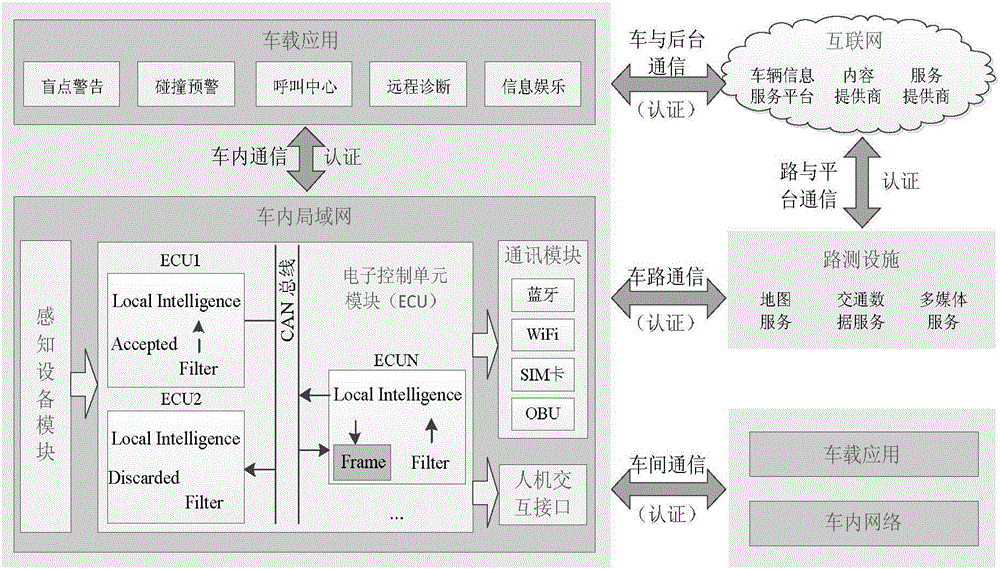
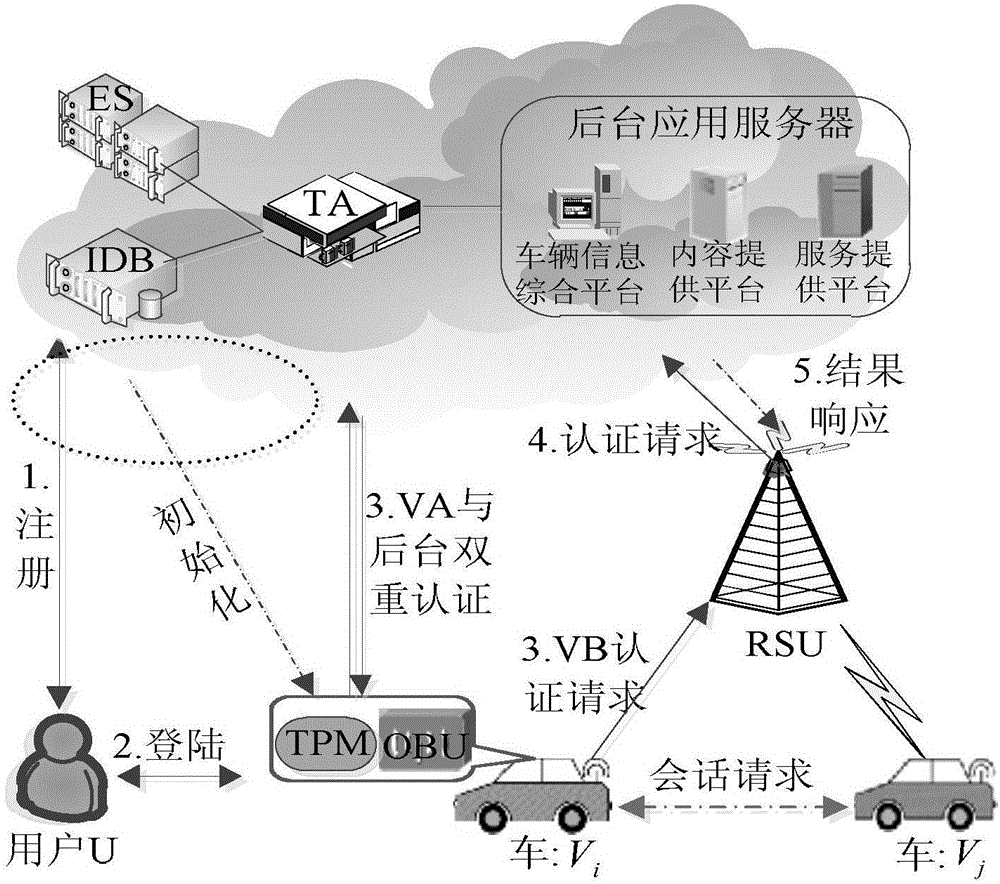
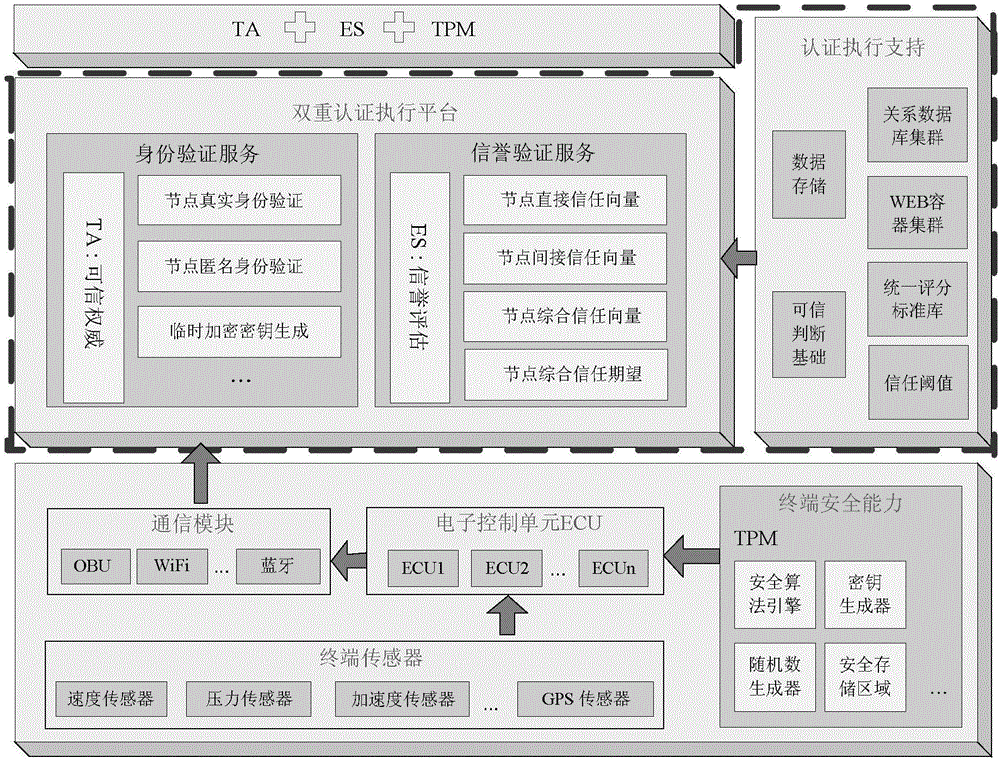
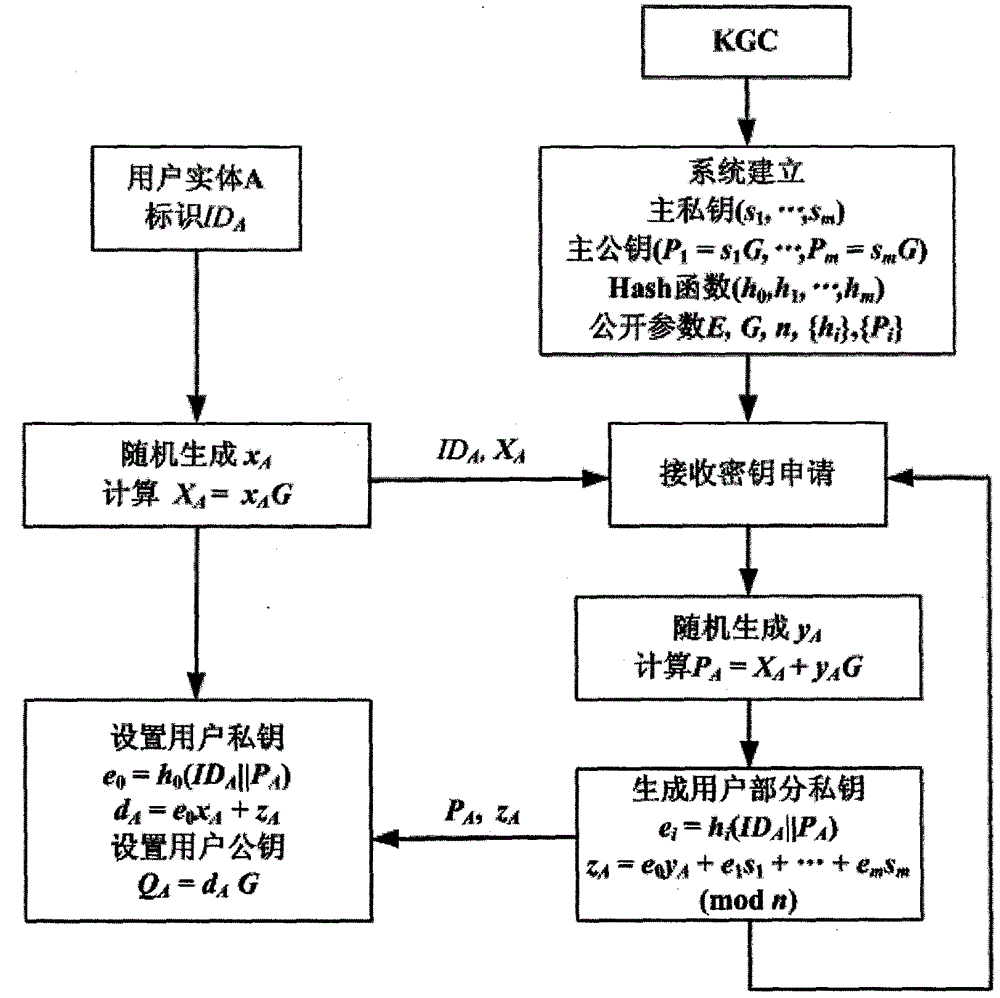
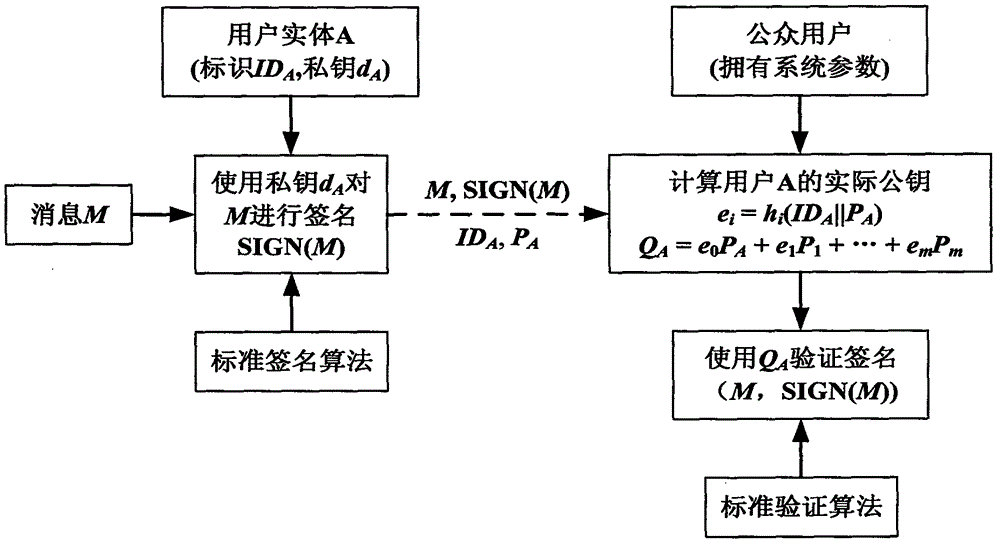
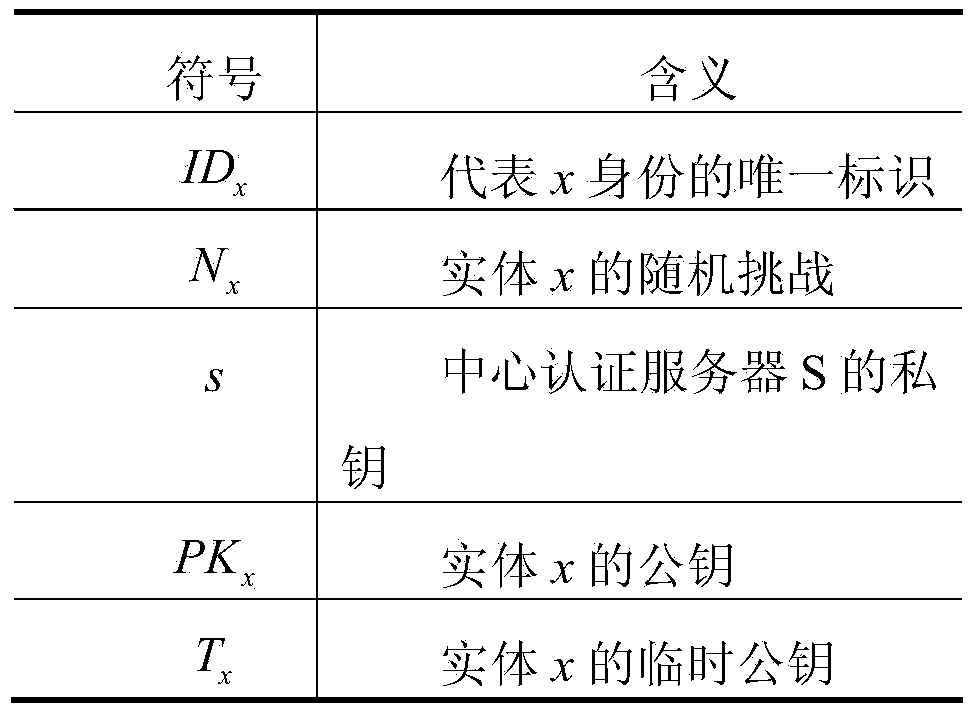
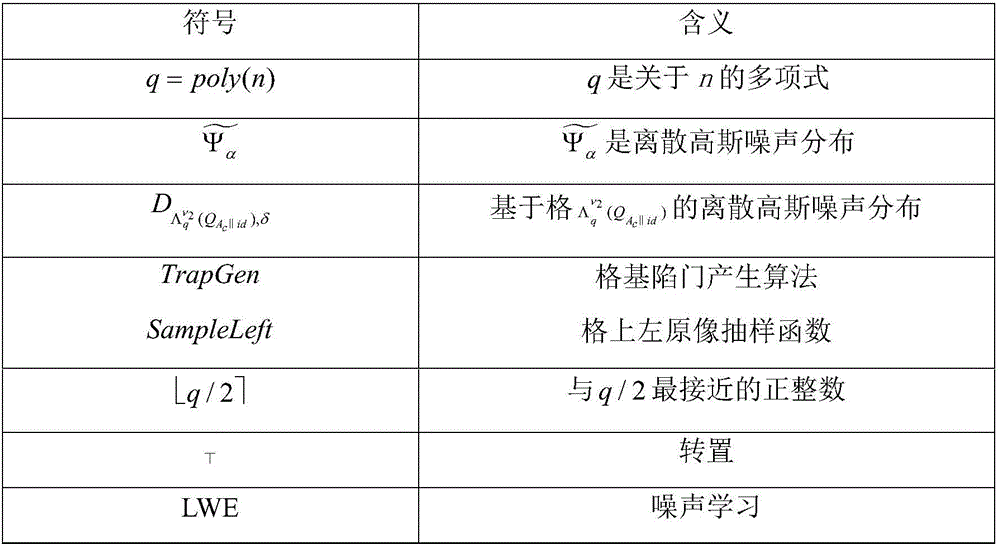
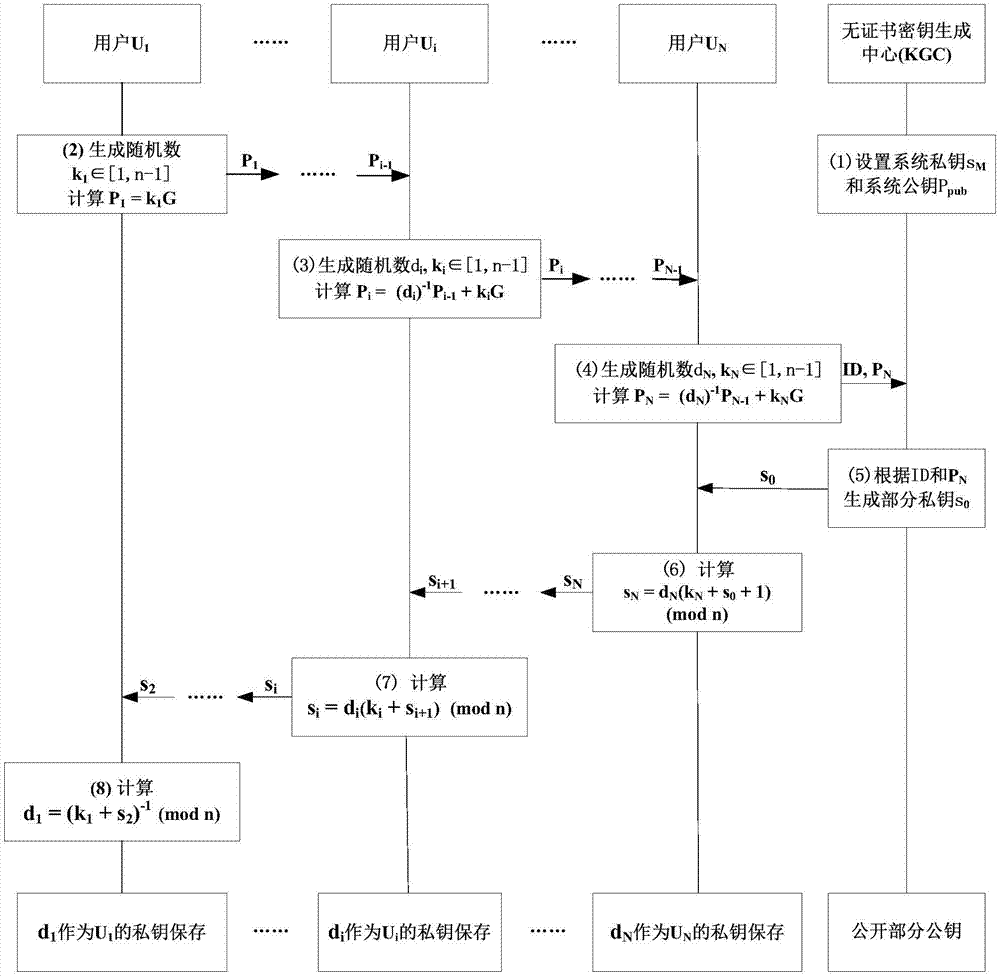
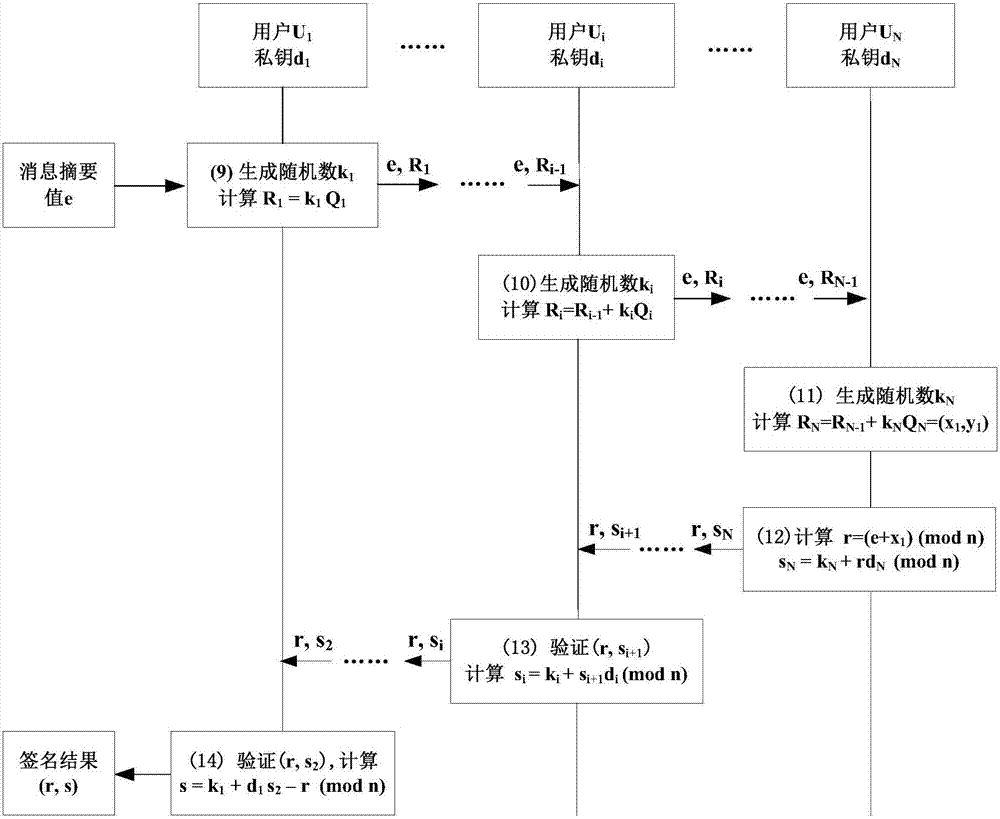
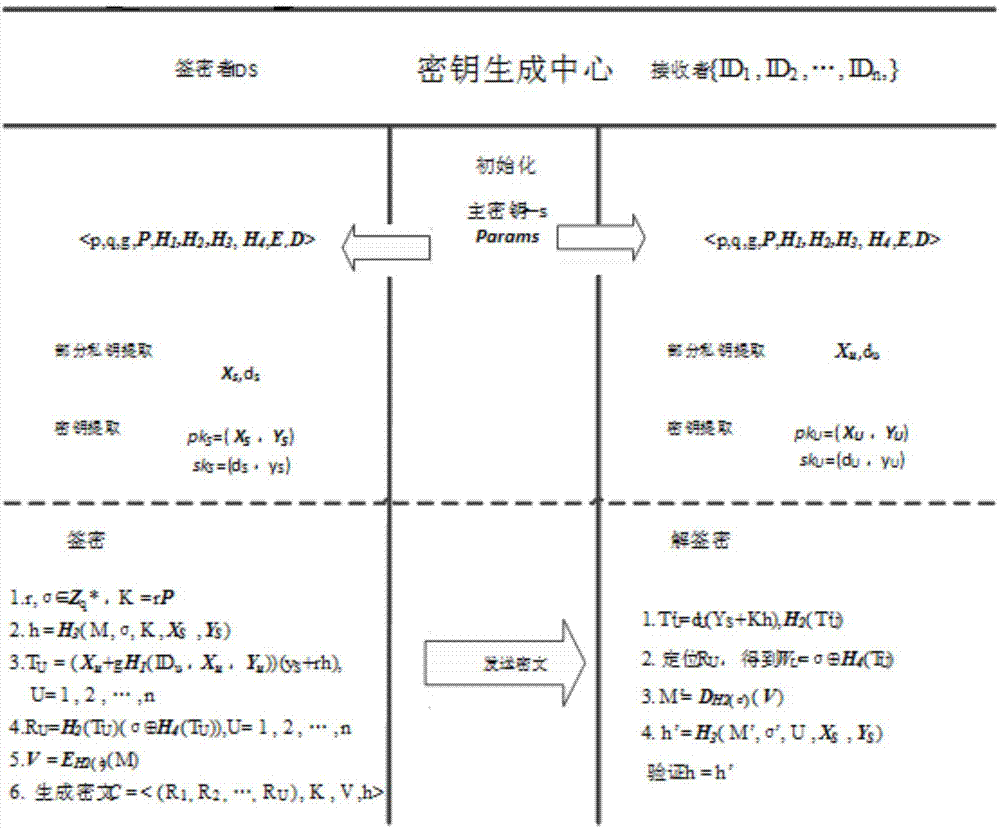
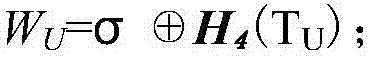
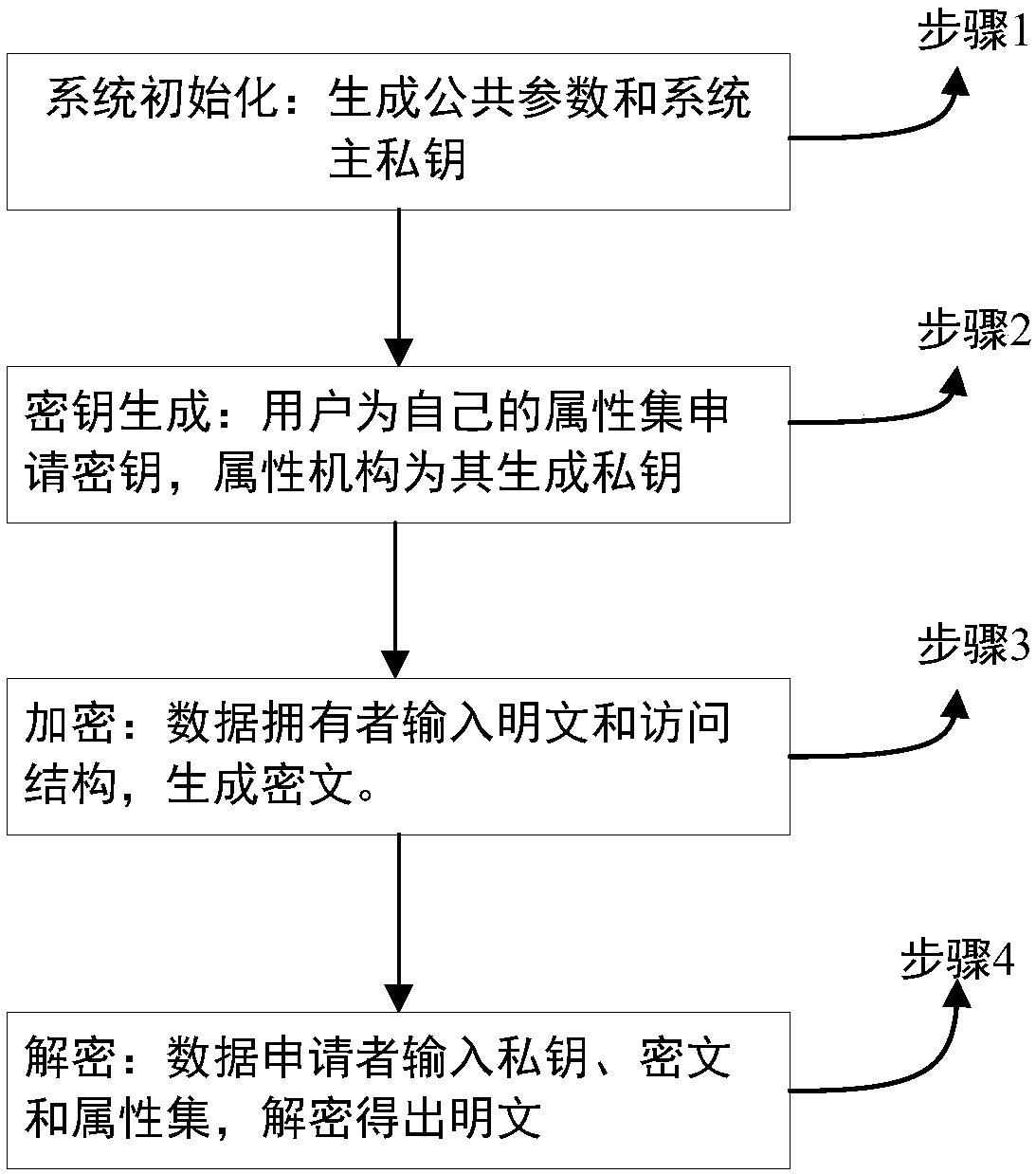
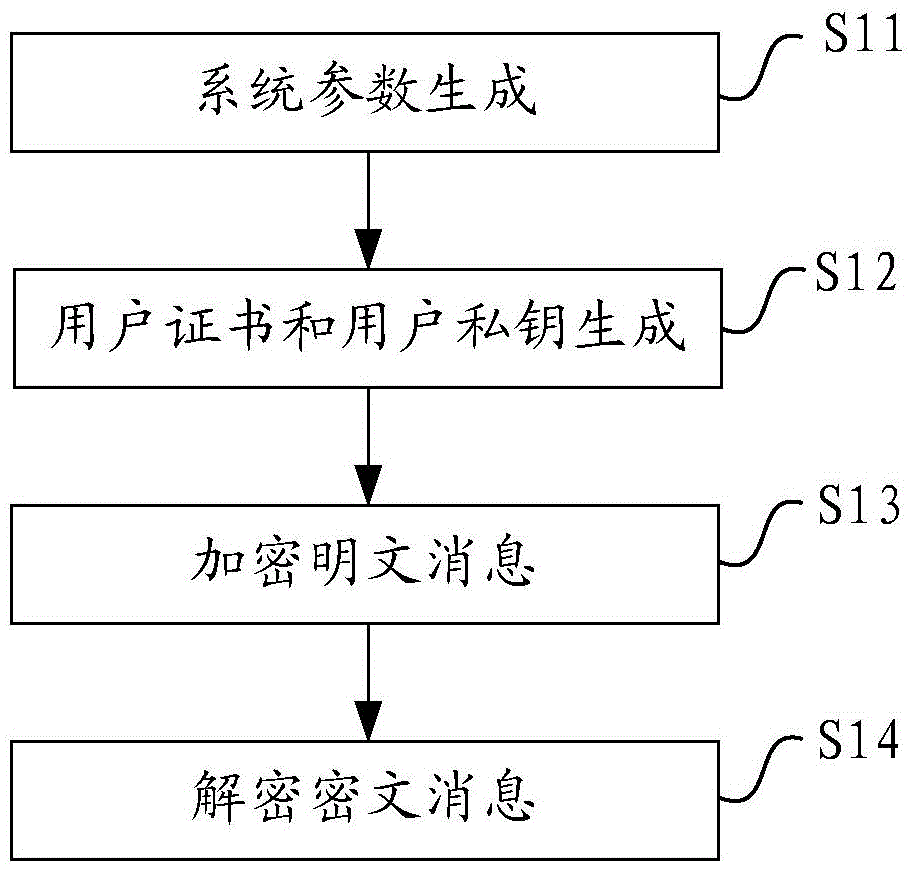
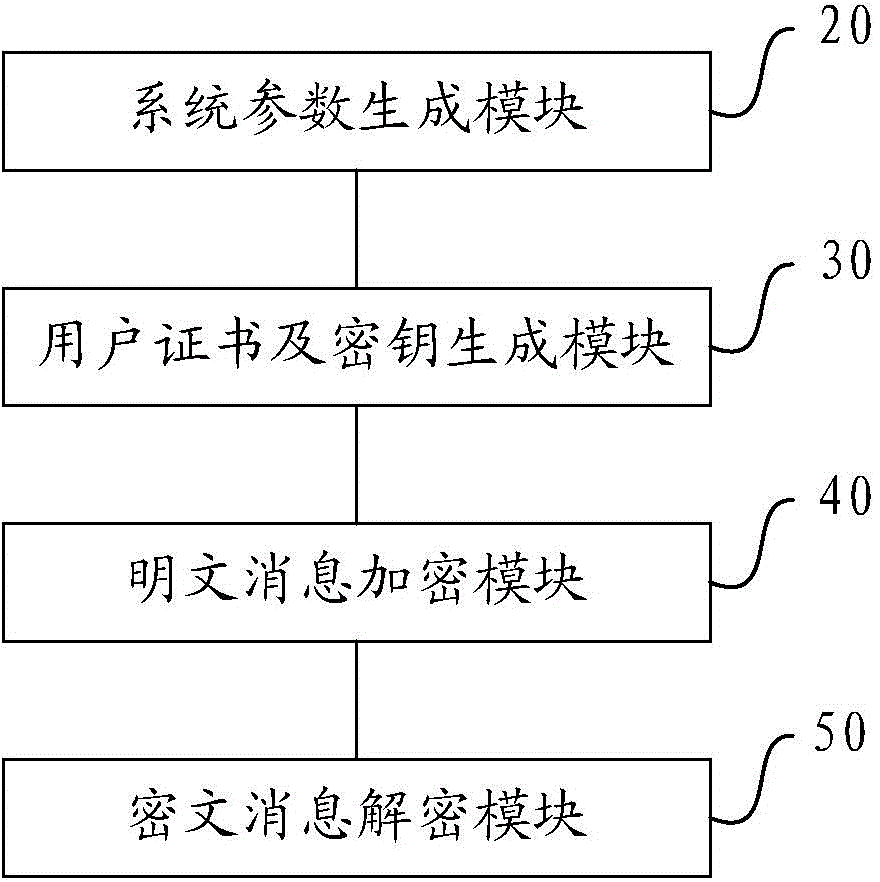
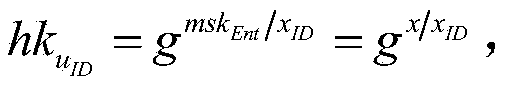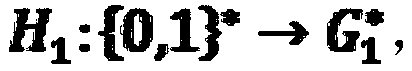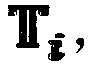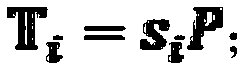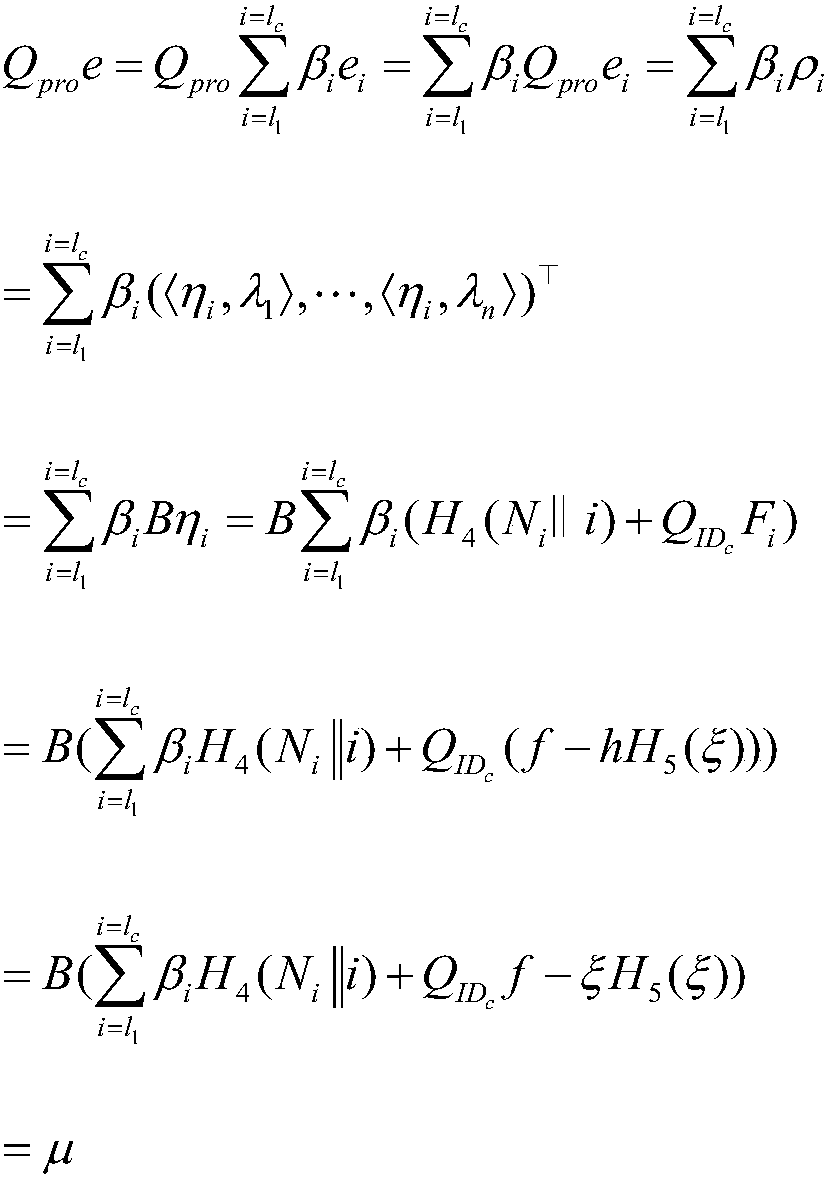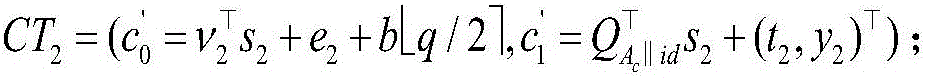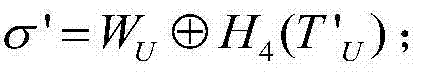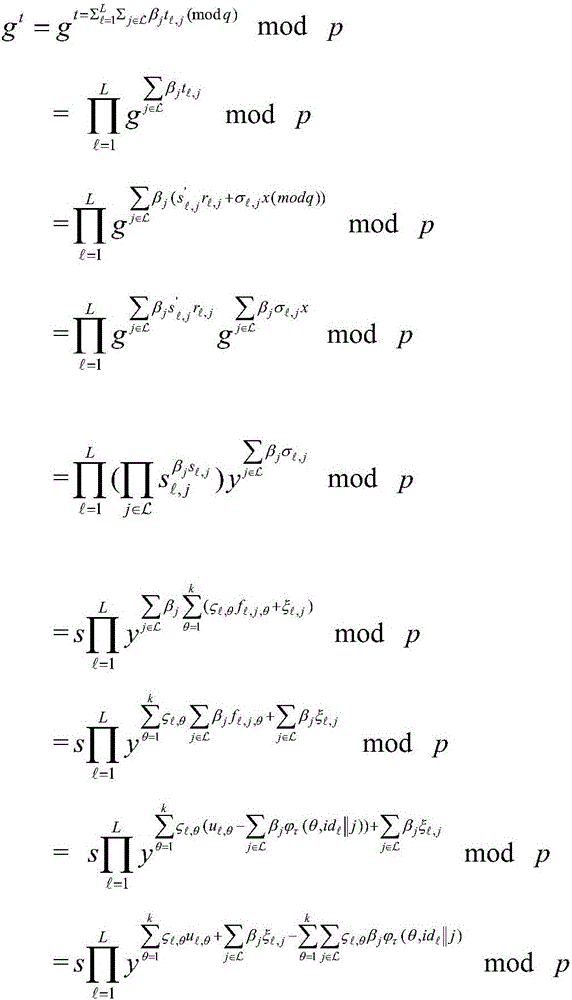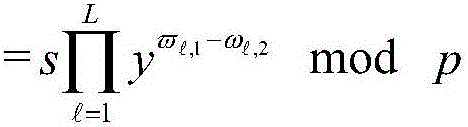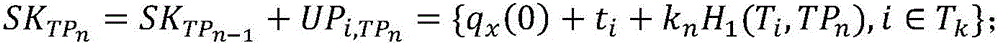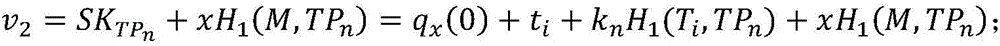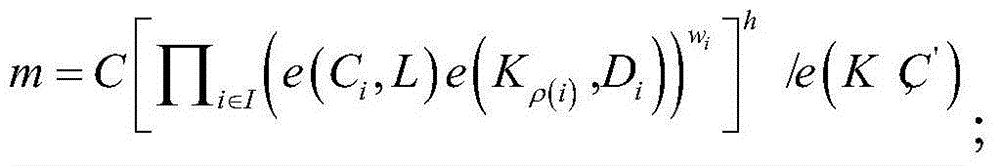Patents
Literature
220 results about "Bilinear pairing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The bilinear pairing is a bilinear, non-degenerate map between G_1 and G_2 to an element in G_T. The users can build complex pairing-based software by the Pairing library without much.
Strong privacy protection dual authentication method based on node identities and reputations in Internet of vehicles
The invention discloses a strong privacy protection dual authentication method based on node identities and reputations in Internet of vehicles. A user registers with an authentication center to obtain unique secret information shared with the authentication center; the user stores vehicle node initialization parameter information into a TPM security storage area; when the user expects interaction between vehicle applications on vehicle nodes and a background application server, the user needs to input identity information and an authentication process of the vehicle nodes and a background is executed by TA; the authentication process is as follows: a temporary encryption key with the TA is established to carry out symmetrical encryption transmission on the information through a bilinear pairing principle, the TA carries out integrity and consistency detection on the received information, verifies legality of real and temporary identities of the vehicle nodes and calls an ES to compute the node reputation, if the identities of the vehicle nodes are legal finally and the reputations exceed a threshold, the authentication of communication between the vehicle nodes and the background is completed. According to the method, the authentication security is enhanced, the identity privacy and the trajectory privacy of the user are protected, the authentication efficiency is improved and the authentication time delay is reduced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Achievement method of certificate-less public key cryptosystem without bilinear pairing operation
