Patents
Literature
218 results about "Artificial neuron" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
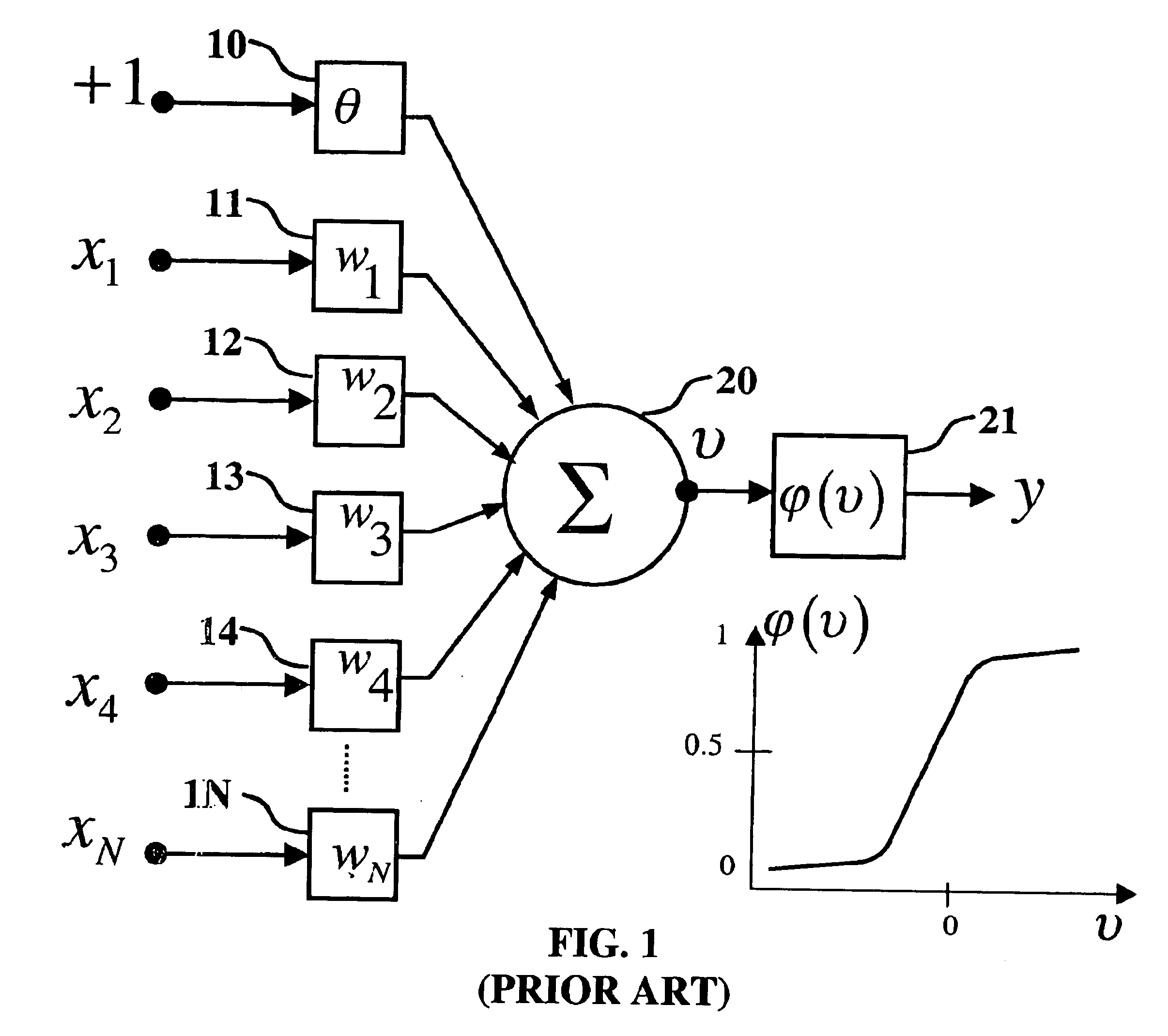
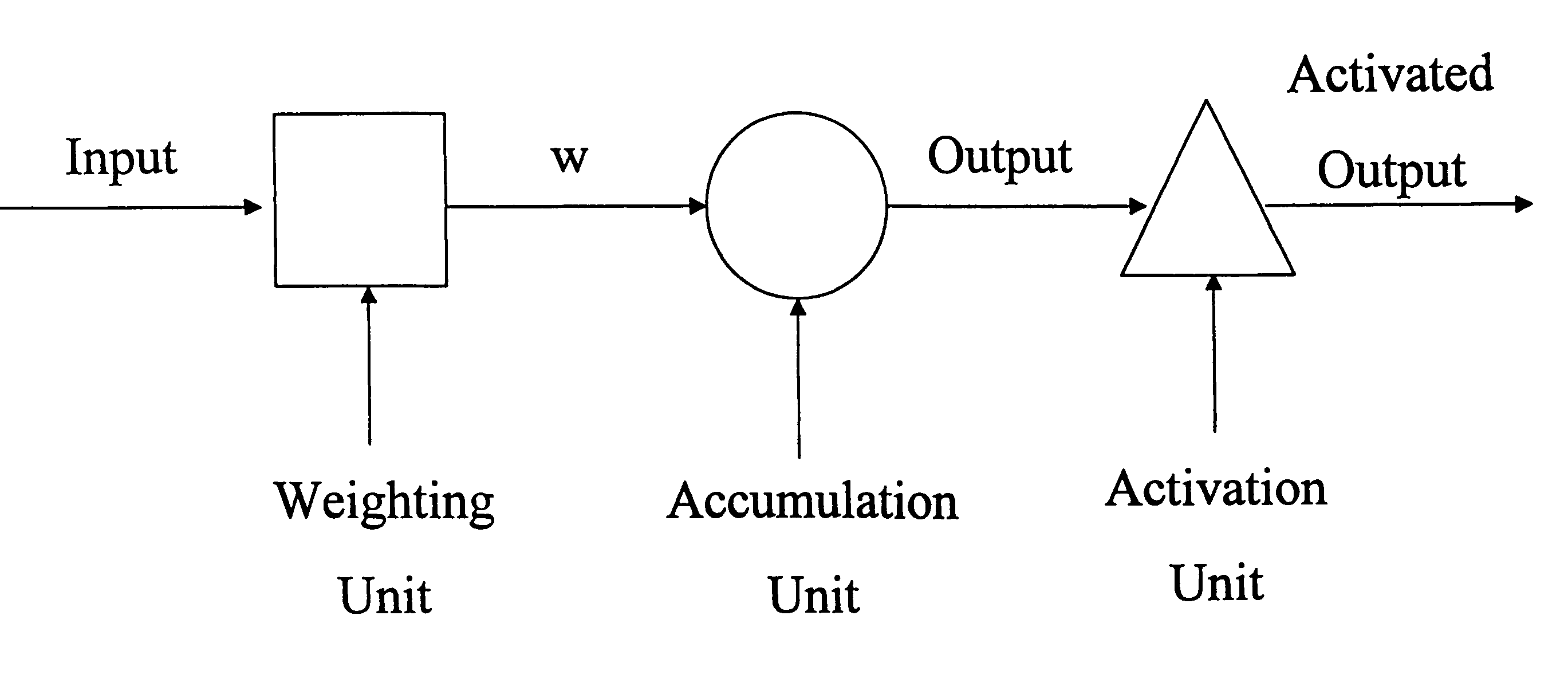
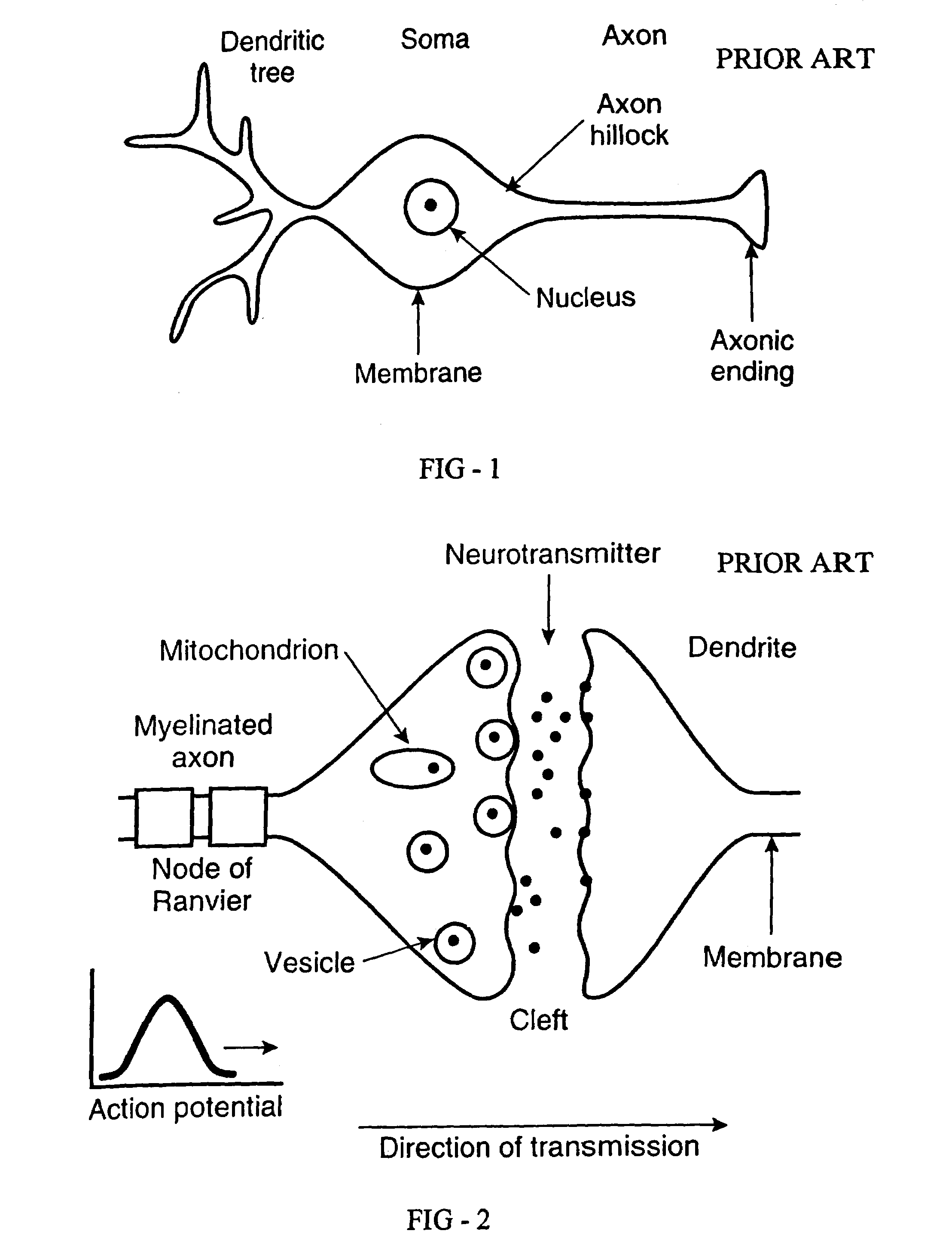
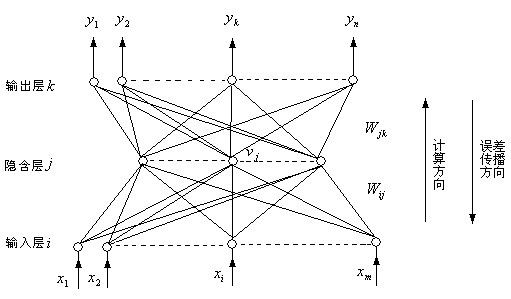
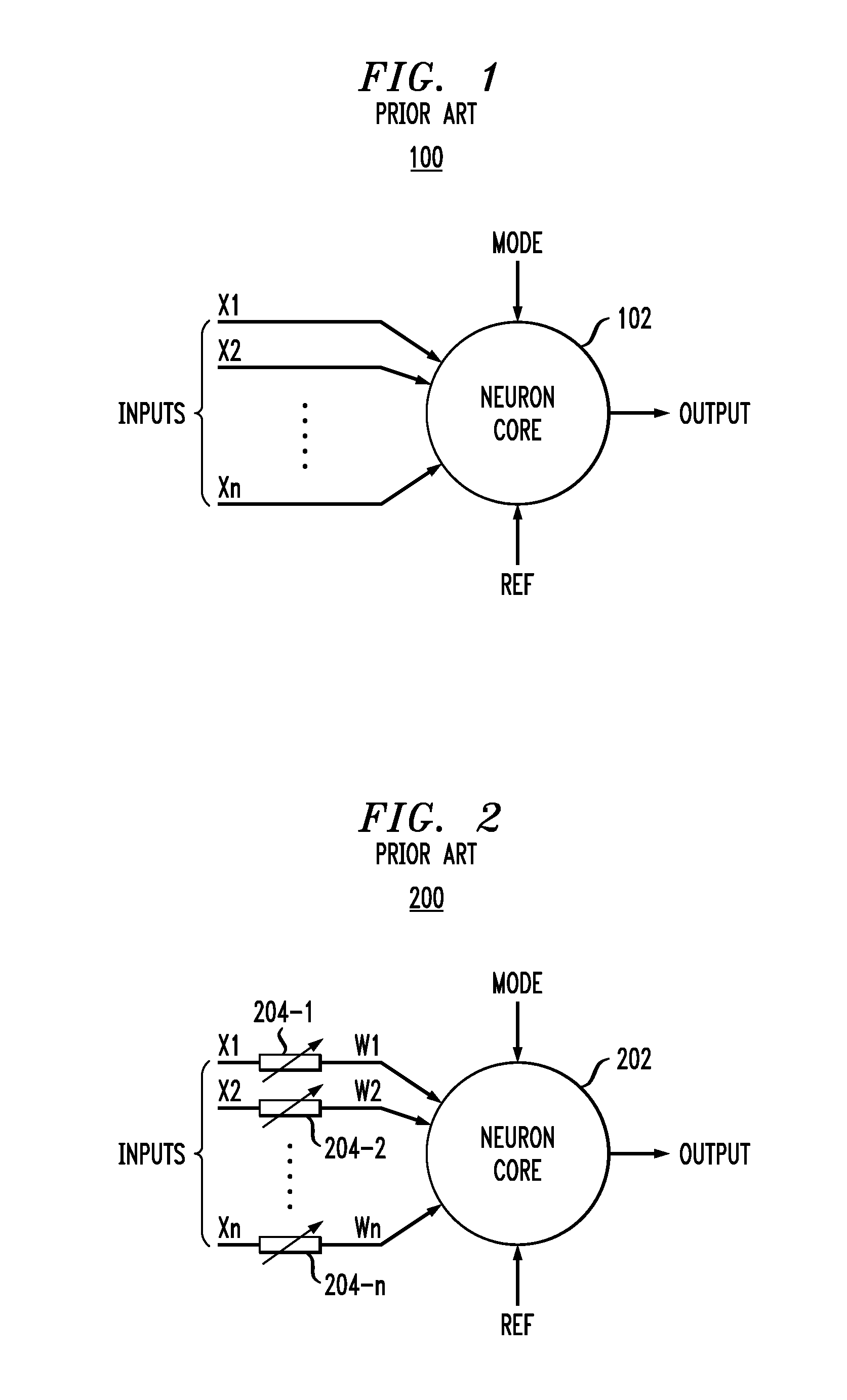
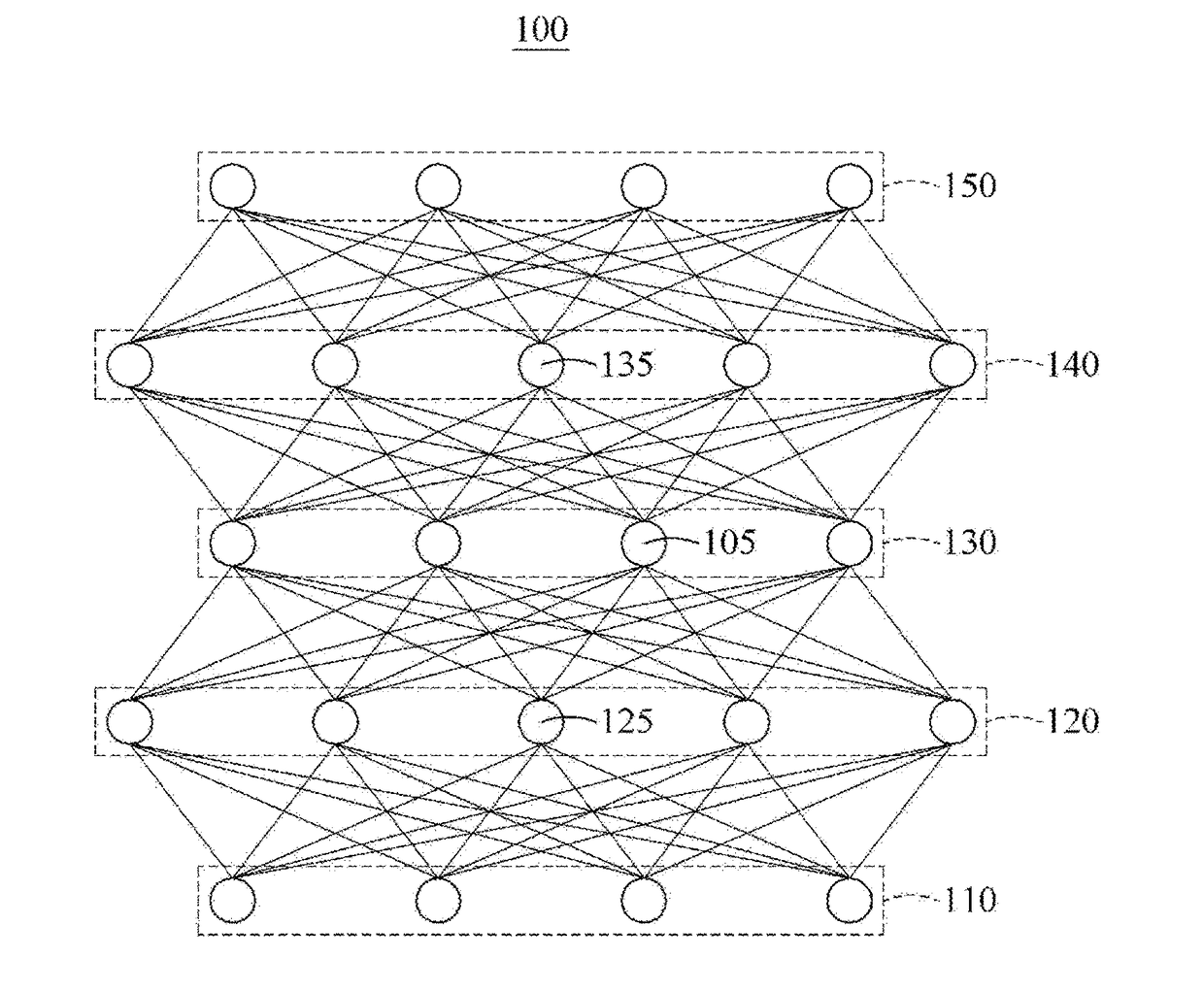
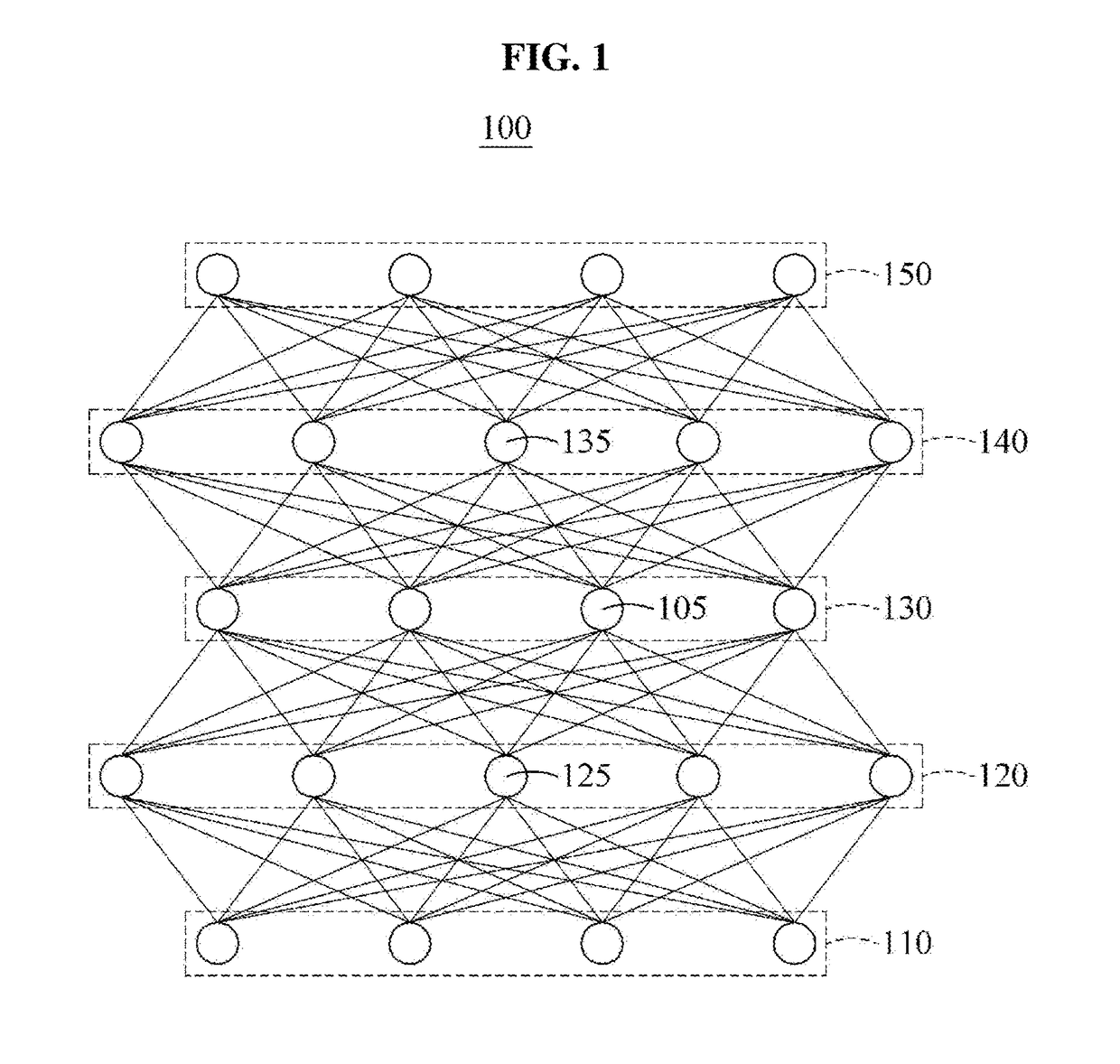
An artificial neuron is a mathematical function conceived as a model of biological neurons, a neural network. Artificial neurons are elementary units in an artificial neural network. The artificial neuron receives one or more inputs (representing excitatory postsynaptic potentials and inhibitory postsynaptic potentials at neural dendrites) and sums them to produce an output (or activation, representing a neuron's action potential which is transmitted along its axon). Usually each input is separately weighted, and the sum is passed through a non-linear function known as an activation function or transfer function. The transfer functions usually have a sigmoid shape, but they may also take the form of other non-linear functions, piecewise linear functions, or step