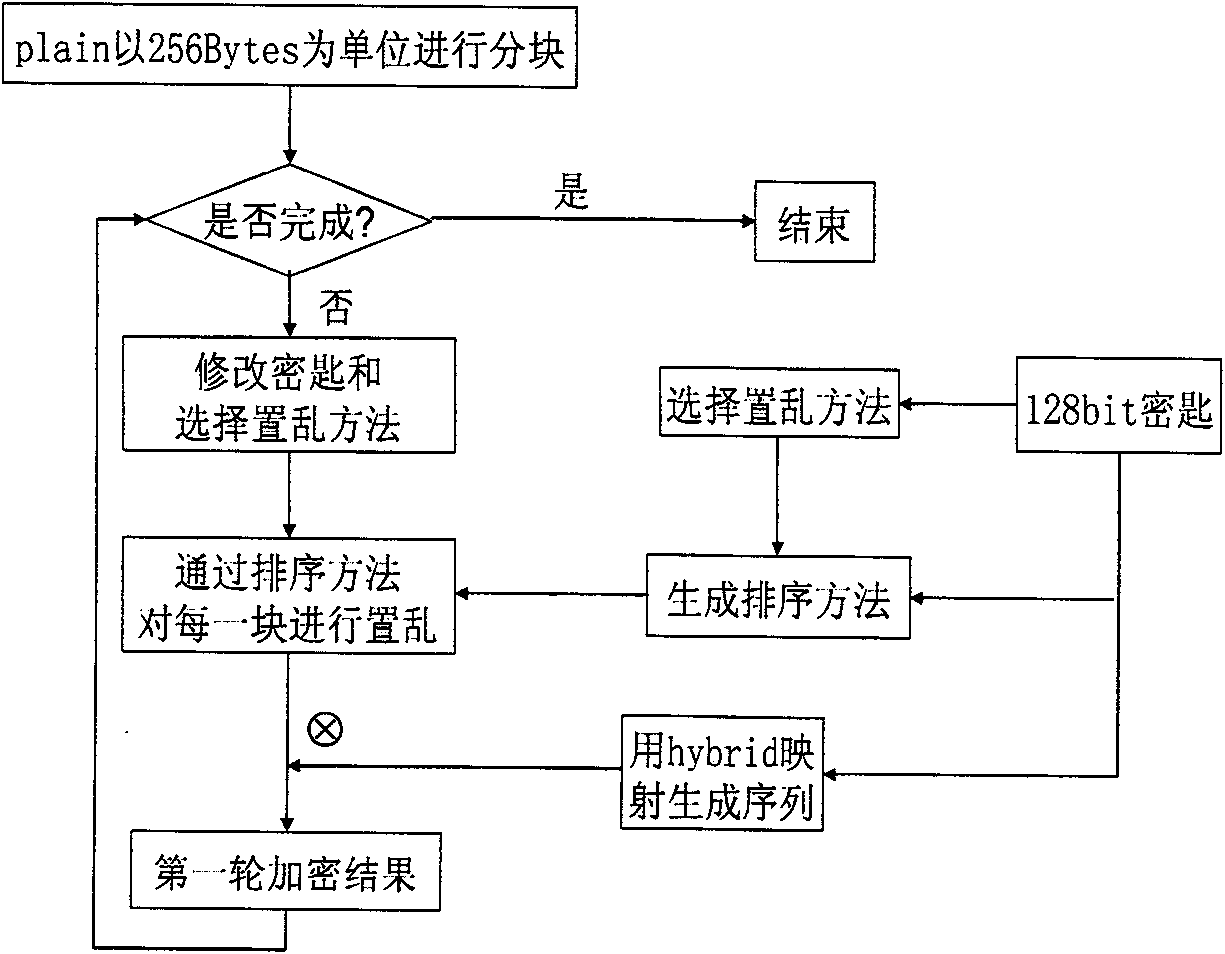
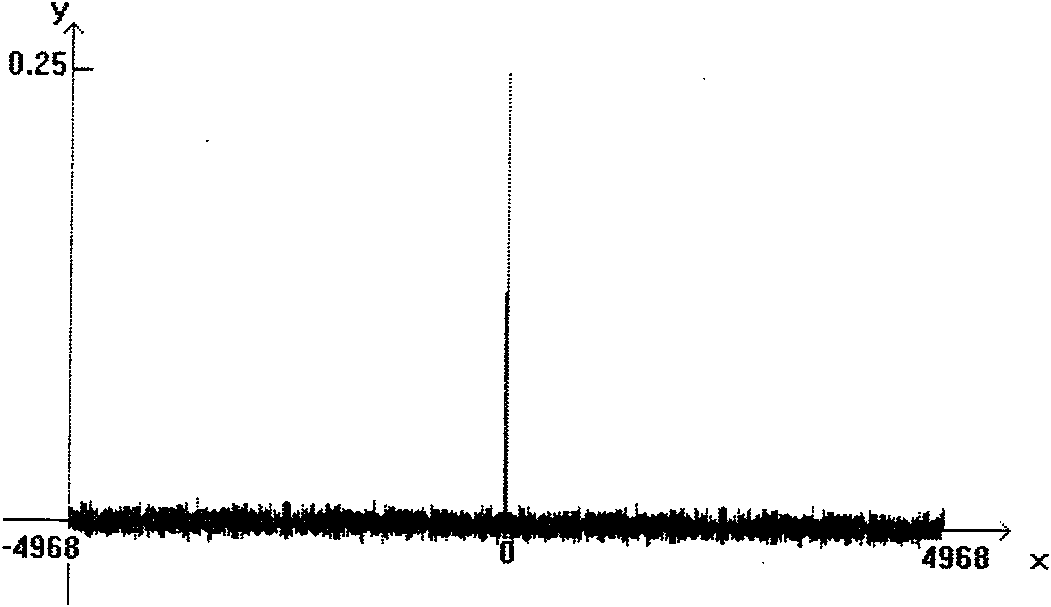
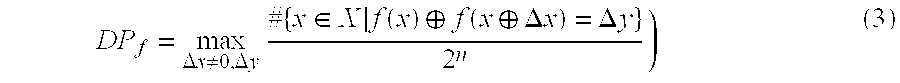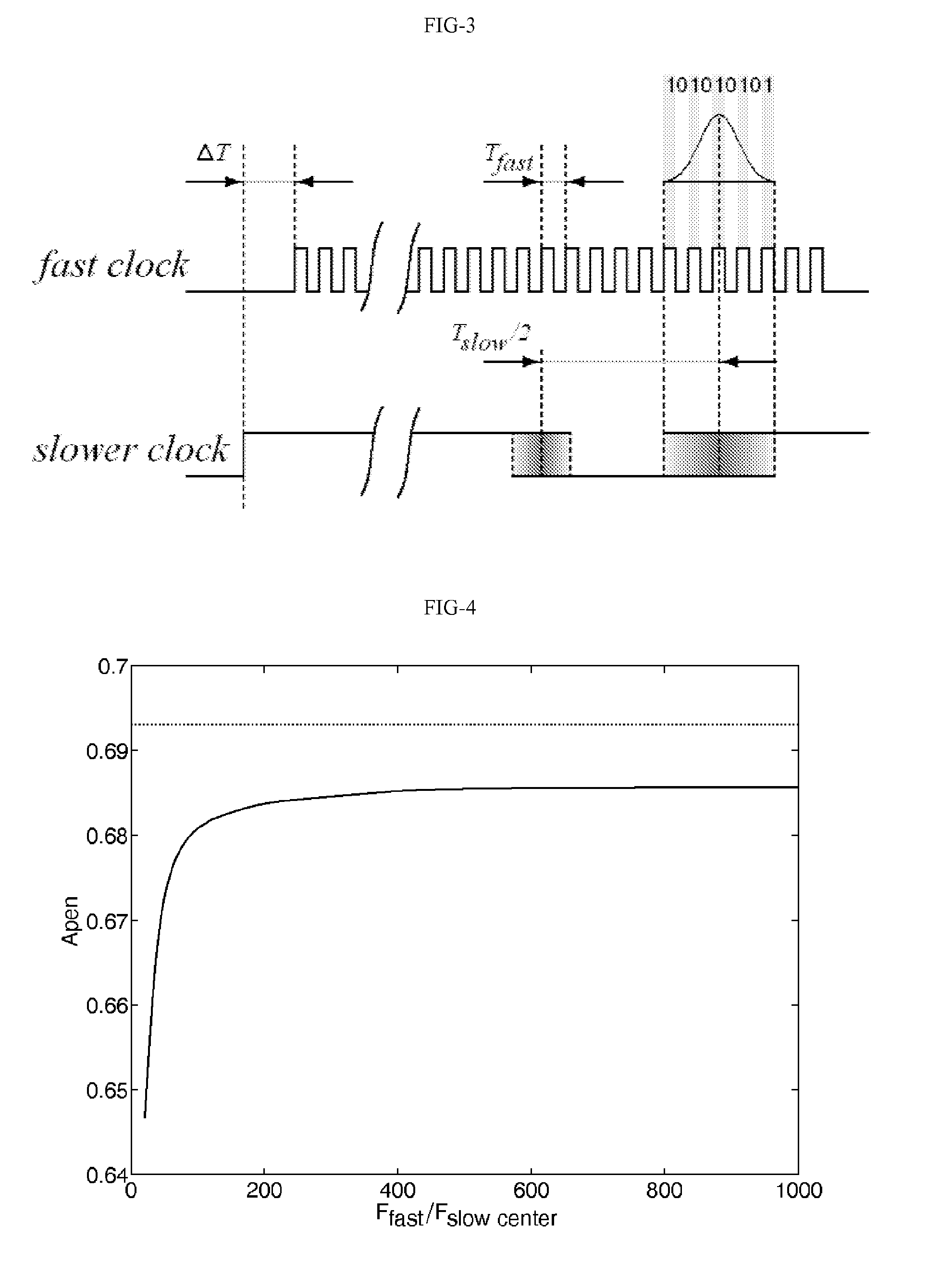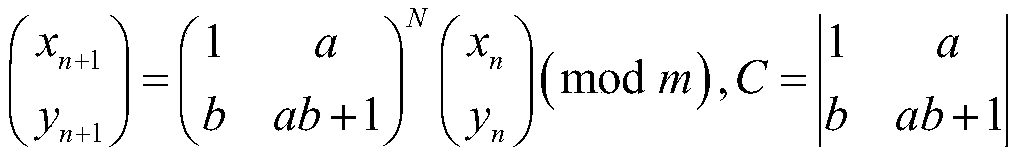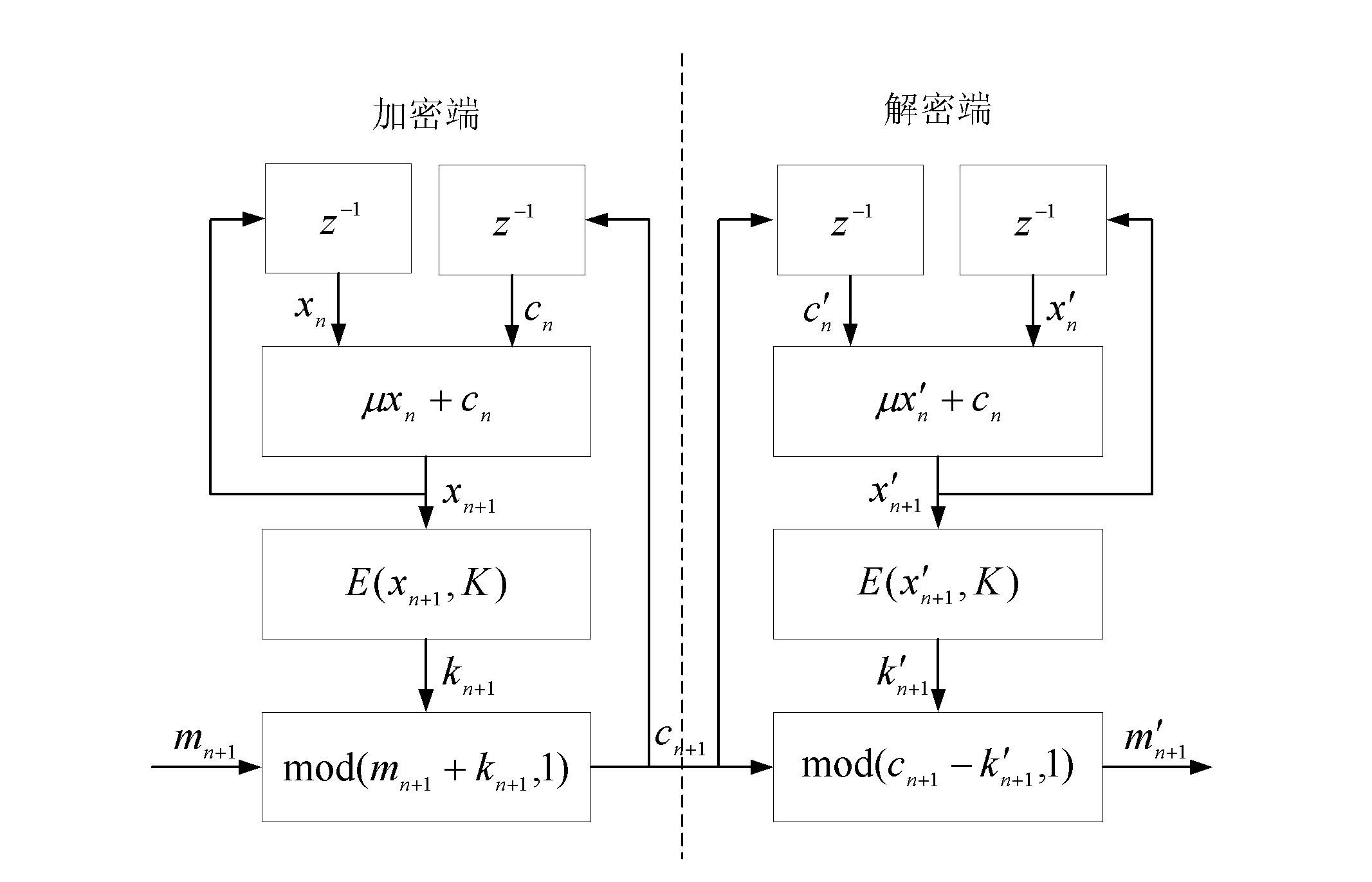Patents
Literature
82 results about "Chaotic map" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
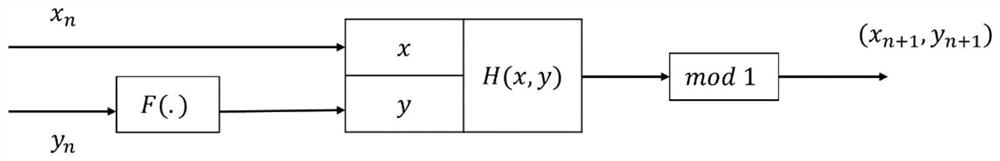
In mathematics, a chaotic map is a map (= evolution function) that exhibits some sort of chaotic behavior.Maps may be parameterized by a discrete-time or a continuous-time parameter. Discrete maps usually take the form of iterated functions.Chaotic maps often occur in the study of dynamical systems.. Chaotic maps often generate fractals.Although a fractal may be constructed by an iterative ...
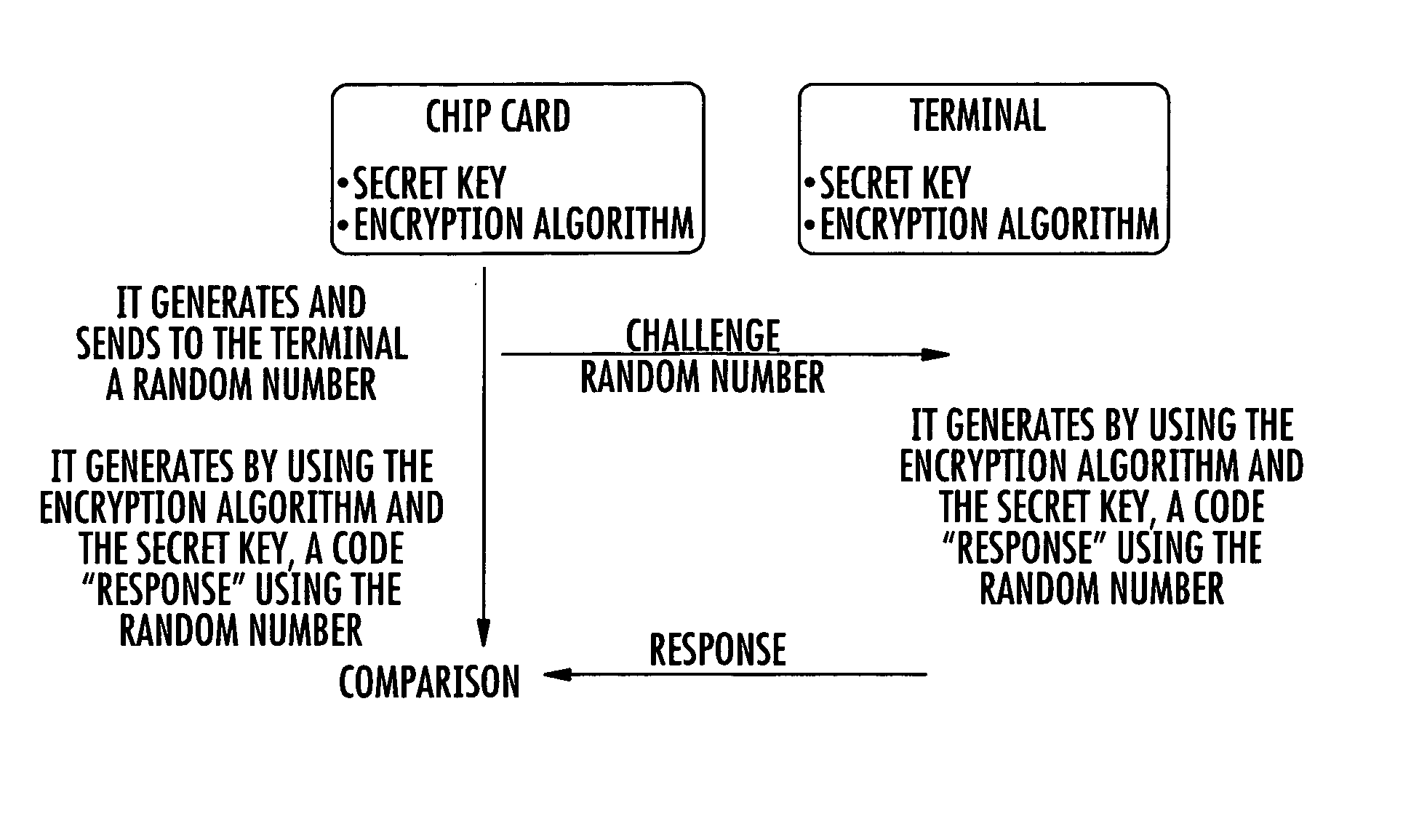
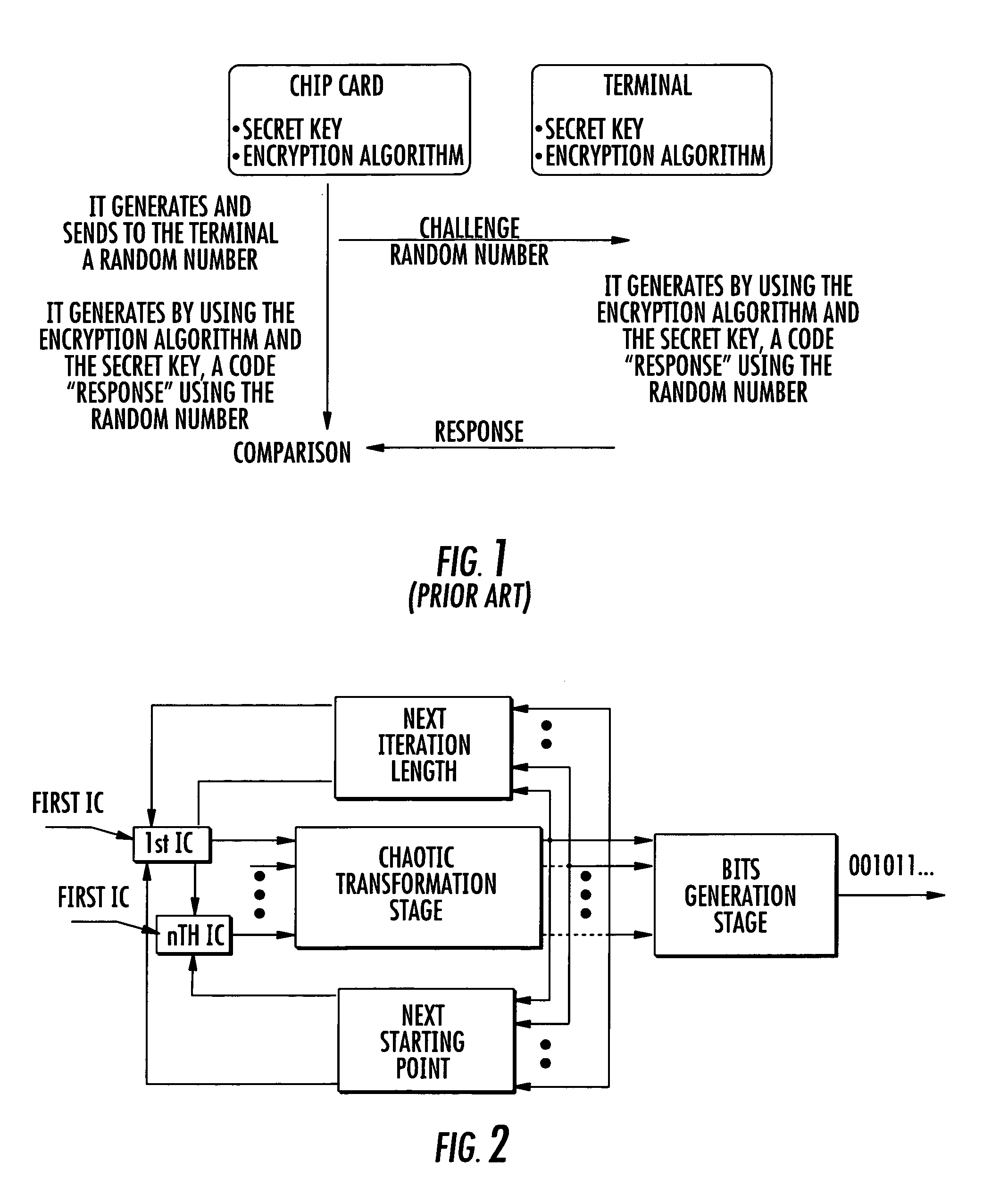
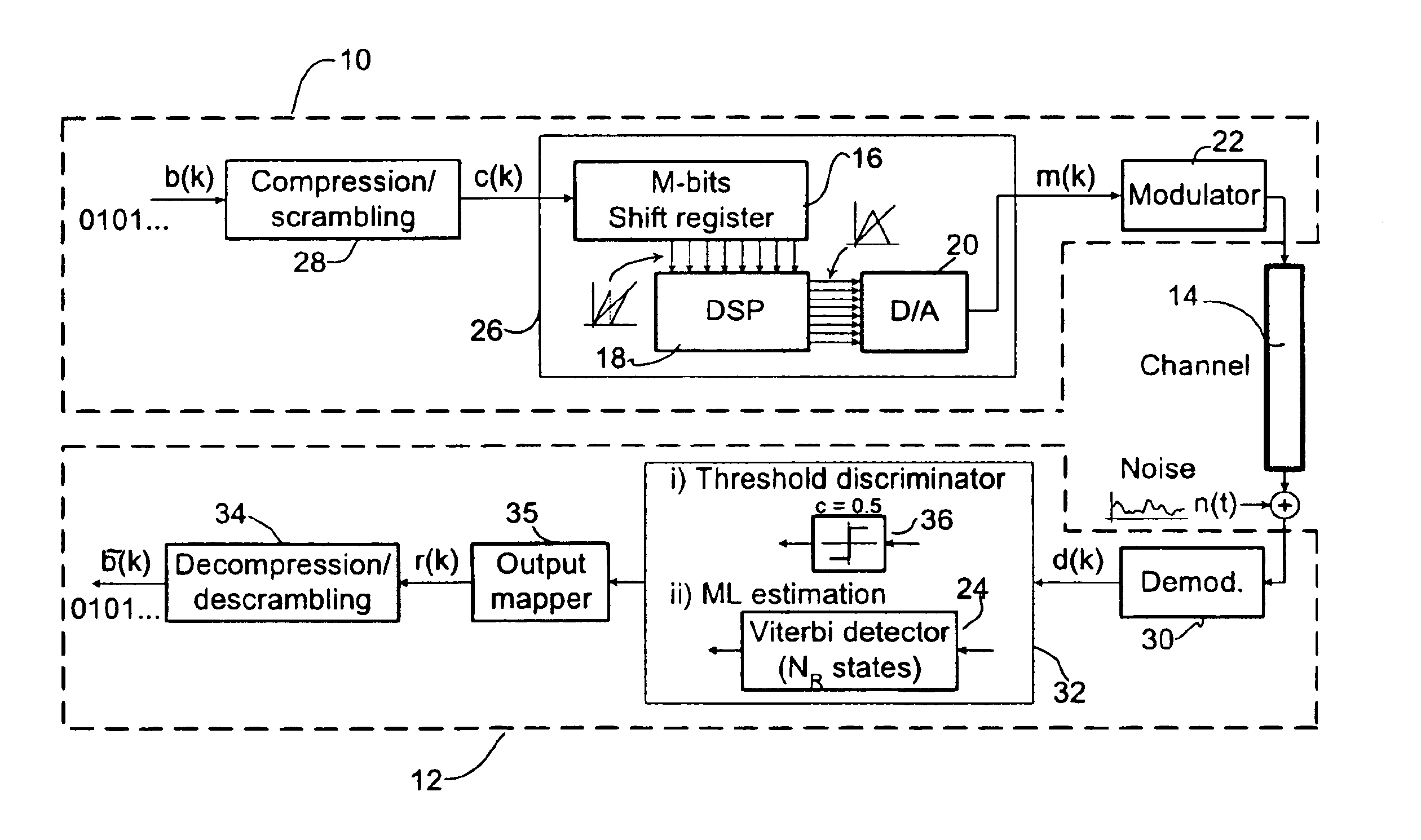
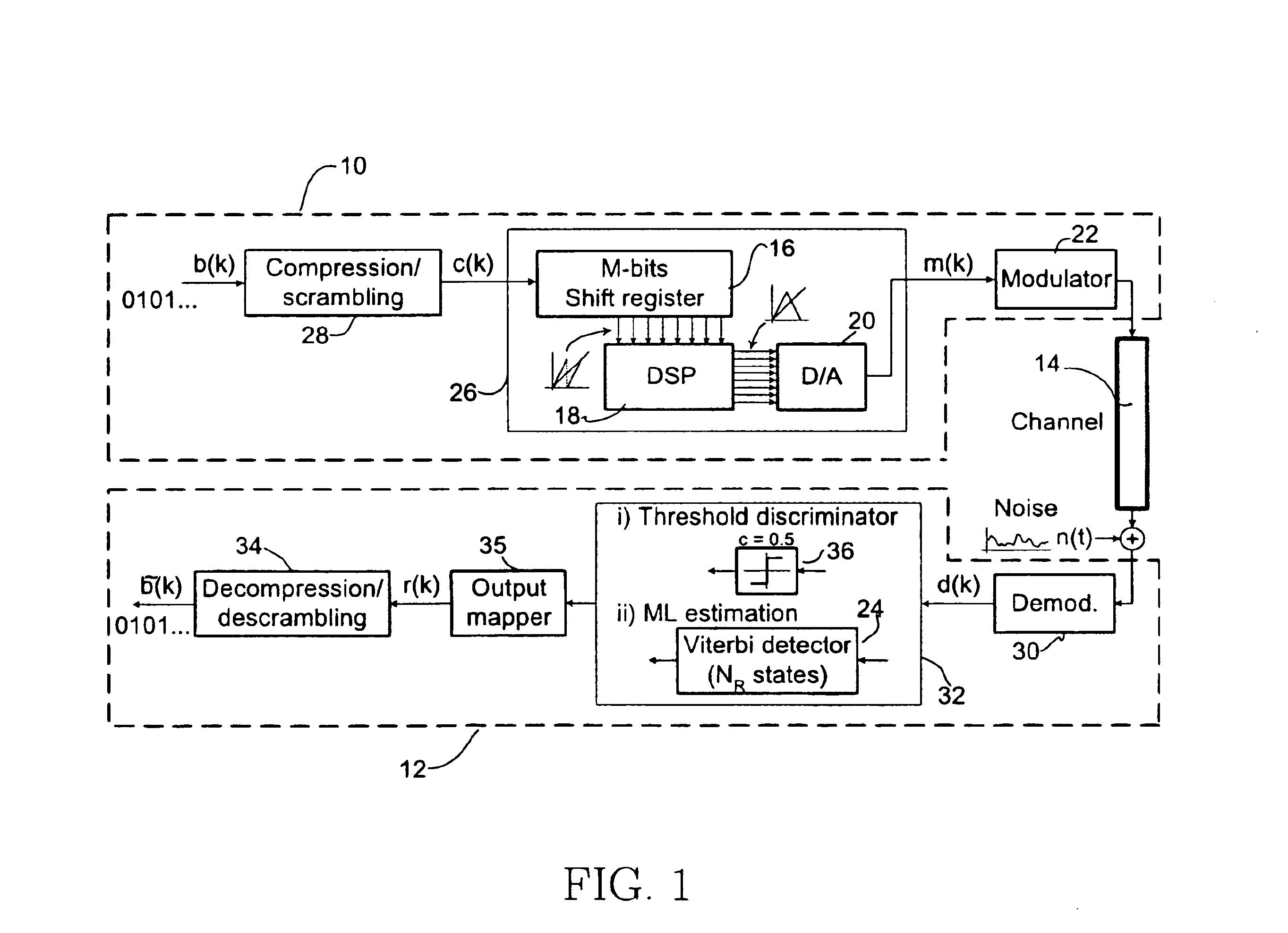
Method of generating successions of pseudo-random bits or numbers
InactiveUS20060251250A1Conveniently implementedReduce computing costSecuring communication by chaotic signalsTheoretical computer scienceChaotic map
A method for generating a succession of pseudo-random numbers includes choosing at least one chaotic map, and choosing a seed for the chaotic map and a number of iterations for the chaotic map. The succession of pseudo-random numbers are generated by executing iteratively generating a pseudo-random number as a function of a final state reached by the chaotic map iterated for the current number of iterations starting from the current seed, and generating a new seed for the chaotic map or a new number of iterations as a function of the final state.