ActiveCN104539423AEfficient managementImprove computing efficiencyPublic key for secure communicationUser identity/authority verificationCommunications securityInformation security
The invention provides an achievement method of a certificate-less public key cryptosystem without bilinear pairing operation and belongs to the field of information safety. The achievement method is used for solving the problems of generation of a secret key of a user, usage and authentication of a public key of the user. According to the achievement method, firstly, a user sets a secret value and calculates a temporary public key, then a secret key generating center generates the other part of the secret key for the user and enables the two parts to be bound, and finally the user synthesizes a his / her actual public and secret key pair. The defect that public key replacement and signature counterfeit possibly exist in a common certificate-less cryptosystem is overcome, the user has complete control right on the secret key, the secret key can be revoked and re-generated, and the signature of the user has non-repudiation. The achievement method adopts a public key cryptographic algorithm of a standard elliptic curve, does not adopt the bilinear pairing operation, is few in occupied resources and high in safety and can operate without the secret key generating center when being applied to signature, authentication and secret key negotiation. By means of the achievement method, identity authentication, communication security and non-repudiation application demands of large-scale systems and low-power-consumption devices can be met.
Owner:北京百旺信安科技有限公司 +1
Method for keyword searchable encryption based on bilinear pairs in cloud storage
ActiveCN104021157AEnsure safetyImprove efficiencyDigital data protectionTransmissionCiphertextMulti user environment
The invention discloses a method for keyword searchable encryption based on bilinear pairs in cloud storage. The method includes the steps that firstly, system parameters are initialized; users are added; thirdly, encryption and security indexes for files are generated; fourthly, search tokens, relative to keywords, of the users are generated; fifthly, a cloud storage server is searched for keywords relative to ciphertexts; sixthly, the ciphertexts are decrypted by the users; seventhly, the users are logged out. According to the method, the authorized users can look for the encrypted files through a trap door connected with the keywords. The keywords used by the users for search cannot be known even by the cloud storage server, so that security of user information can be guaranteed; Compared with an existing scheme, the comprehensive efficiency of the aspects of communication and calculation cost, namely the aspects of the search speed of the size of the trap door, the encryption and search speed of the keywords, of the provided scheme is improved, and the method is suitable for multi-user environments.
