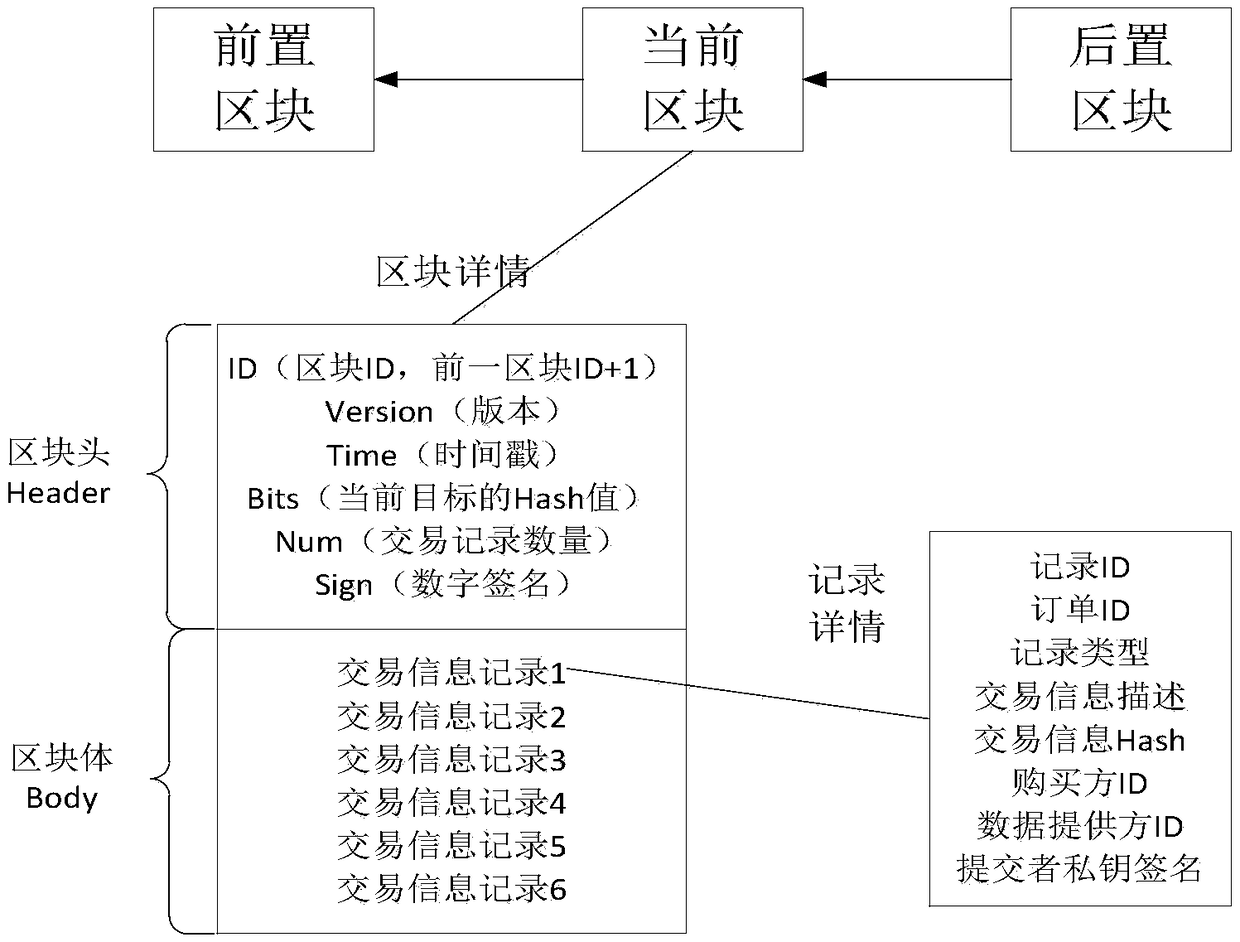
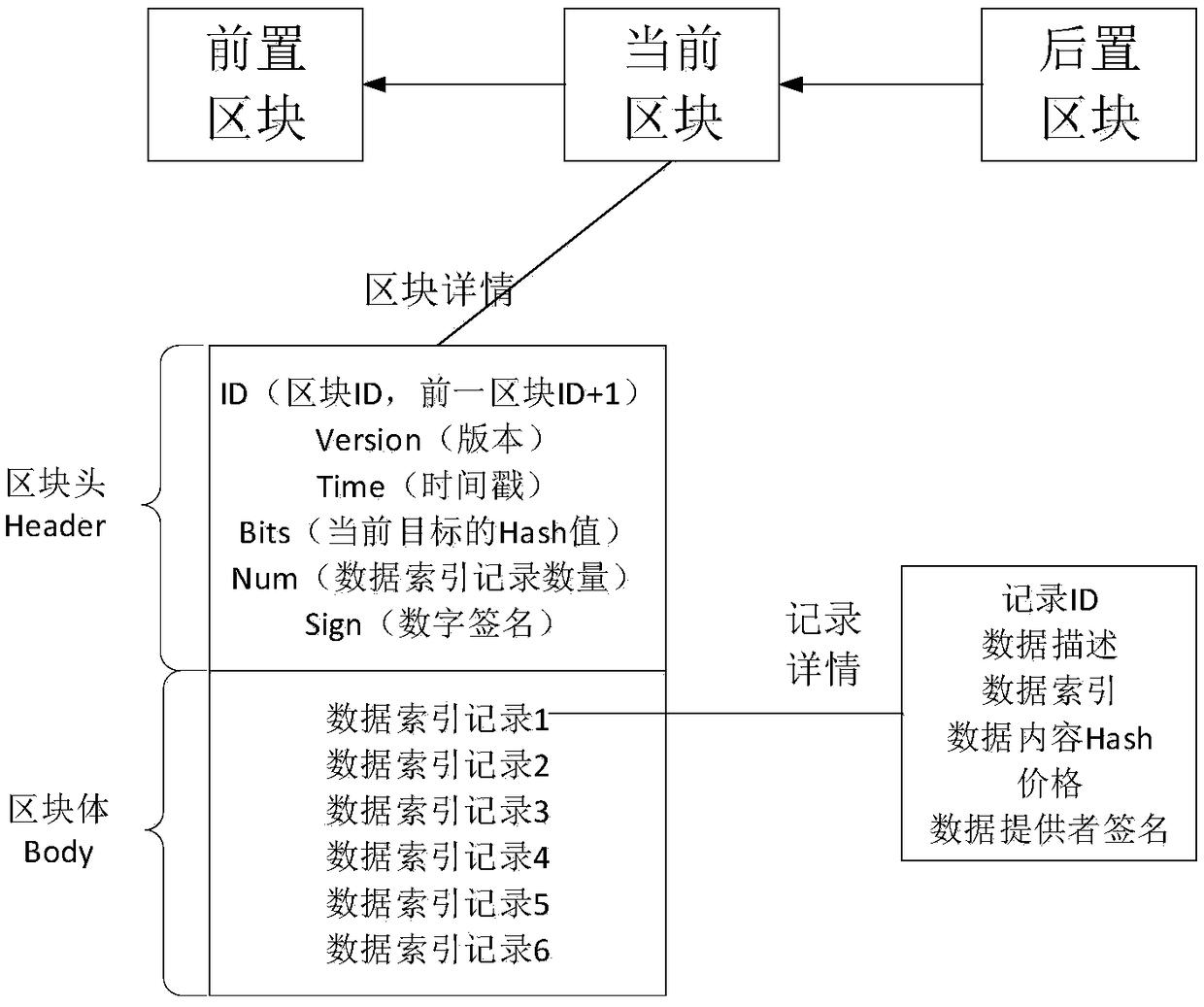
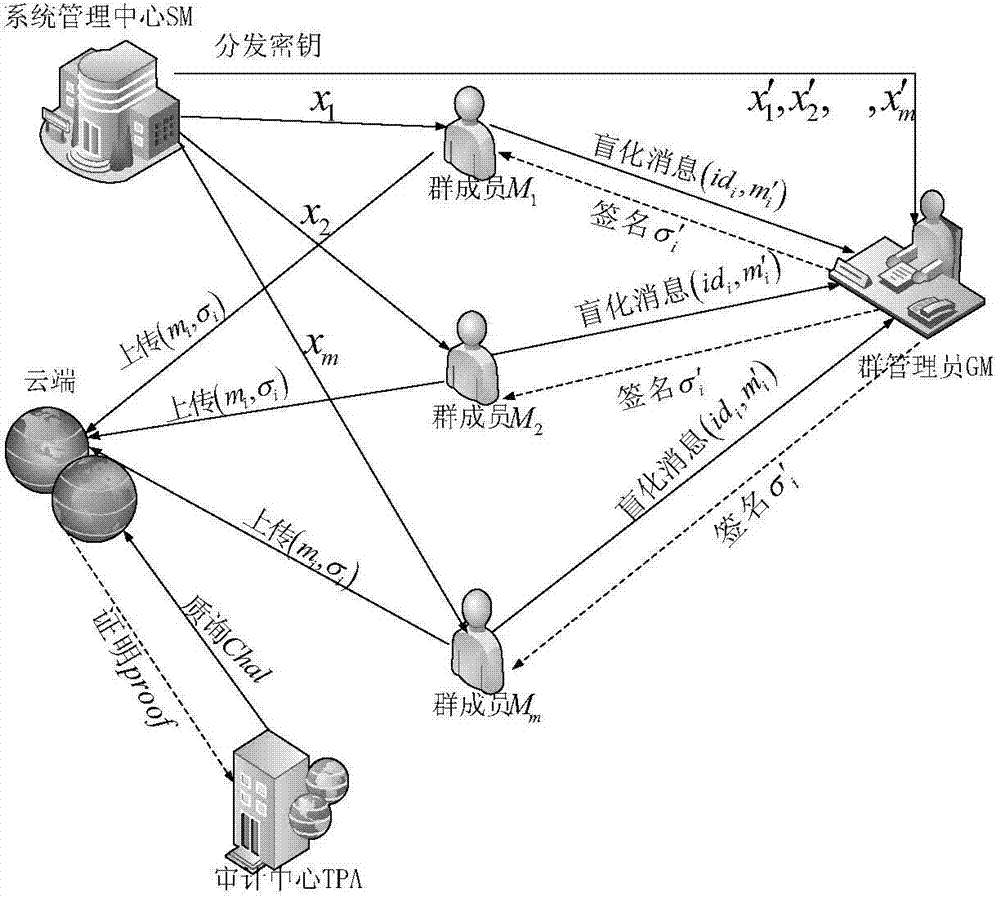
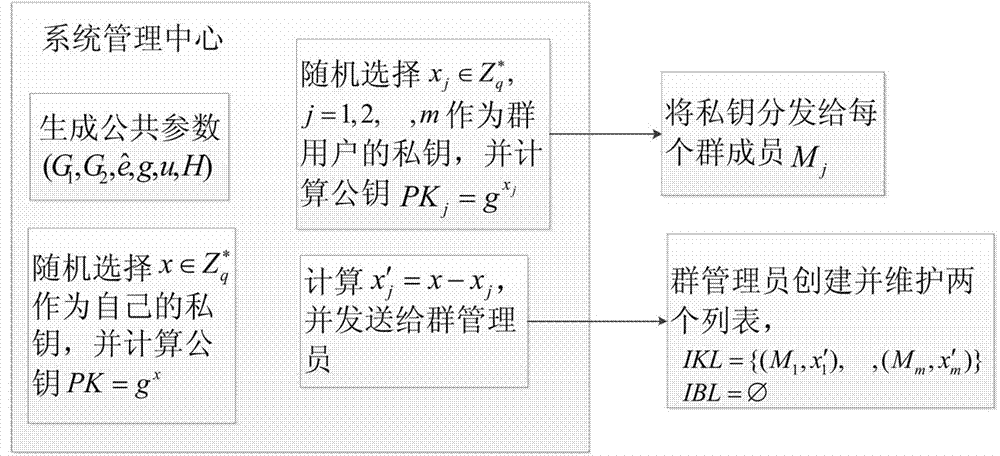
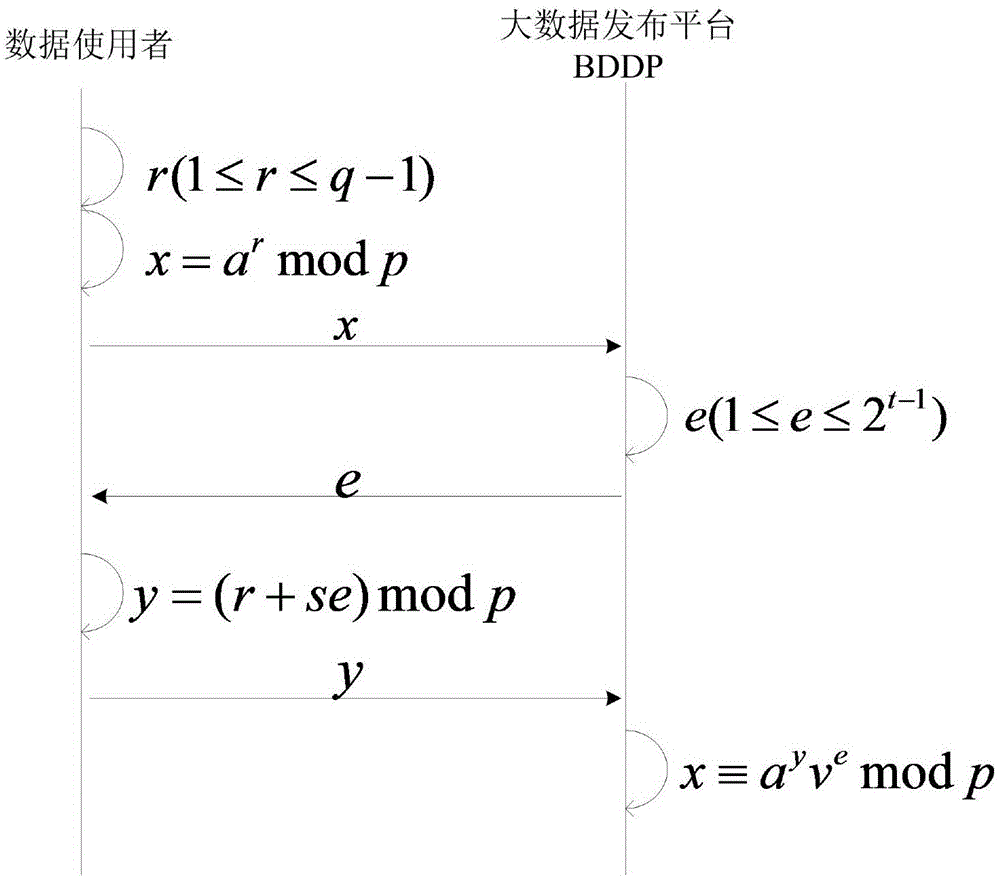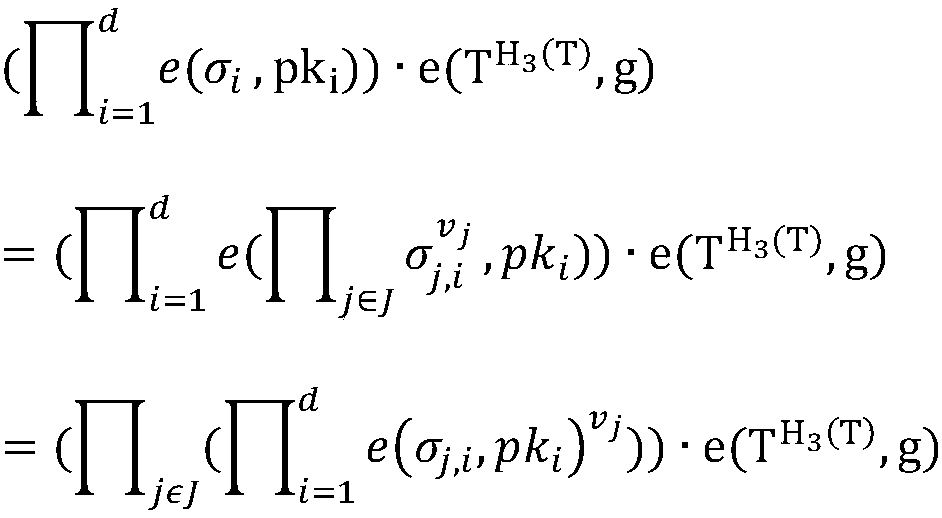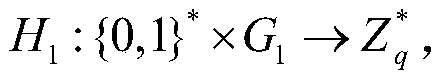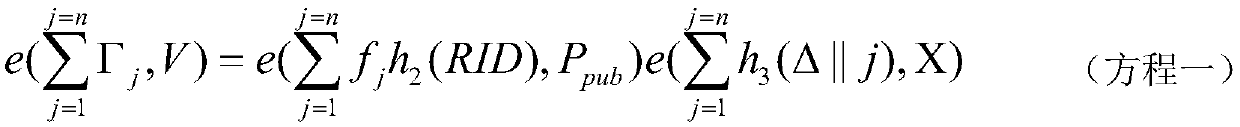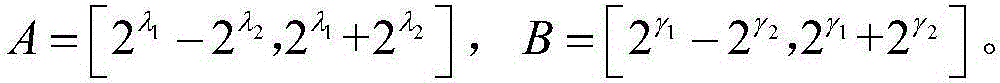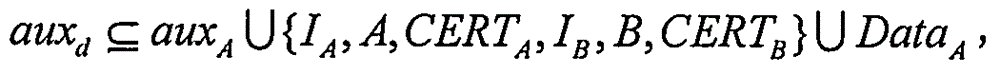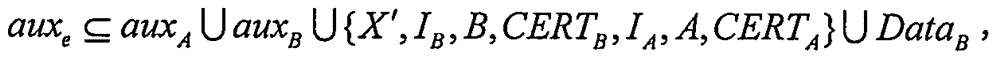Patents
Literature
155 results about "Identity privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Privacy Risk Metrics in Online Systems
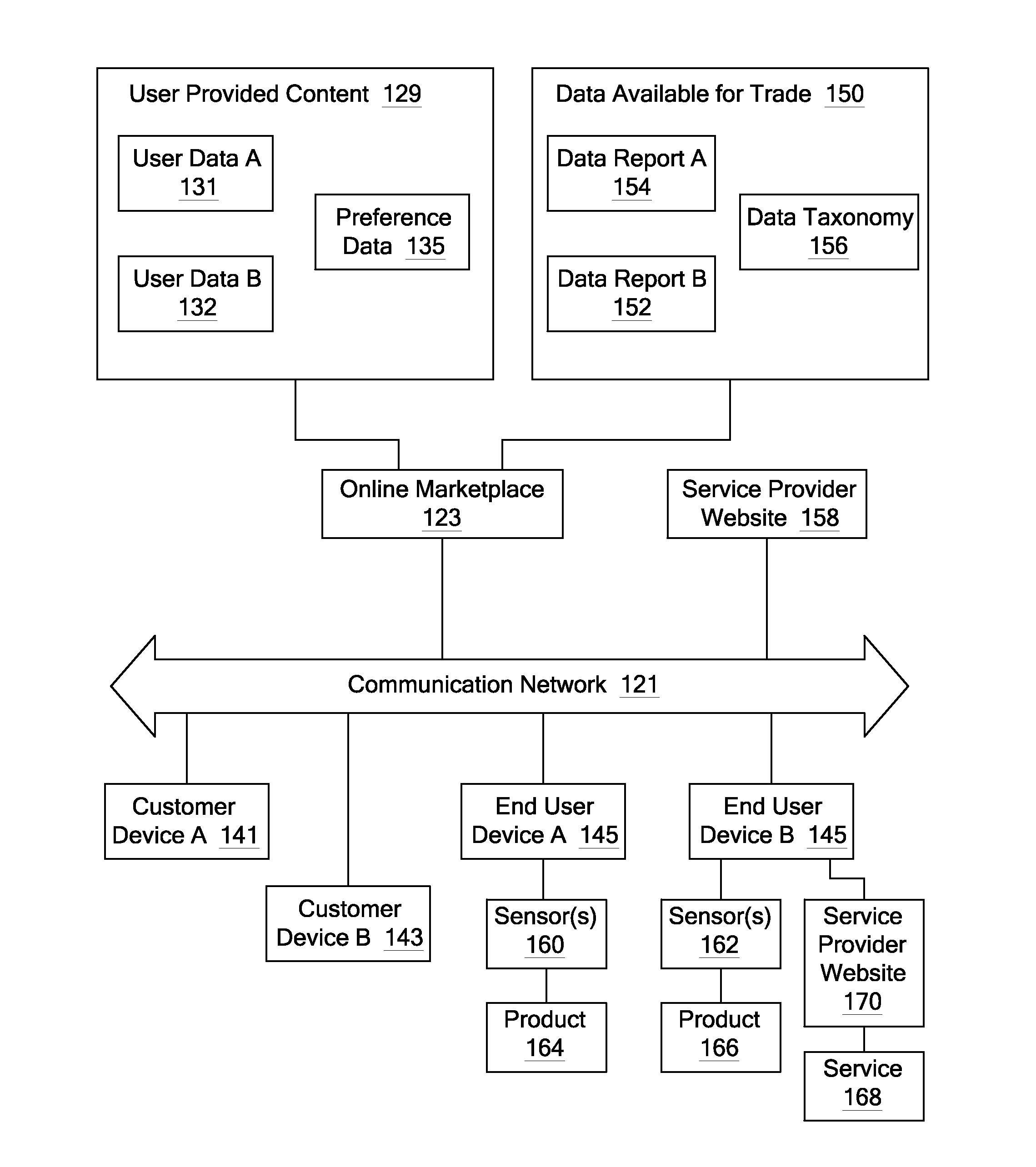
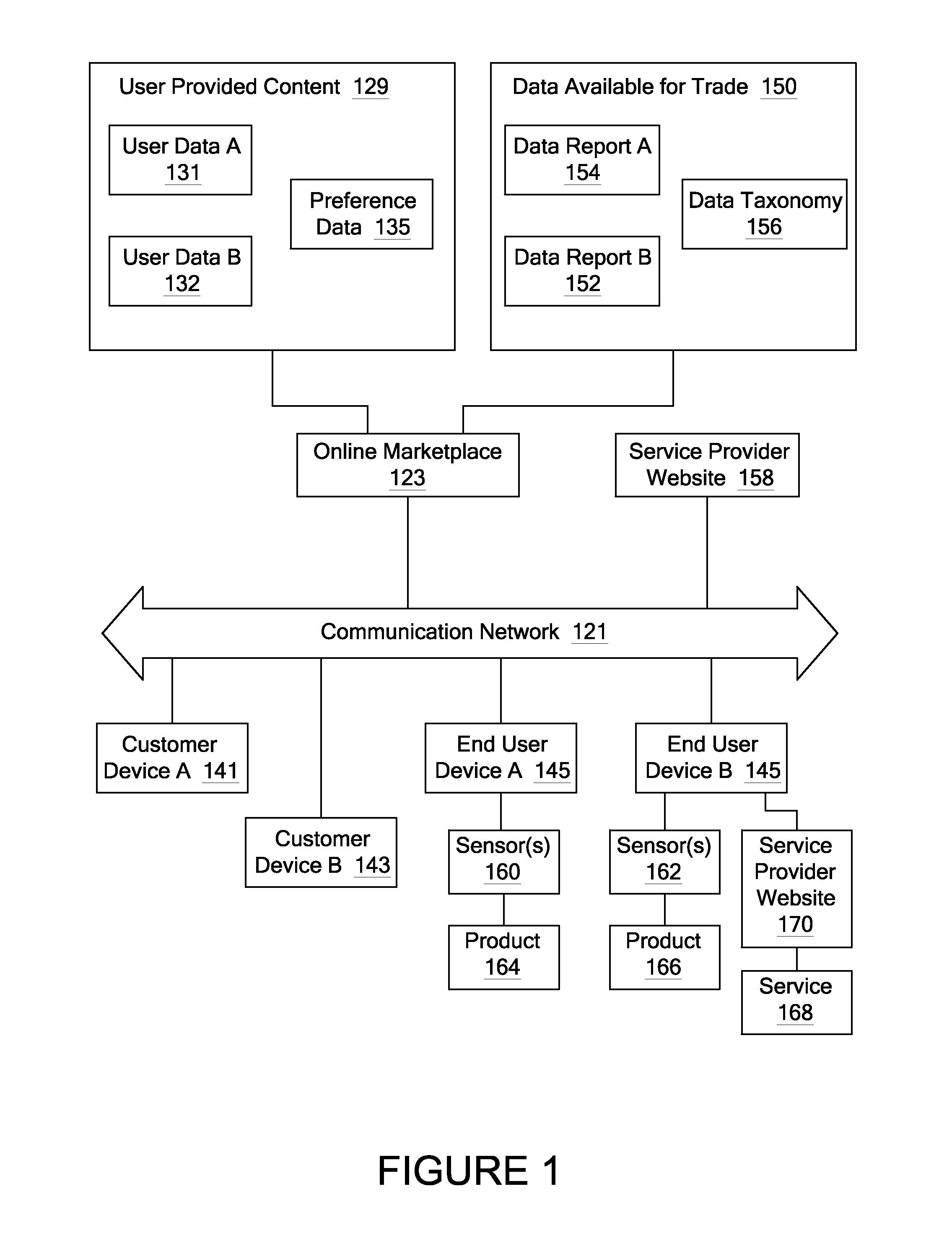
A plurality of persona attributes are identified within a data set received from a data seller. A persona privacy risk associated with the persona attributes of the dataset is determined. The persona privacy risk comprises an estimate of the potential sensitivity of the persona attributes. A plurality of identity attributes within a data set received from a data seller are identified. An identity privacy risk associated with the plurality of identity attributes is determined. The persona privacy risk comprises an estimate of the risk that the plurality of identity attributes identify the data seller. A total privacy risk is then determined using the persona privacy risk and the identity privacy risk associated with the dataset, the total privacy risk comprising an estimate of a total risk to the privacy of the data seller that disclosure of the dataset represents.