functions. They are also often monotonically increasing, continuous, differentiable and bounded. The thresholding function has inspired building logic gates referred to as threshold logic; applicable to building logic circuits resembling brain processing. For example, new devices such as memristors have been extensively used to develop such logic in recent times.
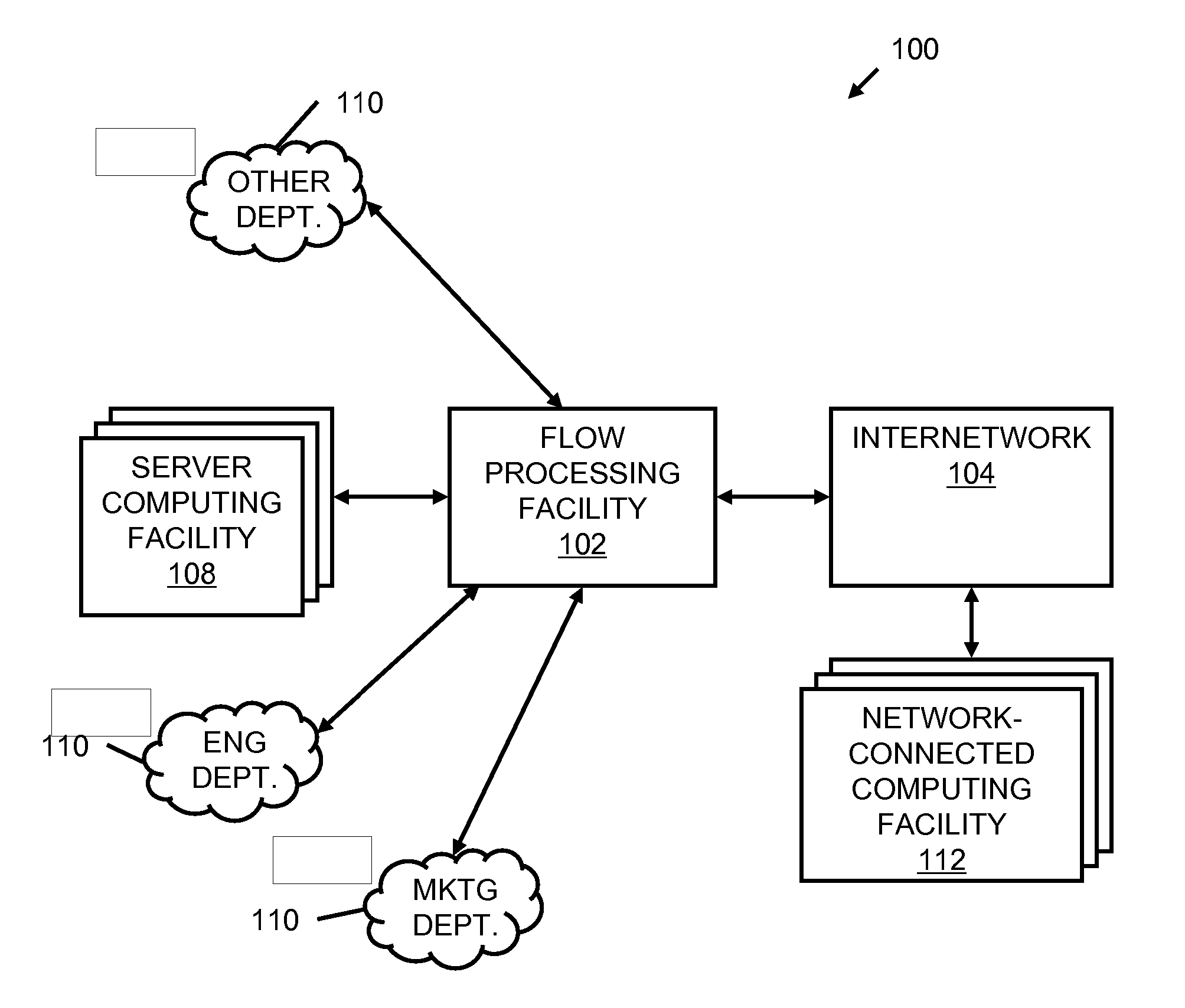
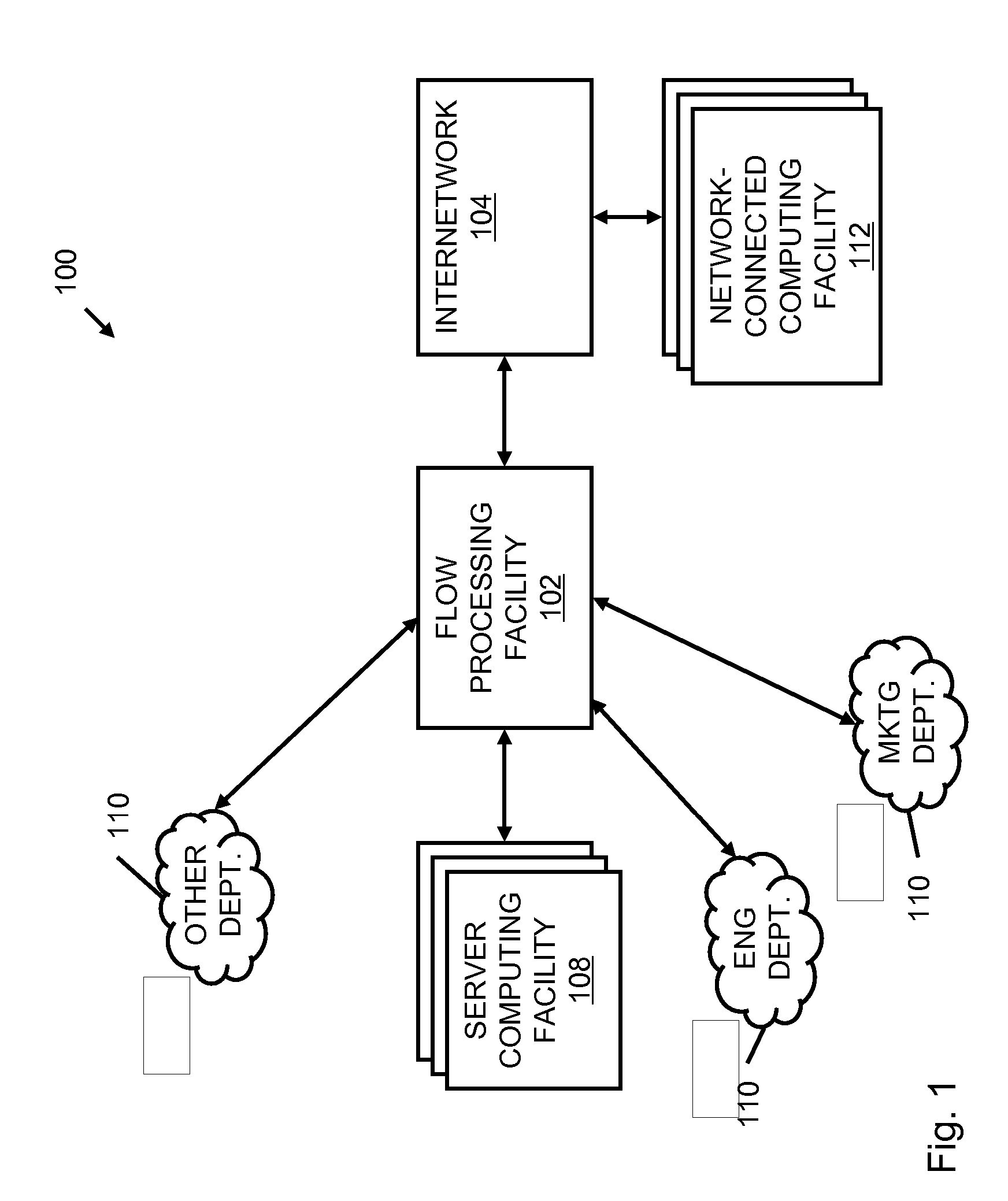
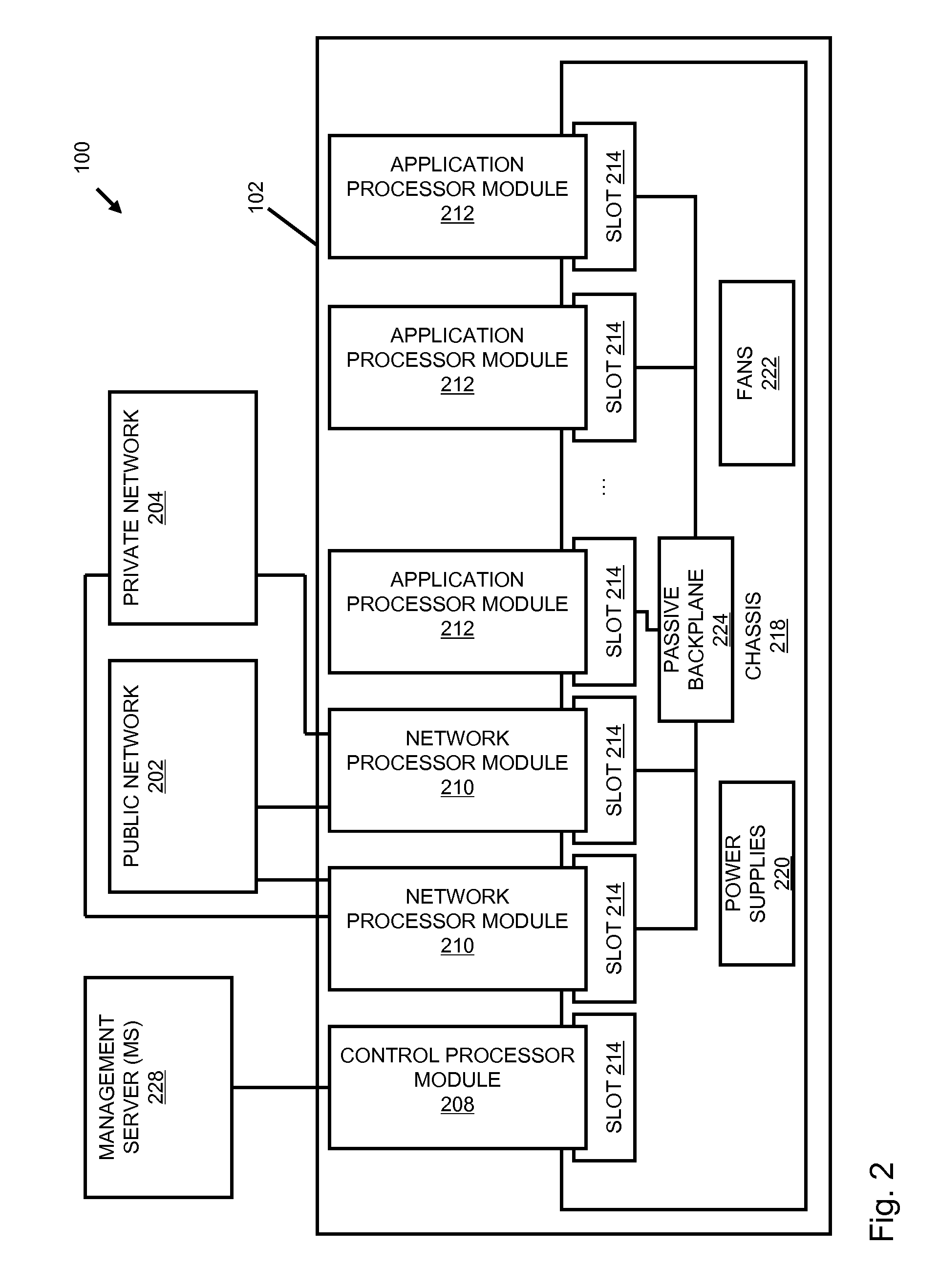
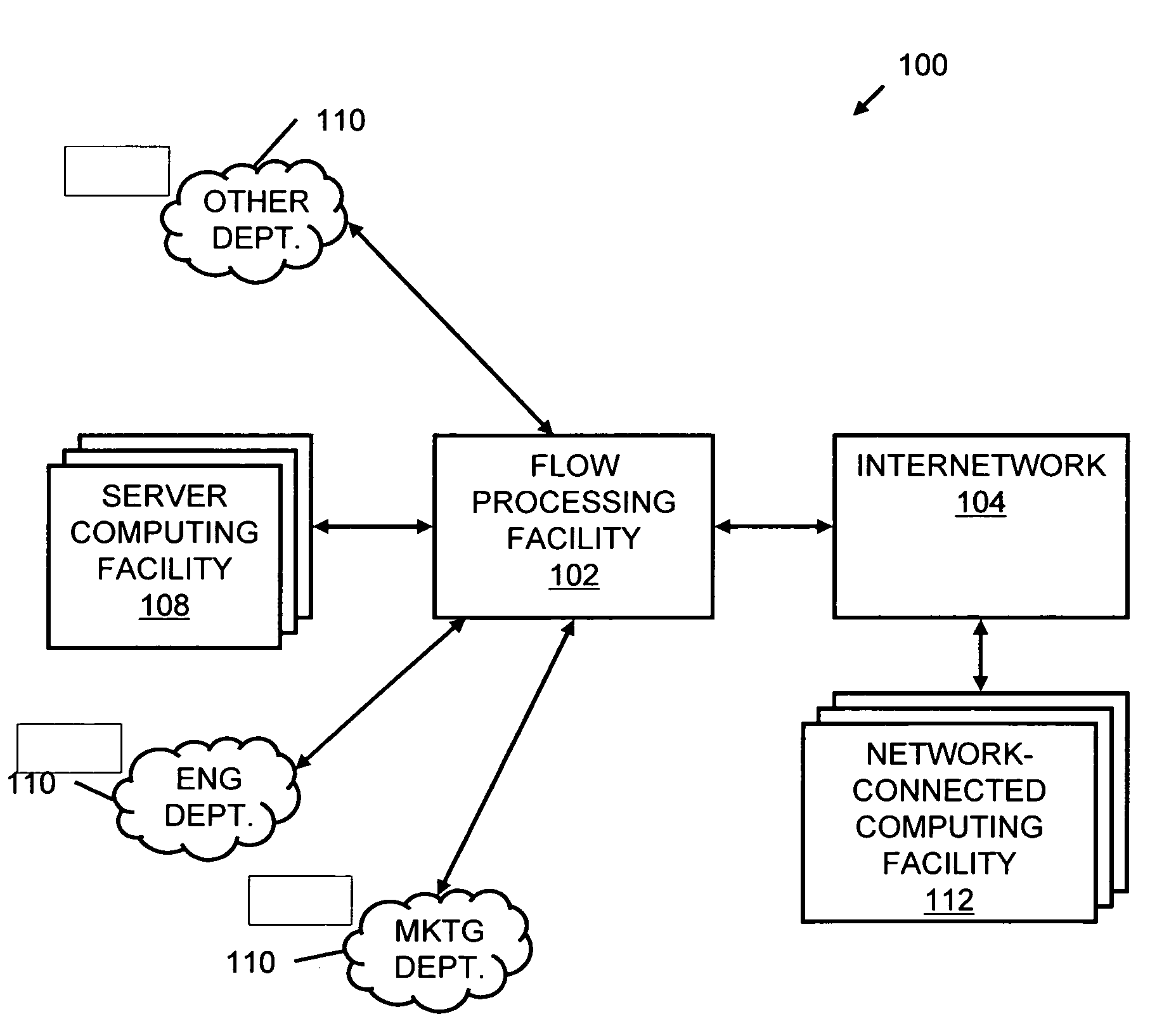
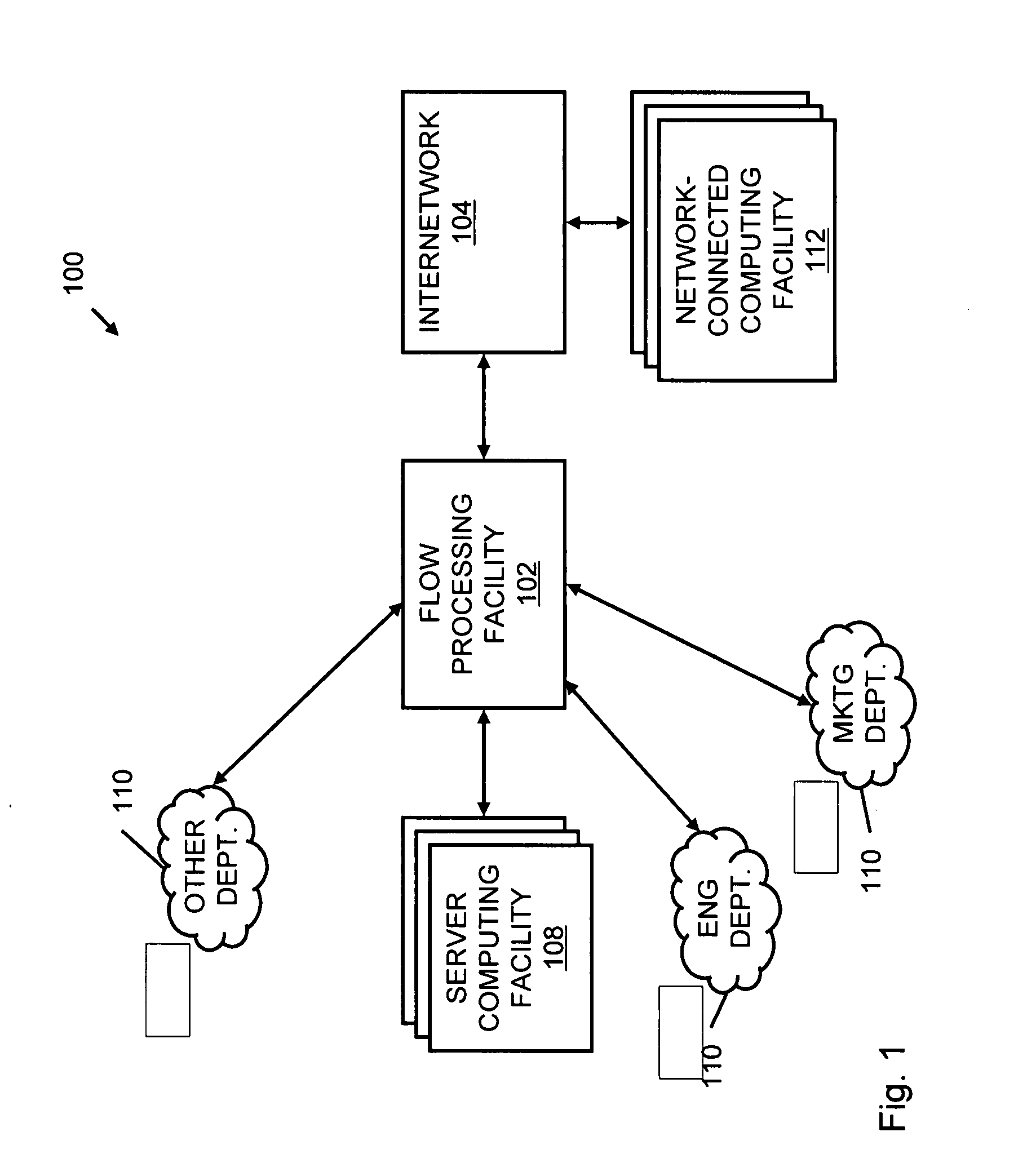
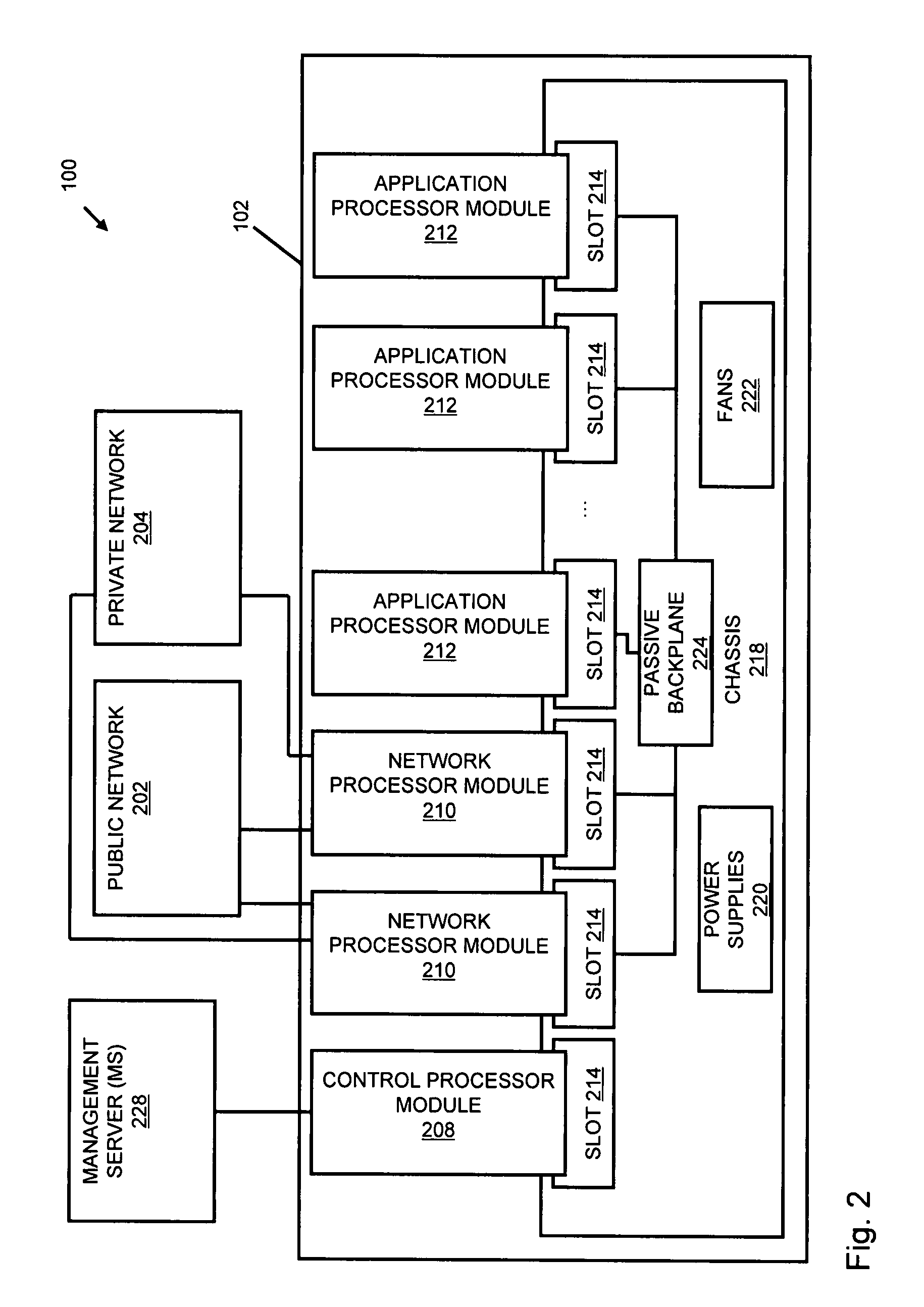
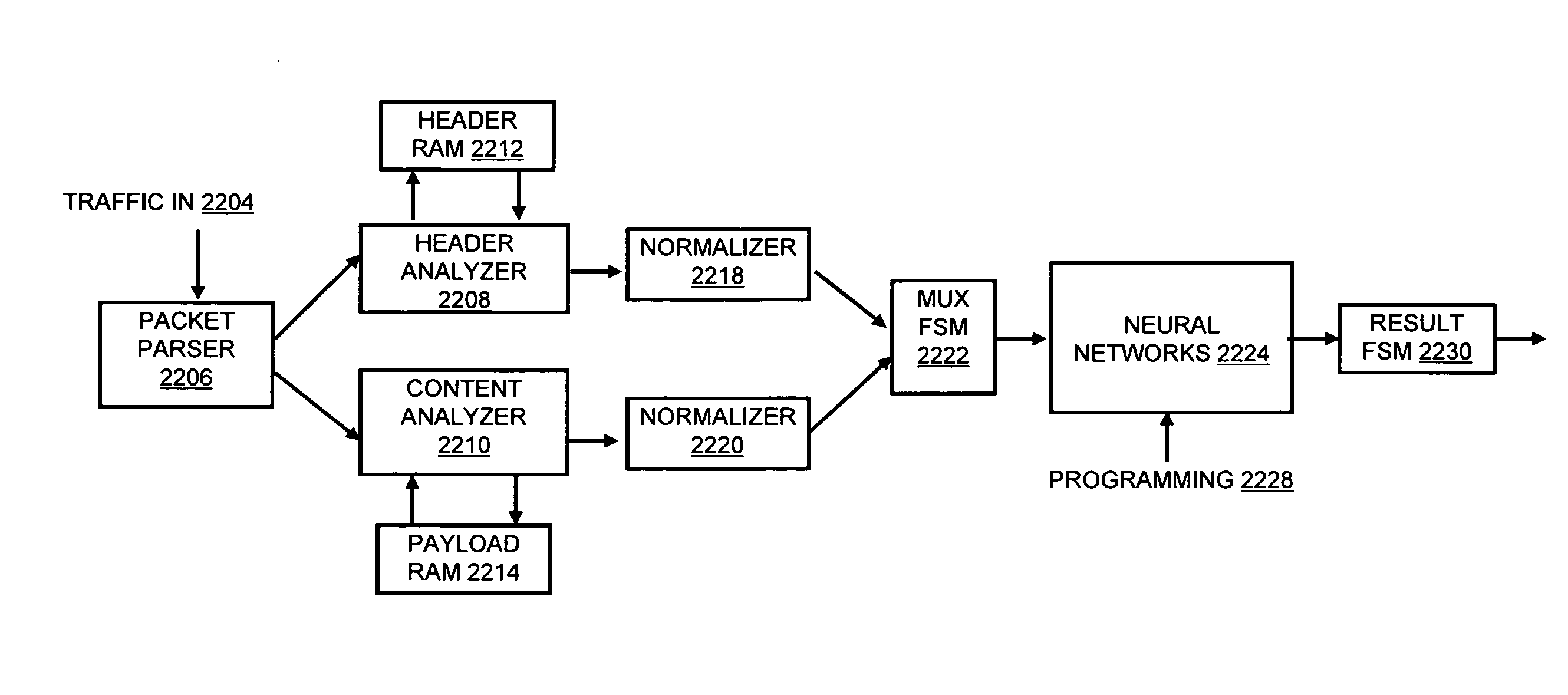
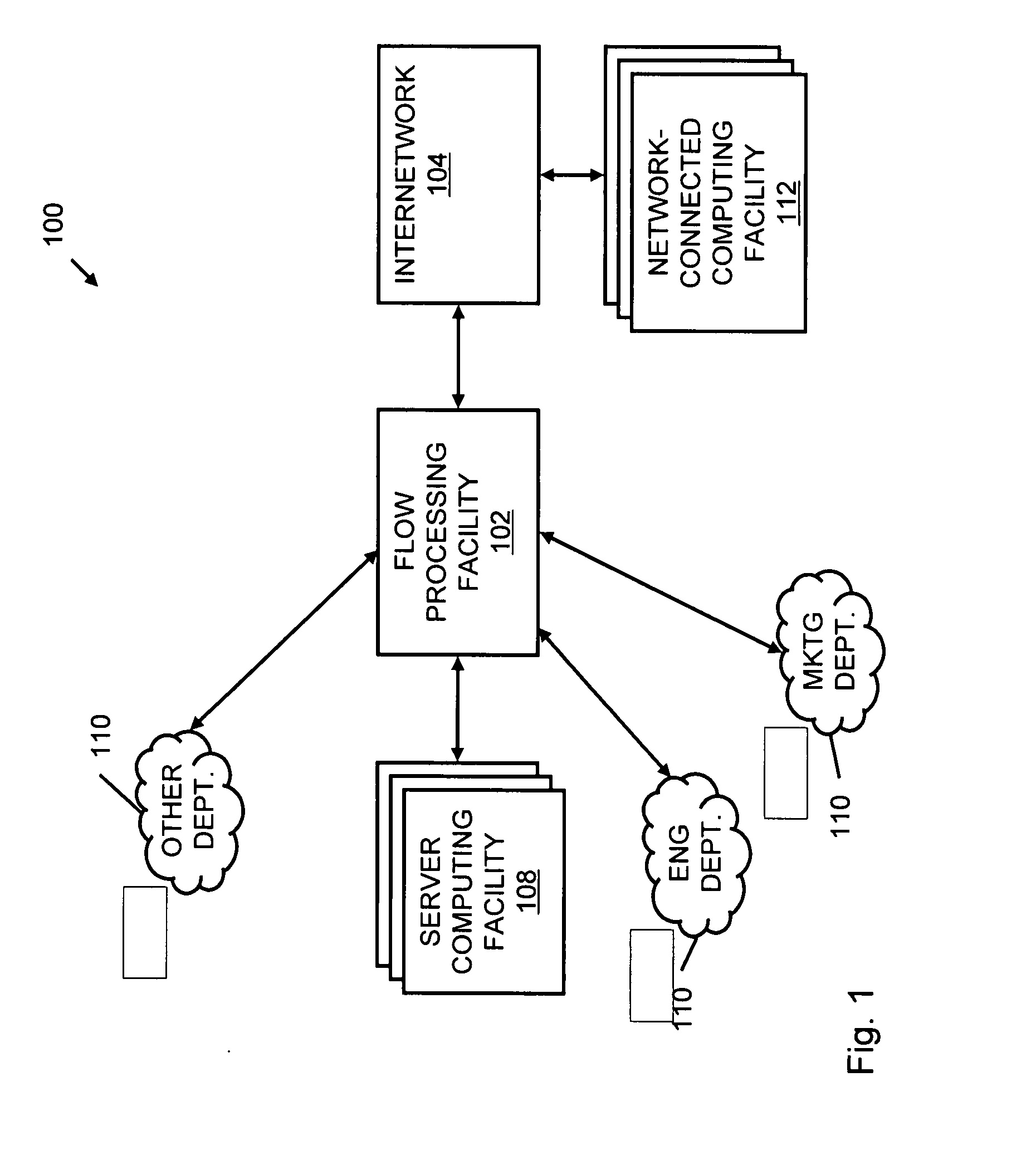
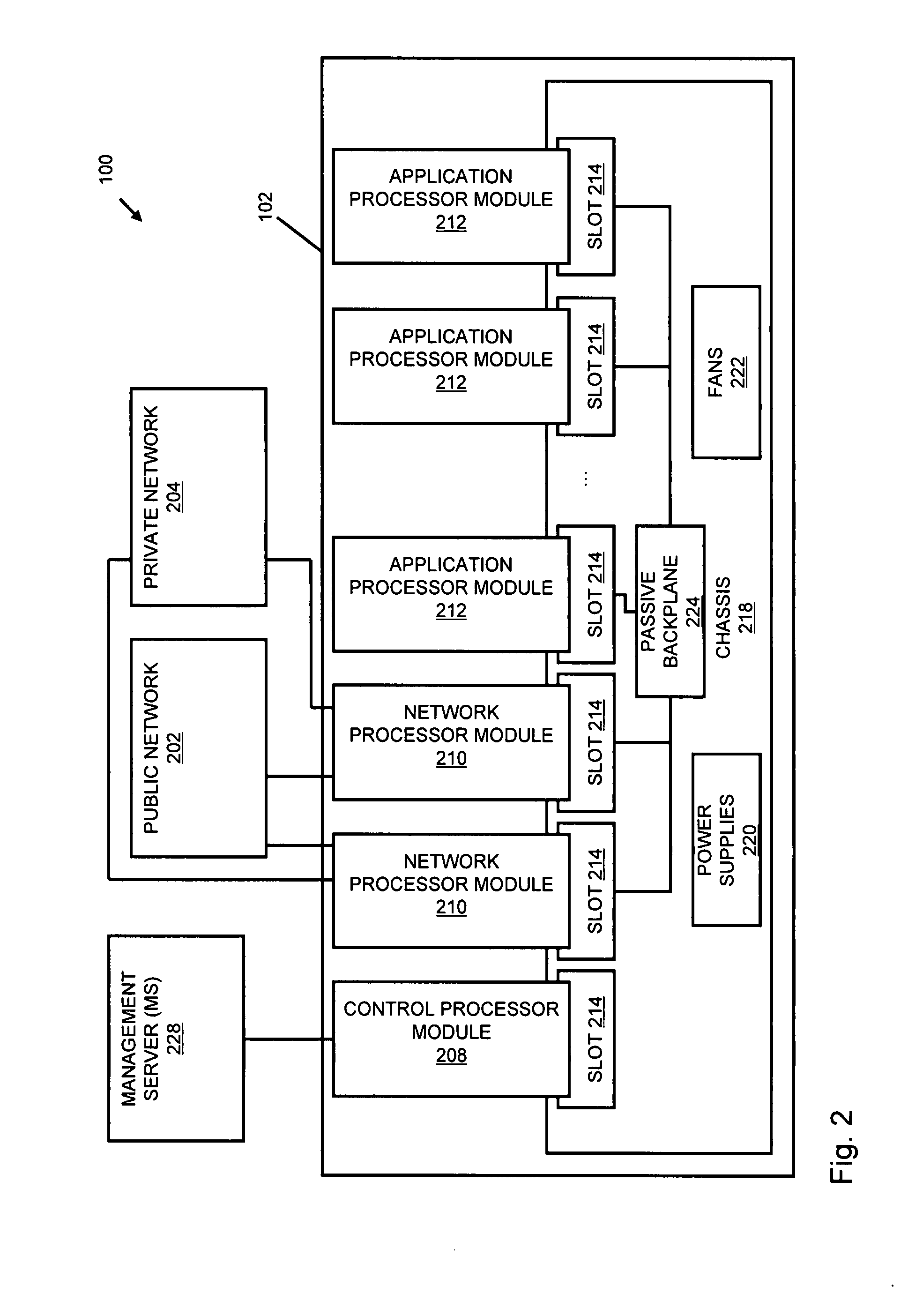
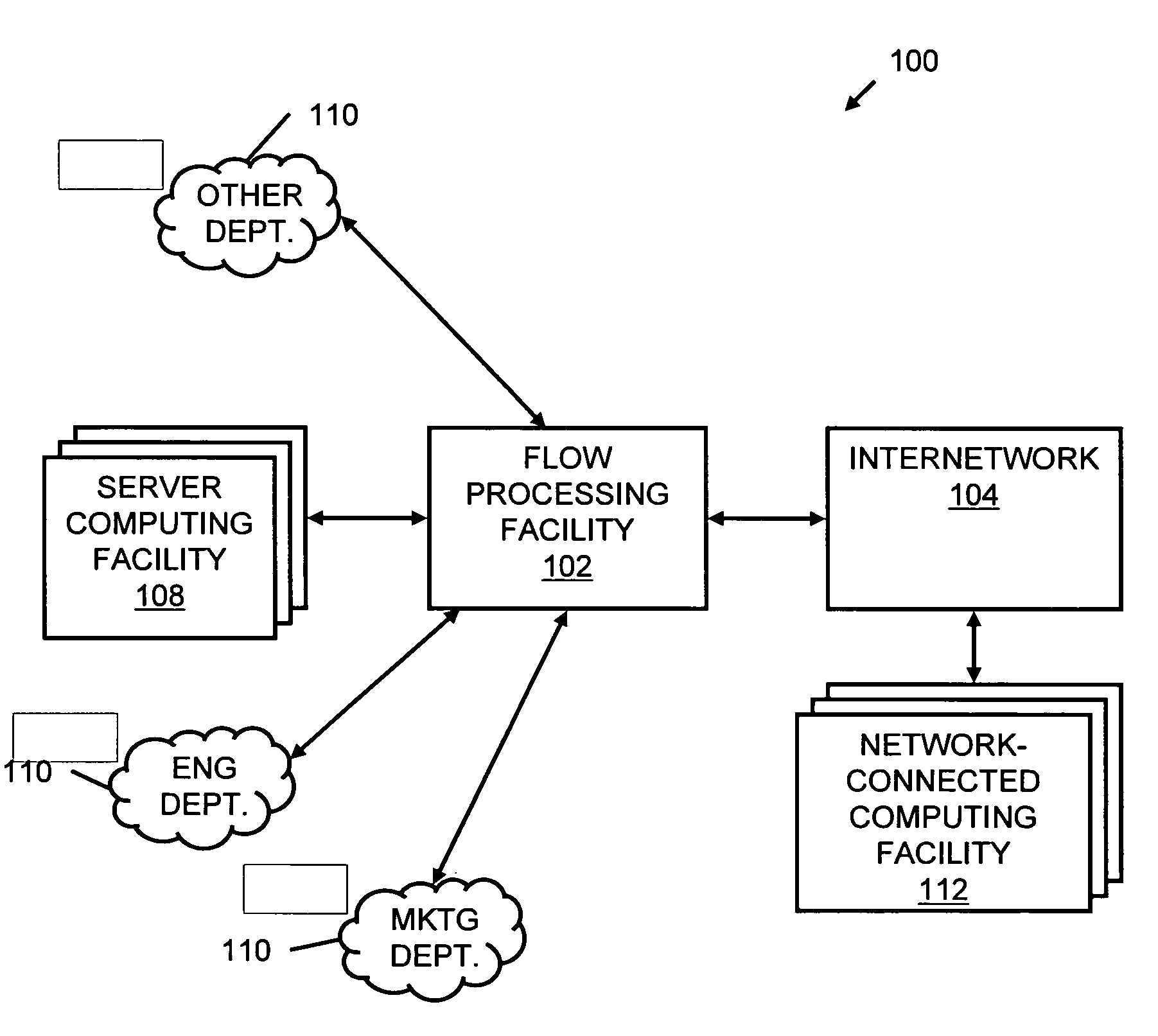
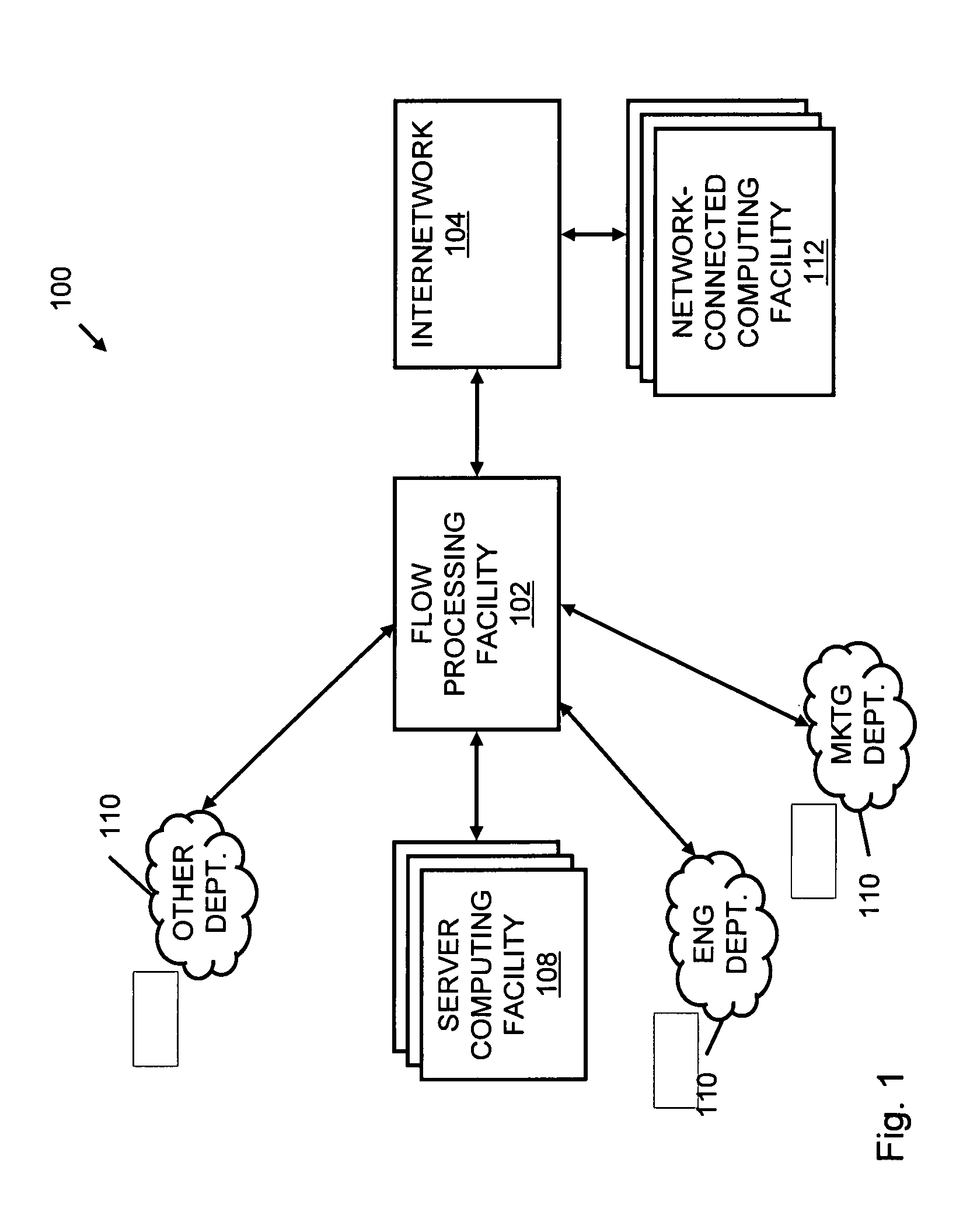
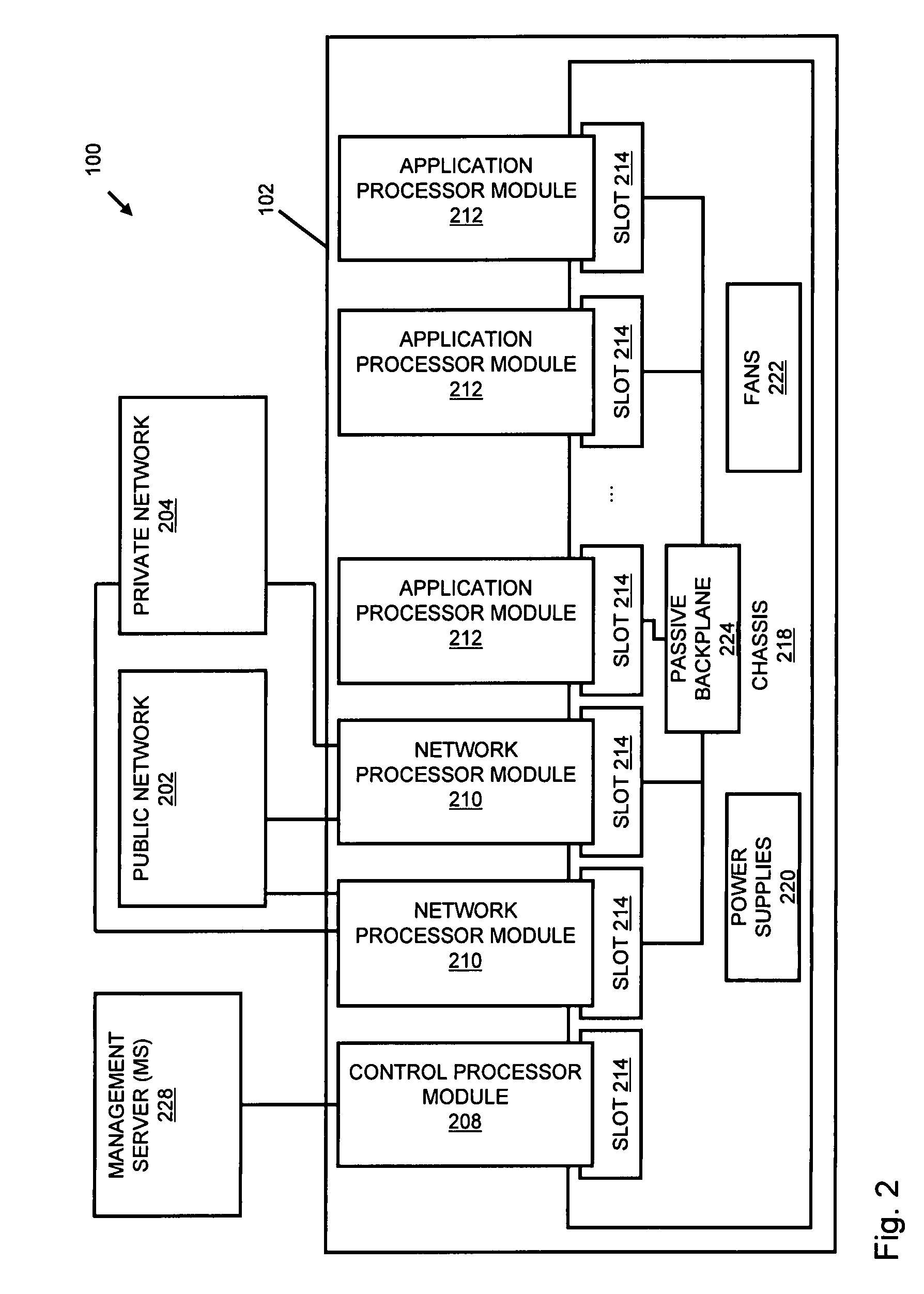
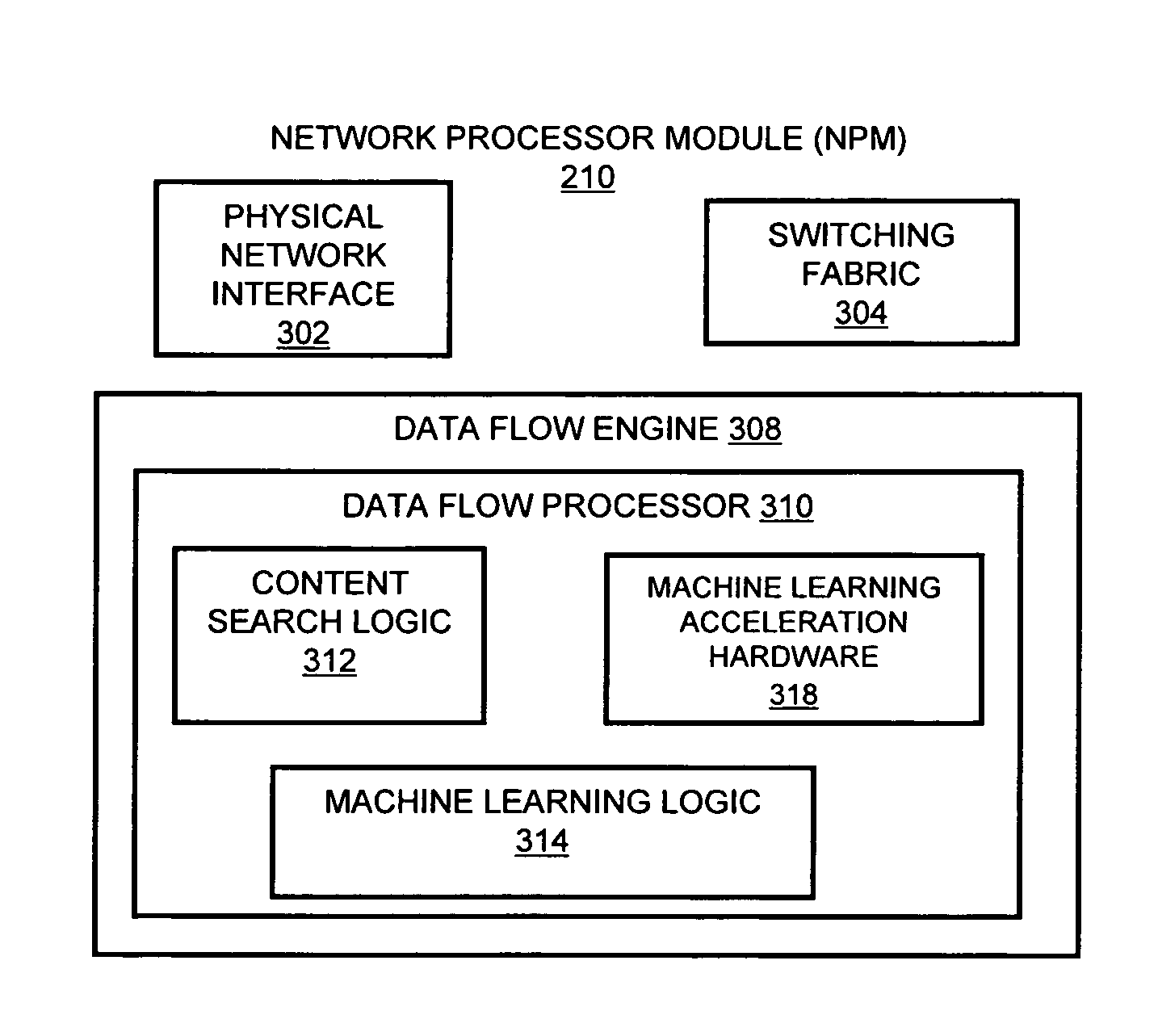
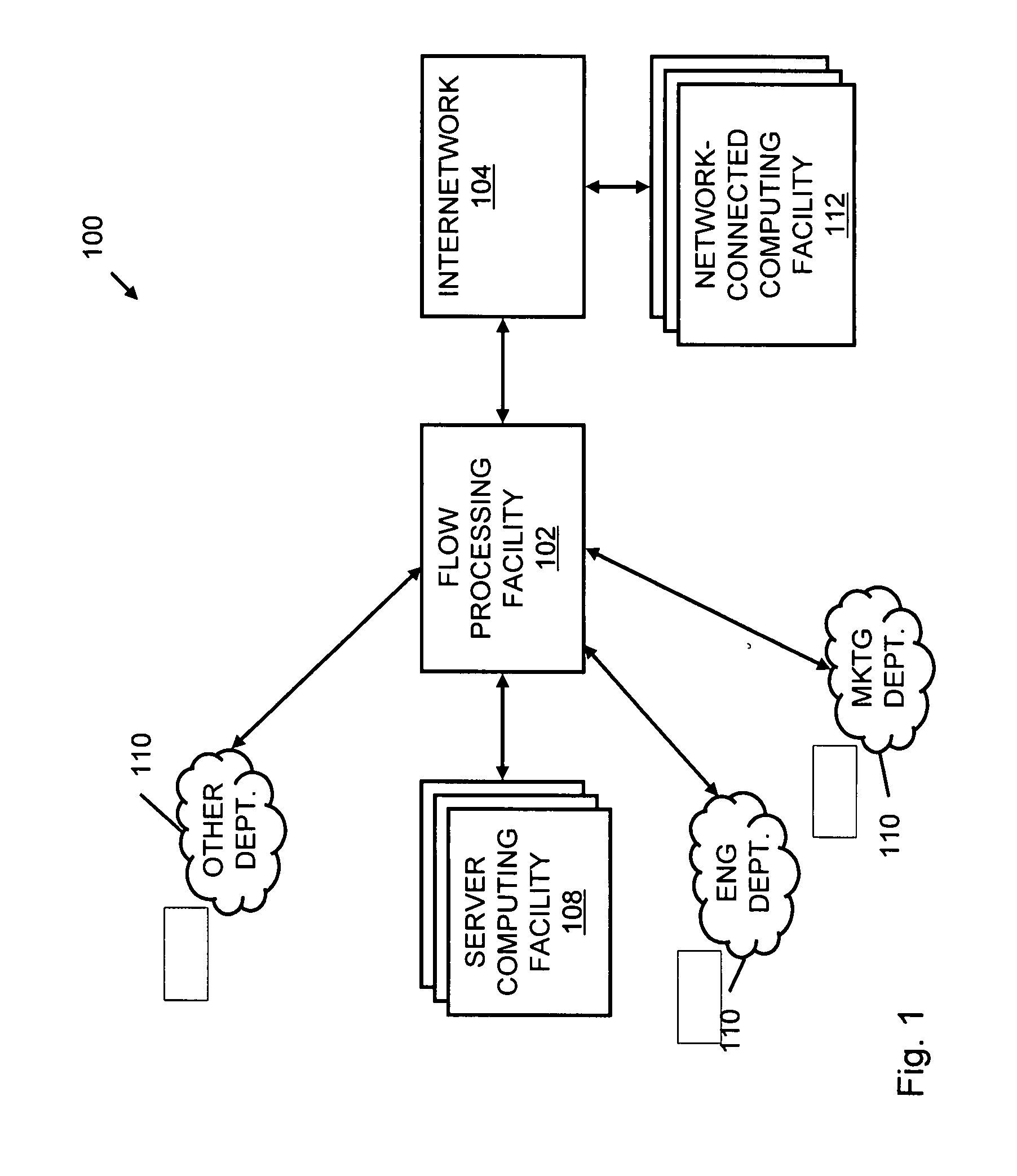
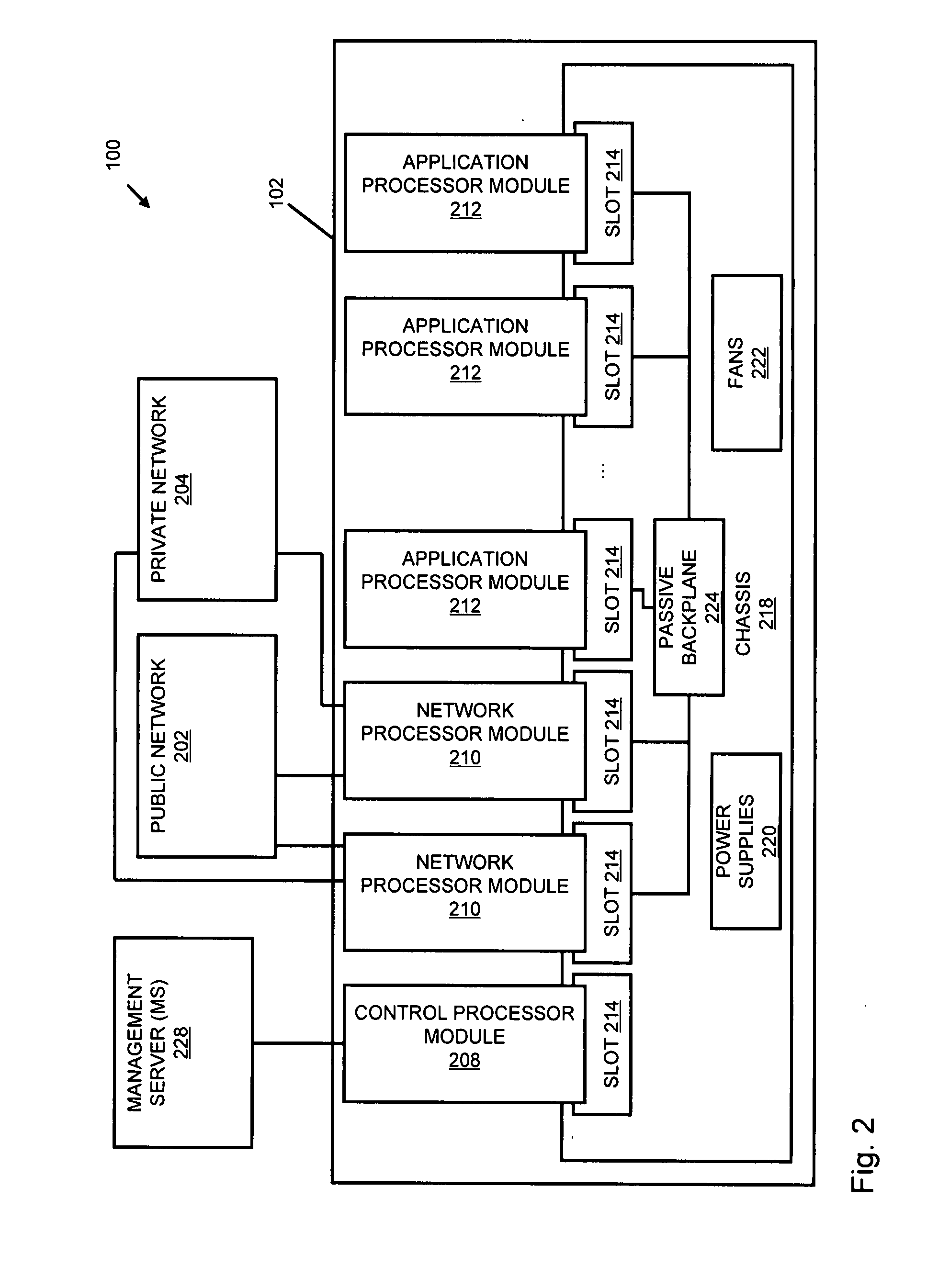
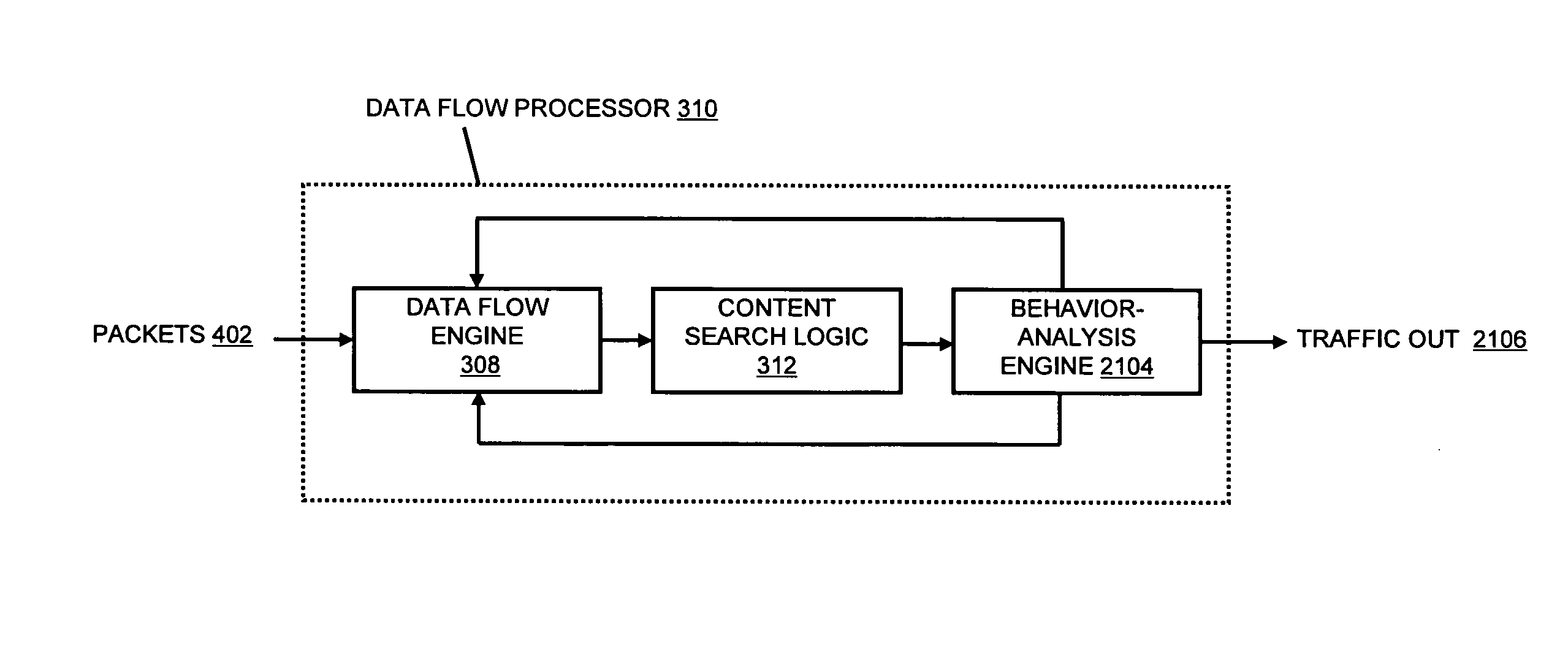
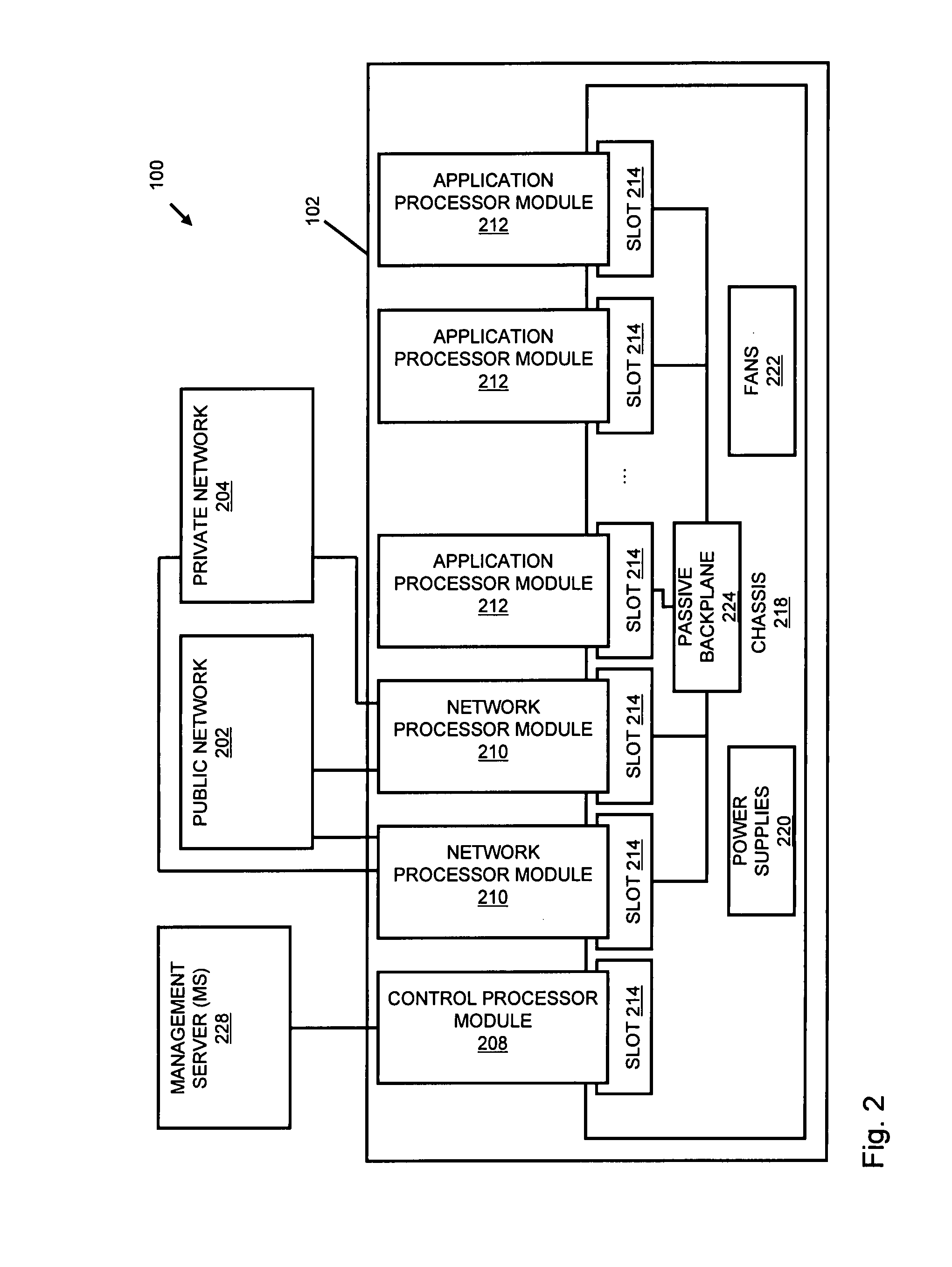
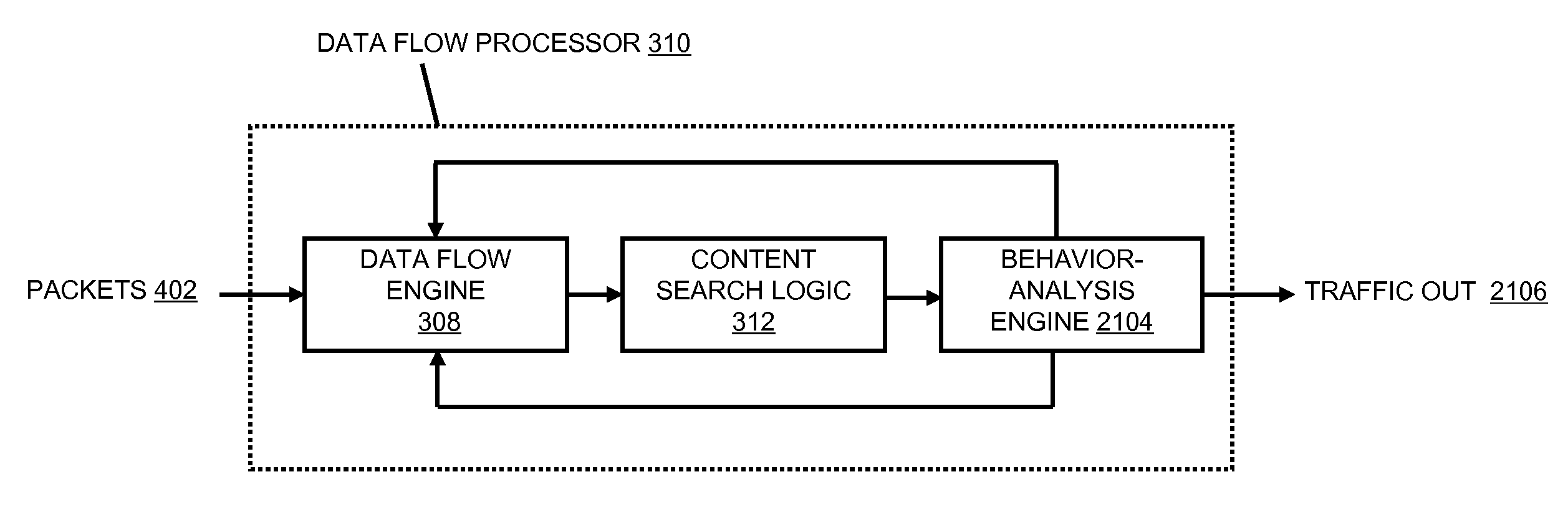
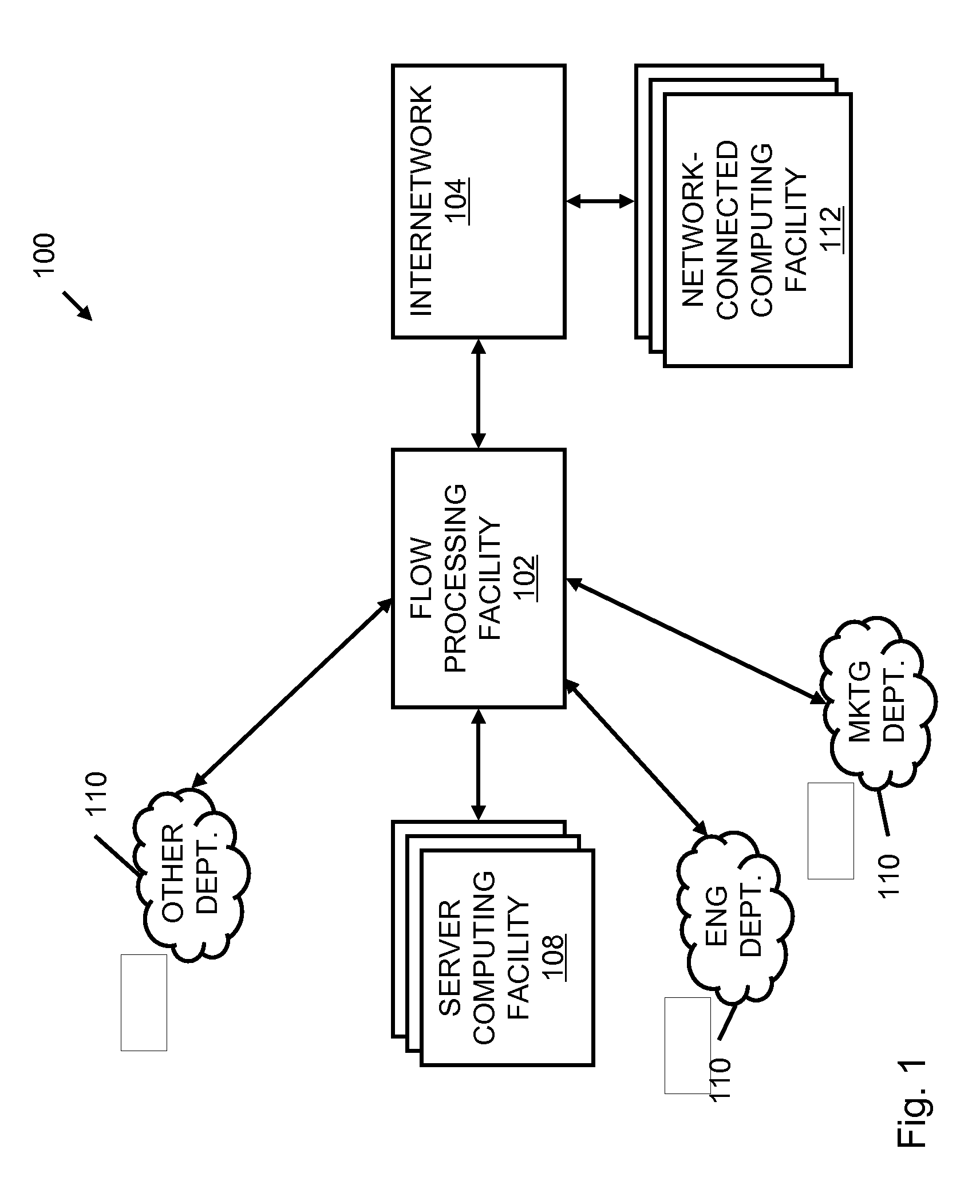
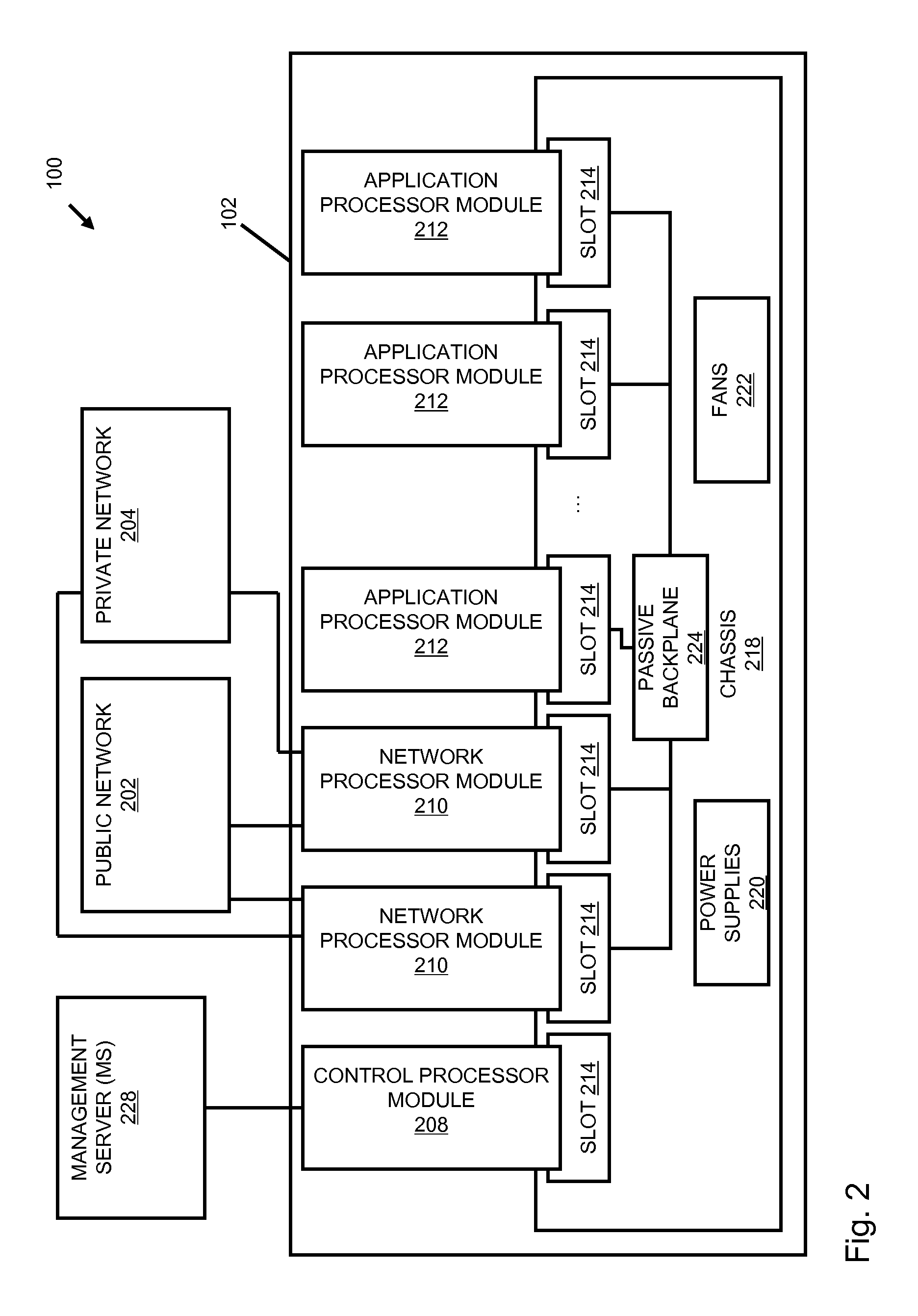
