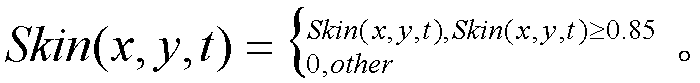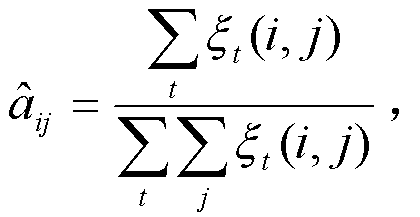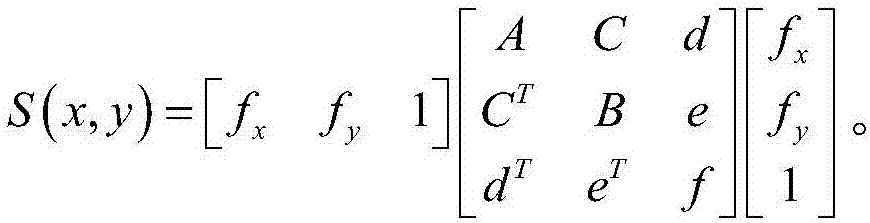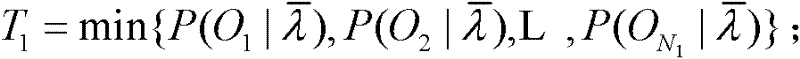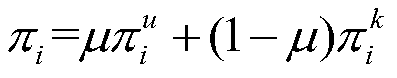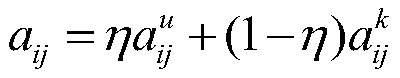Patents
Literature
74 results about "Forward algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
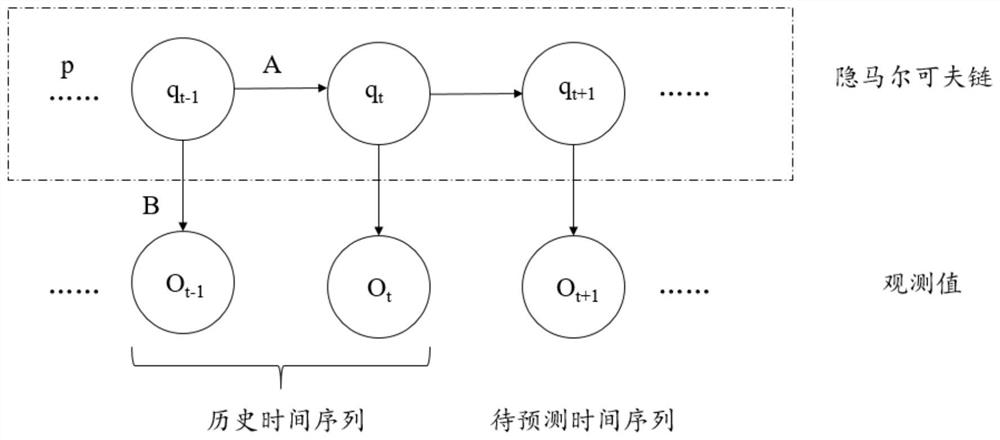
The forward algorithm, in the context of a hidden Markov model (HMM), is used to calculate a 'belief state': the probability of a state at a certain time, given the history of evidence. The process is also known as filtering. The forward algorithm is closely related to, but distinct from, the Viterbi algorithm. For an HMM such as this one: this probability is written as P(xₜ|y₁:ₜ). Here x(t) is the hidden state which is abbreviated as xₜ and y₁:ₜ are the observations 1 to t.
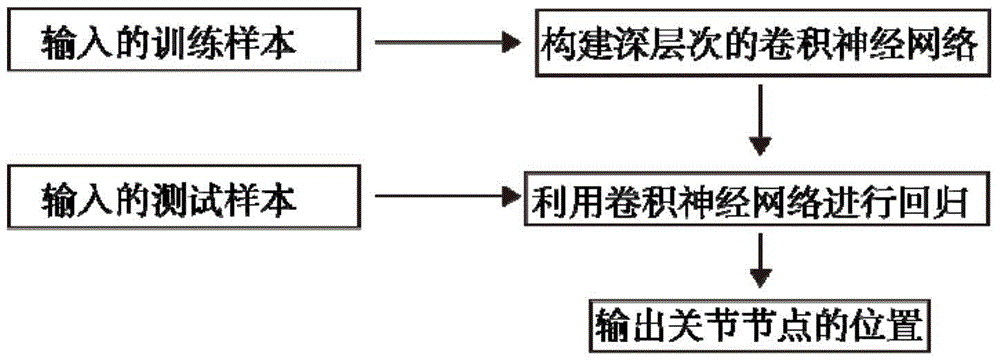
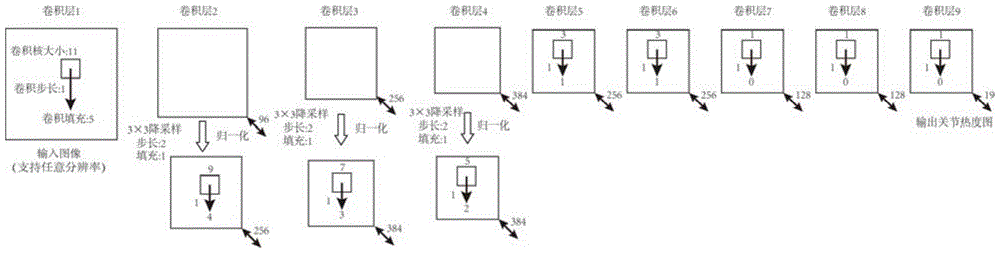
Depth image human body joint positioning method based on convolution nerve network
ActiveCN105787439ACharacter and pattern recognitionNeural learning methodsHuman bodyForward algorithm
The invention discloses a depth image human body joint positioning method based on a convolution nerve network. The method is characterized by comprising a training process and an identification process. The training process comprises the following steps: 1, inputting a training sample; 2, initializing a deep convolution nerve network and its parameters, wherein the parameters comprise a weight and a bias of each layer edge; and 3, by use of a forward algorithm and a backward algorithm, learning the parameters of the constructed convolution nerve network. The identification process comprises the following steps: 4, inputting a test sample; and 5, performing regression on the input test sample by use of the trained convolution nerve network to find positions of human body joints. According to the invention, by use of the deep convolution nerve network and large data, multiple challenges such as shielding, noise and the like can be resisted, and the accuracy is quite high; and at the same time, by means of parallel calculation, the effect of accurately positioning the human body joints in real time can be realized.
