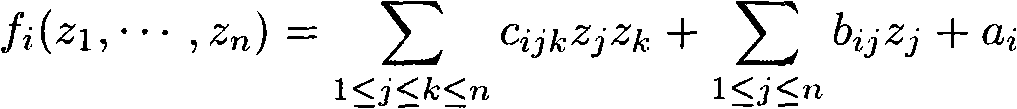Patents
Literature
201 results about "Authenticated encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
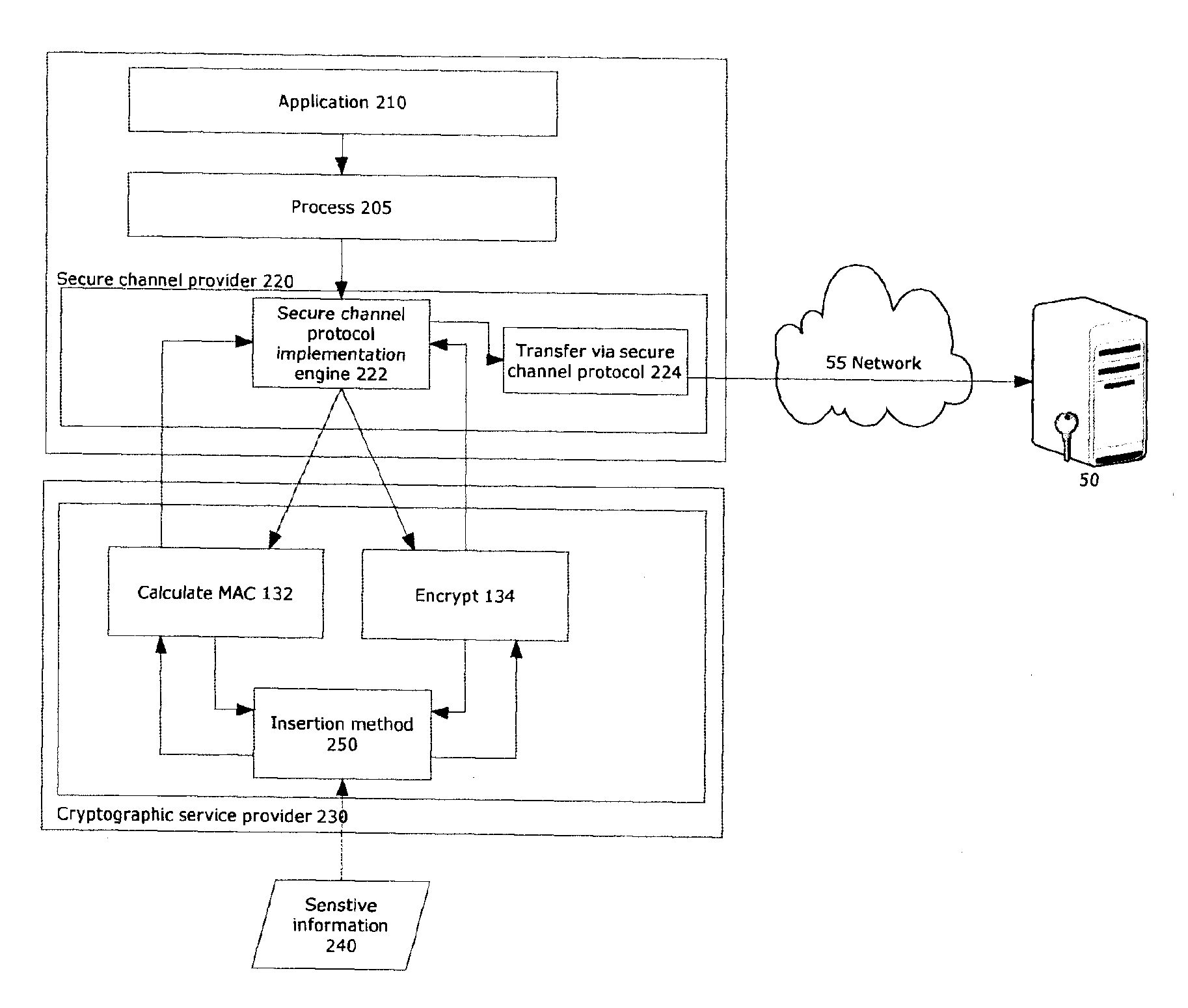
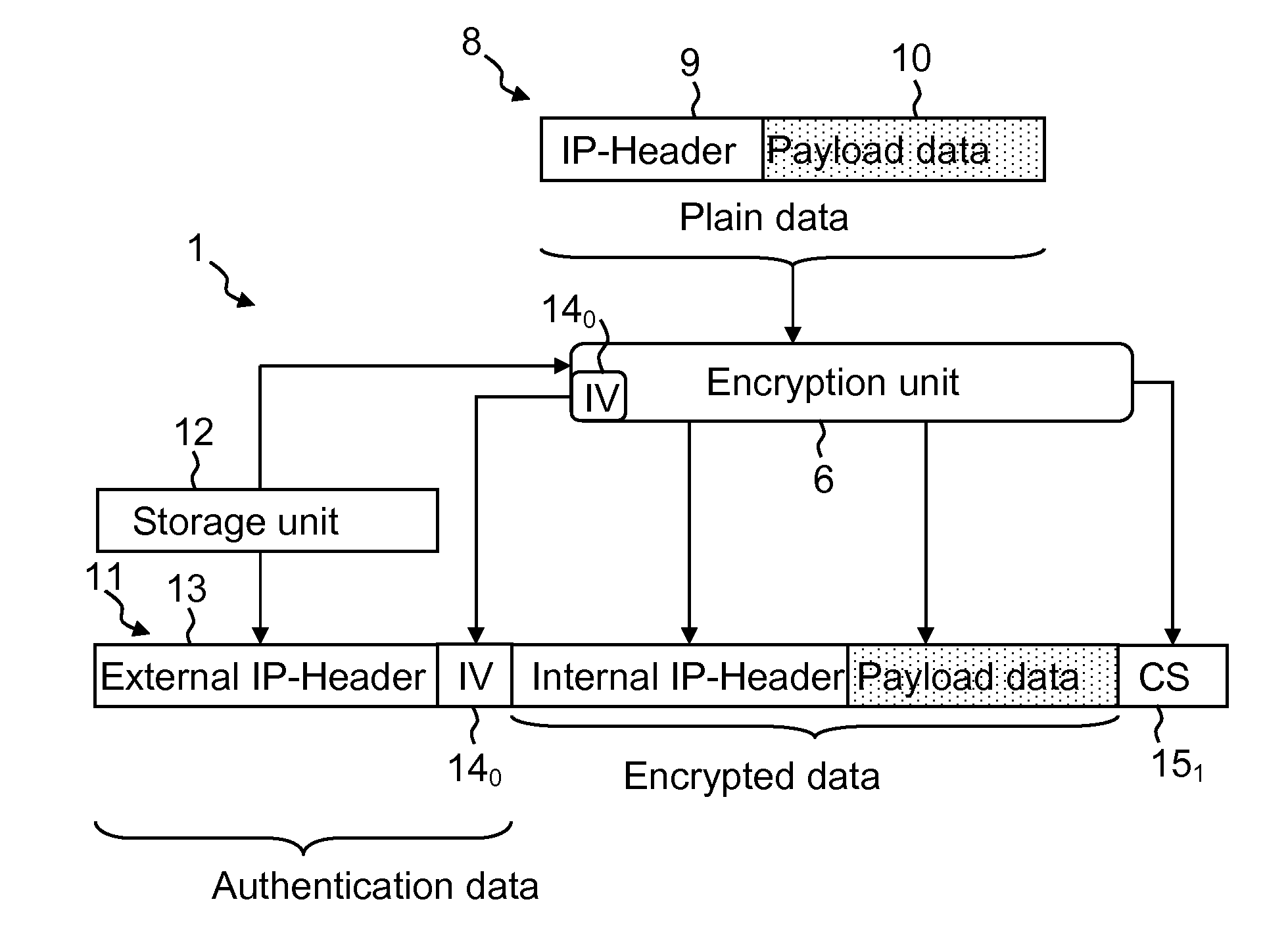
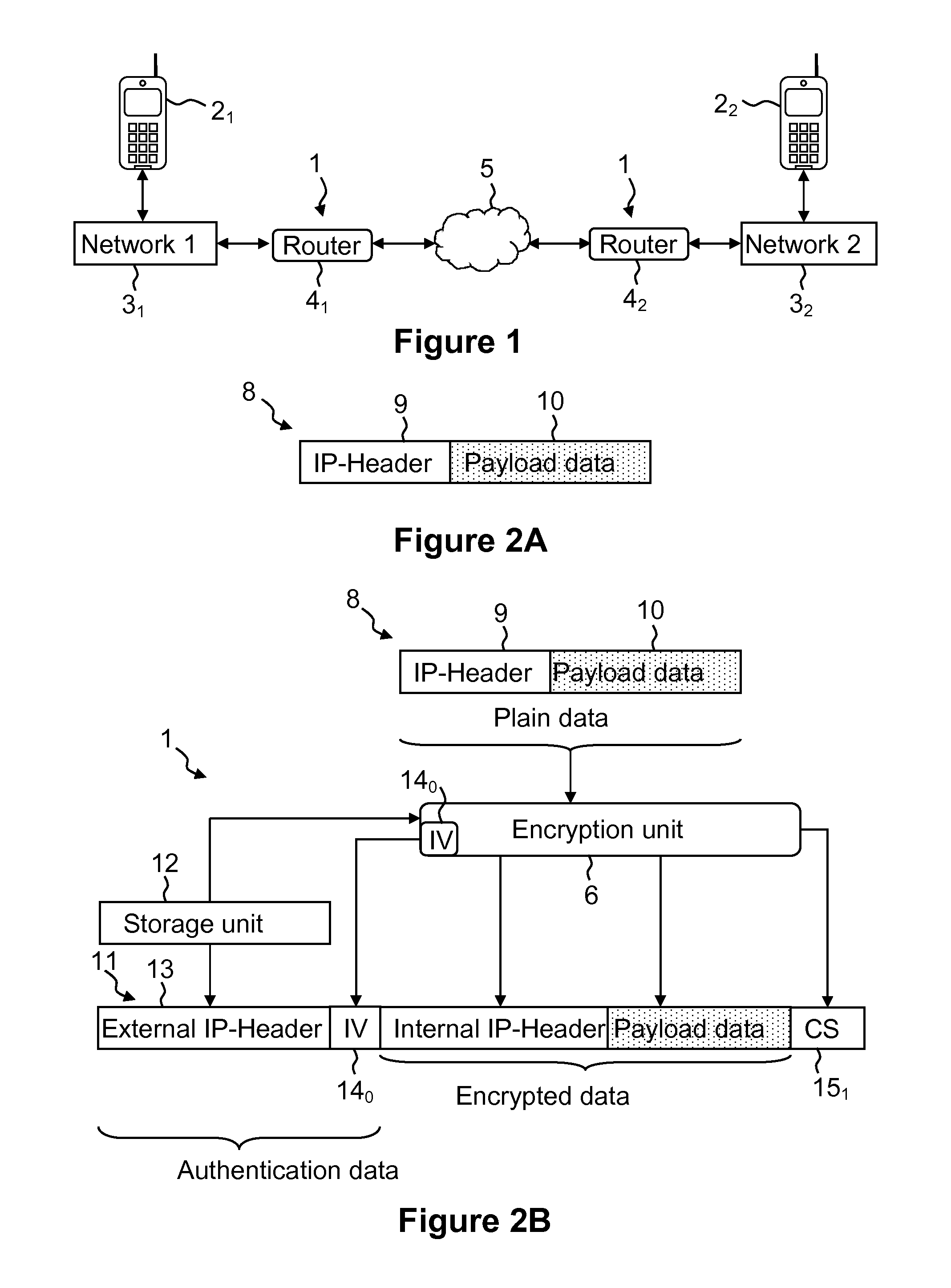
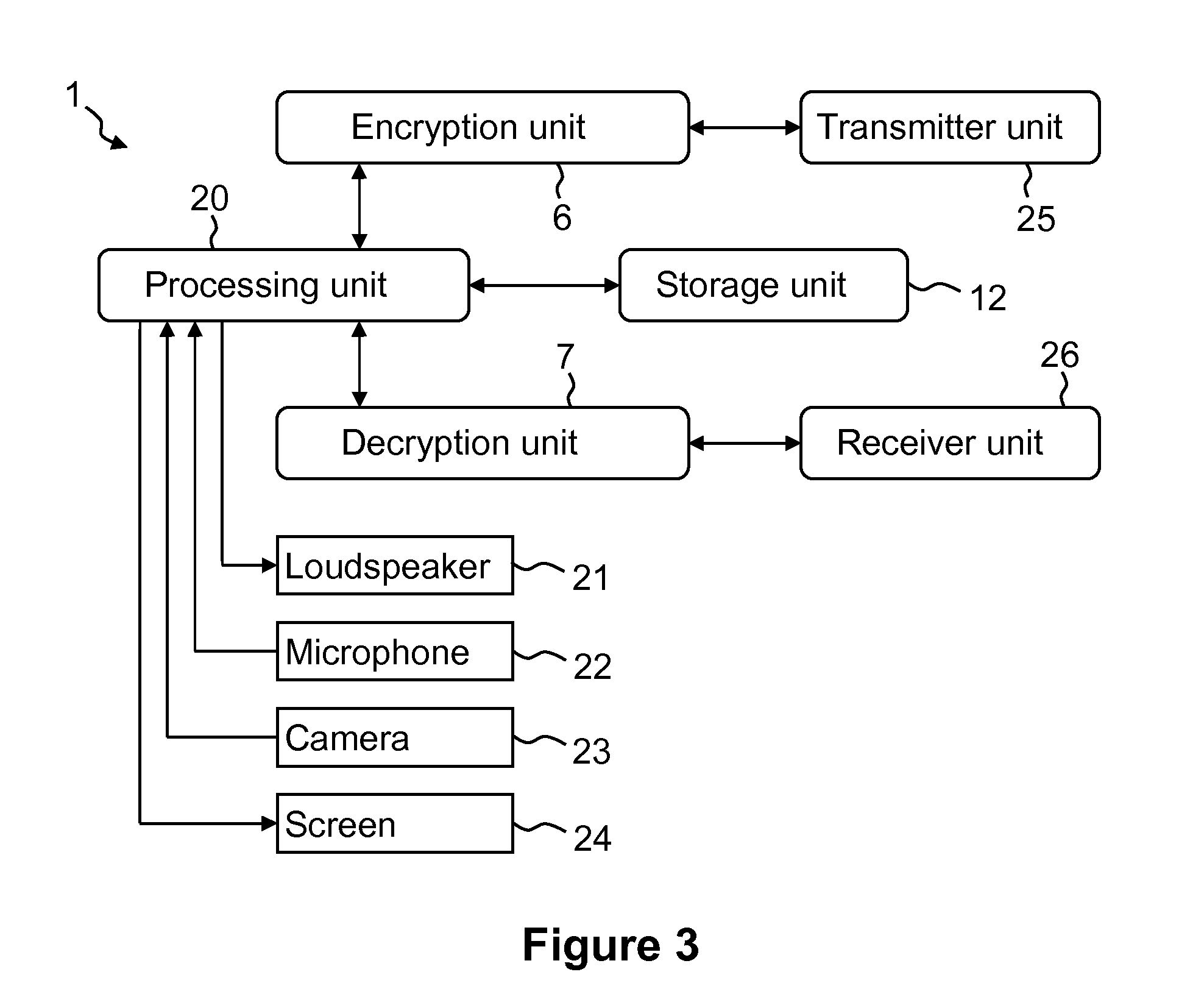
Authenticated encryption (AE) and authenticated encryption with associated data (AEAD) are forms of encryption which simultaneously assure the confidentiality and authenticity of data. These attributes are provided under a single, easy to use programming interface.
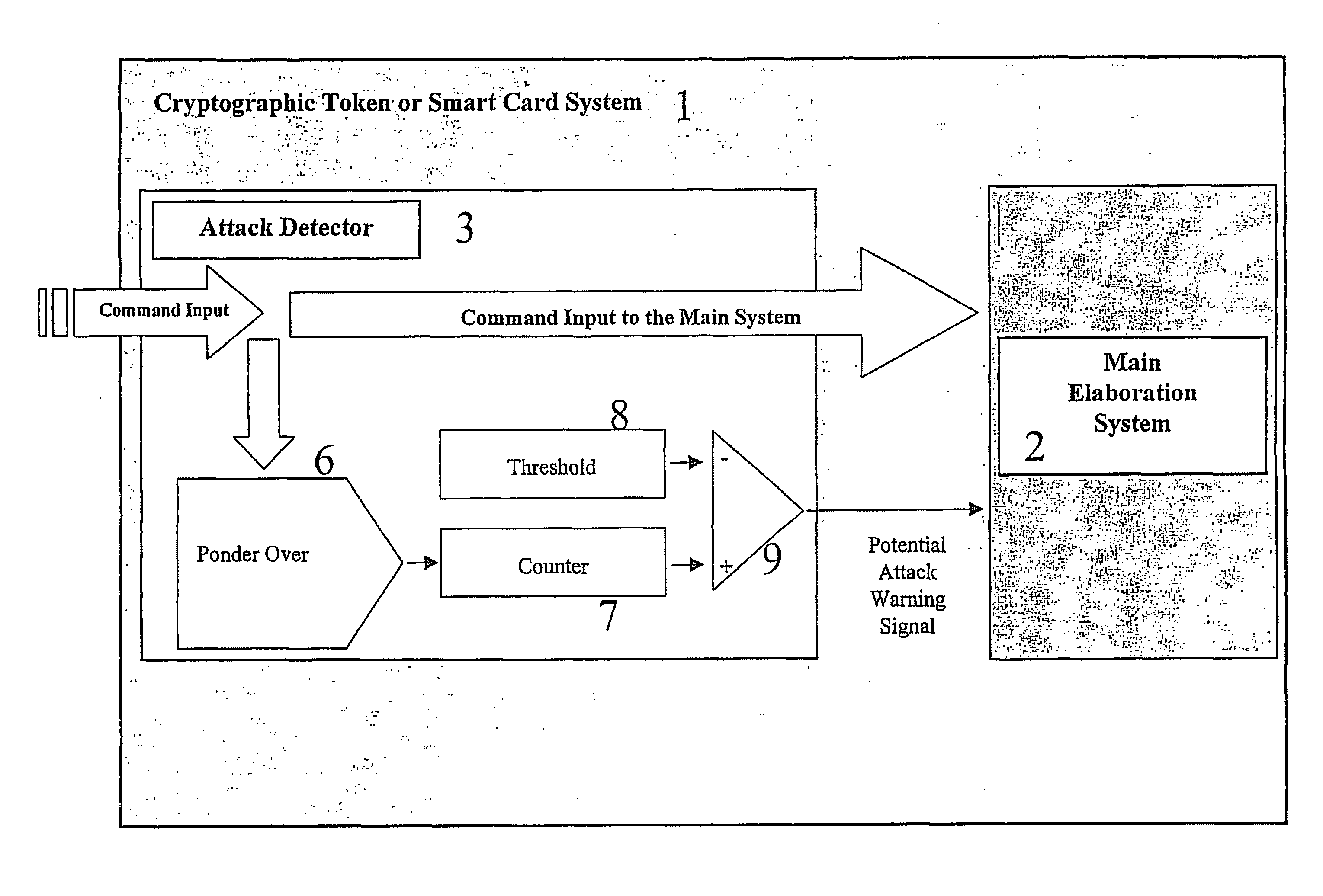
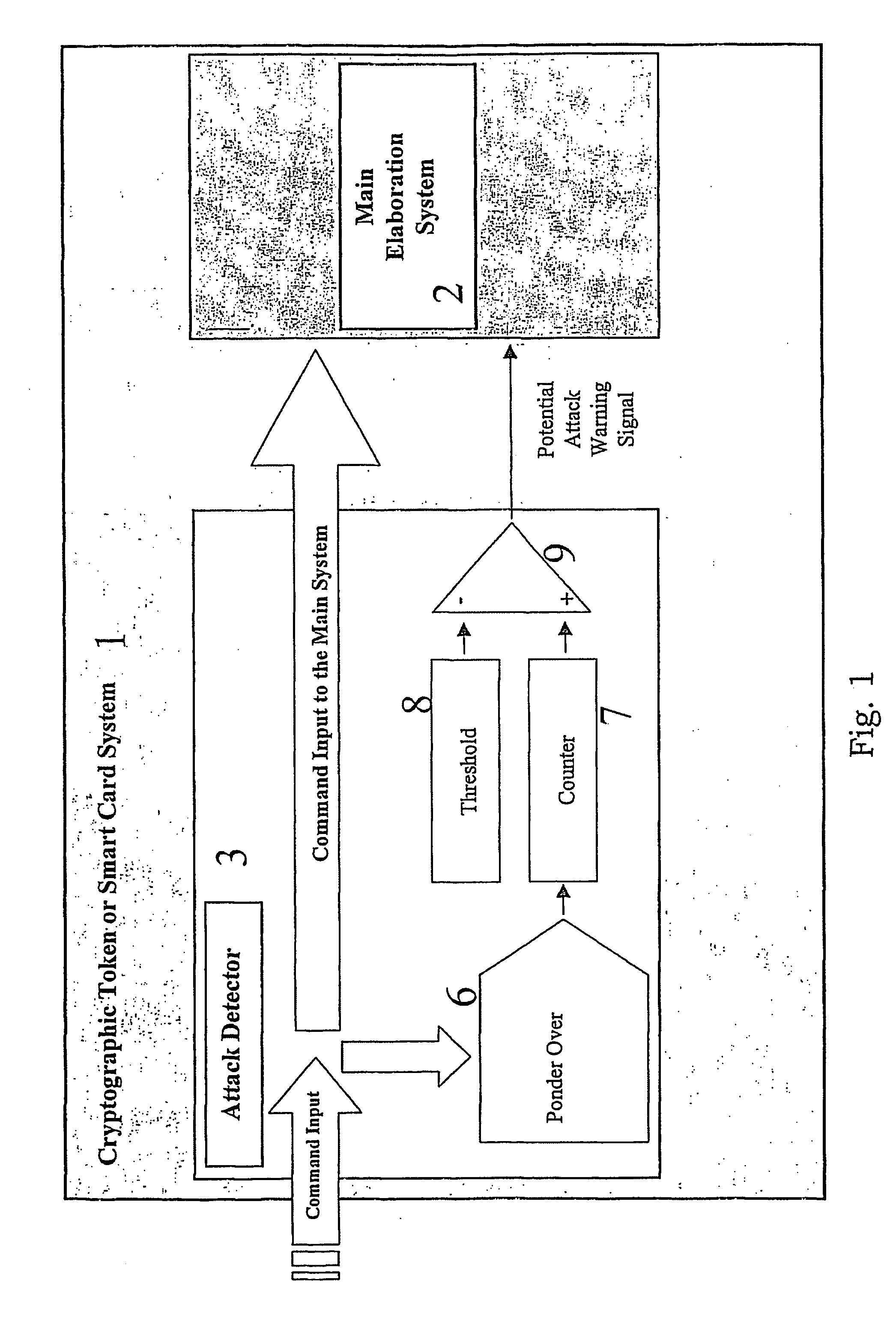
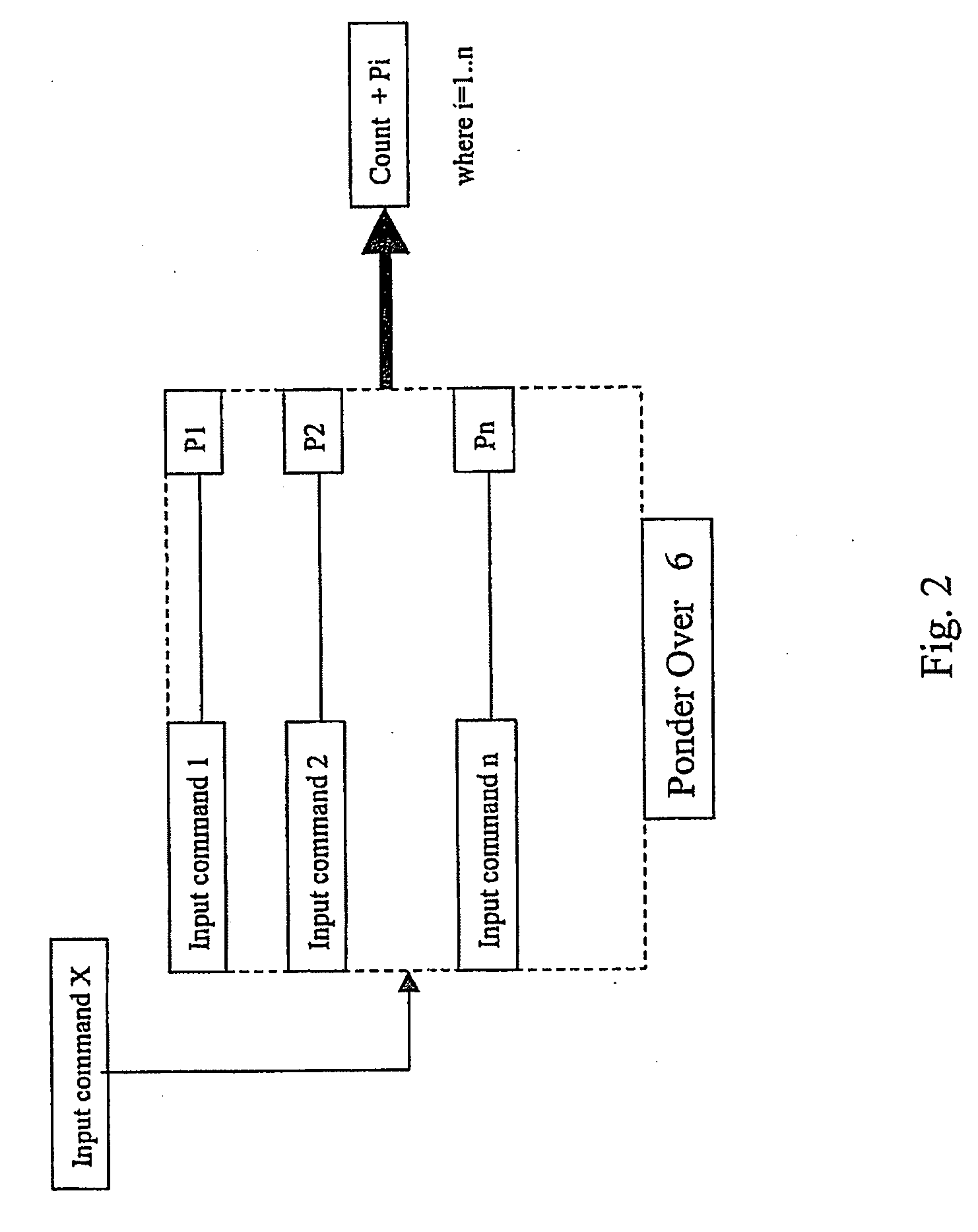
Method For Detecting and Reacting Against Possible Attack to Security Enforcing Operation Performed by a Cryptographic Token or Card
InactiveUS20080209550A1Assured protectionEfficient methodMemory loss protectionError detection/correctionAuthentication systemAuthenticated encryption
The approach defines a protection mechanism against attacks to a security enforcing operation performed by cryptographic token or smart card. It is based on an attack detector which signals the main elaboration or processing system regarding a potential attack situation. The approach addresses SIM cloning problems of telecommunications operators who use old and breakable cryptographic algorithms such as the COMP-128 and do not want to invest in updating the network authentication systems with more resistant authentication cryptographic algorithms. The approach may be applicable to the typical telecommunications operator in an emerging market that does not use state of the art technology.
Owner:STMICROELECTRONICS INT NV
Secure and Authenticated Transactions with Mobile Devices
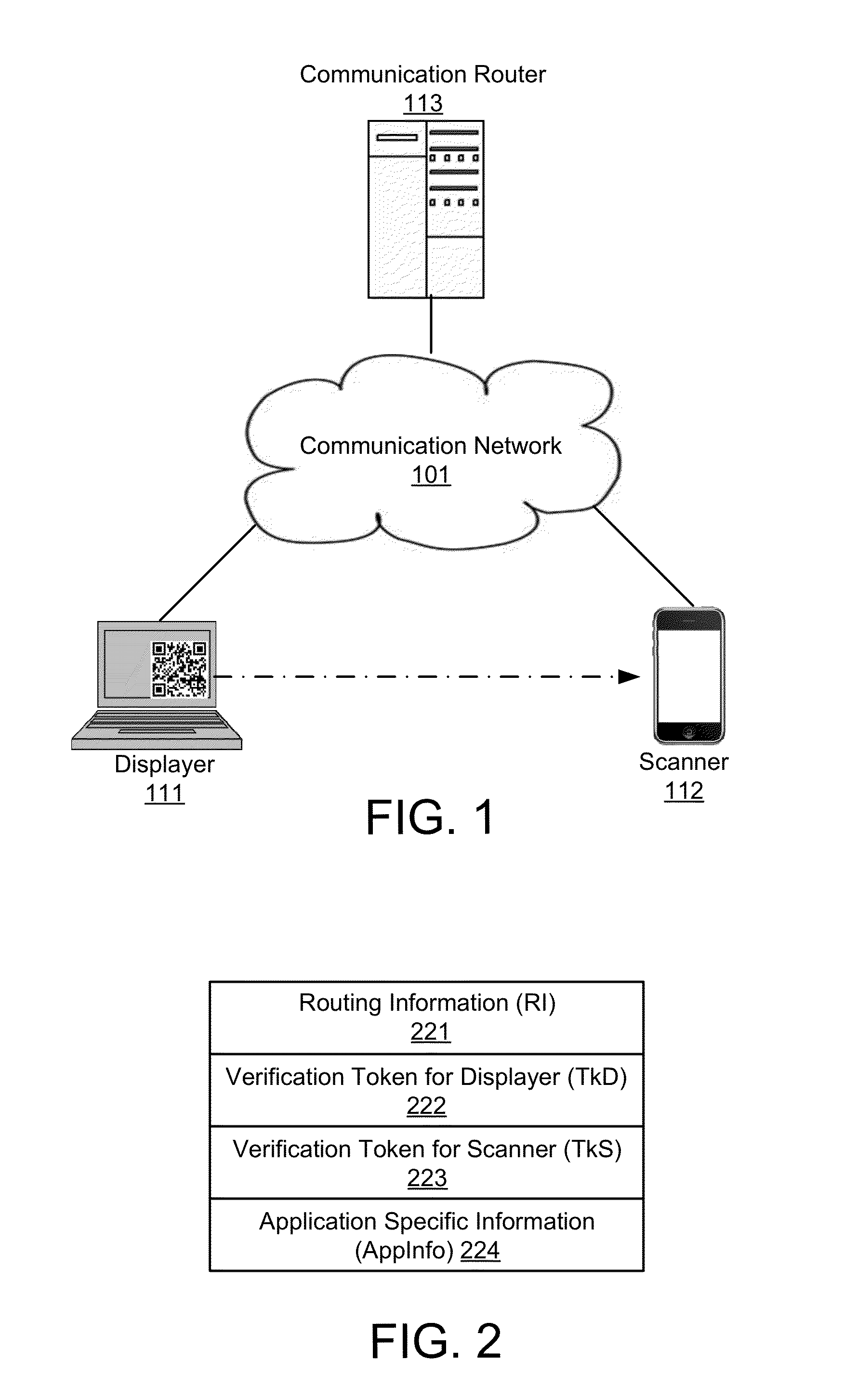
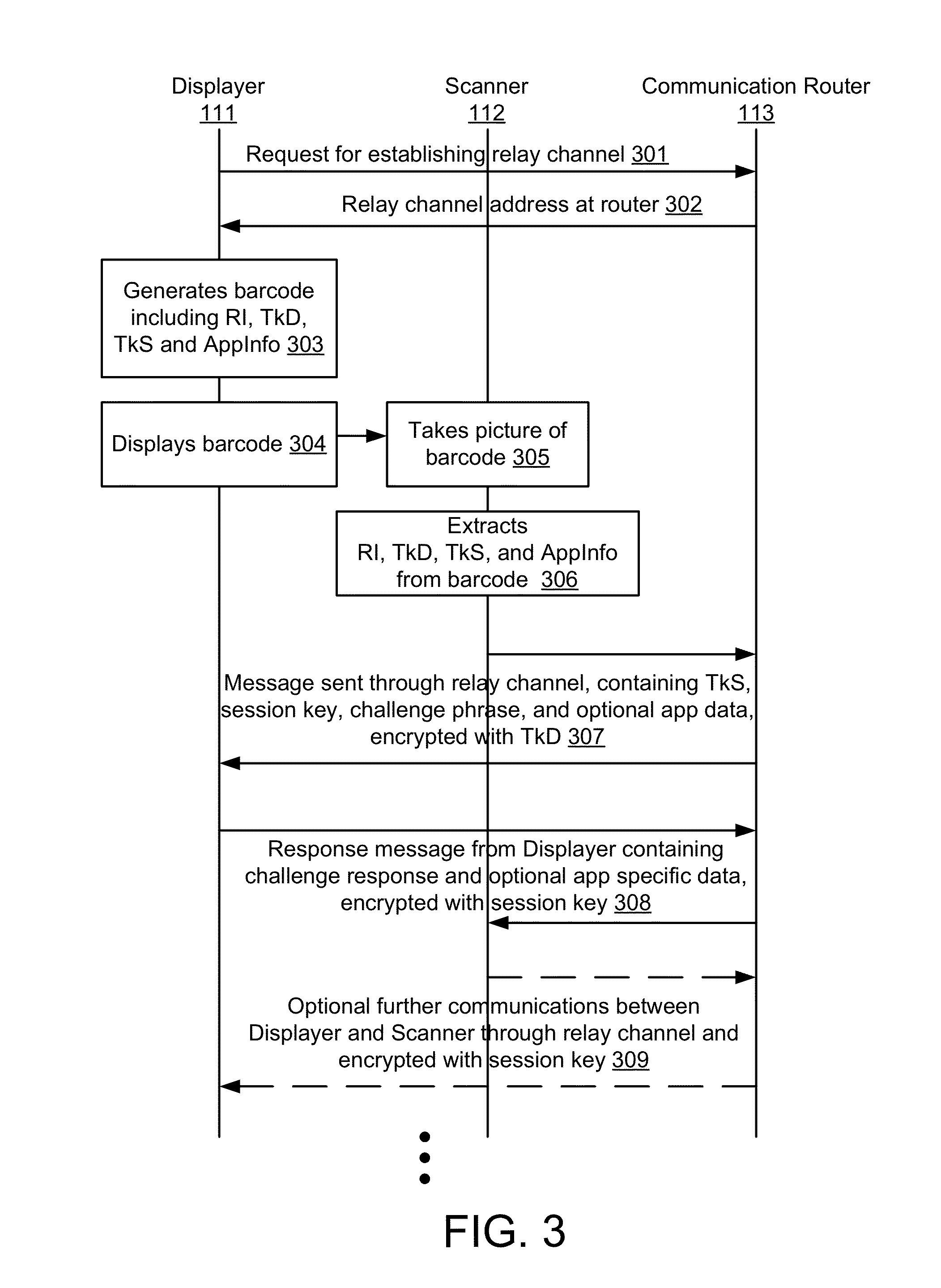
Embodiments of the invention include a platform for using 2D barcodes to establish secure authenticated communication between two computing devices that are in proximity to each other. A two-tier application architecture using a single base app and dynamic add-on applets is used. 2D barcodes can be distinctively visually branded. According to other aspects, the security of mobile payment systems are enhanced by (1) a triangular payment settlement in which the sender and receiver of payment each submit transaction information independently to the same payment server; (2) sensitive information is split into two parts, one of which is stored on a mobile device, and the other of which is stored on a payment server, and the two parts are only combined and exist transiently in the payment server's volatile memory when executing a transaction; and (3) a process to securely update profile pictures associated with payment accounts.
