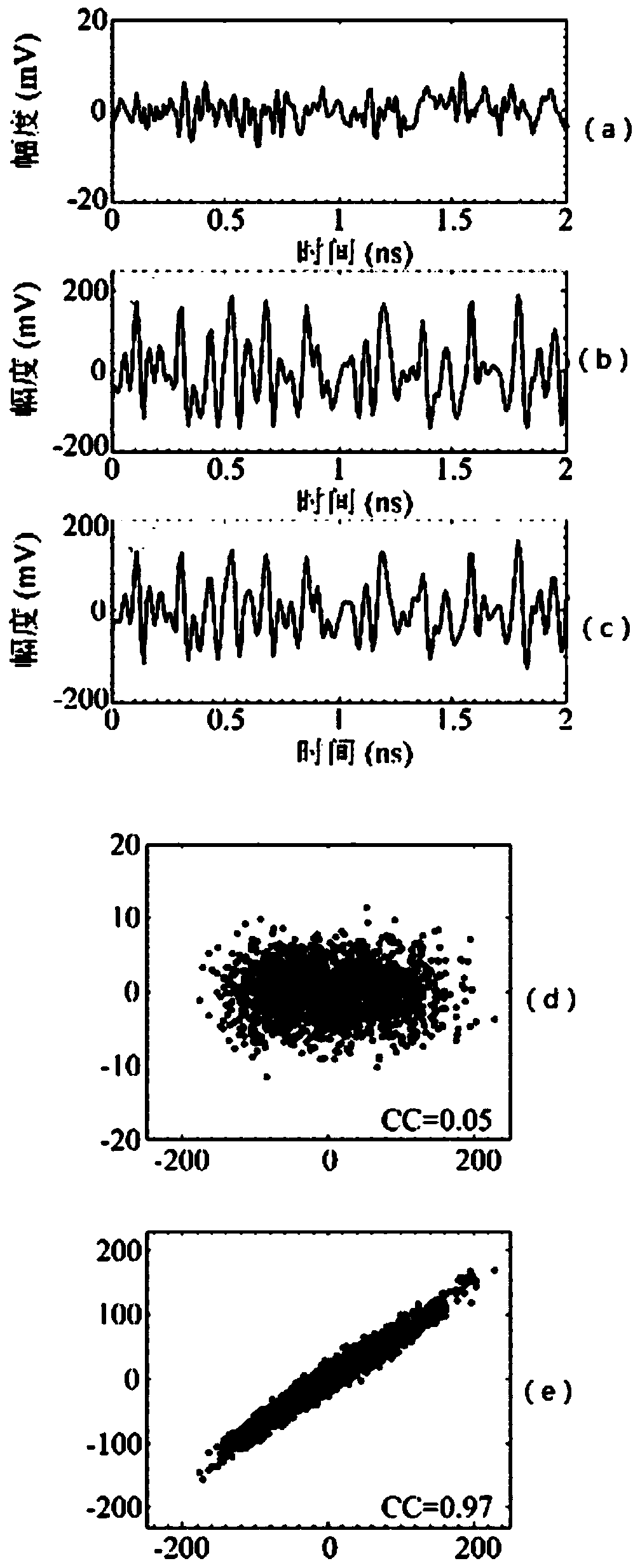
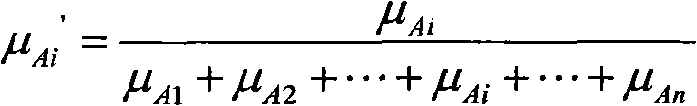Patents
Literature
576results about How to "Implement encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
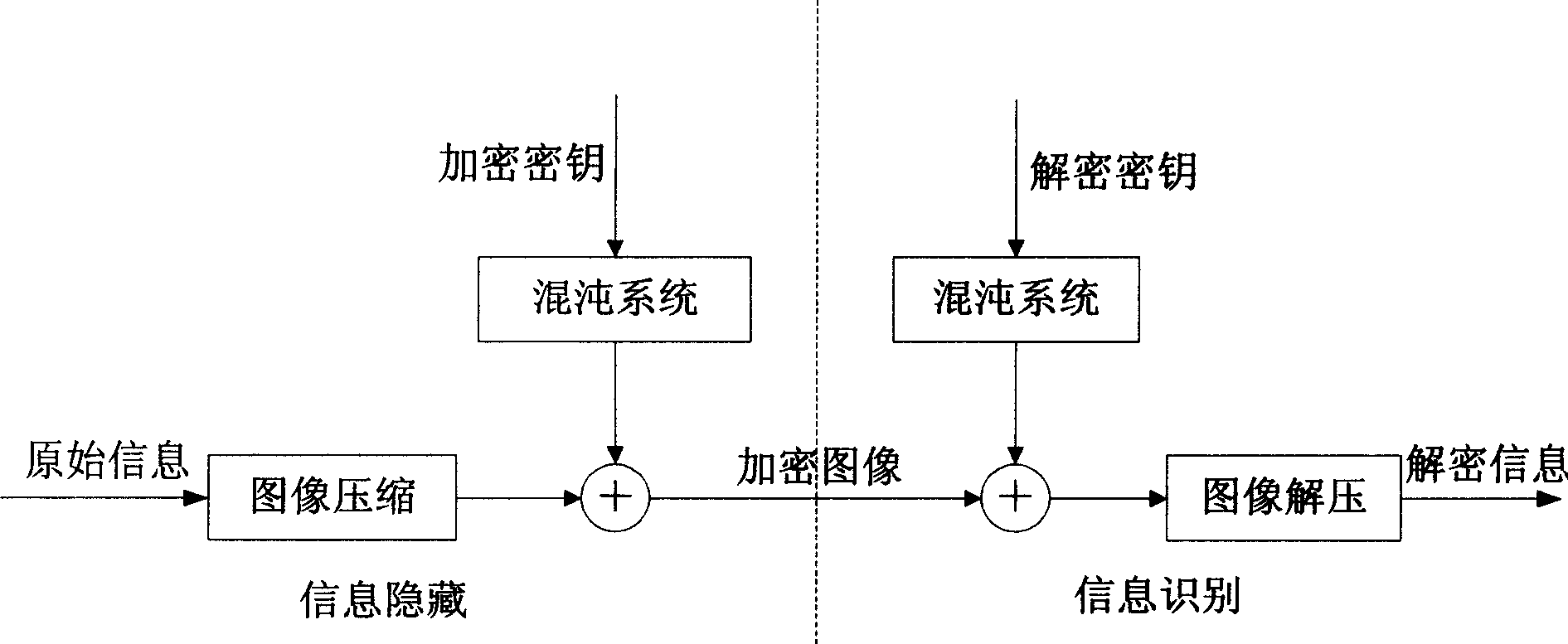
CPK credibility authorization system
InactiveCN1832403AEliminate Collusion AttacksImprove securityUser identity/authority verificationKey exchangeHash function
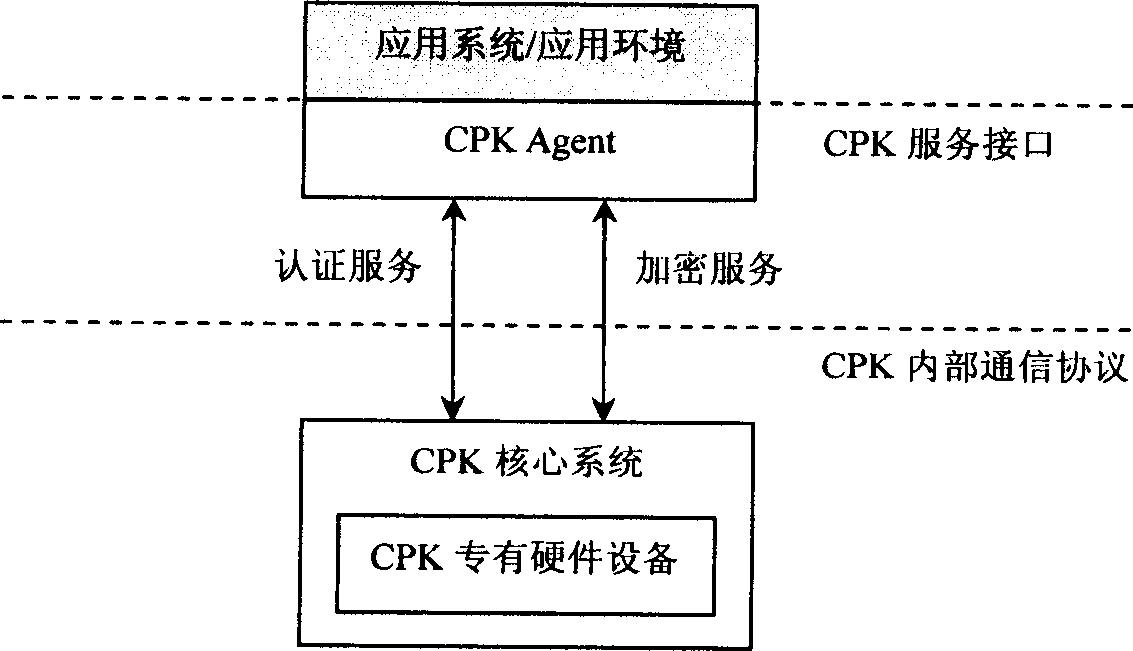
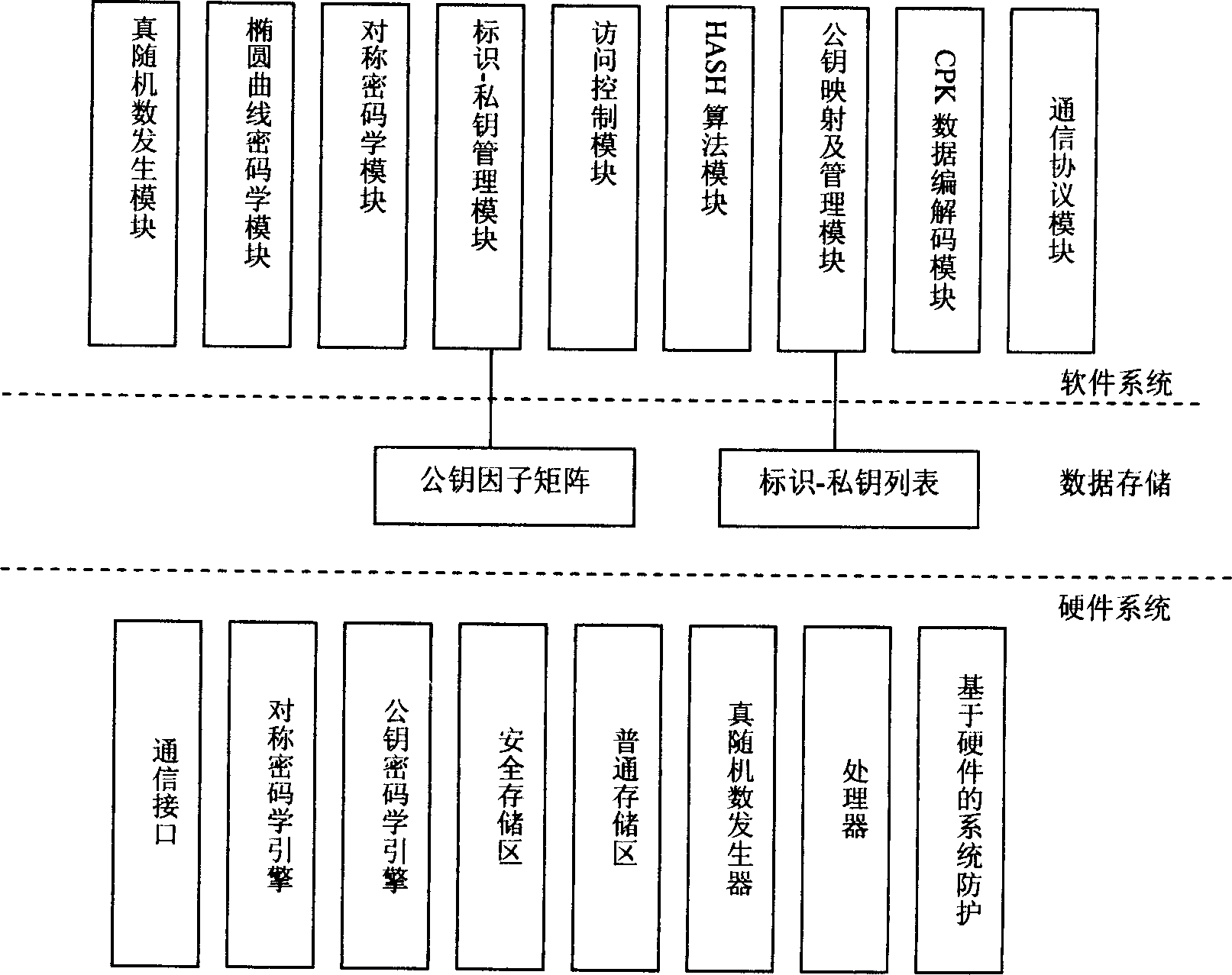
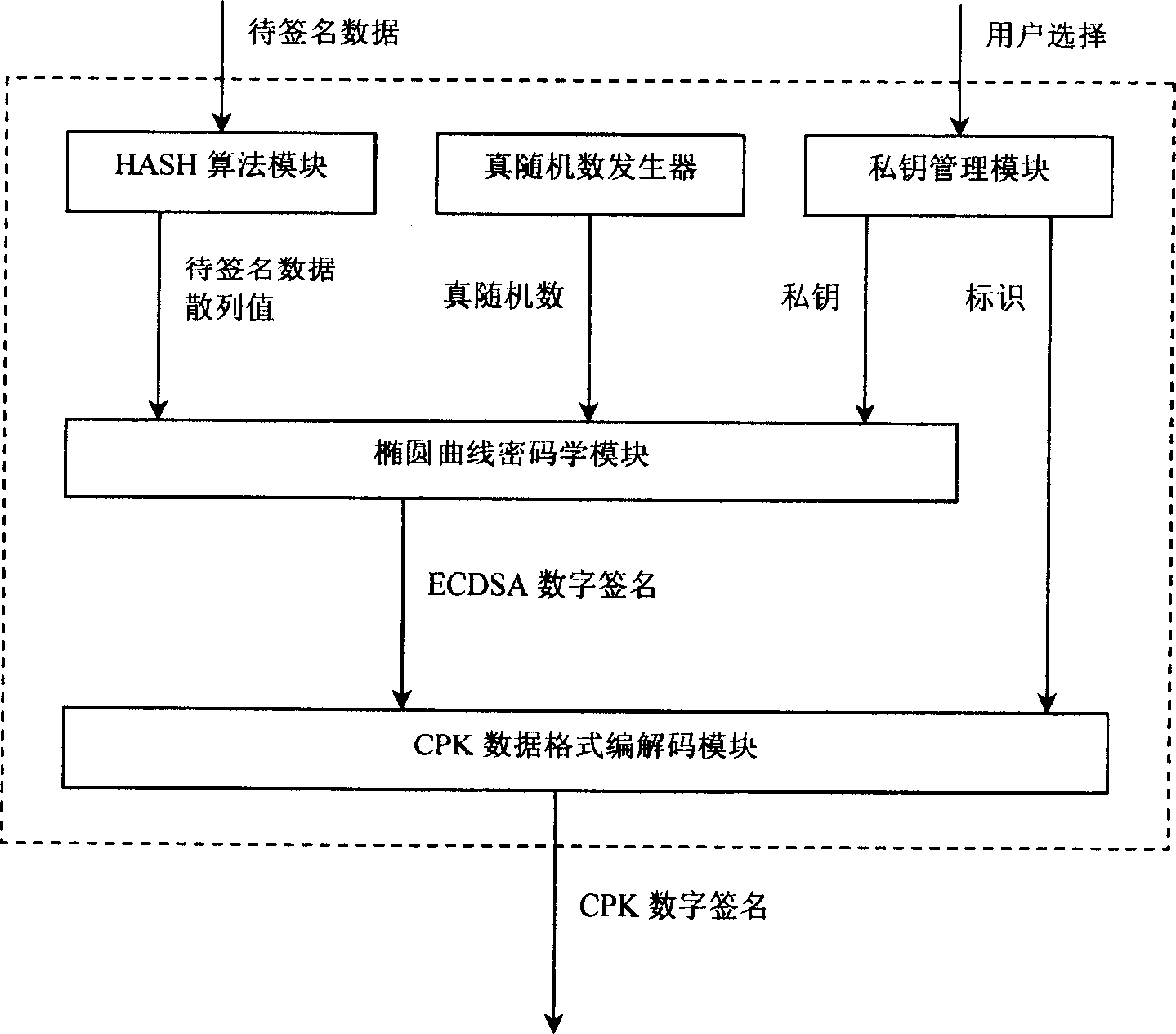
This invention discloses a CPK trustable certification system with a chip including special COS, CPK algorithm, ID certificates, signature protocol, a cryptographic key exchange protocol, a ciphering algorithm and HASH function and divided into intelligent card, USB Key, Flash card and cell phone SIM card. One chip can bear the functions of a cipher machine, signature verification, cryptographic key storage and management.
Owner:BEIJING E HENXEN AUTHENTICATION TECH
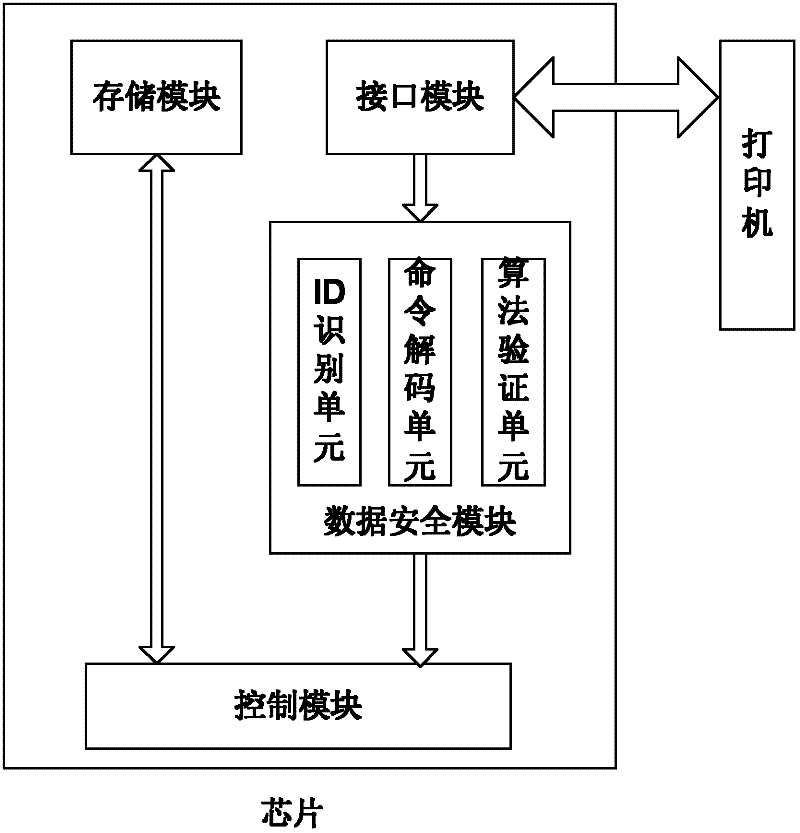
Chip, data communication method for chip, consumable container and imaging equipment
InactiveCN102231054AImprove reliabilityAvoid crackingElectrographic process apparatusPrintingExternal dataStructure of Management Information
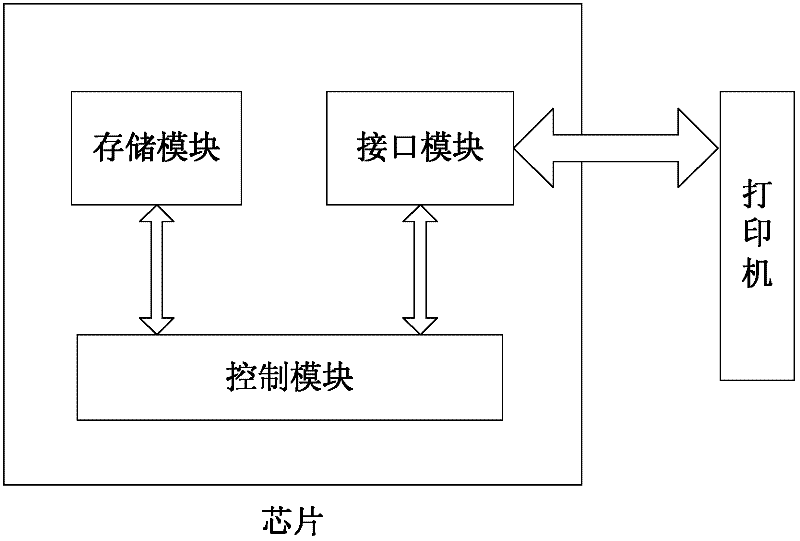
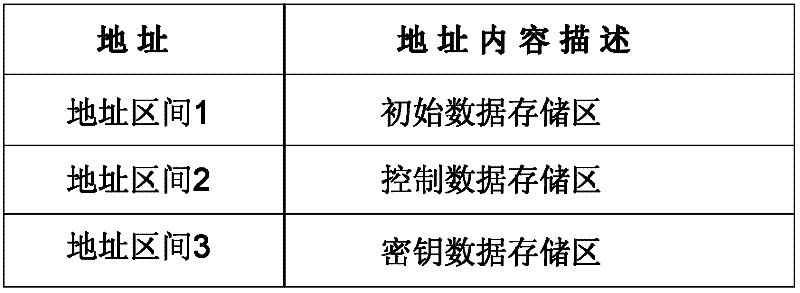
The invention provides a chip of a consumable container, which comprises a storage module, a control module, an interface module and a data safety module. The storage module is used for storing initial data, printing data, control data and key data; the interface module is used for realizing data communication between the storage module and the control module; the data safety module is respectively connected with the interface module and the control module, and is used for identifying a type and a content of data communicated between a printer and the chip, encrypting matched data in a selected safe mode and decrypting the data; the control module is connected with the storage module and is used for controlling data communication between the chip and the printer and the access operation of the data of the storage module and external data and sending a corresponding control command to the chip according to a safety module processing result so as to realize data communication; and the same keys are stored in the printer and the chip. The invention also provides a data communication method for the chip, the consumable container with the chip structure, and imaging equipment with the consumable container. The safety of the communication data of the chip can be protected.