Owner:STMICROELECTRONICS SRL
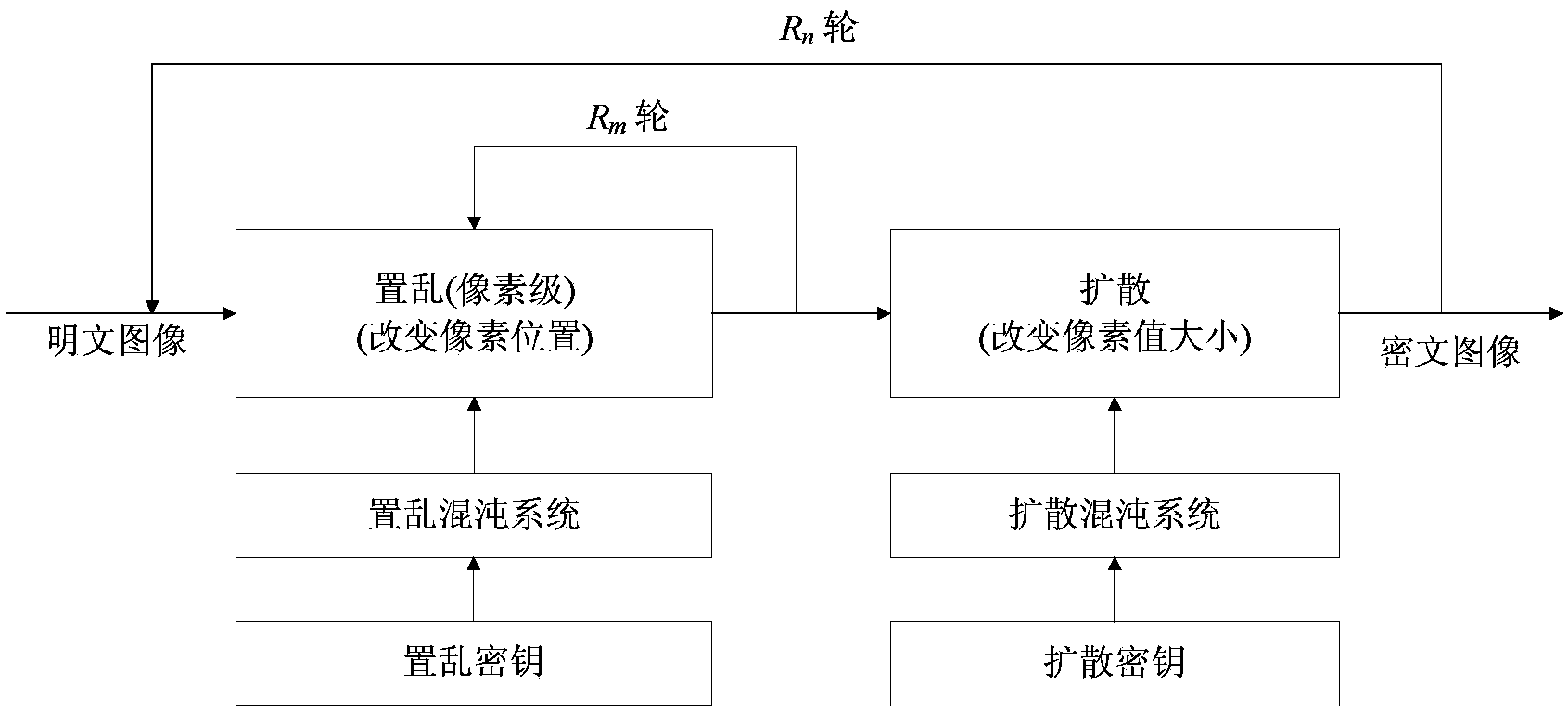
Chaos medical image encryption method applied to privacy protection
ActiveCN103916234AImprove performanceDoes not affect operational efficiencySecuring communicationPlaintextPrivacy protection
The invention relates to a chaos medical image encryption method applied to privacy protection, and belongs to the technical field of image encryption. The chaos medical image encryption method includes the steps that driving is carried out through three independent logistic chaotic maps, in the scrambling stage, each pixel point in an image is exchanged with another pixel point, and the position of a target pixel point is generated by two logistic chaotic maps; key streams used in the diffusion stage are generated by the third logistic chaotic map; in the key stream generating process, each key stream element is controlled by plaintext pixels to conduct circulating shifting operation to achieve the aim of relating the key streams and plaintexts. By means of the medical image encryption method, the scrambling effect and the scrambling speed overall performance are superior to those of an existing scrambling method, and the overall speed of an encryption system is remarkably superior to a common grouping encryption method in the modern cryptography; the cryptography analysis results show that the provided encryption method can effectively resist to various common attack techniques.
Owner:辽宁康恒科技有限公司
Encryption process employing chaotic maps and digital signature process
ActiveUS6892940B2Easy to implementShorten the timeSecret communicationSecuring communication by chaotic signalsComputer hardwareDigital signature
An encryption process includes choosing a secret key and a set of permutable functions defined on a phase space for encrypting / decrypting messages, choosing a code for encoding messages to be sent as a number belonging to the phase space. The set of permutable functions includes chaotic maps generated by a composite function of first and second functions, and an inverse of the first function. The secret key is defined by the second function.
Owner:STMICROELECTRONICS SRL
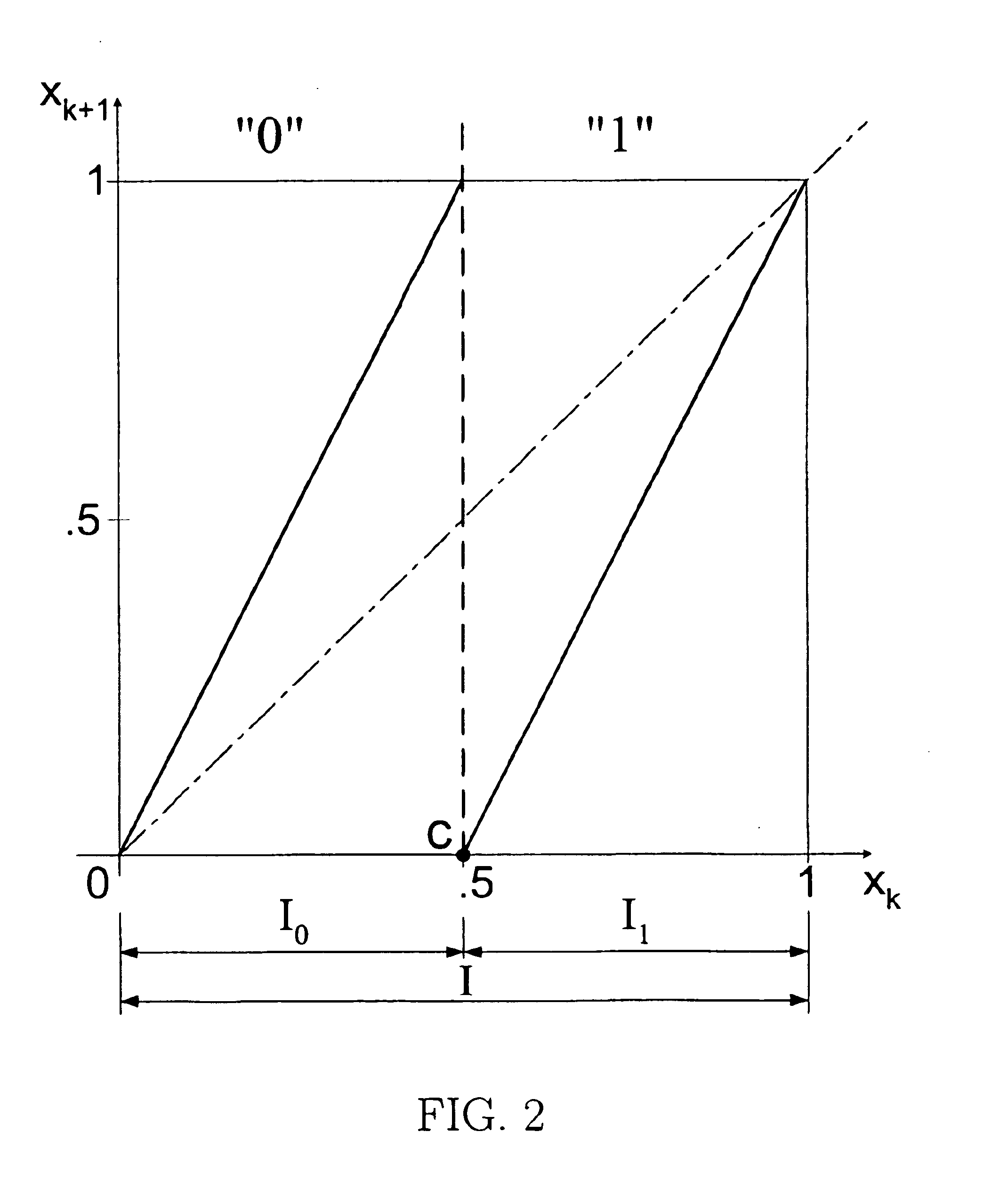
Pseudo-chaotic communication method exploiting symbolic dynamics
InactiveUS6882689B2Receiver scalabilityAmplitude-modulated carrier systemsAmplitude demodulationShift registerData signal
A pseudo-chaotic coding / modulation method. The coding method exploits symbolic dynamics of a chaotic map at the transmitter to encode data. The encoding synthesizes the chaotic map based upon the data to be transmitted. In a preferred embodiment, pseudo-chaotic iterates are generated from a digital implementation of a Bernoulli shift map. The output of the shift map is translated by a mapping, preferably implemented by a digital signal processor, to allow transitions between states in a transmitted signal to differ, and the translated map is used to drive a modulator (for example PPM, FSK, PSK, QAM, etc.). In the specific case of pulse-position modulation (PPM) the translated map is used to modulate pulse train positions within a periodic synchronization frame. The preferred embodiment uses a shift register to implement an approximation of the Bernoulli shift map acting as a form of convolutional code with a number of states equal to the symbolic states defined on the chaotic map. A receiver may use fewer states and still decode the data signal, allowing receiver scalability.
Owner:RGT UNIV OF CALIFORNIA
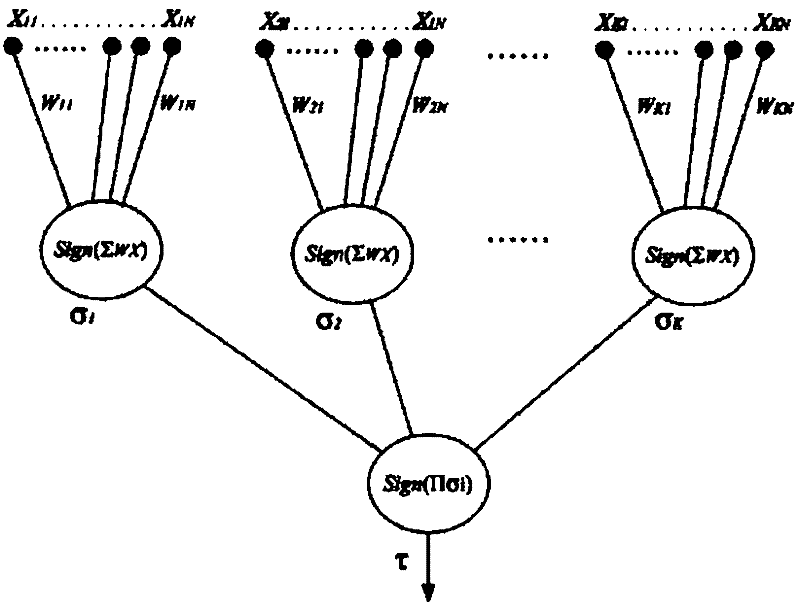
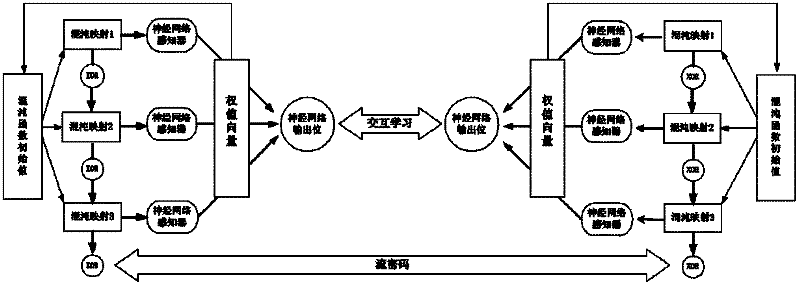
A Stream Cipher Key Control Method Fused with Neural Network and Chaotic Map
ActiveCN102263636AImprove security featuresImprove securityKey distribution for secure communicationKey generatorComputer science
The invention provides a stream cipher key control method for fusing a neural network with chaotic mappings. A sending party and a receiving party are configured to have neural network weight synchronization models with same parameters and three chaotic mapping functions with the same initial value, and the sending party and the receiving party are set to have the same initial value of the chaotic functions. The method comprises the following steps: (1) determining a hybrid stream key generator based on three chaotic mappings; and (2) realizing a chaotic function initial value update mechanism based on neural network weight synchronization. The method provided by the invention can be used for updating the chaotic initial values and strengthening the safe application of stream ciphers.
Owner:ZHEJIANG UNIV OF TECH
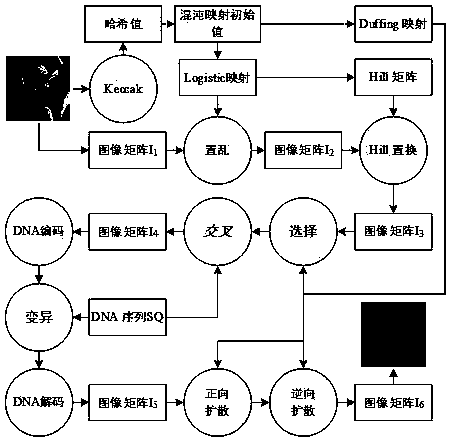
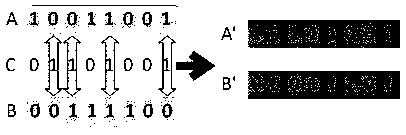
An image encryption method based on Duffing mapping and genetic operation
ActiveCN109376540AIncreased sensitivityIncrease the difficulty of decipheringDigital data protectionPlaintextExclusive or
The invention provides an image encryption method based on Duffing mapping and genetic operation. The hash value of a plaintext image is calculated by using a Keccak algorithm as an initial value input key of a chaotic system; the sensitivity and pseudo-randomness of the chaotic map to the initial conditions are used, the pseudo-random sequence is obtained by iterating the Logistic map and the Hill encryption matrix is generated to scramble and replace the image matrix. Combined with Duffing map and DNA coding technology, pixel selection, crossover and mutation are realized by genetic operation to achieve pixel diffusion and scrambling, and bidirectional exclusive OR operation with chaotic sequence to enhance its confusion and diffusion characteristics. The invention utilizes the pseudo-randomness of Duffing mapping and Logistic mapping, ergodicity and the crossover mutation operation of genetic algorithm, has strong sensitivity to key, can effectively resist statistical attack and differential attack, etc., has good security and application potential, and the image encryption effect and performance are remarkably improved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
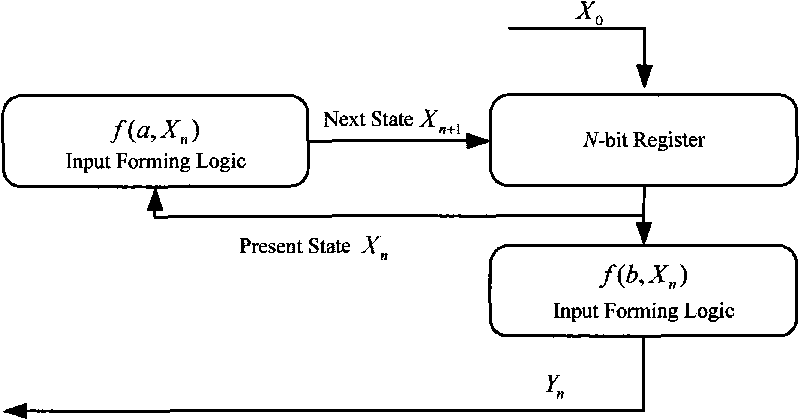
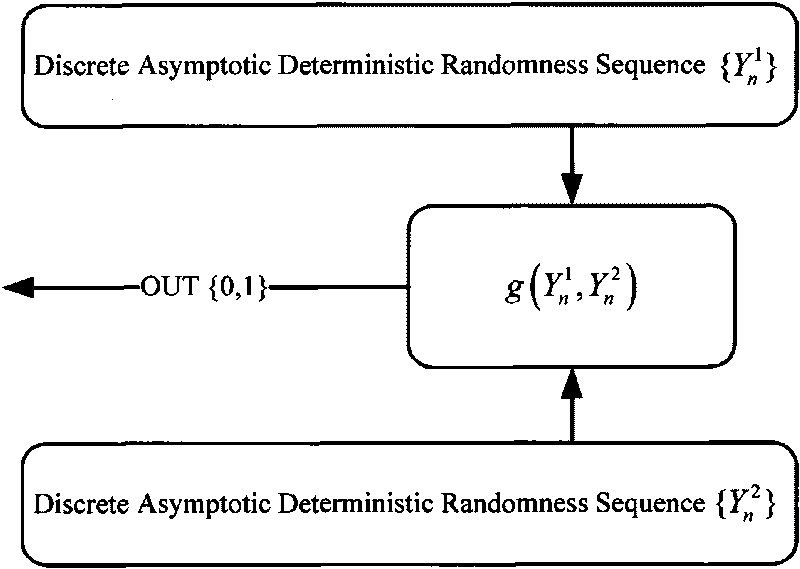
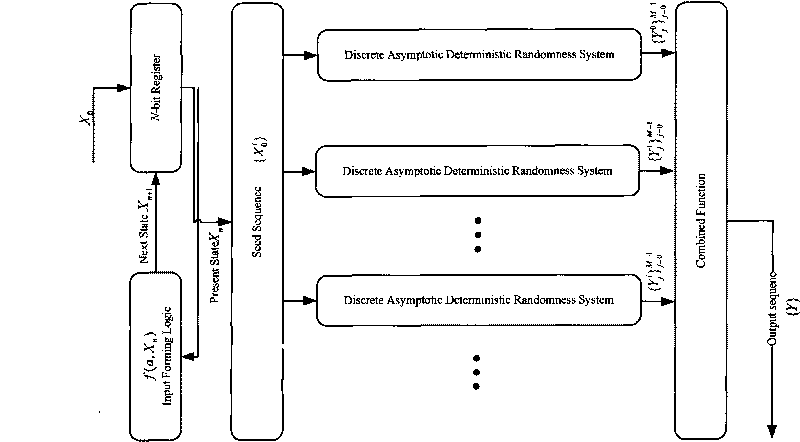
Method for generating random pseudorandom sequence based on discrete progressive determinacy
The invention provides a method for generating a random pseudorandom sequence based on a discrete progressive determinacy, which comprises the steps of: (1) selecting a discrete or chaotic map Xn+1=aXnmod2N, setting an initial value X0 and a chaotic control parameter a, and performing iterative operation with an input value Xn at the time of n, namely, the current time, so as to obtain output Xn+1 of a chaotic system at the time of Xn+1, namely, the next time; (2) nonlinearly changing the Xn into Yn=bXnmod2N to obtain the corresponding random pseudorandom Yn of the discrete progressive determinacy, wherein the nonlinear control parameter b=2k, and k is a positive integer; and (3) building a discrete progressive determinacy random system from step (1) to step (2), and changing an integer sequence Y two value into 0-1 sequence Z with a coupling method to obtain a random sequence output Z. The method has good balance, ideal run distribution, and the statistical characteristic of self correlation and mutual correlation similar to white noise, and can be taken as the pseudorandom sequence with high safety.
