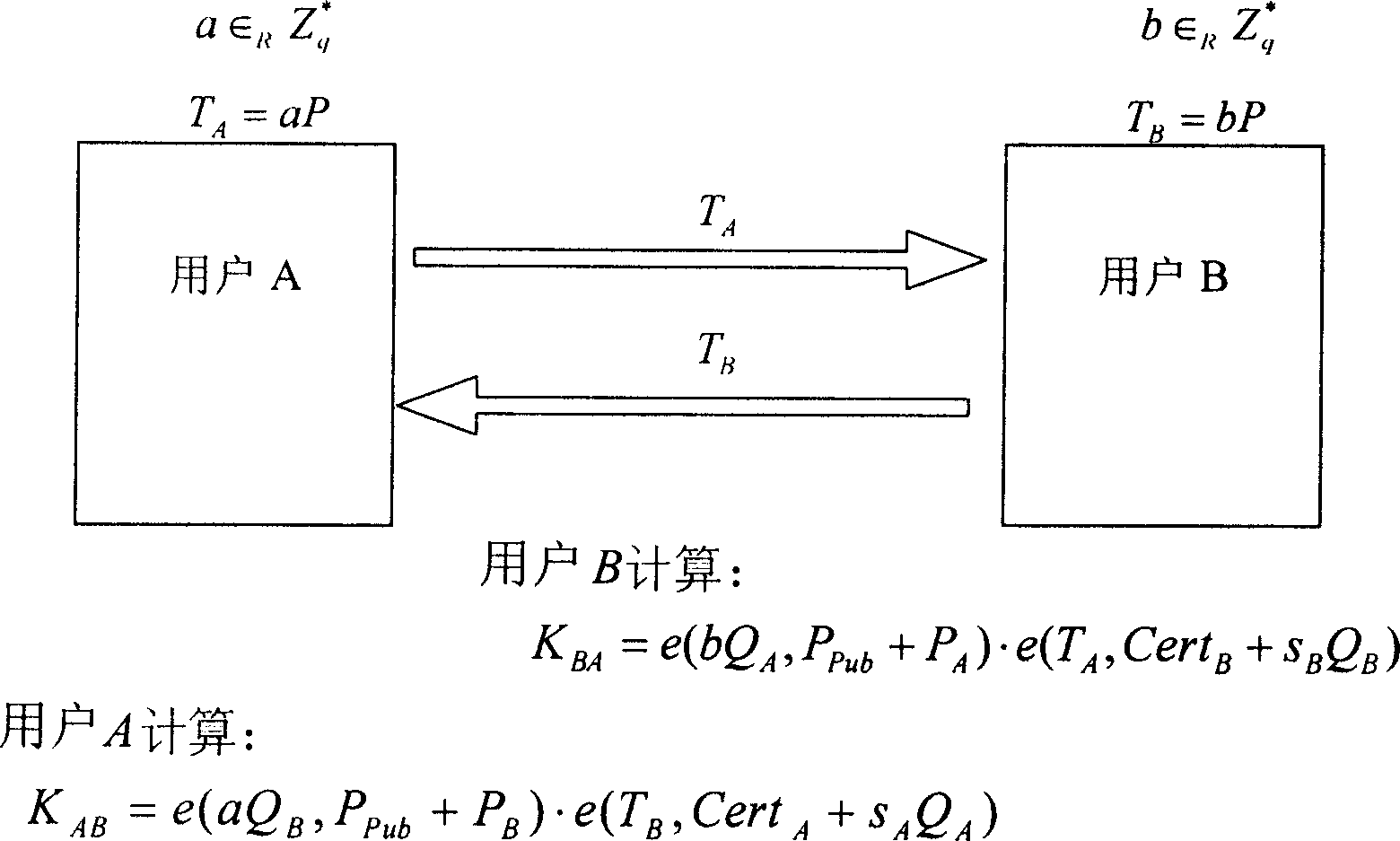
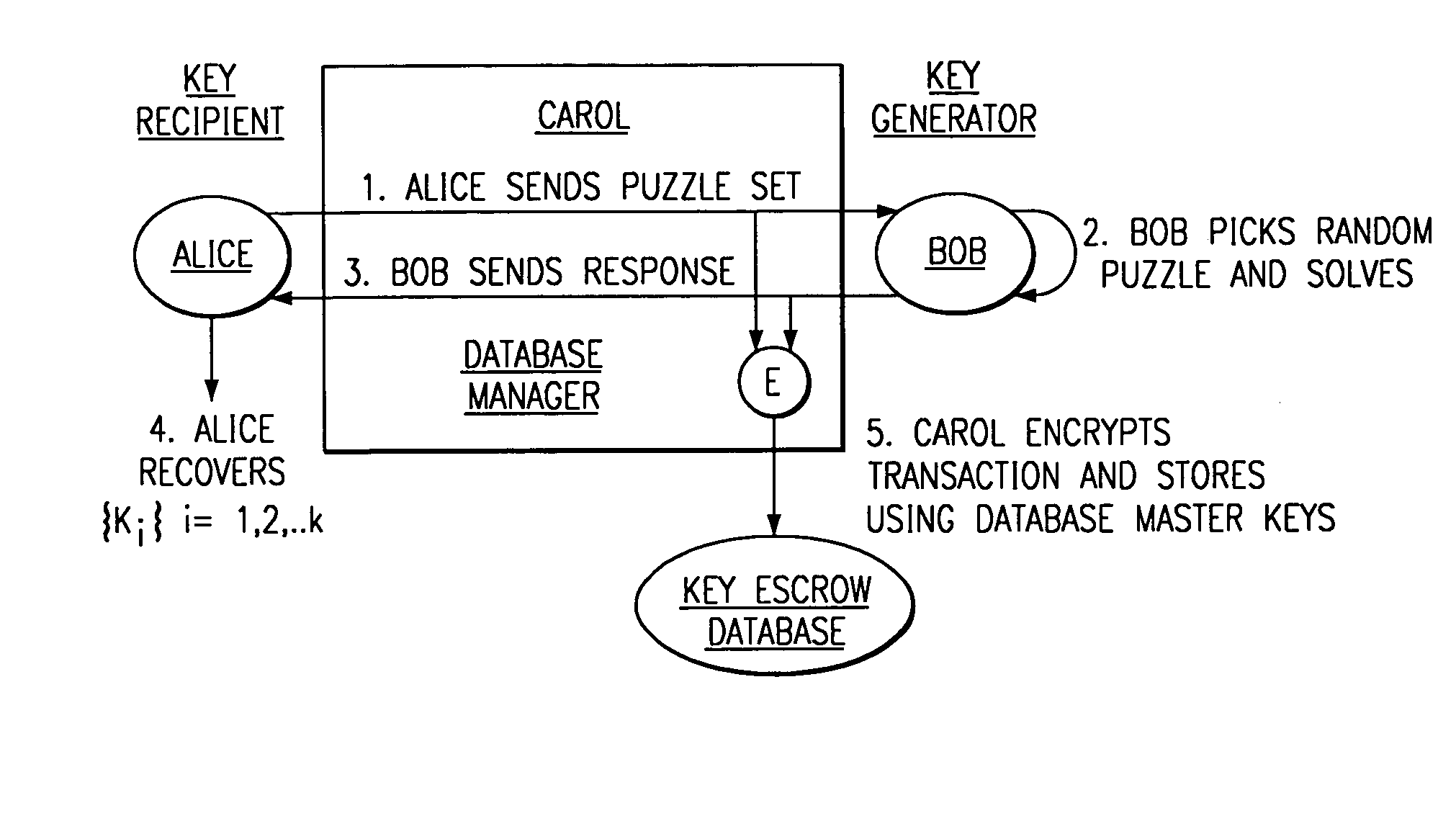
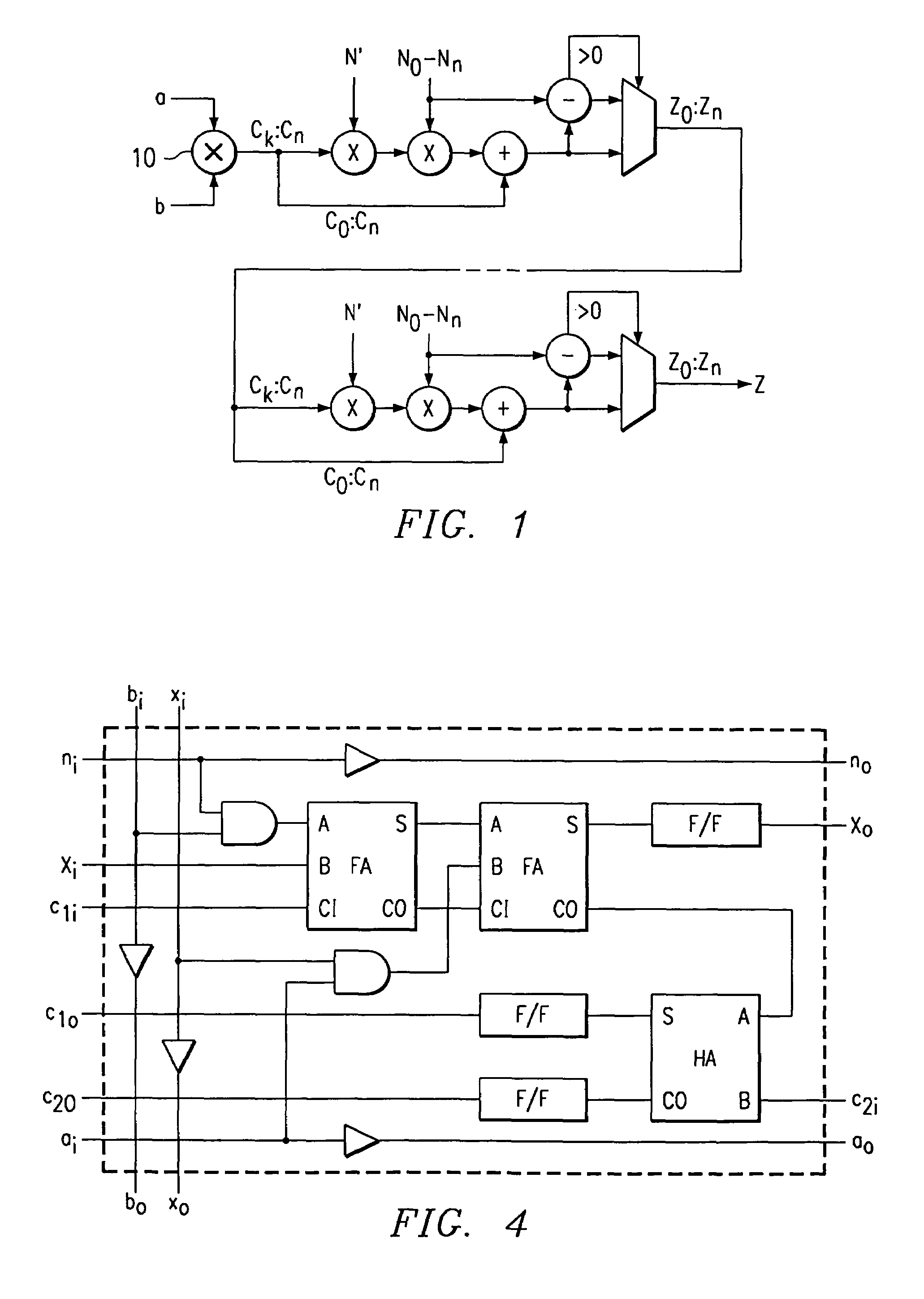
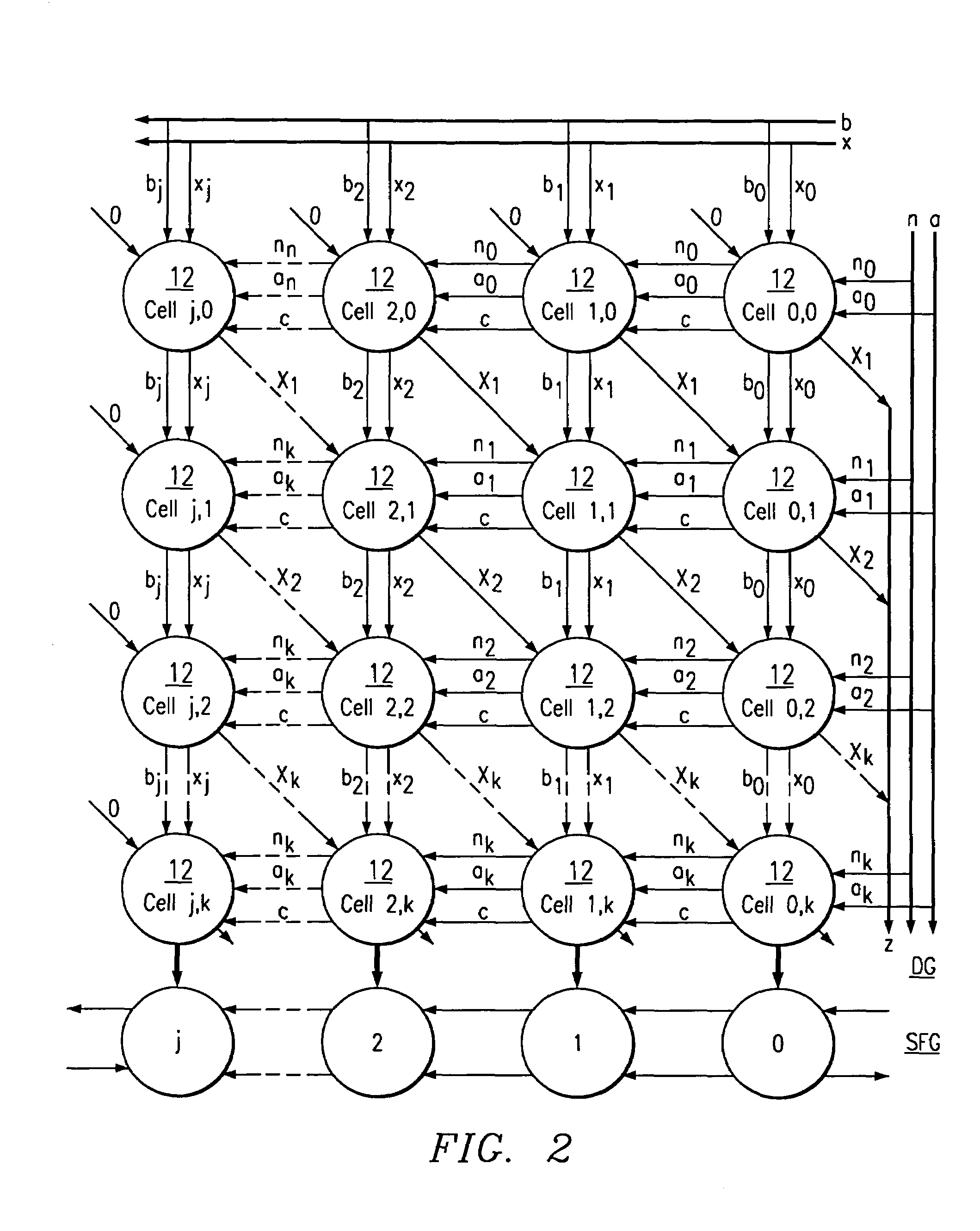
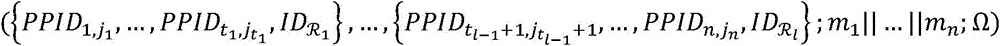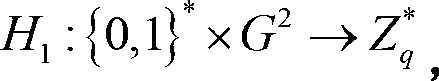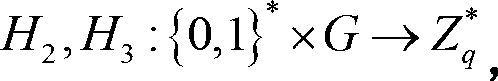Patents
Literature
198 results about "Key escrow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
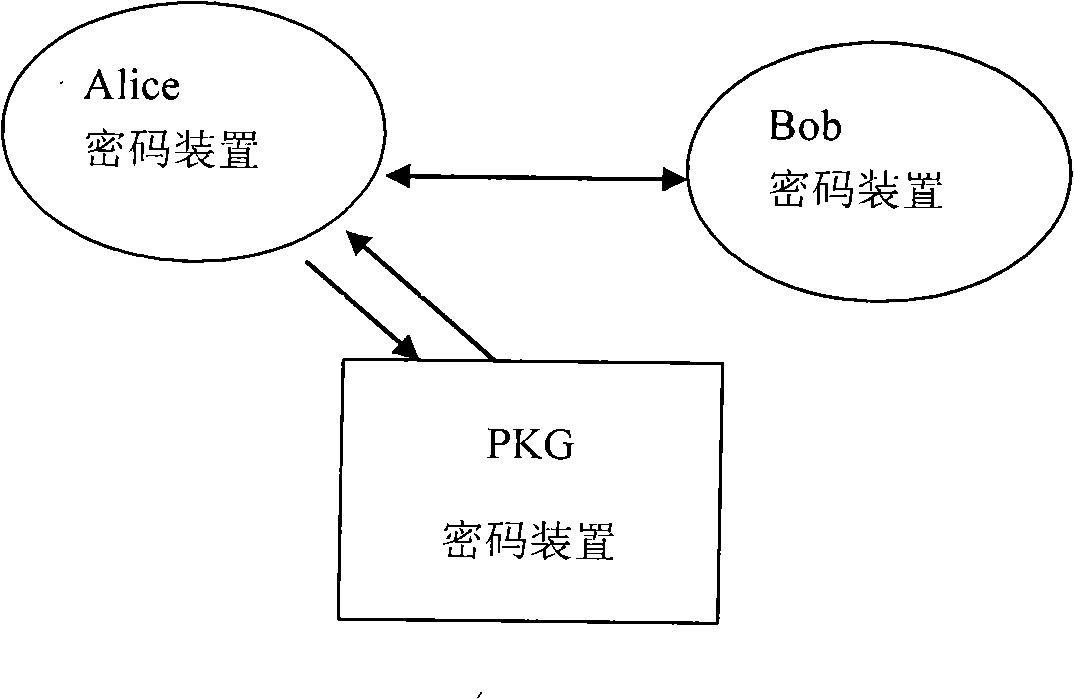
Key escrow (also known as a “fair” cryptosystem) is an arrangement in which the keys needed to decrypt encrypted data are held in escrow so that, under certain circumstances, an authorized third party may gain access to those keys. These third parties may include businesses, who may want access to employees' private communications, or governments, who may wish to be able to view the contents of encrypted communications.
Method for authenticating electronic documents
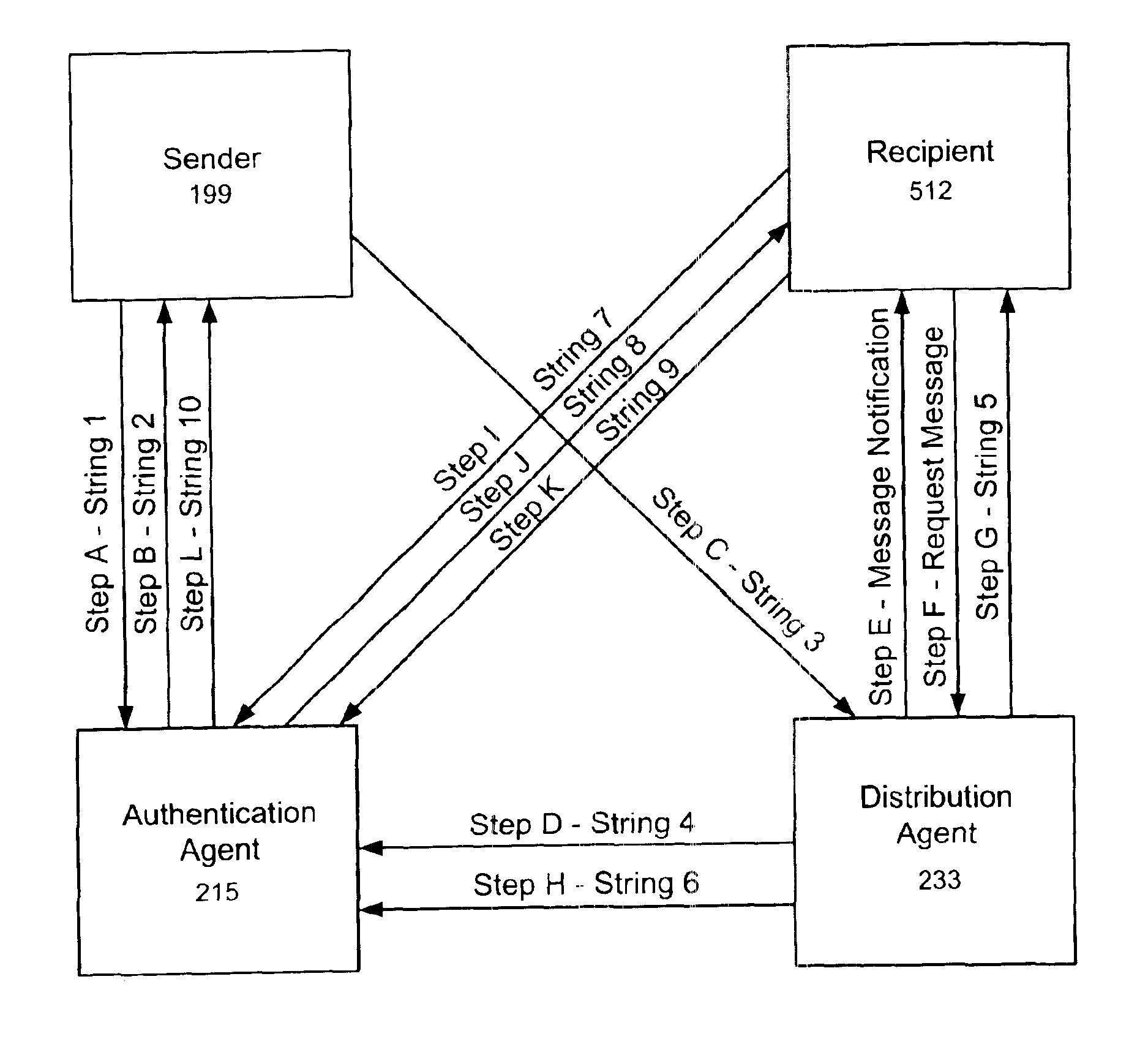
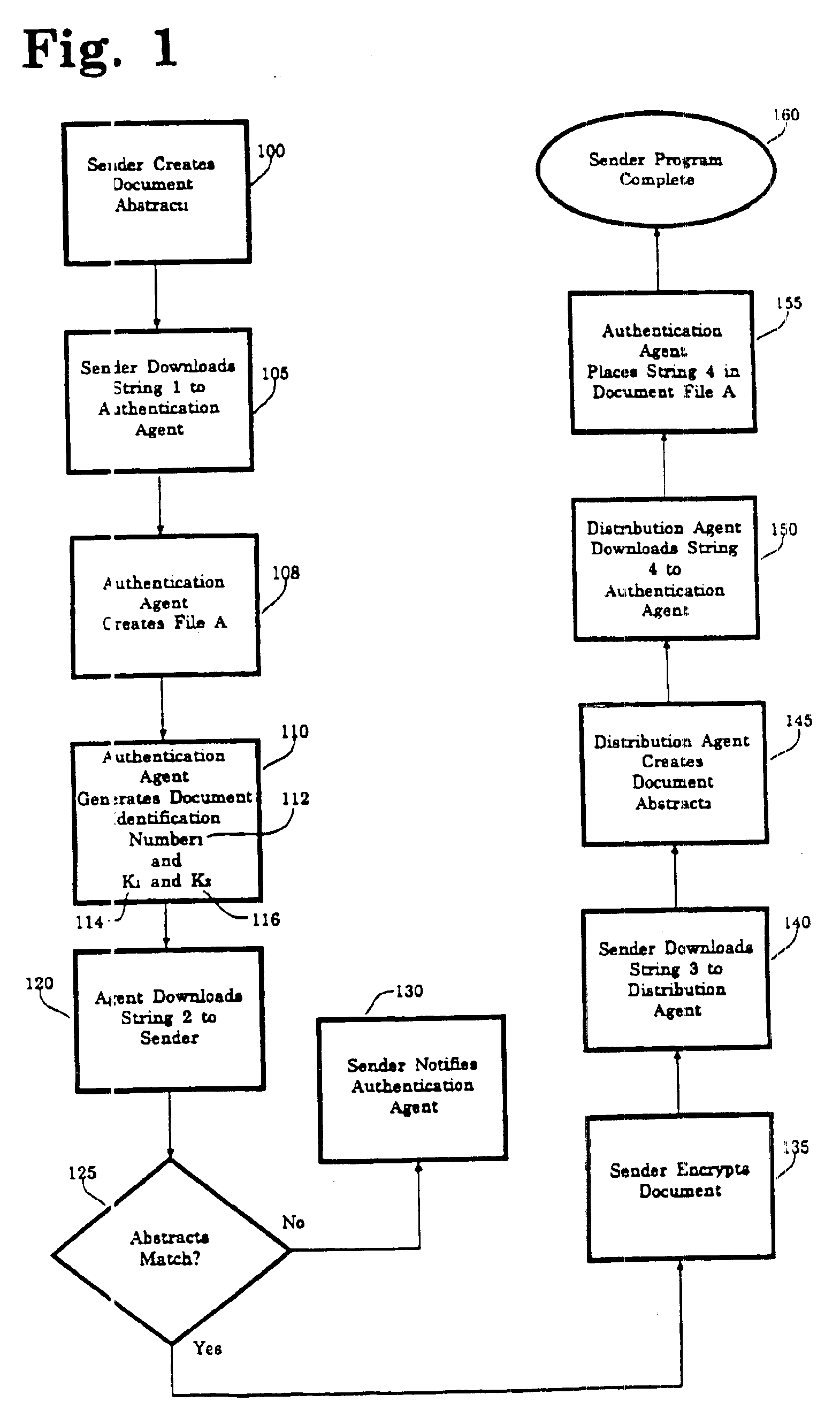
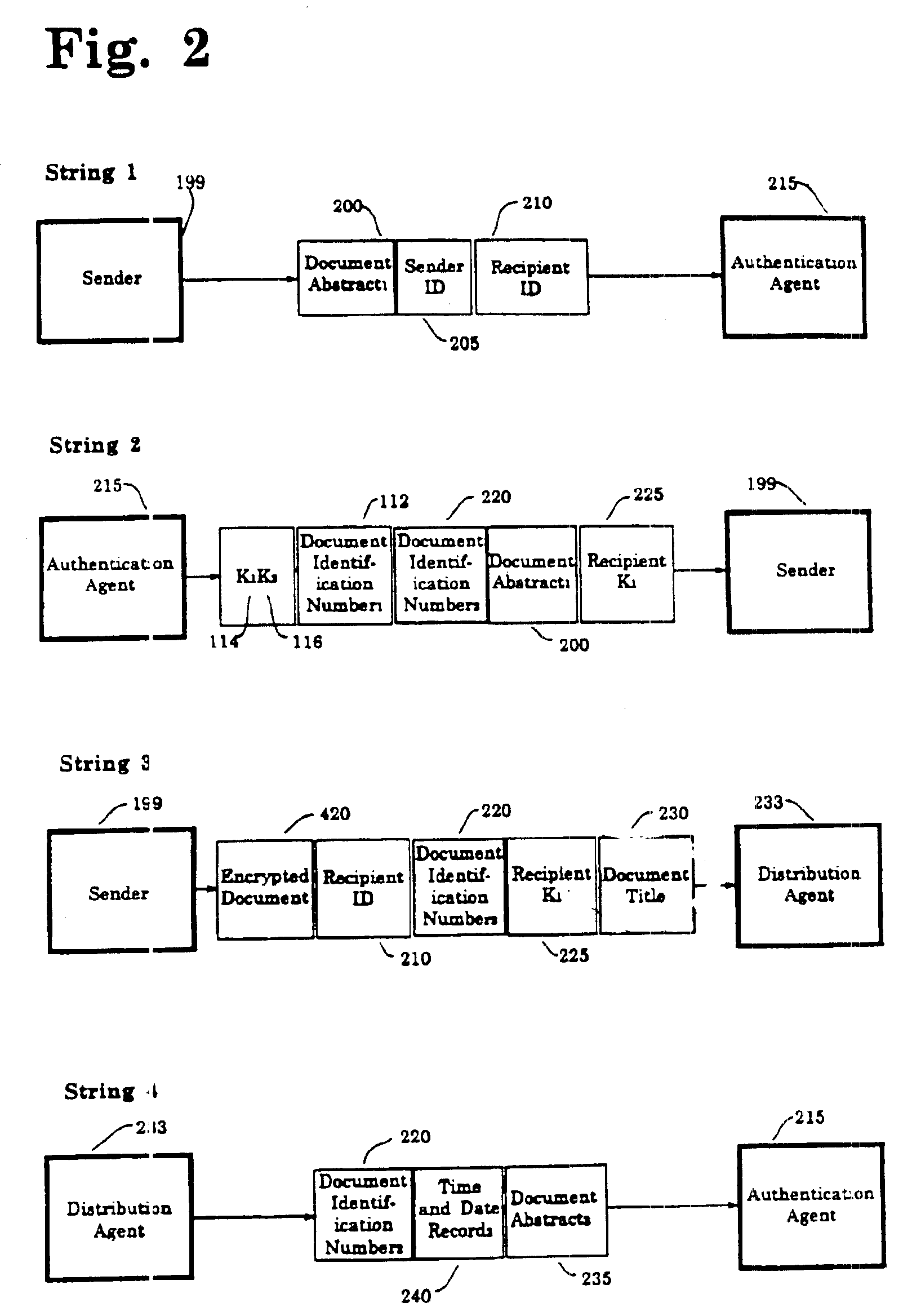
InactiveUS6963971B1Improve privacyImprove user securityKey distribution for secure communicationUser identity/authority verificationThird partyElectronic document
A secure method for sending registered, authenticated electronic documents. The invention validates sender and recipient identities, provides for non-repudiation of authenticated documents by sender and recipient, provides an evidence trail, and protects the integrity of the document. The invention is constructed so that a sender can be supplied with proof that the intended recipient received and opened an authenticated document. A neutral third party acts as a document registration agent, and witness to the transmission and receipt of the authenticated document. In the event of a dispute between sender and recipient, the third party can provide an irrefutable record of the contents of the document and of the history of the transmission and receipt of the document Because the third party never has possession of the electronic document, the method provides maximum privacy for sender and recipient. The method is readily adaptable to both key recovery and key escrow.