Owner:广州爱范儿科技股份有限公司
Authentication group key management method based on identity
InactiveCN101431414AAvoid hostingSolve tough problemsKey distribution for secure communicationUser identity/authority verificationGroup sessionKey escrow
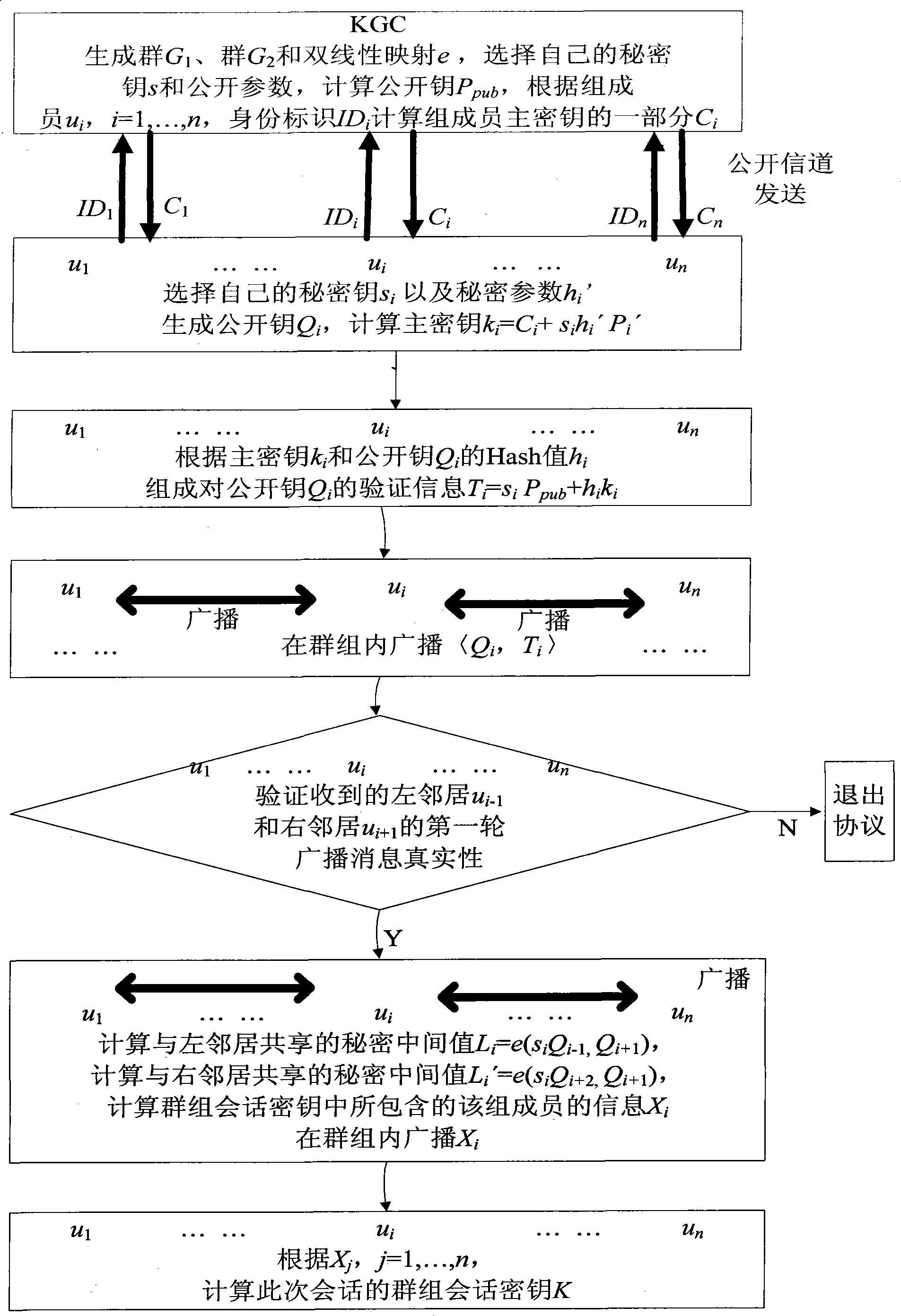
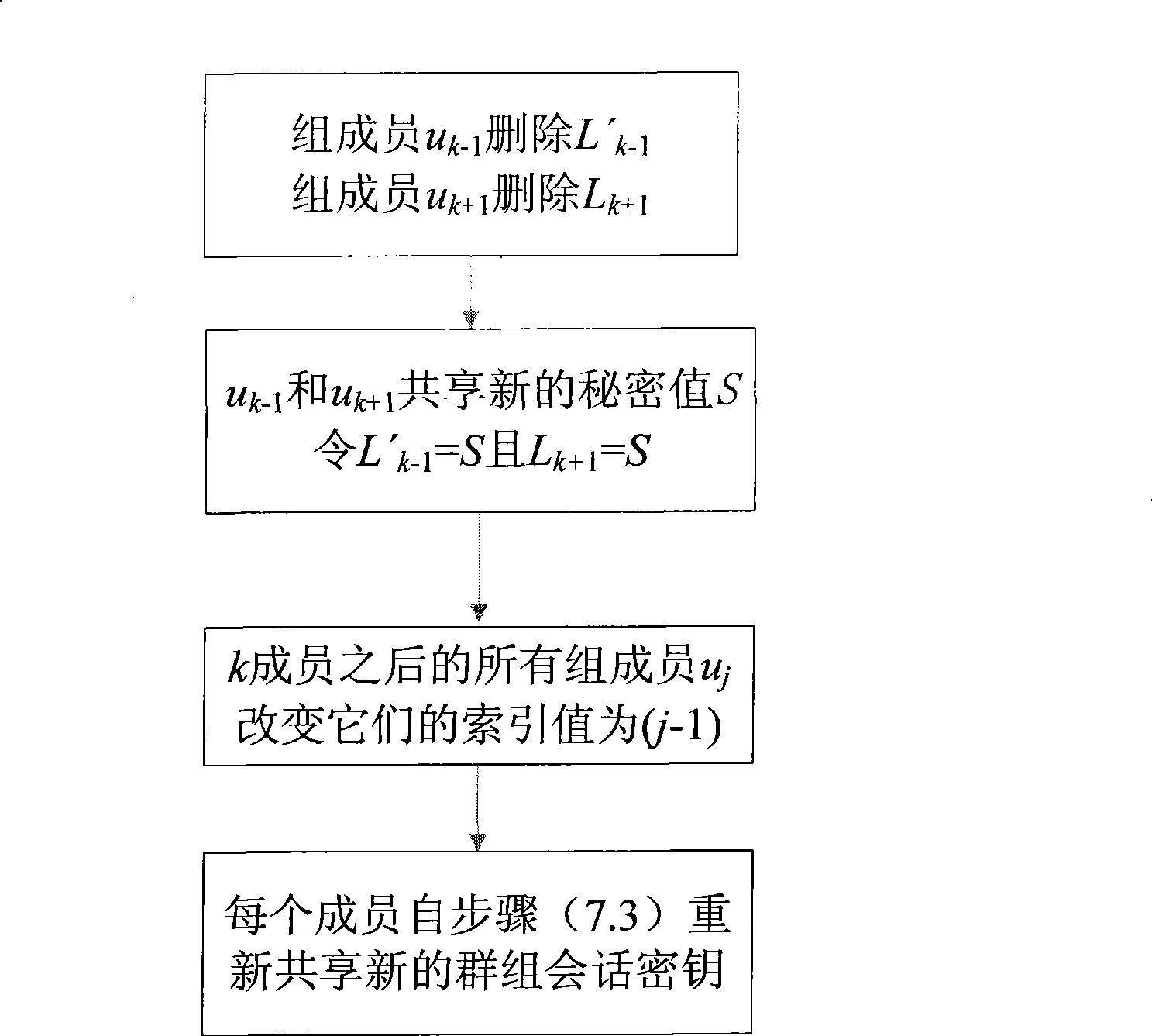
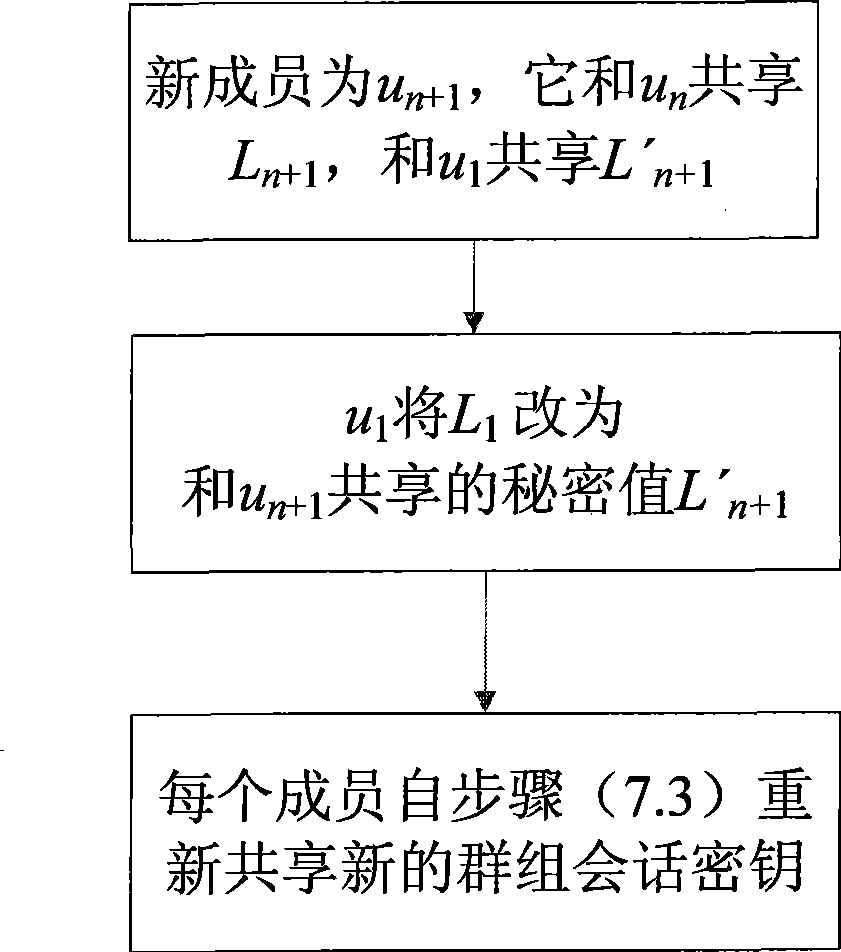
The present invention discloses a identity-based authentication group key management method which comprises the following steps: embedding ID into key with bilinear pairing in elliptic curve; generating Ci as part of main key ui according to the secret key and ID of group member ui by key generating center, and transmitting the Ci to ui through overt channel; generating main key according to Ci and its own secret key by each group member ui; calculating overt key verification information according to Hash value of main key and over key by each group member, and broadcasting the link between over key and verification information inside the group; calculating the secret value sharing with left and right neighbors when the received information is verified to be true by each group member, and calculating the group member information Xi included in group session key according to the secret value, and then broadcasting the Xi inside the group; calculating group session key K according to all Xj, j=1, ...,n, by each group member. The invention has the advantages of no key escrow and no need of secure channel, which can be applied in coordination and distributed network as secure reliable group communication.
Owner:XIDIAN UNIV
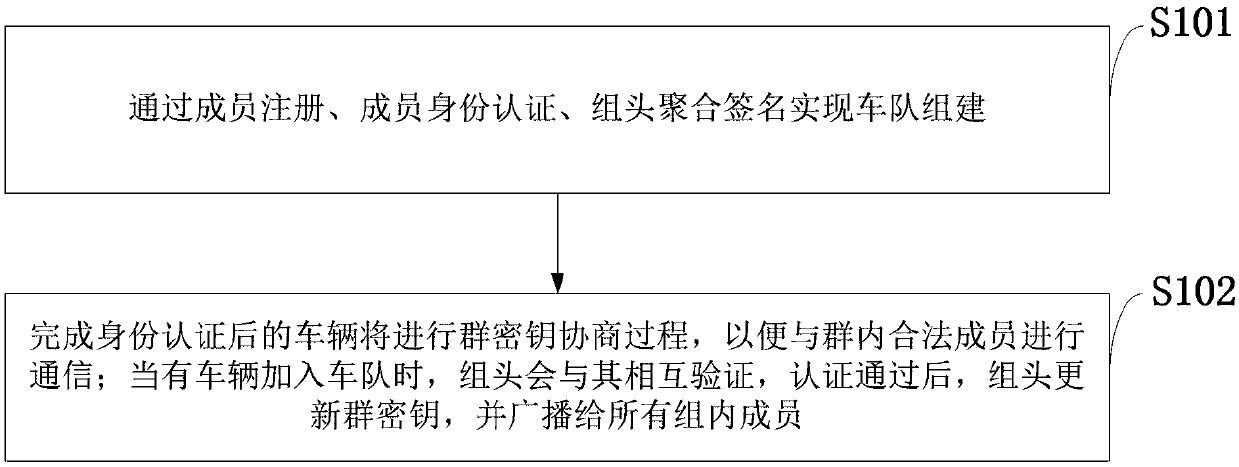
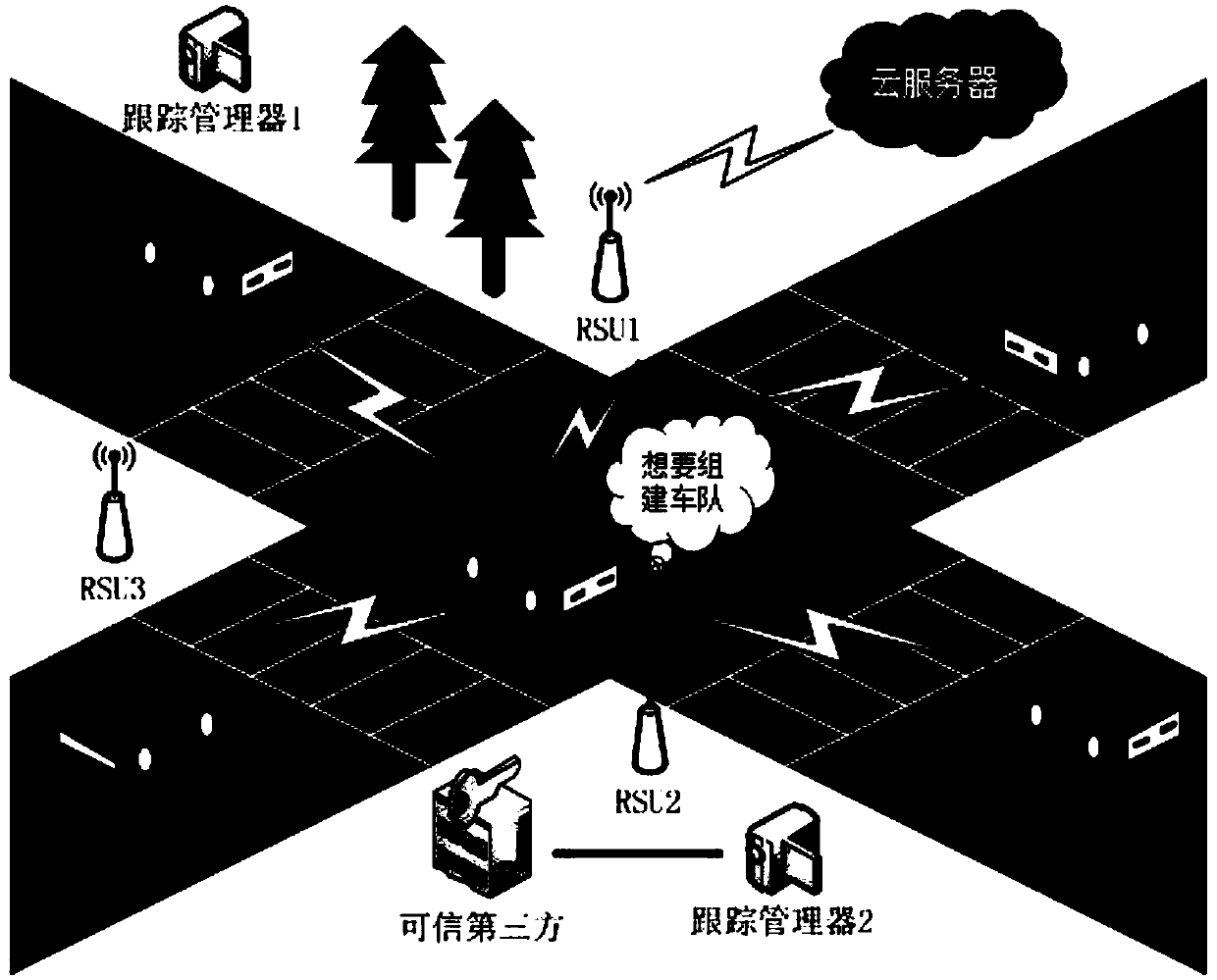
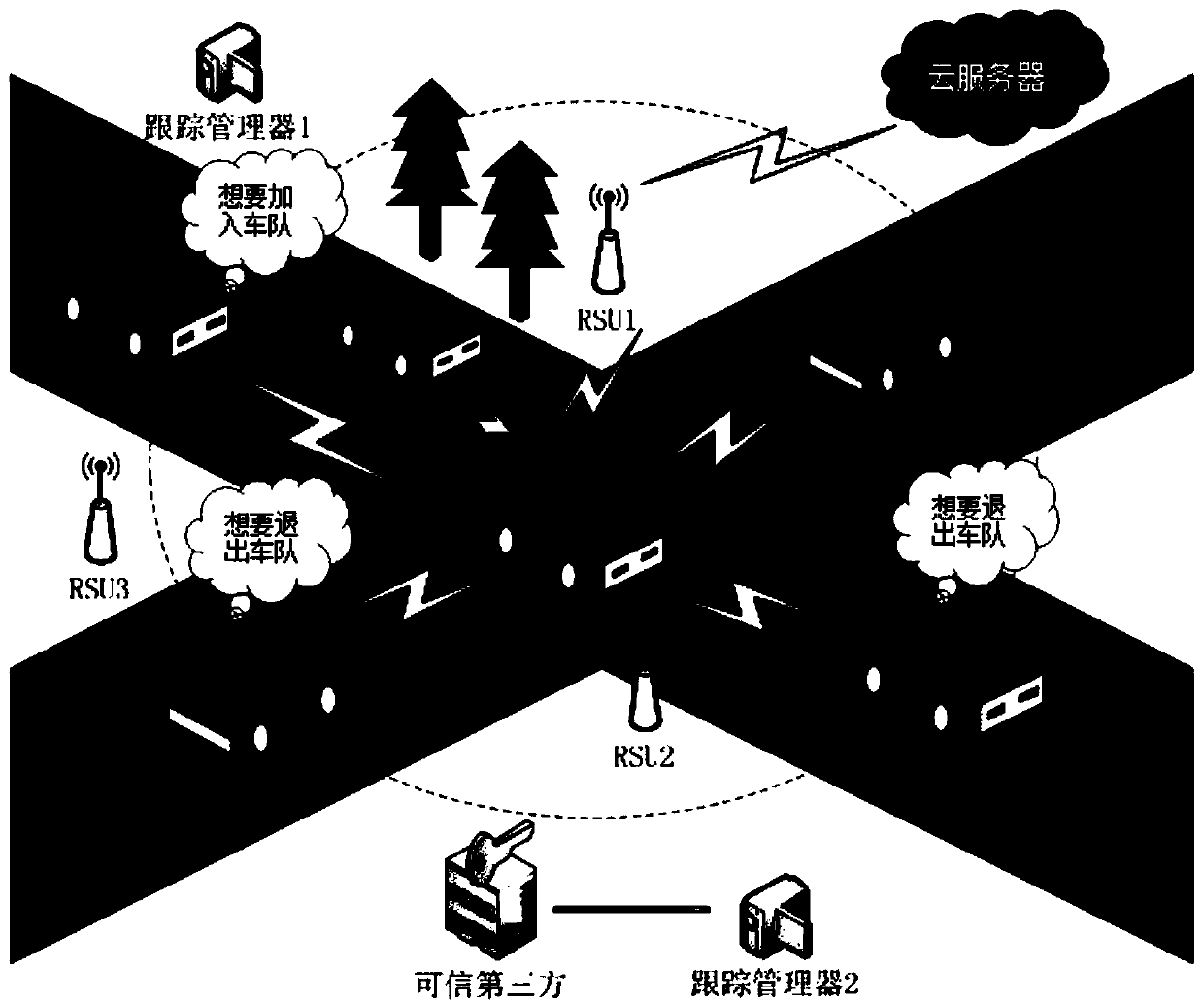
Motorcade establishment and management method and system based on block chain and PKI authentication mechanism
ActiveCN109687976ASolve authentication problemsTroubleshoot account management issuesKey distribution for secure communicationParticular environment based servicesSecure communicationThe Internet
The invention belongs to the technical field of safety communication between motorcades in Internet of Vehicles, and discloses a motorcade establishment and management method and system based on a block chain and a PKI authentication mechanism. The method is mainly divided into two parts of motorcade establishment and group key agreement and update; the motorcade establishment part comprises the following main processes of member registration, member identity authentication and group head aggregate signature; and the group key agreement and update part comprises the following main processes ofgroup key agreement and group key update for dynamic joining and exiting of a vehicle. According to the method and the system, the block chain is combined with the PKI authentication mechanism, a problem of identity authentication of the vehicle, a server and an RSU in the Internet of Vehicles is solved; the motorcade establishment is completed based on an elliptic curve, a bilinear pairing technology and an aggregate signature; and the group key agreement and update can be realized based on a DDH difficulty problem, the forward and backward safety is achieved, and the safety of member communication in the motorcade is ensured.
Owner:XIAN UNIV OF POSTS & TELECOMM
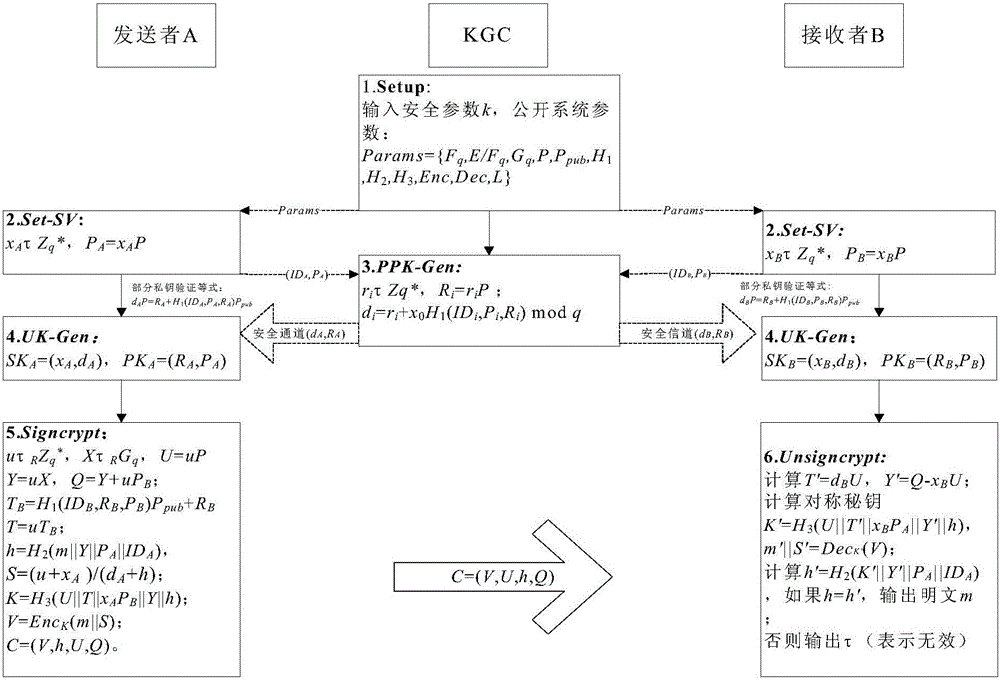
Secure certificateless hybrid signcryption method without pairing
InactiveCN105024994AResistant to Substitution AttacksImprove security levelPublic key for secure communicationPlaintextSigncryption
The invention discloses a secure certificateless hybrid signcryption method without pairing. The method is used for solving a technical problem of low efficiency of a conventional certificateless hybrid signcryption method. The method is characterized by a KGC is restricted by a user part public key in a stage of generating a part secret key by prescribing a fixed secret key generation sequence of a user so as to bind the user part public key when a signcryption user performs signcryption on a plaintext and guarantee enough resistance to public key replacing attack; before a user complete private key is generated, using a part private key bound with user identity information and a part public key to verify an equality in order that the user timely detects an invalid behavior of the active dishonest KGC, resists to malicious KGC attack, improves a system security level, and eliminates unnecessary computation consumption; in a unsigncryption stage, substituting scalar multiply operation on a elliptical curve to for expensive time-consuming bilinear pairings to complete message signcryption and unsigncryption processes, thereby improving computation efficiency.
Owner:东莞市三航军民融合创新研究院
Identity-based unmanned aerial vehicle key management and networking authentication system and method
ActiveCN109218018AImprovements to computing inequalityImprove reliabilityKey distribution for secure communicationPublic key for secure communicationAuthentication serverAuthentication system
The invention belongs to the technical field of a device for verifying the identity or credentials of a system user, and discloses an identity-based unmanned aerial vehicle key management and networking authentication system and a method thereof. The ground authentication server is responsible for generating and distributing system parameters, identity information and keys required by the unmannedaerial vehicle for key management and network authentication. UAV authentication client is the main body of the system; Through mutual cooperation, the key pairs of UAV for network authentication canbe generated in a distributed manner, and the identity authentication and key agreement between UAV can be realized by using the key pairs. The invention improves the problem of unequal calculation of nodes in the key management of the UAV network existing in the prior art, enhances the reliability of the system, and realizes the key management of the UAV self-organization. The two-way authentication between UAV nodes ensures the credibility and authenticity of both sides of the communication. Using identity public key and bilinear pairing implementation, the computational overhead is less and the implementation efficiency is improved.
