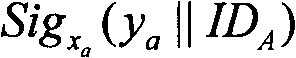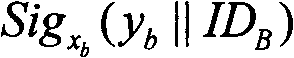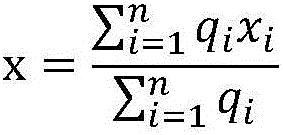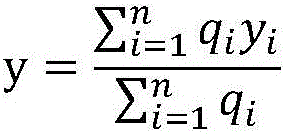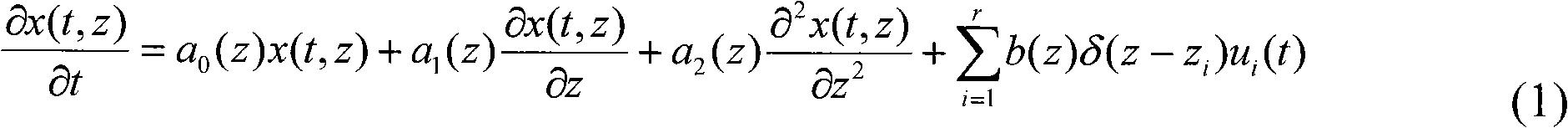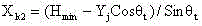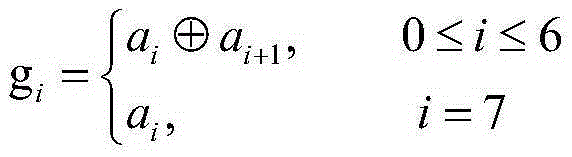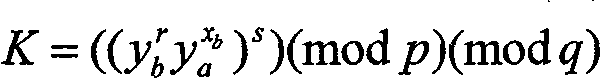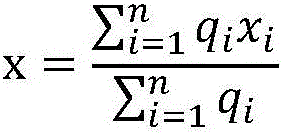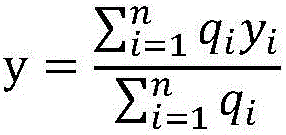Patents
Literature
53results about How to "Optimize the total calculation amount" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
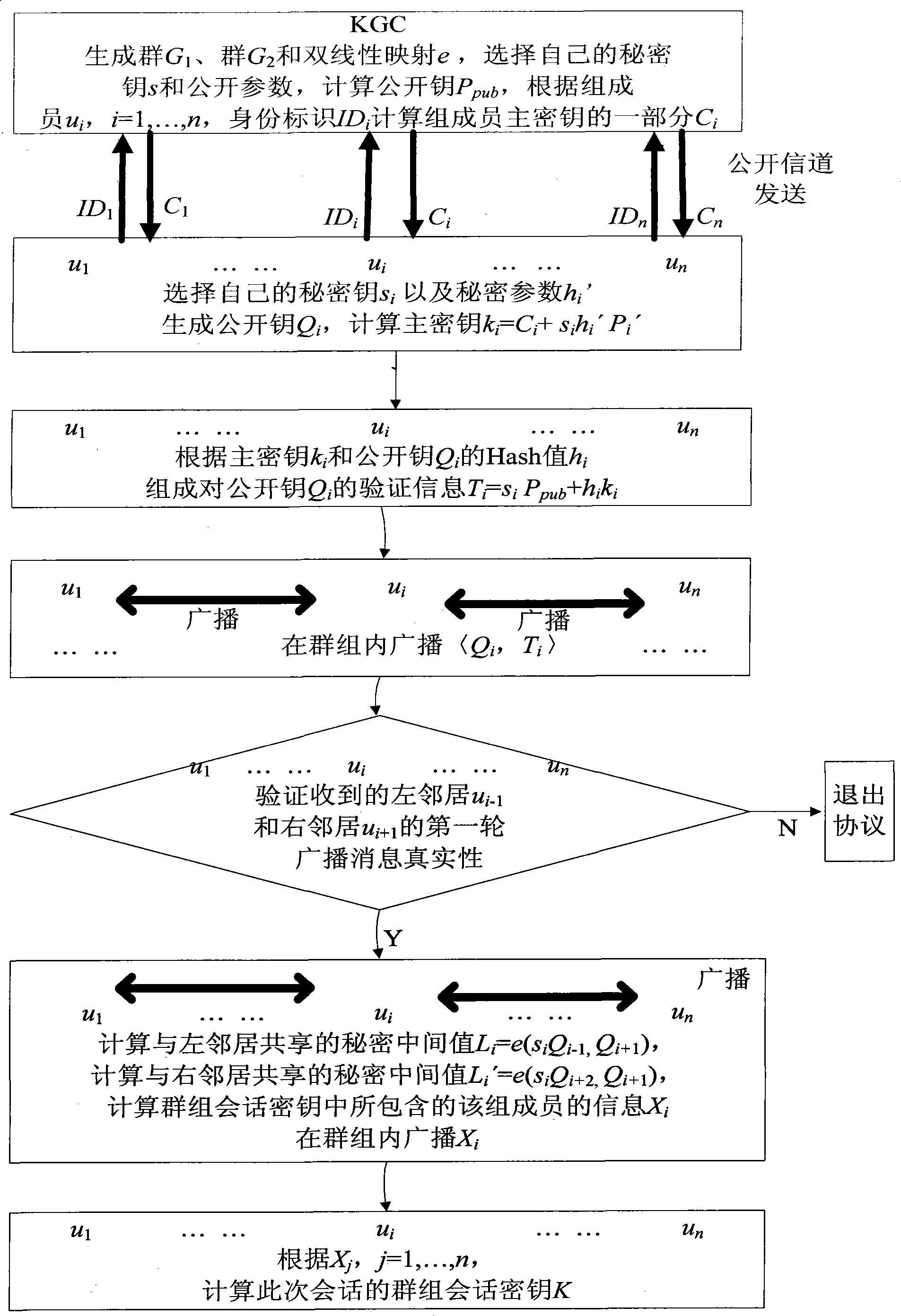
Authentication group key management method based on identity
InactiveCN101431414AAvoid hostingSolve tough problemsKey distribution for secure communicationUser identity/authority verificationGroup sessionKey escrow
The present invention discloses a identity-based authentication group key management method which comprises the following steps: embedding ID into key with bilinear pairing in elliptic curve; generating Ci as part of main key ui according to the secret key and ID of group member ui by key generating center, and transmitting the Ci to ui through overt channel; generating main key according to Ci and its own secret key by each group member ui; calculating overt key verification information according to Hash value of main key and over key by each group member, and broadcasting the link between over key and verification information inside the group; calculating the secret value sharing with left and right neighbors when the received information is verified to be true by each group member, and calculating the group member information Xi included in group session key according to the secret value, and then broadcasting the Xi inside the group; calculating group session key K according to all Xj, j=1, ...,n, by each group member. The invention has the advantages of no key escrow and no need of secure channel, which can be applied in coordination and distributed network as secure reliable group communication.
Owner:XIDIAN UNIV
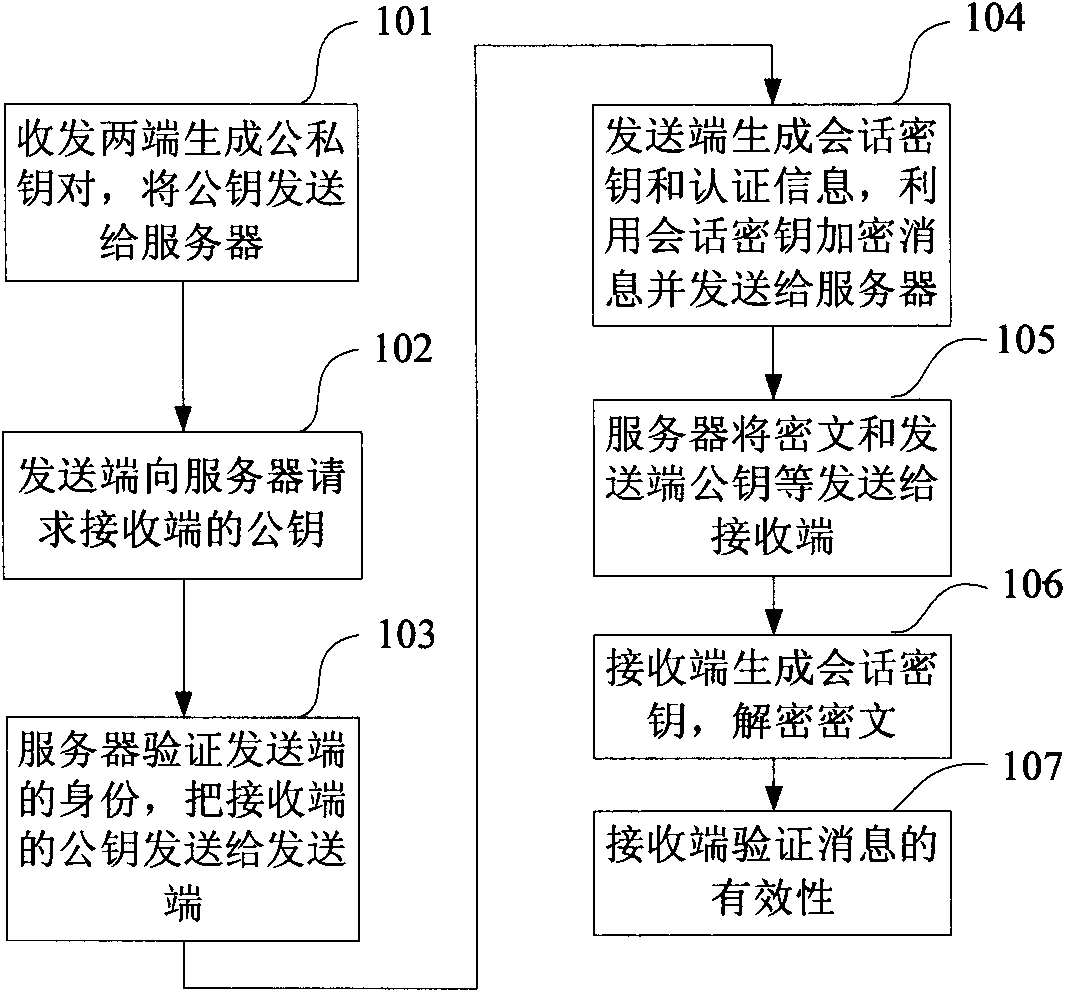
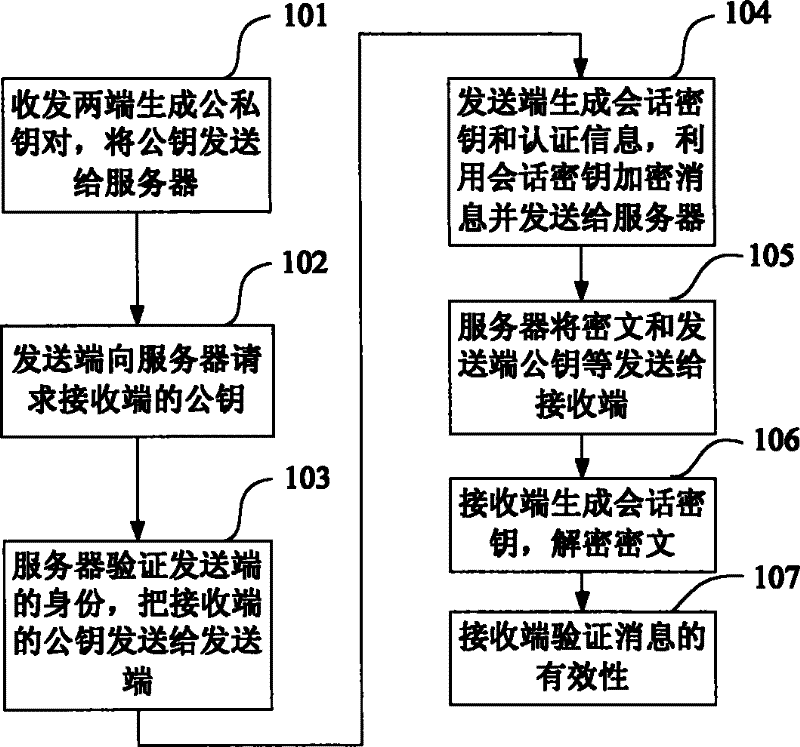
Authenticated encryption method and encryption system based on symmetric encryption
InactiveCN101667913AAchieve authenticationImplement encryptionKey distribution for secure communicationUser identity/authority verificationThird partyCommunications security
The invention discloses an authenticated encryption method and a system, relating to the field of communication security. The restorable signature of a message and the symmetric encryption technologyare combined; a commitment value which only can be calculated by a designated message receiving end is used as a session key encryption message; and the message receiving end validates the validity ofthe message by the restorable signature, thus realizing encryption and authentication in one logical step. A key generation unit of a sending end generates a session key of the sending end; an encryption unit encrypts a message to be sent; the receiving end generates a session key of the receiving end; a decryption unit utilizes the session key of the receiving end to decrypts the encrypted message; and the authentication and confirmation message is generated according to the decrypted message, thus validating the validity of the message. When disputes occur, the message receiving end transforms the authenticated and encrypted message signature into a common signature so as to lead a third party to validate the validity of the signature. The invention has the advantages of high security,low calculated amount and transmission cost, and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
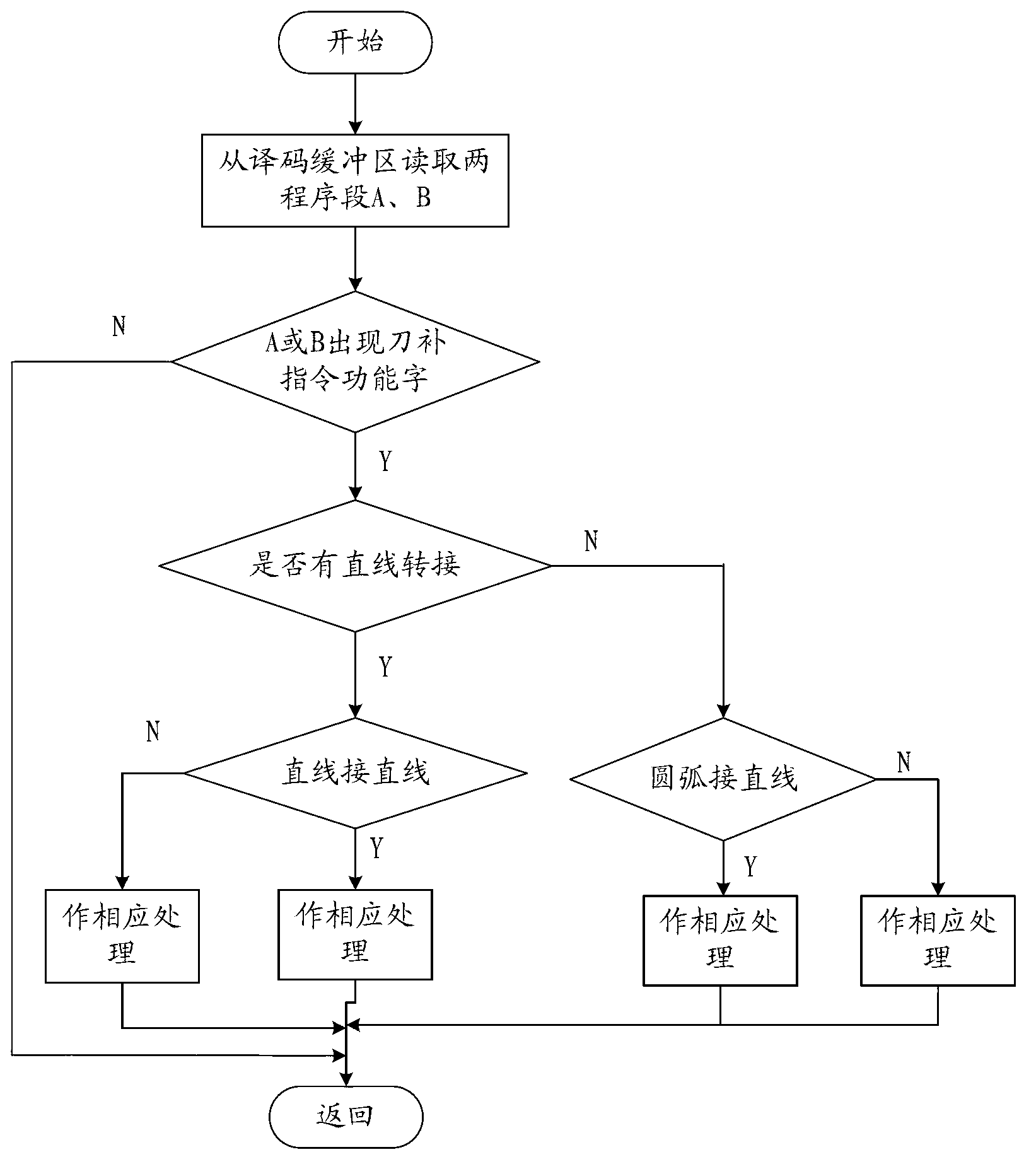
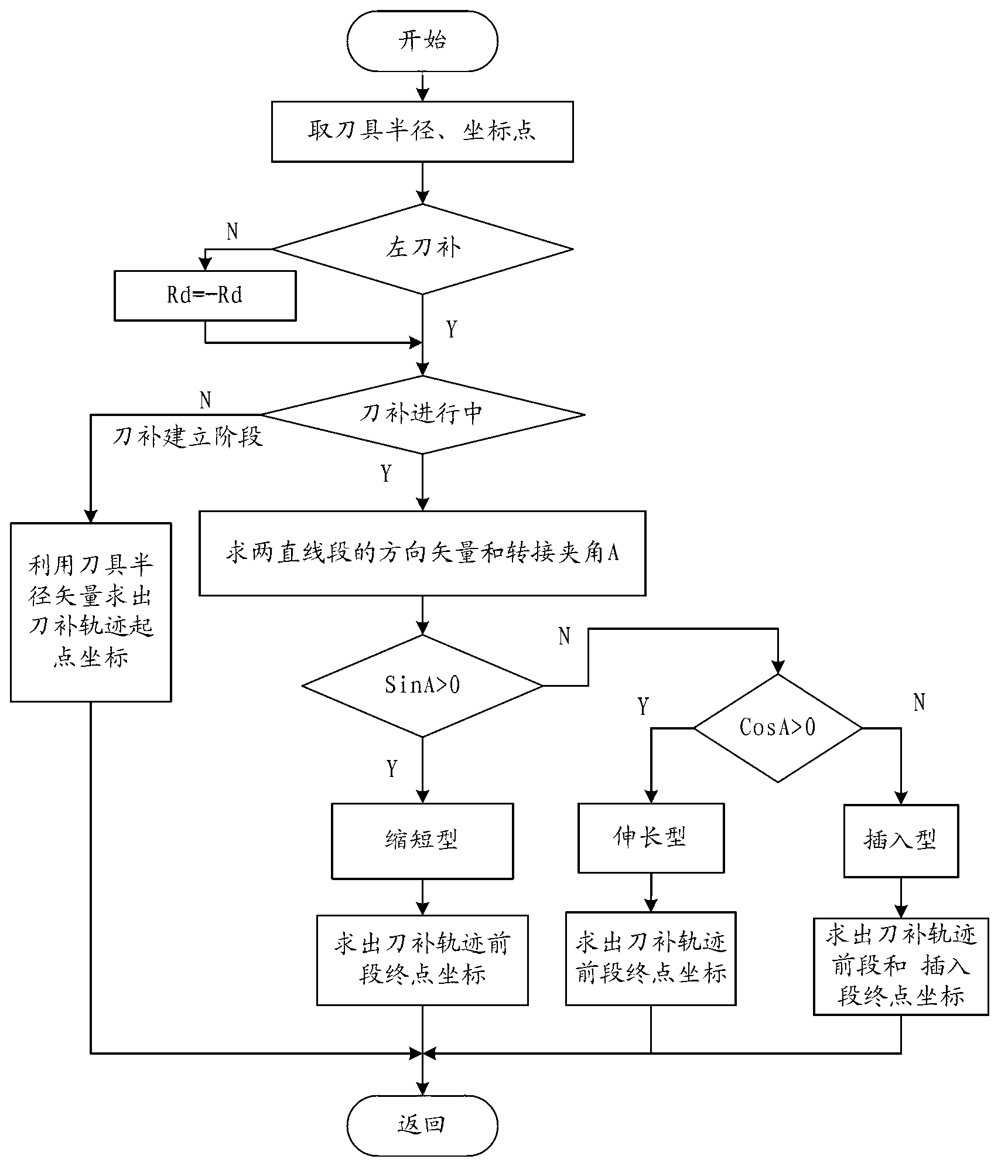
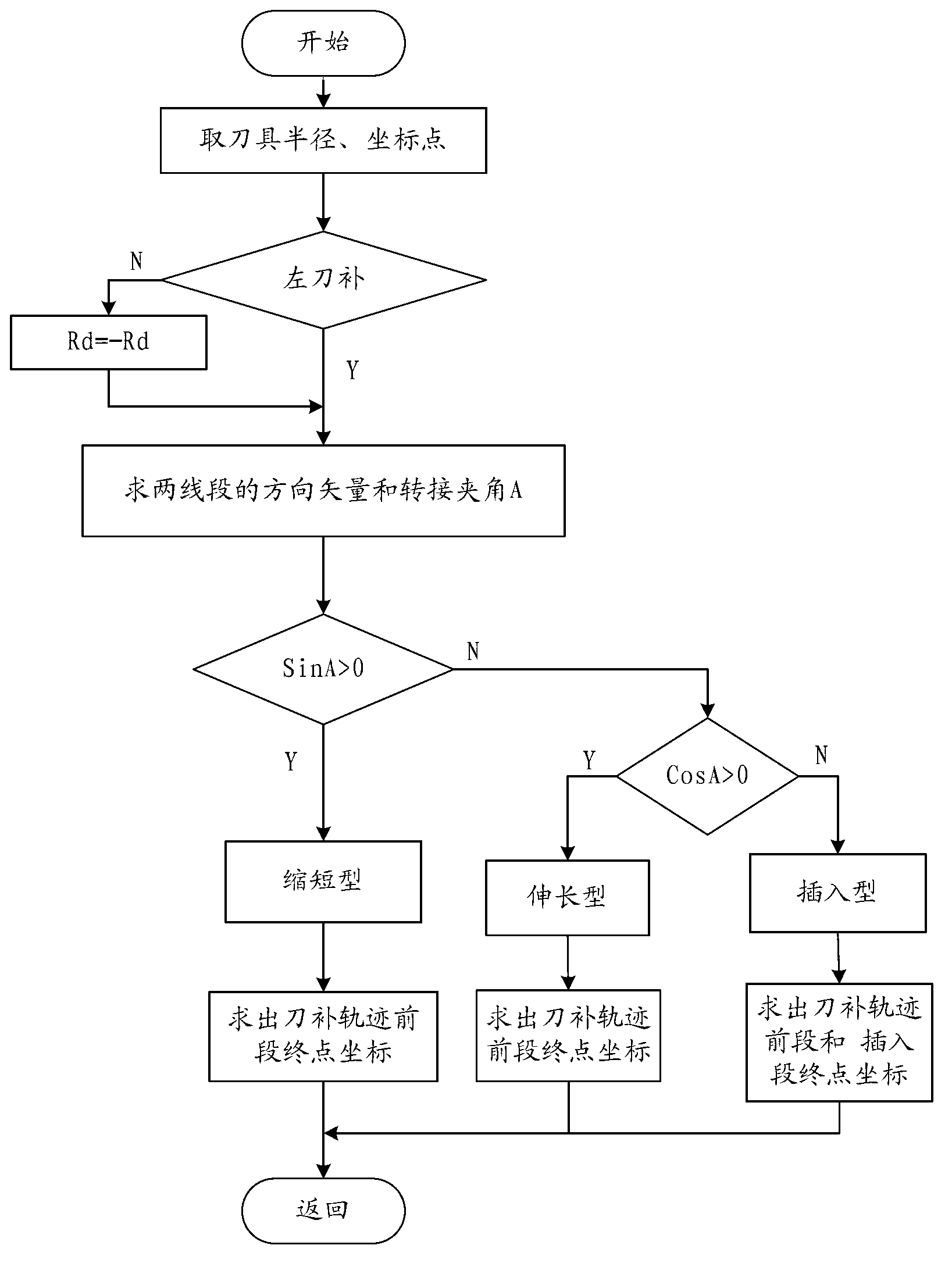
Numerical control system-based tool radius compensation vector calculating method
InactiveCN103076761AHigh feasibilityOptimize the total calculation amountProgramme controlComputer controlComputer scienceCalculation methods
The invention provides a numerical control system-based tool radius compensation vector calculating method which comprises the steps of: judging different switching-over types through analyzing the distribution condition of a vector angle of a tangent line on the switching-over point of a processing segment on a plane coordinate system, and calculating the coordinate point after cutter compensation according to a specific computing method; analyzing the processing segment according to the information of the tool radius, the cutter compensation direction and a workpiece outline coordinate point and the like after collecting and processing the information of a to-be-processed workpiece, calculating vectors of two tangent lines on the switching-over point, and obtaining a switching-over angle of two straight lines according to the vectors of the two tangent lines, drawing the distribution condition of the switching-over angle in the plane coordinate system, and judging the switching-over type of the two straight lines so as to figure out coordinates of the switching-over point by adopting a vector calculating method; and sending information of the coordinates to a numerical control system for next step of interpolation. The numerical control system-based tool radius compensation vector calculating method has the advantages of being simple in calculating method and small in calculating quantity, and being beneficial to the realization of programming especially for the calculation of the switching-over point, thereby increasing the processing efficiency.
