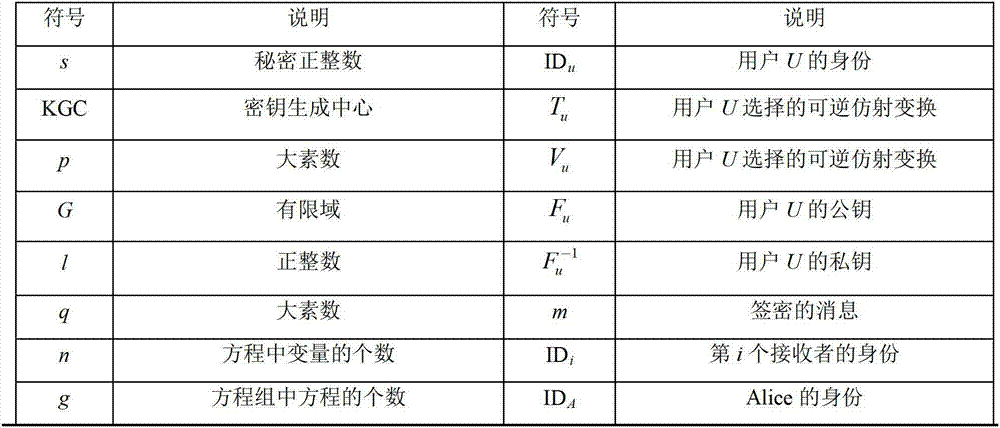
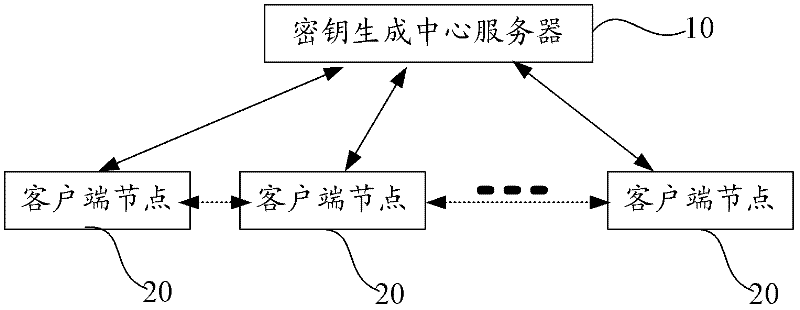
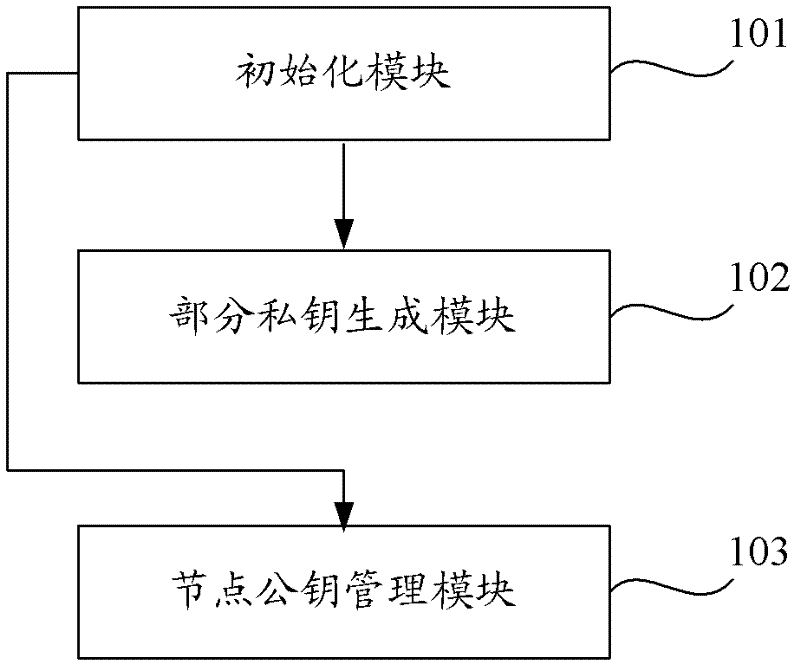
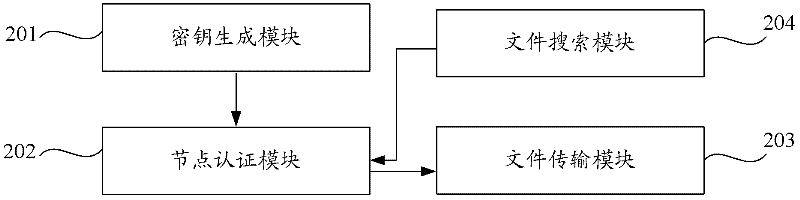
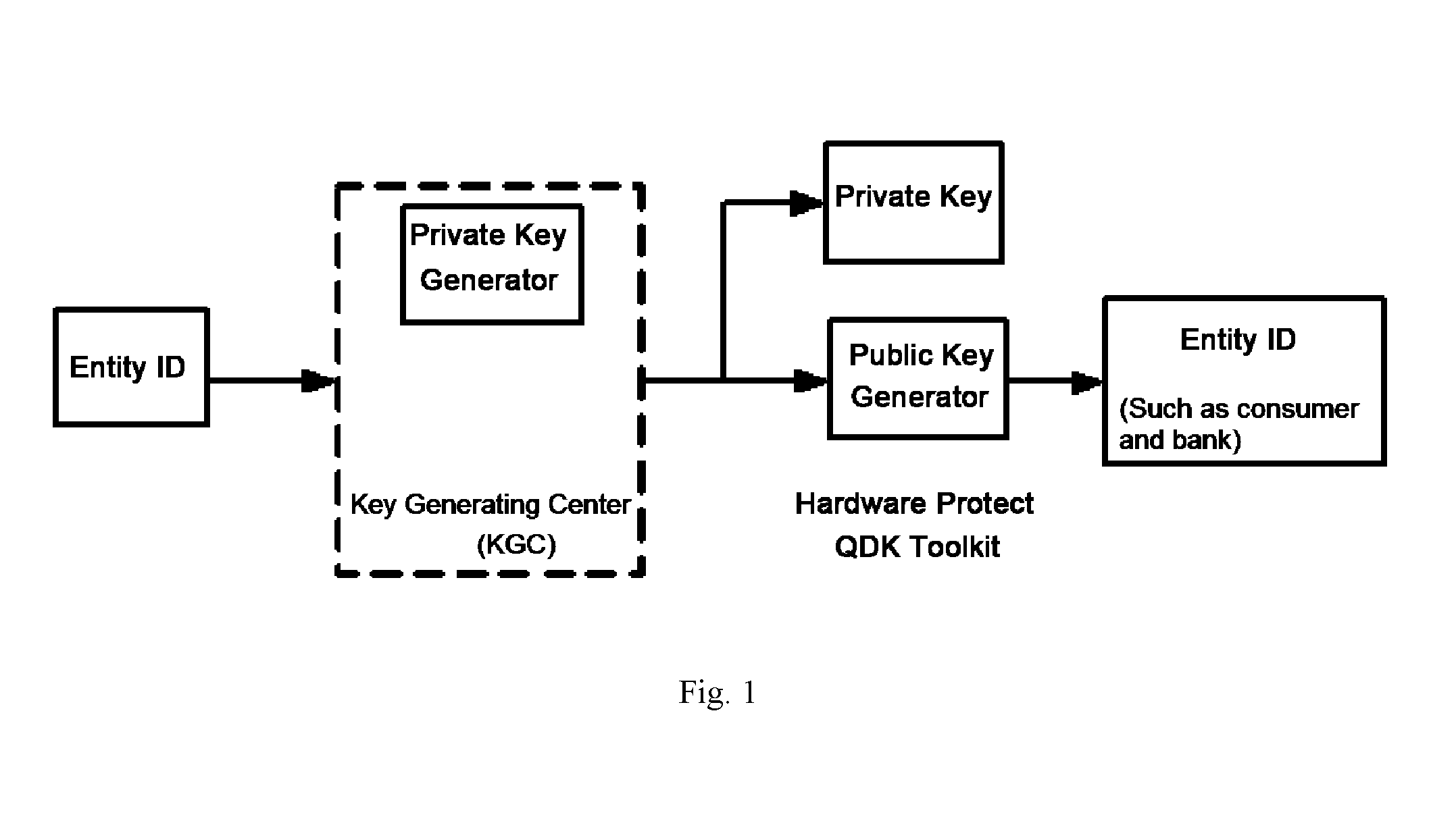
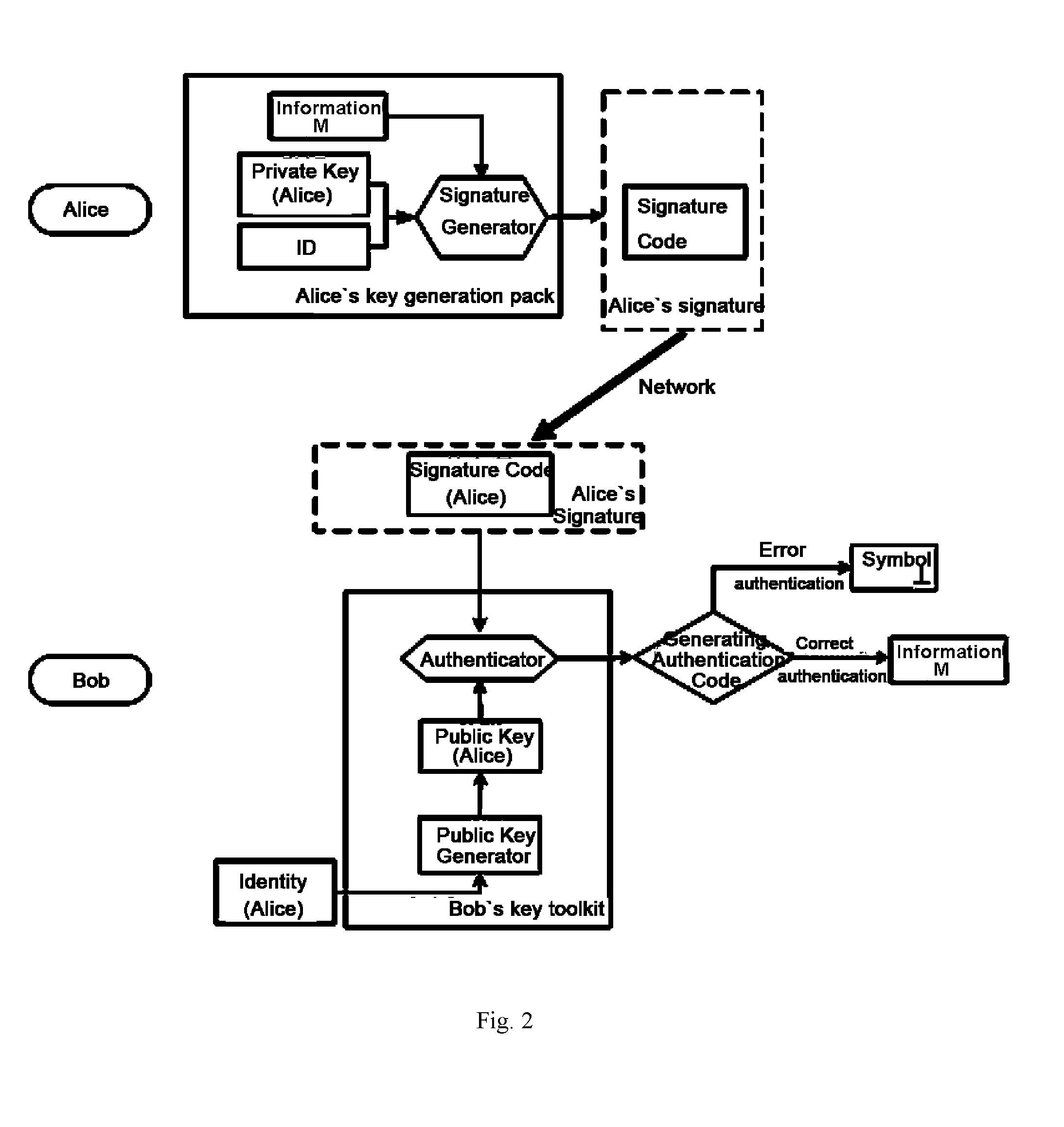
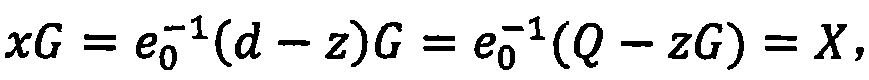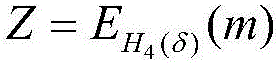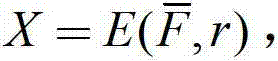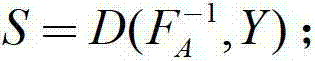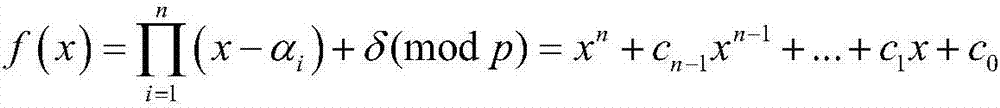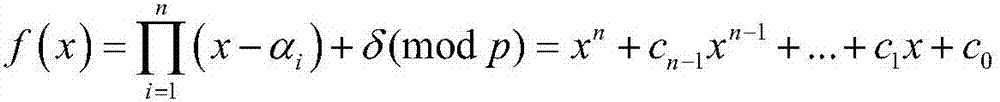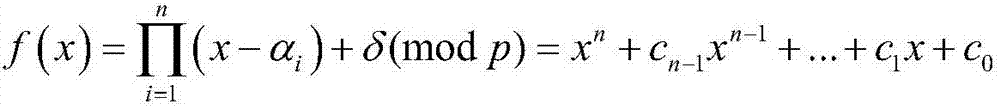Patents
Literature
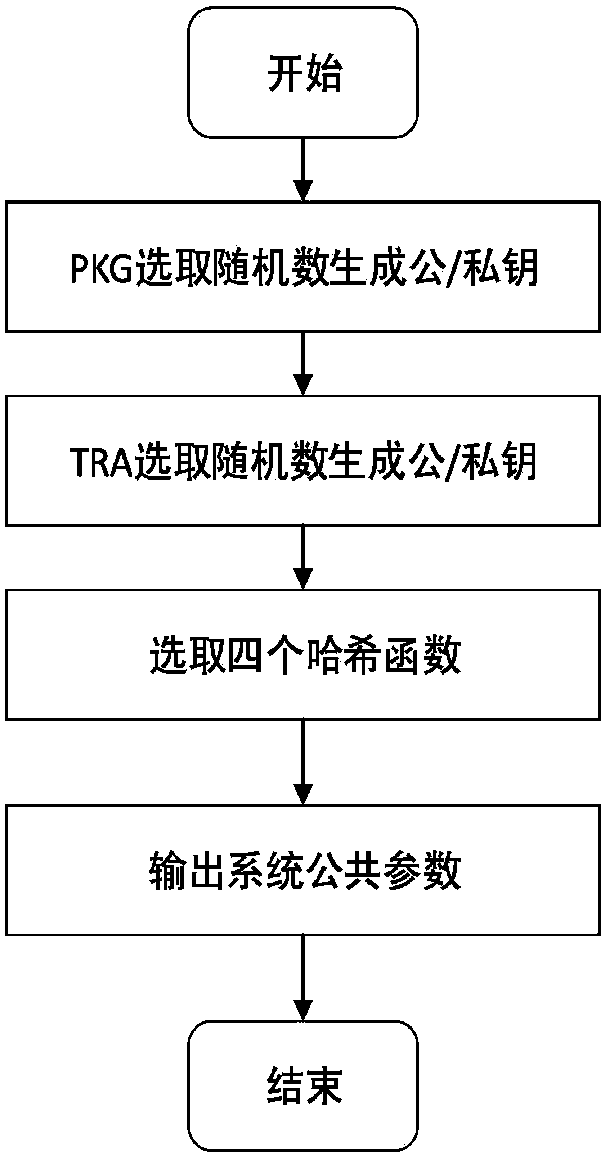
369 results about "Key generation center" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Achievement method of certificate-less public key cryptosystem without bilinear pairing operation
ActiveCN104539423AEfficient managementImprove computing efficiencyPublic key for secure communicationUser identity/authority verificationCommunications securityInformation security
The invention provides an achievement method of a certificate-less public key cryptosystem without bilinear pairing operation and belongs to the field of information safety. The achievement method is used for solving the problems of generation of a secret key of a user, usage and authentication of a public key of the user. According to the achievement method, firstly, a user sets a secret value and calculates a temporary public key, then a secret key generating center generates the other part of the secret key for the user and enables the two parts to be bound, and finally the user synthesizes a his / her actual public and secret key pair. The defect that public key replacement and signature counterfeit possibly exist in a common certificate-less cryptosystem is overcome, the user has complete control right on the secret key, the secret key can be revoked and re-generated, and the signature of the user has non-repudiation. The achievement method adopts a public key cryptographic algorithm of a standard elliptic curve, does not adopt the bilinear pairing operation, is few in occupied resources and high in safety and can operate without the secret key generating center when being applied to signature, authentication and secret key negotiation. By means of the achievement method, identity authentication, communication security and non-repudiation application demands of large-scale systems and low-power-consumption devices can be met.
Owner:北京百旺信安科技有限公司 +1
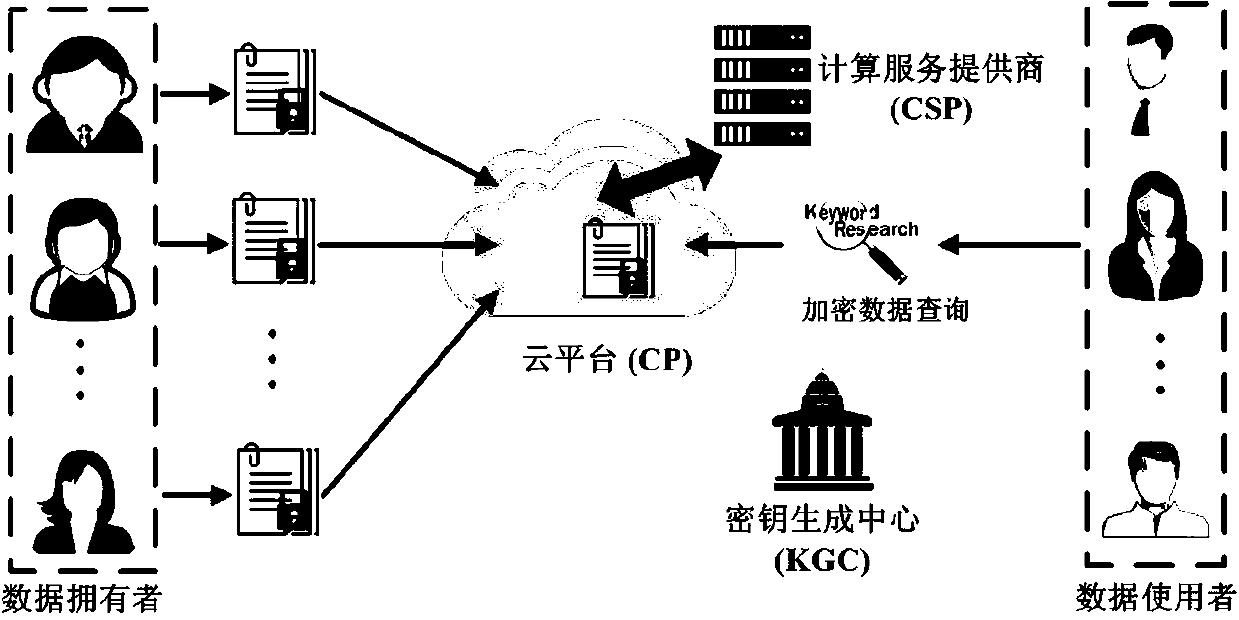
Key escrow-free secure multi-keyword sorting and searching system
ActiveCN108632032ADoes not affect search resultsExpandable and flexibleKey distribution for secure communicationUser identity/authority verificationCiphertextSecurity index
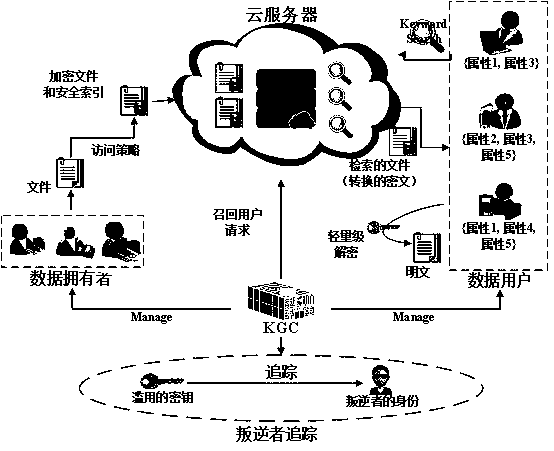
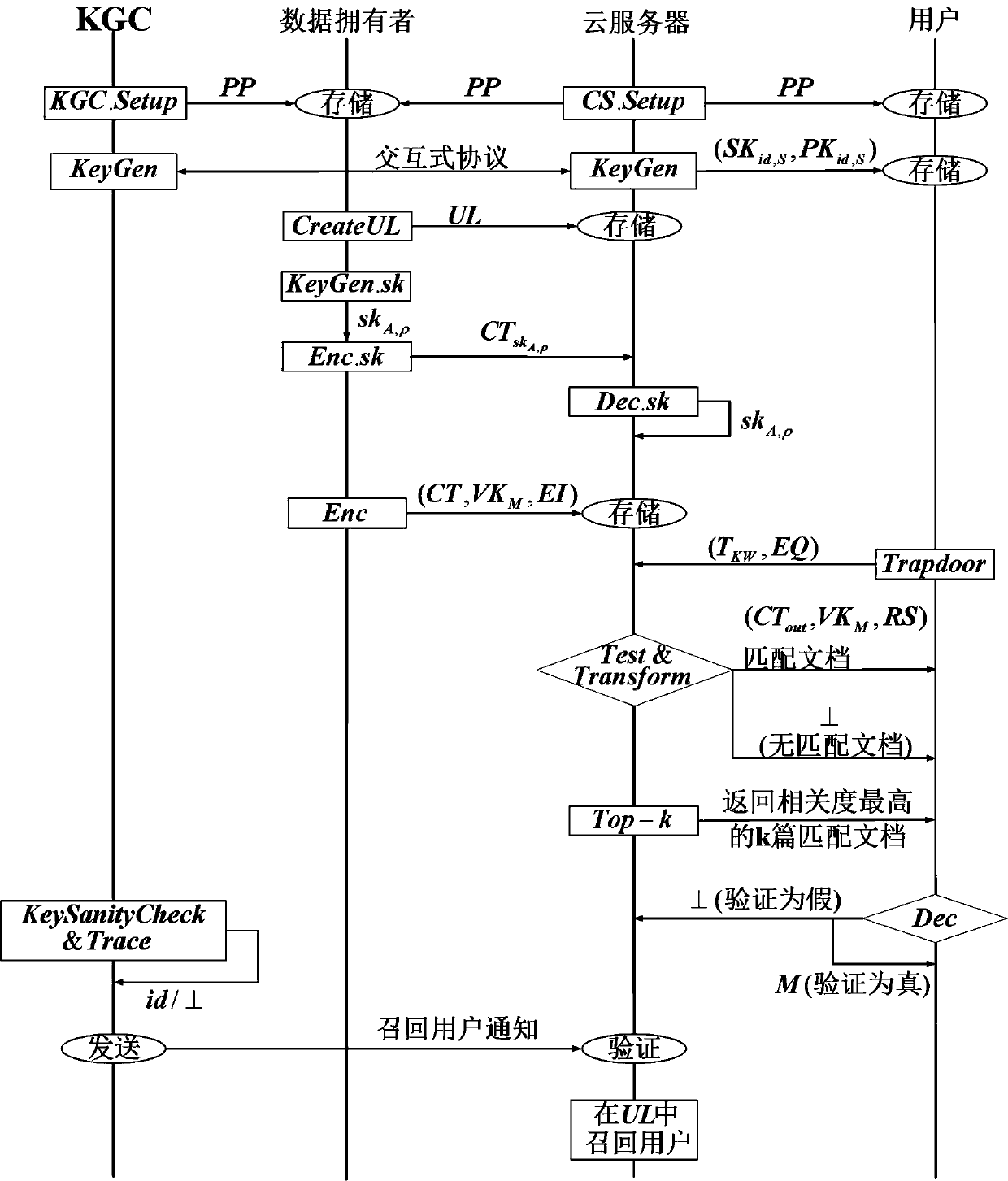
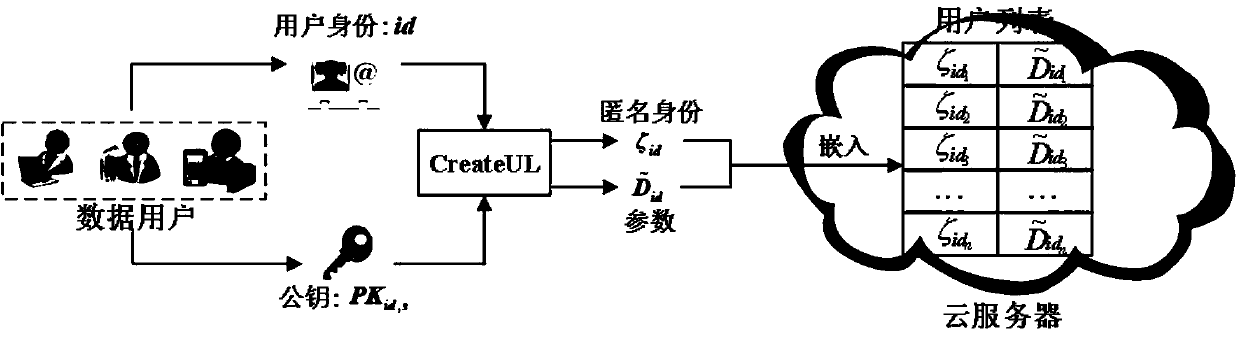
The invention relates to a key escrow-free secure multi-keyword sorting and searching system. The system comprises a key generation center, a cloud server, a data owner and a data user; the key generation center is used for achieving interactive computing with the cloud server to jointly generate a public parameter of the system and a property public key-private key pair of the data user; the cloud server is used for storing a file of the data owner and responding to a searching query request of the data user; the data owner extracts a keyword set from the file, encrypts the keyword set into asecure index, encrypts the file, makes an access strategy and embeds the access strategy into ciphertext; and the data user defines the searched keyword set and generates a trap door by using the property private key of the data user to search for the encrypted file stored in the cloud server. According to the system, the key escrow problem is solved, flexible authorization keyword searching andfine-grained data access authorization are achieved, multi-keyword subset searching is supported, and the searching result is not influenced by changes of the keyword query order.
