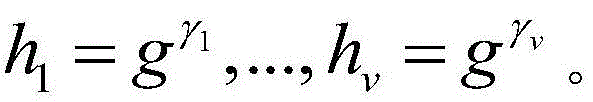Patents
Literature
1744results about How to "Reduce computational overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
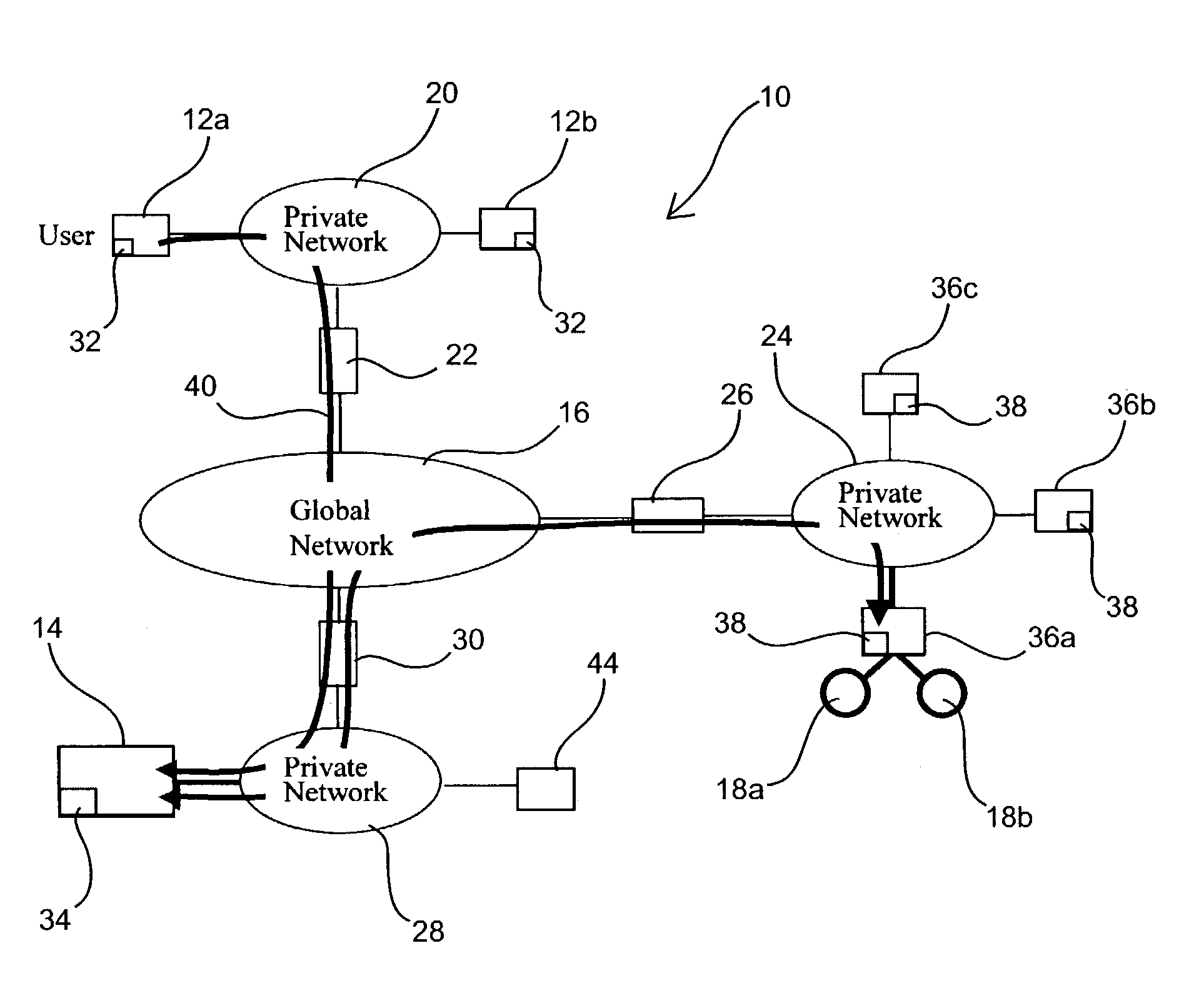
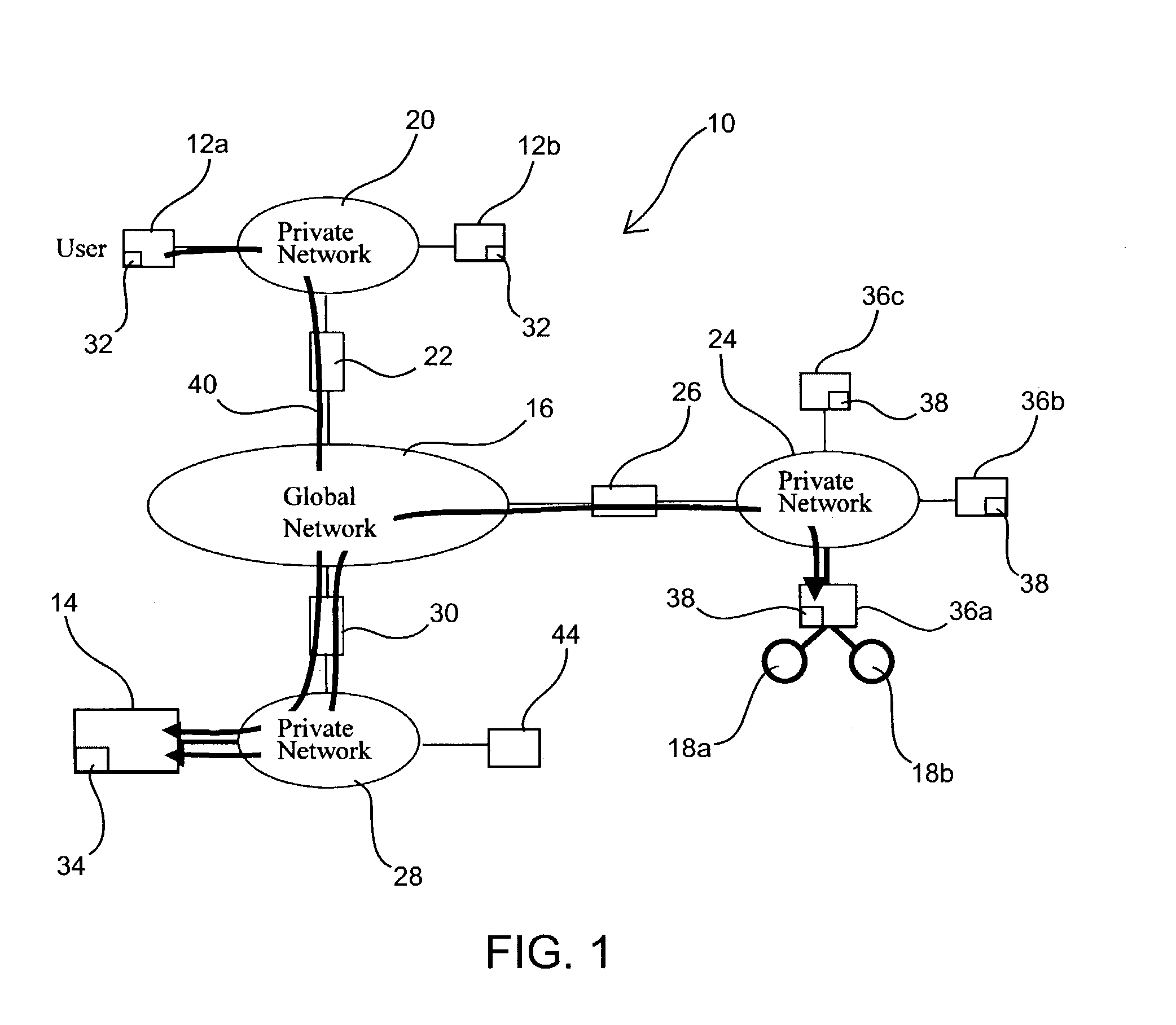
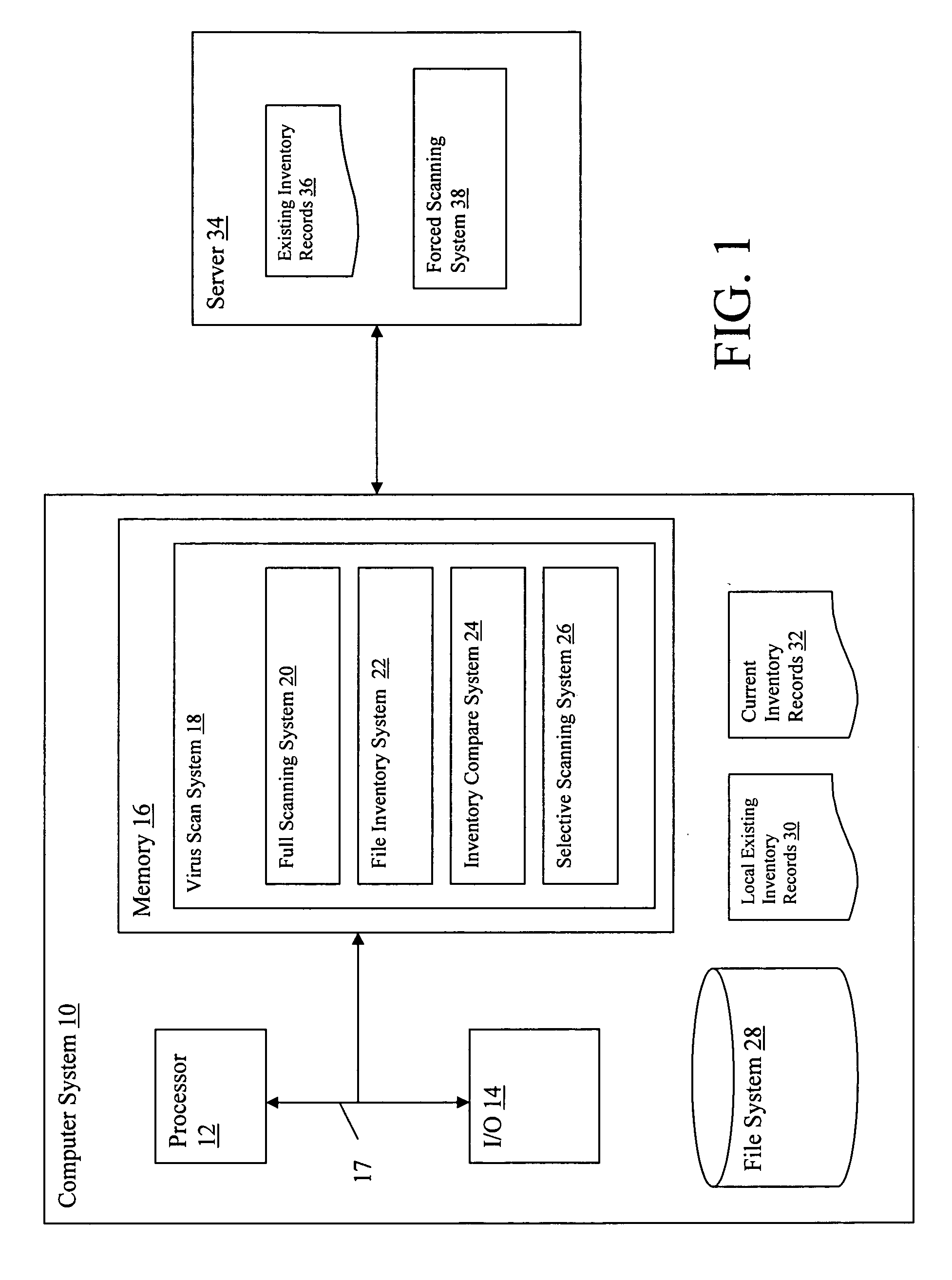
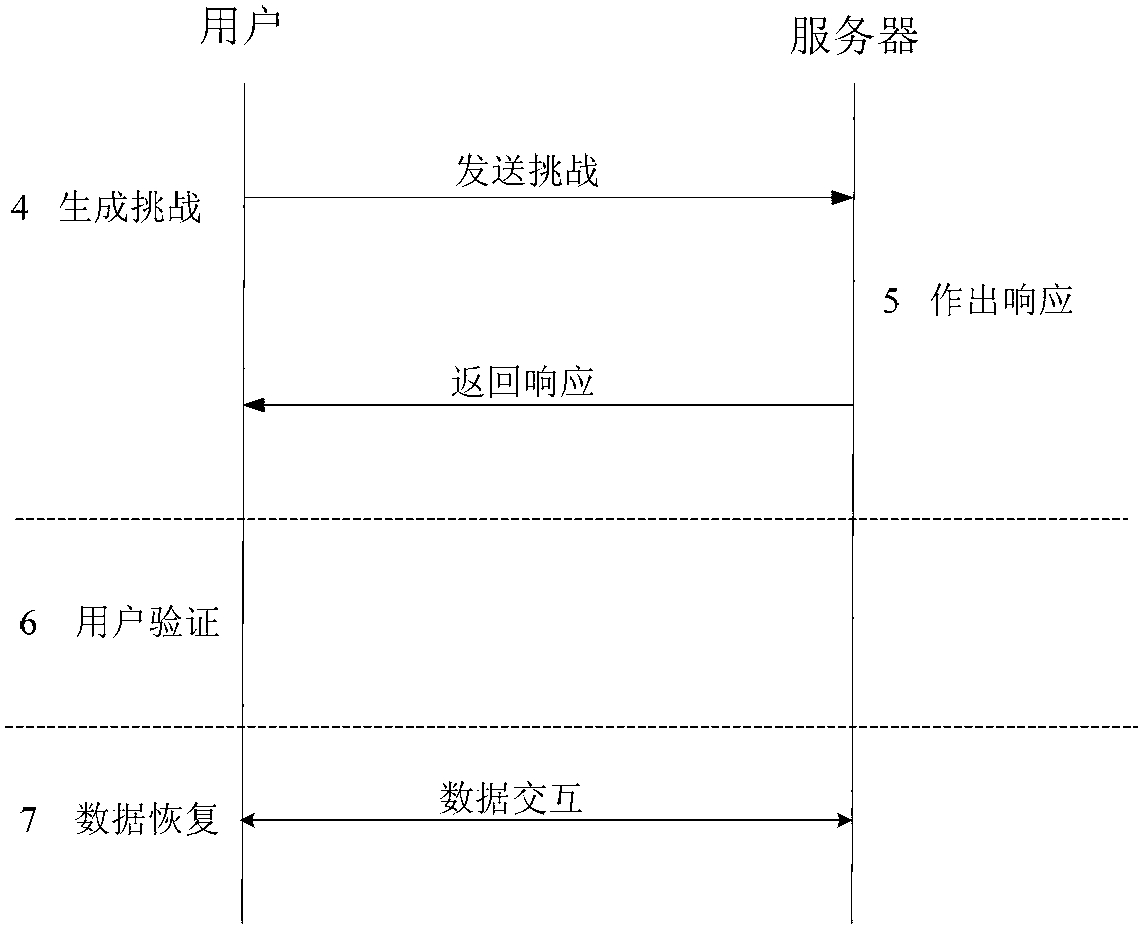
Access and control system for network-enabled devices
InactiveUS7120692B2Reduce computational overheadReduce communicationMultiple digital computer combinationsProgram controlControl systemSecure transmission
Owner:WESTERN DIGITAL TECH INC
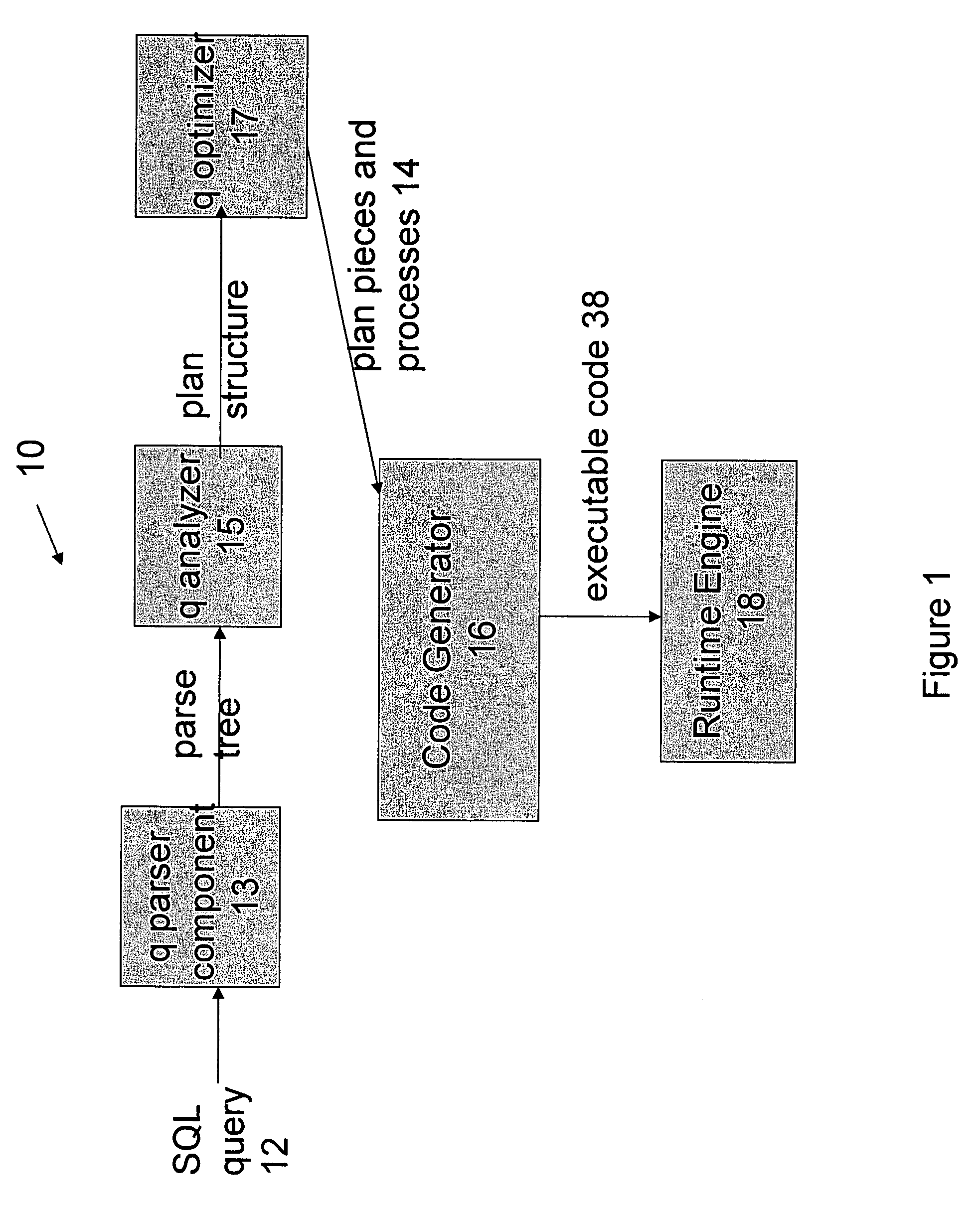
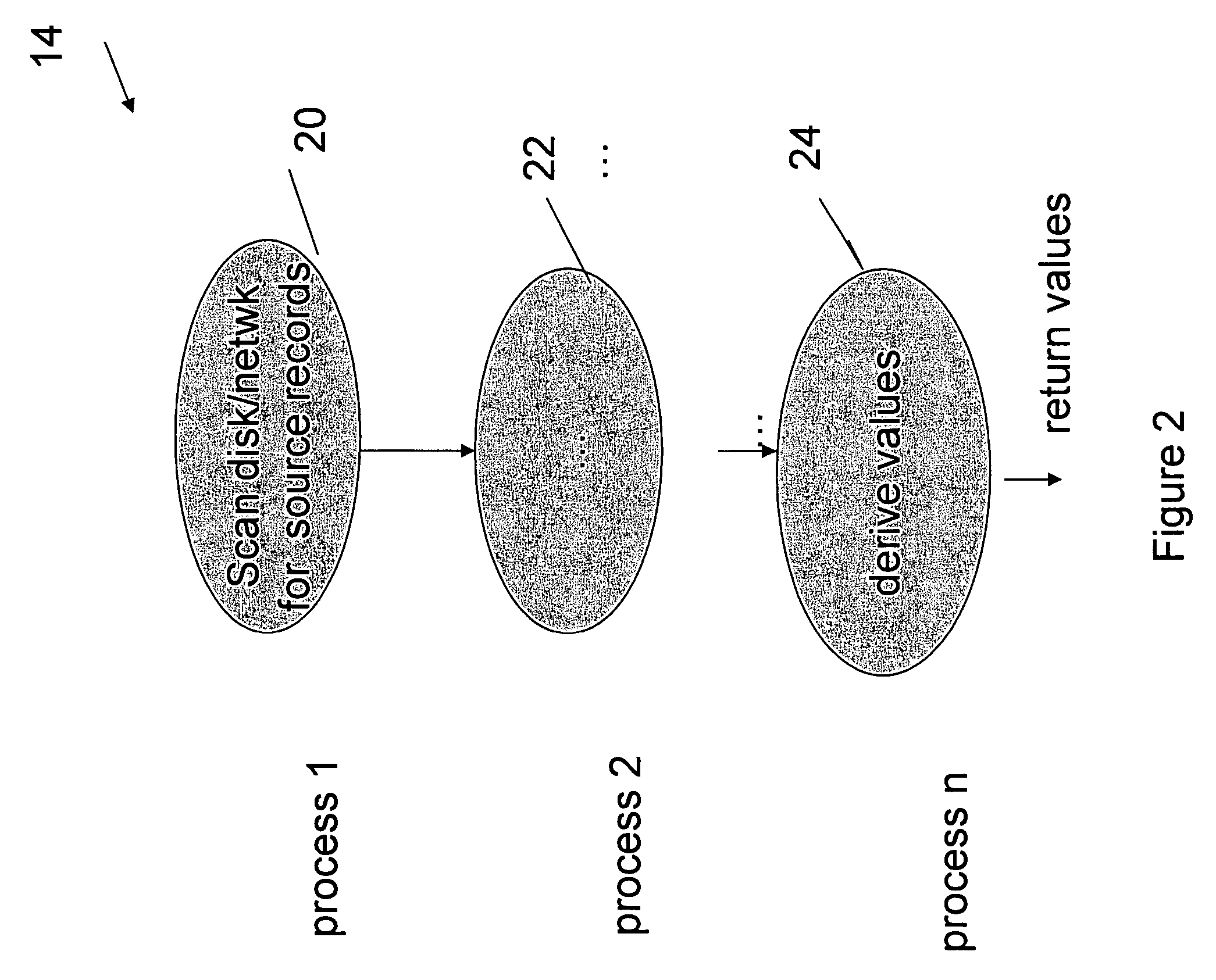
Optimized SQL code generation
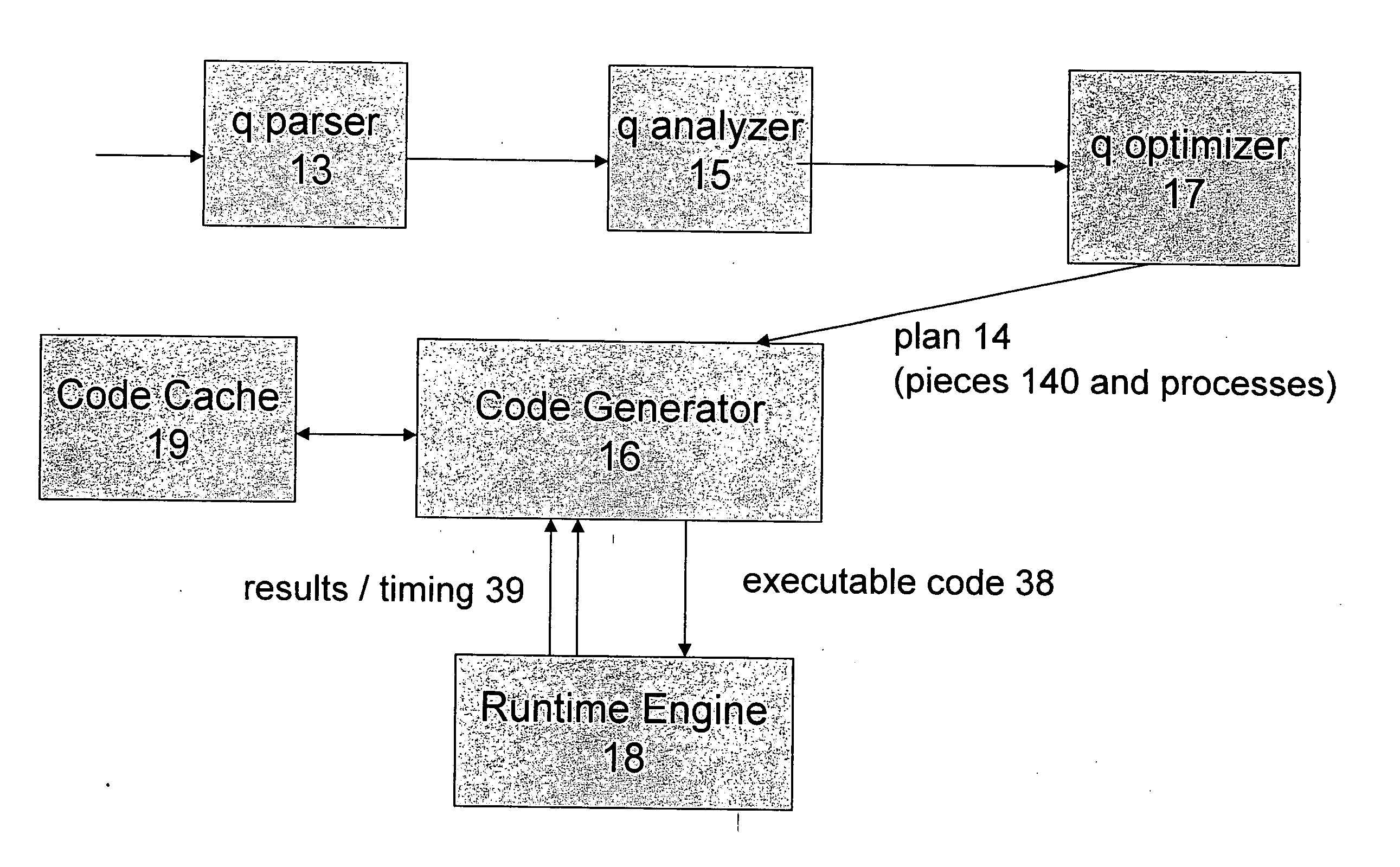
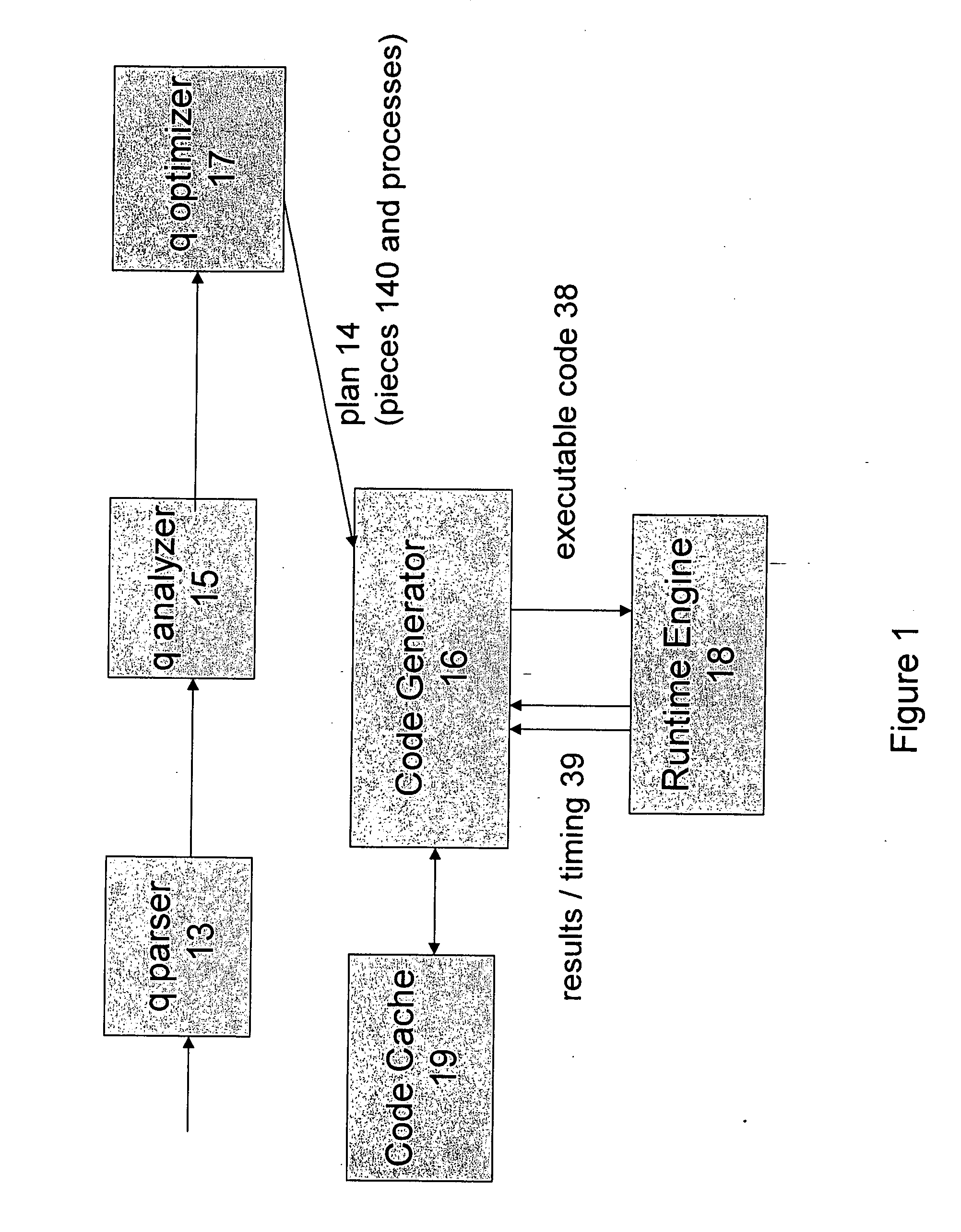
ActiveUS7430549B2Reduce and minimize compilation timeReduce and minimize execution timeDigital data information retrievalData processing applicationsExecution planCode generation
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. The present invention provides a method for generating executable machine code for query execution plans, that is adaptive to dynamic runtime conditions, that is compiled just in time for execution and most importantly, that avoids the bounds checking, pointer indirection, materialization and other similar kinds of overhead that are typical in interpretive runtime execution engines.