Owner:FUJIAN UNIV OF TECH
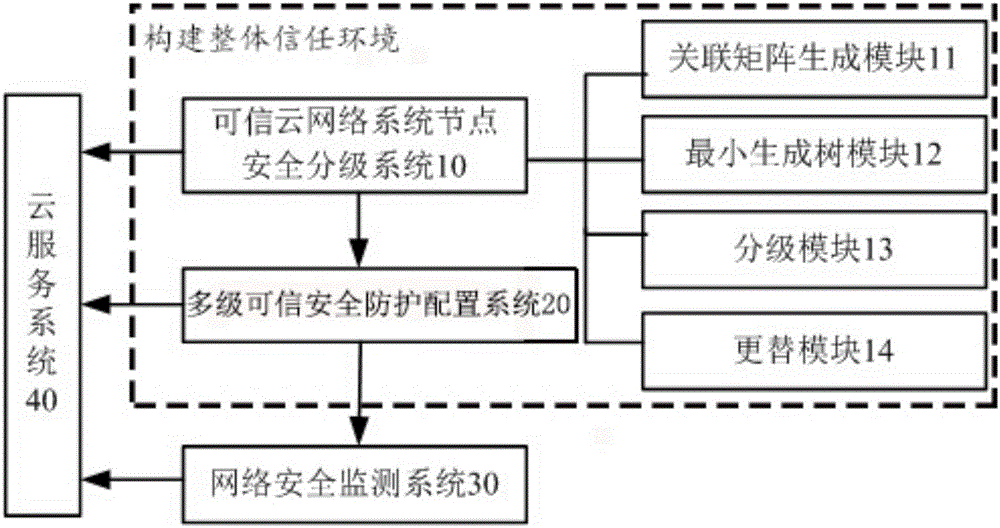
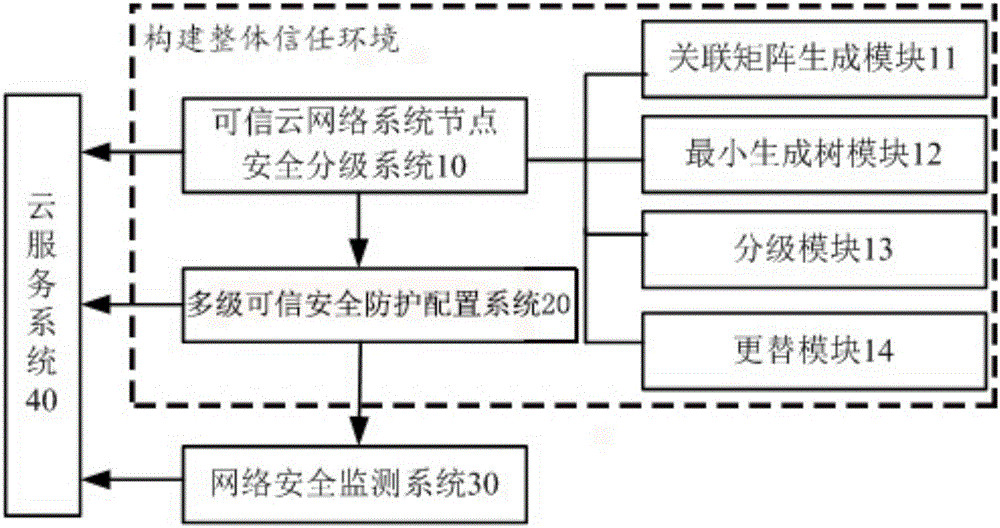
Big data security protection cloud system based on trusted calculation
InactiveCN105933361ATimely collectionOptimize the total calculation amountTransmissionTrusted ComputingBig data security
The invention discloses a big data security protection cloud system based on trusted calculation. The big data security protection cloud system constructs a security configuration system based on a trusted security grading system and minimal trees on the basis of systems having security grading functions and trusted security configuration functions, and provides a trusted calculating environment for the security protection of information through the cooperation with a security network monitoring system. The trusted protection cloud system starts from the acquisition and security grading of basic data, divides the network nodes into four different security grades by calculating the importance values of the network nodes, and constructs an integral trusted environment, and by means of the security grading configuration with high credibility, the trusted security of information security and protection is guaranteed, the data cannot be acquired randomly, and a good balance between the calculated quantity and trusted security configuration is achieved.
Owner:GUANGXI POWER GRID CORP
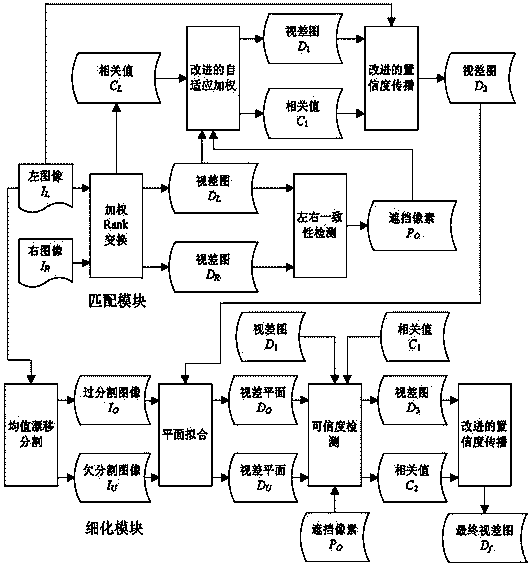
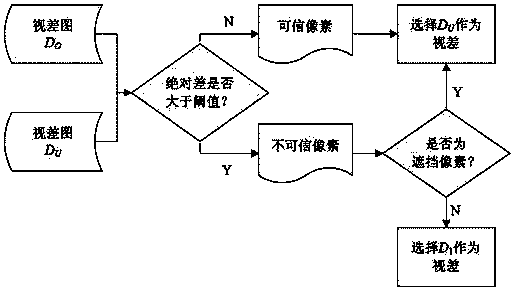
Parallax estimation method based on improved adaptive weighted summation and belief propagation
InactiveCN104166987AReduce mismatchImprove quality and efficiencyImage analysisGlobal optimizationBelief propagation
The invention discloses a parallax estimation method based on improved adaptive weighted summation and confidence propagation, belonging to the computer stereo visual sense technology field. The invention solves the problems that matching accuracy of the parallax calculated by the current matching algorithm in the shielding area and depth discontinuous area is low, that the high accuracy matching algorithm has heavy calculation quantity, that the implementation is poor, and the refinement method parallax plane estimation based on the segmentation is not accurate. The parallax estimation method comprises steps of computing correlated values among matching pixels by utilizing the weight class changing method, performing matching on shielding pixels afresh through improving the adaptive weight method, using the improved confidence propagation algorithm to perform global optimization on a disparity map, using a refinement module to perform refinement on the disparity map, and utilizing the improved confidence propagation algorithm again and the correlated value and the disparity map to perform global optimization. The invention can be applied in segmentation of the stereo image, encoding of the stereo video, robot vision, target tracking, etc.
Owner:HARBIN NORMAL UNIVERSITY
A combined detection method for decreasing complexity in mobile communication system
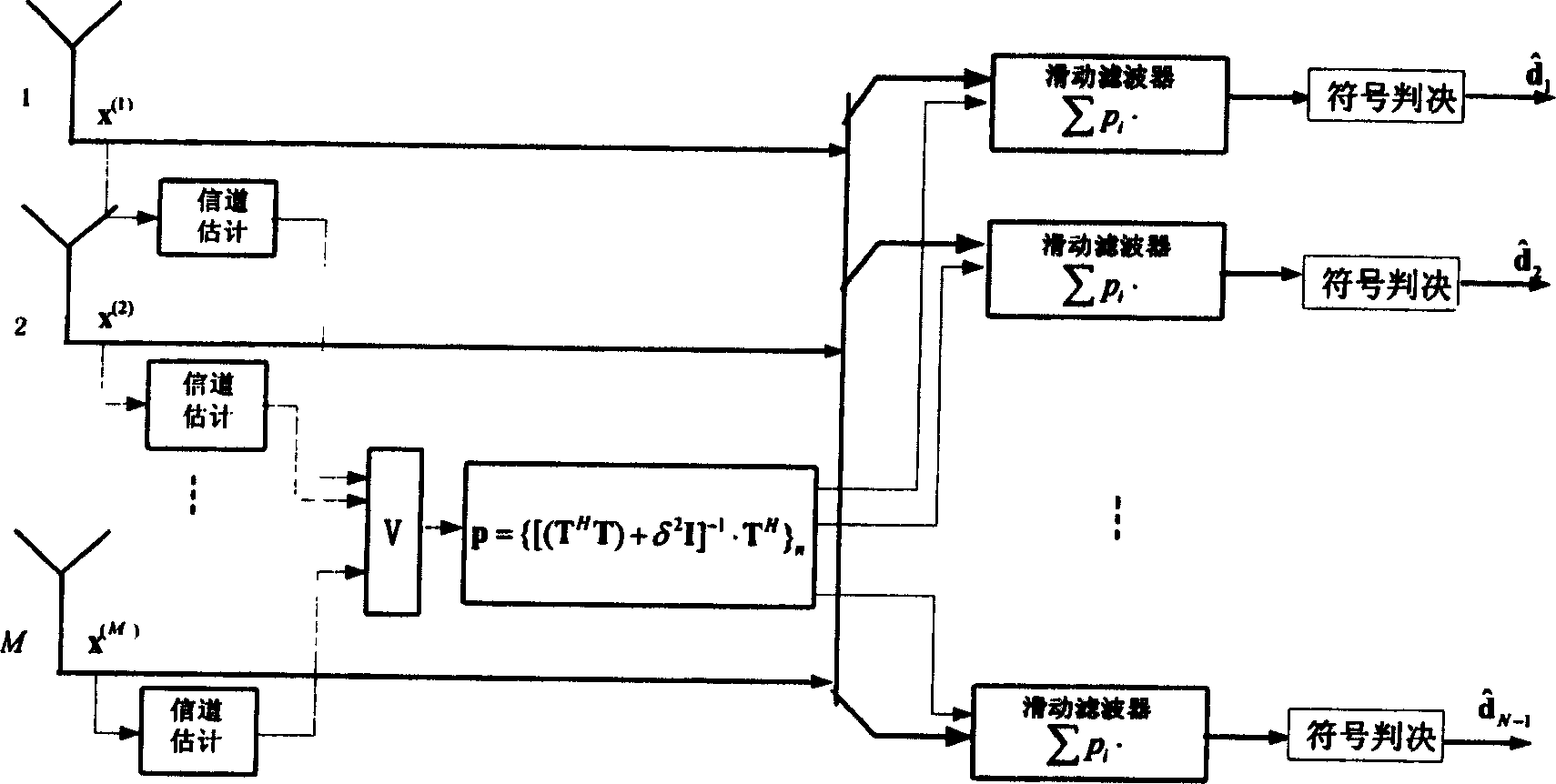
InactiveCN1595825AHeavy calculationOptimize the total calculation amountSpatial transmit diversityCode division multiplexFir systemTD-SCDMA
The invention is a combined detecting method of reducing complexity in mobile communication system, including the steps: processing the signal received by array antenna by sampling, A / D conversion, etc, and then sending the data to a base band processing part for base-band digital processing; according to TD-SCDMA time gap structure, a user training sequence in the middle of the time gap is known, and using the user training sequence to make channel estimation so as to compose a system matrix; according to the block characteristic of TD-SCDMA system matrix, inverting a small matrix composed of blocks on principal and minor diagonals to stand for the system matrix inverse, making slide filtration on the received data and thus able to find a corresponding transmitted data. It has not great quantity of calculation on the conduction of obtaining relatively good code error ratio, easy to implement in engineering.