Owner:ZHUHAI TIANWEI TECH DEV CO LTD
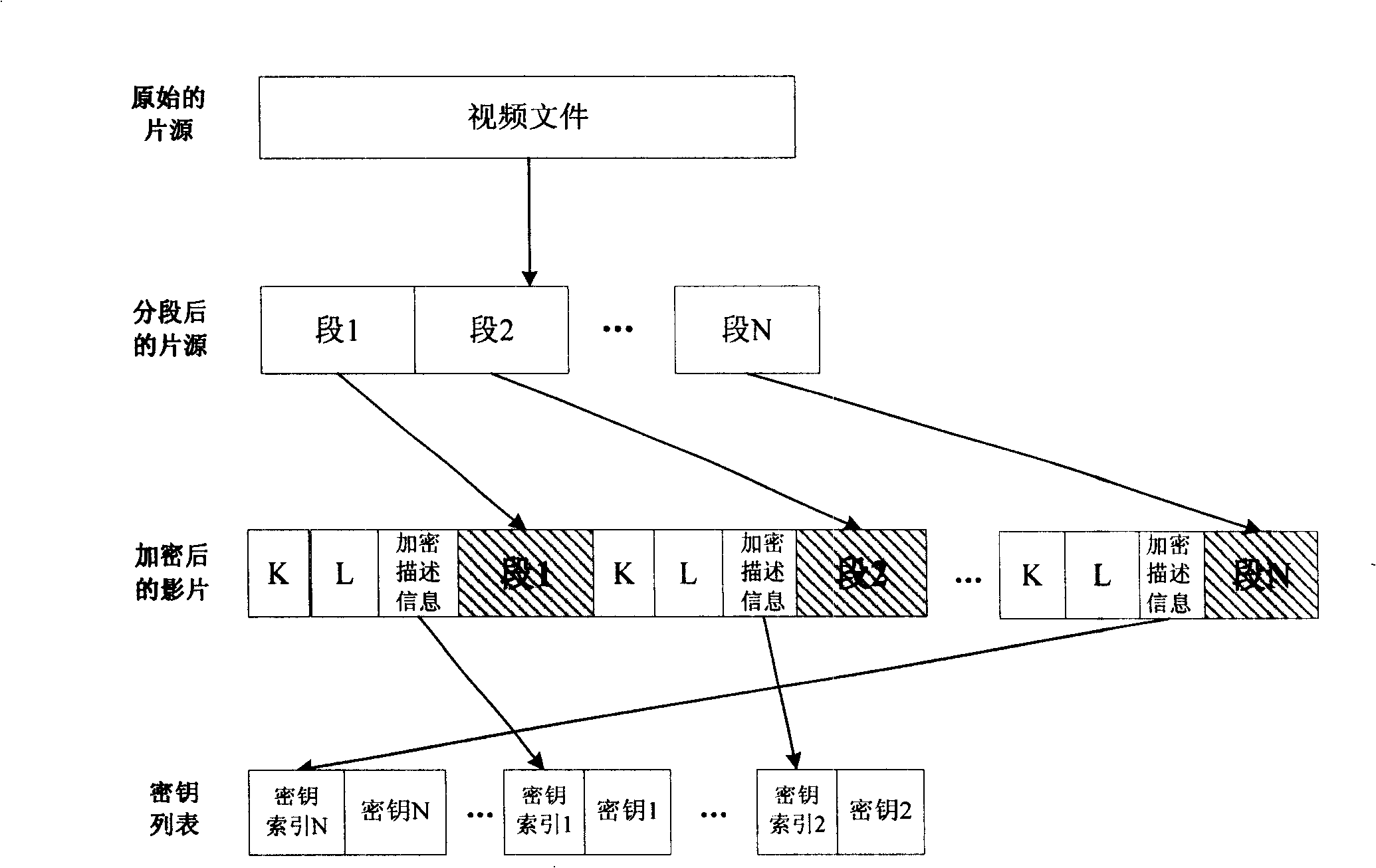
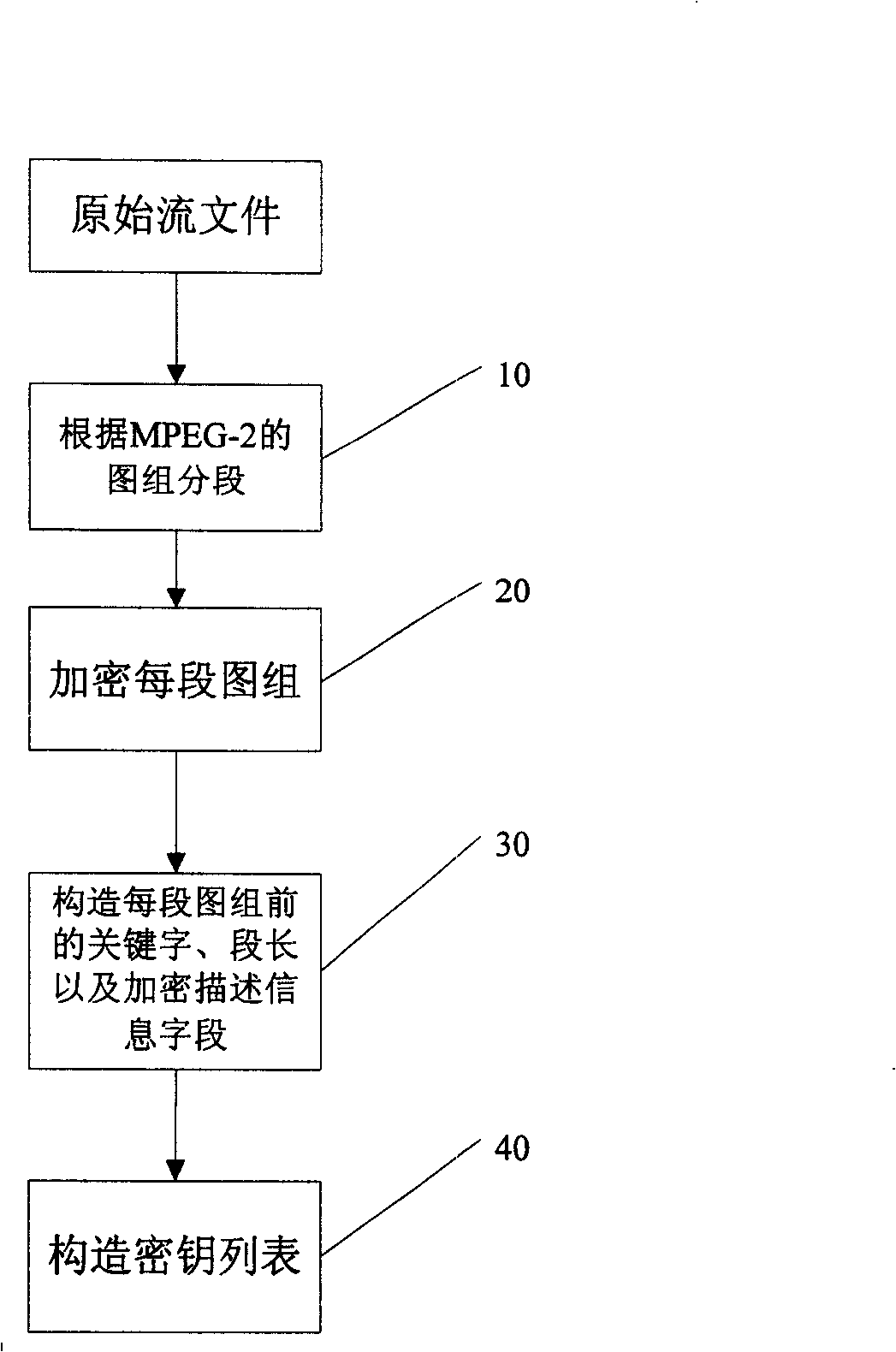
File enciphering method and enciphered file structure in digital media broadcasting system
InactiveCN101247506AImprove securityIncrease flexibilityAnalogue secracy/subscription systemsDigital video signal modificationDigital Video BroadcastingParagraph
The present invention discloses a method for encrypting the file in the digital medium playing system and the encrypted file structure thereof, wherein, the method comprises the following procedures: (1) dividing the file to a plurality of segments according to the format character of the file; (2) encrypting the segment content which needs to be encrypted; (3) including paragraph identifier in each segment; and (4) forming all the key values correlative to the file to a key list which is used for transmitting to the subscriber. The encrypted file structure comprises a medium file which is composed of a plurality of segments and a key list that is composed of a plurality of key index values and the corresponding keys. Each segment comprises medium content and the segment length field which is used for indicating the total length of this segment of data. The invention possesses the advantage that the functions of speeding, quickly returning, jumping broadcasting and the like are realized and the security of the encrypted file is increased.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
Intelligent vending machine
ActiveCN105825583AImprove experienceImplement encryptionCoin-freed apparatus detailsApparatus for dispensing discrete articlesSystems managementIntelligent city
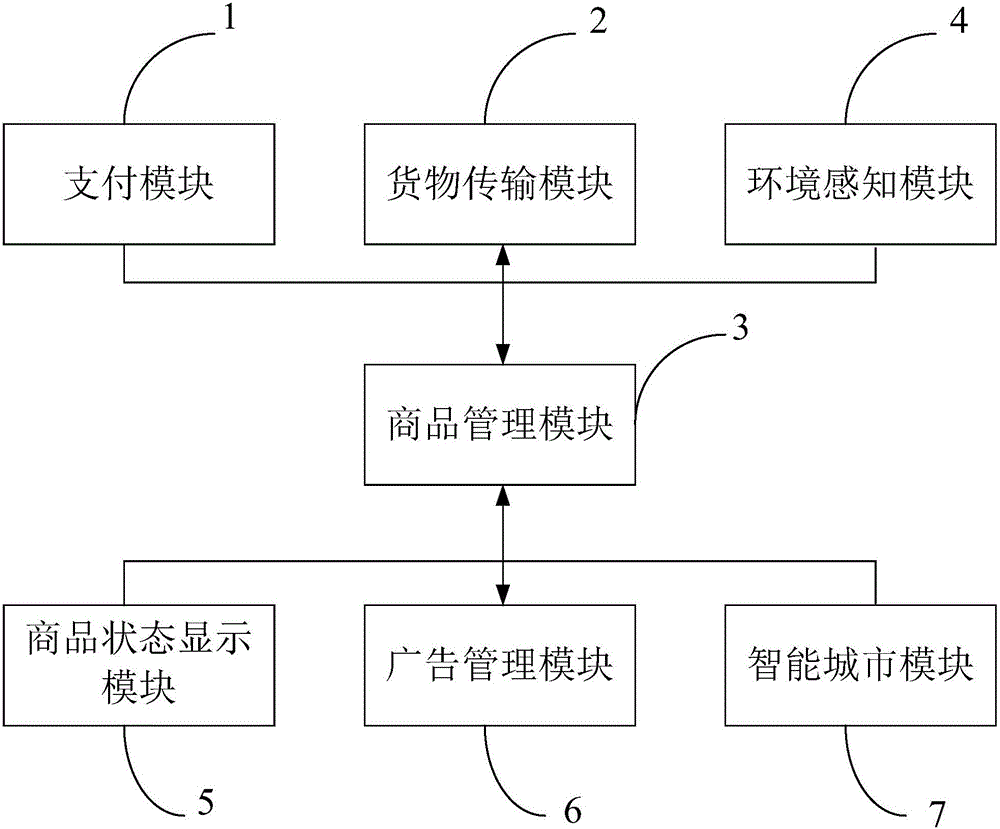
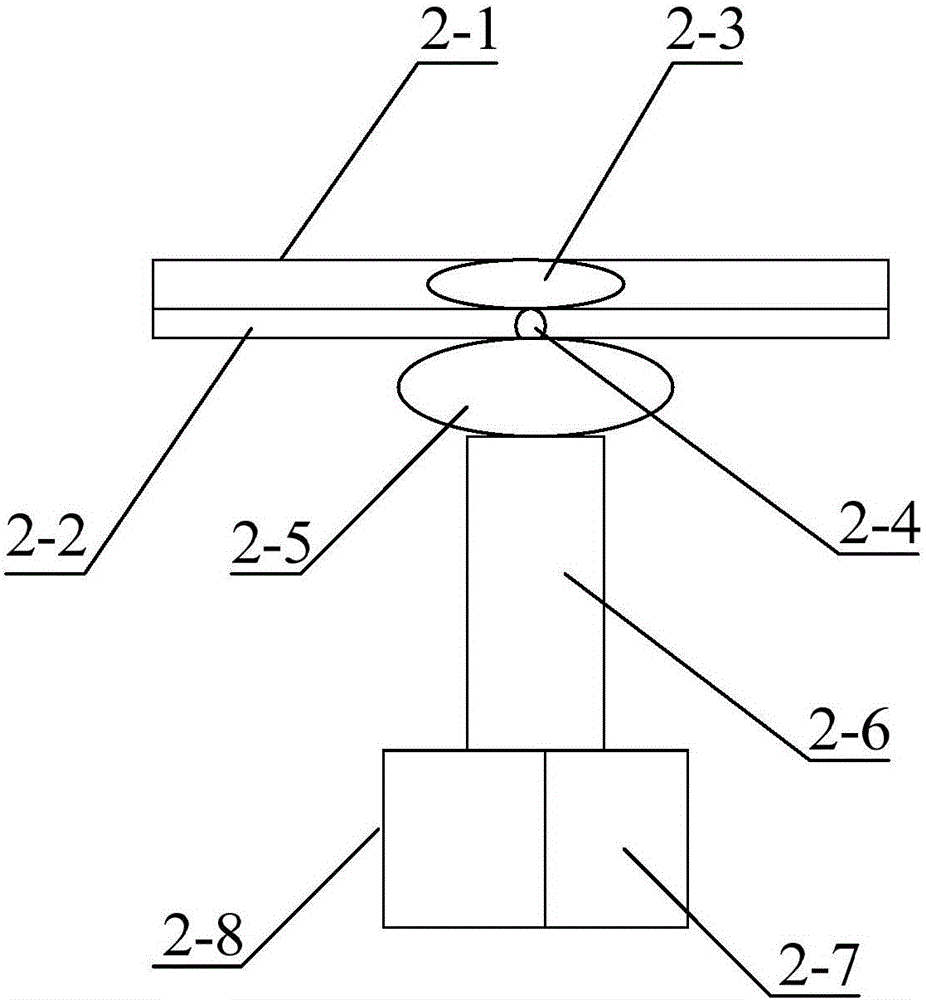
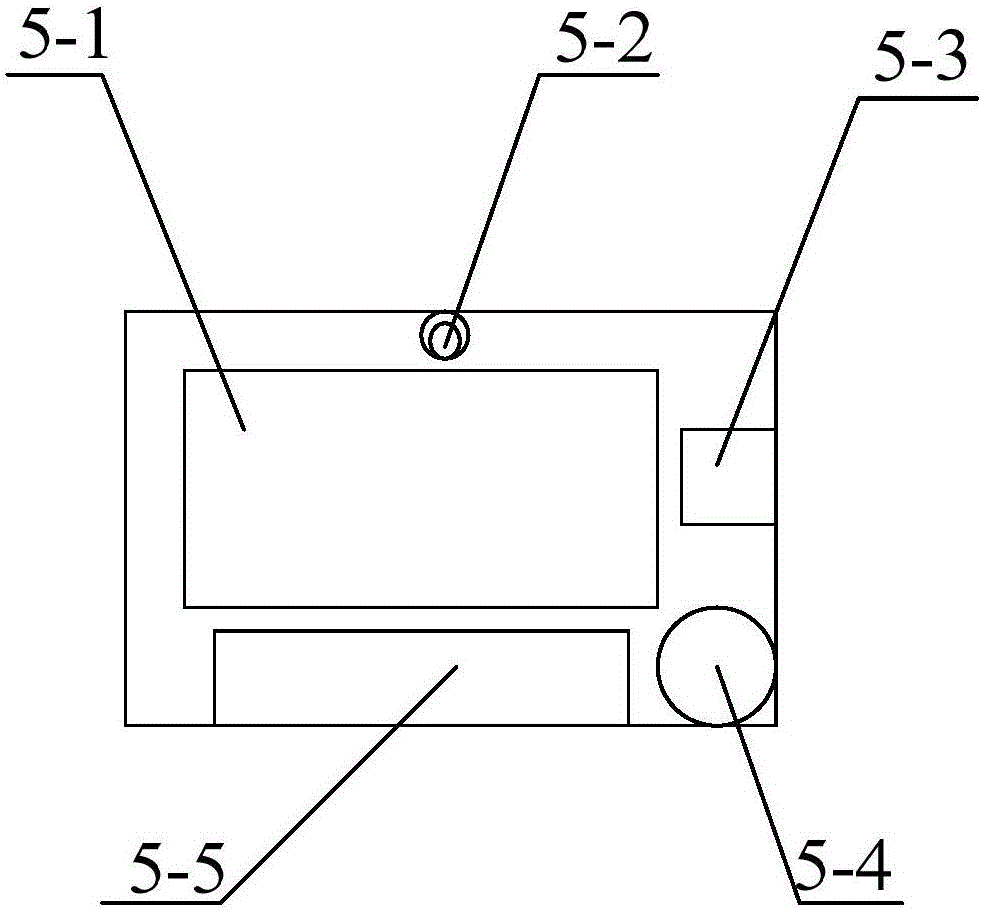
The invention discloses an intelligent vending machine. A payment module, a cargo transmission module, a commodity management module, an environment sensing module, a commodity state display module, an advertisement management module and an intelligent city module are arranged inside a machine body, wherein the commodity management module comprises a system management and communication center, a mobile display hand set and a remote vending machine operation terminal; the payment module comprises a mobile payment module, an iris payment module and a face payment module; the intelligent city module and the advertisement management module are used for displaying and inquiring relevant city information. The intelligent vending machine has the advantages that a manager can be timely notified to supplement cargos in time; the function of reminding the concrete position of the vending machine with the short lacked commodity distance is achieved; the cloud server can recommend buying commodity to the user according to the weather, temperature, geographic position and health preserving information sensed by the vending machine according to seasons; the user experience is enhanced; various payment functions are realized; convenience and high speed are realized.
Owner:永州巨米智能科技有限公司
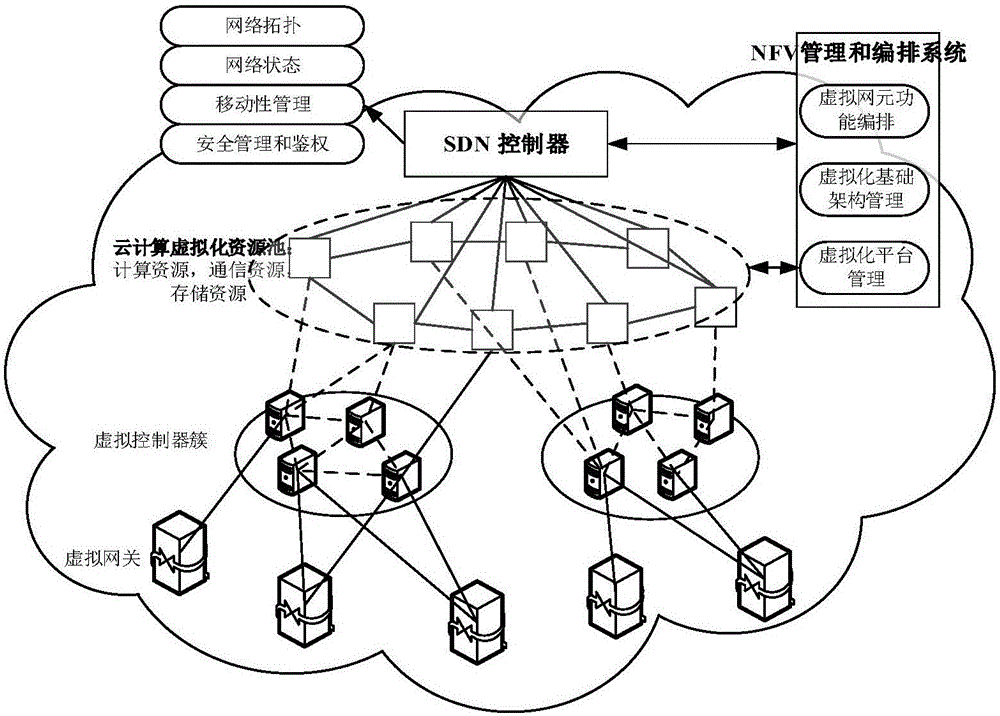
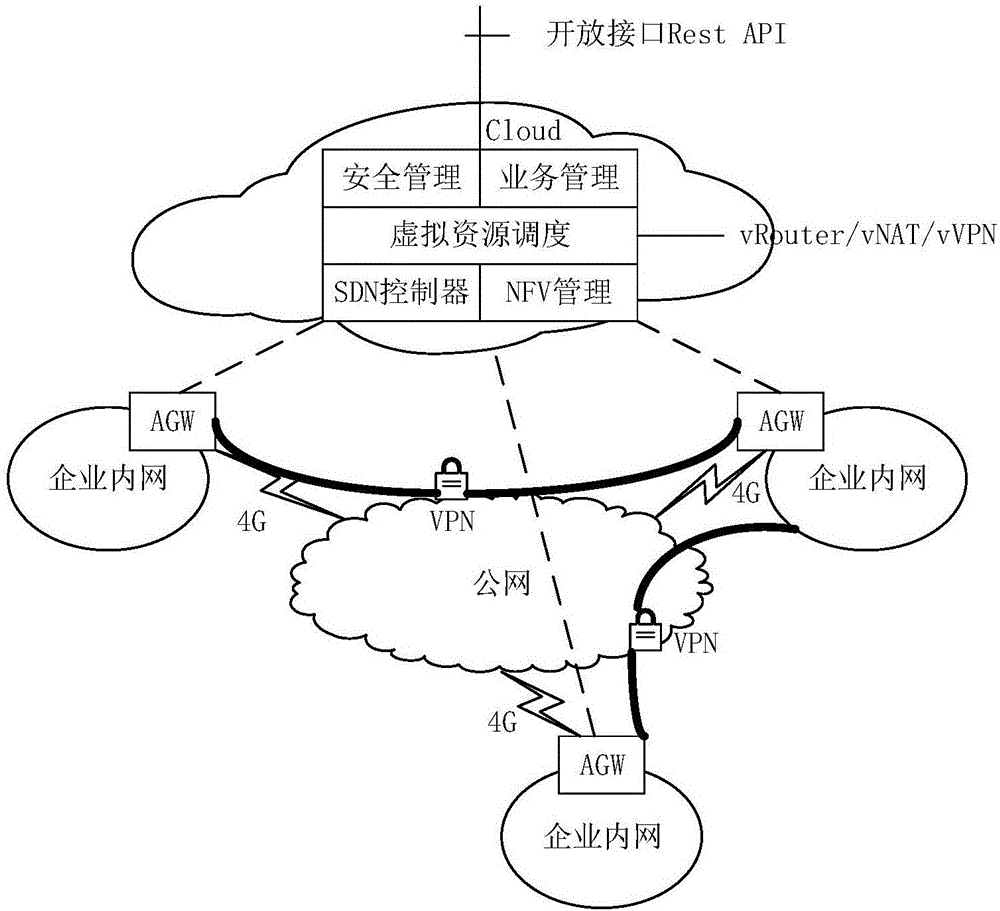
Intelligent manufacturing special network data acquisition scheduling system
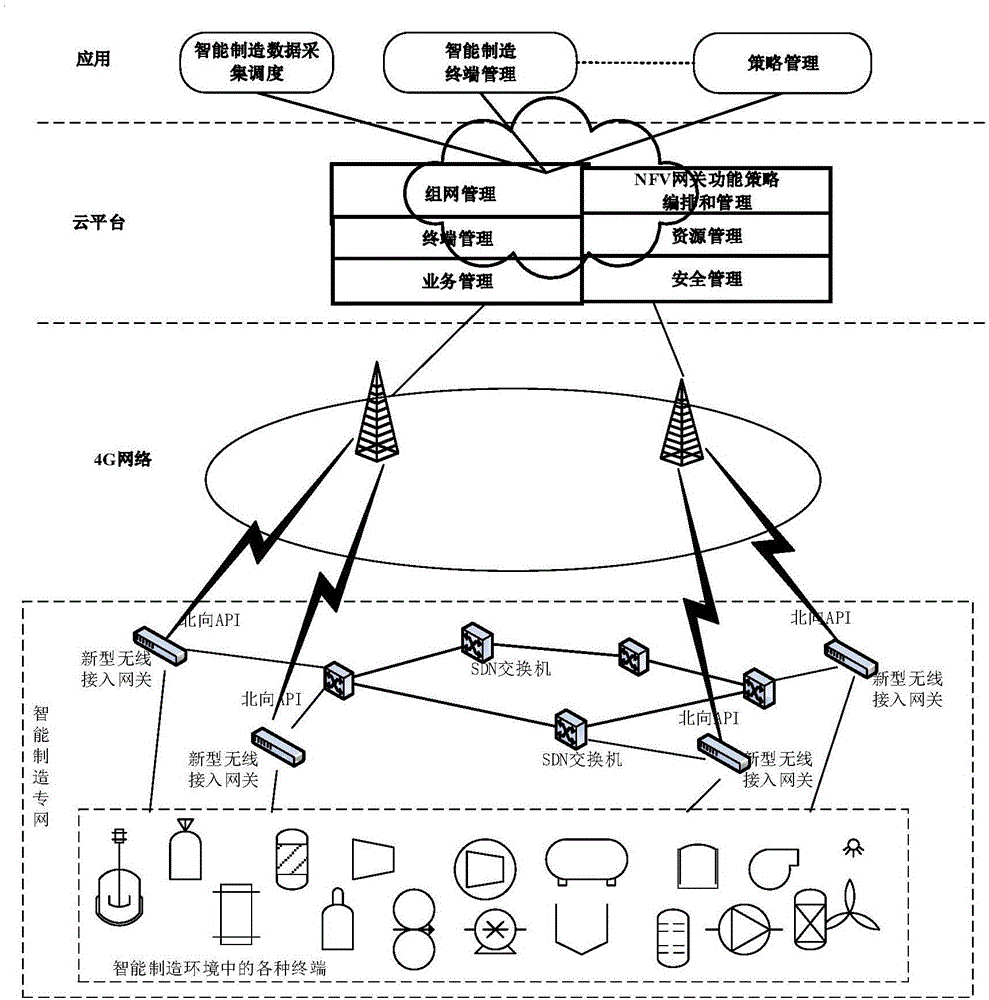
ActiveCN106603659ARealize control function refactoringRapid realization of control function reconfigurationTransmissionData acquisitionSmart manufacturing
The invention discloses an intelligent manufacturing special network data acquisition scheduling system. On the basis of conception of forwarding and control plane separation, a 4G special line intelligent scheduling system facing intelligent manufacturing is constructed, moreover, the system further satisfies concentrated scheduling and decentralized domain management functions, flexible network resource calling and rapid disposition capability are realized, standard northwards API interfaces are provided for the external, and concentrated management of wireless access equipment, on-demand scheduling and rapid security and other value-added service business opening are realized through SDN and NFV technologies. The system comprises five parts, including an internal network connected with manufacturing equipment in enterprises, a wireless access network based on 4G, a novel wireless access gateway connected with the internal network and an external network, a cloud platform used for carrying out concentrated network scheduling management, and various applications for intelligent manufacturing. The full-network configuration is realized through employing the cloud platform, network interconnection is realized through the novel access gateway, for network element functions, an SDN method is employed to separate a control plane from a data plane in an adaptive mode.