Owner:STATZ
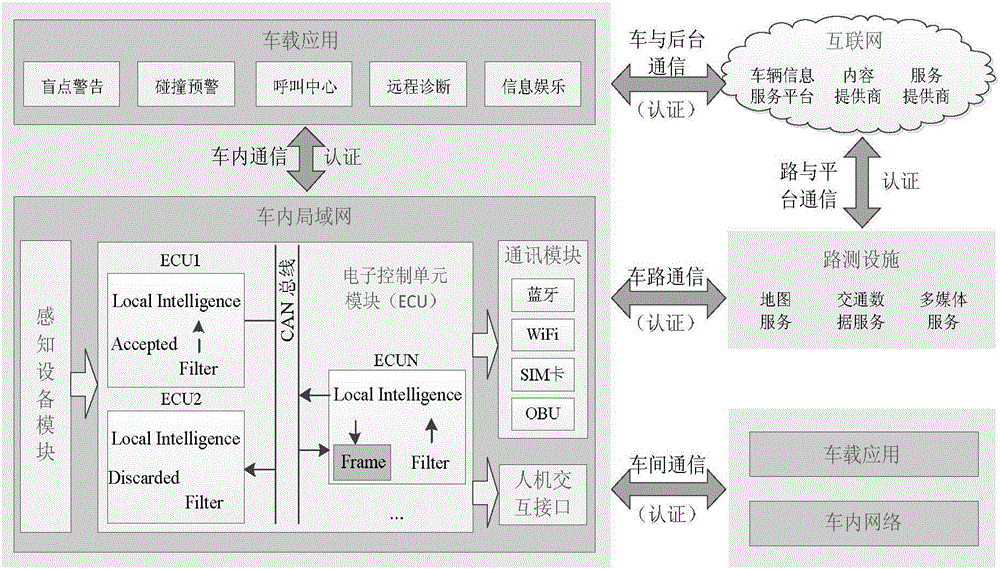
Strong privacy protection dual authentication method based on node identities and reputations in Internet of vehicles
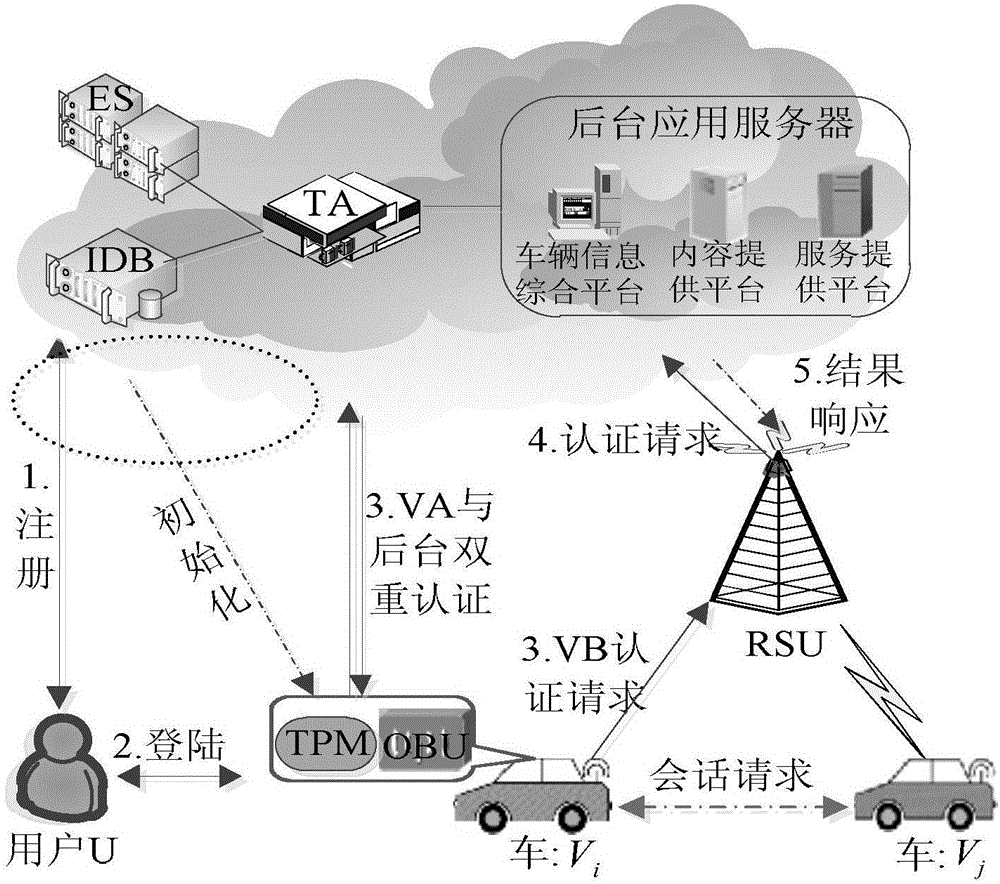
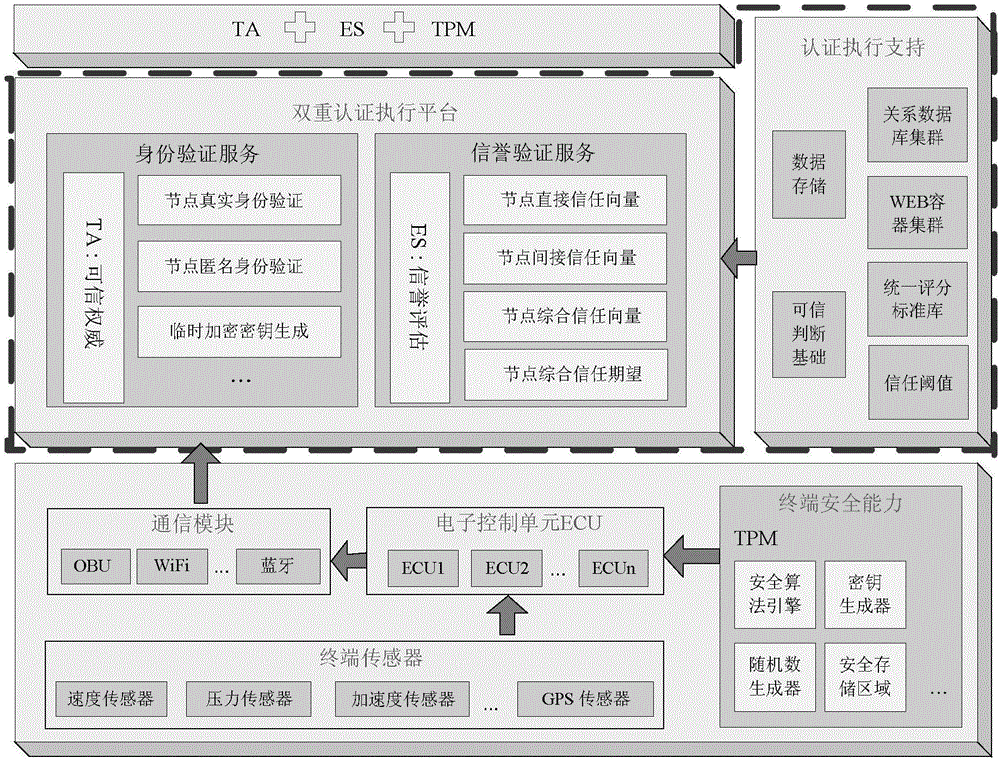
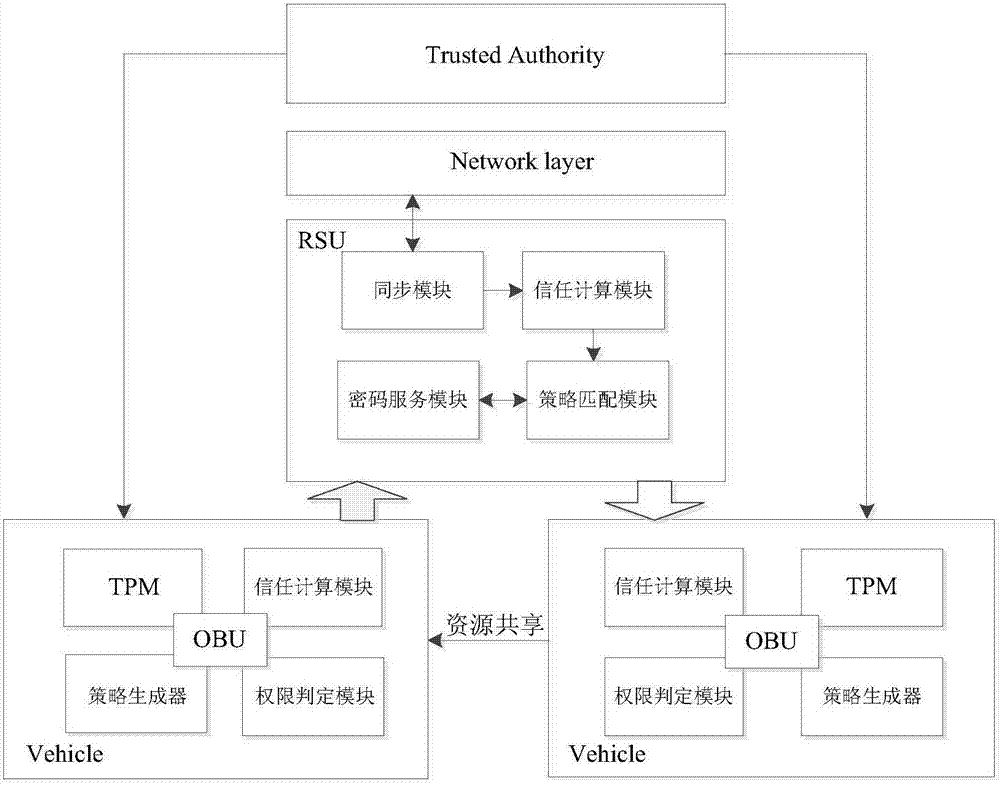
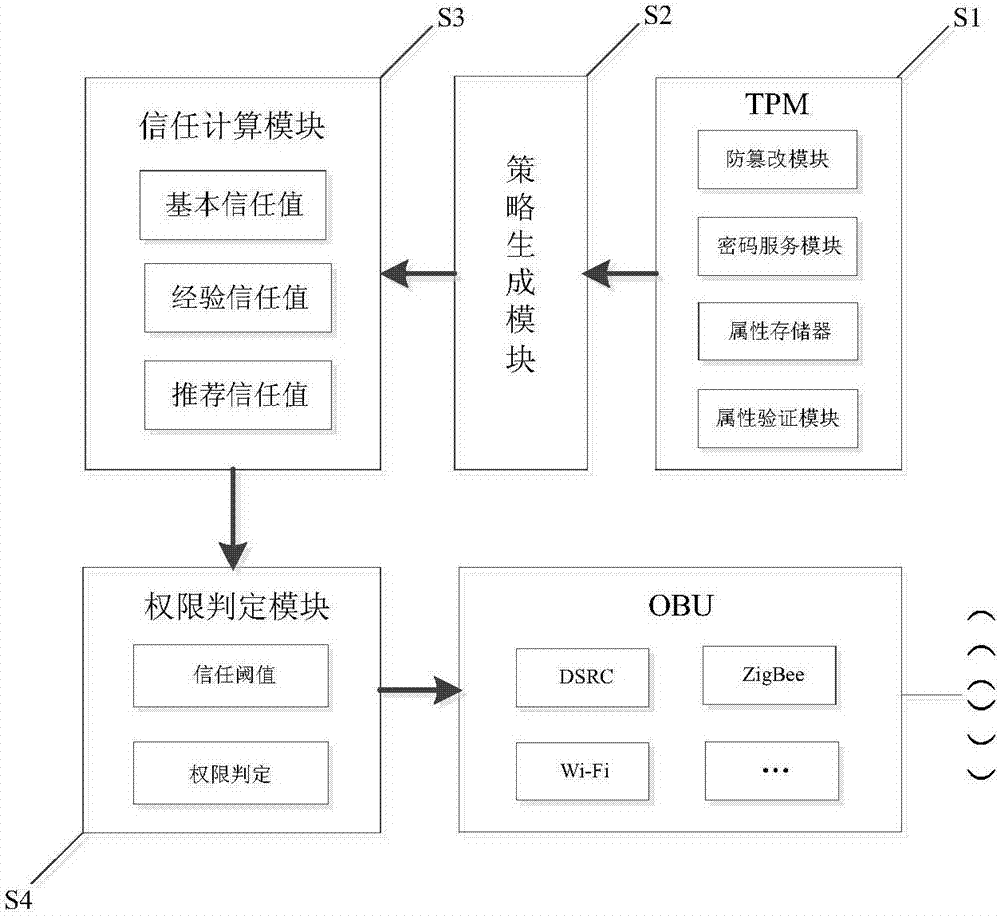
The invention discloses a strong privacy protection dual authentication method based on node identities and reputations in Internet of vehicles. A user registers with an authentication center to obtain unique secret information shared with the authentication center; the user stores vehicle node initialization parameter information into a TPM security storage area; when the user expects interaction between vehicle applications on vehicle nodes and a background application server, the user needs to input identity information and an authentication process of the vehicle nodes and a background is executed by TA; the authentication process is as follows: a temporary encryption key with the TA is established to carry out symmetrical encryption transmission on the information through a bilinear pairing principle, the TA carries out integrity and consistency detection on the received information, verifies legality of real and temporary identities of the vehicle nodes and calls an ES to compute the node reputation, if the identities of the vehicle nodes are legal finally and the reputations exceed a threshold, the authentication of communication between the vehicle nodes and the background is completed. According to the method, the authentication security is enhanced, the identity privacy and the trajectory privacy of the user are protected, the authentication efficiency is improved and the authentication time delay is reduced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
A vehicle networking architecture based on block chain and a working method thereof
ActiveCN109068299ASolve the centralization problemSolve the problem of mutual distrust between entitiesParticular environment based servicesUser identity/authority verificationUndirected graphIn vehicle
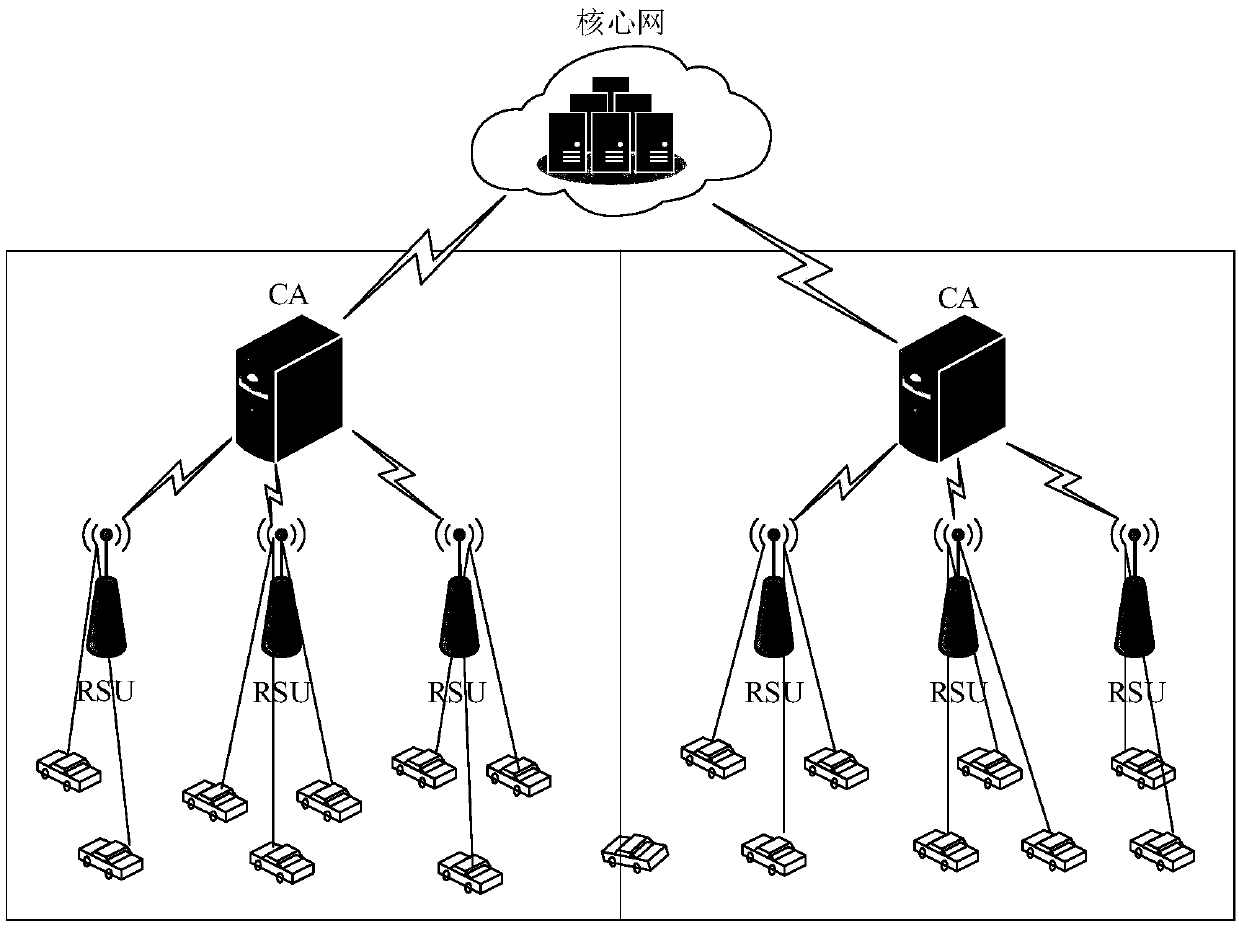
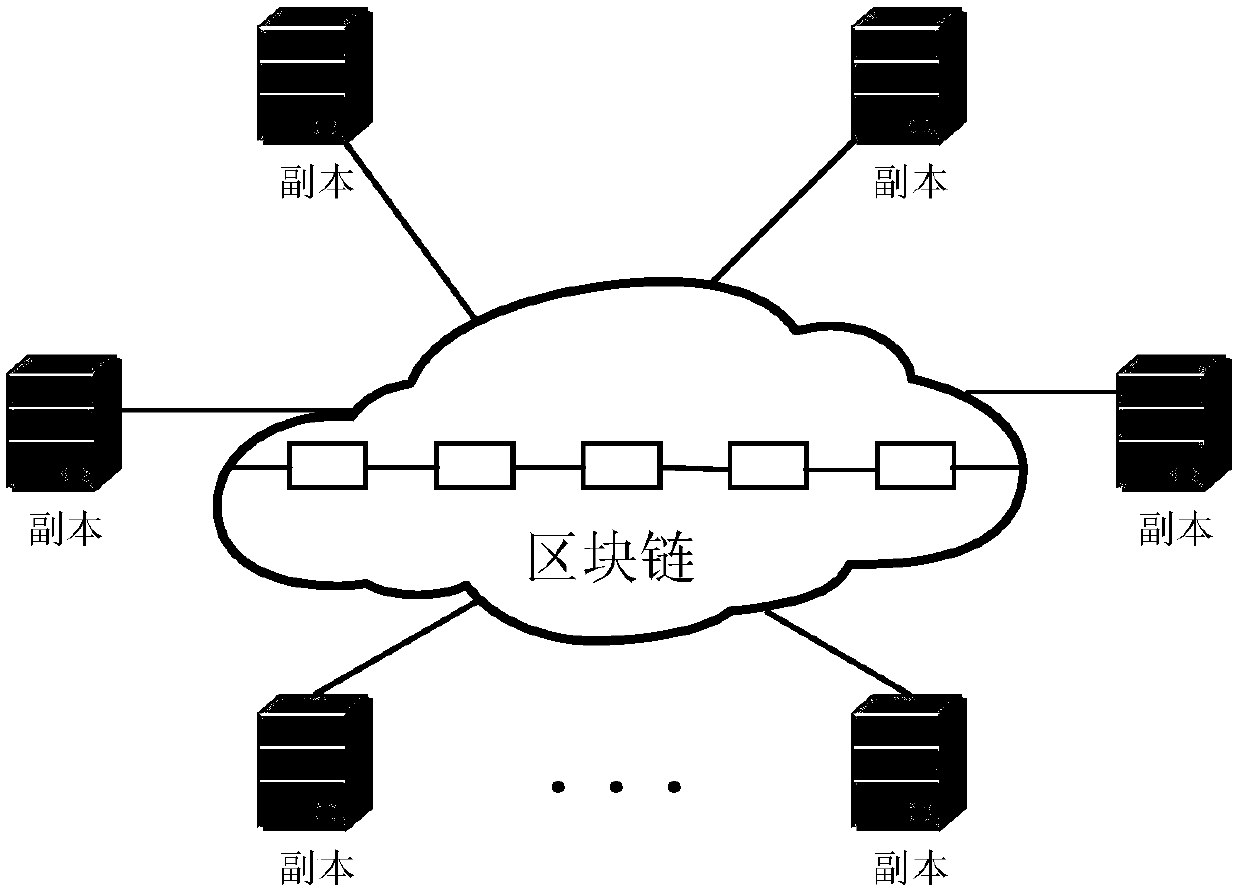
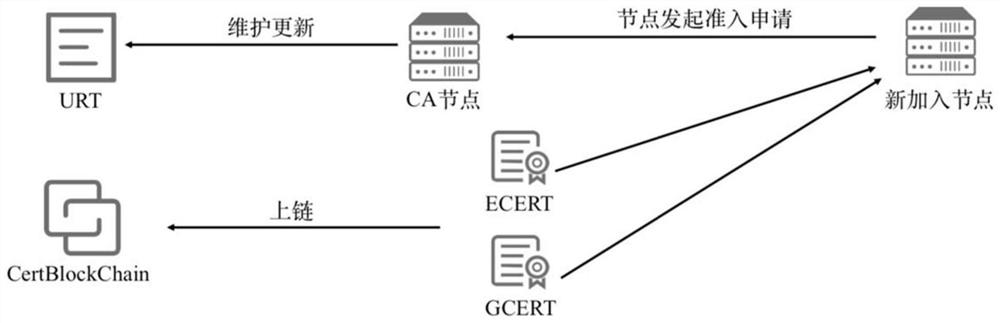
The invention discloses a vehicle networking structure based on a block chain and a working method thereof. The vehicle networking structure comprises an interconnected vehicle entity, a vehicle-mounted unit OBU, a roadside unit RSU, a core network and a block chain network. It has the typical characteristics of decentralization, distribution, collective maintenance and incapability of tampering.It can effectively solve the problem of centralization of traditional vehicle networking architecture and mutual distrust between entities. At that same time, the invention provides an undirected graph generation method, an identity privacy protection method and a location privacy protection method when the beacon information is uploaded by a vehicle, thereby solving the problem of identity and location privacy disclosure of a vehicle networking architecture based on a block chain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
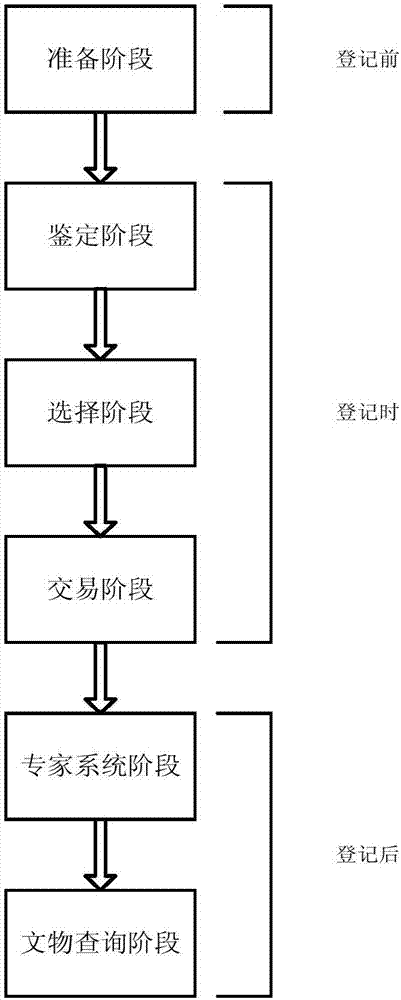
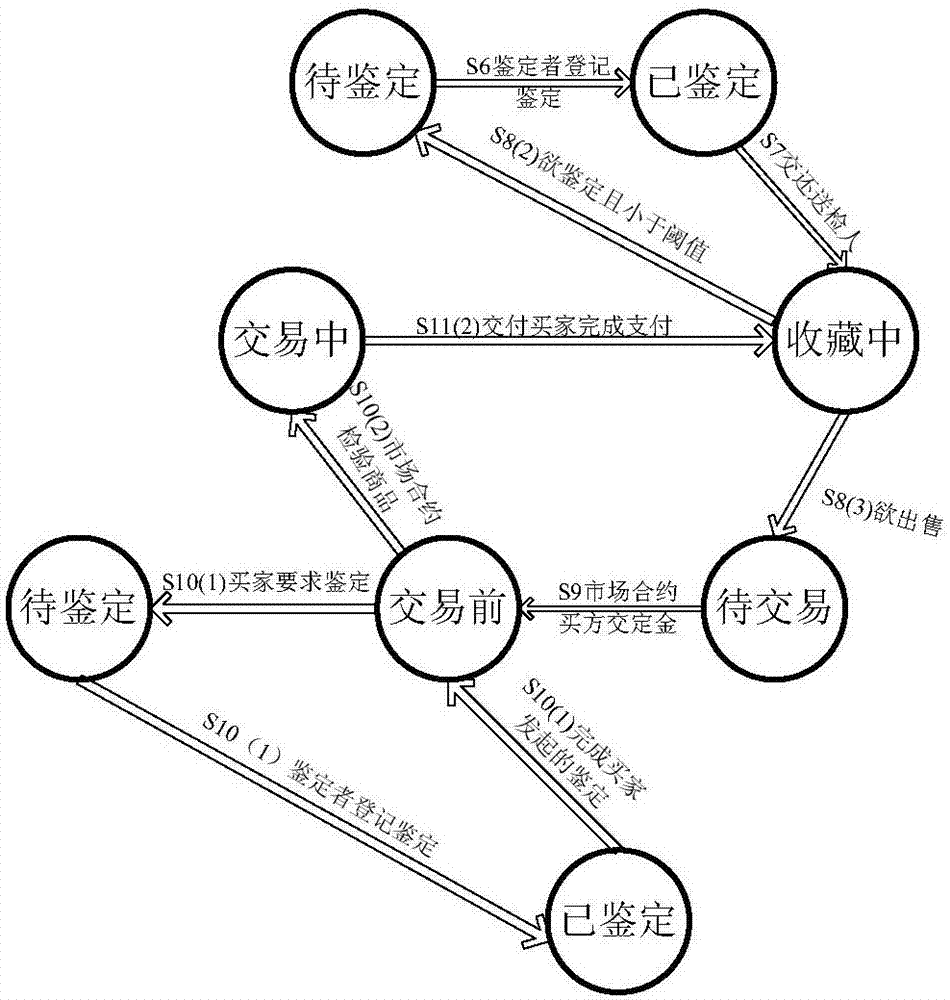
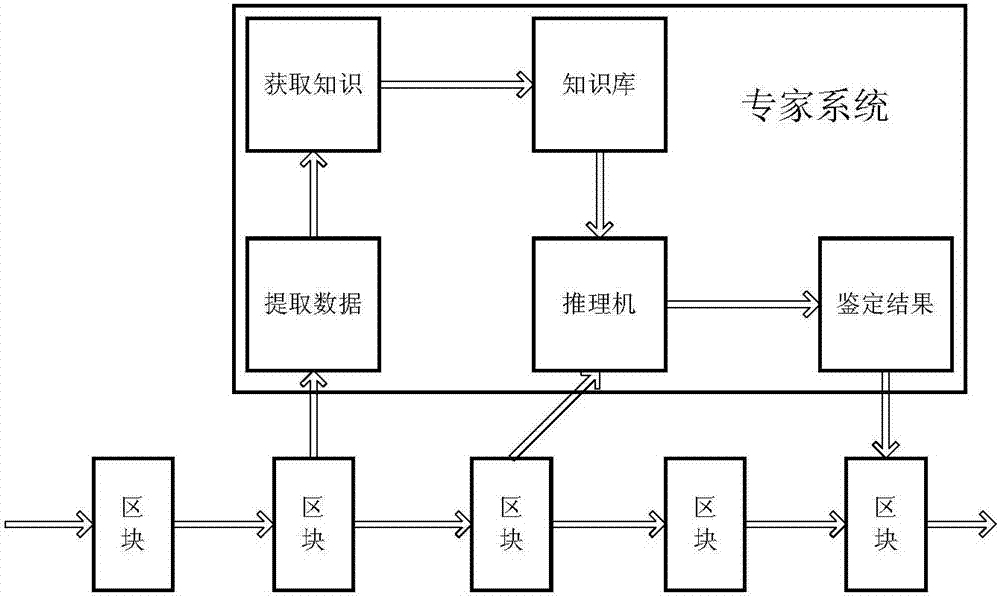
Artwork circulation, authentication and registration method based on blockchain and expert system
InactiveCN107194587APrevent repudiationAvoid harmBuying/selling/leasing transactionsResourcesSmart contractIdentity privacy
The invention discloses an artwork circulation, authentication and registration method based on a blockchain and an expert system. According to the method, registration for an authentication result of an artwork is completed by smart contracts of authentication markets, and then the artwork is allowed to be circulated and recorded in smart contracts of trading markets. According to the method, block information accumulated in the smart contracts of the authentication markets is utilized, and knowledge is acquired outside the blockchain by machine learning of authentication information, the expert system is established, and a need for the commodity authentication validity and authentication result checking is met through providing an authentication suggestion for the artwork of which an inquiry is to the expert system. In addition, under the premise of protecting the identity privacy of a trader from disclosure, the smart contracts of the trading markets and the smart contracts of the authentication markets are combined, and cultural relic registration is established to specifically record a circulation state and an authentication result of a cultural relic. Ultimately, decentralization is realized in a trading process of the artwork by virtue of the above-mentioned method, and gain effects of creditability, convenience and a low cost are achieved at the same time.
