Patents
Literature
9247 results about "Virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms, storage devices, and computer network resources.
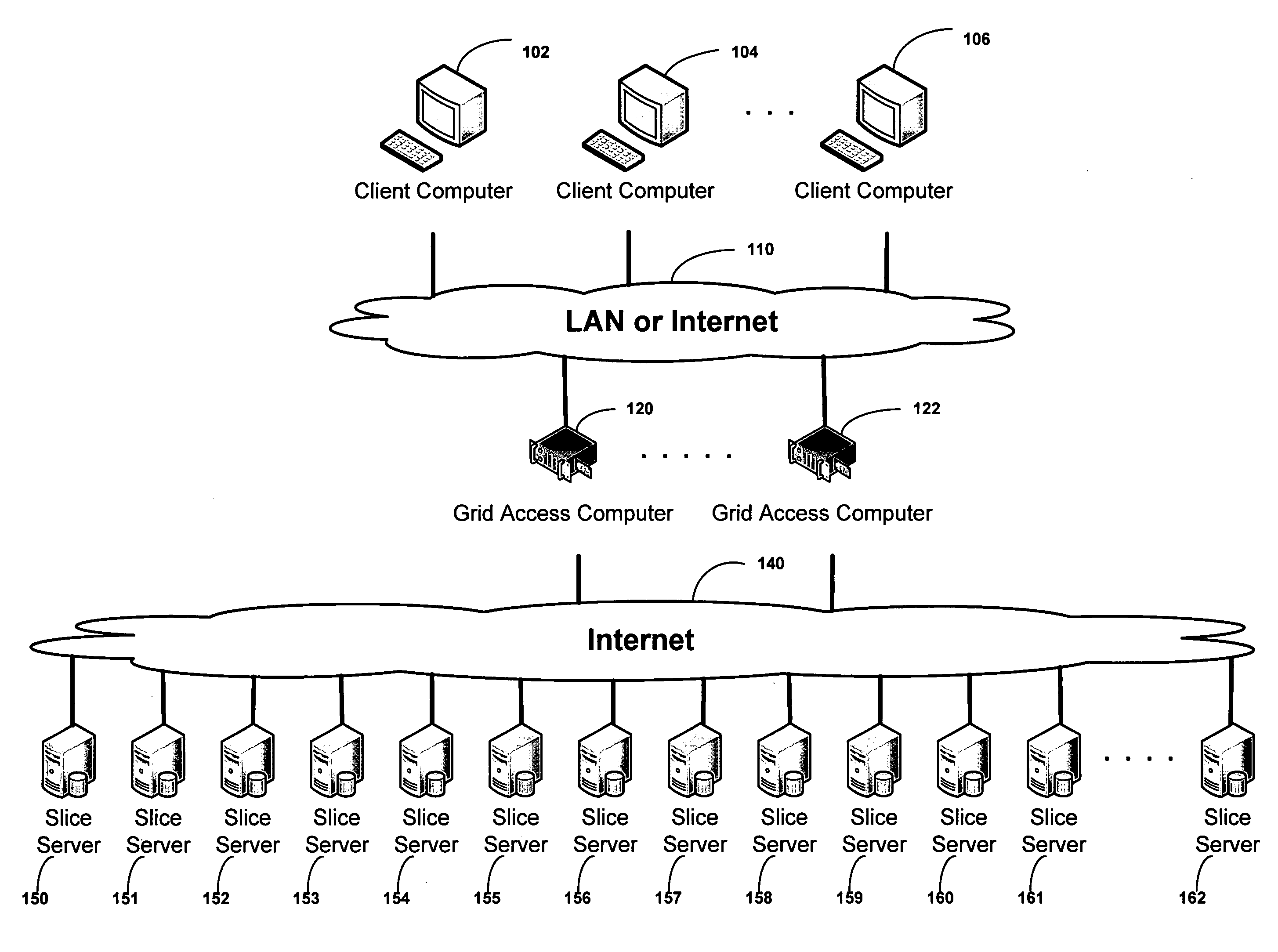
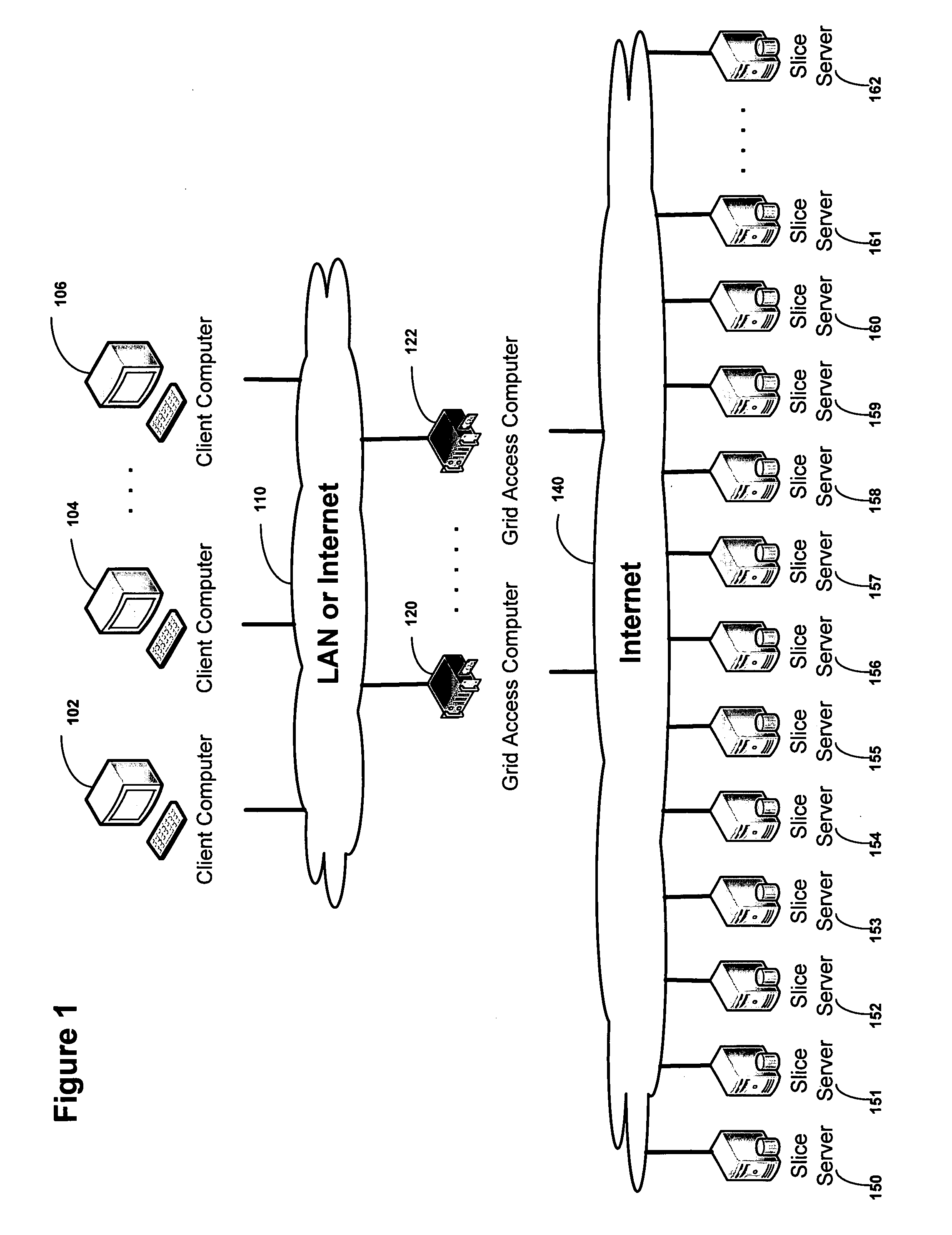
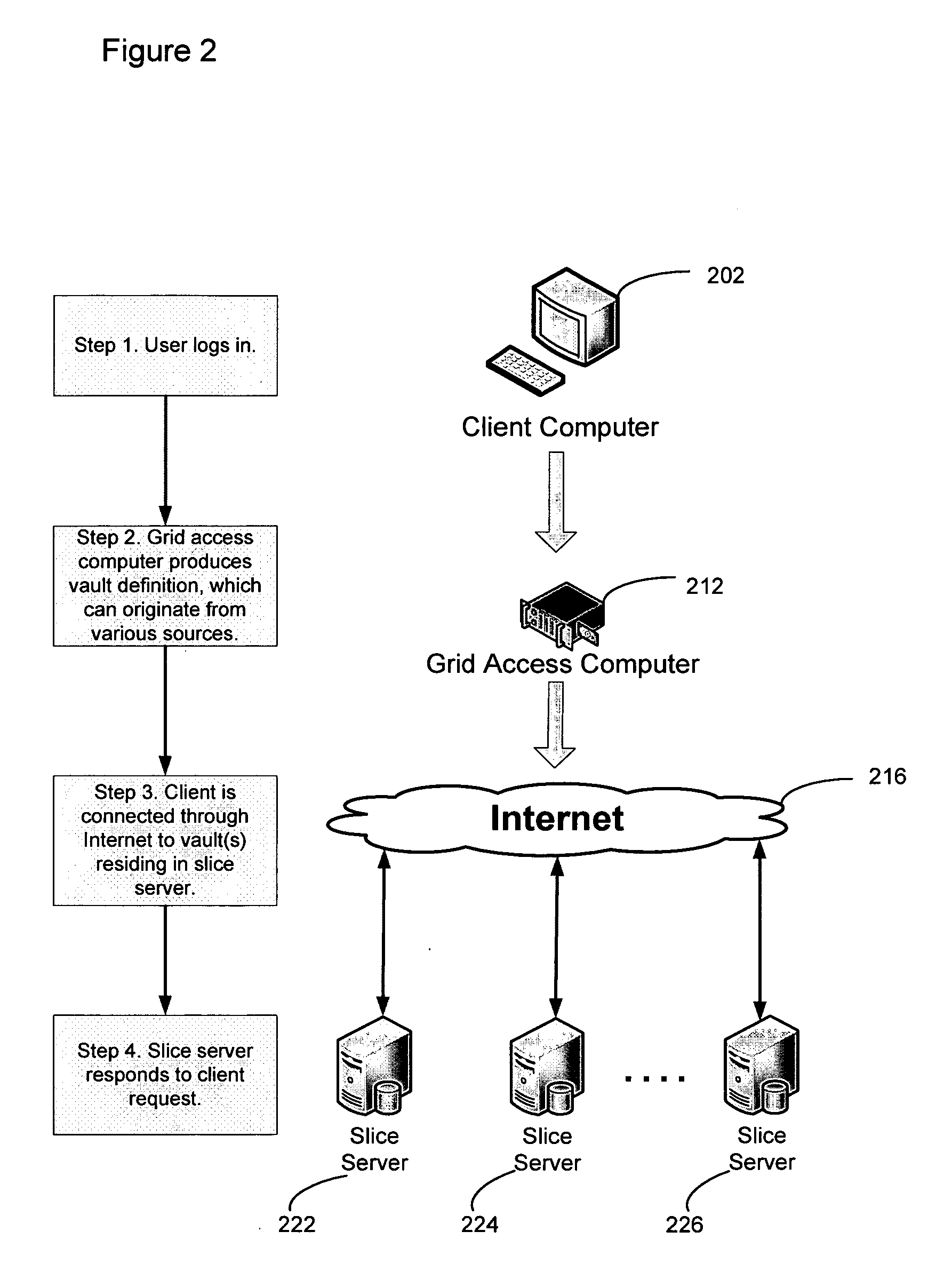
Virtualized data storage vaults on a dispersed data storage network
ActiveUS20090094251A1Efficient managementData processing applicationsDigital data processing detailsInformation dispersalVirtualization
A system, method, and apparatus for implementing a plurality of dispersed data storage networks using a set of slice servers are disclosed. A plurality of information records are maintained, with each information record corresponding to a dispersed data storage network. The information record maintains what slice servers are used to implement the dispersed data storage network, as well as other information needed to administer a DDSN, such as the information dispersal algorithm used, how data is stored, and whether data is compressed or encrypted.
Owner:PURE STORAGE
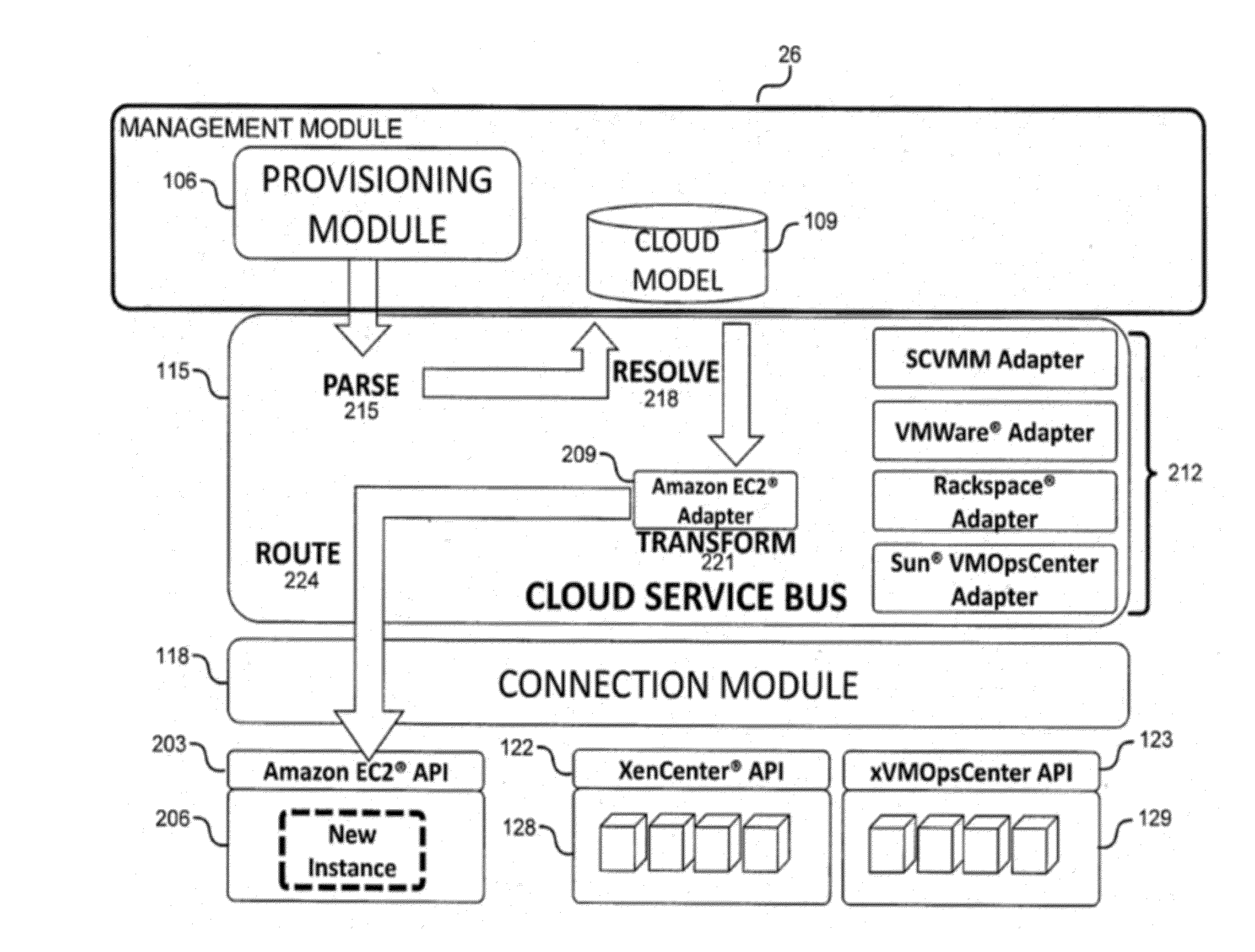
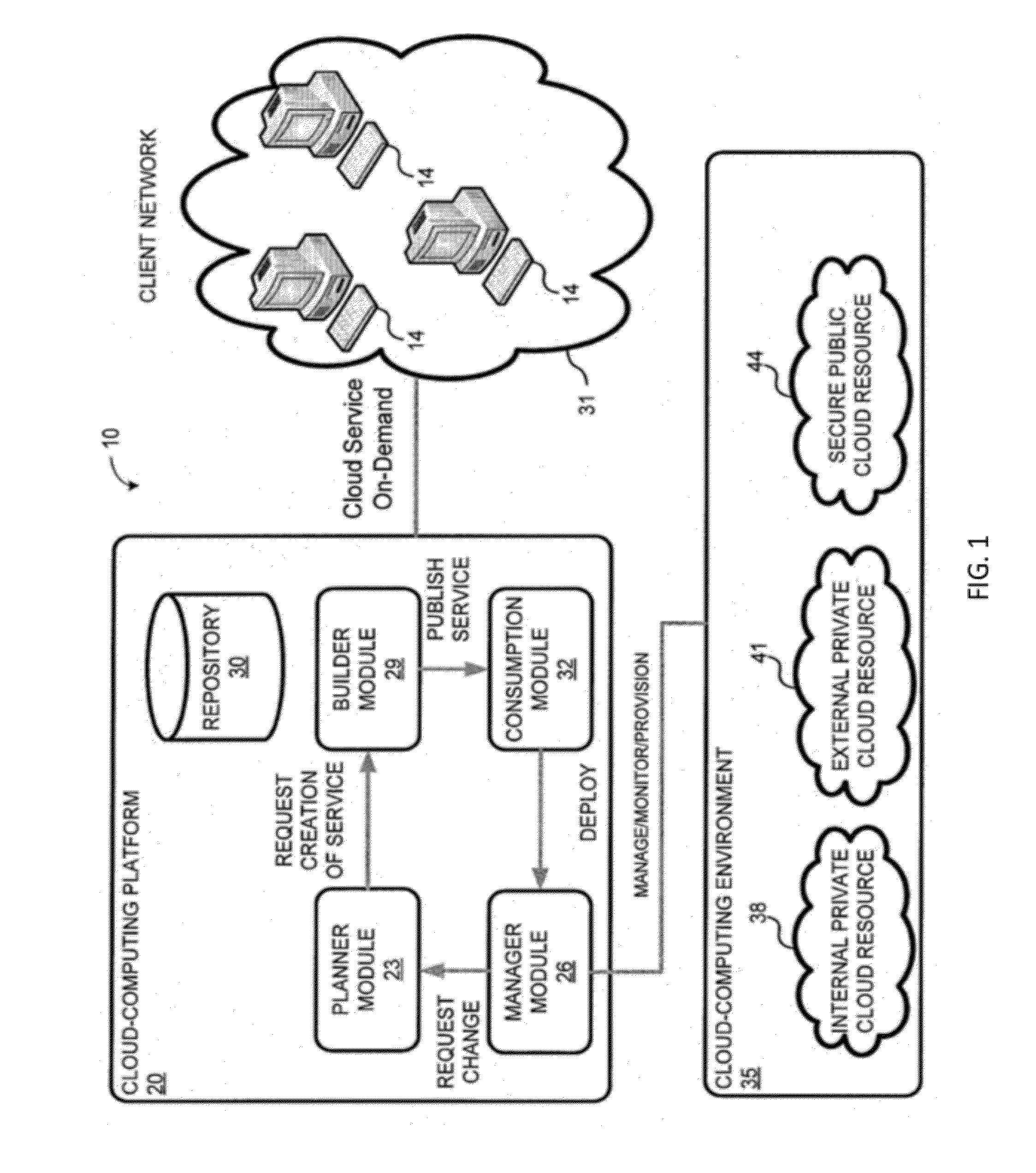
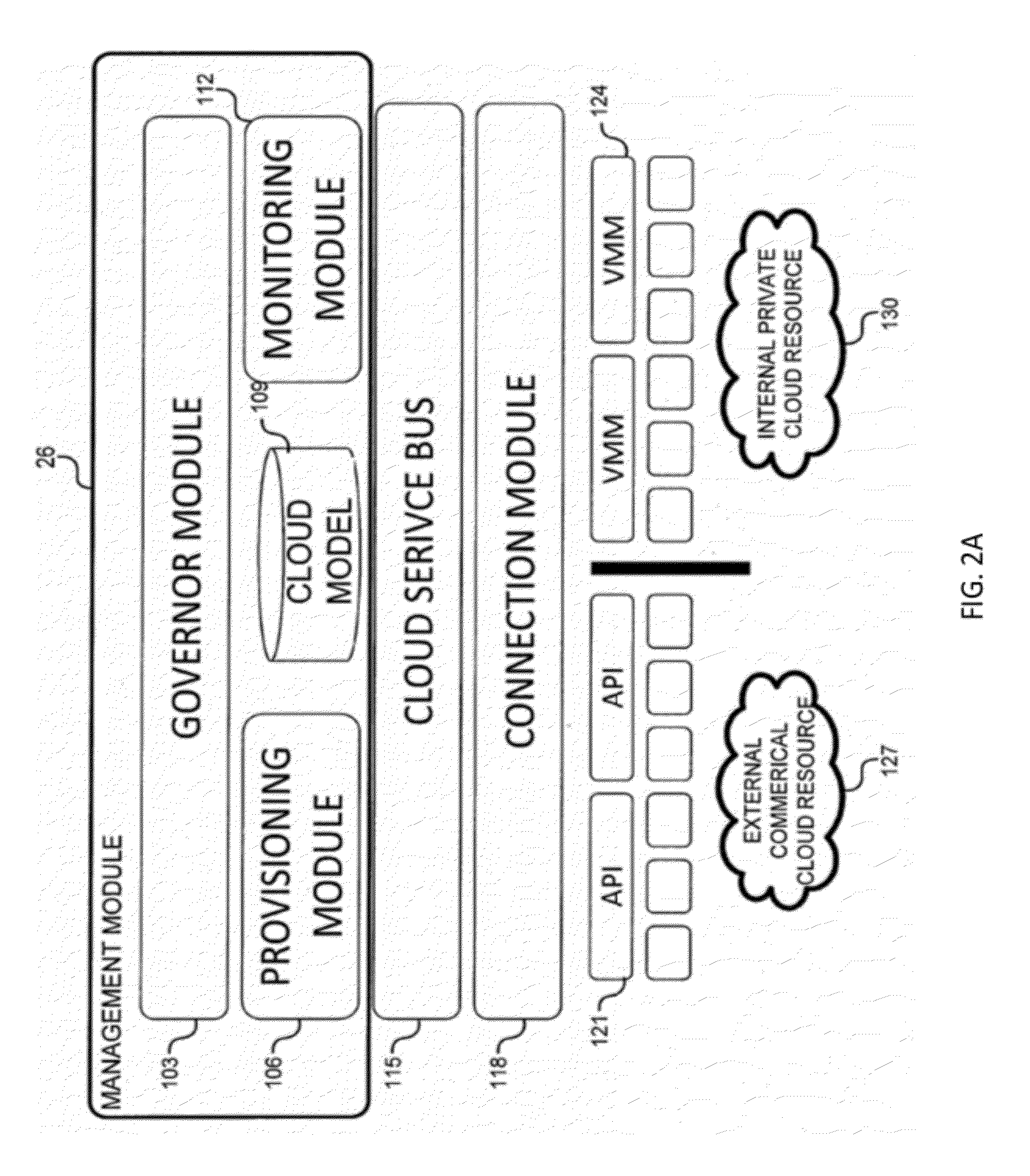
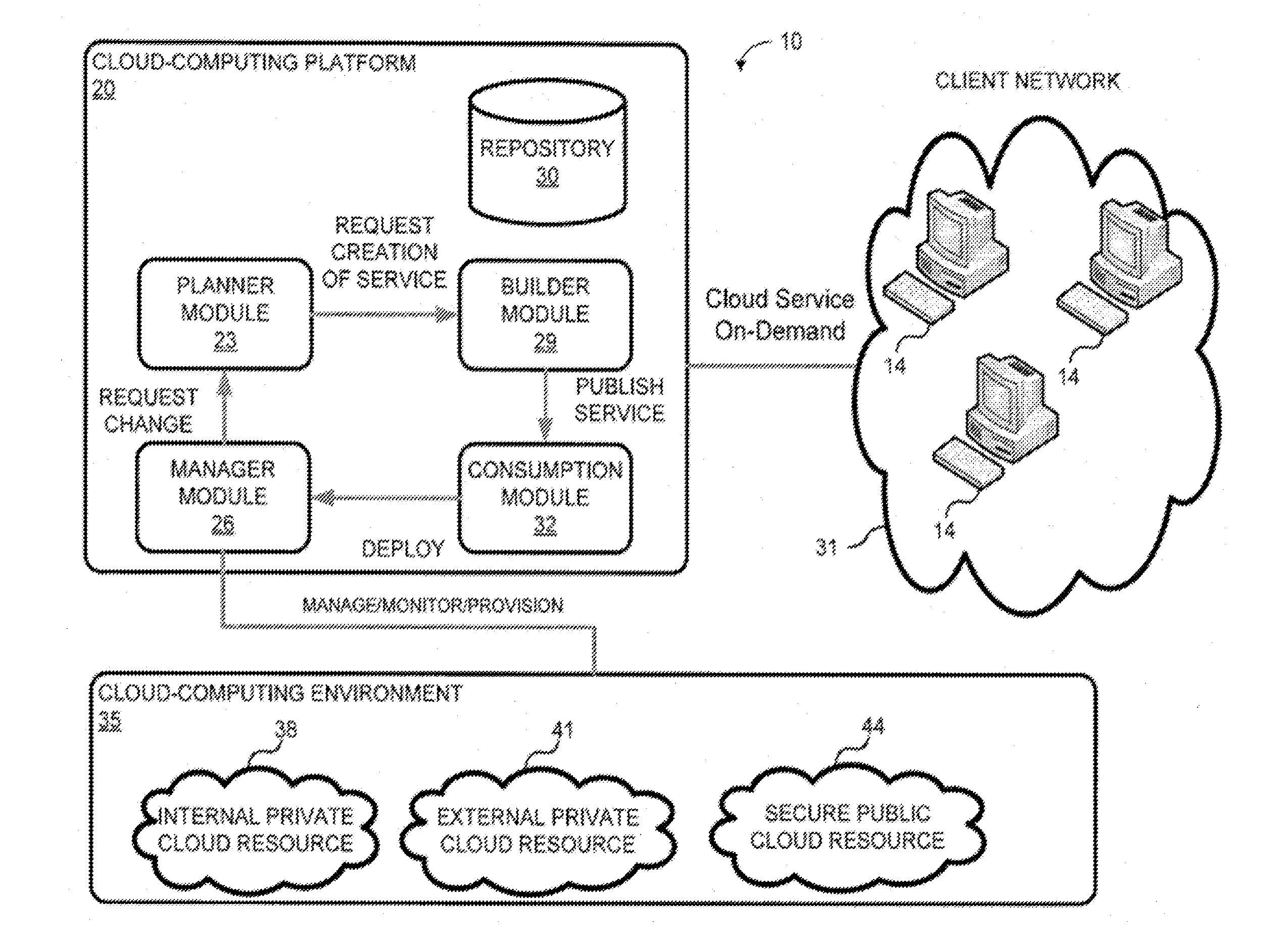
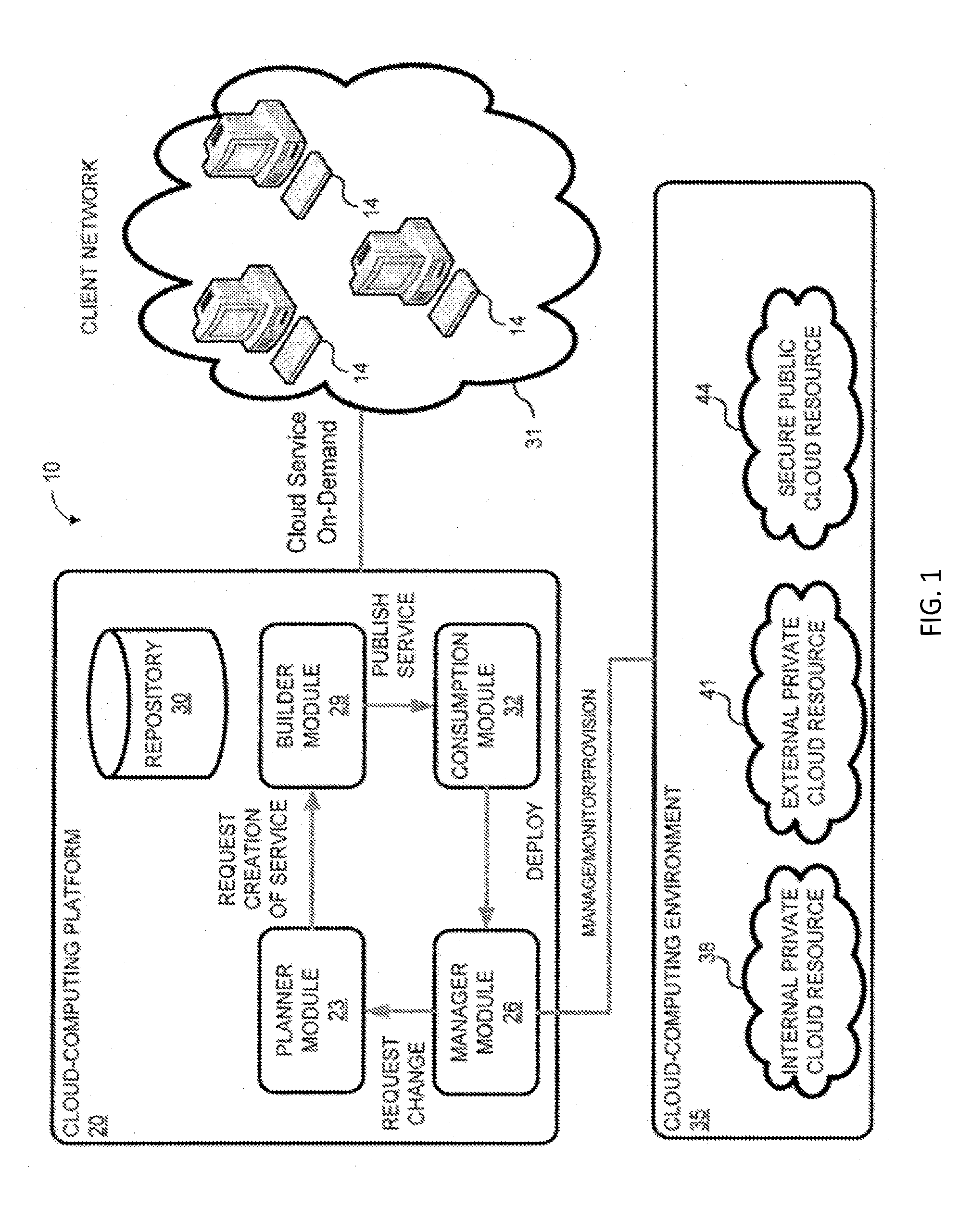
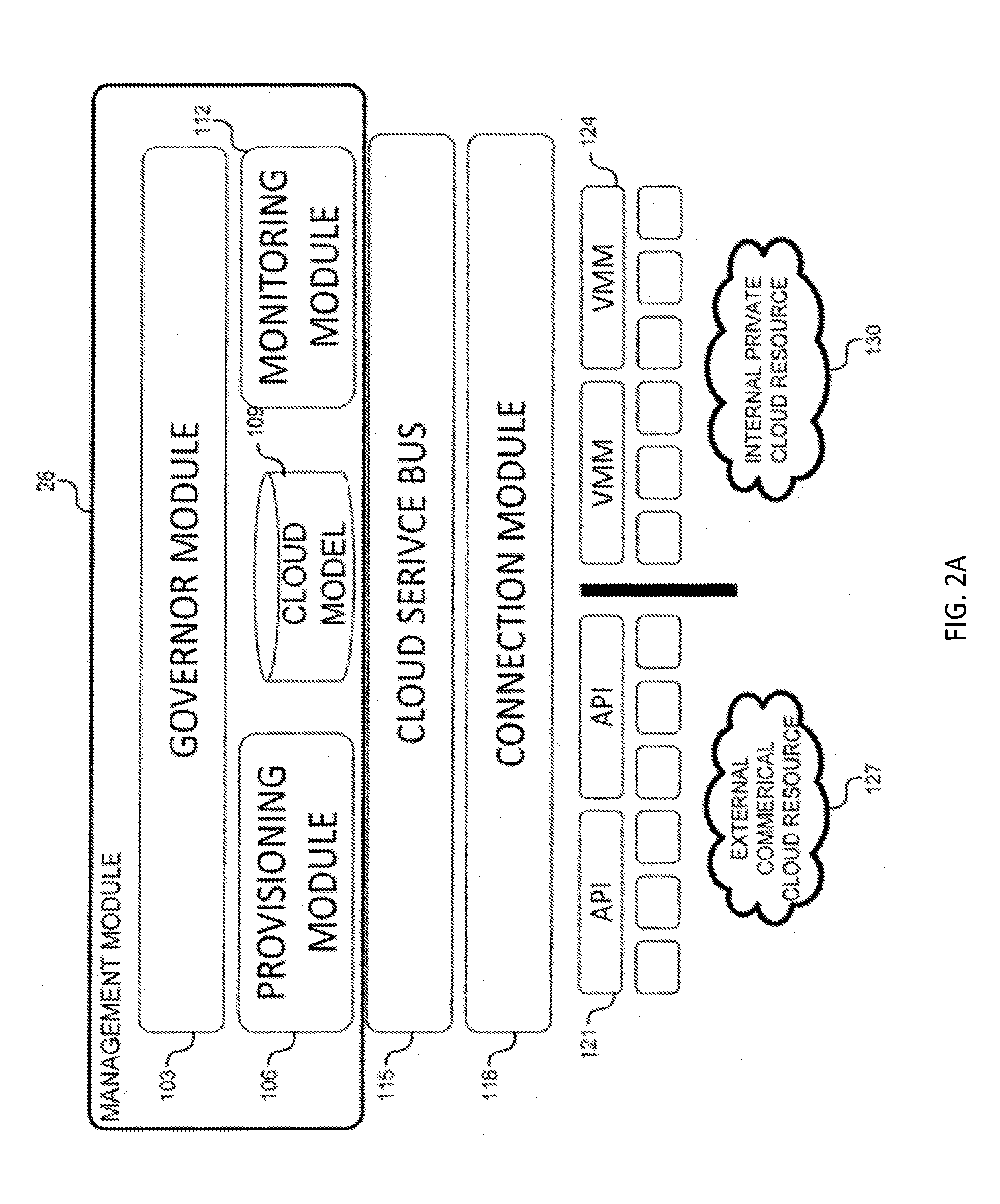
System and method for a cloud computing abstraction layer with security zone facilities
ActiveUS20120185913A1Rapid and dynamic deployment and scalingShorten the timeComputer security arrangementsHybrid transportVirtualizationAbstraction layer
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload. This allows a developer to define a security zone and to apply at least one type of security policy with respect to the security zone including the type of security zone policy in the metamodel framework such that the type of security zone policy can be associated with the software workload upon development of the software workload, and if the type of security zone policy is associated with the software workload, automatically applying the security policy to the software workload when the software workload is deployed within the security zone.