Owner:NANJING UNIV OF POSTS & TELECOMM
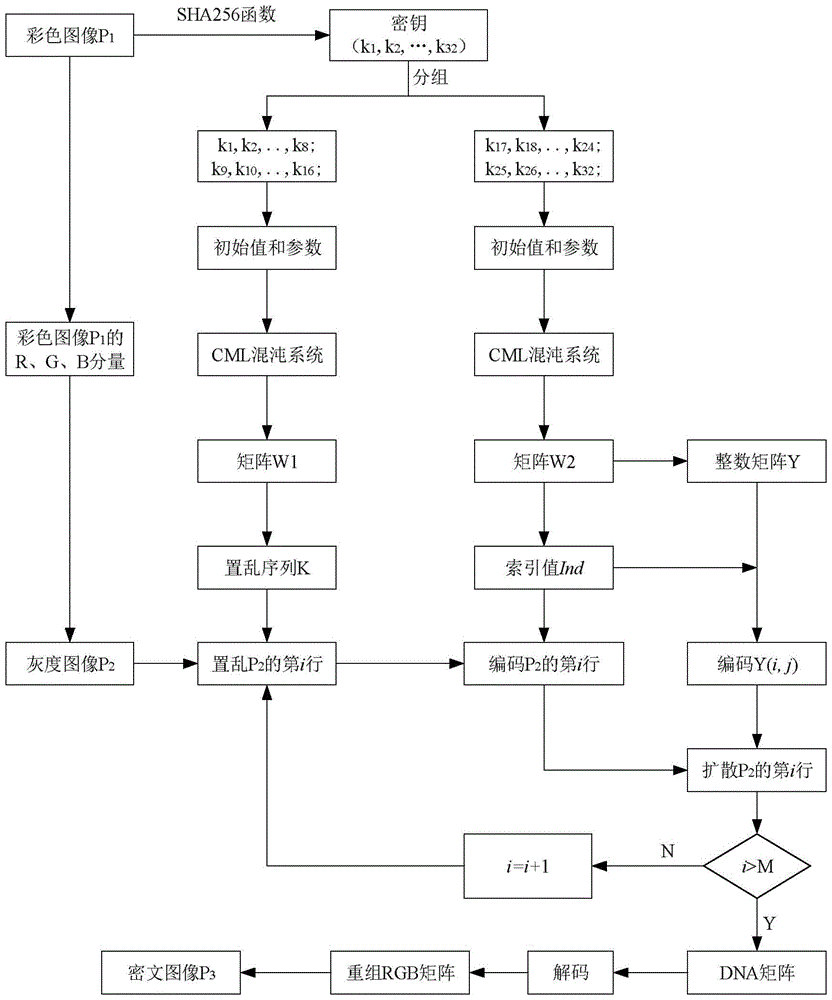
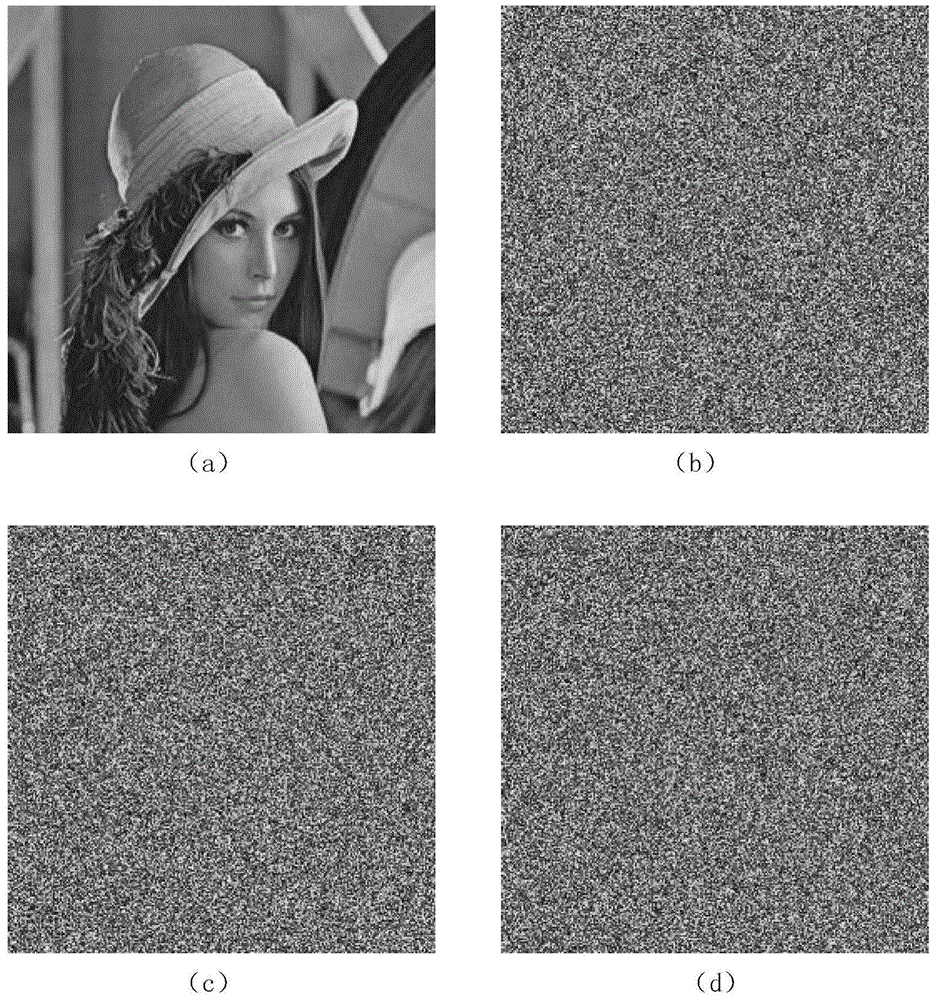
DNA dynamic coding based colored image encryption method
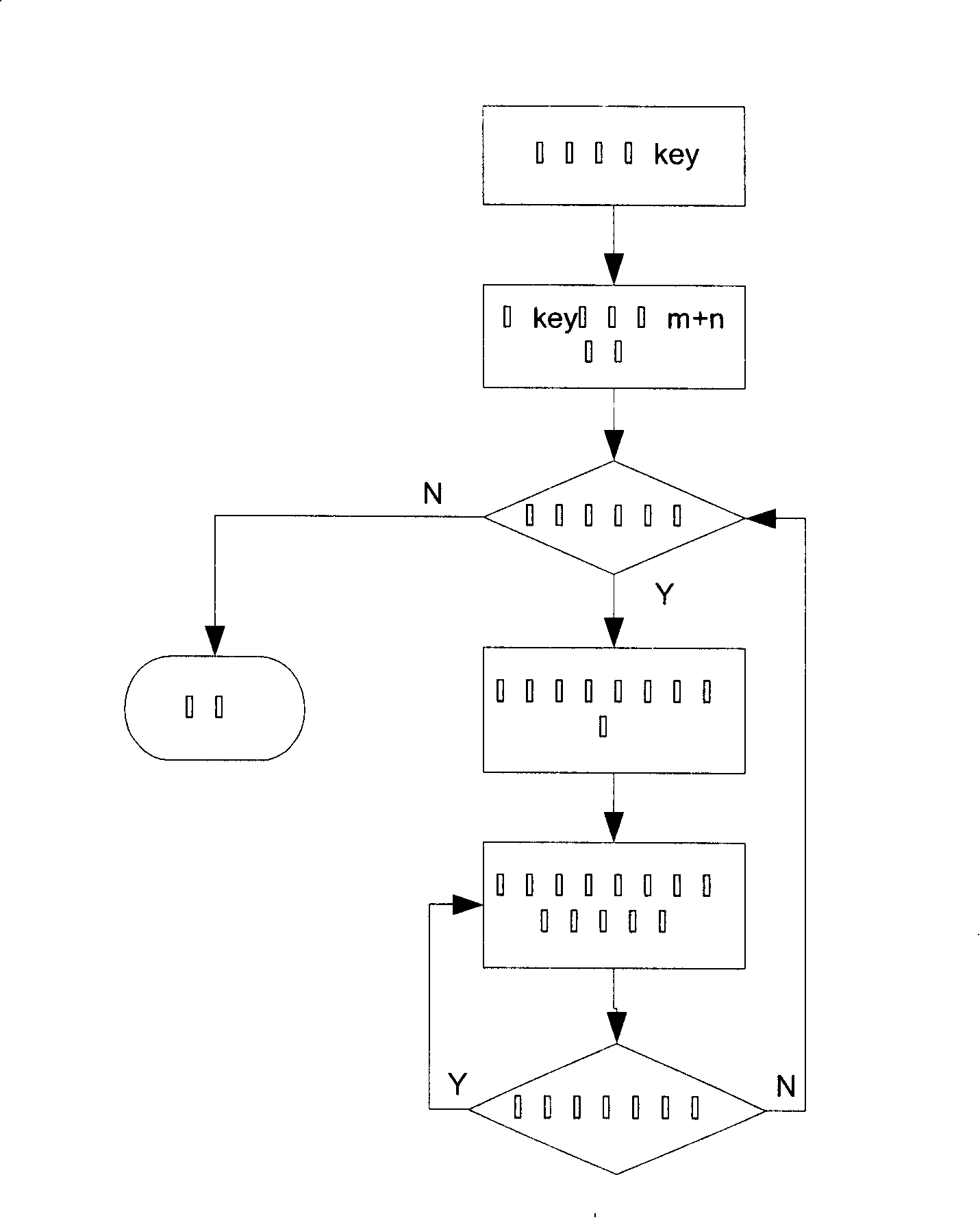
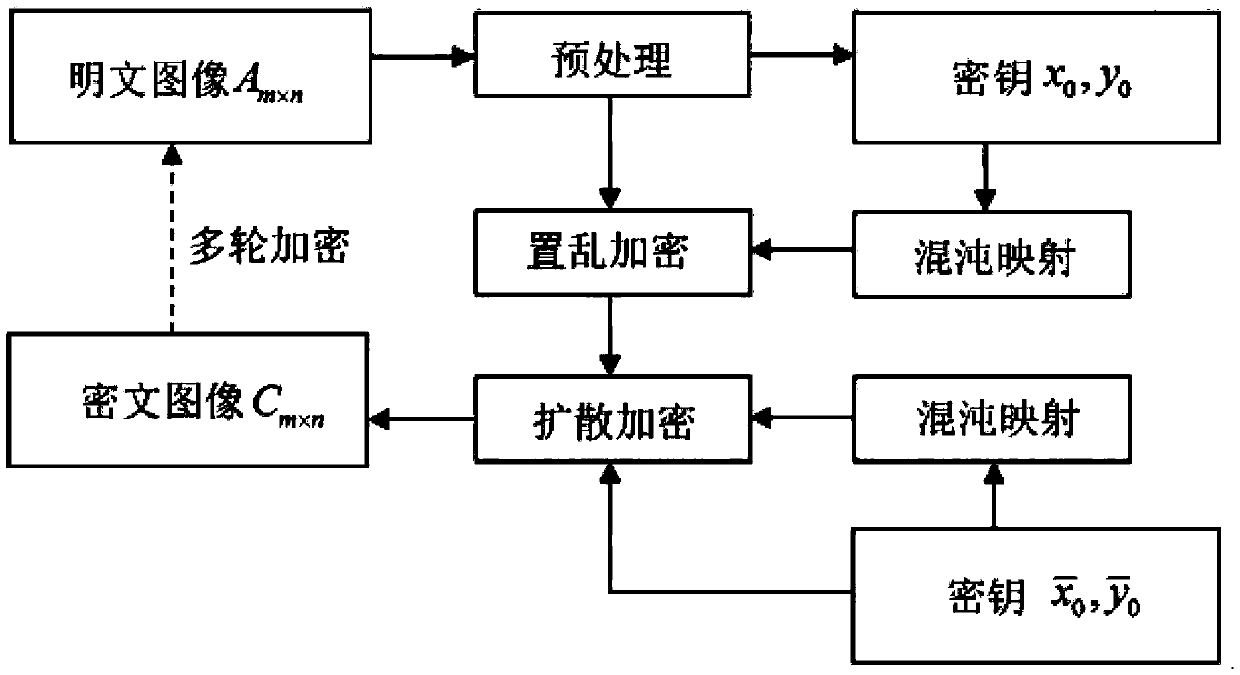
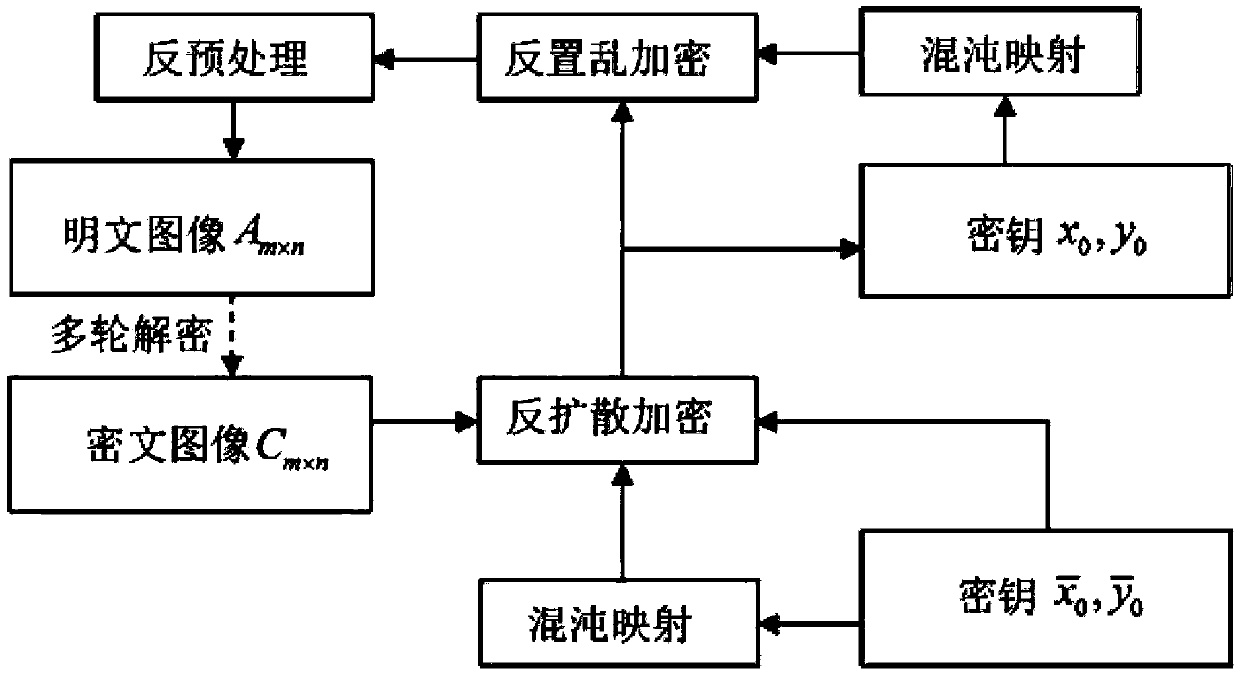
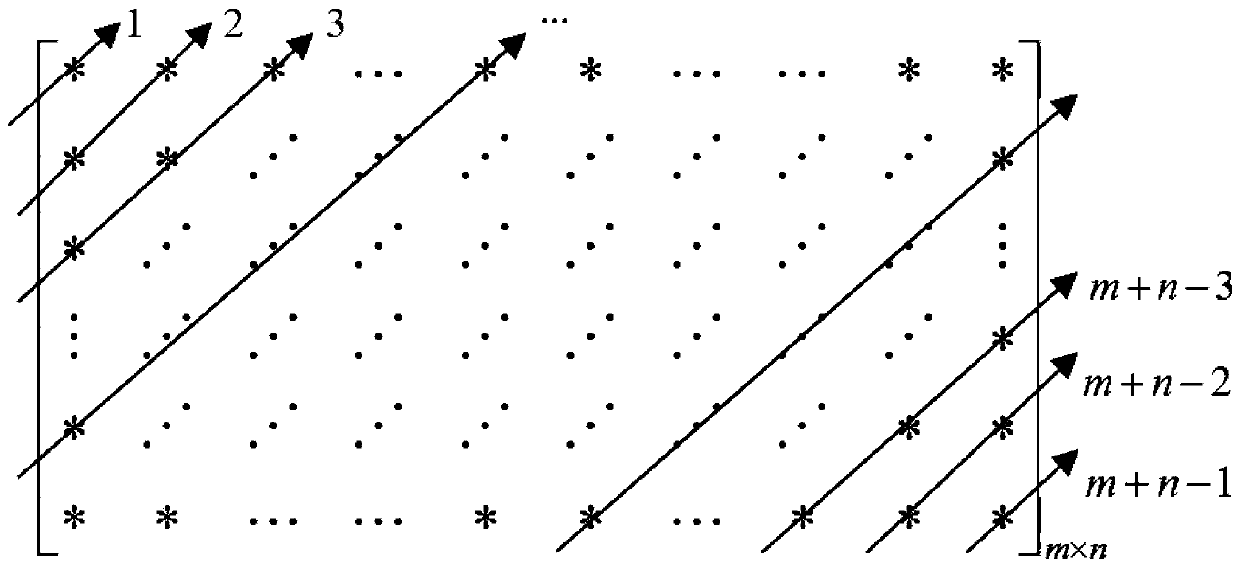
The present invention relates to a DNA dynamic coding based colored image encryption method, comprising: obtaining a key through a colored plain-text image; by the key, calculating an initial value and a parameter of a chaotic system used in scrambling and diffusion processes; substituting the initial value and the parameter to the chaotic system for iteration to obtain W1 and W2, obtaining a scrambling matrix K from W1, obtaining an integer matrix Y and an index matrix Ind from W2, and performing DNA coding on Y according to the index matrix Ind; and performing scrambling on the plain-text image row by row by using the matrix K, then performing coding and diffusion until all rows finish DNA coding, and finally performing decoding and recomposing on a DNA matrix, to obtain a final colored ciphertext image. According to the method, a function SHA256 is used to generate the key, so that the key space is expanded; the generation of the key depends on a plain-text, so that plain-text attack can be effectively resisted; chaotic characteristics are combined with DNA dynamic coding, so that the security is further improved; and meanwhile, scrambling and diffusion operations are performed according to the row of images, so that parallel computing is facilitated and the efficiency is improved.
Owner:HENAN UNIVERSITY
Data encrypting method and device and data decrypting method and device
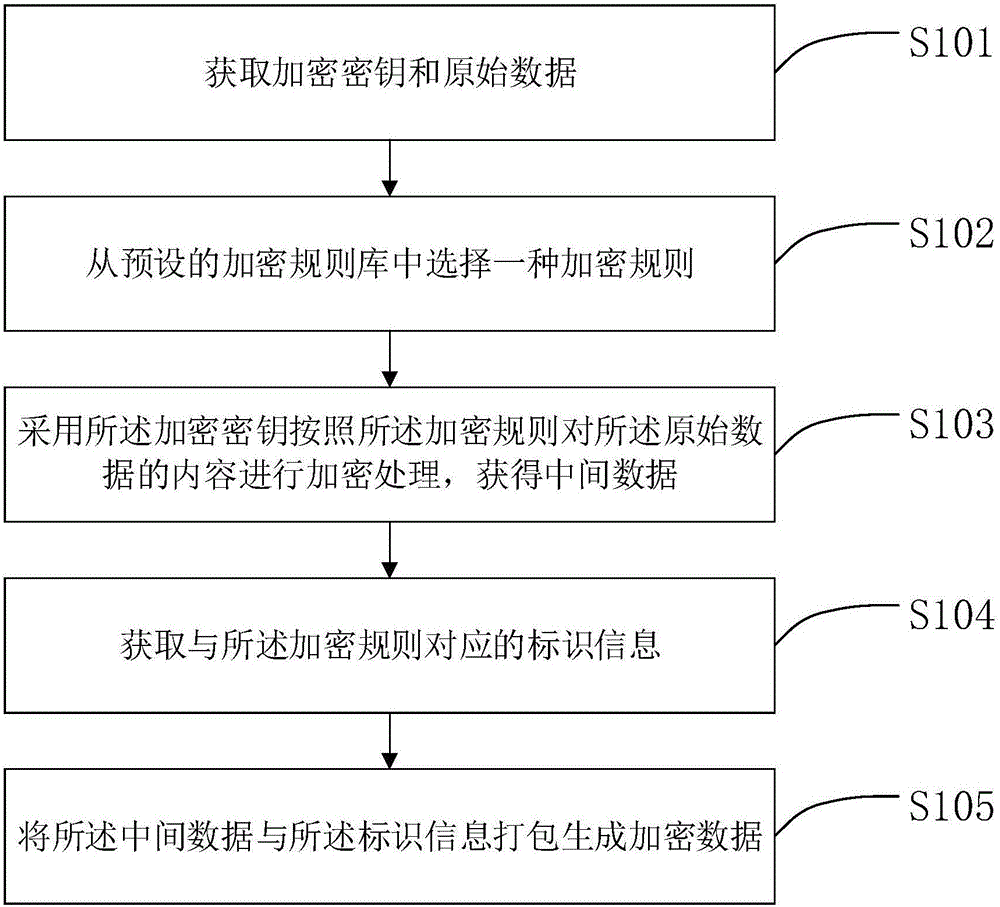
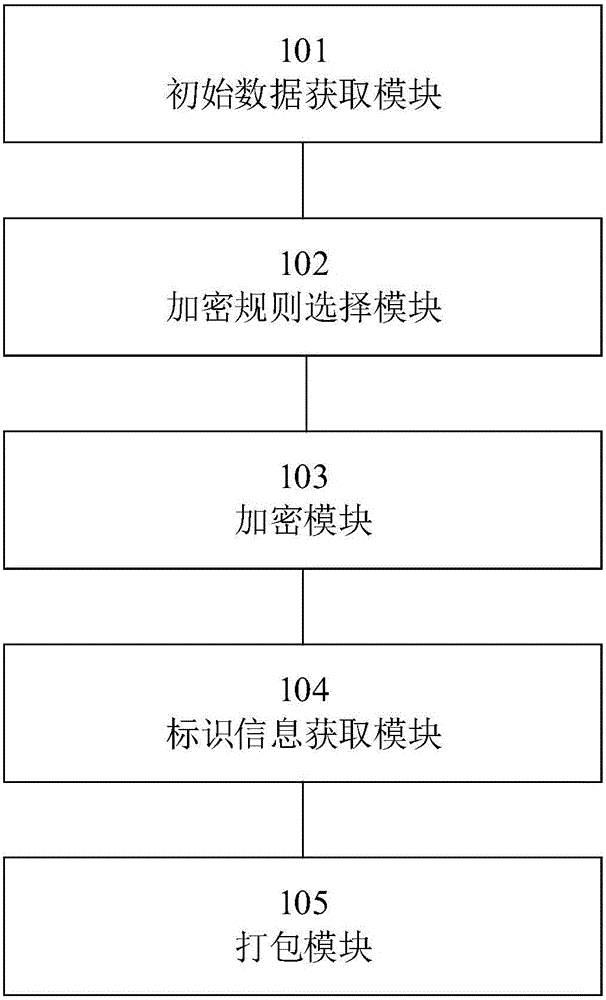
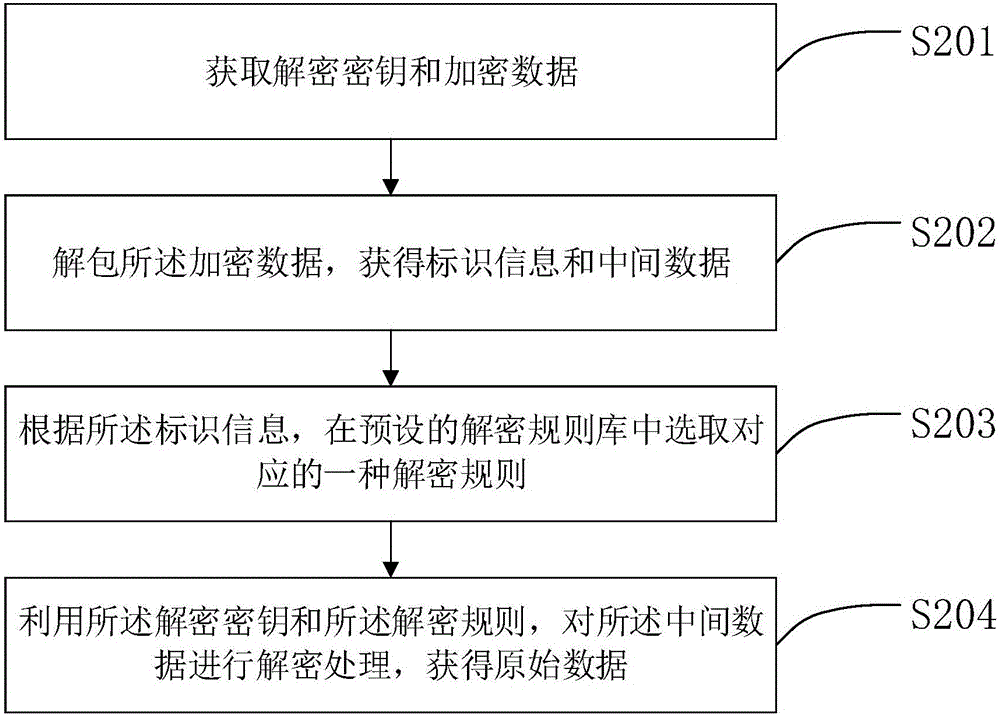
ActiveCN105760765ARealize multi-dimensional encryptionAvoid crackingEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareOriginal data
The invention relates to the field of data encrypting and decrypting, in particular to a data encrypting method and device and a data decrypting method and device.The data encrypting method comprises the steps that at first, an encryption key and original data are obtained; then, an encryption rule is selected from a preset encryption rule base; the encryption key is adopted for encrypting the original data according to the encryption rule to obtain intermediate data; then, identification information corresponding to the encryption rule is obtained; finally, the intermediate data and the identification information are packaged to generate encrypted data.Compared with the prior art, encryption information does not only depend on the carrier key, the encryption rule is selectively used, and the encryption rule is encrypted; meanwhile, in the file transmitting process, only the identification information of the encryption rule exists in the transmission information, and the specific content of the encryption rule does not exist, so that multi-dimensional encryption is achieved, the encryption means is more complex, the key can not be decrypted easily, and encryption safety is higher.