Owner:INT BUSINESS MASCH CORP
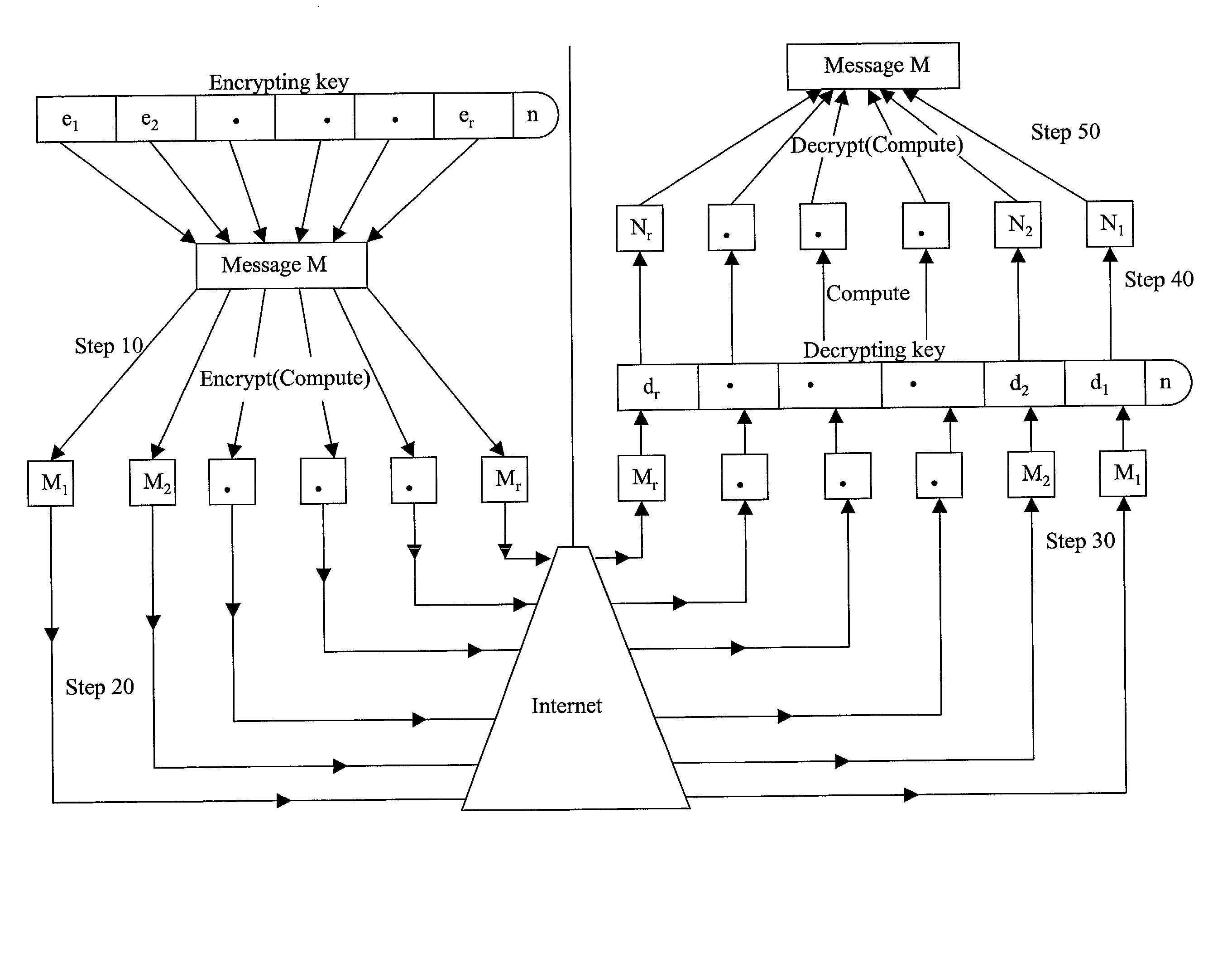
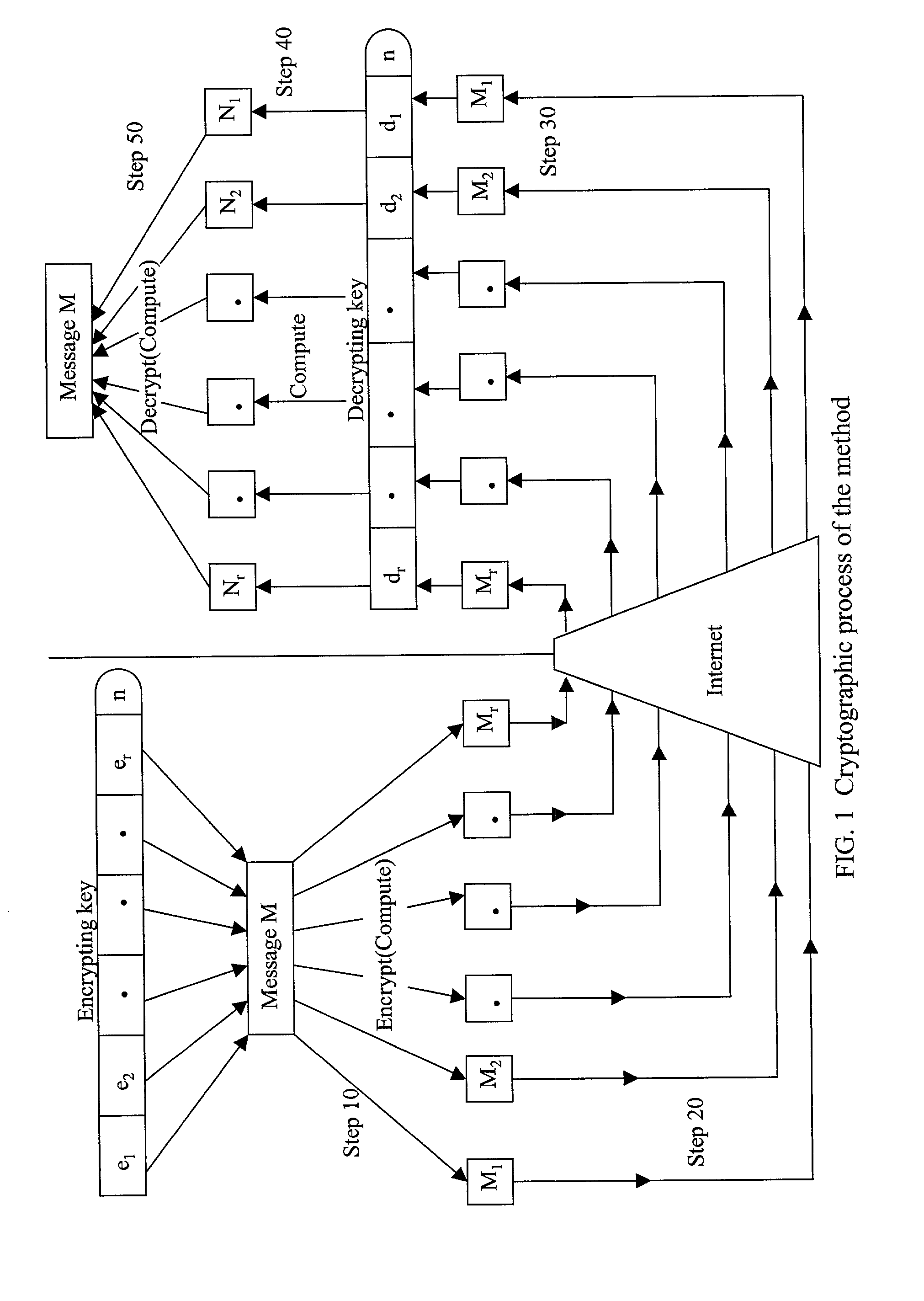
Absolute public key cryptographic system and method surviving private-key compromise with other advantages
InactiveUS20020186848A1Less powerful processorOvercomes shortcomingKey distribution for secure communicationPublic key for secure communicationEncryption systemTwo-way communication
Owner:KIOBA PROCESSING LLC
System and Method for Enabling Coordinated Beam Switching and Scheduling
ActiveUS20100075705A1Reduce computational overheadReduce communication overheadSite diversitySubstation equipmentCommunications systemBeam pattern
A system and method for enabling coordinated beam switching and scheduling in a wireless communications system. A method for controller operation includes indicating that the controller is operating in a cooperative beam switching mode, transmitting a beam formed reference signal (BFRS), from each communications device being served by the controller, receiving a measurement of a communications channel between the controller and the communications device and an indicator indicating a transmission unit corresponding to the measurement of the communications channel, receiving a transmission intended for a communications device, and causing the transmission to be transmitted to the communications device. The BFRS is beam formed using a plurality of beam patterns, the beam pattern used in beam forming the BFRS changes once per transmission unit, and the transmission is transmitted using measurement of the communications channel and the indicator from the communications device.
Owner:FUTUREWEI TECH INC
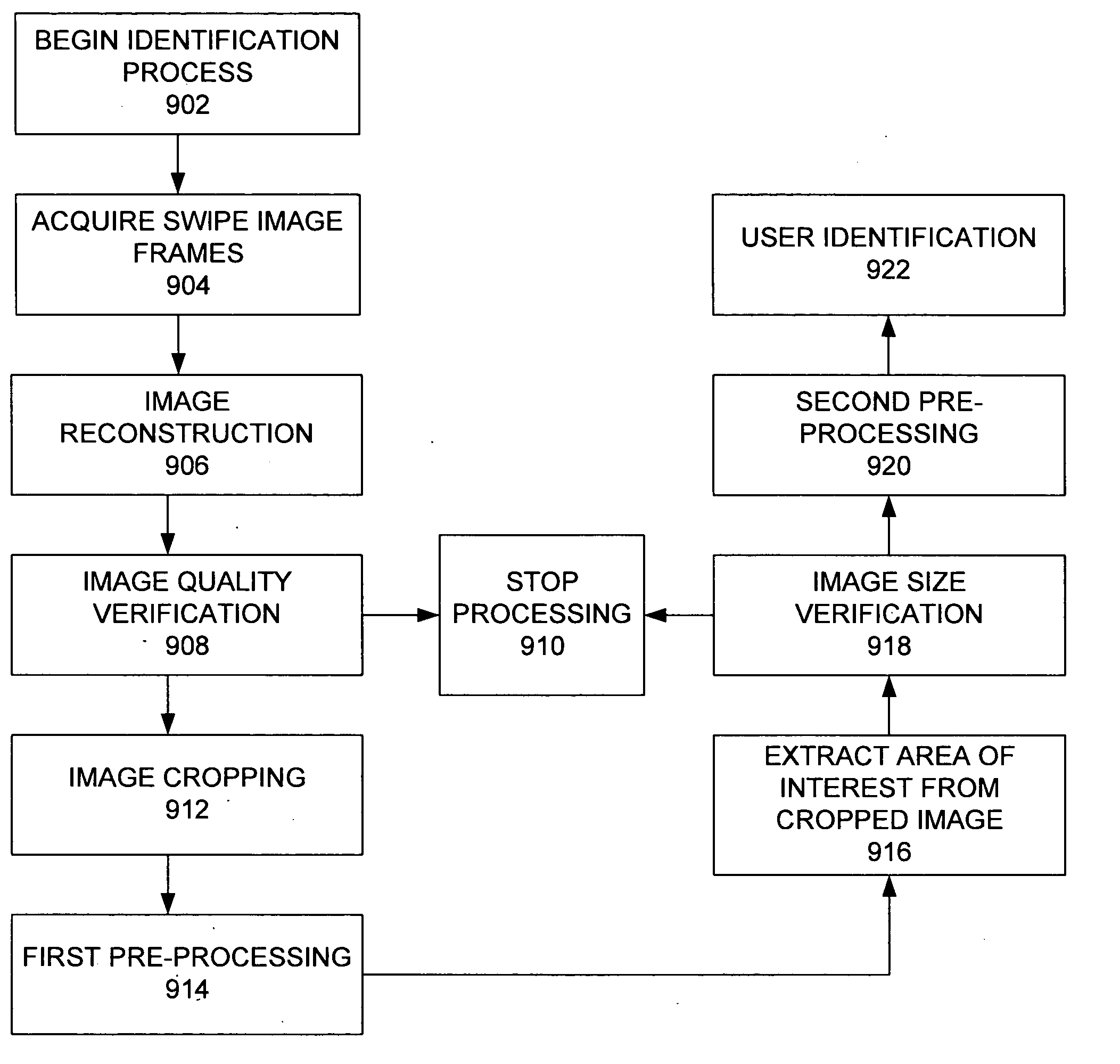
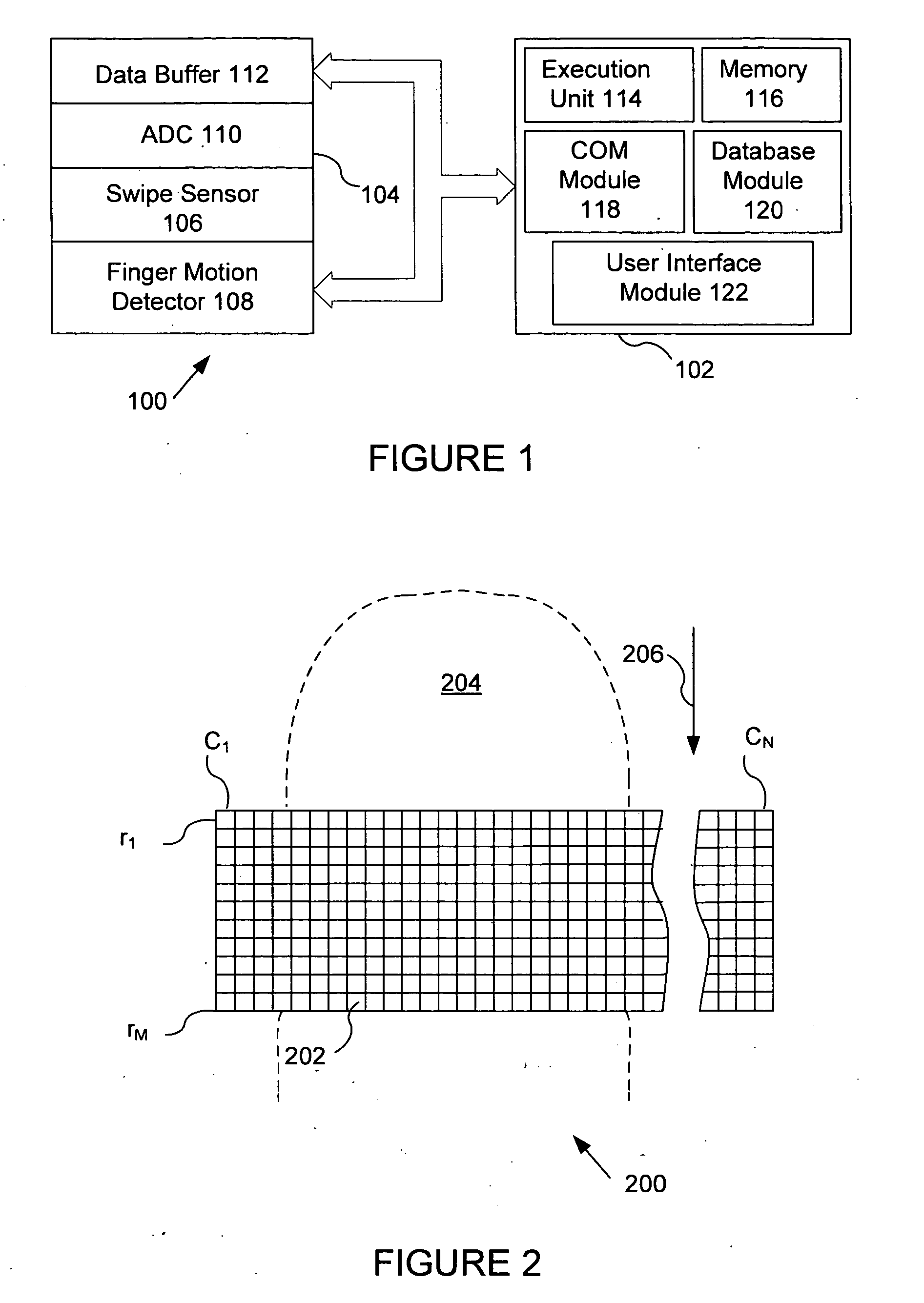
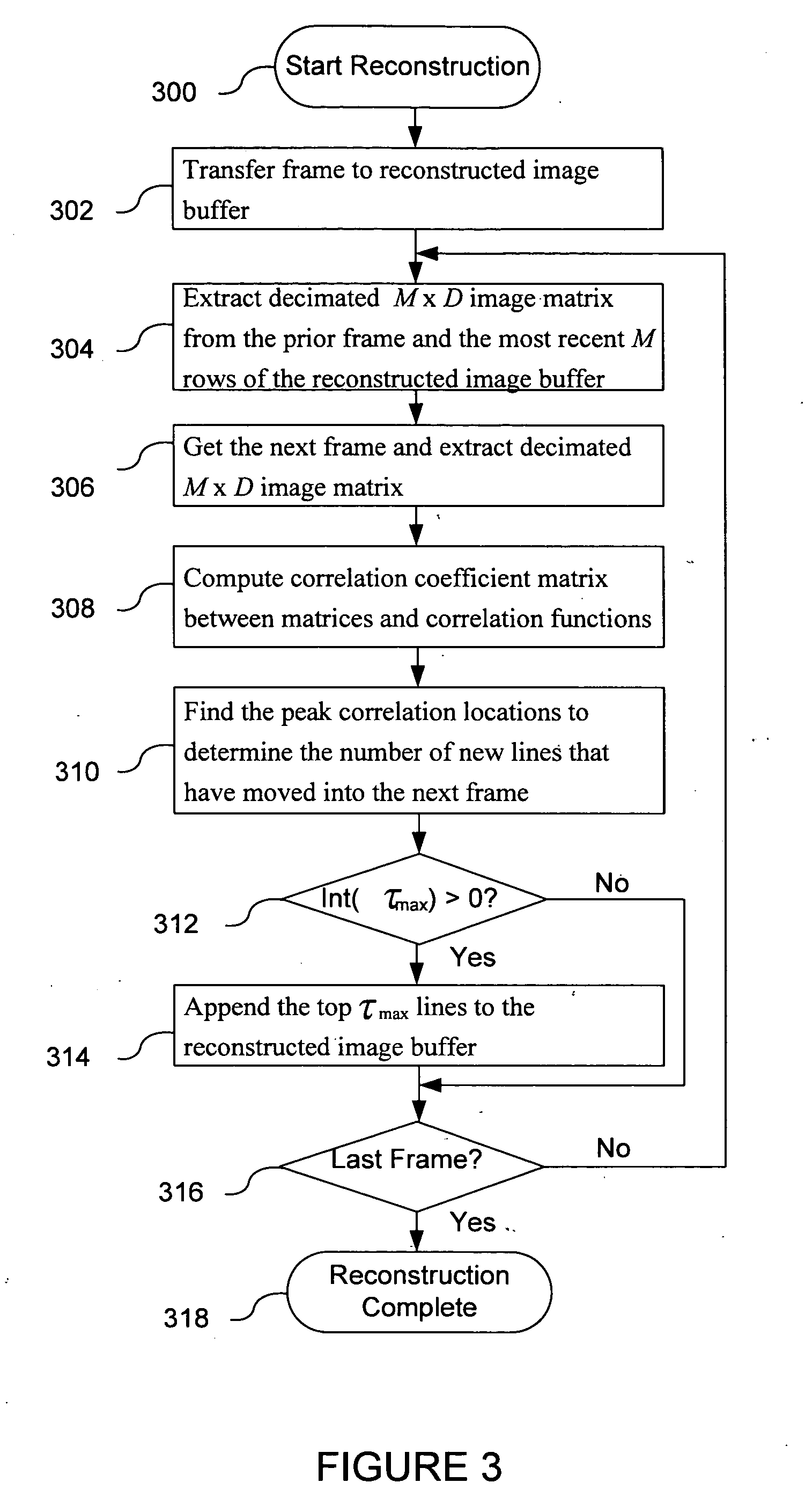
System for fingerprint image reconstruction based on motion estimate across a narrow fingerprint sensor
ActiveUS20050238212A1Valid conversionLow costCharacter and pattern recognitionPattern recognitionSensor system
In accordance with an embodiment of the present invention, an efficient and accurate system and method are described for detecting a fingerprint from swipe sensor system. A swipe sensor module is coupled to a microprocessor module. The swipe sensor module collects fingerprint image data as a plurality of frames and passes the frames of data to the microprocessor module. The microprocessor module assembles the frames of data into a complete image of the fingerprint that is cropped and processed to remove noise and artifacts. The cropped image is used to generate a template in a first instance and to compare an extracted portion of the cropped image to existing templates in a second instance.
Owner:SONY CORP +1
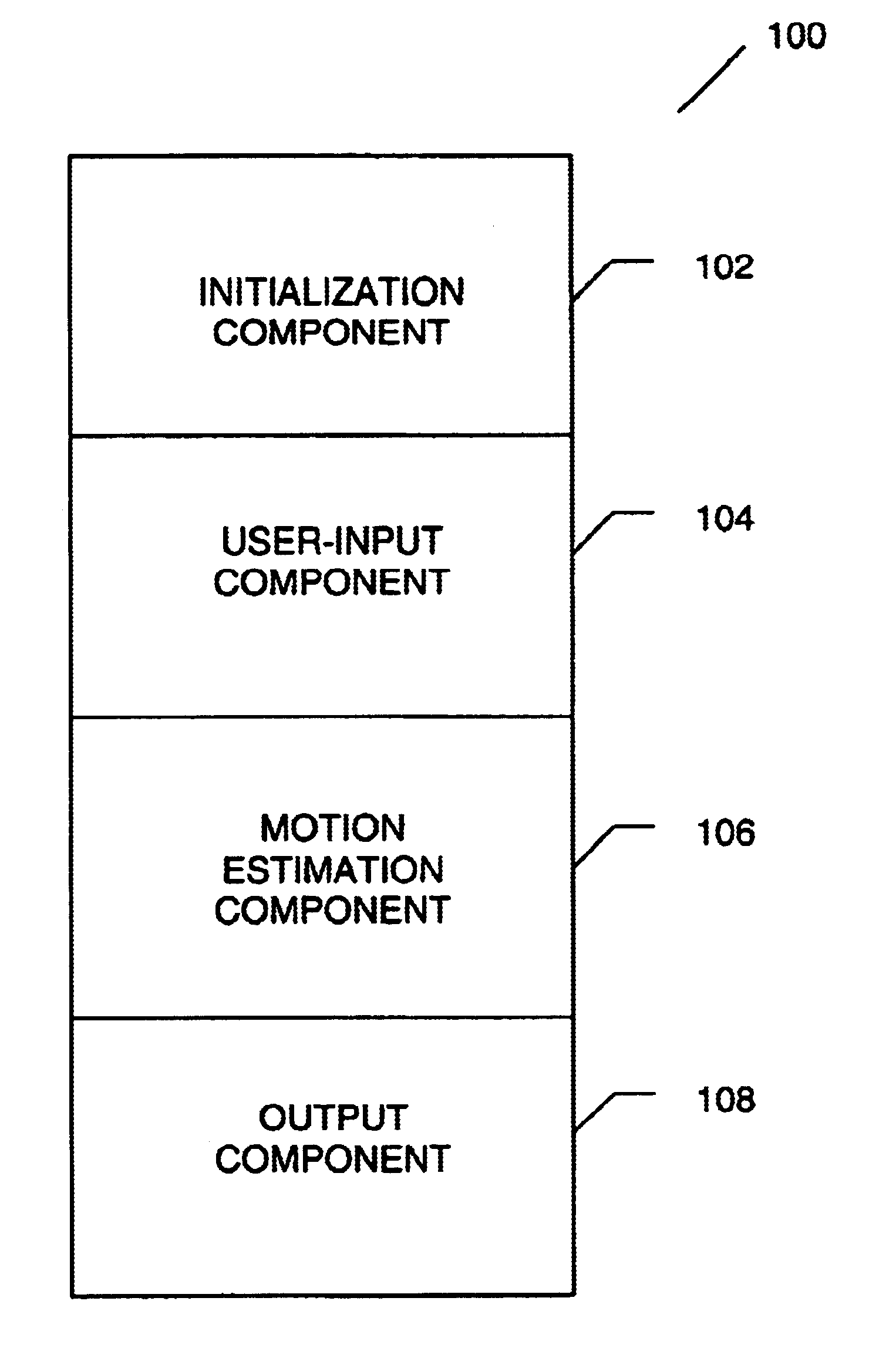
Systems and methods for tracking objects in video sequences
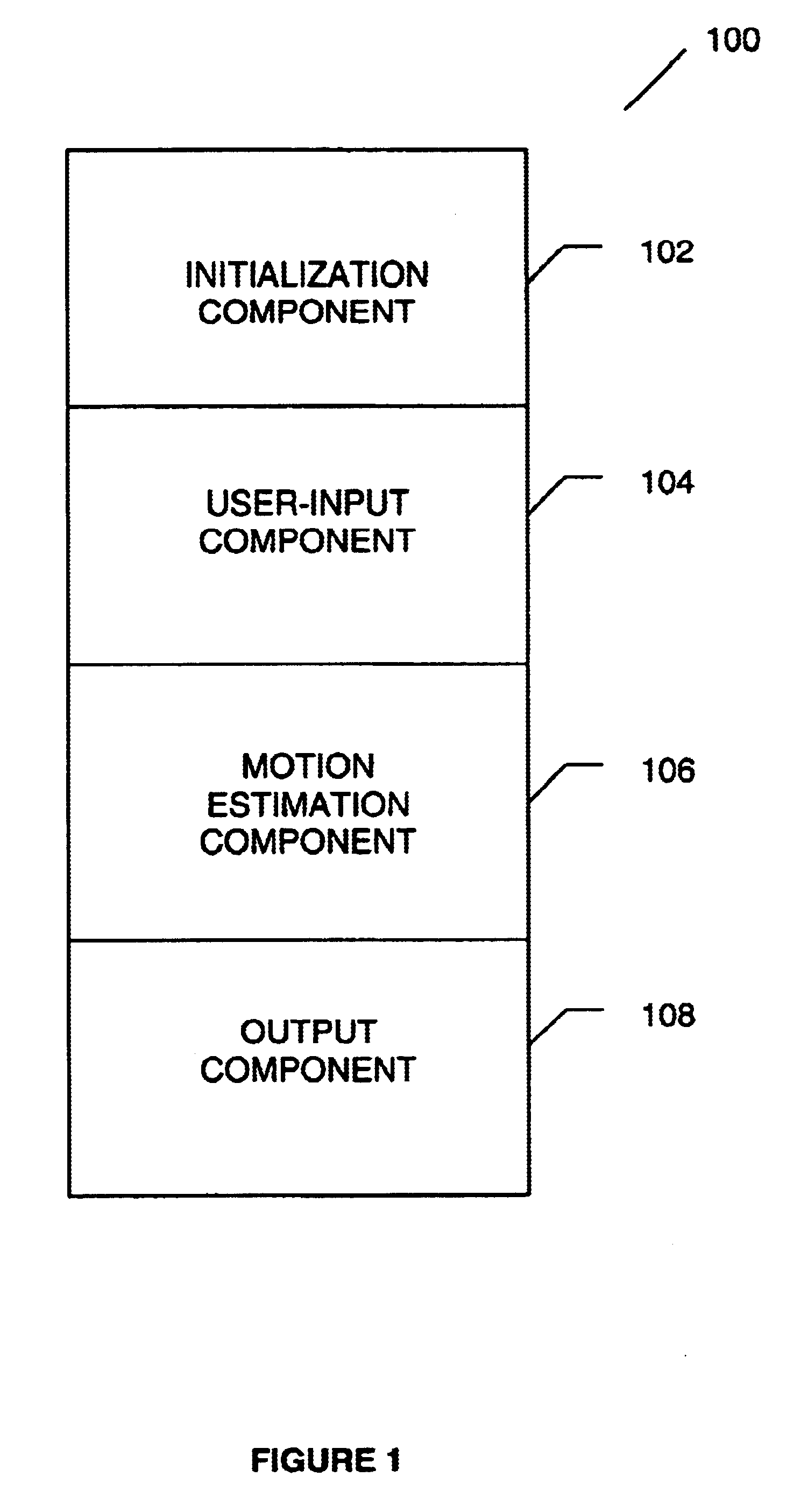
InactiveUS6901110B1Reduce computational overheadPrevent steppingImage enhancementTelevision system detailsMotion vectorMean difference
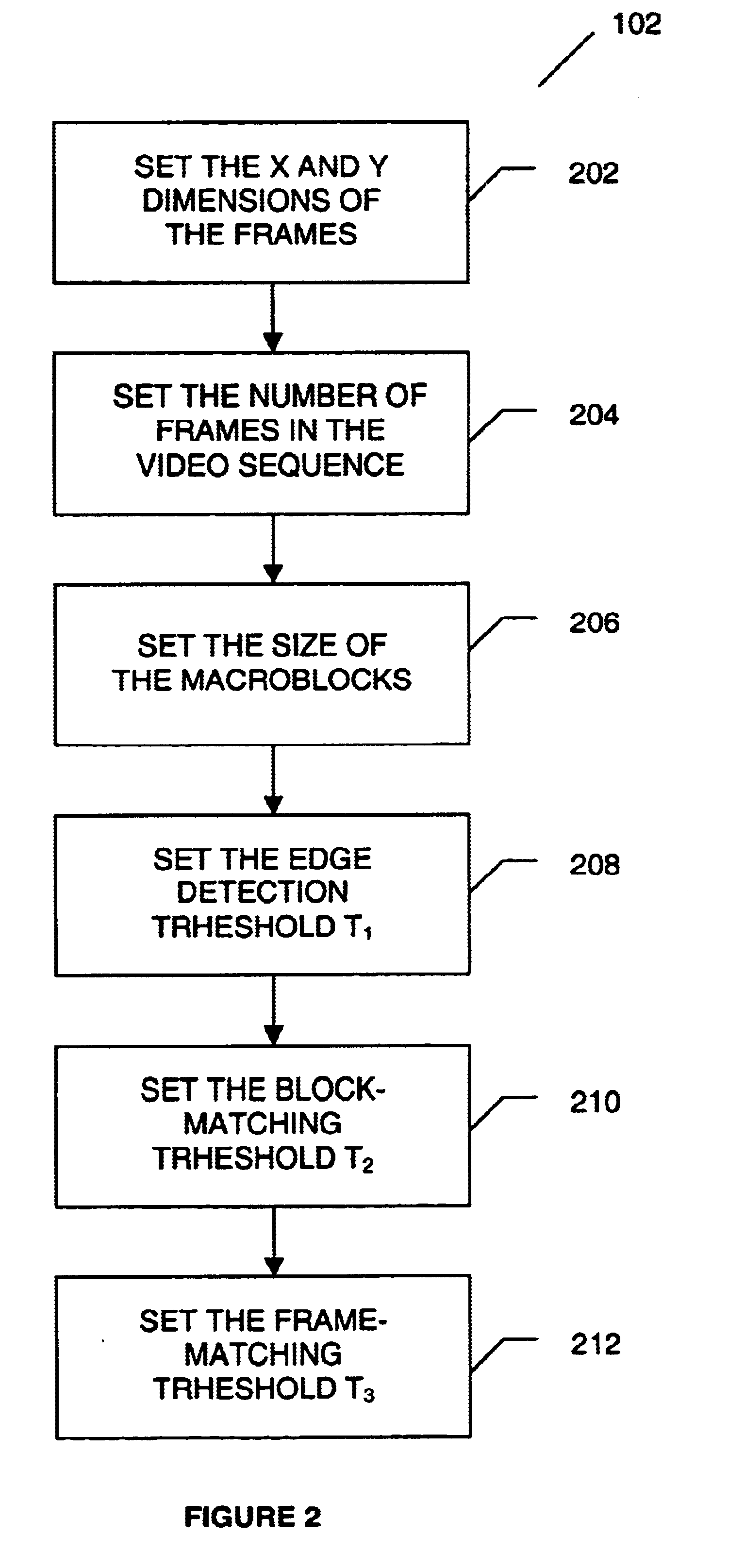
A method for tracking one or multiple objects from an input video sequence allows a user to select one or more regions that contain the object(s) of interest in the first and the last frame of their choice. An initialization component selects the current and the search frame and divides the selected region into equal sized macroblocks. An edge detection component computes the gradient of the current frame for each macroblock and a threshold component decides then which of the macroblocks contain sufficient information for tracking the desired object. A motion estimation component computes for each macroblock in the current frame its position in the search frame. The motion estimation component utilizes a search component that executes a novel search algorithm to find the best match. The mean absolute difference between two macroblocks is used as the matching criterion. The motion estimation component returns the estimated displacement vector for each block. An output component collects the motion vectors of all the predicted blocks and calculates the new position of the object in the next frame.
