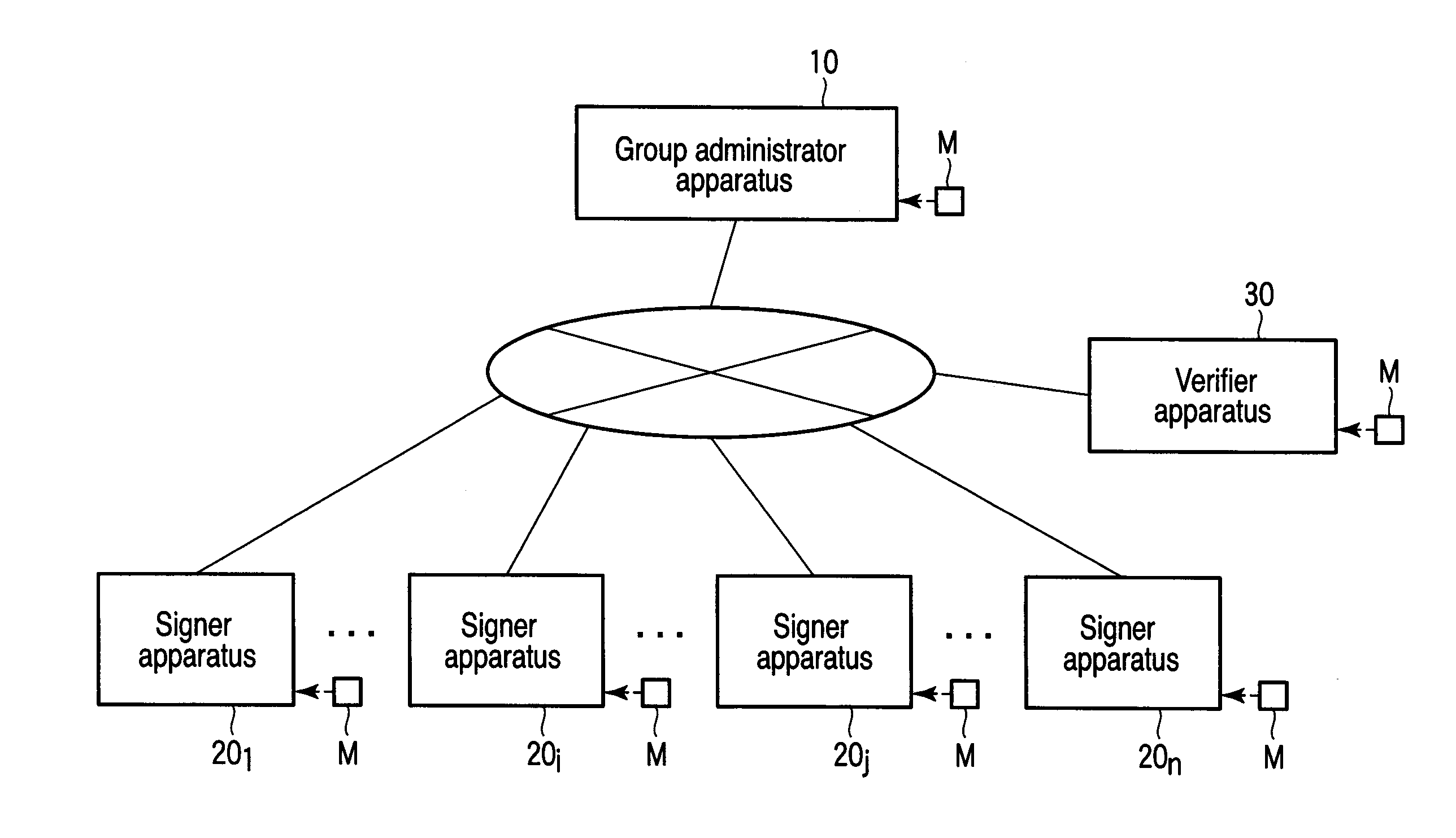
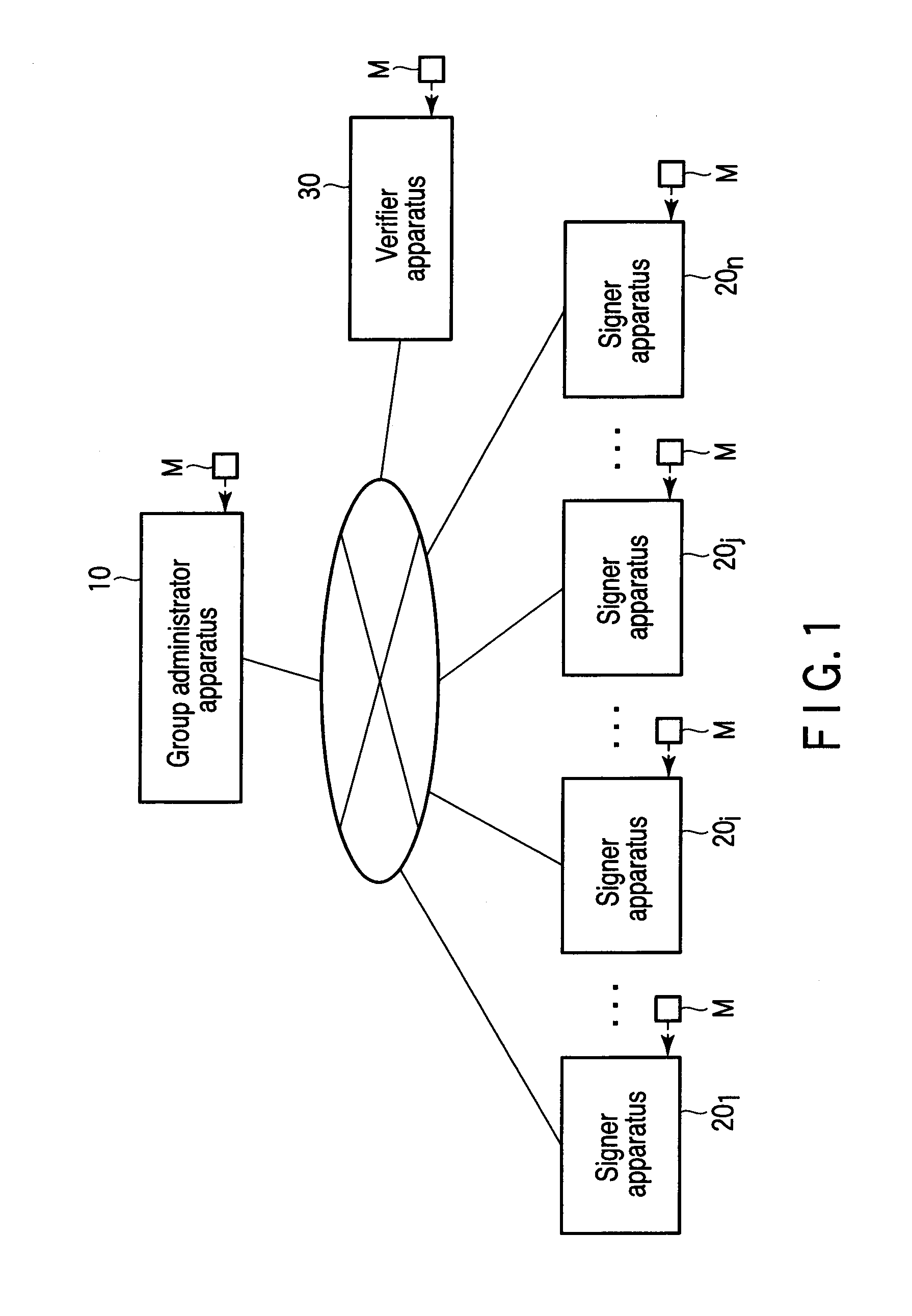
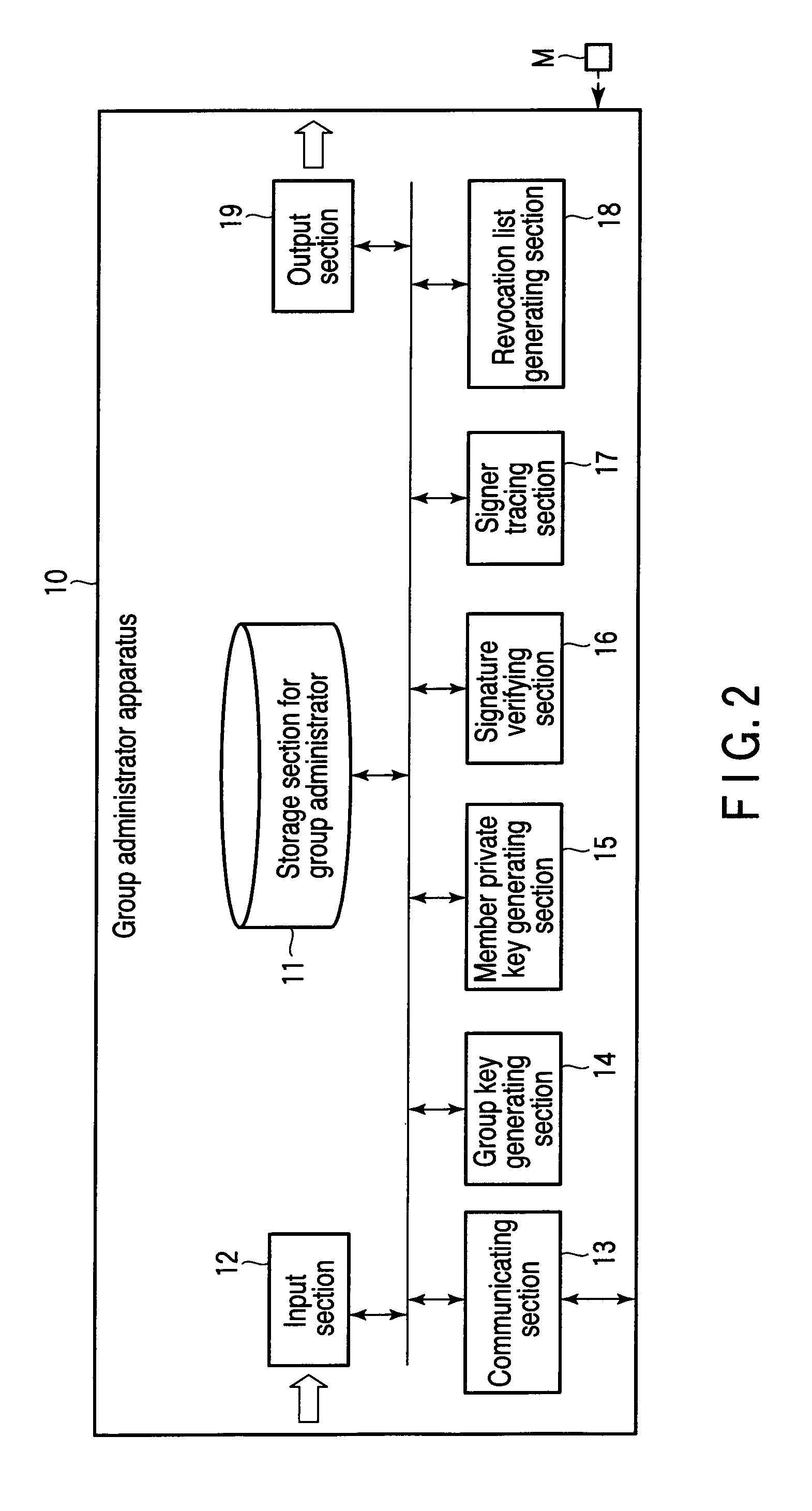
Patents
Literature
235 results about "Group signature" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A group signature scheme is a method for allowing a member of a group to anonymously sign a message on behalf of the group. The concept was first introduced by David Chaum and Eugene van Heyst in 1991. For example, a group signature scheme could be used by an employee of a large company where it is sufficient for a verifier to know a message was signed by an employee, but not which particular employee signed it. Another application is for keycard access to restricted areas where it is inappropriate to track individual employee's movements, but necessary to secure areas to only employees in the group.
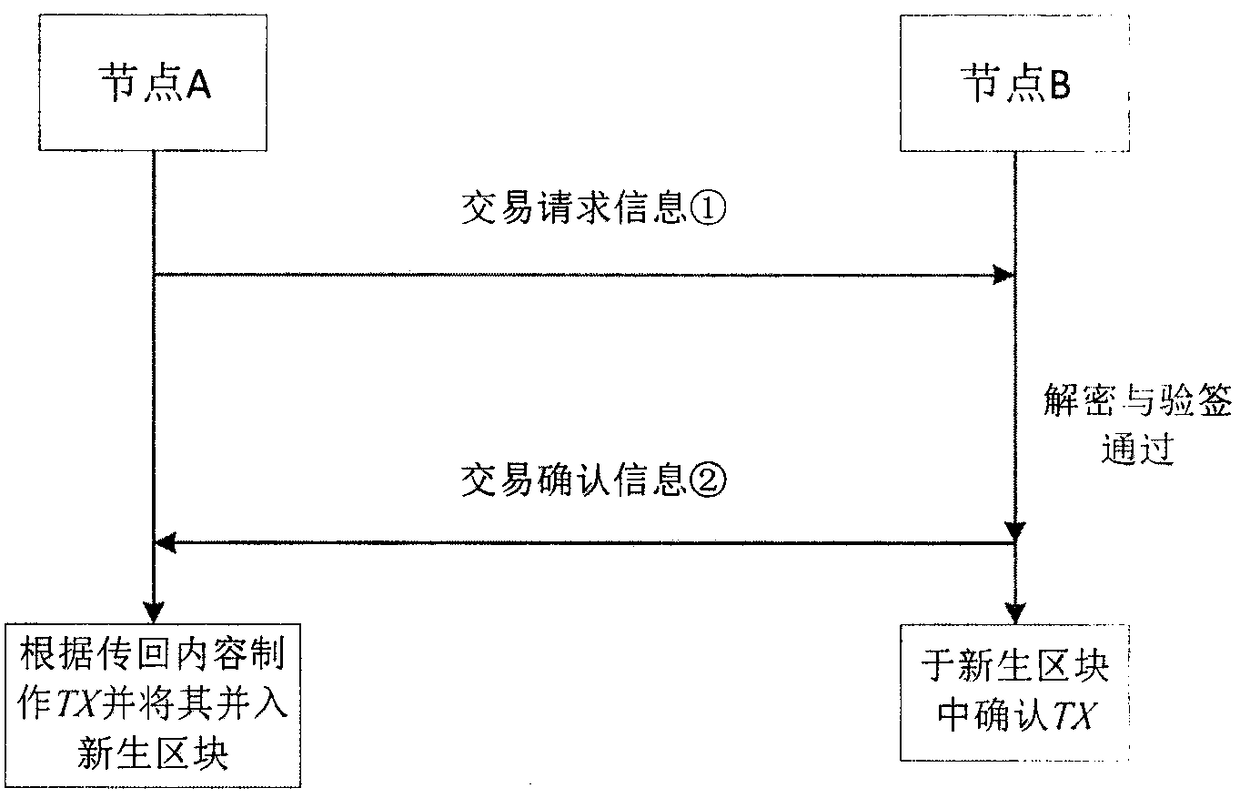
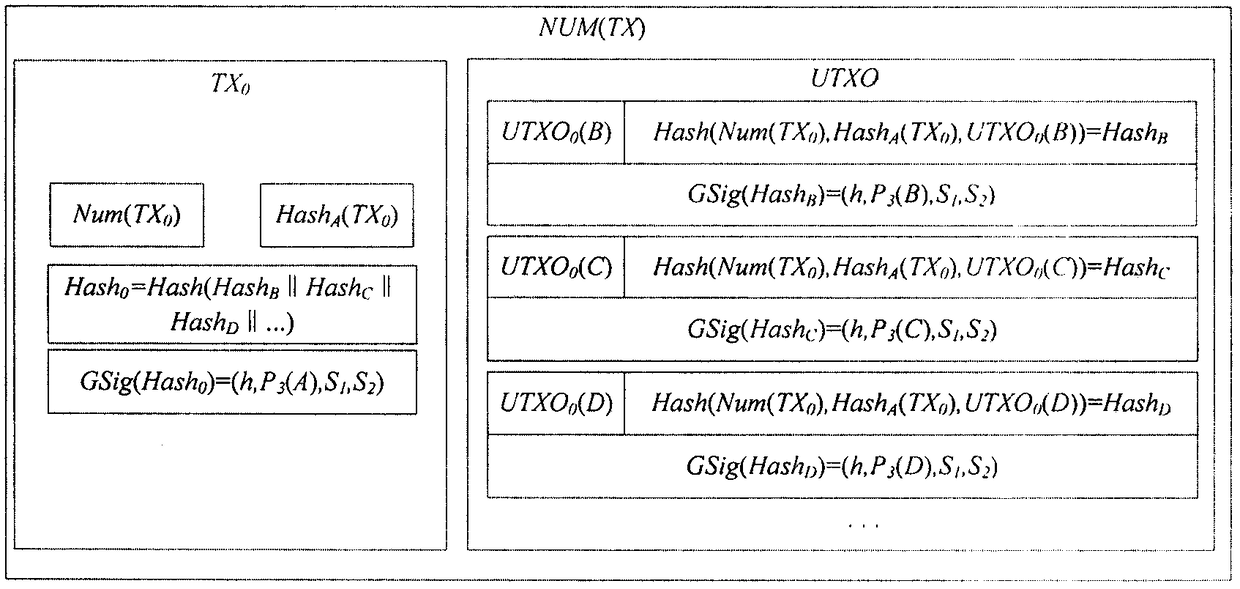
Method and system for privacy protection of block chain transaction
ActiveCN107911216ARealize regulationSupport reviewKey distribution for secure communicationFinancePublic accountPrivacy protection
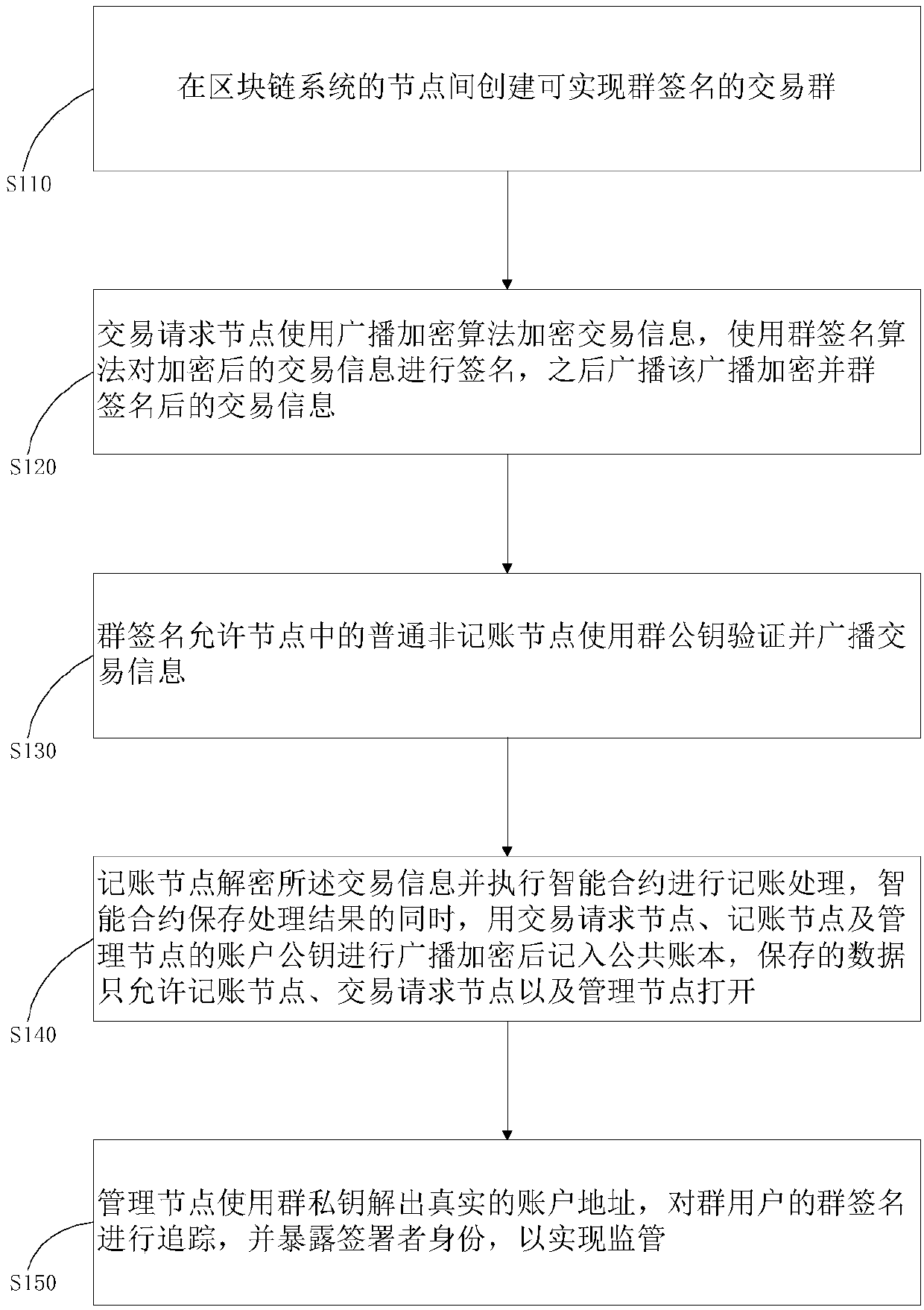
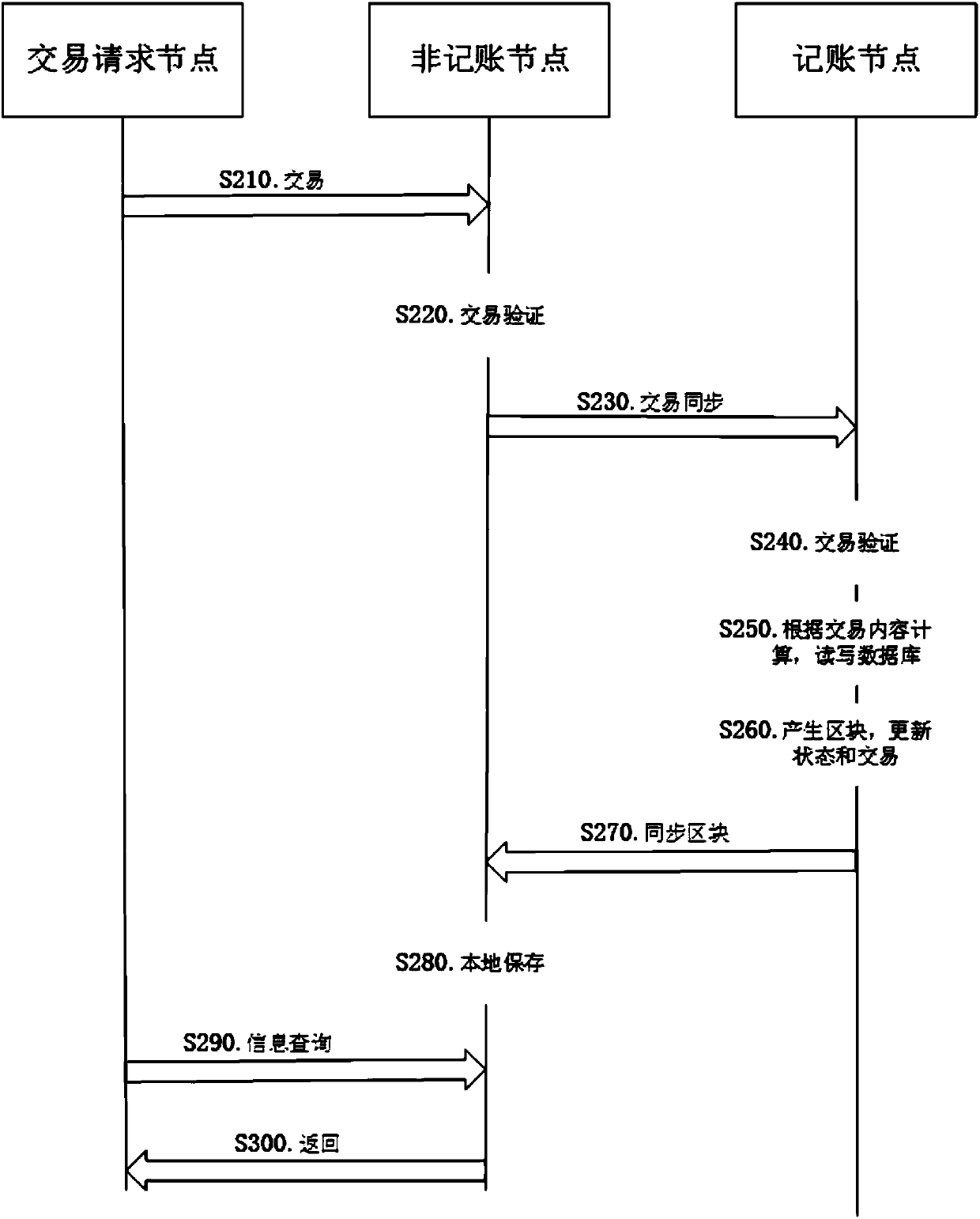
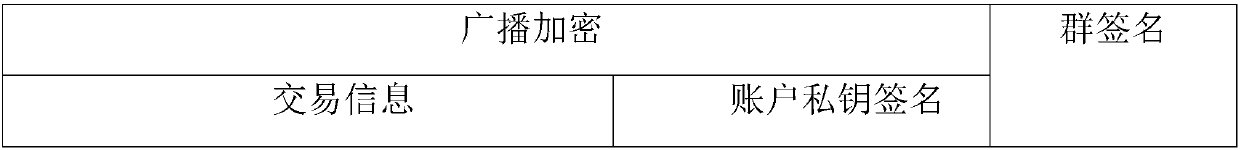
The invention provides a method and system for privacy protection of block chain transaction. The method comprises: a transaction group is established between nodes of a block chain system, a user establishes an account at a node, and the node generates public and private key information of the account and then joining of a group is carried out; a transaction request node encrypts transaction information by using a broadcast encryption algorithm, carries out group signature processing on the encrypted transaction information, and then broadcasts the transaction information after broadcast encryption and group signature processing; a common non-account-recording node verifies the transaction information and then broadcasts the transaction information, an account-recording node decrypts thetransaction information and performs an intelligent contract to carry out account recording, broadcast encryption is carried out and then the information is recorded into a public account book, wherein the stored data are only allowed to be opened by the account-recording node, the transaction request node and an administration node. With the broadcast encryption algorithm and group signature technology, a privacy protection problem in the block chain system is solved and the traceability of the transaction is ensured.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Peer-to-peer group management and method for maintaining peer-to-peer graphs
InactiveUS7493363B2Timely and useful communicationImprove practicalityMultiple digital computer combinationsSecuring communicationGraphicsInformation transfer
A system and method of serverless peer-to-peer group management and maintenance is presented. Group formation and discovery of private, public, and enumerated groups are provided, as is a method of joining such a peer-to-peer group. Group information management provided by the present invention ensures that each node maintains a current database from the initial joining of the group through the run phase of membership. Group graph maintenance utilizes a group signature to ensure that partitions in a graph may be detected and repaired. The utility of connections within the graph are also monitored so that non-productive connections may be dropped to increase the efficiency of the group. The diameter of the graph is also monitored and adjusted to ensure rapid information transfer throughout the group. A disconnect procedure is used to maintain the graph integrity and prevent partitions resulting from the departure of a group member.