Owner:SOUTHEAST UNIV
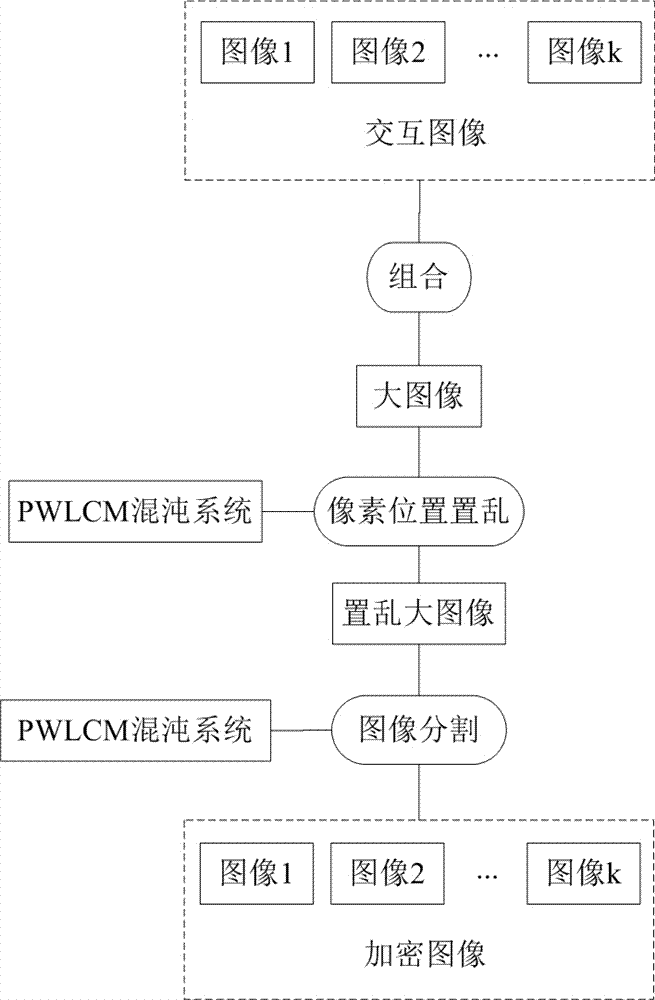
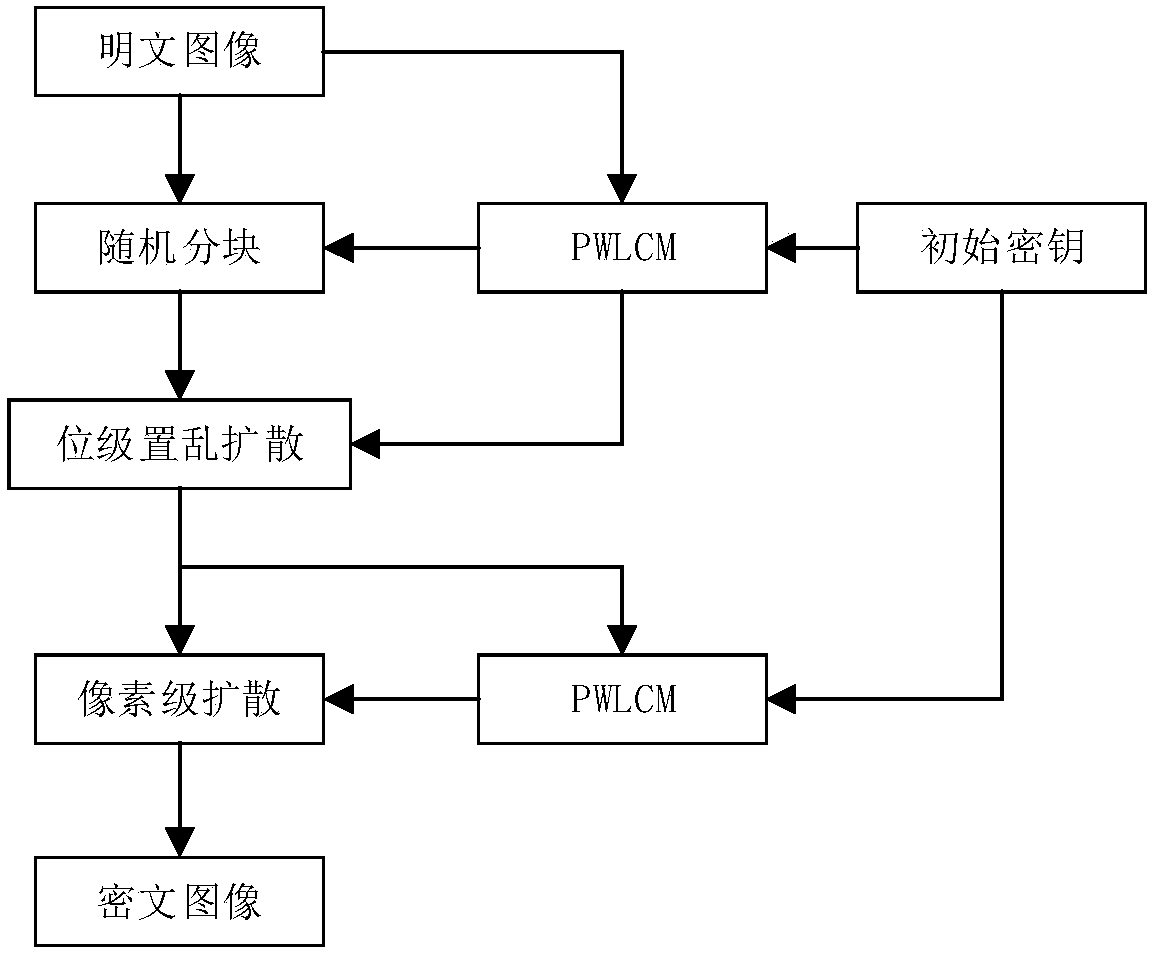
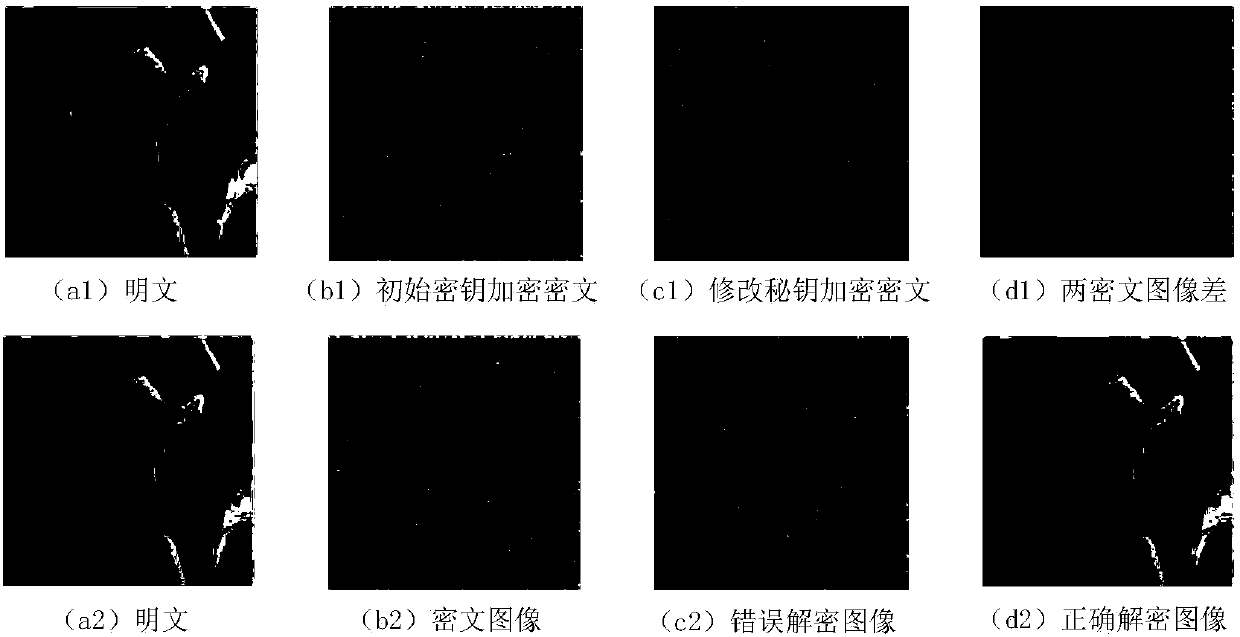
Multi-image encryption method based on piecewise linear chaotic map (PWLCM)
InactiveCN105450899AAchieve protectionLarge key spacePictoral communicationCommunications securityMulti-image
A multi-image encryption method based on piecewise linear chaotic map (PWLCM) belongs to the field of information encryption, and aims to solve the problems that most of the conventional image encryption methods take a single image as an encryption object, and cannot adapt to mass image encryption, and the encryption efficiency of the conventional image encryption methods is relatively low. Being different to the conventional image encryption methods, the multi-image encryption method takes multiple images as encryption objects, and adopts the steps of converting the multiple images into a single large image, encrypting the single large image, and converting the encrypted single large image into multiple encrypted images, so as to protect contents in the multiple images. The multi-image encryption method comprises the key steps of combining k interactive images into a large image, encrypting the large image according to PWLCM to obtain an encrypted large image, dividing the encrypted large image into k encrypted images, and naming the k encrypted images sequentially according to a chaotic sequence generated based on PWLCM. Test results show that the method is easy to implement, the encryption effect is favorable, the encryption efficiency and security are high, and communication security of contents of any multiple images can be protected simultaneously.
Owner:CHINA UNIV OF MINING & TECH
Method for encrypting bit-level synchronous promiscuous diffusion images and pixel-level annular diffusion images
InactiveCN108319859ASmall amount of calculationEnhanced defense against differential attacksDigital data protectionSecuring communication by chaotic signalsComputer hardwareDiffusion methods
The invention provides a method for encrypting bit-level synchronous promiscuous diffusion images and pixel-level annular diffusion digital images. According to the method, bit-level encryption and pixel-level encryption are carried out on an image by utilizing a chaos sequence generated by piecewise linear chaotic map, so that ideal encryption effect can be obtained through one round of encryption. In the bit-level encryption stage, random blocking is carried out on the image by utilizing the chaos sequence to destroy the correlation of adjacent pixels, a low four-bit plane, a previous ciphertext pixel and a key stream are combined, synchronous promiscuous diffusion encryption is carried out on a high four-bit plane with a high information amount, overall scrambling is carried out on thelow four-bit plane with an extremely low information amount through cyclic shift, and inter-block diffusion is realized through parameter transfer. In the pixel-level encryption stage, a transverse sequential diffusion and longitudinal reversed diffusion combined annular diffusion method is adopted, so that phenomena such as plaintext sensitivity non-uniformity and break points caused by diffusionof each pixel along one direction are avoided.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
A method to obtain uniform distributed pseudo random sequence in random chaos system
InactiveCN101217360AEvenly distributedEasy to implementSecret communicationSecuring communicationRight shiftSign bit
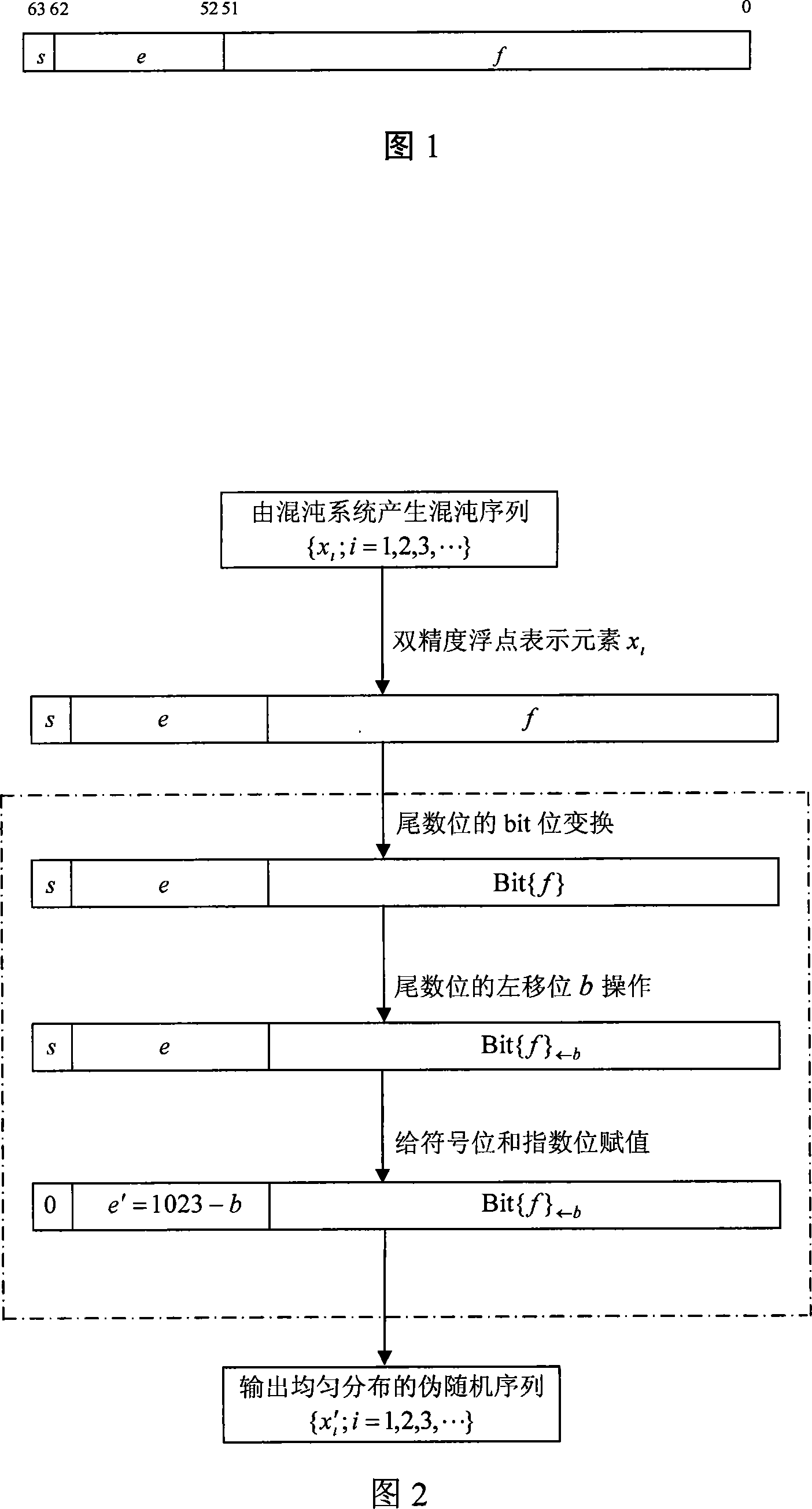
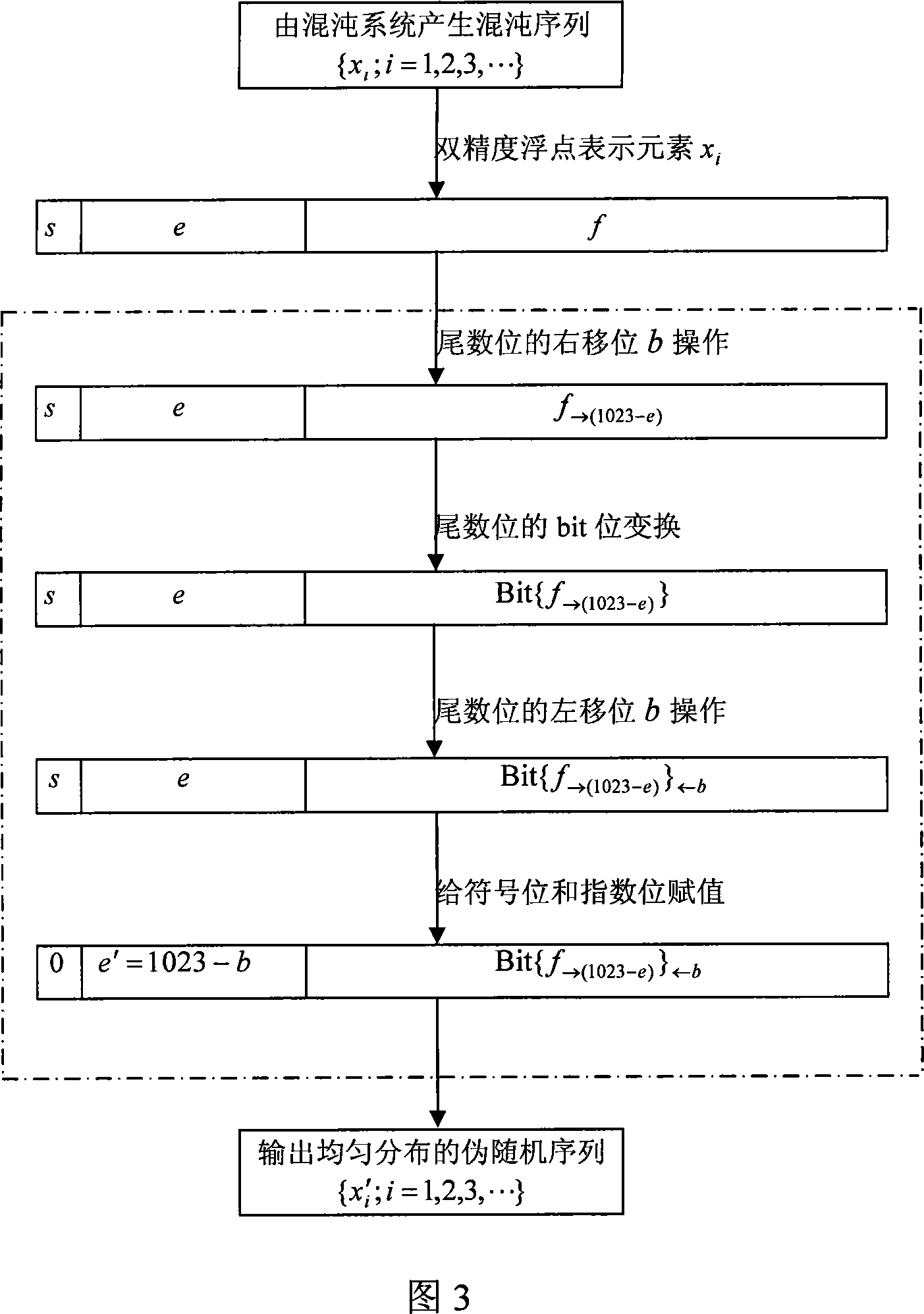
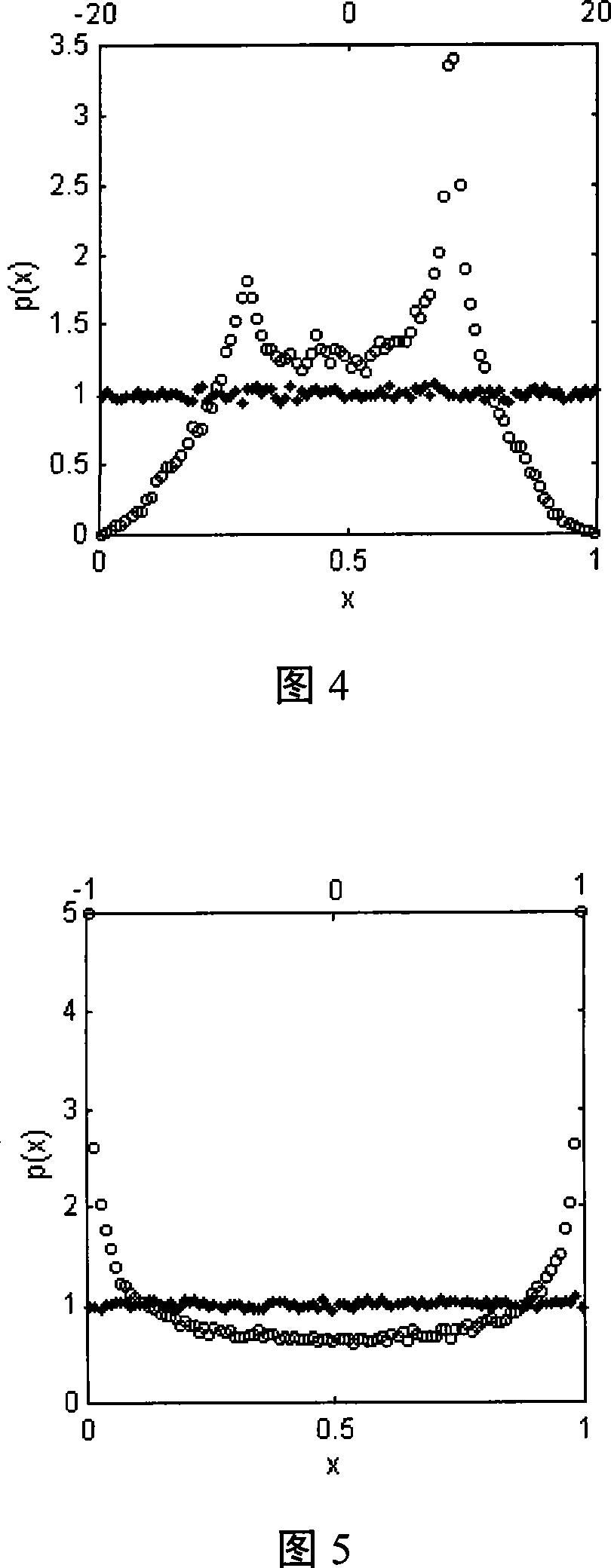
The invention discloses a pseudo-random sequence even obtaining method from an arbitrary chaotic system. The invention comprises the following steps: for an arbitrary solid pattern chaotic sequence from a chaotic map system or a chaotic differential dynamic system, if the field of definitions of the chaotic sequence is (-1, 1), a real number converter carries on right shift b operations successively to the mantissas of each element in the arbitrary solid pattern chaotic sequence, switches the bit position of mantissa and carries on left shift b operations to the mantissas; the sign bit is endowed with a value '0' and an asynchronous exponential bit is endowed with a value '1023-b' to obtain an even-distributed pseudo-random sequence; or the real number converter switches the position of bit successively of the mantissas of each element in the arbitrary solid pattern chaotic sequence, carries on left shift b operations to the mantissas; the sign bit is endowed with a value '0' and an asynchronous exponential bit is endowed with a value '1023-b' to obtain the even-distributed pseudo-random sequence. The invention can obtain good-homogeneity pseudorandom number from an arbitrary chaotic system, in particular to be convenient for the realization of digital system.
