Certificateless partially blind signature method
A partially blind and certificateless technology, applied in the field of information security, can solve problems such as poor practicability, low execution efficiency, and complex algorithms, and achieve the effect of eliminating the disadvantages of fully blind signatures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
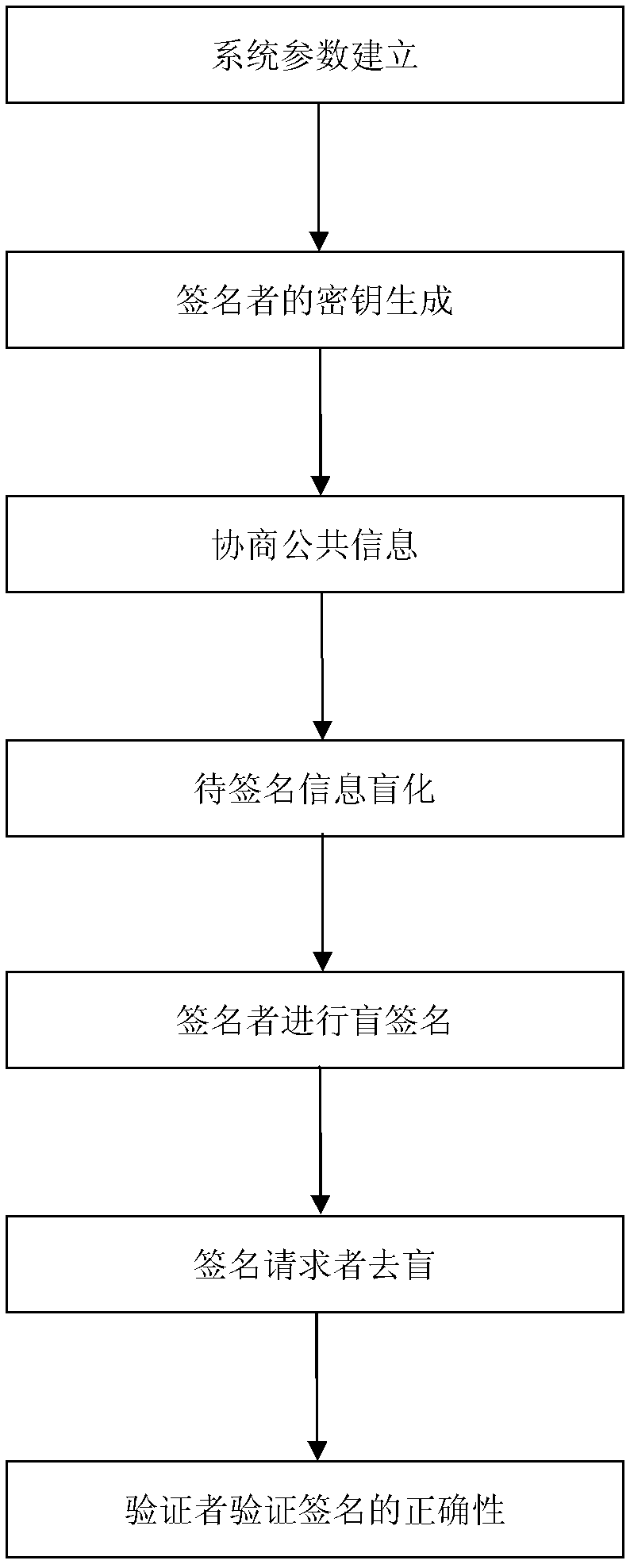
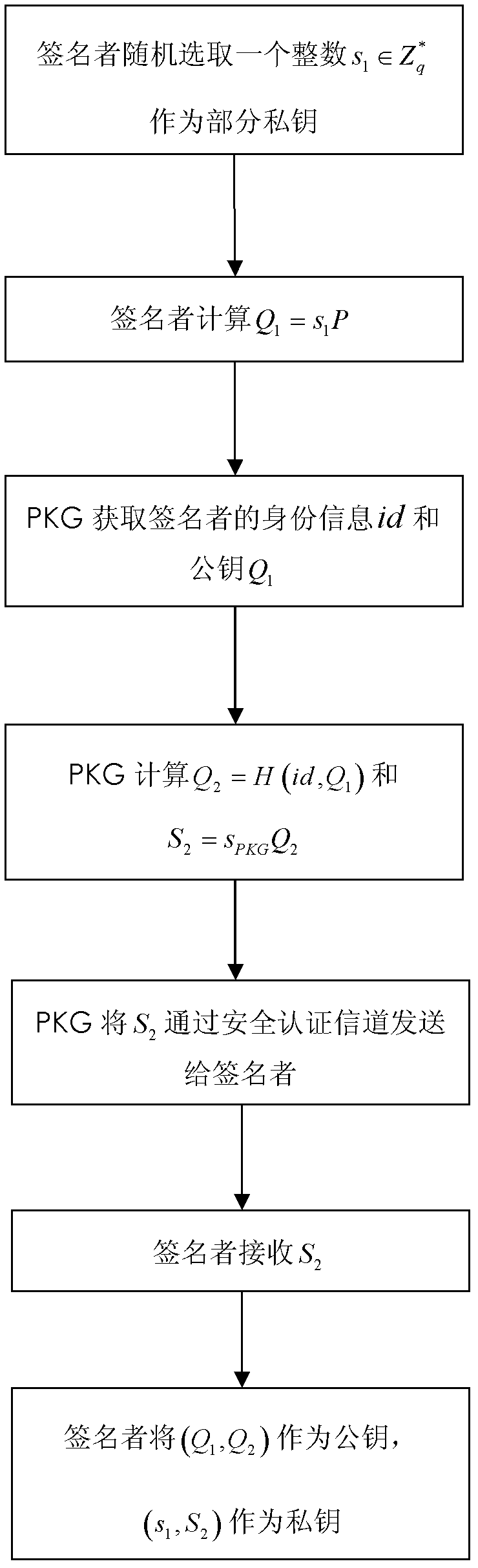
[0028] Reference figure 1 , The present invention is a certificate-free partial blind signature method, and its implementation steps are:
[0029] Step 1. The key generation center PKG establishes system parameters. The specific steps are as follows:
[0030] (1a) Determine the size of the safety factor l and the prime number q according to safety requirements, and use the elliptic curve to construct the bilinear mapping e(G 1 , G 1 )→G 2 Cyclic additive group 1 , +> And cyclic multiplication group 2 ,·> For simplicity, this embodiment uses the P-192 elliptic curve in the prime number domain recommended by the National Institute of Standards and Technology (NIST);
[0031] (1b) Choose the following collision-free hash function H: {0, 1} * →G1 and In this embodiment, the hash function SHA-1 is selected;
[0032] (1c) From the integer multiplication group of mod q Randomly select an integer s PKG As own private key and calculate Q PKG =s PKG P as its own public key;
[0033] (1d) Publi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com