Owner:NETABPECTRUM
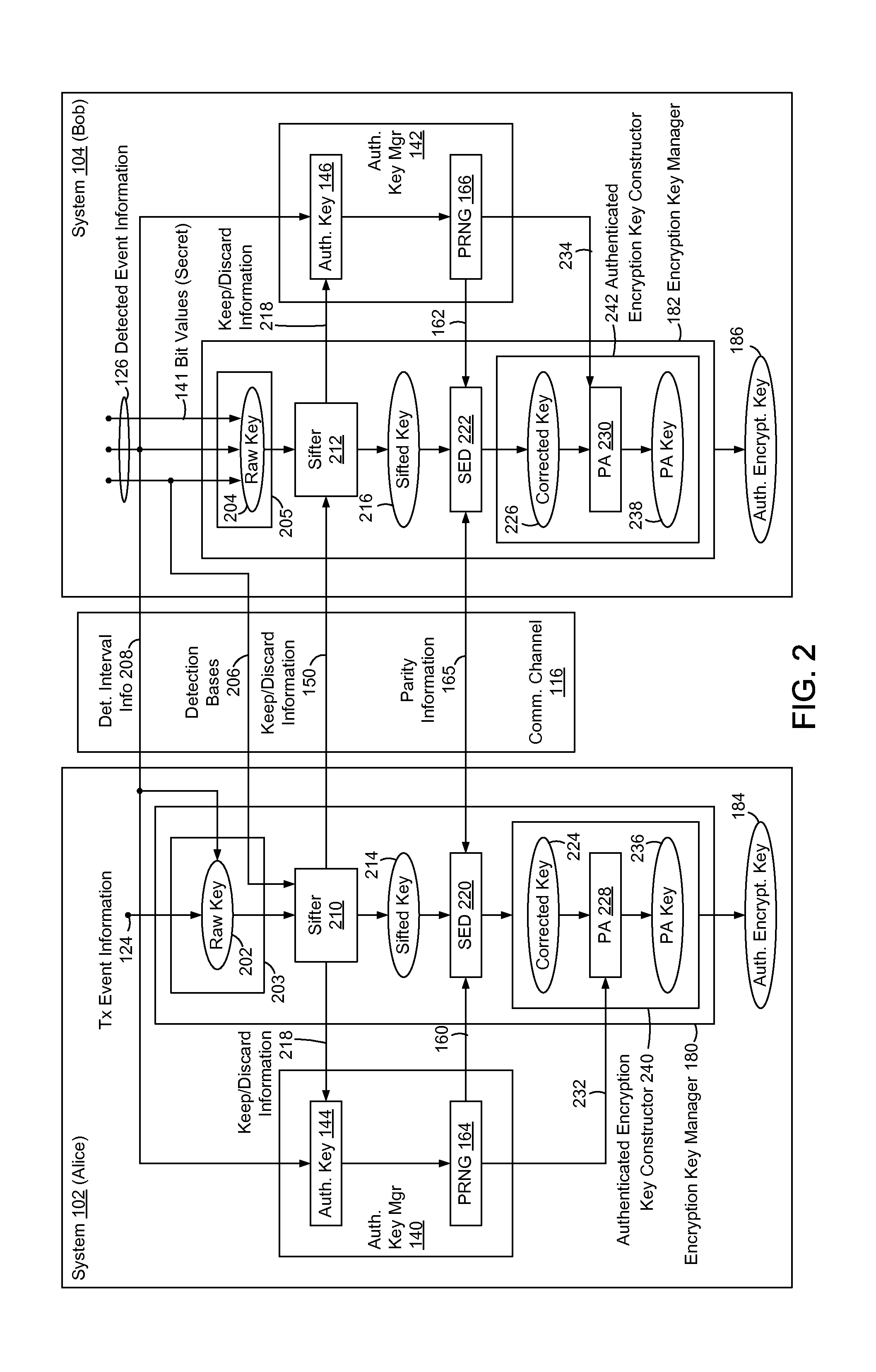
Embedded Authentication Protocol for Quantum Key Distribution Systems
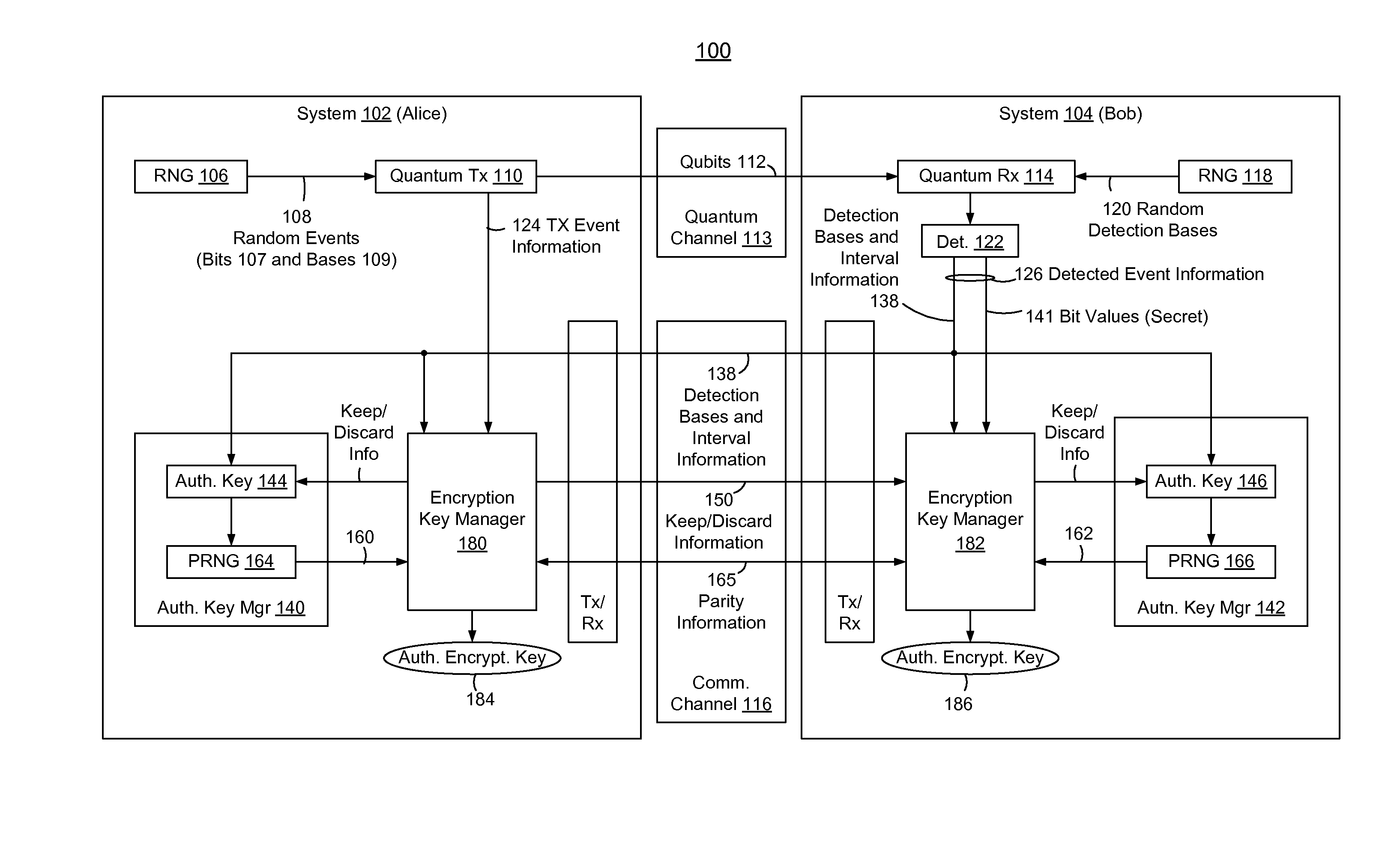
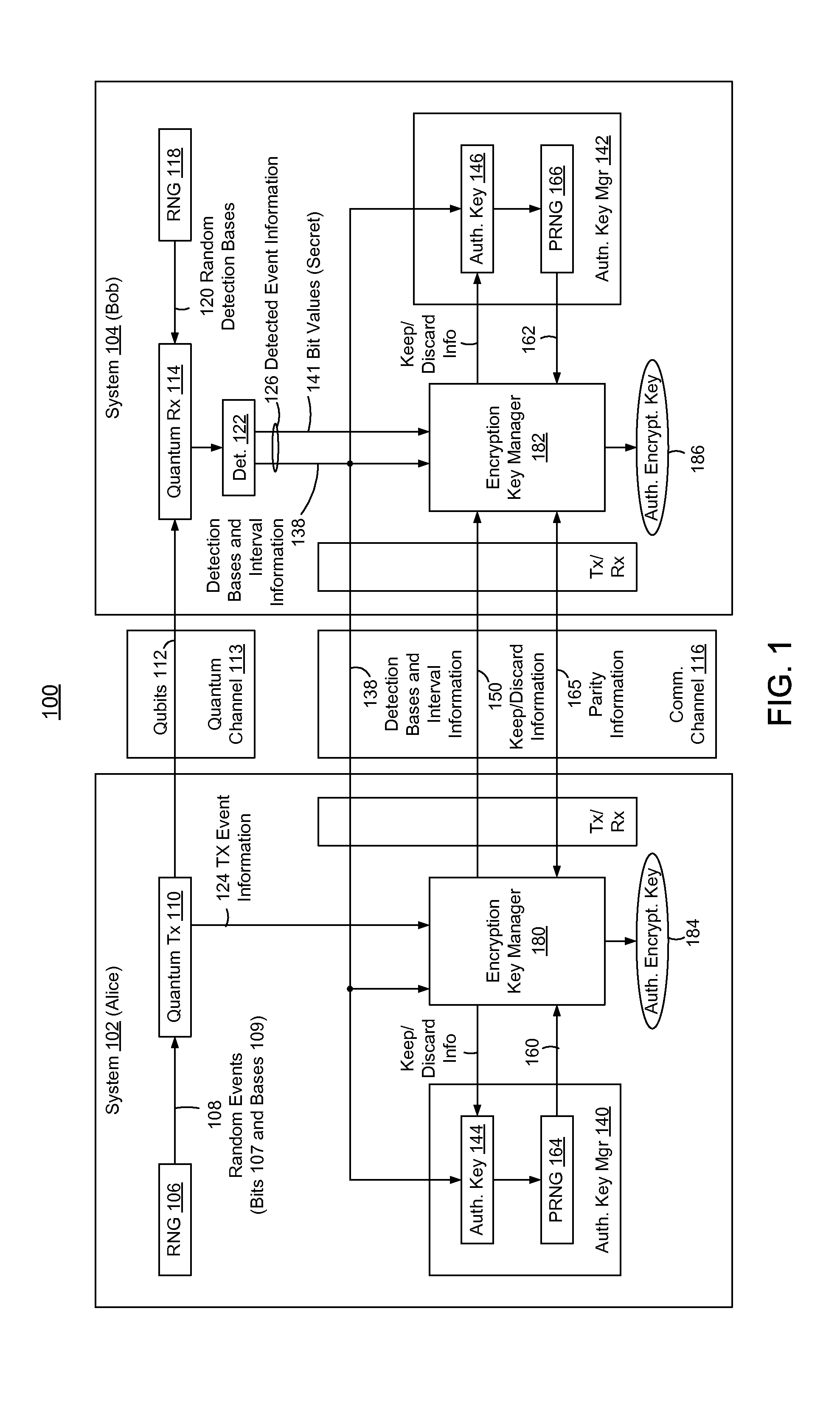
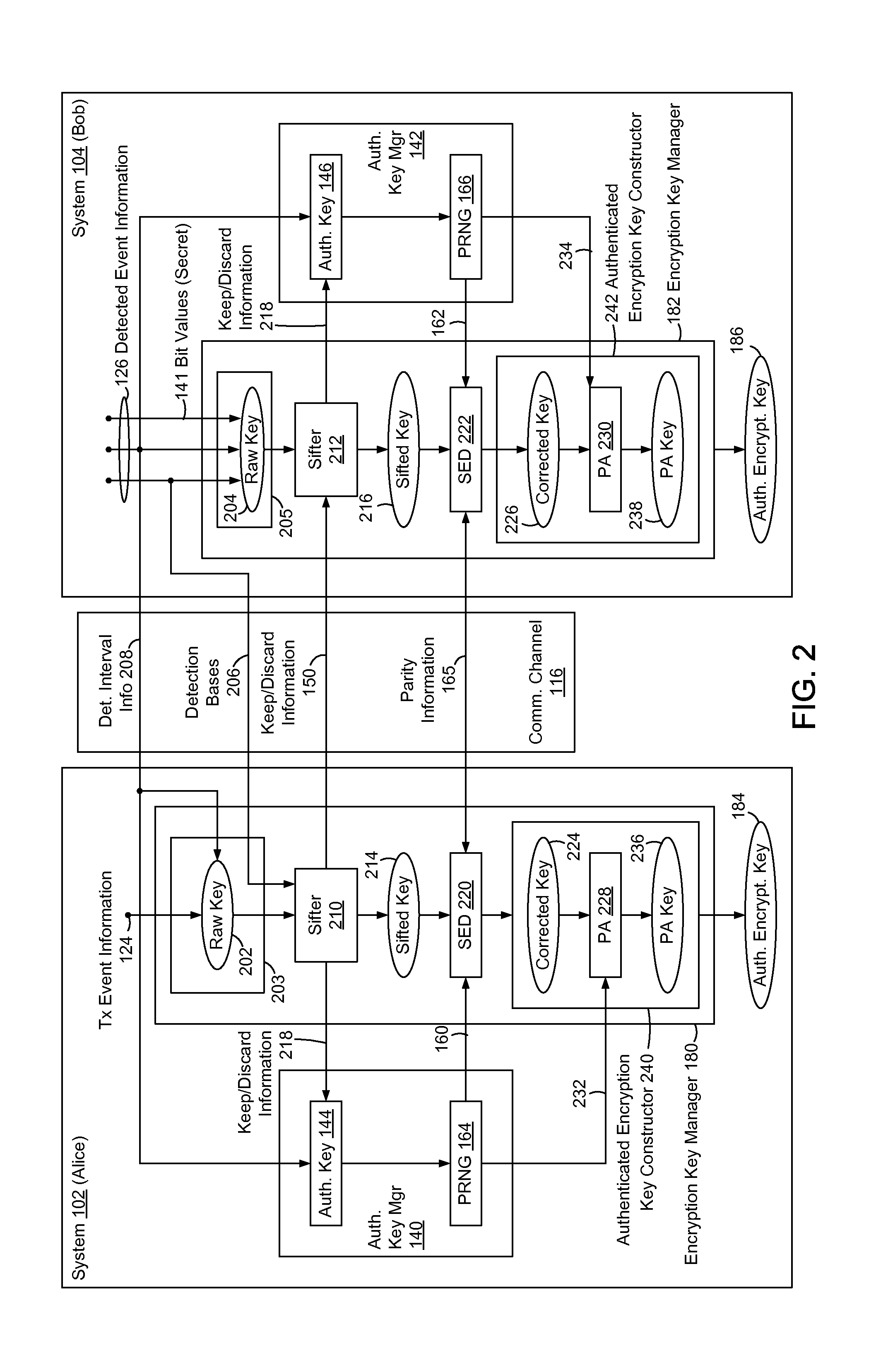
ActiveUS20130315395A1Reduction of informationReduce overheadKey distribution for secure communicationAuthenticated encryptionQuantum key distribution
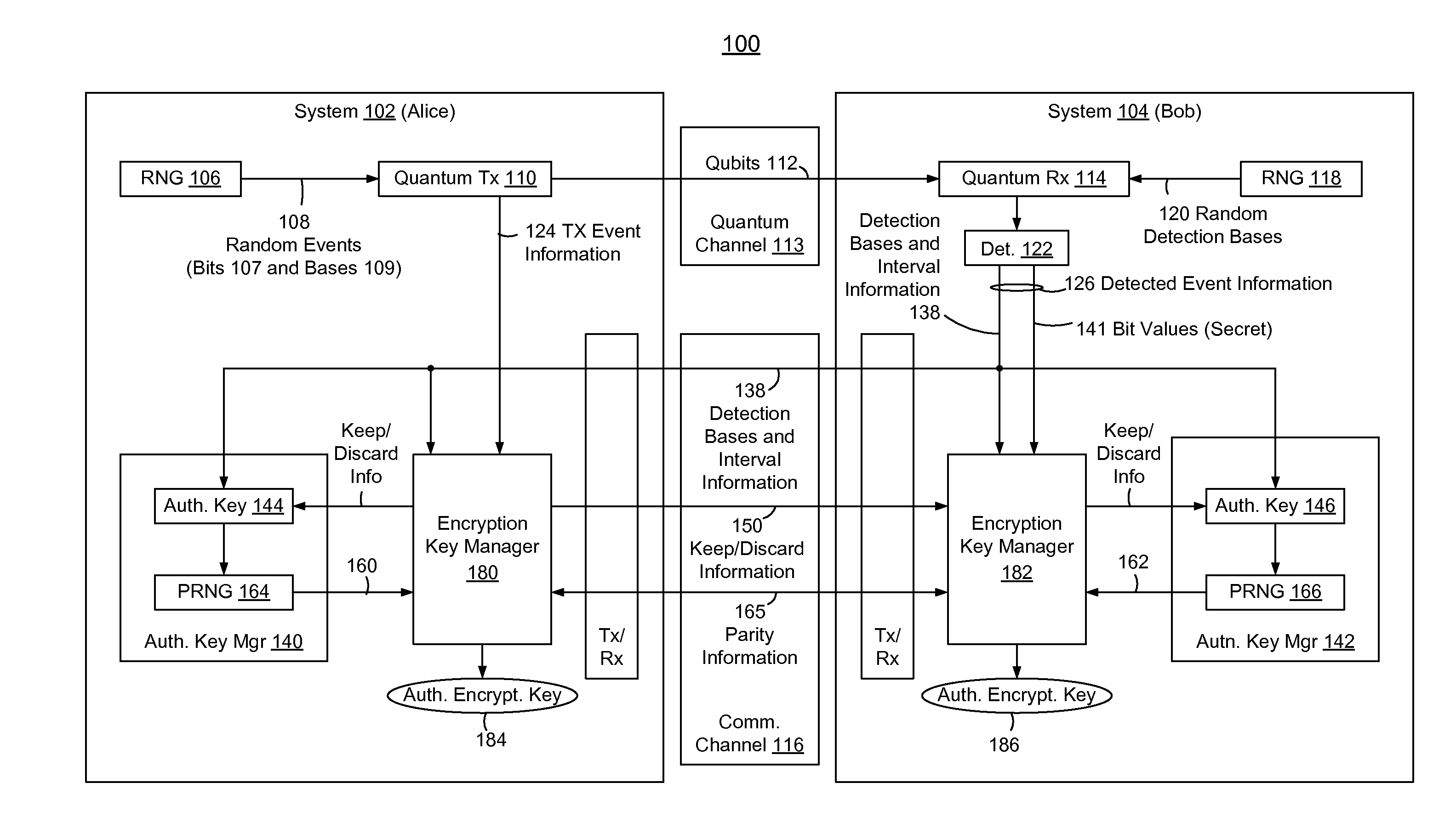
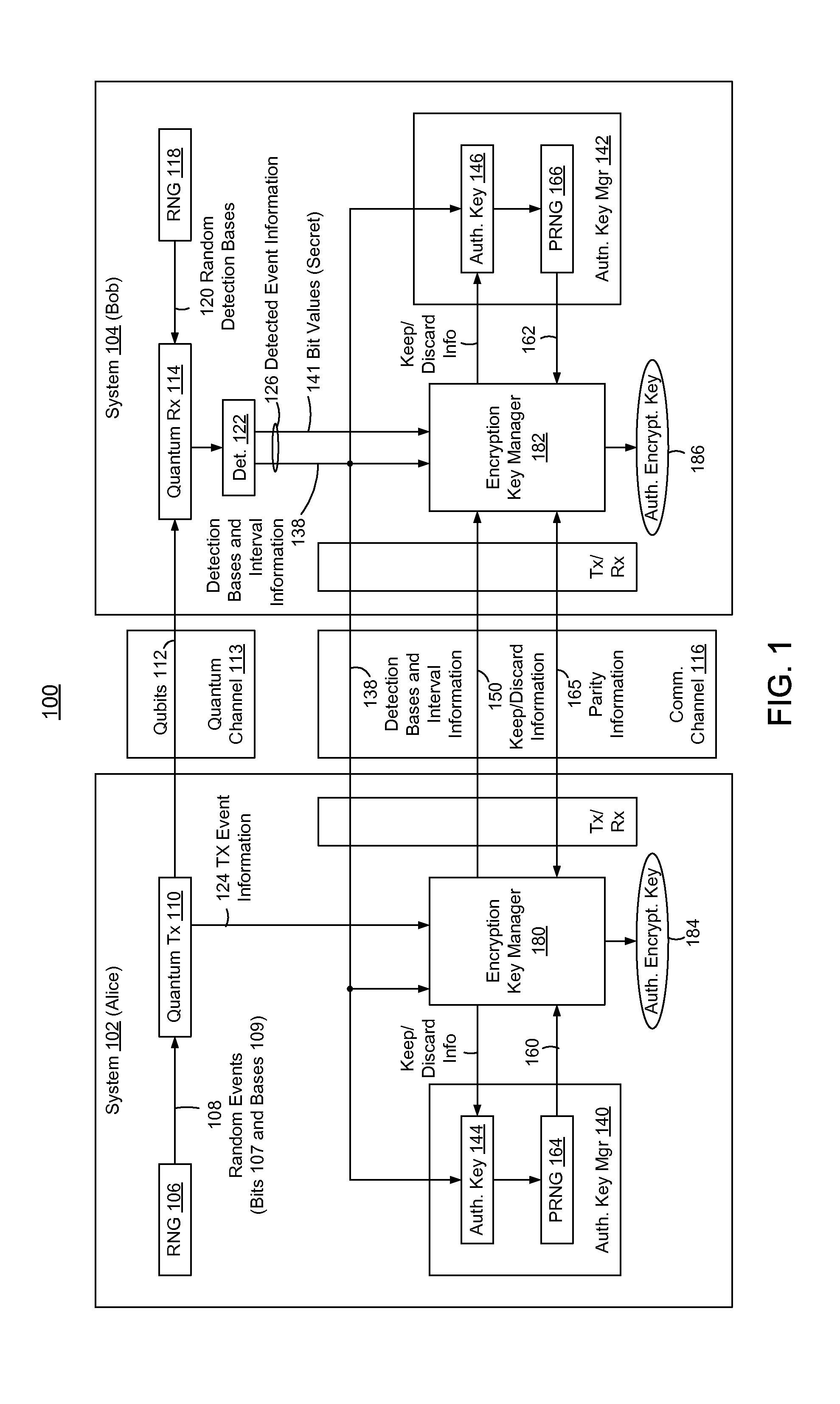
In methods and systems to authenticate systems in a quantum key distribution environment based on limited disclosures and identical, re-usable, pre-provisioned authentication keys, each system constructs an encryption key based on a corresponding one of transmitted events and detected events. Basis-sifting, error detection, error correction, and / or privacy amplification (PA) may be performed on the encryption keys based on limited disclosures (e.g., detection interval information, basis-sifting information, associated detection basis information, and / or parity measures). The authenticated keys may be modified based on disclosed detection information. Error detection and / or PA may be performed with identical pre-provisioned algorithms and pseudo-random values generated from the authenticated keys or modified authenticated keys. Final authenticated encryption keys are selectively constructed depending upon an extent of detected errors. Construction of authenticated encryption keys indicates authentication of the systems. None of the pre-provisioned authentication keys or modified authentication keys is disclosed and may thus be reused.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
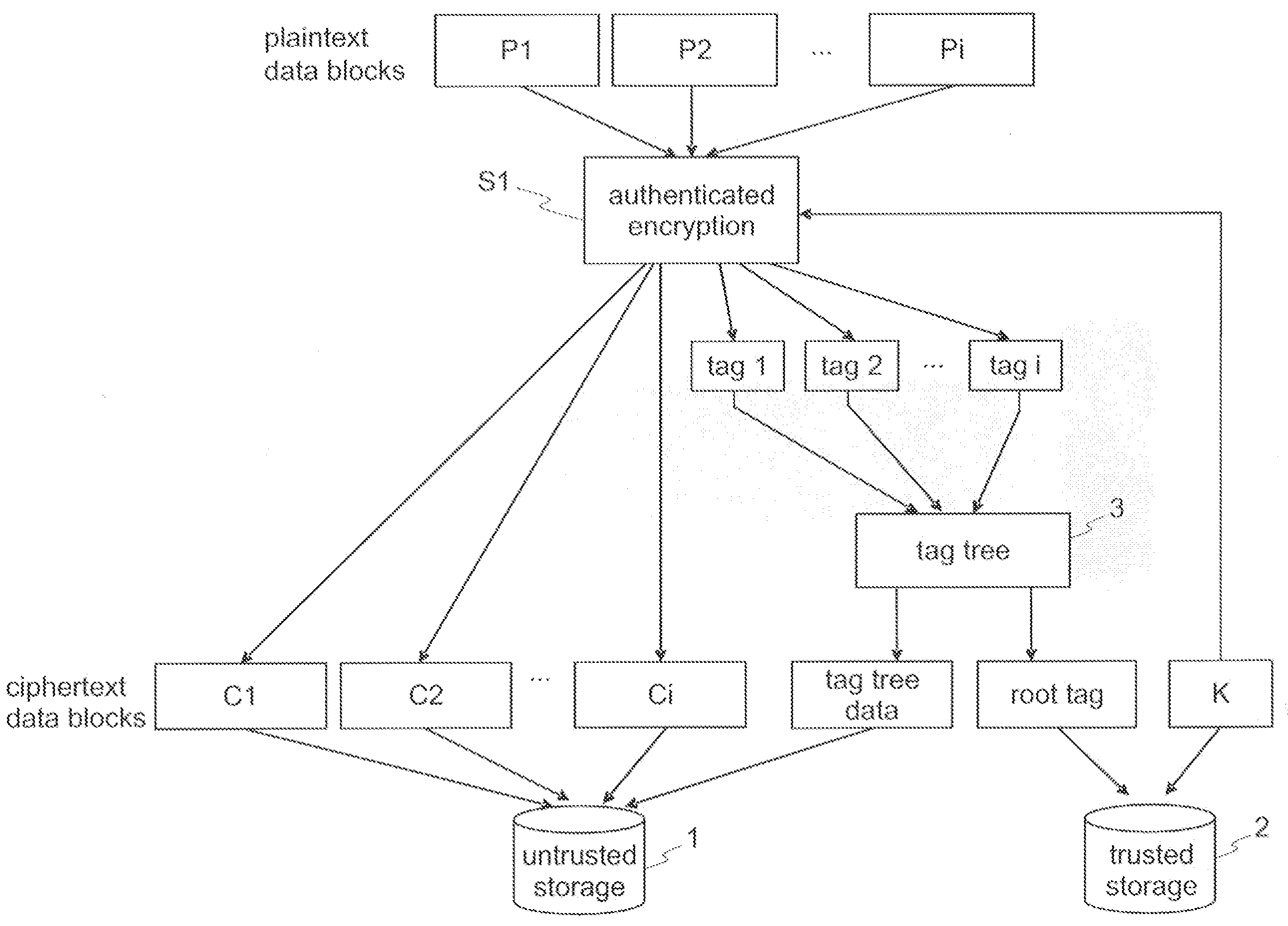
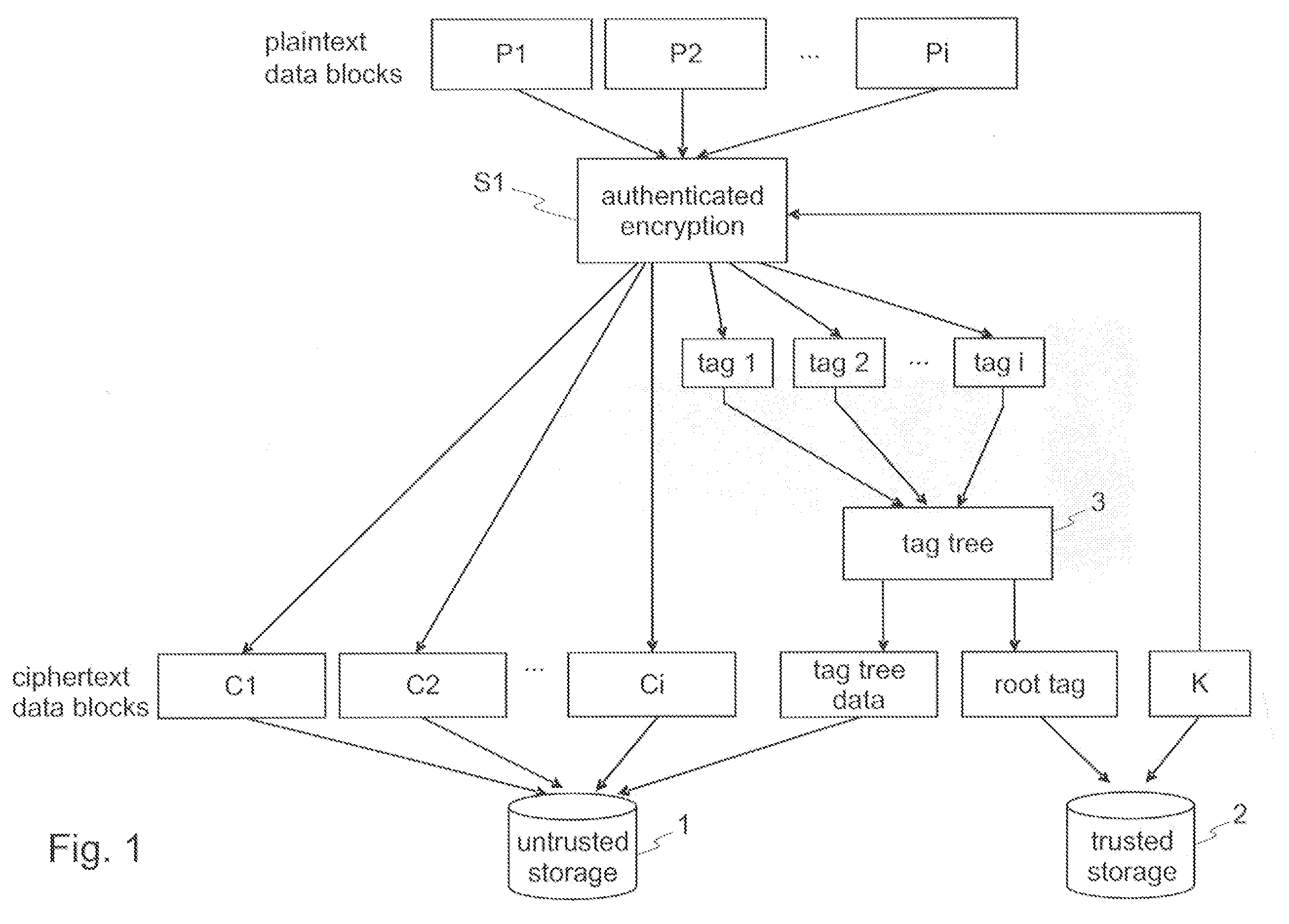
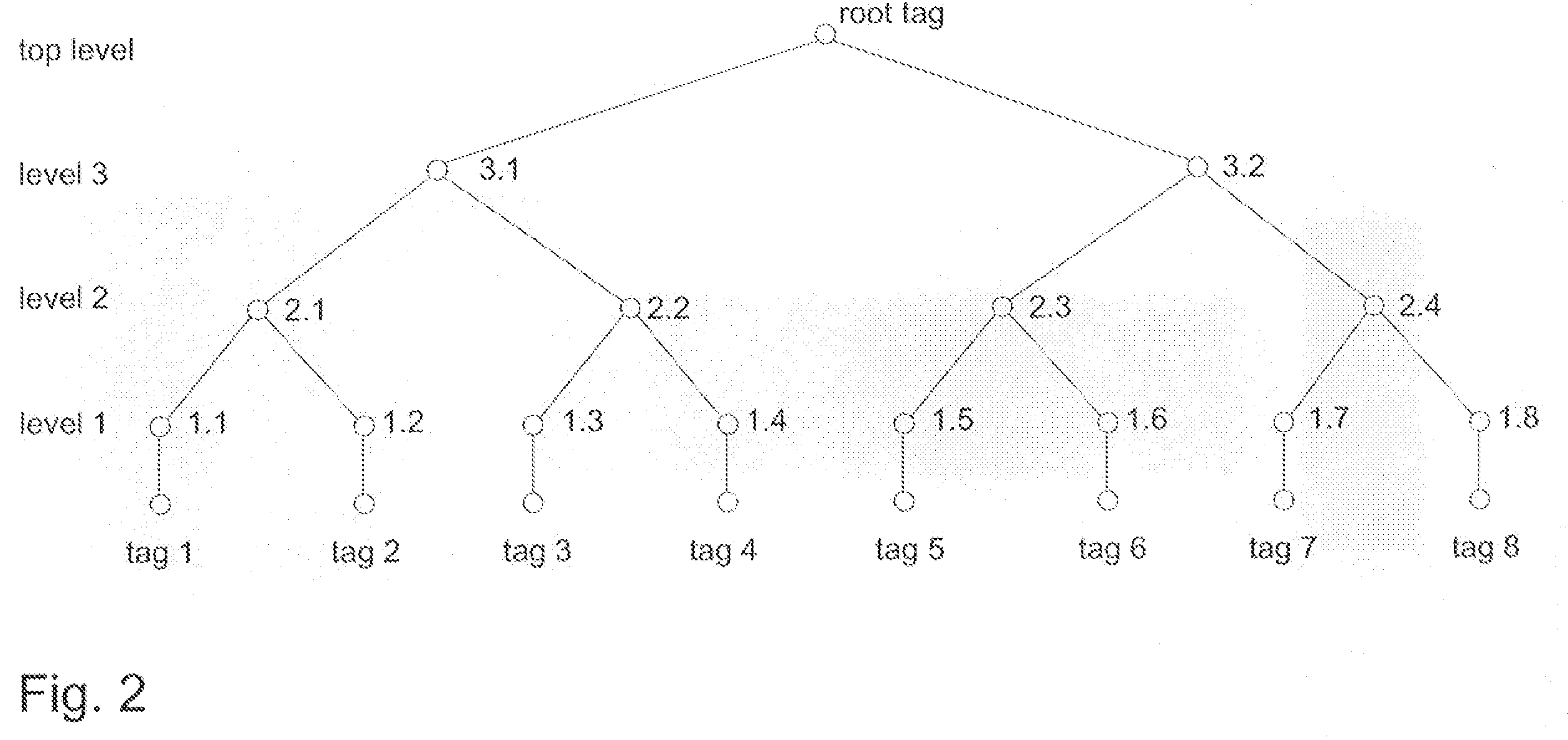
Encryption and authentication of data and for decryption and verification of authenticity of data
InactiveUS20080172562A1Effective timeEasy to implementUnauthorized memory use protectionHardware monitoringPlaintextComputer hardware
Techniques for encryption and authentication of data. One or more plaintext data blocks ciphertext data blocks and corresponding authentication tags are generated by means of authenticated encryption. A tag tree is generated by means of the authentication tags. The ciphertext data blocks and the tag tree data of the tag tree are stored in an untrusted storage, and the root tag of the tag tree is stored in a trusted storage.