Owner:SONY CORP
SQL code generation for heterogeneous environment
ActiveUS20050028134A1Avoiding runtime interpretationAnalysis latencyData processing applicationsDigital data information retrievalDatabase queryExecution plan
This invention relates generally to a system for processing database queries, and more particularly to a method for generating high level language or machine code to implement query execution plans. In one preferred embodiment, the method begins by receiving a subject query, and then forming an execution plan corresponding to the subject query. The execution plan will typically have a sequence of component snippets or pieces and corresponding processes for implementing the pieces. For at least one piece in the plan, the process then (a) generates source code using different code generation techniques as a function of expected runtime processing machine types; and then (b) compiles the generated source code to form machine executable code for implementing the subject query. As a result, the query executed directly as machine executable code thereby avoiding runtime interpretation of the pieces in the execution plan.
Owner:IBM CORP
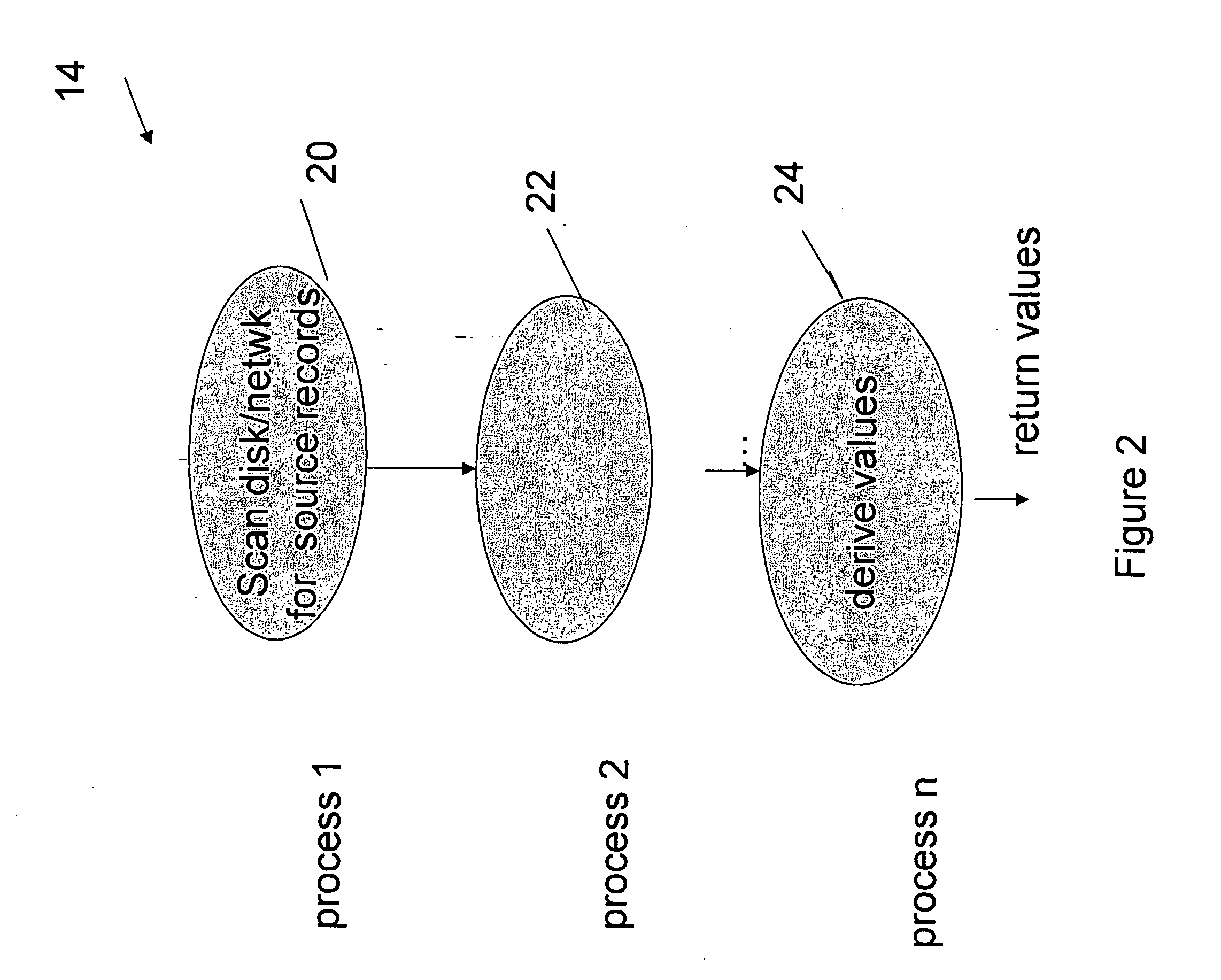
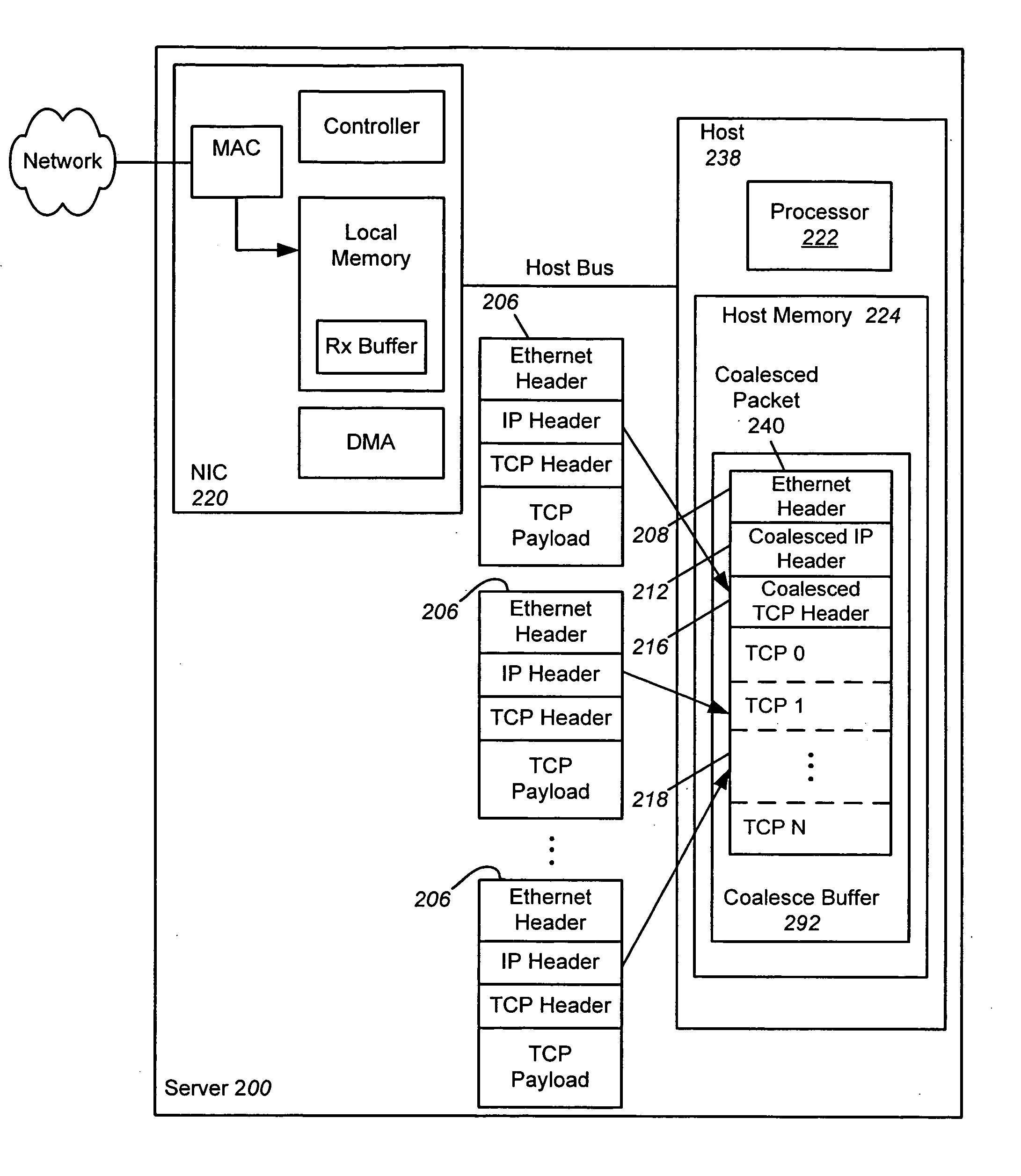
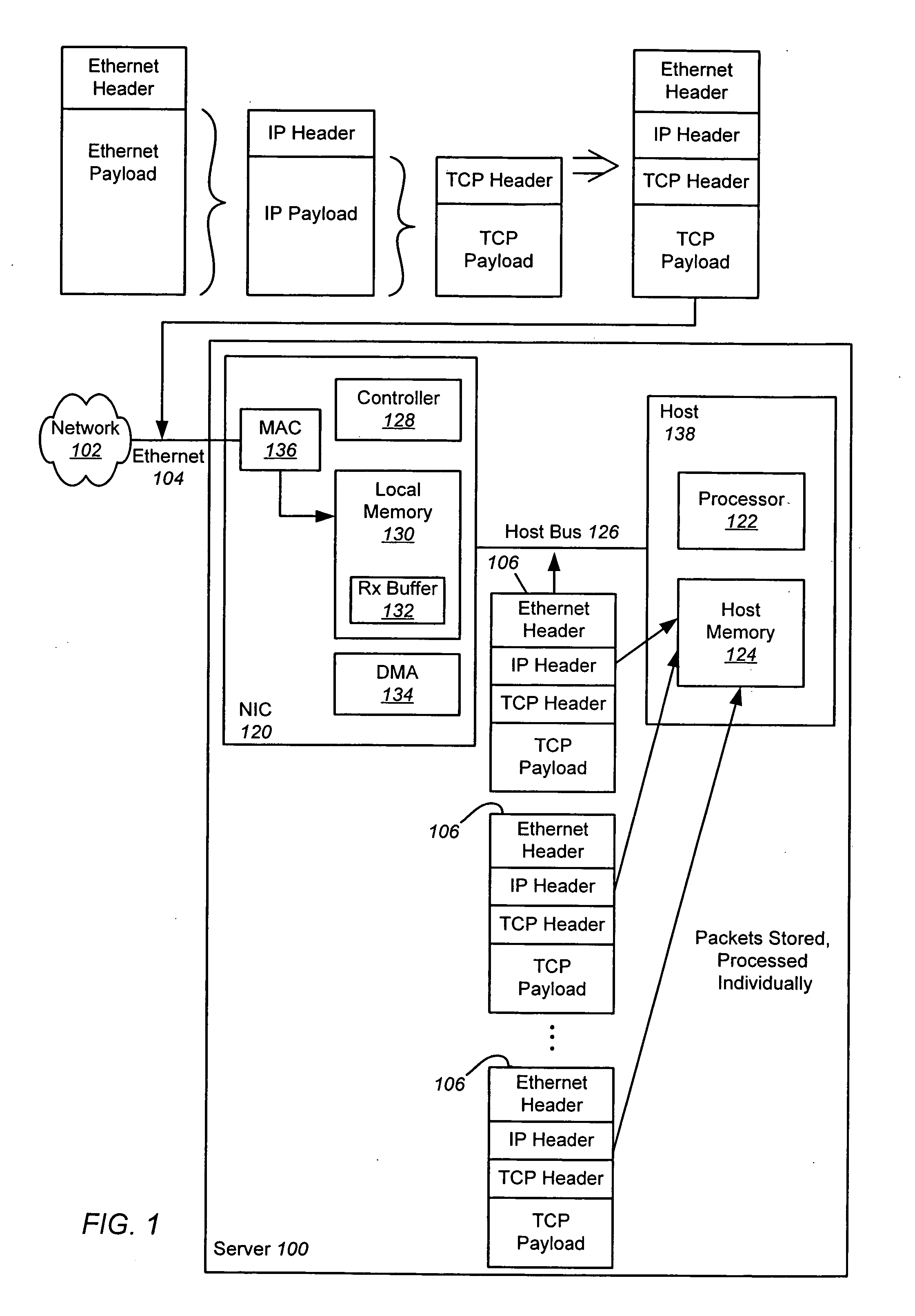
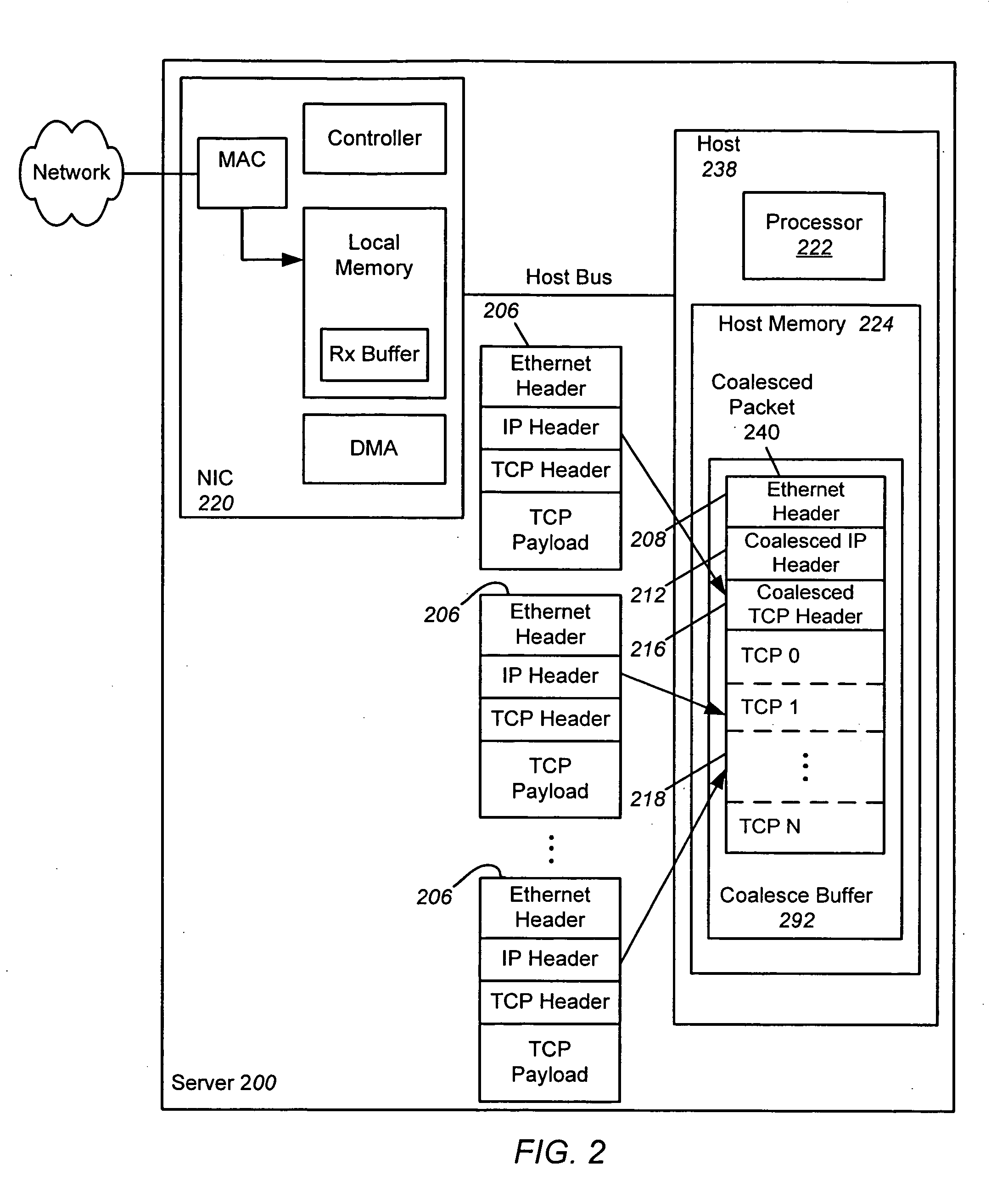
Receive coalescing and automatic acknowledge in network interface controller
ActiveUS20070064737A1Reduce computational overheadImprove network performanceTime-division multiplexTransmissionHost memoryInternet Protocol
An apparatus and method is disclosed for reducing the computational overhead incurred by a host processor during packet processing and improving network performance by adding additional functionality to a Network Interface Controller (NIC). Under certain circumstances the NIC coalesces multiple receive packets into a single coalesced packet stored within a coalesce buffer in host memory. The coalesced packet includes an Ethernet header, a coalesced Internet Protocol (IP) header, a coalesced Transmission Control Protocol (TCP) header, and a coalesced TCP payload containing the TCP payloads of the multiple receive packets. By coalescing received packets into fewer larger coalesced packets within the host memory, the host software needed to process a receive packet will be invoked less often, meaning that less processor overhead is incurred in the host.
Owner:AVAGO TECH INT SALES PTE LTD
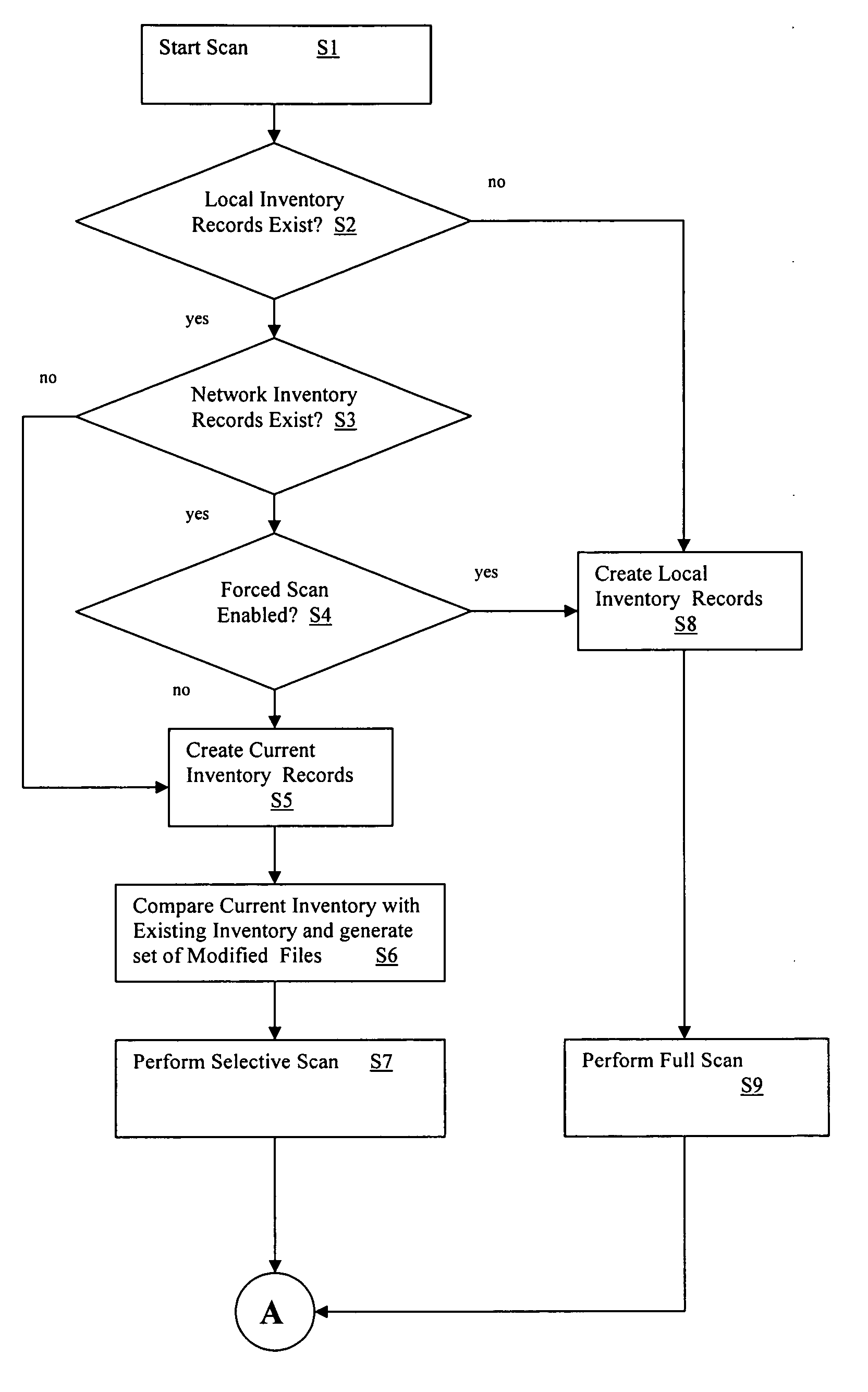
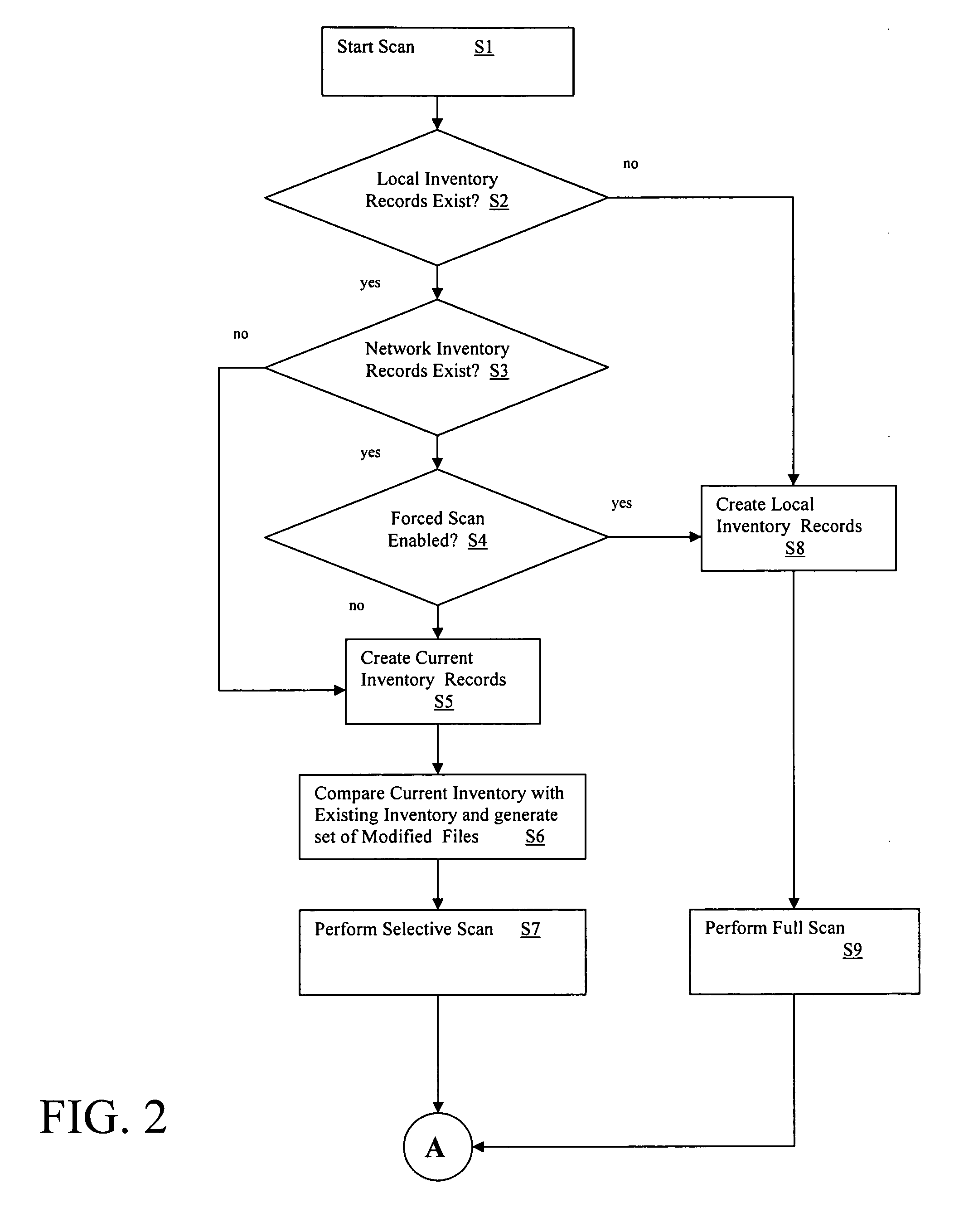
Selective virus scanning system and method
InactiveUS20060236398A1Reduce computational overheadMemory loss protectionUnauthorized memory use protectionRecordsetFile system
A virus scanning system and method. A system is provide that includes: a full scanning system for performing a full scan of each file in a file system; a file inventory system for inventorying each file in the file system and generating a set of inventory records, wherein each inventory record includes a unique key associated with each file in the file system; an inventory compare system for comparing a current set of inventory records with an existing set of inventory records to identify files in the file system that were modified since the existing set of inventory records was generated; and a selective scanning system for selectively scanning only files in the file system that were identified as modified by the inventory compare system.