Owner:BEIJING SEEYON INTERNET SOFTWARE CORP
Image false-proof method based on chaotic characteristic
InactiveCN1738235AImplement encryptionAchieve decryptionImage data processing detailsSensing record carriersChaotic systemsImage segmentation
The invention discloses a image counterfeit deterrence method based on the chaotic feature, comprising: first, by the chaotic mapping system, using the information needed keep secret and counterfeit deterrence to generate the chaotic sequence which is used to encode the information, then, printing the encoded information to the two-dimension bar code image according to the PDF417 bar code; collecting the two-dimension bar code image by the scanner, and operating the preprocessing of image segmentation, filtration, geometric correction and stratified on collected image, then decoding the bar code according to the decoding rule of national standard PDF417 bar code to attain the chaotic encoded information carried by bar code image. The invention fully utilizes the features of chaotic system and two-dimension bar code technique which are combined for image counterfeit deterrence. The invention has the characters as strong secret-keeping property and large information carried, while it can recognize automatically.
Owner:XI AN JIAOTONG UNIV
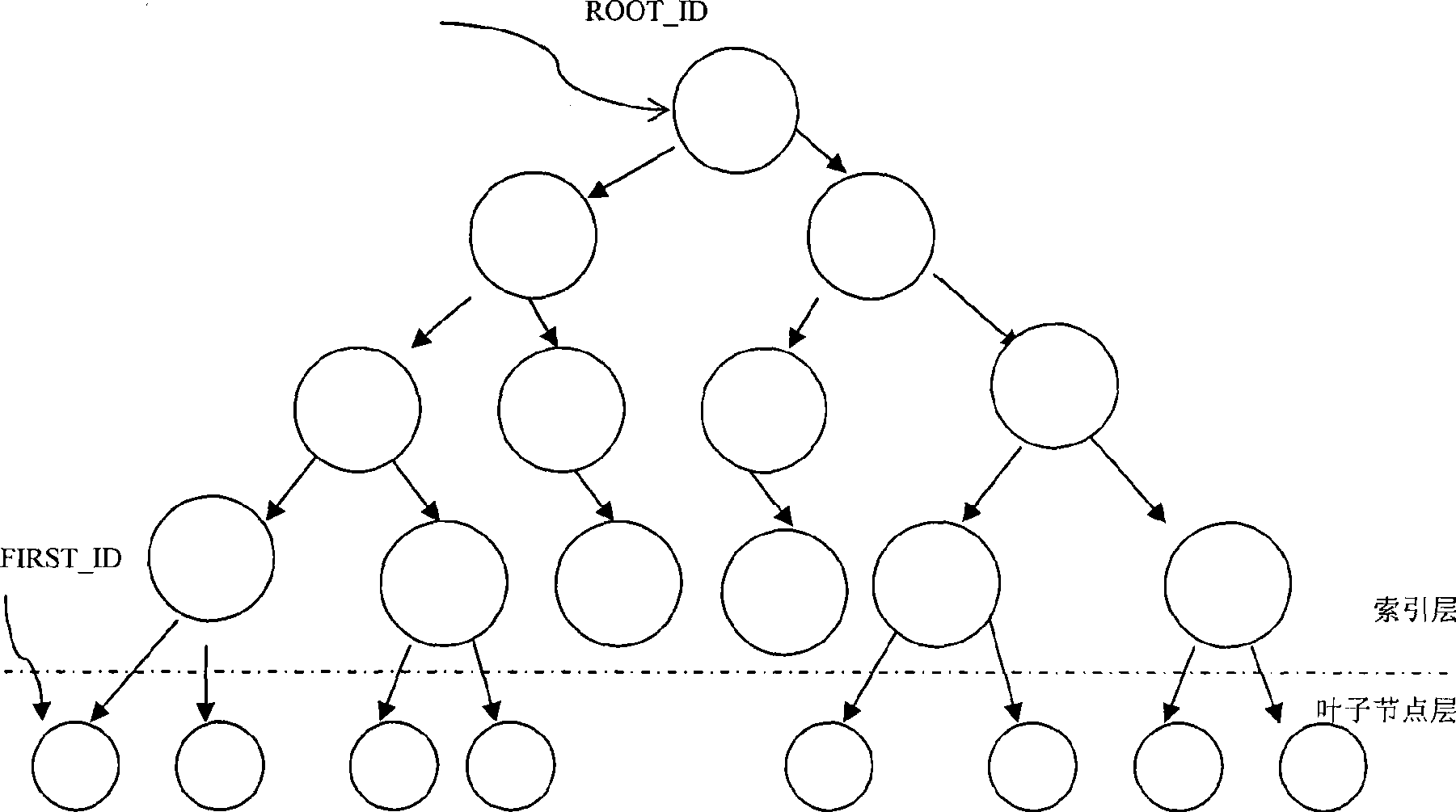
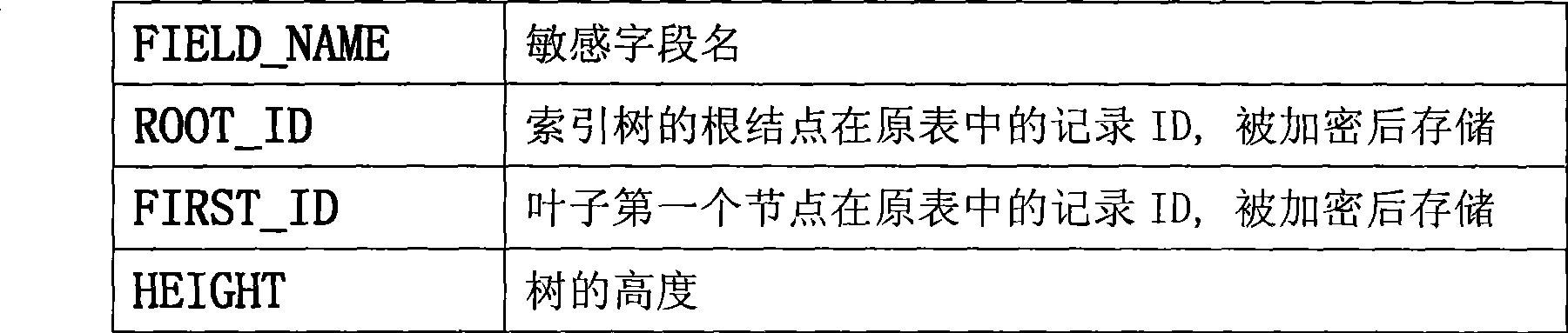
Cryptograph index supported database transparent encryption method
InactiveCN101504668AImplement automatic decryptionImplement encryptionSpecial data processing applicationsDatabase securitySQL
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
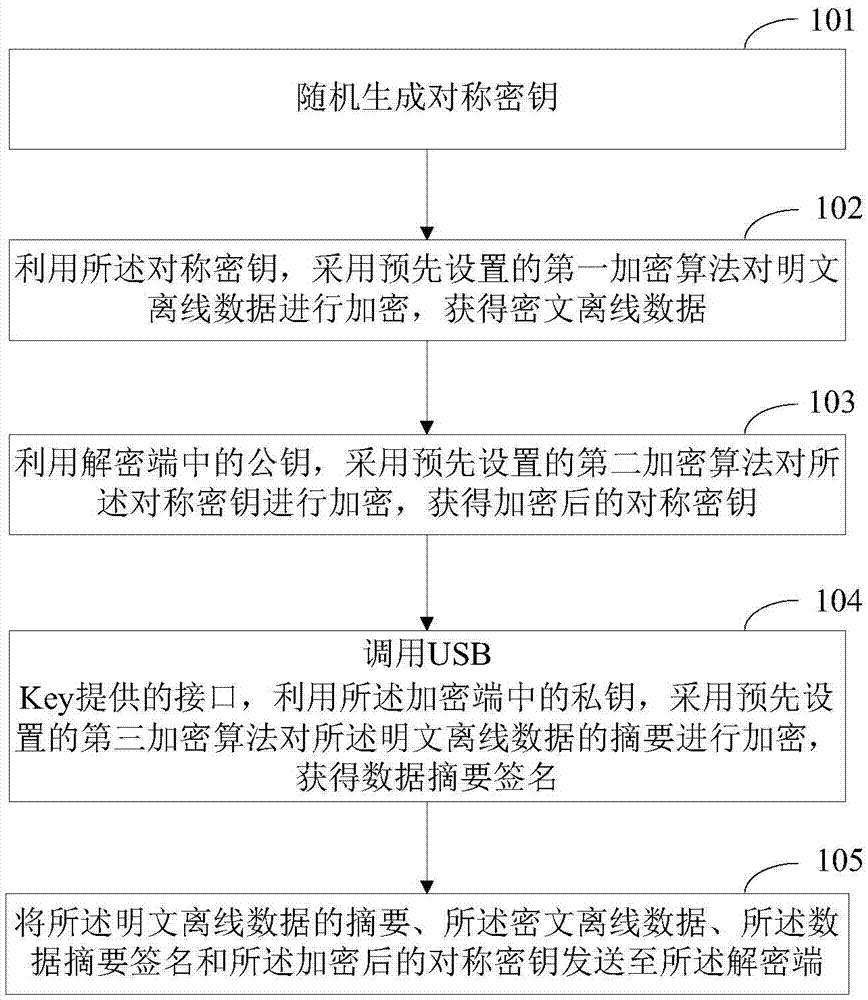
Off-line data encryption method and decryption method and corresponding apparatus and system
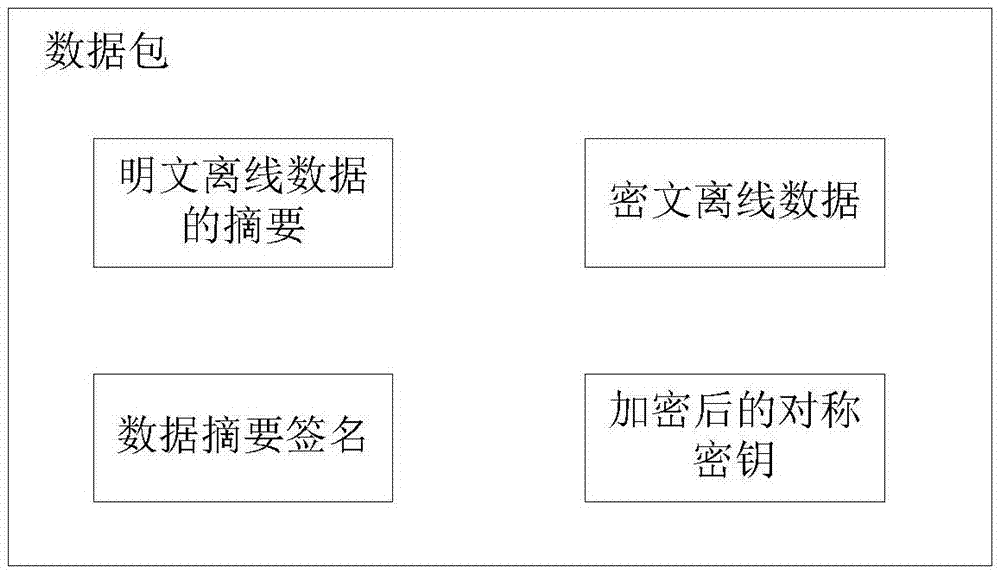
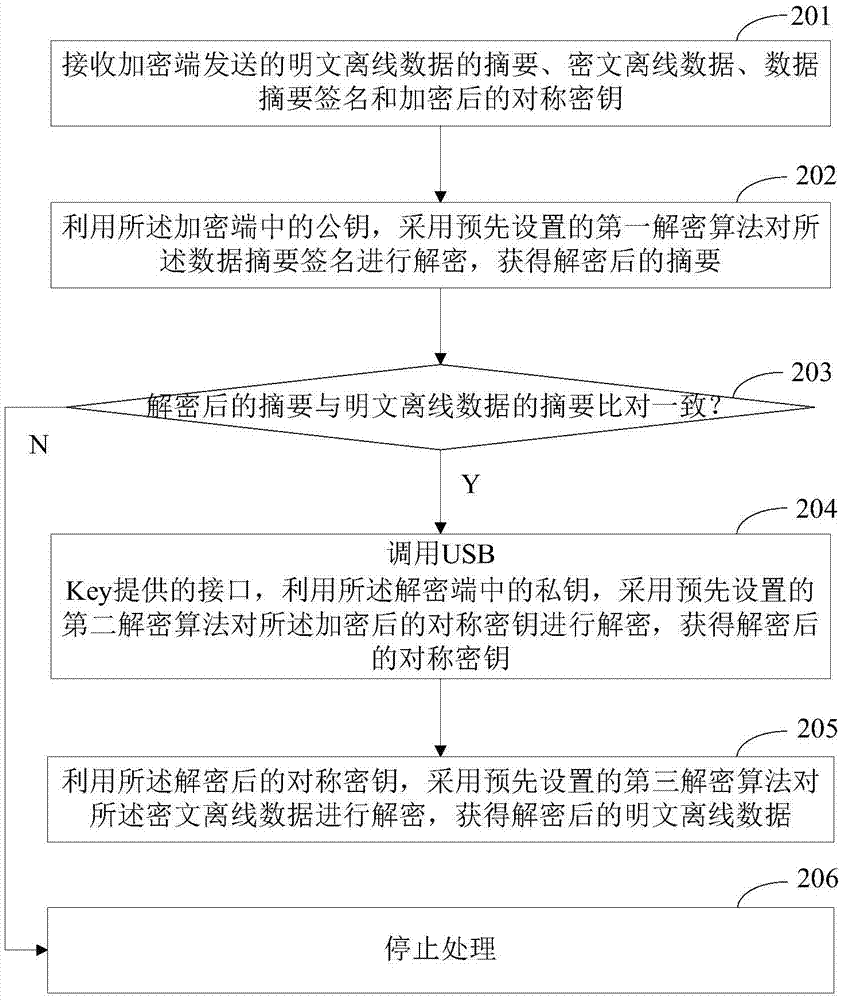
The present invention provides an off-line data encryption method and decryption method and a corresponding apparatus and system. The encryption method comprises: randomly generating a symmetric key; performing encryption for plain-text off-line data by using the symmetric key and by using a preset first encryption algorithm, to obtain cipher-text off-line data; performing encryption for the symmetric key by using a public key at a decryption end and by using a preset second encryption algorithm, to obtain an encrypted symmetric key; invoking an interface provided by a USB Key, performing encryption for an abstract of the plain-text off-line data by using a private key at an encryption end and by using a preset third encryption algorithm, to obtain a data abstract signature; and sending the abstract of the plain-text off-line data, the cipher-text off-line data, the data abstract signature, and the encrypted symmetric key to the decryption end. According to the method provided by the present invention, encryption for plain-text off-line data, the symmetric key, and the abstract of the plain-text off-line data is implemented, thereby greatly improving security of off-line data.
Owner:CHINA CONSTRUCTION BANK
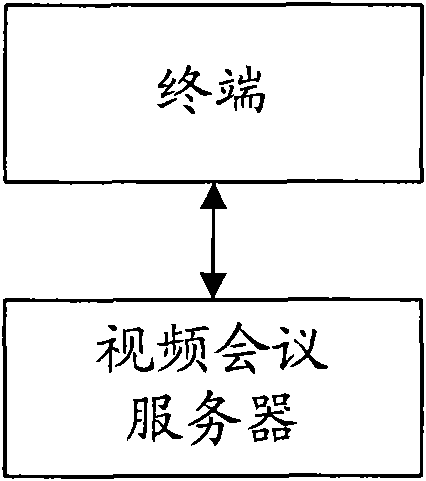
Method and system of terminal for encrypting videoconference data
ActiveCN101635823AEnsure confidential transmissionPrevent eavesdroppingTelevision conference systemsUser identity/authority verificationEavesdroppingWeb authentication
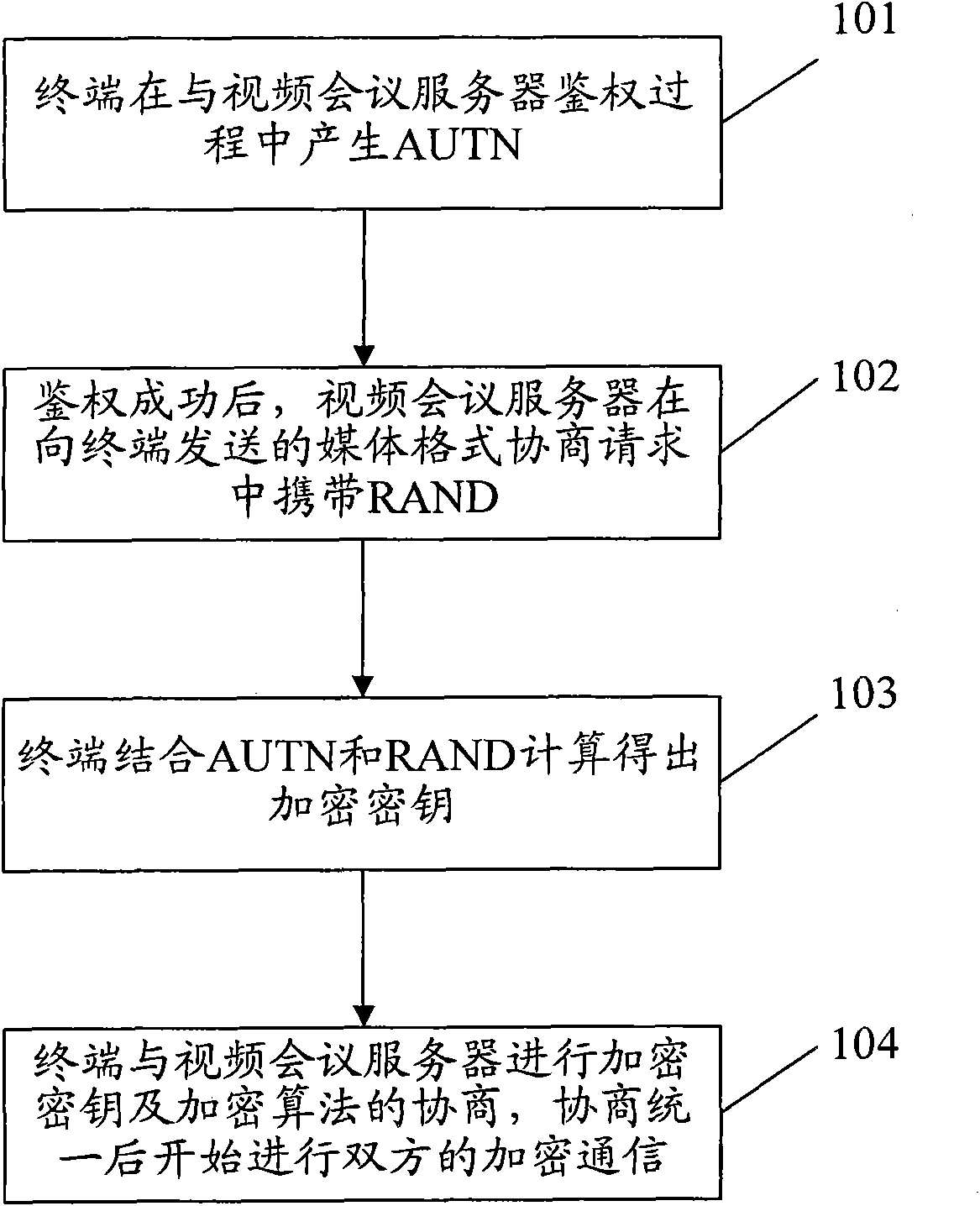
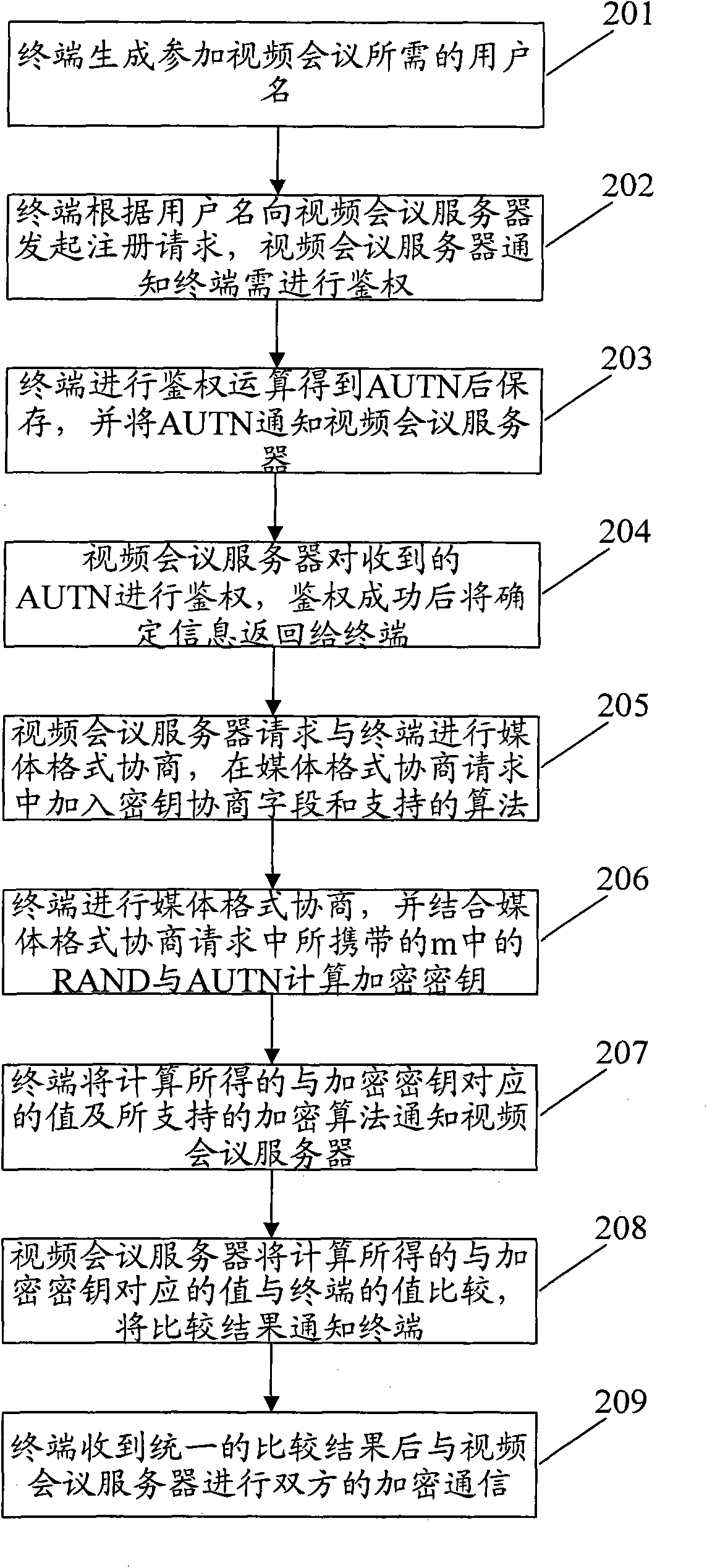
The invention discloses a method of a terminal for encrypting videoconference data, which comprises the following steps: generating a network authentication token (AUTN) by a terminal in authentication with a videoconference server; carrying random passwords (RAND) by the videoconference server in media format negotiation requests sent to the terminal after the authentication is succeeded; calculating an encryption key by the terminal by combining the AUTN and the RAND; carrying out negotiation of encryption key and encryption calculation with the videoconference server; and carrying out encryption communication between the two parties after the negotiation is unified. The invention also discloses a system of a terminal for encrypting videoconference data. The method and the system can be used for encrypting videoconference data and ensuring the confidential transmission of the videoconference data. Because user names registered in each terminal are different in a videoconference, encryption keys generated by each terminal are different. In the communication between a terminal and a server, the invention can effectively prevent a third party from eavesdropping.