Owner:ZTE CORP
Wireless transmitter recognition method based on multi-core double-channel network
ActiveCN111050315AGood performanceSimplified Computational ComplexityCharacter and pattern recognitionNeural architecturesPath networkChannel network
The invention discloses a wireless transmitter recognition method based on a multi-core double-channel network, and belongs to the field of electromagnetism. The method specifically comprises the following steps: firstly, performing power amplification on a modulation signal through a transmitter, transmitting the modulation signal to a receiver for sampling and receiving, performing statistical characteristic processing on a received signal to obtain a cyclic spectrum, and extracting a high peak density value in the cyclic spectrum as a characteristic; then, inputting all the characteristic values into a fully connected multi-core double-channel network module, learning the characterization characteristics of each transmitter from the cyclic spectrum, and fusing the obtained result unionsets; after a multi-core double-path network model is trained, the fused feature result is tested, and normalized feature vectors corresponding to all test features are obtained; and obtaining a probability value corresponding to each feature through a softmax classifier, and selecting the wireless transmitter with the maximum probability value as the final wireless transmitter to be identified and classified. According to the method, the calculation complexity is simplified, and the situation that the classification effect is not ideal due to noise interference is reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM
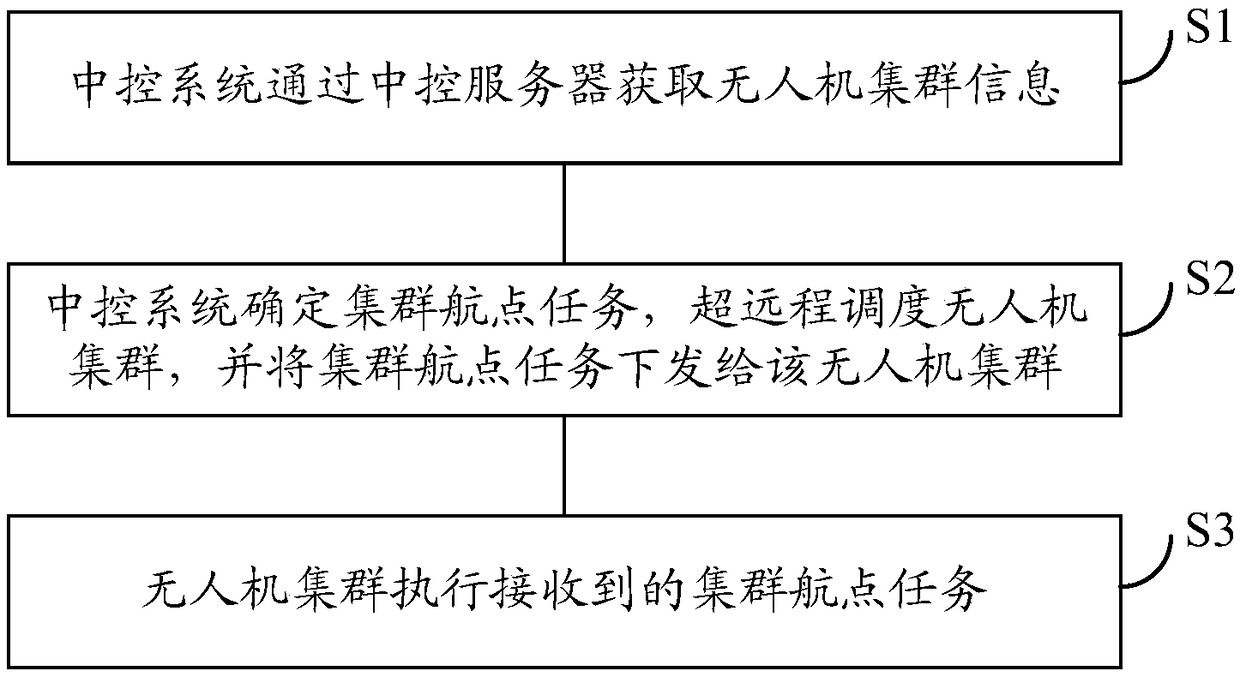
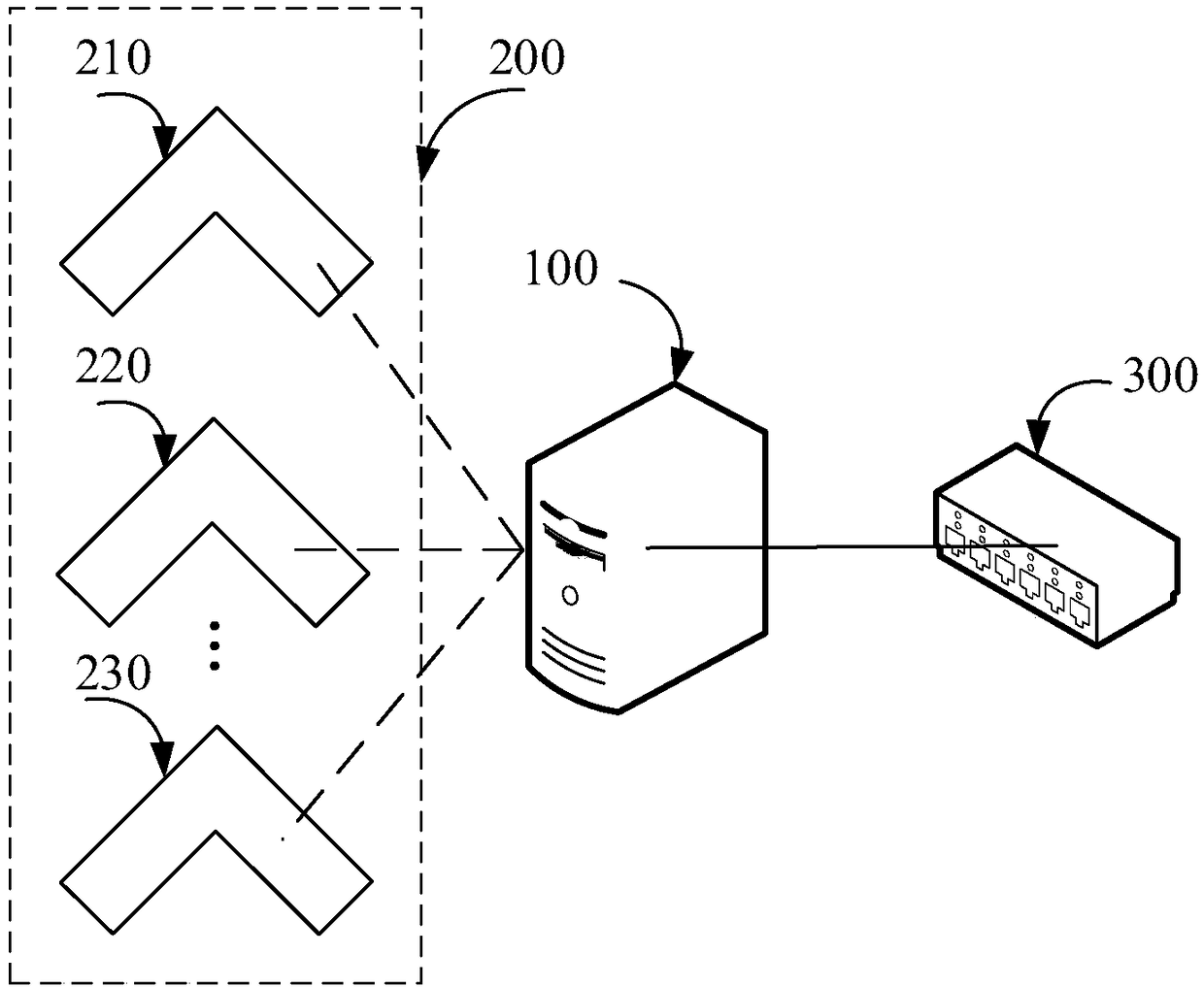
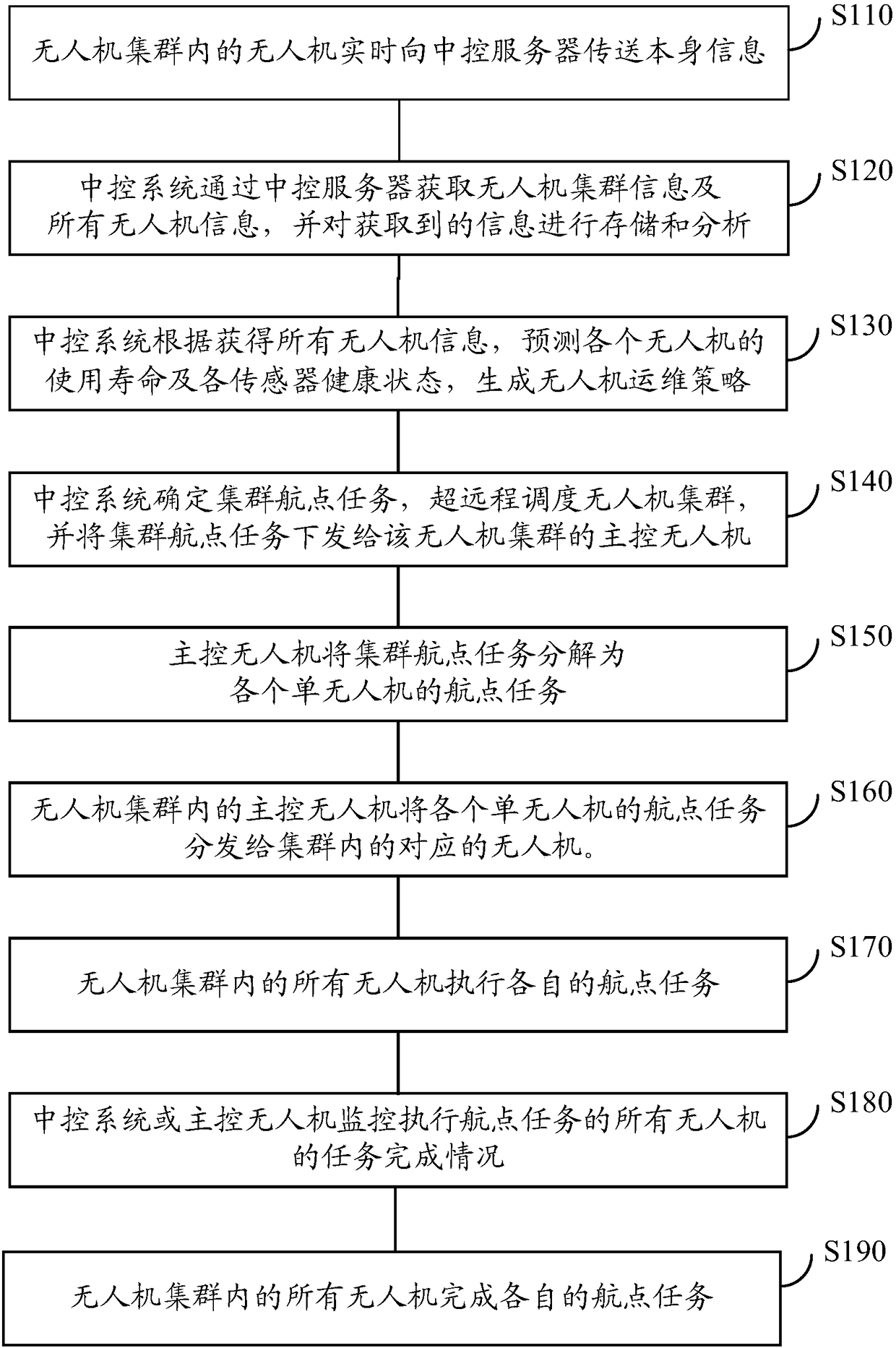
UAV(unmanned aerial vehicle) cluster scheduling method and computer storage medium
InactiveCN108490975AIncrease freedomImprove scheduling efficiencyPosition/course control in three dimensionsControl systemDegrees of freedom
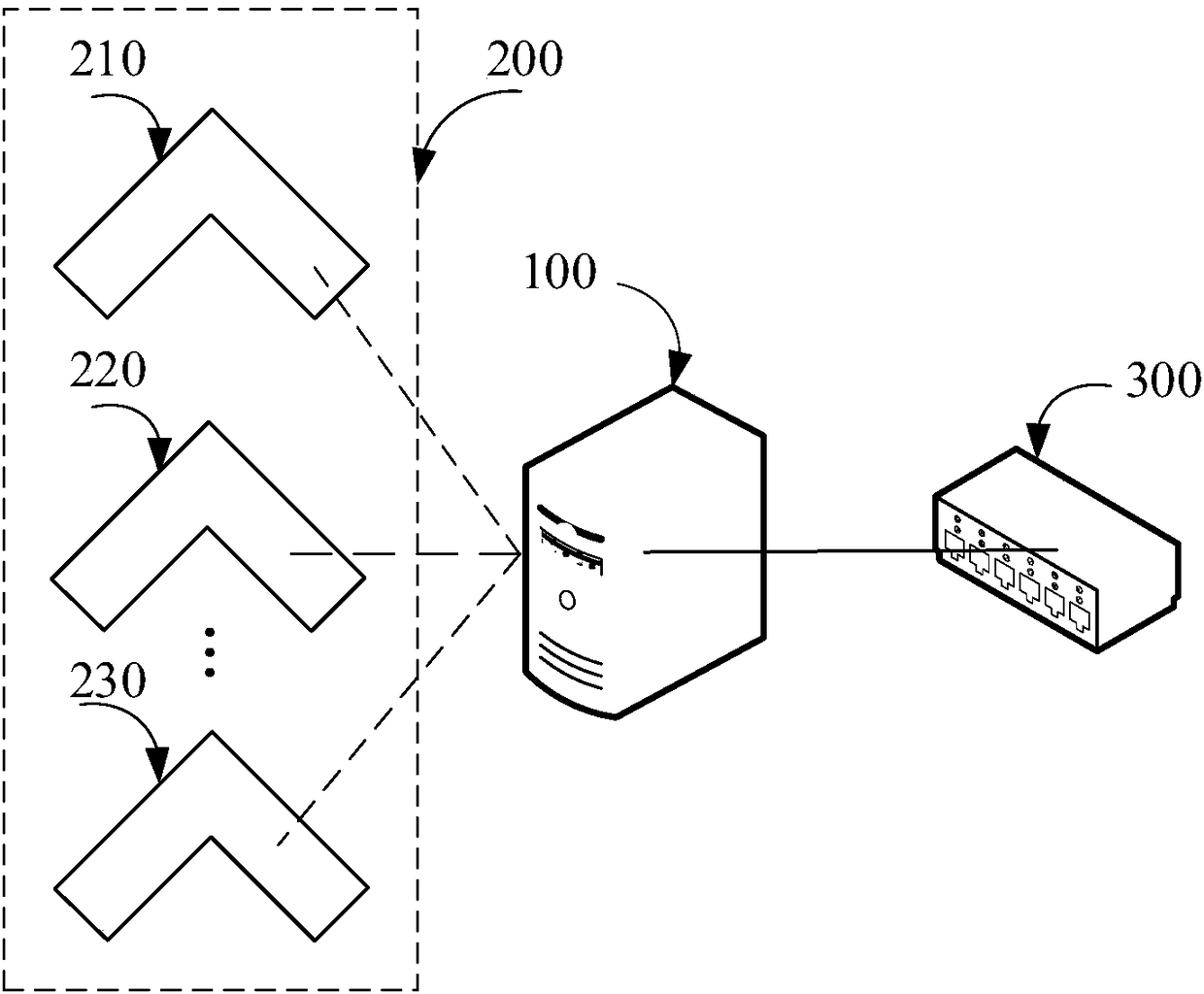
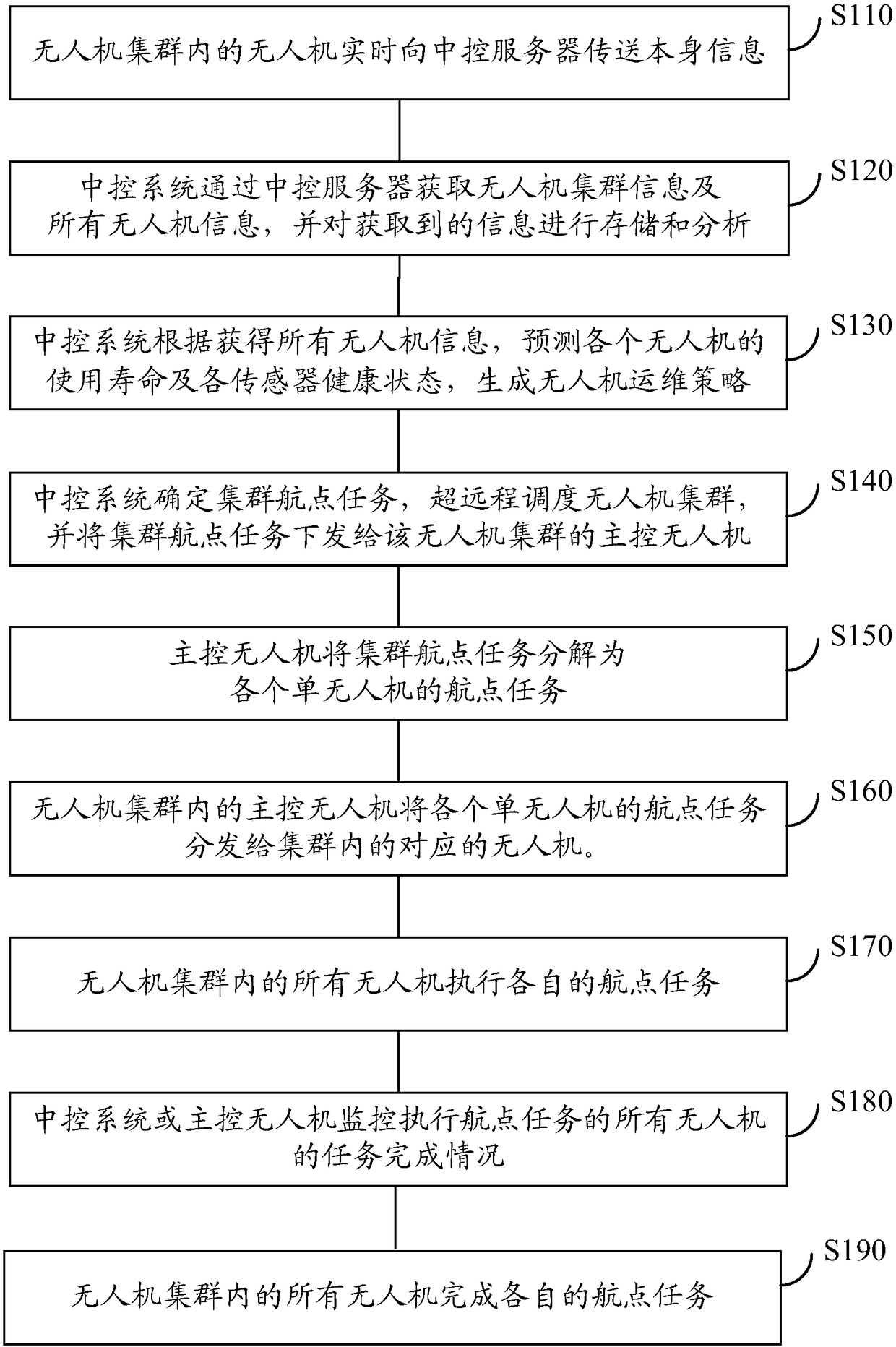
The invention discloses an UAV(unmanned aerial vehicle) cluster scheduling method and a computer storage medium, and belongs to the UAV field. The UAV (unmanned aerial vehicle) cluster scheduling method comprises the following steps: a central control system obtains UAV cluster information through a central control server; the central control system determines a cluster waypoint task, carries outultra-remote scheduling of a UAV cluster and sends the cluster waypoint task to the UAV cluster; and the UAV cluster executes the received cluster waypoint task. Since the cluster waypoint task is sent to the UAV cluster, and the UAV cluster decomposes the waypoint task, pressure of the central control server can be reduced, and meanwhile, greater flight degree of freedom can be provided for the UAV cluster, and scheduling efficiency of the UAV cluster is improved.