Owner:MICROSOFT TECH LICENSING LLC
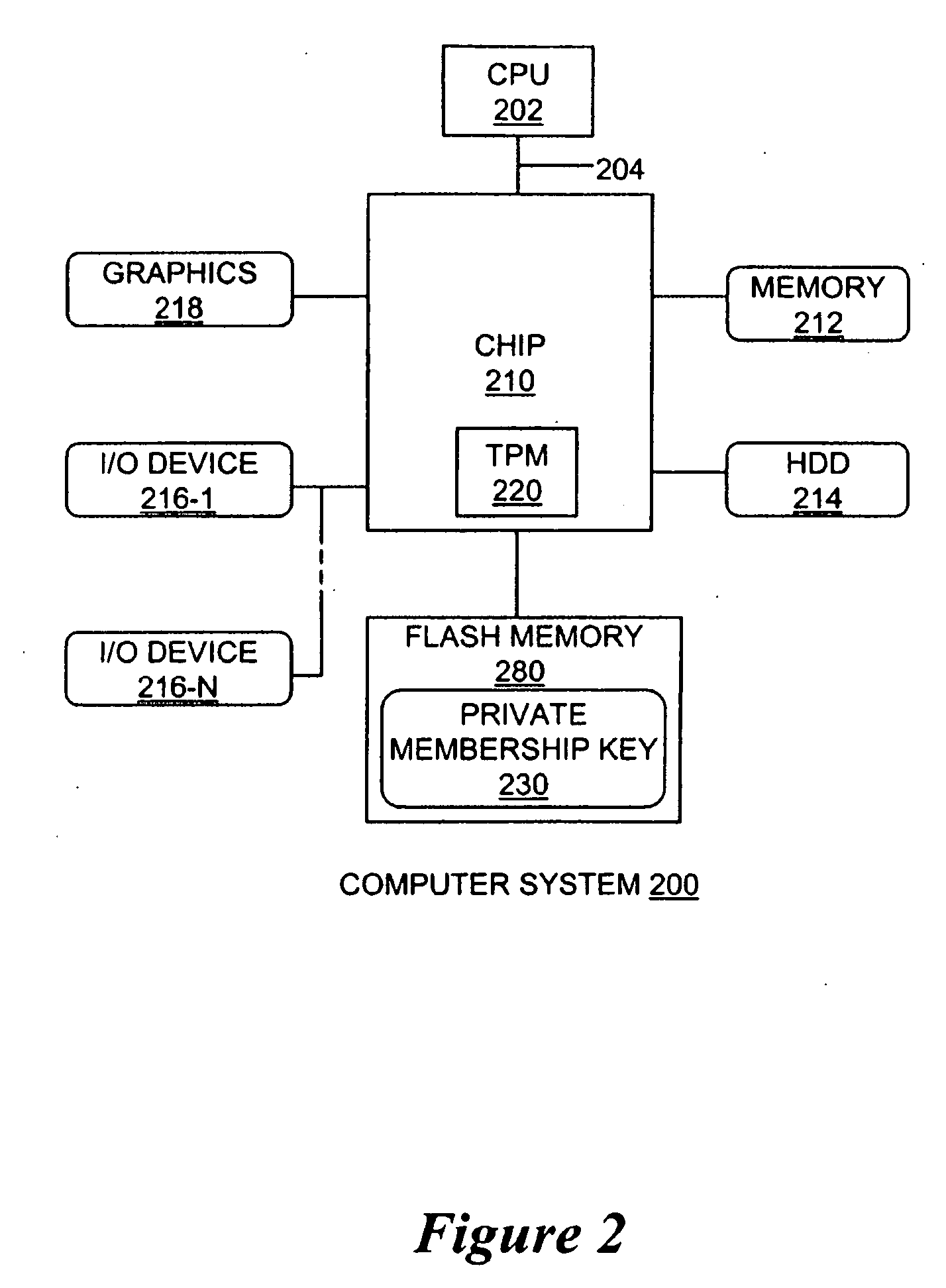
Apparatus and method for a direct anonymous attestation scheme from short-group signatures
InactiveUS20090129600A1Key distribution for secure communicationPublic key for secure communicationDigital signatureTrusted Platform Module
An apparatus and method is provided for a direct anonymous attestation scheme from short-group signatures. The method may include the creation of a group public / private key pair for a trusted membership group defined by an issuer; and assigning a cryptographic pair that is combined with a unique private member value to form a private membership key. A trusted member device generates the unique private member value during a join procedure of a trusted membership group. In one embodiment, the private member value of the private membership key is unknown to the issuer. A member may sign a message with the private membership key to form a short-group digital signature that is verified using a public key of the trusted membership group to maintain anonymity of trusted member devices. A size of the private membership key may be reduced to enable storage within a trusted platform module. Other embodiments are described and claimed.
Owner:INTEL CORP
Mobile ad hoc authentication method, network and system
InactiveCN101192928AImprove efficiencyMake the most of processing resourcesEnergy efficient ICTUser identity/authority verificationNetwork structureMobile ad hoc network
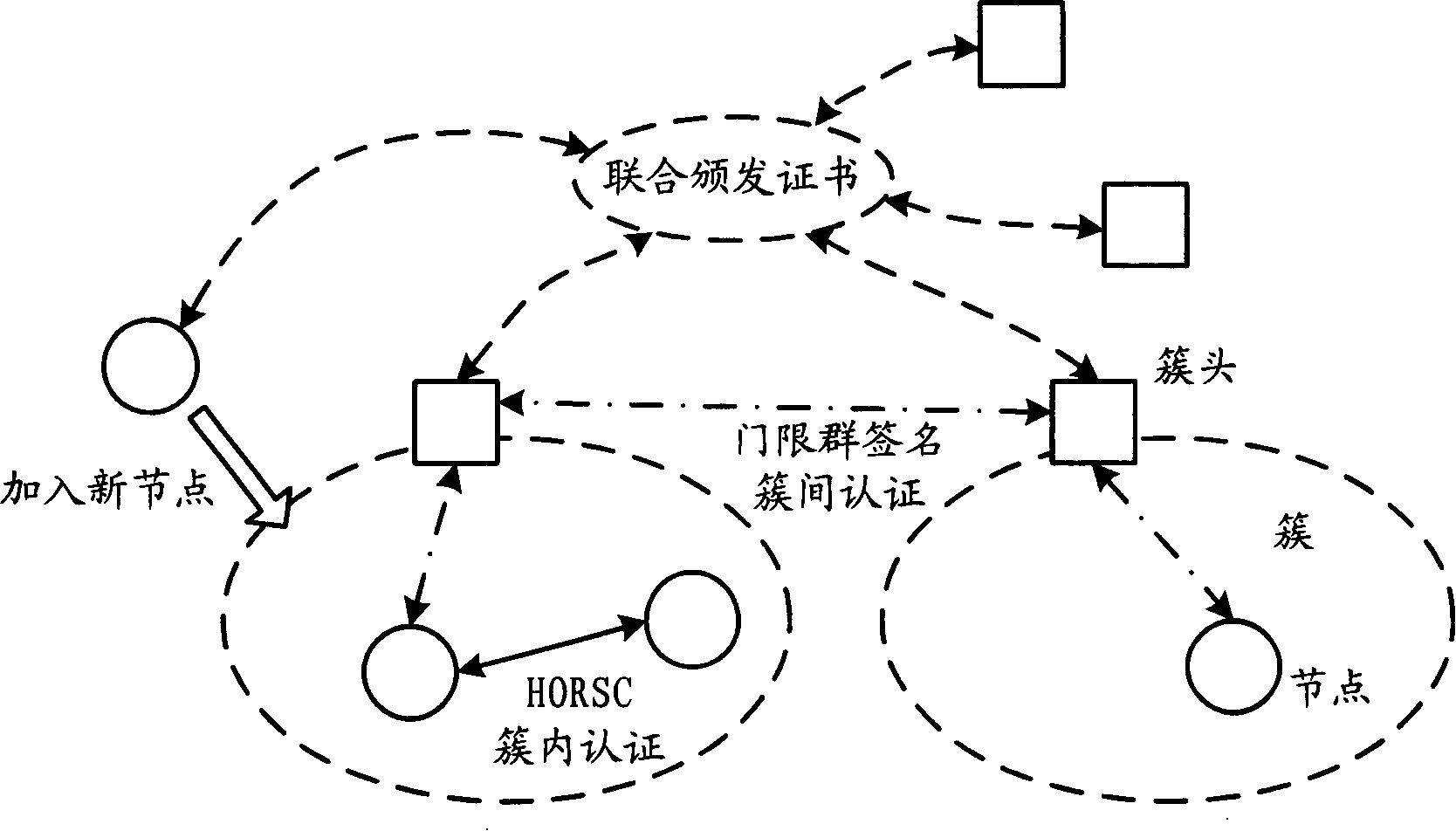
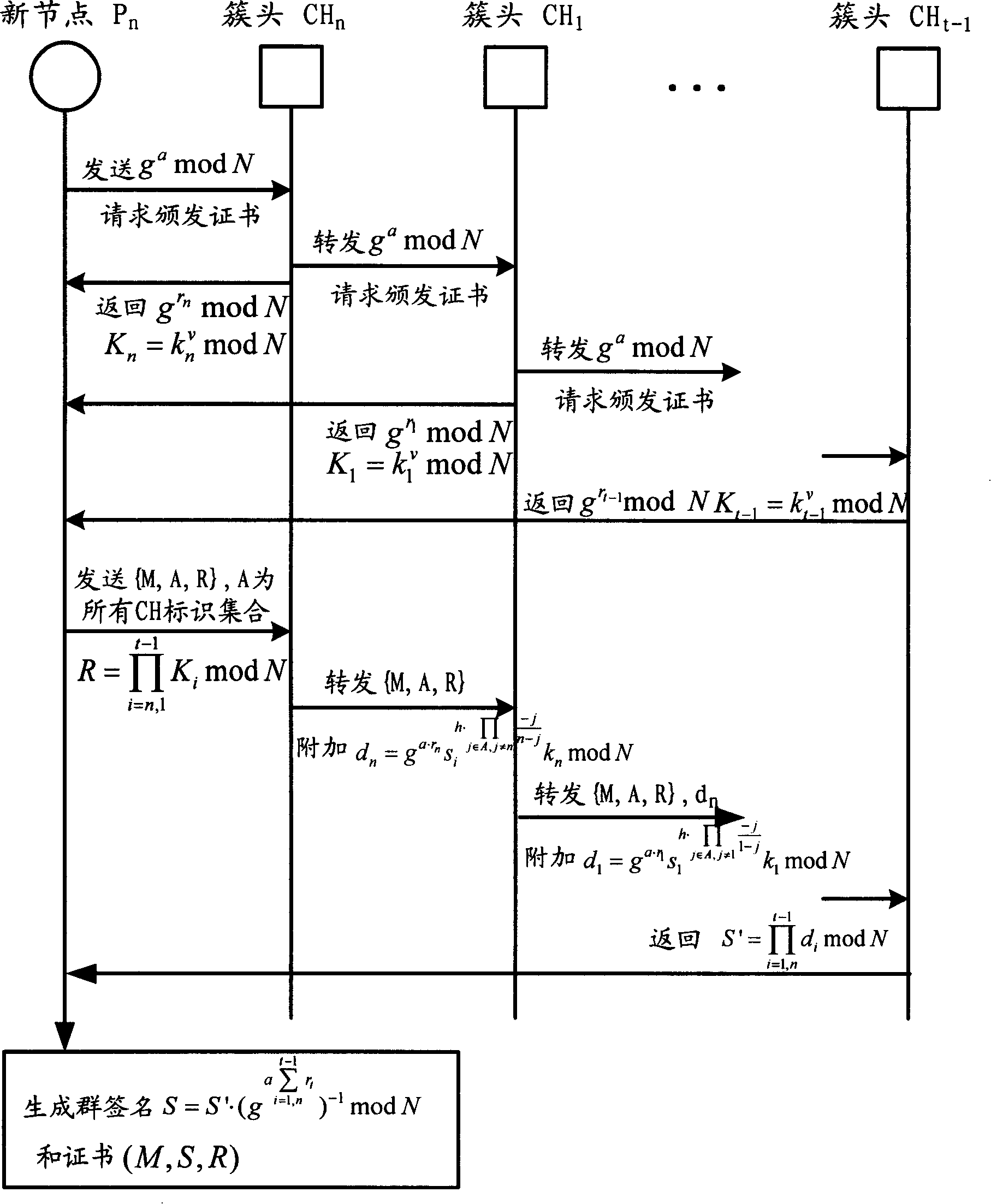
The invention relates to the communication field and discloses an authentication method, a network and a system of mobile ad hoc network, which ensures the realization of layer distribution type authentication scheme of cluster mobile ad hoc network; and the requirement on computer processed resources is rational, which can be realized in practical application environment. The invention adopts a group network structure of cluster mobile ad hoc network and advocates layer distribution identity authentication scheme; and the inter-cluster communication used an improved new threshold group signature protocol which improves the original threshold group signature method based on GQ and decreases power index calculation times, improves calculation parallelism and reduces the requirement on processed resources; at the time of initialization, a certificate and a sub key are issued by the system uniformly; cluster heads which have enough numbers of sub keys can jointly recover system keys, thereby carrying out the group signature to issue certificates to new added nodes and using multi-leap serial communication for realizing united group signature.
Owner:HUAWEI TECH CO LTD +1
Group signature generation system using multiple primes
InactiveUS7093133B2User identity/authority verificationHardware monitoringComposite numberDigital signature
A method is provided for generating a group digital signature wherein each of a group of individuals may sign a message M to create a group digital signature S, wherein M corresponds to a number representative of a message, 0≦M≦n−1, n is a composite number formed from the product of a number k of distinct random prime factors p1·p2· . . . ·pk, k is an integer greater than 2, and S≡Md(mod n). The method may include: performing a first partial digital signature subtask on a message M using a first individual private key to produce a first partial digital signature S1; performing at least a second partial digital signature subtask on the message M using a second individual private key to produce a second partial digital signature S2; and combining the partial digital signature results to produce a group digital signature S.
Owner:HEWLETT PACKARD DEV CO LP
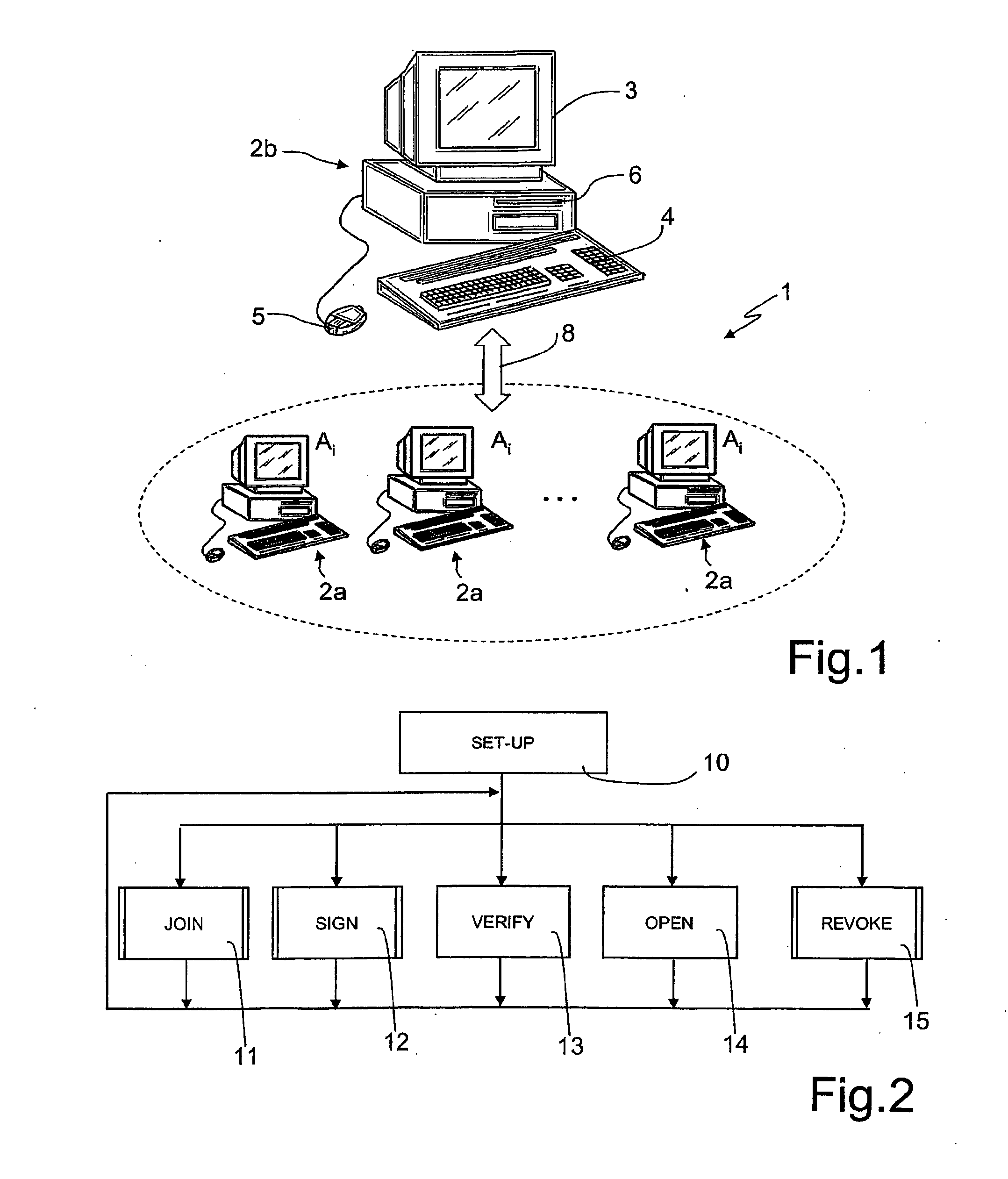
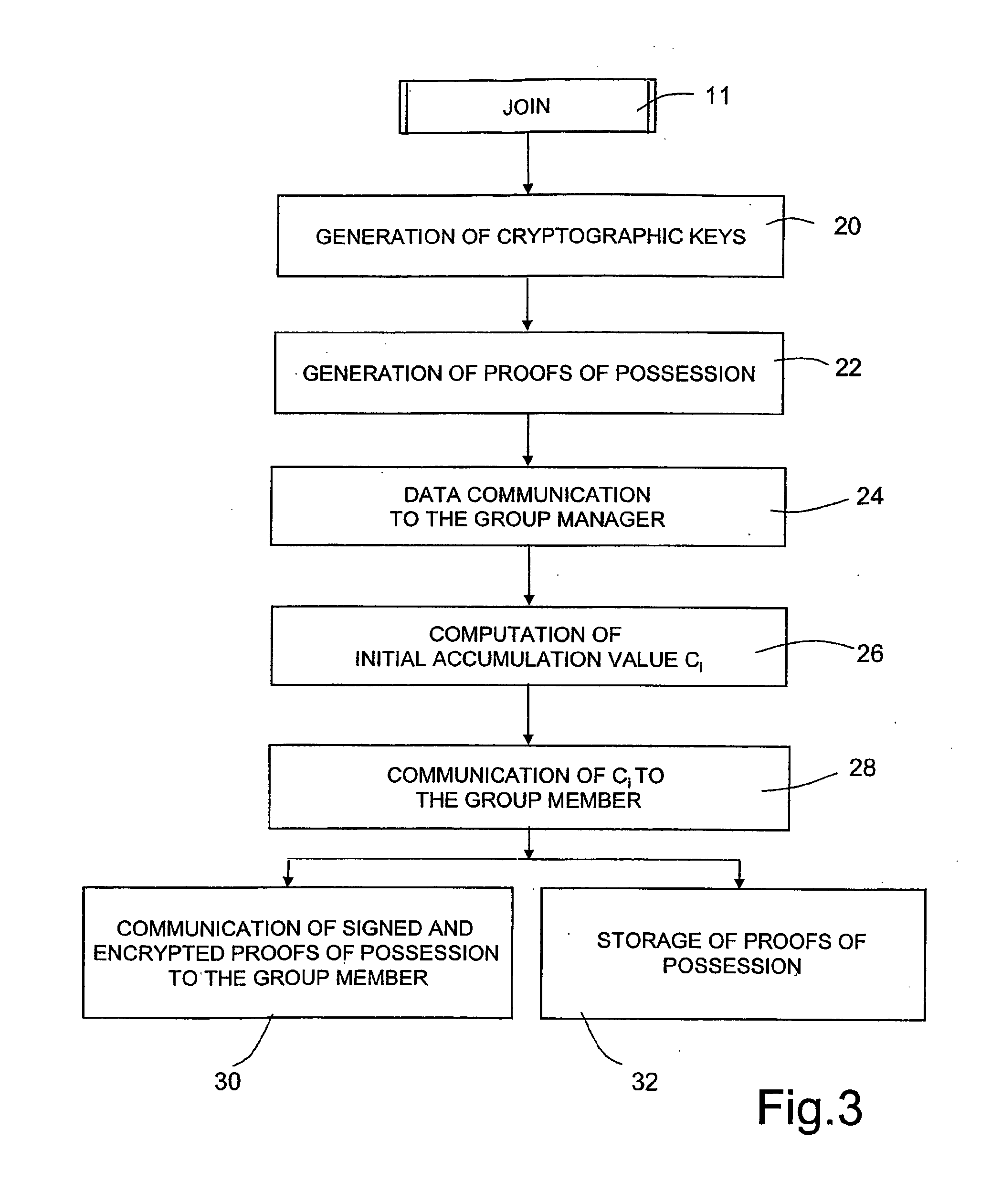
Group Signature Scheme With Improved Efficiency, in Particular in a Join Procedure
ActiveUS20090222668A1Avoiding possible attackImprove system securityKey distribution for secure communicationMultiple keys/algorithms usageGroup signatureDistributed computing
A method for managing a group signature scheme includes in a setup procedure for group initialization, generating, by a group manager, a group public key. In a join procedure for the group manager to add a new member to the group, the method includes generating by the new member, user information, and providing the generated user information to the group manager, and computing, by the group manager, membership information for the new member based on the user information received by the new member and on the group public key, and providing to the new member the computed membership information. In particular, the membership information is computed, by the group manager, as a function of the inverse of a given hash function of the user information. In a signing procedure for a group member to sign a message on behalf of the group, the method includes: using, by the group member, the membership information and the user information. The method further includes the use of digital certificates, in order for the group member to prove to the group manager the possession of said user information.