Owner:BUSH GEORGE +4
Cloud key escrow system
ActiveUS20120321086A1Data augmentationKey distribution for secure communicationDigital data processing detailsThird partyData access
Owner:MICROSOFT TECH LICENSING LLC
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
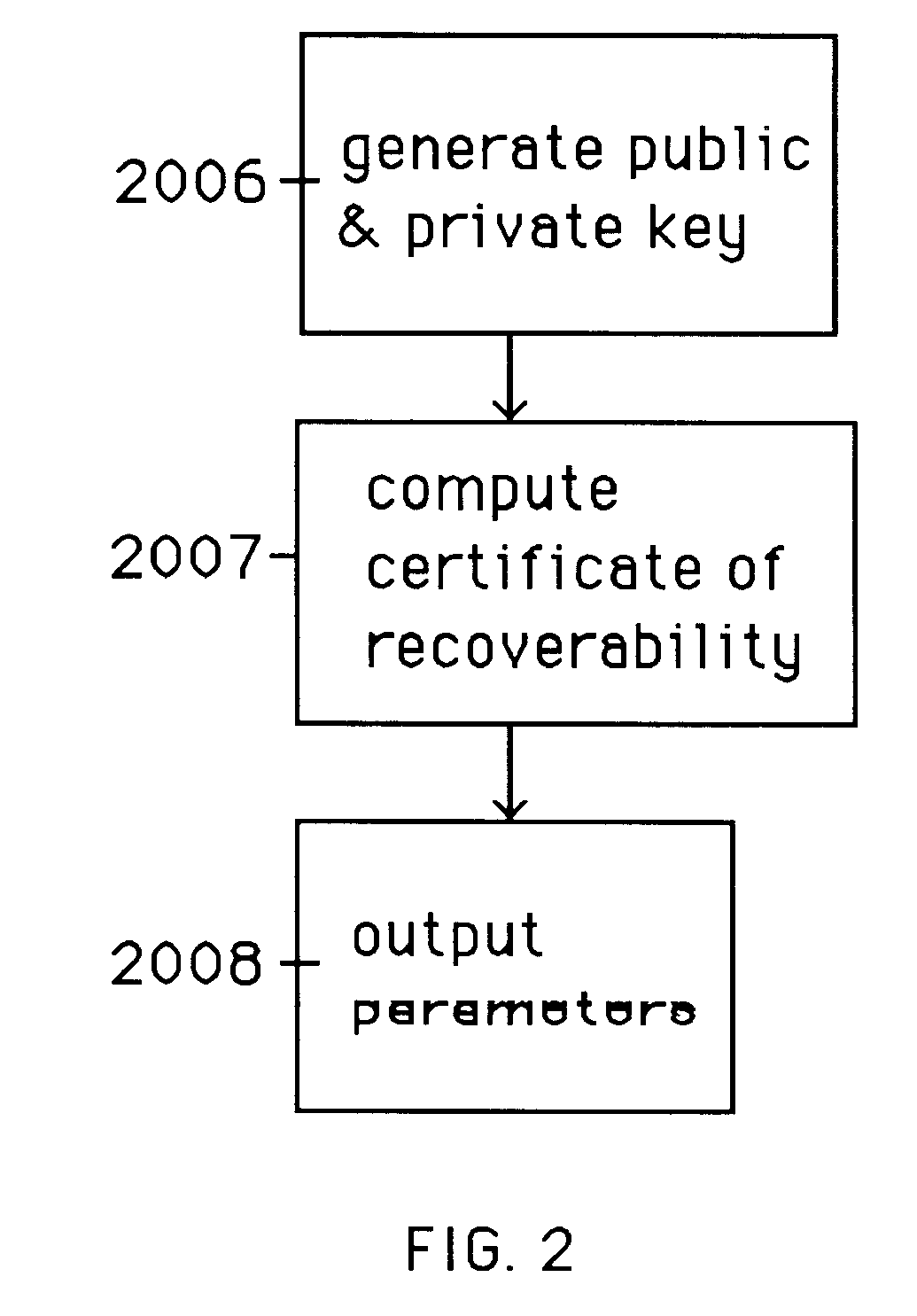
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
Management of ssl certificate escrow
ActiveUS20120170753A1Key distribution for secure communicationComputer security arrangementsInternet privacyKey escrow
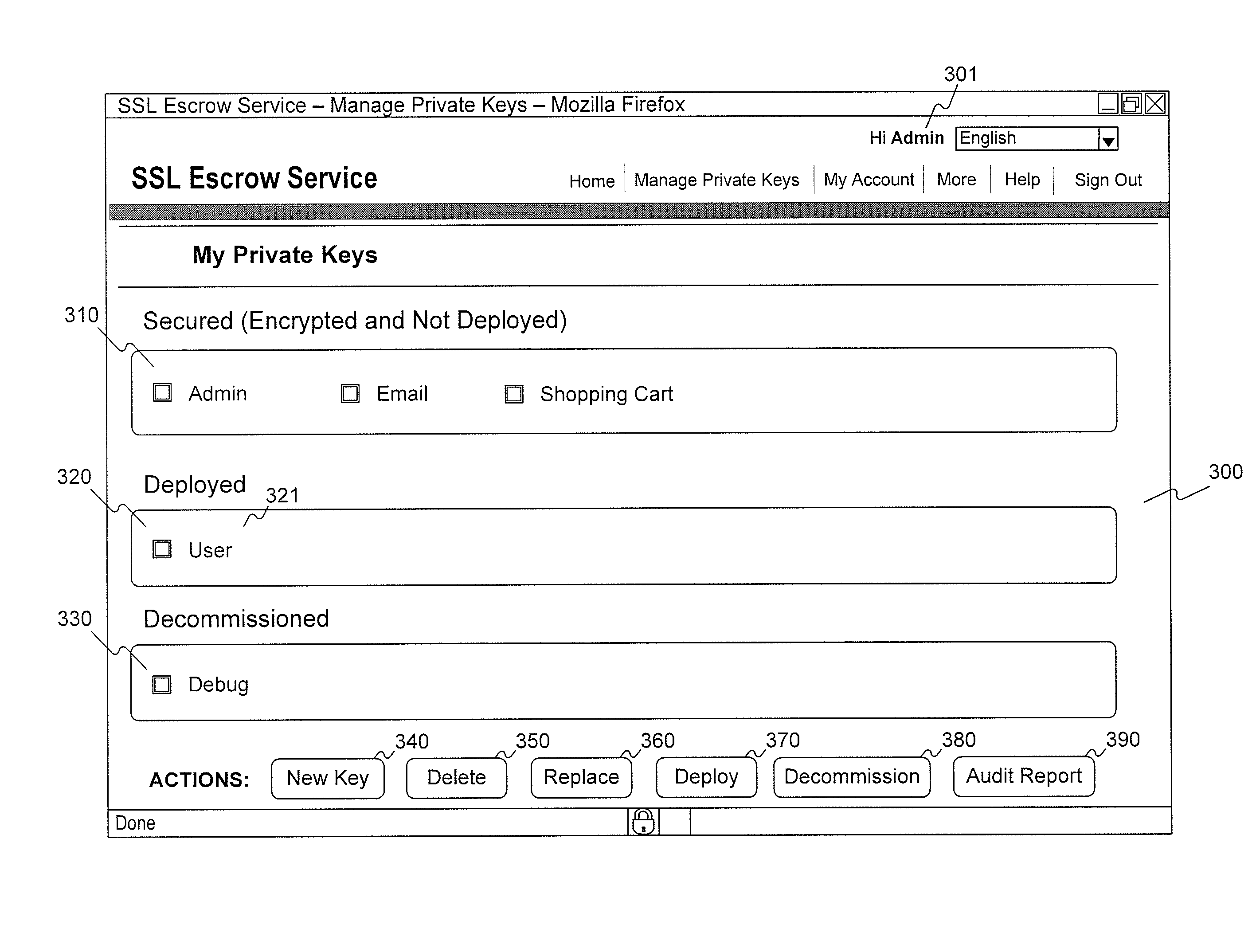
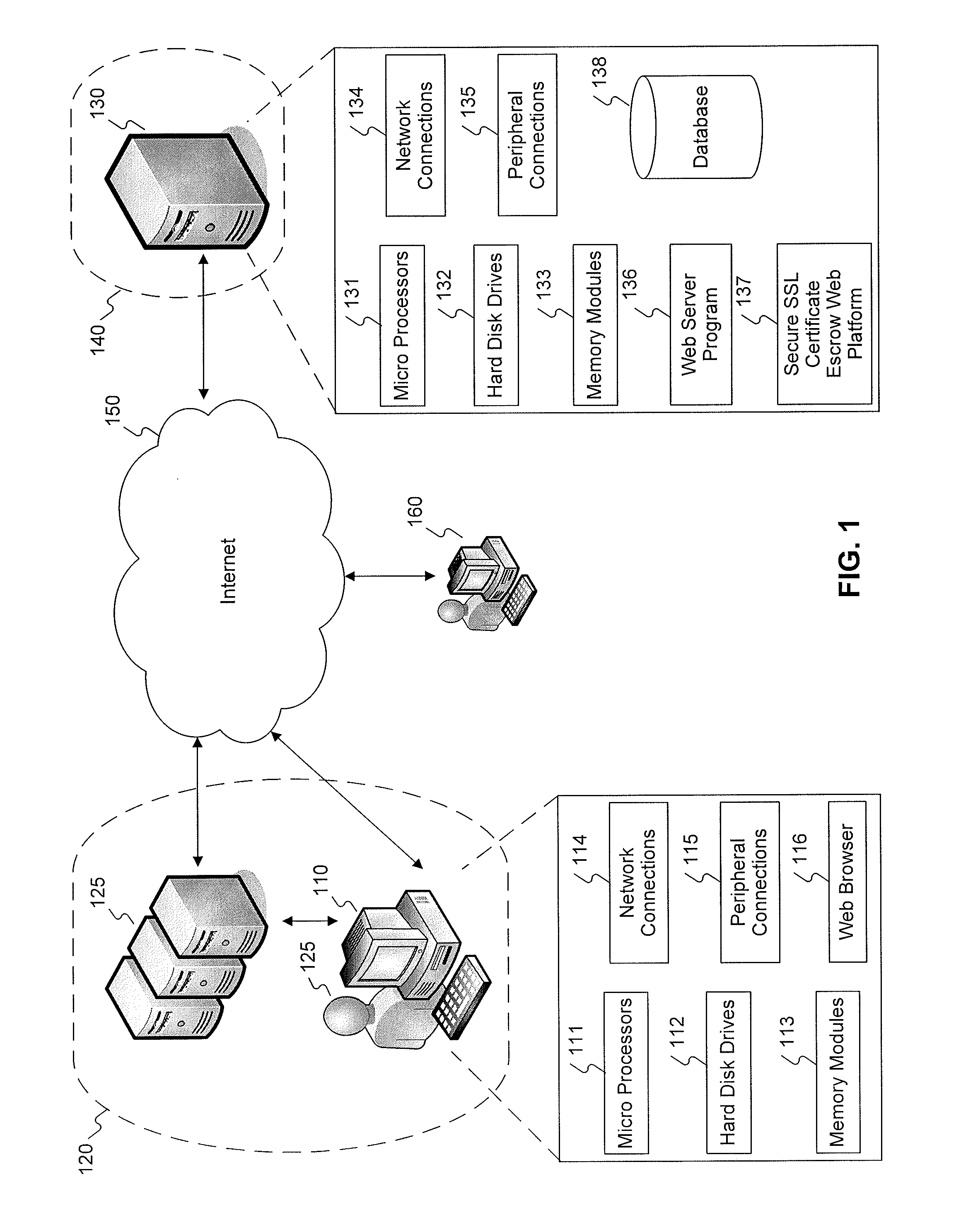
Methods and systems for providing a secure SSL certificate escrow service comprise: providing a secure upload webpage for a private key holder to upload an encrypted copy of a private key; receiving the encrypted copy of the private key from the private key holder via the secure upload webpage; storing the encrypted copy of the private key in memory; providing a secure decryption webpage for the private key holder to enable the private key escrow service to decrypt the private key; receiving an instruction to decrypt the private key from the private key holder through the secure decryption webpage; and decrypting the private key in response to the instruction to decrypt the private key.
Owner:VERISIGN
Distributed aggregation authentication method having privacy protection function for vehicle-mounted self-organizing network
InactiveCN105763558ASatisfy unlinkable privacyKey distribution for secure communicationSecurity arrangementPrivate communicationPrivacy protection
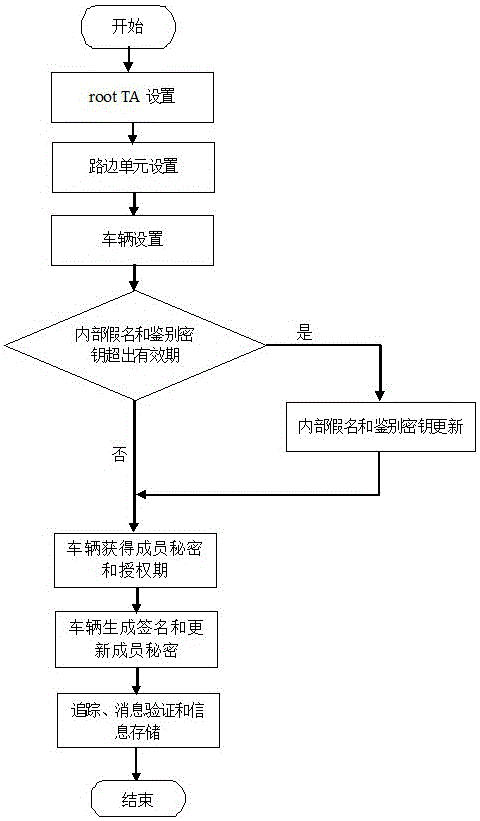
The invention discloses a distributed aggregation authentication method having a privacy protection function for a vehicle-mounted self-organizing network. The method comprises the following steps: a step of trusted root mechanism arrangement, a step of road side unit arrangement, a step of vehicle arrangement, a step of internal pseudonym and authentication key updating, a step of a vehicle obtaining secrets of members and authorization terms, a step of the vehicle generating signatures and updating the secrets of the members, a step of tracking and a step of message verification and information storage. The distributed aggregation authentication method is characterized in that conditional privacy is not associable, the method is independent of an ideal and strict anti osmosis device, and no secret key trusteeship problem can be caused. Safe and private communication of a the vehicle-mounted self-organizing network can be realized through the distributed aggregation authentication method.
Owner:EAST CHINA NORMAL UNIV
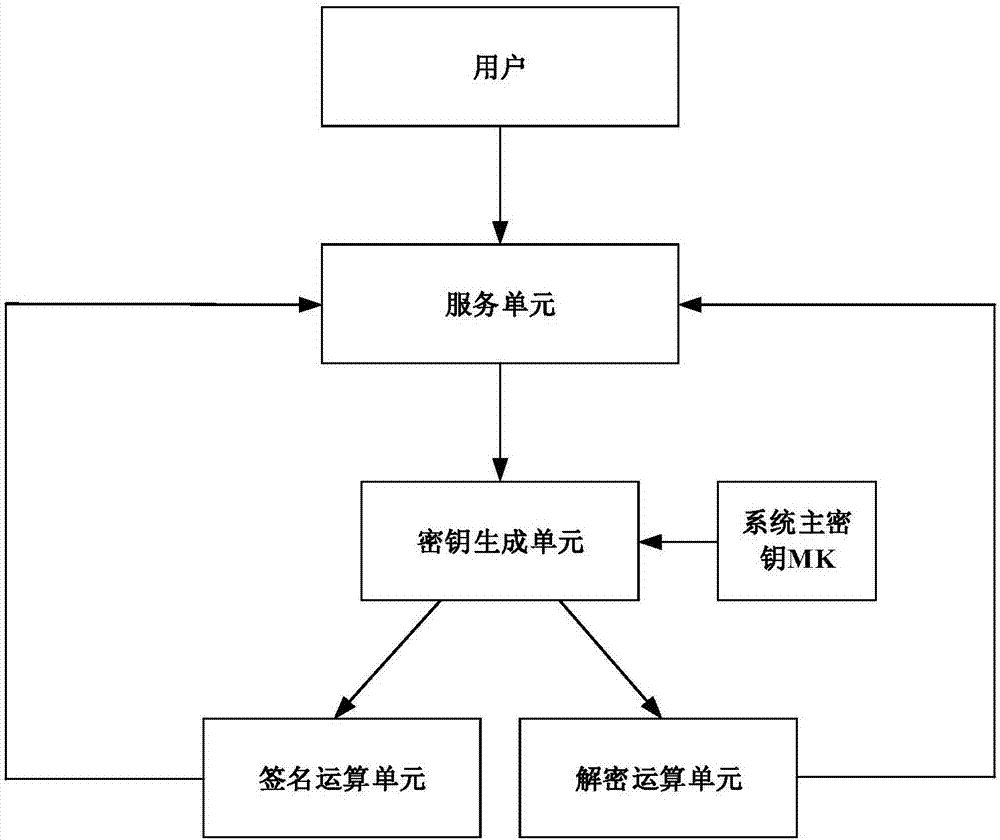
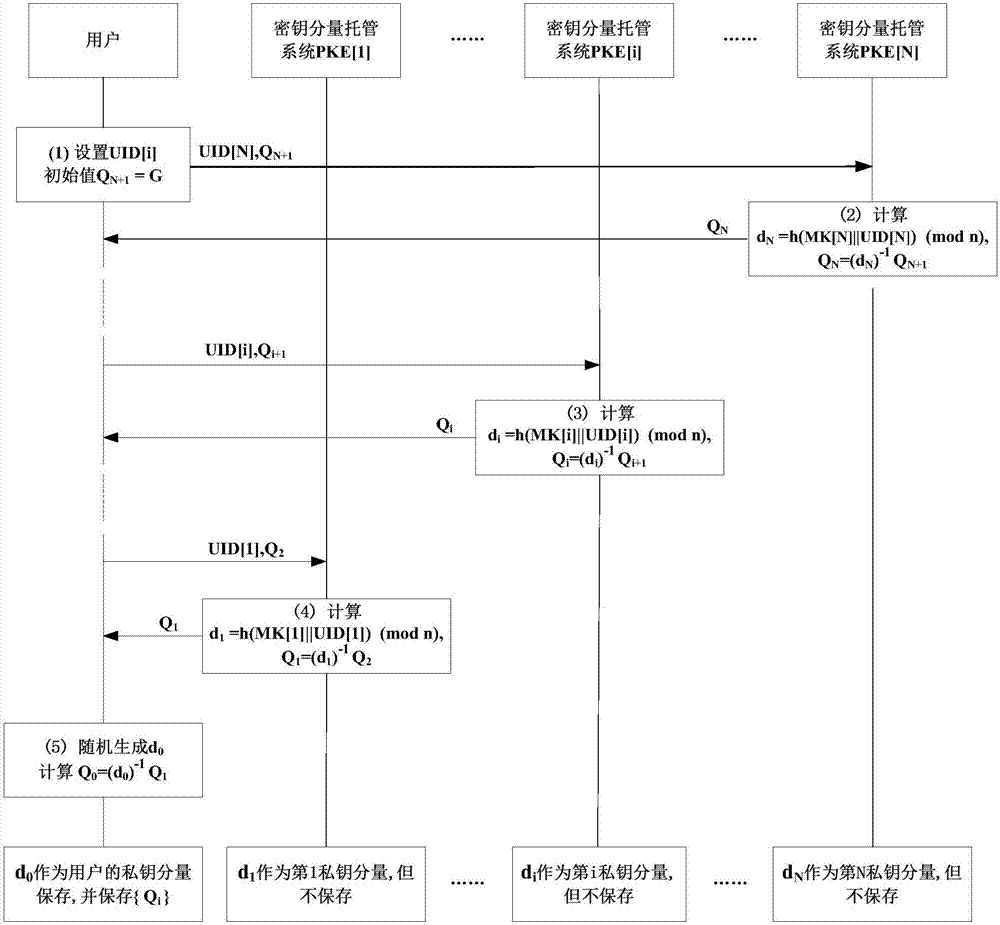
PKE method and system based on SM2 algorithm
ActiveCN106961336AKey distribution for secure communicationUser identity/authority verificationMapping algorithmKey escrow
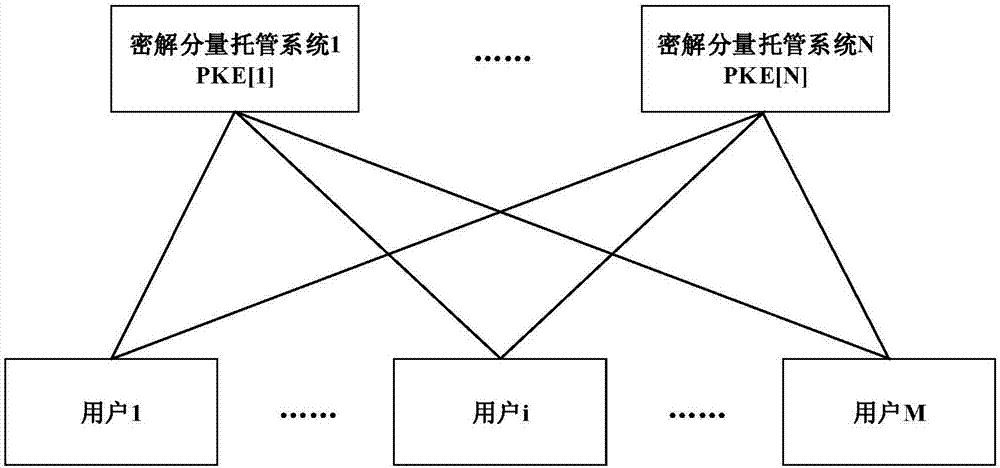
The invention provides a partial key escrow (PKE) method and system based on a public key cryptographic algorithm SM2, and belongs to the field of information security. N (N is not less than 1) different PKE systems form one key escrow network. An SM2 private key of a user is divided into N+1 partial keys by utilizing key partition storage and multiparty combined calculation modes; the user and the N different PKE systems perform scatter storage; and the user and the N different PKE systems are combined to complete a correlation calculation when the private key needs to be used. At user key generation and use stages, the PKE system generates user partial private keys by utilizing a labeling mapping algorithm, but does not practically save the user partial private keys; therefore, the construction scale of the system can be largely reduced, investment costs of the system are reduced, and operation efficiency and service level of the system are improved.
Owner:北京百旺信安科技有限公司 +1
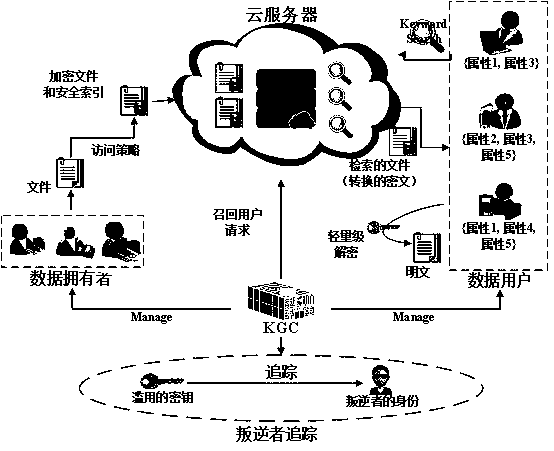
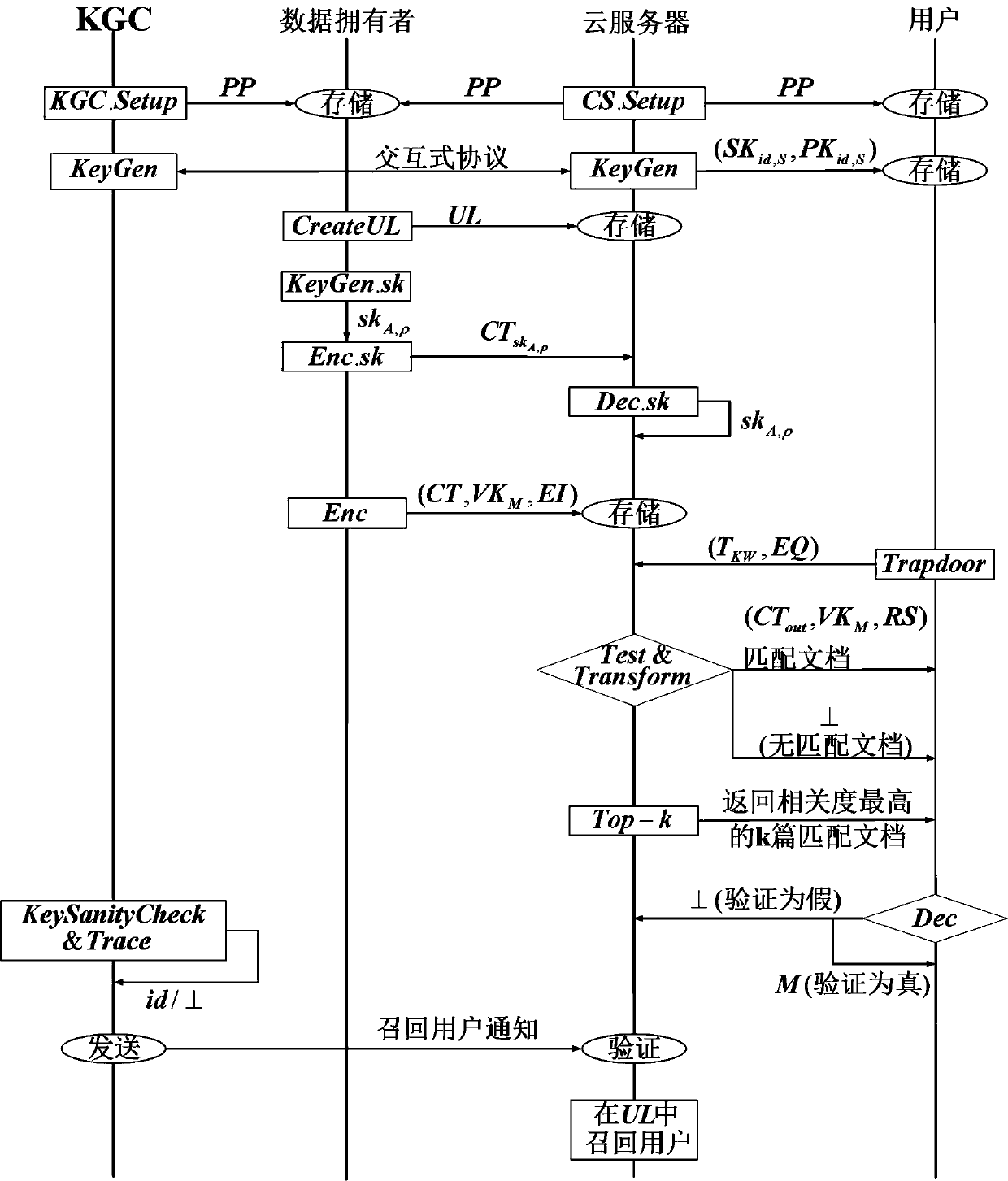
Key escrow-free secure multi-keyword sorting and searching system
ActiveCN108632032ADoes not affect search resultsExpandable and flexibleKey distribution for secure communicationUser identity/authority verificationCiphertextSecurity index
The invention relates to a key escrow-free secure multi-keyword sorting and searching system. The system comprises a key generation center, a cloud server, a data owner and a data user; the key generation center is used for achieving interactive computing with the cloud server to jointly generate a public parameter of the system and a property public key-private key pair of the data user; the cloud server is used for storing a file of the data owner and responding to a searching query request of the data user; the data owner extracts a keyword set from the file, encrypts the keyword set into asecure index, encrypts the file, makes an access strategy and embeds the access strategy into ciphertext; and the data user defines the searched keyword set and generates a trap door by using the property private key of the data user to search for the encrypted file stored in the cloud server. According to the system, the key escrow problem is solved, flexible authorization keyword searching andfine-grained data access authorization are achieved, multi-keyword subset searching is supported, and the searching result is not influenced by changes of the keyword query order.
