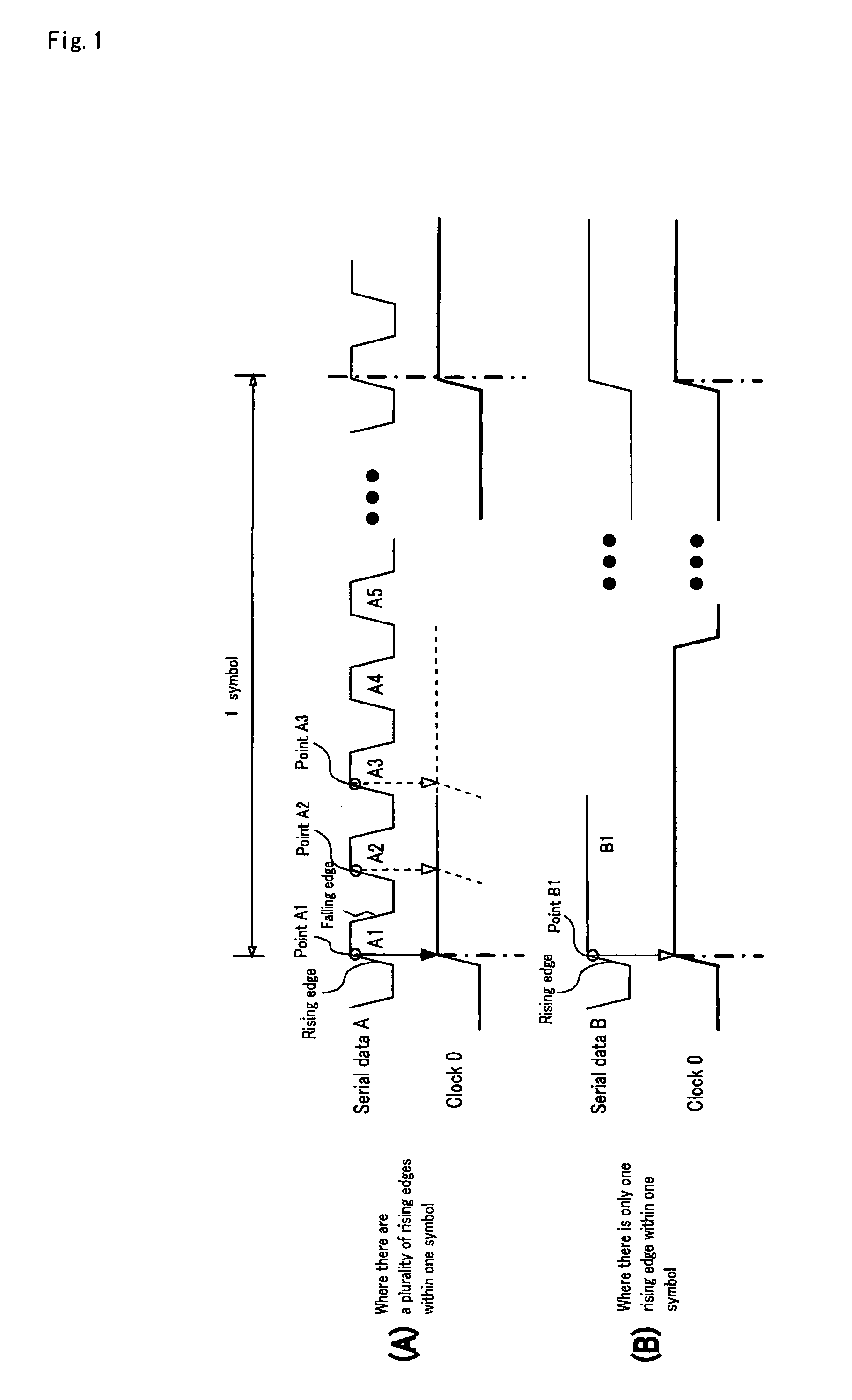
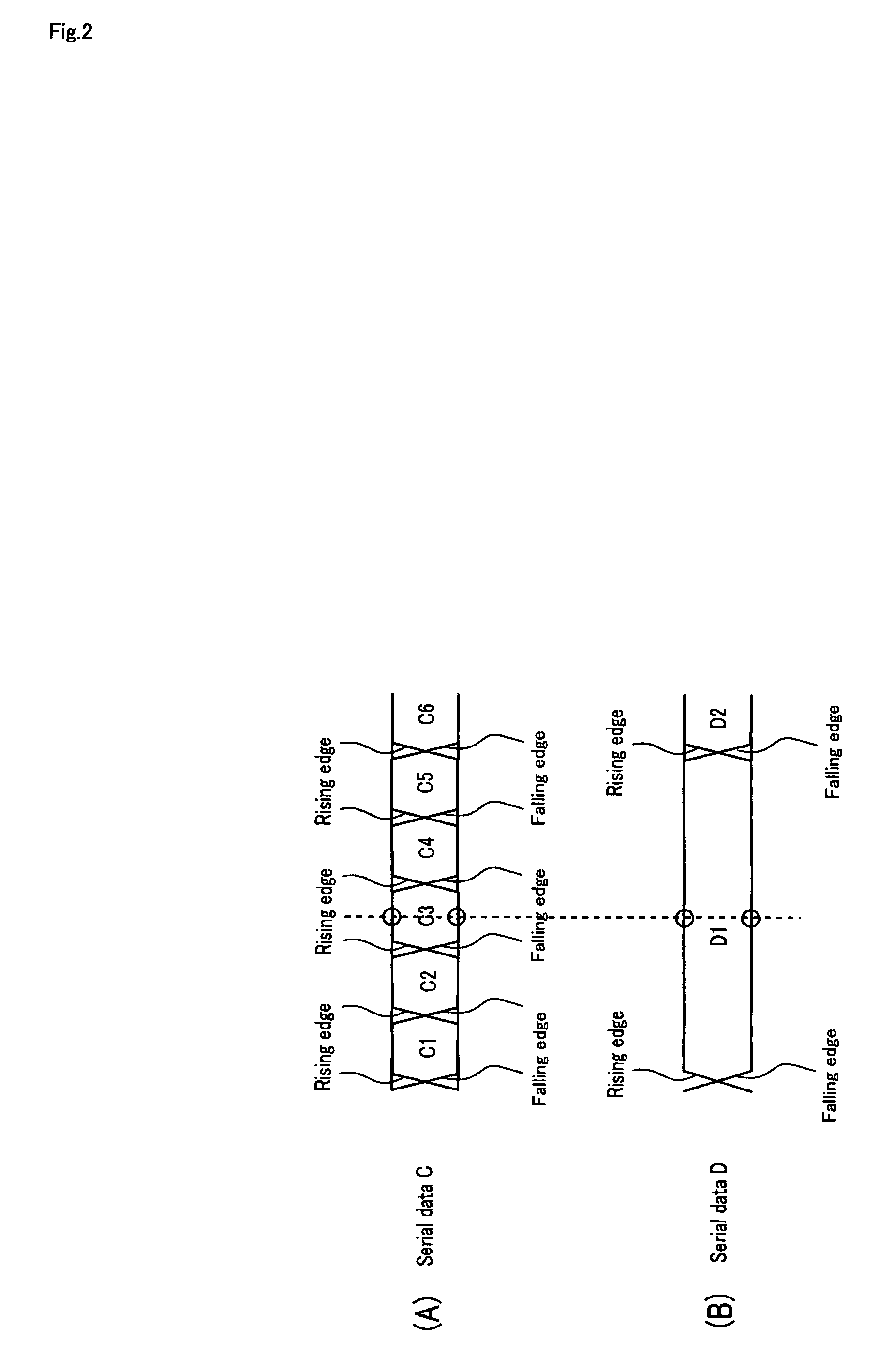
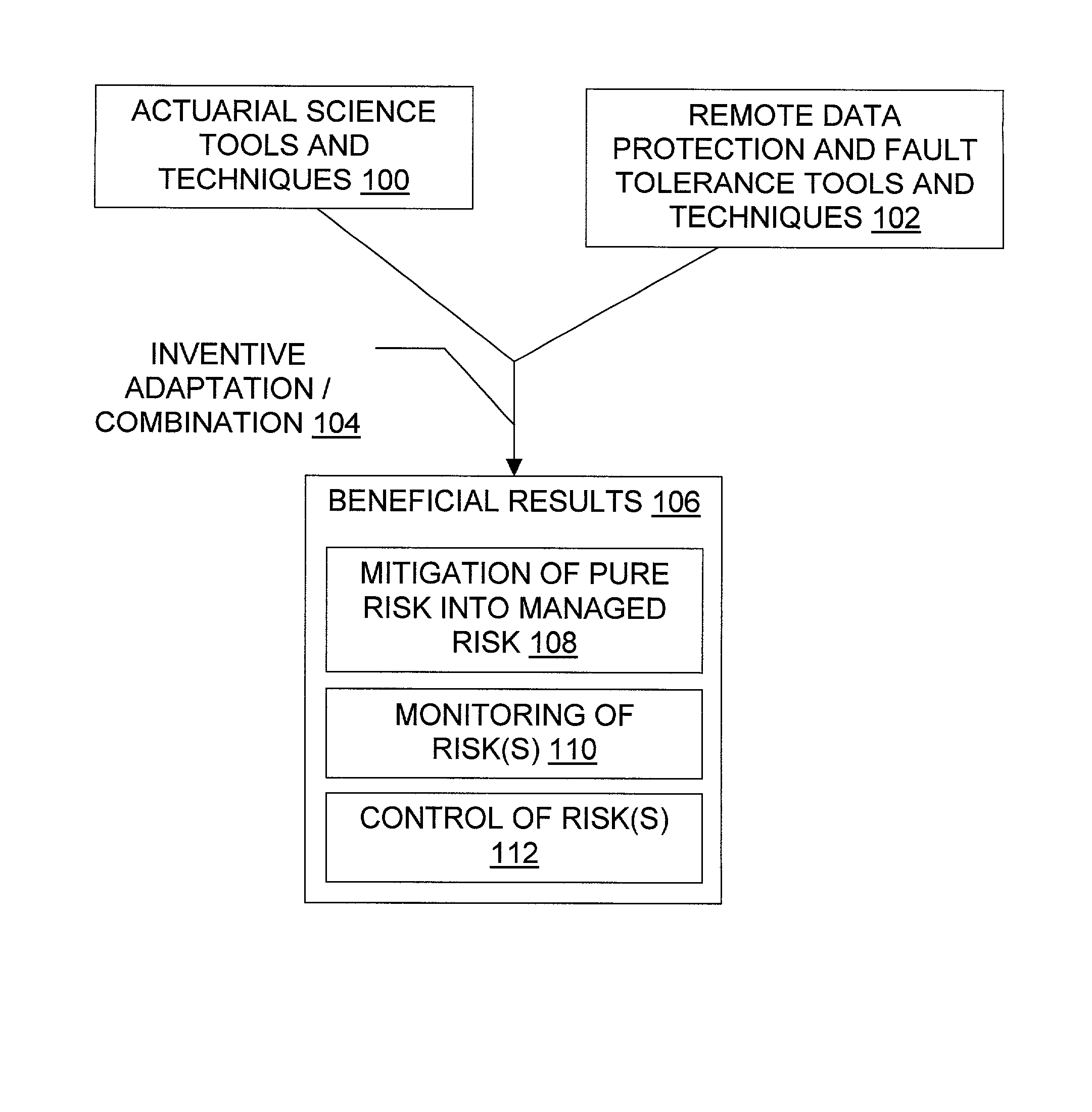
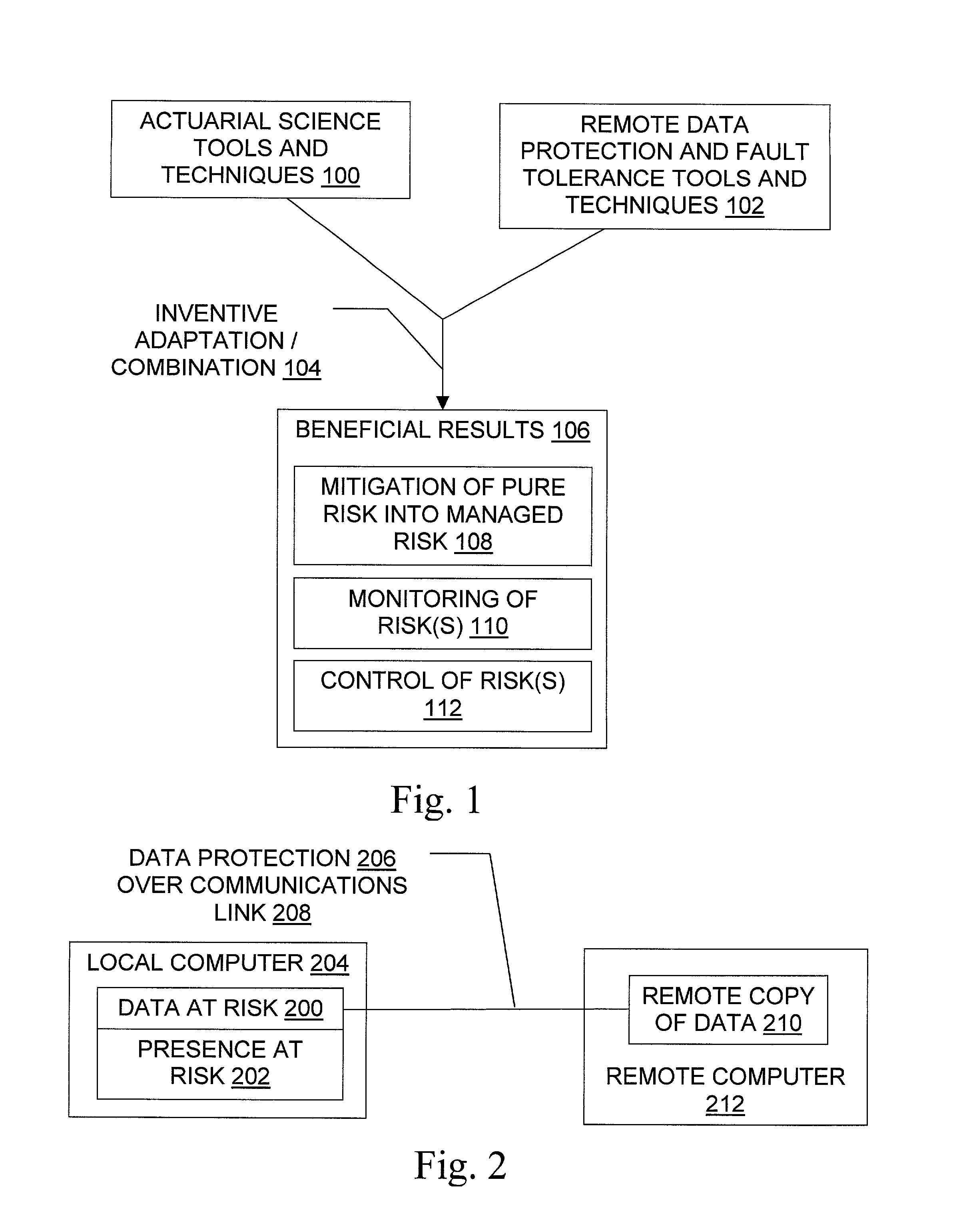
Patents
Literature
4248 results about "Data recovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, data recovery is a process of salvaging (retrieving) inaccessible, lost, corrupted, damaged or formatted data from secondary storage, removable media or files, when the data stored in them cannot be accessed in a normal way. The data is most often salvaged from storage media such as internal or external hard disk drives (HDDs), solid-state drives (SSDs), USB flash drives, magnetic tapes, CDs, DVDs, RAID subsystems, and other electronic devices. Recovery may be required due to physical damage to the storage devices or logical damage to the file system that prevents it from being mounted by the host operating system (OS).
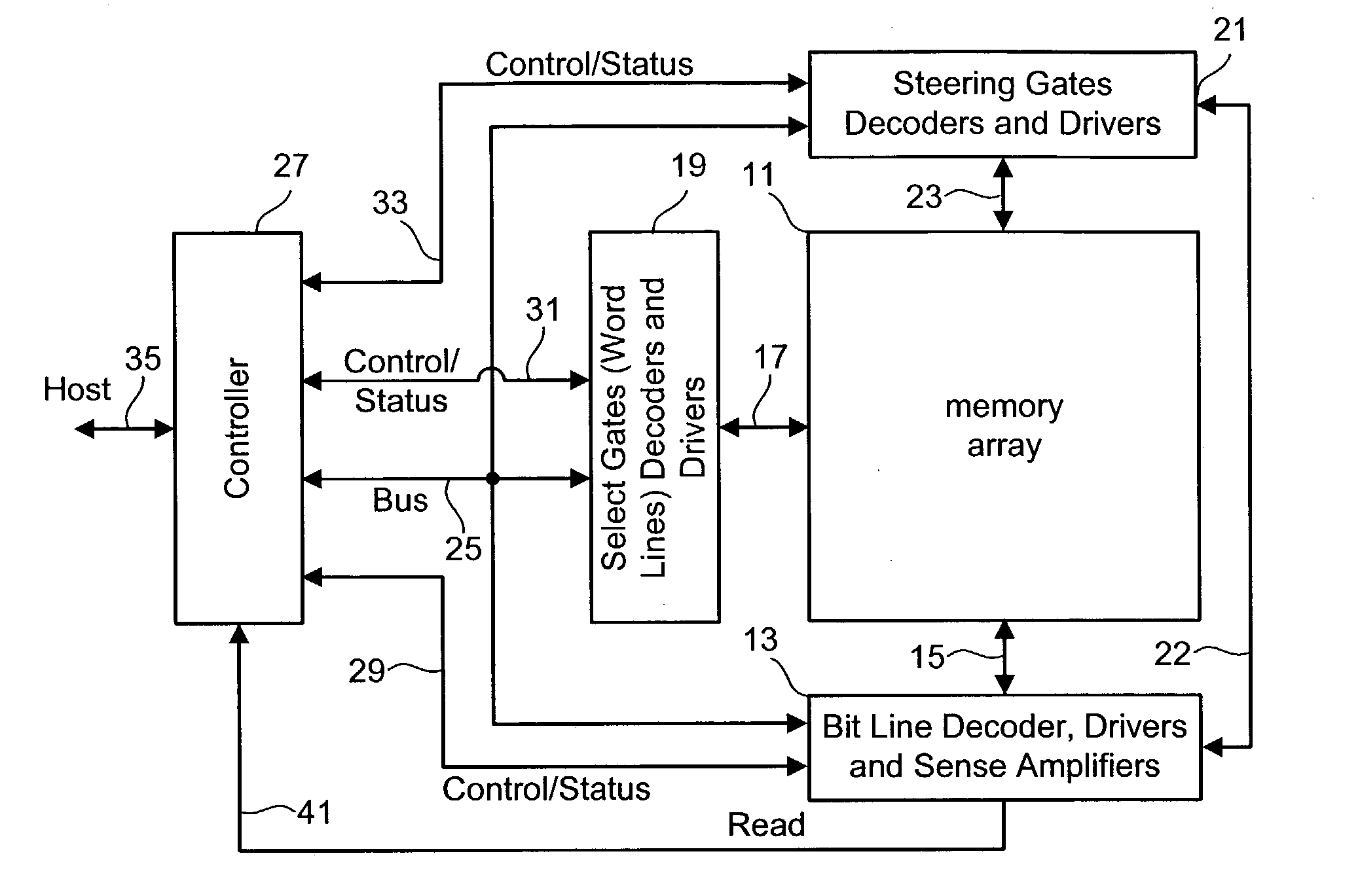
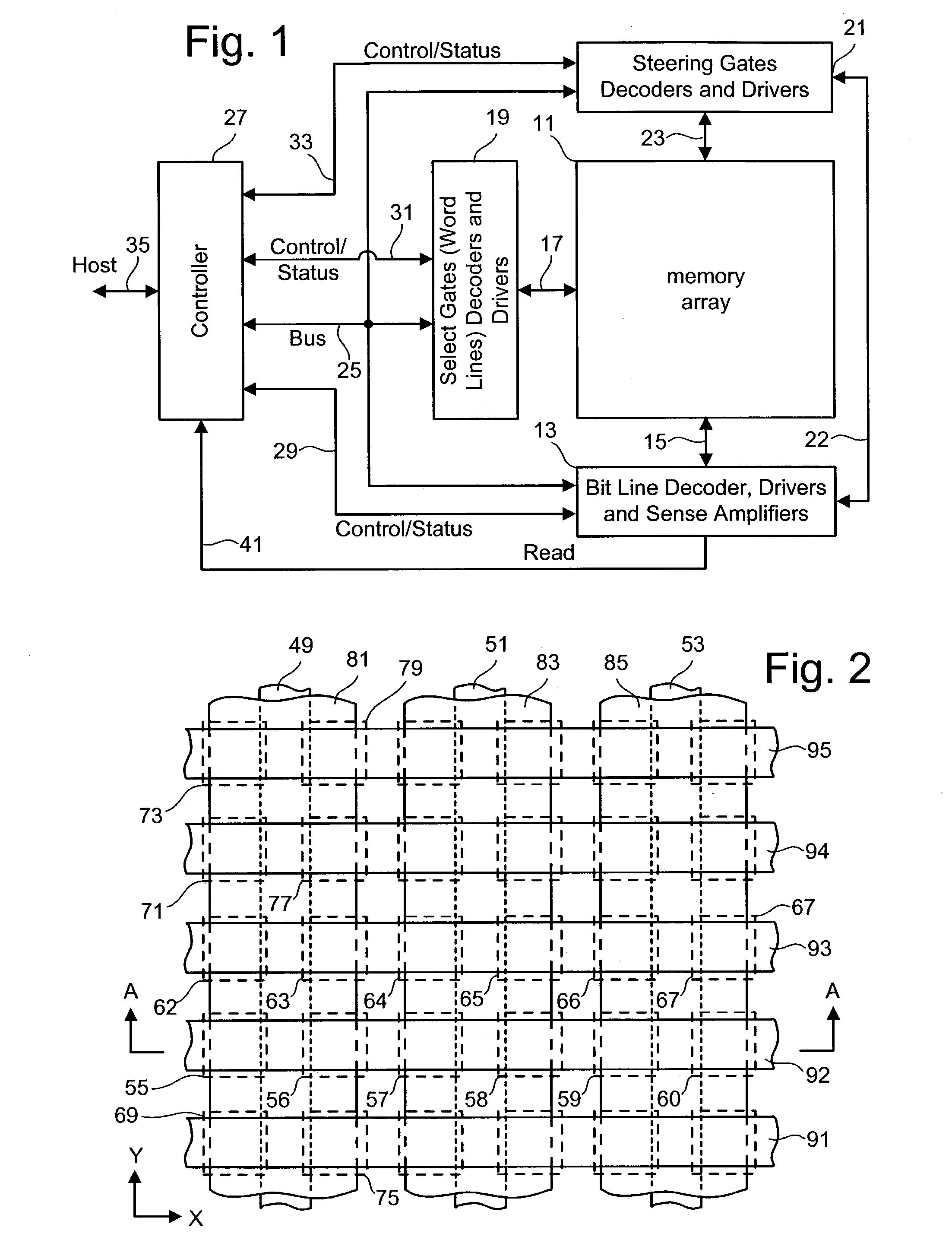
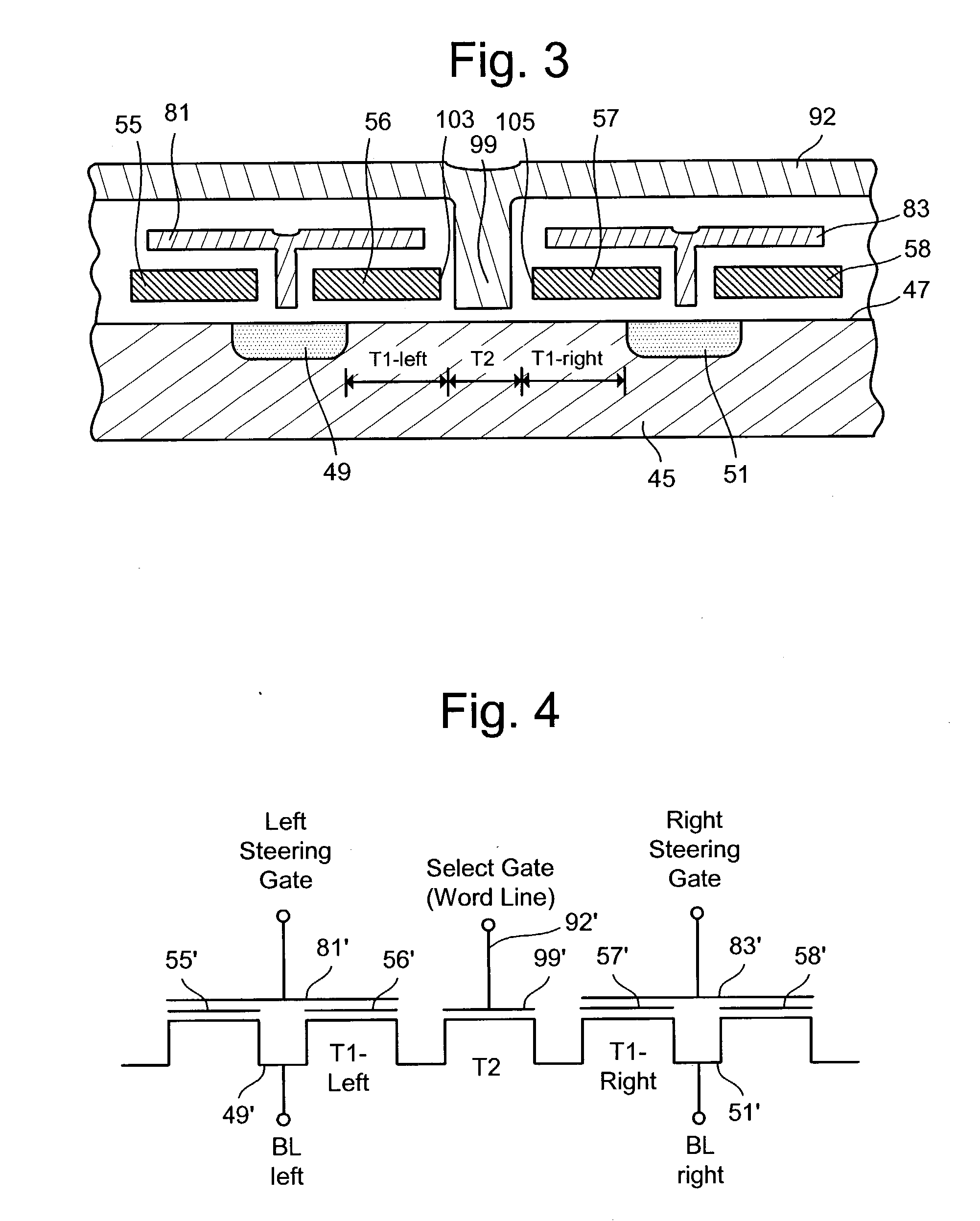
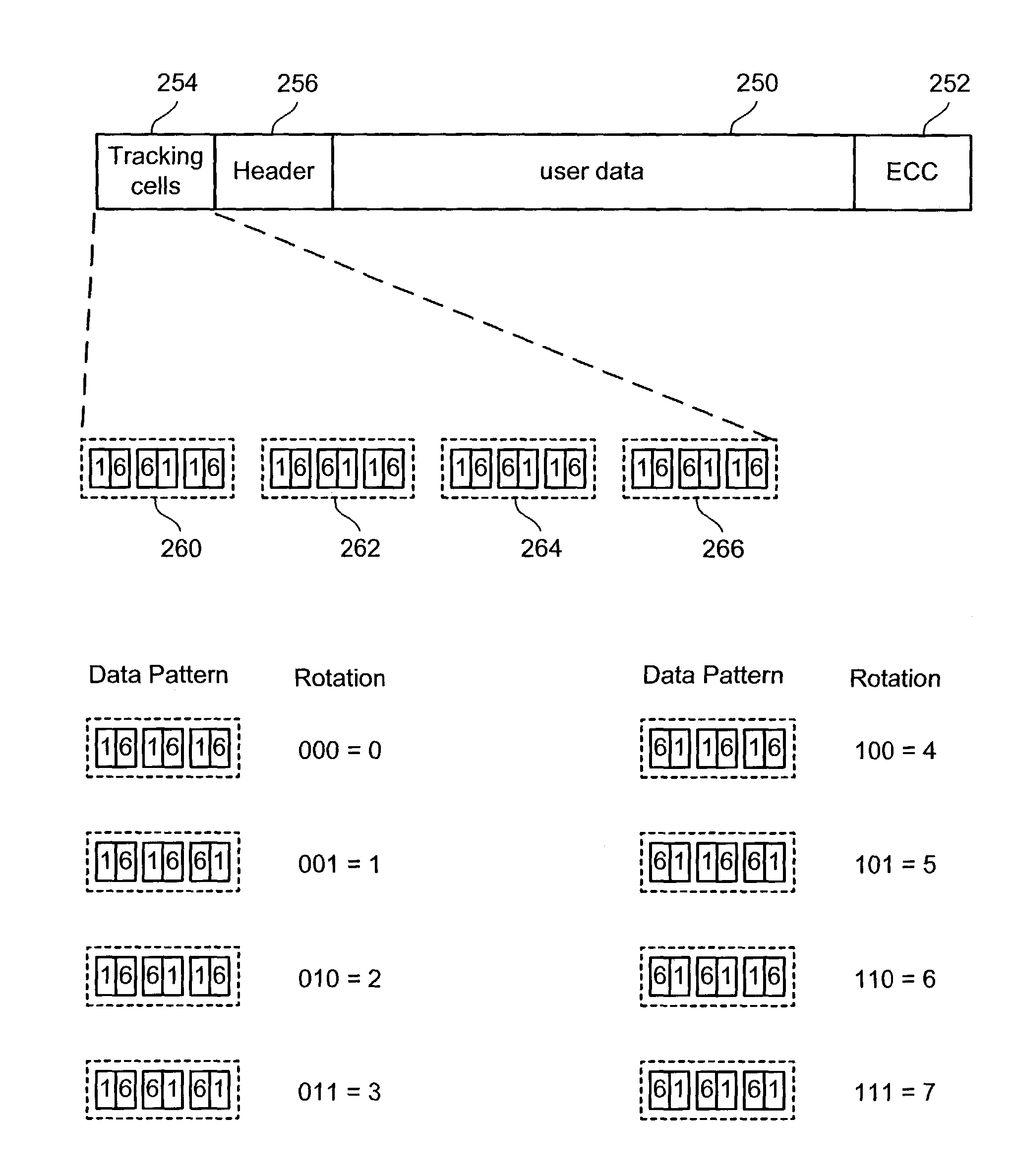
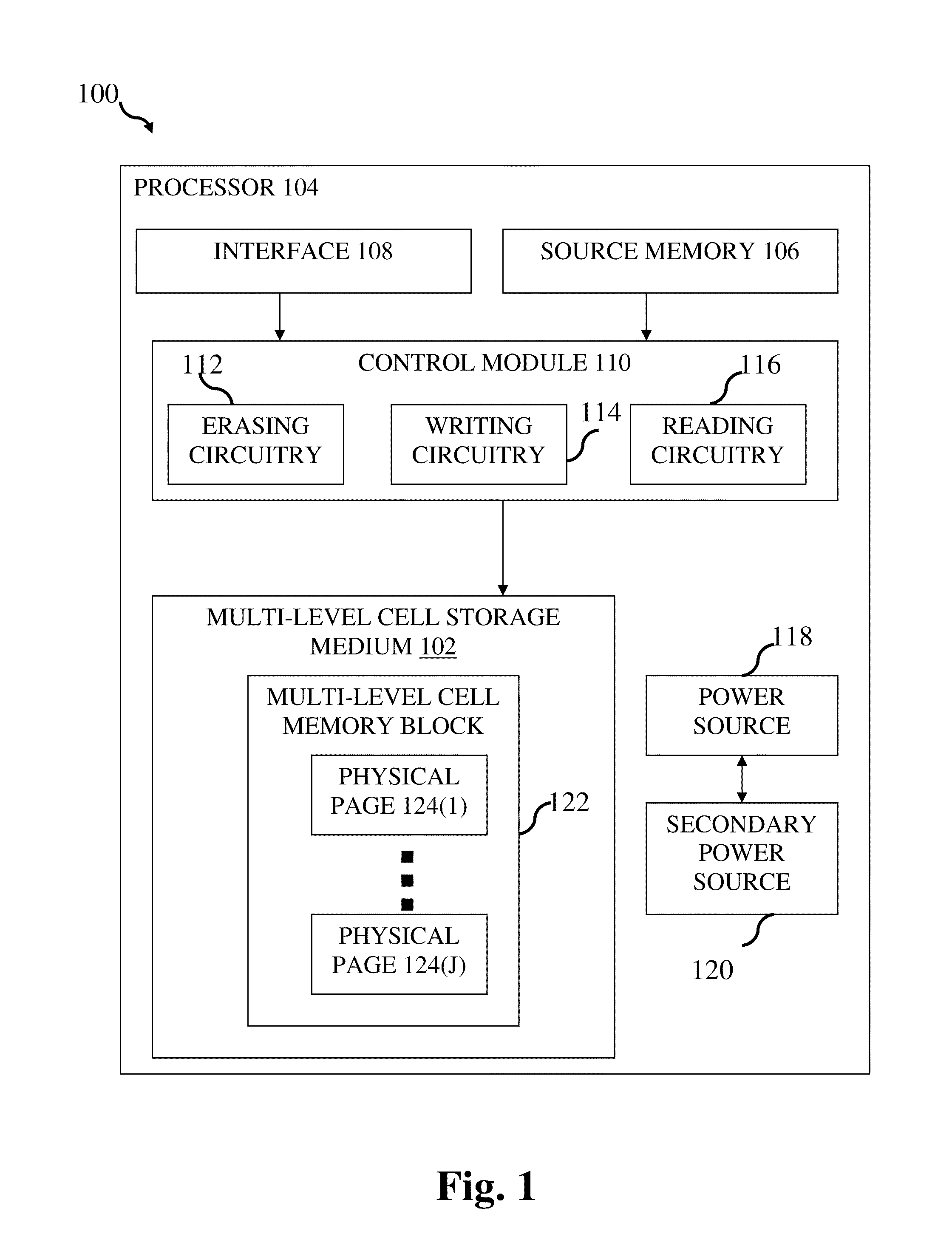
Tracking cells for a memory system
Tracking cells are used in a memory system to improve the read process. The tracking cells can provide an indication of the quality of the data and can be used as part of a data recovery operation if there is an error. The tracking cells provide a means to adjust the read parameters to optimum levels in order to reflect the current conditions of the memory system. Additionally, some memory systems that use multi-state memory cells will apply rotation data schemes to minimize wear. The rotation scheme can be encoded in the tracking cells based on the states of multiple tracking cells, which is decoded upon reading.
Owner:SANDISK TECH LLC
Tracking cells for a memory system
Tracking cells are used in a memory system to improve the read process. The tracking cells can provide an indication of the quality of the data and can be used as part of a data recovery operation if there is an error. The tracking cells provide a means to adjust the read parameters to optimum levels in order to reflect the current conditions of the memory system. Additionally, some memory systems that use multi-state memory cells will apply rotation data schemes to minimize wear. The rotation scheme can be encoded in the tracking cells based on the states of multiple tracking cells, which is decoded upon reading.