Owner:CENT SOUTH UNIV
Static synchronization compensator chaos balance control system based on cascade type DC-to-AC converter
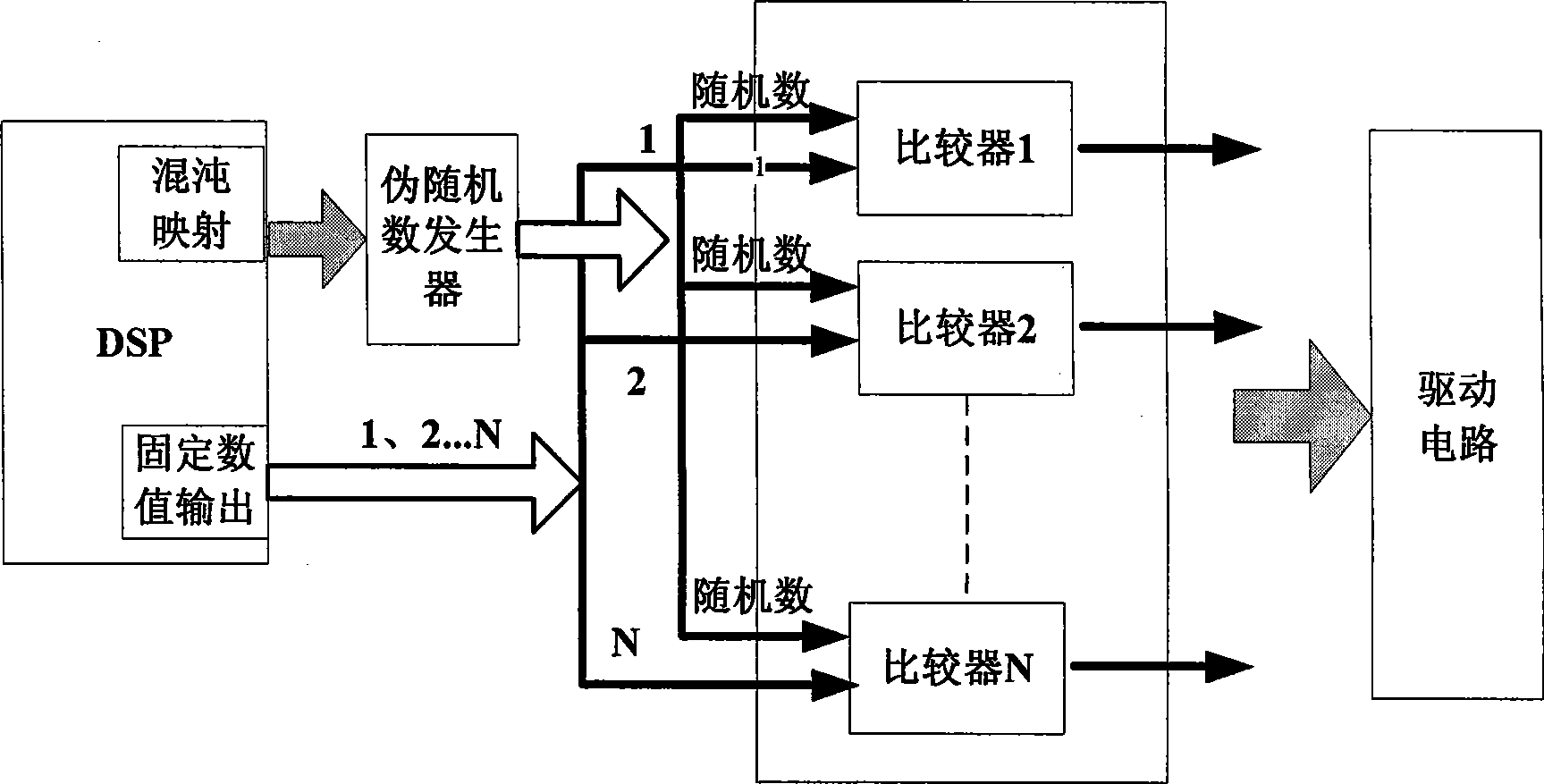
InactiveCN101459340AAchieve normal workAutomatically balance usageFlexible AC transmissionEfficient power electronics conversionDigital signal processingControl system
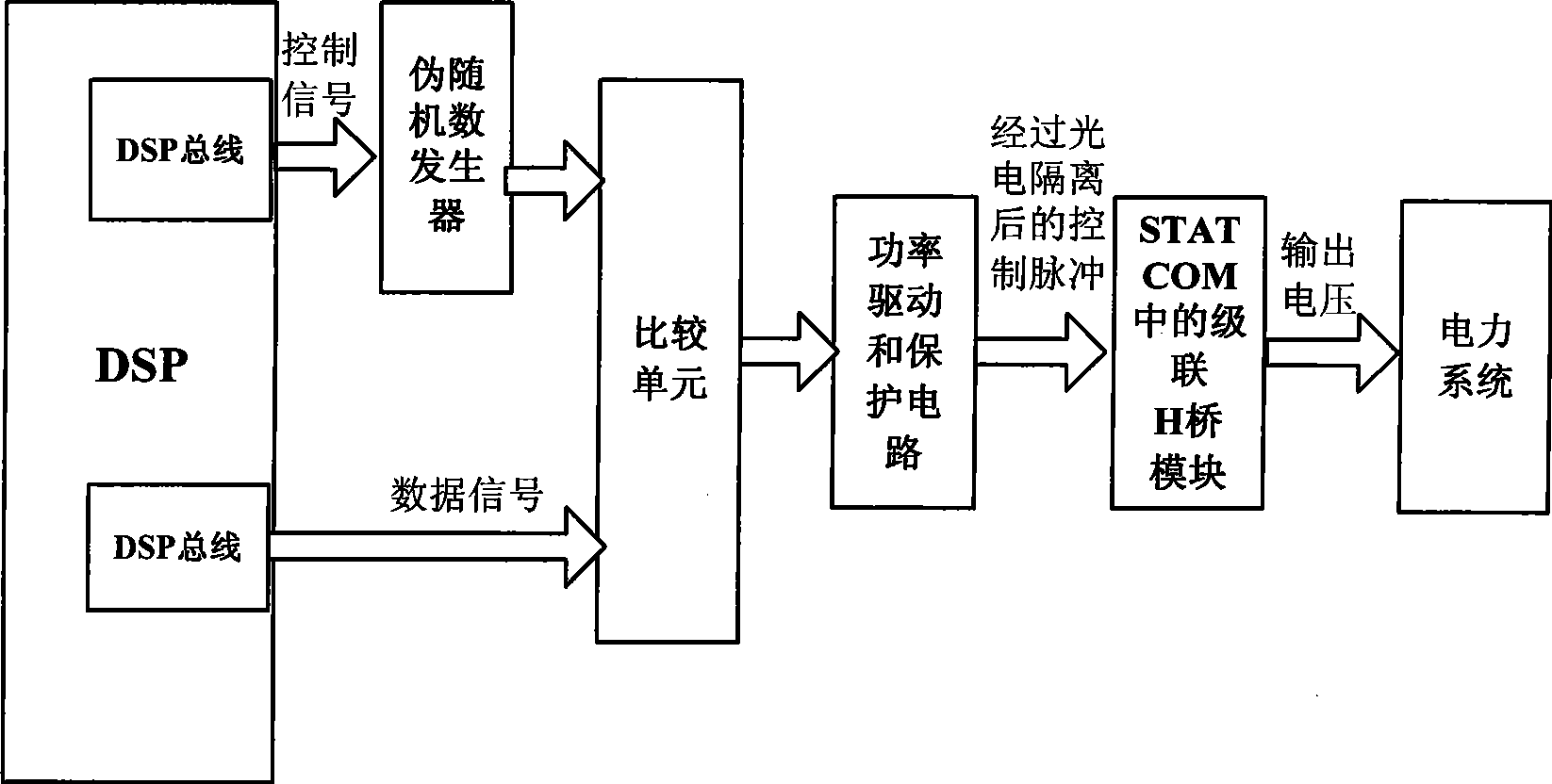
The invention relates to a chaotic balanced control system of a static synchronous compensator based on a cascade inverter, which is characterized in that the chaotic balanced control system comprises a digital signal process, a pseudorandom number generator unit, a comparing unit, a power driving circuit unit and a gate pole turn-off cascade H bridge circuit unit. The chaotic balanced control system has the advantages that the work of a pseudorandom number generator is controlled through using a high performance digital signal treatment chip and a method of chaotic map to produce a random number, thereby achieving to automatically balance the use rate of various cascade inverter units, and leading the use rate of various cascade units to be basically identical. On one side, the design cost of the cascade inverter is reduced, and the service life is prolonged. On the other side, the normal work of STATCOM is achieved, and the reliability and continuity demands of a circuit system are guaranteed.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
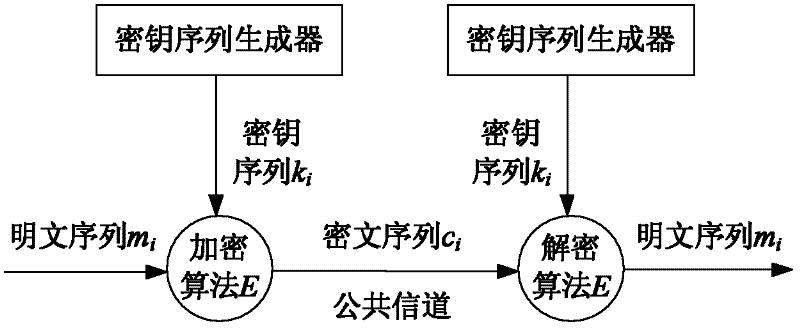
Chaos-based data protection using time-discrete dynamical systems
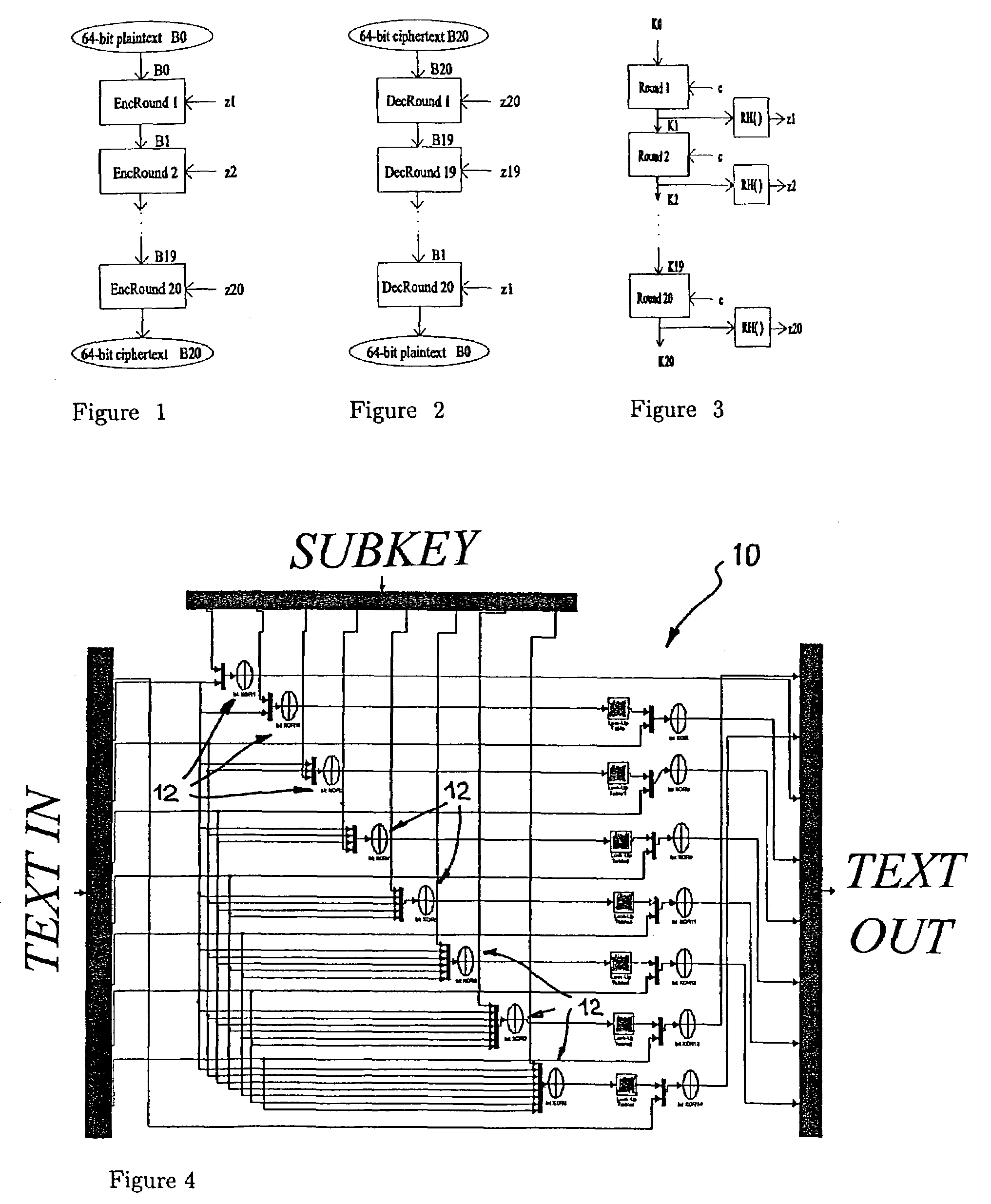
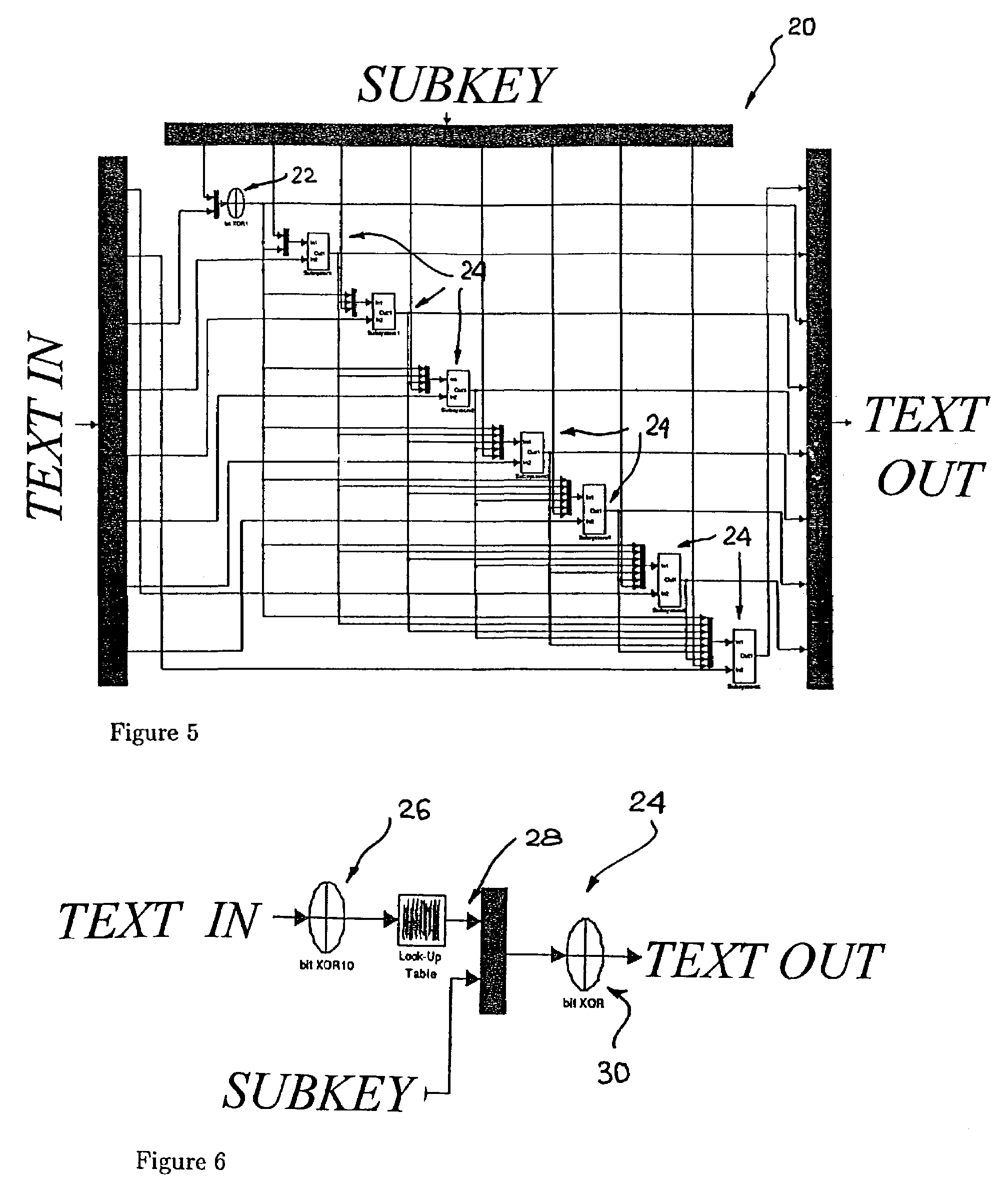
ActiveUS7106864B2Encryption apparatus with shift registers/memoriesSecret communicationPlaintextDiscrete dynamical system
In an encryption / decryption system for converting data signals between an unencrypted plaintext format and an encrypted ciphertext format plurality of round modules are provided permitting a respective set of input data signals (TEXT IN) to generate a respective set of output data signals (TEXT OUT) by means of transformation controlled by a round key (SUBKEY). The transformation is identified by at least one map function derived from a chaotic map.
Owner:STMICROELECTRONICS SRL
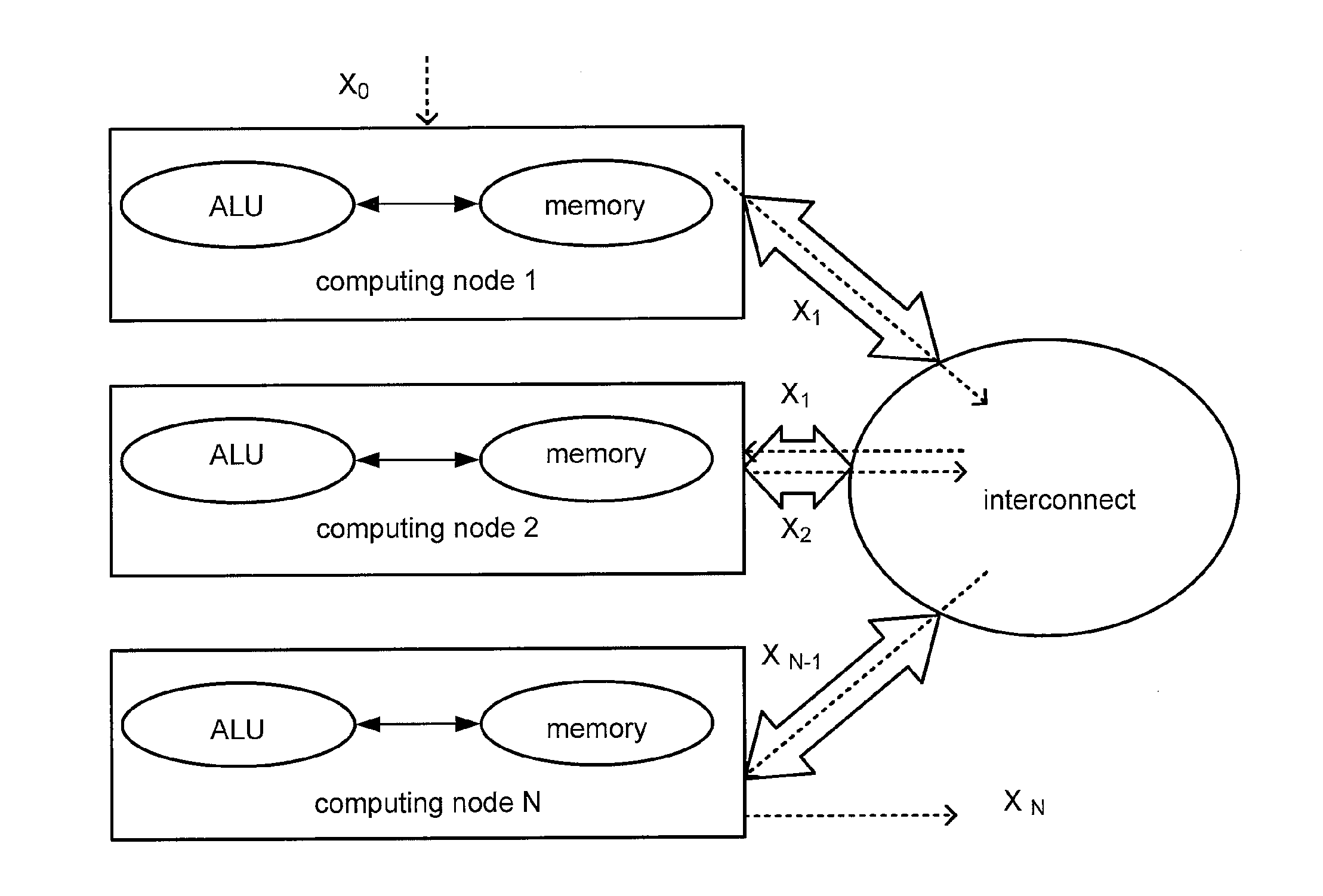
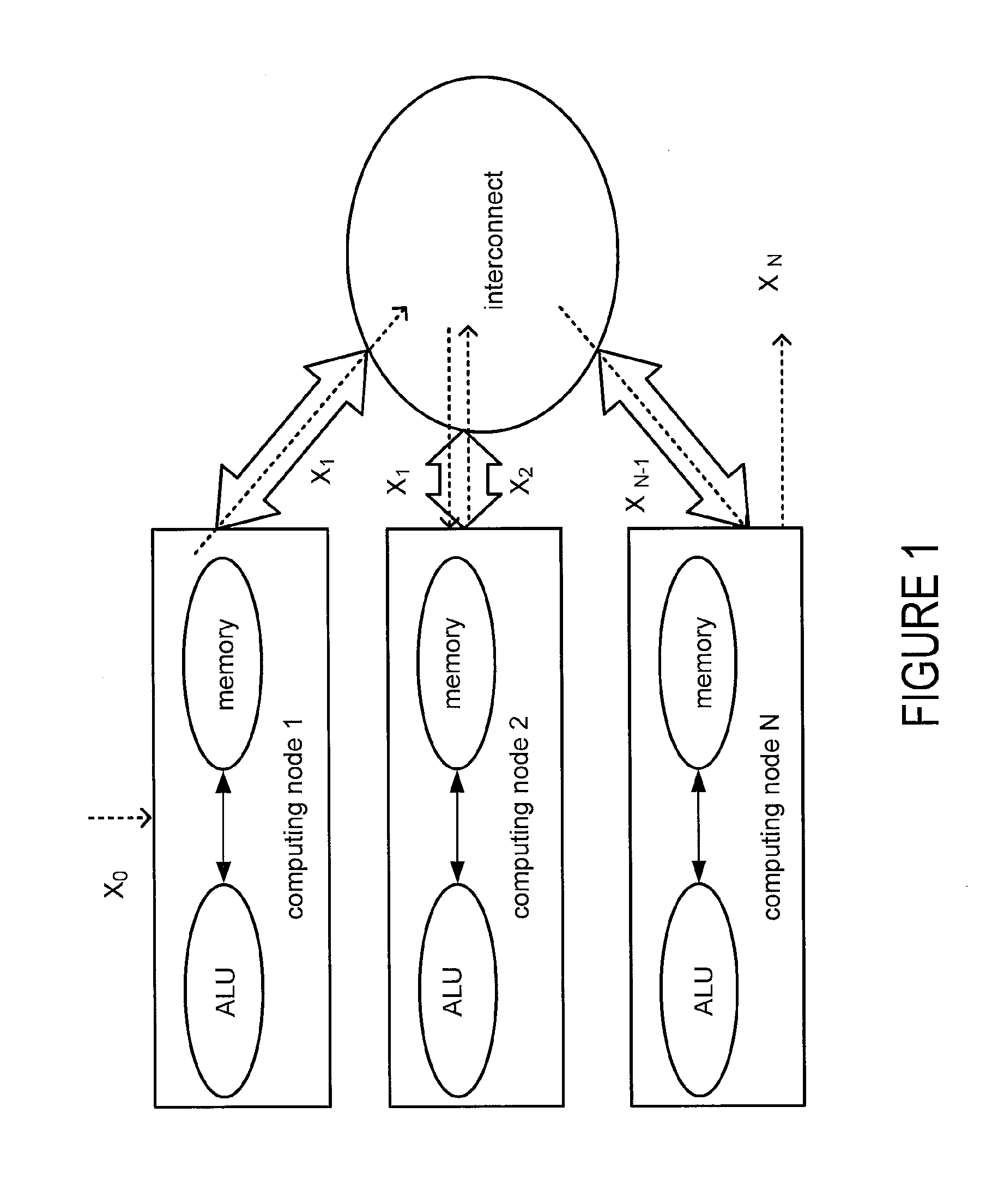
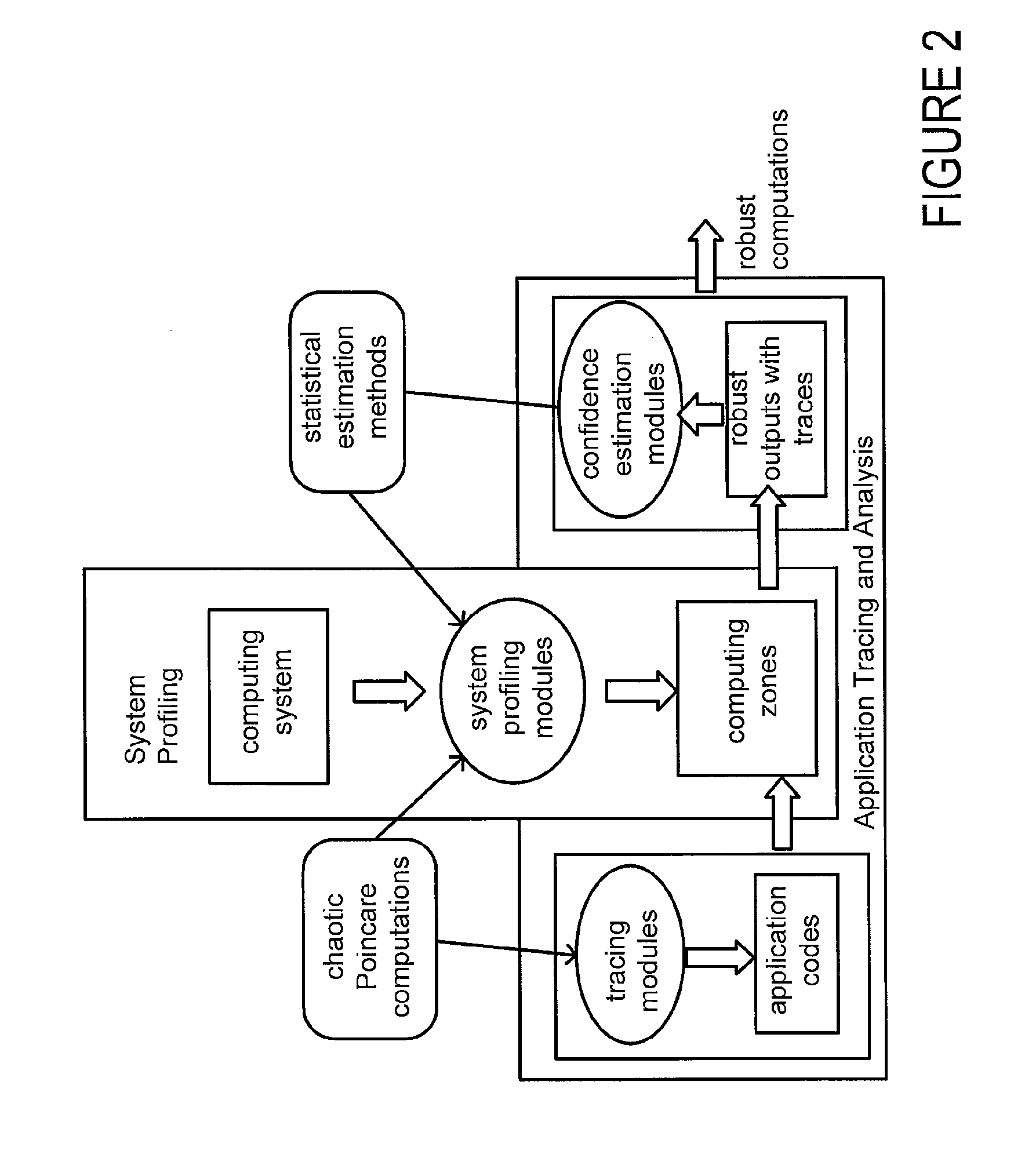
Failure detection in high-performance clusters and computers using chaotic map computations
A programmable media includes a processing unit capable of independent operation in a machine that is capable of executing 1018 floating point operations per second. The processing unit is in communication with a memory element and an interconnect that couples computing nodes. The programmable media includes a logical unit configured to execute arithmetic functions, comparative functions, and / or logical functions. The processing unit is configured to detect computing component failures, memory element failures and / or interconnect failures by executing programming threads that generate one or more chaotic map trajectories. The central processing unit or graphical processing unit is configured to detect a computing component failure, memory element failure and / or an interconnect failure through an automated comparison of signal trajectories generated by the chaotic maps.