Owner:DXC US AGILITY PLATFORM INC
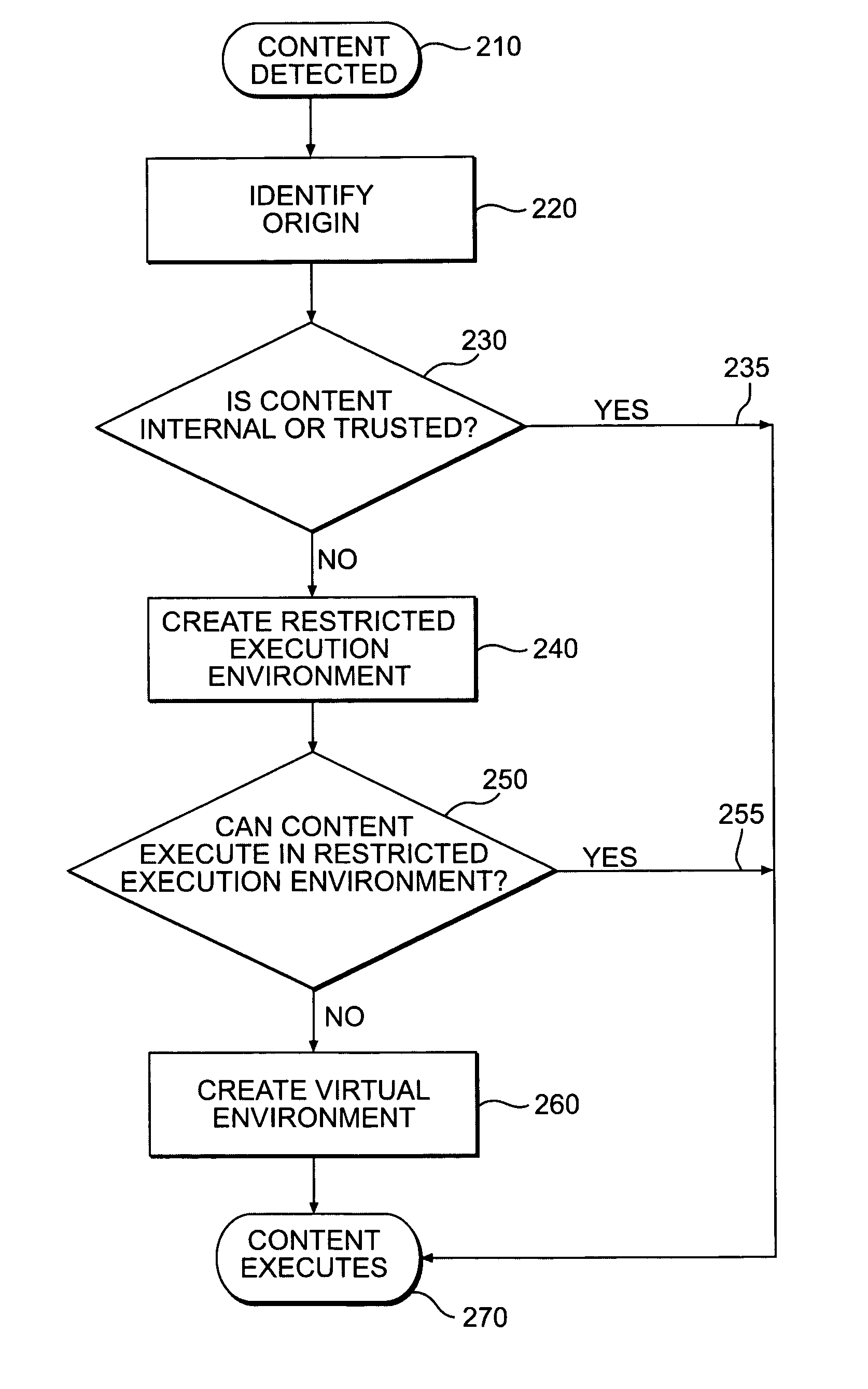
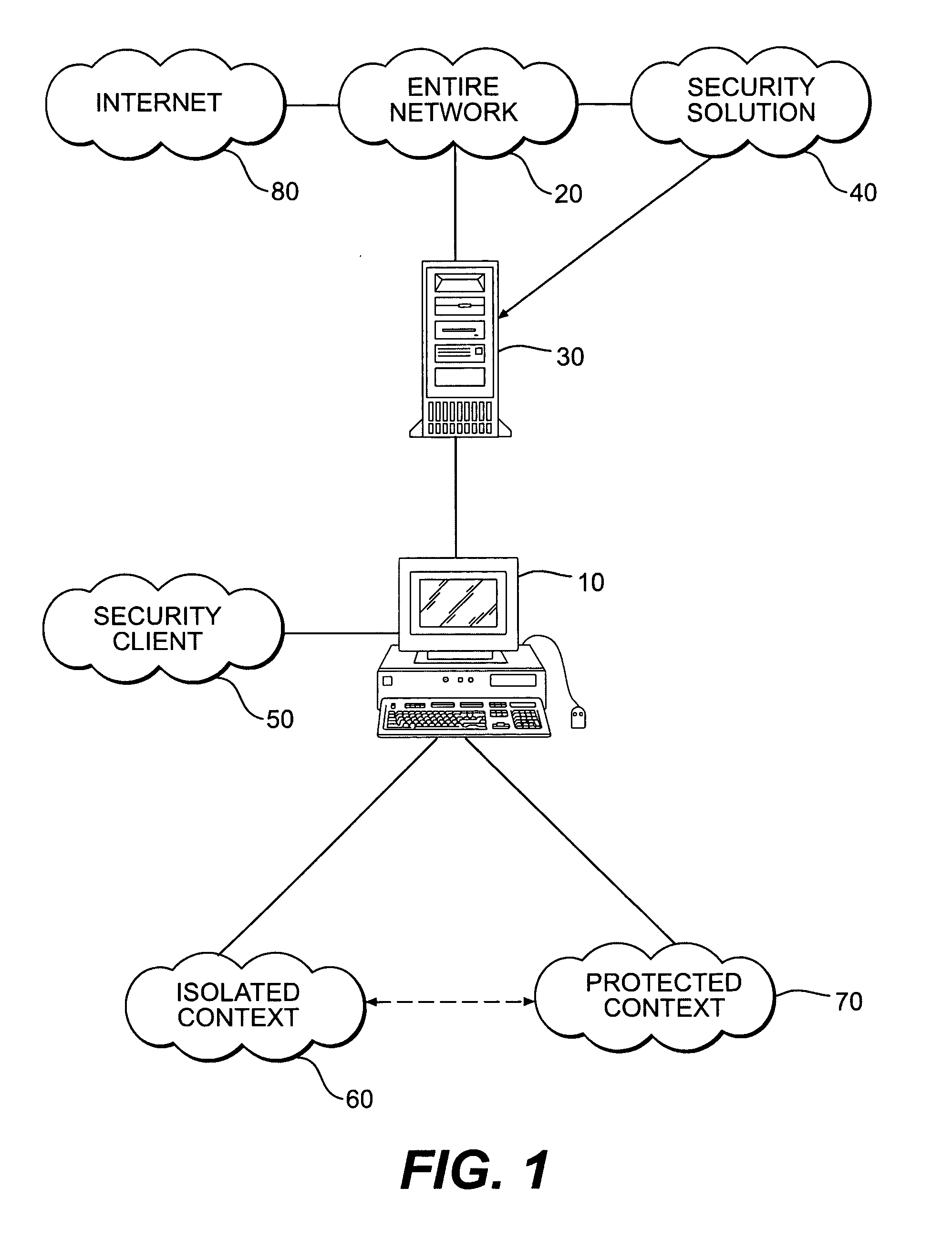
Systems and methods for secure client applications
ActiveUS20050149726A1Avoid attackMinimize impactDigital data processing detailsHardware monitoringVirtualizationClient-side
An innovative security solution which separates a client into a Protected Context, which is the real files and resources of the client, and an Isolated Context, which is a restricted execution environment which makes use of virtualized resources to execute applications and modify content in the Isolated Context, without allowing explicit access to the resources in the Protected Context. The solution further consolidates user interfaces to allow users to seamlessly work with content in both contexts, and provide a visual indication of which display windows are rendered from content executed in the Isolated Context.
Owner:GOOGLE LLC
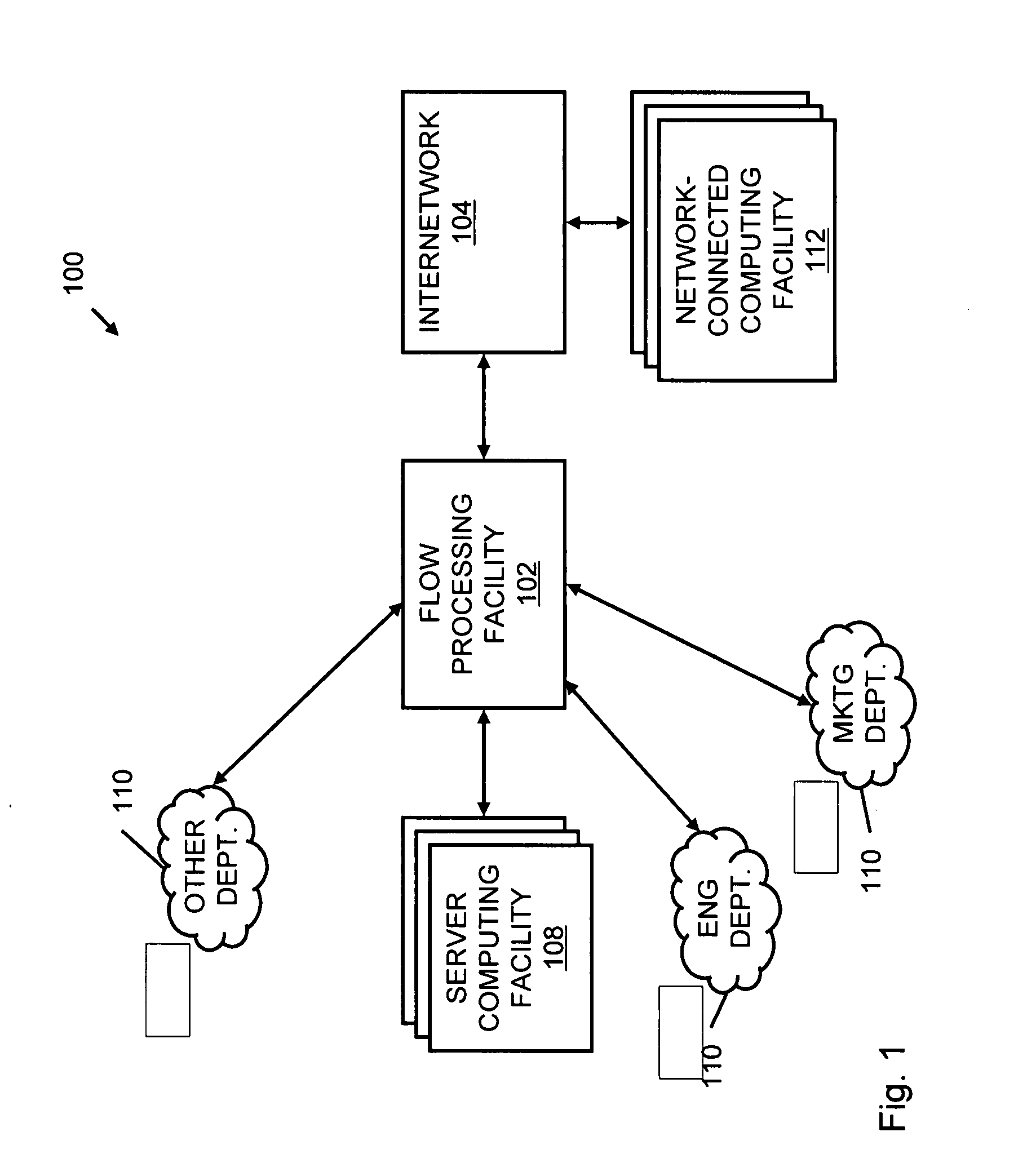
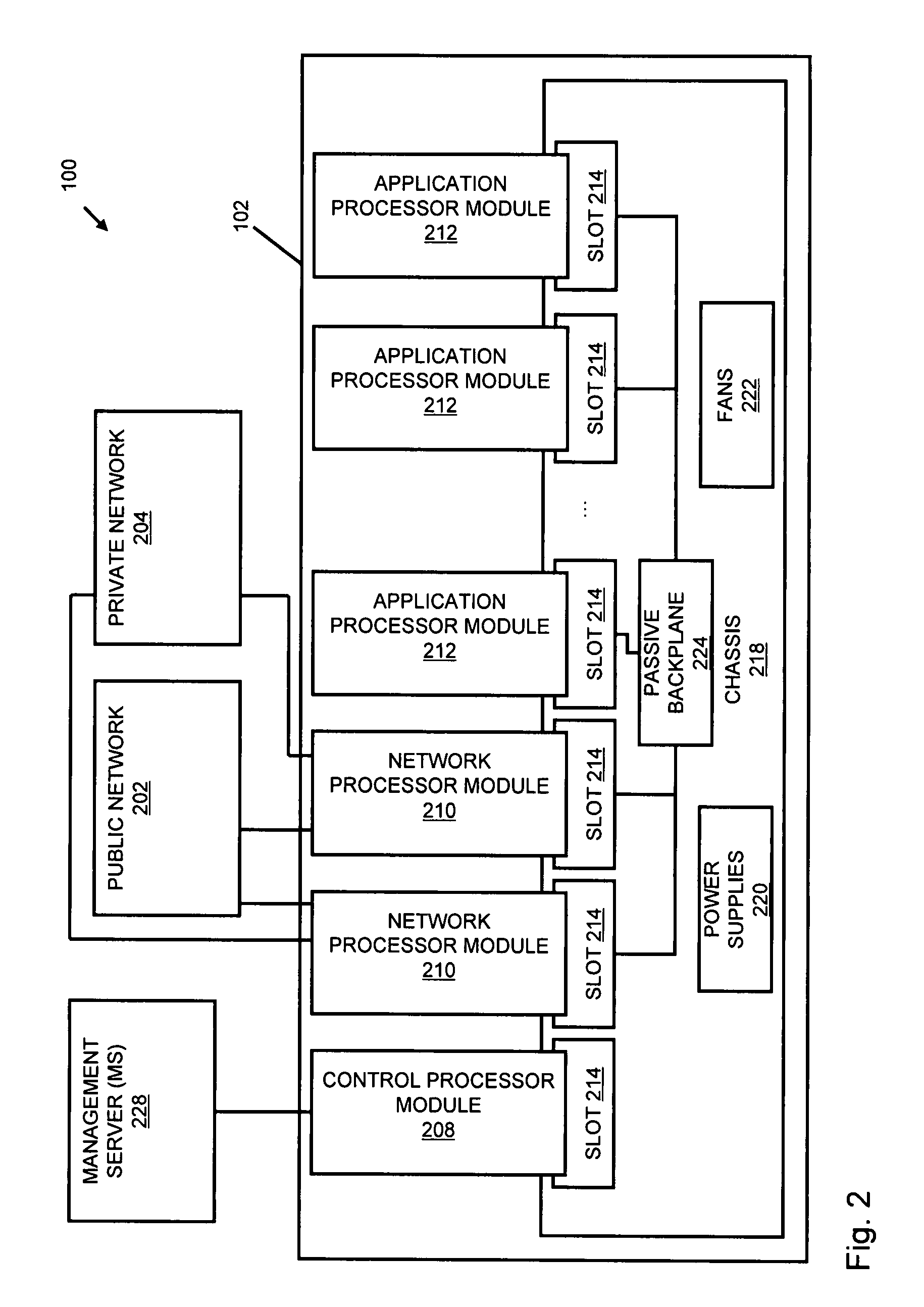
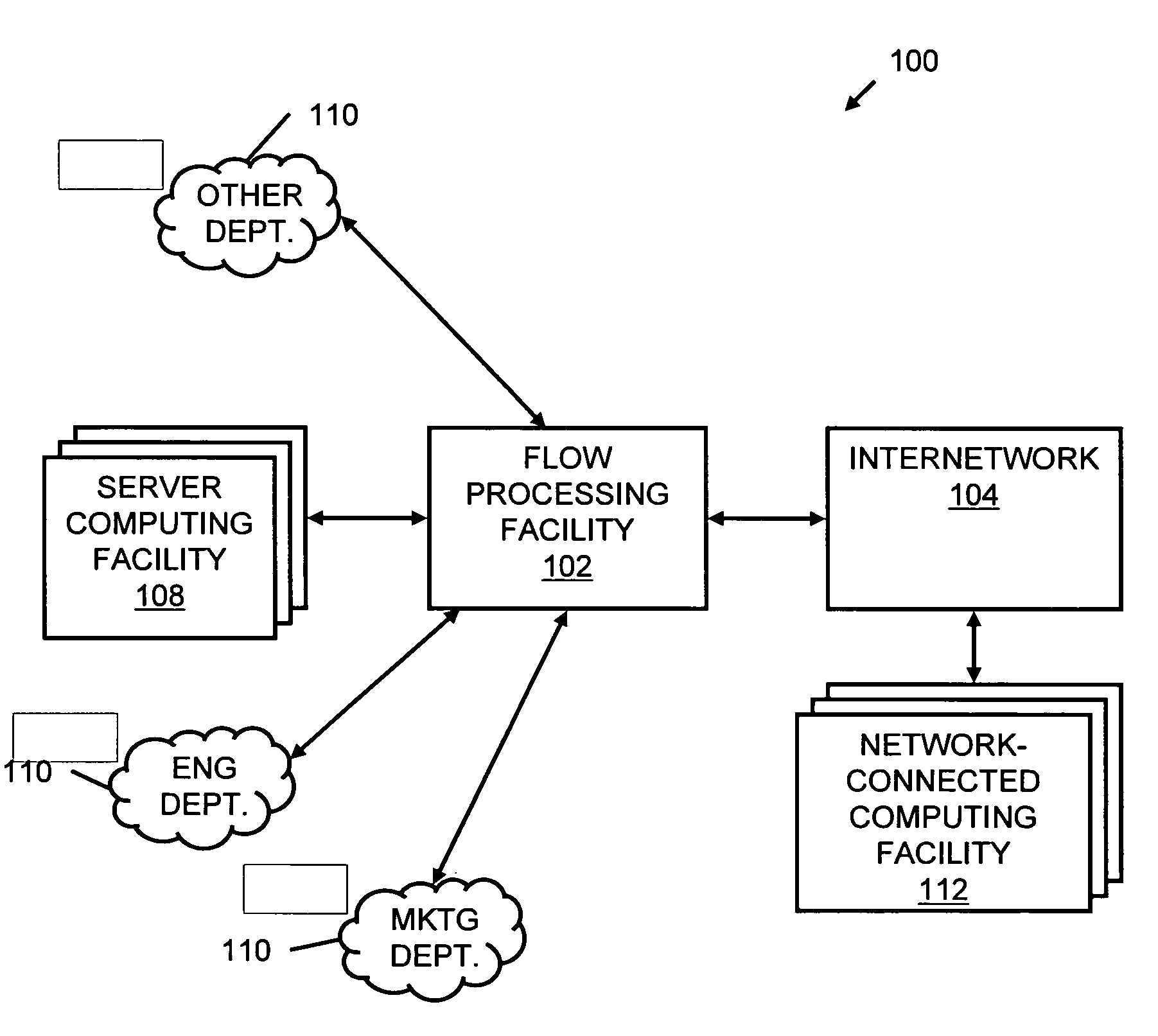
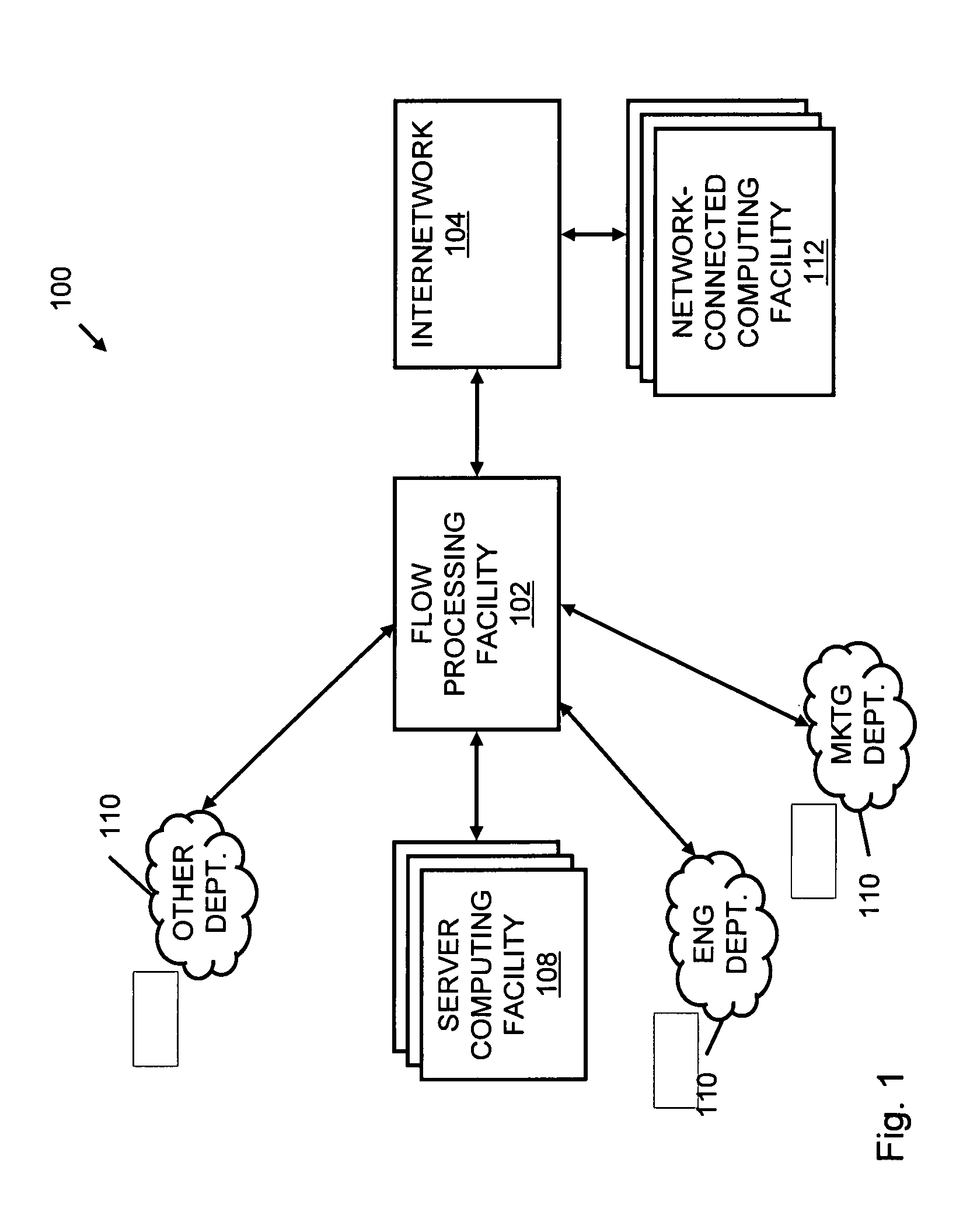
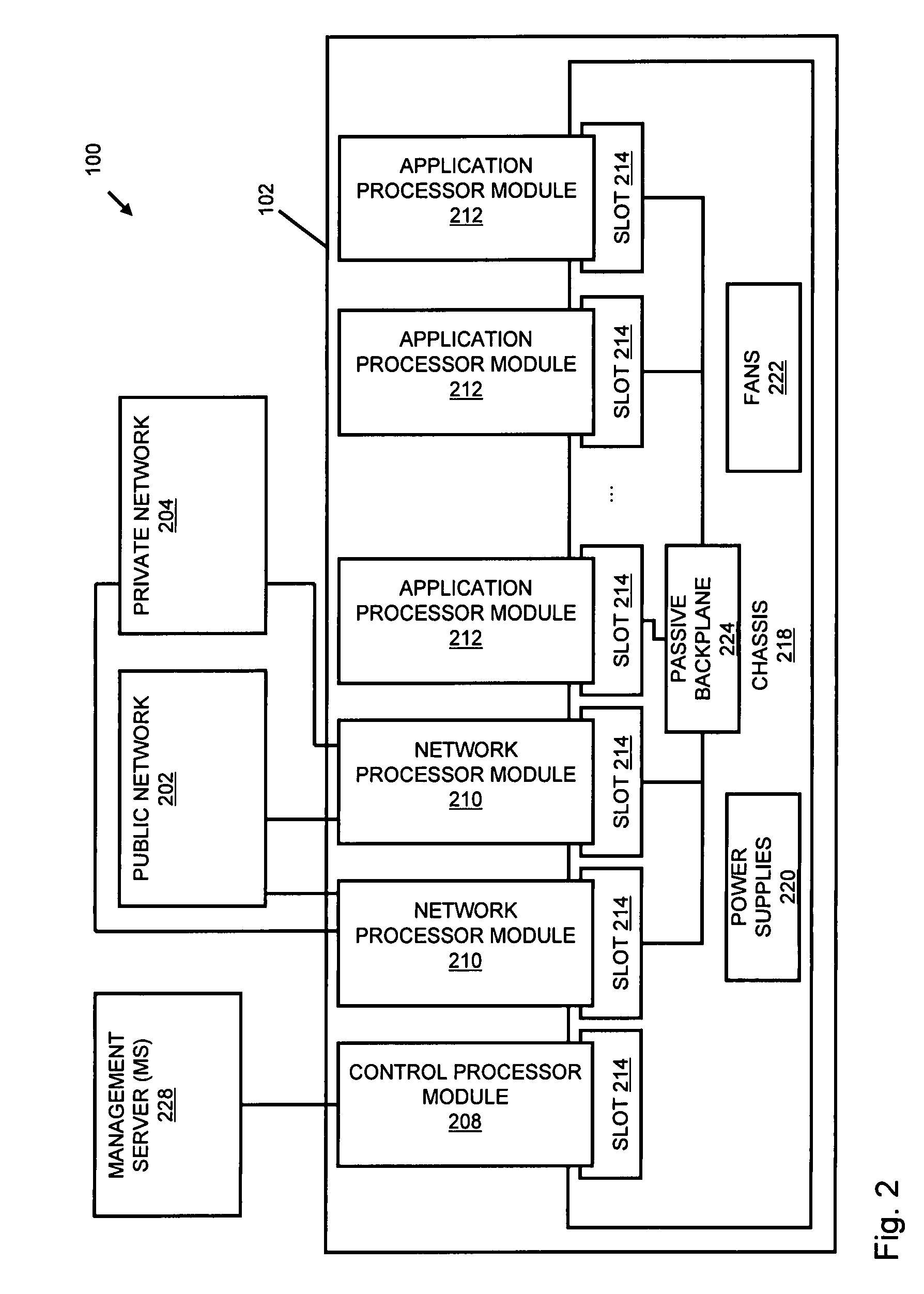
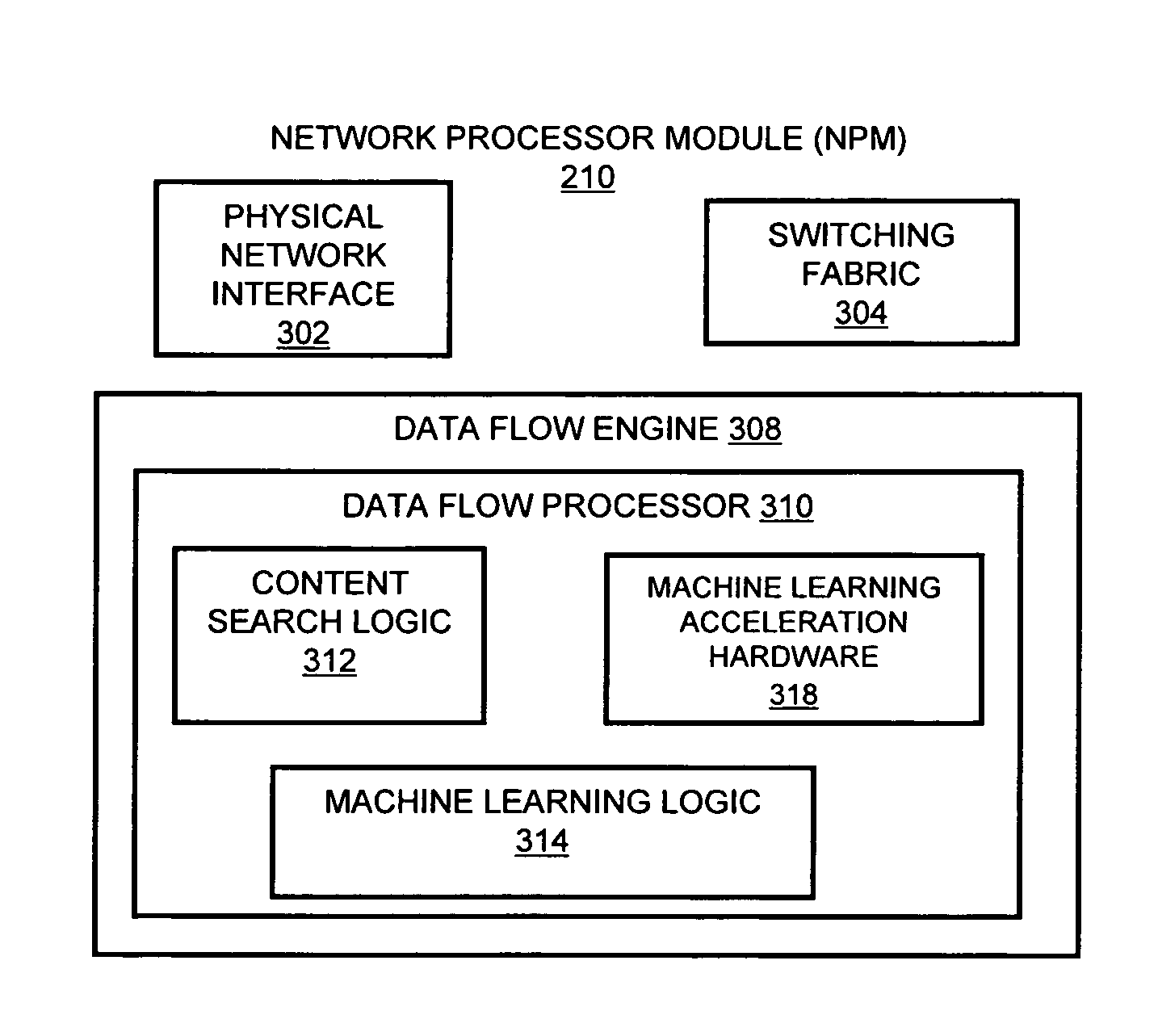
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
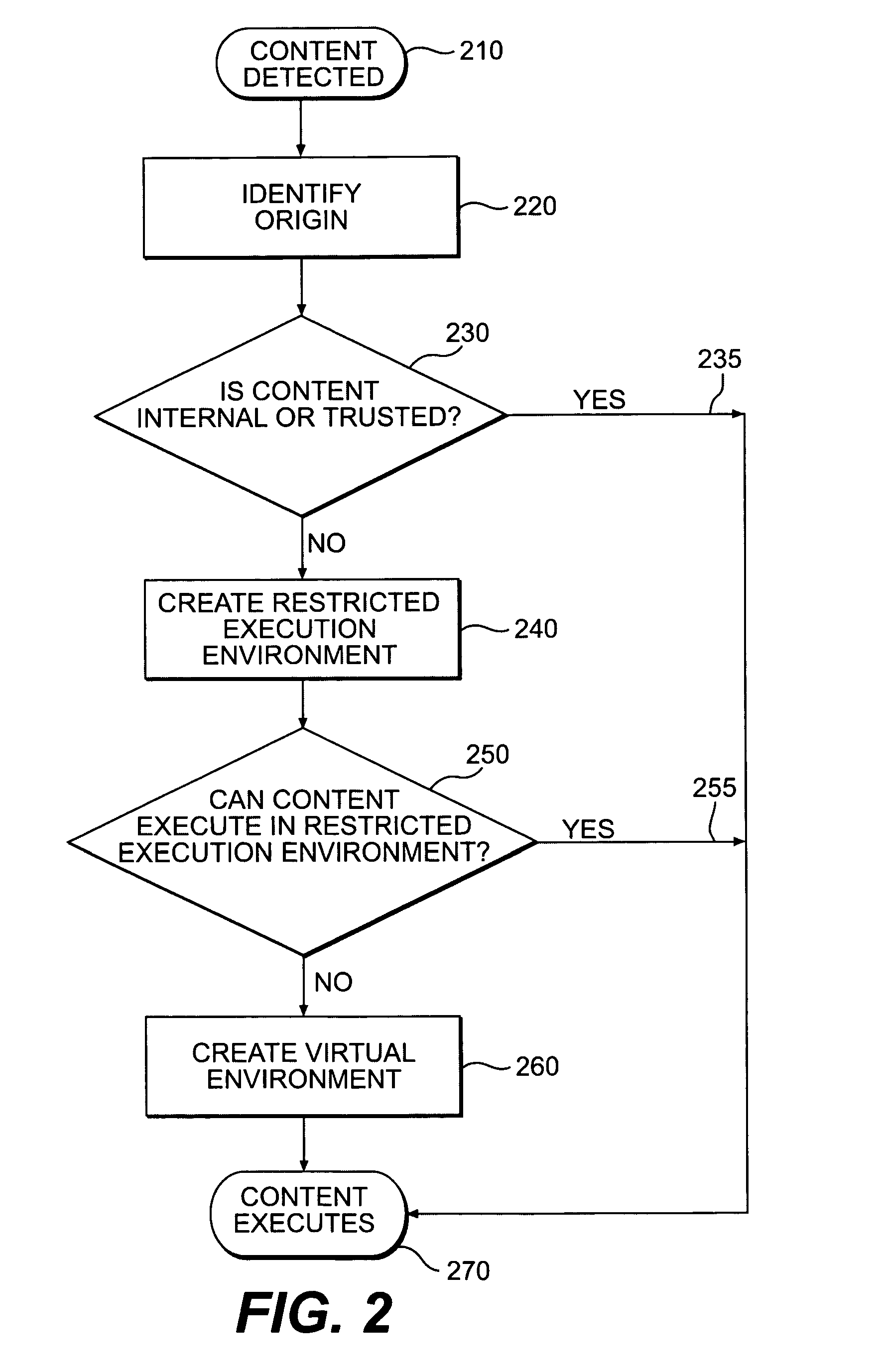
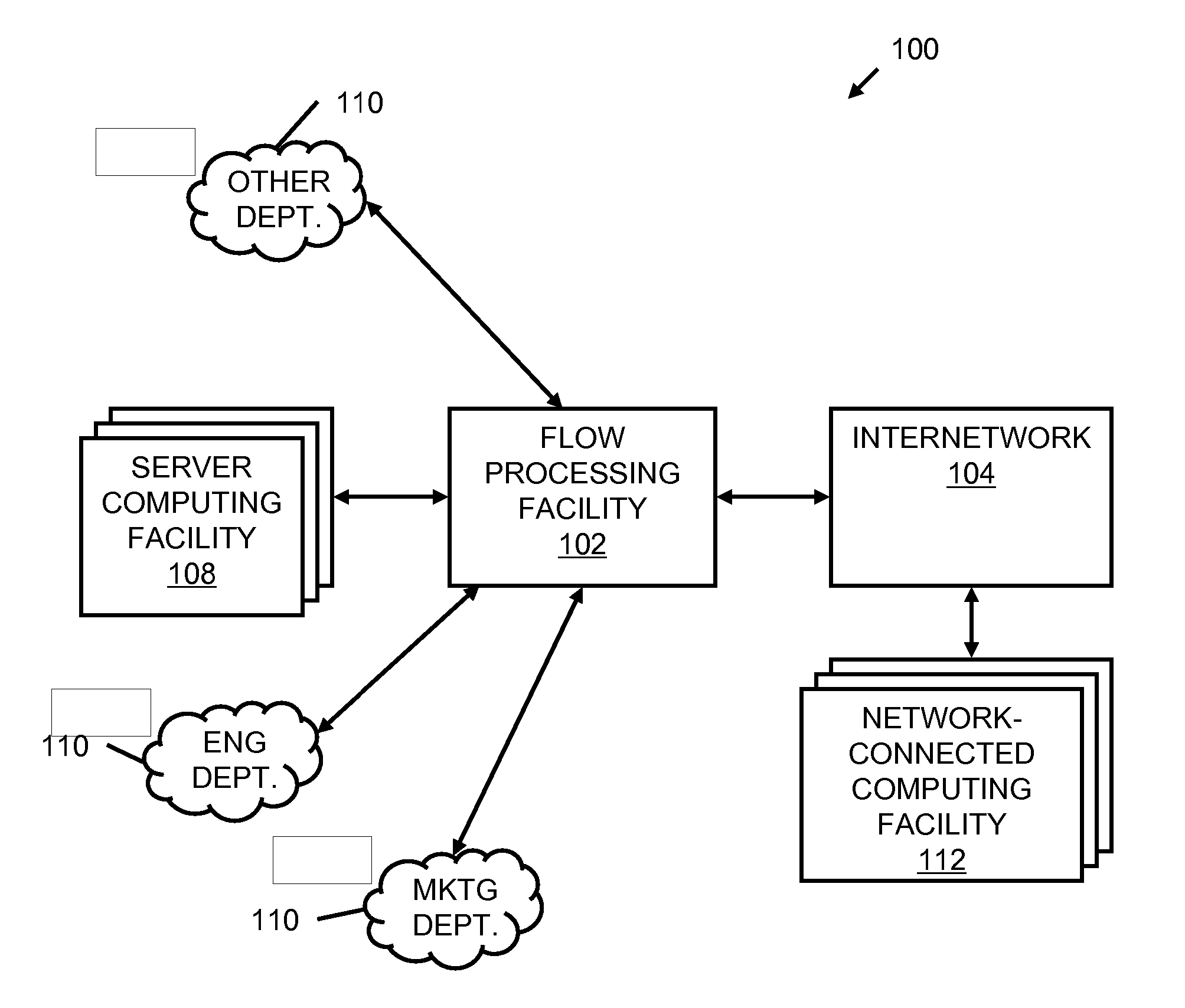
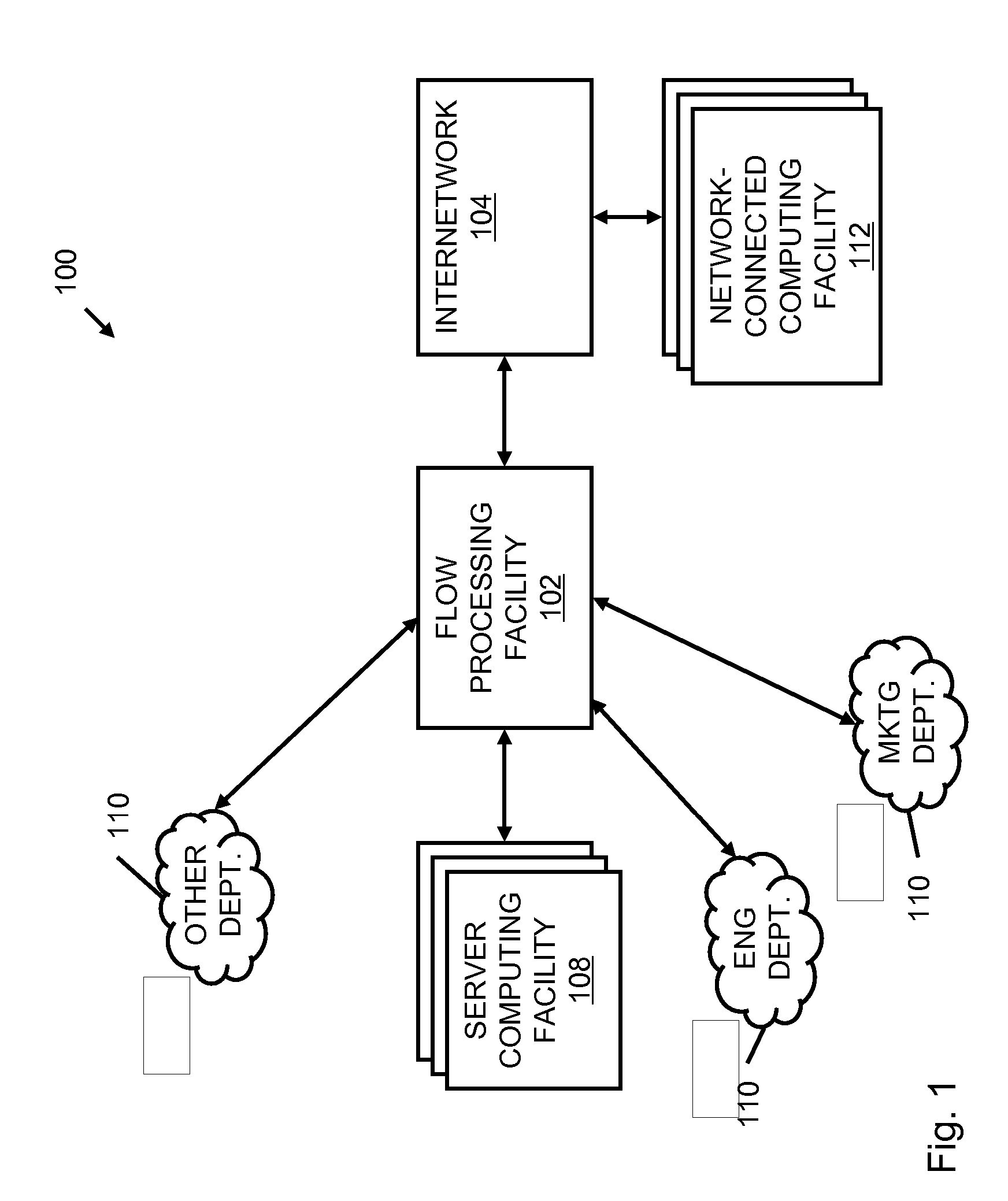
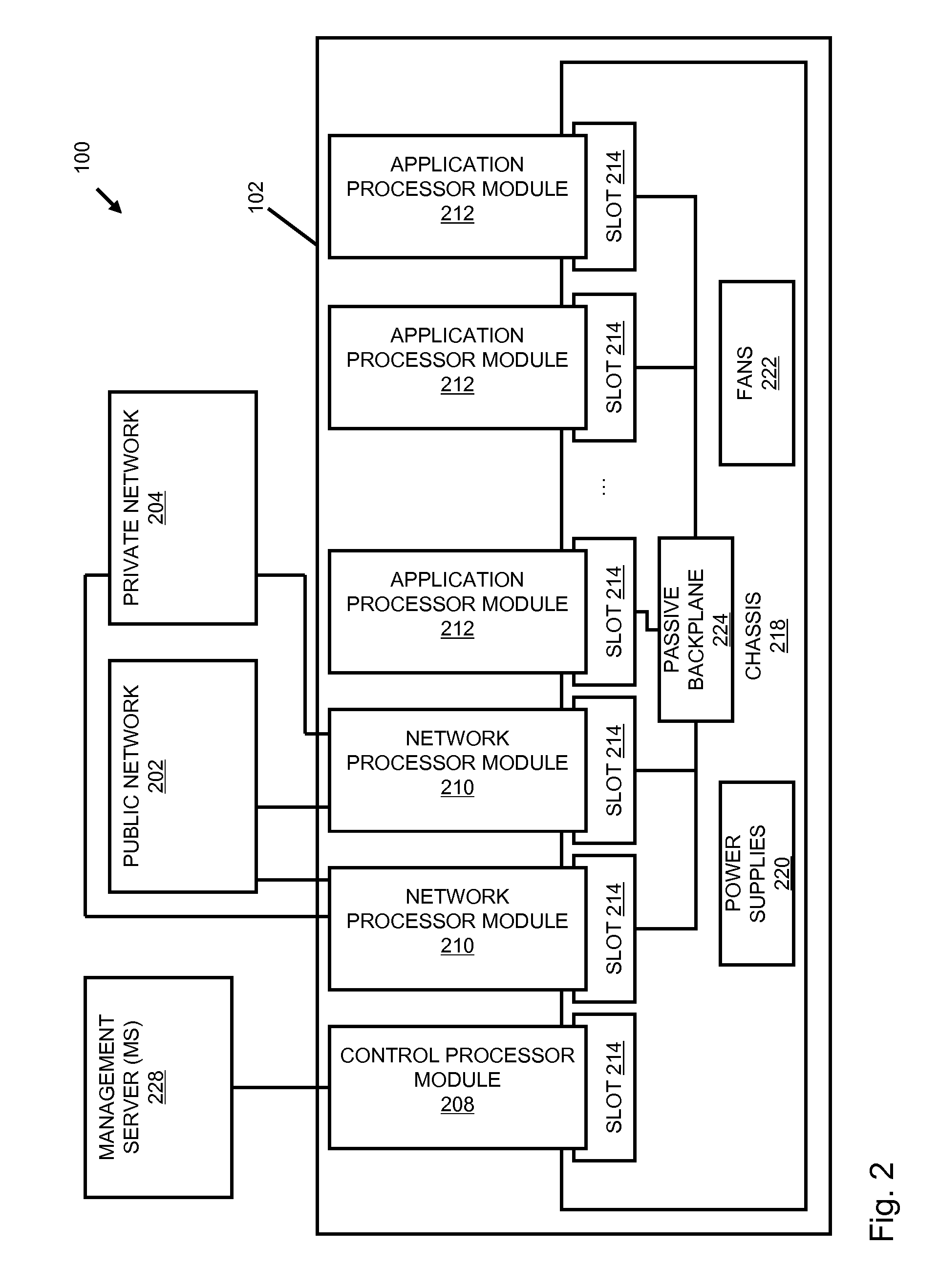
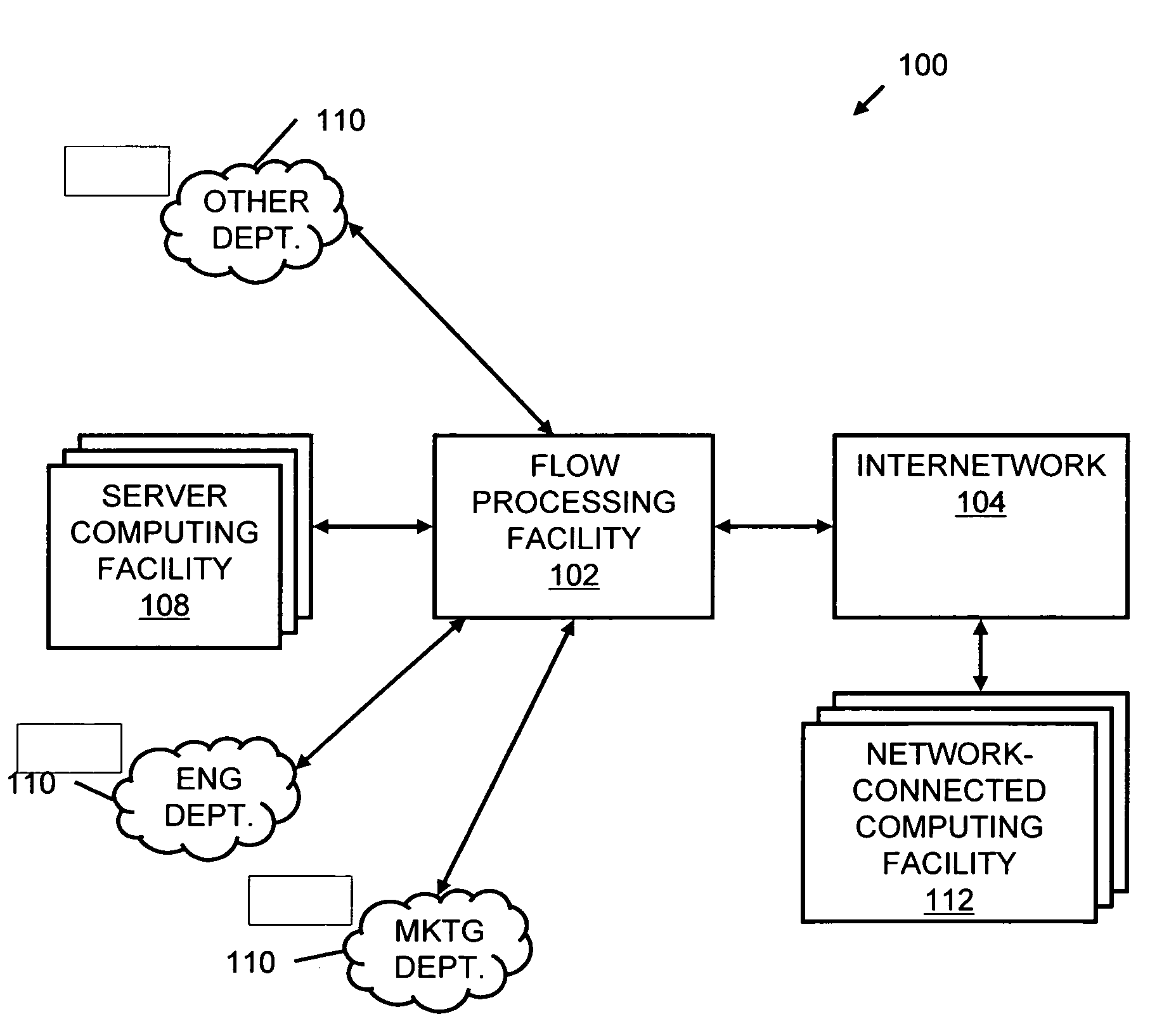
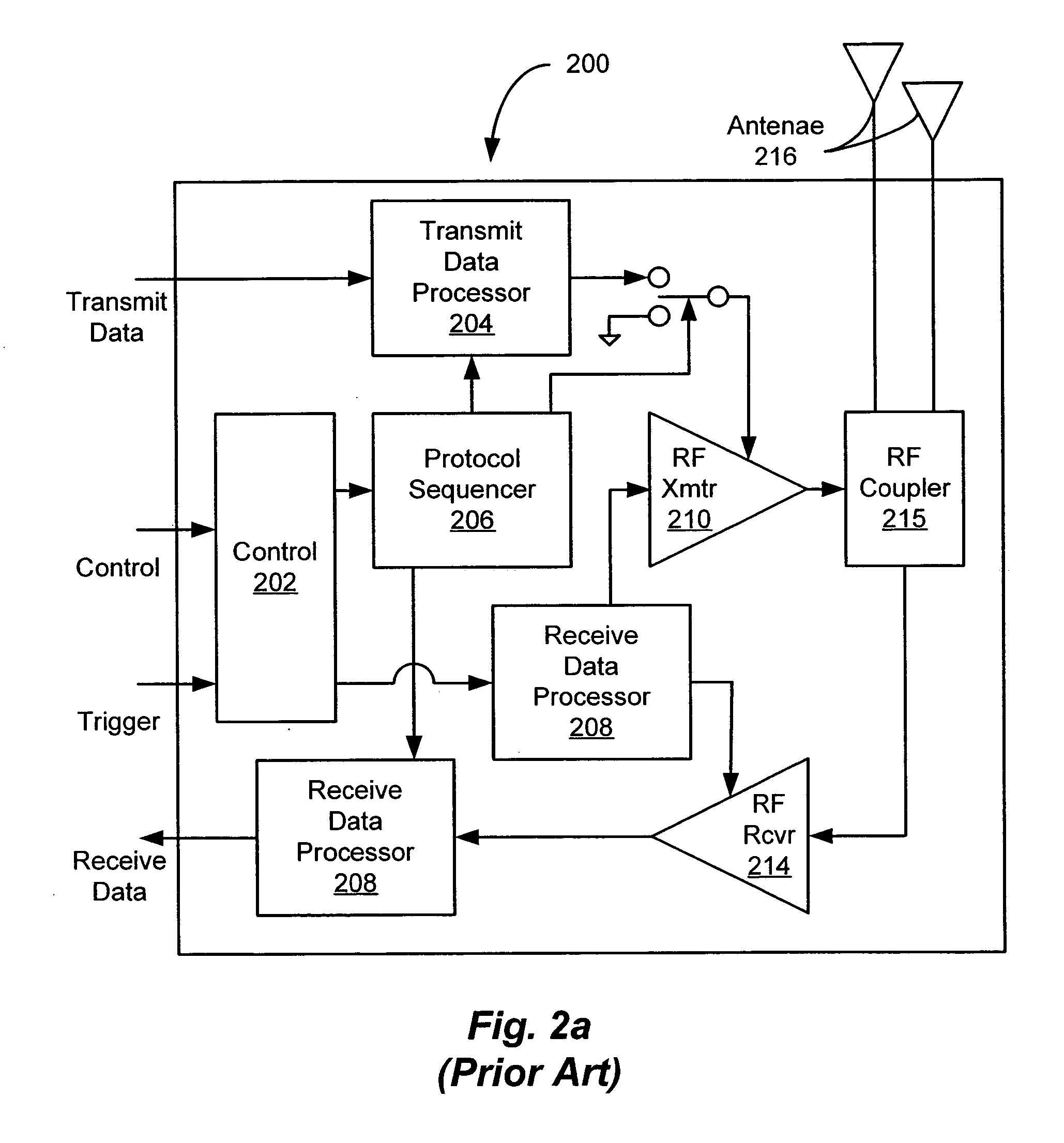
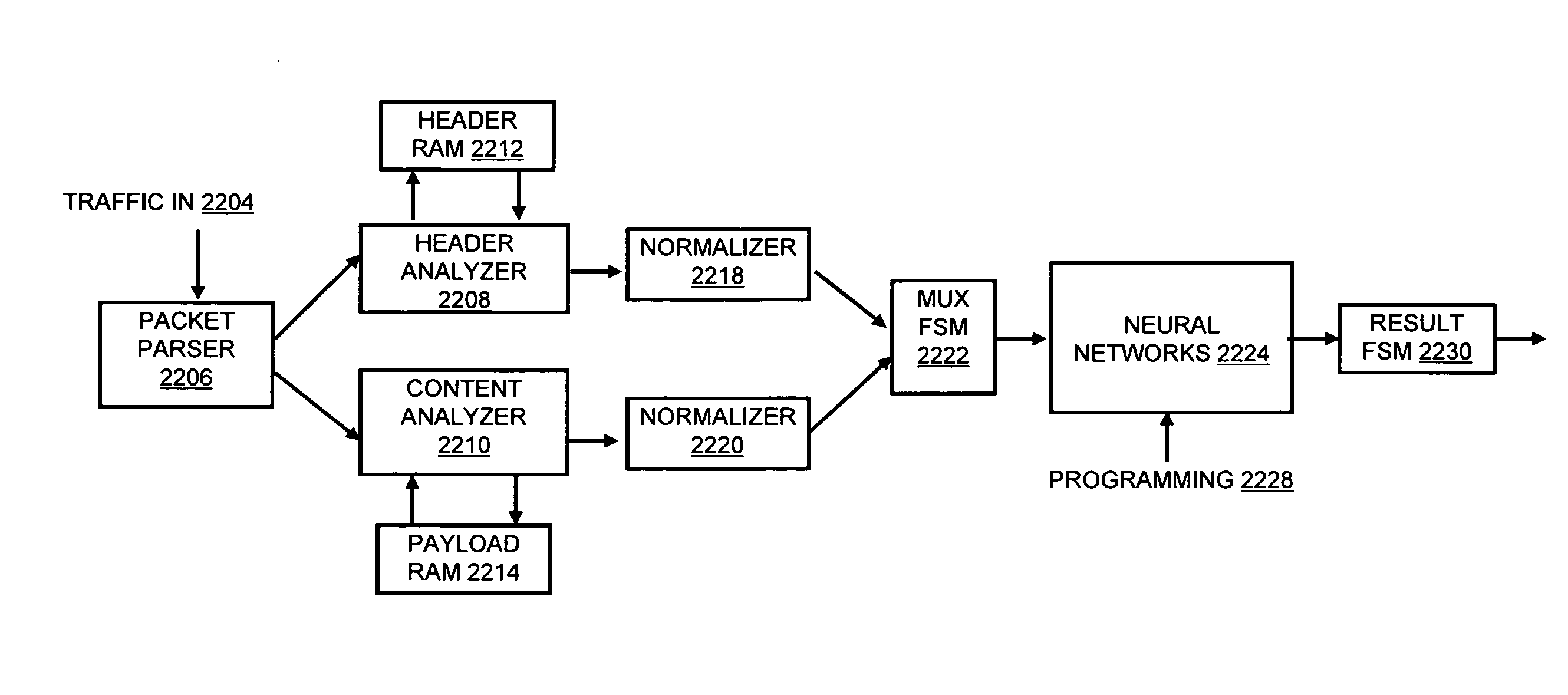
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Virtual systems management
Automatic configuration management of a network is provided by determining an inventory of resources at a virtualization layer of a node of the network, assigning prioritization to members of a set of network configuration elements, allocating virtual resources among the set of network configuration elements, establishing a network configuration. The configuration is managed by determining real time performance metrics for the configuration, producing a reallocation