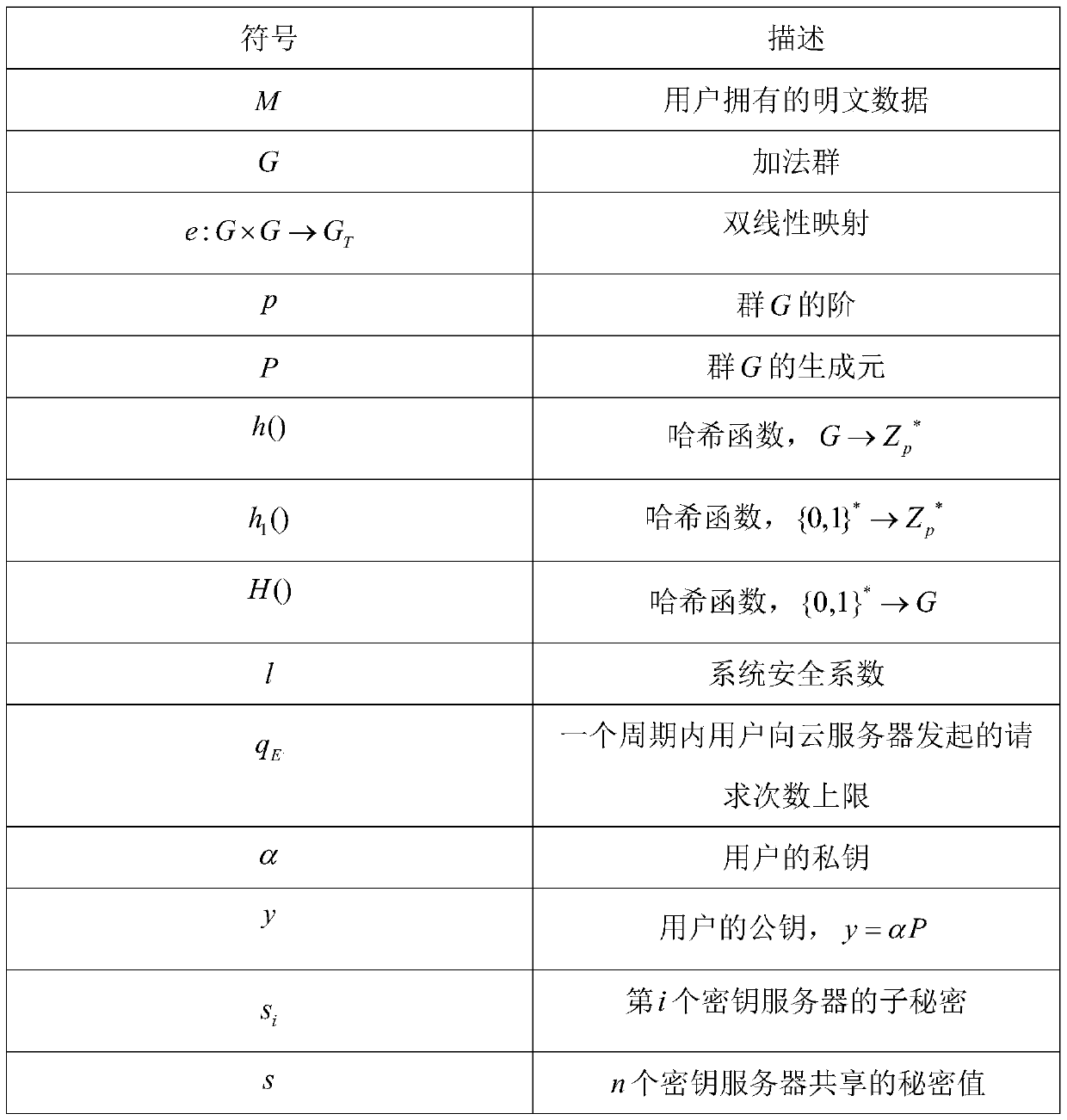
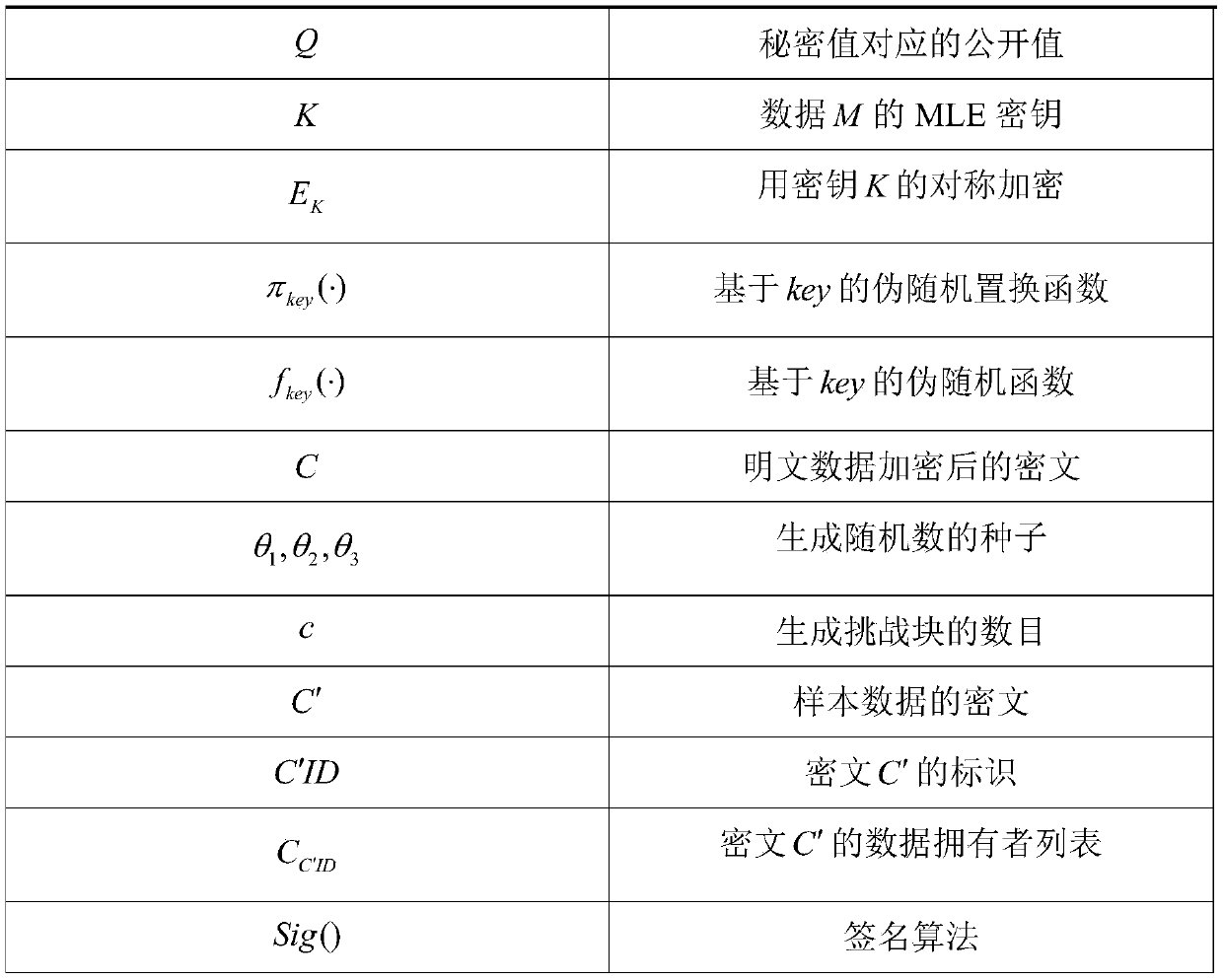
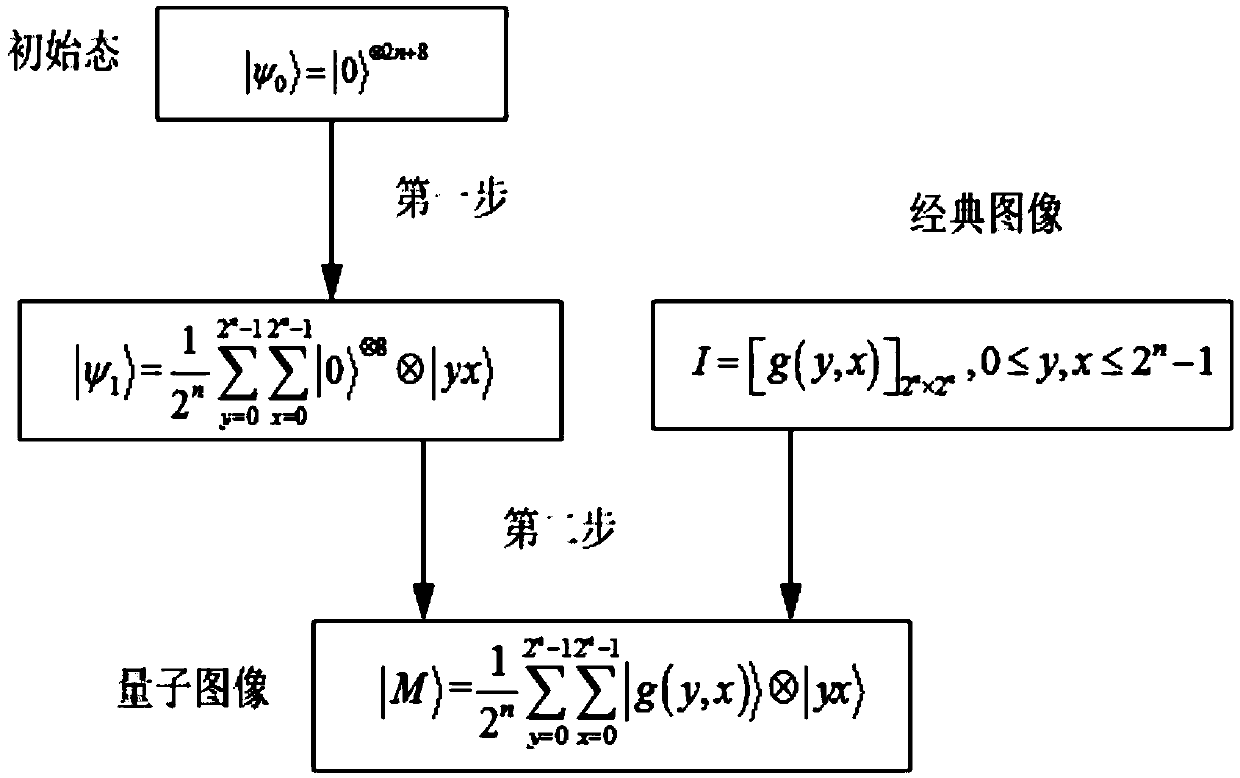
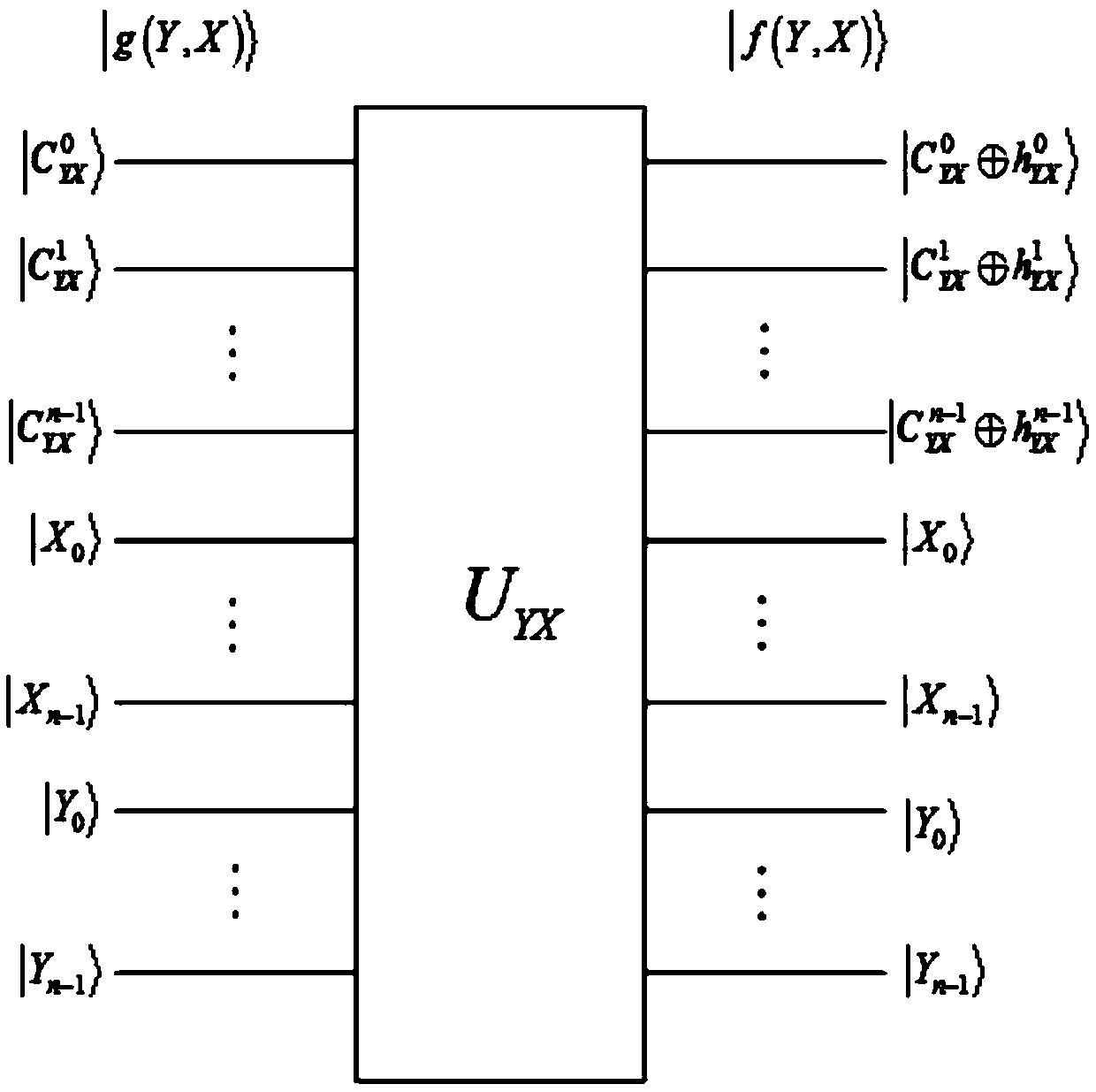
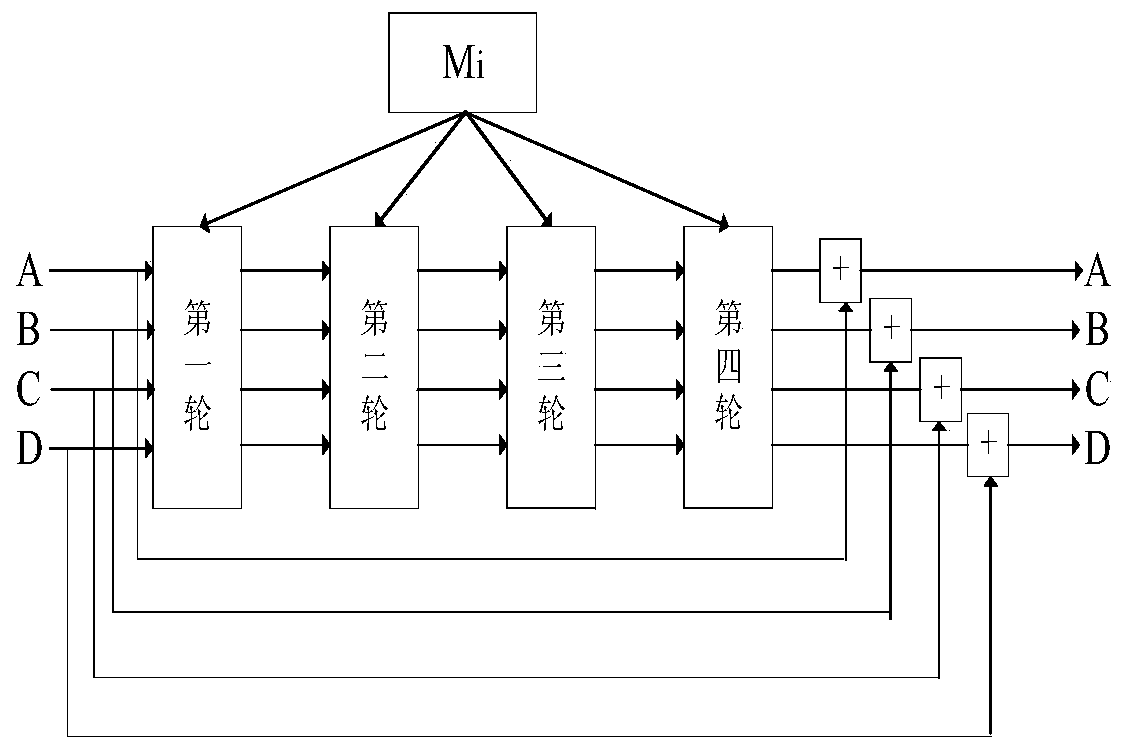
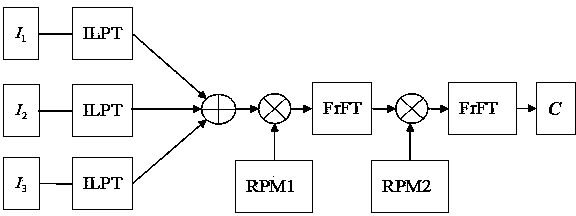
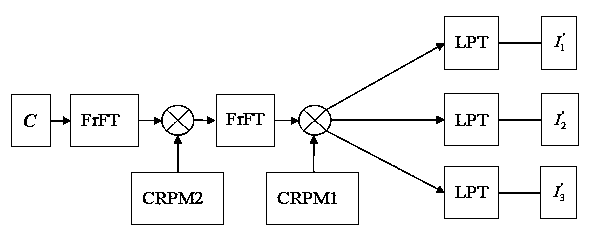
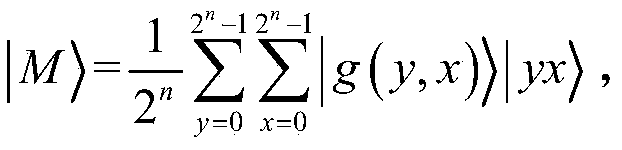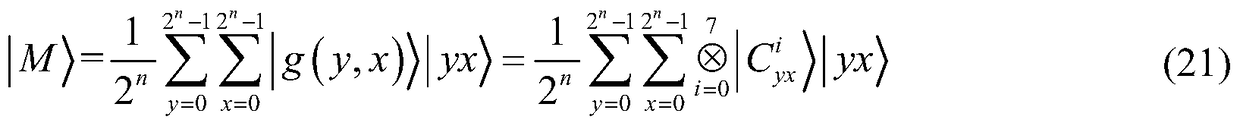Patents
Literature
38results about How to "Resist Brute Force Attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
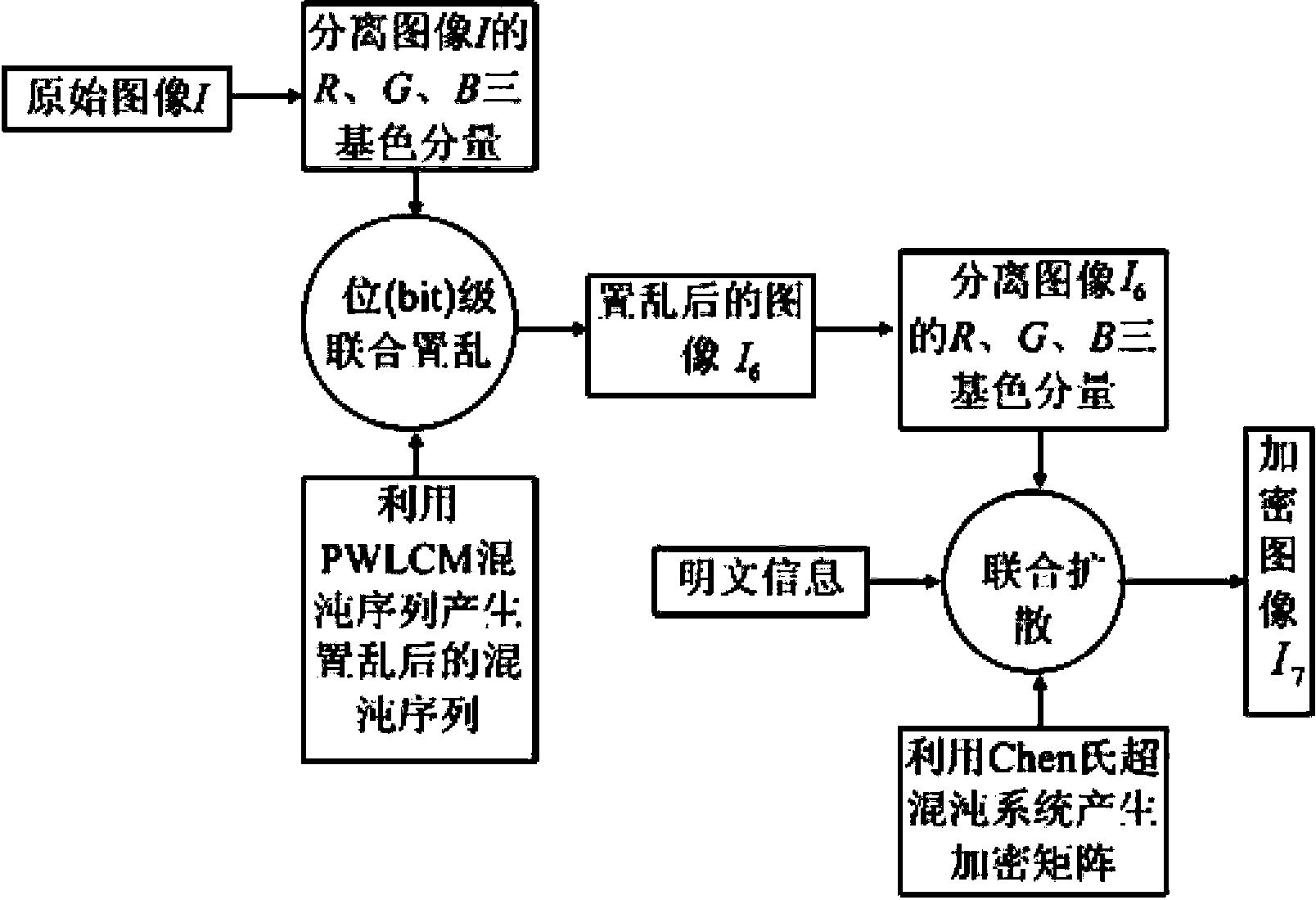
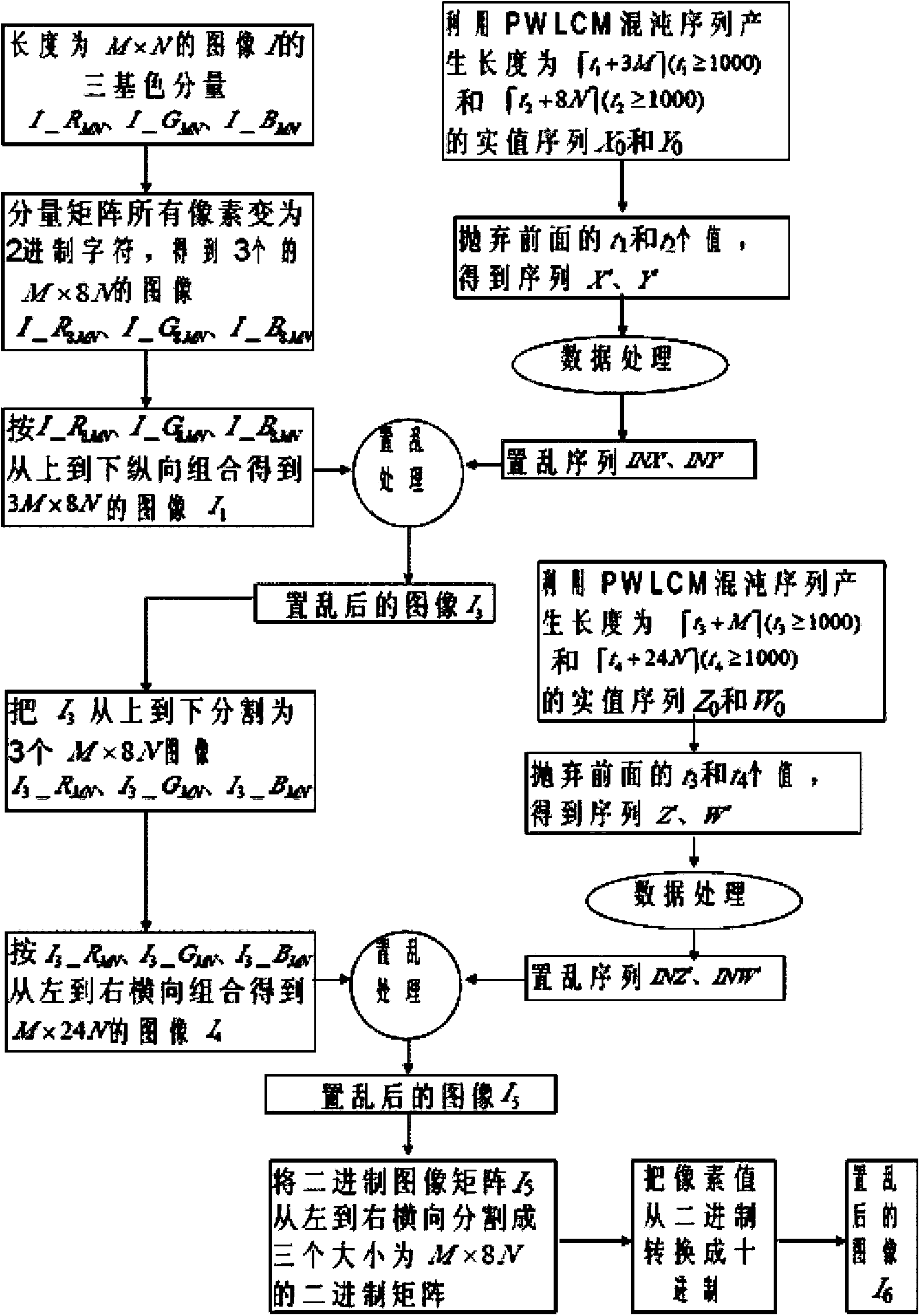
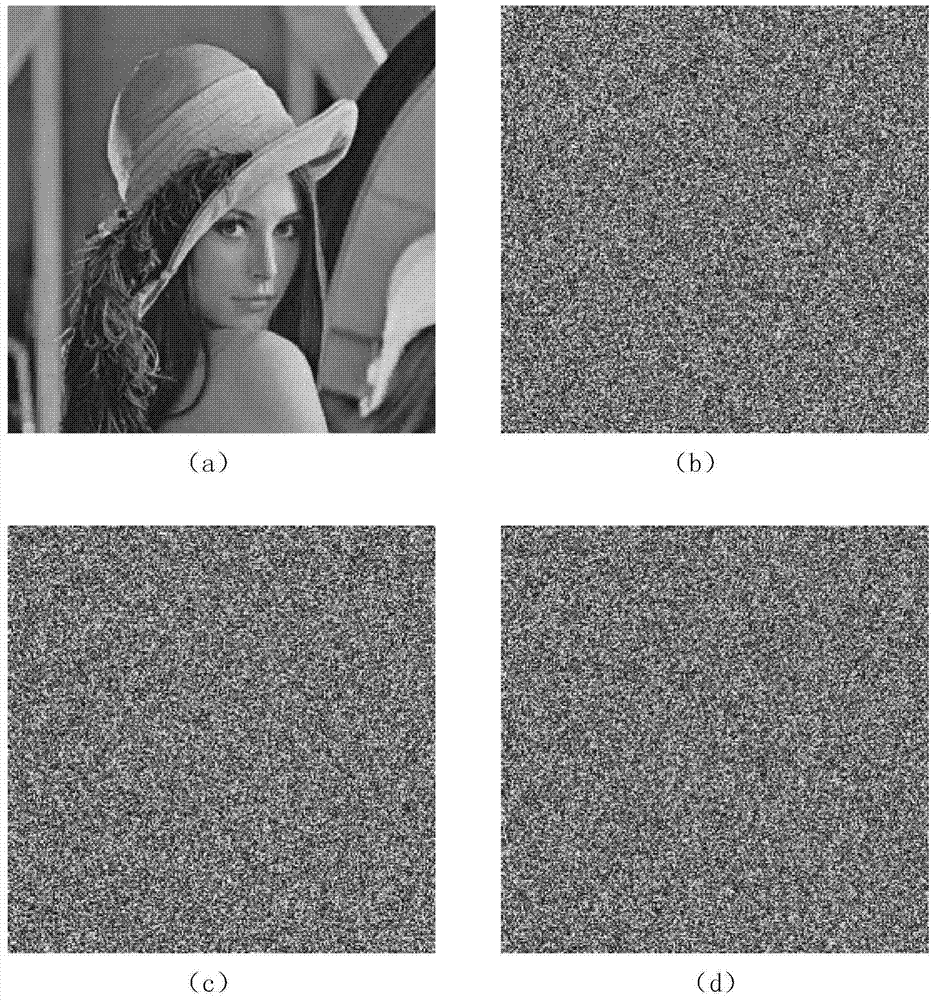
Color image encryption method based on chaos sequence and hyper-chaos system
InactiveCN103489151AImprove securityLarge key spaceImage data processing detailsChaotic systemsDiffusion
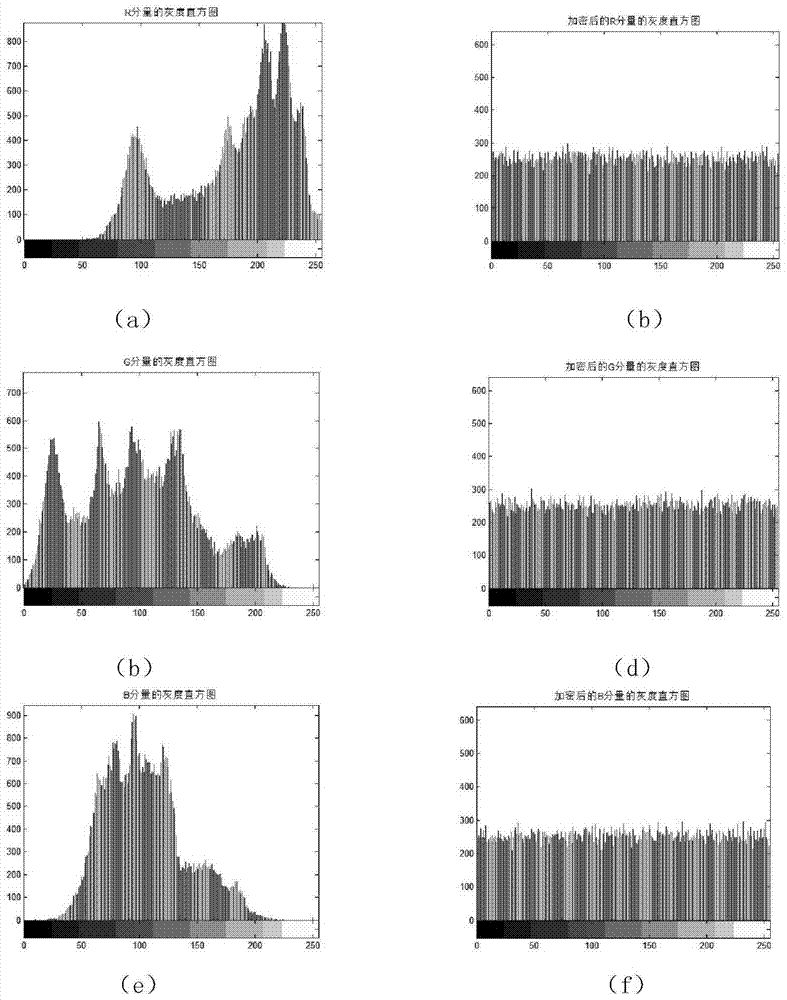
The invention relates to a color image encryption method based on a chaos sequence and a hyper-chaos system. The color image encryption method mainly comprises the following steps: an original color image is subjected to bit level united scrambling to obtain a scrambled image; the scrambled image is decomposed into three primary color components, that is R, G and B, and the hyper-chaos system is used for generating an encryption matrix which is used for encrypting the scrambled image; all pixel values of the three primary color components of the scrambled image are changed by utilizing the encryption matrix in combination with plaintext information and information of the three primary color components, united diffusion is conducted to obtain the three primary color components of the image after the united diffusion, and therefore a final encrypted image is obtained. By means of the color image encryption method, a secret key space is greatly enlarged, the safety, the encryption effect and the sensitivity of a secret key are higher, the anti-attack ability is stronger, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
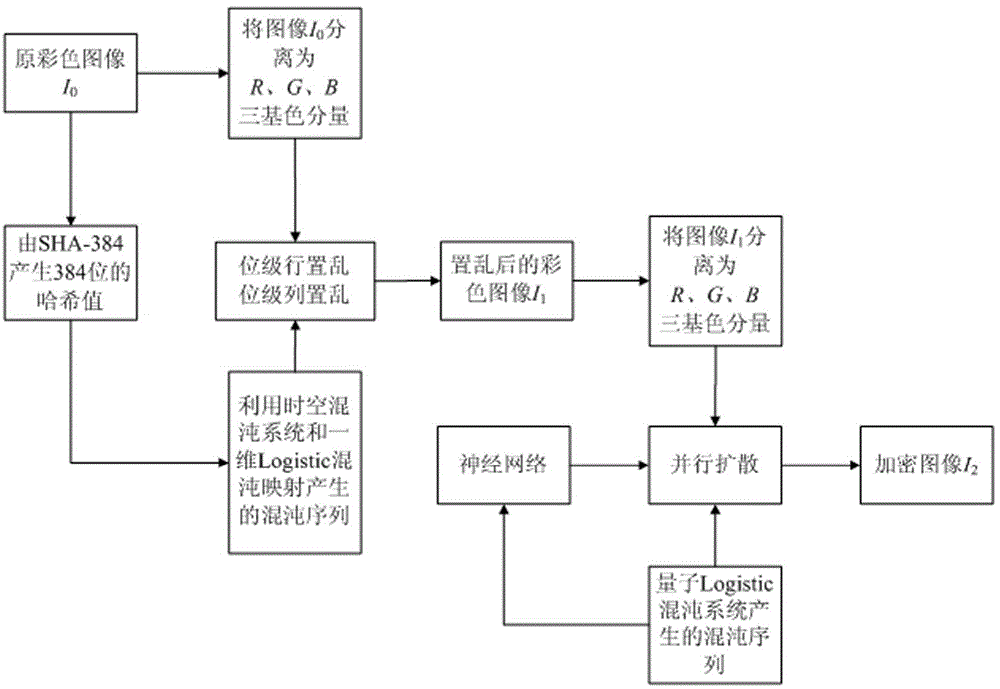
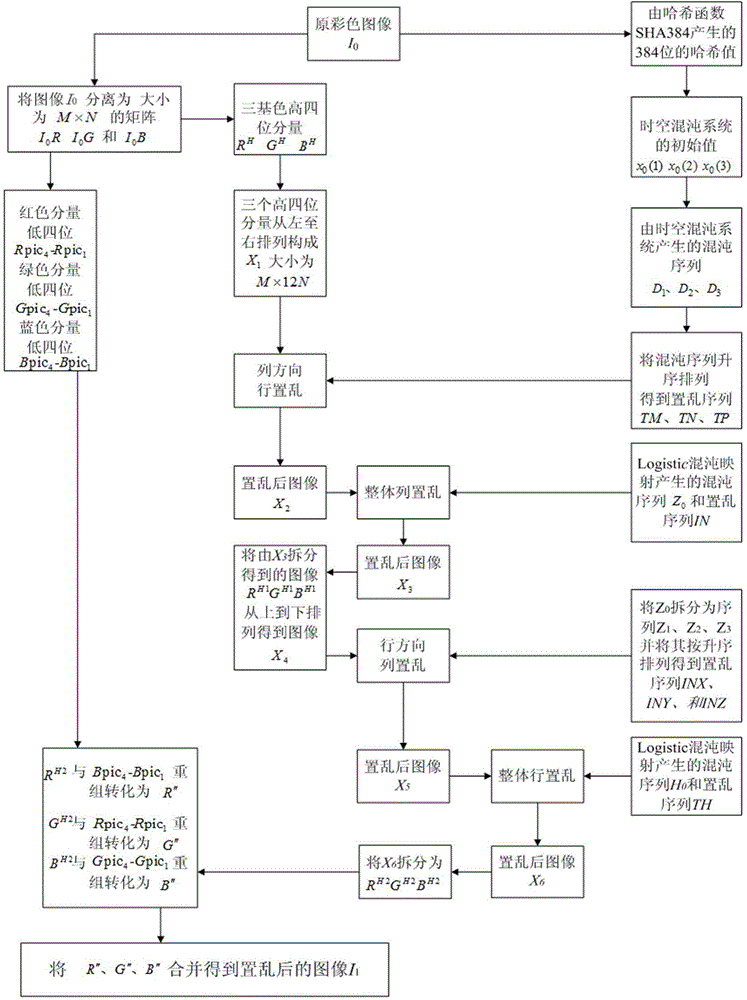
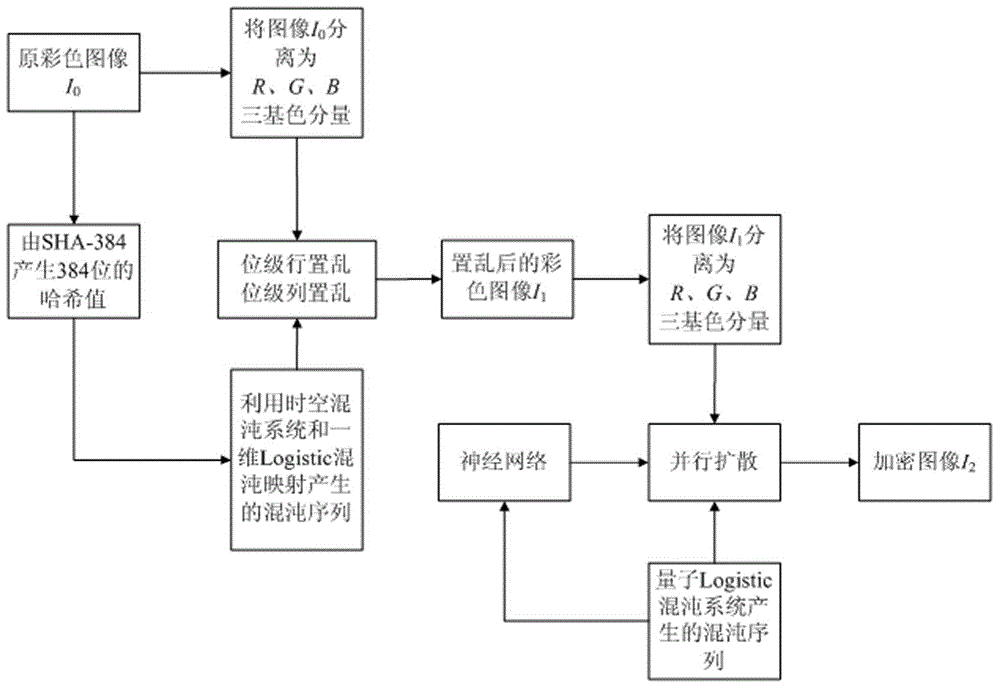
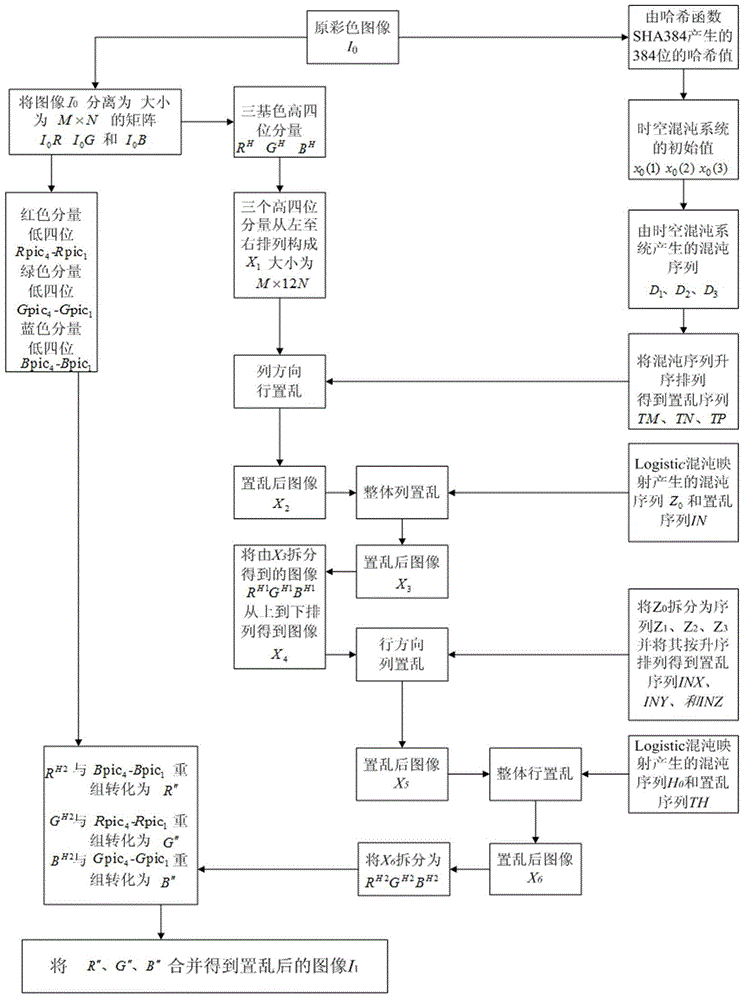
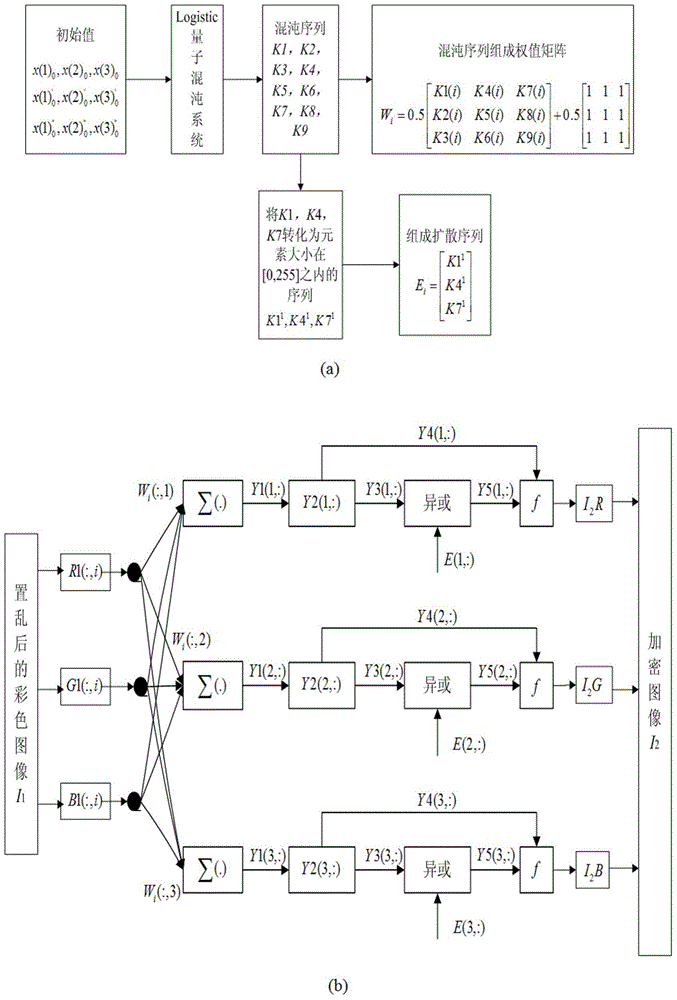