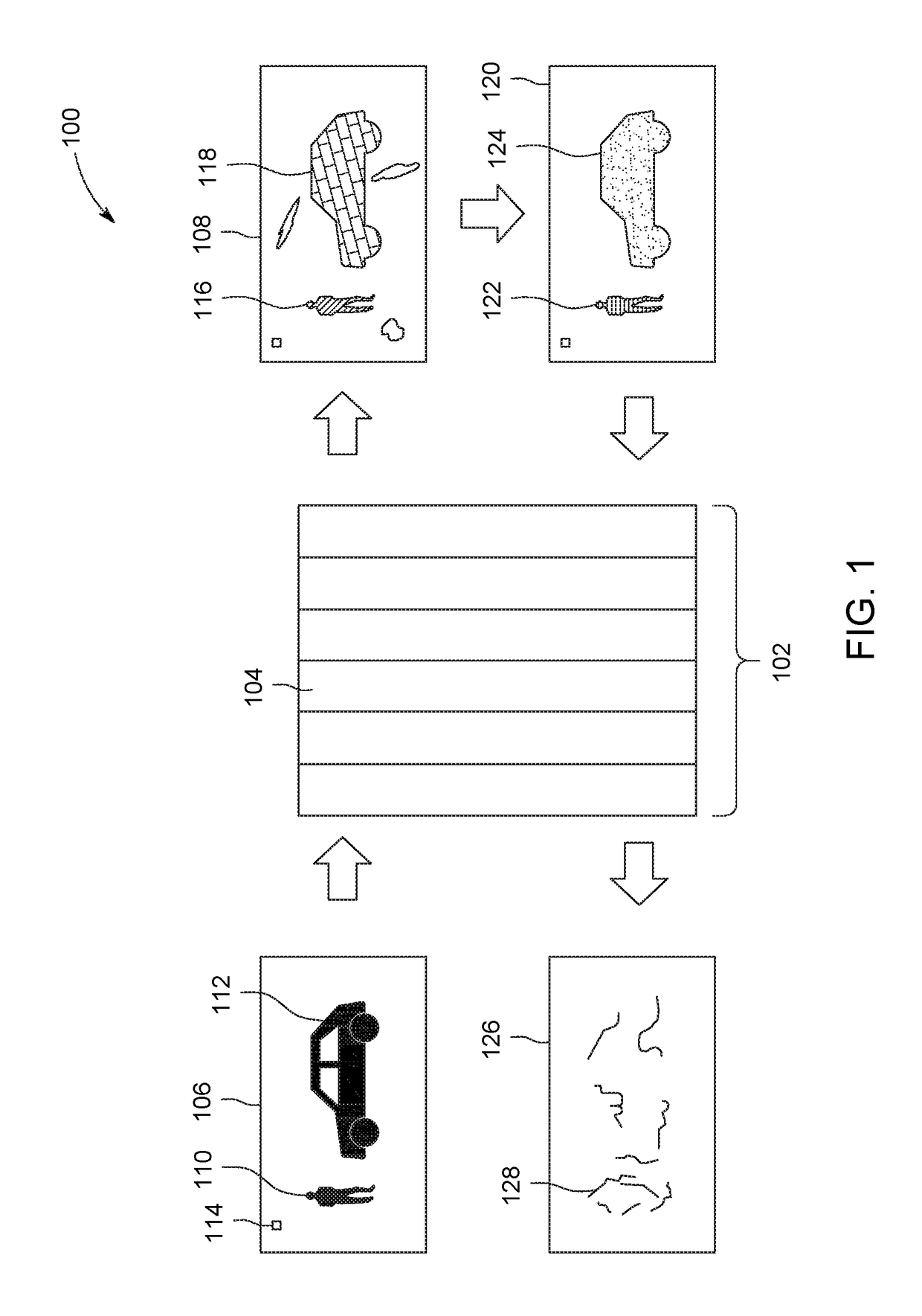
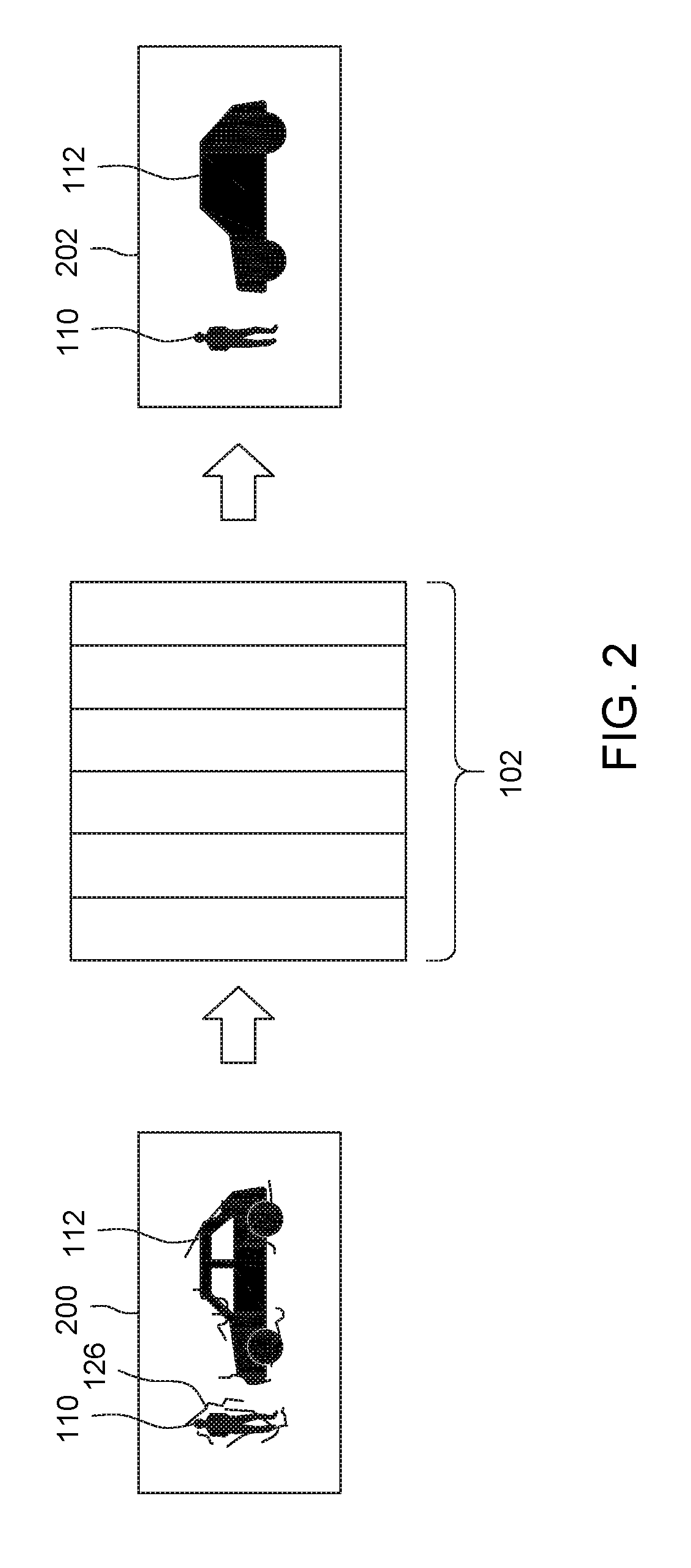
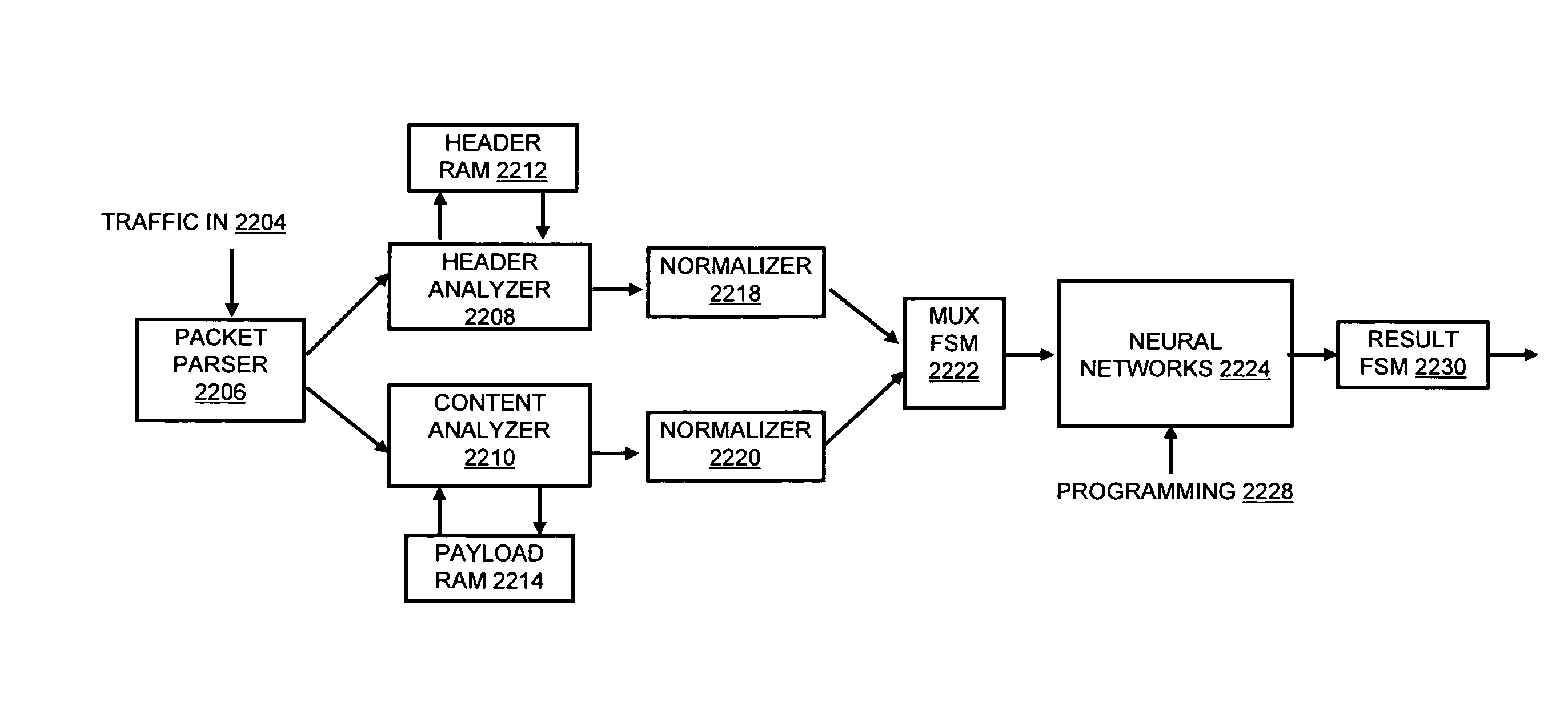
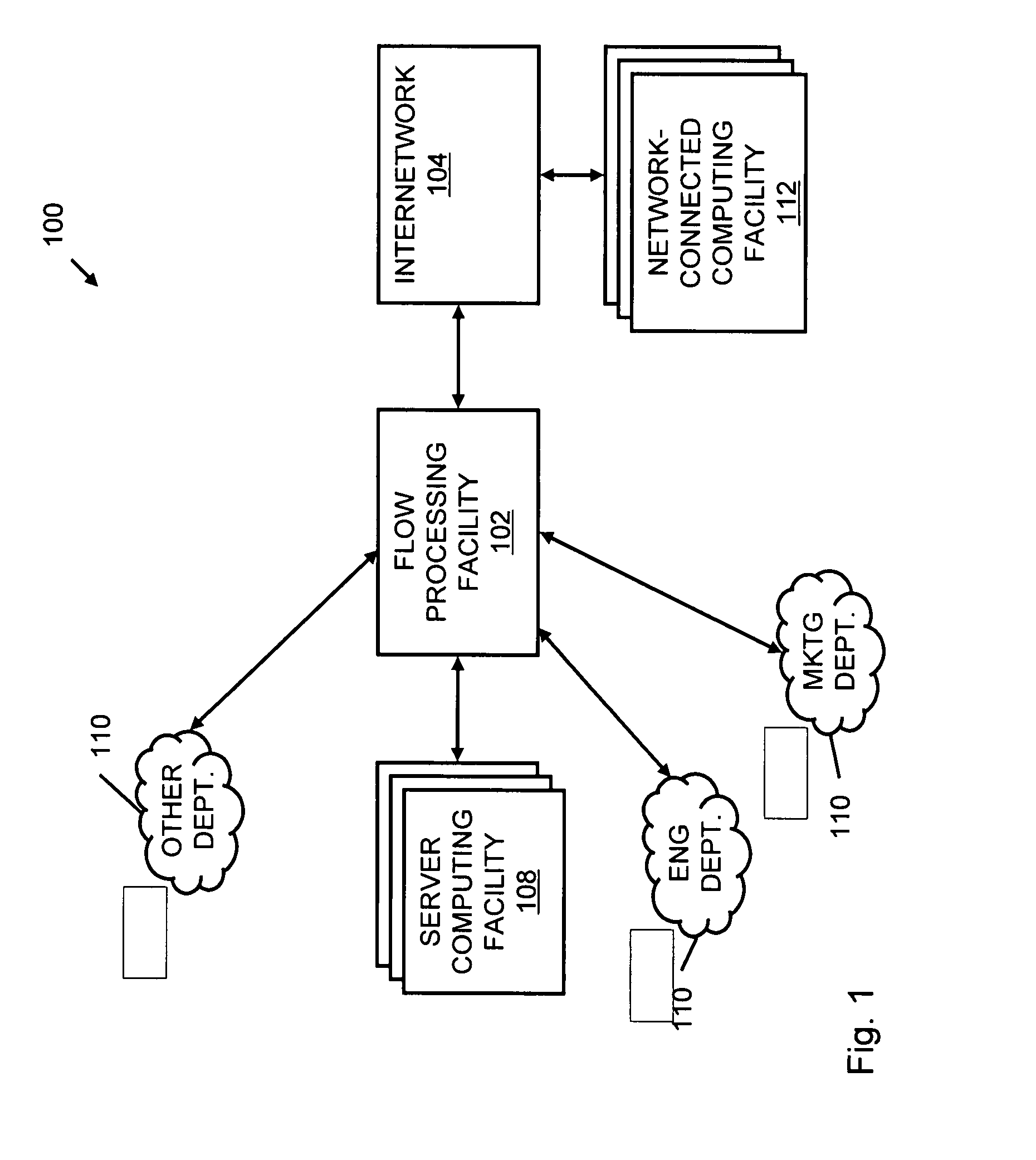
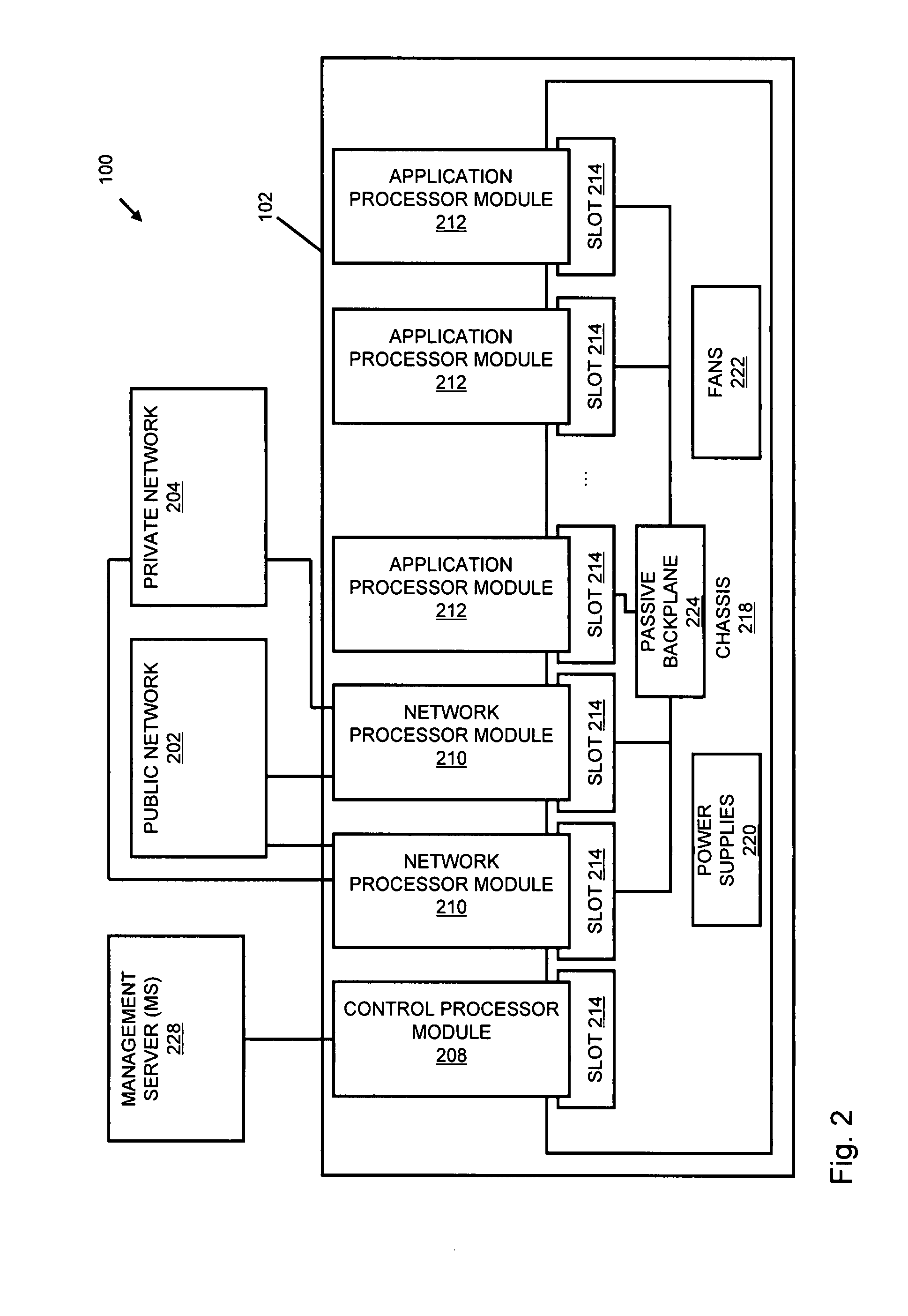
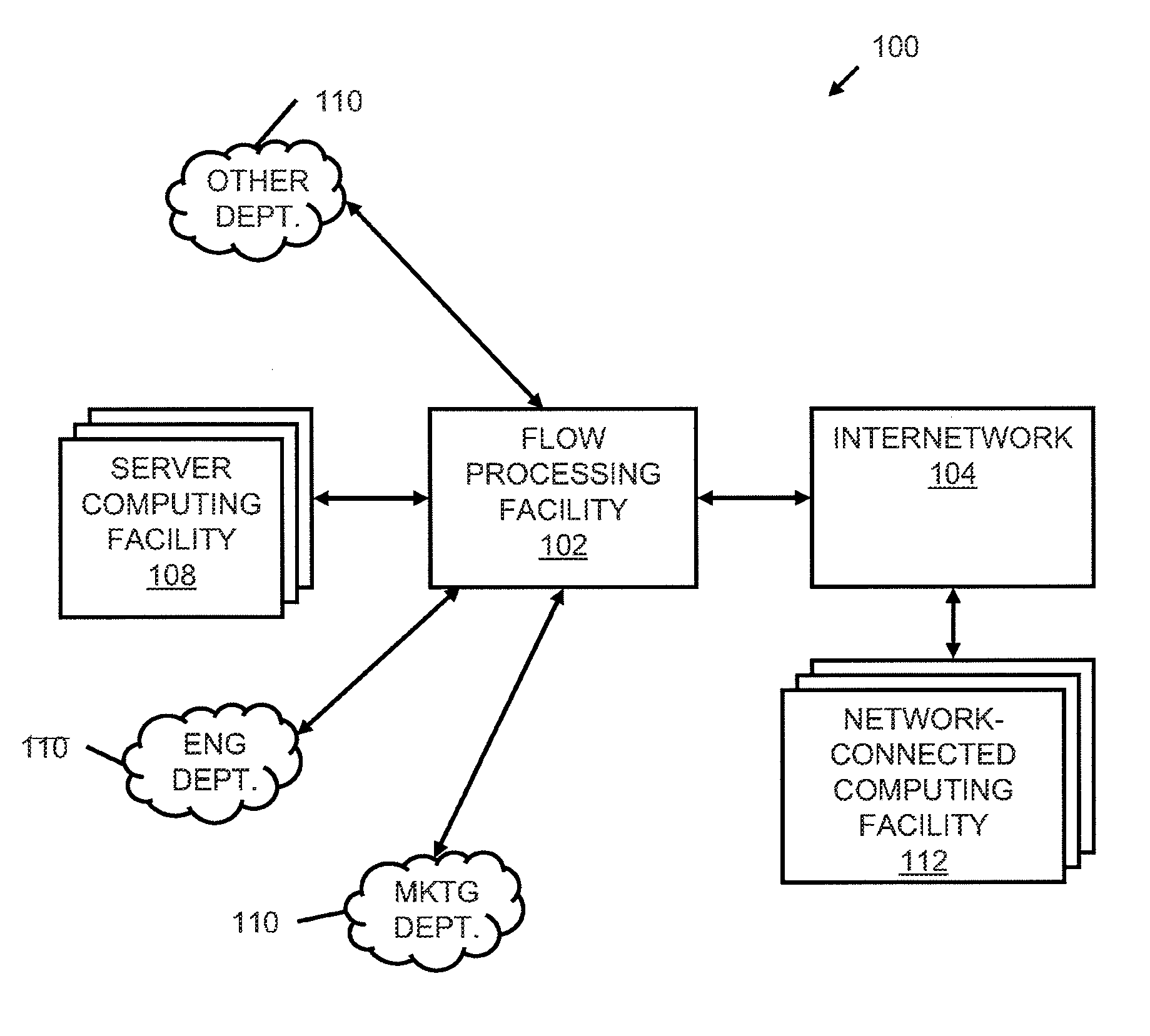
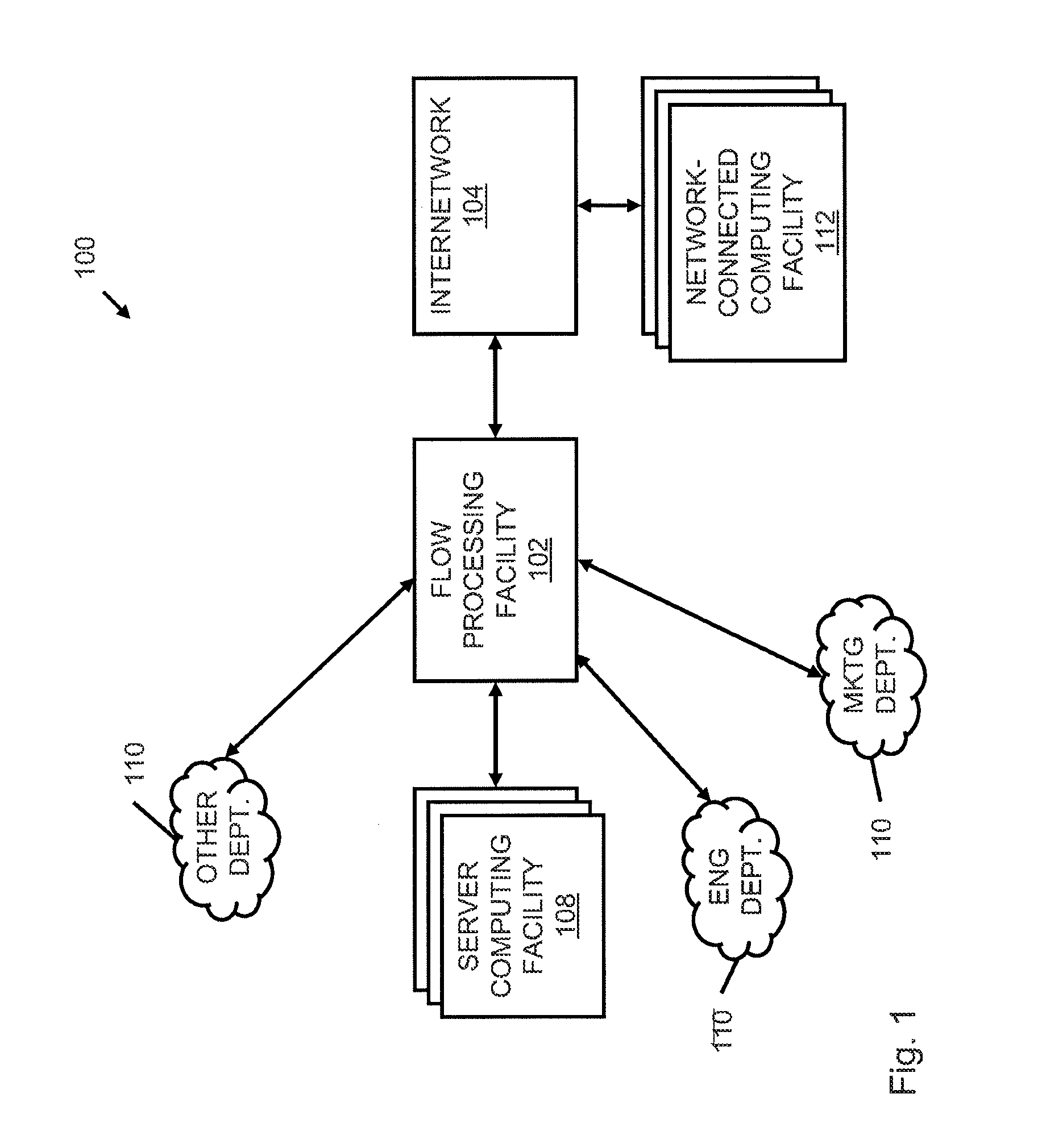
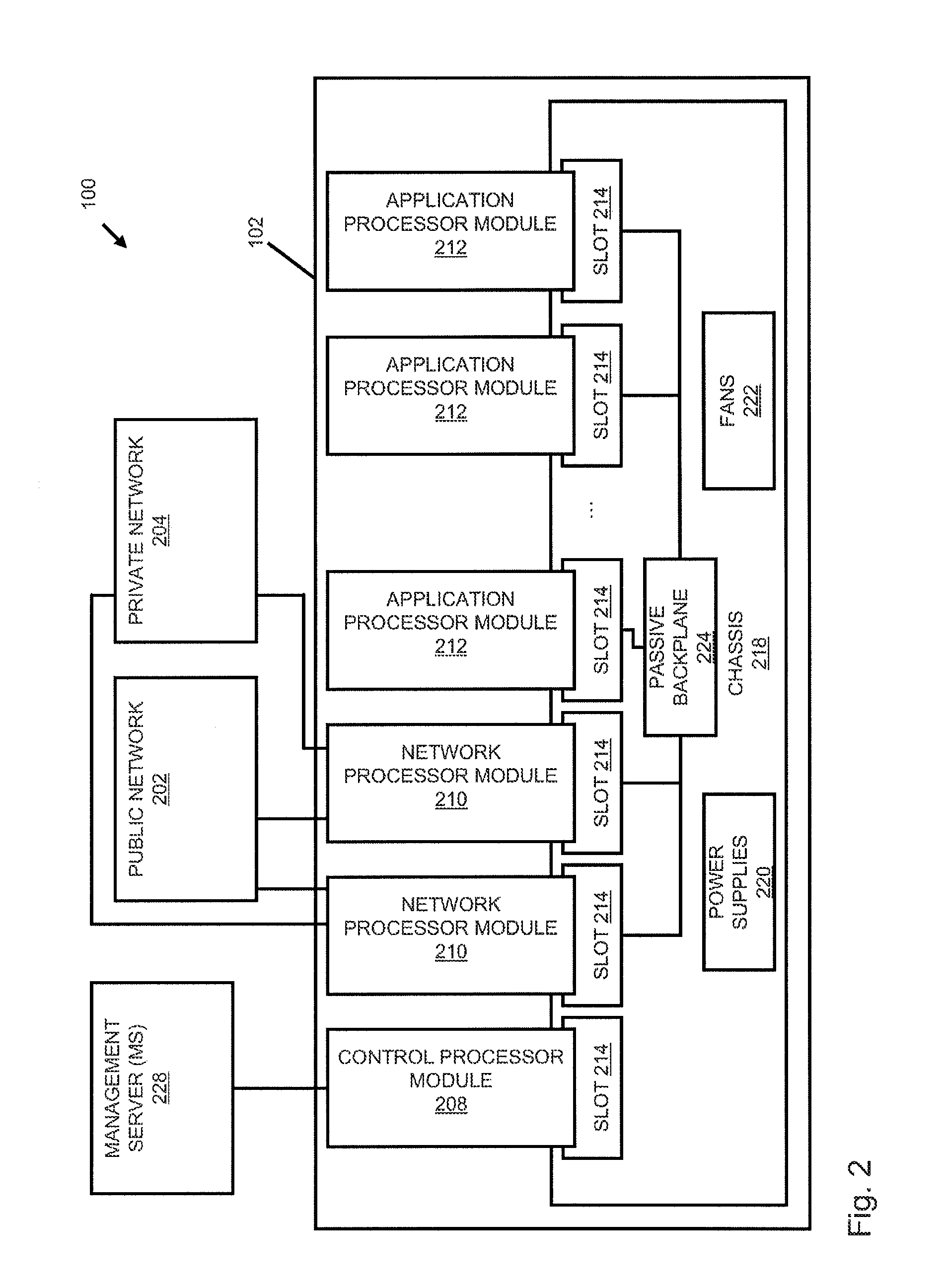
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
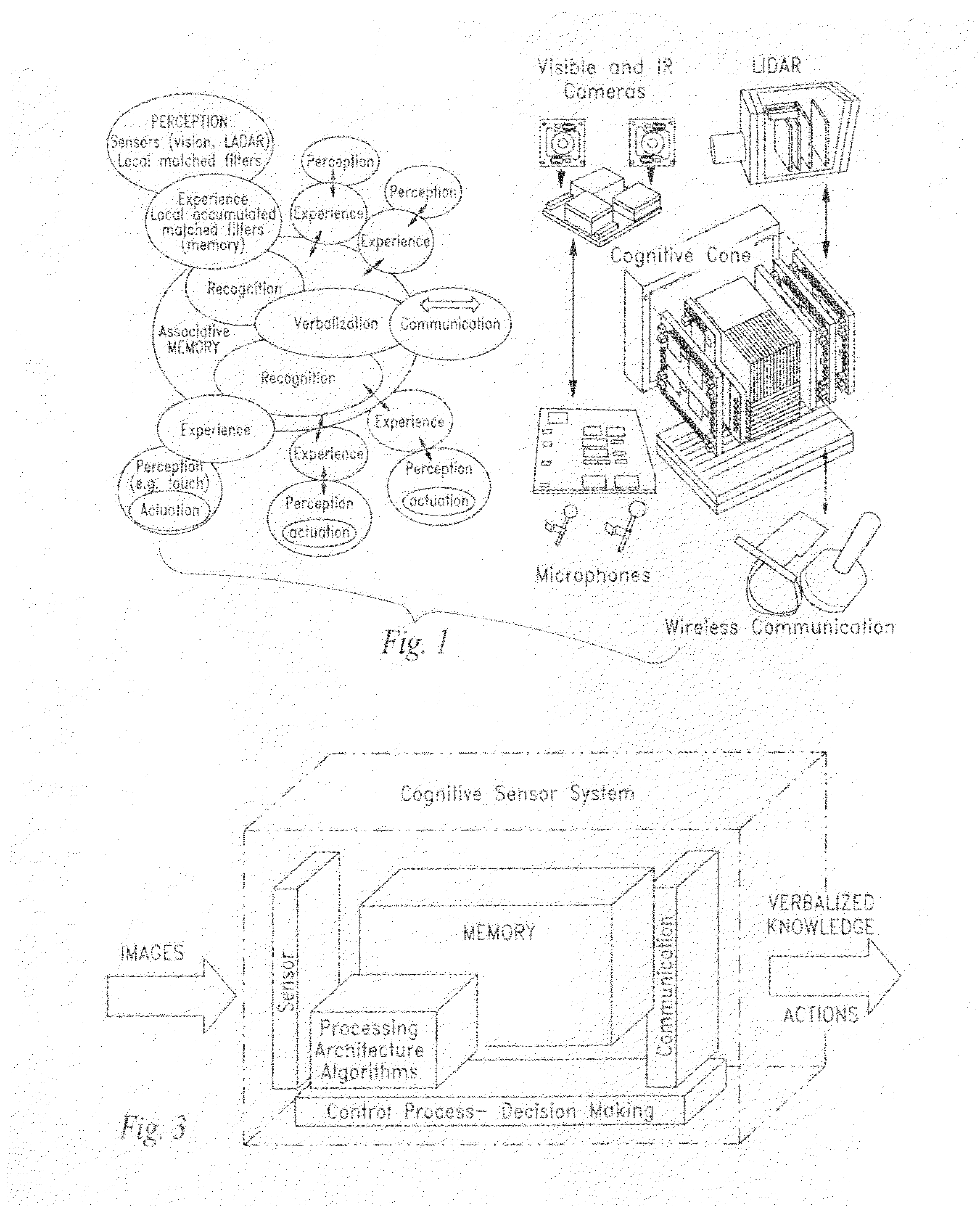
Apparatus comprising artificial neuronal assembly
ActiveUS20100241601A1Augment sensory awarenessDigital computer detailsDigital dataVisual cortexRetina
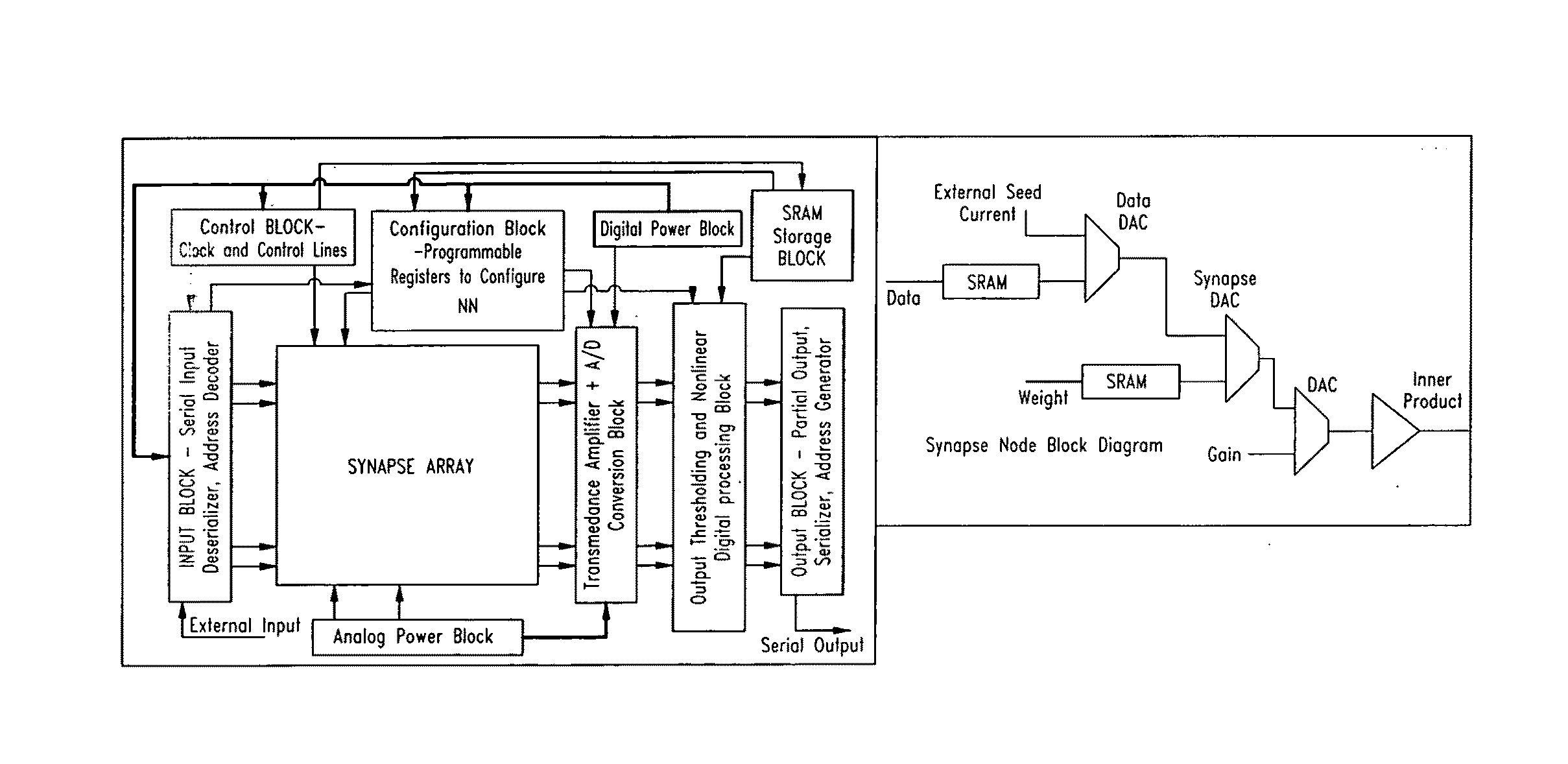
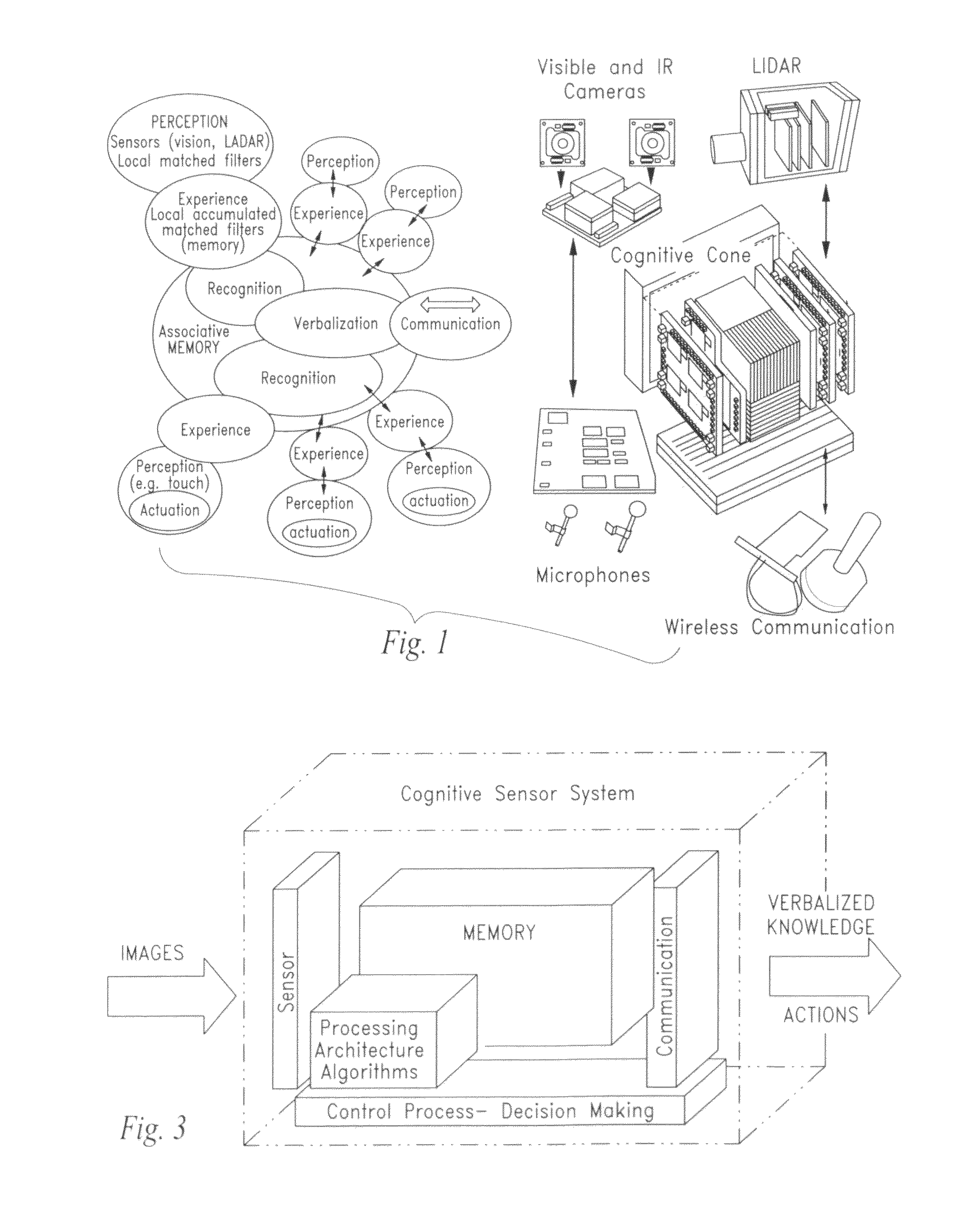
An artificial synapse array and virtual neural space are disclosed.More specifically, a cognitive sensor system and method are disclosed comprising a massively parallel convolution processor capable of, for instance, situationally dependent identification of salient features in a scene of interest by emulating the cortical hierarchy found in the human retina and visual cortex.
Owner:PFG IP +1
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
Systems and methods for processing data flows