of the virtual resources based on the performance metrics that are estimated to change the established configuration, change the performance metrics, and initiating the reallocation of the virtual resources. This Abstract is provided for the sole purpose of complying with the Abstract requirement that allows a reader to quickly ascertain the subject matter of the disclosure contained herein. This Abstract is submitted with the understanding that it will not be used to interpret or to limit the scope or the meaning of the claims.
Owner:TOUTVIRTUAL
Distributed trusted virtualization platform
InactiveUS20090204964A1Key distribution for secure communicationMultiple digital computer combinationsVirtualizationEnd to end security
A platform architecture shifts the networked computing paradigm from PC+Network to a system using trusted mobile internet end-point (MIEP) devices and cooperative agents hosted on a trusted server. The MIEP device can participate in data flows, arbitrate authentication, and / or participate in implementing security mechanisms, all within the context of assured end-to-end security. The MIEP architecture improves platform-level capabilities by suitably (and even dynamically) partitioning what is done at the MIEP nodes, the network, and the server based infrastructure for delivering services.
Owner:MOTEGRITY +1
Method and apparatus for providing virtual computing services
InactiveUS20050044301A1Easy to manageLow costResource allocationMemory adressing/allocation/relocationVirtualizationOperational system
A level of abstraction is created between a set of physical processors and a set of virtual multiprocessors to form a virtualized data center. This virtualized data center comprises a set of virtual, isolated systems separated by a boundary referred as a partition. Each of these systems appears as a unique, independent virtual multiprocessor computer capable of running a traditional operating system and its applications. In one embodiment, the system implements this multi-layered abstraction via a group of microkernels, each