Owner:FUZHOU UNIV
Certificate-based agent heavy encryption method and system
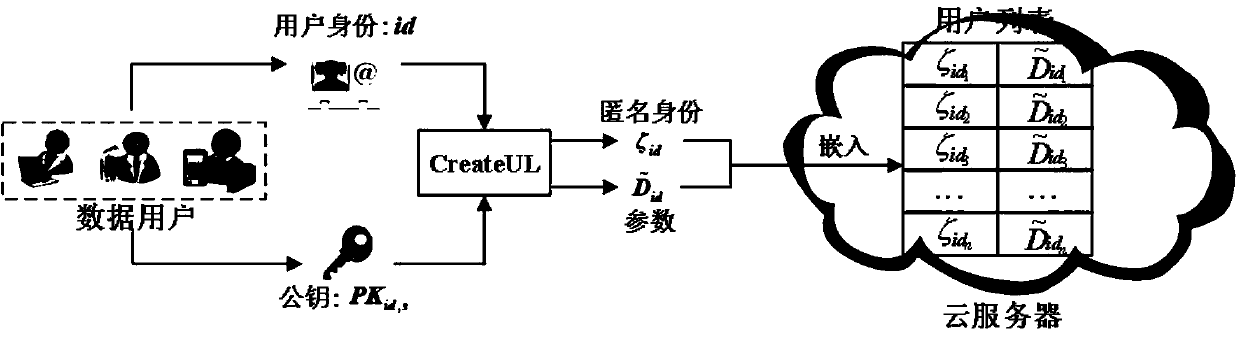
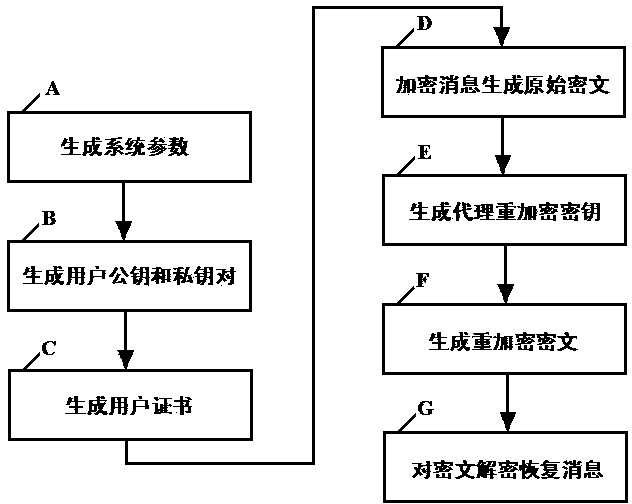
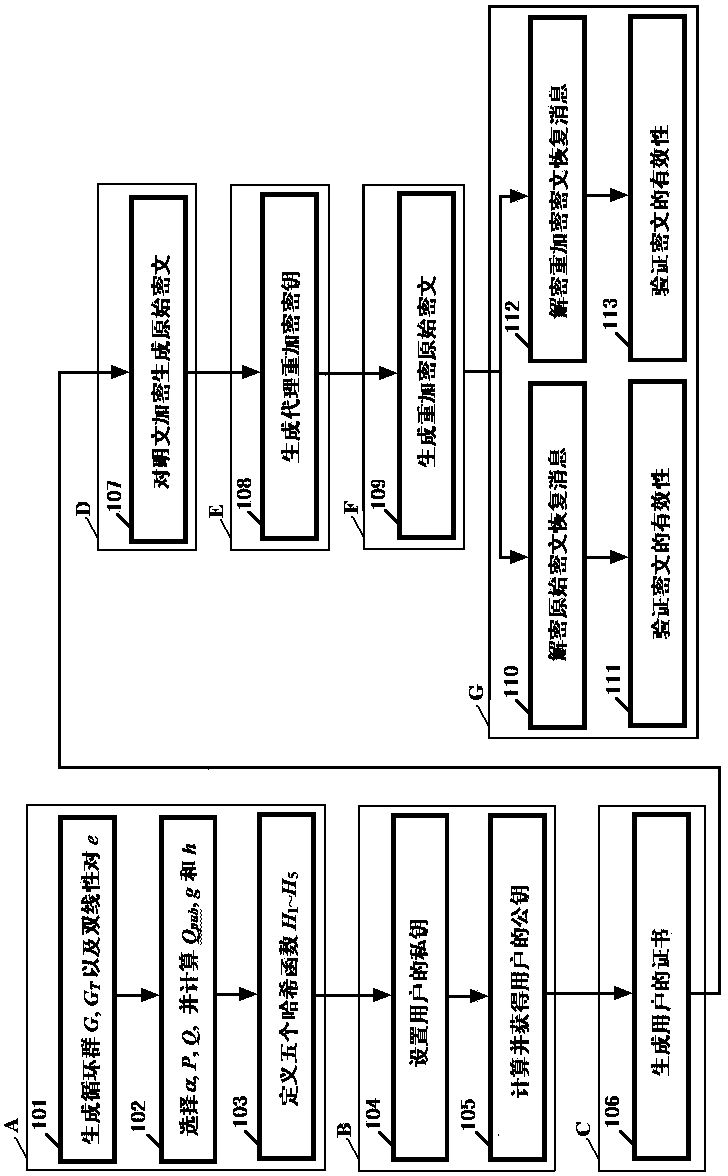
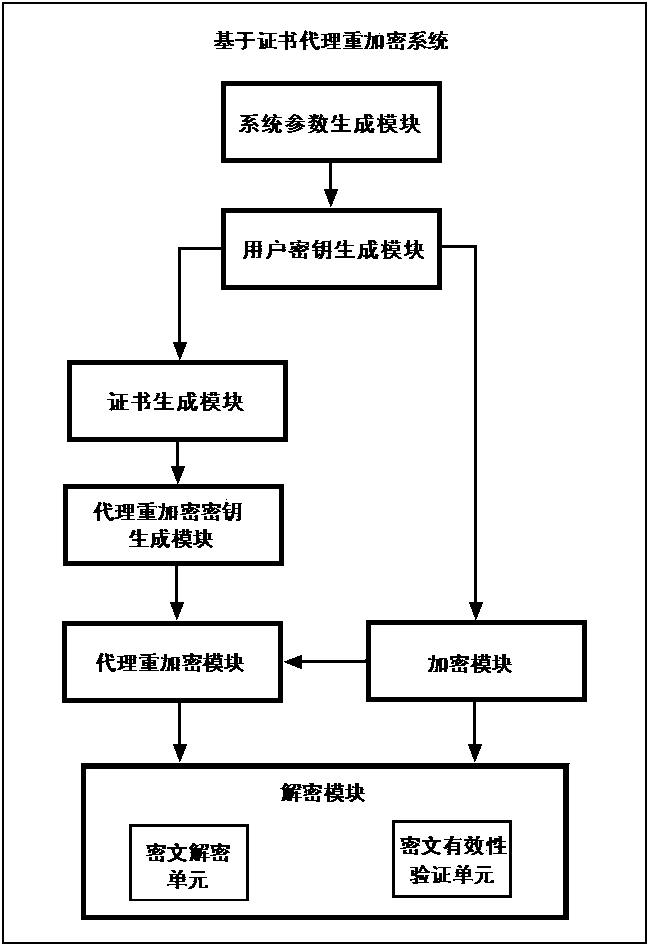
InactiveCN103647642AOvercome problemsSimplify the undo problemKey distribution for secure communicationPublic key for secure communicationCryptographic key generationPassword
The invention relates to the technical field of data encryption in information security, and discloses a certificate-based agent heavy encryption method and system, for solving the defect of a conventional agent heavy encryption method. The invention provides a certificate-based agent heavy encryption method by combining a certificate password system and agent heavy encryption. The method comprises the steps of generating system parameters, generating a user public key and private key pair, generating a user certificate, encrypting messages, generating agent heavy encryption secret key, agent heavy encrypting and message recovery. The invention also provides a certificate-based agent heavy encryption system. The system comprises a system parameter generation module, a user secret key generation module, a certificate generation module, an encryption module, an agent heavy encryption secret key generation module, an agent heavy encryption module and a decryption module. The technical scheme provided by the invention not only simplifies a certificate management process, but also eliminates the problems of secret key distribution and secret key hosting and facilitates application in open network environment.
Owner:HOHAI UNIV
Methods and systems for key escrow
An embodiment pertains generally to a method of storing keys. The method includes receiving a request for generating a subject private key at a token processing system and generating a subject key pair, where the subject key pair includes a subject public and the subject private key. The method also includes archiving the subject private key within the token processing system.
Owner:RED HAT
Authentication group key management method based on identity
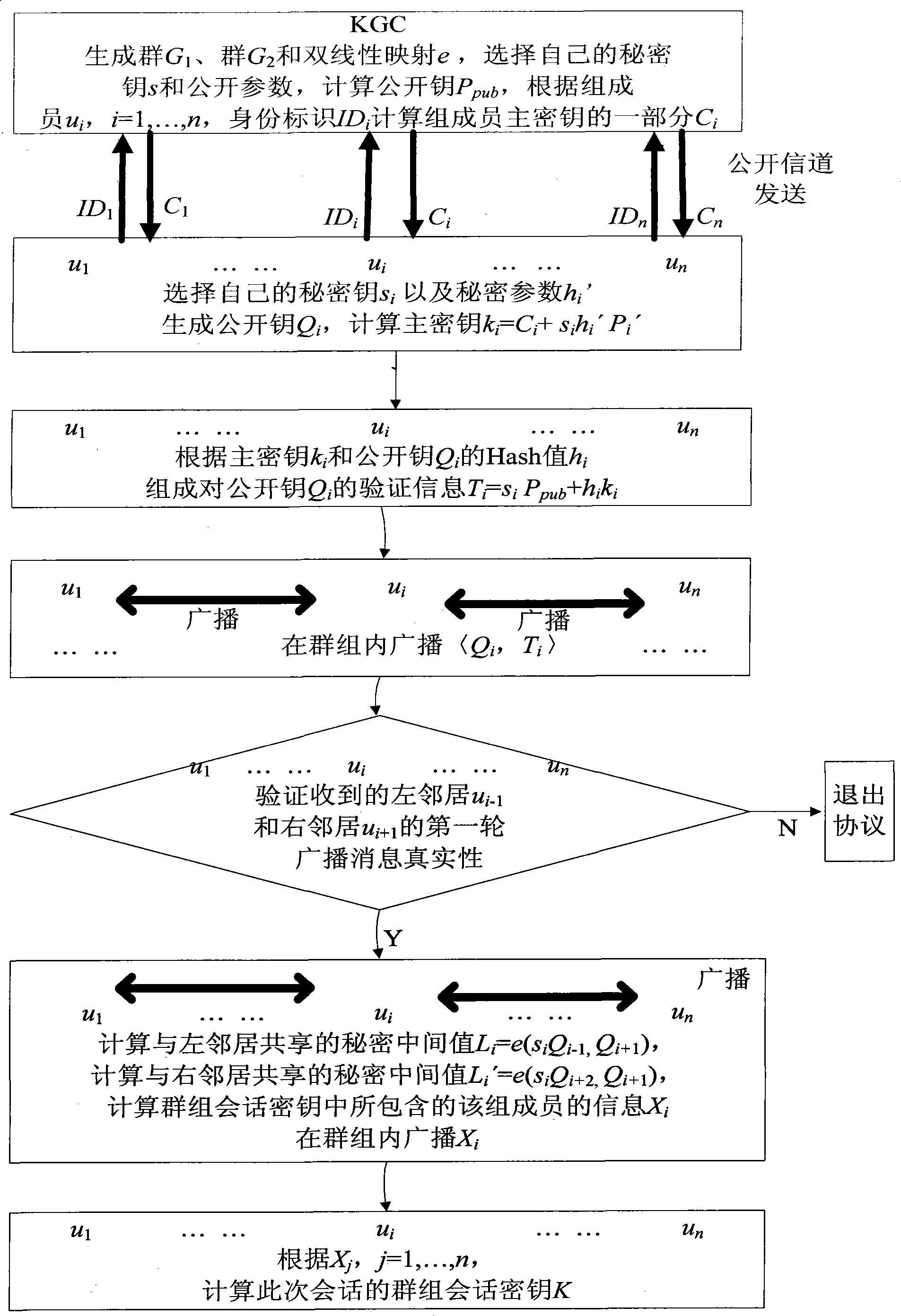
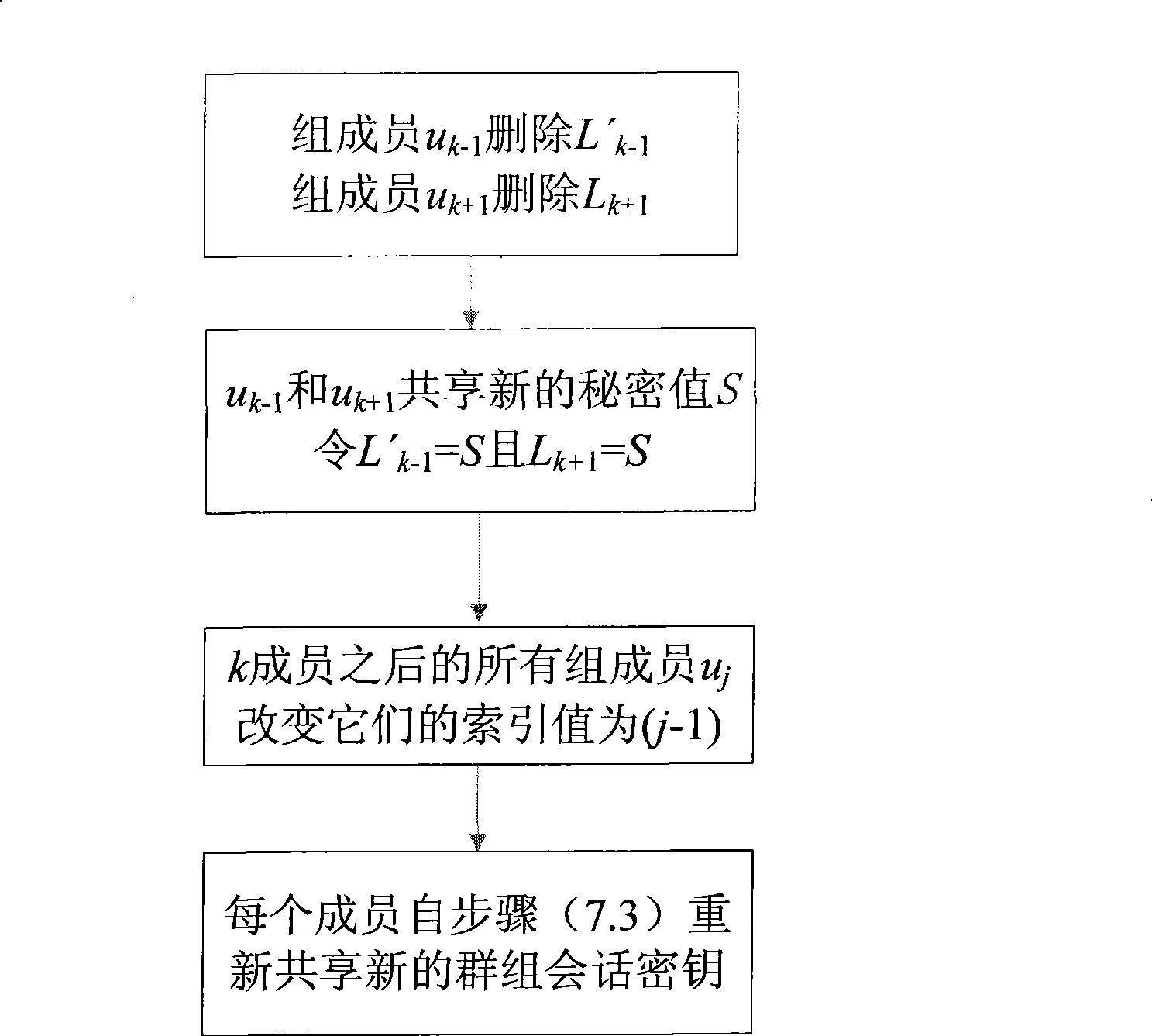
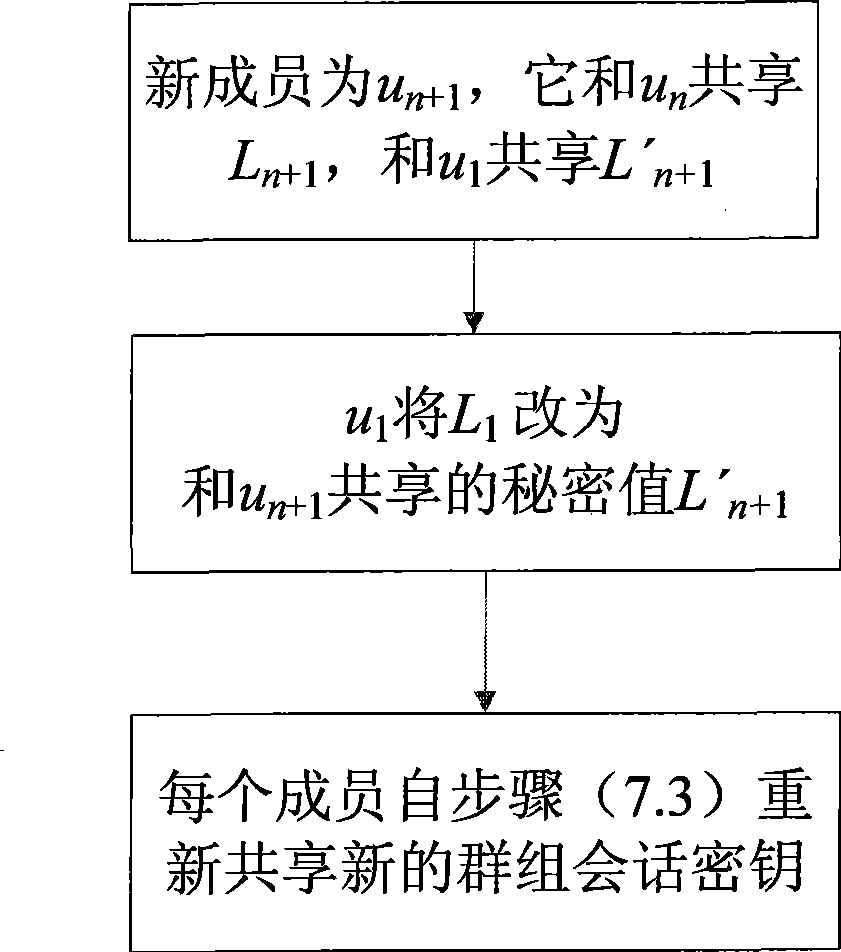
InactiveCN101431414AAvoid hostingSolve tough problemsKey distribution for secure communicationUser identity/authority verificationGroup sessionKey escrow
The present invention discloses a identity-based authentication group key management method which comprises the following steps: embedding ID into key with bilinear pairing in elliptic curve; generating Ci as part of main key ui according to the secret key and ID of group member ui by key generating center, and transmitting the Ci to ui through overt channel; generating main key according to Ci and its own secret key by each group member ui; calculating overt key verification information according to Hash value of main key and over key by each group member, and broadcasting the link between over key and verification information inside the group; calculating the secret value sharing with left and right neighbors when the received information is verified to be true by each group member, and calculating the group member information Xi included in group session key according to the secret value, and then broadcasting the Xi inside the group; calculating group session key K according to all Xj, j=1, ...,n, by each group member. The invention has the advantages of no key escrow and no need of secure channel, which can be applied in coordination and distributed network as secure reliable group communication.
Owner:XIDIAN UNIV
Mutual identifying key consultation method and system based on hidden common key certificate
InactiveCN1889433AComputationally efficientEfficient calculation loadSynchronising transmission/receiving encryption devicesPublic key for secure communicationThree stageKey escrow
This invention relates to a negotiation method and a system for both party certificated cryptographic keys based on hidden public key certificates, which applies three stages of system initialization, user end registration, generation of hidden public key certificates and distribution and certificated cryptographic key negotiations to utilize the traditional cipher plan of PKI and identity base to eliminate unnecessary trusteeship of the cryptographic keys on one hand and keep the advantages of part of identity base ciphers on the other, besides, this invention also discloses a system for realizing negotiation method of both party certified keys based on hidden public key certificates.
Owner:SHANGHAI JIAO TONG UNIV +1
Key escrow systems
ActiveUS7269261B1Easy to changePermit multiplicationKey distribution for secure communicationComputer hardwareKey escrow
The storage and retrieval of cryptographic key materials from a storage database utilizes a limited one-way function to create computational barriers. The limited one-way function is asymmetric in nature, in terms of work to compute and work to invert, to store and retrieve encryption keys. The limited one-way function is not intractable, but alternatively, there is some measurable difference in the amount of work required to invert a stored encryption key, compared to the work required for a calculation of the output of the one-way function for storage of an encryption key in a database.
Owner:FORCEPOINT FEDERAL
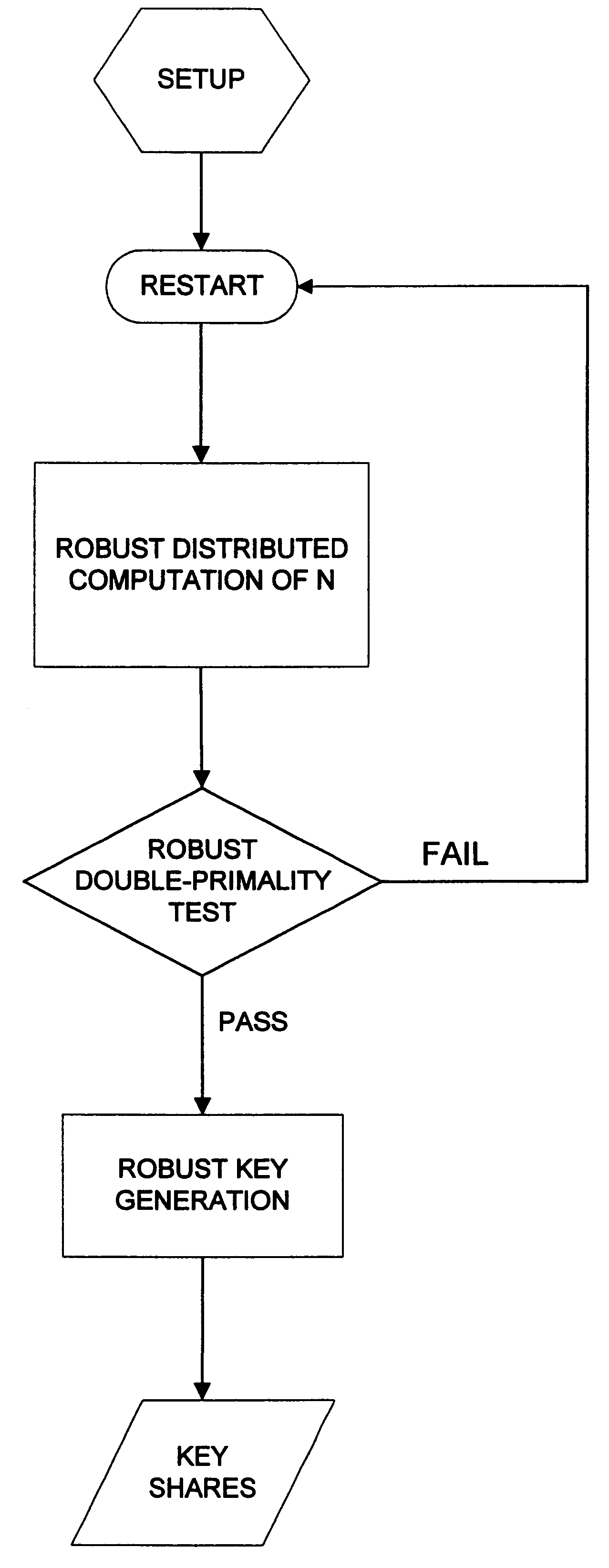
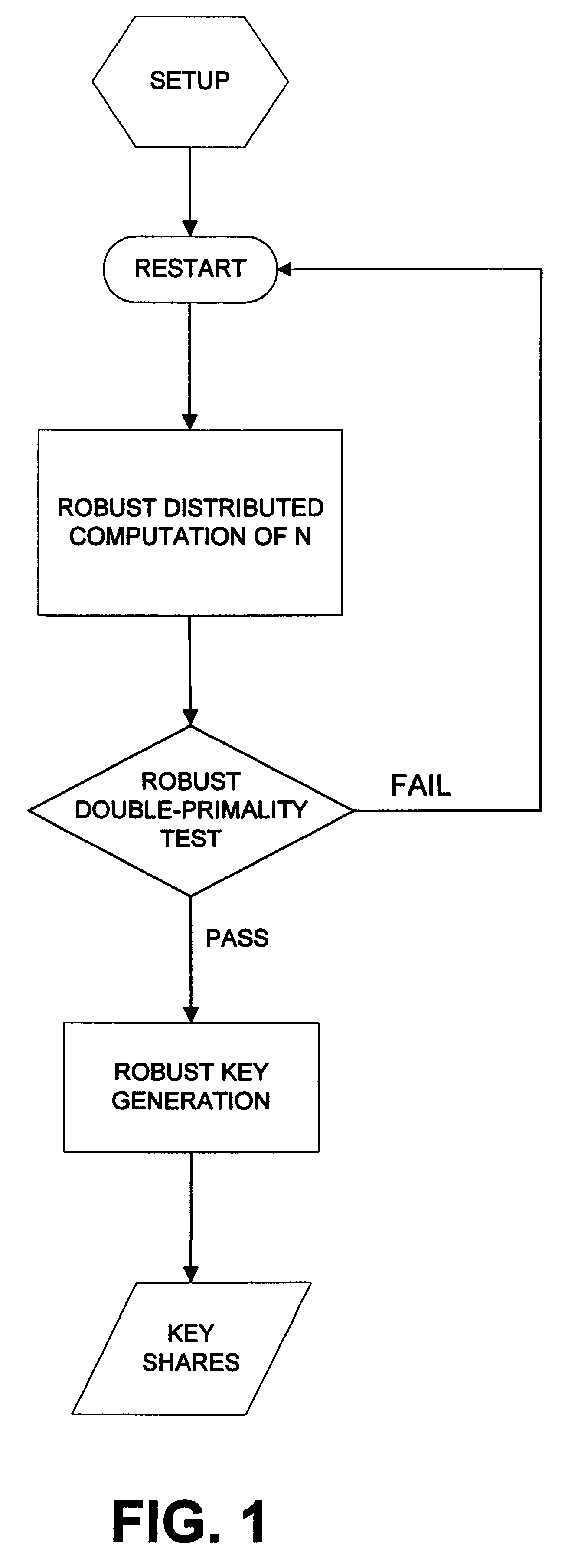
Robust efficient distributed RSA-key generation
InactiveUS6237097B1Reduce in quantityConfidenceKey distribution for secure communicationPublic key for secure communicationParallel computingEngineering
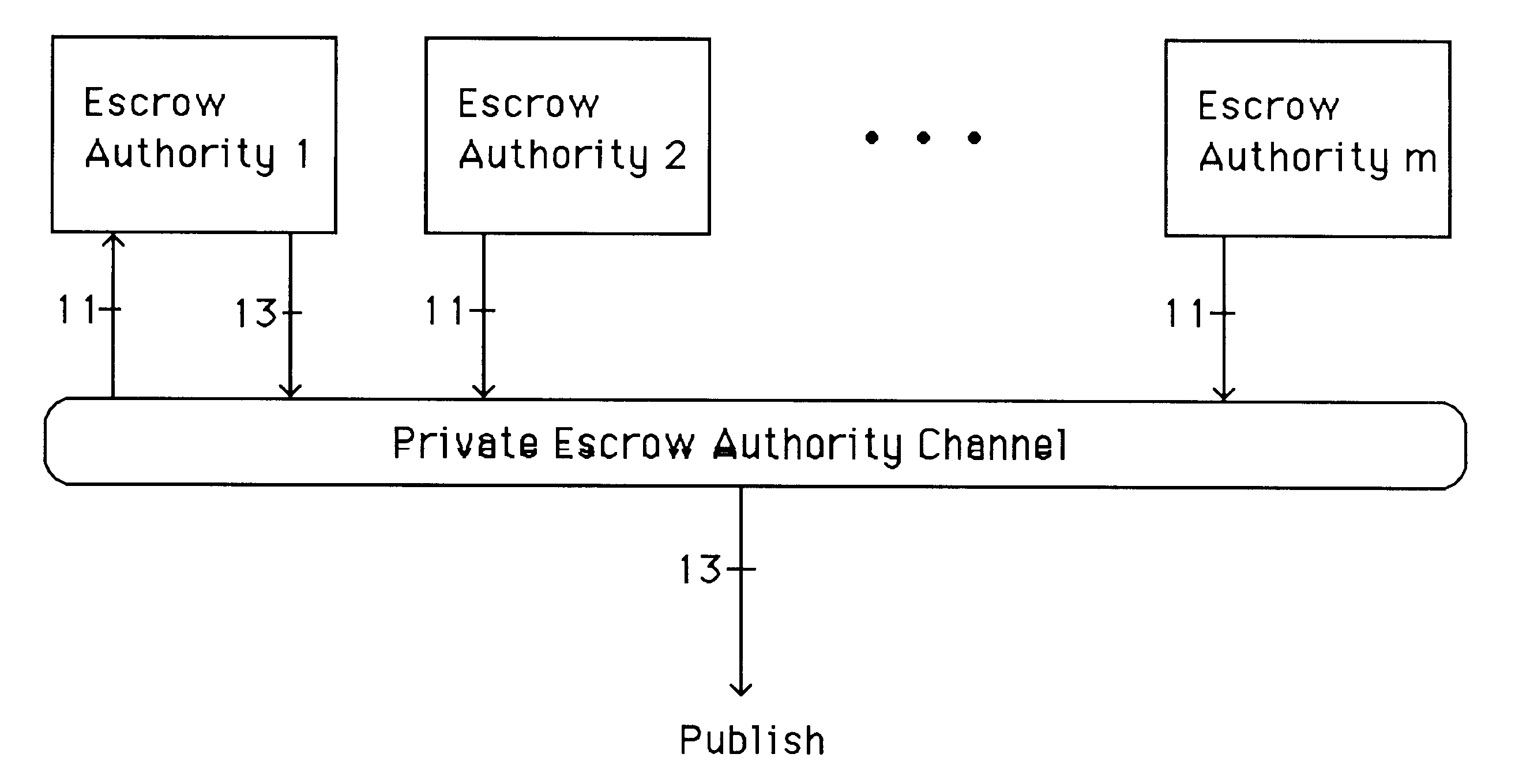
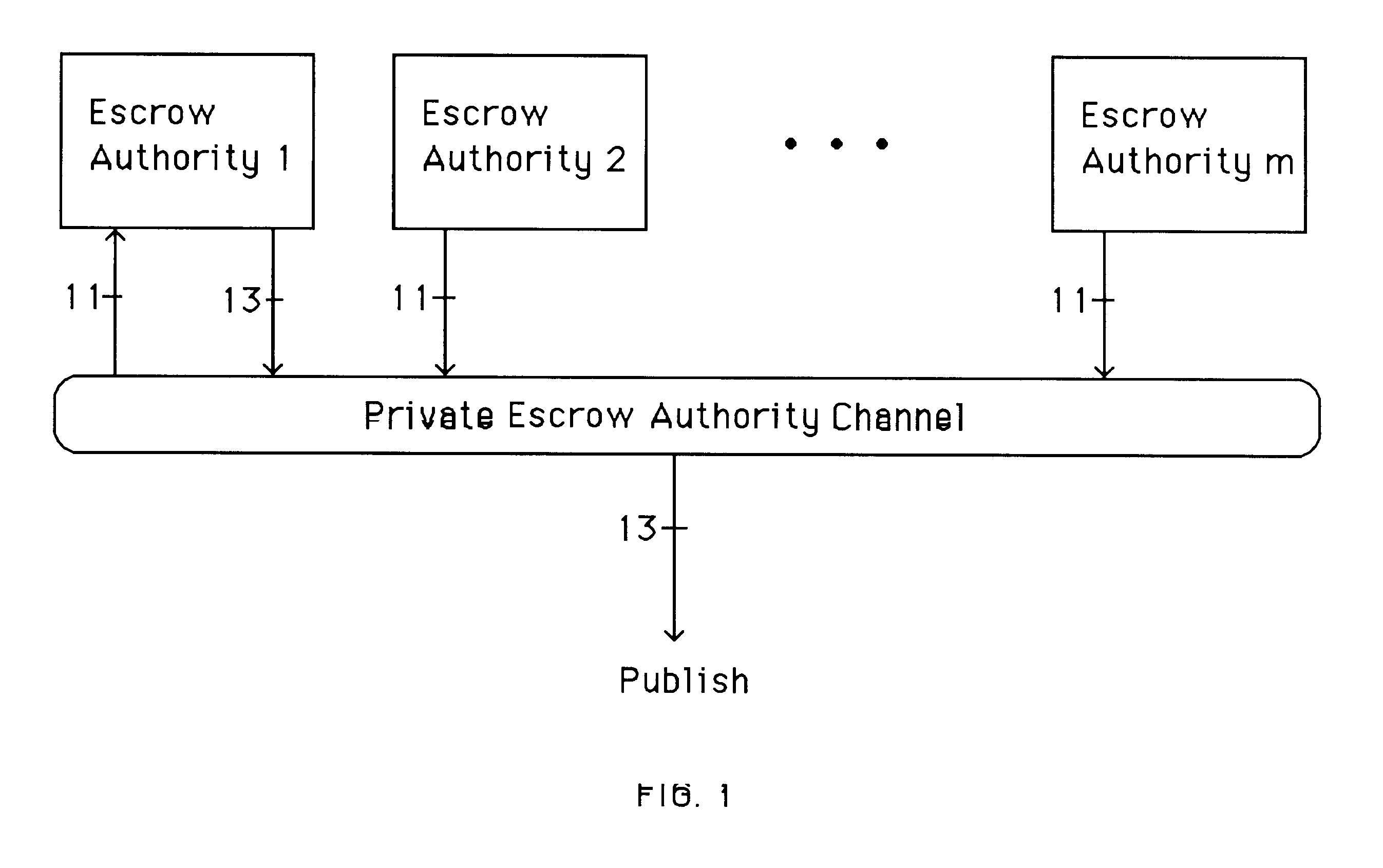
The invention provides for robust efficient distributed generation of RSA keys. An efficient protocol is one which is independent of the primality test "circuit size", while a robust protocol allows correct completion even in the presence of a minority of arbitrarily misbehaving malicious parties. The disclosed protocol is secure against any minority of malicious parties (which is optimal). The disclosed method is useful in establishing sensitive distributed cryptographic function sharing services (certification authorities, signature schemes with distributed trust, and key escrow authorities), as well as other applications besides RSA (namely: composite ElGamal, identification schemes, simultaneous bit exchange, etc.). The disclosed method can be combined with proactive function sharing techniques to establish the first efficient, optimal-resilience, robust and proactively-secure RSA-based distributed trust services where the key is never entrusted to a single entity (i.e., distributed trust totally "from scratch"). The disclosed method involves new efficient "robustness assurance techniques" which guarantee "correct computations" by mutually distrusting parties with malicious minority.
