A Quantum Key Based Group Signature System
A quantum key and group signature technology, applied in the field of cryptography, can solve the problems that the technology is difficult to adapt to the complex group signature environment, the group signature scheme is difficult to resist joint attacks or collusion attacks, and it is difficult to adapt to the dynamic changes of group members.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
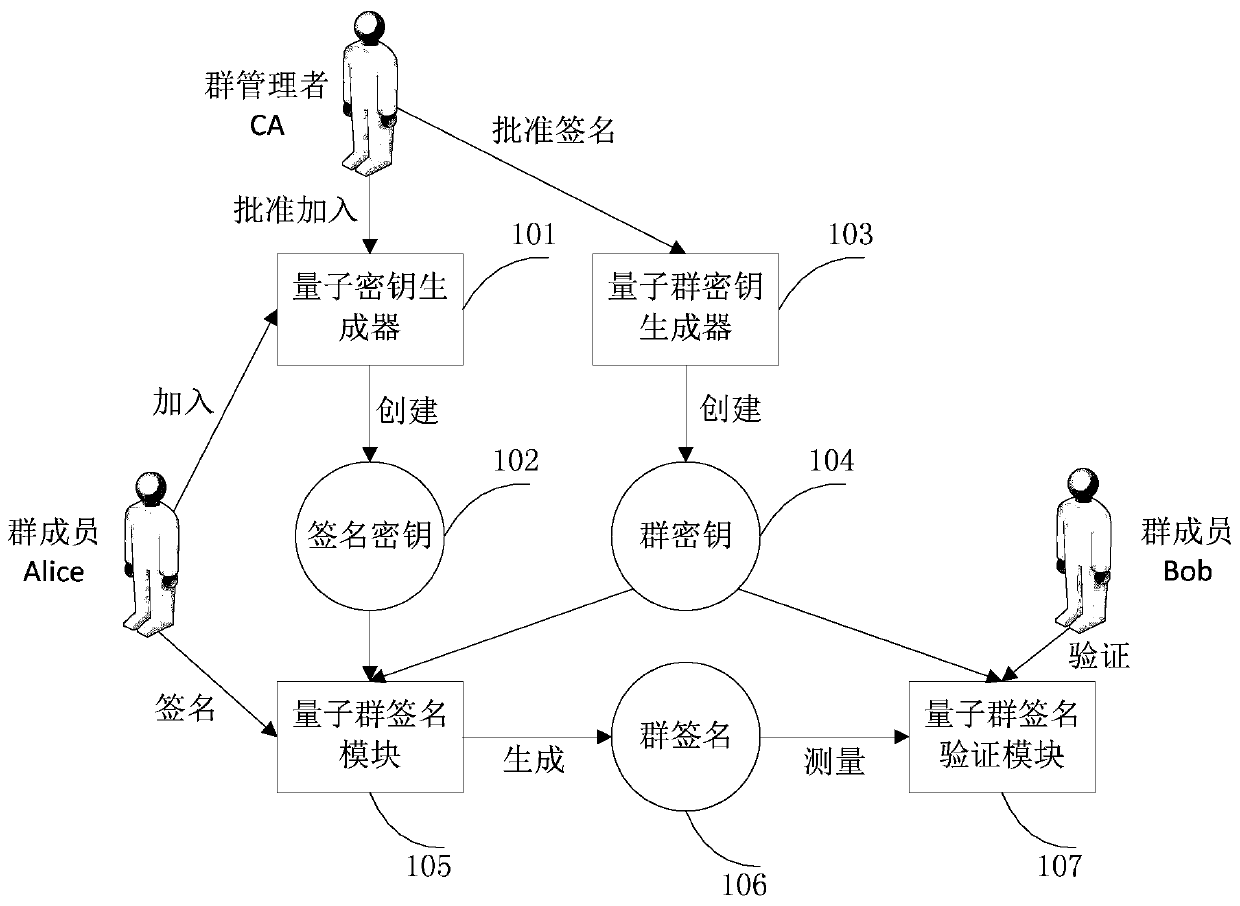
[0042] Such as figure 1 As shown, a quantum key-based group signature method and system includes: quantum key generator 101, signature key 102, quantum group key generator 103, group key 104, quantum group signature module 105, group Signature 106, quantum group signature verification module 107.