Color image encryption method based on SHA-384 function, spatiotemporal chaotic system, quantum chaotic system and neural network
ActiveCN104008520AImprove securityLarge key spaceImage data processing detailsComputer hardwareDiffusion
The invention relates to a color image encryption method based on an SHA-384 function, a spatiotemporal chaotic system, a quantum chaotic system and a neural network. The method includes the steps that an original color image I0 is calculated through the SHA-384 function, a Hash value is obtained as a secret key, the Hash value, a CML and one-dimension Logistic chaotic mapping are utilized for generating a chaos sequence, bit-level line-column scrambling is carried out on high four-digit images of components of three primary colors of the I0 through the chaos sequence, and a scrambled image I1 is obtained; the Logistic quantum chaotic system is utilized for generating a chaos sequence for encrypting the scrambled image, and is combined with the neural network to carry out parallel diffusion processing on all pixel values of components of three primary colors of the I1, and a final encrypted image I2 is obtained. By the method, the space of the secret key is greatly enlarged, the safety, encryption effect and secret key sensibility are higher, the attack resistance capacity is higher, the scrambling process and the encryption time are shorter, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
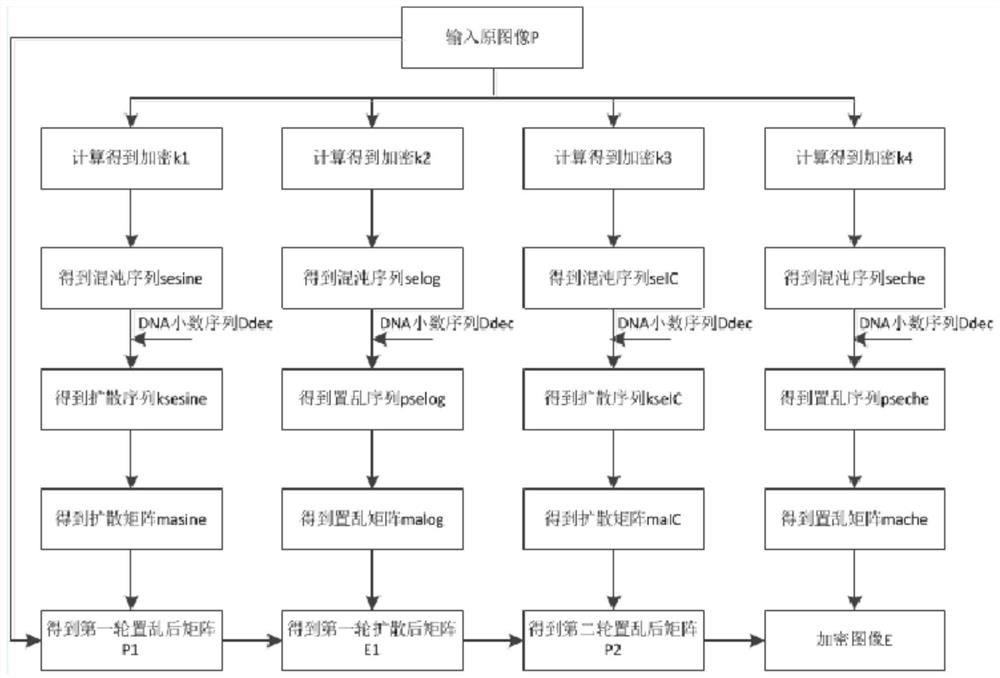
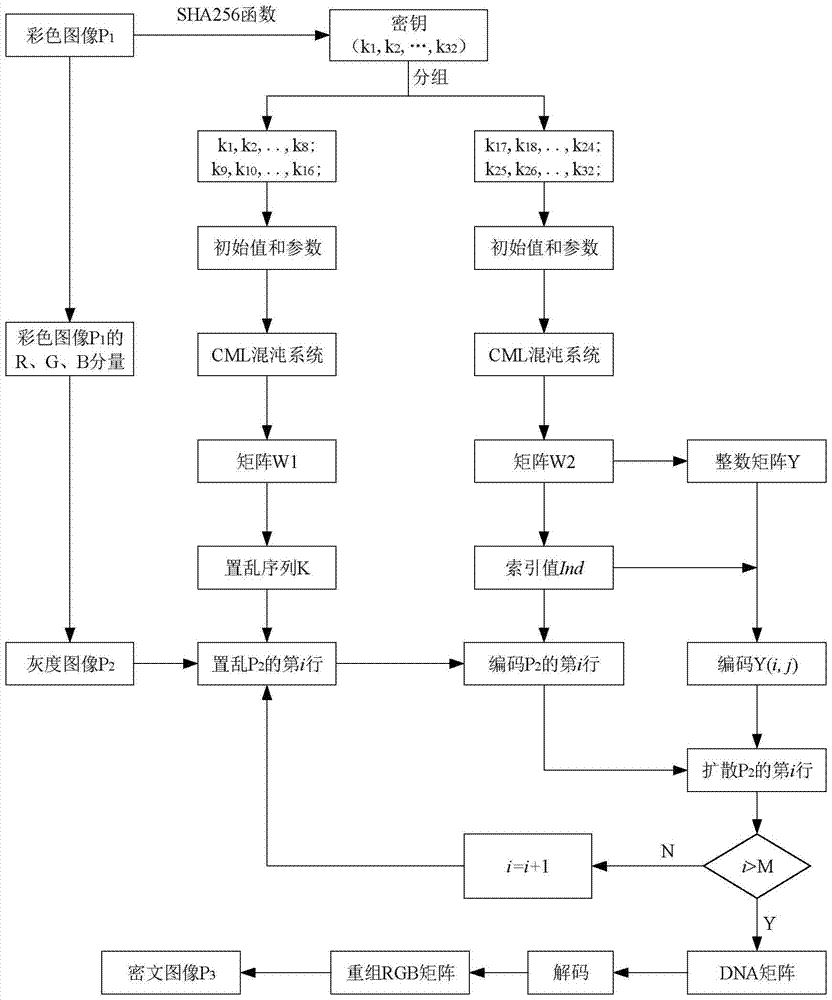
DNA dynamic coding based colored image encryption method
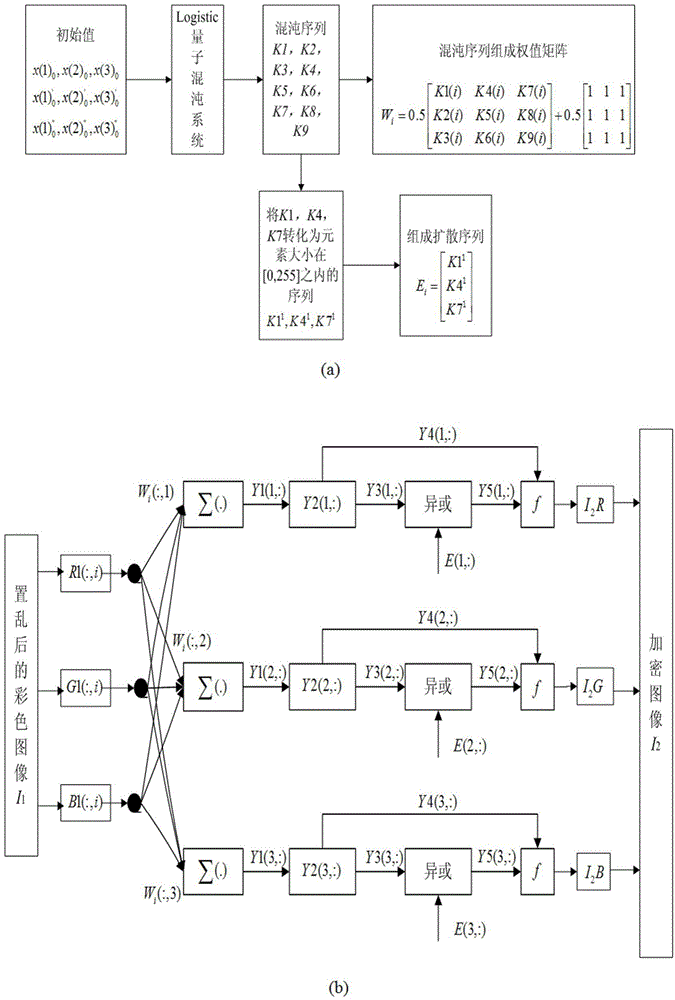
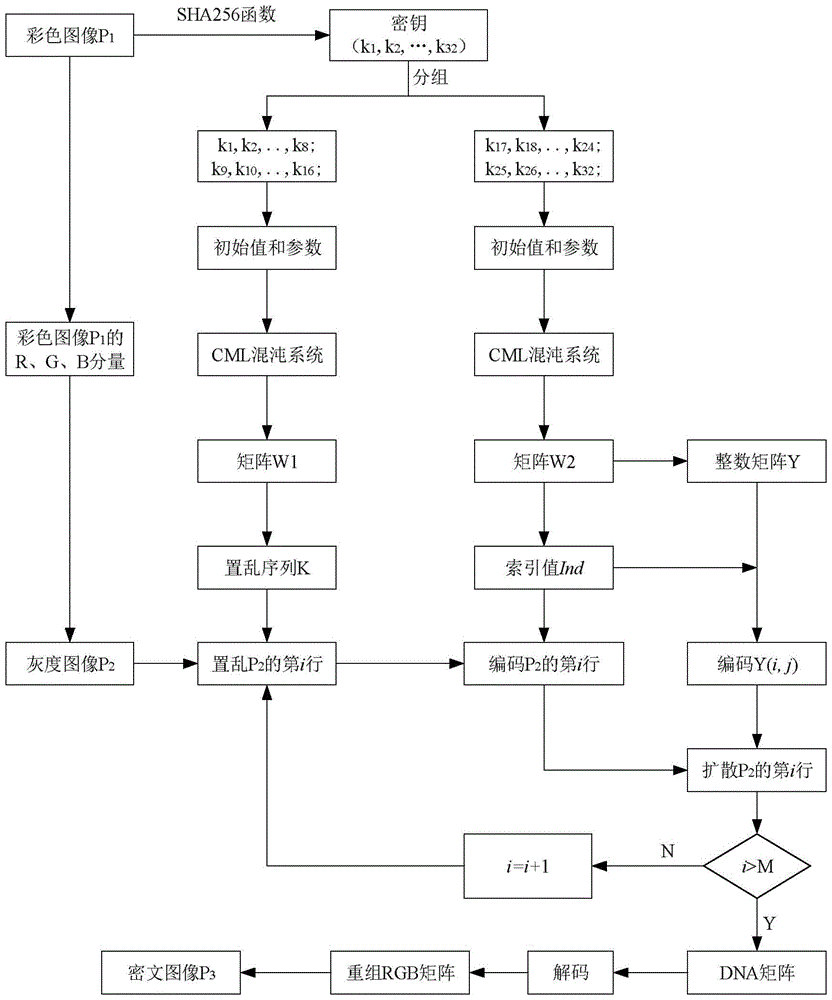
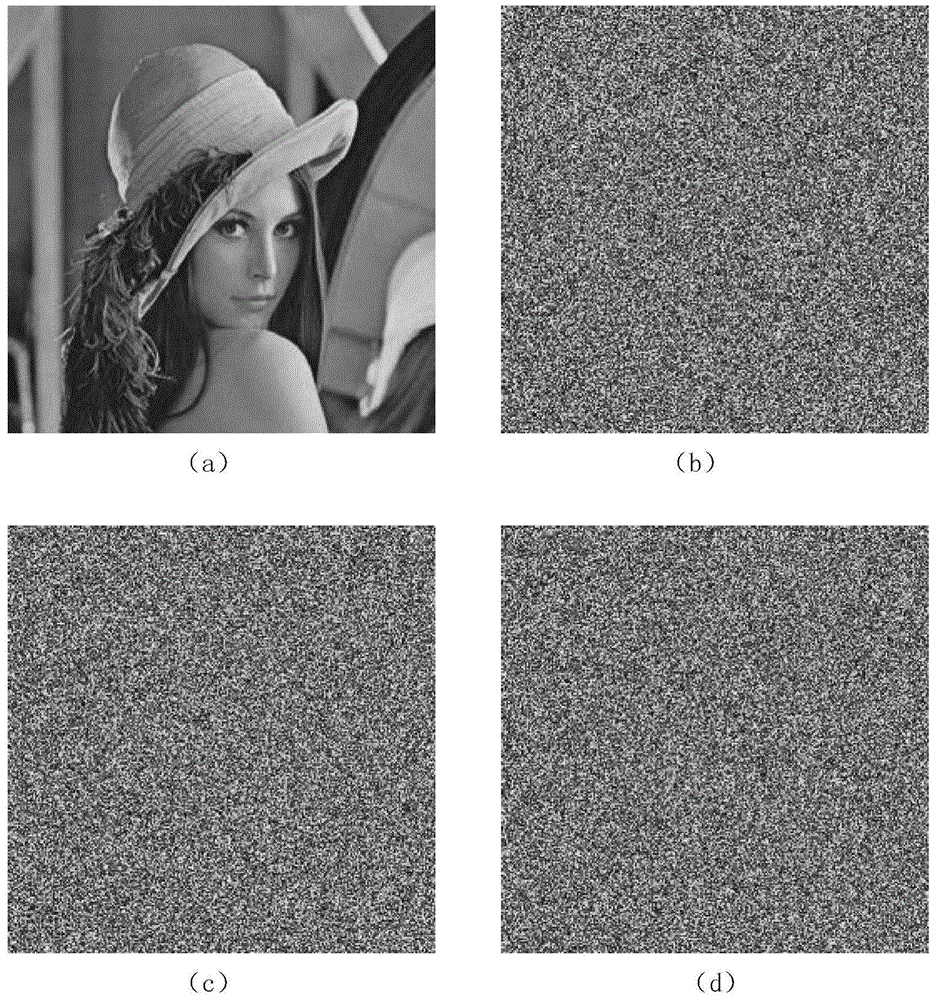
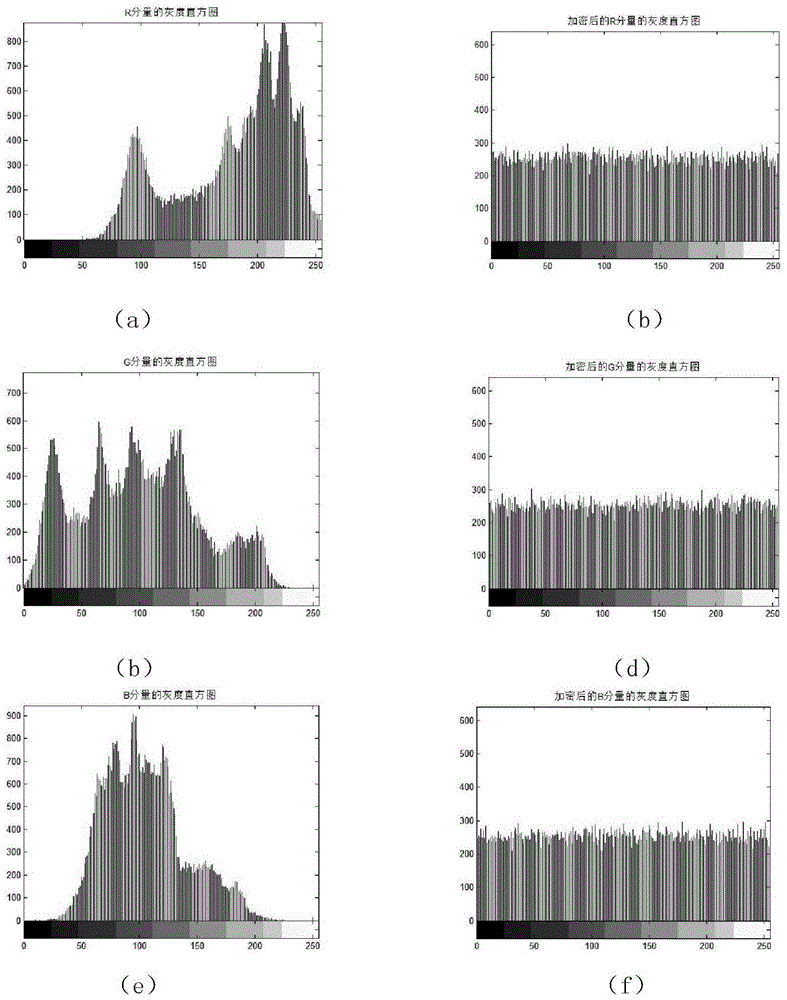
The present invention relates to a DNA dynamic coding based colored image encryption method, comprising: obtaining a key through a colored plain-text image; by the key, calculating an initial value and a parameter of a chaotic system used in scrambling and diffusion processes; substituting the initial value and the parameter to the chaotic system for iteration to obtain W1 and W2, obtaining a scrambling matrix K from W1, obtaining an integer matrix Y