Patents
Literature
1578results about "Securing communication by chaotic signals" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Applications of fractal and/or chaotic techniques
InactiveUS20030182246A1Increase pixel densityEasy to controlKey distribution for secure communicationChaos modelsImaging processingComputer science
This invention relates to the application of techniques based upon the mathematics of fractals and chaos in various fields including document verification, data encryption and weather forecasting. The invention also relates, in one of its aspects, to image processing.
Owner:JOHNSON WILLIAM NEVIL HEATON +2
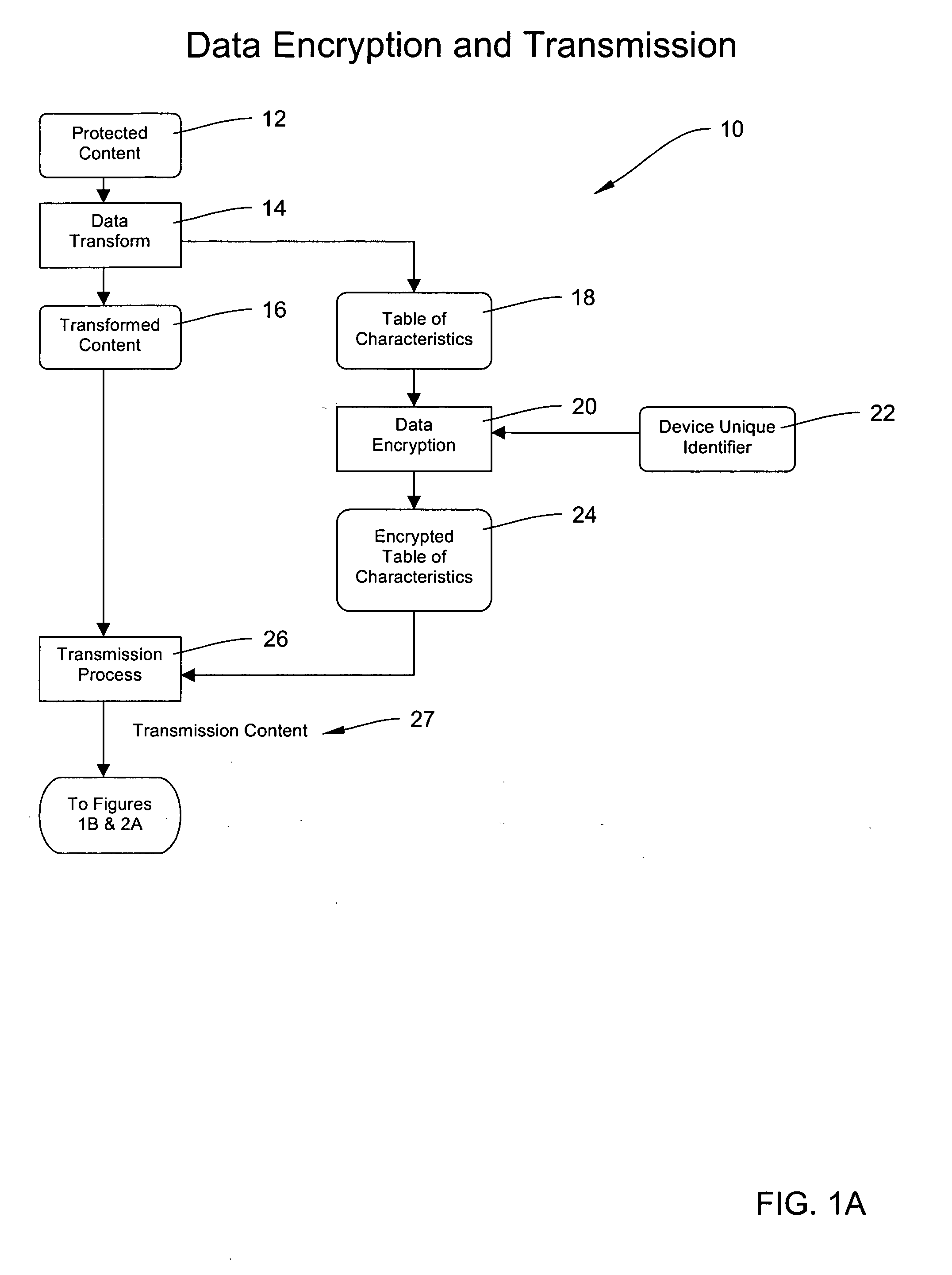
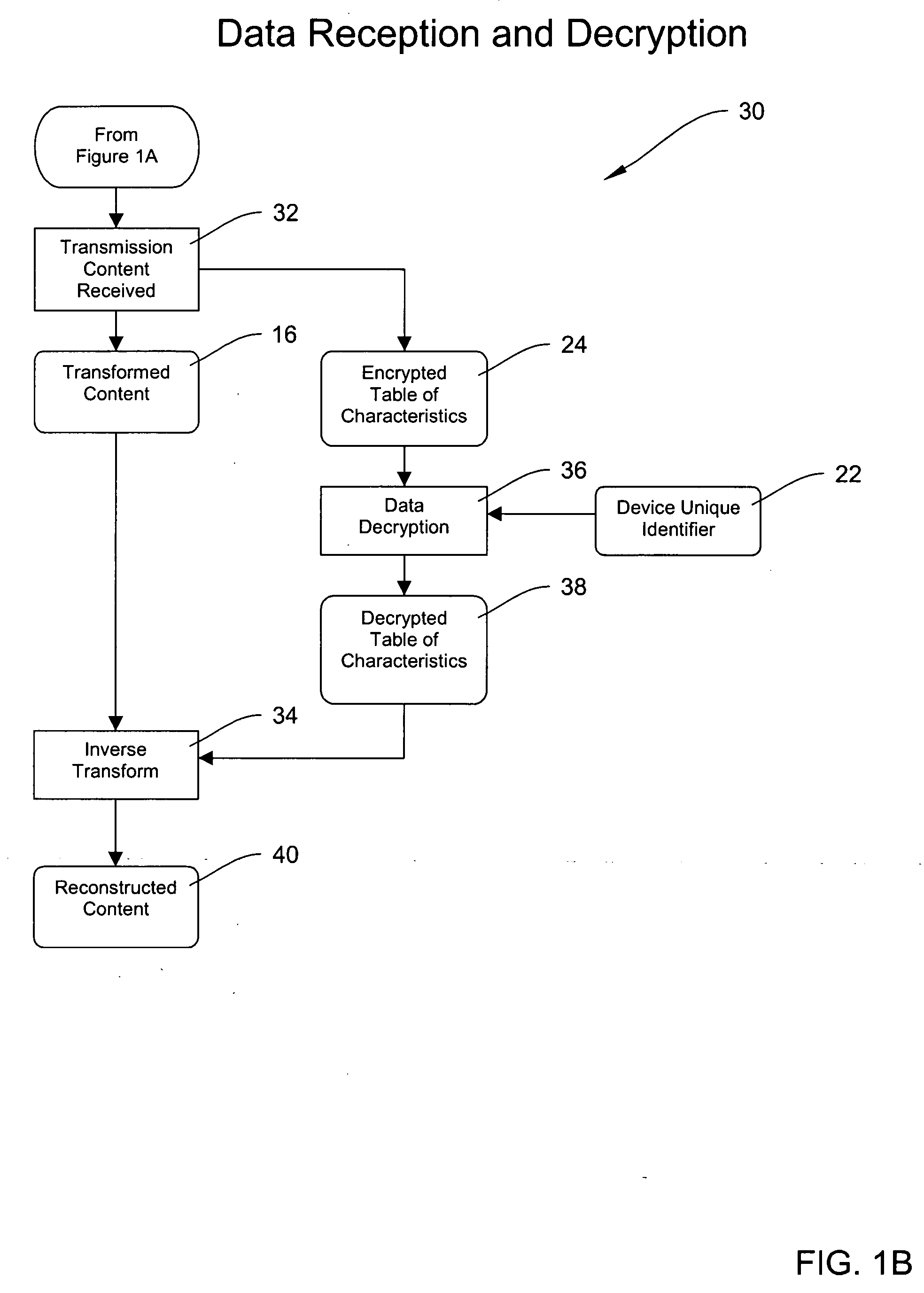
Methods and systems for digital rights management of protected content
InactiveUS20050021539A1Limit length of timeTimely controlDigital data processing detailsCode conversionDigital contentNumber content
The invention is directed, in one embodiment, to systems and methods relating to managing rights associated with digital content.
Owner:CHAOTICOM
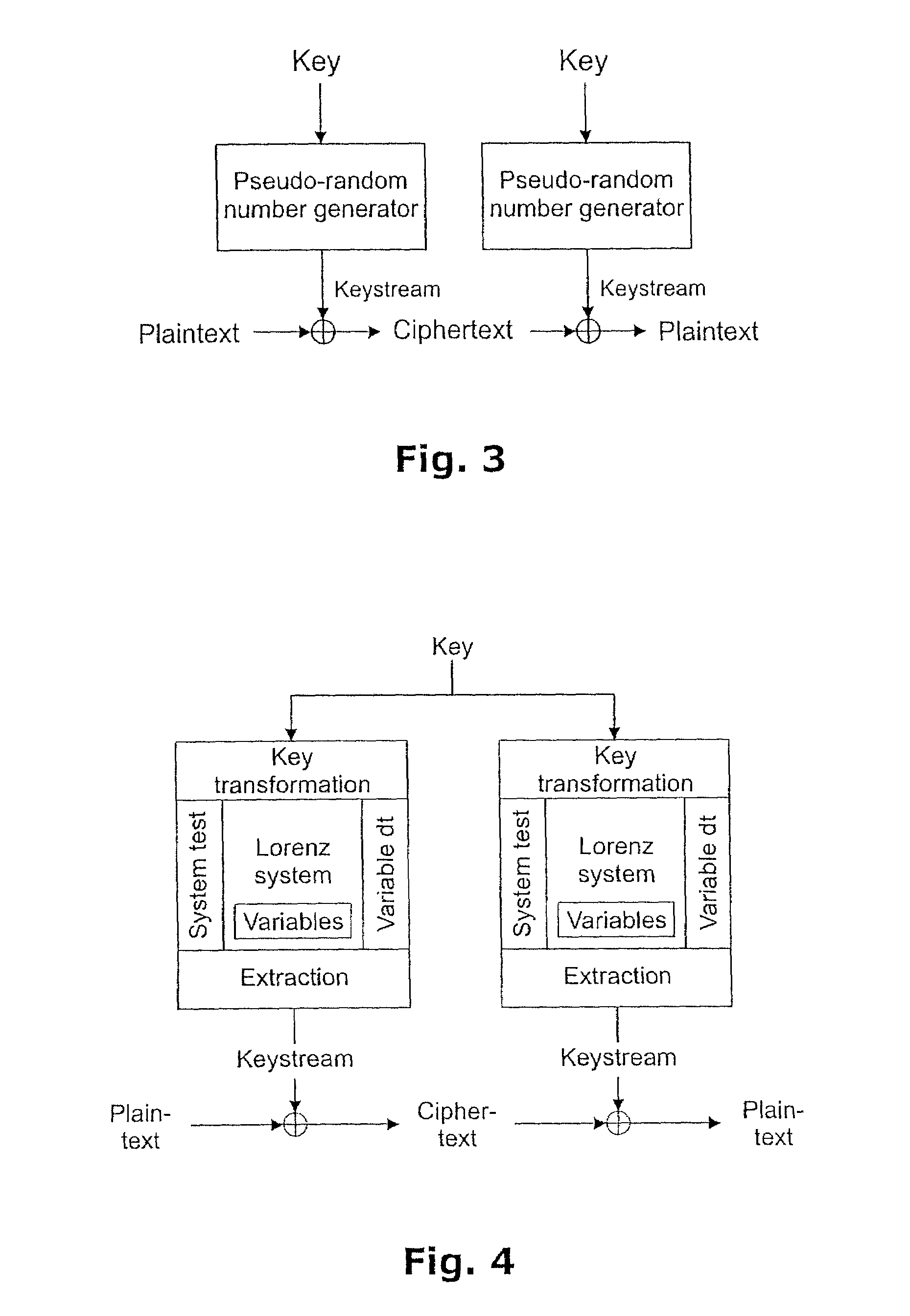
Method of generating pseudo-random numbers in an electronic device, and a method of encrypting and decrypting electronic data
InactiveUS7170997B2Compromise safetyQuick buildRandom number generatorsSecret communicationTheoretical computer scienceElectronic data
A method of performing numerical computations in a mathematical system with at least one function, including expressing the mathematical system in discrete terms, expressing at least one variable of the mathematical system as a fixed-point number, performing the computations in such a way that the computations include the at least one variable expressed as a fixed-point number, obtaining, from the computations, a resulting number, the resulting number representing at least one of at least a part of a solution to the mathematical system, and a number usable in further computations involved in the numerical solution of the mathematical system, and extracting a set of data which represents at least one of a subset of digits of the resulting number, and a subset of digits of a number derived from the resulting number.
Owner:CRYPTICO
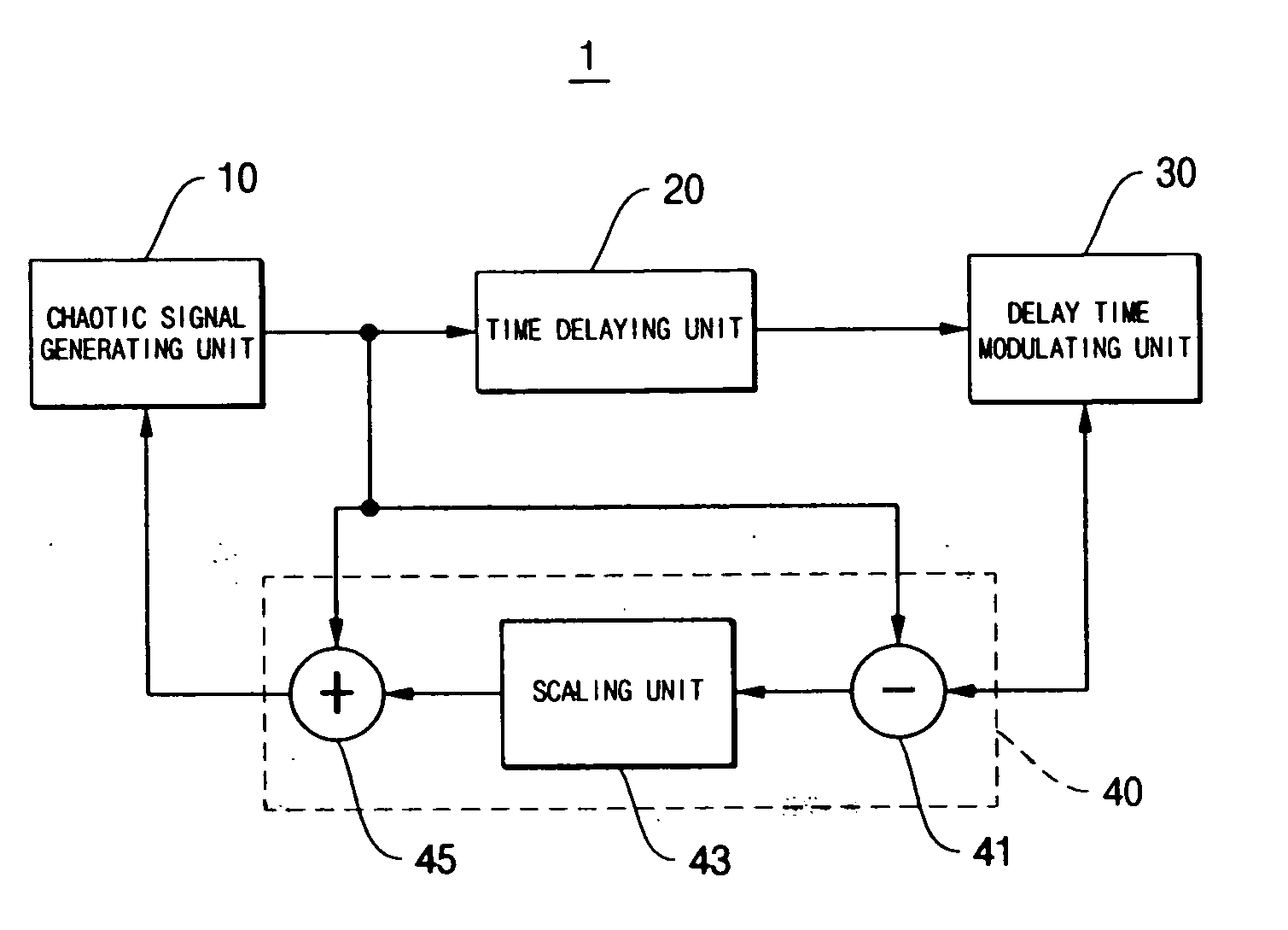
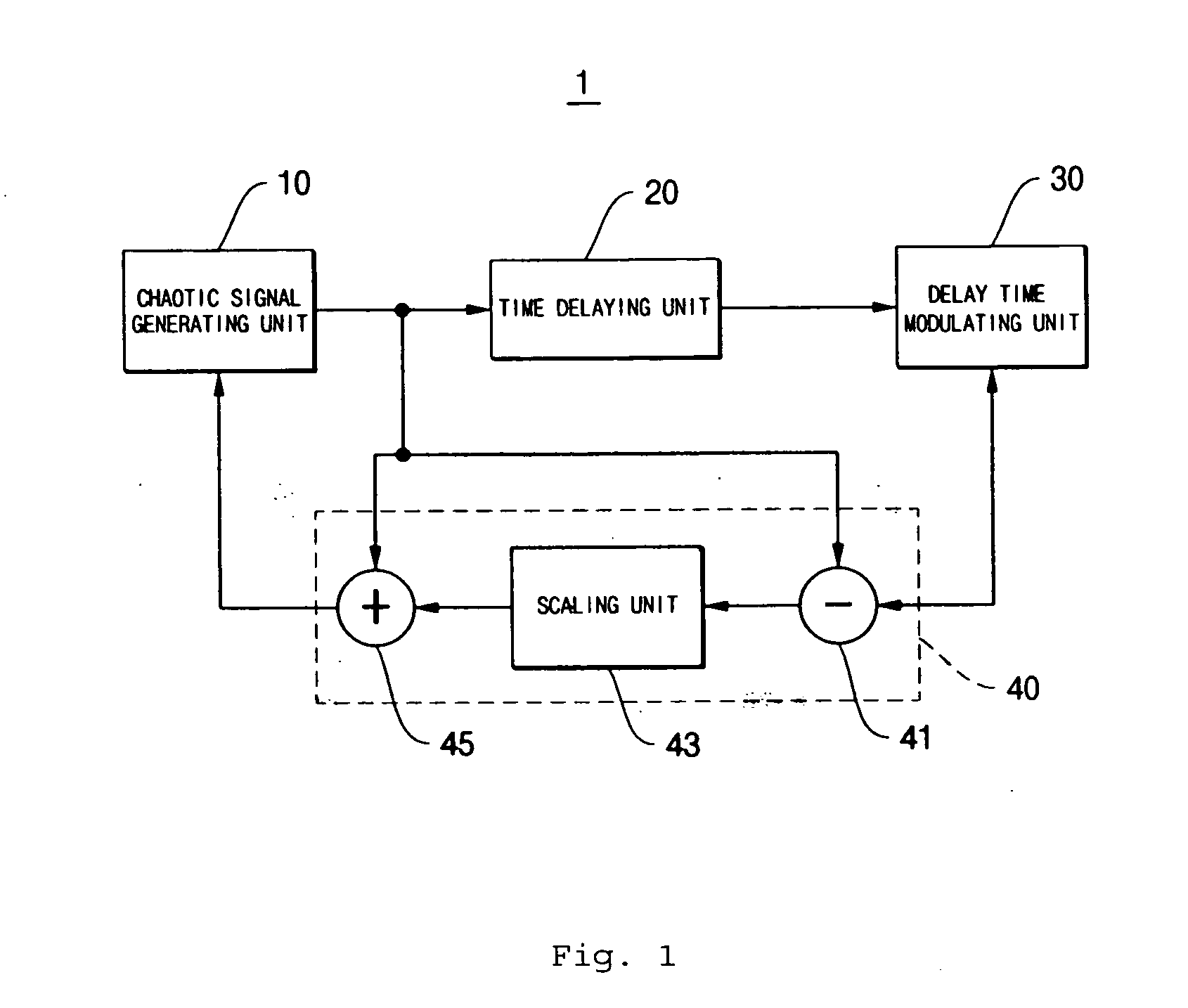
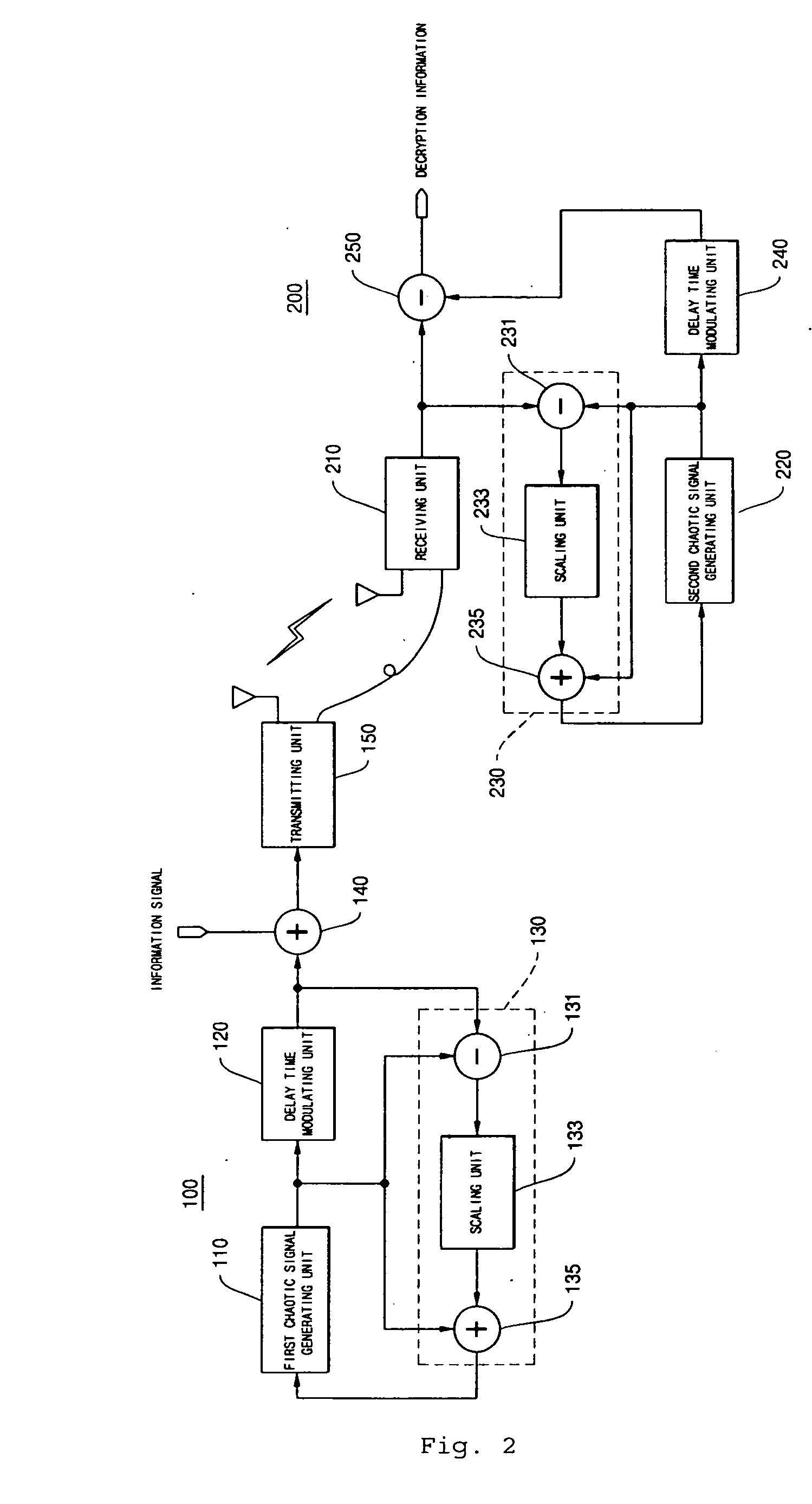
Encryption and communication apparatus and method using modulated delay time feedback chaotic system
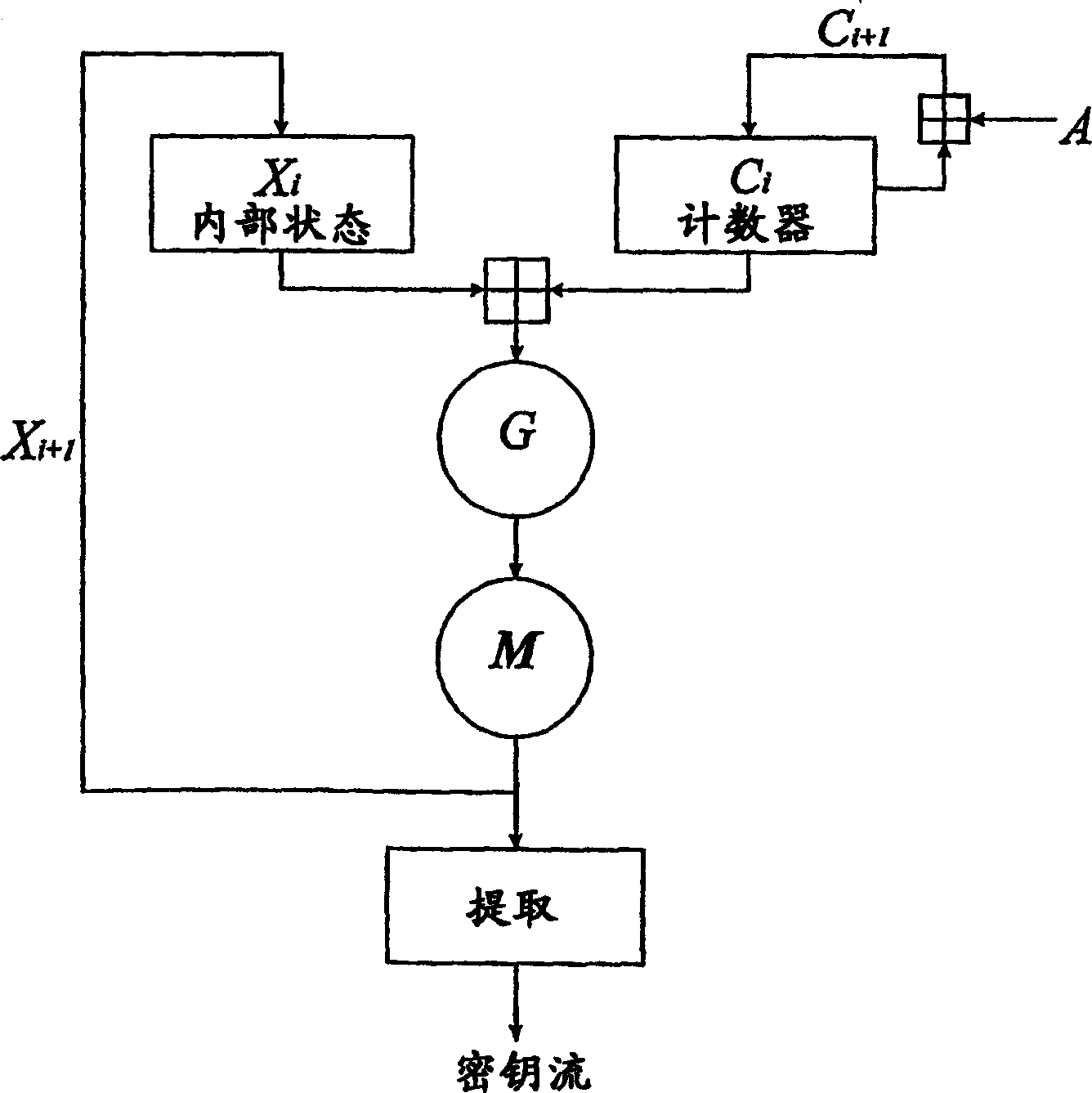
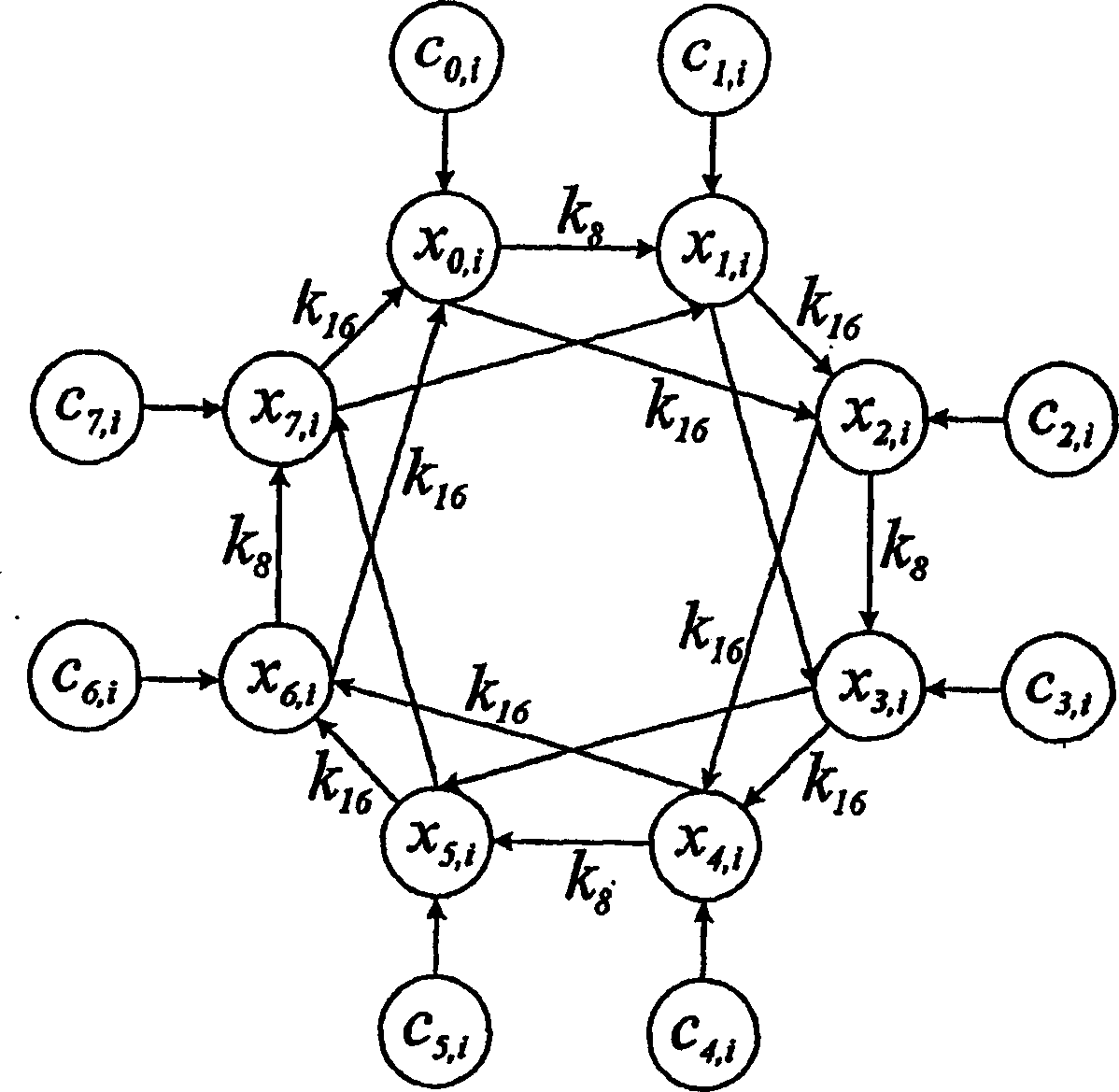
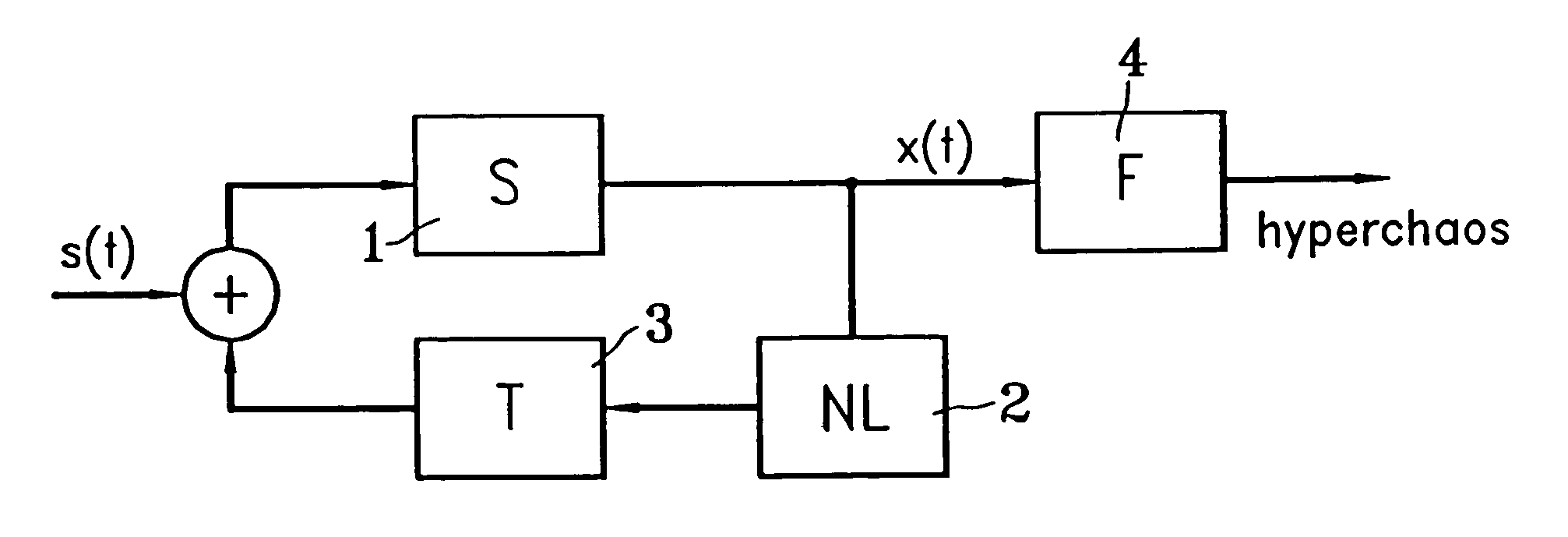
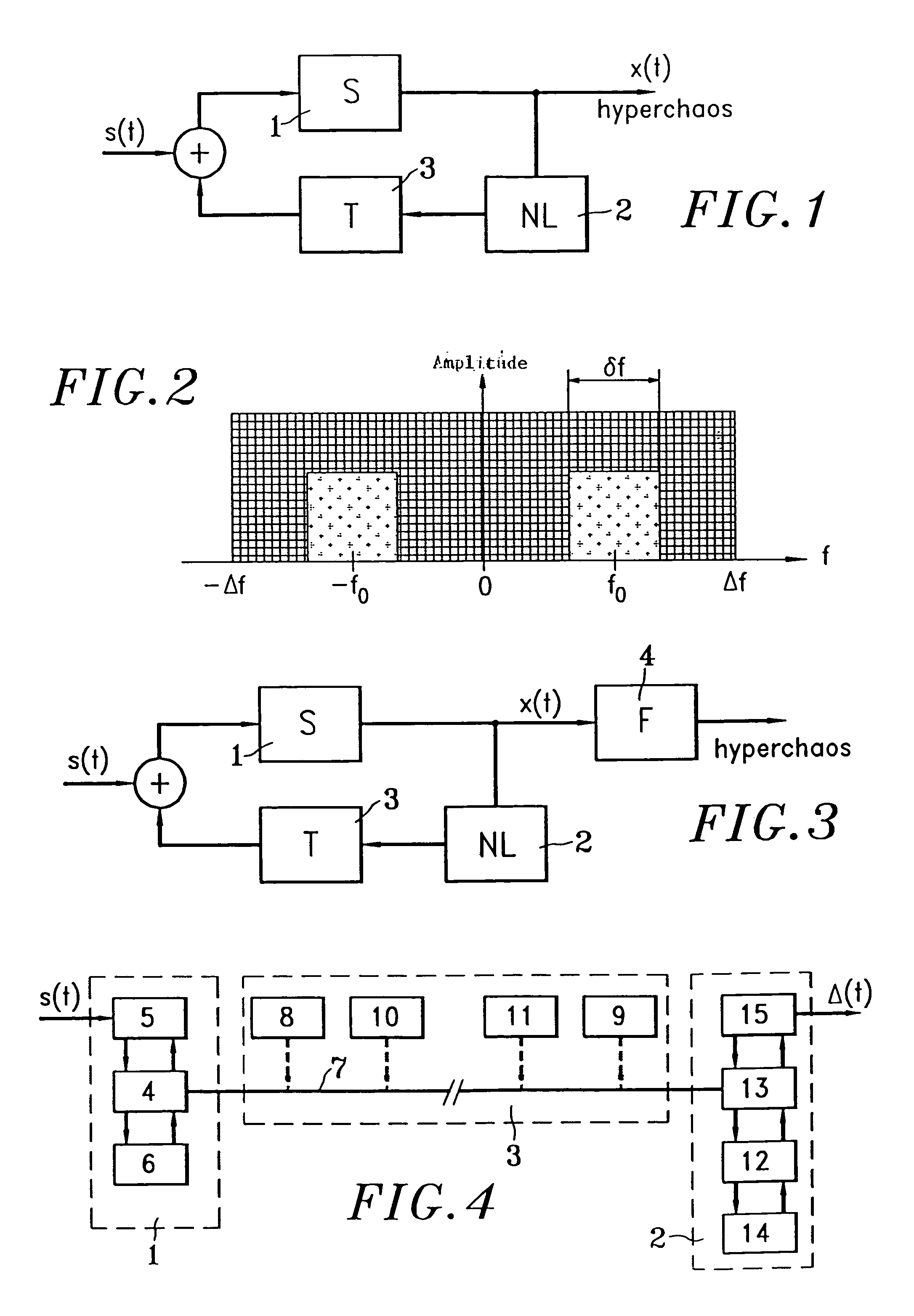
InactiveUS20050089169A1Avoid attackImpossible to detectEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsDelayed timeChaotic systems
Disclosed herein is an encryption and communication apparatus and method using a modulated delay time feedback chaotic system. The encryption apparatus of the present invention includes chaotic signal generating means for generating a high-dimensional chaotic signal in response to an original chaotic signal and a predetermined feedback chaotic signal, delay time modulating means for delaying the high-dimensional chaotic signal output from the chaotic signal generating means by a predetermined time and modulating the time-delayed chaotic signal, and feedback means for receiving the chaotic signal output from the chaotic signal generating means and the modulated time-delayed signal output from the delay time modulating means, performing addition and subtraction operations with respect to the received signals, and feeding the operated result back to the chaotic signal generating means. Accordingly, the present invention is advantageous in that it modulates a delay time so as to prevent an information signal contained in a chaotic signal from being attacked from the outside, so that it is impossible to detect an exact delay time contained in a modulated time-delayed chaotic signal and to decrypt the information signal, thus constructing a more robust and reliable encryption system.