Owner:SANDISK TECH LLC
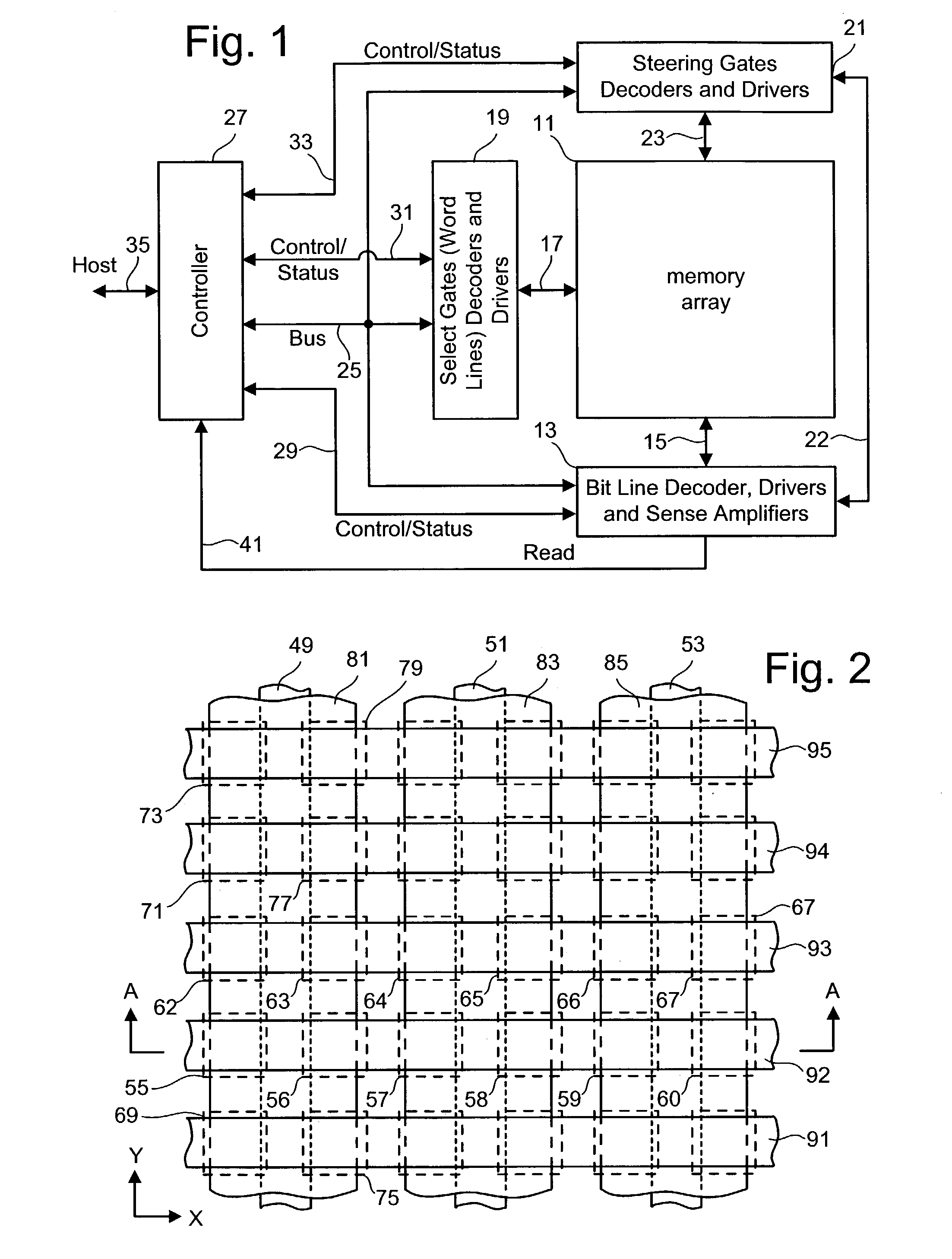
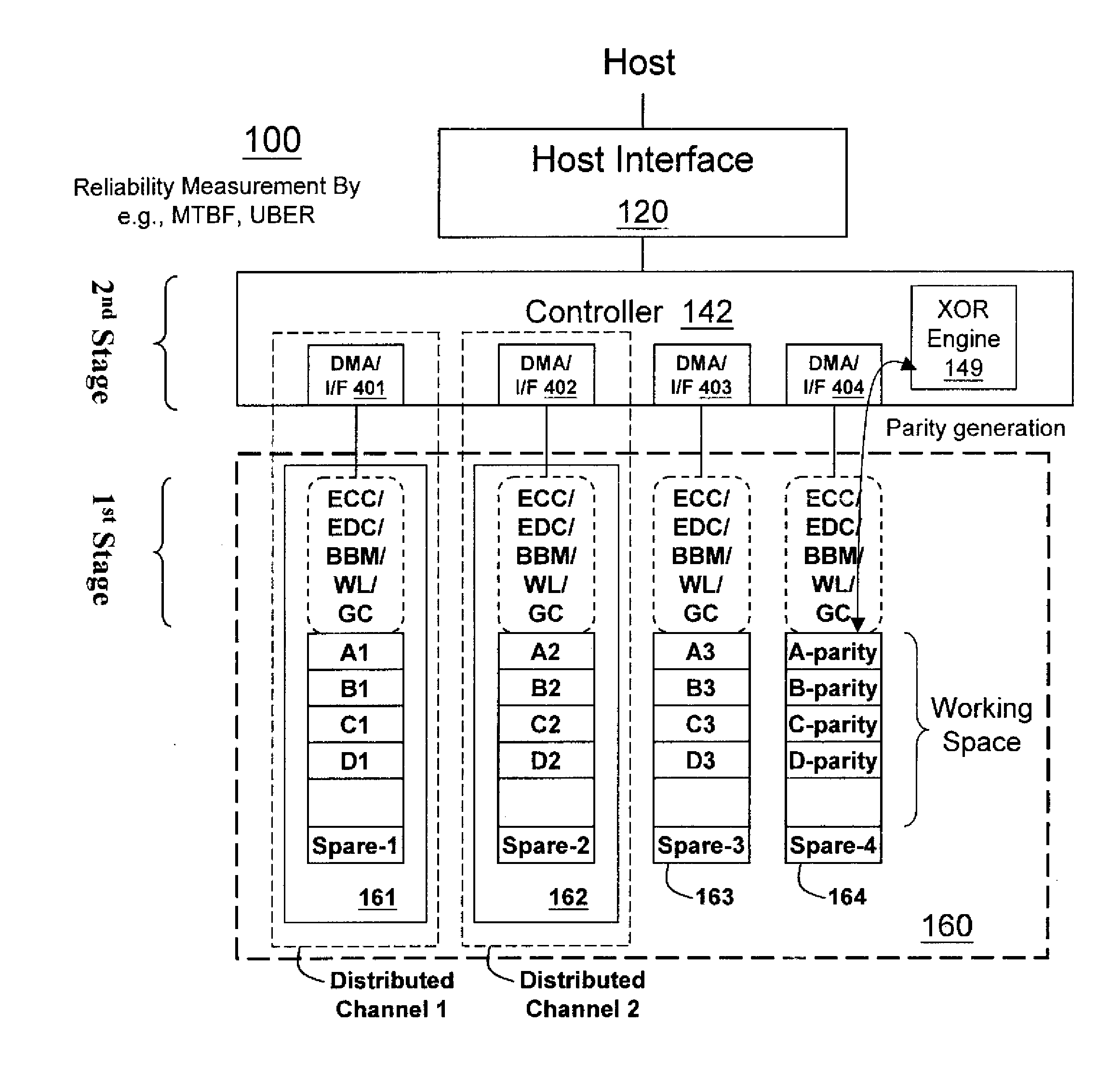
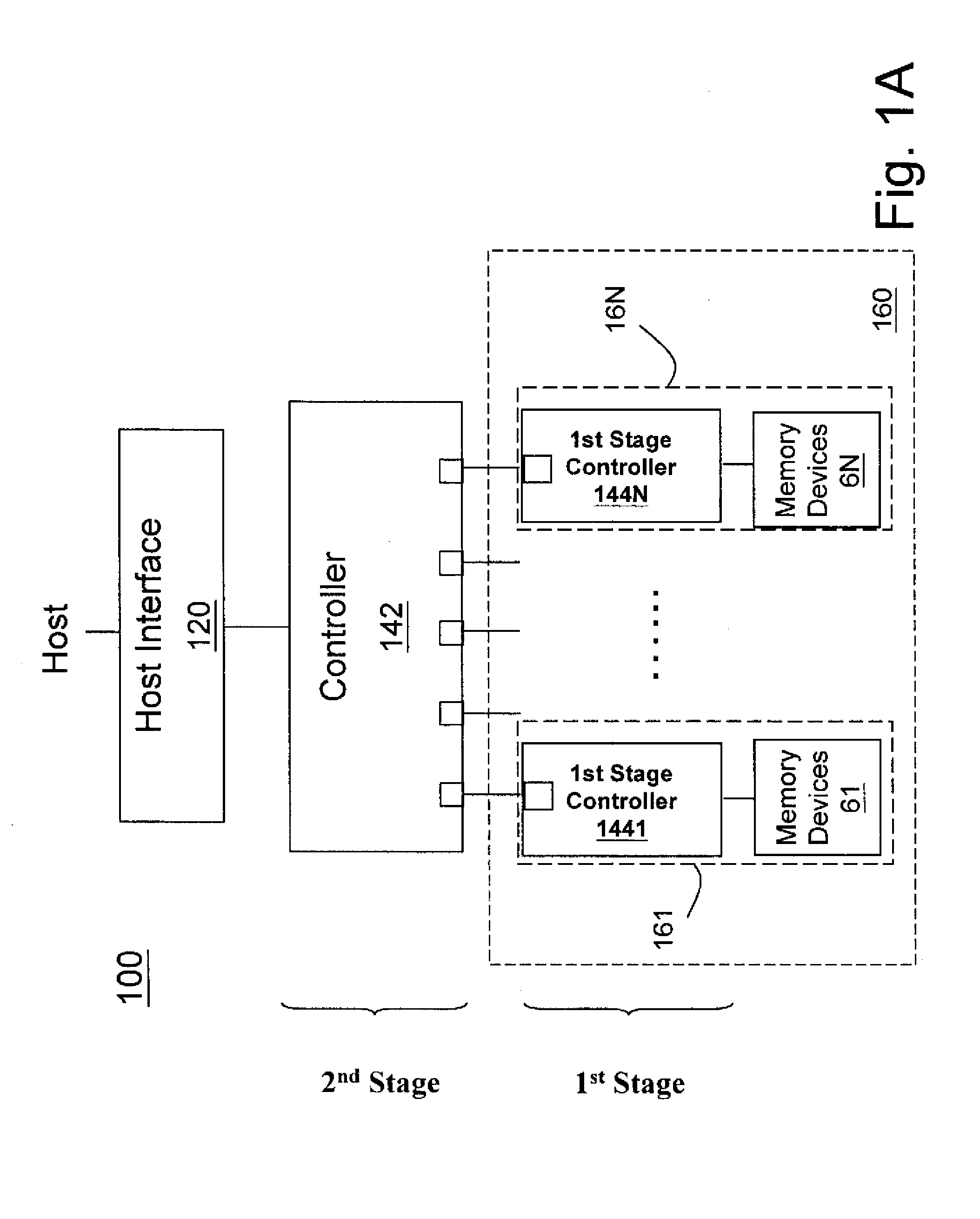
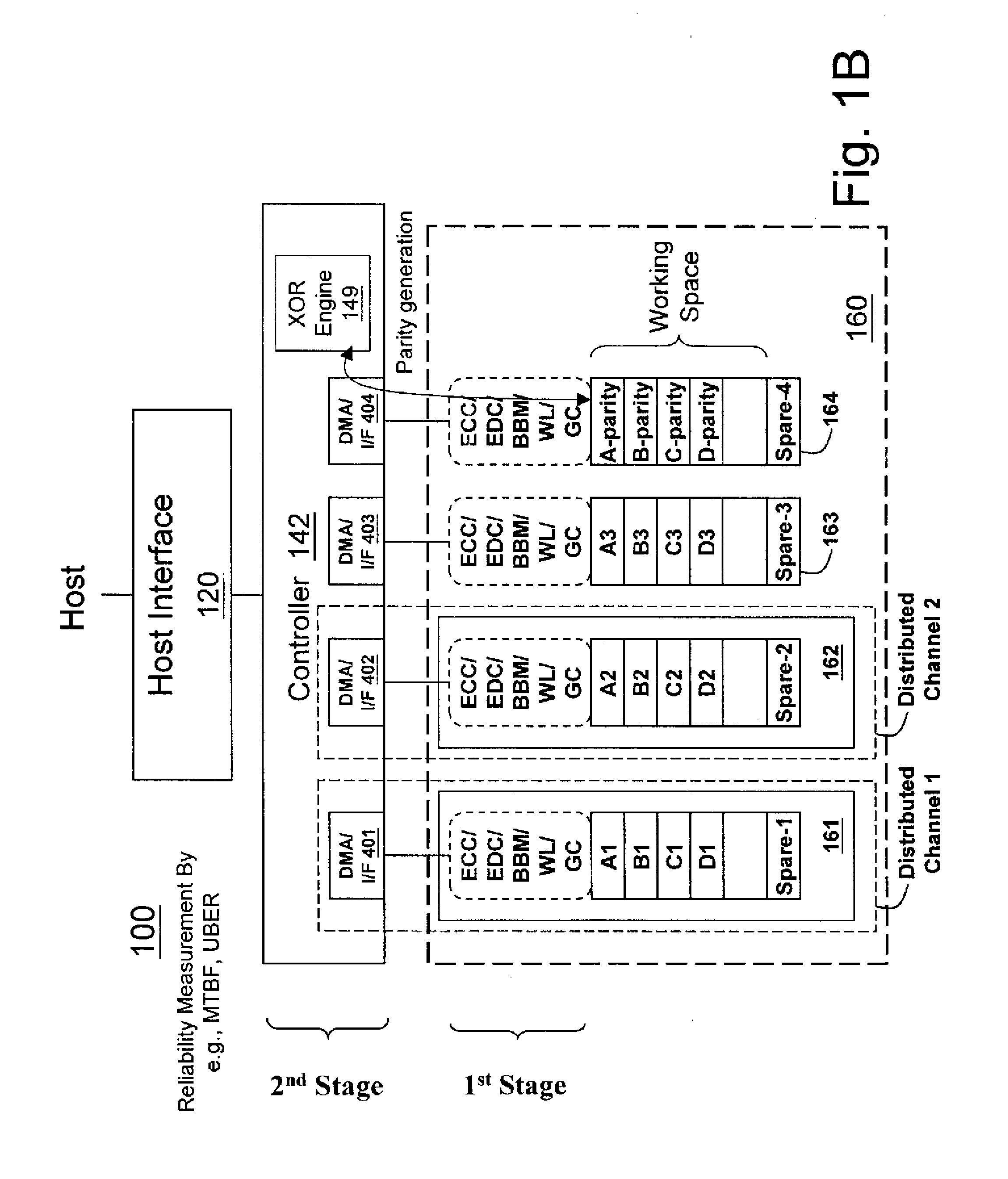
Non-volatile memory data storage system with reliability management
InactiveUS20100017650A1Improve reliabilityReliable managementMemory loss protectionMemory adressing/allocation/relocationRAIDData recovery
A non-volatile memory data storage system, comprising: a host interface for communicating with an external host; a main storage including a first plurality of flash memory devices, wherein each memory device includes a second plurality of memory blocks, and a third plurality of first stage controllers coupled to the first plurality of flash memory devices; and a second stage controller coupled to the host interface and the third plurality of first stage controller through an internal interface, the second stage controller being configured to perform RAID operation for data recovery according to at least one parity.
Owner:NANOSTAR CORP
Controlling data storage in an array of storage devices
ActiveUS20140325262A1Reduce mismatchLow costRedundant hardware error correctionData storeDevice failure
Methods, apparatus and computer programs have been provided for mitigating a problem of non-optimal recovery from storage device failures. A method involves determining a required write performance for rebuilding data of a failed device, based at least partly on the potential read performance of storage devices in a data rebuild; and allocating a virtual storage area within available storage, which allocation of virtual storage is based at least partly on the required write performance. Data is rebuilt by writing to the allocated virtual storage area, and data recovery is completed by migrating this rebuilt data to at least one data storage device such as a spare physical storage device within the array.
Owner:GLOBALFOUNDRIES US INC
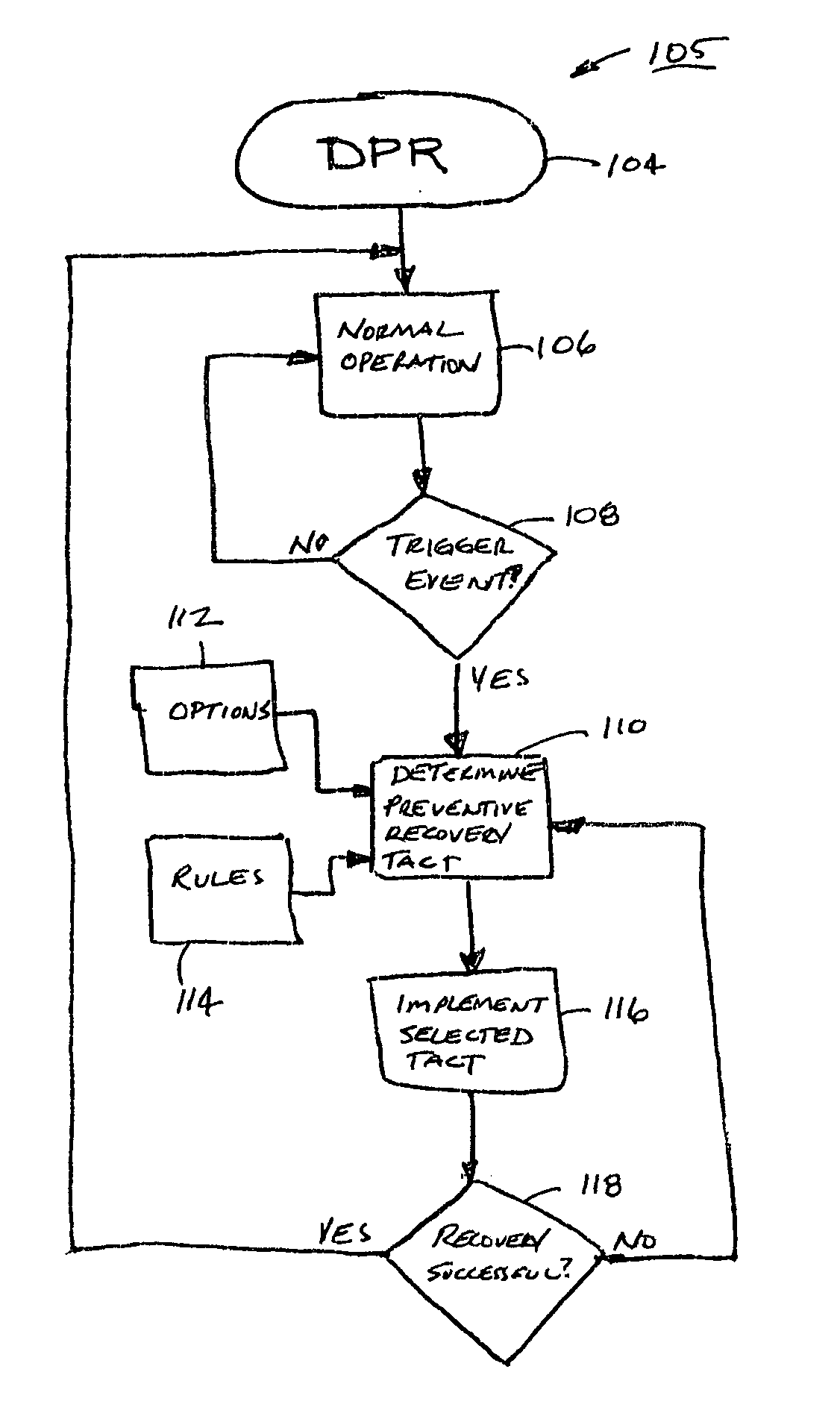
Deterministic preventive recovery from a predicted failure in a distributed storage system
A data storage subsystem in a distributed storage system having a plurality of predictive failure analyzing data storage devices. The subsystem furthermore has a circuit that is responsive to a predicted failure indication by a data storage device in relation to predetermined rules stored in memory for deterministically initiating a preventive recovery either by a data recovery procedure in the data storage device or by a fault tolerance storage arrangement in the subsystem.
Owner:SEAGATE TECH LLC
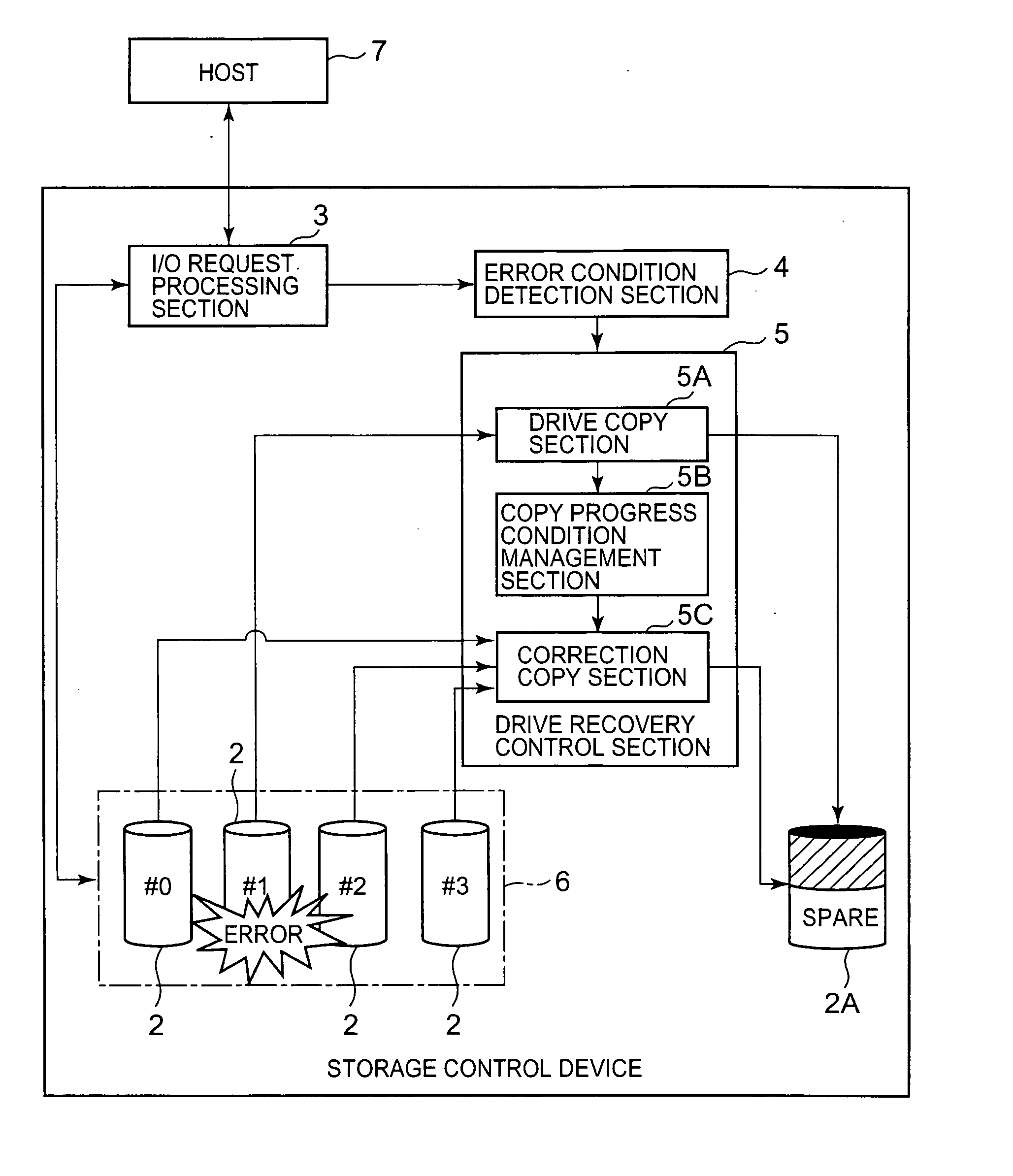
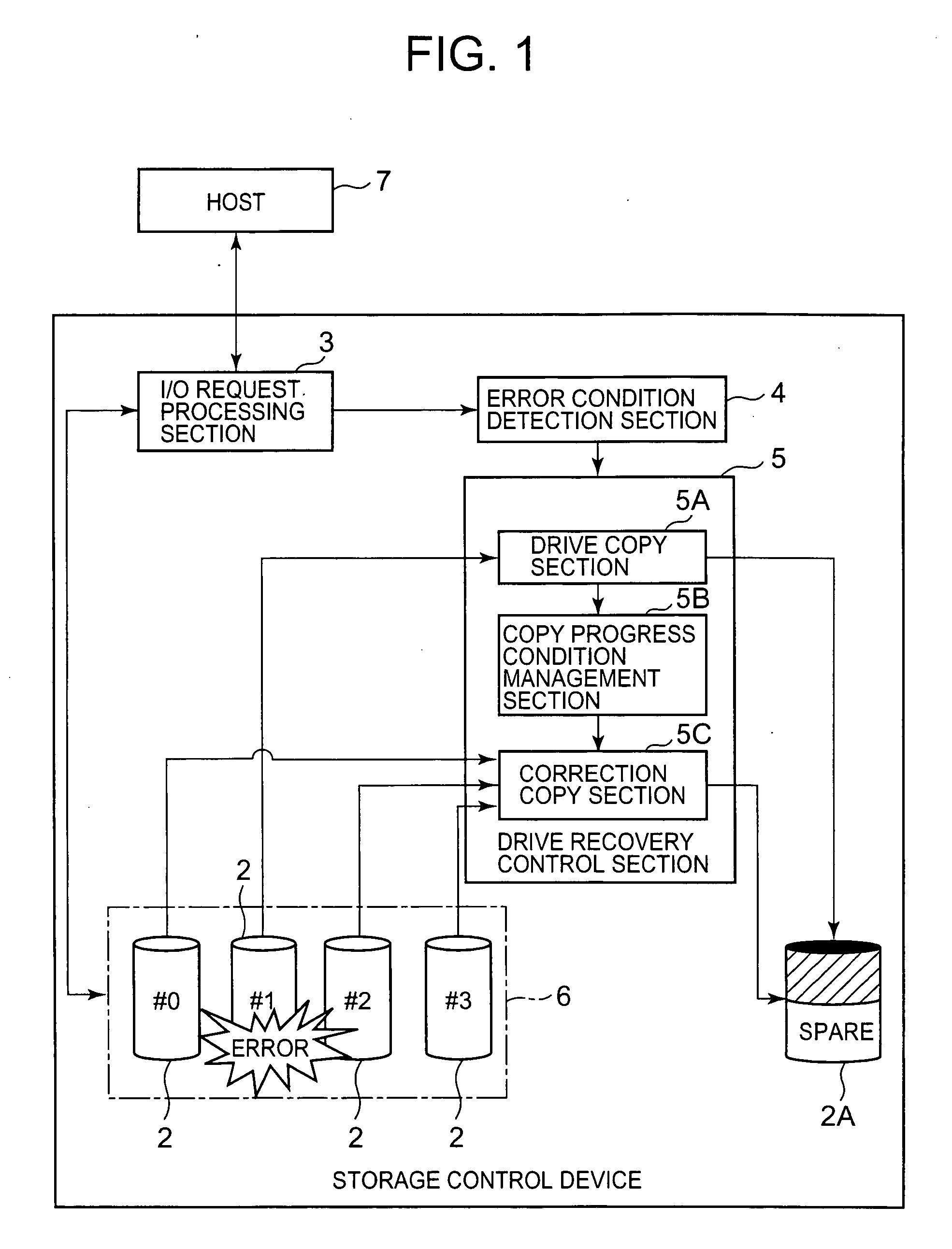
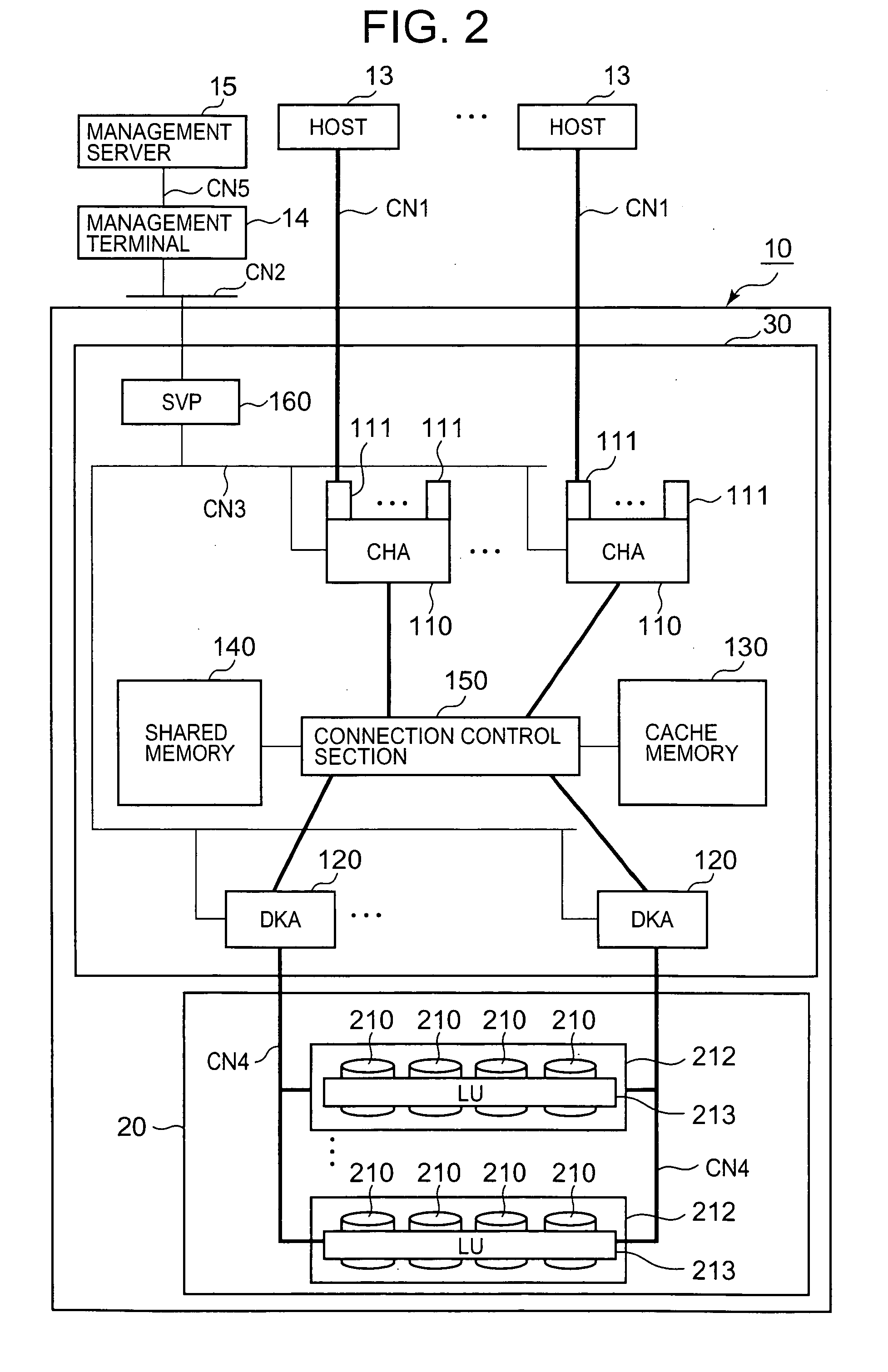
Storage control device and data recovery method for storage control device
The present invention efficiently recovers an error drive by suppressing futile copying. When the number of errors of the disk drive is equal to or more than a first threshold, data stored in the disk drive is copied to a spare drive by a drive copy section. When the number of errors of the disk drive is equal to or more than a second threshold prior to completion of the drive copy, the disk drive is closed, and a correction copy by a correction copy section is started in place of the drive copy. The correction copy section starts the correction copy from the position where the drive copy is interrupted by taking over the drive copy completion position (copy interrupt position) managed by a copy progress condition management section.
Owner:HITACHI LTD
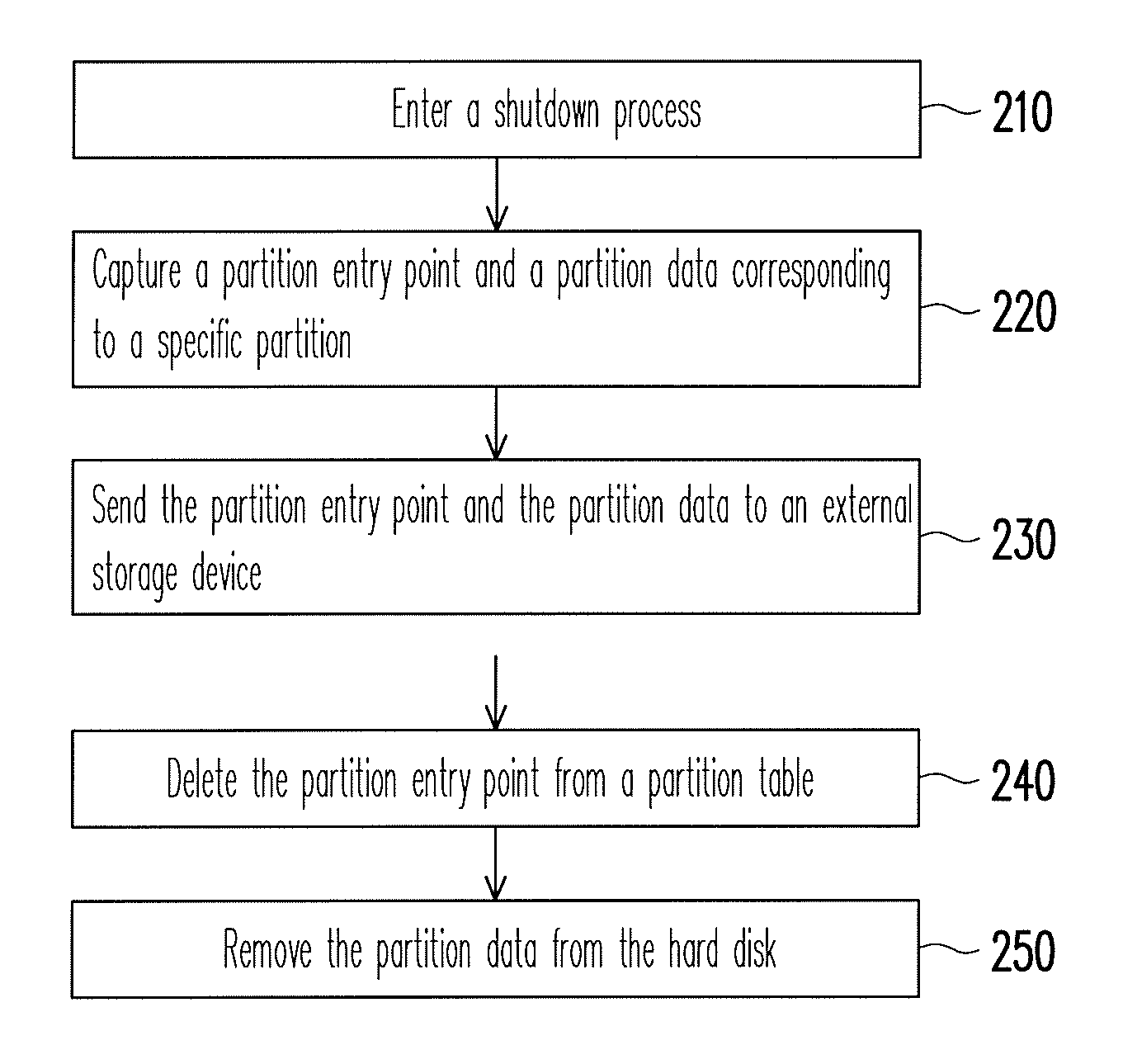
Data protection method
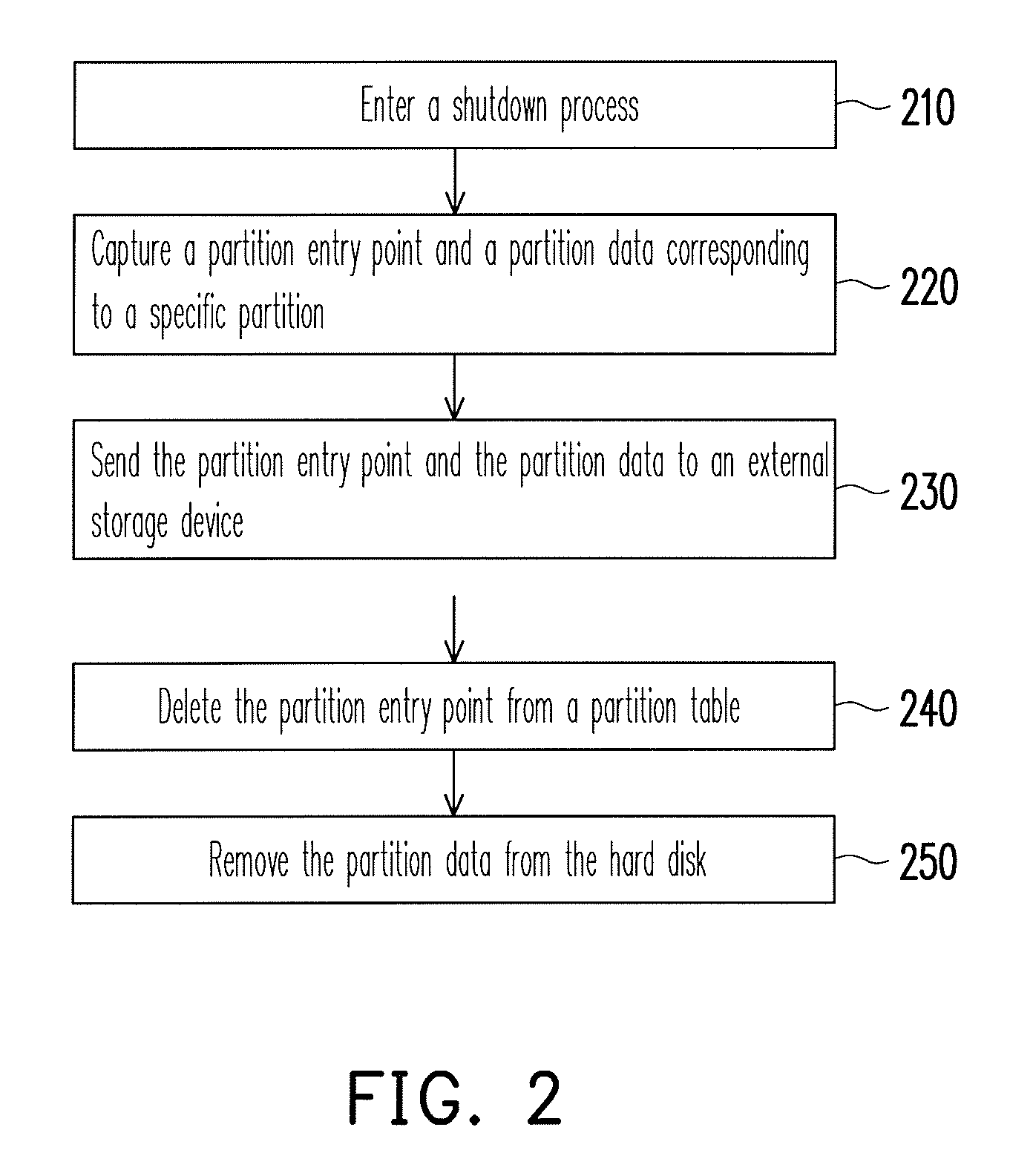
ActiveUS8041913B2Data SecurityEnsure safetyDigital data processing detailsUnauthorized memory use protectionExternal storageEntry point
A data protection method for an electronic device having a storage medium is provided, wherein the storage medium includes a plurality of partitions and a partition table. In the data protection method, a partition entry point and a partition data corresponding to the specific partition are captured and sent to an external storage device when the electronic device enters a shutdown process. Then, the partition entry point is deleted from the partition table and the partition data is removed from the storage medium. When the electronic device is turned on, a user has to provide the corresponding external storage device to restore the partition entry point and the partition data back to the storage medium. Thereby, personal data stored in the storage medium is protected and accordingly data security is ensured.