Owner:FUZHOU UNIV
Authentication group key management method based on identity
InactiveCN101431414AAvoid hostingSolve tough problemsKey distribution for secure communicationUser identity/authority verificationGroup sessionKey escrow
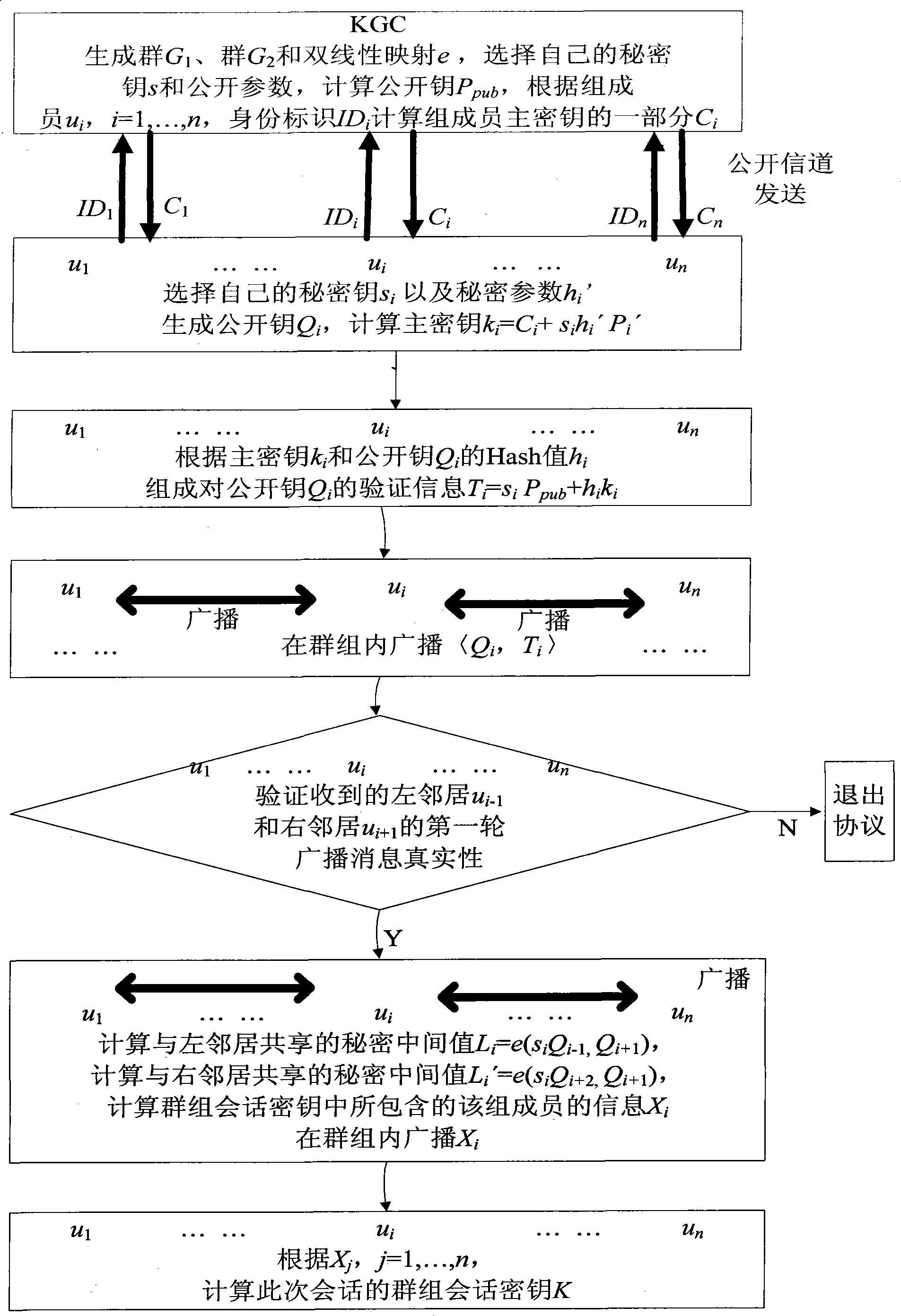
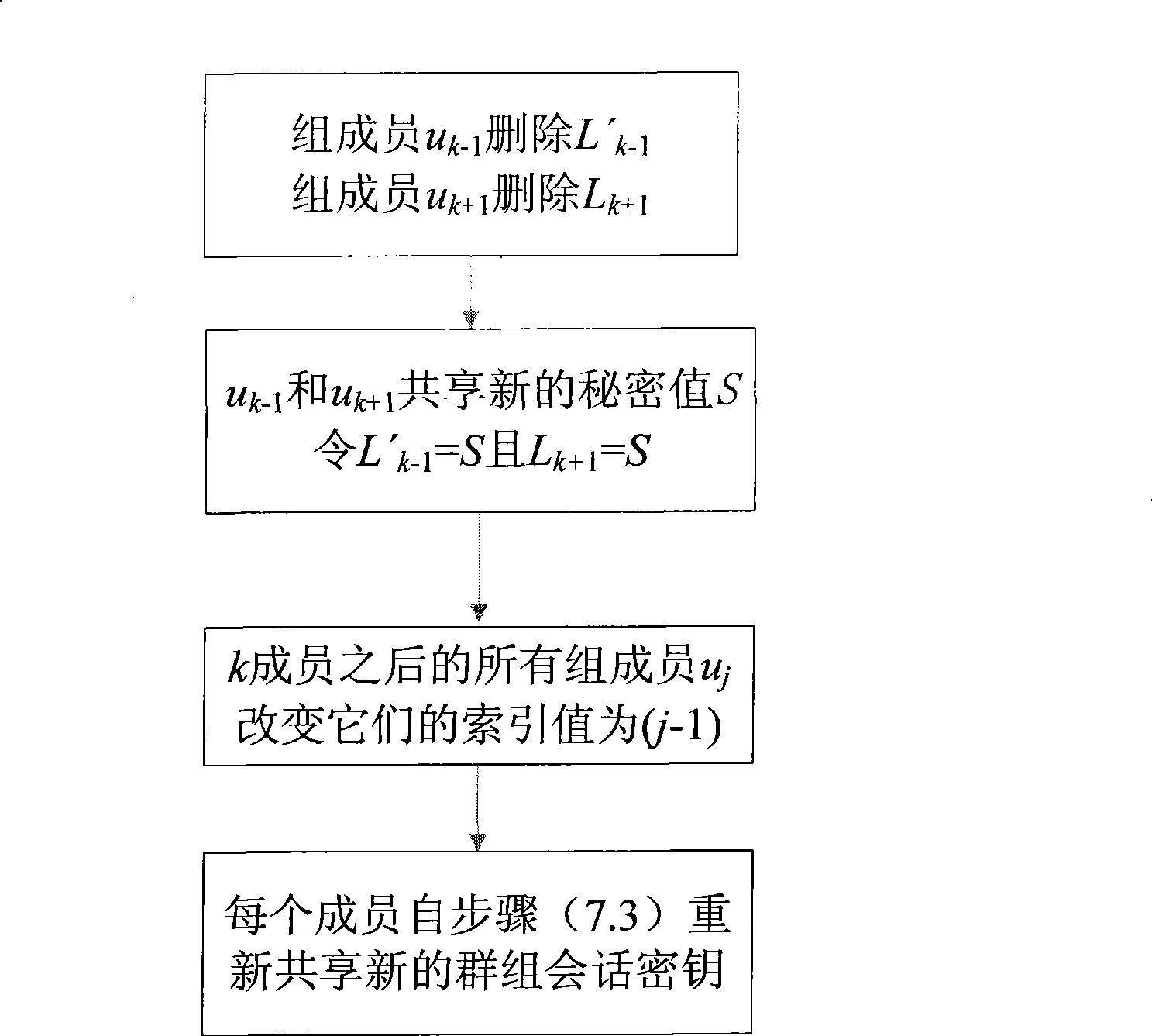
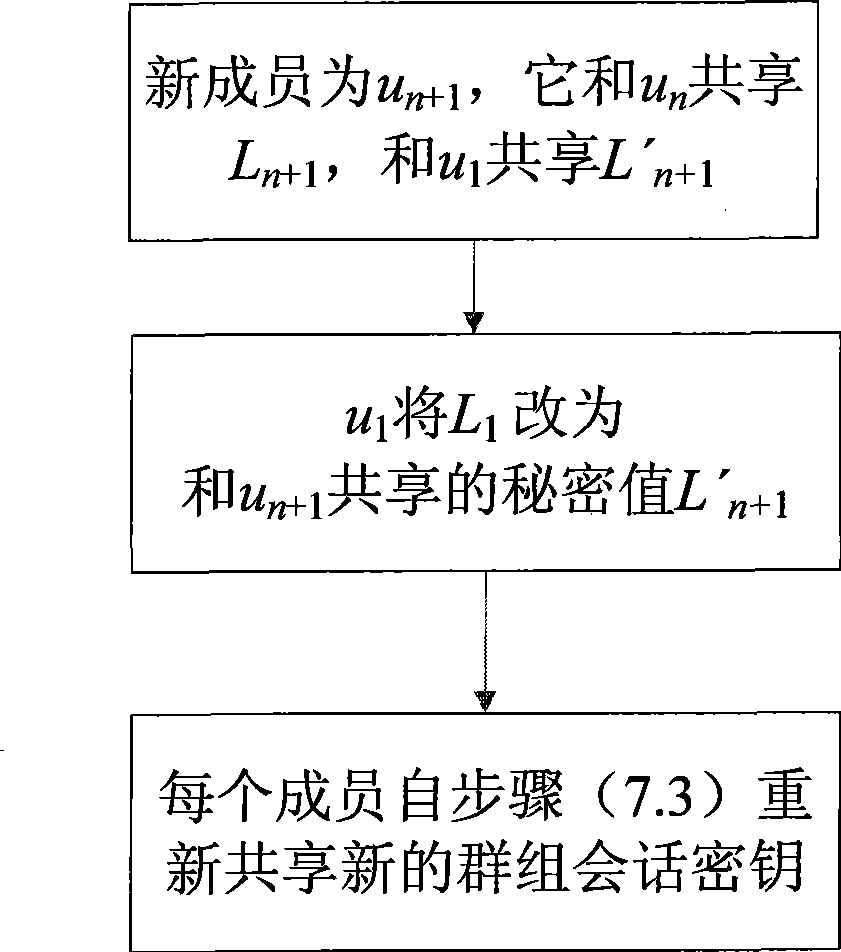
The present invention discloses a identity-based authentication group key management method which comprises the following steps: embedding ID into key with bilinear pairing in elliptic curve; generating Ci as part of main key ui according to the secret key and ID of group member ui by key generating center, and transmitting the Ci to ui through overt channel; generating main key according to Ci and its own secret key by each group member ui; calculating overt key verification information according to Hash value of main key and over key by each group member, and broadcasting the link between over key and verification information inside the group; calculating the secret value sharing with left and right neighbors when the received information is verified to be true by each group member, and calculating the group member information Xi included in group session key according to the secret value, and then broadcasting the Xi inside the group; calculating group session key K according to all Xj, j=1, ...,n, by each group member. The invention has the advantages of no key escrow and no need of secure channel, which can be applied in coordination and distributed network as secure reliable group communication.
Owner:XIDIAN UNIV
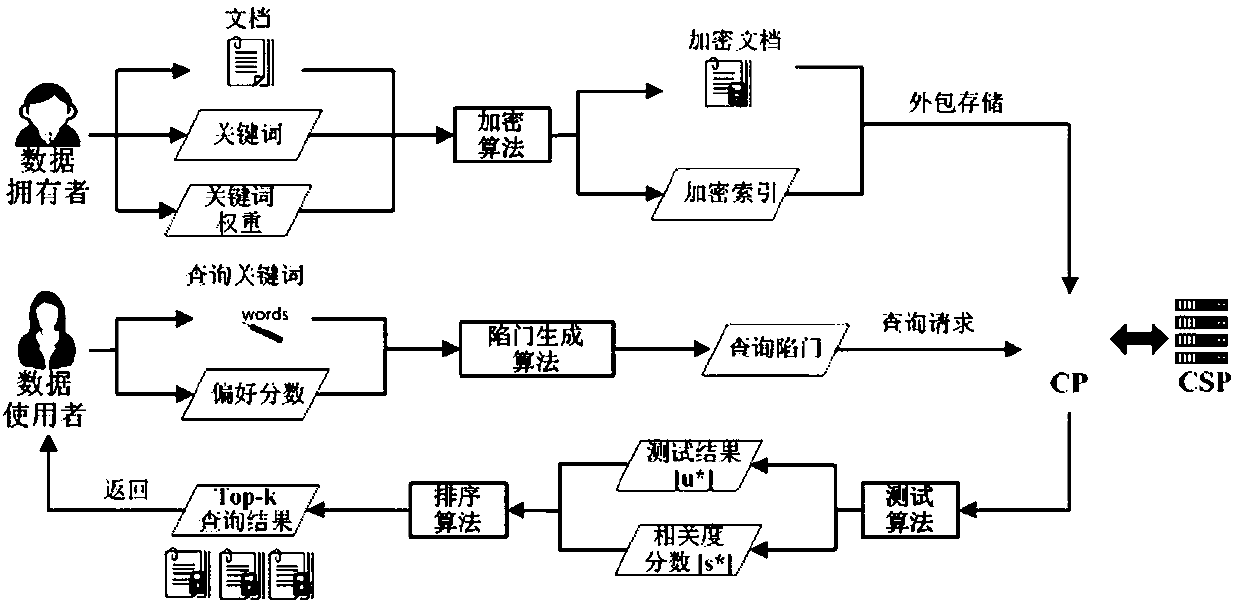
Multi-user multi-keyword sorting searchable encryption system supporting any language query
ActiveCN107491497AAdd arbitrarilyReduce storage overheadKey distribution for secure communicationUnstructured textual data retrievalEngineeringServer
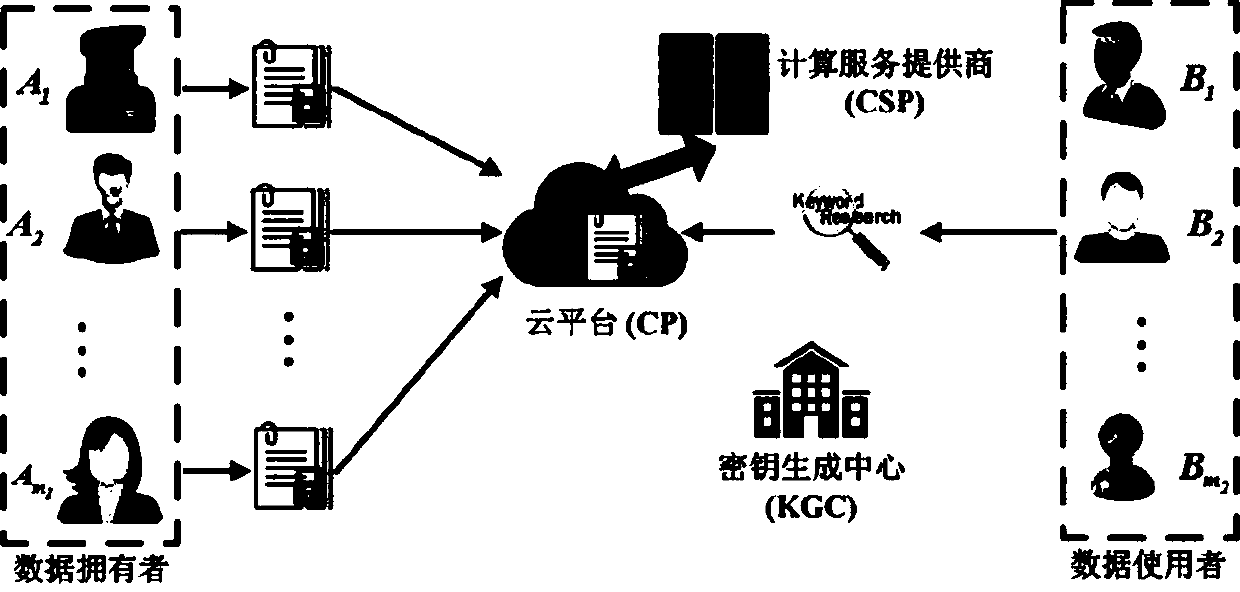
The invention relates to a multi-user multi-keyword sorting searchable encryption system supporting any language query. A key generation center generates a key for each entity in the system; a cloud platform stores a document of a user in an encrypted form and makes a response to a data retrieval request of the user; a computing service provider provides an online computing server for online computing; a data owner encrypts keywords and the document, and sends the encrypted keywords and document to the cloud platform for performing storage; and the user generates a keyword trap door and initiates the data retrieval request to the cloud platform. According to the multi-user multi-keyword sorting searchable encryption system supporting any language query, provided by the invention, the storage overhead is small; any language is supported; flexible authorization mechanism and time-based user cancellation mechanism are realized; data of multiple data owners is searched at the same time; flexible keyword weight and preference score setting is realized; and user privacy is protected.
Owner:FUZHOU UNIV
Cross-domain anonymous authentication method and system based on block chain
ActiveCN112039872ANo additional overheadNo secondary registration requiredKey distribution for secure communicationUser identity/authority verificationPrivacy protectionEngineering
The invention provides a cross-domain anonymous authentication method and system based on a blockchain. A trusted key generation center is set to issue a public and private key pair to a registrationcenter, and deploy key information of a blockchain smart contract management communication party; the registration center provides registration service for a common user, generates a signature to realize certificate authentication service, and stores communication party identification information and public key information related to a service system into the blockchain intelligent contract in a privacy protection mode; when two communication parties carry out mutual authentication, authentication information is sent in an anonymous mode, a blockchain intelligent contract query interface is called to check identification information of a user, and whether a public key of the user is registered or not is checked and authenticated; the smart contract manages the identification information and the key information, provides real-time update of the user identification information and the key information, so that the method avoids the problems of introduction of single-point fault attacks, asynchronous update, high communication overhead and the like, and supports user cross-domain authentication service. The anonymous authentication technical scheme has good security, stability and reliability.