Owner:XIDIAN UNIV +1
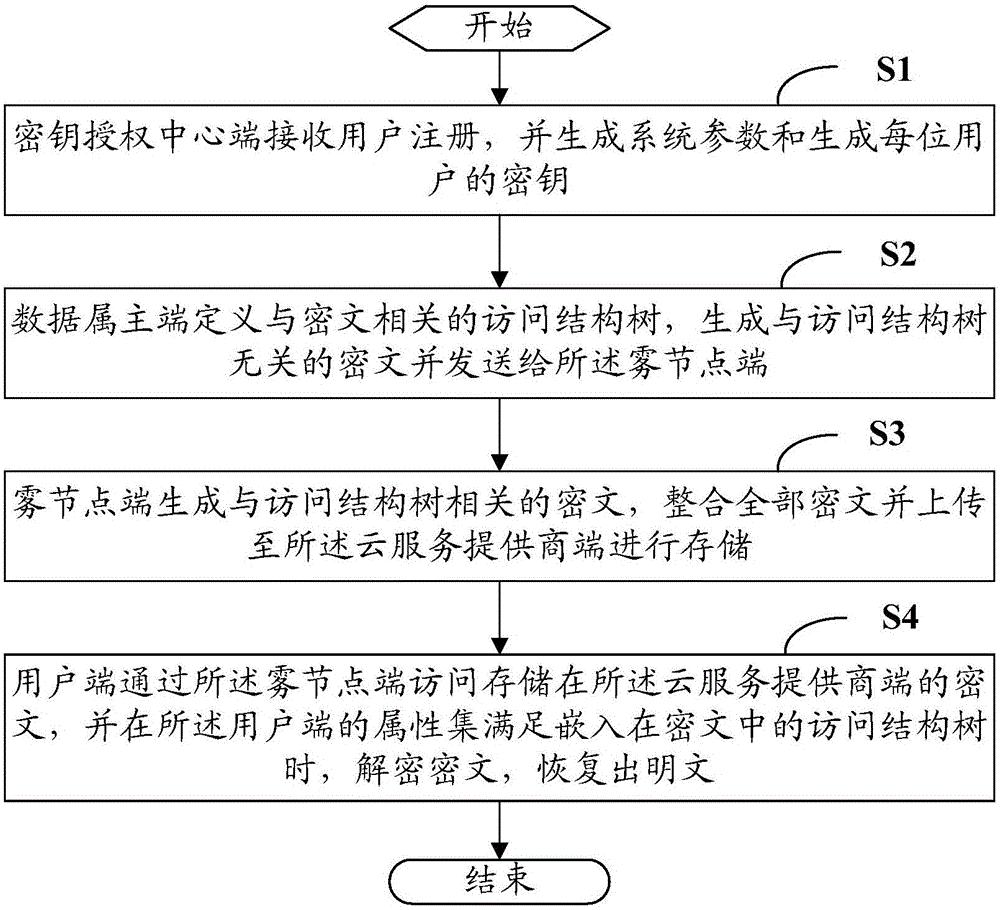
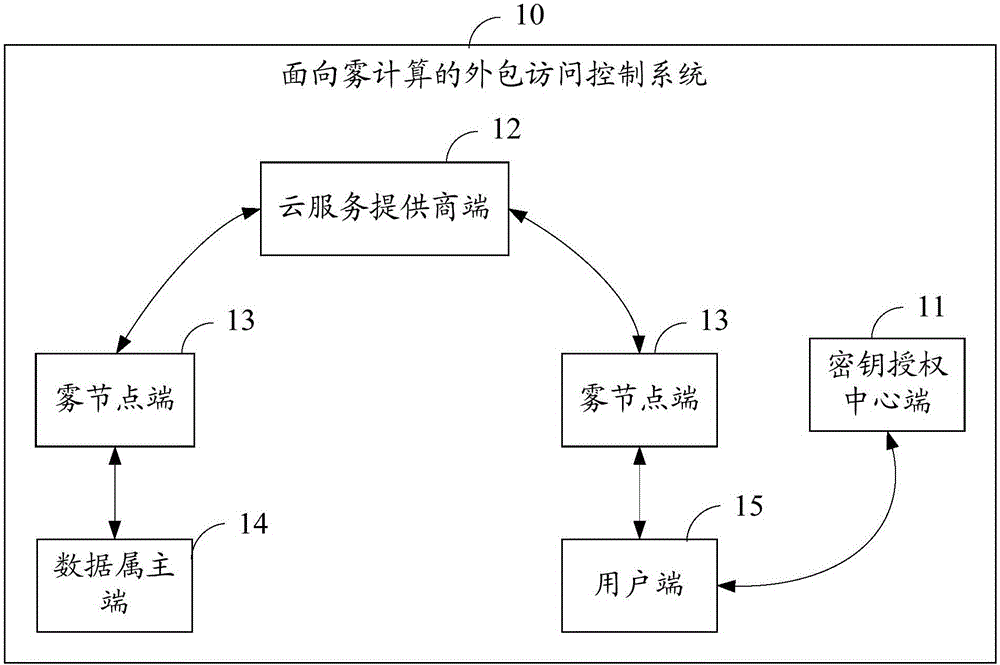
Outsourcing access control method and system aiming at fog computing
ActiveCN106357395AReduce computational overheadLighten the computational burdenKey distribution for secure communicationCiphertextFog computing
The invention belongs to the technical field of cloud storage services and provides an outsourcing access control method and system aiming at fog computing. The method includes: a key authorizing central terminal receives user registration and generates system parameters and a key for each user; a data owner terminal defines an access structural tree related to cipher text, generate cipher text unrelated to the access structural tree and transmits the generated cipher text to a fog node terminal; the fog node terminal generates cipher text related to the access structural tree, integrates all cipher text, and uploads the integrated cipher text to a cloud service provider terminal for storage; a user terminal accesses the cipher text stored at the cloud service provider terminal through the fog node terminal, the cipher text is decrypted to display plain text when the attribute set of the user terminal satisfies the access structural tree embedded into the cipher text. By the method, the computing burden of the data owner terminal can be lowered greatly, a user only needs to execute one bilinear-pair operation and two multiplication so as to successfully decrypt the cipher text, and the computing burden of the user is lowered greatly.
Owner:SHENZHEN UNIV
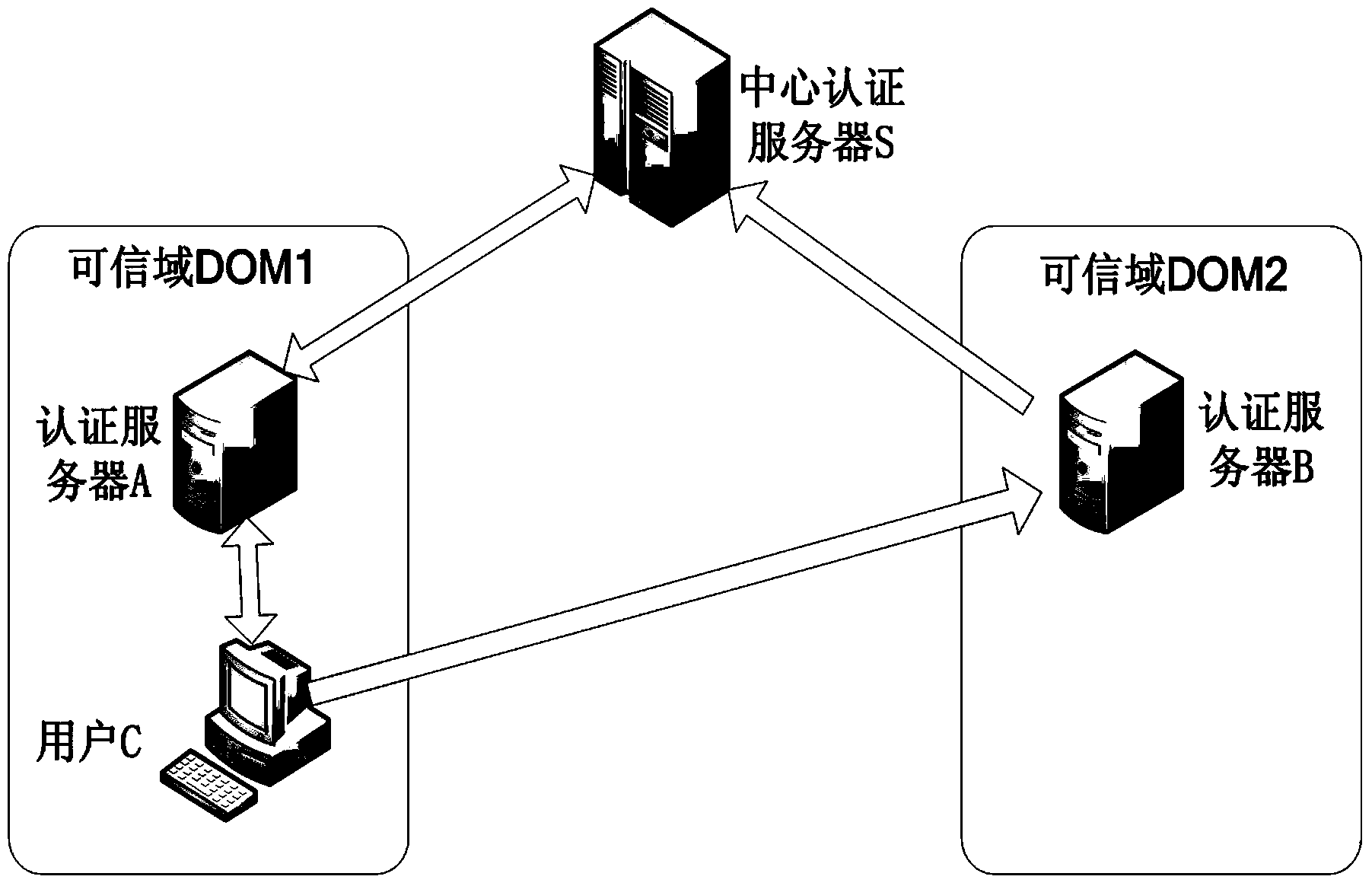
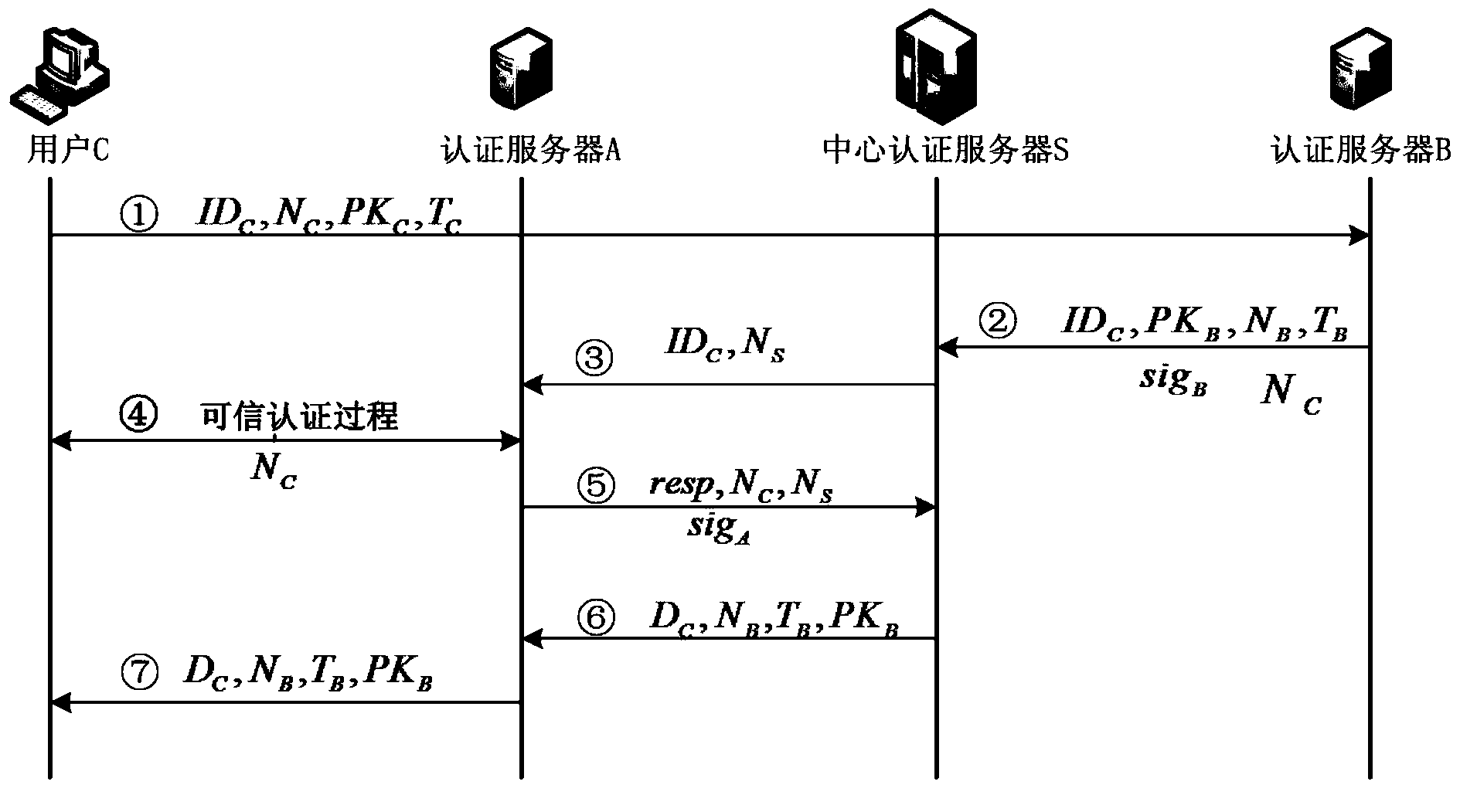
Method for certificateless cross-domain authentication in credible could computing environment
ActiveCN103546567AAddress certificate maintenance overheadReduce overheadKey distribution for secure communicationHypothesisAuthentication server
The invention relates to a method for certificateless cross-domain authentication in a credible cloud computing environment and belongs to the technical field of cloud computing safety. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, the certificateless public key cryptography technology is introduced into cross-domain authentication, credible cross-domain authentication is achieved in the process of credible cloud computing, a certificateless public key cryptosystem is applied, the problem of the certificate maintenance expense of a traditional digital certificate authentication system and the problem of private key trusteeship of a public key cryptography system based on the identity are solved. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, a user public key is generated based on the identity, a part of a private key of a user is generated by the user, and the other part of the private key of the user is generated by a center authentication server. According to the method for certificateless cross-domain authentication in the credible cloud computing environment, a certificate system is abandoned, the expense of the authentication system is reduced, the private key of the user is protected at the same time, bilinear pairing computation is applied to the certificateless public key cryptosystem, it is proved that a safety hypothesis based on bilinear pairing computation is high in safety, the certificateless public key cryptosystem is used for identity authentication and session key negotiation, and therefore it is ensured that the system is high in safety.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND +1
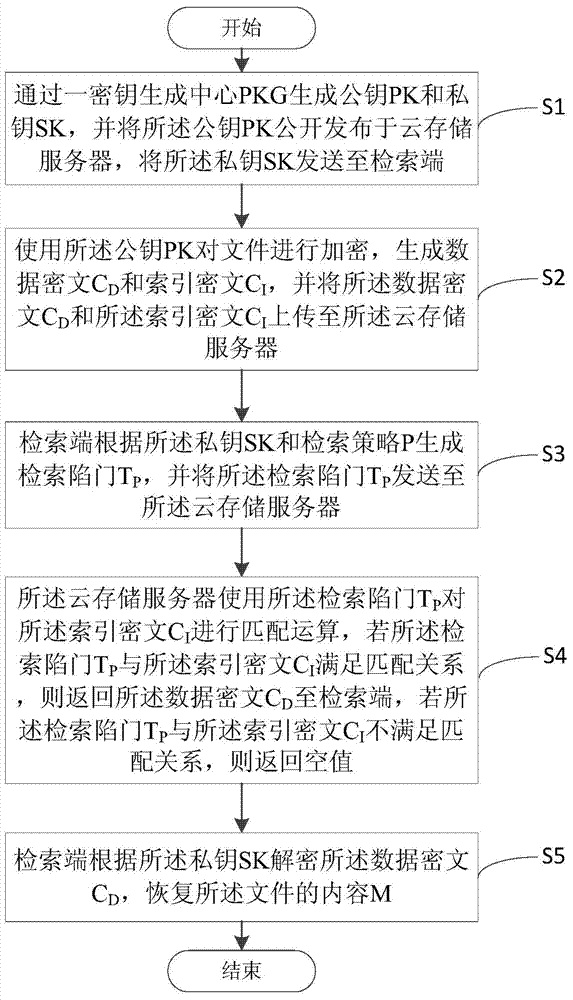
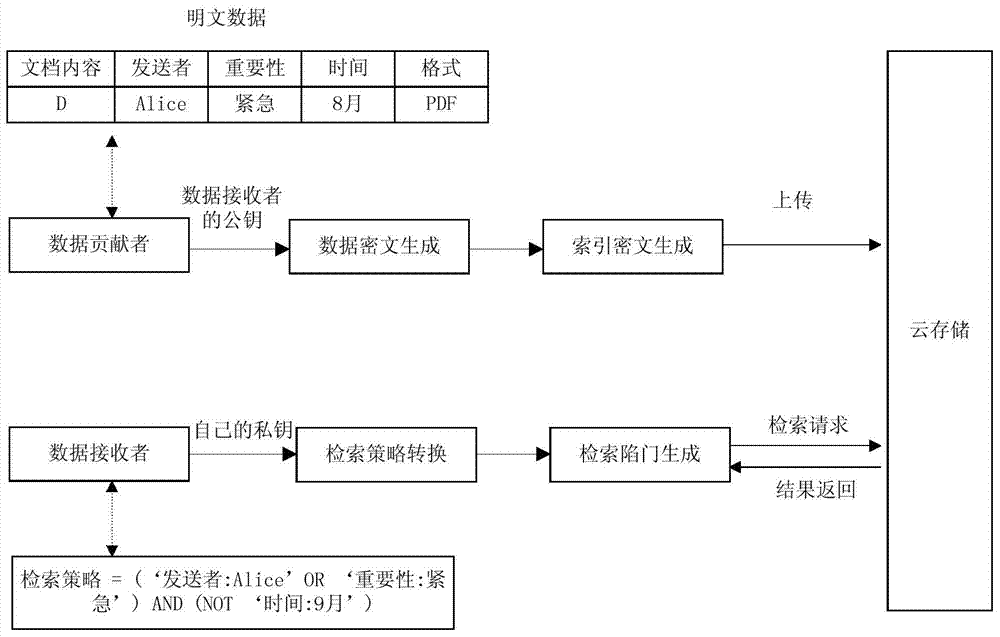
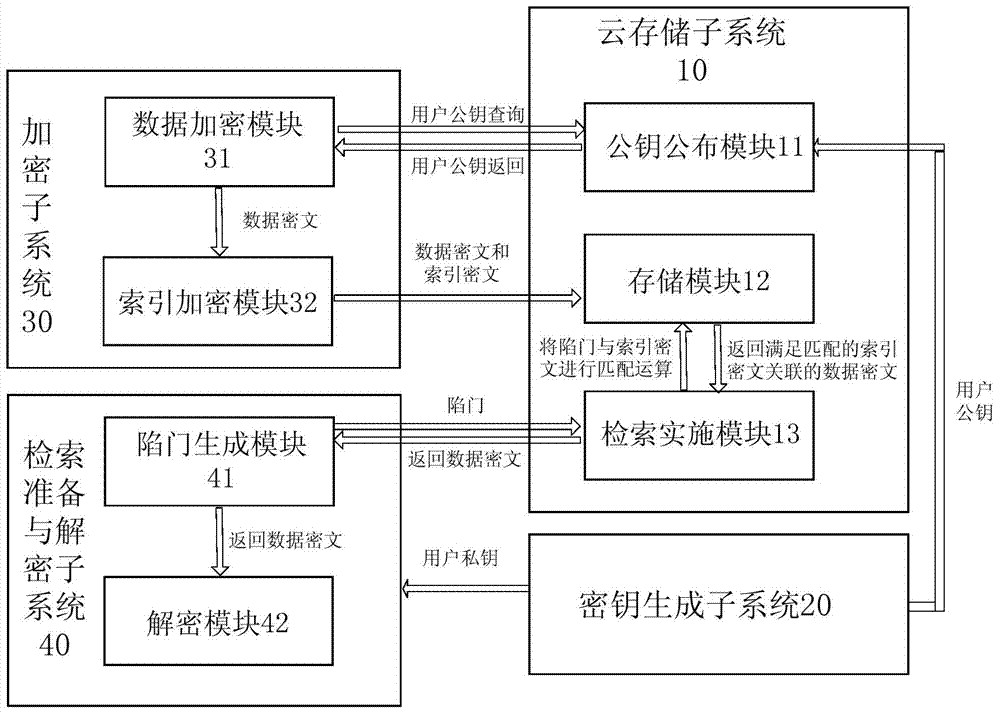
Cloud storage ciphertext retrieval method and system
ActiveCN103944711AAccurately obtainedReduce transmission costKey distribution for secure communicationSpecial data processing applicationsComposite numberCiphertext
The invention discloses a cloud storage ciphertext retrieval method and system. The method includes the following steps: (1) a step of generating a public key and a private key at a retrieval end; (2) an encryption step; (3) a step of generating a retrieval trap door; (4) a retrieval implementation step; (5) a decryption step. Through implementation of the cloud storage ciphertext retrieval method and system, the cloud storage ciphertext retrieval supports a retrieval strategy of nest of logic words such as AND, OR and NOT and the like and users are helped to accurately obtain needed data and thus the transmission cost is reduced and the method and system have the advantages of being simple in process and high in calculation efficiency. At the same time, the cloud storage ciphertext retrieval method and system adopt composite number order group and bilinear pairing for construction and thus known plaintext distribution regularity attacks and attacks targeted at access modes are effectively prevented and thus the security is comparatively high.