Owner:UT BATTELLE LLC
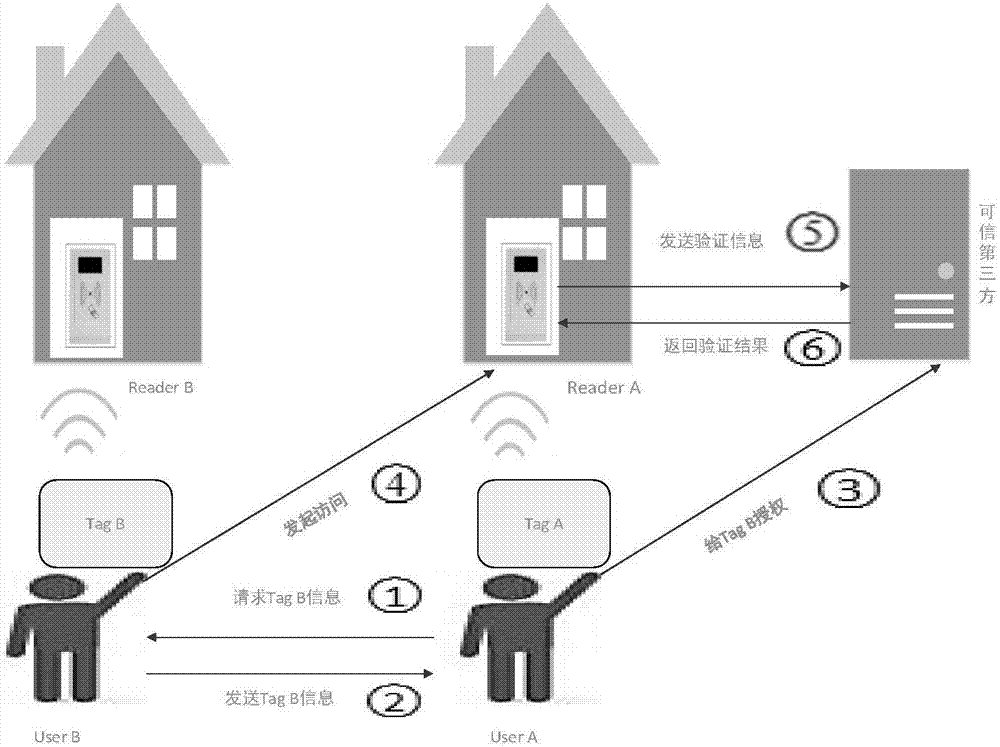
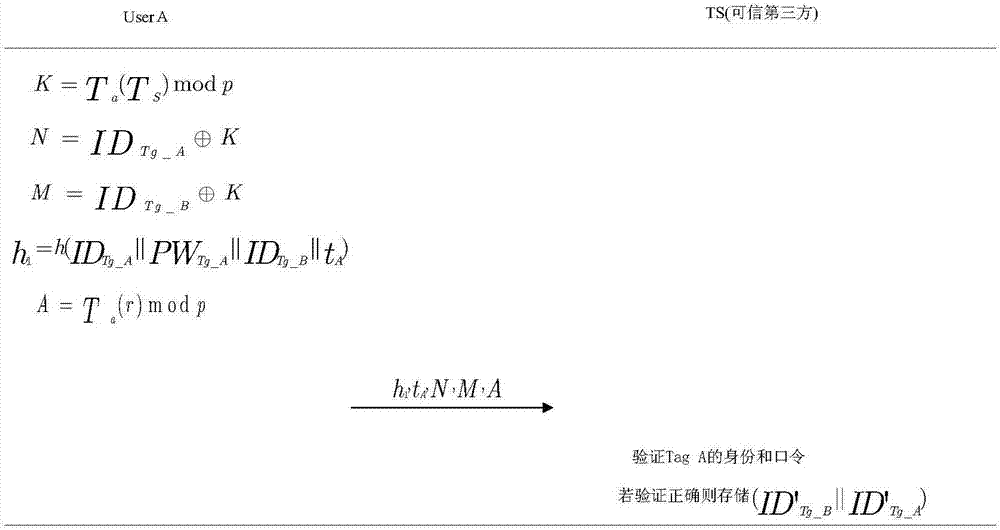
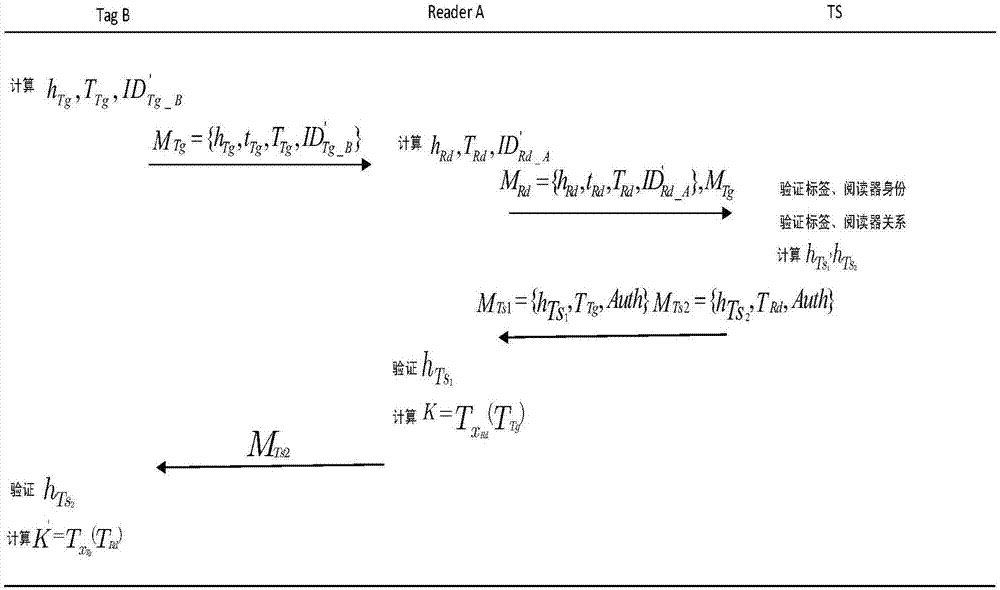
RFID entrusted authentication method for smart home
ActiveCN107423647AReduce overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareRfid authentication
The invention claims the protection for a RFID entrusted authentication method for smart home, and relates to the field of smart home. A RFID-based access control system is widely applied to resolutions for smart home. Current access control verification plans fail to be entrusted to scenarios, such as when a user travels or is on business trip and can not entrust other to enter his / her home to complete certain tasks. The invention provides a RFID entrusted authentication plan which can be authorized on the user's own to address the problem. According to the invention, firstly, a general RFID authentication protocol is designed and is applied to general authentication scenarios in smart home; and on the basis of the general RFID authentication protocol, for matters entrusted, an entrusted authentication protocol is provided. The technical solution is designed based on Chebyshev chaotic map, such that the user can remote complete matters entrusted.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
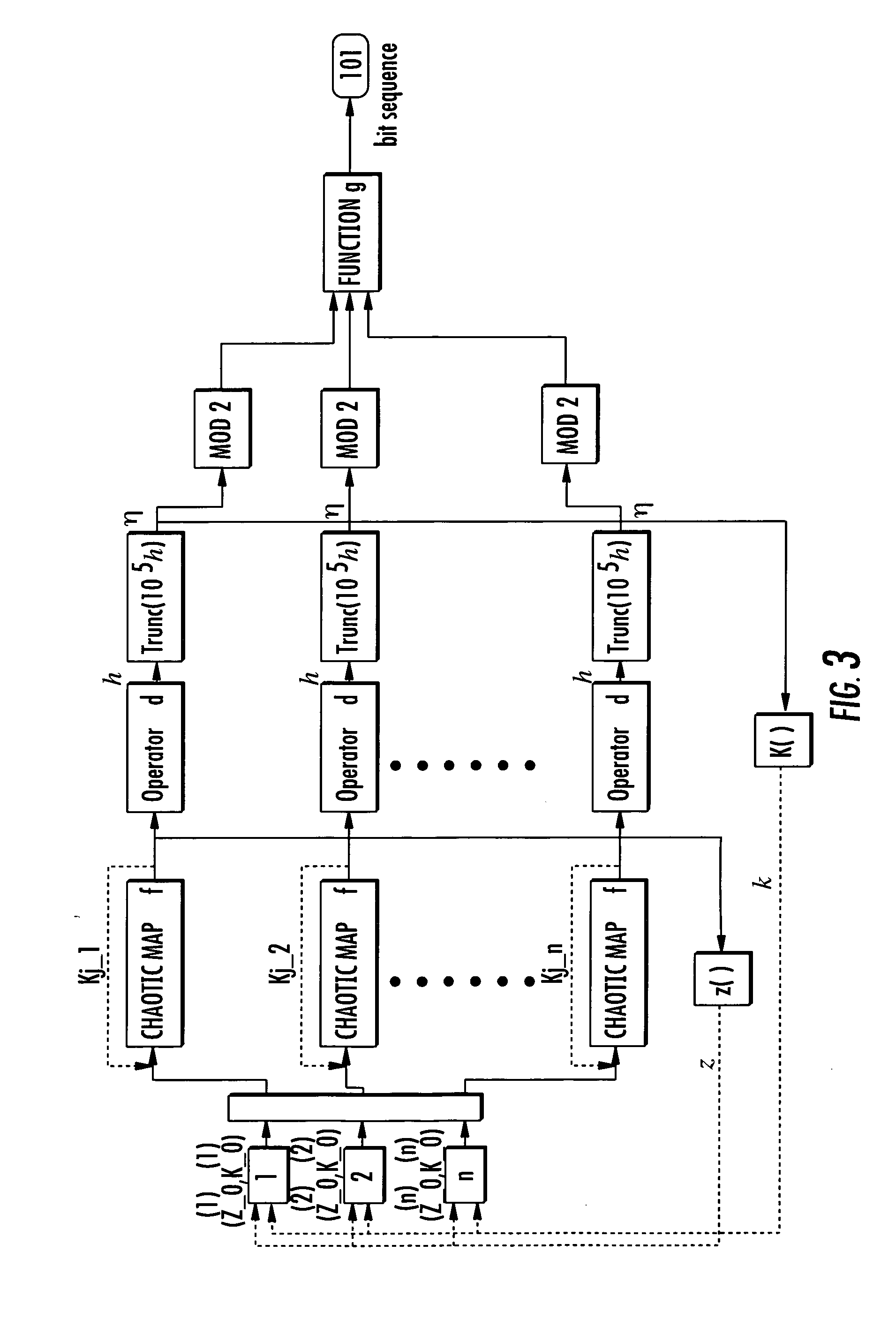
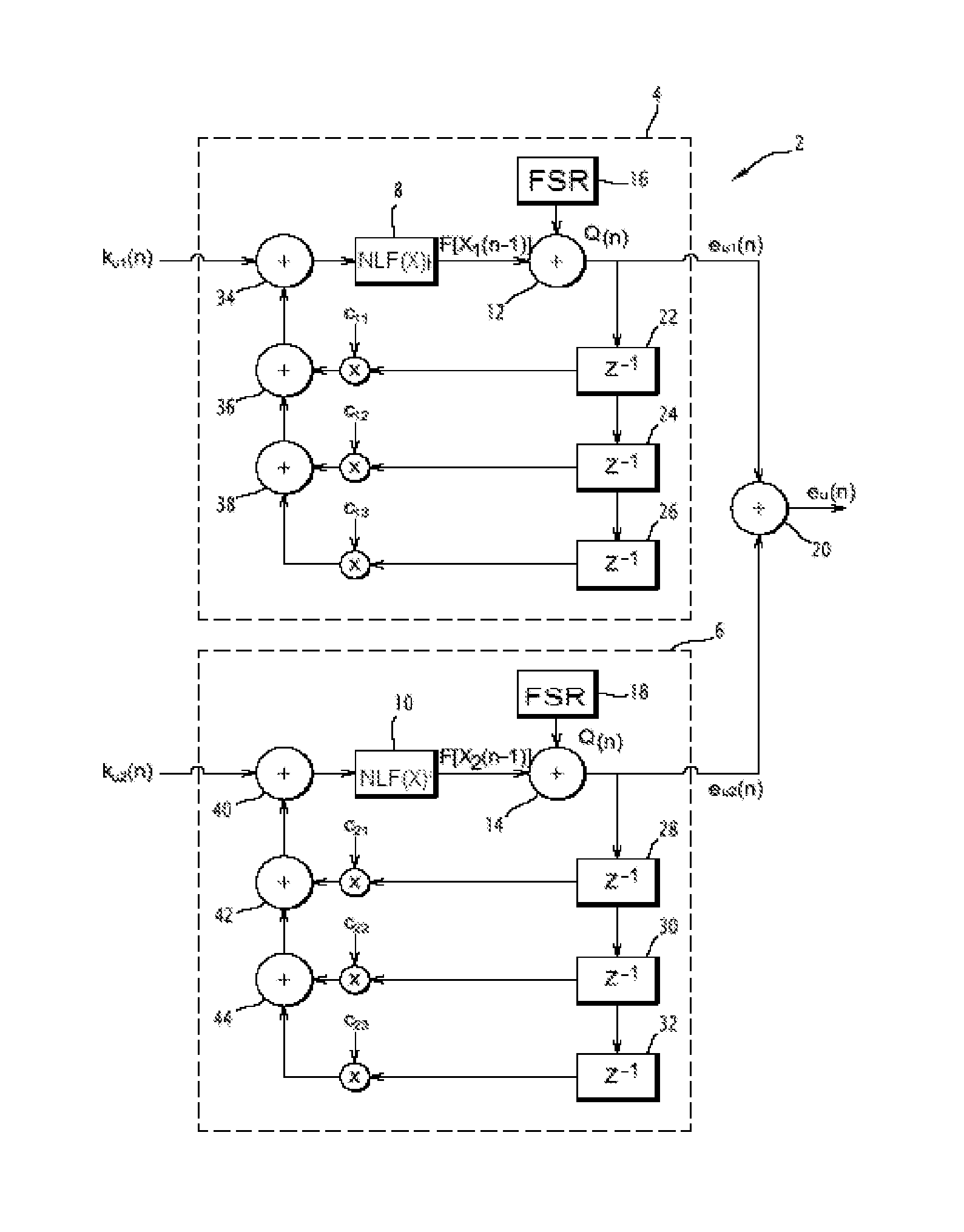
Generator of Chaotic Sequences and Corresponding Generating System
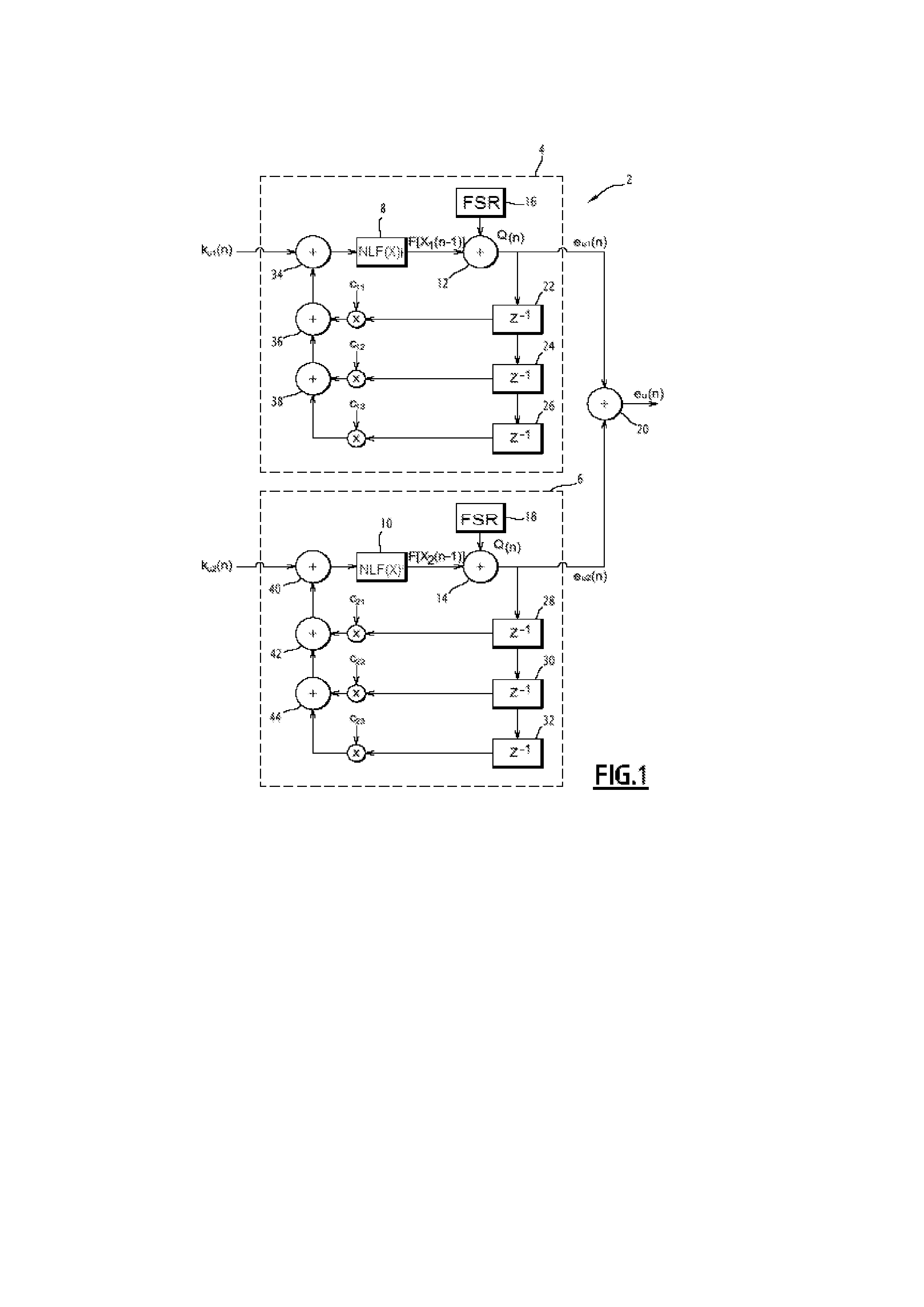
InactiveUS20130170641A1Small sizeAccurate measurementKey distribution for secure communicationDigital data processing detailsExclusive orNon linear functions
A generator of chaotic sequences of integer values is provided. The generator includes at least two discrete recursive filters at least of first-order, generating an output chaotic sequence of integer values, each recursive filter comprising means for implementing a nonlinear function connected via an exclusive-or gate to means for generating a perturbation sequence of integer values. The two filters are mounted in parallel. The chaotic sequence output from the generator is equal to an exclusive-or of the chaotic sequences output from the recursive filters, and in the means for implementing the nonlinear function includes a chaotic map.
