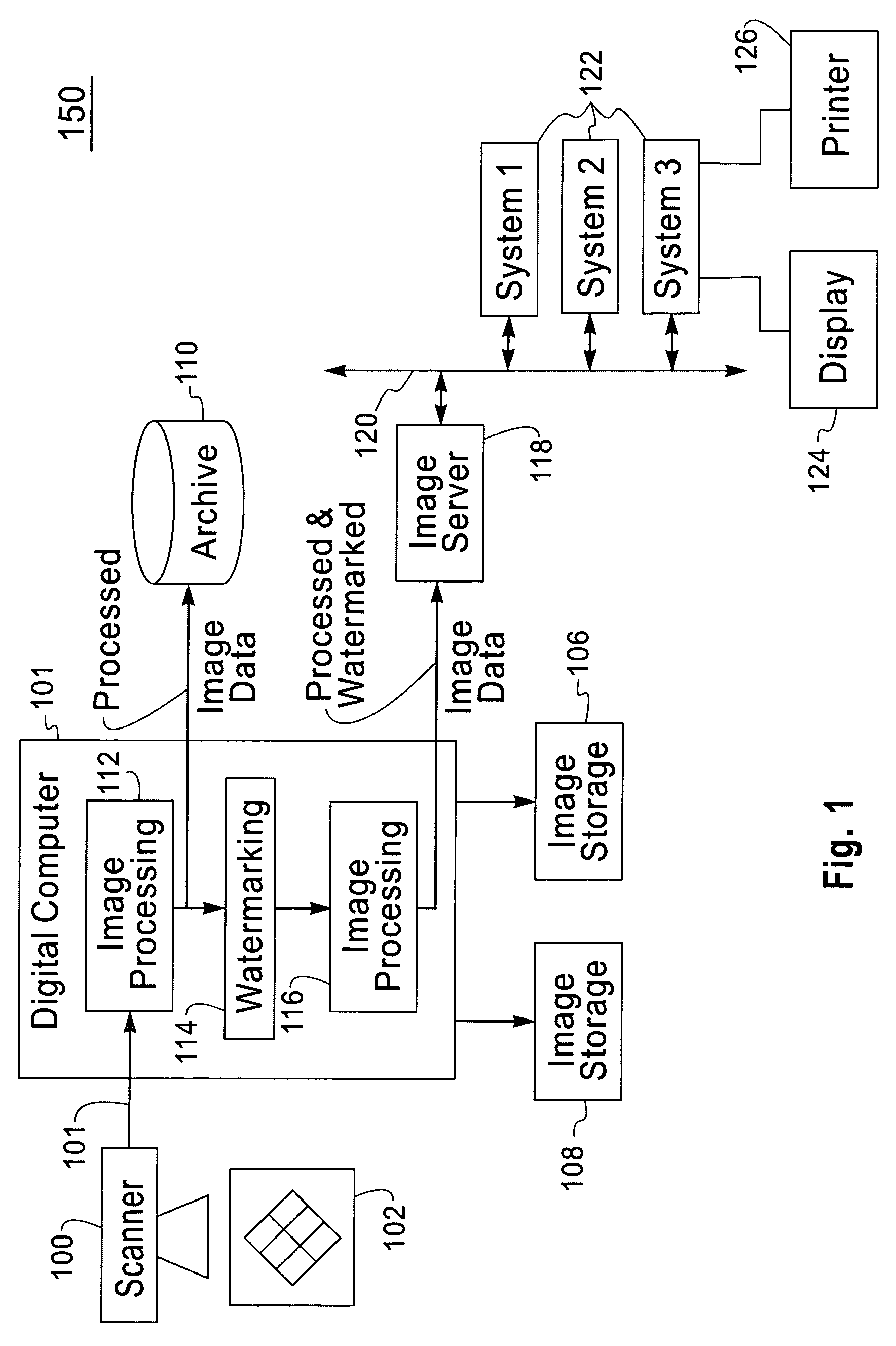
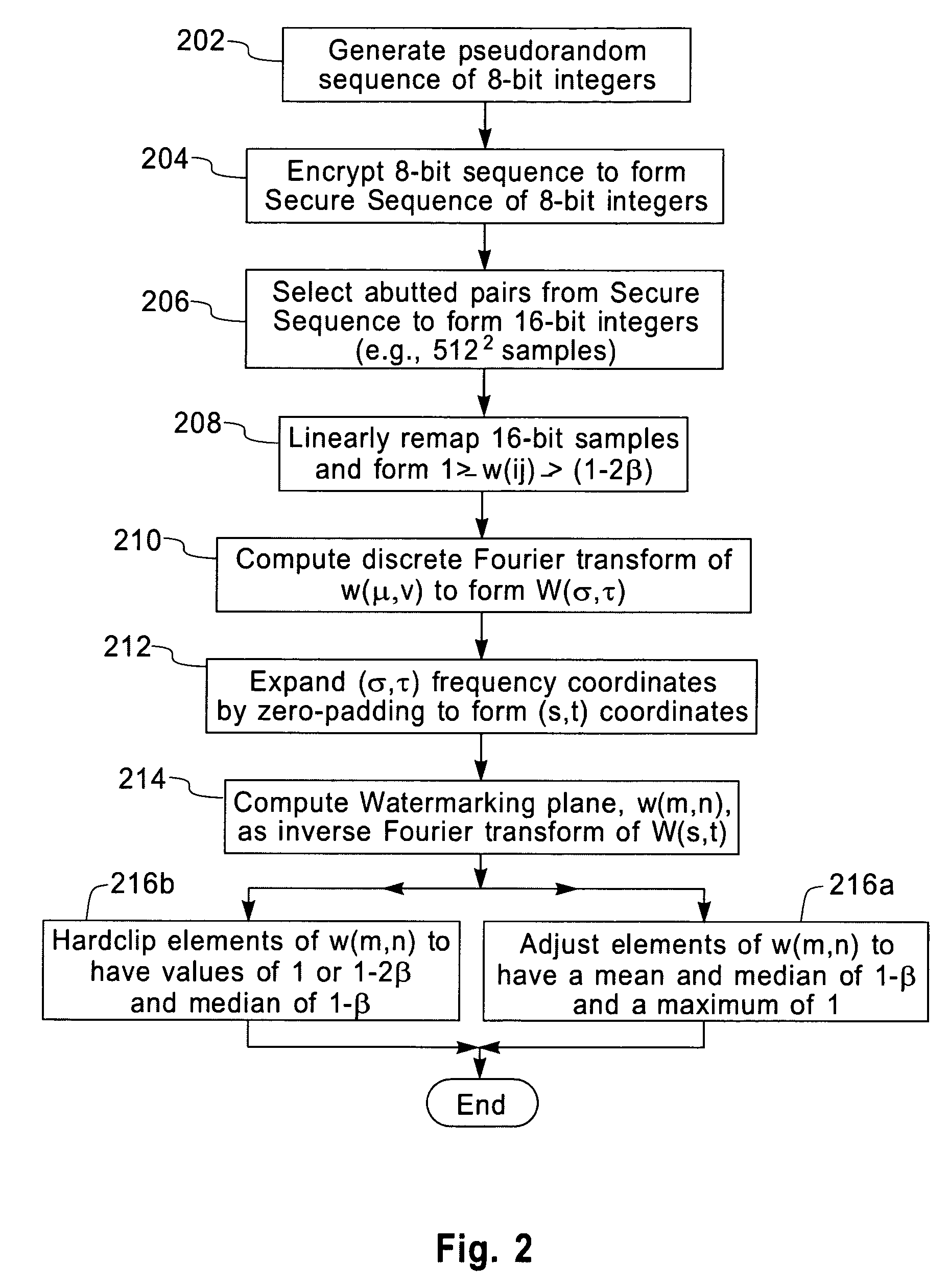
InactiveUS7130442B2Improve detection rateCharacter and pattern recognitionSecret communicationPixel brightnessLightness
A robust means of watermarking a digitized image with a highly random sequence of pixel brightness multipliers is presented. The random sequence is formed from ‘robust-watermarking-parameters’ selected and known only by the marker and / or the marking entity. A watermarking plane is generated having an element array with one-to-one element positional correspondence with the pixels of the digitized image being marked. Each element of the watermarking plane is assigned a random value dependent upon a robust random sequence and a specified brightness modulation strength. The so generated watermarking plane is imparted onto the digitized image by multiplying the brightness value or values of each pixel by its corresponding element value in the watermarking plane. The resulting modified brightness values impart the random and relatively invisible watermark onto the digitized image. Brightness modulation is the