and an index matrix Ind from W2, and performing DNA coding on Y according to the index matrix Ind; and performing scrambling on the plain-text image row by row by using the matrix K, then performing coding and diffusion until all rows finish DNA coding, and finally performing decoding and recomposing on a DNA matrix, to obtain a final colored ciphertext image. According to the method, a function SHA256 is used to generate the key, so that the key space is expanded; the generation of the key depends on a plain-text, so that plain-text attack can be effectively resisted; chaotic characteristics are combined with DNA dynamic coding, so that the security is further improved; and meanwhile, scrambling and diffusion operations are performed according to the row of images, so that parallel computing is facilitated and the efficiency is improved.
Owner:HENAN UNIVERSITY
Diffusion mapping scrambling and chaotic system combined image encryption method
InactiveCN108133445ALarge key spaceResist key brute force attackImage data processing detailsBit planeChaotic systems
The invention provides a diffusion mapping scrambling and chaotic system combined image encryption method, which is characterized by forming a diffusion matrix and an Arnold mapping matrix through a chaotic sequence generated by a two-dimensional nonlinear dynamical system constructed by a Logistic system; then, carrying out diffusion on a color image in primary colors, and carrying out scramblingon the color image on different bit planes; finally, carrying out encryption on a scrambled image file through a chaos sequence generated by a Chen system; and under the action of a key, generating achaos sequence through the Chen system and module operation, and carrying out multiple XOR operation to decrypt the encrypted image. The method adopts the Chen chaotic system and chaotic system combined encryption, has a very large key space and can resist key exhaustive attack; statistical distribution of the encrypted image is completely destroyed, and the method has a very good ability to resist statistical analysis; and the file encryption method can effectively resist attacks using pixel correlation analysis.