Owner:GUANGZHOU EHANG INTELLIGENT TECH
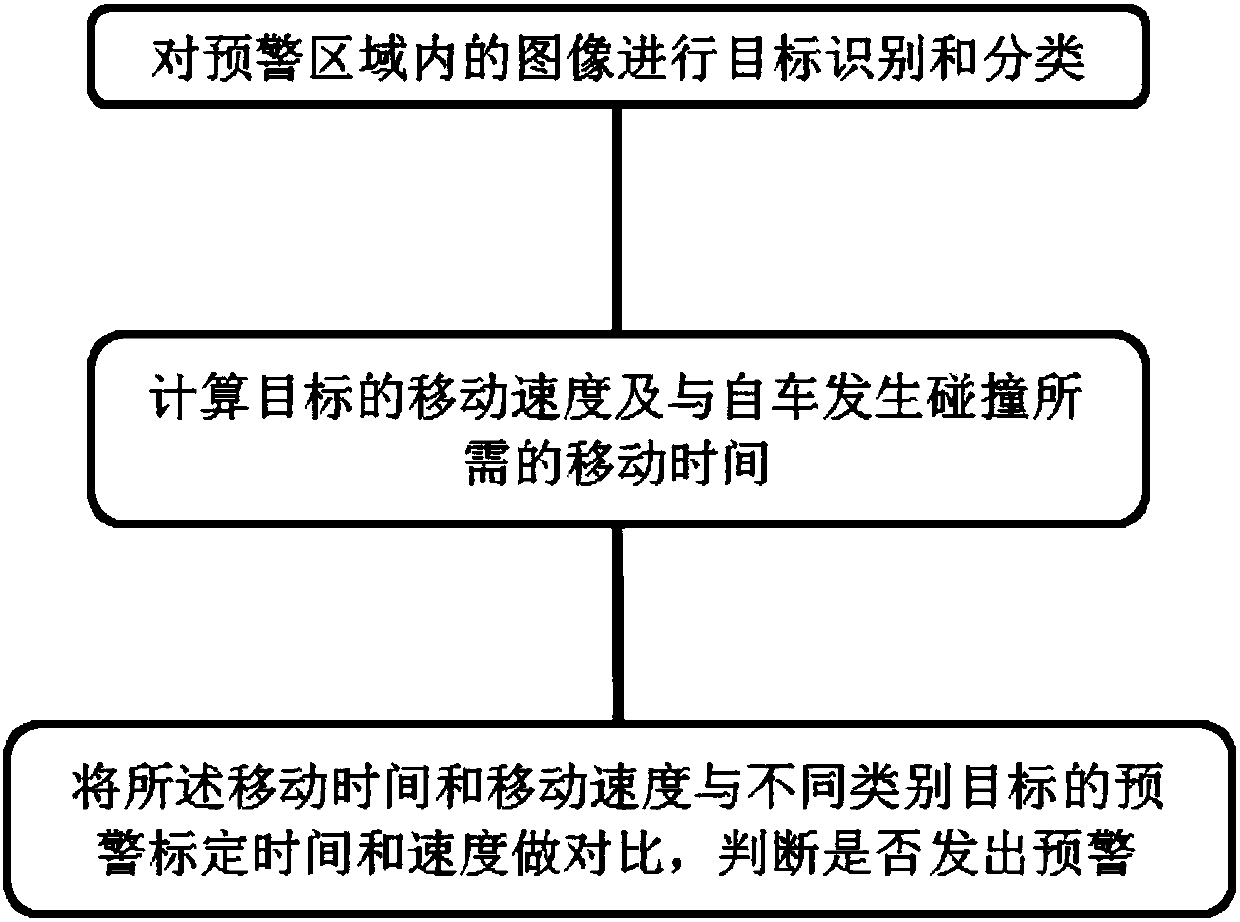
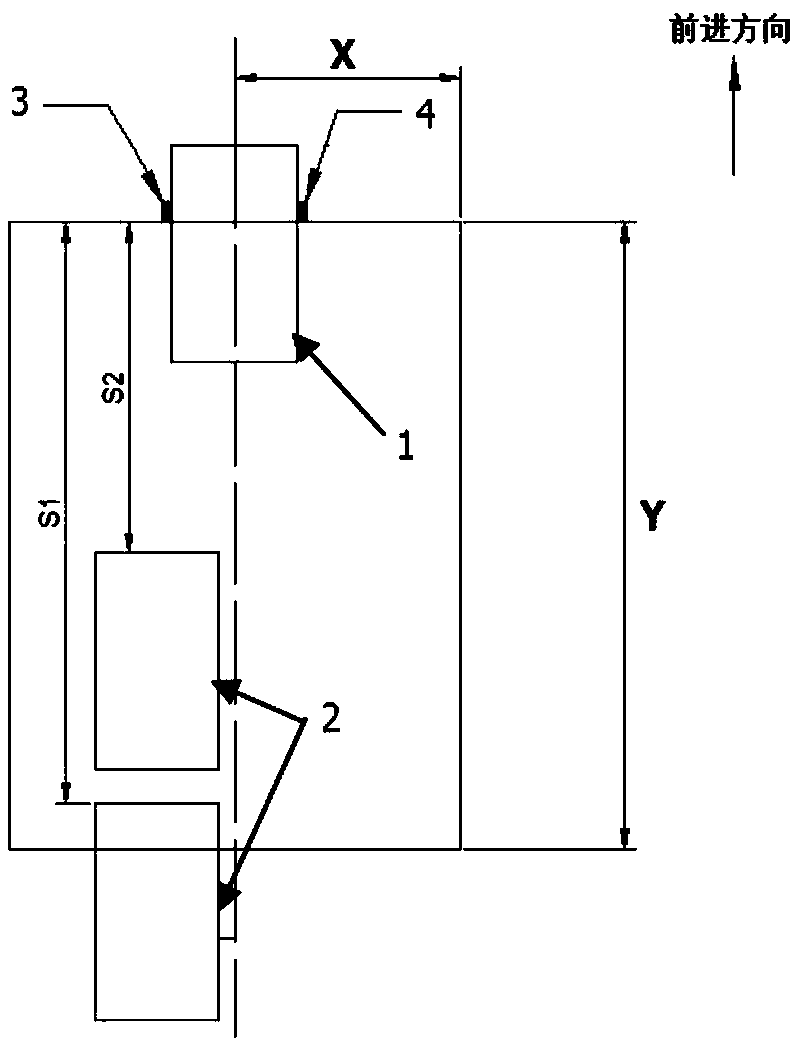
Pre-warning method and system for automobile parking door opening and based on image processing
InactiveCN107650640AFast operationImprove stabilityPedestrian/occupant safety arrangementSignalling/lighting devicesMoving speedElectronics
The invention belongs to the technical field of automobile electronics, and discloses a pre-warning method for automobile parking door opening and based on image processing. The pre-warning method comprises the steps that target identification and classification are conducted on images in a pre-warning area; the moving speed of a target and the moving time of a target needed to collide with an automobile are calculated; and the moving time and the moving speed are compared with the pre-warning calibration time and speed of different categories of targets to determine whether pre-warning is issued or not. The pre-warning method for automobile parking door opening and based on image processing utilizes SIFT feature extraction technology to quickly identify vehicles and pedestrians and the like in the pre-warning area, the calculation speed is high, and stability is high; and the binocular vision ranging technology can be utilized to accurately measure the distance and collision time of the passed vehicles, pedestrians and the like with the automobile, the calculation amount is greatly optimized, environment information of the rear part of the automobile can be processed in real time,almost no delay occurs, and a reliable pre-warning system is provided for parking door opening.
Owner:SHANGHAI UNIV OF ENG SCI
Real-time digital organ cutting method based on metaball model and mixed drive method
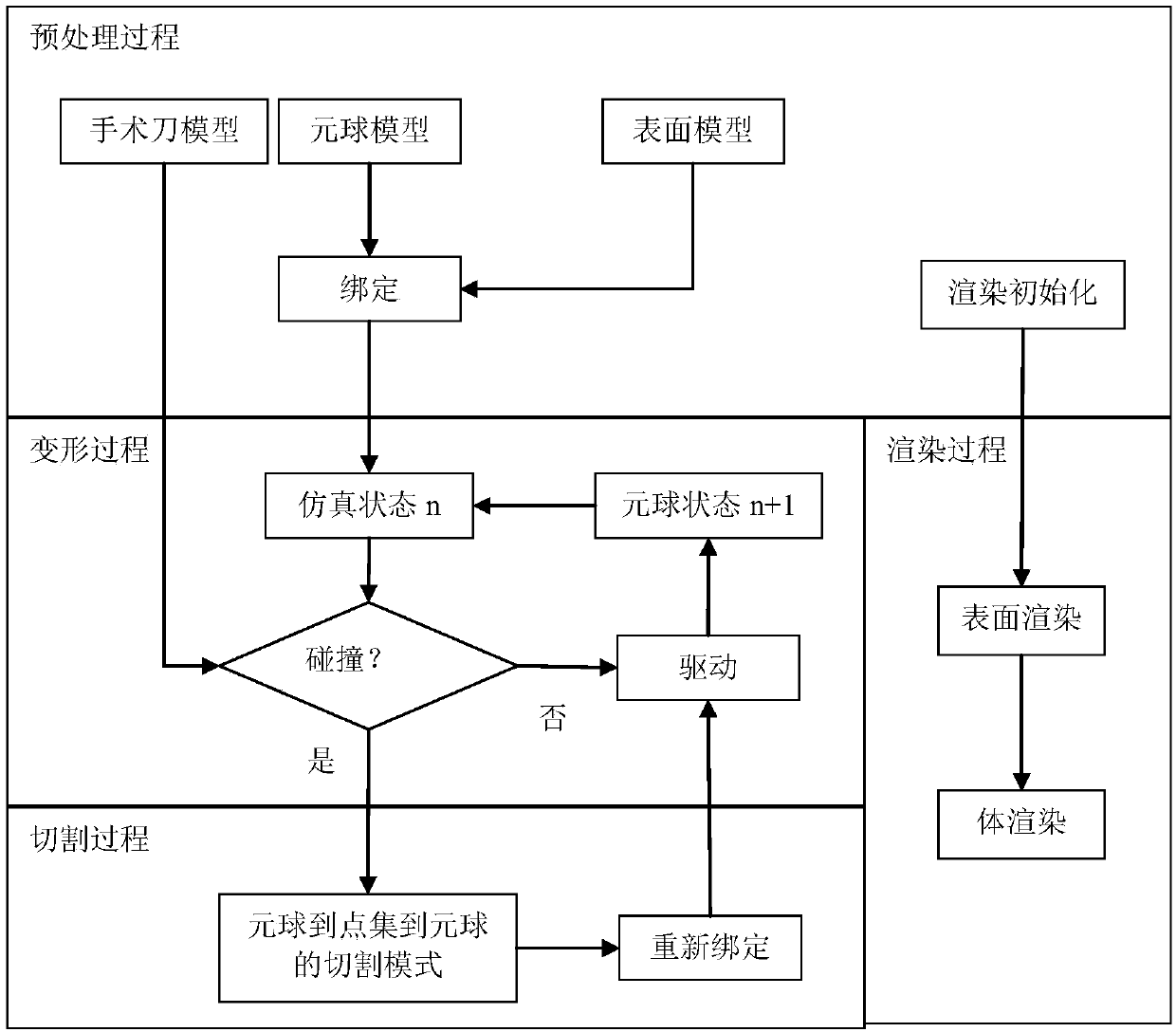
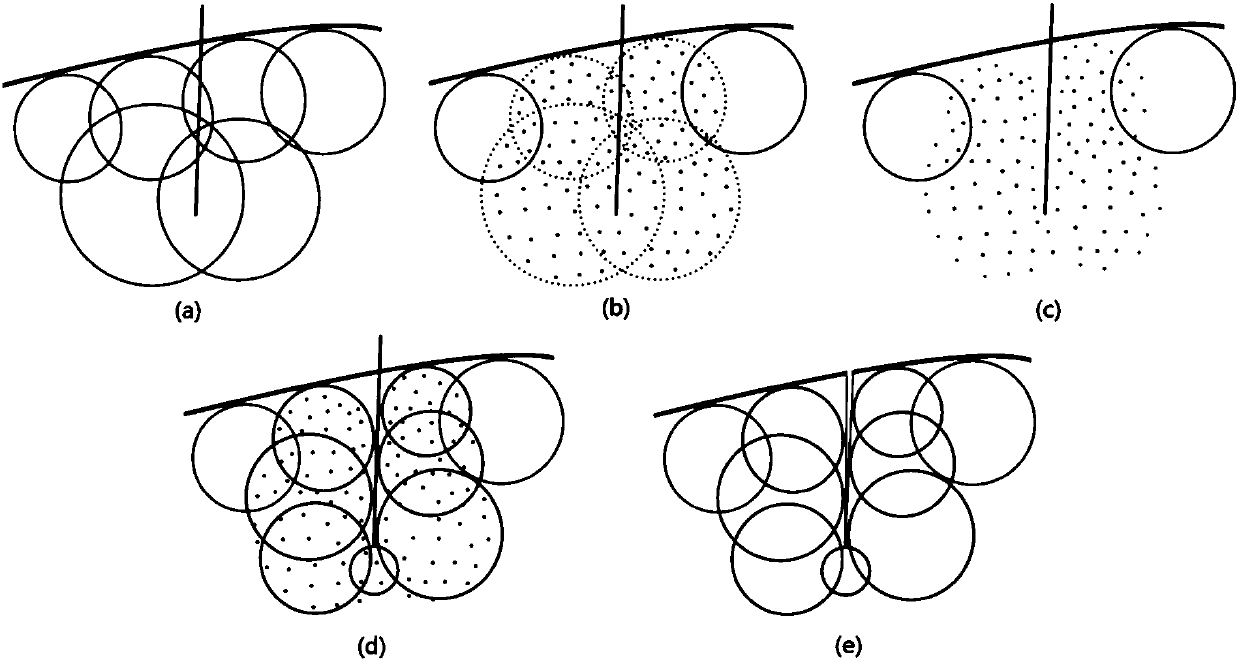
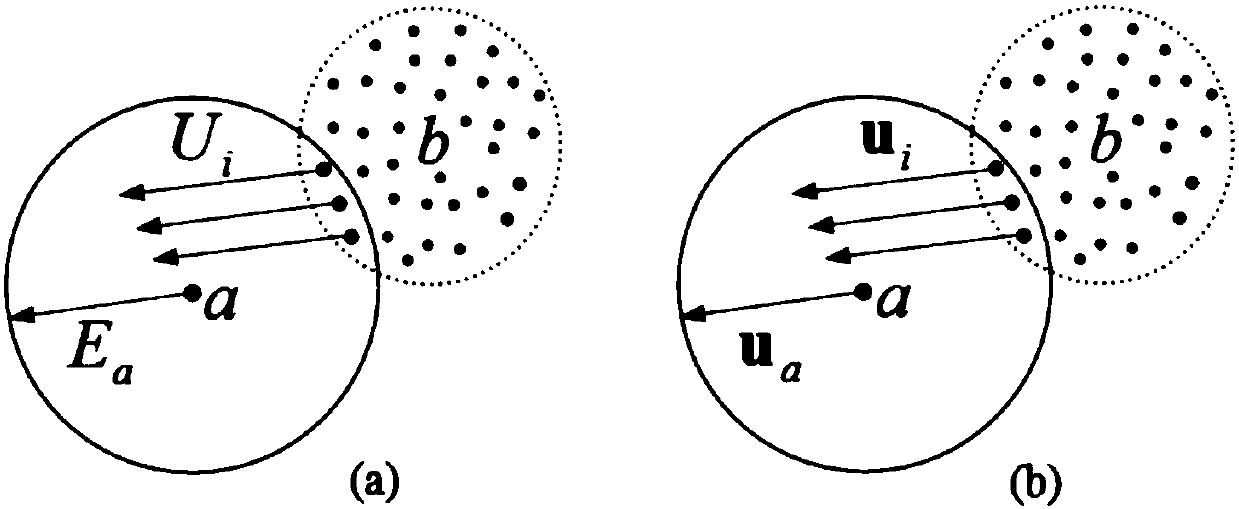
ActiveCN106875462AReduce fillingFast convergenceComputer-aided planning/modellingEducational modelsDynamic methodSimulation
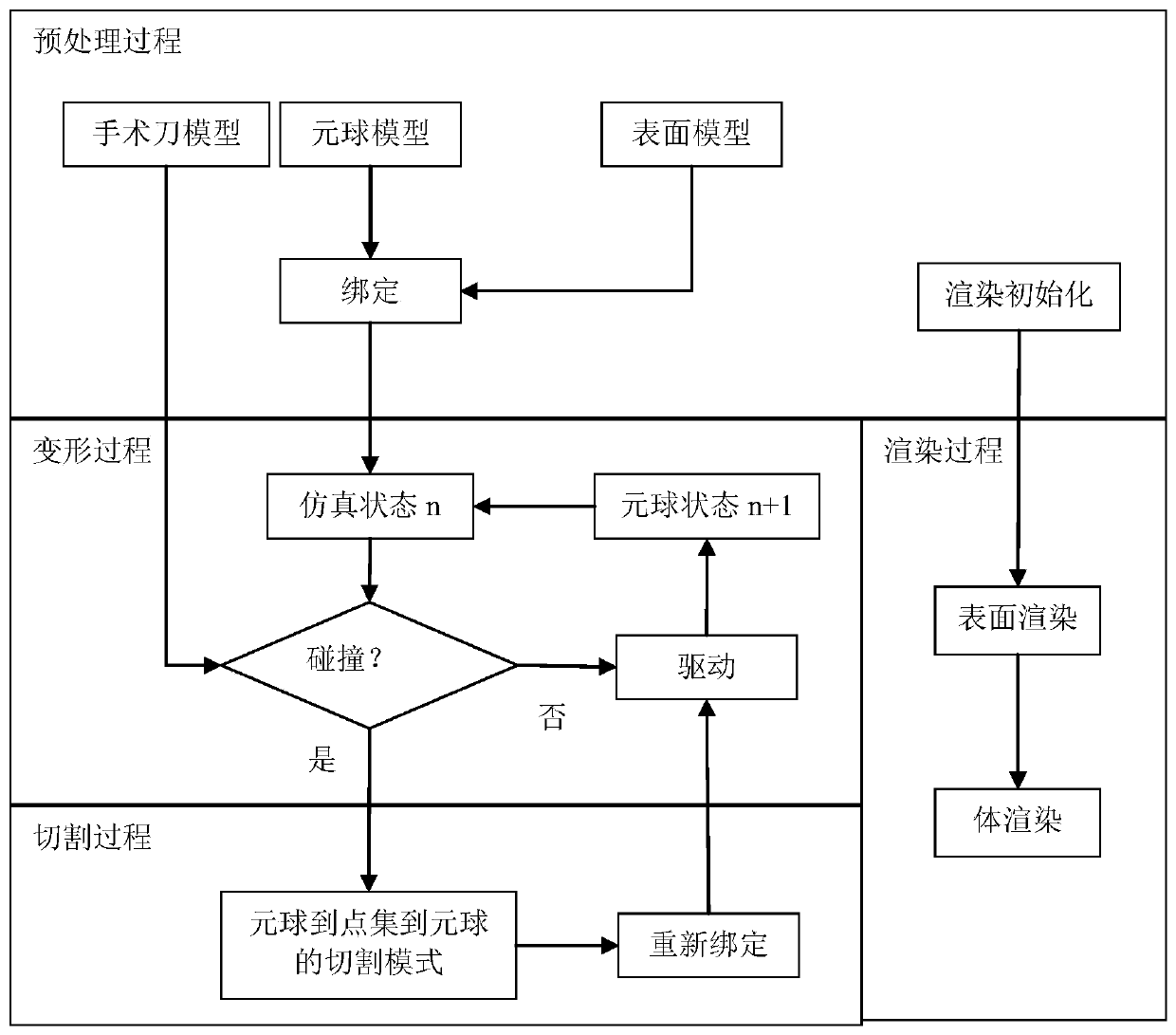
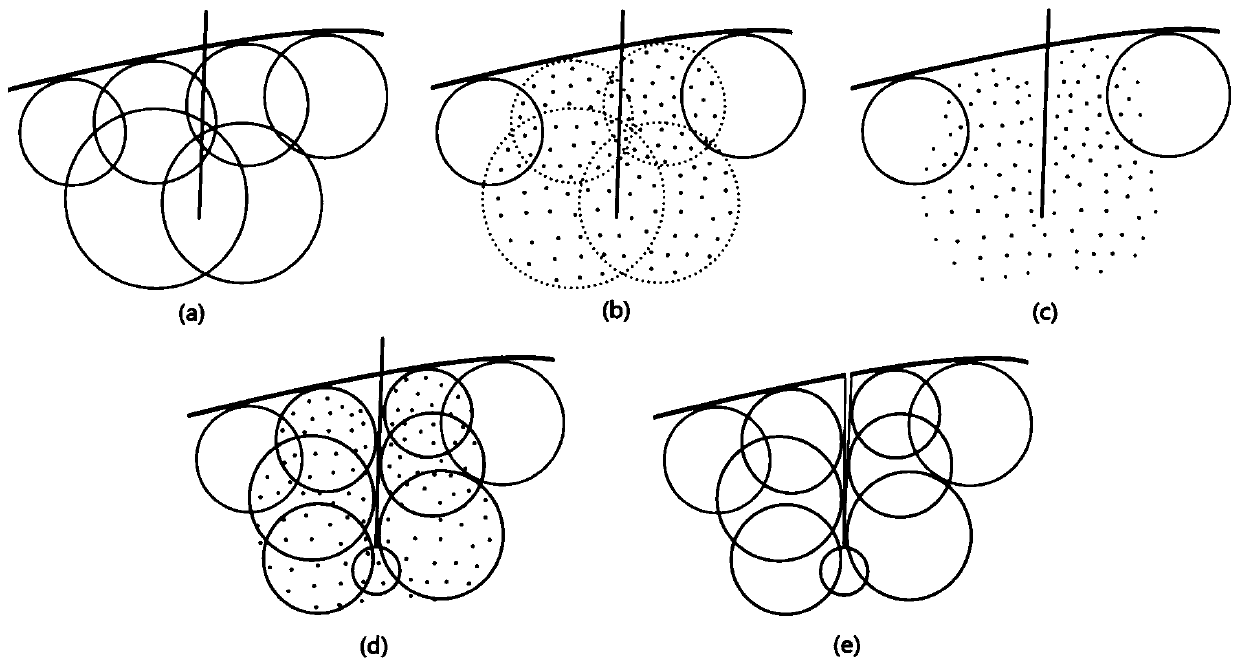
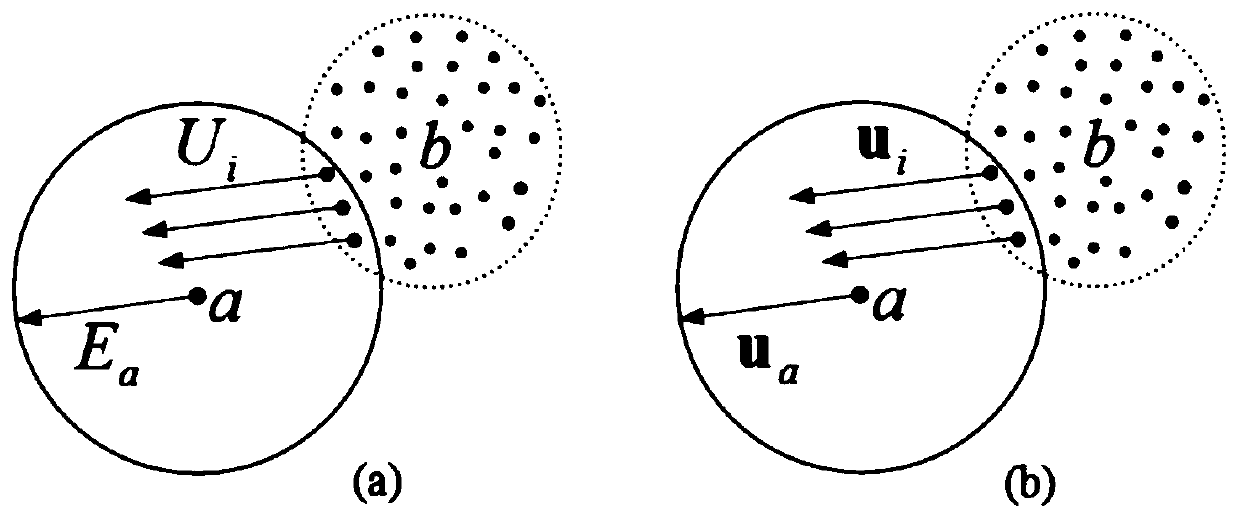
The invention provides a real-time digital organ cutting method based on a metaball model and a mixed drive method. The method takes the metaball as the basis, and employs a position dynamics and a no-grid method to drive the model at the same time. In order to solve a problem that a metaball needs to be split and combined frequently in a cutting process, the method employs a cutting mode of metaball to a point set to the metaball, and employs the position dynamics method to drive the metaball in the mode, and employs the no-grid method drive a point set generated by the metaball. The method comprises four steps: 1, a preprocessing process: carrying out some initialization operation while reading a model file; 2, a deformation process: carrying out the model drive based on the position dynamics method; 3, a cutting process: driving the model through the mixed drive method, and carrying out the cutting in the mode of metaball to a point set to the metaball; 4, a rendering process: carrying out the rendering of the models at steps 2 and 3. The method can truly simulate the process of cutting a soft tissue in a virtual operation, and is higher in controllability and real-time performance.