Owner:GUANGZHOU NEWTEMPO TECH
Method and system for path based network congestion management
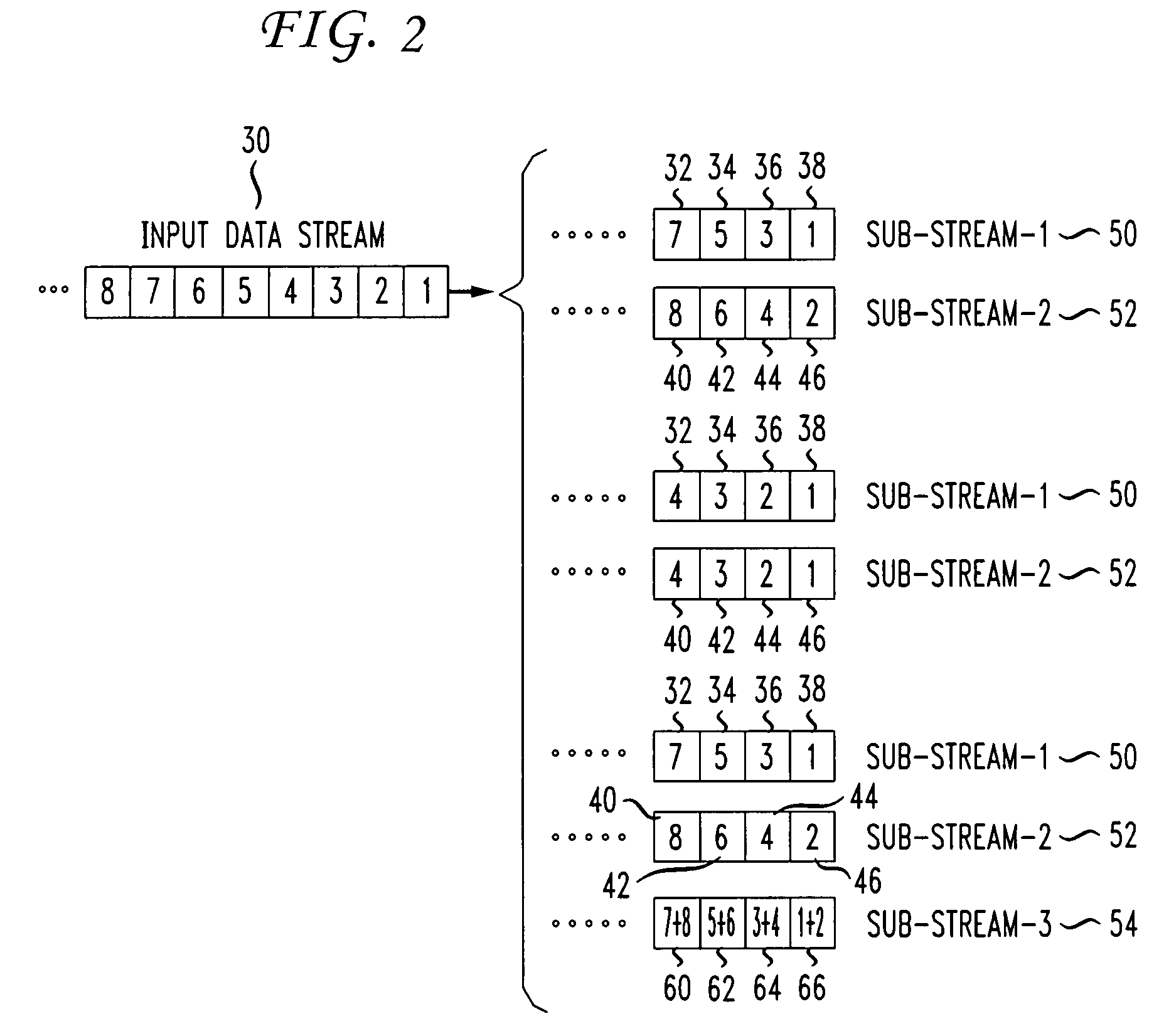
InactiveUS20090300209A1Multiple digital computer combinationsTransmissionForward algorithmData stream
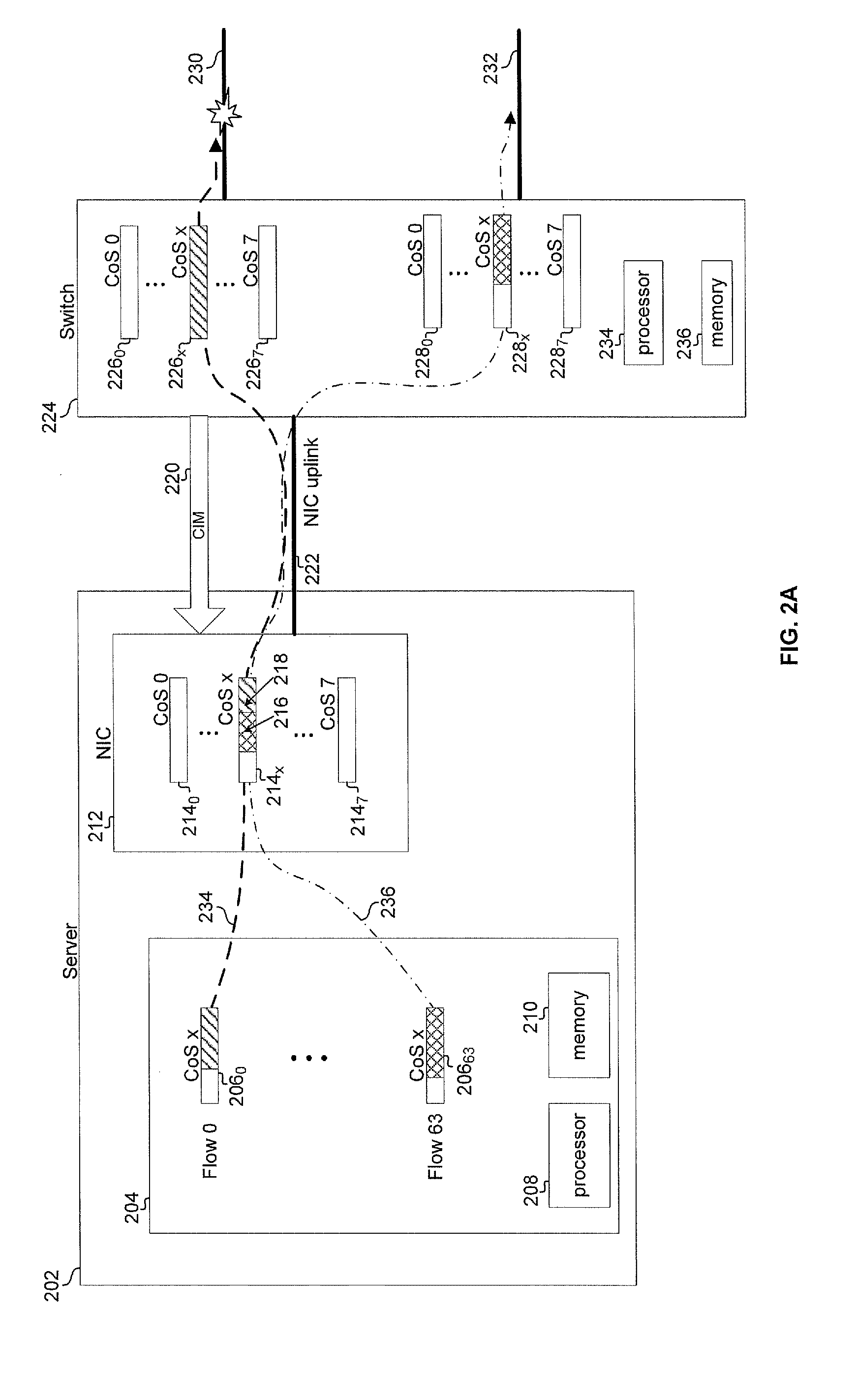
Aspects of a method and system for path based network congestion management are provided. In this regard, an indication of conditions, such as congestion, in a network may be utilized to determine which data flows may be affected by congestion in a network. A path table may be maintained to associate conditions in the network with flows affected by the conditions. Flows which are determined as being affected by a condition may be paused or flagged and transmission of data belonging to those flows may be deferred. Flows affected by a condition such as congestion may be identified based on a class of service with which they are