Owner:JINAN UNIVERSITY
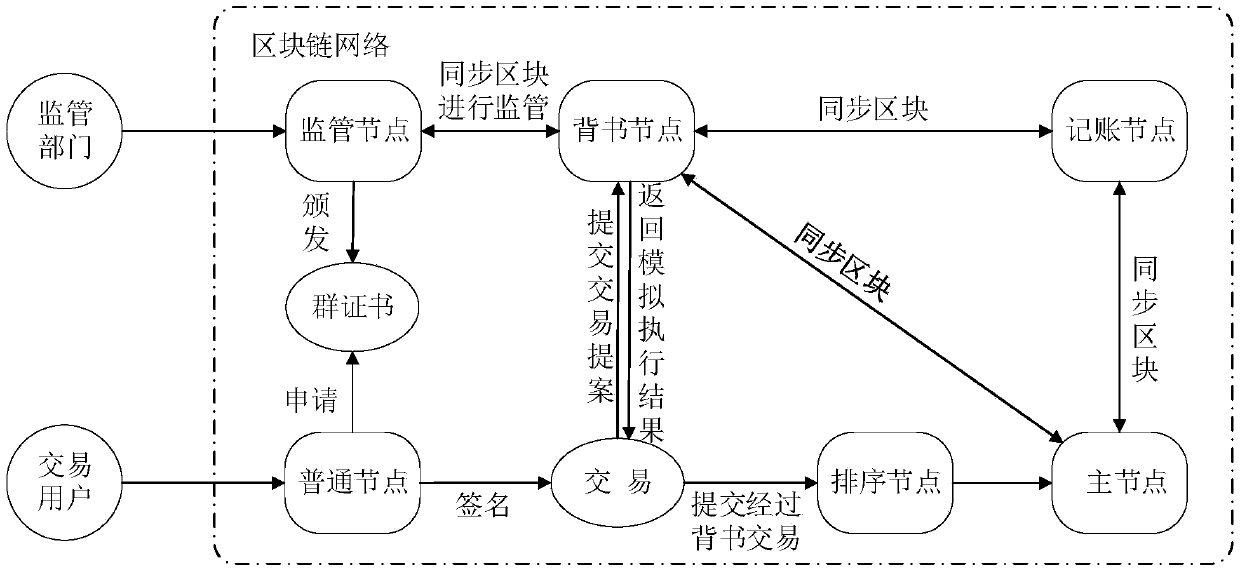
Permission block chain privacy protection and supervision method based on group signatures
InactiveCN109636599AProtect identity privacyGood anonymityFinanceDigital data protectionPrivacy protectionIdentity privacy
The invention discloses a permission block chain privacy protection and supervision method based on group signatures. In a transaction process, whether the endorsement verification of the endorsementnode, the sequencing service of the sequencing node and the consensus process of the main node and the accounting node can only verify the legality of the identities of the two parties of the transaction, and cannot correspond the signature to the real identity of the user, so that the identity privacy of the user is guaranteed. After the transaction is completed, the supervision department can synchronize the block with other nodes through the supervision node, then open the signature contained in the transaction, and enable the signature to correspond to the real identity of the transactionuser, so as to supervise the block chain.
Owner:GUANGXI NORMAL UNIV
Internet of Vehicles system based on block chain and working method
ActiveCN110446183AAvoid participationReduce participationParticular environment based servicesUser identity/authority verificationInvestigation methodsPrivacy protection
The invention provides an Internet of Vehicles system based on a block chain. The system comprises a certificate issuing mechanism, a vehicle-mounted unit deployed on a vehicle, a block chain networktaking a roadside unit as a peer node, and a cloud server for providing cloud service for the vehicle-mounted unit and the roadside unit. The working process of the system comprises four stages of vehicle registration, vehicle authentication, vehicle announcement and vehicle forwarding. The system provided by the invention has the characteristics of distribution, data collective maintenance, no tampering and conditional privacy protection. Meanwhile, a vehicle identity privacy protection method, a malicious vehicle responsibility investigation method and a transaction data storage method are provided, so that the problems of dependence on trusted third parties and mutual trust between entities in the traditional Internet of Vehicles architecture can be effectively solved.
Owner:XIAN UNIV OF POSTS & TELECOMM
Internet of vehicles group key management method oriented to multiple services and privacy protection
ActiveCN105554105ASolve the problem of multiple groups ordering multiple servicesProtect identity privacyTransmissionComputer networkPrivacy protection
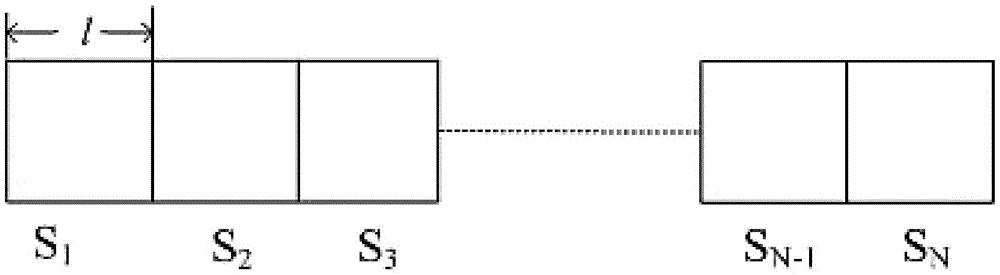
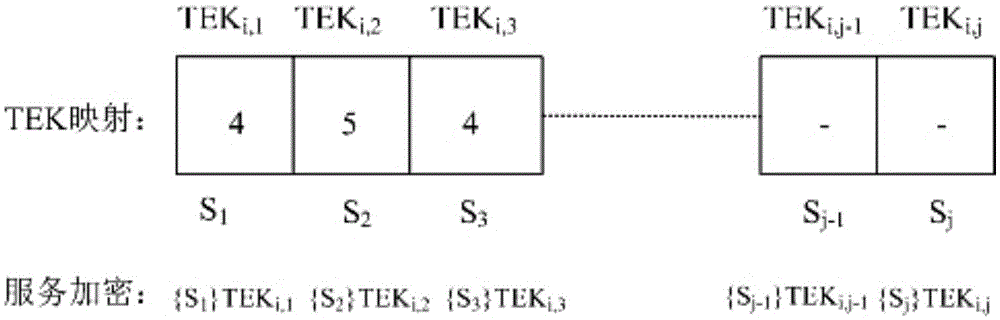
The invention discloses an Internet of vehicles group key management method oriented to multiple services and privacy protection. The method sequentially comprises the following steps: (1) establishing a two-layer network model of Internet of vehicles (colons are deleted); (2) describing a scene in which multiple groups subscribe multiple services in the Internet of vehicles based on the network model in the step (1); (3) protecting identity privacy of vehicles through a pseudonym mechanism, wherein TA can reveal real identities of the vehicles when service disputes occur; (4) using key update slot KUS by a TEK update strategy; and (5) after turnover of the vehicles, performing TEK update in a target region to ensure backward security, and performing TEK update in an original region to ensure forward security. Through adoption of the method, the identity privacy of the vehicles, non-repudiation of vehicle subscription services and service continuity during inter-regional turnover of the vehicles can be ensured.