essence of watermark imparting. Detection of an imparted watermark requires knowing the watermarking plane with which the watermark was imparted. Regeneration of the watermarking plane requires knowledge of the robust-marking-parameters used in its formulation. This is generally only known to the marker and / or marking entity. Once regenerated, the watermarking plane is used together with a verifying image located in a ‘visualizer’ to demonstrate the existence of the watermark. The process of watermark detection is enhanced by application of a blurring filter to the marked image before detection is attempted.
Owner:RPX CORP
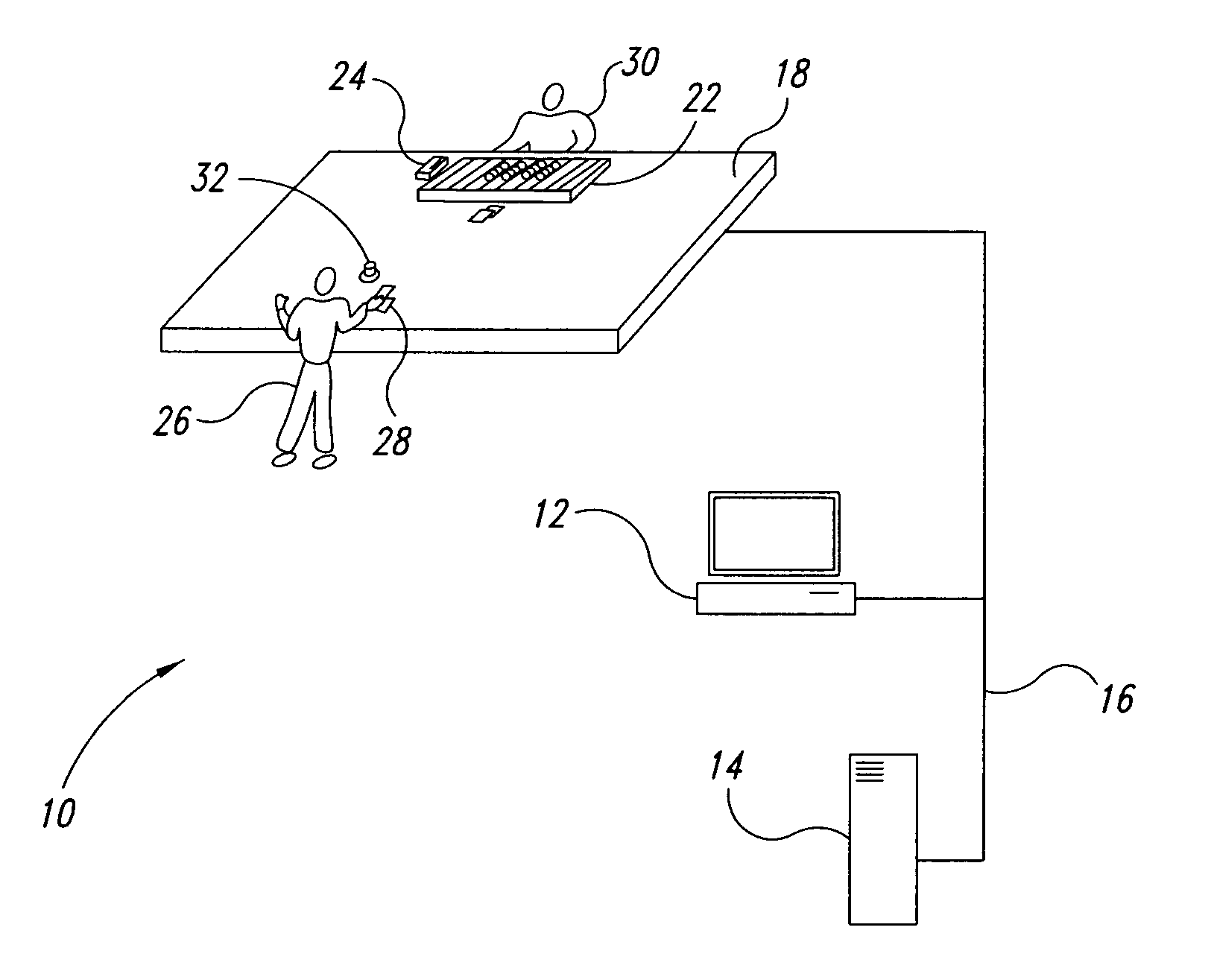
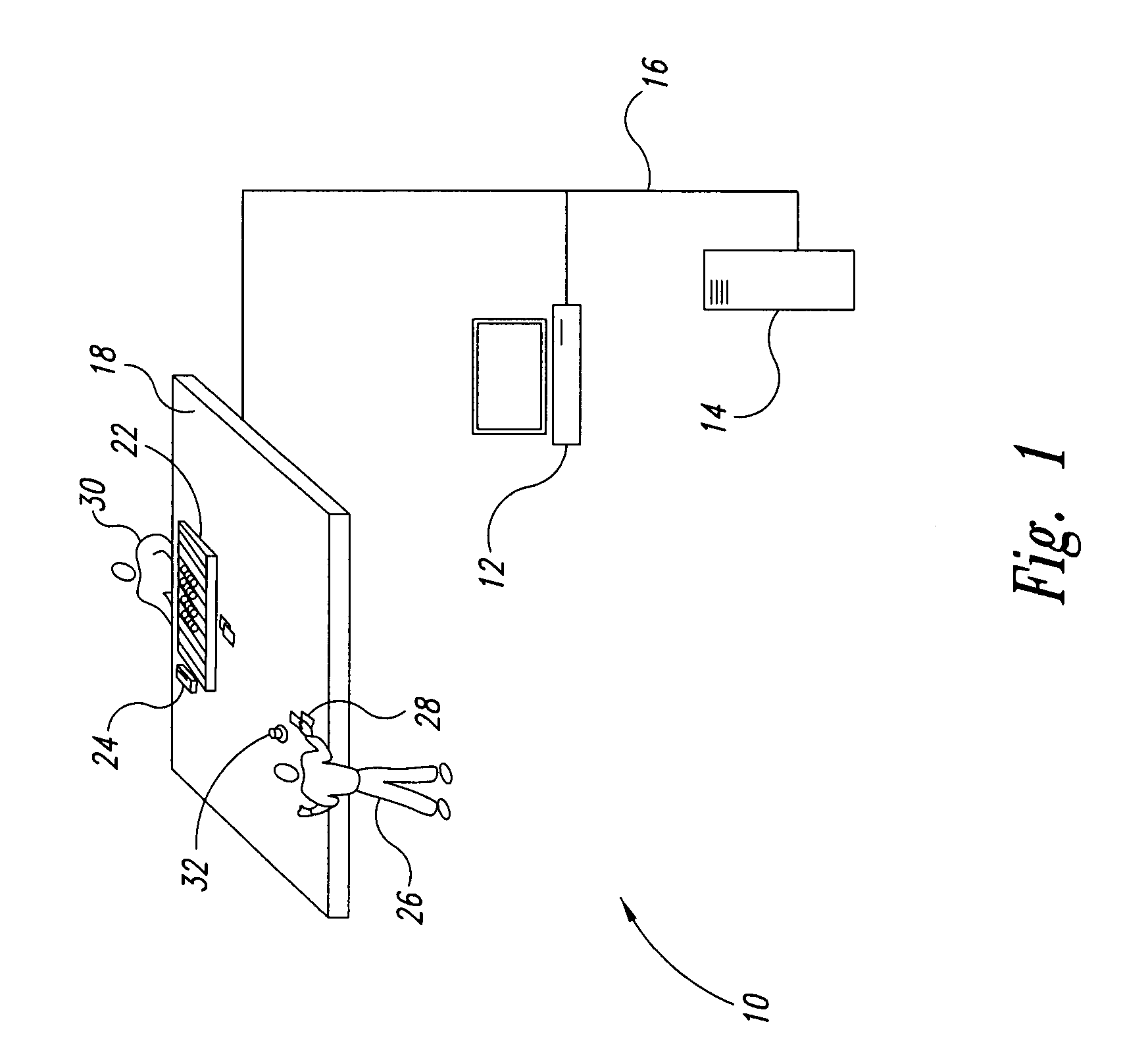
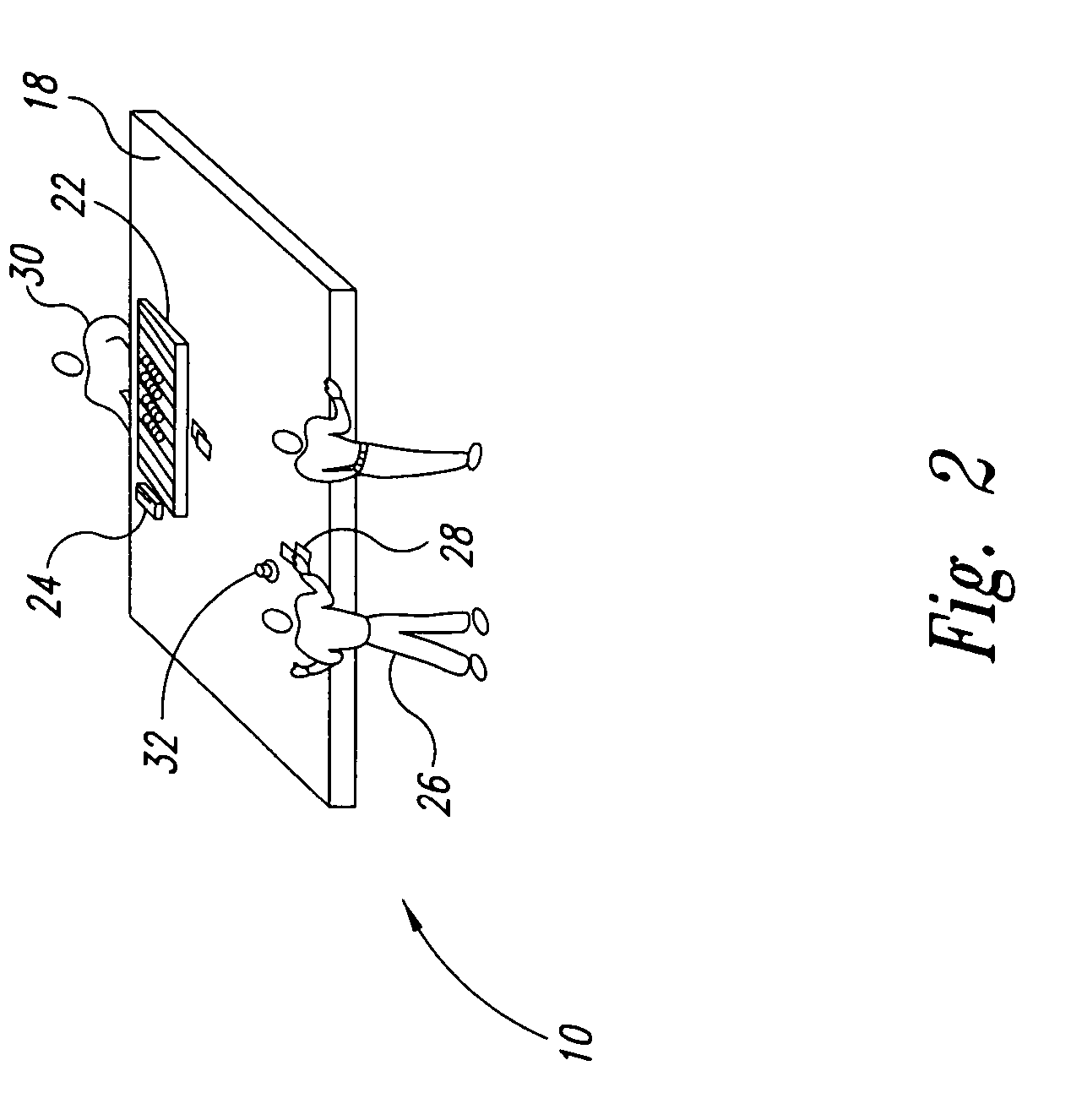
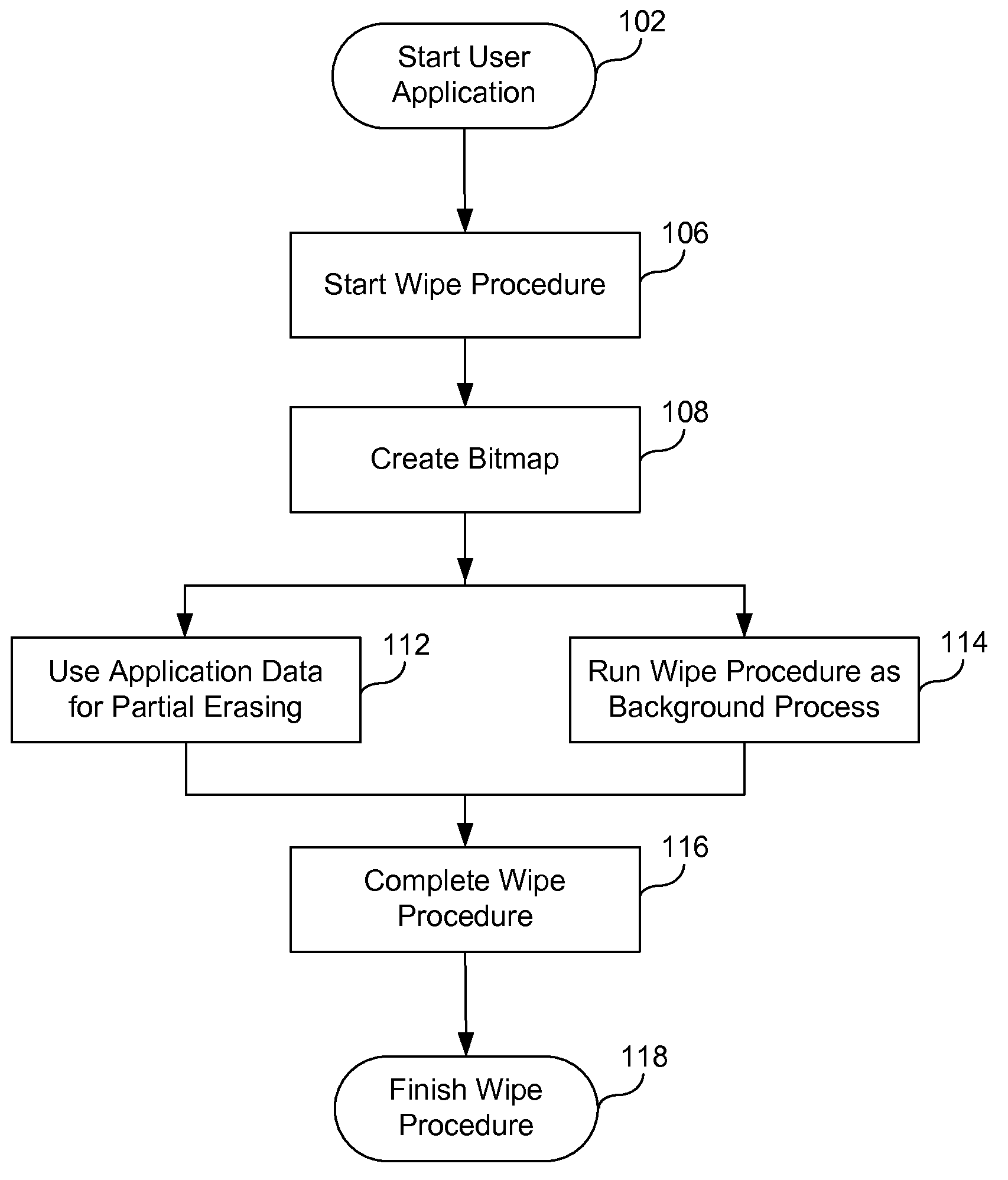
Secure deletion of information from hard disk drive
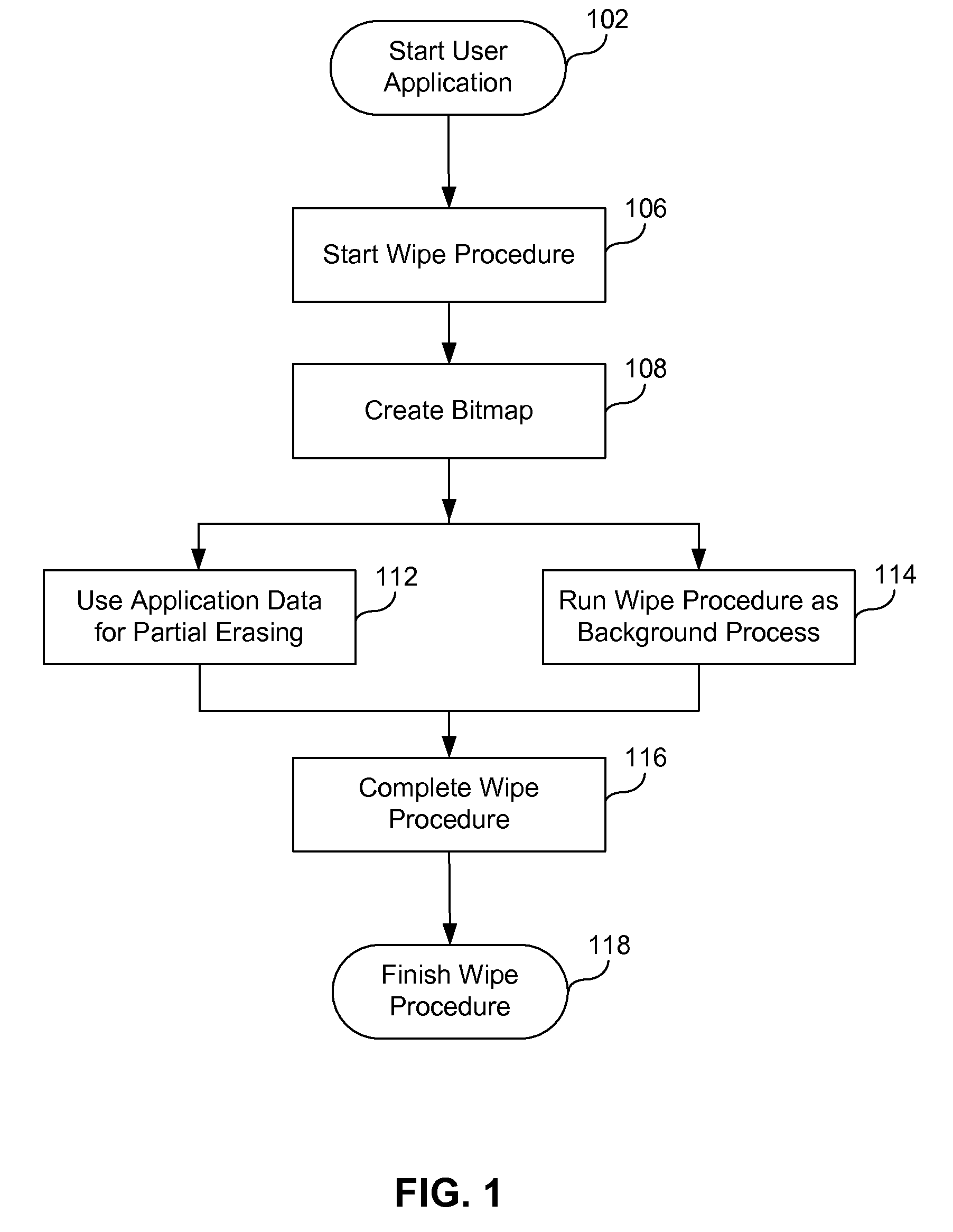
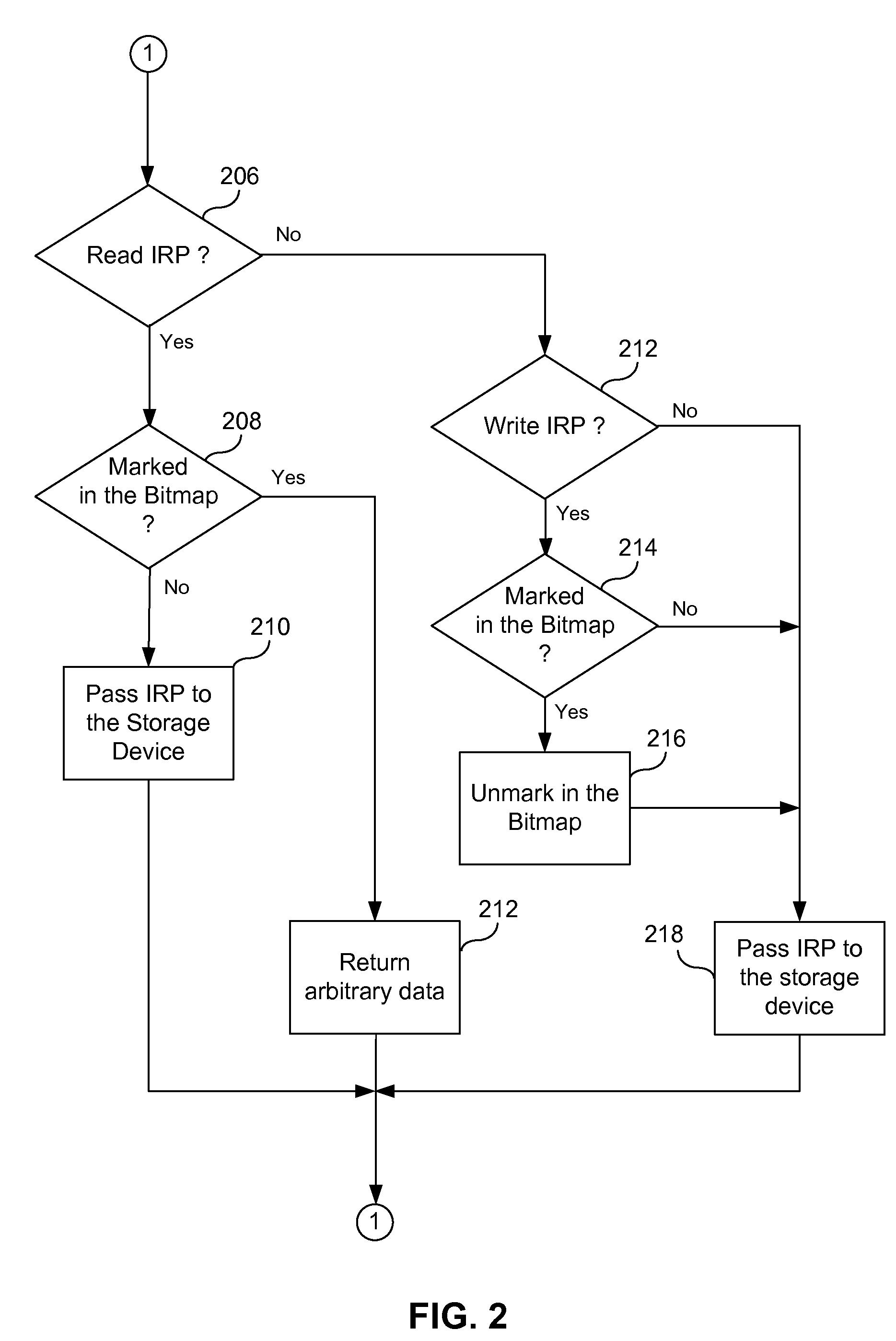
ActiveUS7650473B1Digital data processing detailsAnalogue secracy/subscription systemsHard disc driveApplication software
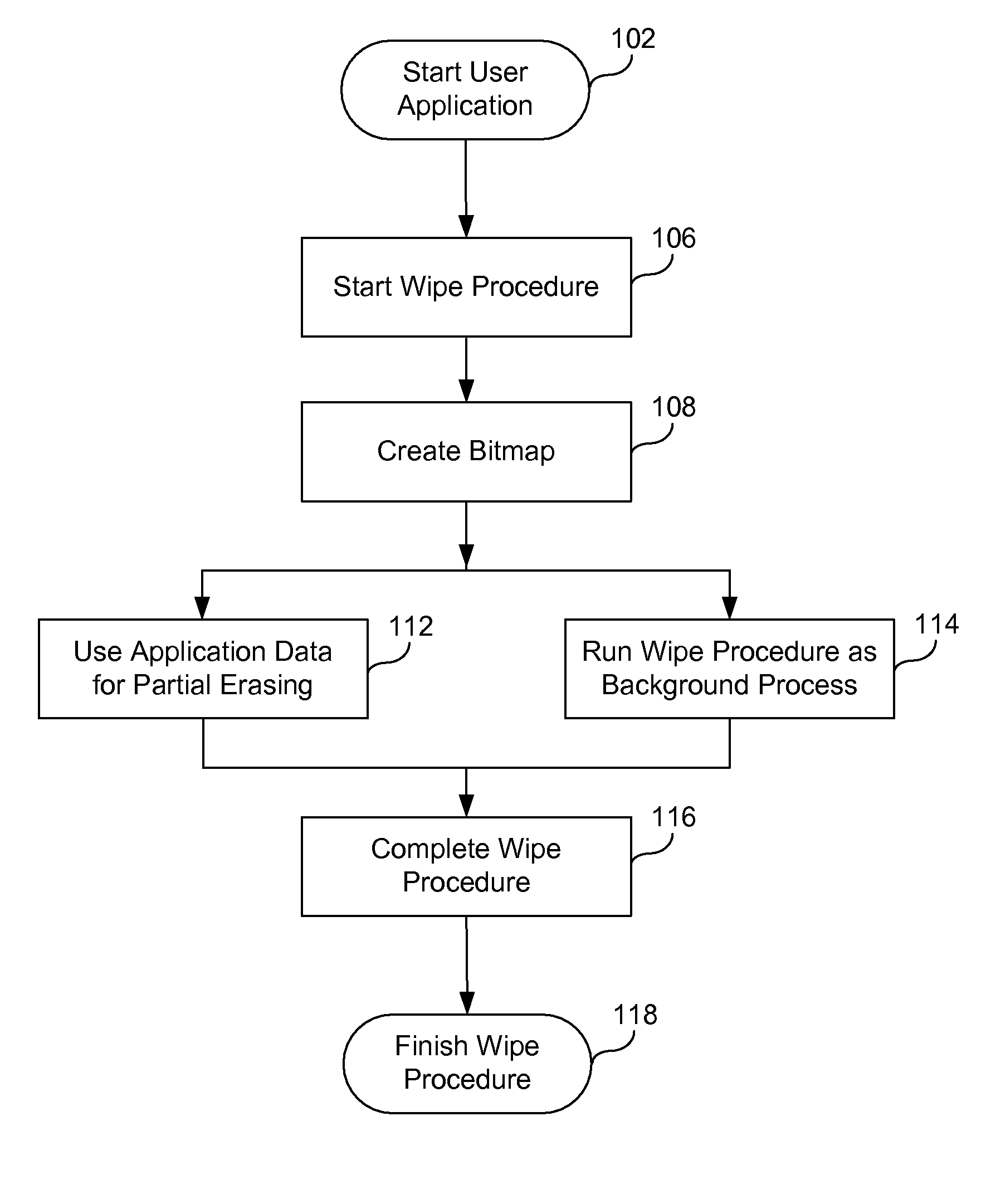
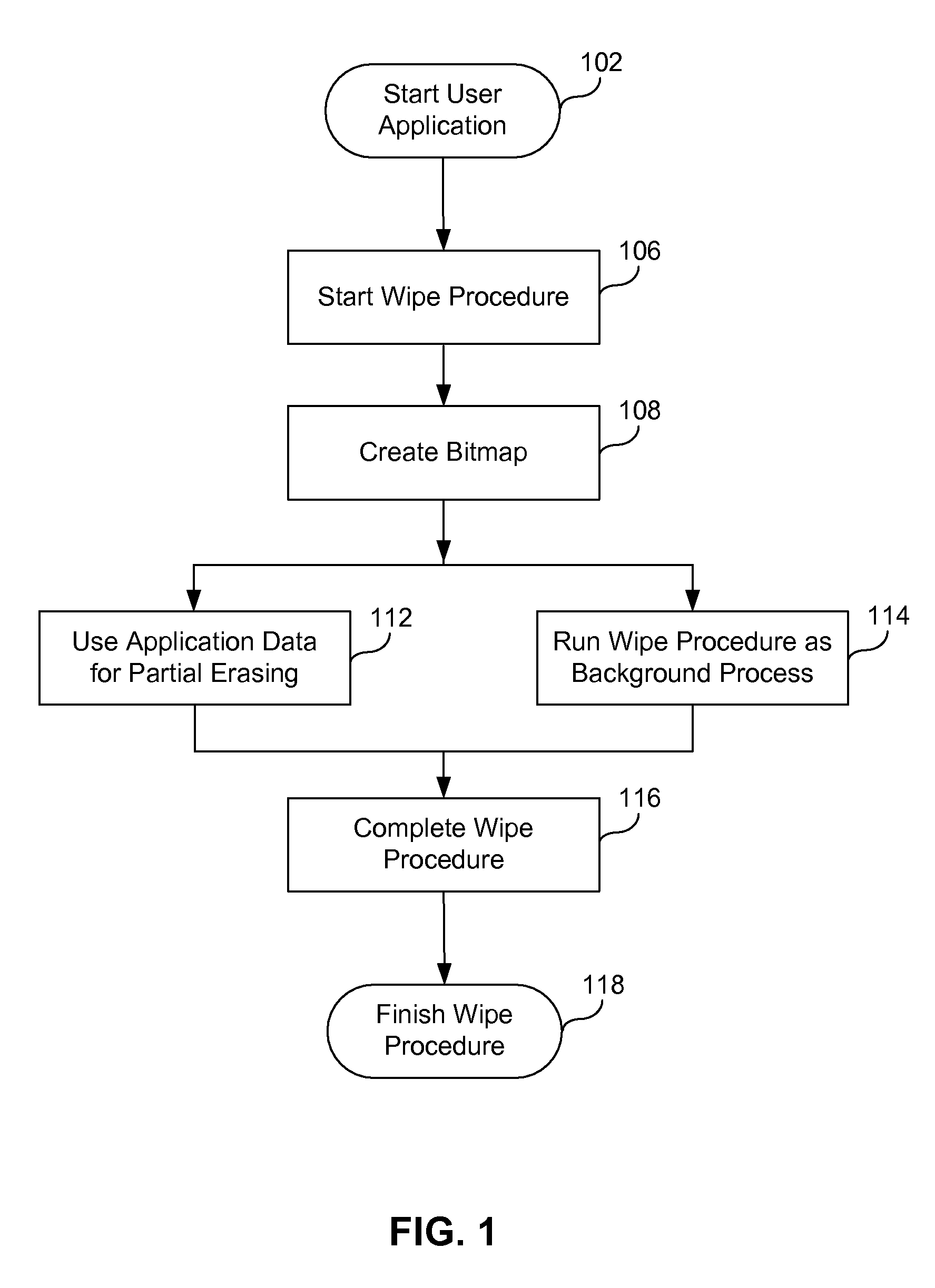