Owner:IBM CORP
Symmetric key authenticated encryption schemes
InactiveUS6963976B1Low costSame level of securityData processing applicationsEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
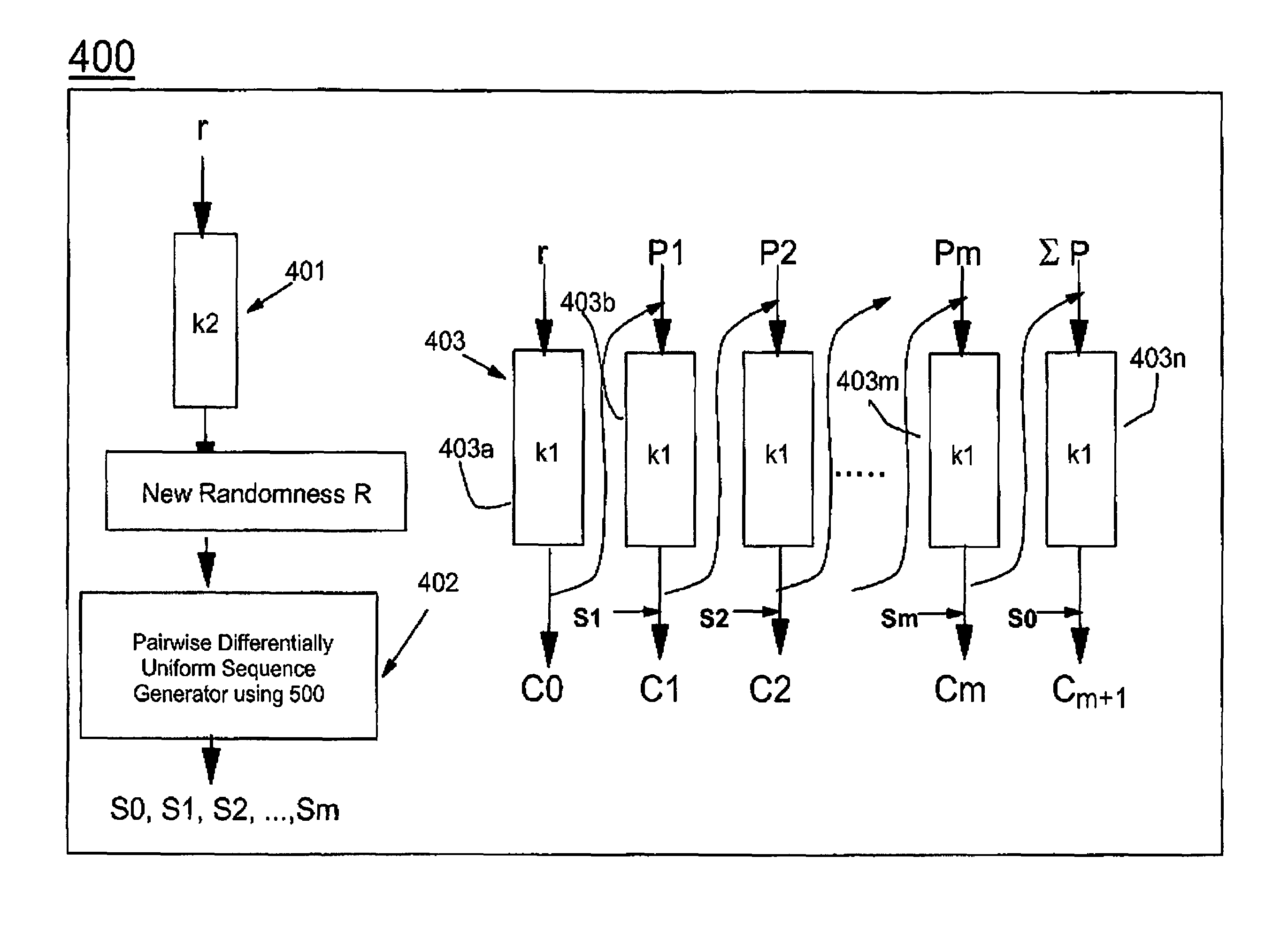
The present invention provides encryption schemes and apparatus which securely generate a cipher-text which in itself contains checks for assuring message integrity. It also provides compatible decryption schemes confirming message integrity. The encryption scheme generates a cipher-text with message integrity in a single pass with little additional computational cost, while retaining at least the same level of security as schemes based on a MAC. One embodiment encrypts a plain-text message by dividing the plain-text message into a multitude of plain-text blocks and encrypting the plain-text blocks to form a multitude of cipher-text blocks. A single pass technique is used in this process to embed a message integrity check in the cipher-text block. A message integrity check is embedded in the cipher-text blocks by embedding a set of pseudo random numbers, which may be dependent, but are pair-wise differentially uniform. We also describe an embodiment which is highly parallelizable.
Owner:IBM CORP +1
Method and apparatus for facilitating efficient authenticated encryption
InactiveUS20060285684A1Efficient processLow costSecret communicationSecuring communicationComputer hardwareCiphertext
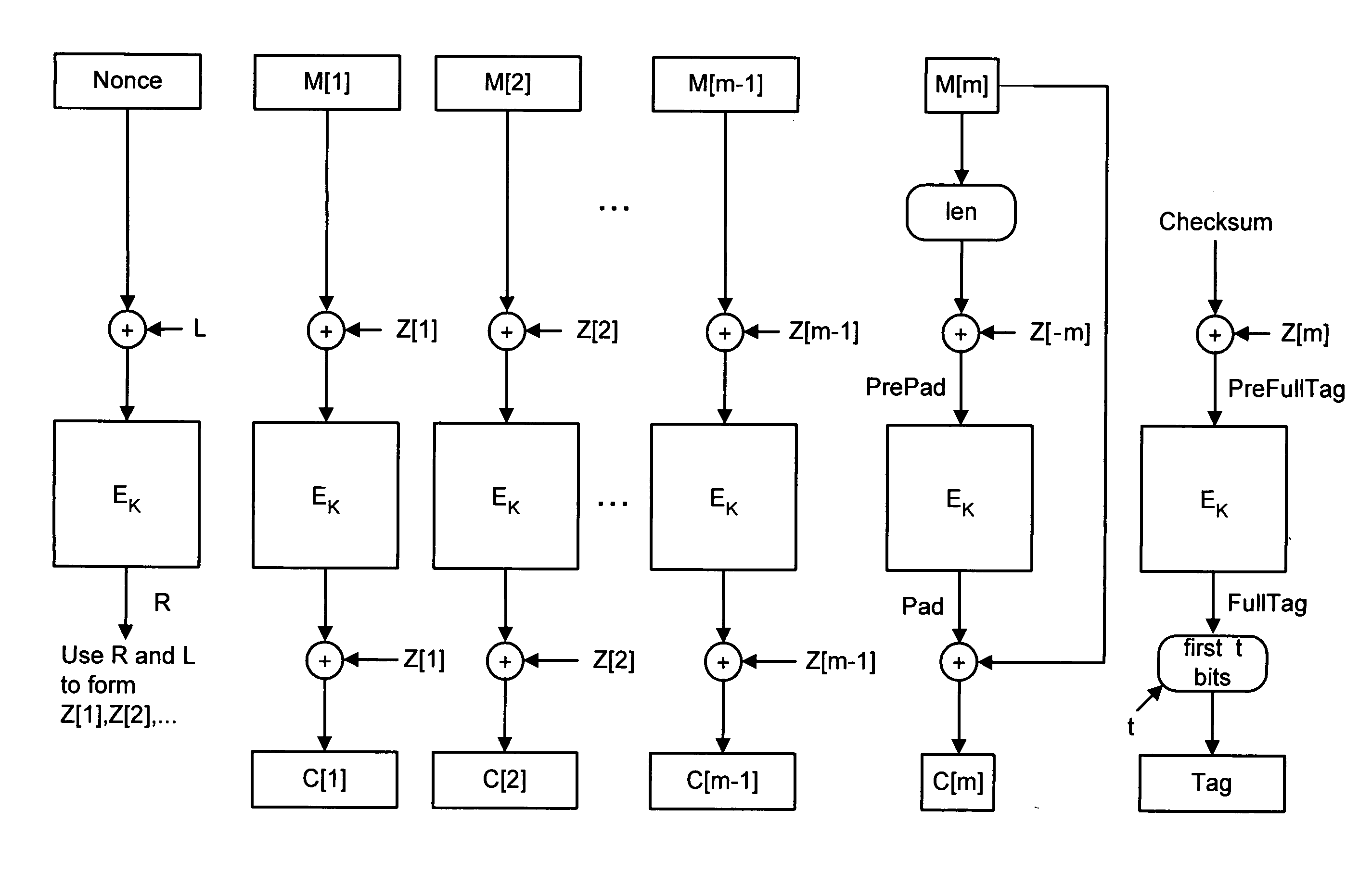
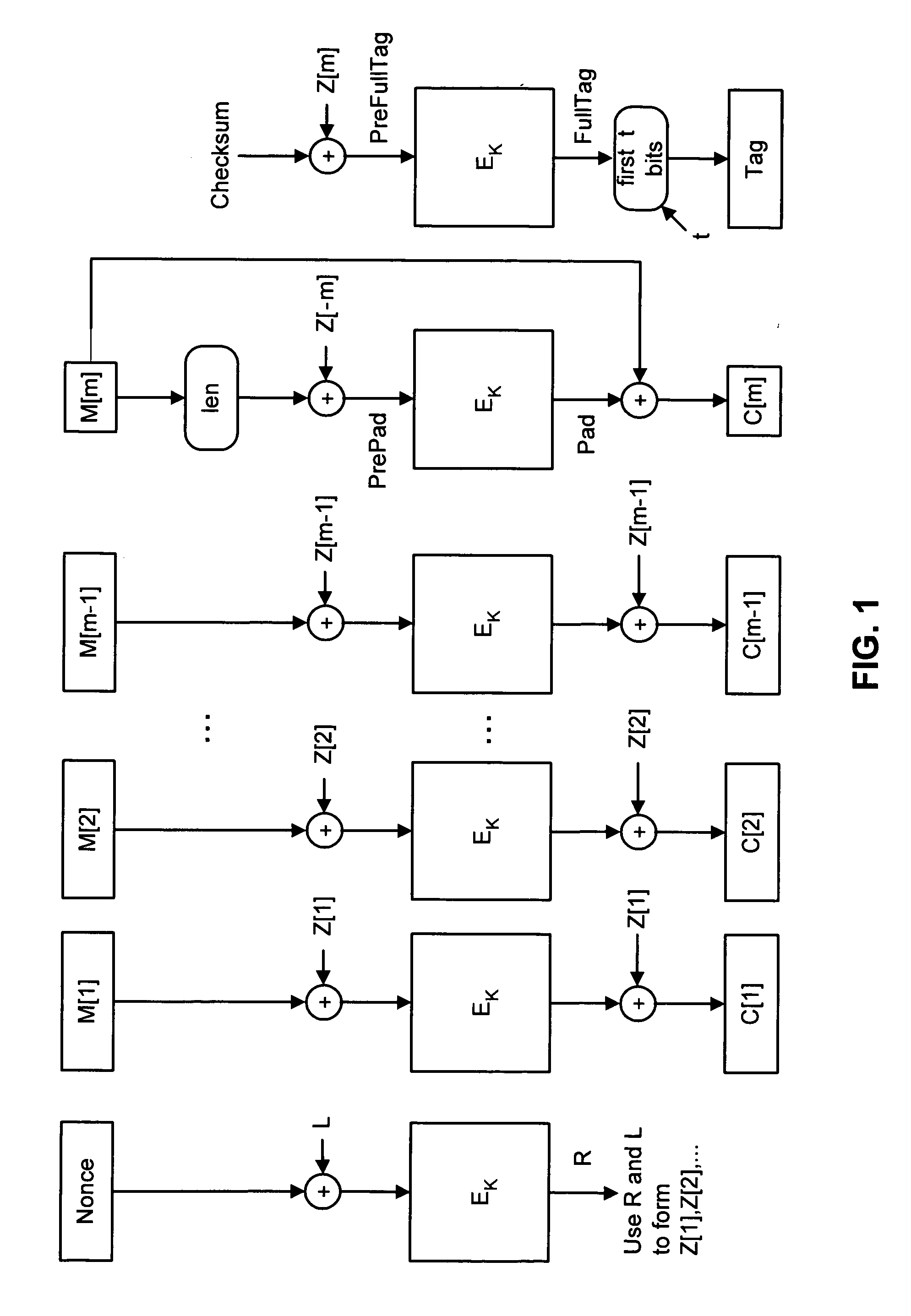
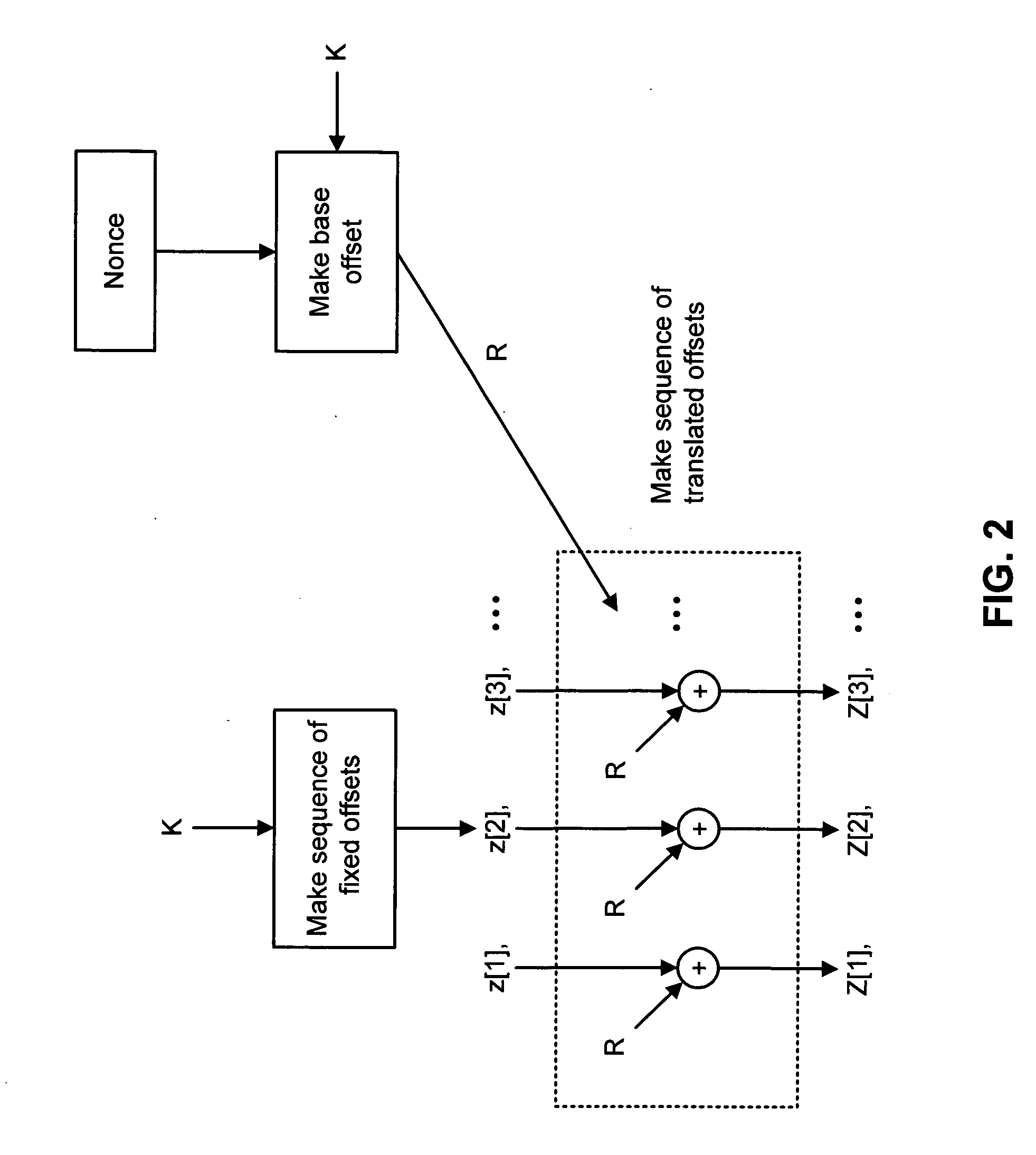
A shared-key encryption scheme that uses identically keyed block-cipher calls, low additional overhead, supports the encryption of arbitrary-length strings, produces a minimal-length-ciphertext, and is fully parallelizable. In one embodiment, “OCB”, a key shared between communicating parties is mapped to a key variant using the block cipher. The key variant is mapped into a sequence of basis offsets using shifts and conditional xors. To encrypt a message using a nonce, a nonce-dependent base offset is formed, and then a sequence of offsets is constructed by starting with the base offset and then xoring, for each offset, an appropriate basis offset. The message is partitioned into message blocks of the same length as the block length of the block cipher, along with a message fragment that may be shorter. Each message block is combined with a corresponding offset, enciphered, and then combined again with the offset, yielding a ciphertext block. The message fragment is xored with an appropriately computed pad to give a ciphertext fragment. A checksum is formed using the message blocks, the message fragment, and the pad. The checksum is combined with an offset and enciphered to yield a tag. The encrypted message includes the ciphertext blocks, the ciphertext fragment, and the tag.
Owner:ROGAWAY PHILLIP
Methods and Systems for Distributing Cryptographic Data to Authenticated Recipients
ActiveUS20120179905A1Digital data authenticationSelective content distributionIdentity providerClient-side
A method for distributing cryptographic data to authenticated recipients includes receiving, by an access control management system, from a first client device, information associated with an encrypted data object. The method includes receiving, by the access control management system, from a second client device, a request for the information associated with the encrypted data object. The method includes verifying, by the access control management system, that a user of the second client device is identified in the received information associated with the encrypted data object. The method includes authenticating, by the access control management system, with an identity provider, the user of the second client device. The method includes sending, by the access control management system, to the second client device, the received information associated with the encrypted data object.
Owner:VIRTRU
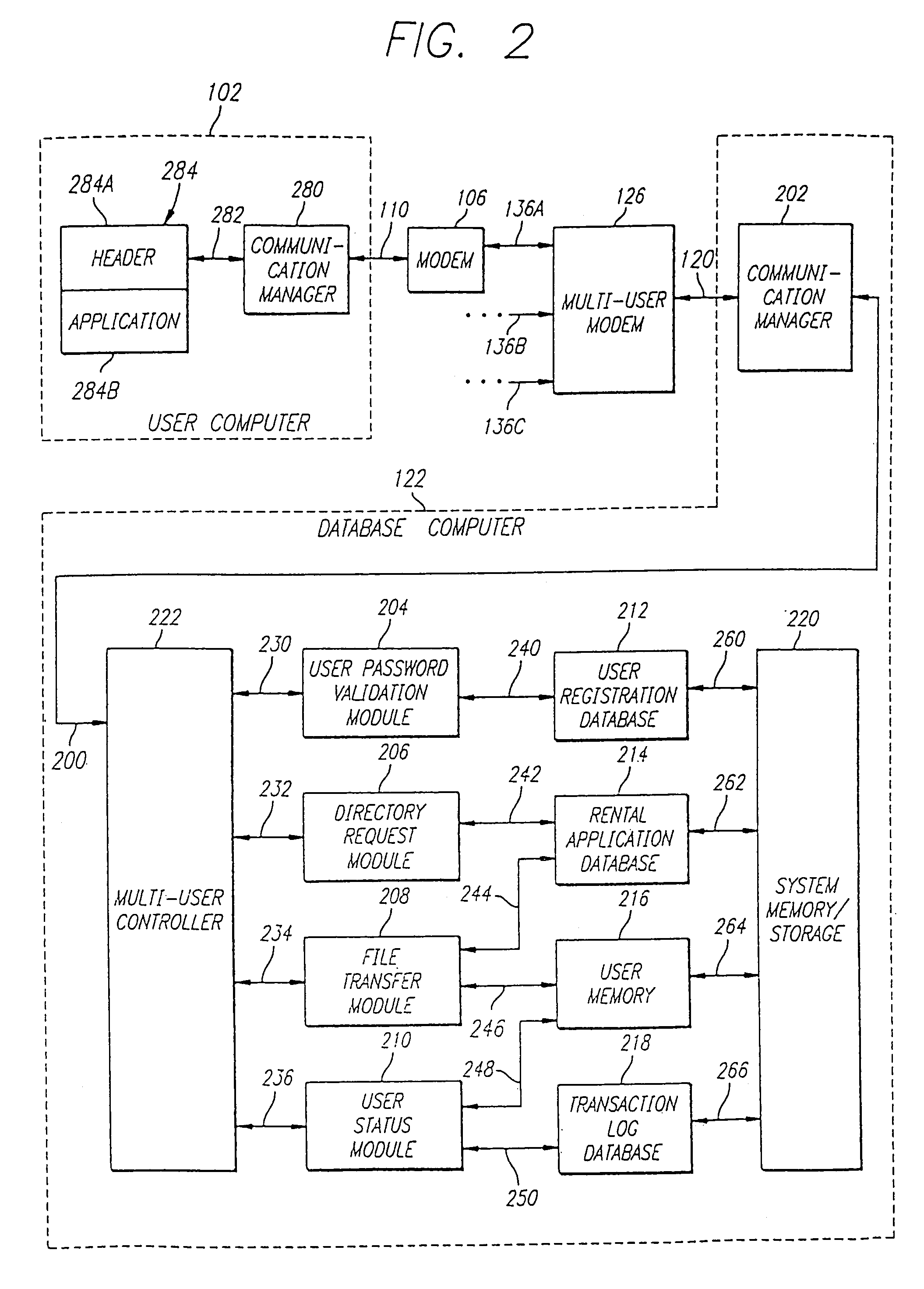
Method and system for providing authentication service for Internet users
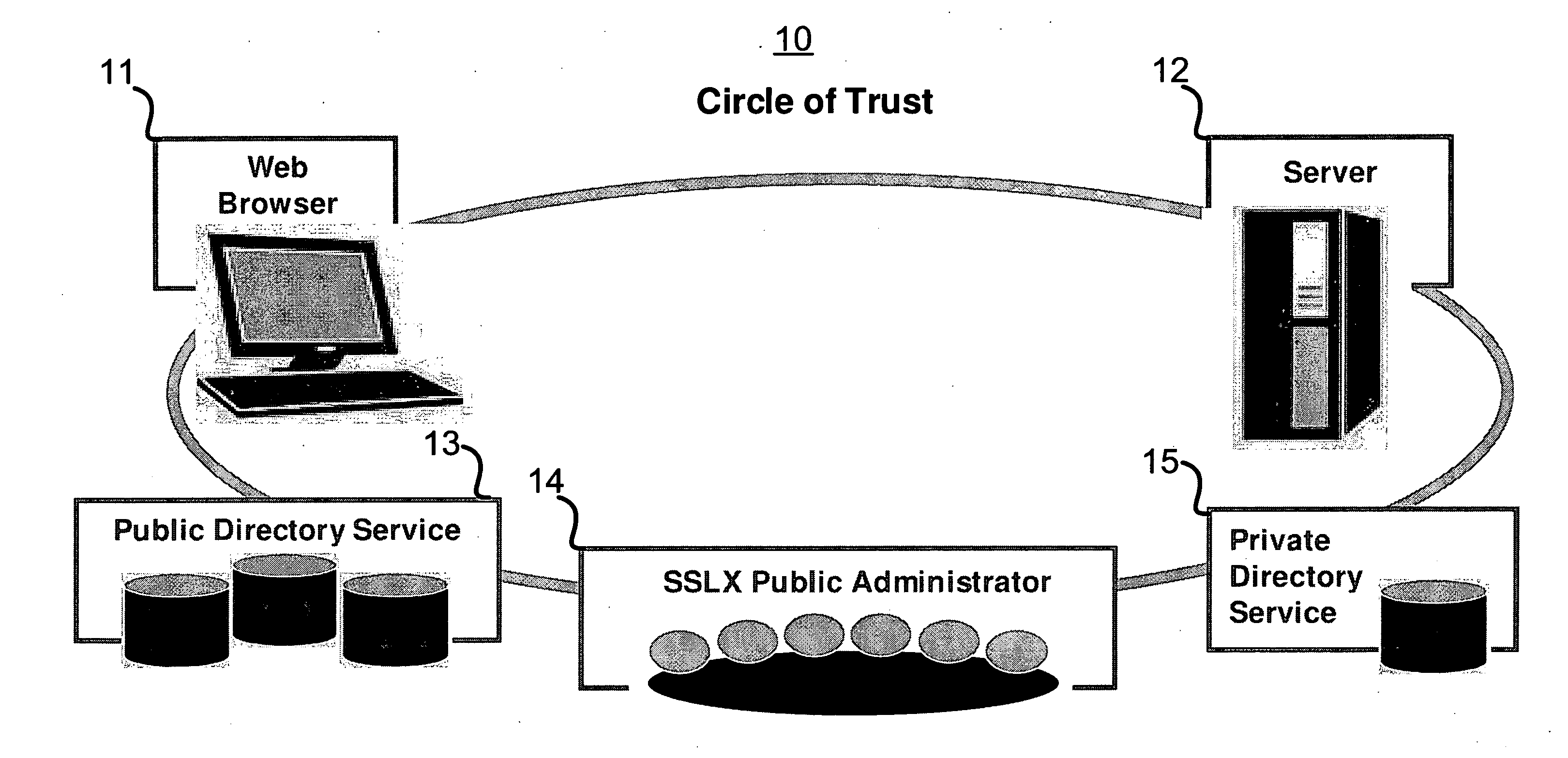
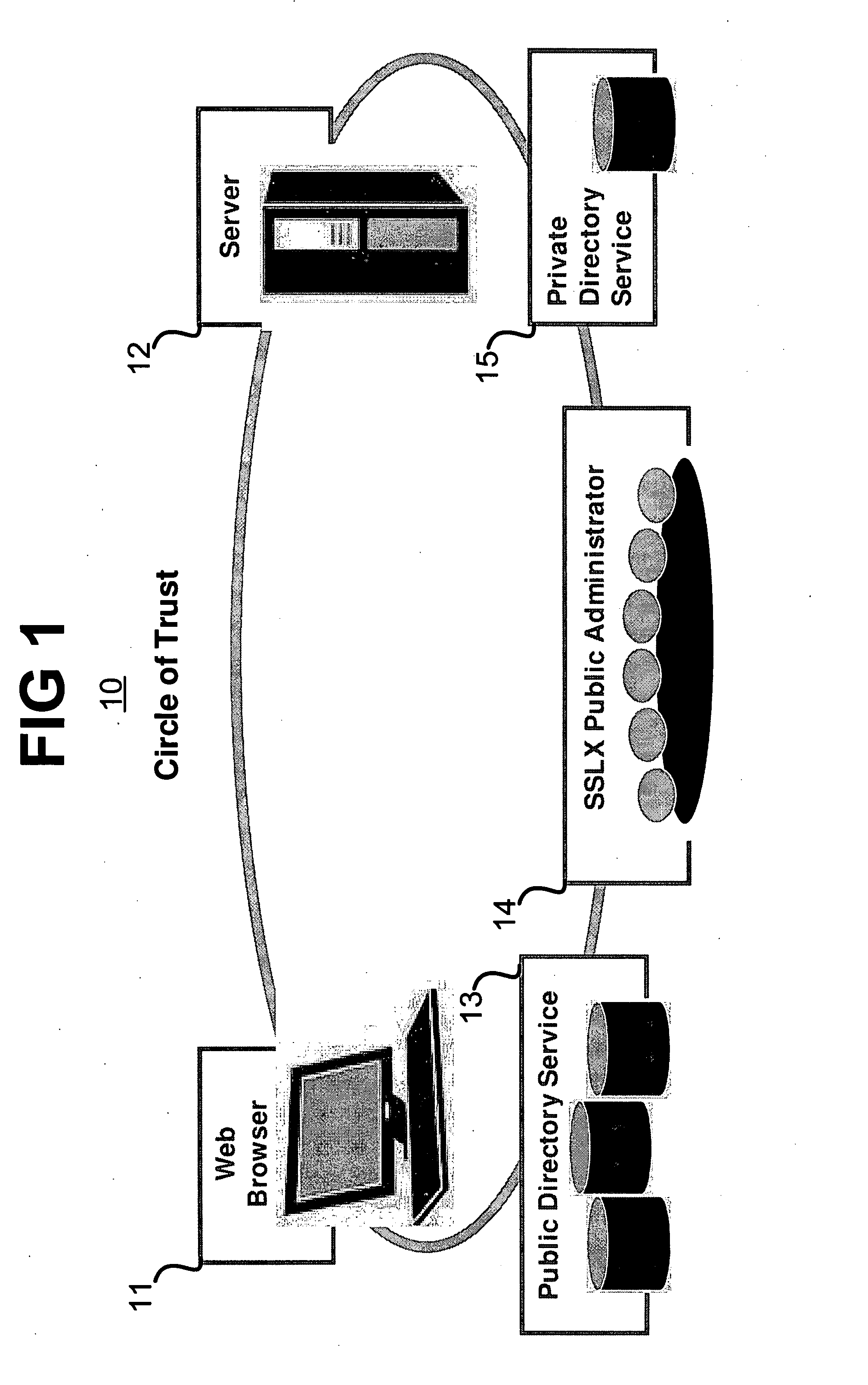
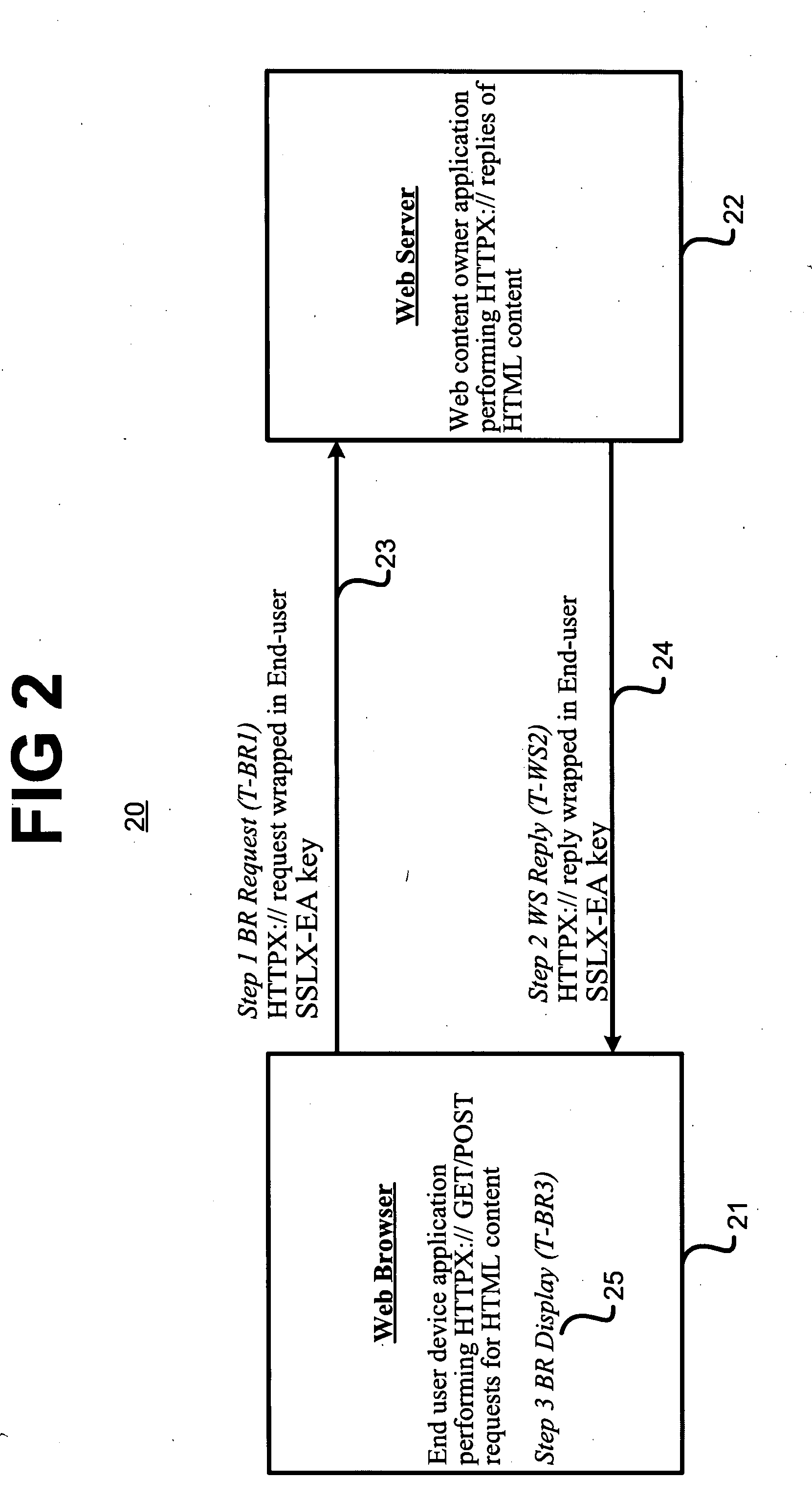
ActiveUS20080056501A1Faster delivering a single-pass handshakeKey distribution for secure communicationPublic key for secure communicationInternet usersPublic network
A system and method comprising a computer useable medium having computer readable program code means embodied therein for authenticating and encrypting and decrypting information transferred over a public network between a client application program running in a client computer and a server application program running in a server computer and a directory service application program running in a server computer. A method for obtaining a session master key by an application from a server includes sending an open request to the server for the session master key and receiving a first reply by the application from the server with a first portion of the session master key. The first reply identifies a directory server from which a second portion of the session master key may be obtained. The application sends an open request to the directory server specified by the server in the first reply for the second portion of the session master key and receives it from the directory server. The session master key is generated by the application using the first portion of the session master key received from the server and the second portion of the session master key received from the directory server.