Owner:ANHUI UNIVERSITY
Zero-knowledge proof-based method and system for protecting user identity privacy
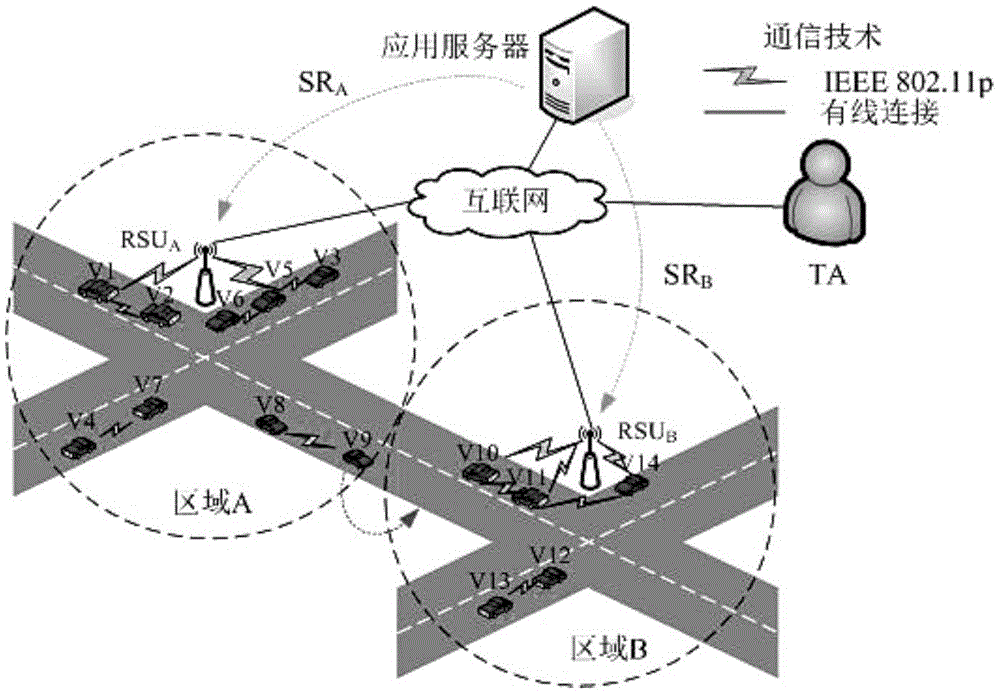
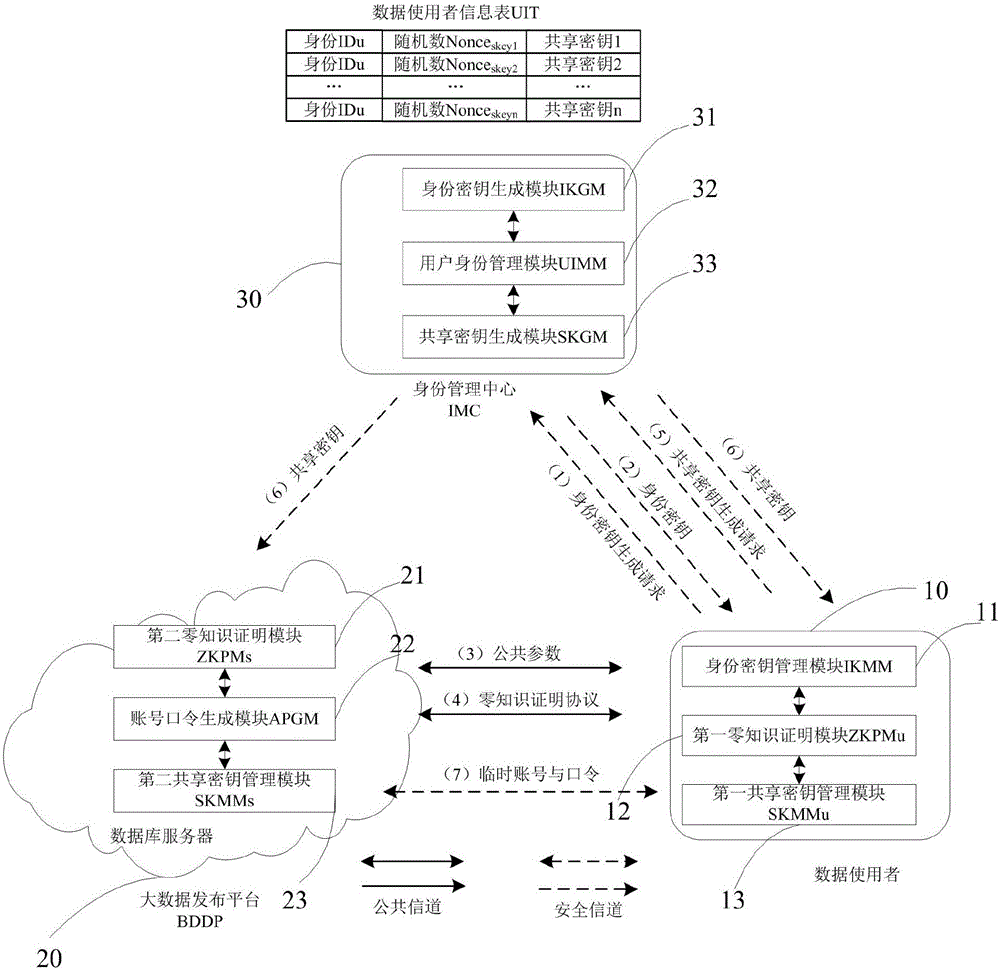
ActiveCN105024823ANormal analysisDo not reveal identity informationUser identity/authority verificationTemporary Account NumberPassword
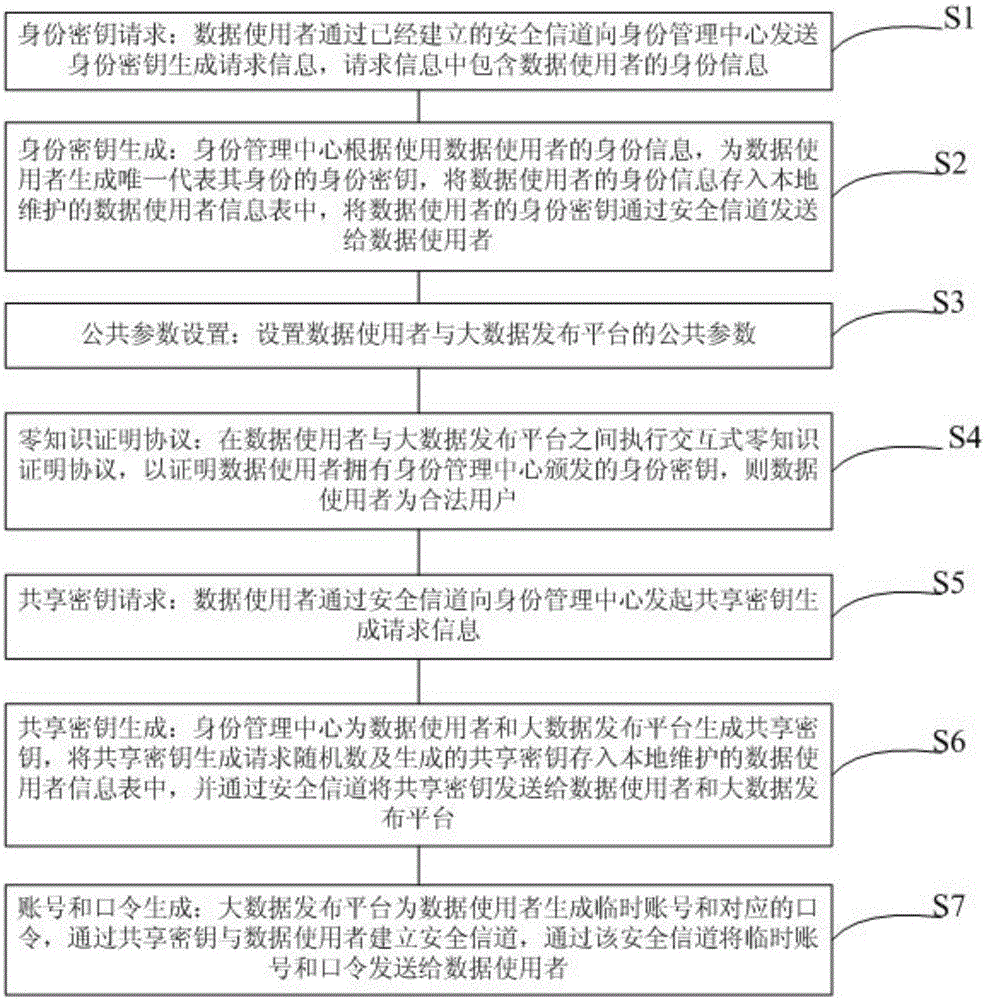
A zero-knowledge proof-based method for protecting user identity privacy comprises the steps as follows: S1, identity secret key requesting: a data user transmits identity secret key generation request information to an identity management centre via an established secure channel; S2, identity secret key generation: the identity management centre uses the identity information of the data user; S3, public parameter setting: public parameters of the data user and a big-data releasing platform are set; S4, zero-knowledge proof protocol execution: an interactive zero-knowledge proof protocol is executed between the data user and the big-data releasing platform; S5, shared secret key requesting: the data user transmits shared secret key generation request information to the identity management centre via the secure channel; S6, shared secret key generation: the identity management centre generates a shared secret key for the data user and the big-data releasing platform; S7, account number and password generation: the big-data releasing platform generates a temporary account number and a corresponding password for the data user and establishes the secure channel.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
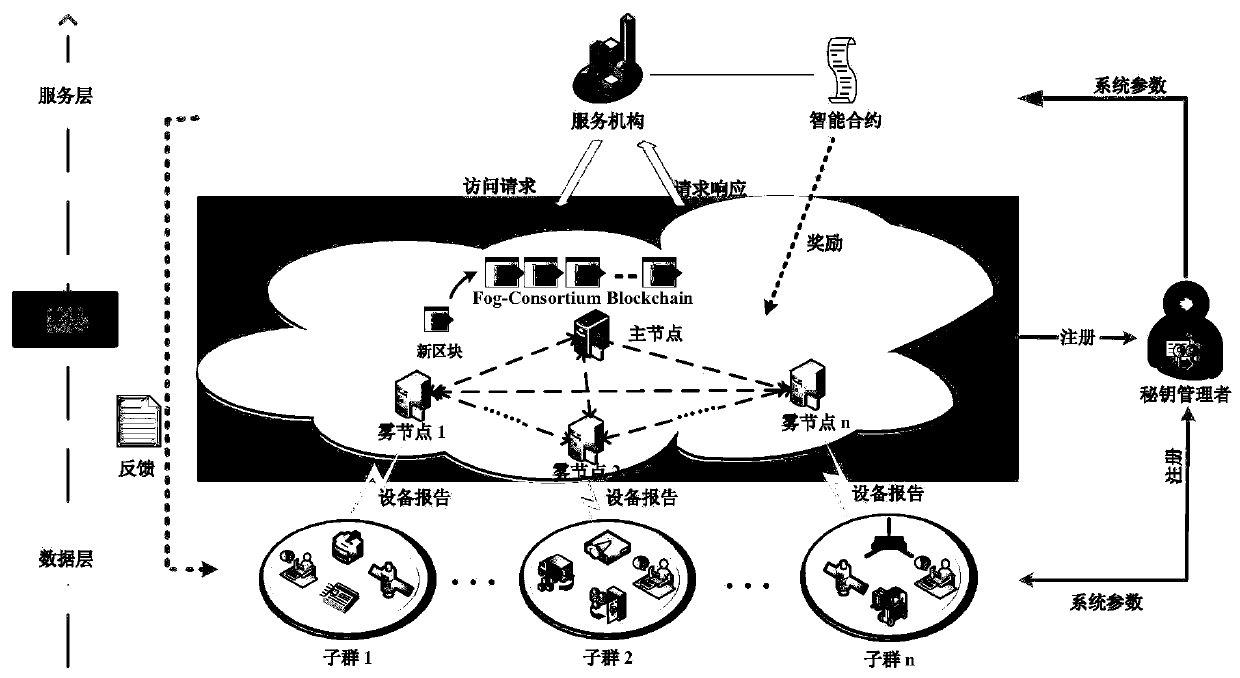
Security distributed aggregation and access system and method based on fog alliance chain
ActiveCN111372243AReduce transmission overheadResist curiosityPublic key for secure communicationSecurity arrangementData integrityConfidentiality
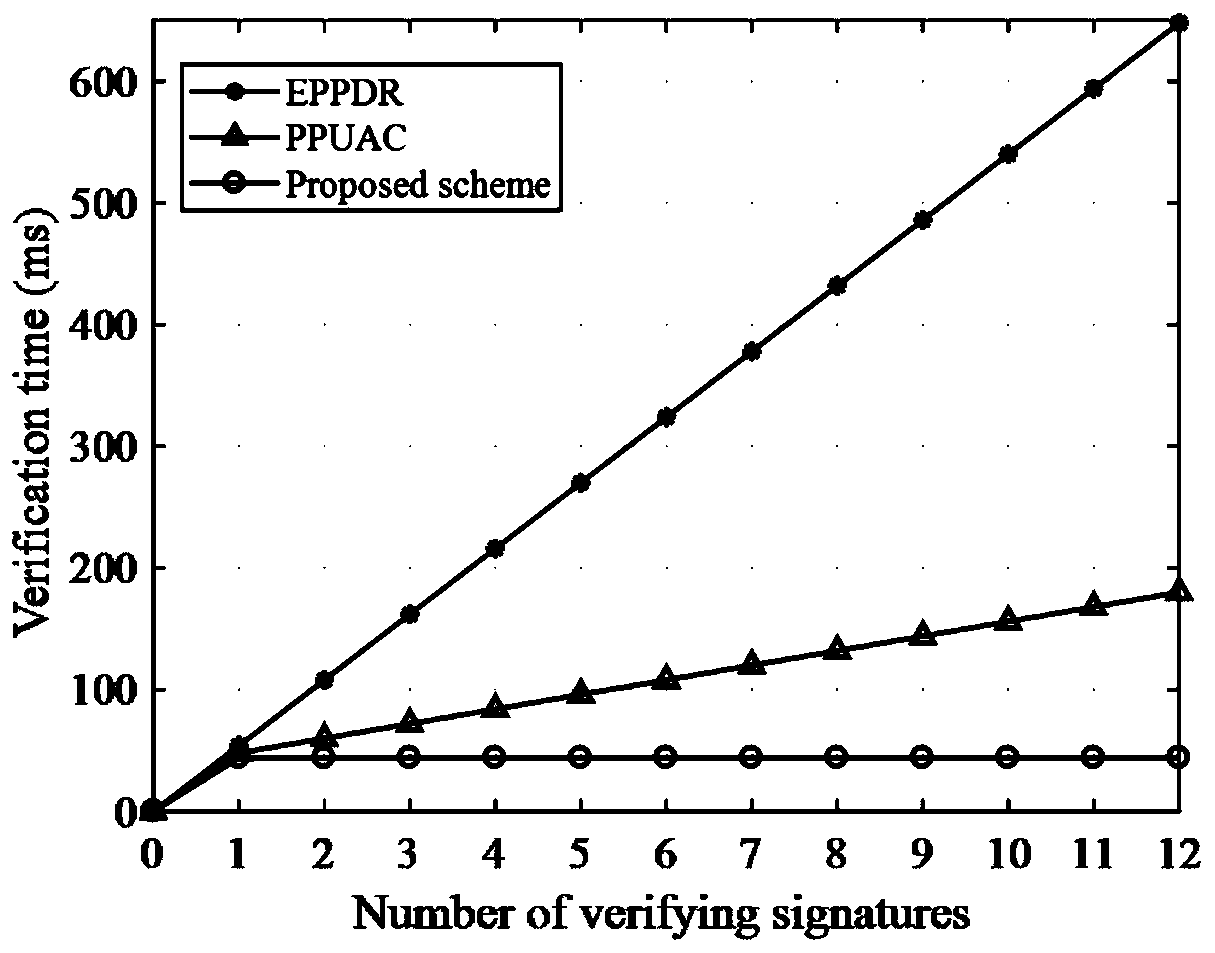
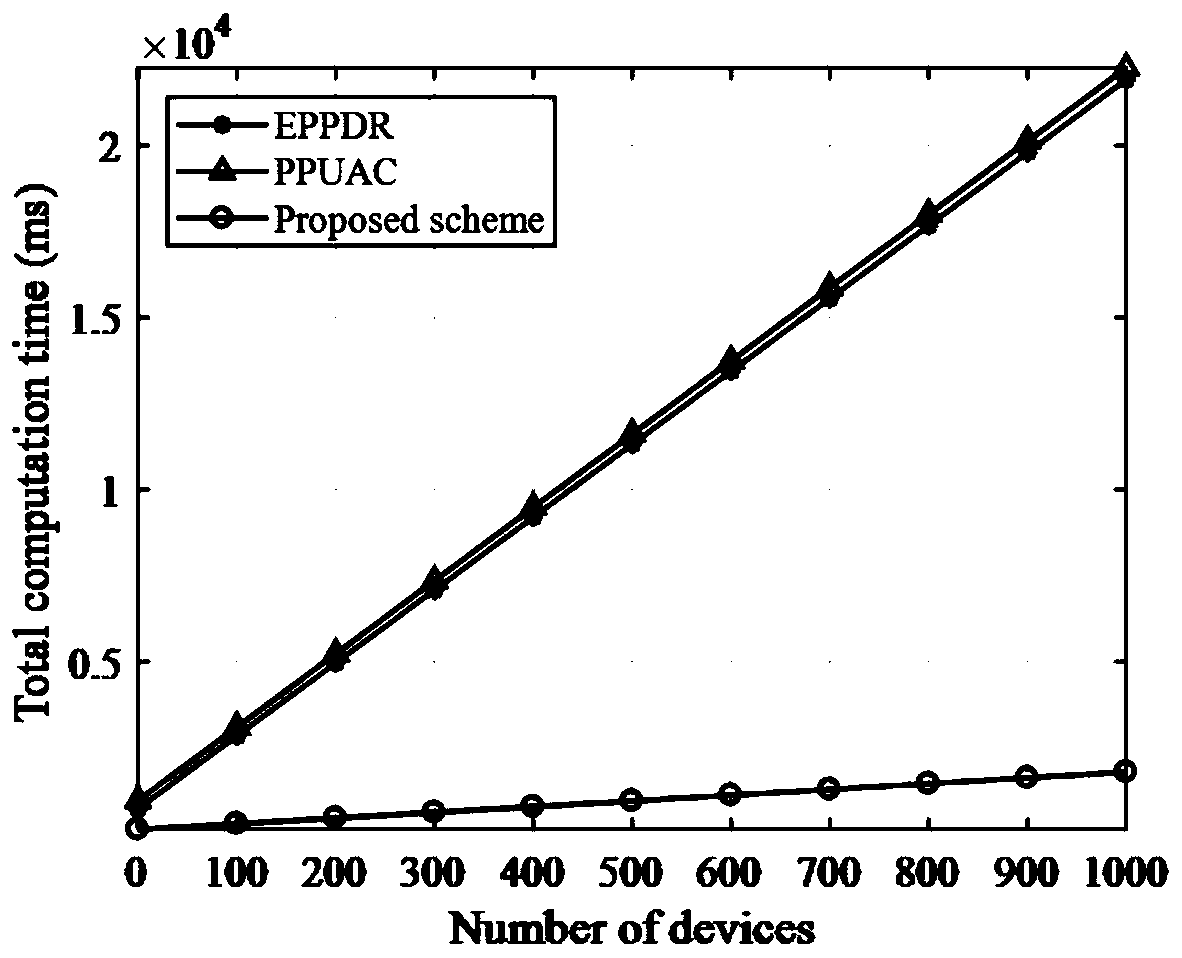
The invention discloses a security distributed aggregation and access system and method based on a fog alliance chain, and aims to solve the problem that most of current data aggregation schemes are designed based on a centralized mode, face single-point faults and tampering threats, and have security and performance improvement space. In order to solve the challenge, a distributed aggregation framework is designed in combination with fog computing and an alliance chain, single-point faults and tampering crisis are solved, and powerful support is provided for safe collection, communication andstorage of data. Meanwhile, a Paillier homomorphic algorithm of a threshold version is fused, a safe access control mechanism with a fault-tolerant function is designed, and confidentiality and privacy of data on a chain are guaranteed. Meanwhile, an efficient anonymous authentication method is provided, and identity privacy and data integrity can be guaranteed. Finally, the comparative analysisresult of the method and the existing method shows that the method can resist malicious attacks and ensure the system security, and compared with other existing methods, the method has lower calculation and communication costs.
Owner:NANJING UNIV OF POSTS & TELECOMM
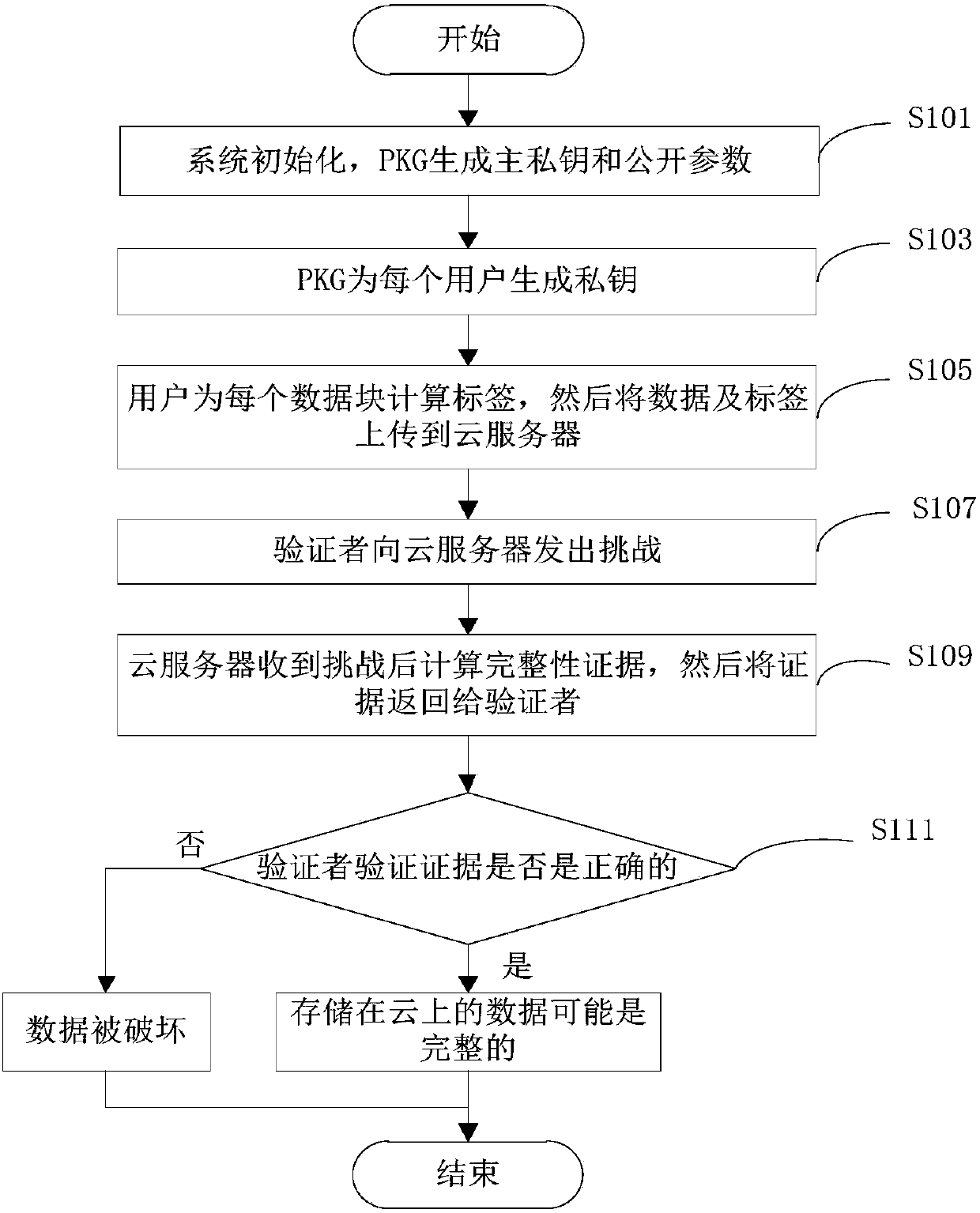
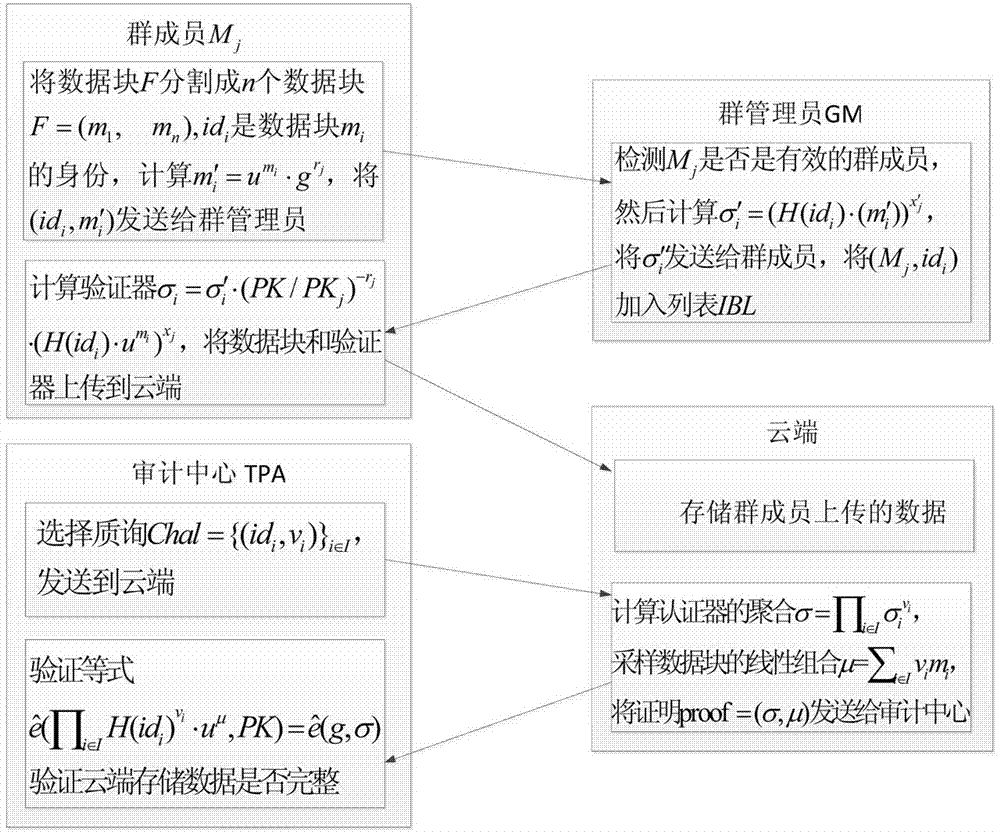
Identity-based privacy protection integrity detection method and system in cloud storage
ActiveCN107948143AReduce overheadReduce public key certificate management workUser identity/authority verificationThird partyData integrity
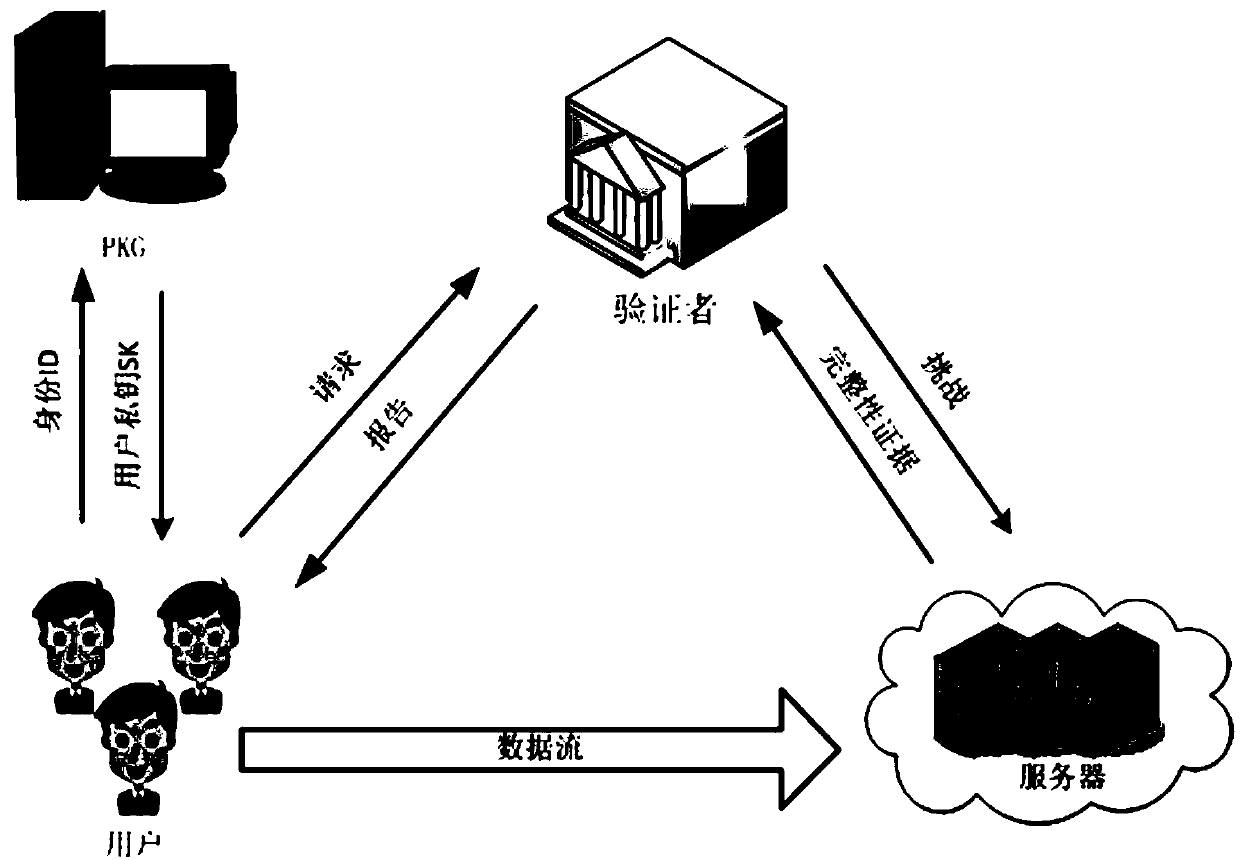
The invention discloses an identity-based privacy protection integrity detection method and system in a cloud storage. The method comprises the following steps of (1) a system initialization stage that a trusted third-party PKG generates a main private key and a public parameter; (2) a secret key extraction stage that the trusted third-party PKG generates a private key for a user according to useridentity; (3) a label generation stage that the user generates a data label for each data block by using the private key and uploads data and the corresponding data label to a cloud server; (4) a challenge inquiry stage that a verifier sends a challenge to the cloud server; (5) an evidence generation stage that the cloud server computes an integrity evidence according to challenge information andreturns the integrity evidence to the verifier; and (6) a verification stage that the verifier verifies the data integrity according to the evidence. According to the method and the system, the public key certificate management and calculation cost of the system is reduced based on an identity signature, and meanwhile, the identity privacy and the data privacy of the user are protected in a process of verifying the data integrity, and the safety of the system is improved.