of which communicates with one or more peer microkernel over a high-speed, low-latency interconnect and forms a distributed virtual machine monitor. Functionally, a virtual data center is provided, including the ability to take a collection of servers and execute a collection of business applications over a compute fabric comprising commodity processors coupled by an interconnect. Processor, memory and I / O are virtualized across this fabric, providing a single system, scalability and manageability. According to one embodiment, this virtualization is transparent to the application, and therefore, applications may be scaled to increasing resource demands without modifying the application.
Owner:ORACLE INT CORP
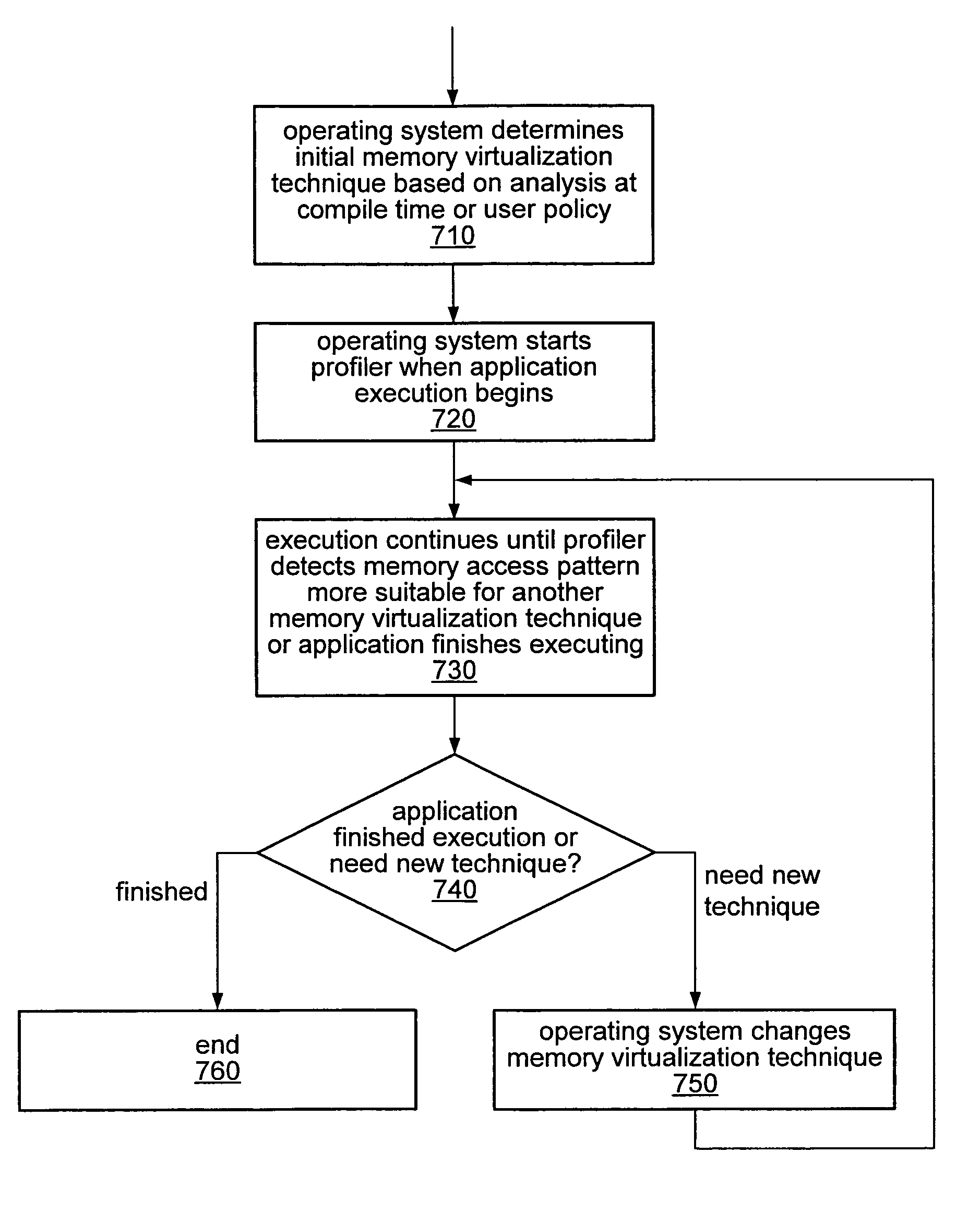
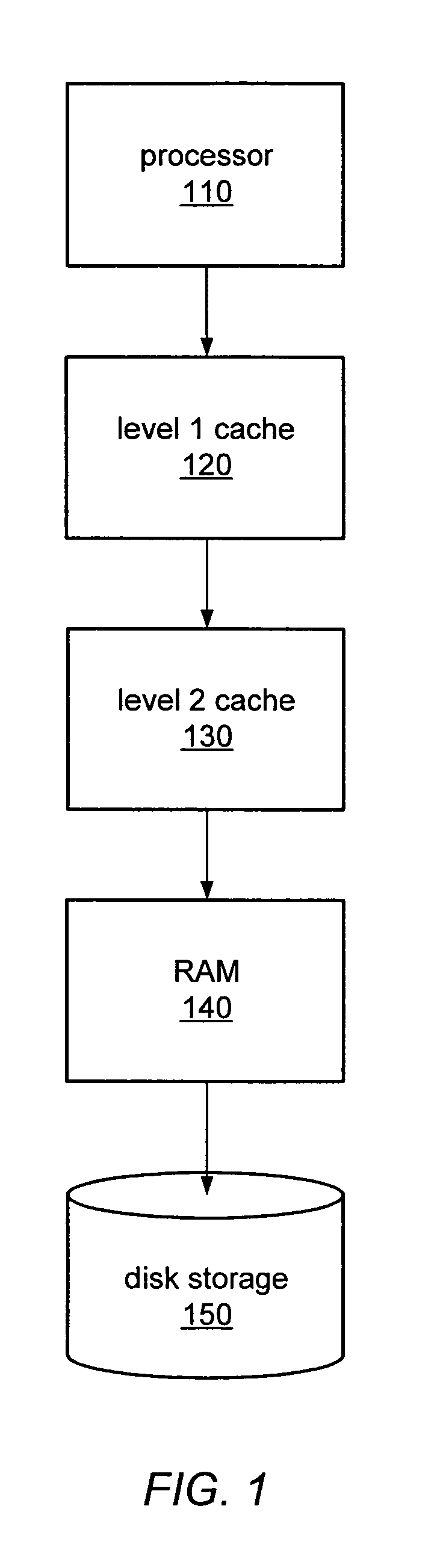
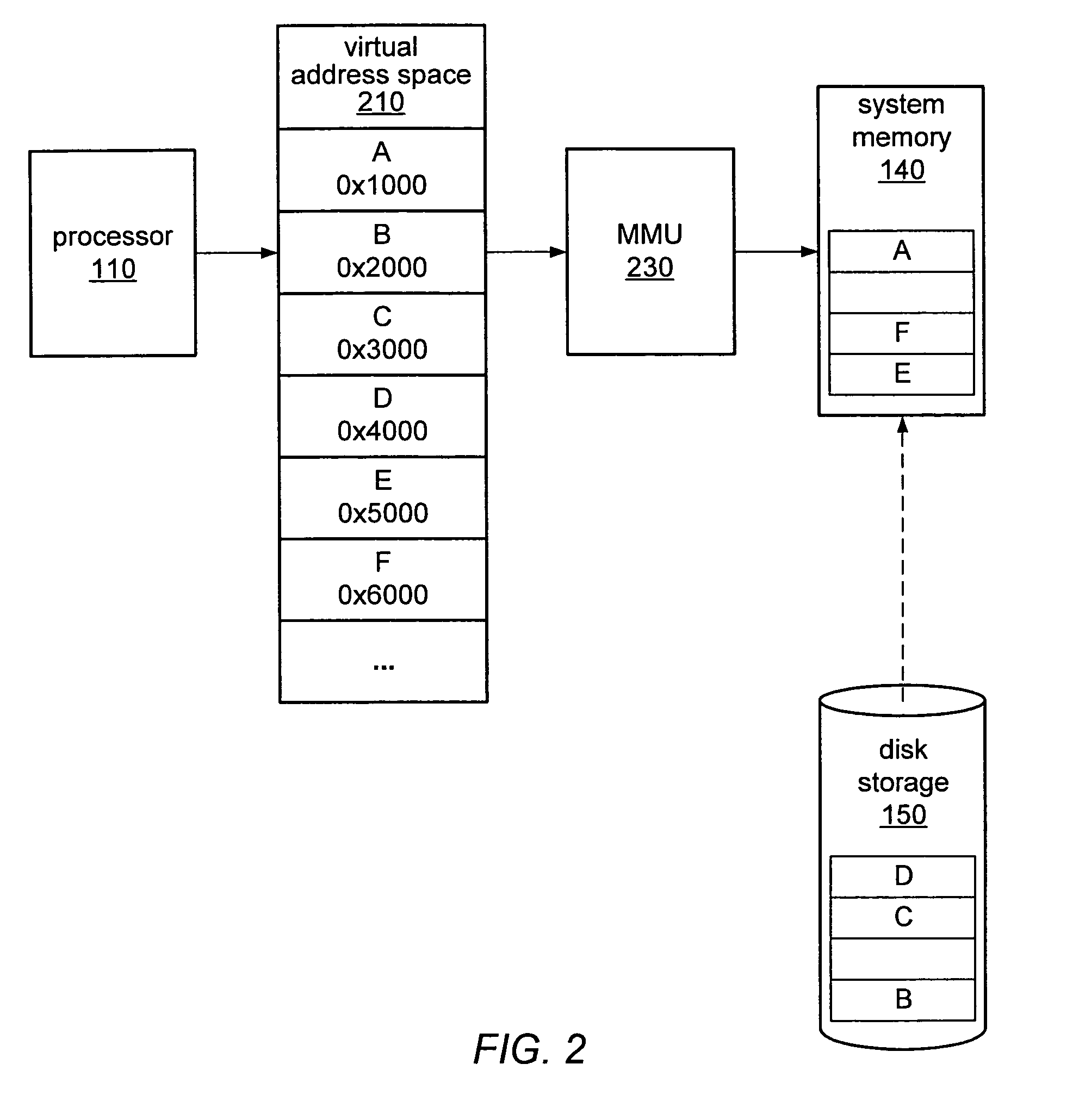
Dynamic selection of memory virtualization techniques
ActiveUS7752417B2Error detection/correctionMemory adressing/allocation/relocationVirtualizationComputerized system
A computer system may be configured to dynamically select a memory virtualization and corresponding virtual-to-physical address translation technique during execution of an application and to dynamically employ the selected technique in place of a current technique without re-initializing the application. The computer system may be configured to determine that a current address translation technique incurs a high overhead for the application's current workload and may be configured to select a different technique dependent on various performance criteria and / or a user policy. Dynamically employing the selected technique may include reorganizing a memory, reorganizing a translation table, allocating a different block of memory to the application, changing a page or segment size, or moving to or from a page-based, segment-based, or function-based address translation technique. A selected translation technique may be dynamically employed for the application independent of a translation technique employed for a different application.