Owner:QWYIT LLC
Apparatus and method to prevent man in the middle attack
InactiveUS20110154021A1Digital data processing detailsUser identity/authority verificationThird partyMan-in-the-middle attack
A system, peripheral device, and method for authenticating an encryption key before transmitting encrypted messages containing sensitive information are provided. Authentication of a client device during the coordination of data transfer among multiple computer devices is possible by providing a peripheral device that does not have a direct connection to a network, but rather, any message to be transmitted over the network must be relayed through a client device. Any sensitive information to be transferred to a remote device is inserted into a message, then the message is encrypted in the peripheral device. This prevents any process running on the client device from fooling the client device into communicating confidential information to a third party rather than the desired remote computer, because the client device never sees the sensitive information in an unencrypted form; only the peripheral device has access to the sensitive information in an unencrypted form.
Owner:NETABECURE INNOVATIONS
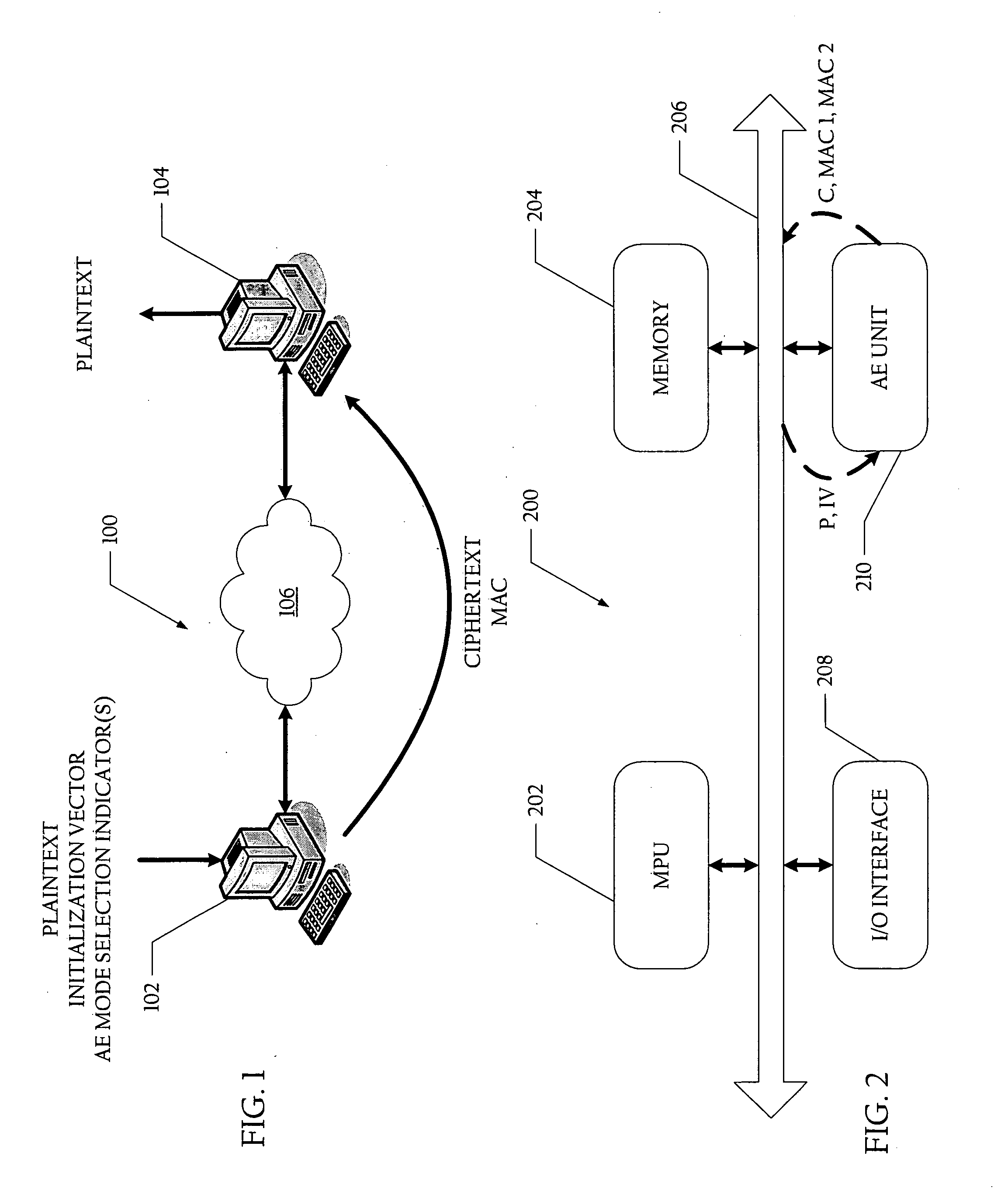
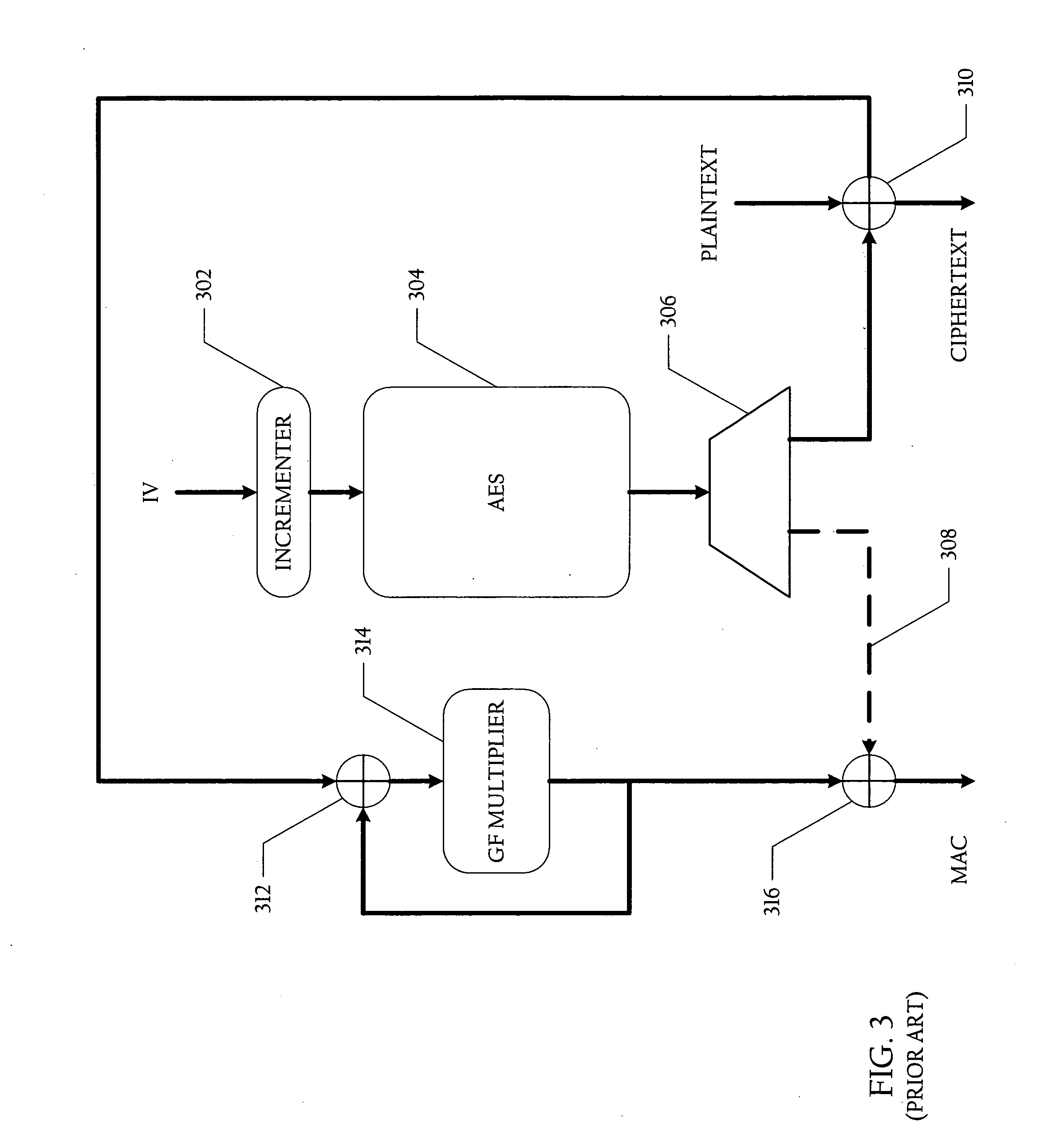
Method and system for generating ciphertext and message authentication codes utilizing shared hardware
A method and system for generating ciphertext and message authentication codes utilizing shared hardware are disclosed. According to one embodiment, a method is provided of generating ciphertext message data and message authentication codes utilizing shared authenticated encryption unit hardware. In the described embodiment, plaintext message data is received at an authenticated encryption unit which comprises first and second authenticated encryption hardware modules. Thereafter, a first message authentication code (MAC) associated with a first authenticated encryption mode and a second MAC associated with a second authenticated encryption mode are generated. More specifically, the first MAC is generated utilizing the plaintext message data and first authenticated encryption hardware module and ciphertext message data and the second MAC are generated utilizing the plaintext message data and second authenticated encryption hardware module.
Owner:IBM CORP
Embedded authentication protocol for quantum key distribution systems
ActiveUS8693691B2Reduction of informationReduce overheadKey distribution for secure communicationProtocol for Carrying Authentication for Network AccessKey generation
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
Identity authentication system and method based on electronic identification card
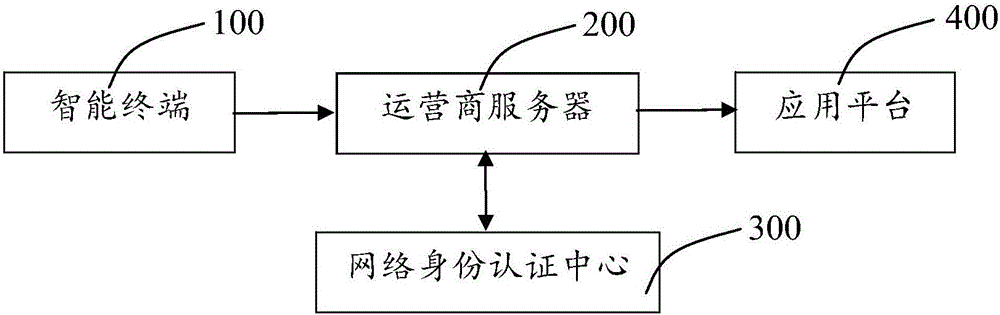
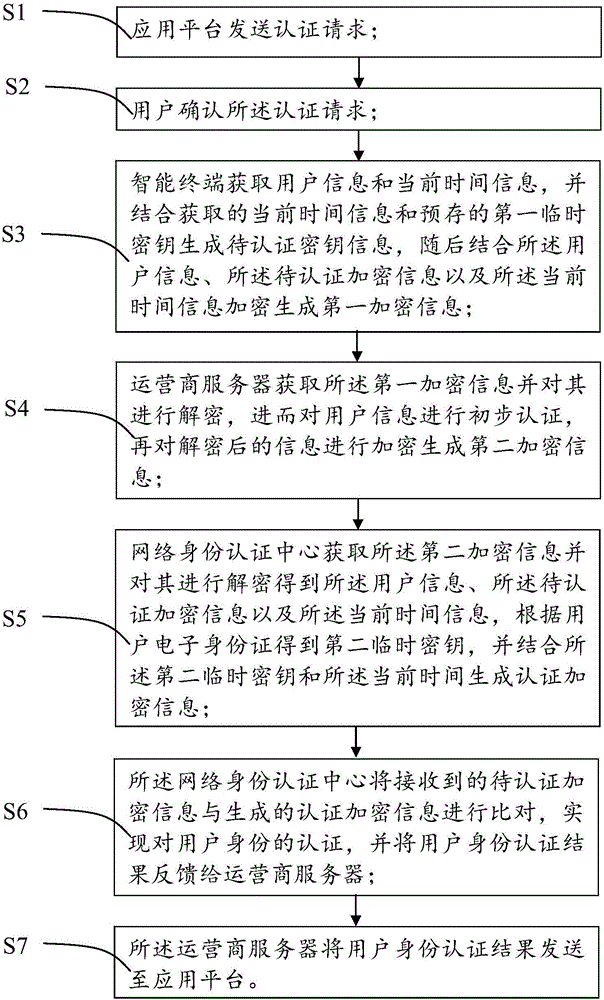
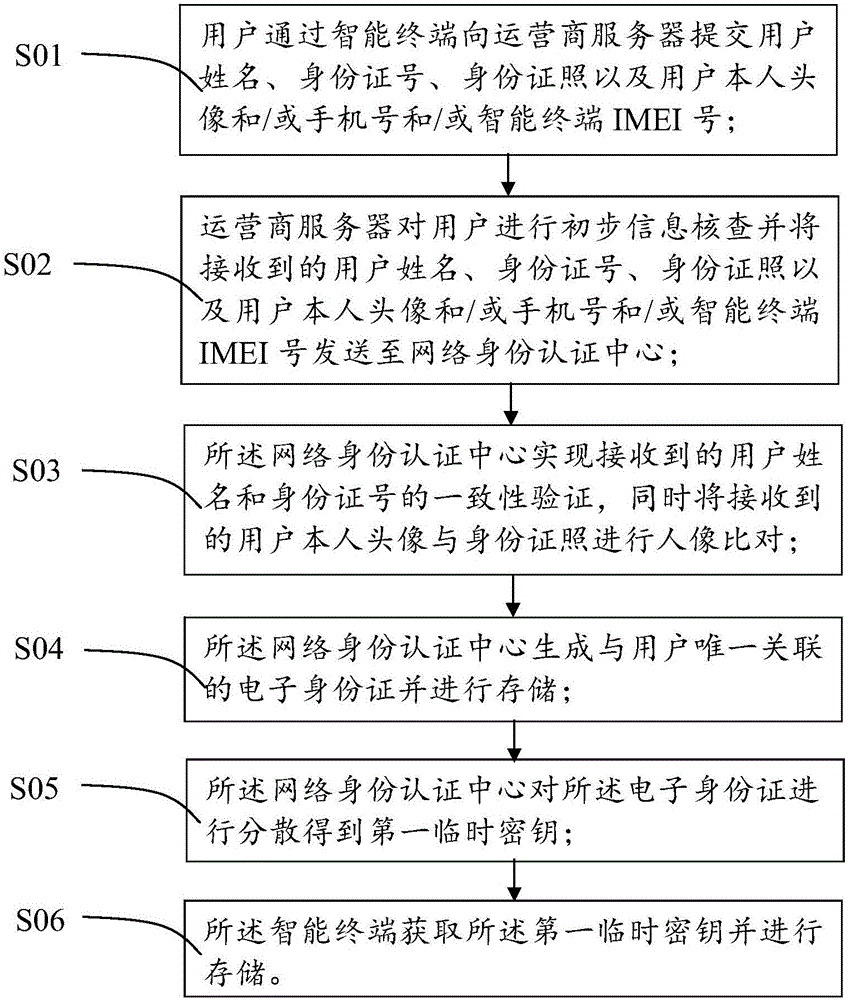
ActiveCN104994114AProtect identity privacyImprove reliabilityUser identity/authority verificationElectronic identificationOnline identity
The invention provides an identity authentication system and method based on an electronic identification card. The identity authentication system comprises an intelligent terminal, an operator server, a network identity authentication center and an application platform. The intelligent terminal is used for storing a first temporary secret key only associated with the electronic identification card of a user, and generating to-be-authenticated encryption information and first encryption information. The operator server is used for acquiring the first encryption information, authenticating the first encryption information preliminarily, and then generating second encryption information. The network identity authentication center is used for acquiring the second encryption information, generating a second temporary secret key and authenticated encryption information, and comparing the to-be-authenticated encryption information with the authenticated encryption information so as to realize authentication of the user identity. The application platform is connected with a secret key server. The application platform sends an authentication request and is used for acquiring a result of user identity authentication from the operator server. The first temporary secret key is stored in a safe area of the intelligent terminal, so that the user does not need to carry a hardware carrier and are not worry about risks, such as information leakage and so on when in online payment or online identity authentication.
Owner:尤磊
System and method for transferring items having value
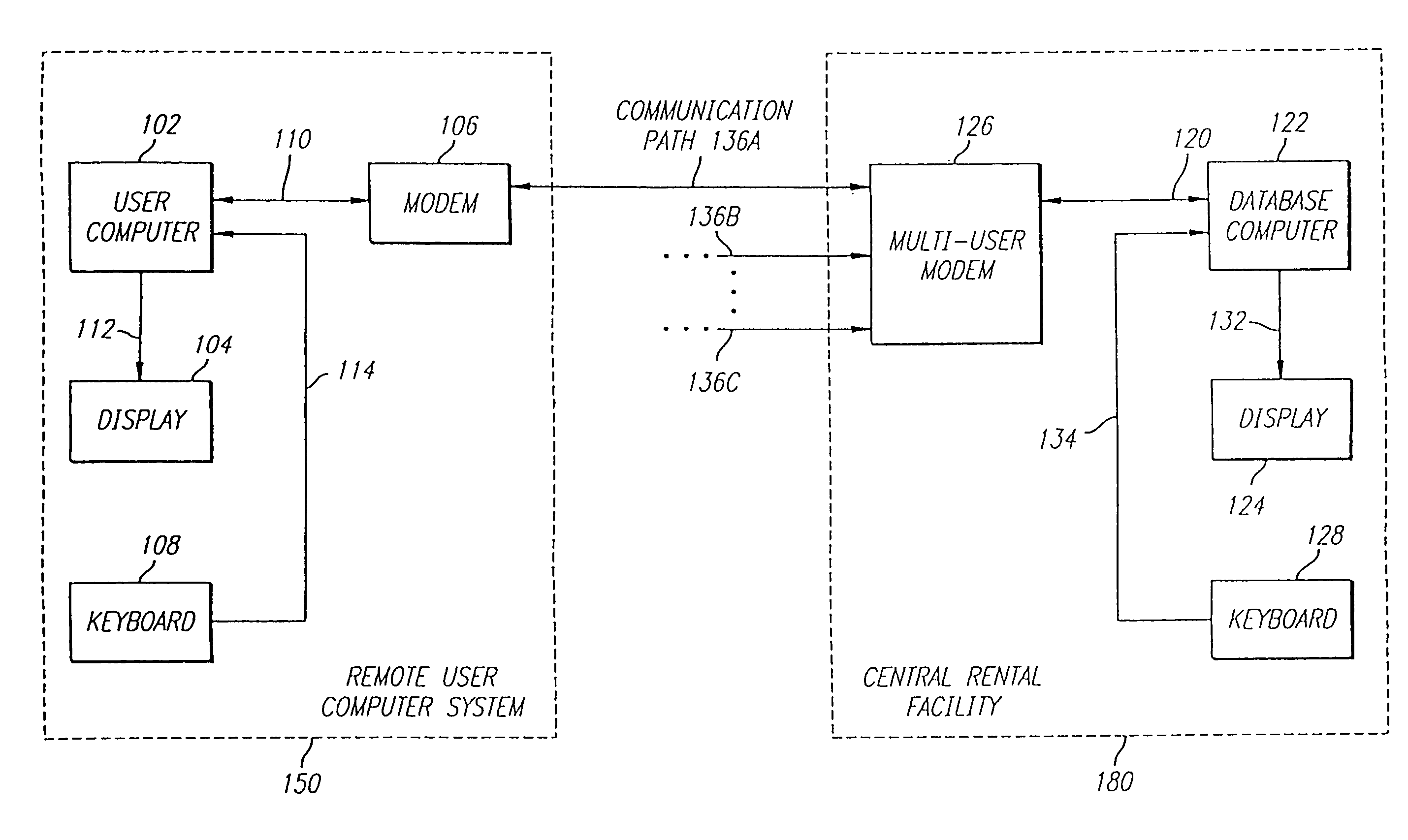
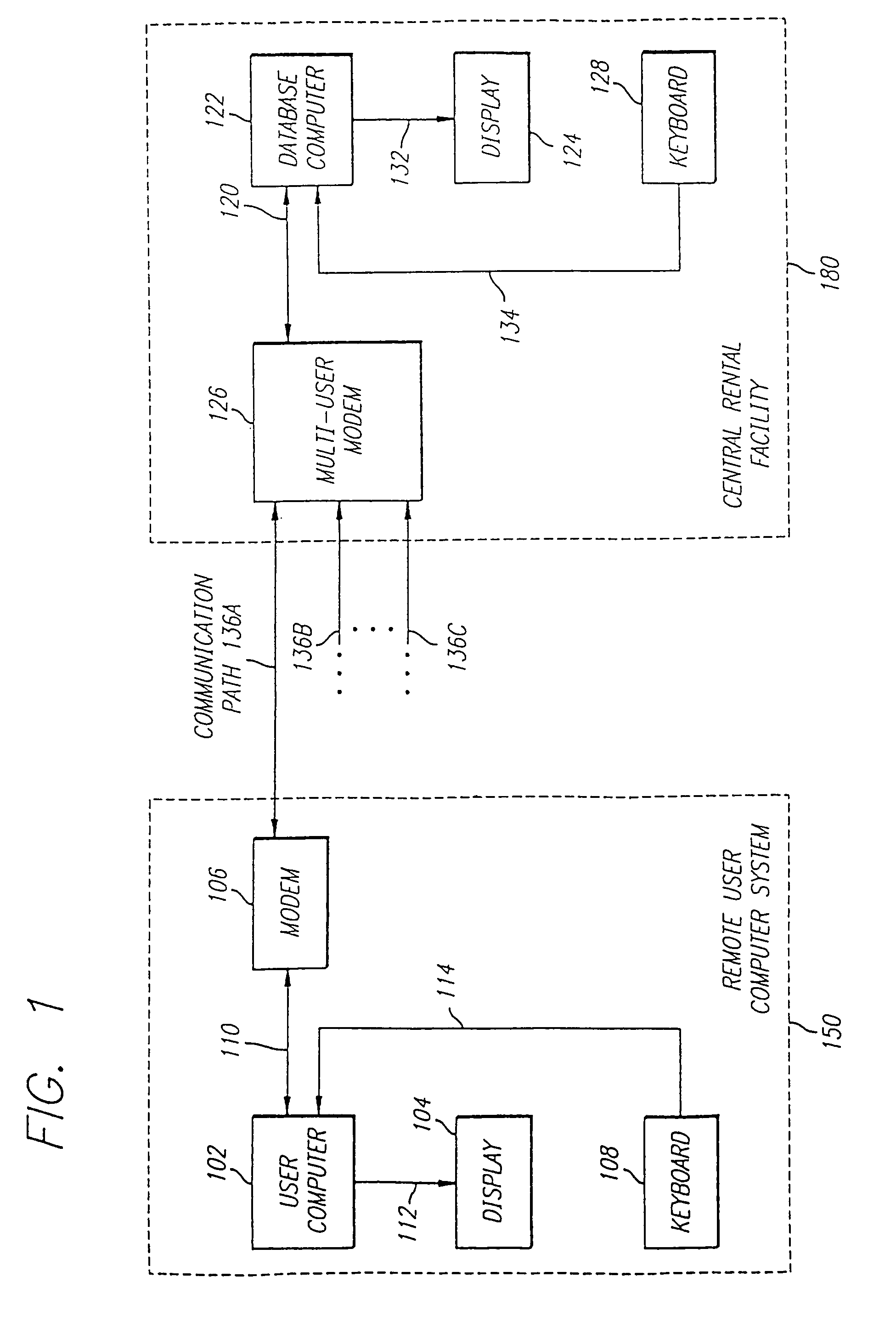
InactiveUS7778924B1Ensure protectionComputer security arrangementsFranking apparatusRelevant informationDigital signature
The present invention is directed to a system for providing secured access to a software rental or a postage metering system. The virtual postage meter software of this invention enables a user to print postage indicia on documents, envelopes or labels. To generate valid postage indicia the virtual meter software is executed on a first computer while it is in communication with the remotely located second computer. All communication between the first computer and the second computer utilize data encryption algorithms to preserve the security and integrity of the data transferred. In one embodiment, the second computer is a collection of one or more computers with virtual postage meter enabling software capable of communicating simultaneously to a number of user computers that are concurrently executing the virtual postage meter software. The second computer is connected to one or more US FIPS 140-1 security level 3 or better certified cryptographic devices identified as Postal Security Devices (PSD). The printed postage indicia appears as a two-dimensional barcode that includes digital signature, amount of postage, ZIP code and other relevant information.