InactiveUS20080133517A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
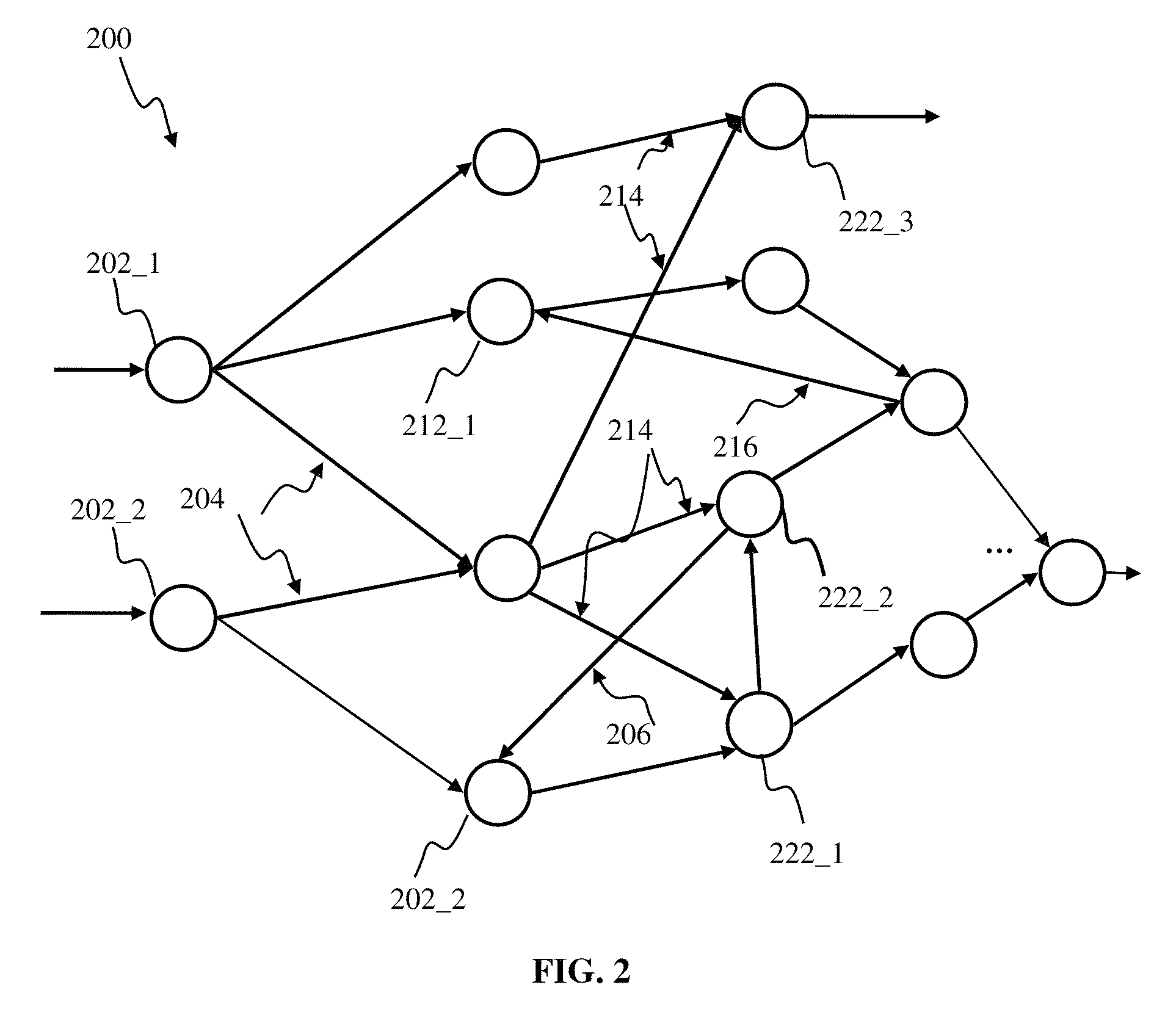
Apparatus and methods for efficient updates in spiking neuron network
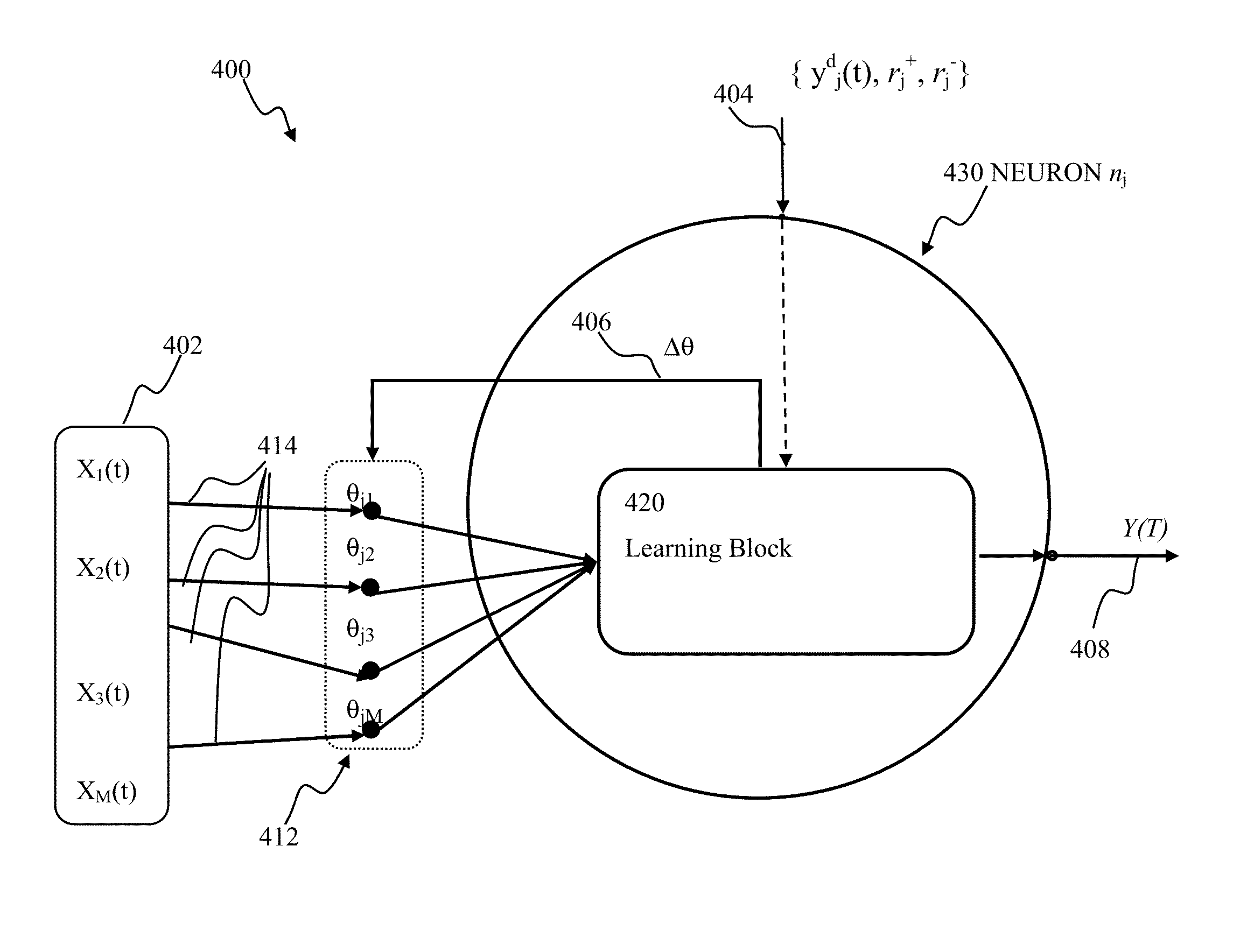
Efficient updates of connections in artificial neuron networks may be implemented. A framework may be used to describe the connections using a linear synaptic dynamic process, characterized by stable equilibrium. The state of neurons and synapses within the network may be updated, based on inputs and outputs to / from neurons. In some implementations, the updates may be implemented at regular time intervals. In one or more implementations, the updates may be implemented on-demand, based on the network activity (e.g., neuron output and / or input) so as to further reduce computational load associated with the synaptic updates. The connection updates may be decomposed into multiple event-dependent connection change components that may be used to describe connection plasticity change due to neuron input. Using event-dependent connection change components, connection updates may be executed on per neuron basis, as opposed to per-connection basis.