Owner:ASUSTEK COMPUTER INC
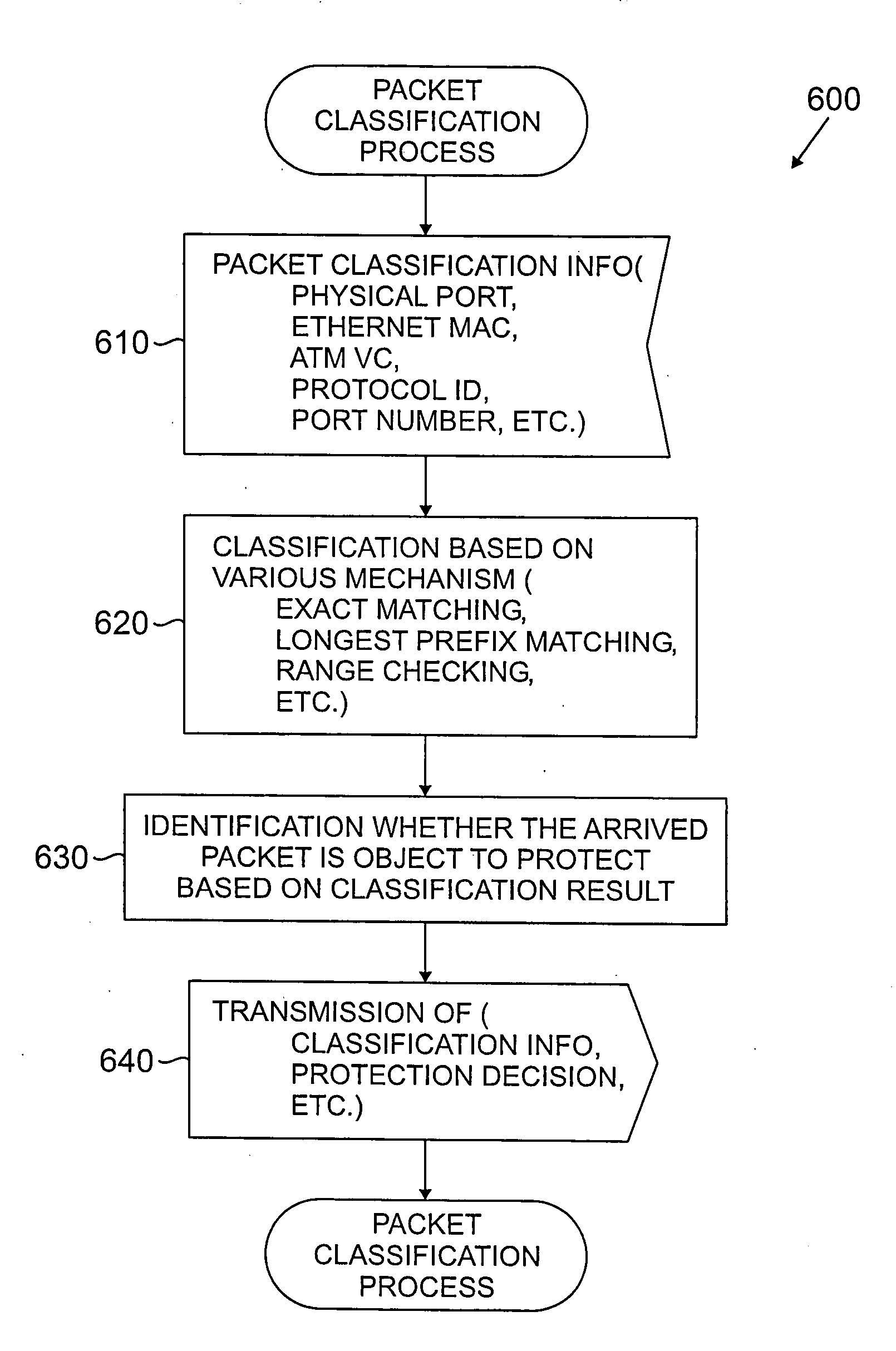
Method and apparatus for per-service fault protection and restoration in a packet network
InactiveUS20060013210A1Quickly and efficiently restoredLower Level RequirementsError preventionTransmission systemsService flowTraffic capacity
A method and apparatus are disclosed for per-service flow protection and restoration of data in one or more packet networks. The disclosed protection and restoration techniques allow traffic to be prioritized and protected from the aggregate level down to a micro-flow level. Thus, protection can be limited to those services that are fault sensitive. Protected data is duplicated over a primary path and one or more backup data paths. Following a link failure, protected data can be quickly and efficiently restored without significant service interruption. A received packet is classified at each end point based on information in a header portion of the packet, using one or more rules that determine whether the received packet should be protected. At an ingress node, if the packet classification determines that the received packet should be protected, then the received packet is transmitted on at least two paths. At an egress node, if the packet classification determines that the received packet is protected, then multiple versions of the received packet are expected and only one version of the received packet is transmitted.
Owner:AGERE SYST INC
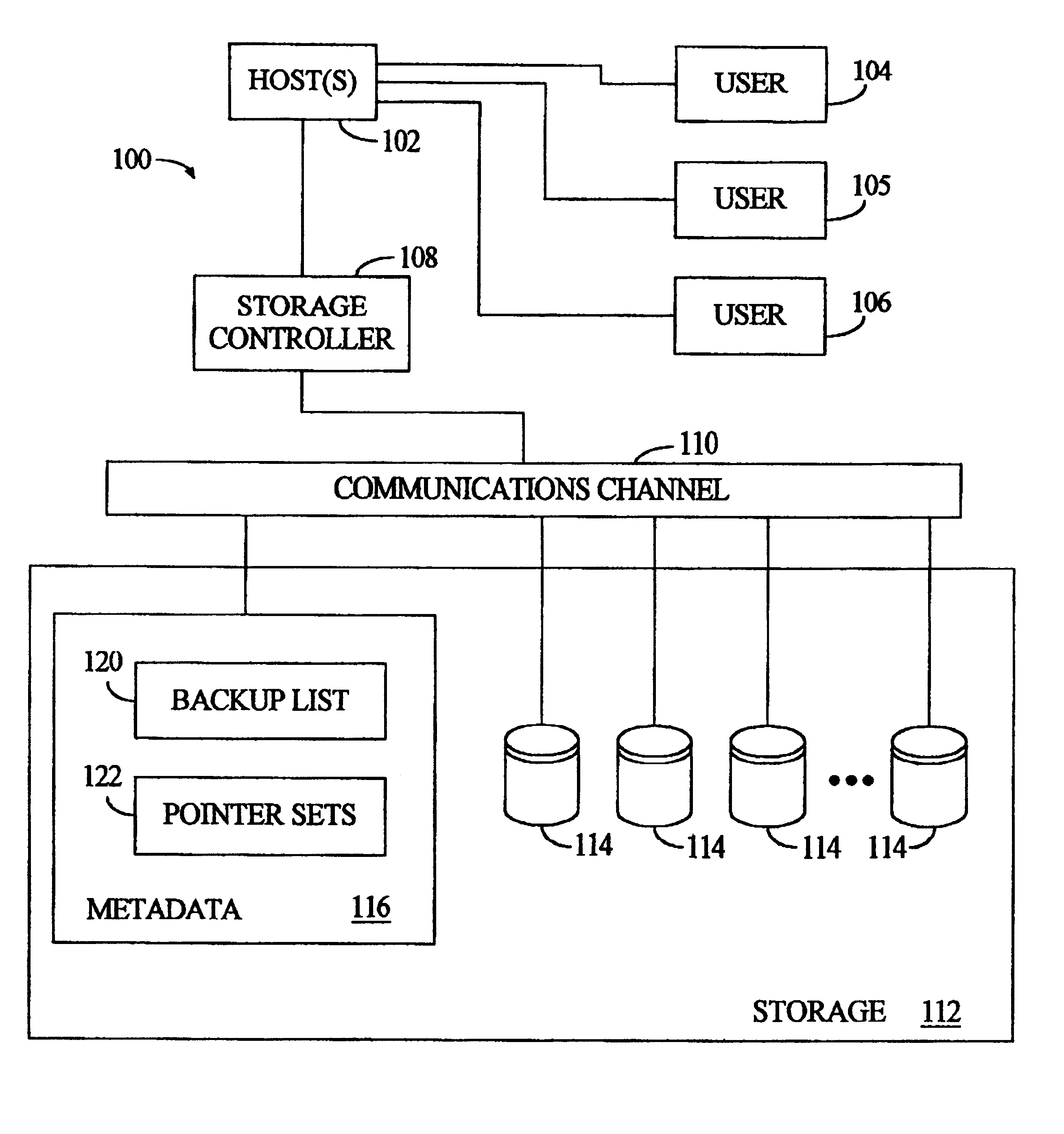
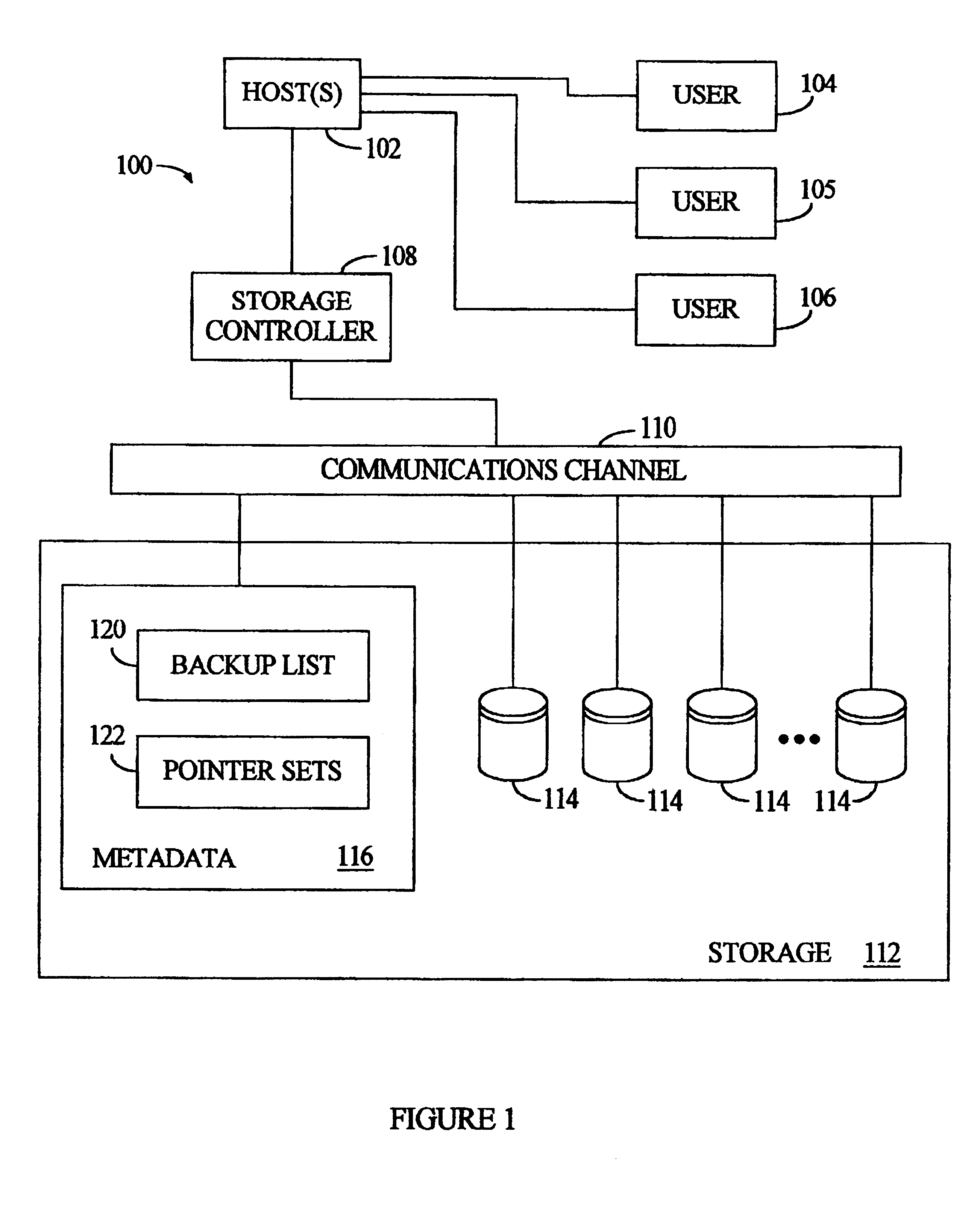
Method and apparatus for immediate data backup by duplicating pointers and freezing pointer/data counterparts
InactiveUS6226759B1Data processing applicationsMemory adressing/allocation/relocationData setOriginal data
An expedited data backup is performed by creating a duplicate set of pointers to a current dataset already identified by an original pointer set, then designating the dataset as a backup dataset, and thereafter preventing changes to the pointed-to-data and the duplicate pointers, where changes to the current dataset are nonetheless effected by storing new data and modifying the original pointer set alone. More specifically, the backup involves an original dataset having multiple subparts residing at various original storage locations, which are pointed-to by a primary set of pointers. A virtual backup copy is created by duplicating the primary set of pointers to create a backup set of pointers. The backup set of pointers are entered in a backup list, in association with the virtual backup copy and the original dataset. To preserve the backup copy, the system prevents changes to the original dataset and the backup set of pointers. When any changes are directed to subparts of the original dataset, the system creates a changed dataset by storing the changes at one or more change storage locations and updating the primary set of pointers to identify the change storage locations along with any original storage locations still containing unchanged subparts of the original dataset. In addition to expediting data backups, fast data recovery is possible by updating the primary set of pointers to duplicate the backup set of pointers.
Owner:IBM CORP
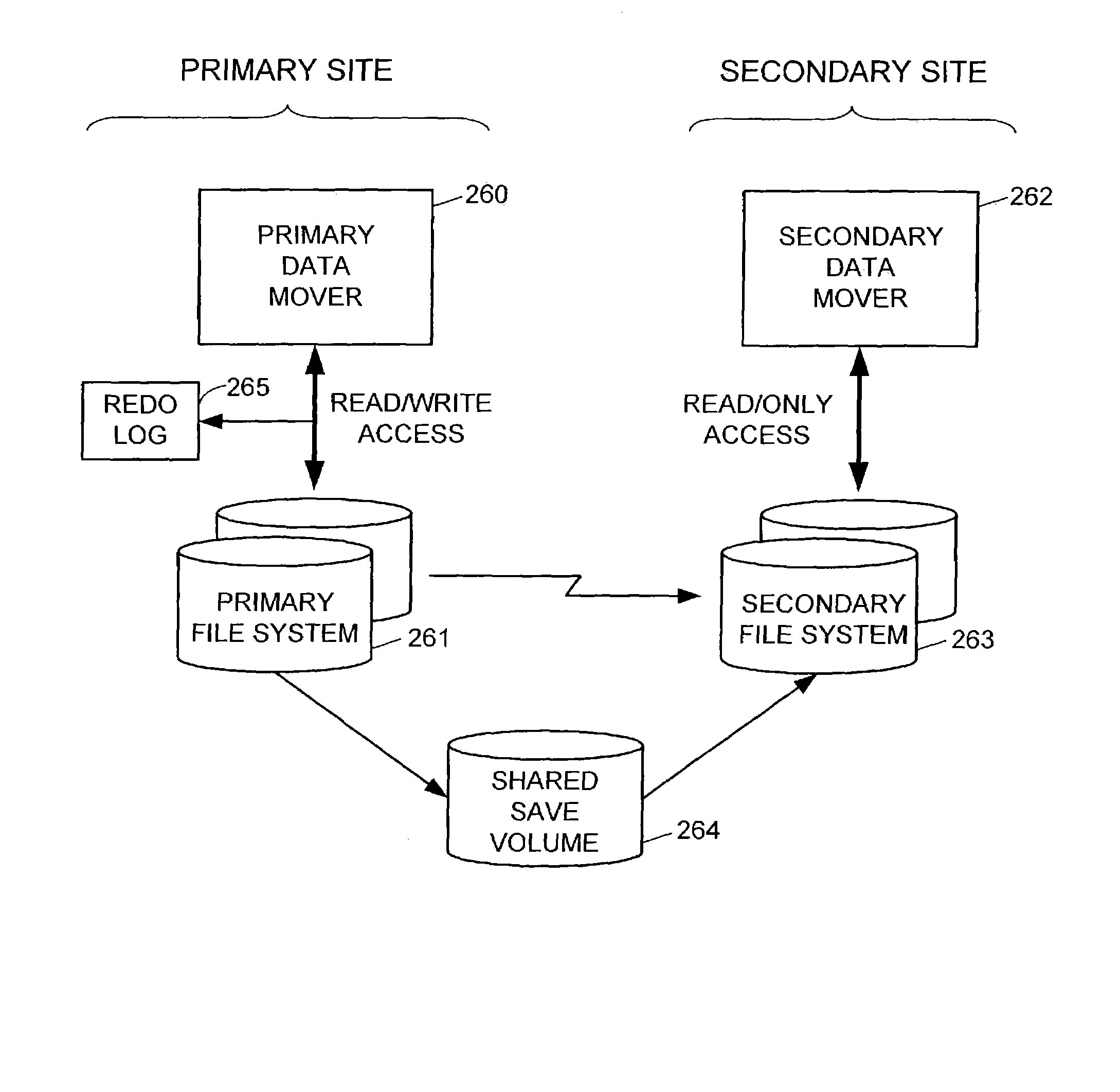
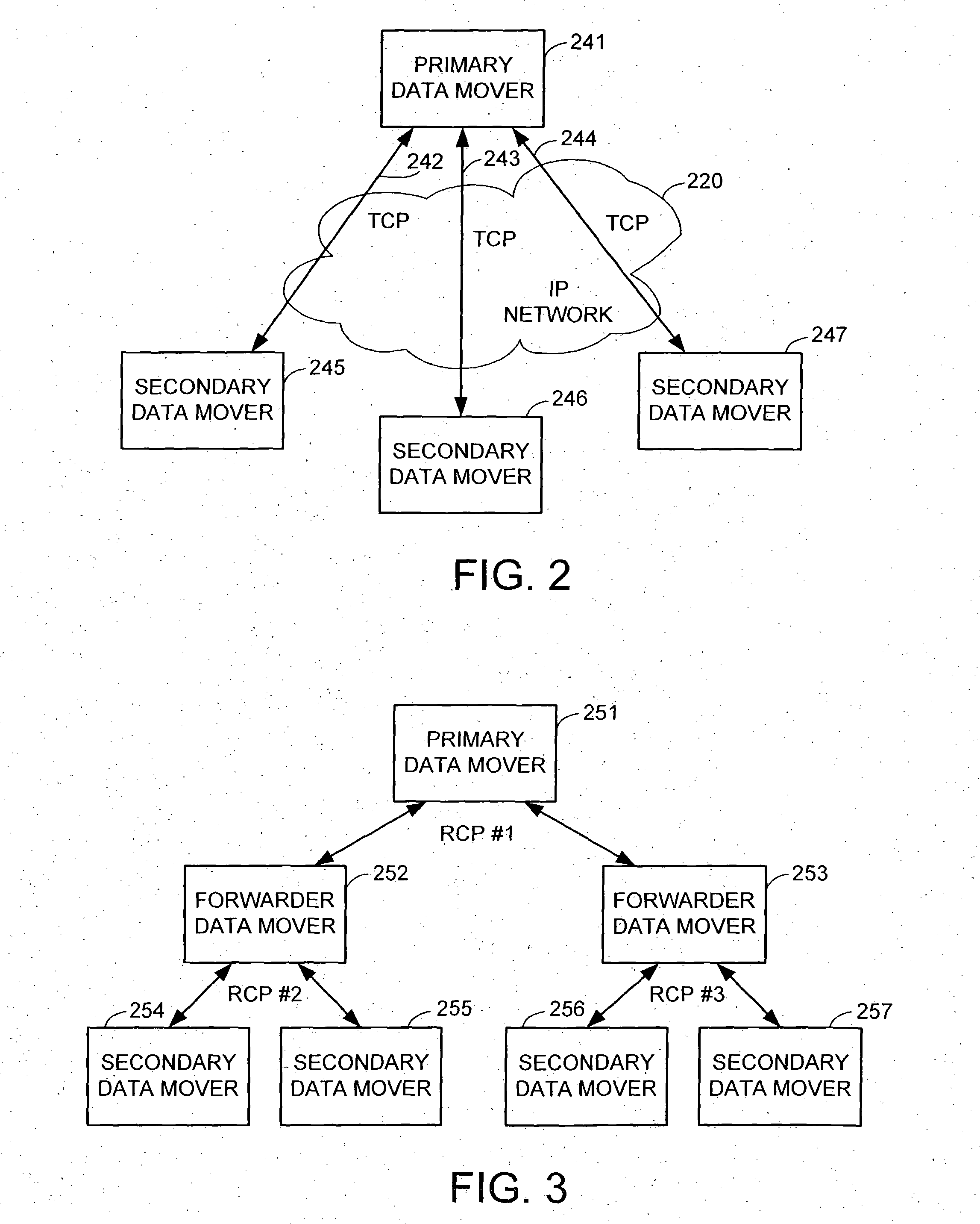
Data recovery with internet protocol replication with or without full resync
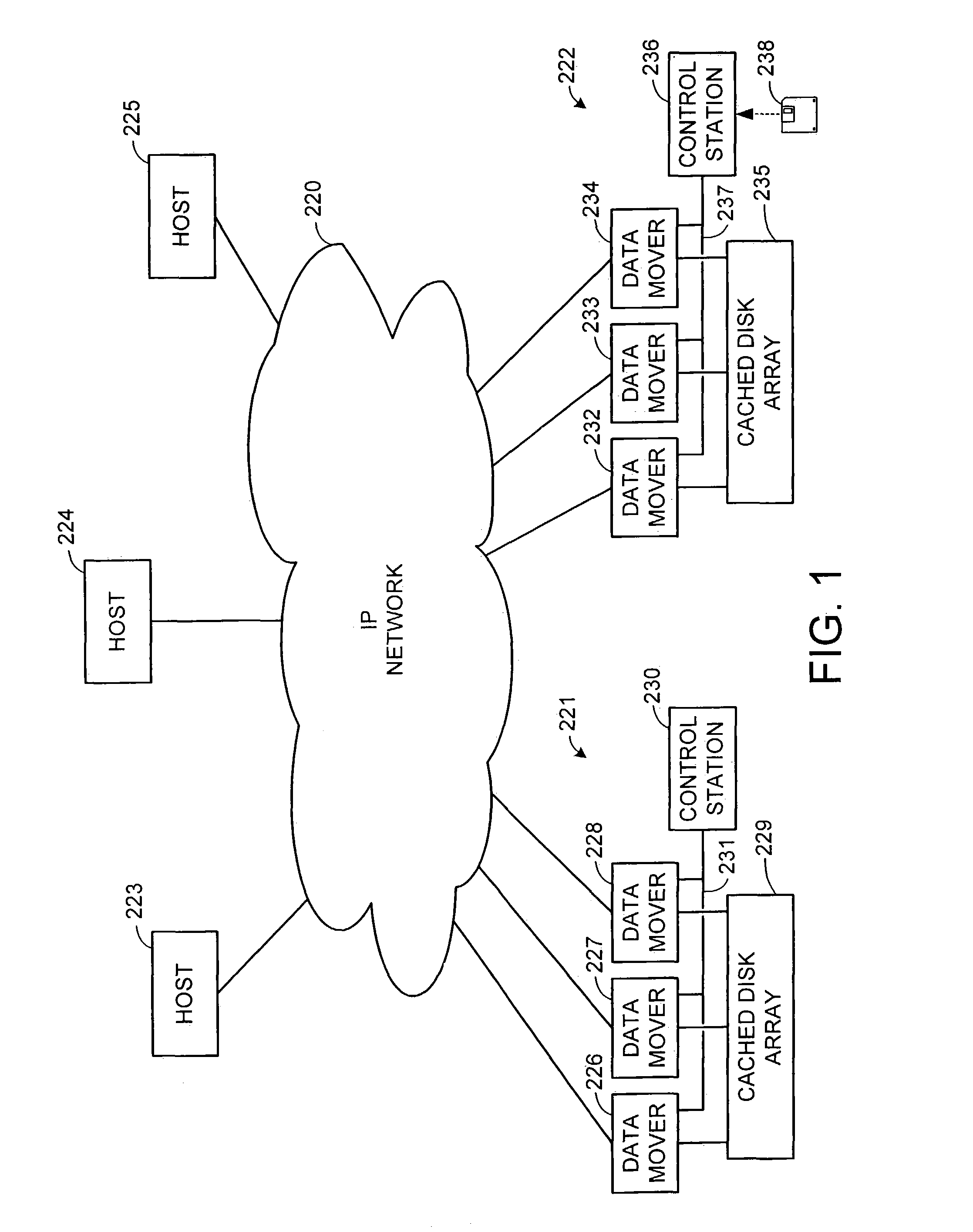
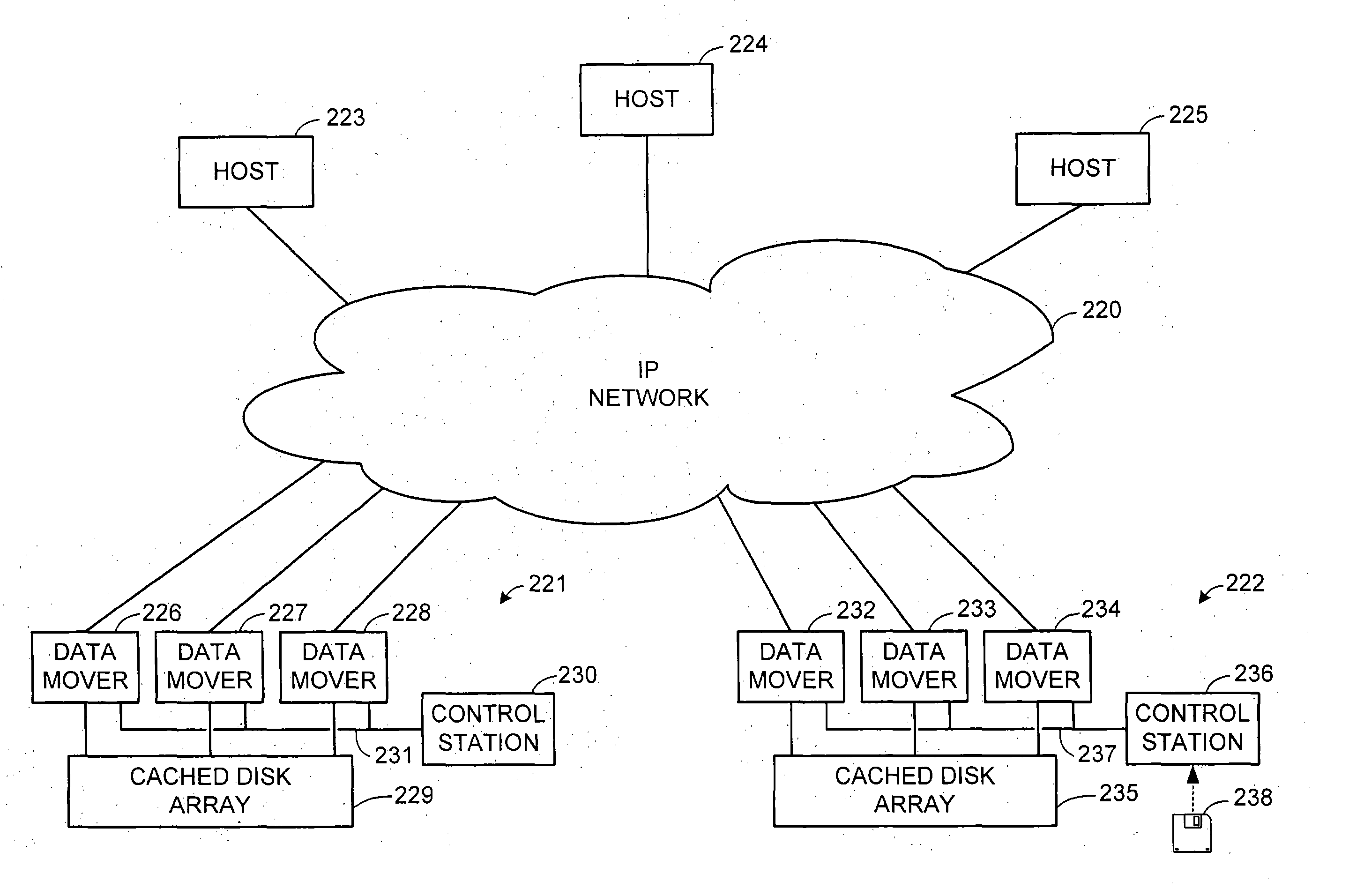
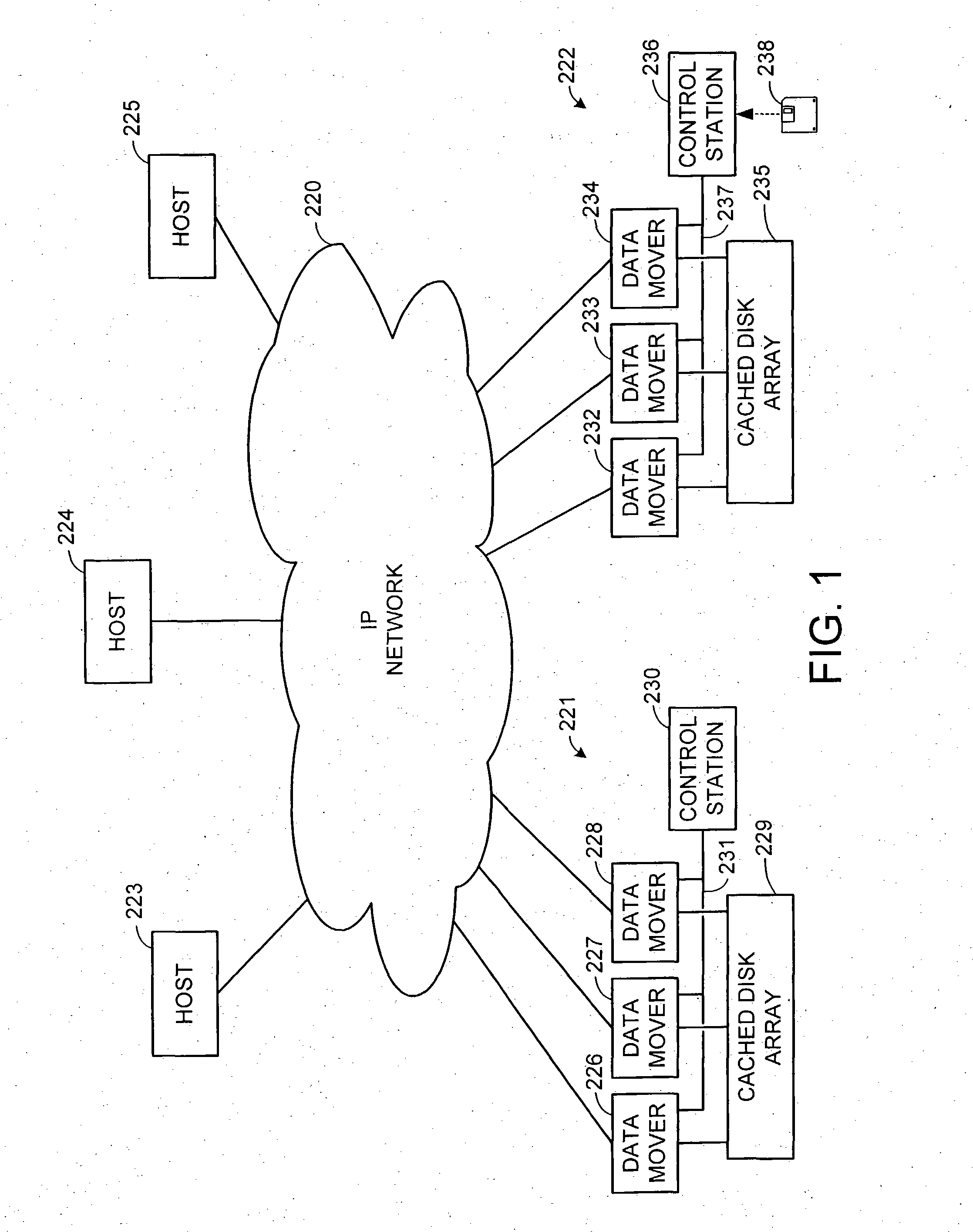
ActiveUS7275177B2Data processing applicationsEmergency protective arrangements for automatic disconnectionPrimary sitesFile system
In an asynchronous remote copy system, a primary site keeps a list of data blocks for which changes have been made to a primary file system and transmitted to a secondary file system at a secondary site. When the primary site becomes inoperative, the secondary site begins read / write access to the secondary file system and keeps a snapshot copy of the restart point. Once the primary site becomes operative, the primary file system is restored to the state of the secondary file system at the restart point by using the list of data blocks for obtaining from the snapshot copy the data of the blocks for which changes had been made to the primary file system after the restart point. Then the primary file system is synchronized to the secondary file system, and read / write access is switched back from the secondary file system to the primary file system.
Owner:EMC IP HLDG CO LLC
Data recovery with internet protocol replication with or without full resync
ActiveUS20050015663A1Data processing applicationsEmergency protective arrangements for automatic disconnectionPrimary sitesFile system
In an asynchronous remote copy system, a primary site keeps a list of data blocks for which changes have been made to a primary file system and transmitted to a secondary file system at a secondary site. When the primary site becomes inoperative, the secondary site begins read / write access to the secondary file system and keeps a snapshot copy of the restart point. Once the primary site becomes operative, the primary file system is restored to the state of the secondary file system at the restart point by using the list of data blocks for obtaining from the snapshot copy the data of the blocks for which changes had been made to the primary file system after the restart point. Then the primary file system is synchronized to the secondary file system, and read / write access is switched back from the secondary file system to the primary file system.