Owner:ZTE CORP
Large-capacity hiding method for reversible data in bitstream encryption domain of JPEG image
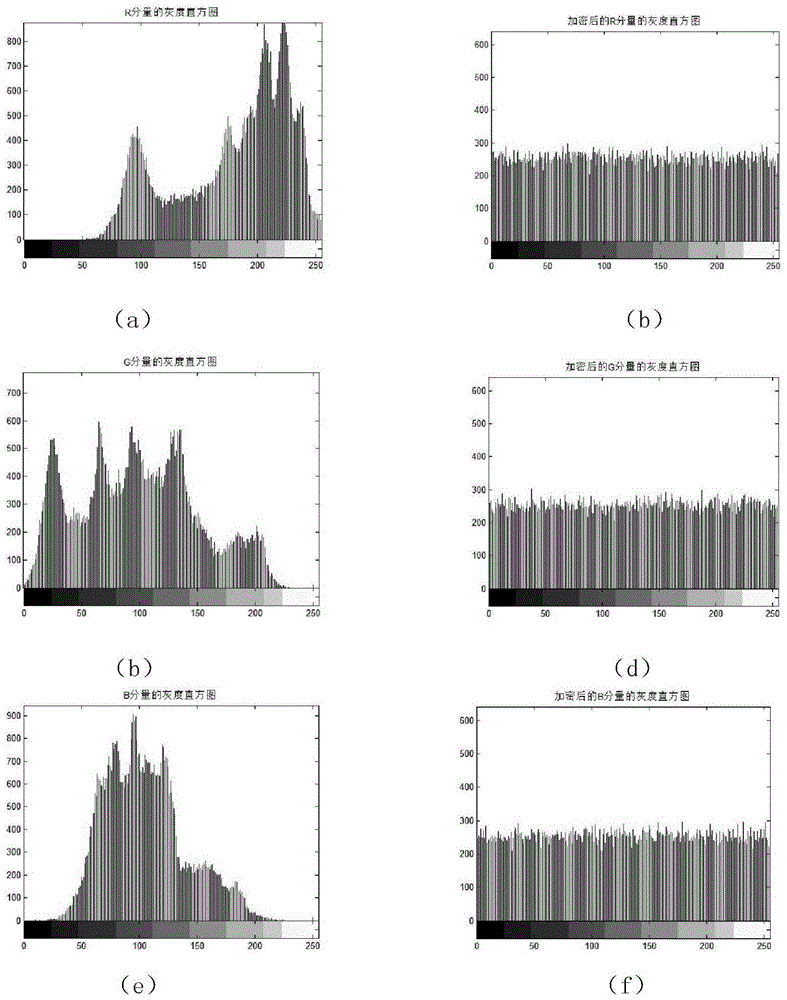
ActiveCN109151486AImplement encryptionImprove securityEncryption apparatus with shift registers/memoriesDigital video signal modificationAc coefficientHistogram
The invention discloses a large-capacity hiding method for reversible data in a bitstream encryption domain of a JPEG image. According to the method, a user performs exclusive or encryption on extension bits of entropy coding in each of image blocks according to an encryption key in JPEG bitstreams, performs pseudo-random scrambling on remaining AC coefficients except a last non-zero AC coefficient, and then performs the pseudo-random scrambling on the entropy coding of all the image blocks; a cloud performs embedding of extraneous information by a histogram shifting method on the AC coefficients in a bitstream ciphertext according to a hiding key, and can perform non-destructive extraction; and a receiver performs pseudo-random scrambling resumption on the entropy coding of ciphertext image blocks in the bitstream ciphertext according to the encryption key, and then the pseudo-random scrambling resumption and exclusive or decryption of the AC coefficients are performed in the entropycoding of each of the ciphertext image blocks to obtain decrypted bitstreams same as original JPEG bitstreams. The method not only achieves encryption of the extension bits of the entropy coding, butalso encrypts Huffman coding of the entropy coding; and the steganographic capacity is large, and the safety is high.
Owner:SOUTHWEST JIAOTONG UNIV
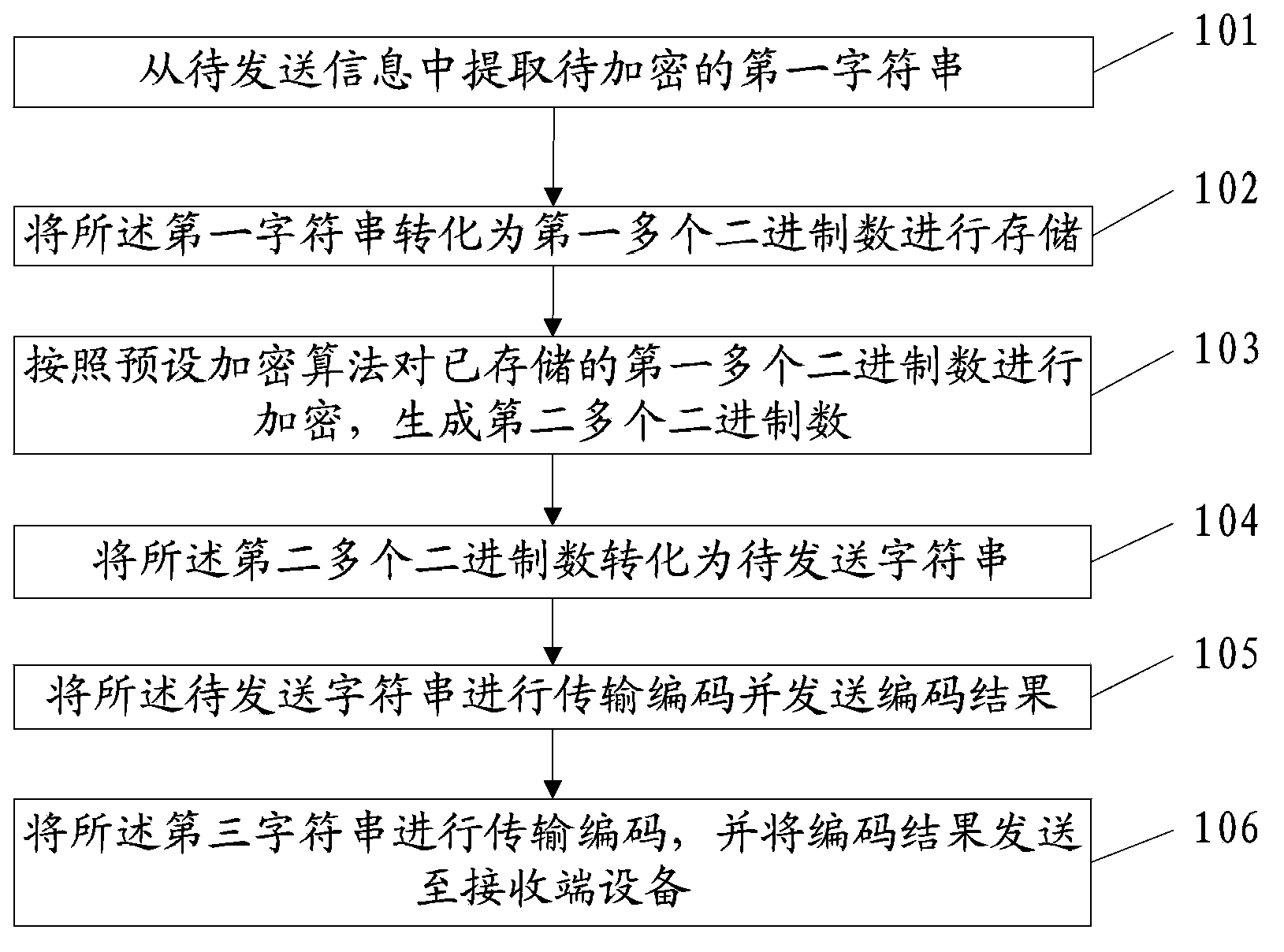
Method, device and system for encryption and decryption of communication
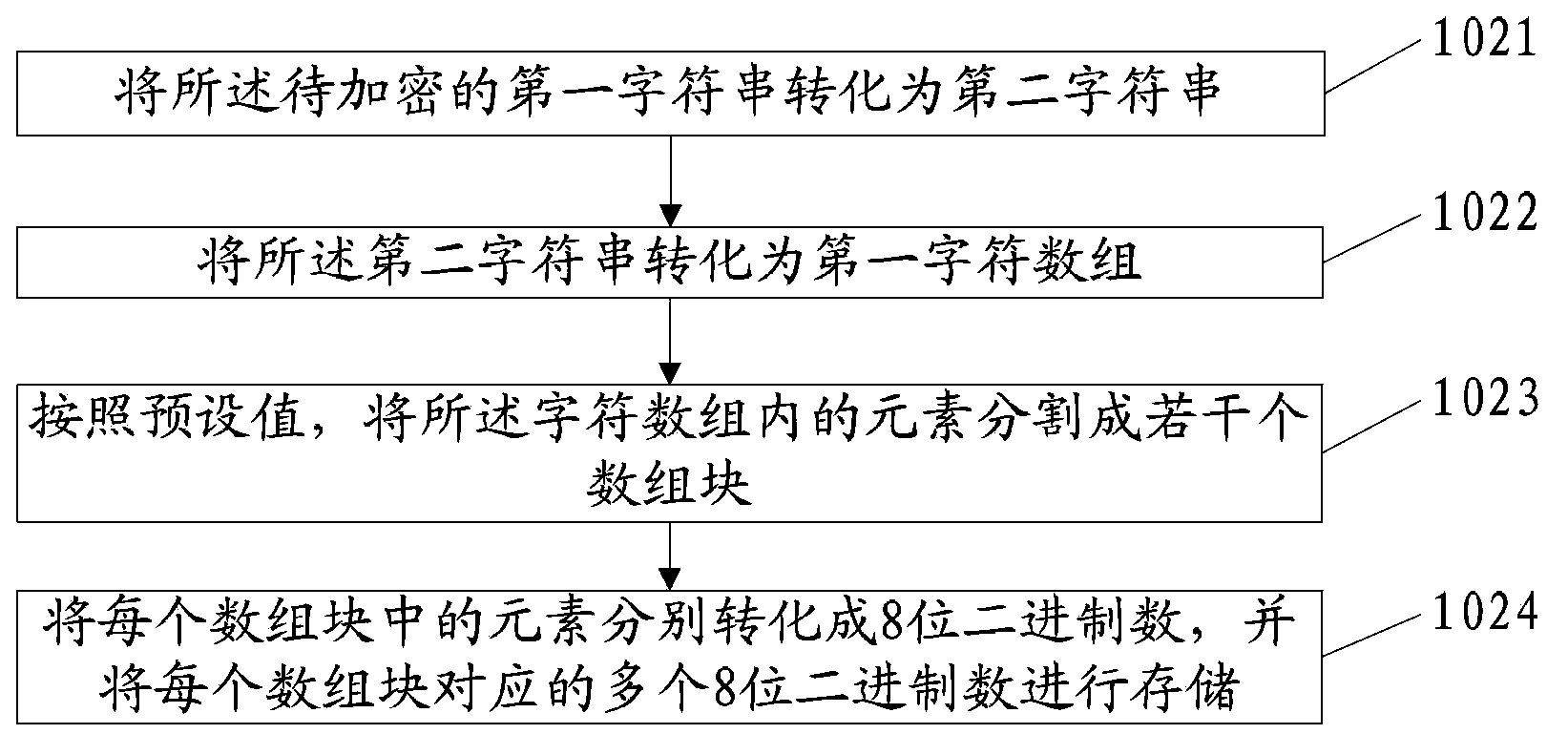
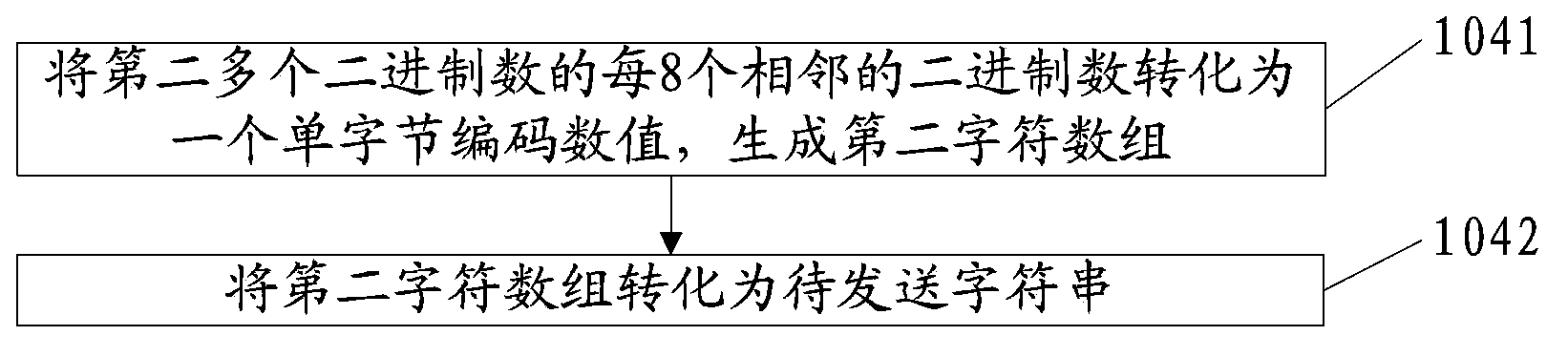
The invention discloses a method, a device and a system for encryption and decryption of communication, and relates to the field of information processing. A Javascript is utilized to realize encryption and decryption of communication so that safety of user information is guaranteed. The invention comprises an encryption process of communication and a decryption process of communication. The encryption process of communication comprises that: a first character string to be encrypted is extracted from information to be sent; the first character string is converted into first multiple binary numbers to be stored; the stored first multiple binary numbers are encrypted according to a preset encryption algorithm so that second multiple binary numbers are generated; the second multiple binary numbers are converted into a character string to be sent; and transmission encoding is performed on the character string to be sent and an encoding result is sent. The decryption process of communication comprises that: the information which is to be processed and is sent by a sending end is received; transmission decoding is performed on the information to be processed so that a third character string is obtained; the third character string is converted into third multiple binary numbers to be stored; the stored third multiple binary numbers are decrypted according to a preset decryption algorithm so that fourth multiple binary numbers are generated; and the fourth multiple binary numbers are converted into a fourth character string.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method on a network element for the purpose of synchronization of clocks in a network
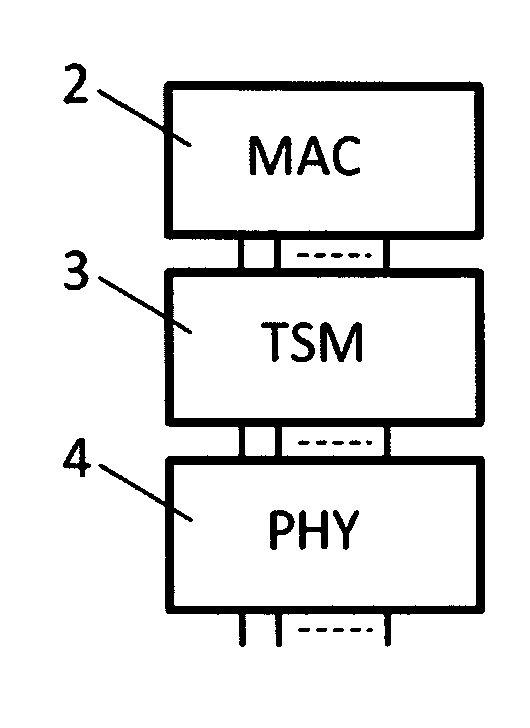
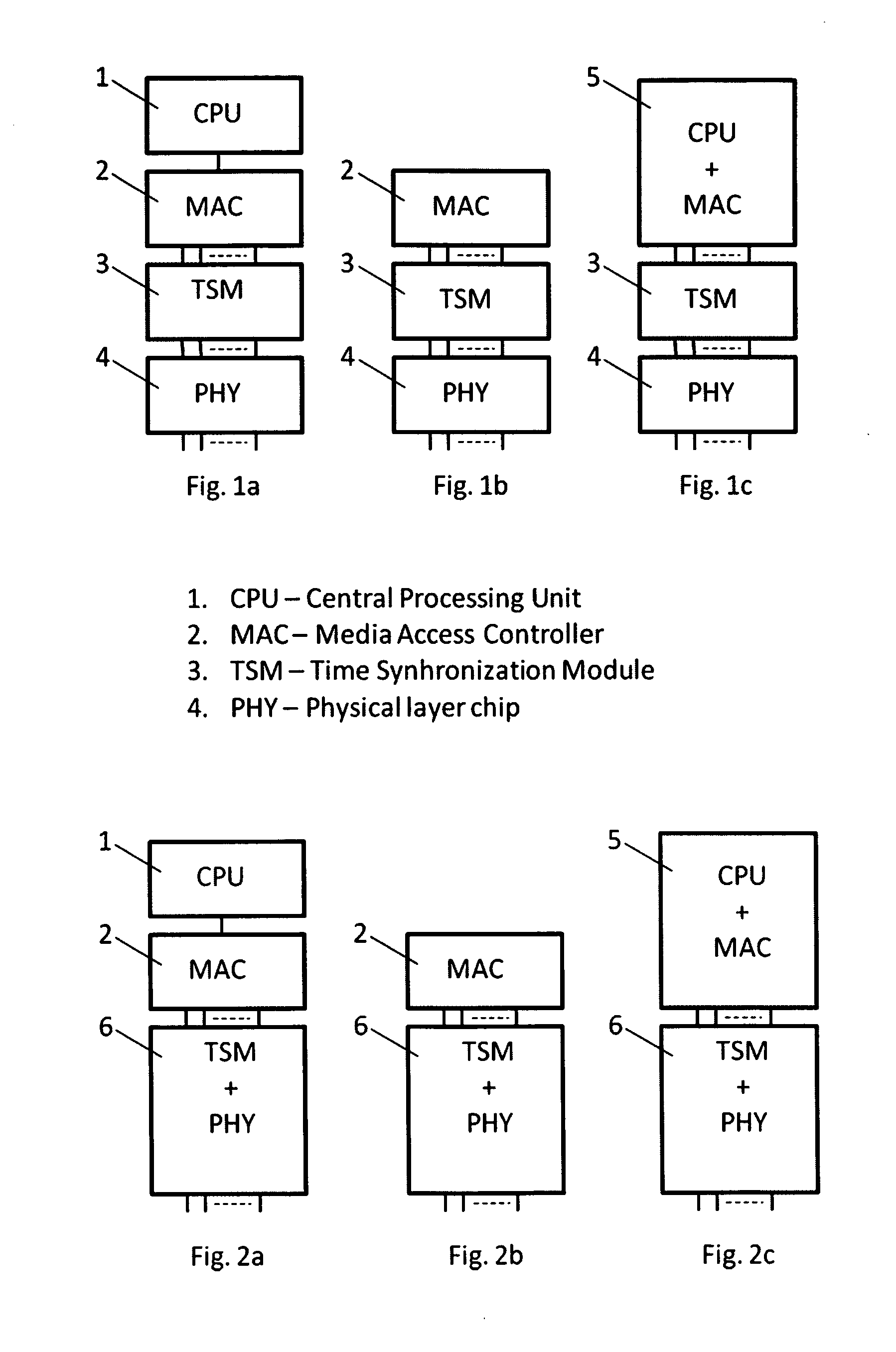
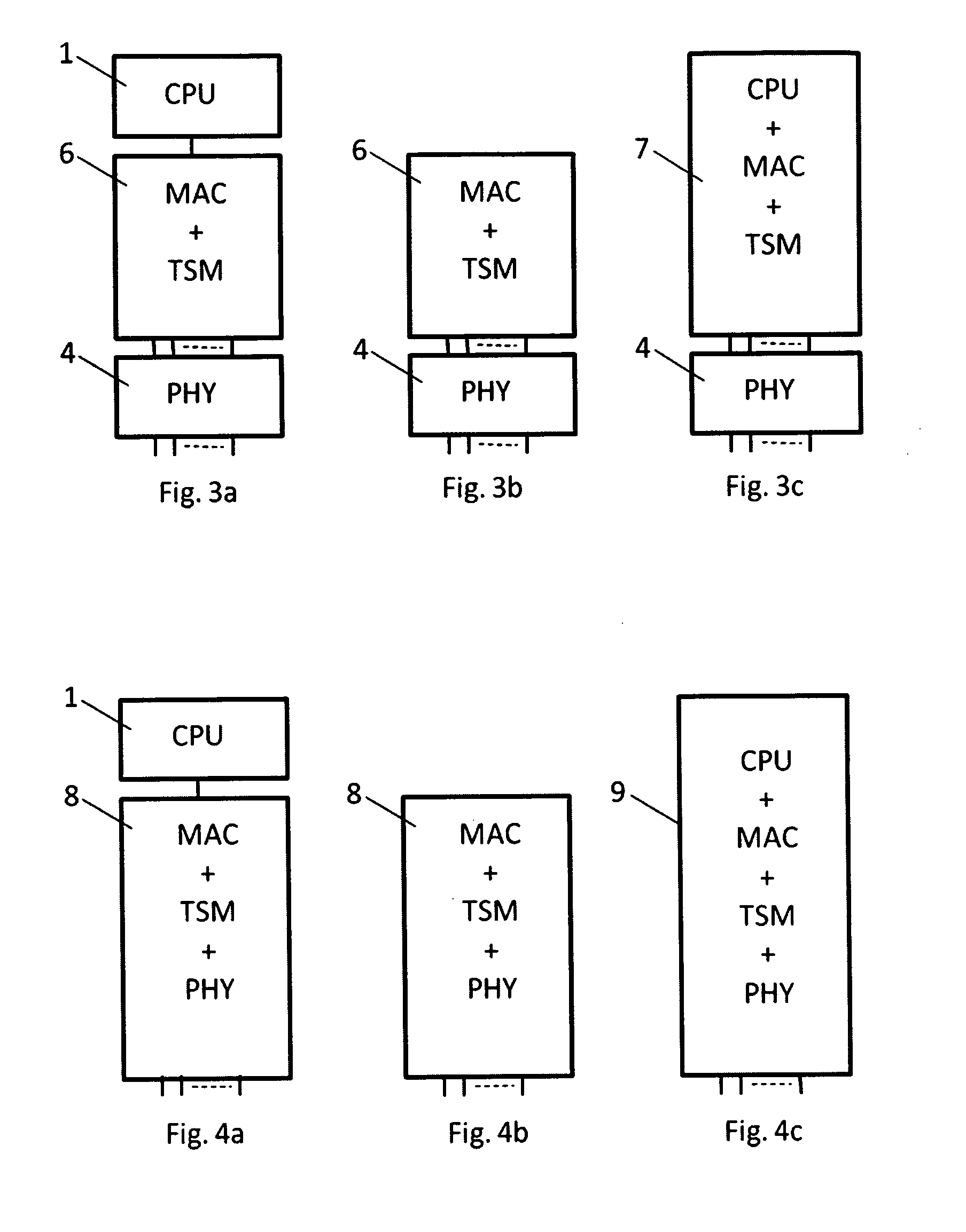
InactiveUS20120128011A1Reduces and removes time synchronization loadGood timing synchronization performanceTime-division multiplexTransmissionData synchronizationSynchronous network
It is described a method on a network element with one or more communication ports for transmitting and receiving data packets to and from other network elements in a network for the purpose of synchronization of clocks in a network, said network element comprising a time synchronization module, a time synchronization module clock and a database.