Owner:TELECOM ITALIA SPA
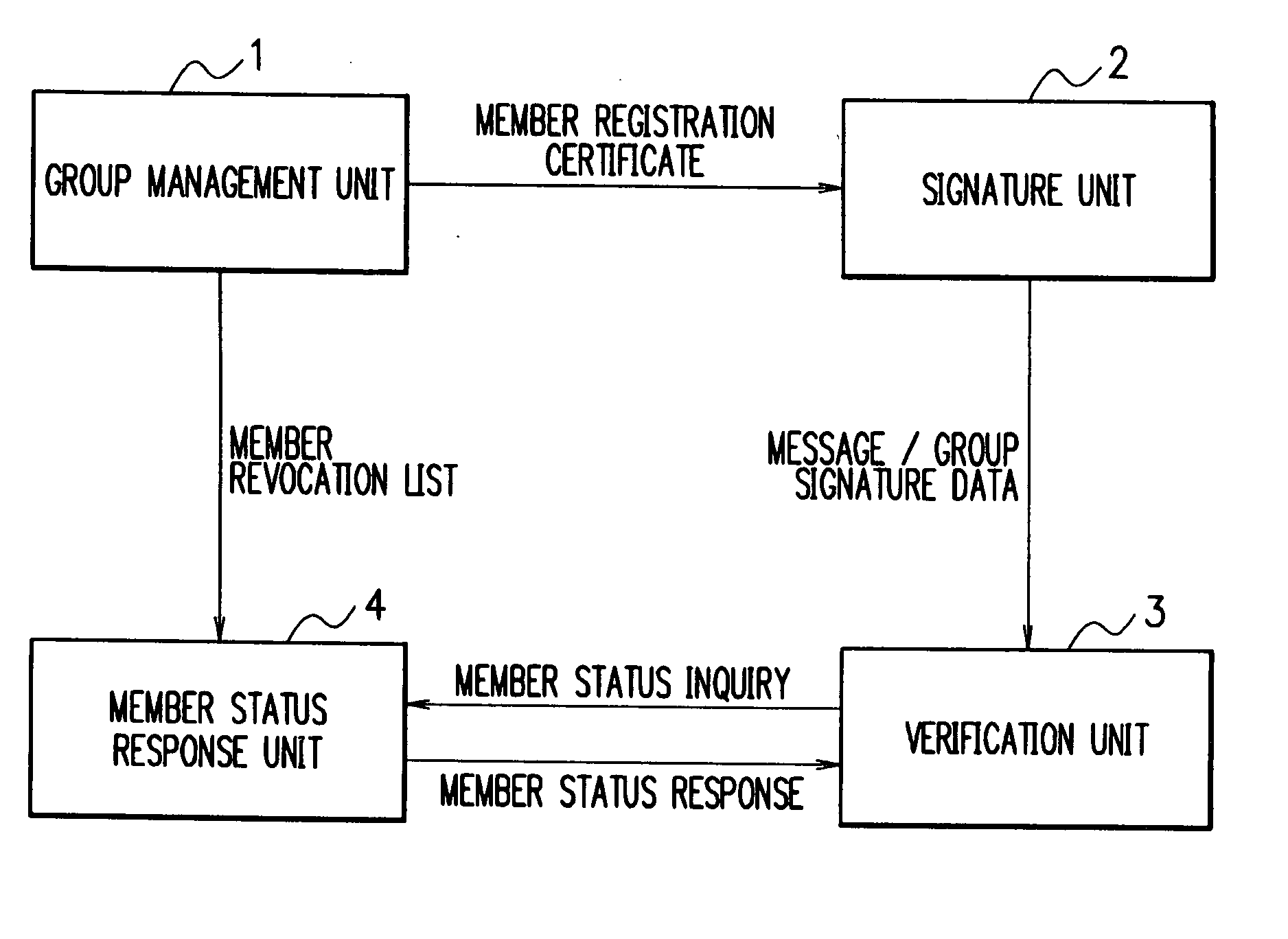
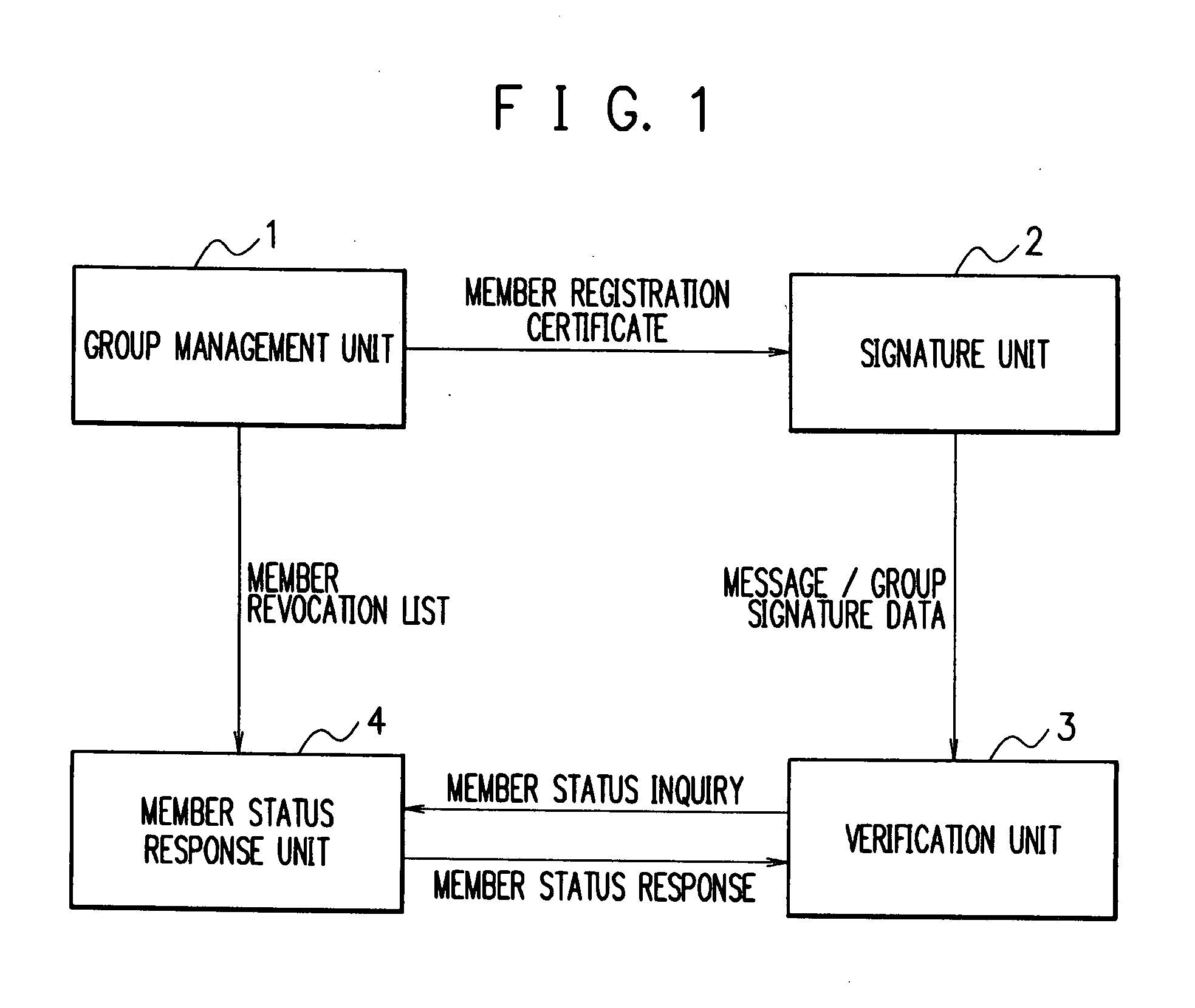
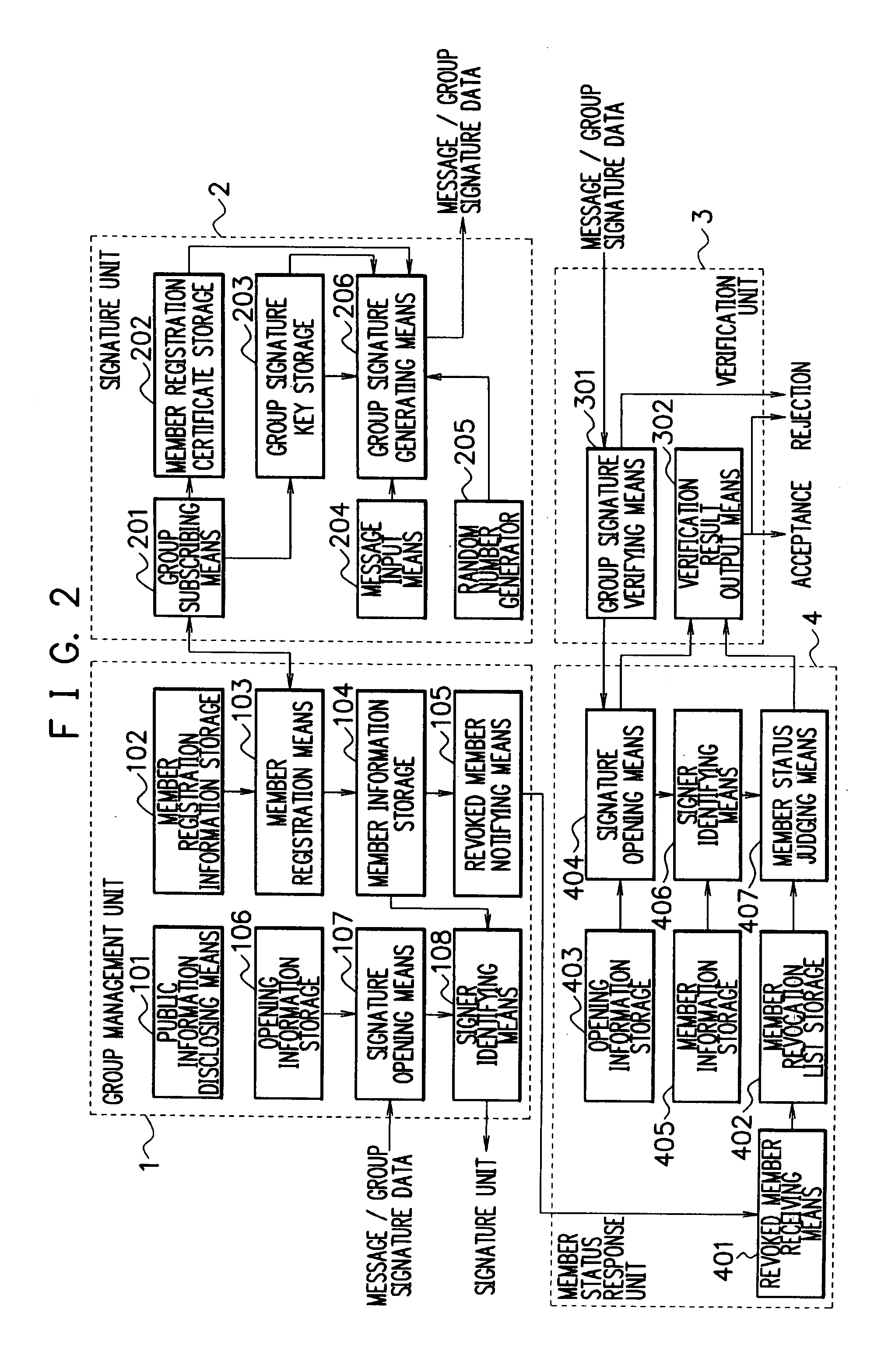
Group Signature System, Member Status Judging Device, Group Signature Method And Member Status Judging Program
InactiveUS20080091941A1User identity/authority verificationSpecial data processing applicationsManagement unitAnonymity
For group signature data capable of keeping anonymity, it is possible to efficiently determine whether the user having created the group signature data is a valid member of the group. When a message and group signature data are received, the verification unit 3 authenticates the data and inquires, of the member status response unit 4, whether the user of the signature unit 2 having created the group signature data is a valid member of the group. In response to the inquiry, the response unit 4 determines the member status of the user having created the group signature data, according to a member revocation list notified from the group management unit 1. The response unit 4 then transmits a judge result of the member status to the verification unit 3.
Owner:NEC CORP
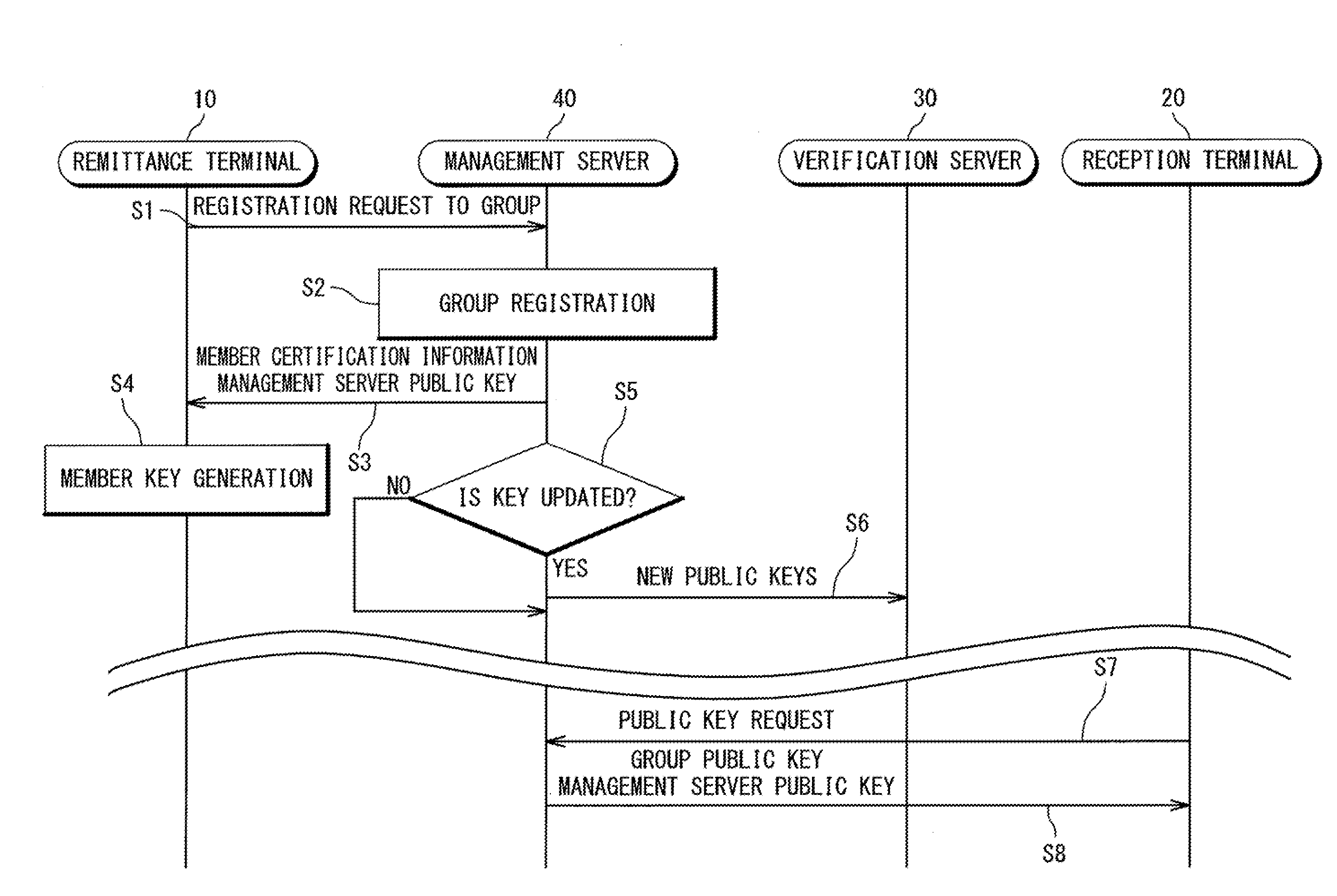
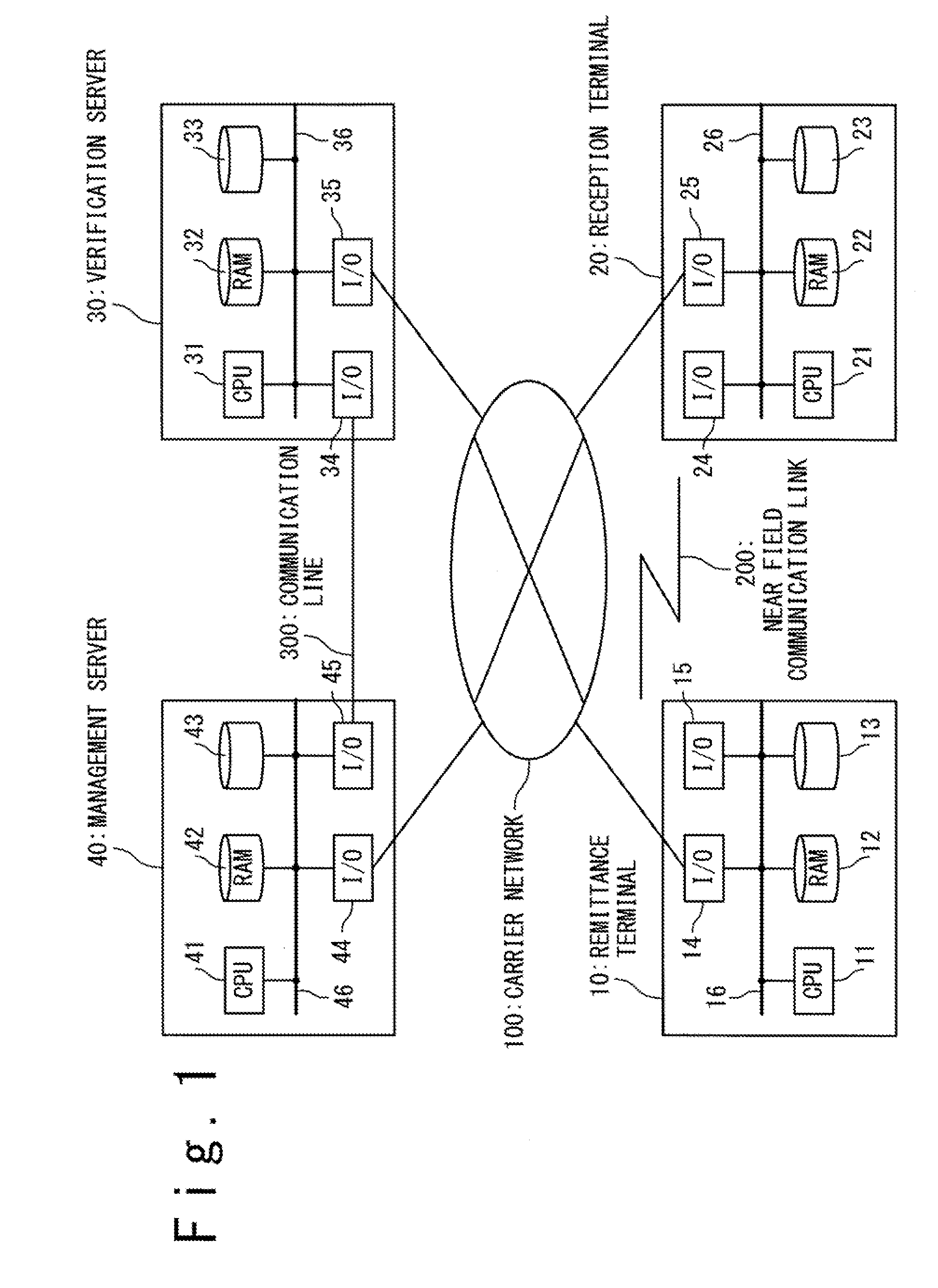
Electronic money system and electronic money transaction method
ActiveUS20100217710A1Illegal useComplete banking machinesNear-field transmissionComputer terminalComputer security
An electronic money system is directed to avoid unauthorized use of certificate-type electronic money. The electronic money system is provided with a management server, a verification sever, a remittance terminal, and a receptor terminal. In response to a request from the remittance terminal, the management server issues an inactive electronic certificate including a certificate ID and notifies the verification server of the certificate ID. The remittance terminal gives a group signature to the inactive electronic certificate to generate an active electronic certificate. The reception terminal verifies the active electronic certificate obtained from the remittance terminal on the basis of the group signature. The verification server matches the certificate ID notified from the management server with the certificate ID included in the active electronic certificate verified by the reception terminal to verify availability of the active electronic certificate.
Owner:NEC CORP
Group signature system, apparatus and storage medium
ActiveUS20110060903A1Increase computing speedReduce the amount of calculationUser identity/authority verificationComputer scienceBilinear group
A group signature system according to one embodiment of the present invention comprises a group administrator apparatus, signer apparatuses and a verifier apparatus which can communicate with one another. Here, in a group signature method used by the apparatuses, a multiplication cyclic group or a bilinear group in which an order is unknown as in RSA is not used at all, but a multiplication cyclic group gG of a prime order q is only used, and representation parts ki1 and ki2 are used as a member private key. Moreover, as information for tracing a signer, Ti=G1̂{ki1} is utilized, and ki1 is utilized for verifying revocation. In consequence, a calculation amount can be decreased to increase a calculation speed as compared with conventional [CG04], [FI05] and [DP06] systems.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
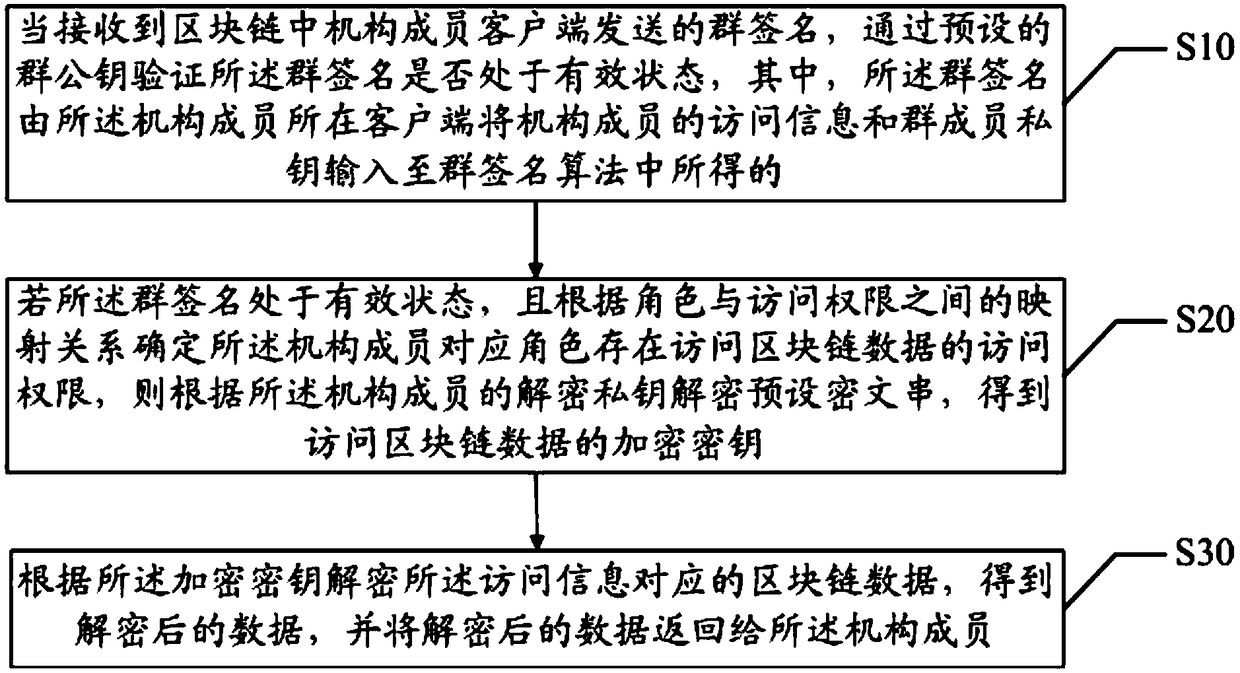
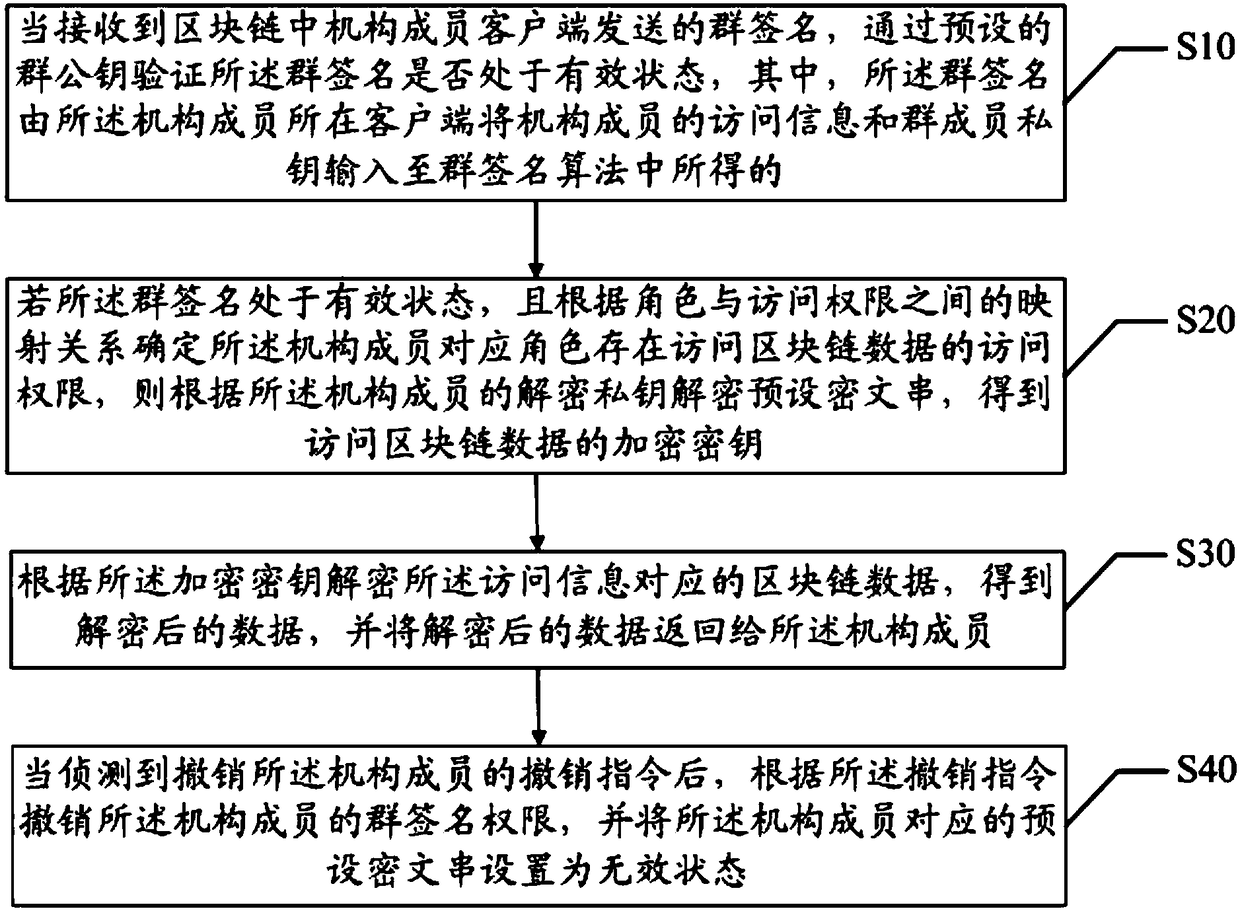
Blockchain access control method, device and computer readable storage medium
ActiveCN108768988AImprove operational efficiencyAchieve accessKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInter agencyRelational database
The invention discloses a blockchain access control method, a blockchain access control device and a computer readable storage medium. The blockchain system provided by the invention completes the identity authentication of a member of a role corresponding institution by a group signature algorithm, and implements the access of encryption data by using a digital envelope technology; through the concept of groups and roles, each group corresponds to a role, and each role may correspond to multiple institutional members, so that the blockchain system supports the scenarios of multi-user data access. Compared to the traditional relational database-based data access system, the blockchain system in the application is strong in scalability, and capable of easily implementing inter-agency accesscontrol. And in this embodiment, the signature operation of the group signature algorithm and the verification time for verifying the group signature are independent of the number of group members, thereby improving the operation efficiency of the blockchain system during data access.
Owner:WEBANK (CHINA)
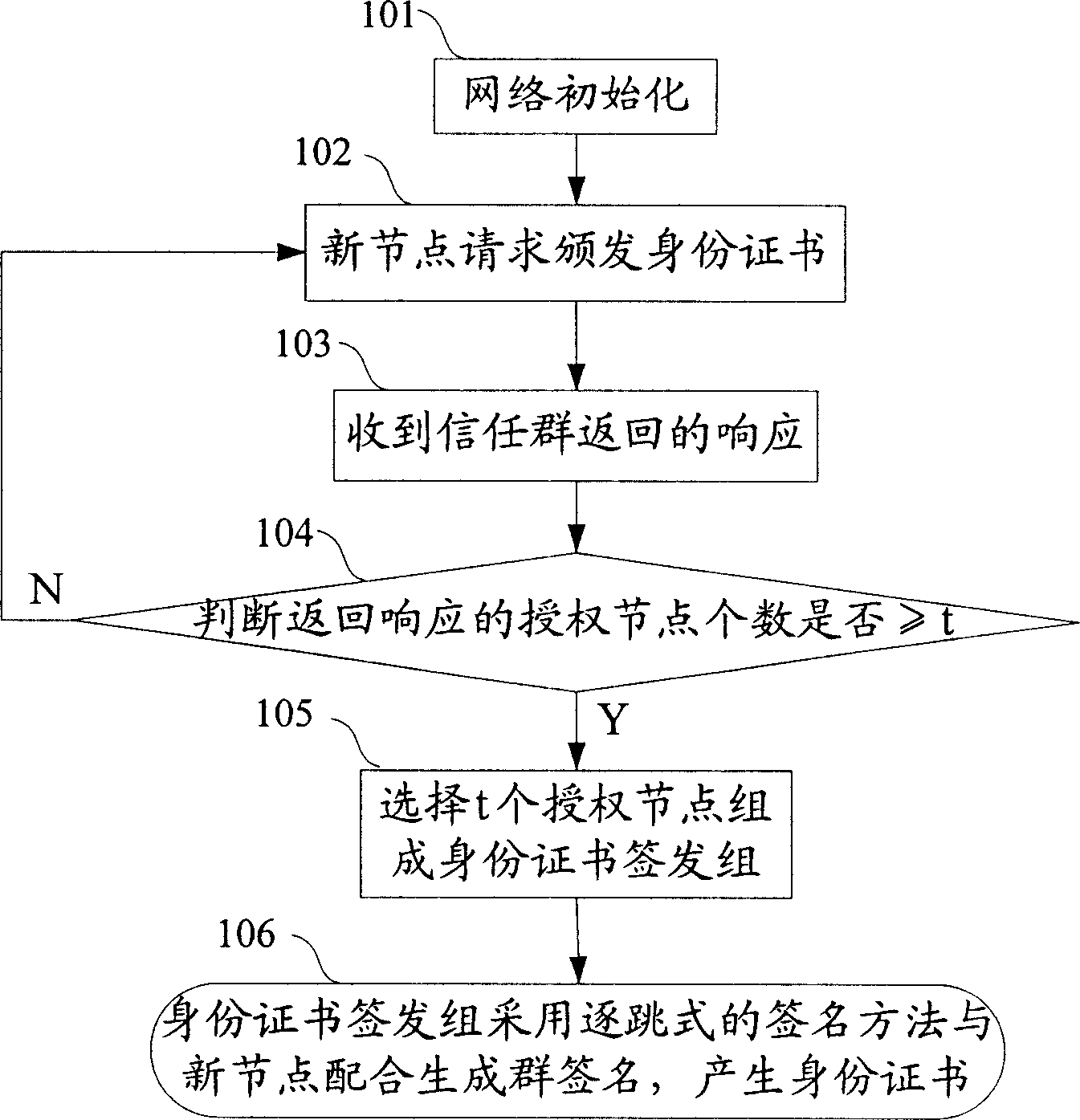
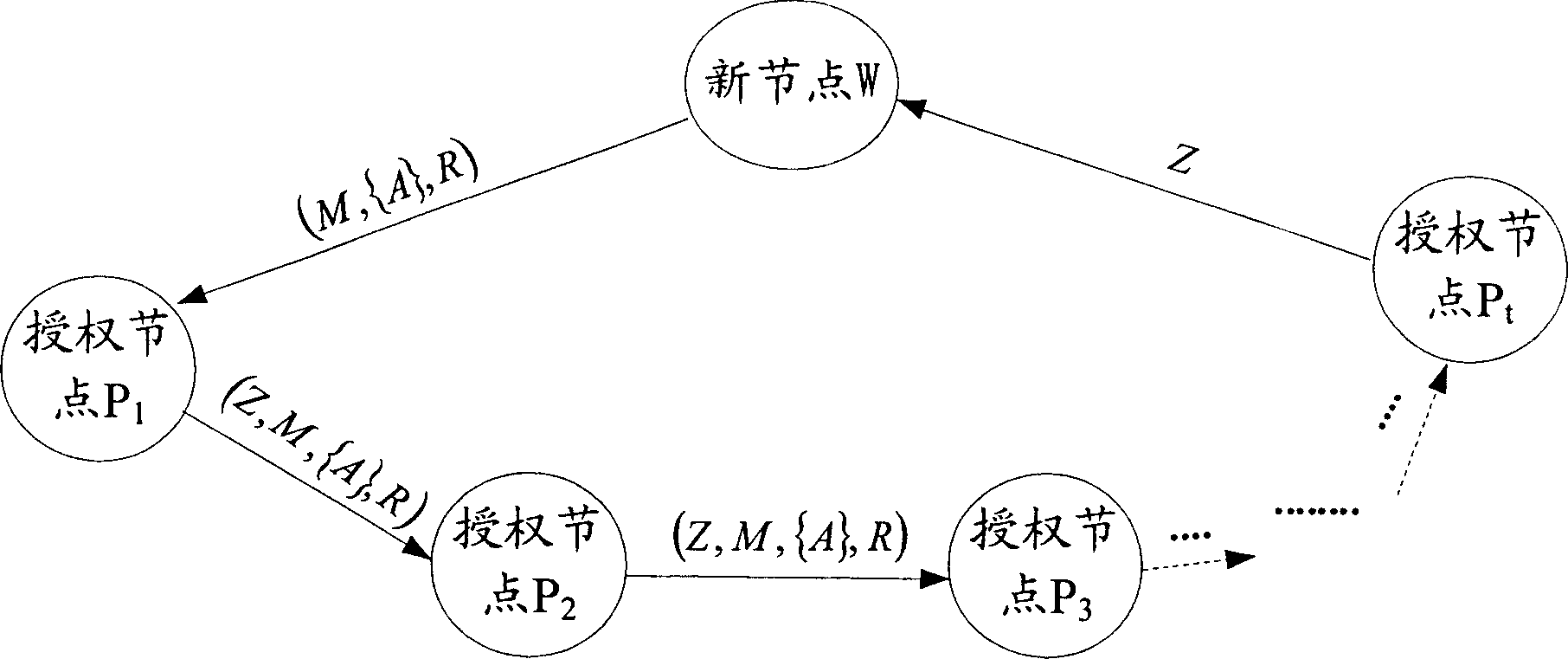
Distributed identity-card signature method
ActiveCN1897518AAvoid security breachesAchieve reuseKey distribution for secure communicationUser identity/authority verificationAuthorizationGroup signature
The method comprises: new node initiates an identification letter issuing request to all authorization node; after receiving the responses for agreeing to participate in issuing identification letter from at least t authorization nodes, the new node selects t authorization nodes from them; the selected authorization nodes use a hop-by-hop signature approach to incorporate with the new node to generate the group signature and to generate identification letter.