Owner:EMC IP HLDG CO LLC
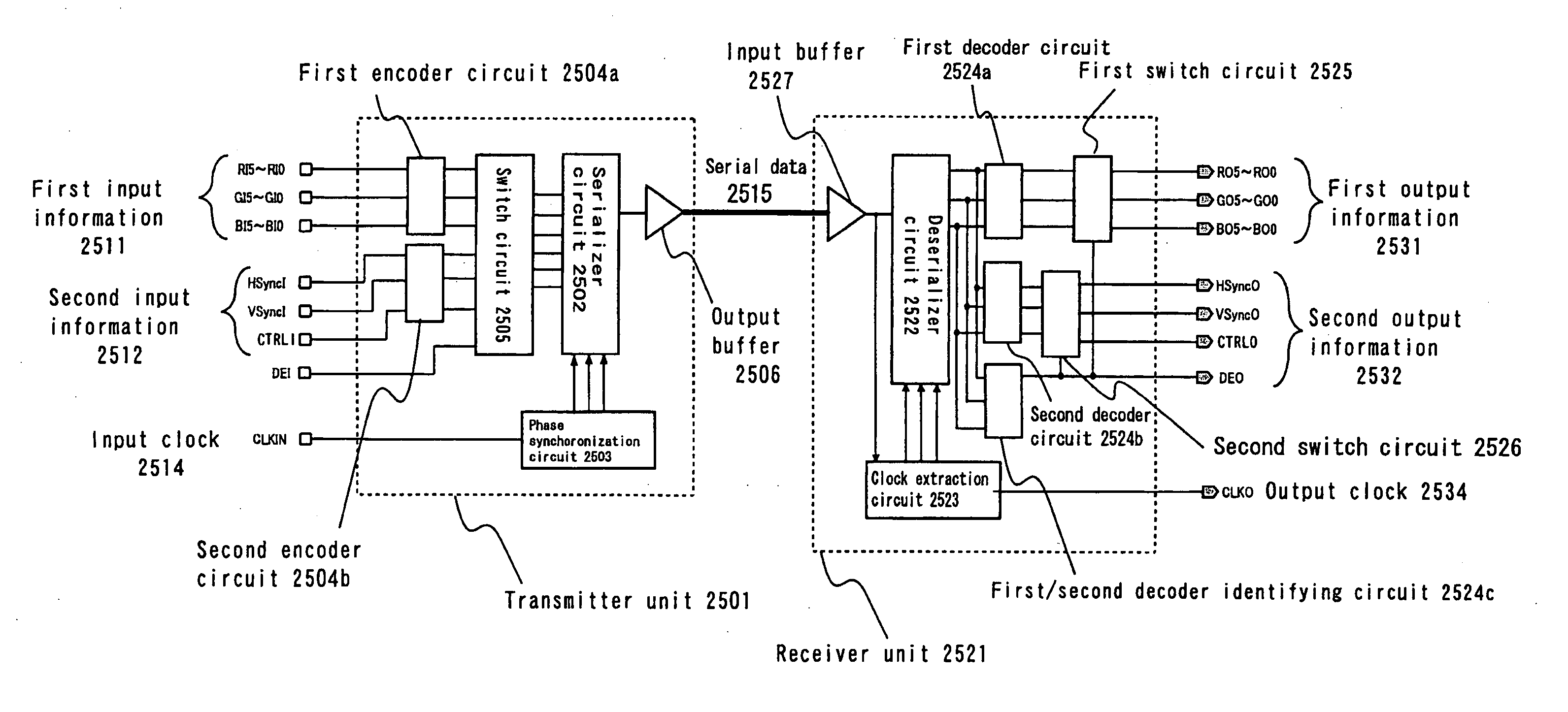
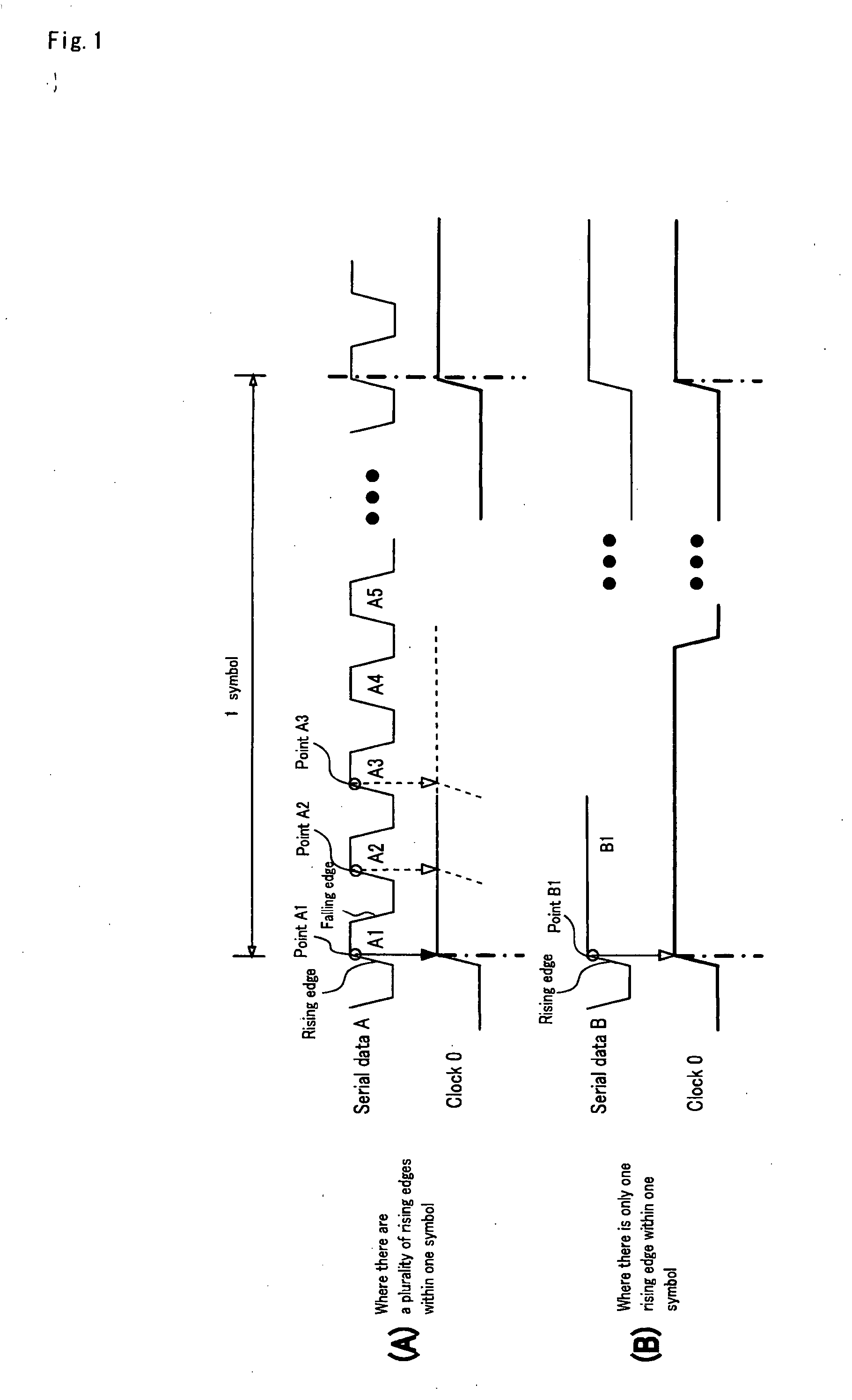
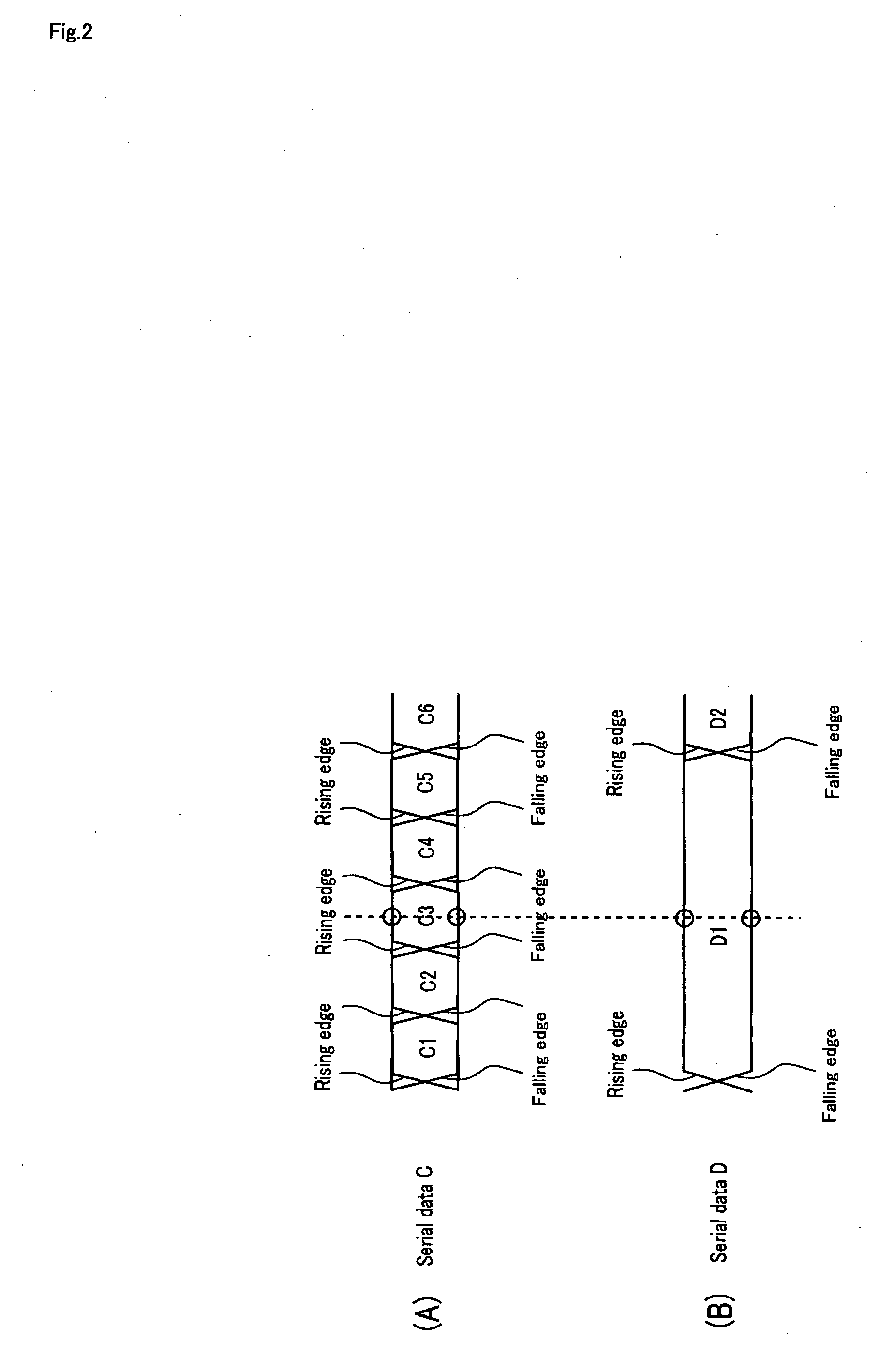
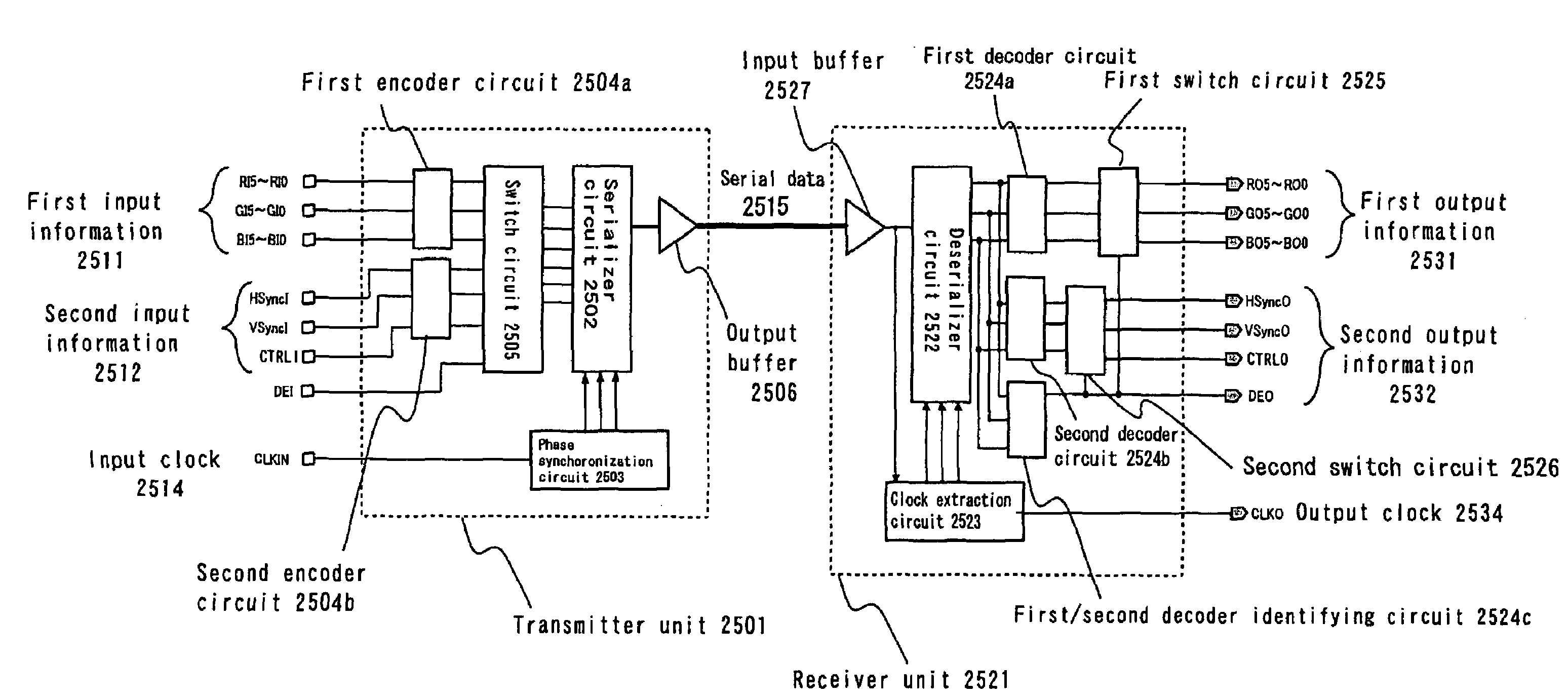
Transmitter circuit, receiver circuit, clock data recovery phase locked loop circuit, data transfer method and data transfer system
ActiveUS20050286643A1Reduce errorsData transmission is stableTelevision system detailsFrequency/rate-modulated pulse demodulationDigital dataPhase locked loop circuit
[Problems] To realize a reliable and stable transfer of digital data that does not require a reference clock and a handshake operation. [Means for Solving the Problem] The present invention provides a digital data transfer method for alternately and periodically transferring first information and second information respectively in a first period and in a second period, wherein: an amount of information of the first information per unit time in the first period is greater than an amount of information of the second information per unit time in the second period; and the second information in the first period is transferred as pulse-width-modulated serial data.
Owner:THINE ELECTRONICS
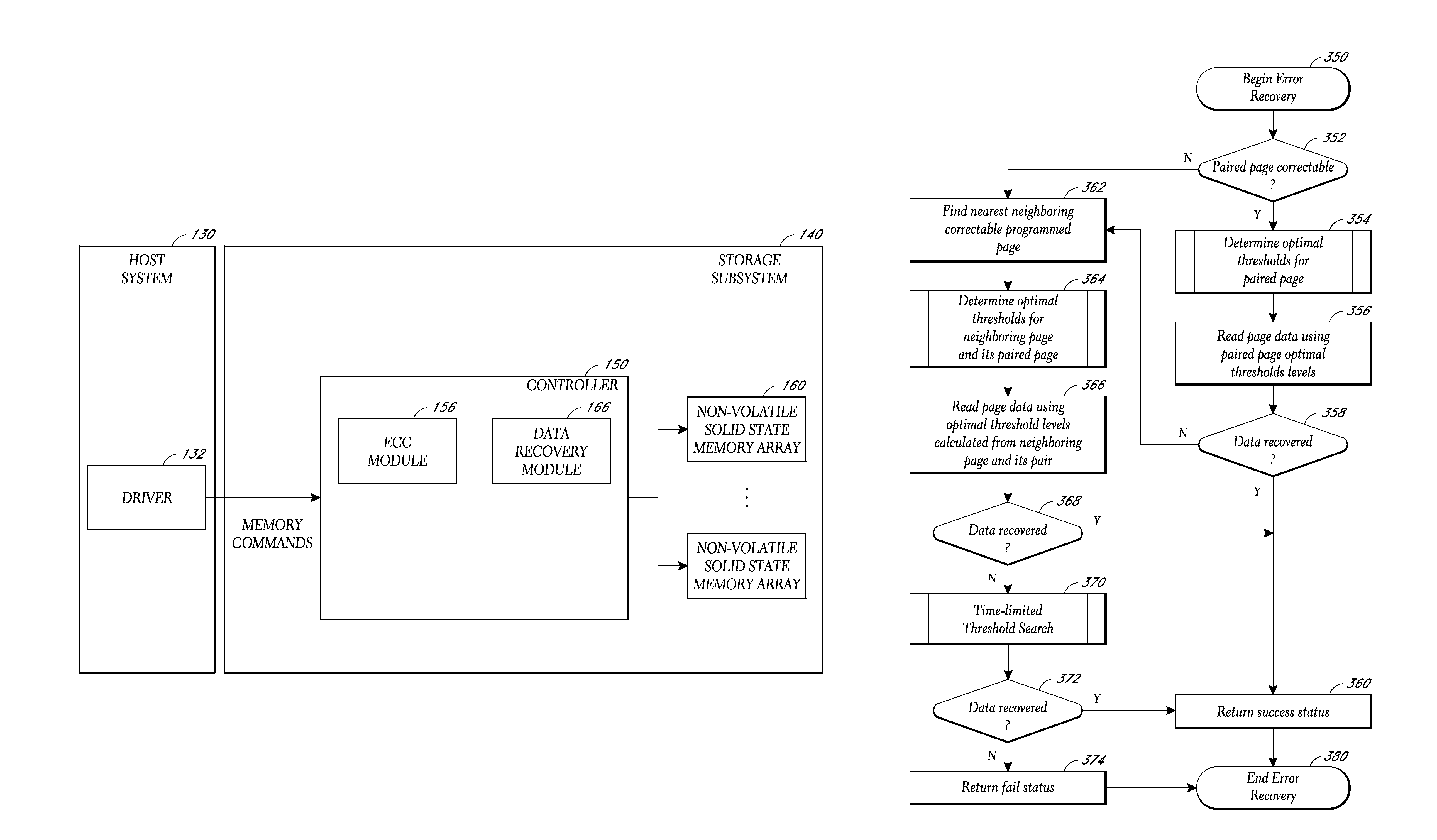
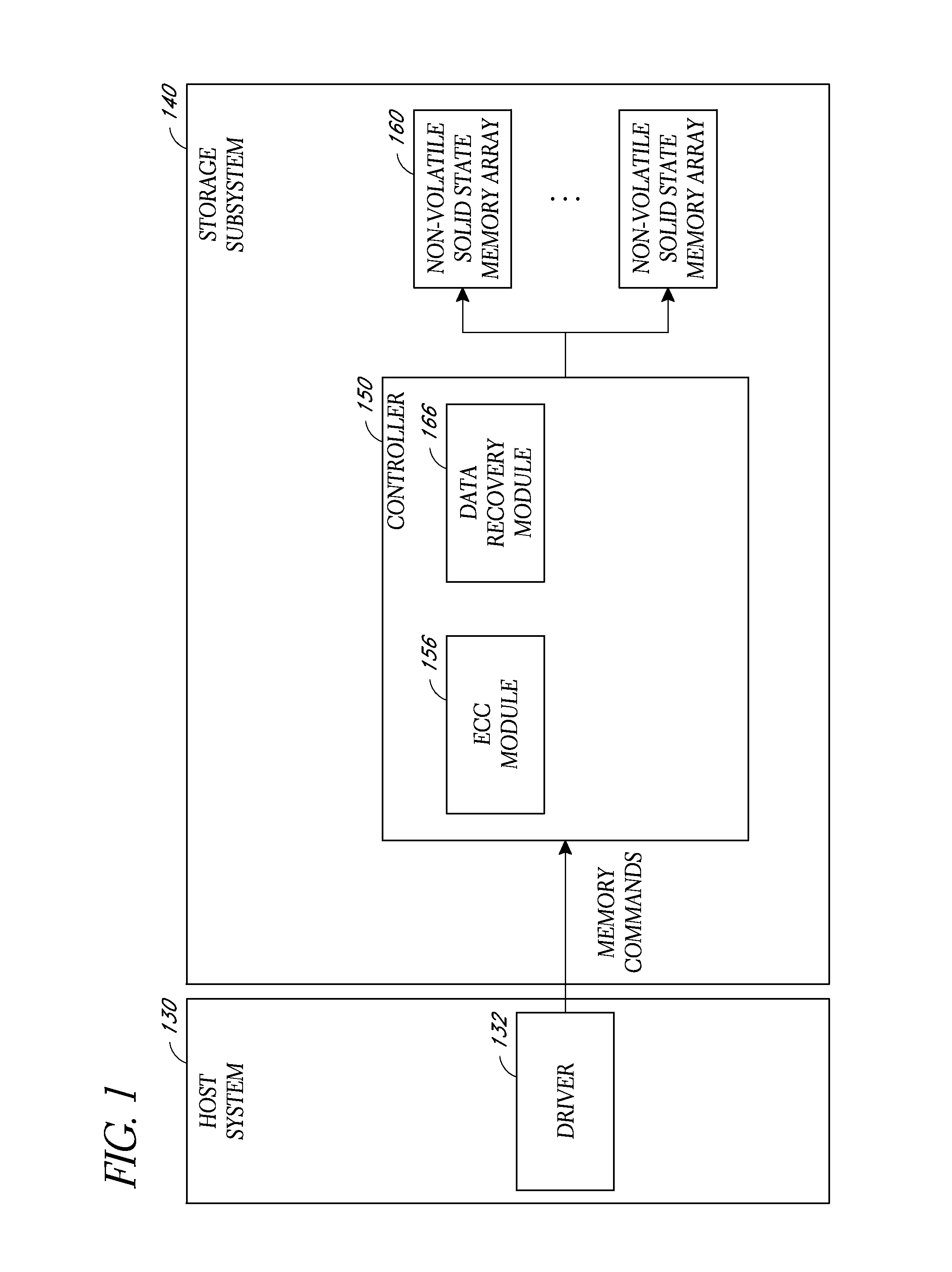
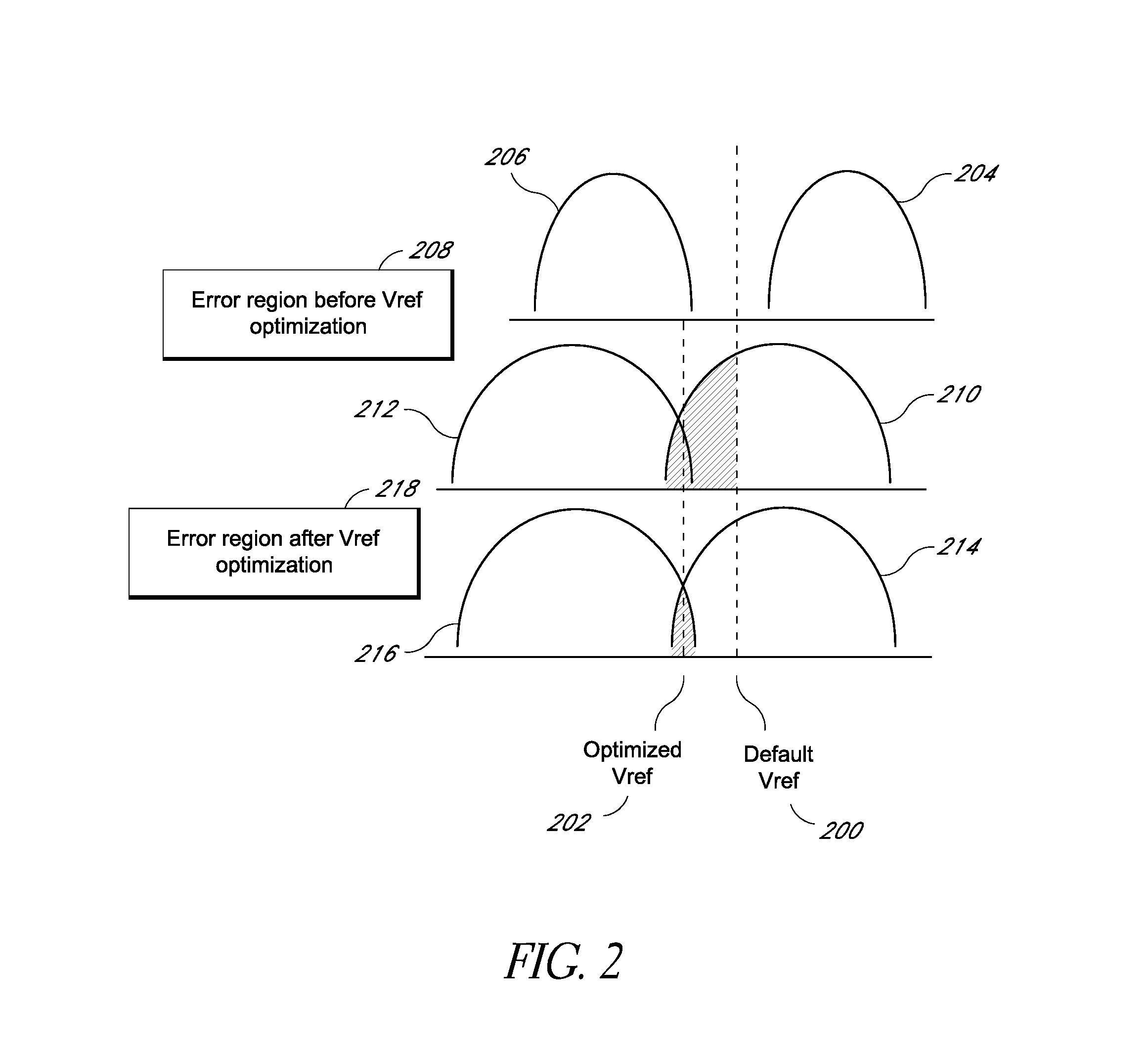
System and method for data recovery in a solid state storage device
Embodiments of solid-state storage system are provided herein include data recovery mechanism to recover data upon detection of a read error (e.g., an uncorrectable ECC error) in a storage element such as a page. In various embodiments, the system is configured to determine optimal reference voltage value(s) by evaluating the reference voltage value(s) of page(s) that are related to the page where the failure occurred. The related page(a) may include a page that is paired with the initial page where the failure occurred (e.g., the paired pages reside in a common memory cell), or a neighboring page that is physically near the page where the initial page, and / or a paired page of the neighboring page. In another embodiment, the system is configured to perform a time-limited search function to attempt to determine optimal reference voltage values through an iterative process that adjusts voltage values in a progression to determine a set of values that can retrieve the data.
Owner:WESTERN DIGITAL TECH INC
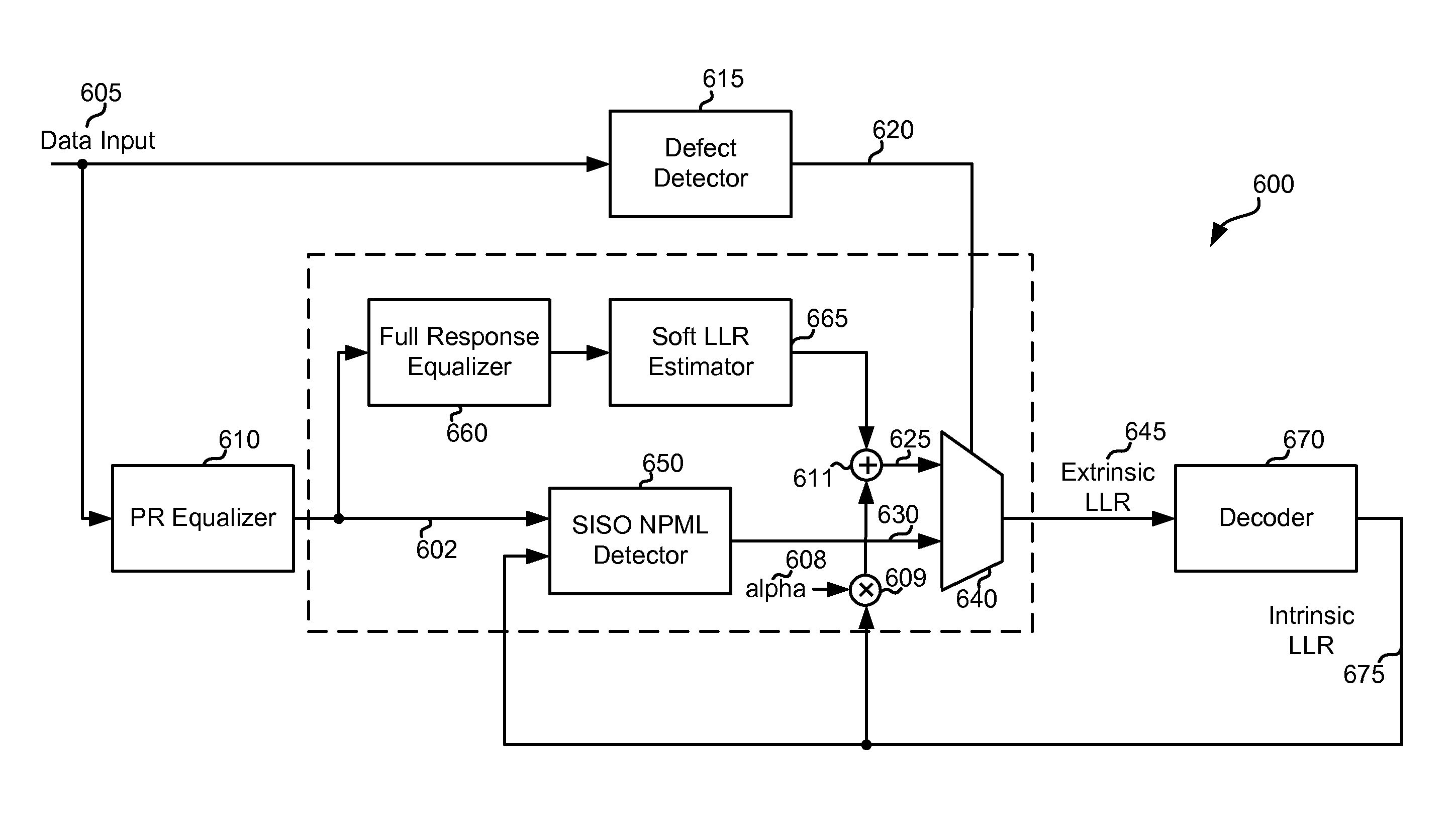
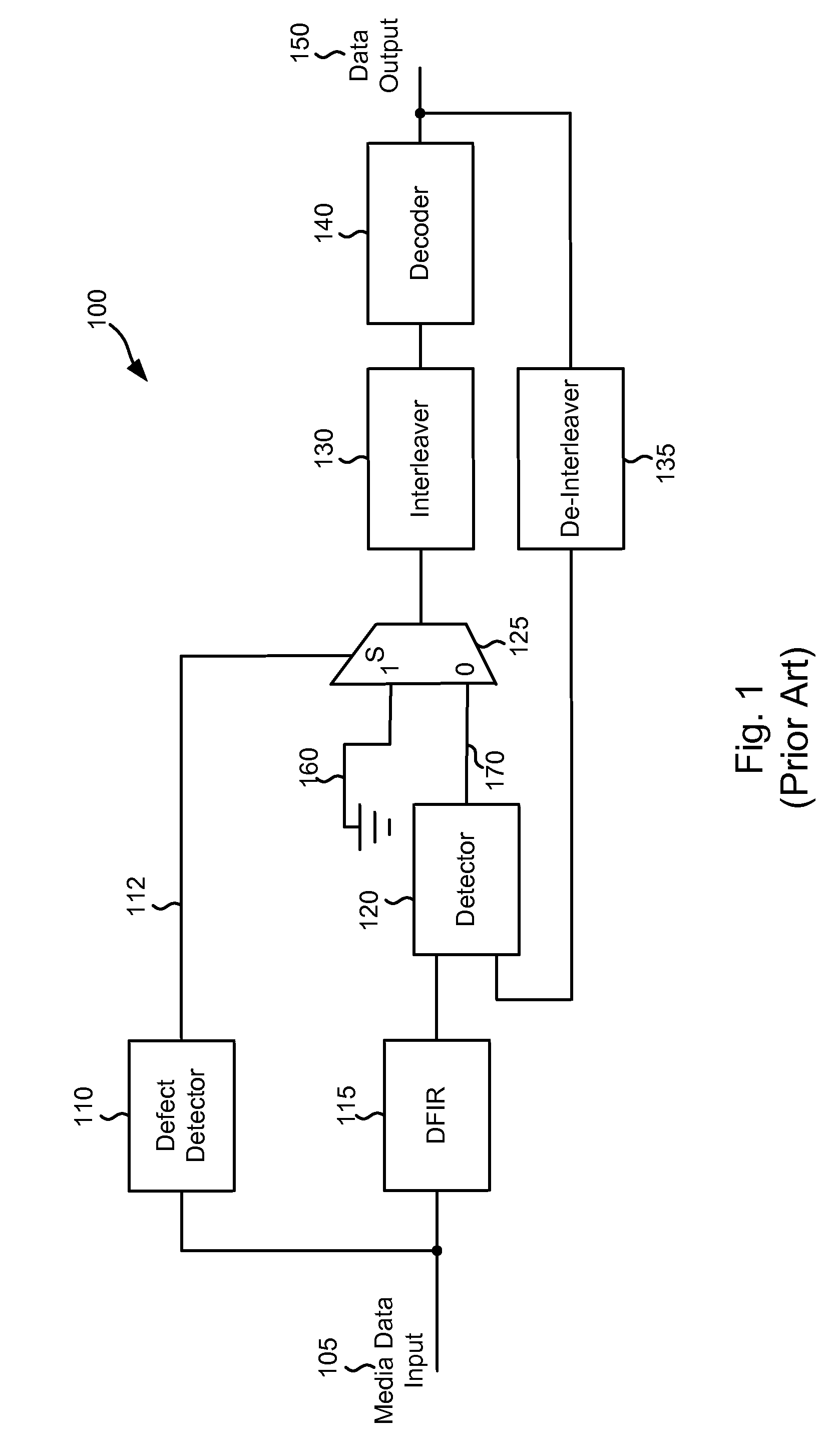
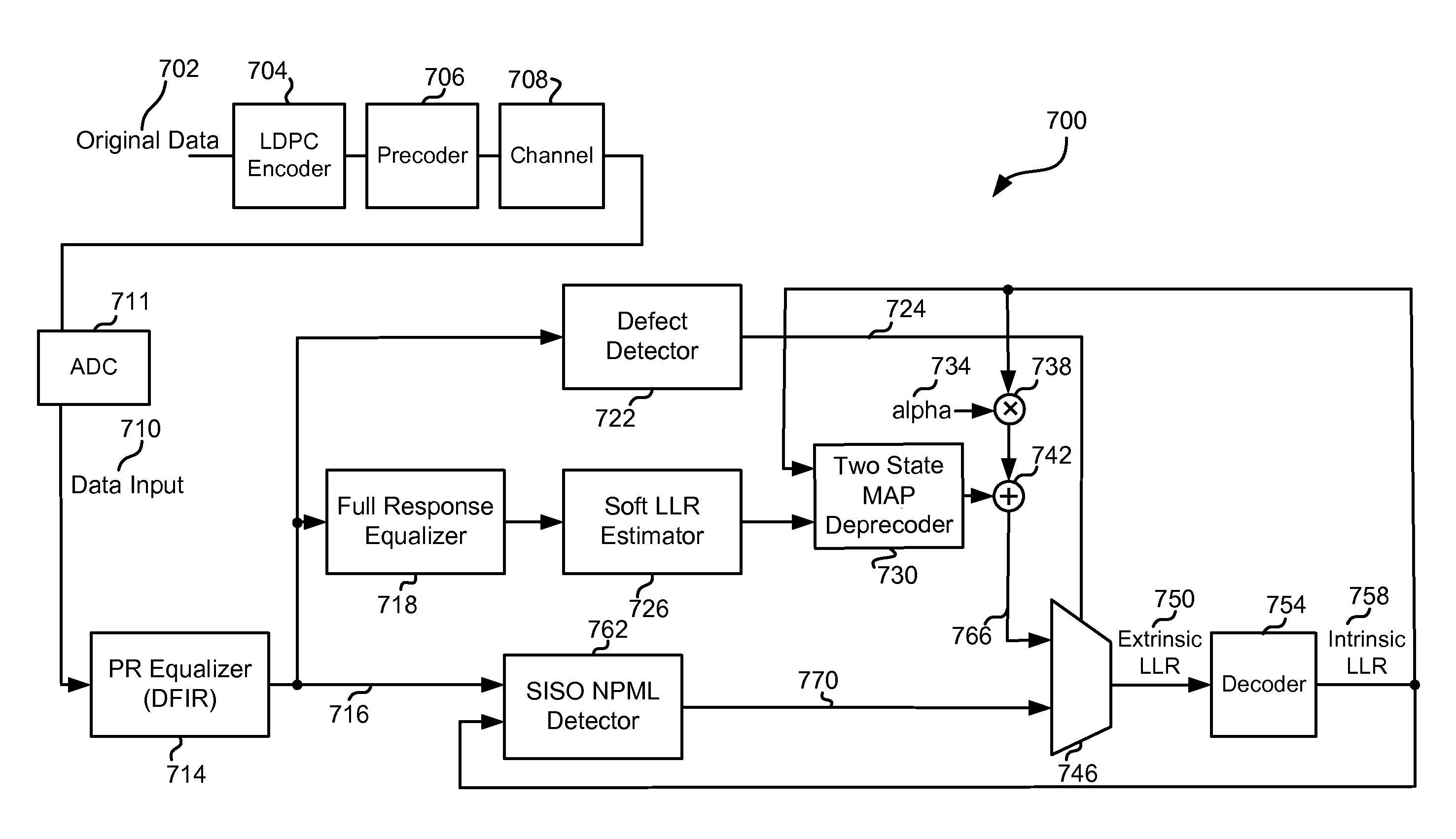
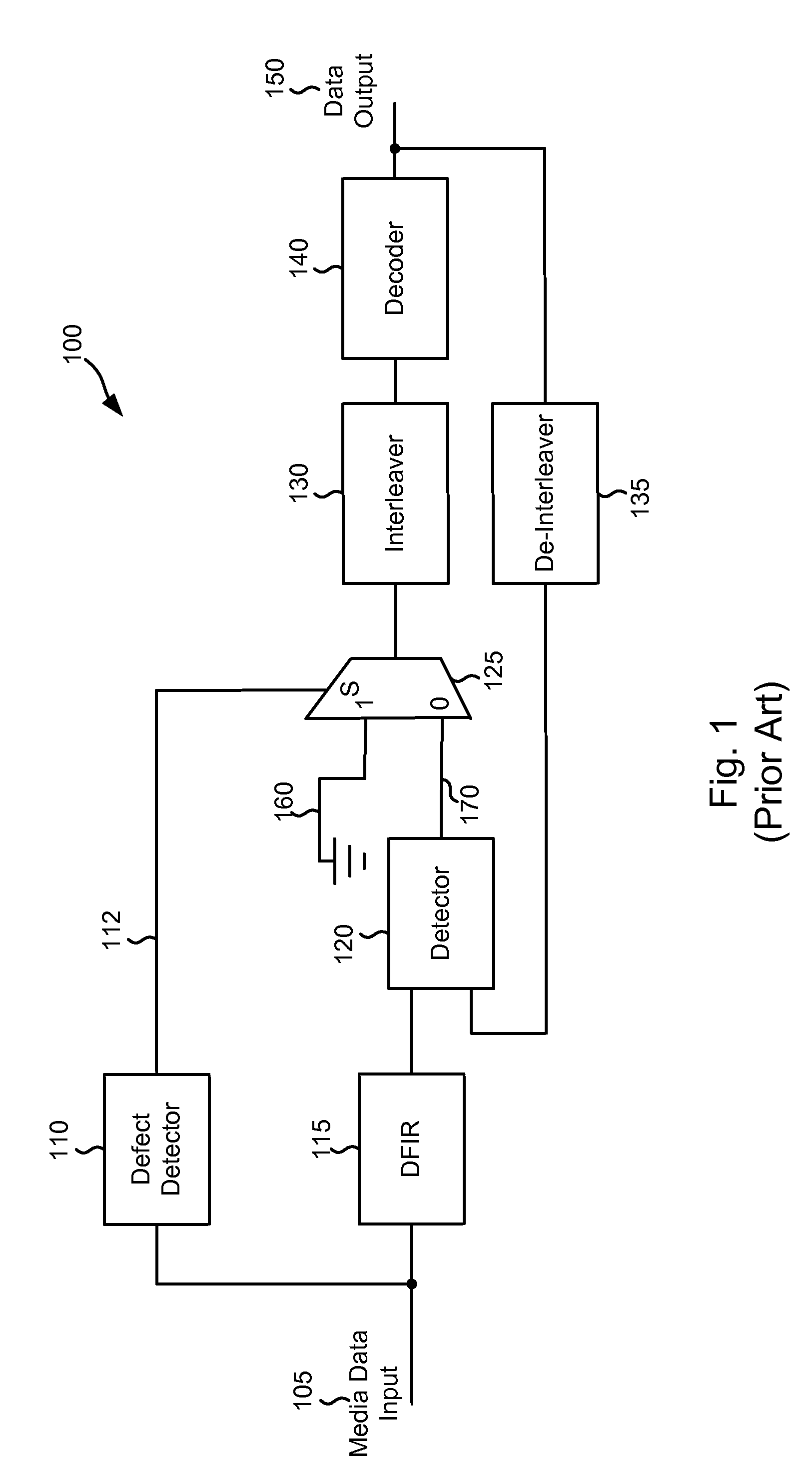
Systems and Methods for Using Intrinsic Data for Regenerating Data from a Defective Medium
ActiveUS20090235146A1Error prevention/detection by using return channelData representation error detection/correctionMultiplexerData recovery
Various embodiments of the present invention provide systems and methods for data regeneration. For example, a system for data regeneration is disclosed that includes a data input derived from the medium. A data detector and a data recovery system receive the data input. The data detector provides a first soft output, and the data recovery system provides a second soft output. The first soft output and the second soft output are provided to a multiplexer. A media defect detector performs a media defect detection process, and provides a defect flag that indicates whether the data input is derived form a defective portion of the medium. The defect flag is provided to the multiplexer where it is used to select whether the first soft output or the second soft output is provides as an extrinsic output.