Owner:QUALCOMM INC
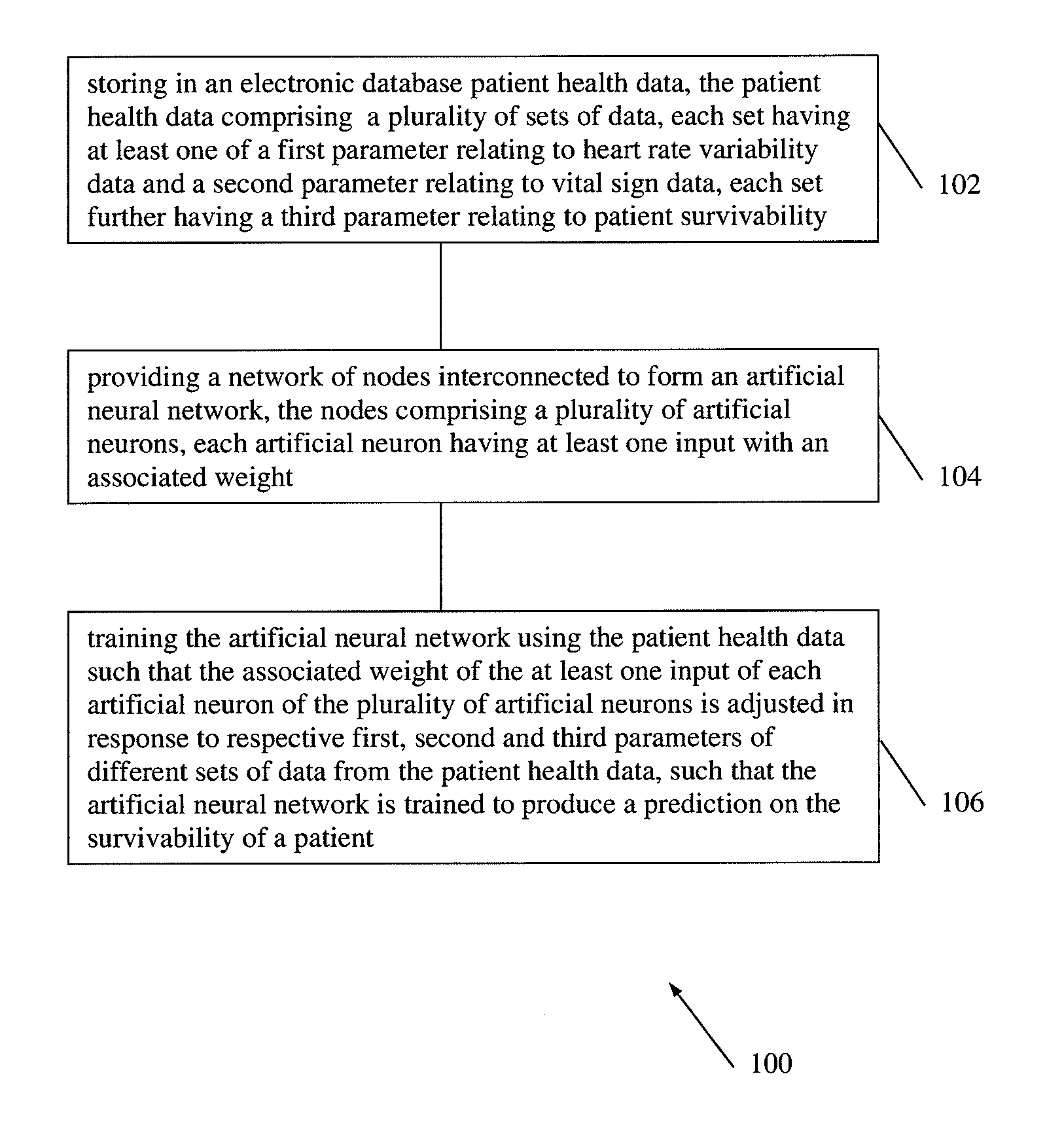
Method of predicting acute cardiopulmonary events and survivability of a patient
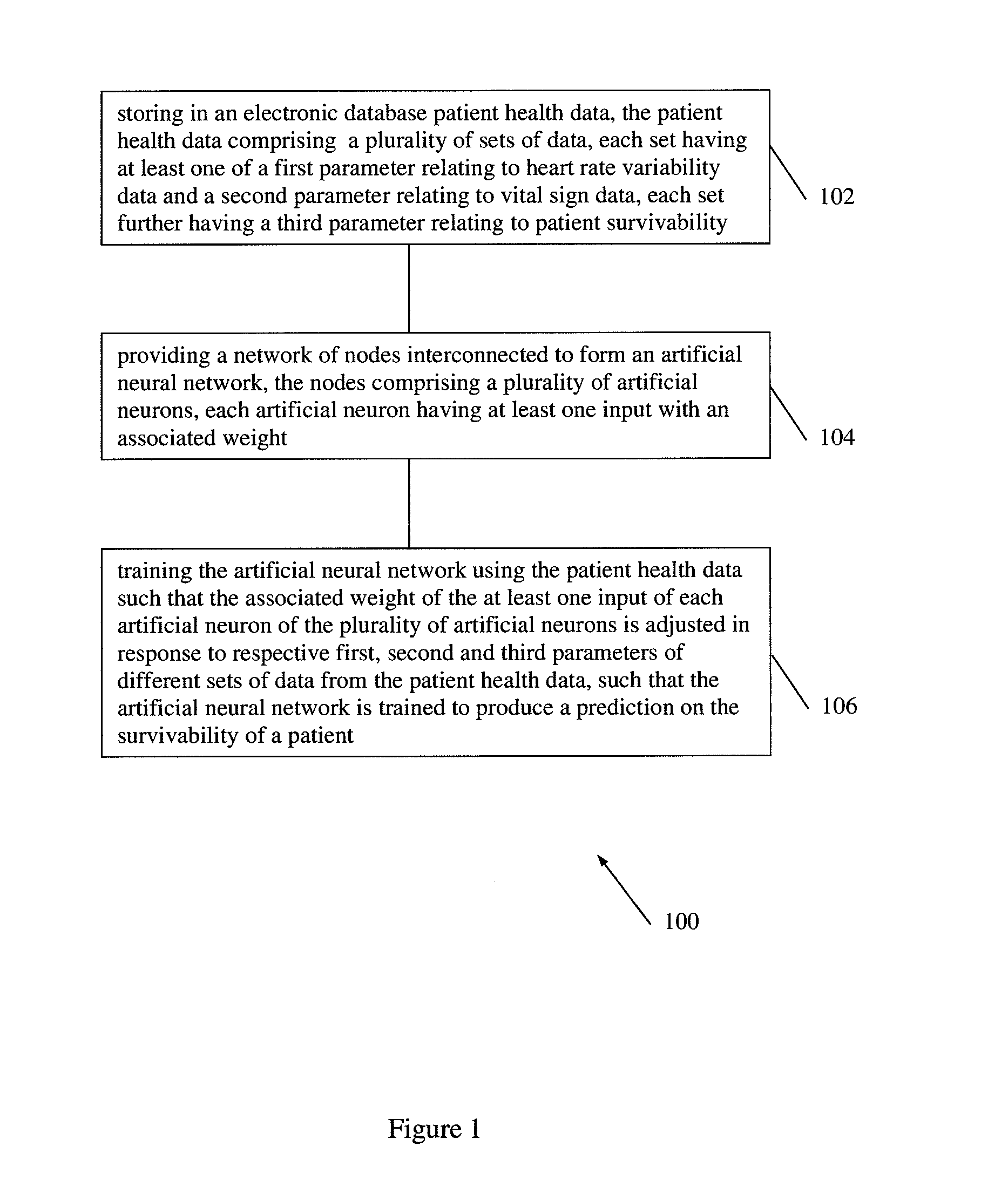
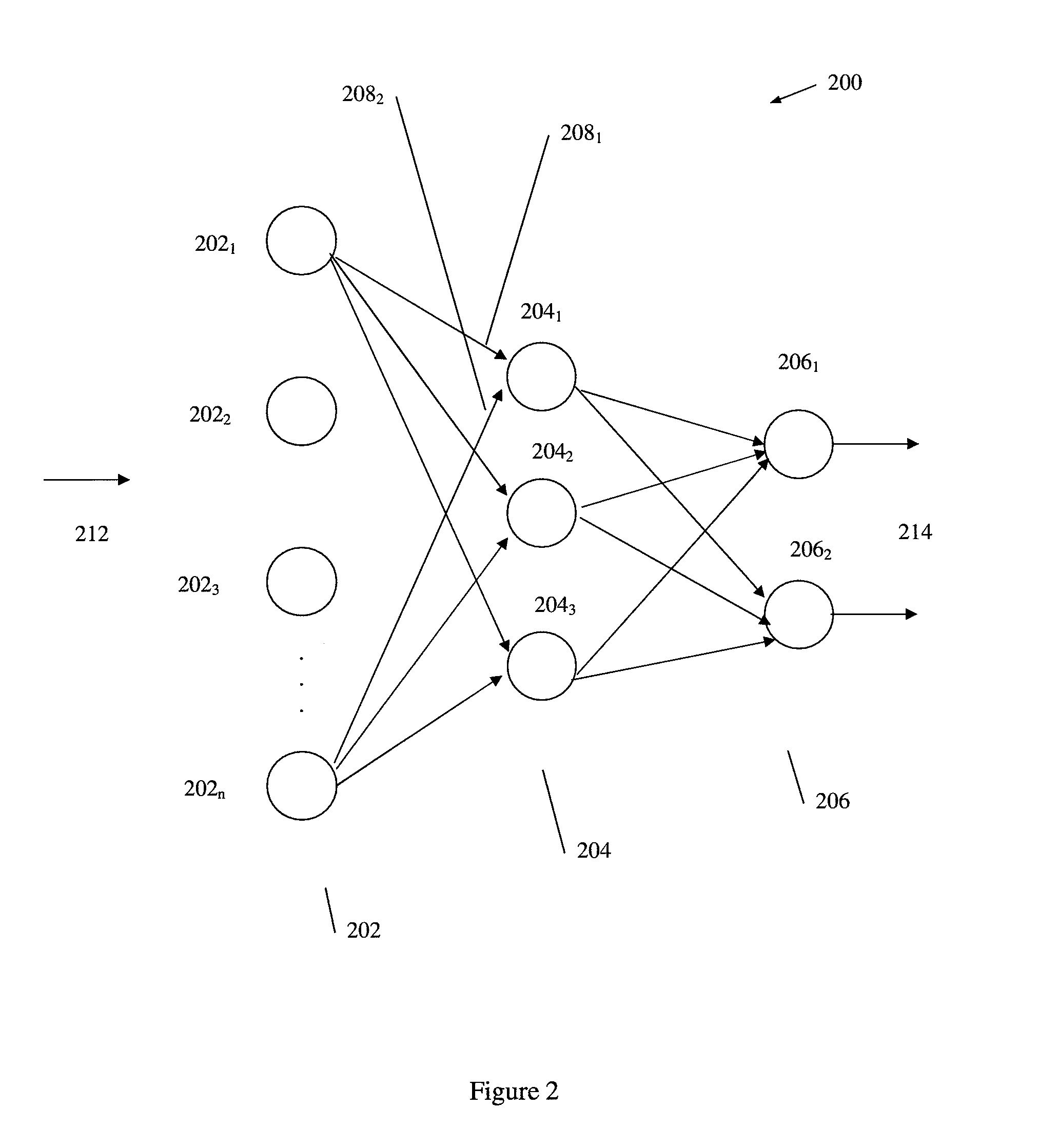
According to embodiments of the invention, there is provided a method of producing an artificial neural network capable of predicting the survivability of a patient, the method including: storing in an electronic database patient health data, the patient health data comprising a plurality of sets of data, each set having at least one of a first parameter relating to heart rate variability data and a second parameter relating to vital sign data, each set further having a third parameter relating to patient survivability; providing a network of nodes interconnected to form an artificial neural network, the nodes comprising a plurality of artificial neurons, each artificial neuron having at least one input with an associated weight; and training the artificial neural network using the patient health data such that the associated weight of the at least one input of each artificial neuron of the plurality of artificial neurons is adjusted in response to respective first, second and third parameters of different sets of data from the patient health data, such that the artificial neural network is trained to produce a prediction on the survivability of a patient.
Owner:SINGAPORE HEALTH SERVICES PTE +1
Apparatus and methods for generalized state-dependent learning in spiking neuron networks
ActiveUS20140032459A1Easy to implementDigital computer detailsDigital dataNeuron networkArtificial intelligence
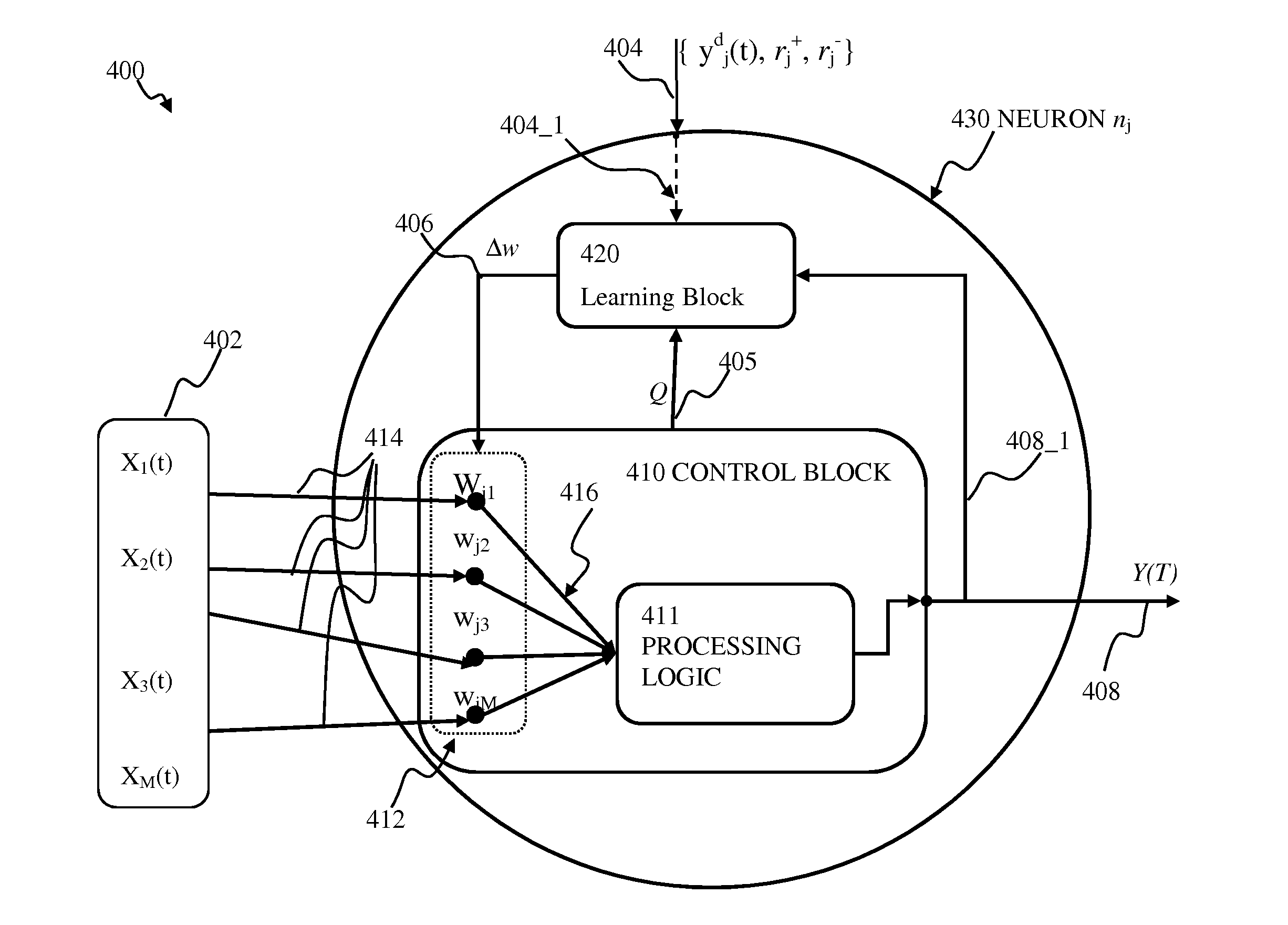
Generalized state-dependent learning framework in artificial neuron networks may be implemented. A framework may be used to describe plasticity updates of neuron connections based on connection state term and neuron state term. The state connections within the network may be updated based on inputs and outputs to / from neurons. The input connections of a neuron may be updated using connection traces comprising a time-history of inputs provided via the connections. Weights of the connections may be updated and connection state may be time varying. The updated weights may be determined using a rate of change of the trace and a term comprising a product of a per-neuron contribution and a per-connection contribution configured to account for the state time-dependency. Using event-dependent connection change components, connection updates may be executed on per neuron basis, as opposed to per-connection basis.
Owner:BRAIN CORP
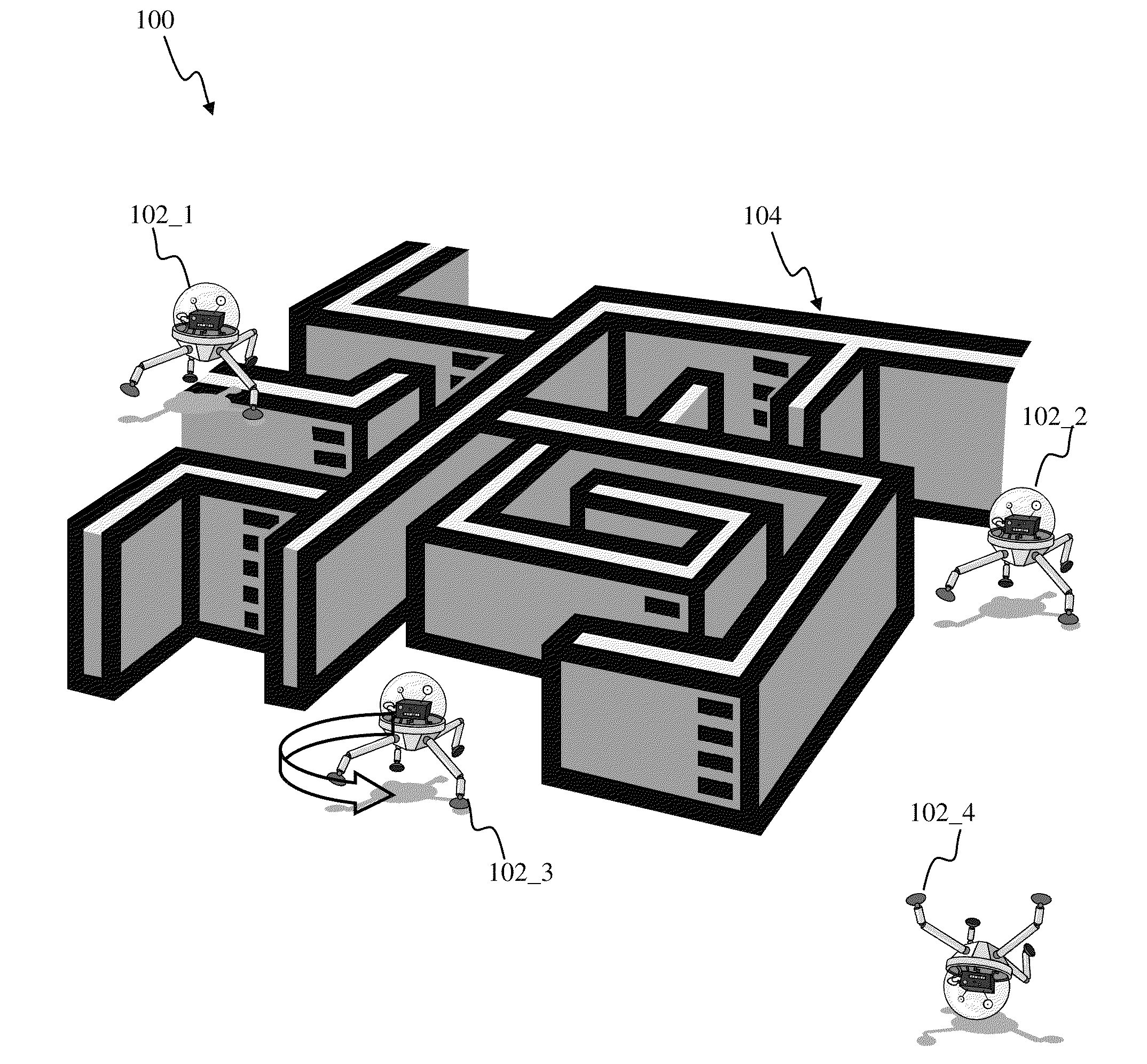
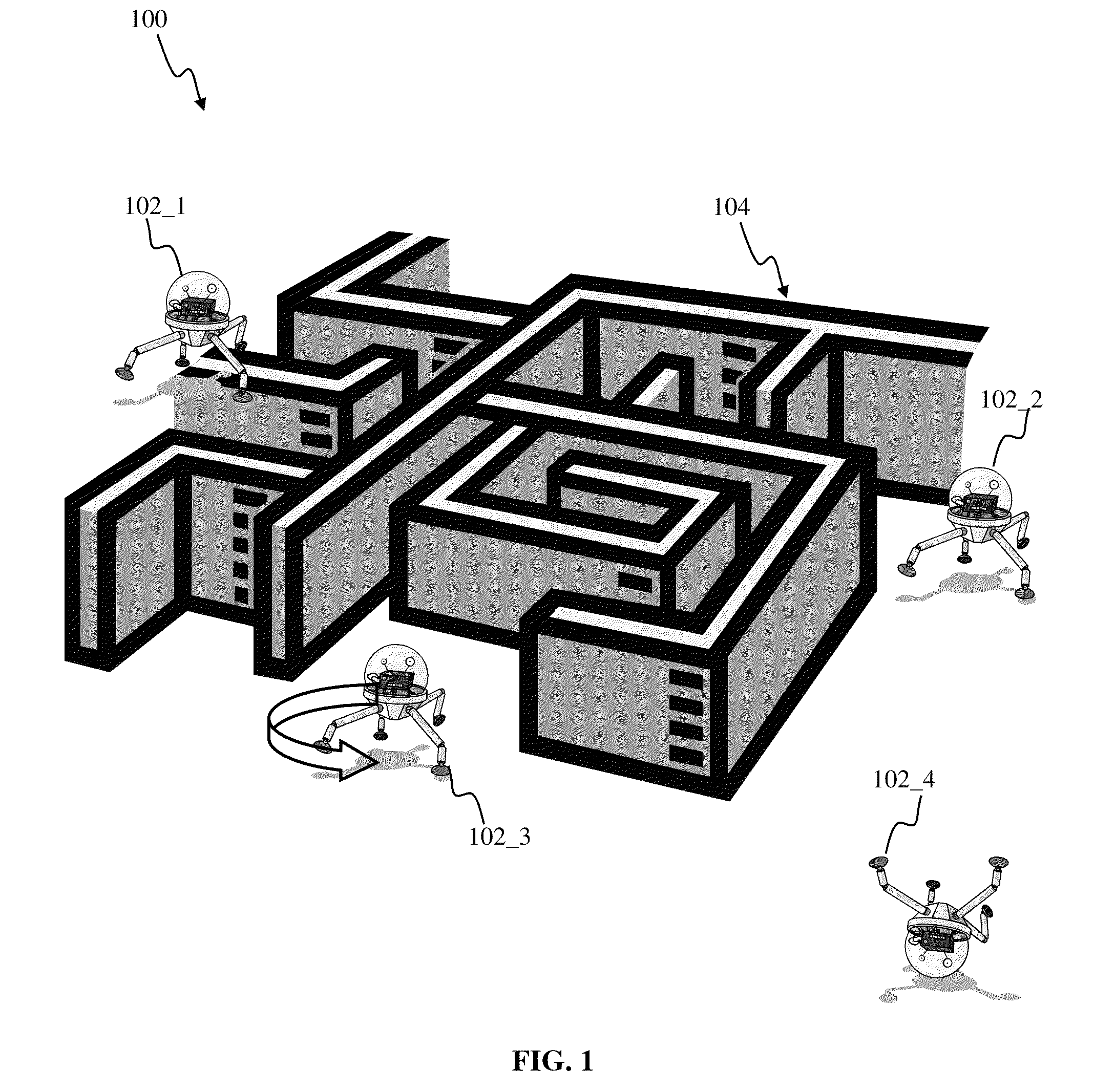
Robotic learning and evolution apparatus
ActiveUS8793205B1Inhibition of reproductionEasy to optimizeDigital computer detailsArtificial lifeArtificial neuronHuman–computer interaction
Apparatus and methods for implementing robotic learning and evolution. An ecosystem of robots may comprise robotic devices of one or more types utilizing artificial neuron networks for implementing learning of new traits. A number of robots of one or more species may be contained in an enclosed environment. The robots may interact with objects within the environment and with one another, while being observed by the human audience. In one or more implementations, the robots may be configured to ‘reproduce’ via duplication, copy, merge, and / or modification of robotic. The replication process may employ mutations. Probability of reproduction of the individual robots may be determined based on the robot's success in whatever function trait or behavior is desired. User-driven evolution of robotic species may enable development of a wide variety of new and / or improved functionality and provide entertainment and educational value for users.
Owner:BRAIN CORP
Apparatus and methods for state-dependent learning in spiking neuron networks
State-dependent supervised learning framework in artificial neuron networks may be implemented. A framework may be used to describe plasticity updates of neuron connections based on a connection state term and a neuron state term. Connection states may be updated based on inputs and outputs to and / or from neurons. The input connections of a neuron may be updated using input traces comprising a time-history of inputs provided via the connection. Weight of the connection may be updated and connection state may be time varying. The updated weights may be determined using a rate of change of the input trace and a term comprising a product of a per-neuron contribution and a per-connection contribution configured to account for the state time-dependency. Using event-dependent connection change components, connection updates may be executed on a per neuron basis, as opposed to a per-connection basis.
Owner:BRAIN CORP
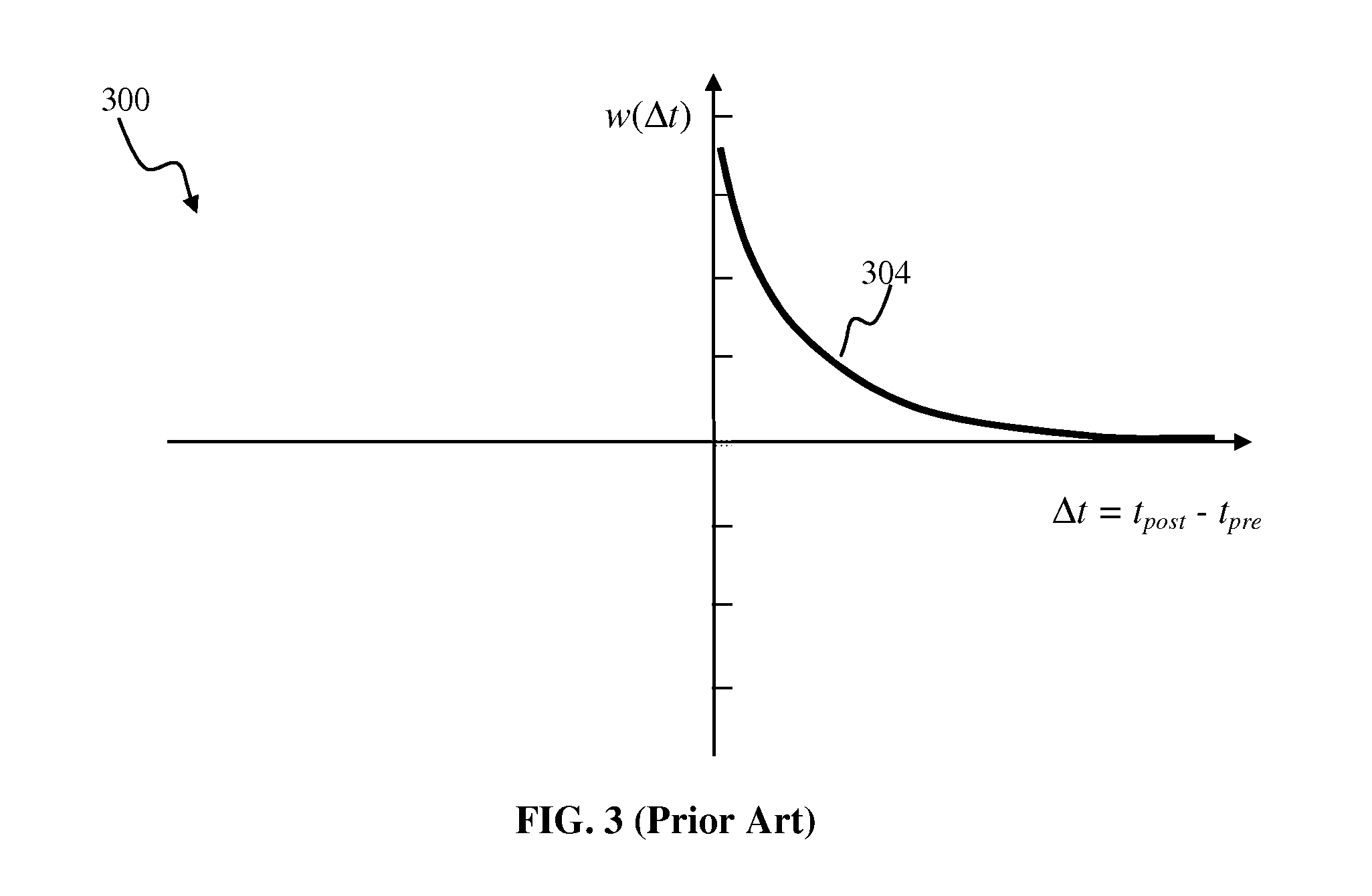
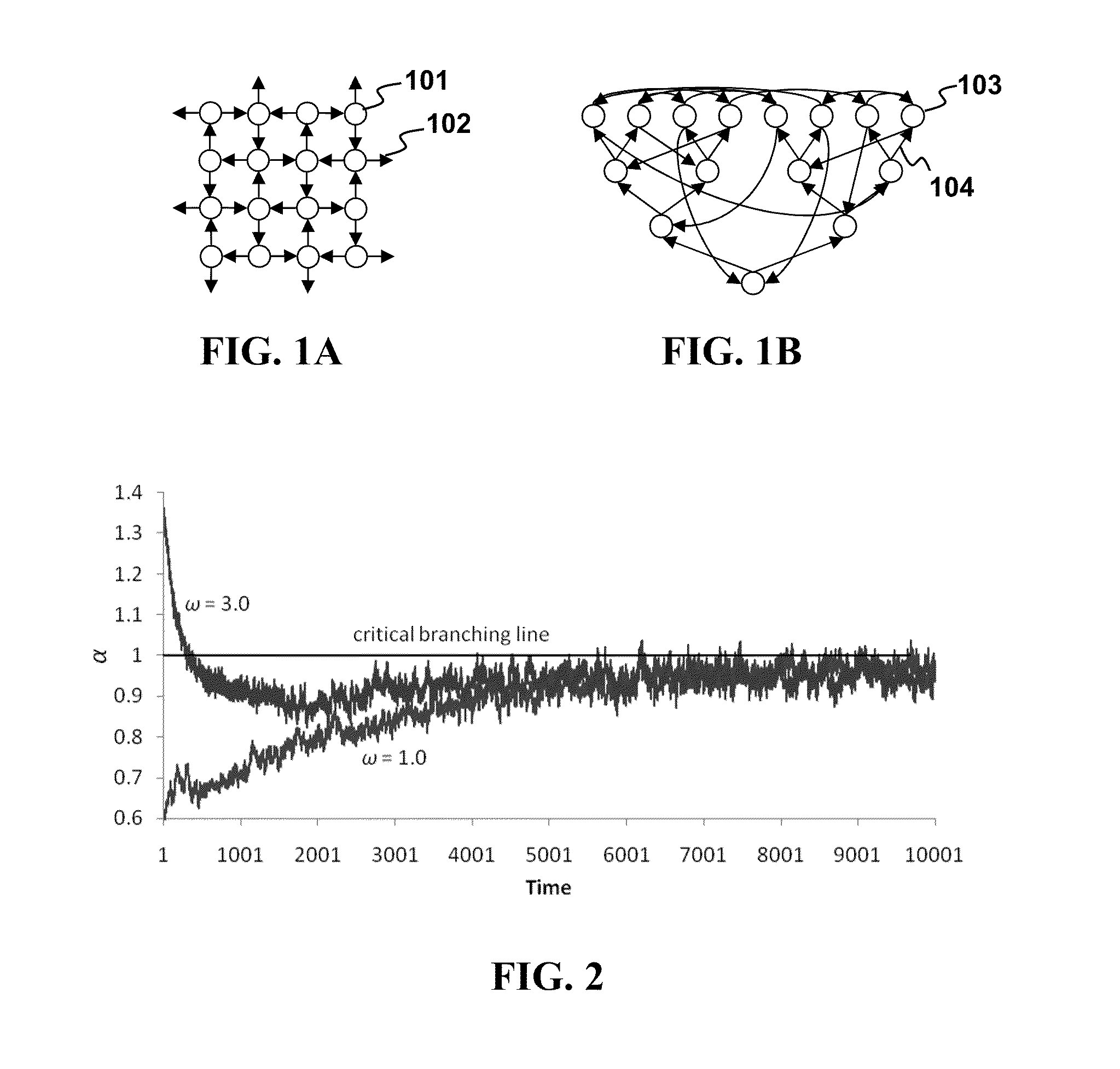
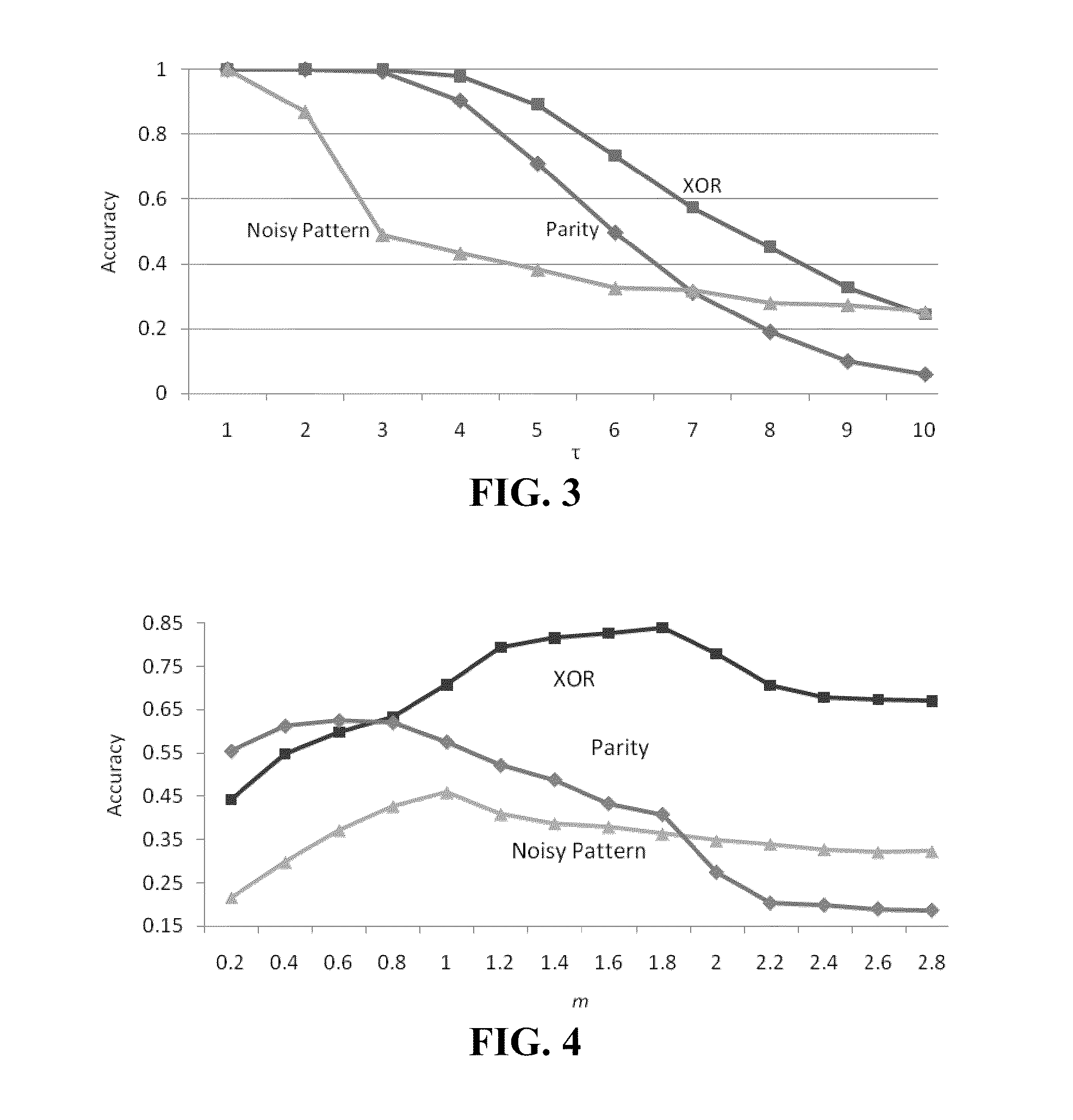
Critical Branching Neural Computation Apparatus and Methods
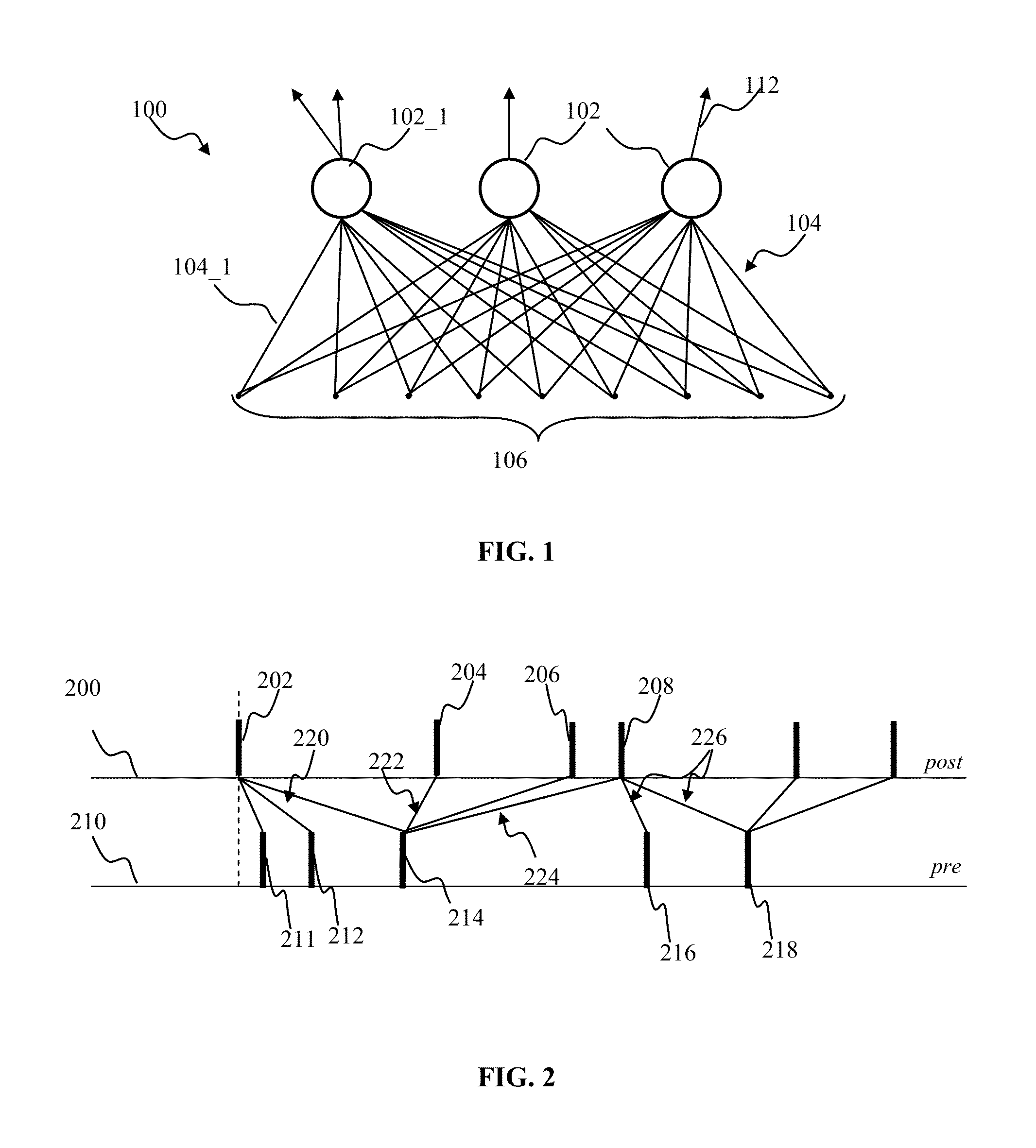
A neural network comprising artificial neurons interconnected by connections, wherein each artificial neuron is configured to receive an input signal from and send an output signal to one or more of the other artificial neurons through one of the connections; each input and output signal is either positive or negative valued; and each artificial neuron has an activation at a time point, the activation being determined by at least input signals received by the artificial neuron, output signals sent by the artificial neuron, and a plurality of weights, wherein at least one weight is self-tuned at the time point. Also provided are methods of tuning neural networks.