associated. Transmission of one or more of the plurality of flows may be scheduled based on the determination. The determination may be based on one or both of a forwarding table and a forwarding algorithm of the downstream network device.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
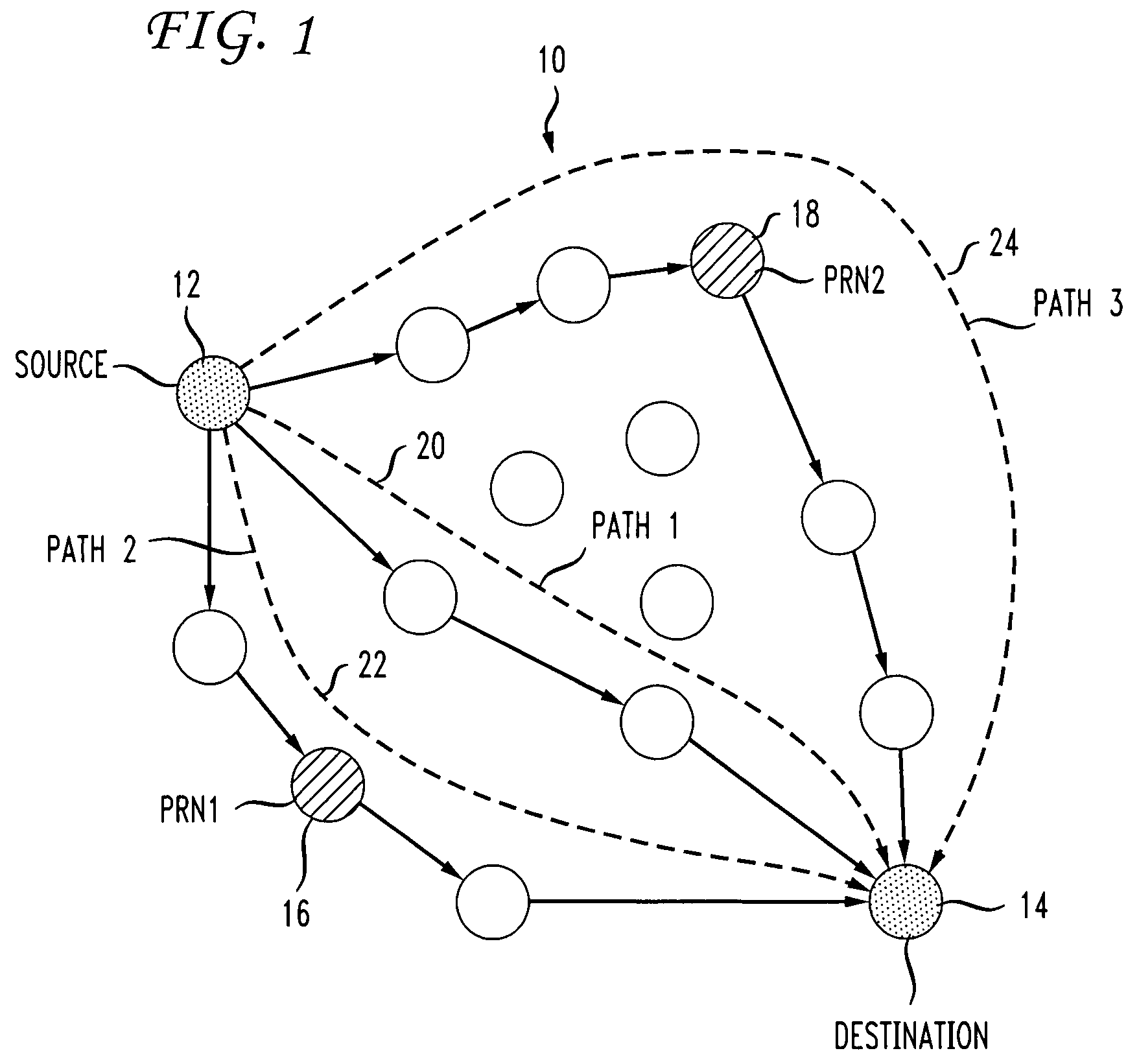
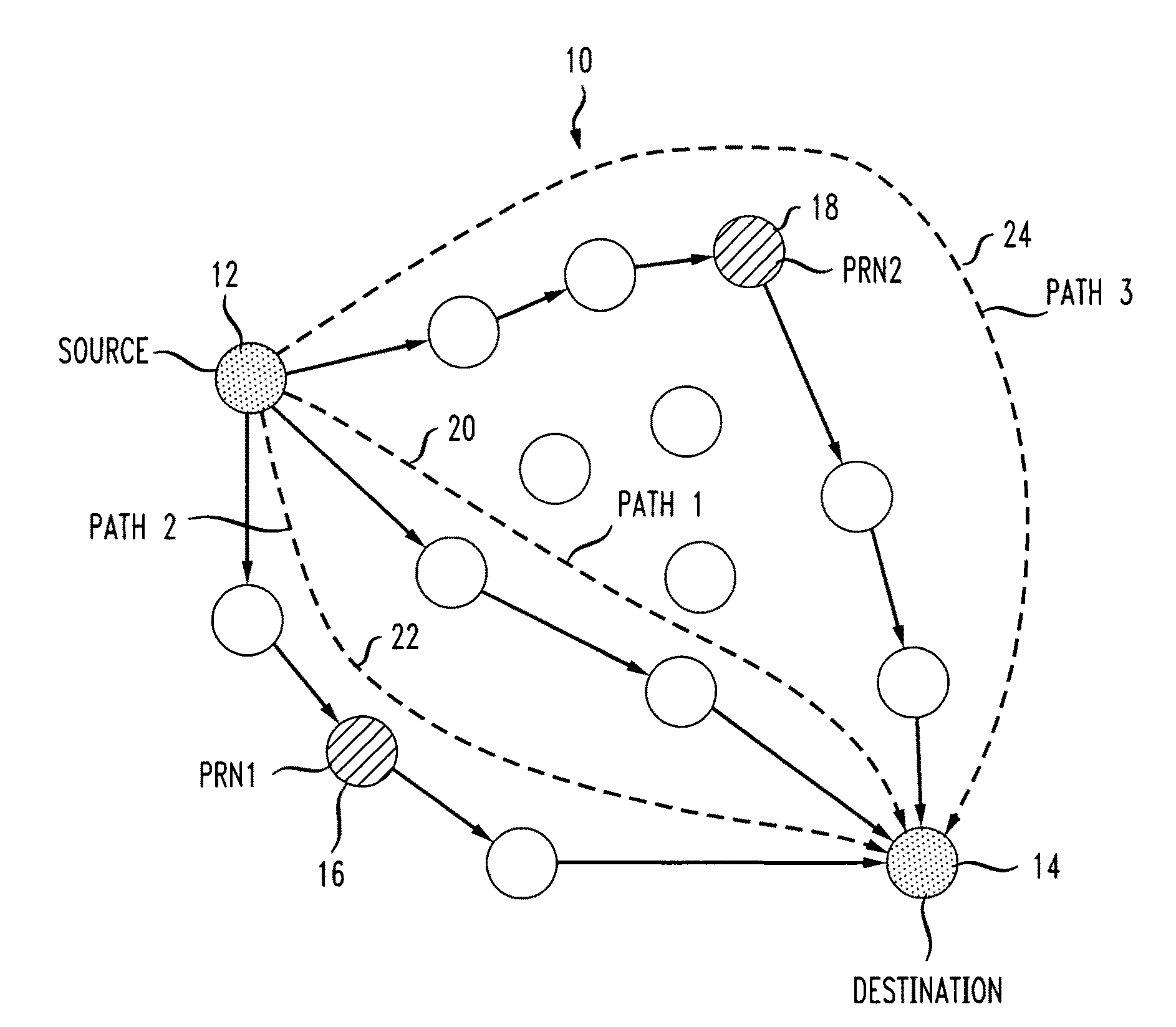
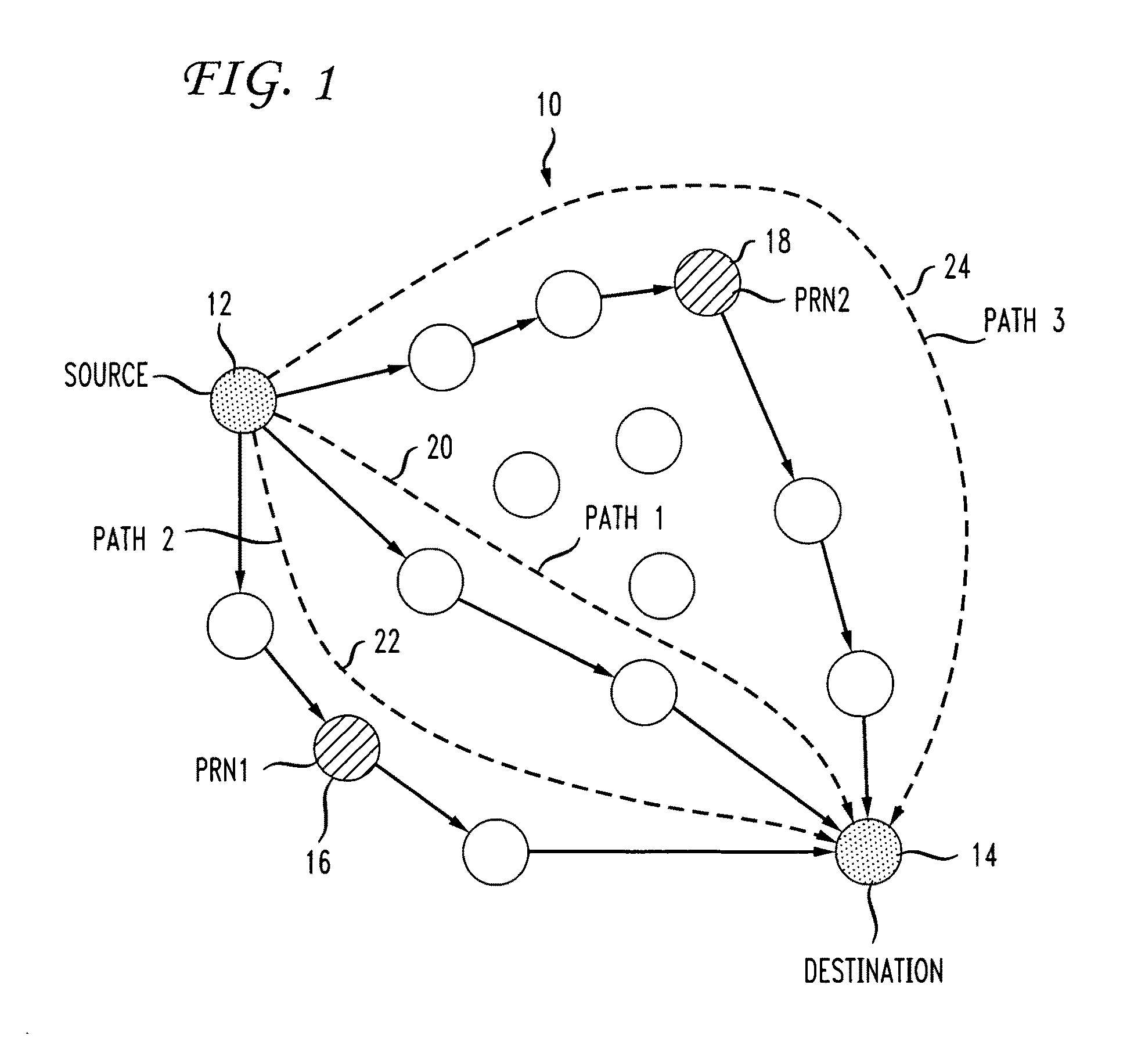
Data forwarding in hybrid mesh networks
ActiveUS20090073921A1Enhanced data path controlImprove service qualityNetwork traffic/resource managementNetwork topologiesForward algorithmWireless mesh network
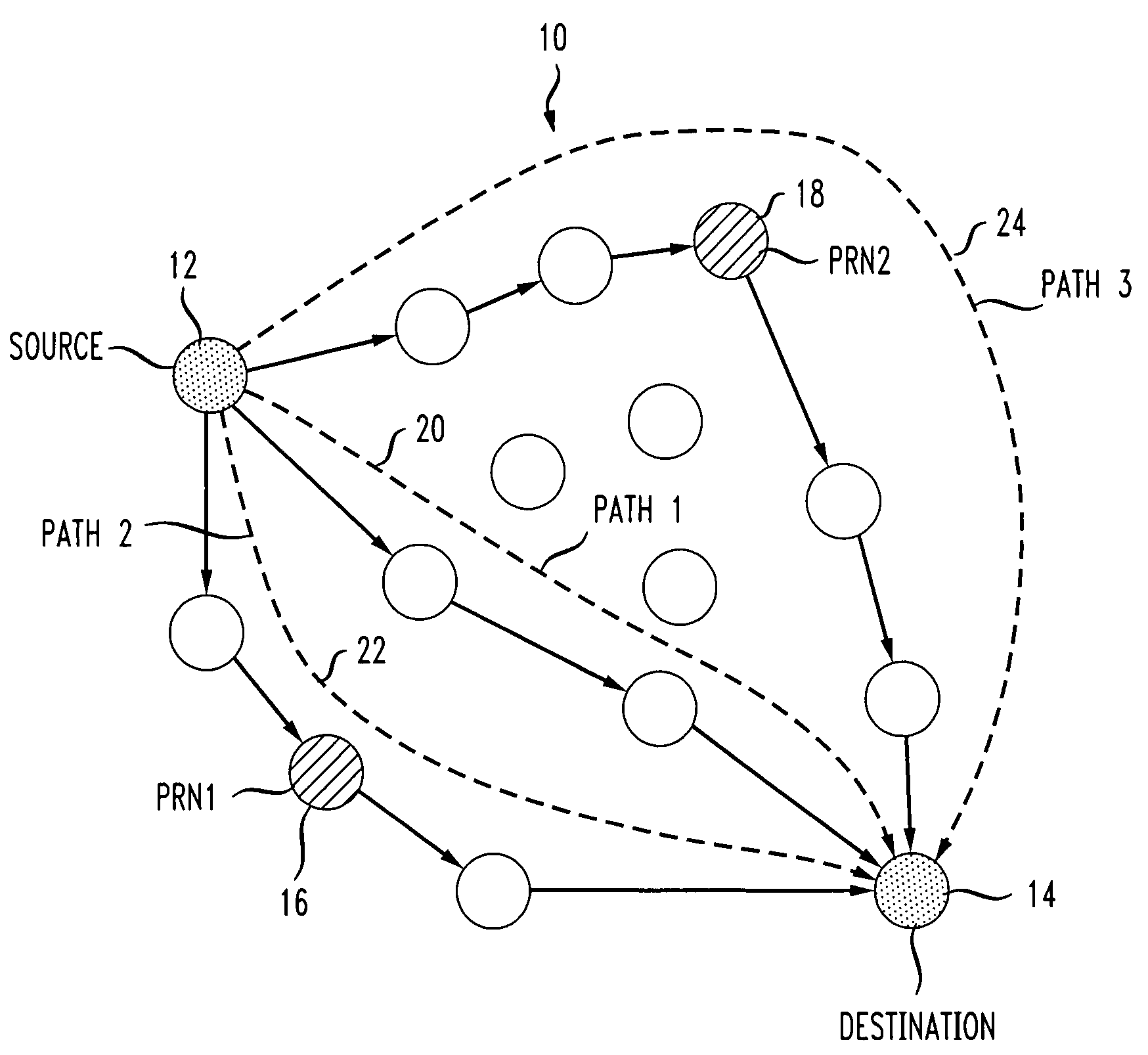
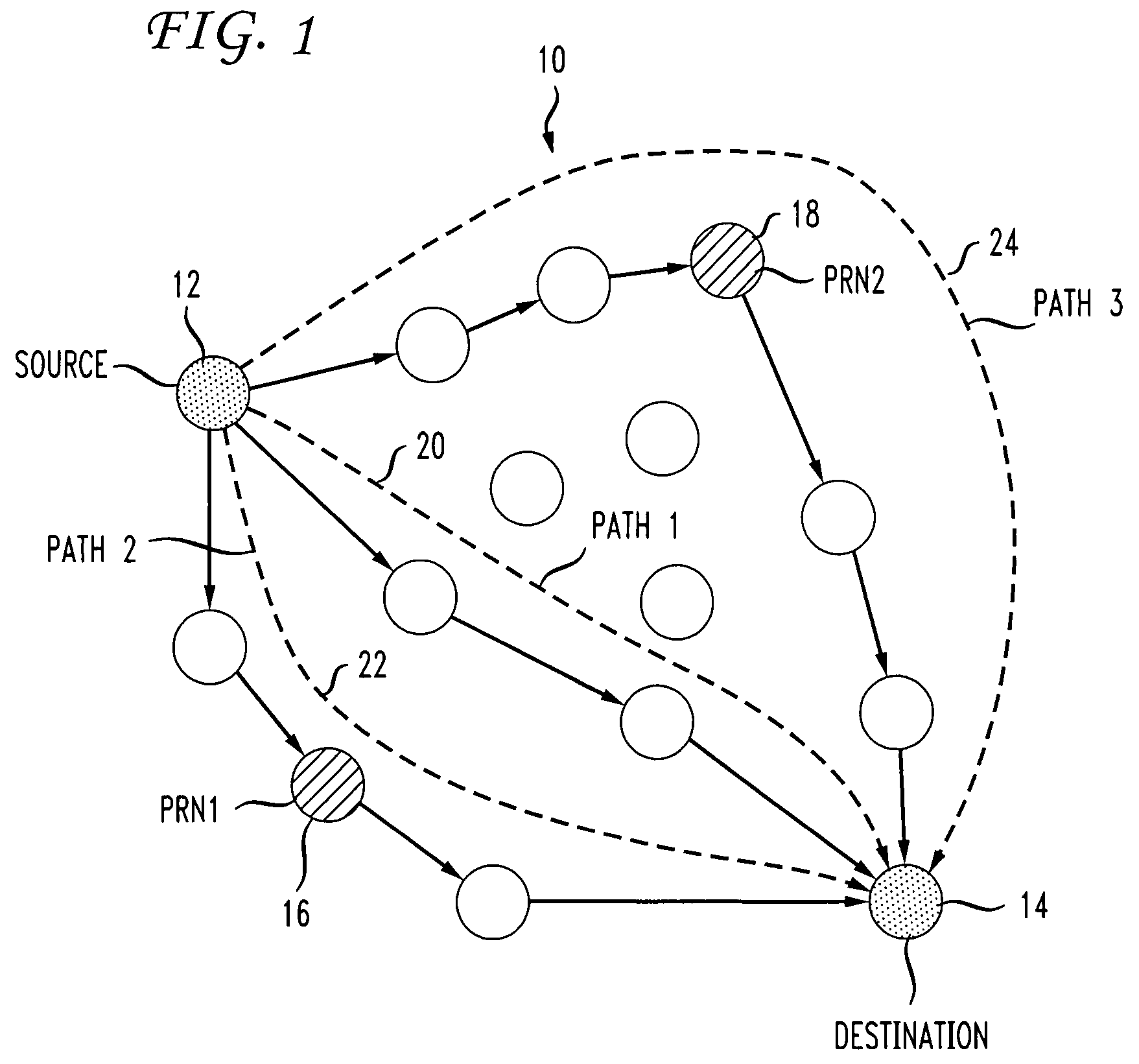
A system and method are disclosed for forwarding data in hybrid wireless mesh networks. The method includes configuring a number of mesh network nodes as Potential Relay Nodes (PRNs) in an overlay network associated with a