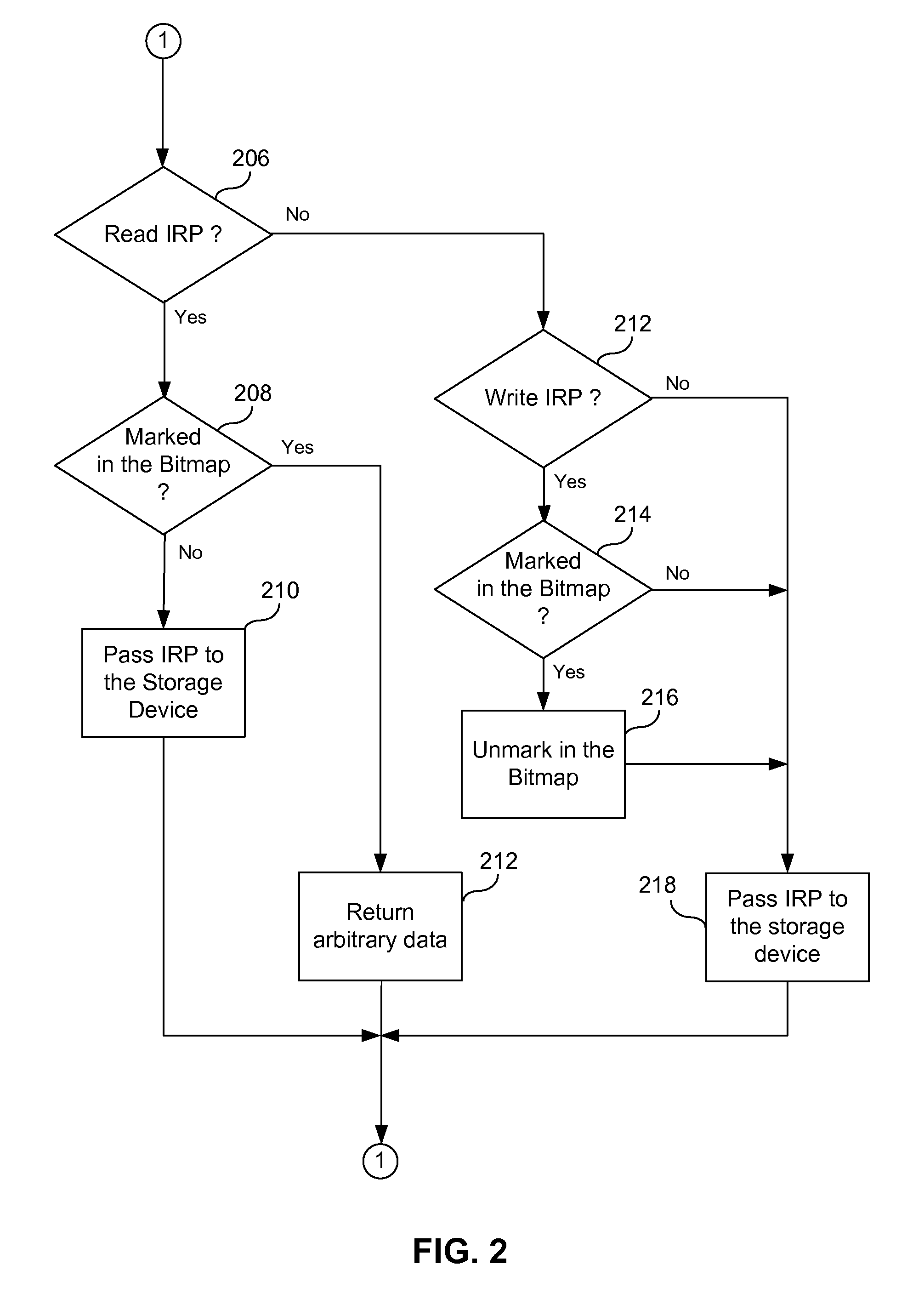
A method of securely deleting data from a storage medium includes generating a bitmap that corresponds to unused locations on the storage medium; initiating a background process that wipes the unused locations, where the background process runs asynchronously with a user application; wiping the unused locations; and updating the bitmap to reflect that the unused locations have been wiped. The wiping replaces data at the unused locations with random sequences, with pseudo-random sequences, with data generated by a secure deletion algorithm, with application data from the user application, or with all zeros. The wiping includes repeated writing of predetermined sequences to the unused locations. The wiping replaces data at unused locations that represent portions of any of blocks, clusters and sectors, and can wipe any metadata associated with files previously stored at any of the unused locations. Upon a request for access of data from a wiped location, data that does not correspond to data originally stored at the wiped location can be returned.