Owner:ONTIME NETWORKS
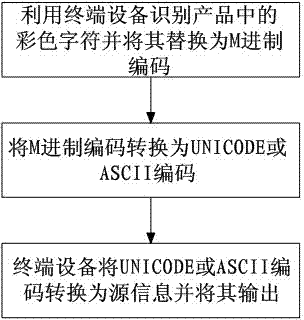
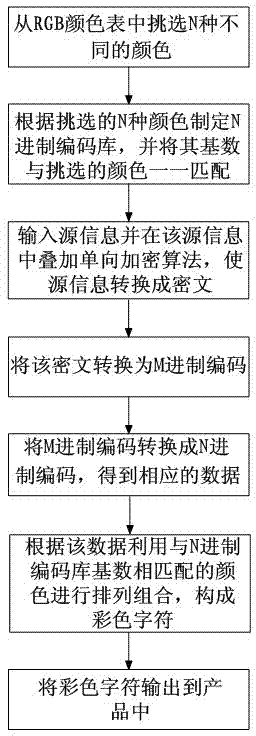
Color character encoding method and decoding method
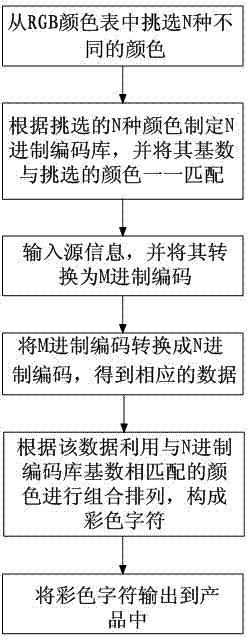
InactiveCN103310255AIngenious ideaThe principle is simpleRecord carriers used with machinesPattern recognitionDecoding methods
The invention discloses a color character encoding method and a decoding method which solve the problems of an anti-counterfeiting code technology that the security is low and the appearance effect of a product is affected. The color character encoding method comprises the following steps that (1) N different colors are selected; (2) an N system encoding library is set up and the base of the encoding library is matched with the selected colors; (3) source information is input and converted into an M system code; (4) the M system code is converted into an N system code to obtain corresponding data; (5) the data is substituted through the colors which are matched with the base of the N system encoding library, lined and combined into a color character; and (6) the color character is output. The color character decoding method comprises the following steps that (1) the color character is identified and substituted into the M system code by terminal equipment; (2) the M system code is converted into a Unicode or an ASCII code; and (3) the terminal equipment converts the Unicode or ASCII code into source information and outputs the same. According to the color character encoding method and the decoding method, an anti-counterfeiting code manufacturing method is novel and the security is high.
Owner:曾芝渝 +3
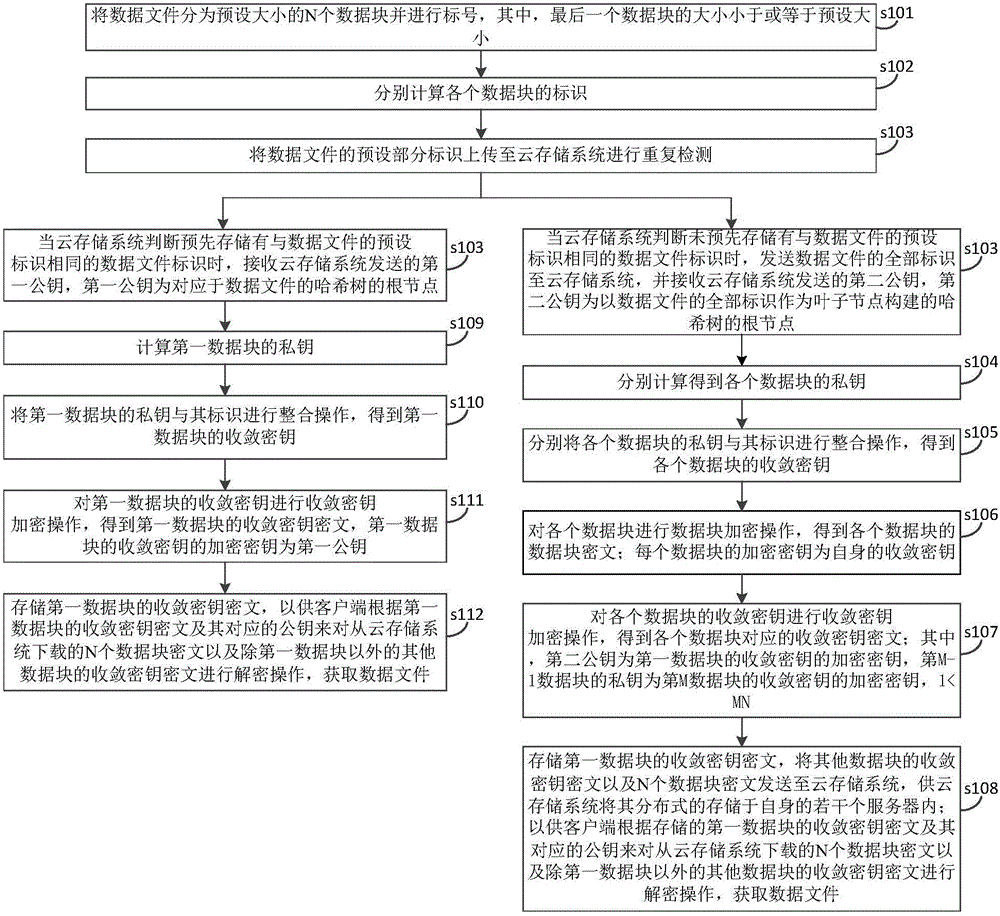
Cloud storage encryption and dereplication method and cloud storage encryption and dereplication system
ActiveCN105915332AImplement encryptionAchieve repetitionData stream serial/continuous modificationComputer hardwareCiphertext
The invention discloses a cloud storage encryption and dereplication method and a cloud storage encryption and dereplication system. The method comprises the following steps of: dividing a data file into a plurality of blocks, firstly transmitting an identification of each data block to a cloud storage system to perform the repetition detection, if the data file is not repeated, encrypting each data block by virtue of a convergence key, respectively encrypting each convergence key, storing a convergence key ciphertext of a first data block by virtue of a client, and storing convergence key ciphertexts of rest data blocks and all data block ciphertexts; and if the data file is repeated, generating a convergence key of the first data block, encrypting the convergence key by utilizing a root node of a hash tree transmitted by the cloud storage system, and storing the generated convergence key ciphertext of the first data block. By adopting the method and the system, the security of the data file can be improved when the convergence encryption and dereplication are adopted, a dictionary can be prevented from being cracked when in attack as far as possible, and the storage space of the client can be saved.
Owner:GUANGDONG UNIV OF TECH
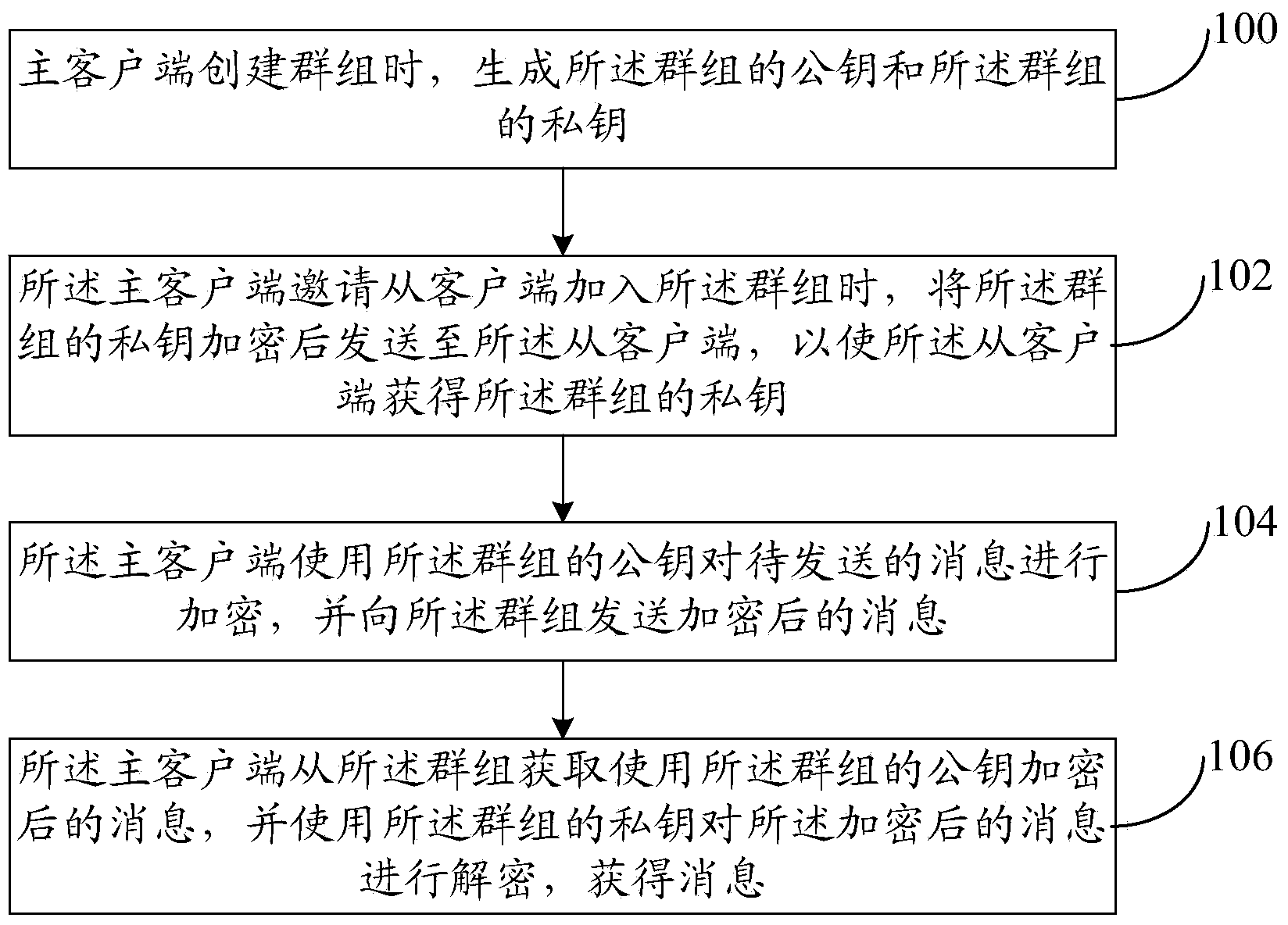
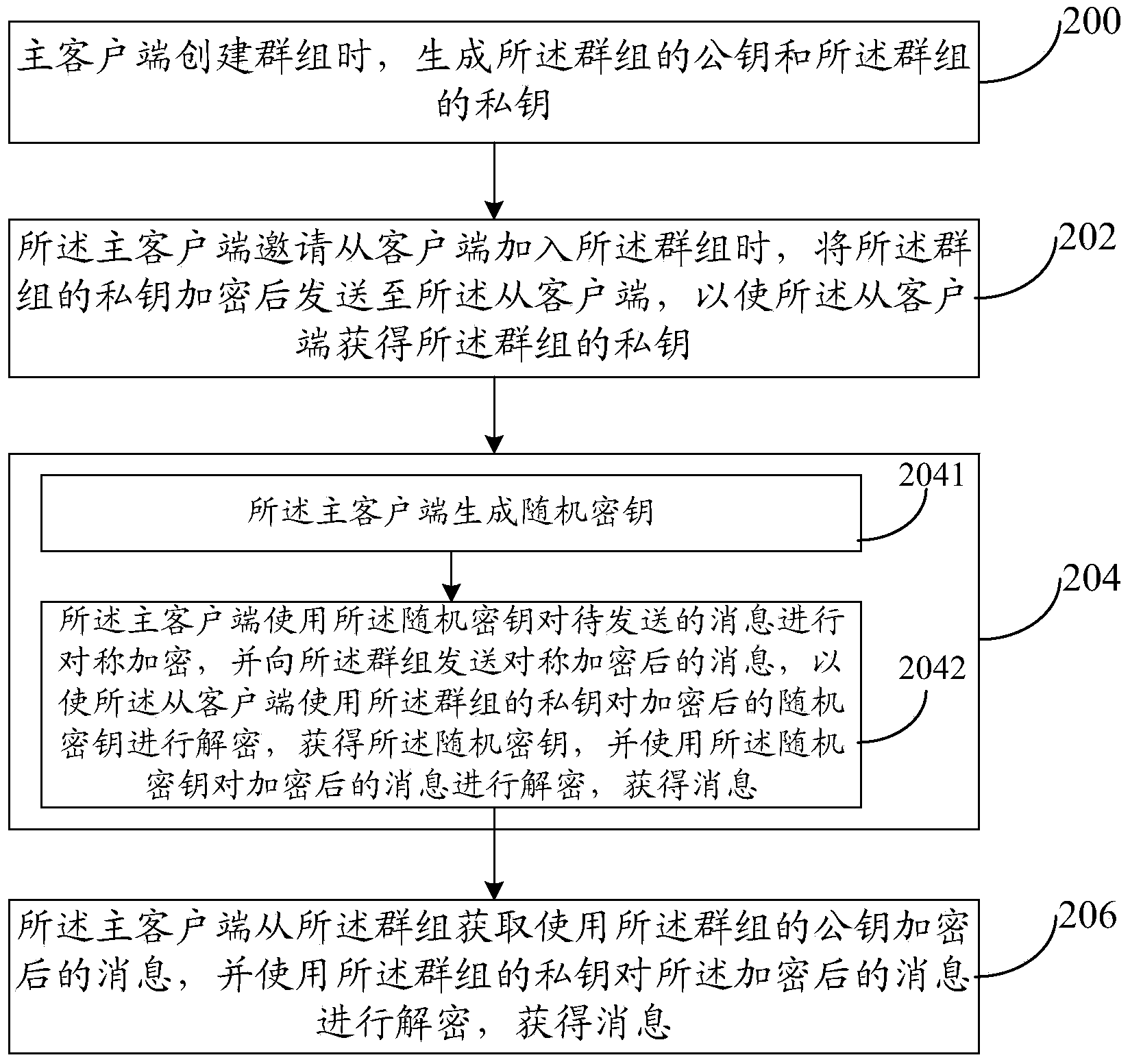
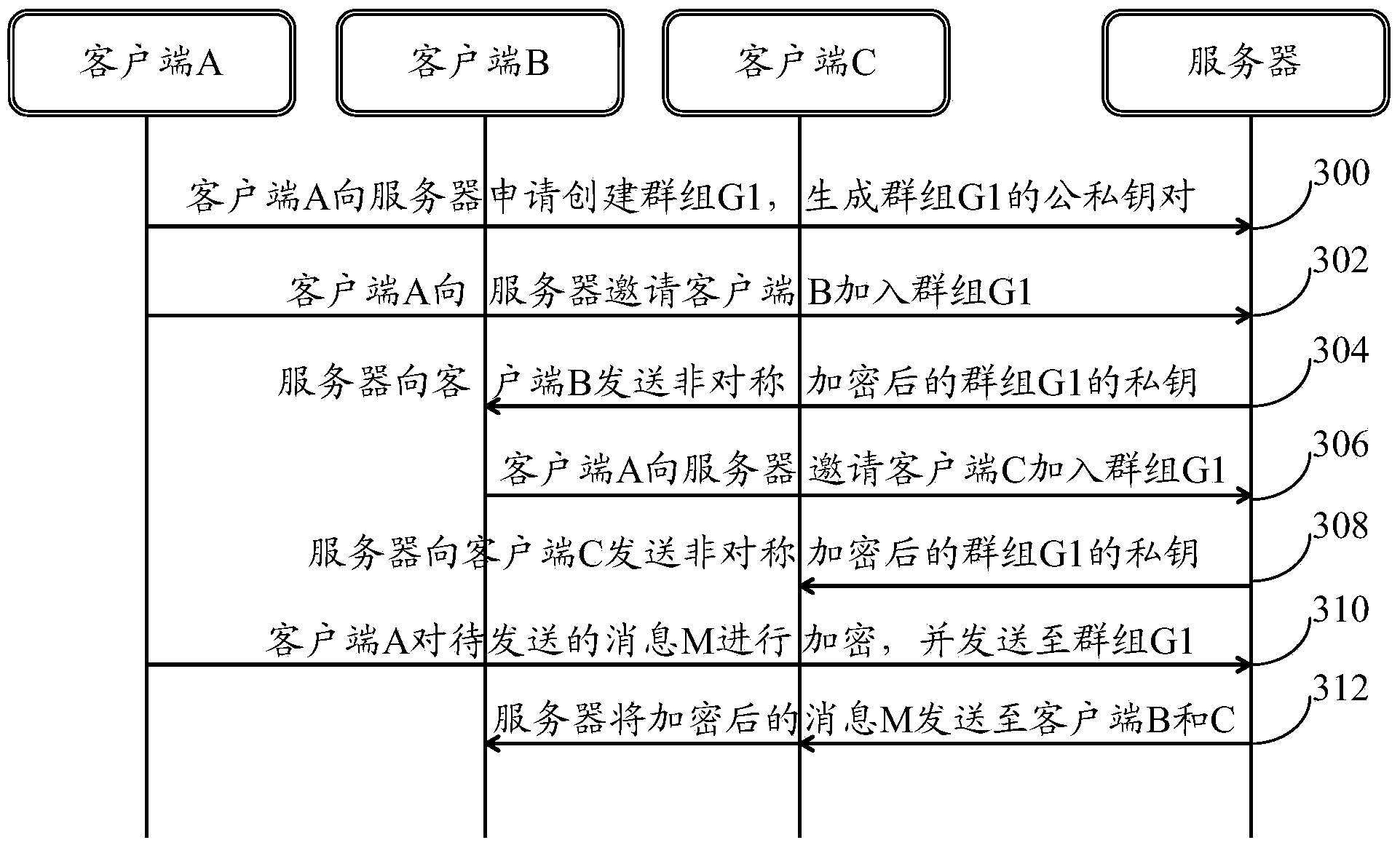
In-group message communication method and system
ActiveCN104219051AIncrease flexibilityImprove securityKey distribution for secure communicationUser identity/authority verificationEnd-to-end encryptionClient-side
The invention provides an in-group message communication method and system. The in-group message communication method includes: generating a public key of a group and a private key of the group when the group is established in a master client side; when the master client side is invited to join the group, transmitting the encrypted private key of the group to a slave client side so as to acquire the private key of the group from the slave client side; sharing the public key of the group between the master client side and the slave client side; the master client side using the public key of the group to have to-be-transmitted information encrypted and transmitting the encrypted information to the group; and / or the master client side acquiring information of the encrypted public key of the group from the group and using the private key of the group to decrypt the encrypted information to acquire messages. By the in-group message communication method and system, end-to-end encryption in the group is realized, and flexibility and safety in communication are improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Encryption method applied to MQTT-SN protocol
InactiveCN107708112AImplement encryptionAchieve authenticationNetwork topologiesTransmissionComputer hardwarePlaintext
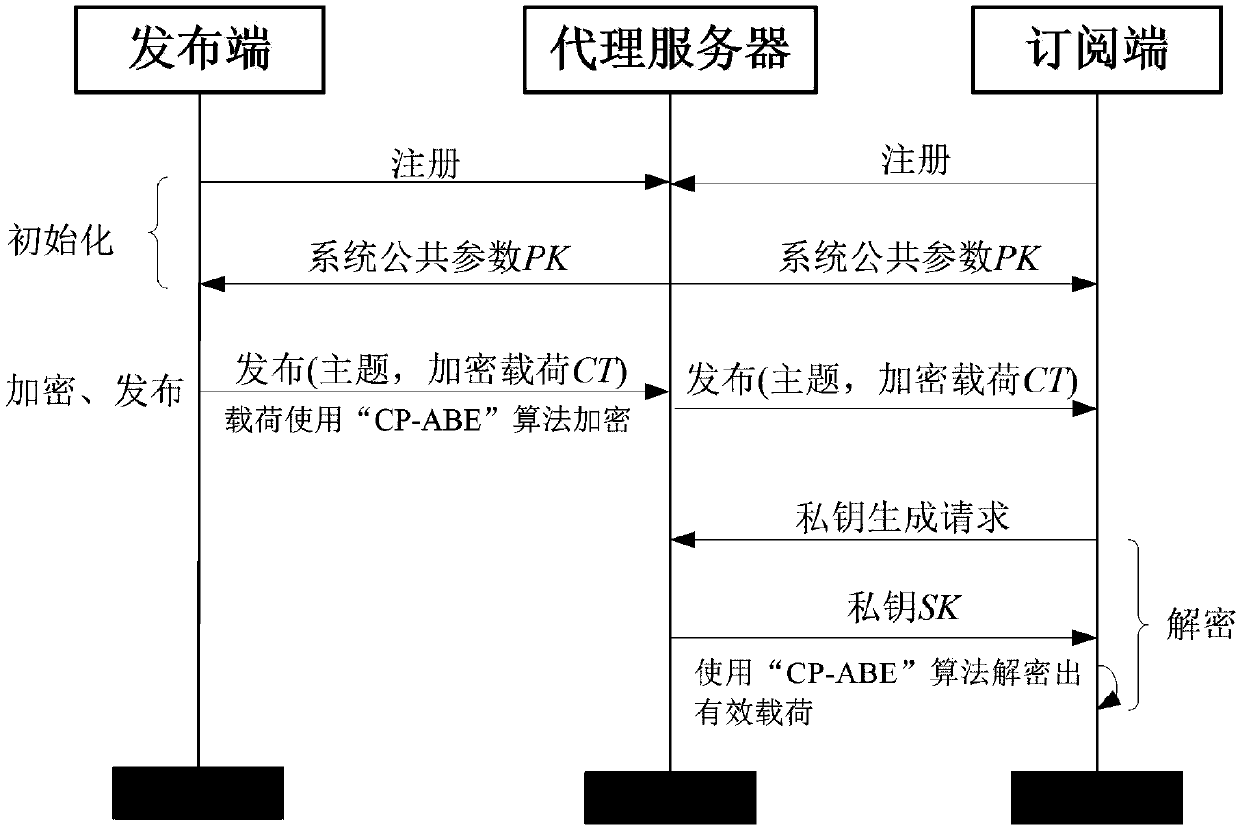
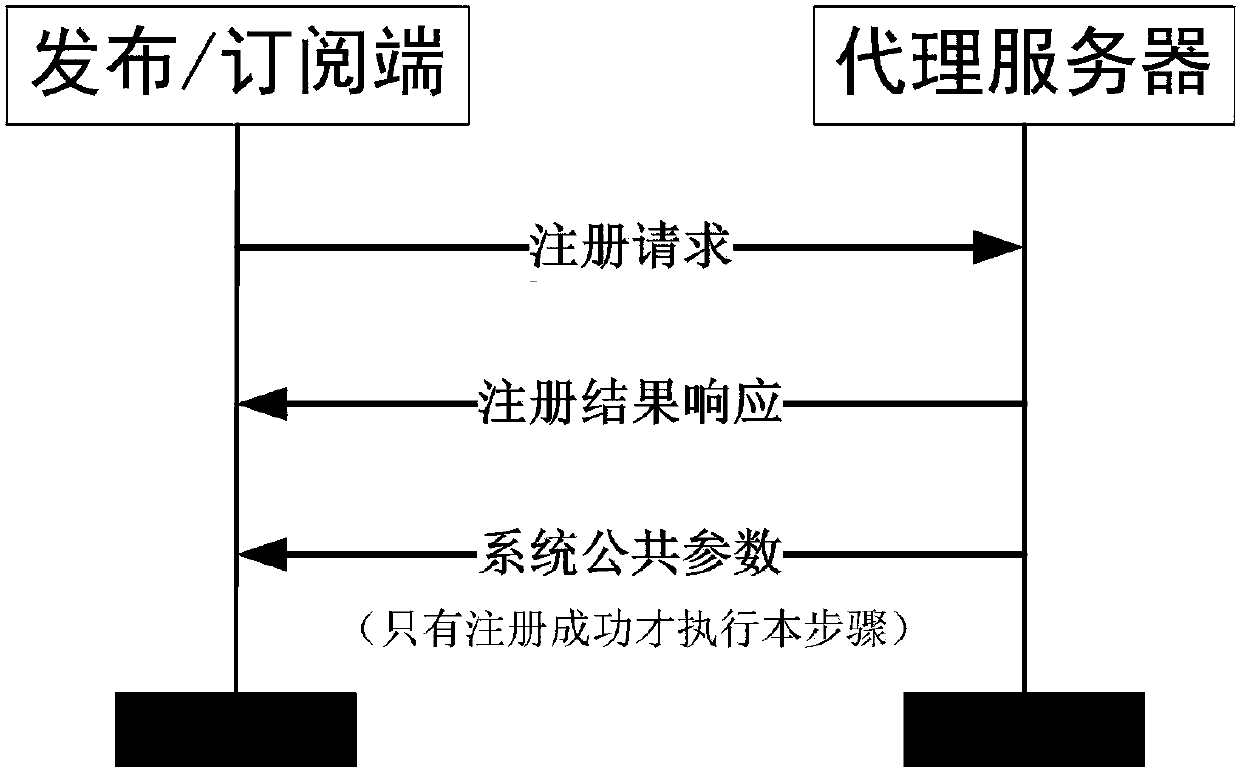
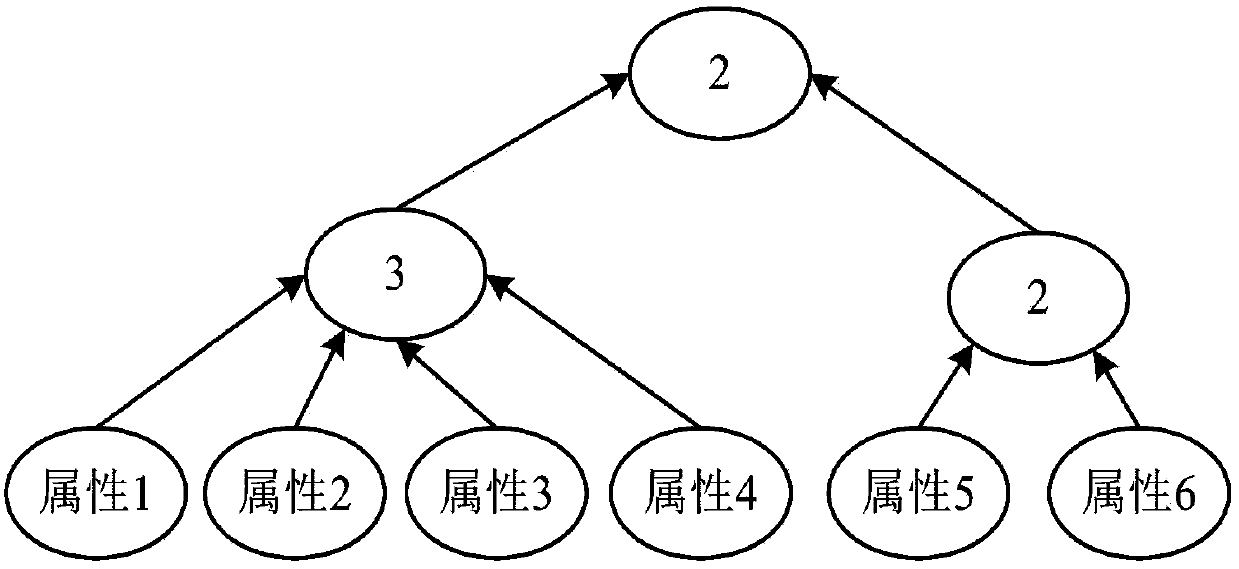
The invention relates to an encryption method applied to a MQTT-SN protocol, and relates to the field of communication. The method employs a harsh algorithm and ciphertext-policy attribute-based encryption method, so that a publishing terminal, an agent server and one or a plurality of subscription terminals can complete encrypted communication. The method herein includes the following steps: an agent server verifying the identity of a publishing / subscription terminal, performing registration of the publishing / subscription terminal, and generating a system common parameter; the publishing terminal encrypting a plaintext load by using the ciphertext-policy attribute-based encryption method; the publishing terminal transmitting the encrypted load to the agent server, the agent server forwarding the encrypted load to one or a plurality of subscription terminals; and the subscription terminal applying for a secrete key from the agent server, decrypting the encrypted load, obtaining a plaintext. According to the invention, the method can implement identity verification of a MQTT-SN protocol publishing / subscription terminal, data integrity verification, and data confidentiality protection, and better addresses the safety issues faced by the MQTT-SN protocol in terminals of wireless sensor network applications.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Authenticated encryption method and encryption system based on symmetric encryption
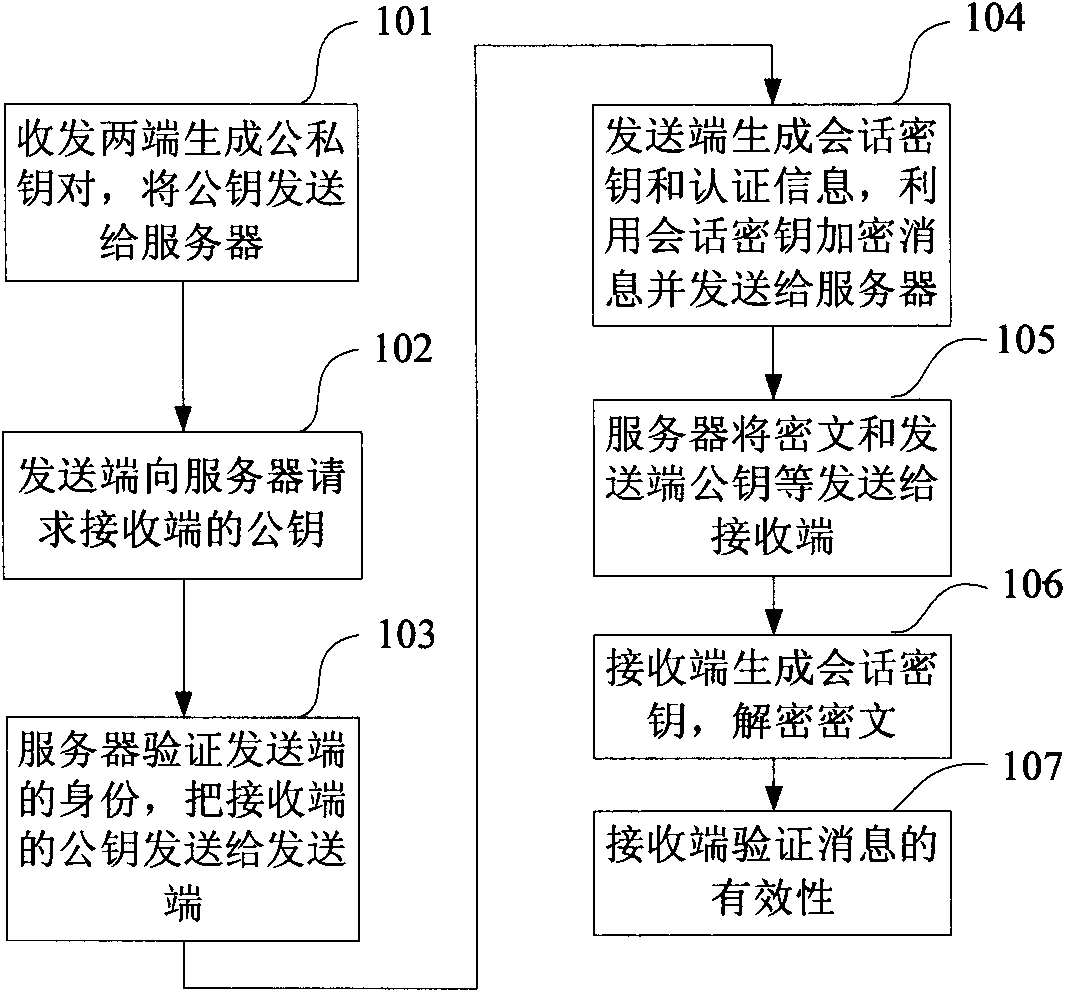
InactiveCN101667913AAchieve authenticationImplement encryptionKey distribution for secure communicationUser identity/authority verificationThird partyCommunications security
The invention discloses an authenticated encryption method and a system, relating to the field of communication security. The restorable signature of a message and the symmetric encryption technologyare combined; a commitment value which only can be calculated by a designated message receiving end is used as a session key encryption message; and the message receiving end validates the validity ofthe message by the restorable signature, thus realizing encryption and authentication in one logical step. A key generation unit of a sending end generates a session key of the sending end; an encryption unit encrypts a message to be sent; the receiving end generates a session key of the receiving end; a decryption unit utilizes the session key of the receiving end to decrypts the encrypted message; and the authentication and confirmation message is generated according to the decrypted message, thus validating the validity of the message. When disputes occur, the message receiving end transforms the authenticated and encrypted message signature into a common signature so as to lead a third party to validate the validity of the signature. The invention has the advantages of high security,low calculated amount and transmission cost, and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
