Multi-distributed SM9 decryption method, medium and key generation method
A technology of key generation and key generation center, which is applied to the public key and key distribution of secure communication, and can solve problems such as the inability to obtain encryption keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
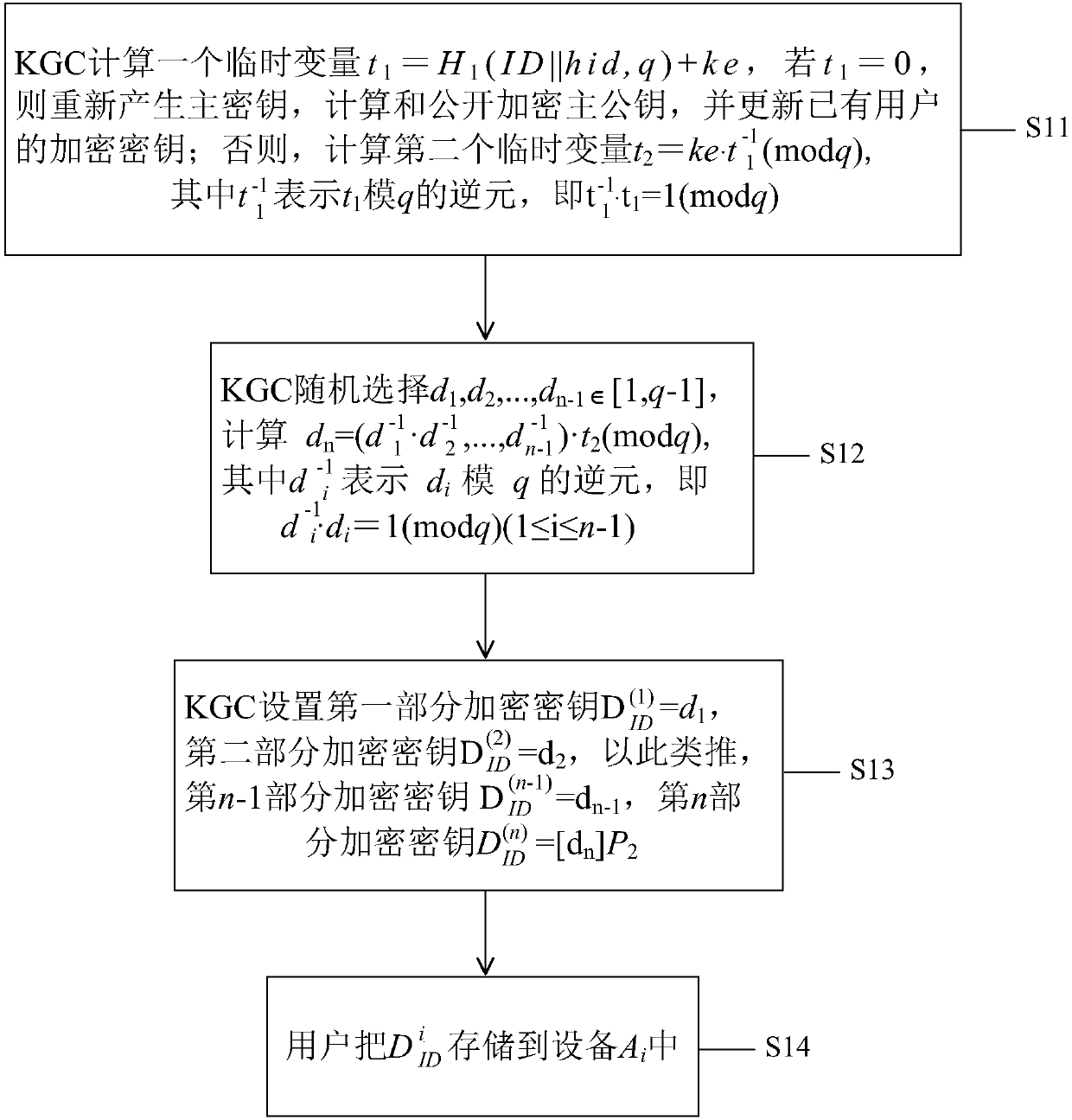
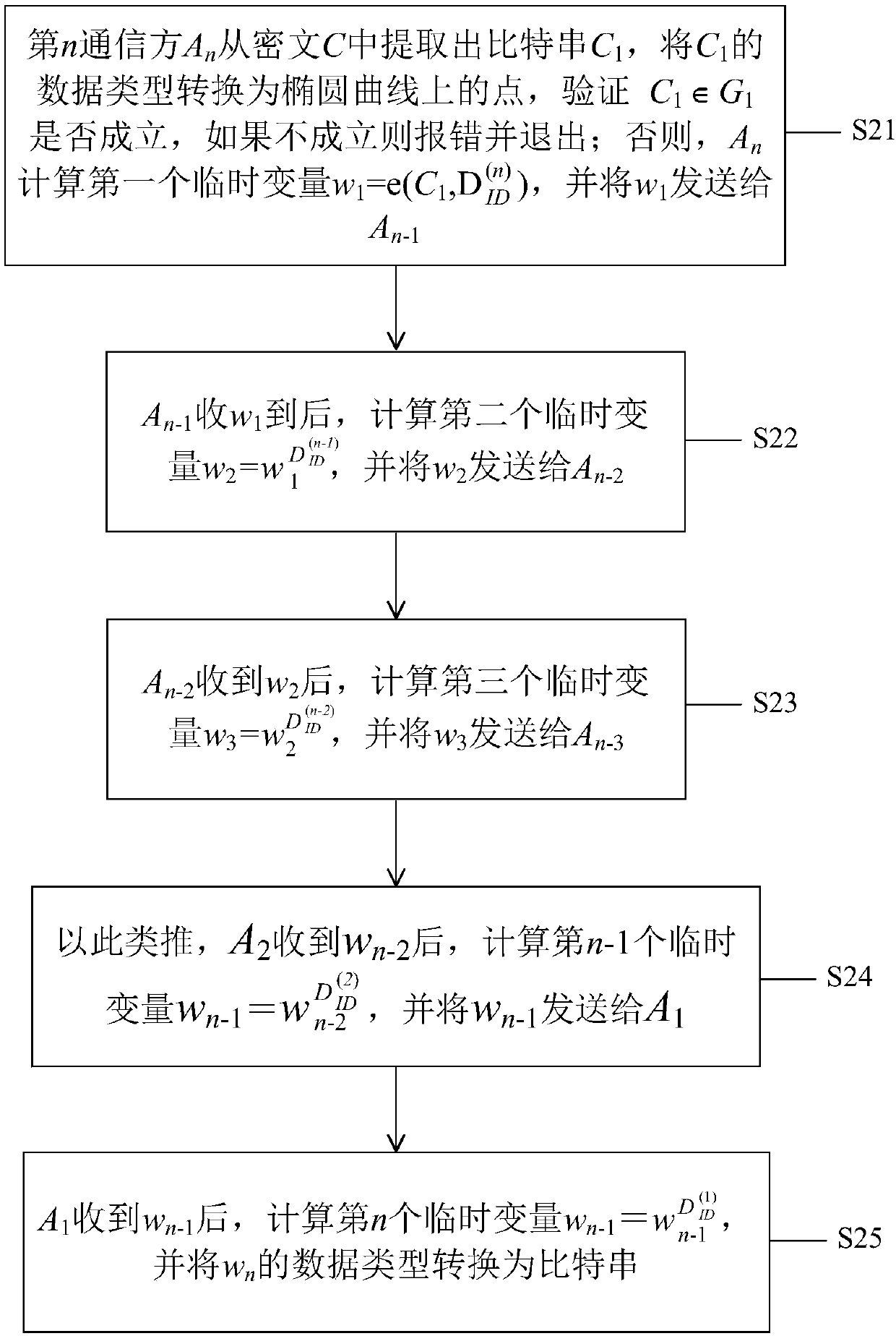
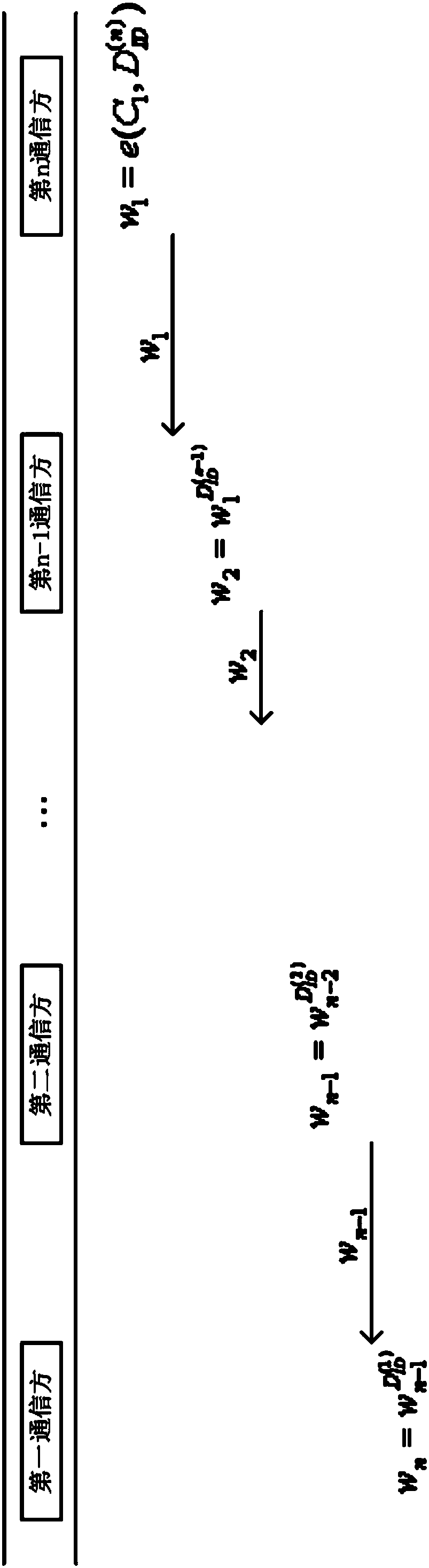
[0048]The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments. Note that the aspects described below in conjunction with the drawings and specific embodiments are only exemplary, and should not be construed as limiting the protection scope of the present invention.
[0049] Before starting to describe the technical solutions of the embodiments of the present invention, the symbols and their definitions that will appear in the following description are listed first.
[0050] KGC: Key Generation Center. It is a trusted organization, mainly responsible for generating system parameters, master private key and encryption key.
[0051] KDF(·): key derivation function.
[0052] MAC(·): Message authentication code function.
[0053] G 1 ,G 2 : The additive cyclic group of order prime q.
[0054] G T : The multiplicative cyclic group of order prime q.
[0055] e: from G 1 ×G 2 to G T bilinear pairing.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com