Owner:ORACLE INT CORP
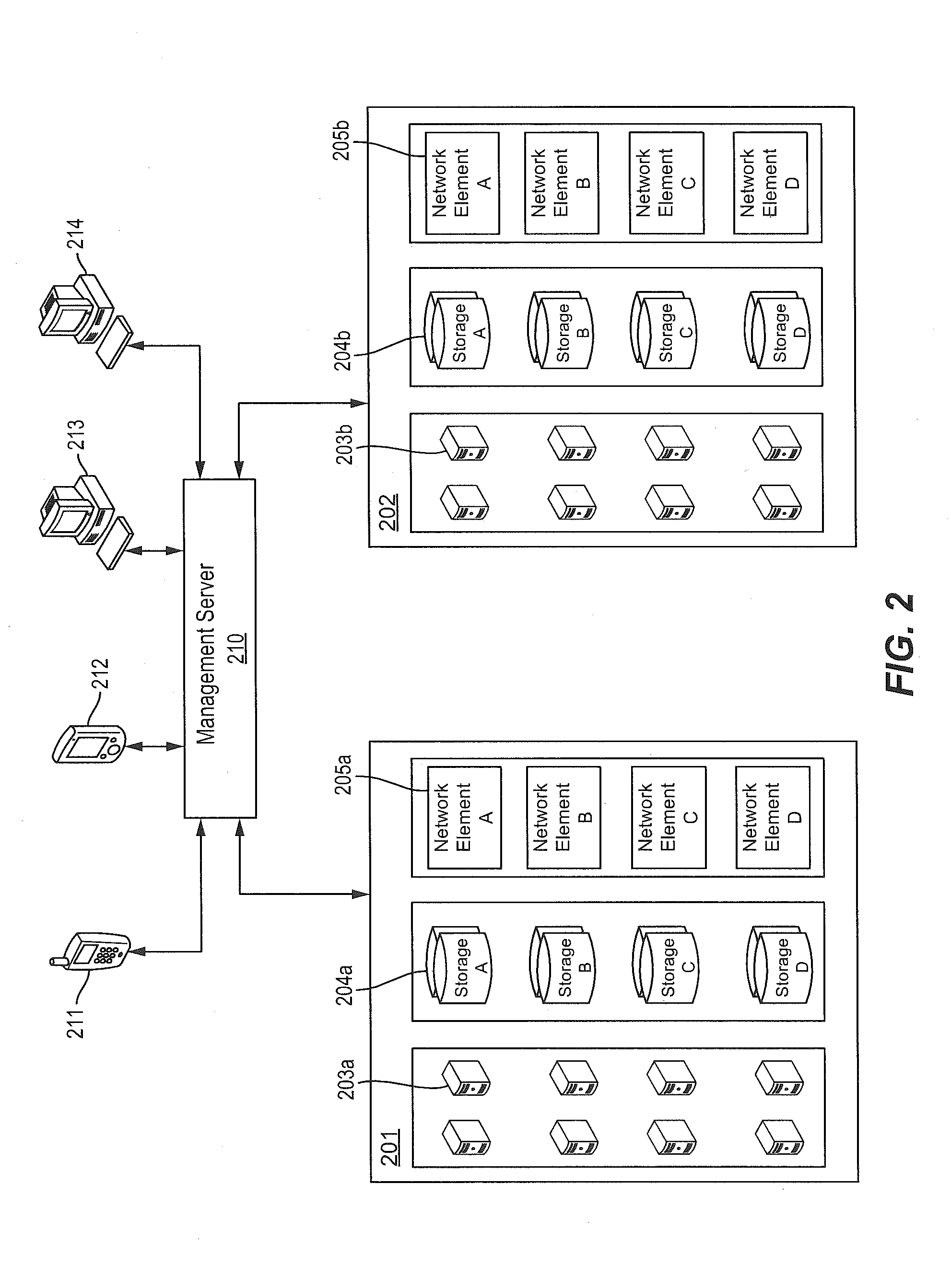
System and method for discovery enrichment in an intelligent workload management system
InactiveUS20110126275A1Free computational resourceAgile and flexible managementDigital data processing detailsUser identity/authority verificationVirtualizationService-oriented architecture
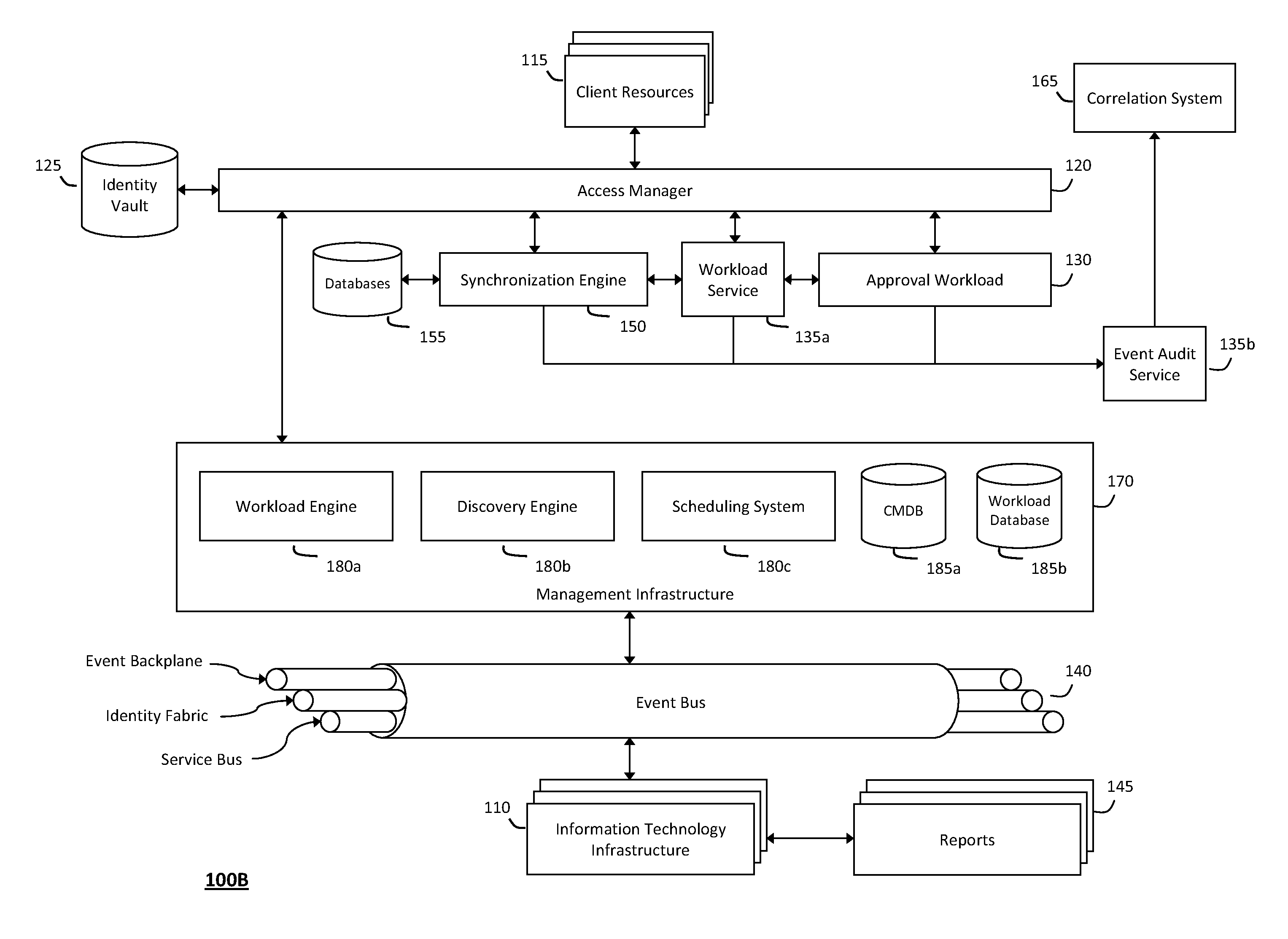
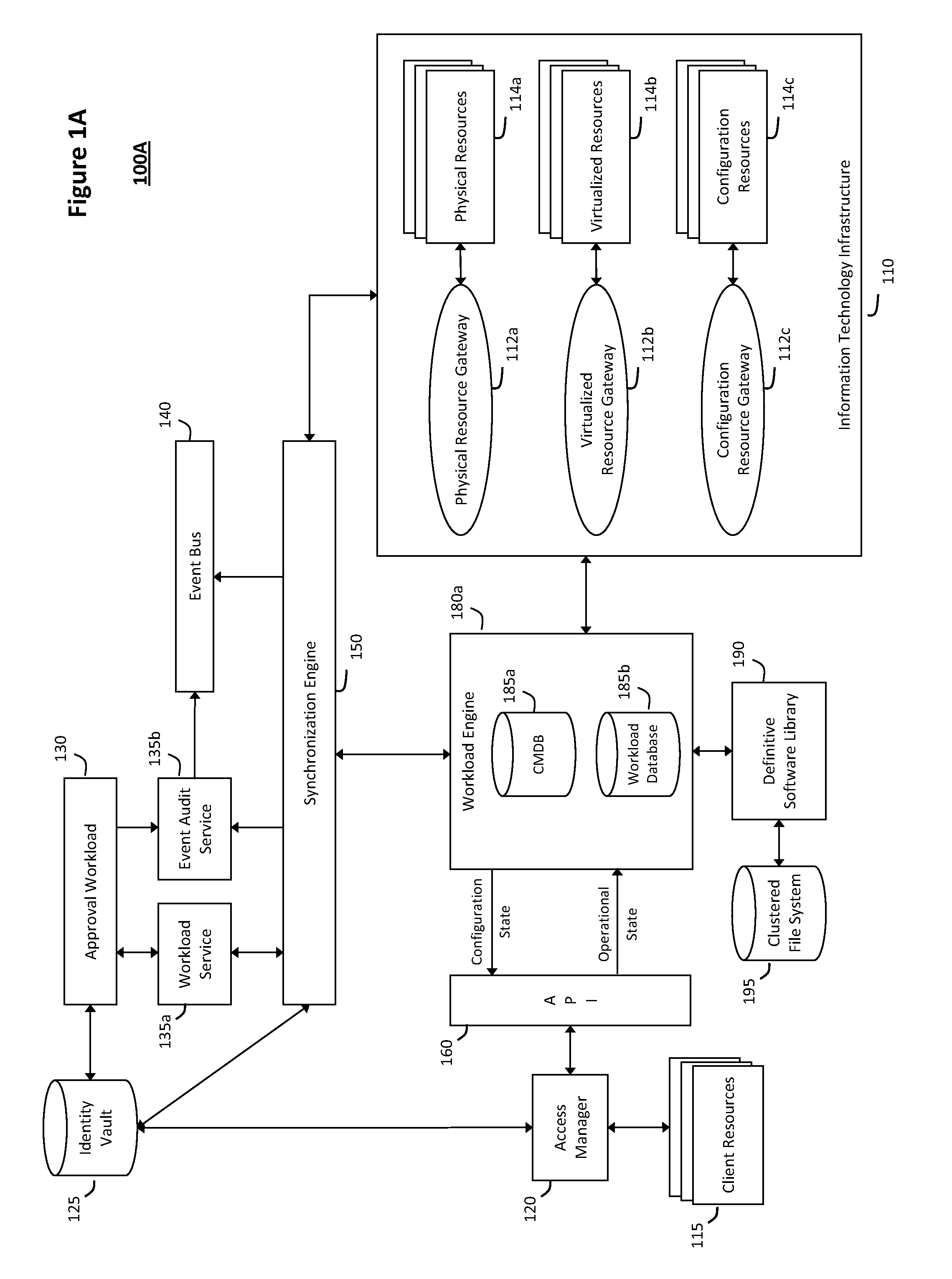
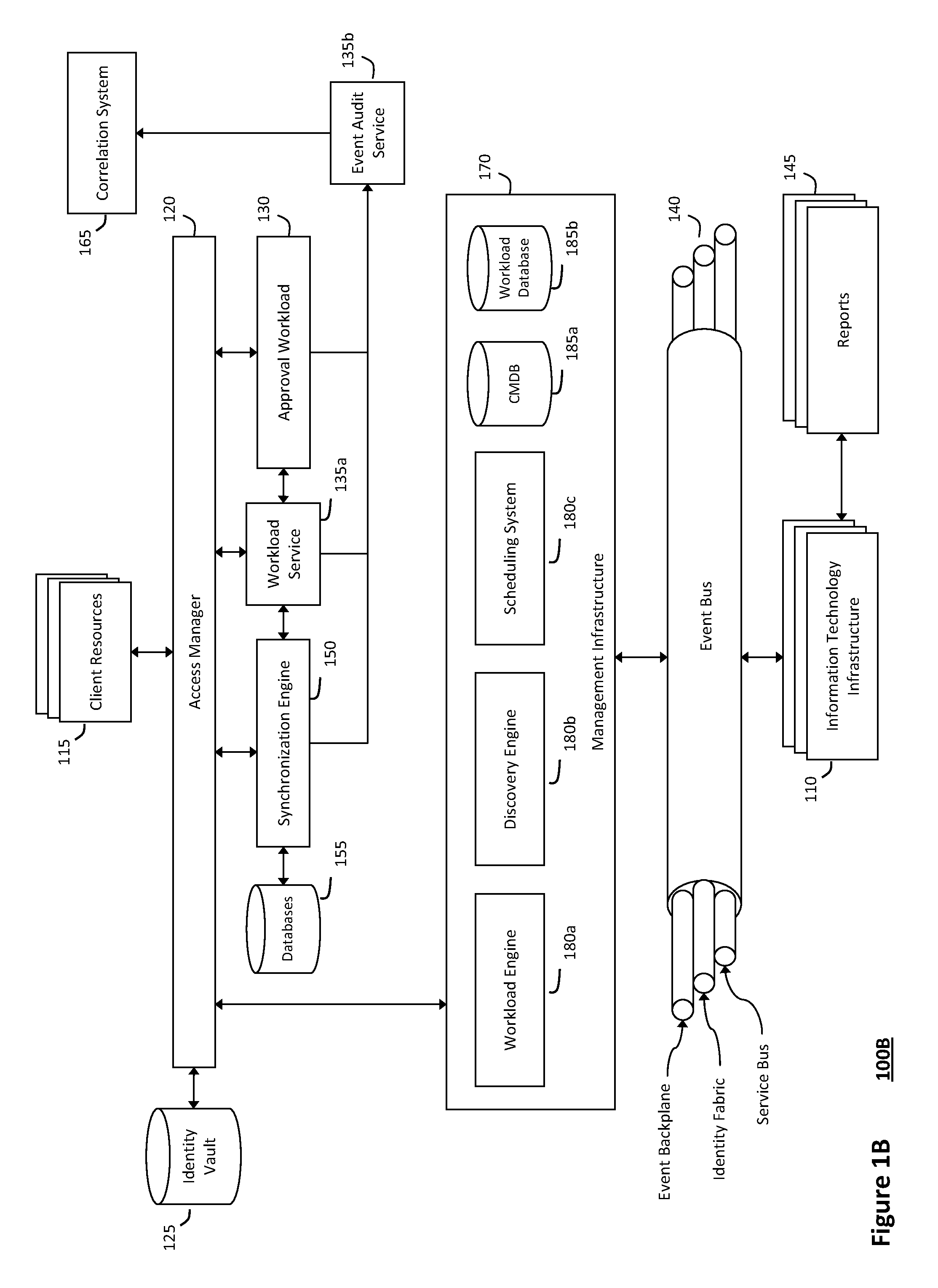
The system and method described herein for discovery enrichment in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing identities and access credentials, which may provide information that can enrich discovery of physical and virtual infrastructure resources. For example, a discovery engine may reference federated identity information stored in an identity vault and enrich a discovered infrastructure model with the federated identity information. Thus, the model may generally include information describing physical and virtualized resources in the infrastructure, applications and services running in the infrastructure, and information derived from the federated identity information that describes dependencies between the physical resources, the virtualized resources, the applications, and the services.
Owner:MICRO FOCUS SOFTWARE INC
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Apparatus, method and system for rapid delivery of distributed applications
ActiveUS20070078988A1Virtualized networkFirmly connectedEnergy efficient ICTMultiple digital computer combinationsVirtualizationVirtual device
An apparatus, method and system are disclosed for visually constructing and rapidly delivering distributed applications. The system includes a virtual appliance apparatus and a composite appliance apparatus, as well as a system for virtualizing hardware resources and for provisioning, executing and scaling distributed applications.
Owner:CA TECH INC
Policy-Based Application Management
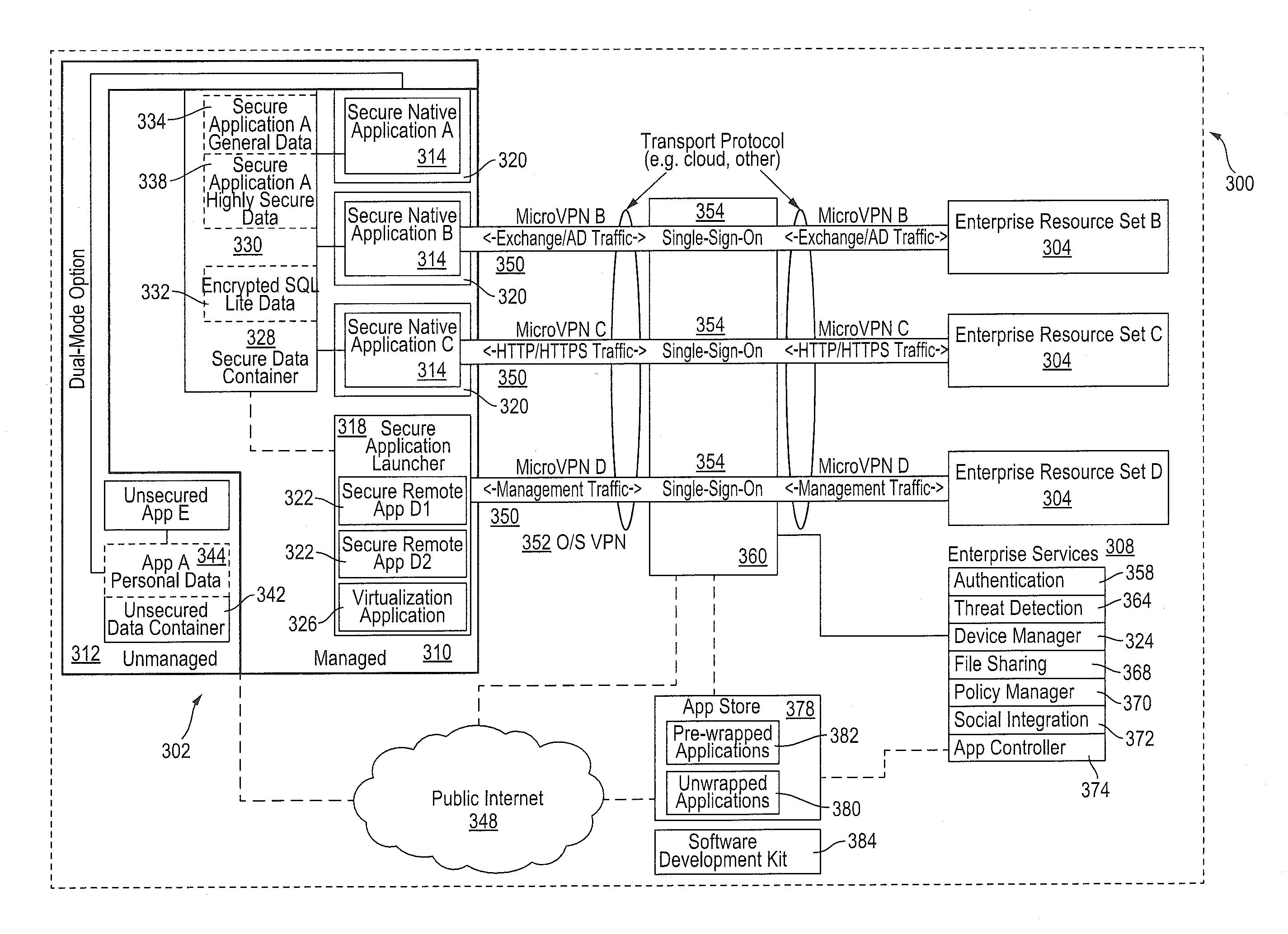
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
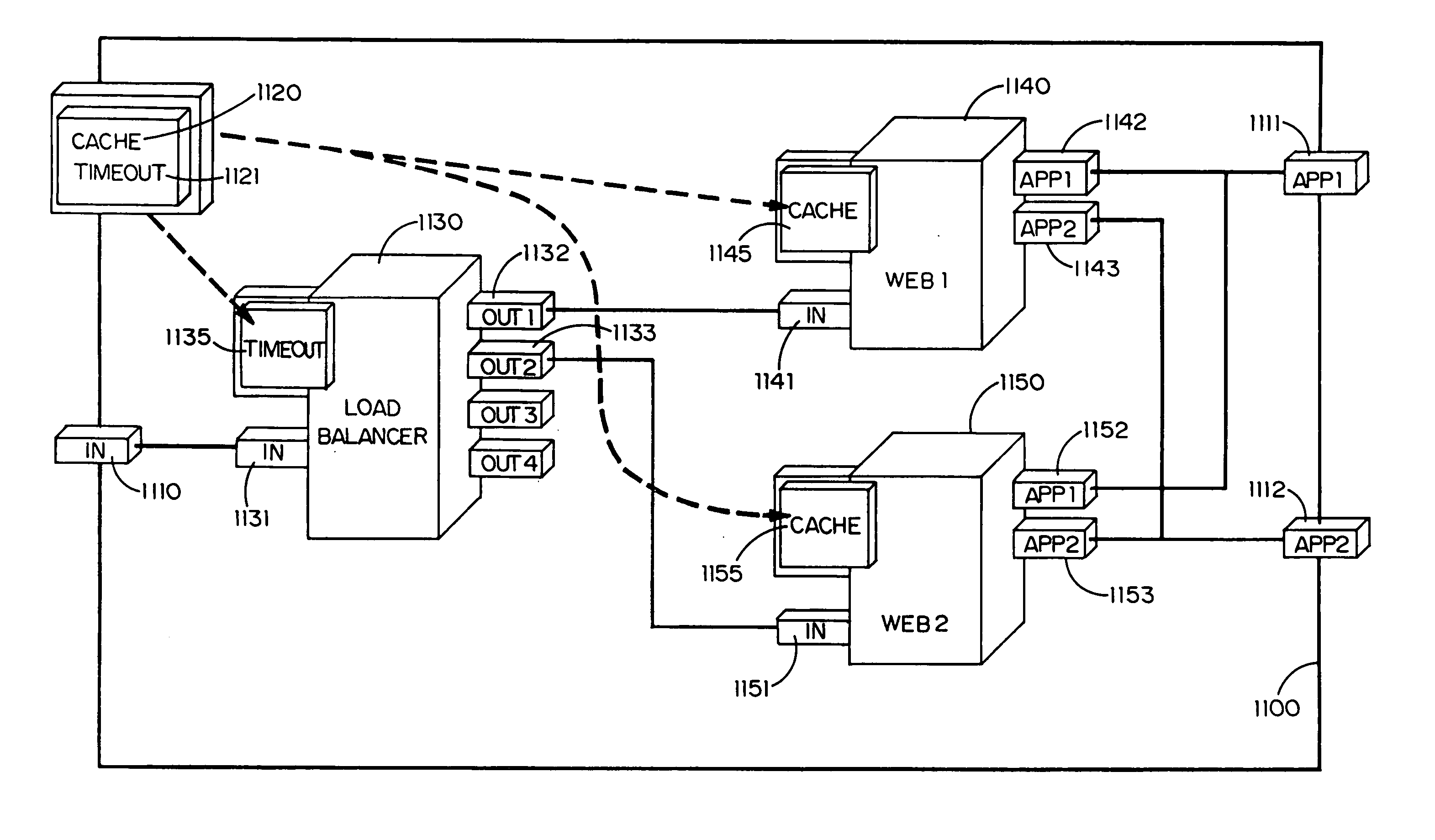
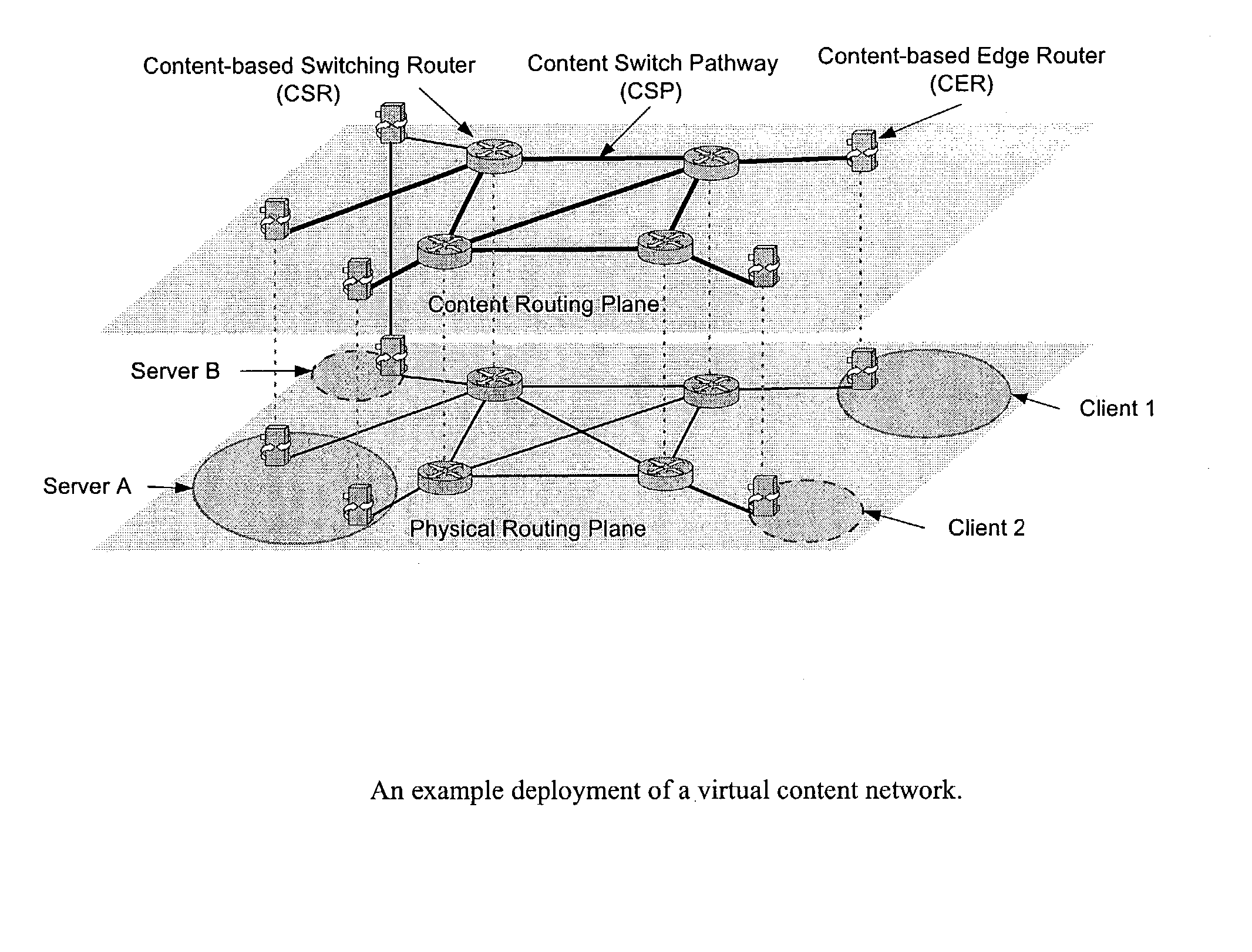
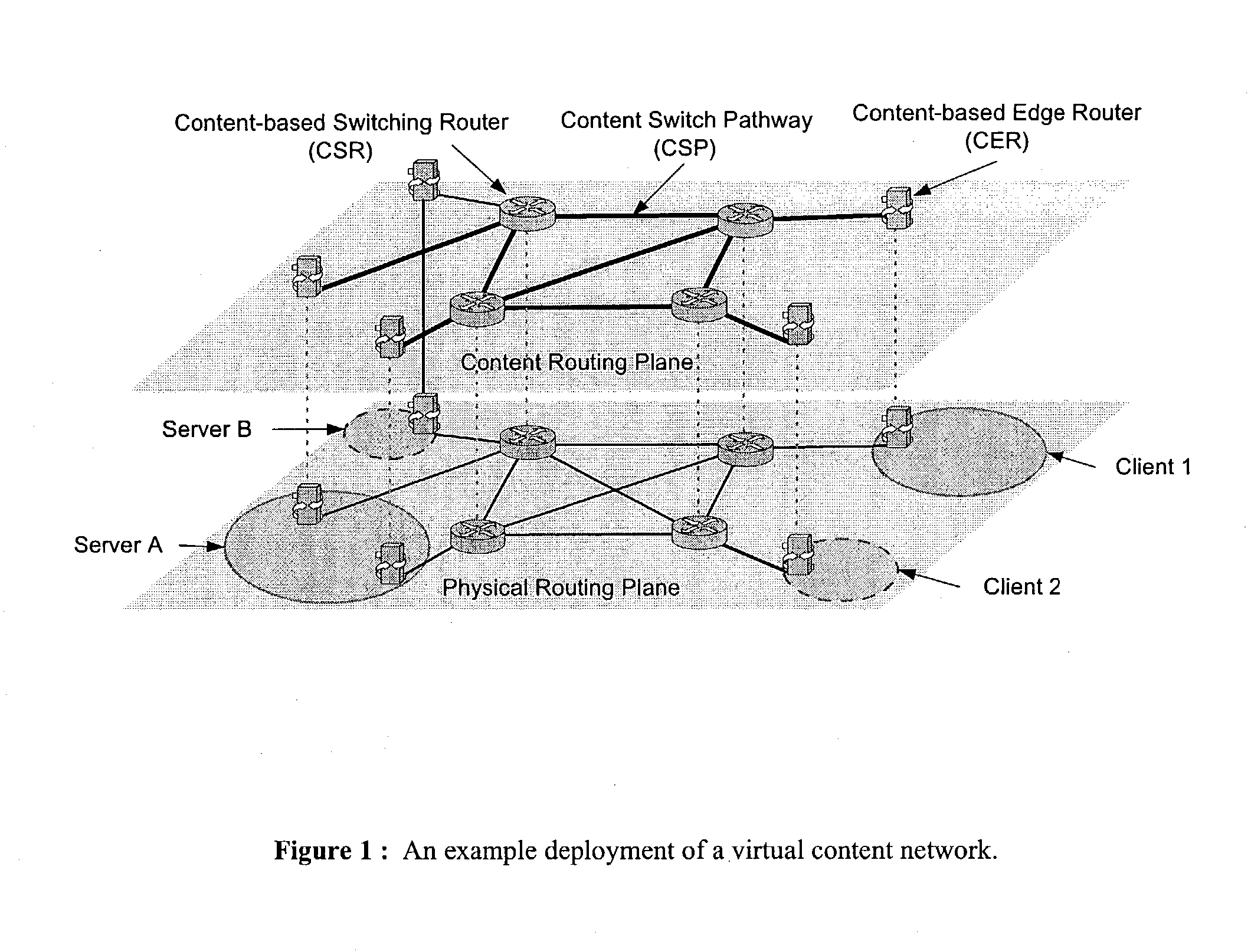
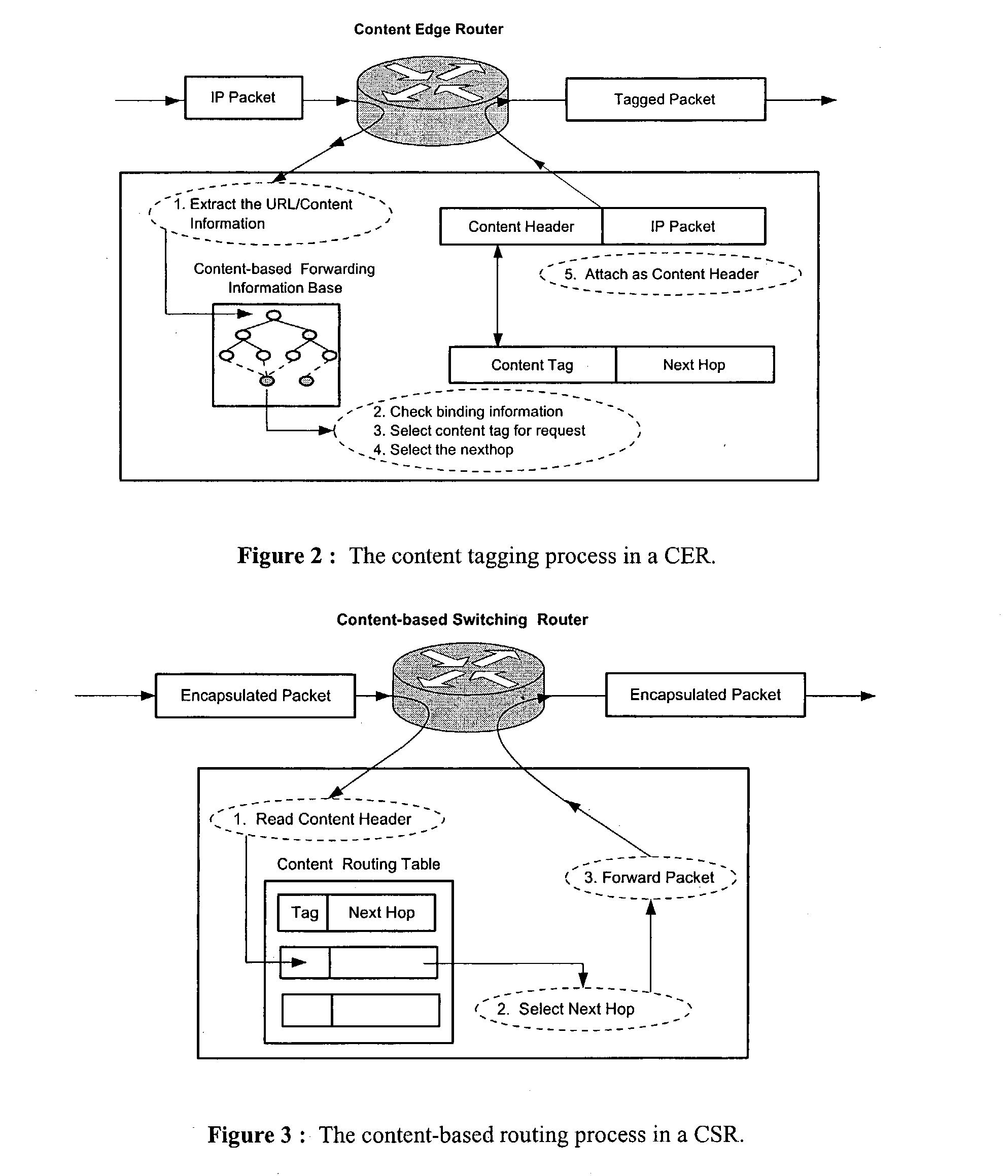
Wide-area content-based routing architecture
InactiveUS20030099237A1Easy to manageMaximum connectivityData switching by path configurationWide areaVirtualization
Content networking is an emerging technology, where the requests for content accesses are steered by "content routers" that examine not only the destinations but also content descriptors such as URLs and cookies. In the current deployments of content networking, "content routing" is mostly confined to selecting the most appropriate back-end server in virtualized web server clusters. This invention presents a novel content-based routing architecture that is suitable for global content networking. In this content-based routing architecture, a virtual overlay network called the "virtual content network" is superimposed over the physical network. The content network contains content routers as the nodes and "pathways" as links. The content-based routers at the edge of the content network may be either a gateway to the client domain or a gateway to the server domain whereas the interior ones correspond to the content switches dedicated for steering content requests and replies. The pathways are virtual paths along the physical network that connect the corresponding content routers. The invention is based on tagging content requests at the ingress points. The tags are designed to incorporate several different attributes of the content in the routing process. The path chosen for routing the request is the optimal path and is chosen from multiple paths leading to the replicas of the content.