Owner:CERTCO
Public key cipher system private key escrowing system based on identification
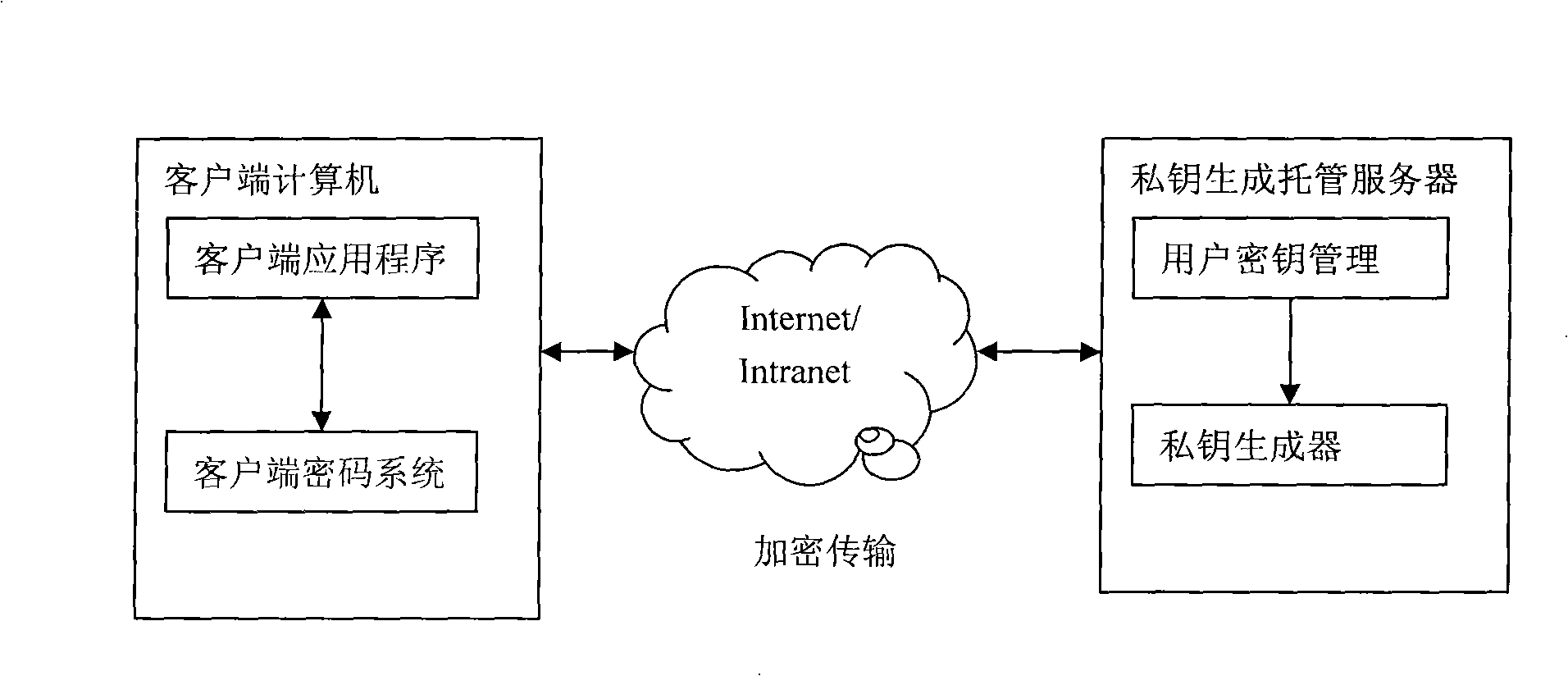
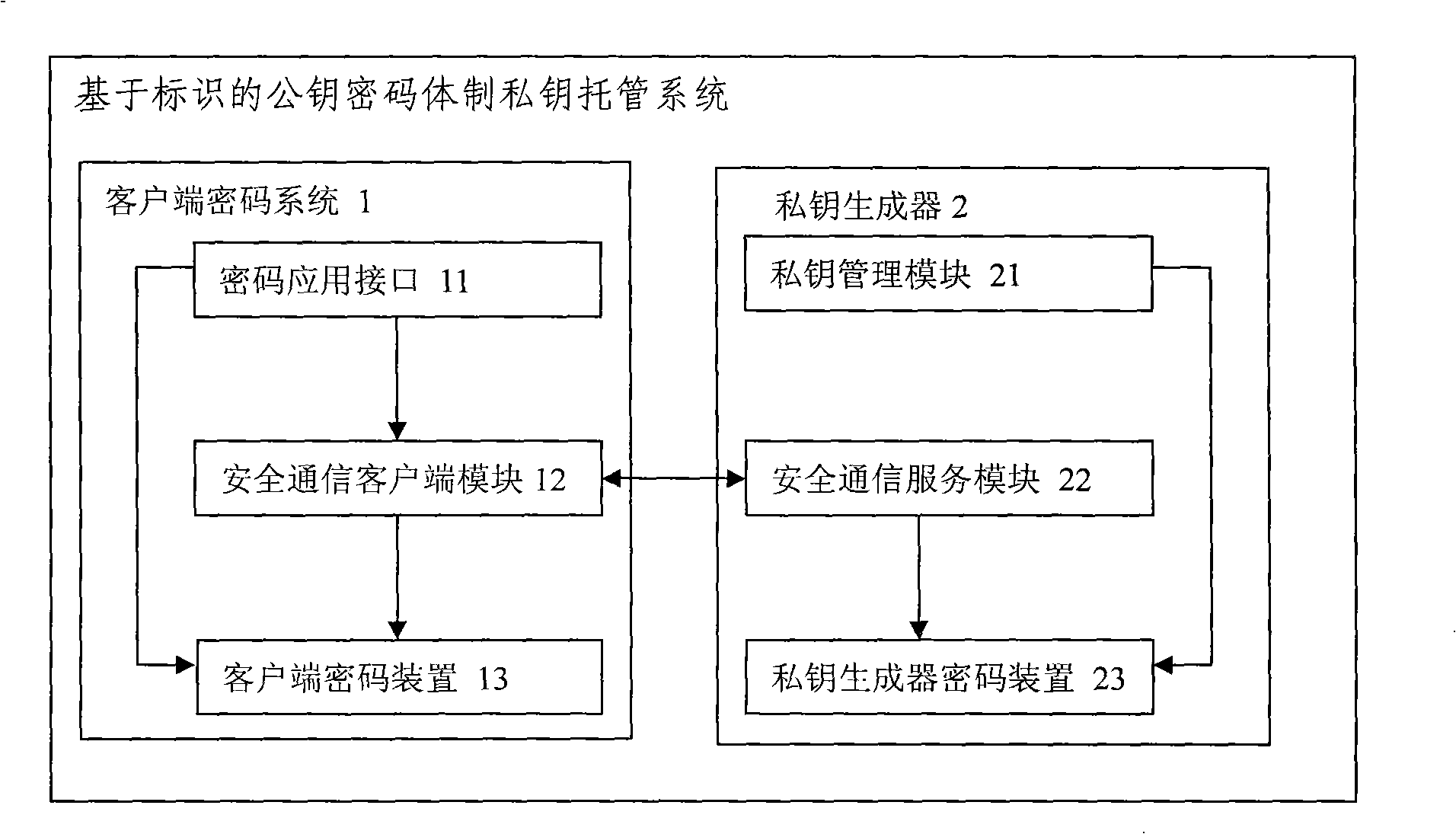
InactiveCN101359991AEnsure safetyIncrease attack difficultyUser identity/authority verificationTamper resistanceKey escrow
The invention relates to a public key cryptosystem private key escrow system based on identification. A client cryptosystem transmits the information of a user to a private key generator for requesting authentication; a user private key is generated and stored at the client cryptosystem after the authentication of the private key generator is passed; and the client cryptosystem provides an operation interface for an application program, and realizes the cryptographic operation internally. The public key cryptosystem private key escrow system dynamically acquires the private key form the private key generator when a user is logged in, a tamper-proofing authentication protocol and the technology of a cipher device can ensure the user to acquire the private key safely. Because the user neither stores the private key statically nor dynamically exposes the private key out of the cipher device, so the hacking difficulty of a hacker is increased. The public key cryptosystem private key escrow system can effectively resist various dynamic and static analysis methods.
Owner:湖北电力信息通信中心 +1
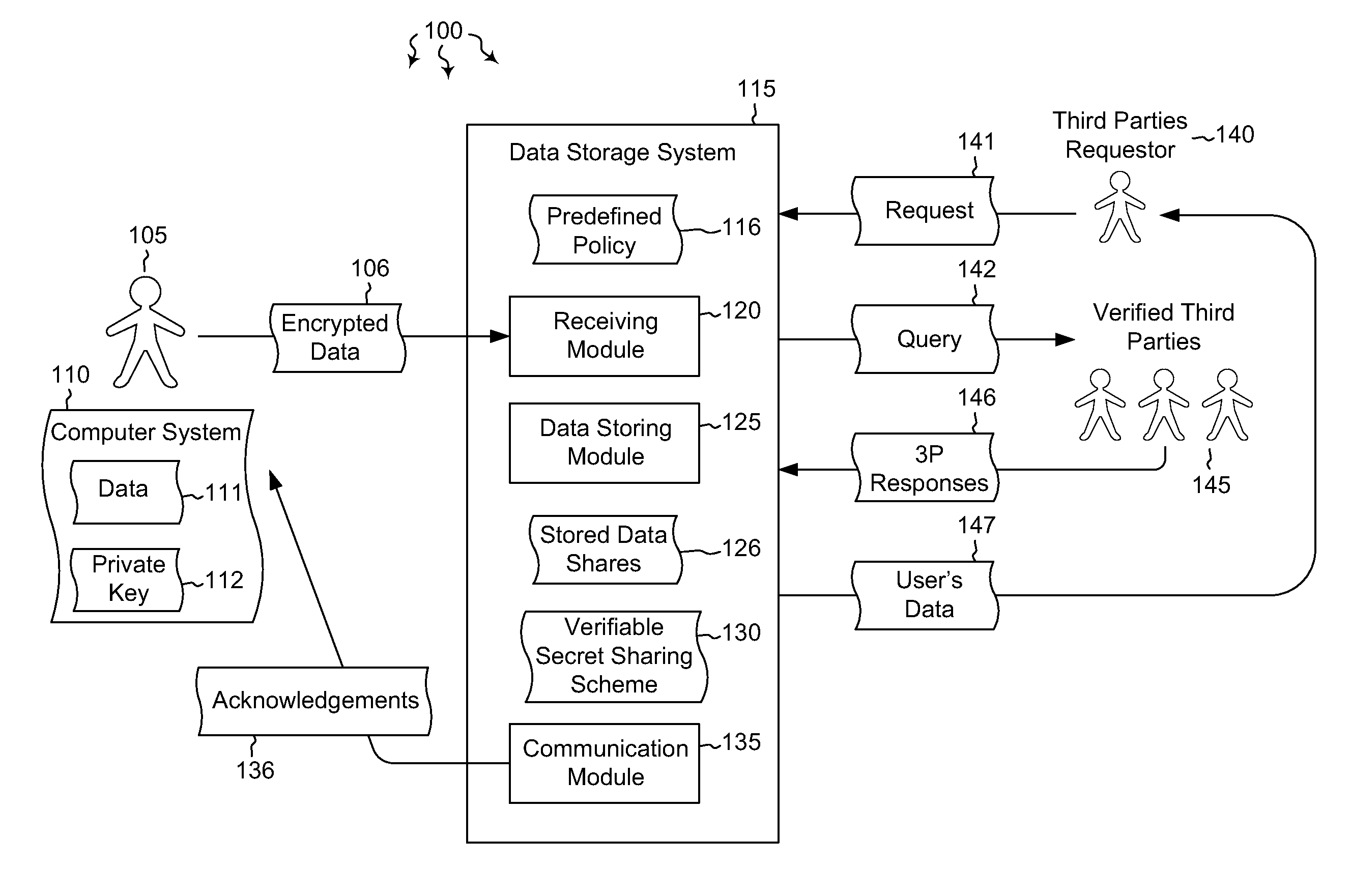
Cloud key escrow system
ActiveUS8891772B2Key distribution for secure communicationDigital data processing detailsThird partyData access
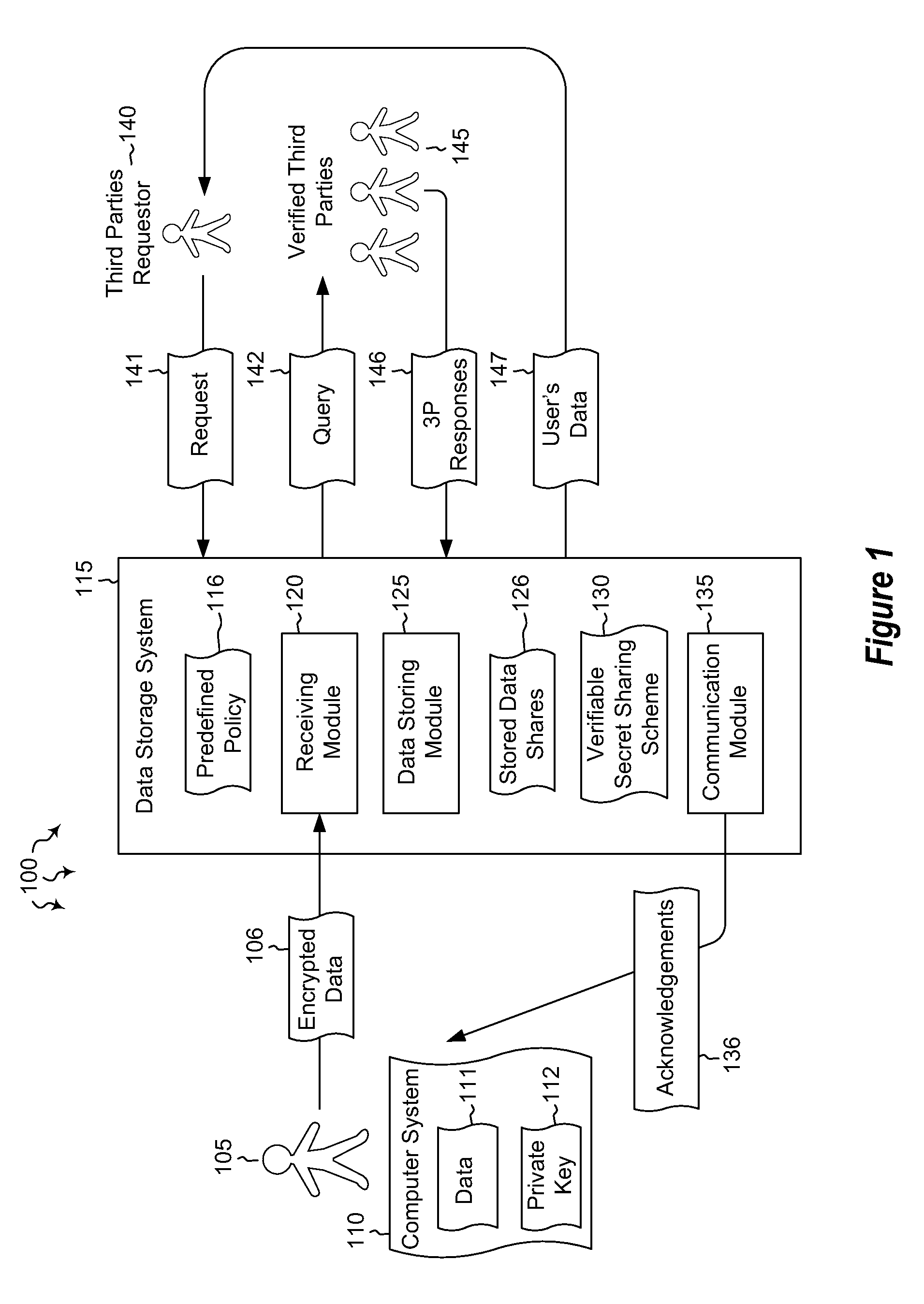
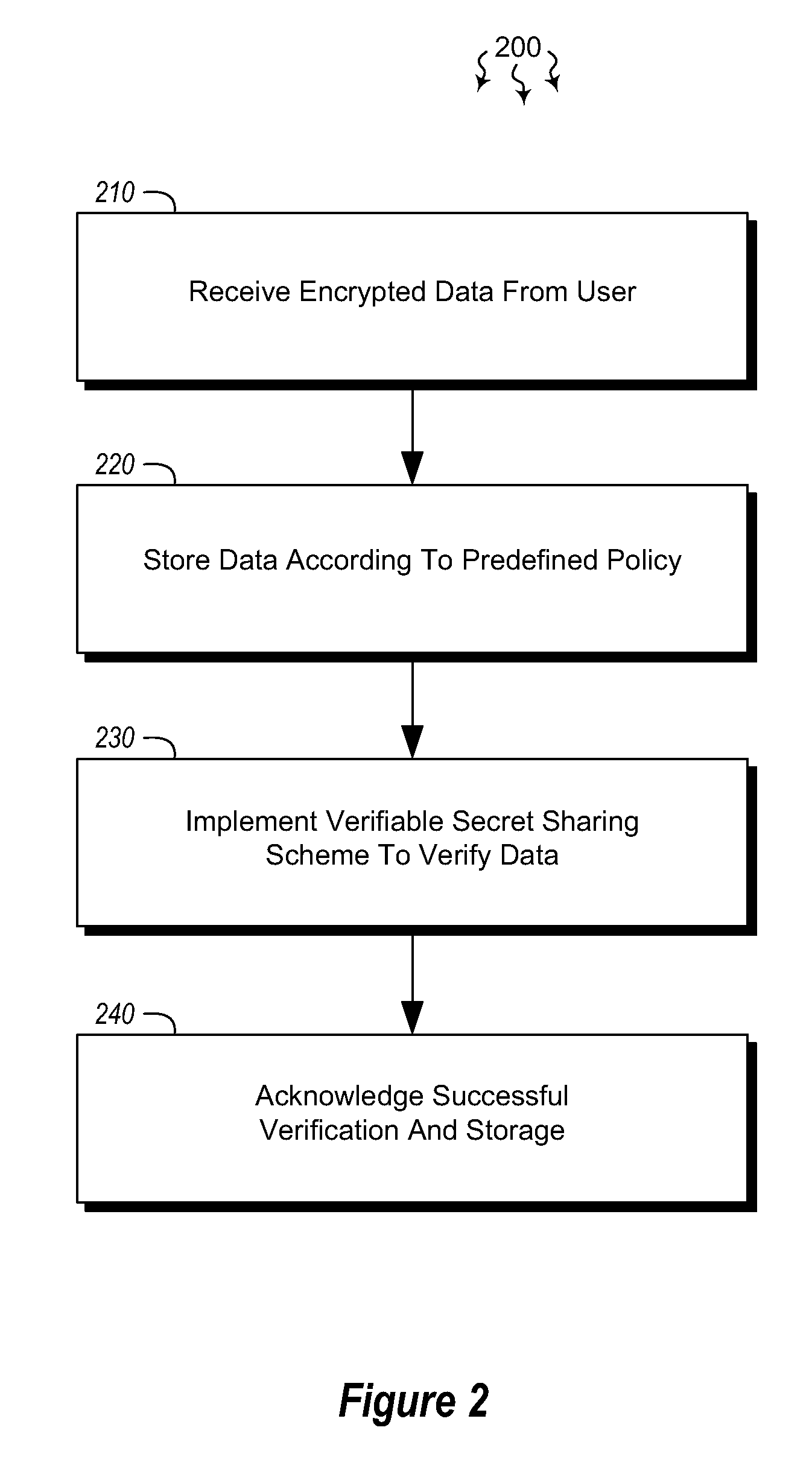
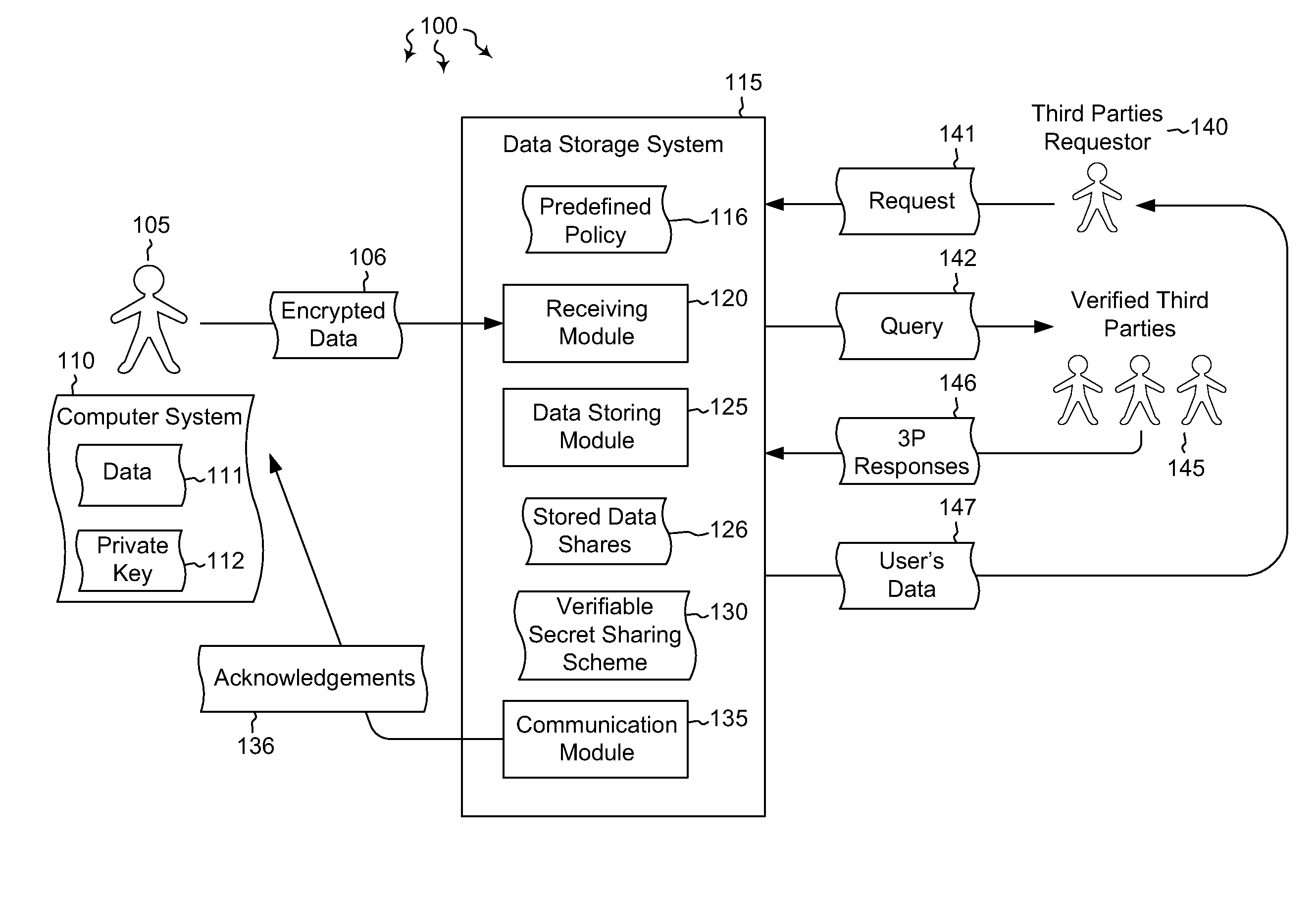
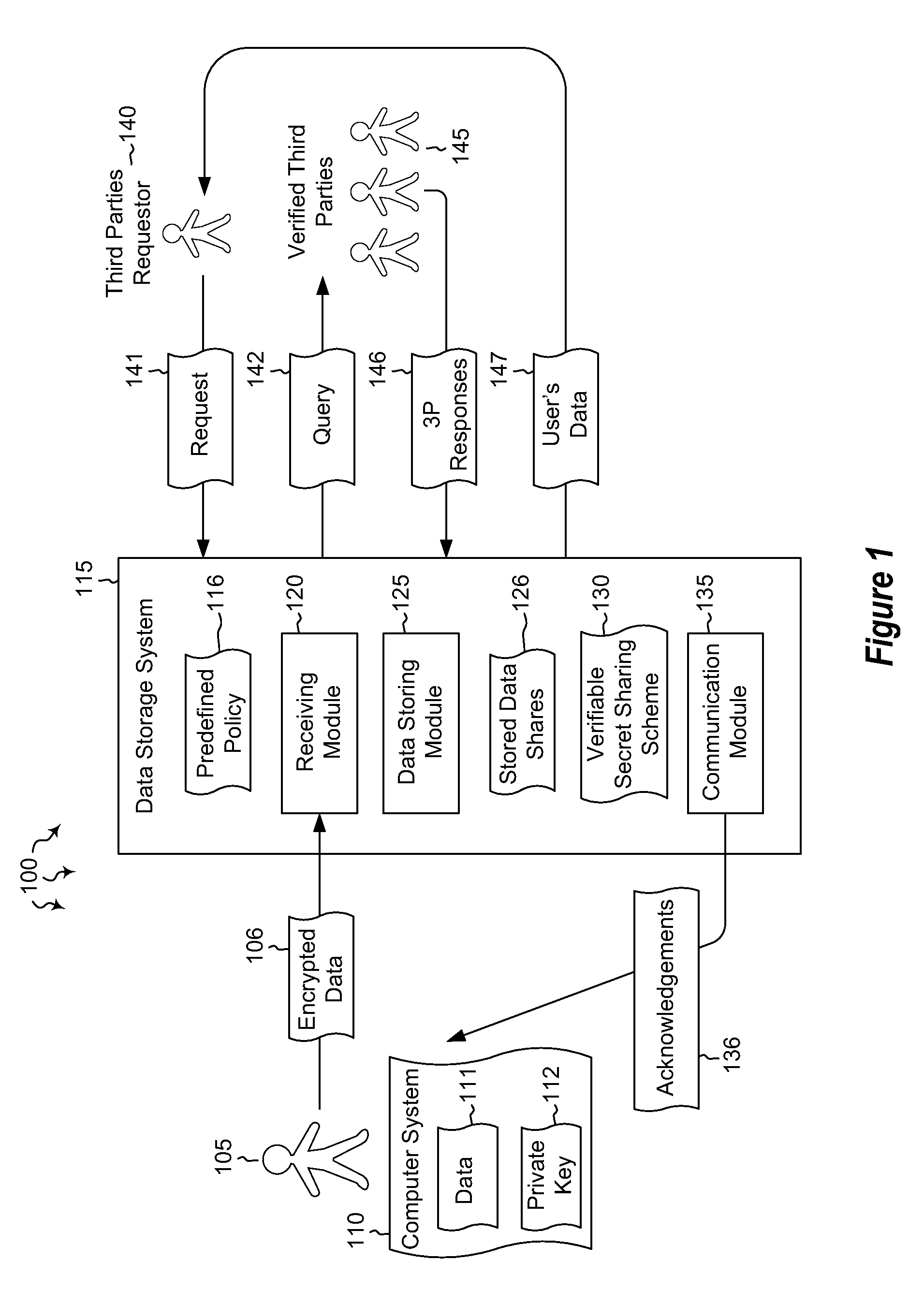
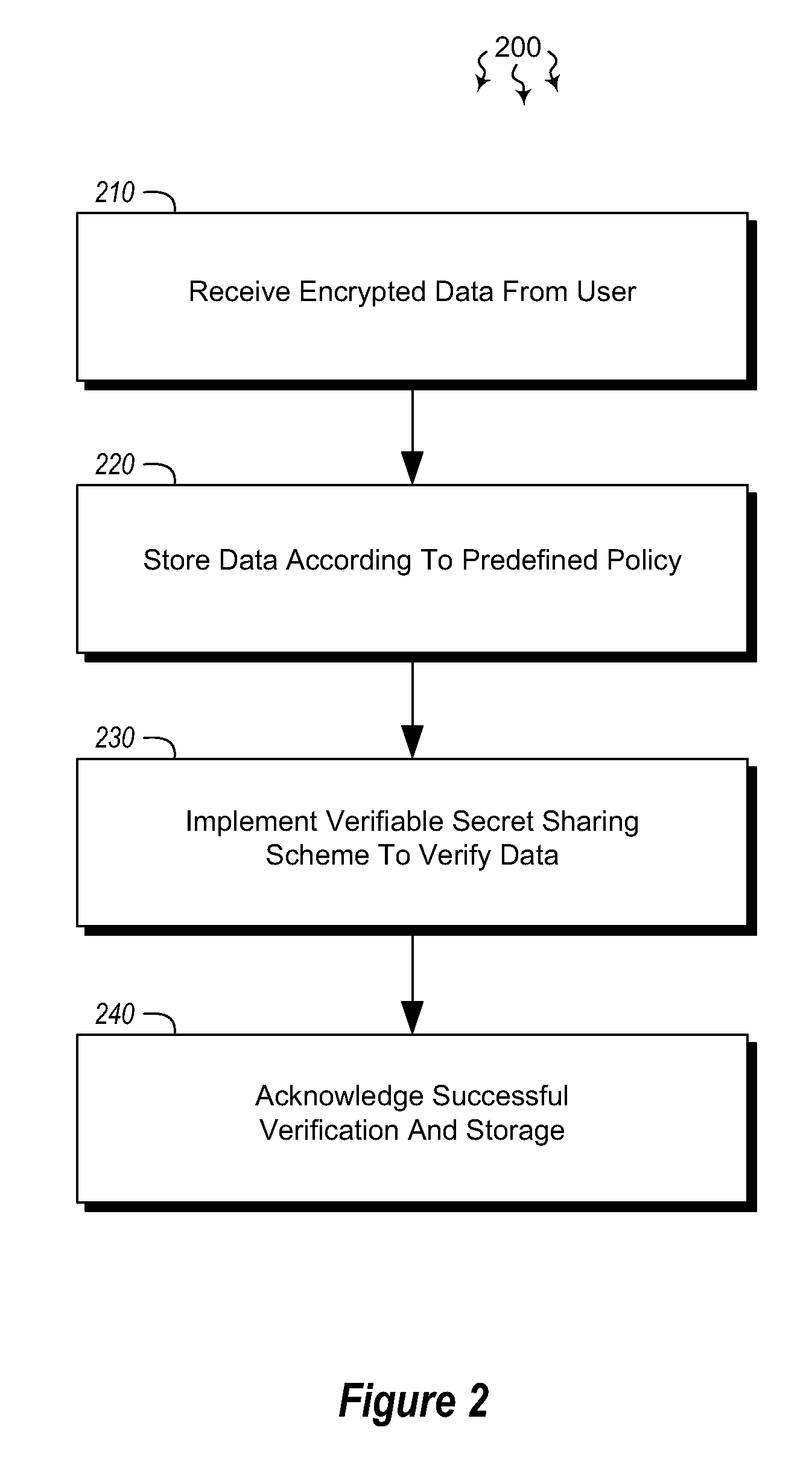
Embodiments are directed to allowing a user to store encrypted, third-party-accessible data in a data store and to providing third party data access to a user's encrypted data according to a predefined policy. A data storage system receives encrypted data from a user at a data storage system. The data is encrypted using the user's private key. The data storage system stores the received encrypted data according to a predefined policy. The encryption prevents the storage system from gaining access to the encrypted data, while the policy allows the encrypted data to be released upon receiving a threshold number of requests from verified third parties. The data storage system implements a verifiable secret sharing scheme to verify that the encrypted data can be reconstituted without the data storage system accessing the encrypted data. The data storage system synchronously acknowledges that the received encrypted data has been verified and successfully stored.