Owner:QINZHOU JINGTONG TECH CO LTD
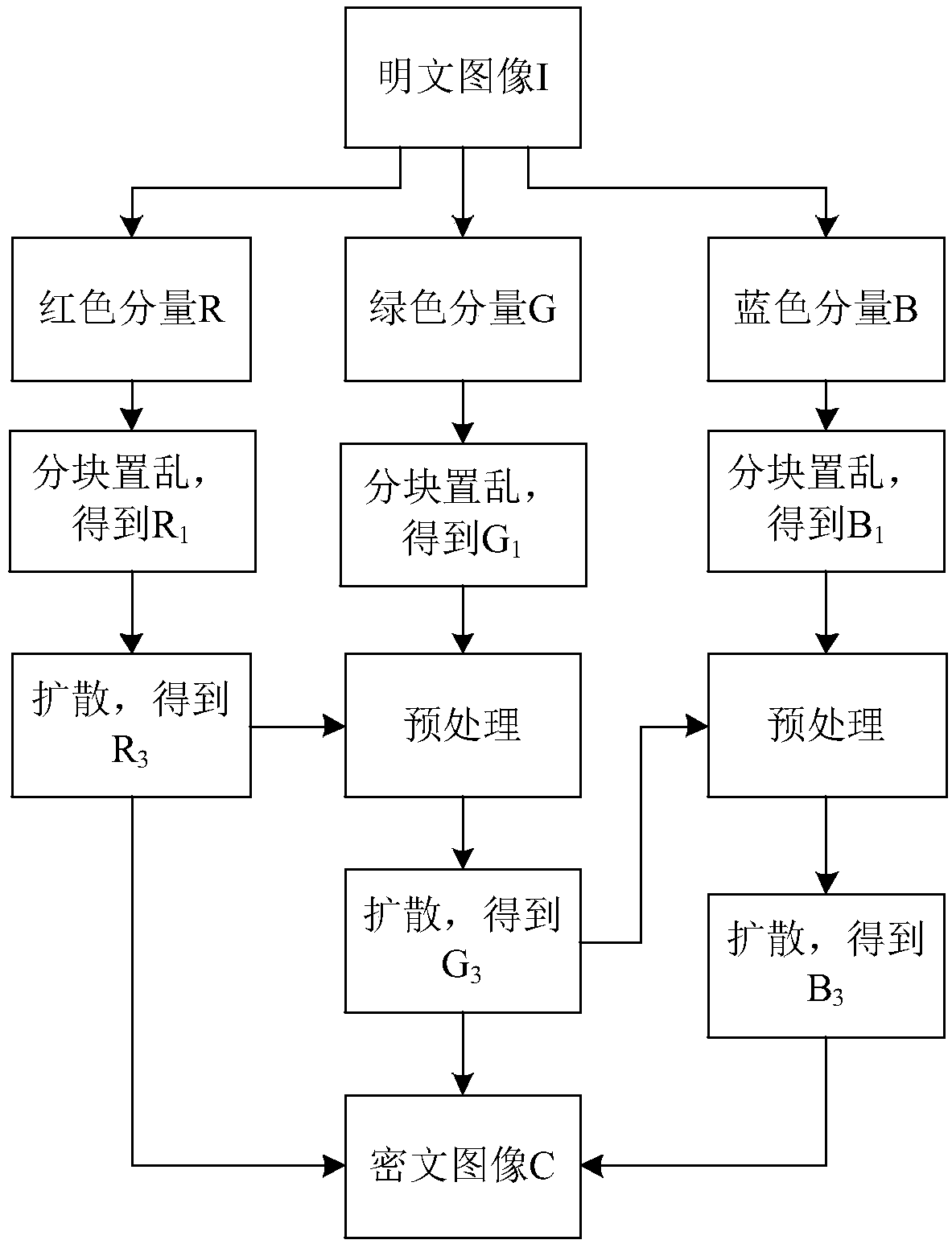
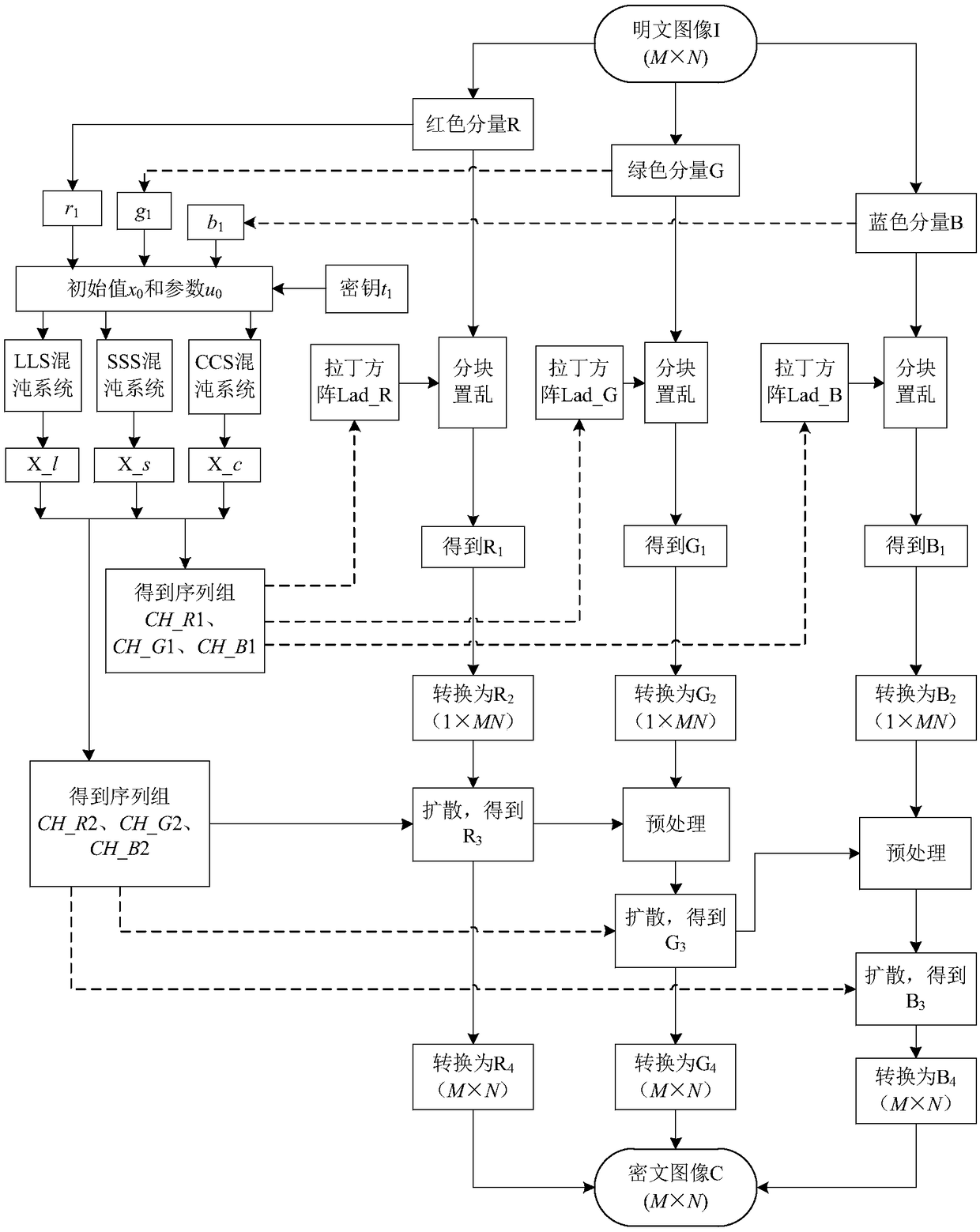
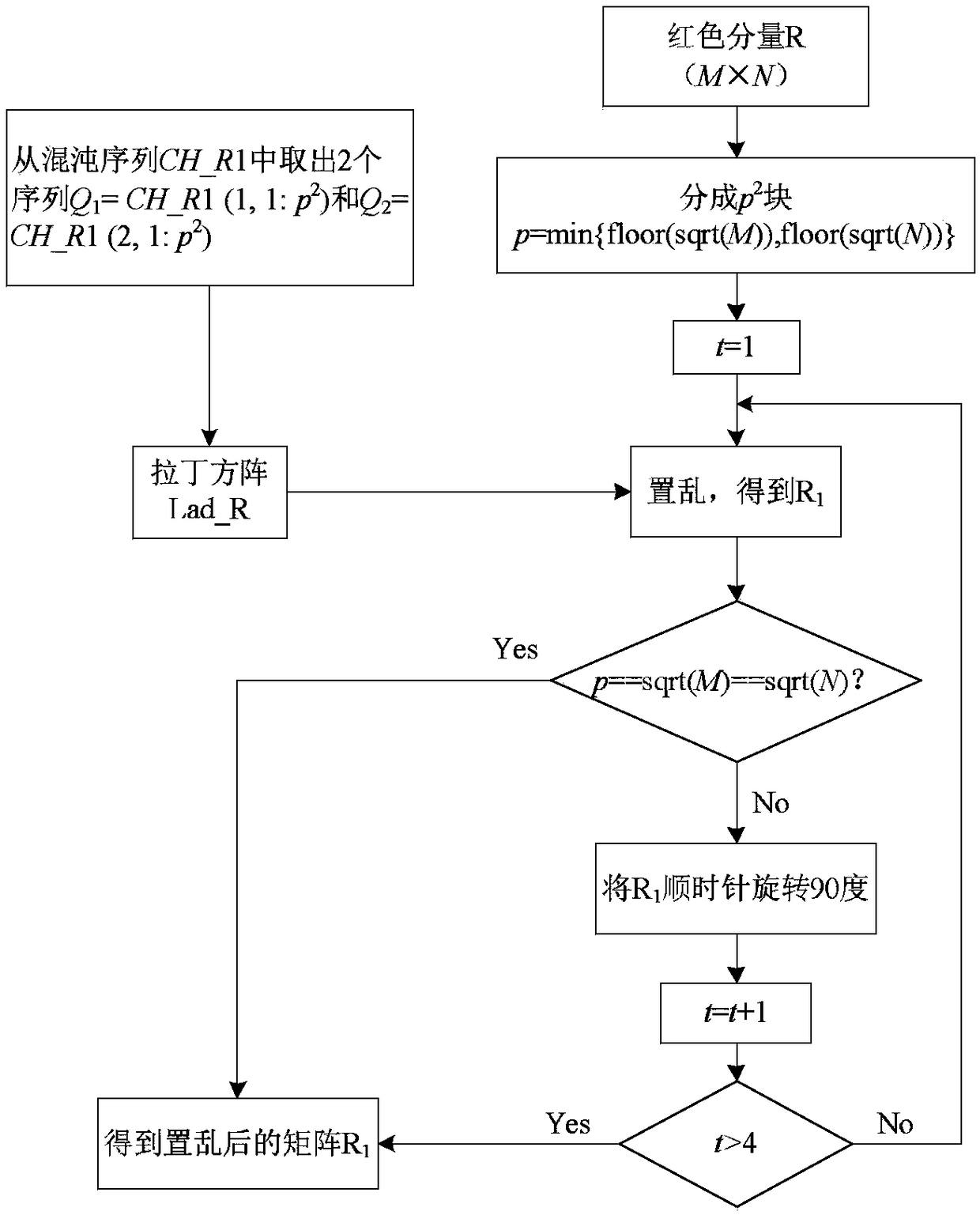
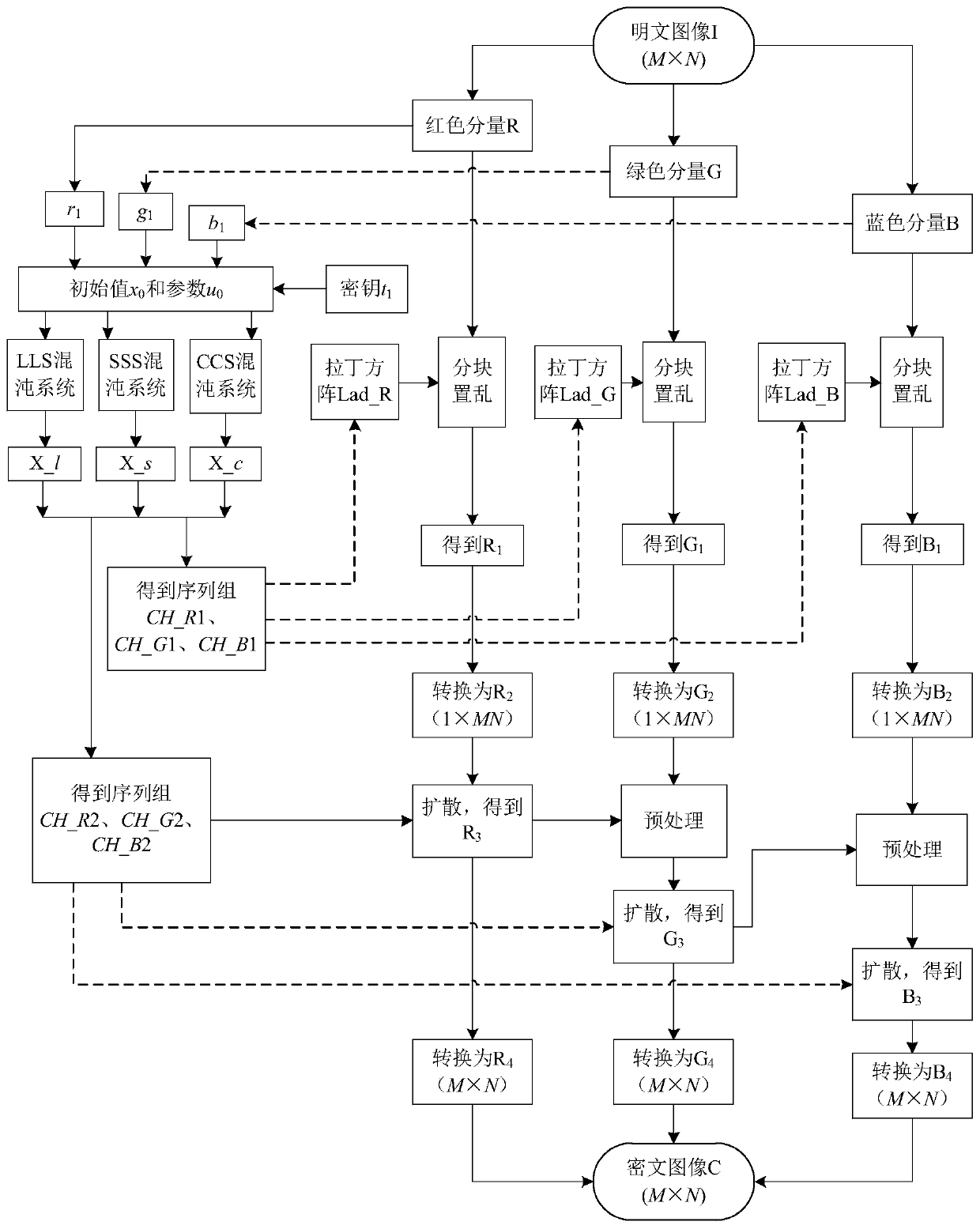
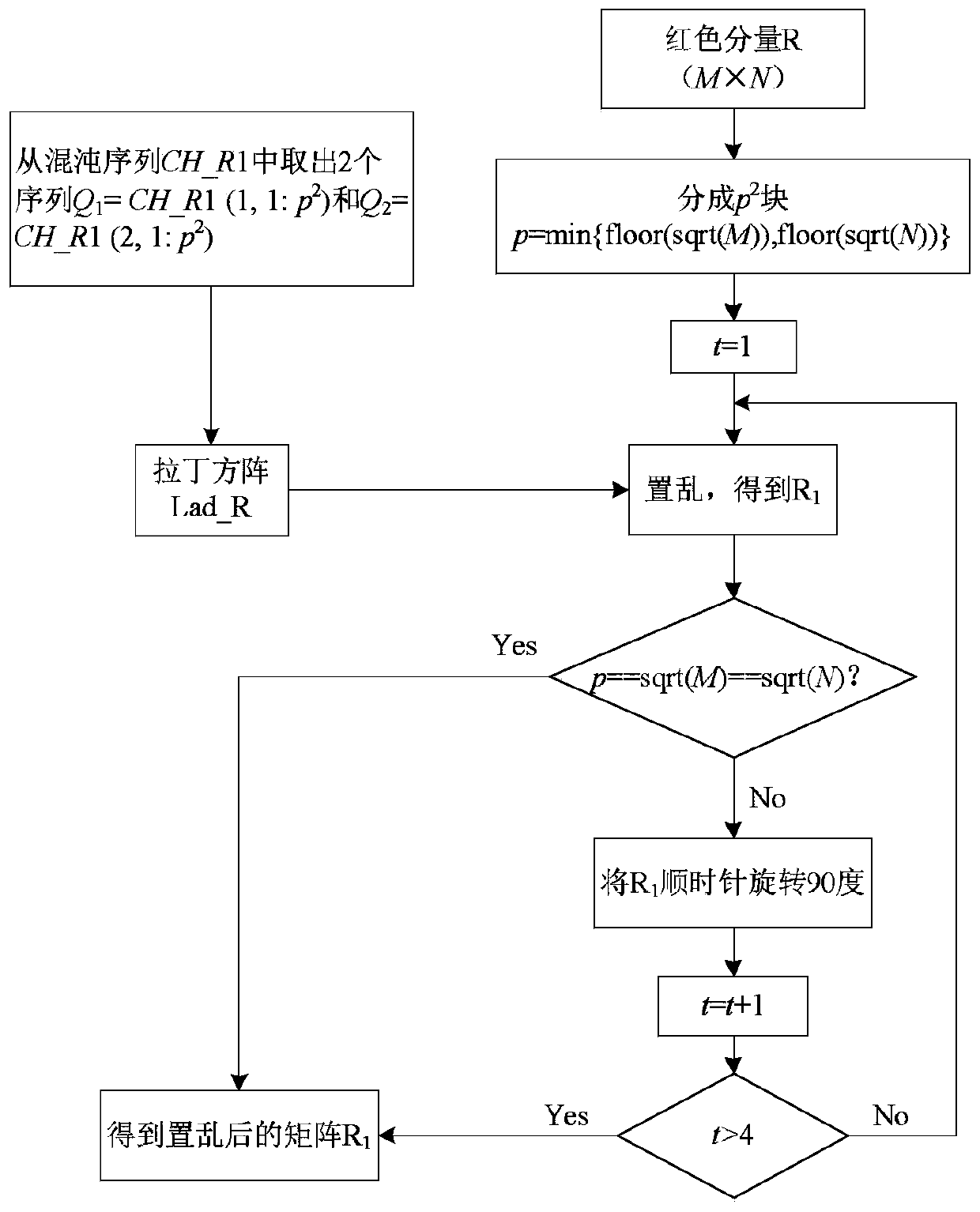
Color image encryption method based on Latin square scrambling
ActiveCN108696666AImprove resistance to attackReduce strong correlationSecuring communication by chaotic signalsPictoral communicationPlaintextComputer hardware
The invention relates to a color image encryption method based on Latin square scrambling. Plaintext keys r1, g1 and b1 are calculated through utilization of R, G and B components of a color plaintextimage, an initial value and a parameter obtained through calculation based on the keys are substituted into a chaotic system, and three groups of chaotic sequences are generated; the chaotic sequences for scrambling and diffusion are selected through utilization of a chaotic sequence selection mechanism based on the plaintext and digital arrangement; and a final ciphertext image is obtained through adoption of a block scrambling policy based on a Latin square and the chaotic sequences, and diffusion operation based on the plaintext and a scrambled image. The encryption method is closely related to the plaintext, so the plaintext attack resistance is improved. The employed chaotic system is an improved chaotic system, a chaotic characteristic is good, the randomness is high and a key spaceis great, so a security level is further improved. A simulation result and safety analysis show that according to the encryption provided by the invention, an image complete encryption demand can besatisfied, the encryption efficiency is high, and the robustness is high.
Owner:HENAN UNIVERSITY
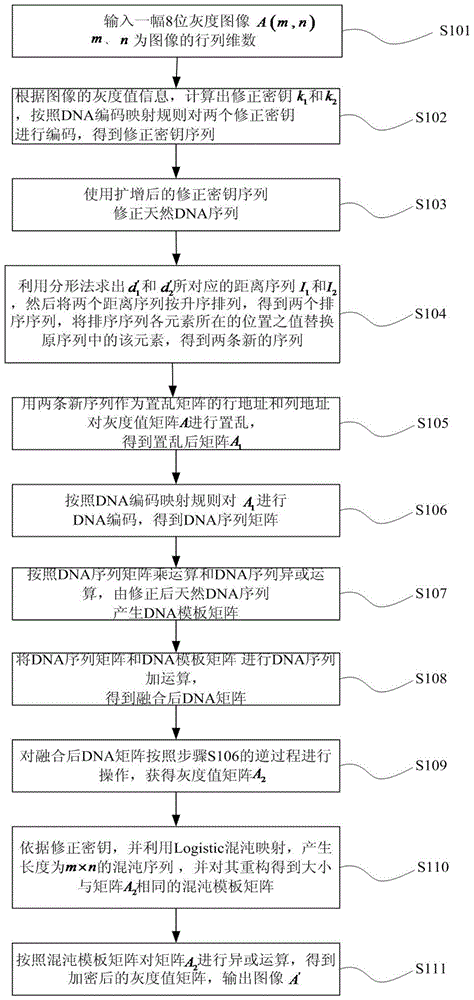
Image encryption method based on fractal and DNA sequence operation
ActiveCN105701755AImprove securityGood encryptionImage data processing detailsThe InternetLogistic map
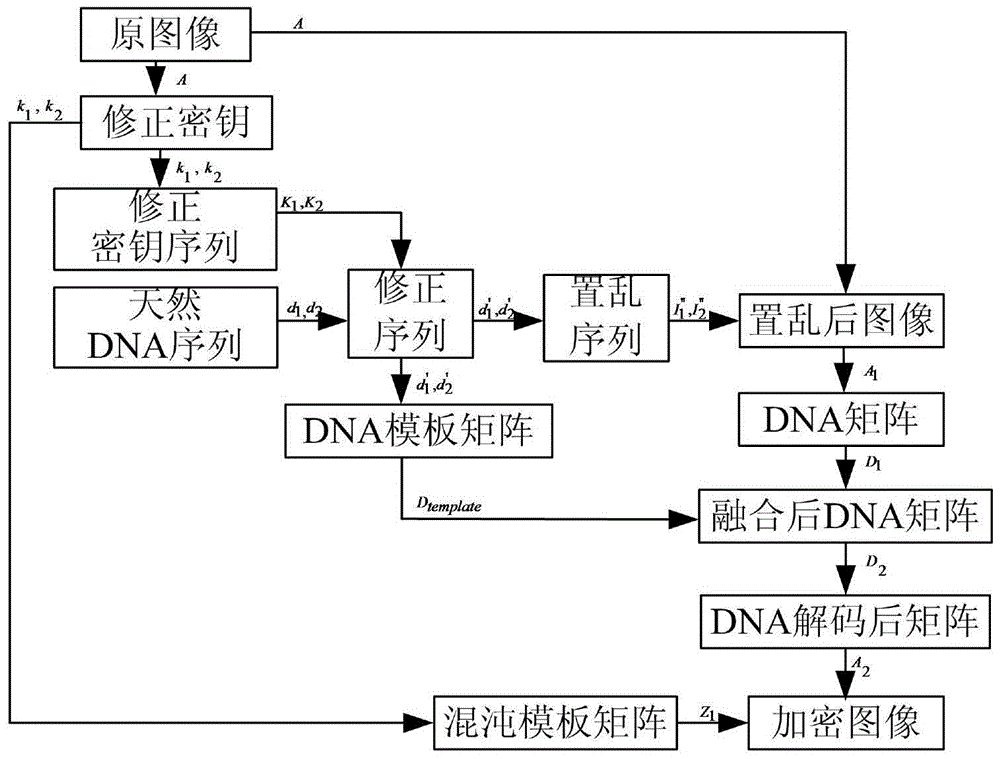
The invention discloses an image encryption method based on fractal and DNA sequence operation, which mainly comprises the steps of: scrambling an original image by utilizing a scrambling sequence generated by adopting a fractal method; then acquiring a DNA template matrix by utilizing a corrected natural DNA sequence; then encoding the scrambled image, and carrying out DNA sequence add operation on a result and the DNA template matrix; and finally utilizing a chaos template matrix generated by Logistic mapping and a matrix obtained after DNA decoding to interact to obtain an encrypted image. The image encryption method has the advantages of high security, good encryption effect and large secret key space, and can effectively resist exhaustive attacks, statistical attacks and differential attacks. And the algorithm is easy to implement, the cost is low, and the encryption results can be transmitted through the Internet.