Owner:EDUCATIONAL
Cryptographic key, encryption device, encryption/decryption device, cryptographic key management device, and decryption device
ActiveUS7269258B2Random number generatorsSecuring communication by chaotic signalsComputer hardwareCryptographic nonce
Owner:YAZAKI CORP
Method of generating successions of pseudo-random bits or numbers
InactiveUS20060251250A1Conveniently implementedReduce computing costSecuring communication by chaotic signalsTheoretical computer scienceChaotic map
A method for generating a succession of pseudo-random numbers includes choosing at least one chaotic map, and choosing a seed for the chaotic map and a number of iterations for the chaotic map. The succession of pseudo-random numbers are generated by executing iteratively generating a pseudo-random number as a function of a final state reached by the chaotic map iterated for the current number of iterations starting from the current seed, and generating a new seed for the chaotic map or a new number of iterations as a function of the final state.
Owner:STMICROELECTRONICS SRL
Cryptographic system incorporating a digitally generated chaotic numerical sequence
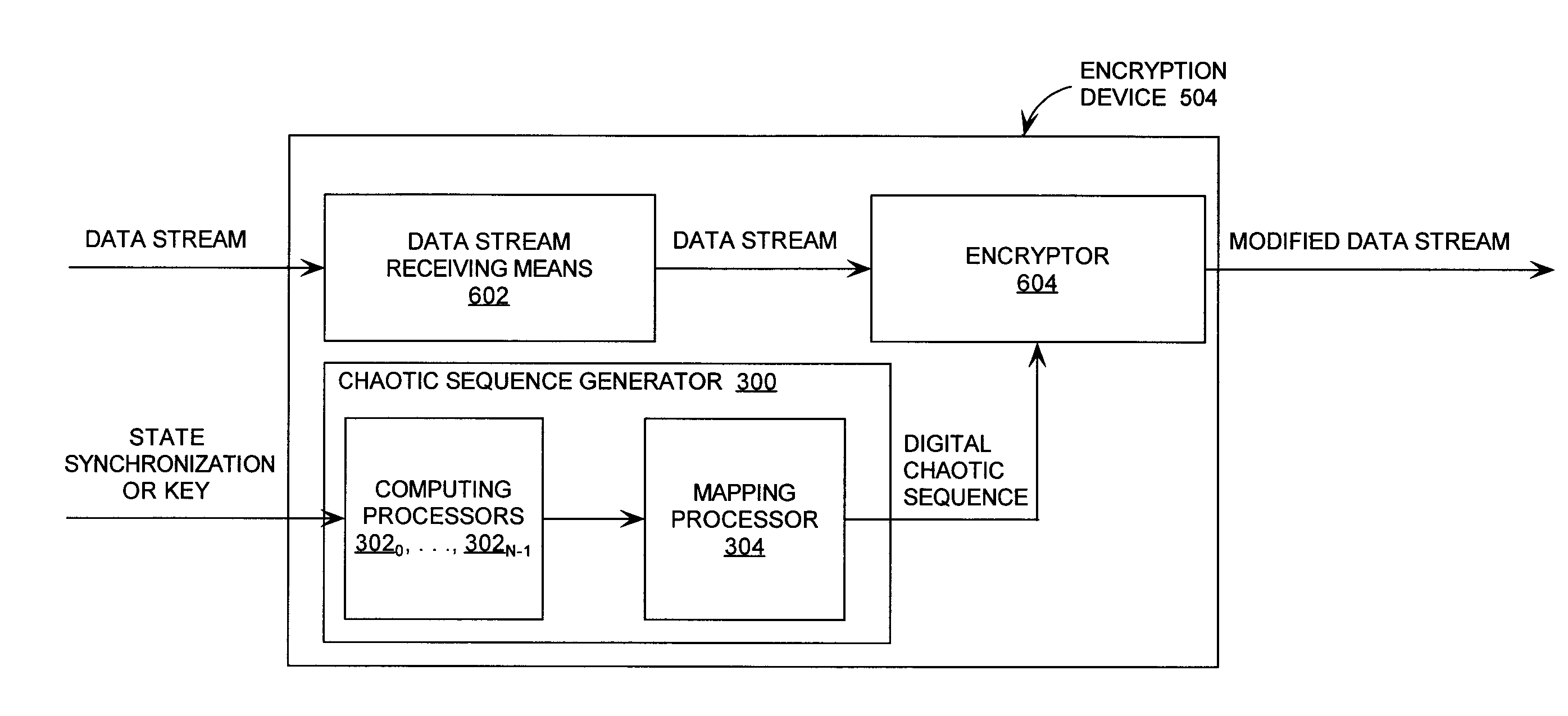
ActiveUS20090196420A1Data stream serial/continuous modificationSecret communicationNumbering systemData stream
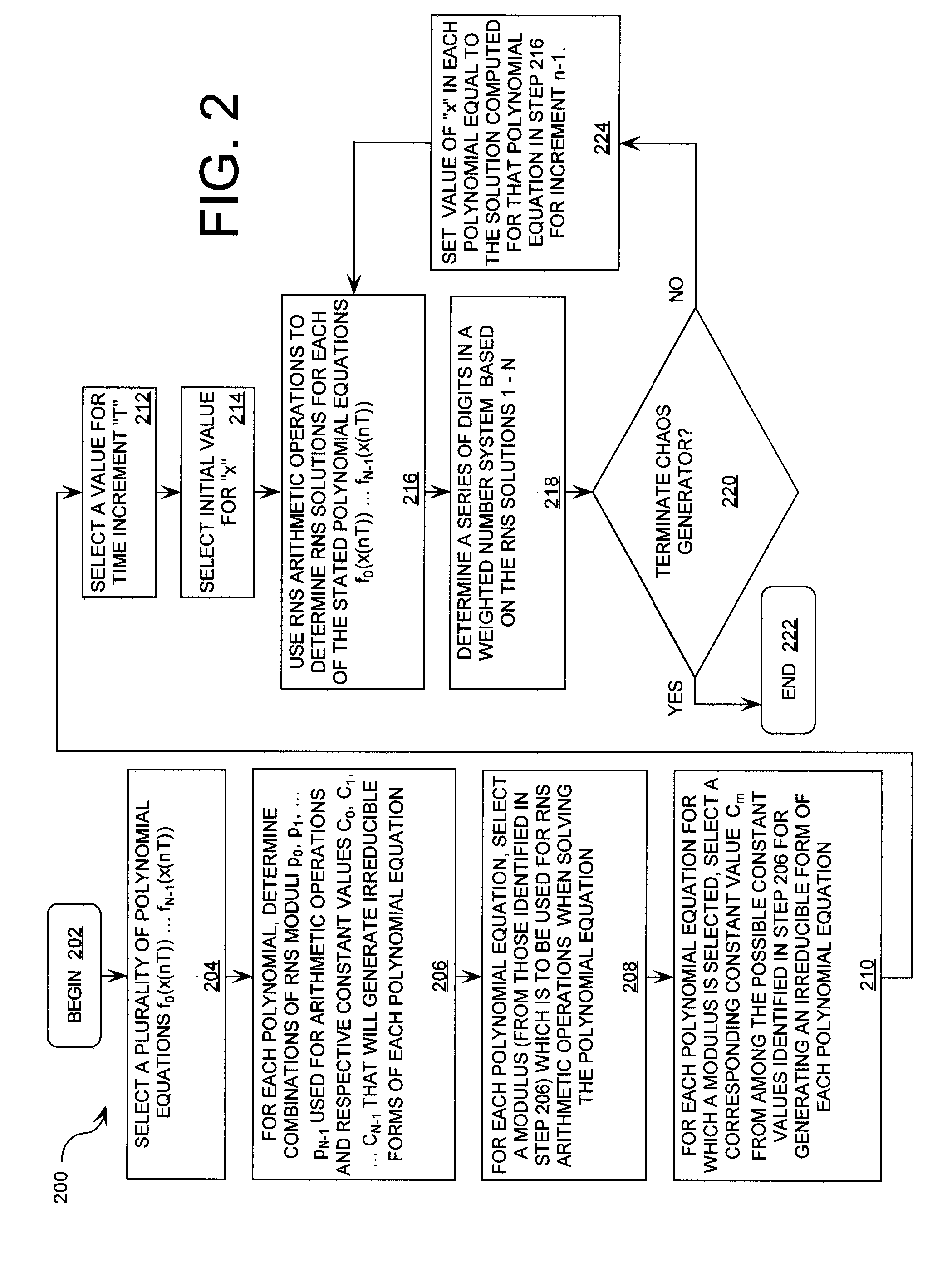
A cryptographic system (CS) is provided. The CS (500) is comprised of a data stream receiving device (DSRD), a chaotic sequence generator (CSG) and an encryptor. The DSRD (602) is configured to receive an input data stream. The CSG (300) includes a computing means (3020, . . . , 302N-1) and a mapping means (304). The computing means is configured to use RNS arithmetic operations to respectively determine solutions for polynomial equations. The solutions are iteratively computed and expressed as RNS residue values. The mapping means is configured to determine a series of digits in the weighted number system based on the RNS residue values. The encryptor is coupled to the DSRD and CSG. The encryptor is configured to generate a modified data stream by incorporating or combining the series of digits with the input data stream.
Owner:HARRIS CORP
Chaotic privacy system and method
InactiveUS7076065B2Multiple keys/algorithms usageSecuring communication by chaotic signalsComputer scienceTransmitter
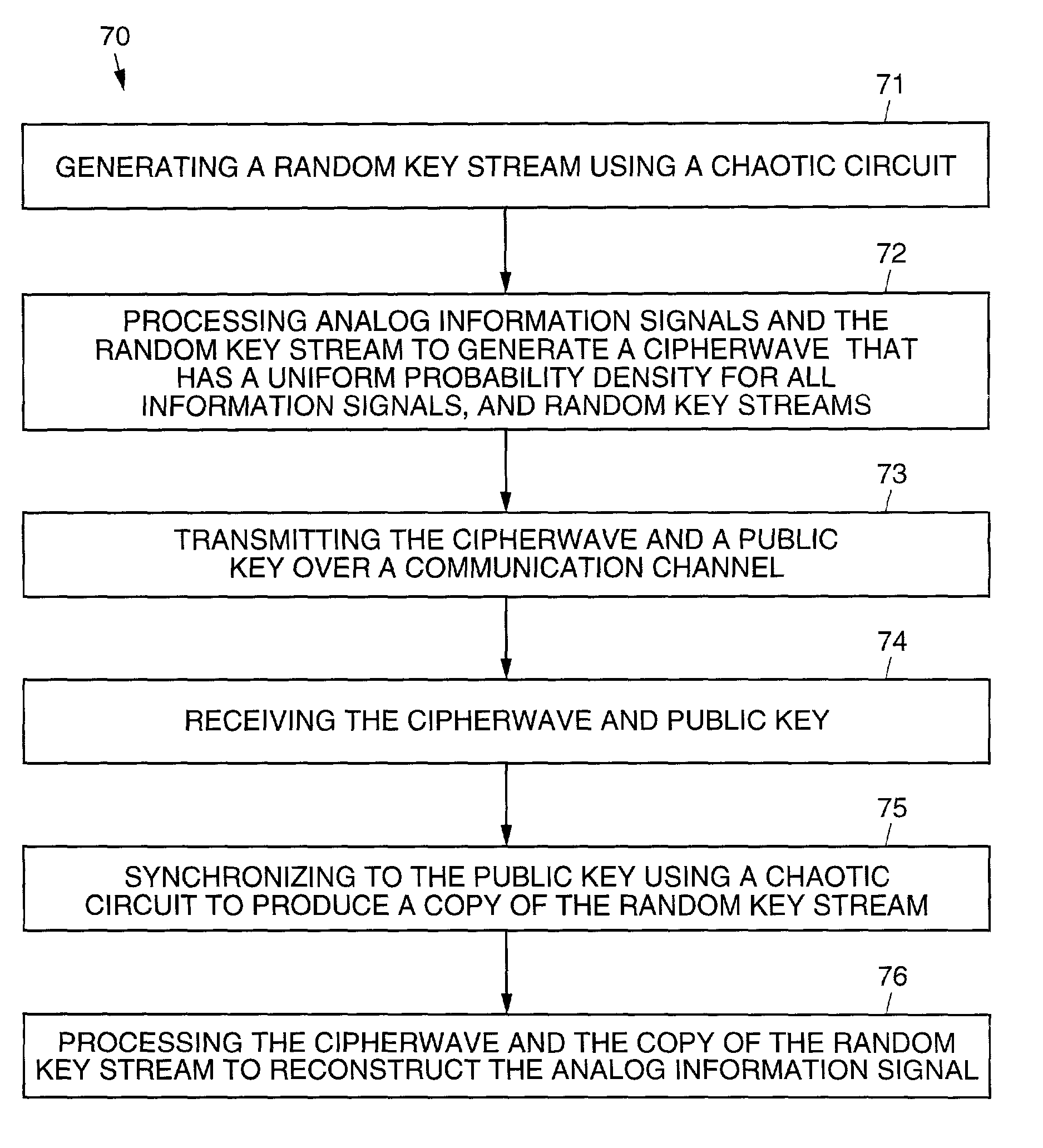
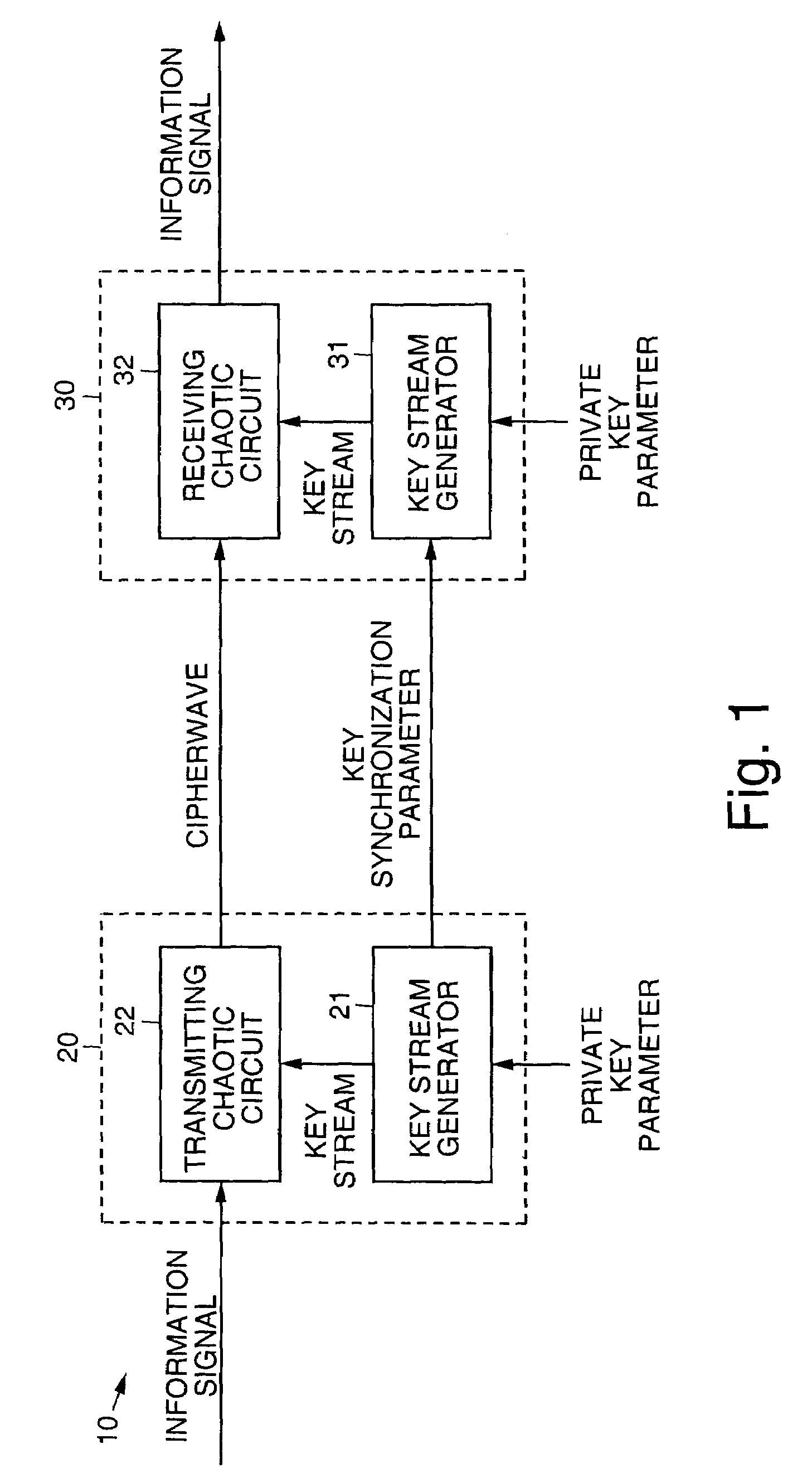
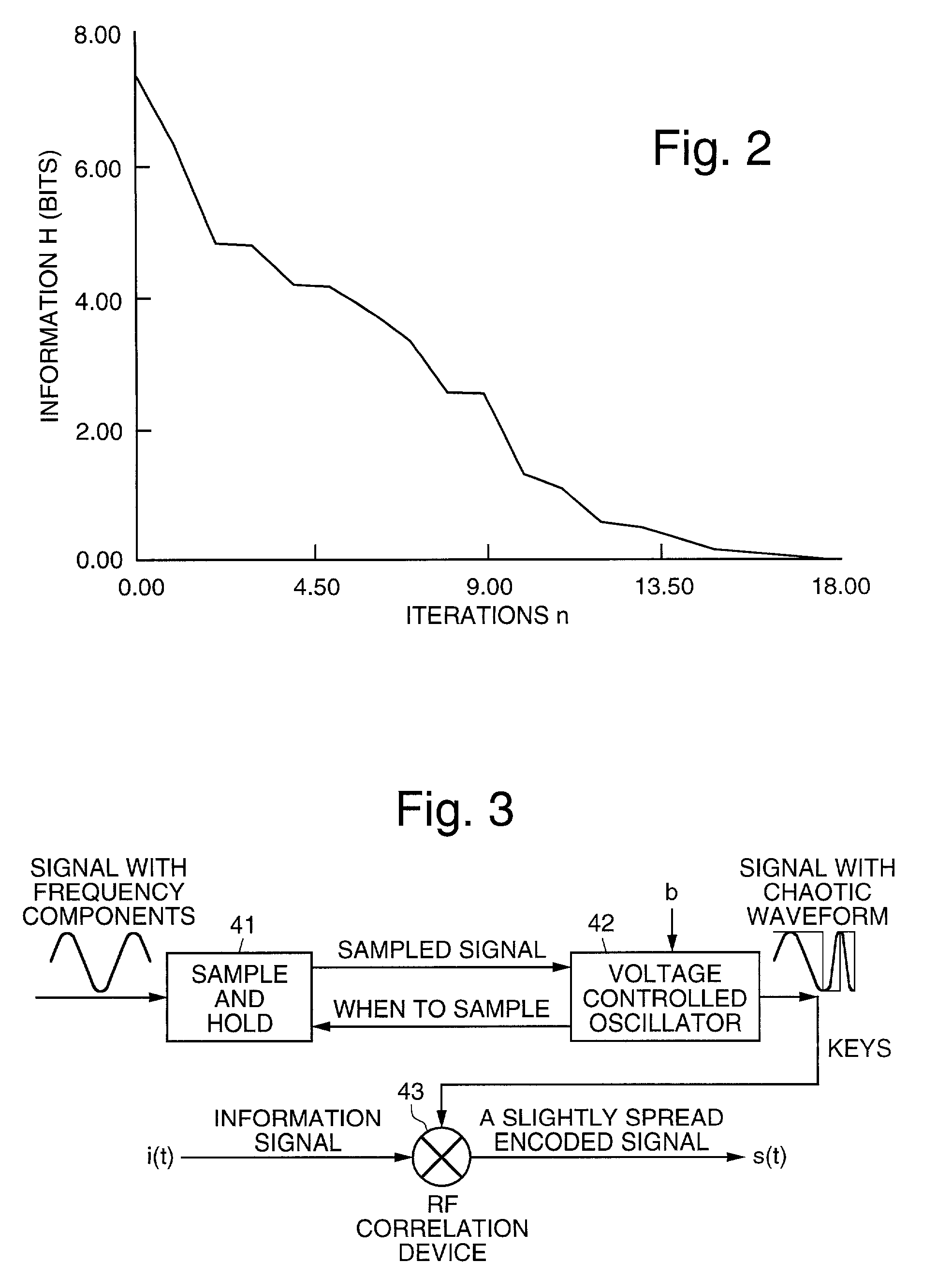
Systems and methods for protecting privacy in transmitting an analog information signal. The present invention combines the information signal with an analog random signal generated by a chaotic circuit and transmits the signal. The received signal is synchronized using a receiving chaotic circuit. The received signal is demodulated using a synchronized replica of the analog random signal. The information signal is recovered since the product of the random signals generated in the transmitter and in the receiver, is unity. Techniques used in the present invention for generating chaos, synchronization, and signal recovery are also disclosed.