Owner:MICROSOFT TECH LICENSING LLC
Key management to protect encrypted data of an endpoint computing device
ActiveUS8588422B2Digital data processing detailsUnauthorized memory use protectionComputer moduleKey escrow
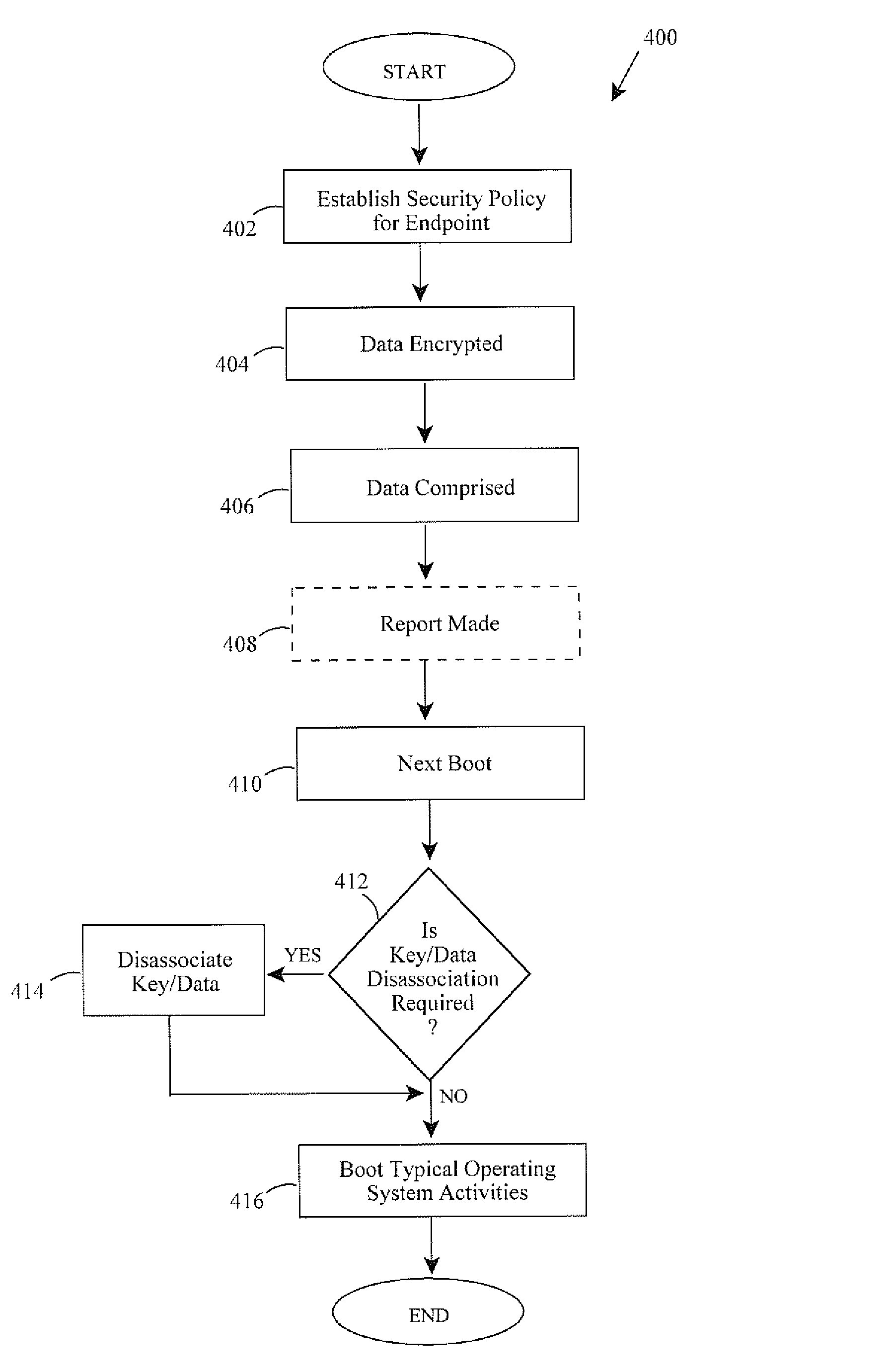
Methods and apparatus involve protecting encrypted data of endpoint computing assets by managing decryption keys. The endpoint has both a traditional operating system for applications, and the like, and another operating system during a pre-boot phase of operation. During use, the pre-boot operating system prevents users of the endpoint from accessing the encrypted data and the key. Upon determining the encrypted data has been compromised, the key is disassociated from the encrypted data. Disassociation can occur in a variety of ways including deleting or scrambling the key and / or data or re-encrypting the encrypted data with a new key. Key escrowing and updating through the pre-boot is further contemplated. The pre-boot phase also contemplates a limited computing connection between the endpoint and a specified authentication server and approved networking ports, USB devices and biometric equipment. Security policies and enforcement modules are also disclosed as are computer program products, computing arrangements, etc.
Owner:MICRO FOCUS SOFTWARE INC
Nearly-stateless key escrow service
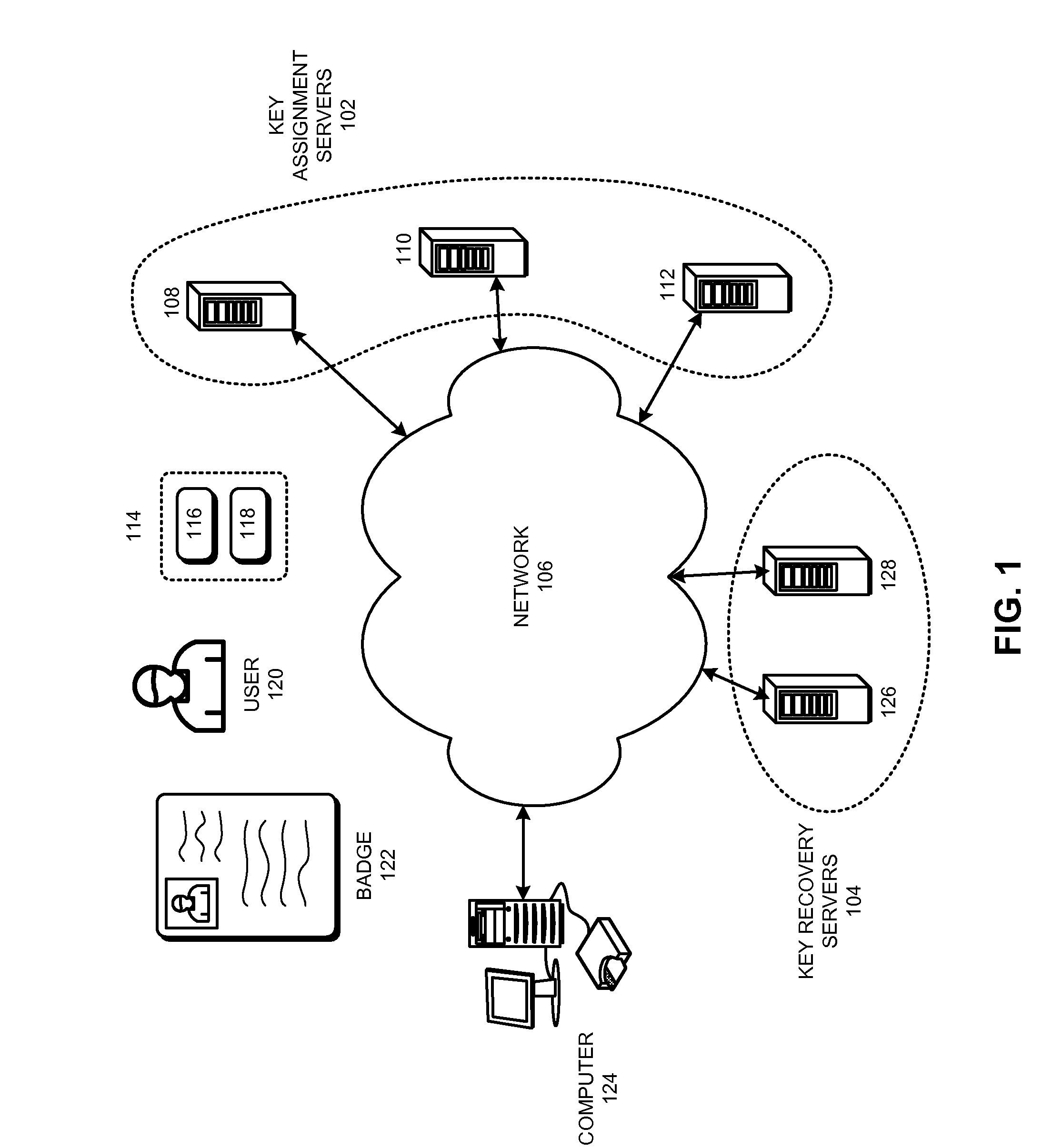
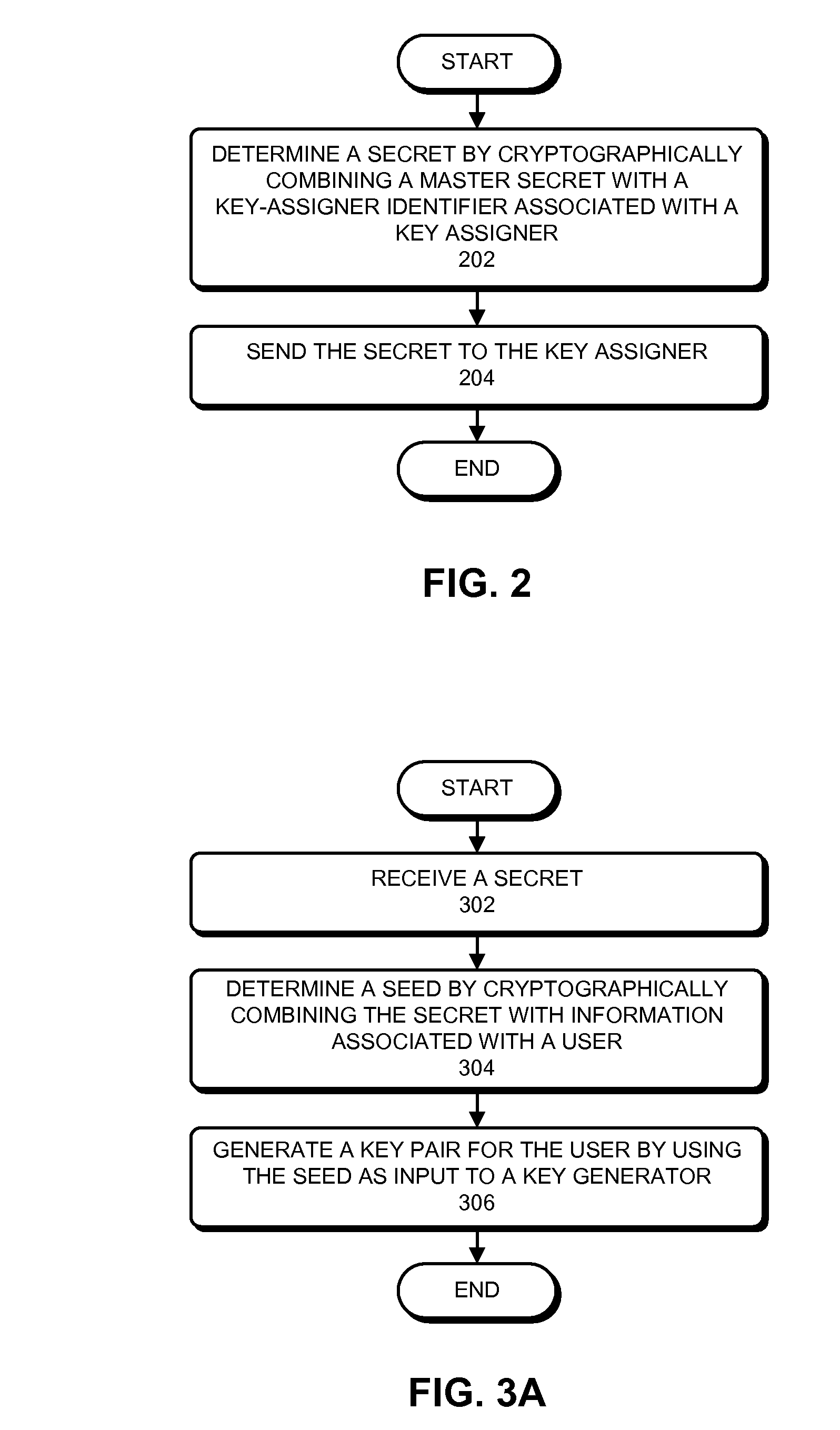
ActiveUS20100142713A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionKey escrow
Some embodiments provide a system to generate a key pair. During operation, the system can receive a request to generate the key pair, wherein the key pair is generated by a key assigner, and wherein the key pair is associated with a user. Next, the system can determine a secret associated with the key assigner. Specifically, the system can determine the secret by determining an initial secret associated with the key assigner, and by applying a one-way hash function to the initial secret one or more times. The system can then determine a seed based on the secret. Specifically, the system can determine the seed by cryptographically combining the secret with information associated with the user. Next, the system can generate the key pair by using the seed as an input to a key generator. The system can then return the key pair to a requestor.
Owner:ORACLE INT CORP
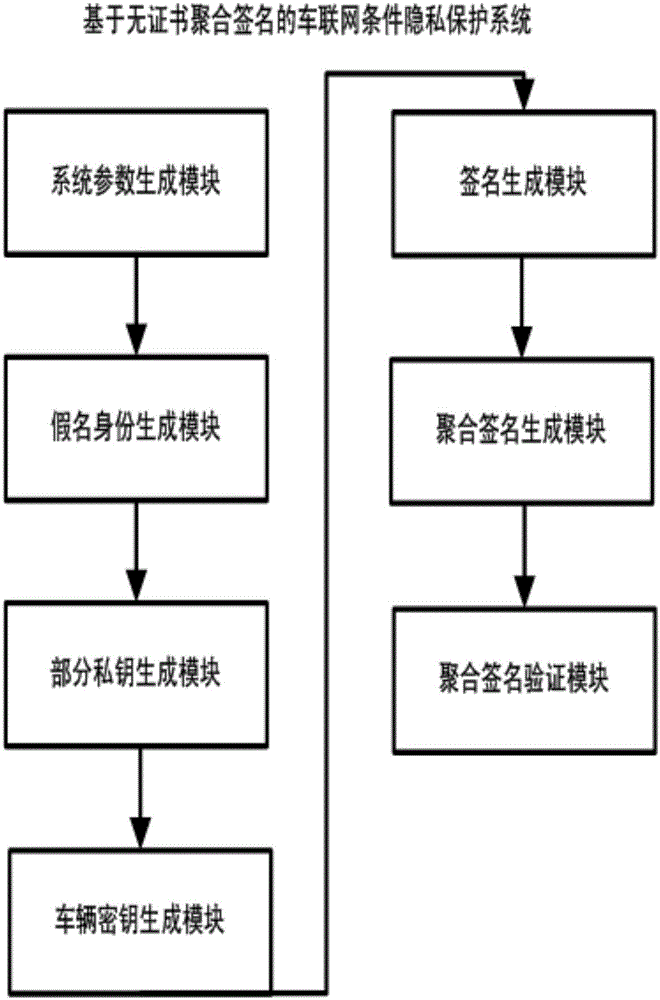
Internet of vehicles conditional privacy protection method and system based on certificateless aggregation signature
ActiveCN106131059AAvoid managementAvoid key escrow issuesKey distribution for secure communicationPrivacy protectionThe Internet
The invention discloses an internet of vehicles conditional privacy protection method and system based on certificateless aggregation signature. The internet of vehicles conditional privacy protection method based on certificateless aggregation signature is provided based on a certificateless cryptosystem. On the basis of internet of vehicle conditional privacy protection of a traditional public key cryptosystem, an aggregation signer aggregates various different signatures into one signature, the internet of vehicles conditional privacy protection scheme is realized by employing a key generation center KGC and a tracking authentication center TRA, the problems of certificate management and key hosting are avoided, the computing efficiency of an internet of vehicles is improved when the aggregation signature is authenticated, the conditional privacy protection of internet of vehicles users is realized, and the method and the system can be applied in the open internet of vehicles safely.
Owner:HOHAI UNIV
Multi-receiver signcryption method based on keyless trusteeship problem of elliptic curve
ActiveCN106027239AOvercome the problem of not being able to resist malicious KGC attacksResistance to malicious KGC attacks hasKey distribution for secure communicationPublic key for secure communicationSigncryptionKey escrow
This invention discloses a multi-receiver signcryption method based on keyless trusteeship problem of elliptic curve, and solves the technical problem of private key trusteeship existed in the existing multi-receiver signcryption method. The method comprises the following steps: a user randomly selects a secret value as own private key, calculates a verification share according to own private key, and sends the verification share and own identity information to a private key generating center KGC; the private key generating center KGC generates a public key, a public key verification parameter and a public key hiding parameter of the user according to the verification share and the identity information sent by the user, and sends the public key, the public key verification parameter and the public key hiding parameter to the user; and after receiving the parameters sent by the private key generating center KGC, the user verifies the public key. Since the private key of the user is the secret value randomly selected by the user, the private key generating center KGC only knows the public key and corresponding identity information of the user, and cannot acquire the private key of the user to realize keyless trusteeship. Simultaneously, the signcryption efficiency is improved; and the bandwidth is reduced.
Owner:XIDIAN UNIV
Random encryption method for decrypting by adopting exhaustion method
InactiveCN102013980AEnsure safetyPublic key for secure communicationUser identity/authority verificationPasswordKey escrow
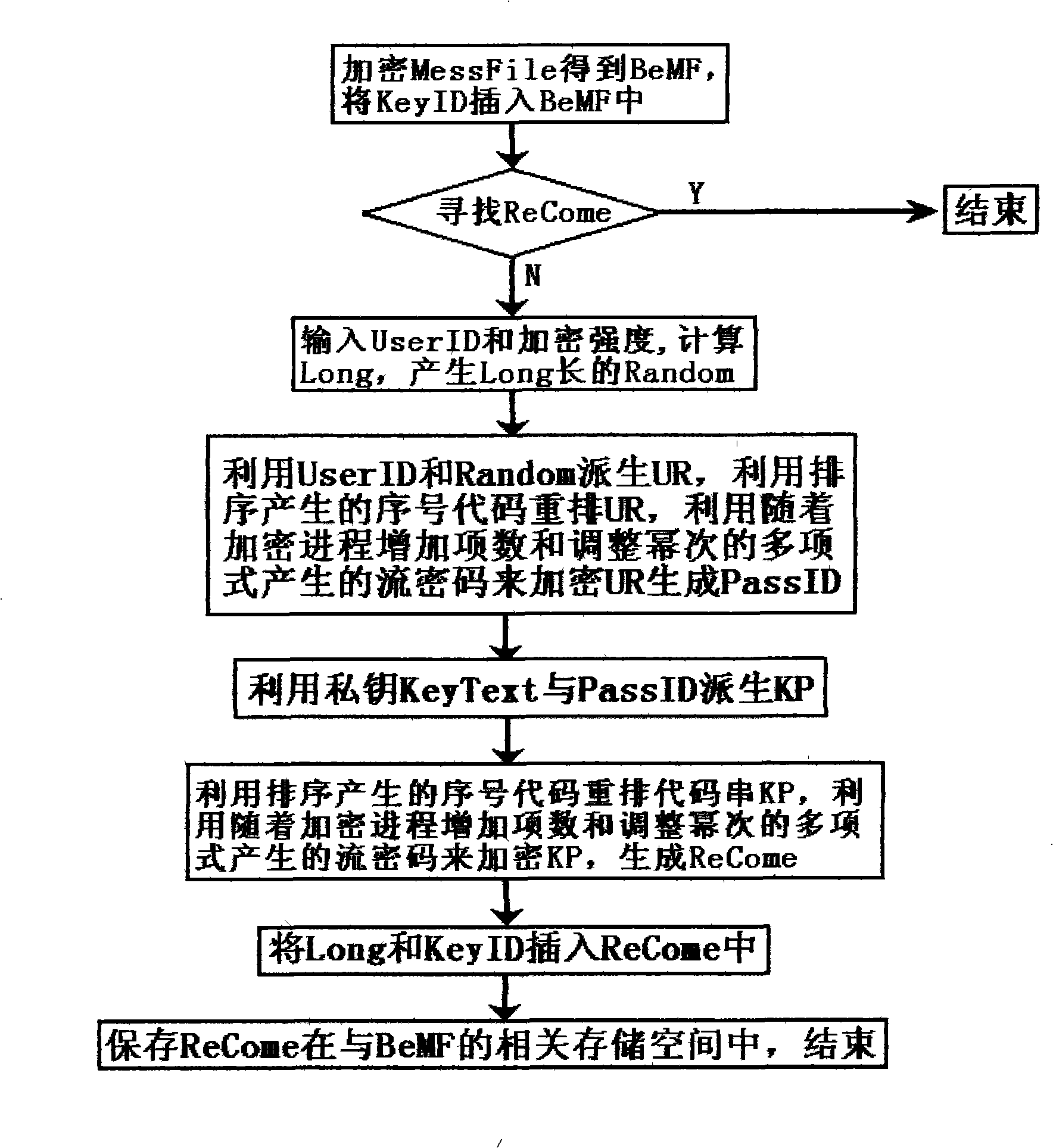
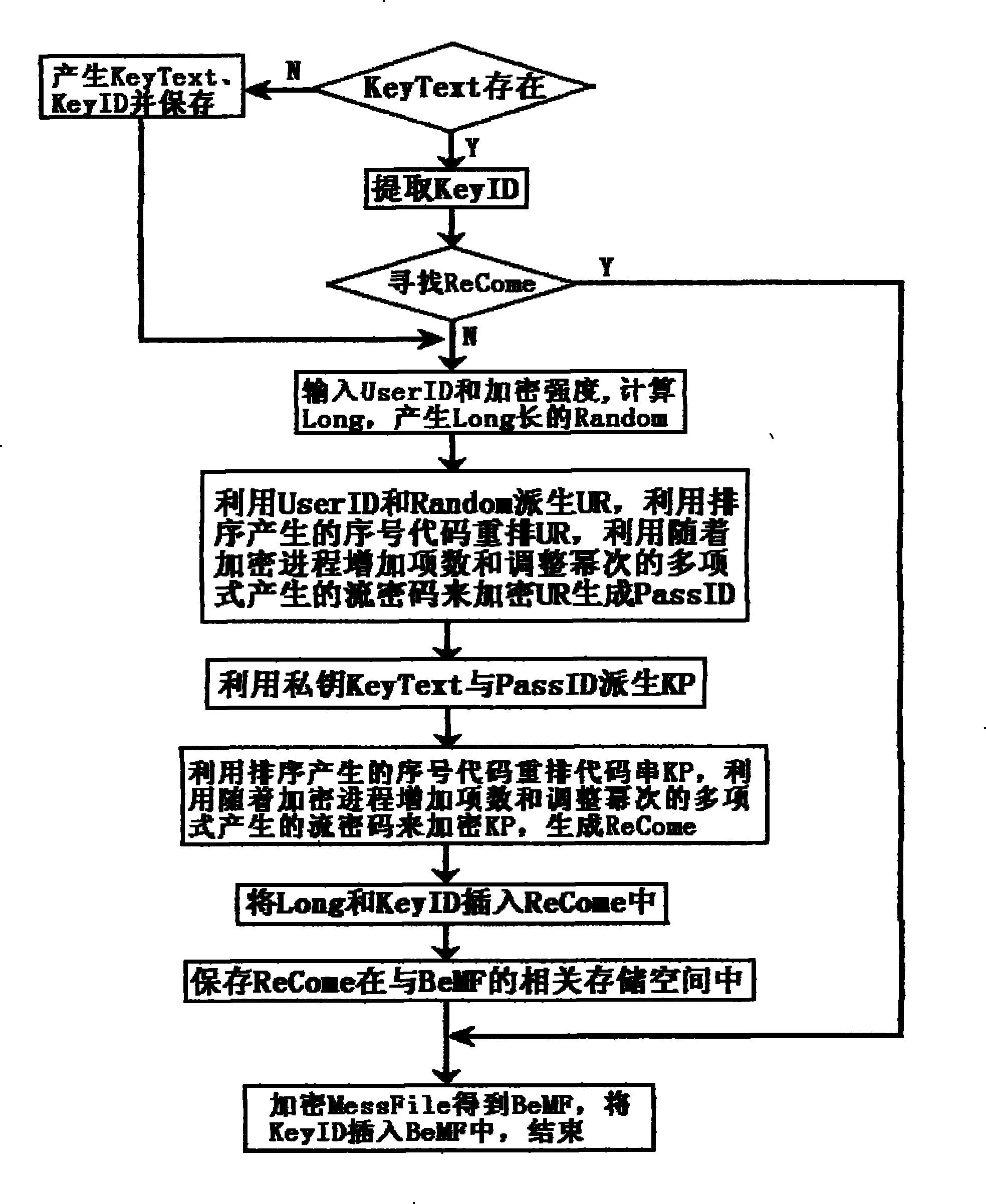
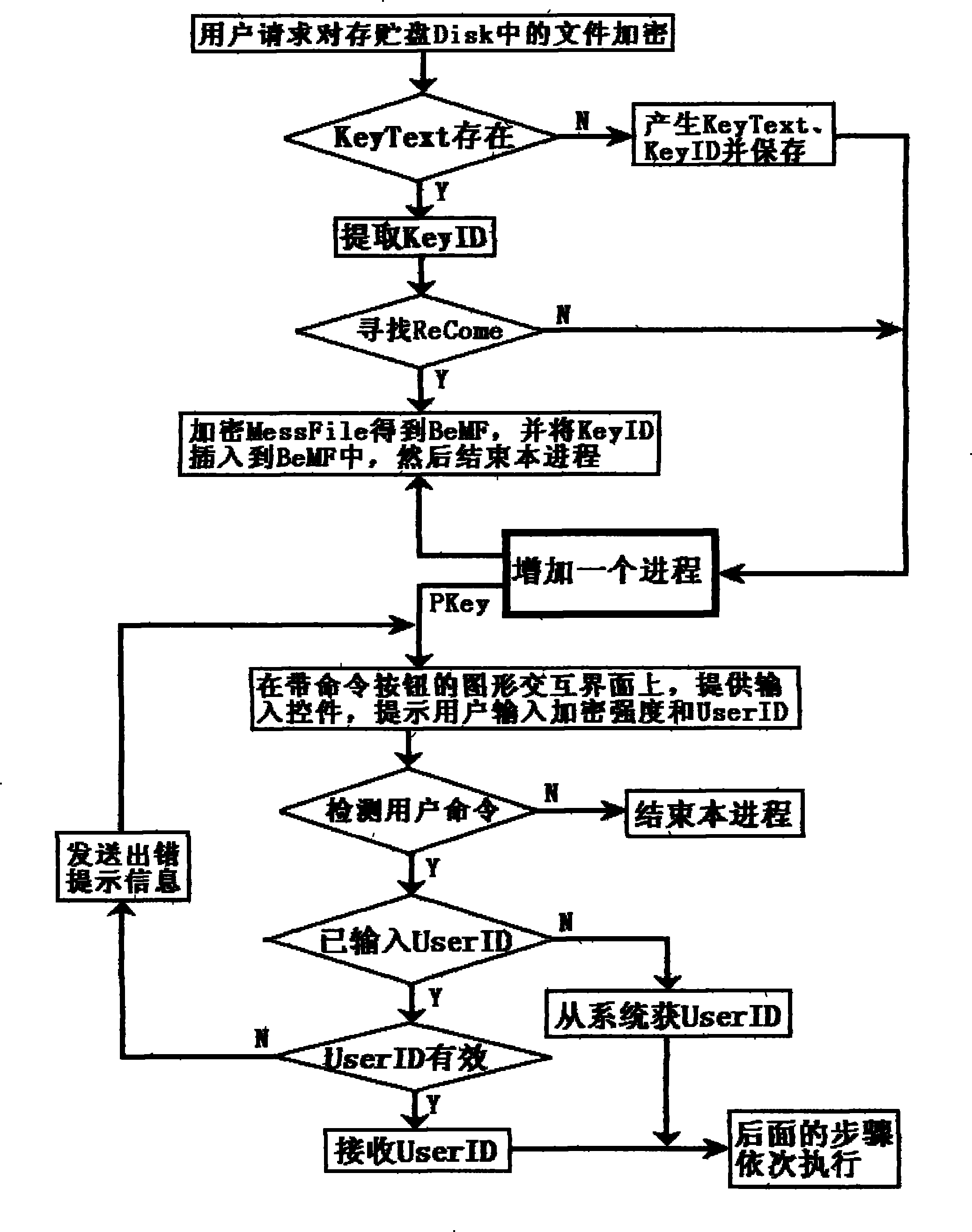
The invention provides a random encryption method for decrypting by adopting an exhaustion method, which is mainly used for encrypting backup keys, certificates and important documents. The random encryption method comprises the following encryption flow: inputting use identity information and encryption strength; calculating the random length of a random key and generating the random key of the random length according to the relationship among encryption strength and other factors; and encrypting the key and the certificate by using the user identity information and the random key according to the encryption algorithm to obtain backups of the encrypted key and certificate and locking the user identity information and the random key in password identification information by using the encryption algorithm determined by the program. The backups generated by the encryption method are decrypted by using the exhaustion method no matter how to write the decryption program even if the correct user identity is input; in addition, the user and the random key are required to be respectively compared. The method is not only applied to a stand-alone system, but also can be applied to key escrow services in clouds.