Owner:HUAWEI TECH CO LTD +1
Group signature method based on elliptic curve
ActiveCN101977110ASignature length advantageComputational overhead advantagePublic key for secure communicationUser identity/authority verificationDigital Signature AlgorithmKey generation
The invention discloses a group signature method based on an elliptic curve, comprising the following six steps: 1, selecting two multiplication cyclic groups G1 and G2 with the order of p from the elliptic curve as well as a nonsingular bilinear mapping e which can map elements in the G1 and G2 into GT, namely e:G1*G2->GT; 2, operating a secret key generation algorithm by a group administrator, generating a group public key, and generating signature secrete keys for members in the groups; 3, operating a signature algorithm after members in the groups obtain corresponding signature secret keys through the secret key generation algorithm; 4, verifying the validity of signatures delta by adopting the group public key to operate a verification algorithm by a verifier; 5, as for a given signature, adopting a signature tracking algorithm to substitute revocation identification of a time slot in which the signature is generated into a revocation identification inequation, and if the inequation is true, indicating that the signature is signed by a group member corresponding to the revocation identification; and 6, in some cases, adopting a member revocation algorithm to revoke the signature qualification of some members, which requires to calculate the revocation identification of the members in corresponding time intervals and publish the revocation identification in a revocation list.
Owner:BEIHANG UNIV
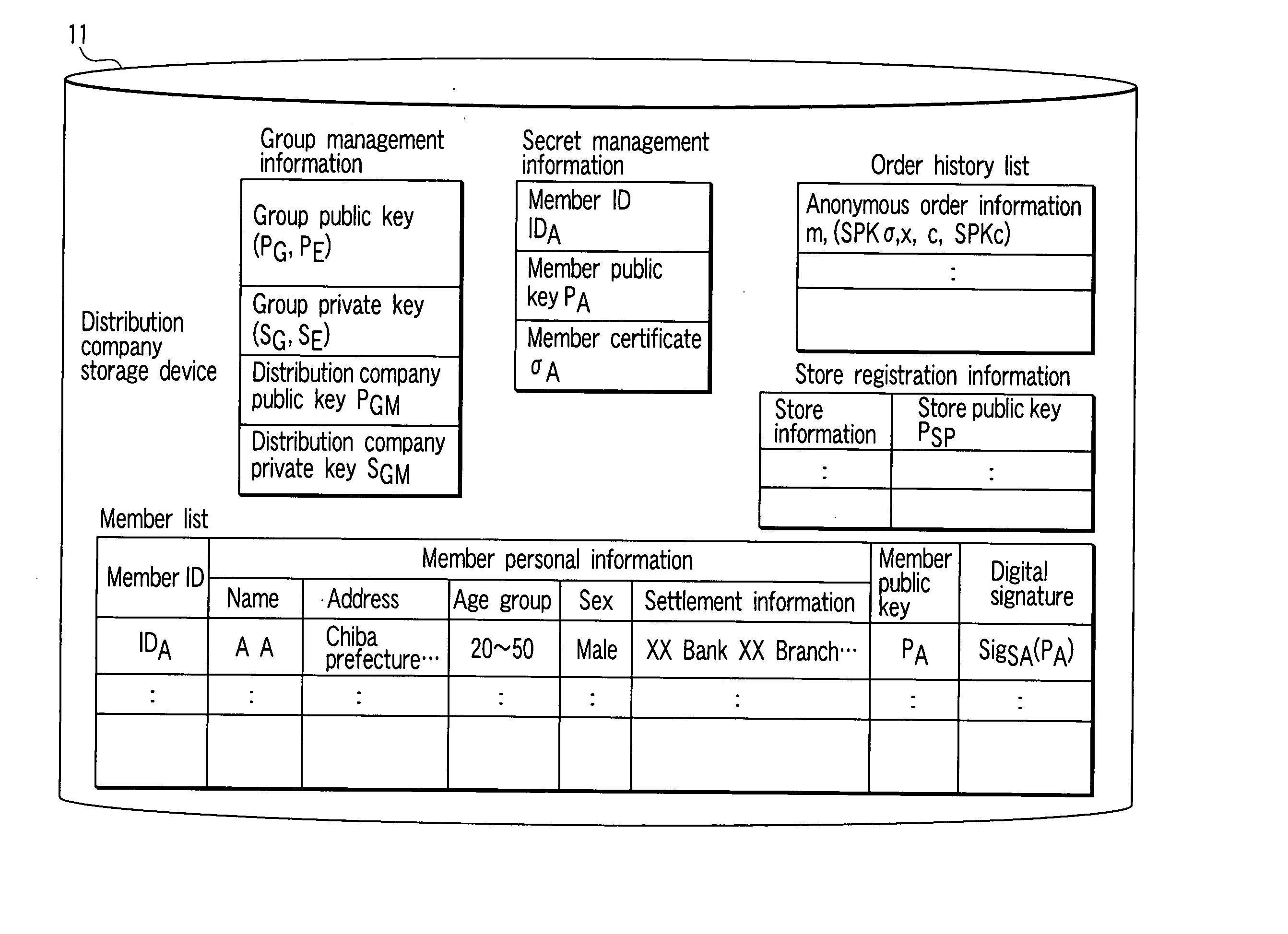
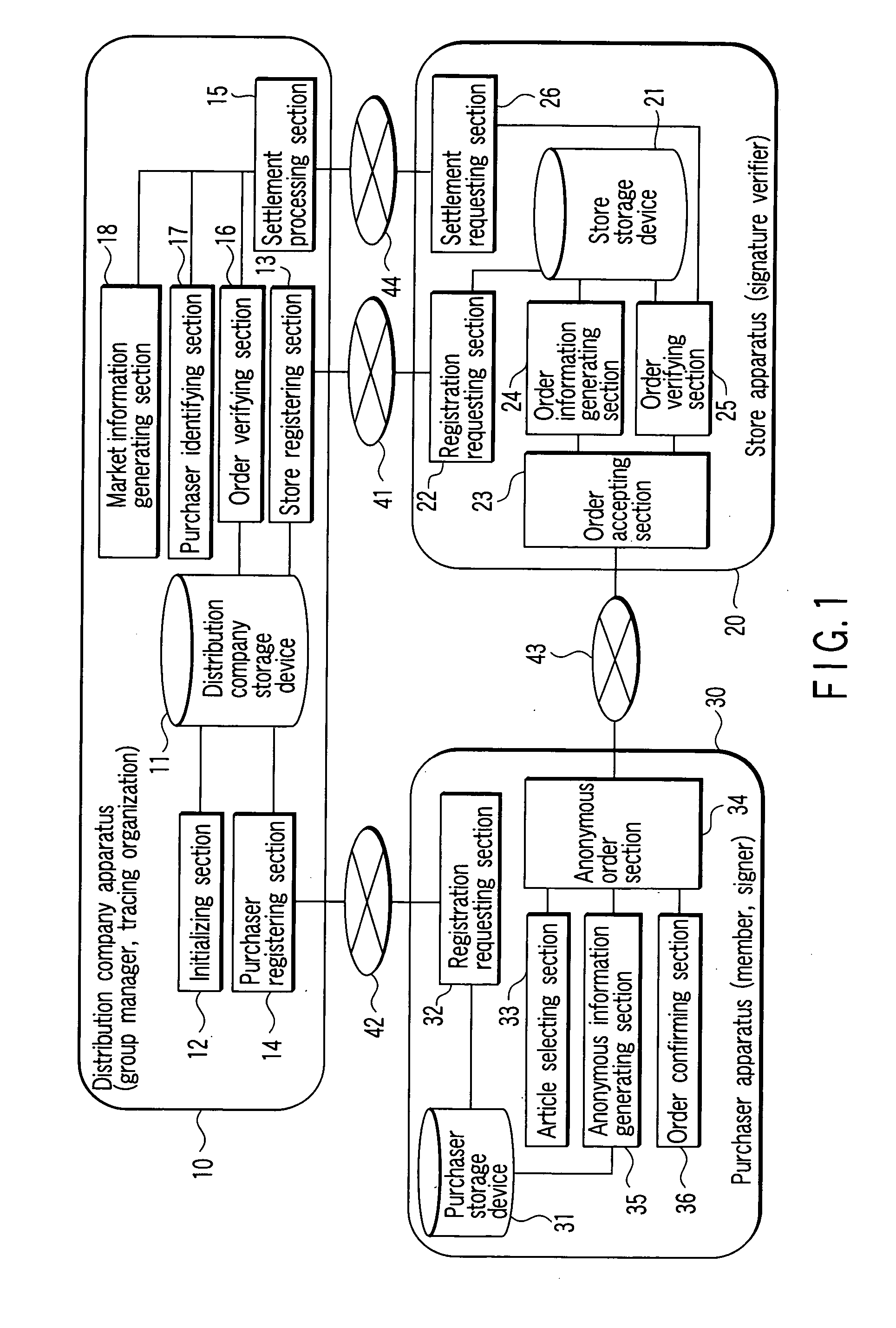
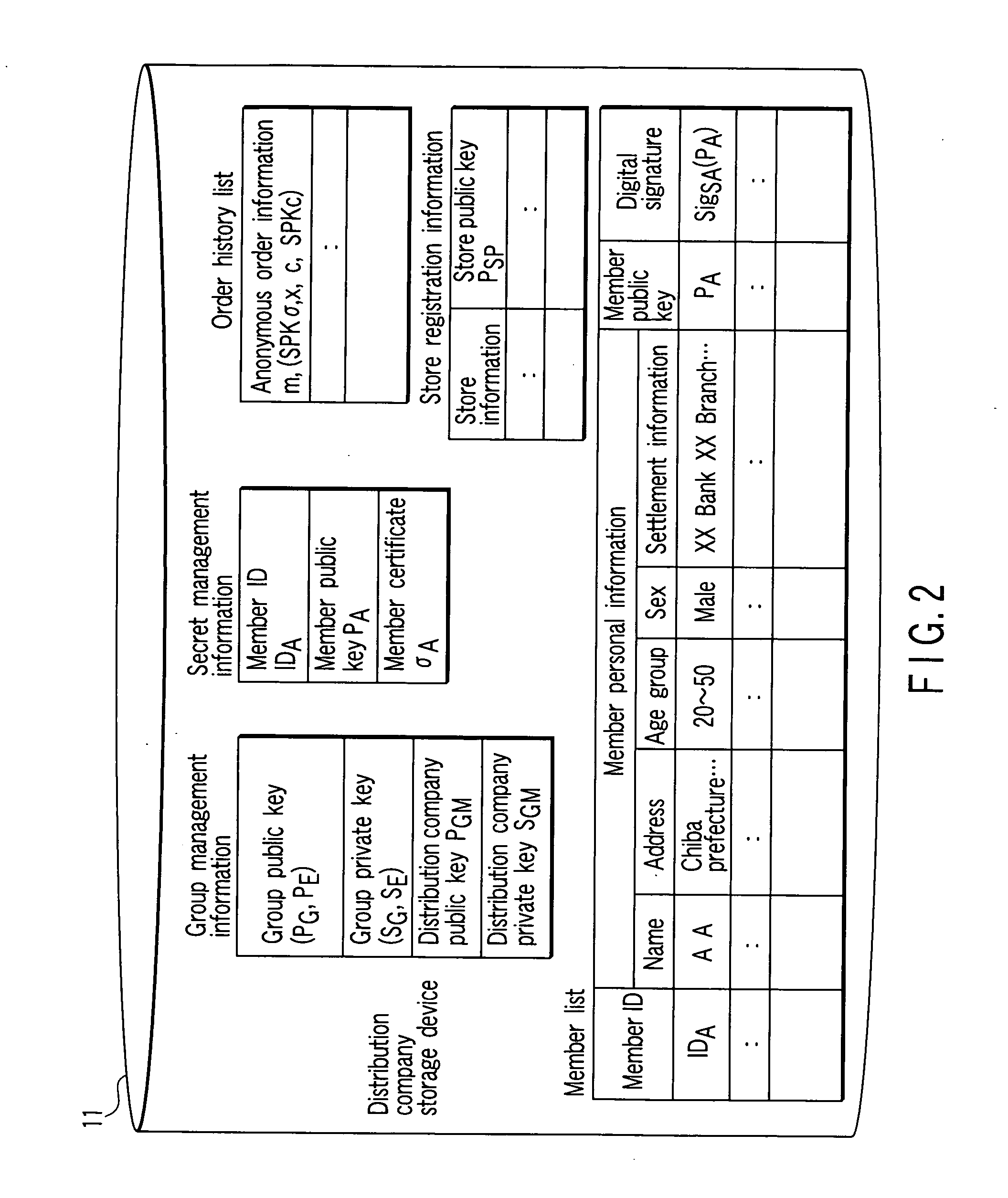
Anonymous order system, an anonymous order apparatus, and a program therefor
InactiveUS20070255661A1Privacy protectionPrivacy of the contentsUser identity/authority verificationSecret communicationService provisionData mining
A store apparatus receives anonymous order information including an order ID and a group signature from a purchaser apparatus. The store apparatus verifies the group signature. When the group signature is verified to be valid, the store apparatus sells an article corresponding to the anonymous order information and order ID to a purchaser via a manager apparatus so as to keep the name of the article secret. Consequently, the store apparatus, serving as a service provider, need not manage personal information. This enables a user to remain anonymous. Further, the manager apparatus handles the article the name of which is kept secret. This makes it possible to protect the privacy of the contents of the order from the manager apparatus.
Owner:KK TOSHIBA +1
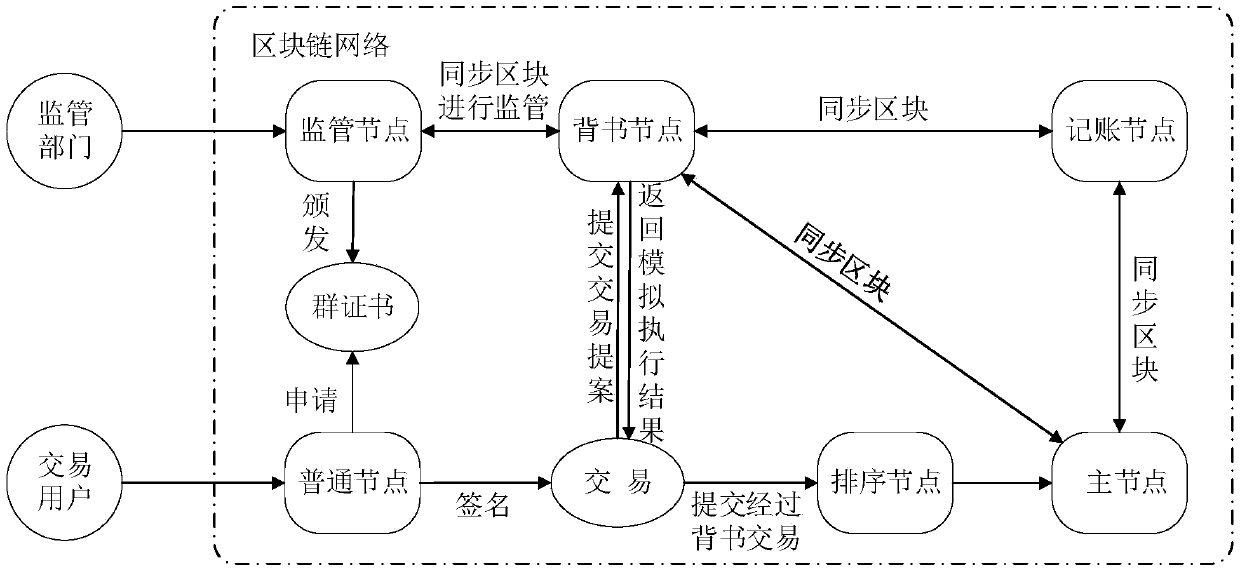
Permission block chain privacy protection and supervision method based on group signatures
InactiveCN109636599AProtect identity privacyGood anonymityFinanceDigital data protectionPrivacy protectionIdentity privacy
The invention discloses a permission block chain privacy protection and supervision method based on group signatures. In a transaction process, whether the endorsement verification of the endorsementnode, the sequencing service of the sequencing node and the consensus process of the main node and the accounting node can only verify the legality of the identities of the two parties of the transaction, and cannot correspond the signature to the real identity of the user, so that the identity privacy of the user is guaranteed. After the transaction is completed, the supervision department can synchronize the block with other nodes through the supervision node, then open the signature contained in the transaction, and enable the signature to correspond to the real identity of the transactionuser, so as to supervise the block chain.
Owner:GUANGXI NORMAL UNIV
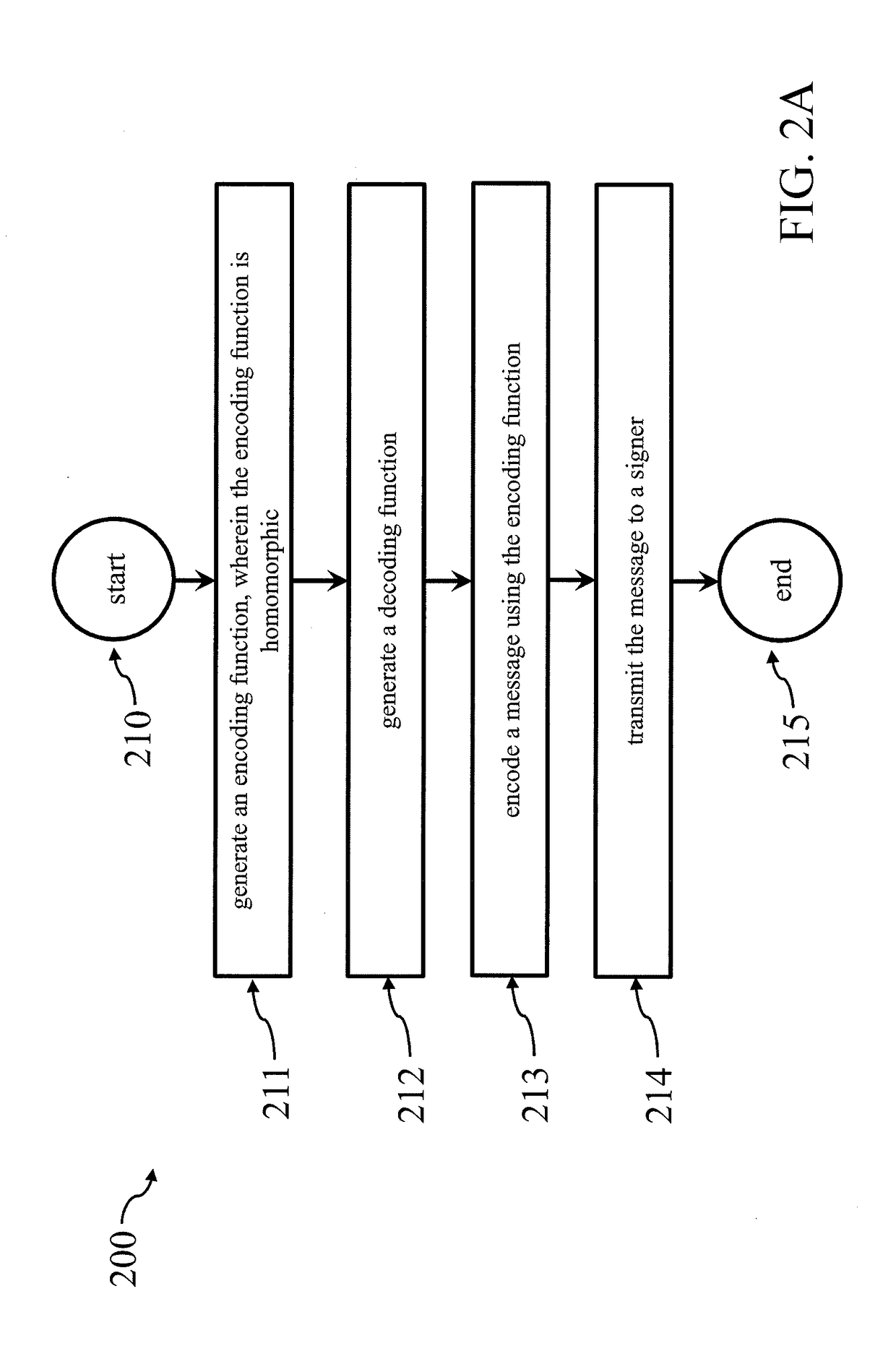
Signature scheme for homomorphic message encoding functions
ActiveUS20180234254A1Key distribution for secure communicationMultiple keys/algorithms usageMessage encodingComputer security
A method for cryptographic signing. The disclosure provides for a signature scheme to secure digital communication using homomorphic message encoding functions. The signature may be applied to hidden messages, and the knowledge of a signature can be proved without the value of the signature being revealed. Applications of the present invention may include anonymous credentials, electronic voting, and group signatures.