Owner:武汉见邦融智科技有限公司 +1
Multi-user searchable encryption system and method with index validation and tracing
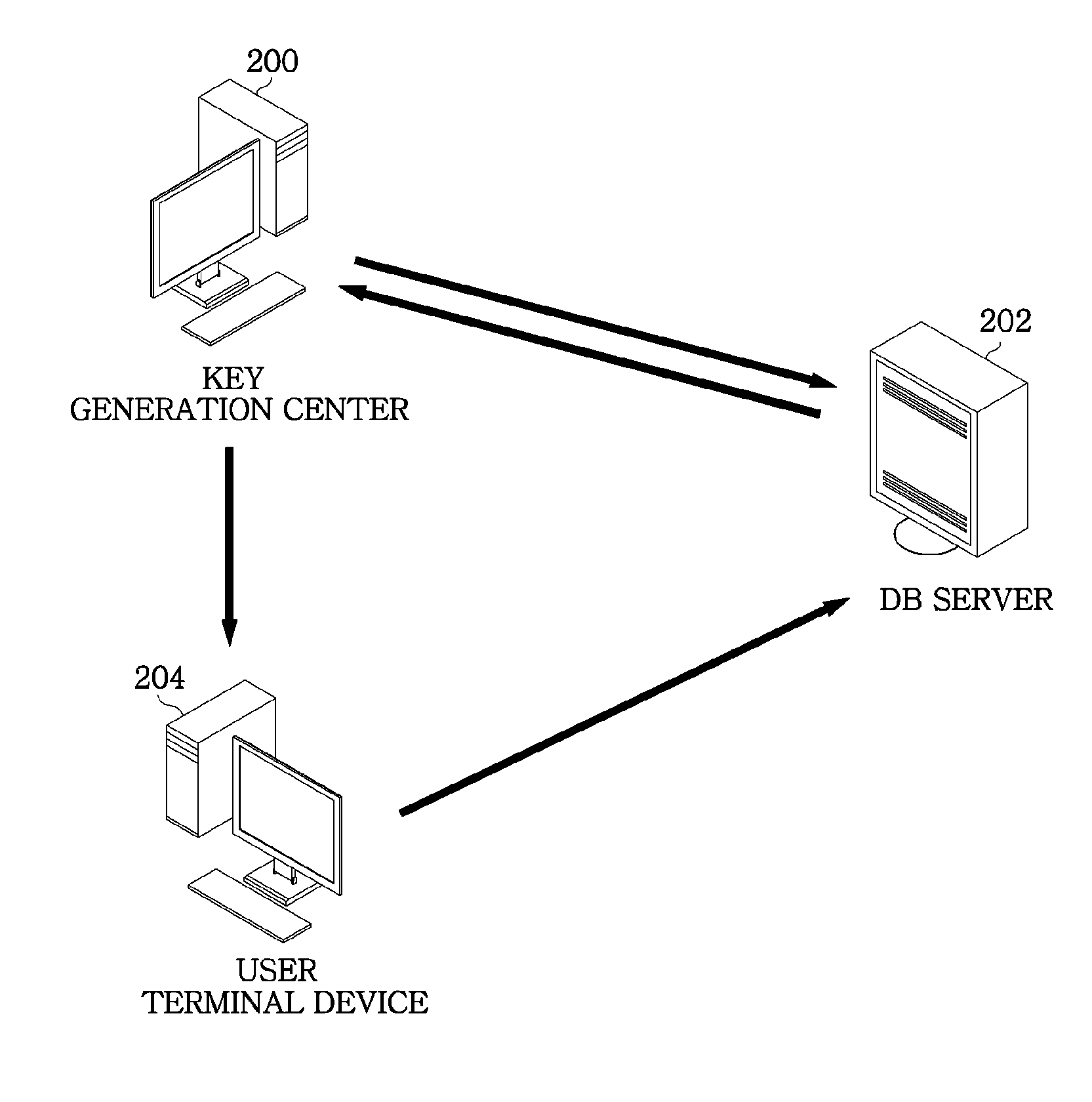
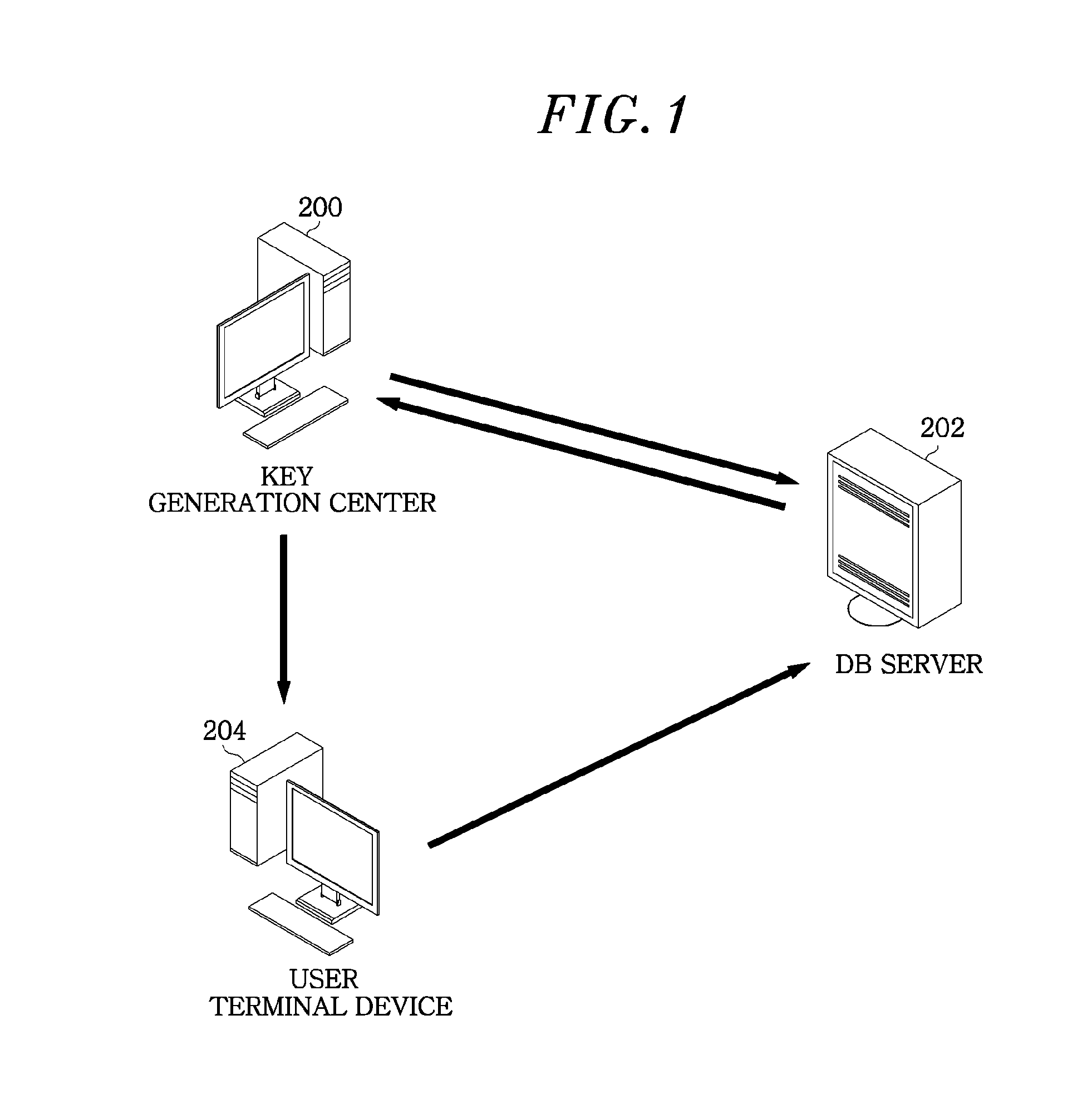
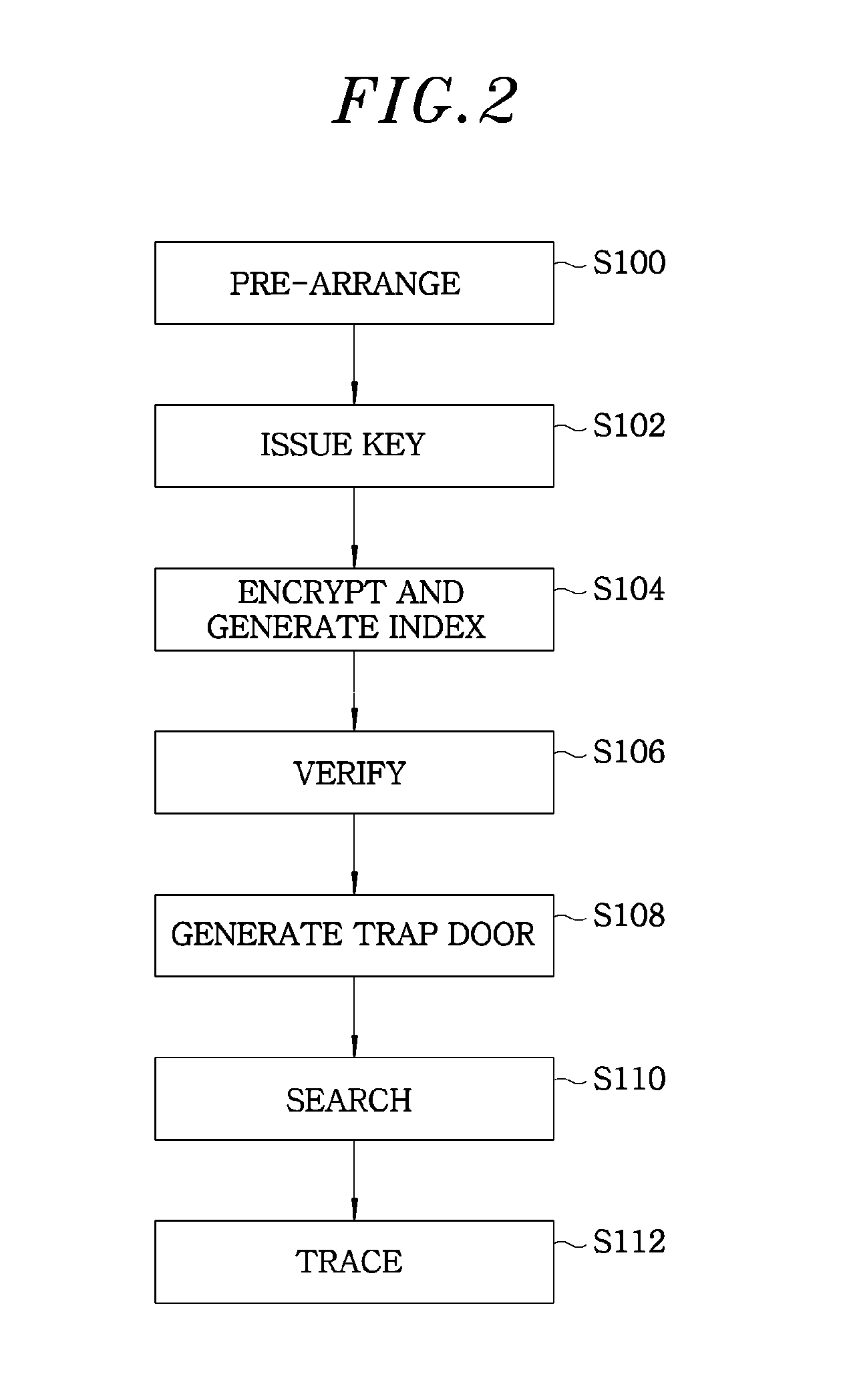
InactiveUS20130148803A1Key distribution for secure communicationDigital data protectionTerminal equipmentKey generation center
A multi-user searchable encryption system includes a key generation center to issue a private secret key to a user and trace information regarding a user who has generated an index, and a user terminal device to generate an index for searching for a database using the private secret key. The multi-user searchable encryption system includes a database (DB) server that verifies the index generated by the user terminal device and searches for corresponding data to the verified index.
Owner:ELECTRONICS & TELECOMM RES INST
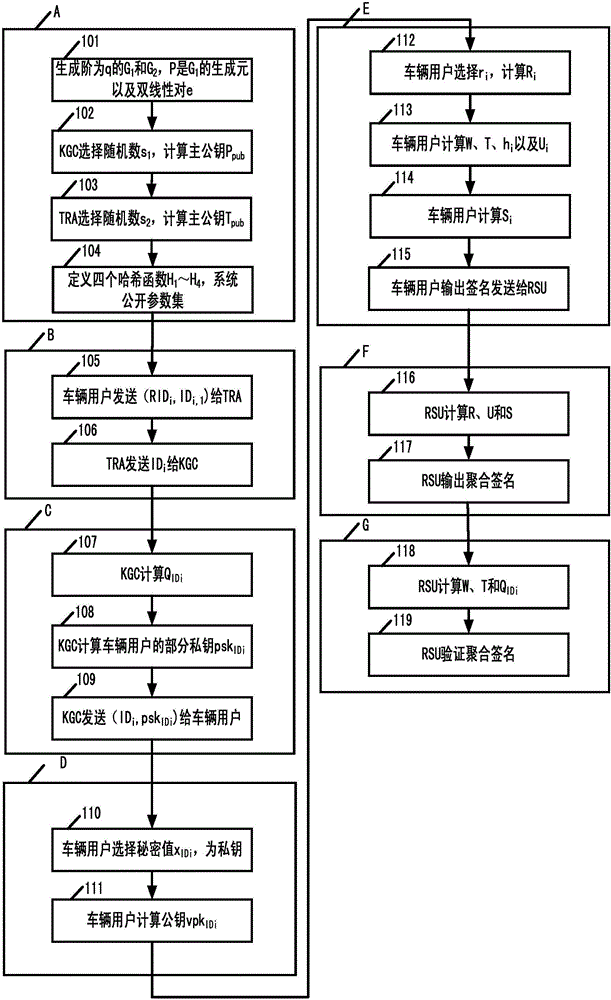
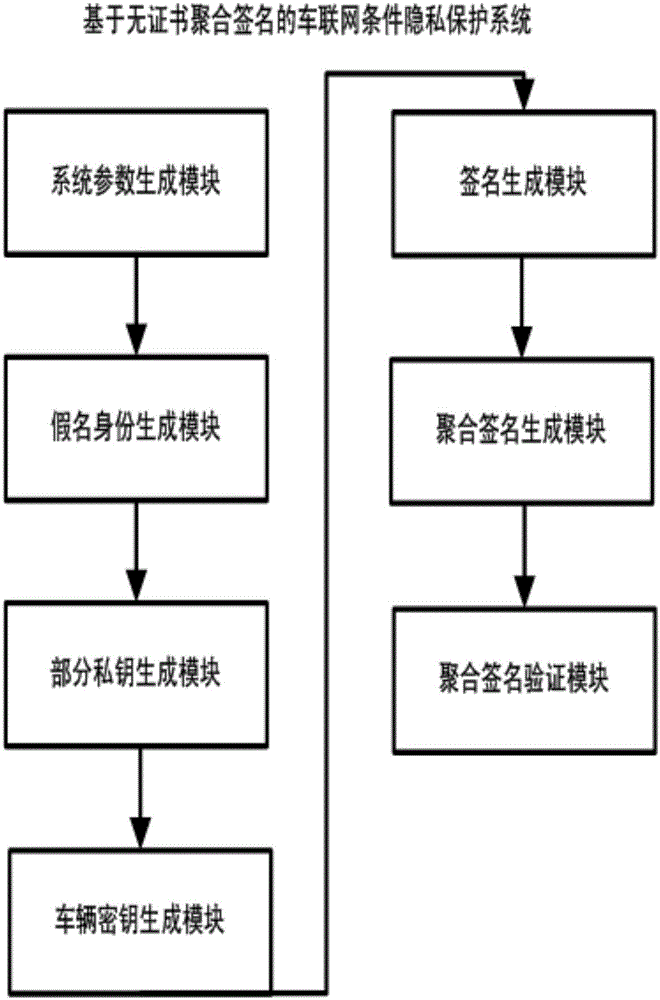
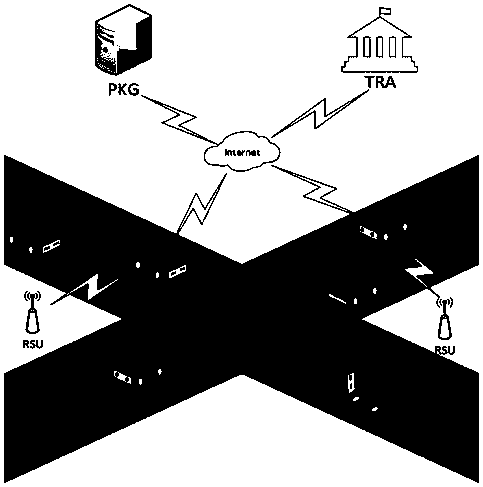
Internet of vehicles conditional privacy protection method and system based on certificateless aggregation signature
ActiveCN106131059AAvoid managementAvoid key escrow issuesKey distribution for secure communicationPrivacy protectionThe Internet
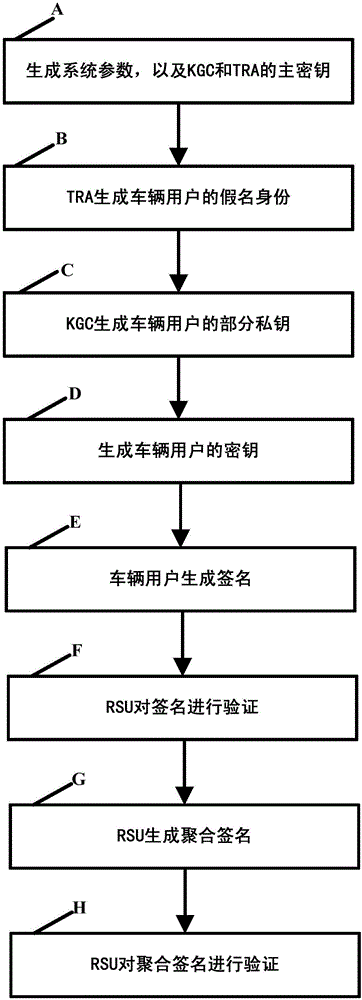
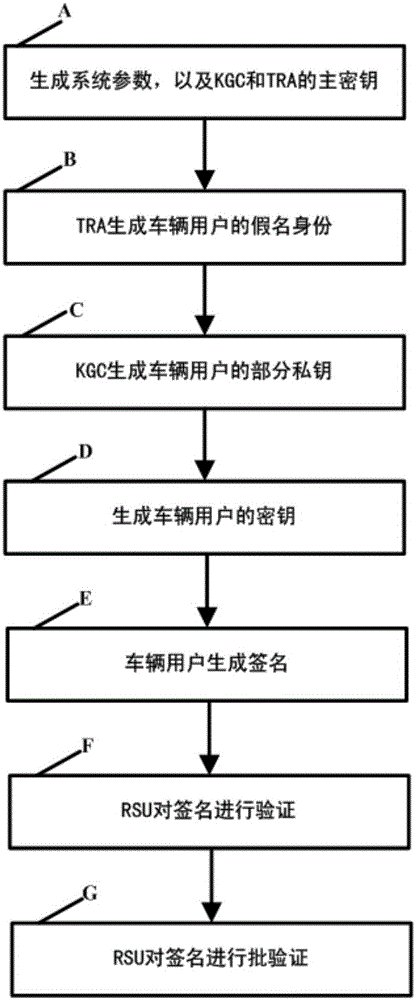
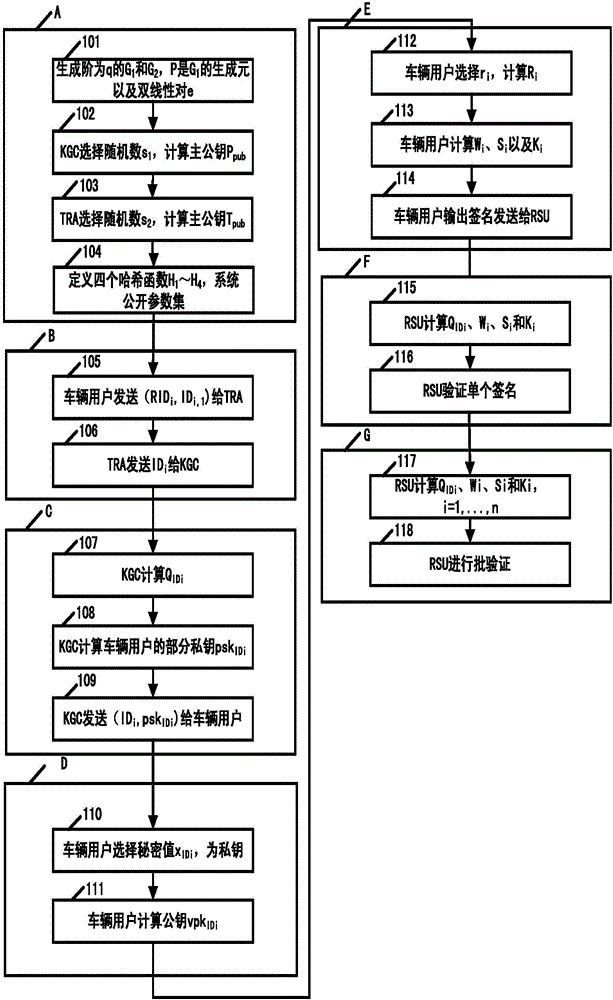
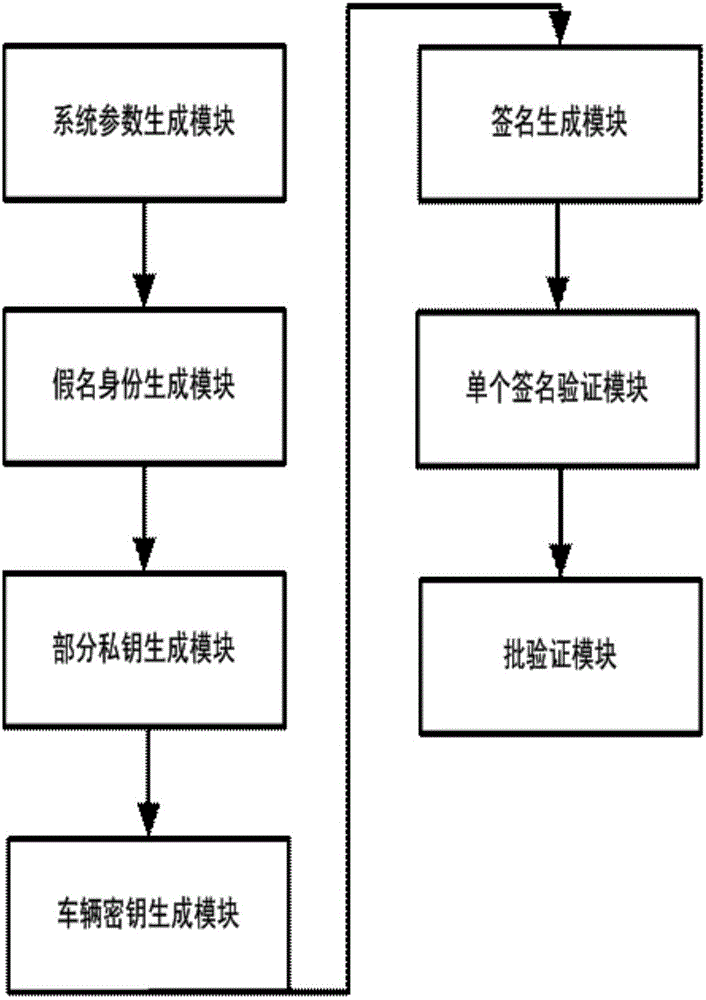
The invention discloses an internet of vehicles conditional privacy protection method and system based on certificateless aggregation signature. The internet of vehicles conditional privacy protection method based on certificateless aggregation signature is provided based on a certificateless cryptosystem. On the basis of internet of vehicle conditional privacy protection of a traditional public key cryptosystem, an aggregation signer aggregates various different signatures into one signature, the internet of vehicles conditional privacy protection scheme is realized by employing a key generation center KGC and a tracking authentication center TRA, the problems of certificate management and key hosting are avoided, the computing efficiency of an internet of vehicles is improved when the aggregation signature is authenticated, the conditional privacy protection of internet of vehicles users is realized, and the method and the system can be applied in the open internet of vehicles safely.