Owner:TELECOMM RES LAB
Policy-Based Application Management
ActiveUS20140032691A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
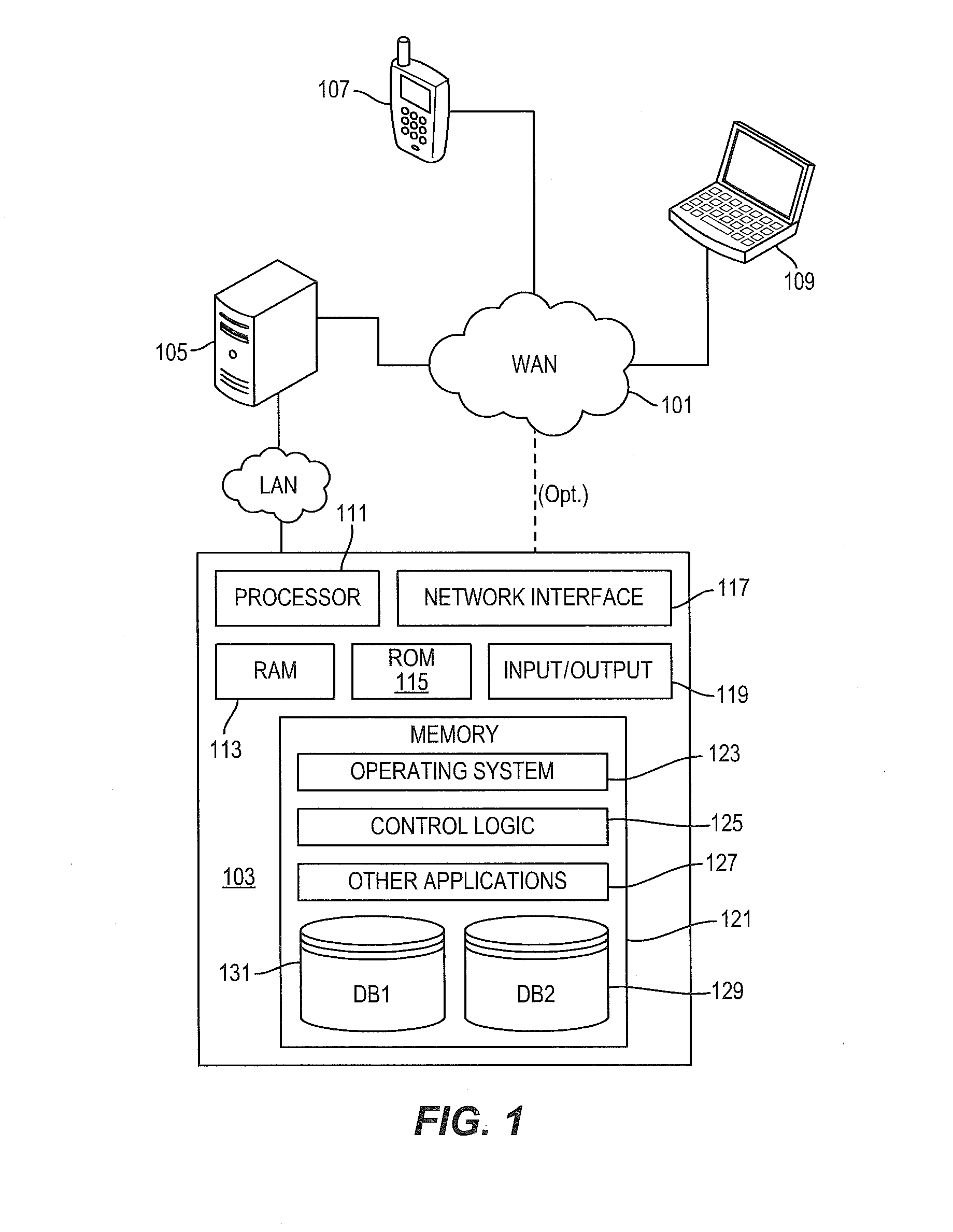
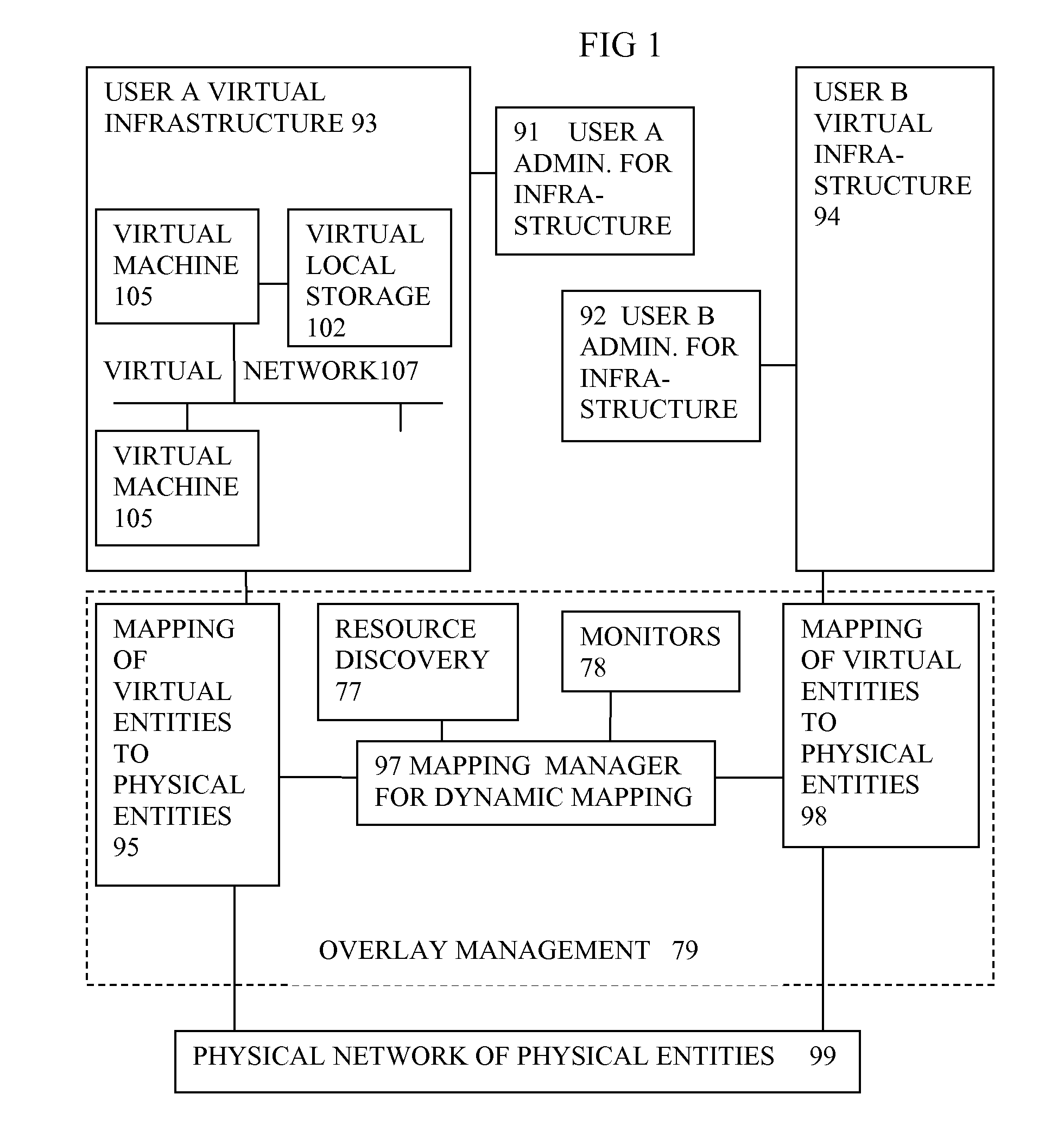
Virtual computing infrastructure
InactiveUS20090199177A1Overcome disadvantagesCritical applicationResource allocationTransmissionVirtualizationNetwork communication
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. The system has a mapping manager to dynamically alter the mapping for balancing, performance, and redundancy. There can be more independence from the underlying physical configuration, compared to known methods of virtualizing only some of the entities. The mapping manager can be distributed across a number of entities on different physical servers arranged to cooperate with each other.
Owner:HEWLETT PACKARD DEV CO LP
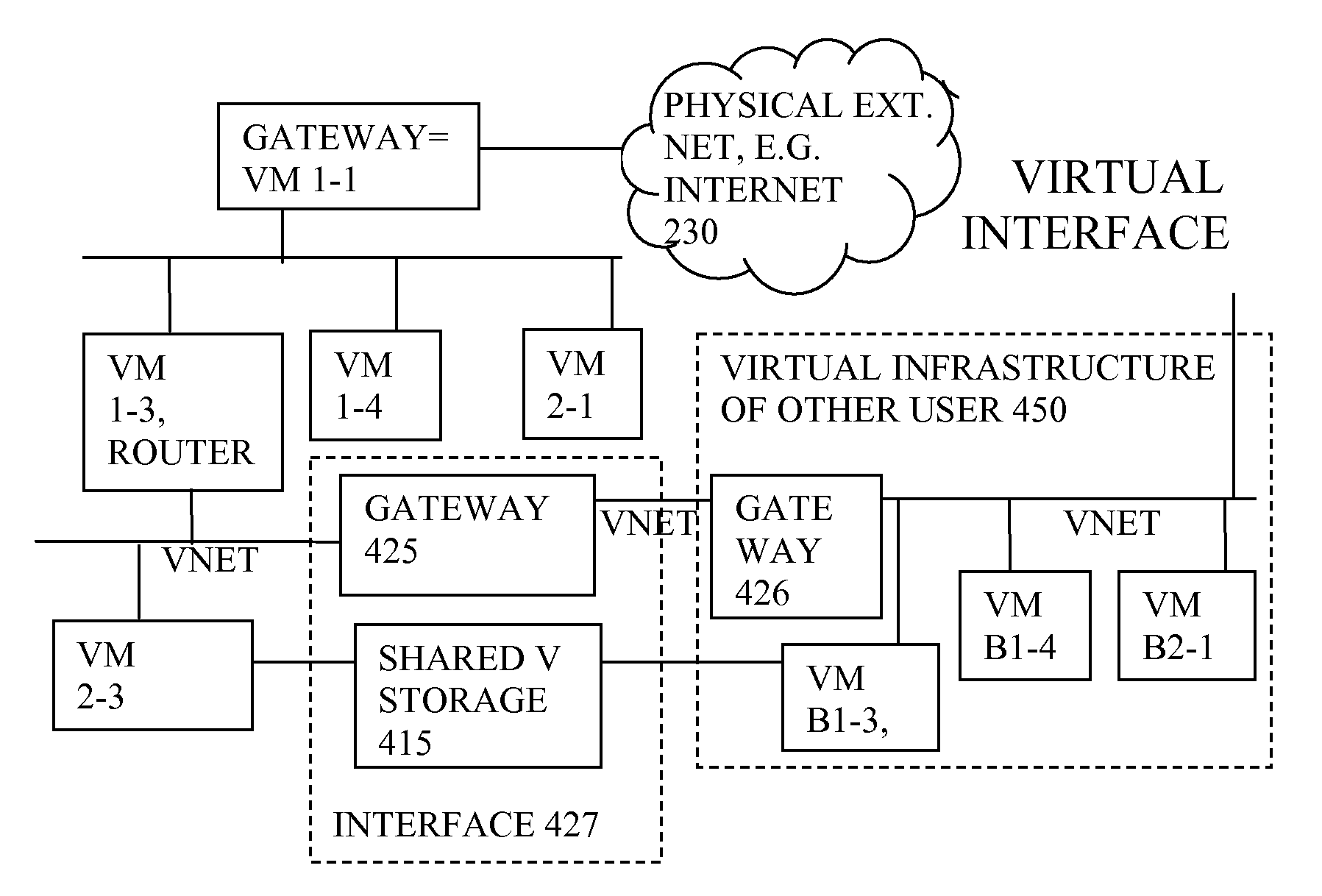
Distributed virtual storage cloud architecture and a method thereof
ActiveUS20130204849A1Prevent lockInput/output to record carriersDigital data information retrievalThird partyVirtualization
The present disclosure relates to a distributed information storage system which functions as virtual cloud storage overlay on top of physical cloud storage systems. The disclosure discloses transparently solving all the data management related security, virtualization, reliability and enables transparent cloud storage migration, cloud storage virtualization, information dispersal and integration across disparate cloud storage devices operated by different providers or on-premise storage. The cloud storage is owned or hosted by same or different third-party providers who own the information contained in the storage which eliminates cloud dependencies. This present disclosure functions as a distributed cloud storage delivery platform enabling various functionalities like cloud storage virtualization, cloud storage integration, cloud storage management and cloud level RAID.
Owner:CHACKO PETER
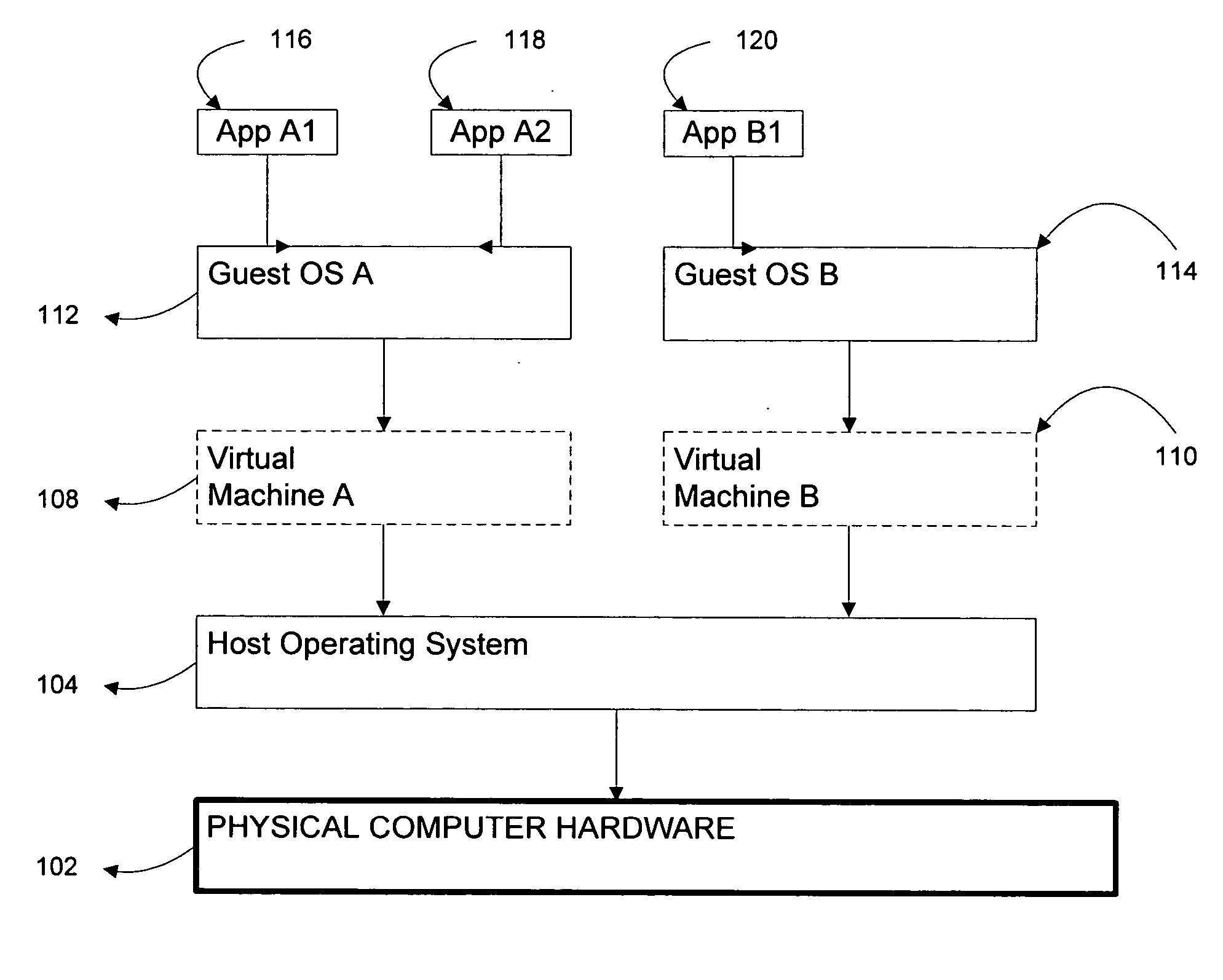
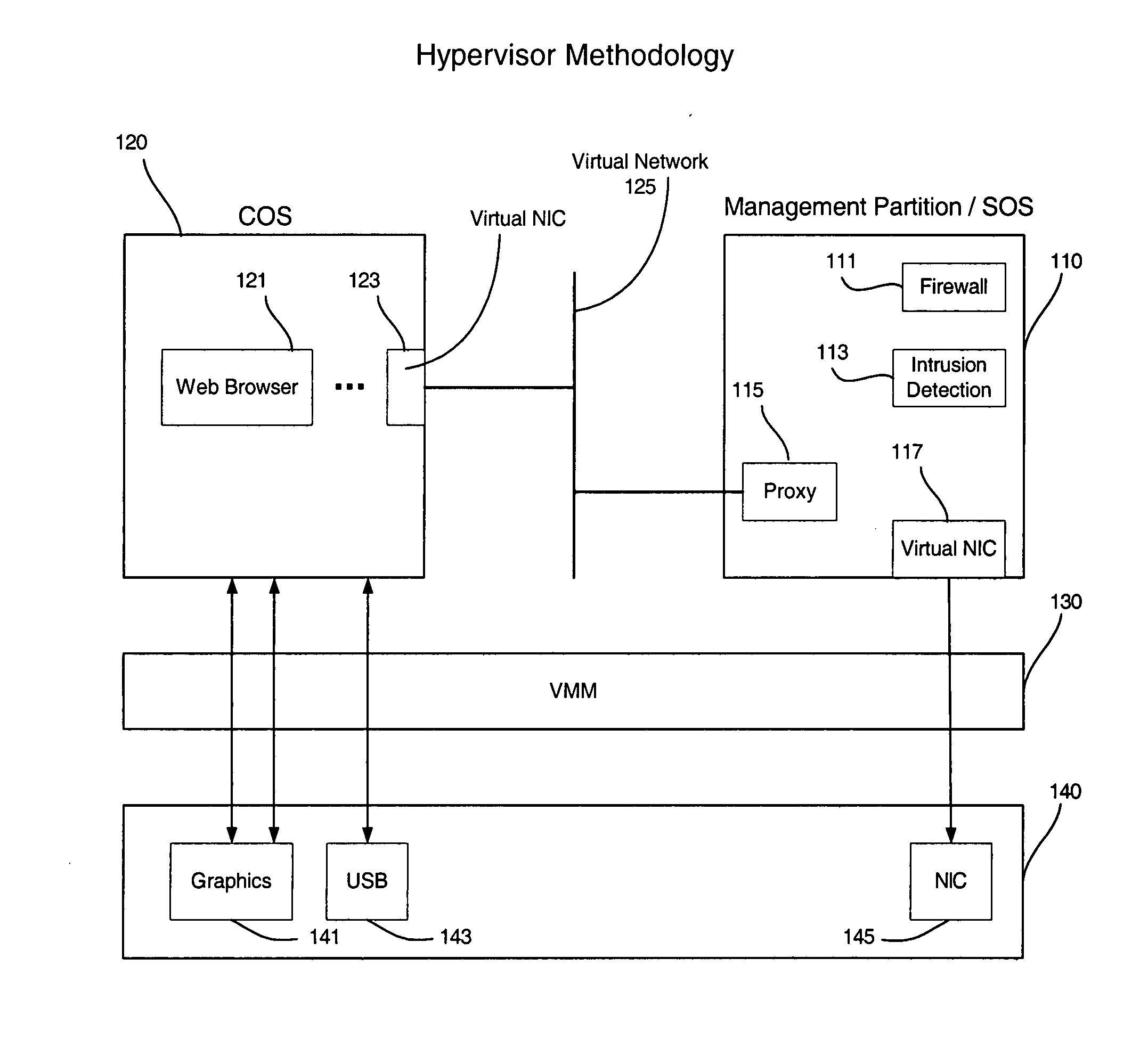
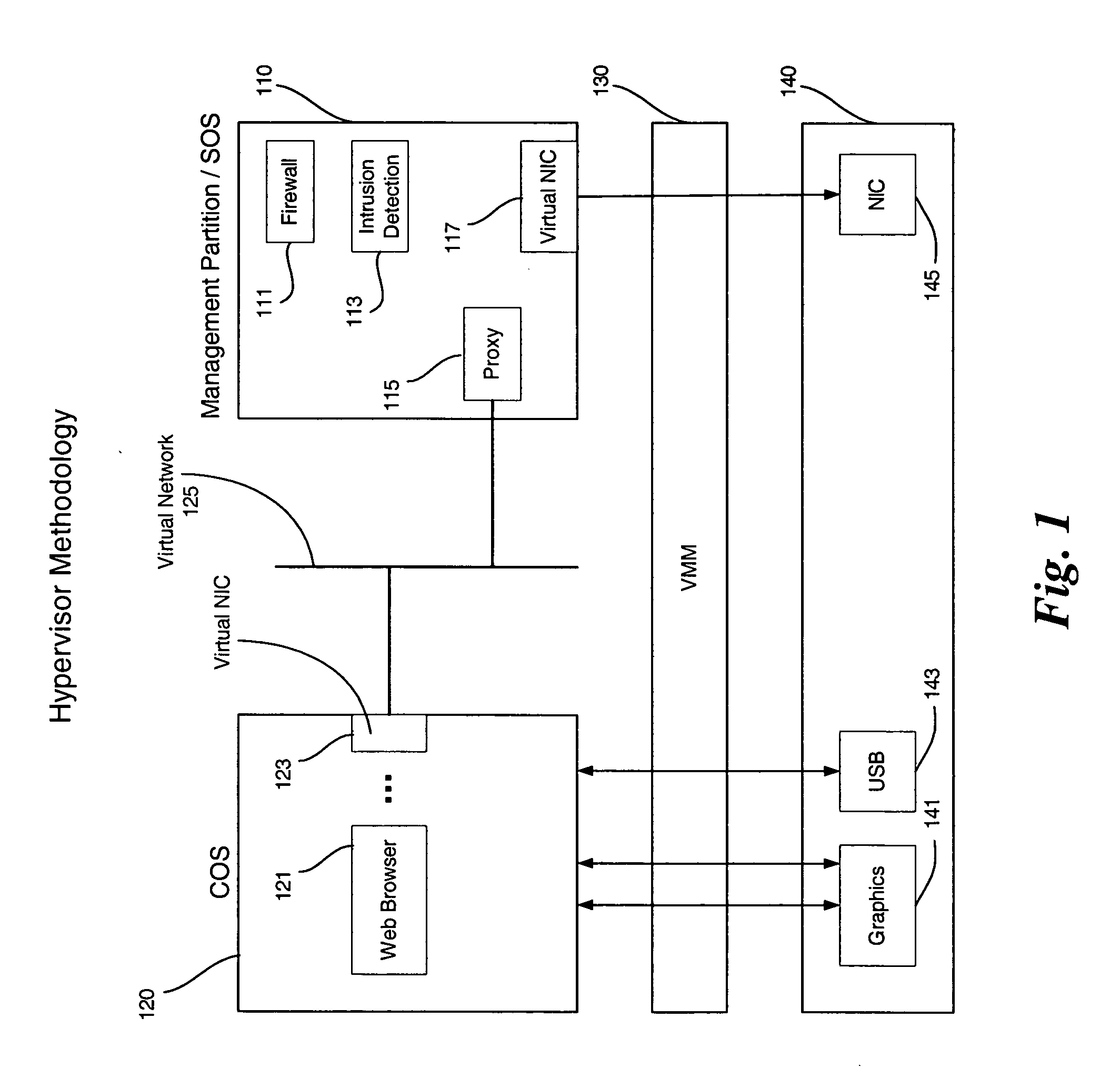
Systems and methods for virtualizing graphics subsystems
ActiveUS20060146057A1Program control using stored programsProcessor architectures/configurationVirtualizationOperational system
Systems and methods for applying virtual machines to graphics hardware are provided. In various embodiments of the invention, while supervisory code runs on the CPU, the actual graphics work items are run directly on the graphics hardware and the supervisory code is structured as a graphics virtual machine monitor. Application compatibility is retained using virtual machine monitor (VMM) technology to run a first operating system (OS), such as an original OS version, simultaneously with a second OS, such as a new version OS, in separate virtual machines (VMs). VMM technology applied to host processors is extended to graphics processing units (GPUs) to allow hardware access to graphics accelerators, ensuring that legacy applications operate at full performance. The invention also provides methods to make the user experience cosmetically seamless while running multiple applications in different VMs. In other aspects of the invention, by employing VMM technology, the virtualized graphics architecture of the invention is extended to provide trusted services and content protection.
Owner:MICROSOFT TECH LICENSING LLC
Isolating network traffic in multi-tenant virtualization environments
ActiveUS7885276B1Frequency-division multiplex detailsData switching by path configurationVirtualizationDistributed computing
Managing data in a server system includes providing a plurality of servers, each having an internal gateway / switch that is accessible from outside the server, providing a plurality of virtual servers on at least some of the servers, where each of the virtual servers is accessible by the internal gateway / switch of the corresponding server, and accessing the data using the internal gateway / switch, where the internal gateway / switch determines which particular one of the virtual servers contain the data and then accesses the particular virtual server to provide the data. Managing data in a server system may also include associating portions of the data to tenants of the server system. Each of the servers may maintain a table that correlates tenants with the virtual servers maintained thereby and the internal gateway / switch may use the table to determine which particular one of the virtual servers contains data for a particular tenant.