Owner:国家超级计算深圳中心 +1
Apparatus and method for generating and verifying ID-based blind signature by using bilinear parings
InactiveUS20050005125A1Multiple keys/algorithms usageUser identity/authority verificationTrusted authorityBlind signature
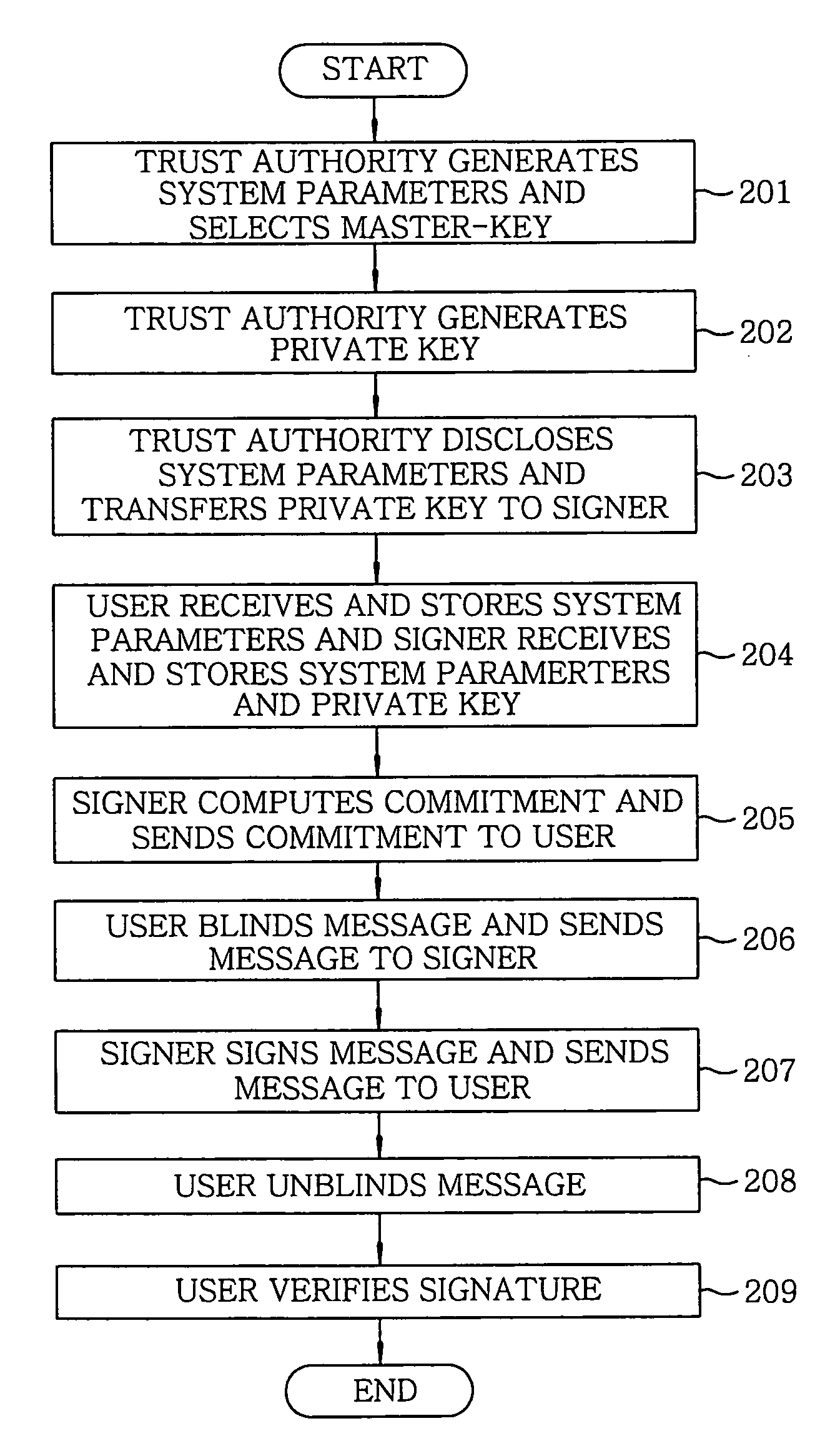
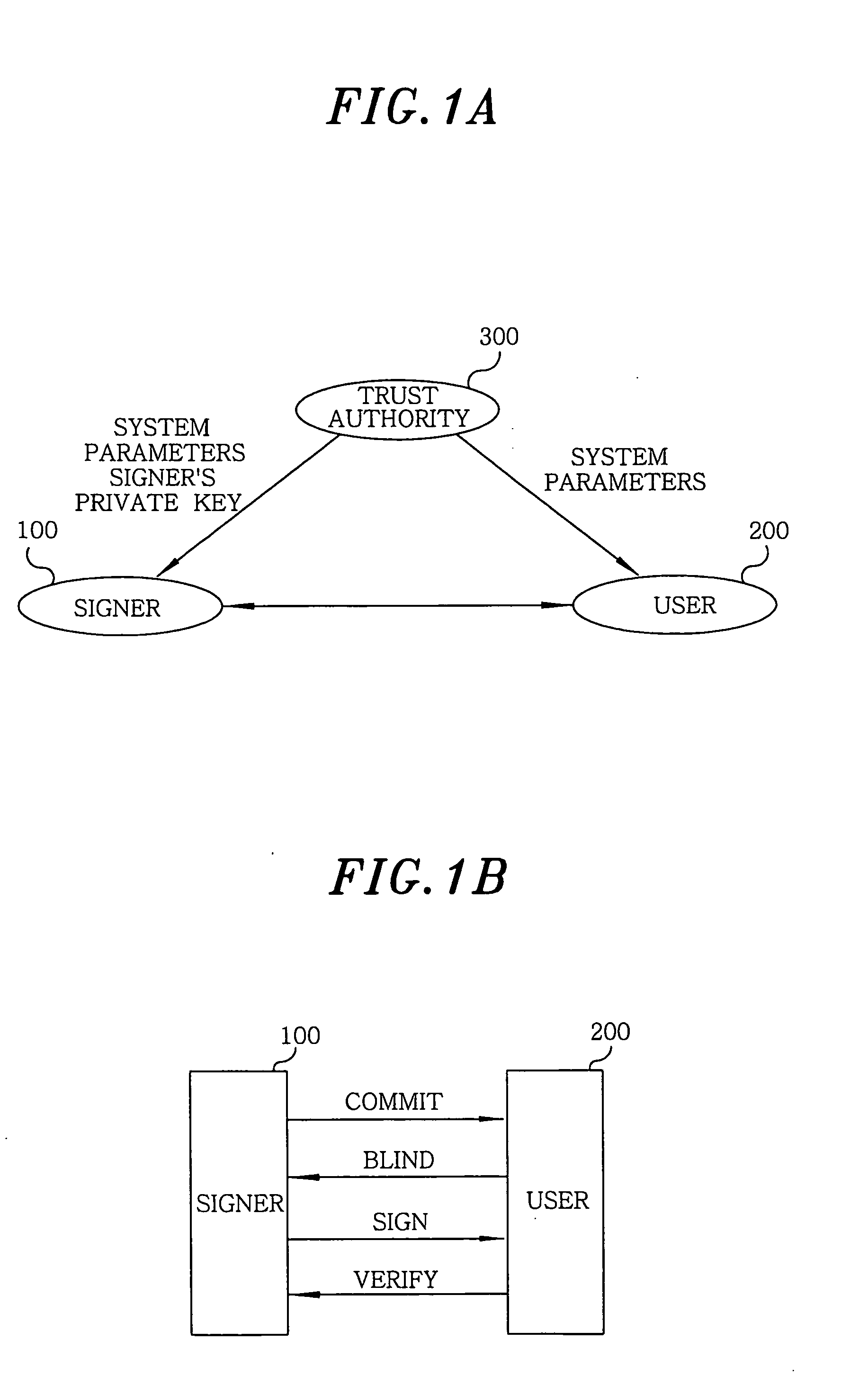
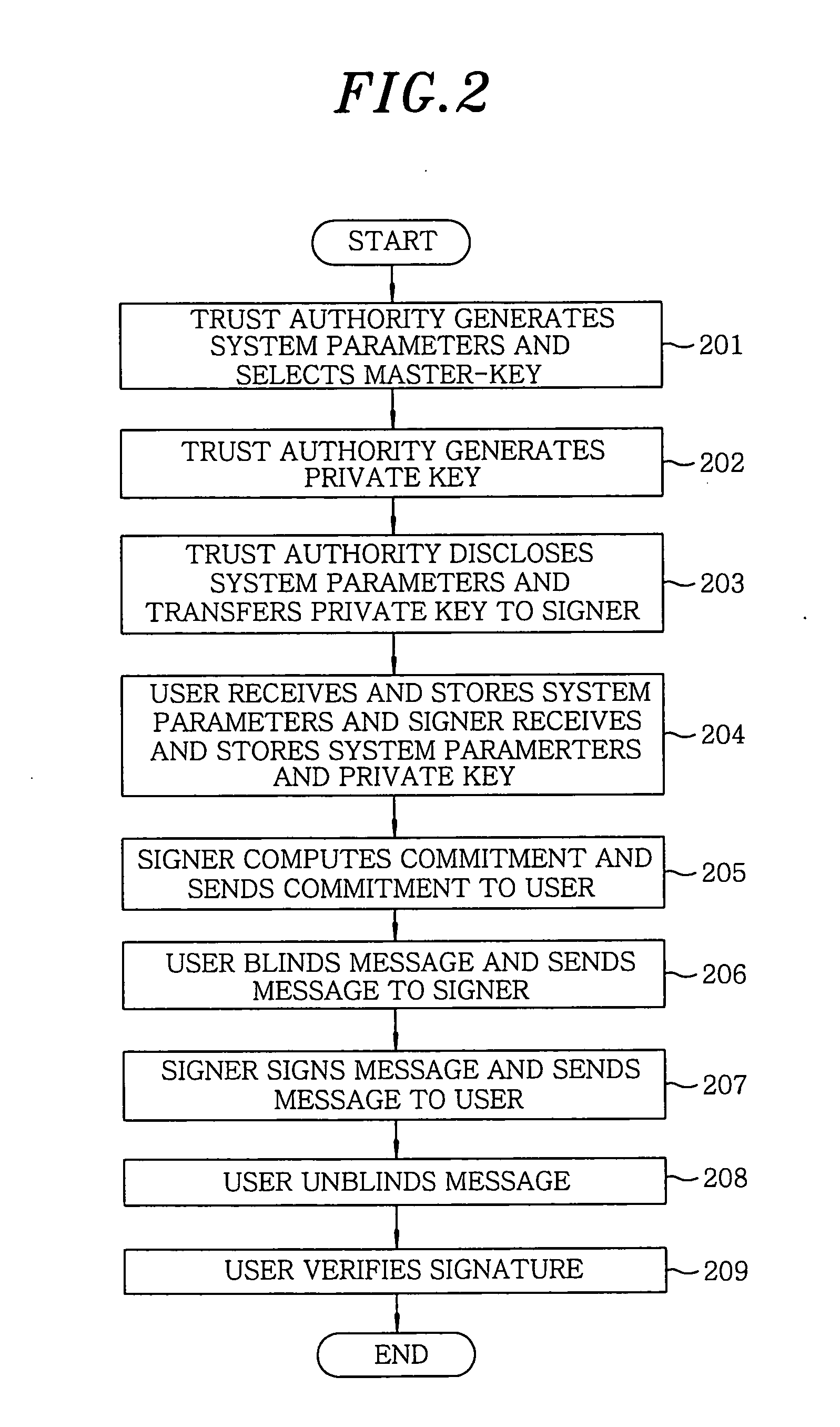
In an apparatus and a method for generating and verifying an identity based blind signature by using bilinear parings, a trust authority generates system parameters and selects a master key. Further, the trust authority generates a private key by using a signer's identity and the master key. The signer computes a commitment and sends the commitment to the user. The user blinds a message and sends the blinded message to the signer. The signer signs the blinded message and sends the signed message to the user. Thereafter, the user unblinds the signed message and then verifies the signature.
Owner:INFORMATION & COMM UNIV EDUCATIONAL FOUND
Attribute-based hybrid encryption method capable of tracing leaked secret key
ActiveCN104168108AEnsure safetyAvoid destructionEncryption apparatus with shift registers/memoriesUser identity/authority verificationTrusted authorityHash function
Disclosed is an attribute-based hybrid encryption method capable of tracing a leaked secret key. The method comprises the following steps: a trusted authority: 1, inputting a coefficient lambda, and outputting a system parameter; 2, running a randomized number generation algorithm; 3, selecting one anti-bump Hash function, and calculating a Hash value; 4, running a fingerprint code generation algorithm GenFC; 5, calculating a bilinear pair exponentiation operation; 6, distributing a fingerprint code to a user, and specifying an attribute set S; 7, running the randomized number generation algorithm, multiplication and exponentiation operation; and 8, embedding the fingerprint code in a user private key; a data holder: 9, carrying out AES data encryption; 10, generating an access control matrix; 11, running an attribute-based hybrid encryption algorithm Encapsulate, and encrypting an AES session secret key; and 12, running a bilinear pair and multiplication and division operation to obtain a session secret key; a data user: 13, running an AES data decryption algorithm; and the trusted authority: 1*, searching for an adaptability code word; 2*, calculating pj and Z; and 3, calculating a weight sum, and outputting a set C.
Owner:BEIHANG UNIV
Bilinear pairing-based multi-user multi-keyword searchable encryption method in cloud storage
ActiveCN105024802AUndo implementationGuaranteed privacySpecial data processing applicationsSecuring communicationCiphertextTheoretical computer science
The invention discloses a bilinear pairing-based multi-user multi-keyword searchable encryption method in cloud storage. The specific steps include: 1. initialization of system parameters; 2. addition of users; 3. file encryption by a file owner and generation of a safe index; 4. index re-encryption by a server; 5. generation of a keyword search token by the users; 6. search of ciphertext keywords by a cloud storage server; 7. decryption of ciphertext by the users; and 8. cancellation of the users. The bilinear pairing-based multi-user multi-keyword searchable encryption method provided by the invention solves the problem existing in the prior art that keyword search cannot be realized after cloud storage data are encrypted.
Owner:WUHAN FIBERHOME INFORMATION INTEGRATION TECH CO LTD
Lattice-based cloud storage data safety auditing method supporting data proxy uploading
InactiveCN107124272AAvoid complex managementResist attackKey distribution for secure communicationUser identity/authority verificationCommunications securityOriginal data
The invention belongs to the technical field of information safety, and in particular relates to a lattice-based cloud storage data safety auditing method supporting data proxy uploading. The auditing method provided by the invention helps a data owner authorize a proxy signature generating data to a proxy signer and upload the proxy signature to a cloud server, and also helps a credible auditor to audit completeness of the cloud storage data. The auditing method provided by the invention achieves construction of a random mask code based on an original image sampling algorithm on the lattice, so that the credible auditor can be effectively prevented from recovering original data block information of an original signer from a data file. The credible auditor only needs to compute a linear combination with limited a computation amount instead of computing bilinear pairings with higher cost and modular exponentiation during a cloud storage data completeness verification process, so that the auditing method is very beneficial to the credible auditor in the aspect of computing efficiency. Meanwhile the method provided by the invention can effectively resist attacks of a quantum computer, and thus have very important application value in cloud computing environment of post-quantum communication security.
Owner:SOUTHWEST PETROLEUM UNIV
Method and device of two-side authentication secret key negotiation based on certificateless
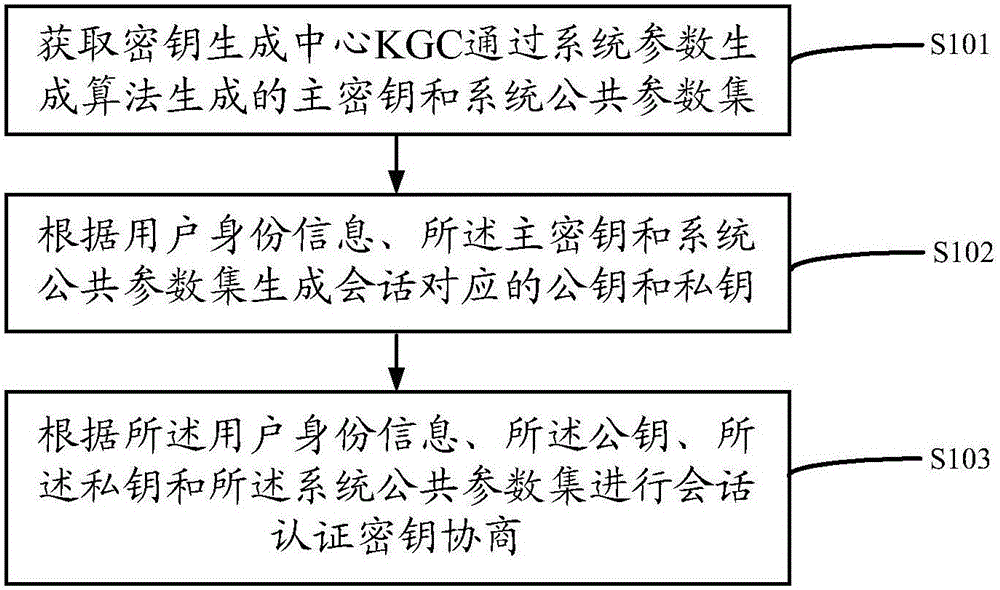
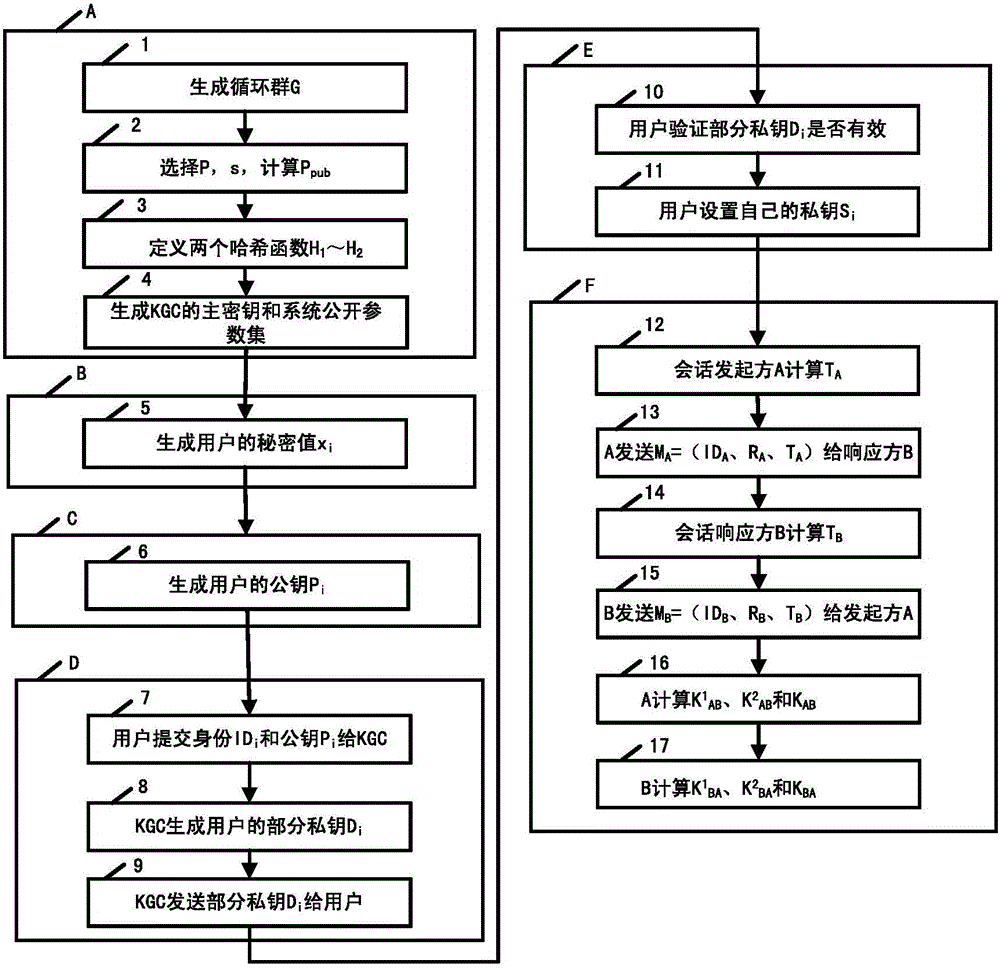
The present invention discloses a method and device of two-side authentication secret key negotiation based on certificateless. The device comprises a parameter module and a negotiation module, a system public parameter set and the master key, part of secret keys, the secret value, the private key and the public key of a key generation center (KGC) are generated, and the two-side secret key negotiation is performed so as to overcome the problem of complex certificate management in a traditional public key cryptosystem and the problem of inherent secret key trusteeship based on the identity of the cryptosystem, and the method and device of two-side authentication secret key negotiation based on certificateless do not depend on the bilinear pairing operation so as to improve the system efficiency and are specially suitable for a wireless mobile device with limited capability.
Owner:ZTE CORP
PEKS (public-key encryption with keyword search) method for lattice-based cloud stored cyphertext data under standard model
ActiveCN106789044AReaction securityResist attackKey distribution for secure communicationUser identity/authority verificationTechnical standardModular exponentiation
The invention belongs to the technical field of cyberspace security and particularly relates to a PEKS (public-key encryption with keyword search) method for lattice-based cloud stored cyphertext data under standard model. The method of the invention has no need for a random oracle so that the security of the designed PEKS method can more truly reflected; a designed cryptographic algorithm is based on assumption of LWE (learning with errors) hard problems, quantum computer attacks can be resisted effectively. The method of the invention has a need for specifying a unique cloud server to perform testing and return corresponding search results, so that no malicious servers are able to execute search test operation, and malicious server attacks are partly avoided accordingly. In addition, the algorithm can ensure that cyphertext is undistinguishable. Furthermore, in keyword cyphertext generation phase, the method of the invention needs no computing of high-overhead modular exponentiation and bilinear pairing operation, but the computing of finite linear algebraic operation, and accordingly is highly worthy of practical application in post-quantum communication environments.
Owner:SOUTHWEST PETROLEUM UNIV
Certificateless security signature method based on SM2 algorithm
ActiveCN107248909AThe signing process is simpleImprove computing efficiencyKey distribution for secure communicationPublic key for secure communicationDigital signatureCryptosystem
A certificateless security signature method based on an SM2 algorithm belongs to the application field of public key cryptography. The method is used to solve the problem on how to generate private keys of N (N>=2) users in a certificateless public key cryptography system without bilinear pairing operation on an elliptic curve and complete SM2 signature of one message through the N users. In the invention, each user cannot acquire the private key information of other users, a user subset containing less than N users cannot generate a complete digital signature, and the security of signature is fully ensured. Attackers cannot forge a valid signature without stealing all the N private keys. The security signature process is simple. The computation efficiency is high. The signature result accords with the standard of the national cipher SM2 signature algorithm.
Owner:北京百旺信安科技有限公司 +1
Multi-receiver hybrid signcryption algorithm without bilinear pairings
ActiveCN104734857APrevent forgeryDefend against forgery attacksKey distribution for secure communicationUser identity/authority verificationSigncryptionTwo-way communication
The invention discloses a multi-receiver hybrid signcryption algorithm without bilinear pairings. The multi-receiver hybrid signcryption algorithm includes the five processes of secret key generation center initialization, extraction of a part of private keys, secret key extraction, signcryption and unsigncryption. Two-way communication signcryption of multiple receivers is achieved, the signcryption algorithm in the scheme is achieved without the bilinear pairings, calculation expenses are greatly reduced, and universality is better; compared with traditional schemes, counterfeit attacks of a positive and dishonest secret key generation center can be defended, and safety is higher.