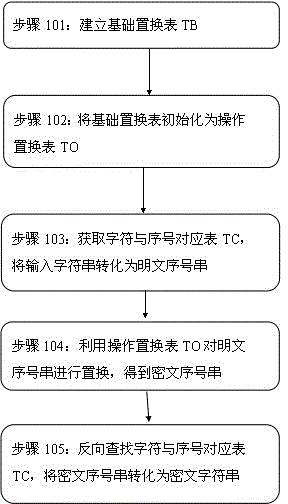
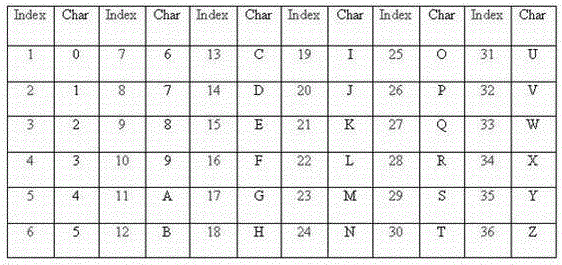
Encryption method and?device
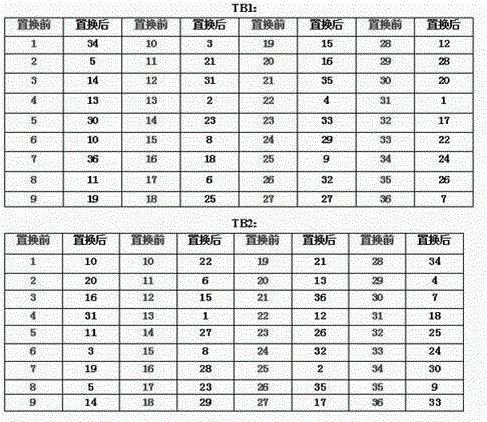
ActiveCN103825723AAccelerateImplement encryptionEncryption apparatus with shift registers/memoriesVisibilityComputer hardware
The invention discloses an encryption method based on characters. The method comprises steps of building a basic transposition table?TB and using a secret key to initialize the basic transposition table to an operation transposition table?TO, converting an input character string into a plaintext sequence number string according to a pre-defined character and sequence number corresponding?table TC, using the operation transposition table?TO for carrying out transposition on the plaintext sequence number string to obtain a ciphertext sequence number string, and converting the ciphertext sequence number string into a ciphertext character string. According to the method, a character?position services as a basic processing unit, dynamic variable data length encryption is realized, length?consistency and?visibility of the ciphertext and the plaintext can be ensured, and platform adaptability and high calculation efficiency are realized.
Owner:深圳市太和物联信息技术有限公司
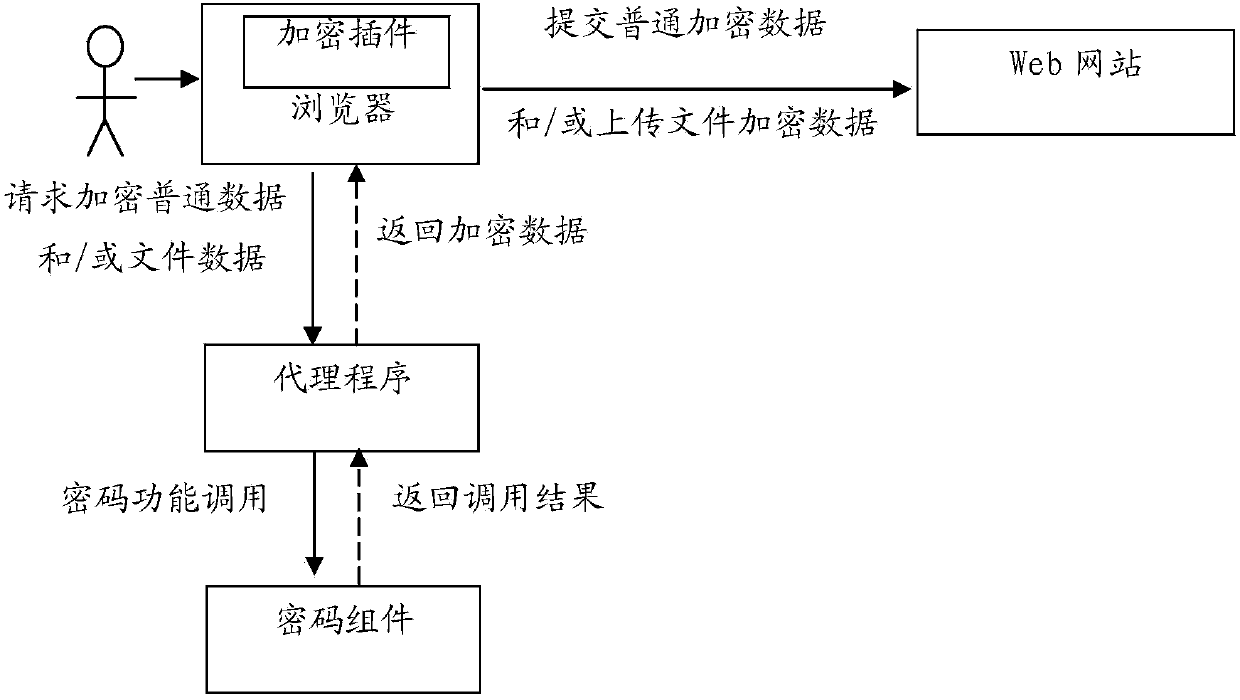
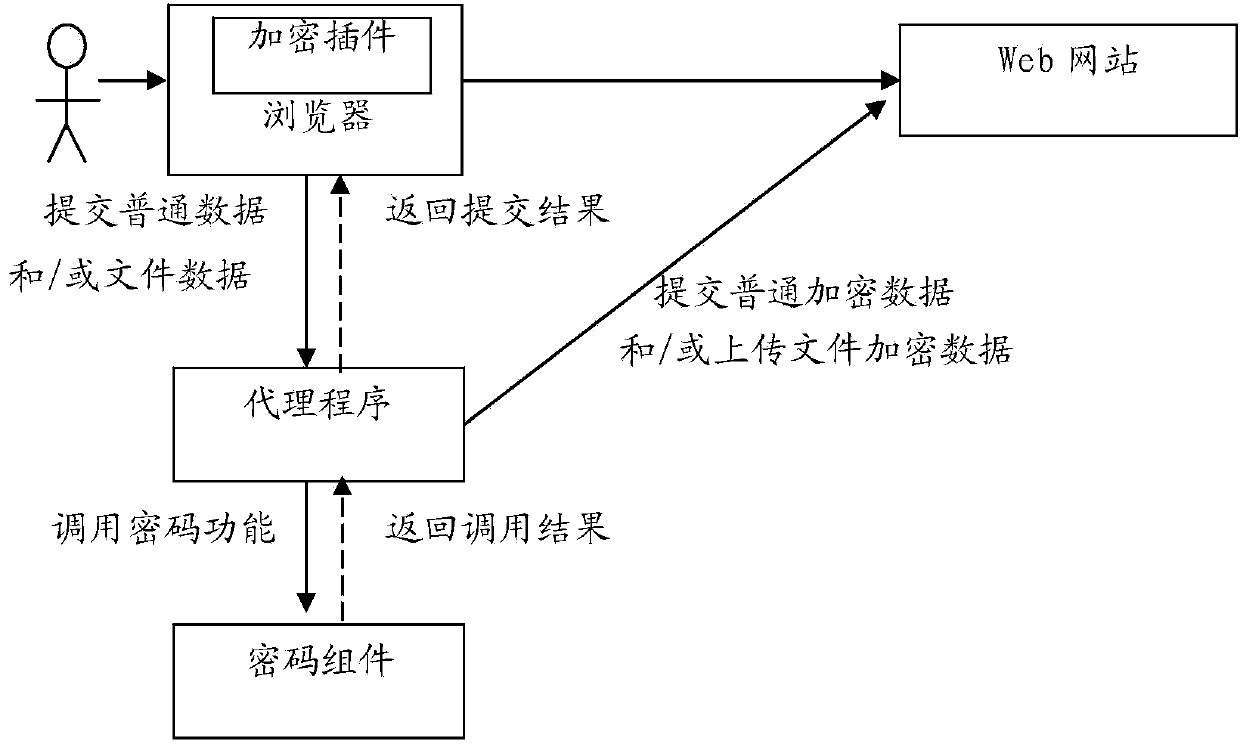
Method of encrypting data and files for browser
The invention relates to a method of encrypting data and files for a browser. The method comprises the following steps that an encryption plug-in modifies a code for submitting data and / or uploading a file part in a page code, which returns to a user browser, of a Web website; when a user submits the data and / or uploads a file through the browser, the modified page code for submitting the data and / or uploading the file submits data to be submitted or the file data to be uploaded by the user to a local agent program of the user browser, the agent program calls a password module to encrypt the data to be submitted or the file data to be uploaded, and then the browser submits or uploads the encrypted data or the file data to the Web website, or the agent program submits or uploads the encrypted data or the file data to the Web website. According to the method, the submitted data and / or the uploaded file data can be encrypted without modifying the Web website and calling the plug-in of the browser.
Owner:WUHAN UNIV OF TECH
Information encryption method and mobile terminal
ActiveCN104270517AImplement encryptionSolve the security problem of leaking user informationKey distribution for secure communicationSubstation equipmentComputer hardwarePlaintext
The invention provides an information encryption method and a mobile terminal and relates to the field of mobile communication. The security problem of leaking information of a user through a terminal is solved. The method includes the steps that an encryption instruction is obtained; according to the encryption instruction, plaintext inside an input box is encrypted to obtain ciphertext; the ciphertext is used for replacing the plaintext to be displayed. According to the technical scheme, the information encryption method and the mobile terminal are suitable for communication software, and input information in the communication software is encrypted.
Owner:ZTE CORP
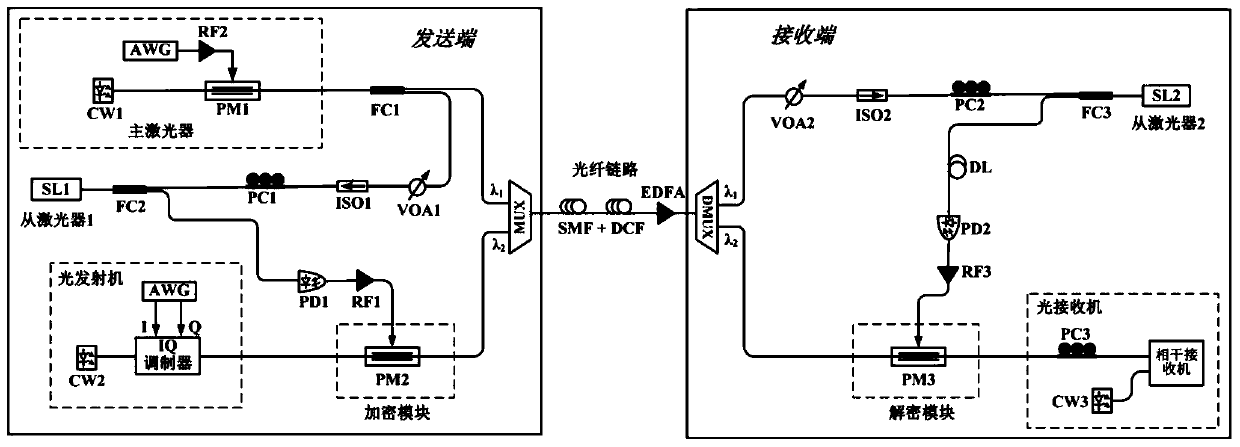
Physical layer secret optical fiber communication system based on chaotic phase encryption
ActiveCN111277337AImplement encryptionAchieve decryptionSecuring communication by chaotic signalsElectromagnetic transmission optical aspectsEngineeringMechanical engineering
The invention discloses a physical layer secret optical fiber communication system based on chaotic phase encryption, and the system comprises the steps: dividing a broadband random light source generated by a main laser into two identical optical signals, and respectively injecting the two optical signals into slave lasers of two communication sides, thereby generating a synchronous chaotic signal; and then the generated synchronous chaotic signal is used as a phase modulator driving signal, and high-speed optical signals generated by high-order modulation are encrypted and decrypted at a sending end and a receiving end.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Two-dimensional code compiling method
InactiveCN103177281AImprove aestheticsAvoid influenceRecord carriers used with machinesData compressionTerra firma
The invention discloses a two-dimensional code compiling method. The two-dimensional code compiling method comprises the following steps of: on the basis of a self-adaptive code compiling extended black and white code compiling technology and a code compiling scheme applicable to different multimedia, introducing an interweaving technology into an error-correcting code compiling technology by using a data compression technology with an open structure during compression code compiling; and adopting an advanced morphologic image pre-processing technology based on multi-scale structural analysis. The two-dimensional code compiling method has the advantages that a two-dimensional code is superior to the conventional two-dimensional code standard in terms of information bearing capacity, robustness, safety, reliability and adaptability; and coding and decoding bottom-layer supporting software provides technical support for various types of application of the two-dimensional code to the field of the internet of things in an open interface mode, the market monopoly position of the conventional foreign two-dimensional code standard can be broken, the chaotic situation of the conventional domestic two-dimensional code application is changed, and a firm foundation is laid for the development of the internet-of-things industry.
Owner:江苏圆坤二维码研究院有限公司
Identity-based wireless sensor network security trust method
InactiveCN101600198AExchangeImplement encryptionNetwork topologiesSecurity arrangementTrusted systemAuthentication
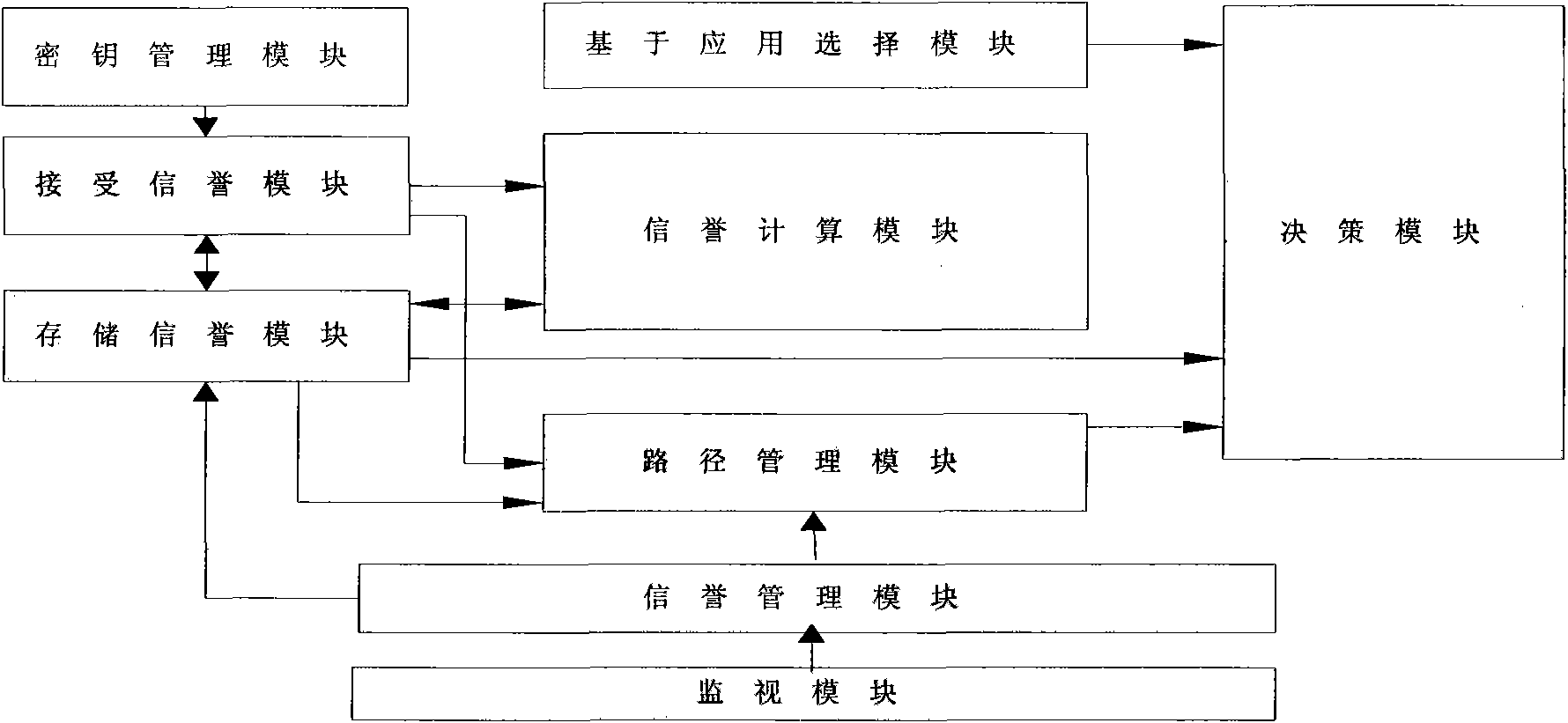
The invention discloses an identity-based wireless sensor network security trust method. In the method, firstly each node in the network is loaded with a trust management structure; wherein the trust management structure is composed of a secret key management module, a receiving credit module, a storage credit module, a credit calculating module, an application selecting module, a route management module, a decision making module, a credit management module and a monitoring module. On the basis of the trust management structure, a trust communication network is established by broadcasting query node information among nodes, receiving query respond and updating node credit and by identity-based public key password encryption and authentication among nodes, so as to realize safe communication of credit information among nodes. The invention reduces complexity of credit calculation in the wireless sensor network, improves security of communication of the wireless sensor network trust system, solves communication problem of a source node and a destination node under multi-hop condition, and can meet the requirement of large-scale self-organized network application.