Owner:AVAGO TECH INT SALES PTE LTD
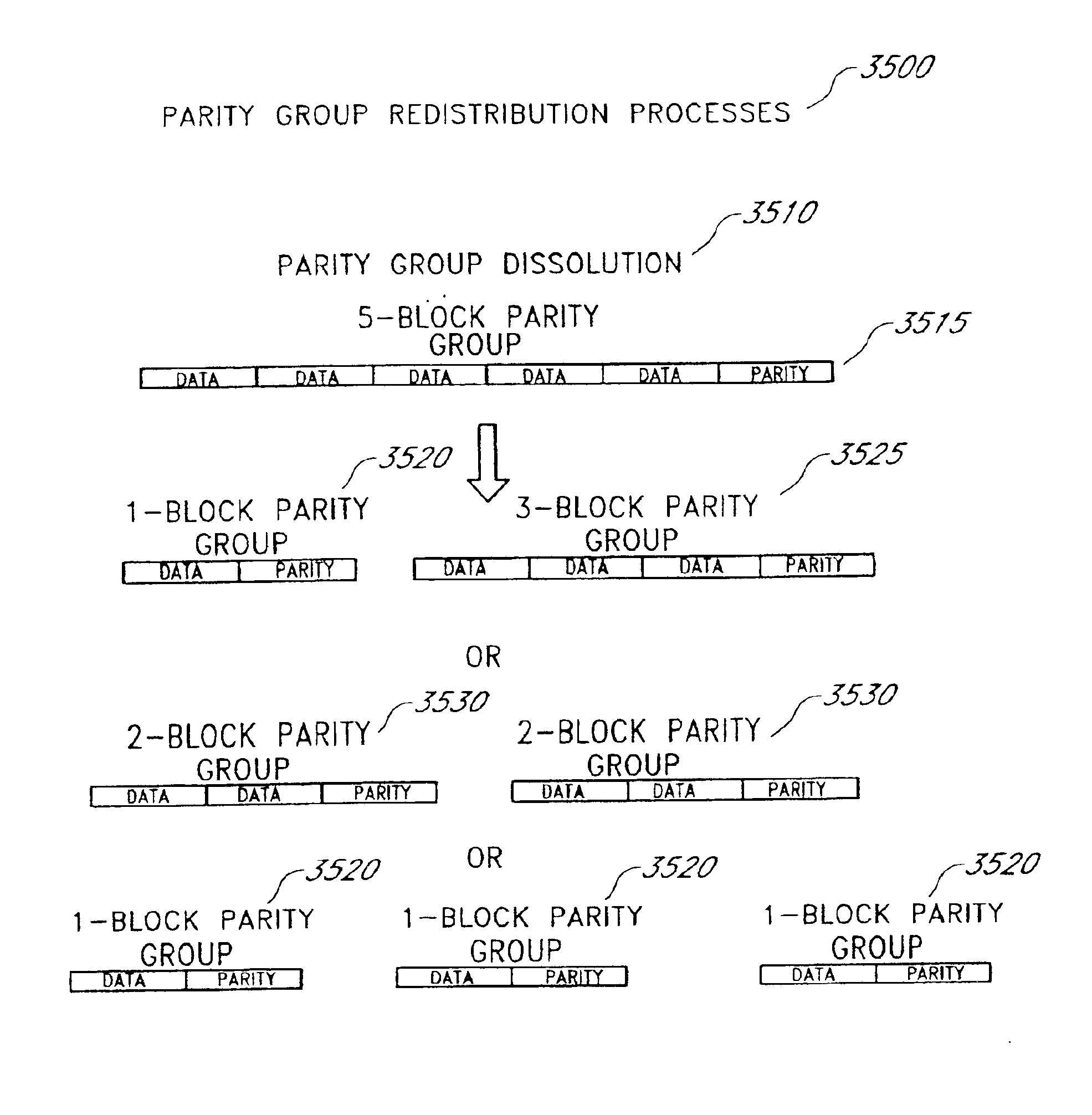
Dynamic data recovery
InactiveUS6871295B2Increase capacityImprove throughputMemory loss protectionDigital data processing detailsDynamic dataData recovery
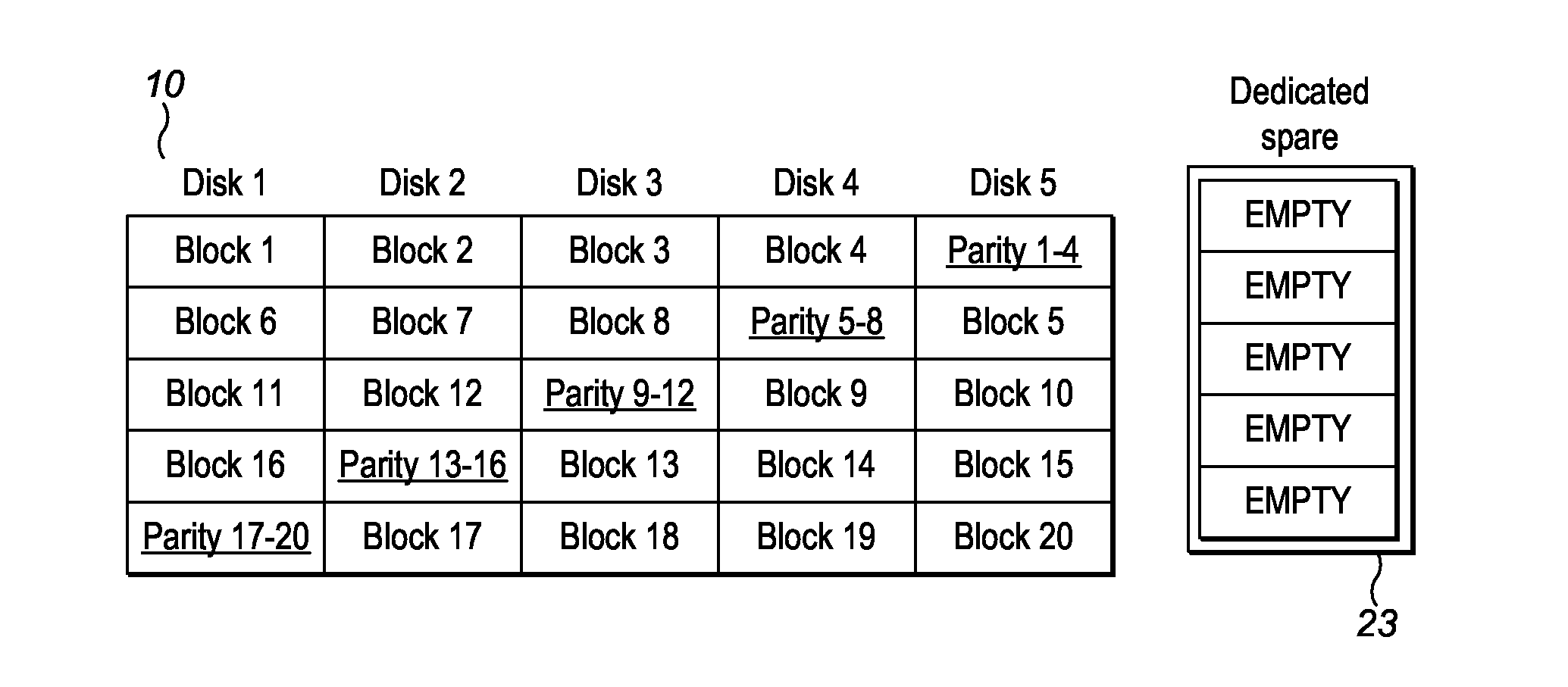
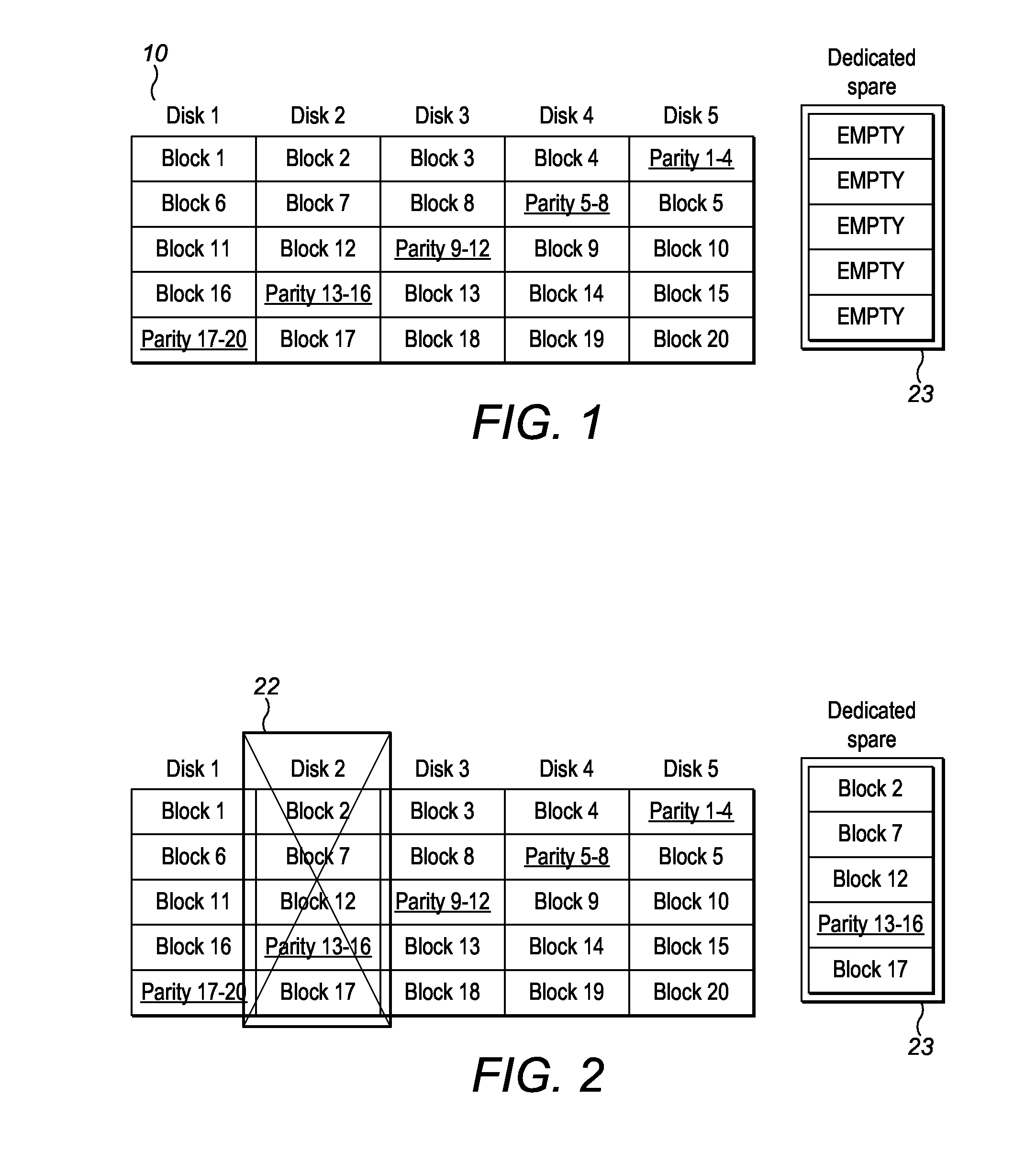
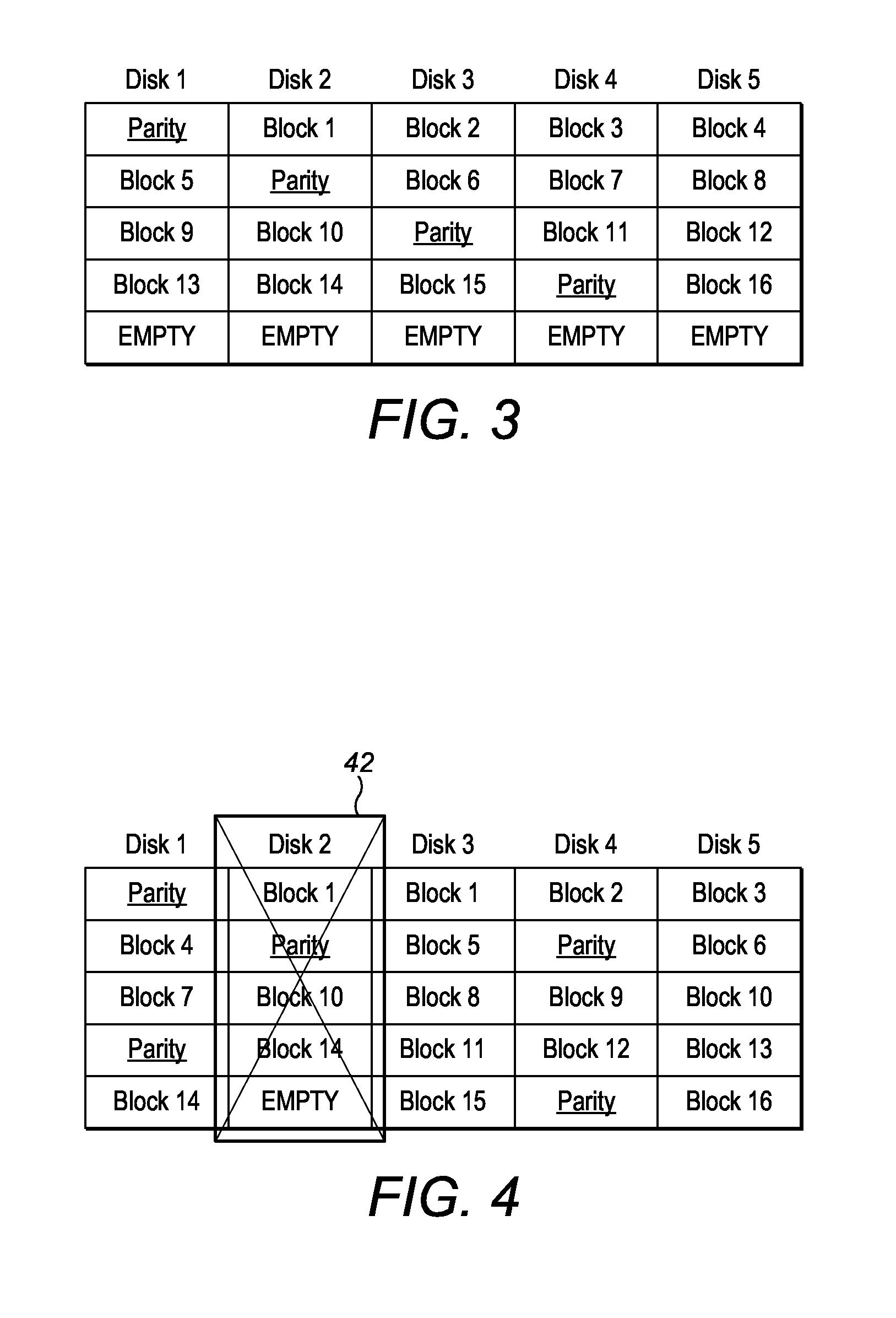
A system and method for dynamic data recovery is described. The system and method for dynamic data recovery operates on a computer storage system that includes a plurality of disk drives for storing parity groups. Each parity group includes storage blocks. Each of the storage blocks is stored on a separate disk drive such that no two storage blocks from a given parity set reside on the same disk drive. The computer storage system further includes a recovery module to dynamically recover data that is lost when at least a portion of one disk drive in the plurality of disk drives becomes unavailable. The recovery module is configured to produce a reconstructed block by using information in the remaining storage blocks of a parity set that corresponds to an unavailable storage block. The recovery module is further configured to split the parity group corresponding to an unavailable storage block into two parity groups if the parity group corresponding to the unavailable storage block spanned all of the drives in the plurality of disk drives.
Owner:OVERLAND STORAGE
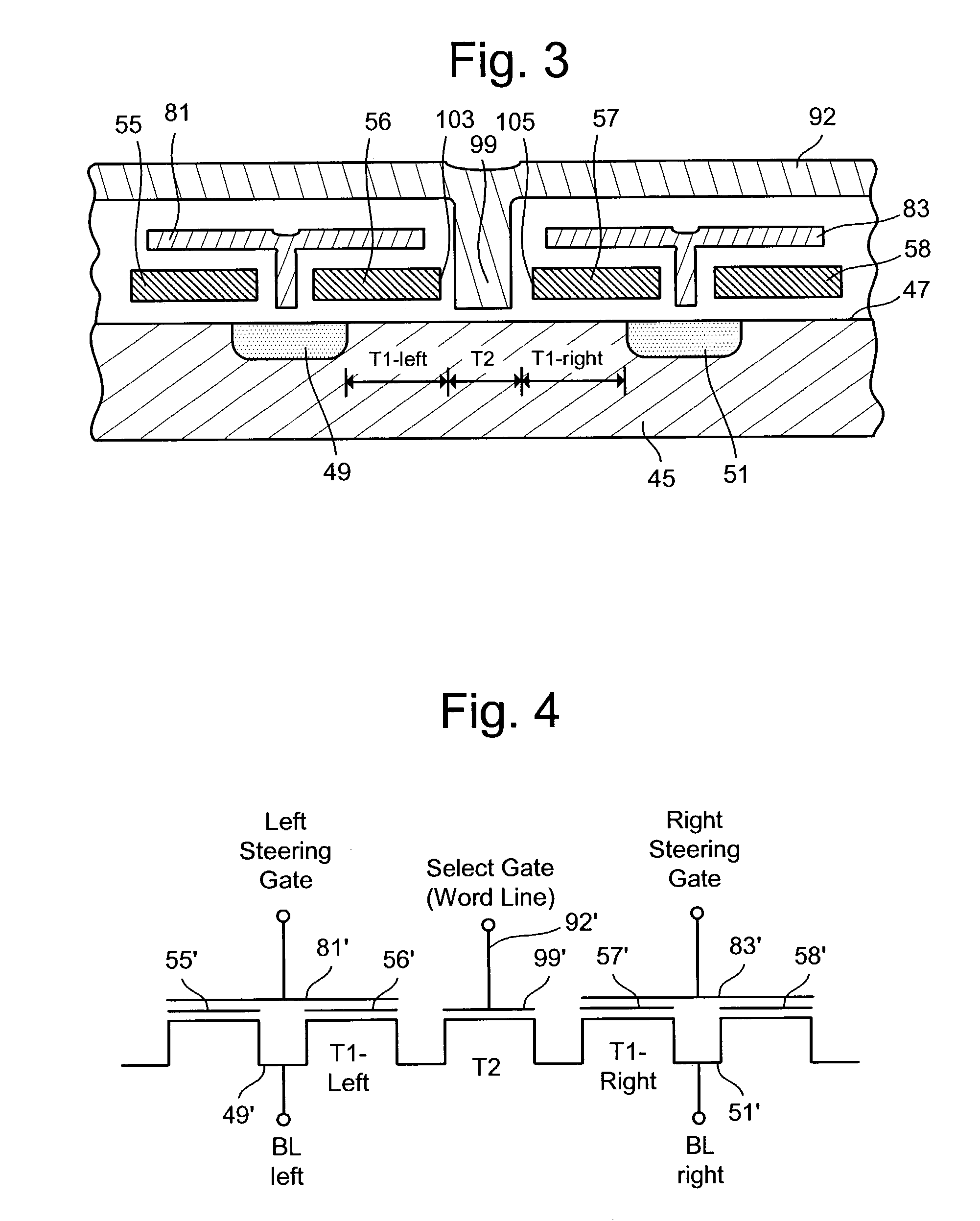
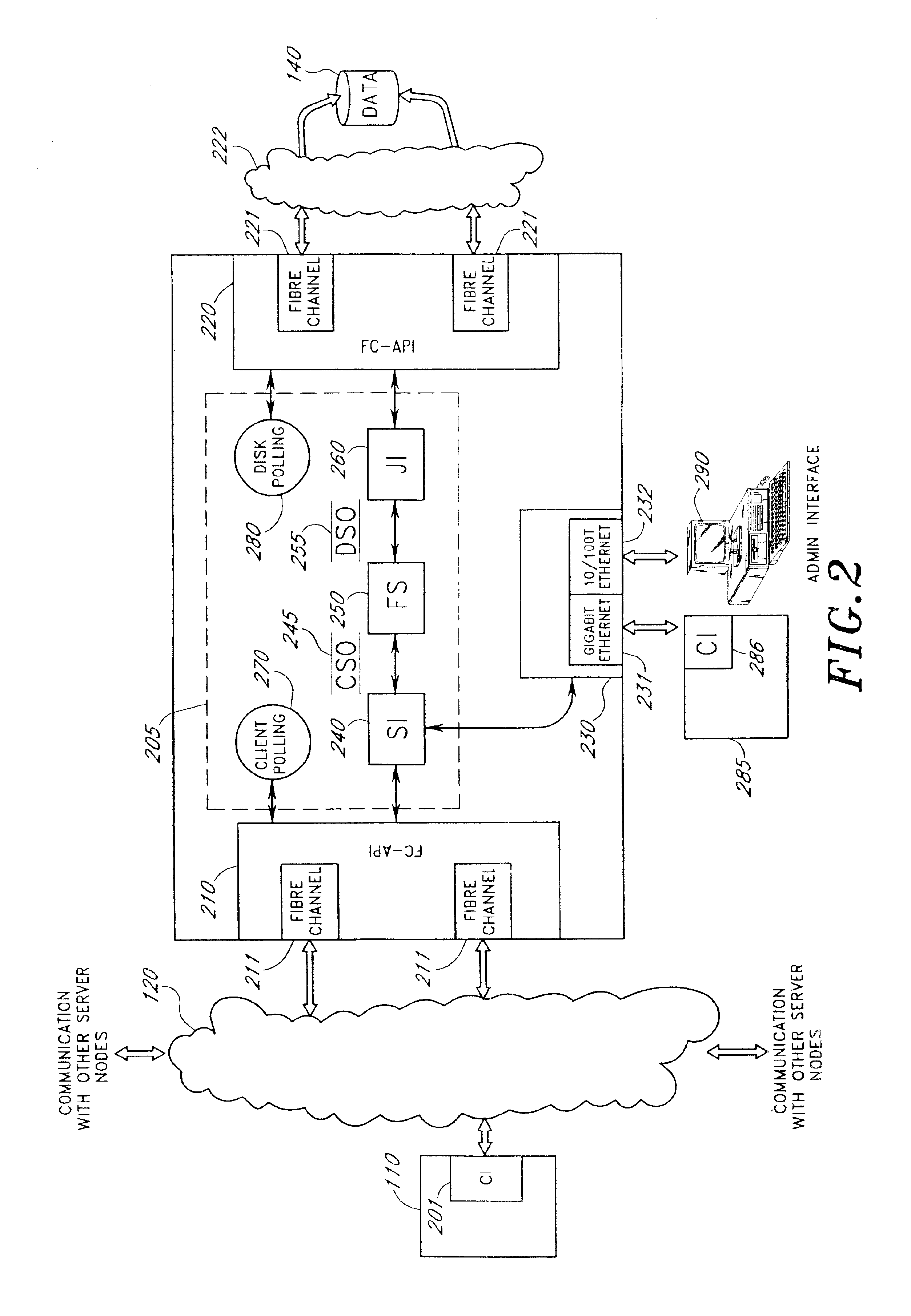
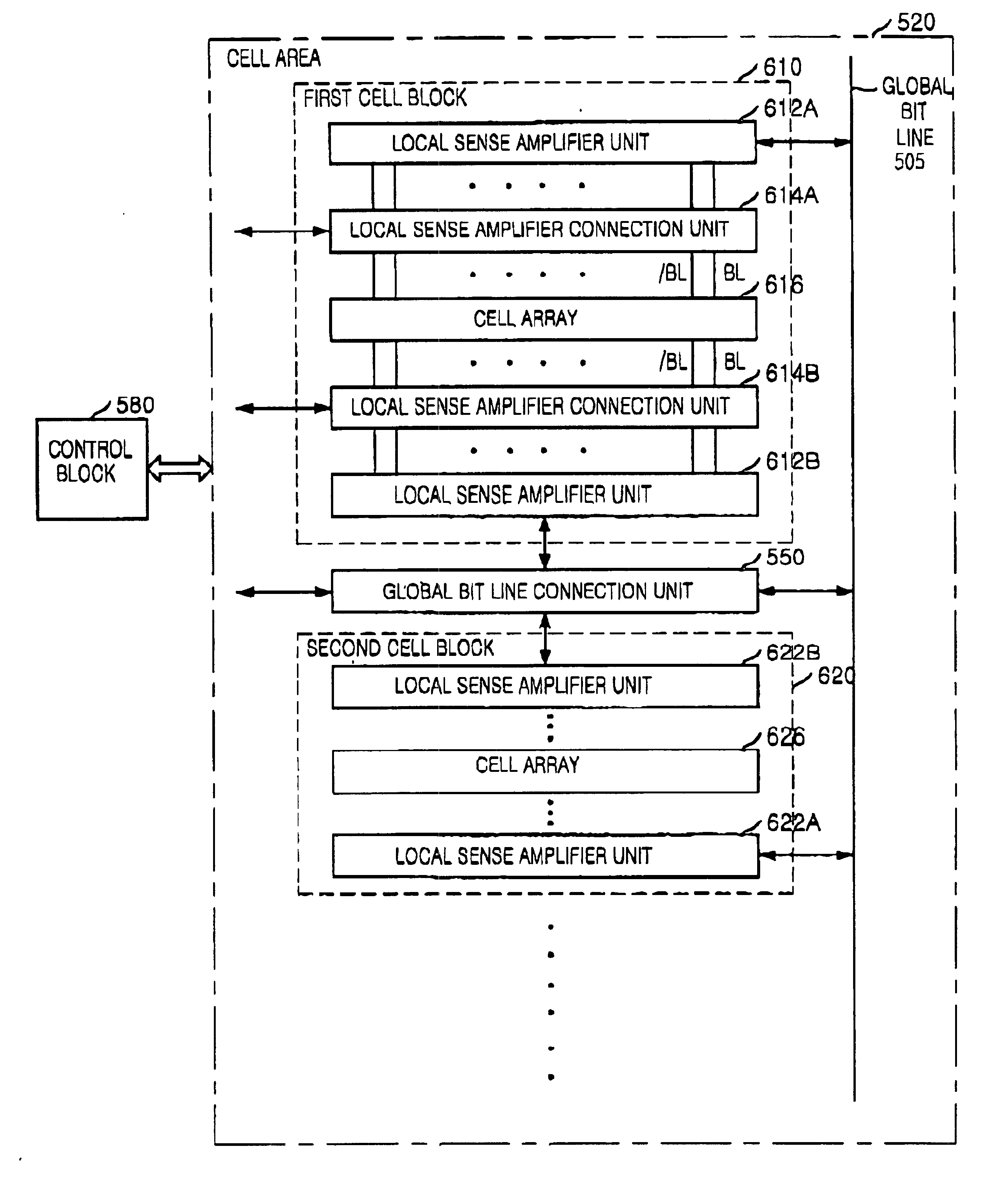
Semiconductor memory device with reduced data access time
A memory device includes at least two cell blocks connected to a global bit line for outputting data in response to an instruction; at least one global bit line connection unit for selectively connecting the global bit line to each cell block under control of a control block, one global bit line connection unit being allocated between the two cell blocks; and said control block for controlling output of data stored in each cell block to the global bit line and restoration of the outputted data of the global bit line to the original cell block or another cell block which is determined by depending upon whether data in response to a next instruction is outputted from the original cell block or another cell block.
Owner:SK HYNIX INC
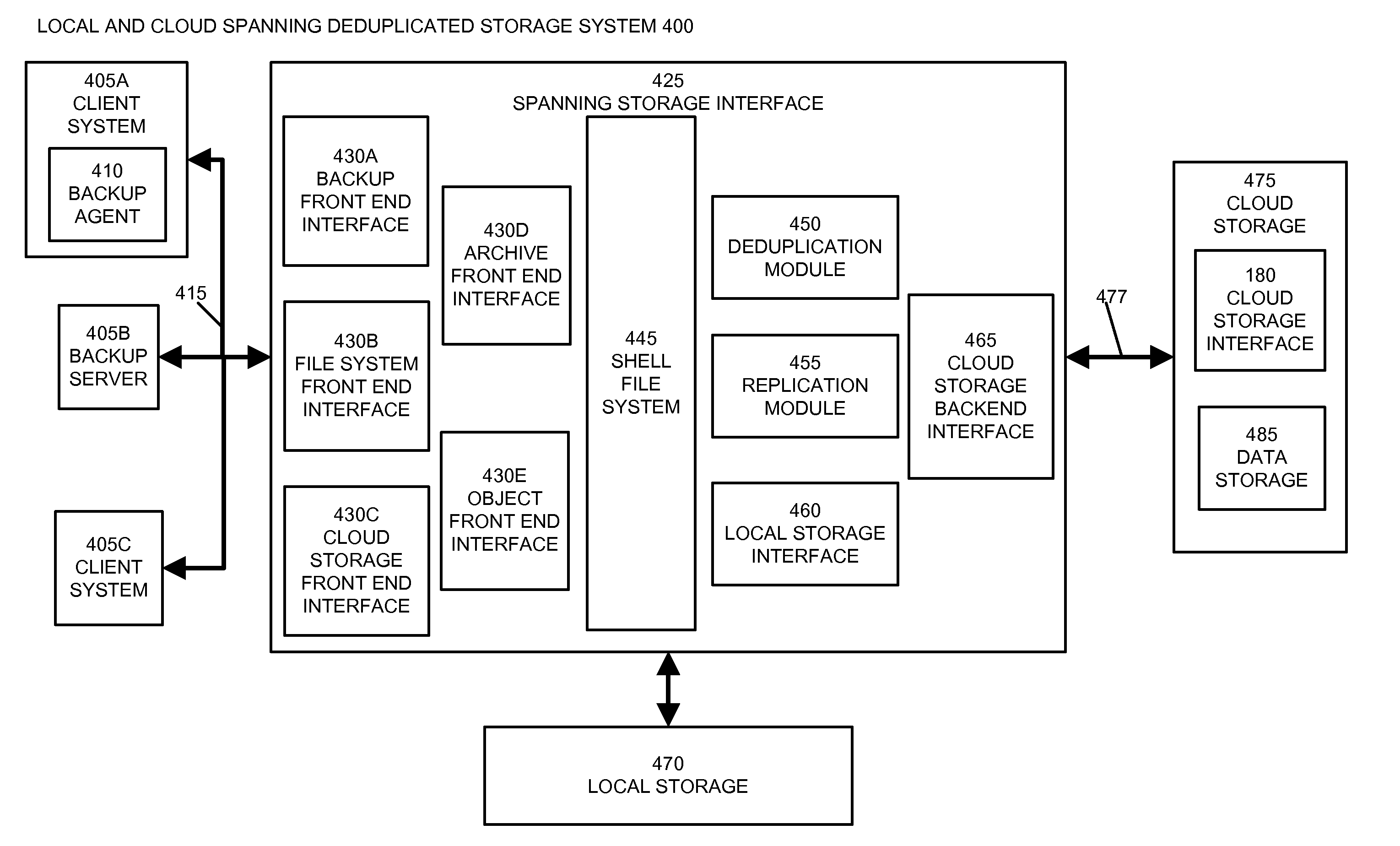
Cloud-based disaster recovery of backup data and metadata
ActiveUS20120084261A1Inexpensive and easily configuredEliminate needError detection/correctionDigital data processing detailsData streamCloud base
Cloud storage services can be used to facilitate secondary backup and disaster data recovery without the need for specialized backup servers at the secondary location or cloud storage service. Backup data streams are transferred to a cloud storage service. In addition to the backup data streams, backup metadata is generated for each backup data stream. The backup metadata is adapted to configure a backup server to retrieve and access data in the backup data stream. The backup metadata is also transferred to the cloud storage service. To access data from the backup data stream, a recovery backup system is connected with the cloud storage service. Backup metadata is transferred from the cloud storage service to the recovery backup system. The recovery backup system is updated with the backup metadata, which configures the recovery backup system to retrieve and access data in the backup data stream.
Owner:NETWORK APPLIANCE INC
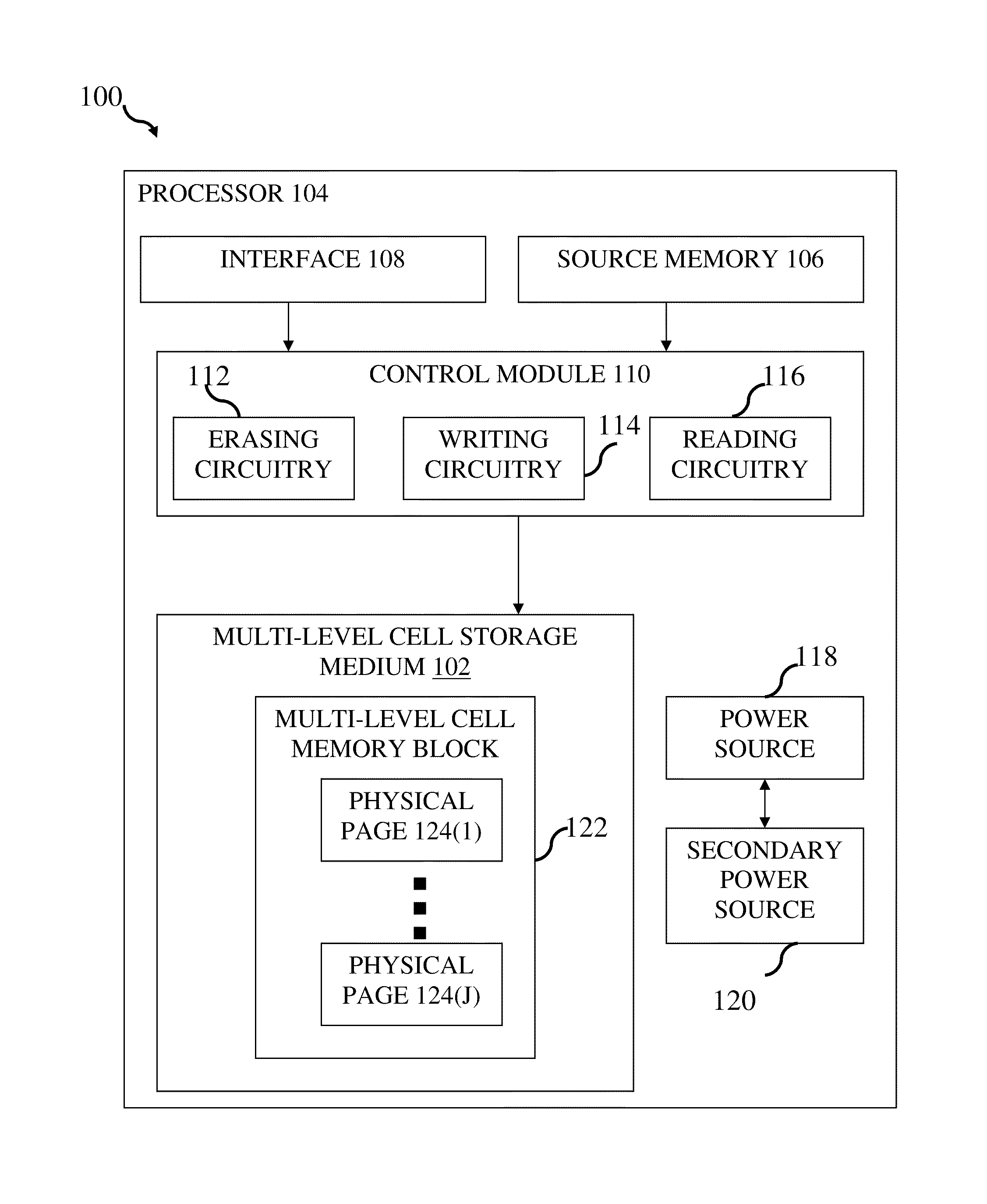
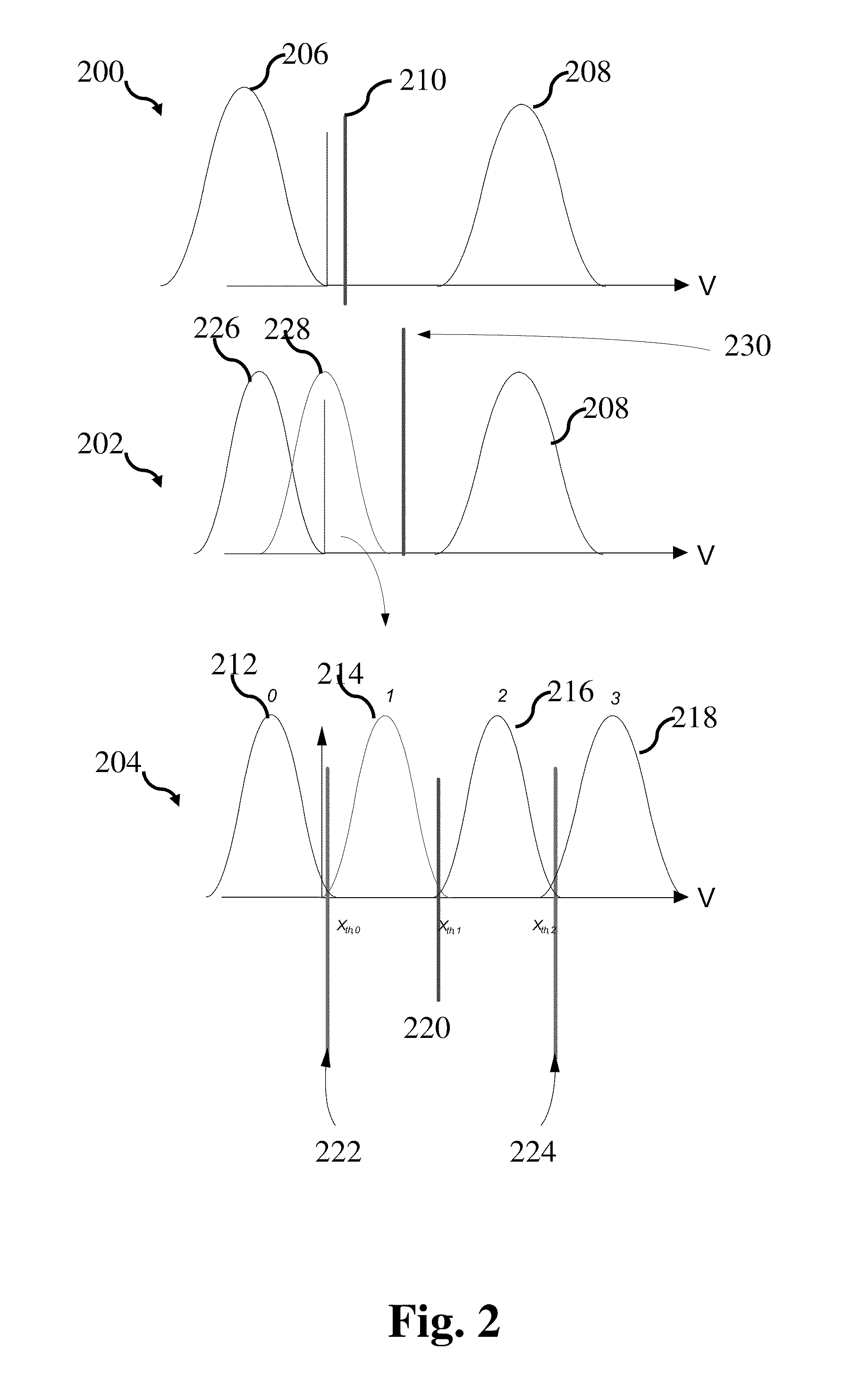
System and method for data recovery in multi-level cell memories
ActiveUS20120005558A1Read-only memoriesError correction/detection using block codesParallel computingMulti-level cell
A system and method are provided for data recovery in a multi-level cell memory device. One or more bits may be programmed sequentially in one or more respective levels of multi-level cells in the memory device. An interruption of programming a subsequent bit in a subsequent second or greater level of the multi-level cells may be detected. Data may be recovered from the multi-level cells defining the one or more bits programmed preceding the programming interruption of the second or greater level.