Owner:NANJING UNIV OF POSTS & TELECOMM
Cloud storage medical data batch self-auditing method based on wireless body area network
InactiveCN106789082AUser identity/authority verificationCommunication with homomorphic encryptionCloud userBody area network
The invention belongs to the technical field of information security, and particularly relates to a cloud storage medical data batch self-auditing method based on a wireless body area network. The security of a cryptographic algorithm designed by the method is based on discrete logarithm problems, and thus it is guaranteed that a malicious cloud server cannot produce a piece of forged auditing proof response information which cheats a cloud user and makes the user pass an auditing verification process. In the cloud storage medical data batch self-auditing method based on the wireless body area network, the cloud user makes use of a linear homomorphic aggregation signature algorithm to construct a homomorphic linear identifier, and can conduct batch auditing on the completeness of multiple medical data files simultaneously, and in the auditing process, the bilinear pairing operation with large expenses does not need to be conducted, and the cloud storage medical data batch self-auditing method is particularly applicable to an application scenario in which the lightweight class calculated amount is needed, the memory space is limited and the wireless body area network needs to be efficiently achieved.
Owner:SOUTHWEST PETROLEUM UNIV
Method and device for negotiating group cipher
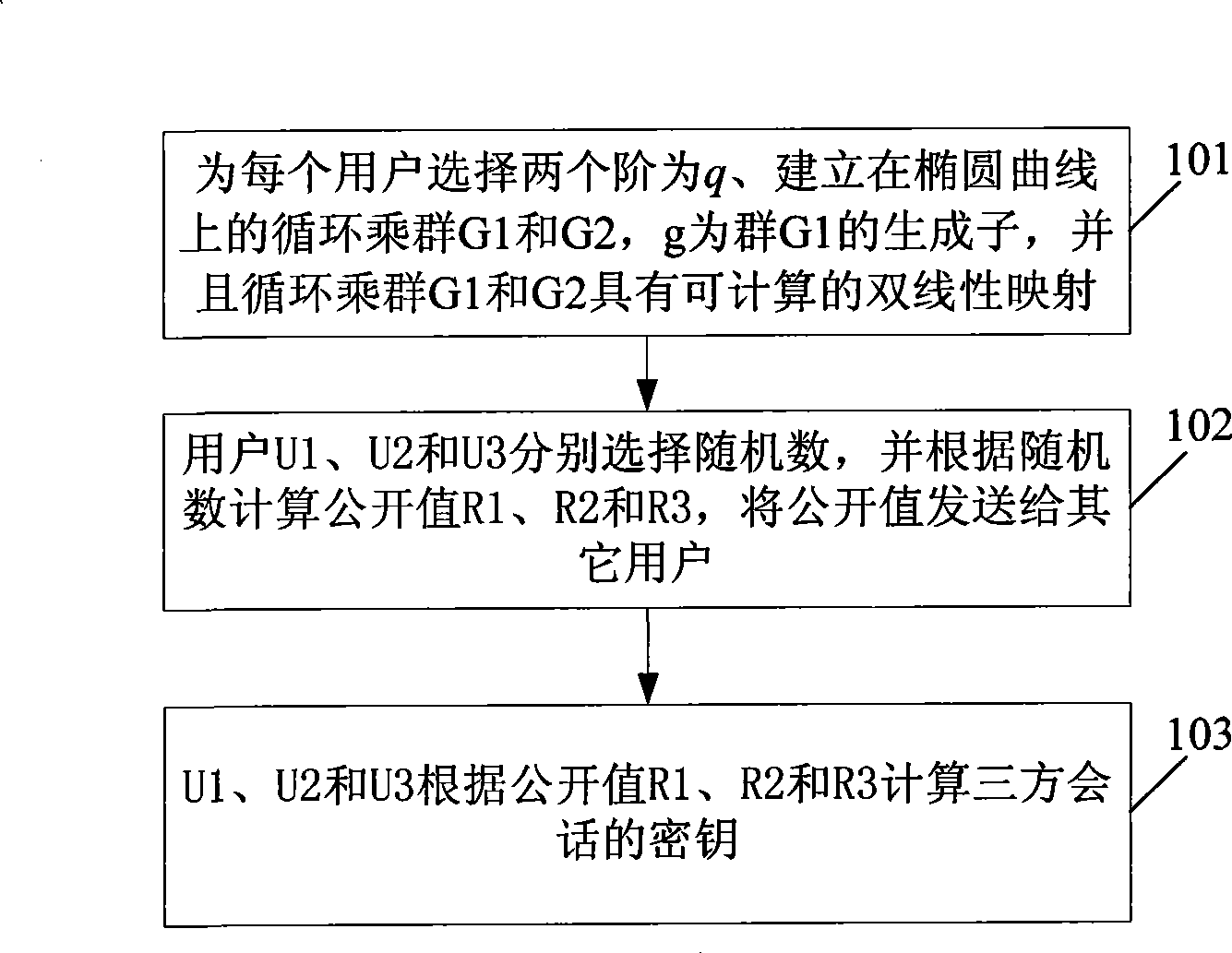
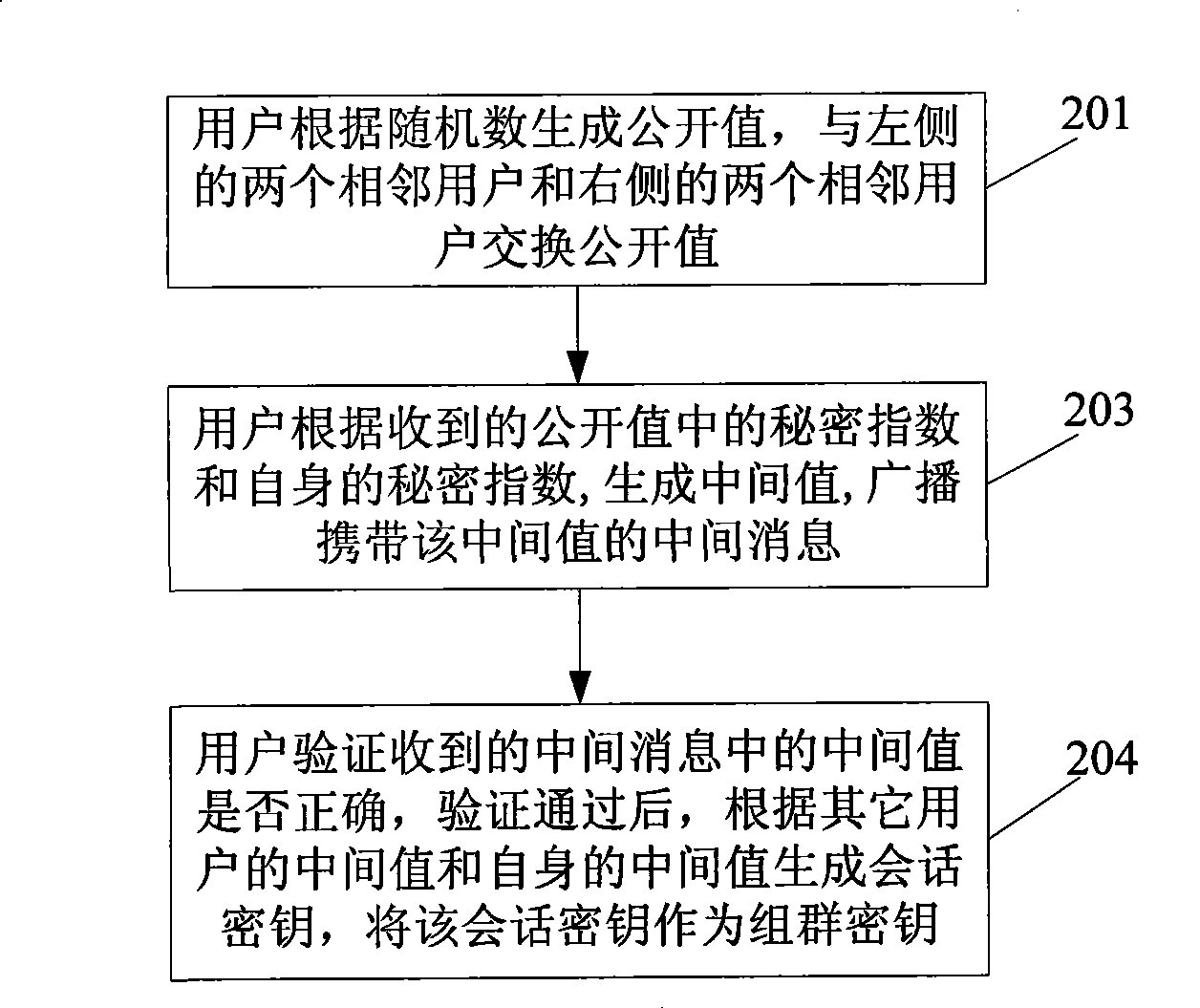
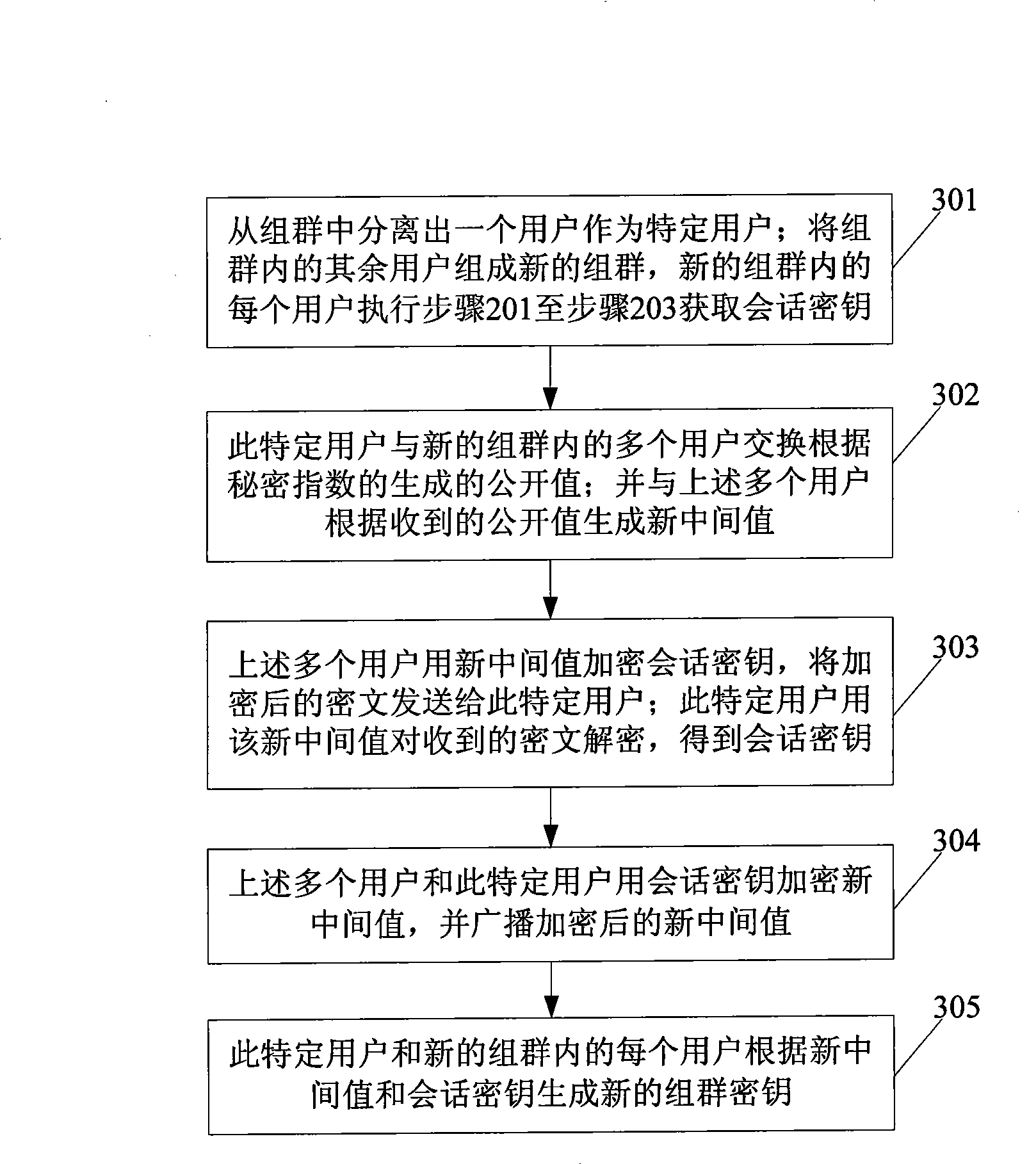
InactiveCN101399660AReduce trafficImprove real-time performanceData switching by path configurationSecuring communicationKey generationBilinear pairing
The invention discloses a method for negotiating group keys and equipment thereof, which belongs to the communication field. In the method, each subscriber in the group generates the same group keys by information interaction with other subscribers based on bilinear pairings mapping of elliptical curve by the method of selecting negotiating group keys according to the parity of total number of subscribers in the group. The equipment can be three types, wherein, one equipment comprises an information interaction module, an intermediate value generating module and a group key generating module; another equipment comprises an information interaction module, an intermediate value generating module, a conversation key generating module, a new intermediate value generating module and a group key generating module; and the third equipment comprises an information interaction module, an intermediate value generating module, a conversation key decoding module and an intermediate value encrypting module. The method and the equipment have small number of communication rounds during the process of key negotiation, thereby improving the immediacy of communication. Furthermore, the rounds number of key negotiation is independent of the number of members, so that the communication volume of the key negotiation is reduced.
Owner:HUAWEI TECH CO LTD +1
Anonymous signcryption method from identity public key system to certificate public key system
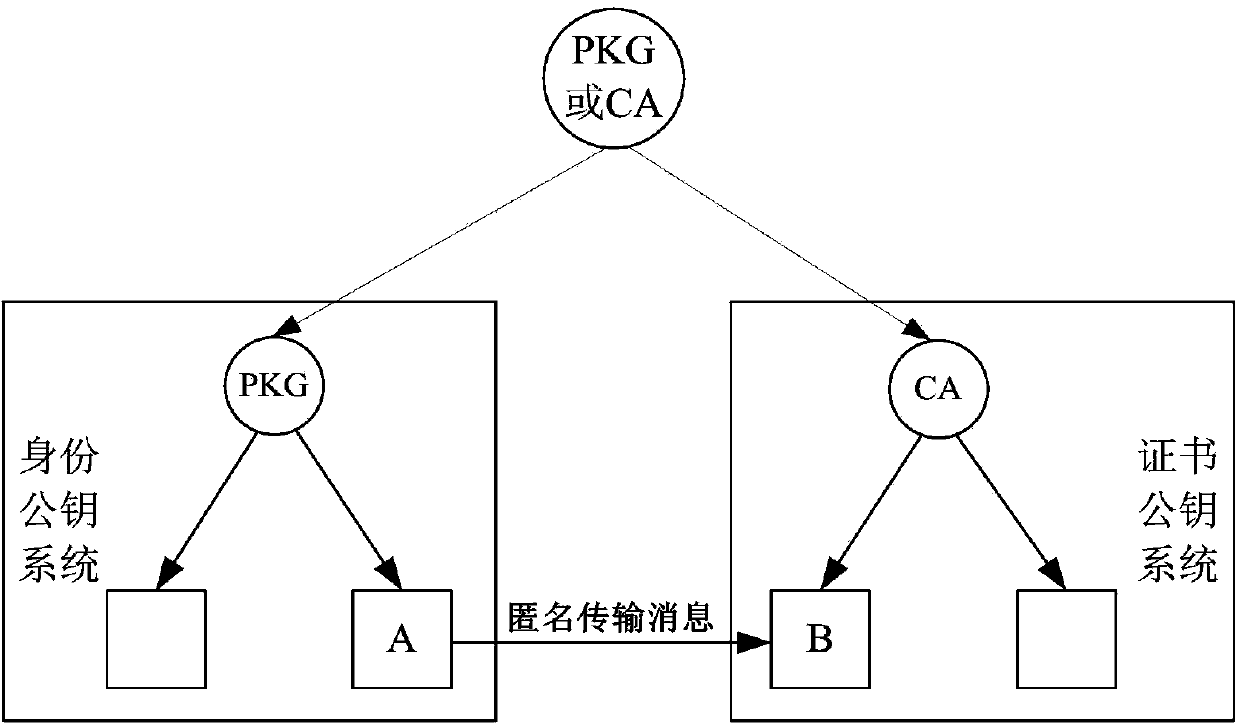
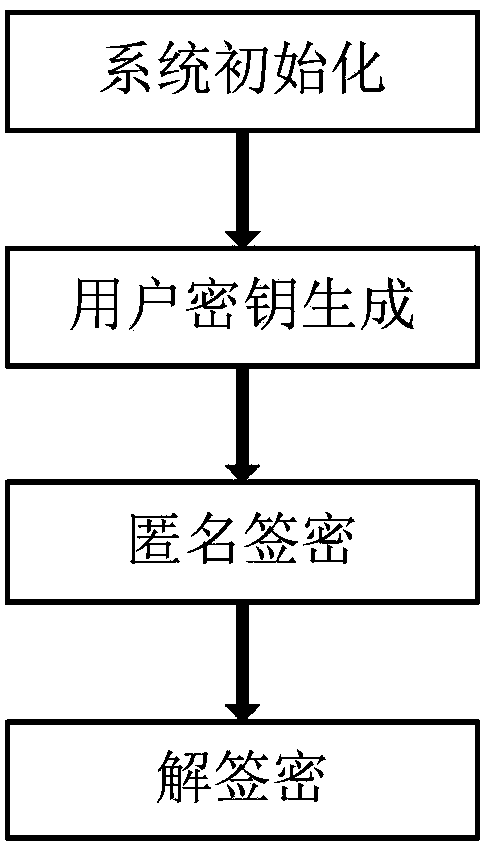
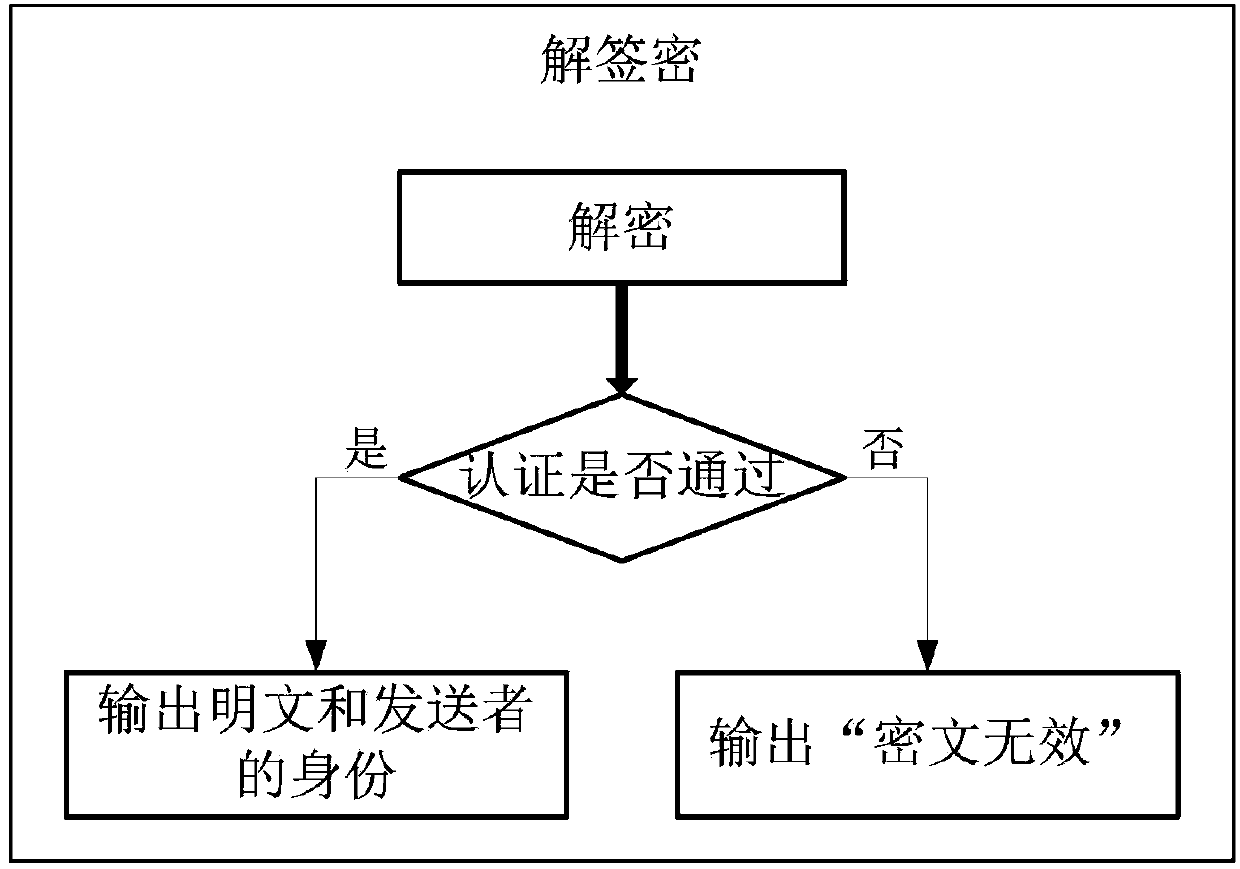
ActiveCN103746811APrivacy protectionImprove securityUser identity/authority verificationCiphertextConfidentiality
The invention discloses an anonymous signcryption method from an identity public key system to a certificate public key system. The anonymous signcryption method specifically comprises the steps that parameters are randomly selected from a public key function database and system public keys and system private keys of the identity public key system and the certificate public key system are generated; a public key and a private key of a user are generated according to the public keys and the private keys and the system parameters; anonymous signcryption is performed to a message by using a bilinear pair, the private key of the user of the identity public key system and the public key of the user of the certificate public key system, and a ciphertext is sent to a receiver; the receiver performs designcryption to the ciphertext according to the bilinear pair and the private key of the receiver and simultaneously authenticates the identity of a sender. The anonymous signcryption method from the identity public key system to the certificate public key system has the advantages of simple implementation process and high transmission efficiency, and can be used for realizing the confidentiality, authentication and anonymity of information transmitted from the identity public key system to the certificate public key system.