Owner:UNIV DE NANTES
Multi-image encryption method based on hyperchaotic Chen system
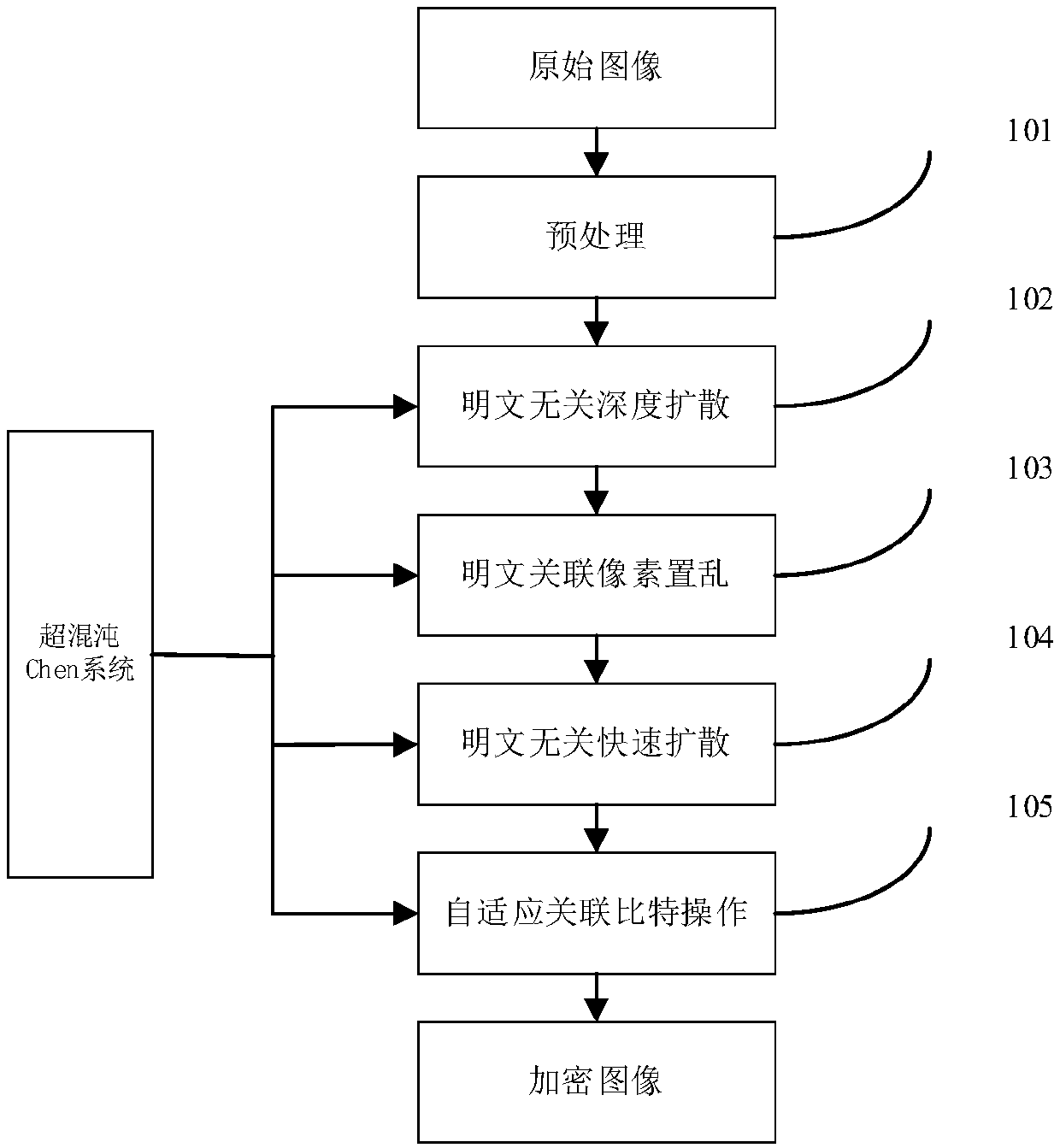
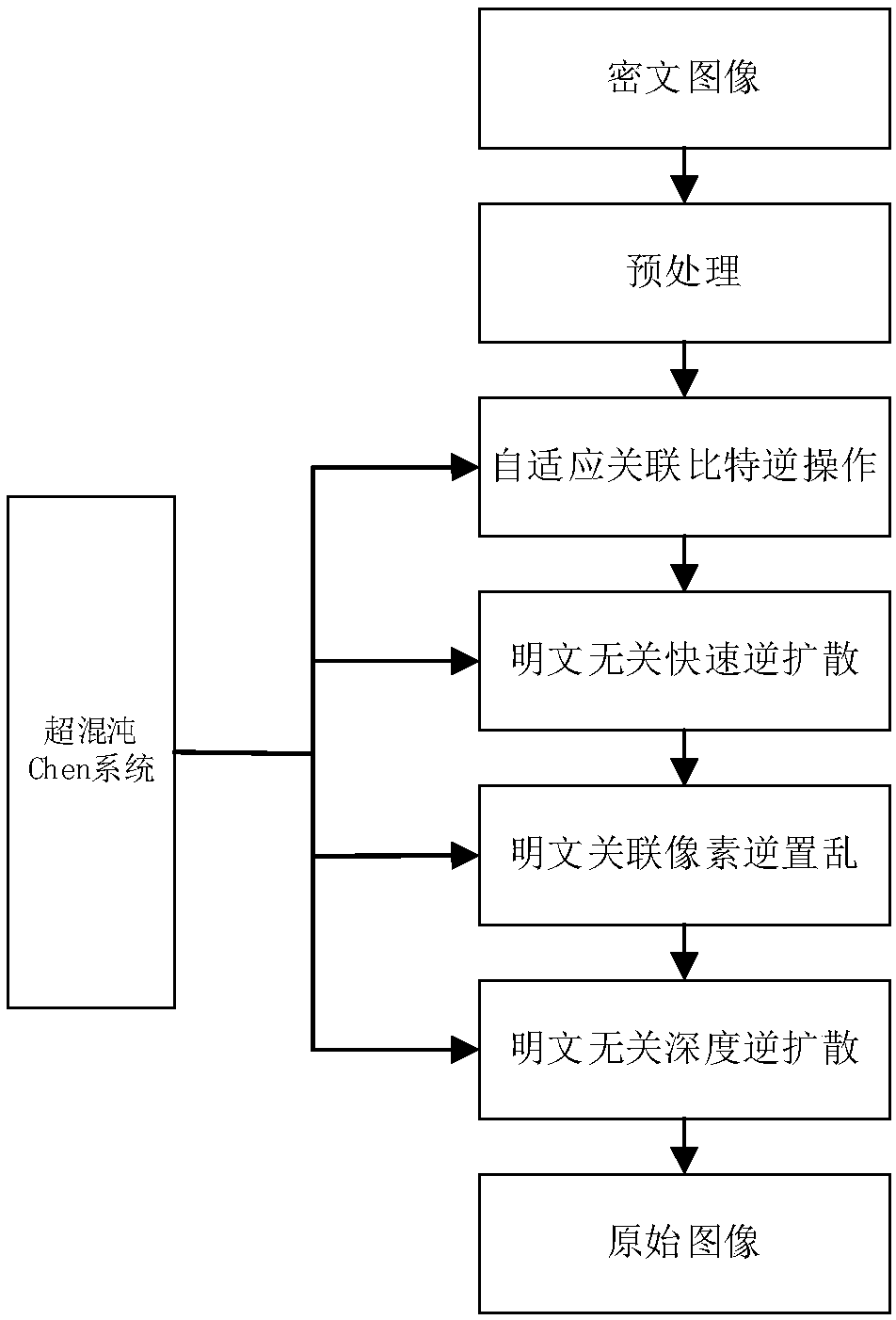
InactiveCN109618073AStrong correlationImprove efficiencySecuring communicationPictoral communicationComputer hardwarePlaintext
The invention relates to a multi-image encryption method based on a hyperchaotic Chen system. The method aims at the problems that in an existing chaotic image encryption algorithm, system security isnot high, a plaintext attack cannot be resisted, encryption images are mutually independent, and efficiency is low. A hyperchaotic system generates a chaotic stochastic matrix related to plaintext images according to the plaintext images. Plaintext irrelevant deep diffusion is carried out on the plaintext images. One of the images is selected, plaintext related scrambling operation and plaintextirrelevant rapid bit diffusion are carried out on the image, and a first ciphertext is generated. Adaptive relation bit operation is carried out on the rest images, the rest ciphertexts are generated,and multi-image related image encryption is finished. An experiment simulation result shows that the algorithm has relatively high efficiency and relatively high plaintext attack resistance. The plaintext image corresponding to a ciphertext cannot be obtained through utilization of only one ciphertext, so security is relatively high. The algorithm has a good application scene.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
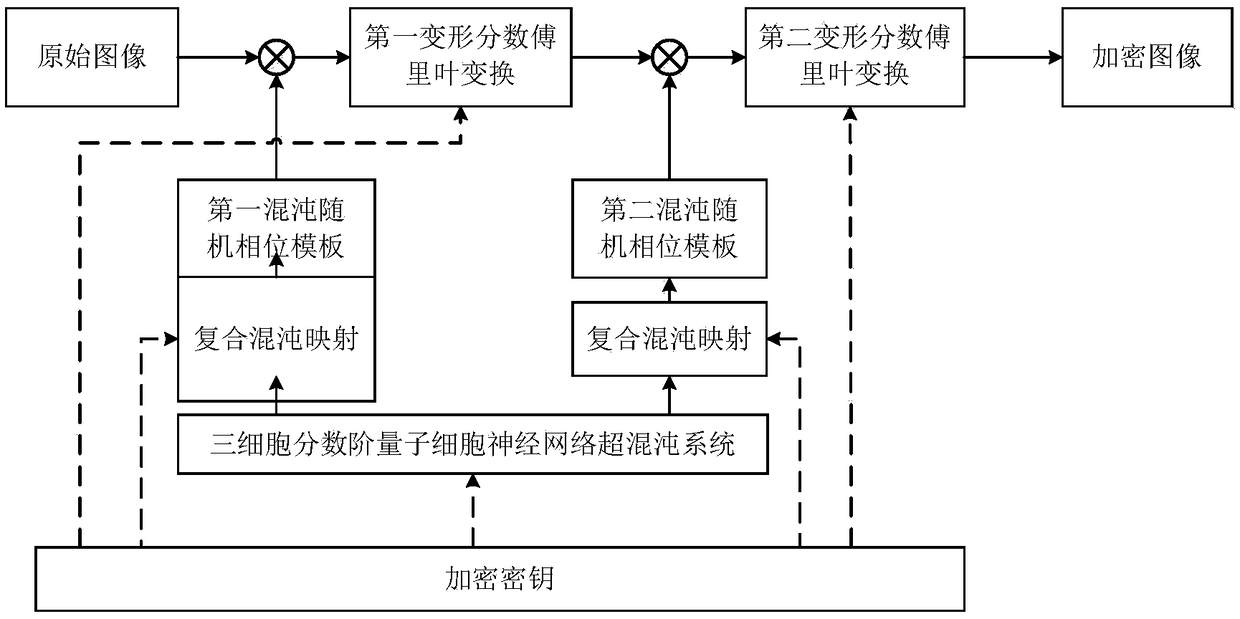
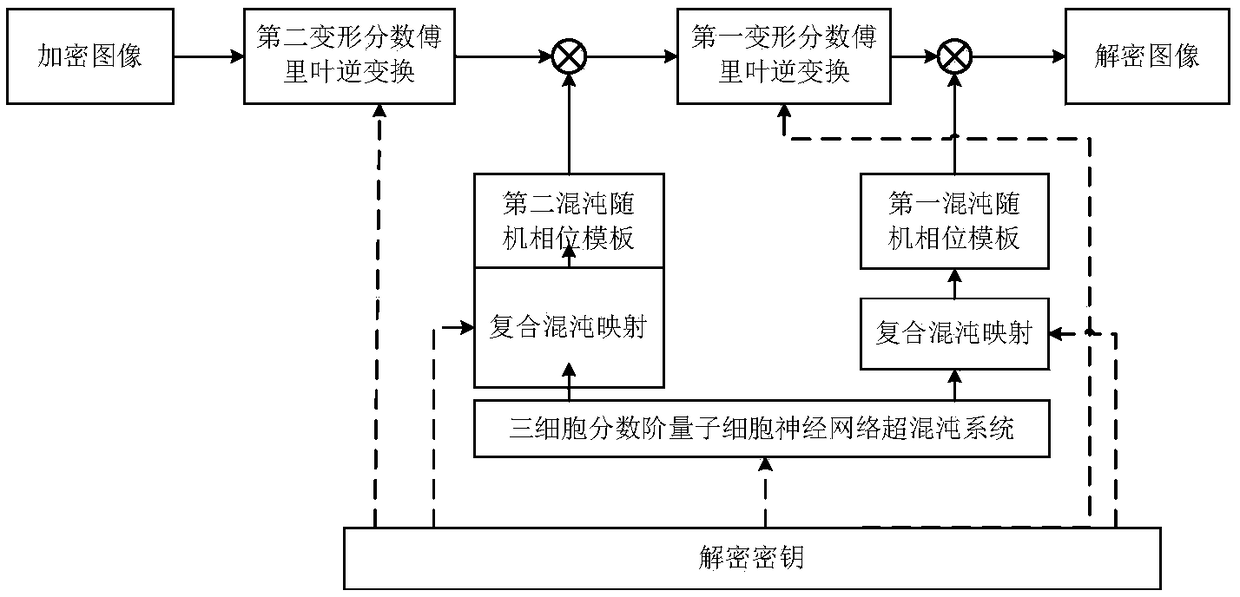
Optical image encryption and decryption based on composite chaos and quantum chaos
ActiveCN109190393AMake up for the security flaws of the lack of linear featuresHigh key dimensionDigital data protectionChaos modelsQuantum cellular automatonInformation security
An optical image encryption and decryption method based on compound chaos and quantum chaos is provided, which relates to the field of optical information security technology and solves the security defect of the non-linear shortage of the existing optical image encryption technology, the method comprising an encryption process and a decryption process, wherein the user encryption key and the decryption key are respectively set, which consist of the initial value, the control parameter and the order of the hyperchaotic system of a three-cell fractional quantum cellular neural network, the initial value and the control parameters of the composite chaotic map, and the series of the deformed fractional Fourier transform. The invention makes up for the security defect that the linear characteristic of the traditional optical image encryption technology is insufficient, and the fractional-order quantum chaotic system has a higher key dimension, bigger secret key space and greater sensitivity and can better resist all kinds of security attacks; the quantum chaotic system is a new type of nano-device, which is characterized in that quantum dots and quantum cellular automata transmit information mutually by the Coulomp action.
Owner:CHANGCHUN UNIV OF SCI & TECH
Method and hardware for generating random numbers using dual oscillator architecture and continuous-time chaos
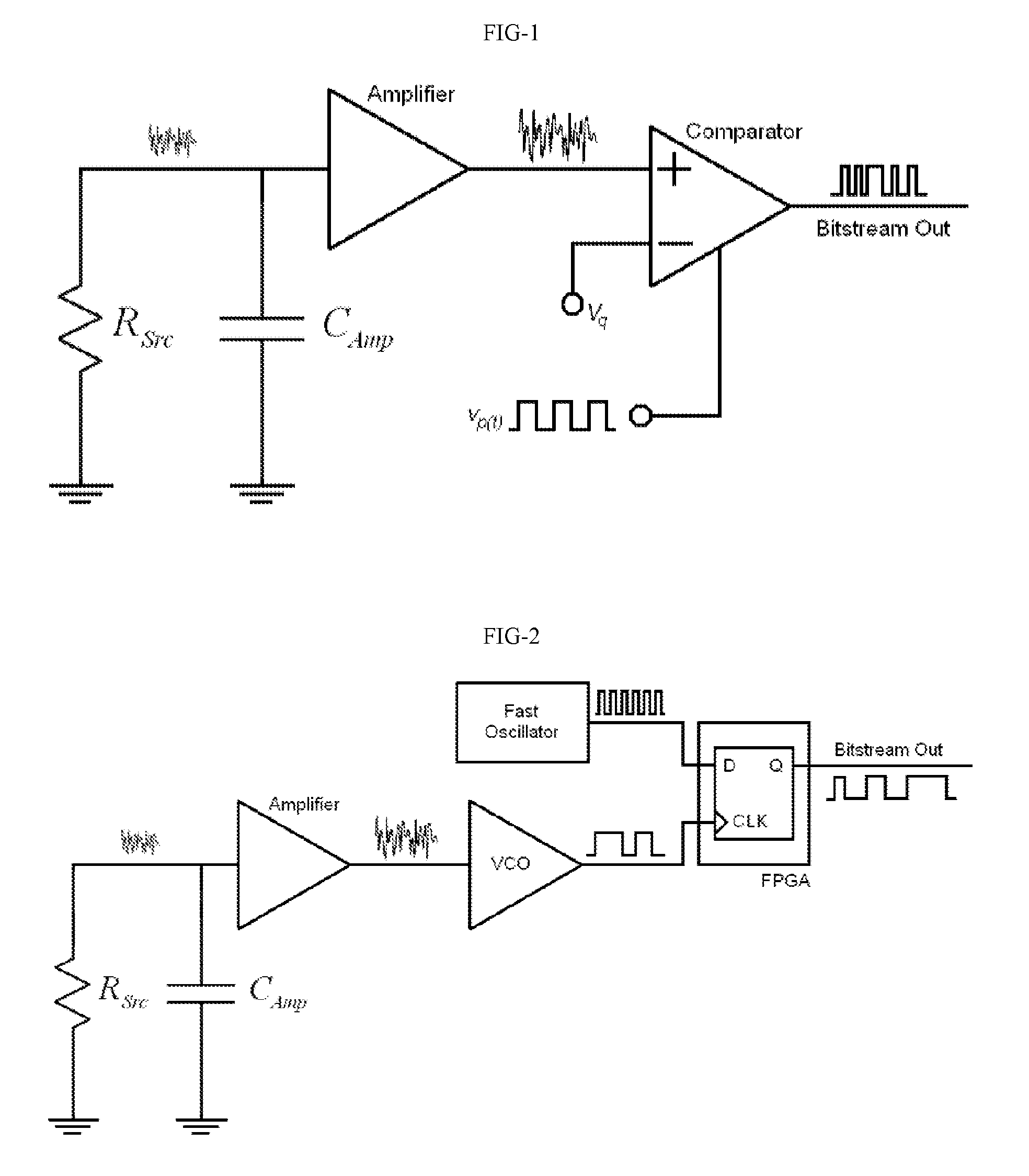
ActiveUS8612501B2Improve throughput speedQuality improvementRandom number generatorsSecuring communication by chaotic signalsStatistical qualityNumber generator
Novel random number generation methods and novel random number generators based on continuous-time chaotic oscillators with dual oscillator architecture are presented. Numerical and experimental results not only verify the feasibility of the proposed circuits, but also encourage their use as a high-performance IC TRNG. In comparison with RNG's based on discrete-time chaotic maps, amplification of a noise source and jittered oscillator sampling, which are advantageous in the sense that true random behavior can be mathematically proven thanks to an analytical model that has been developed, it is seen that RNG's based on continuous-time' chaotic oscillators can offer much higher and constant data rated without post-processing. The proposed innovation increases the throughput, maximizes the statistical quality of the output sequence and is robust against external interference, parameter variations and attacks aimed to force throughout. The proposed circuits can be integrated on today process at GHz range.