Owner:STAMPS COM
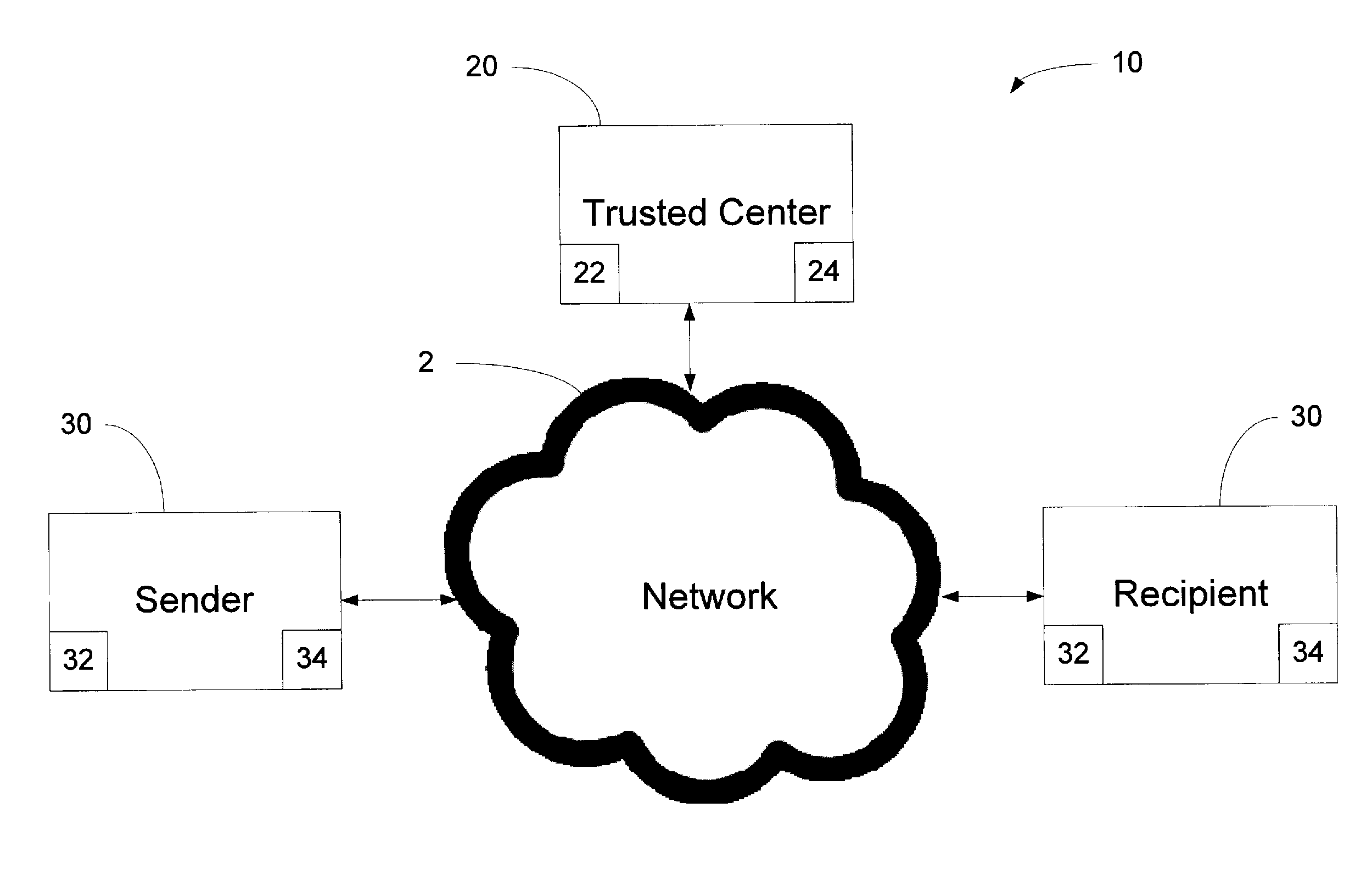
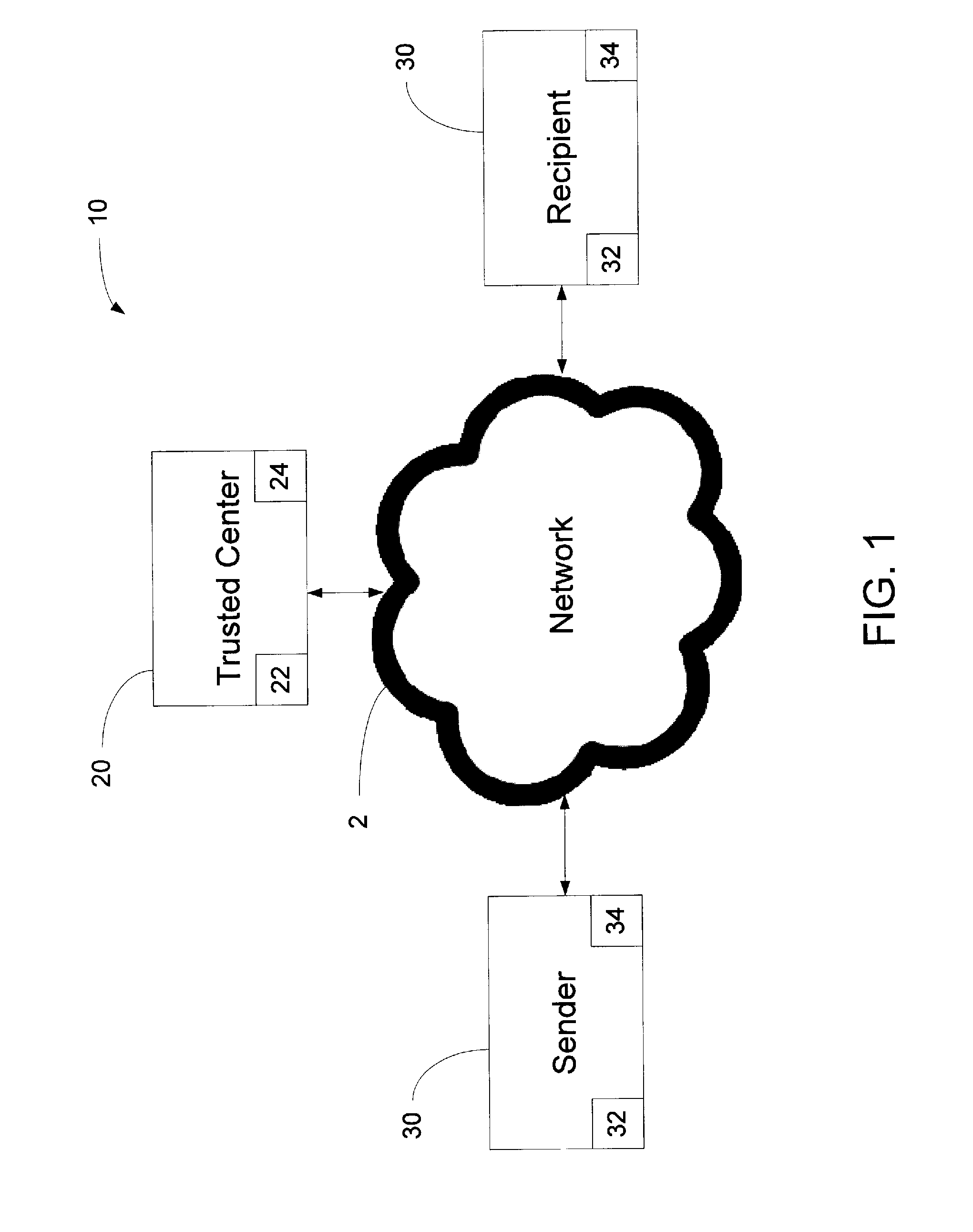
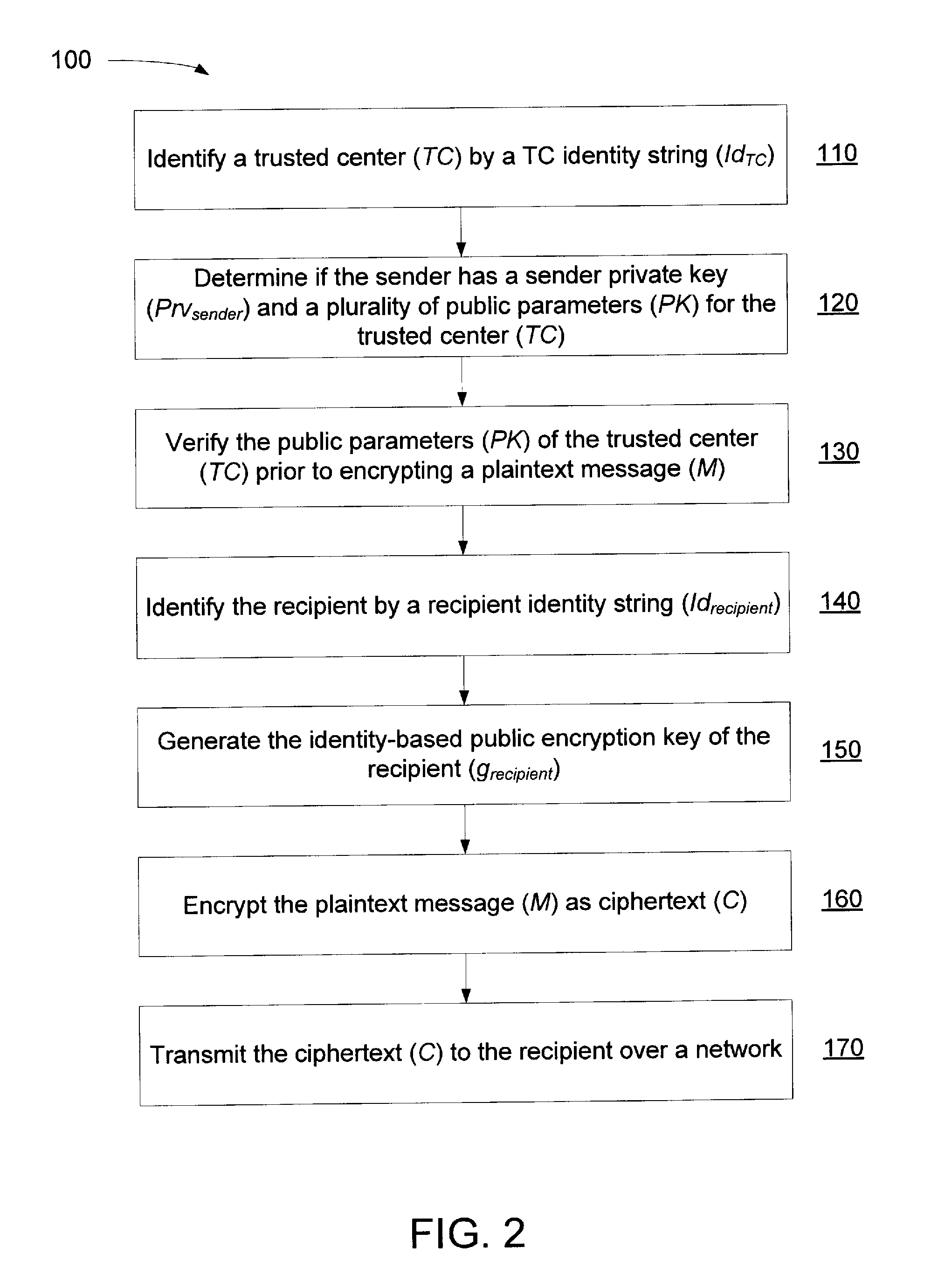
Method and System for a Certificate-less Authenticated Encryption Scheme Using Identity-based Encryption
ActiveUS20130212377A1Good flexibilityEliminate needPublic key for secure communicationUser identity/authority verificationPlaintextID-based encryption
A method of verifying public parameters from a trusted center in an identity-based encryption system prior to encrypting a plaintext message by a sender having a sender identity string may include: identifying the trusted center by a TC identity string, the trusted center having an identity-based public encryption key of the trusted center based on the TC identity string; determining if the sender has a sender private key and the public parameters for the trusted center including the public encryption key of the trusted center and a bilinear map; and verifying the public parameters using the TC identity string prior to encrypting the plaintext message into a ciphertext by comparing values of the bilinear map calculated with variables from the trusted center. The ciphertext may include a component to authenticate the sender once the ciphertext is received and decrypted by the recipient using the private key of the recipient.
Owner:VIBE CYBERSECURITY IP LLC
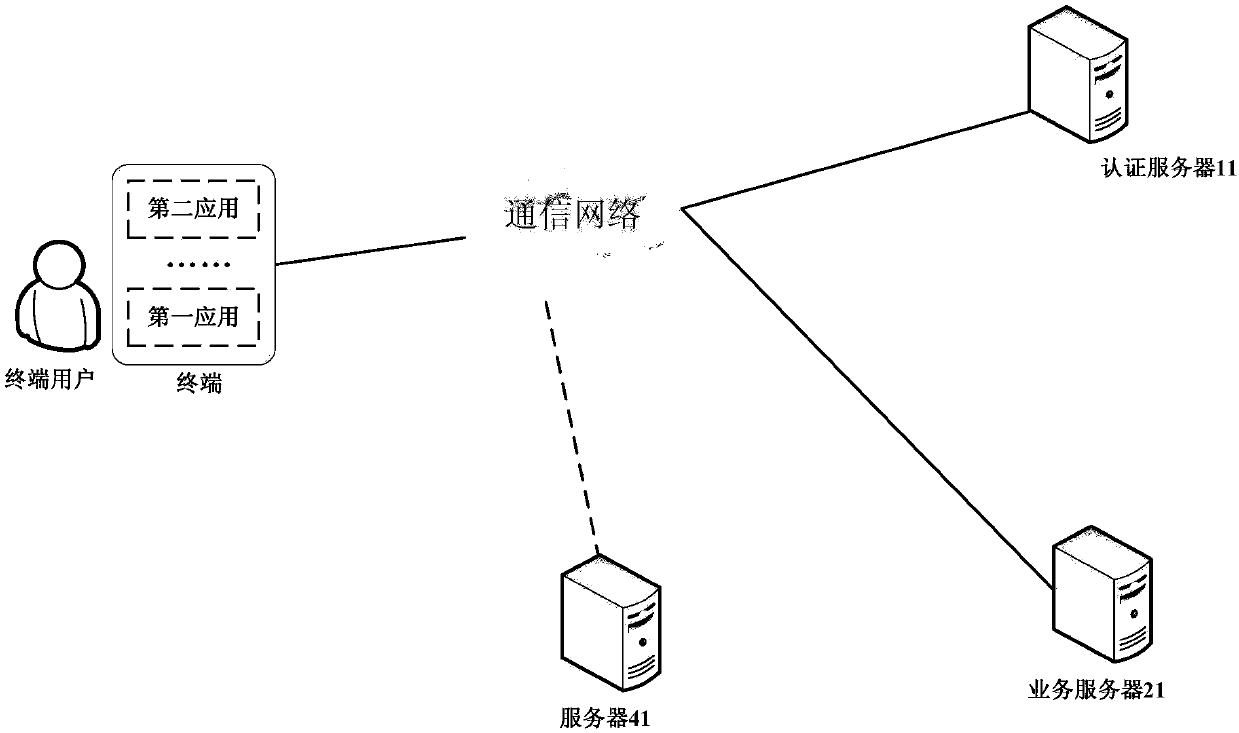
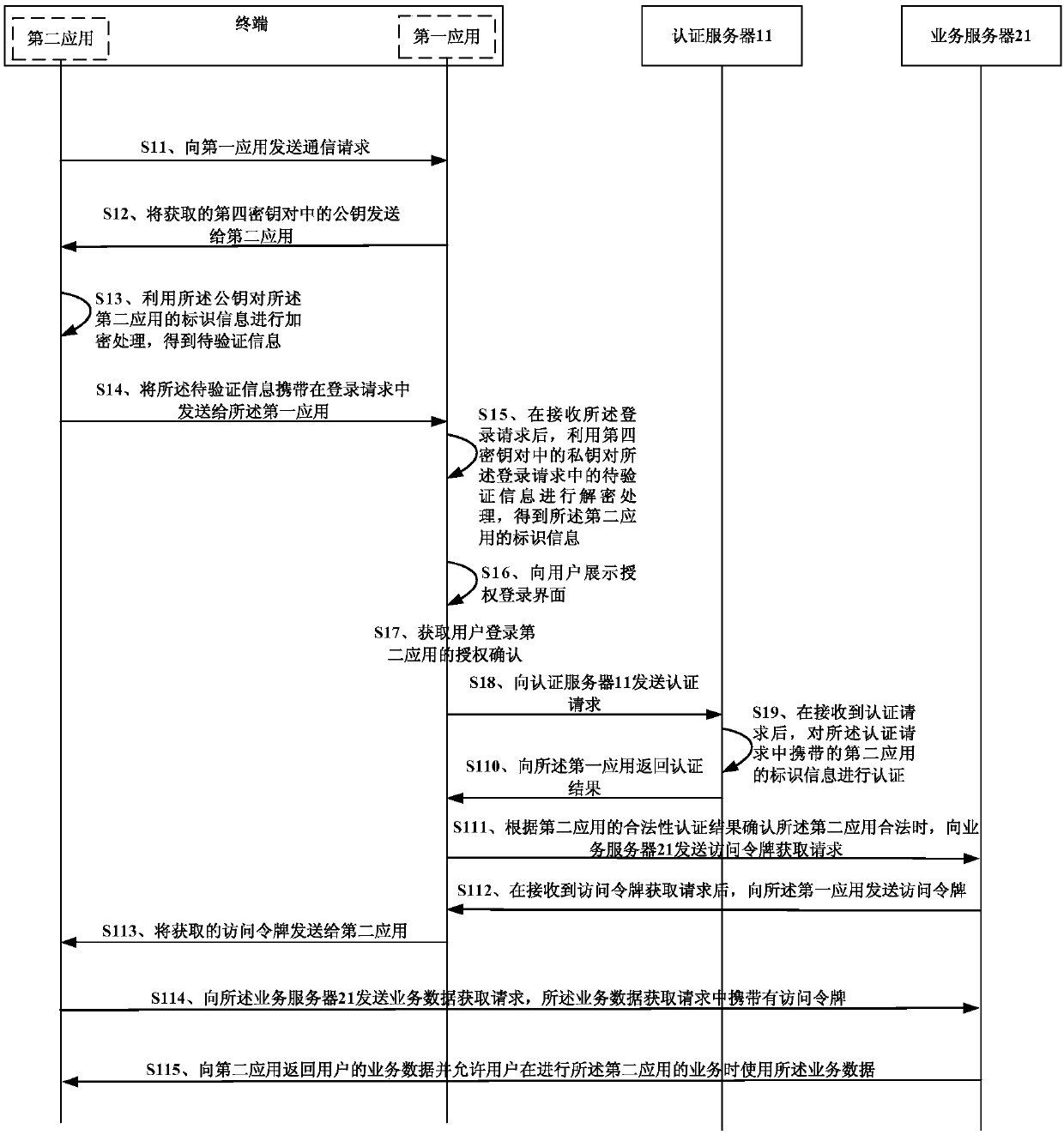
Application login method and system, terminal and electronic equipment
ActiveCN110324276AEnsure safetyPrevent leakageUser identity/authority verificationTransfer procedureBusiness data
The invention discloses an application login method and system, a terminal and electronic equipment, and belongs to the technical field of information security. The method comprises the following steps of: when a first application in a terminal acquires authorization confirmation that a user permits to use user identity information of the first application to log in a second application, sending an authentication request of authentication encryption information carrying the identification information of the second application to an authentication server; when it is determined that the second application is legal according to an authentication result returned by the authentication server, obtaining the access token from the business server of the first application and sending the obtained access token to the second application, so that the second application can obtain the business data of the user from the business server by utilizing the access token, and meanwhile, the user is allowed to use the business data when carrying out the business of the second application. The data is transmitted in an encryption mode, information is prevented from being stolen in the transmission process, and therefore the safety of the data recorded on the service server by a user is guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
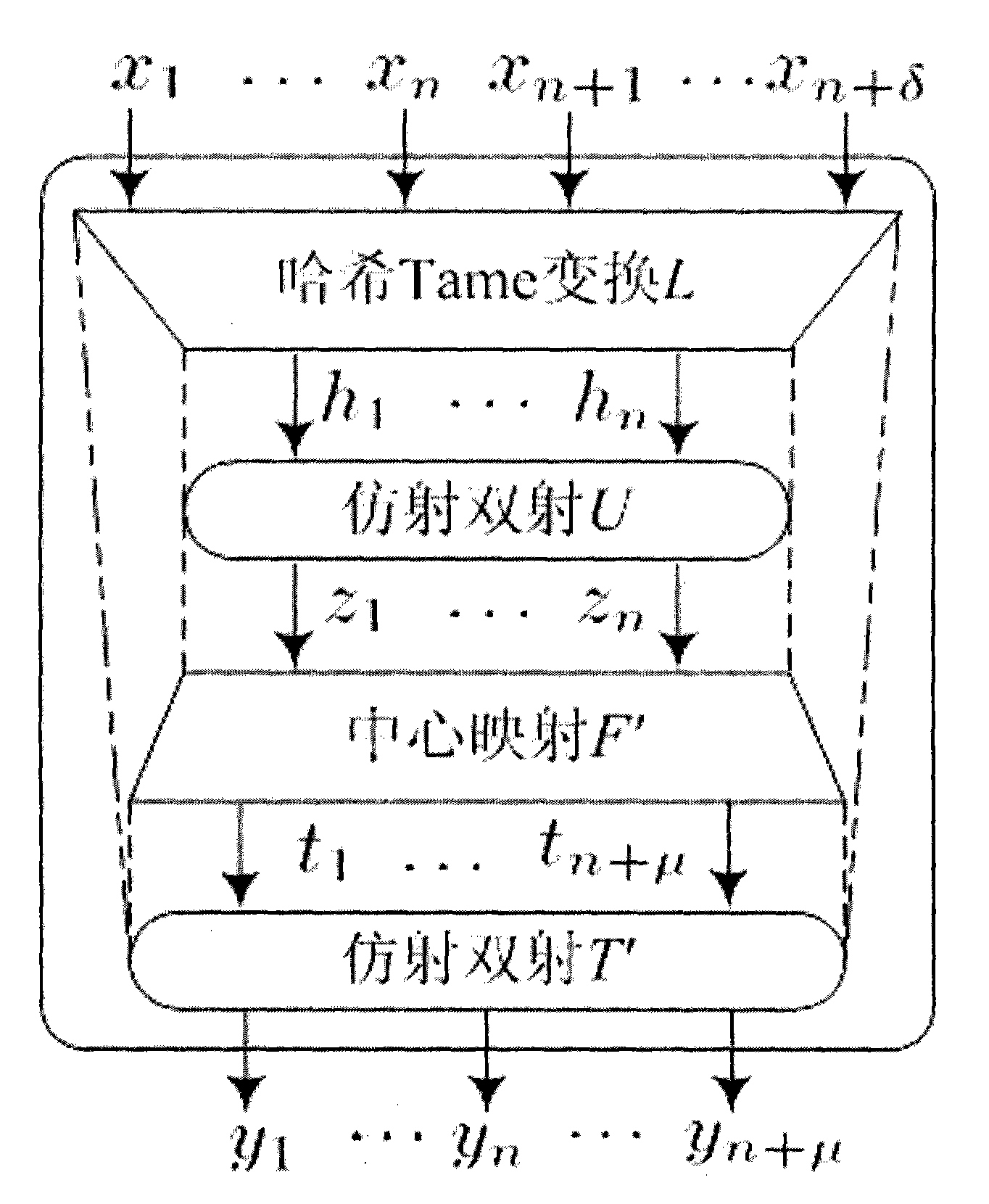
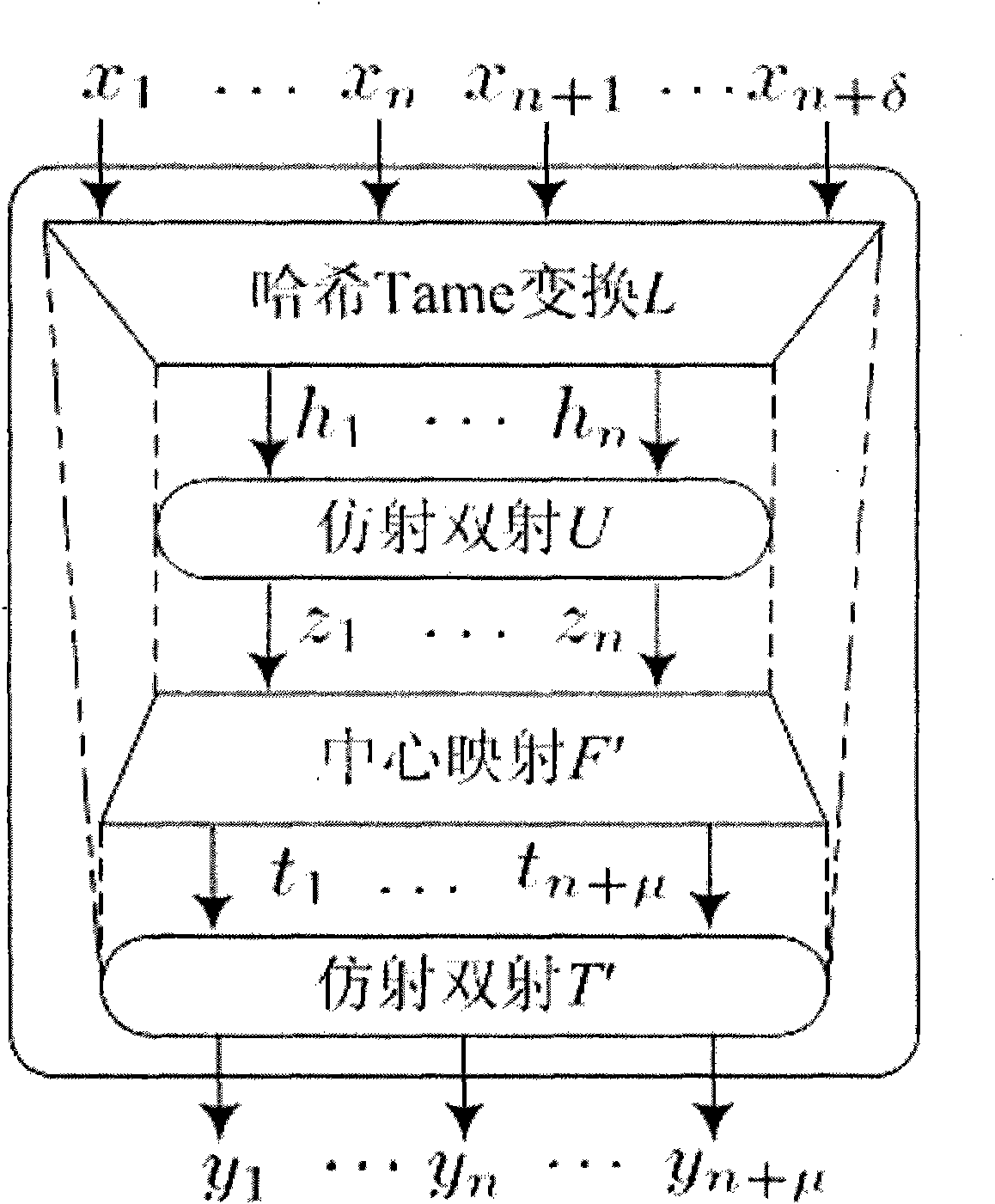
Authenticated encryption method of public key and digital signature method
ActiveCN101834724AResist attackImprove securityPublic key for secure communicationUser identity/authority verificationHash functionCoprocessor
The invention relates to the technical field of information safety and particularly discloses an authenticated encryption method of a public key and a digital signature method. The invention adopts a multivariable public key password system as a main body part, is combined with a Hash function authentication technology and provides double safety protection by efficiently compounding the multivariable public key password system and the Hash function authentication technology. When applying the scheme to carry out encryption or digital signature, the invention has the advantages of high realization efficiency, no need for a password algorithm coprocessor high safety, impact resistance of a quantum computer and the like and has more superiority in the safety field of intelligent cards, wireless sensing networks and the like compared with the traditional public key encryption algorithm such as RSA (Rivest-Shamir-Adleman), ECC (Elliptic Curve Crypto) and the like. The methods can be widely applied to the field of information safety systems of network safety, electronic commerce, bill, identity authentication and the like.
Owner:常熟紫金知识产权服务有限公司
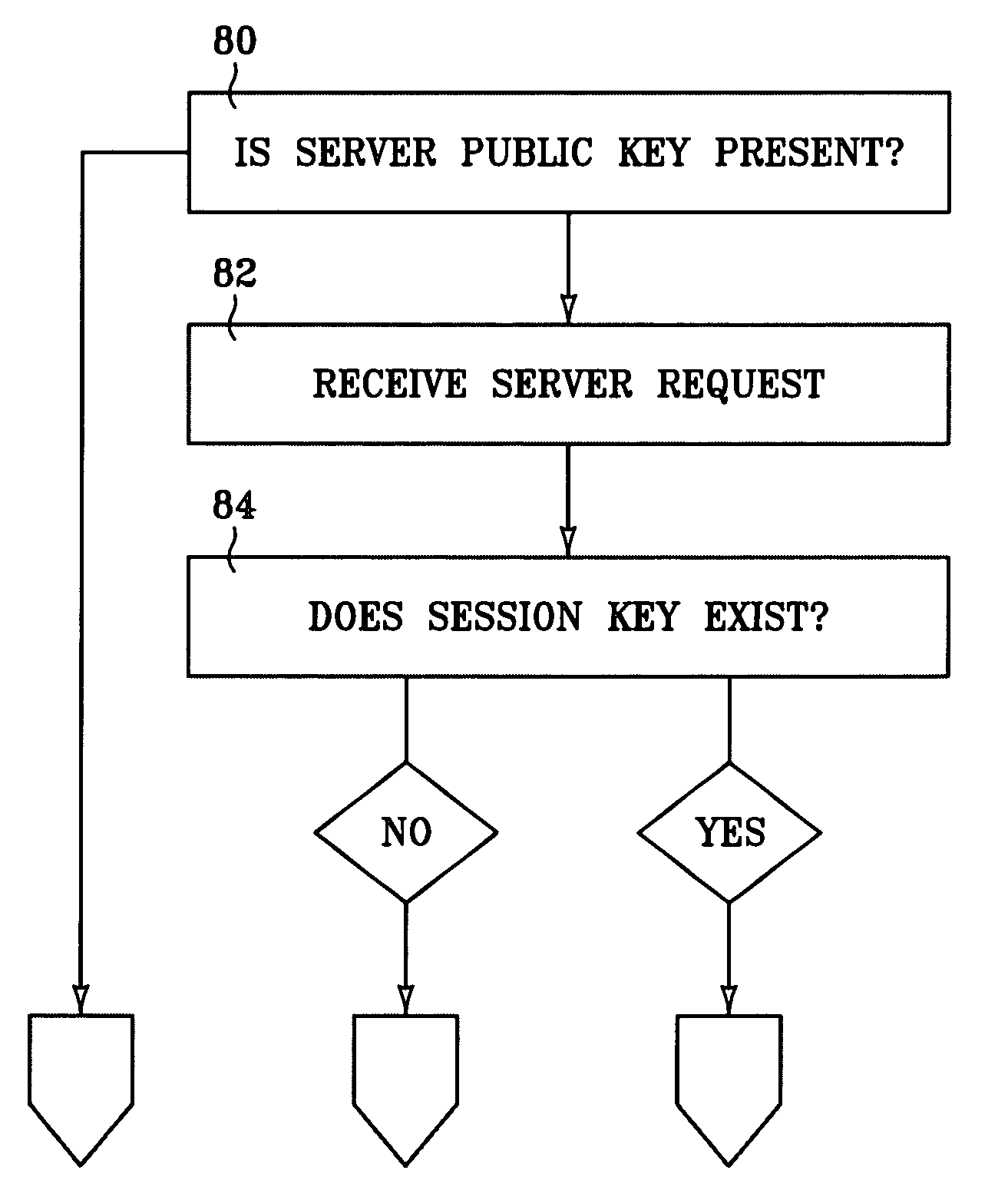
One pass security
InactiveUS7281128B2Digital data processing detailsPublic key for secure communicationOne passInternet Authentication Service
A system and method for secure network communication. In various embodiments of the present invention, data needed for authentication an encryption is included in each communication pass between network devices, so that when a network connection is broken, a secure connection can be reestablished with the next pass. A client authentication service on the client receives a server request and searches for a current client-side session key. If one is not present, the client authentication service generates and encrypts an initial session key, acquires credentials, adds the credentials to the server request, and encrypts the server request with the initial session key. The encrypted server request and the encrypted session key are sent to the server, where a server authentication service decrypts the initial session key, decrypts the server request with the initial session key, and authenticates the credentials before allowing the server request to be acted upon. Where a current client-side session key is detected, the client authentication service acquires the current client-side session key, generates a next step session key, adds the next step session key to the server request, and encrypts the server request with the current client-side session key. The encrypted server request is sent to the server where the server authentication service decrypts the server request with a current server-side session key allowing the server request to be acted upon.