hybrid wireless mesh network, streaming data packets from a source node to a destination node using a native data forwarding algorithm of the hybrid wireless mesh network, dynamically identifying Relay Nodes (RNs) among PRNs in the overlay network, creating secondary paths for sending data packets towards selected RNs in the overlay network, and relaying data packets from RNs to the destination node using the overlay network.
Owner:AT&T INTPROP I L P
Human gesture recognizing method based on depth convolution condition random field
ActiveCN105095862AMeet various needs in practical applicationsCharacter and pattern recognitionForward algorithmConditional random field
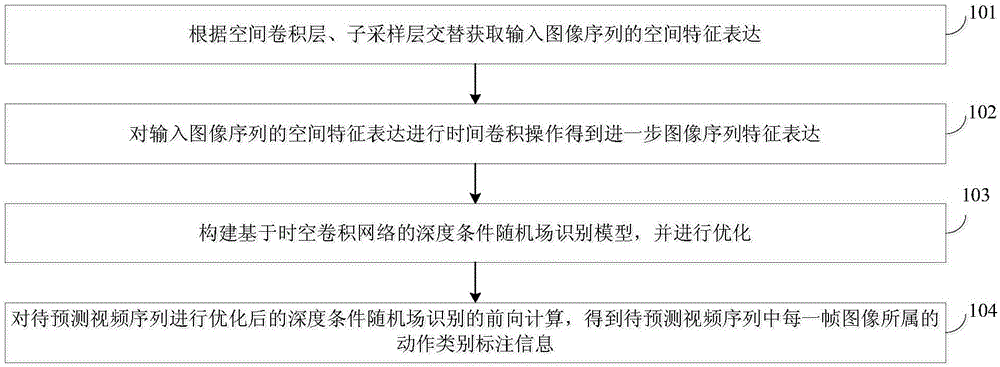
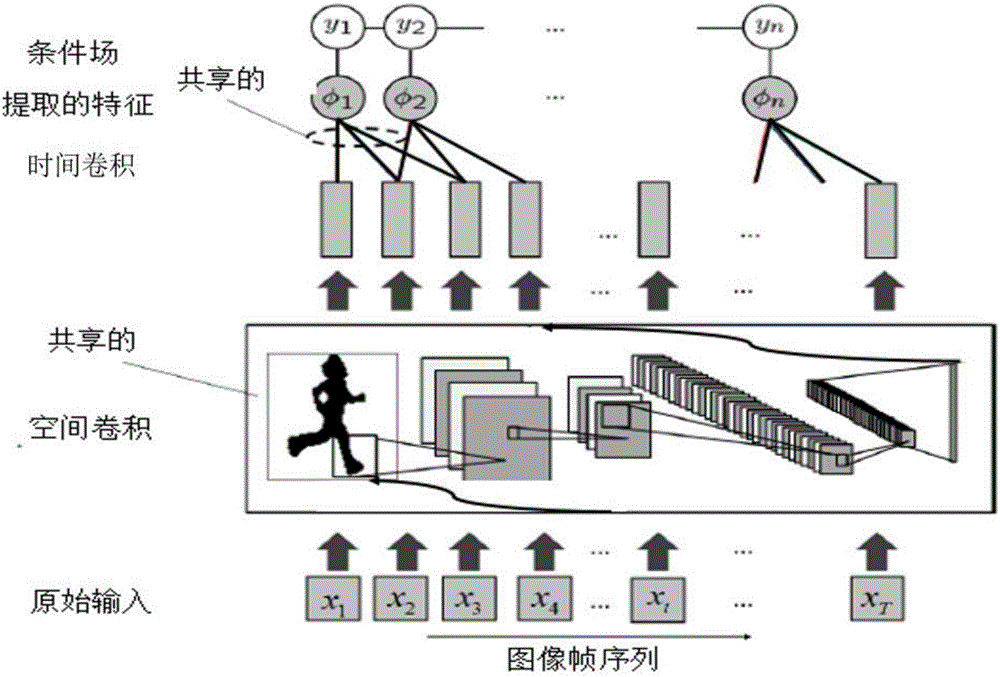
The invention discloses a human gesture recognizing method based on a depth convolution condition random field. The method comprises the following steps: alternately obtaining expressions of spatial characteristics of an inputted image sequence according to a space convolution layer and a sub-sampling layer; performing time convolution on the obtained expressions of spatial characteristics of the inputted image sequence to further obtain expressions on the image sequence; building a depth condition random field recognizing model based on a time convolution network and optimizing the model; conducting forward algorithm on the depth condition random field recognizing after the optimization of a to-be-predicted video sequence to obtain marked information for the movement category to which each frame image in the to-be-predicted video sequence belongs. According to the embodiments of the invention, the method is capable of building a model on the change of image sequence data from time to space, and therefore, a good human movement recognizing effect is achieved.