Owner:RGT UNIV OF CALIFORNIA
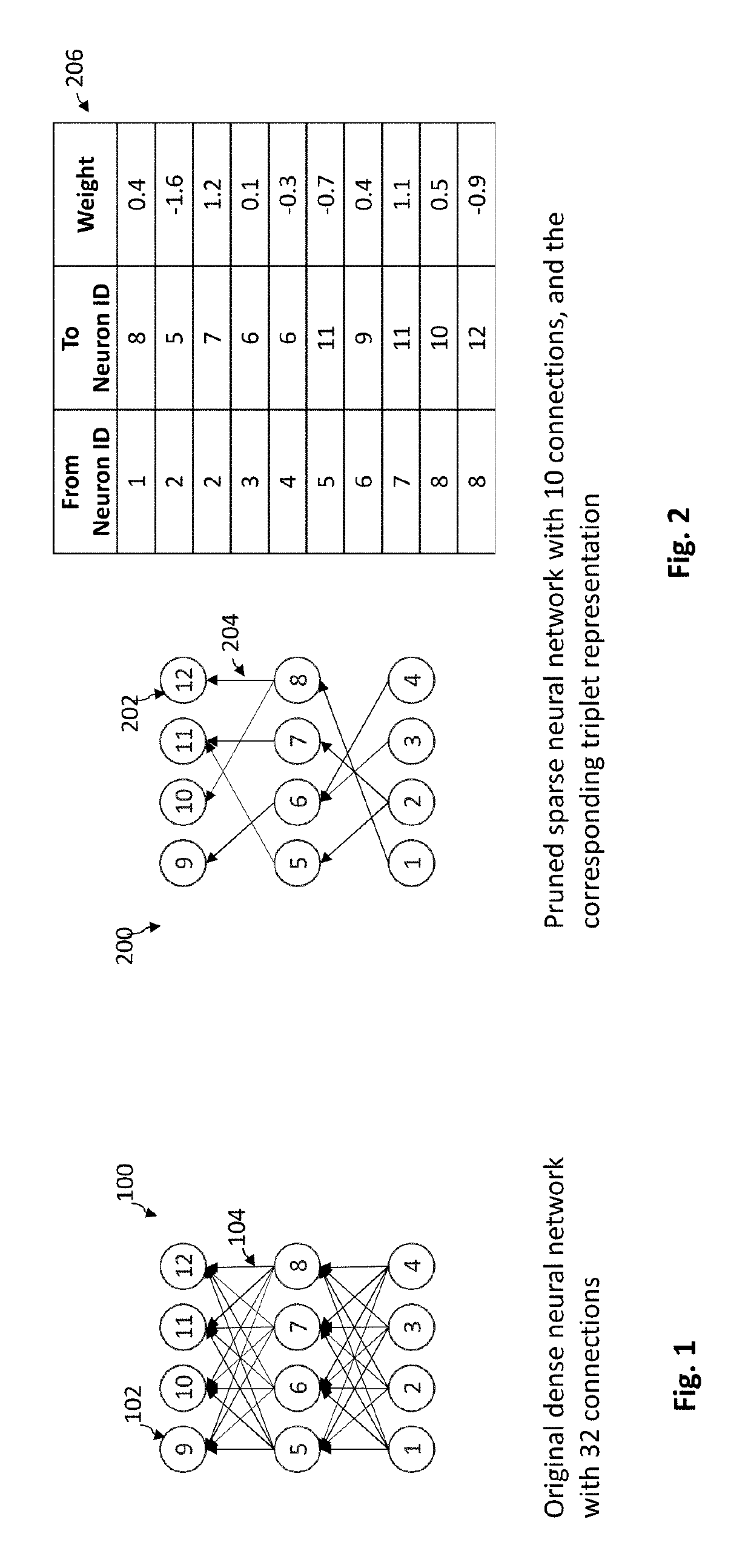
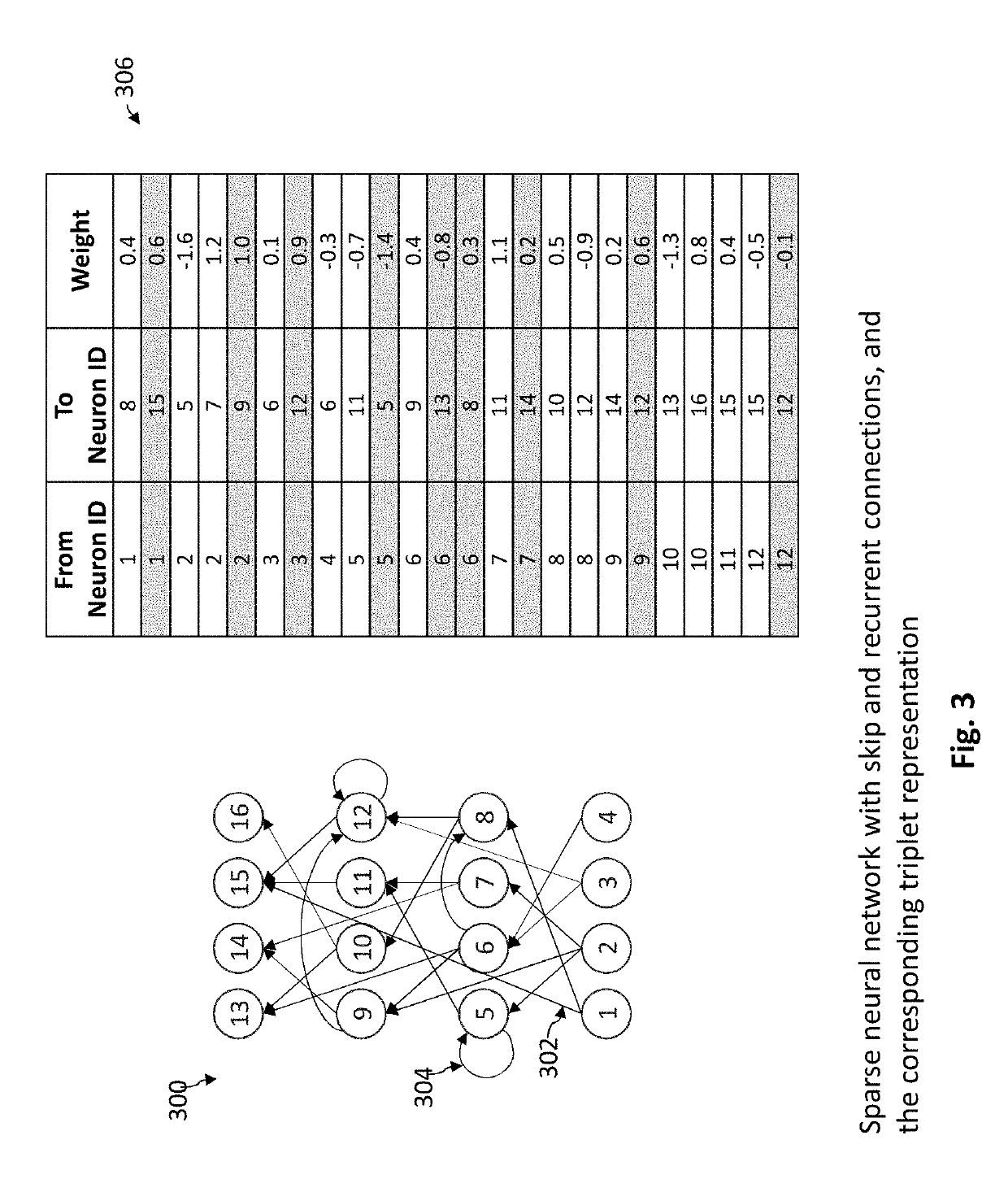
System and method for compact and efficient sparse neural networks
A device, system, and method is provided for storing a sparse neural network. A plurality of weights of the sparse neural network may be obtained. Each weight may represent a unique connection between a pair of a plurality of artificial neurons in different layers of a plurality of neuron layers. A minority of pairs of neurons in adjacent neuron layers are connected in the sparse neural network. Each of the plurality of weights of the sparse neural network may be stored with an association to a unique index. The unique index may uniquely identify a pair of artificial neurons that have a connection represented by the weight. Only non-zero weights may be stored that represent connections between pairs of neurons (and zero weights may not be stored that represent no connections between pairs of neurons).
Owner:NANO DIMENSIONS TECH LTD
Convolutional neural network
ActiveUS20170200078A1Improve energy efficiencyIncrease speedNeural architecturesPhysical realisationNerve networkWeight coefficient
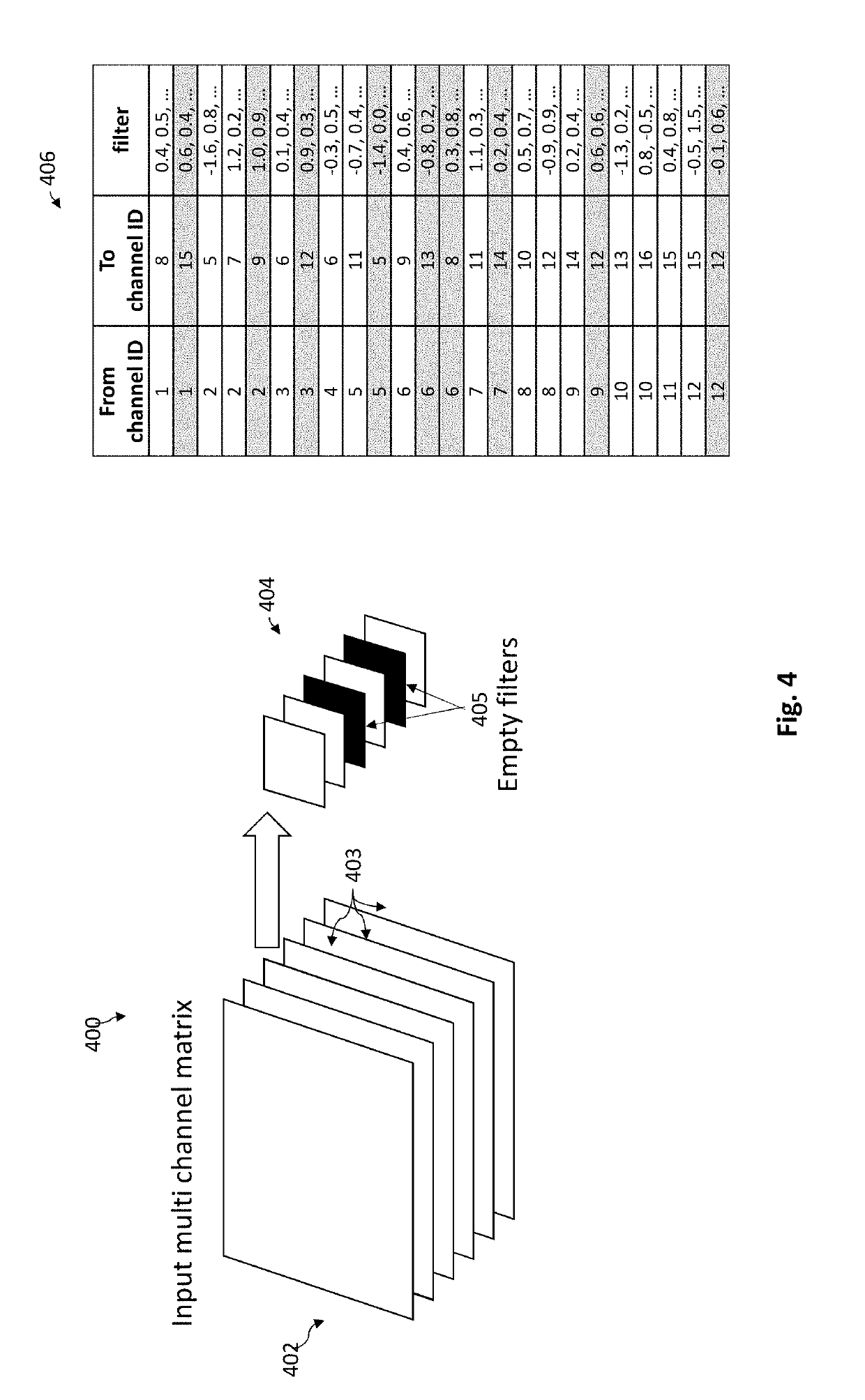
A convolutional neural network comprises a plurality of artificial neurons arranged in one or more convolution layers, each convolution layer comprising one or more output matrices, each output matrix comprising a set of output neurons, each output matrix being connected to an input matrix, comprising a set of input neurons, by artificial synapses associated with a convolution matrix. The convolution matrix comprises the weight coefficients associated with the output neurons of the output matrix, the output value of each output neuron being determined from the input neurons of the input matrix to which the output neuron is connected and the weight coefficients of the convolution matrix associated with the output matrix. Each synapse consists of a set of memristive devices comprising at least one memristive device, each set of memristive devices storing a weight coefficient of the convolution matrix. In response to a change of the output value of an input neuron of an input matrix, the neural network is capable of dynamically associating each set of memristive devices storing a coefficient of the convolution matrix with an output neuron connected to the input neuron. The neural network further comprises an accumulator for each output neuron, the accumulator being configured to accumulate the values of the weight coefficients stored in the sets of memristive devices dynamically associated with the output neuron, the output value of the output neuron being determined from the value accumulated in the accumulator.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Prediction by single neurons
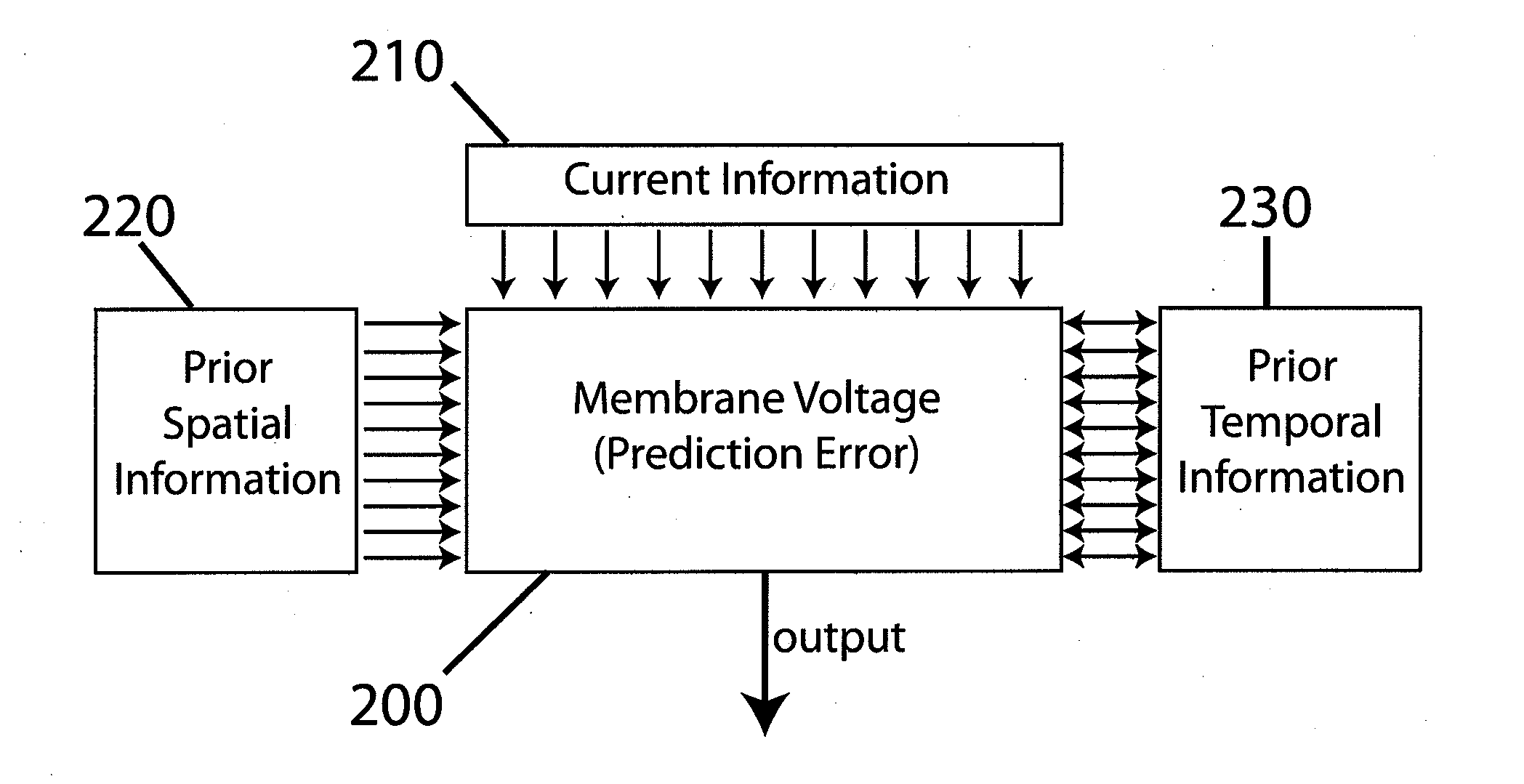
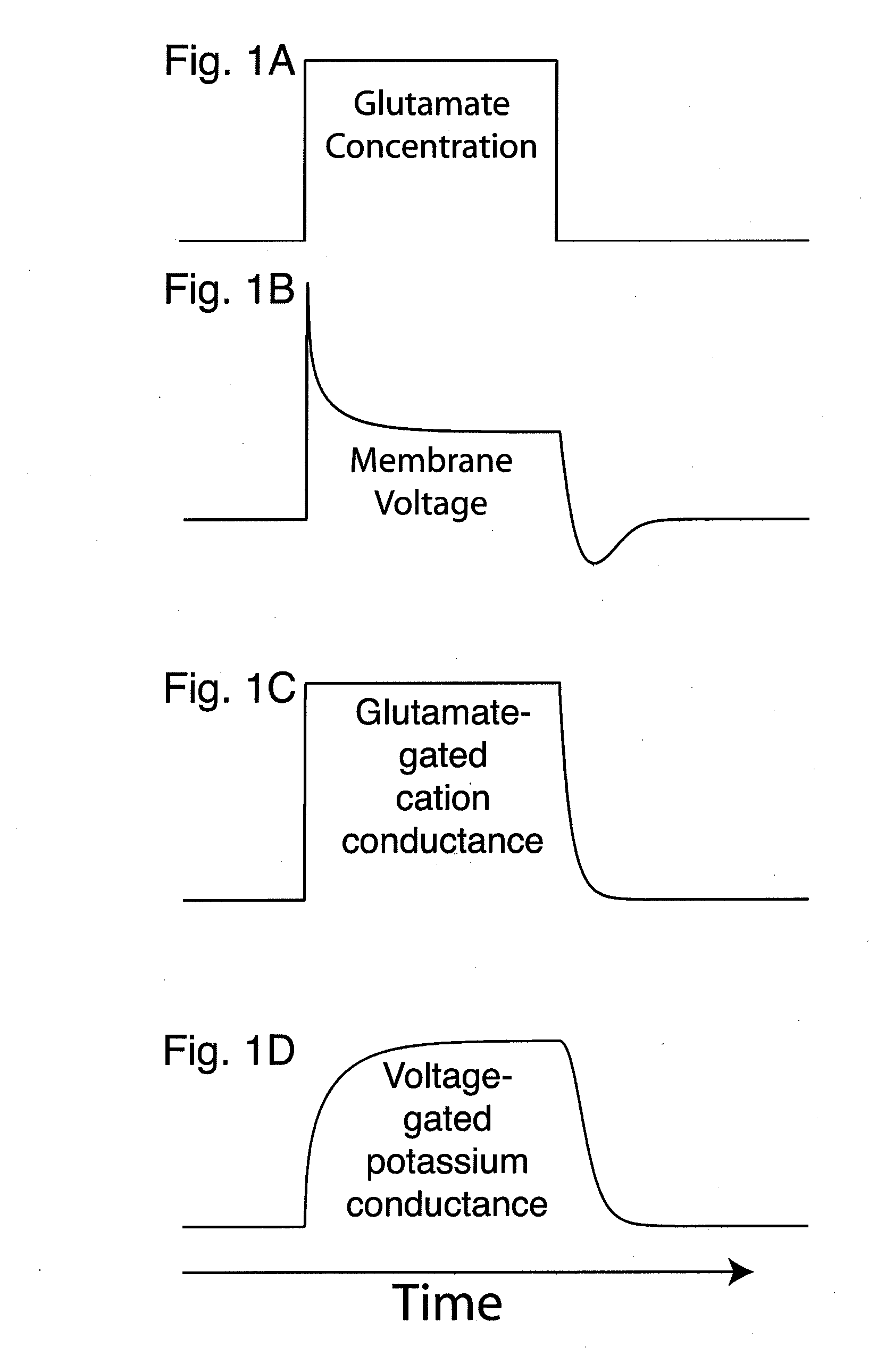
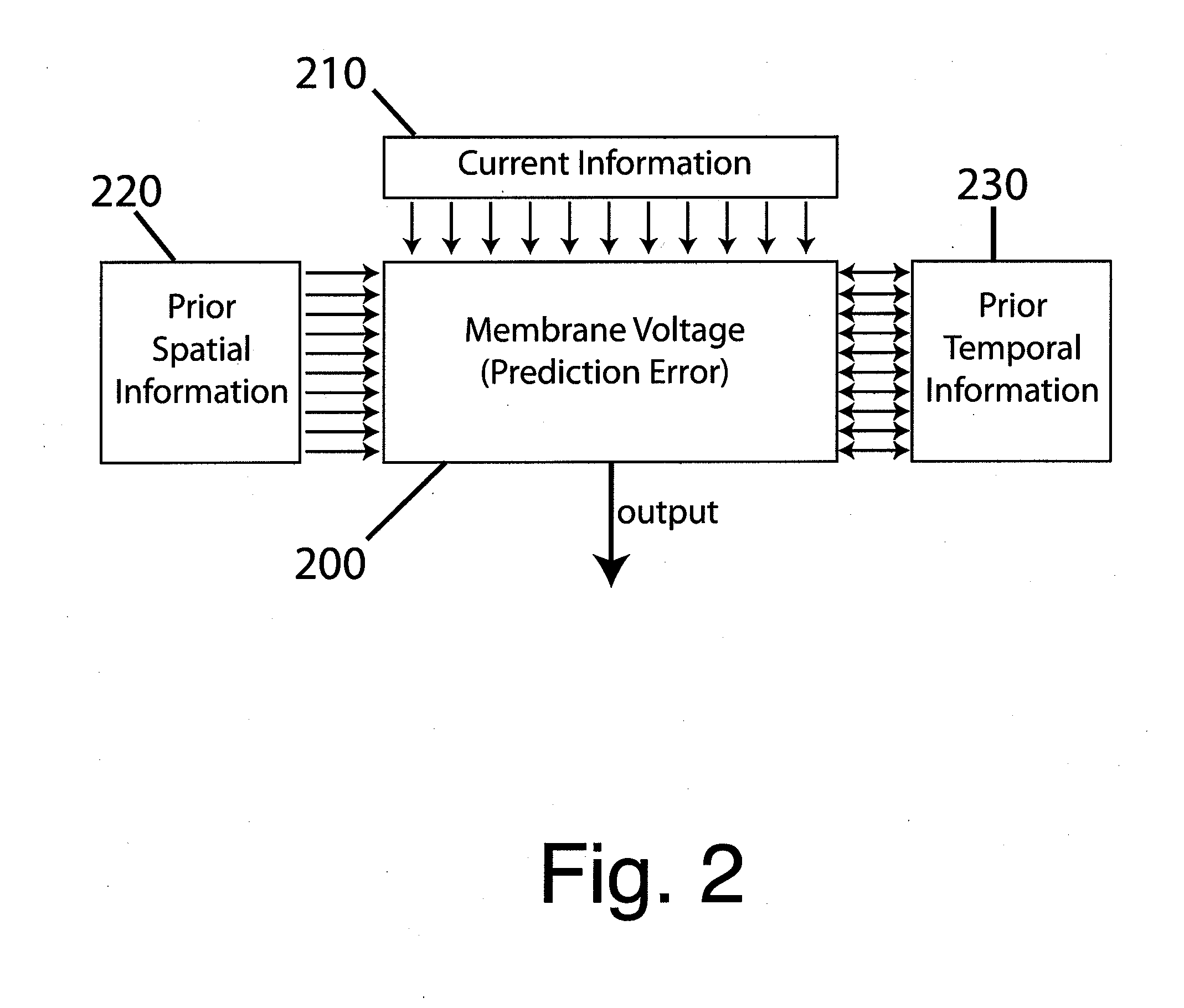
Associative plasticity rules are described to control the strength of inputs to an artificial neuron. Inputs to a neuron consist of both synaptic inputs and non-synaptic, voltage-regulated inputs. The neuron's output is voltage. Hebbian and anti-Hebbian-type plasticity rules are implemented to select amongst a spectrum of voltage-regulated inputs, differing in their voltage-dependence and kinetic properties. An anti-Hebbian-type rule selects inputs that predict and counteract deviations in membrane voltage, thereby generating an output that corresponds to a prediction error. A Hebbian-type rule selects inputs that predict and amplify deviations in membrane voltage, thereby contributing to pattern generation. In further embodiments, Hebbian and anti-Hebbian-type plasticity rules are also applied to synaptic inputs. In other embodiments, reward information is incorporated into Hebbian-type plasticity rules. It is envisioned that by following these plasticity rules, single neurons as well as networks may predict and maximize future reward.
Owner:FIORILLO CHRISTOPHER
Image analysis neural network systems
A method includes determining object class probabilities of pixels in a first input image by examining the first input image in a forward propagation direction through layers of artificial neurons of an artificial neural network. The object class probabilities indicate likelihoods that the pixels represent different types of objects in the first input image. The method also includes selecting, for each of two or more of the pixels, an object class represented by the pixel by comparing the object class probabilities of the pixels with each other, determining an error associated with the object class that is selected for each pixel of the two or more pixels, determining one or more image perturbations by back-propagating the errors associated with the object classes selected for the pixels of the first input image through the layers of the neural network without modifying the neural network, and modifying a second input image by applying the one or more image perturbations to one or more of the first input image or the second input image prior to providing the second input image to the neural network for examination by the neurons in the neural network for automated object recognition in the second input image.
Owner:GENERAL ELECTRIC CO
Systems and methods for processing data flows
InactiveUS7979368B2Increased complexityAvoid problemsDigital computer detailsDigital dataData packData stream
Owner:CA TECH INC
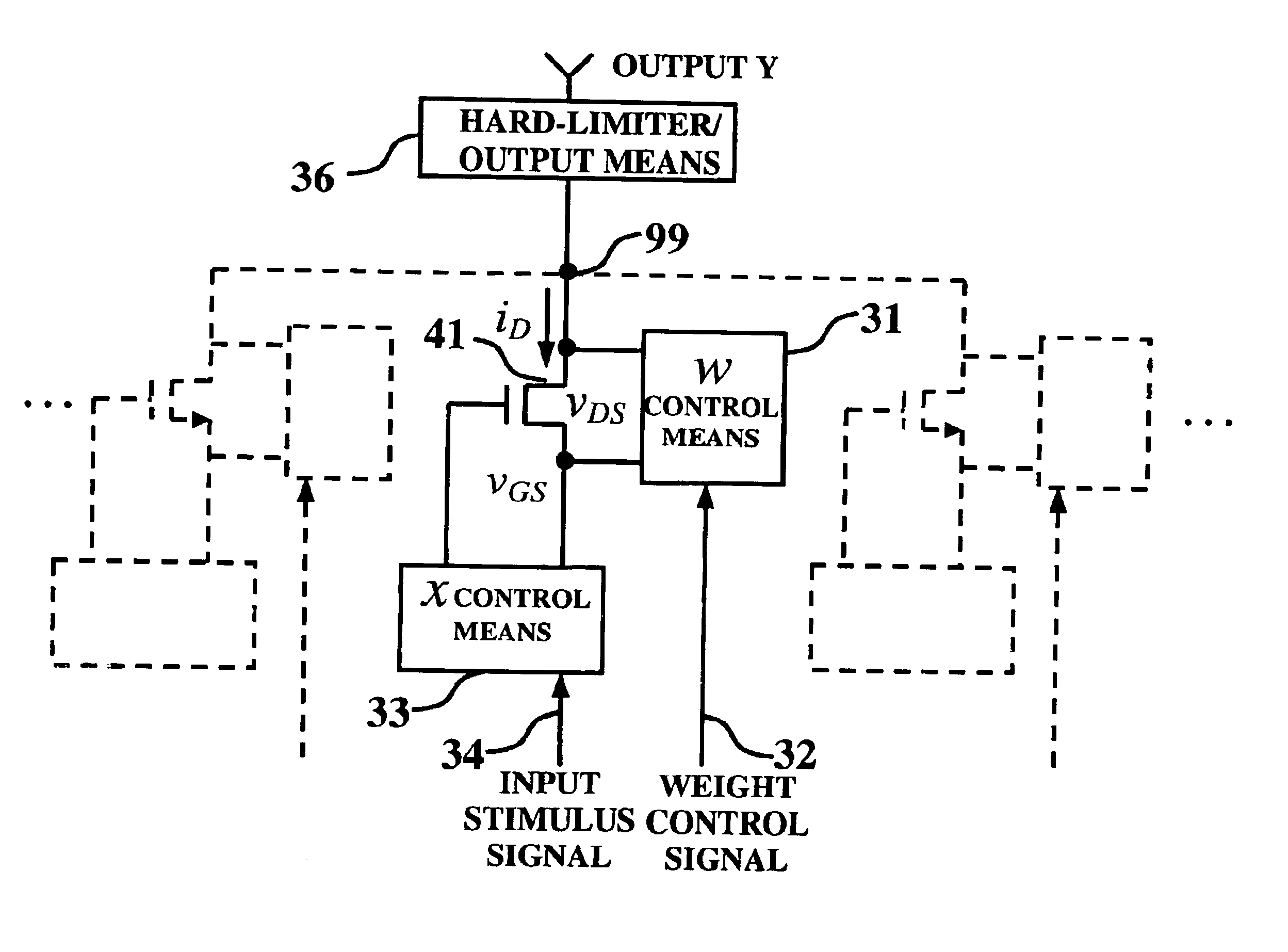
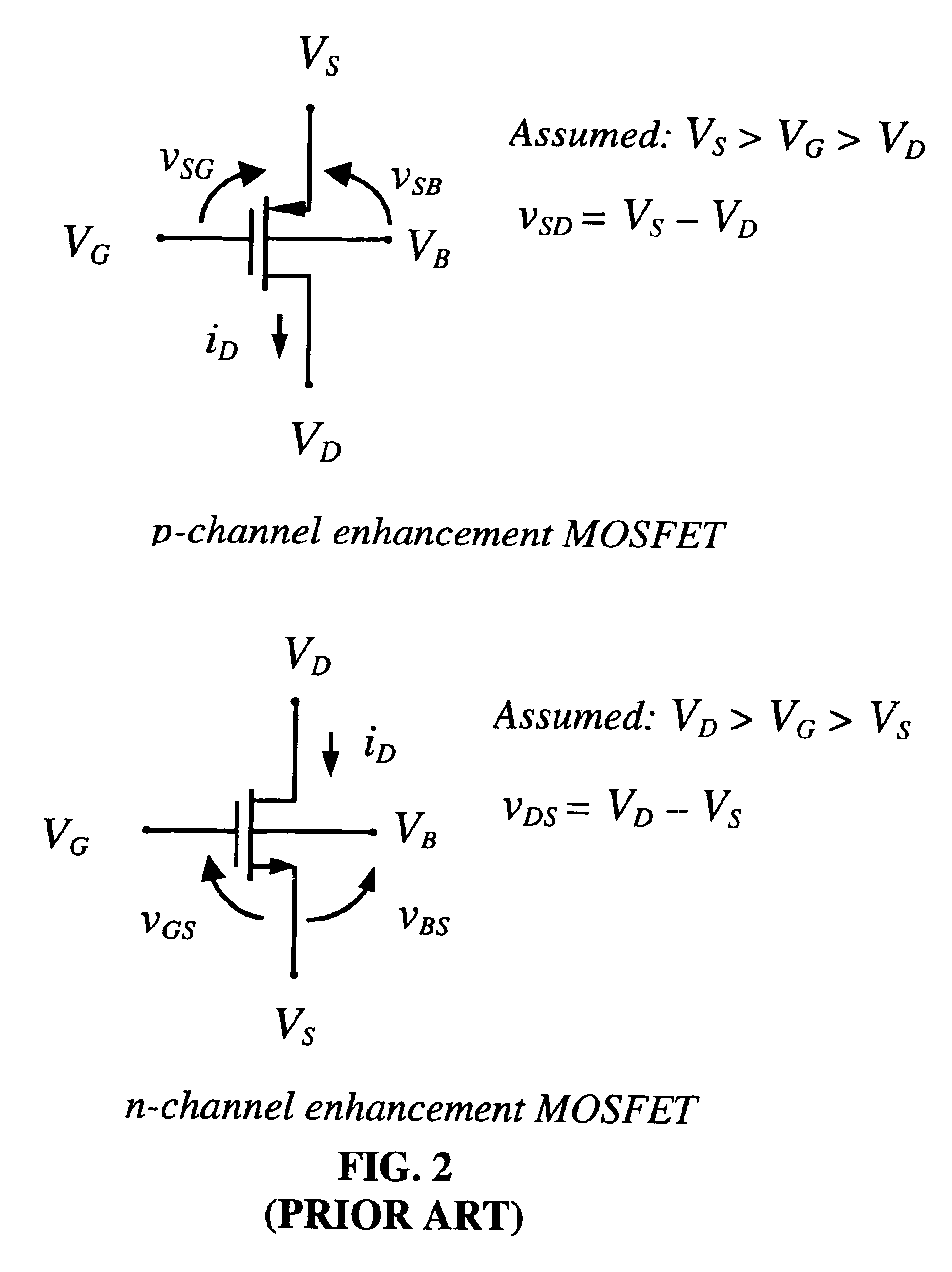
Method and apparatus for modeling a neural synapse function by utilizing a single conventional MOSFET
InactiveUS6829598B2Great potentialSimple methodDigital computer detailsDigital storageMOSFETFunctional modeling
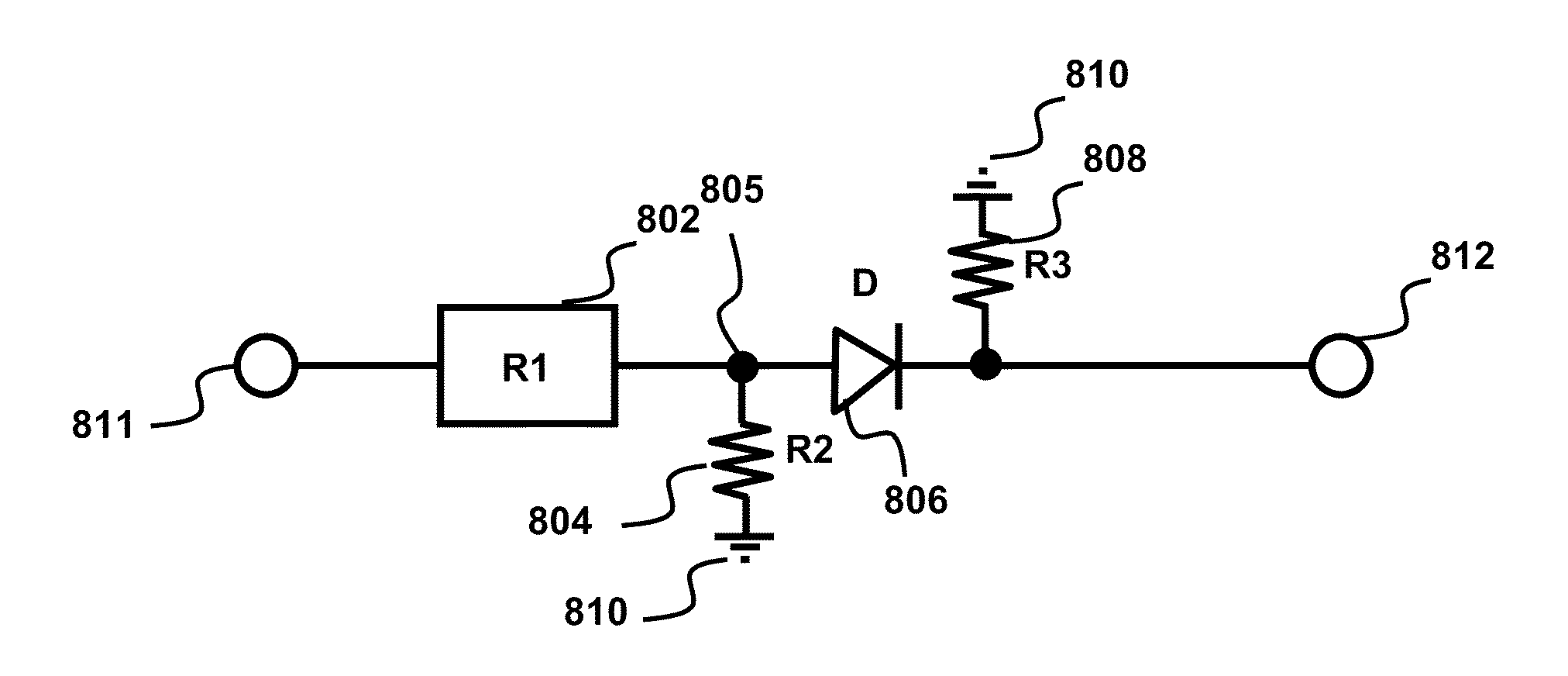
A method and apparatus for modeling a neural synapse function in analog hardware whereby the multiplication function inherent to the operation of a neural synapse is computed by applying a voltage on the gate-source terminals and an independent voltage on drain-source terminals of a MOSFET further using the resultant drain current of the latter device in non-saturation mode as function implementing a computation essentially close to multiplication function between the aforesaid voltages. Analog circuit is provided, capable of generating an output current signal which is proportional in magnitude, within a certain range, to a function computing essentially a sum of weighted input signals-products of corresponding pair of current input signal, and voltage control signal applied to a plurality of inputs thus capable of constructing an artificial neuron model.