Owner:EXTENDED SYST
System and method for providing authenticated encryption in GPON network
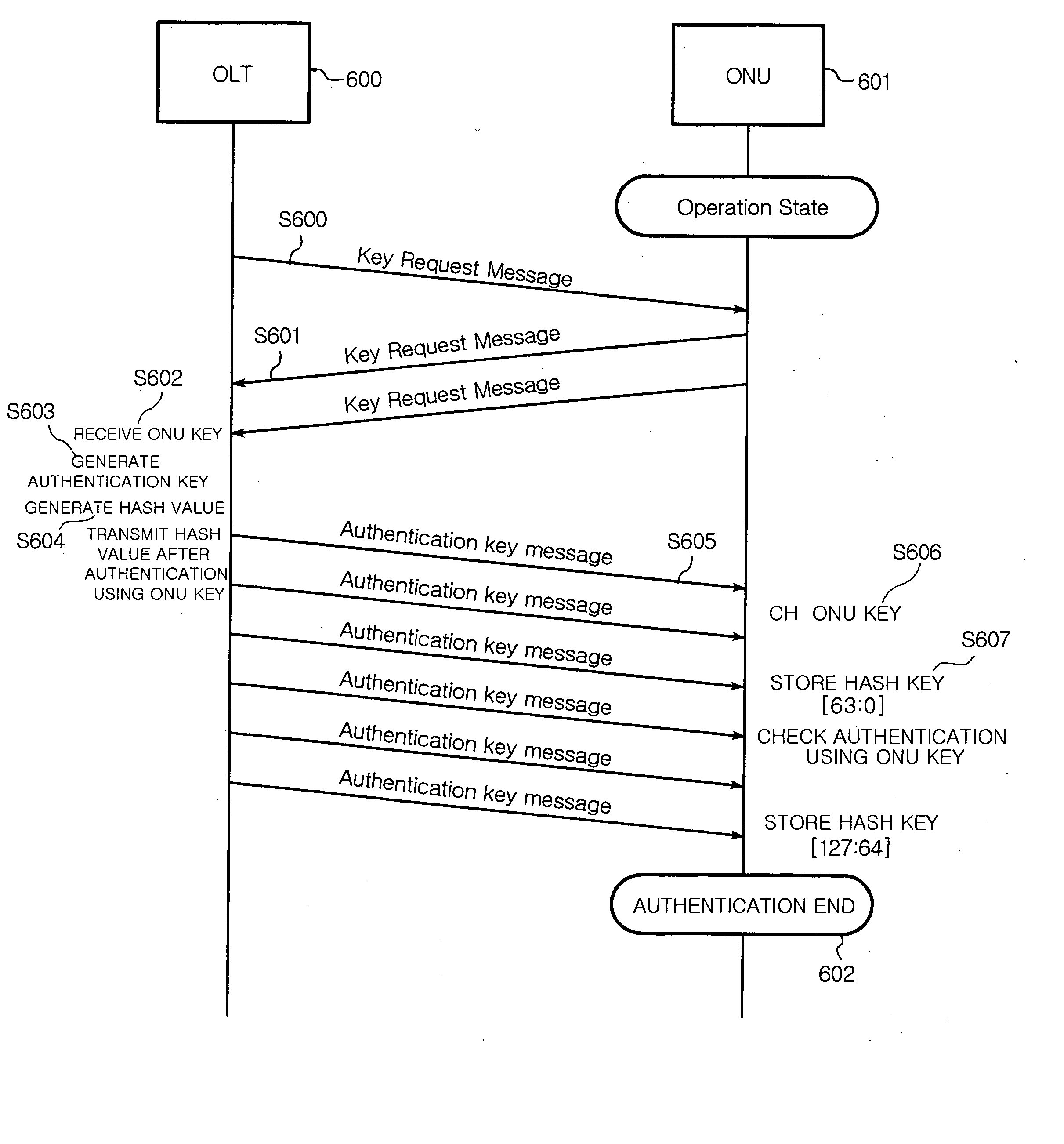
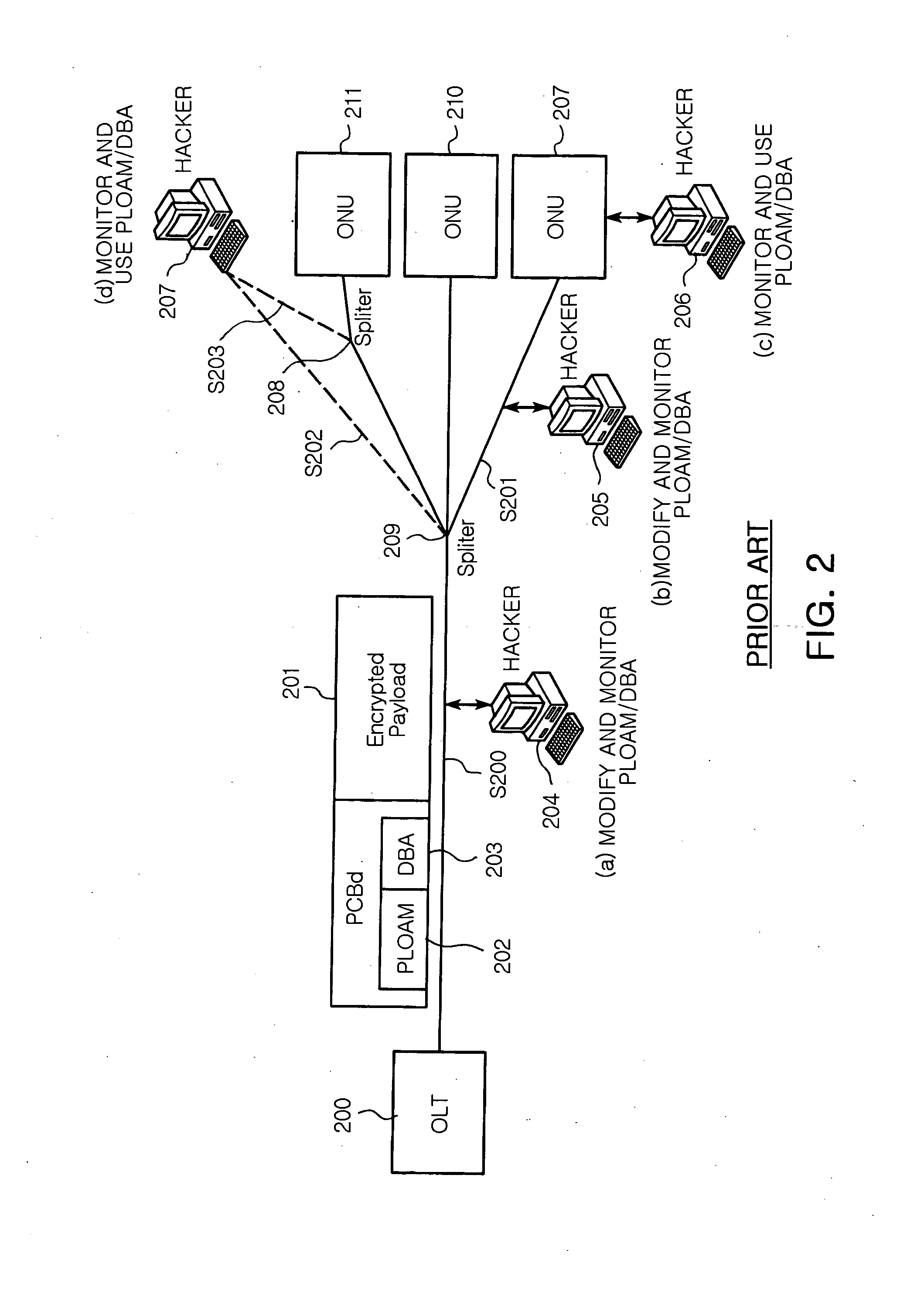
InactiveUS20080040604A1Error preventionFrequency-division multiplex detailsSecure transmissionService provision
A system and a method for providing a secured transmission through an authenticated encryption for each ONU in downlink transmission of an OLT in GPON are provided. The GPON system includes an OLT for generating a GTC downlink frame by receiving data from an external service provider and ONUs for receiving the GTC downlink frame from the OLT and processing the received GTC downlink frame. The OLT performs the authenticated encryption for the generated GTC downlink frame according to the ONU by including an authentication generator and the ONU determines whether the GTC downlink frame is allowed to be processed or not by checking the authentication of the received GTC downlink frame through an authentication checker.
Owner:ELECTRONICS & TELECOMM RES INST
Cloud Storage Encryption
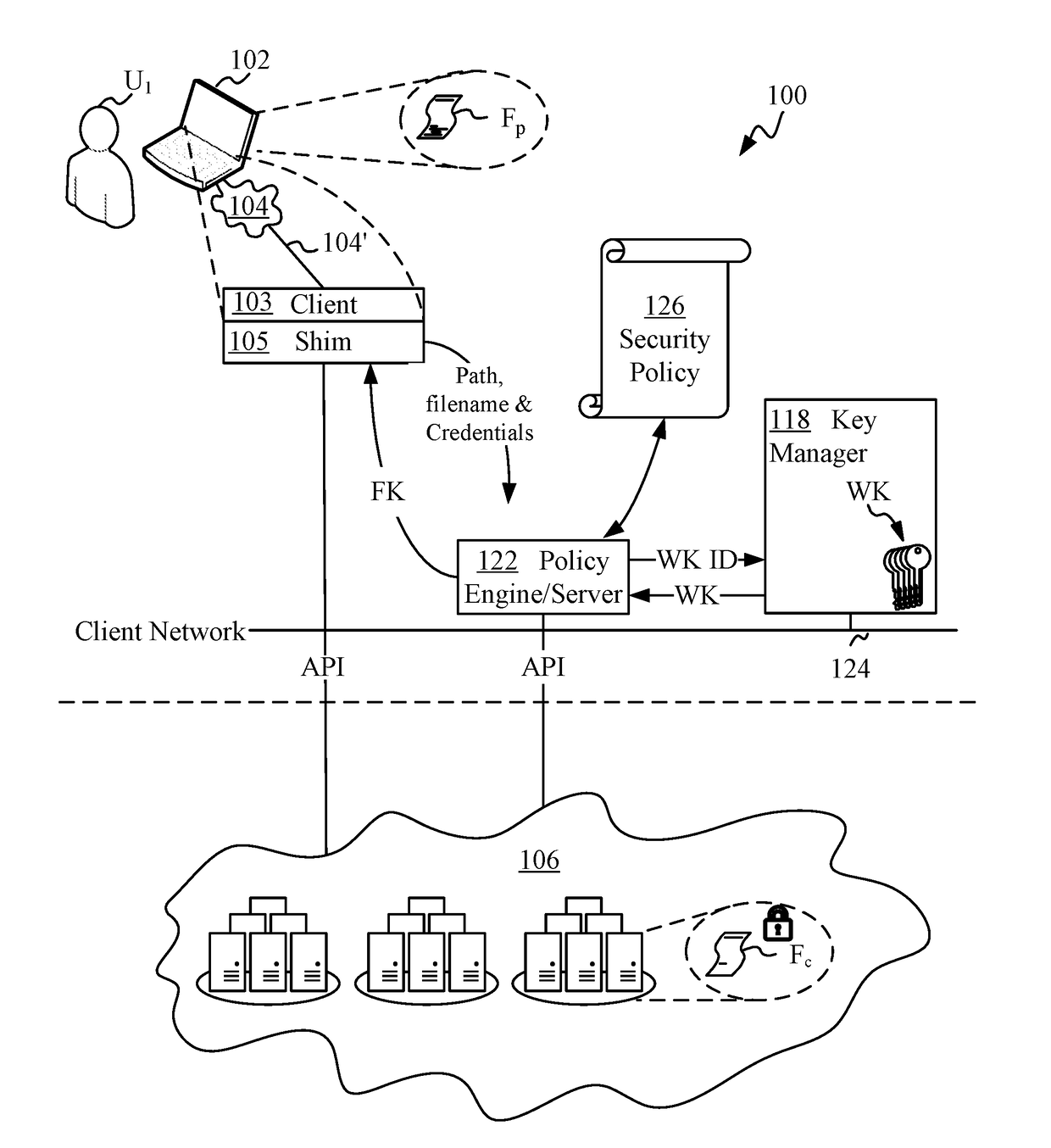
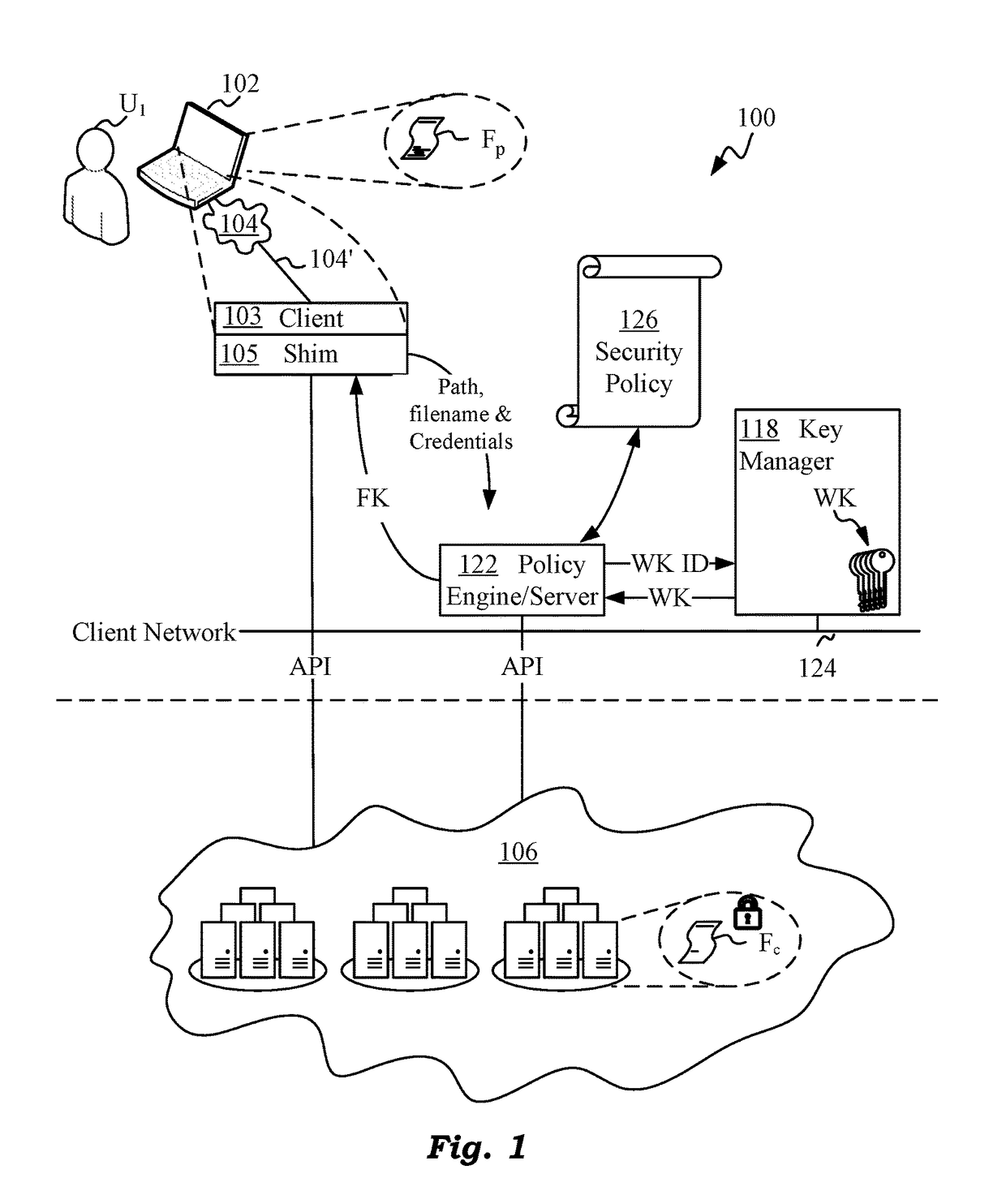
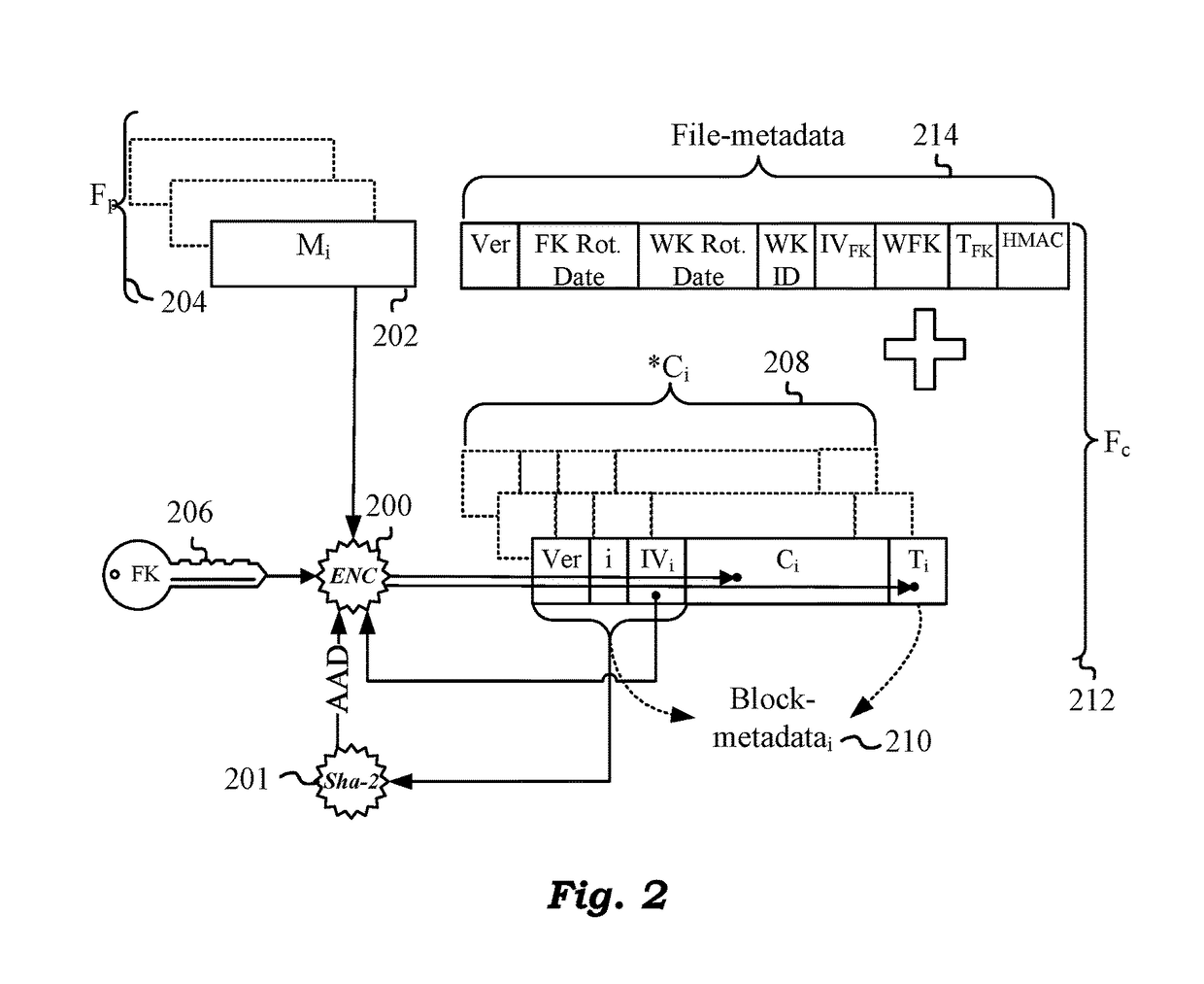
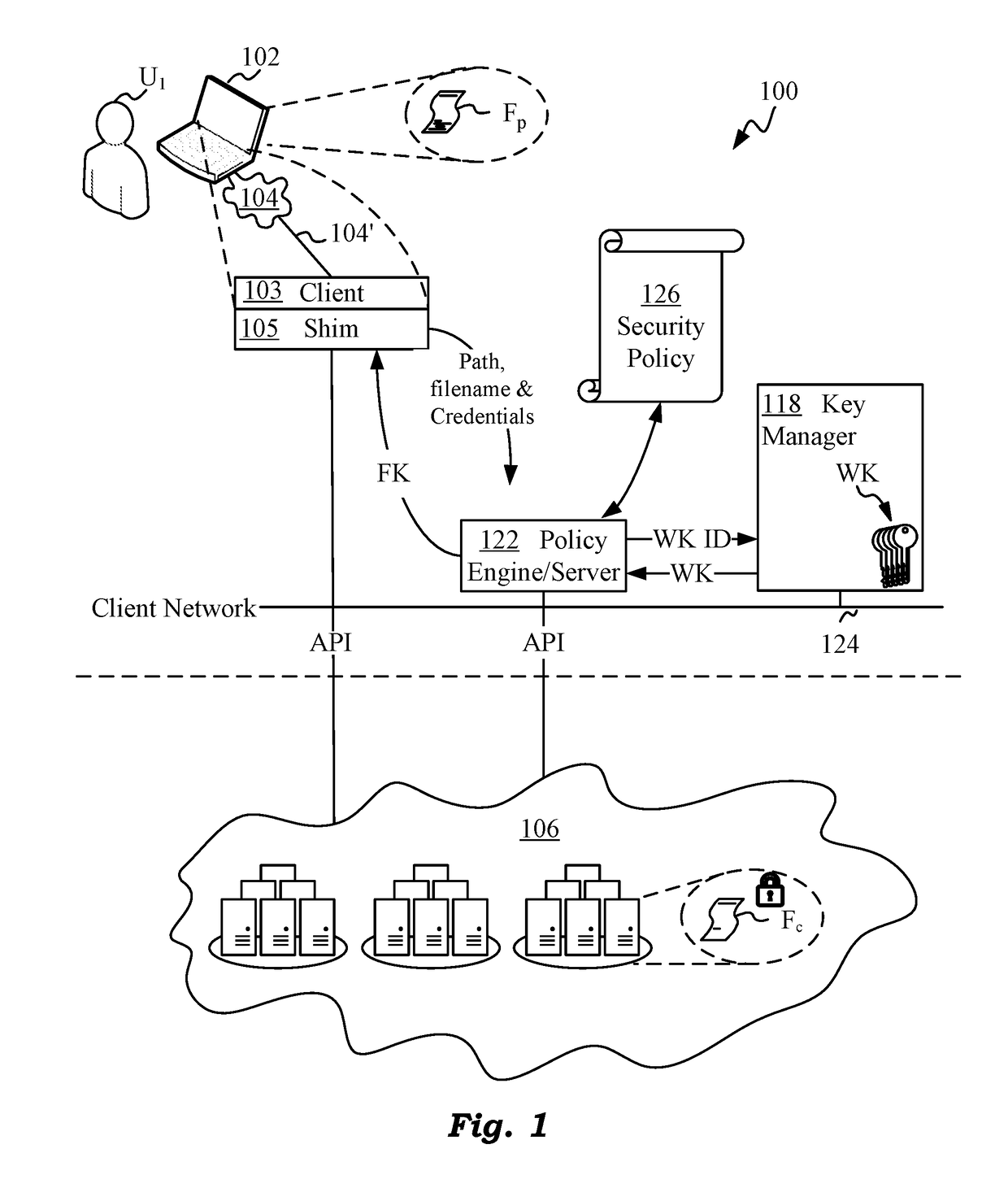
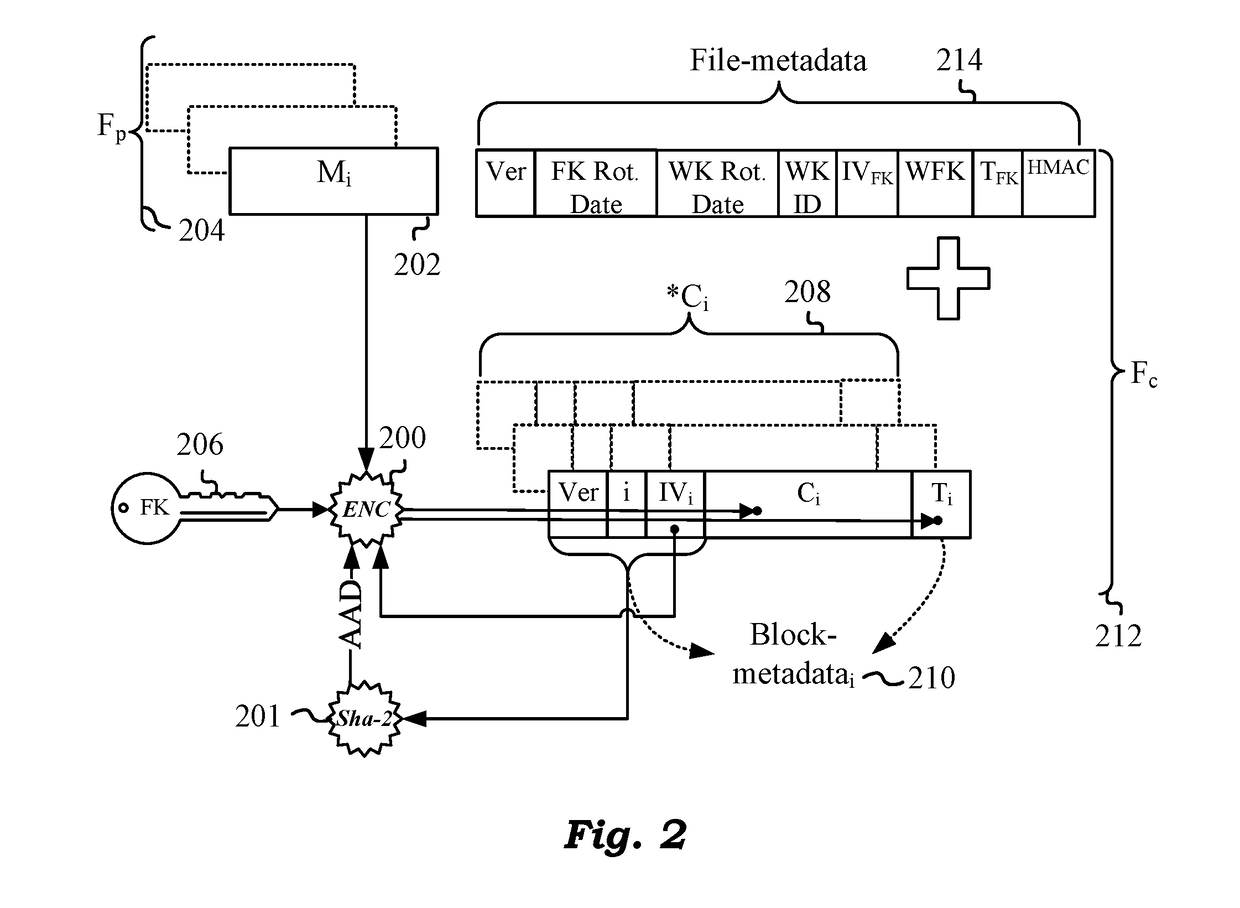
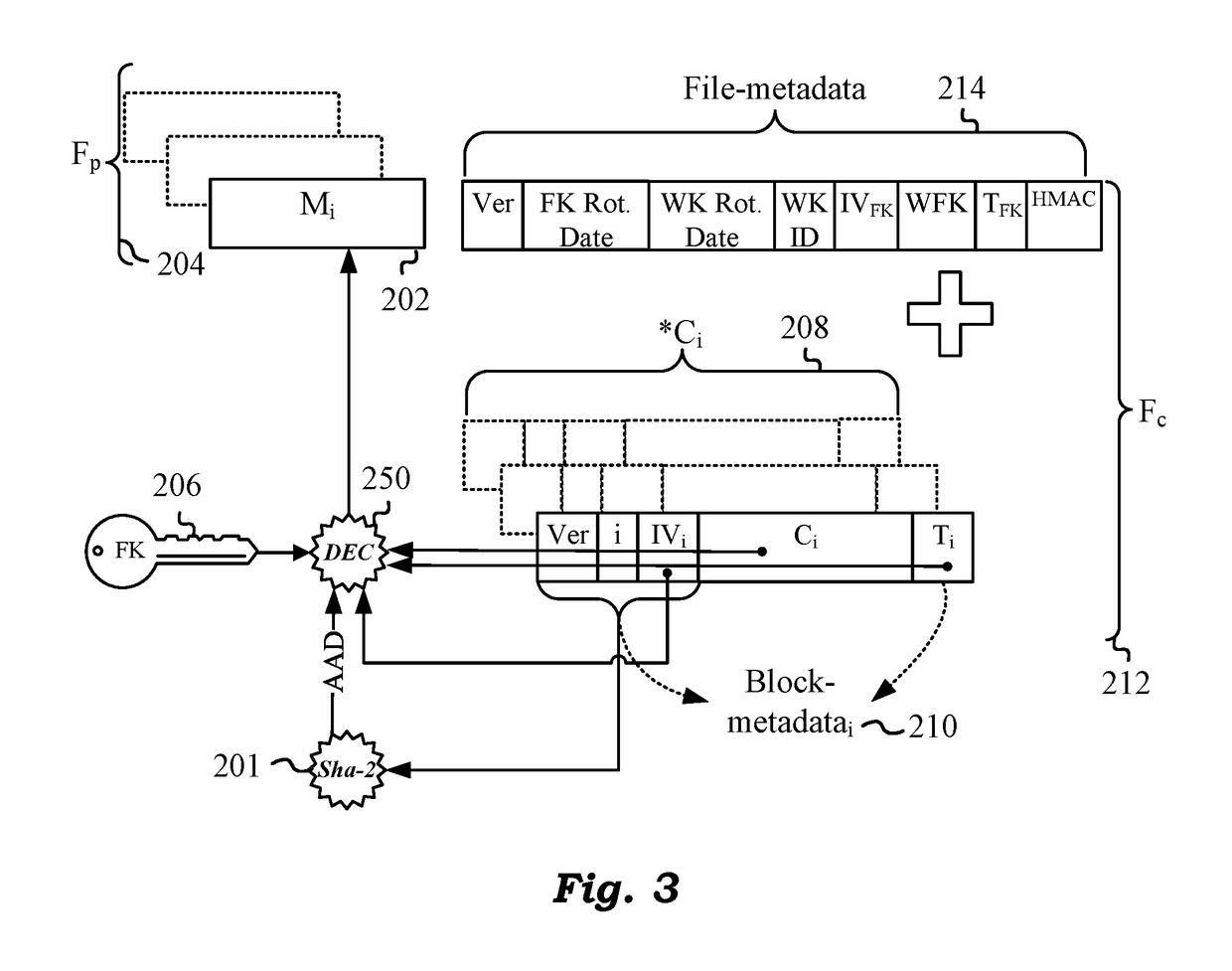
ActiveUS20180082076A1Improve integrityMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesManagement toolHardware security module
Techniques are disclosed for securing data in a cloud storage. Plaintext files are stored as secured, encrypted files in the cloud. The ciphering scheme employs per-block authenticated encryption and decryption. A unique file-key is used to encrypt each file. The file-key is wrapped by authenticated encryption in a wrapping-key that may be shared between files. A centralized security policy contains policy definitions which determine which files will share the wrapping-key. Wrapping-keys are stored in a KMIP compliant key manager which may be backed by a hardware security module (HSM). File metadata is further protected by a keyed-hash message authentication code (HMAC). A policy engine along with administrative tools enforce the security policy which also remains encrypted in the system.