Owner:EMC IP HLDG CO LLC
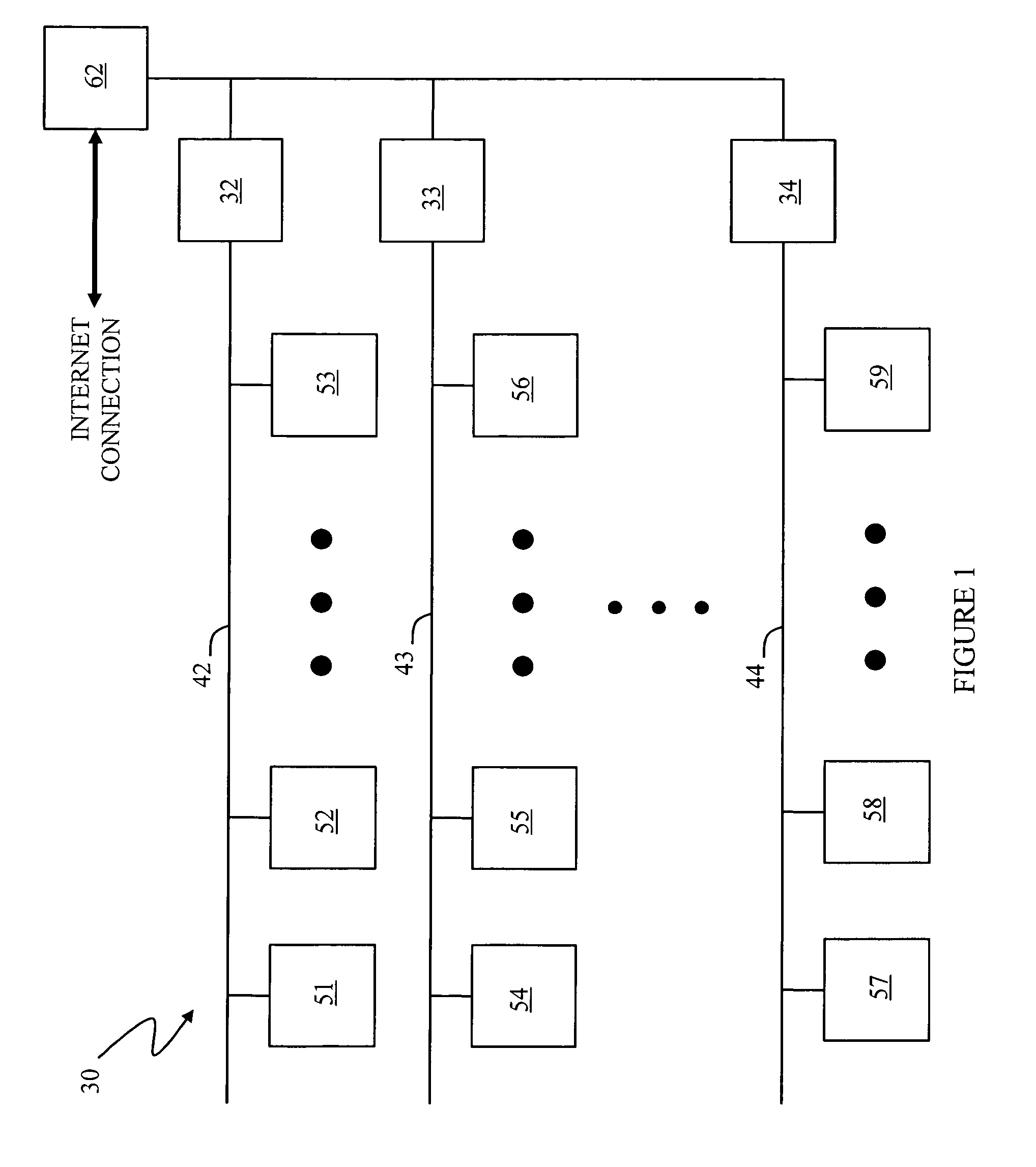
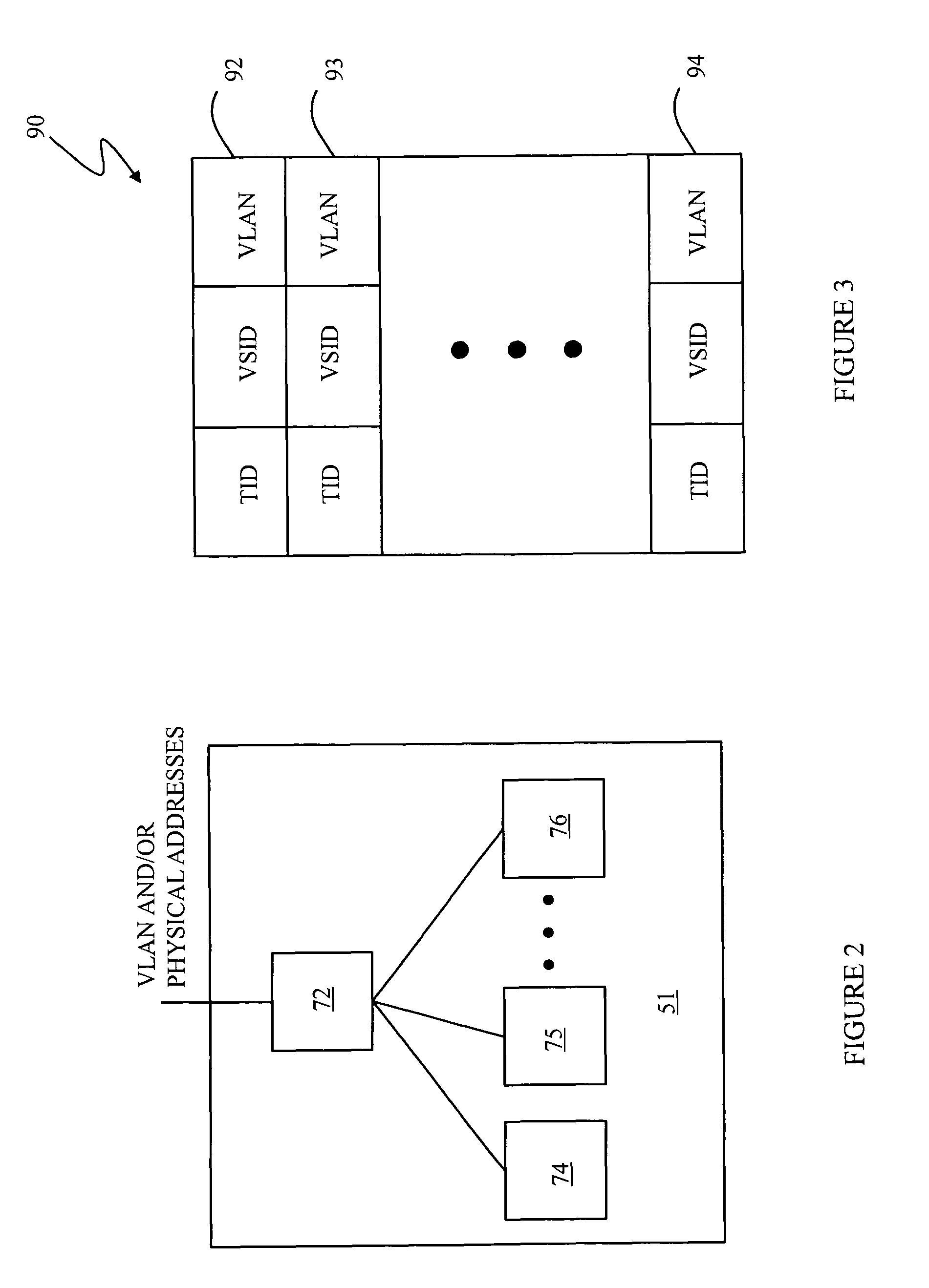
Location virtualization in an RFID system
ActiveUS20060170565A1Improve reliabilityRandom number generatorsFrequency-division multiplex detailsVirtualizationRadio frequency
A system and method of determining locations of one or more RFID tags within an RFID environment. The system includes a plurality of RFID readers, each operative to transmit and receive RF signals for scanning a tag disposed within an RF coverage region associated with the reader, and for receiving tag data in response to the scanning of the tag. A plurality of sub-locations is determined within the environment, each corresponding to at least a portion of at least one of a plurality of RF coverage regions associated with the readers. The sub-locations are mapped to a plurality of predefined locations within the environment. A reader scans a tag, and receives tag scan data from the tag in response to the scanning of the tag. The tag scan data includes a tag identifier associated with the scanned tag. The tag scan data is mapped to the sub-locations based on the RF coverage region associated with the reader. The location of the scanned tag is then determined with reference to the predefined locations within the environment, based on the tag identifier included in the tag scan data, the mapping of the tag scan data to the sub-locations, and the mapping of the sub-locations to the predefined locations.
Owner:ODIN SOFTWARE INC +1
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
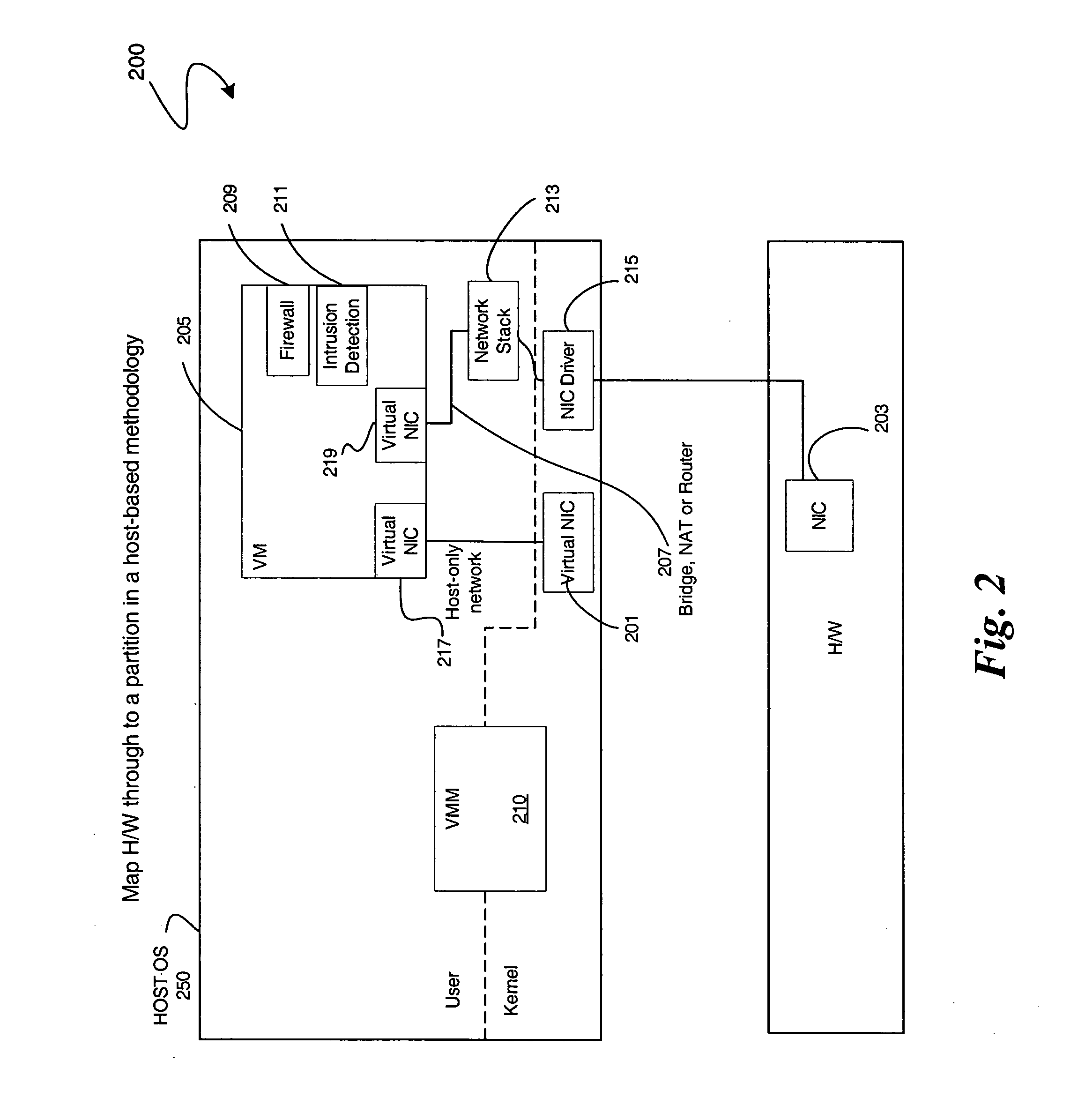
Enabling platform network stack control in a virtualization platform
InactiveUS20060070066A1TransmissionSoftware simulation/interpretation/emulationVirtualizationData pack
In some embodiments, the invention involves protecting network communications in a virtualized platform. An embodiment of the present invention is a system and method relating to protecting network communication flow using packet encoding / certification and the network stack. One embodiment uses a specialized engine or driver in the network stack to encode packets before being sent to physical network controller. The network controller may use a specialized driver to decode the packets, or have a hardware implementation of a decoder. If the decoded packet is certified, the packet is transmitted. Otherwise, the packet is dropped. An embodiment of the present invention utilizes virtualization architecture to implement the network communication paths. Other embodiments are described and claimed.
Owner:INTEL CORP
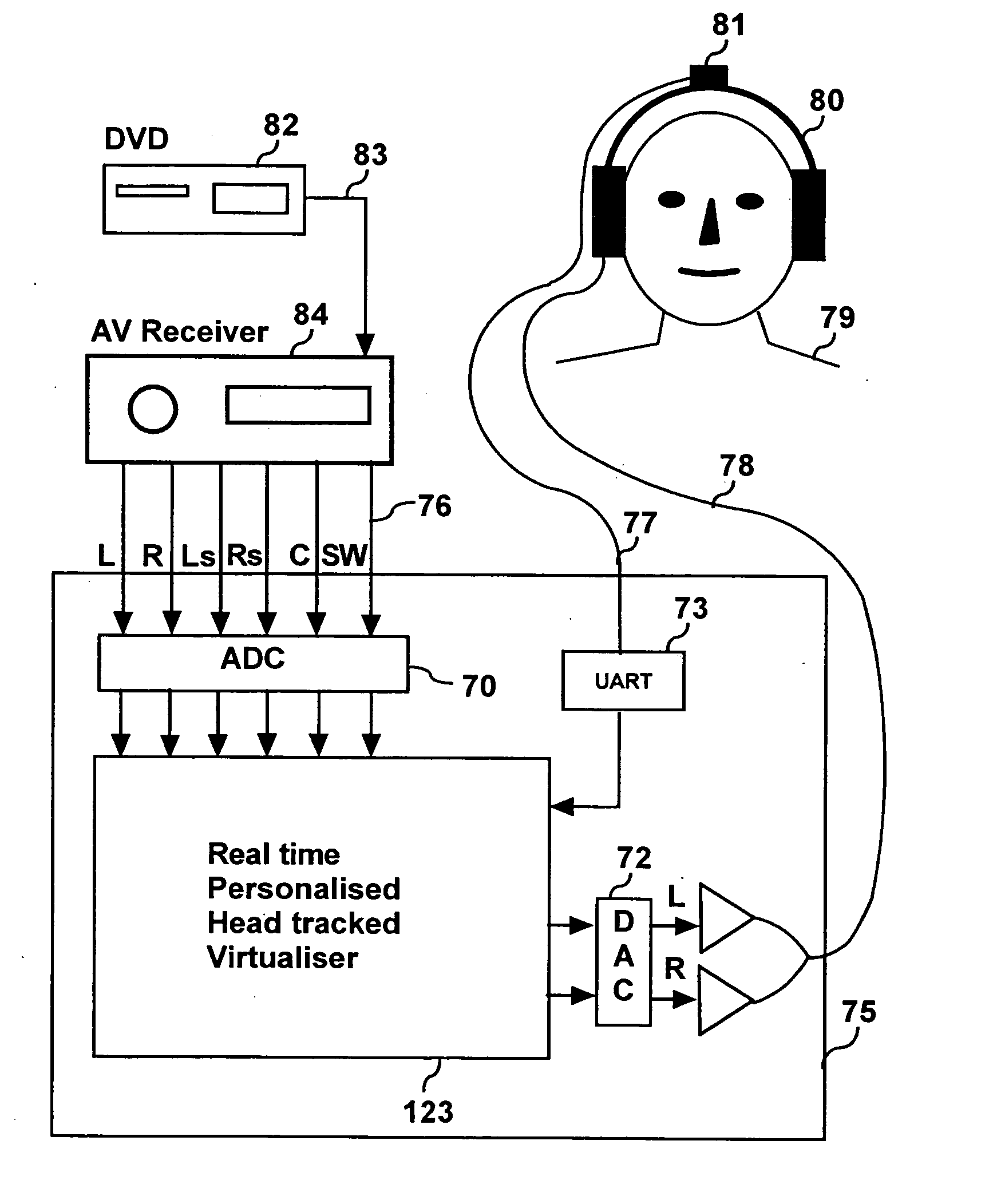
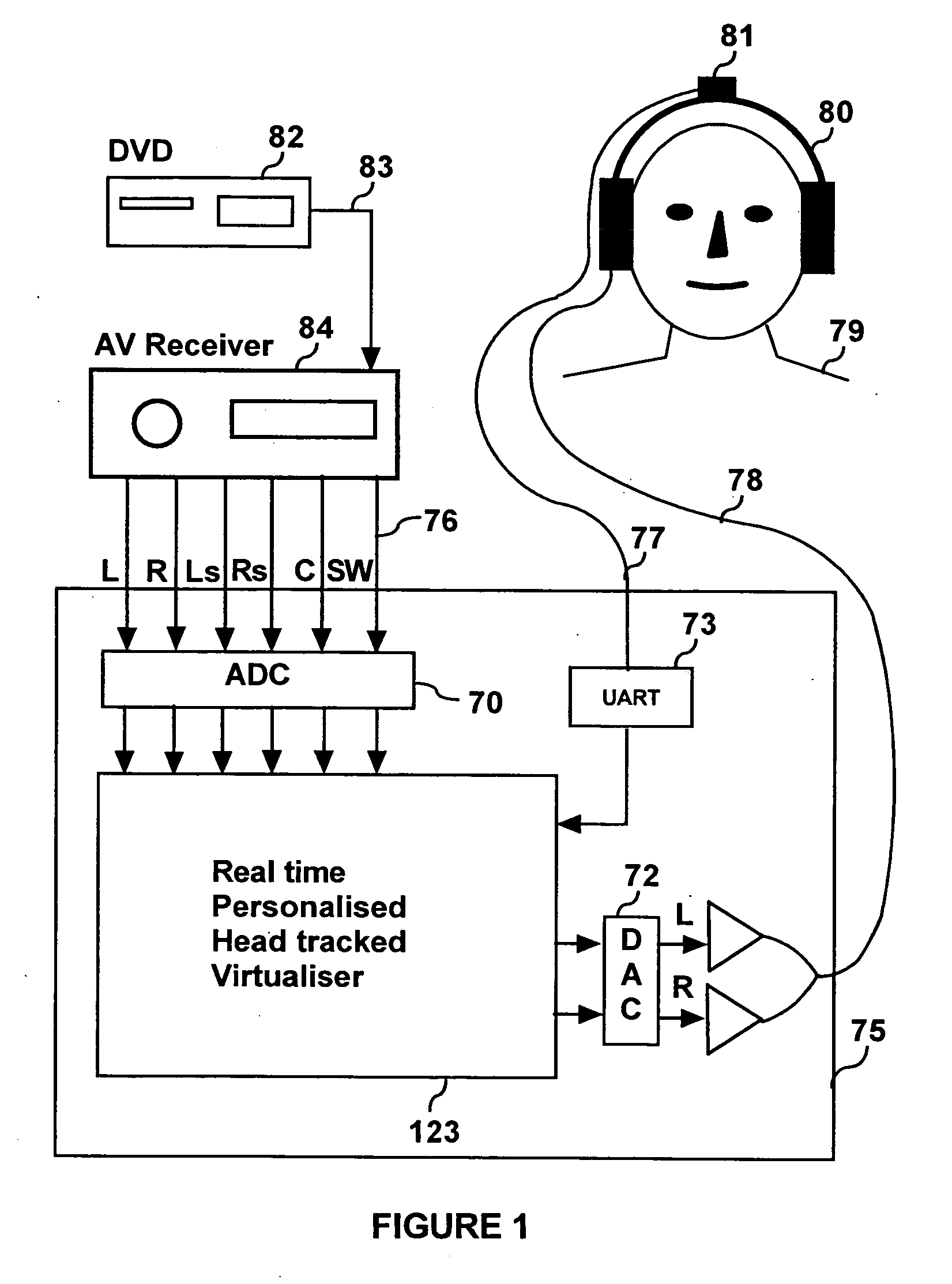
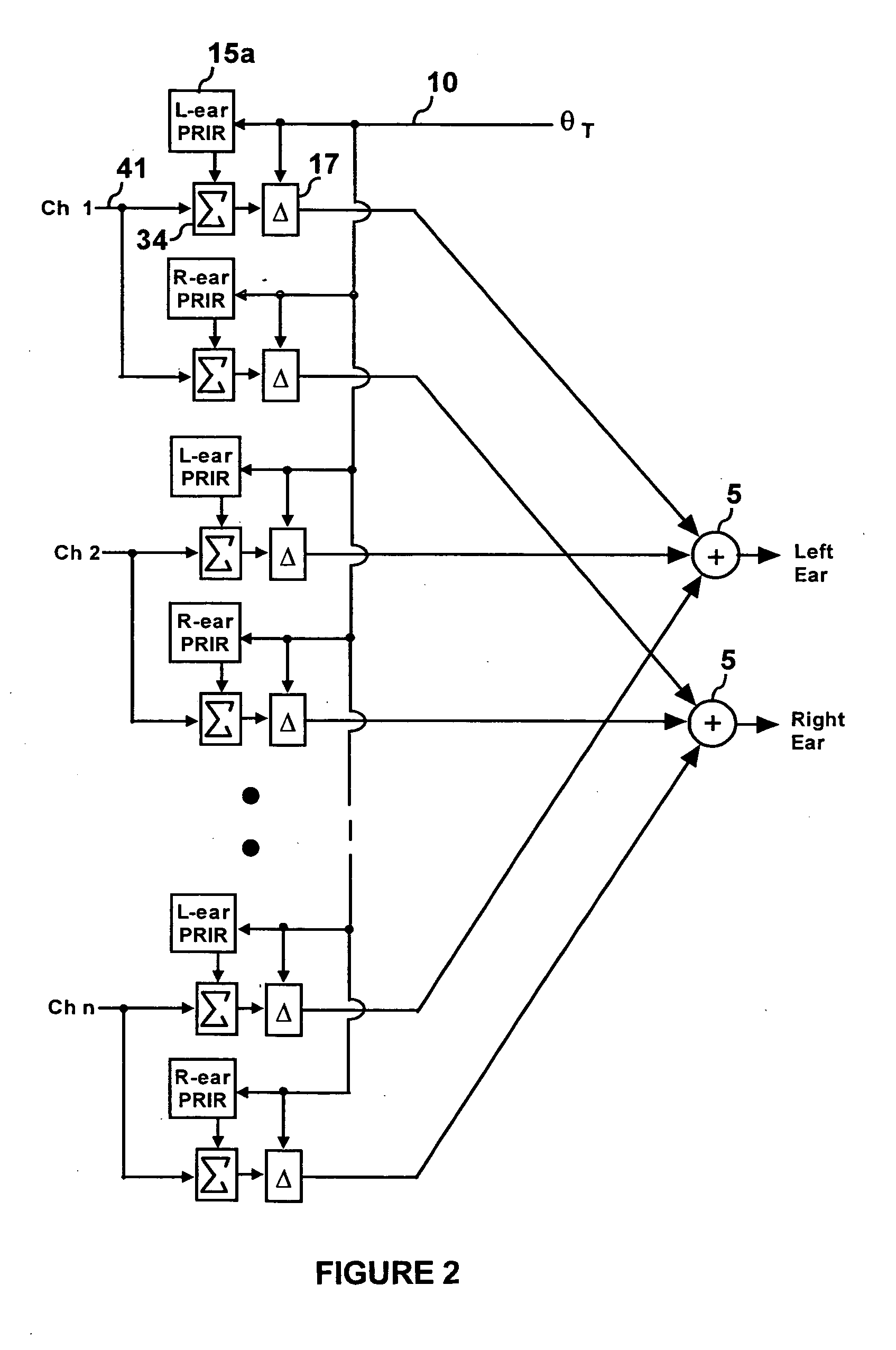
Personalized headphone virtualization
ActiveUS20060045294A1Improve accuracySound qualityHeadphones for stereophonic communicationEarpiece/earphone attachmentsVirtualizationPersonalization
A listener can experience the sound of virtual loudspeakers over headphones with a level of realism that is difficult to distinguish from the real loudspeaker experience. Sets of personalized room impulse responses (PRIRs) are acquired for the loudspeaker sound sources over a limited number of listener head positions. The PRIRs are then used to transform an audio signal for the loudspeakers into a virtualized output for the headphones. Basing the transformation on the listener's head position, the system can adjust the transformation so that the virtual loudspeakers appear not to move as the listener moves the head.