Owner:AVAGO TECH INT SALES PTE LTD
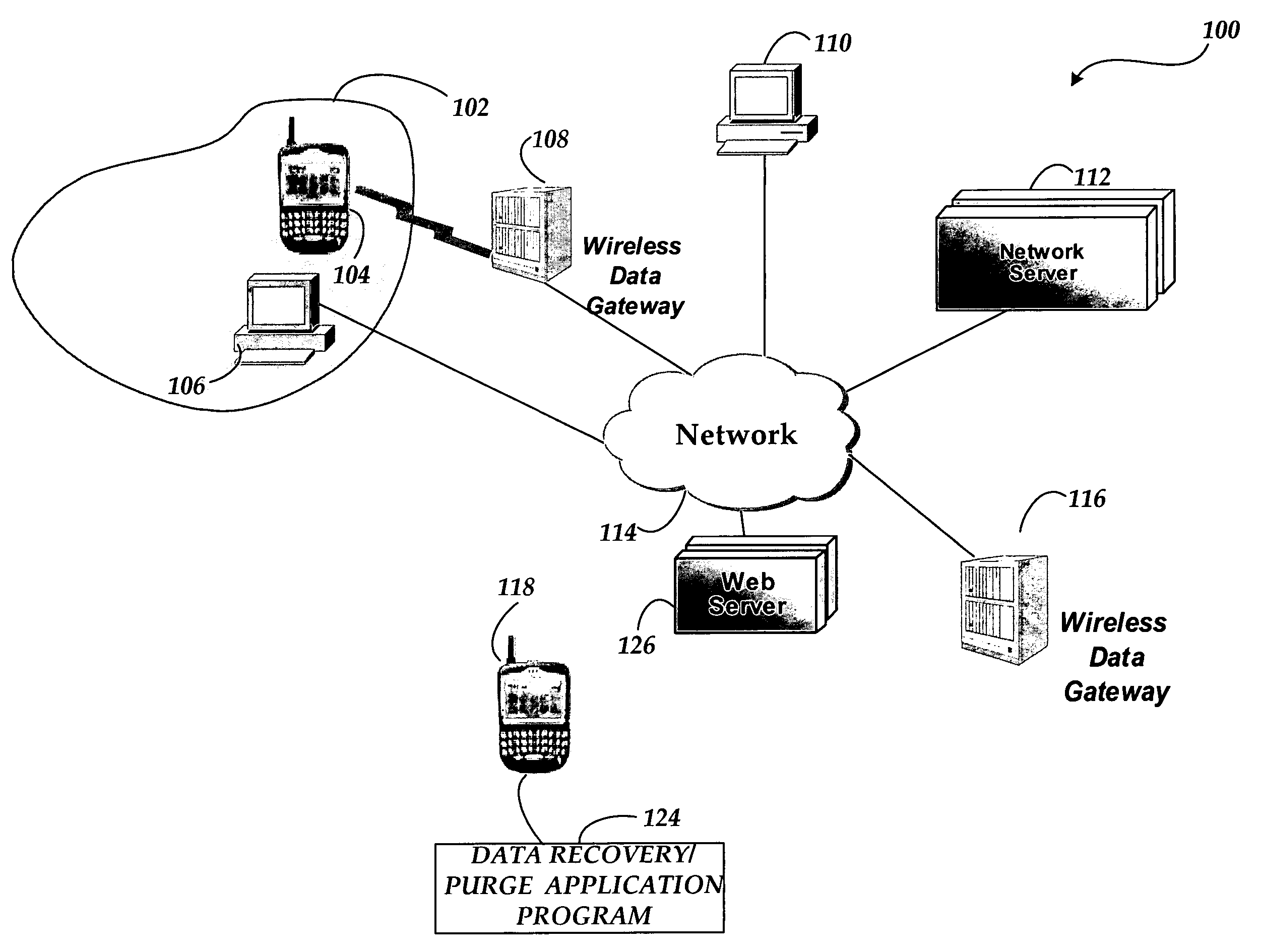
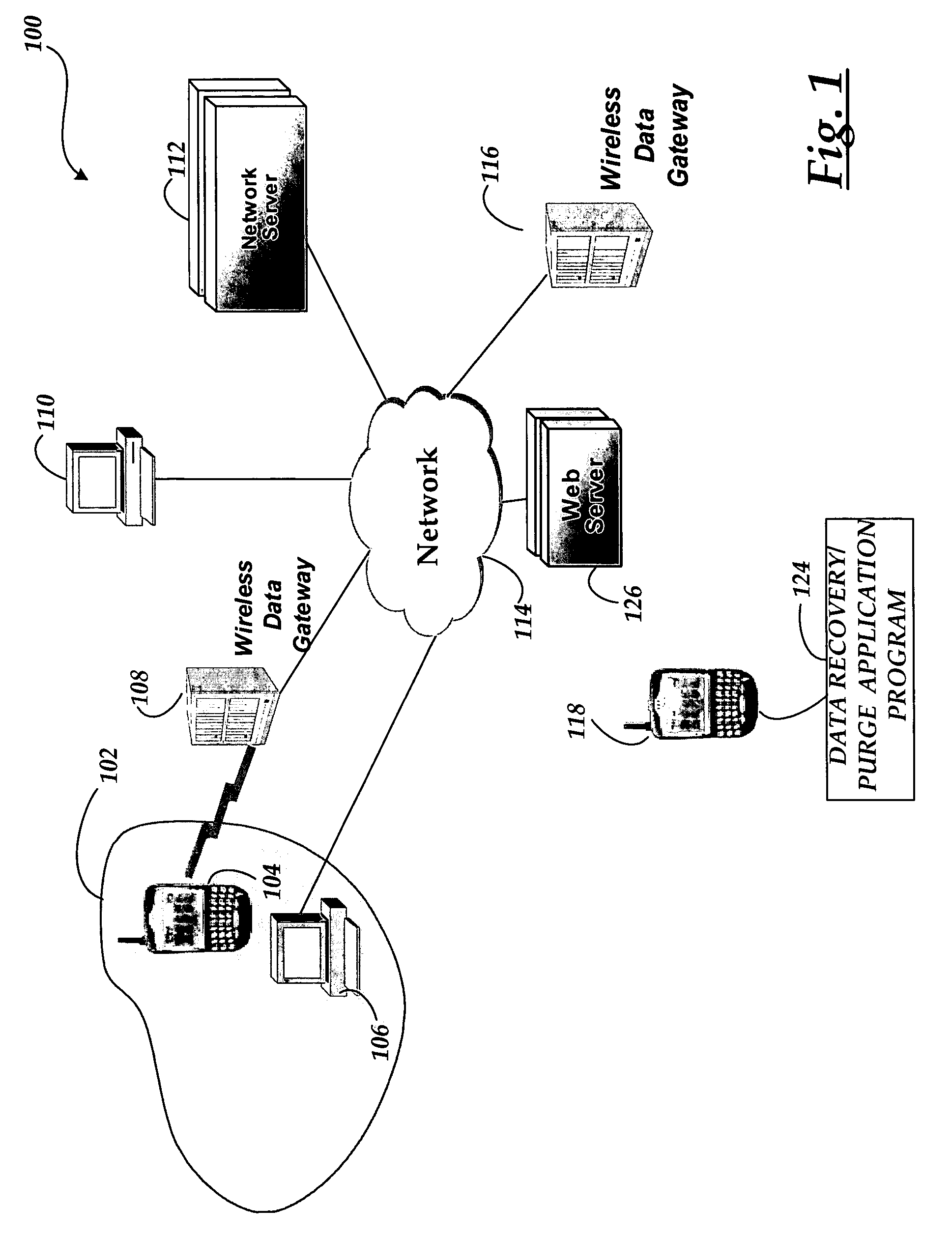
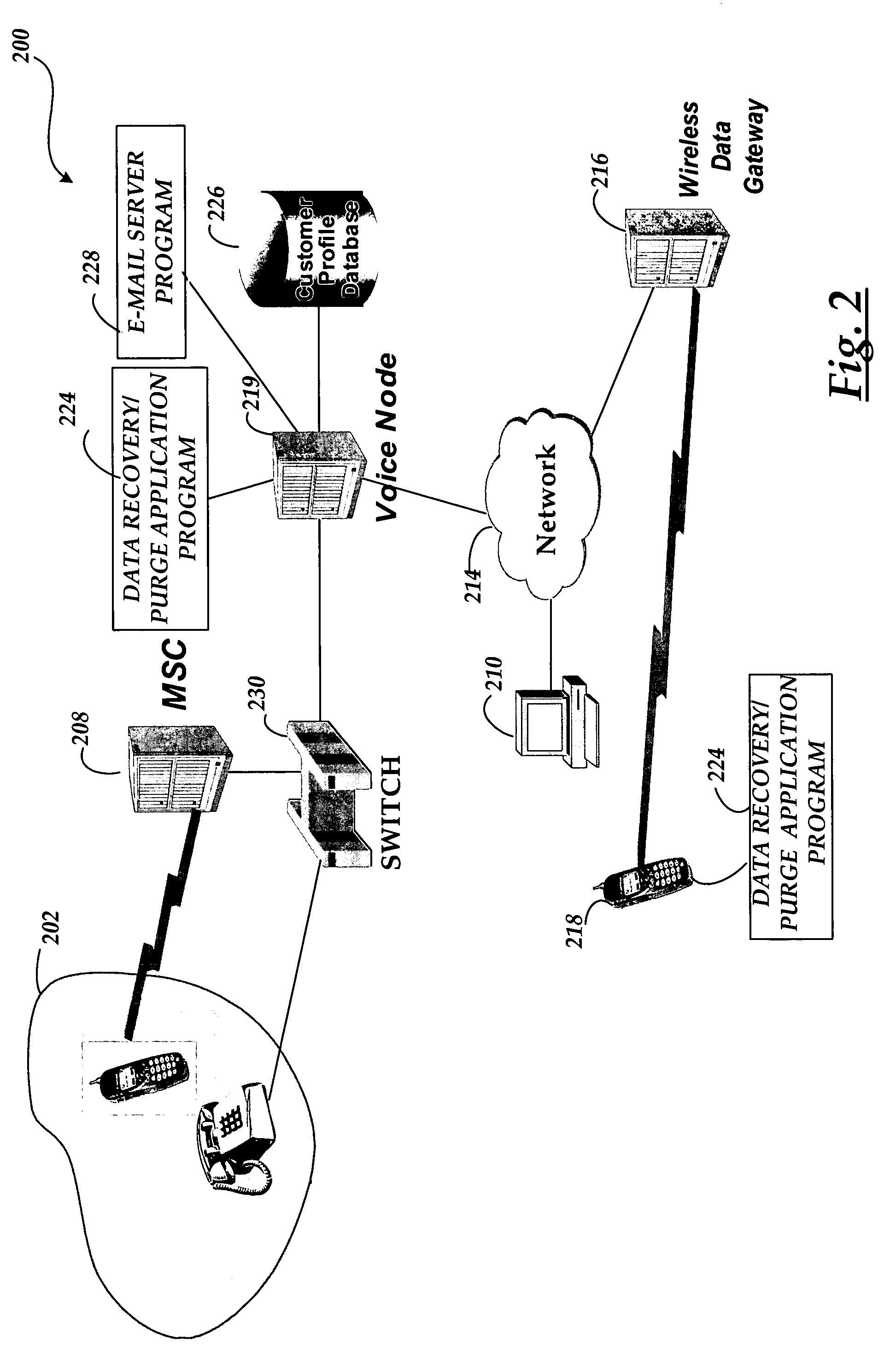
System and methods for remotely recovering and purging data from a wireless device in a communications network
ActiveUS7849161B2Avoid accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer networkData recovery
A system and methods are provided for remotely recovering and purging data from a wireless device in a communications network. The system includes a wireless device capable of executing a data recovery / purge application program for receiving a message from a communications device in the network. The application program retrieves the data in the wireless device, purges the data from the wireless device, and sends a return message, including the data retrieved from the wireless device, to the communications device.
Owner:RAKUTEN GRP INC
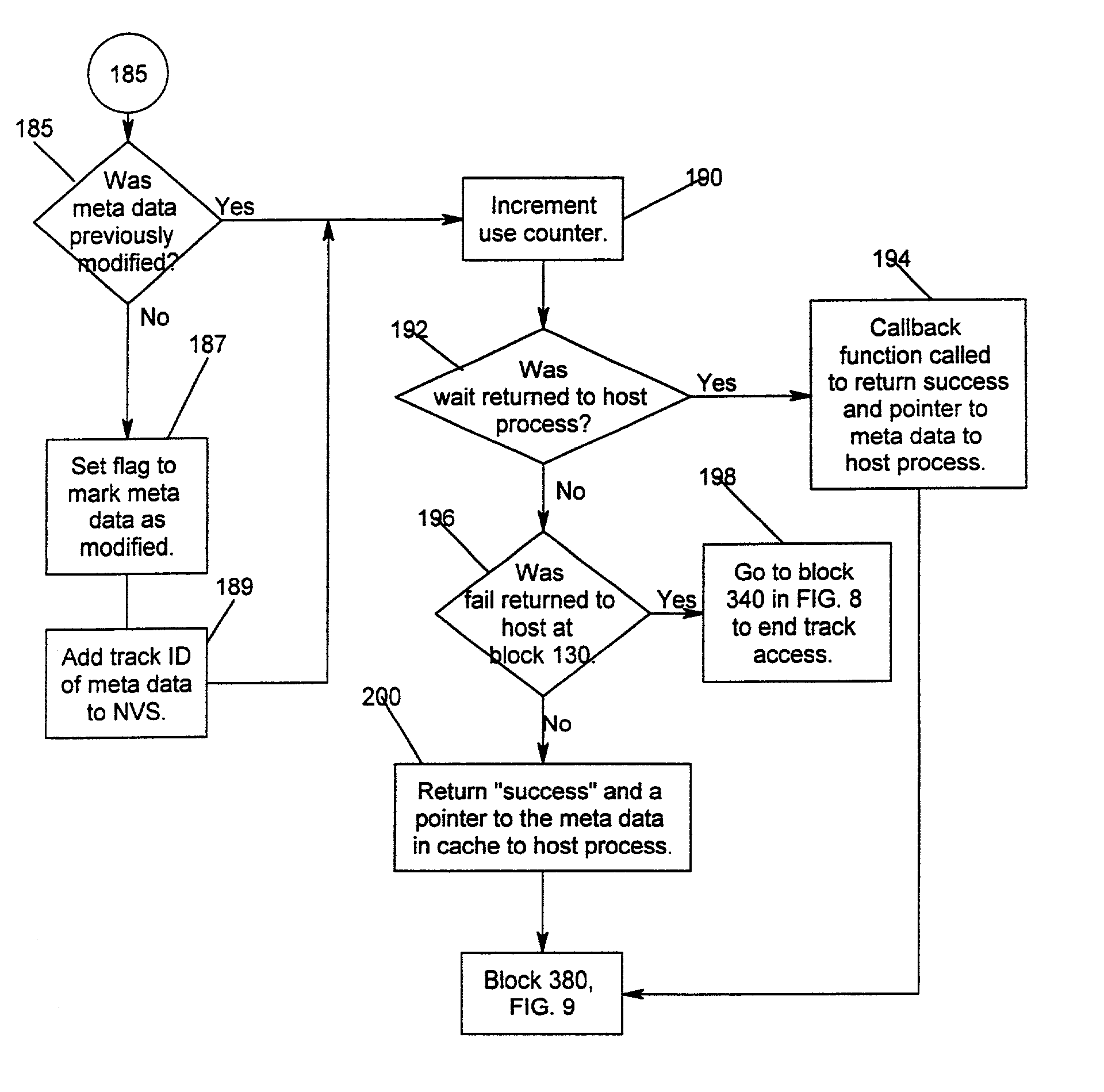
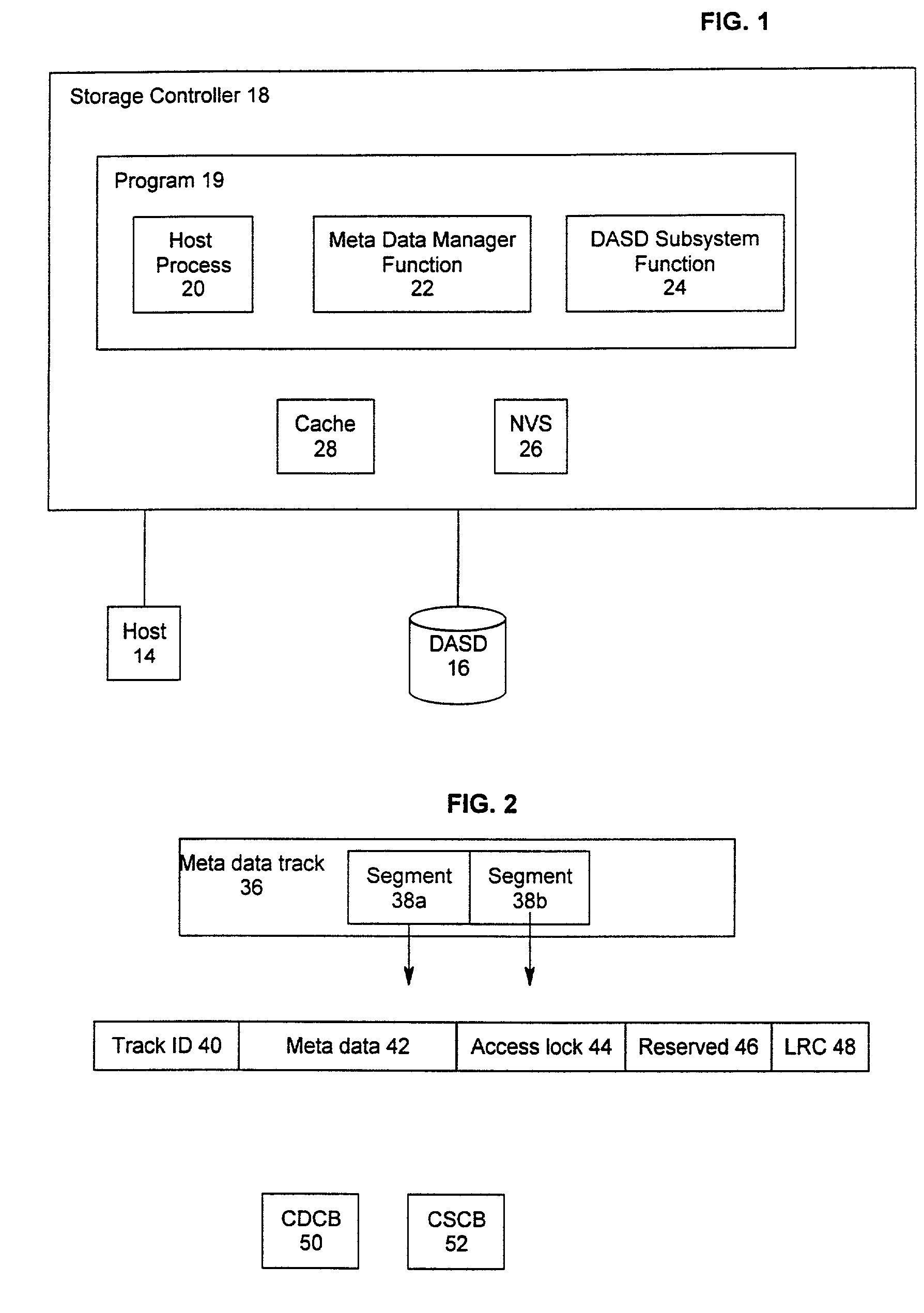
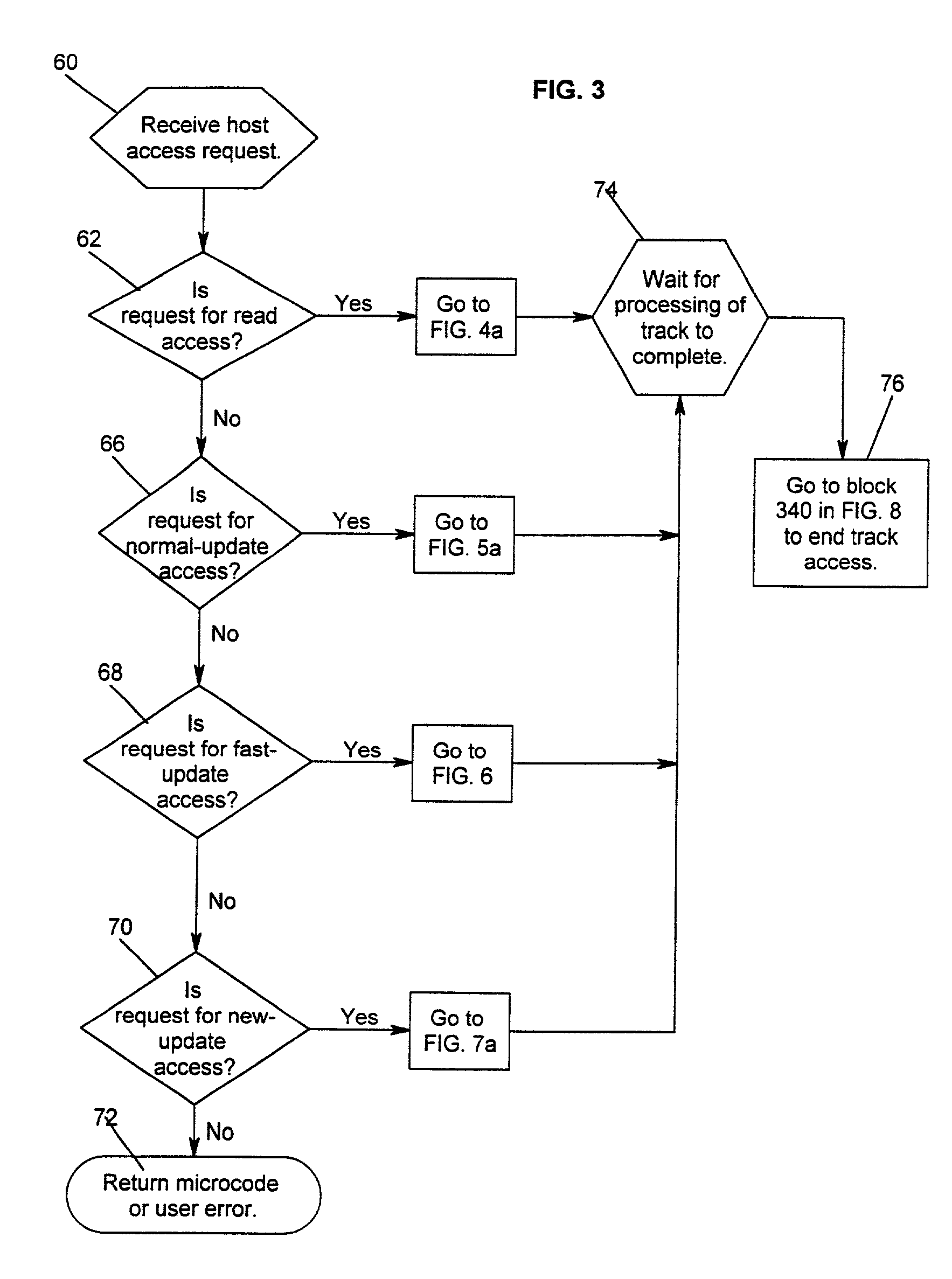
Method and system for recovery of meta data in a storage controller
InactiveUS6988171B2Data processing applicationsMemory adressing/allocation/relocationSystem failureComputer science
Disclosed is a method, system, and article of manufacture for processing modified meta data for data recovery operations. The meta data provides information on user data maintained in a storage device. The system determines whether meta data tracks maintained in a cache were modified and indicates in a non-volatile memory that the determined meta data tracks were modified. Data recovery operations may be initiated as a result of a system failure, such as a warmstart or coldstart recovery. During such data recovery operations, the system processes the non-volatile memory and the indications of modified meta data tracks therein to rebuild lost meta data tracks in the cache.
Owner:IBM CORP
Codes For Limited Magnitude Asymetric Errors In Flash Memories
ActiveUS20080168320A1Increase speedReach levelError preventionTransmission systemsReduced sizeErrors and residuals
Error correction is tailored for the use of an ECC for correcting asymmetric errors with low magnitude in a data device, with minimal modifications to the conventional data device architecture. The technique permits error correction and data recovery to be performed with reduced-size error correcting code alphabets. For particular cases, the technique can reduce the problem of constructing codes for correcting limited magnitude asymmetric errors to the problem of constructing codes for symmetric errors over small alphabets. Also described are speed up techniques for reaching target data levels more quickly, using more aggressive memory programming operations.
Owner:CALIFORNIA INST OF TECH
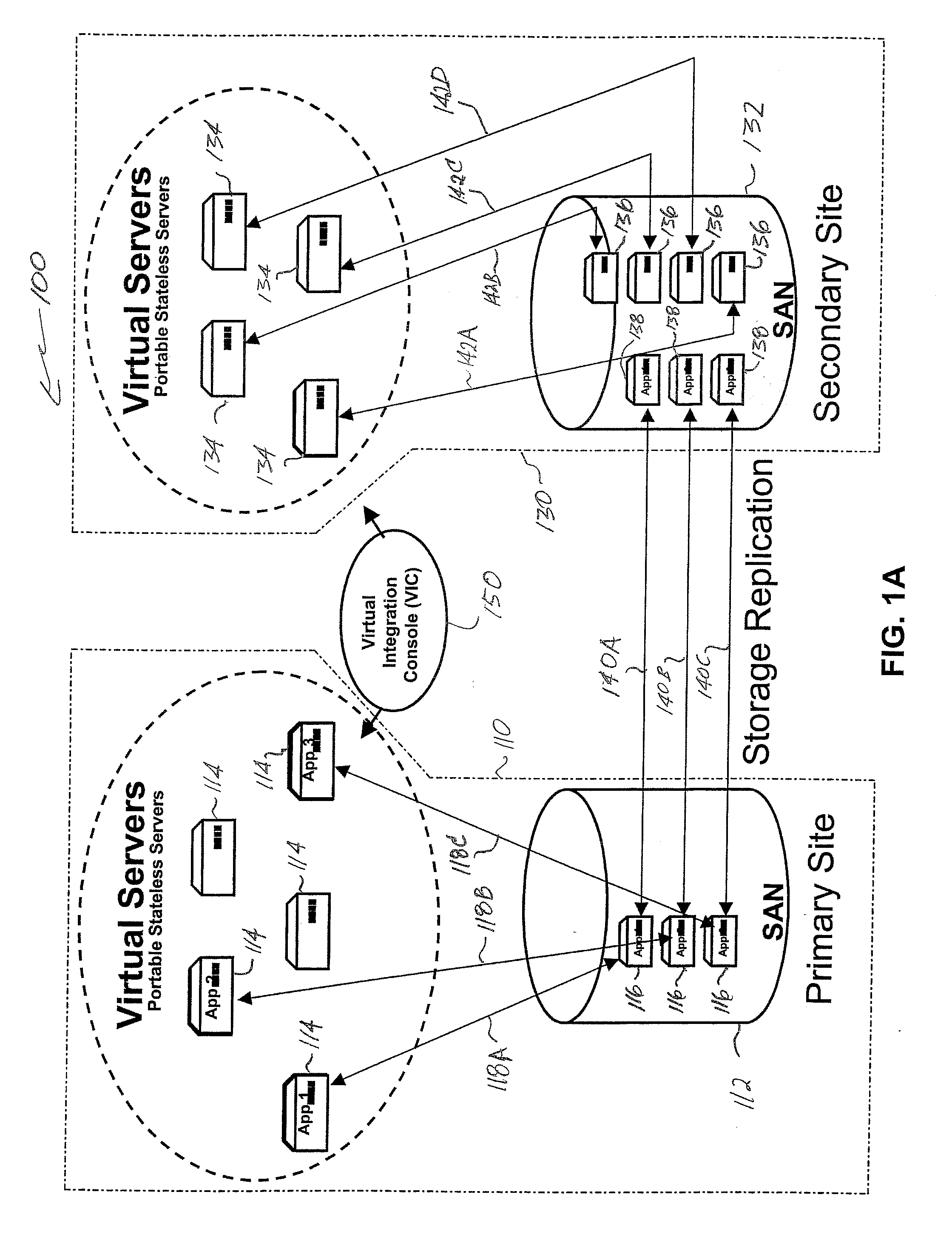
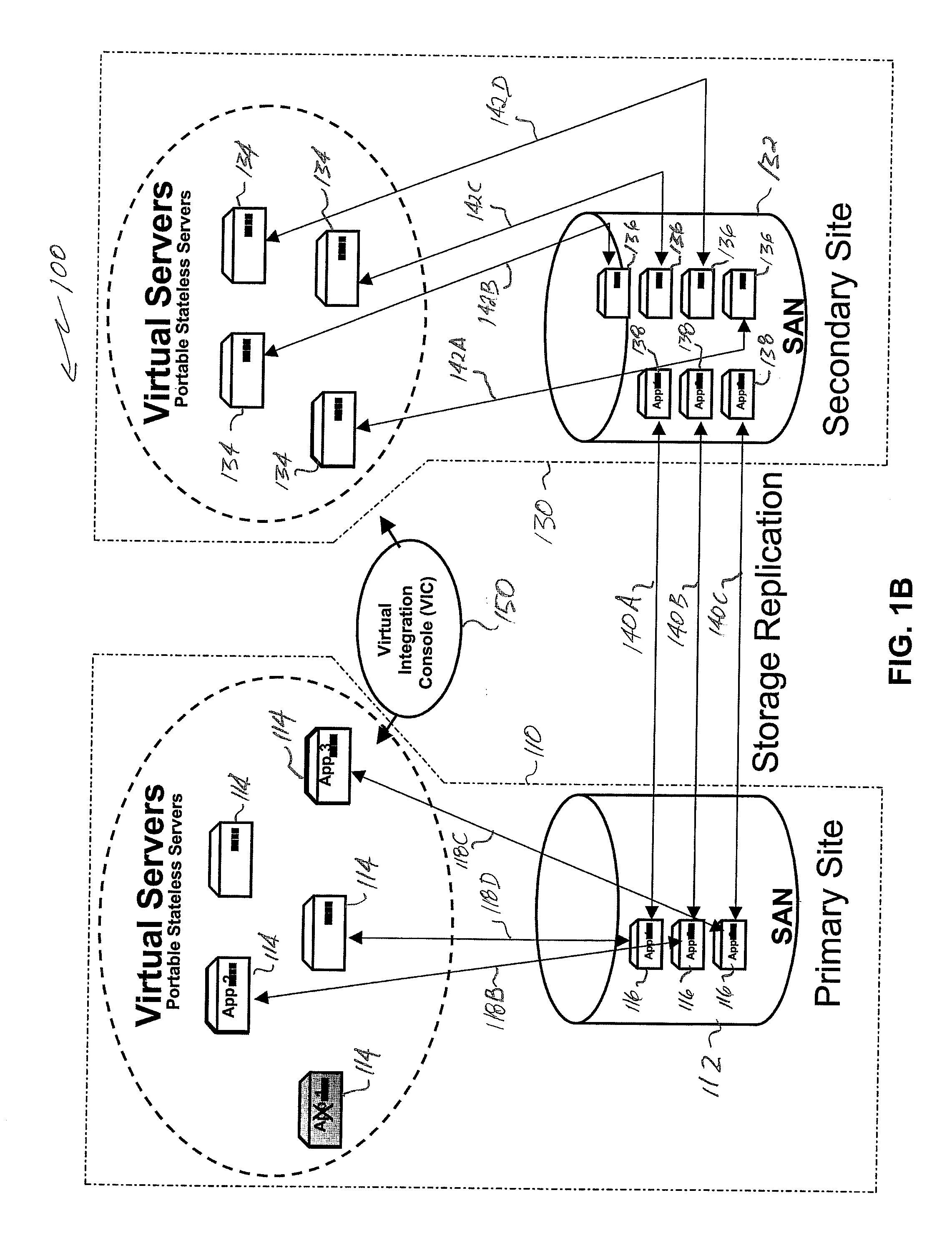
Application of virtual servers to high availability and disaster recovery soultions
InactiveUS20070078982A1Improve availabilityHigh dataError detection/correctionMultiple digital computer combinationsVirtualizationStorage area network
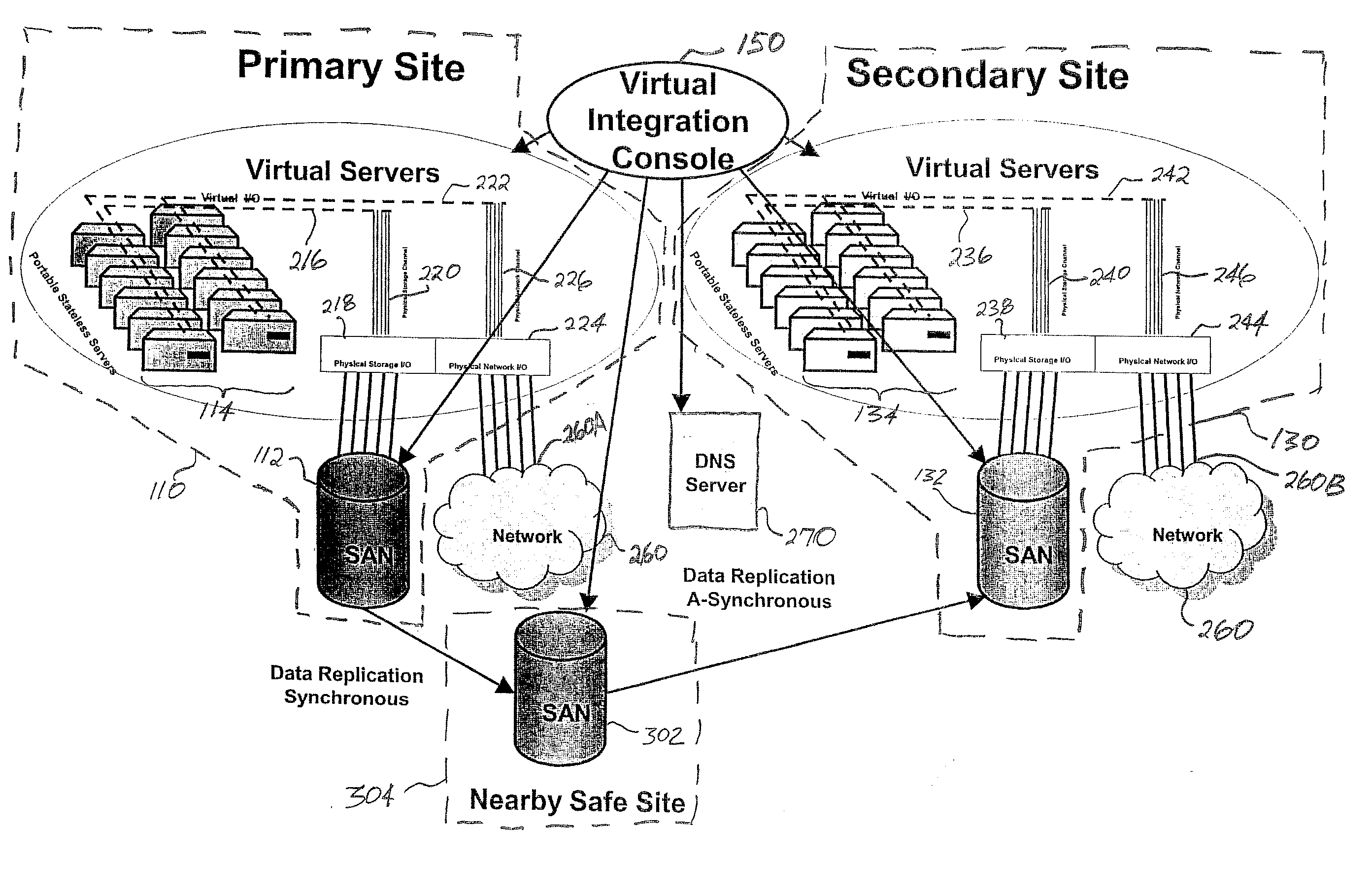
Server virtualization technology is applied to virtualize and encapsulate all unique information of a server as an image that is stored on a storage area network at one site and replicated on a storage area network at another site to provide high availability of system resources and data recovery capabilities. In one embodiment, a virtualized server system (100) includes a primary site (110), a secondary site (130), and a computer executable control application (150). The primary site (110) includes a storage area network (112), at least one primary virtual server platform (114), and at least one primary virtual server stored as at least one image (116) on the storage area network (112). The control application (150) directs replication of the primary virtual server image (116) onto a storage area network (132) at the secondary site (130) to create a corresponding replicated virtual server image (138). The control application (150) also monitors operation of the primary virtual server platform (114) and associates the replicated virtual server image (138) with a secondary virtual server (134) at the secondary site (130) in the event that a problem is detected with the primary site virtual server (114).