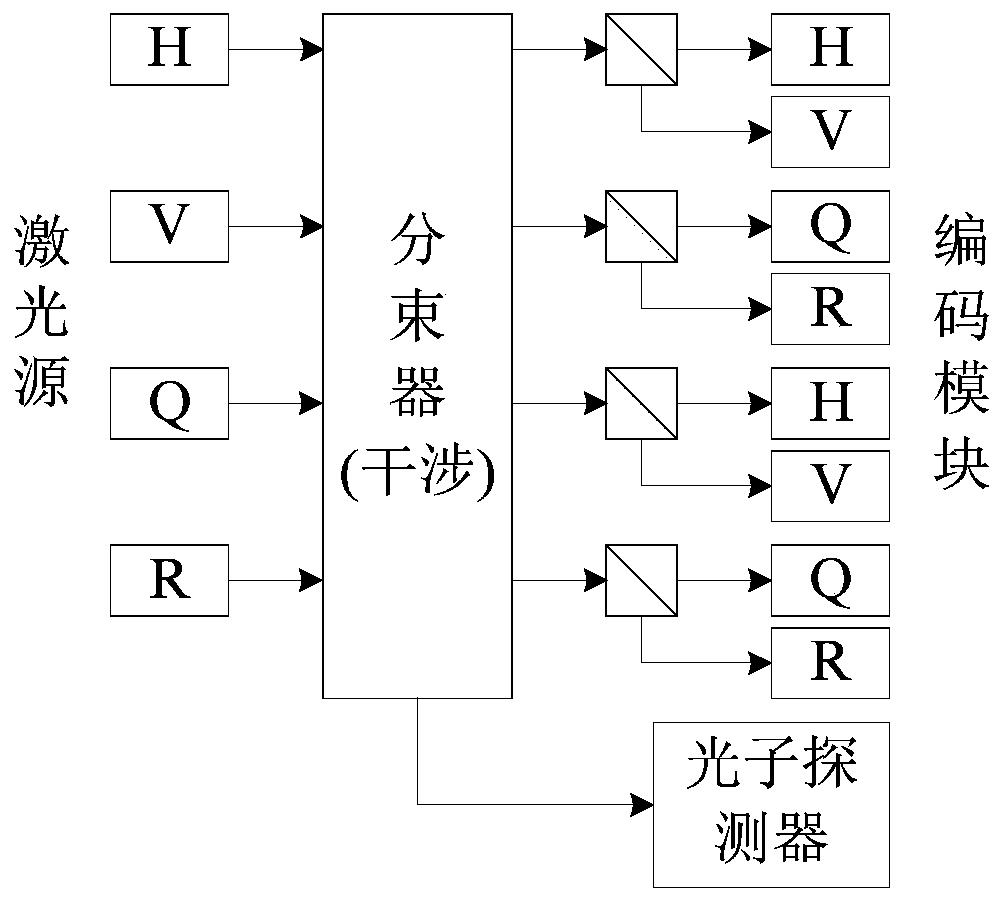
[0043] The quantum key generator 101 is a quantum sequence device generated by a laser light source, preferably, it is composed of a laser source, a beam splitter, an encoding module, and a photon detector, and is used to generate a quantum sequence and its encoding; further Ground, the group manager CA divides the quantum sequence into two photons through the beam splitter, and sends the photons to the group manager CA and the group member Alice through the beam splitter to form the group manager CA and the newly joined group Member Alice's shared key K CA ; Similarly, when the group member Bob joins the group, the shared key K between the group manager CA and the newly joined gr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com