Owner:LOCKHEED MARTIN CORP
Method and system for chaotic digital signature, encryption, and authentication
InactiveUS20050271207A1Improve securityImprove usabilityPublic key for secure communicationSecuring communication by chaotic signalsDigital signatureEncryption
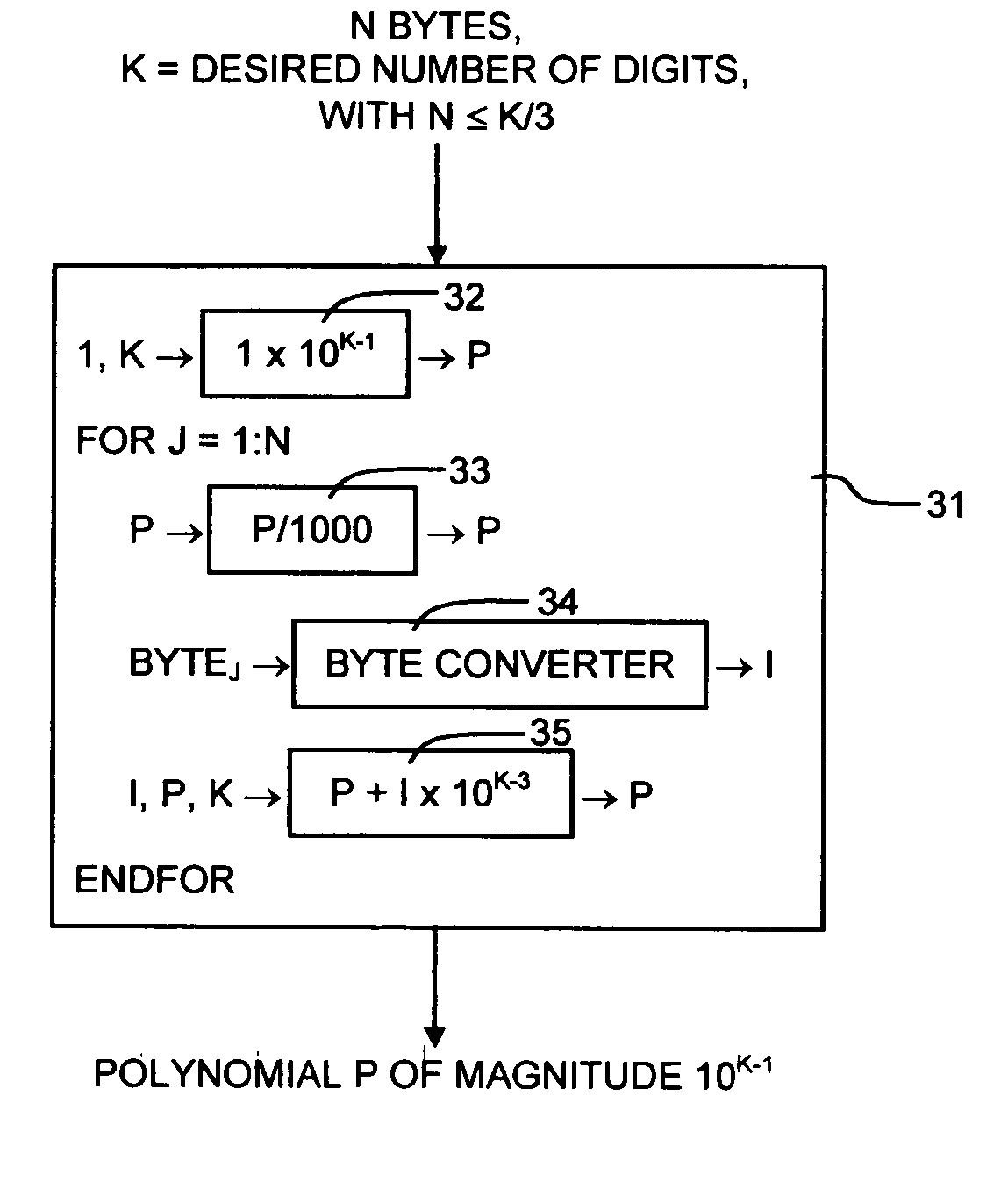
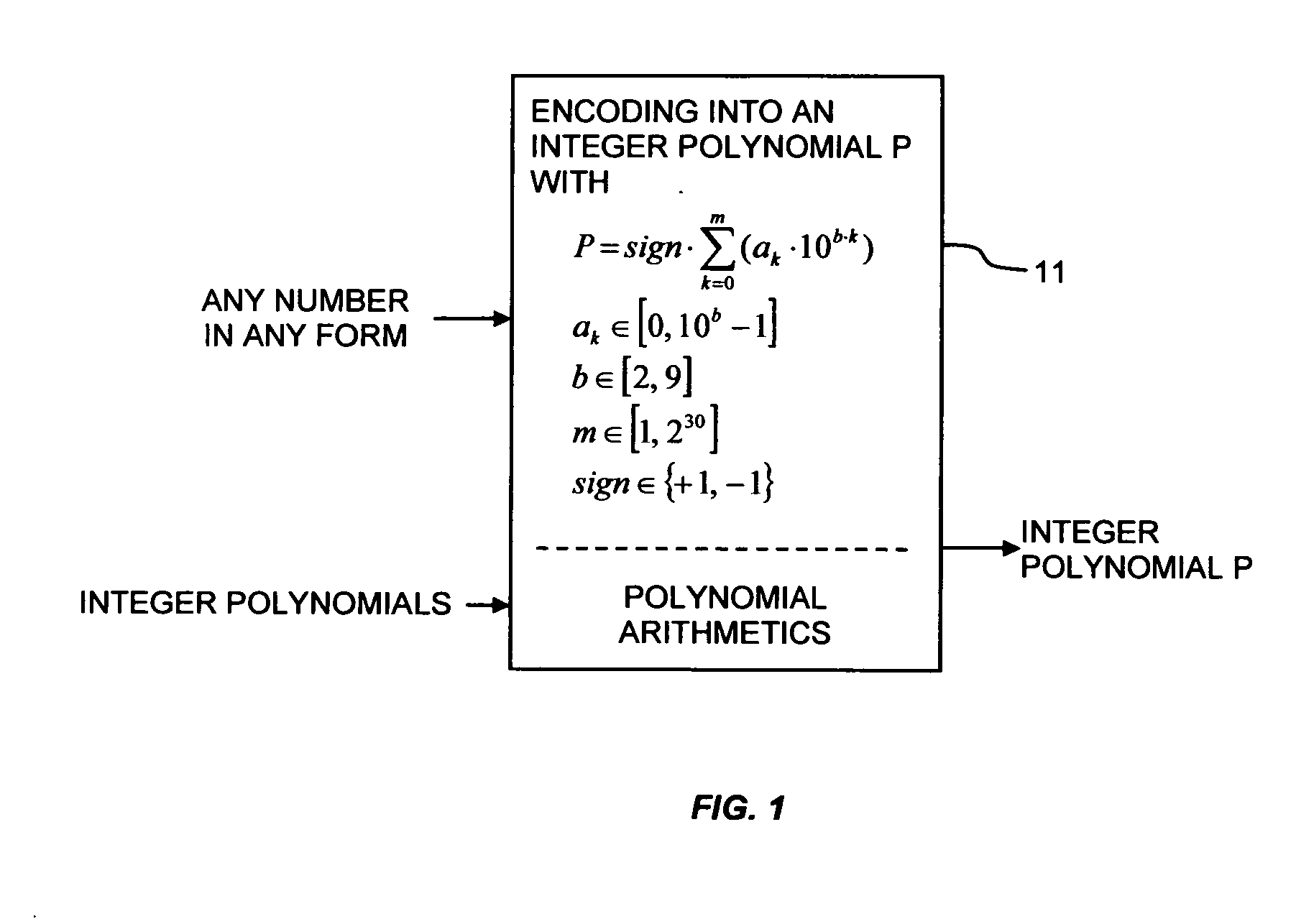
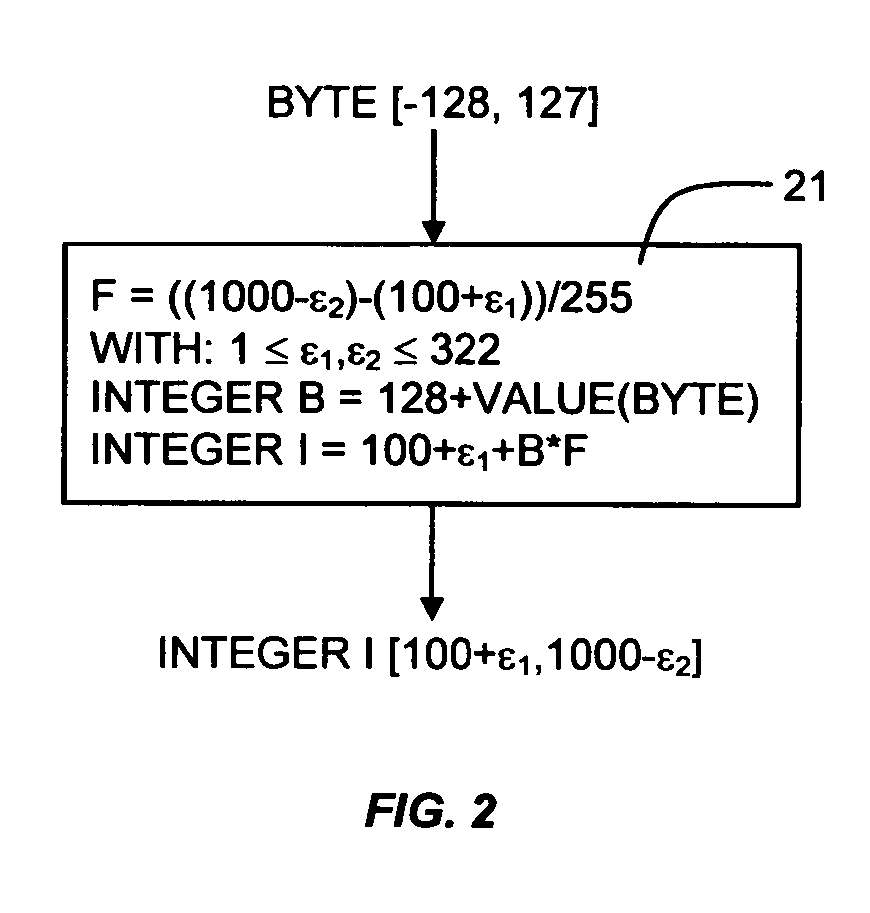
The method and system for chaotic digital signature, encryption, and authentication using a chaos generator, which operates in the domain of polynomial integer numbers of arbitrary magnitude.
Owner:FREY HELMUT
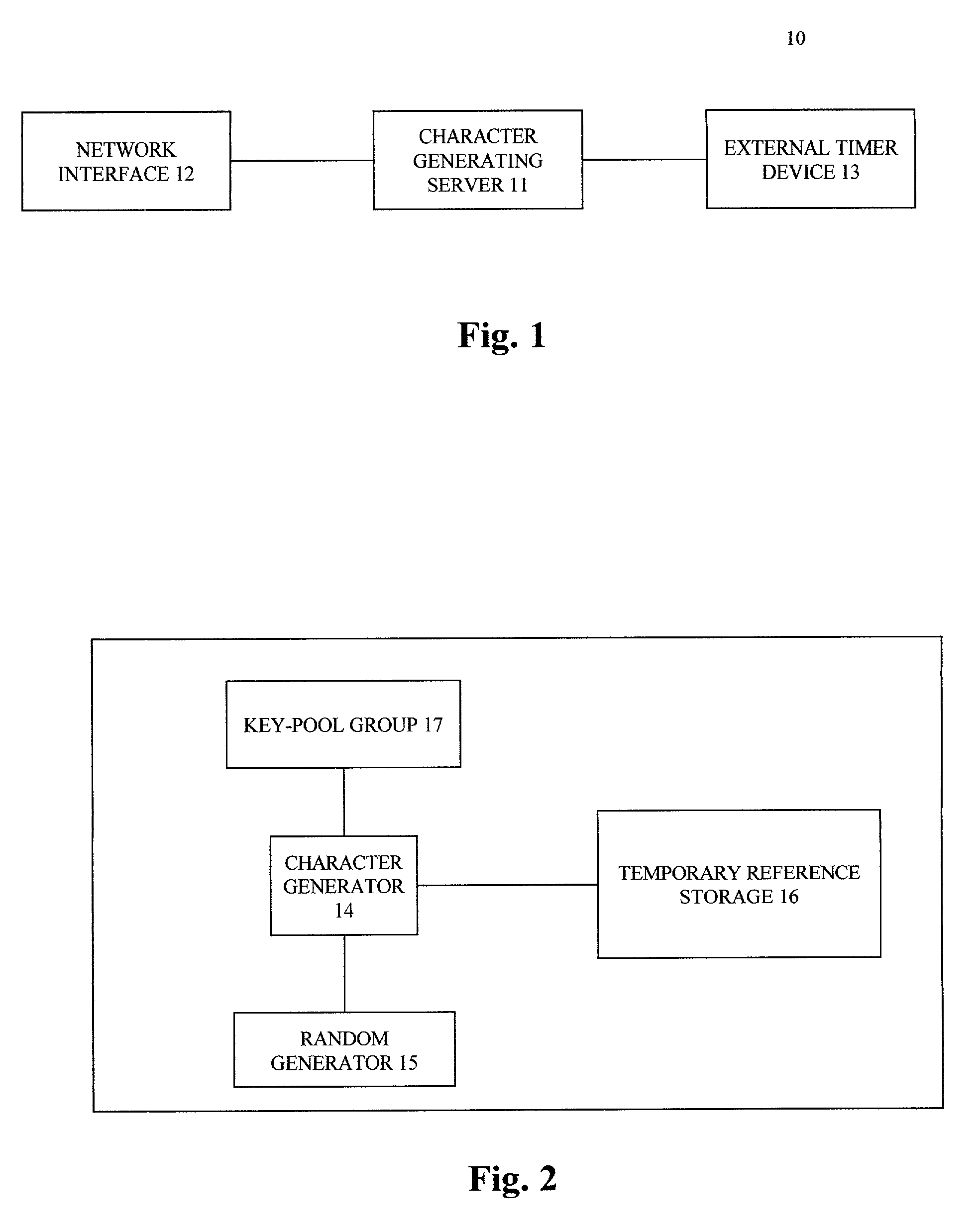
Method and apparatus for generating a group of character sets that are both never repeating within certain period of time and difficult to guess
InactiveUS6987853B2Prevent forgeryKey distribution for secure communicationSecuring communication by chaotic signalsAlgorithmTime segment
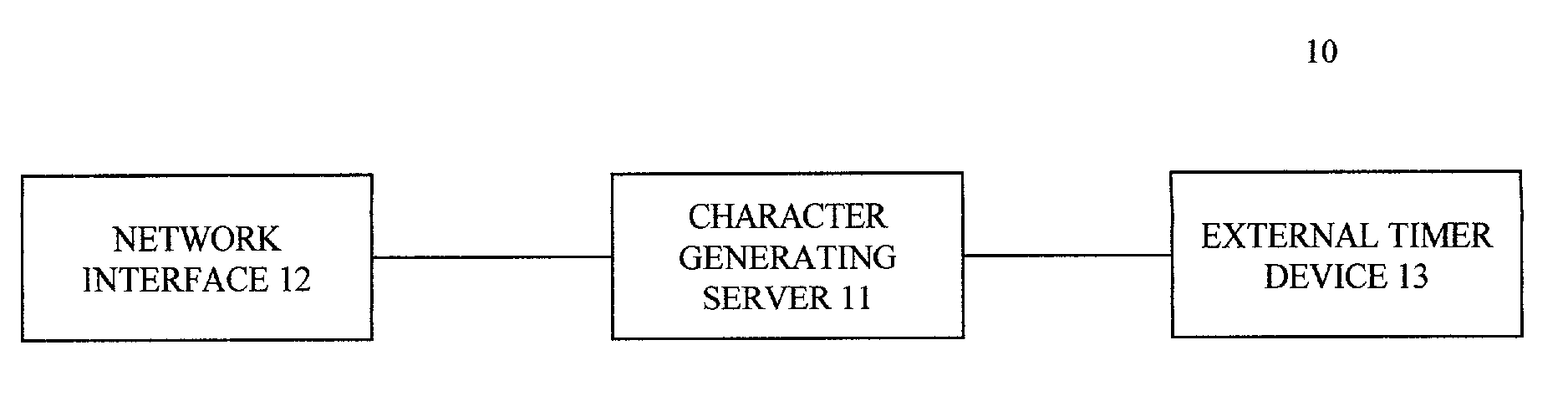
A method and apparatus for generating a group of non-repetitive, difficult-to-guess character sets is disclosed. The method includes (a) generating a request for a character set by a client of a character-generating server, (b) sending the request to the character-generating server, (c) generating a pseudo random number required by the character generator; (d) sending the pseudo random number to the character generator; (e) generating a character for the character set by the character generator, (f) sending the character set along with a related key to the client; (g) sending the character set along with the related key to a target server, (h) sending related key to the character-generating server by the target server; (i) re-creating the character set from the related key by the target server; and (j) sending the character set along with the related key to the target server.
Owner:BODACION TECH
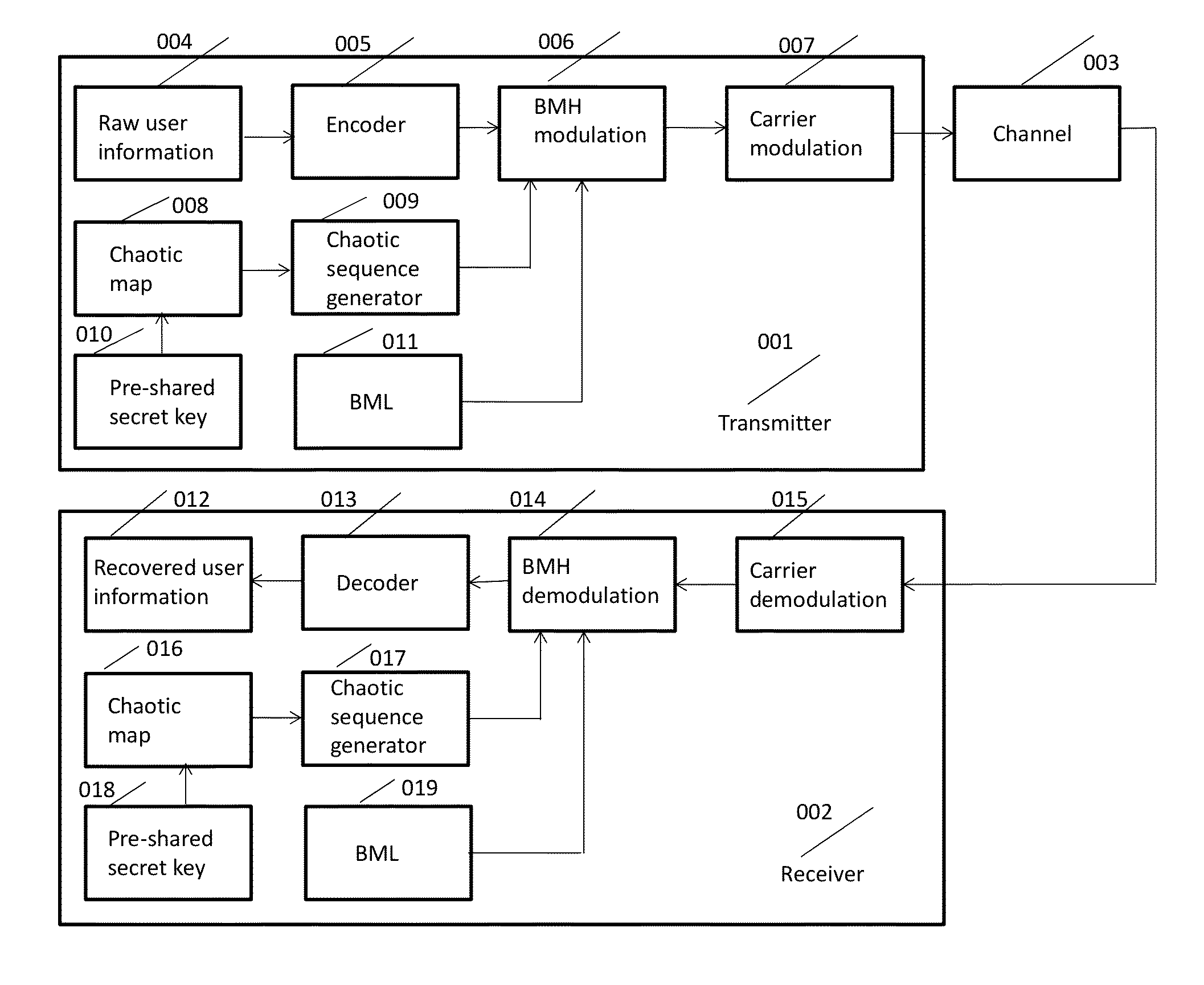
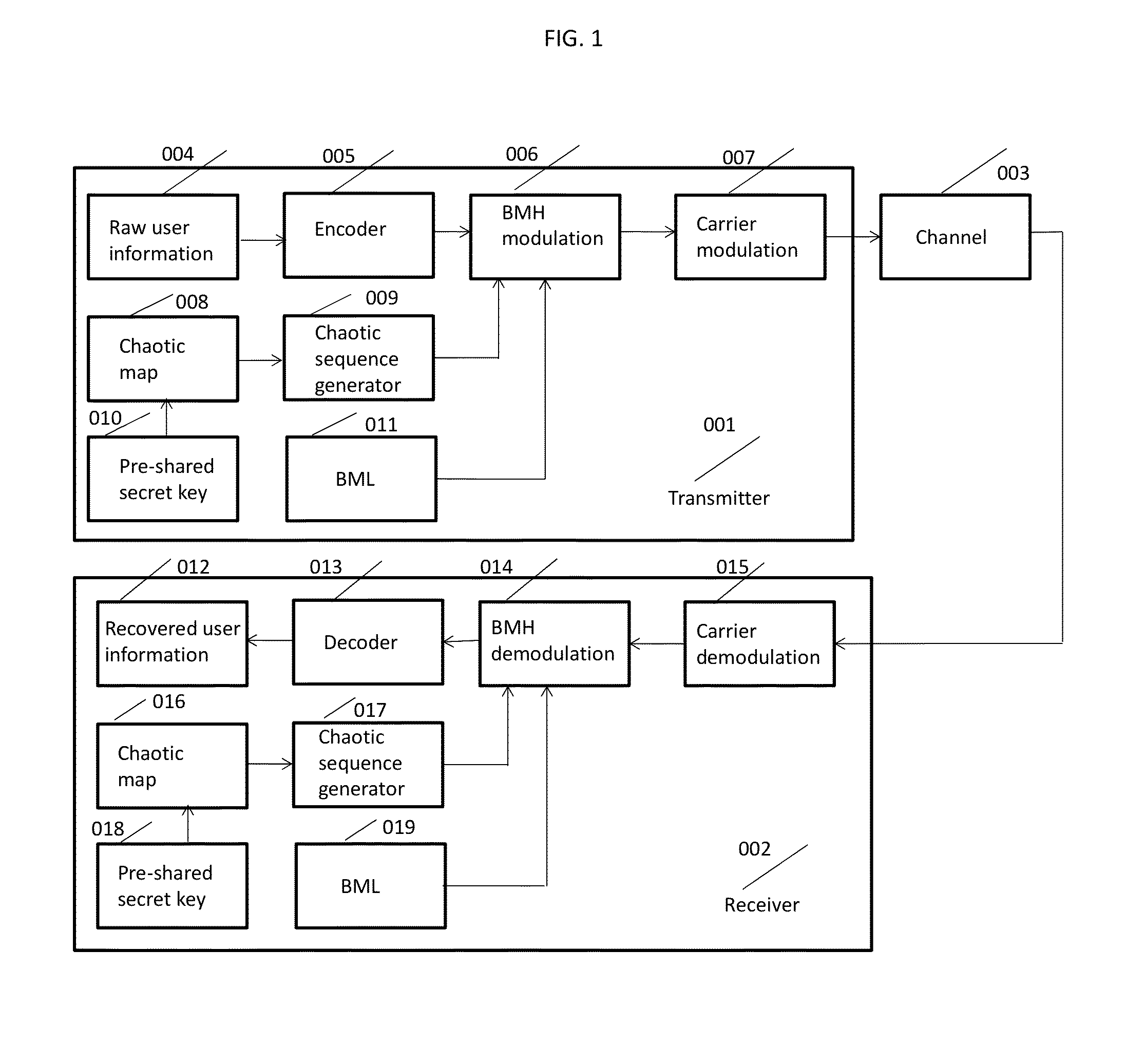
Chaotic Baseband Modulation Hopping Based Post-Quantum Physical-Layer Encryption
A post-quantum physical-layer encryption / decryption system based on chaotic Baseband Modulation Hopping (BMH). The baseband constellation, mapping, power level, and phase will vary symbol-by-symbol according to assigned random sequences. Pre-shared secret keys are used as the chaotic system parameters, initialization, and quantization parameters to generate the BMH codes. The BMH physical-layer encryption / decryption system can be combined with digital-domain based encryption algorithms such as AES, code-based post-quantum cryptography, and other physical-layer secure communication techniques such as Frequency Hopping (FH) and Direct Sequence Spread Spectrum (DSSS). It can also be combined with Quantum Key Distribution (QKD) to provide mutual authenticated key distribution. This invention can be applied to all kinds of communication systems including wireless (radio frequency, optical, quantum channel, sonar) and wire (optical fiber, power-line, telephone line, wire quantum channel, etc.), single carrier and multi-carrier, OFDM, MIMO channels.