Owner:HOHAI UNIV
Multi-receiver signcryption method based on keyless trusteeship problem of elliptic curve
ActiveCN106027239AOvercome the problem of not being able to resist malicious KGC attacksResistance to malicious KGC attacks hasKey distribution for secure communicationPublic key for secure communicationSigncryptionKey escrow
This invention discloses a multi-receiver signcryption method based on keyless trusteeship problem of elliptic curve, and solves the technical problem of private key trusteeship existed in the existing multi-receiver signcryption method. The method comprises the following steps: a user randomly selects a secret value as own private key, calculates a verification share according to own private key, and sends the verification share and own identity information to a private key generating center KGC; the private key generating center KGC generates a public key, a public key verification parameter and a public key hiding parameter of the user according to the verification share and the identity information sent by the user, and sends the public key, the public key verification parameter and the public key hiding parameter to the user; and after receiving the parameters sent by the private key generating center KGC, the user verifies the public key. Since the private key of the user is the secret value randomly selected by the user, the private key generating center KGC only knows the public key and corresponding identity information of the user, and cannot acquire the private key of the user to realize keyless trusteeship. Simultaneously, the signcryption efficiency is improved; and the bandwidth is reduced.
Owner:XIDIAN UNIV
File ownership proof method based on convergence encryption
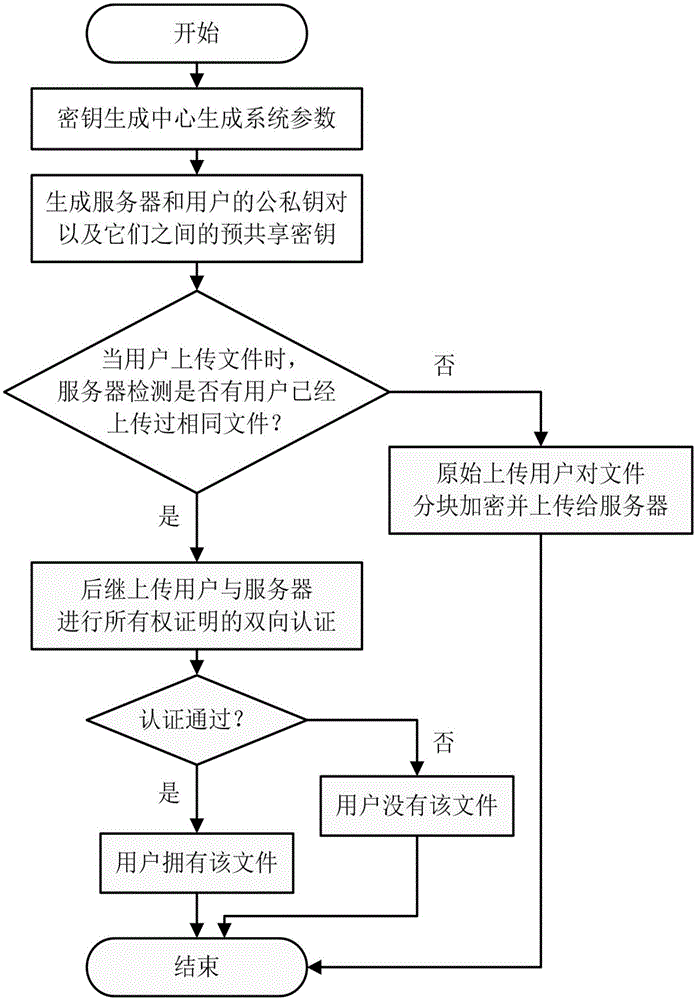
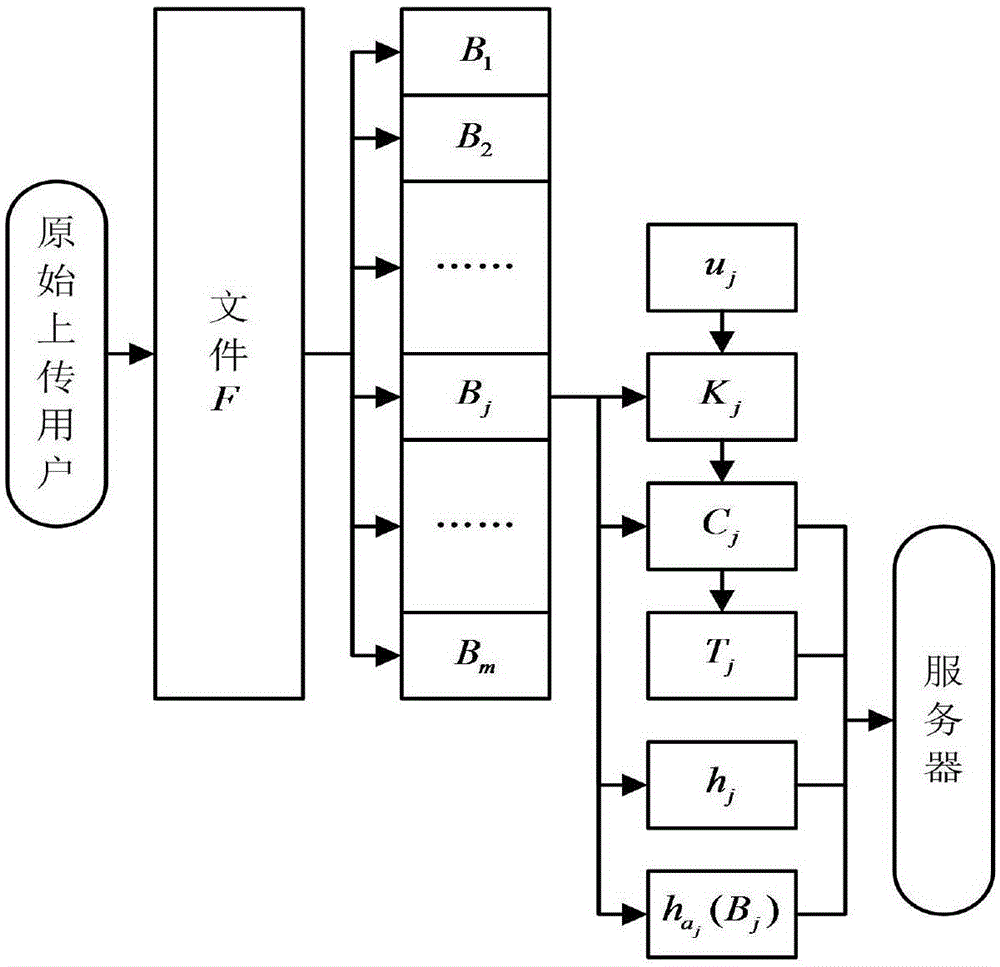
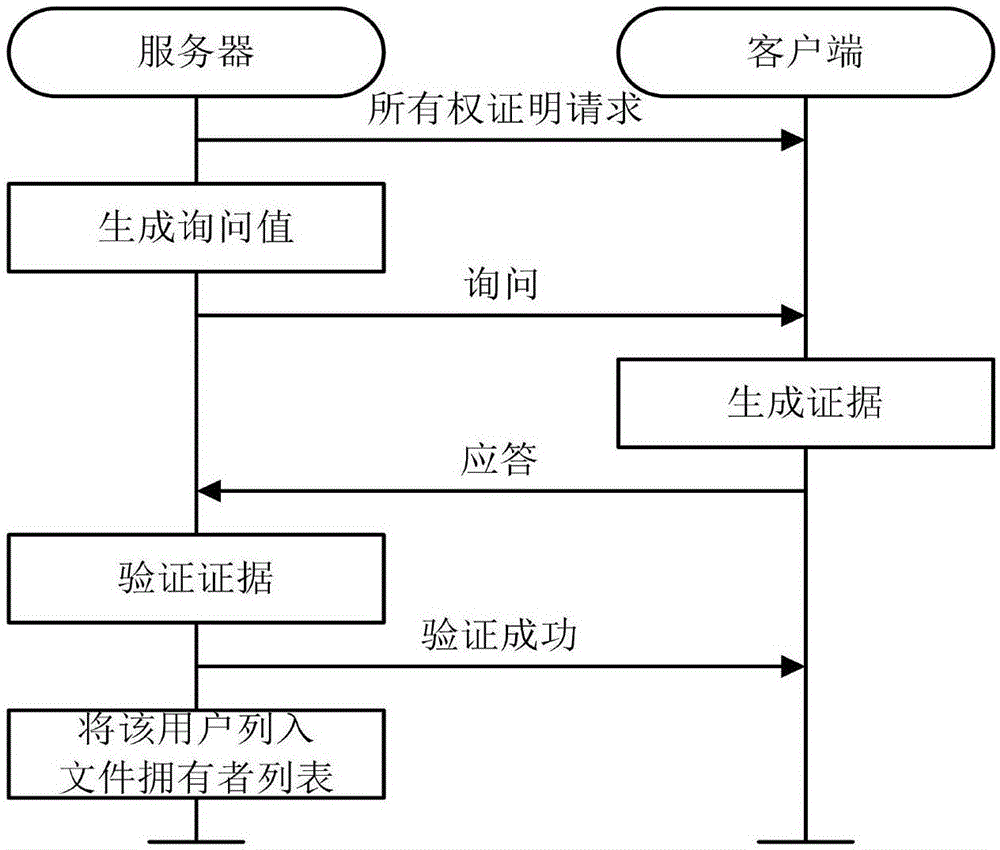
InactiveCN105141602AResist attackPrevent leakageUser identity/authority verificationOriginal dataClient data
The invention discloses a file ownership proof method based on convergence encryption, which mainly solves the problem in the prior art that the security of taking a hash value as an ownership evidence is bad. The implementation steps are as follows: step 1 of generating a system parameter, a server key and a user key by a key generation center; step 2 of detecting whether the user is a first user that uploads files by the server; step 3 of performing block encryption on the files by the first uploading user and uploading the files; step 4 of issuing an ownership proof request by the server, generating an inquiry value and transmitting the inquiry value to the client; step 5 of performing ownership proof the client receives the inquiry value; step 6 of performing ownership verification after the server receives a reply by the server, and after that, continuing to upload a bidirectional authentication between the user and the client. According to the file ownership proof method based on the convergence encryption provided by the invention, a signature of an original data block is adopted as an evidence of owning the files, thus the security of the evidence can be improved, the network upload bandwidth and cloud server storage overhead can be reduced, and the method can be used for supporting a cloud storage system across client data deduplication.
Owner:XIDIAN UNIV
Method and system for protecting condition privacy of internet of vehicles based on certificateless batch verification
ActiveCN106059766AAvoid managementAvoid key escrow issuesKey distribution for secure communicationUser identity/authority verificationCertificateless cryptographyThe Internet
The invention discloses a method and a system for protecting a condition privacy of an internet of vehicles based on certificateless batch verification. The method comprises the following steps: a key generation center KGA and a track authentication center TRA jointly generate a master key and a system parameter of the internet of vehicles; according to the system parameter and vehicle user real identity information, the TRA generates a pseudonym identity of a vehicle user; the KGC generates a partial private key of the vehicle user; the vehicle user generates an own key; the vehicle user signs a message; an RSU carries out verification on a signature; and the RSU carries out the batch verification on the signature. According to the method and the system disclosed by the invention, by adopting a certificateless cryptography system, the unsolvable inherent certificate management problem and the certificate maintenance problem in the traditional public key cryptography system are effectively solved; and meanwhile, the key escrow problem caused by an identity-based cryptography system is also avoided; by adopting a batch verification technology, the signature verification efficiency in the internet of vehicles is improved; and in the internet of vehicles, the key generation center KGA and the track authentication center TRA are adopted to realize the condition privacy protection on the internet of vehicles.
Owner:HOHAI UNIV
Two-dimension code electronic key implementation method based on digital signature
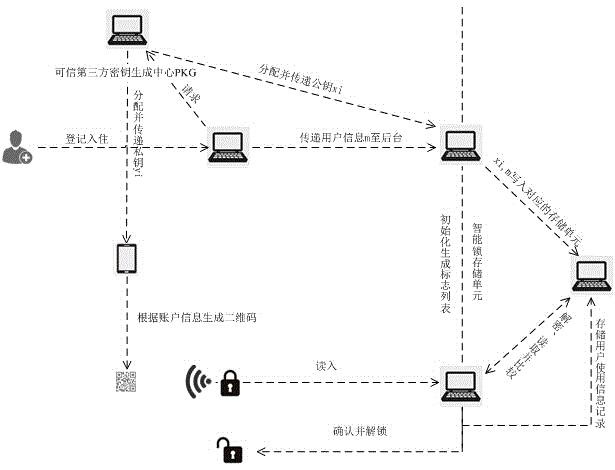
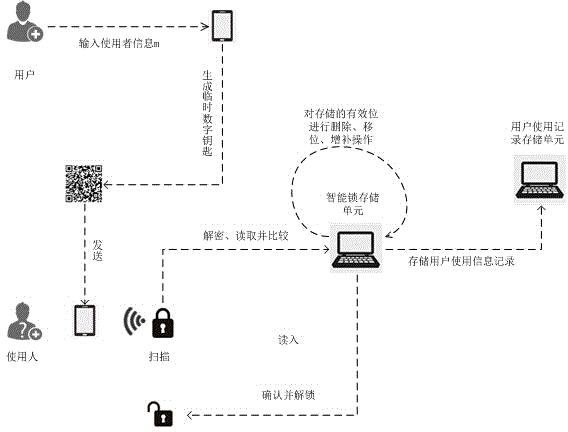
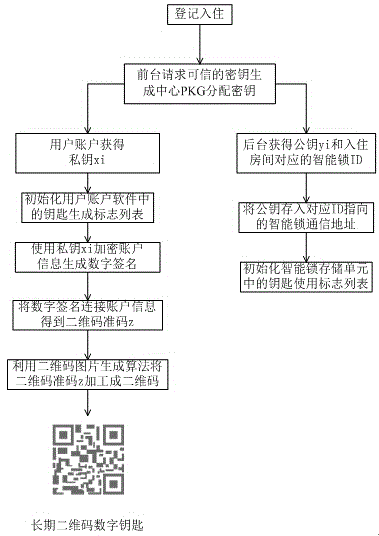
ActiveCN104933793AUniqueness guaranteedGuarantee authenticityIndividual entry/exit registersDigital Signature AlgorithmMobile device
The invention relates to a method for encoding information of a user and generating a two-dimension code digital key by adopting a digital signature technique. A mobile phone and other mobile devices are taken as carriers of the two-dimension code digital key. The method comprises steps as follows: a credible key generation center allocates a unique private / public key pair for a user account and a smart lock storage unit during starting; a digital signature algorithm is adopted, that is, a private key is used for encrypting the information of the user and a public key is used for decrypting a read-in two-dimension code sequence; the information of the user is stored and read by field. Normal use of the two-dimension code key of the user can be guaranteed, the reliability and the authenticity of the source of a generated temporary two-dimension code key can be guaranteed, meanwhile, temporary two-dimension code keys received by different people can be effectively distinguished, and the flexibility and the safety of a whole two-dimension code smart lock system are unified.
Owner:宁波飞拓电器有限公司
Communication method, device and system based on combined public key cryptography system
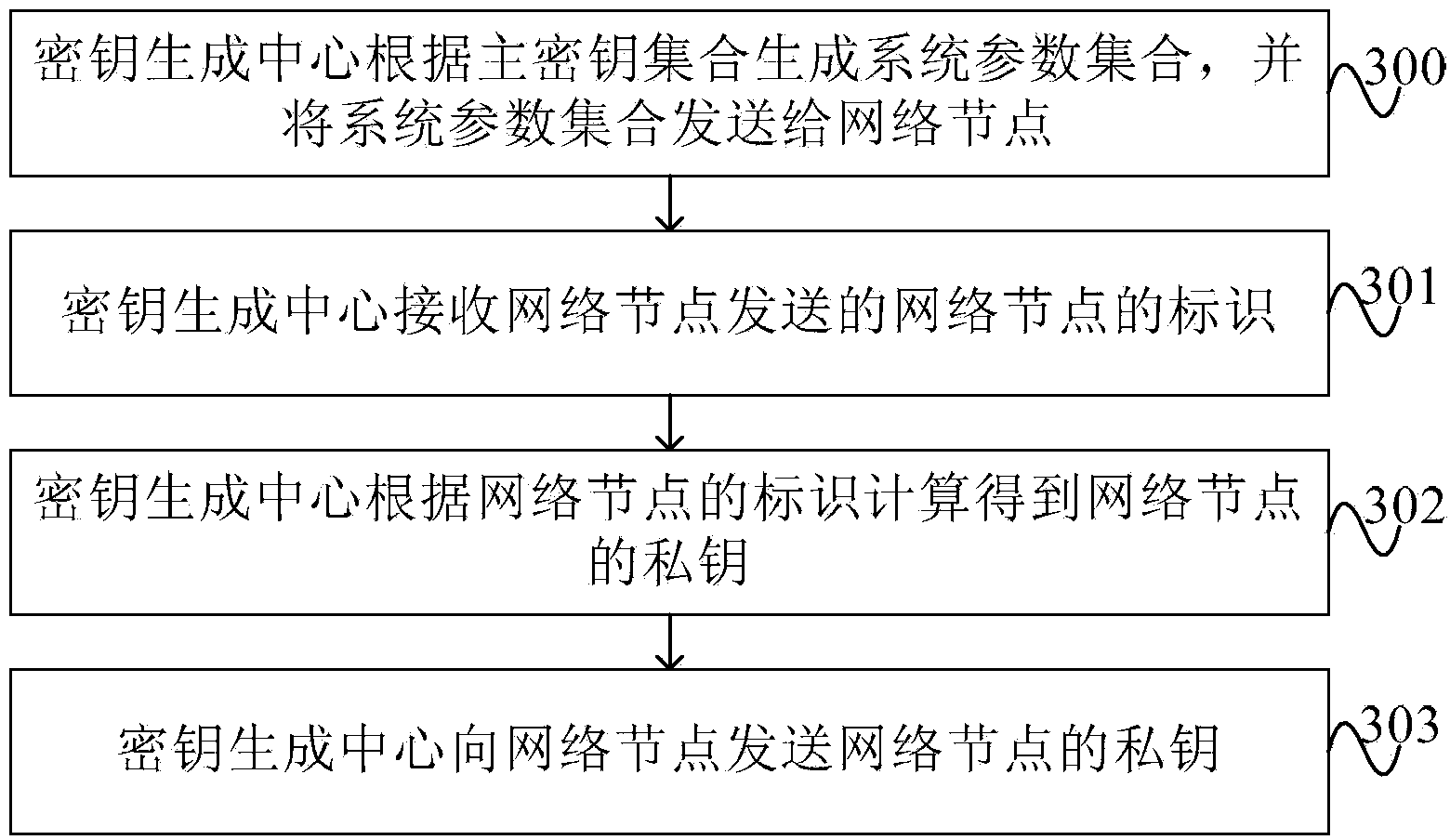
InactiveCN103825733AReduce the number of interactionsImprove authentication efficiencyKey distribution for secure communicationPublic key for secure communicationKey generation centerComputer security
The invention provides a communication method, device and system based on a combined public key cryptography system. The method includes the steps of obtaining a private key of a first node from a secret key generating center through the first node, obtaining identification of a second node according to an adjacent node identification list, calculating a public key of the second node according to the identification of the second node, calculating a shared secret key parameter of the first node according to the secret key of the first node and the public key of the second node, then, calculating a shared secret key of the first node according to the shared secret key parameter of the first node, generating a first secret key verification code corresponding to the shared secret key of the first node, sending shared secret key verification information with the first secret key verification code to the second node, and receiving shared secret key response information from the second node. The calculation steps can be completed offline, the number of times of interaction between the nodes is lowered, and therefore when the first node starts verification, verification can be completed in a quite short period of time, and verification efficiency is improved.
