Test data encryption method based on S box and chaotic map
A technology of chaotic mapping and testing data, which is applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., can solve complex security issues and achieve resistance to exhaustive attacks and large key space Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
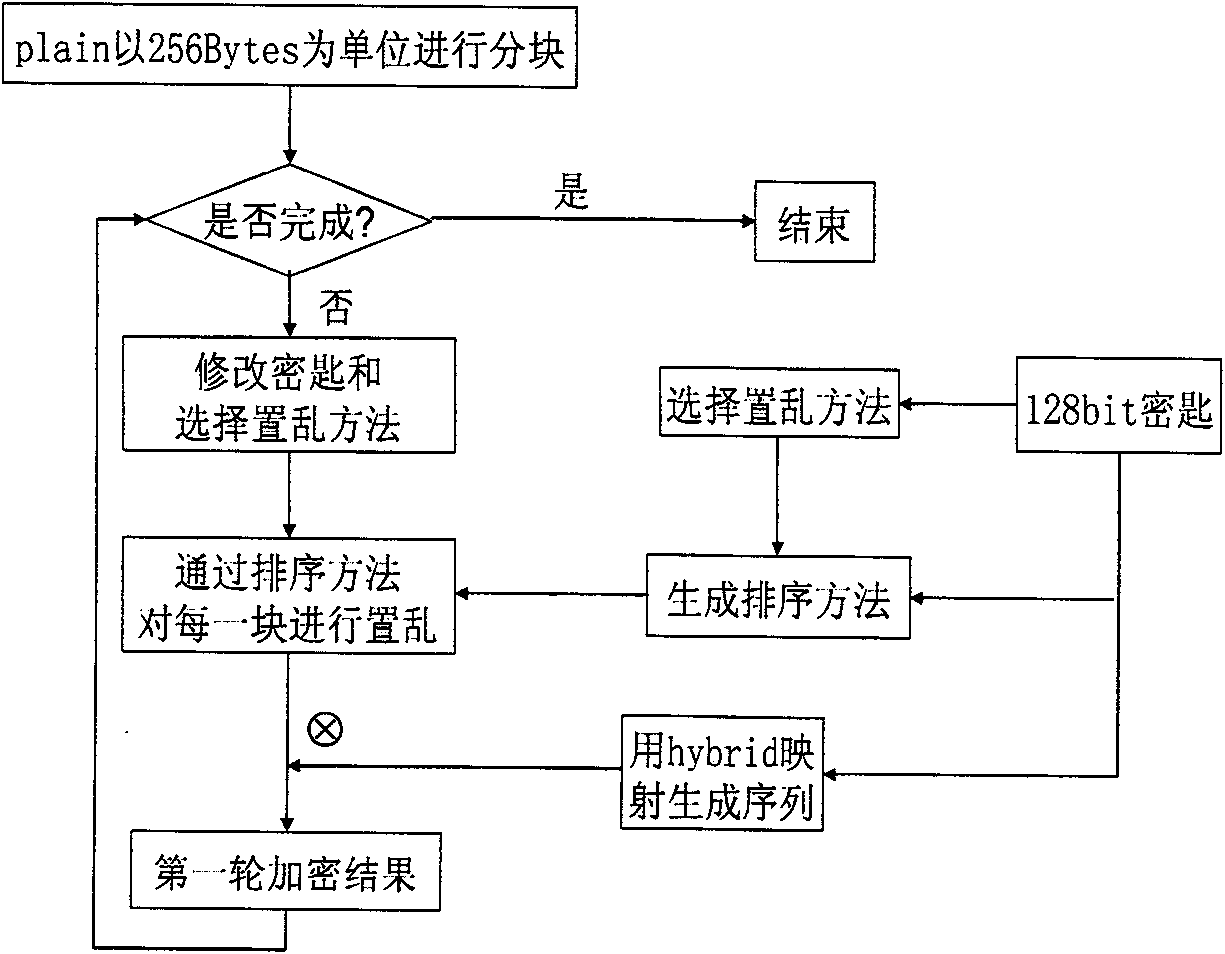
[0080] Now in conjunction with embodiment, accompanying drawing, the present invention will be further described:
[0081] Encryption process:
[0082] The encryption party chooses a 128-bit key, represented by four unsigned integer numbers (key0, key1, key2, key3), and the number of encryption rounds is 20 times.
[0083] Step 1: Generate three key initial values cheKey1, cheKey2, cheKey3:
[0084] 1) The generation process of the initial value cheKey1
[0085] x0=(key0 / 0xffffffff+key1 / 0xffffffff) / 2
[0086] x1=(key2 / 0xffffffff+key3 / 0xffffffff) / 2
[0087] Take x0 and x1 as initial values, parameter k=4.000, map with chebyshev, iterate 100 times respectively to generate x01 and x11;
[0088] x=(x01+x11) / 2
[0089] The chebyshev mapping formula is:
[0090] x n+1 =cos[K arccos(x n )]x n ∈ [-1, 1], K ≥ 2
[0091] Then take x as the initial value, parameter k=3.000, and use chebyshev mapping to iterate 100 times to generate cheKey1.
[0092] 2) Selection process of i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com