Owner:SERVICENOW INC +1
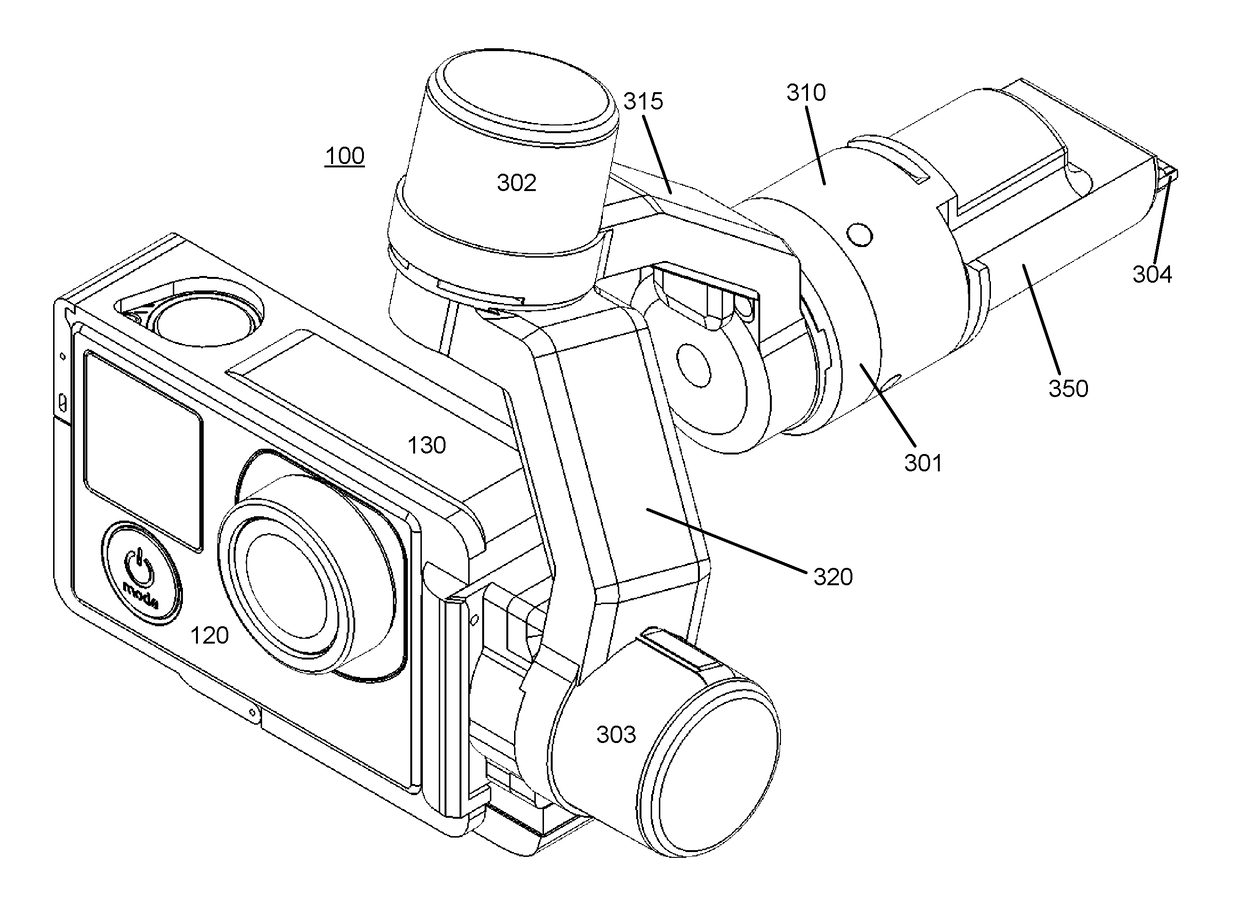
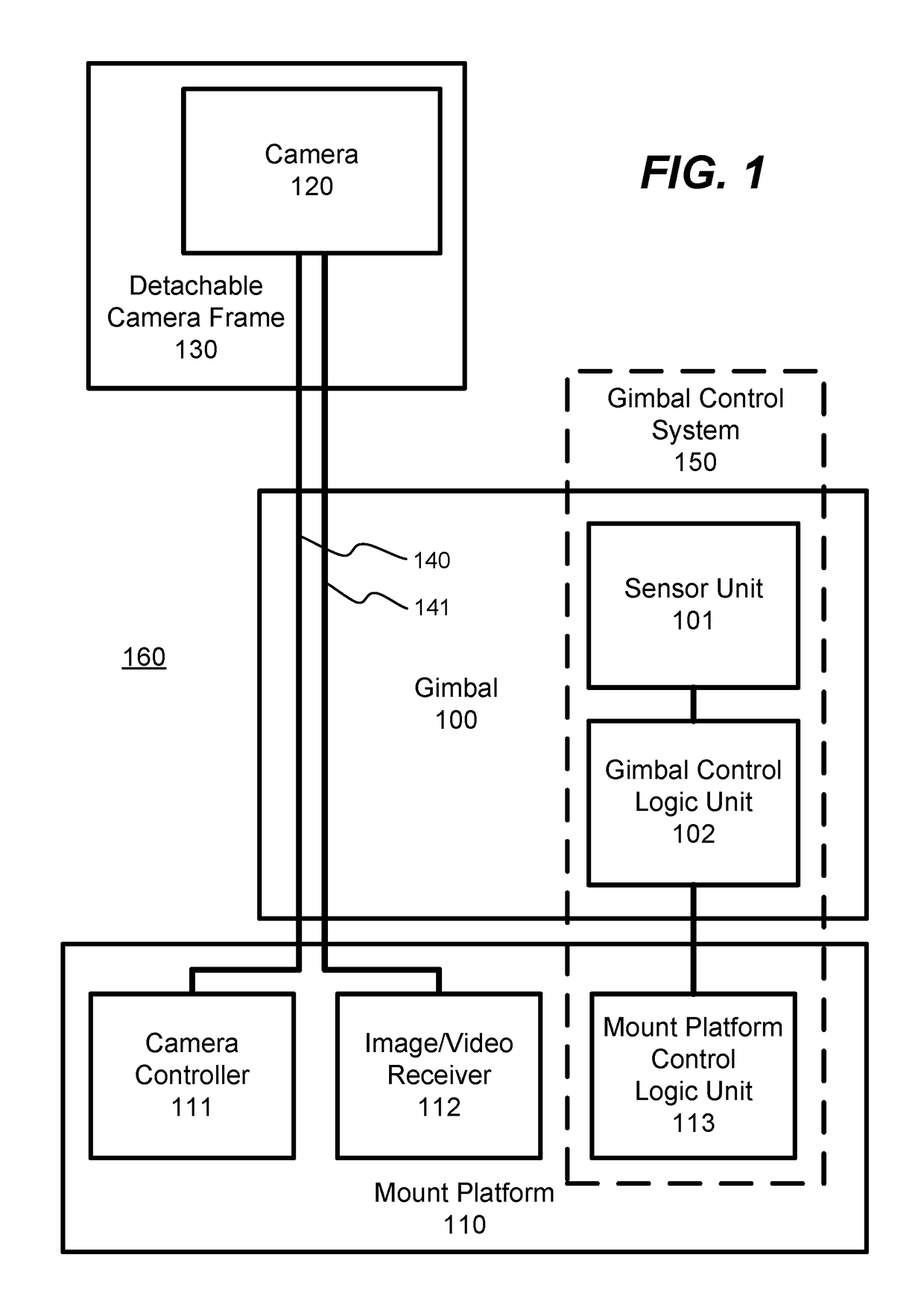
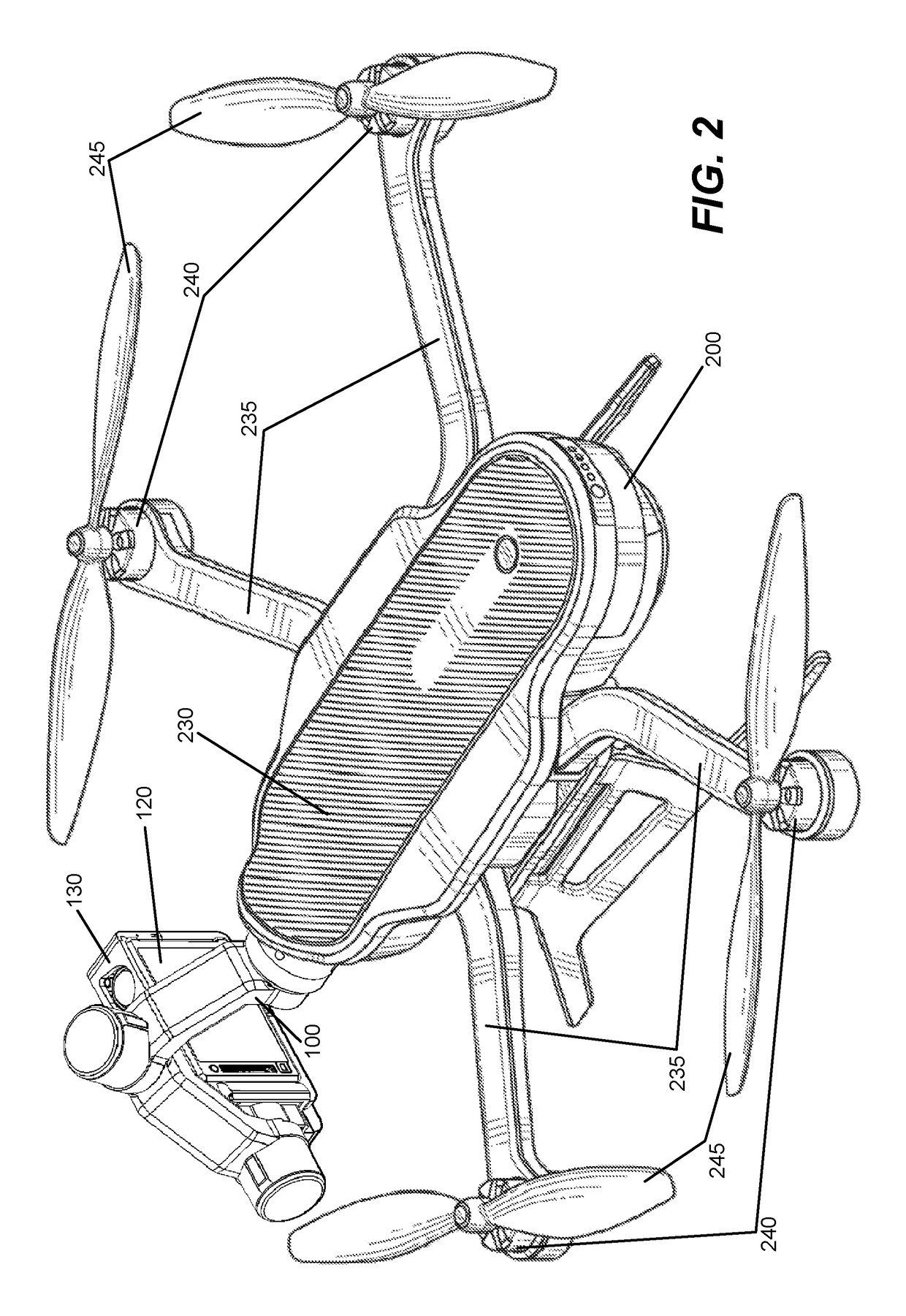
Camera System Using Stabilizing Gimbal
ActiveUS20170227162A1Accurate trackingReduce computational overheadAircraft componentsTelevision system detailsHand heldEngineering
Disclosed is an electronic gimbal with camera and mounting configuration. The gimbal can include an inertial measurement unit which can sense the orientation of the camera and three electronic motors which can manipulate the orientation of the camera. The gimbal can be removably coupled to a variety of mount platforms, such as an aerial vehicle, a handheld grip, or a rotating platform. Moreover, a camera can be removably coupled to the gimbal and can be held in a removable camera frame. Also disclosed is a system for allowing the platform, to which the gimbal is mounted, to control settings of the camera or to trigger actions on the camera, such as taking a picture, or initiating the recording of a video. The gimbal can also provide a connection between the camera and the mount platform, such that the mount platform receives images and video content from the camera.
Owner:GOPRO
Framework for efficient code generation using loop peeling for SIMD loop code with multiple misaligned statements
InactiveUS20050283773A1Reduce computational overheadIncrease computational overheadSoftware engineeringGeneral purpose stored program computerData reorganizationSteady state
A system and method is provided for vectorizing misaligned references in compiled code for SIMD architectures that support only aligned loads and stores. In this framework, a loop is first simdized as if the memory unit imposes no alignment constraints. The compiler then inserts data reorganization operations to satisfy the actual alignment requirements of the hardware. Finally, the code generation algorithm generates SIMD codes based on the data reorganization graph, addressing realistic issues such as runtime alignments, unknown loop bounds, residual iteration counts, and multiple statements with arbitrary alignment combinations. Loop peeling is used to reduce the computational overhead associated with misaligned data. A loop prologue and epilogue are peeled from individual iterations in the simdized loop, and vector-splicing instructions are applied to the peeled iterations, while the steady-state loop body incurs no additional computational overhead.
Owner:IBM CORP
Method for deleting repeated data by using double-fingerprint hash check
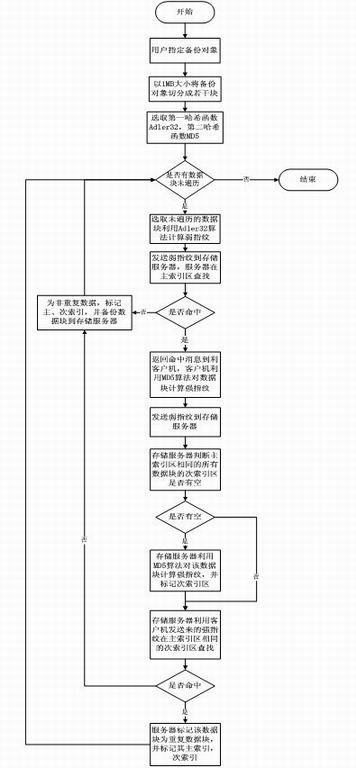
InactiveCN102156727AAvoid parityReduce the amount of fingerprint calculationSpecial data processing applicationsRedundant operation error correctionComputer hardwareHash function
The invention provides a method for deleting repeated data by using double-fingerprint hash check. The method comprises the following steps of: dividing an object to be backed up into data blocks to be backed up with equal lengths; judging whether the weak fingerprint of one of the data blocks to be backed up is the same as the weak fingerprint of any data block in a server; if the weak fingerprint of one of the data blocks to be backed up is different from the weak fingerprint of any data block in the server, backing up the data block; if the weak fingerprint of one of the data blocks to be backed up is the same as the weak fingerprint of any data block in the server, judging whether the strong fingerprint of the data block is the same as the strong fingerprint of any data block in the server; if the strong fingerprint of the data block is different from the strong fingerprint of any data block in the server, backing up the data block; and performing the operation on all data blocks to be backed up. In the method for deleting the repeated data, a hash function with low calculation amount is adopted at the first time to perform weak check on every data block and a has function with high calculation amount is adopted then to perform strong check, so the problem that all the data are checked by the hash function with the high calculation amount is avoided, the fingerprint calculation amount during checking is reduced greatly, the series performance is enhanced, and the appreciable transmission performance is provided for data backup based on mass data storage.
Owner:HUAZHONG UNIV OF SCI & TECH
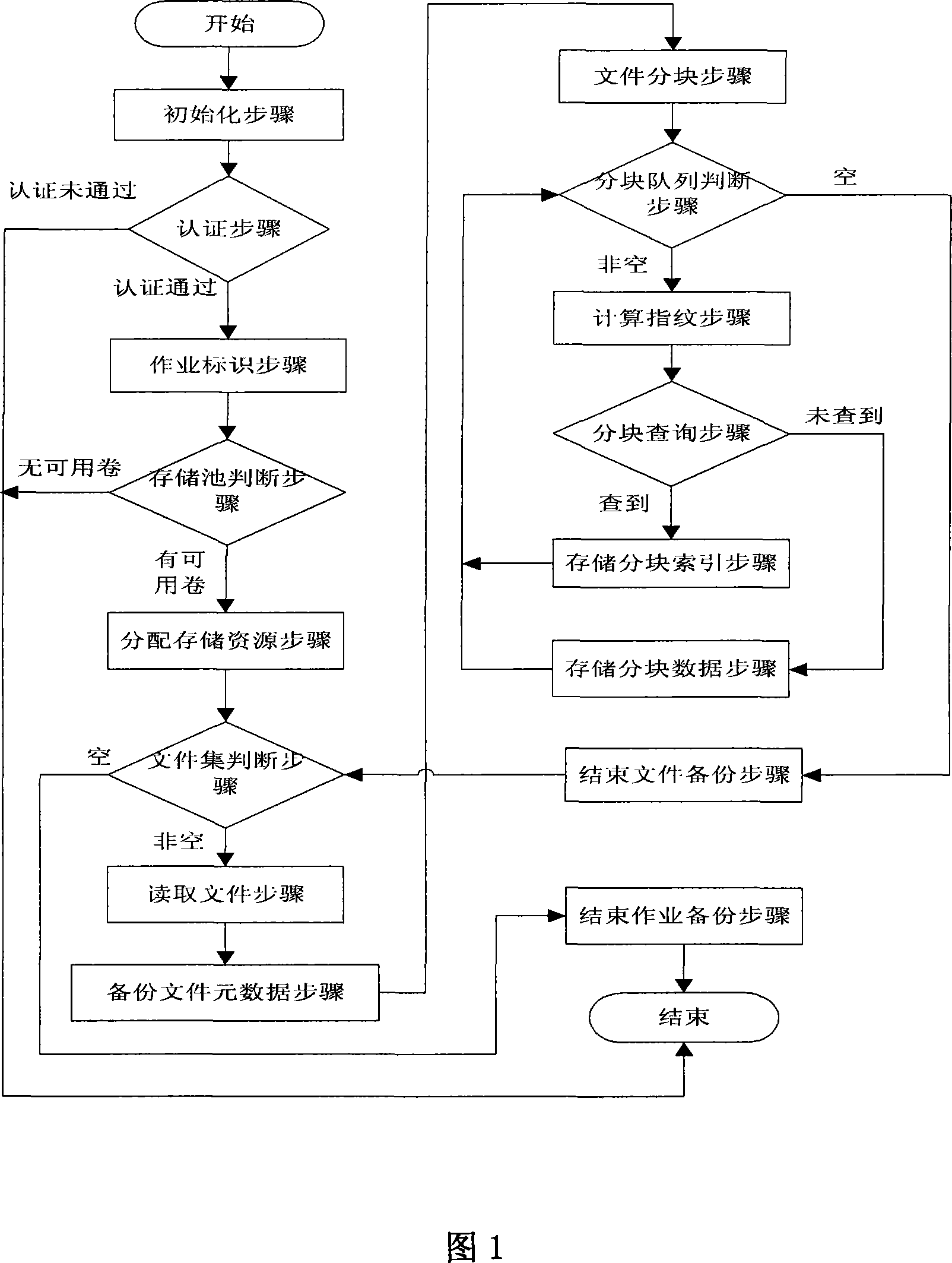
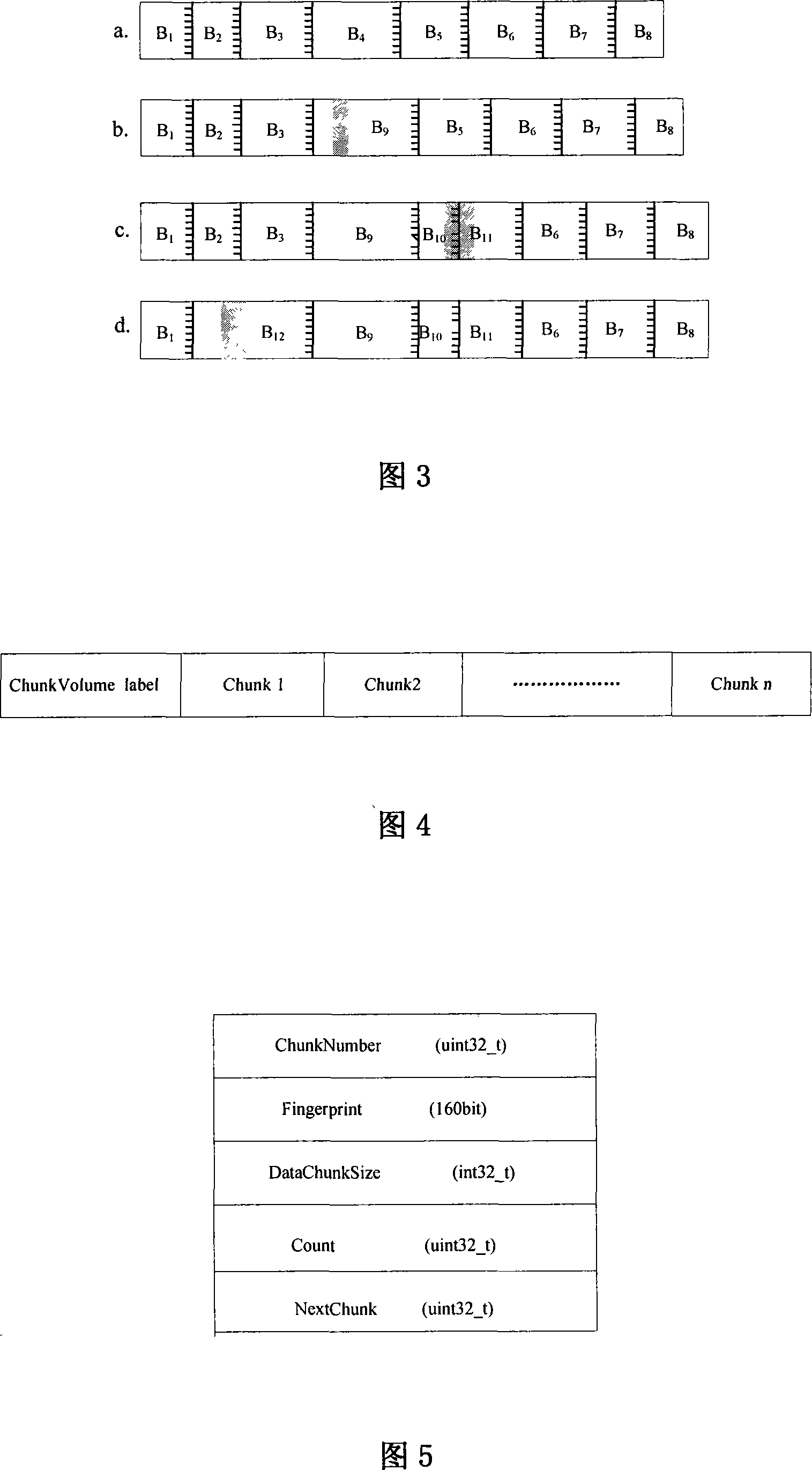
File backup method based on fingerprint
InactiveCN101216791AReduce overall backupSave bandwidthRedundant operation error correctionSpecial data processing applicationsFile sharingComputer science
The invention relates to a file backup method based on fingerprints, belonging to the technical field of storage backup in a computer. The invention is amied at reducing the backup of duplicated data, saving the cost of network bandwidth and storage needed by backup, and improving the backup efficiency. The invention comprises a backup process and a recovery procedure. The invention adopts the file blocking technology based on an anchorage to identify the redundant data of the backup file, the modification is stable, and the computation cost is low; data blocking of the file is memorized in a blocking volume in a storage server by using the fingerprints thereof as an identifier, thereby avoiding the backup of the duplicated data, and facilitating the data blocking to be shared by different files; file metadata and file blocking index are memorized in a storage volume in the storage server, thereby facilitating a user to organize a storage pool, and realizing the personalized management to logical objects.