Owner:SMYTH RES
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
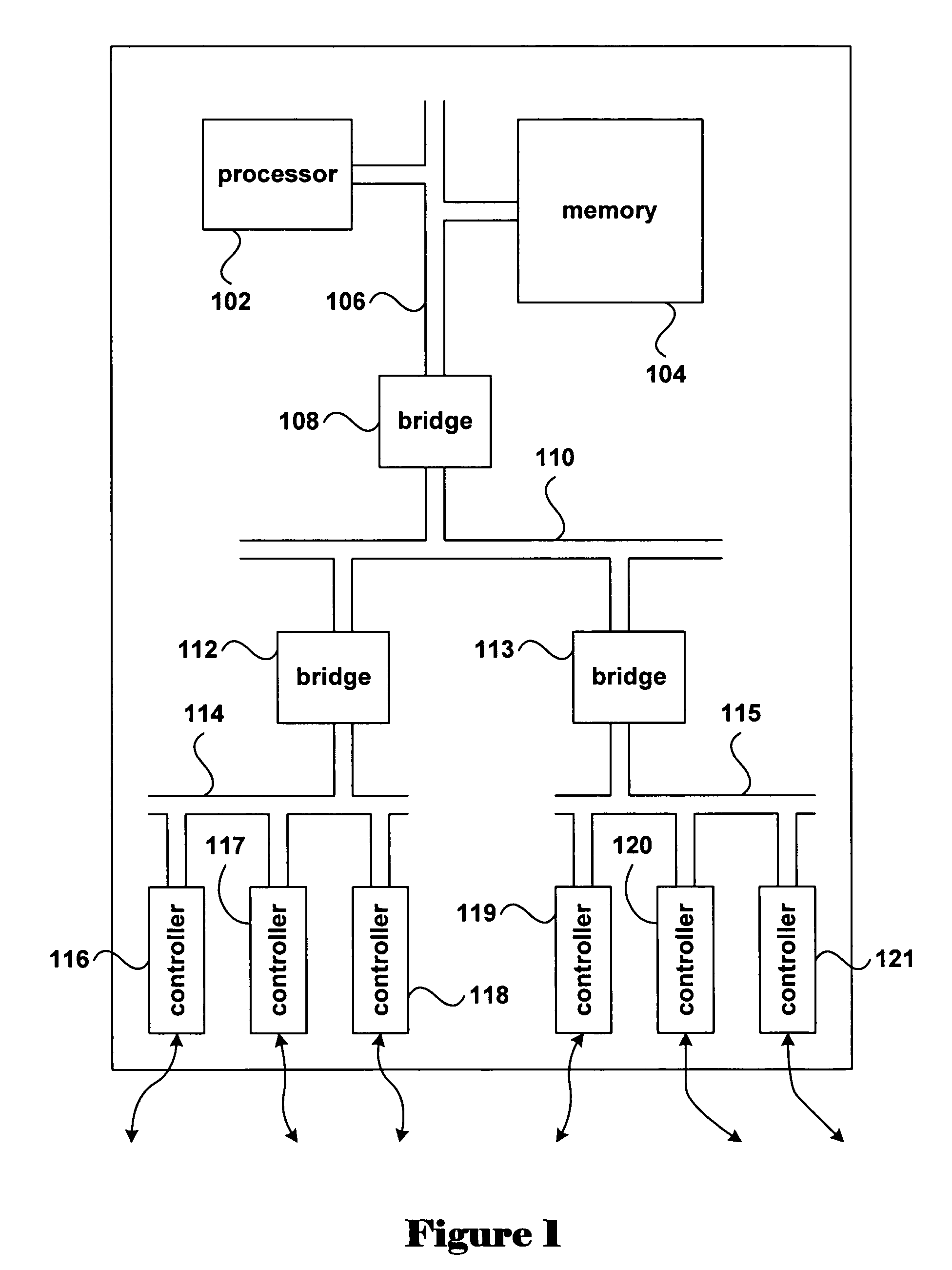
Processor-architecture for facilitating a virtual machine monitor
InactiveUS20050091652A1Easy to operateGeneral purpose stored program computerMultiprogramming arrangementsVirtualizationVirtual address space
Virtual-machine-monitor operation and implementation is facilitated by number of easily implemented features and extensions added to the features of a processor architecture. These features, one or more of which are used in various embodiments of the present invention, include a vmsw instruction that provides a means for transitioning between virtualization mode and non-virtualization mode without an interruption, a virtualization fault that faults on an attempt by a priority-0 routine in virtualization mode attempting to execute a privileged instruction, and a flexible highest-implemented-address mechanism to partition virtual address space into a virtualization address space and a non-virtualization address space.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
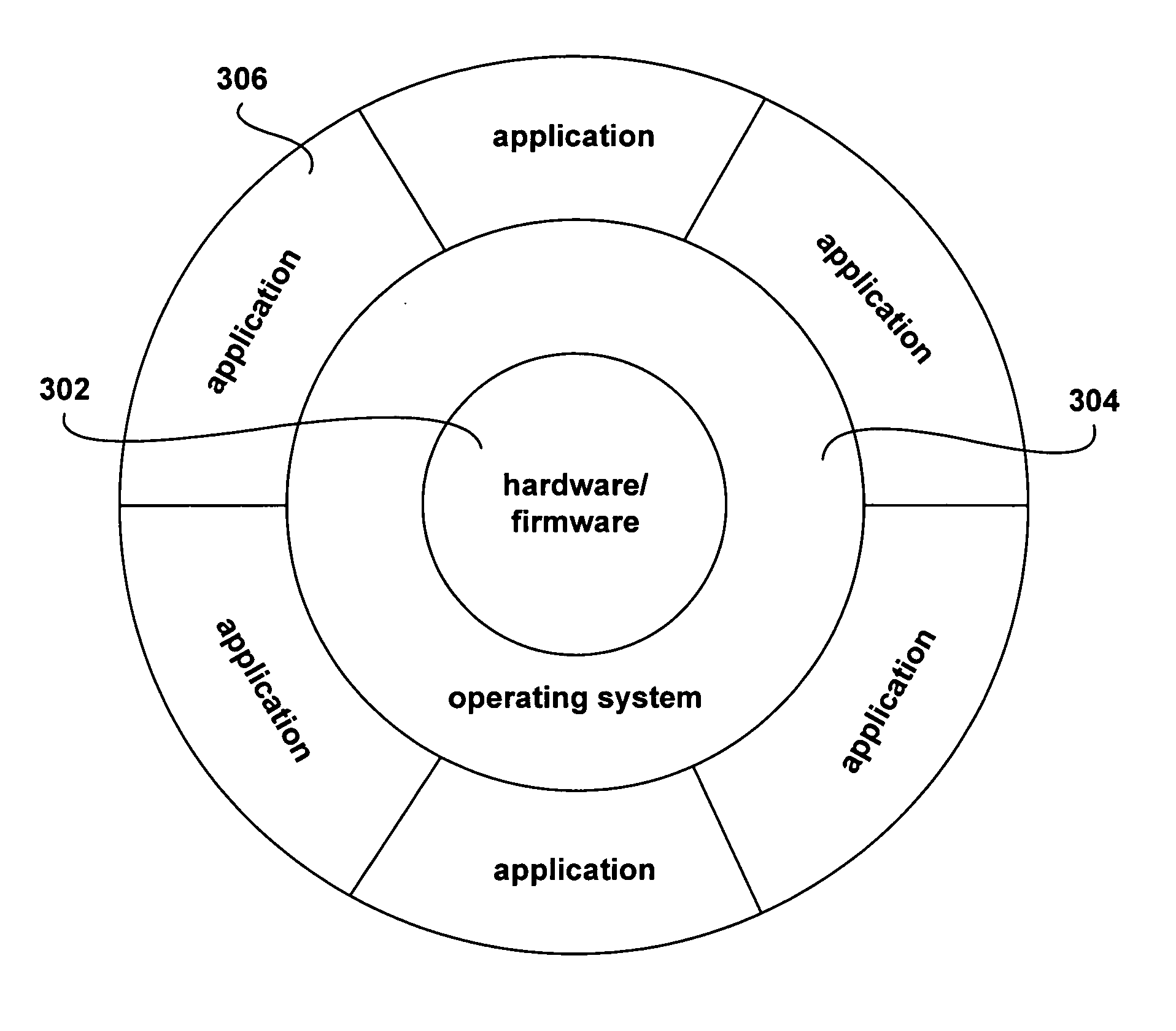
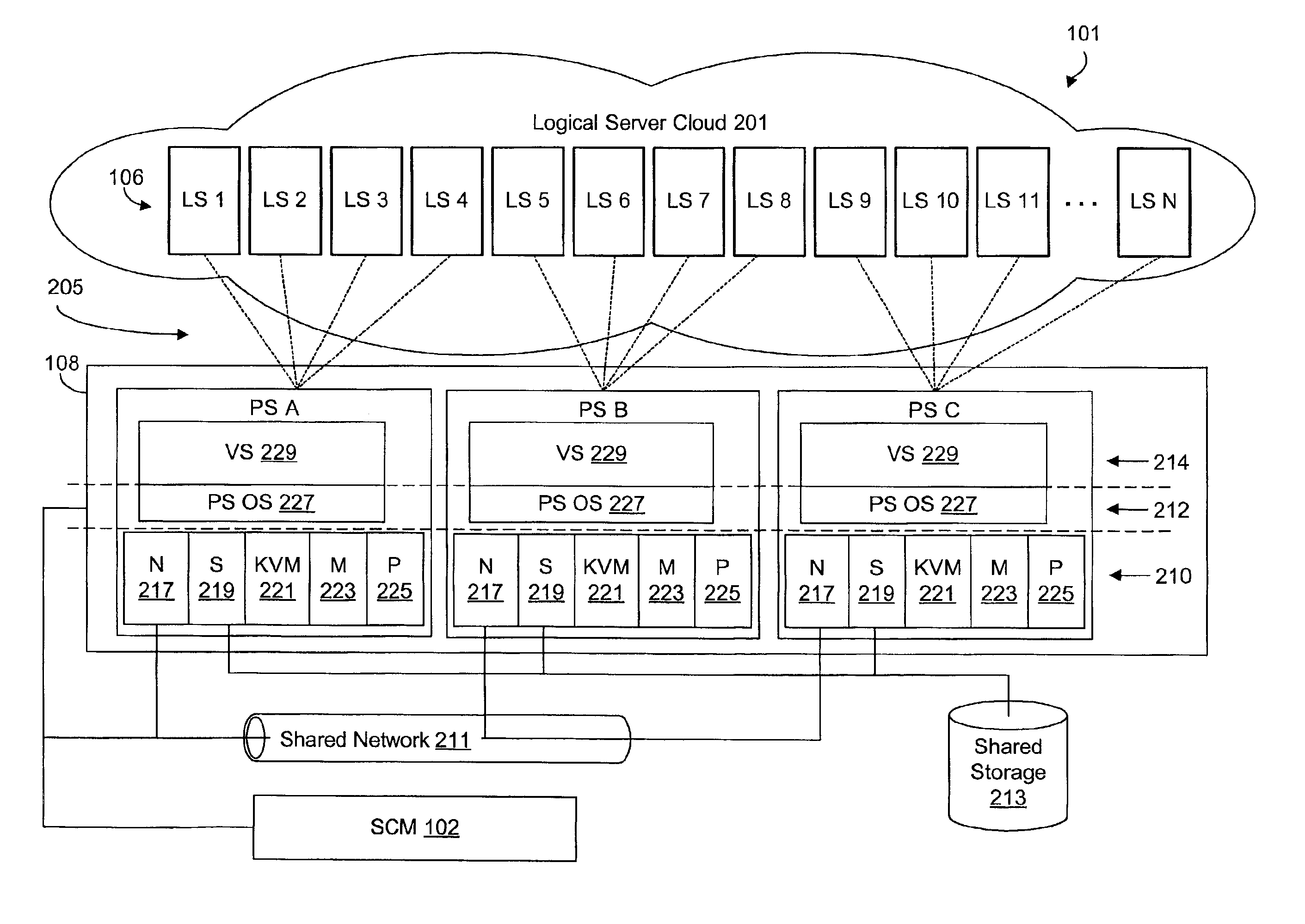
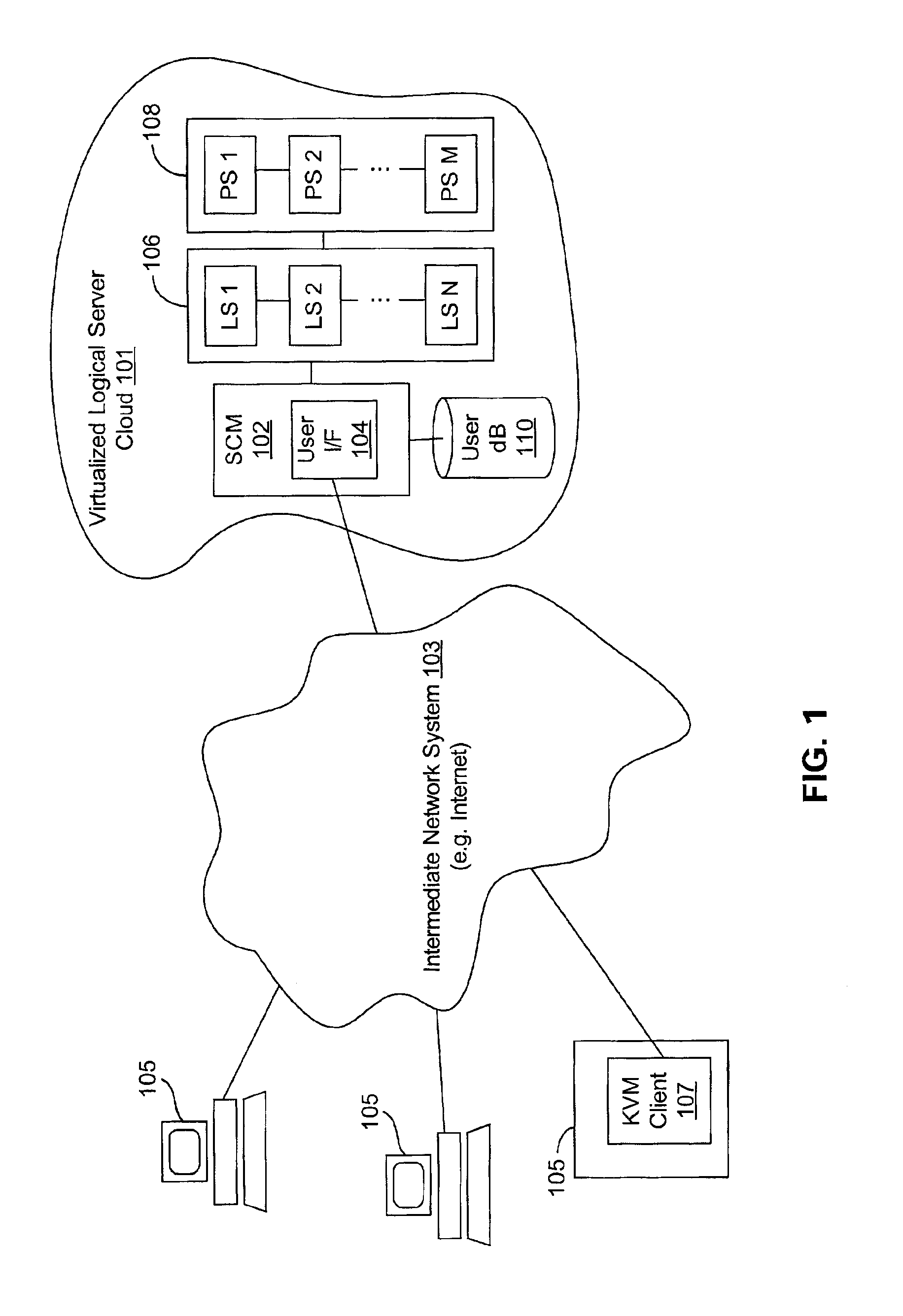
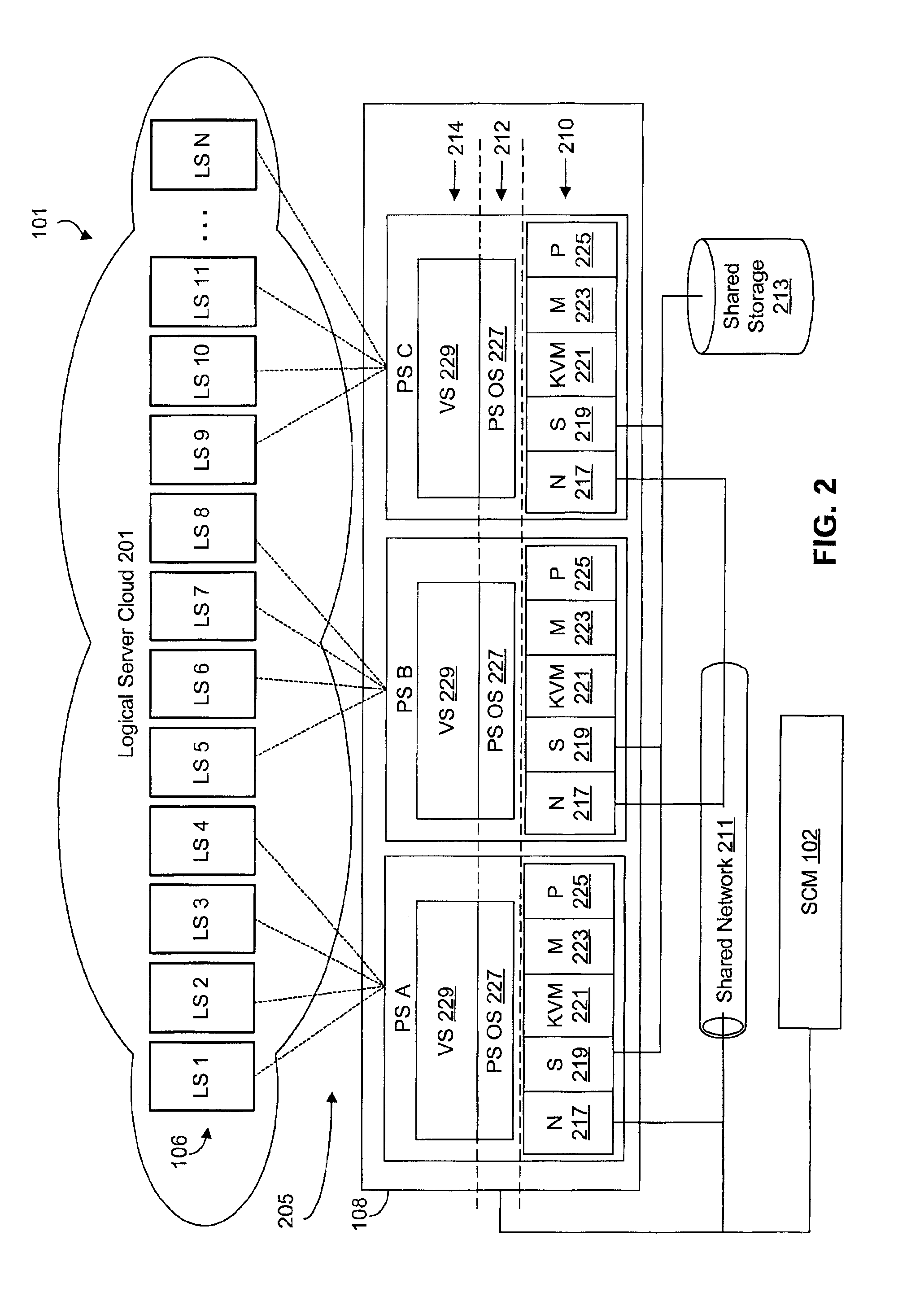
Virtualized logical server cloud providing non-deterministic allocation of logical attributes of logical servers to physical resources
InactiveUS6880002B2Resource allocationMultiple digital computer combinationsVirtualizationData store
A virtualized logical server cloud that enables logical servers to exist independent of physical servers that instantiate the logical servers. Servers are treated as logical resources in order to create a logical server cloud. The logical attributes of a logical server are non-deterministically allocated to physical resources creating a cloud of logical servers over the physical servers. Logical separation is facilitated by the addition of a server cloud manager, which is an automated multi-server management layer. Each logical server has persistent attributes that establish its identity. Each physical server includes or is coupled to physical resources including a network resource, a data storage resource and a processor resource. At least one physical server executes virtualization software that virtualizes physical resources for logical servers. The server cloud manager maintains status and instance information for the logical servers including persistent and non-persistent attributes that link each logical server with a physical server.
Owner:DELL PROD LP
System and method for a cloud computing abstraction with multi-tier deployment policy
ActiveUS20140280961A1Increase and decrease numberScaling downDigital computer detailsData switching networksVirtualizationWorkload
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload.
Owner:CSC AGILITY PLATFORM INC
Virtualized shared protection capacity
The present disclosure relates a network, a network element, a system, and a method providing an efficient allocation of protection capacity for network connections and / or services. These may be for services within a given Virtual Private Network (VPN) or Virtual Machine (VM) instance flow. Network ingress / egress ports are designed to be VM instance aware while transit ports may or may not be depending on network element capability or configuration. A centralized policy management and a distributed control plane are used to discover and allocate resources to and among the VPNs or VM instances. Algorithms for efficient allocation and release of protection capacity may be coordinated between the centralized policy management and the distributed control plane. Additional coupling of attributes such as latency may provide more sophisticated path selection algorithms including efficient sharing of protection capacity.
Owner:CIENA
Intelligent security control system for virtualized ecosystems
ActiveUS20100169948A1Digital data processing detailsPublic key for secure communicationObject handlingVirtualization
Resources of a virtualized ecosystem are intelligently secured by defining and analyzing object handling security control information for one or more logical resources in the virtualized ecosystem and deriving therefrom object properties for each of the logical resources involved in the execution of a virtual machine in any given context within the virtualized ecosystem.
Owner:HYTRUST
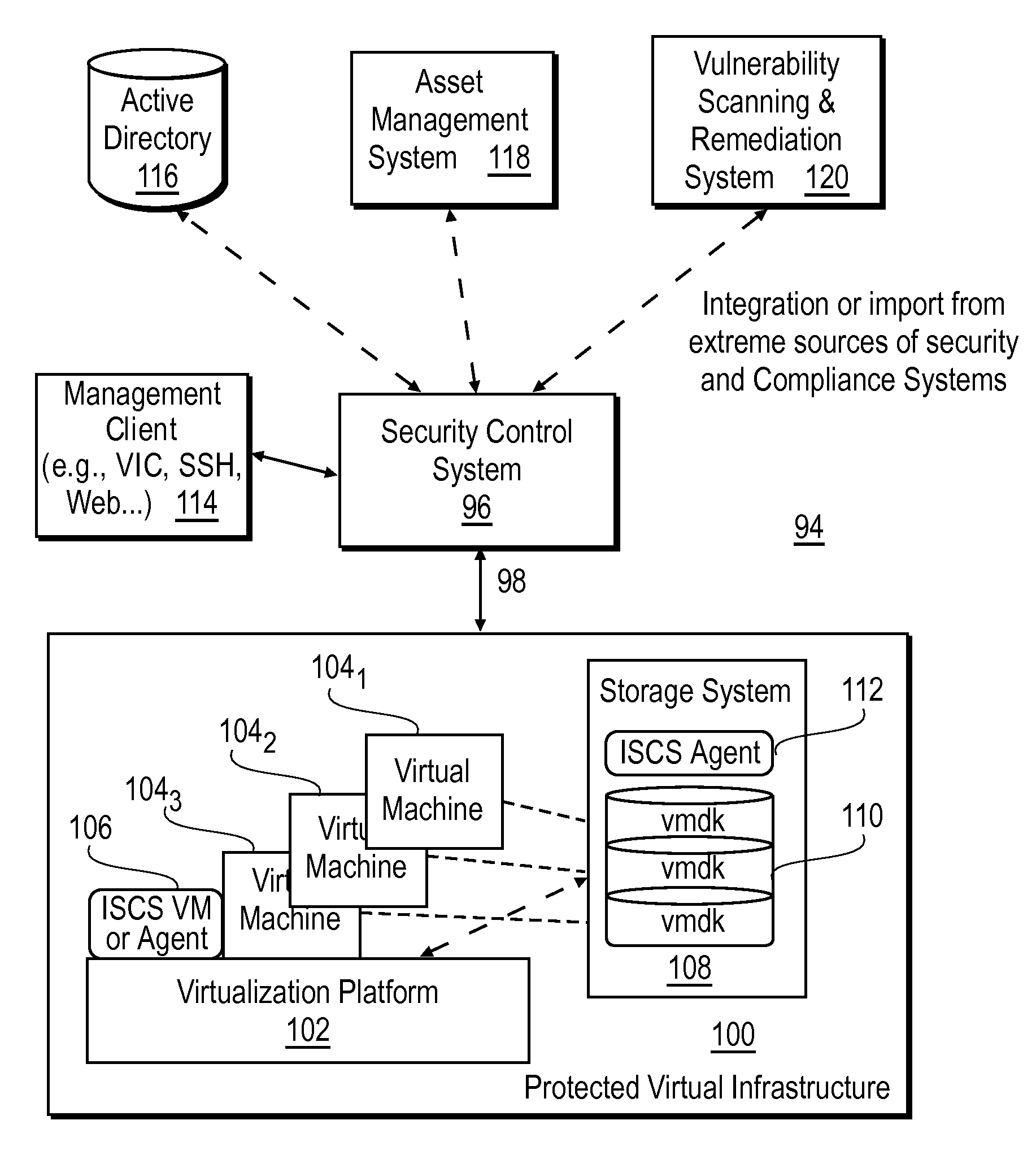
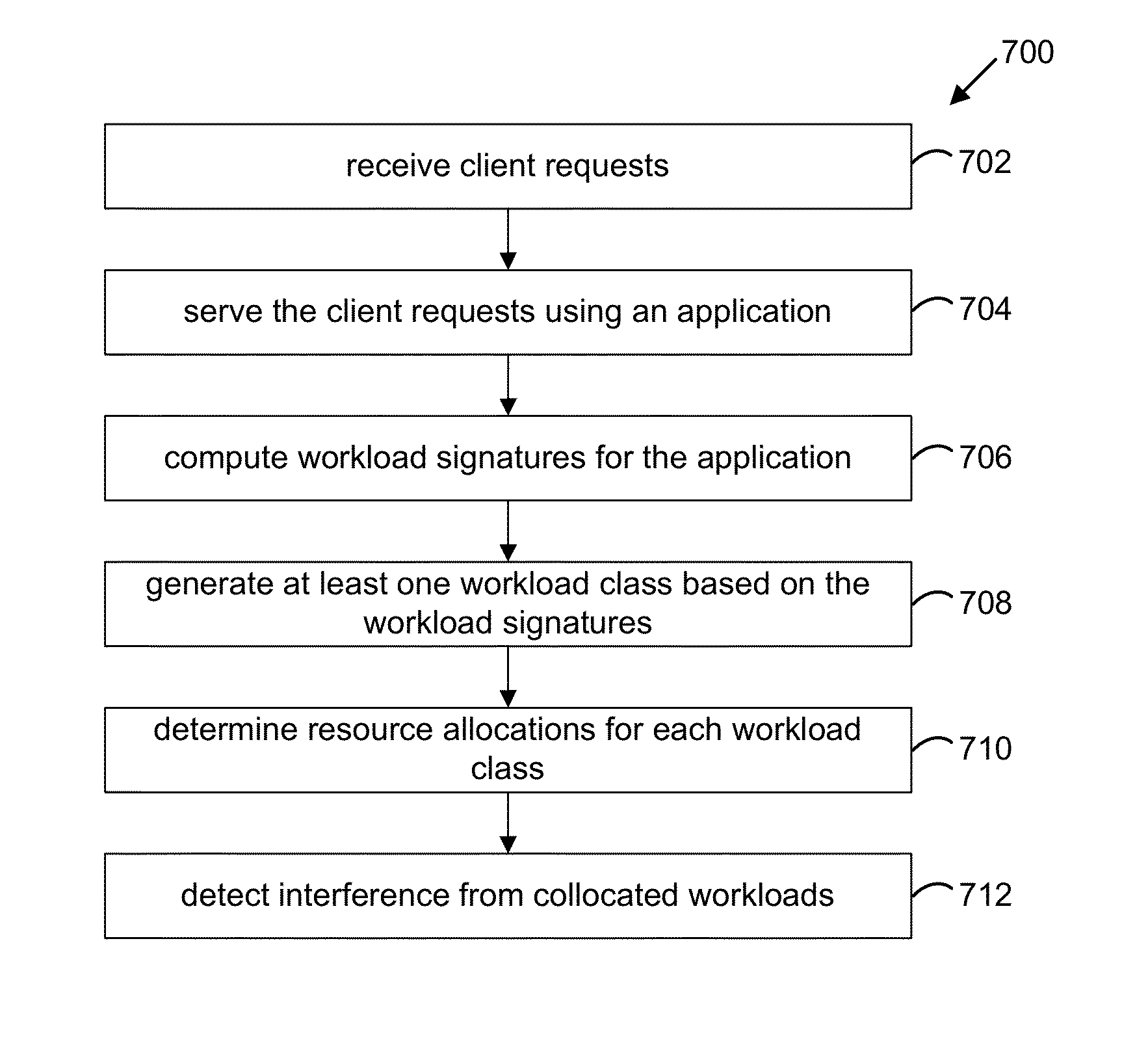
Accelerating resource allocation in virtualized environments using workload classes and/or workload signatures
Systems, methods, and apparatus for managing resources assigned to an application or service. A resource manager maintains a set of workload classes and classifies workloads using workload signatures. In specific embodiments, the resource manager minimizes or reduces resource management costs by identifying a relatively small set of workload classes during a learning phase, determining preferred resource allocations for each workload class, and then during a monitoring phase, classifying workloads and allocating resources based on the preferred resource allocation for the classified workload. In some embodiments, interference is accounted for by estimating and using an “interference index”.
Owner:ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL) +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com