Owner:IBM CORP
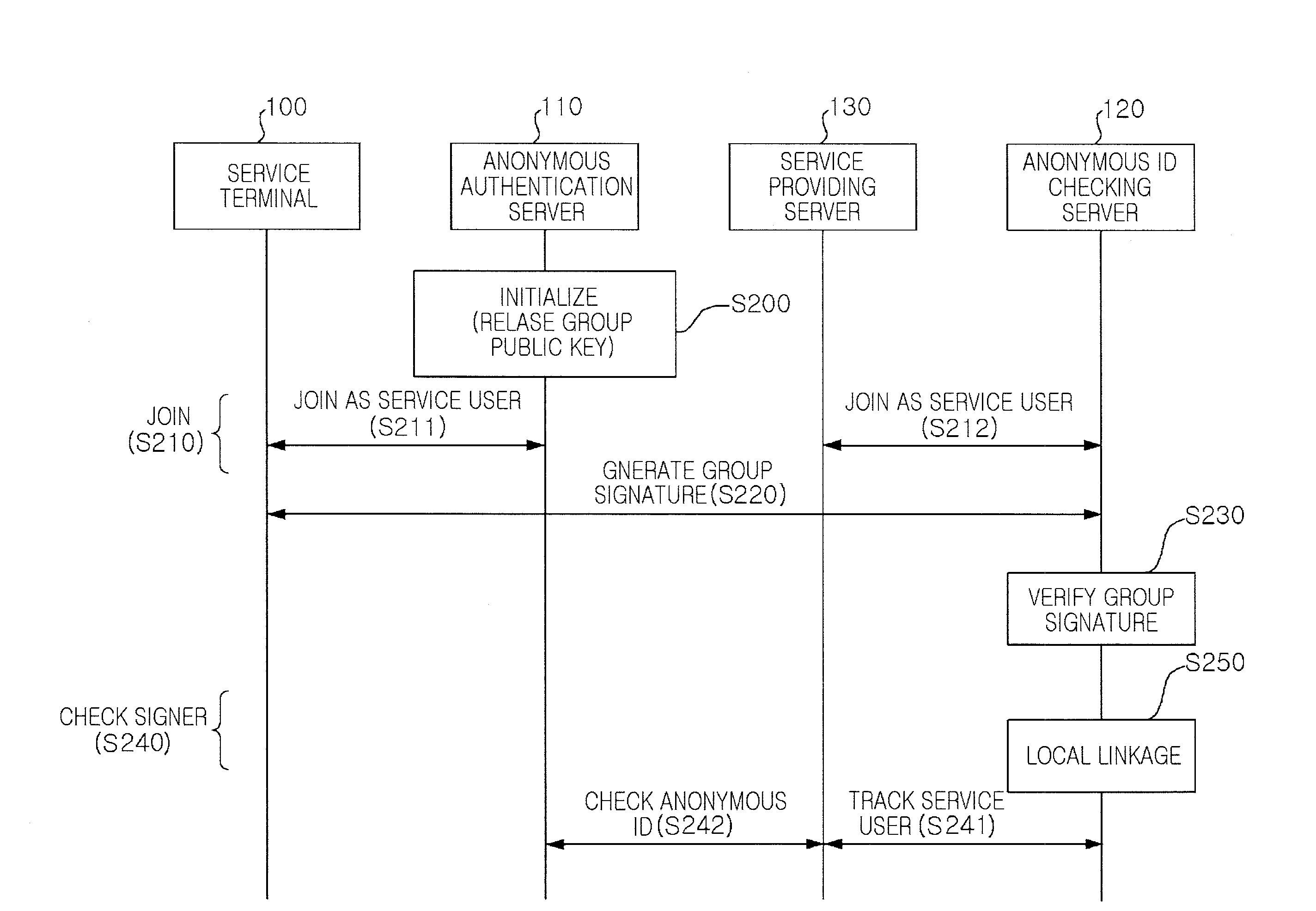
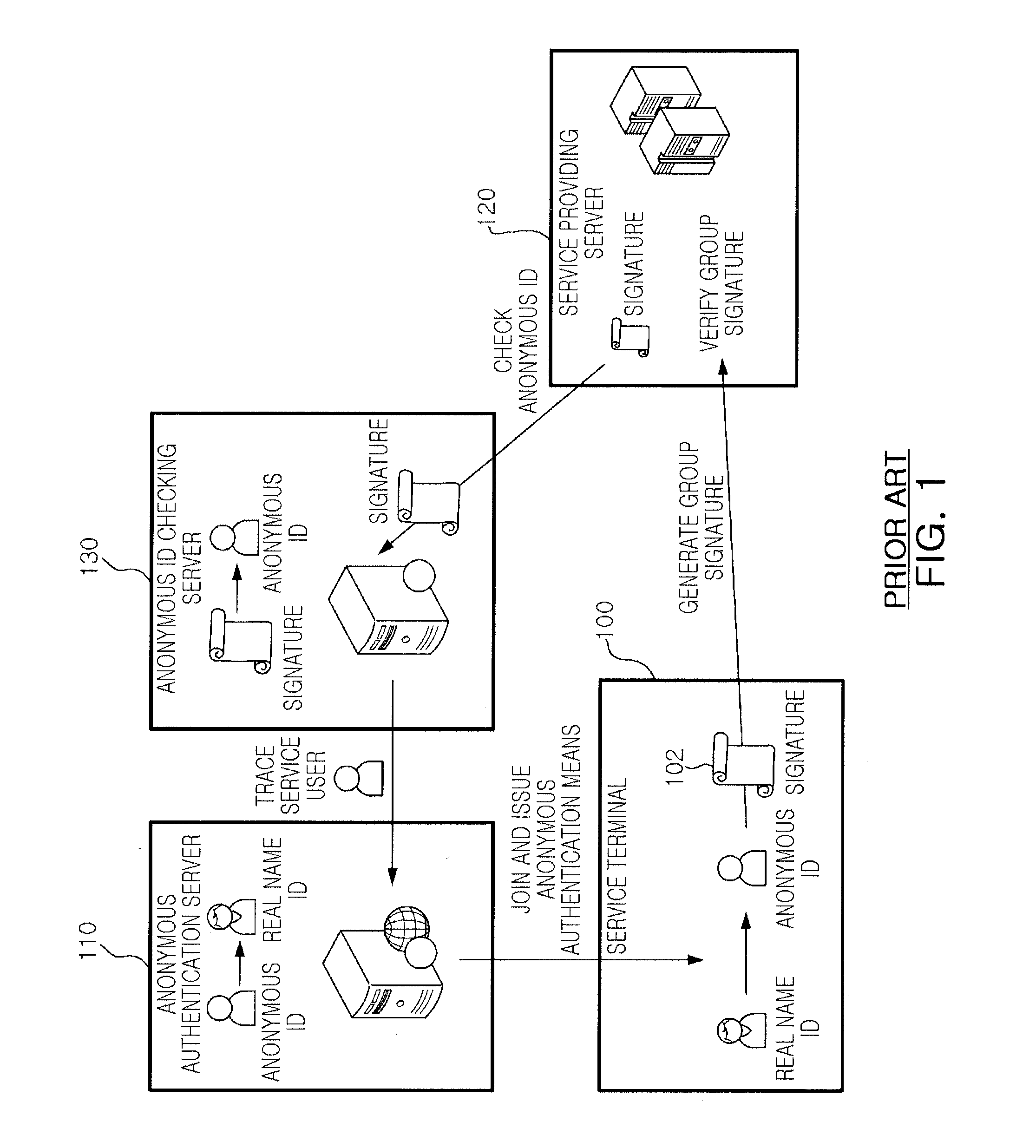
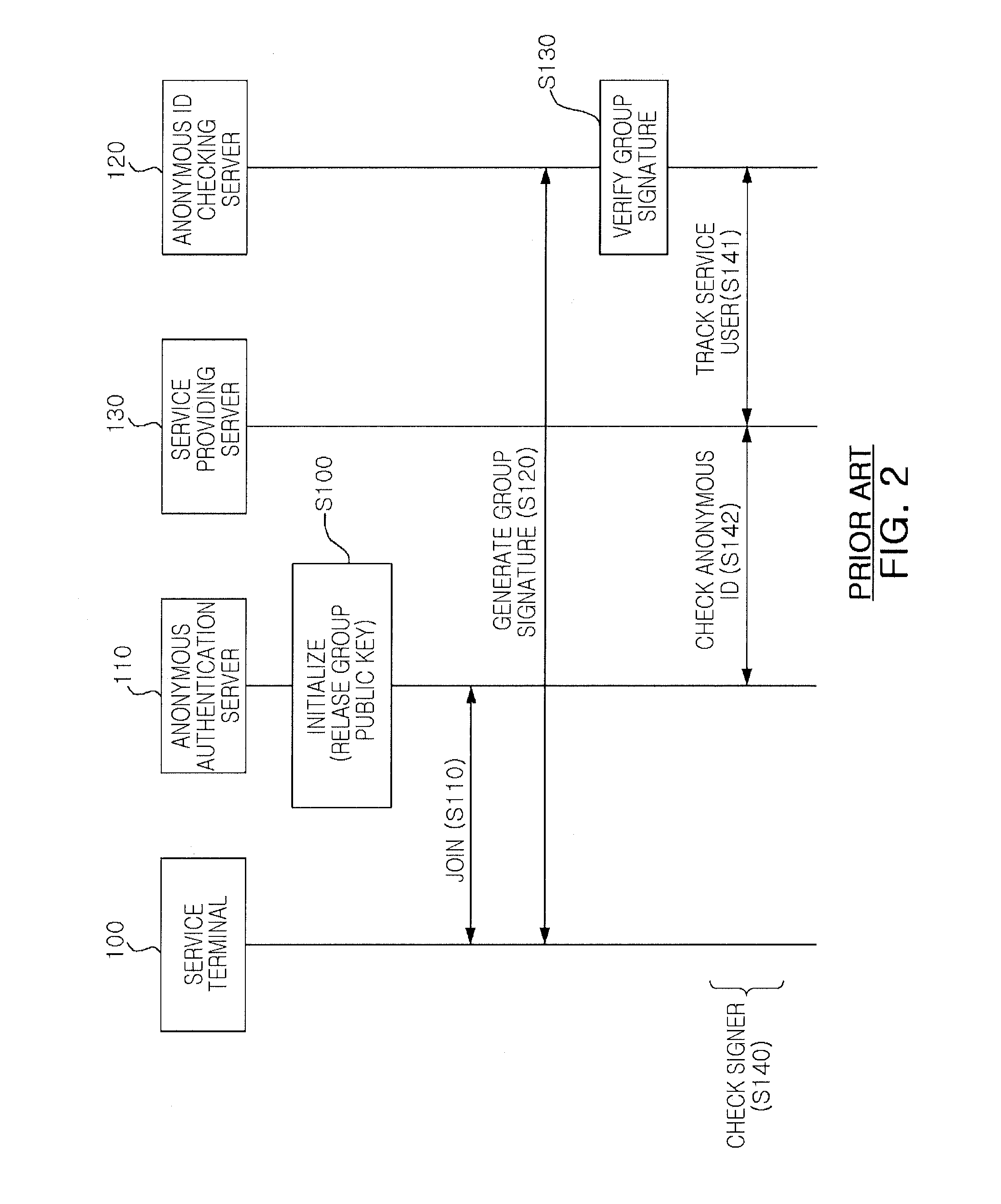
Anonymous authentication service method for providing local linkability
There is provided an anonymous service method of providing local linkability. The anonymous service method providing local linkability according to exemplary embodiments of the invention, an anonymous authentication operation based on a short group signature is performed, for which the concept of a local linkability is introduced to secure linkability within the same service domain. Namely, in the interior of a service provider, a virtual index having a fixed value is calculated for each service user, and in this case, although a plurality of service providers collude with each other, they cannot calculate a virtual index having the same value, whereby the linkability can be secured within the same service domain but not within the interiors of different service domains.
Owner:ELECTRONICS & TELECOMM RES INST
Group signature system, device, and program
ActiveUS20100169656A1Reduce the amount of calculationIncrease computing speedMultiple keys/algorithms usageUser identity/authority verificationZero-knowledge proofComputer security
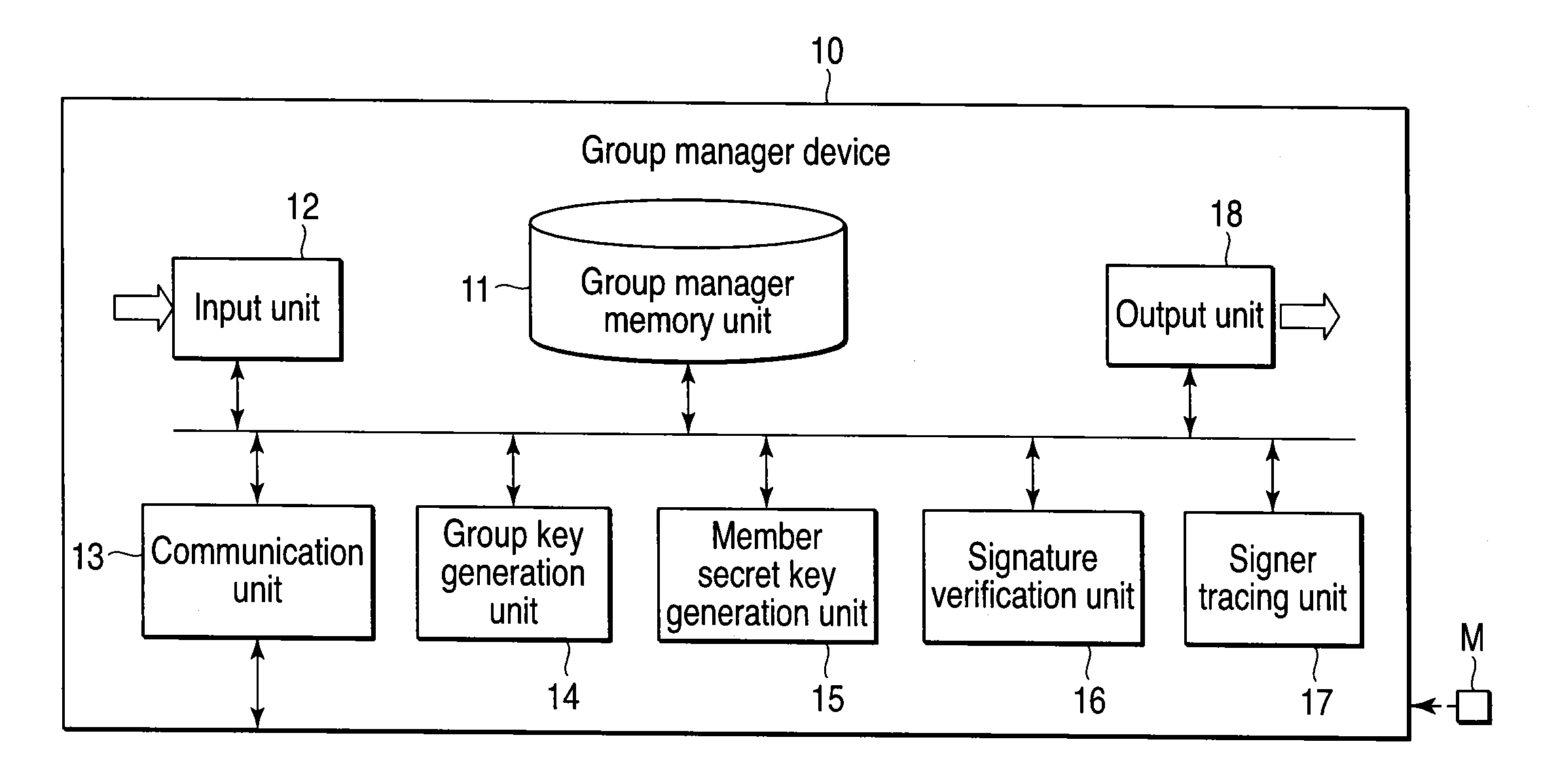
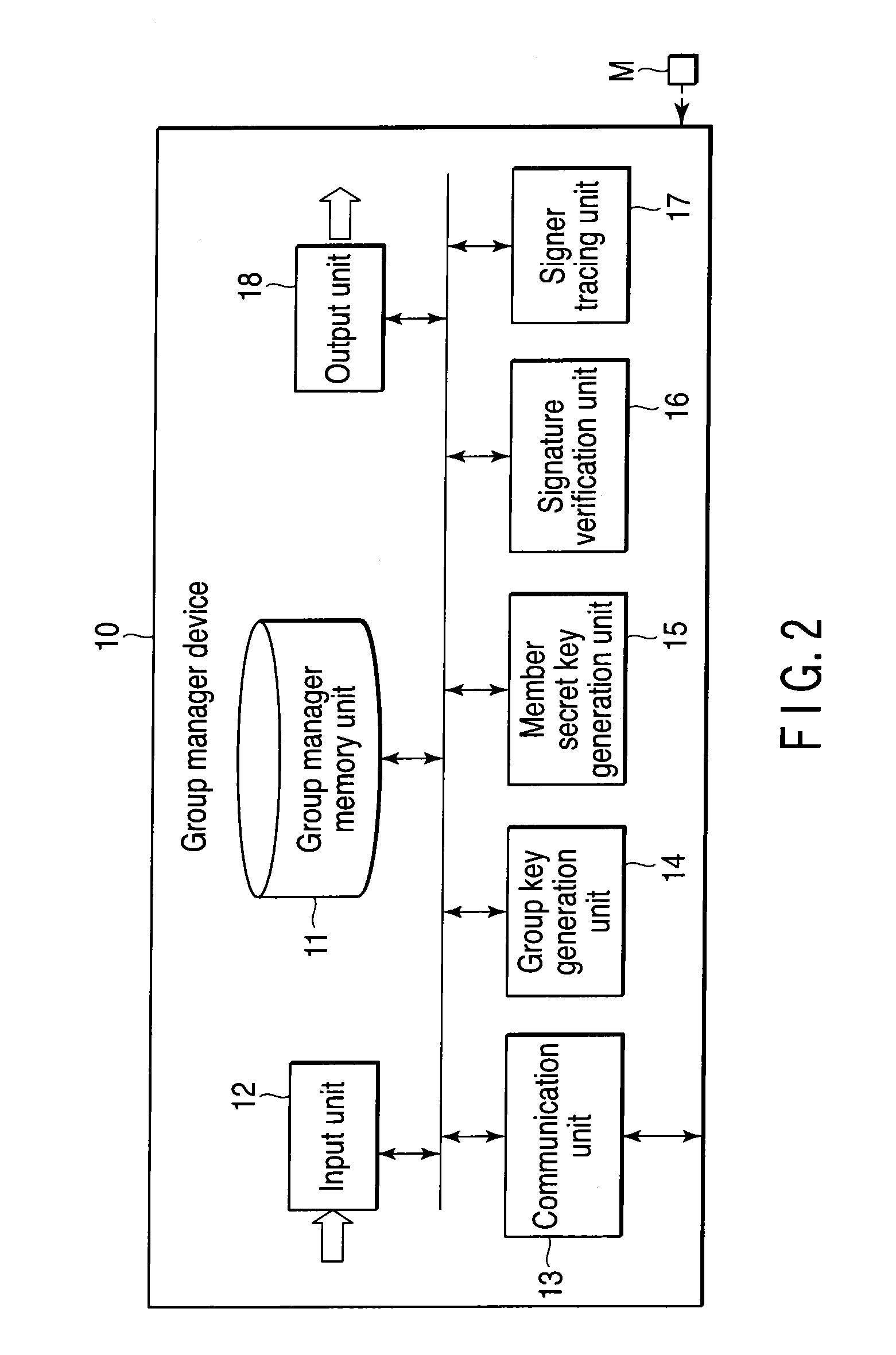
A group signature system includes a group manager device, a signer device and a verifier device capable of communicating with each other, each device using a group signature scheme. The group manager device generates a group secret key, a group public key, a member secret key and a signer tracing information. The signer device generates an encrypted text data of the signer tracing information, and a zero-knowledge proof showing that the signer device knows the member secret key and the encrypted text data is correctly generated based on the signer tracing information. The signer device transmits, to the verifier device, a group signature composed of the encrypted text data and the zero knowledge proof, and the message. The verifier device verifies correctness of the group signature and transmits the verified result to the signer device.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
Group signature method with efficient revocation in vehicle networking
ActiveCN104753683AImprove real-time update efficiencyEfficient undoUser identity/authority verificationIn vehicleBroadcasting
The invention discloses a group signature method with efficient revocation in vehicle networking with an aim to mainly solve the problem that revocation of group members affects key pairs of group members without revocation in the prior art. According to the technical scheme, the group signature method includes: 1, initiating a system and generating parameters and public key pairs of a general trusted mechanism, a local trusted mechanism and a road administration unit; 2, vehicle users registering in the local trusted mechanism before access to the networking and receiving blind certificates; 3, the road administration unit establishing groups, the vehicle users in the jurisdictional scope submitting the blind certificates and joining in the groups after identity legitimacy is verified; 4, after the group members join in the groups, subjecting messages to signing and broadcasting, and anybody verifying the messages; 5, when new users join in the groups or in case of revocation of the members, the road administration unit calculating and publishing new public keys. With the method, efficient and safe joint and revocation in the road administration in the vehicle networking and anonymity of the users to the road administration can be realized, and track on user mobile trajectories is avoided.
Owner:XIDIAN UNIV
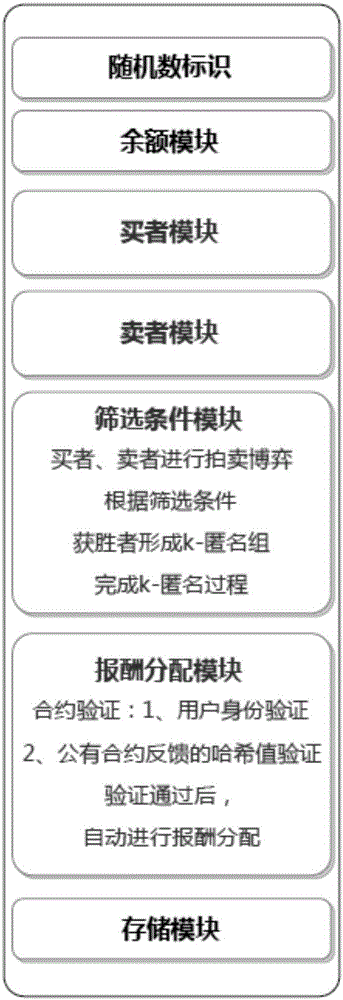
User privacy protection method based on secure smart contract k-anonymity incentive mechanism
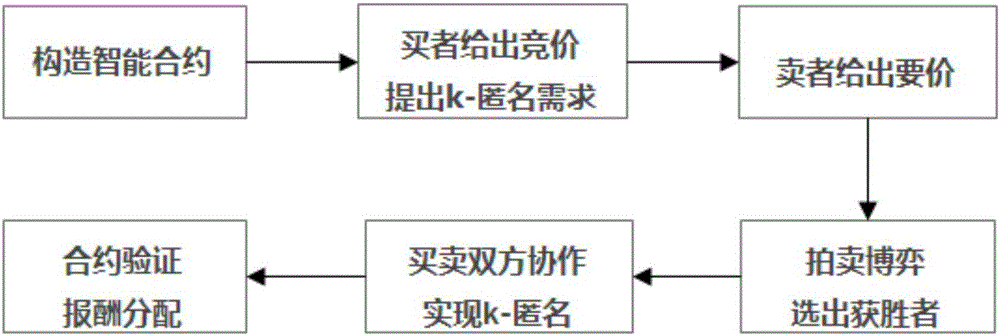
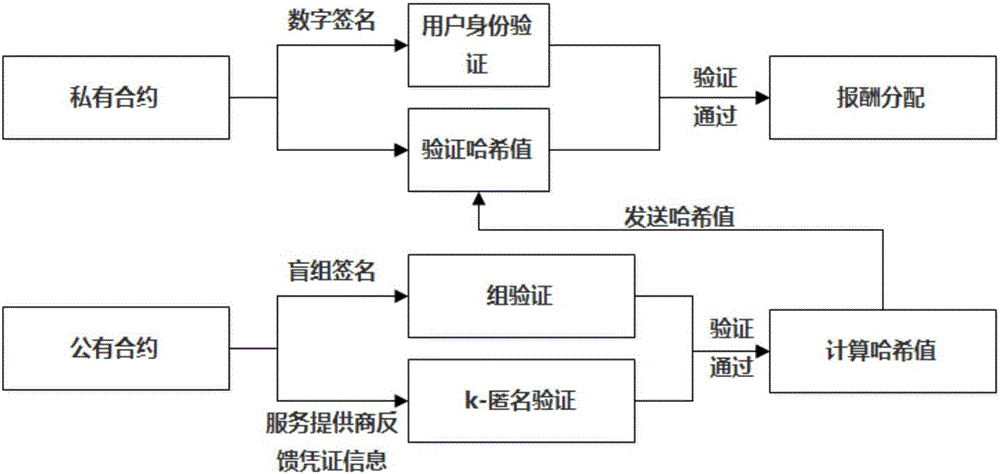
ActiveCN107528835AIncrease success rateAvoid safety hazardsKey distribution for secure communicationUser identity/authority verificationK-anonymityUser privacy
The invention relates to a user privacy protection method based on a secure smart contract k-anonymity incentive mechanism. According to the method, contracts are divided into public contracts and private contracts, the private contracts can be seen only by users in an anonymous group, the public contracts are encrypted through group keys to be prevented from being viewed by outsiders, and the private contracts and the public contracts are jointly verified, such that the security when the users request service is effectively guaranteed. According to the invention, the users can be encouraged to join the k-anonymous group and apply decentralized smart contracts such that potential security risks in a trusted center can be avoided; a part of information of the public contracts is encrypted by use of the group keys so that transaction relations are hidden; and joint verification is carried out by use of the private contracts and the public contracts and group verification is performed by use of a blind group signature such that the k-anonymous success rate is improved while the security is guaranteed.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
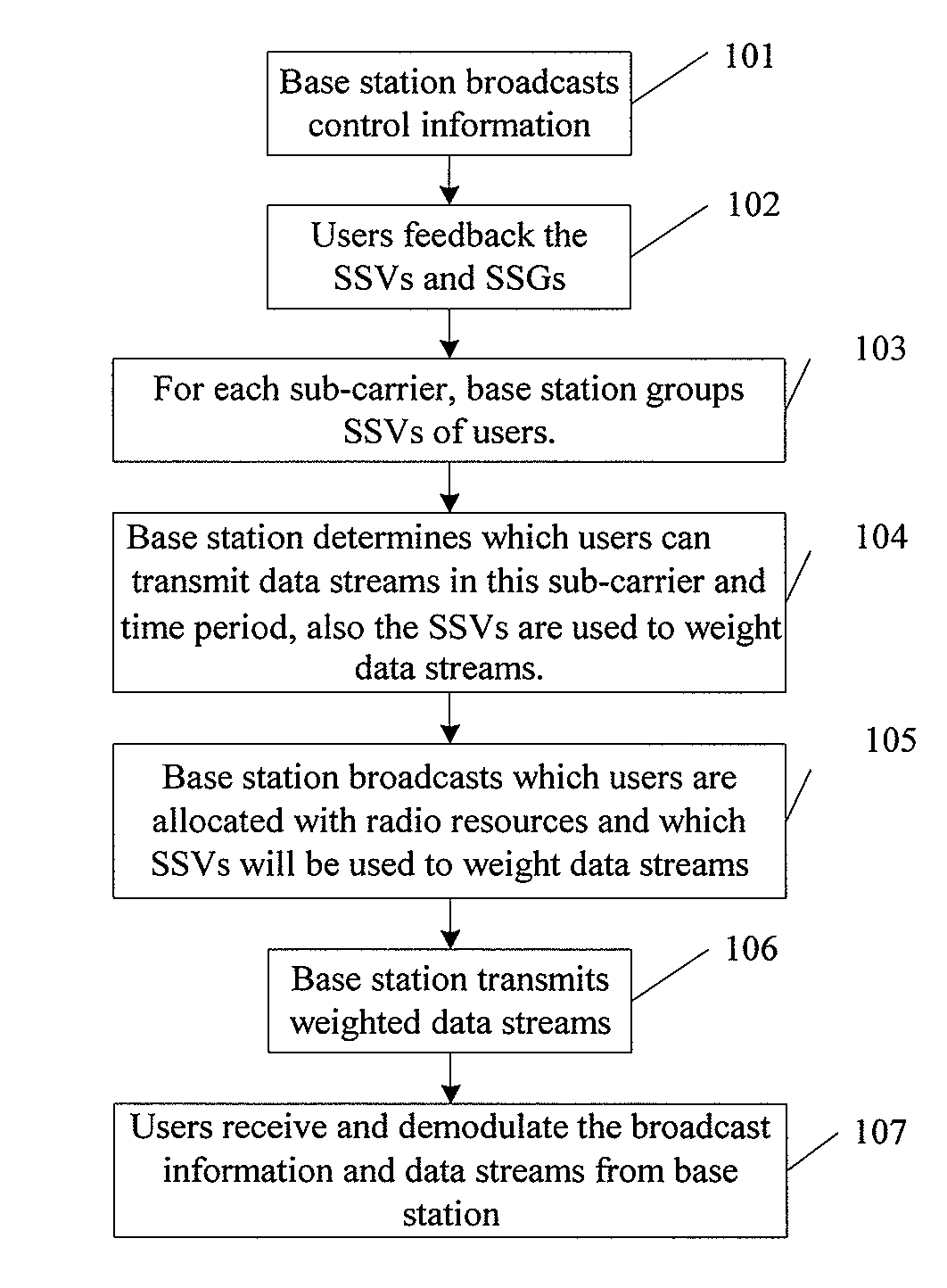
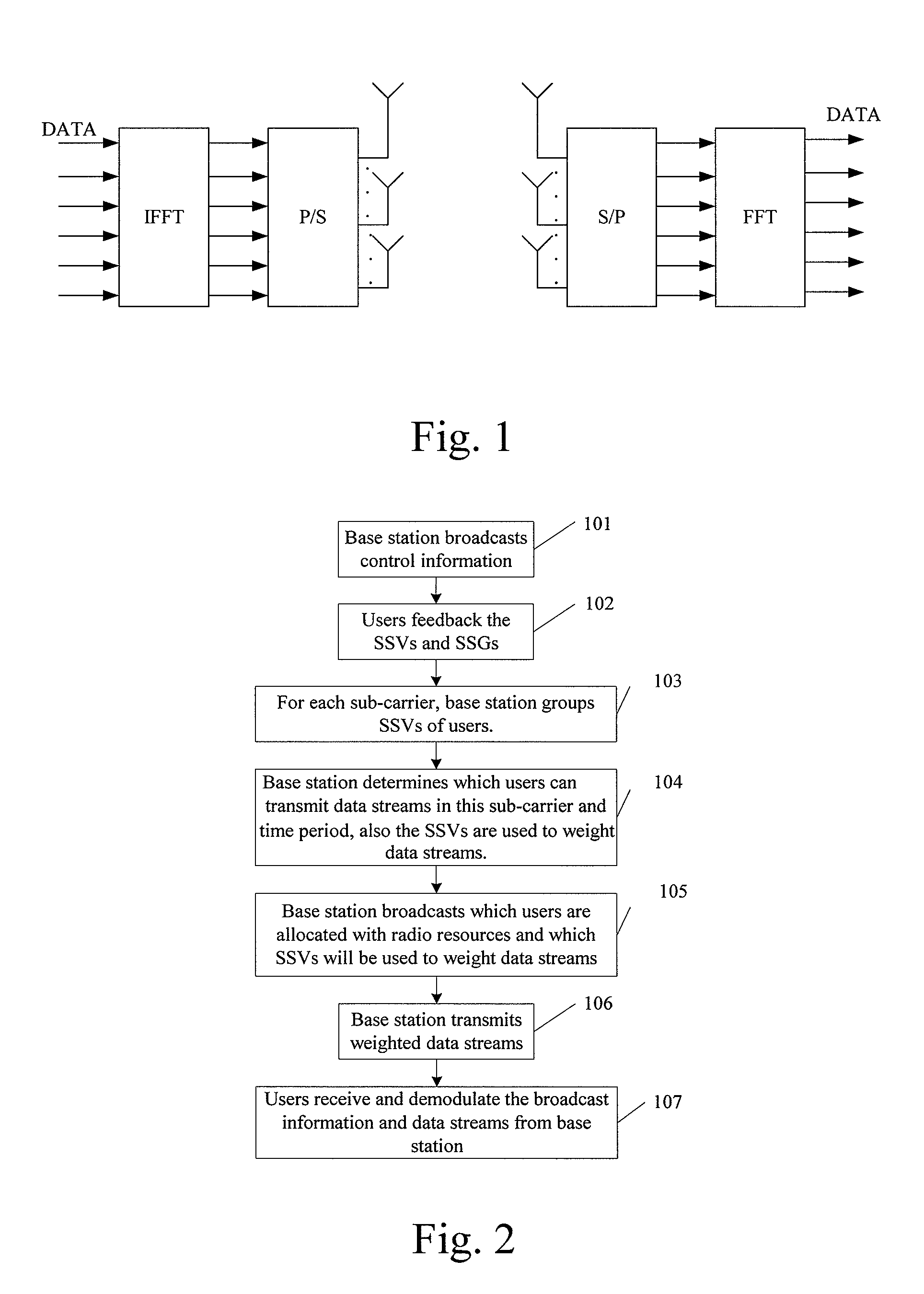
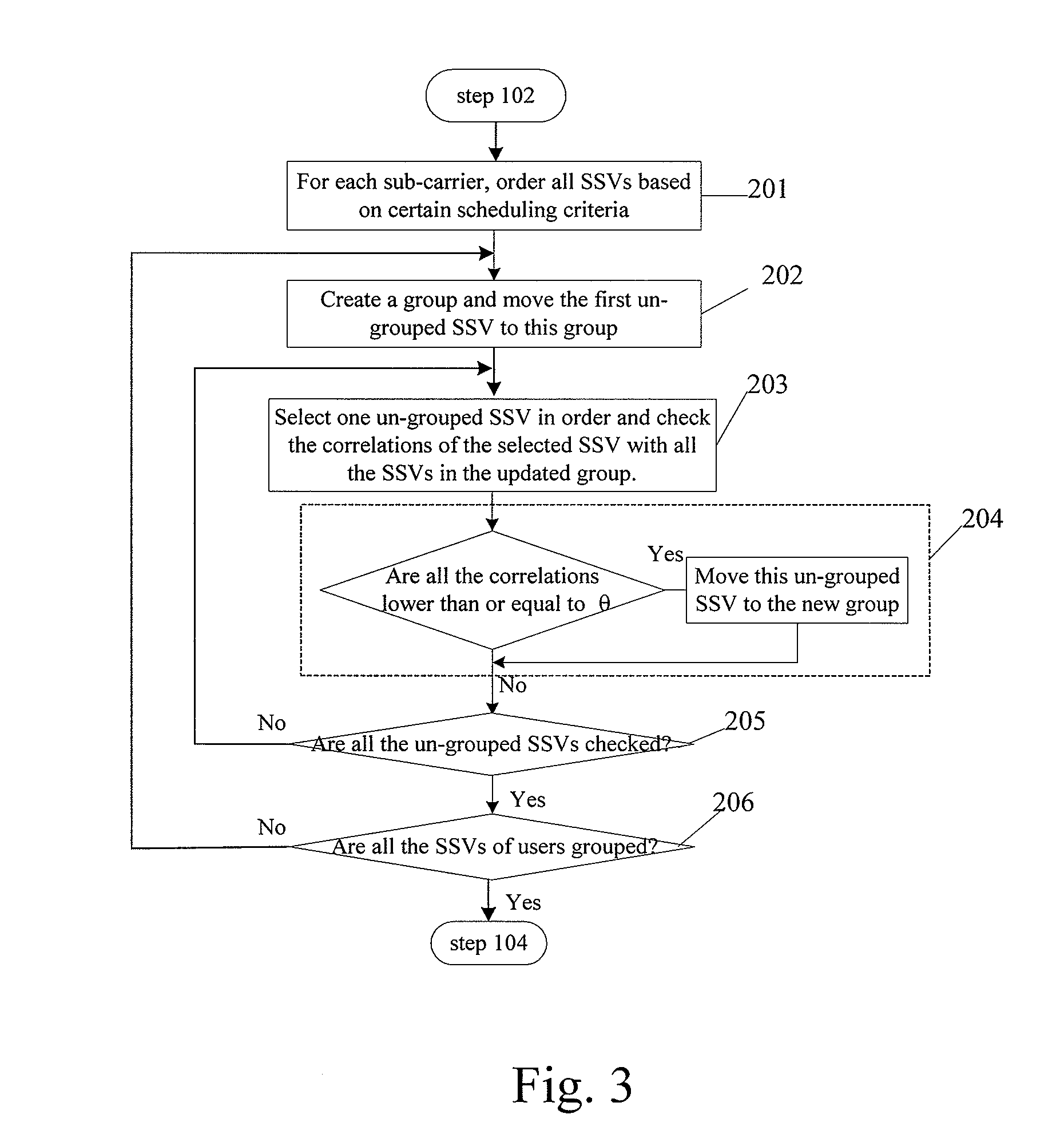
Resource allocation method for mimo-ofdm of multi-user access systems
ActiveUS20080165883A1Reduce complexityQuality improvementModulated-carrier systemsDiversity/multi-antenna systemsMulti inputCo-channel interference
A resource allocation method for MIMO (multi-input multi-output-OFDM (orthogonal frequency-division multiplex) of multi-user access systems includes A) for each sub-carrier or group of sub-carriers of OFDM, grouping signature vectors of users at a time period according to correlations of the signature vectors; B) from the grouping results, selecting the signature vectors according to a scheduling rule; assigning the sub-carrier frequency and time resource to users of which simultaneously the selected signature vectors have low correlations; and assigning spatial resource to the users corresponding to the selected signature vectors. By minimizing the spatial co-channel interference to an acceptable low level, the complexity significantly in the joint multi-user optimization is reduced.