Owner:TUBITAK
Test data encryption method based on S box and chaotic map
InactiveCN101777975AIncrease the number of roundsExtension of timeEncryption apparatus with shift registers/memoriesComputer hardwareS-box
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Method and device for constructing spreading code
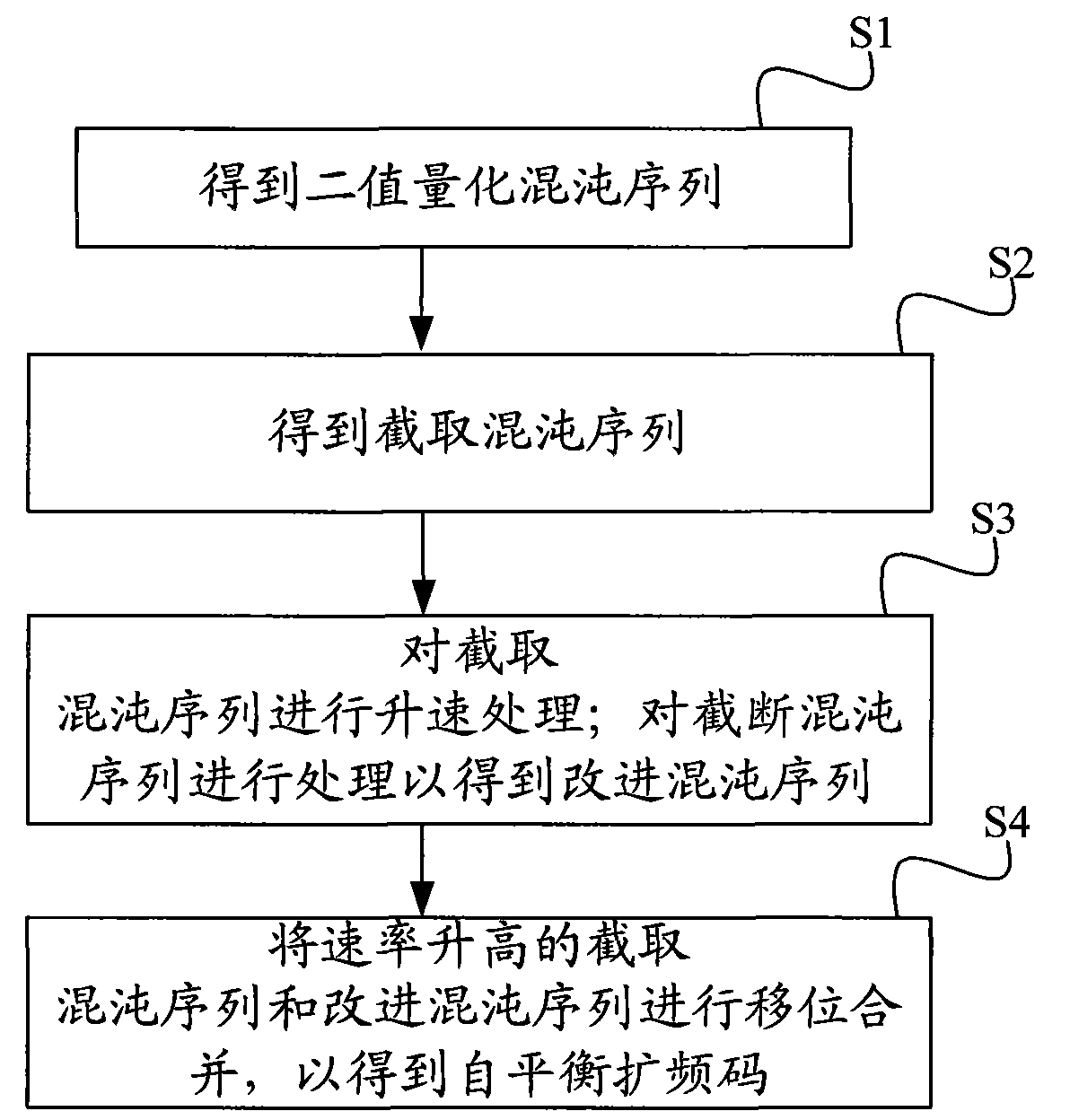
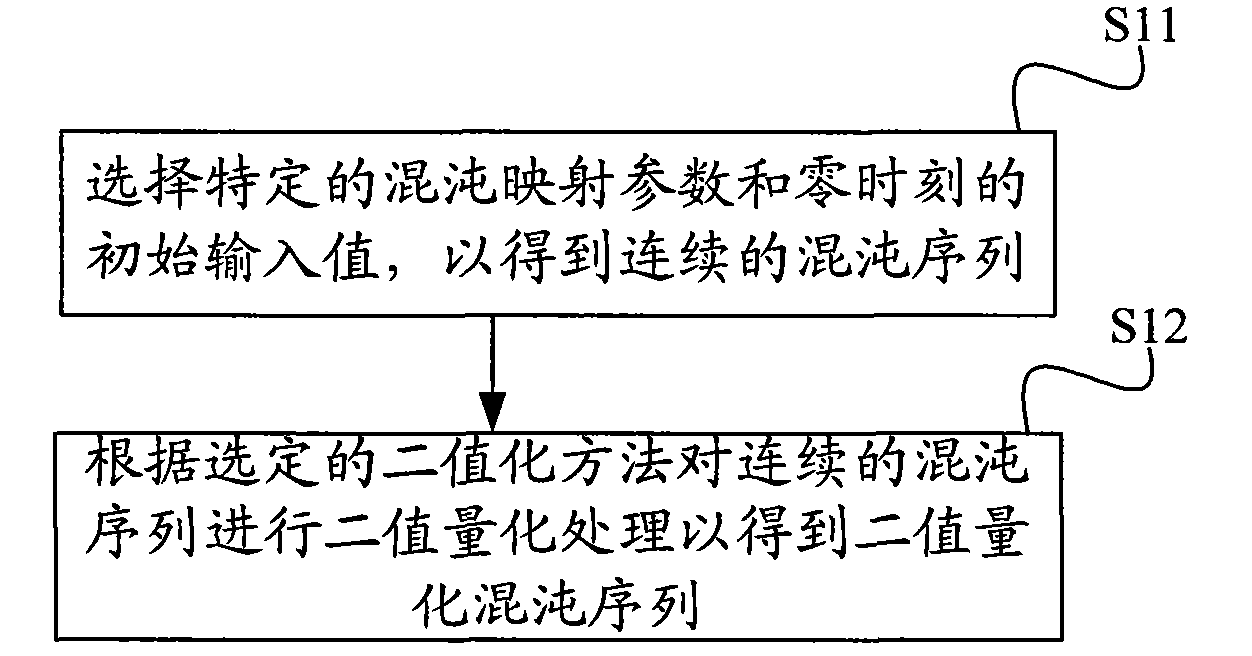
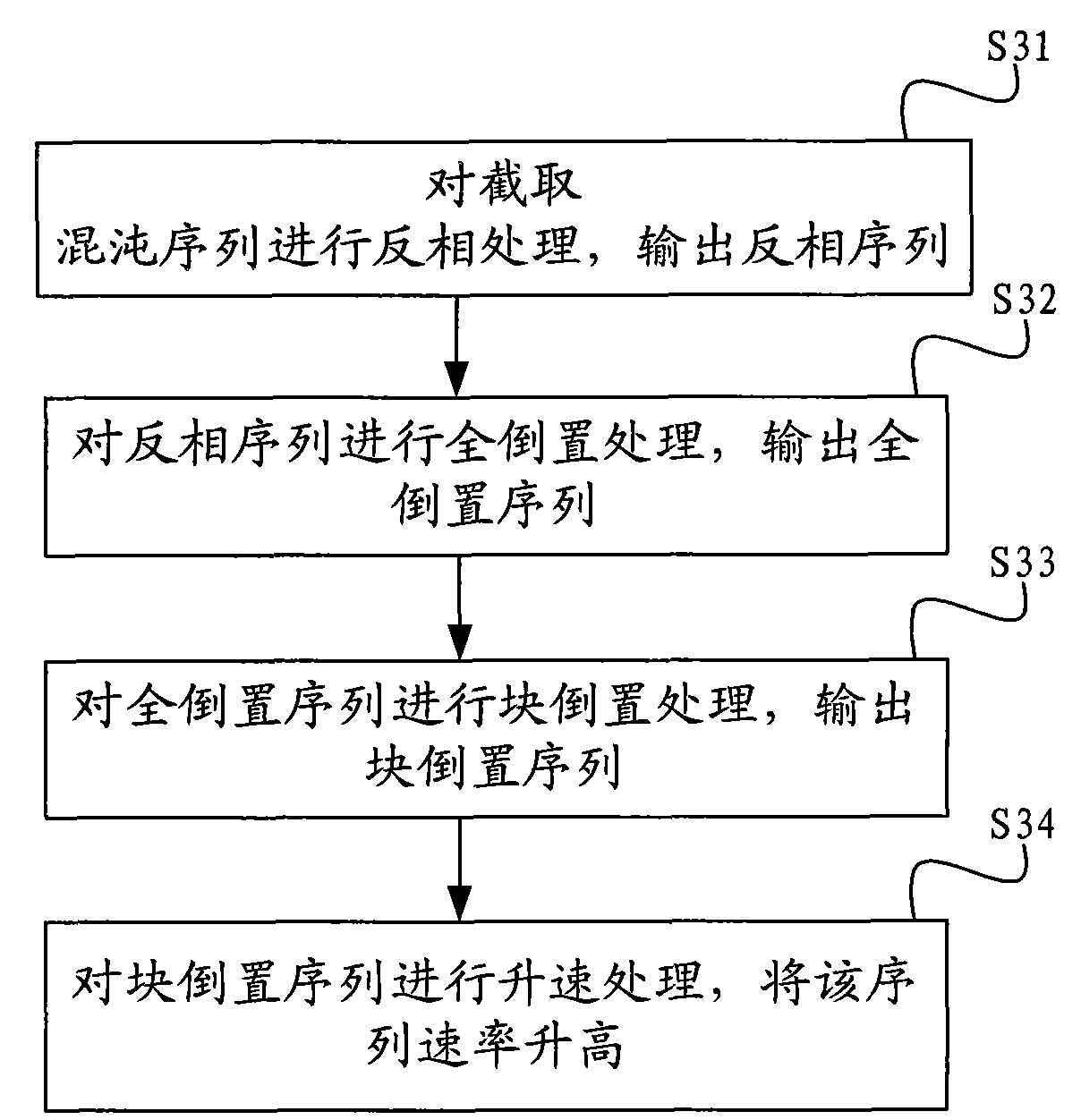
ActiveCN101599775AImprove confidentialityImprove featuresMultiplex code generationTransmissionStart timeConfidentiality
The invention discloses a method for constructing a spreading code, comprising the following steps: using chaotic map and initial condition, obtaining a two-valued quantification chaotic sequence after the two-valued quantification; carrying out intercepting treatment on the two-valued quantification chaotic sequence according to the initial start time and finish time determined by spreading codelength to obtain an intercepted chaotic sequence; carrying out ascending velocity treatment on the intercepted chaotic sequence to improve the velocity thereof; treating the intercepted chaotic sequence to obtain an improved chaotic sequence; carrying out displacement and combination on the intercepted chaotic sequence with improved velocity and the improved chaotic sequence, thus obtaining the self-balancing spreading code. The invention further discloses a device for constructing the spreading code. The invention not only improves the confidentiality of spread spectrum communication but also has good self-correlation characteristic and cross-correlation characteristic of the constructed spreading code.
Owner:SOI MICRO CO LTD
Single-round image encryption method based on hybrid chaotic mapping
ActiveCN111682932AReduce computational complexityReduce computing timeSecuring communication by chaotic signalsChosen-plaintext attackComputation complexity
The invention discloses a single-round image encryption method based on hybrid chaotic mapping. The method comprises the steps of one-dimensional and two-dimensional hybrid chaotic mapping, image encryption and image decryption. The invention provides a mixed one and two dimensional chaotic map (MOTDCM) based on the mixing of one-dimensional chaotic mapping and two-dimensional chaotic mapping, a random and uniformly distributed chaotic sequences can be provided, a full-text dynamic correlation encryption method is designed based on the hyperchaotic system, scrambling and diffusion processes are combined, the calculation complexity and time overhead of a conventional encryption method are reduced, and the capability of the method for resisting selected plaintext attacks is enhanced.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
Rapid chaotic image encryption method capable of simultaneously scrambling and diffusing rows and columns
ActiveCN111683191AReduce computational complexityReduce encryption timesKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputation complexityTheoretical computer science
The invention discloses a rapid chaotic image encryption method capable of simultaneously scrambling and diffusing rows and columns, and aims to provide a novel image encryption method capable of simultaneously scrambling and diffusing rows and columns based on hyperchaos and dynamically related to plaintext pixels, which comprises the following steps of: time-delayed nonlinear combined hyperchaosmapping , image encryption and image decryption. According to the method, a time-delayed nonlinear combined hyperchaos mapping NMHMD is designed on the basis of nonlinear combined mapping provided byZhou Y, and the mapping has the characteristics of wider hyperchaotic interval, no periodic window, more complex dynamic characteristics and better randomness of generated state sequence classes; first-selected plaintext attacks can be effectively resisted; the whole method only needs one round of scrambling and diffusion operation, and the calculation complexity of the method is reduced.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
Random blocking chaotic image encryption method
PendingCN111444522AImprove efficiencyImprove securityDigital data protectionAlgorithmTheoretical computer science
The invention discloses a random blocking chaotic image encryption method, and relates to the technical field of information security. The method comprises the following steps of: reading a plaintextimage A, setting the size of the plaintext image A to be M * N, and aij representing the pixel of the ith row and the jth column in the image A; setting secret keys x0, y0, z0, r and s0 (1); scrambling the image; decomposing the replaced image into four sub-images; and encrypting each sub-image by using integer Logistic mapping, combining all the encrypted sub-images, and storing the combined sub-images as an encrypted image. According to the invention, a random blocking strategy based on chaos is adopted, and the blocking scheme is randomly changed in each encryption, so that the security iseffectively improved. Meanwhile, a random blocking strategy is introduced, and meanwhile it is guaranteed that the image encryption algorithm has high efficiency.
Owner:NANCHANG UNIV
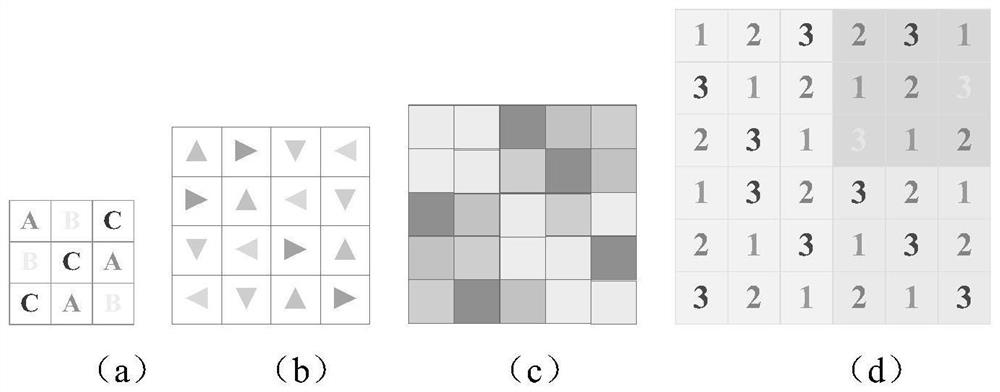
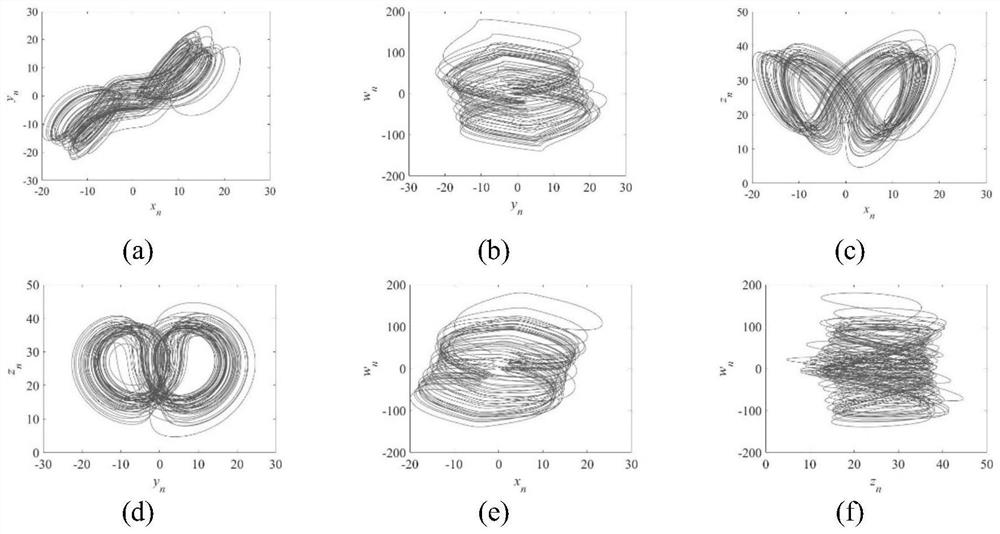
Latin square-based chaotic image encryption method
ActiveCN113300827AIncreased sensitivityIncreased complexitySecuring communication by chaotic signalsPictoral communicationAlgorithmCiphertext
The invention provides a Latin square-based chaotic image encryption method, which comprises the following steps of: generating a key by using an original image matrix, and inputting the key into a hyperchaotic Lorenz system to obtain a chaotic sequence; intercepting the chaotic sequence, converting the chaotic sequence into a matrix, and scrambling an original image matrix; intercepting the chaotic sequence to generate a Latin square matrix as a lookup table; intercepting the chaotic sequence and forming an index matrix, and selecting elements from corresponding coordinates in the lookup table by using the index matrix for replacement to obtain a pixel replacement matrix; and intercepting the chaotic sequence and generating a Latin square matrix, forming a bit matrix by using bit planes of the pixel replacement matrix, performing bit scrambling on the bit matrix by using the Latin square matrix, combining the bit matrix and the Latin square matrix into a bit plane matrix, and converting the bit plane matrix into a decimal system to obtain a ciphertext image. Latin square matrices used in the method are all generated by chaotic sequences, so that the complexity is enhanced, and the safety is improved; the randomness and the sensitivity are effectively improved, differential attacks can be effectively resisted, the decoding difficulty is increased, and the method is suitable for practical application.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
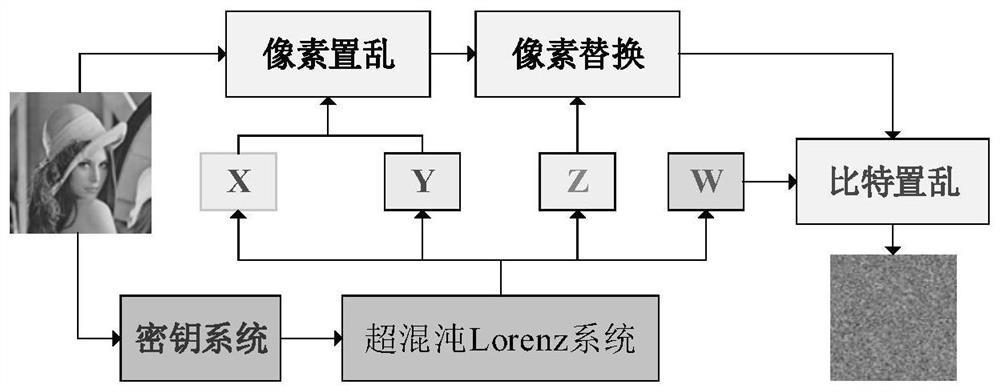
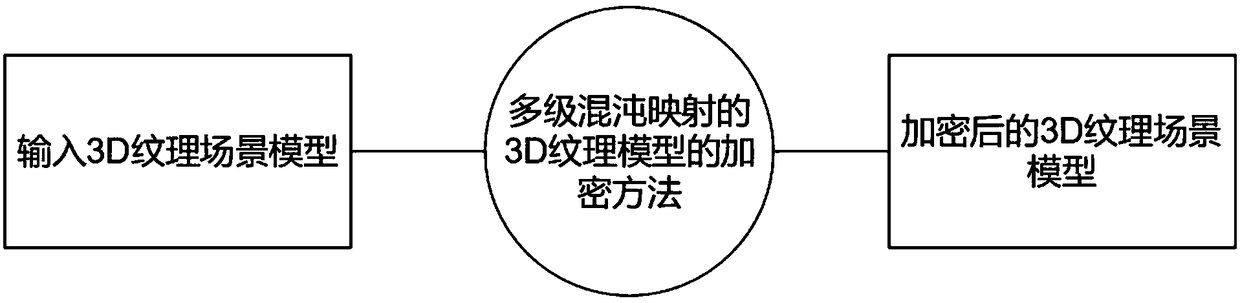
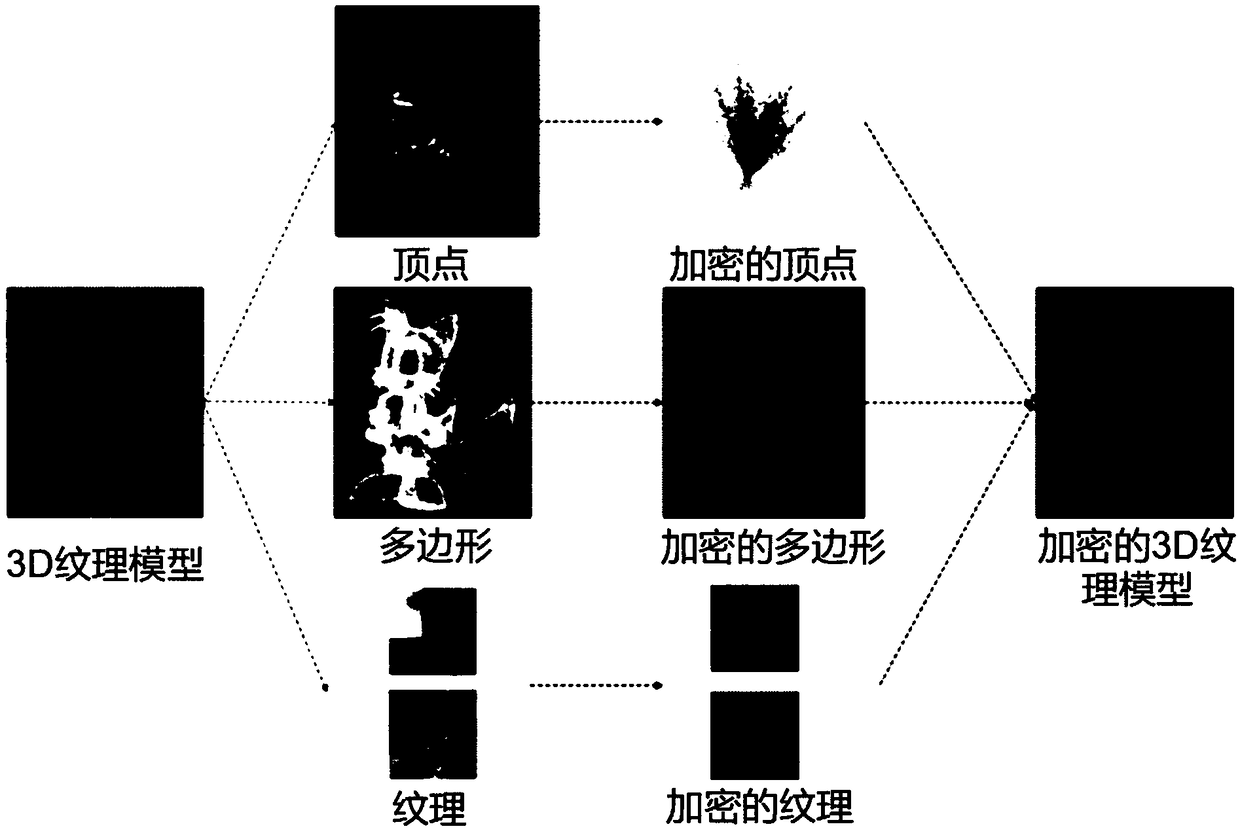
Encryption method of 3D texture model based on multi-level chaotic map
InactiveCN109039577AGood encryptionReduce contributionSecuring communication by chaotic signalsCryptographic attack countermeasuresPoint cloudTexture model
The invention provides an encryption method of 3D texture model based on multi-level chaotic map. Based on the contribution of the vertices (point clouds) of the 3D model, polygons and textures to 3Dmodel recognition, vertices that contribute most to identifying 3D models are encrypted using advanced 3D Lu mappings, and polygons and textures that contribute relatively little to identifying 3D models are encrypted using 2D Arnold mappings and 1D logistic mappings. The method is easily realized by software, and the invention can be widely applied to the fields of 3D printing, 3D modeling, 3D model secrecy and the like.
Owner:中共中央办公厅电子科技学院
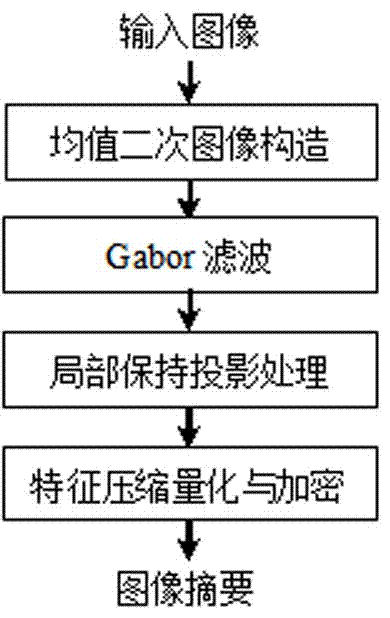
An Image Summarization Method Based on Mean Quadratic Image and Locality Preserving Projection
ActiveCN104778689BEfficient compressionAchieve compressionImage analysisCharacter and pattern recognitionPattern recognitionData compression
The invention discloses an image summarization method based on mean value quadratic image and local preserving projection, which is characterized in that it comprises the following steps: 1) mean value quadratic image construction; 2) Gabor filtering; 3) local preserving projection processing; 4) features Compression quantization and encryption; 5) Similarity calculation. The advantages of this method are: using the strategy of two image blocks to construct the average secondary image, which effectively compresses the image data and makes the average secondary image resistant to certain rotation operations; uses the Gabor filter to process the average secondary image Filtering effectively improves the robust performance of the summary method; using local preservation projection to reduce the dimensionality of the filtering results, quantizing the variance into bits, and further realizing data compression; using the Skew tent chaotic map to perform XOR encryption on the variance bit sequence , which ensures the security of the image summary; the extracted image summary has good robustness, uniqueness and security.