Owner:LEIDOS INNOVATIONS TECH INC
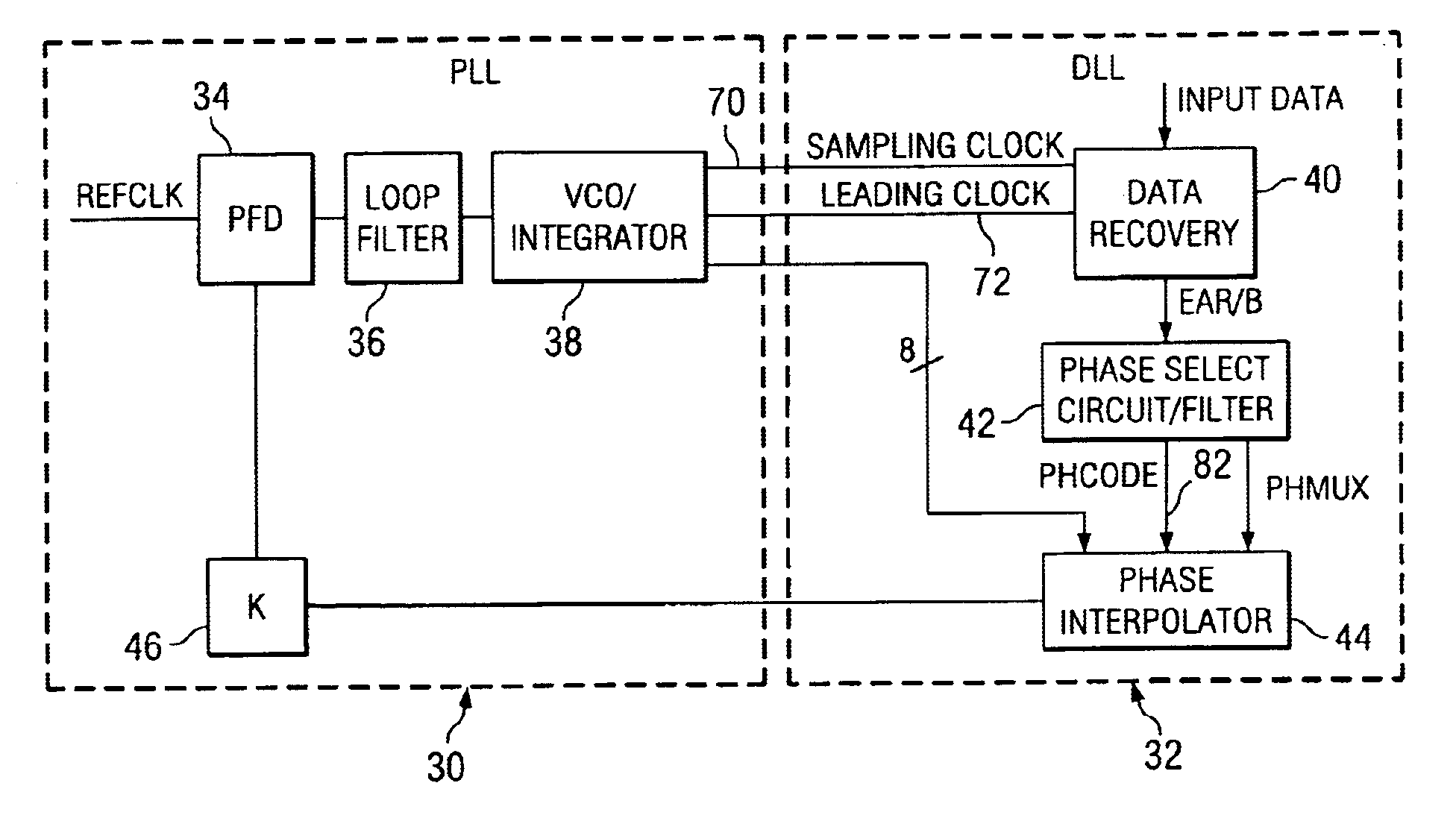
Time division multiplex data recovery system using close loop phase and delay locked loop
InactiveUS6901126B1Alleviate duty cycle issuesHigh bandwidthPulse automatic controlAngle demodulation by phase difference detectionDelay-locked loopClosed loop
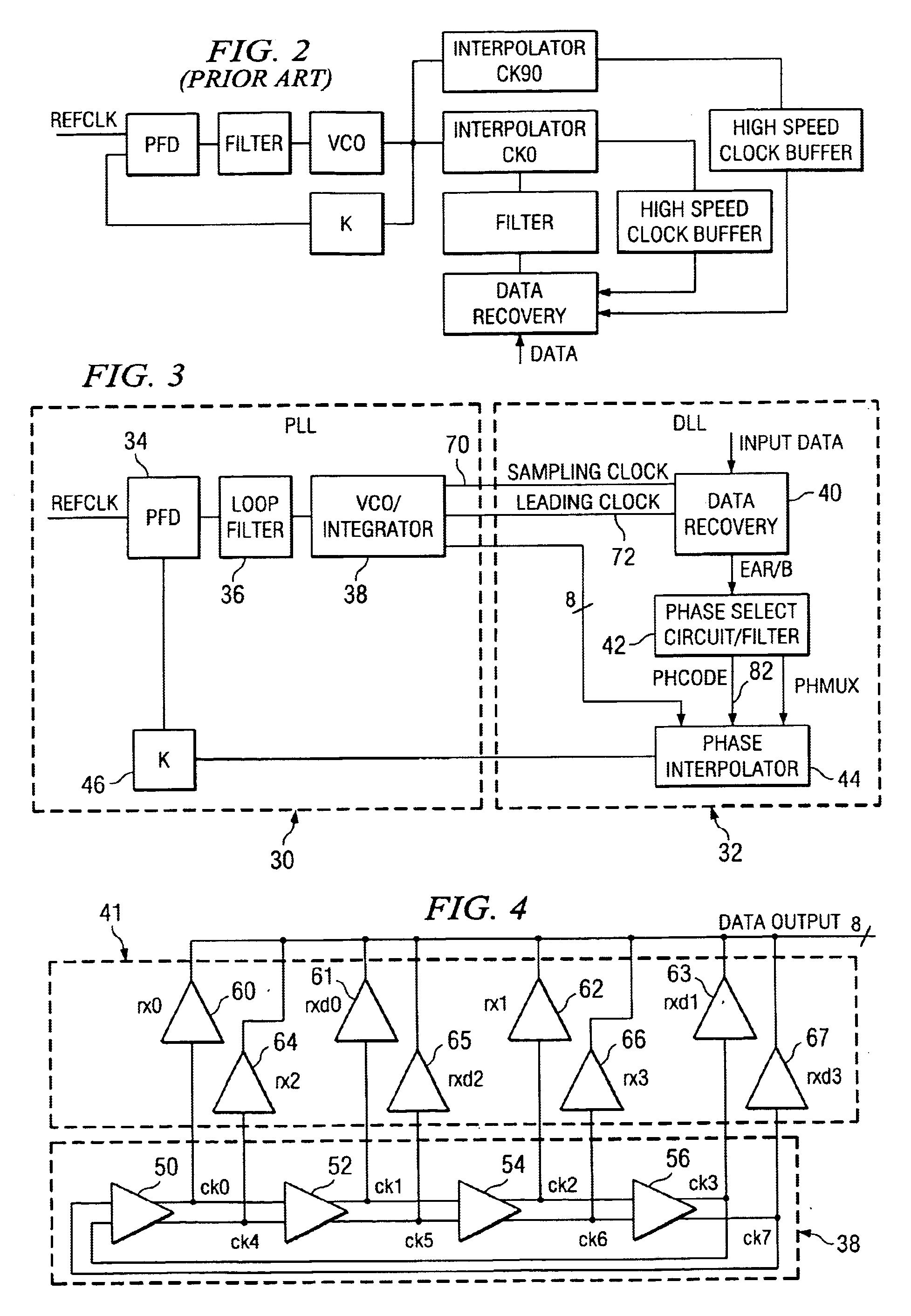
A time division multiplex data recovery system using a closed-loop phase lock loop (PLL) and delay locked loop (DLL) is disclosed. In other words, one closed loop comprises both a phase locked loop (PLL) and a delay locked loop (DLL) in a novel time division multiplex data recovery system. This new architecture comprises a 4 stage Voltage Controlled Oscillator (VCO) used to generate 8 clock signals, 45 degrees phase shifted from one another, for 8 receivers to do the oversampling. An interpolator tracks the received data signal and feeds it back to the Phase / Frequency Detector (PFD). The PFD has a second input of the reference clock which the PFD uses along with the interpolator input to correct the frequency of the PLL. The PLL operates at a high bandwidth. The DLL's bandwidth is several orders lower than the PLL. The DLL activates only a multiplexer and an interpolator continuously, thereby drawing a minimum amount of power.
Owner:TEXAS INSTR INC
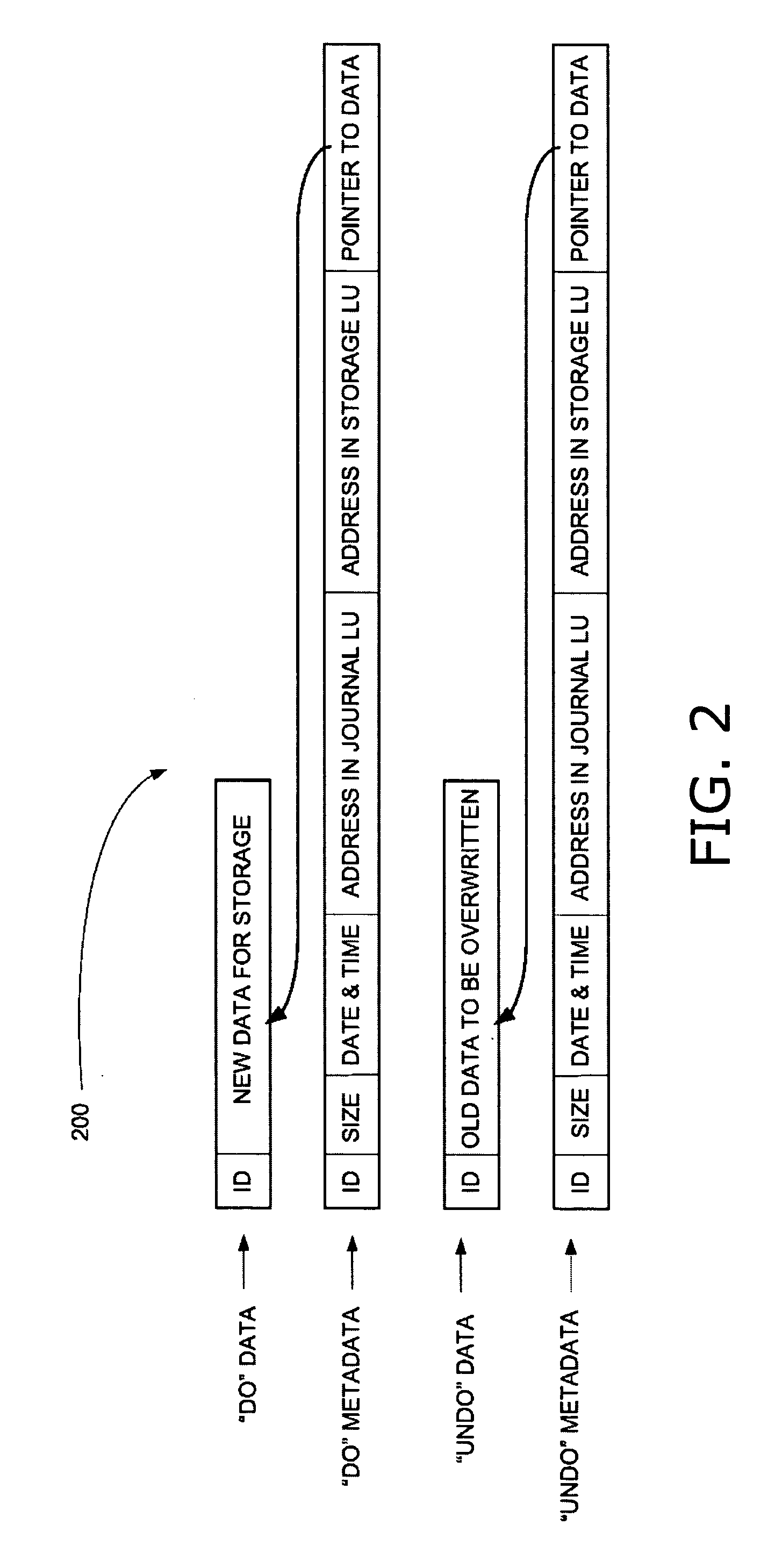
Method and apparatus for data recovery system using storage based journaling
InactiveUS20050028022A1Data processing applicationsError detection/correctionSystem maintenanceDatabase
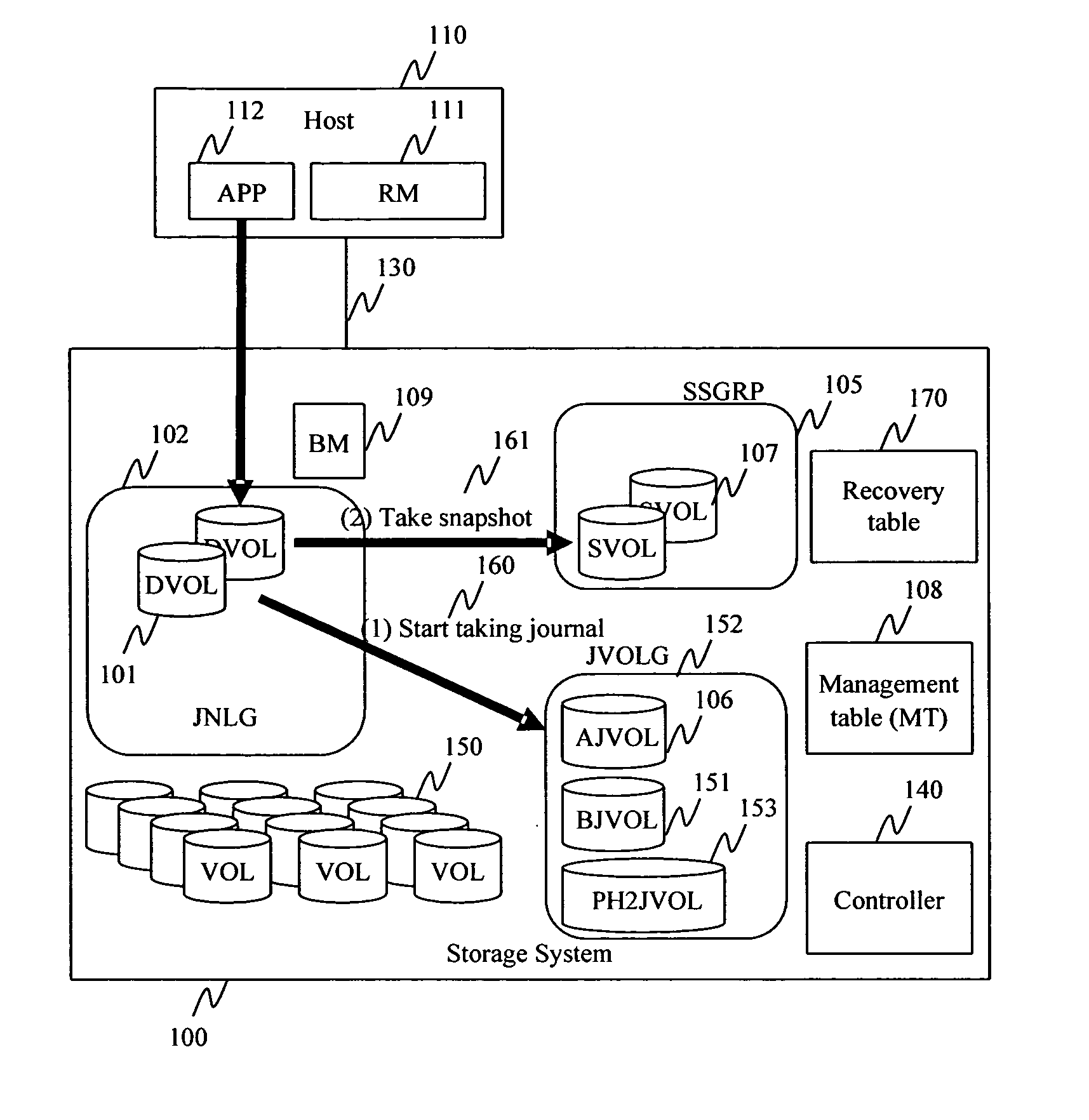
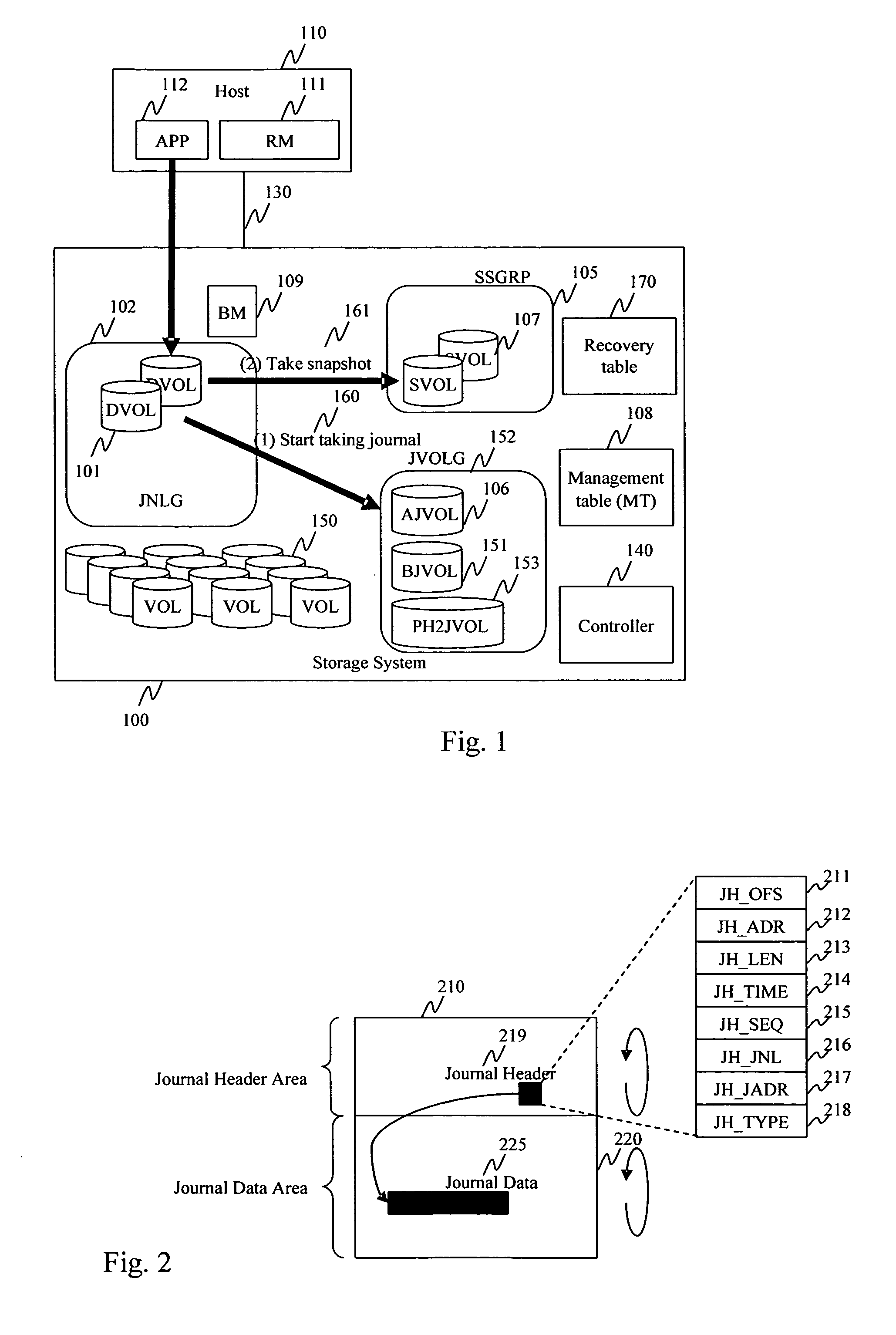
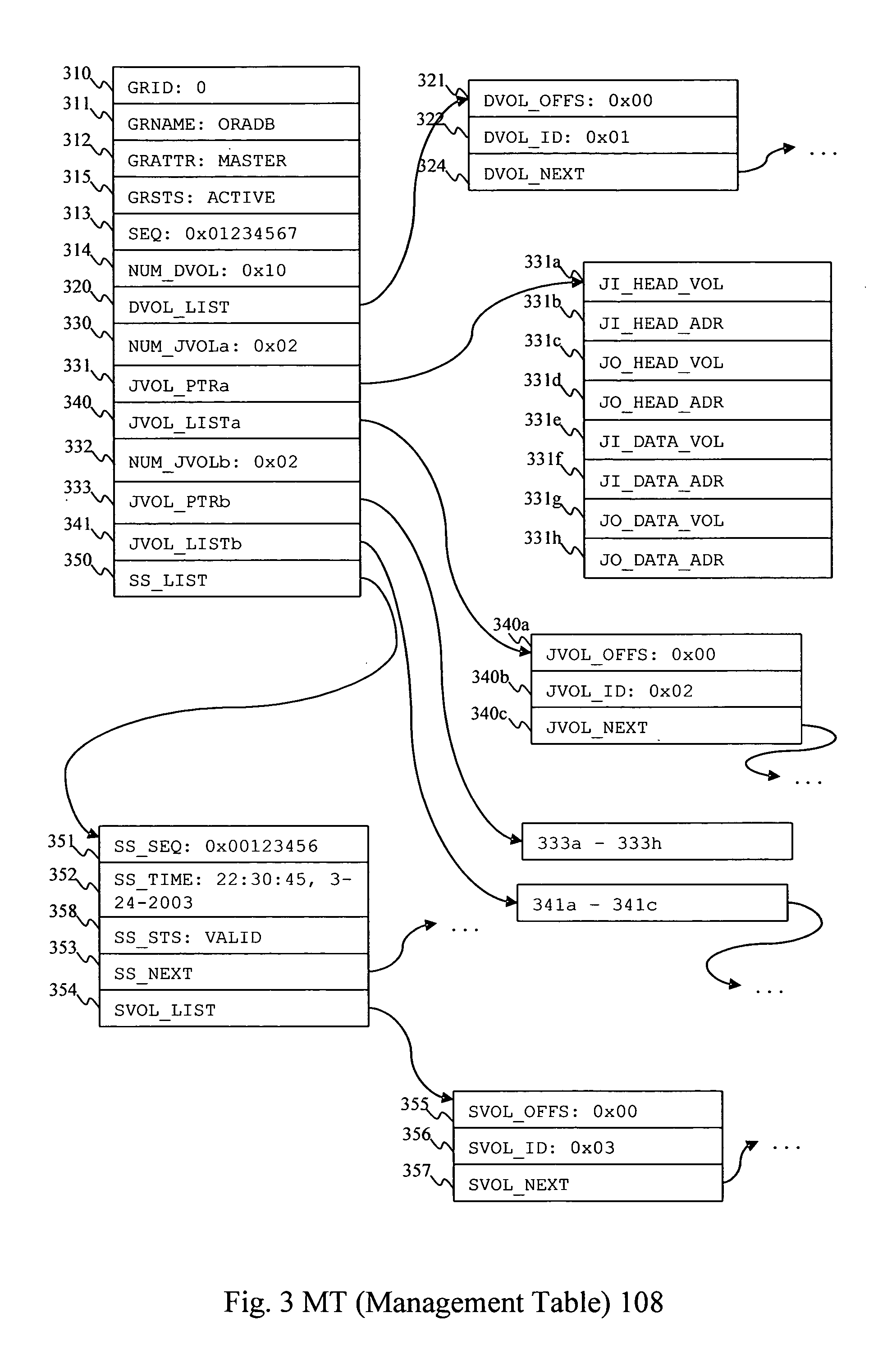
A storage system maintains a journal and a snapshot of one or more data volumes. Two journal entry types are maintained, an AFTER journal entry and a BEFORE journal entry. Two modes of data recovery are provided: “fast” recovery and “undo-able” recovery. A combination of both recovery modes allows the user to quickly recover a targeted data state.
Owner:HITACHI LTD
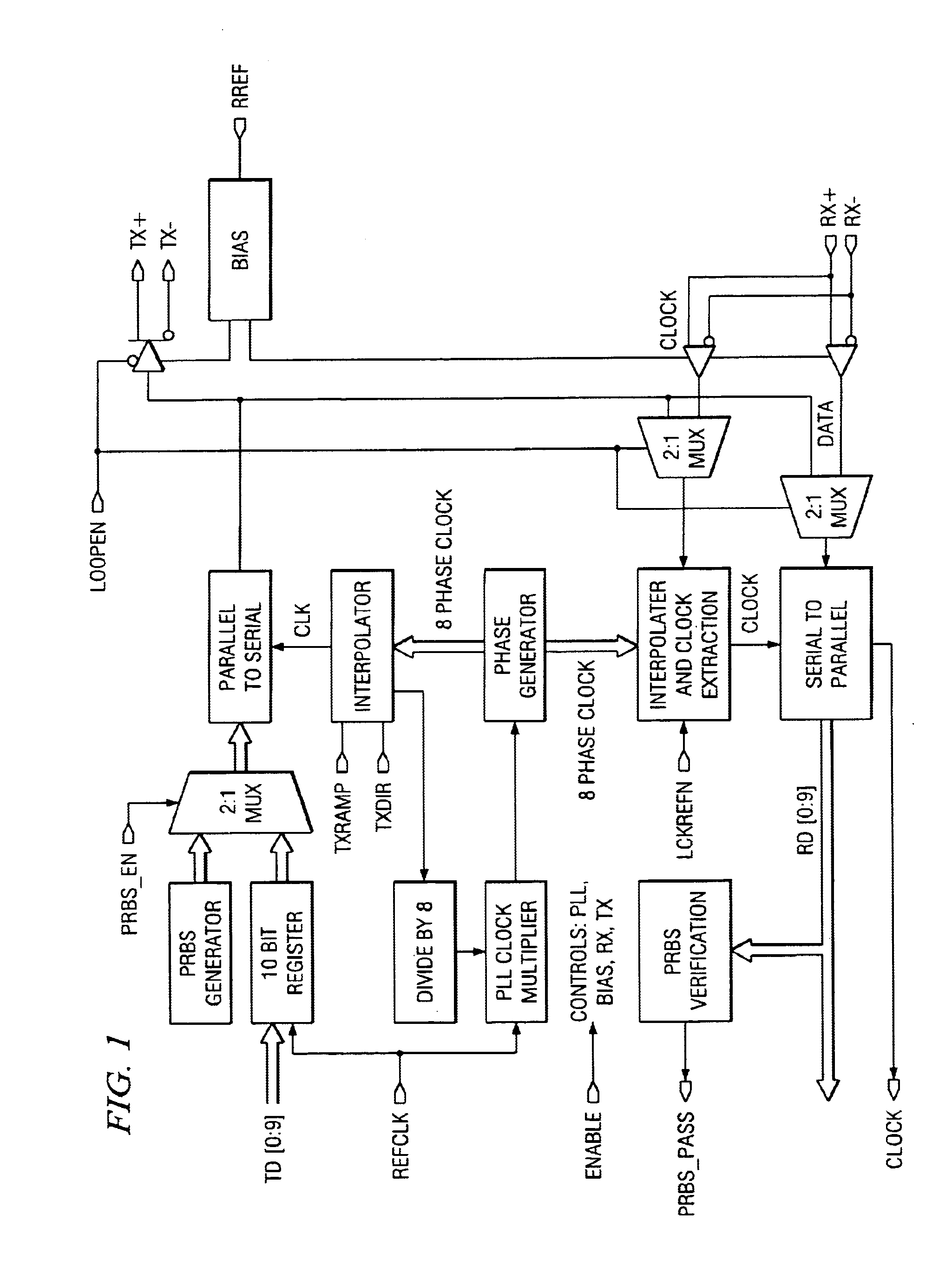
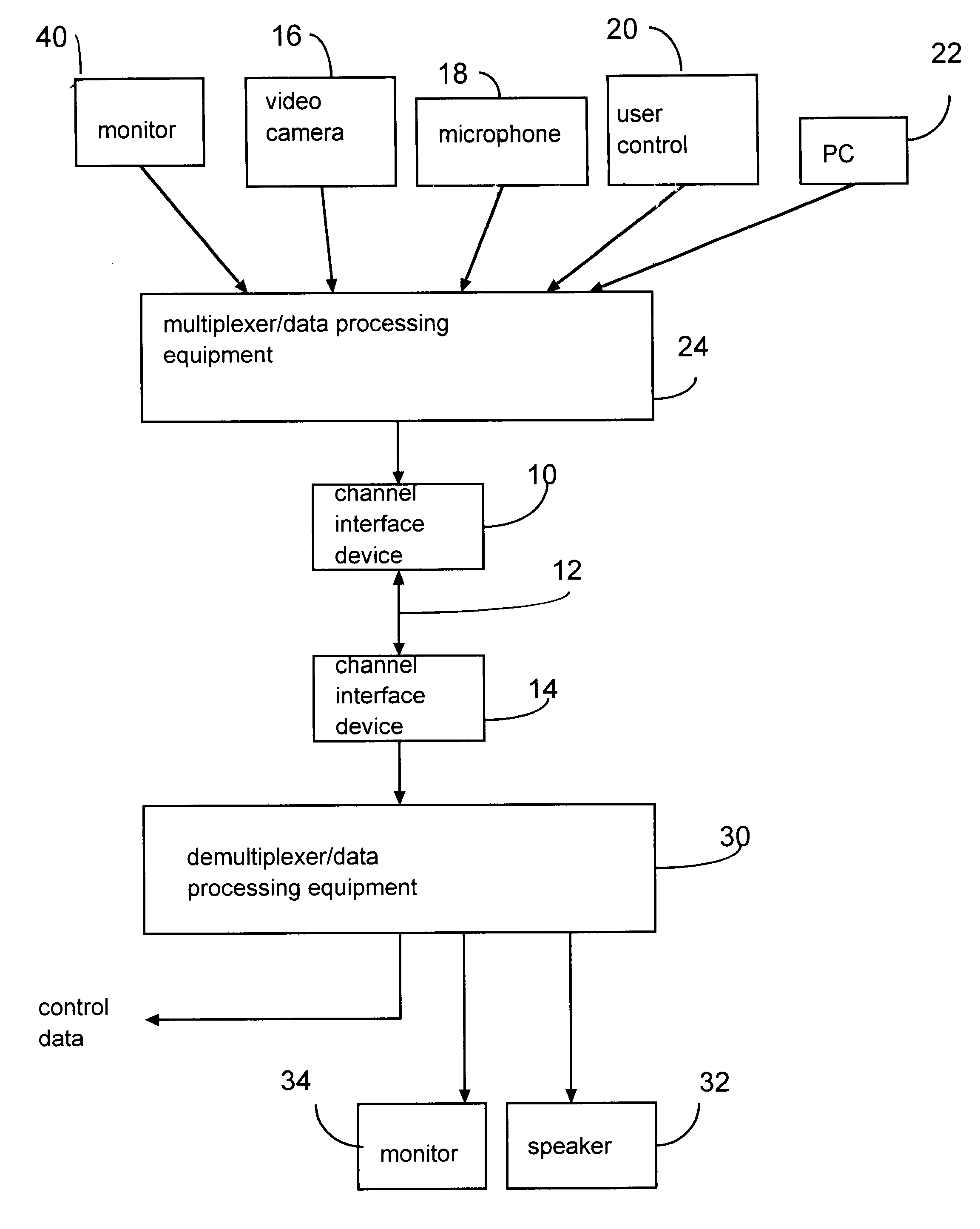
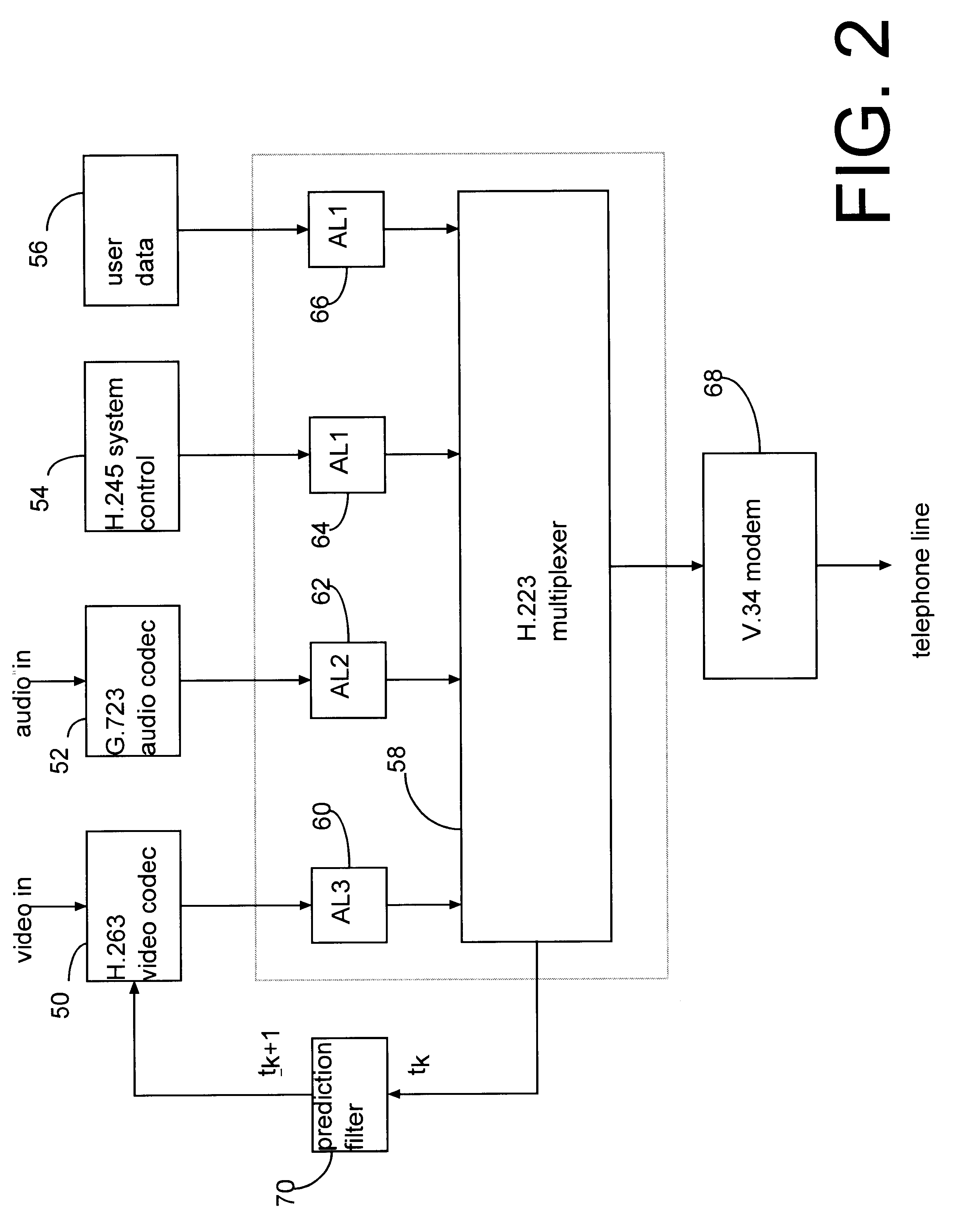
Data processor having controlled scalable input data source and method thereof
InactiveUS6404776B1Pulse modulation television signal transmissionTime-division multiplexModem deviceData recovery
A multimedia communication arrangement processes and multiplexes different types of data, including data from an adaptive data rate data source and a nonadaptive data rate data source, to substantially increase data throughput over a communication channel. The rate at which data is collected from the adaptive data rate data source varies based on the available channel bandwidth of the modem. The transmission rate is optionally adjusted in response to a detected error rate. Furthermore, the amount of filtering performed by a video camera on an image before the image is encoded by a codec can be adjusted. In addition, a data recovery terminal optionally selectively adjusts intervals at which received audio data is sampled to potentially reduce latency periods.