Owner:NANKAI UNIV
Method for determining gesture moving direction based on hidden Markov model
ActiveCN102592112ARealize judgmentOvercoming motion noiseImage analysisCharacter and pattern recognitionForward algorithmHide markov model
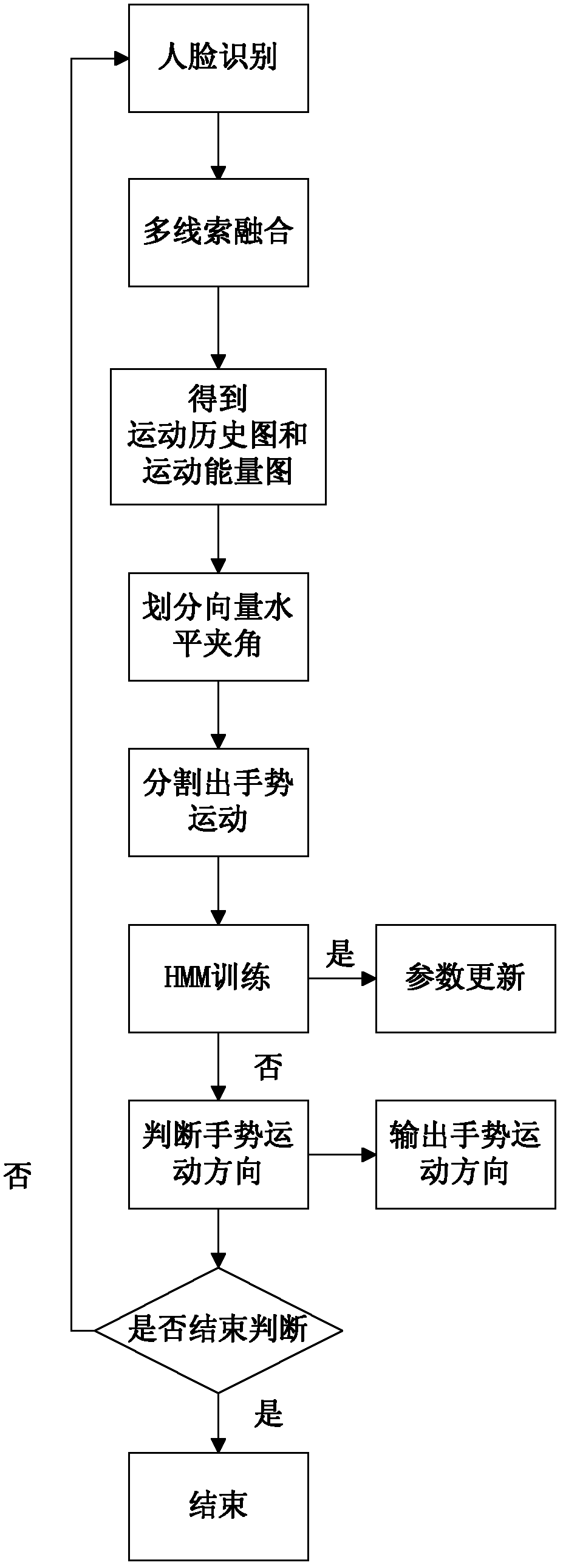
The invention relates to a method for determining a gesture moving direction based on a hidden Markov model. The method comprises the following steps of: a, recognizing a human face; b, acquiring a gesture area gray-scale map through multi-threaded fusion; c, updating a gesture moving history map and acquiring a moving energy map according to the gesture area gray-scale map; d, dividing vector horizontal angles; e, acquiring a starting moment and an ending moment of gesture movement through the moving energy map, and splitting the gesture movement; and f, training hidden Markov model parameters, and presuming the gesture moving direction by the forward algorithm and the backward algorithm of the hidden Markov model. By the method for determining the gesture moving direction based on the hidden Markov model, the gesture moving direction of the hidden Markov model is determined by using a plurality of determining conditions, so that the determination accuracy of the gesture movement can be improved, and the interference of various factors in a determination result can be obviously reduced.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
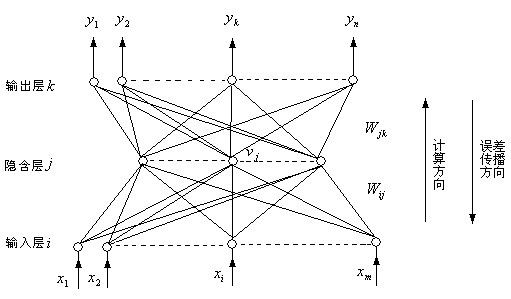
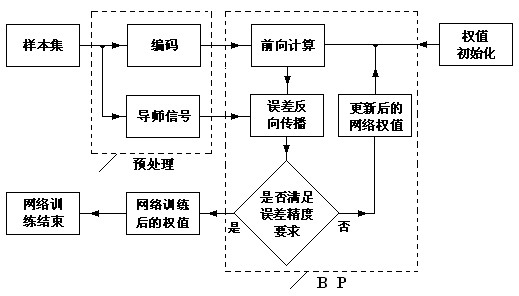
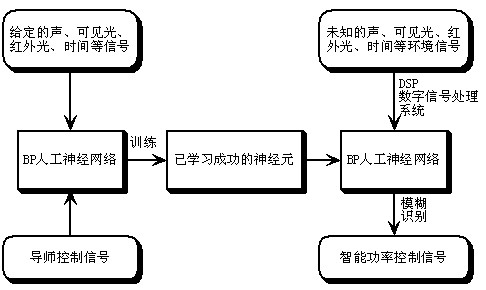
Intelligent street lamp energy-saving control system based on artificial neutral network
ActiveCN102413605ARealize intelligent energy-saving controlRealize energy-saving controlElectric light circuit arrangementEnergy saving control techniquesForward algorithmPower controller
The invention discloses an intelligent street lamp energy-saving control system based on an artificial neutral network. The intelligent street lamp energy-saving control system comprises a sensor system, an energy-saving control system and a power controller. An output signal of the sensor system is connected with an input terminal of the energy-saving control system; and an output signal of the energy-saving control system is connected with the power controller. Besides, the intelligent street lamp energy-saving control system is characterized in that: the sensor system includes environmental optical signal collection processing module, an infrared signal collection processing module and a sound signal collection processing module; the energy-saving control system consists of a DSP embedded system and an artificial neutral network module that is arranged in a DSP chip; and the artificial neutral network module is formed by a forward algorithm of an artificial neutral network BP algorithm and an artificial neuron that has been trained. According to the invention, according to peripheral environment situations of all street lamp illumination units, intelligent power control can be realized; and on the premise that an illumination requirement is met, energy consumption is effectively reduced.