Owner:LI WENHUA +1
Method and apparatus for encryption of data
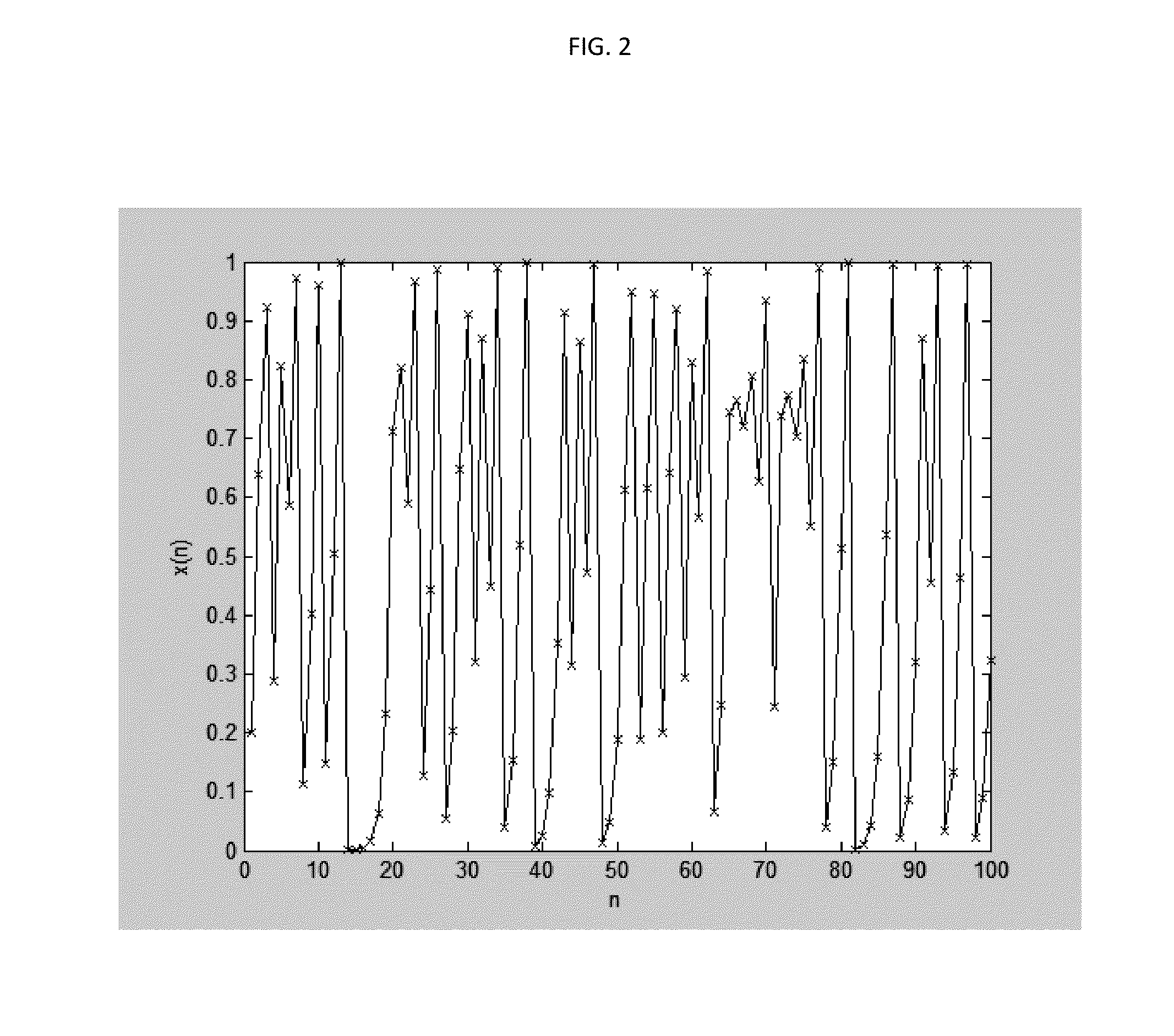
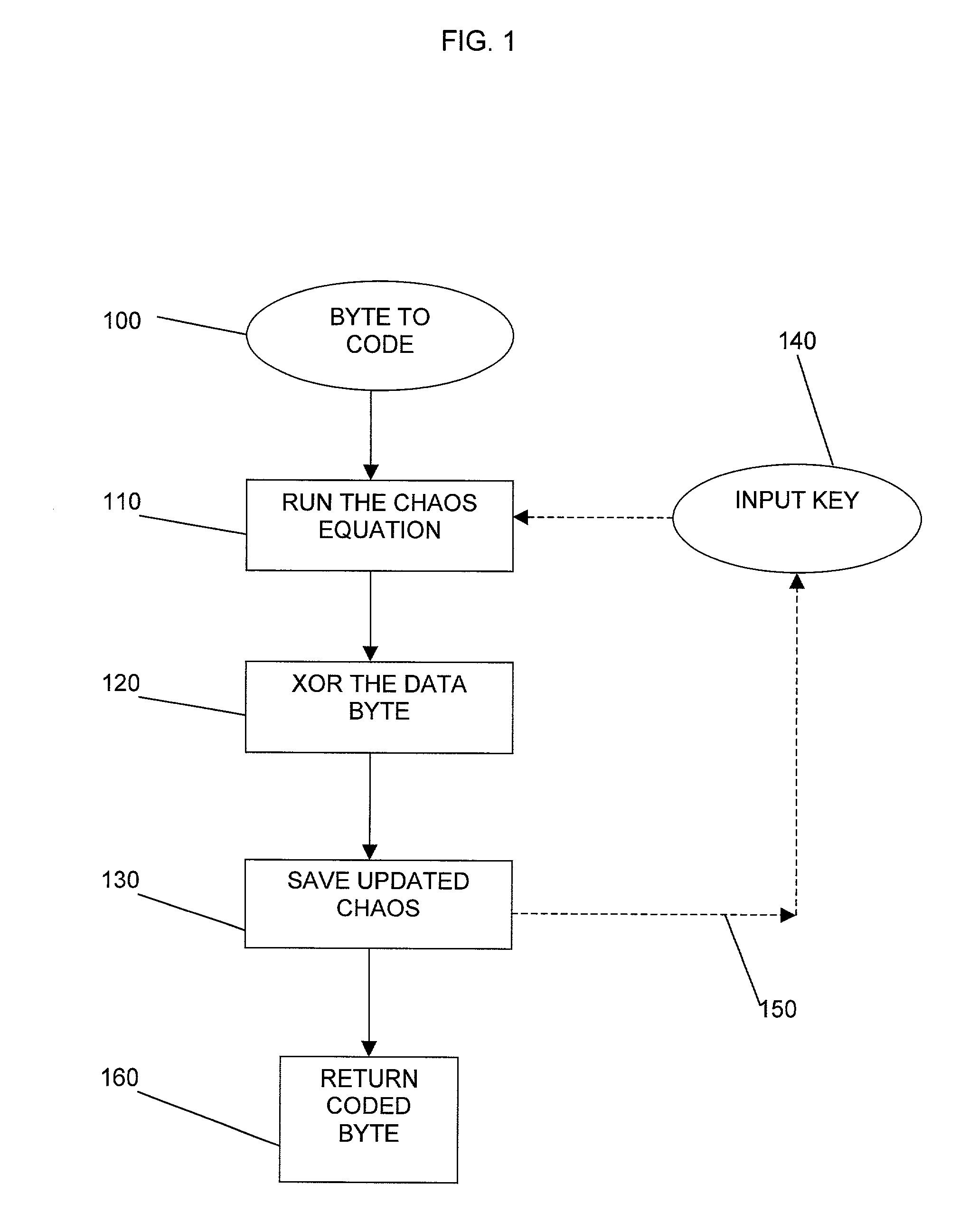
A method for encryption and decryption of data items is provided by defining a cipher key based on variables in a Chaotic Equation. The method includes selecting a Chaotic Equation (110) from a set of Chaotic Equations, defining starting conditions of the variables of the equation (140), and applying the equation to each data item (120). The real and imaginary parts of the result of the iteration of the Chaotic Equation are combined with the data item by an arithmetic operation, for example, an XOR operation (120). Data items in a continuous stream with a rate dependency can be encrypted and decrypted on an item by item basis. The input or cipher key changes for each byte of the data encryption. Blocks of data (700, 701, 702, 703, 704) can be encrypted using the method with an identifier of the order of the blocks in the data stream. If blocks are received out of sequence, the identifiers can be used to maintain the correct decryption order. The method of encryption and decryption can be used in devices (801) to avoid the need for a session key. The continuously updating input or cipher key enables fraudulent use of devices (801) to be identified.
Owner:IBM CORP
Randomized value generation
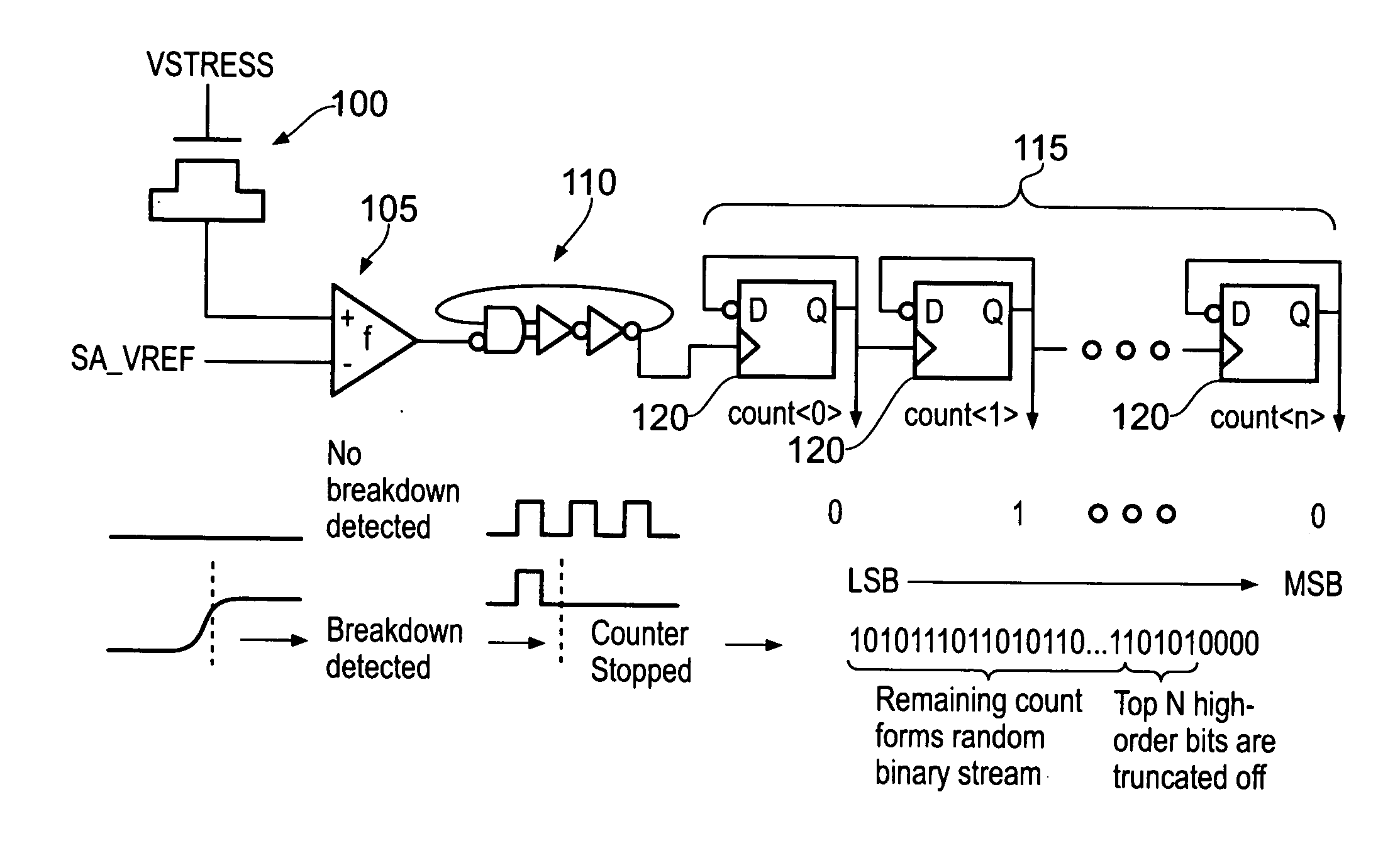
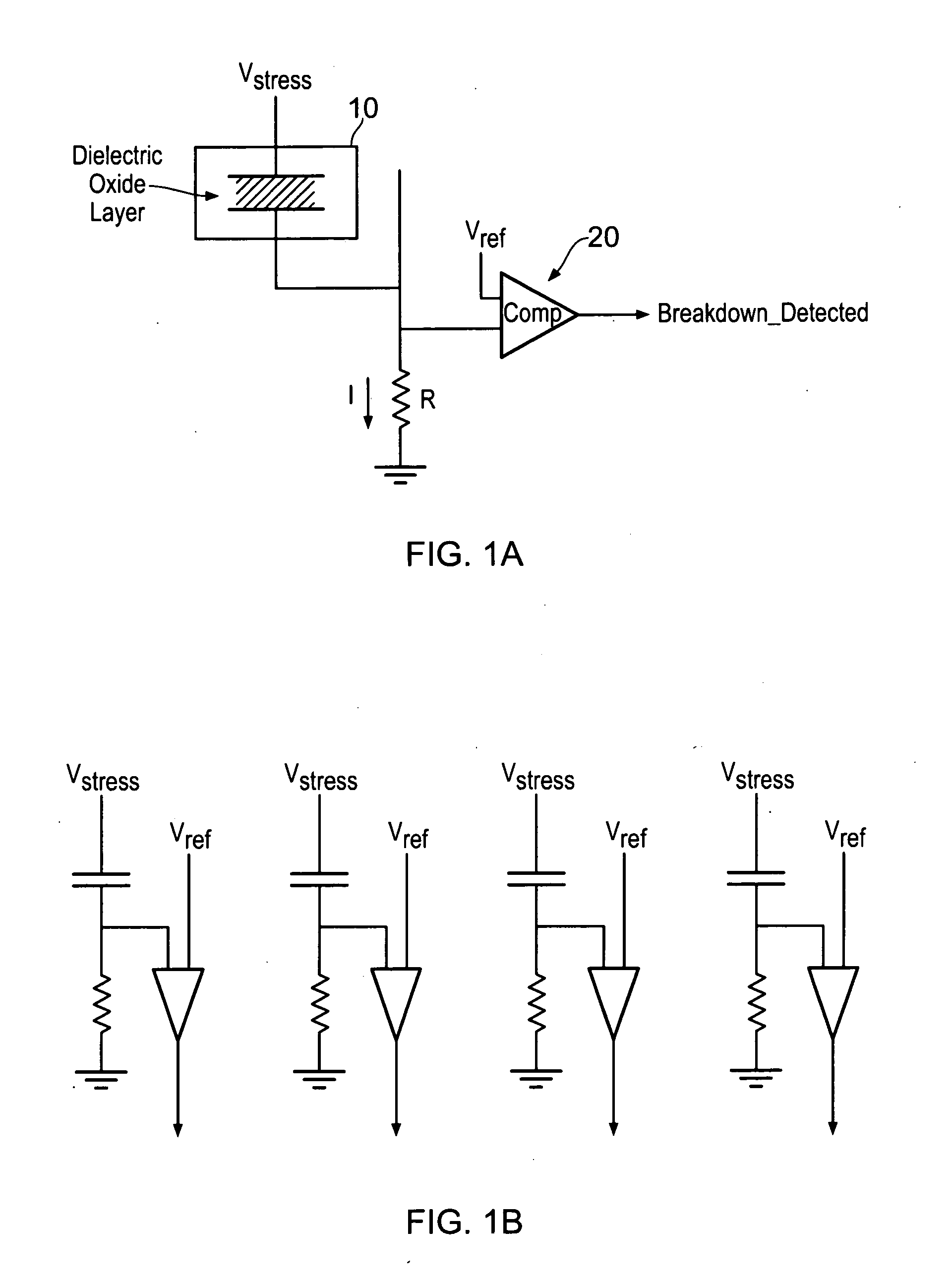
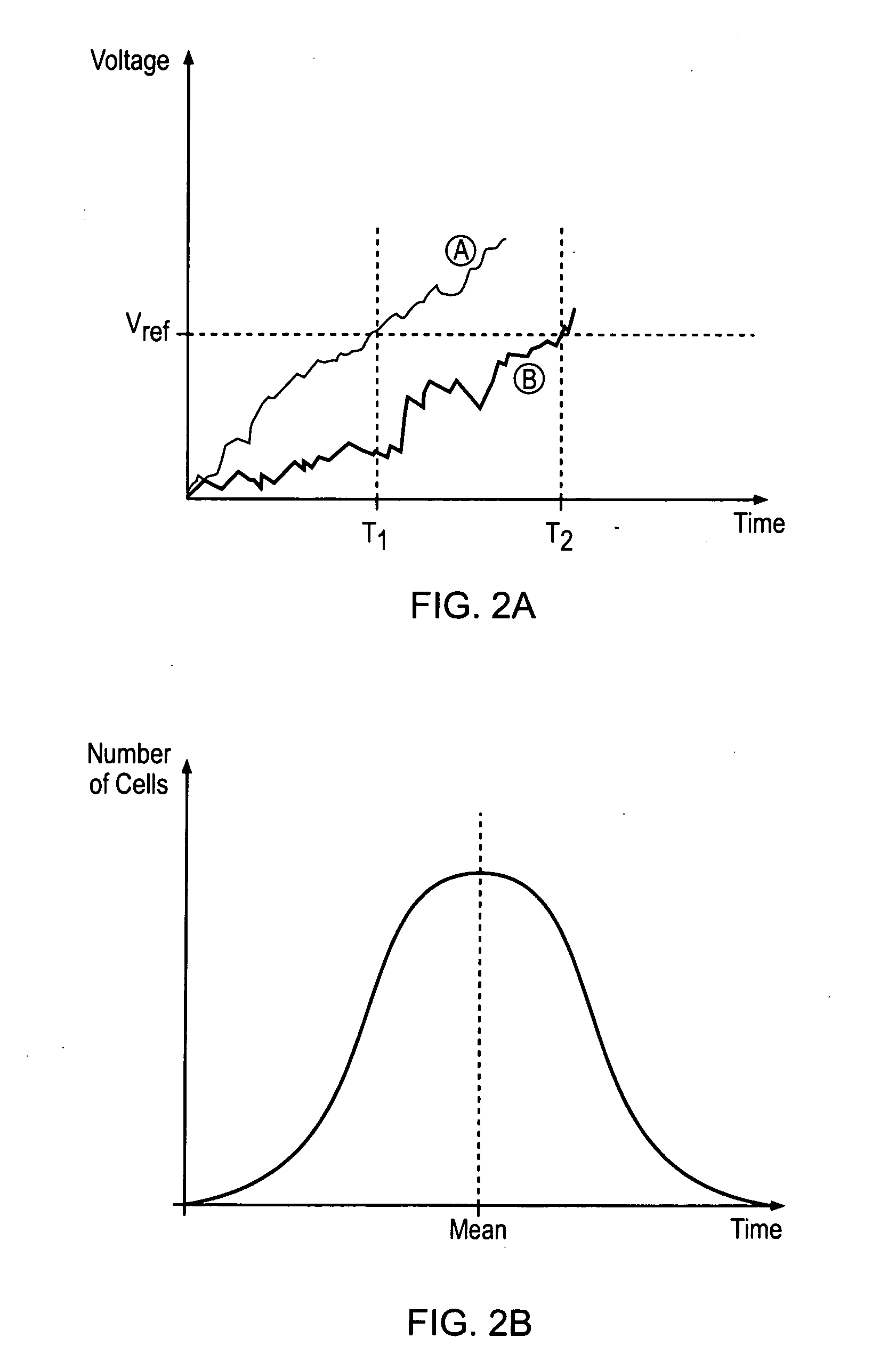
InactiveUS20120030268A1Effective monitoringMaximize lengthRandom number generatorsSecuring communication by chaotic signalsRandomizationVoltage
A data processing apparatus is provided for producing a randomized value. A cell in the data processing apparatus comprises a dielectric oxide layer and stress voltage circuitry is configured to apply a stress voltage across the dielectric oxide layer of the cell to cause an oxide breakdown process to occur. Oxide breakdown detection circuitry is configured to determine a current extent of the oxide breakdown process by measuring a response of the dielectric oxide layer to the stress voltage and randomized value determination circuitry is configured to determine a randomized value in dependence on the current extent of the oxide breakdown process.
Owner:RGT UNIV OF MICHIGAN
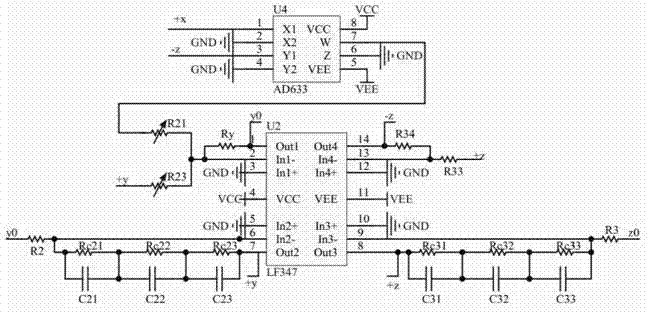
Method for realizing fractional-order three-system automatic-switchover chaotic system and analog circuit
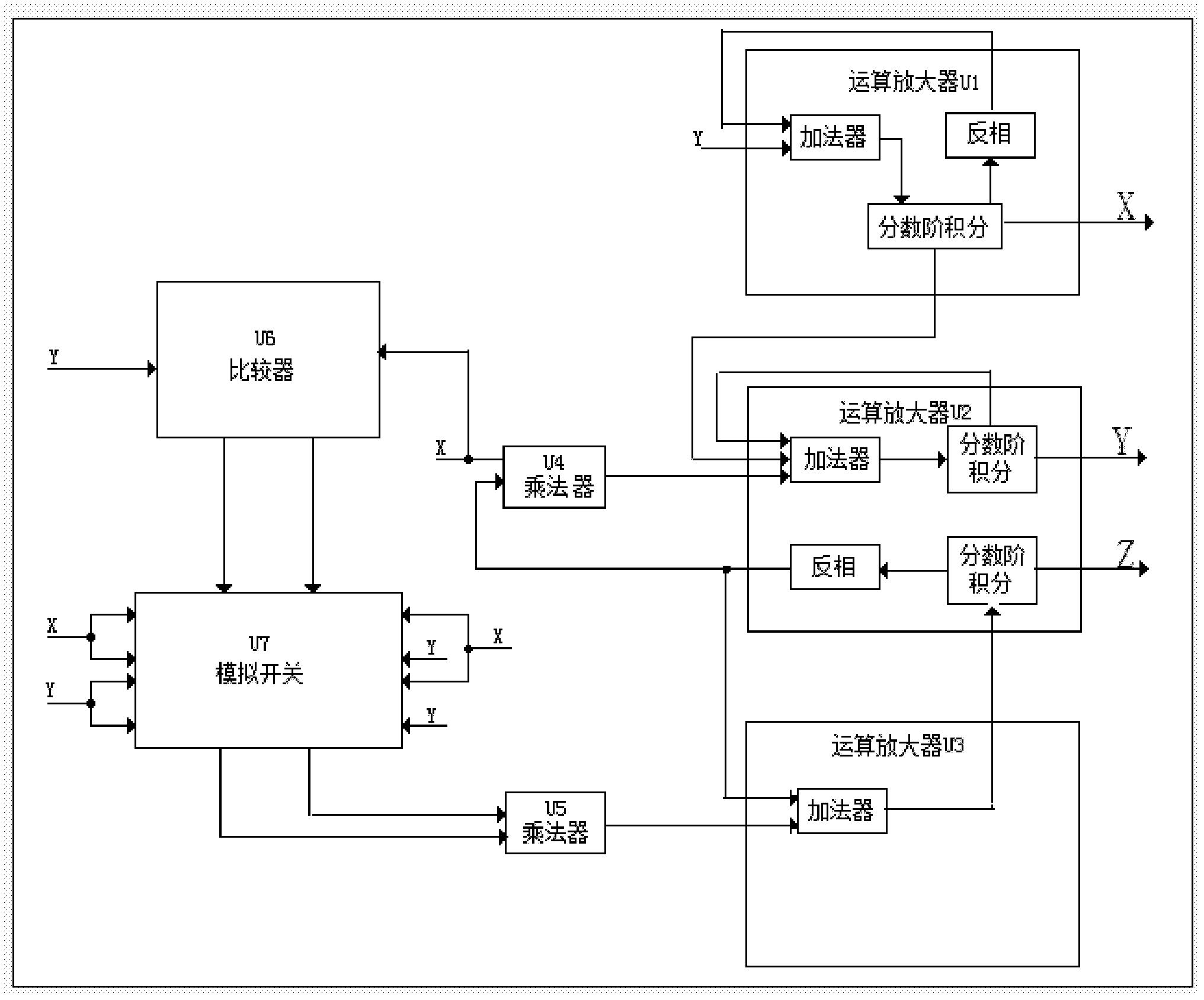
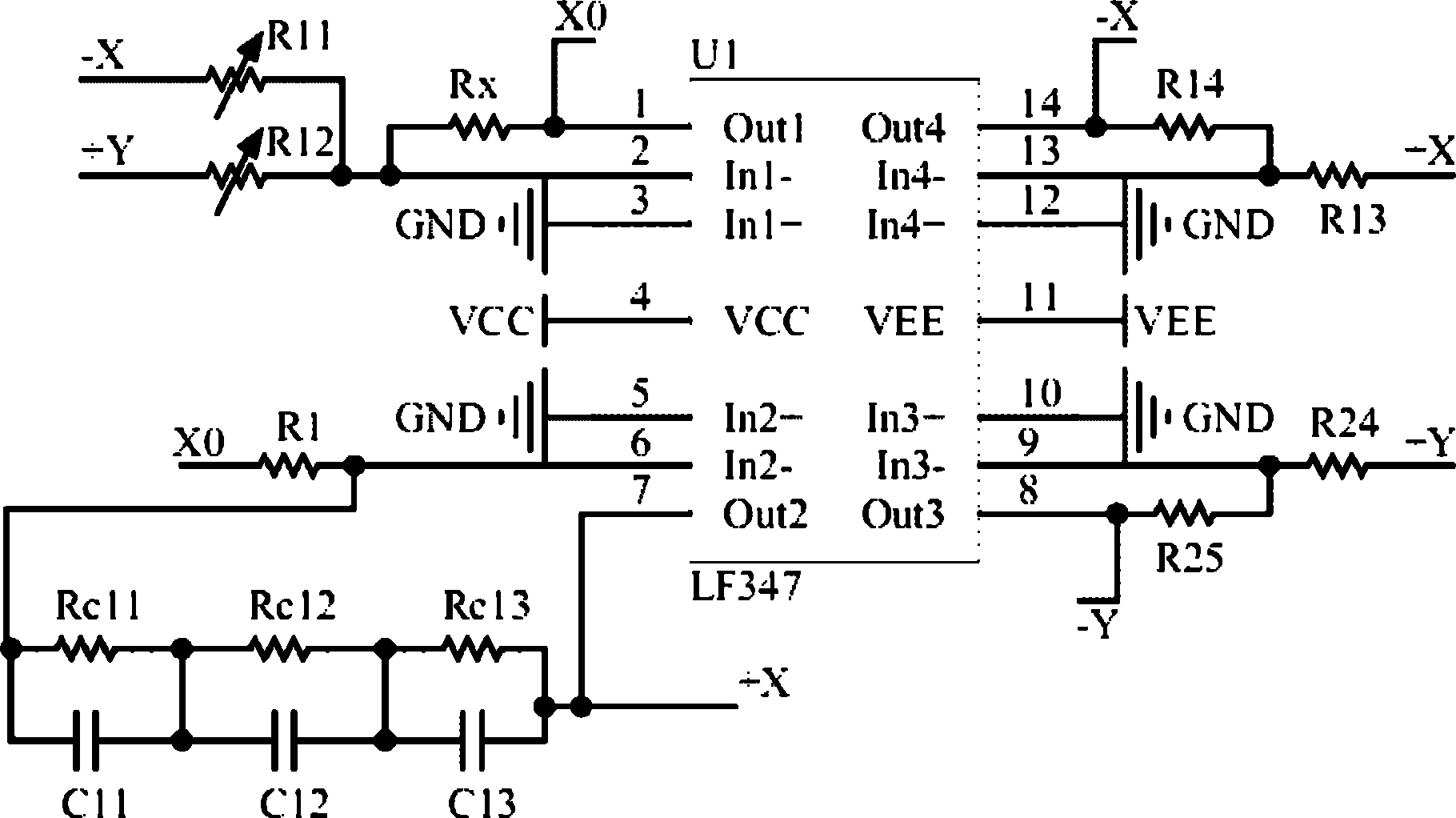
ActiveCN102385659ADigital data processing detailsCAD circuit designAudio power amplifierChaotic systems
The invention discloses a method for realizing the construction of a fractional-order three-system automatic-switchover chaotic system and an analog circuit. The method comprises the following steps: three chaoses and sub-chaoses form an automatic-switchover fractional-order system; the automatic-switchover fractional-order chaotic system is realized by the analog circuit; operational amplifiers U1, U2 and U3 adopt LF346; multiplying units U4 and U5 adopt AD633JN; a voltage comparator U6 adopts LM339; an analog switch U7 adopts CD4052; the operational amplifier U1is connected with the voltage comparator U6, the analog switch U7, the multiplying unit U4 and the operational amplifier U2, the operational amplifier U2 is connected with the voltage comparator U6 and the analog switch U7; the operational amplifier U3 is connected with the operational amplifier U2 and the multiplying unit U4; and the analog switch U7 is connected with the multiplying unit U5; and the multiplying unit U5 is connected with the operational amplifier U3. In the method, the analog circuit is utilized to realize the fractional-order chaotic system in which three subsystems are switched automatically, and the fractional-order three-system automatic-switchover chaotic system is more complicated and has stronger randomness as compared with an automatic-switchover chaotic system composed of two chaotic subsystems and a non-switched fractional-order chaotic system. Therefore, the fractional-order three-system automatic-switchover chaotic system can be a new choice of the signal source of secret communication and has a better application prospect in the secret communication.