Owner:广东英视科技有限公司
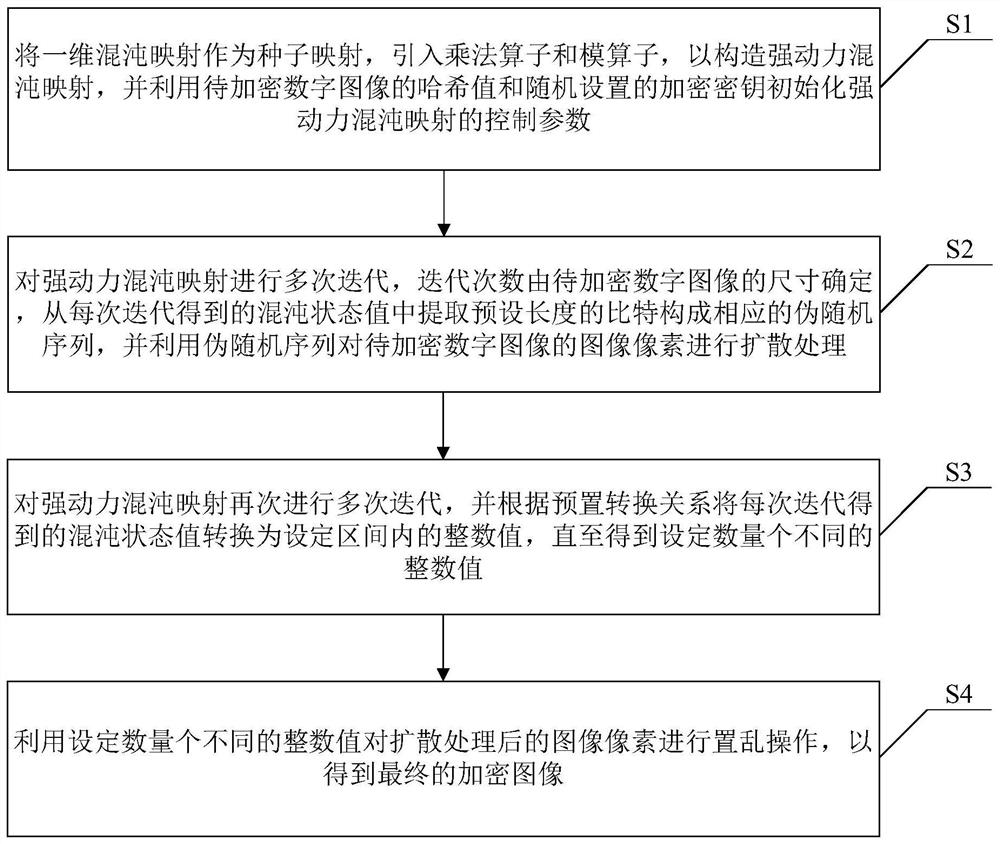
Digital image encryption method, decryption method and system based on chaotic system
PendingCN114157408ALarge dynamic propertiesStrong dynamic propertiesSecuring communication by chaotic signalsChaotic systemsDigital image
The invention discloses a digital image encryption method, decryption method and system based on a chaotic system, and belongs to the field of chaotic image encryption, and the encryption method comprises the steps: taking a one-dimensional chaotic mapping as a seed mapping, introducing a multiplication operator and a modular operator, constructing a strong dynamic chaotic mapping, initializing a control parameter of strong dynamic chaotic mapping by using the hash value of the digital image to be encrypted and the encryption key; iterating the strong dynamic chaotic mapping for multiple times, extracting bits with a preset length from a chaotic state value obtained by each iteration to form a corresponding pseudo-random sequence, and diffusing image pixels of the digital image to be encrypted by using the pseudo-random sequence; and performing multiple iterations on the strong dynamic chaotic mapping again, converting a chaotic state value obtained by each iteration into an integer value in a set interval until a set number of different integer values are obtained, and performing scrambling operation on image pixels after diffusion processing to obtain a final encrypted image. And the digital image is encrypted safely and effectively.
Owner:HUAZHONG UNIV OF SCI & TECH
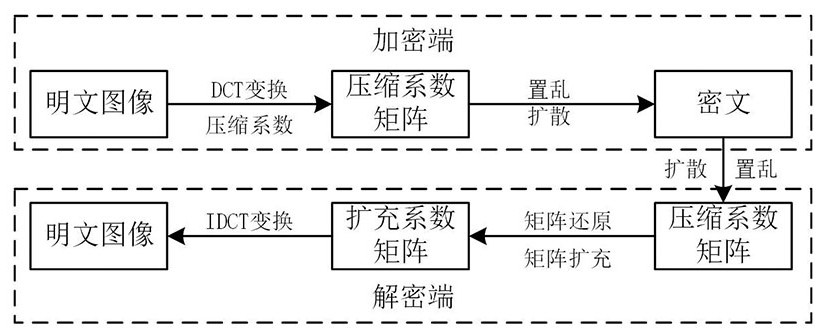
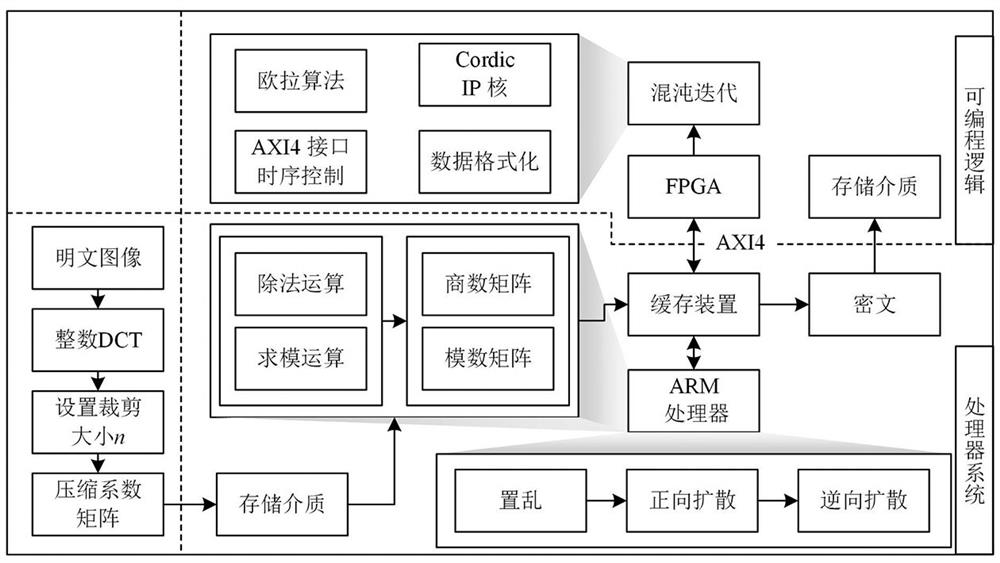
Compressible six-dimensional non-degenerate hyperchaotic image secrecy system and method
PendingCN113890722AImprove discretization speedReduce data volumeSecuring communication by chaotic signalsDigital video signal modificationConcurrent computationAlgorithm
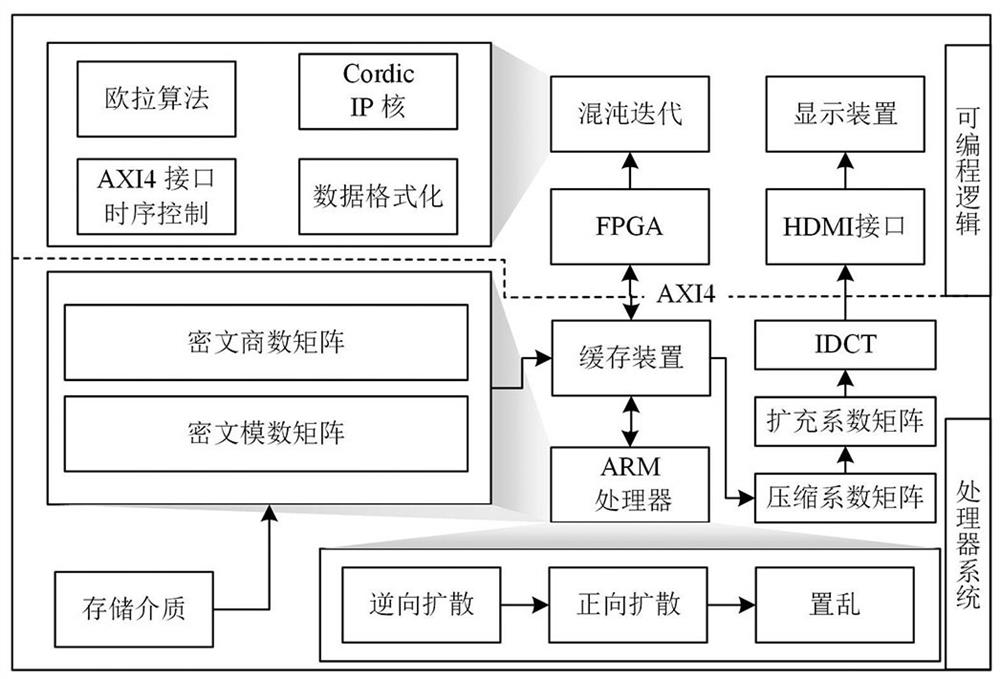
The invention discloses a compressible six-dimensional non-degenerate hyperchaotic image secrecy system and method. Image data are compressed at an encryption end to obtain a compression coefficient matrix, and the matrix is encrypted by combining a hyperchaotic sequence at the encryption end to obtain ciphertext data. And the decryption end sets an initial value of the hyper-chaotic system according to the key, decrypts the ciphertext data by a chaotic sequence of the hyper-chaotic system of the decryption end, and further reduces the ciphertext data to obtain a plaintext image. The encryption end and the decryption end complete encryption and decryption operations by using SOPC resources, the FPGA performs parallel acceleration on the hyperchaotic discretization process in the SOPC, and the ARM processor completes the image encryption and decryption process in combination with a chaotic sequence. According to the method, hardware resources can be effectively saved in the application process, the discretization speed of the hyperchaotic system is increased by applying the parallel computing advantages of the FPGA, and then the working efficiency of an image secrecy system is improved.
Owner:HUNAN UNIV OF SCI & TECH
Selective satellite image compression encryption method based on Chacha20 and CCSDS
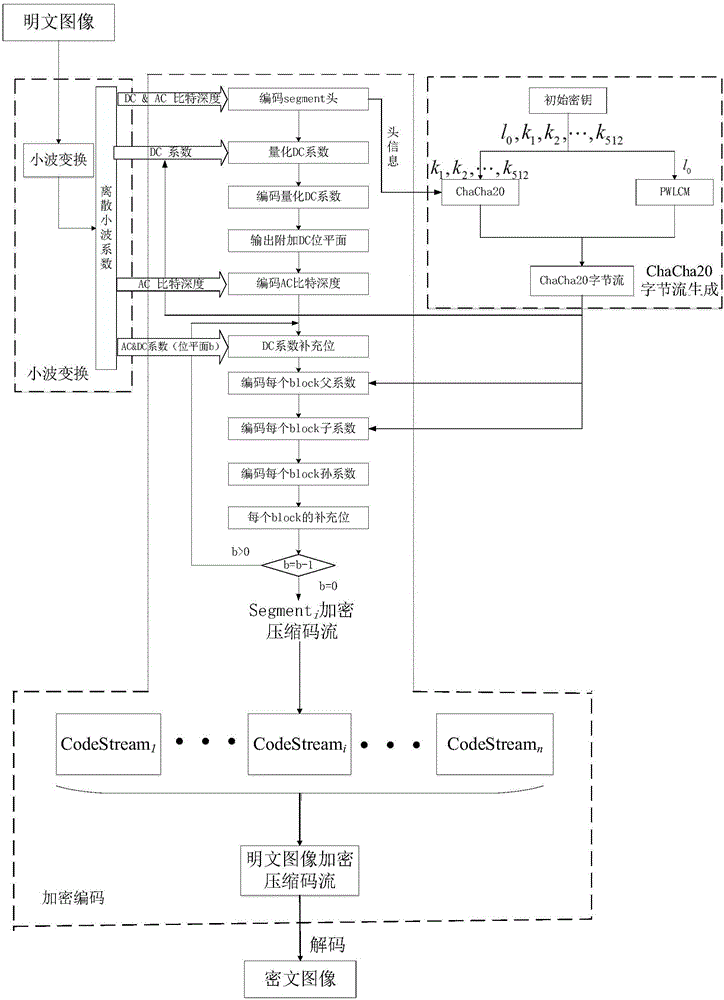
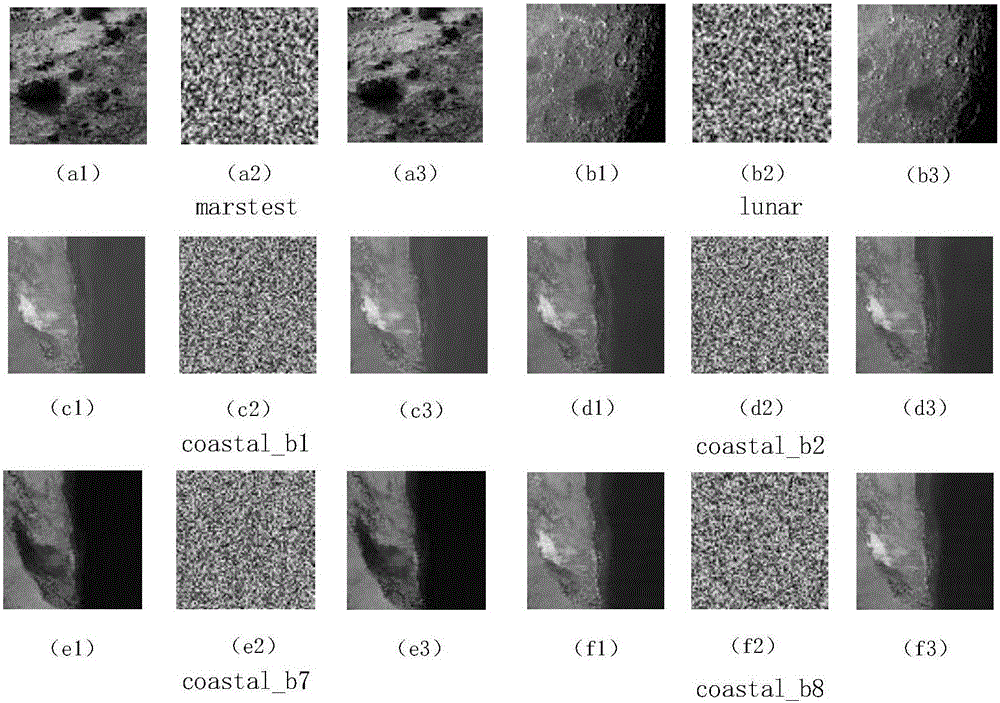
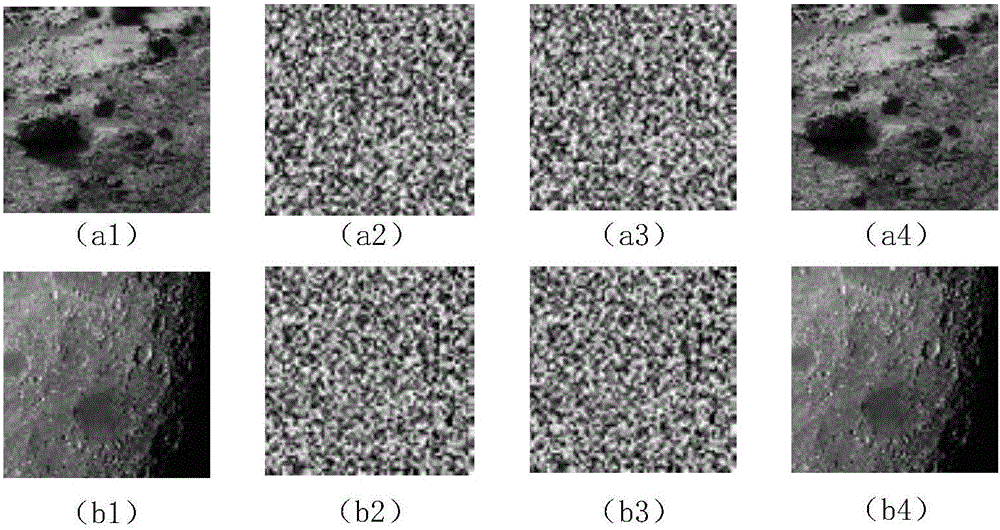
InactiveCN105704499AIncreased sensitivityHigh encryption strengthDigital video signal modificationPlaintextAc coefficient
The invention provides a selective satellite image compression encryption method based on Chacha20 and CCSDS. Aiming the characteristics of a satellite image, the method comprises the steps: firstly carrying out the three-stage two-dimensional discrete wavelet transformation through employing a 9 / 7 integral wavelet in a CCSDS image compression algorithm, and obtaining a DC coefficient and an AC coefficient after transformation; secondly generating a ChaCha20 initial byte stream through the head information in a coding item and a 512-bit initial secret key and ChaCha20 Hash; thirdly carrying out the summation and modular operation of a chaos initial secret key and a plaintext image normalization value through the byte stream generated by PWLCM (Piecewise Linear Chaotic Map) and the ChaCha20 initial byte stream, and generating a ChaCha20 byte stream; fourthly carrying out the XOR encryption of the ChaCha20 byte stream and the DC coefficient and AC coefficient (the father and son coefficients in each block) and all AC coefficient symbol bites; finally enabling the encrypted DC and AC coefficients to be coded and compressed, and completing the compression and encryption of the satellite image. The generation of the ChaCha20 byte stream is related with the to-be-encrypted satellite image and a compression coding parameter, thereby improving the encryption adaptability.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Encryption and decryption method based on self-synchronizing chaotic stream ciphers of 1D-ICMIC (One Dimensional-Iterative Chaotic Maps with Infinite Collapses)
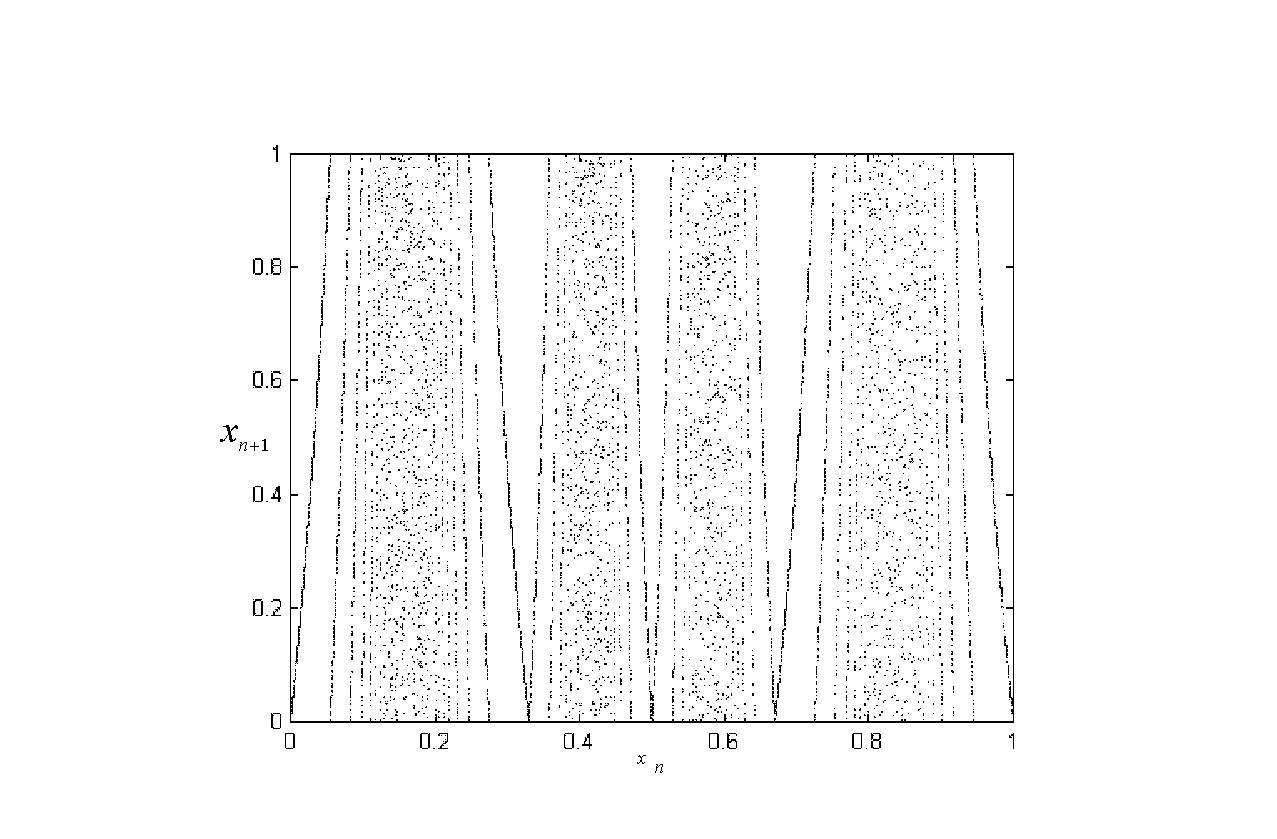
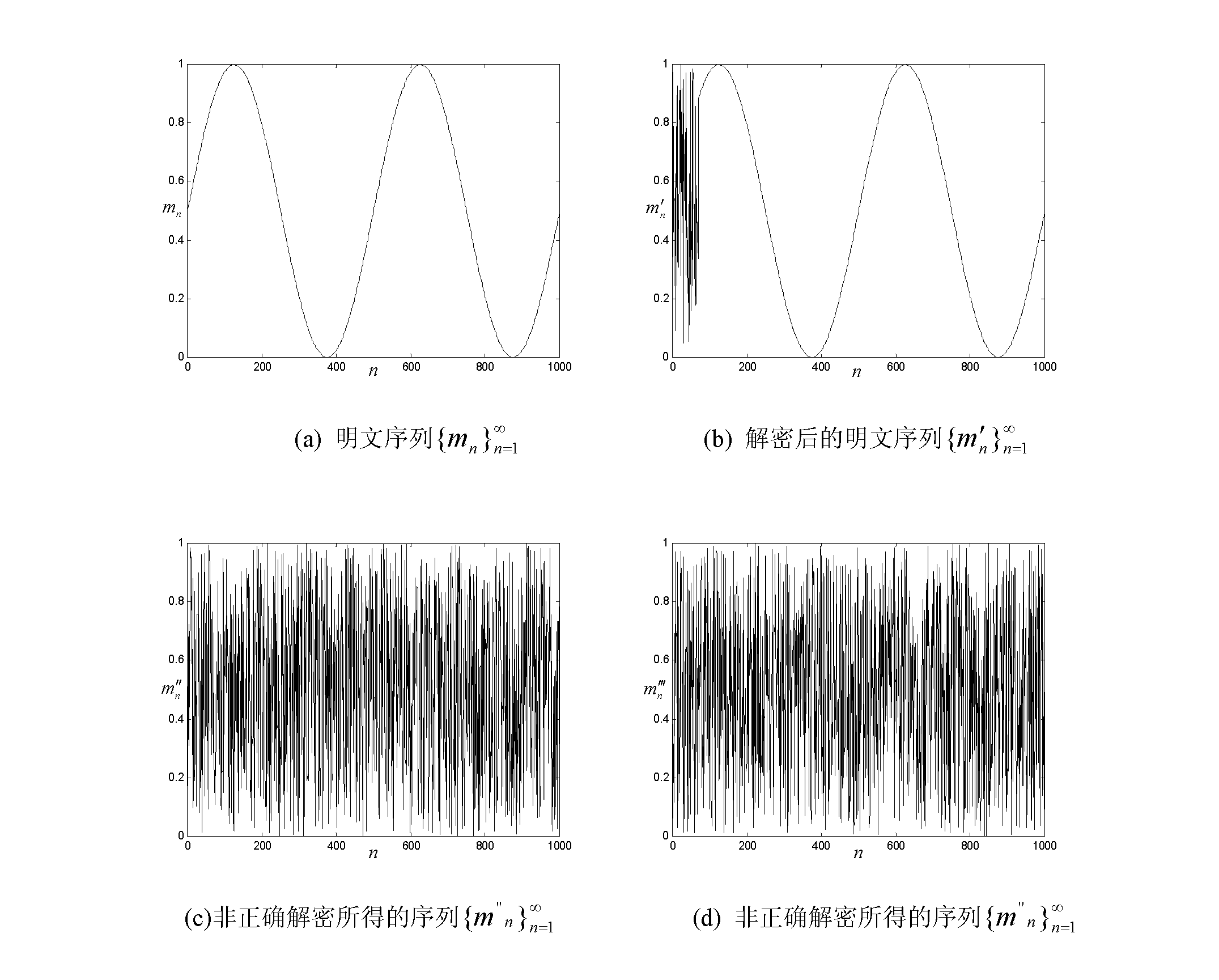
InactiveCN102629899ASimple encryption and decryption methodEfficient encryption and decryption methodsSecuring communicationComputer hardwareCiphertext
The invention relates to an encryption and decryption method based on self-synchronizing chaotic stream ciphers of 1D-ICMIC (One Dimensional-Iterative Chaotic Maps with Infinite Collapses). The encryption and decryption method comprises the following steps: (1) generating a key stream sequence Kn+1 by using the self-synchronizing chaotic stream ciphers of the 1D-ICMIC through an encryption terminal; and (2) encrypting a clear text sequence Mn+1 by using the key stream sequence Kn+1 and then obtaining a mod value, and generating a ciphertext sequence Cn+1, wherein cn+1=mod (mn+1+kn+1, 1). The invention provides the simple, efficient and safe encryption and decryption method for encryption functions based on the self-synchronizing chaotic stream ciphers of the 1D-ICMIC according to the composite mapping formed by one-dimensional piecewise linear mapping (ID-PLM) and the 1D-ICMIC.
Owner:XI'AN INST OF OPTICS & FINE MECHANICS - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com