Owner:ANHUI UNIVERSITY
Cross-domain identity authentication method based on edge computing network architecture
ActiveCN111355745AReduce computational overheadLow costKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEdge nodeNetwork architecture
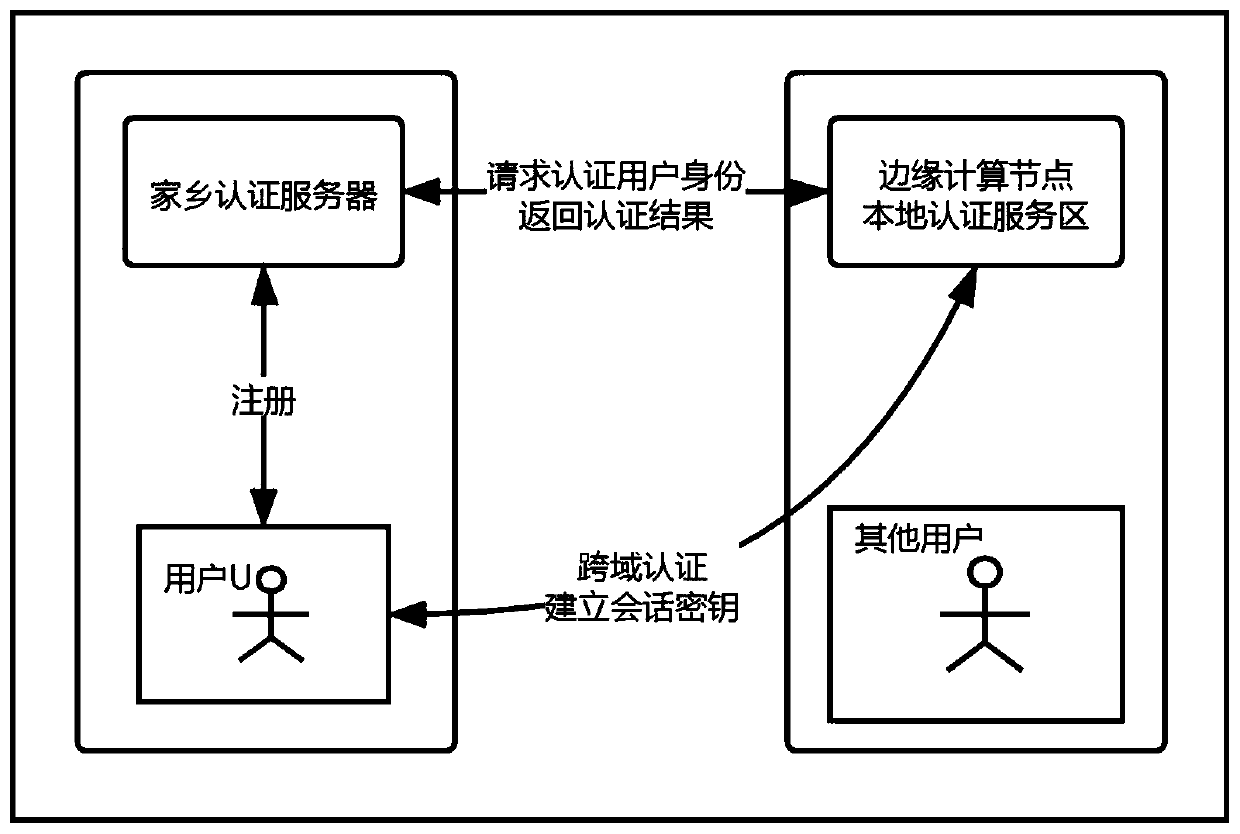
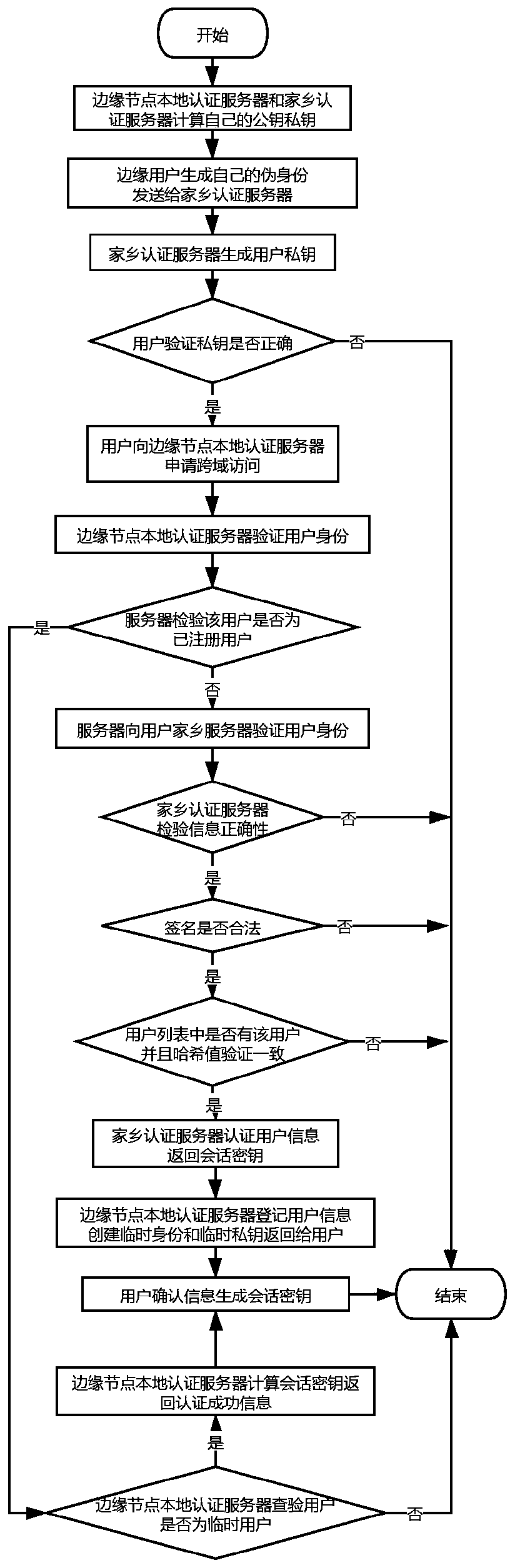
The invention discloses a cross-domain identity authentication method based on an edge computing network architecture, and mainly solves the technical problems that in the prior art, key management and distribution are difficult, and user privacy is difficult to protect. The method comprises the following steps: 1) an edge node local authentication server and a home authentication server calculaterespective public and private keys; 2) the home authentication server generates a private key constructed by the user by using the pseudo identity; 3) the user applies for cross-domain access to theedge node local authentication server; 4) the edge node local authentication server sends information to a home authentication server of the user to verify the identity of the user; 5) the home authentication server authenticates the user information and returns a session key; 6) the local authentication server of the edge node calculates the session key and returns the authentication information;7) the user confirms the information to generate the session key. According to the method, the bidirectional verification security of the edge node equipment and the user can be effectively improved,the problems that the identity privacy of the user is exposed and the session is tracked are solved, and the method can be used for modern Internet of Things equipment.
Owner:XIDIAN UNIV
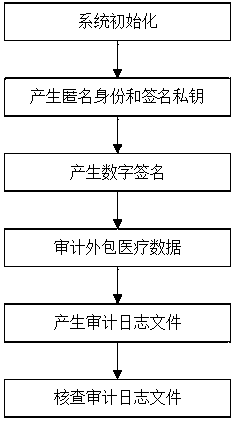
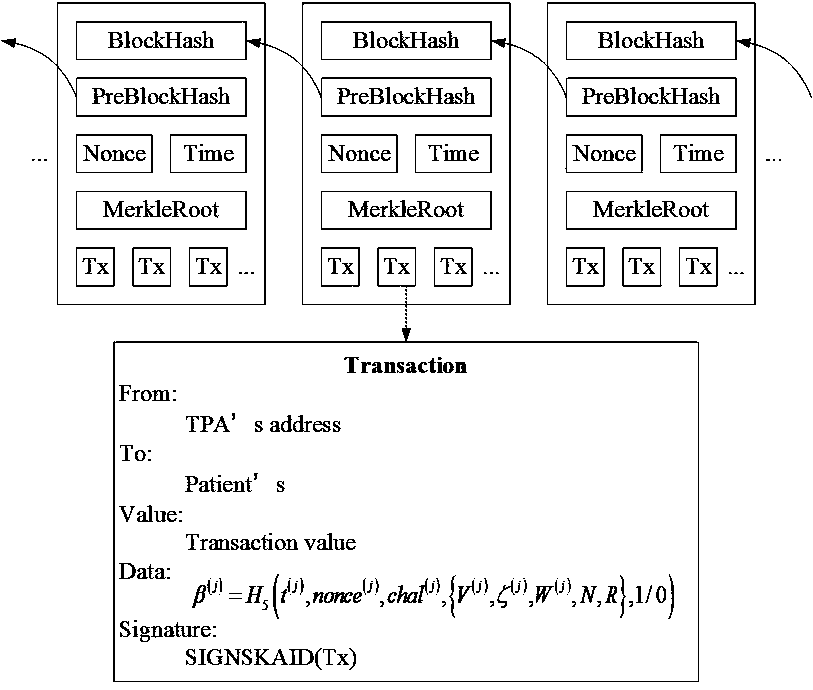
Medical cloud storage public auditing method of anonymous identity based on blockchain technology
ActiveCN109639420AChallenge - Verify IntegrityPrivacy protectionKey distribution for secure communicationFinanceThird partyData integrity
The invention discloses a medical cloud storage public auditing method of anonymous identity based on the blockchain technology. The method comprises an outsourcing medical data integrity verificationstep and a third party auditor behavior checking step, wherein the outsourcing medical data integrity verification step comprises an initialization sub-step, an anonymous identity and signature private key generation sub-step, a digital signature generation sub-step and an outsourcing medical data auditing sub-step, and the third party auditor behavior checking step comprises an auditing log filegeneration sub-step and an auditing log file inspection sub-step. In the medical cloud storage public auditing method disclosed by the invention, a user sends the real identity to a key generation center to obtain the corresponding anonymous identity, thereby ensuring the identity privacy of the user, and a third party auditor periodically challenges-verifies the integrity of the outsourcing medical data stored by the user on a cloud server and defends a data linear recovery attack of an auditor by using the random mask technology.
Owner:SOUTHWEST PETROLEUM UNIV
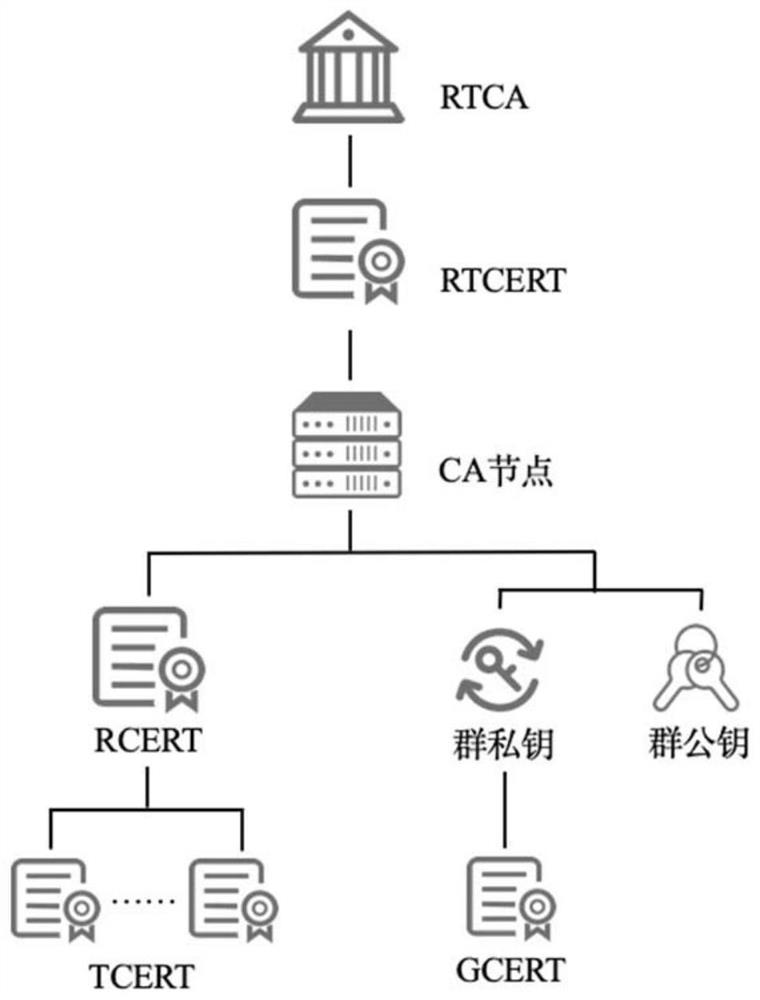
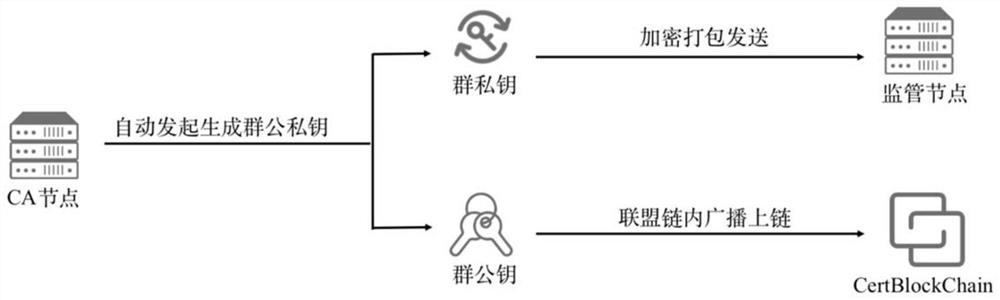
A block chain privacy protection scheme and system based on SM9 algorithm
InactiveCN109409884ASolve problems that are difficult to apply to real-world scenariosSolve application problemsDigital data protectionProtocol authorisationChain structurePrivacy protection
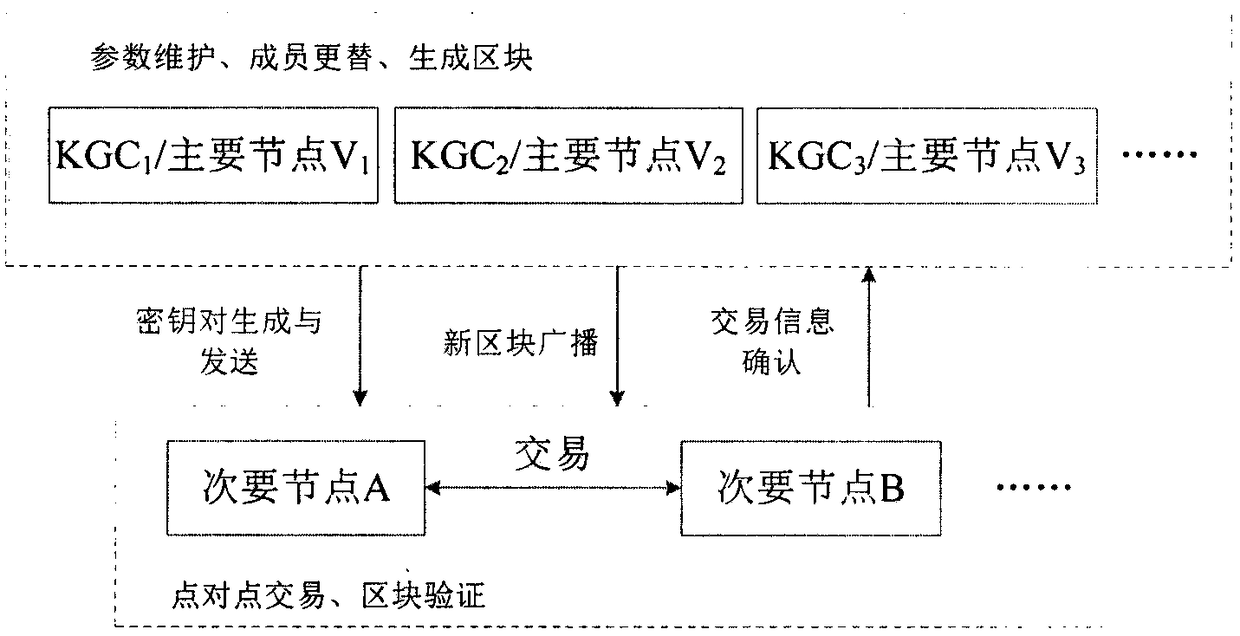
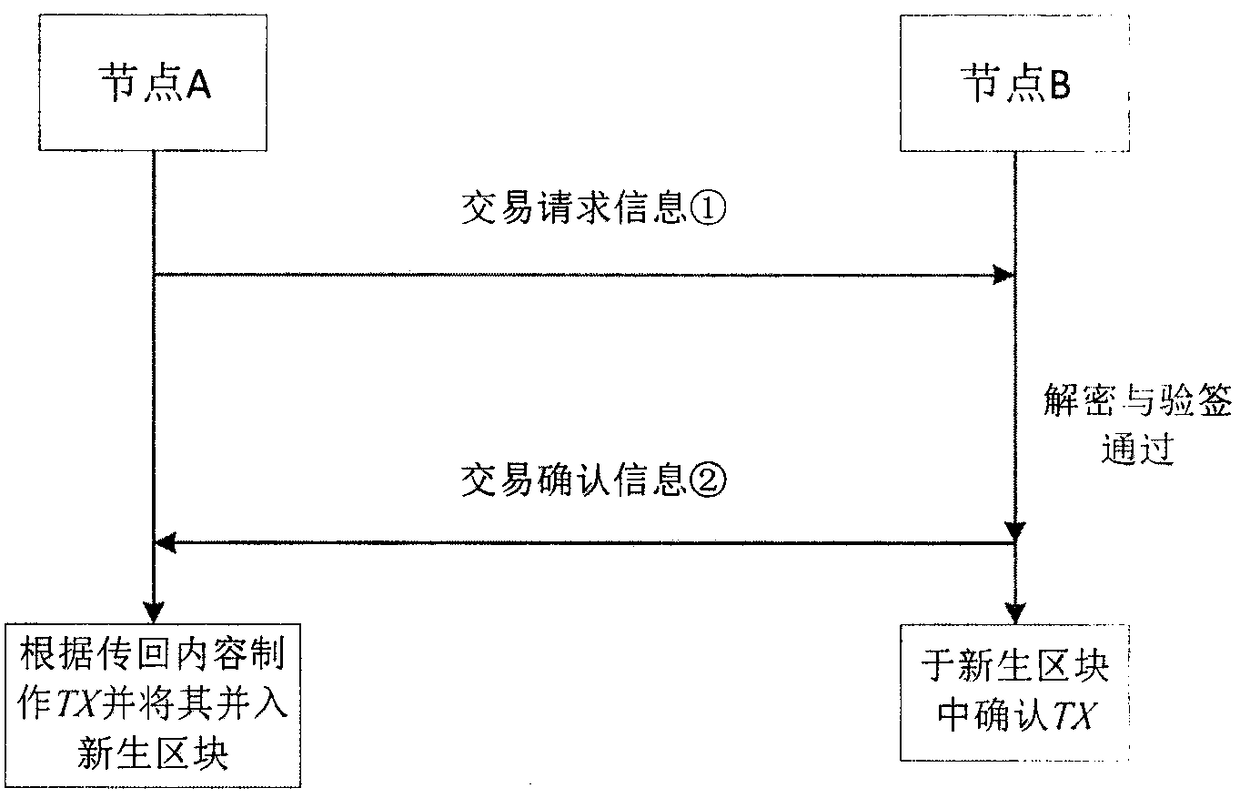
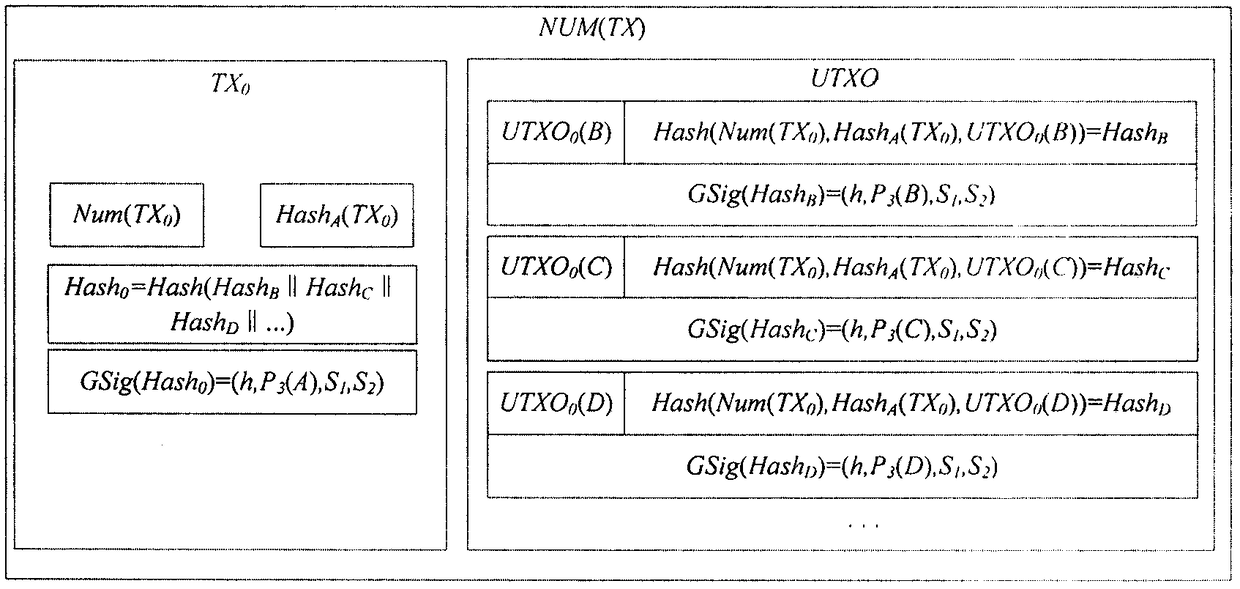
The invention discloses a block chain privacy protection scheme and a block chain privacy protection system based on an SM9 commercial cryptographic algorithm in China, belonging to the field of blockchain security and privacy protection. This invention provides an inter-node transaction platform based on federation chain, defines the permissions and functions of various nodes in the platform, and supports node transaction, information verification, parameter maintenance, block generation and other functions. This invention describes an improved SM9 multi-KGC (Key Generation Center) signaturealgorithm, which improves the working mode of single KGC in SM9 algorithm, adapts to the federation chain structure, and adopts this algorithm to determine the identity of the opposite party in the transaction between nodes. A group signature scheme based on SM9 algorithm is proposed. The identity verification of SM9 algorithm is improved to group signature verification, which effectively protects the identity privacy of the signatory. The transaction information is signed by the node through the algorithm and written into the block chain after the transaction, which can effectively hide theidentity information of both parties of the transaction, protecting the privacy of the node and ensuring the legitimacy of the transaction.