Owner:BEIHANG UNIV
Gear residual life prediction method based on MMALSTM
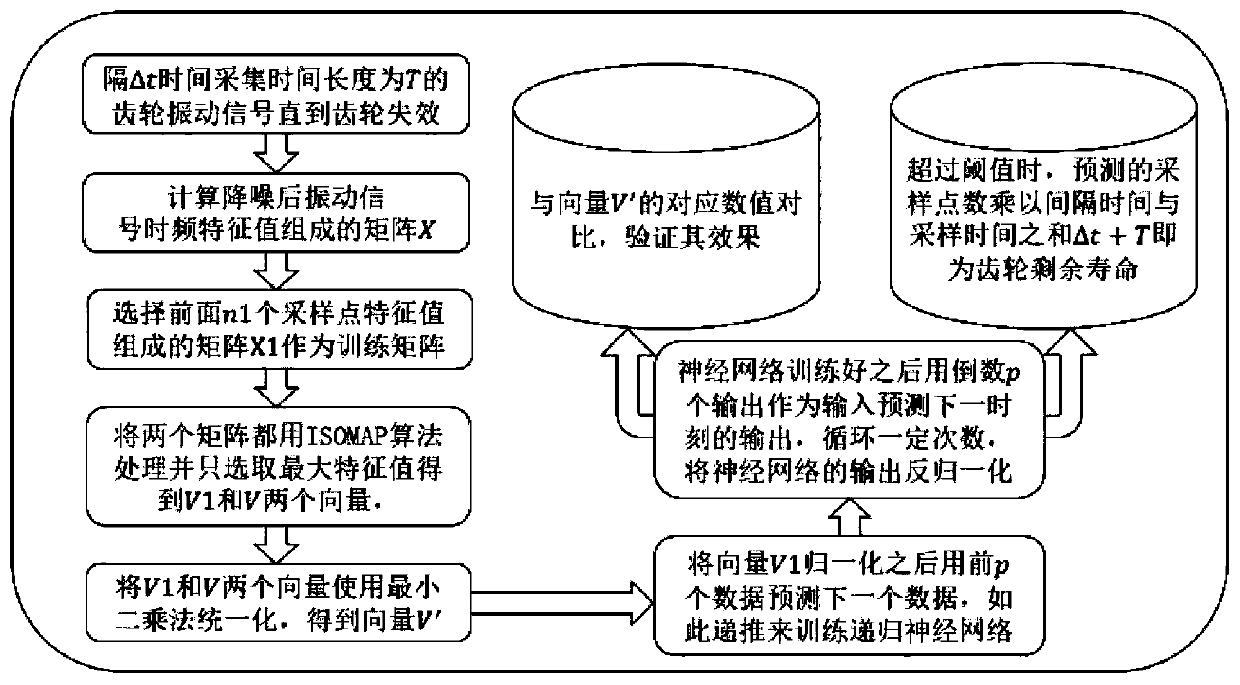
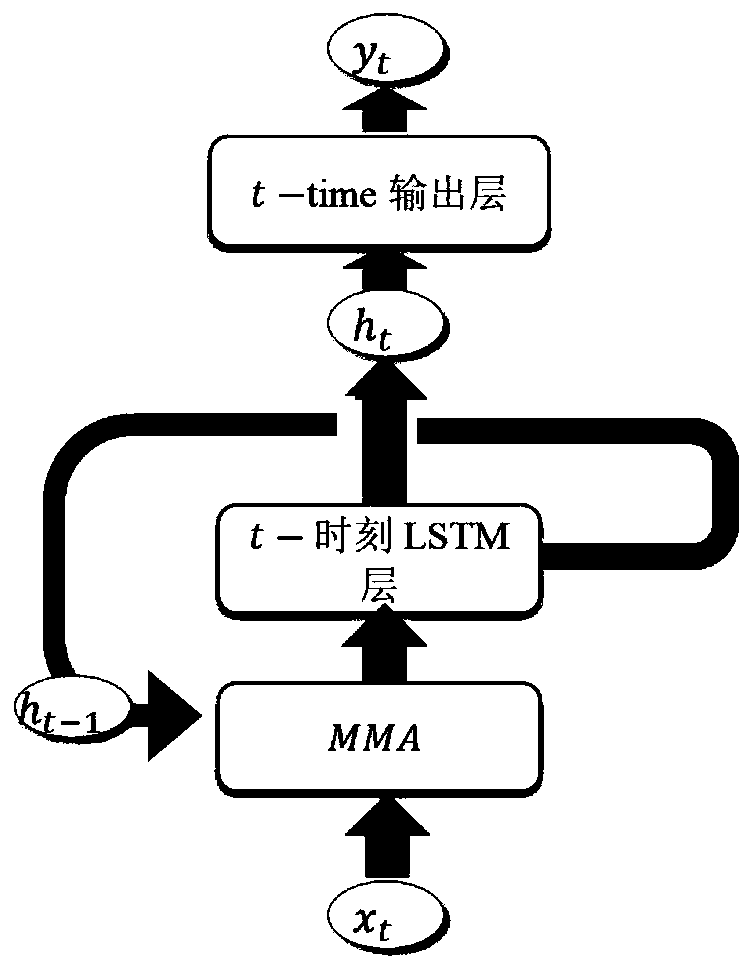
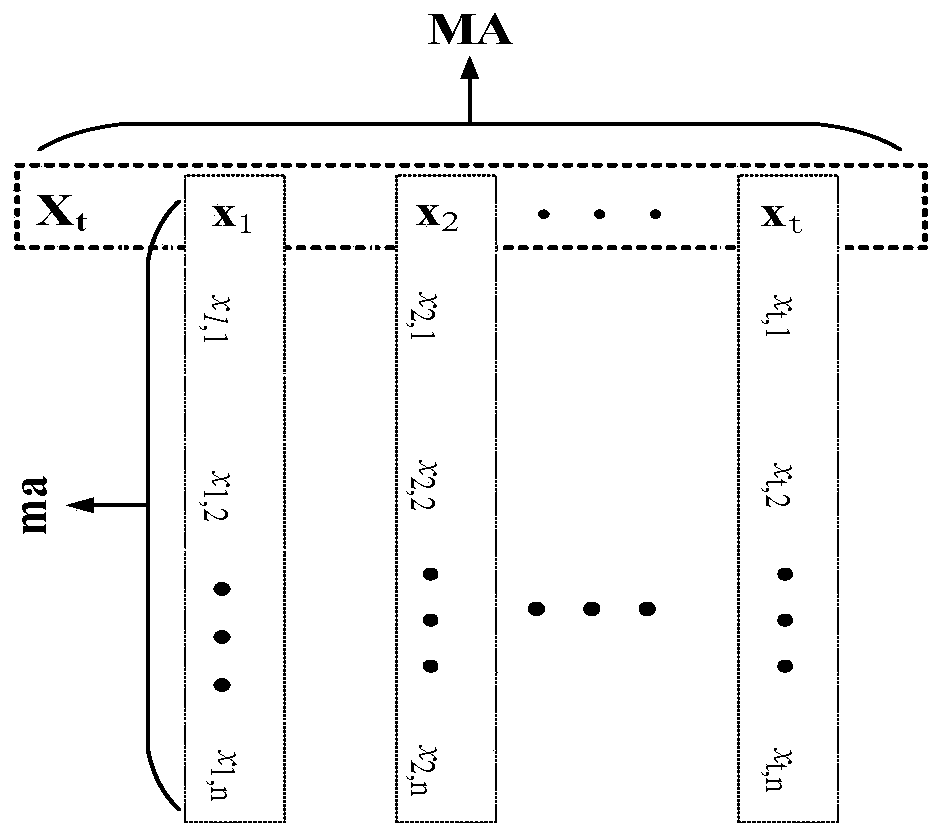
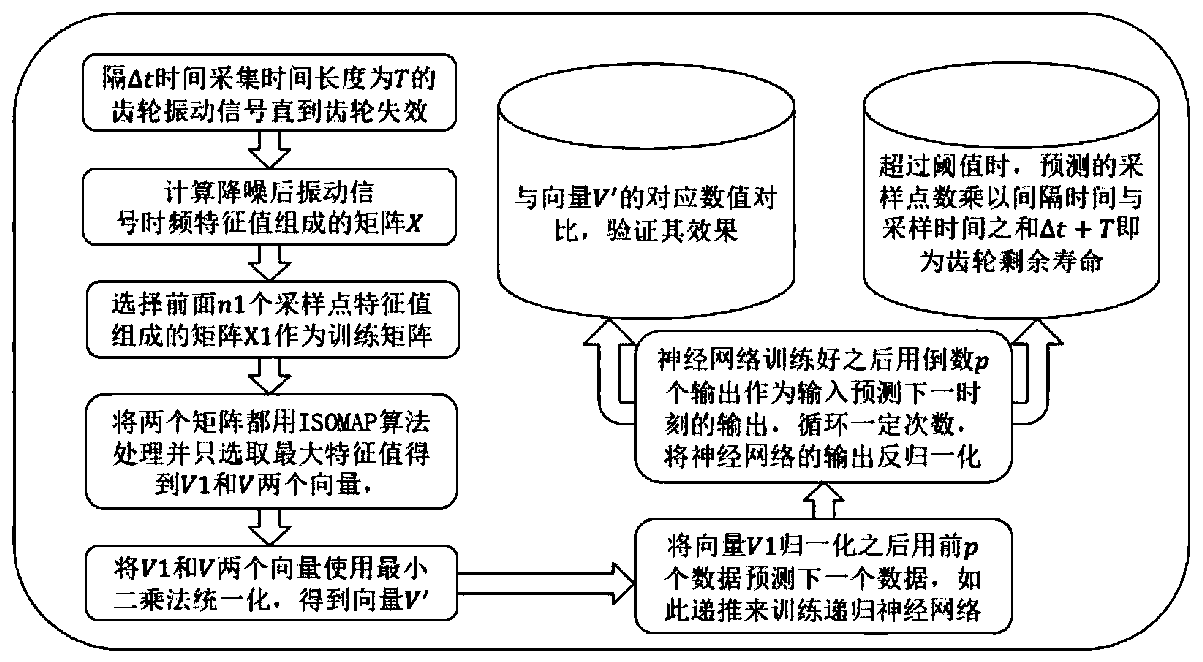
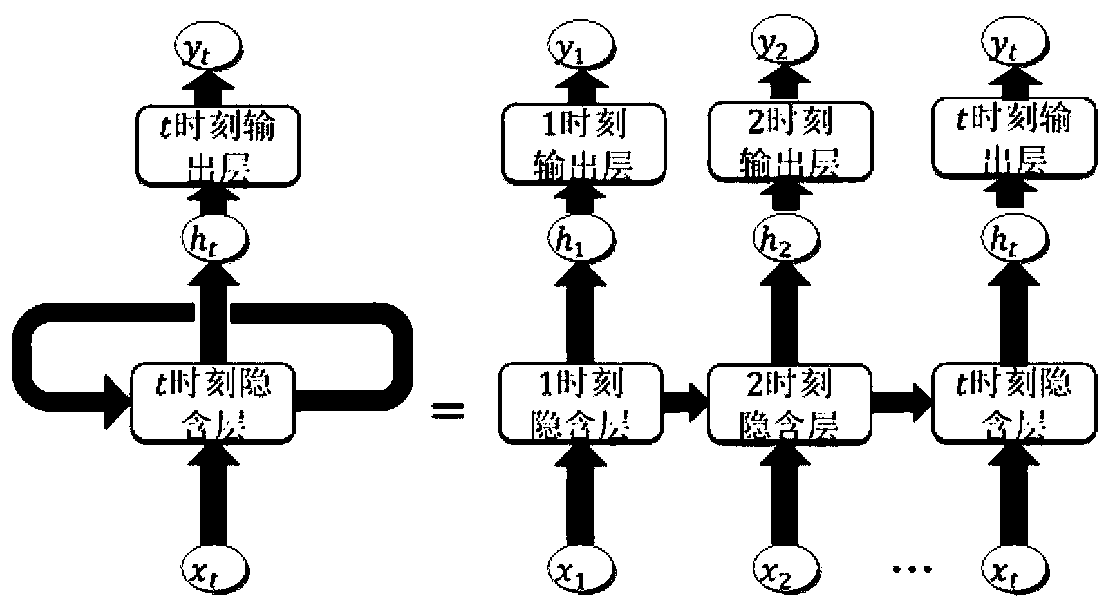
ActiveCN110175425AComprehensive and in-depth differentiated treatmentOptimize the total calculation amountGeometric CADSustainable transportationFeature dataHigh dimensional
The invention relates to a gear residual life prediction method based on MMALSTM, and belongs to the field of big data and intelligent manufacturing. The method comprises the following steps: firstly,simplifying and fusing high-dimensional features of acquired gear vibration signals; then using the fusion feature information subjected to dimension reduction for multi-step prediction of MMALSTM, and performing macro and micro processing on the fusion feature data by adopting MMA according to the characteristic that different feature information contains different information amounts; and finally, amplifying the weights of the input data and the recursive data according to the result of the MMA, and performing automatic and different degrees of processing on the fusion feature data. The prediction speed and precision of the residual life of the gear can be improved while the calculated amount is reduced.