Owner:ZETTASET
System for encrypting and decrypting a plaintext message with authentication
InactiveUS20120008767A1Lower levelLow levelSecret communicationSecuring communicationComputer hardwarePlaintext
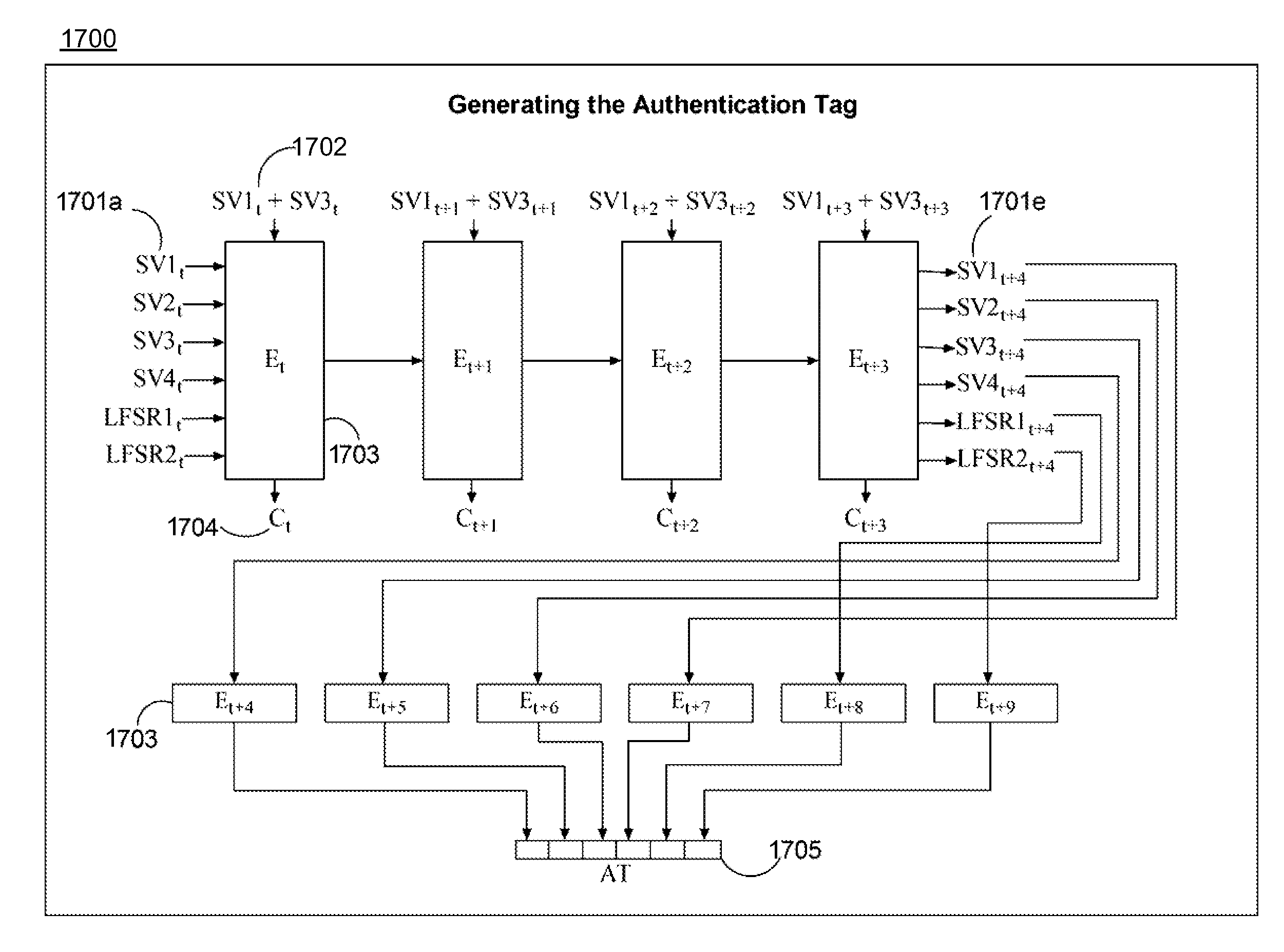
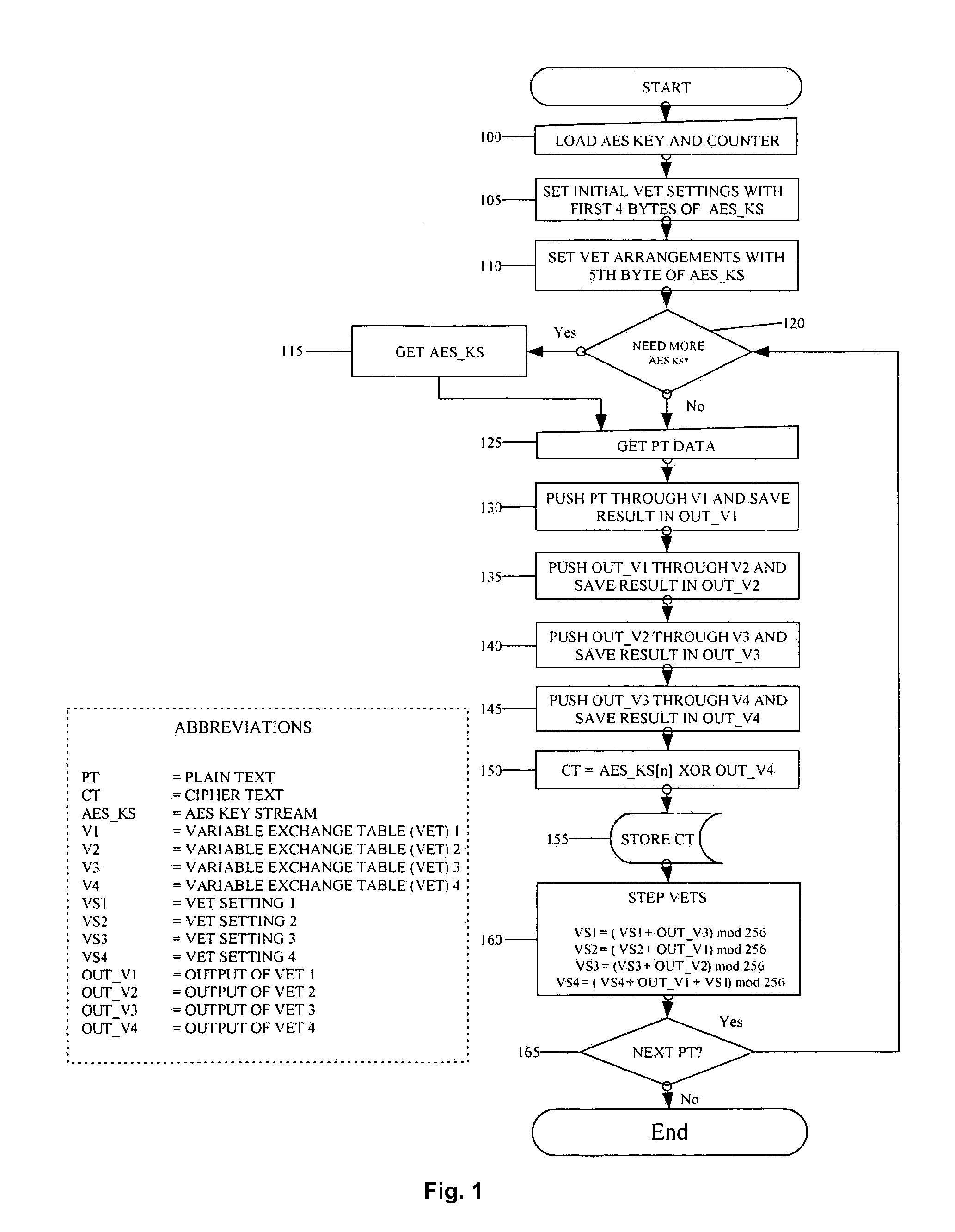
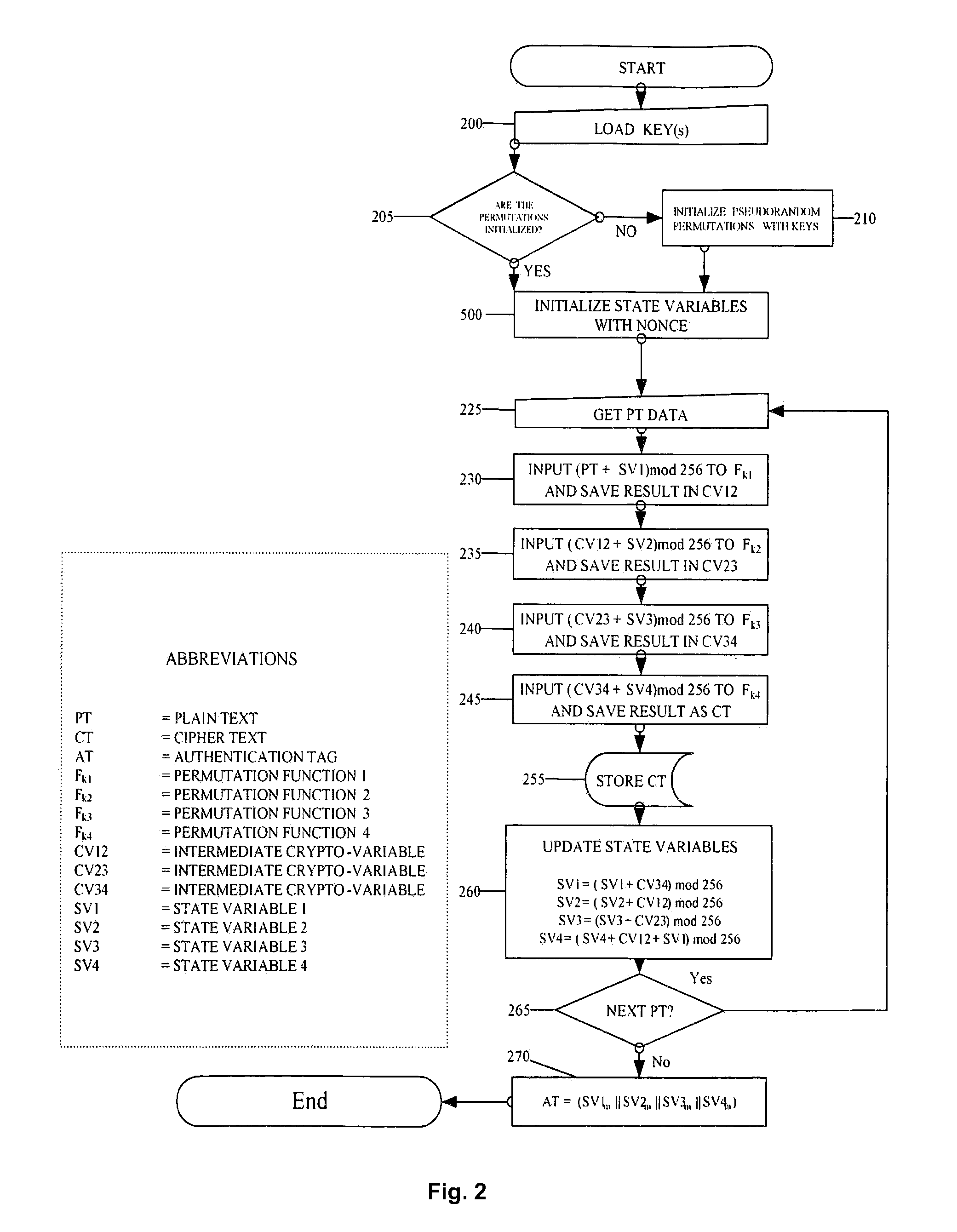
The described system and method provide for an encryption and authentication technique that achieves enhanced integrity verification through assured error-propagation using a multistage sequence of pseudorandom permutations. The method generates intermediate data-dependent cryptographic variables at each stage, which are systematically combined into feedback loops. The encryption technique also generates an authentication tag with minimal post processing that is the size of the state. The size of the state is dependent on the number of pseudorandom permutations and the size of the LFSR. The authentication tag provides a unique mapping to the plaintext for any number of plaintext blocks that is less than or equal the size of the state. In addition to being a stand alone encryption algorithm, the disclosed technique is applicable to any mode that uses pseudorandom permutations such as, key dependent lookup tables, S-Boxes, and block ciphers such as RC5, TEA, and AES.
Owner:SMITH ERIC MYRON +3
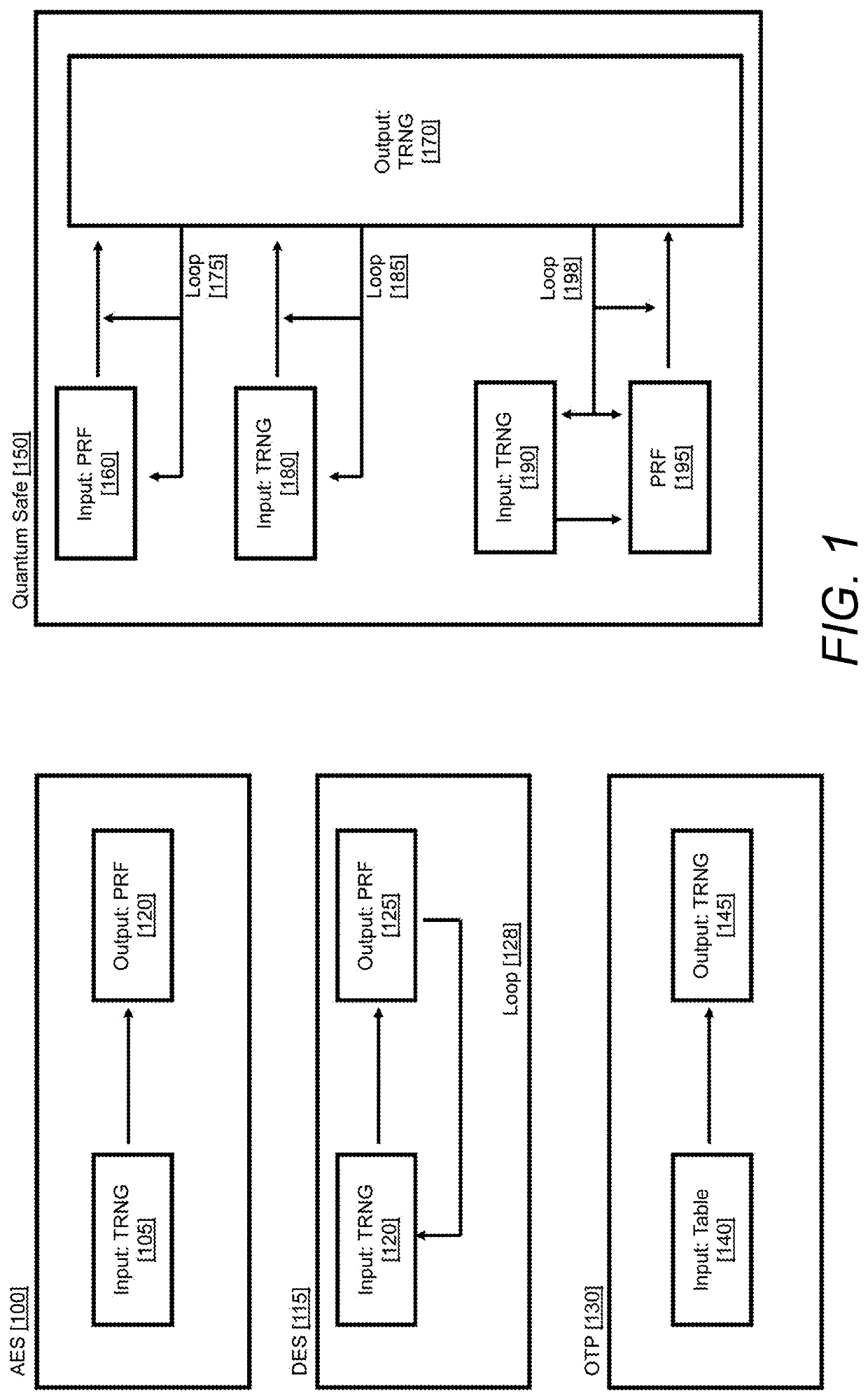
A system and method for quantum-safe authentication, encryption, and decryption of information
ActiveUS20200328886A1Improve securityIncrease the number ofKey distribution for secure communicationAlgorithmTheoretical computer science
Aspects and embodiments of the present invention relate to a method and system for generating a private cryptographic key for use in a secure cryptogram for transmission between a first entity and a second entity. The method may comprise: selecting a random vector defined in an n-dimensional vector space shared between the first entity and the second entity, the vector comprising one or more component coordinates defined in the n-dimensional vector space, each component coordinate being associated with one or more bits; determining the one or more bits associated with each component coordinate comprised in the random vector, and generating the private key in dependence on the one or more bits associated with each component coordinate comprised in the random vector.
Owner:BTQ AG
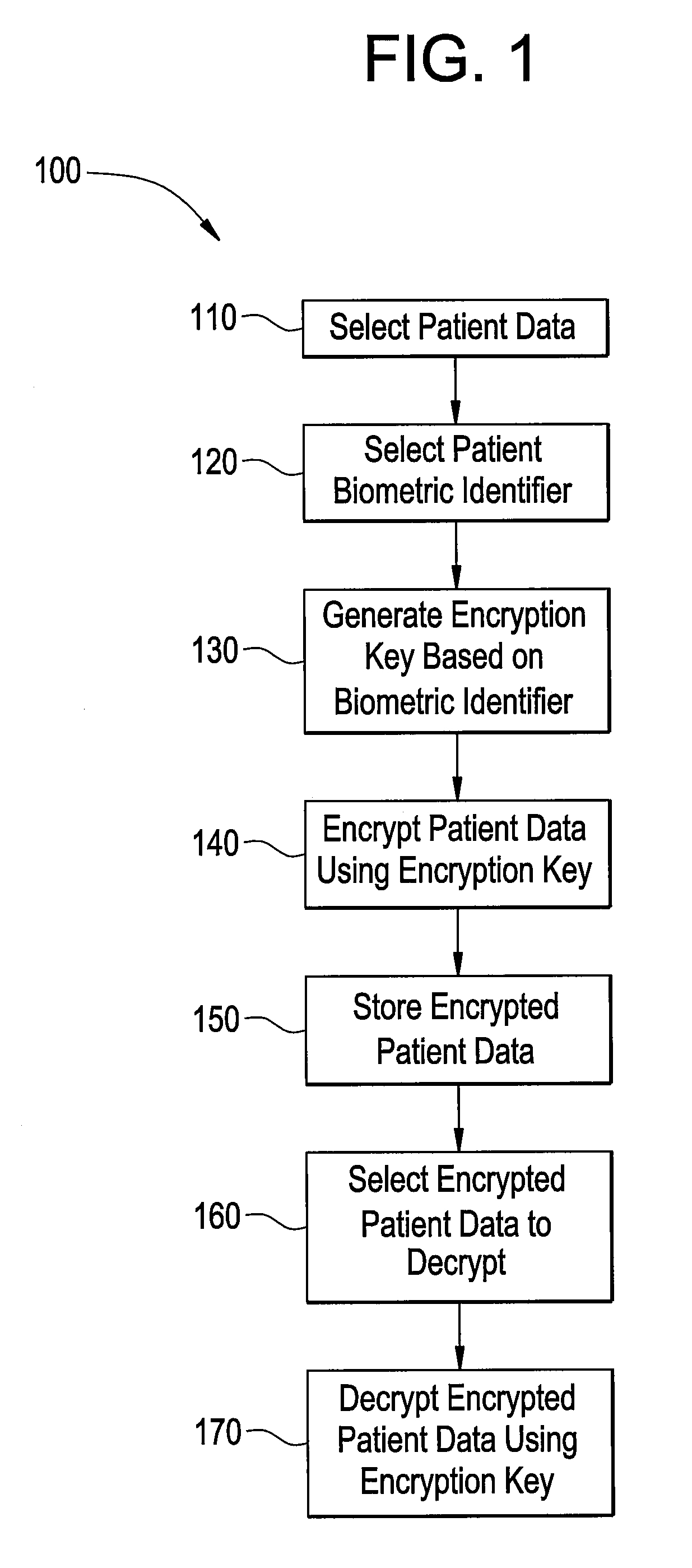
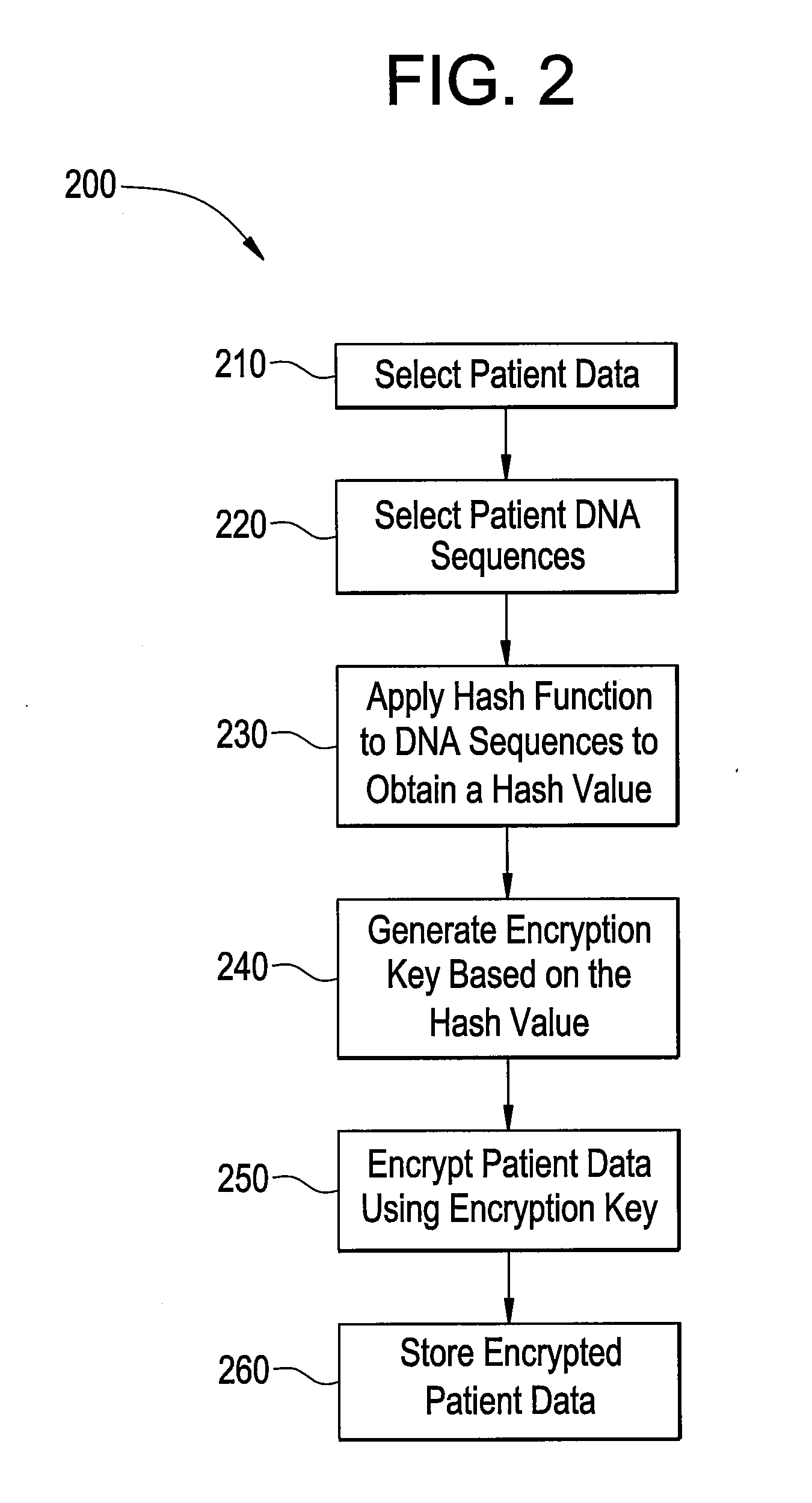
Systems and methods for encrypting patient data
Certain embodiments of the present invention provide a method for protecting electronic patient data in a healthcare environment. The method includes selecting the patient data to be protected, selecting a biometric identifier from a patient, generating an encryption key based on the biometric identifier, and encrypting the patient data. The method may also include authenticating the encrypted patient data. The biometric identifier may be a DNA sequence. The method may also include applying a hash function to the DNA sequences to obtain a hash value. The encryption key may be based at least in part on the hash value.
Owner:GENERAL ELECTRIC CO
Smart password key authentication based cross-platform heterogeneous system login method
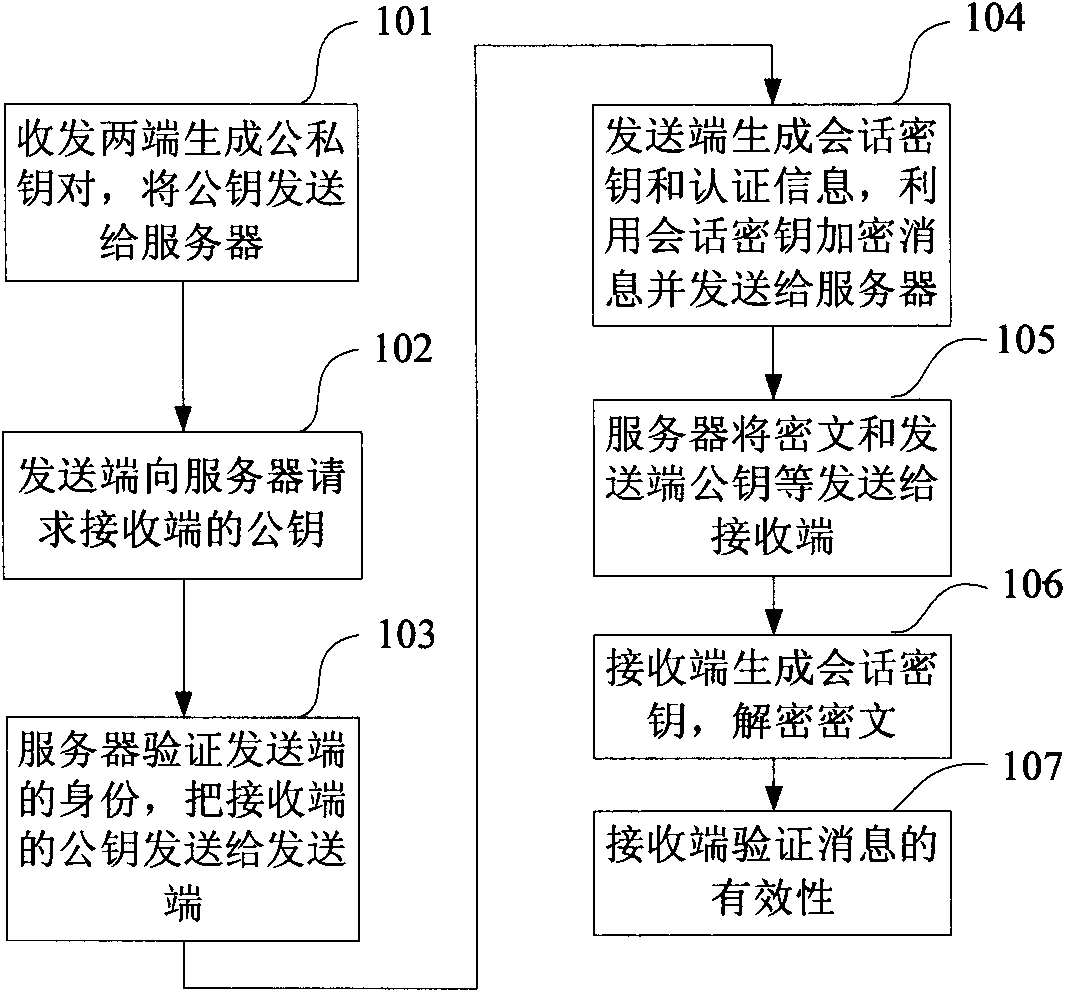
InactiveCN107508837ARealize authentication sharingAchieve single sign-onKey distribution for secure communicationUser identity/authority verificationInformation resourceKey authentication
The invention provides a smart password key authentication based cross-platform heterogeneous system login method. The method is to provide a uniform authentication service platform for a multi-service system user by utilizing a smart password key, a digital signature and a digital certificate authentication mechanism based on a PKI theoretical system and to perform uniform authentication of the user identity and access control through integrating service systems and content, thereby realizing single-point login and integration of information resources of each service system. An enterprise employee, as long as remembering a command, can log in multiple heterogeneous systems in the access process of an application system; uniform user identity information is provided, so information sharing can be carried out even the user identity information content and data format of each application system are non-uniform, and interconnection and mutual communication are realized; after the smart password key authentication is encrypted, the data transmitted by the user are guaranteed to be the original text without being tampered maliciously; and the identity of the user can be confirmed.
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
Authenticated encryption method and encryption system based on symmetric encryption
InactiveCN101667913AAchieve authenticationImplement encryptionKey distribution for secure communicationUser identity/authority verificationThird partyCommunications security
The invention discloses an authenticated encryption method and a system, relating to the field of communication security. The restorable signature of a message and the symmetric encryption technologyare combined; a commitment value which only can be calculated by a designated message receiving end is used as a session key encryption message; and the message receiving end validates the validity ofthe message by the restorable signature, thus realizing encryption and authentication in one logical step. A key generation unit of a sending end generates a session key of the sending end; an encryption unit encrypts a message to be sent; the receiving end generates a session key of the receiving end; a decryption unit utilizes the session key of the receiving end to decrypts the encrypted message; and the authentication and confirmation message is generated according to the decrypted message, thus validating the validity of the message. When disputes occur, the message receiving end transforms the authenticated and encrypted message signature into a common signature so as to lead a third party to validate the validity of the signature. The invention has the advantages of high security,low calculated amount and transmission cost, and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
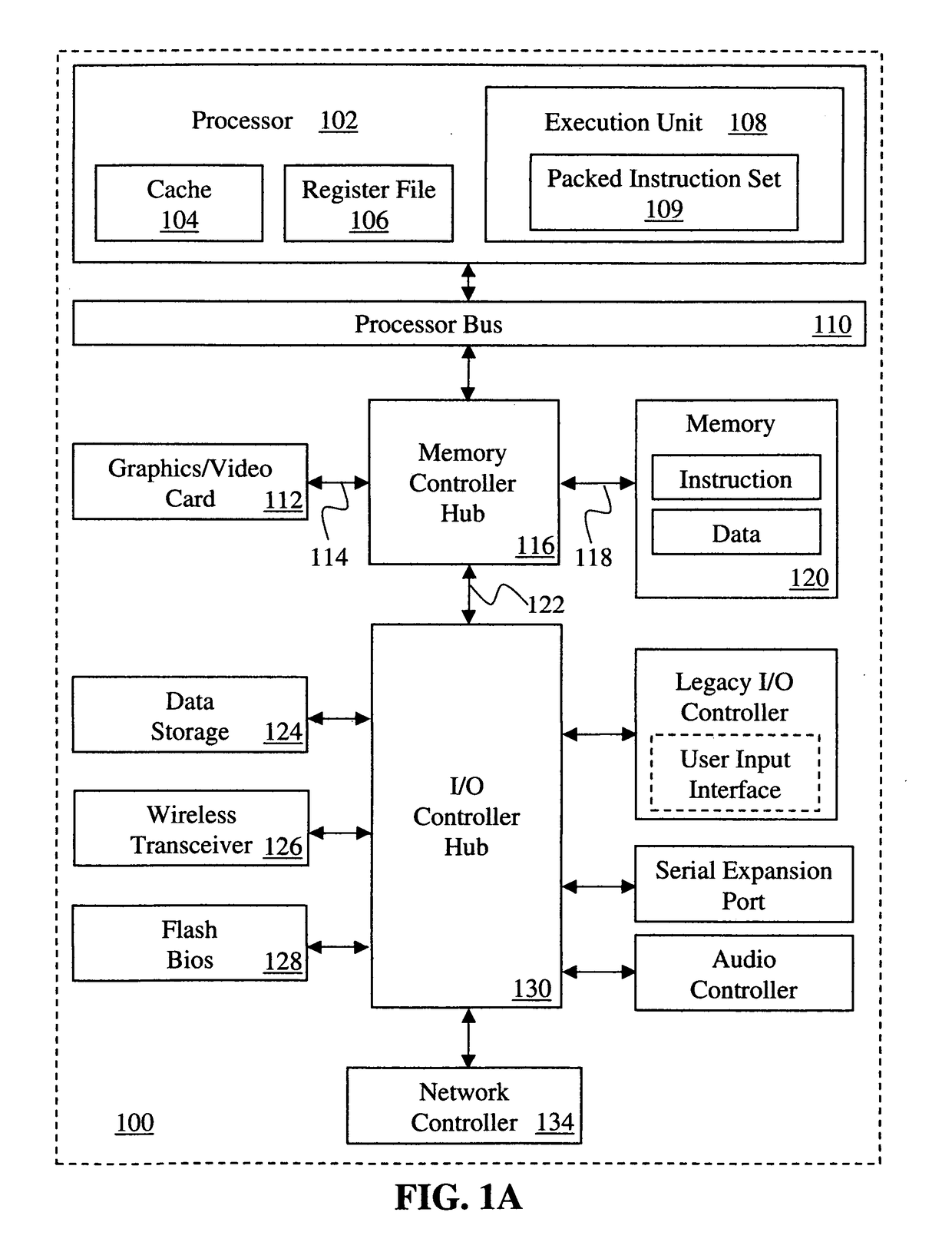
Instructions and logic to suspend/resume migration of enclaves in a secure enclave page cache
ActiveUS20170185533A1Memory architecture accessing/allocationMultiple keys/algorithms usageExternal storageManagement process
Instructions and logic support suspending and resuming migration of enclaves in a secure enclave page cache (EPC). An EPC stores a secure domain control structure (SDCS) in storage accessible by an enclave for a management process, and by a domain of enclaves. A second processor checks if a corresponding version array (VA) page is bound to the SDCS, and if so: increments a version counter in the SDCS for the page, performs an authenticated encryption of the page from the EPC using the version counter in the SDCS, and writes the encrypted page to external memory. A second processor checks if a corresponding VA page is bound to a second SDCS of the second processor, and if so: performs an authenticated decryption of the page using a version counter in the second SDCS, and loads the decrypted page to the EPC in the second processor if authentication passes.