Owner:HUAZHONG UNIV OF SCI & TECH
Revocable key external package decryption method based on content attributes
ActiveCN104486315APrevent unauthorized accessProtection securityUser identity/authority verificationComputer hardwareTrusted authority
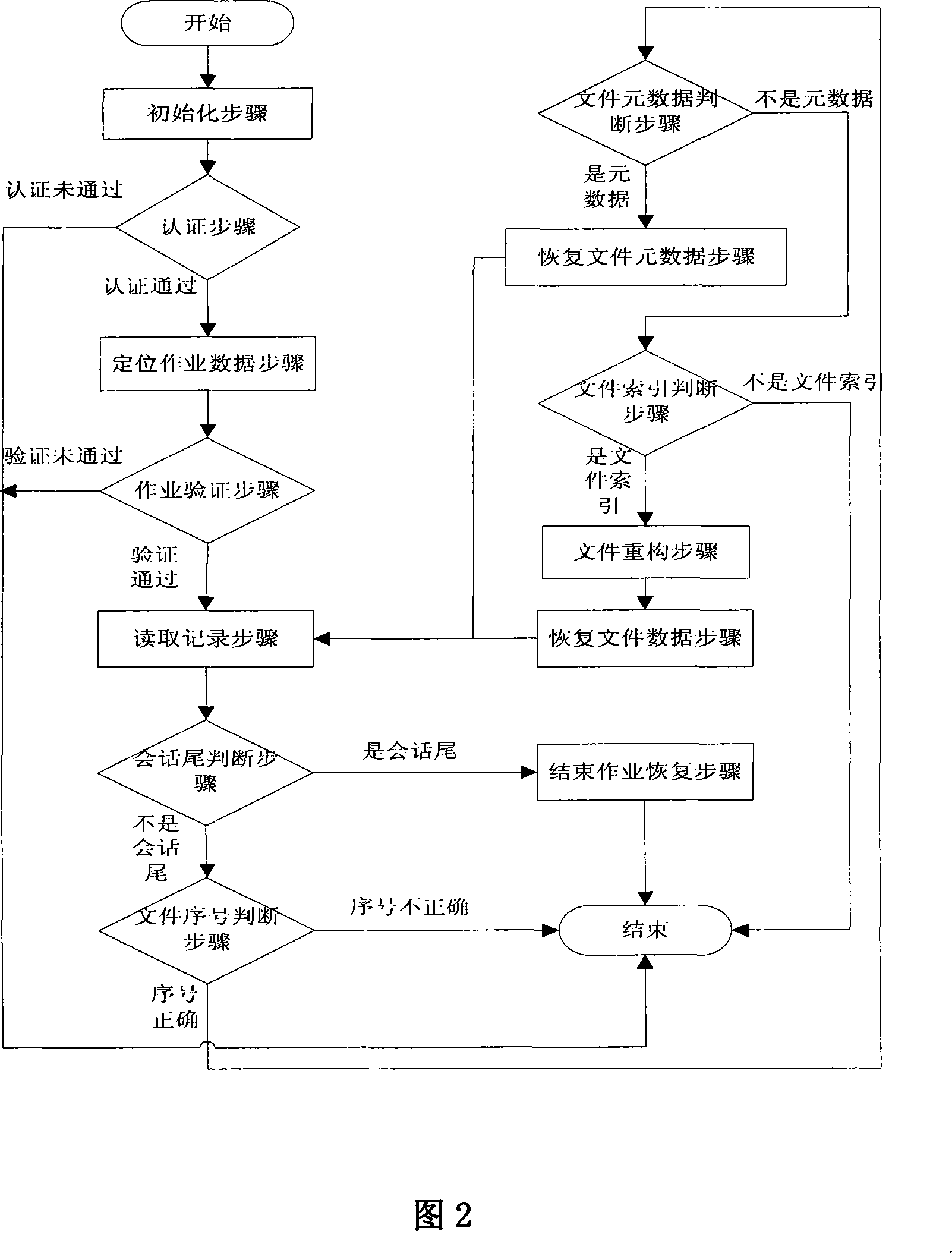
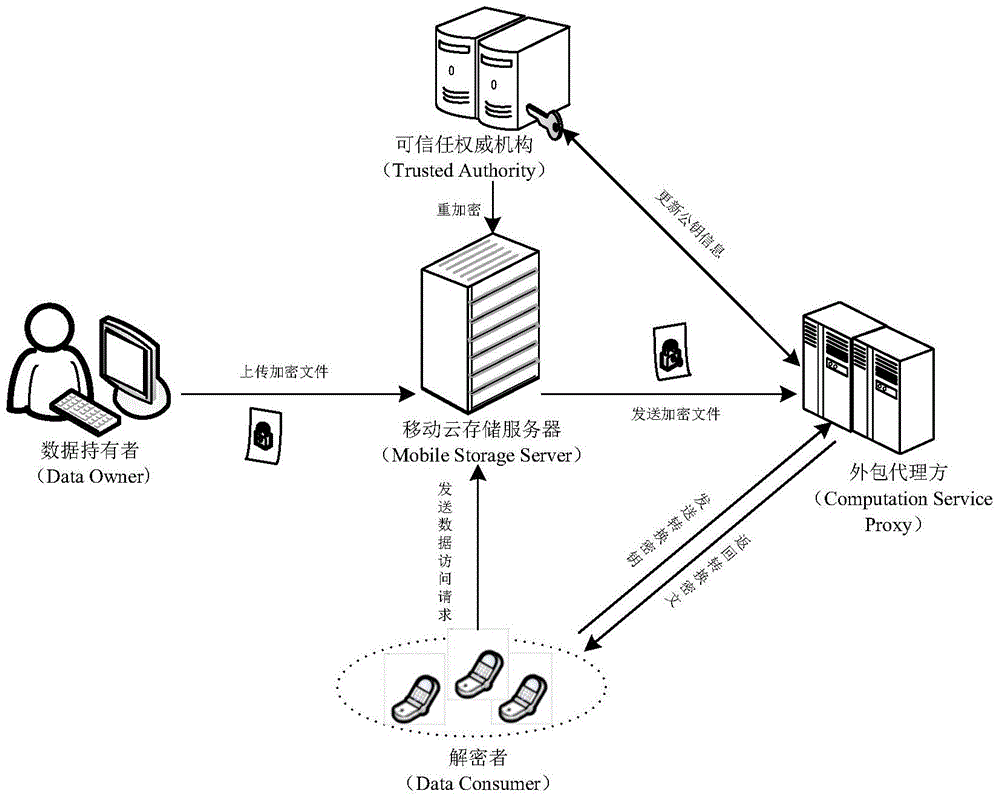
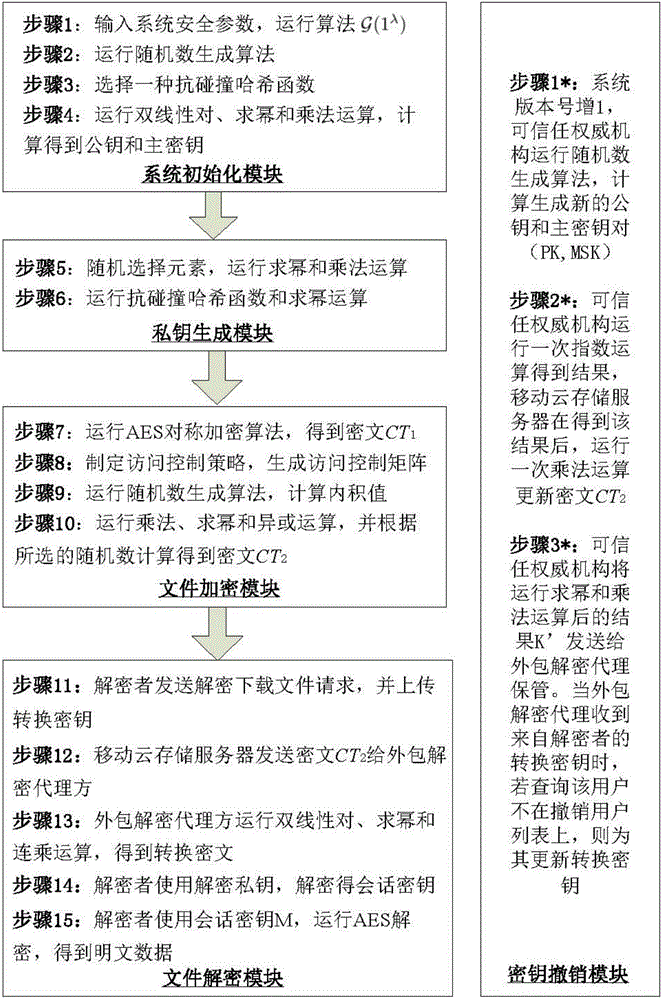
The invention relates to a revocable key external package decryption method based on content attributes. For a trusted authority, 1, initialization is carried out, and system parameters are output; 2, a random number generation algorithm operates; 3, a collision-resistant Hash function is selected, and the Hash value is calculated; 4, a public key and a main key are calculated; 5, the random number is selected, and exponentiation calculation and multiplication are carried out; 6, the collision-resistant Hash function operates, the exponentiation operation is carried out, and a decryption key is obtained. For a data holder, 7, AES data encryption is carried out; 8, an access control matrix is generated; 9, a random number is selected, and an inner product is calculated; 10, multiplication, exponentiation and exclusive-or operation is operated, and ciphertexts are obtained. For a decryption operator, 11, a decryption request and a transformation key are sent. For a mobile storage serve provider, 12, CT2 is sent to an external package decryption agency. For the external package decryption agency, 13, the transformation key is utilized, and the transformation ciphertext is calculated. For the decryption operator, 14, a conversation key is obtained through calculation; 15, AES data decryption is carried out.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
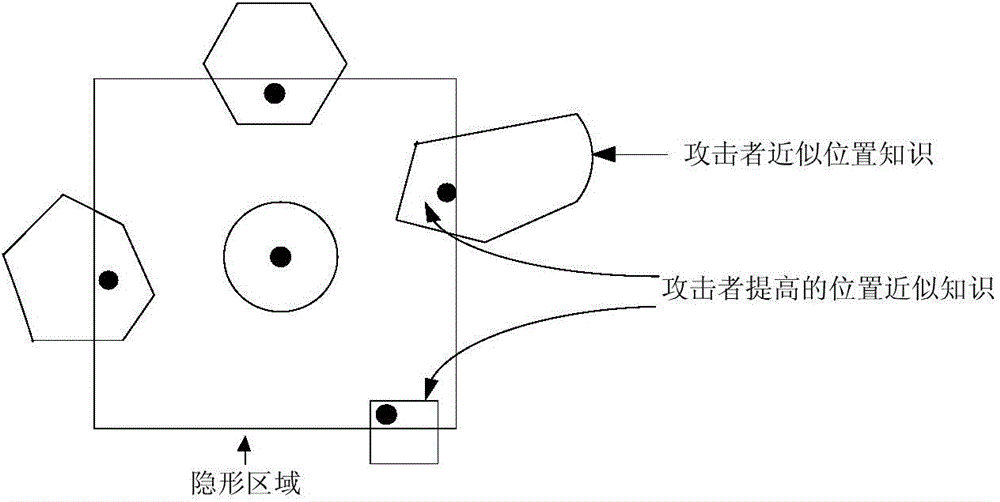
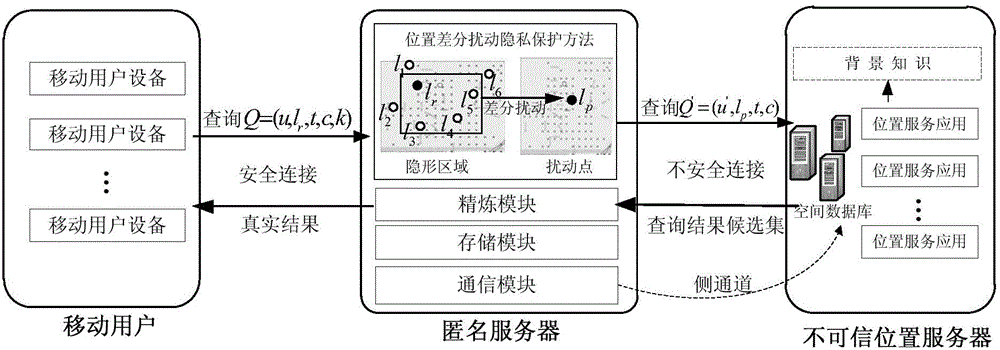
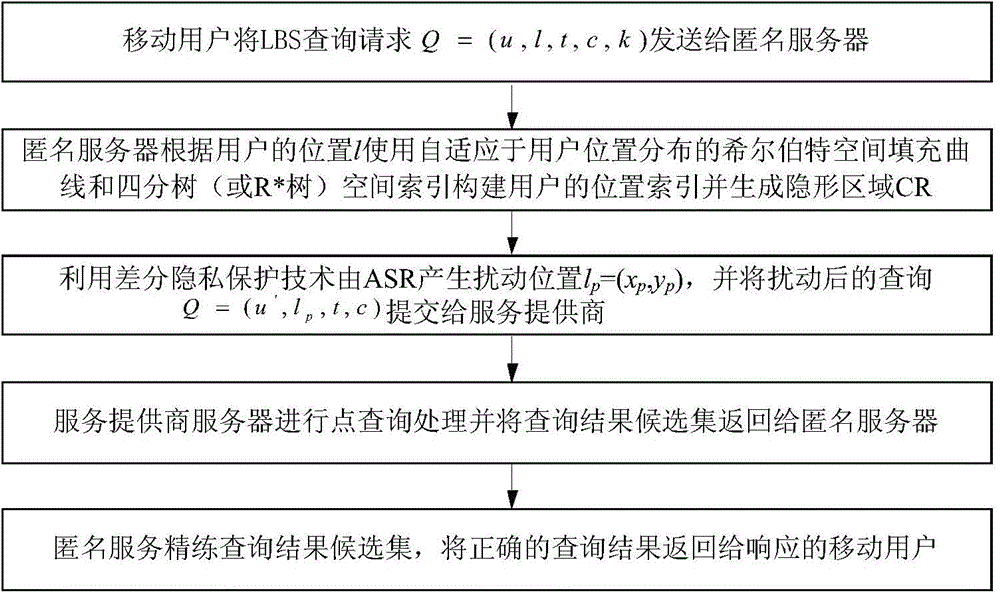
High-efficiency difference disturbance location privacy protection system and method
ActiveCN104394509AGenerate efficientlyGuaranteed correctnessTransmissionLocation information based serviceK-anonymitySide information
The invention discloses a high-efficiency difference disturbance location privacy protection system and a method, considering that the attacker has the challenge to the location privacy protection method based on the location disturbance and fuzzy technology about the background knowledge of the user side information, the difference privacy protection technology is guided to the location fuzzy privacy protection method, the Hilbert space filling curve capable of self-adaption transition on the user location according to the distributed change features in the geographic space of the mobile user and the current fashionable quadtree or R tree spatial index are used for forming the location index for all mobile users in the geographic space, and the K anonymity contact area satisfying the principle of reciprocity is effectively generated. Then, the difference privacy protection technology is used for generating the location disturbance point reasonable near user real location of k location points of the contact area as the query location of LBS user for requesting service from the LBS service provider, the problems and deficiencies of the existing method can be overcome.
Owner:XI AN JIAOTONG UNIV
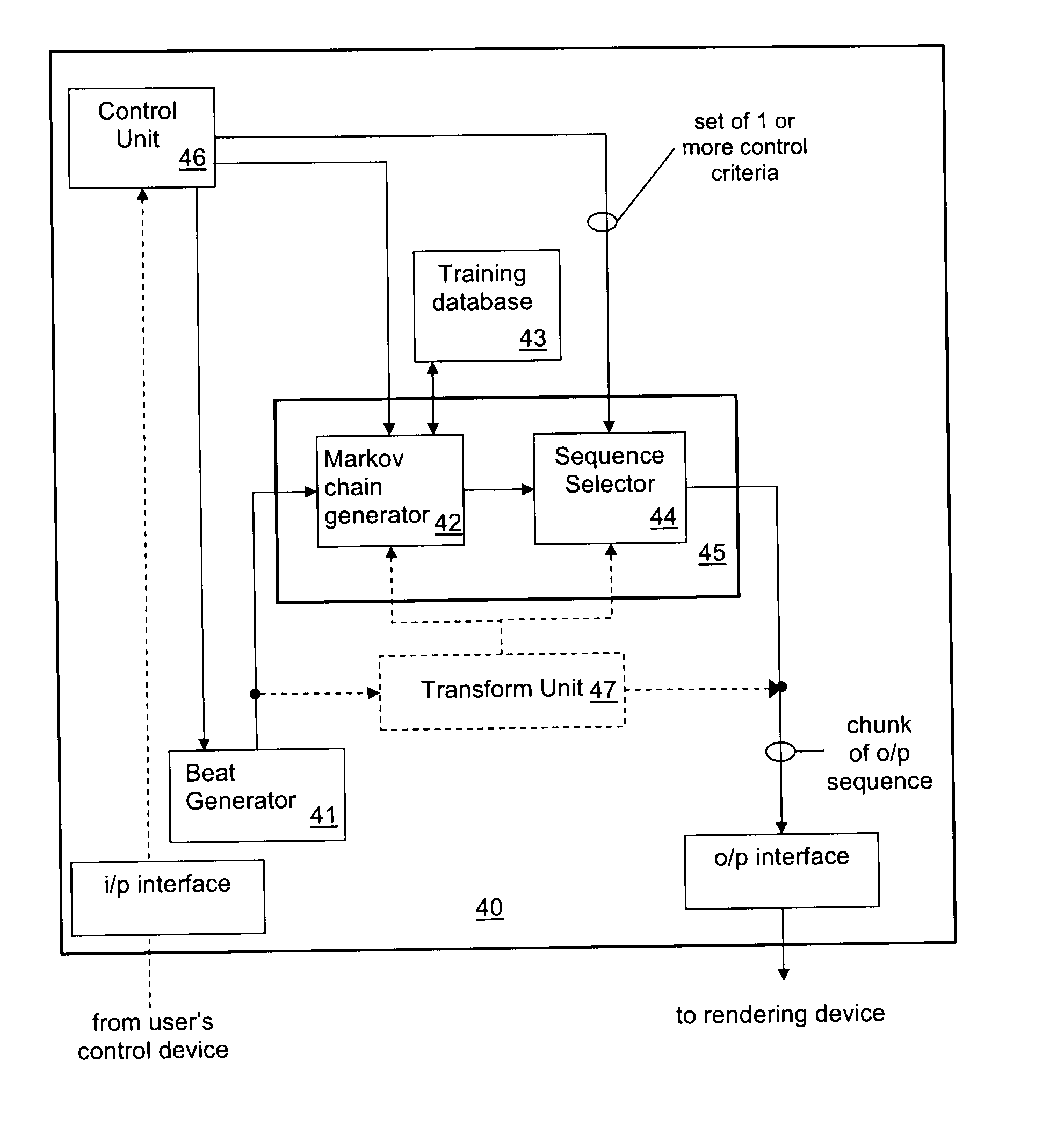
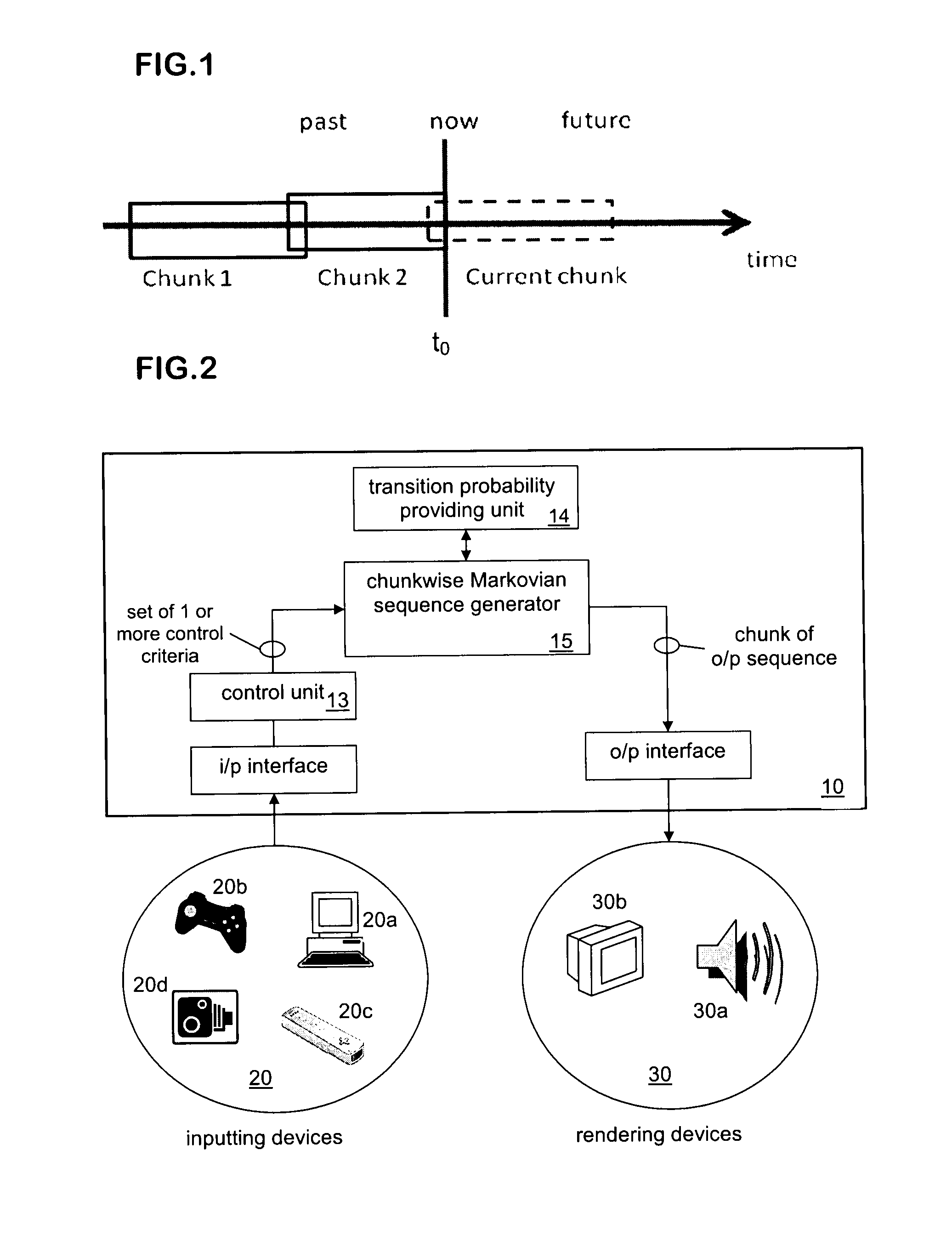
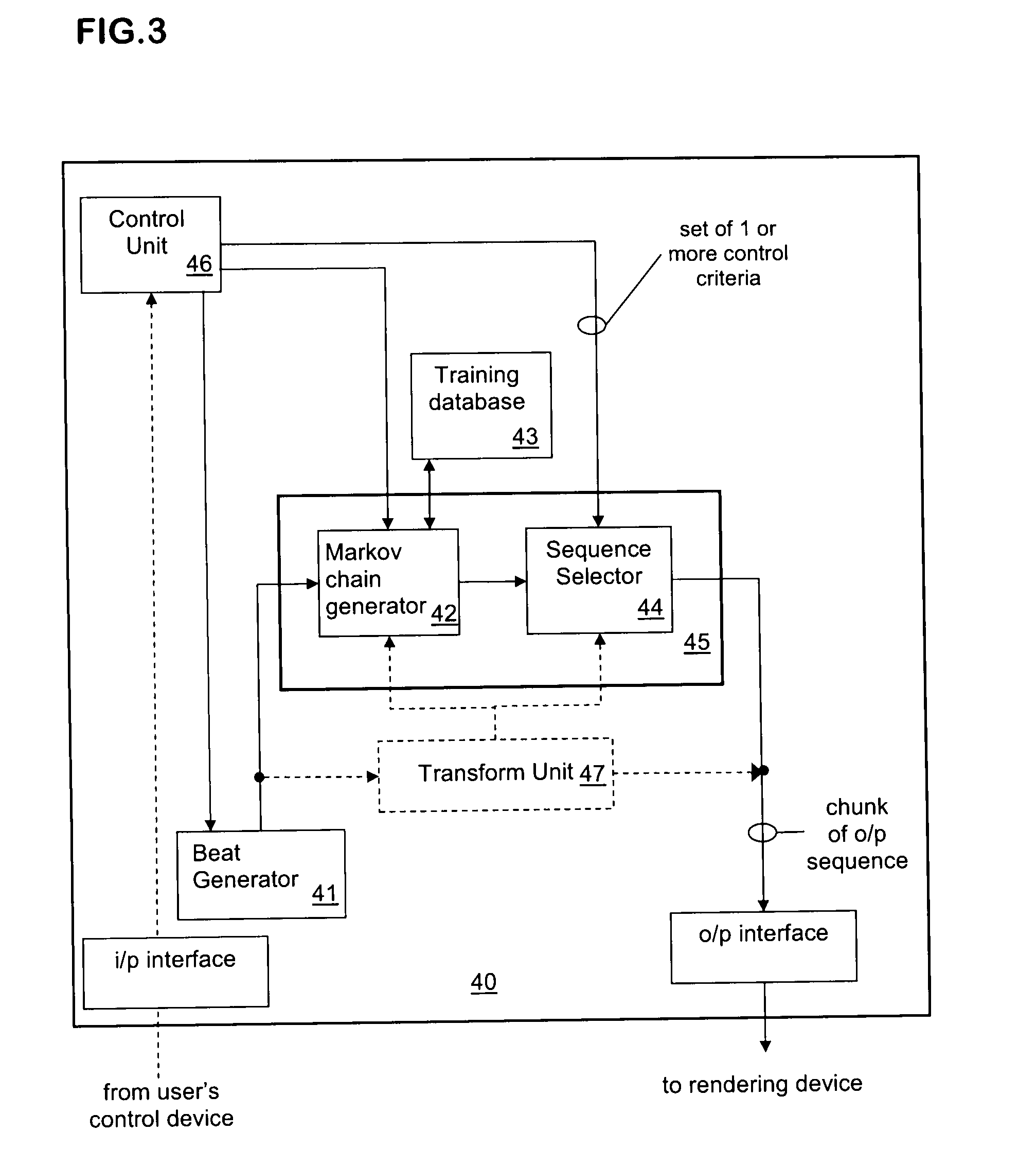
Markovian-sequence generator and new methods of generating markovian sequences
ActiveUS20110010321A1Extensive controlMore “costly”Mathematical modelsElectrophonic musical instrumentsConstraint satisfaction problemExecution control
A new type of Markovian sequence generator and generation method generates a Markovian sequence having controllable properties, notably properties that satisfy at least one control criterion which is a computable requirement holding on items in the sequence. The Markovian sequence is generated chunkwise, each chunk containing a plurality of items in the sequence. During generation of each chunk a search is performed in the space of Markovian sequences to find a chunk-sized series of items which enables the control criterion to be satisfied. The search can be performed using a generate and test approach in which chunk-sized Markovian sequences are generated then tested for compliance with the requirement(s) of the control criteria. Alternatively, the search can be performed by formulating the sequence-generation task as a constraint satisfaction problem, with one or more constraints ensuring that the generated sequence is Markovian and one or more constraints enforcing the requirement(s) of the control criteria. The sequence generator can be used in an interactive system where a user specifies the control criterion via an inputting device (20).
Owner:SONY CORP
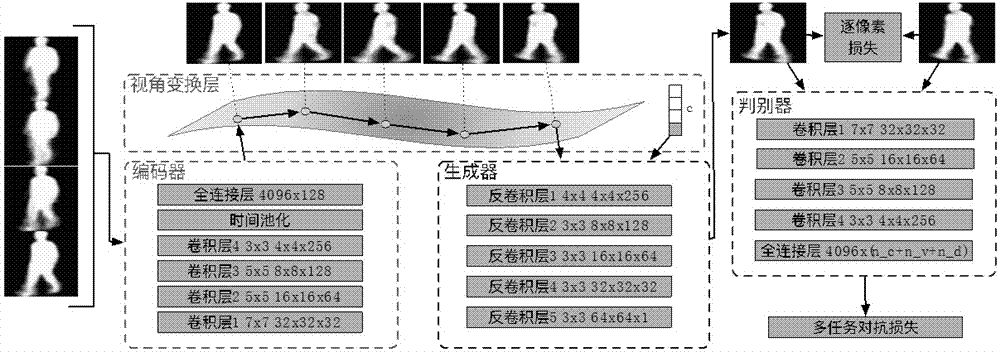
Cross-visual angle gait recognition method based on multitask generation confrontation network
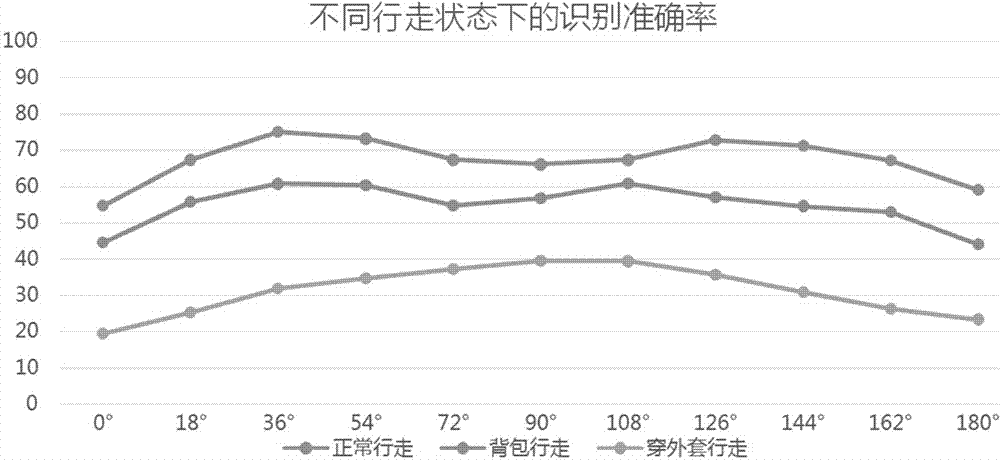
ActiveCN107085716AReduce computational overheadExpressiveCharacter and pattern recognitionNeural architecturesPattern recognitionFrame sequence
The invention belongs to the field of computer vision and machine learning, and particularly relates to a cross-visual angle gait recognition method based on a multitask generation confrontation network. The objective of the invention is to solve a problem of reduced generalization performance of a model under big visual angle change of the gait recognition. The method comprises steps of firstly carrying out pretreatment on each frame of image for an original pedestrian video frame sequence, and extracting gait template features; carrying out gait hidden expression through neural network coding and carrying out angle transformation in a hidden space; generating a confrontation network through multiple tasks and constructing gait template features of other visual angles; and finally using the gait hidden expression to carry out recognition. Compared with methods based on classification or reconstruction, the method has quite strong interpretability and recognition performance can be improved.
