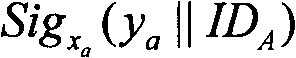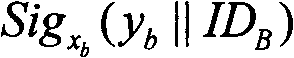Authenticated encryption method and encryption system based on symmetric encryption
A technology for authentication encryption and authentication information, applied in user identity/authority verification and key distribution, which can solve the problems of inability to publicly verify signatures by third parties, inability to resist forgery attacks by message receivers, and low security, so as to ensure reliability and reliability. Integrity, small amount of computation, improved effect of transmission cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
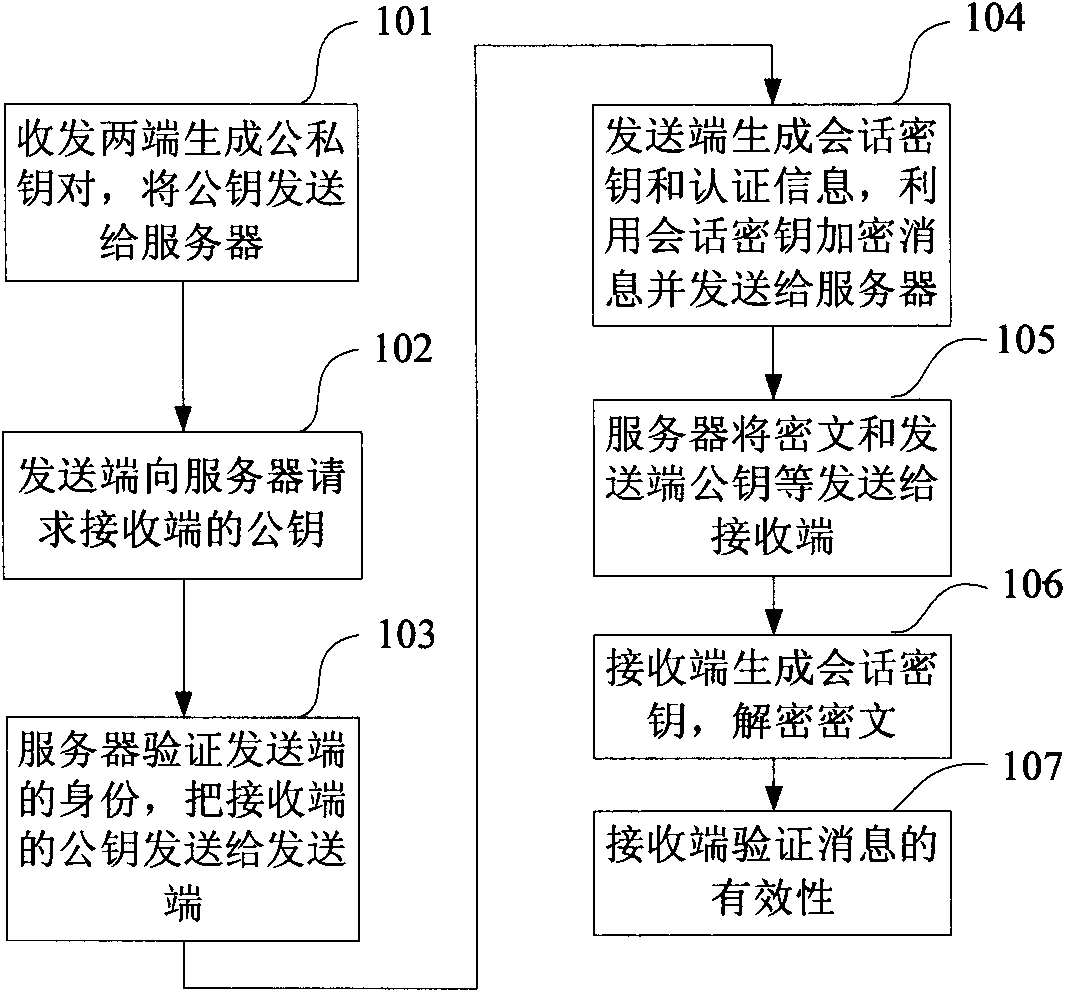
[0019] The invention proposes an authentication encryption method and system based on symmetric encryption and message recoverable signature technology. Specifically include the following steps.
[0020] Step A: The sending end and the receiving end automatically generate public and private keys, and send the public key and their corresponding identities to the server;
[0021] Step B: The sending end receives the public key of the receiving end through the server, the key generation unit of the sending end generates the session key of the sending end according to the public key of the receiving end and the selected random number, and the encryption unit uses the session key of the sending end to pair the message to be sent Encrypt, and use the selected random number, the message to be sent and its own private key to generate authentication information, and the sending unit sends the encrypted message and authentication information to the receiving end through the server;
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com