Owner:PHICOMM (SHANGHAI) CO LTD
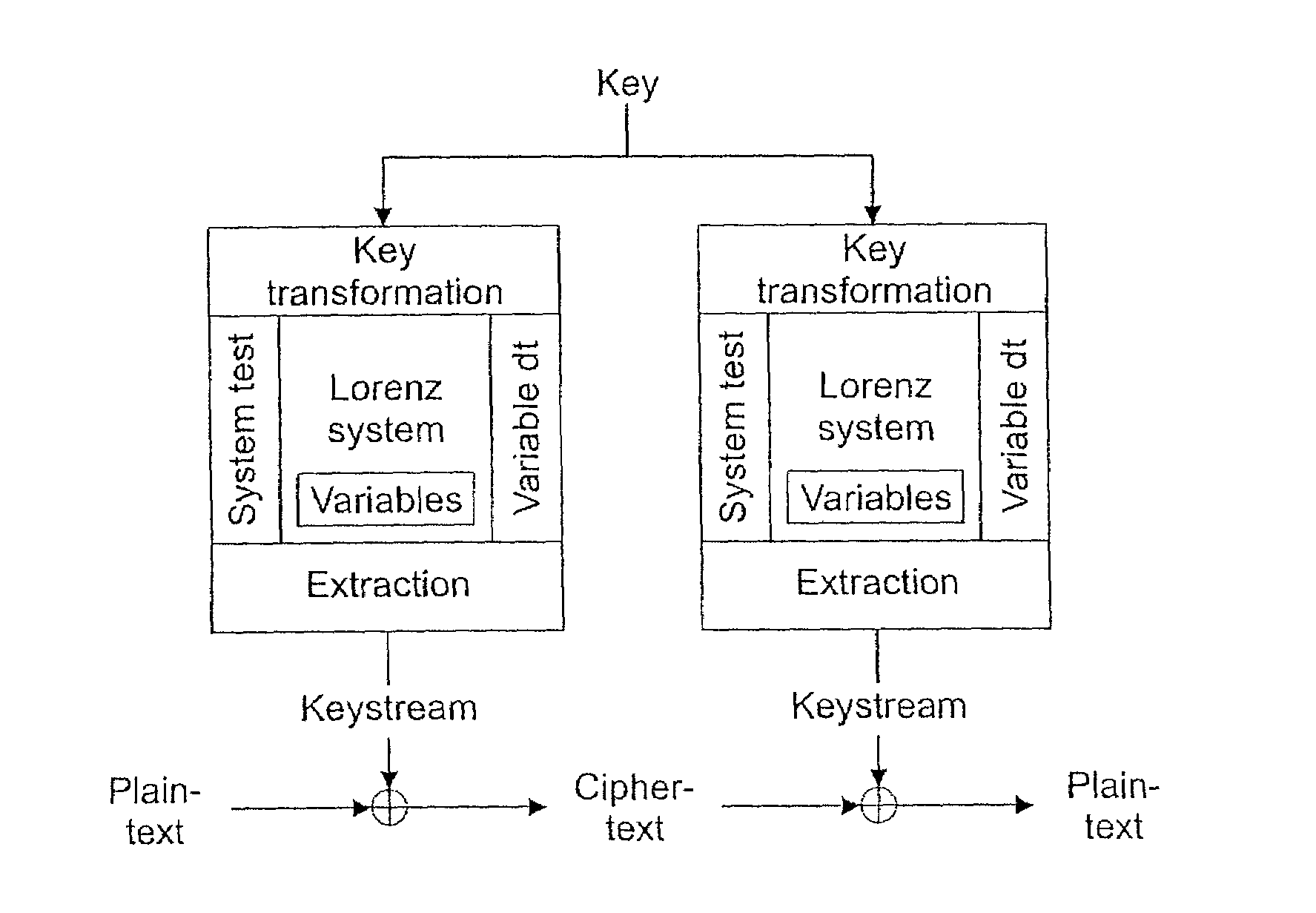
Method and Apparatus for Secure Digital Communications Using Chaotic Signals
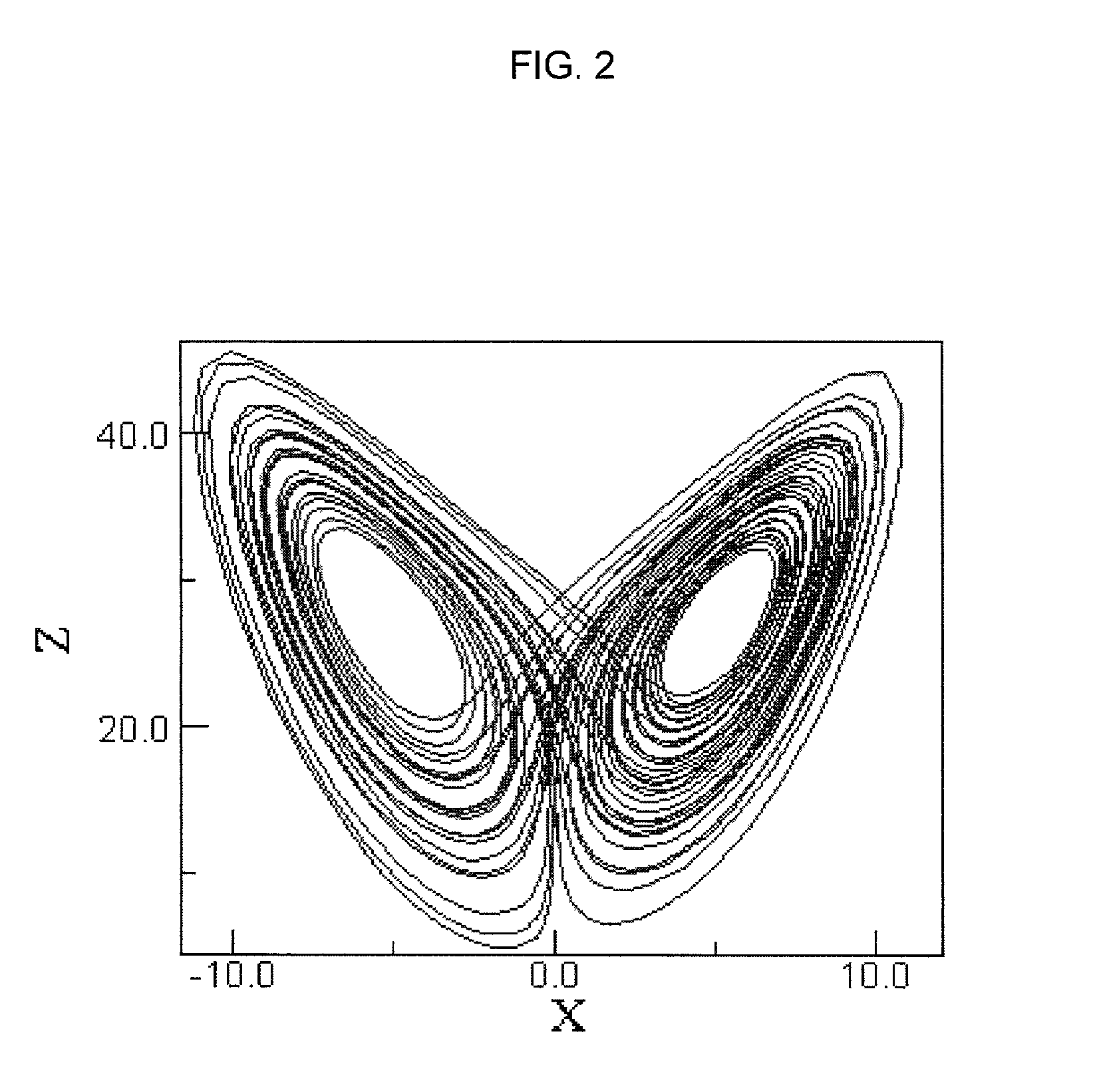
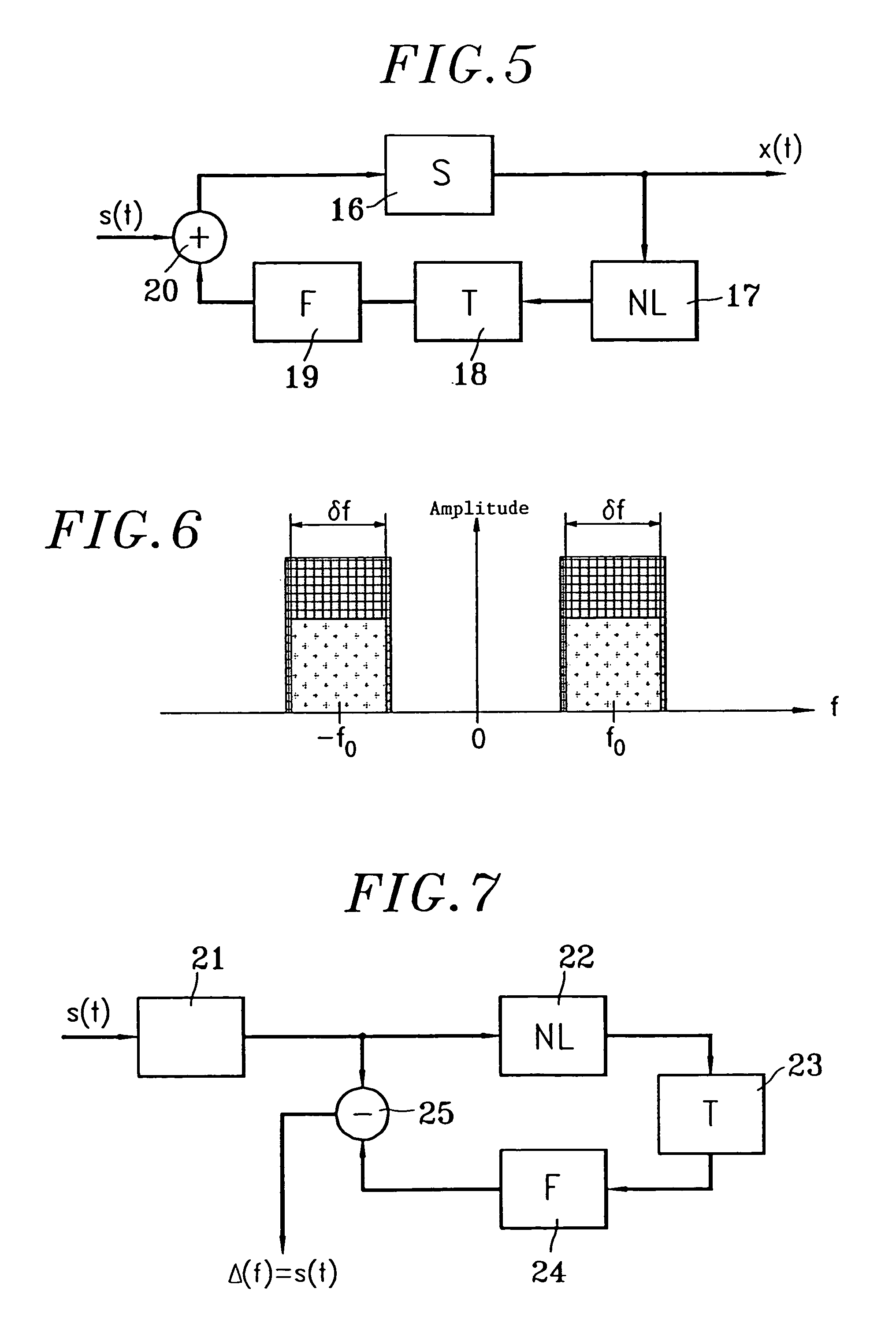
InactiveUS20080107268A1Modulated-carrier systemsEncryption apparatus with shift registers/memoriesChaotic systemsLorenz system
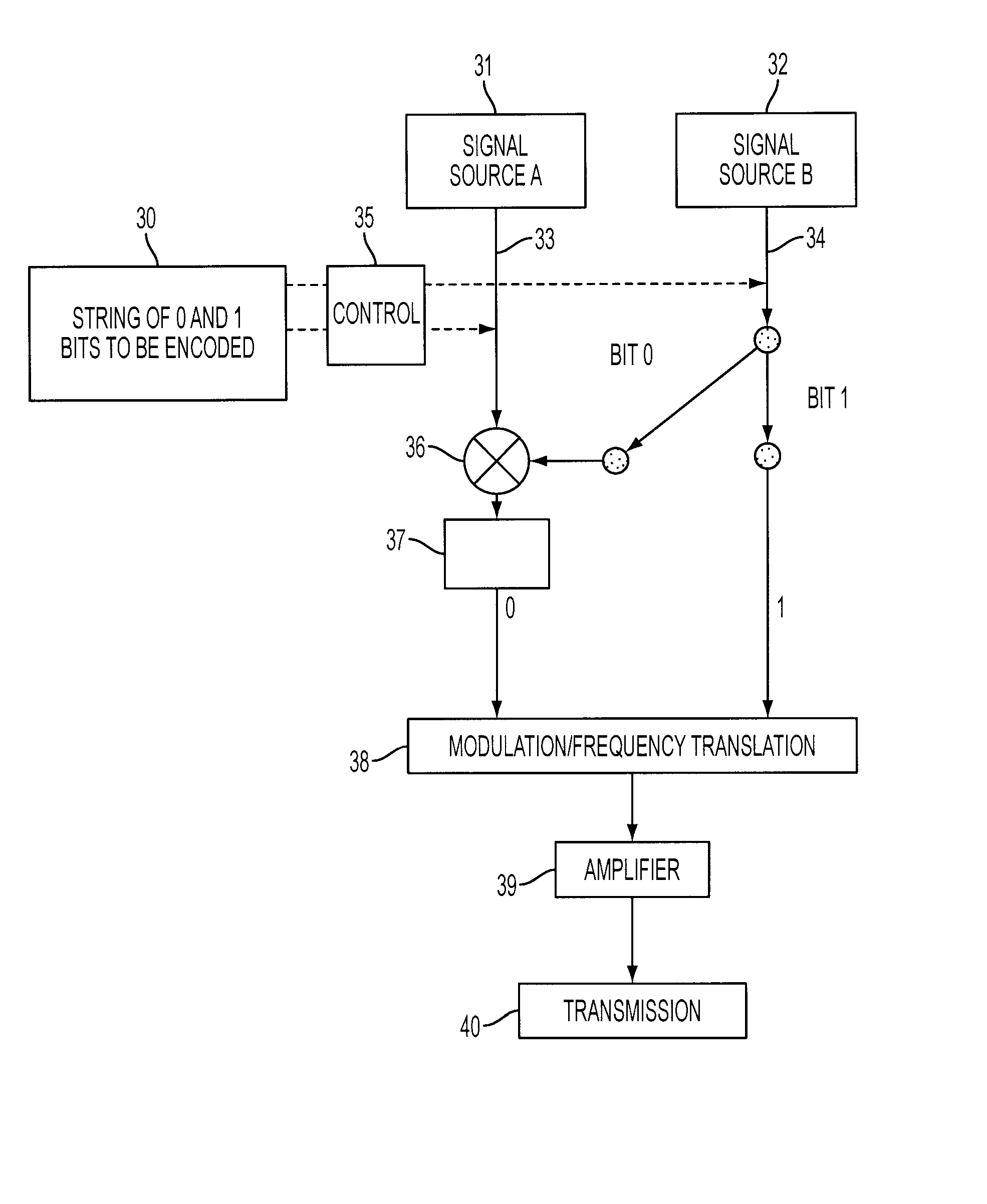
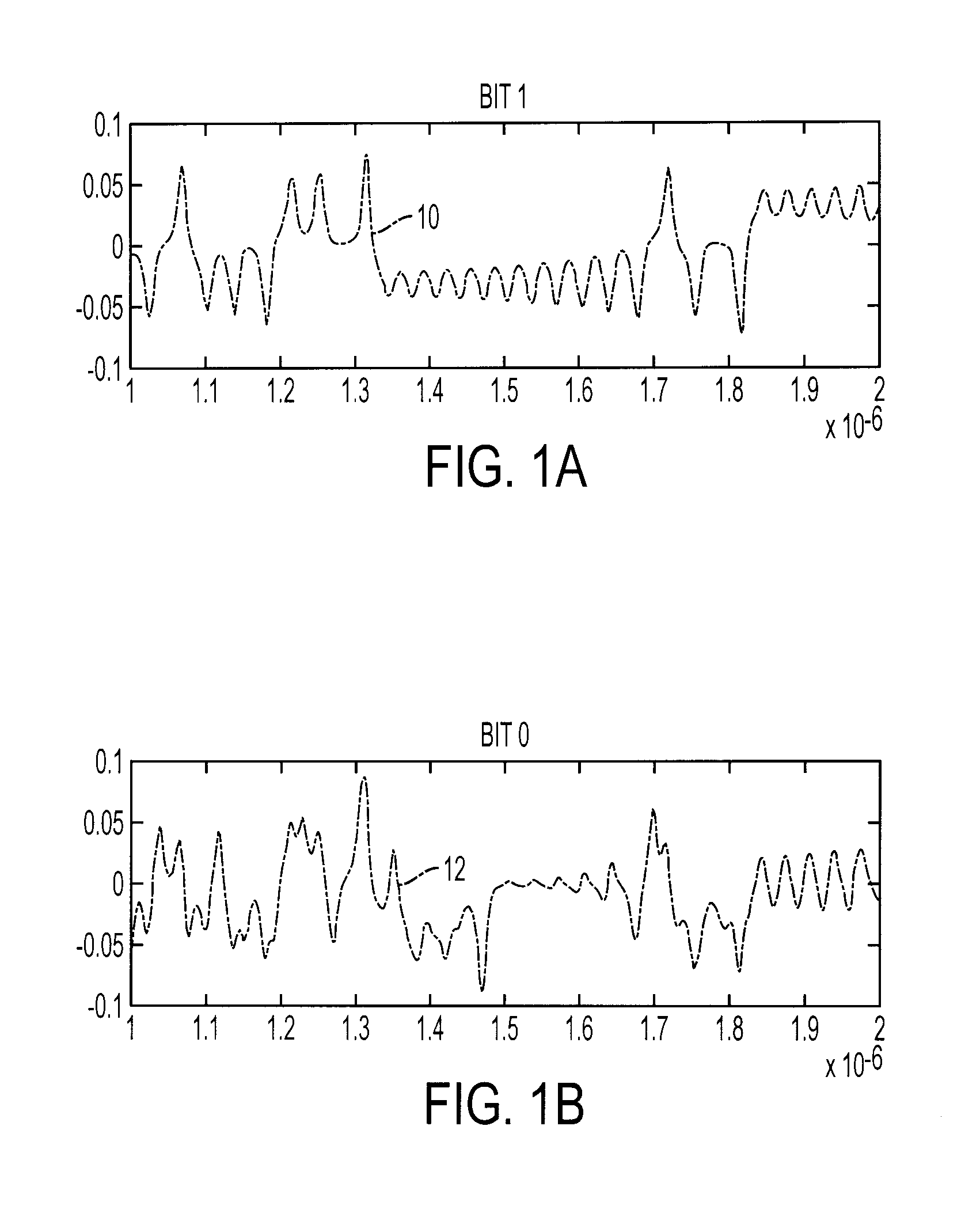
A system and method for encoding zero and one bits for transmission, including generating a first signal from a non-linear chaotic system to represent the one bit, with the signal's embedded vectors being within the non-linear system's attractor set, and generating a second signal from the non-linear system to represent the zero bit, with the signal's embedded vectors being outside the non-linear system's attractor set. The second signal encoding the zero bit can be generated by adding together two chaotic signals arising from the non-linear system initialized with different initial conditions, and weighting the second signal to have approximately the same energy as the first signal. One suitable chaotic systems is a Lorenz system. Systems and methods for decoding a transmitted stream of signals compare a detection statistic of the received stream of signals to a threshold value that depends on the chaotic system.
Owner:NAVY GOVERNMENT OF THE UNITED STATES OF AMERICA THE AS REPRESENTED BY THE SEC OF THE
System for scrambling and methods for use therewith
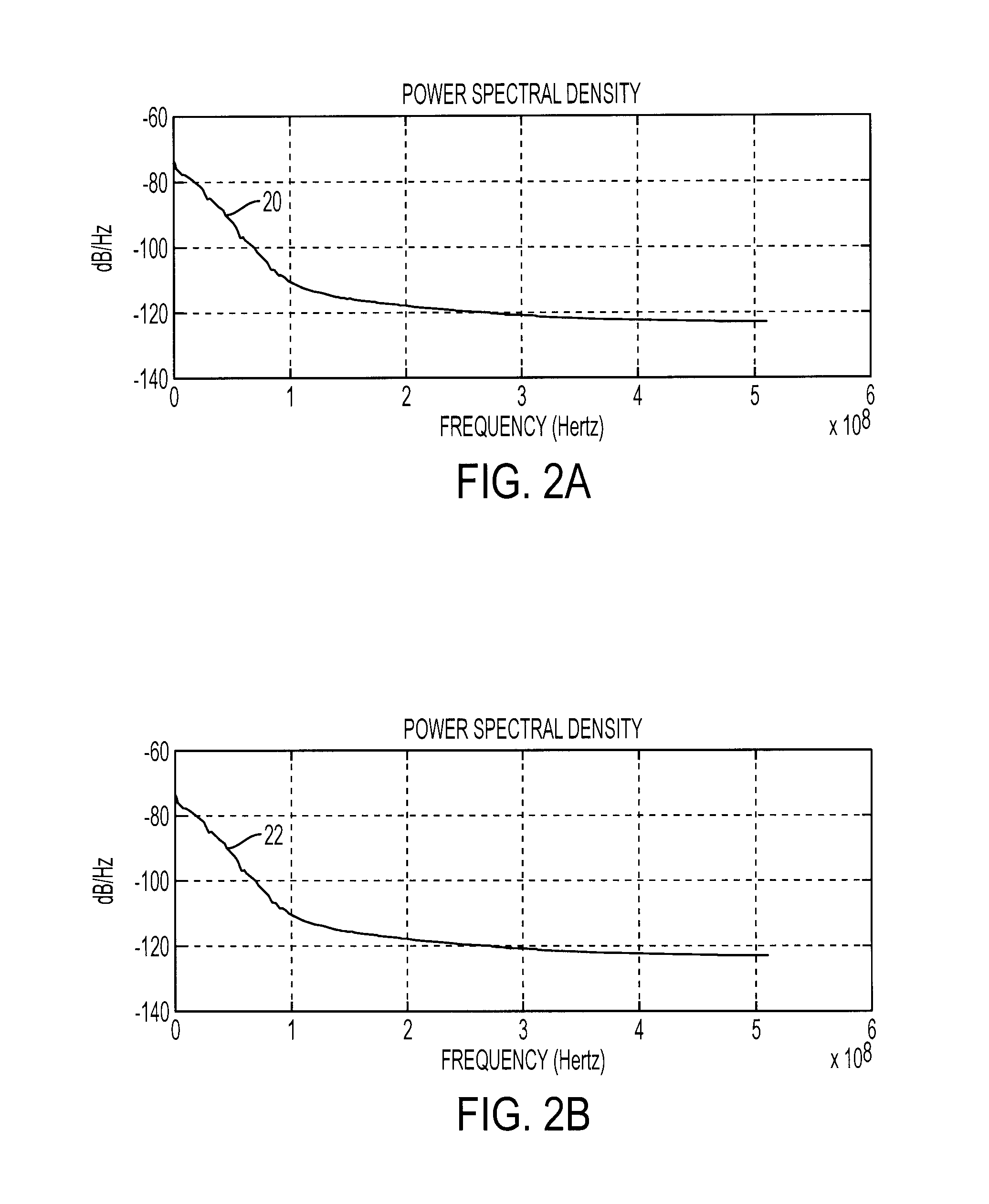
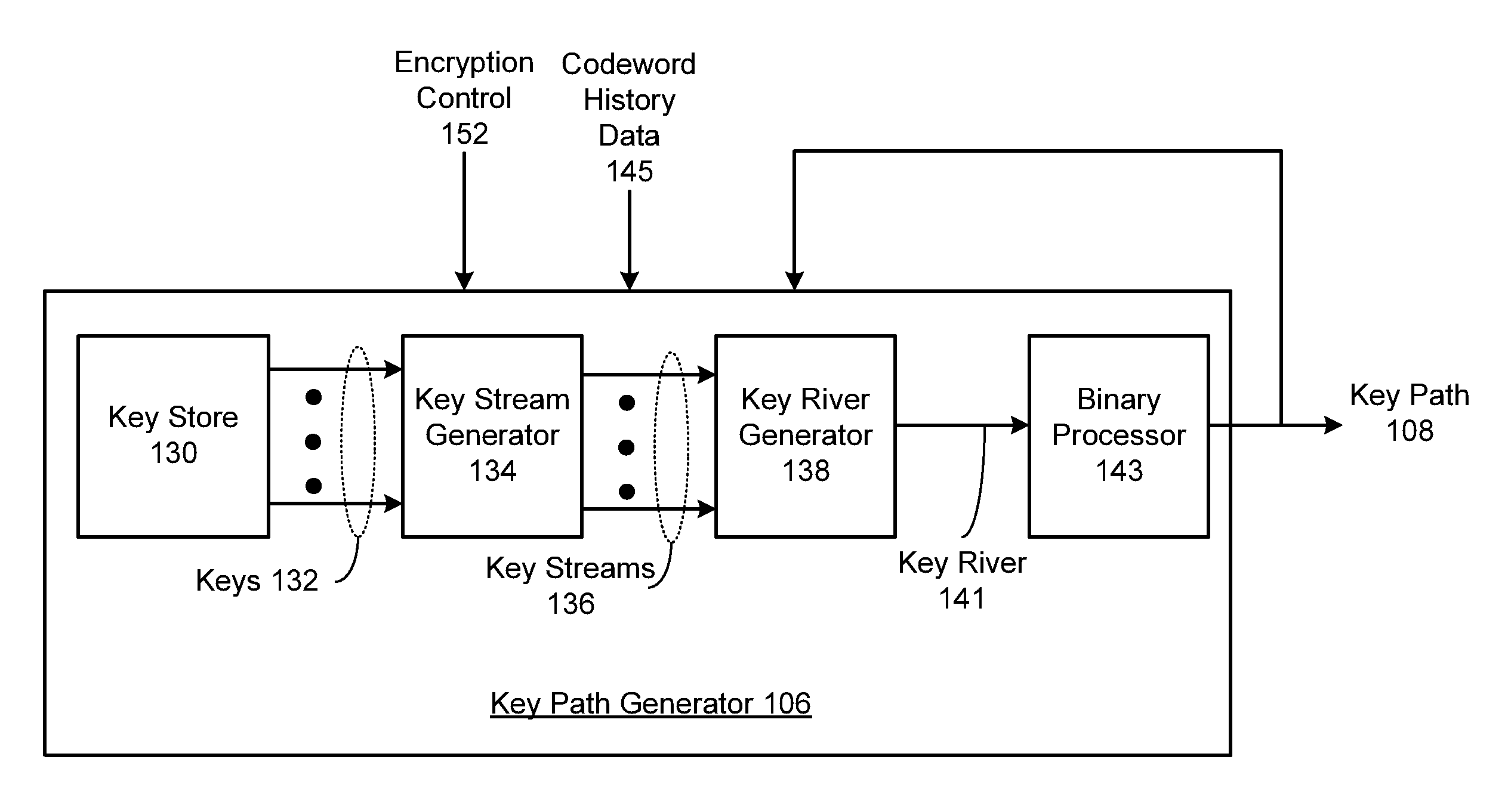
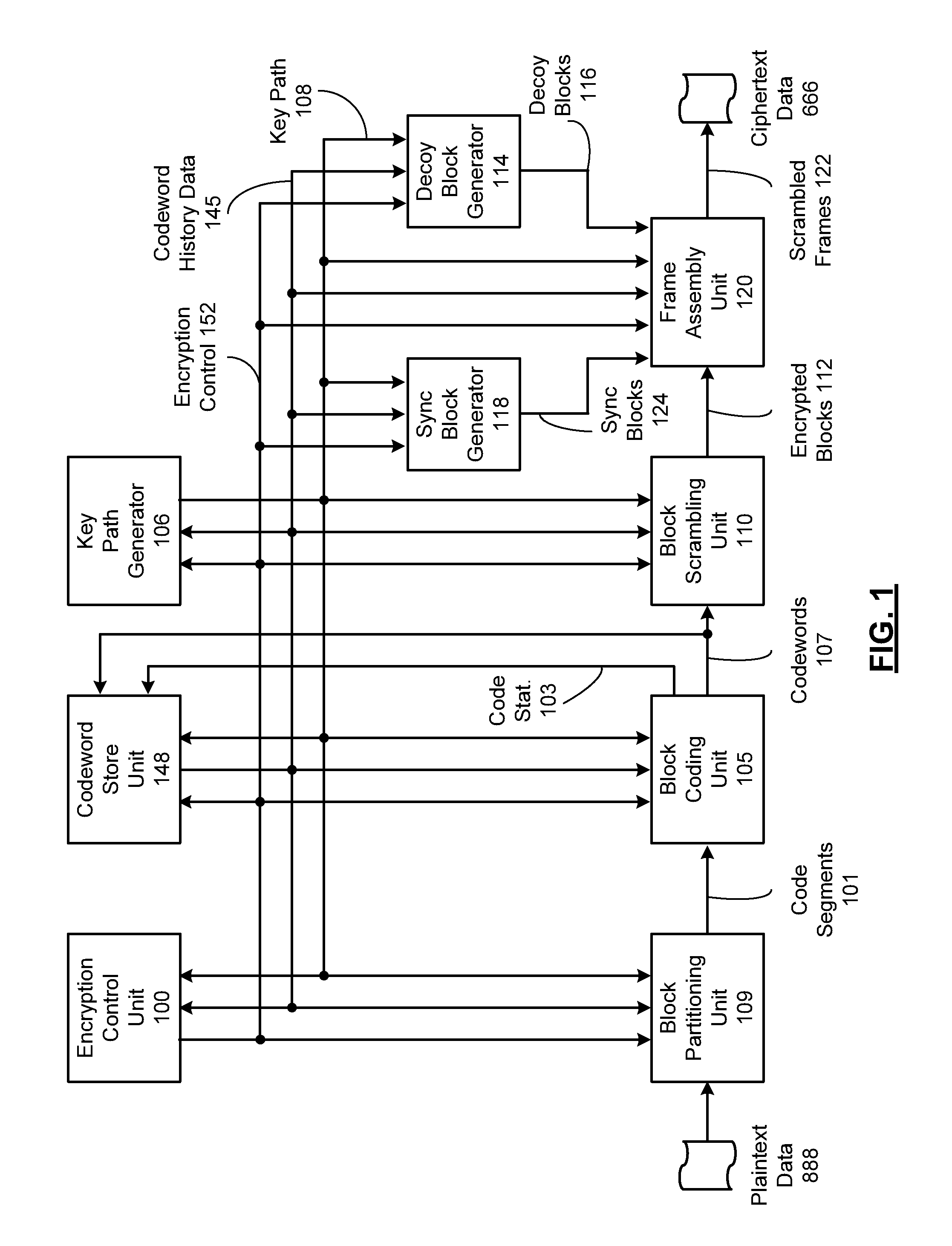
ActiveUS20120033809A1Unauthorized memory use protectionHardware monitoringCryptographic key generationBlock code
A system includes a key path generator that generates a key path based on a plurality of encryption keys. A block coding unit generates a plurality of codewords based on a plurality of data blocks. A block scrambling unit scrambles the plurality of codewords to generate a plurality of encrypted blocks by entropy processing, chaos processing and permutation processing each of the plurality of codewords, based on the plurality of encryption keys.