Owner:FUDAN UNIV
Distributed cloud storage data integrity protection method
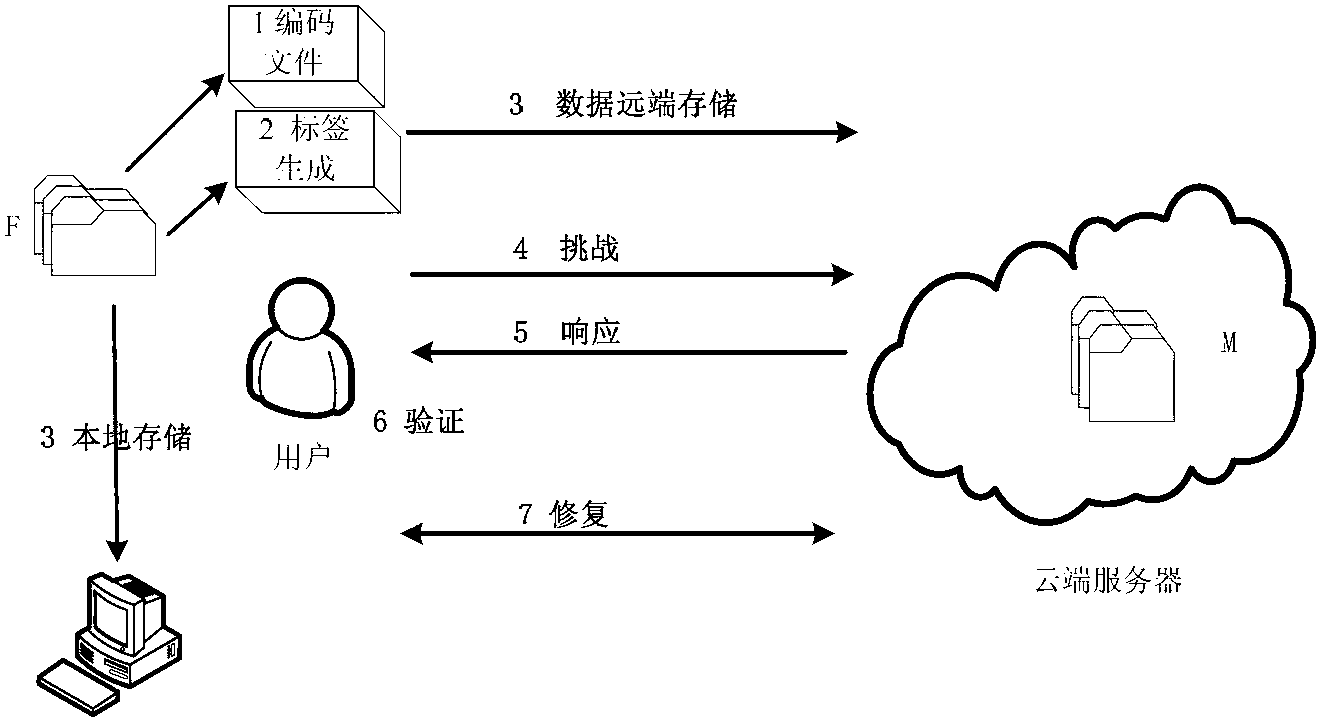
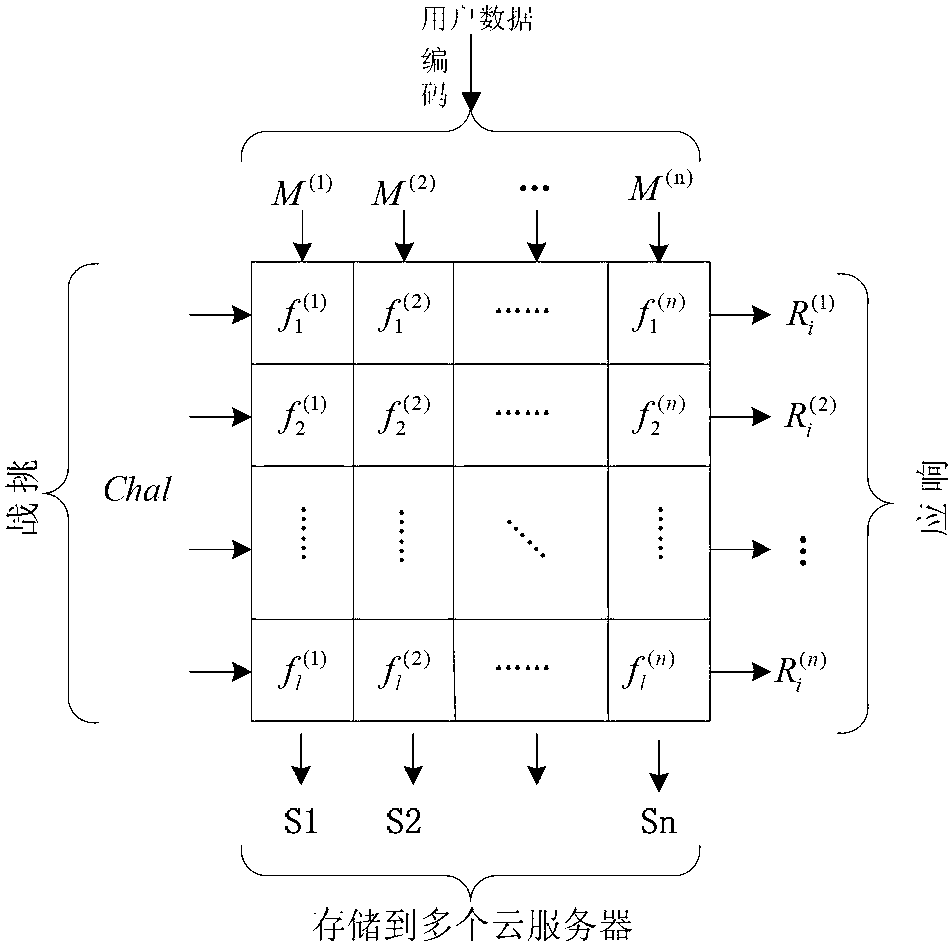
InactiveCN102710757AAchieve positioningSmall amount of local storageTransmissionData integrityLinear coding
The invention relates to a distributed cloud storage data integrity protection method. The method comprises: (1) data division and coding {F--M}; (2) generation of homomorphic verifiable tags (HVTs) {(sk,F)--HVTs}; (3) remote data storage {(M(j),HVT--Sj)}; (4) a user launching a challenge {chal}; (5) a server making a response {R}; (6) verification{(R,sk)--('success', 'failure')}; and (7) data recovery {(M*,P)--F}. According to the method provided by the invention, the communication cost is reduced by adopting random data block sampling; data error location and error recovery can be realized by using linear coding; and the method has no limits to the number of times for data possession verification, is high in the verification confidence, safe and reliable. Accordingly, the method provided by the invention has good practical value and wide application prospect in the technical field of cloud security.
Owner:BEIHANG UNIV
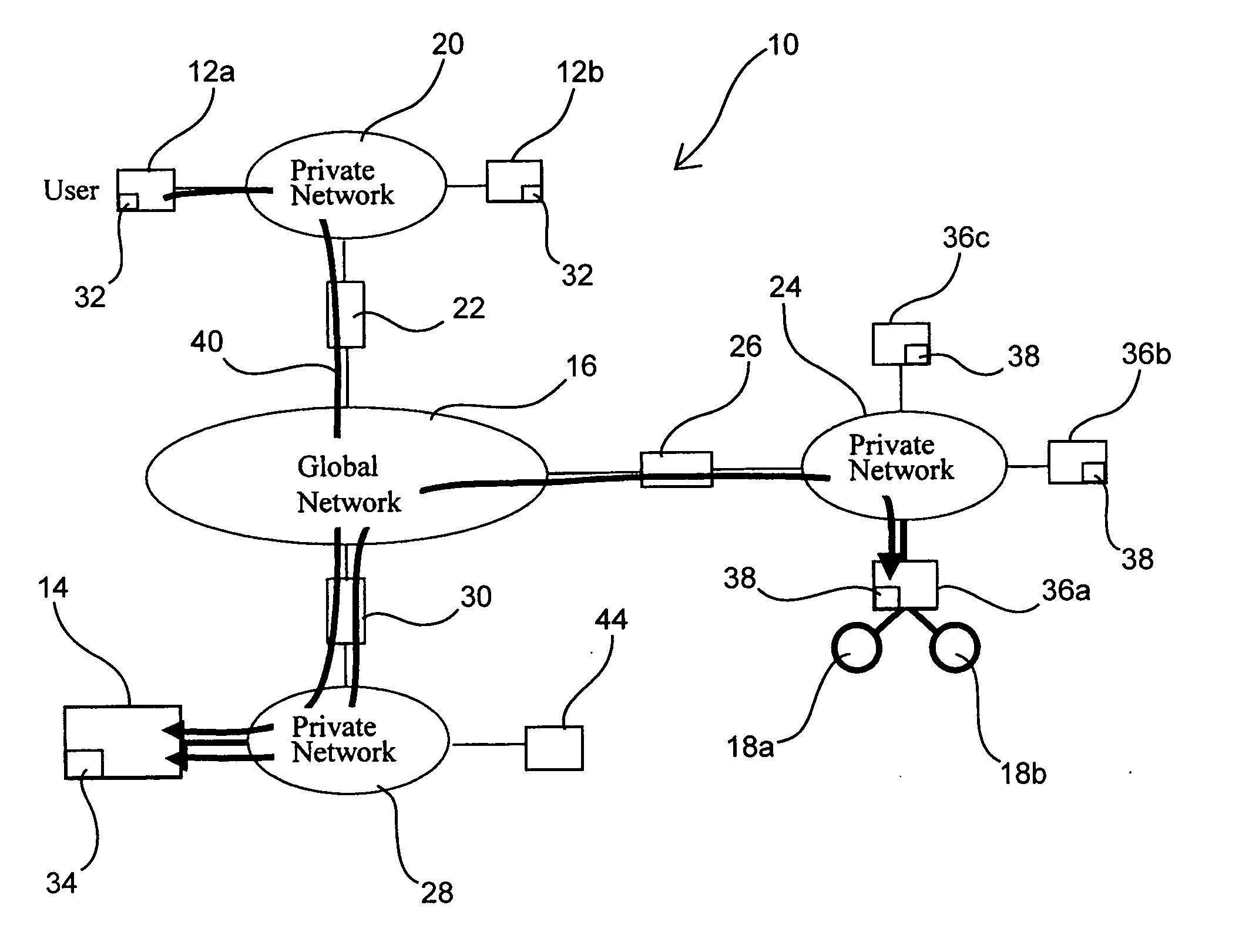
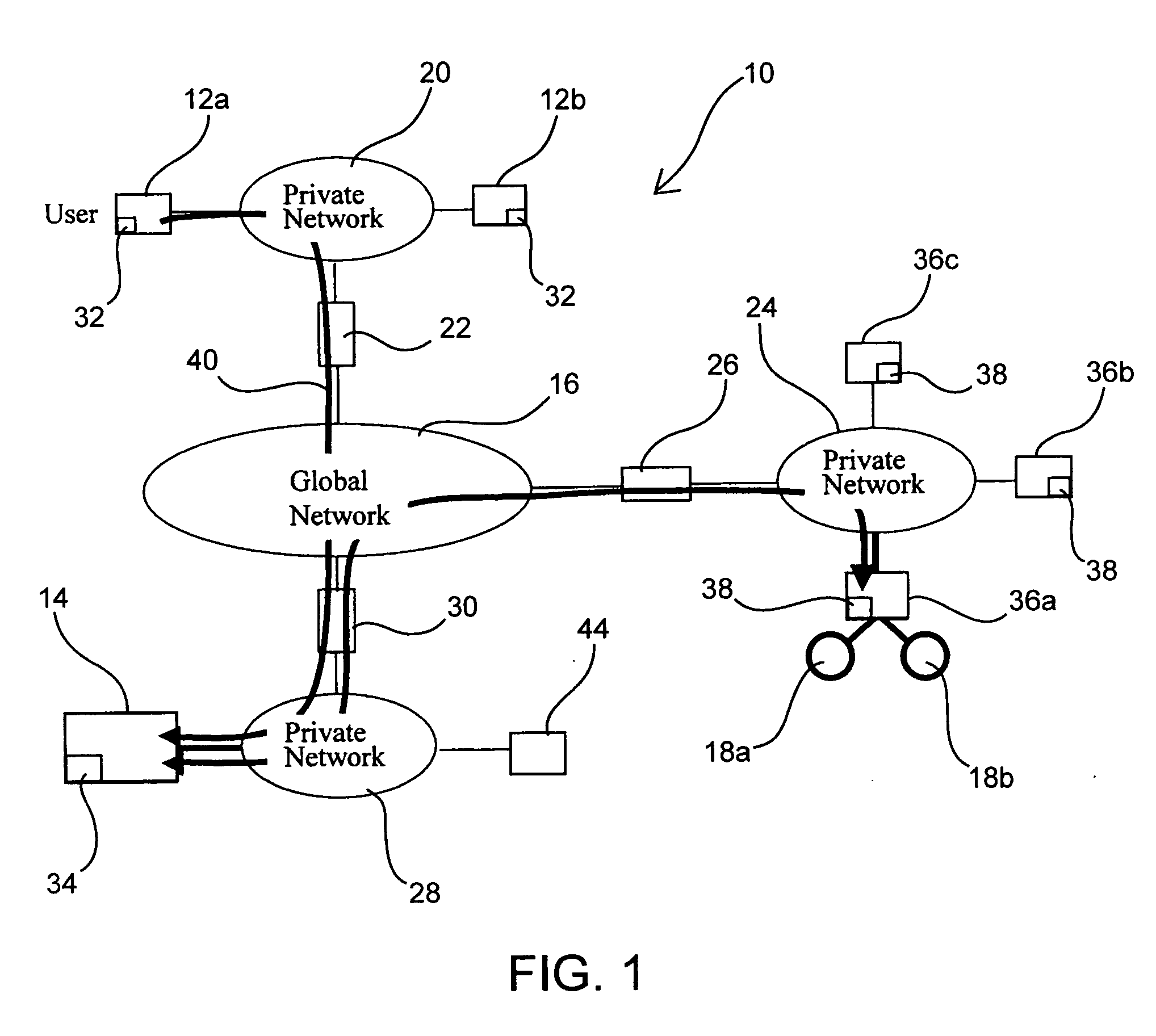
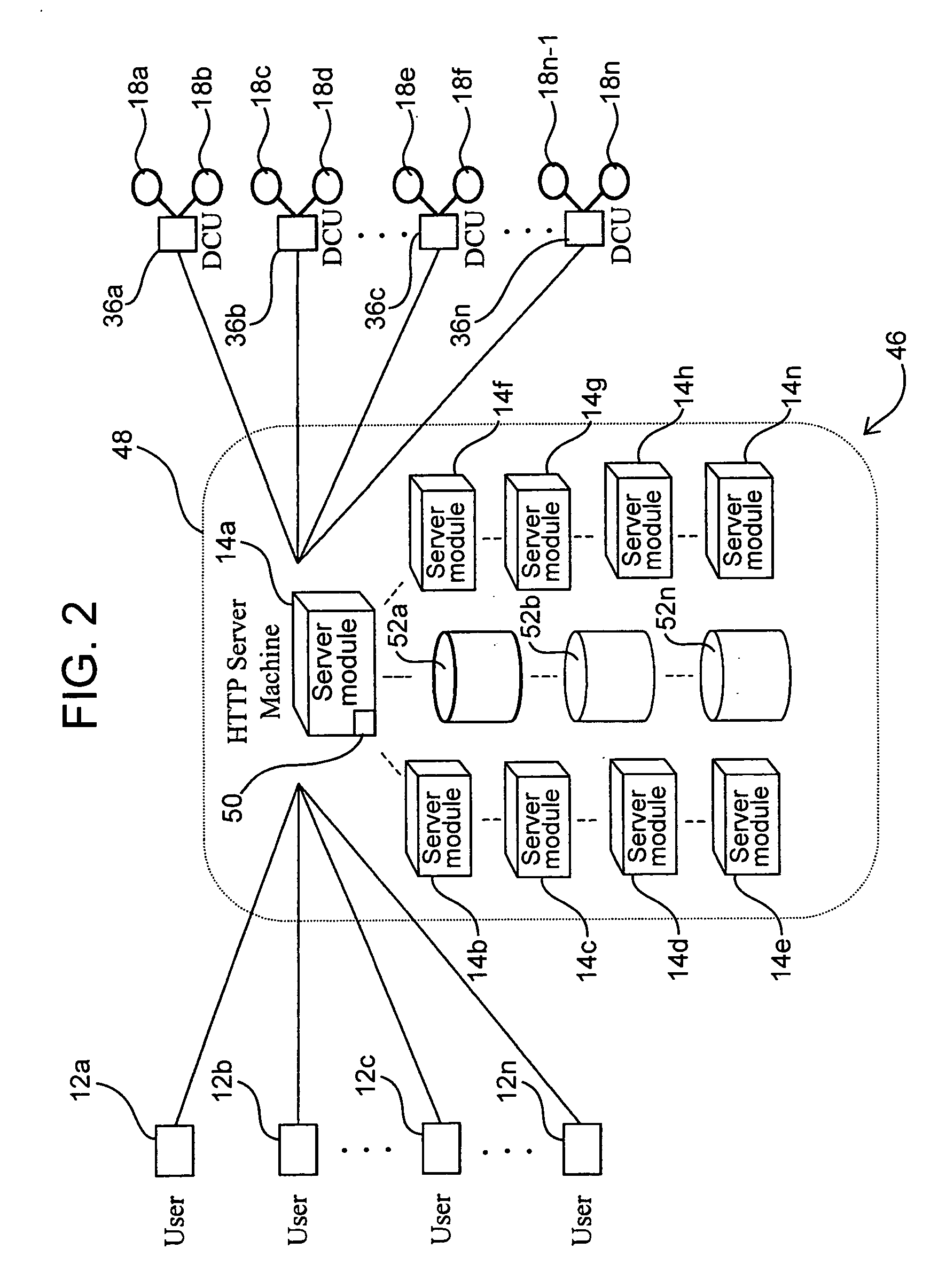
Access and control system for network-enabled devices
InactiveUS20050268334A1Reduce computational overheadReduce communicationMultiple digital computer combinationsProgram controlControl systemSecure transmission
Systems and methods for remote access of network-enabled devices that provide seamless, firewall-compliant connectivity between multiple users and multiple devices, that allow collaborative operations by multiple users of remote devices, that allow point to multipoint control of multiple devices and which allow rapid, secure transmission of data between remote users and devices. In general terms, the system includes at least one connection server, and at least two computers operatively coupled to the connection server via a public or global network. In an example where at least one client computer is operatively connected to at least one network-enabled device through a connection sever via the public or global network, the connection server is configured to route control instructions from the client to the network-enabled device, and route data from the network-enabled device to the client.
Owner:WESTERN DIGITAL TECH INC
Navigation system with intersection and three-dimensional landmark view
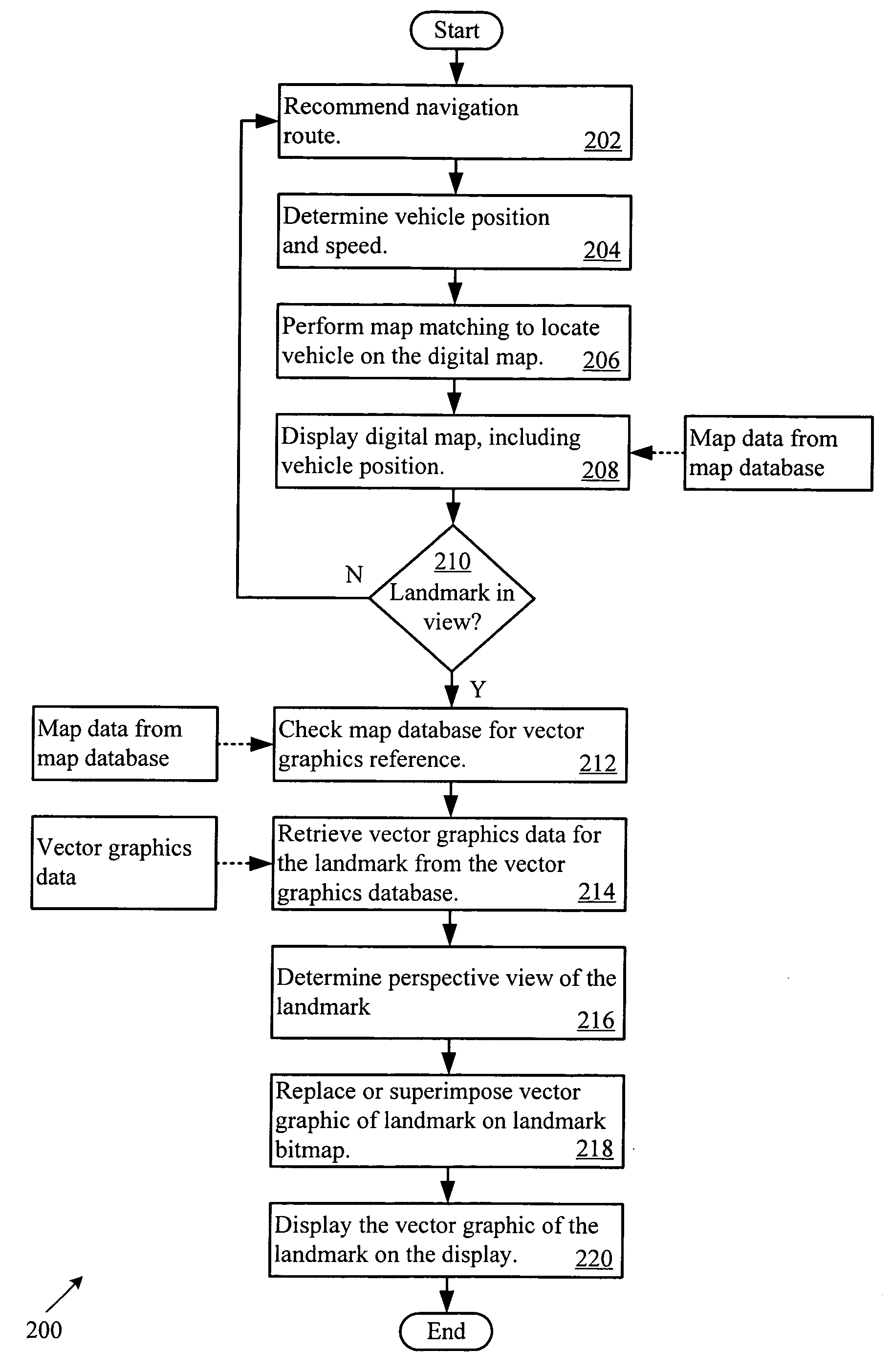
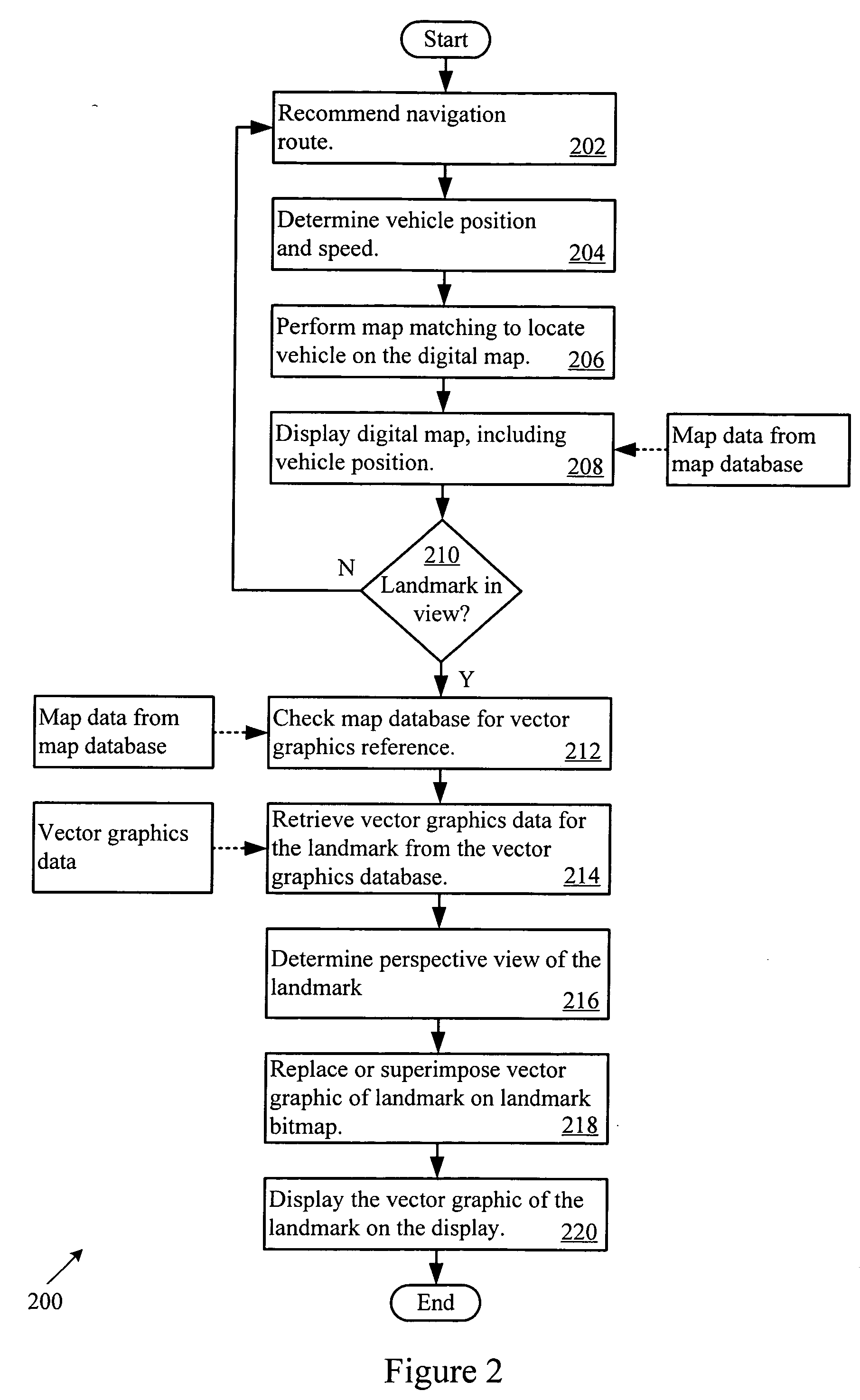
InactiveUS20060287819A1Reduce computational overheadEnhance image qualityInstruments for road network navigationRoad vehicles traffic controlDistortionImage resolution
A vehicle navigation system helps guide a driver to a destination by enhancing visualization of landmarks and upcoming intersections. The navigation system stores resolution independent representations of the landmarks and intersections. The representations allow the navigation system to quickly and efficiently resize and render the landmarks and intersections without distortion and with reduced computational burden. When the vehicle approaches a landmark or intersection, the navigation system may retrieve the representation, mathematically scale the representation, adjust the perspective of the representation, and render a view of the upcoming landmarks and intersection to aid the driver with reaching the destination.
Owner:HARMAN BECKER AUTOMOTIVE SYST
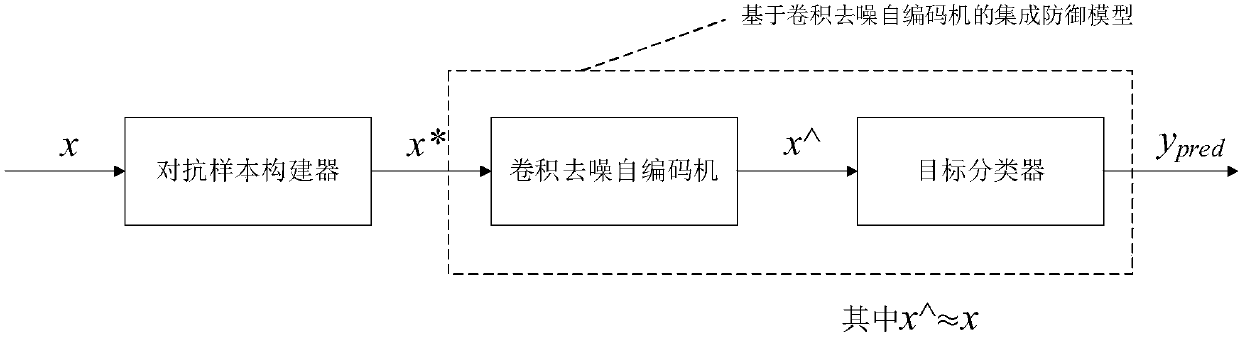
Method for defense of attack of adversarial examples based on convolutional denoising auto-encoder
ActiveCN108537271AImprove classification accuracyStrong explainabilityCharacter and pattern recognitionPattern recognitionDenoising auto encoder
The present invention relates to a method for defense of attack of adversarial examples based on a convolutional denoising auto-encoder. Adversarial image examples x* (output tags identified by an image classification device is y*) are constructed by manual addition of adversarial disturbance on clean image samples x without modification (output tags identified by the image classification device is y), the fraud purpose that y* is not equal to y can be achieved, even though the image classification device classifies two images essentially showing the same meaning to two classes by mistake. Thepresent invention designs an integration defense model connected with a target image classifier based on a convolutional denoising auto-encoder (CDAE), namely input samples are subjected to coding and decoding at the internal portion of a well trained CDAE to remove most of adversarial disturbances in the input samples so as to output denoising samples close to original clean samples, and then are transmitted to the target image classifier so as to improve the classification correction of the target classifier and have an effect for defense of attack of adversarial examples.