Owner:DALIAN UNIV
Joint channel security coding method based on balance index and polarization code
InactiveCN106341208AIncrease valueReduce overheadError preventionComputer hardwareChosen-plaintext attack
The invention discloses a joint channel security coding method based on a balance index and a polarization code. The method comprises the steps that after polarization code coding is carried out on all message sequences, the sequences are encoded into balance code words with the same number of 0 and 1; the balance index is used to carry out one-time pad sequence password encryption with small complexity on the balance code words; and private key encryption system encryption is carried out on the balance index based on the polarization code. The code words have dual functions of error correction and encryption, which can reduce the overhead of a system. In the design of the private key encryption system, the redundant information freeze bit of the polarized code is used as one private key which has the tasks of error correction and encryption; a randomly generated error vector ensures that the system is resistant to the existing exhaustive attack and selection plaintext attack; and the decoding complexity is reduced.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
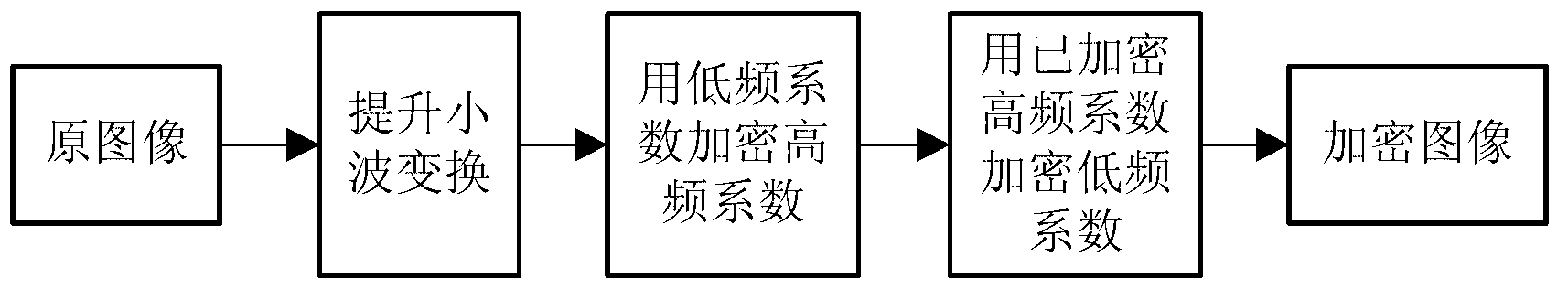
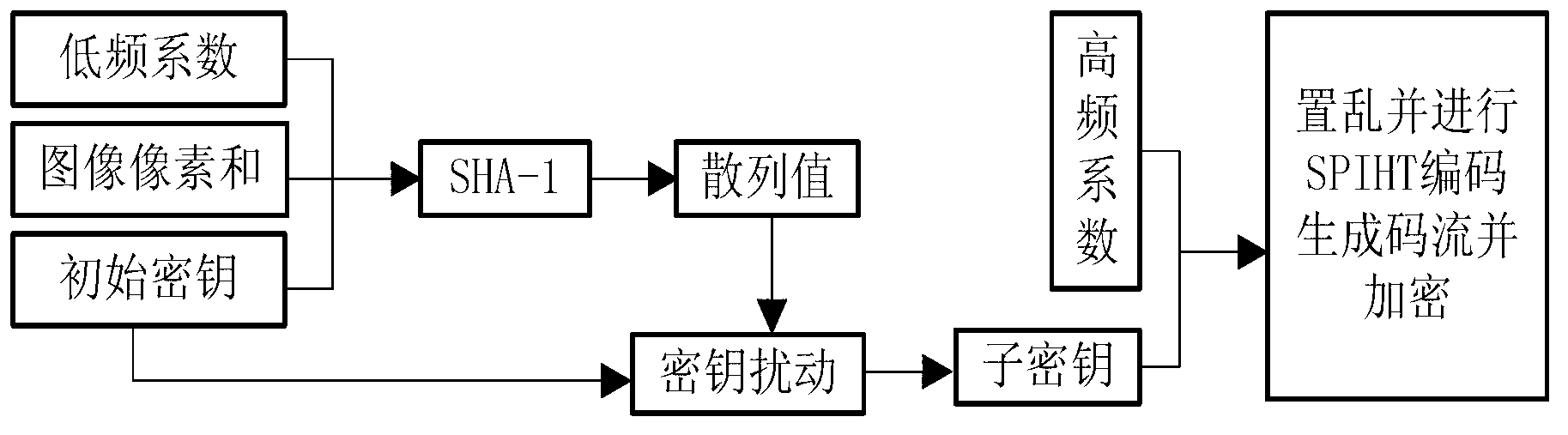
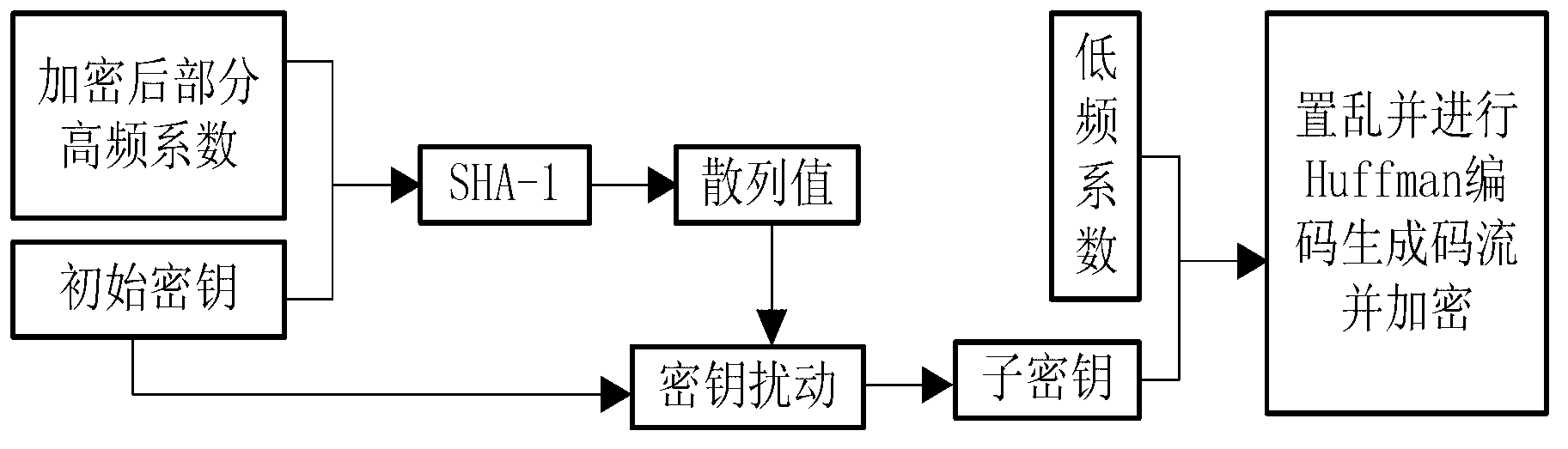
Image compression and encryption method based on wavelet transform and SHA-1 (secure has algorithm-1)
InactiveCN103002281AEnsure safetyImplement encryptionTelevision systemsDigital video signal modificationData streamDecomposition
The invention relates to an image compression and encryption method based on wavelet transform and SHA-1 (secure has algorithm-1) and aims to encrypt in image compression process. According to the algorithm, an image is subjected to four-layer wavelet decomposition first, and coefficients are divided into a low-frequency portion and a high-frequency portion after decomposition. Low-frequency coefficients, initial keys and original image pixels are used to generate 160-bit hashed values by SHA-1, and the hashed values generate subkey scrambled high-frequency coefficients. The scrambled high-frequency coefficients are subjected to SPIHT (set partitioning in hierarchical trees) encoding, and the initial keys disturbed by the hashed values are used to partially encrypt encoded data streams. Part of the encrypted high-frequency coefficients and the initial keys are used as input messages for SHA-1. The subkey scrambled low-frequency coefficients are generated by the hashed values, the scrambled low-frequency coefficients are subjected to Huffman encoding, and then the initial keys are disturbed by the hashed values to encrypt the encoded data streams, so that low-frequency coefficients are encrypted. Input information is sensitized by SHA-1, the low-frequency portion and the high-frequency portion are mutually encrypted, and accordingly image information safety is guaranteed.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
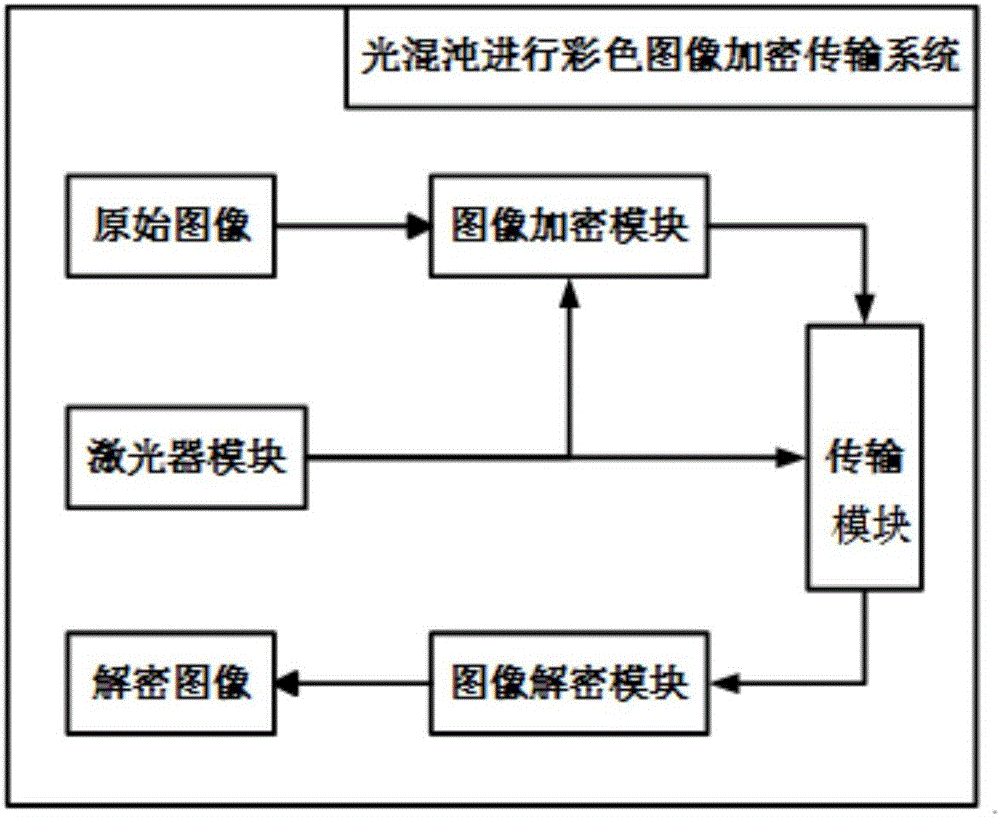
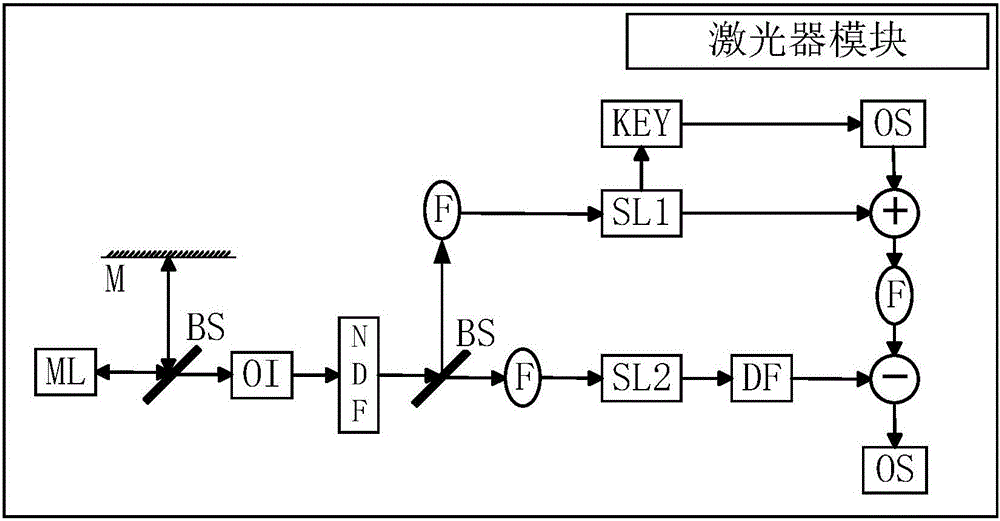
Light chaos-based color image encrypted transmission method and system thereof
ActiveCN106791266AHigh bandwidthReduce lossImage data processing detailsSecuring communication by chaotic signalsComputer visionEncryption
The present invention discloses a light chaos-based color image encrypted transmission method and a system thereof. The system comprises a laser module, an image encryption module and an image decryption module. First, a laser generates chaos output under the action of light feedback, and an encrypted key is extracted from a generated chaos signal; a scrambling and diffusion encryption processing is performed on an original image through 3D cat mapping and Logistic chaos mapping and other methods; and an encrypted image is transmitted in an optical fiber by using a chaos concealment technology, and then the encrypted image is decrypted correspondingly, so as to recover the original image. The color image encrypted transmission method and the system thereof have high security and fast transmission speed.
Owner:SOUTHWEST UNIVERSITY
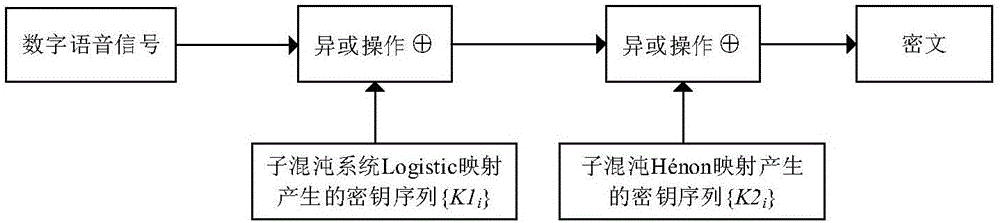
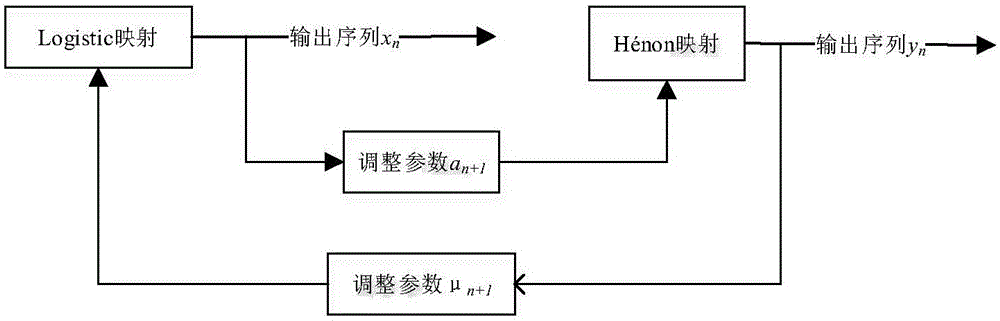
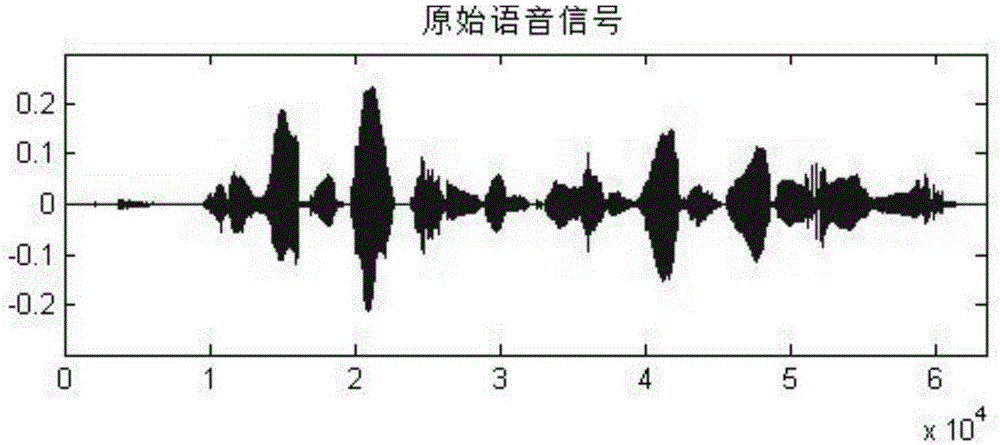
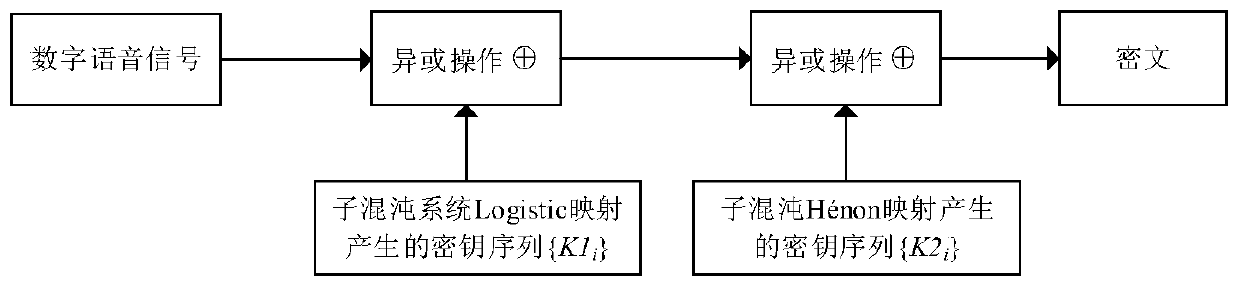
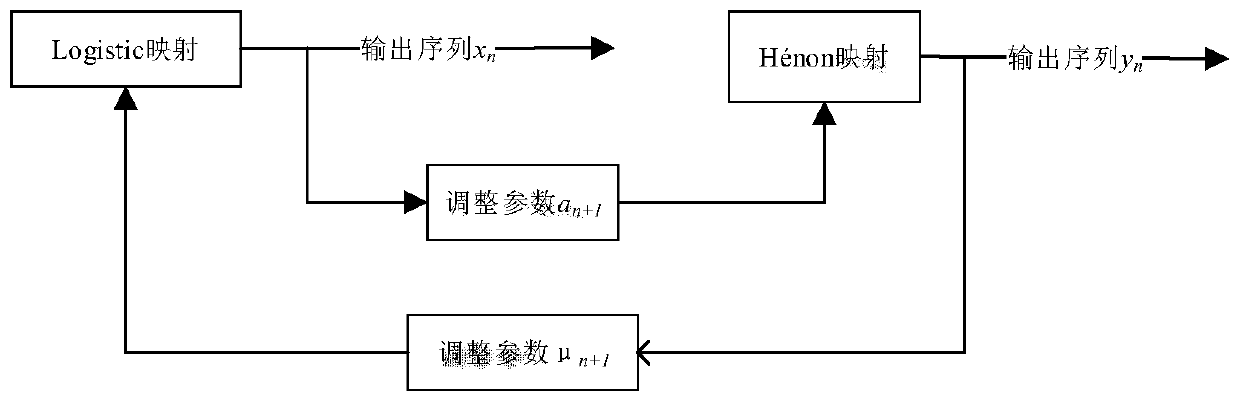
Chaotic encryption method for voice information
ActiveCN106375079AGood pseudorandomnessExtended cycleSecuring communication by chaotic signalsPlaintextComputer hardware
The invention discloses a chaotic encryption method for voice information. The method is characterized in comprising the steps of 1), establishing a dynamic variable parameter composite chaotic system and generating a real-value chaotic sequence of which length is the same to that of a plaintext voice sequence through utilization of the system; 2), carrying out binarization processing on the real-value chaotic sequence, thereby obtaining a chaotic key sequence of which length is the same to that of the plaintext voice sequence; and 3), through combination of the chaotic key sequence, carrying out bit-by-bit exclusive or operation on the plaintext voice sequence, thereby obtaining a ciphertext. According to the method, under limited calculation precision, the chaotic sequence with good pseudo-randomness can be generated, the valid precision effect is reduced, and a chaotic sequence cycle is prolonged; and through adoption of a chaotic system cascading mode, the encryption security is improved, a sufficient key space can be generated, and an exhaustive attack can be resisted effectively.
Owner:HUAQIAO UNIVERSITY
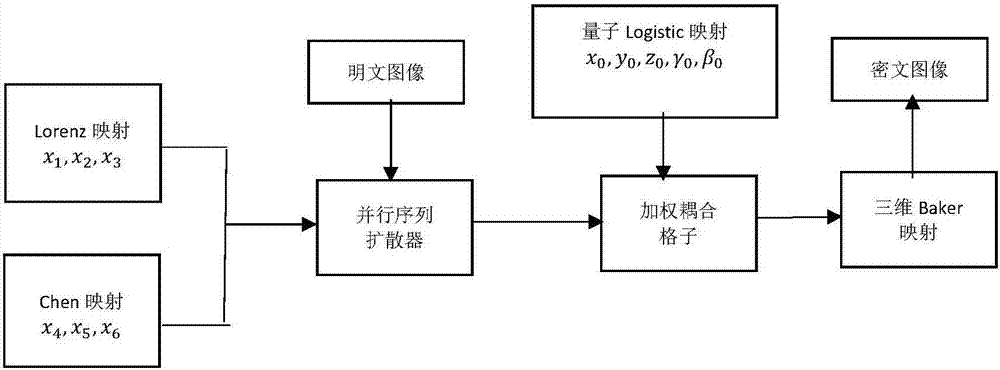
Quantum chaos-based parallel image encryption method
InactiveCN107292802ASmooth connectionResist Differential AttacksImage data processing detailsPlaintextComputer hardware
The invention relates to a quantum chaos-based parallel image encryption method. The invention aims to solve the defects of a current traditional serial chaotic encryption algorithm. According to the method of the invention, a sequence generated by hyperchaotic Lorenz mapping and Chen mapping is used as an input sequence for parallel encryption; a generated intermediate ciphertext is adopted as the input of quantum logistic mapping; three-dimensional Baker scrambling operation is performed; and therefore, plaintext information can be hidden. As indicated by experimental simulation, the encryption speed of the algorithm of the invention is higher than that of the traditional serial encryption algorithm, the algorithm of the invention can effectively resist statistical attacks and differential attacks to achieve a very good encryption effect.