Owner:NOKIA TECHNOLOGLES OY
Group signature method suitable for large groups
InactiveCN101800641AImprove efficiencyShorten the timePublic key for secure communicationUser identity/authority verificationSystem parametersComputer security
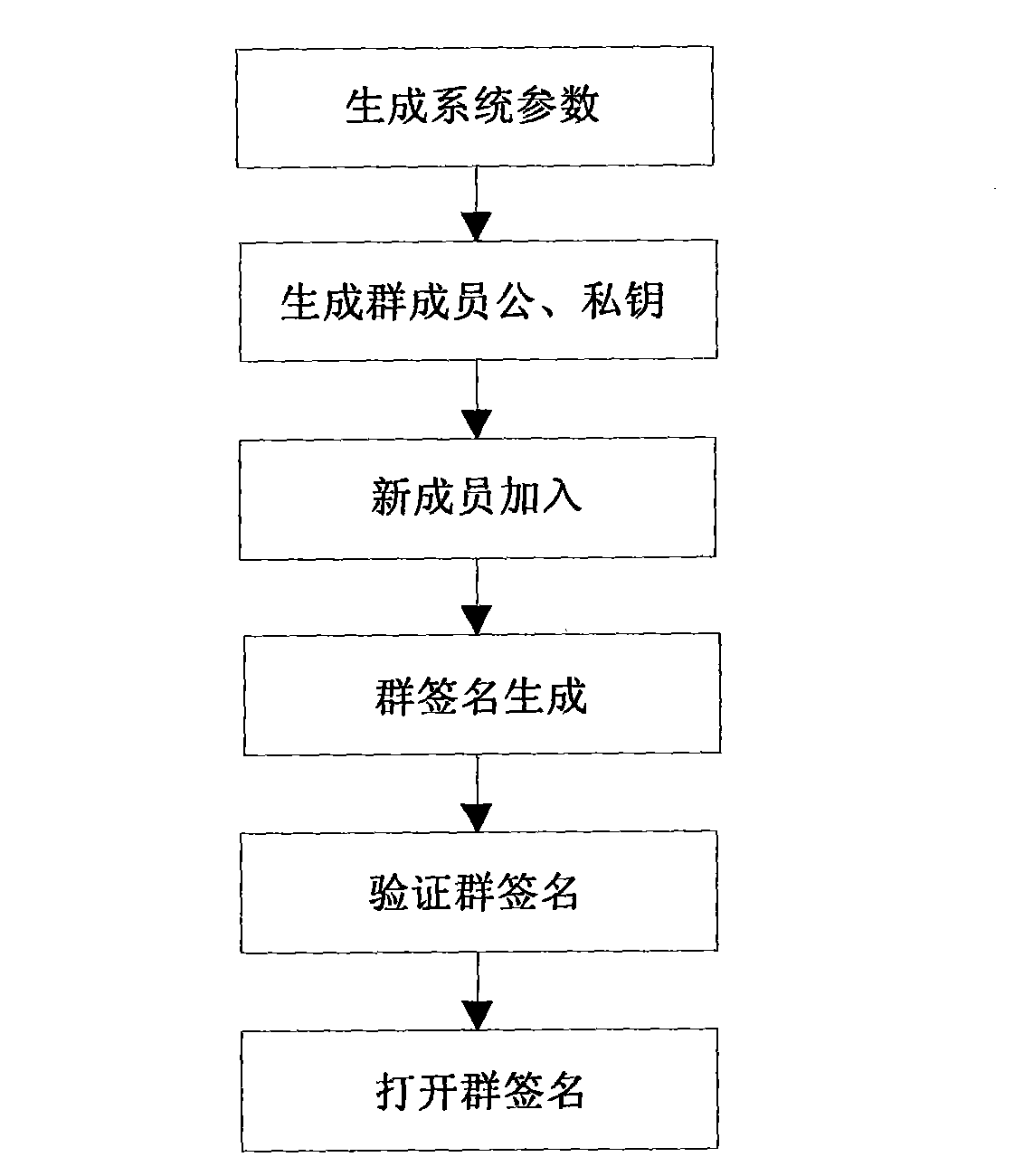
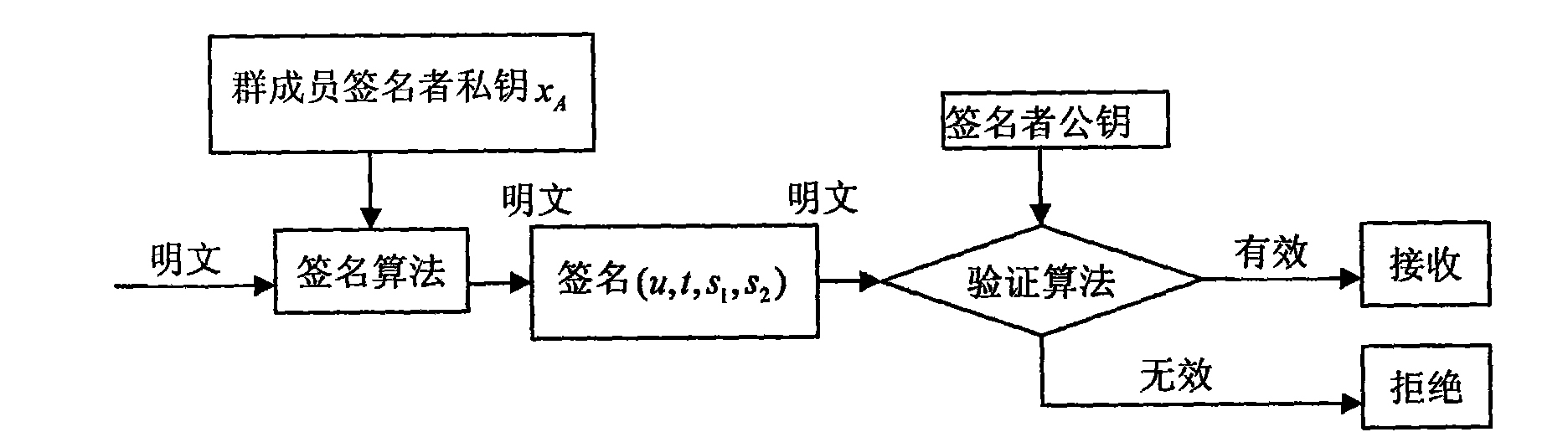
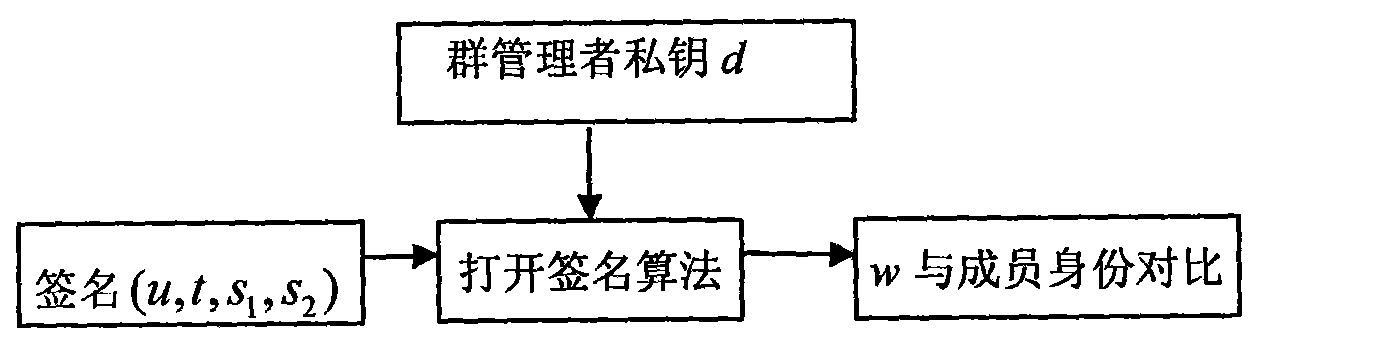
The invention discloses a group signature method suitable for large groups, which comprises the following steps: generating system parameters, adding new members, generating a group signature, and verifying the group signature, wherein a group trusted center selects a group private key and a group public key for a group administrator; when a new member joins in the group, the new member randomly selects (xA, z), stores xA as the private key thereof and transmits z to the group administrator, the group administrator signs z by using the private key thereof, the signature result is (r, s, w), and the group administrator stores the member identity information (w, z) and transmits the (r, s, w) to the new member; after receiving the (r, s, w), the new member verifies whether the (r, s, w) is valid by using the group public key (e, n), and if so, the new member accepts (s, w) as the member certificate and joins successfully; any member in the group can generate a group signature (u, t, s1, s2) for the message m of a signature requester according to the signature algorithm by utilizing the member certificate and the private key xA; and after obtaining the signature the (u, t, s1, s2), a verifier calculates a verification equation. When a new member joins in, the invention does not need to update the group public key and the member private keys, thereby saving time; and when opening the signature, the identity of a signer can be traced.
Owner:HENAN UNIV OF URBAN CONSTR
Group signature system, method, device, and program
InactiveUS20090024852A1User identity/authority verificationCoding/ciphering apparatusGroup signatureComputer security
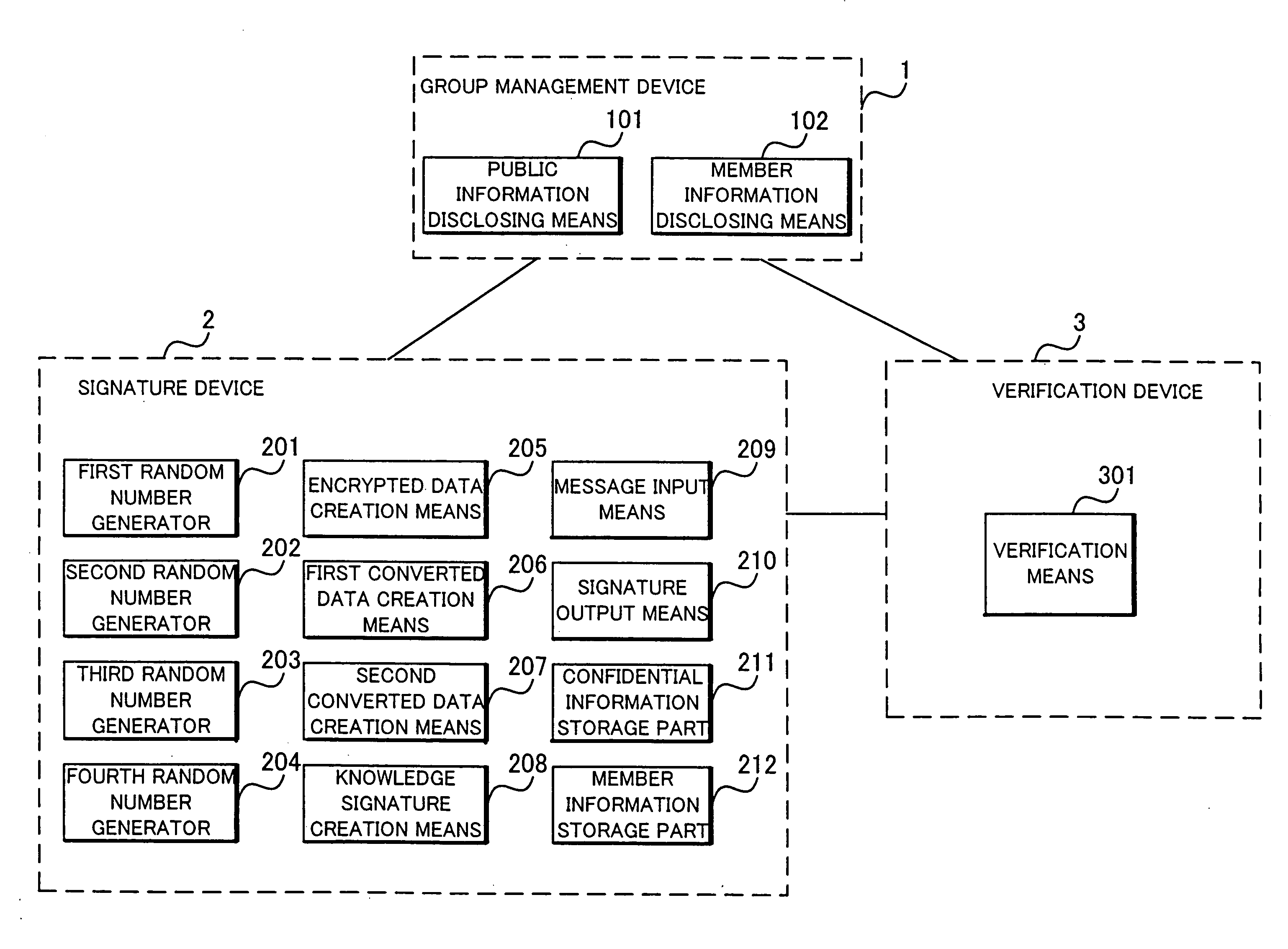
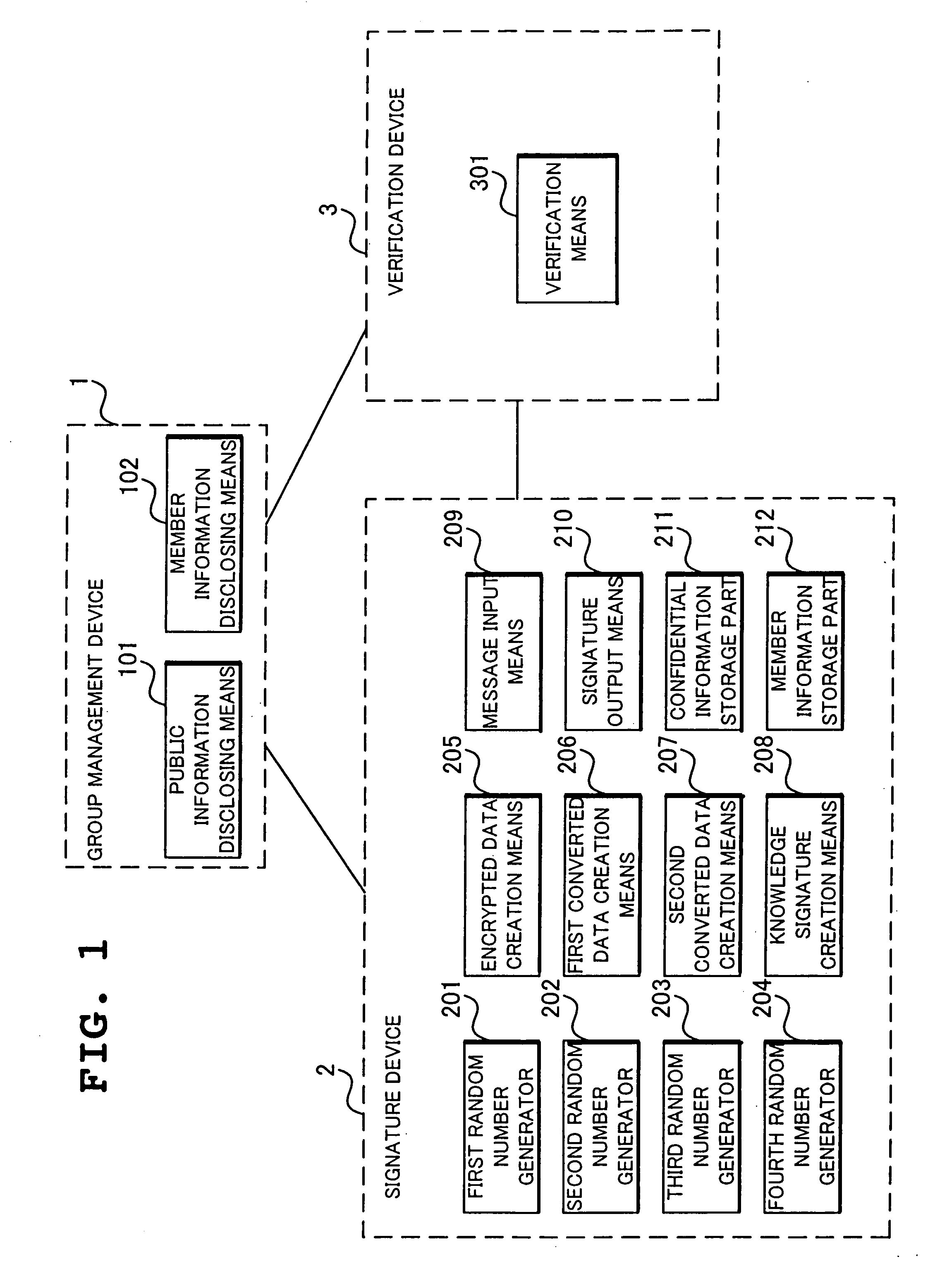
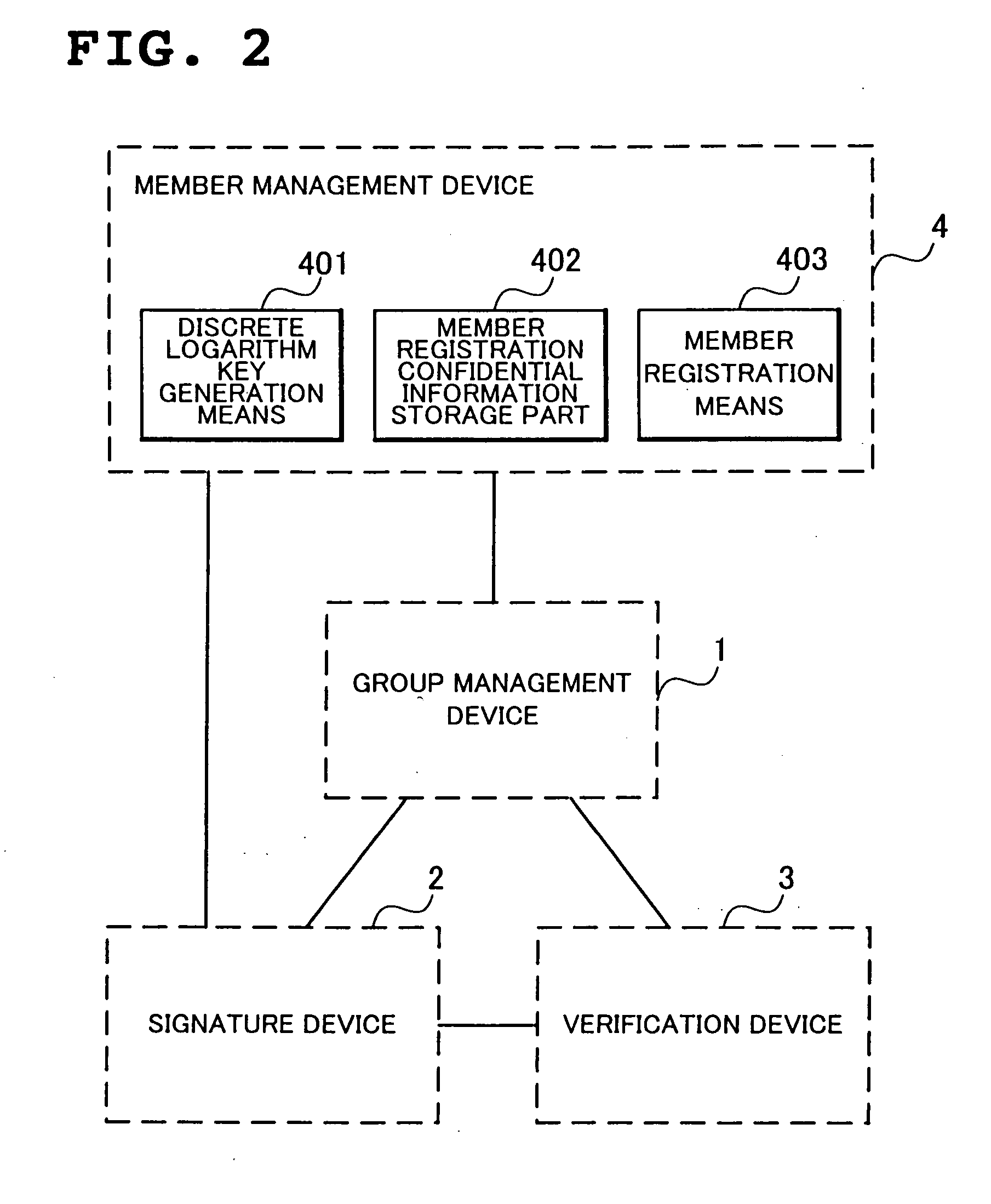
A signature device 2 creates encrypted data by encrypting a first element of a member certificate through use of a first random number and public information disclosed by said group management device 1. The signature device 2 also creates first and second converted data by converting the first element through use of a random number and public information. The signature device 2 further creates knowledge signature data from which information concerning the first element, the second element, and the signature key will not be divulged, and outputs a group signature which contains the knowledge signature data together with a message. A verification device 3 verifies whether a group signature has been created by using a member certificate of one of the registered members in the group and a signature key, based on the message, the group signature, and the public information.