Owner:CHONGQING UNIV
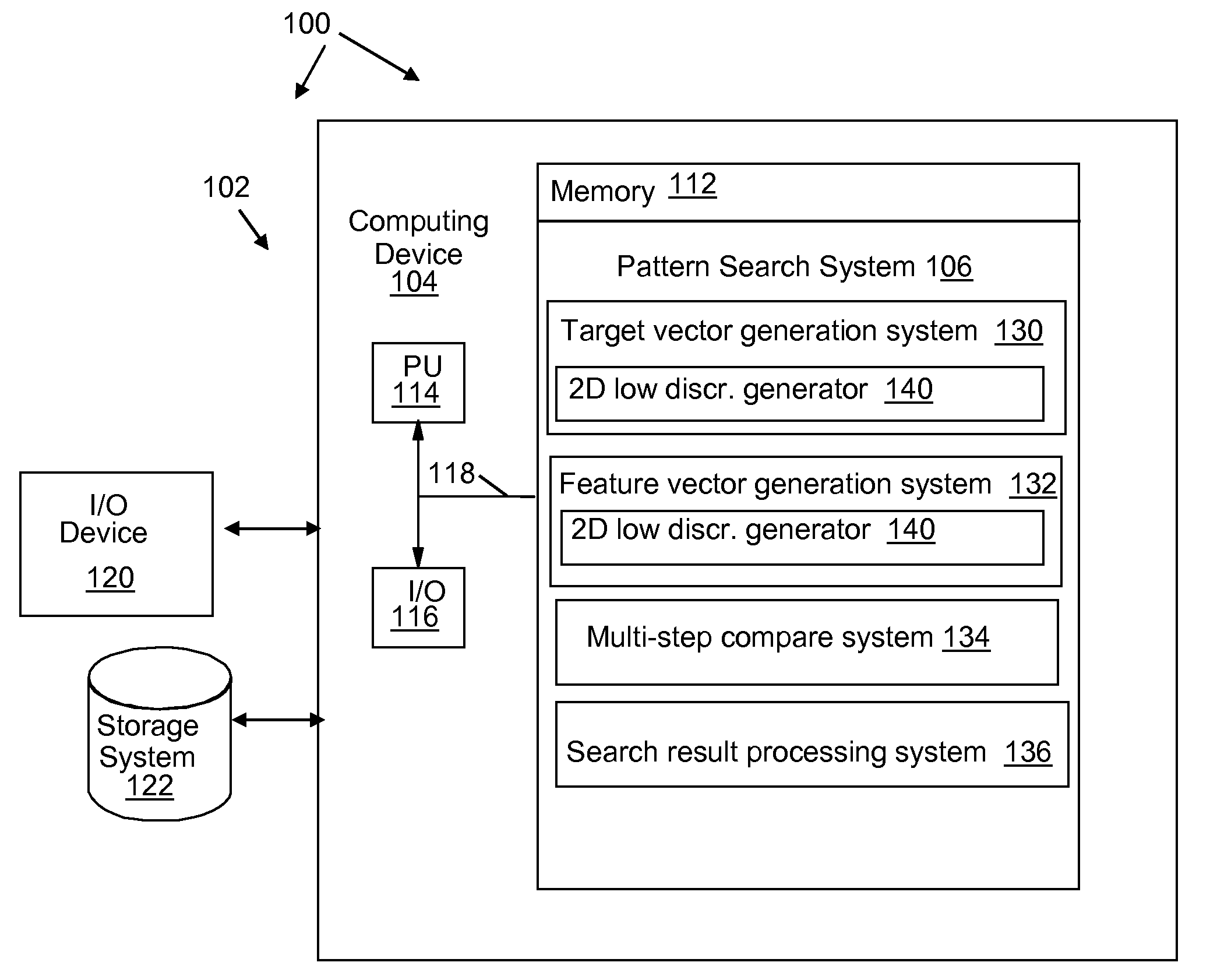
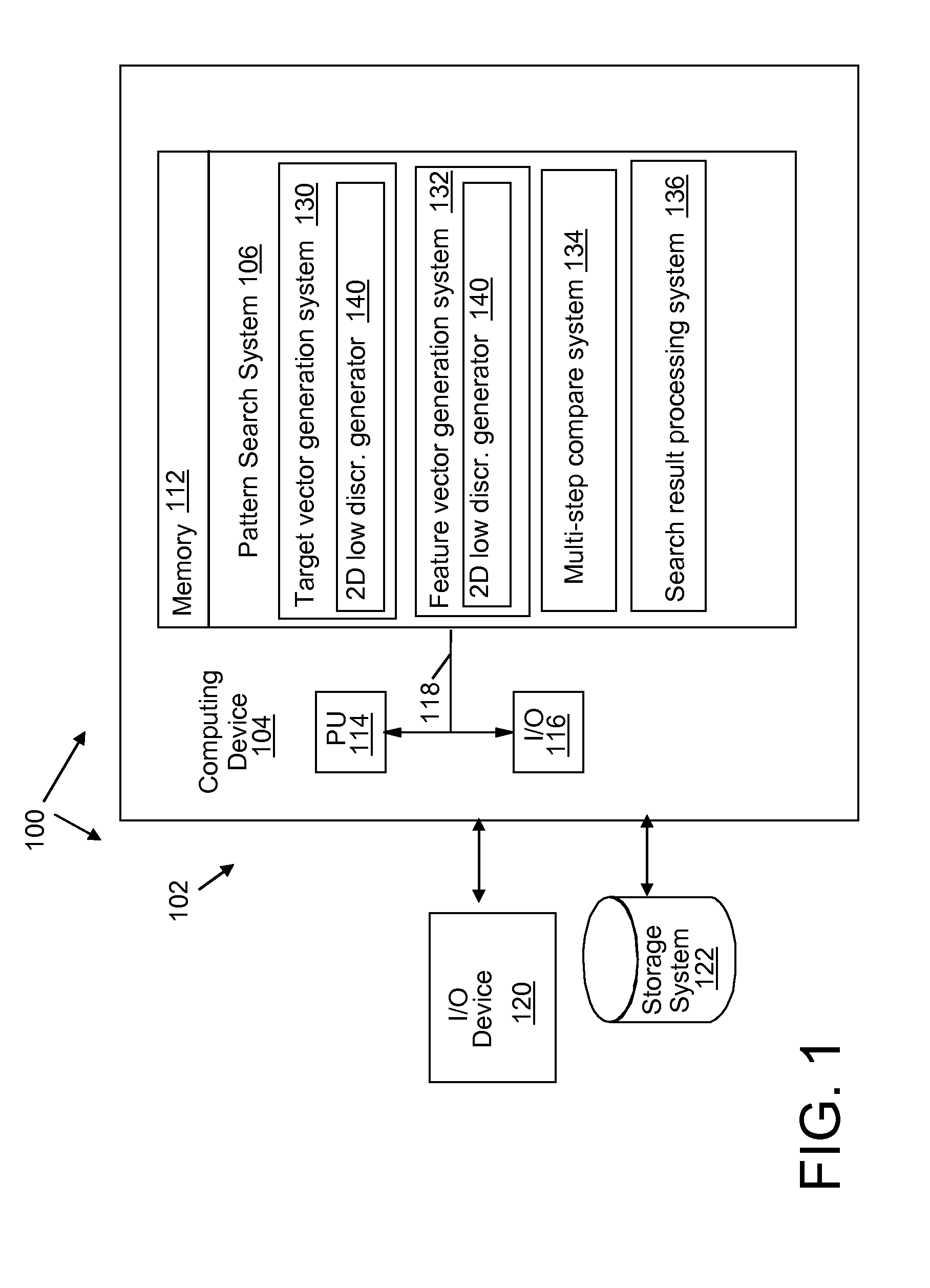
Feature extraction that supports progressively refined search and classification of patterns in a semiconductor layout
InactiveUS20080320421A1Reduce computational overheadLow sequenceDetecting faulty computer hardwareComputer aided designFeature vectorFeature extraction
A system, method and program product for searching and classifying patterns in a VLSI design layout. A method is provided that includes generating a target vector using a two dimensional (2D) low discrepancy sequence; identifying layout regions in a design layout; generating a feature vector for a layout region; comparing a subset of sequence values in the target vector with sequence values in the feature vector as an initial filter, wherein the system for comparing determines that the layout region does not contain a match if a comparison of the subset of sequence values in the target vector with sequence values in the feature vector falls below a threshold; and outputting search results.
Owner:IBM CORP
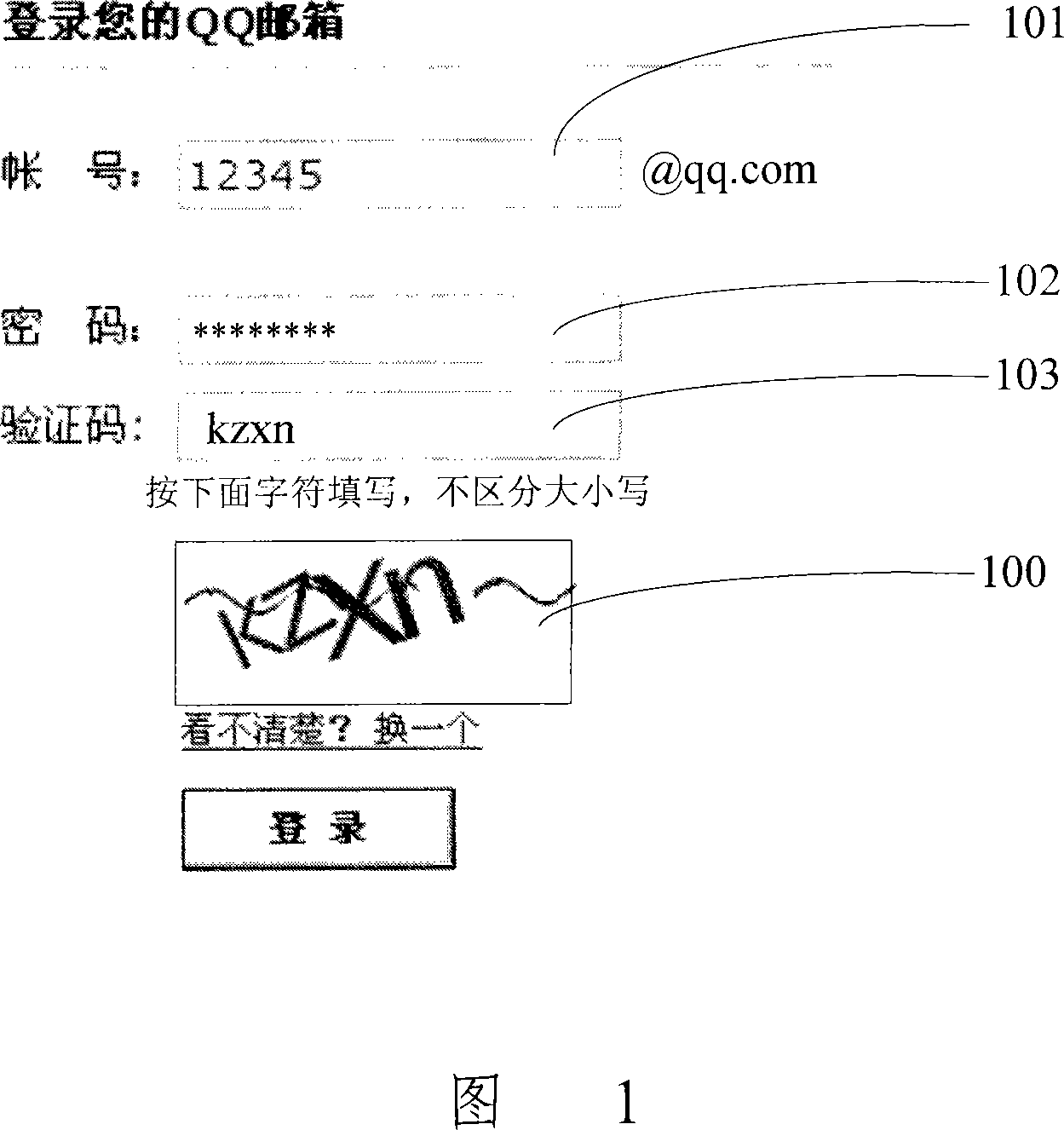
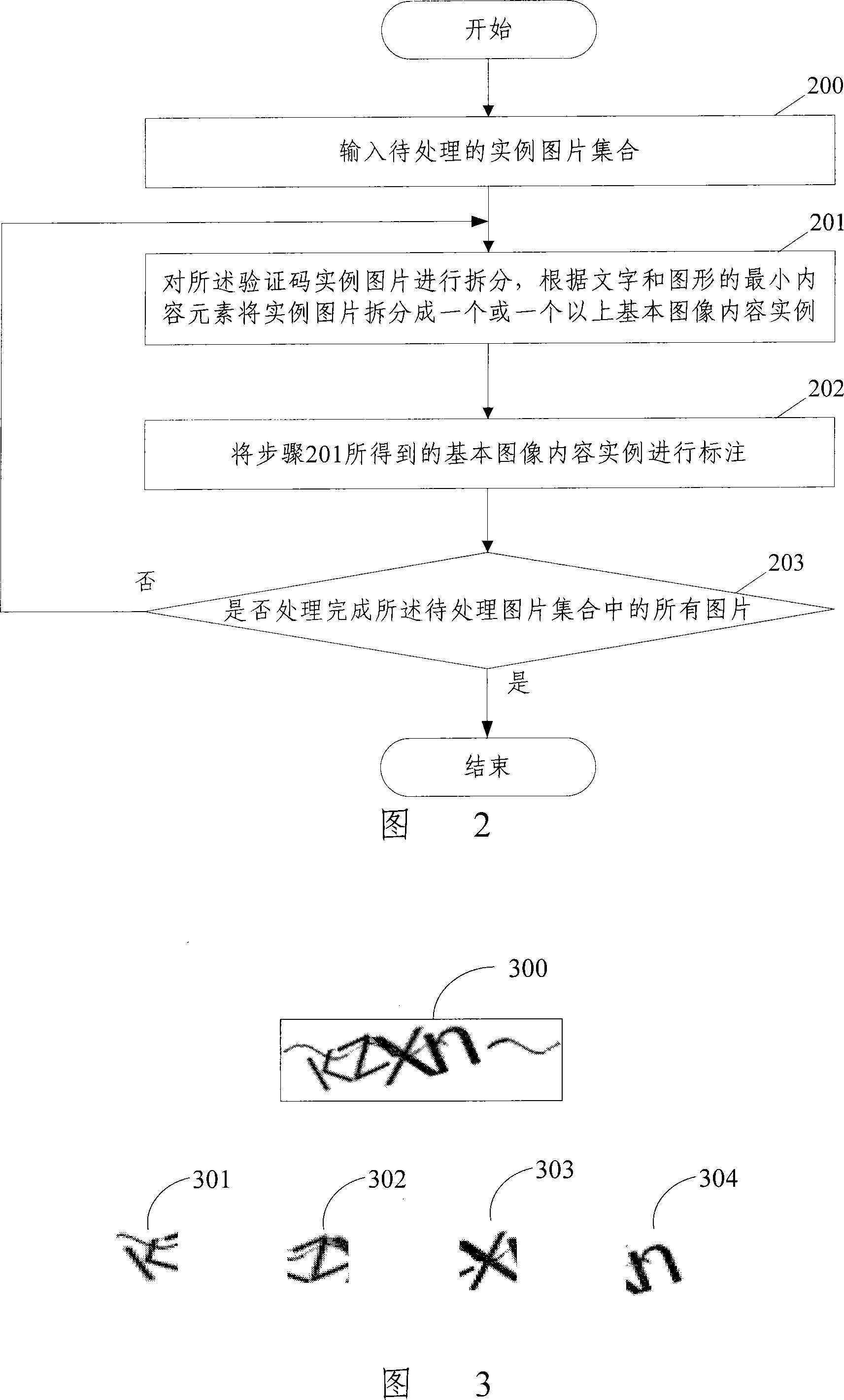
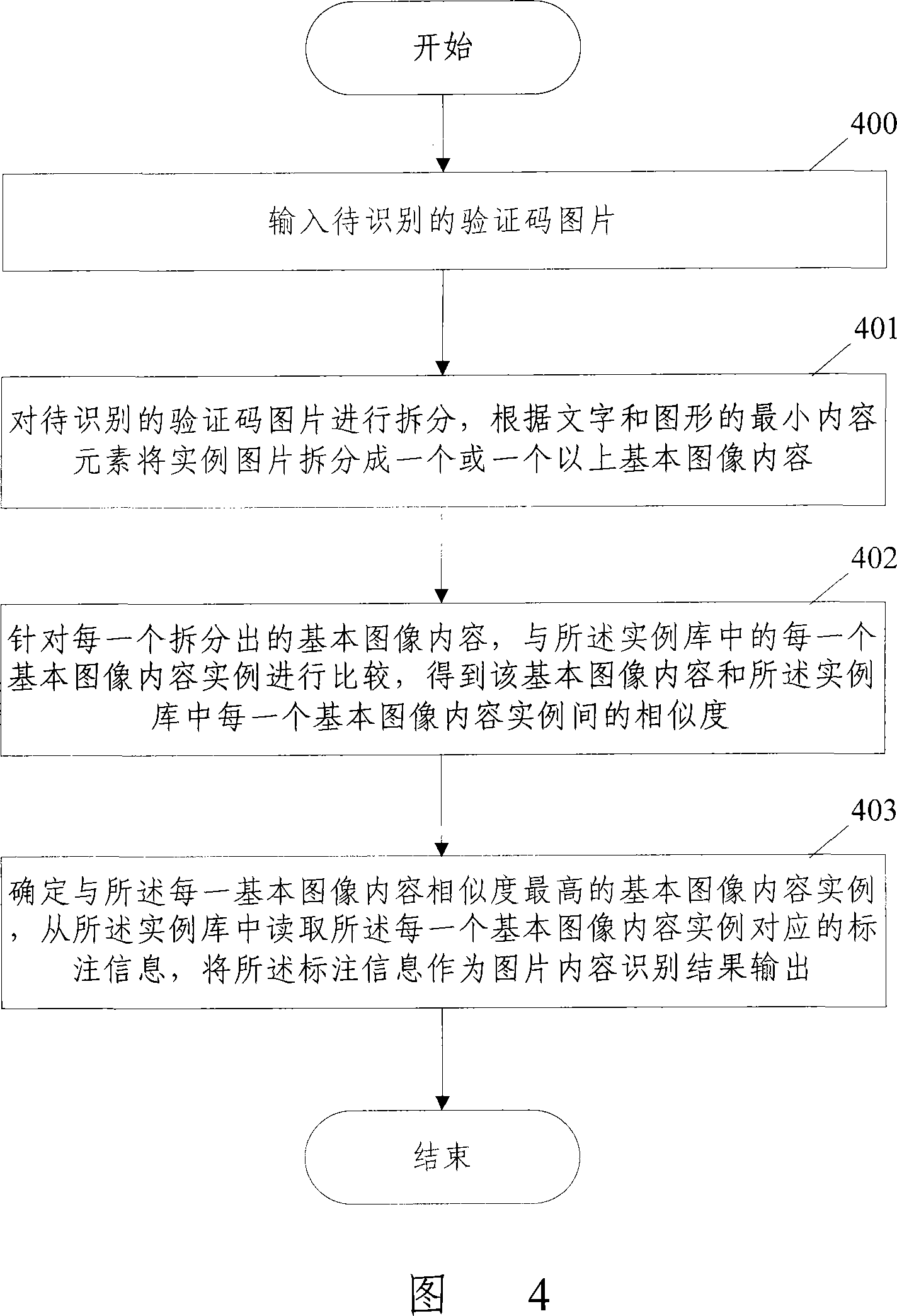
Image content recognizing method and recognition system
ActiveCN101196994AReduce computational overheadReduce occupancyUser identity/authority verificationCharacter and pattern recognitionComputer moduleComputer science
The present invention discloses a picture content identification method and system, wherein the method comprises the following steps that basic image content examples and corresponding marking information are stored in an example base beforehand. During identification, one or more than one item of basic image content is split from a to-be-identified picture by a split module; the split basic image content is compared with the basic image content examples in the example base by a similarity comparison module, obtaining corresponding similarity; a result output module determines the basic image content example having the highest similarity with each item of the basic image content, and outputs the marking information corresponding to the basic image content examples as a picture content identification result. The present invention can decrease the computation cost of computers and the occupancy to system resources, and can enlarge the species of recognizable content.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
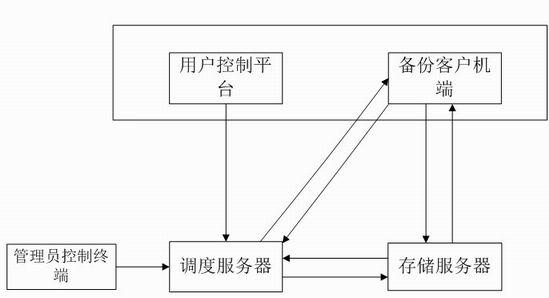
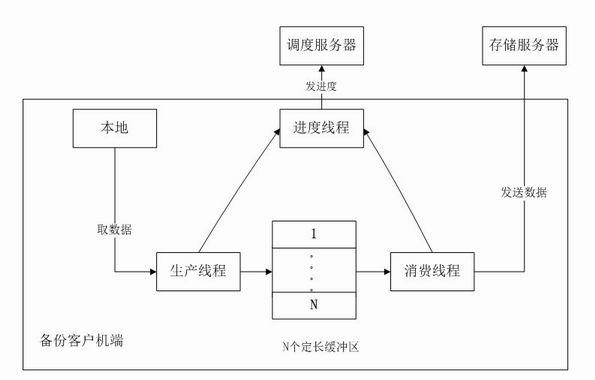
Data stand-by system based on finger print
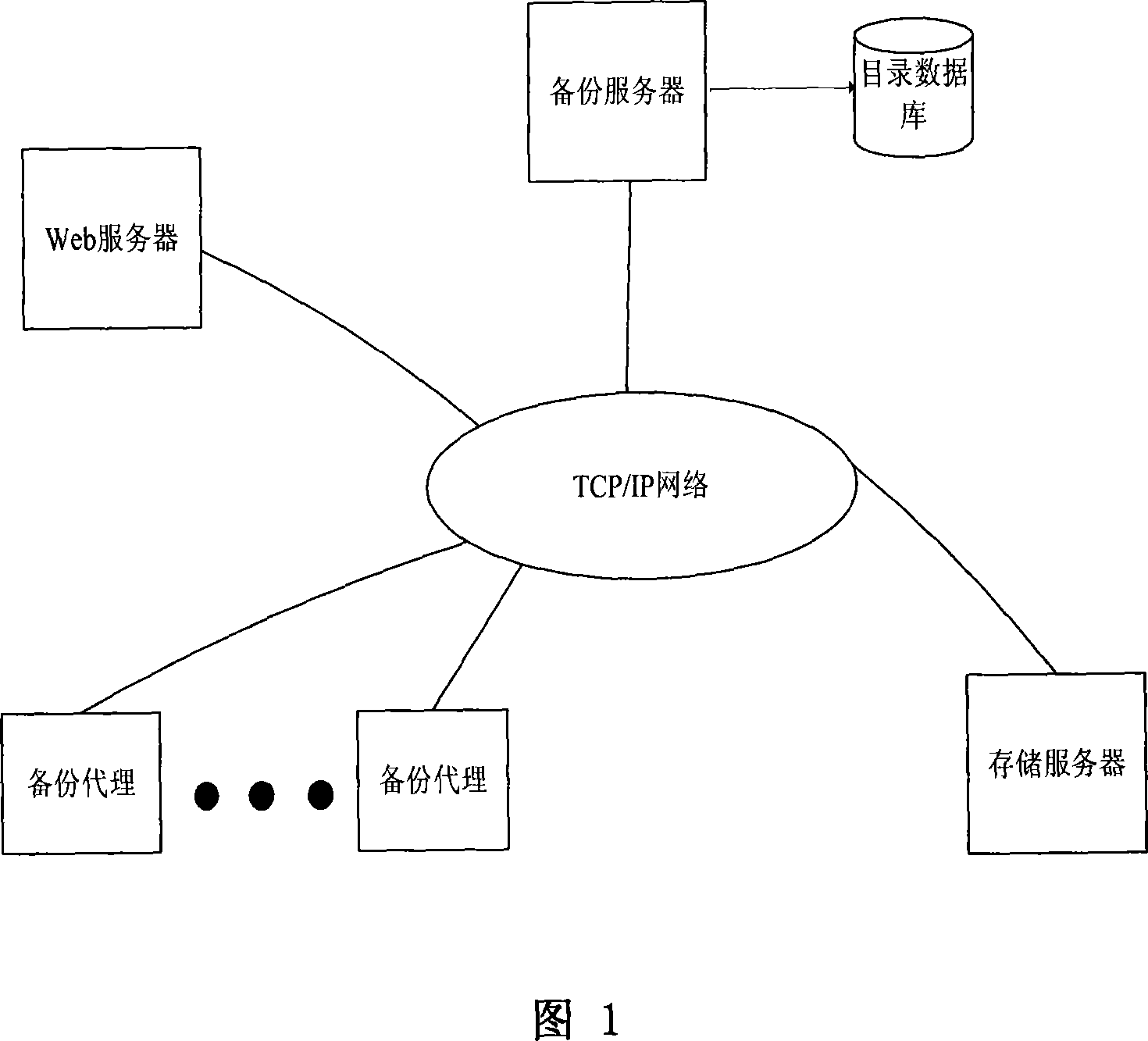
InactiveCN101183323AReduce computational overheadHas modification stabilityMultiprogramming arrangementsTransmissionComplete dataApplication server
The invention relates to a data backup system based on fingerprints, belonging to the technical field of computer storage backup, which aims at reducing management, storage and network overhead of data backup and improving backup performance. The invention comprises a backup server, a backup agent, a storage server and a Web server which complete data backup and recovery through mutual network communication. The invention is characterized in that redundant data of backup files is recognized with the file segmentation technology based on anchors, thus the invention has the advantages that the modification stability is good and computation cost is low; data segmentations with fingerprints as the index are stored on a plurality of disk arrays of the storage server so as to eliminate backup of redundant data and save disk storage space; the data segmentations are not erased once stored and can be continuously appended on the disk so as to eliminate disk storage fragments; since the effective backup buffer strategy is adopted, the invention also has the advantages of reduced network overhead of backup, increased data backup speed and lowered backup influence to application servers.
Owner:HUAZHONG UNIV OF SCI & TECH
Access and control system for network-enabled devices
InactiveUS20060277314A1Reduce computational overheadReduce communicationMultiple digital computer combinationsElectric digital data processingControl systemSecure transmission
Systems and methods for remote access of network-enabled devices that provide seamless, firewall-compliant connectivity between multiple users and multiple devices, that allow collaborative operations by multiple users of remote devices, that allow point to multipoint control of multiple devices and which allow rapid, secure transmission of data between remote users and devices. In general terms, the system includes at least one connection server, and at least two computers operatively coupled to the connection server via a public or global network. In an example where at least one client computer is operatively connected to at least one network-enabled device through a connection server via the public or global network, the connection server is configured to route control instructions from the client to the network-enabled device, and route data from the network-enabled device to the client.