Owner:GUANGDONG UNIV OF TECH
Transparent data integrity auditing and transparent encrypted data deduplication protocol based on block chain
ActiveCN110278076AEnsure safetyIntegrity guaranteedKey distribution for secure communicationEncryption apparatus with shift registers/memoriesData integrityInformation security
The invention belongs to the field of information security, and particularly relates to a transparent data integrity auditing and transparent encrypted data deduplication protocol based on a block chain. The scheme of the invention comprises four modules: parameter initialization, encryption key acquisition, bidirectional upheaval checking, transparent integrity auditing and transparent de-duplication. Compared with the prior art, the protocol can resist the bias audit and delay audit of the cloud server, and meanwhile, the situation that the cloud server claims an erroneous duplicate removal level to charge additional fees can be avoided. According to the protocol, single-point failure attacks and exhaustion attacks can be prevented, and bidirectional ownership proof of a user and a cloud server can be provided. The invention realizes a secure and effective protocol based on the block chain, and can simultaneously realize transparent data integrity auditing and transparent data de-duplication.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Hyperchaotic system based quantum image encryption method
ActiveCN105373739AImprove resistance to attackImprove securityChaos modelsDigital data protectionComputer hardwareQuantum
The invention discloses a hyperchaotic system based quantum image encryption method. The method comprises: finishing quantum image encryption by utilizing CNOT operation to realize XOR operation of a quantum image, namely, generating a hyperchaotic sequence by a Chen's hyperchaotic system, controlling unit transformation and NOT gate by a processed hyperchaotic sequence to construct CNOT transformation, and then, utilizing the CNOT operation to realize the XOR operation of the quantum image, thereby finishing the quantum image encryption. According to the method, the XOR operation of the quantum image is constructed for the first time and applied to the quantum image encryption, so that the attack resistance and security of an encryption algorithm can be enhanced; an initial condition of the Chen's hyperchaotic system serves as a secret key of the encryption algorithm, so that the effect of expanding secret key space is achieved; and the algorithm can resist strong attack, so that the secret key is easier to allocate, store and memorize.
Owner:NANCHANG UNIV
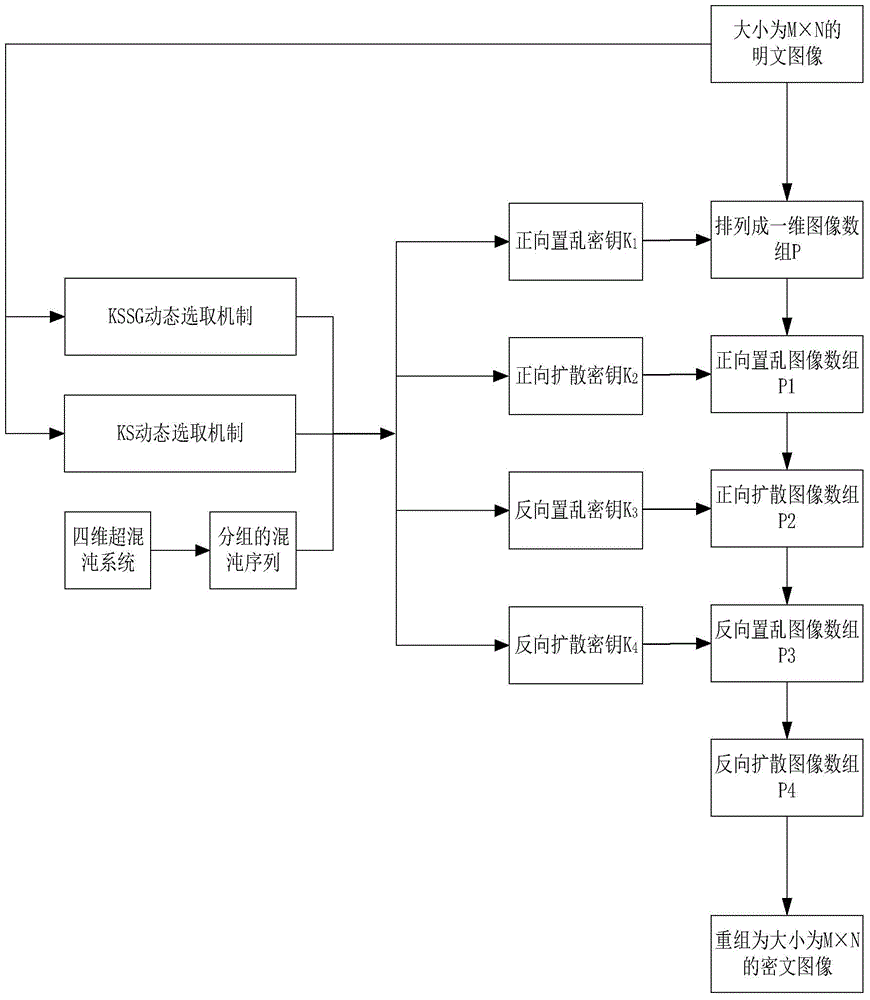
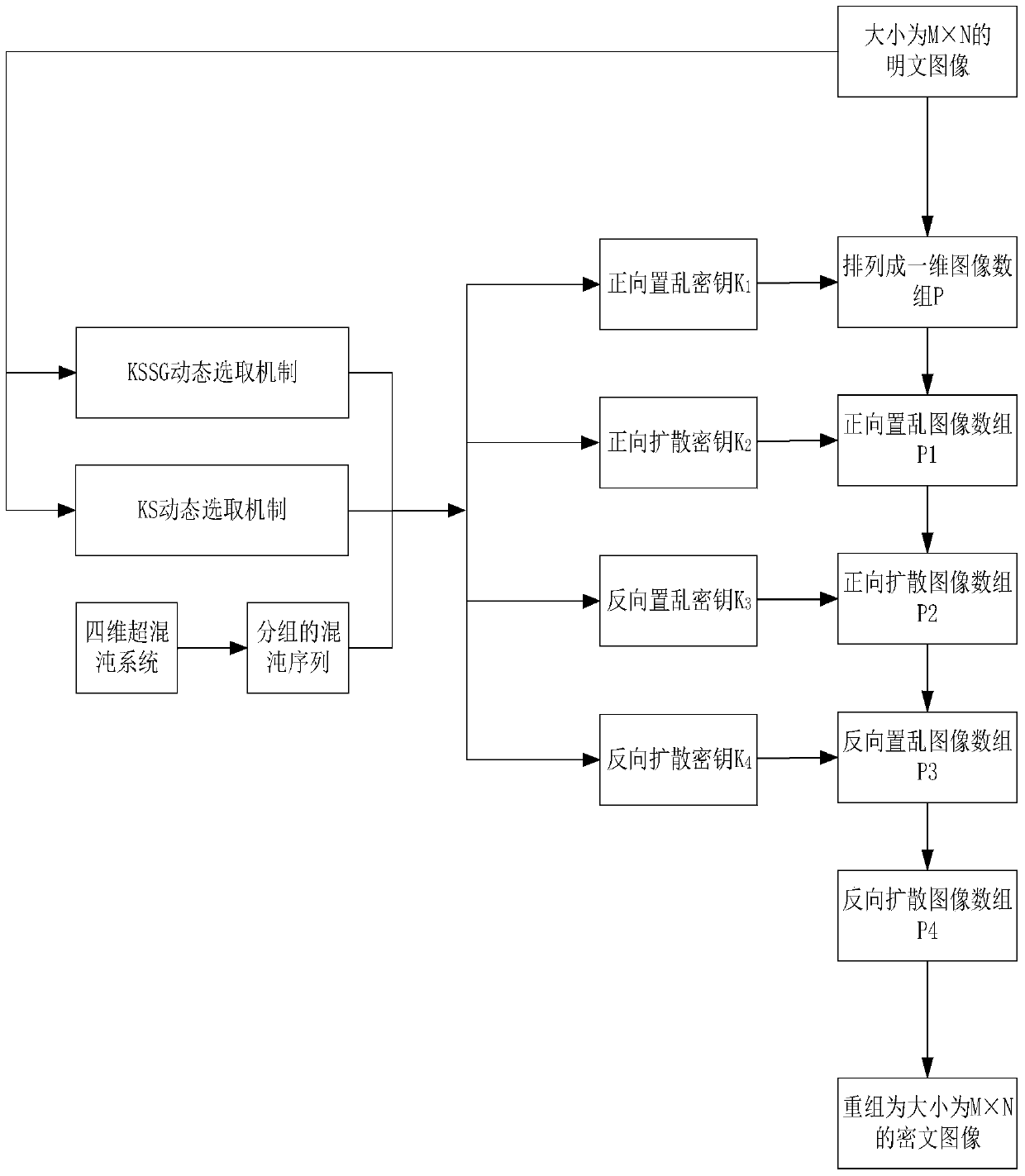
Hyper-chaotic system-based secret key dynamic selection image encryption algorithm
The invention relates to a hyper-chaotic system-based secret key dynamic selection image encryption algorithm. The algorithm mainly comprises the following steps of arranging original plaintext images into an image array P, using a hyper-chaotic system to generate a chaotic sequence, and performing grouping; generating a forward scrambling secret key K1 with the combination of a KSSG and KS dynamic selection mechanism based on a plaintext and performing forward scrambling of the P to obtained P1; generating a forward diffusion secret key K2 with the combination the KSSG and KS dynamic selection mechanism and performing forward diffusion of the P1 to obtain a P2; generating a backward scrambling secret key K3 with the combination of the KSSG and KS dynamic selection mechanism and performing backward scrambling of the P2 to obtain a P3; and generating a backward diffusion secret key K4 with the combination the KSSG and KS dynamic selection mechanism, performing forward diffusion of the P3 to obtain a P4, and performing regrouping of the P4 to obtain a final cryptograph image. The abovementioned method provided by the invention increases the secret key space, enables the security, the encryption effect and the secret key sensitivity to be higher and the anti-attach performance to be stronger, and is easy in hardware implementation.
Owner:HENAN UNIVERSITY
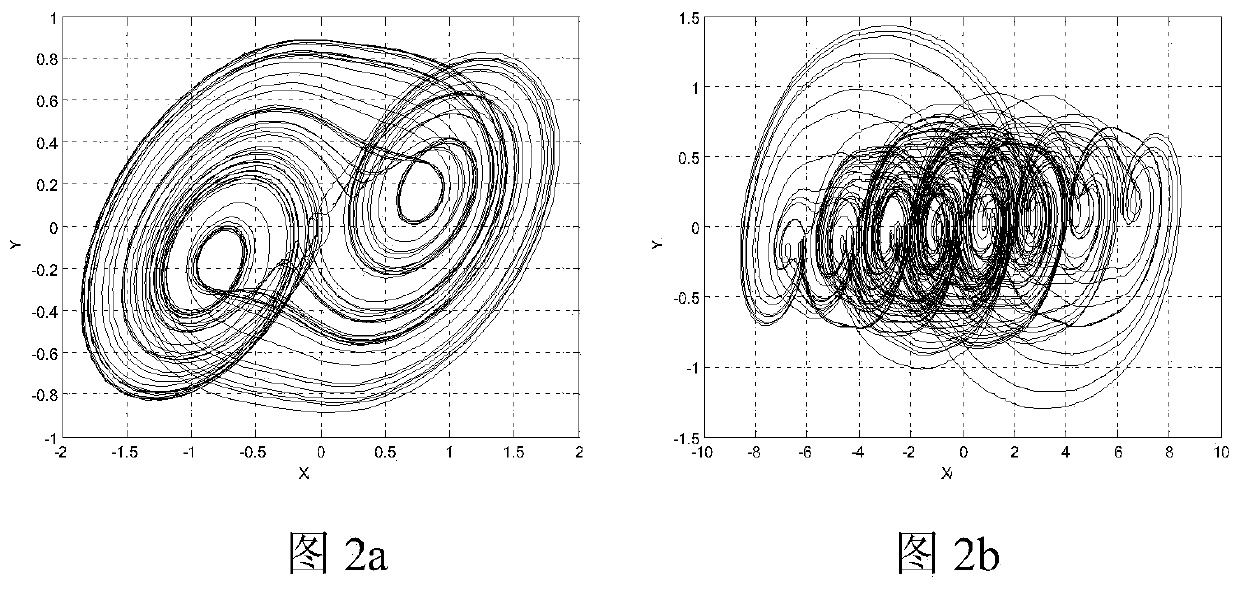
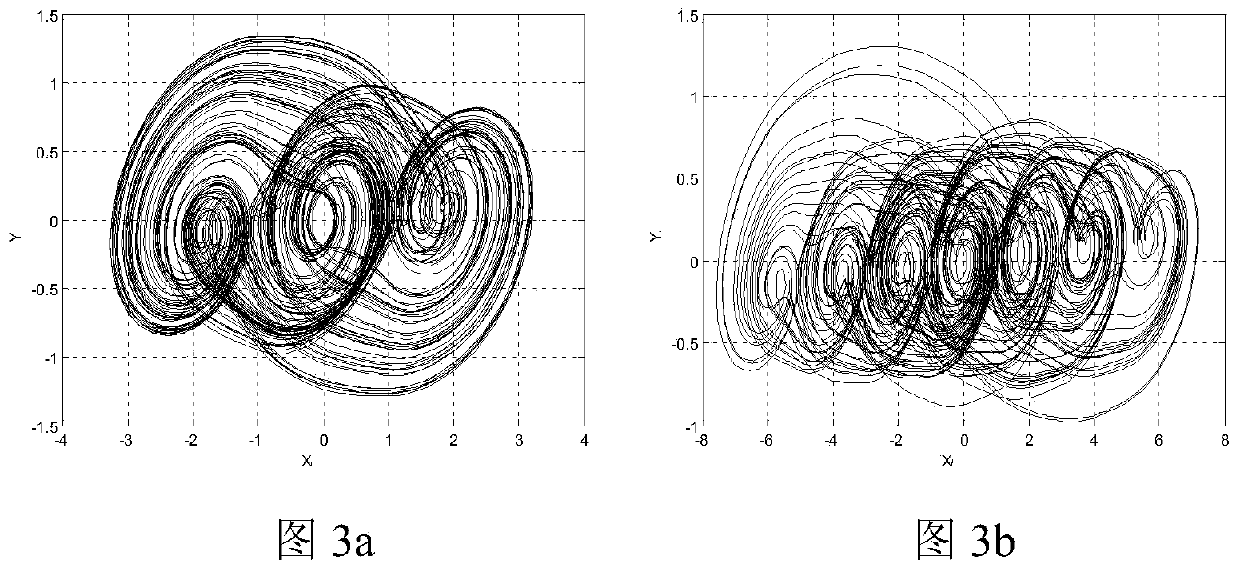
Image encryption and decryption method based on fractional order translation chaotic system
PendingCN110572252AHigh dimensional spaceStrong initial value sensitivityDigital data protectionSecuring communication by chaotic signalsComputer hardwarePlaintext
The invention discloses an image encryption and decryption method based on a fractional order translation chaotic system, and relates to the fields of computer cryptography, image encryption processing and communication and network engineering, which can solve the problems that initial conditions of an existing chaotic system are not associated with plaintexts, plaintext attacks cannot be resisted, and the safety is poor. According to themethod, translation transformation is conducted on the fractional order chaotic system by introducing a piecewise function, parameters are set, different numbers of scroll attractors can be generated, and the fractional order translation chaotic system perfects the field of fractional order chaotic systems composed of three-dimensional one-time autonomousconstant differential. Meanwhile, the fractional order multi-scroll chaotic system has higher dimension space and higher initial value sensitivity, the image encryption and decryption algorithm basedon the system is high in randomness and multiple in secret key parameters, a multi-iteration mode is adopted in the encryption process, an encrypted ciphertext matrix becomes very uniform, and therefore the purpose of effectively hiding original image information is achieved.