Owner:ROVI TECH CORP
Transmitter circuit, receiver circuit, clock data recovery phase locked loop circuit, data transfer method and data transfer system
ActiveUS7535957B2Reduce errorsData transmission is stableTelevision system detailsFrequency/rate-modulated pulse demodulationDigital dataPhase locked loop circuit
[Problems] To realize a reliable and stable transfer of digital data that does not require a reference clock and a handshake operation.[Means for Solving the Problem] The present invention provides a digital data transfer method for alternately and periodically transferring first information and second information respectively in a first period and in a second period, wherein: an amount of information of the first information per unit time in the first period is greater than an amount of information of the second information per unit time in the second period; and the second information in the first period is transferred as pulse-width-modulated serial data.
Owner:THINE ELECTRONICS
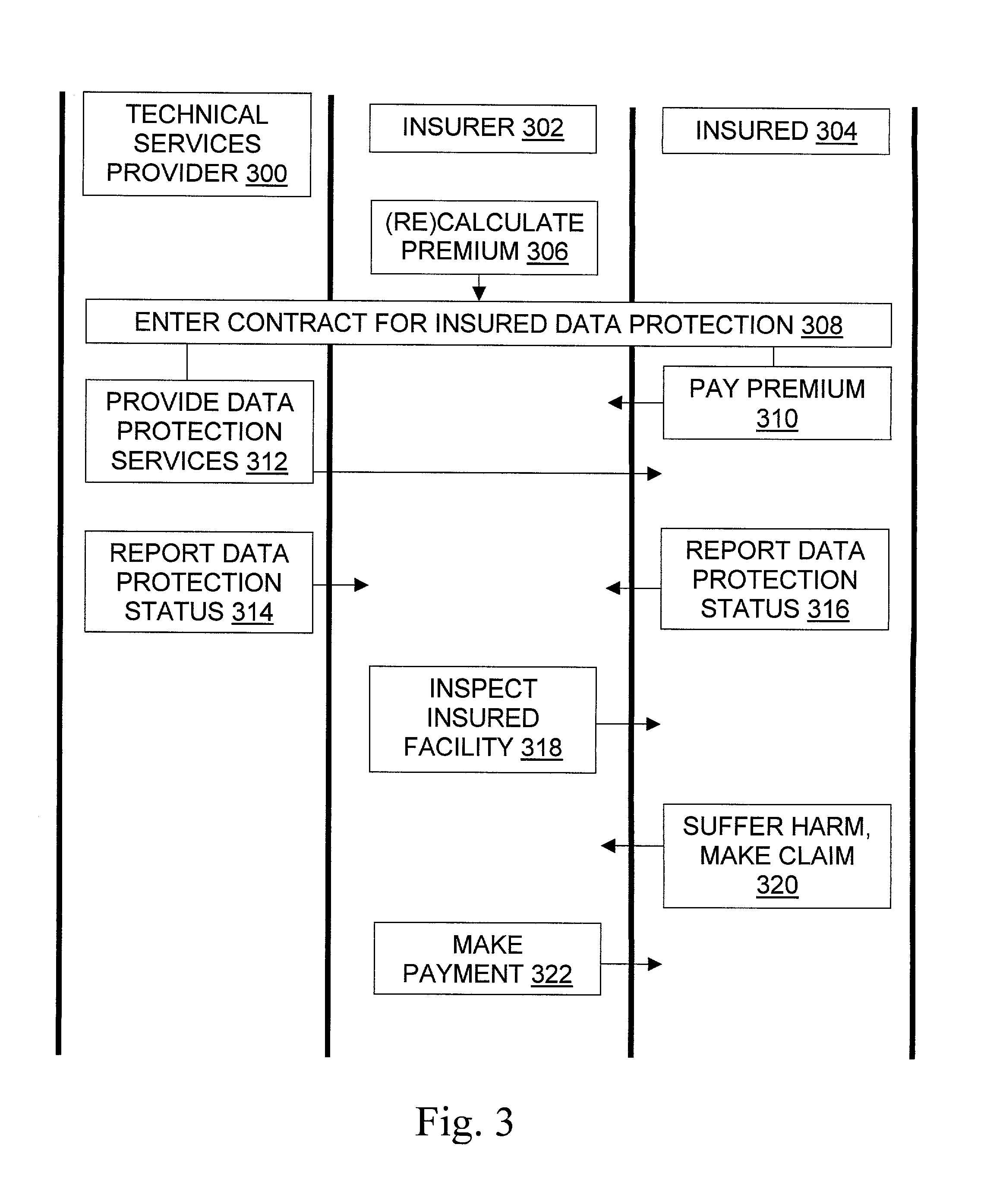
Data/presence insurance tools and techniques
Methods for insurance of online presence (202) and / or data (200) are described. An insurer (302) contracts with an insured entity (304) in an agreement (308) under which a premium (310) is paid for insurance coverage. The premium is calculated (306) using a pure premium method (400) or a loss ratio premium method (402), in a manner that depends on factors such as expected virus scan results (404), expected data recovery time (406), expected geographic spread (408), use of multiple recovery methods (410), and other information regarding the insured entity's business and the technical protection services (206) to be used. In some embodiments, the technical protection services are provided under the agreement by a third party technical services provider (300). Systems, signals, and configured media are also described.
Owner:INTELLECTUAL VENTURES II
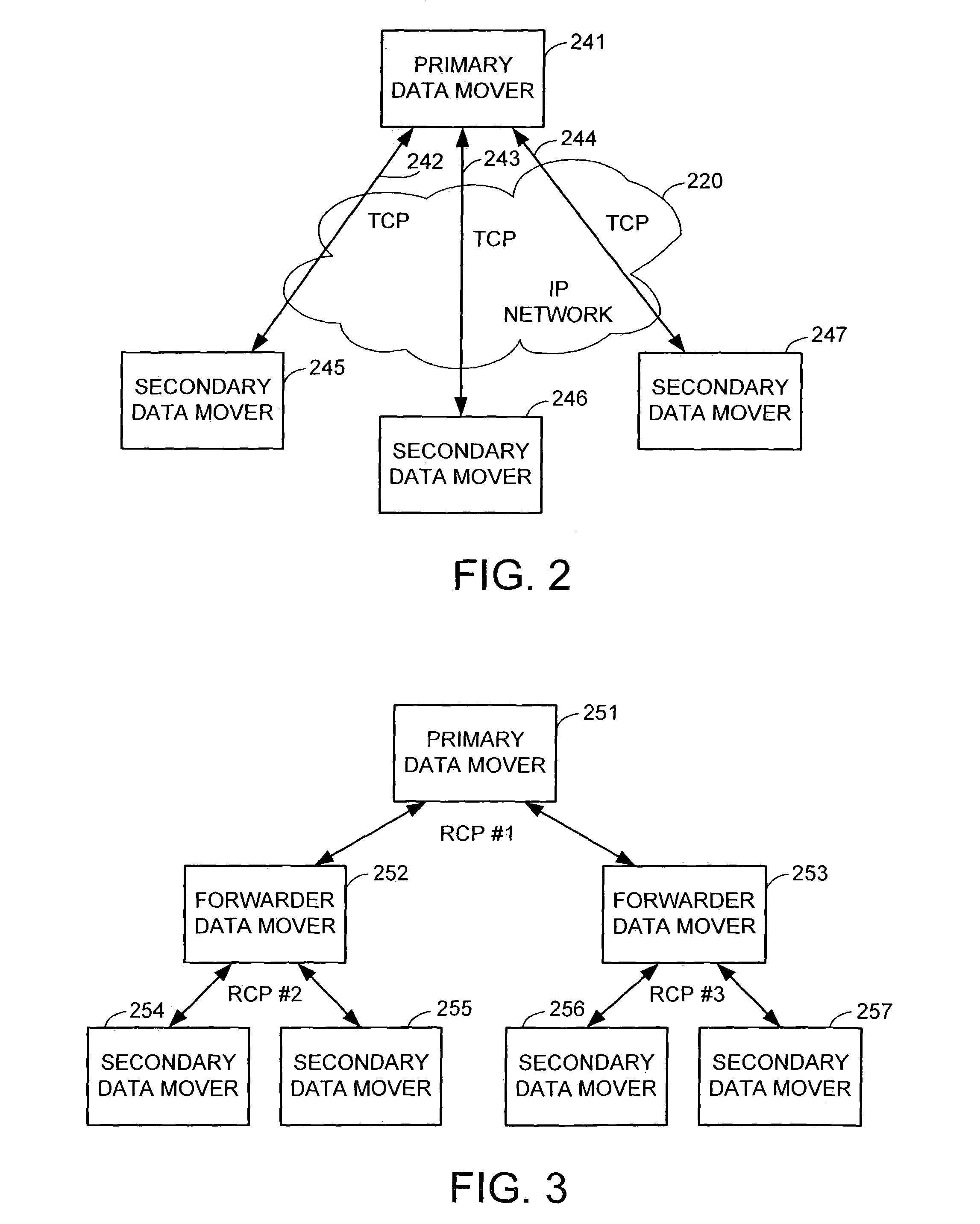
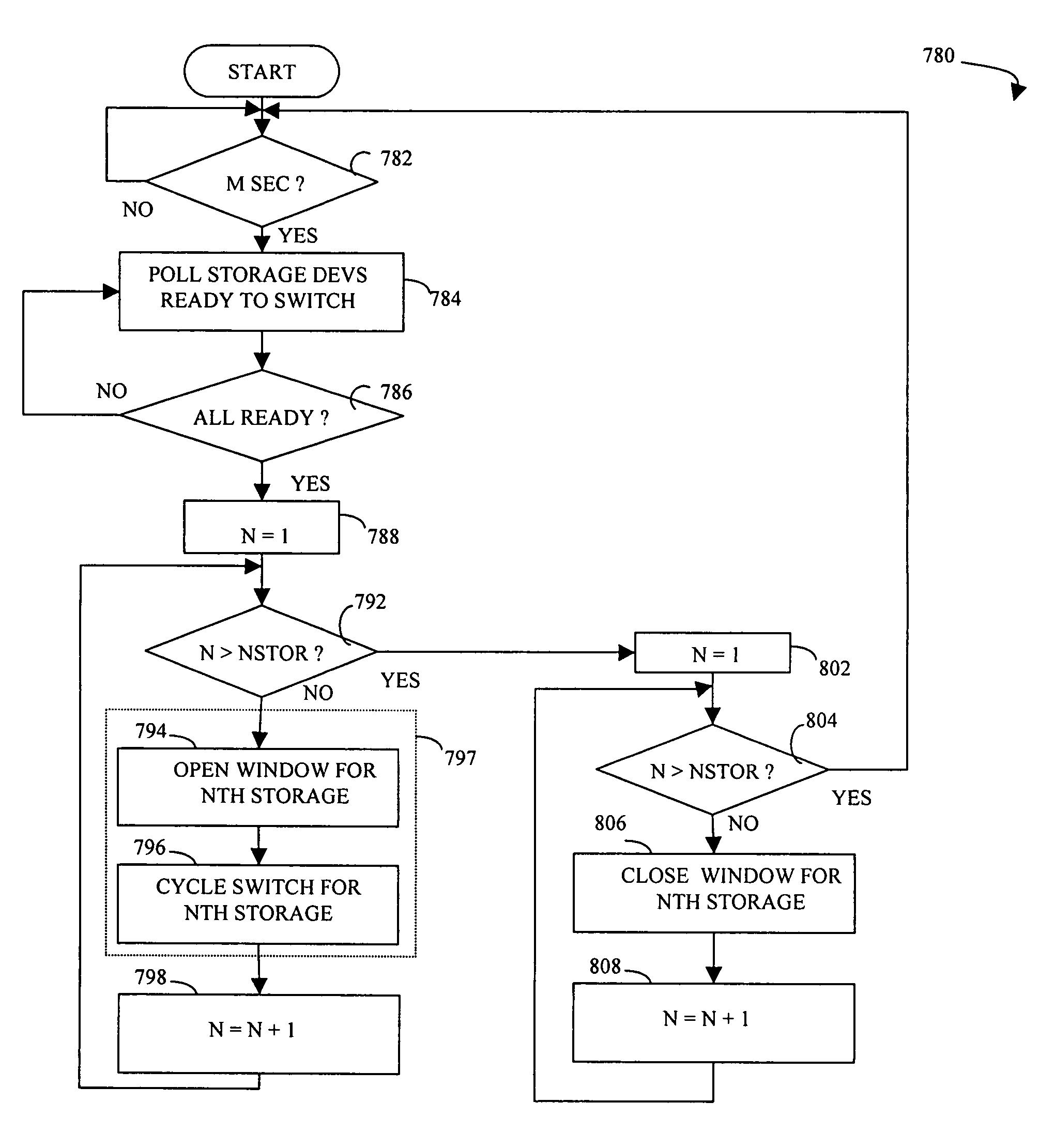
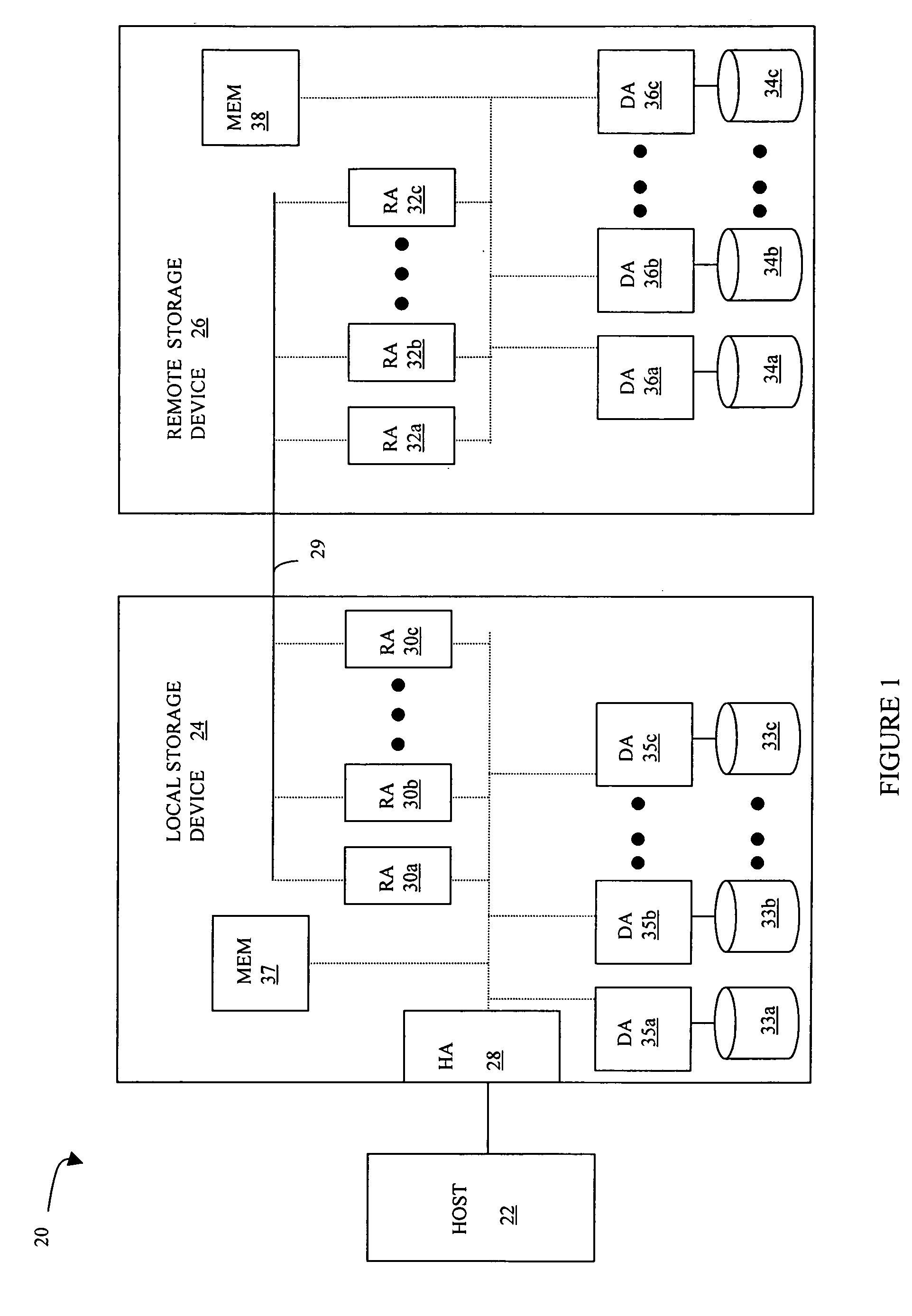
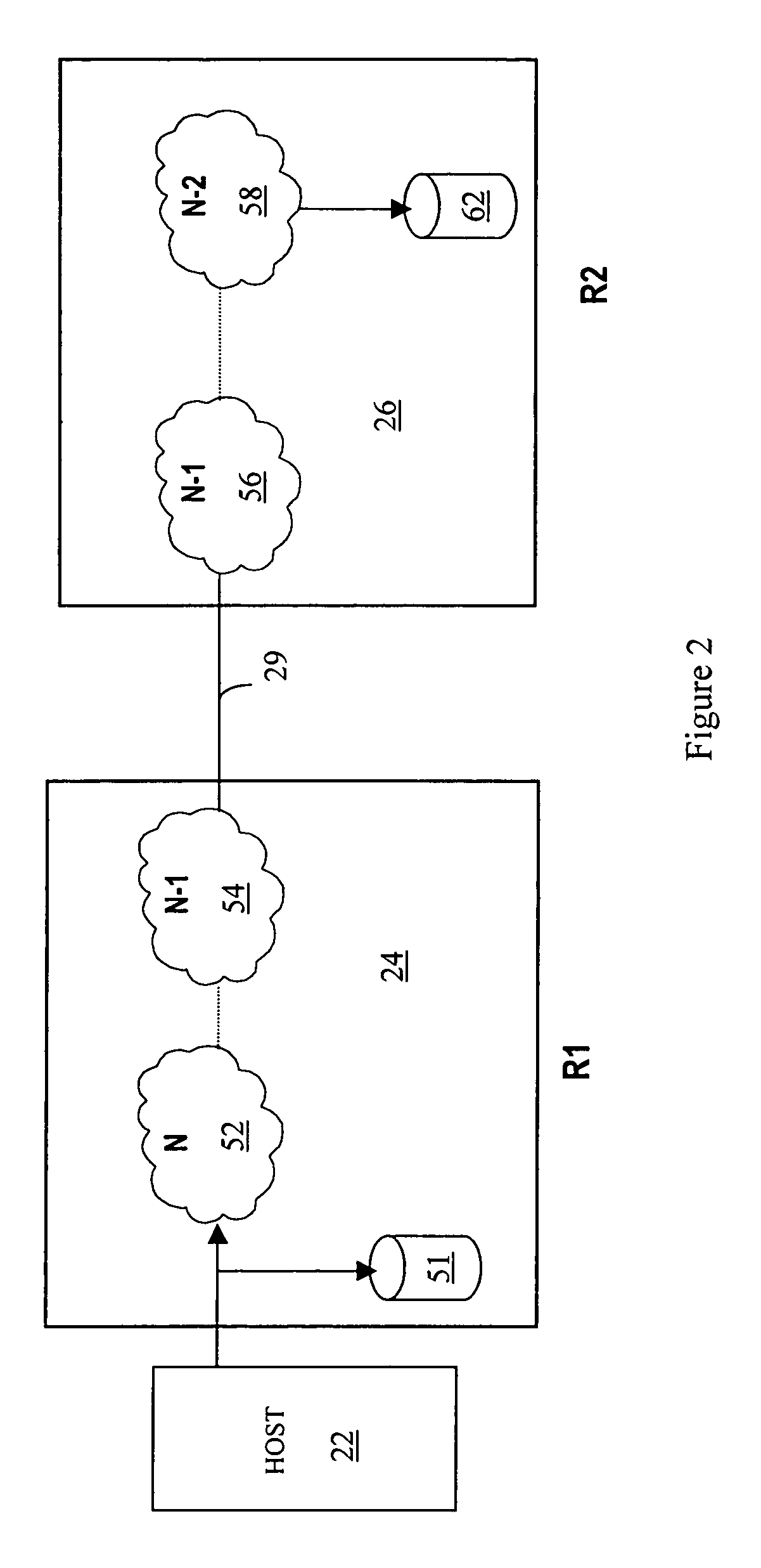
Data recovery for virtual ordered writes for multiple storage devices
Recovering data provided in chunks to a plurality of secondary storage devices includes, for each of the secondary storage devices, discarding data corresponding chunks for which all data thereof has not been received, and, for each of the secondary storage devices, restoring a chunk of data thereto where all of the chunks of data restored to the plurality of secondary storage devices correspond to a particular transmission cycle of primary storage devices that provide data to the plurality of secondary storage devices. Recovering data may also include, following discarding and prior to restoring, for each of the plurality of secondary storage devices having two different chunks, waiting for external intervention to indicate whether to restore a particular one of the chunks. The external intervention may be provided by a host computer that is proximate to at least one of the secondary storage devices or may be provided by a host computer that is proximate to at least one of the primary storage computers.
Owner:EMC IP HLDG CO LLC
Cross tagging of data for consistent recovery
ActiveUS20070220311A1Overcome limitationsConsistent imageError detection/correctionStorage area networkData recovery
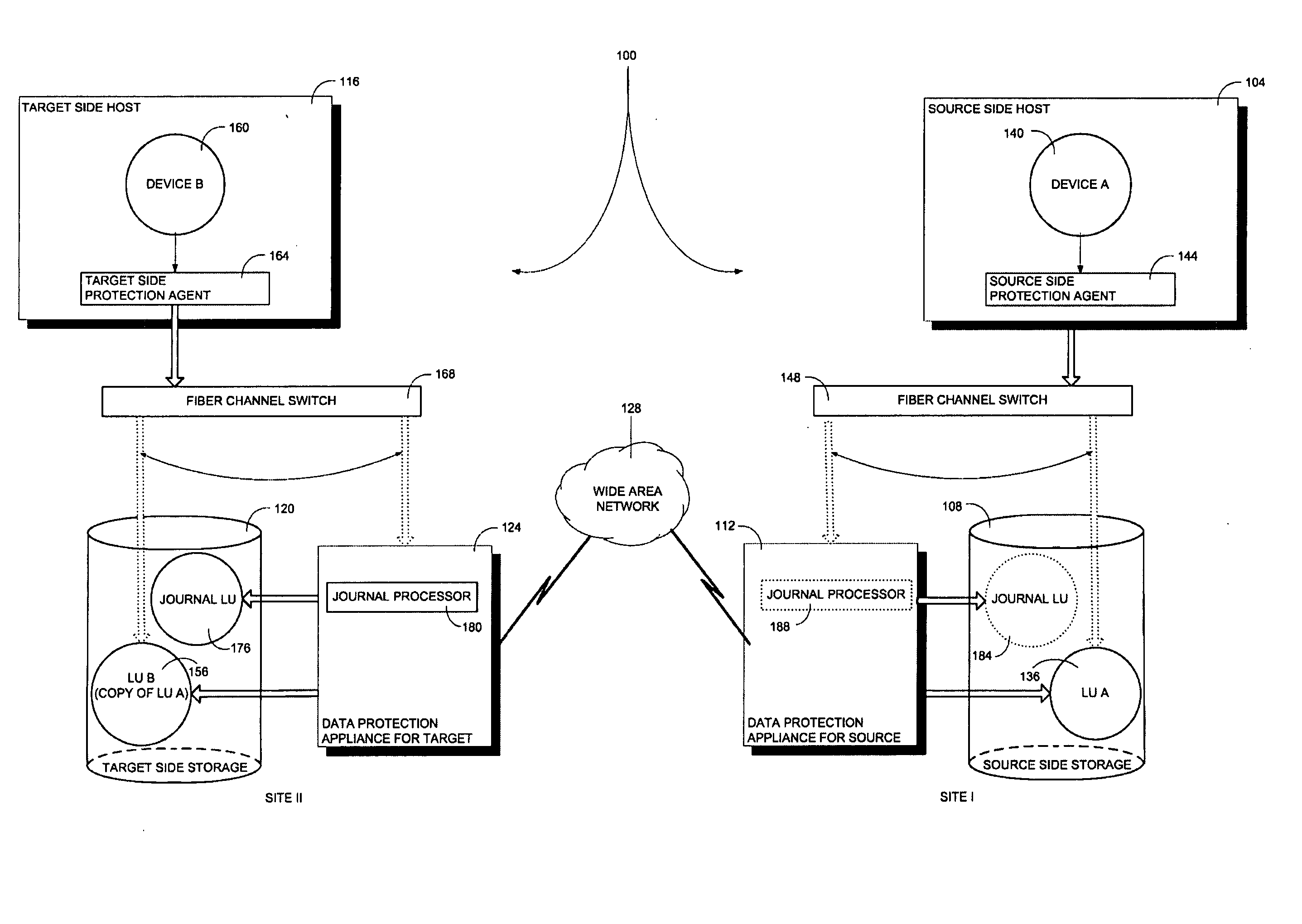
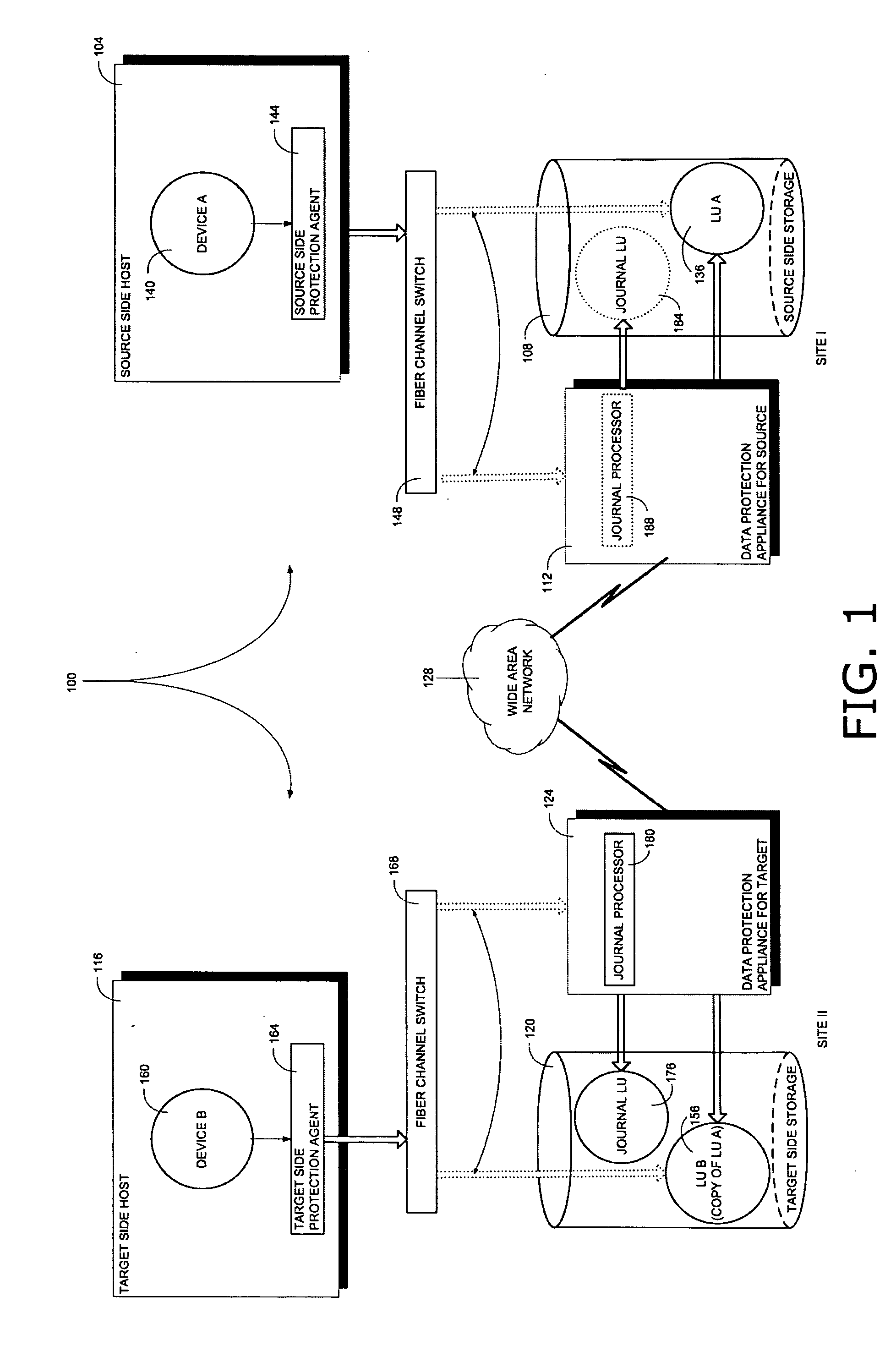
A system for consistent data recovery, including a storage area network (SAN) of initiator nodes and target nodes, wherein initiator nodes issue I / O requests and target nodes respond to I / O requests, the SAN being represented logically as a plurality of consistency groups of nodes, G1, . . . , Gn, each consistency group representing at least one logical storage unit (LU), each LU acting as a target node within the SAN, at least one host device, each host device acting as an initiator within the SAN, each host device including a transmitter for issuing I / O requests to at least one LU, and each host device being associated with a host device agent, the host device agent including an interceptor for intercepting I / O requests issued by the host device, and a router for forwarding the intercepted I / O requests to a data protection appliance, a data protection appliance (DPA) acting as both an initiator node and a target node within the SAN.
Owner:EMC CORP +1
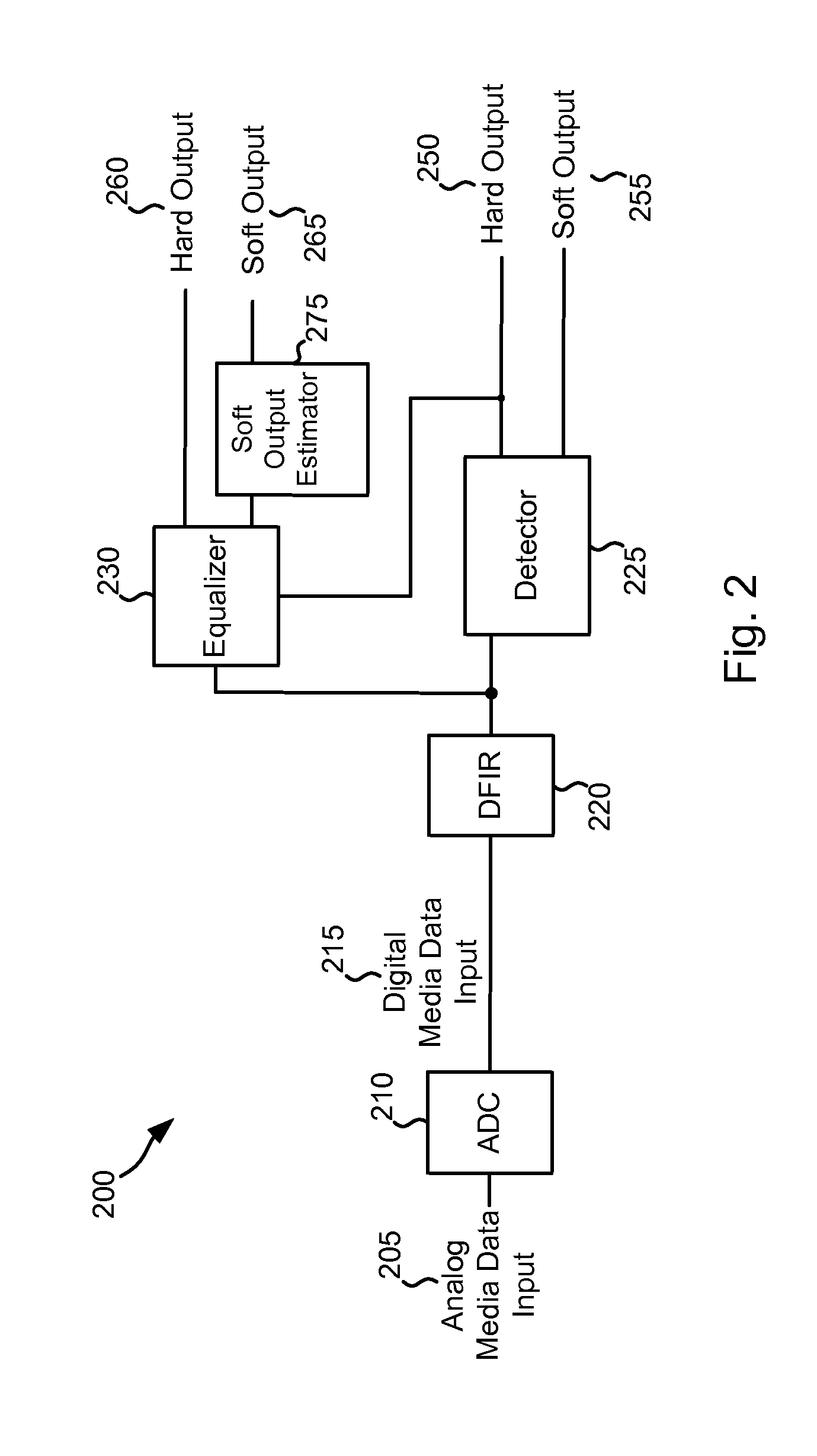
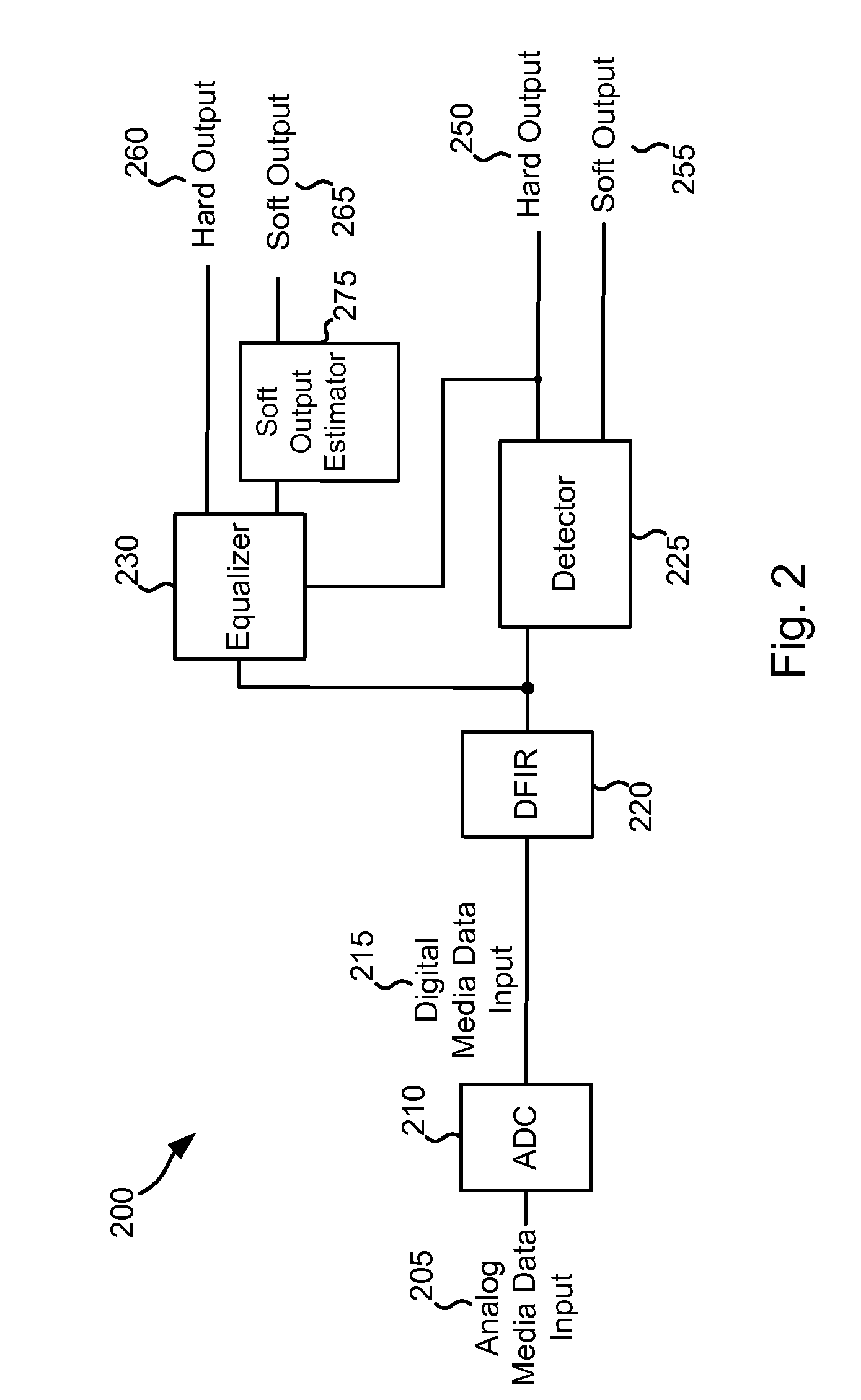
Systems and Methods for Regenerating Data from a Defective Medium
Various embodiments of the present invention provide systems and methods for data regeneration. For example, a system for data regeneration is disclosed that includes a data input derived from the medium. A data detector and a data recovery system receive the data input. The data detector provides a first soft output, and the data recovery system provides a second soft output. The first soft output and the second soft output are provided to a multiplexer. A media defect detector performs a media defect detection process, and provides a defect flag that indicates whether the data input is derived form a defective portion of the medium. The defect flag is provided to the multiplexer where it is used to select whether the first soft output or the second soft output is provides as an extrinsic output.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com