Owner:INTEL CORP
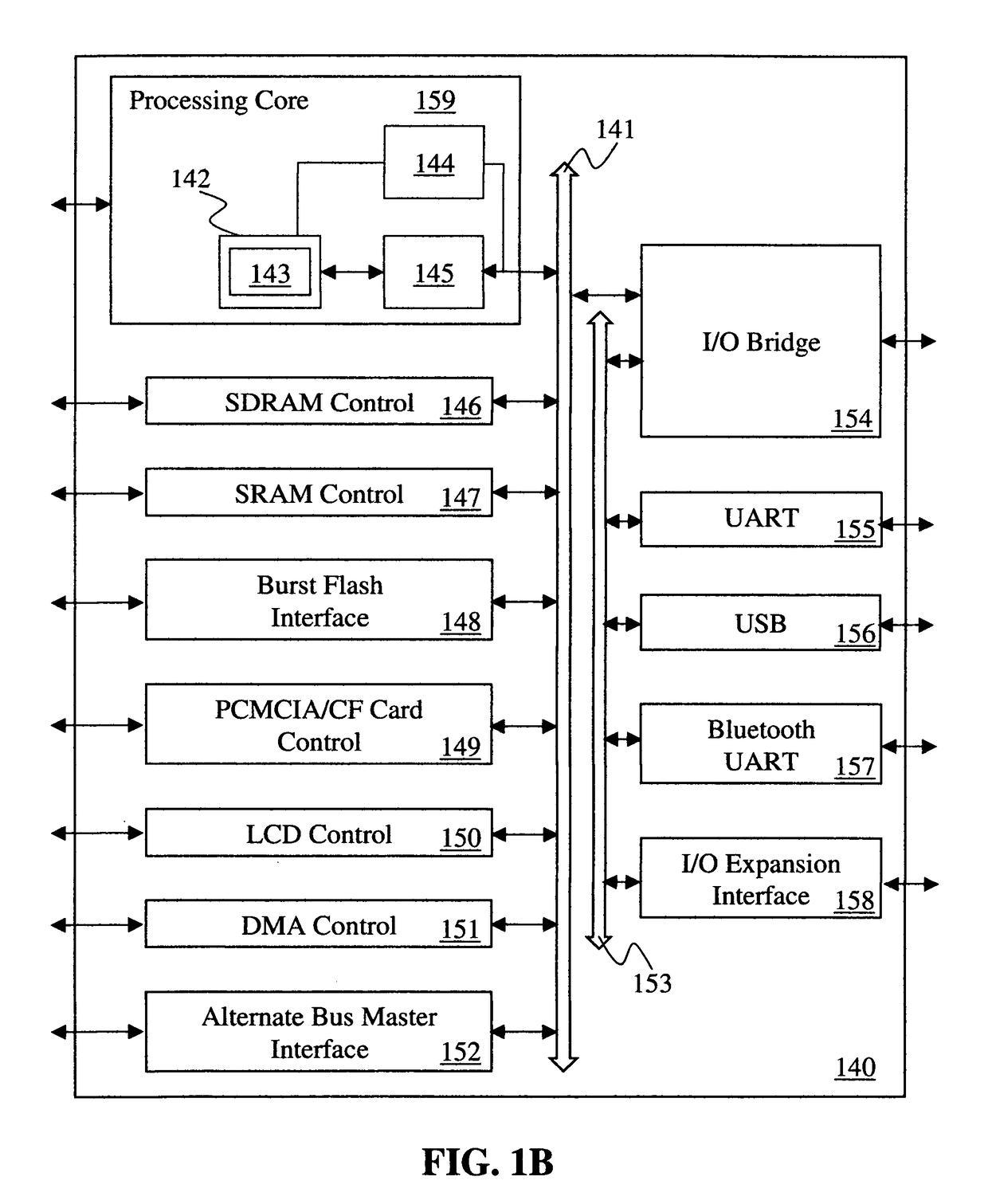
Efficient Internet-Of-Things (IoT) Data Encryption/Decryption
ActiveUS20210044972A1Lighten the computational burdenAvoid contactUser identity/authority verificationDigital data protectionInternet privacyConfidentiality
Techniques are disclosed for encrypting internet-of-things (IoT) data of an IoT network only once at its inception until its final consumption without intervening encryption / decryption stages / cycles. The present encrypt-decrypt-once design thus eliminates potential exposure of the IoT data in its plaintext form of a traditional approach employing intervening encryption / decryption cycles. The present design is also efficient and reduces the burden on IoT resources by eliminating the need for encrypting and decrypting the data multiple times. To accomplish these objectives, a number of schemes for device enrollment, authentication, key distribution, key derivation, encryption and encoding are disclosed. The devices employ authenticated encryption because it provides confidentiality, integrity, and authenticity assurances on the encrypted data. The final consumption of the IoT data may be at a designated gateway or a corporate system.
Owner:ZETTASET
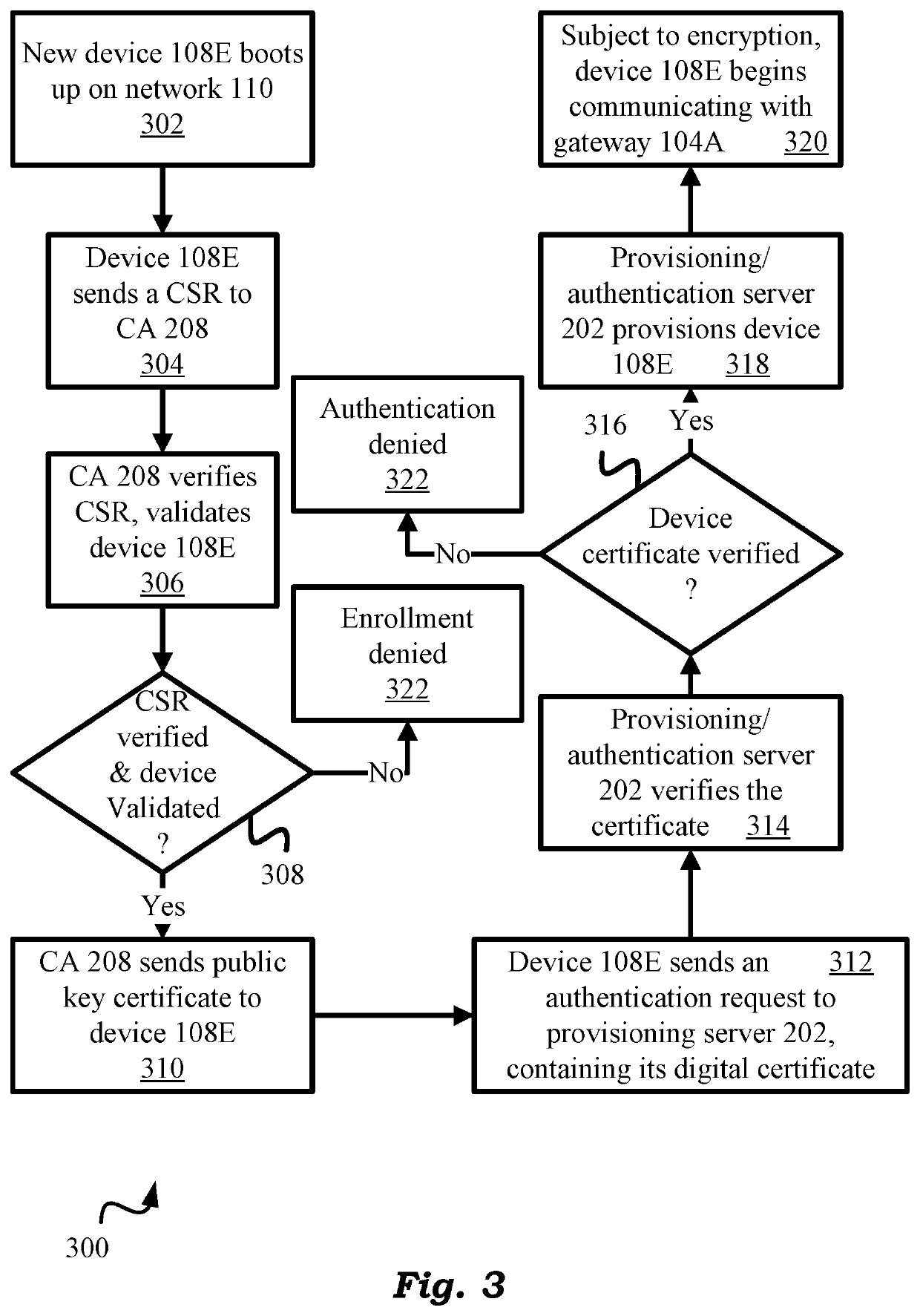
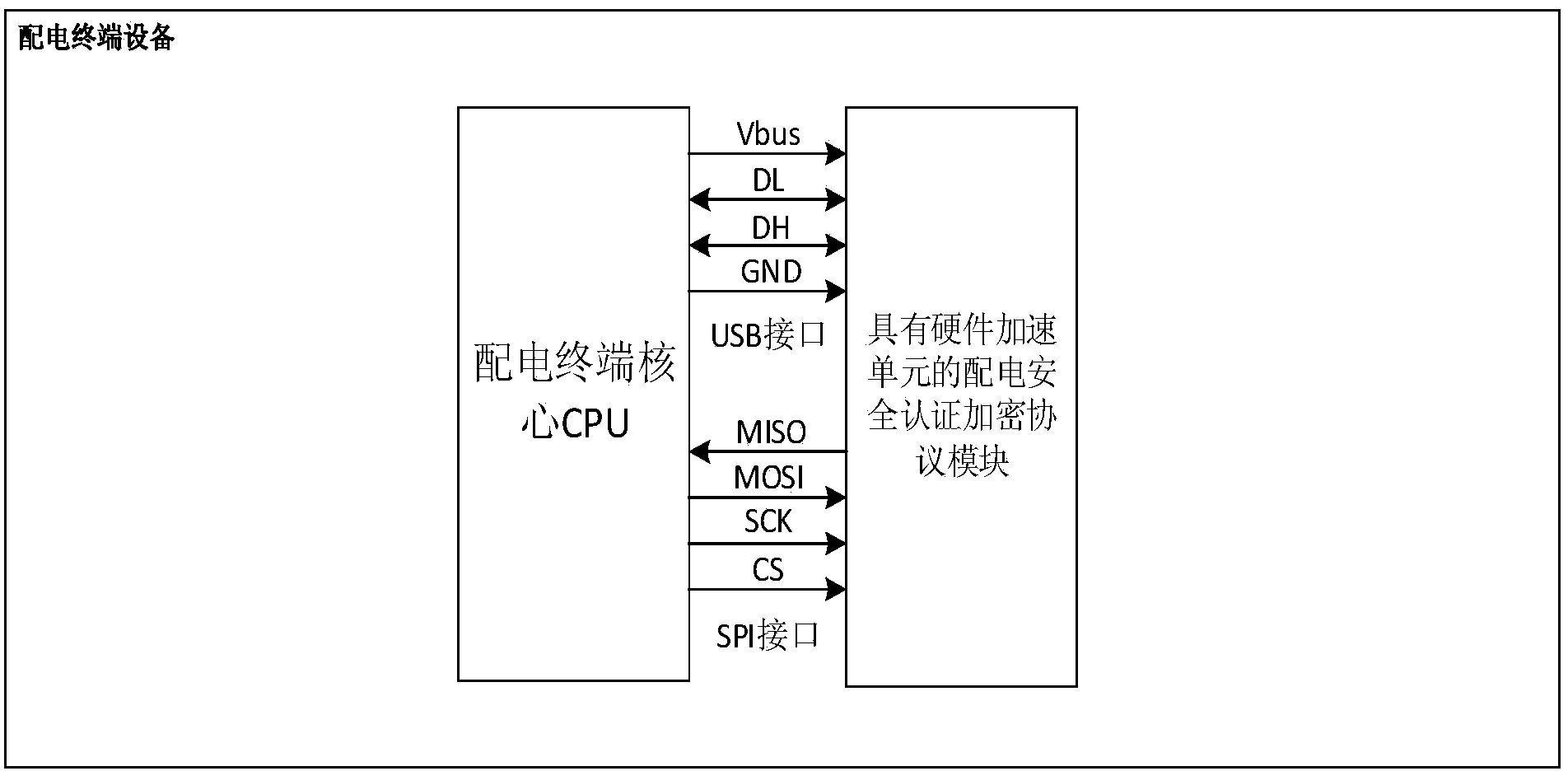
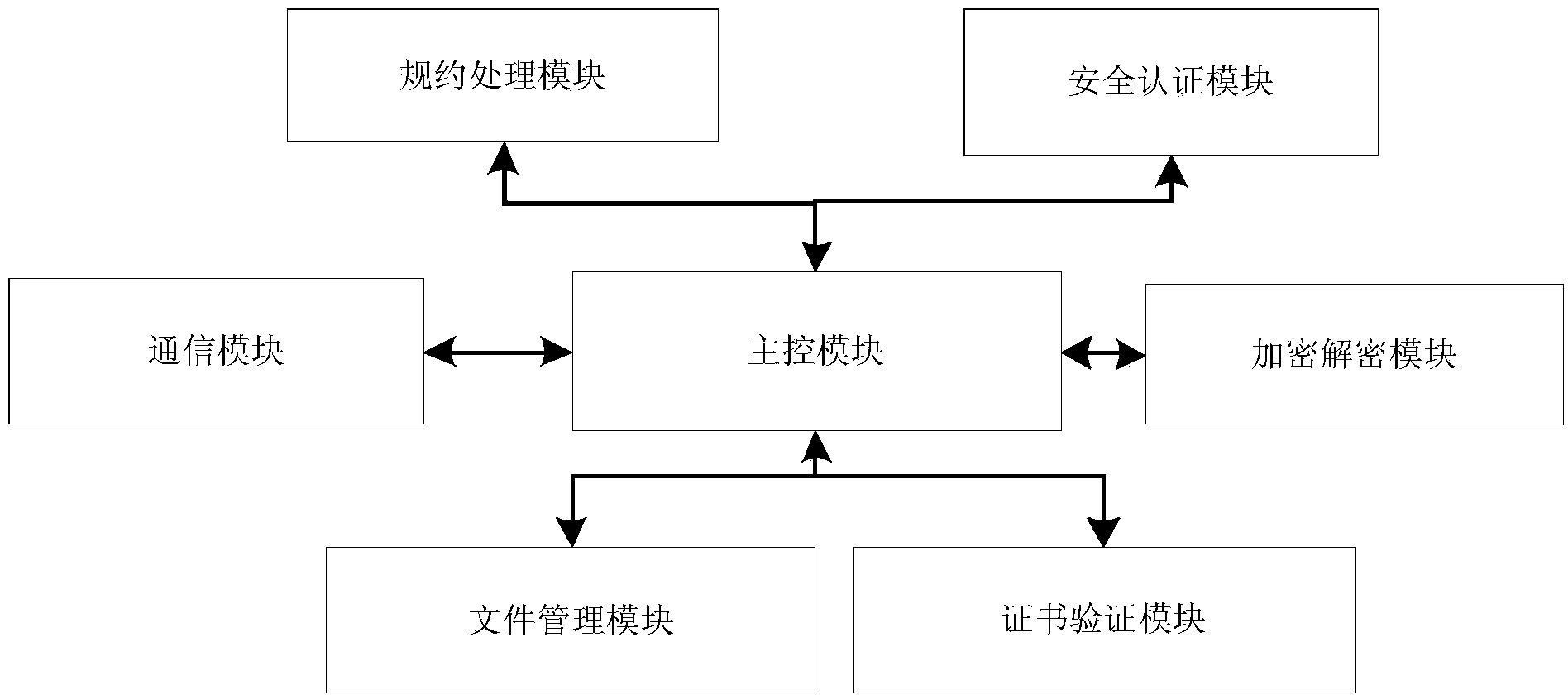
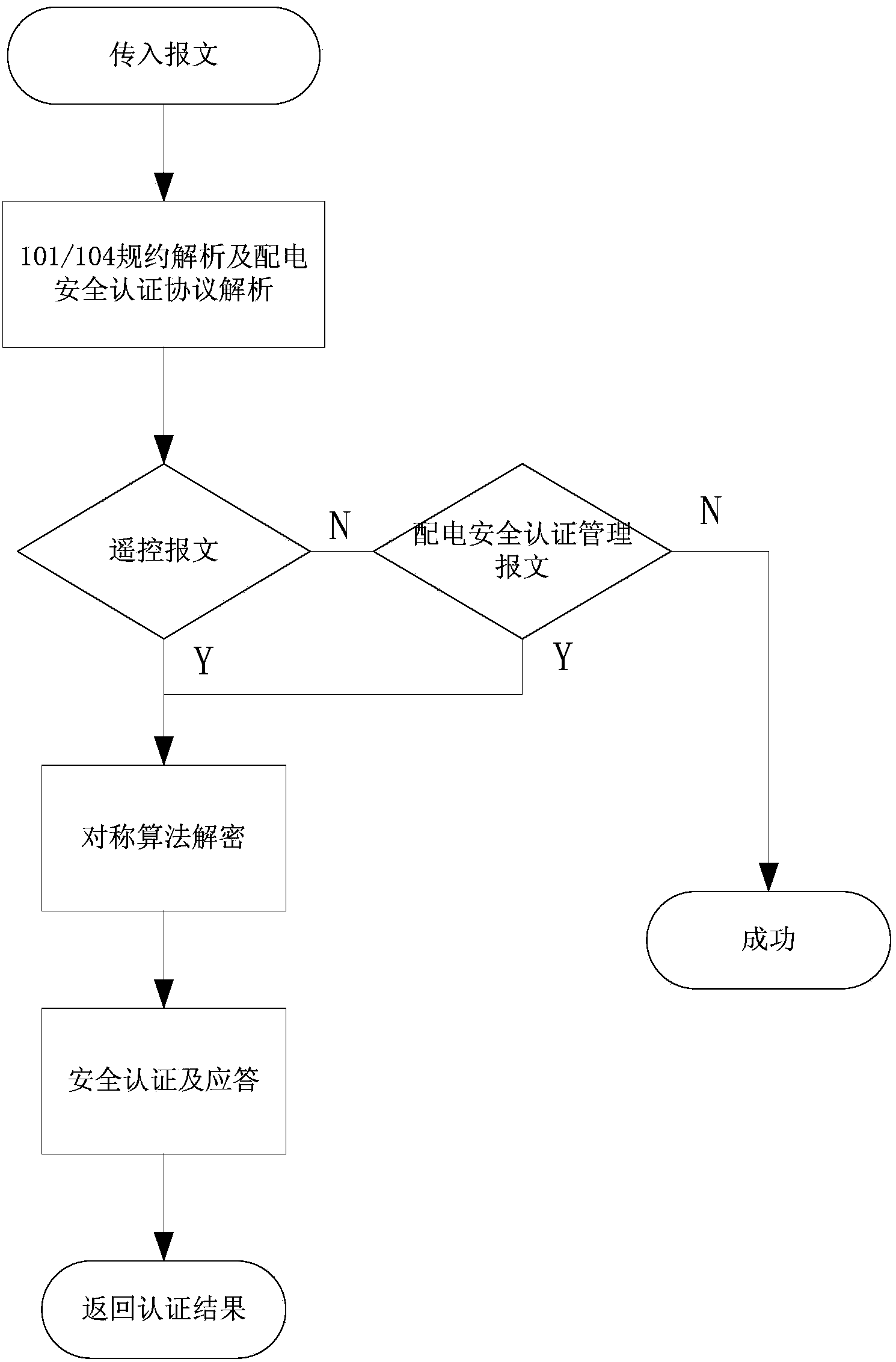
Distribution safety authentication device and method
InactiveCN103888444AImplement parsingAchieve effectivenessCircuit arrangementsUser identity/authority verificationRemote controlEncryption decryption
The invention discloses a distribution safety authentication device and a method. The distribution safety authentication device comprises a communication management module, a protocol parsing module, a safety authentication module, a file management module, a certificate verification module and a master control module. The communication module receives messages and transmits the messages to the protocol parsing module for parsing the protocol; and the parsed message is transmitted to the safety authentication module after decryption processing by the decryption module; the safety authentication module performs safety authentication on the decrypted message. If the transmitted message is a distribution safety management message, the certificate authentication module is invoked to perform validity versification on the certificate, and if the message is a remote control message, the master control module returns response information according to the authentication result after validity verification. The invention integrates a distribution safety authentication decrypted protocol, realizes parsing of the protocol and validity verification, and provides unified, easy, highly efficient and reliable distribution safety authentication service to the distribution terminal.
Owner:STATE GRID CORP OF CHINA +3
Authentication of encrypted data blocks
ActiveUS20130301827A1Improve efficiencyFast rateSecret communicationSecuring communicationChecksumComputer science
An authentication-encryption unit provides at least one encryption element, where each encryption element encrypts a plain-data block and accordingly generates a cipher-data block. A common checksum is calculated over each cipher-data block. It is possible to select via a selection unit in each encryption element which data bits in each cipher-data block are to be used to calculate the common checksum.
Owner:ROHDE & SCHWARZ GMBH & CO KG
Authenticated encryption device, authenticated encryption method, and program for authenticated encryption
ActiveUS20160173276A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextAlgorithm
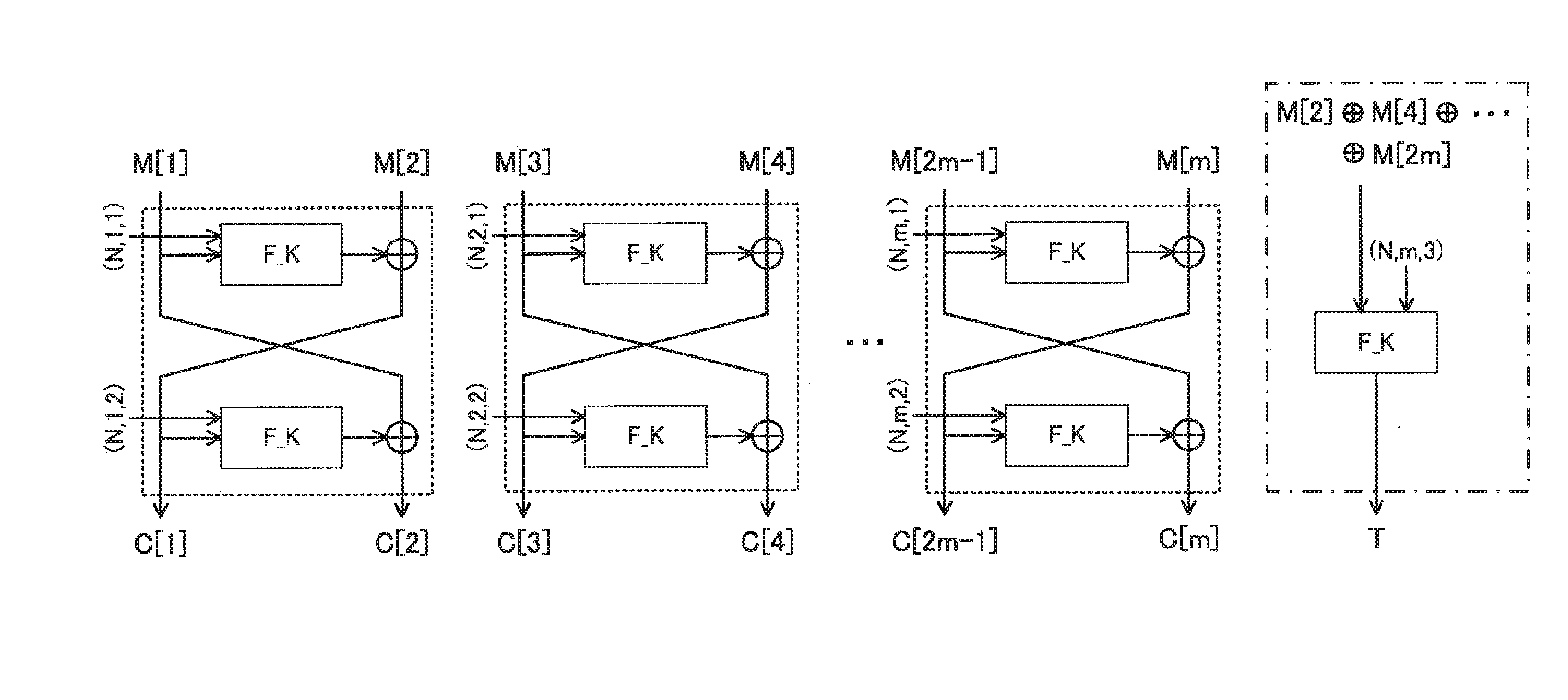
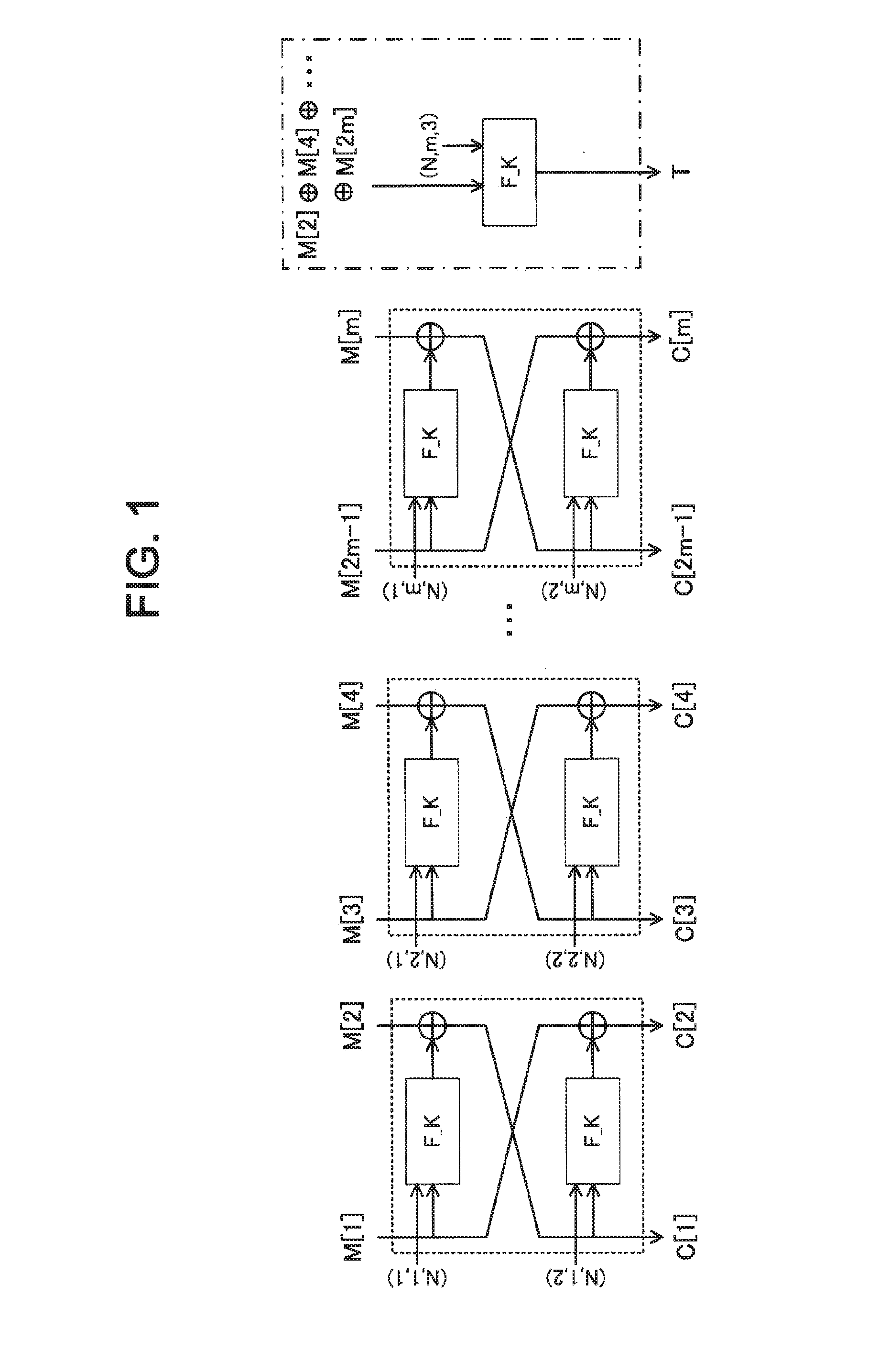
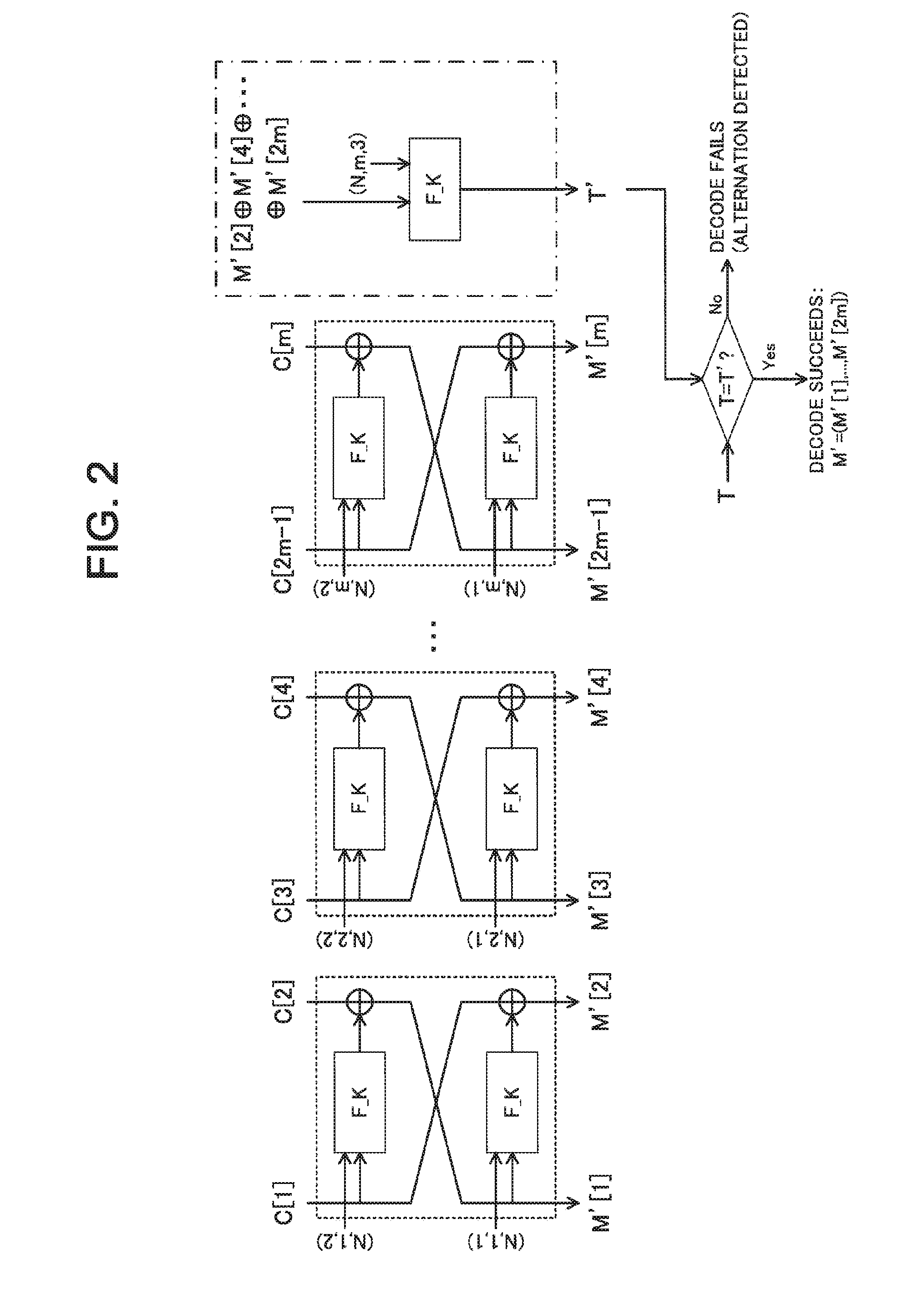
To achieve one-pass and one-rate authenticated encryption capable of performing parallel processings and totally performing encryption and decode processings by only one encryption function. An authenticated encryption device comprises an authenticated encryption means for applying a two-round Feistel structure using an encryption function assigned with an auxiliary variable for a round function per two blocks to an input plaintext or encrypted text thereby to generate an encrypted text or decoded plaintext. The authenticated encryption means finds an encrypted text chunk CC[i]=(C[i_1], C[i_2]) corresponding to an i-th plaintext chunk MC[i]=(M[i_1], M[i_2]) when dividing a plaintext into chunks per two blocks as:C[i_1]=F_K((N,Tw_i_1),M[i_1]) xor M[i_2],C[i_2]=F_K((N,Tw_i_2),C[i_1]) xor M[i_1].
Owner:NEC CORP
Cloud Storage Encryption With Variable Block Sizes
ActiveUS20190013936A1Key distribution for secure communicationDigital data protectionPlaintextManagement tool
Techniques are disclosed for securing data in a cloud storage. Plaintext files are stored as secured, encrypted files in the cloud. The ciphering scheme employs per-block authenticated encryption and decryption. A unique file-key is used to encrypt each file. The file-key is wrapped by authenticated encryption in a wrapping-key that may be shared between files. A centralized security policy contains policy definitions which determine which files will share the wrapping-key. Wrapping-keys are stored in a KMIP compliant key manager which may be backed by a hardware security module (HSM). File metadata is protected by a keyed-hash message authentication code (HMAC). A policy engine along with administrative tools enforce the security policy which also remains encrypted in the system. Various embodiments support blocks of fixed as well as variable sizes read / written from / to the cloud storage.
Owner:ZETTASET
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com