Owner:NEC CORP
Vehicle-mounted-network anonymous-communication system based on ring signature and method
ActiveCN109412816AProtect privacy and securityGuarantee authentication efficiencyUser identity/authority verificationSecurity arrangementThird partyCommunications system
The invention relates to the technical field of network security, and provides a vehicle-mounted-network anonymous-communication system based on ring signature. The system includes a third-party trustinstitution, road side units and vehicles. The invention also provides a method of using the above system for vehicle-mounted-network anonymous-communication. The third-party trust institution firstly publishes public parameters, then the vehicles and the road side units apply for registration to the third-party trust institution, the third-party trust institution issues pseudonyms and public andprivate keys for the vehicles, and issues public and private keys and initial pseudonym ring members for the road side units, and then states of the vehicles in a vehicle-mounted network are monitored; and initial accessing authentication is carried out with a road side unit RSU if a vehicle accesses the vehicle-mounted network for the first time, and switching accessing authentication is carriedout with a road side unit RSU' if the vehicle does out access the vehicle-mounted network for the first time, and two-way authentication is carried out under assistance of a road side unit if a vehicle Vi is ready to communicate with a vehicle Vj. The system and the method integrate pseudonym certificate and group signature technology, and can fully protect privacy safety of communicators on thepremise of ensuring authentication efficiency.
Owner:NORTHEASTERN UNIV
Confounding method of encrypted group signatures
ActiveCN104917617AImplement encryption group signature functionImprove confidentialityUser identity/authority verificationCiphertextEngineering
The invention relates to a confounding method of encrypted group signatures, thereby protecting signature private keys of members in a group. The method comprises the following steps that: (1), a group master constructs a signature group and a group parameter sequence pub, a main private key MK, a tracking private key TK are obtained according to a setup algorithm; (2), an information receiver obtains a respective encrypted public key PKe and decrypted private key SKe based on an EKGen algorithm according to the group parameter sequence pub: (3), according to the group parameter sequence pub, the main private key MK, and IDs of the members in the group, the group master obtains signature tracking information sID and signature private keys KID corresponding to the respective IDs of the members in the group by using an Enroll algorithm, and the signature private keys KID are sent to corresponding members in the group; (4) according to a confounding algorithm Obf, confounding processing is carried out on an initial encryption group signature algorithm EGS of the members in the group and the signature private keys KID of the members in the group, thereby obtaining an encryption group signature algorithm Rpub,z,PKe; and (5), according to the encryption group signature algorithm Rpub,z,PKe, information signature encryption is carried out a to-be-sent message M to generate an encrypted ciphertext C and then the encrypted ciphertext C is sent to the information receiver. Compared with the prior art, the confounding method has advantages of function of private key protection and good secret keeping effect and the like.
Owner:TONGJI UNIV
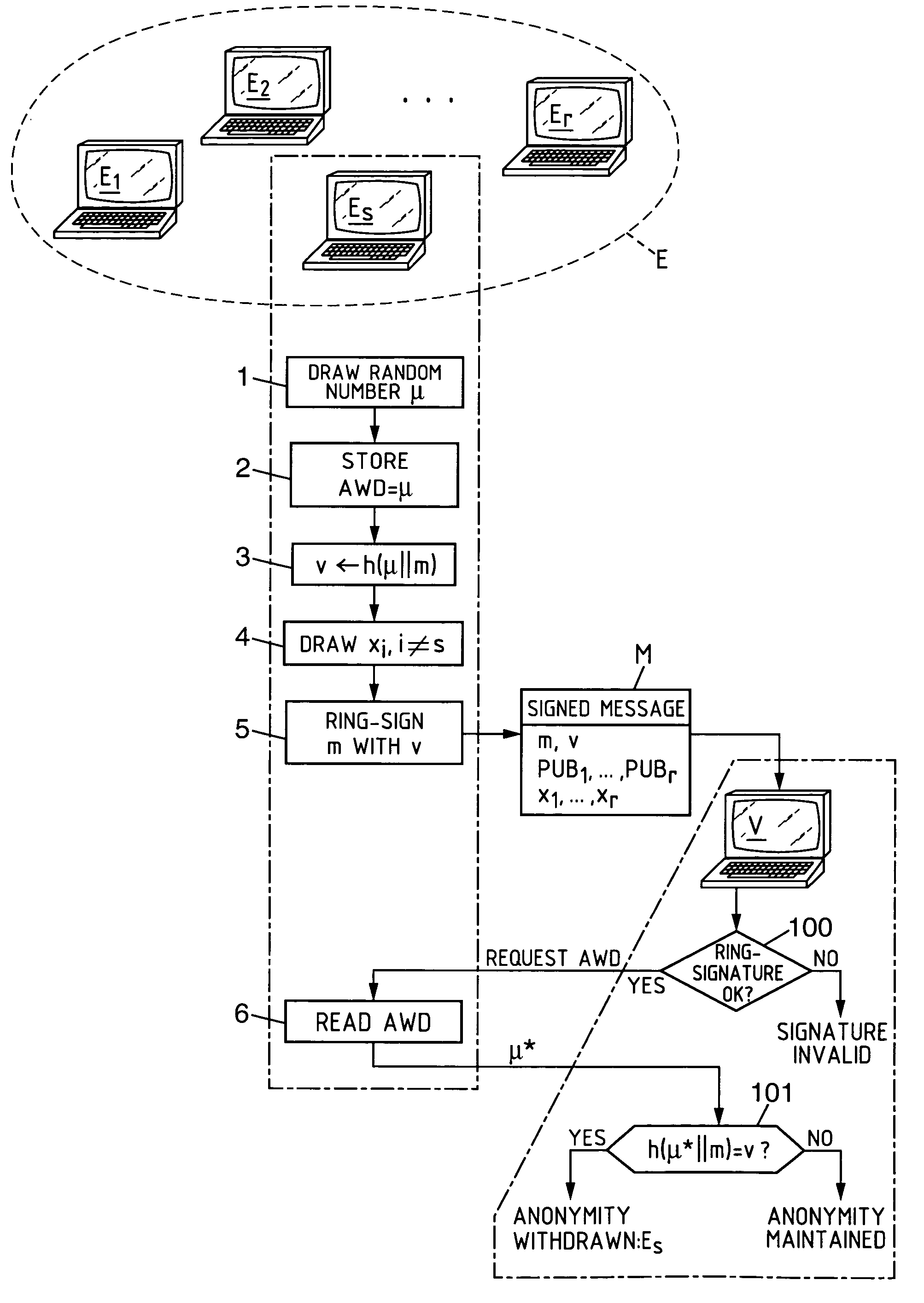
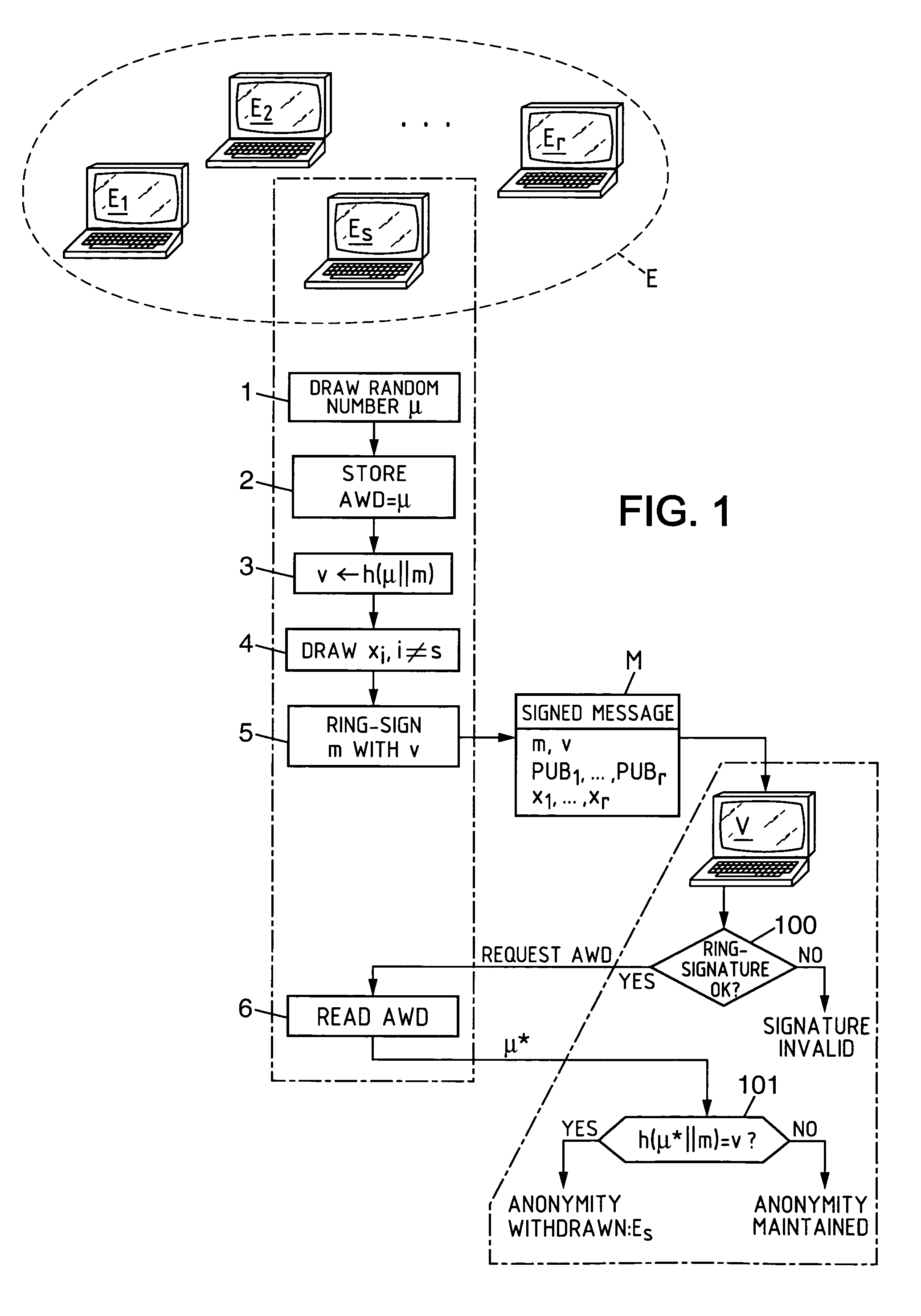
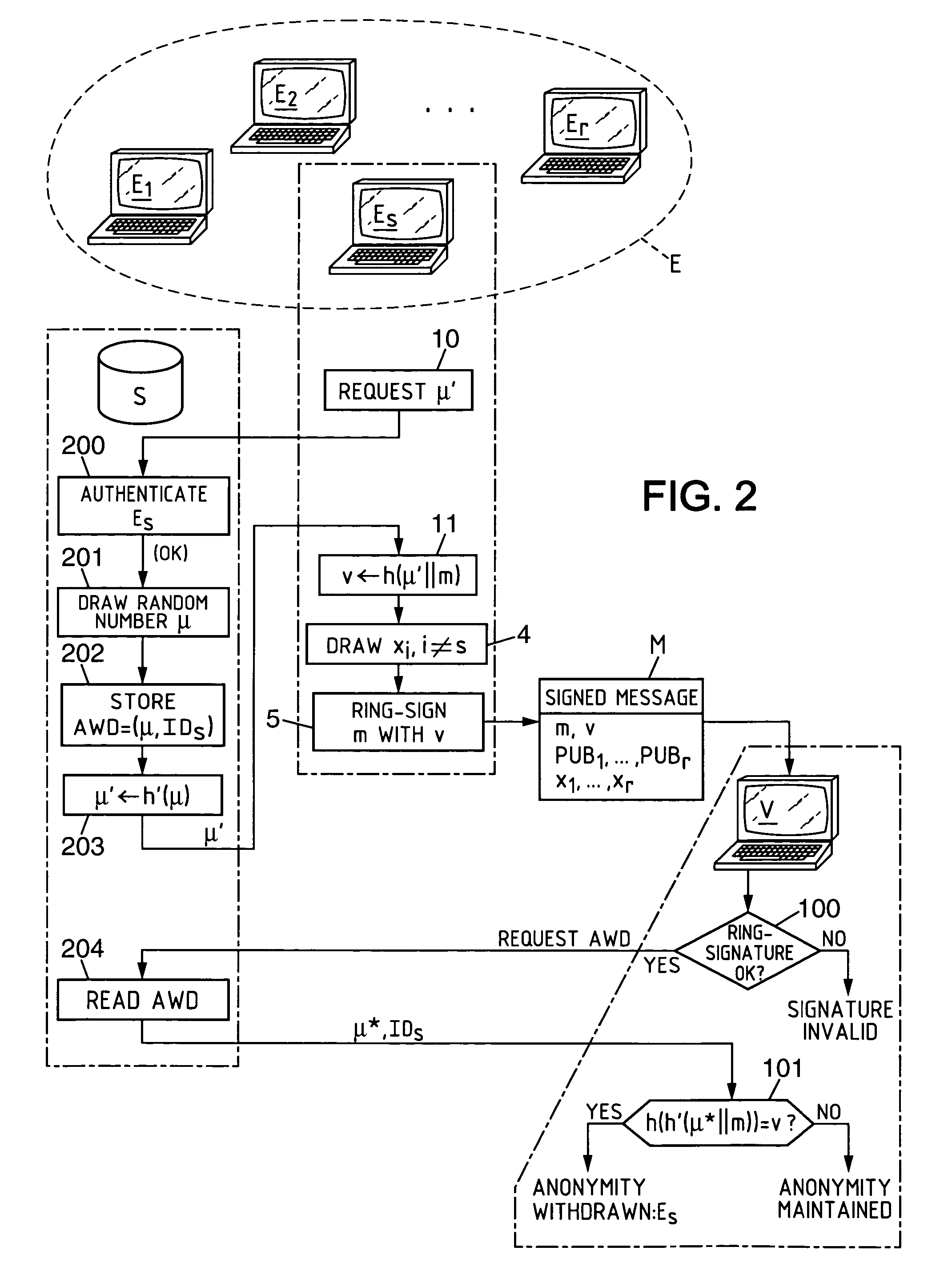
Electronic group signature method with revocable anonymity, equipment and programs for implementing the method
A ring-signature scheme is adapted so that at least one of the variability parameter values used is an identity trace of the anonymous signatory, determined as a function of anonymity withdrawal data stored and held secret by an anonymity withdrawal entity in connection with an identification of the anonymous signatory. This provides a subsequent controlled capacity of withdrawing the anonymity of the signatory, either by an authority, or by the signatory himself.
Owner:FRANCE TELECOM SA
A block chain privacy protection scheme and system based on SM9 algorithm
InactiveCN109409884ASolve problems that are difficult to apply to real-world scenariosSolve application problemsDigital data protectionProtocol authorisationChain structurePrivacy protection
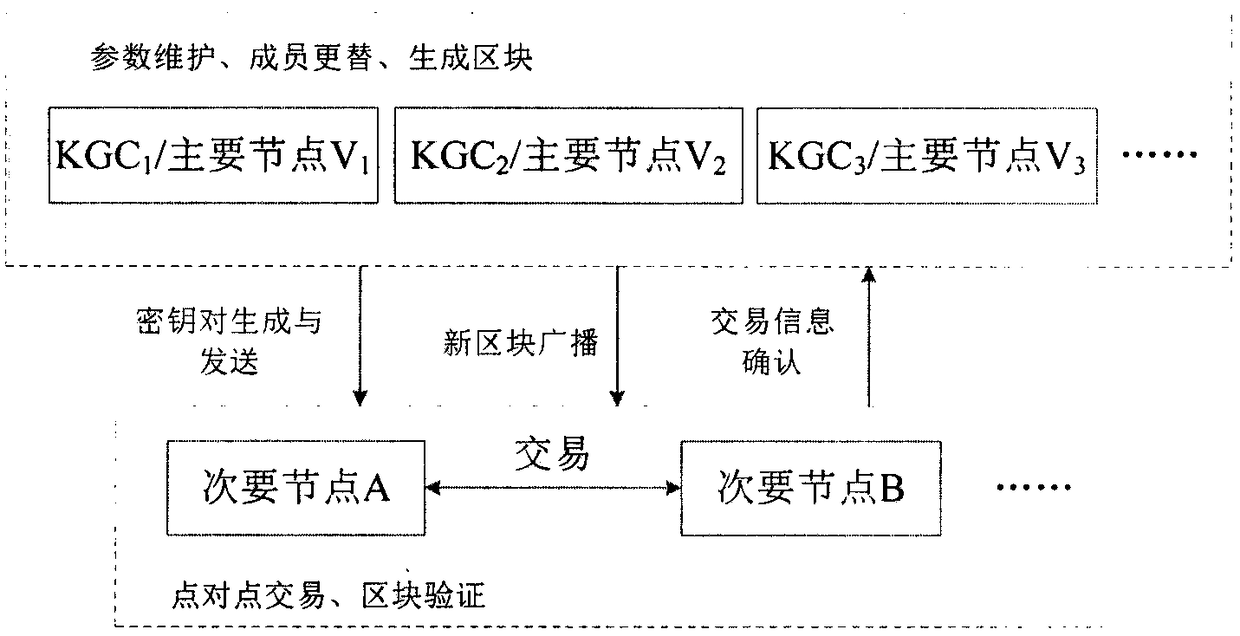
The invention discloses a block chain privacy protection scheme and a block chain privacy protection system based on an SM9 commercial cryptographic algorithm in China, belonging to the field of blockchain security and privacy protection. This invention provides an inter-node transaction platform based on federation chain, defines the permissions and functions of various nodes in the platform, and supports node transaction, information verification, parameter maintenance, block generation and other functions. This invention describes an improved SM9 multi-KGC (Key Generation Center) signaturealgorithm, which improves the working mode of single KGC in SM9 algorithm, adapts to the federation chain structure, and adopts this algorithm to determine the identity of the opposite party in the transaction between nodes. A group signature scheme based on SM9 algorithm is proposed. The identity verification of SM9 algorithm is improved to group signature verification, which effectively protects the identity privacy of the signatory. The transaction information is signed by the node through the algorithm and written into the block chain after the transaction, which can effectively hide theidentity information of both parties of the transaction, protecting the privacy of the node and ensuring the legitimacy of the transaction.
Owner:BEIJING ANRUSHAN CULTURE TECH
System and method for controlling anonymous hospitalizing and security access of medical information based on property
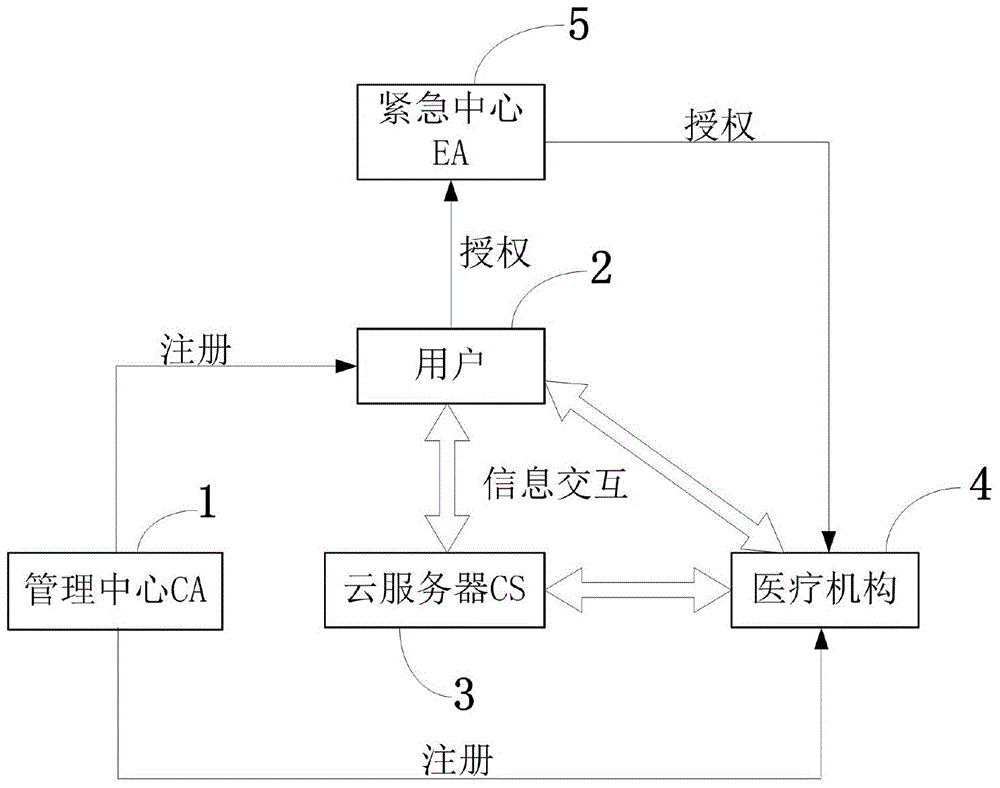
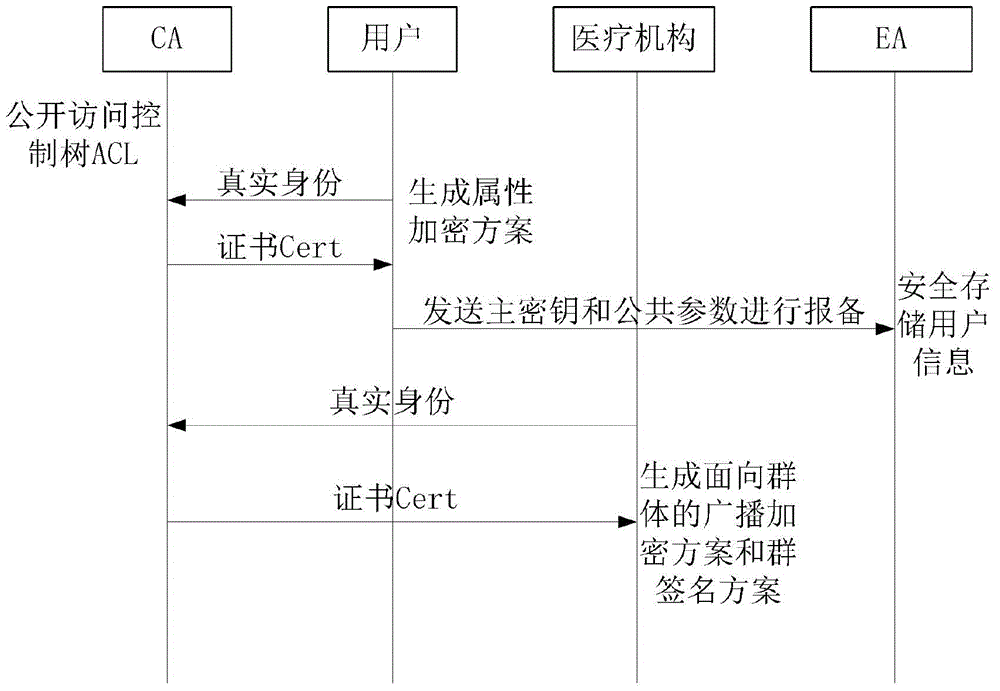
ActiveCN104683351AImprove identityProtecting Medical PrivacyData processing applicationsUser identity/authority verificationMedical recordCiphertext
The invention discloses a system and a method for controlling anonymous hospitalizing and security access of medical information based on property. The method is that the property encrypting and symmetric encrypting technologies are adopted to protect the security and privacy of the medical record information of a patient; the broadcasting encrypting technology and group signature technology based on groups are utilized to achieve anonymous registration and hospitalization of the patient, so as to protect the privacy of the patient. With the adoption of the method, the difficulty in key management caused by the increase of users can be avoided; meanwhile, the calculation burden caused by frequent key updating and ciphertext updating due to canceling of authorization can be reduced; in addition, a detailed scheme is provided according to the actual hospitalization process, and moreover, the authorization process in emergency conditions is provided according to the emergency conditions in actual life.