Owner:CHONGQING UNIV
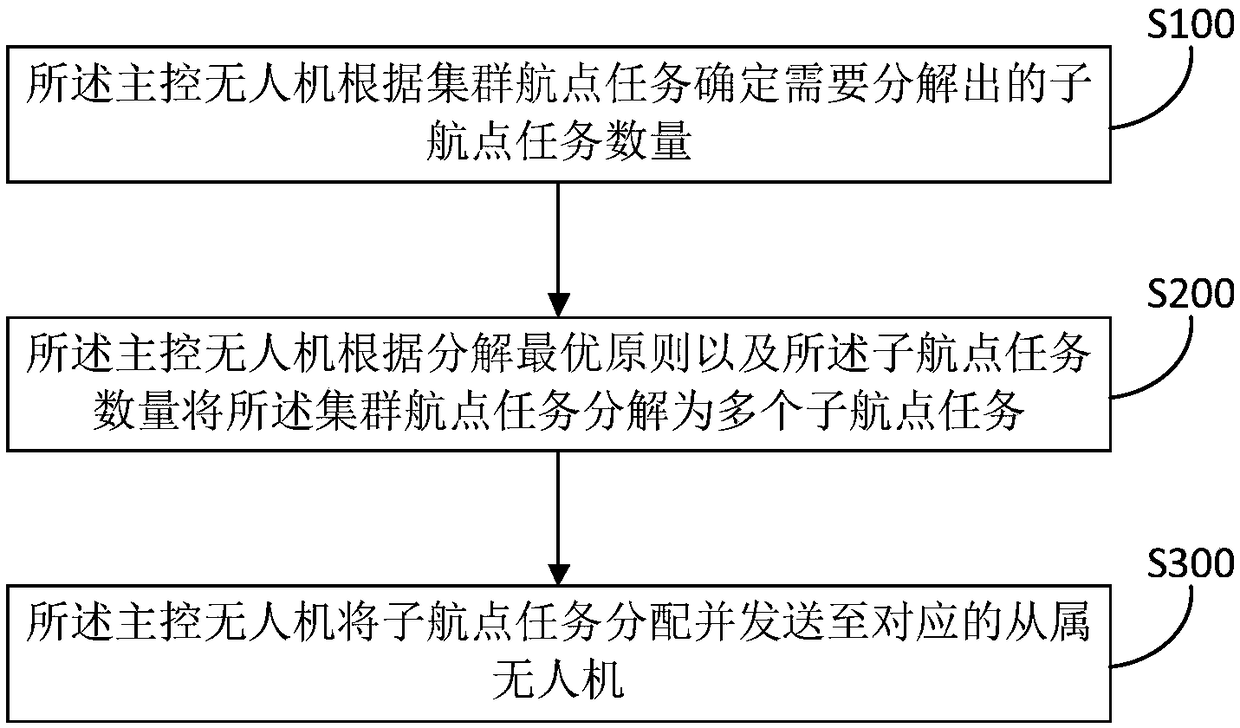
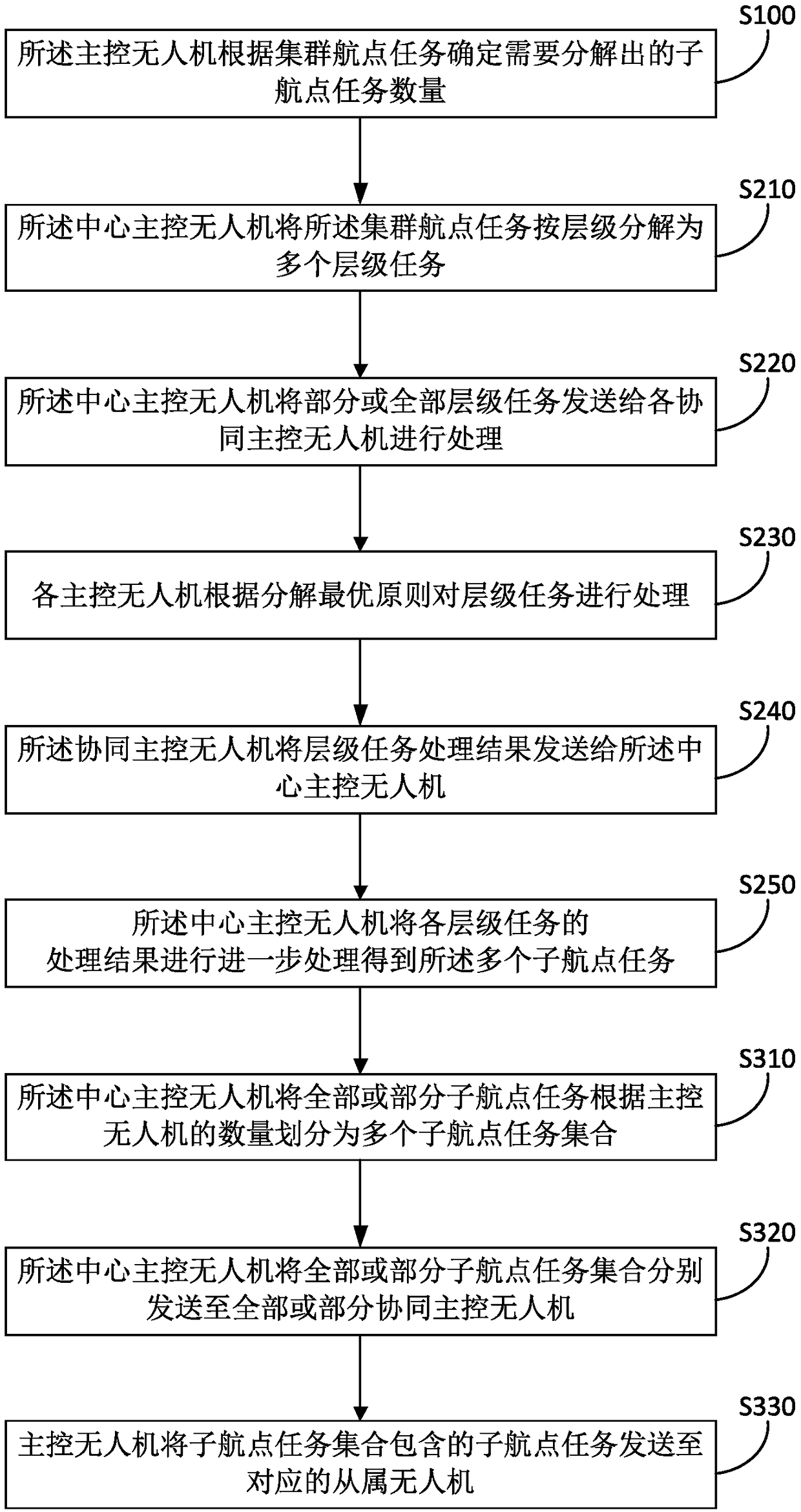
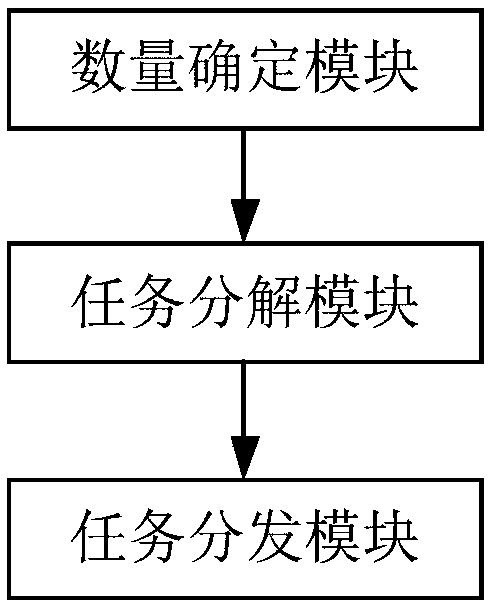
Unmanned aerial vehicle cluster task decomposition and sending method and system
PendingCN108830448ARelieve stressIncrease freedomForecastingResourcesInformation processingDecomposition
The invention relates to the technical field of unmanned aerial vehicle control and particularly provides an unmanned aerial vehicle cluster task decomposition and sending method and system. The method particularly comprises steps: a master unmanned aerial vehicle determines the number of sub navigation point tasks which need to be decomposed according to a cluster navigation point task; the master unmanned aerial vehicle decomposes the cluster navigation point task to multiple sub navigation point tasks according to a decomposition optimality principle and the number of sub navigation point tasks; and the master unmanned aerial vehicle distributes and sends the sub navigation point tasks to corresponding subordinate unmanned aerial vehicles. In the method, the master unmanned aerial vehicle is in charge of decomposition, distribution and sending of a cluster task, the unmanned aerial vehicles shoulder one part of the work of a central control system, the information processing pressure of the central control system is lessened, a greater degree of freedom is given to the unmanned aerial vehicle cluster, management on mass data of the unmanned aerial vehicles is also facilitated, and the total computation amount of formation task distribution is optimized.
Owner:GUANGZHOU EHANG INTELLIGENT TECH
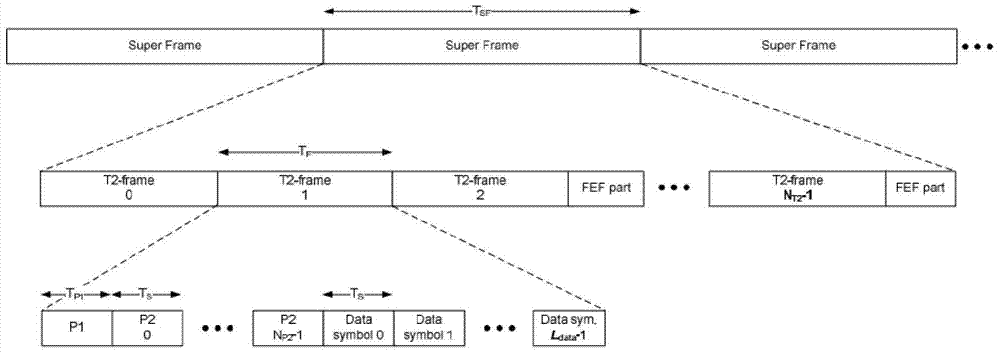
Method of synchronizing precise timing of DVB-T2 (Digital Video Broadcasting-Terrestrial 2) system
ActiveCN103501284AReduce power consumptionGood repeatabilityMulti-frequency code systemsSelective content distributionFast Fourier transformTime domain
The invention discloses a method of synchronizing precise timing of a DVB-T2 (Digital Video Broadcasting-Terrestrial 2) system. The method comprises the steps: extracting the pilot frequency of a first P2 symbol in the received T2 frame, performing pseudo random sequence correction, and carrying out IFFT (Inverse Fast Fourier Transform) to obtain channel impulse response; according to the average power and envelope of the channel impulse response, separating the effective path in the channel impulse response; making relation with a time domain P2 signal by using the time domain signal of the locally generated P2 pilot frequency according to the position of the effective path in the channel impulse response and the imaging position of the effective path, analyzing and judging the true position of the path in the channel impulse response; judging the characteristic of a channel by judging whether a path exists before a main path of a CIR, thus regulating the window of FFT (Fast Fourier Transform) in time domain by utilizing the minimal intersymbol interference principle. By utilizing the method, the computation amount and locking time can be greatly reduced, the synchronization accuracy of the precise timing can be improved, and the power consumption of the DVT-T2 system can be decreased.
Owner:HUNAN GOKE MICROELECTRONICS
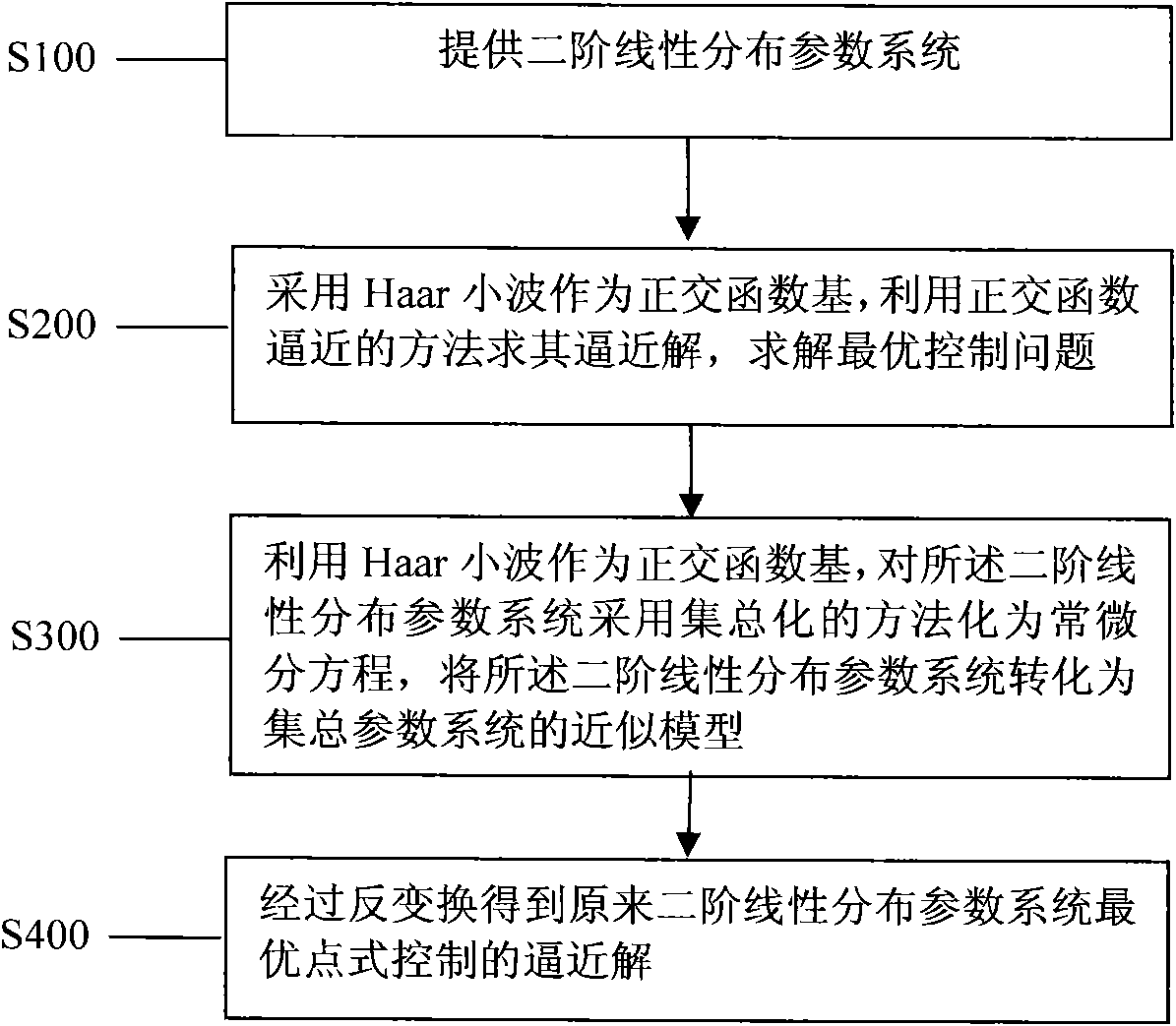
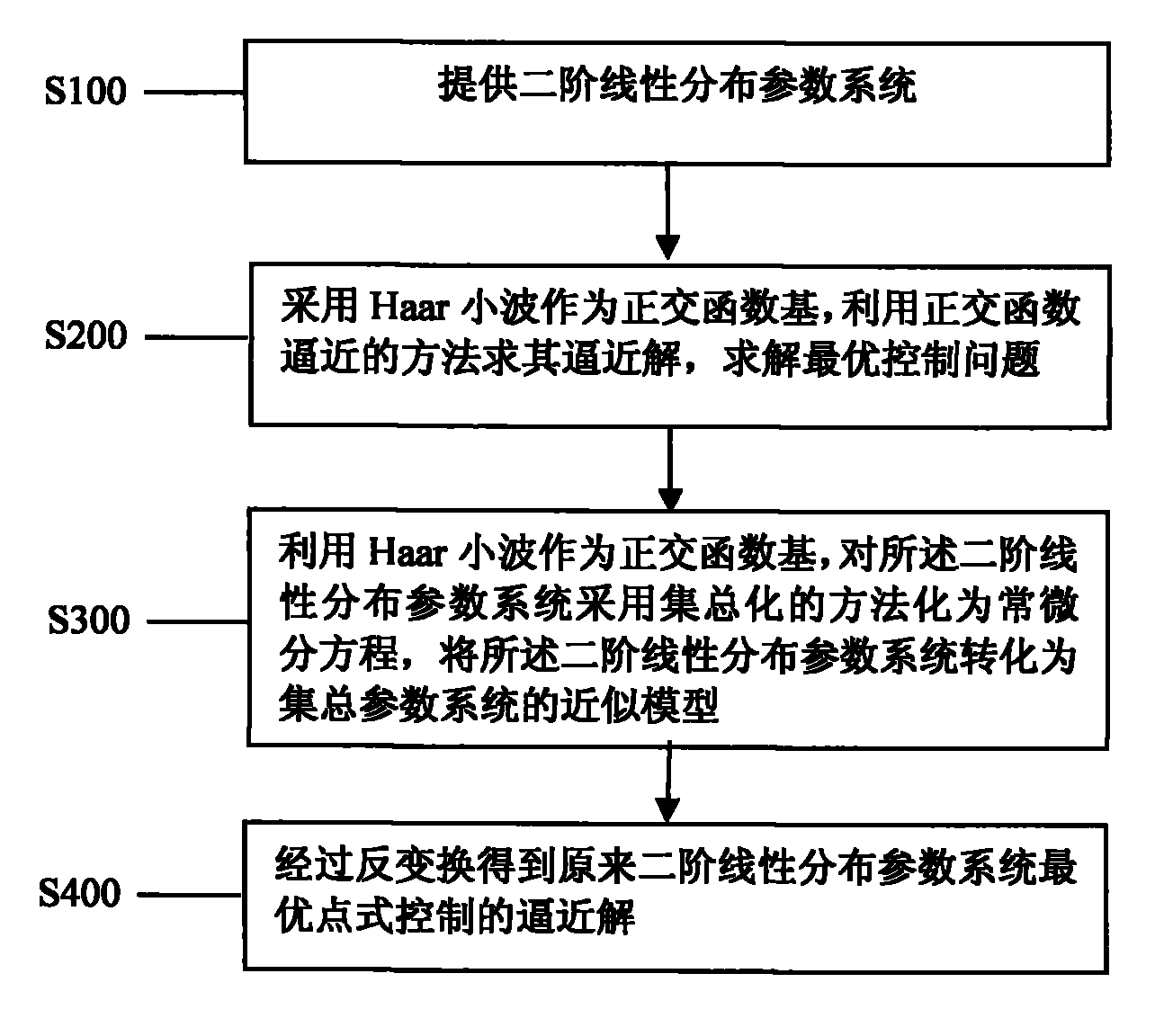
Wavelet analysis method of optimal point-wise control of distributed parameter system
InactiveCN101819412AGood effectSmall amount of calculationAdaptive controlDistributed parameter systemAlgorithm
The invention discloses a wavelet analysis method of the optimal point-wise control of a distributed parameter system, comprising the following steps of: detruding a differential operation matrix, a product integral operation and an element product operation matrix corresponding to Haar wavelet with the aid of an orthogonal function approximating method, and applying the differential operation matrix, the product integral operation and the element product operation matrix to the research of the problem of the optimal point-wise control of the distributed parameter system, converting the problem of the optimal pint-wise control of the distributed parameter system into a lumped parameter problem, and obtaining an approximating solution of the original optimal point-wise control of the distributed parameter system by an inverse transformation, such that the problem hardly to be solved is easy to solve and a wavelet approximating algorithm with better performance is obtained. In the invention, the provided Haar wavelet approximating algorithm is a method with better control effect, and the method provides a new way for solving the problem of the optimal point-wise control of the distribution parameter system.
Owner:SHANGHAI DIANJI UNIV
An Expectation-Maximization Parameter Estimation Method for Gaussian Mixture Models
ActiveCN103748985BEasy to calculateImprove accuracyImage analysisCharacter and pattern recognitionEstimation methodsAlgorithm
The invention discloses a method for estimating parameters of expectation maximization in a Gaussian mixture model. The method improves the specific calculation process of the EM algorithm on the basis of sample clustering, and provides the estimation of three parameters of w, μ and ∑ method, making it suitable for sample reduction and the input parameters of GMM are fuzzy color features. Due to the reduction in the number of samples, the parameter estimation process will not introduce unnecessary noise, thereby improving the accuracy of parameter estimation; due to the reduction in the number of samples, the improved EM algorithm is also improved in terms of storage capacity, calculation capacity, and running time. , which is beneficial to improve the efficiency of parameter estimation.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Unmanned aerial vehicle cluster and flight method thereof
PendingCN108594854AIncrease freedomImprove scheduling efficiencyPosition/course control in three dimensionsControl systemReal-time computing
The invention discloses an unmanned aerial vehicle cluster and a flight method thereof and belongs to the field of unmanned aerial vehicles. The flight method of the unmanned aerial vehicle cluster includes the steps that the unmanned aerial vehicle cluster accepts ultra-long-distance scheduling of a central control system, and a main control unmanned aerial vehicle receives a cluster waypoint task sent by the central control system; the main control unmanned aerial vehicle decomposes the cluster waypoint task into single unmanned aerial vehicle waypoint tasks and distributes the decomposed single unmanned aerial vehicle waypoint tasks to corresponding unmanned aerial vehicles in the cluster; all the unmanned aerial vehicles in the cluster perform their own waypoint tasks. The cluster waypoint task is decomposed by the main control unmanned aerial vehicle in the unmanned aerial vehicles so that the pressure of a central control server can be reduced, and meanwhile, a greater freedom degree of flight is provided for the unmanned aerial vehicle cluster, so that the scheduling efficiency of the unmanned aerial vehicle cluster is improved.
Owner:GUANGZHOU EHANG INTELLIGENT TECH
Universal killing area calculation method and universal launching area calculation method
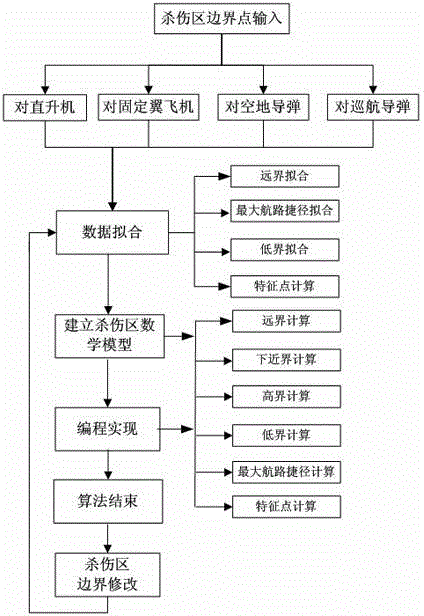
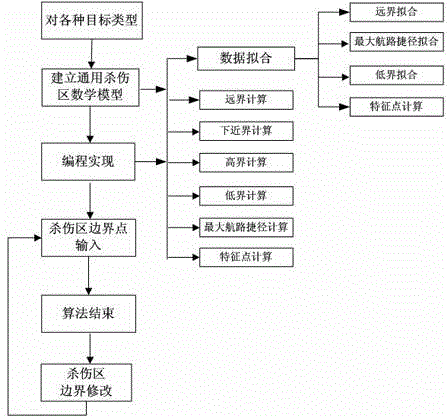
InactiveCN105224778AEfficient modificationImprove versatilitySpecial data processing applicationsModel NumberWeapon system
The invention discloses a universal killing area calculation method and a universal launching area calculation method. The method can be well applied to killing area calculation of various tactical types and various target types, so that a killing area is quickly and efficiently modified in different stages of type research and development. The method abstracts various killing area boundary calculation methods and extracts common parts for establishing a universal mathematic model, thereby realizing complete isolation of killing area boundary parameters and an algorithm model. As only the killing area boundary parameters are different for different tactical types, the required killing area can be obtained by only changing initial parameters. The algorithm well solves the problems of an existing killing area in incompatibility among different types, incompatibility among different target types and complex and low-efficiency killing area calculation after change of boundary parameters, has the advantages of quickness, high efficiency, high universality and the like, can effectively reduce research and development expenditures and manpower resource costs, and can meet the requirements of killing area calculation of weapon systems of different tactical types.