Owner:TEXAS INSTR INC
Apparatus comprising artificial neuronal assembly
Owner:PFG IP +1
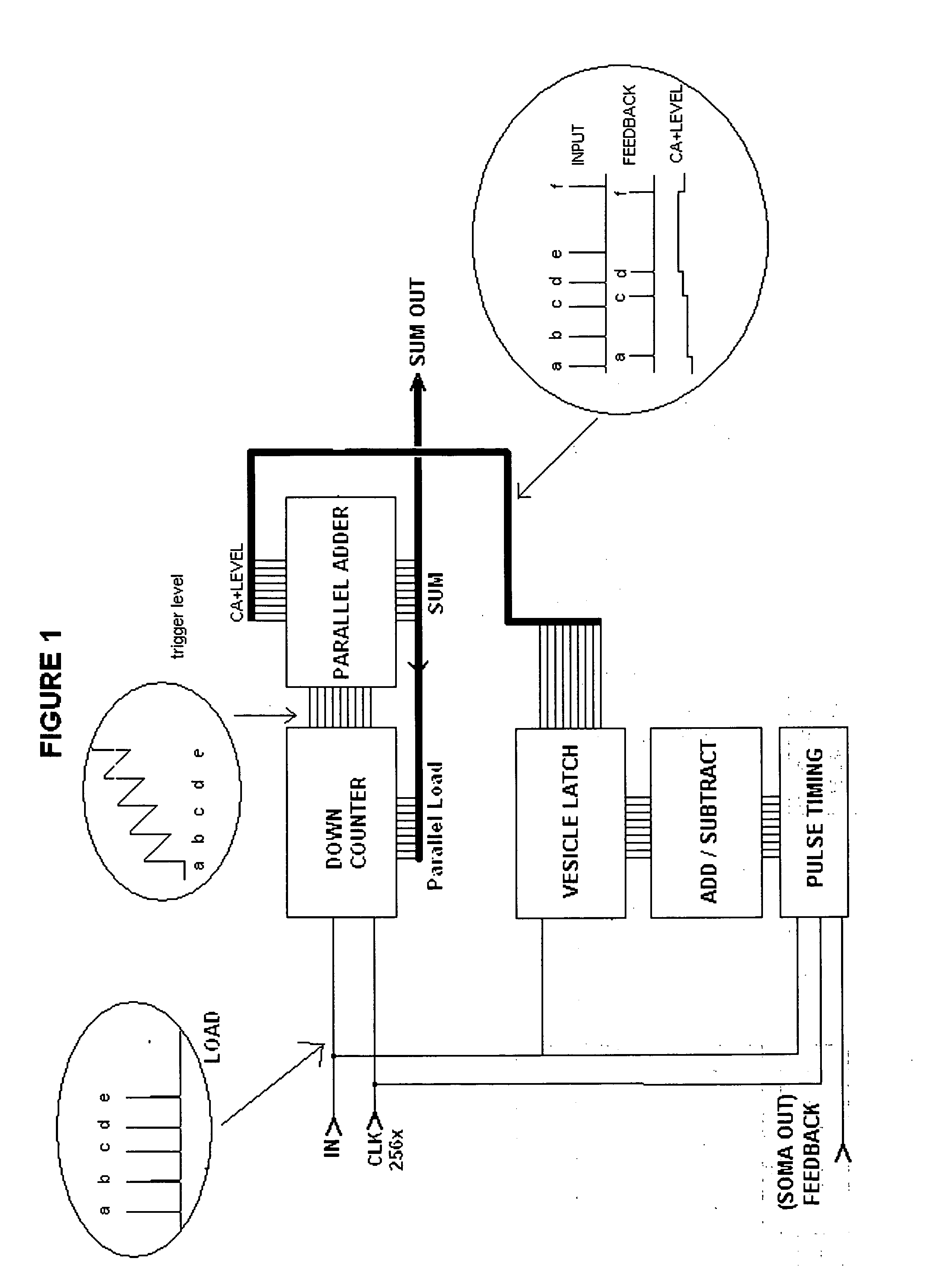
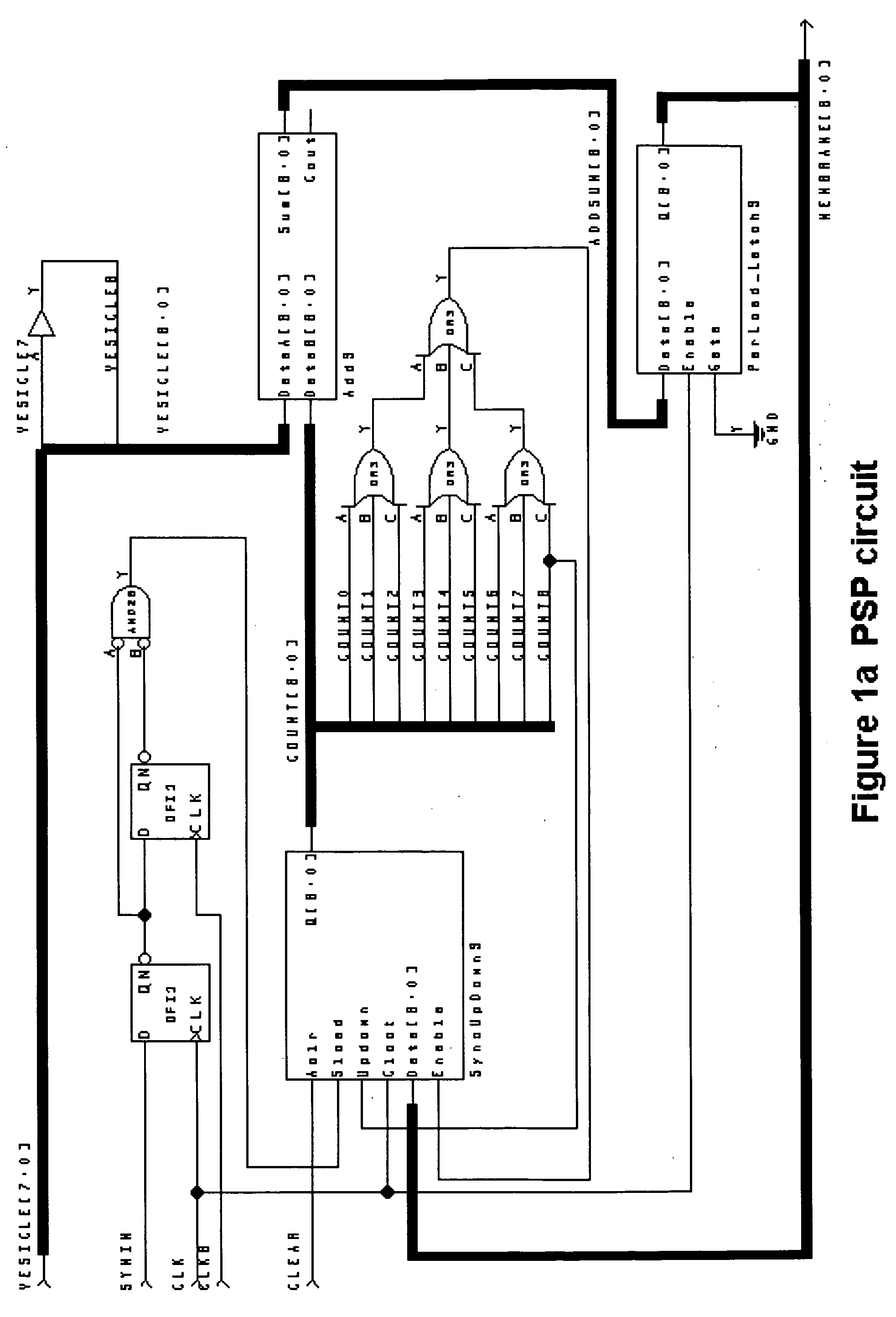
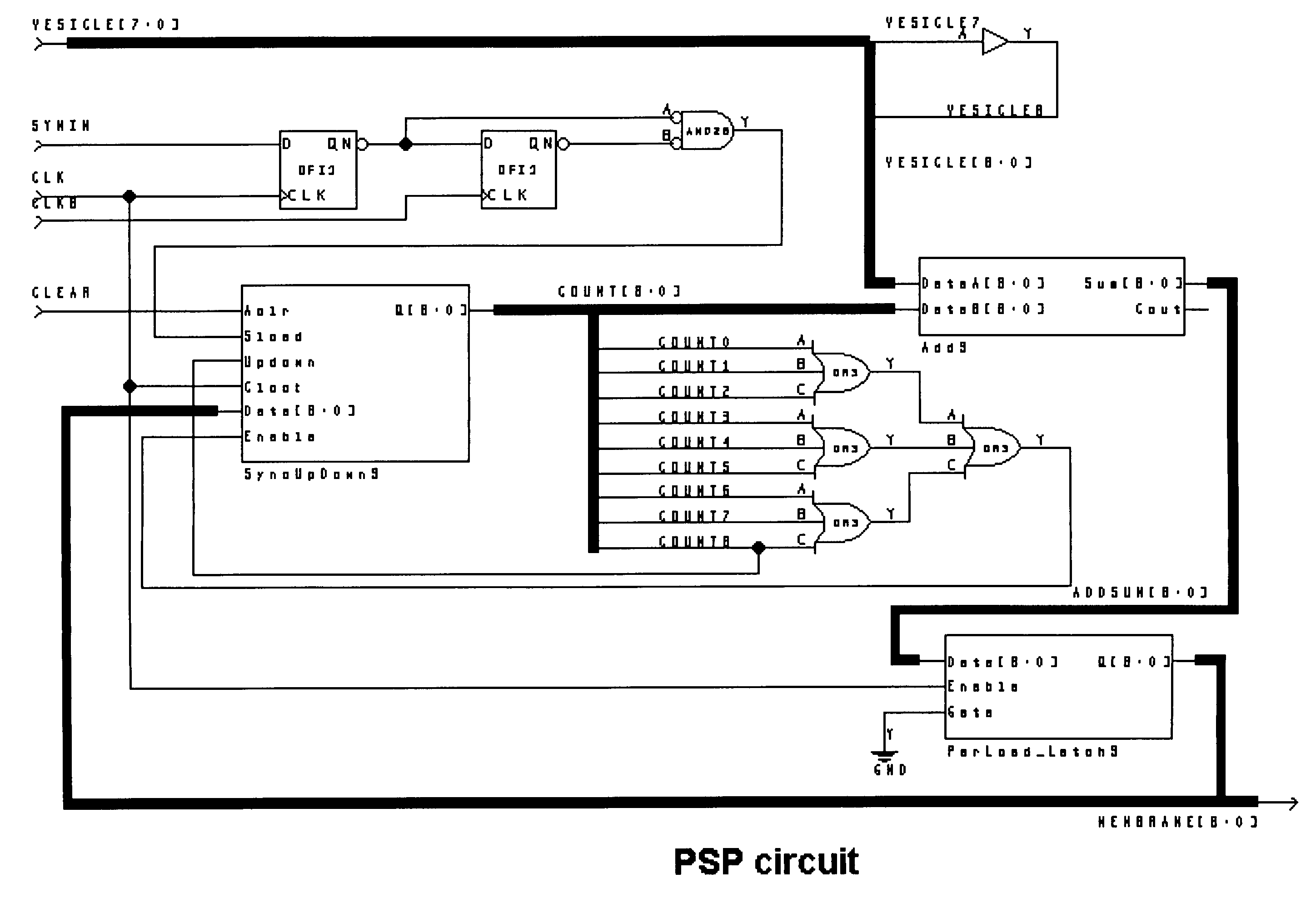
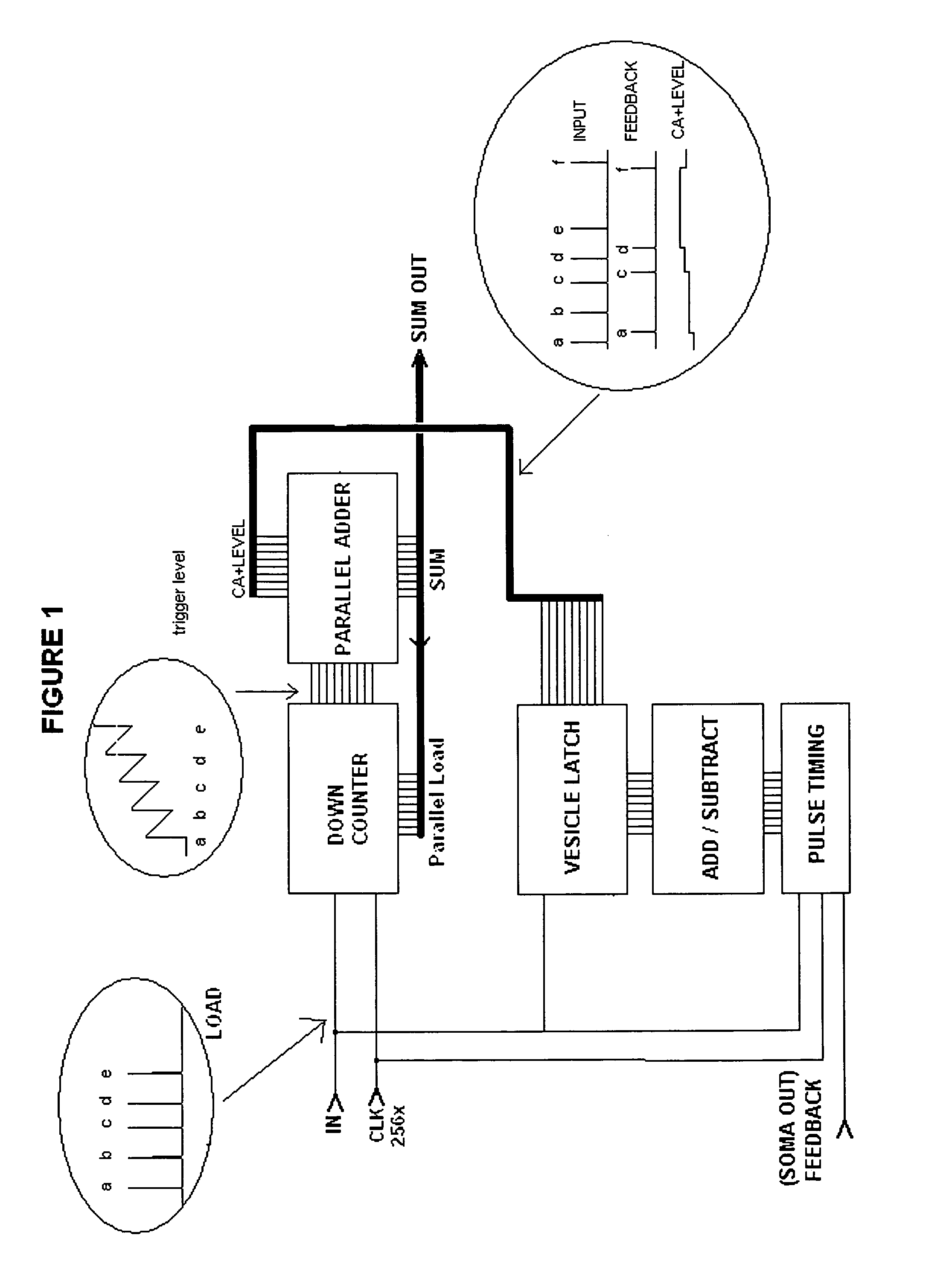
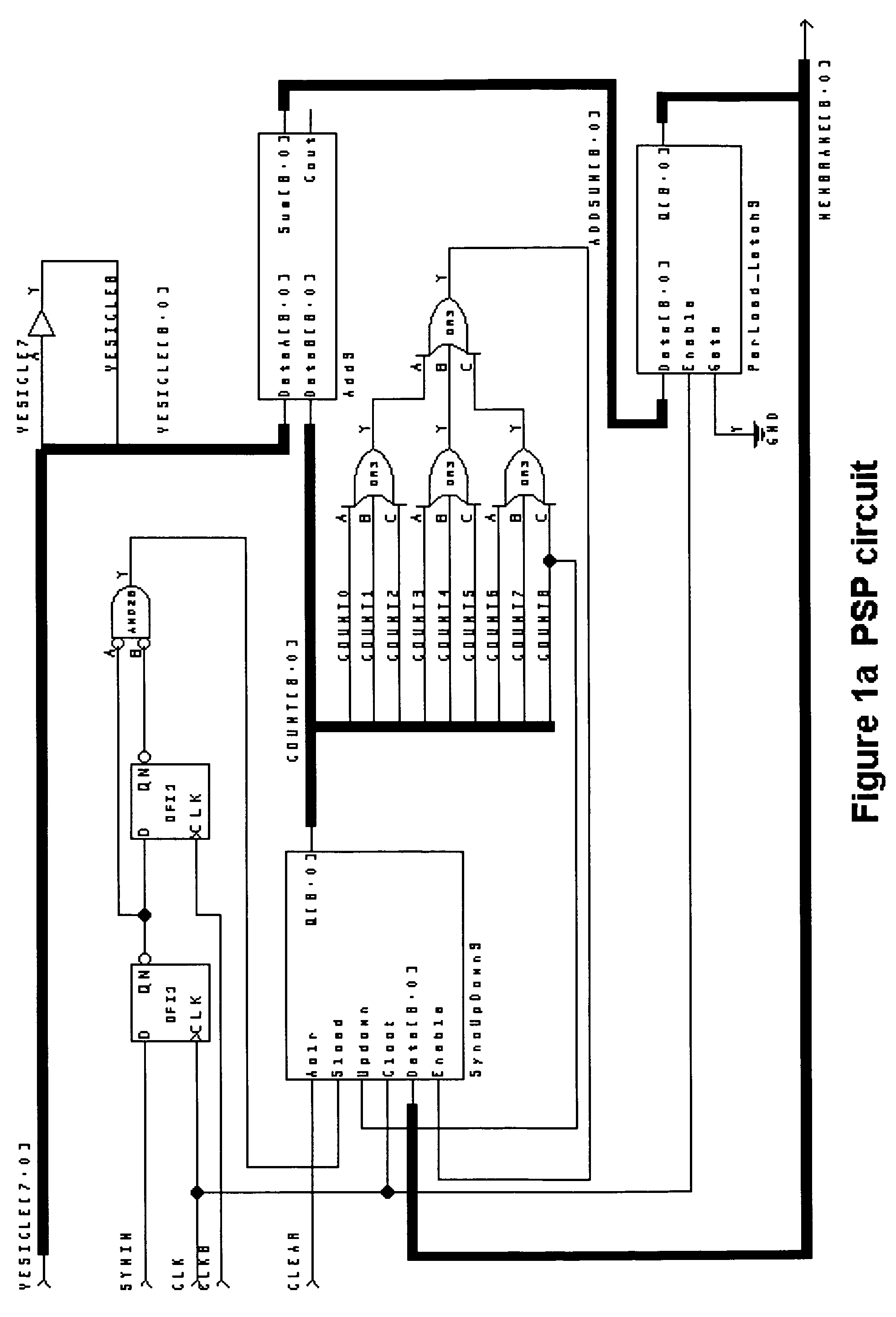
Autonomous Learning Dynamic Artificial Neural Computing Device and Brain Inspired System
ActiveUS20100076916A1Digital computer detailsAnalogue computers for chemical processesInformation processingNervous system
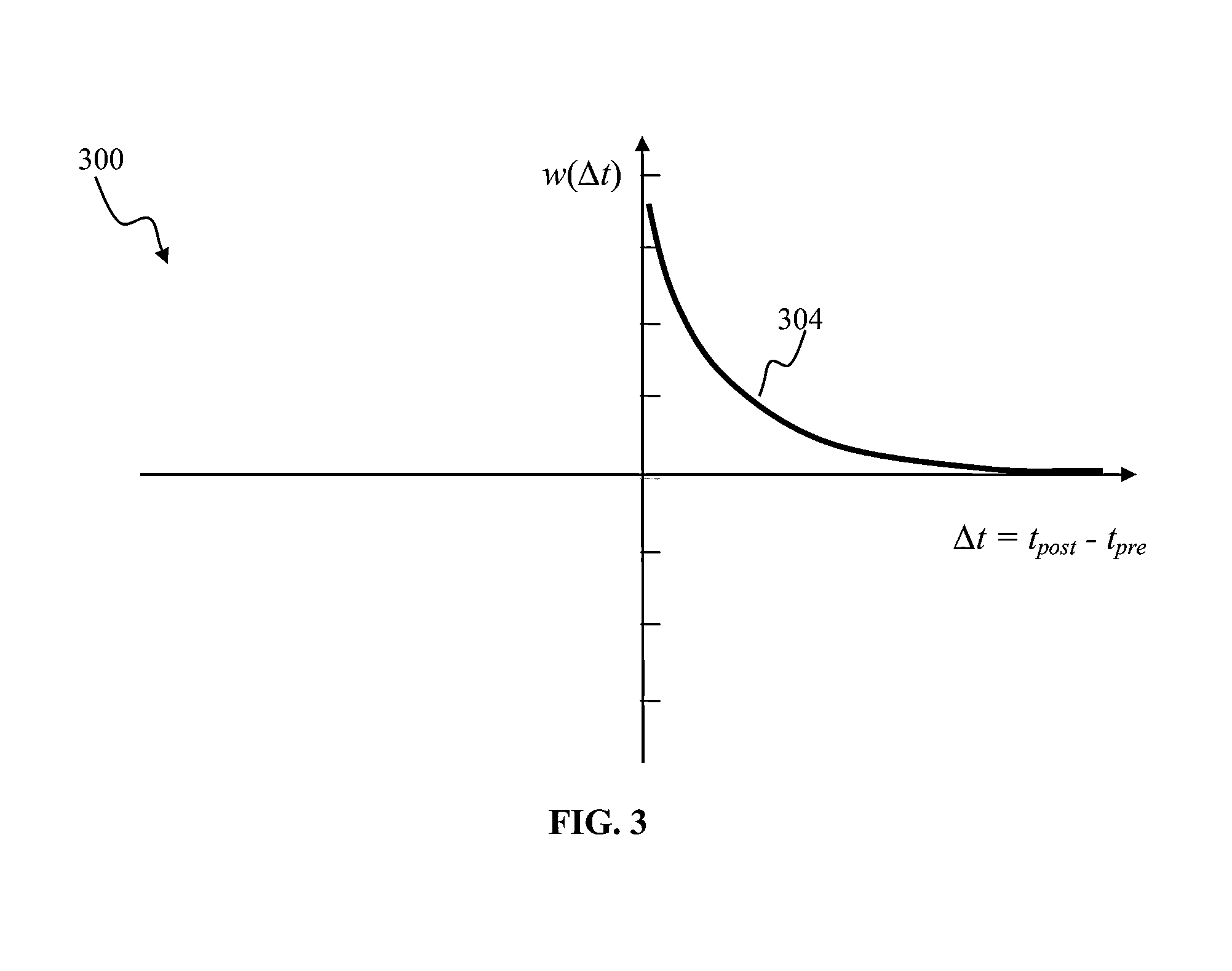
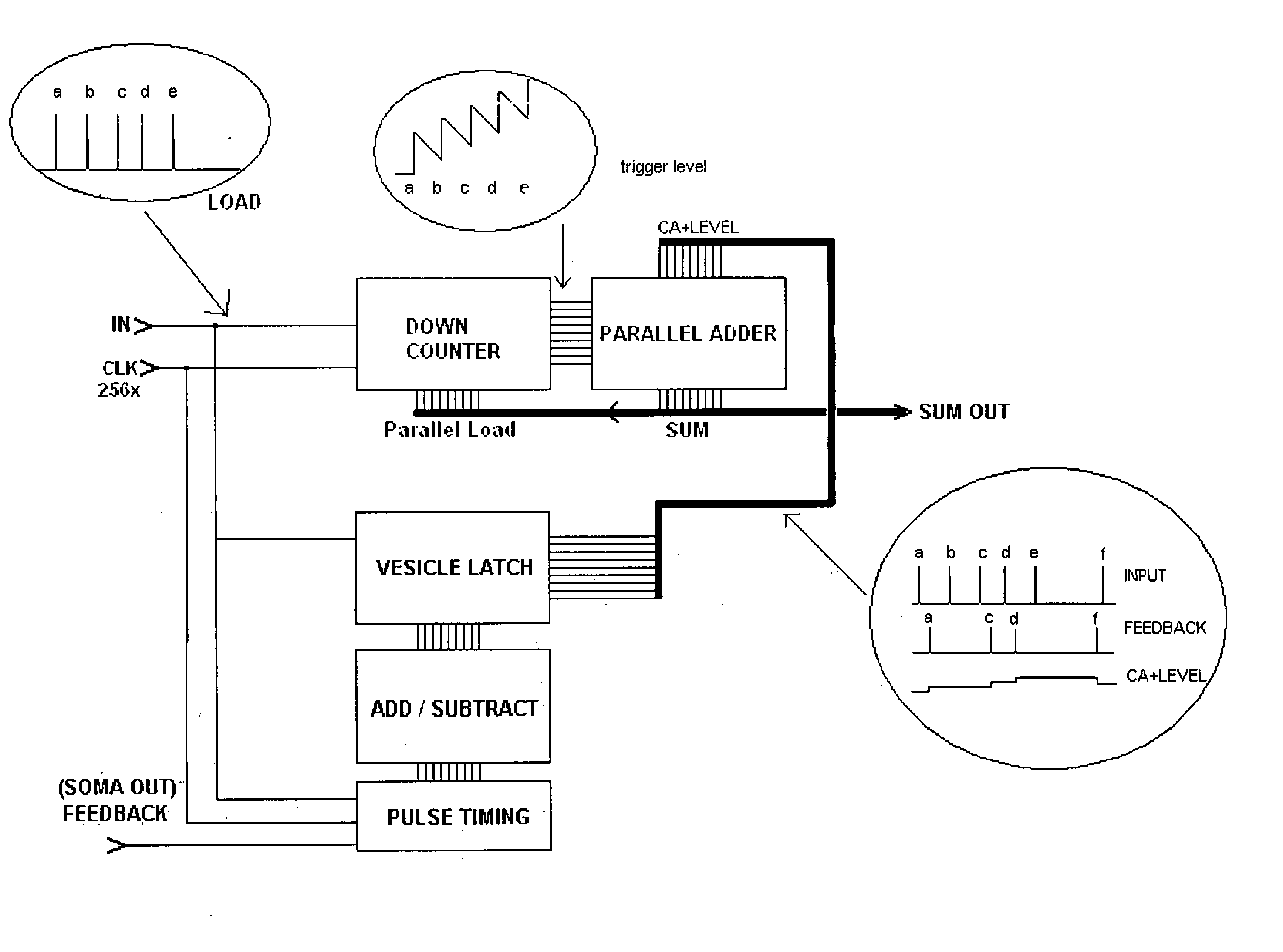
A hierarchical information processing system is disclosed having a plurality of artificial neurons, comprised of binary logic gates, and interconnected through a second plurality of dynamic artificial synapses, intended to simulate or extend the function of a biological nervous system. The system is capable of approximation, autonomous learning and strengthening of formerly learned input patterns. The system learns by simulated Synaptic Time Dependent Plasticity, commonly abbreviated to STDP. Each artificial neuron consisting of a soma circuit and a plurality of synapse circuits, whereby the soma membrane potential, the soma threshold value, the synapse strength and the Post Synaptic Potential at each synapse are expressed as values in binary registers, which are dynamically determined from certain aspects of input pulse timing, previous strength value and output pulse feedback.
Owner:BRAINCHIP INC
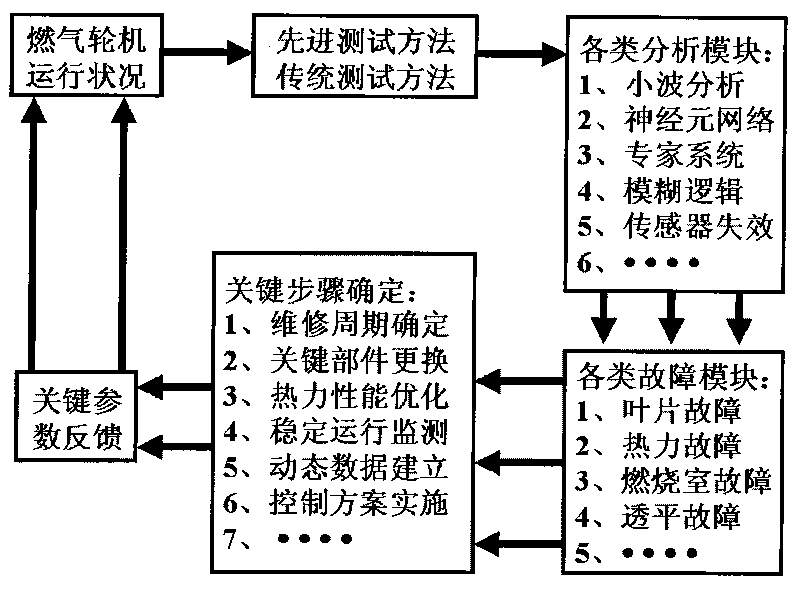
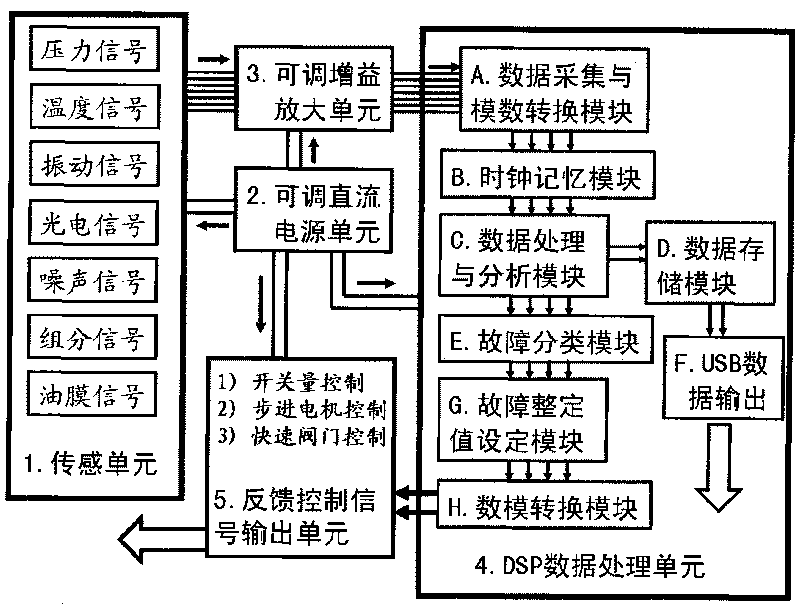
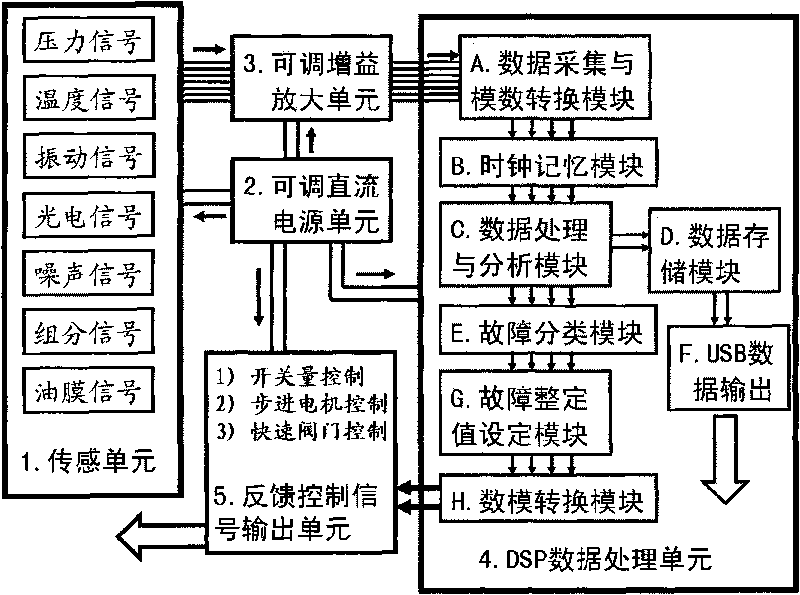
On-line failure diagnosis, prediction and feedback control method of small/medium size gas turbine and device thereof
InactiveCN101694182AGuaranteed uptimeImprove usabilityGas turbine plantsJet propulsion plantsArtificial neuronFeedback control
The invention discloses an on-line failure diagnosis, prediction and feedback control method of a small / medium size gas turbine and a device thereof, being used for carrying out on-line analysis on parameters representing running states of the gas turbine. The method comprises the following steps: adopting an artificial neural network (ANN) to analyze the operating characteristics of all working conditions of a gas turbine set; constructing an expert analysis database; adopting a fuzzy logic analysis block and combining a Kalman filtering module for failure isolation; constructing a multi-parameter analysis module to carry out on-line detection on the thermal performance and the running state of the gas turbine set; and finally, outputting the setting values of related control parameter by the on-line analysis on the parameters representing the running states of the gas turbine. A dynamic data processor (DSP) is adopted to cure the analysis means into a chip, and the invention can realize accurate evaluation of the states of parts in the gas turbine, improves the availability of equipment, prolongs time between overhaul, enhances the capability of preventing sudden failures and improves the operation level of the gas turbine on the basis of analysis technologies such as failure category, advanced failure analysis methods, failure experts and the like.