Owner:MIDCAP FINANCIAL TRUST
Secure data transmission from unsecured input environments
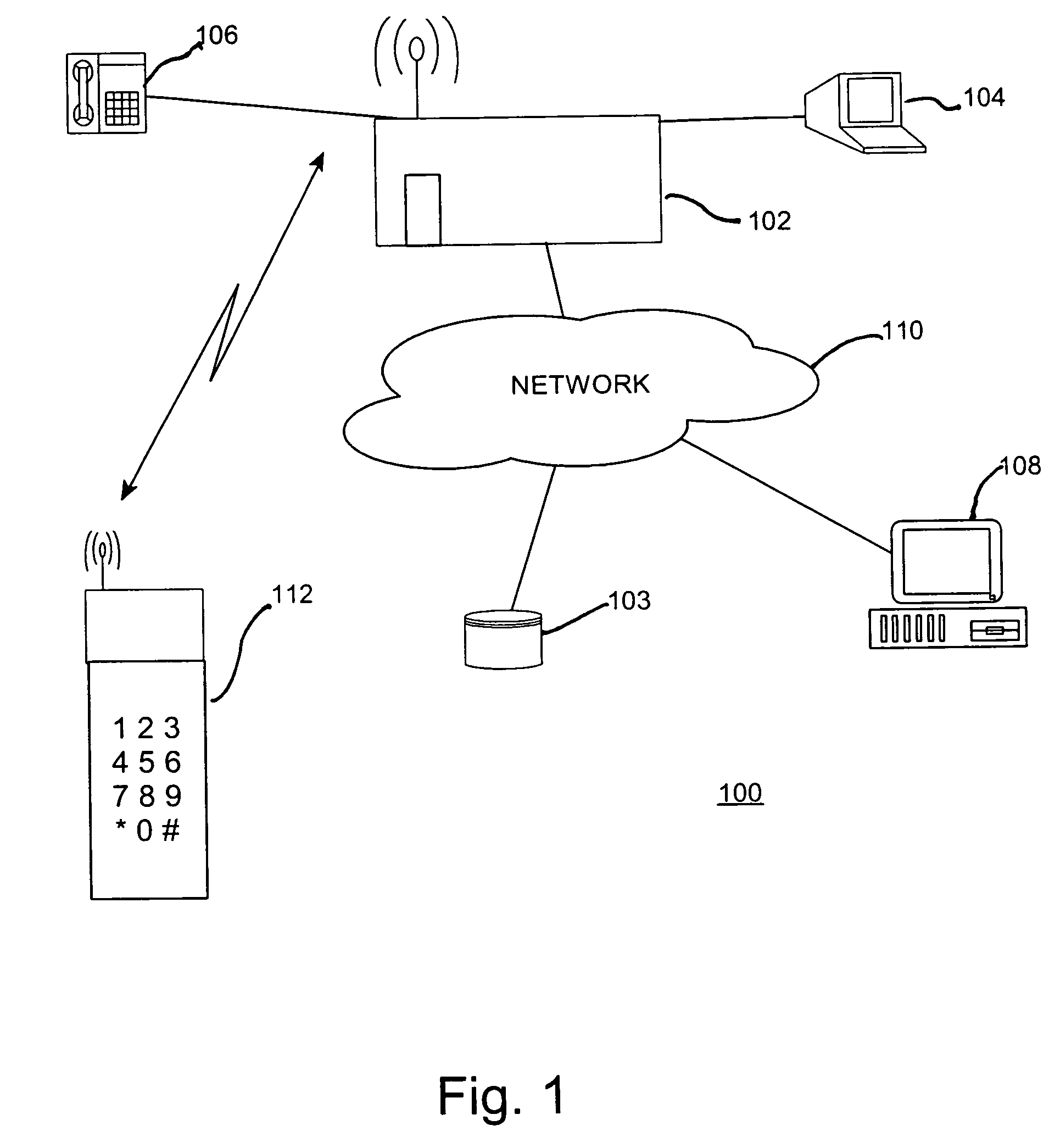
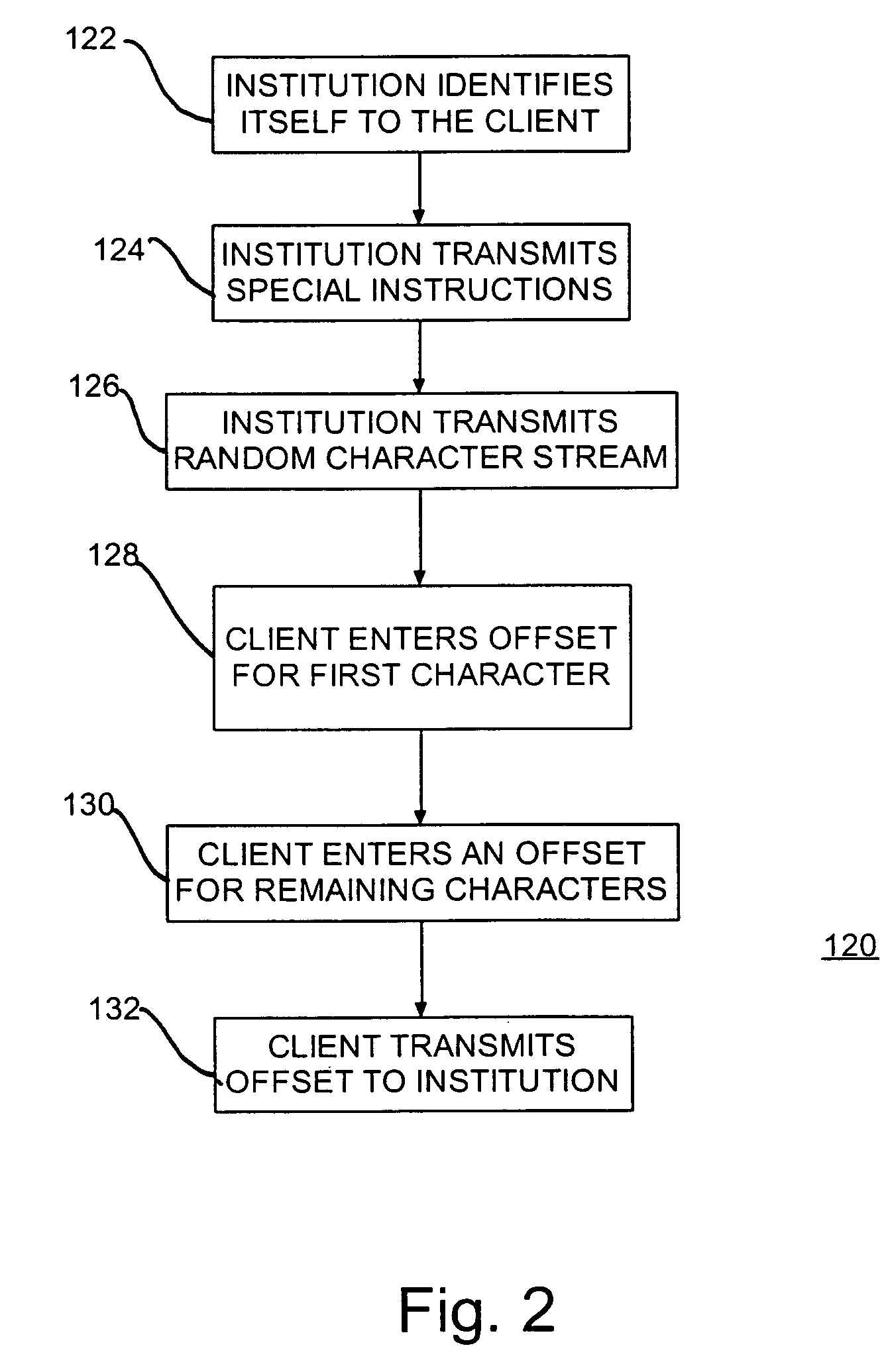
ActiveUS6990586B1Selectively accessedVolume/mass flow measurementUser identity/authority verificationPasswordClient-side
An apparatus, business method and program product for selectively providing access to a service facility such as a financial institution or bank. Client access codes (passwords, PINs) are maintained by the service facility in a database. When a client seeks access to the service facility, e.g., access to the client's account, a random sequence of character is generated and passed to the client. The client responds with an offset that when combined with the random character sequence is the client's access code. The client sends the code to the service facility and is granted access to the client's account. Optionally, the service facility may specify an intended relationship between the offset and the random character sequence, e.g., the offset is added / subtracted from the random character sequence. For additional security, dummy characters may be embedded in the random character sequence.
Owner:IBM CORP
Method and Apparatus for Generating Random Data
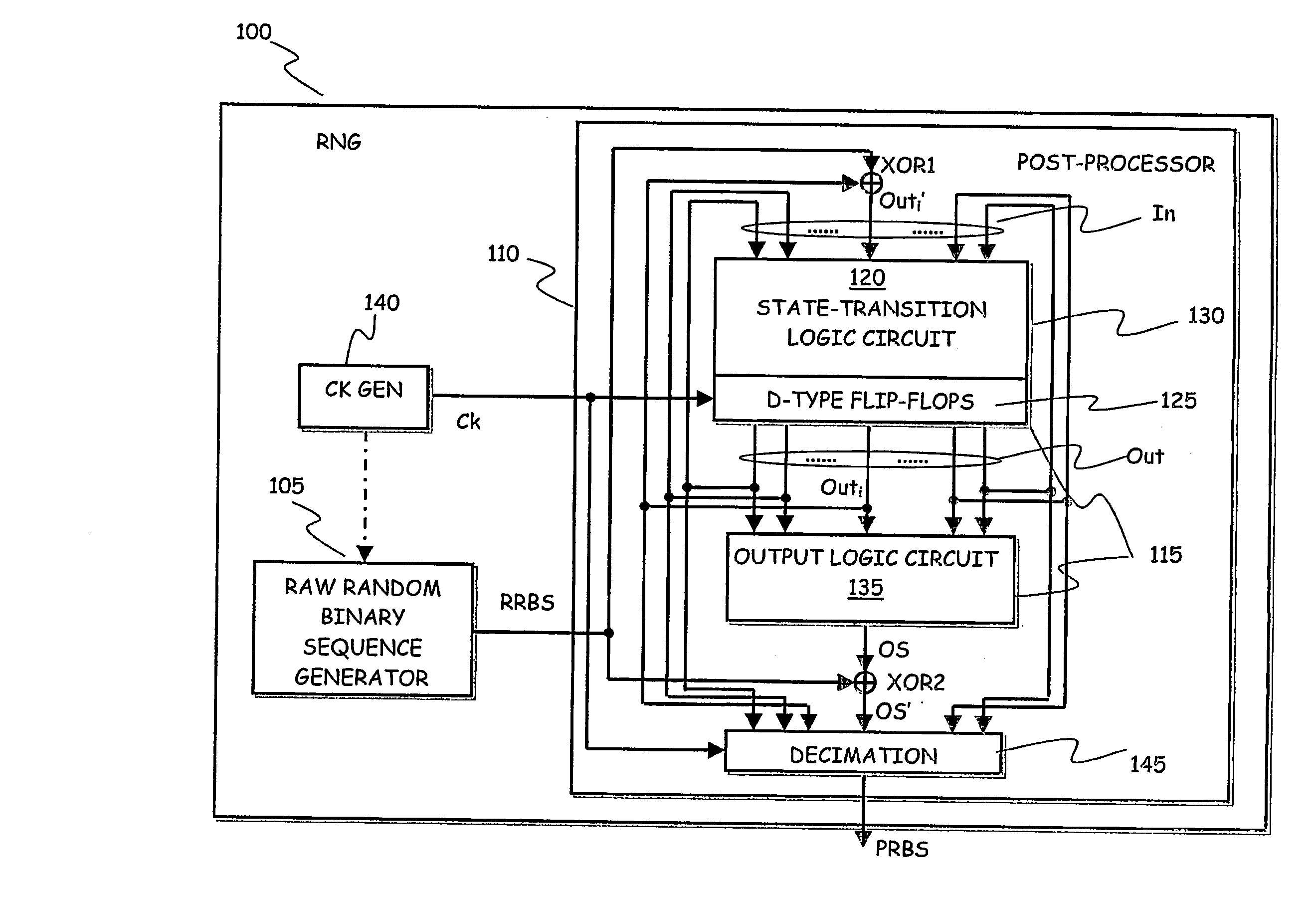
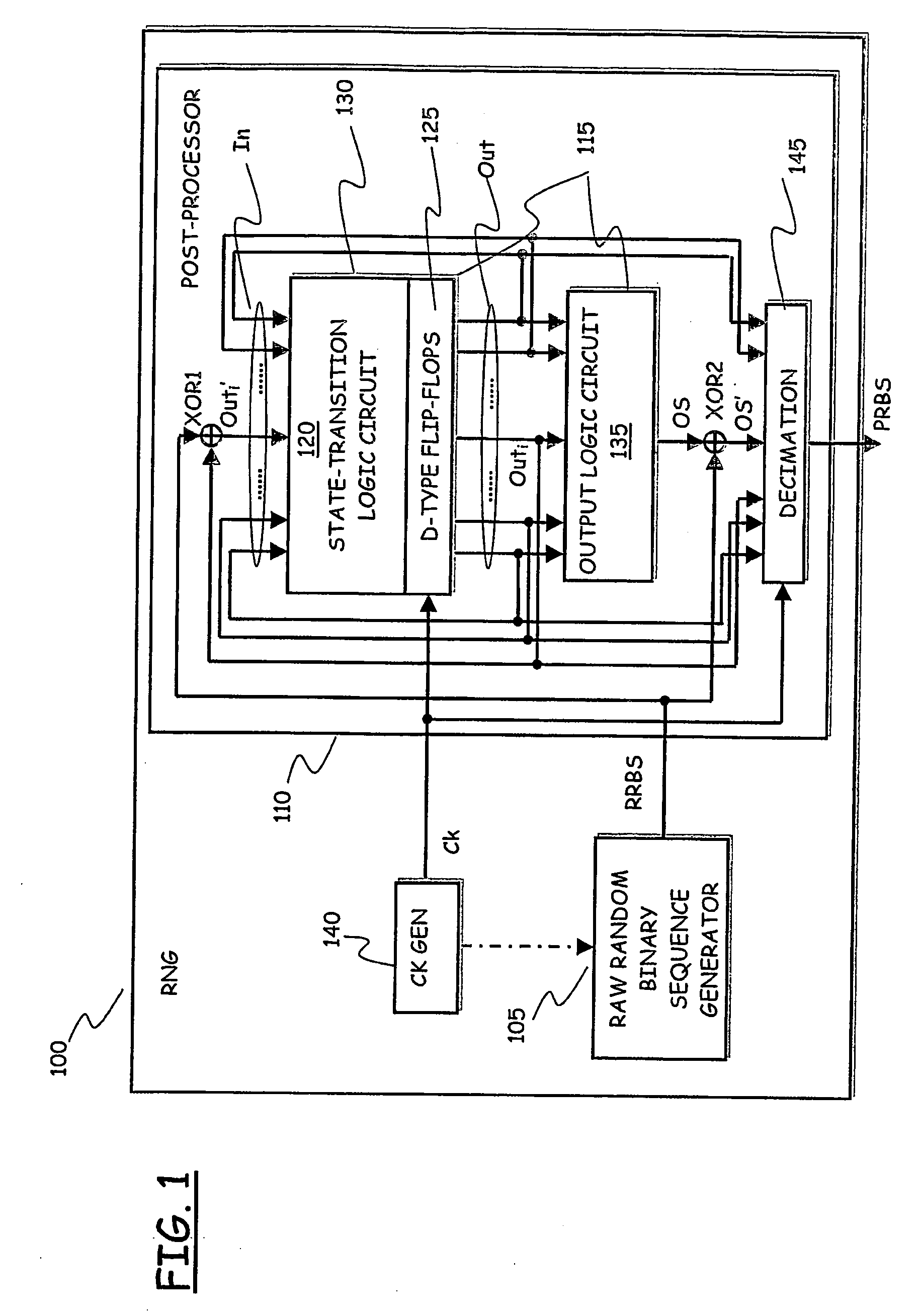
ActiveUS20070244950A1Efficient implementationRandom number generatorsDigital function generatorsPost processorFinite-state machine
An apparatus for generating random data includes a raw random sequence source adapted to generate a raw random sequence and a digital post processor adapted to process the raw random sequence to generate the random data, wherein the digital post-processor includes a synchronous finite state machine having at least one input adapted to repeatedly receive a current value of the raw random sequence and at least one output to provide a current output value depending on previous values of the raw random sequence.