Owner:付志
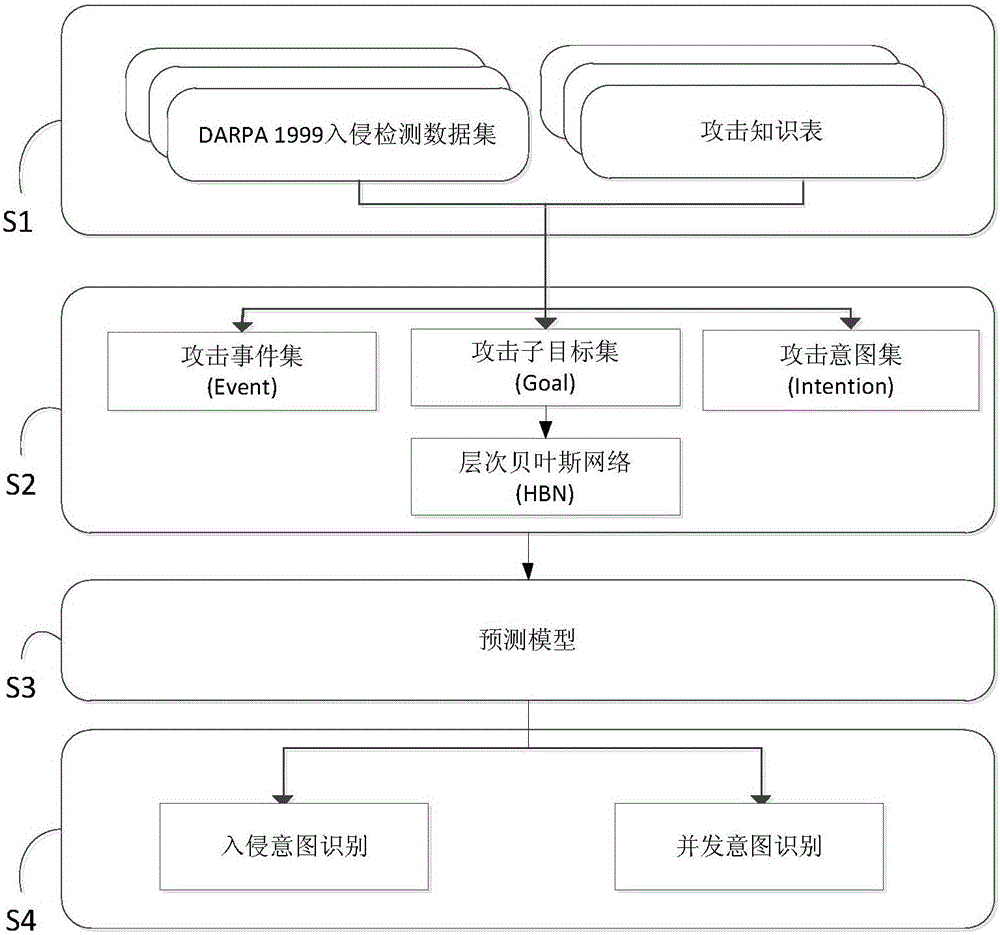
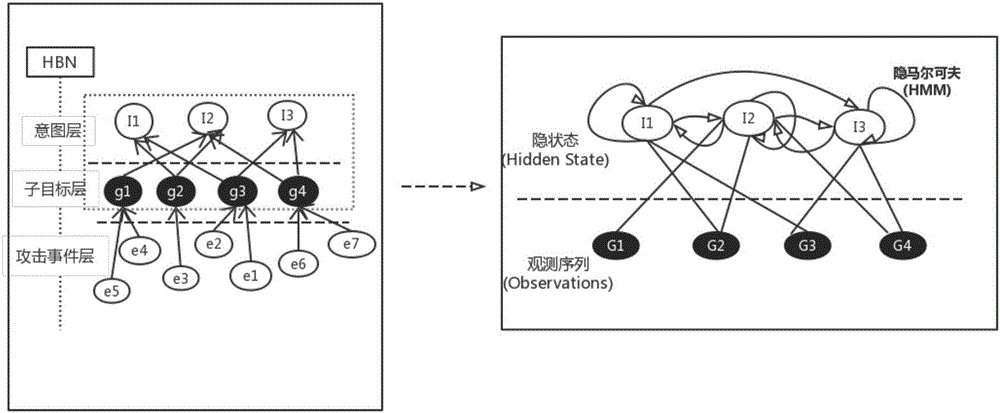
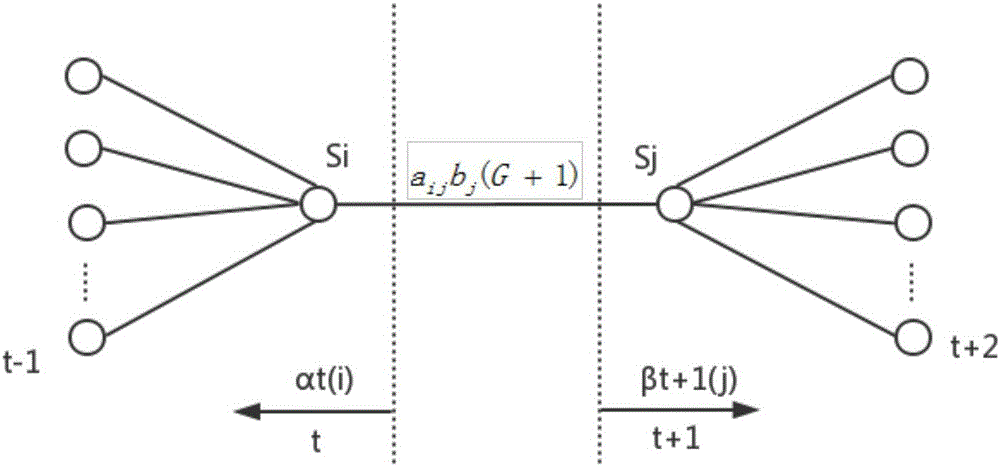
Intrusion intension recognition system and method based on hidden markov and probability inference
ActiveCN106682502AThe problem of optimizing a single probability outputAvoid subjectivityPlatform integrity maintainanceData switching networksForward algorithmLearning based
The invention discloses an intrusion intension recognition system and method based on hidden markov and probability inference, and belongs to the technical field of computer security. The method comprises the steps that firstly, due to the causal relationship existing among attack events, subgoals and intentions, a hierarchical bayesian network (HBN) is built for representing the causal relationship between the layers; secondly, the subgoals have the obvious time-order characteristics, and the hidden relationship for a target layer and an intention layer is learned based on a hidden markov model (HMM); finally, a multi-output hidden markov model (MO_HMM), a loop believable propagation algorithm (LBP) is introduced for optimizing the problem of single-probability output of a forward algorithm and a backward algorithm in HMM, and a plurality of possible intentions and probability can be reported.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
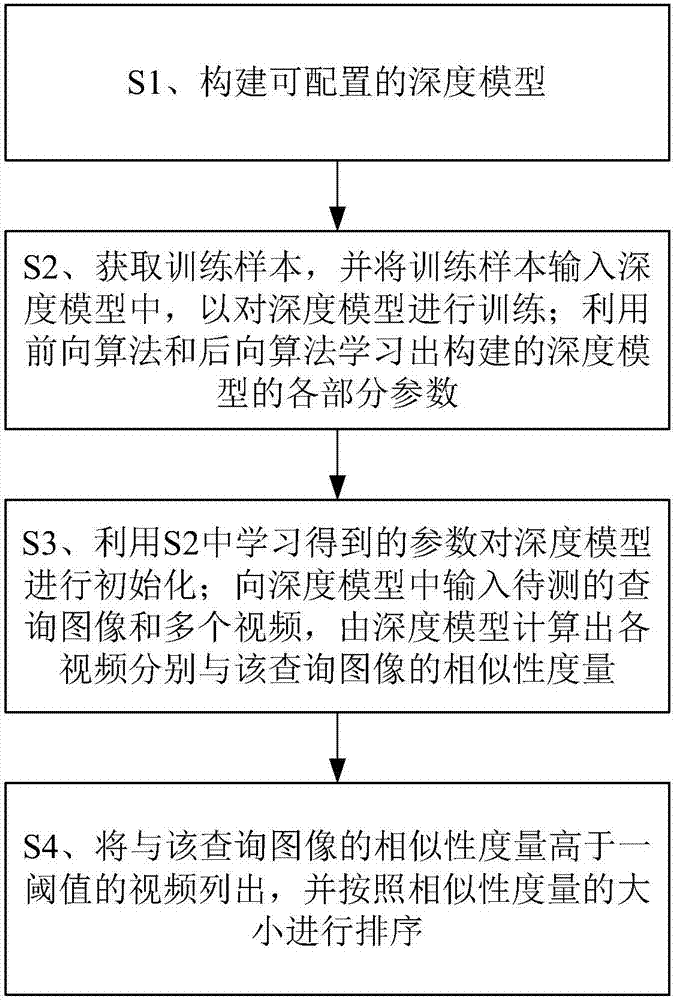
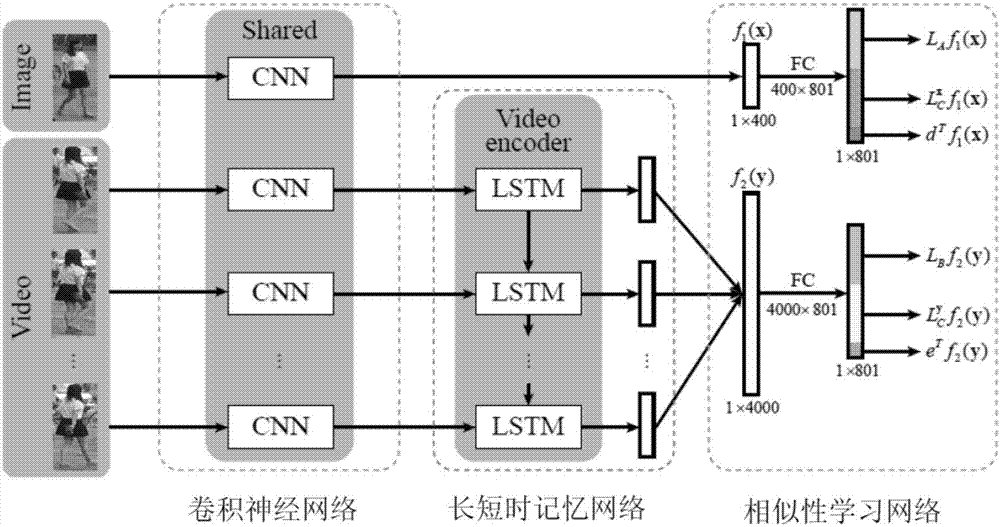
Pedestrian recognition method based on cross modal comparison between image and video
ActiveCN107480178ASolving a major problem in pedestrian re-identification technologyCharacter and pattern recognitionNeural architecturesForward algorithmPedestrian recognition
The invention provides a pedestrian recognition method based on the cross modal comparison between image and video, and is used for retrieving a video containing the corresponding characters in an input query image from multiple videos. The method includes the steps of S1, building a configurable depth model; S2, acquiring training samples, inputting the training samples into the depth model, training the depth model, and learning various parts of the parameters of the built depth model by utilizing the forward algorithm and the backward algorithm; S3, initializing the depth model by utilizing the obtained parameters learned in S2; inputting the query image and multiple videos to be measured in the depth model, and calculating the similarity measure between each video and the query image by utilizing the depth model; S4, listing the video with one threshold value higher than the similarity measure of the query image, and sorting according to the size of the similarity measure. According to the pedestrian recognition method, the pedestrian recognition based on the cross modal comparison between image and video under the precondition of guaranteeing high precision is achieved.
