Certificateless security signature method based on SM2 algorithm
A security signature, certificateless technology, applied in the field of public key cryptography, which can solve the problems of key sharing and joint signature difficulties, undiscovered, difficult signatures, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
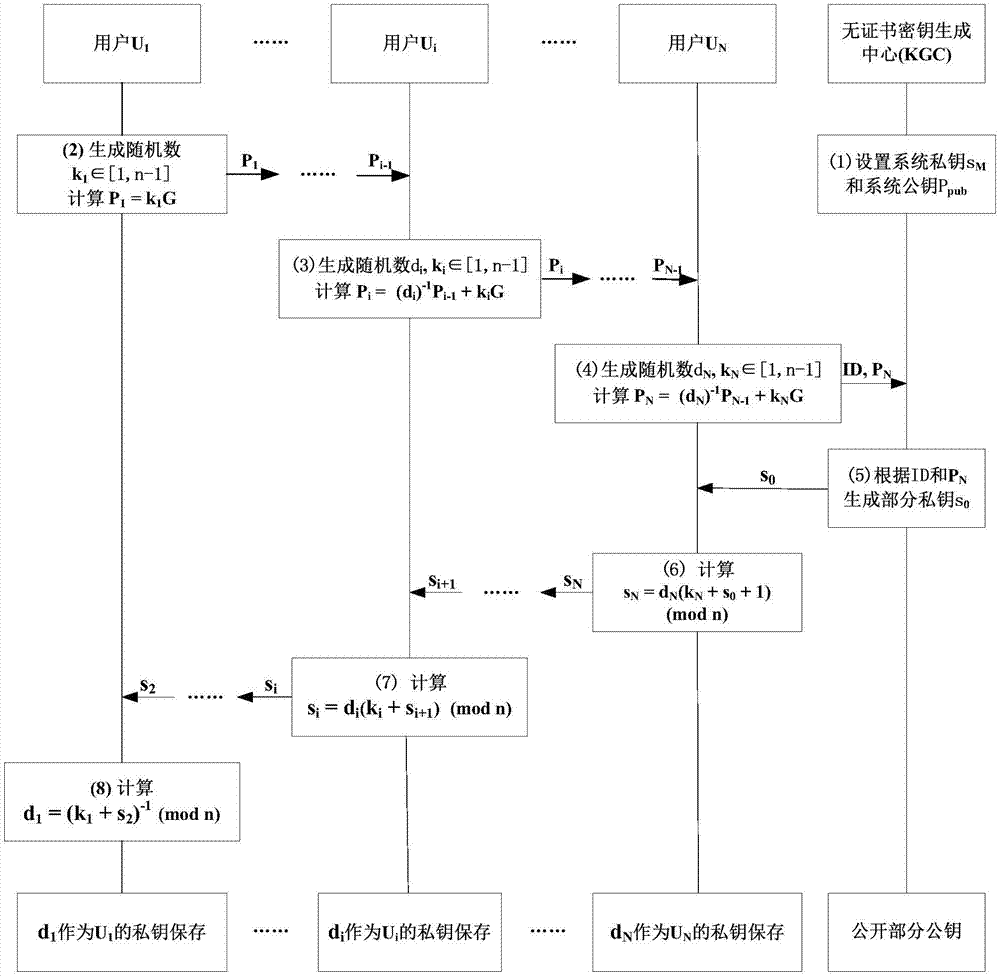
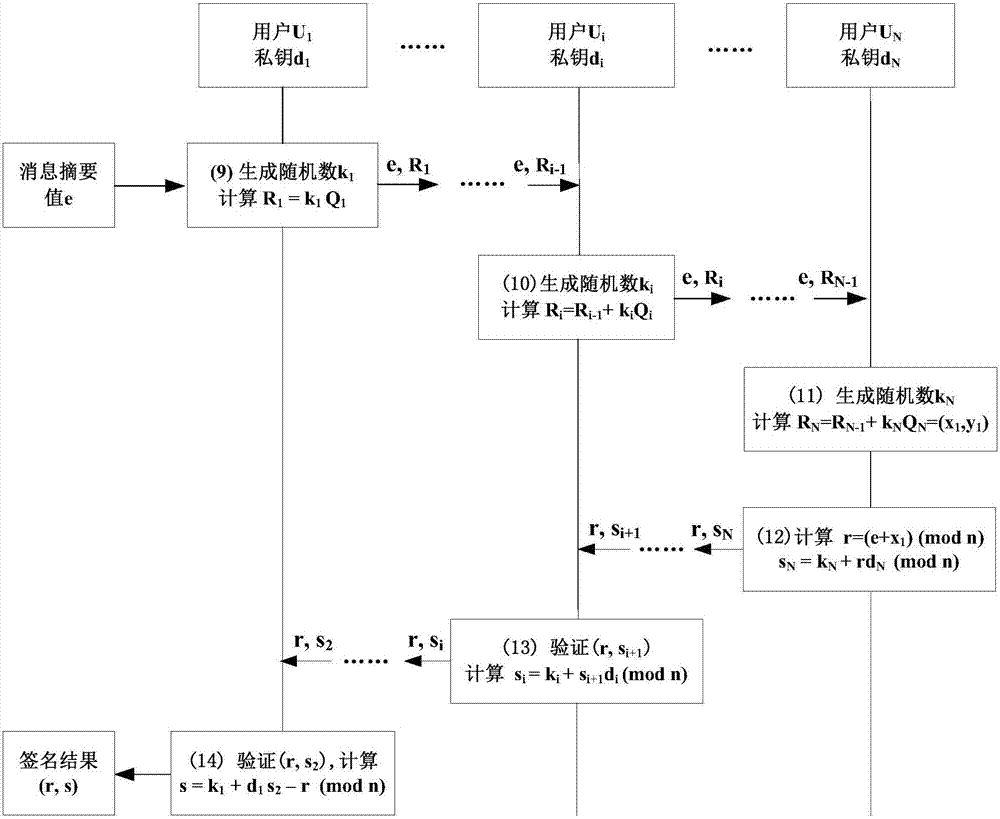
[0058] The present invention proposes a secure signature scheme for a certificateless public key cryptosystem based on the SM2 algorithm, and the implementation of the present invention will be described in detail below with reference to the accompanying drawings.
[0059] figure 1 Shown is the key generation implementation process based on the certificateless public key cryptosystem. The elliptic curve parameters on the finite field involved in the present invention are set by the national secret SM2 algorithm standard, and the elliptic curve on the finite field used is denoted as E (Fq), and its base point is G, and the order of G is prime number n, h (x) is the SM3 hash function.
[0060] The non-certificate key generation center is called KGC, and the N users who share the key are respectively recorded as U 1 ,U 2 ,...,U N , they share a user ID.
[0061] The KGC in step (1) sets the system private key s M and system public key P pub , to complete the system establi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com