Owner:HUAWEI TECH CO LTD
Signcryption method from certificateless environment to identity environment
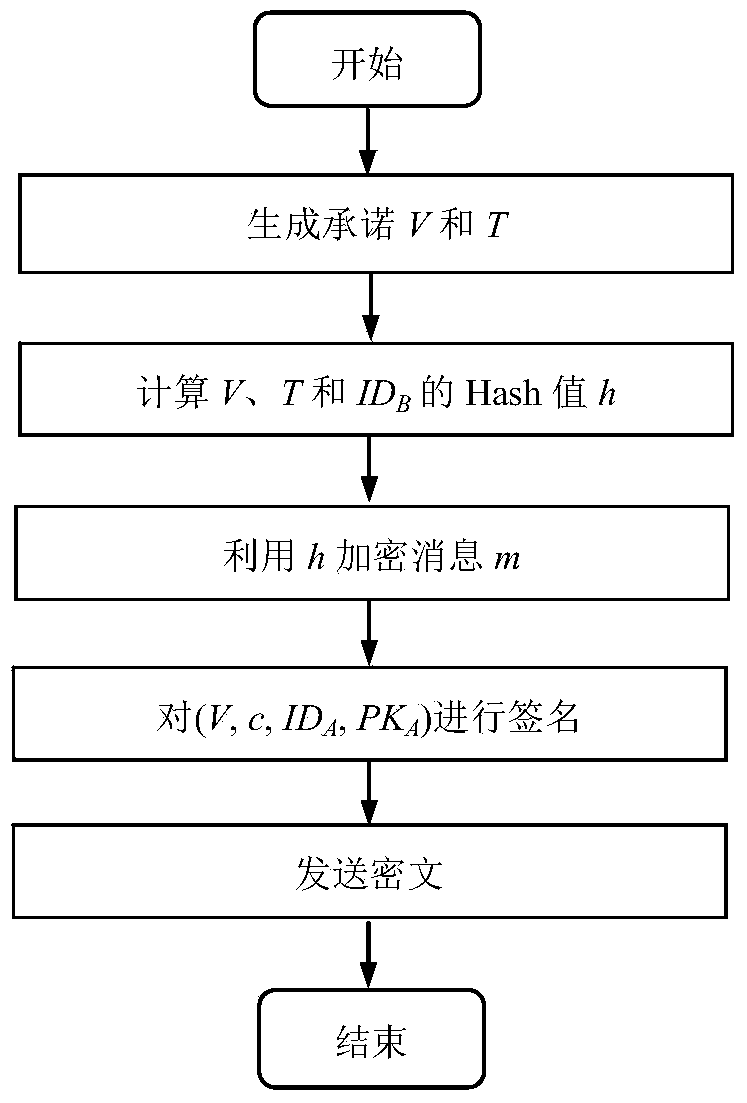
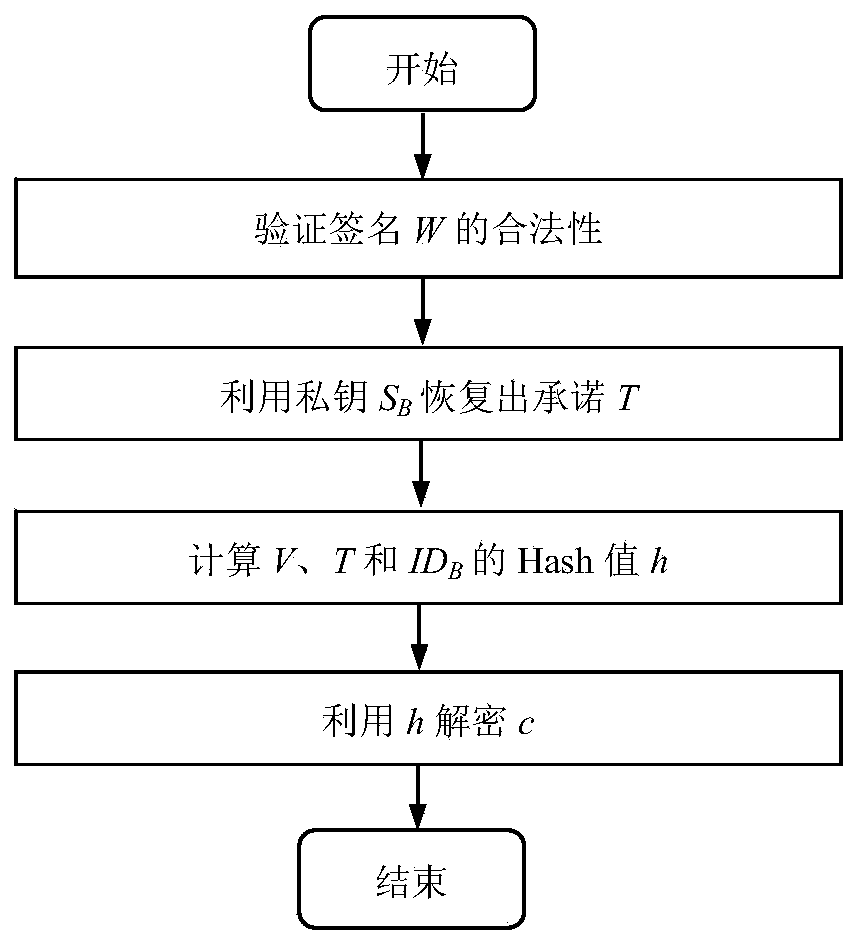
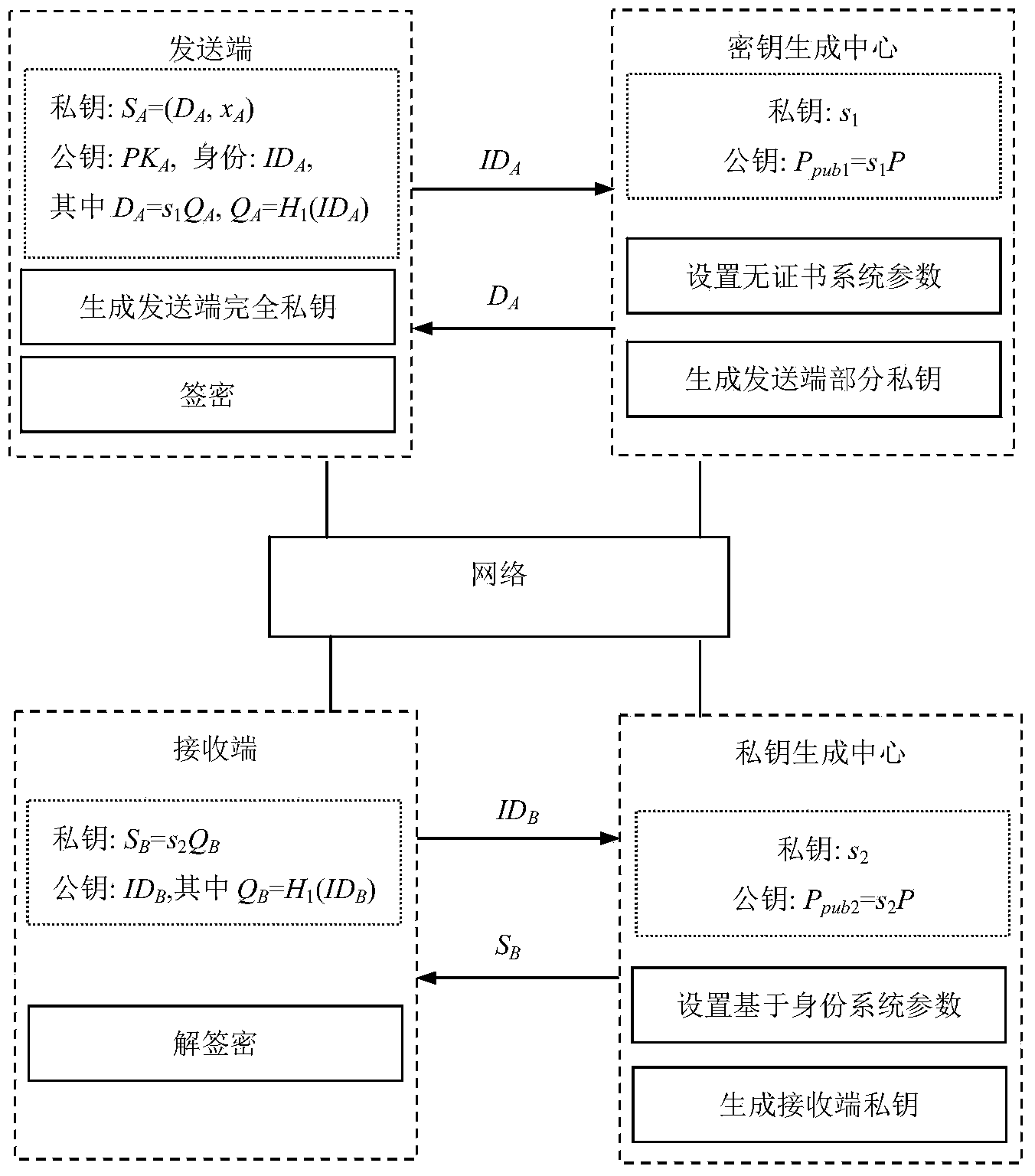
InactiveCN104270249AProvide confidentialityProvide integrityUser identity/authority verificationSecure communicationCiphertext
The invention discloses a signcryption method from a certificateless environment to an identity environment and belongs to the field of secure communication. In order to enable a sending end based on the certificateless environment to send messages to a receiving end based on the identity environment through the signcryption method, the signcryption method includes the steps that after system parameters are initialized, a key generation center generates a part private key DA and sends the part private key DA to the sending end, and the sending end generates a secrete value randomly based on the system parameters, and a complete private key SA and a public key PKA are arranged with the part private key DA; a private key generation center generates a private key SB and sends the private key SB to the receiving end; the sending end generates a signcryption ciphertext according to the system parameters, the identity of the sending end, the complete private key SA, the public key PKA, the identity of the receiving end and the messages m, and the ciphertext, the identity of the sending end and the public key PKA are sent to the receiving end to conduct signcryption treatment. The signcryption method is used for signcryption communication of a heterogeneous network, and end-to-end secrete, complete, certificated and undeniable services are provided for users in the certificateless environment and users based on the identity environment.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
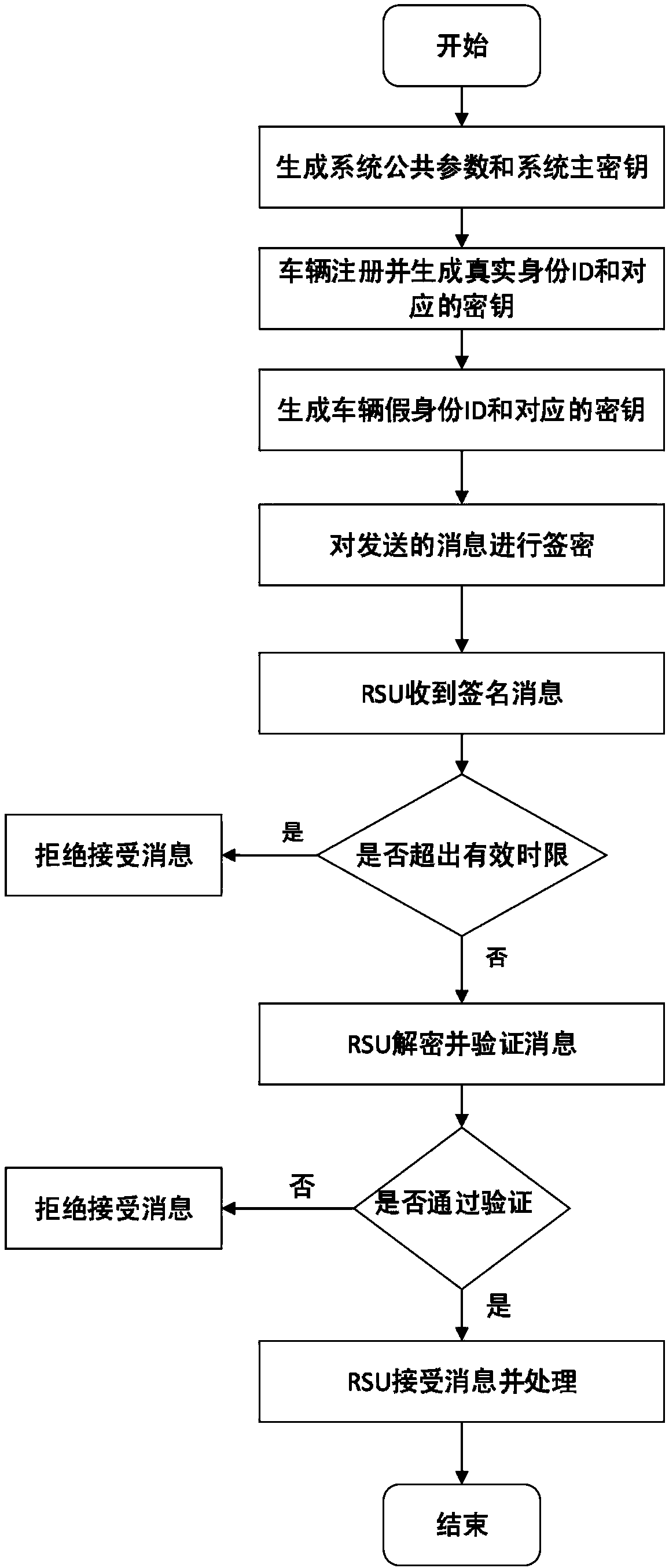
Method for protecting privacy of vehicle ad hoc network based on signcryption
InactiveCN107682149AEffective calculationProtect identity privacyKey distribution for secure communicationParticular environment based servicesDigital signatureSigncryption
The invention request to protect a method for protecting privacy of a vehicle ad hoc network based on signcryption. The method is used for solving a privacy protection problem when a vehicle node (OBU) under an environment of the Internet of vehicles communicates with a road side unit (RSU). On the basis of a digital signature mechanism and a pseudonym mechanism, the invention provides a signcryption mechanism which is an integrated scheme synthesizing encryption and signature; in the method, privacy protection on the vehicle node is achieved via the pseudonym mechanism. Under the environmentof the Internet of vehicles, the vehicle node sends own identity information to a TRA to generate a pseudonym, a secret key generation center generates a secret key corresponding to a private key of the pseudonym, the vehicle node uses the generated pseudonym and the secrete key to perform signcryption on a message and sends the message to the road side unit, after receiving the message, the roadside unit uses the private key to decrypt the message and verify the same, and the message is accepted if the verification is passed.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
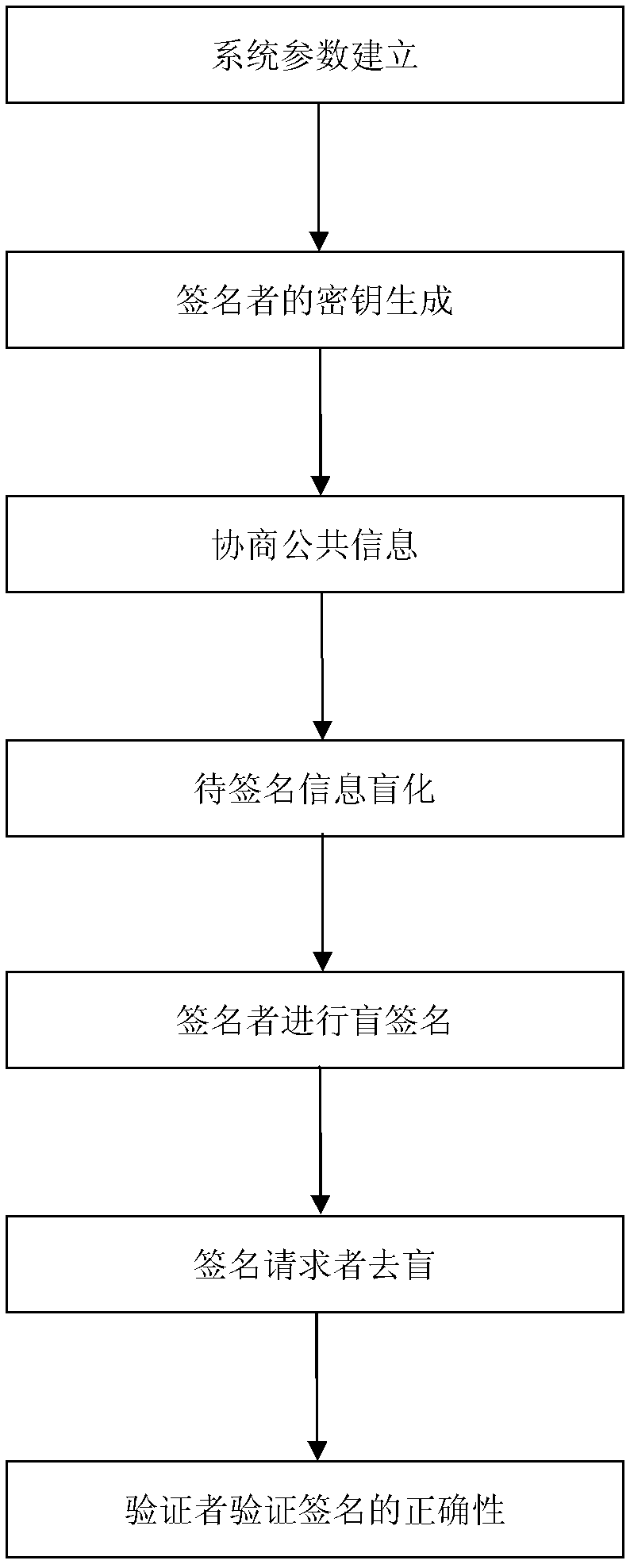
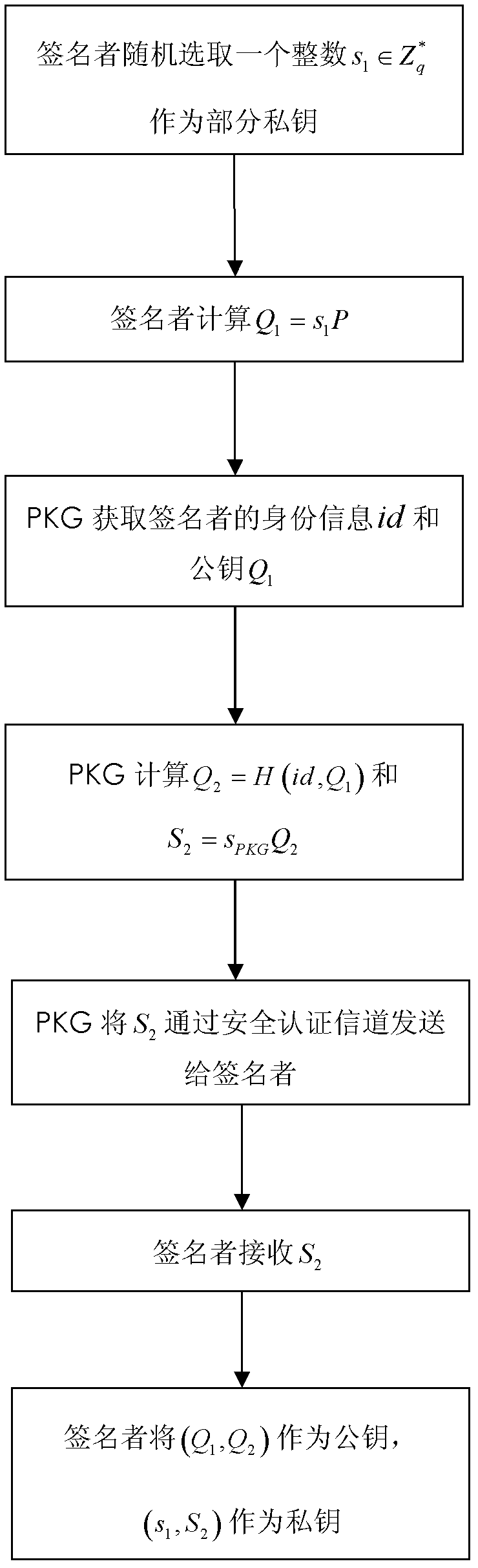
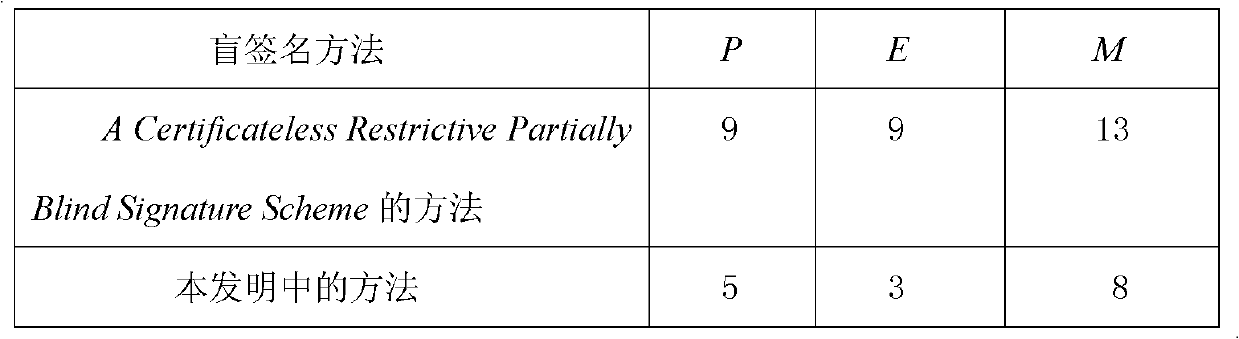
Certificateless partially blind signature method
InactiveCN102387019AEliminate demandTroubleshoot hosting issuesPublic key for secure communicationUser identity/authority verificationElectronic cashKey escrow
The invention relates to a certificateless partially blind signature method. In the prior art, practicality of the partially blind signature method is low. The method of the invention is mainly used to solve the above problem. The method comprises the following steps that: 1) a secret key generation center randomly selects an integer sPKG as a private key in an integer multiplication group of mod q and stores secretly, and discloses a system parameter: (G1, q, 1, P, G2, e, H, h, QPKG); 2) a signer generates the partial private key s1 and a partial public key Q1, the secret key generation center generates the other partial private key S2 and the public key Q2 and sends to the signer through a safe authentication channel, and the signer acquires a private key pair (s1, S2) and a public key pair (Q1, Q2); 3) the signer carries out signature; 4) an authenticator verifies validity of the signature by using the public key pair (Q1, Q2) of the signer. By using the method of the invention, a demand to a certificate can be eliminated. There is no disadvantage of secret key escrow. A partial blind characteristic is possessed. Simultaneously, the method is simple and high efficient and possesses good practicality and security. The method can be used in an electronic cash transaction and electronic voting.
Owner:XIDIAN UNIV
Retrieval system of encrypted data in secure cloud storage
PendingCN107734054APrevent Malicious BehaviorOffline KG attack preventionKey distribution for secure communicationDatabase queryingCloud storageDocumentation
The invention relates to a retrieval system of encrypted data in secure cloud storage. The retrieval system comprises a key generation center used for managing and distributing a public key / private key generated in the system; a cloud platform used for providing a data storage service to a data owner and responding to a search request of a user, that is, a data owner encrypts the data by utilizingthe public key and sends the encrypted data to the cloud platform for storage; and the user generates a query trap door and sends the query door to the cloud platform so as to search the encrypted data; and a calculation service provider for providing an online calculation service and interacting with the cloud platform to carry out calculation. The retrieval system of encrypted data in secure cloud storage supports multiple search and query modes; the system allows the user to search the encrypted documents from multiple data owners by utilizing one query trap door and supports flexible userauthorization and revocation mechanisms; and the system prevents offline keyword guessing attacks.