Owner:HUANG LAWRENCE P
Encryption process employing chaotic maps and digital signature process
ActiveUS6892940B2Easy to implementShorten the timeSecret communicationSecuring communication by chaotic signalsComputer hardwareDigital signature
An encryption process includes choosing a secret key and a set of permutable functions defined on a phase space for encrypting / decrypting messages, choosing a code for encoding messages to be sent as a number belonging to the phase space. The set of permutable functions includes chaotic maps generated by a composite function of first and second functions, and an inverse of the first function. The secret key is defined by the second function.
Owner:STMICROELECTRONICS SRL
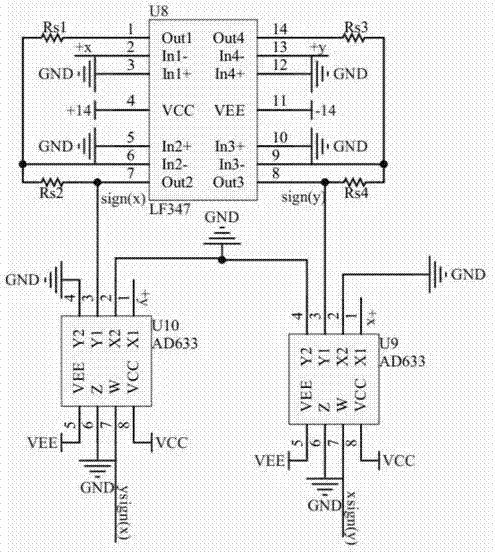
Method for realizing integer order and fractional order automatic switching chaotic system and analog circuit
InactiveCN102497263ASecuring communication by chaotic signalsLogic circuitsChaotic systemsIndustrial engineering
The invention discloses a construction of an integer order and fractional order automatic switching chaotic system and an analog circuit realization method. The construction comprises an automatic switching system which is formed by an integer order chaotic system and a fractional order chaotic system, and the automatic switching system is realized by utilizing an analog circuit. According to the invention, automatic switching of the integer order chaotic system and the fractional order chaotic system is realized by utilizing the analog circuit, the integer order and fractional order automatic switching chaotic system is more complex than the integer order chaotic system, the fractional order chaotic system and the automatic switching system, and superiority of the above three systems are concentrated. The system provided by the invention has an important meaning in secret communication based on chaos and signal detection and has good application prospect.
Owner:JINZHONG POWER SUPPLY COMPANY OF STATE GRID SHANXI ELECTRIC POWER
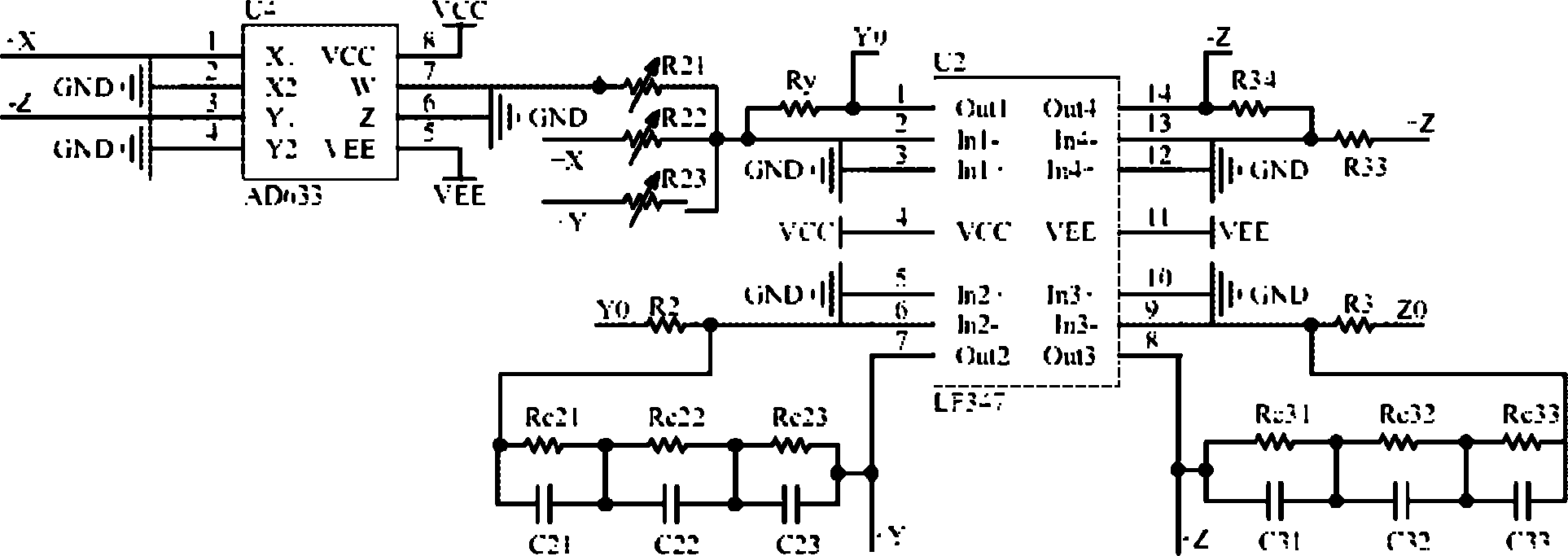
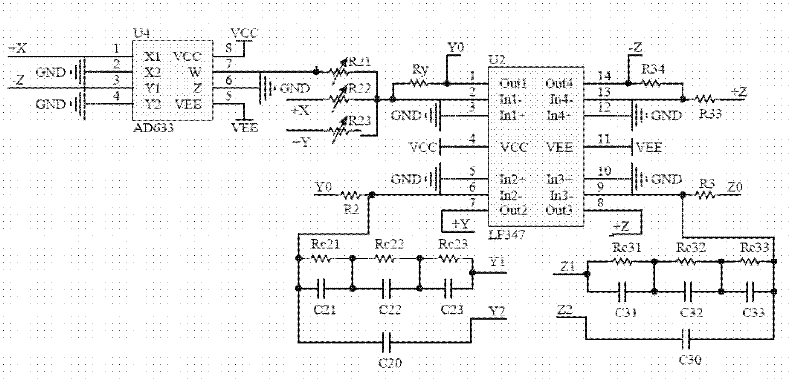
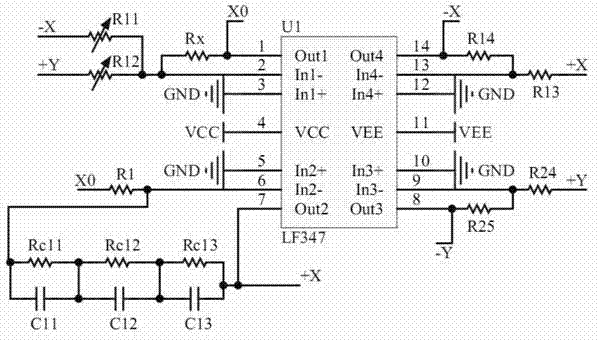
Method for automatically switching fractional-order chaotic system by four systems based on Lu-type system and analog circuit
ActiveCN102904708AModulated-carrier systemsSecuring communication by chaotic signalsChaotic systemsEngineering
The invention discloses a method for automatically switching a fractional-order chaotic system by four systems based on a Lu-type system and an analog circuit. The analog circuit comprises an operational amplifier U1, an operational amplifier U2, an operational amplifier U3, an operational amplifier U5, an operational amplifier U8, a multiplier U4, a multiplier U9, a multiplier U10, a voltage comparator U7 and an analog switch U6. By the analog circuit, the fractional-order chaotic system can be automatically switched by four Lu-type subsystems. The analog circuit is more complex than automatically switched chaotic systems formed by two or three sub-chaotic systems and fractional-order chaotic systems that are not switched, has higher randomness, can be a new choice for a signal source for confidential communication, and has brighter application prospect in confidential communication.
Owner:STATE GRID CORP OF CHINA +2
Encryption method, program for encryption, memory medium for storing the program, and encryption apparatus, as well as decryption method and decryption apparatus
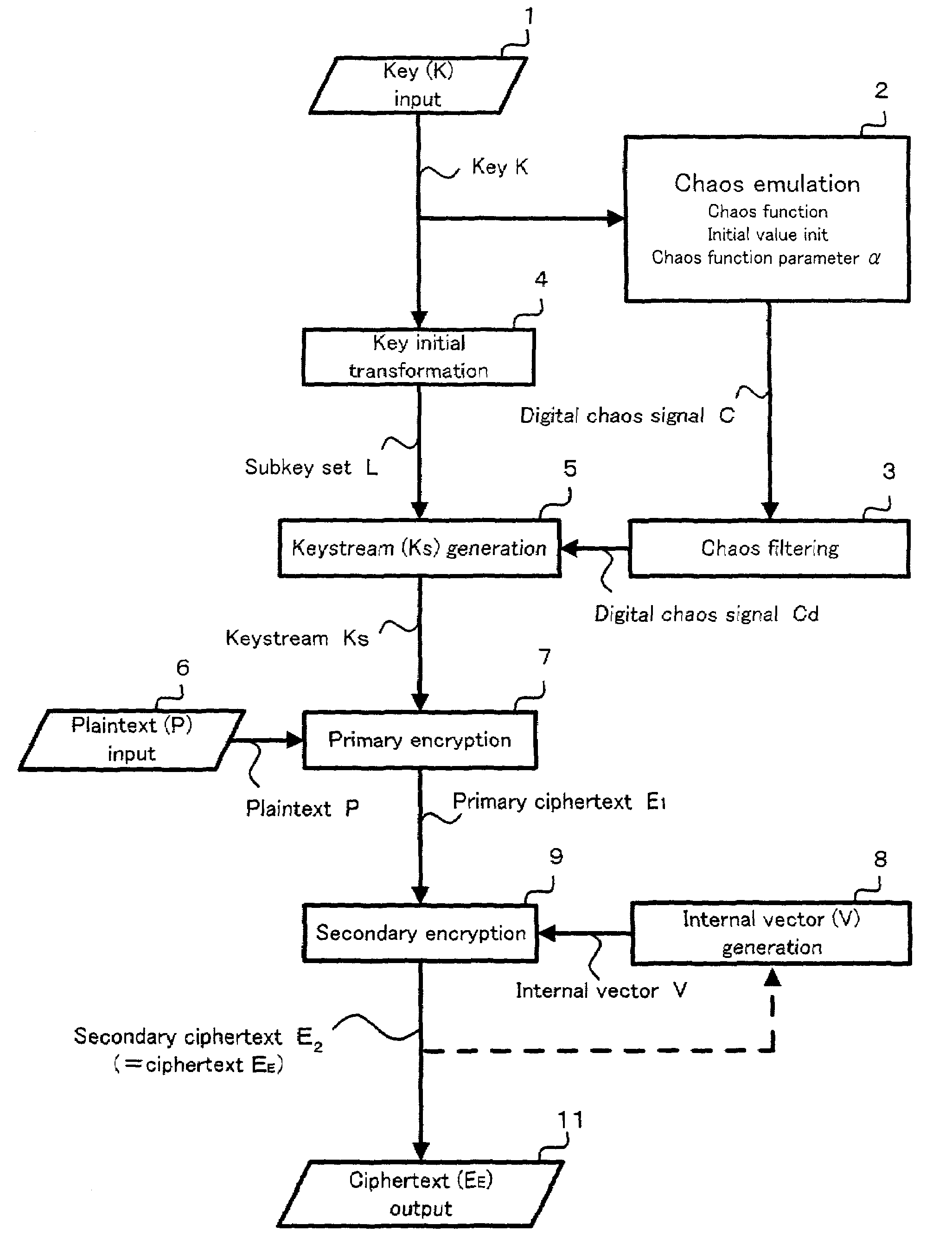
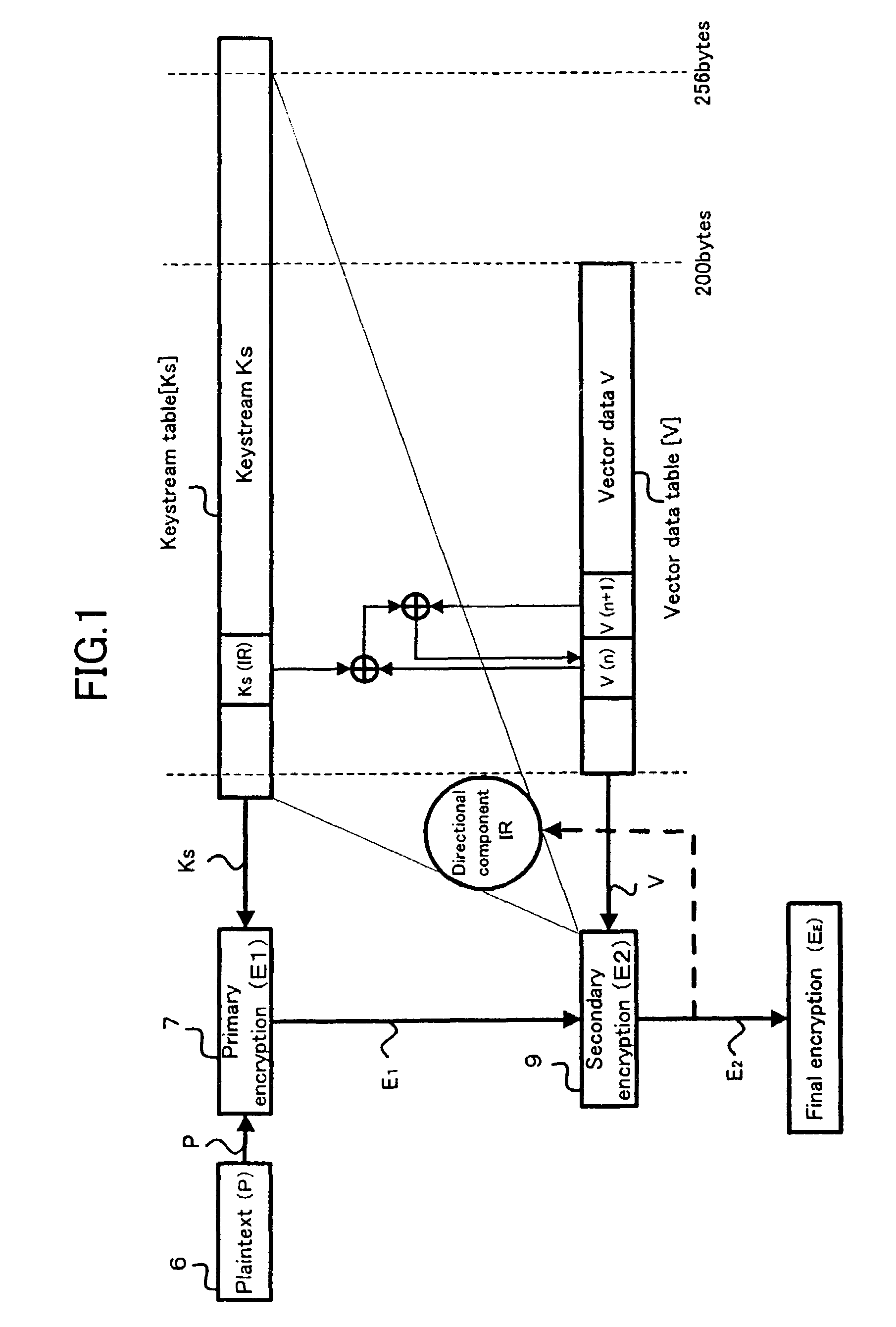
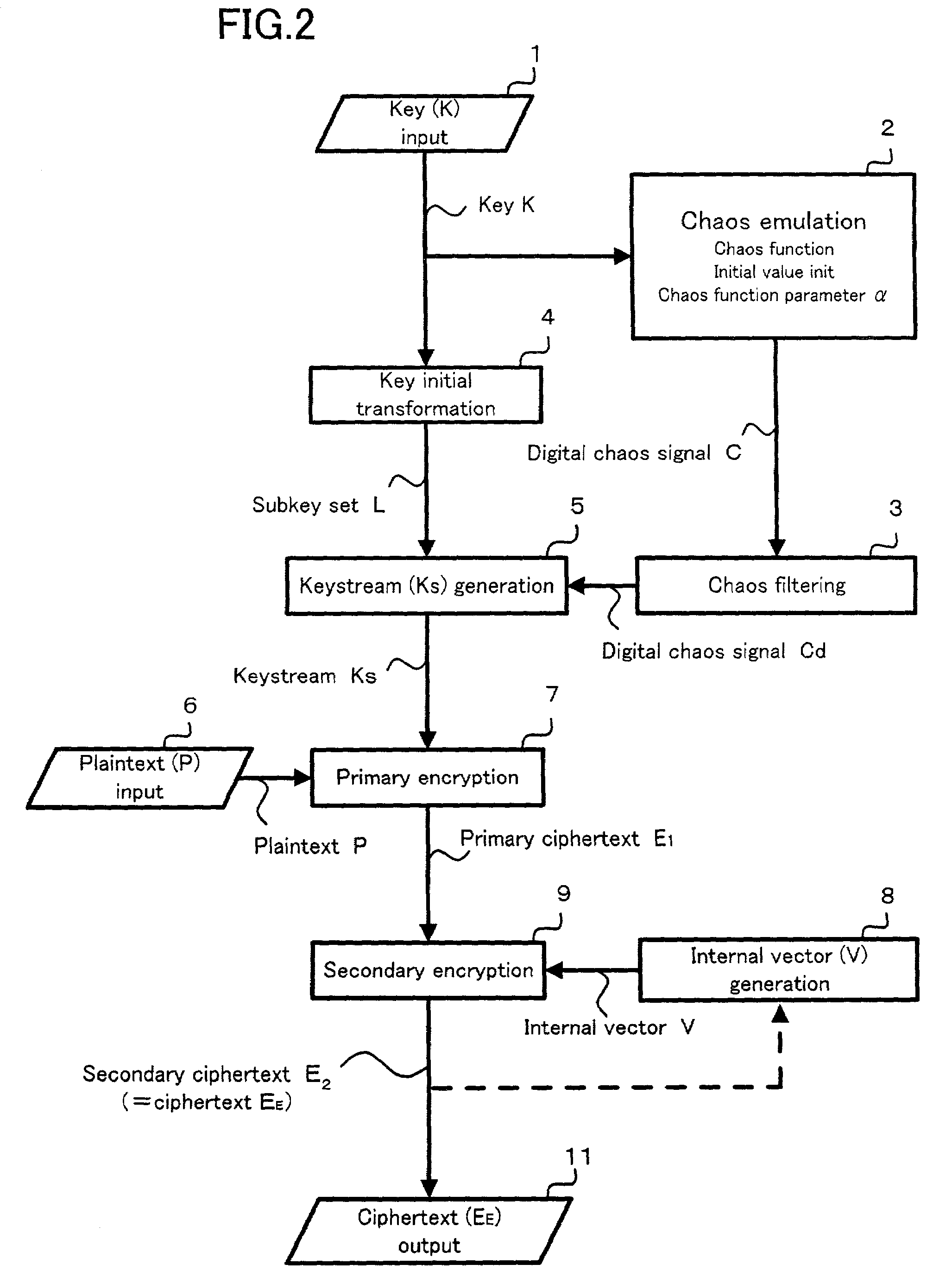
InactiveUS7218733B2Easy loadingIncrease speedData stream serial/continuous modificationSecret communicationData spaceKeystream
The present invention relates to a cryptosystem. A keystream table [Ks] is a virtual data space. Every data of 1 byte in a secondary ciphertext E2 provides a vector directional component IR. The data Ks (IR) in the keystream table [Ks] designated by the directional component IR of the vector is recognized as the quantitative component of the vector. By handling a secondary ciphertext E2 of 1 byte as the address in the keystream table [Ks], the secondary ciphertext E2 can be recognized as the directional component of the vector. A logical operation for the data Ks (IR) is performed, and the internal vector data V is sequentially replaced every 1 byte. An exclusive OR operation is performed between the internal vector data V and the primary ciphertext E1 for generating a secondary ciphertext E2.
Owner:C4 TECH
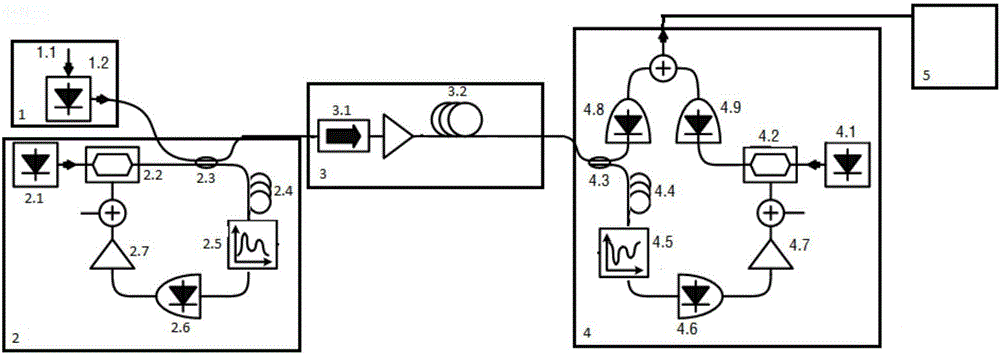
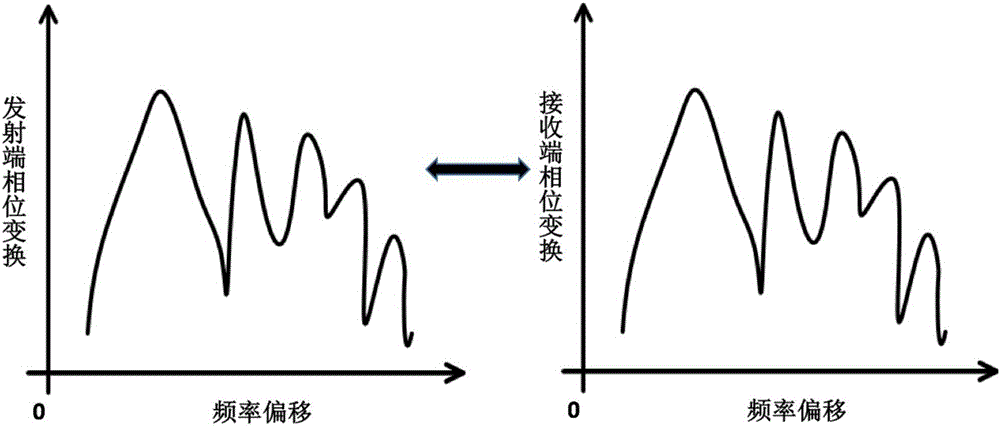
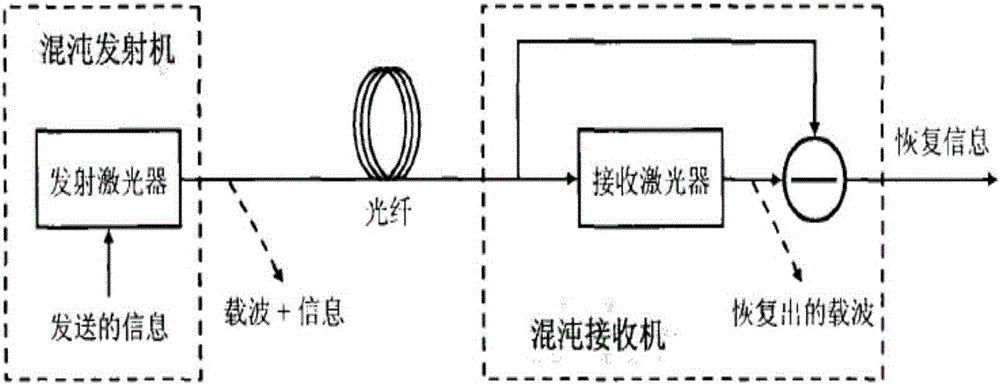
Secondary chaotic encryption optical communication system based on phase transformation
InactiveCN106330428AEasy to adjustThere are many adjustable parameters for encryptionSecuring communication by chaotic signalsElectromagnetic receiversConfidentialityOptical communication
The invention discloses a secondary chaotic encryption optical communication system based on phase transformation. The system comprises an optical signal transmitting device, a chaotic combined phase transformation encryption device, a transmission fiber, a chaotic combined phase transformation decryption device and a signal receiving device. The signal encryption part is a chaotic encryption module added with a phase transformation decryption device in a feedback loop, and the signal decryption device is an open-loop chaotic laser receiving module comprising a phase transformation decryption device. The system overcomes the defect that encryption variables of a chaotic encryption system are few; by combining phase transformation decryption with chaotic encryption, an eavesdropper is difficult in analyzing and attacking the energy; high-speed signals can be supported, and 10 Gb / s high-speed signals can be directly encrypted; a light emitting source of an existing WDM (Wavelength Division Multiplexing) system can be directly used for encrypting, and a special ultra-short pulse light source is not needed; and decryption can be implemented by using the same phase transformation modules at the receiving end as at the transmitting end, so that the adjusting difficulty is reduced without changing the confidentiality.