Owner:CHANGCHUN UNIV OF TECH
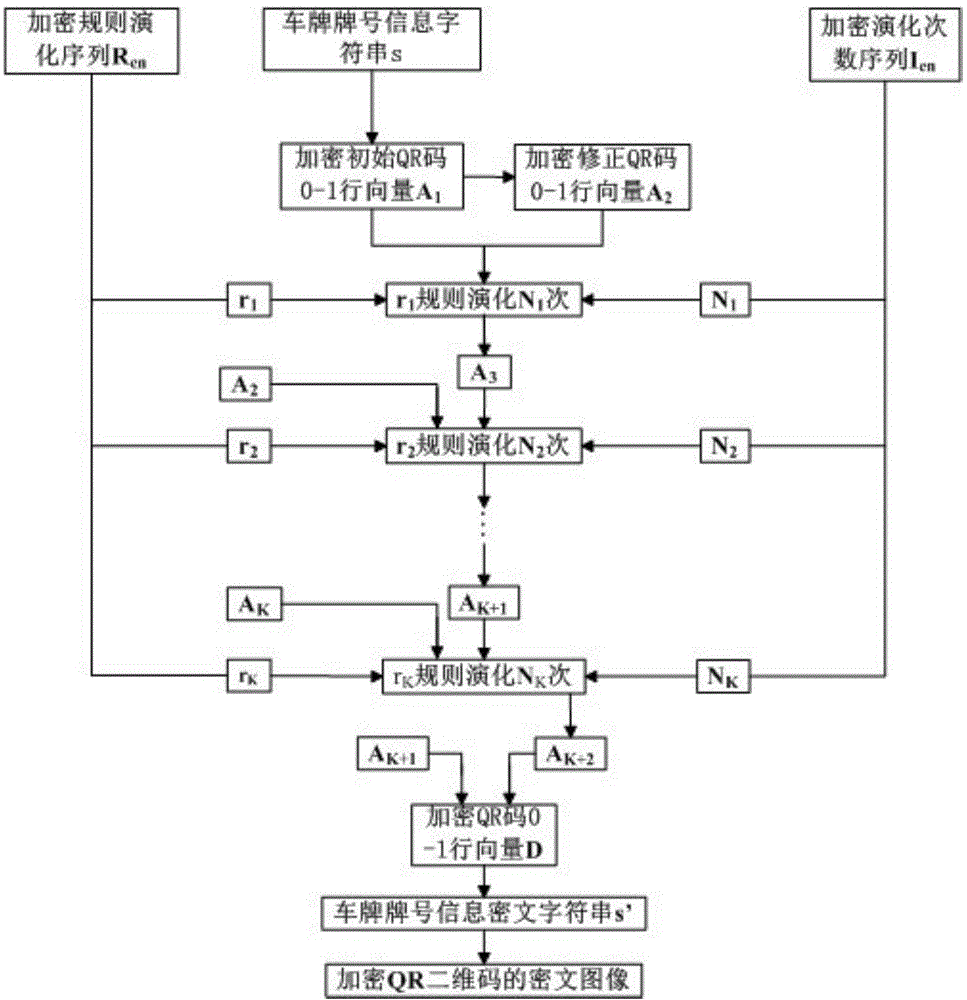
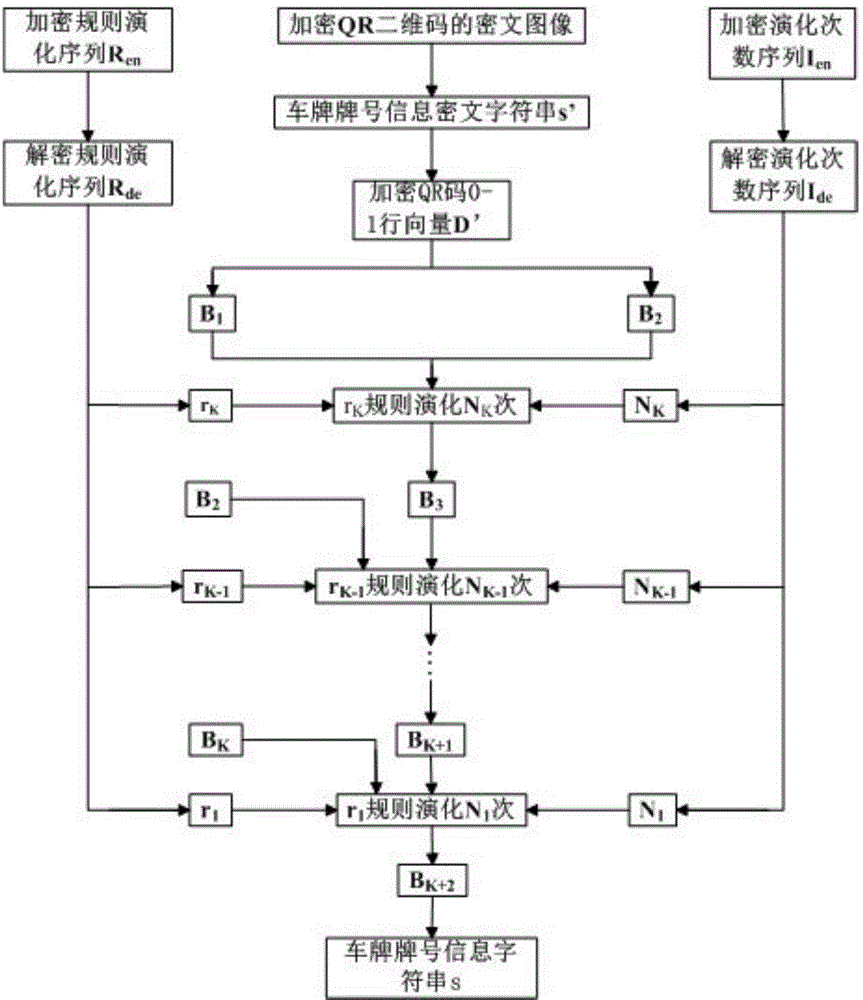
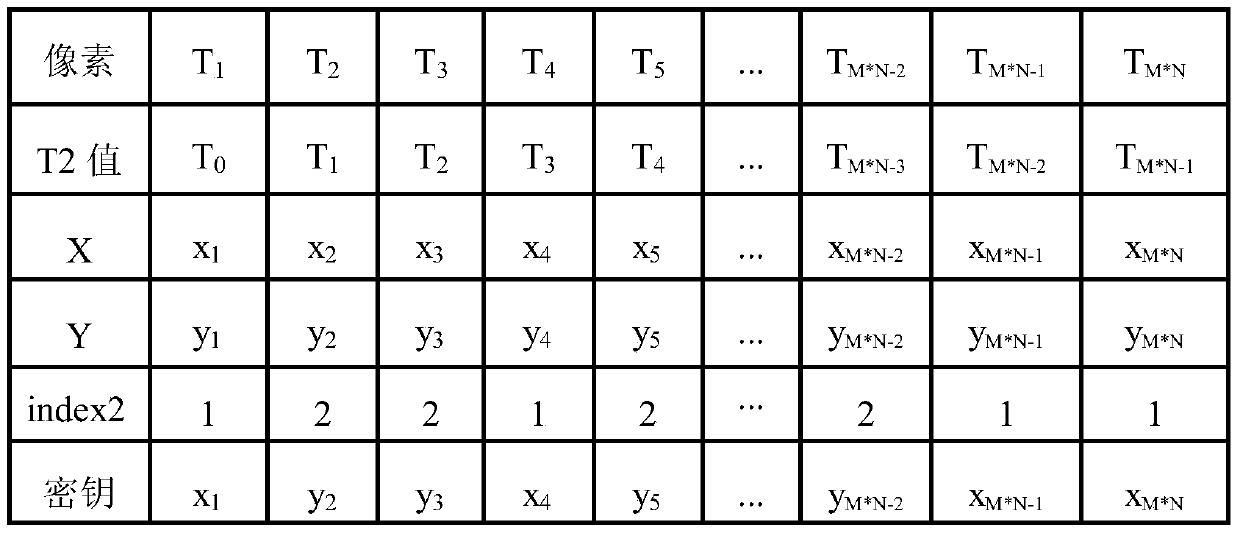
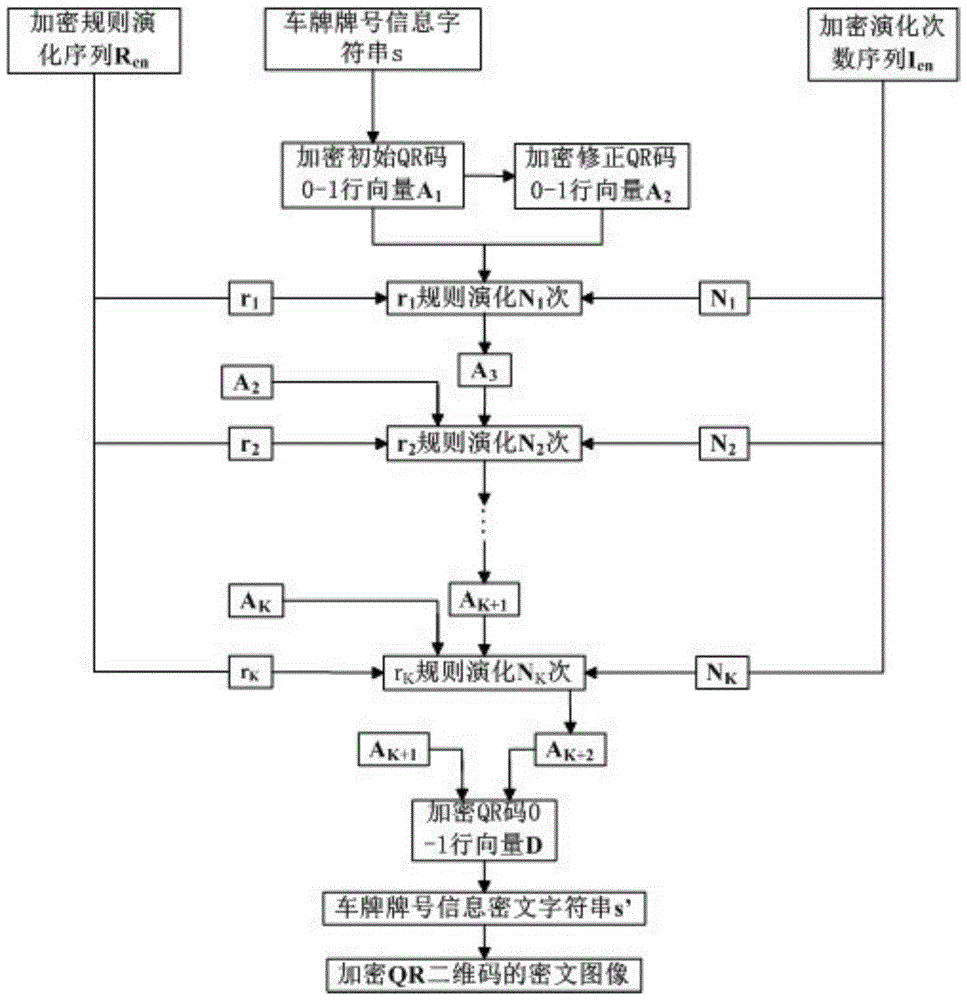
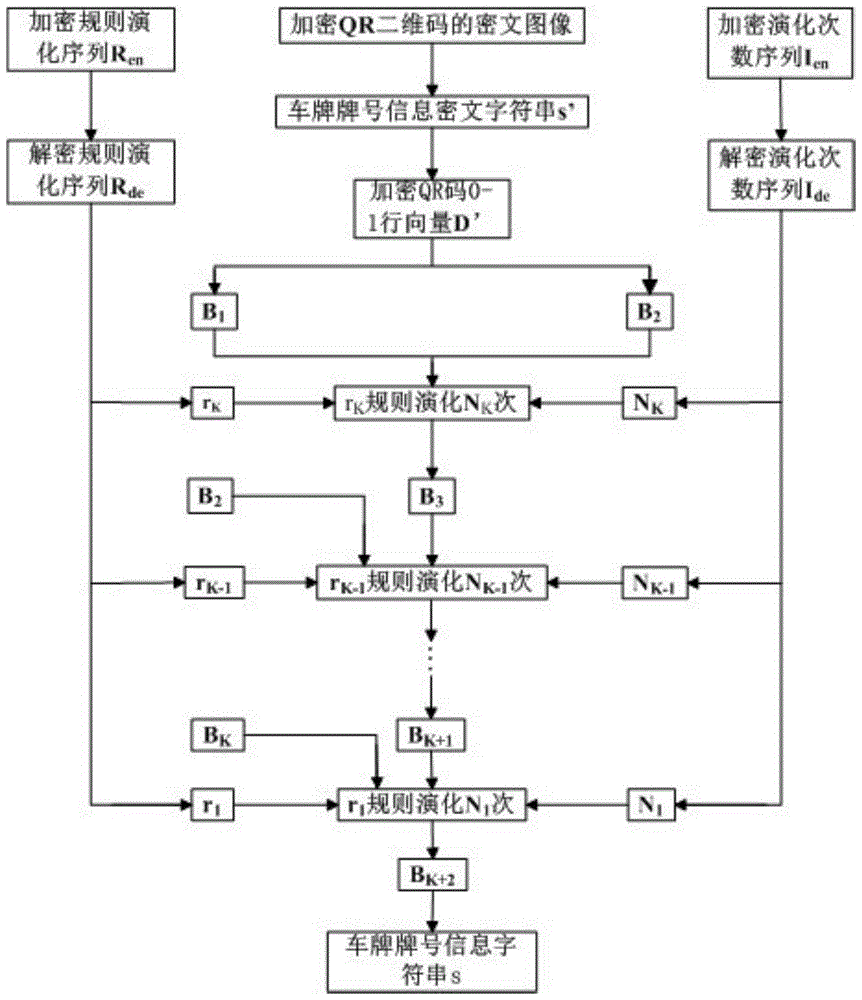
Automobile license plate with encrypted QR two-dimensional code
InactiveCN104527535AEasy accessOvercoming inefficiencyCharacter and pattern recognitionVehicle componentsCiphertextSoftware engineering
The invention discloses an automobile license plate with an encrypted QR two-dimensional code. The automobile license plate is characterized in that the obverse of an automobile license plate contains an encrypted QR two-dimensional code cipher text image and license plate number text. The automobile license plate can be identified quickly and accurately by an intelligent traffic system, meanwhile, the accuracy and time efficiency of identification are improved, and the cost of artificial identification is reduced; a quite strong anti-counterfeiting function is achieved by adopting the encrypted QR two-dimensional code, so the adverse effect of a counterfeit license plate is reduced; besides, a license plate QR two-dimensional code information interface is provided for intelligent traffic management through the automobile license plate, and the automobile license plate allows research and development of related portable devices and implementation of intelligentialization, normalization and lightening of traffic police enforcement to be possible, thereby having broad application prospects.
Owner:HEFEI UNIV OF TECH
DNA one-time pad image encryption method based on multiple keys
ActiveCN111988144AImprove securityGood encryptionMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesInverse discrete fourier transformDNA
The invention provides a DNA one-time pad image encryption method based on multiple secret keys, and the method comprises the steps: obtaining four encryption parameters through the calculation of two-dimensional discrete cosine transform, two-dimensional inverse discrete cosine transform, two-dimensional discrete Fourier transform and two-dimensional inverse discrete Fourier transform according to a to-be-encrypted image; taking the four encryption parameters as initial values of four chaos respectively to generate four chaotic sequences; selecting a natural DNA sequence, and processing the four chaotic sequences by using the natural DNA sequence to obtain two diffusion matrixes and two scrambling matrixes; and alternately performing two rounds of diffusion operation and two rounds of scrambling operation on the to-be-encrypted image to obtain an encrypted image. According to the invention, the initial values of all chaotic functions are obtained by calculating the original image information, so that the differential attack can be well resisted. Meanwhile, the problem that one-time pad messy codebooks are difficult to store is solved by utilizing massive DNA sequences, the one-time pad encryption effect is achieved, and the security of the encryption method is improved to a great extent.
Owner:DALIAN UNIV
Color Image Encryption Method Based on DNA Dynamic Coding
The present invention relates to a DNA dynamic coding based colored image encryption method, comprising: obtaining a key through a colored plain-text image; by the key, calculating an initial value and a parameter of a chaotic system used in scrambling and diffusion processes; substituting the initial value and the parameter to the chaotic system for iteration to obtain W1 and W2, obtaining a scrambling matrix K from W1, obtaining an integer matrix Y and an index matrix Ind from W2, and performing DNA coding on Y according to the index matrix Ind; and performing scrambling on the plain-text image row by row by using the matrix K, then performing coding and diffusion until all rows finish DNA coding, and finally performing decoding and recomposing on a DNA matrix, to obtain a final colored ciphertext image. According to the method, a function SHA256 is used to generate the key, so that the key space is expanded; the generation of the key depends on a plain-text, so that plain-text attack can be effectively resisted; chaotic characteristics are combined with DNA dynamic coding, so that the security is further improved; and meanwhile, scrambling and diffusion operations are performed according to the row of images, so that parallel computing is facilitated and the efficiency is improved.
Owner:HENAN UNIVERSITY
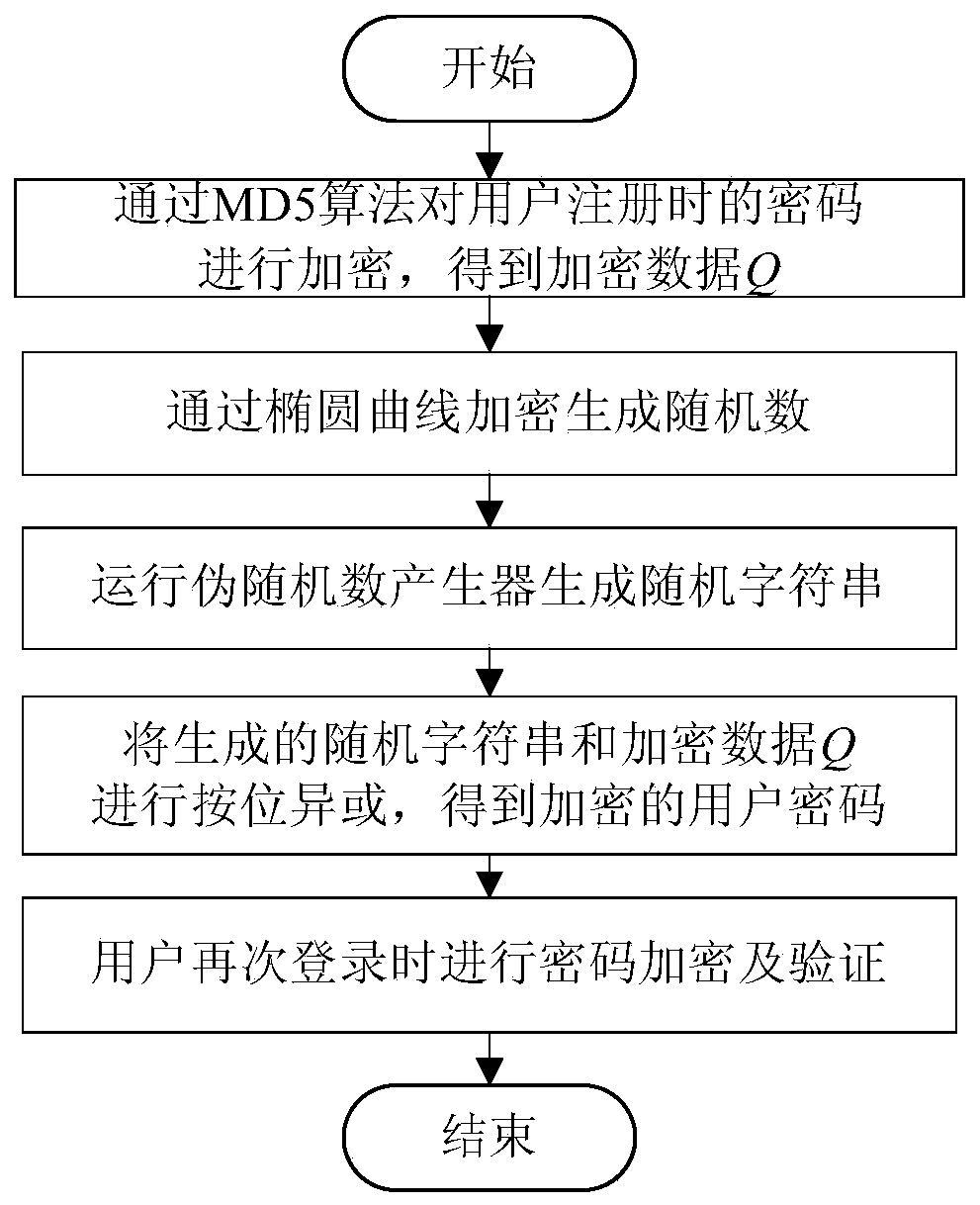
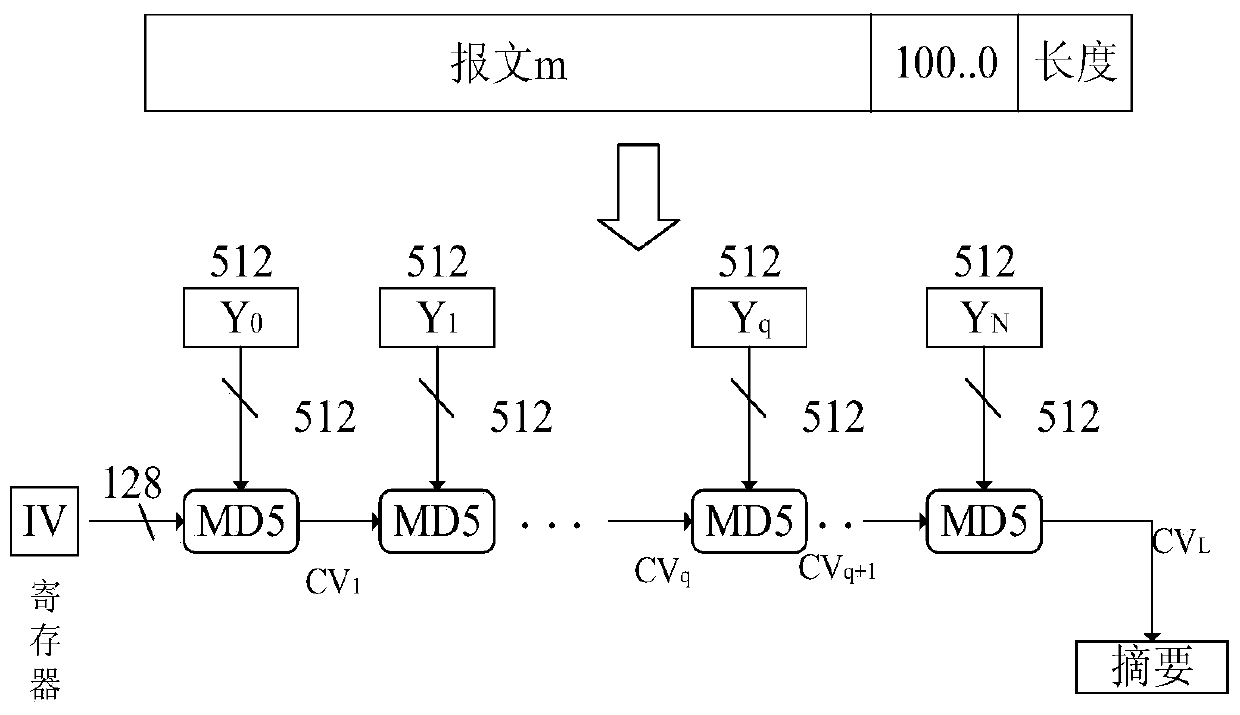
User password encryption method based on improved MD5 encryption algorithm
ActiveCN110943837AIncrease randomnessImprove collision resistanceKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAlgorithmCiphertext
The invention provides a user password encryption method based on an improved MD5 encryption algorithm, and relates to the technical field of information security. The method comprises the following steps: firstly, encrypting a password input by a user during registration through an MD5 algorithm to obtain the initial encrypted data, generating a random number through an elliptic curve, sending the random number to a pseudo-random number generator, generating a random character string by the elliptic curve and the pseudo-random number generator, performing bitwise exclusive OR on the random character string and the encrypted data generated by an MD5 algorithm to generate new encrypted data as a message abstract, and storing the new encrypted data in a database. And when the user logs in again, the input password is encrypted, and the encrypted ciphertext is compared with the ciphertext stored in the database for verification. According to the method, based on the improved MD5 encryption algorithm, the random character string is added after the original MD5 algorithm is operated to perform exclusive OR operation, so that the randomness and the collision resistance of the algorithm are improved, the security of the algorithm is improved, and exhaustion attack, birthday attack and differential attack can be effectively resisted.
Owner:LIAONING TECHNICAL UNIVERSITY
Multi-Image Encryption Method Based on Logarithmic Polar Coordinate Transformation
InactiveCN102800042BPromote recoveryEliminate crosstalkImage data processing detailsMulti-imageAlgorithm
The invention discloses a multi-image encryption method based on log-polar transform. The method comprises the following steps of: with log-polar transform, encoding different images to different annular ranges, wherein the inner and outer radiuses of the different annular ranges are not overlapped; and superposing all annular images to obtain one image; and performing double-random phase encoding encryption on the superposed image on the basis of fractional Fourier transform in an optical mode, wherein the transform order of the fractional Fourier transform and the random phase template are used as keys and the inner diameter and outer diameter of the transform annular area can be used as secondary keys. The method disclosed by the invention is simple and easy to operate, improves the image encryption efficiency, and has relatively good attack resistance and relatively high safety.
Owner:NANCHANG UNIV
Color image encryption method based on SHA-384 function, spatiotemporal chaotic system, quantum chaotic system and neural network
ActiveCN104008520BImprove securityLarge key spaceImage data processing detailsComputer hardwareDiffusion
The invention relates to a color image encryption method based on an SHA-384 function, a spatiotemporal chaotic system, a quantum chaotic system and a neural network. The method includes the steps that an original color image I0 is calculated through the SHA-384 function, a Hash value is obtained as a secret key, the Hash value, a CML and one-dimension Logistic chaotic mapping are utilized for generating a chaos sequence, bit-level line-column scrambling is carried out on high four-digit images of components of three primary colors of the I0 through the chaos sequence, and a scrambled image I1 is obtained; the Logistic quantum chaotic system is utilized for generating a chaos sequence for encrypting the scrambled image, and is combined with the neural network to carry out parallel diffusion processing on all pixel values of components of three primary colors of the I1, and a final encrypted image I2 is obtained. By the method, the space of the secret key is greatly enlarged, the safety, encryption effect and secret key sensibility are higher, the attack resistance capacity is higher, the scrambling process and the encryption time are shorter, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
Color Image Encryption Method Based on Latin Square Scrambling
ActiveCN108696666BImprove resistance to attackReduce strong correlationSecuring communication by chaotic signalsPictoral communicationPlaintextComputer hardware
The invention relates to a color image encryption method based on Latin square scrambling. Plaintext keys r1, g1 and b1 are calculated through utilization of R, G and B components of a color plaintextimage, an initial value and a parameter obtained through calculation based on the keys are substituted into a chaotic system, and three groups of chaotic sequences are generated; the chaotic sequences for scrambling and diffusion are selected through utilization of a chaotic sequence selection mechanism based on the plaintext and digital arrangement; and a final ciphertext image is obtained through adoption of a block scrambling policy based on a Latin square and the chaotic sequences, and diffusion operation based on the plaintext and a scrambled image. The encryption method is closely related to the plaintext, so the plaintext attack resistance is improved. The employed chaotic system is an improved chaotic system, a chaotic characteristic is good, the randomness is high and a key spaceis great, so a security level is further improved. A simulation result and safety analysis show that according to the encryption provided by the invention, an image complete encryption demand can besatisfied, the encryption efficiency is high, and the robustness is high.