Owner:TELECOM ITALIA SPA
Fast multi-photon key distribution scheme secured by quantum noise
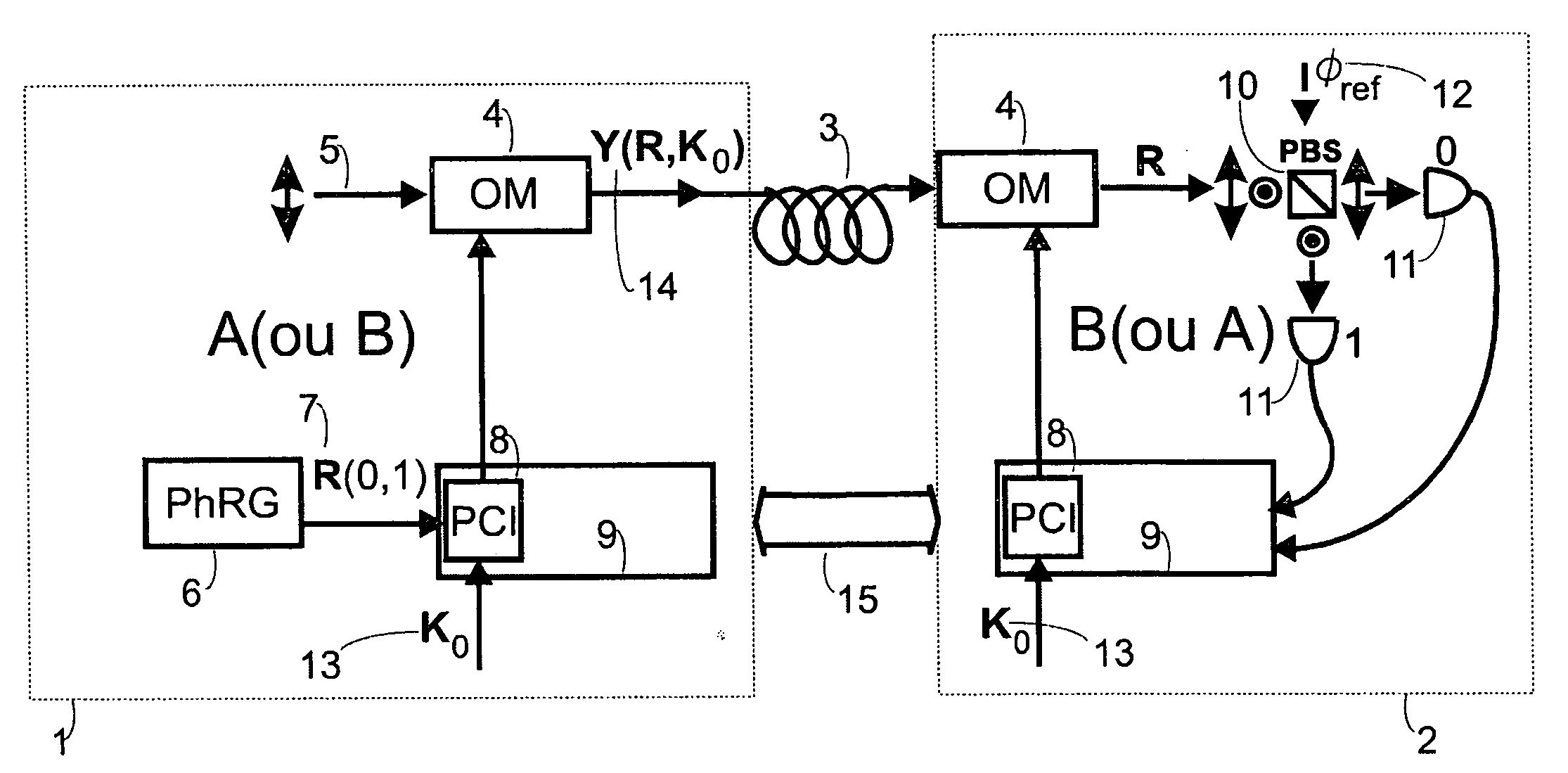
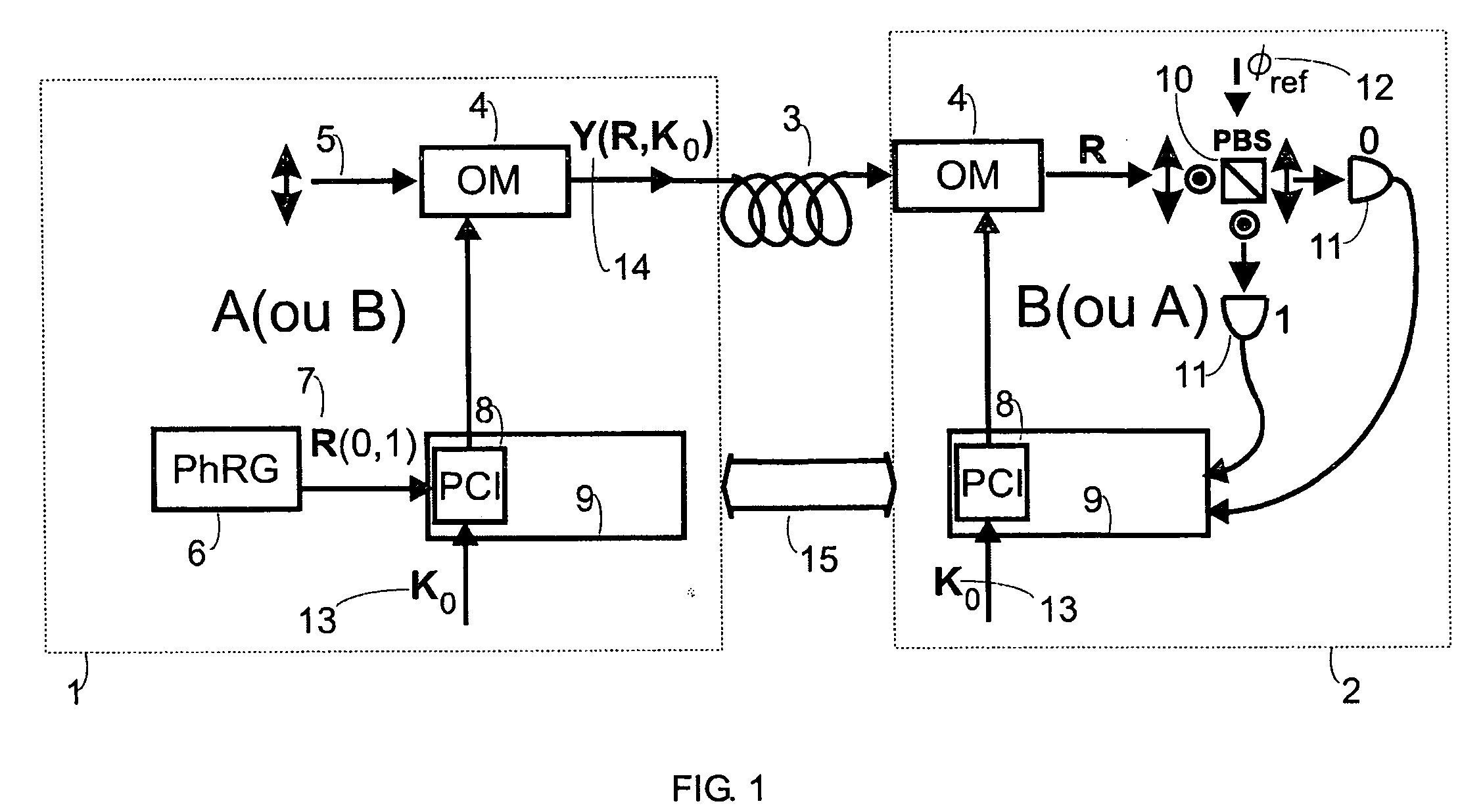
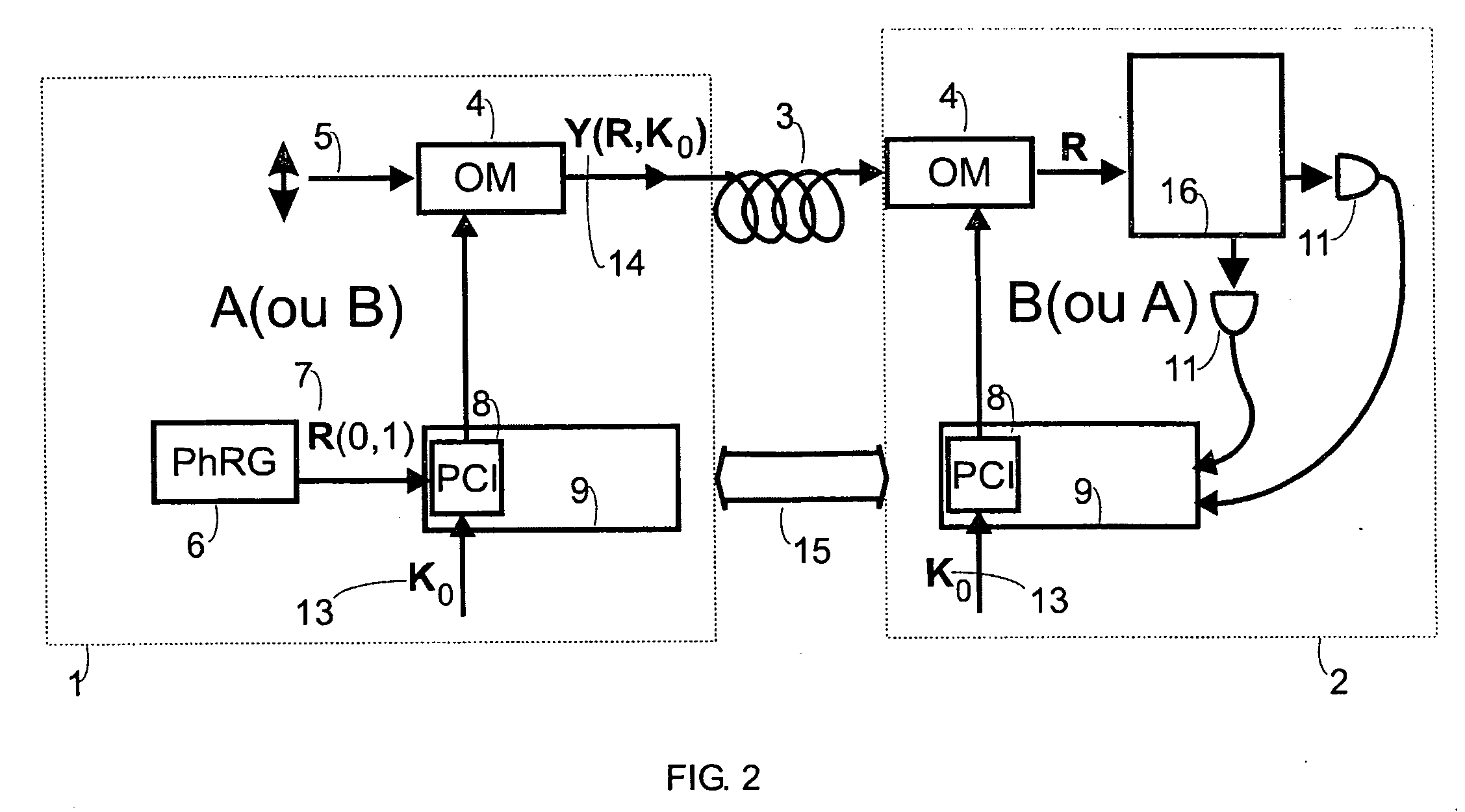
ActiveUS20050152540A1Fast and secure key distributionRaise the ratioKey distribution for secure communicationSecret communicationComputer hardwareQuantum noise
A key distribution scheme comprising a generation and reception system and a specific operation protocol is described. This system allows fast and secure key distribution in optical channels by two stations A and B. One or two true-random physical sources are used to generate random bits and a random sequence received provides the cipher to the following one to be sent. A starting shared secret key is used and the method can be described as a one-time-pad unlimited extender. The minimum probability of error in signal determination by an eavesdropper can be set arbitrarily close to the pure guessing level of one-half and the security of the method comes from the quantum noise of light as well as from the starting secret key. This system allows for optical amplification without security degradation within its operational boundaries.