Owner:CENT FOR CLEAN ENERGY TECH OF SHANGHAI +1
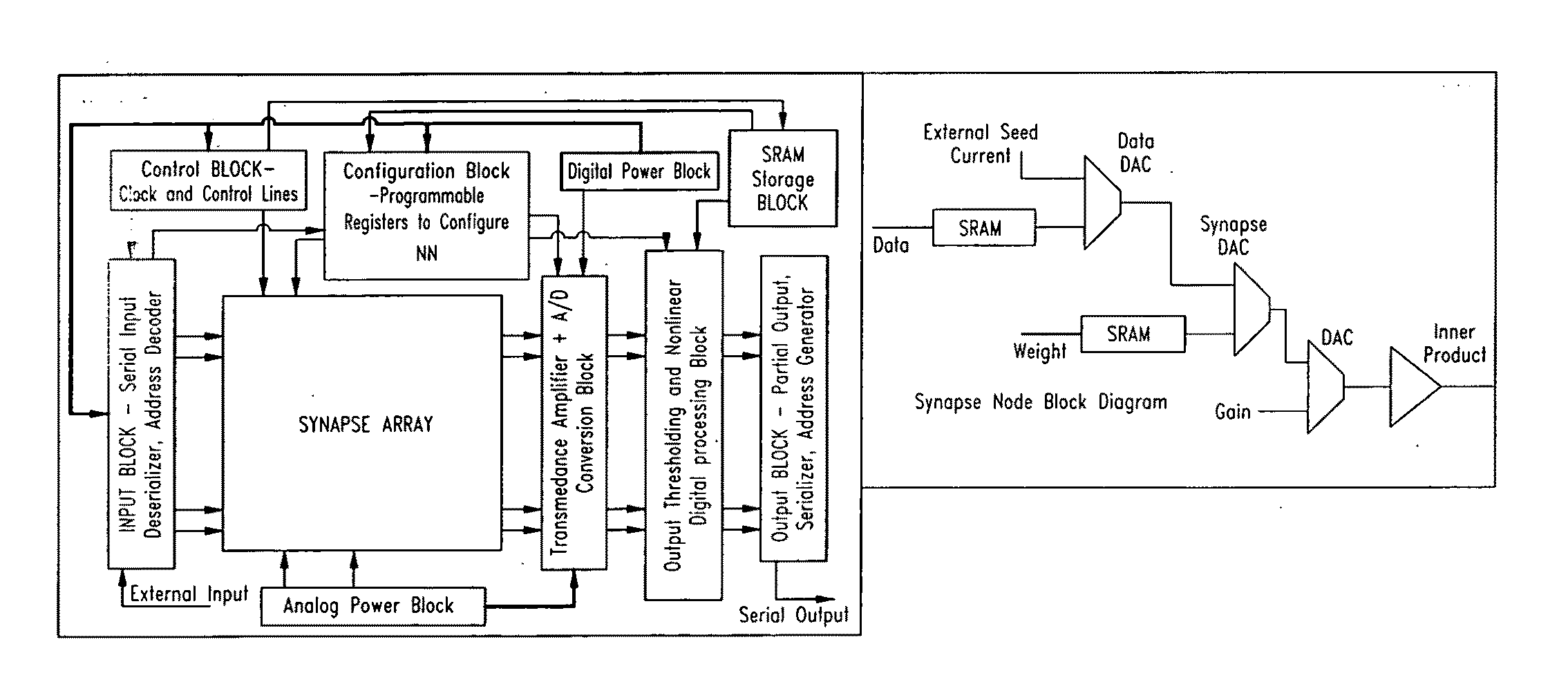
Analog neurons and neurosynaptic networks
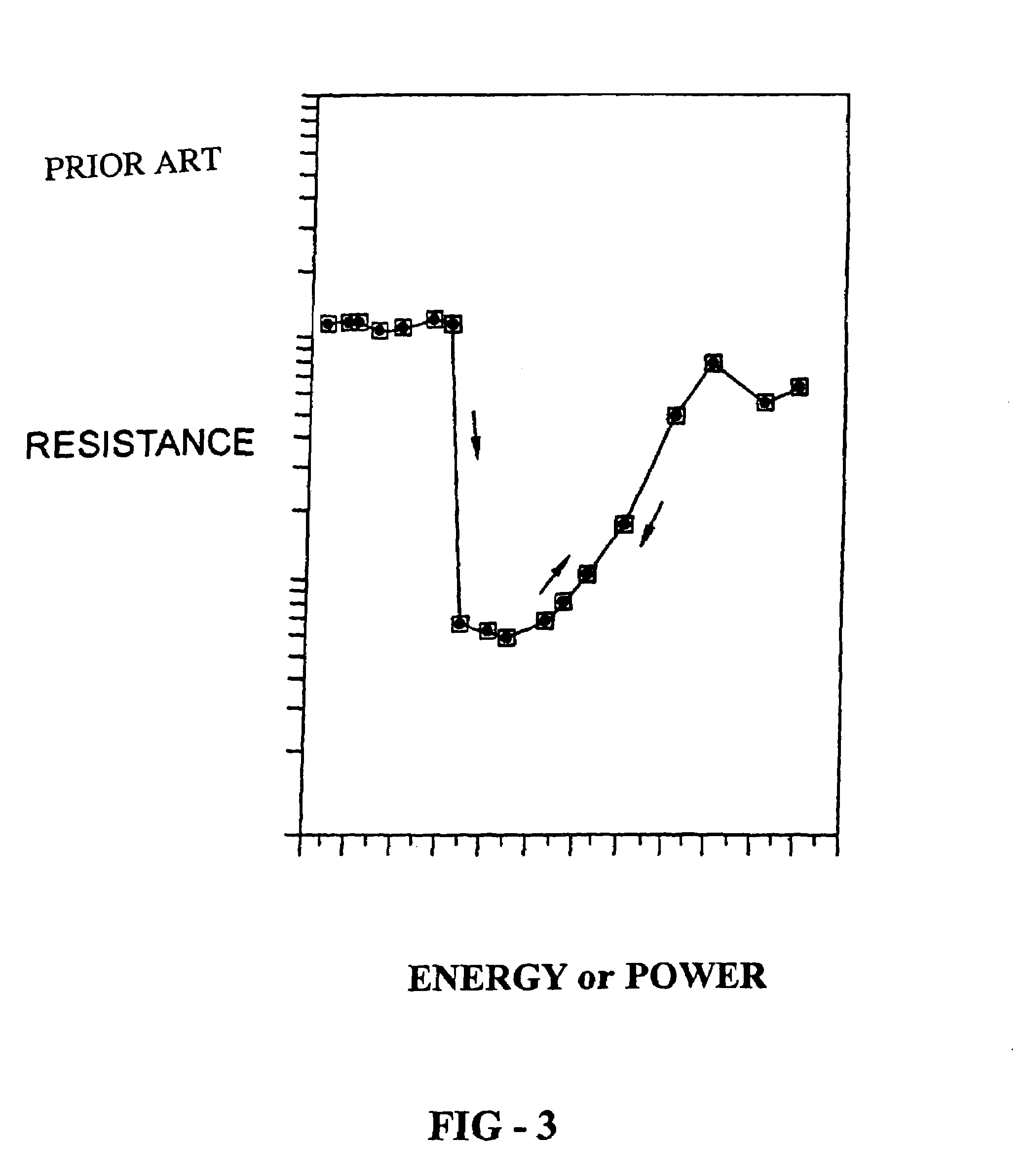
InactiveUS6999953B2Lower resistanceImprove conductivityDigital computer detailsDigital storageElectrical resistance and conductanceNerve network
An analog neural computing medium, neuron and neural networks are disclosed. The neural computing medium includes a phase change material that has the ability to cumulatively respond to multiple input signals. Input signals induce transformations among a plurality of accumulation states of the disclosed neural computing medium. The accumulation states are characterized by a high electrical resistance. Upon cumulative receipt of energy from one or more input signals that equals or exceeds a threshold value, the neural computing medium fires by transforming to a low resistance state. The disclosed neural computing medium may also be configured to perform a weighting function whereby it weights incoming signals. The disclosed neurons may also include activation units for further transforming signals transmitted by the accumulation units according to a mathematical operation. The artificial neurons, weighting units, accumulation units and activation units may be connected to form artificial neural networks.
Owner:OVONYX MEMORY TECH LLC
Systems and Methods for Processing Data Flows
InactiveUS20160366160A1Increased complexitySignificant expenseData switching networksNeural learning methodsData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
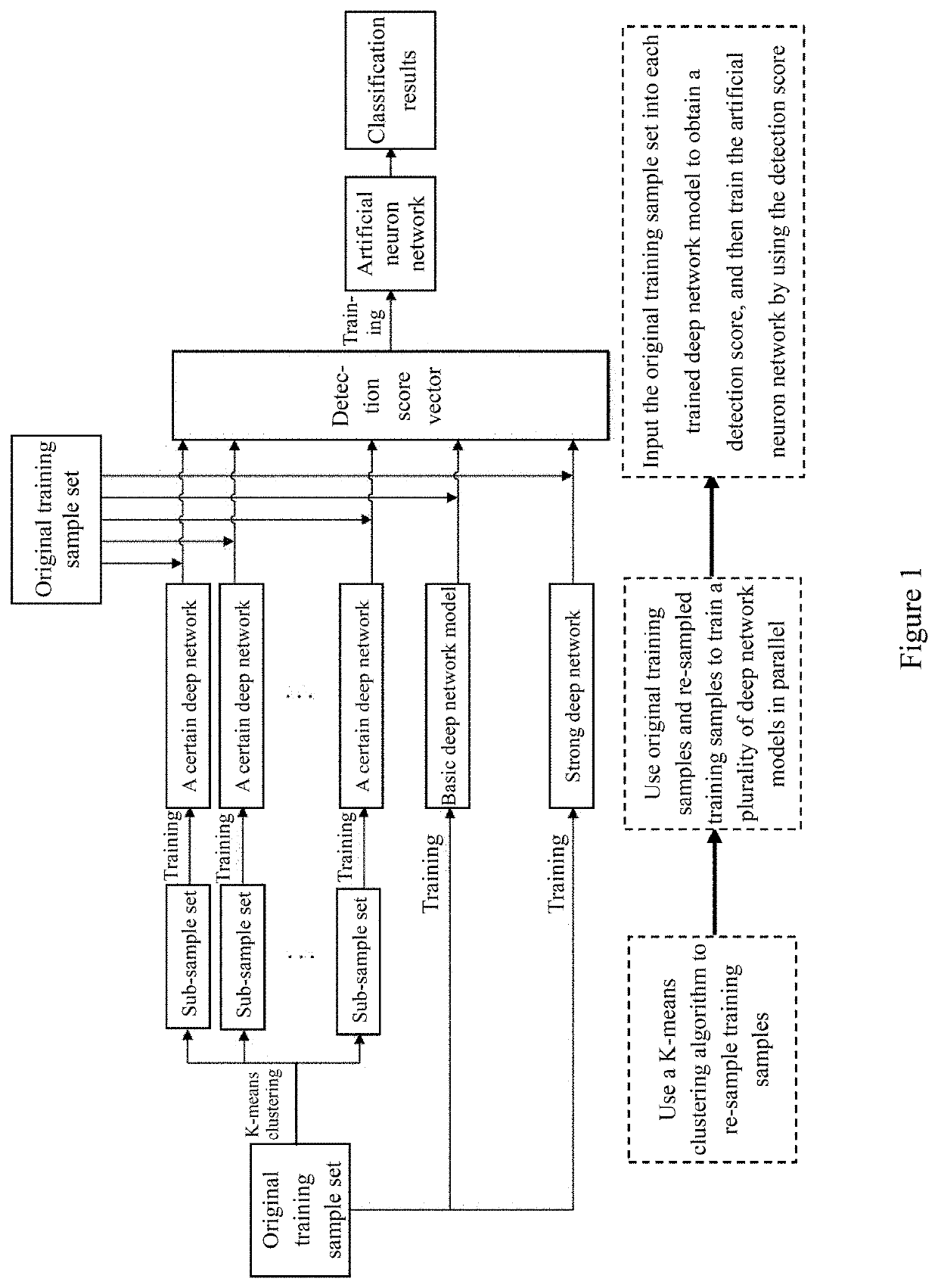
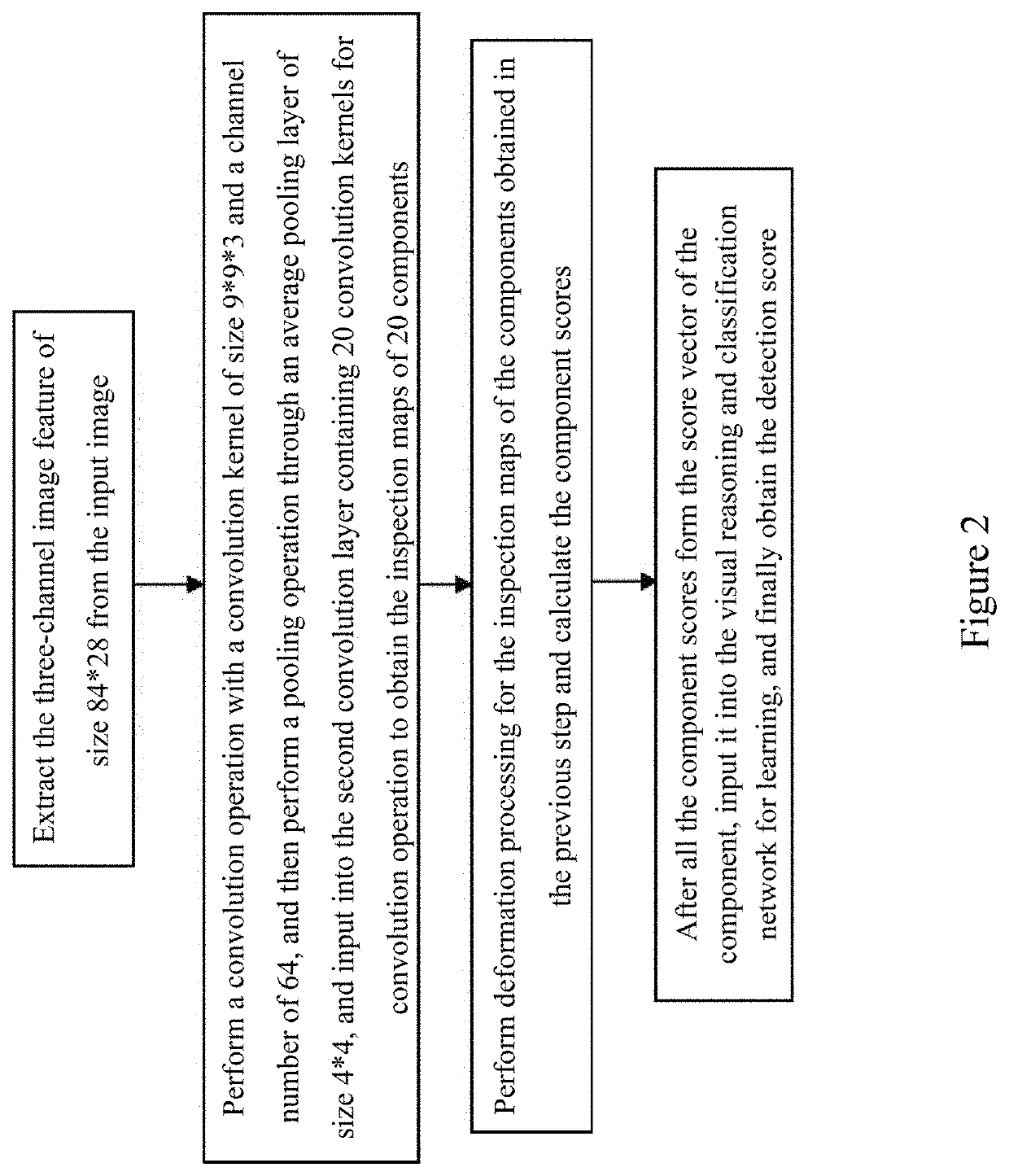
Collaborative deep network model method for pedestrian detection
ActiveUS20200082165A1Avoid restrictionsAccurate detectionBiometric pattern recognitionNeural architecturesData setOriginal data
A Collaborative Deep Network model method for pedestrian detection includes constructing a new collaborative multi-model learning framework to complete a classification process during pedestrian detection; and using an artificial neuron network to integrate judgment results of sub-classifiers in a collaborative model, and training the network by means of the method for machine learning, so that information fed back by sub-classifiers can be more effectively synthesized. A re-sampling method based on a K-means clustering algorithm can enhance the classification effect of each classifier in the collaborative model, and thus improves the overall classification effect. By building a collaborative deep network model, different types of training data sets obtained using a clustering algorithm are used for training a plurality of deep network models in parallel, and then classification results, on deep network models, of an original data set are integrated and comprehensively analyzed, which achieves more accurate sample classification.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
Autonomous learning dynamic artificial neural computing device and brain inspired system
ActiveUS8250011B2Analogue computers for chemical processesDigital computer detailsInformation processingSynapse
A hierarchical information processing system is disclosed having a plurality of artificial neurons, comprised of binary logic gates, and interconnected through a second plurality of dynamic artificial synapses, intended to simulate or extend the function of a biological nervous system. The system is capable of approximation, autonomous learning and strengthening of formerly learned input patterns. The system learns by simulated Synaptic Time Dependent Plasticity, commonly abbreviated to STDP. Each artificial neuron consisting of a soma circuit and a plurality of synapse circuits, whereby the soma membrane potential, the soma threshold value, the synapse strength and the Post Synaptic Potential at each synapse are expressed as values in binary registers, which are dynamically determined from certain aspects of input pulse timing, previous strength value and output pulse feedback.
Owner:BRAINCHIP INC
Intelligent street lamp energy-saving control system based on artificial neutral network
ActiveCN102413605ARealize intelligent energy-saving controlRealize energy-saving controlElectric light circuit arrangementEnergy saving control techniquesForward algorithmPower controller
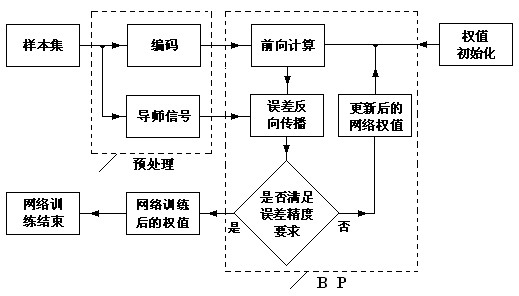
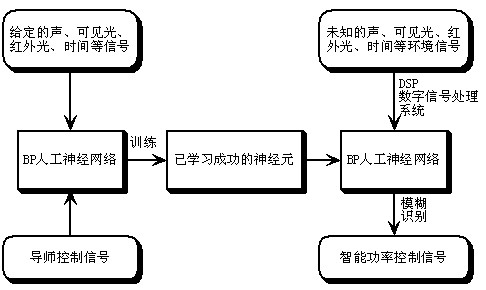
The invention discloses an intelligent street lamp energy-saving control system based on an artificial neutral network. The intelligent street lamp energy-saving control system comprises a sensor system, an energy-saving control system and a power controller. An output signal of the sensor system is connected with an input terminal of the energy-saving control system; and an output signal of the energy-saving control system is connected with the power controller. Besides, the intelligent street lamp energy-saving control system is characterized in that: the sensor system includes environmental optical signal collection processing module, an infrared signal collection processing module and a sound signal collection processing module; the energy-saving control system consists of a DSP embedded system and an artificial neutral network module that is arranged in a DSP chip; and the artificial neutral network module is formed by a forward algorithm of an artificial neutral network BP algorithm and an artificial neuron that has been trained. According to the invention, according to peripheral environment situations of all street lamp illumination units, intelligent power control can be realized; and on the premise that an illumination requirement is met, energy consumption is effectively reduced.
Owner:付志
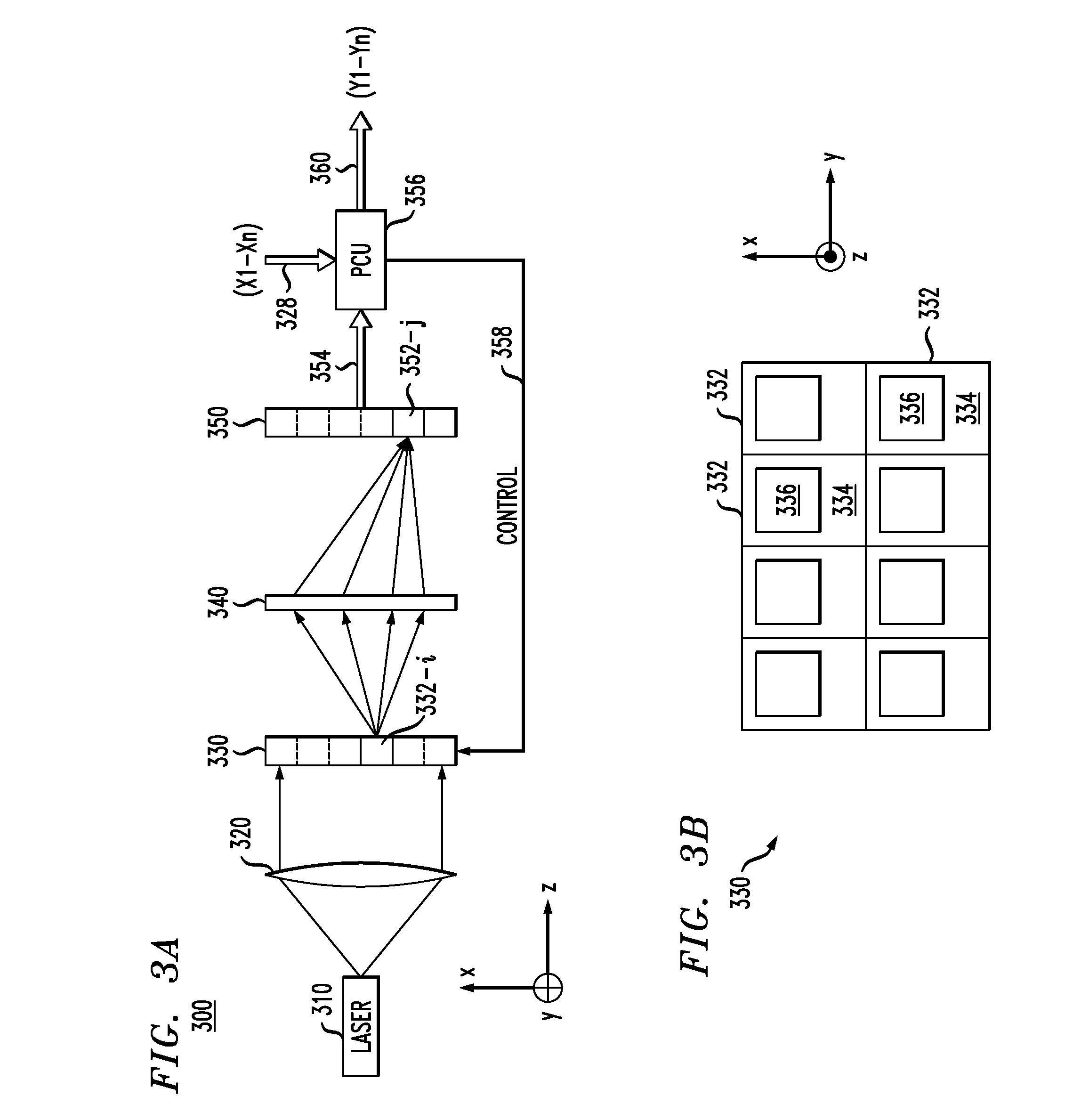
Optical processor for an artificial neural network
InactiveUS20080154815A1Improve processing speedDigital computer detailsDigital dataPattern recognitionSpatially resolved
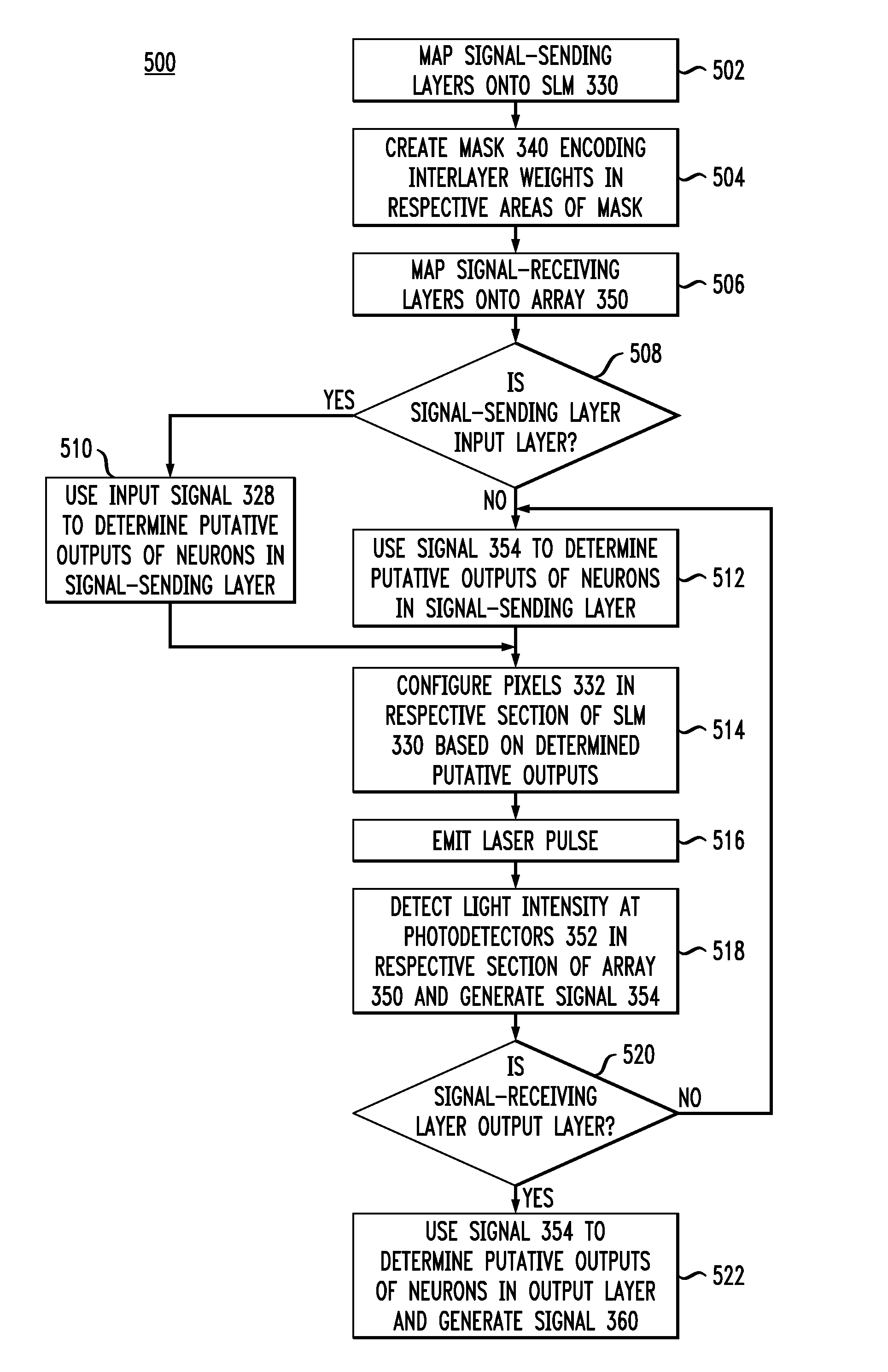
An optical processor adapted to emulate an artificial neural network (ANN) having a plurality of interconnected layers, each layer having one or more artificial neurons, the processor having a spatial light modulator (SLM) optically coupled, via an optical mask, to a photodetector array. In one embodiment, the SLM has a plurality of pixels, each pixel being configurable to emulate an output portion of a corresponding artificial neuron in a signal-sending ANN layer. The optical mask has a hologram that encodes the weights corresponding to interlayer connections in the ANN and spatially modulates the light transmitted by the SLM. The photodetectors of the array spatially resolve the interference pattern produced by the spatially modulated light, with each photodetector being configurable to emulate an input portion of a corresponding artificial neuron in a signal-receiving ANN layer.
Owner:ALCATEL-LUCENT USA INC
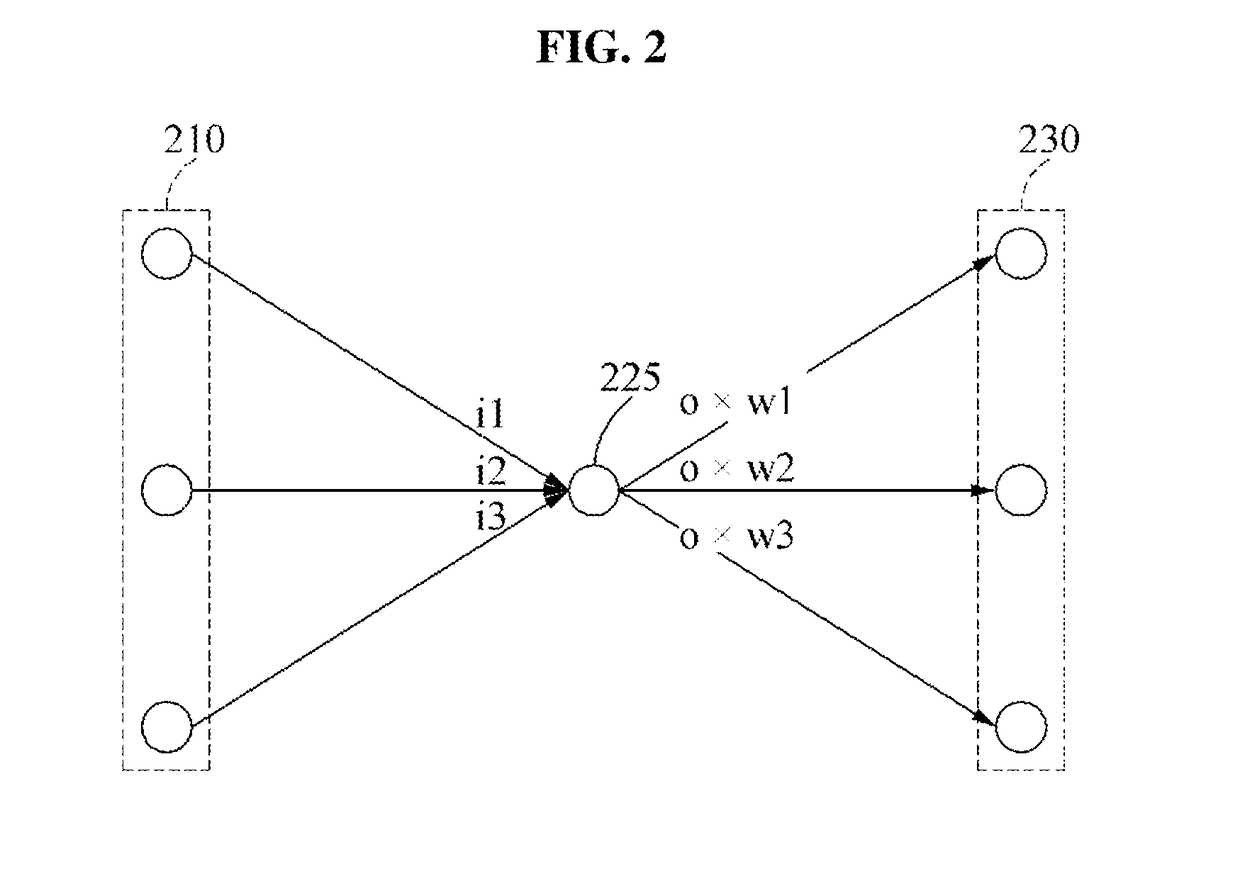
Method for neural network and apparatus performing same method
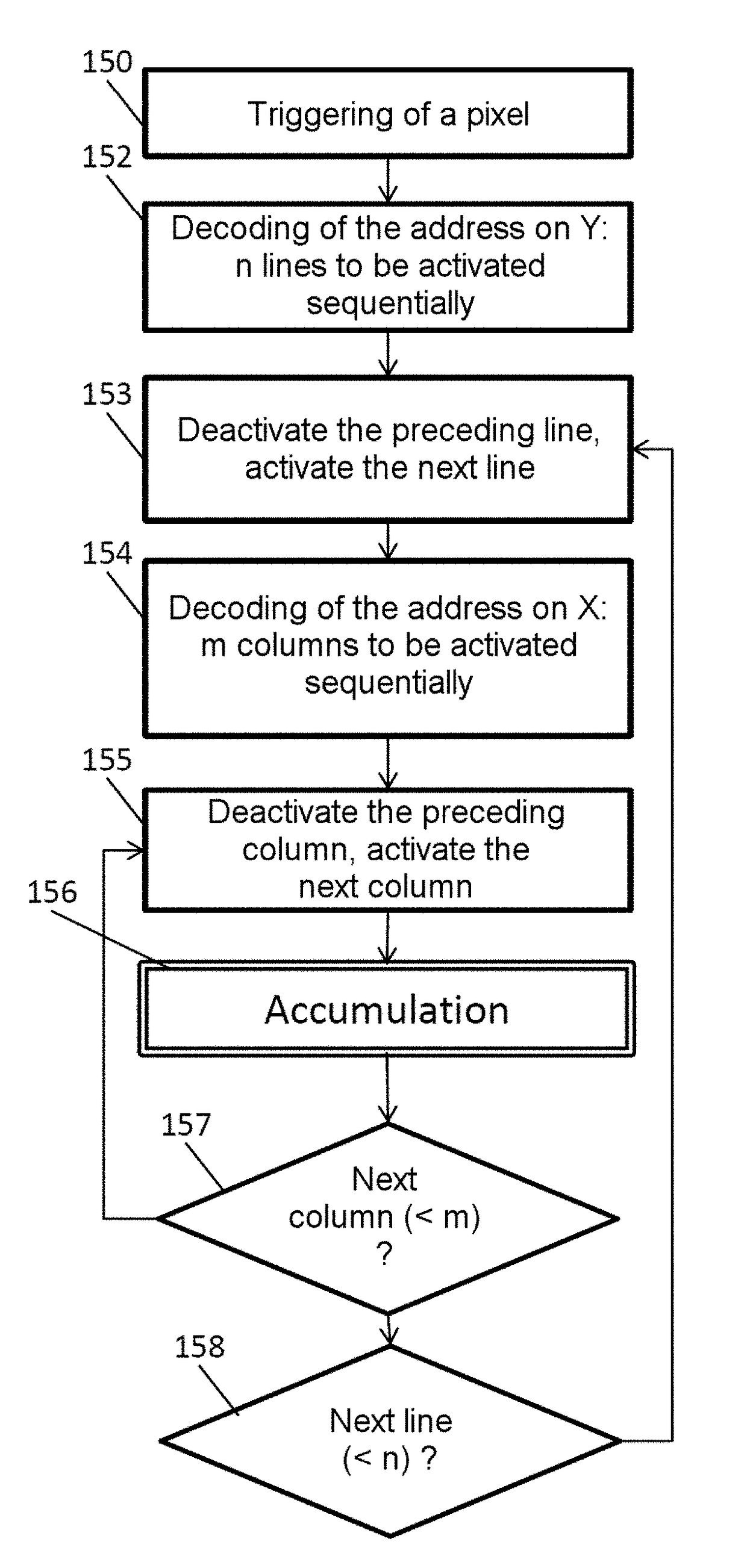
A method for operating an artificial neuron and an apparatus for performing the method are provided. The artificial neuron may calculate a change amount of an activation based on an input signal received via an input synapse, determine whether an event occurs in response to the calculated change amount of the activation, and transmit, to an output synapse, an output signal that corresponds to the event in response to an occurrence of the event.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com