Owner:HENAN UNIVERSITY
Image Encryption Method Based on Dynamic Key Selection of Hyperchaotic System
The invention relates to an image encryption method based on hyperchaotic system key dynamic selection, which mainly includes the following steps: arranging the original plaintext images into an image array P, and then using the hyperchaotic system to generate chaotic sequences and grouping them; combining the plaintext-dependent KSSG and KS dynamic selection mechanism to generate forward scrambling key K1, and perform forward scrambling on P to obtain P1; combine KSSG and KS mechanism to generate forward diffusion key K2, and perform forward diffusion on P1 to obtain P2; combine KSSG and KS The dynamic selection mechanism generates reverse scrambling key K3, reverse scrambles P2 to obtain P3; uses KSSG and KS dynamic selection mechanism to generate reverse diffusion key K4, performs reverse diffusion on P3 to obtain P4, and reorganizes P4 That is, the final ciphertext image is obtained. The above method increases the key space, makes the security, the encryption effect and the key sensitivity higher, the anti-attack ability is stronger, and it is easier to realize by hardware.
Owner:HENAN UNIVERSITY
A car license plate with an encrypted qr two-dimensional code
InactiveCN104527535BEasy accessOvercoming inefficiencyCharacter and pattern recognitionVehicle componentsComputer hardwareCiphertext
Owner:HEFEI UNIV OF TECH
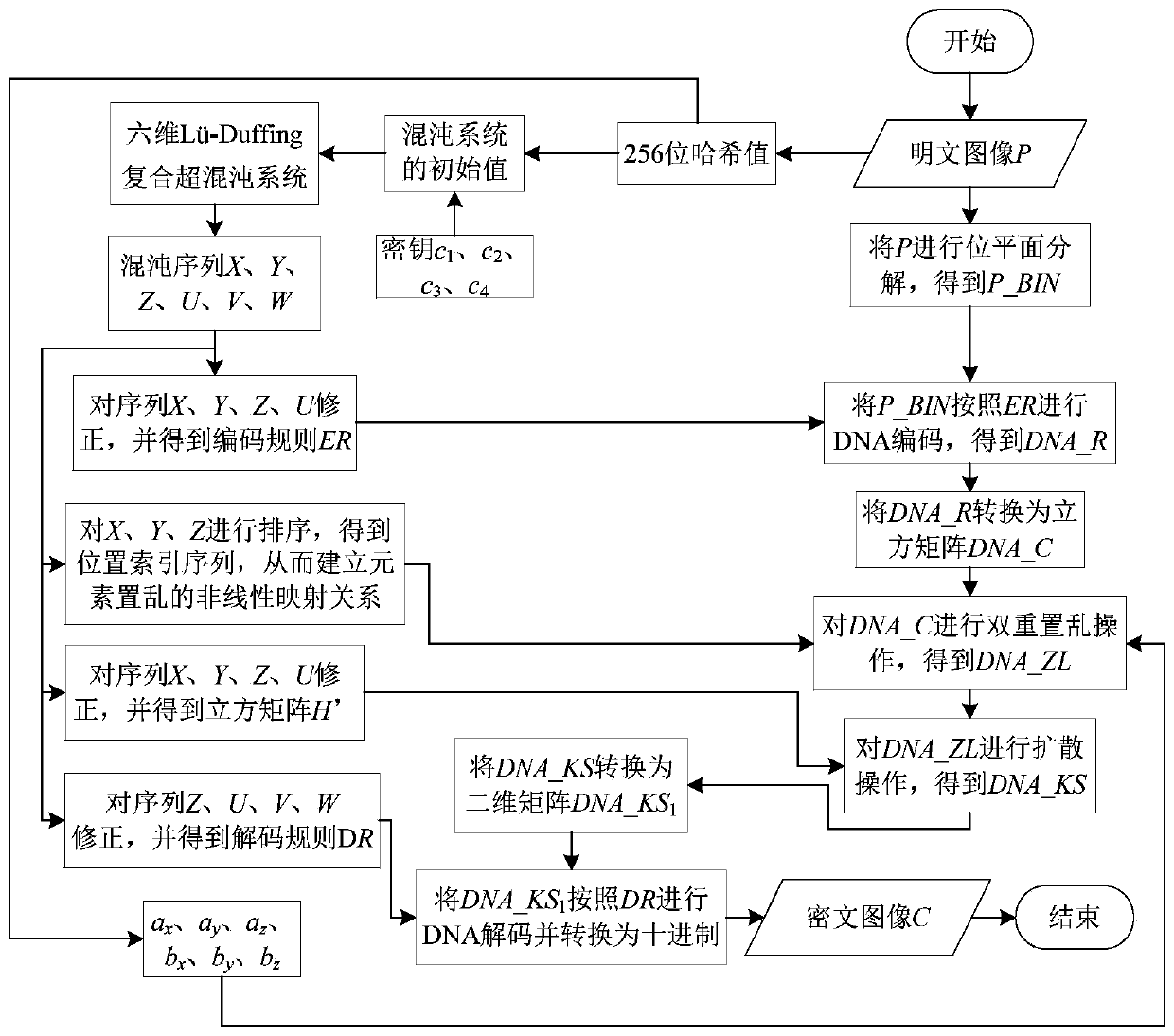
Chaotic Image Encryption Method Based on Double Reset Scrambling and DNA Coding
ActiveCN108898025BAvoid multiple iterationsImprove securityDigital data protectionHash functionAlgorithm
The invention relates to a chaos image encryption method based on dual scrambling and DNA coding, firstly, carrying out bit plane decomposition on a plaintext image and carrying out DNA coding and transformation on the image to turn the image into a three-dimensional DNA matrix; then, scrambling the three-dimensional DNA matrix through the dual scrambling operation, wherein the sequence of the chaotic sequences is scrambled and the DNA sequence is scrambled in a bit level through combining the three-dimensional cat mapping; next, performing diffusion operation on the scrambled three-dimensional DNA matrix, and converting the diffused matrix into a two-dimensional DNA matrix; finally, performing decoding operation on the two-dimensional DNA matrix to obtain a ciphertext image. According tothe invention, the SHA256 hash function of the plaintext image is used to calculate the initial value of the chaotic system, and the parameters of three-dimensional cat mapping are also related to theplaintext image, which enhances the ability of the algorithm to resist the selection of plaintext attack. Experimental results and safety analysis show that the encryption scheme can resist various known attacks, and can effectively protect the security of images and also can improve the security level.
Owner:HENAN UNIVERSITY
A Quantum Image Encryption Method Based on Hyperchaotic System
ActiveCN105373739BImprove resistance to attackImprove securityChaos modelsDigital data protectionComputer hardwareQuantum
Owner:NANCHANG UNIV
A Safe and Effective Client Deduplication Method Based on Possession Proof
ActiveCN108600263BLimit the number of interactionsResist Brute Force AttacksKey distribution for secure communicationEncryption apparatus with shift registers/memoriesKey serverAttack
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
An image encryption method based on h geometric fractal and hilbert curve
ActiveCN109903212BWide application of secure transmissionLarge key spaceImage data processing detailsKey spaceSecure transmission
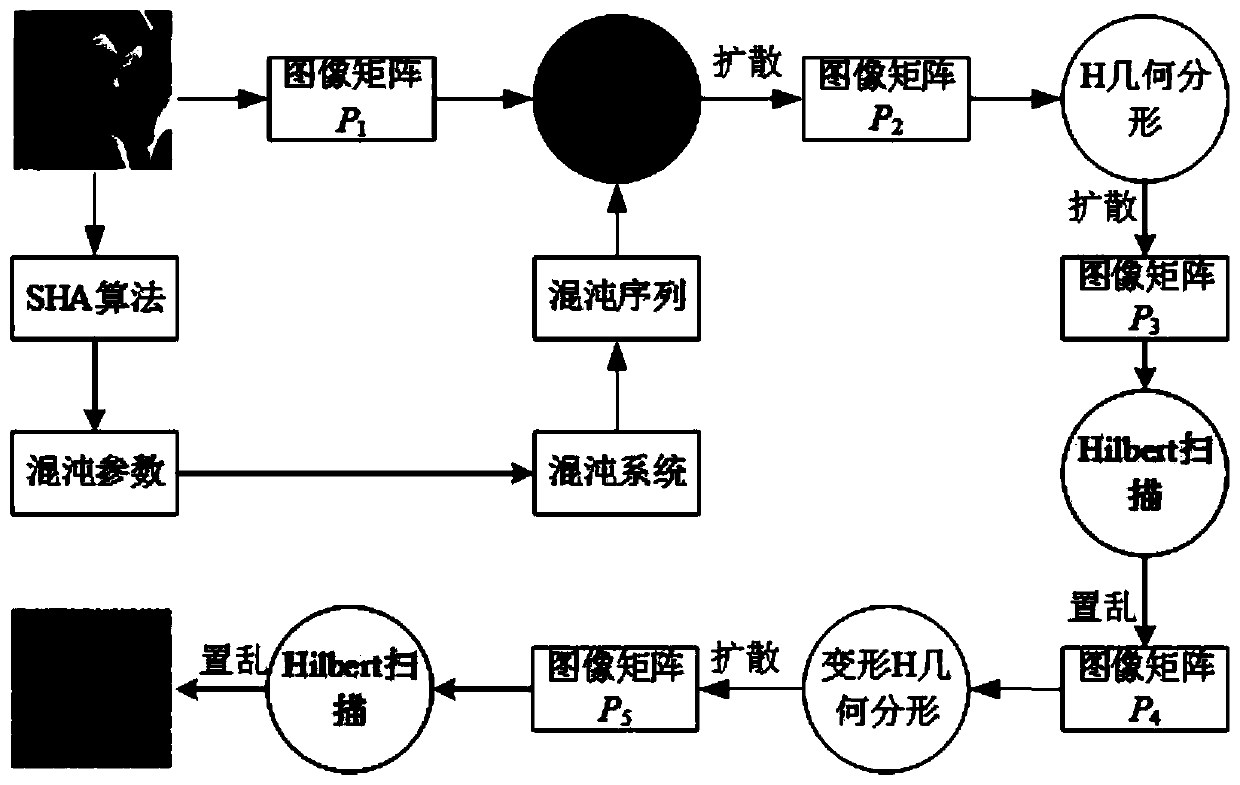
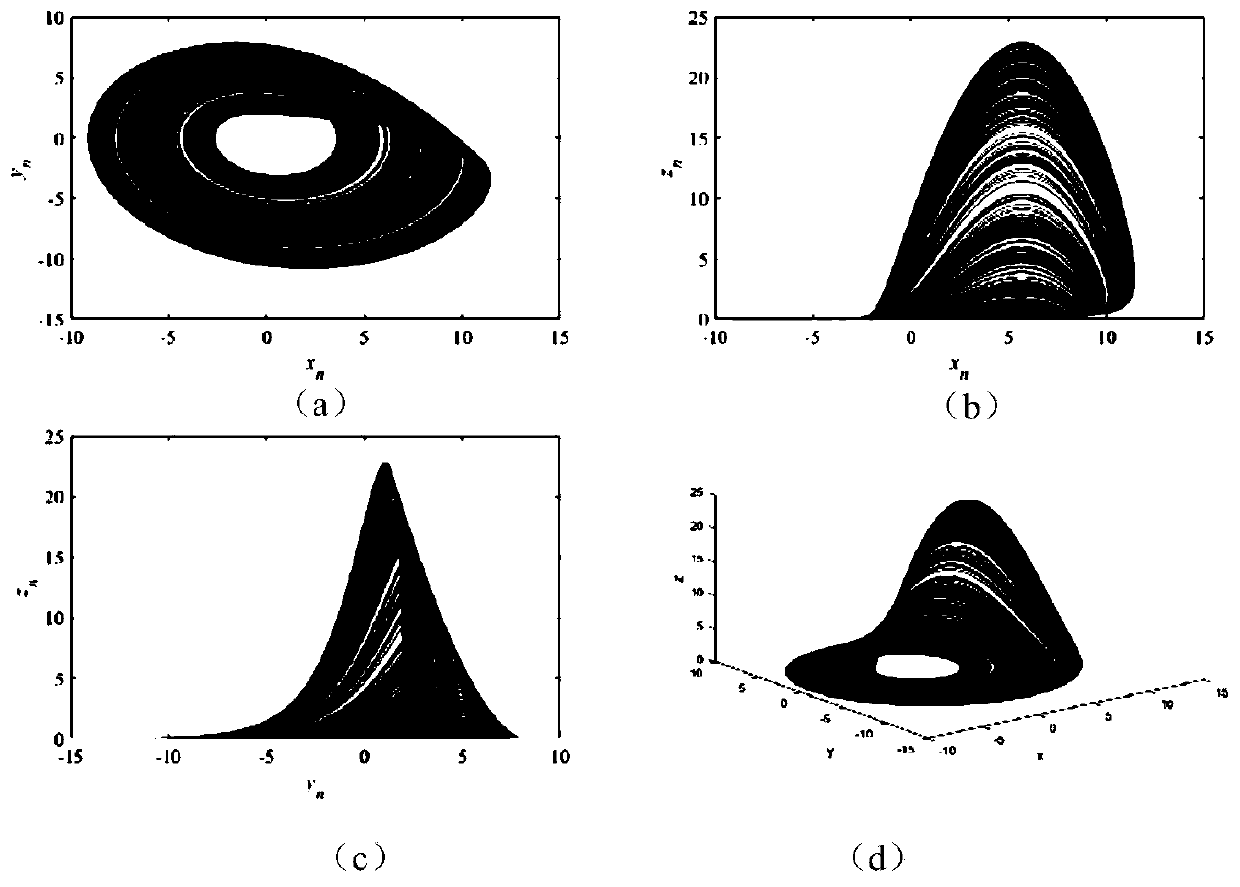
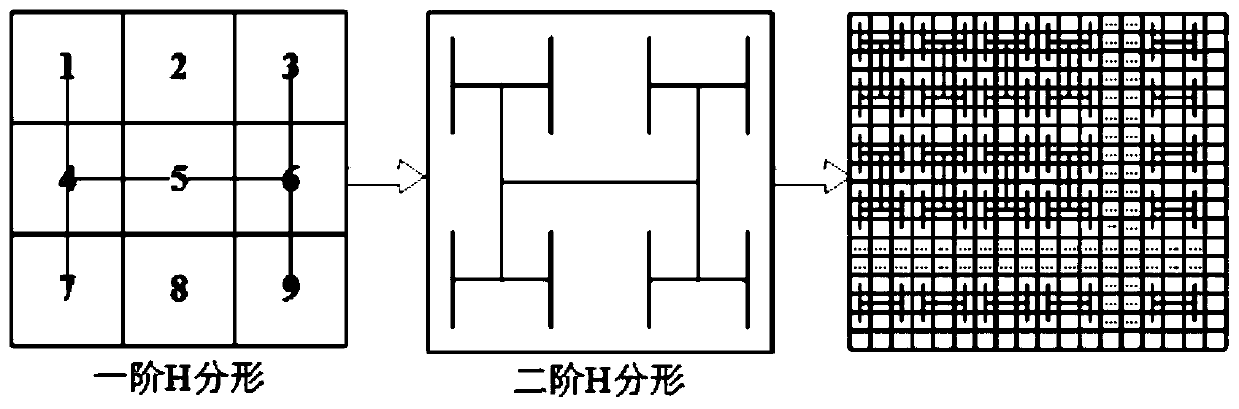
The invention provides an image encryption method based on H geometric fractal and a Hilbert curve. The image encryption method comprises the following steps: calculating a hash value of the originalgray level image as an initial value of a chaotic system by using an SHA-3 algorithm, and carrying out bitwise ratio specificity or diffusion on image pixels by using a sequence generated by the chaotic system; And alternately carrying out diffusion operation and two-dimensional Hilbert scanning curve scrambling operation by using the second-order H fractal to obtain an encrypted image. Accordingto the invention, Hilbert curve scanning scrambling and H geometric fractal diffusion are adopted, and a chaotic system, DNA coding, a Hilbert scanning curve and H fractal are combined to realize tworounds of pixel position scrambling and pixel value diffusion; Experimental results and security analysis show that the method not only has enough key space to resist exhaustive attacks, but also canresist statistical attacks, differential attacks, data loss attacks and noise attacks, and is widely applicable to secure transmission of image information.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
A Chaotic Encryption Method for Speech Information
ActiveCN106375079BGood pseudorandomnessExtended cycleSecuring communication by chaotic signalsKey spaceAlgorithm
The invention discloses a chaotic encryption method for voice information. The method is characterized in comprising the steps of 1), establishing a dynamic variable parameter composite chaotic system and generating a real-value chaotic sequence of which length is the same to that of a plaintext voice sequence through utilization of the system; 2), carrying out binarization processing on the real-value chaotic sequence, thereby obtaining a chaotic key sequence of which length is the same to that of the plaintext voice sequence; and 3), through combination of the chaotic key sequence, carrying out bit-by-bit exclusive or operation on the plaintext voice sequence, thereby obtaining a ciphertext. According to the method, under limited calculation precision, the chaotic sequence with good pseudo-randomness can be generated, the valid precision effect is reduced, and a chaotic sequence cycle is prolonged; and through adoption of a chaotic system cascading mode, the encryption security is improved, a sufficient key space can be generated, and an exhaustive attack can be resisted effectively.
Owner:HUAQIAO UNIVERSITY
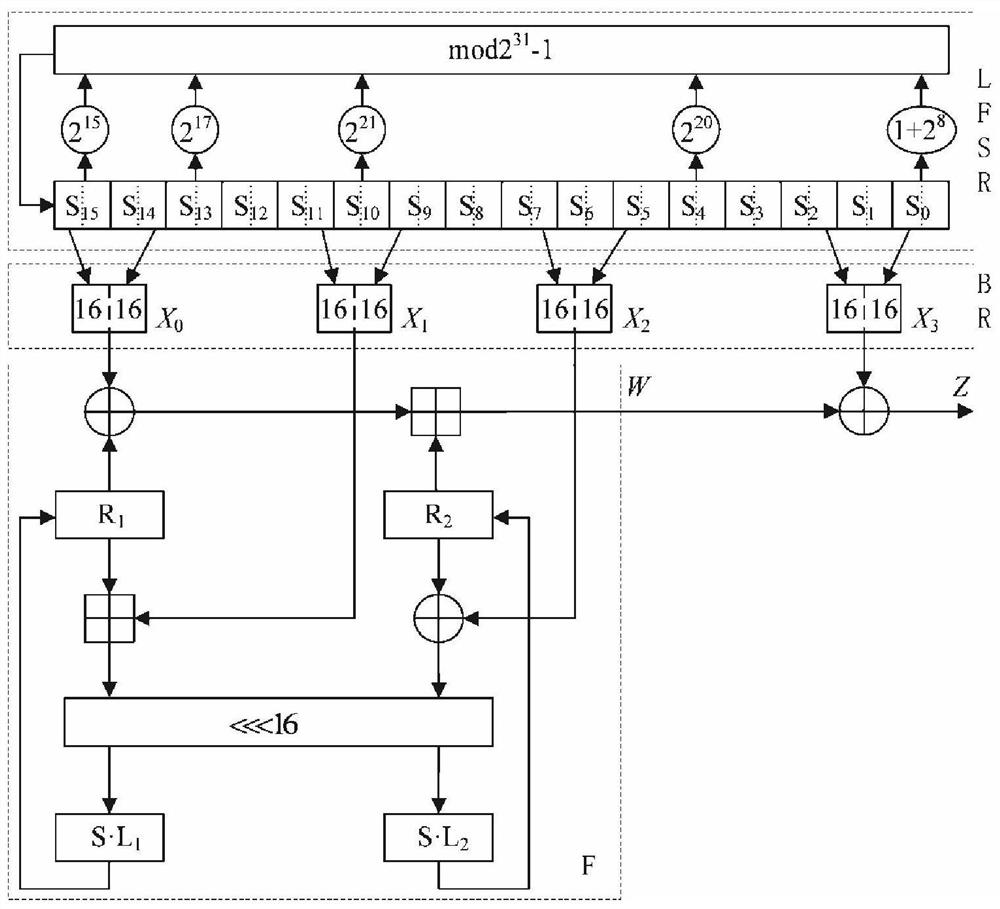
A fpga-based zuc encryption system ip core construction method
ActiveCN112367155BGuaranteed continuityRun fastKey distribution for secure communicationSecuring communication by chaotic signalsStream managementLogisim
The invention provides a method for constructing an IP core of an FPGA-based ZUC encryption system. ZUC is used as a key stream generation algorithm, and the output of an improved one-dimensional discrete chaotic system based on the Logistic chaotic system is used as the initial vector IV of ZUC, which is implemented in hardware. When encrypting the system, the flow management mode is used to realize the data interaction between various modules. In this transmission mode, both the upstream and downstream have the right to stop the other party and the obligation to respond to the other party being stopped. The transmission guarantees the correctness of the handshake logic and the continuity of the data. The FIFO memory is added to the corresponding module to cache, so that the upstream and downstream The latent period of inter-divergence can be converged to 1, so that the advantages of FPGA parallel work can be truly utilized, and the running speed of the entire encryption system can be effectively improved. The present invention combines the sequence cipher with chaos through the important parameter initial vector IV in the sequence cipher, so that the key of the whole system can be replaced regularly, thereby further improving the security performance of the whole system.
Owner:HEILONGJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com