Owner:刘海云
Certificateless signature method based on elliptic curve discrete logarithm problem
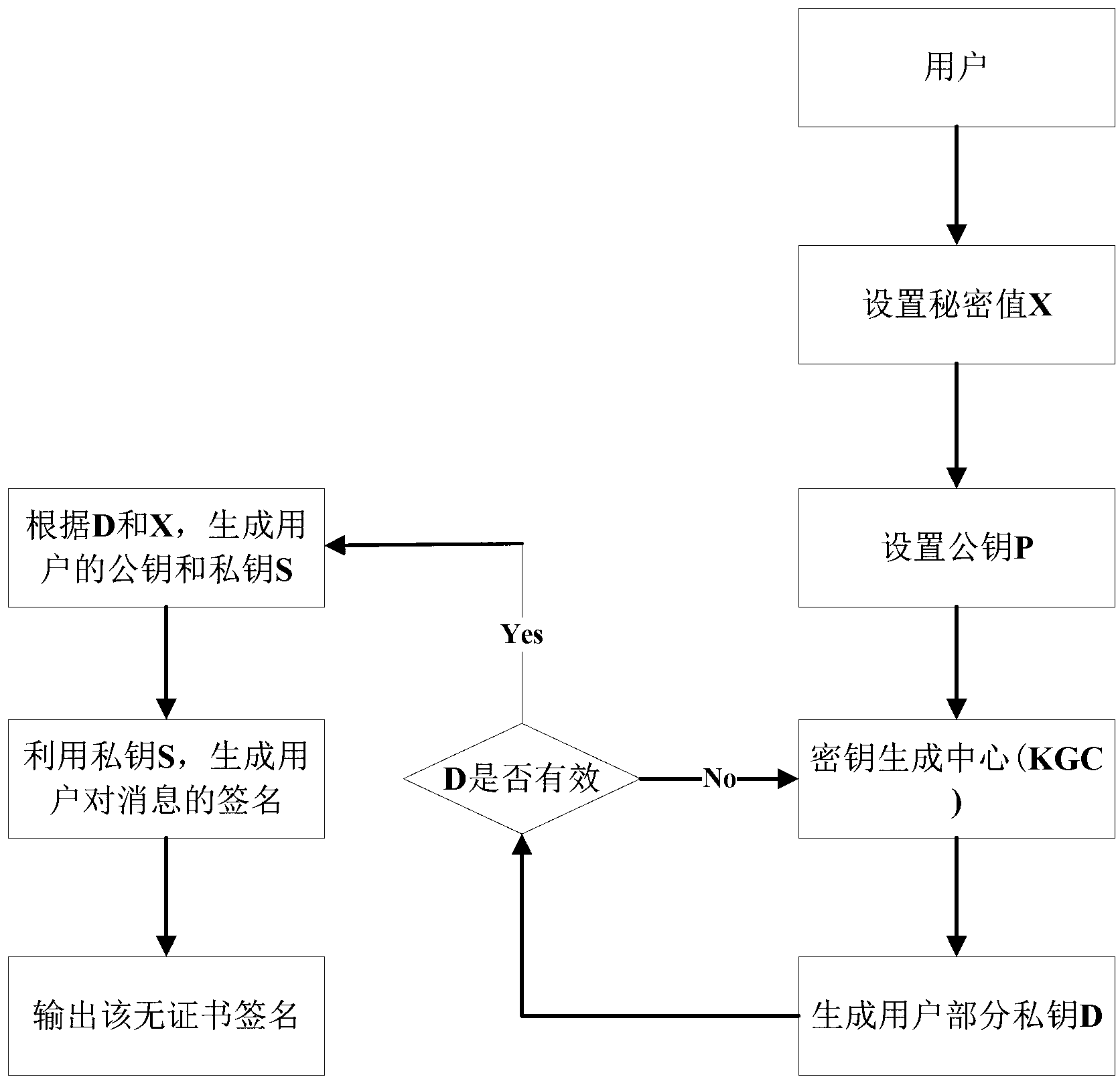
InactiveCN103023648AShort signature lengthResist attackPublic key for secure communicationUser identity/authority verificationElliptic curve discrete logarithm problemPassword
The invention discloses an efficient certificateless signature method based on an elliptic curve discrete logarithm problem. The method has the advantages of a common certificateless signature algorithm, namely a certificate management problem of a traditional public key system and a key escrow problem in an identity password system are eliminated; and the algorithm is simple in calculation process, and time-consuming bilinear operation does not need to use. The algorithm can be efficiently applied to fields such as e-commerce and the like of requiring the electronic signature.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
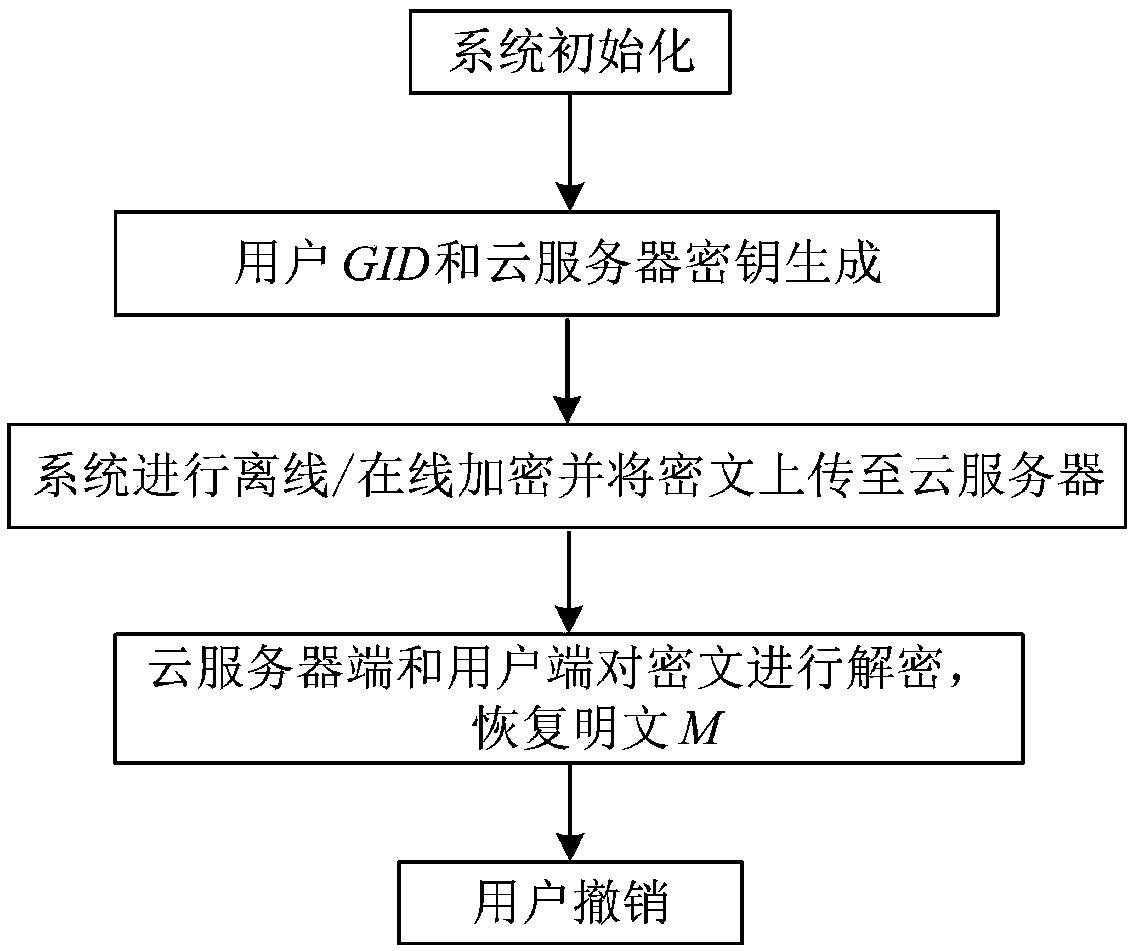
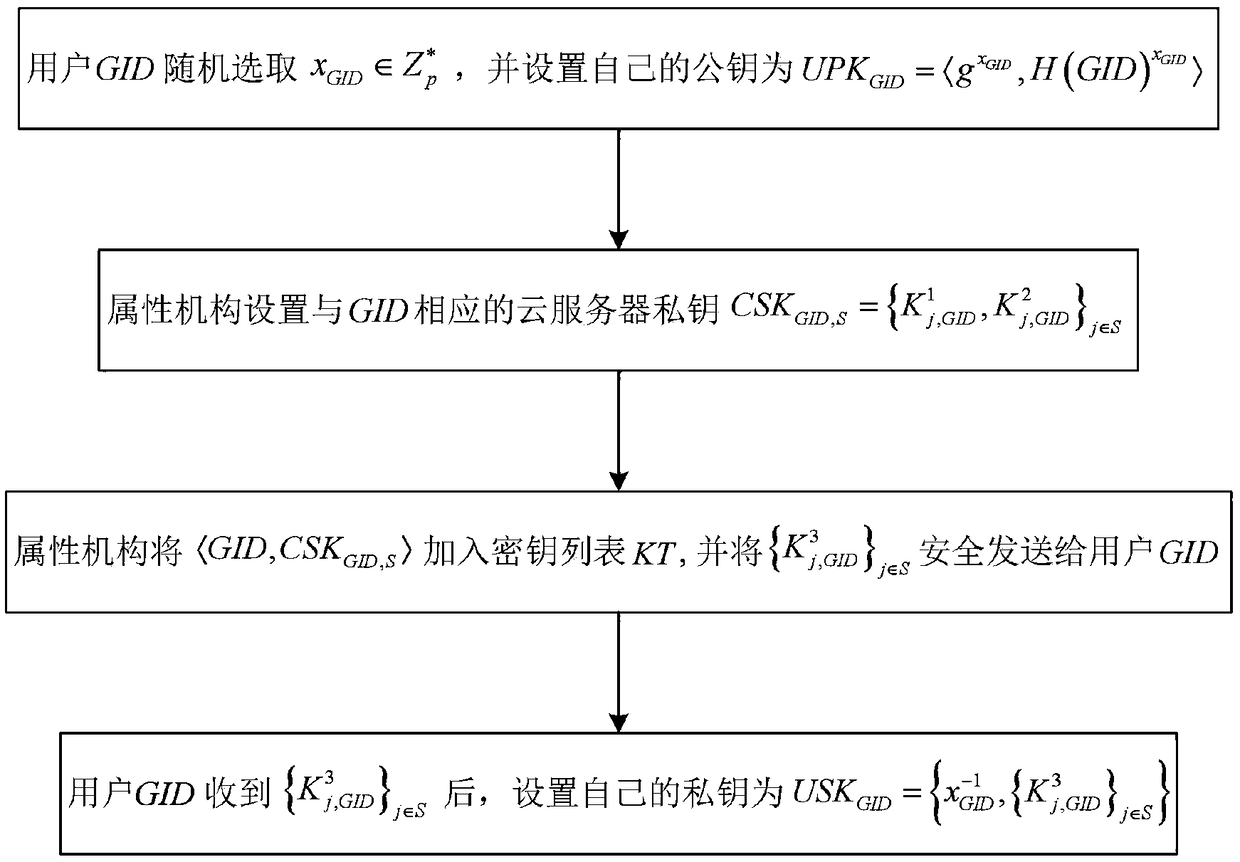
Multifunctional fine-grained access control method for cloud storage
The invention discloses a multifunctional fine-grained access control method for cloud storage, and solves the problem of fine-grained access control of data in cloud storage. The implementation stepsof the method are as follows: performing global initialization and attribute organization initialization; generating the public and private keys of a user and a private key of a cloud server; enabling a system to perform offline / online encryption, wherein the system is provided with a strategy hiding mechanism; uploading a final ciphertext to the cloud server; enabling the cloud server and a userterminal to decrypt and verify the correctness of the keys; enabling the cloud server to delete the corresponding entry from a key list for user revocation. The invention proposes a multi-system CP-ABE scheme with multiple characteristics, and the offline / online encryption mechanism is constructed in detail, which greatly reduces the computational cost of the user. The method has the functions ofattribute revocation, keyless collocation problem, the offline / online encryption mechanism, the strategy hiding and verifiability, and can be applied to fine-grained access control of data in cloud environments such as education, business and medical fields.
Owner:陕西链诚致远科技有限公司
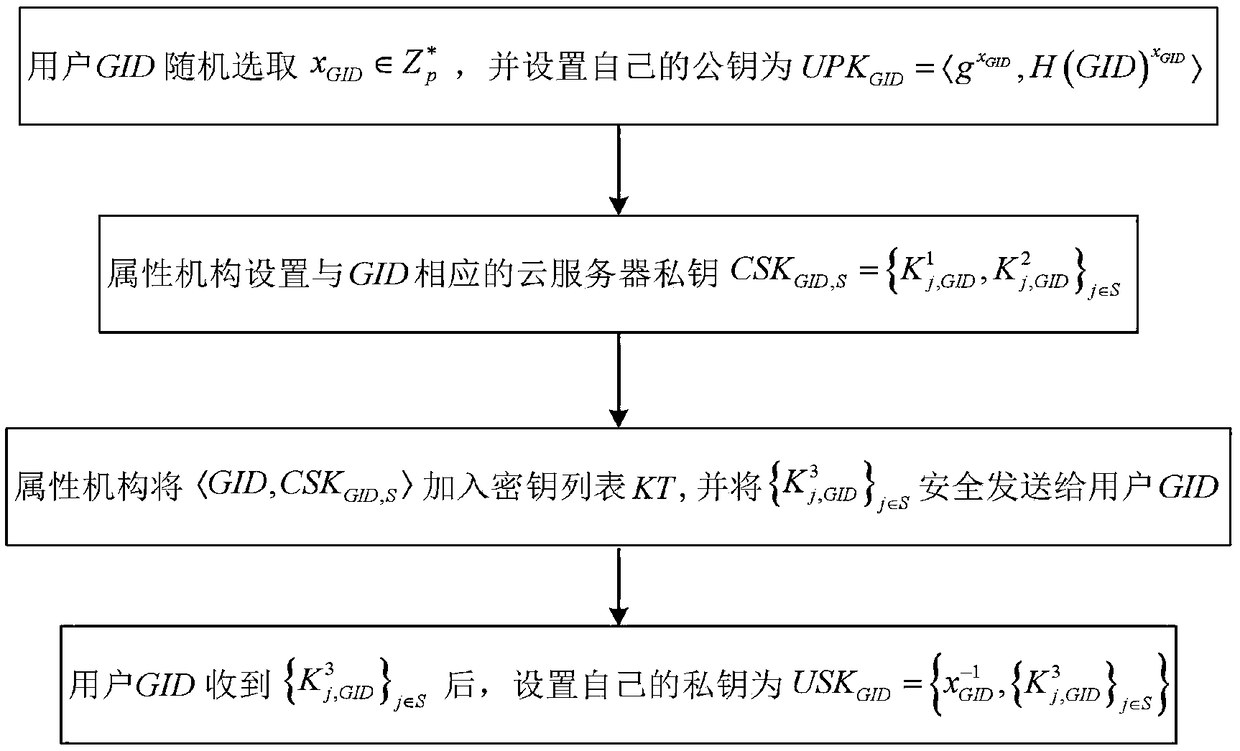
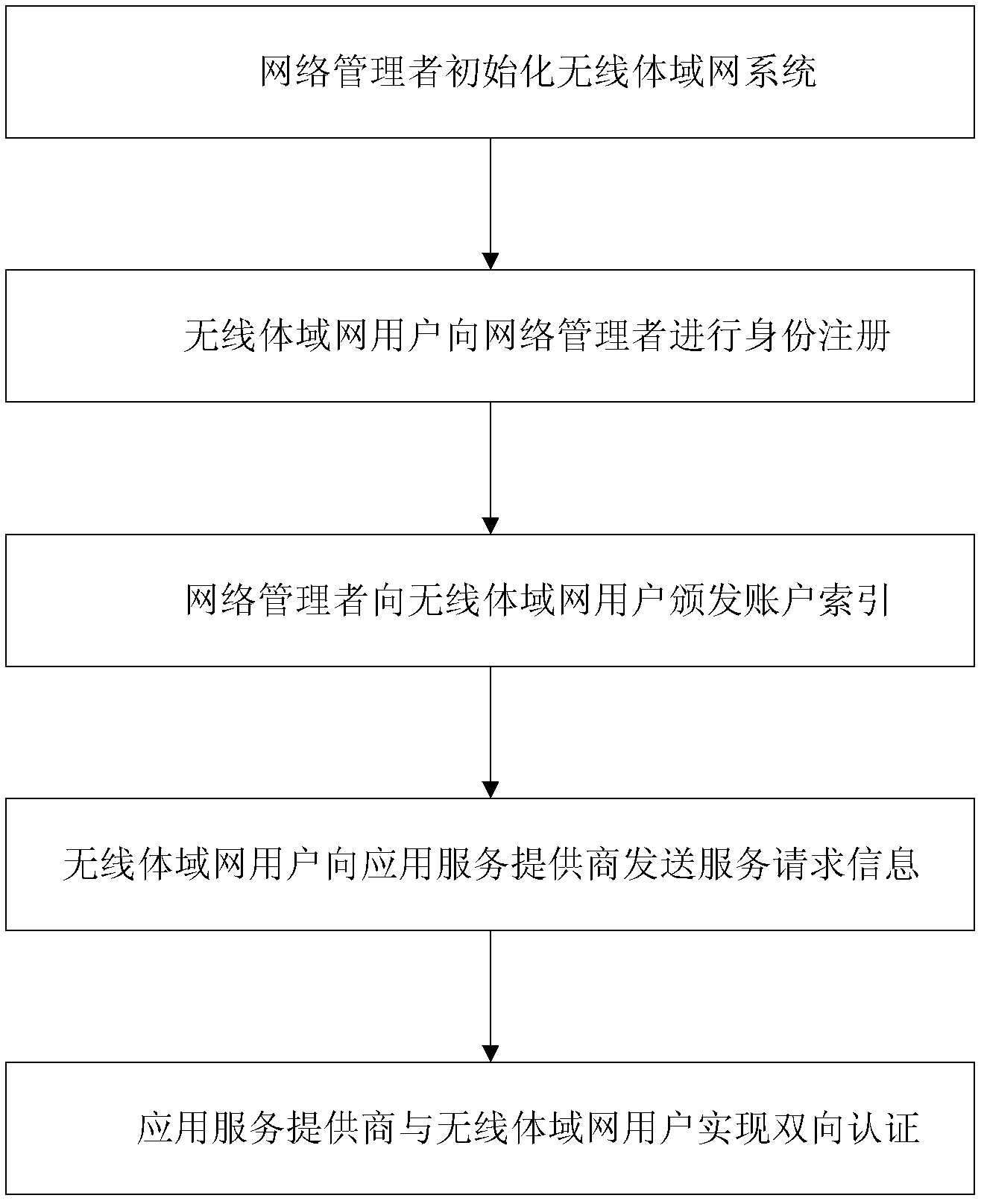
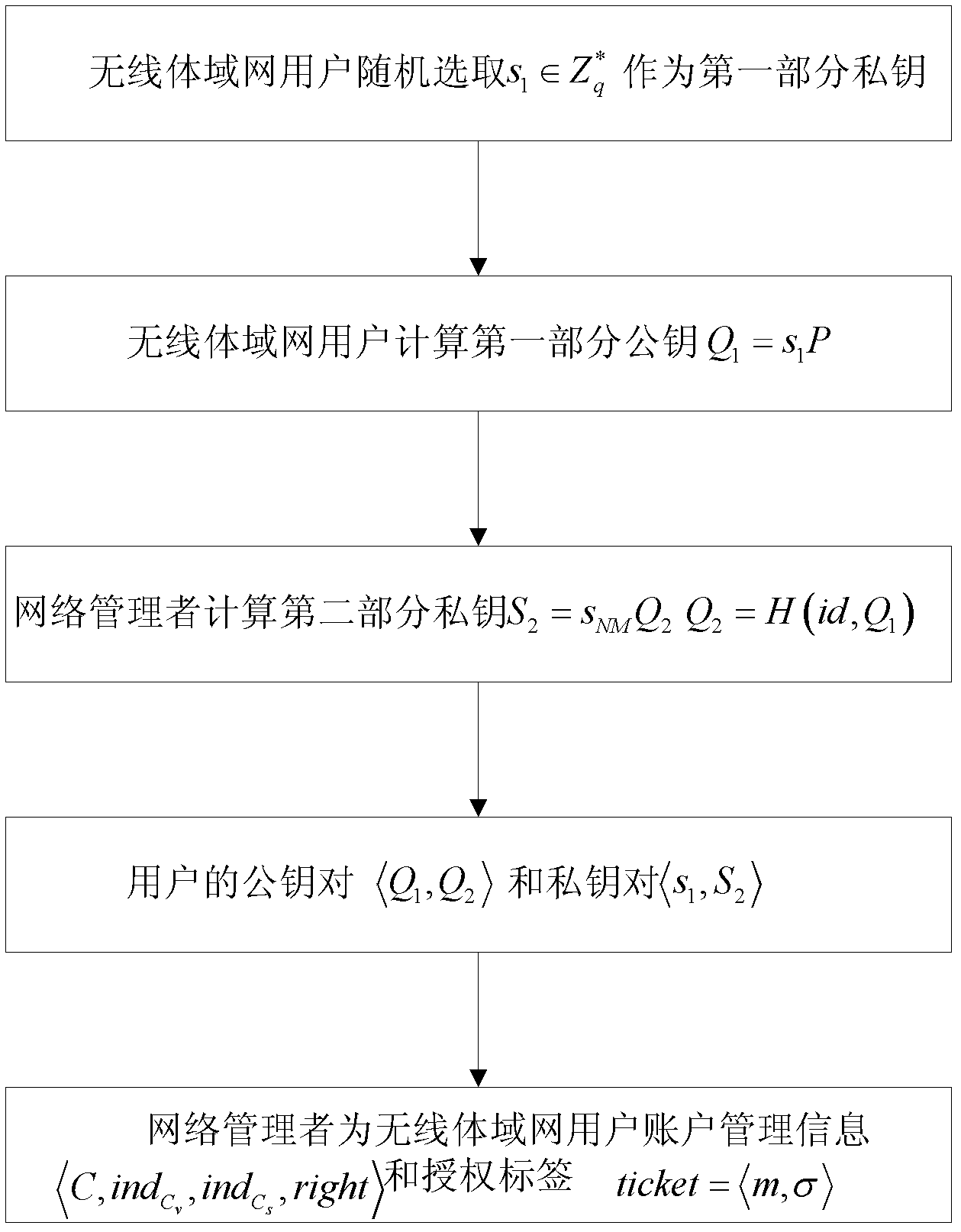
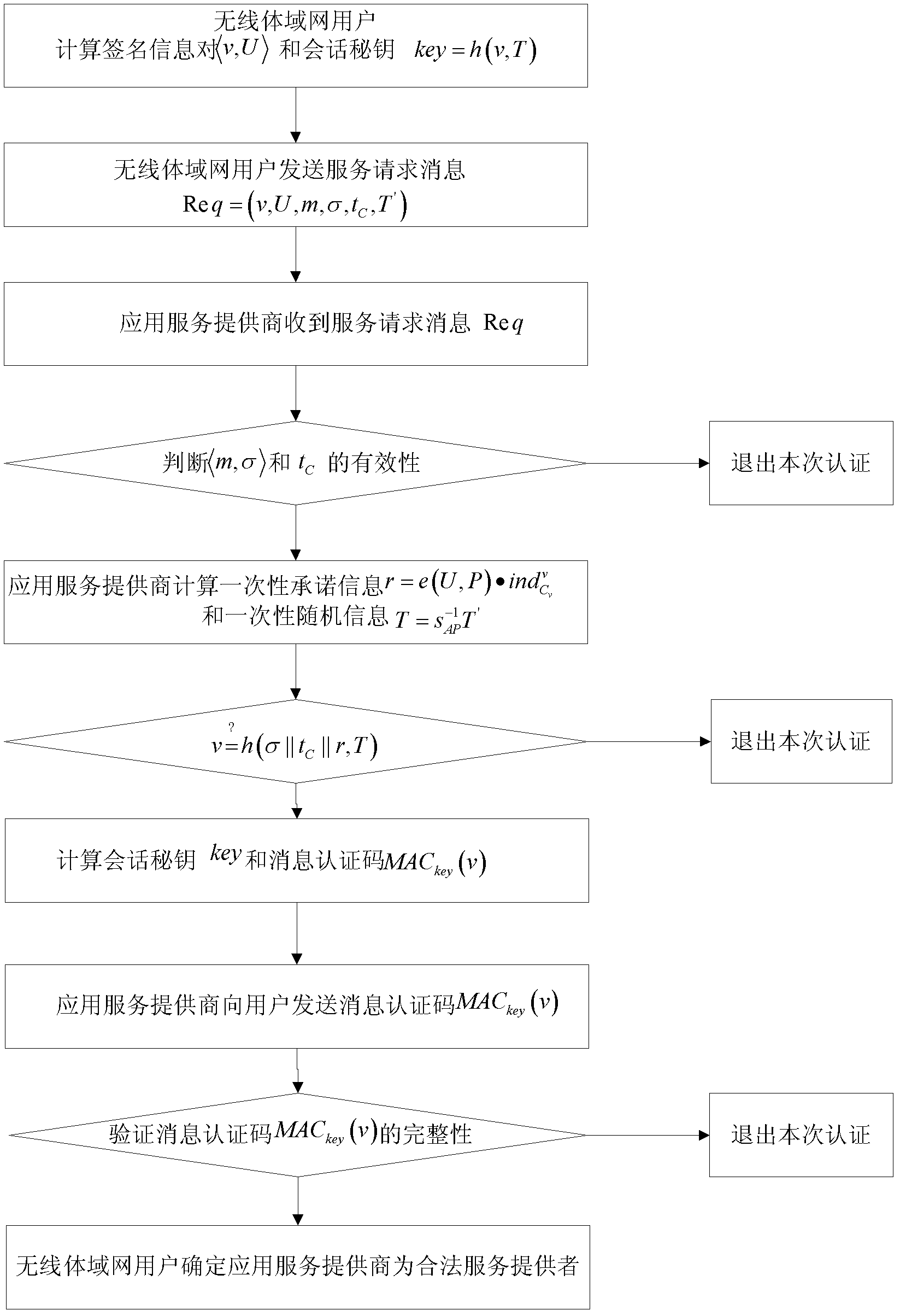
Certificate-free remote anonymous authentication method for wireless body area network
InactiveCN102624530AGood anonymityImprove securityPublic key for secure communicationUser identity/authority verificationComputation complexityBody area network
The invention discloses a certificate-free anonymous authentication method for a wireless body area network, which mainly solves the anonymity problem of wireless body area network remote authentication, and mainly comprises the steps as follows: 1) a network manager initializes a whole wireless body area network system; 2) a wireless body area network user carries out identity register from the network manager; 3) the network manager issues an account index to the wireless body area network user; 4) the wireless body area network user uses the account index to disguisedly send a service request to the network manager; and 5) bidirectional authentication between an application service provider and the wireless body area network user is achieved. According to the invention, a certificate is not required, the defect of no key escrow is avoided, the security performance is high, the degree of complexity of calculation is low, and the method can be used for remote medical treatment monitoring and on other application occasions.