Owner:SHANGHAI INST OF ELECTROMECHANICAL ENG
RSSI weighted ranging method based on equilateral triangle model
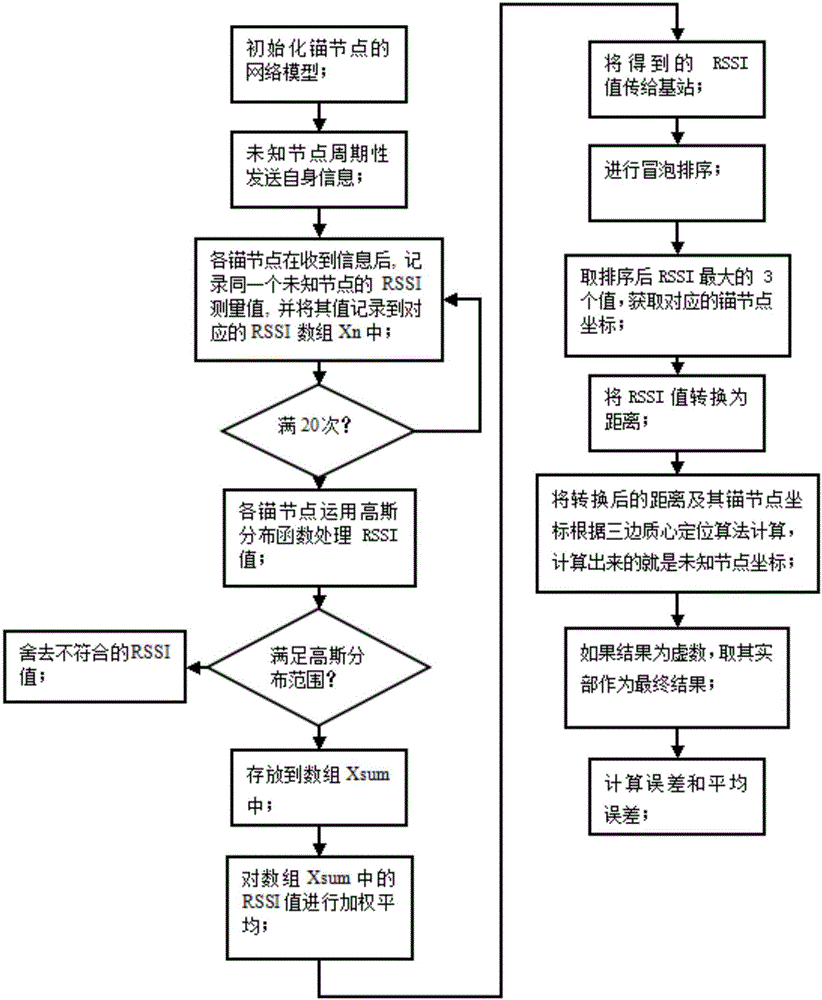
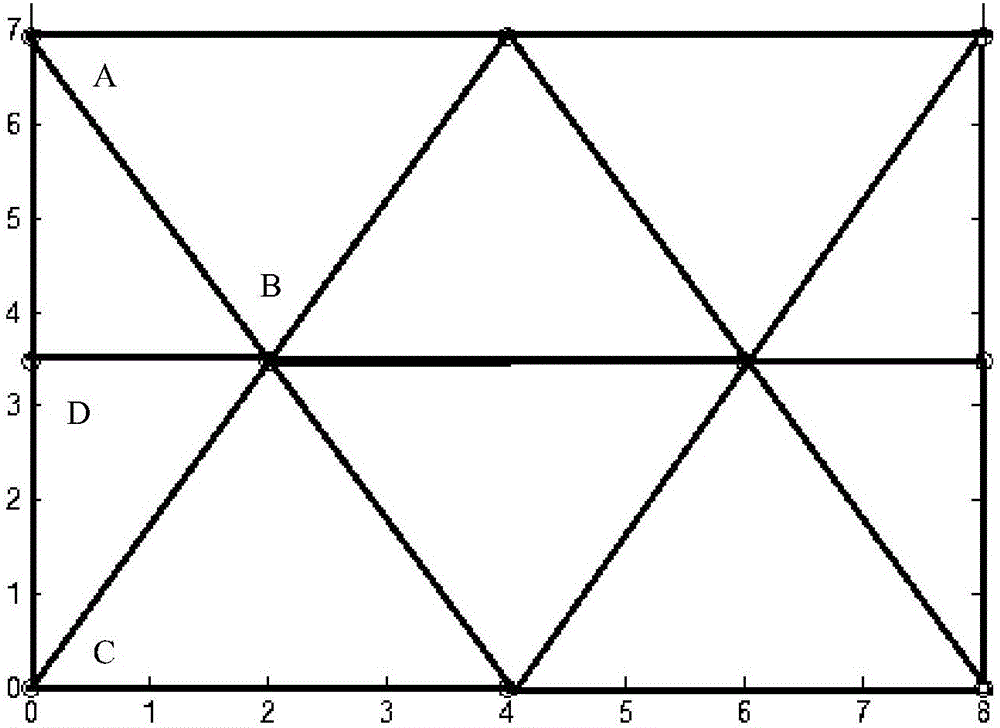
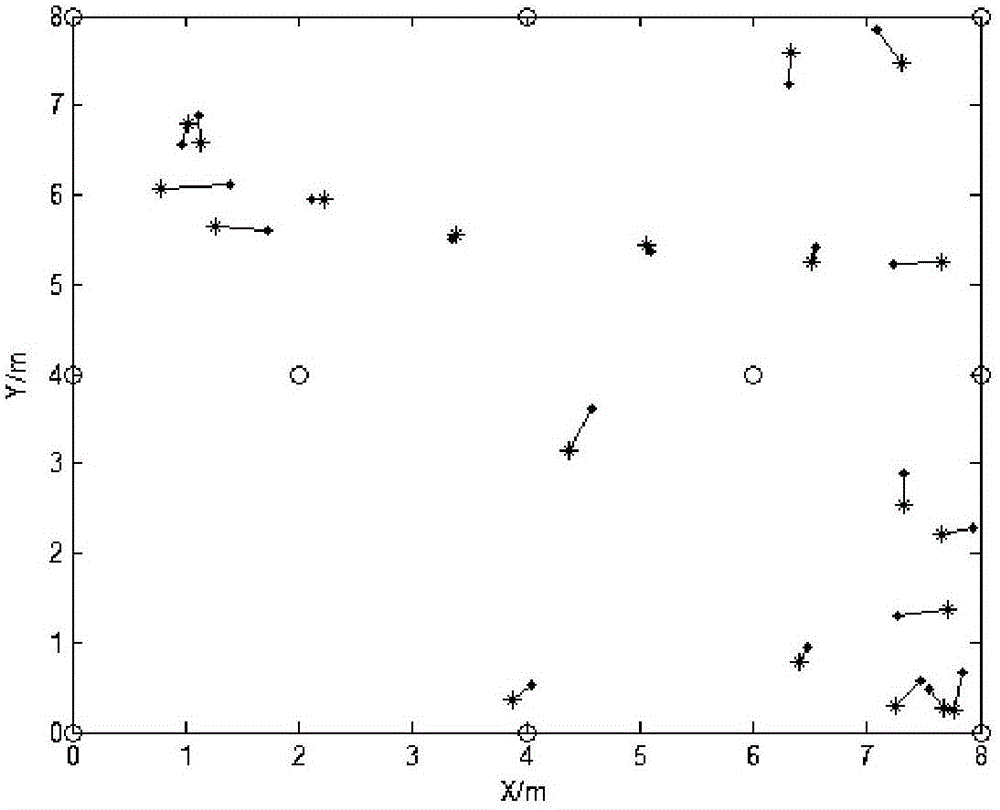
InactiveCN106131951AReduce uncertainty errorsReduce random errorNavigational calculation instrumentsPosition fixationNODALIsoetes triquetra
The invention discloses an RSSI weighted ranging method based on an equilateral triangle model. According to the method, each RSSI is given a weight according to Gaussian distribution, average value calculation is performed to obtain an RSSI optimal value, and the coordinates of an unknown node are calculated according to the RSSI optimal value. Uncertain errors caused by uncertain factors such as walls, various fixed or movable barriers, multi paths and diffraction and the like are reduced. The invention also provides a modified equilateral triangle arrangement model of anchor nodes, a necessary anchor node is added to the marginal area for positioning to reduce the interference of multiple positioning nodes, and the positioning accuracy is improved.
Owner:GUANGZHOU UNIVERSITY
Cultural relic classification method based on lightweight deep learning network
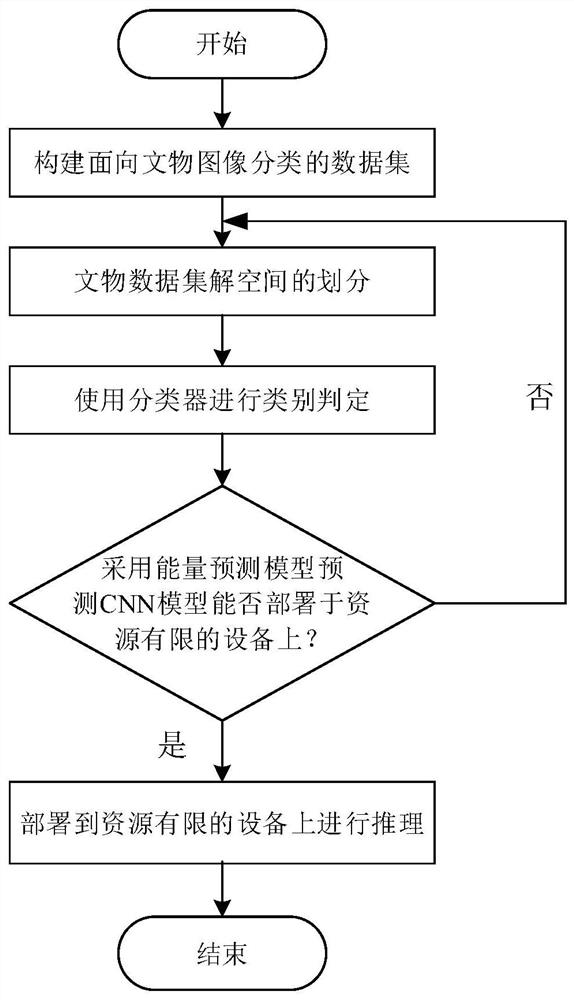
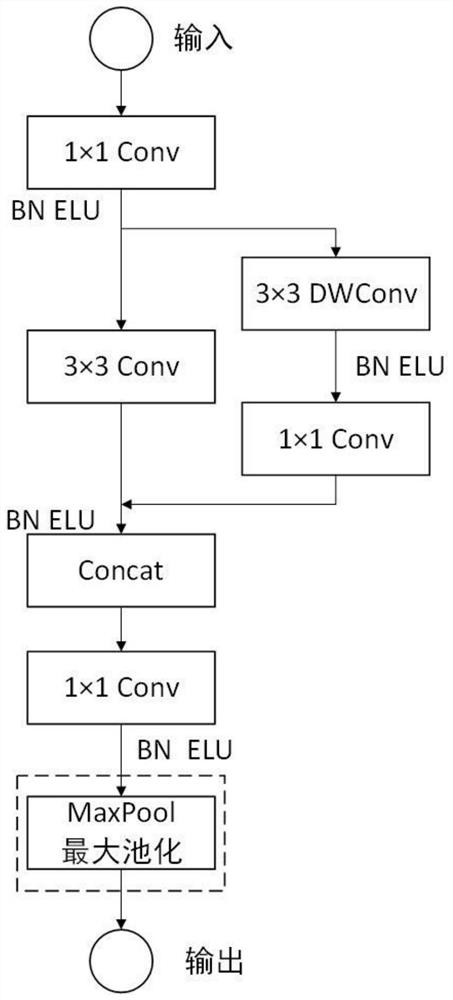
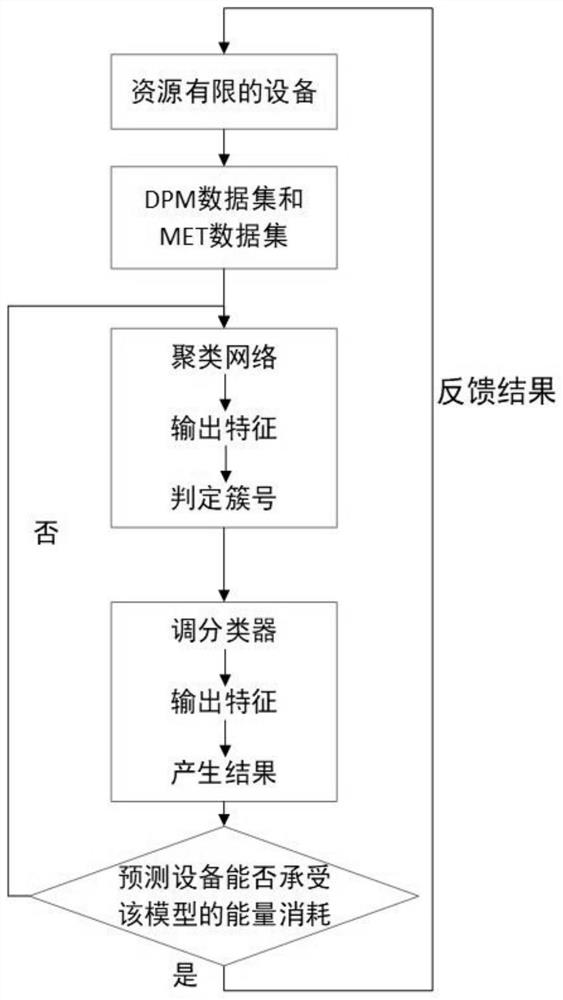
PendingCN113920363AIncrease training speedImprove generalization abilityCharacter and pattern recognitionNeural architecturesNeural network classifierEngineering
The invention provides a cultural relic classification method based on a lightweight deep learning network, and the method comprises the steps: firstly constructing a data set for the classification of cultural relic images, and then dividing an original cultural relic image data set into a plurality of relatively independent small data sets through employing a coarse-grained clustering neural network, for each small data set, using a lightweight neural network classifier designed by the invention to classify data, and finally, using an energy prediction model to measure whether the CNN model can be deployed on a device with limited resources. According to the method, the model structure can be simplified, the training speed can be increased, the reusability is higher, the precision and the calculated amount can be better balanced, and the method is suitable for being deployed on equipment with limited resources.
Owner:NO 20 RES INST OF CHINA ELECTRONICS TECH GRP
Paper defect detection method based on bit planes
InactiveCN105300998AThe method is simple and easy to implementGood anti-interferenceImage analysisOptically investigating flaws/contaminationImage segmentationBit plane
The invention discloses a paper defect detection method based on bit planes. The paper defect detection method comprises the following steps of firstly, obtaining an original image of the tested paper, and converting into a grayscale image; pretreating the grayscale image, so as to eliminate the noise in the image; decomposing the bit plane of the pretreated grayscale image to obtain eight bit planes of the image; using Gray code to enhance the bit planes, so as to obtain eight enhanced bit planes of the grayscale image; finally, selecting the sixth enhanced bit plane, and segmenting the image, so as to obtain the final detection result. The paper defect detection method has the advantages that while the rapidity of algorithm is guaranteed, the defect can be well detected; the anti-interference property and positioning accuracy are better, and the operation is simple.
Owner:SHAANXI UNIV OF SCI & TECH
Prediction method for residual life of gear based on LSTMPP
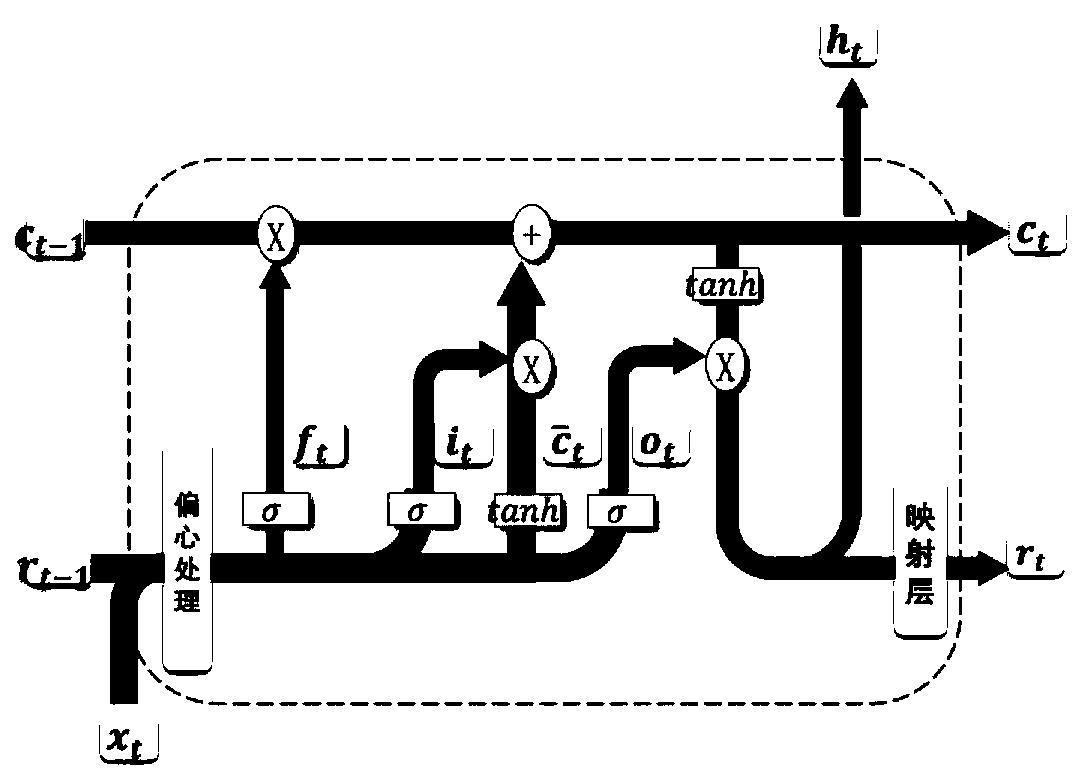
ActiveCN110210126AOptimize the total calculation amountGood predictive speedGeometric CADNeural architecturesTerm memoryFeature data
The invention relates to a gear residual life prediction method based on LSTMPP, and belongs to the field of big data and intelligent manufacturing. The method comprises the steps of firstly, simplifying and fusing high-dimensional features of collected gear vibration signals; then using the fusion feature information subjected to dimension reduction for multi-step prediction of an eccentric longshort-term memory network LSTMPP, and performing eccentric processing on the fusion feature data by adopting an attention mechanism method according to the characteristic that different feature information contains different information amounts; and finally, amplifying the weights of the input data and the recursive data according to an eccentric processing result, and performing automatic and different degrees of processing on the fused feature data. The prediction speed and precision of the residual life of the gear can be improved while the calculated amount is reduced.