Owner:SMARTPLUG
Method, apparatus and article for random sequence generation and playing card distribution
A method, apparatus and article generates a pseudo-random playing card sequence and distributes playing cards according the pseudo-random playing card sequence. For example, the method, apparatus and article generates a pseudo-random playing card sequence and prints playing cards in order of the pseudo-random playing card sequence. Further, the method, apparatus and article generates a pseudo-random playing card sequence based on a house advantage. Yet further, the method, apparatus and article can generate a promotional message on one or more playing cards.
Owner:THE US PLAYING CARD
Secure deletion of information from hard disk drive
ActiveUS7895403B1Digital data processing detailsUnauthorized memory use protectionHard disc driveBitmap
A method of securely deleting data from a storage medium includes generating a bitmap that corresponds to unused locations on the storage medium; initiating a wiping process that wipes the unused locations, where the wiping process runs asynchronously with a application; wiping the unused locations; and updating the bitmap to reflect that the unused locations have been wiped. The wiping replaces data at the unused locations with random sequences, with pseudo-random sequences, with data generated by a secure deletion algorithm, with application data from the application, or with all zeros. The wiping includes repeated writing of predetermined sequences to the unused locations. The wiping replaces data at unused locations that represent portions of any of blocks, clusters and sectors, and can wipe any metadata associated with files previously stored at any of the unused locations. Upon a request for access of data from a wiped location, data that does not correspond to data originally stored at the wiped location can be returned.
Owner:MIDCAP FINANCIAL TRUST
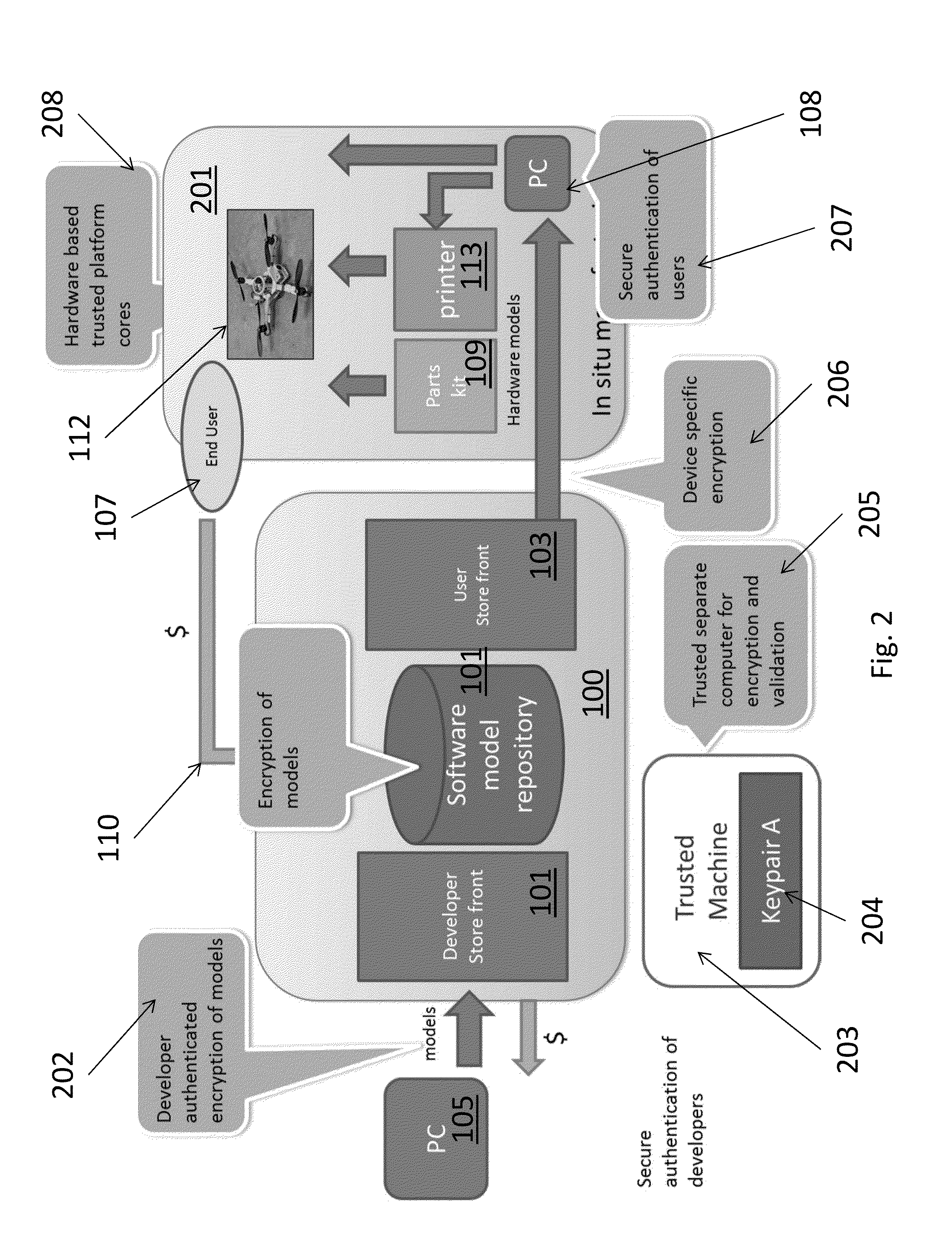
Method for Using Cryptography to Protect Deployable Rapid On-Site Manufacturing 3D Printing Systems and Enable a Single Time Printing Protocol
InactiveUS20150134955A1Key distribution for secure communicationUser identity/authority verificationThird partyWeb service
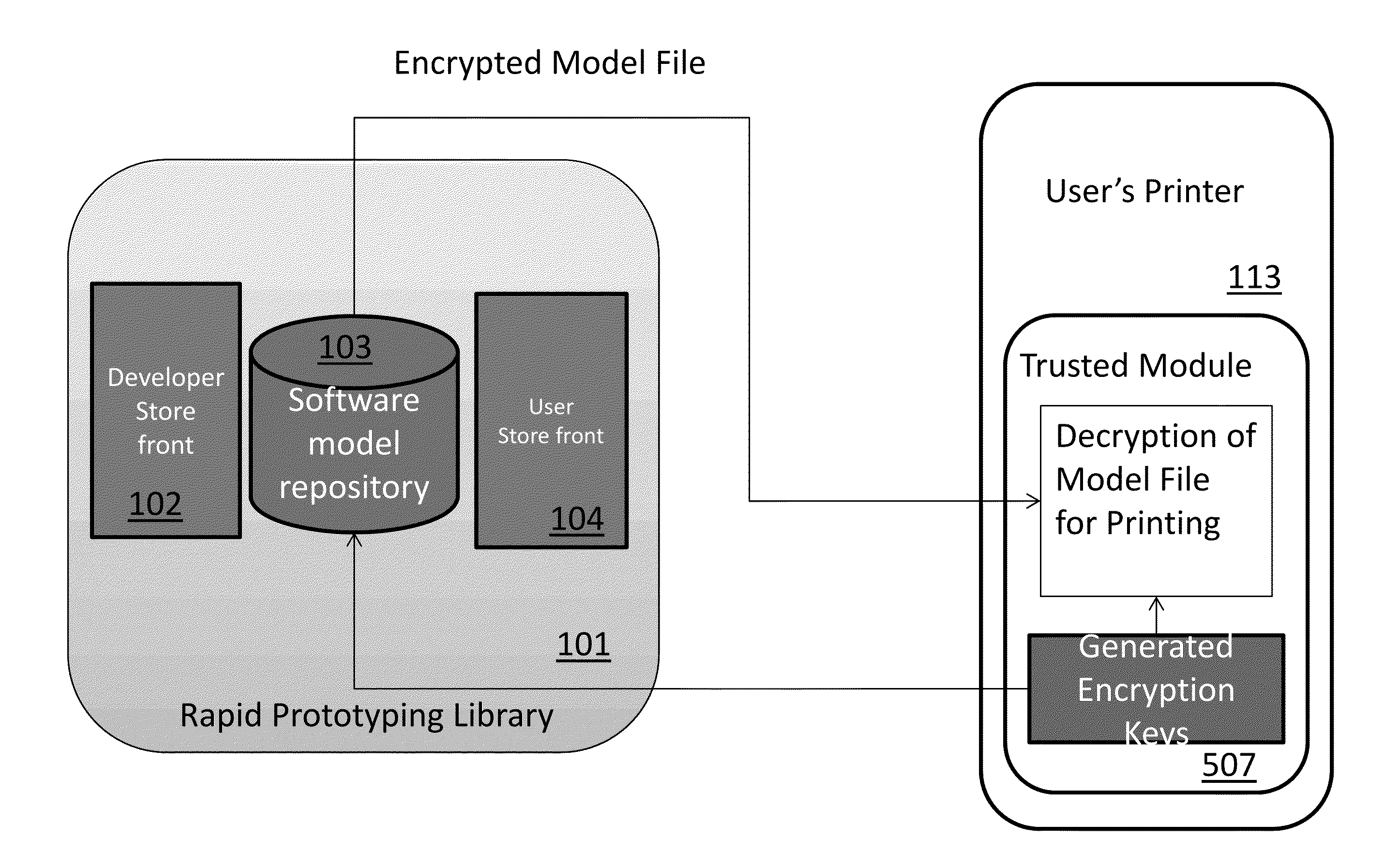
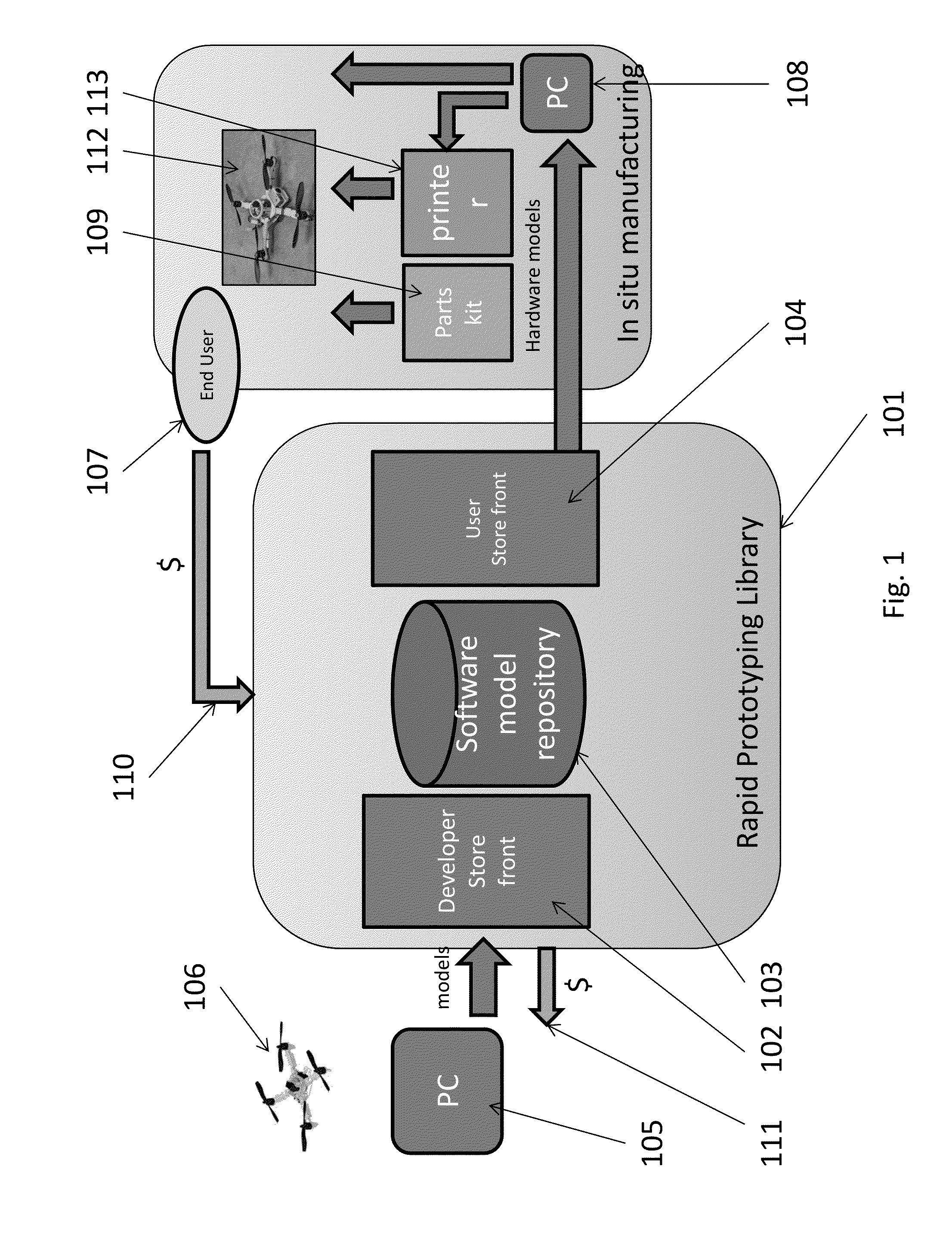
A webserver is comprised of a registry, database, web store, arbiter, and signature verifier with device public keys. An external trusted machine provides a first key pair to the server system. The database contains encrypted copies of developer software / models, using the Trusted Machine to encrypt. The Signature Verifier verifies that devices requesting code are truly safe devices provided from a third party. The Trusted Machine is an extremely secure machine with a first key pair “A” used to encrypt and decrypt entries into the database safely. A trusted module is associated with the printer which comprises a random sequence generator. The printer generates keys required for printing and authorization using a Common Access Card (CAC). Next the server would encrypt the model with the keys generated by the trusted module of the printer to allow for the printer to decrypt the keys and effectuate printing of the encrypted model.