Owner:FUZHOU UNIV
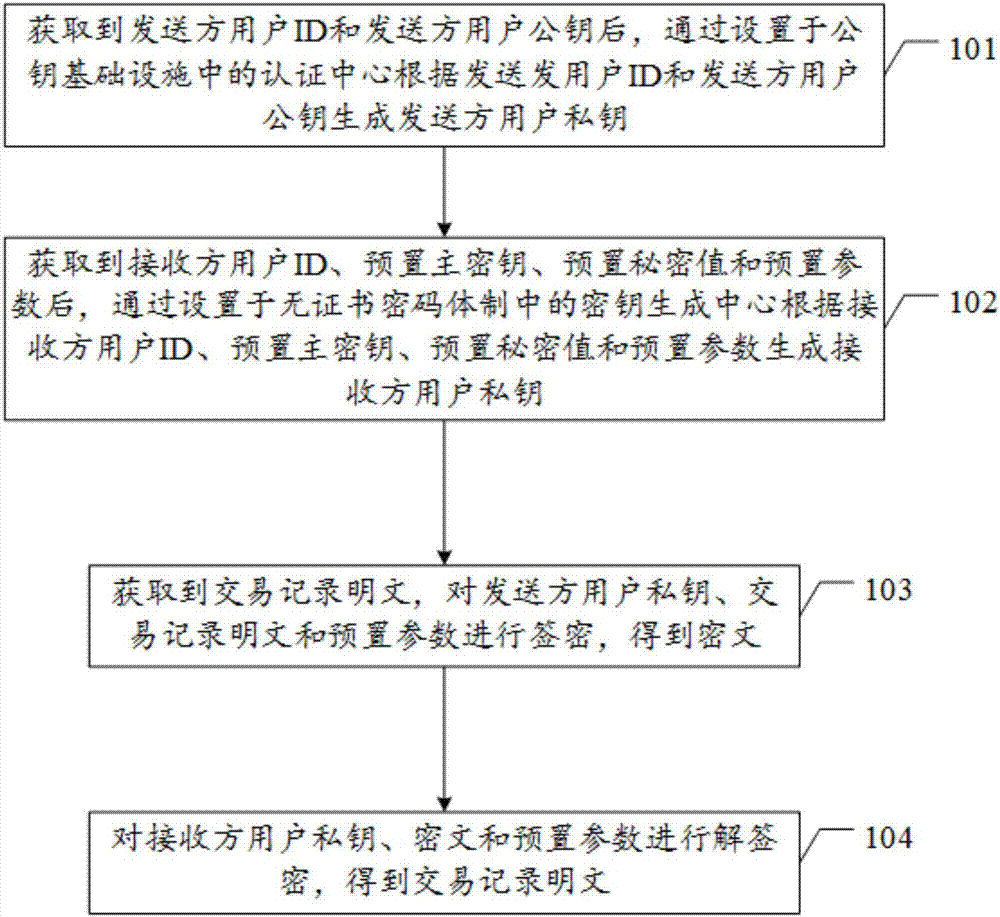
Block chain encryption method based on PKI-CLC heterogeneous aggregation signcryption algorithm
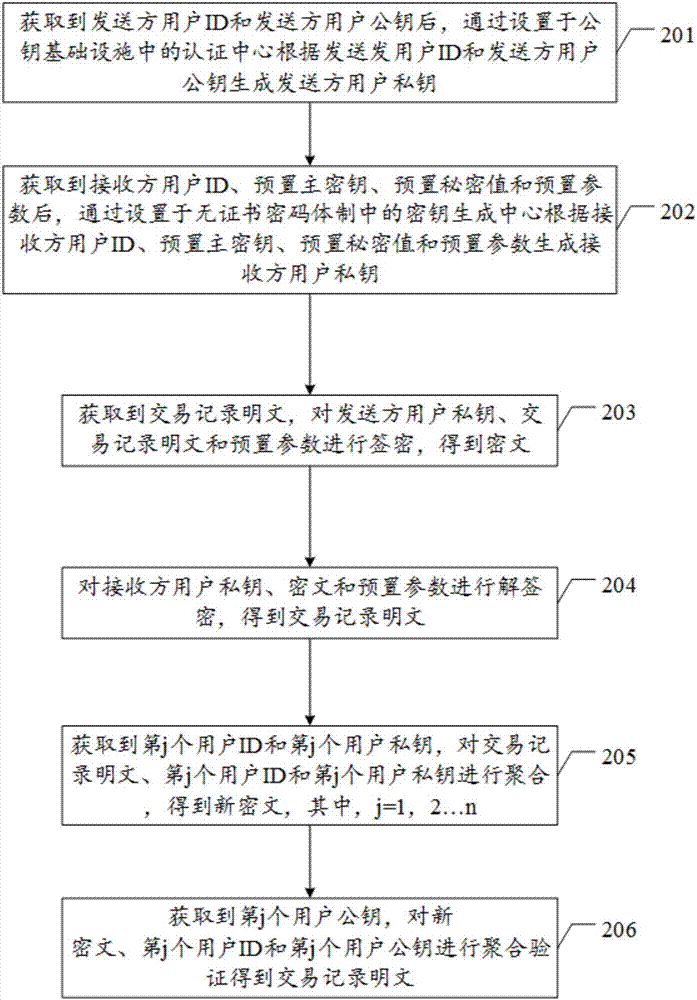
The embodiment of the invention discloses a block chain encryption method based on a PKI (public key infrastructure)-CLC (certificateless cryptography) heterogeneous aggregation signcryption algorithm. The method comprises: generating, after a sender user ID and a sender user public key are obtained, a sender user private key by using an authentication center in the PKI according to the sender user ID and the sender user public key; generating, after a receiver user ID, a preset master secret key, a preset secret value, and a preset parameter, a receiver user private key by using a secret key generation center in the CPC according to the receiver user ID, the preset master secret key, the preset secret value, and the preset parameter; obtaining a transaction record plaintext, subjecting the sender user private key, the transaction record plaintext, and the preset parameter to signcryption to obtain a ciphertext; and subjecting the receiver user private key, the ciphertext, and the preset parameter to unsigncryption to obtain the transaction record plaintext.
Owner:GUANGDONG UNIV OF TECH
Certificateless multi-receiver signcryption method with multivariate-based cryptosystem
InactiveCN102811125APrivacy protectionImprove securityPublic key for secure communicationUser identity/authority verificationCiphertextConfidentiality
The invention discloses a certificateless multi-receiver signcryption method with a multivariate-based cryptosystem. The certificateless multi-receiver signcryption method is used for solving the technical problem of poor security of an existing certificateless signcryption method. The technical scheme includes that the method includes: firstly, using a key generation center to generate system parameters, and selecting a secure multivariable encryption algorithm to generate keys; and enabling a user U to obtain system private keys of the key generation center and generate the private keys to user keys prior to that a user Alice with the identity IDA sends signcryption messages to a user group L={ID1, ID2,...,IDt}, and accepting or refusing ciphertext sigma by means of un-signcryption. By the aid of the multivariate-based cryptosystem, high security of anti-quantum computation is achieved, and the certificateless multi-receiver signcryption method is still high in security facing attack of a quantum computer. Compared with the background art, the certificateless multi-receiver signcryption method is small in computation and high in security, has the advantages of completeness, confidentiality, unforgeability, forward security, backward security, receiver privacy protection and the like and is capable of resisting existing known attack.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Method and system for certificateless and pairing-free identity-based proxy signcryption
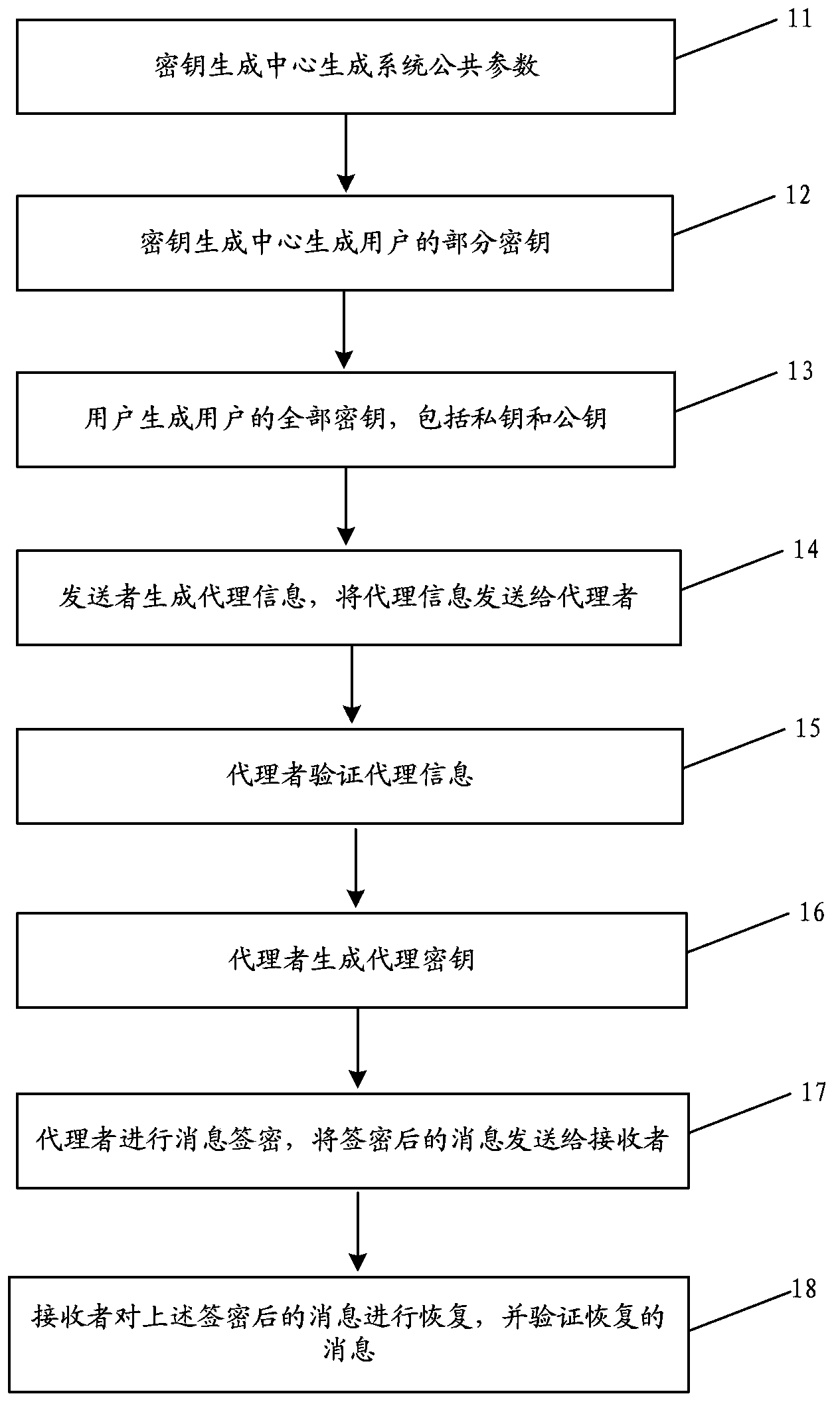
ActiveCN103905189ATroubleshoot hosting issuesPublic key for secure communicationUser identity/authority verificationSurrogate keySigncryption
The embodiment of the invention provides a method and a system for certificateless and pairing-free identity-based proxy signcryption. The method mainly comprises the following steps: a sender generates a private key and a public key thereof according to common parameters of the system and identity information parameters of the sender, generates proxy information based on the private key and the public key thereof, and sends the proxy information to a proxy; after the proxy information passes verification of the proxy, the proxy generates a proxy key, performs signcryption on a message needing to be sent based on the proxy key and the common parameters of the system to obtain a signcrypted message and an intermediate parameter, and sends the signcrypted message and the intermediate parameter to a receiver; and the receiver recovers the signcrypted message with the use of the intermediate parameter and the common parameters of the system to obtain a recovered message, and verifies the recovered message. The certificateless and pairing-free identity-based proxy signcryption scheme provided by the embodiment of the invention has both signature and encryption characteristics and has the feature of proxy. A key generation center only generates part of keys of a user, no certificate is needed, and the problem of key escrow is solved.
Owner:AEROSPACE INFORMATION
Asymmetric group key negotiation method based on block chain
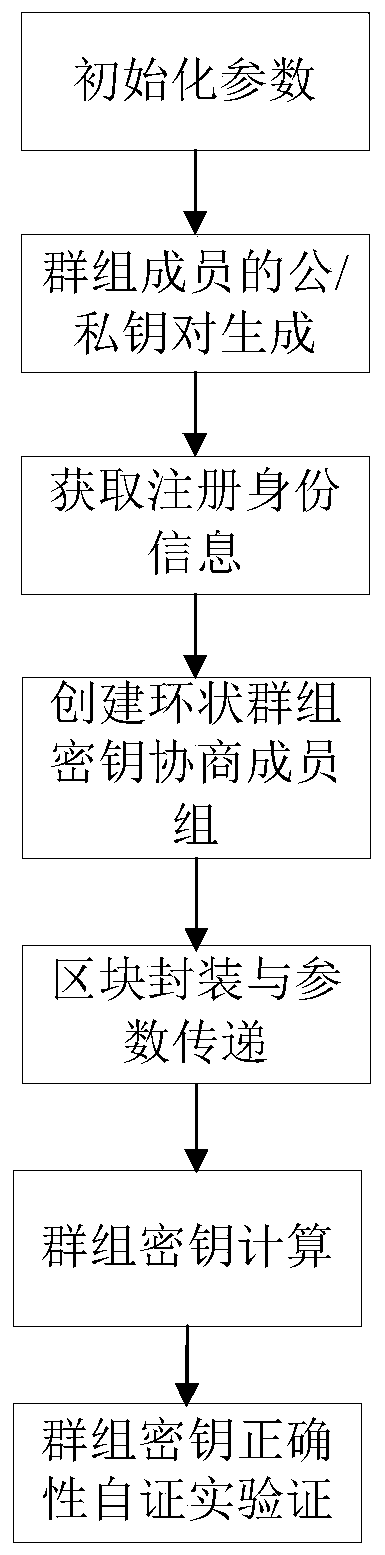
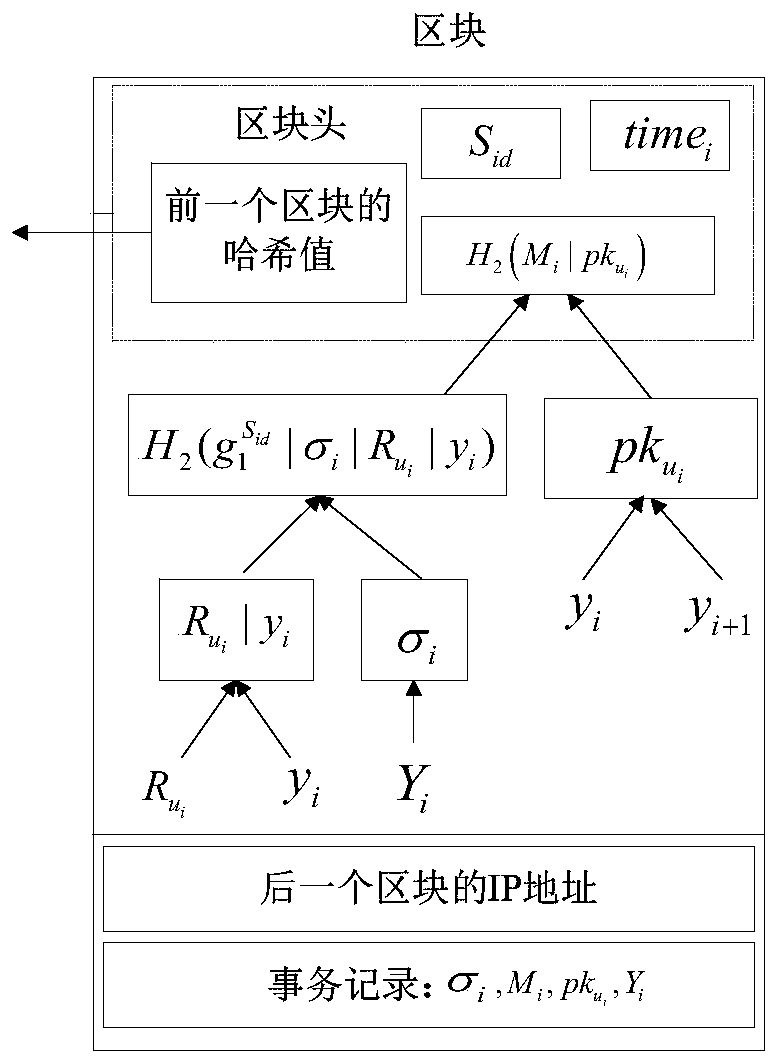
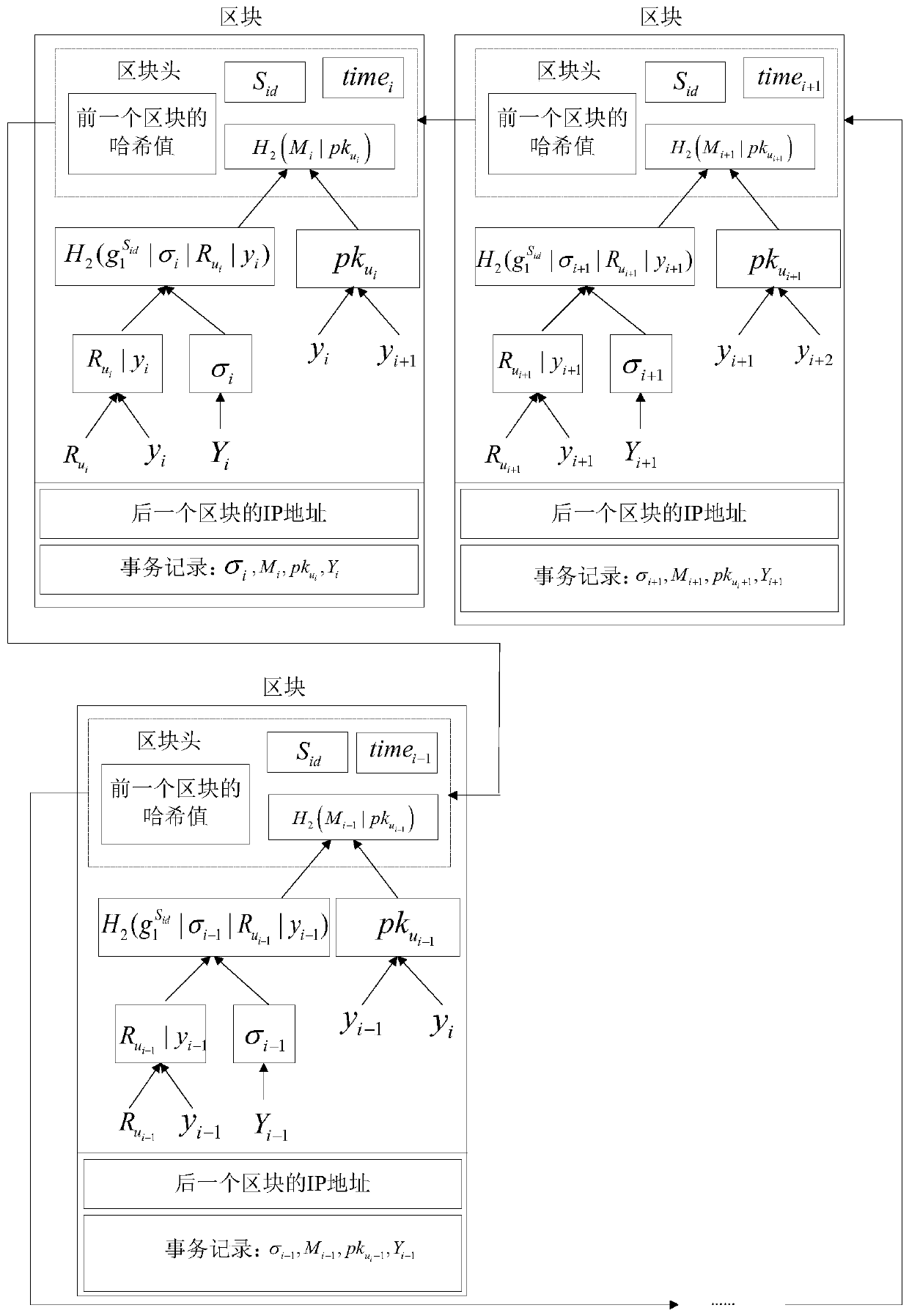
ActiveCN110266482AEnsure safetyGuaranteed normal transmissionKey distribution for secure communicationUser identity/authority verificationIp addressSecurity information
The invention provides an asymmetric group key negotiation method based on a block chain. The asymmetric group key negotiation method comprises the following steps: generating and registering keys of terminal members of a group; enabling the key generation center to arrange the terminal members into an annular set with identifiers according to the IP addresses, the public keys and the registration identification information of the terminal members, broadcast messages among the terminal members and store broadcast information of left and right neighbor nodes of the terminal members; and enabling the terminal member on the initiating node in the annular set to package the message composed of the group key parameters to the first block and transmit the message to the terminal member on the right adjacent node of the first block, carrying out circulation sequentially until the terminal member on the left adjacent node of the initiating node is reached, and calculating a group encryption key and a group decryption key, namely carrying out group key self-verification verification. Security information exchange and security information transmission between group members are achieved through the block chain technology, the asymmetric group key negotiation function and the performance advantage of the block chain technology are achieved, and group key negotiation is more flexible, efficient and practical.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Elliptic curve-based efficient and anonymous certificateless multi-receiver signcryption method
ActiveCN106936593AReduce multiplicationImprove computing efficiencyPublic key for secure communicationUser identity/authority verificationCiphertextSigncryption
The invention discloses an elliptic curve-based efficient and anonymous certificateless multi-receiver signcryption method. The method is used for solving the technical problem in the prior art that an existing certificateless multi-receiver signcryption method is low in operation efficiency. According to the technical scheme of the invention, firstly, a user public key and a partial private key, generated by a private key generation center PKG, are sent to a user. Secondly, after the user receives the user public key and the partial private key, the user calculates its own private key. Meanwhile, the user verifies whether the received user public key and the received partial private key are valid or not. If valid, the operation is continued. Otherwise, the operation is stopped. Thirdly, the signcryption algorithm is adopted to design an elliptic curve and the ciphertext information does not include the identity information of a sender and a recipient. Finally, the ciphertext information is broadcasted. Only authorized recipients can fairly decrypt and verify the ciphertext information. According to the technical scheme of the invention, the signcryption process is designed to conduct based on the elliptic curve. Therefore, the multiplication operation on the elliptic curve is reduced, and the calculation efficiency is improved.
Owner:XIDIAN UNIV
Network file system and method based on certificate-free public key infrastructure
InactiveCN102420810ANo hosting issuesEliminate redundancyUser identity/authority verificationNetwork File SystemClient-side
The invention provides a network file system and method based on a certificate-free public key infrastructure. All client side nodes are registered in a key generating centre server, and node public keys and node private keys of the client side nodes are generated according to system public keys and partial private keys in system parameters generated by the key generating centre server; no key hosting problem exists, the node public keys and identities of the client side nodes are not needed to be bound by certificates, thus the certificate redundancy problem brought by certificate utilization is eliminated, and a secure channel is not needed to be built between the key generating centre server and each client side node; the identity authentication of two communicating client side nodes is directly finished according to the node public keys, the node private keys and the system parameters, and the key generating centre server is not needed anymore; the communication frequency for mutual authentication of the client side nodes is greatly reduced, the bandwidth resources used in the identity authentication process are lowered, and the calculation amount is reduced and higher efficiency is obtained.