Owner:XIDIAN UNIV
Certificateless signature algorithm for user identity authentication in network environment
InactiveCN102983971AImprove computing efficiencyImprove securityKey distribution for secure communicationUser identity/authority verificationPasswordKey escrow
The invention discloses an efficient certificateless signature algorithm which solves the problem of certificate management in a traditional public key cryptosystem and the problem of key escrow based on an identity password system, and safety is guaranteed in a certificateless environment. The certificateless signature is simple and efficient in computational process and high in, specific hush function does not need, and the length of an output signature is also short. The certificateless signature algorithm has high safety and execution efficiency, and can be effectively used in a signature environment which has a high requirement for safety.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
Certificateless partially blind signature method
InactiveCN102387019AEliminate demandTroubleshoot hosting issuesPublic key for secure communicationUser identity/authority verificationElectronic cashKey escrow
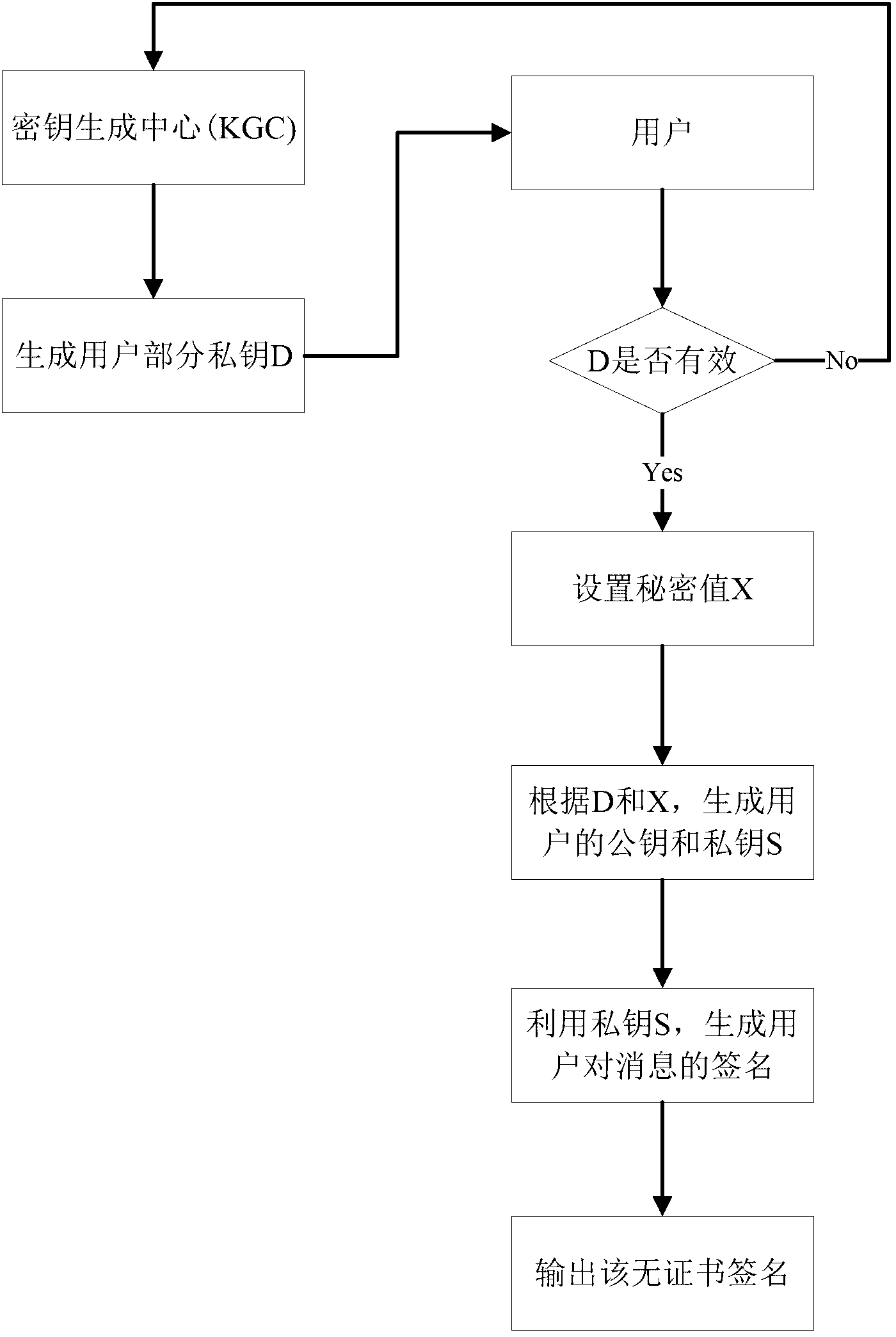
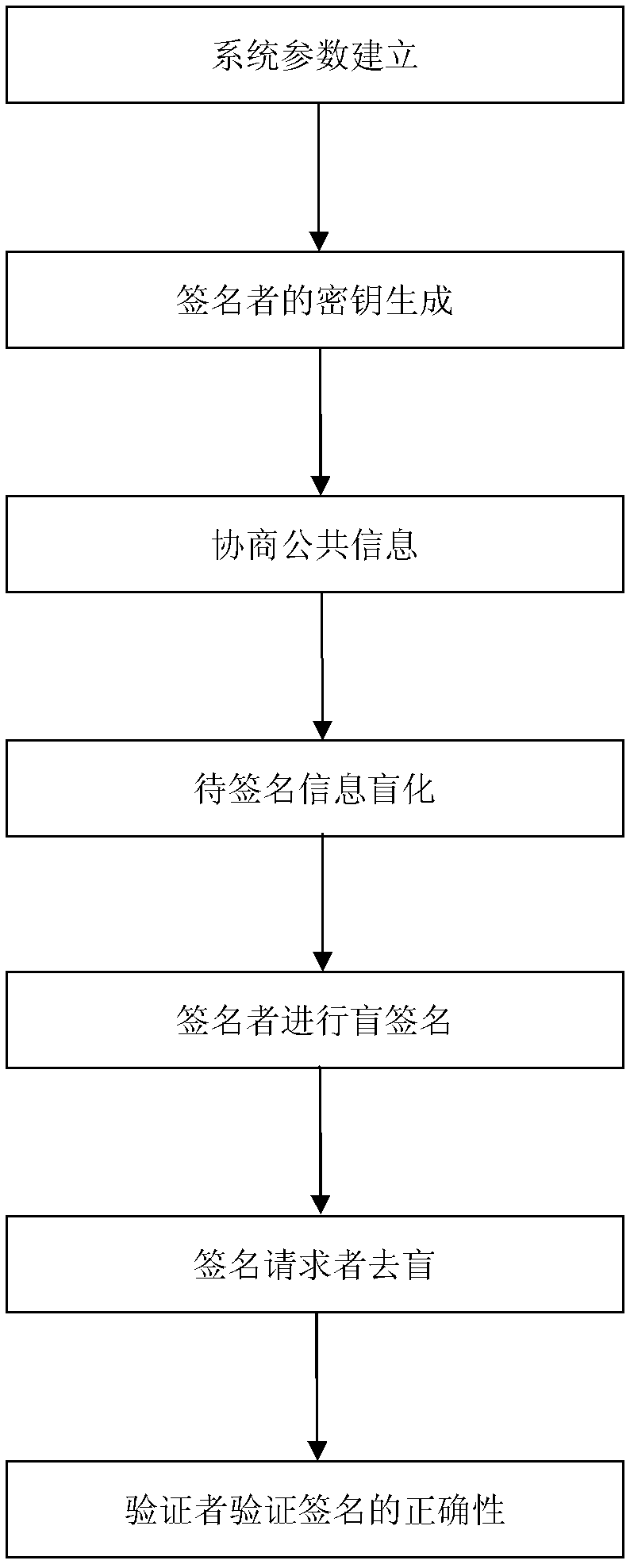
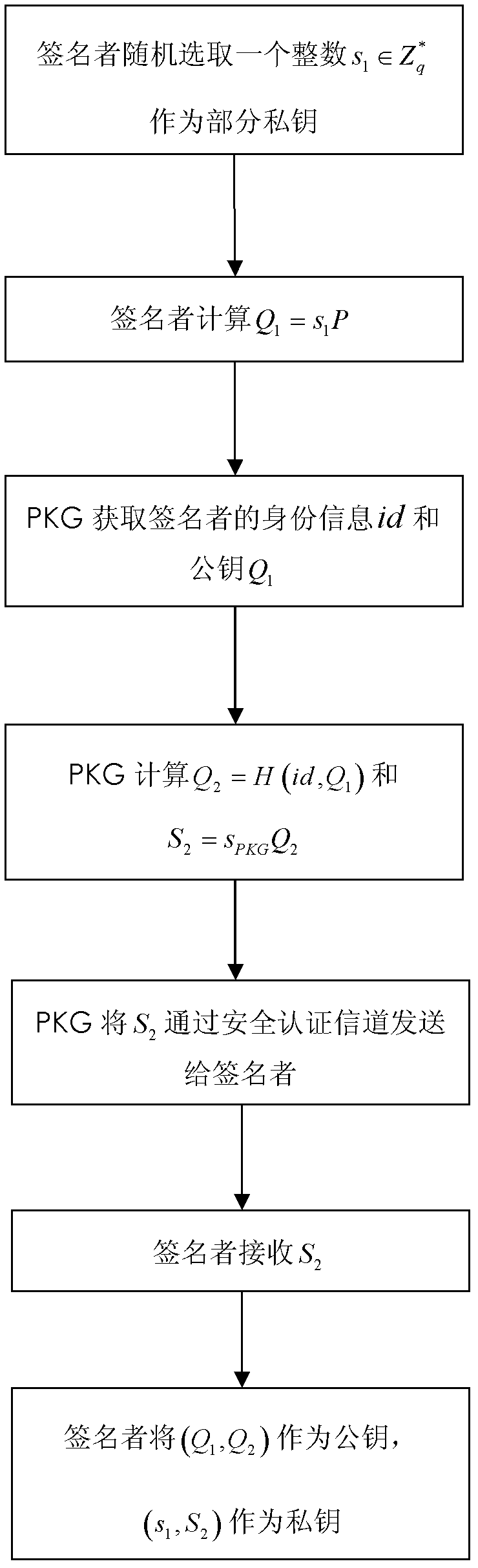
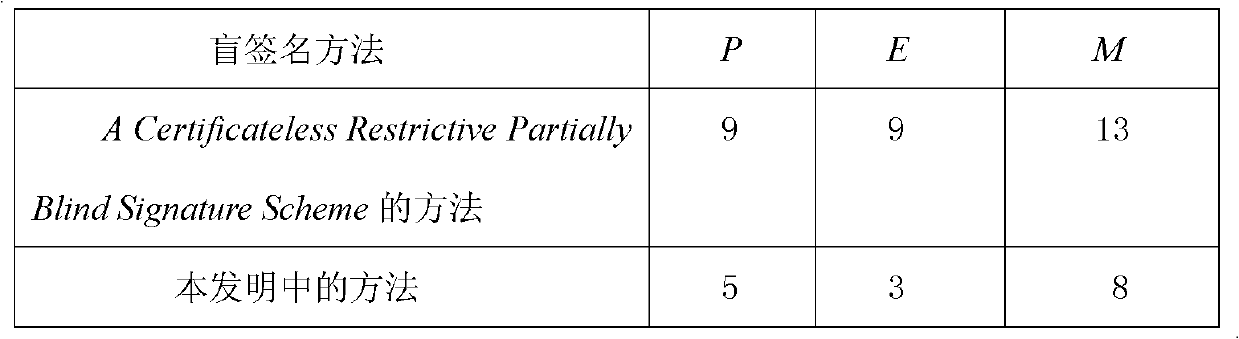
The invention relates to a certificateless partially blind signature method. In the prior art, practicality of the partially blind signature method is low. The method of the invention is mainly used to solve the above problem. The method comprises the following steps that: 1) a secret key generation center randomly selects an integer sPKG as a private key in an integer multiplication group of mod q and stores secretly, and discloses a system parameter: (G1, q, 1, P, G2, e, H, h, QPKG); 2) a signer generates the partial private key s1 and a partial public key Q1, the secret key generation center generates the other partial private key S2 and the public key Q2 and sends to the signer through a safe authentication channel, and the signer acquires a private key pair (s1, S2) and a public key pair (Q1, Q2); 3) the signer carries out signature; 4) an authenticator verifies validity of the signature by using the public key pair (Q1, Q2) of the signer. By using the method of the invention, a demand to a certificate can be eliminated. There is no disadvantage of secret key escrow. A partial blind characteristic is possessed. Simultaneously, the method is simple and high efficient and possesses good practicality and security. The method can be used in an electronic cash transaction and electronic voting.
Owner:XIDIAN UNIV
A method and system for certificating vehicle identity
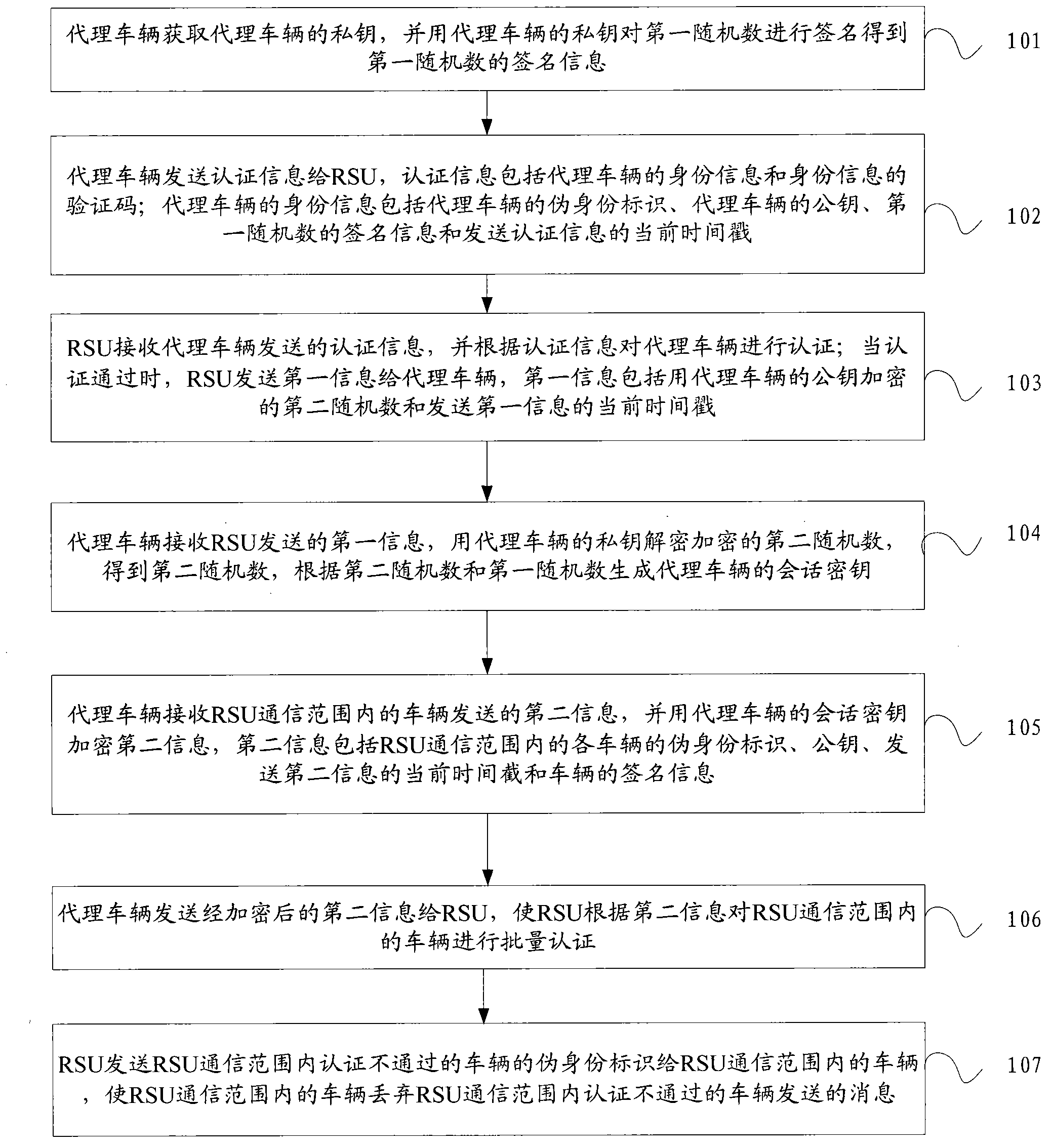
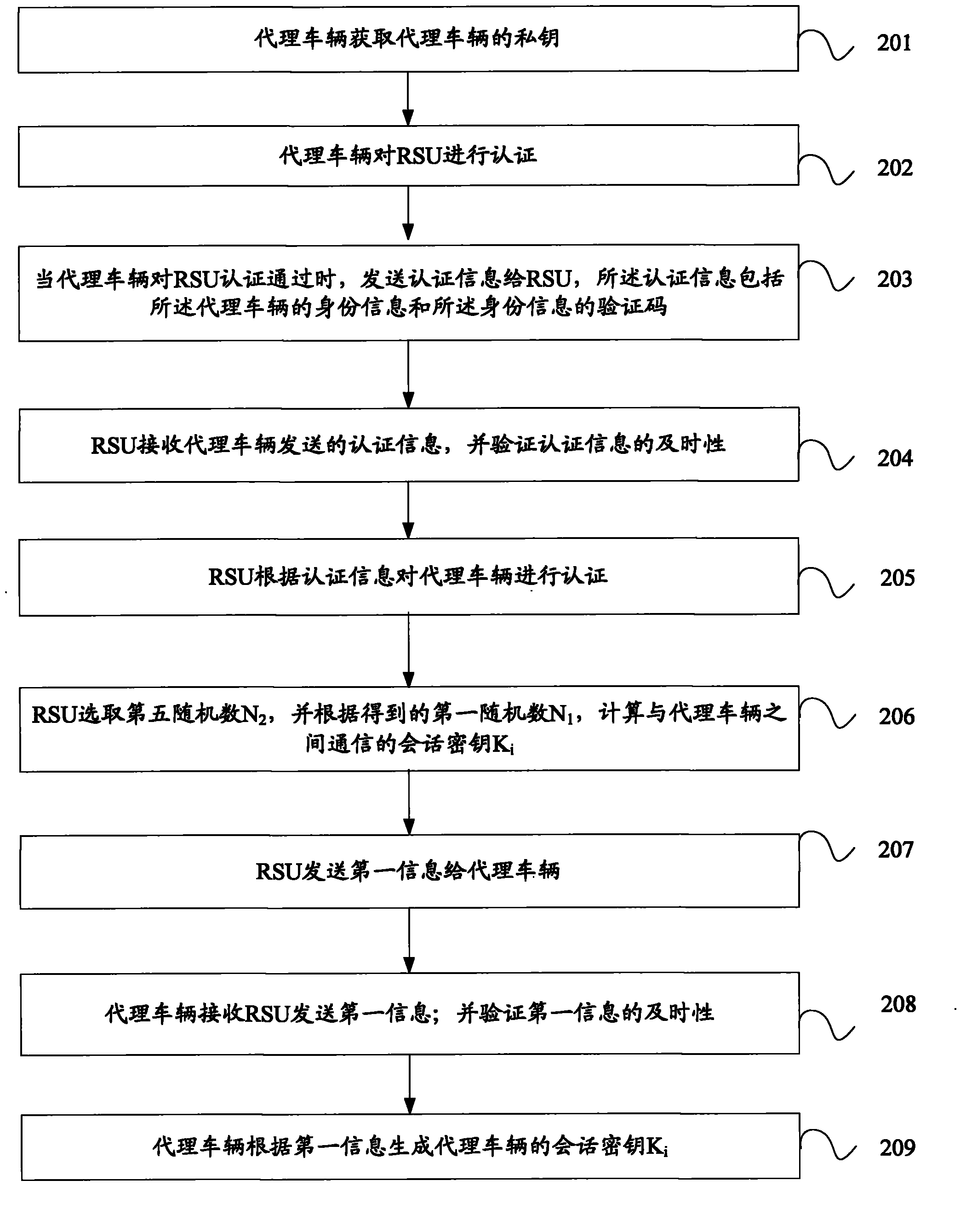
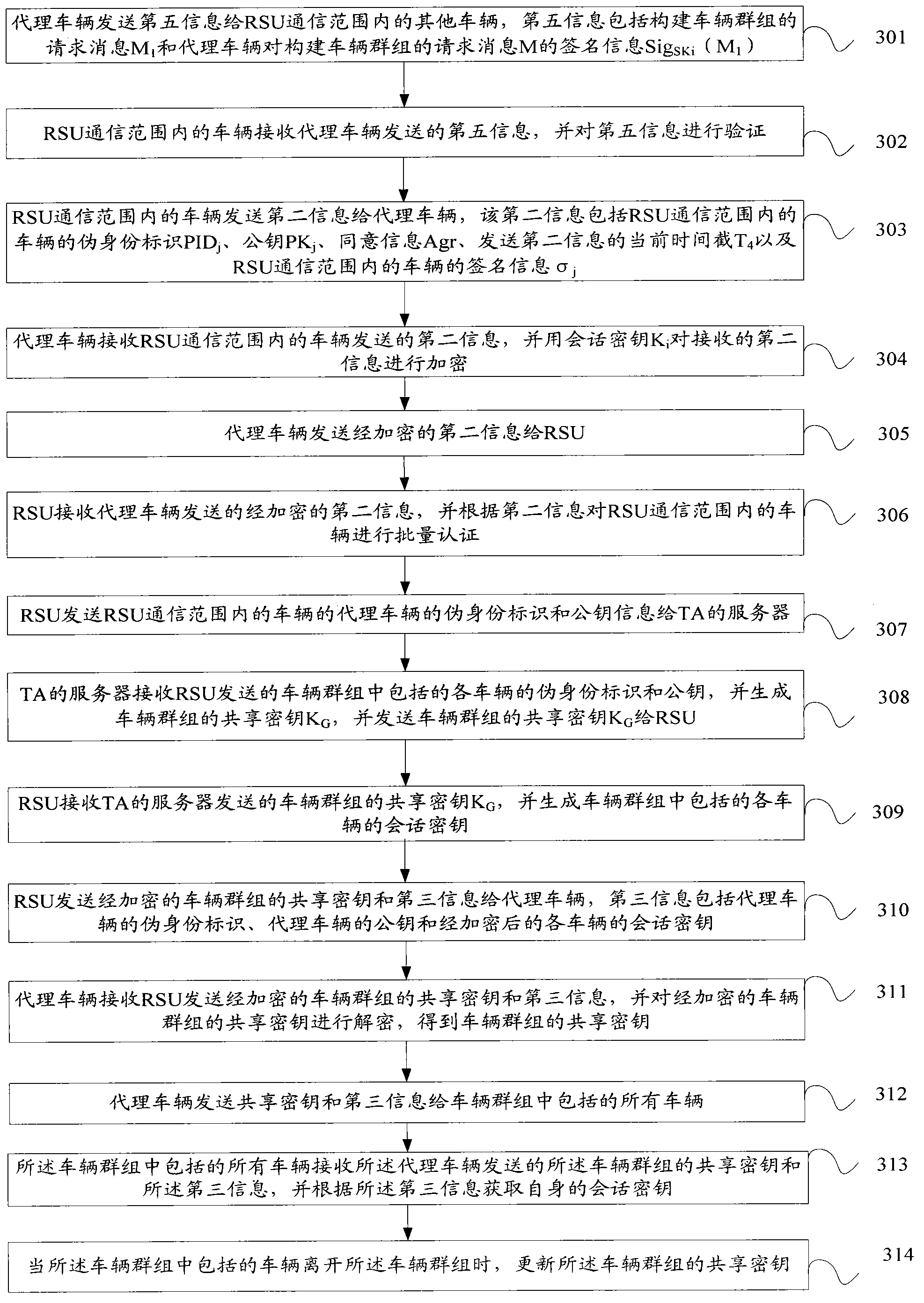
InactiveCN104219663AFast authenticationAvoid key escrow issuesUser identity/authority verificationNetwork topologiesKey escrowSession key
The present invention discloses a method and system for certificating a vehicle identity, and belongs to the field of mobile communication. The method includes: a road side unit RSU certificates an agent vehicle and acquires a session key of the agent vehicle when the certification is passed; the agent vehicle constitutes a vehicle group, and receives second information sent by vehicles within the RSU communication scope; the second information is sent to the RSU after encrypted using the session key of the agent vehicle, so that the RSU certificates the vehicles in the RSU communication scope in a batch according to the second information; and the RSU sends a false identity identification of the vehicle which does not pass the certification within the RSU communication scope to the vehicles in the RSU communication scope. The system includes: an acquiring module, a sending module, a certification module, a generating module and an encryption module. The present invention acquires a private key of the agent vehicle through the agent vehicle, which avoids the problem of secret key hosting; moreover, the RSU sends the false identity identification of the vehicle which does not pass the certification to the vehicles in the RSU communication scope, which considers revocation for illegal vehicles.
Owner:JIANGSU UNIV
Method and system for certificateless and pairing-free identity-based proxy signcryption
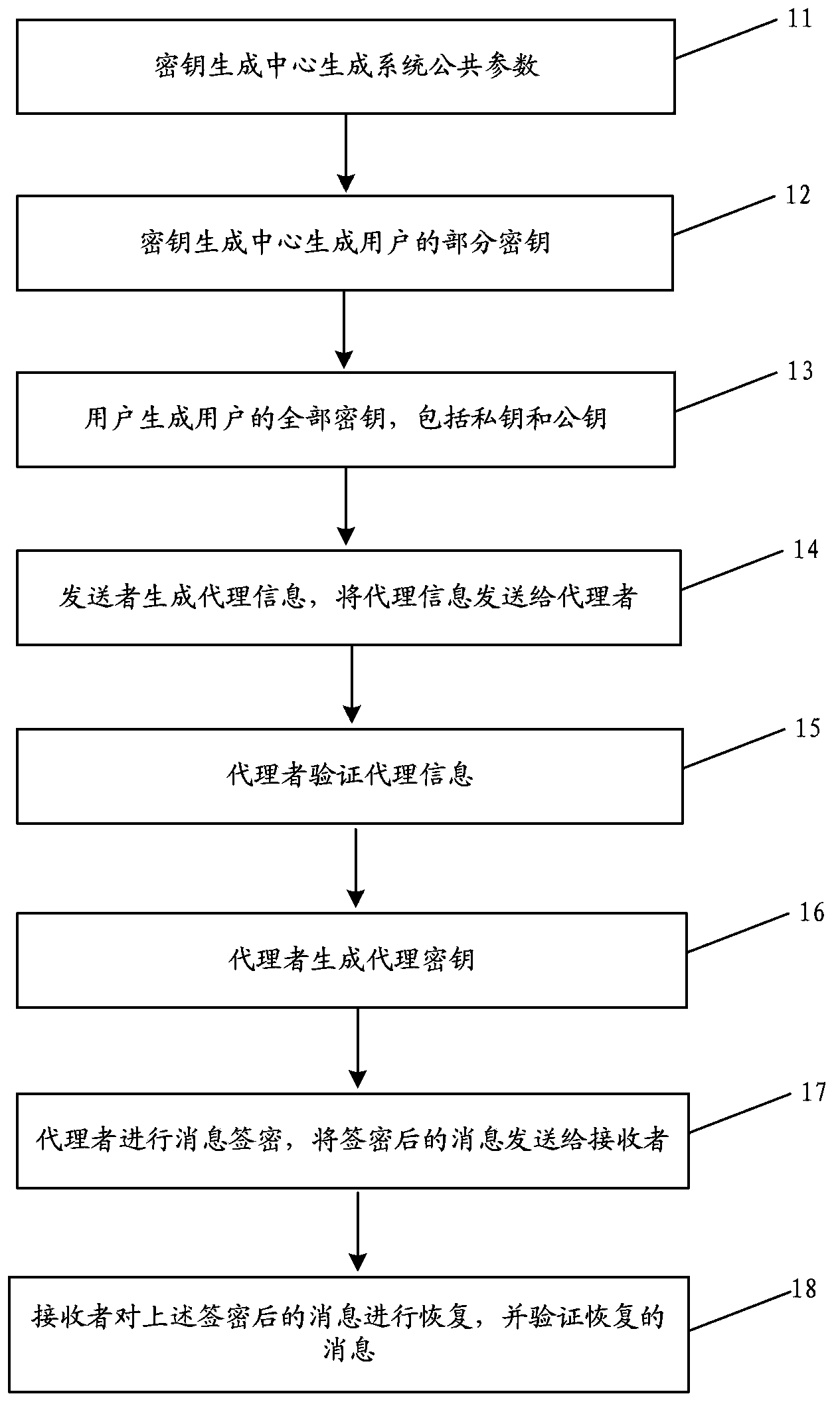
ActiveCN103905189ATroubleshoot hosting issuesPublic key for secure communicationUser identity/authority verificationSurrogate keySigncryption
The embodiment of the invention provides a method and a system for certificateless and pairing-free identity-based proxy signcryption. The method mainly comprises the following steps: a sender generates a private key and a public key thereof according to common parameters of the system and identity information parameters of the sender, generates proxy information based on the private key and the public key thereof, and sends the proxy information to a proxy; after the proxy information passes verification of the proxy, the proxy generates a proxy key, performs signcryption on a message needing to be sent based on the proxy key and the common parameters of the system to obtain a signcrypted message and an intermediate parameter, and sends the signcrypted message and the intermediate parameter to a receiver; and the receiver recovers the signcrypted message with the use of the intermediate parameter and the common parameters of the system to obtain a recovered message, and verifies the recovered message. The certificateless and pairing-free identity-based proxy signcryption scheme provided by the embodiment of the invention has both signature and encryption characteristics and has the feature of proxy. A key generation center only generates part of keys of a user, no certificate is needed, and the problem of key escrow is solved.