Owner:CHONGQING UNIV
Circulating fermentation technology for cowpeas
InactiveCN105192645AShort preparation timeGood nutrition retentionFood preparationRaw materialLactic acid
The invention provides a circulating fermentation technology for cowpeas. The circulating fermentation technology comprises the following steps: adding pickling water with lactic acid bacteria powder into cowpeas for cowpea fermentation; when fermented by the 4nth time, performing centrifugation, water removal, supplementation of new pickling water, lactic acid bacteria powder adding, detection and adjustment on the pickling water for fermentation at the 4nth time, and continuously applying the pickling water to cowpea fermentation, wherein the n adopts a continuous positive integer in sequence; the fermentation is hermitically performed for 40-65 hours under the condition that the temperature of 20 to 24 DEG C; the difference between the new pickling water and the pickling water with the lactic acid bacteria powder is that the new pickling water does not contain the lactic acid bacteria powder. The technology adopts an innovate fermentation method; after performing fermentation by certain times, the pickling water is subjected to centrifugation, water removal, supplementation of new pickling water and the like, so that the pickling water can be recycled; the pickling water raw material and the cost of the preparation technology are reduced, the fermentation time of the cowpeas is shortened, and the quality and the taste of the soaked cowpeas are enhanced; the circulating fermentation technology is suitable for large-scale production and has good economical benefit, and the development of the pickling industry is promoted.
Owner:SICHUAN GAOFUJI BIOLOGICAL TECH
Preparation technology of fresh pickled cowpea
The invention provides preparation technology of fresh pickled cowpea. The technology comprises the following steps: step A, preparing pickle liquid I and pickle liquid II for later use, wherein the difference between the pickle liquid I and the pickle liquid II is that Gaofuji Paolemei Lactobacillus Powder is added in the pickle liquid I while no Gaofuji Paolemei Lactobacillus Powder is added in the pickle liquid II; step B, circulation fermentation, namely fermenting vegetable cowpea by the pickle liquid I prepared in step A, so that the fresh pickled cowpea is obtained; when performing the 4n times of fermentation, the pickle liquid after the 4n-time fermentation is used again for fermenting the cowpea after sequential processes such as centrifugation, water-losing and the like, wherein the n is selected from continuous positive integers; and the fermentation is carried on at 20-24 DEG C for 40-65 hours. According to the technology, the pickle liquid preparation and the circulation fermentation control are utilized, especially the addition of the Gaofuji Paolemei Lactobacillus Powder into the pickle liquid and the controls to the parameters and indexes in the circulation fermentation process are performed, so that the preparation time of the fresh pickled vegetables is shortened and the quality and taste of the fresh pickled vegetables are improved; thus, the technology is suitable for large-scale production and promotes development of the pickled-vegetable industry; moreover, the technology is relatively good in economic benefit.
Owner:SICHUAN GAOFUJI BIOLOGICAL TECH
Generation and authentication method of self-certified public key of mobile self-organized network
InactiveCN101702805AReduce storageReduce communicationPublic key for secure communicationUser identity/authority verificationLimited resourcesSelf certified
The invention discloses a management method of self-certified public key of a mobile self-organized network on the basis of ECC, comprising the following steps: a shared key is distributed to n virtual central nodes by threshold cryptology; a user chooses a secret random number to calculate a public parameter, and identity and the public parameter are sent to a nearby virtual central node A1; A1 contacts with other virtual central nodes and sends the user information to the nodes; each publisher Ai chooses a random secret integer and calculates as well as broadcasts a self-certified public key subblock Qi to other publishers according to the secret integers and parameters published by the user; each publisher Ai calculates a self-certified public key Q, a sub-signature xi and an intermediate quantity Ri and sends (r, I, xi and Ri) to a synthesizer; the synthesizer calculates and synthesizes a signature x after all sub-signatures are qualified after authentication and sends Q and x to the user; the user calculates a secret key s according to the x; and the authenticity of the self-certified public key of the user is verified. The invention has no certificate management, no key escrow and no secure channel, so that the invention is suitable for the safe communication of the mobile self-organization network with limited resource.
Owner:XIDIAN UNIV
Intelligent identification method for tangram toys
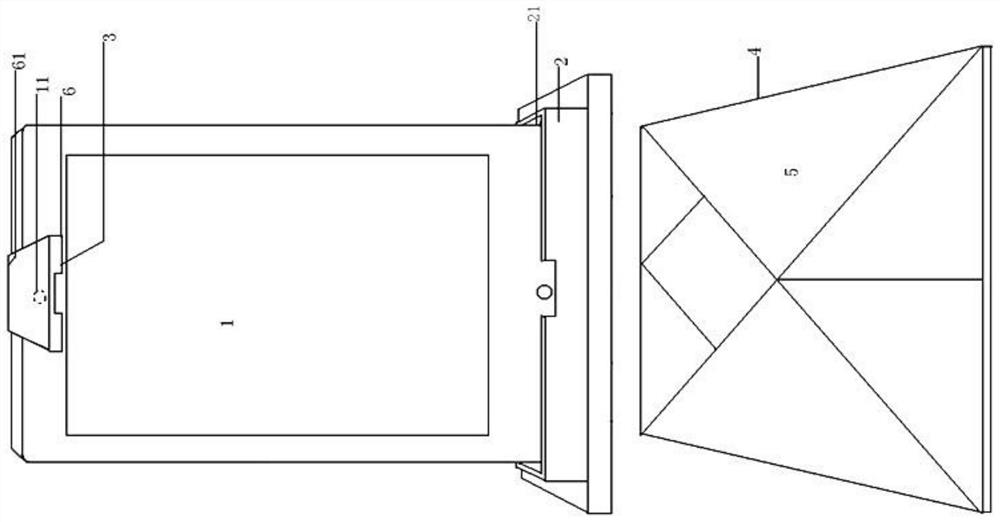
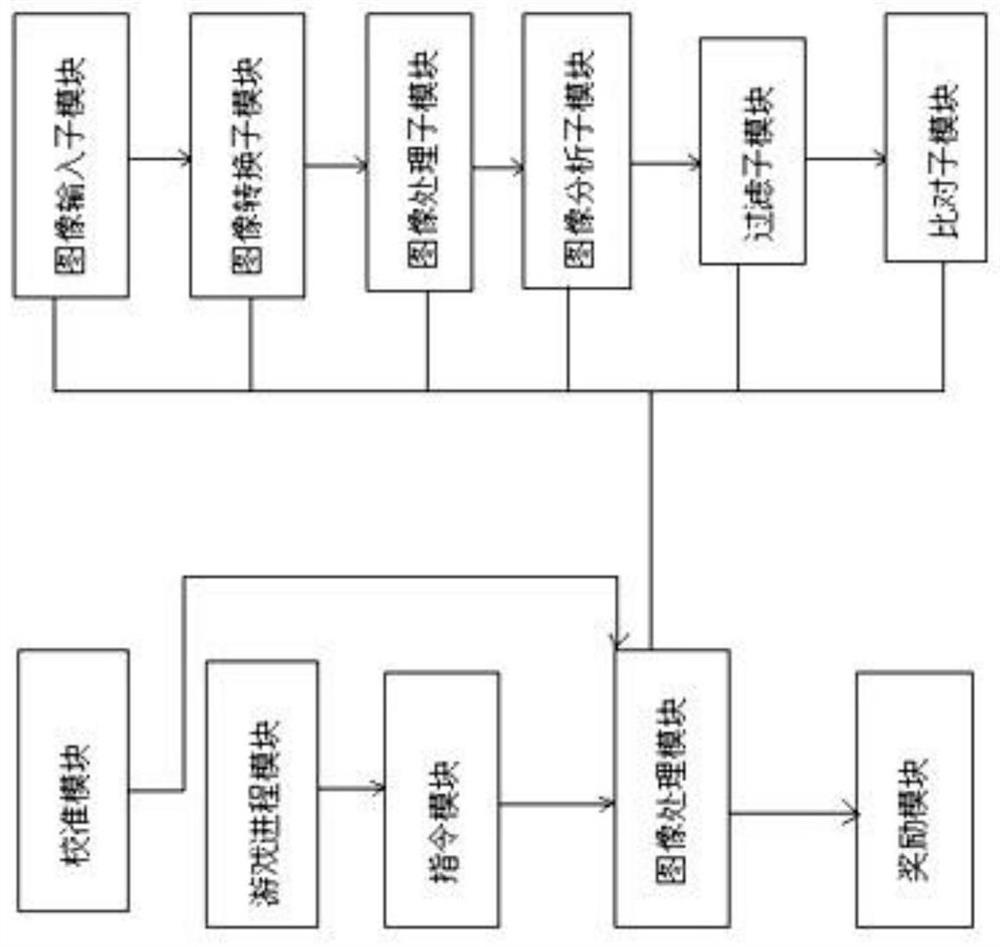
PendingCN112053281AIncrease motivation to playSmall amount of calculationImage enhancementImage analysisApplication softwareEngineering
The invention discloses an intelligent identification method for a tangram toy. Internet equipment, a base, a reflector, a splicing base plate and an application software unit in the Internet equipment are adopted as identification tools; a mobile phone is inserted into a groove of the base, a reflector lens is horizontally installed at the lower end of the shell, and the shell is clamped on the front side of the upper portion of the mobile phone and located on the upper portion of a mobile phone camera. The base plate is positioned at the front end of the base. The application software unit comprises a calibration module, a game process module, an instruction module, an image processing module and a reward module. Identification is divided into eight steps. The method is based on the AI technology, the color of each tangram serves as the judgment basis of the placement position and shape, whether the position and pattern of the single tangram placed in the corresponding area of the base plate are correct or not is directly obtained according to the colors, the calculation amount is reduced, the steps are few, and the probability of image recognition errors is correspondingly reduced; and the method overcomes the defects that an edge matching method adopted in the prior art is large in calculated amount and large in number of steps. Based on the above, the method has a good application prospect.
Owner:上海积跬教育科技有限公司
Three-dimensional target detection method and system based on deep neural network
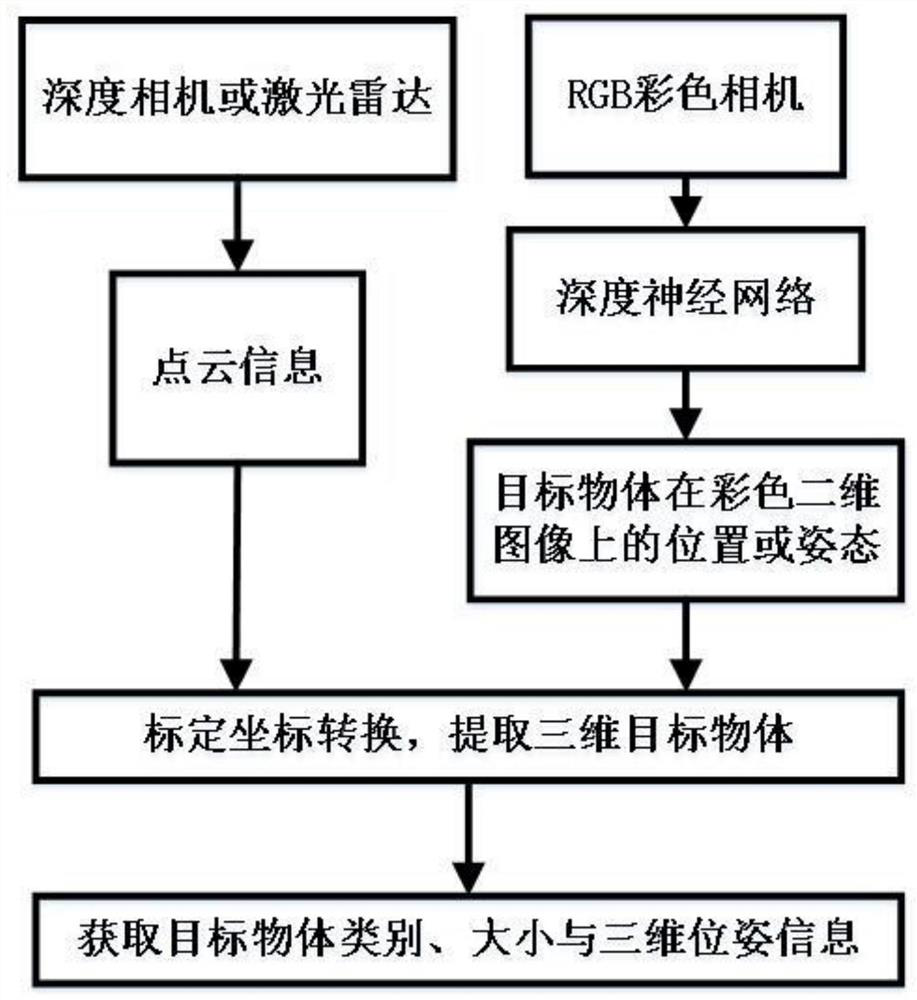
PendingCN112258631ASmall amount of calculationImprove adaptabilityImage enhancementImage analysisPattern recognitionColor image
The invention discloses a three-dimensional target detection method and system based on a deep neural network, and belongs to the technical field of three-dimensional target detection. The three-dimensional target detection method and system based on the deep neural network have the advantages of being accurate in target detection, small in neural network layer number, small in calculated amount,low in hardware requirement, high in universality and real-time performance and the like. The method comprises the steps of obtaining a color image and point cloud information of an environment wherea target object is located; adopting a deep neural network YOLO6D and YOLOv2 to carry out joint detection on the color image, and respectively obtaining a 2D bounding box and a 3D bounding box of thetarget object on the color image; mapping the point cloud information to an image coordinate system of the color image, and obtaining coordinate information of the point cloud information in the colorimage; according to the 2D bounding box and the 3D bounding box of the target object on the image and combining the coordinate information of the point cloud information in the color image, respectively obtaining depth information of the 2D bounding box and the 3D bounding box; and according to the depth information of the 2D bounding box and the 3D bounding box and combining the dimension of thepoint cloud information, obtaining the category, size and pose information of the target object.
Owner:HOHAI UNIV CHANGZHOU
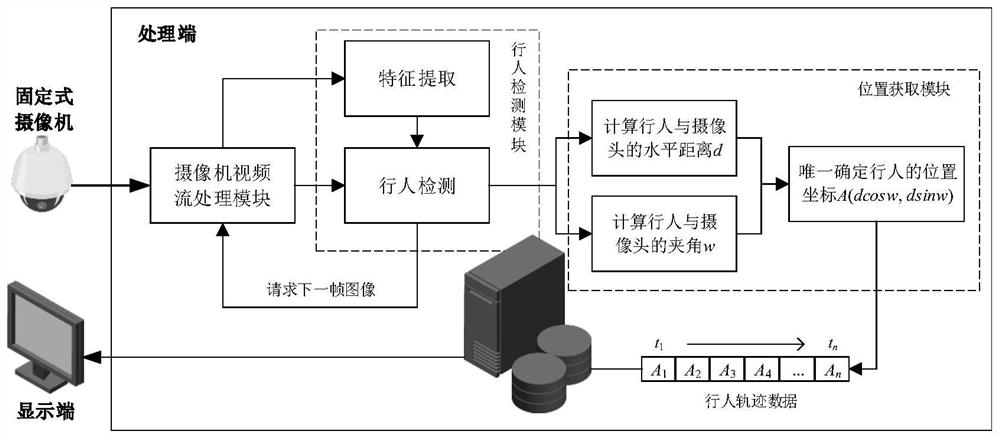
Pedestrian positioning and track obtaining method based on camera video stream
ActiveCN111914699AReduce in quantitySolve the costImage enhancementImage analysisFeature extractionComputer graphics (images)
A pedestrian positioning and track acquisition method based on a camera video stream is characterized by sequentially comprising two steps: 1, a feature extraction and detection algorithm of an indoortarget person; wherein the pedestrian detection module is used for performing pedestrian detection on each frame of image of a camera video stream; 2, a pedestrian position information and a moving track acquisition algorithm thereof; wherein the algorithm is used for acquiring position information and moving tracks of pedestrians detected in each frame of image of a camera video stream. According to the method, the space models of the indoor camera and the pedestrian are established, the related models are established from the vertical section and the horizontal section of the pedestrian respectively, the established models are simple and efficient, the required calculation amount is small, the accuracy of the acquired position information is high, the calculation force can be saved, thetime consumption is reduced, and the real-time performance is ensured.
Owner:TONGJI UNIV
A real-time digital organ cutting method based on metasphere model and hybrid drive method
ActiveCN106875462BReduce fillingFast convergenceComputer-aided planning/modellingAnimationPhysical medicine and rehabilitationPhysical therapy
The invention provides a real-time digital organ cutting method based on a metaball model and a hybrid driving method. Based on the metaball model, the position dynamics and the meshless method driving model are used simultaneously in the cutting process. In order to solve the problem of metaball For problems that require frequent splitting and merging during the cutting process, a metaball-to-pointset-to-metaball cutting mode is adopted, in which positional dynamics is used to drive metaballs, and meshless methods are used to drive meta The set of points generated by the ball. The method consists of four steps. First, the preprocessing process, which requires some initialization operations while reading the model file; second, the deformation process, which uses a method based on positional dynamics to drive the model; third, the cutting process, which uses The hybrid-driven method drives the model, using the method of metaball to point set and then returning to the metaball to cut; the fourth, the rendering process, renders the model in the second and third processes. The invention can truly simulate the process of cutting soft tissue in virtual surgery, and has high controllability and real-time performance.
Owner:BEIHANG UNIV
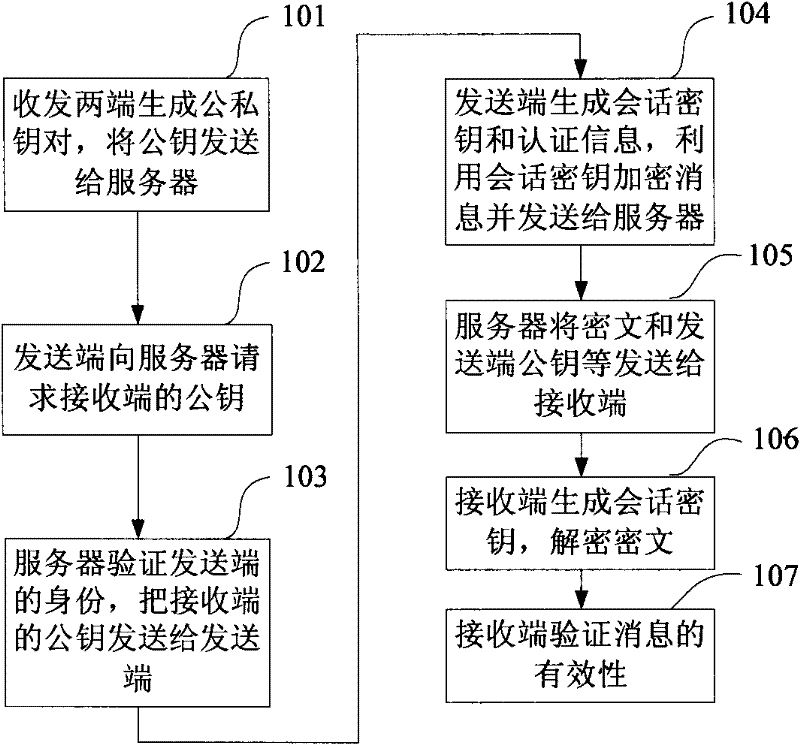
Authentication Encryption Method and Encryption System Based on Symmetric Encryption
InactiveCN101667913BAchieve authenticationImplement encryptionKey distribution for secure communicationUser identity/authority verificationSecure communicationThird party
The invention requests protection of an authentication and encryption method and system, which relate to the field of communication security. Combining message recoverable signature and symmetric encryption technology, using the commitment value that only the specified message receiving end can calculate as the session key to encrypt the message, the message receiving end verifies the validity of the message through the recoverable signature, so that it can be realized simultaneously in one logical step encryption and authentication. The key generating unit at the sending end generates a session key at the sending end, the encryption unit encrypts the message to be sent, the receiving end generates a session key at the receiving end, and the decryption unit uses the session key at the receiving end to decrypt the encrypted message. The message generates authentication confirmation information to verify the validity of the message. When a dispute occurs, the message receiver can convert the authenticated encrypted message signature into a common signature, allowing a third party to publicly verify the validity of the signature. The invention has the advantages of high security, low calculation amount and transmission cost, and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Big data security protection cloud system based on trusted computing
InactiveCN105933361BTimely collectionOptimize the total calculation amountTransmissionBig data securityTrusted Computing
Owner:GUANGXI POWER GRID CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com