Owner:SHANGHAI JIAO TONG UNIV
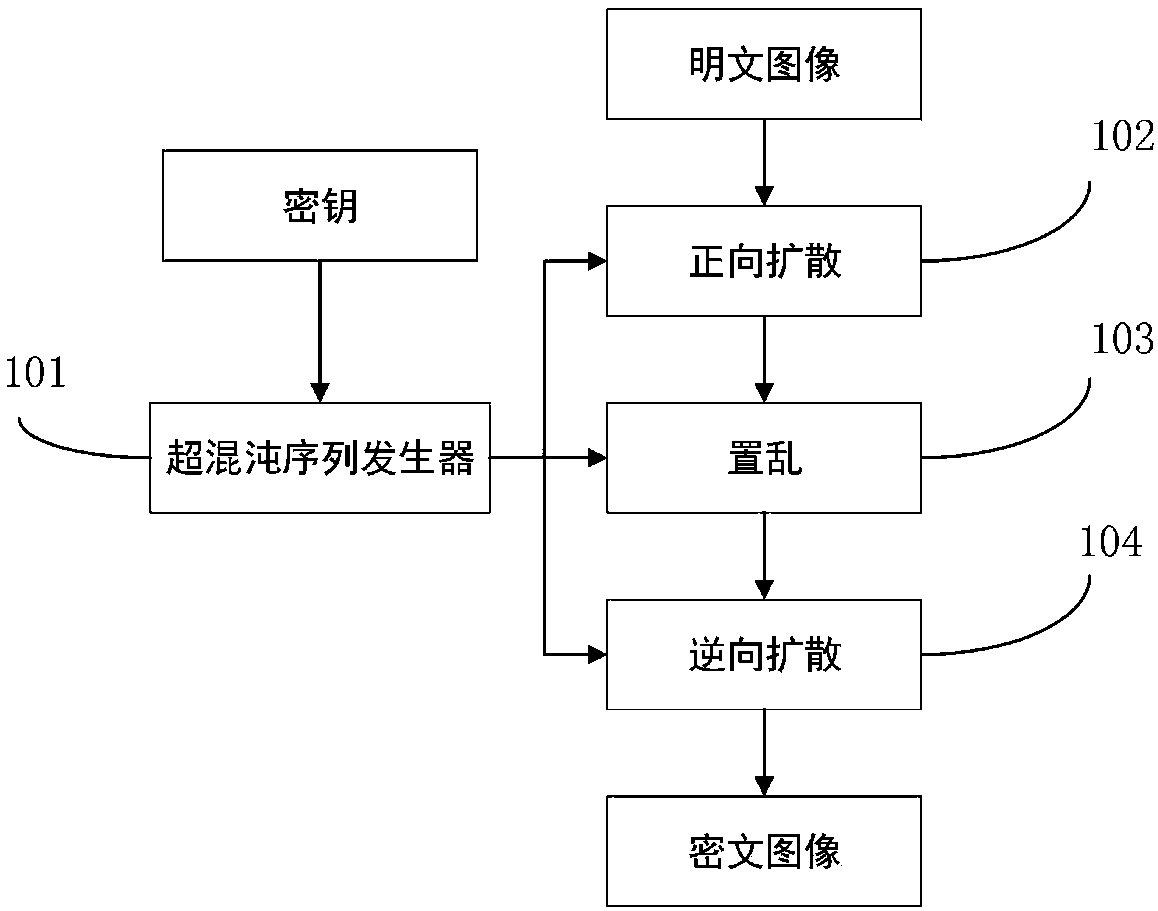
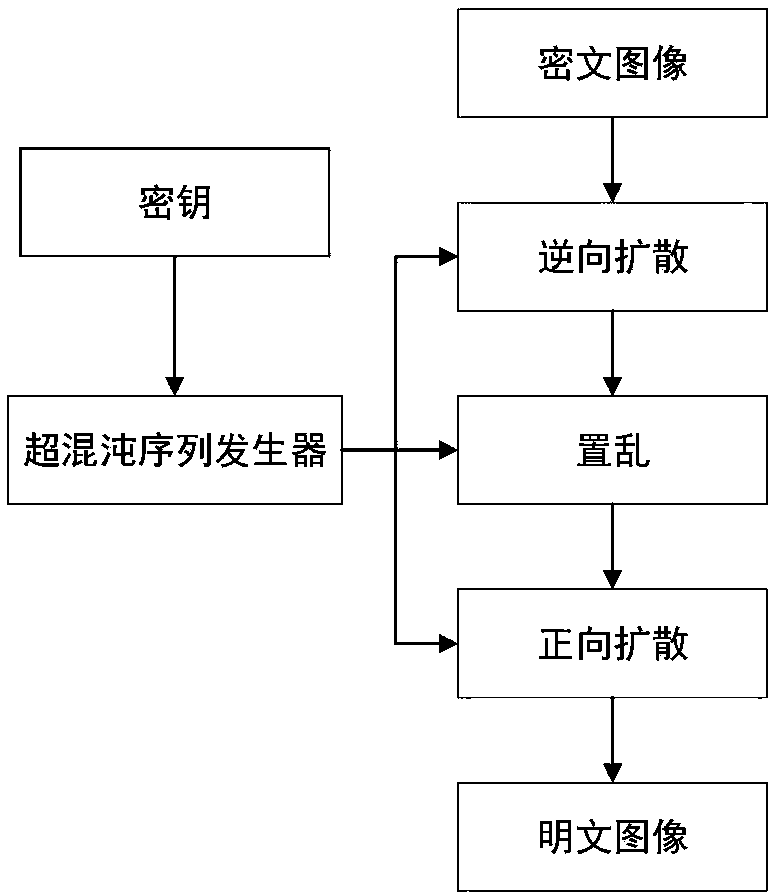
Plaintext associated image encryption algorithm based on hyperchaos Chen system
InactiveCN108234813AReduce the number of iterationsImprove the ability to resist known plaintext attacksKey distribution for secure communicationSecuring communication by chaotic signalsChosen-plaintext attackRelevant information
The invention relates to an image encryption algorithm based on a chaotic system, used for solving security problems that the image encryption algorithm is small in key space and poor in capacity of resisting to plaintext attacks. The algorithm comprises four modules such as a hyperchaos sequence generator, a forward diffusion module, a scrambling module and a reverse diffusion module. Firstly thehyperchaos Chen system is used for generating four chaotic pseudorandom sequences, a chaotic sequence and a plaintext image are used for performing forward diffusion operation to acquire a matrix A,then computation is performed in combination with the pseudorandom sequences and information related to the plaintext image to acquire a scrambled coordinate, the coordinate scrambling is performed onthe matrix A to acquire a matrix B, and at last the chaotic pseudorandom sequences and the matrix B are used for performing reverse diffusion operation to acquire a ciphertext image C. An experimentsimulation result expresses that the algorithm can improve the defect that the image encryption algorithm is small in key space, effectively resist to statistical attacks, differential attacks, and chosen-plaintext attacks, and achieve good encryption effect.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
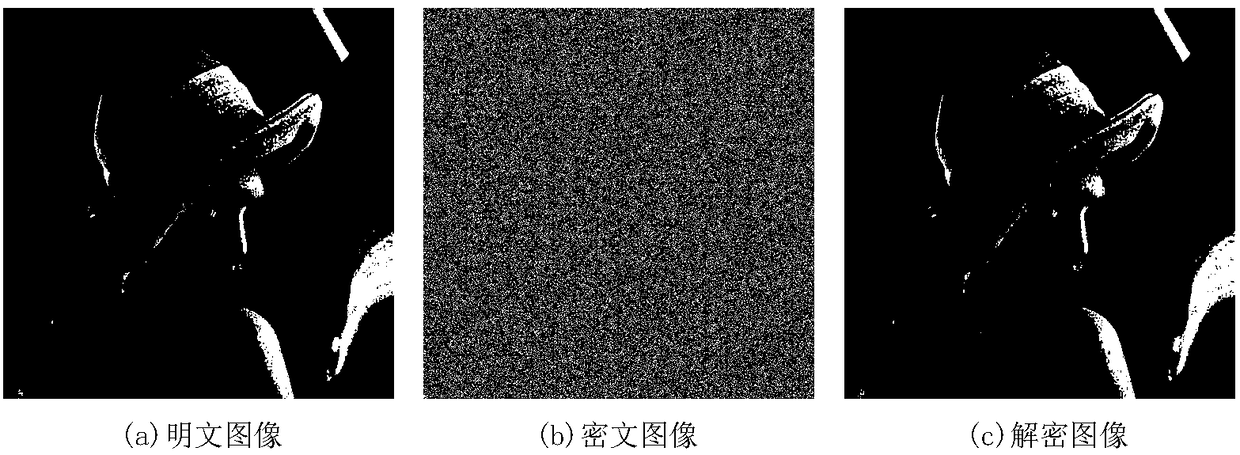
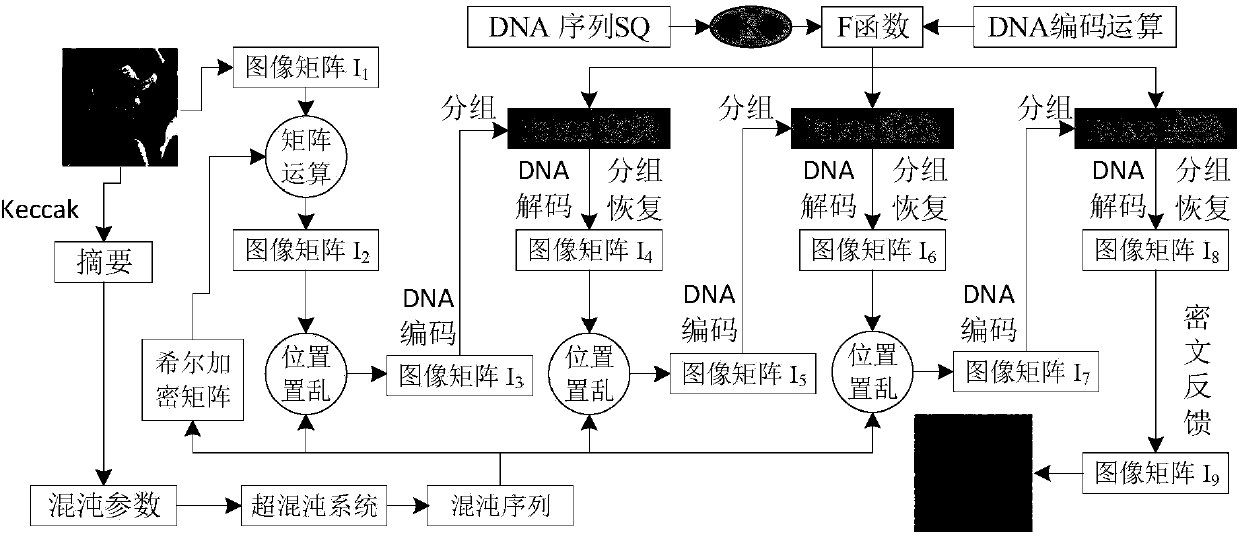
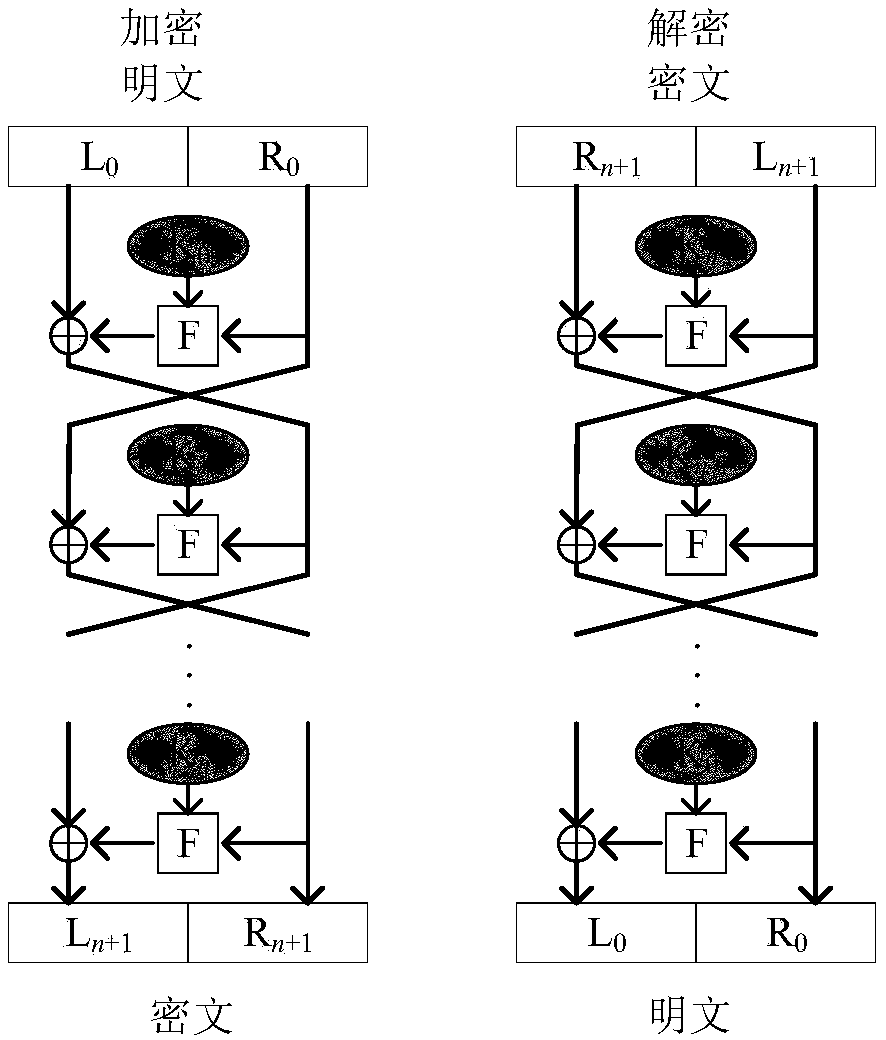
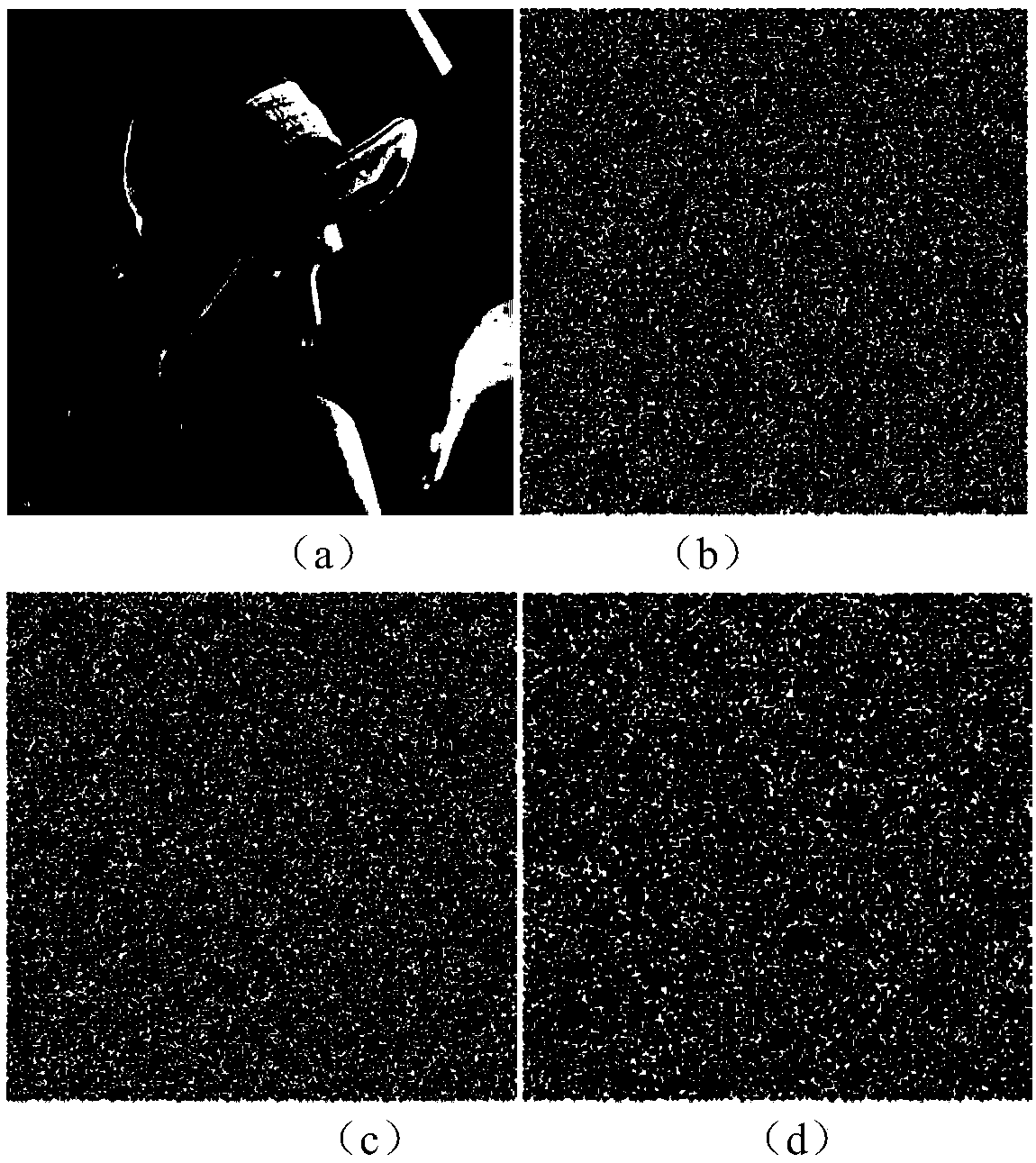
Image encryption method based on Feistel network and dynamic DNA encoding
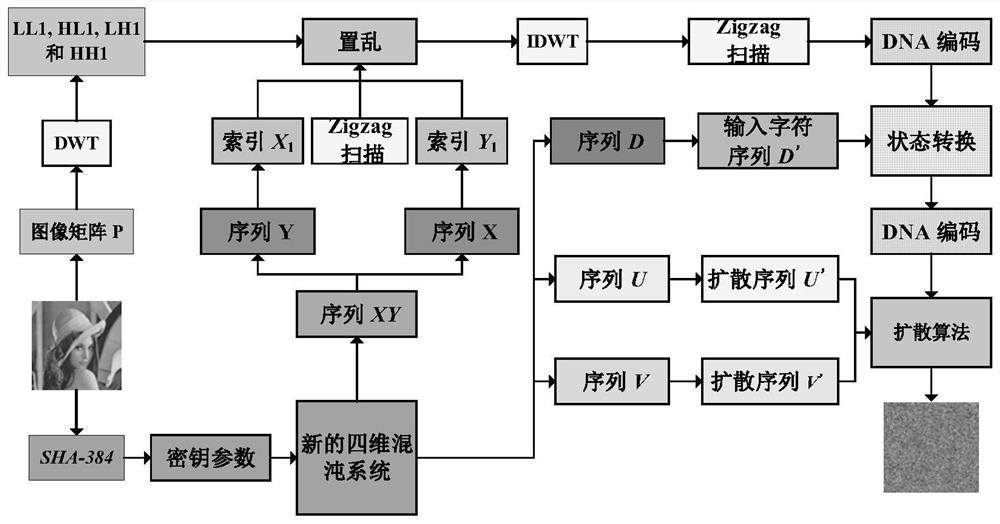
ActiveCN108365947AStrong randomnessStrong resistance to attackKey distribution for secure communicationSecuring communication by chaotic signalsPlaintextCiphertext
The invention provides an image encryption method based on a Feistel network and dynamic DNA encoding. The method comprises the following steps: computing a Hash value of an original plaintext image by using a Keccak algorithm, and taking the Hash value as an initial value of a hyper-chaotic Chen system, generating a Hill encryption matrix by using a chaotic sequence generated by the hyper-chaoticChen system so as to replace pixels of an original image; realizing image pixel value diffusion by using the DNA encoding operation as a F function of the Feistel network, and a DNA sequence base asa key of the Feistel network; and performing further diffusion through ciphertext feedback. Through three turns of chaotic scrambling-DNA encoding-Feistel conversion-DNA decoding, the ciphertext randomness and attack resistance are stronger, the scrambling conversion of the image pixel location and the diffusion of the pixel value are realized, and the encryption turn is reduced due to repeated scrambling and DNA encoding and decoding. Through the image encryption method provided by the invention, the image can be effectively encrypted, the plaintext sensitivity is strong, the plaintext attack, the differential attack and the statistical attack can be effectively resisted
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Image encryption method based on chaotic mapping and bit-level replacement
ActiveCN112084517ALarge key spaceImprove securityDigital data protectionSecuring communication by chaotic signalsKey spaceAlgorithm
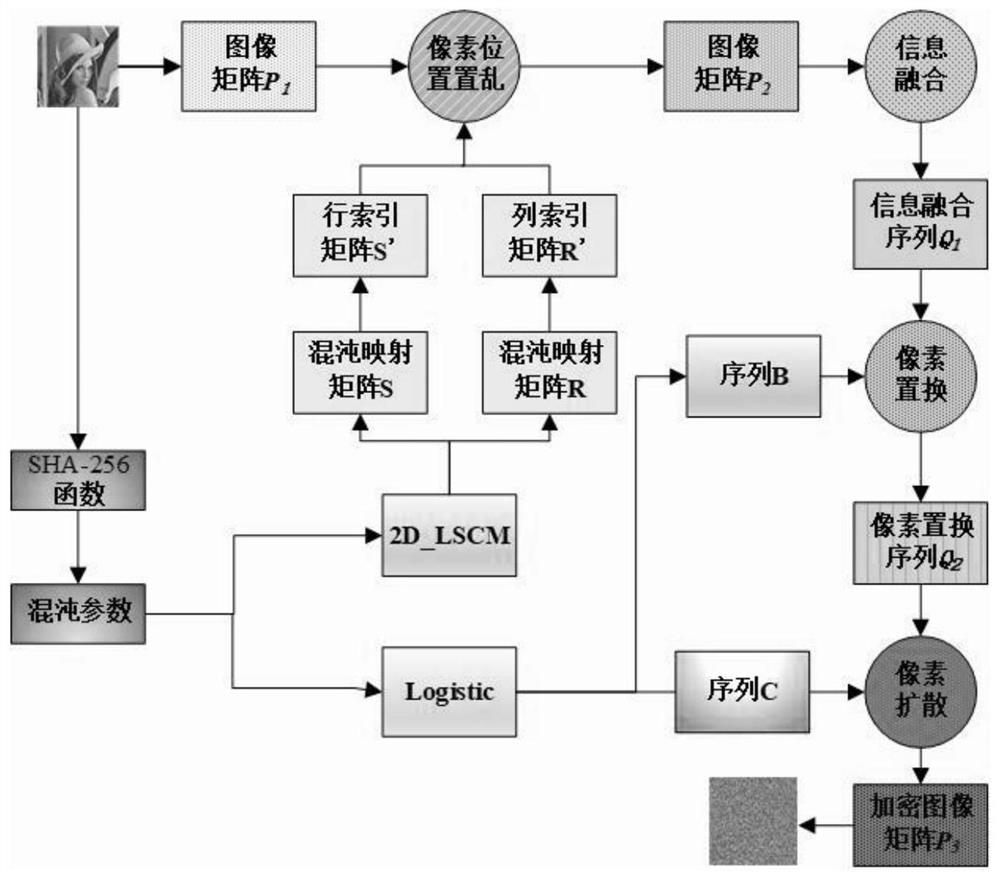
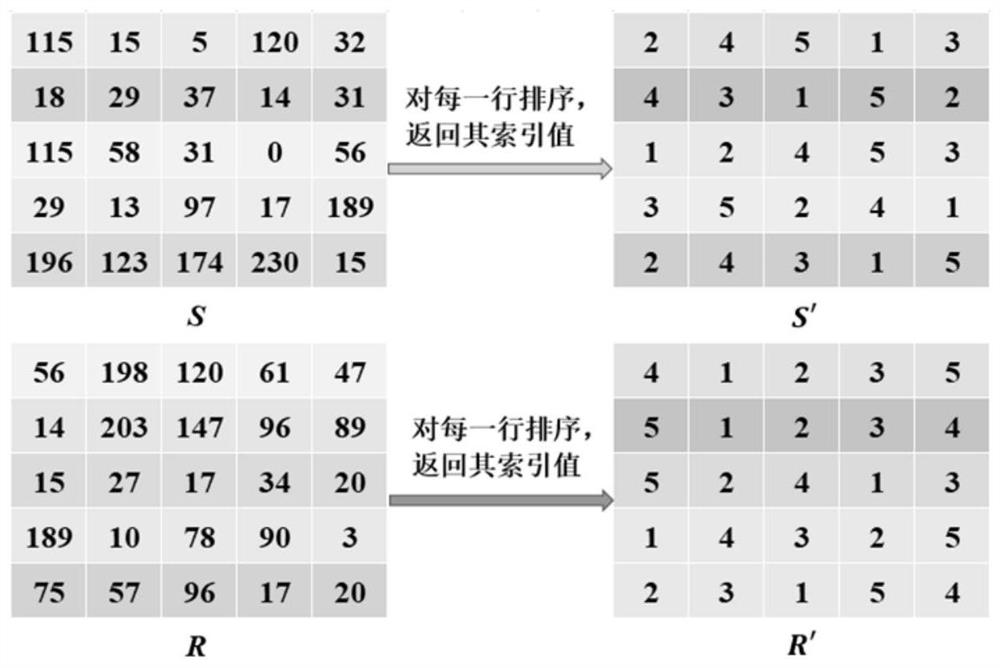
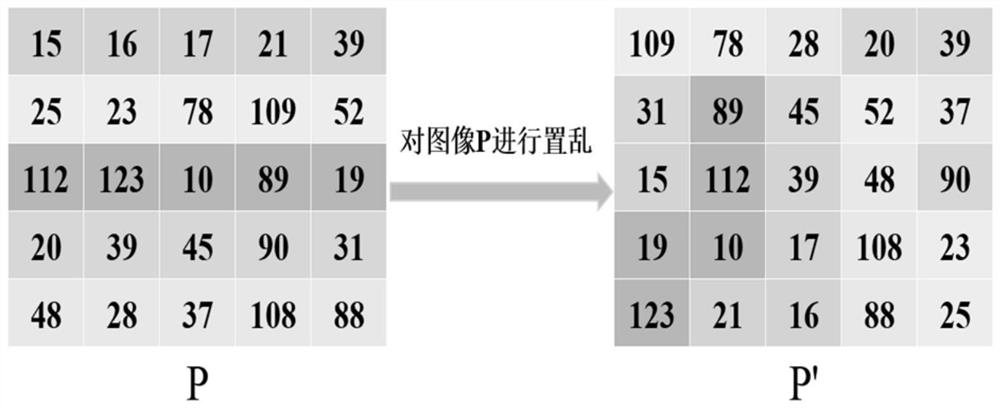
The invention provides an image encryption method based on chaotic mapping and bit-level replacement. The method comprises the following steps: converting a grayscale image into an image matrix; iterating 2D-LSCM mapping to generate a chaotic sequence and mapping the chaotic sequence into a matrix, and returning a position index to perform pixel position exchange on the image matrix after descending sorting of each row; sequentially exchanging the lowest three bits in every two pixel bits to obtain an information fusion sequence of the image; performing iteration on the Logistic mapping to generate a chaotic sequence, and performing operation on the information fusion sequence and the chaotic sequence to obtain a pixel replacement column of the image; and performing pixel diffusion on thepixel replacement sequence of the image by using a chaotic sequence and a ciphertext diffusion technology to obtain an encrypted image. The chaotic mapping and scrambled images are used for replacement operation, the differential attack resistance is enhanced through bit information fusion operation and an image pixel-based diffusion method, the secret key space is large enough, violent attack canbe better resisted, and good safety is achieved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Method for improving unpredictability of output of pseudo-random number generators
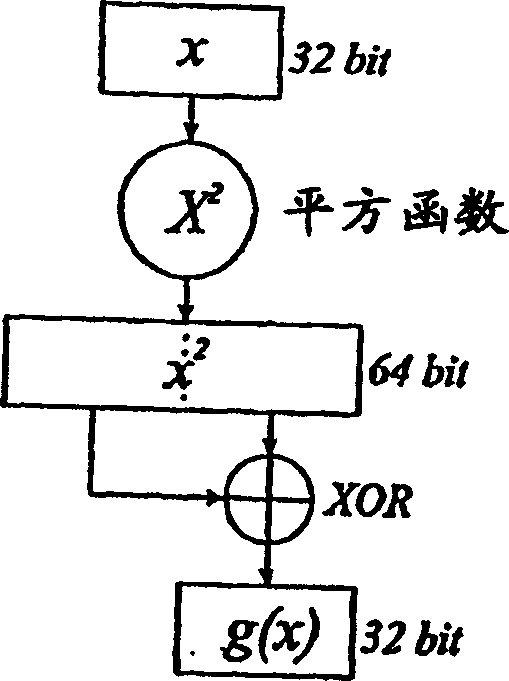
InactiveCN1668995AGood bit mixingImprove unpredictabilityRandom number generatorsChaos modelsData setTheoretical computer science
A method for performing computations in a mathematical system which exhibits a positive lyapunov exponent, or exhibits chaotic behavior, comprises varying a parameter of the system. When employed in cryptography, such as, e.g., in a pseudo-random number generator of a stream-cipher algorithm, in a block-cipher system or a HASH / MAC system, unpredictability may be improved. In a similar system, a computational method comprises multiphying two numbers and manipulating at least one of the most significant bits of the number resulting from the multiplication to produce an output. A number derived from a division of two numbers may be used for deriving an output. In a system for generating a sequence of numbers, an array of counters is updated at each computational step, whereby a carry value is added to each counter. Fixed-point arithmetic may be employed. A method of determining an identification value and for concurrently encrypting and / or decrypting a set of data is disclosed.