Owner:西安千喜网络科技有限公司
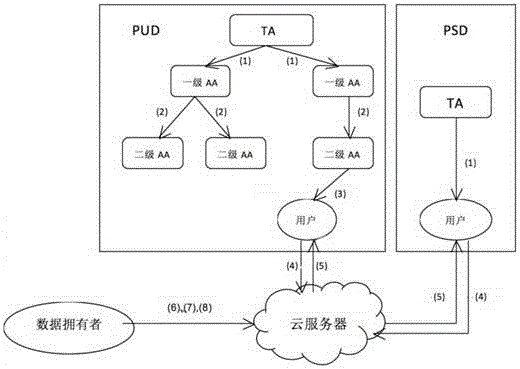
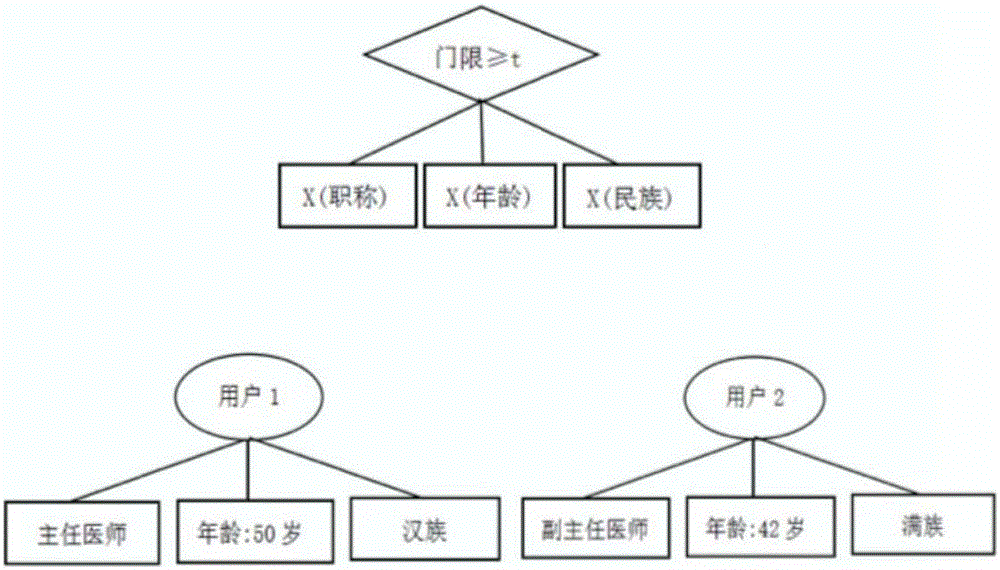
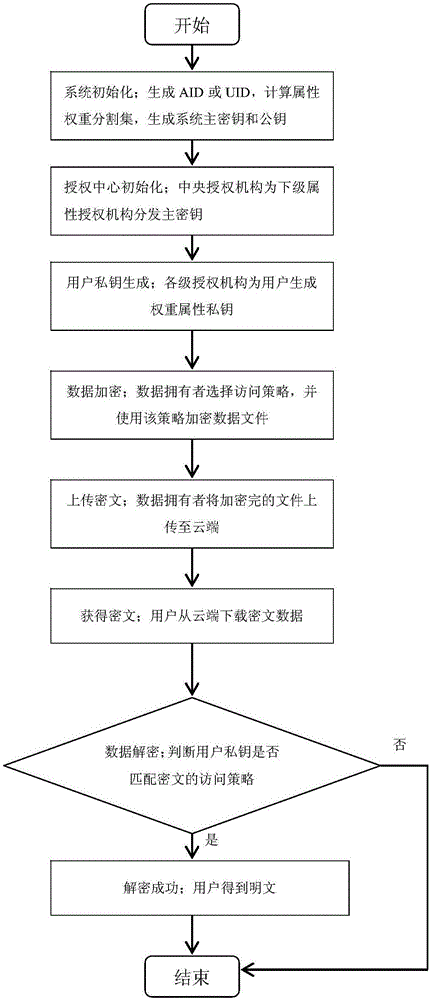
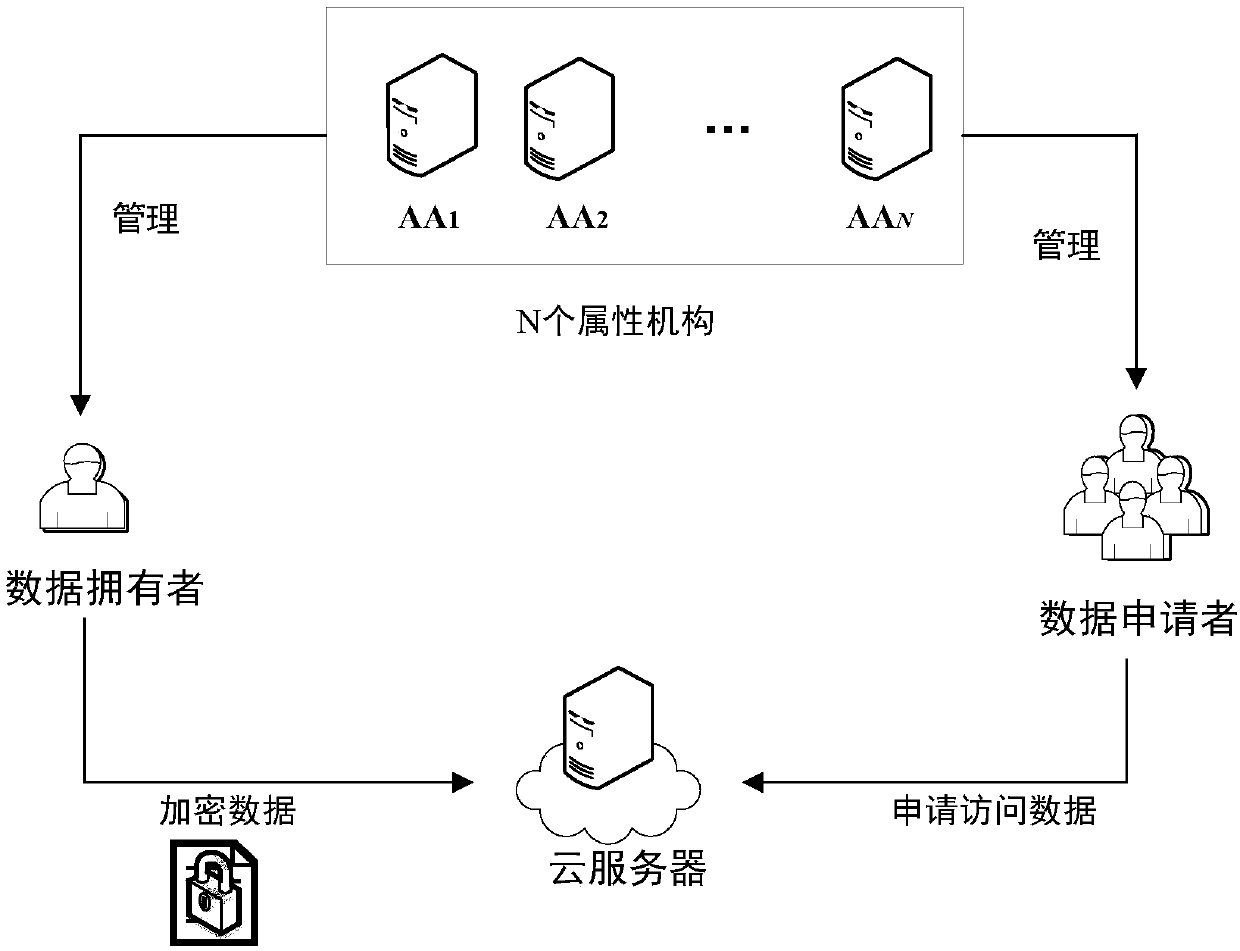
Attribute-based multi-mechanism hierarchical ciphertext-policy weight encryption method under cloud environment
ActiveCN106059763ABuild safe and reliableKey distribution for secure communicationPlaintextAttribute weight
The invention discloses an attribute-based multi-mechanism hierarchical ciphertext-policy weight encryption method under a cloud environment. The method comprises steps: a central authority mechanism generates a global identifier AID or UID for a subordinate attribute authority mechanism or a user, and calculates an attribute weight segmentation set for each attribute in a system; the central authority mechanism randomly selects a bilinear pairing and a bilinear group, generates a system main key MK and a public key PK, retains the MK and publishes the PK; the central authority mechanism distributes the main key or a weight attribute private key for the subordinate attribute authority mechanism or the user; a data owner selects an access policy, encrypts a file and uploads the file to a cloud server; the user requests the cloud server for accessing to the encrypted file, the cloud server returns back a ciphertext CT, the user decrypts the file through the weight attribute private key, and if the attribute in the private key satisfies the access policy, the user obtains a plaintext. With the method provided by the invention, a graded hierarchical multiple-authority mechanism is established, and the authorities of different grades can be in charge of different attributes and distribute private key components.
Owner:NANJING UNIV OF POSTS & TELECOMM
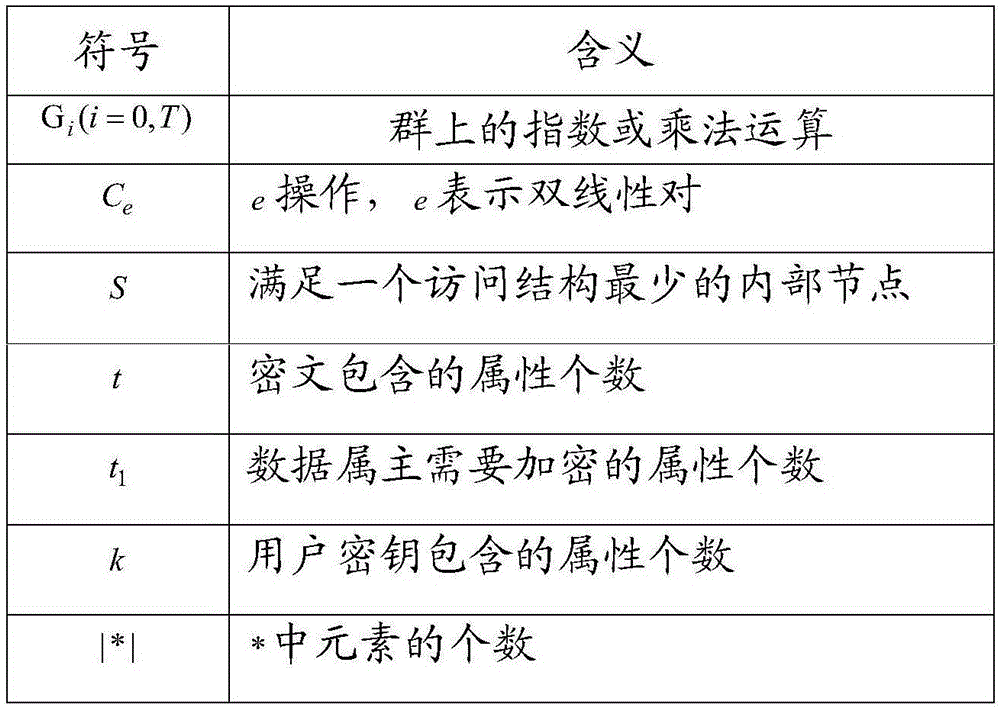
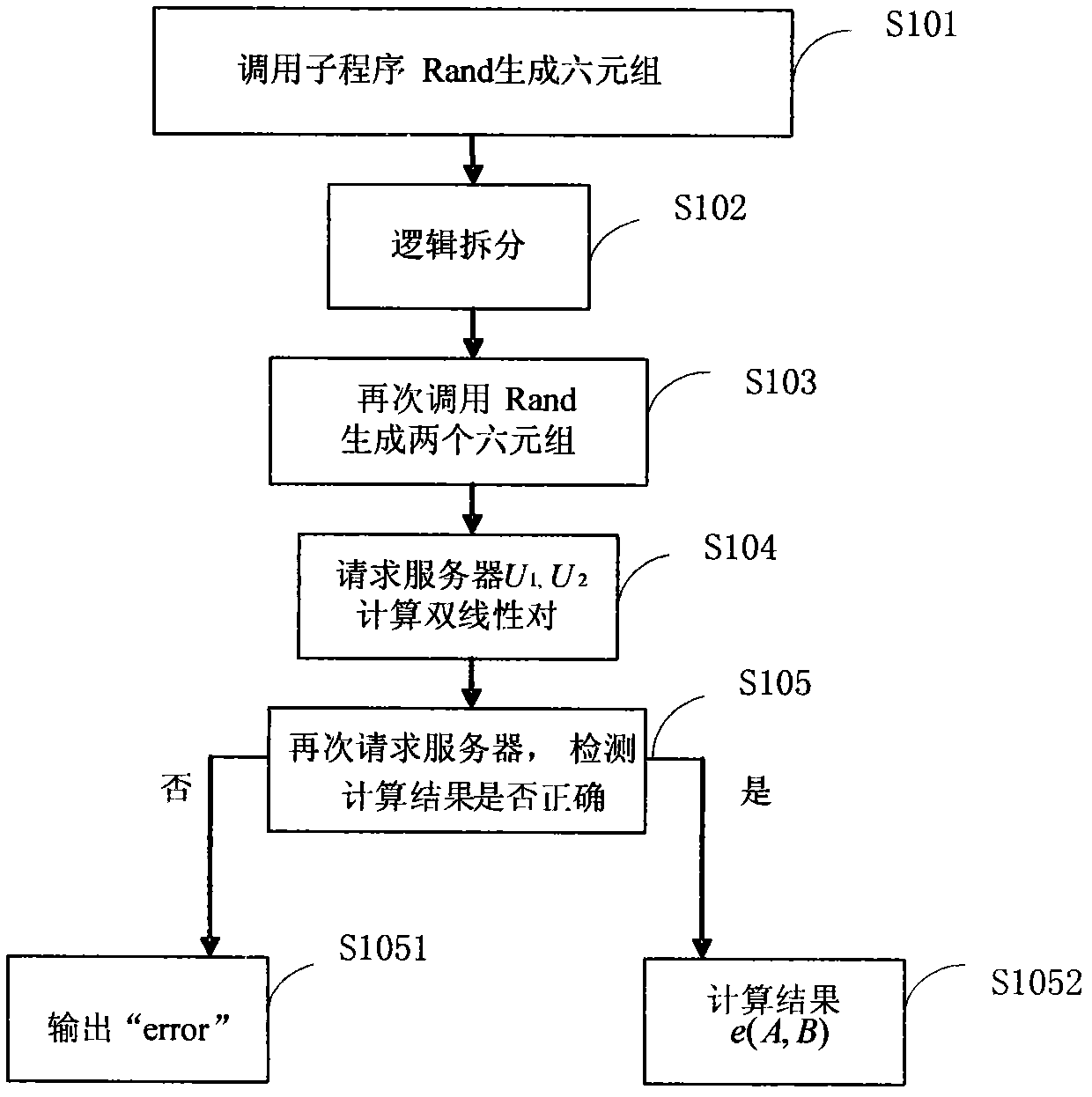
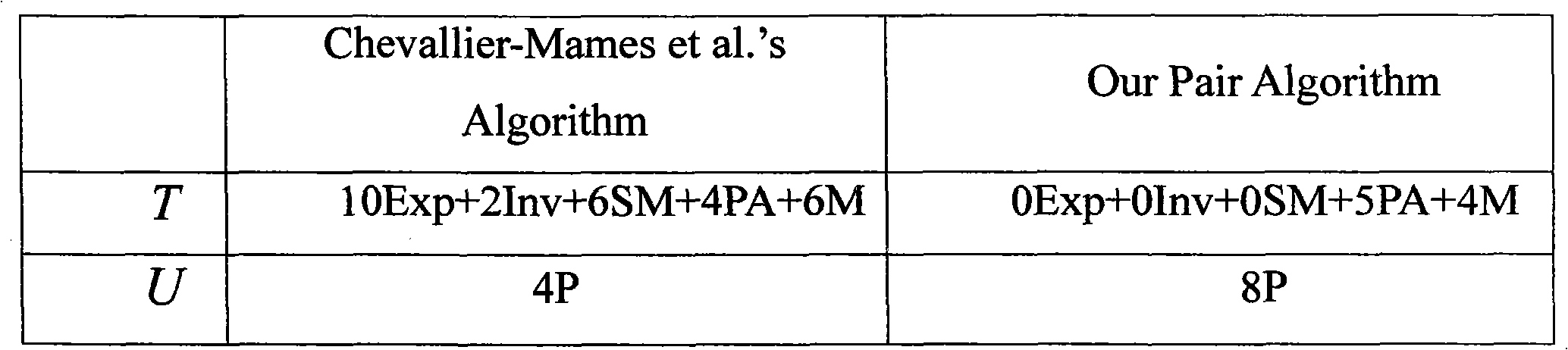
Security outsourcing method for bilinear pairings under cloud computing environment
The invention discloses a security outsourcing method for bilinear pairings under a cloud computing environment. A user T needing to perform outsourcing computing first calls a subroutine Rand for improving computing speed to generate a six-tuple, a number of elements in the six-tuple are utilized to divide e(A, B) logic into five parts, then Rand is called to generate two new six-tuples, inquiry is performed on computing servers U1 and U2 for eight times, the servers work out bilinear pairing results, four parts of the bilinear pairing results serve as intermediate computing results, and the other four parts of the bilinear pairing results serve as test data. Finally the T detects whether output results of the U1 and the U2 are correct and works out results according to response of the servers. The method is suitable for resource-constrained devices. The security outsourcing method is high in computing efficiency, operational times is little, and a subcontractor T does not need to carry out SM and Exp operation high in cost any longer. In addition, by utilizing the method to serve as a subroutine, an encryption scheme of Boneh-Franklin based on identity and security outsourcing of a signature scheme of Cha-Cheon based on identity can be achieved.
Owner:XIDIAN UNIV
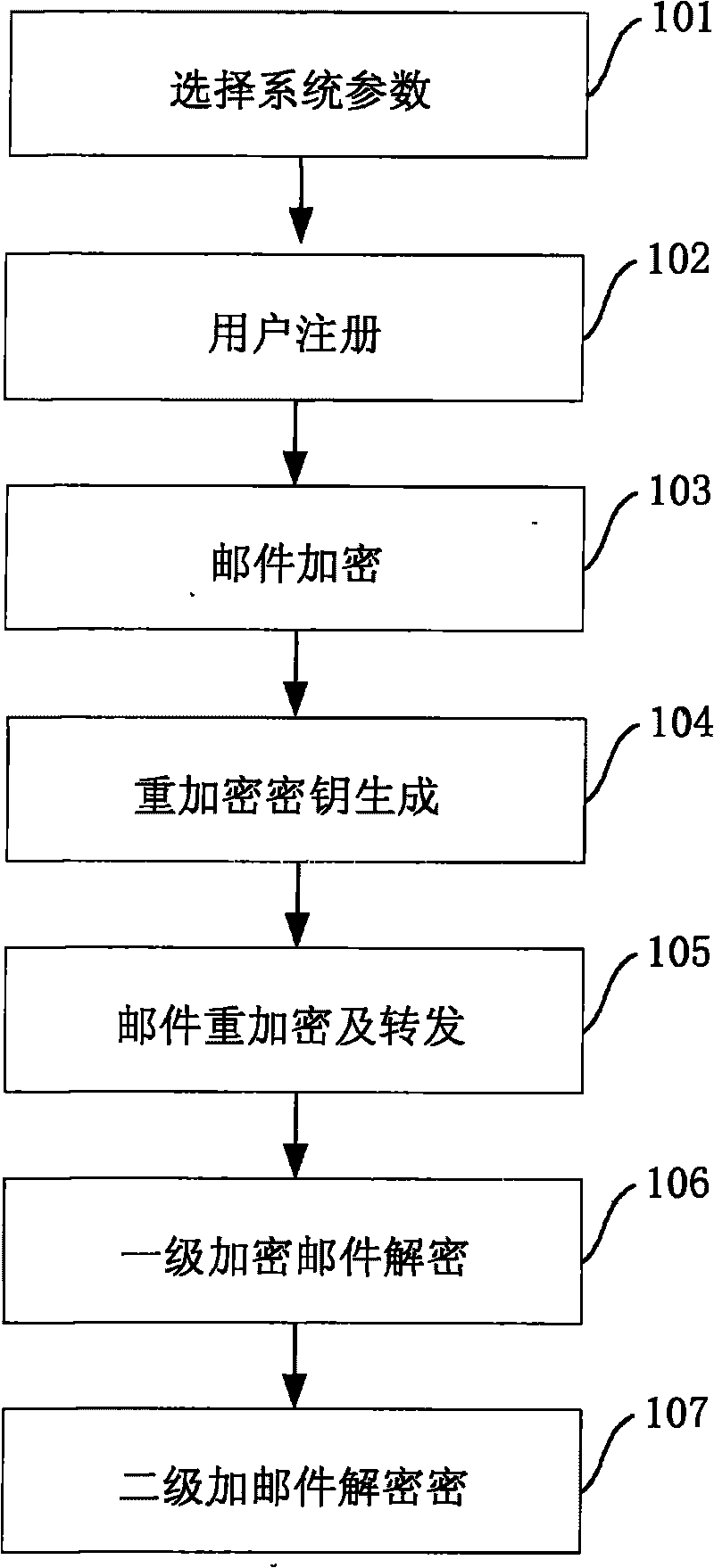
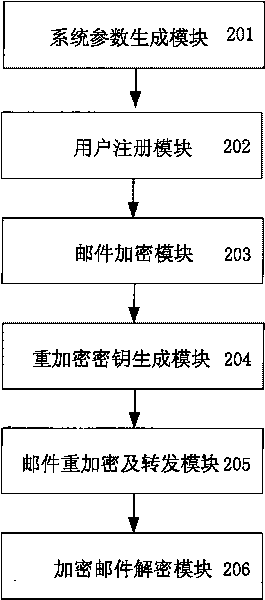
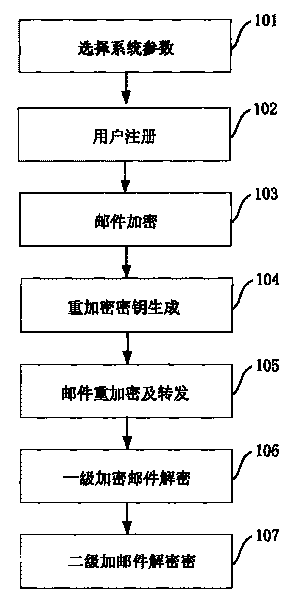
Novel identity-based privacy enhanced mail forwarding system
The invention discloses a novel identity-based privacy enhanced mail forwarding system, which belongs to the field of communication. A method comprises the following steps of: selecting system parameters according to system security requirements, and generating a system master private key (namely the private key of a private key generation center PKG); receiving a user registration application by the PKG, and generating a private key for a user according to an e-mail address selected by the user; generating a first-stage encrypted e-mail according to the e-mail address of the user; generating a re-encrypted private key according to the system parameters; generating a second-stage encrypted e-mail according to the first-stage encrypted e-mail and the re-encrypted private key, and forwarding the second-stage encrypted e-mail; and decrypting the first-stage or the second-stage encrypted e-mail according to the private key of the user. The novel identity-based privacy enhanced mail forwarding system is realized on the basis of the bilinear pairing defined on an elliptic curve, uses a novel random filling mode to ensure the non-scalability of a cipher text, and enhances the security of the first-stage and the second-stage encrypted e-mails.