Owner:BEIJING ANRUSHAN CULTURE TECH
Cross-domain anonymous resource sharing platform and implementing method thereof
ActiveCN106992988AAchieve authenticationRealize cross-domain authorization managementUser identity/authority verificationInternet privacyStrategy making
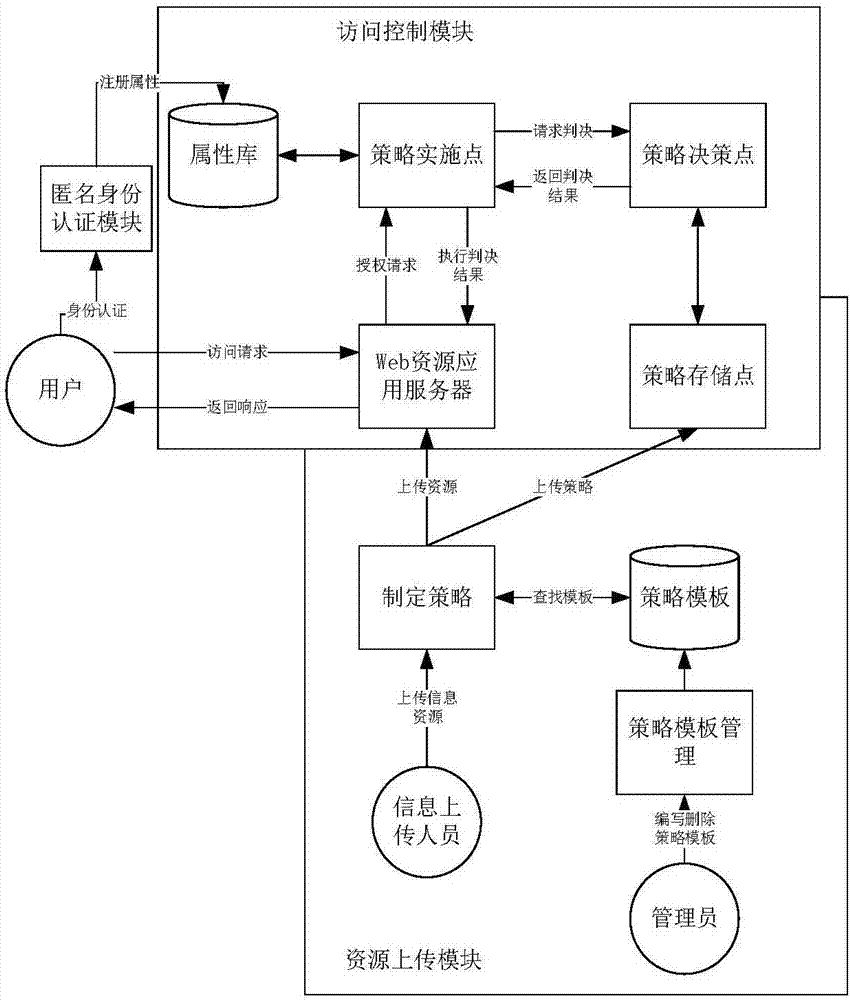
The invention discloses a cross-domain anonymous resource sharing platform and an implementing method thereof. The platform comprises an anonymous identity authentication module, a resource uploading module and an access control module. According to the invention, anonymous identity authentication on a user is implemented by the anonymous identity authentication module, and authorization management on the user is implemented by methods of access control and the like. According to the invention, firstly, by analysis on an attribute certification structure, anonymous identity authentication on the user and construction of a user attribute library on the basis of protecting user identity privacy are implemented. Based on identity authentication, access strategy making for uploaded resources is implemented by the resource uploading module, the access control module judges whether a visitor has an access permission according to each entity attribute and strategy so as to ensure security of resources, and finally, anonymous cross-domain authentication management on the user is implemented and a fine-grained resource sharing mode is implemented. Meanwhile, the cross-domain anonymous resource sharing platform and the implementing method thereof have effectiveness, dynamics and the like.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
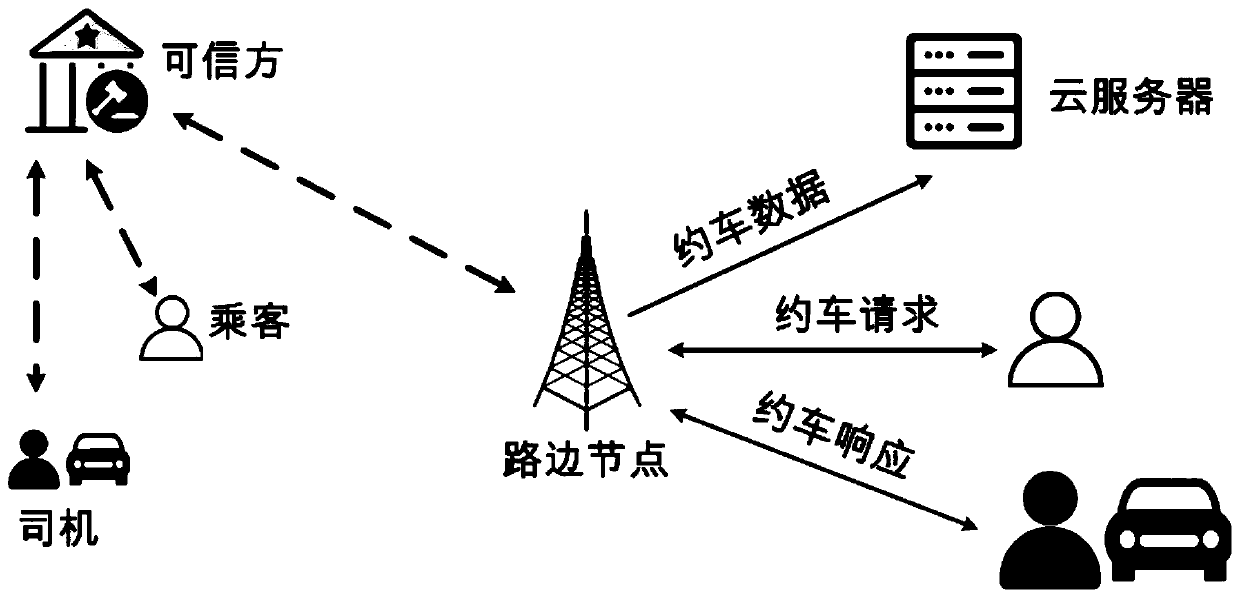
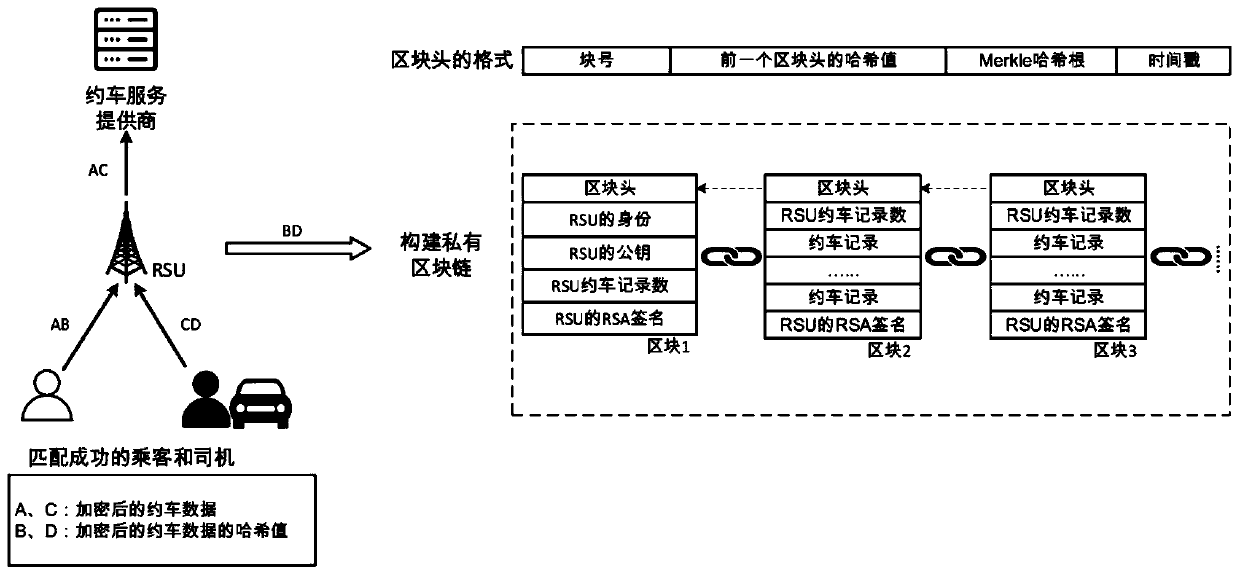
User privacy protection scheme for car hailing based on blockchain
InactiveCN110365485AProtect identity privacyProtect location privacyUser identity/authority verificationDigital data protectionInternet privacyThe Internet
The invention relates to a user privacy protection scheme for car hailing based on a blockchain, and belongs to the technical field of communication of the Internet of Vehicles. The user privacy protection scheme includes the steps: a TA initializes a whole car-hailing system; a passenger, a driver and a roadside node register to the TA to obtain corresponding secret keys; the passenger sends a car hailing request to the nearest roadside node; the roadside node and the driver respond to the car hailing request of the passenger; the roadside nodes match drivers for the passengers and return successfully matched information to the corresponding passengers and drivers; and the passenger and the driver which are successfully matched send confirmation information to the roadside node to start ajourney, and after the journey is finished, the car hailing record is sent to the roadside node, and the roadside node sends car hailing data to the cloud server to be stored and sends a car hailingdata signature to the blockchain network. Compared with the prior art, the identity privacy, the position privacy and the request / report privacy of the user can be protected; rapid matching between passengers and drivers is realized; and a data auditing function of the car-hailing data is realized by using the block chain.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
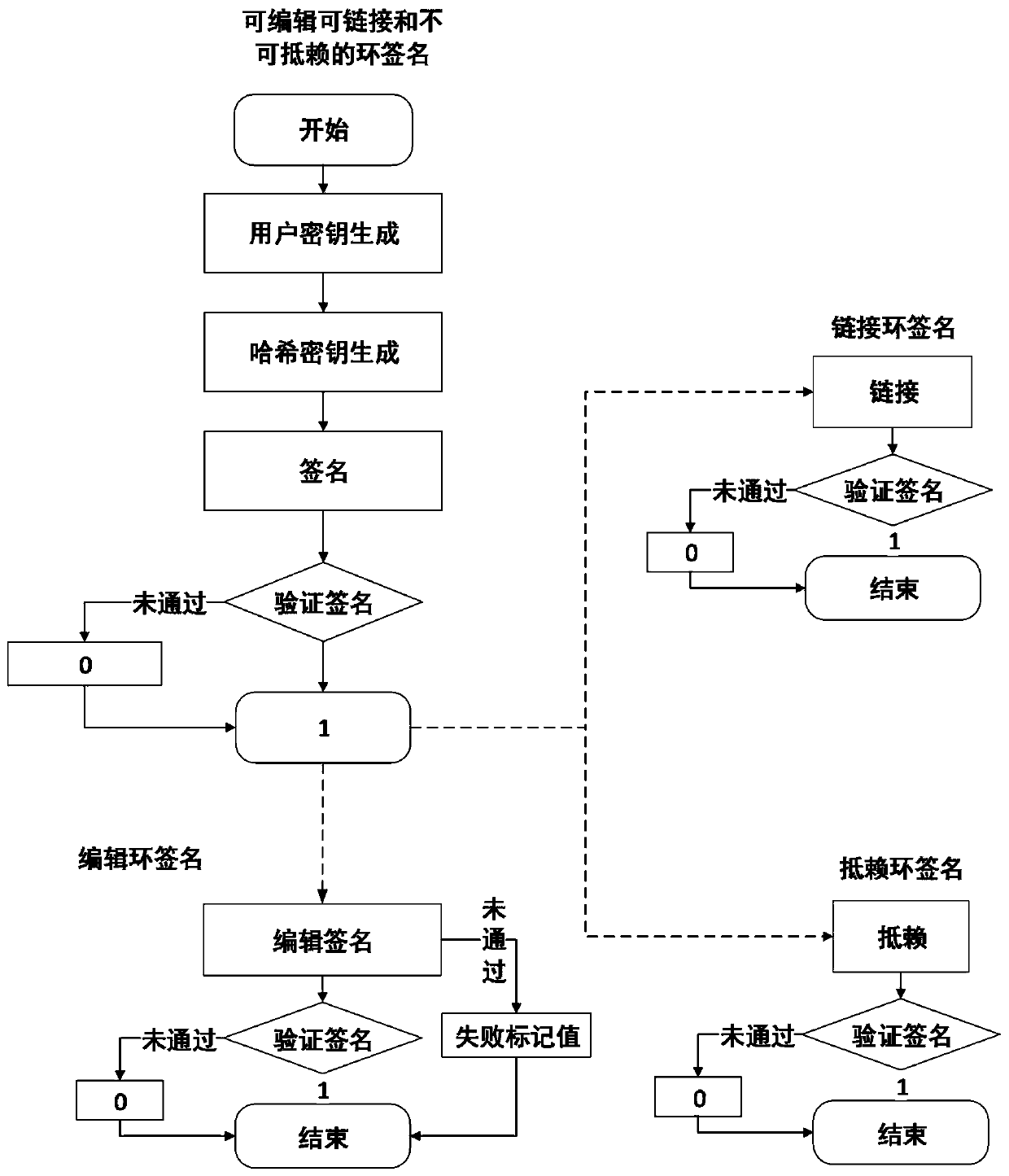
Editable, linkable and non-repudiation ring signature method
ActiveCN110071812APrivacy is not abusedAchieve traceabilityUser identity/authority verificationRing signaturePrivacy protection
The invention discloses an editable, linkable and non-repudiation ring signature method, belongs to the field of network security, and solves the problems of difficulty in revocation of a ring signature, difficulty in tracing identity information of a malicious user, capability of being authenticated by the signature after being edited, no privacy protection, no flexible authentication mechanism and the like in the prior art. The method is used for sequentially carrying out system initialization, user key generation, hash key generation and signature and providing conditional revocation identity privacy, editable and non-repudiation ring signatures. After the signature is edited, if the signature is required to be edited and whether the signature can be linked or repudiated is judged, thesignature is verified respectively, and after the verification is passed, the signature is edited and whether the signature can be linked or repudiated and the like is judged to be used for providingidentity privacy capable of being revoked, editable and non-repudiated ring signatures.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Automobile maintenance data storage method based on alliance chain
ActiveCN111159750AAchieve sharingAvoid the problem of too large blocksFinanceDigital data protectionCloud storageData store
The invention provides an automobile maintenance data storage method based on an alliance chain. At present, a traditional storage mode of the automobile maintenance data mainly adopts paper materialsand scattered local database storage, and the storage mode shows many defects in the aspects of integrity and usability of the maintenance data. According to the invention, a blockchain technology taking an alliance chain as a main part and a cloud storage technology are used, logic blockchain storage and physical cloud storage of maintenance data are realized, so that real maintenance data cannot be tampered and traceable once generated and submitted to a verification node and written into a block by a P-DPoS consensus mechanism, and a user can know the integrity of submitted data in time through a Merkle root verification method. Meanwhile, related cryptography technologies such as a public key encryption algorithm, a proxy re-encryption algorithm, an SOK protocol and the like are adopted, so that disclosure and sharing of part of maintenance data are realized under the condition of ensuring that personal identity privacy is not leaked, and great convenience is provided for a claimprocess of a user.
Owner:NANJING UNIV OF POSTS & TELECOMM
System and method for controlling untrusted resource transmission in Internet of vehicles
The invention requests to protect a system and method for controlling untrusted resource transmission in Internet of vehicles. The method comprises the following steps: designing an access control strategy and a node trust value calculation method for nodes of a resource output vehicle, limiting fixed attributes and dynamic attributes of the resource output vehicle, and dynamically generating a fine-grained access control strategy according to the traveling track of the vehicle to ensure that the access control strategy has better extensibility and flexibility. Thereby, the anonymous directional transmission of messages can be achieved, the waste of resources can be reduced, and the identity privacy of communication vehicles can be effectively protected; the calculation of node trust values can guarantee the trust degree of resource communicators and meet the security and privacy requirements of security related messages in Internet of vehicles; and malicious nodes can be effectively identified, and the injection of malicious resources and the transmission of untrusted resources can be prevented. The method disclosed by the invention can be widely applied to the related fields of mobile Internet, wireless sensor network and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
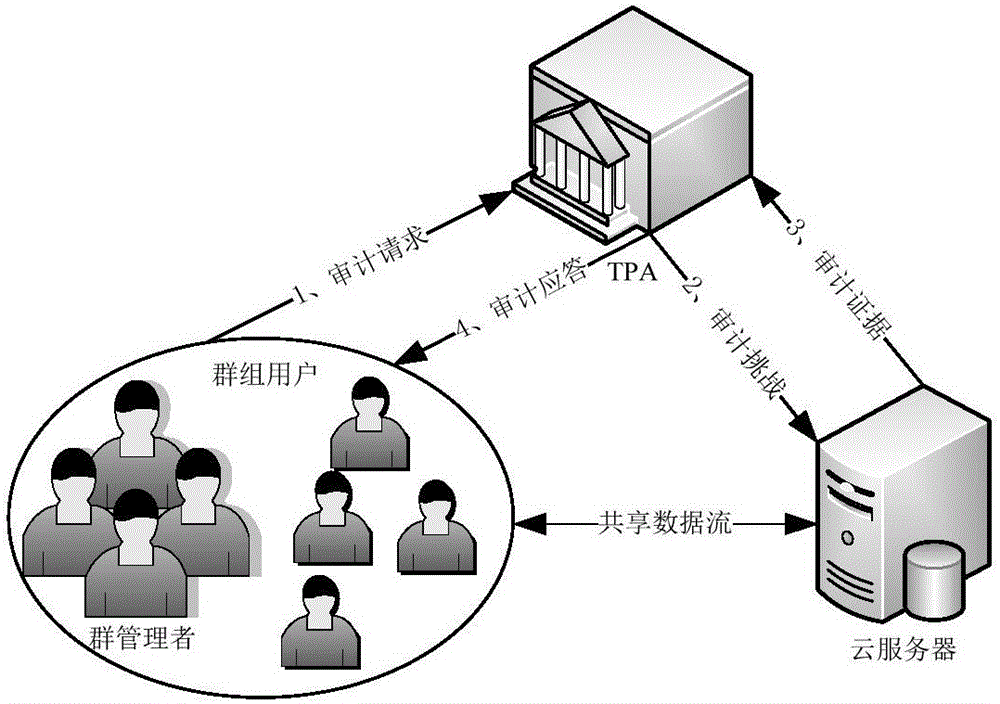
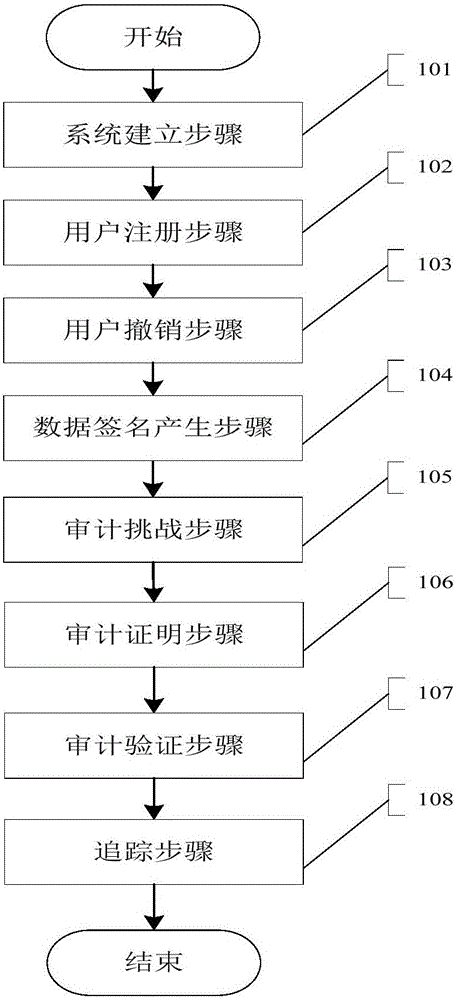
Public auditing method with privacy protection for shared data of multi-manager group
ActiveCN105007284AGuaranteed unframeabilityEnable traceabilityTransmissionPrivacy protectionIdentity privacy
The invention discloses a public auditing method with privacy protection for shared data of a multi-manager group, which comprises the steps of (1) system establishment; (2) user registration; (3) user cancellation; (4) data signature generation; (5) audit challenge; (6) audit certification; (7) audit verification; and (8) user tracking. According to the invention, a homomorphous verifiable group signature scheme supporting multiple managers is constructed based on a forward-security cancelable group signature and (t, s) secret sharing, thereby having high efficiency; the integrity of outsourced data is confirmed in allusion to a cloud server; and the identity privacy of group users is protected in allusion to an auditor, the identity of the users is traceable, and the whole tracing process is fair, so that the users are not maliciously framed.