Owner:SHANGHAI SHENGPAY E PAYMENT SERVICE CO LTD
Self-authenticated method with timestamp
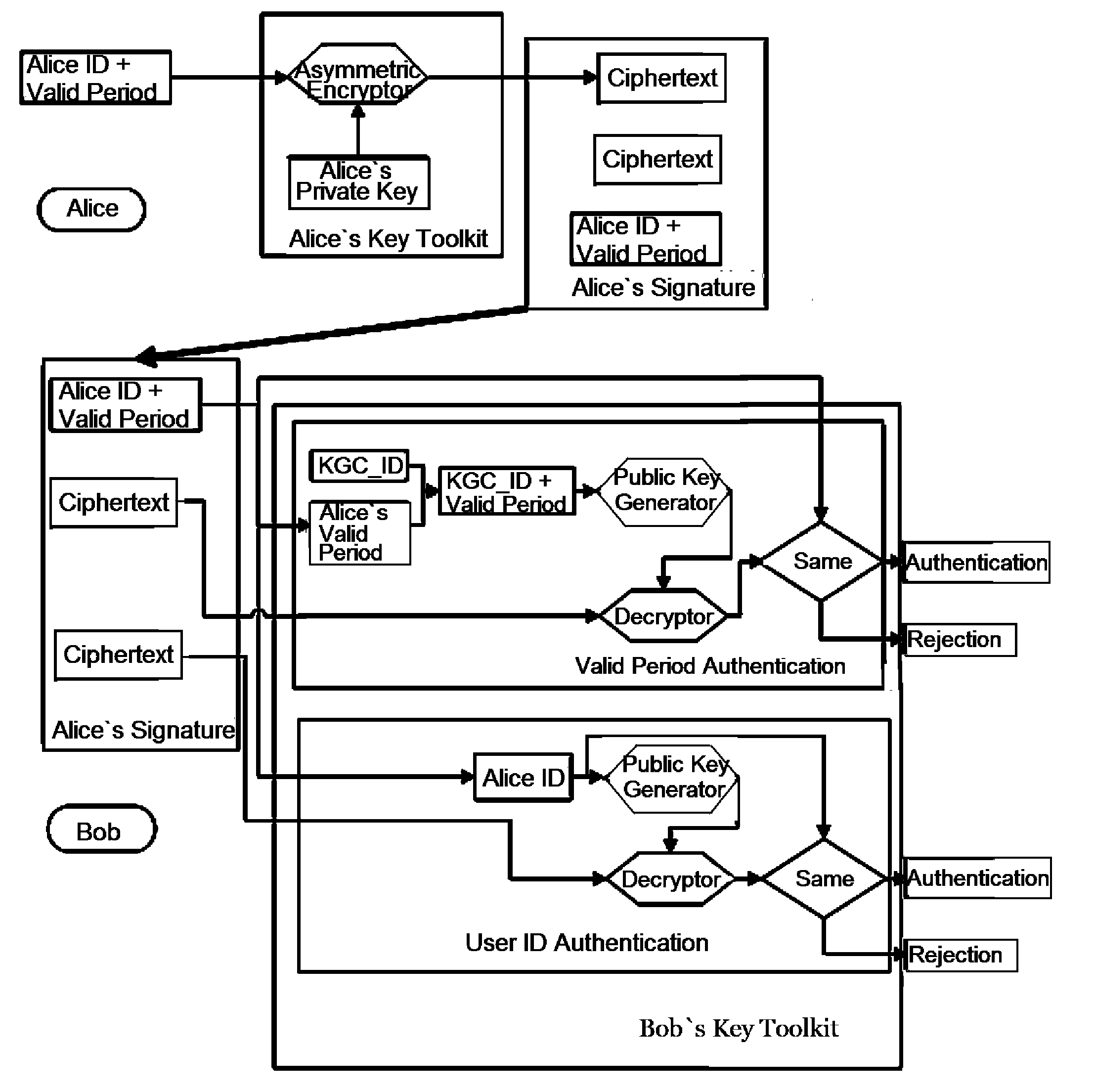
InactiveUS20140325225A1Ensures effectiveness of communicationAvoid wastingUser identity/authority verificationPlaintextTimestamp
A self-authenticated method with timestamp consists of key generating process and self-authenticated process between sender and receiver. The key generating center generates public key generator and private key according to sender's ID; combines the ID of the key generating center and the applied valid time of the sender to generate a identity of the key generating center with timestamp, and generating the corresponding coupled public and private keys; encrypting sender's ID and timestamp by using the private key of the coupled public and private keys, and obtains the first ciphertext of the sender's ID valid period; key generating center packs the sender's valid period, ID plaintext, first ciphertext of ID valid period, sender's public key generator and private key as a tool kit, and send the tool kit key to the sender; the sender encrypts its own ID and valid period by using sender's private key, to form the second ciphertext of the ID valid period, then sends the plaintext of the valid period, the second ciphertext and the first ciphertext of the ID valid period to the receiver; at the same time, performs valid period authentication and identity authentication. The present invention solves the problem in the existing self-authenticated system that the system cannot define valid period of a user's key.
Owner:SHENZHEN DECHUANGTONG INFORMATION TECH
An implementation method of certificateless public key cryptosystem based on elliptic curve
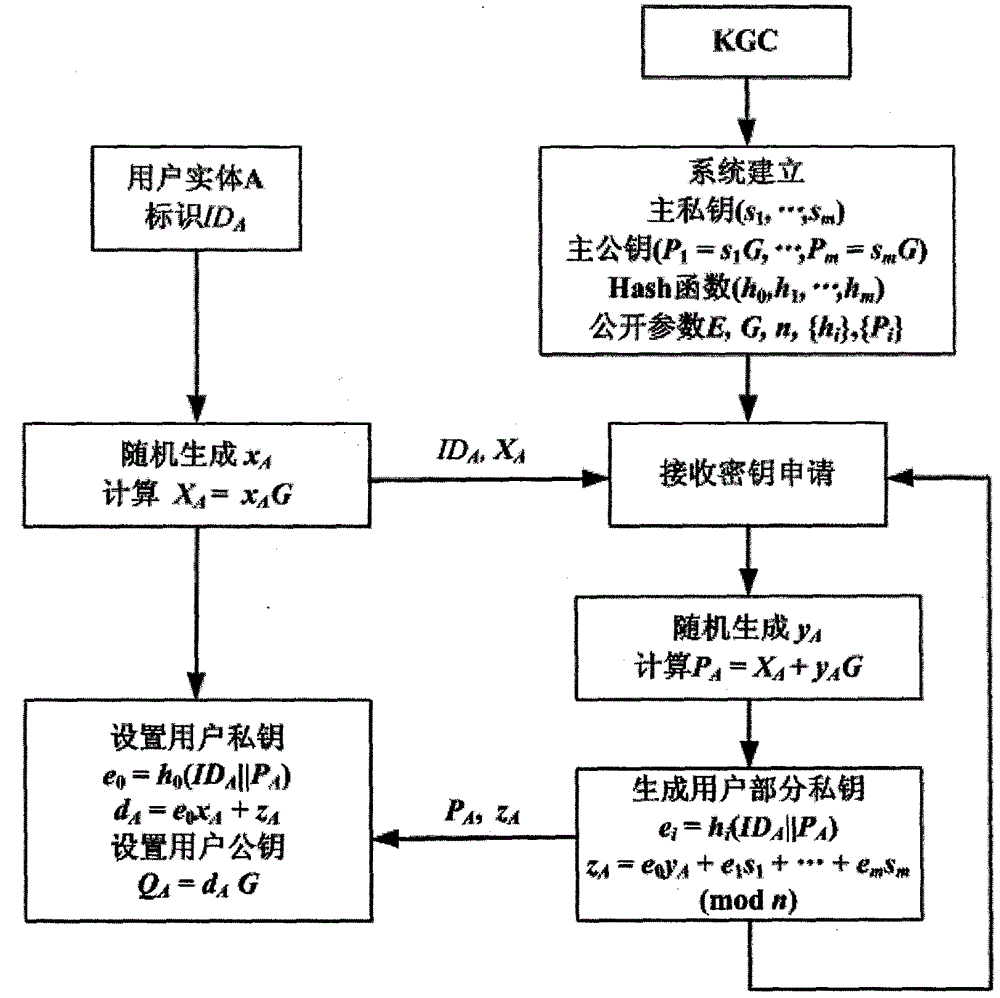
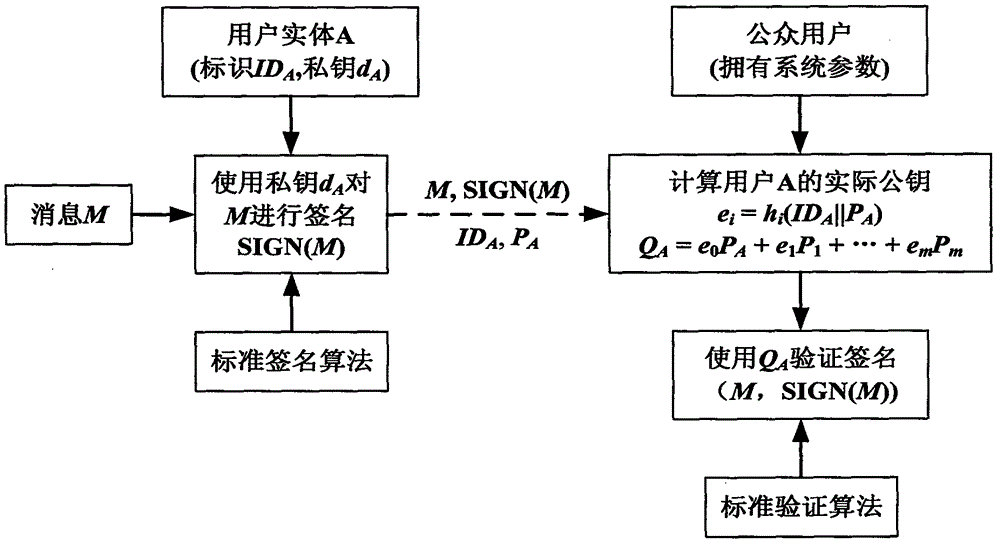
ActiveCN108989053AAvoid managementAvoid using effectsPublic key for secure communicationUser identity/authority verificationPublic key cryptosystemKey generation
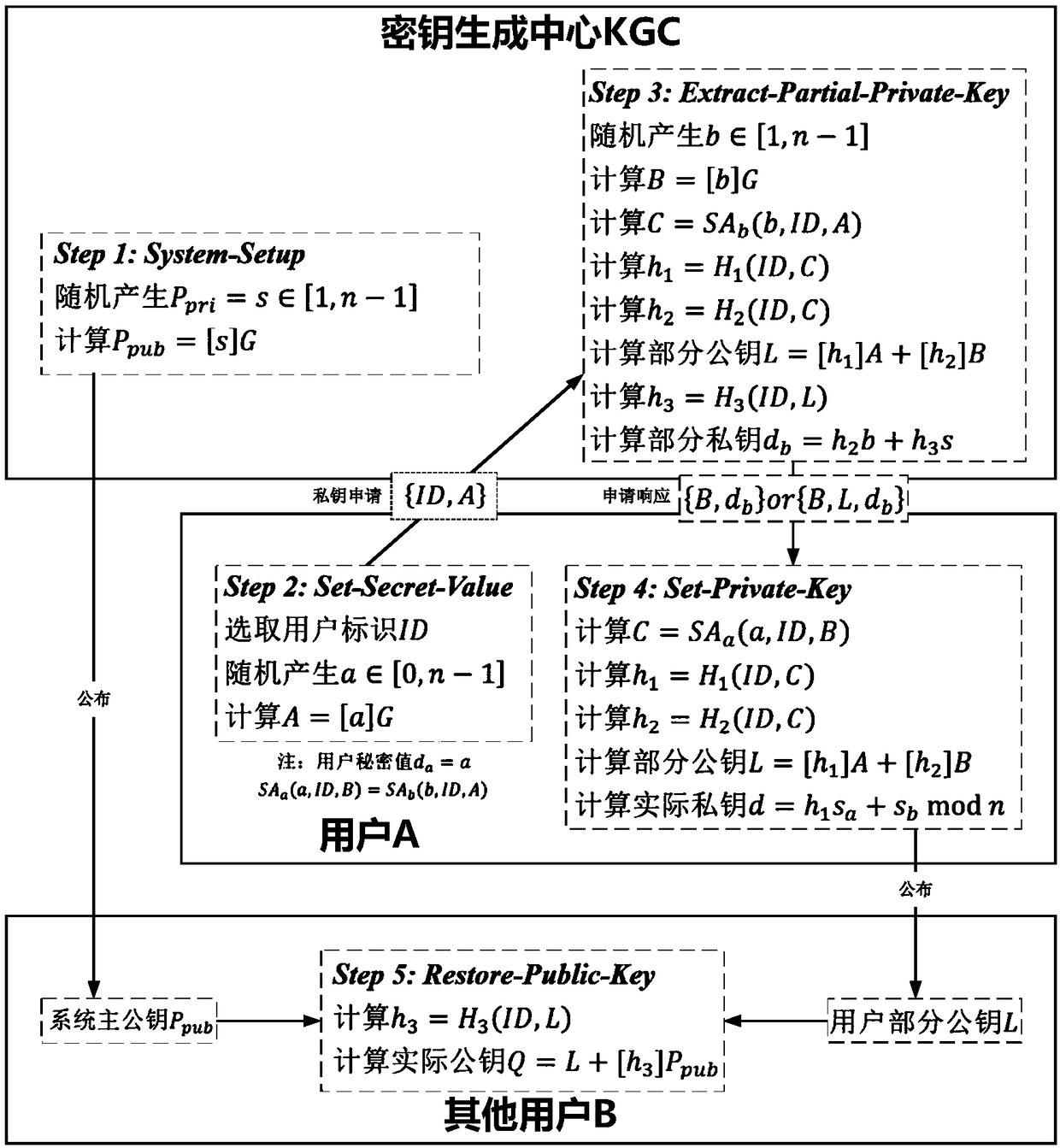
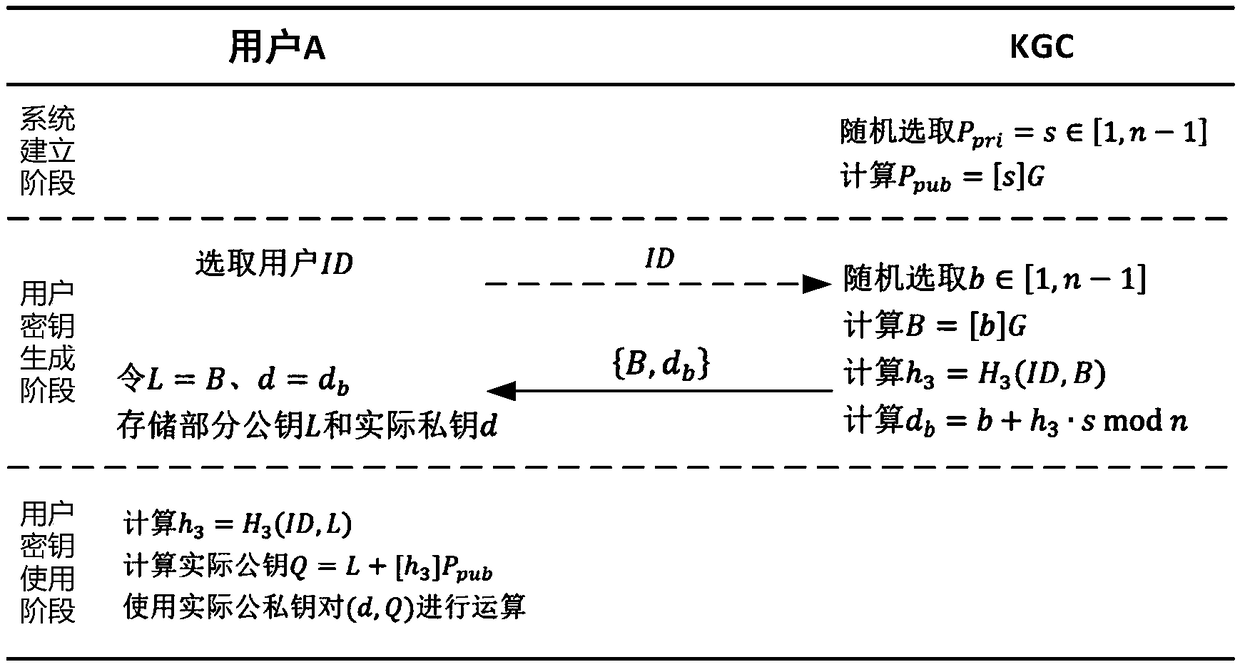
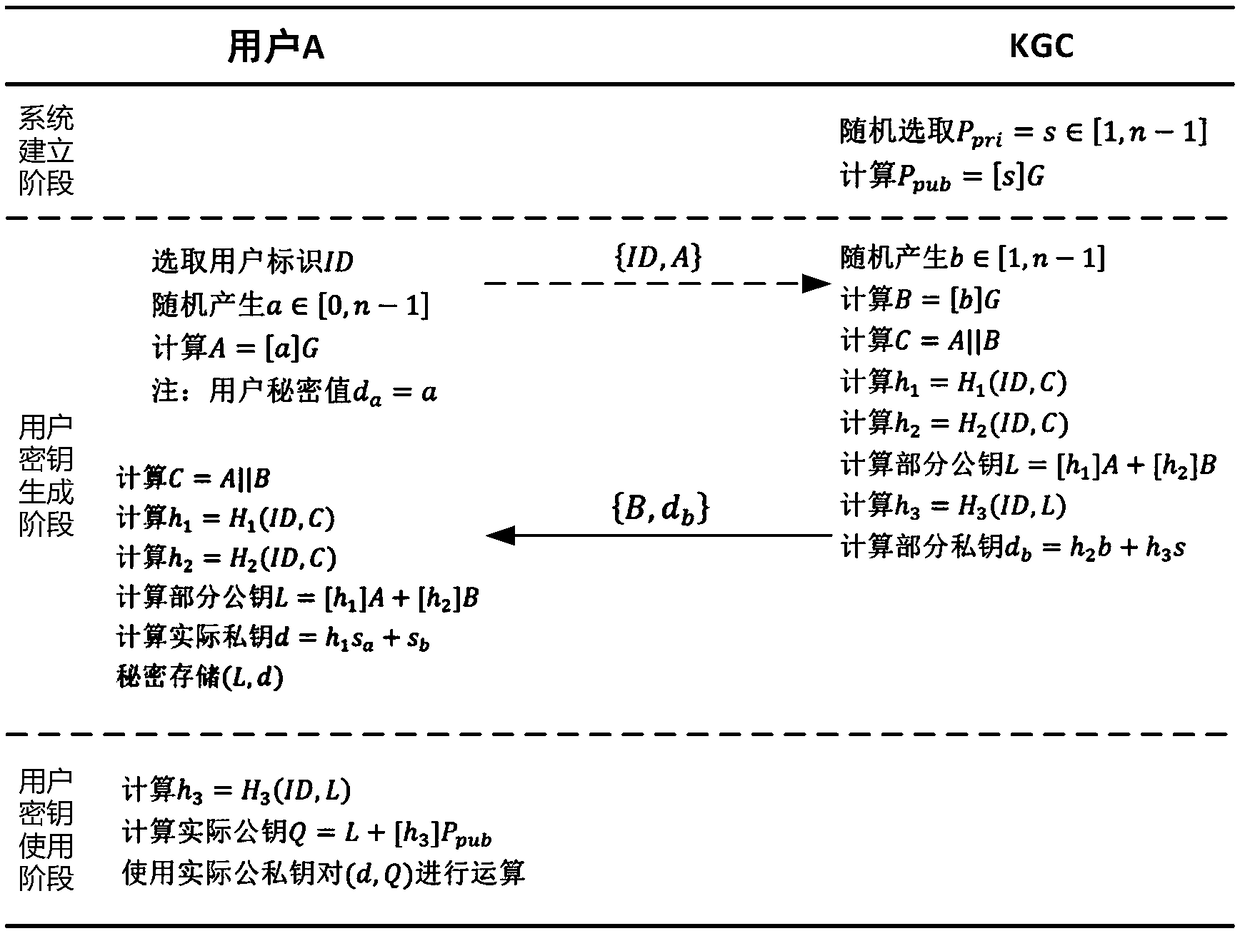
The invention discloses an implementation method of a certificateless public key cryptosystem based on an elliptic curve, which is used for solving the problems of system establishment, user key generation and use under the certificateless cryptosystem. In the present invention, the key generation center determines system parameters and publishes them. Then, the user submits an application to thekey generation center based on the randomly selected secret value, and the key generation center randomly generates a user partial private key based on the system master private key and the application information and returns the user partial private key, and finally the user calculates the actual private key and the partial public key based on the partial private key. In use, other users first get the actual public key based on the user identity and partial public key restoration, and then calculate according to the standard cryptographic algorithm. The invention effectively avoids the use problem of the certificate, can realize the binding of the user identification and the public key, and ensures that only the user can know the private key. The invention has the characteristics of highcomputational efficiency, strong security and the like, and can be applied to various standard elliptic curve cryptographic algorithms without changing the algorithm logic.