Owner:XIDIAN UNIV
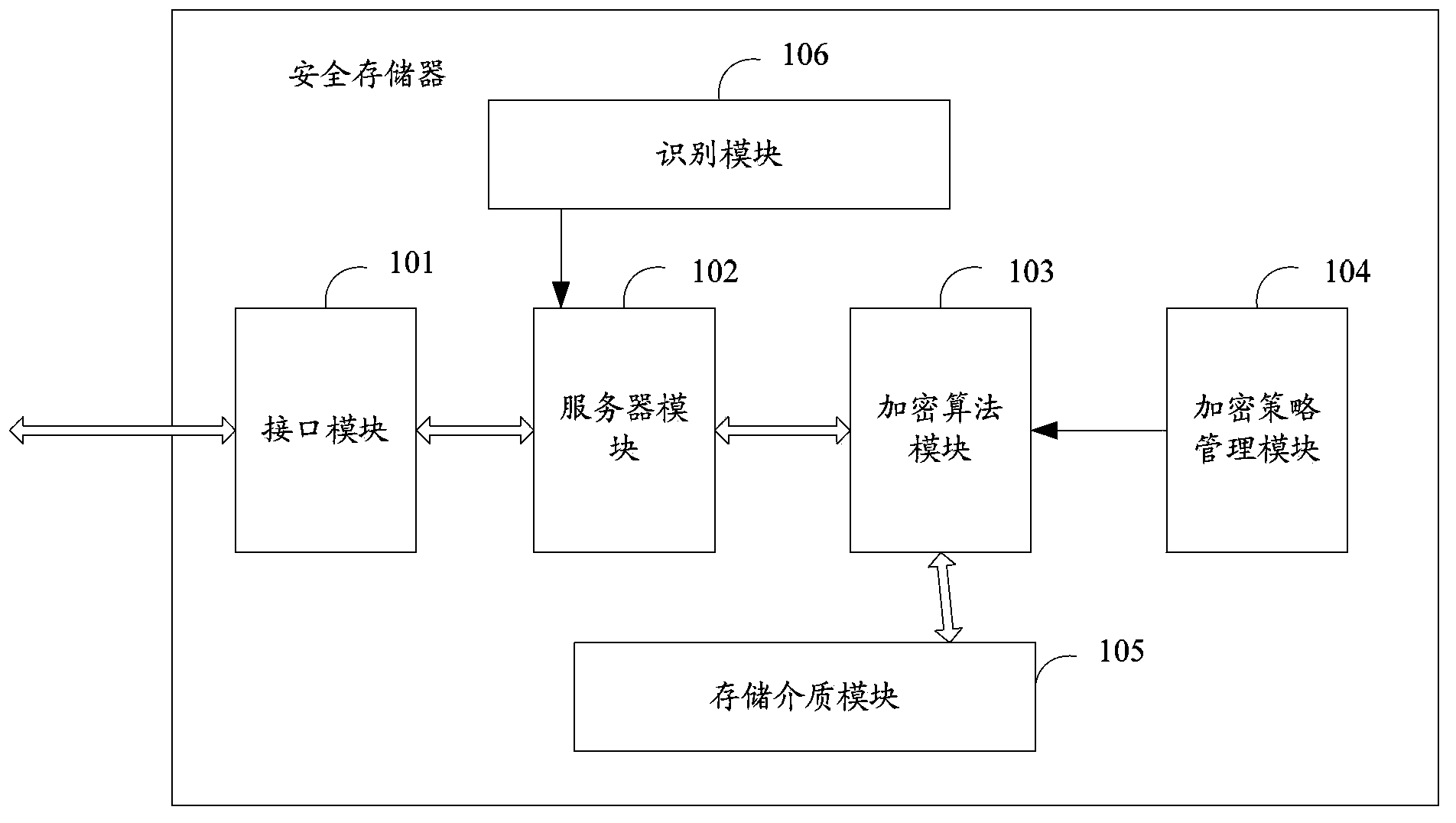
Secure storage device
ActiveCN104239820AAchieve securityPrevent Data LeakageInternal/peripheral component protectionLocal machineComputer hardware
The invention discloses a secure storage device which comprises an interface module, a server module, an encryption algorithm module, an encryption strategy management module, a recognition module and a storage medium module. The server module is used for providing an operating system and file processing programs of the storage device, receiving file access requests from a local computer of a user, converting operation results into images, and transmitting the images to the local computer of the user through the interface module. The encryption algorithm module is used for extracting an encryption strategy from the encryption strategy management module, adopting the encryption strategy to carry out encryption on files according to random seeds formed by the recognition module and file characteristic information and then storing the files in the storage medium module and is also used for adopting the encryption strategy to carry out decryption on the files stored in the storage medium module according to encryption seeds formed by the recognition module and the file characteristic information. The recognition module is used for receiving information input by the user to generate the random seeds which are used as initial indexes of other secret keys.
Owner:POTEVIO INFORMATION TECH
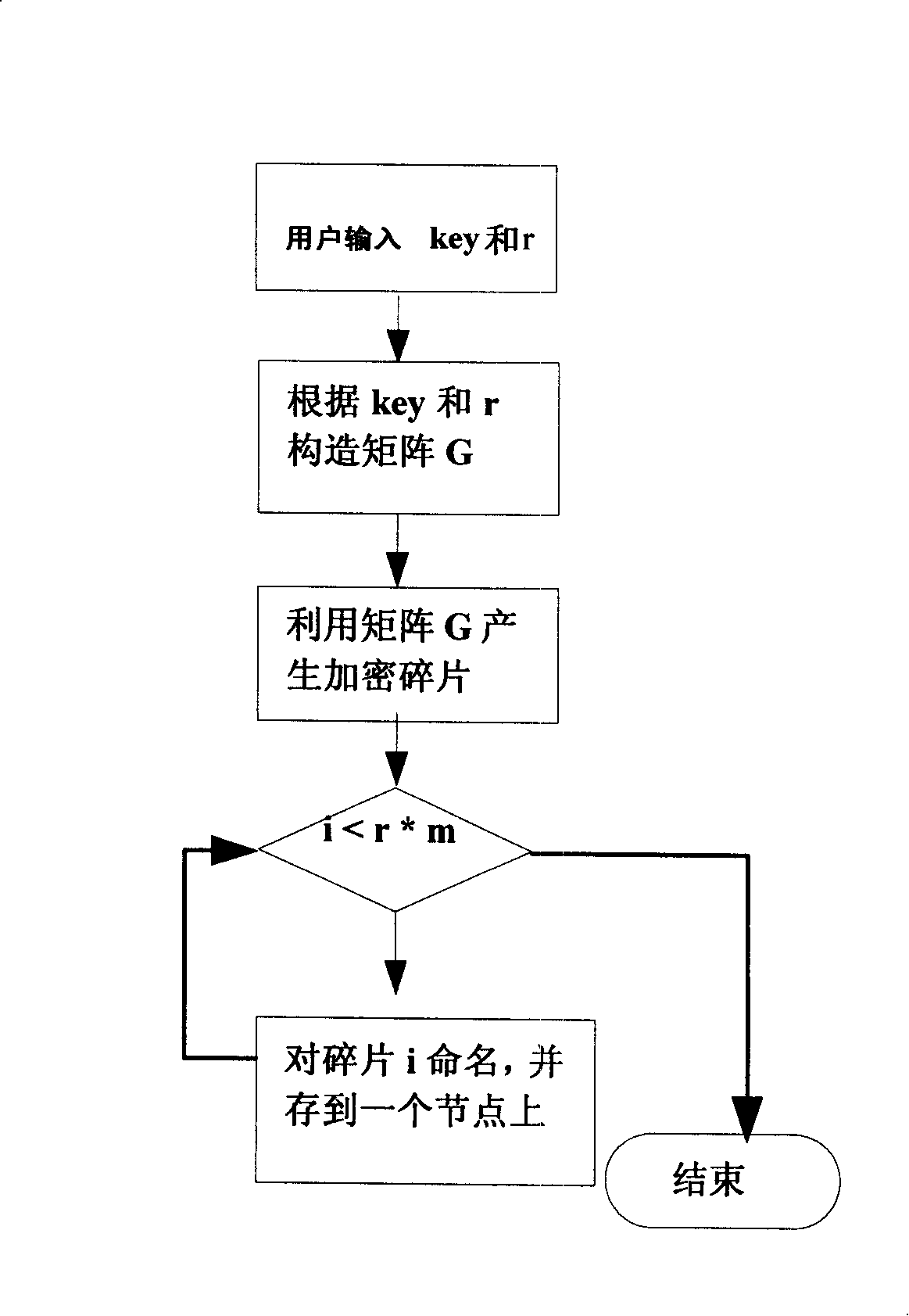
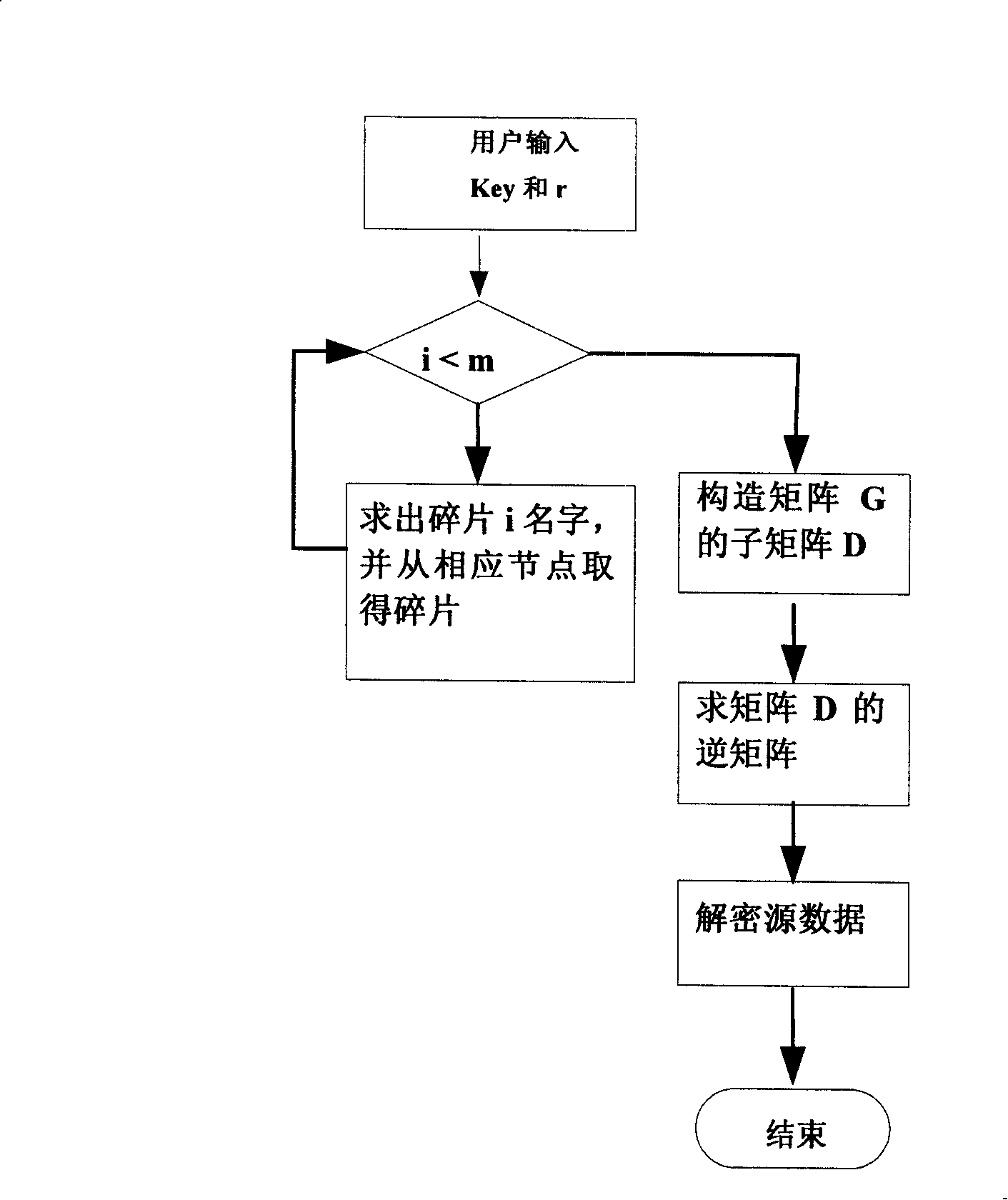
P2P storage system coding method based on Reed-Solomon code
InactiveCN101192924AEnsure safetyGuaranteed reliabilityPublic key for secure communicationSpecial data processing applicationsComputer hardwareOriginal data
A coding method based on a point-to-point storage system comprises the following encryption steps that: 1) an encryption matrix G is generated according to a key entered by the user and a redundancy r required by the user; 2) the original data is coded into the encrypted data fragments, the number of which is the product of r multiplied by m; 3) the fragments are named and different fragments are made to have the independent names, which are distributed into the point-to-point storage system; and the following decryption steps that: 4) when the user wants to read the data, the name of the data fragment is regenerated and the m fragments are collected from the point-to-point system according to the name of the fragment; and 5) a decryption matrix D<-1> corresponding to the encryption matrix G is constructed according to the key and the original data can be obtained through decryption. Combined with the characteristics and the bottom protocols of the P2P storage system, the invention can simultaneously ensure the security and reliability of the data and solve the defect of the present technical proposal in the application of the P2P storage system.
Owner:PEKING UNIV
Novel image encryption method based on correlation between chaos and plaintext
InactiveCN105513002ABreak strong correlationImplement encryptionImage watermarkingPlaintextDiffusion
The invention provides a novel image encryption method based on correlation between chaos and plaintext. The method comprises the steps: carrying out row and column updating of a plaintext image A, and obtaining a processed image E; employing the modular operation of a gray level 256, changing the pixel sum of the image through the modular operation between rows and the modular operation between columns, and breaking the strong correlation between the adjacent rows and the adjacent columns of an original plaintext image; enabling the pixel sum s of the image E to serve as the feature of the image, extracting the feature of the image, participating the generation of a key stream, carrying out the second layer encryption through scrambling encryption, and obtaining an image Q; and solving a problem that a conventional algorithm employs the same key stream while encrypting different images. Through the gray value diffusion of the image, the method builds the mutual influence between two adjacent pixels, and a secret key directly participates in the output of a ciphertext image. In order to achieve an avalanche effect, the mutual influence between two adjacent pixels is built through the key stream. Meanwhile, a second group of secret keys are designed to participate in the output of the ciphertext image, thereby achieving the third layer encryption.
Owner:GUANGDONG OCEAN UNIVERSITY
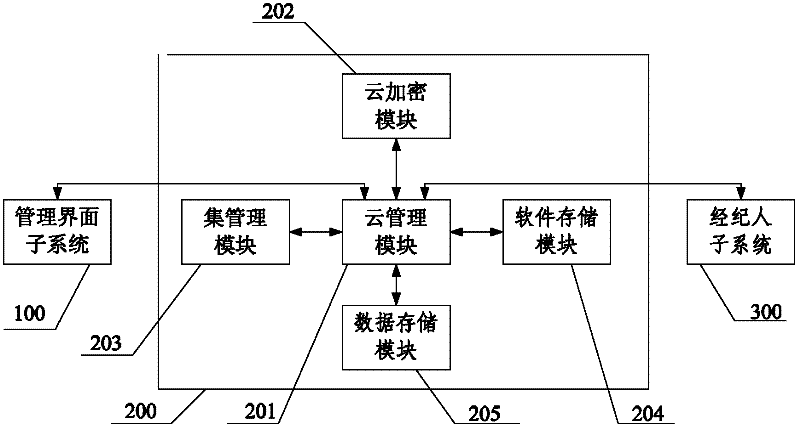
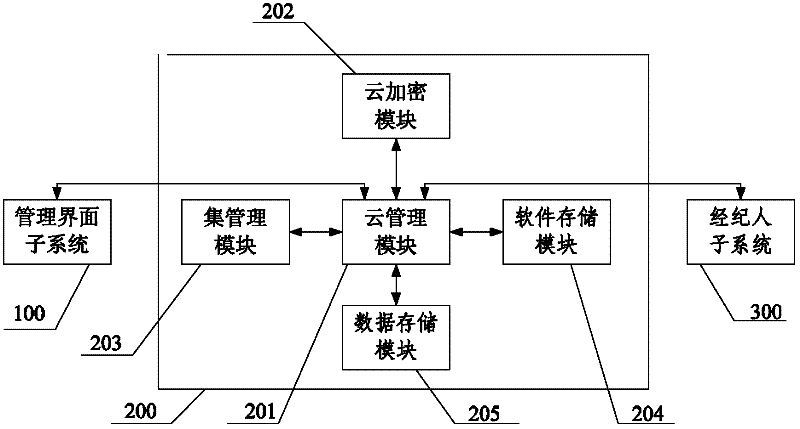
Cloud computing system
ActiveCN102546741AControl and monitor operationsImplement encryptionTransmissionComputing systemsEncryption
The invention discloses a cloud computing system, and relates to the field of cloud computing. The cloud computing system comprises a management interface subsystem, a management service subsystem and a broker subsystem, wherein the management interface subsystem is used for receiving a user instruction, transmitting the user instruction to the management service subsystem and displaying the running state and instruction execution result of the cloud computing system; the management service subsystem is used for managing and maintaining the cloud computing system according to the user instruction, and encrypting and decrypting data in a virtual machine; and the broker subsystem is used for controlling and acquiring the running states of the virtual machine and a computer running the virtual machine according to the control information of the management service subsystem. The cloud computing system is provided with a cloud encryption module, so that the data in the virtual machine can be encrypted and decrypted, and the security of the data in the cloud computing system is effectively improved.
Owner:苏州市卓博科技咨询有限公司
Electronic cigarette controlled through mobile phone software, and control method thereof
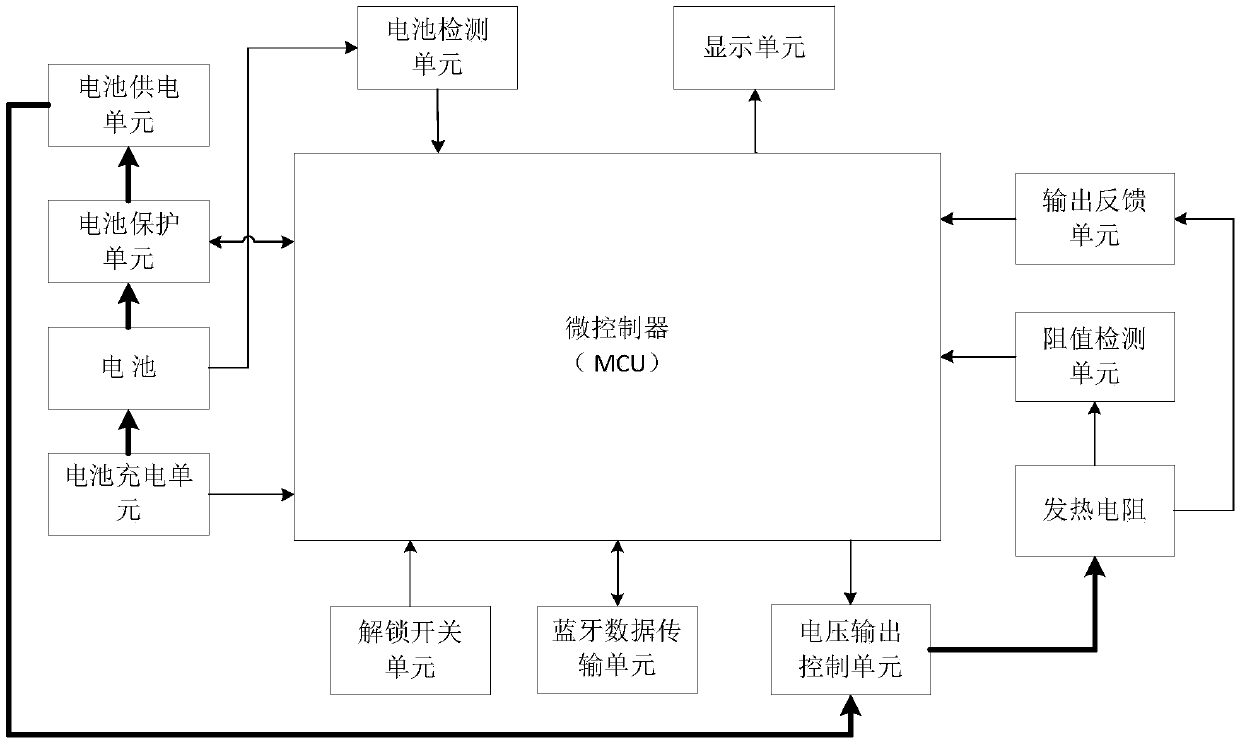
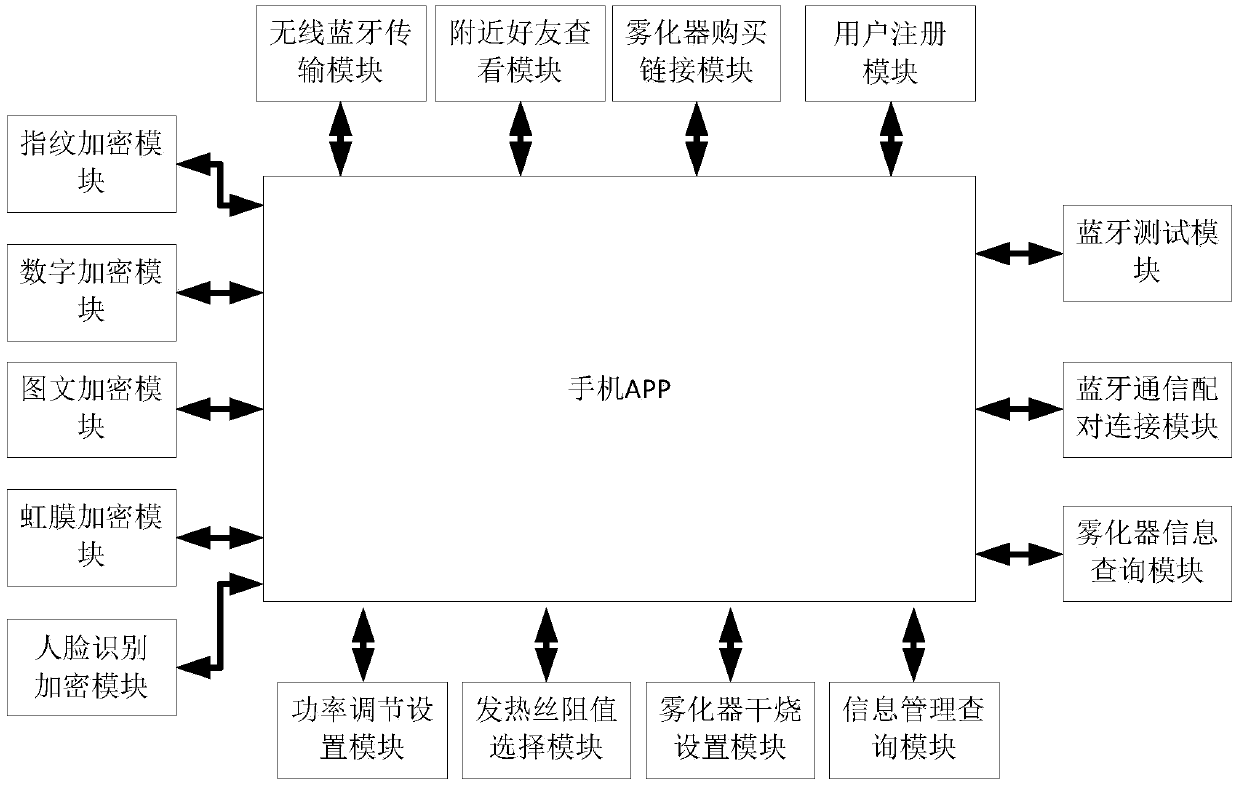
PendingCN109581937AImplement encryptionRealize the use effectProgramme controlComputer controlMicrocontrollerElectronic cigarette
The invention discloses an electronic cigarette controlled through mobile phone software, and a control method thereof. The electronic cigarette comprises an atomizer and a battery component, whereinthe atomizer comprises a heating resistor which is used for heating and atomizing the tobacco liquid of the electronic cigarette; the battery component comprises a battery and a circuit control board,an element and a circuit arranged on the circuit control board comprise a microcontroller, a Bluetooth data transmission unit and an unlocking switch unit; the Bluetooth data transmission unit is provided with a mobile phone software control terminal which is a mobile phone APP installed on a smartphone; the mobile phone APP is provided with encryption information; the encryption information is sent to the Bluetooth data transmission unit through mobile phone Bluetooth, and is then transmitted to the microcontroller; and after the microcontroller identifies the encryption information, throughthe unlocking switch unit, unlocking startup is carried out. The electronic cigarette has the beneficial effects that the encryption of the electronic cigarette and the customization of personal usecan be effectively realized through the control of the mobile phone APP, and juveniles can be prevented from smoking the electronic cigarette so as to avoid bad influences for the society and families.
Owner:HUIZHOU HAPPY VAPING TECH LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com