Owner:NANJING UNIV OF SCI & TECH
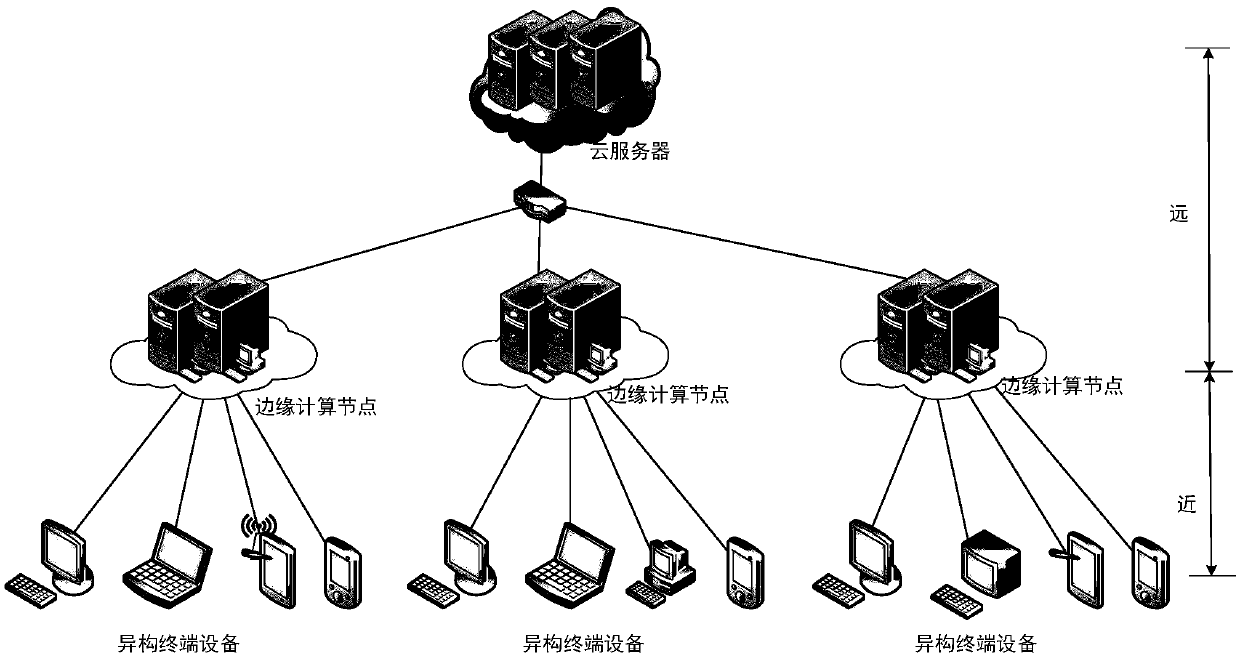
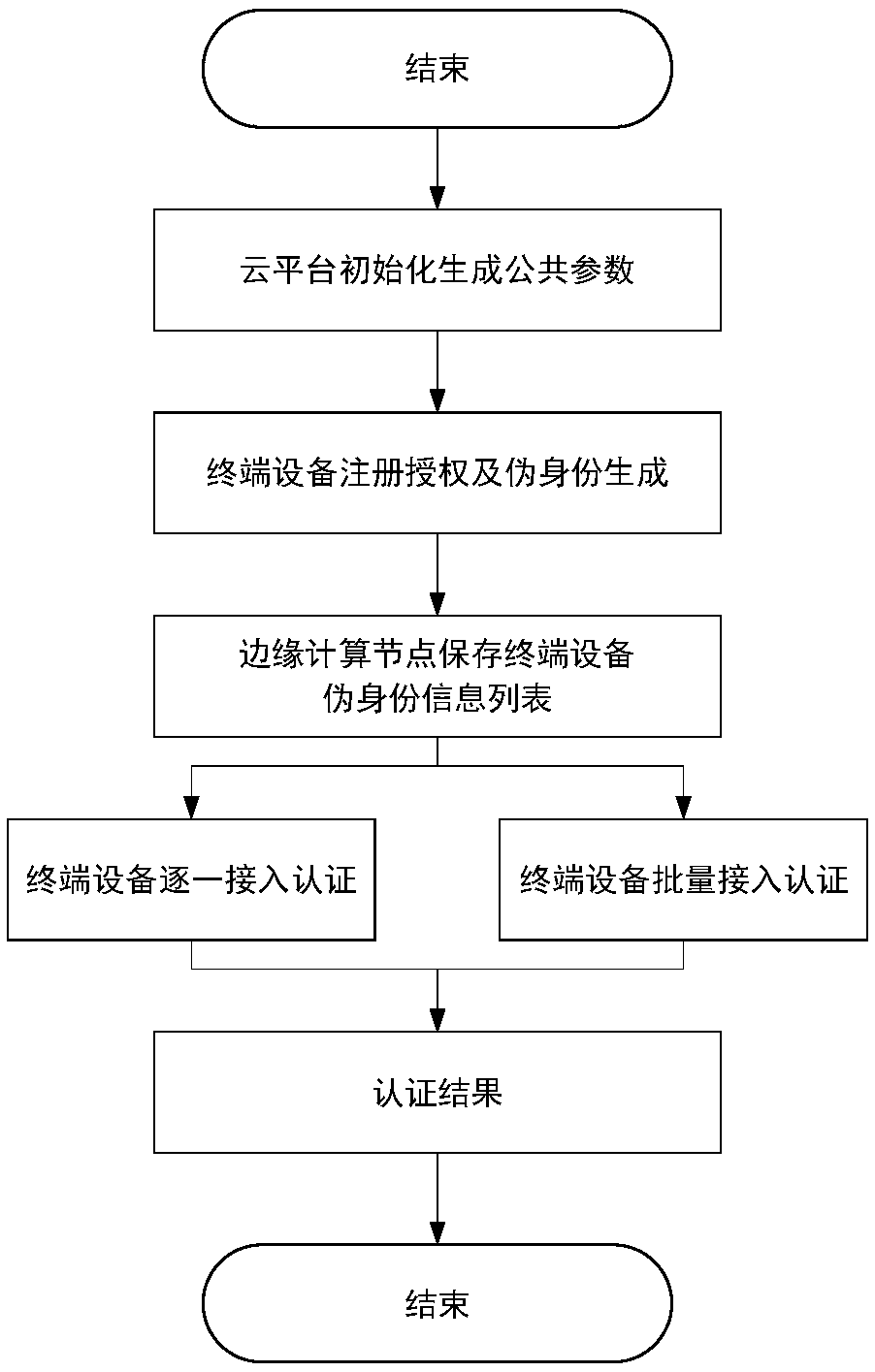
Lightweight authentication method for supporting anonymous access of heterogeneous terminal in edge computing scene
ActiveCN111371730AImplement anonymous authenticationRealize traceabilityKey distribution for secure communicationUser identity/authority verificationEdge computingTerminal equipment
The invention provides a lightweight authentication method for supporting anonymous access of a heterogeneous terminal in an edge computing scene. According to the invention, a pseudo identity is created for each terminal device by using a cloud platform to hide the real identity information of the terminal device; meanwhile, malicious terminal equipment can be traced back; the invention disclosesa method for authenticating an access edge computing node of terminal equipment. The edge computing node can verify the legality of the identities of all accessed devices under the condition of not communicating with the cloud platform; according to the method and the device, the real identity information of the terminal cannot be learned, the identity privacy of the terminal equipment is guaranteed, the access authentication efficiency is improved, common threats such as replay attacks can be resisted, the safety and reliability of the whole edge computing system are enhanced, and the problem of access authentication of the terminal equipment with limited resources in an edge computing scene is solved.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Supervisable anonymous authentication method based on zero knowledge proof
ActiveCN109450645AGuaranteed anonymityProtect identity privacyKey distribution for secure communicationUser identity/authority verificationAnonymous authenticationIdentity privacy
The invention discloses a supervisable anonymous authentication method based on zero knowledge proof, comprising three types of participants: a CA, a user and a verifier, wherein the CA generates an issuer key pair and a group key, the CA allocates a pair of private keys to the user during registration of the user, and meanwhile the CA issues a relevant certificate to the user according to the attribute information submitted by the user; when the user presents the certificate, the verifier specifies an attribute that needs to be presented on the certificate of the user, and the user signs thecertificate and hides attribute values that do not need to be presented; and the verifier verifies the signature, if the signature passes the verification, the certificate presented by the user is valid, or otherwise, the certificate presented by the user is invalid. By adoption of the supervisable anonymous authentication method disclosed by the invention, the anonymity of the user is also ensured while increasing a mandatory supervision function, thereby greatly improving the identity privacy of the user compared with the general identity supervision scheme. By adoption of the supervisable anonymous authentication method disclosed by the invention, a supervisable function is also added.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
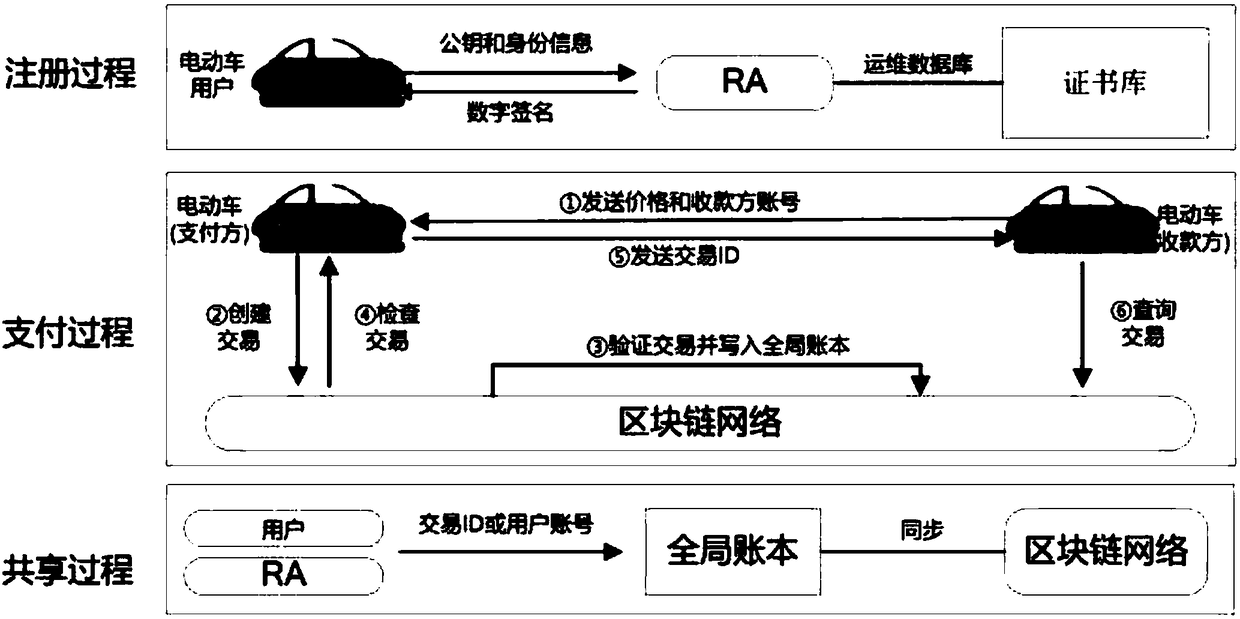
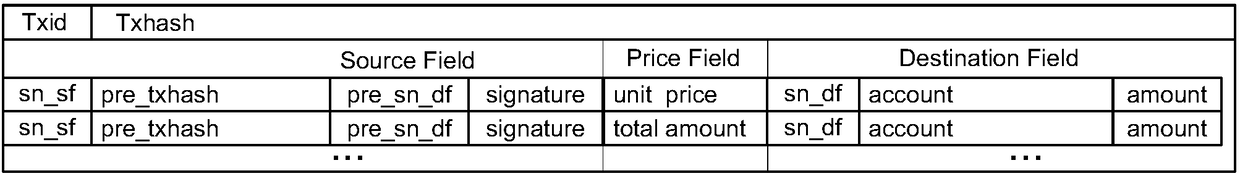
Block chain-based intelligent electric car grid security payment system and method
ActiveCN108510252AAddress data sharingSolve the problem of identity privacy protectionPayment circuitsAnonymous user systemsRegistration authorityPrivacy protection
The invention relates to a block chain-based intelligent electric car grid security payment system and method, and belongs to the field of V2G network payments. According to role definition, the system comprises electric car users, a registration authority (RA) and a block chain network. According to function partitioning, the system comprises a registration module, a payment execution module anda data share module. Based on a block chain technology and a cryptology technology, a special registration mechanism, a verification mechanism and a new payment mechanism are adopted. According to themethod, the problems of data share and user identity privacy protection in the field of V2G network payment can be solved, and effective supervision and privacy protection can be realized. The systemand the method are capable of reducing external attack threats and realizing data share, more accord with practical application scenes, are capable of supporting effective audition and protecting privacy data under the condition that audition is supported, and are capable of considering the demands in the two aspects of transaction data share and privacy information leakage prevention.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
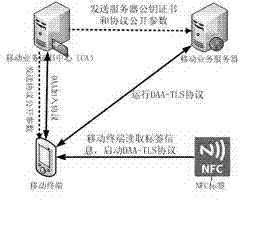
Method to protect communication security and privacy function of mobile client
InactiveCN102761556AGuaranteed anonymityGuaranteed confidentialityKey distribution for secure communicationUser identity/authority verificationCommunications securityEngineering
The invention relates to a method to protect a communication security and privacy function of a mobile client. The method comprises the following steps: combining a direct anonymous authentication (DAA) protocol and a transport layer security (TLS) protocol, and utilizing the identity privacy of a DAA protocol protection client with an NFC (Near Field Communication) function, as well as the privacy between the TLS protocol protection client and a server; reading the service website information and a website connecting with the server by the client with the NFC function, realizing the protection for the client identity privacy and the communication privacy through operating a modified TLS protocol between the client and the server; adopting an ellipse curve cryptography to realize the DAA protocol, wherein the client with a DAA certificate can complete the signature; and combining the DAA protocol and the TLS protocol so as to uniformly realize the anonymity and privacy of the communication between the mobile client and the server.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
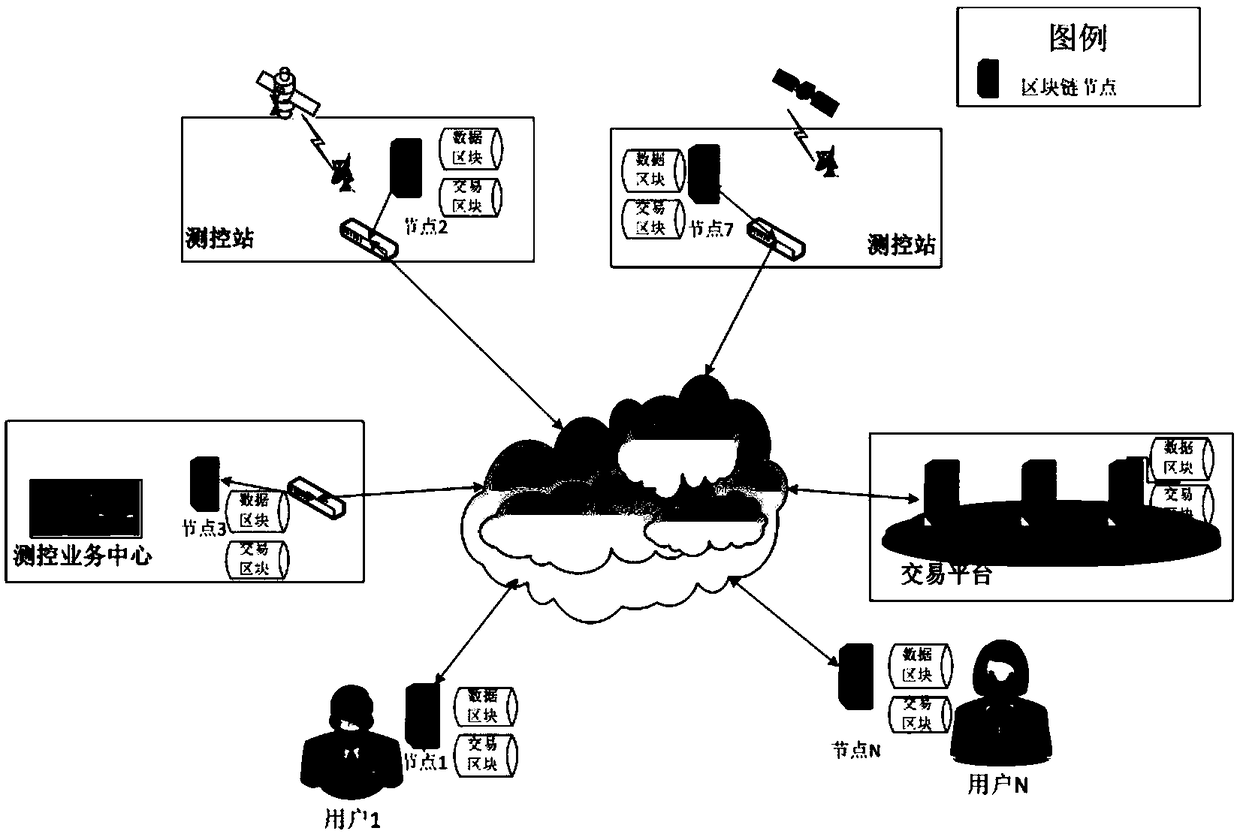
A block chain-based data trading method for an aerospace TTC network
ActiveCN109190331AGuaranteed identity privacyGuarantee managementFinanceDigital data protectionThird partyIdentity privacy
The invention discloses a block chain-based data trading method for an aerospace TTC network. The method introduces the concept of user identity ID in the order management process, and ensures the user identity privacy through the mode of user information Hash. By constructing the transaction record block chain, the transaction record management is strengthened, which can effectively resist the malicious order attack from the third party, ensure the normal operation and scheduling of the tasks of the measurement and control business center to a certain extent, and at the same time, make the transaction records be queried and appealed. By constructing the data index block chain, the security of data transaction is enhanced, and the supervision of the transaction platform is formed, which makes the transaction platform unable to retain the data, ensures the security of the data, and also makes the transaction results undeniable for both parties, and provides evidence for the subsequent transaction traceability and complaint. By using the DRM copyright management technology to strengthen the protection of data copyright, the illegal copying and resale of of data are prevented.
Owner:电信科学技术第五研究所有限公司
Shared data cloud audit method with identity tracking function
ActiveCN104243169AImplement identity trackingPrevent forgeryUser identity/authority verificationSystems managementData file
The invention provides a shared data cloud audit method which adopts a shared data cloud audit system with an identity tracking function for identity tracking. The method includes: step one, system initialization; step two, data file uploading and auditing; step three, identity tracking; step four, member addition and removal. The shared data cloud audit system with the identity tracking function comprises a cloud module, a system management center module, a group administrator module, a group member module and an audit center module. According to the method, group members can upload data to the cloud in the name of a group, and accordingly identity privacy of data owners is protected; when cloud data are disputed, a group administrator can open identities of the data owners, so that the problem that the group members viciously upload wrong data is avoided; in addition, addition and removal of the group members are convenient.
Owner:QINGDAO UNIV
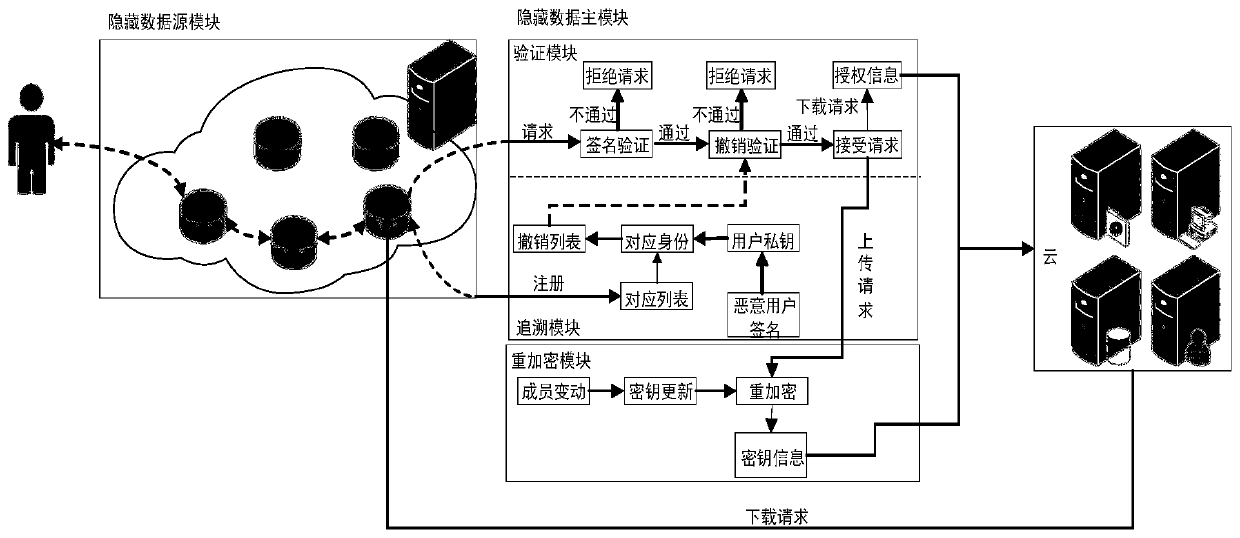
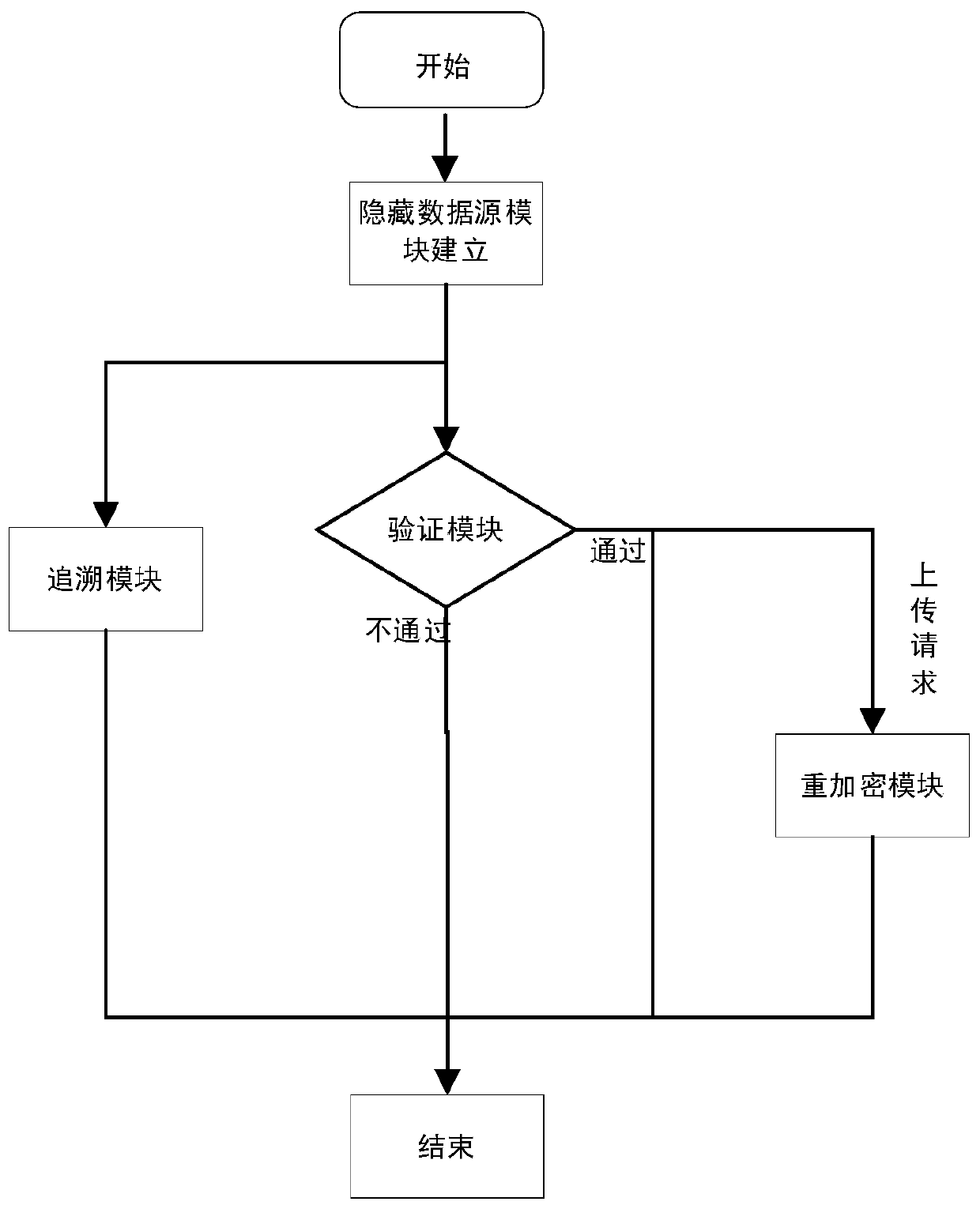
Anonymous data sharing method and system based on data source and data main hiding
ActiveCN111600875APrivacy protectionReduce overheadKey distribution for secure communicationIp addressData source
The invention discloses an anonymous data sharing method and system based on a data source and data main hiding. In the stages of registration and request initiating, effective access control is achieved through group signature, anonymous authentication is completed to protect user identity privacy, and meanwhile the problem that the user identity is associated due to leakage of the user IP address is solved by hiding the user IP address through onion routing. In the file uploading stage, the group administrator re-encrypts the uploaded file by using a re-encryption technology and generates key information; in the file downloading stage, after revocation verification and signature verification are completed, a group administrator generates authorization information for a user, so that theuser can obtain a decryption and re-encryption key from key information, and the forward security of the scheme is ensured; and in the group dynamic stage, the group administrator performs key updating and updates encryption of the cloud file, so that the expenditure of the user side is greatly reduced.