Owner:武汉珈港科技有限公司
Key threshold algorithm based on level identity encryption
InactiveCN102594570AWill not affect normal operationImprove securityKey distribution for secure communicationUser identity/authority verificationPlaintextAlgorithm
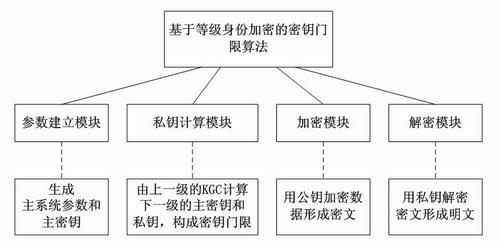
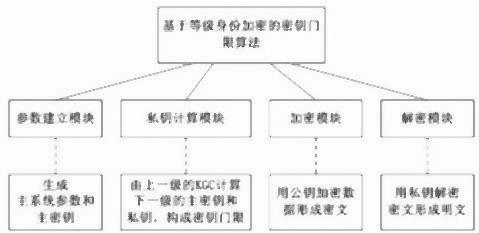
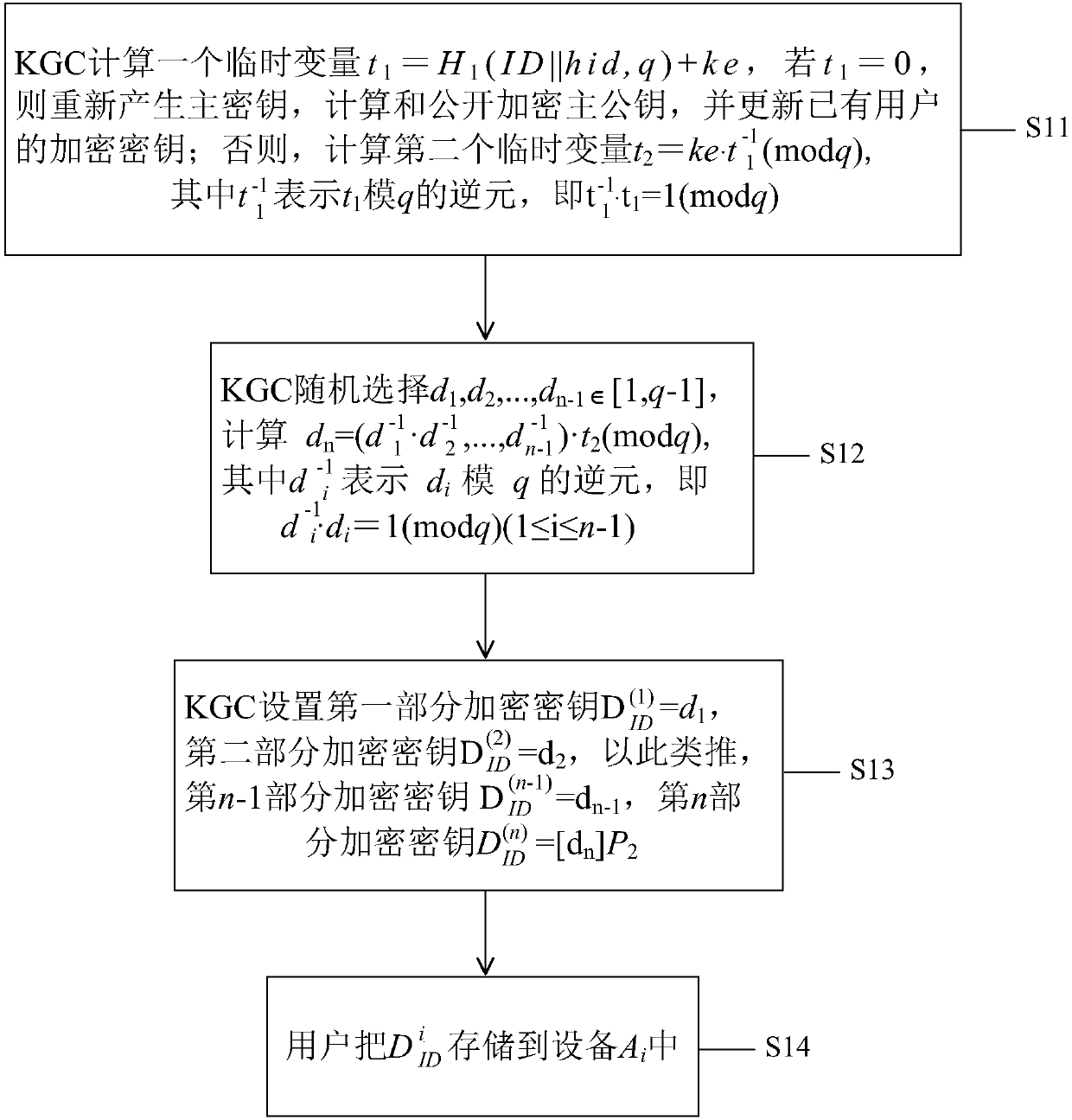
The invention relates to the technical field of identity passwords, in particular to a key threshold algorithm based on level identity encryption. A parameter establishment module, a private key calculation module, an encryption module and a decryption module are included, wherein the parameter establishment module is used for outputting a master system parameter and a master key, and the master key is managed by a highest-level KGC (Key Generation Center); the private key calculation module is used for calculating the master key and the private key at the i level by ni-1 KGCs at the i-1 level and forming a key threshold; the encryption module encrypts data M by using the public key and returns a ciphertext C; and the decryption module is used for decrypting the ciphertext C by using the private key SKID, and returning a plaintext M. Due to adoption of the algorithm, the security and the flexibility of key distribution are enhanced.
Owner:FUJIAN NORMAL UNIV
Multi-distributed SM9 decryption method, medium and key generation method
ActiveCN108418686AEnsure safetyImprove securityKey distribution for secure communicationPublic key for secure communicationTemporary variablePlaintext
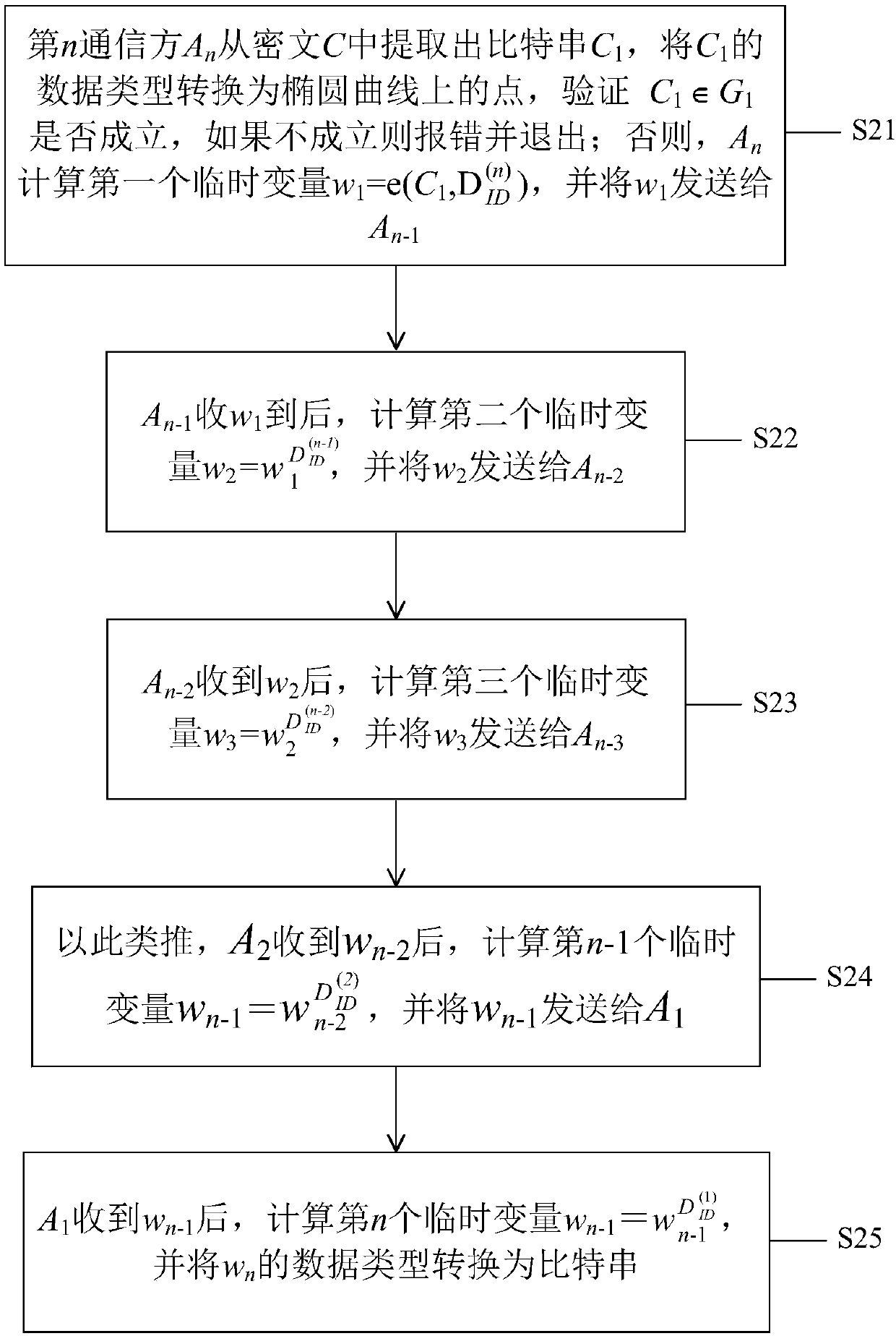
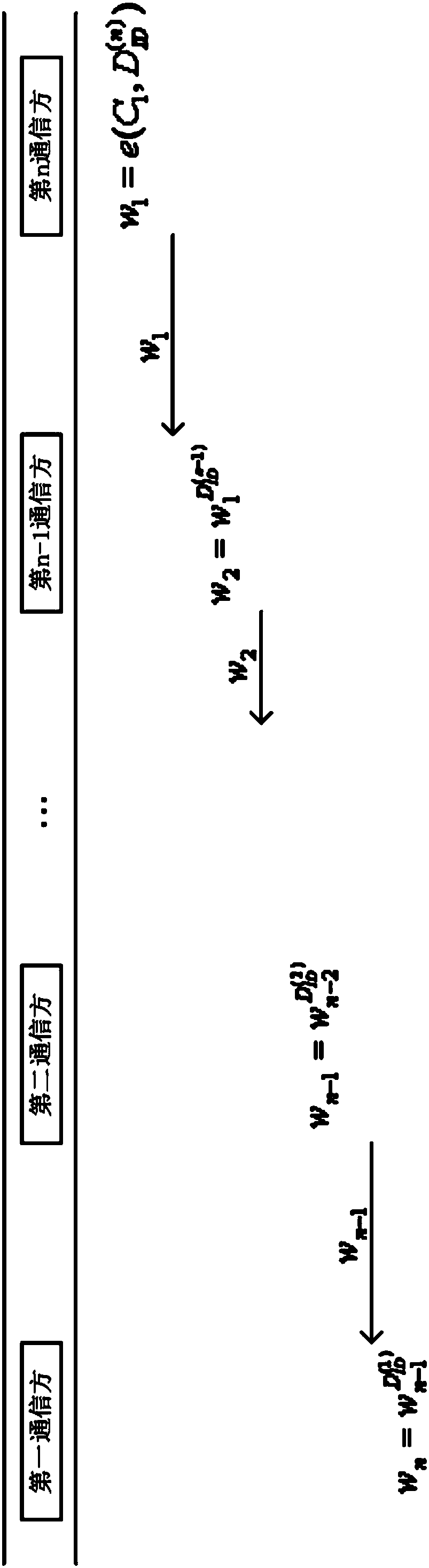
The invention discloses a multi-distributed SM9 decryption method, a medium and a key generation method. Multiple communication methods jointly complete a message decryption process under the condition of not leaking respective part of encryption keys and being unable to acquire the complete encryption key. The technical scheme of the method is as follows: a key generation center (KGC) generates the corresponding part of keys for communication parties participating into an SM9 decryption system. After the key is received, an n-th communication party An computes a first temporary variable, andreturns the first temporary variable back to the An-1. After the An-1 receives w1, a second temporary variable is computed, and returned back to An-2, and so on, until the A1 receives the wn-1, the n-th temporary variable is computed, and is subjected to decryption computing in a classified manner according to a plaintext encryption method, and finally plaintext M' is output.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Disposable public key encryption structuring method based on fuzzy identity
InactiveCN104158661APrevent and reveal malicious activityAnonymityKey distribution for secure communicationPublic key for secure communicationUser needsComputerized system
The invention discloses a disposable public key encryption structuring method based on fuzzy identity. According to the method, a computer system is utilized to complete disposable public key anonymous encryption structure based on fuzzy identity and comprises a user A, a user B, a PKG (a public key generation center) and a KGC (a private key generation center), wherein two users need to send and receive messages to / from each other. The method comprises five steps: initialization, user secret key generation, disposable public key generation, encryption and decryption. Compared with the conventional method, the method has anonymity, unforgeability and traceability, and can effectively prevent disposable attack of malicious users and untrusted attack from a trusted center in the system. Meanwhile, compared with the conventional method, the method provided by the invention has relatively high calculation efficiency and relatively low communication expenditure.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Machine-type communication authentication and key agreement method based on proxy
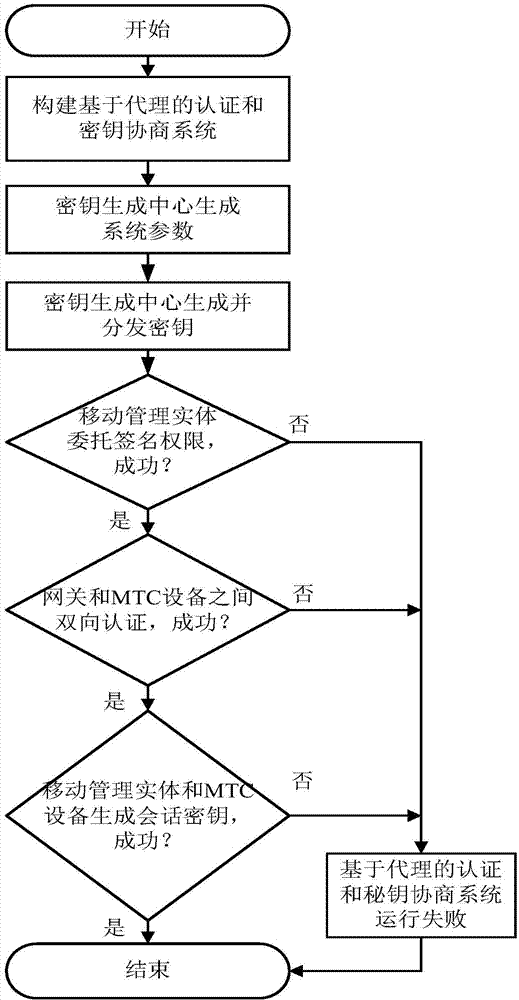
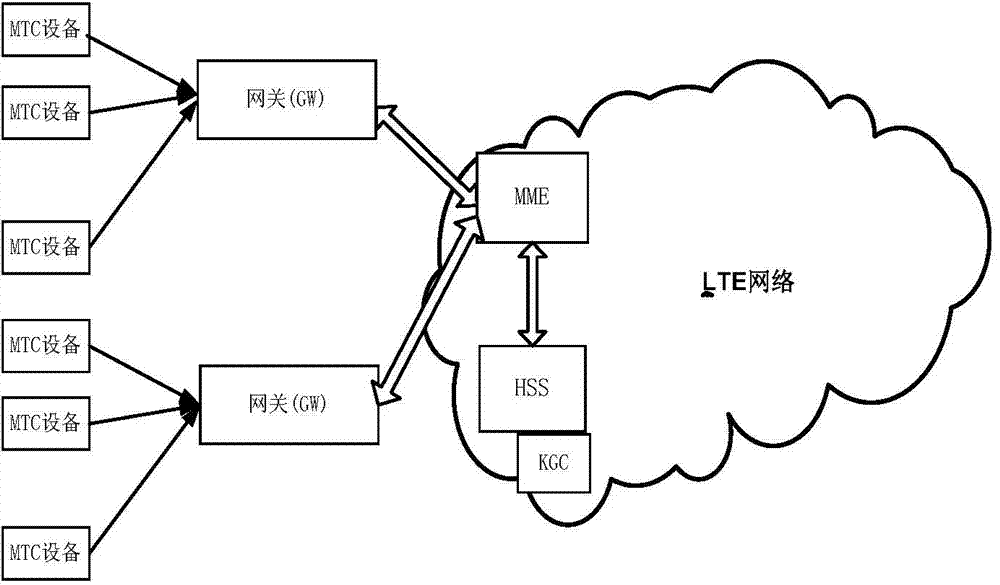
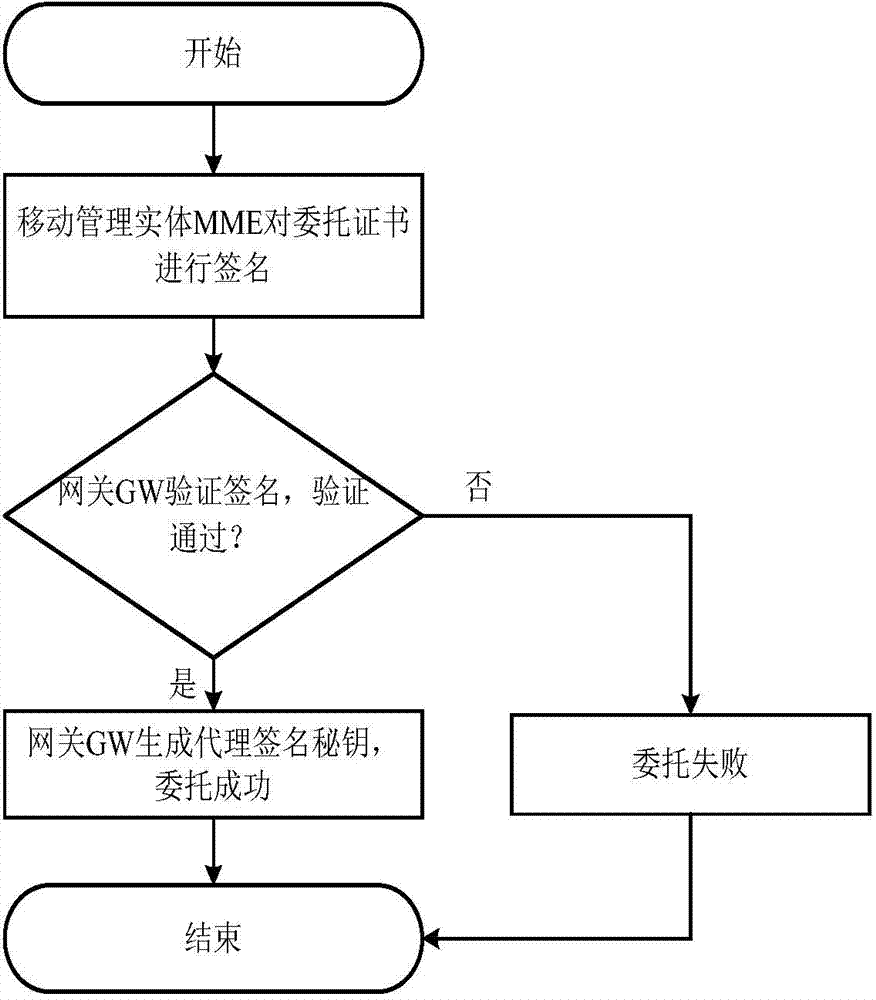
ActiveCN103596167AAvoid signaling congestionReduce loadSecurity arrangementMobility managementComputer science
The invention discloses a machine-type communication authentication and key agreement method based on proxy, and mainly aims to solve the signaling jamming problem in the prior art. The method includes the steps that an authentication and key agreement system based on the proxy is established; a key generation center generates system parameters and calculates and distributes keys corresponding to identity information of mobility management entities, identity information of gateways and identity information of machine-type communication equipment; the mobility management entities entrust the gateways with signature permission; bidirectional authentication is conducted between the entrusted gateways and the machine-type communication equipment; the machine-type communication equipment and the mobility management entities generate session keys. The degree of signaling jamming caused when a large amount of machine-type communication equipment simultaneously has access to networks is reduced through proxy signatures by utilizing the gateways to achieve authentication and key agreement of the machine-type communication equipment in the LTE networks, and the method can be widely applied to the LTE networks in future.
Owner:XIDIAN UNIV
Method and device of two-side authentication secret key negotiation based on certificateless
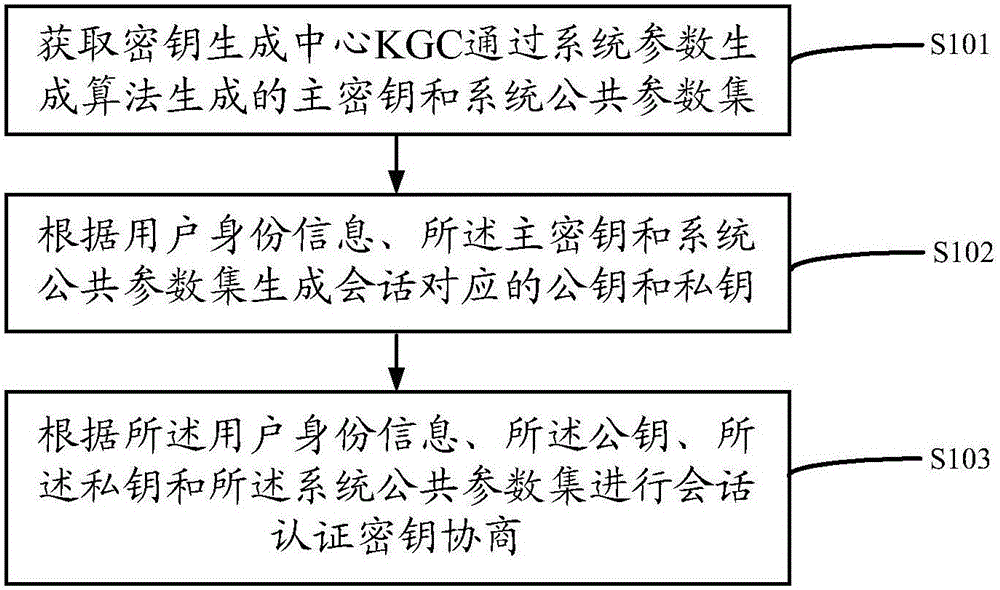
The present invention discloses a method and device of two-side authentication secret key negotiation based on certificateless. The device comprises a parameter module and a negotiation module, a system public parameter set and the master key, part of secret keys, the secret value, the private key and the public key of a key generation center (KGC) are generated, and the two-side secret key negotiation is performed so as to overcome the problem of complex certificate management in a traditional public key cryptosystem and the problem of inherent secret key trusteeship based on the identity of the cryptosystem, and the method and device of two-side authentication secret key negotiation based on certificateless do not depend on the bilinear pairing operation so as to improve the system efficiency and are specially suitable for a wireless mobile device with limited capability.
Owner:ZTE CORP
Multi-receiver hybrid signcryption algorithm without bilinear pairings
ActiveCN104734857APrevent forgeryDefend against forgery attacksKey distribution for secure communicationUser identity/authority verificationSigncryptionTwo-way communication
The invention discloses a multi-receiver hybrid signcryption algorithm without bilinear pairings. The multi-receiver hybrid signcryption algorithm includes the five processes of secret key generation center initialization, extraction of a part of private keys, secret key extraction, signcryption and unsigncryption. Two-way communication signcryption of multiple receivers is achieved, the signcryption algorithm in the scheme is achieved without the bilinear pairings, calculation expenses are greatly reduced, and universality is better; compared with traditional schemes, counterfeit attacks of a positive and dishonest secret key generation center can be defended, and safety is higher.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com