Owner:ROBOTIC RES OPCO LLC
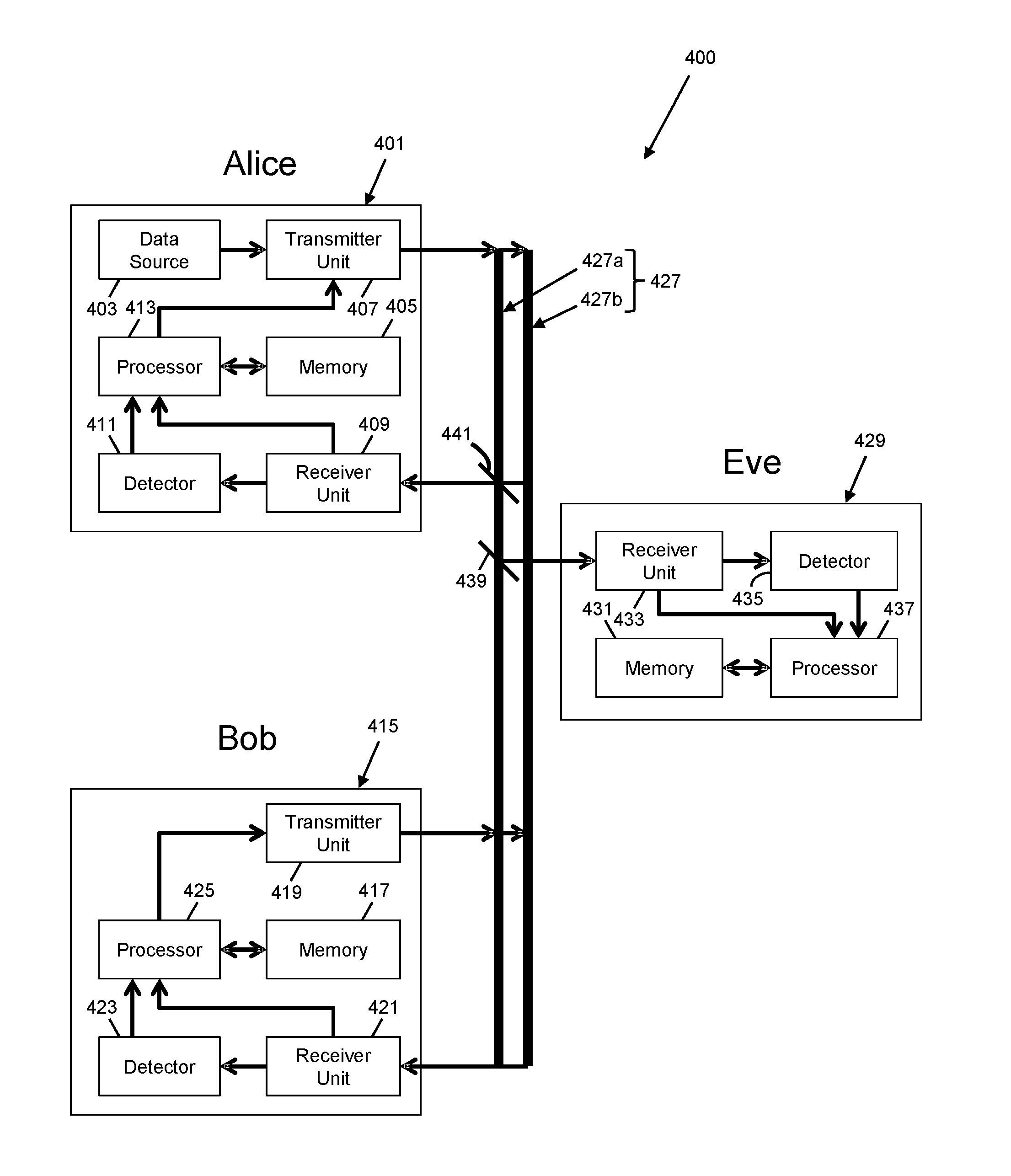
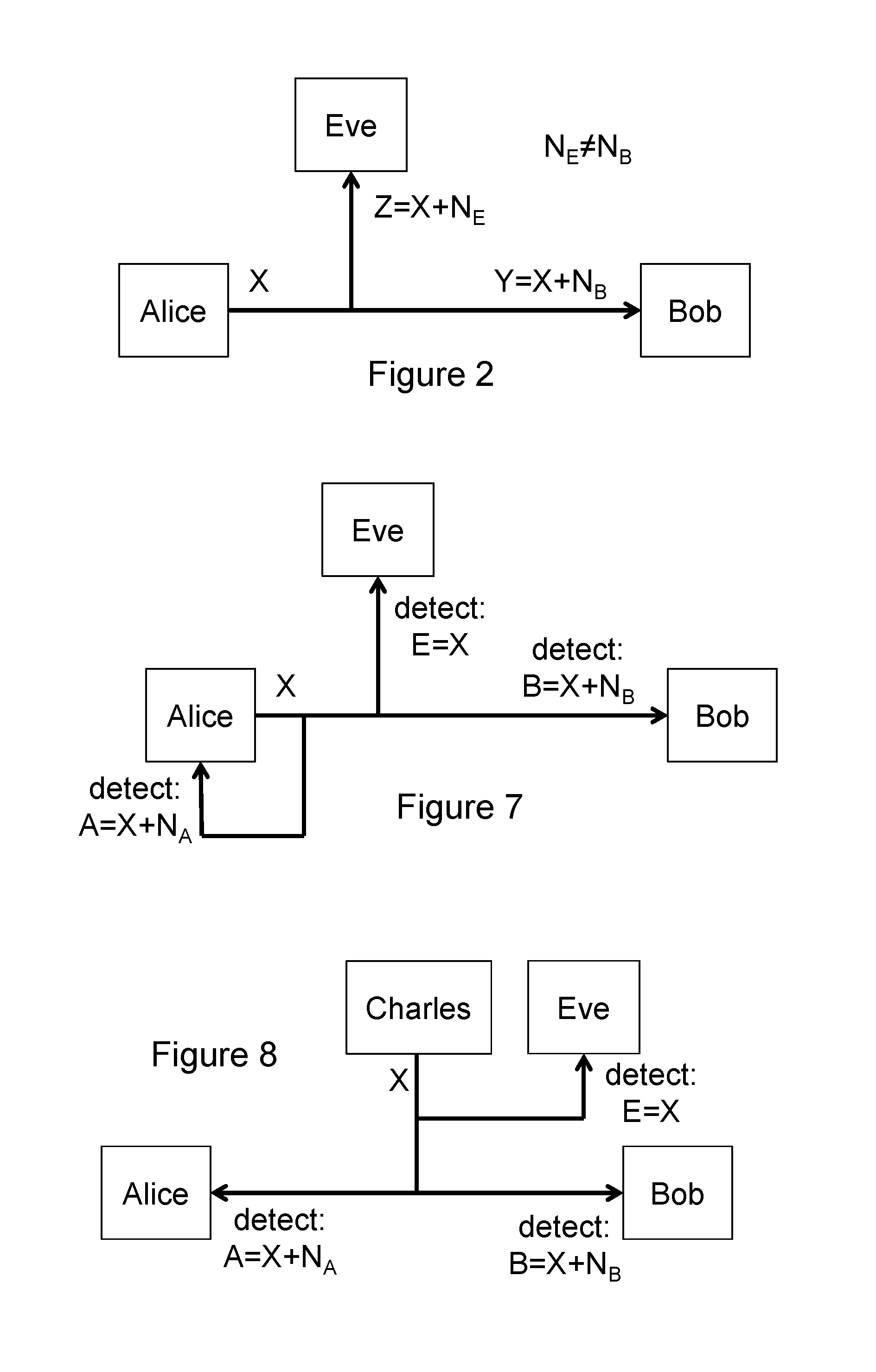
Secure communication
A method for allowing a first party and a second party to obtain shared secret information is provided. The method comprises the steps of: obtaining, by the first party, a sequence of values A=X+NA where X is a sequence of values and NA is a random sequence associated with the first party; obtaining, by the second party, a sequence of values B=X+NB where NB is a random sequence associated with the second party; performing, by the first and second parties, a data matching procedure to identify corresponding pairs of values, a, b in respective sequences A and B that match, wherein sequences A and B are discrete-valued sequences equal to, derived from, or derived using, sequences A and B; wherein the shared secret information is equal to, or derived from, or derived using, the matching values in sequences A and B.
Owner:UNIV OF LEEDS
Establishing method of uncertainty mid-term and long-term hydrological forecasting model
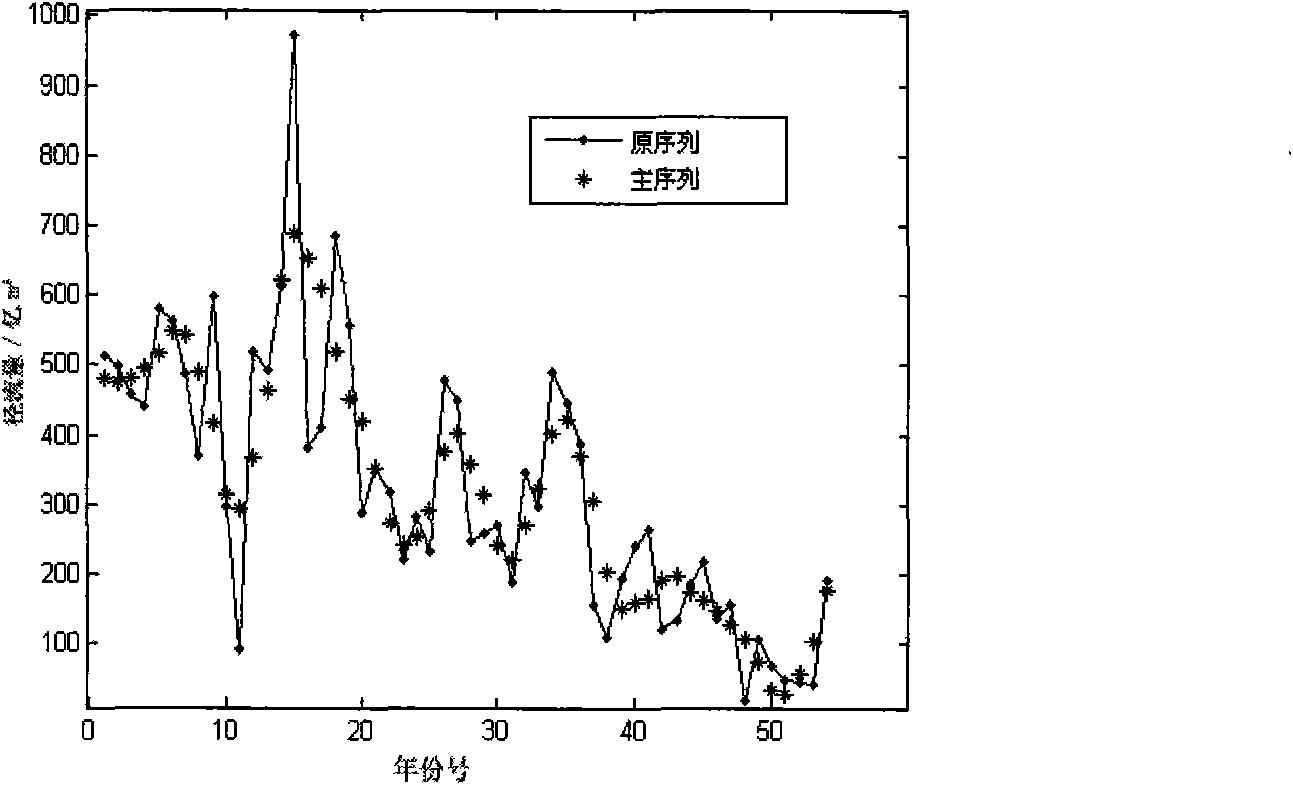
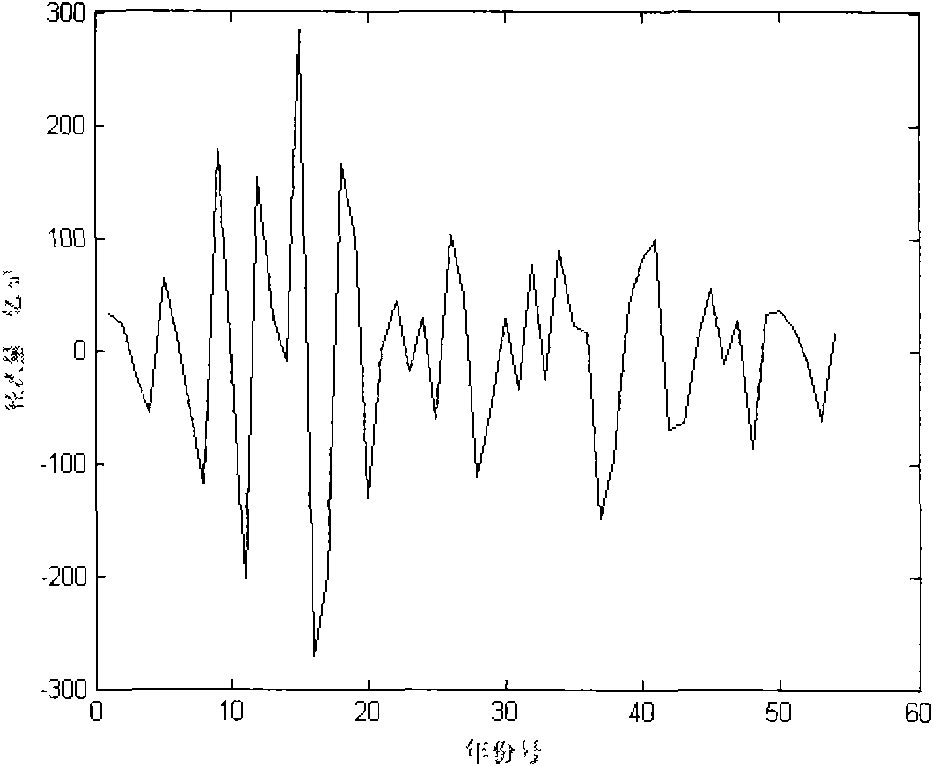
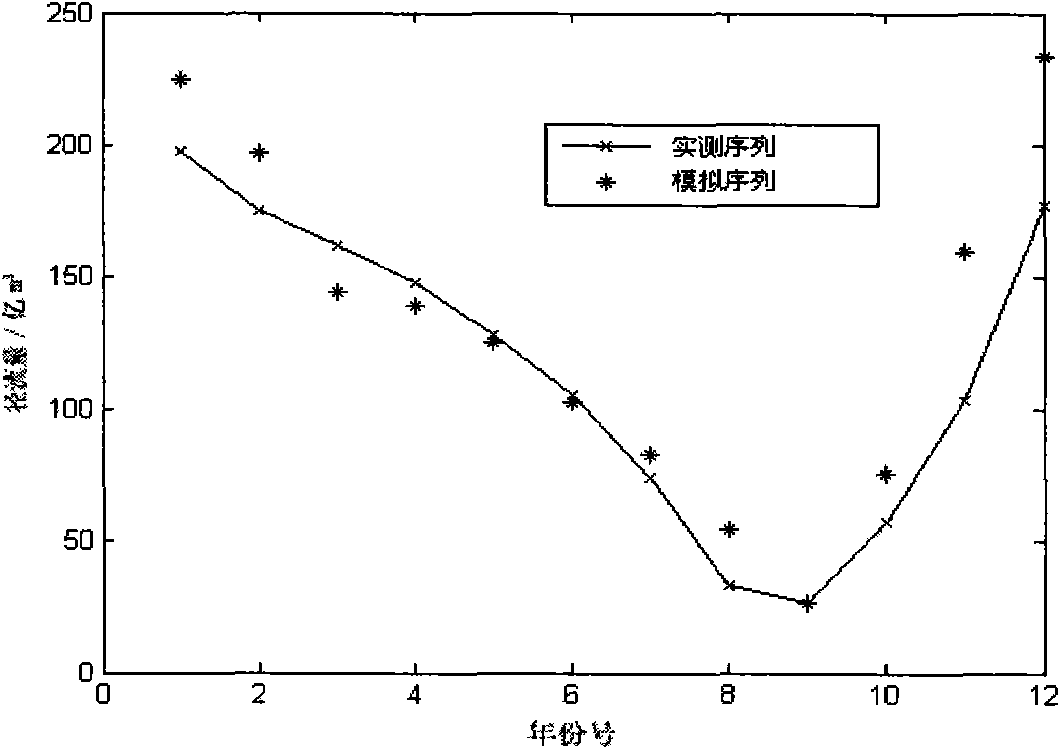
InactiveCN101604356AReveal detailed variation characteristicsReduce blindnessOpen water surveyPhysical realisationMain sequenceBusiness forecasting
The invention discloses an establishing method of an uncertainty mid-term and long-term hydrological forecasting model, comprising the following steps: using a wavelet analysis (WA), an artificial neural network (ANN) and a hydrological frequency analysis (HFA) in combination to establish the uncertainty mid-term and long-term hydrological forecasting model; dividing the original sequence into two sections of a main sequence and a random sequence on the basis that WA is used to reveal multiple time dimension variation characteristics of the hydrological sequences, adopting ANN for analogue forecasting on the main sequence and hydrological frequency analysis on the random sequence and overlapping the results of the two sections to be a final forecasting value. The model is used for the mid-term and long-term hydrological forecasting in the Yellow River estuary area, and compared with the traditional method, the results show that the model can reveal the time and frequency structures and variation characteristics of the sequences, has high forecast value result precision and acceptance rate, can quantitatively analyze and describe the impact of hydrological uncertain factors on the forecasting result and can obtain the analogue forecasting value of different frequencies to corresponding hydrological sequences.