Owner:COMMUNICATION UNIVERSITY OF CHINA
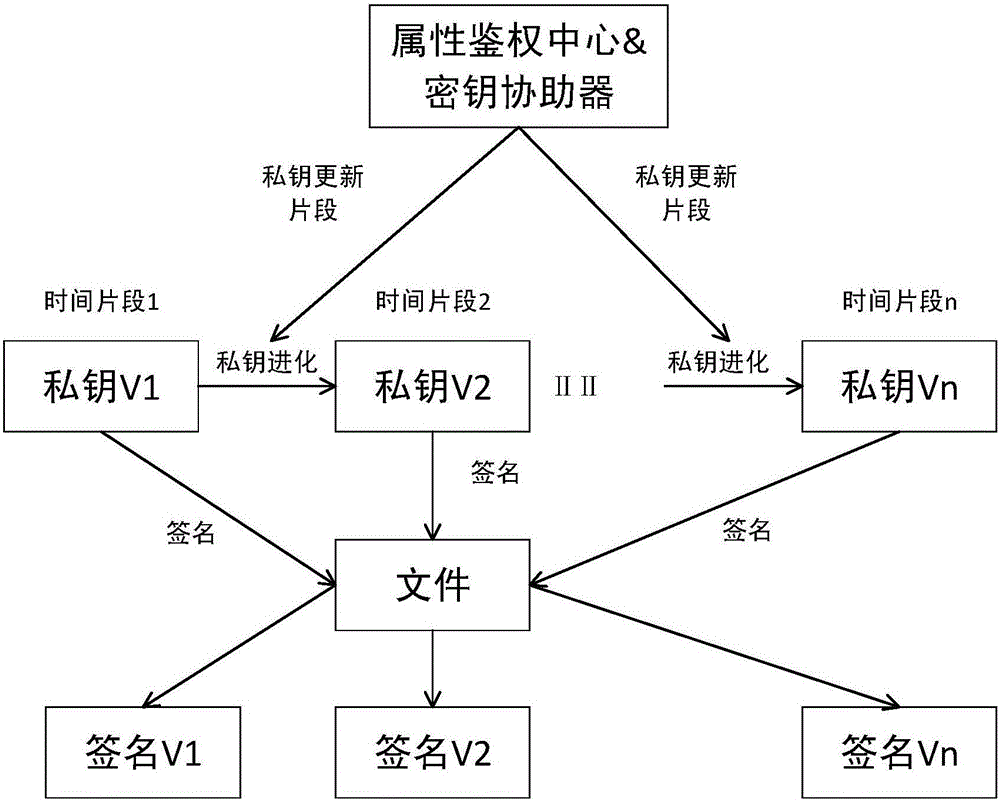
Key isolation signing method based on attribute
ActiveCN106027240APublic authenticationFront and rear safety assuranceKey distribution for secure communicationPublic key for secure communicationSystem timeBilinear pairing
The invention discloses a key isolation signing method based on attribute, which aims at problems of lack of protective measures for key leakage and increase of computation overhead of a terminal caused by bilinear pairing operation in the prior art. A whole signing system is divided into several independent time slices, when the system enters into a new time slice, a key helper generates a private key updating slice, and a user updates a private key. For a certain file, the user signs with the private key corresponding to the current time slice, and verification result of a signature is also corresponding to a certain time slice of the system. If the private key of the user is leaked within a certain time slice, the system also can keep forward security and backward security in other time slices, and thus, harm of private key leakage is minimized. In a process of signing, any operation of bilinear pairing is not required, and computation overhead of a user terminal is reduced. When system time slices evolve, system public parameters are not required to be updated again, and communication overhead caused by synchronization of the public parameters is reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
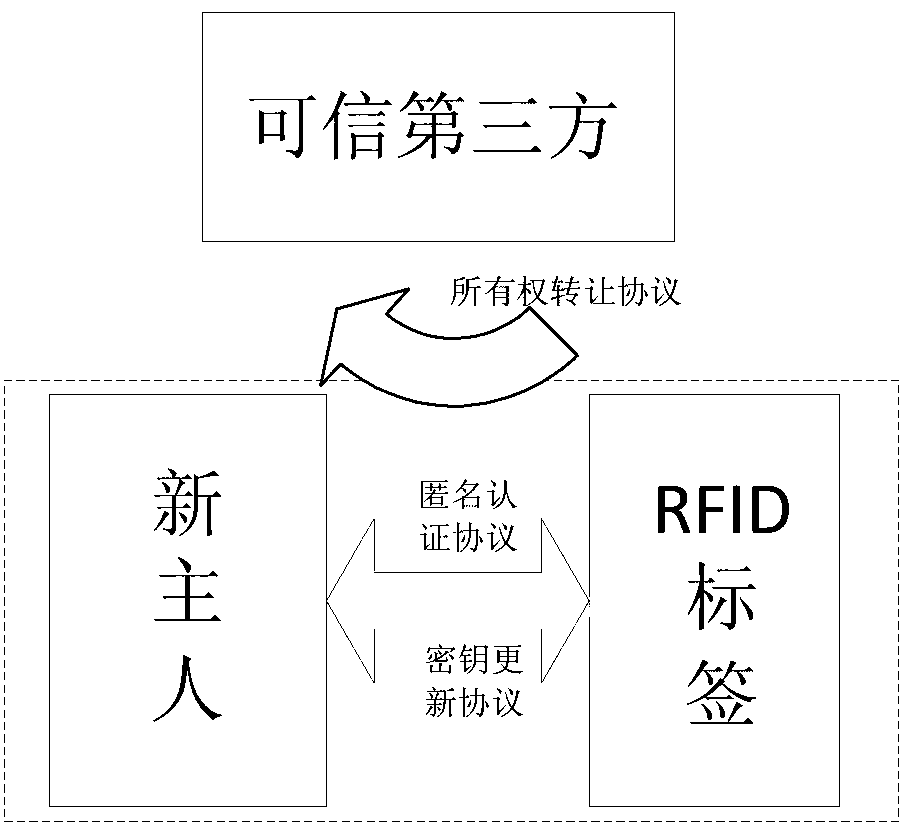
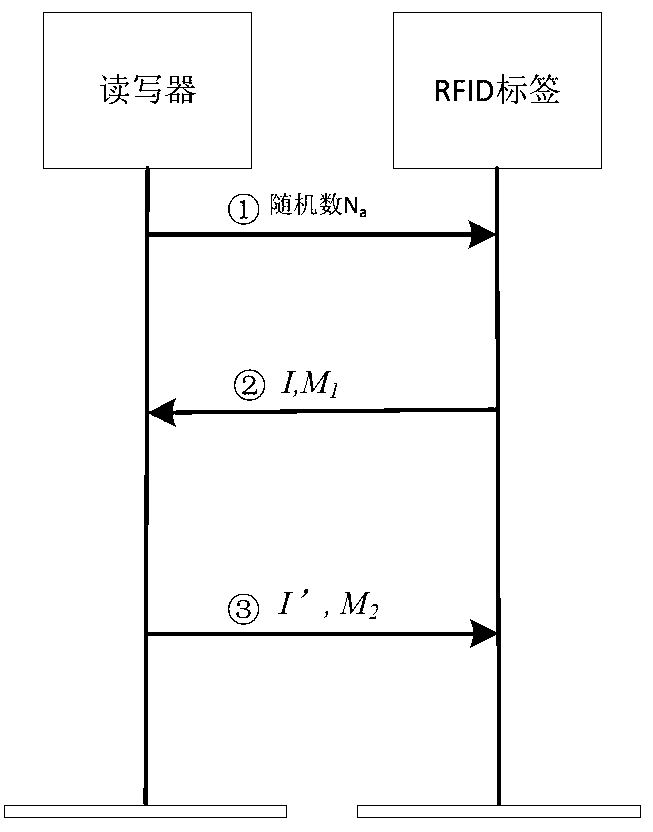
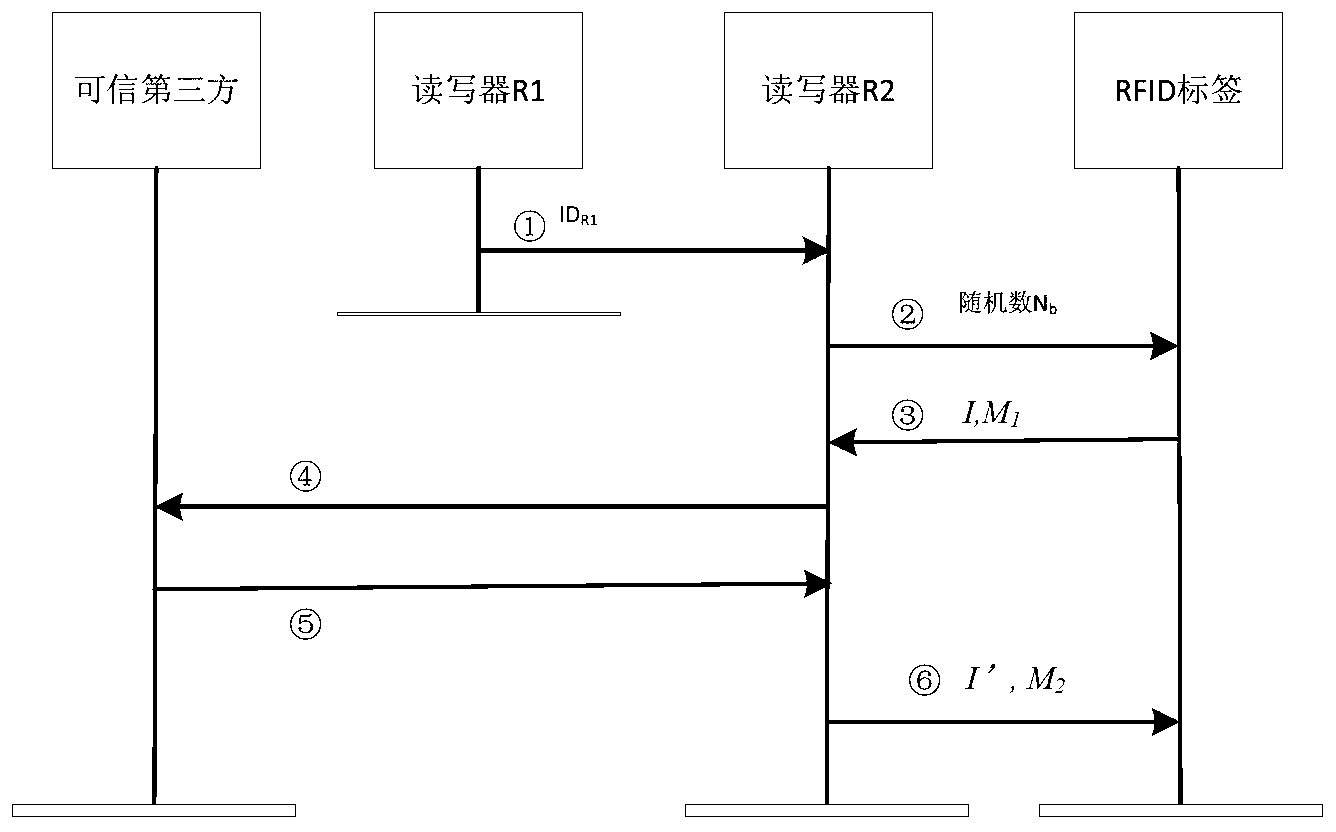
Safe and lightweight class RFID ownership transferring method based on bilinear pairings
InactiveCN103281194AEmphasis on privacy protectionImprove computing efficiencyUser identity/authority verificationThird partyPrivacy protection
A safe and lightweight class RFID ownership transferring method based on bilinear pairings is realized in a mode that a reliable third party, an FRID label, a manufacturer, an old owner, a new owner and a reader-writer execute two initializing sub-processes and three safe sub-protocols. The method has the advantages that through a safe and lightweight class RFID ownership transferring mechanism based on the bilinear pairings, good effects on improving safety of an RFID system, mainly emphasizing privacy protection to an RFID label owner, and resisting to aggressivity are achieved, operation efficiency is relatively high, and application value is obvious.
Owner:杨涛
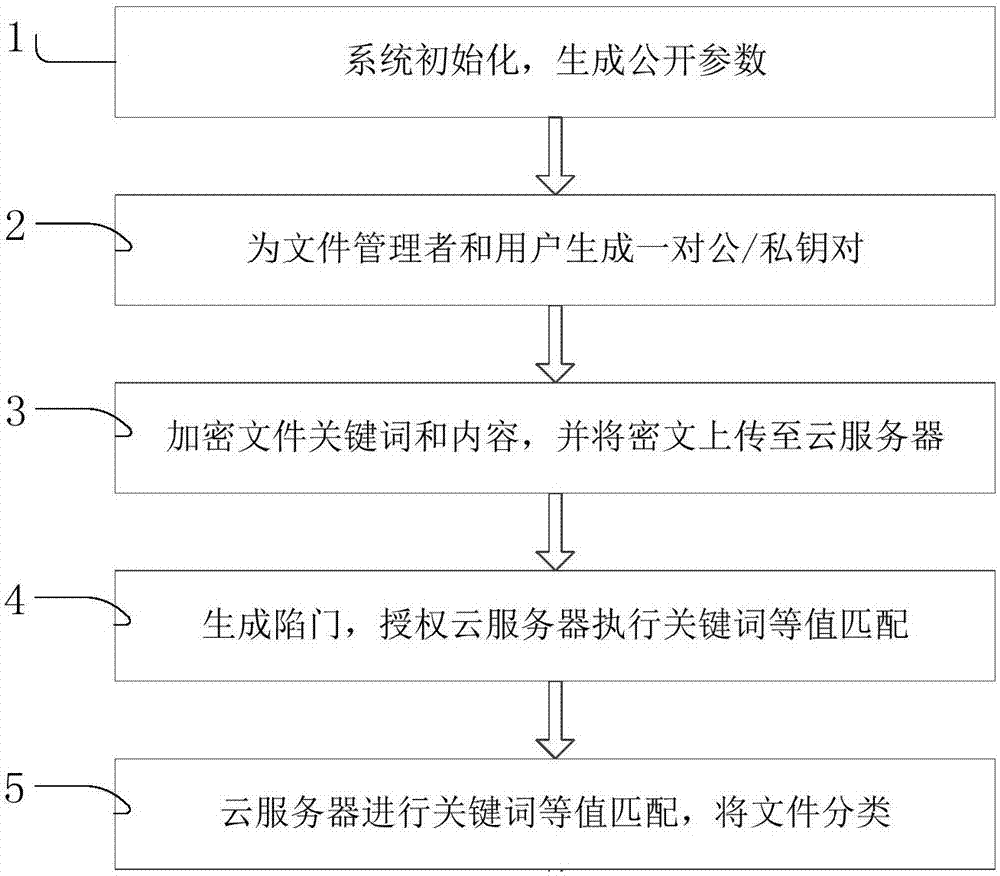
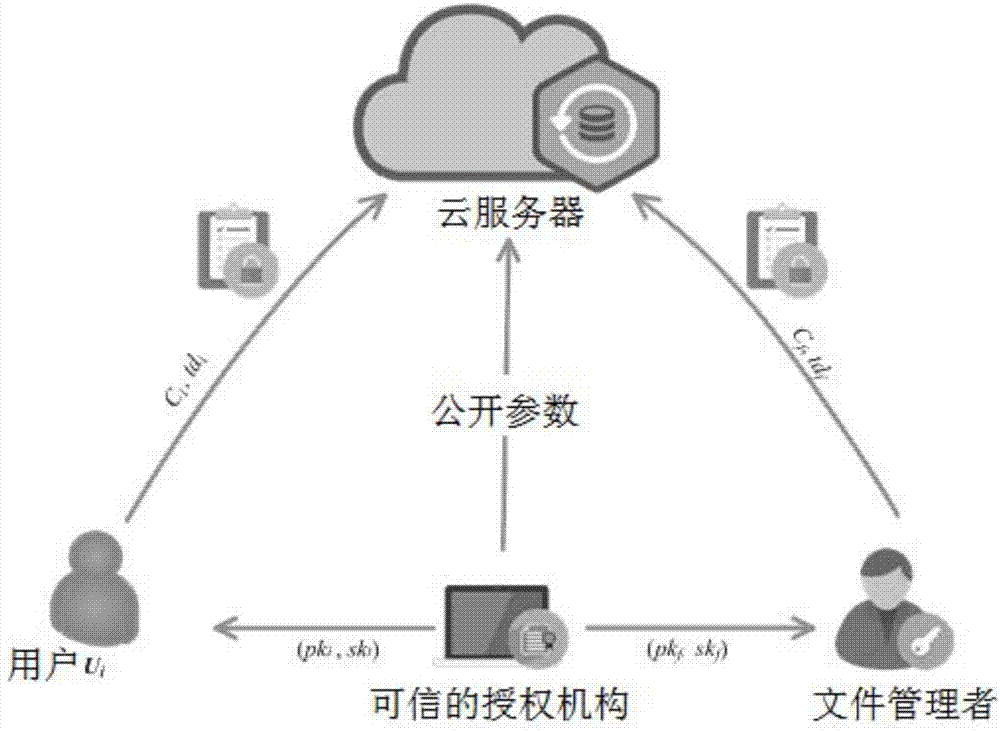
File classification method and system based on public key encryption under multi-user environment
InactiveCN107122449APrivacy protectionReduce manpower consumptionKey distribution for secure communicationDigital data protectionCiphertextMulti user environment
The invention discloses a file classification method and system based on public key encryption under a multi-user environment. The method comprises the following steps that: (1) carrying out system initialization, and generating a public parameter; (2) generating one pair of public / private keys for a file administrator and each user in the system; (3) encrypting the keyword and the file content of the file, and carrying out outsourced storage on the encrypted keyword and a content ciphertext to a cloud server; (4) independently generating trap door authorization to the cloud server by the user and the file administrator to enable the cloud server to own rights for executing keyword equivalent matching; and (5) executing the keyword equivalent matching by the cloud server, and carrying out classified arrangement on the file according to keyword categories. A public key encryption method is adopted to construct a mechanism for utilizing a public key encryption algorithm to carry out the keyword equivalent matching under the multi-user environment, the properties of bilinear pairings are flexibly applied, and the file is classified according to the keyword of the file.
Owner:ANHUI UNIVERSITY
Novel on-lattice MA-ABE (Multi-Authority Attribute Based Encryption) method based on LWE
InactiveCN107682157AIncrease flexibilityLow storage costPublic key for secure communicationCryptographic attack countermeasuresLattice basisAttribute-based encryption
The invention discloses a novel on-lattice MA-ABE (Multi-Authority Attribute Based Encryption) method based on LWE, which comprises four steps of system initialization, secret key generation, encryption and decryption. According to the invention, a plurality of attribute mechanisms manage different attribute sets and respectively distribute secret keys to users in permissions of the attribute mechanisms so as to improve integral efficiency of a system when ensuring security; and meanwhile, a Shamir threshold secret sharing technology is applied, three operations of an access strategy, i.e., anAND operation, an OR operation and a threshold operation, are implemented by adopting an access tree structure, and flexibility is high. Moreover, according to the invention, bilinear pairing is replaced with a lattice principle, a lattice basis delegation algorithm without dimension growth is introduced, encryption and decryption speeds are improved, and storage cost of private keys and ciphertexts of users is reduced. The novel on-lattice MA-ABE method disclosed by the invention is comprehensive in consideration, perfect in function, optimal in system performance and can be better applied to a cloud storage environment.
Owner:HENAN POLYTECHNIC UNIV
Identity-based encryption method with certificates and attributes
ActiveCN104639322ATroubleshoot key escrow issuesRich choiceUser identity/authority verificationPlaintextCiphertext
An embodiment of the invention provides an identity-based encryption method with certificates and attributes. The identity-based encryption method includes enabling a certificate authorization center CA to select elliptical curves and sets of all the attributes, selecting master keys and security parameters and generating and distributing system parameters; enabling users to provide information for the certificate authorization center CA and acquire the certificates, verifying the certificates, generating private keys of the users by the aid of the certificates and the system parameters, and disclosing public keys of the users; allowing senders to use identities and the public keys of receivers, selecting linear key sharing schemes, encrypting messages in plain texts to obtain messages in cipher texts and sending the messages in the cipher texts to the receivers; enabling the receivers to verify whether requirements of access structures in the messages in the cipher texts are met by message receiver attribute sets or not, and decrypting the messages in the cipher texts by the aid of the private keys of the receivers to obtain the messages in the plain texts if the requirements of the access structures in the messages in the cipher texts are met by the message receiver attribute sets. The identity-based encryption method has the advantages that the identity-based encryption schemes are constructed by means of asynchronous bilinear pairing of the elliptical curves, and accordingly problems in the aspect of key recovery can be solved.
Owner:AEROSPACE INFORMATION
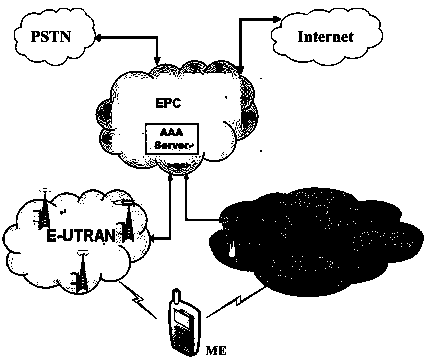
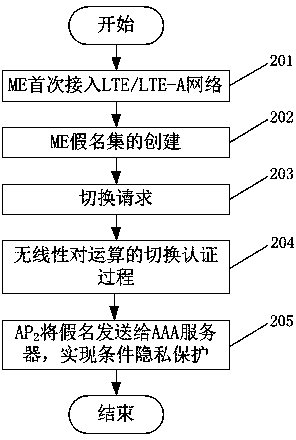
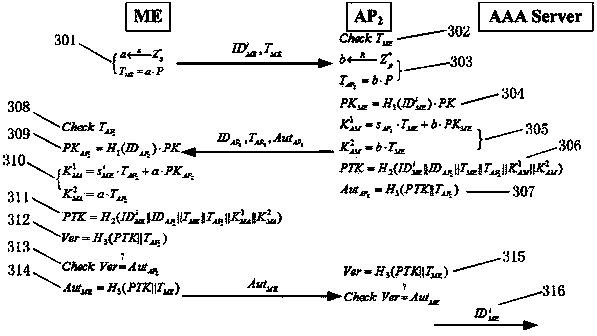
Authentication switching method with privacy protection in LTE (long term evolution)/LTE-A (LTE-advanced) network
InactiveCN103781067ARealize privacy protectionReduce handover authentication delaySecurity arrangementKey exchangeHash function
The invention discloses an authentication switching method with privacy protection in an LTE (long term evolution) / LTE-A (LTE-advanced) network. After ME (mobile equipment) is accessed to the LTE / LTE-A network for the first time and successfully finishes access authentication with an AAA (authentication, authorizing and accounting) server, the AAA server generates a pseudonym set for the ME. When the ME needs to be switched to a new AP (access point) due to movement, only one unused pseudonym needs to be selected from the pseudonym set to perform identity authentication, the real identity of the ME does not need to be provided, so that leakage of a user identity and position privacy can be avoided, and anonymity and untraceability are realized. In the authentication switching process, key agreement is realized based on a Diffie-Hellman key exchange algorithm, the mutual authentication process is finished by hash function value verification, bilinear pairing operation is omitted, and authentication delay is reduced.
Owner:NANJING UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com