Owner:WESTERN DIGITAL TECH INC
Efficient cryptograph image retrieval method capable of supporting privacy protection under cloud environment
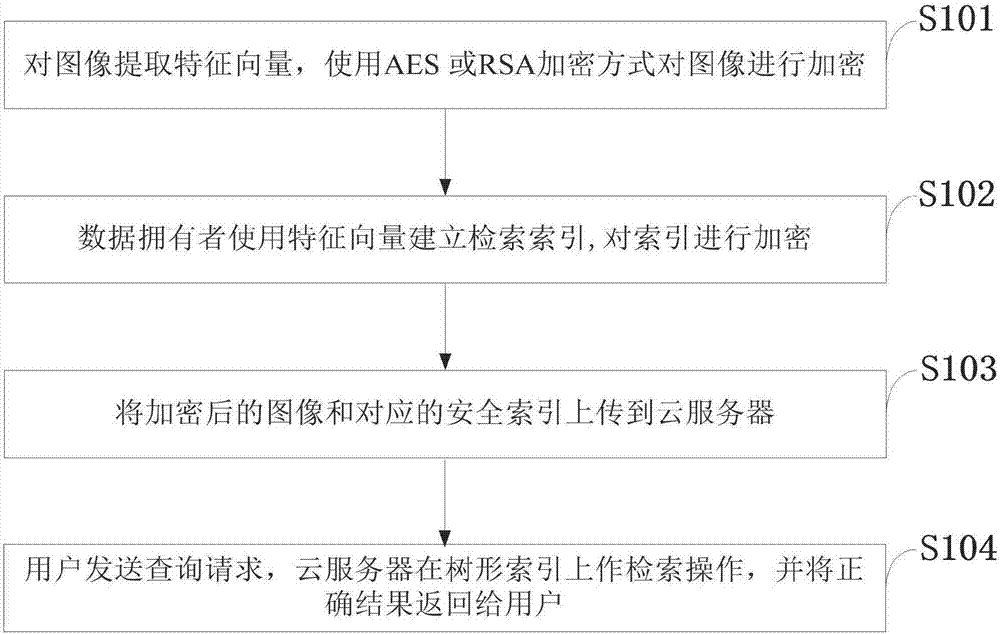
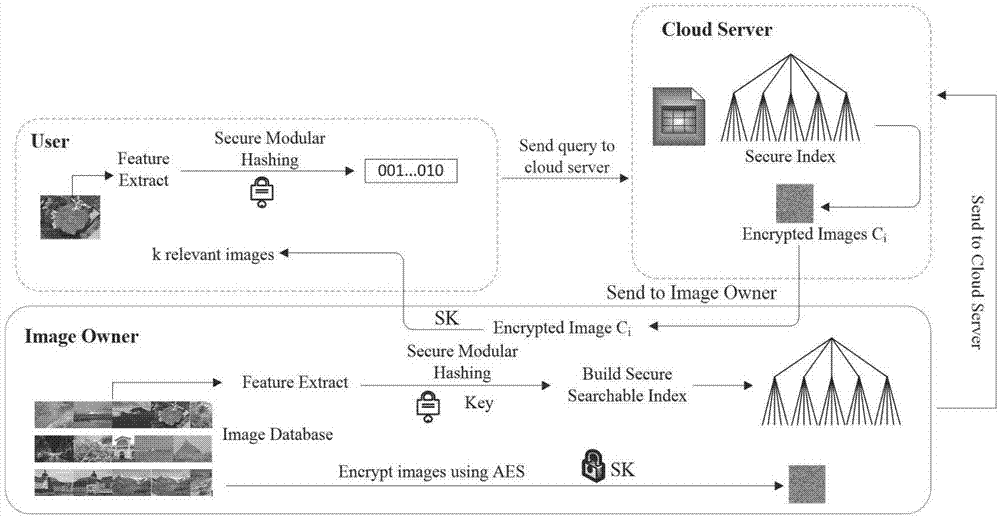
ActiveCN107480163AGuaranteed privacyReduce computational overheadImage data processing detailsTransmissionImage extractionPlaintext
The invention belongs to the technical field of image retrieval and discloses an efficient cryptograph image retrieval method capable of supporting privacy protection under a cloud environment. The efficient cryptograph image retrieval method capable of supporting the privacy protection under the cloud environment comprises the steps that an image owner firstly extracts characteristic vectors of an image in a database and encrypts the image by an AES or RSA encryption manner; the owner establishes indexes using a hierarchical K-means algorithm based on the characteristic vectors and uses a safe mode Hash technology to encrypt the indexes; and the encrypted image and indexes are uploaded to a cloud server, and a retrieval operation is executed. According to the invention, the privacy protection of the cryptograph image retrieval can be achieved, and retrieval accuracy equivalent with public image retrieval can be reached. In addition, detailed safety analysis of the disclosed method is conducted, and experimental assessment of efficiency and accuracy is conducted in different datasets. Results indicate that the method disclosed by the invention can reach expected safety targets, and can increase retrieval efficiency on the premise of ensuring retrieval accuracy.
Owner:XIDIAN UNIV
Dependence-based parallel task packet scheduling method used on multi-core cluster server
ActiveCN103235742AReduce usageReduce idle timeEnergy efficient ICTResource allocationIdle timeResource utilization
The invention particularly discloses a dependence-based parallel task packet scheduling method used on an isomorphic multi-core cluster server. Through calculating the dependence between execution paths and under the premise of not increasing the maximum loads of the execution paths, execution paths with large dependence are combined, compared with the original algorithm, the method can reduce unnecessary task duplication expenditure, communication expenditure between processors and the idle time energy consumption of the processors are reduced, the load of the processors is more balanced, and the overall energy consumption is lowered. The dependence-based parallel task packet scheduling method has the greatest features that the number of the processors is effectively reduced, the resource utilization efficiency is improved, the load of the processors is more balanced, and accordingly, the overall energy consumption is reduced.
Owner:济南云腾智能科技有限公司
Cancellation-supported outsourcing verifiable multi-authorization center access control method, and cloud server
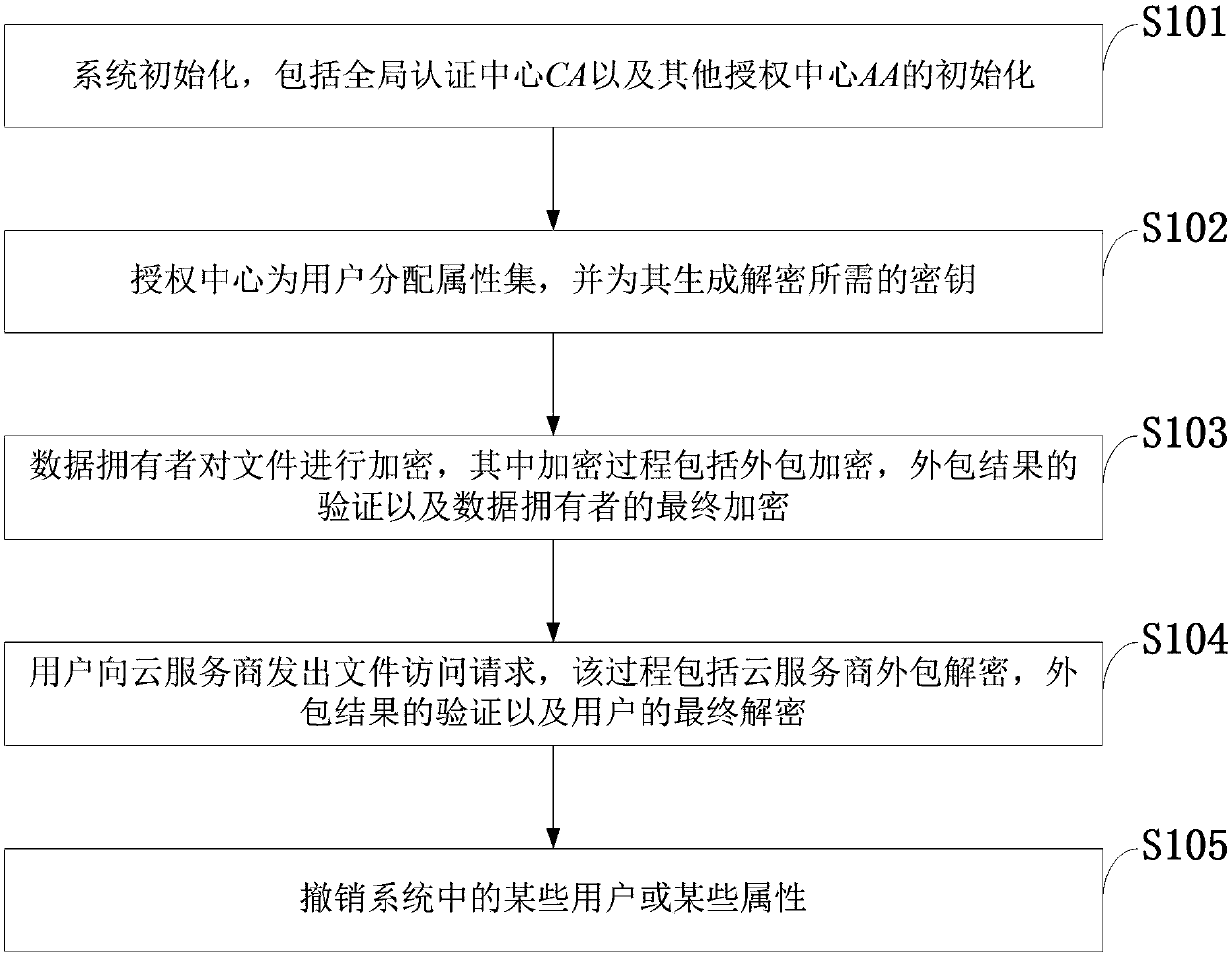
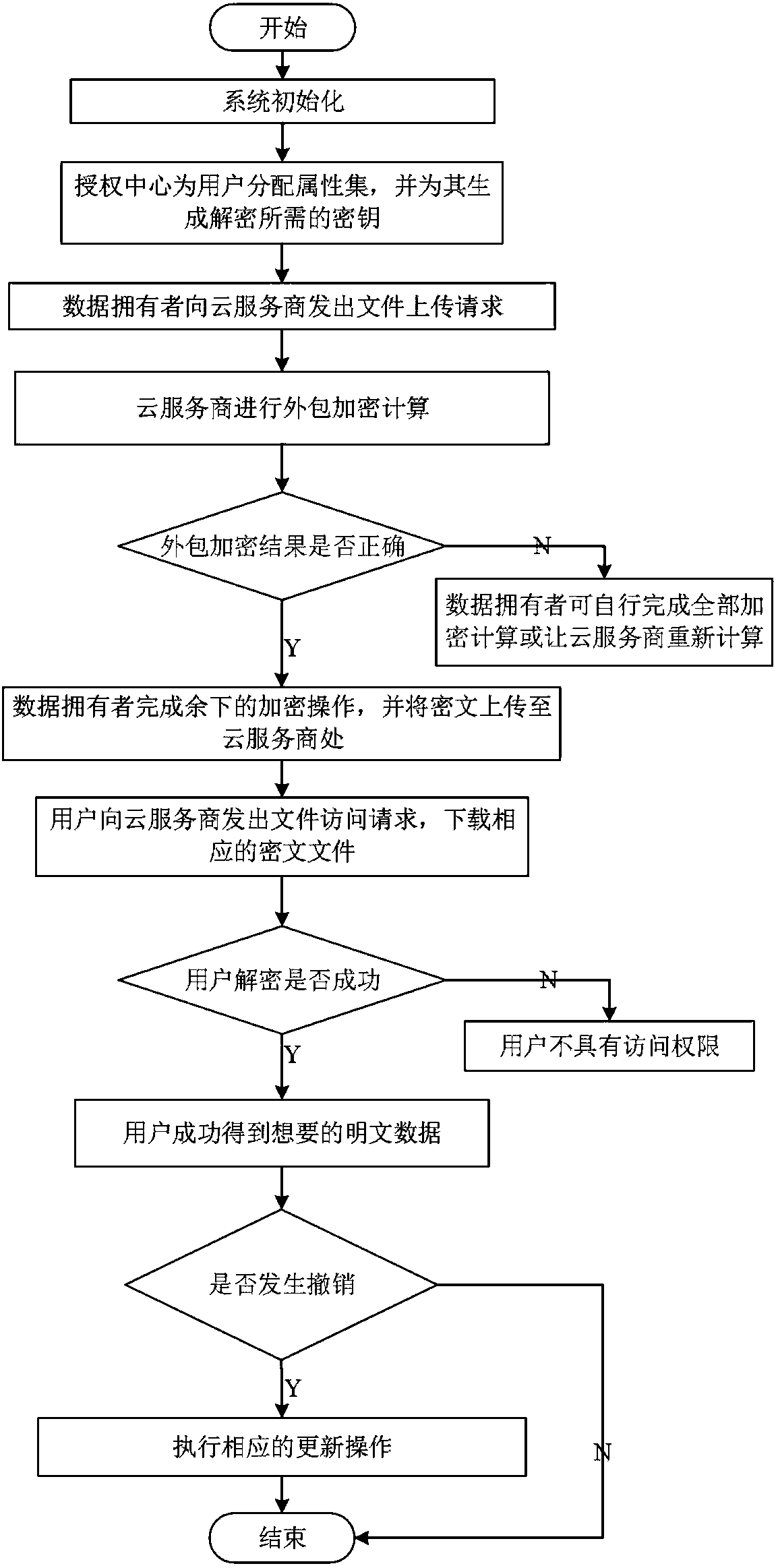
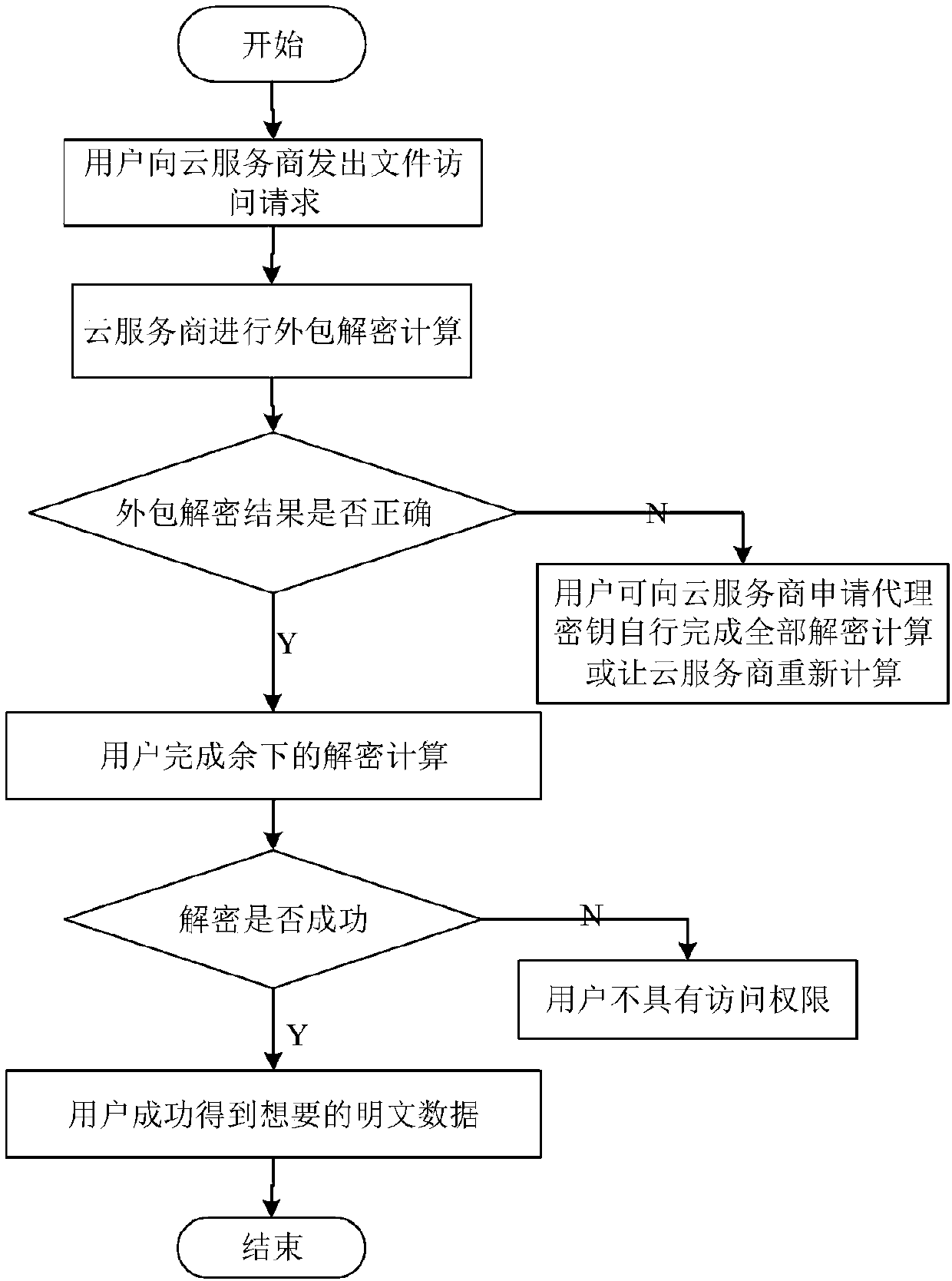
ActiveCN108390876ARich domainImprove efficiencyKey distribution for secure communicationUser PrivilegeCloud storage
The invention belongs to the technical field characterized by a protocol, and discloses a cancellation-supported outsourcing verifiable multi-authorization center access control method, and a cloud server. The method comprises the following steps: system initialization, including the initialization of a global authentication center and other authorization centers; allocating an attribute set for auser by the authorization centers, and generating a secret key needed by decryption for the user; encrypting a file by a data owner, wherein the encryption process comprises outsourcing encryption, the verification of an outsourcing result and the final encryption of the data owner; issuing a file access request to a cloud service provider by the user, wherein the process includes cloud service provider outsourcing decryption, the verification of the outsourcing result, and the final decryption of the user; and cancelling some users or some attributes in a system. The cancellation-supported outsourcing verifiable multi-authorization center access control method provided by the invention has the advantages of being high in system access efficiency, low in computation overhead, capable of supporting dynamic user authority management and the like, and can be used for guaranteeing the privacy data safety of the user in cloud storage, reducing the computation overhead of the user and dynamically managing the authority of the user in the system.
Owner:XIDIAN UNIV
Efficient verifiable multi-keyword sequencing searchable encryption method supporting preference search and logic search
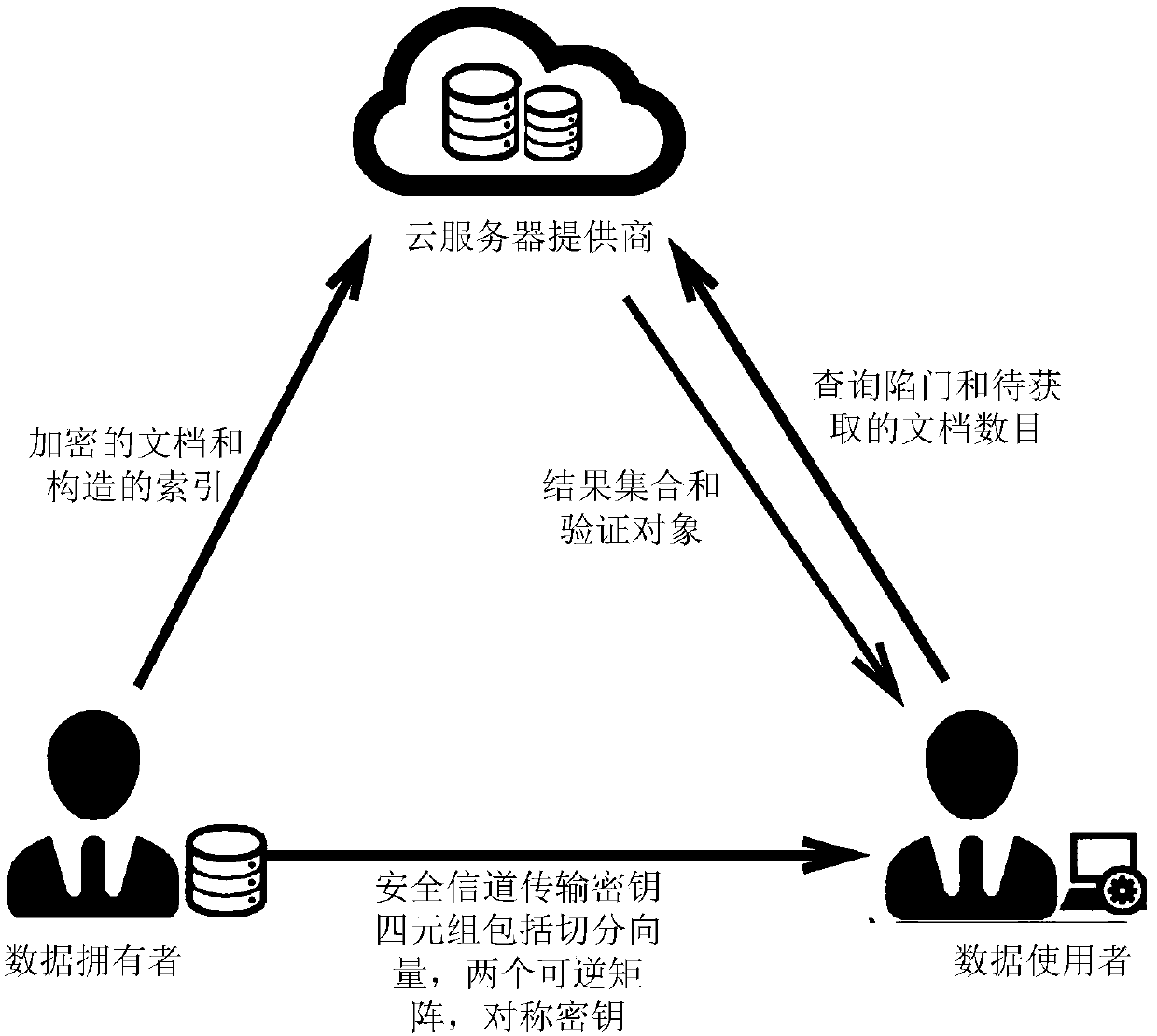
ActiveCN108388807AEffective pruningNarrow down the search spaceDigital data protectionTransmissionCiphertextCryptogram
The invention discloses an efficient verifiable multi-keyword sequencing searchable encryption method supporting a preference search and a logic search. The encryption method comprises the following steps that a data owner encrypts a document, constructs a cryptogram index based on a document collection, generates summary information of the document by utilizing a secret key and the content of thedocument, and then sends a cryptogram document, an encrypted index and the summary information to a cloud server; a data user shares the information of the secret key, which is generated by the dataowner, generates a query trap door according to a query, and sends an encrypted query trap door and the number K of to-be-obtained documents to the cloud server; the cloud server can execute safe inner product operation after receiving the cryptogram index and the query trap door, searches for K documents most relevant to the query of the user, sequences according to relevant values among the K documents and the query, then generates verification objects, and finally returns the most relevant K documents and the verification objects to the data user, and the data user verifies the correctnessand completeness of a return result through a verification algorithm.
Owner:SOUTH CHINA UNIV OF TECH
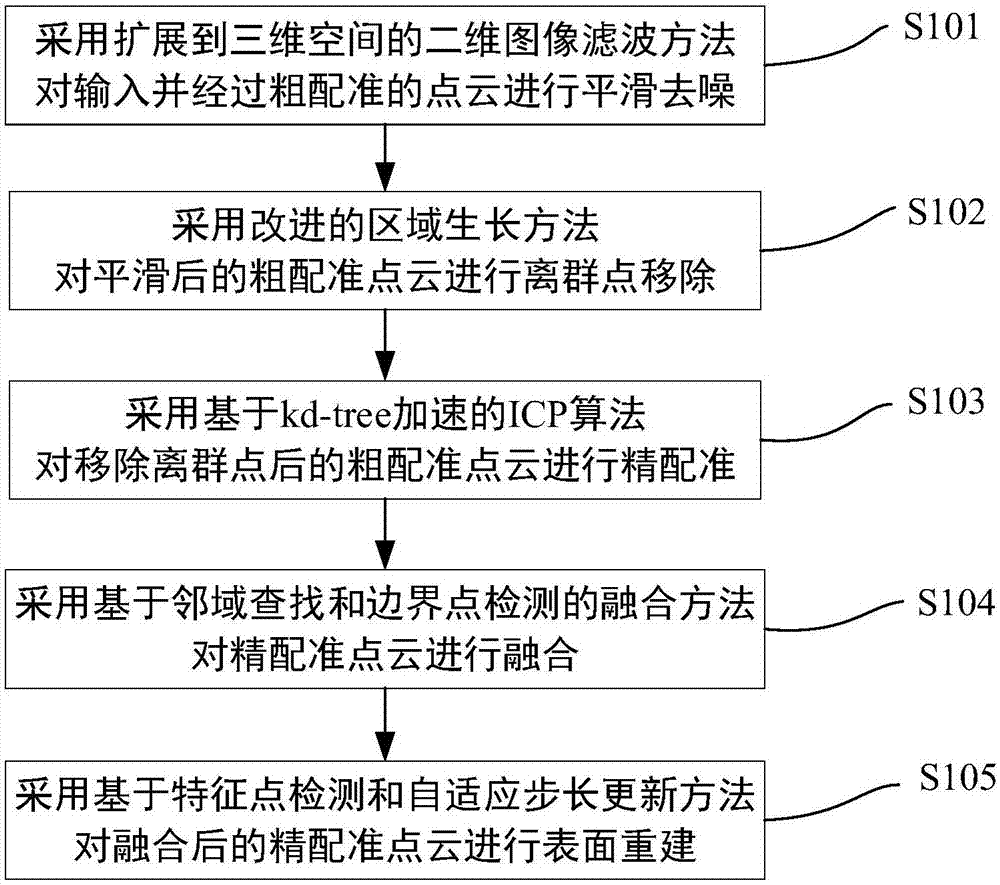
Three-dimensional reconstruction method and system capable of maintaining sharp features
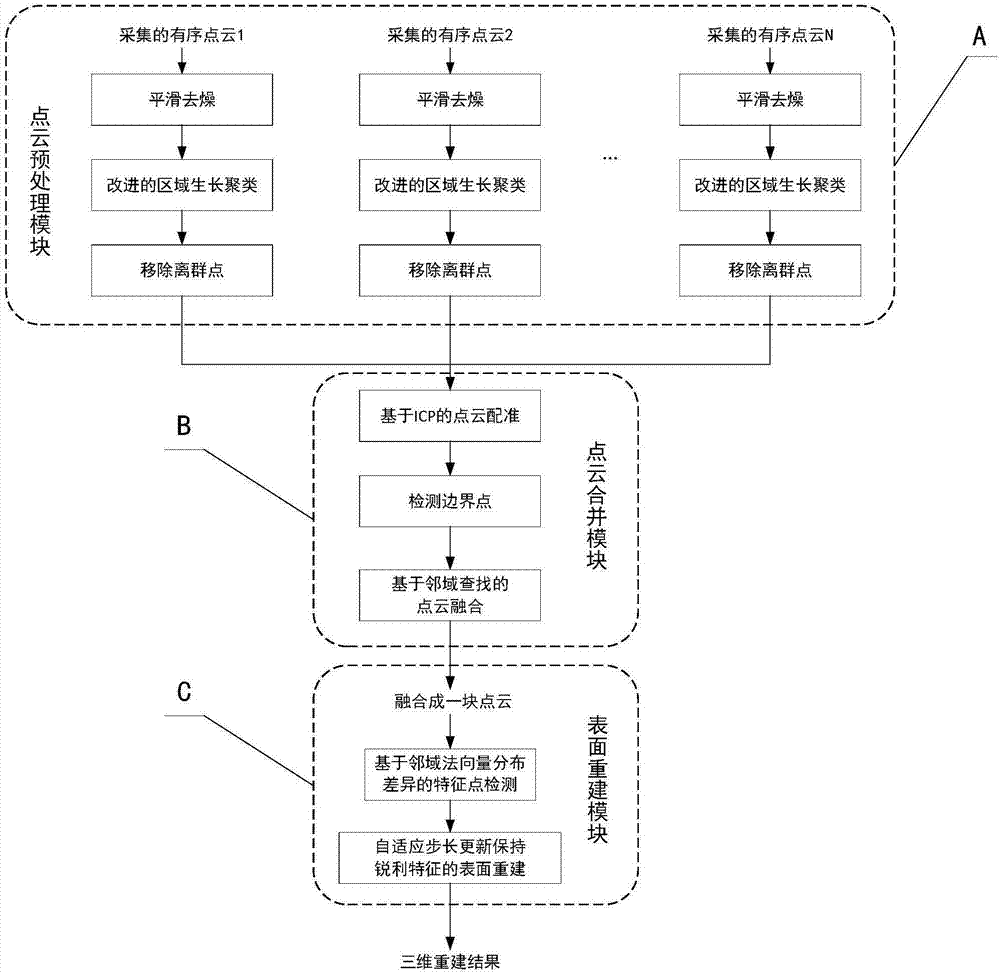
The present invention discloses a three-dimensional reconstruction method and system capable of maintaining sharp features. The method includes the following steps that: 1) a two-dimensional image filtering method extended to a three-dimensional space is adopted to perform smoothing de-noising on inputted roughly-registered point cloud; 2) an improved region growth method is adopted to perform outlier removal on the smoothed roughly-registered point cloud; 3) a kd-tree (k-dimensional tree) acceleration-based ICP (iterative closest point) algorithm is adopted to perform precise registration on the outlier-removed roughly-registered point cloud; 4) a neighborhood search and boundary point detection-based fusion method is adopted to fuse the precisely-registered point cloud; and 5) a feature point detection and adaptive step size update-based method is adopted to perform surface reconstruction on the fused precisely-registered point cloud. The three-dimensional reconstruction system is composed of a point cloud preprocessing module, a point cloud combining module and a surface reconstruction module. The three-dimensional reconstruction system which is realized based on the method of the invention can maintain the sharp features of the edge of a reconstructed model, and therefore, reconstruction speed is considered with accuracy ensured.
Owner:SOUTH CHINA UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com