Owner:JIANGSU UNIV
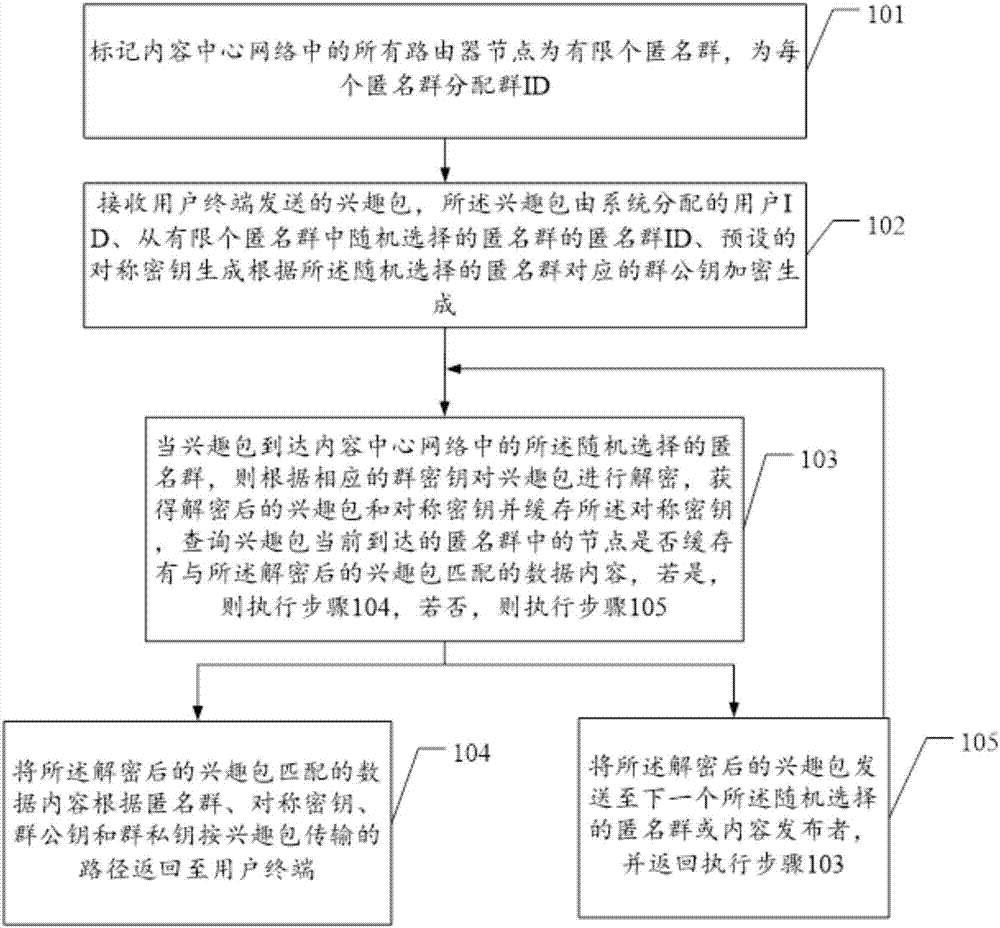
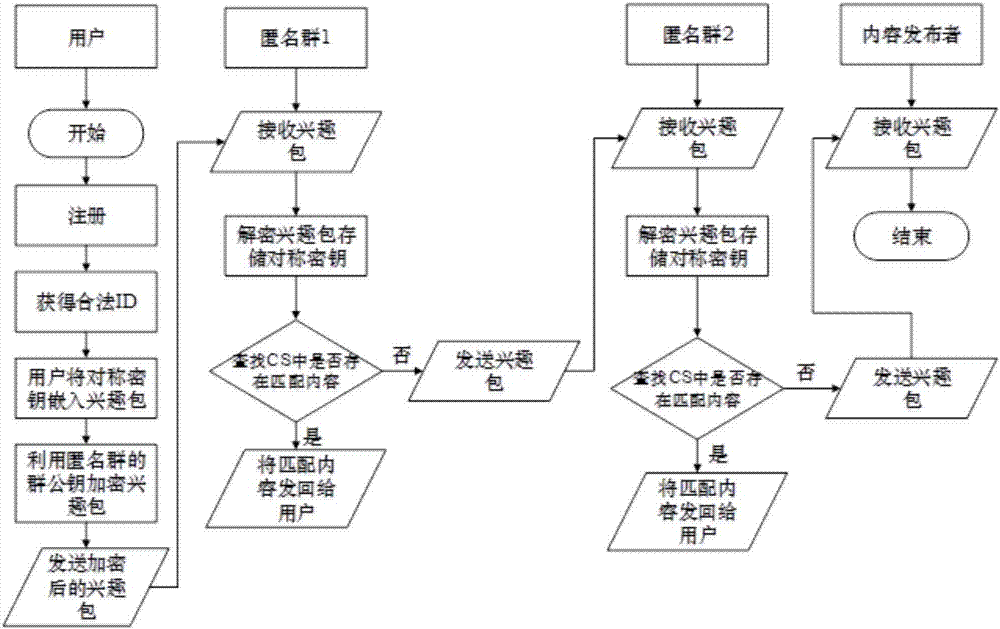
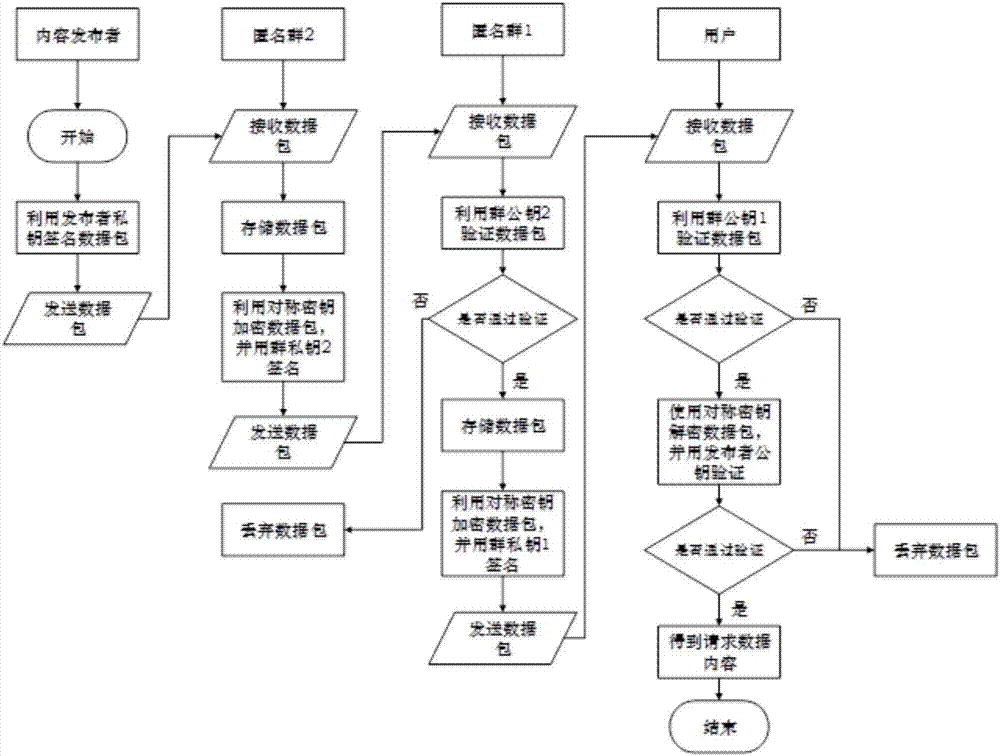
Content centric network privacy protection method based on hybrid encryption and anonymous group
The embodiment of the invention provides a content centric network privacy protection method based on hybrid encryption and an anonymous group. An interest packet is transmitted through the anonymous group, and decrypted into a plaintext interest packet layer by layer in a node of the anonymous group, thereby effectively preventing an attacker from getting association between the interest packet and a user. Hybrid encryption is performed on the interest packet and a data packet through encryption methods such as a user ID, a public key and a private key of a publisher, a symmetric key, and a public key and a private key of the anonymous group, so that the data packet can be protected from being modified in a process from signature to reception by the user, and plaintext content cannot be cracked inversely within certain time even though the attacker gets encrypted communication content by eavesdropping, thereby protecting the privacy of communication data. In the embodiment of the invention, the identity privacy information of a signer is protected through construction of the anonymous group, and meanwhile unlinkability between communication content and both communication parties is realized through a hybrid encryption method.
Owner:GUANGDONG UNIV OF TECH
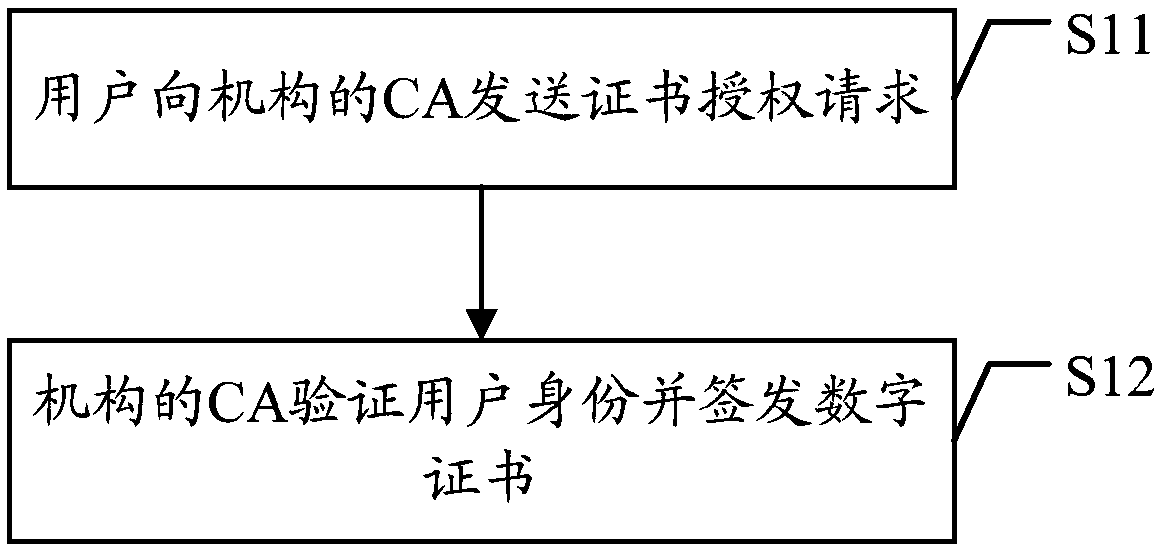
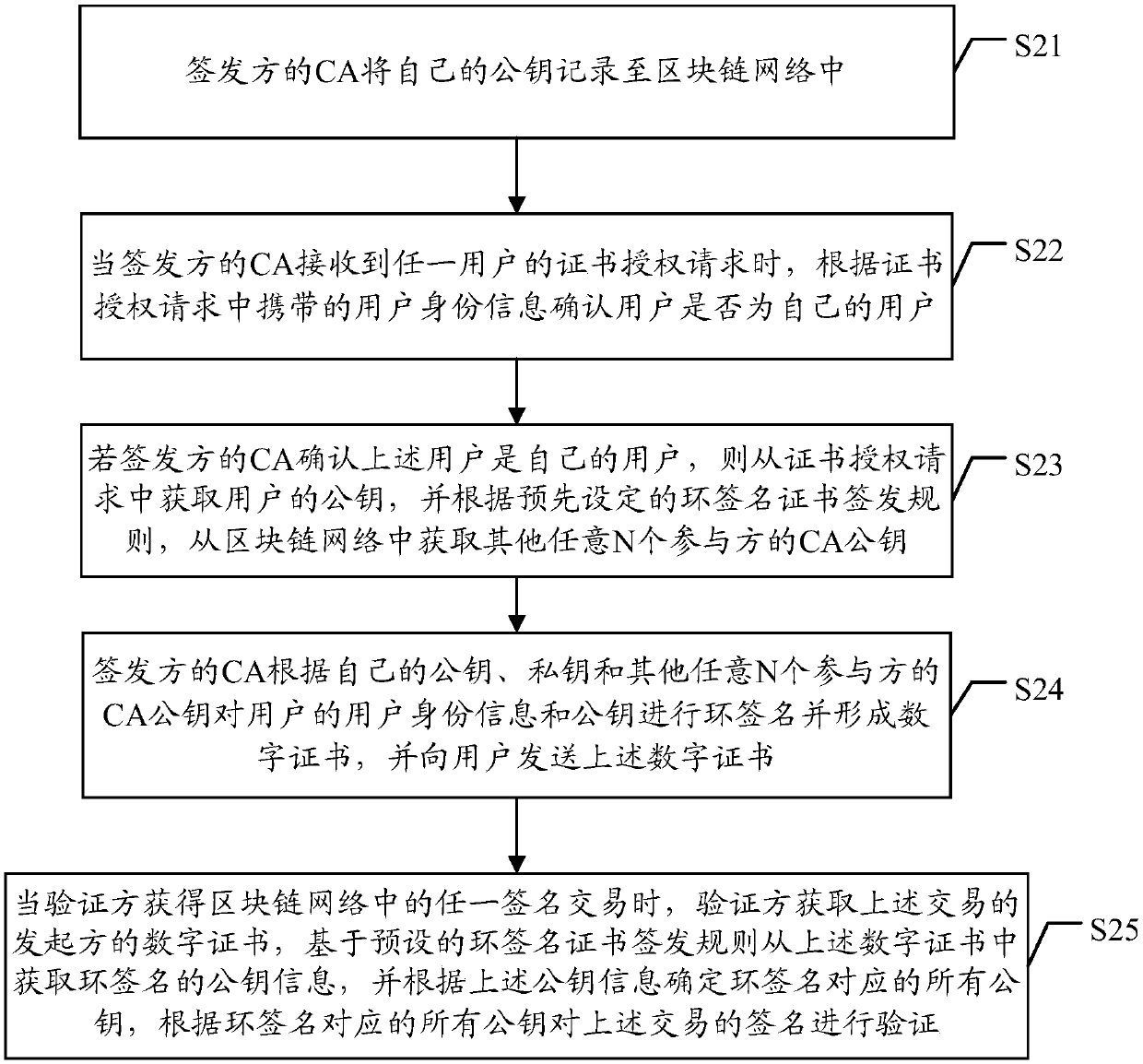
Processing methods and related devices of digital certificate
ActiveCN109547206AAvoid Identity LeakageGuaranteed privacyUser identity/authority verificationRing signatureCertificate authority
The embodiment of the application discloses processing methods and devices of a digital certificate. The method includes: recording a CA (Certificate Authority) public key of a first participant intoa blockchain network by a CA of the first participant of the blockchain network; when the CA of the first participant receives a certificate authorization request of any user, confirming, according touser identity information carried in the certificate authorization request, whether the same is a user of the CA of the first participant; if yes, obtaining a public key of the user from the certificate authorization request, and obtaining CA public keys of any N second participants from the blockchain network according to a ring signature certificate signing and issuing rule, wherein N is equalto a public key number set in the ring signature certificate signing and issuing rule; and carrying out ring signature on the user identity information and the public key of the user by the CA of thefirst participant according to the CA public key and a private key of the first participant and the CA public keys of the N second participants to form the digital certificate, and sending the same tothe user. By adopting the embodiment of the application, identity privacy of signing and issuing sides of digital certificates can be enhanced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Alliance chain cross-chain privacy protection method based on group signature and CA multi-party authentication
ActiveCN112435024AImprove stealthSolve regulationDigital data protectionProtocol authorisationData privacy protectionEngineering
The invention discloses an alliance chain cross-chain privacy protection method based on group signature and CA multi-party authentication. In the alliance chain, full-life-cycle supervision in the chain and privacy protection of cross-chain transactions of the alliance chain are achieved through a technical system integrating certificate distribution uplink and group signature encryption. According to the invention, the certificate blockchain is introduced, and the CA of the alliance chain maintains the certificate blockchain and packages the operation and content of the distributed certificates into a transaction uplink, thereby achieving the later tracing and evidence obtaining of the alliance chain. A group signature technology is introduced, a node of an alliance chain uses a group public key to encrypt a cross-chain transaction to achieve identity privacy protection of the transaction, and an administrator uses a group private key to obtain a signer of the cross-chain transactionto achieve supervision. Generation of a digital certificate and a group public and private key and signature and verification of transaction information are achieved by integrally adopting a currentinternationally universal asymmetric encryption algorithm or an over-encryption algorithm, so that overall data privacy protection of the alliance chain is ensured.
Owner:ZHEJIANG UNIV
Authentication key negotiation method enabling identity privacy and non-malleable security
ActiveCN105099671AEnsure safetyKey distribution for secure communicationModular exponentiationIdentity privacy
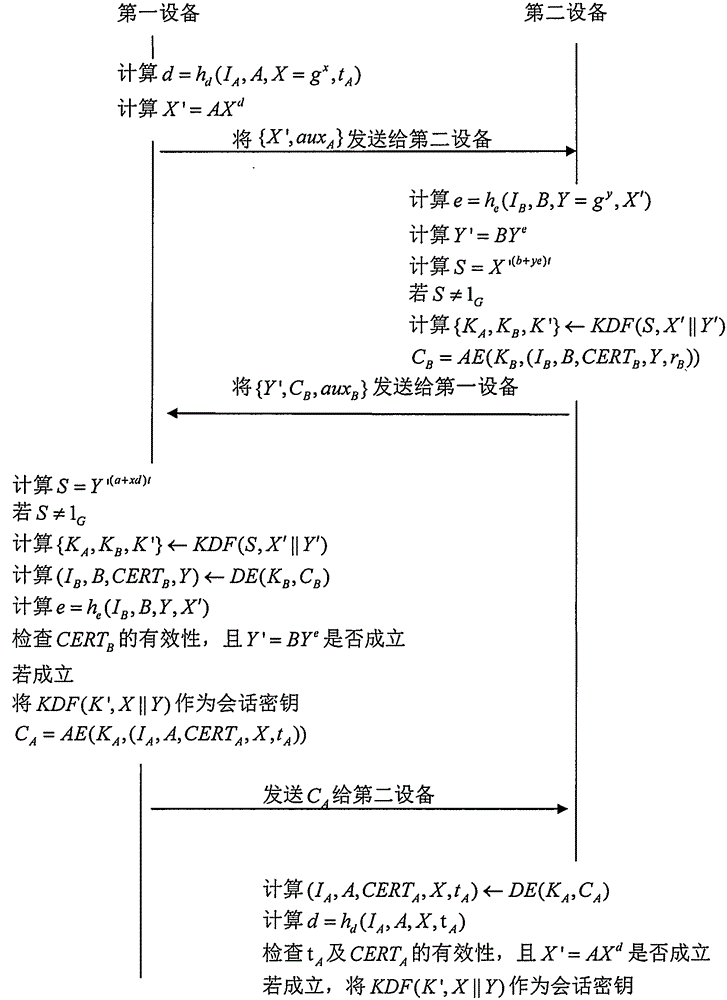
The invention relates to an authentication key negotiation method enabling identity privacy and non-malleable security. The method includes the following steps that: a first device transmits a determined expression, namely, X'=AX<d>, to a second device, wherein A= g is the public key of the first device, X=g<x> and d=h<d>(X, aux<d>); the second device determines an expression, namely, Y'=BY<e>, wherein B=g is the public key of the second device, Y=g<y>, and e=h<e> (Y, aux<e>), and determines S according to a DH- index y, a private key b and X', determines K and K based on S, and determines an expression, namely, C=AE(K,(I, B, CERT(B), Y, Data)) according to K and an authentication encryption function AE, transmits Y' and C to the first device; and the first device determines S according to a DH- index x, a private key a and Y', and determines K and K based on S, and the first device determines an expression, namely, C=AE (K, (I, A, CERT, X, Data)) according to K, and transmits C to the second device. According to the session key negotiation method, based on reasonable parameter setting, each device operations 2.5 modular exponentiation, and therefore, the data computation load of each device can be greatly decreased, and the generation efficiency of session keys can be improved, and the method can be applied more flexibly.
Owner:赵运磊
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com