Owner:西安元智众恒科技服务有限公司
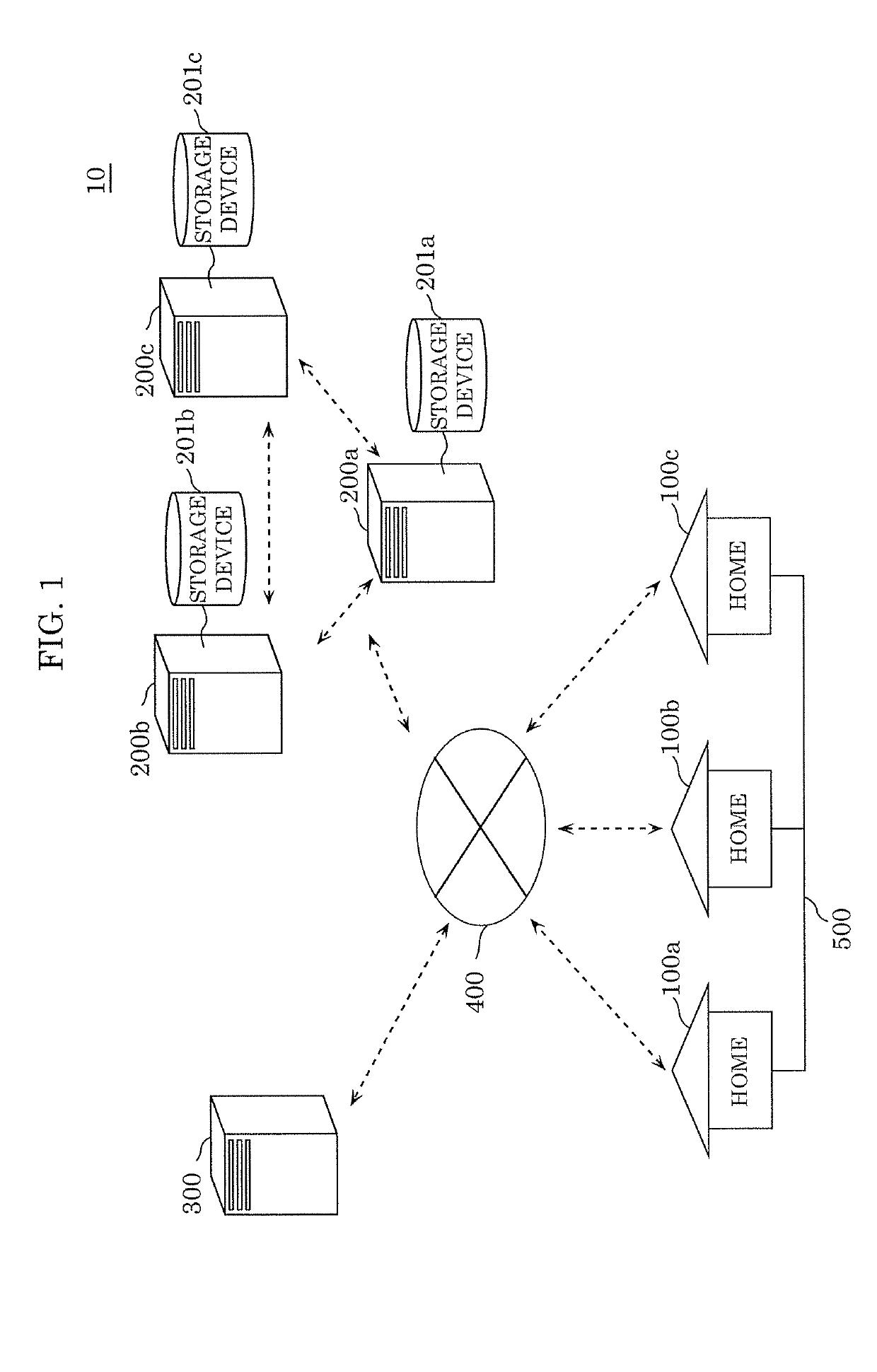
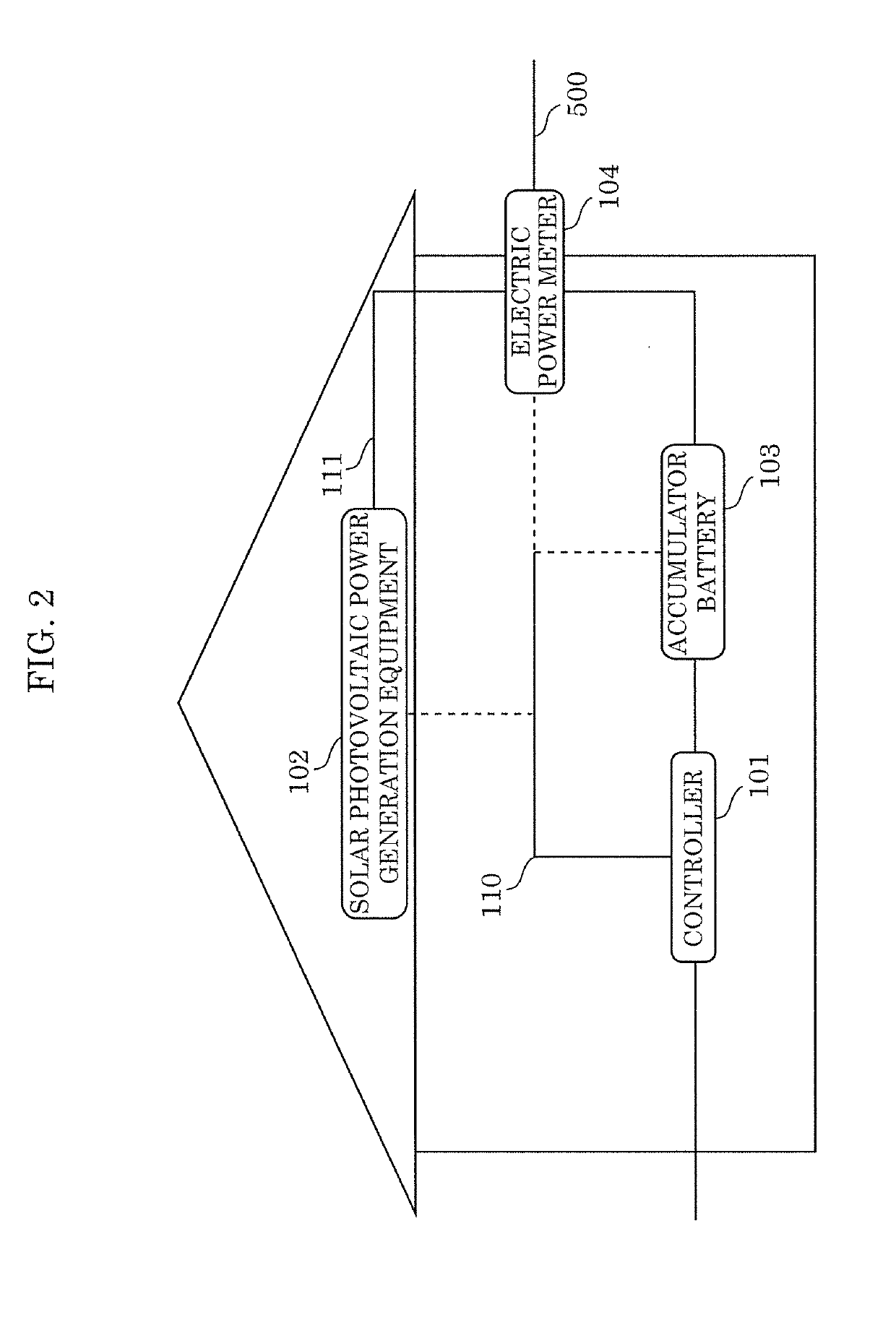
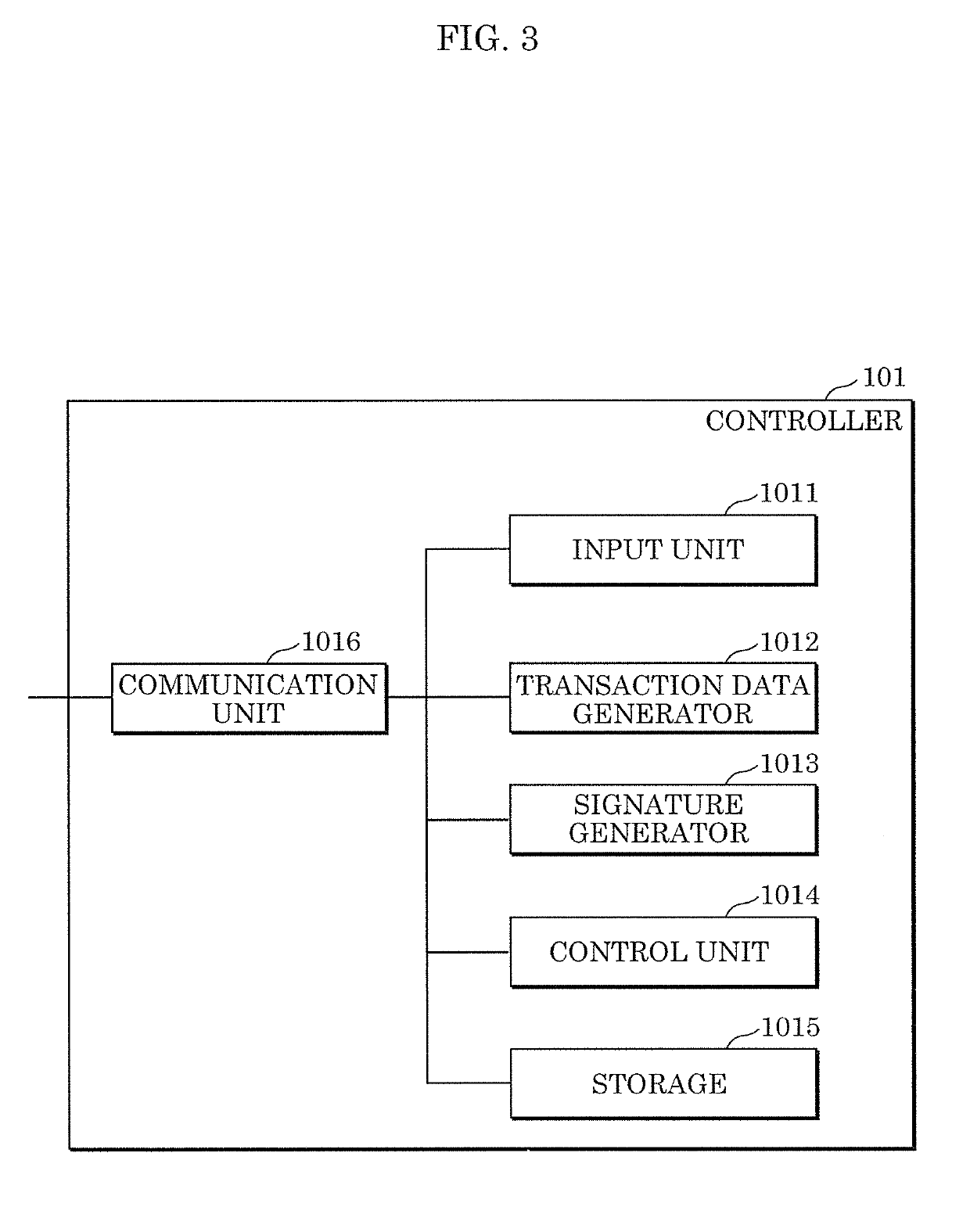
Control method, controller, data structure, and electric power transaction system
ActiveUS20190236726A1Prevent leakageAvoid privacyDiscounts/incentivesFinanceElectric power transmissionTransaction data
A control method including: receiving first transaction data including a first electronic signature from the a home of a first user; verifying whether the received first electronic signature included in the first transaction data is valid; verifying validity of the received first transaction data; when the first electronic signature and the validity of the first transaction data are verified successfully, executing a first consensus algorithm for the first transaction data; and when the validity of the first transaction data is verified according to the first consensus algorithm, recording a block including the first transaction data in a distributed ledger. The first electronic signature is a group signature assigned to a group to which the first user belongs.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Group signature system and method providing controllable linkability
ActiveUS20120084567A1Limit anonymityAnonymity can be controlledUser identity/authority verificationUser deviceComputer security
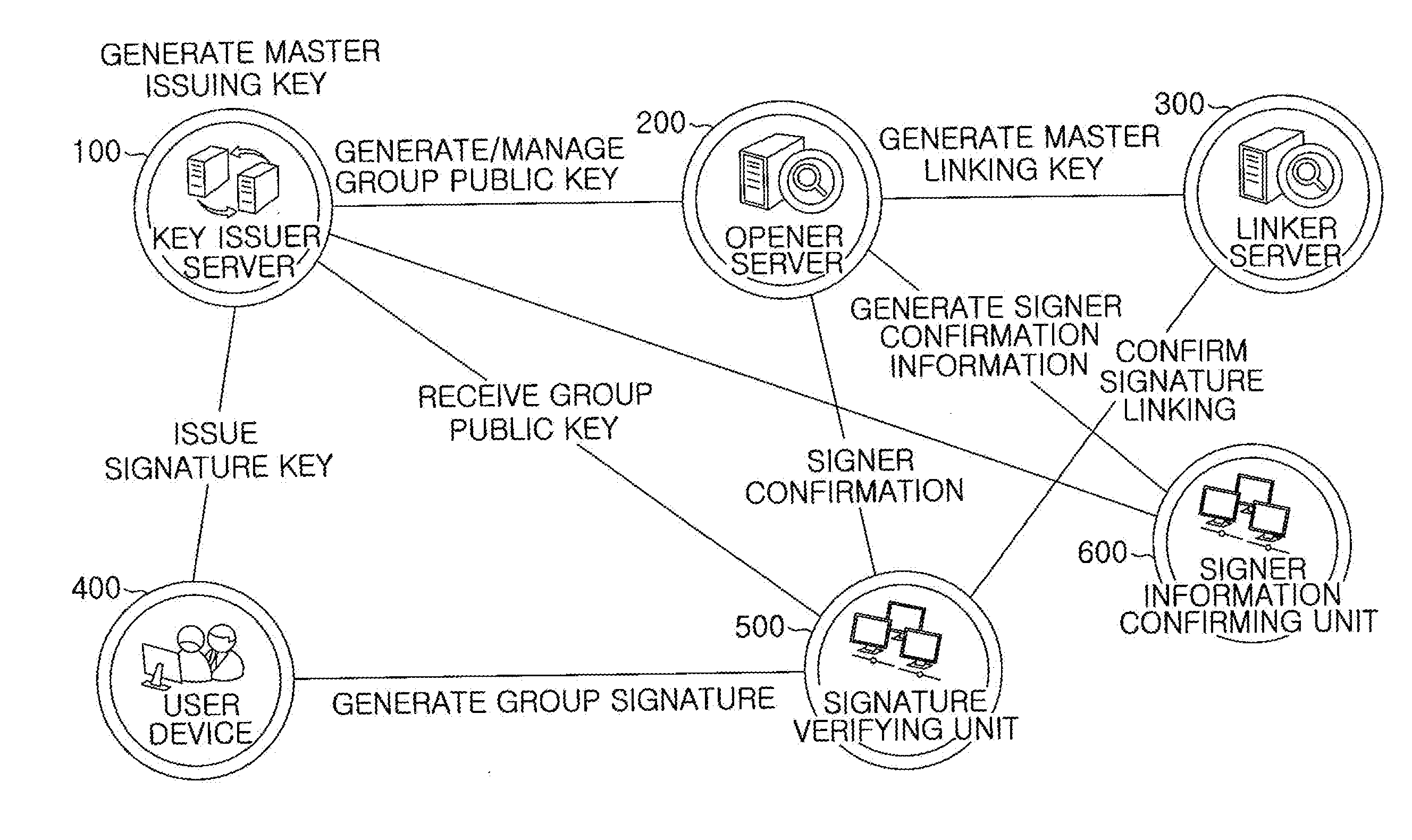
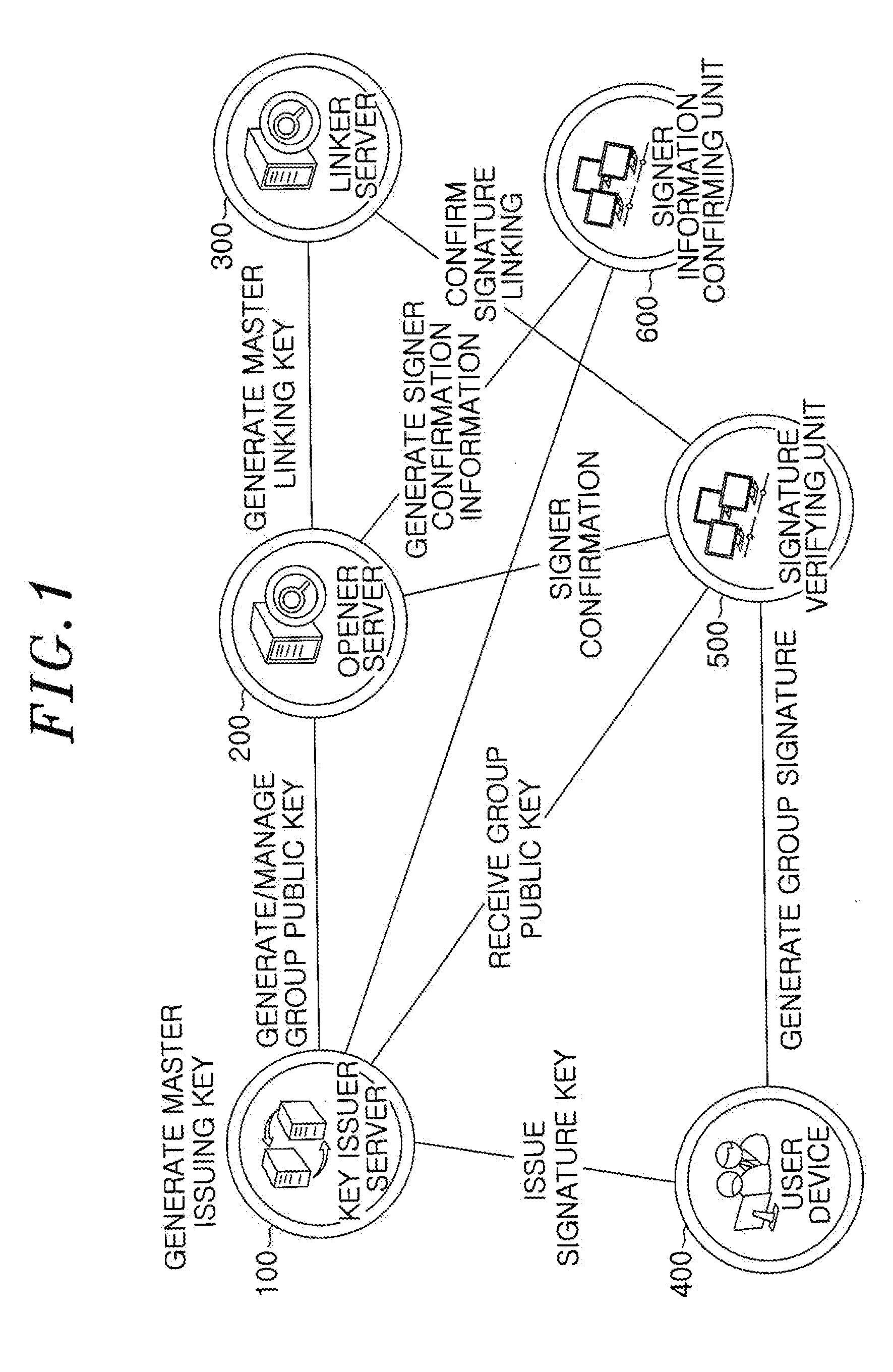
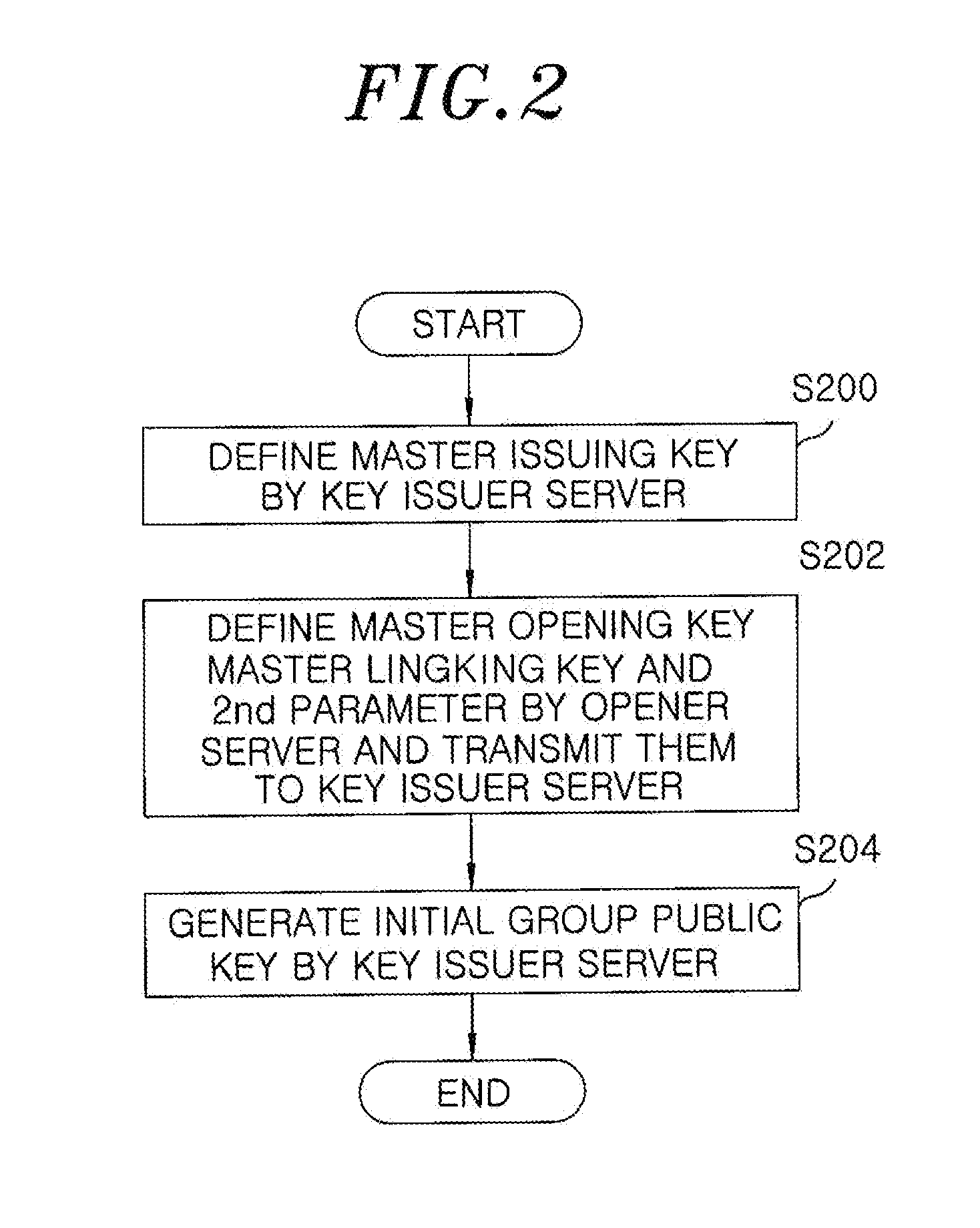
A group signature system includes: a key issuer server for generating a first parameter of a group public key, generating a corresponding master issuing key, and issuing a signature key to a user when a user device joins; an opener server for generating a second parameter of the group public key, and a corresponding master opening key and master linking key; and a linker server for checking whether two valid signatures have been linked by using the master linking key when the two signatures corresponding to a group public key are given. The group signature system further includes: a signature verifying unit for confirming a validity of the given signatures and a signer information confirming unit for confirming a validity of singer confirming information generated by the opener server.
Owner:ELECTRONICS & TELECOMM RES INST
Privacy protection access control method in wireless sensor network supported by IP
ActiveCN109963282AGuaranteed unlinkabilityFlexible revocation processNetwork topologiesSecurity arrangementWireless mesh networkPrivacy protection
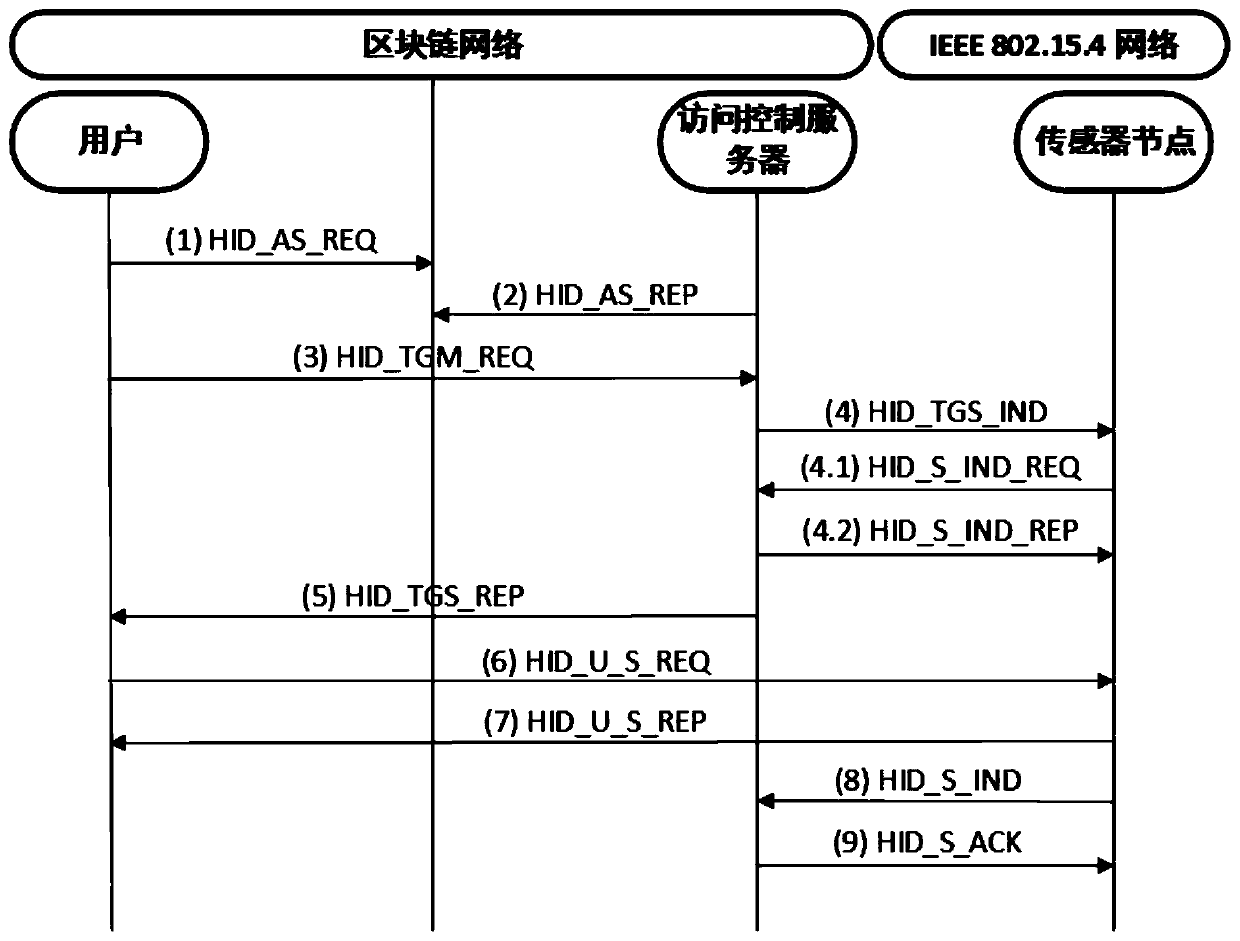
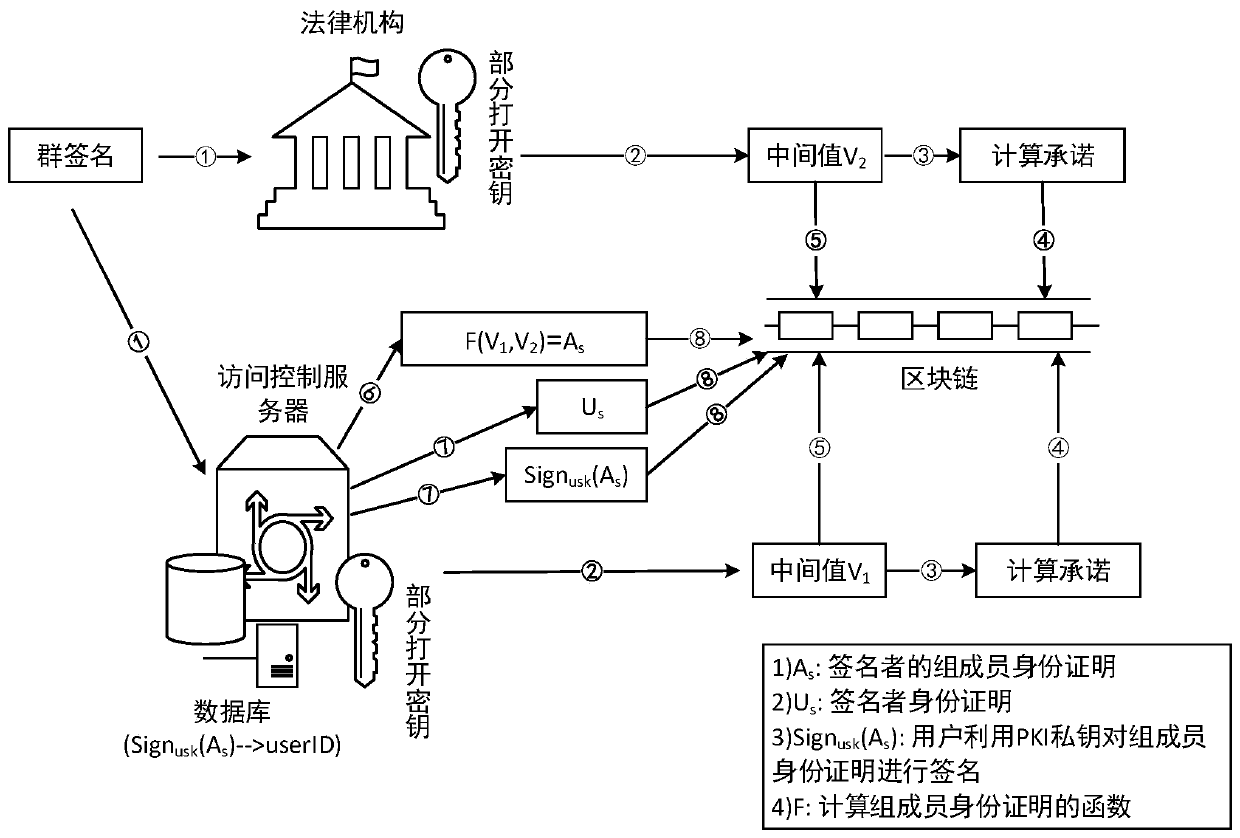
The invention discloses a privacy protection access control method in a wireless sensor network supported by an IP. According to the method, a group signature technology is applied, system users are divided into different user groups according to different access authorities, the group users use group signatures for anonymous access to guarantee user data access privacy, and leakage of user behavior modes is prevented. According to the method, users are divided into different user groups according to different access authorities by utilizing a group signature technology, the group users generate group signatures for identity authentication, and anyone in a network can verify the correctness of the group signatures but cannot know the identities of the signers; the identity authentication and authorization process of the Hidra protocol is improved by utilizing a false ticket mechanism and a self-updating ticket mechanism, so that the unlinkability of a protocol message is ensured; the block chain technology is used for managing the group public key, so that the secret key management and Hidra protocol user revocation process is more flexible; a responsibility investigation mechanismis improved by utilizing a block chain technology, so that the responsibility investigation process is public and transparent, and possible responsibility investigation disputes are solved.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com