Owner:克瑞迪科公司
Devices for emitting or receiving signals encrypted by deterministic chaos, and a transmission system, in particular a radio transmission system, including such devices
InactiveUS7072469B1Low costSynchronising transmission/receiving encryption devicesSecuring communication by chaotic signalsComputer hardwareFrequency spectrum
A sender device for sending an encrypted signal, the device comprising a chaos generator producing an encrypted electrical signal and a feedback loop comprising delayline-forming means, non-linear means, and mixer means which receive the loop signal on one input and the signal to be encrypted on another input, wherein the feedback loop includes filter-forming means which limit the spectrum of the encrypted signals to one or more spectrum bands.
Owner:FRANCE TELECOM SA
Image encryption method based on block scrambling and state conversion
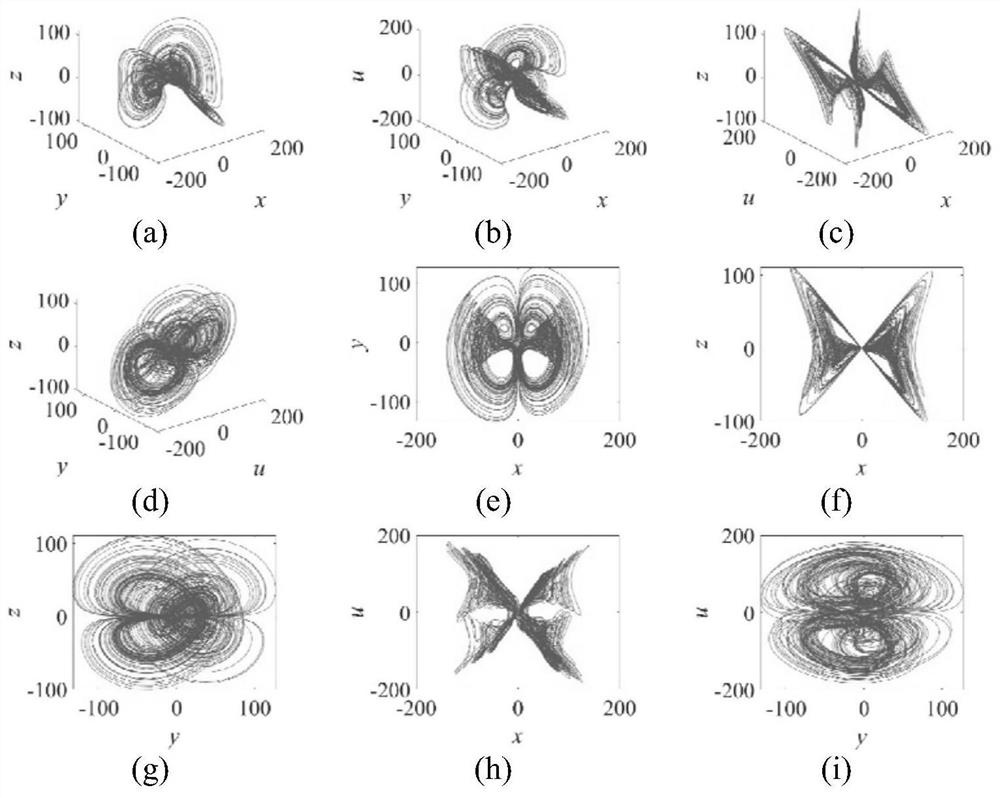
ActiveCN112422268AGuaranteed safe transmissionSuitable for encryptionEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsAlgorithmSecure transmission
The invention provides an image encryption method based on block scrambling and state conversion, and the method comprises the steps: carrying out the processing of an image matrix through a secret key generation system, generating an initial iteration parameter, inputting the initial iteration parameter into a four-wing 4D chaotic system, and carrying out the iteration to generate four chaotic sequences; intercepting the chaotic sequence and performing descending sort to obtain row and column scrambling vectors to generate a scrambling matrix; scrambling the scrambling matrix by using a scanning curve; scrambling the image matrix by using the scrambled matrix to obtain a pixel scrambling matrix, and performing DNA encoding and chaotic sequence input on the pixel scrambling matrix to determine a finite state automaton to obtain a state conversion sequence; performing DNA decoding on the state conversion sequence to obtain a state conversion sequence; and diffusing the state transitionsequence E by using the chaotic sequence to obtain an encrypted image. The scrambling method can effectively break the correlation of adjacent pixels, can resist various attacks, is high in safety, ensures safe transmission of images, and is very suitable for image encryption.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Color Image Encryption Method Based on DNA Strand Displacement Analog Circuit
InactiveUS20200287704A1A large amountShorten the timeKey distribution for secure communicationSecuring communication by chaotic signalsDna strand displacementA-DNA
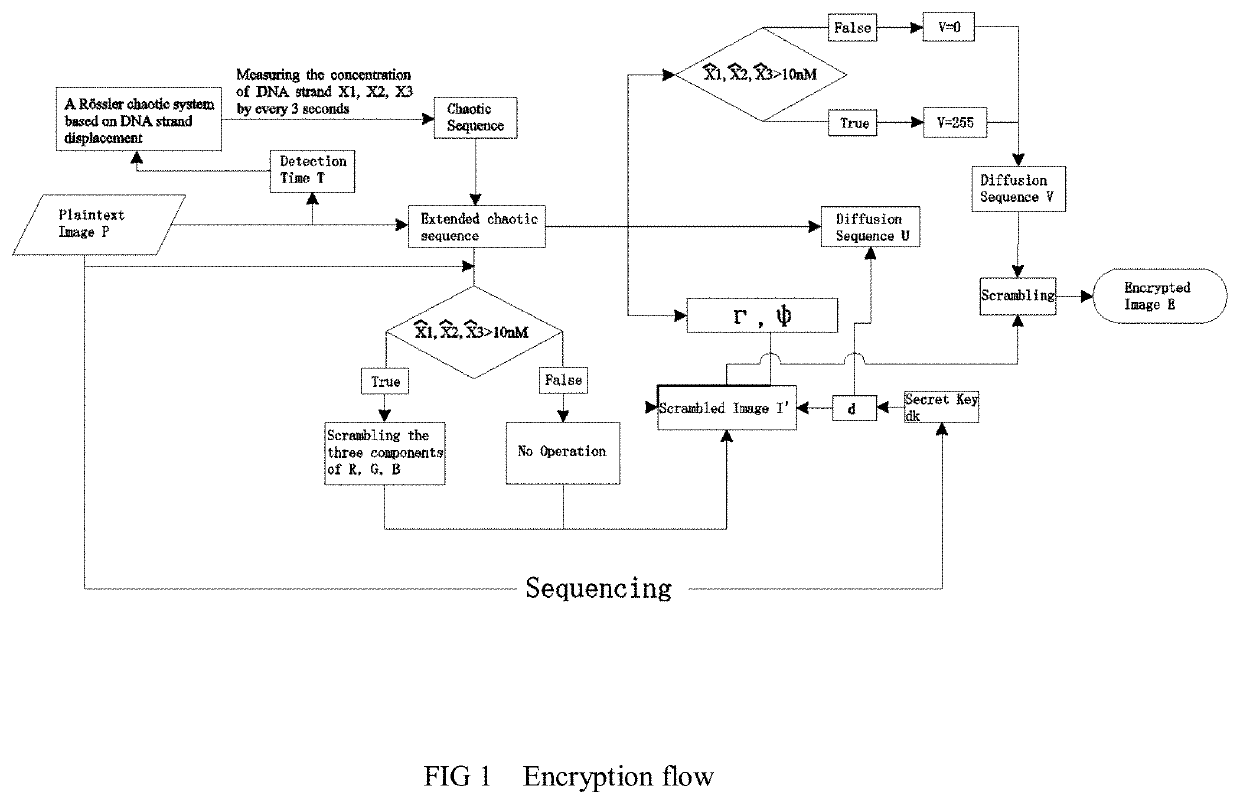
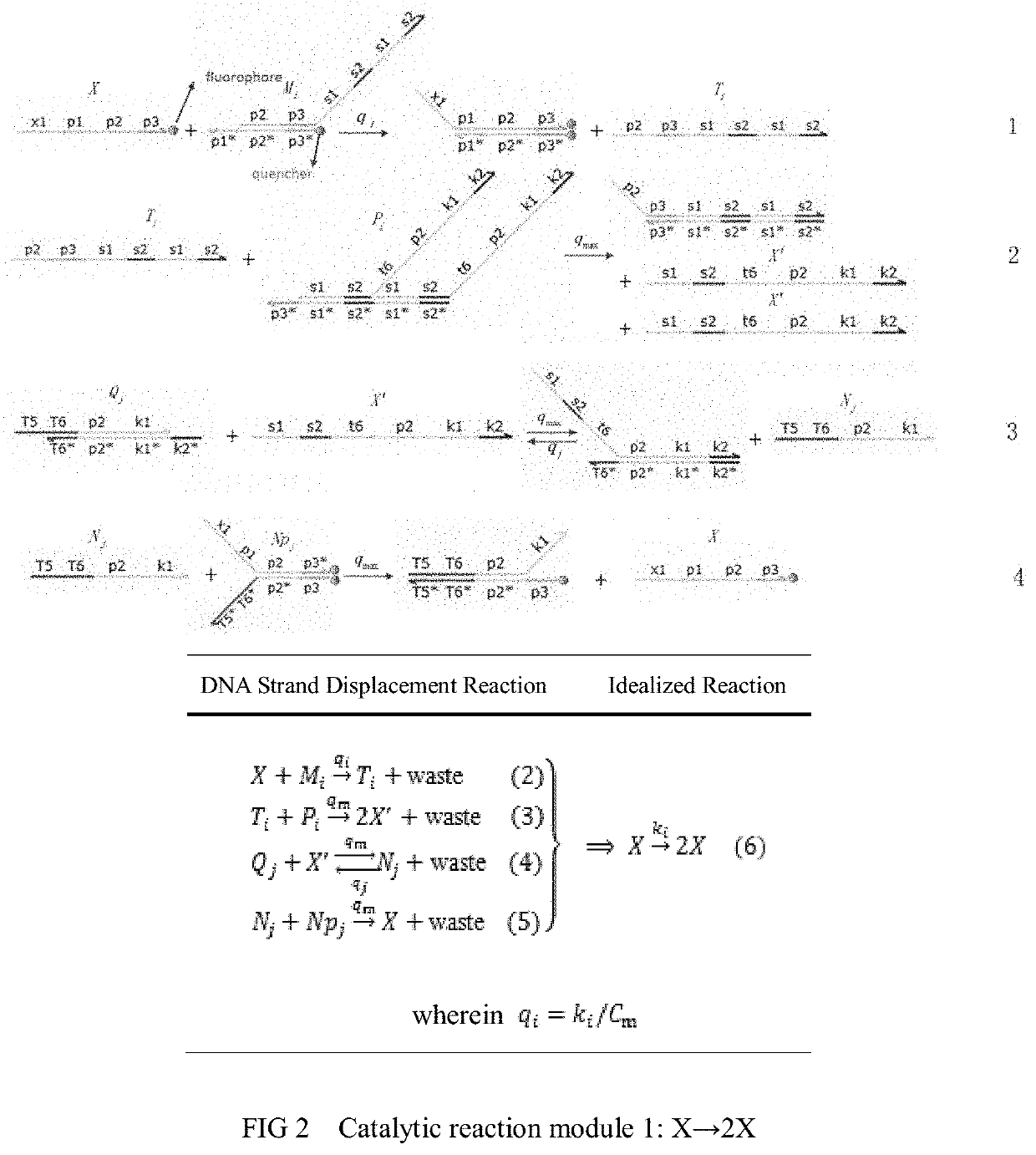
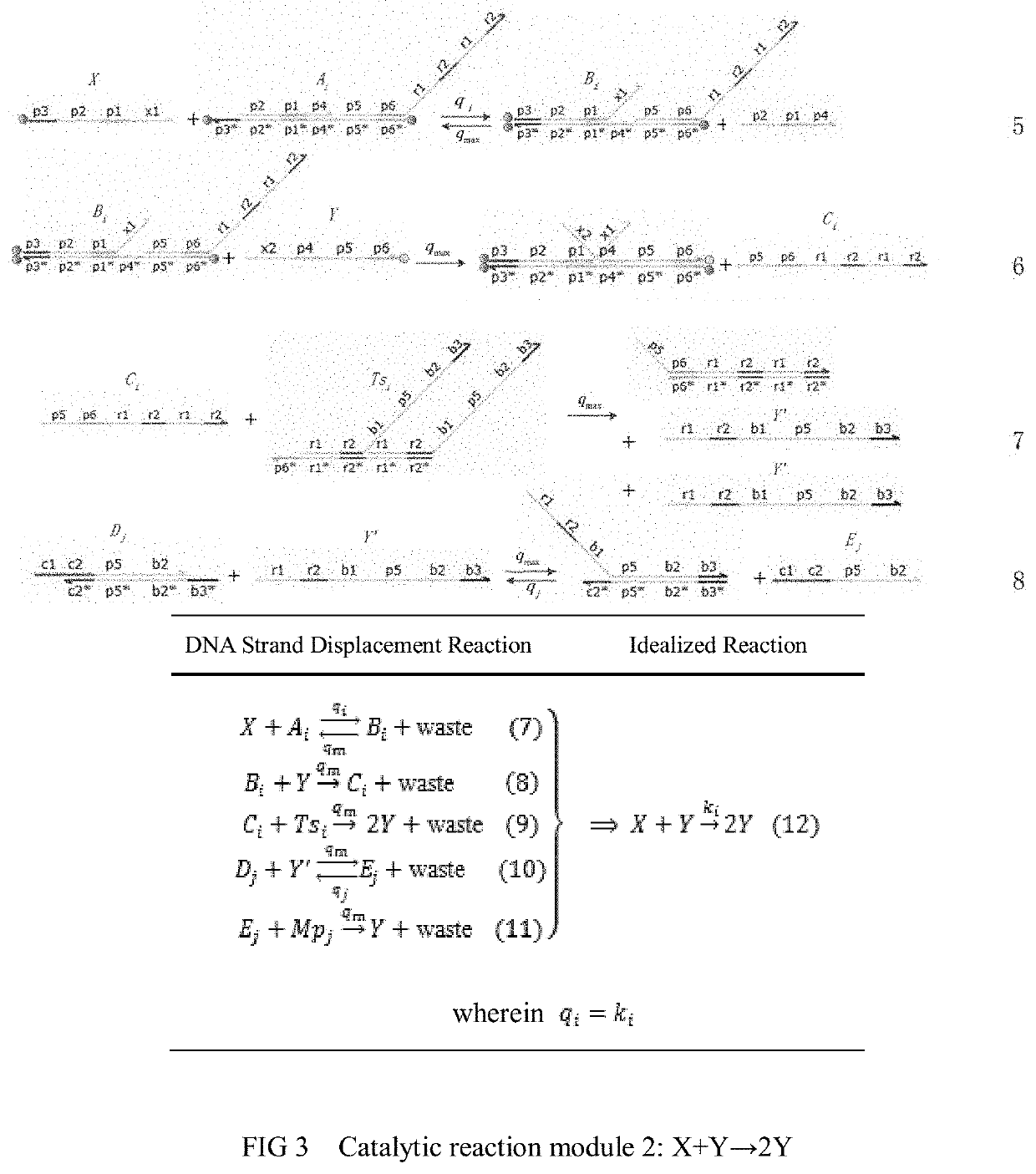
The invention relates to the field of strand displacement, and provides a color image encryption method based on a DNA strand displacement analog circuit. Firstly, a reaction module with a light-emitting group and a quenching group is designed through Visual DSD software, and by utilizing the equivalence of a DNA strand displacement reaction module and an ideal reaction module, an analog circuit formed by the DNA strand displacement reaction module can perform analog on the dynamics characteristics of an ideal reaction network formed by the ideal reaction module, wherein the Rössler chaotic system can be described by the idealized reaction network. Secondly, data generated by the DNA strand displacement analog circuit is converted into a chaotic sequence matched with a plaintext image in size after being extended, and finally, the color image encryption effect is achieved through scrambling and diffusion operations.
Owner:ZHANG QIANG +3
Method and apparatus for encryption of data
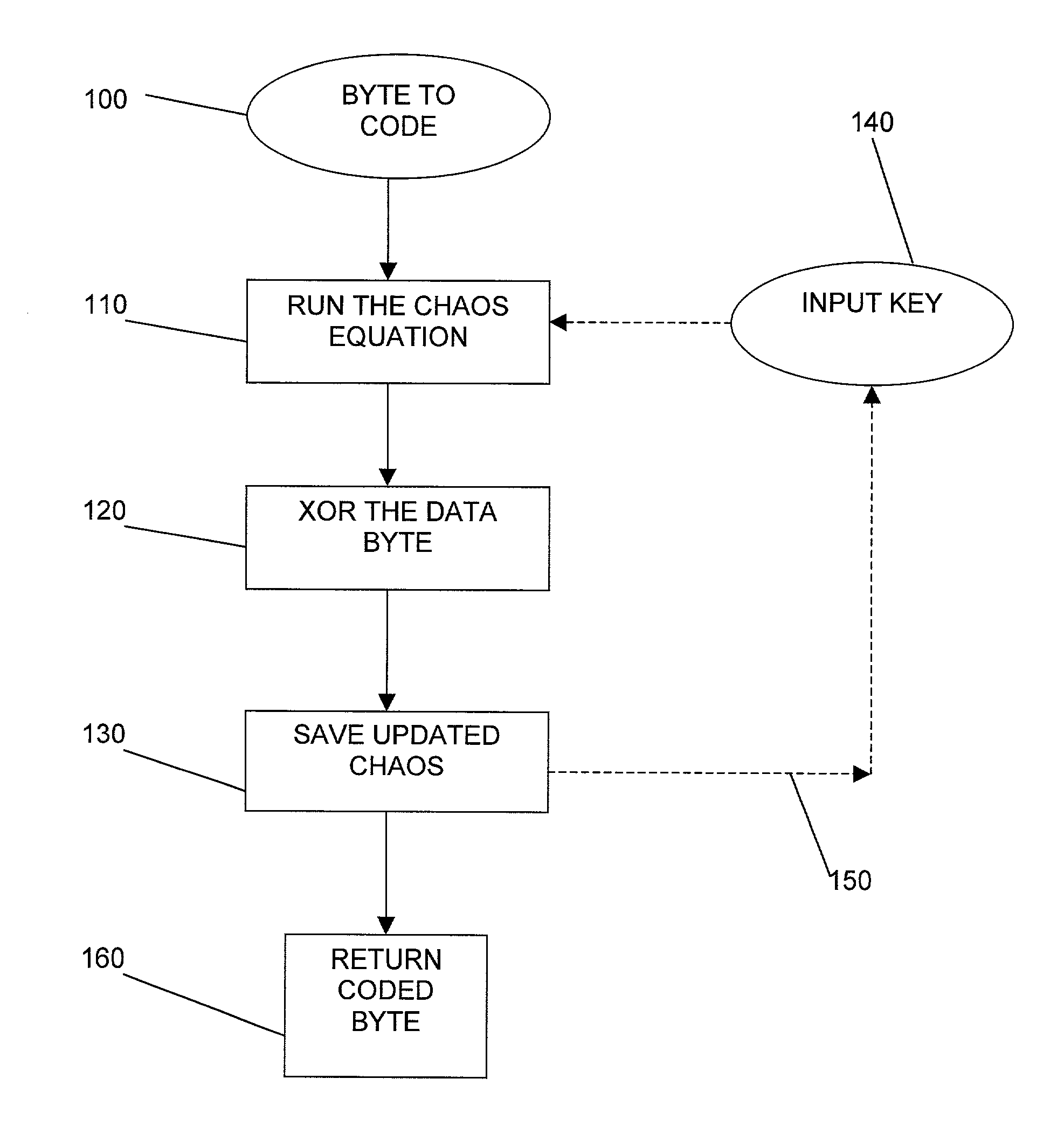
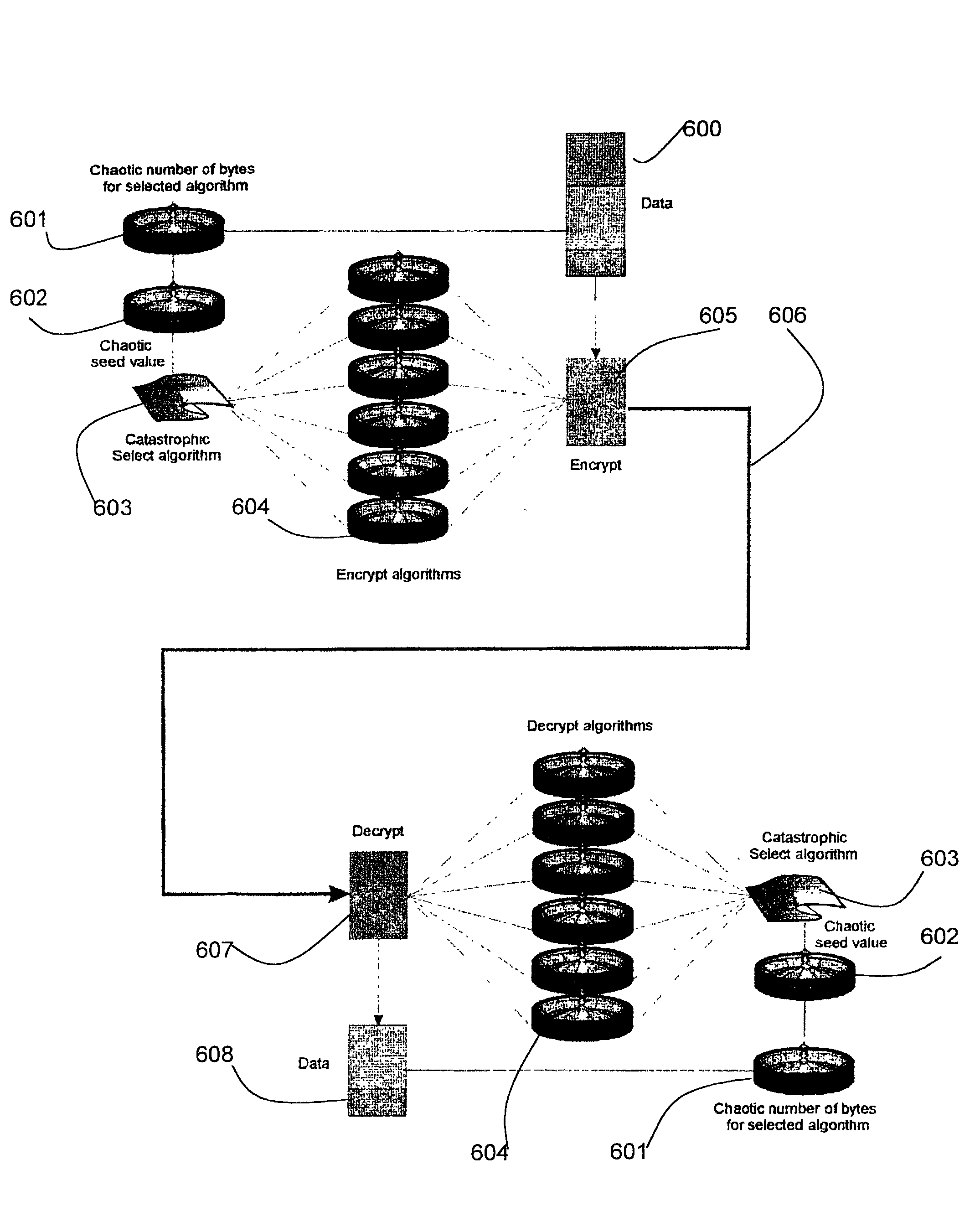
A method and apparatus for encryption of data are provided, in which the data is made up of a series of data items (600). The data items (600) maybe bytes of data or blocks of data. The method includes providing a plurality of encryption algorithms (604), selecting when to change encryption algorithm (601), selecting which encryption algorithm to change to (603), wherein each selection is carried out by applying a Chaotic and / or Catastrophic equation. The plurality of encryption algorithms (604) have index numbers and the generation of an index number by applying the Chaotic or Catastrophic equation selects an encryption algorithm. The selection of when to change encryption algorithm may be determined by a Catastrophic event in the Catastrophic equation and the selection of encryption algorithm may be determined by the surface of a Catastrophic curve on which a point lies, wherein each surface corresponds to an encryption algorithm. The selection of when to change encryption algorithm may be carried out by generating a data item count by applying a Chaotic equation and the encryption algorithm may be selected by generating its index number by applying a Chaotic equation.
Owner:IBM CORP
Color image encryption method based on dynamic chaos and matrix convolution operation
ActiveCN110417539AImprove relevanceIncreased complexityKey distribution for secure communicationDigital data protectionExclusive orChaotic systems
The invention discloses a color image encryption method based on dynamic chaos and matrix convolution operation. According to the method, a cloud model and generalized Fibonacci are combined to propose a new composite chaotic system, dynamic random change of a chaotic sequence is realized, and scrambling transformation of pixel point coordinates is performed on spliced images of R, G and B components of a color image by using the chaotic sequence; then, the chaotic sequence value is used as a matrix convolution cloud side for alternately updating an input value and a pixel value of matrix convolution operation, and replacement transformation of an original pixel value is realized; and finally, positive and negative two-way exclusive OR operation is carried out on the replaced pixel value,a cloud model Fibonacci chaotic sequence and the pixel values of the front (rear) adjacent pixel points to realize linkage diffusion transformation of the pixel values of the whole pixel points causedby the change of any pixel value so as to generate encrypted images in sequence. The method has the characteristics of high encryption security, high anti-interference performance, high robustness and the like.
Owner:QIQIHAR UNIVERSITY
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com