Owner:AEROSPACE INFORMATION
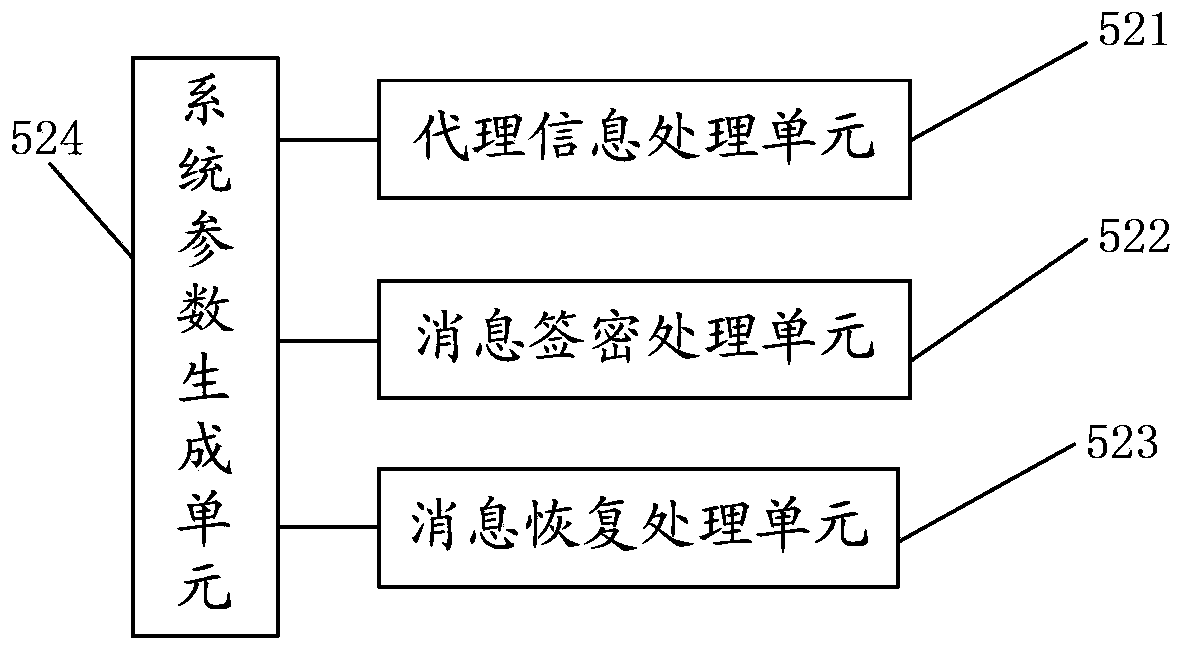
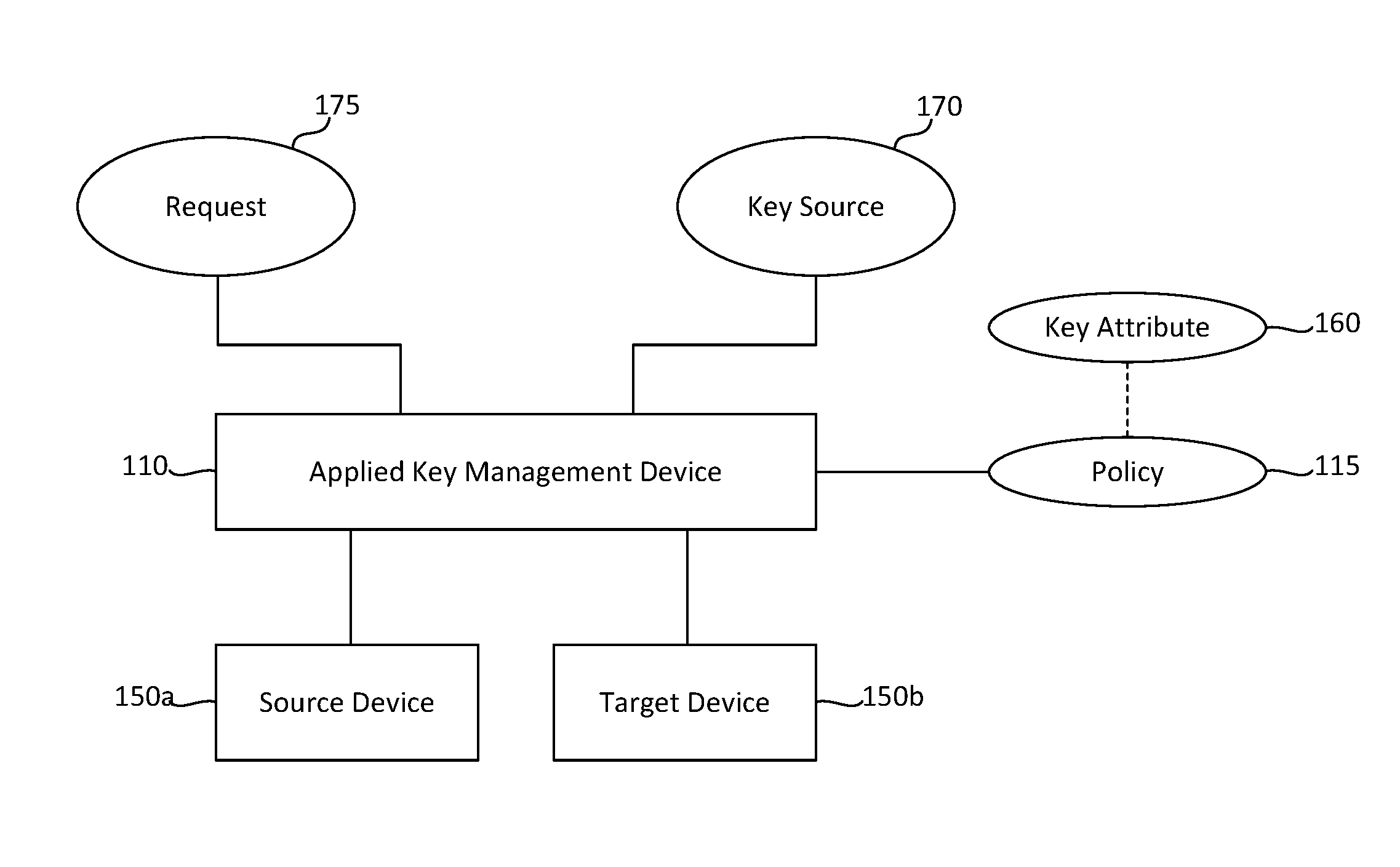
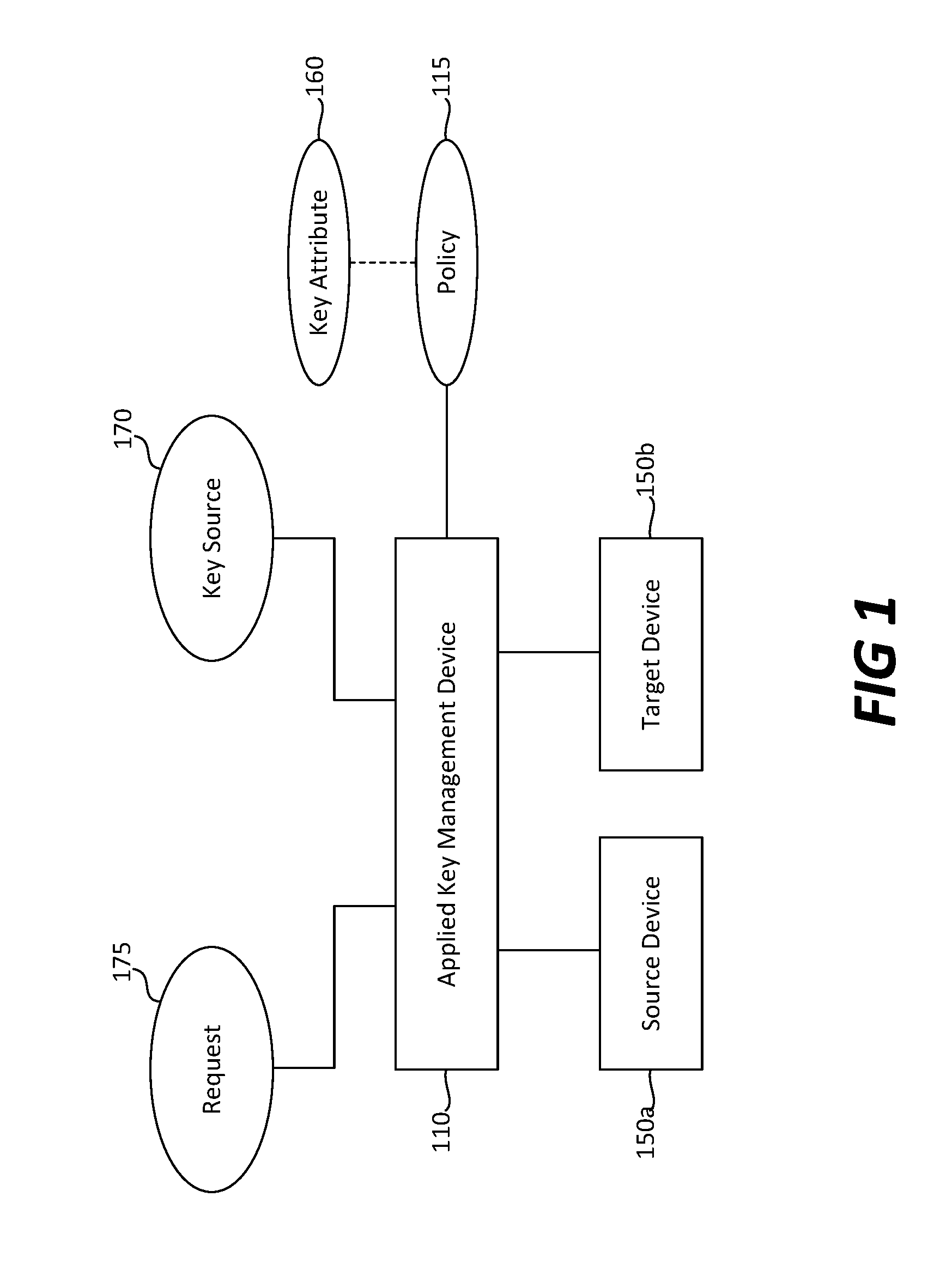
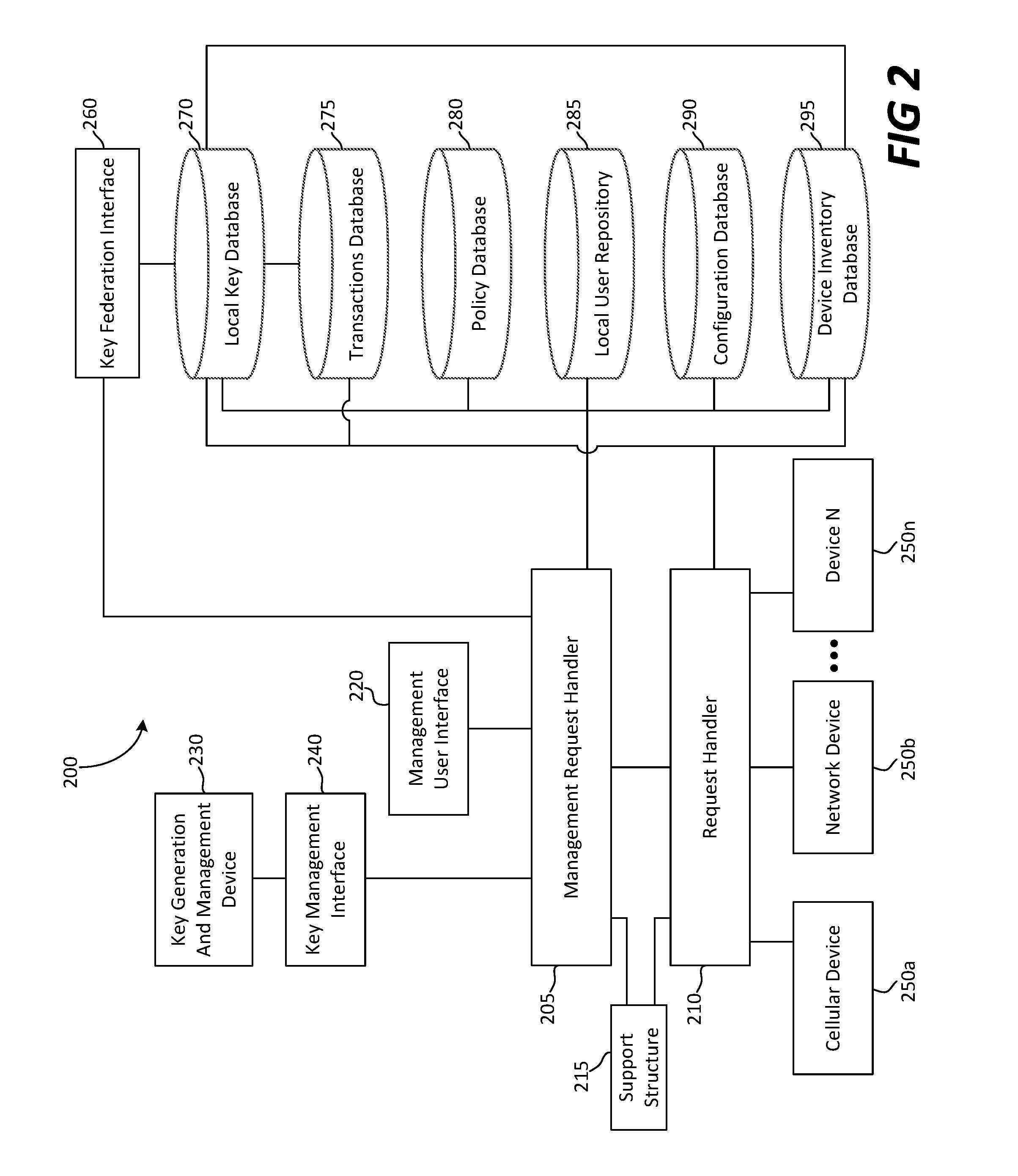
Server-client key escrow for applied key management system and process
Embodiments described herein relate to apparatuses and methods for registering and storing a local key associated with a local application of a communication device, including, but not limited to, receiving a request from the communication device to register and store the local key, evaluating the request based on at least one first policy, and sending the request to register and store the local key to a secure key storage.
Owner:FORNETIX
Cryptographic one time pad technique
InactiveUS20030142821A1Tighter requirementSynchronising transmission/receiving encryption devicesKey escrowKey distribution
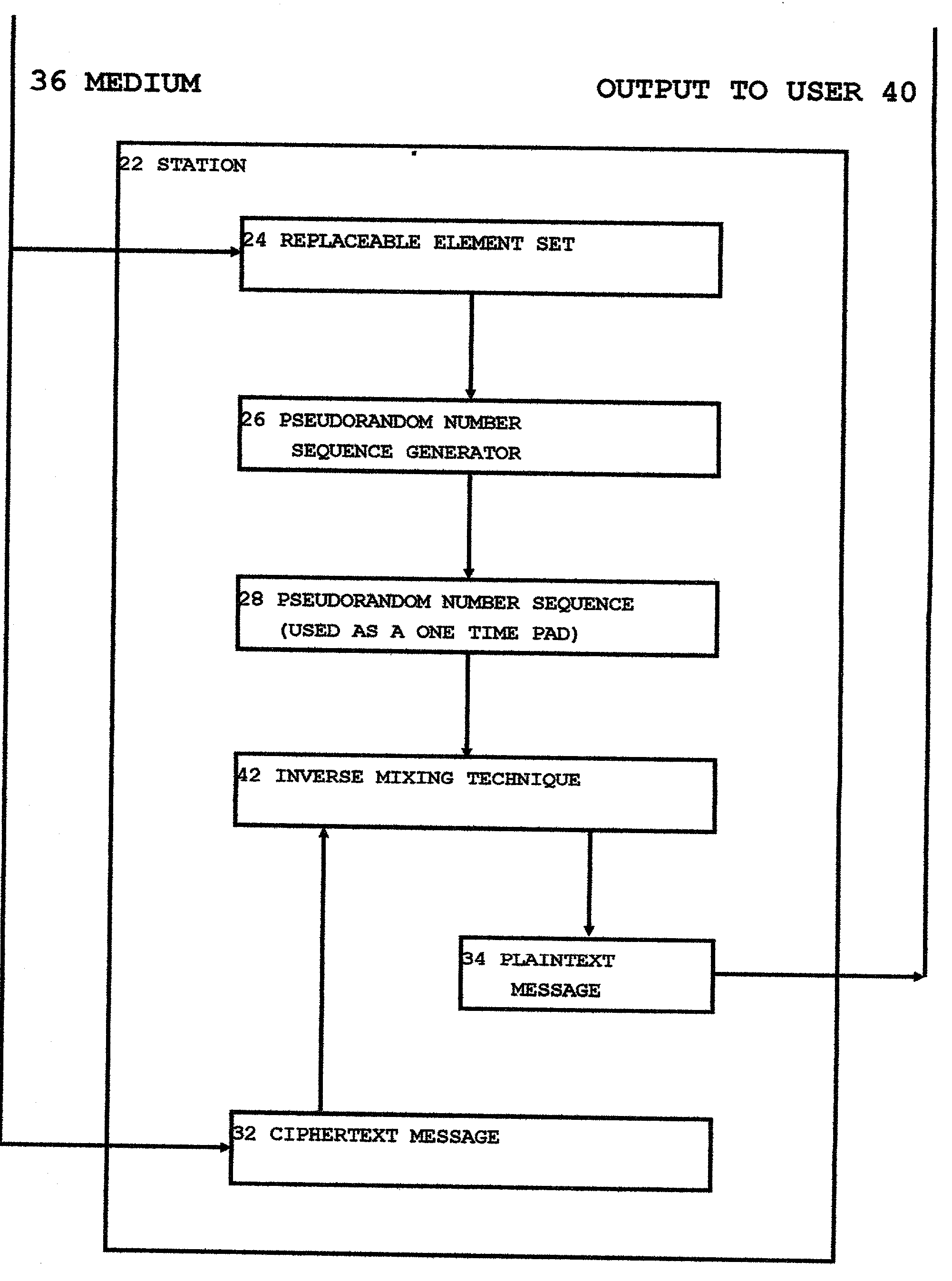
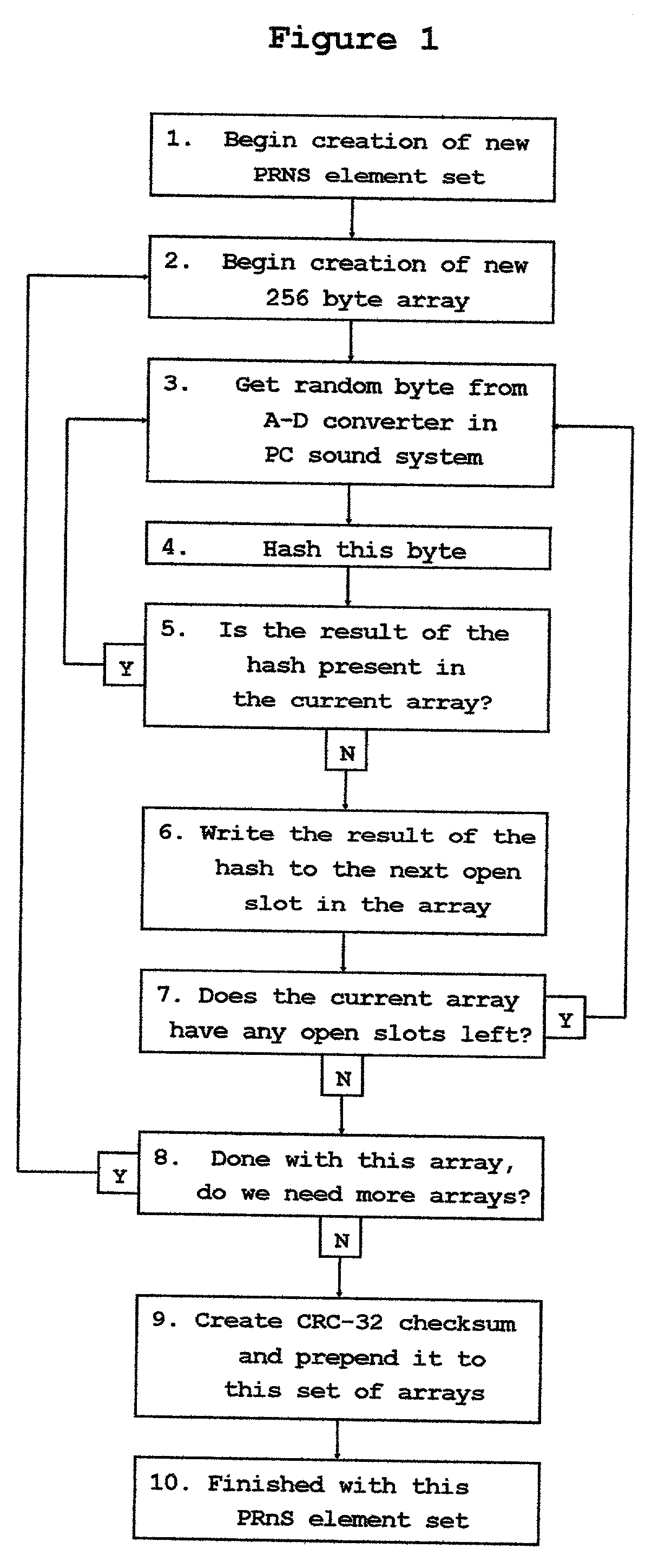
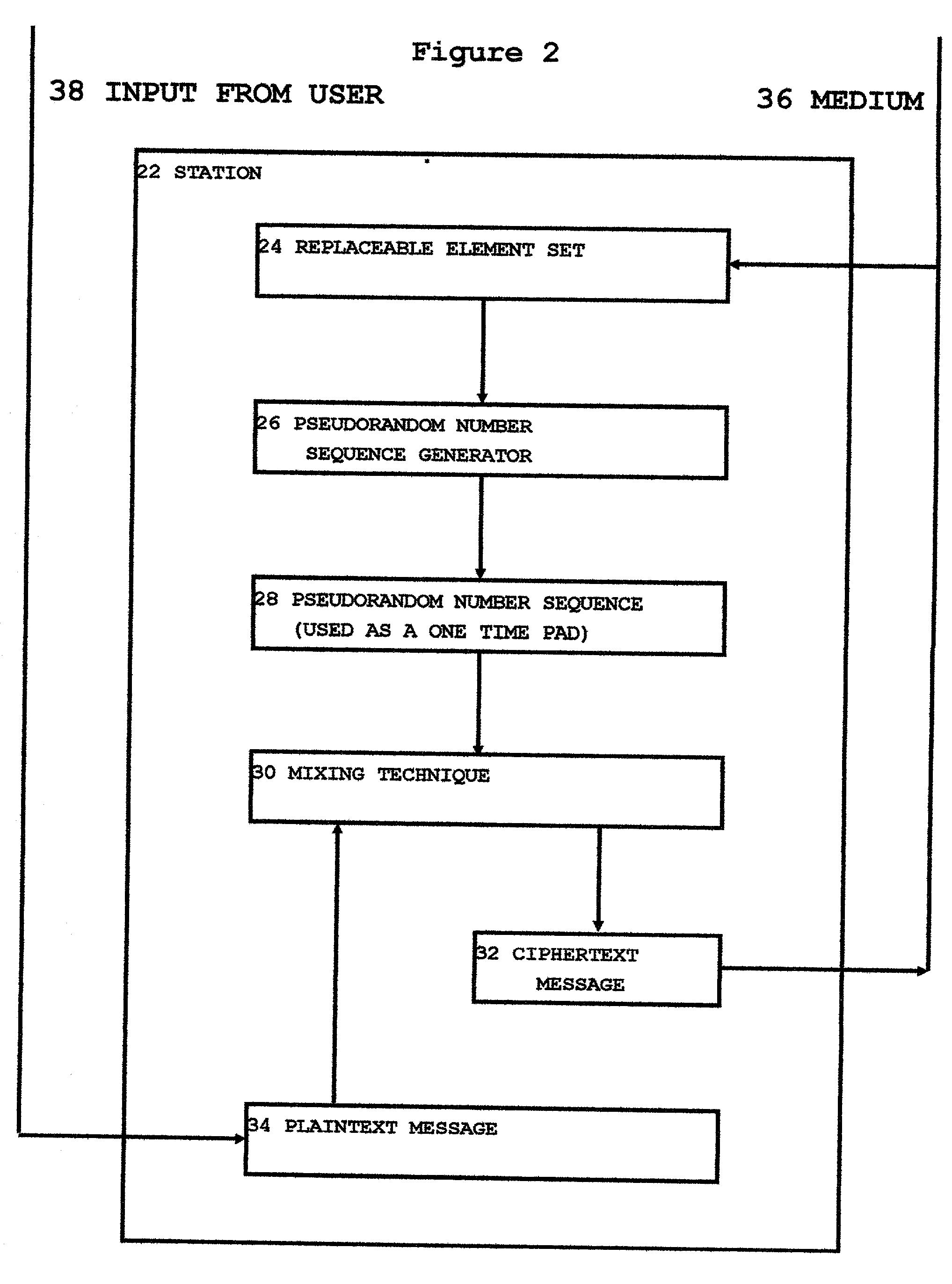
A variant on the "One Time Pad' cipher is used to provide an encrypted link between two or more stations. The main feature of this variant is the use of a unique and easily created Pseudo-Random Number Sequence segment not having any internal repeats. At one station, a mixing function is used to combine a locally created stream of truly random bytes with a portion of this unique PRNS segment, yielding a fresh stream of truly random data. This freshly created stream of truly random data is operated on in such a way as to create a new and unique PRNS element set which is used to control the functioning of a PRNS generator. The PRNS generator is used to create a new and unique PRNS segment which has a repeat period much longer than the length of the PRNS element set used to create it. It is then useful to treat the PRNS element set as a message and transfer it across the encrypted link to other stations. In this fashion, this OTP cipher variant can be re-keyed and used for as long as there is a continuing source of truly random data available at one of the stations on the network. This technique of using unique and freshly created PRNS segments rather than the classic One Time Pad allows encrypted networks to function independently of any central key distribution regimens or Public Key Infrastructures, making such an encrypted network proof against security breaches perpetrated upon, or key escrow schemes propagated through, such external key distribution infrastructures. This technique also provides certain securities against willful betrayals by tempted users or coerced revelations by users under duress.
Owner:ROSS DAVID MARSHALL
Authentication system realizing method supporting exclusive control of digital signature key
InactiveCN102170356AFunction increaseEasy to useKey distribution for secure communicationUser identity/authority verificationKey exchangeThird party
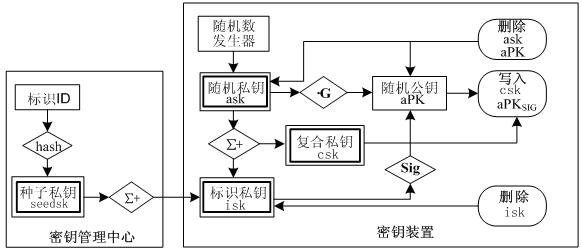
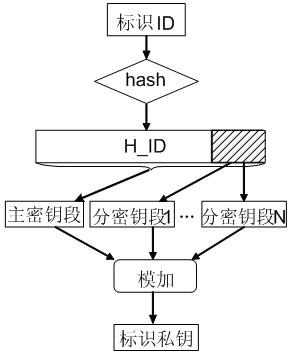
The invention relates to the technical field of information security, in particular to an authentication system supporting exclusive control of a digital signature key on the basis of a combined public key. A seed key consisting of multiple key sections is constructed and comprises a seed public key and a seed private key; by using a user identifier, a key management centre generates a user identifier private key through the seed private key and writes the user identifier private key into a key device; the key device starts an initialization program to automatically generate a composite private key for digital signature and a random public key digitally signed by the user identifier private key while used for the first time; and the composite private key and the digitally signed random public key are written into a secure storage area of the key device, and the user identifier private key and process data are destructed. The digital signature key is automatically produced and controlled by the user so that regulations of relevant laws are satisfied; furthermore, the exclusive control of the digital signature key by the user is assured through a third party of register link; and one-way key exchange, key escrow and key recovery are realized through providing the identifier key for the key exchange.
Owner:北京联合智华微电子科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com