Owner:NANJING UNIV
Pseudo-random number generator
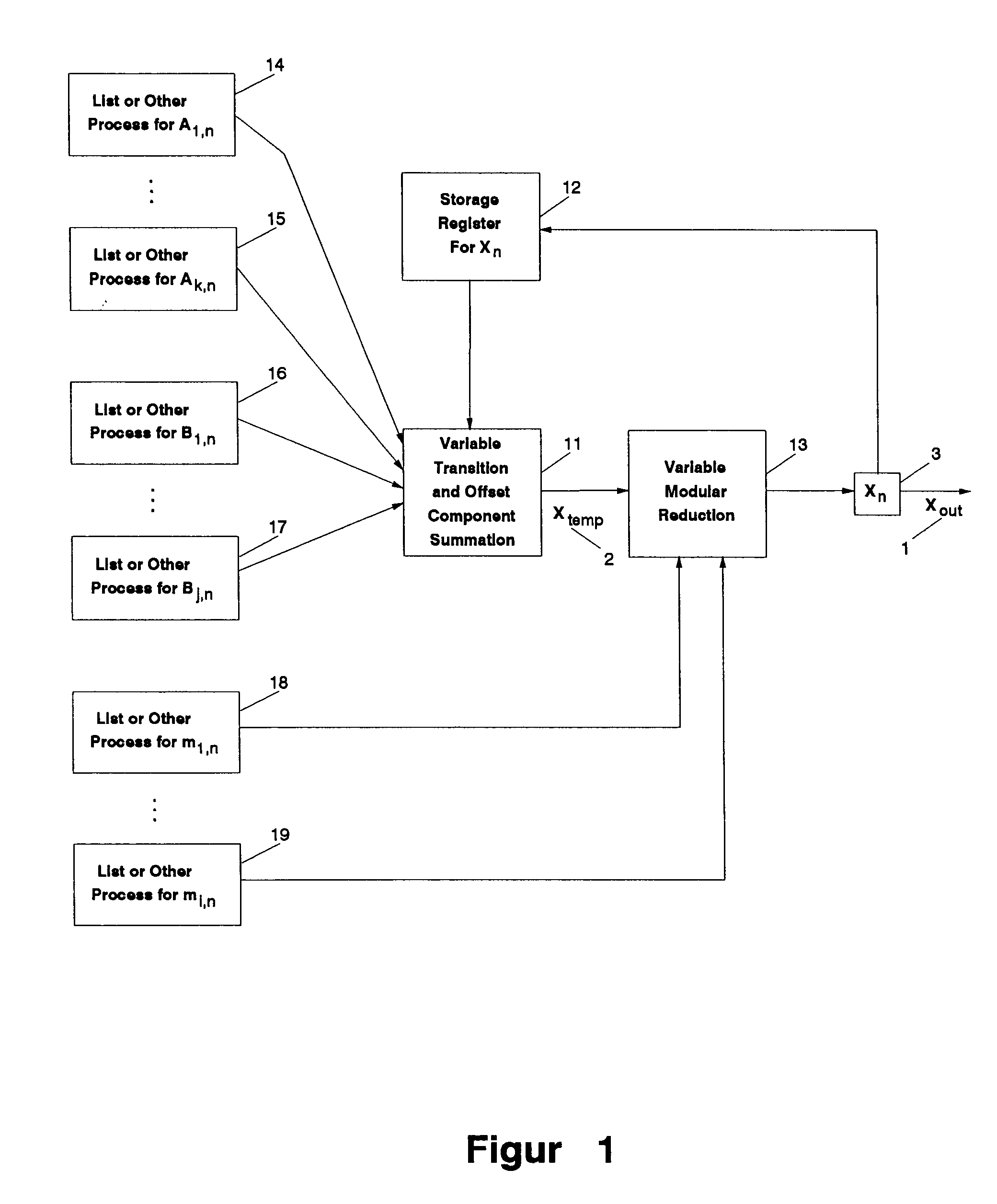
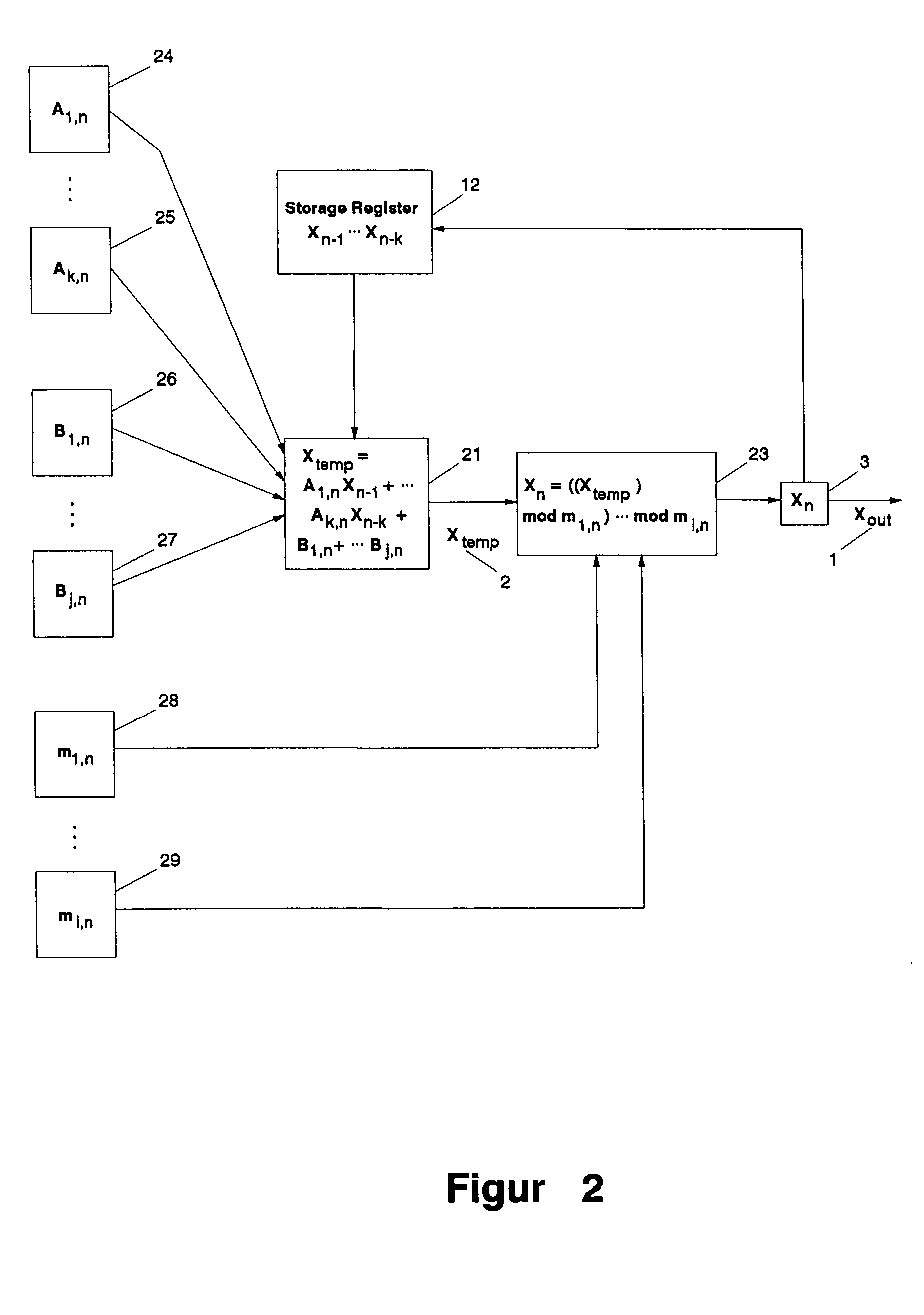
InactiveUS20050044119A1Random number generatorsDigital function generatorsTransition matricesPredictability
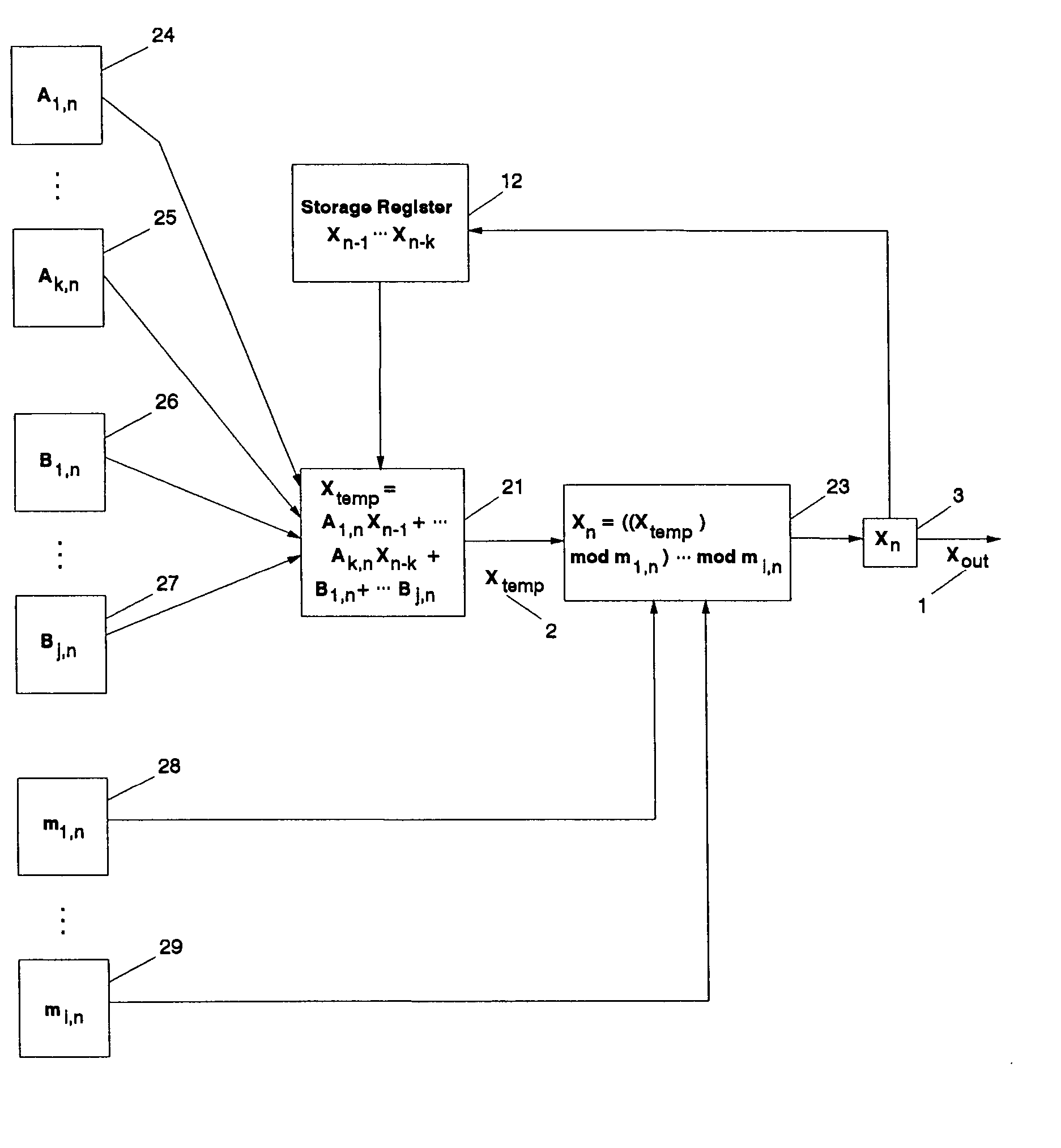
The present invention provides a method and an apparatus for generating pseudo-random numbers with very long periods and very low predictability. A seed random sequence is extended into a much longer sequence by successive iterations of matrix operations. Matrices of candidate output values are multiplied by non-constant transition matrices and summed with non-constant offset matrices; the result is then processed through one or more modulus operations, including non-constant modulus operators, to generate the actual output values. The invention also includes the possibility of introducing non-invertible matrices into the operations. The invention creates final results that are equidistributed over large samples. Secondary pseudo-random and other processes determine the non-constant transition matrices, offset matrices, and modulus operators.
Owner:LANGIN HOOPER JERRY JOE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com