Owner:暗物智能科技(广州)有限公司
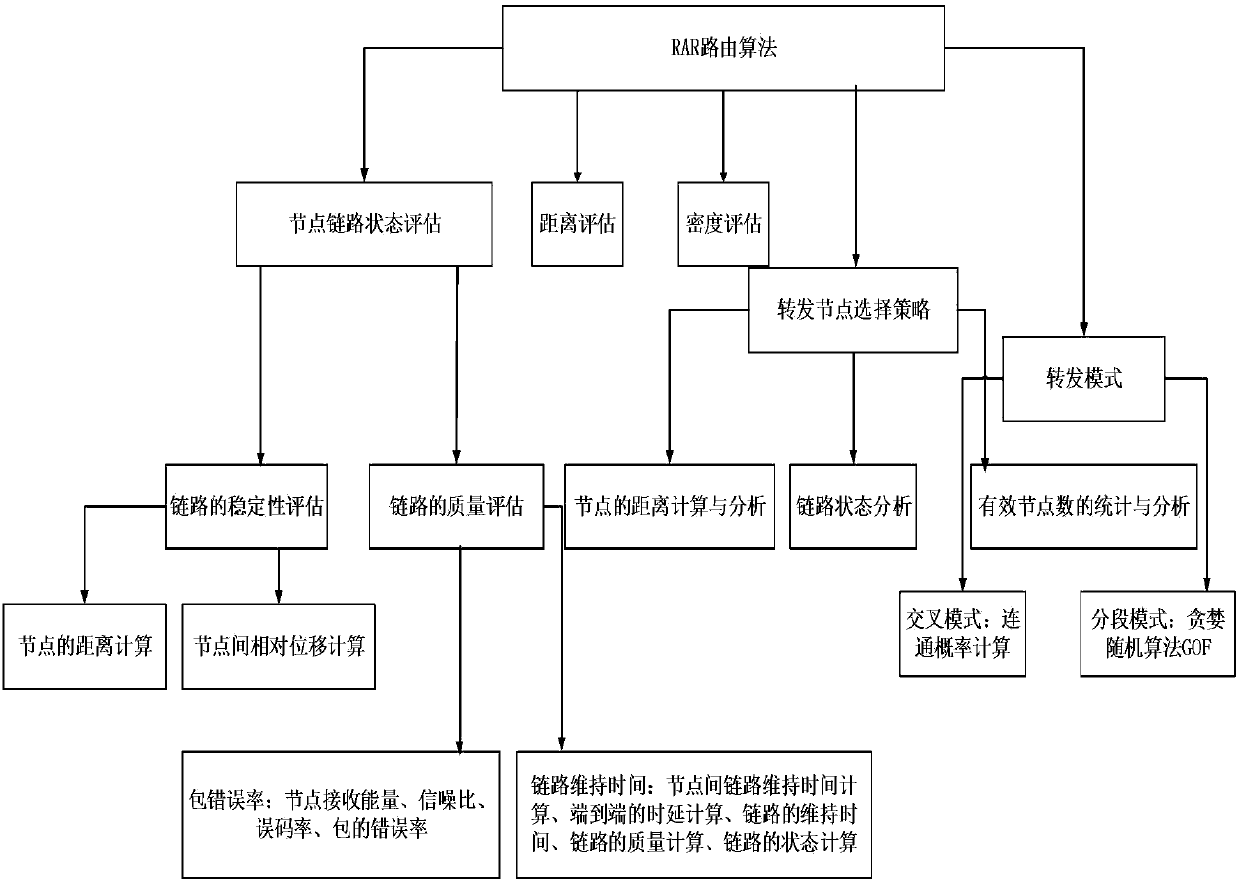
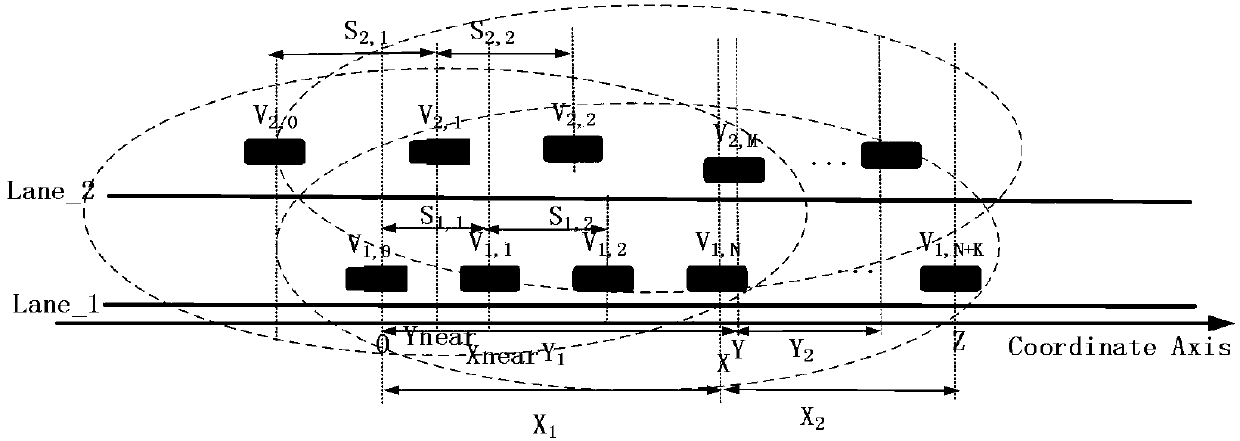
Self-adaptive routing method oriented to highway Internet-of-Vehicles scene
InactiveCN107645417ASolve the local maximization problemImprove delivery rateData switching networksForward algorithmThe Internet
The invention provides a self-adaptive routing method oriented to a highway Internet-of-Vehicles scene. Owing to the high-speed moving of vehicle-mounted ad hoc network nodes, a network topology changes frequently, and a transmission path is very prone to interrupt, thus the routing efficiency is decreased. The self-adaptive routing method comprises the steps of: acquiring an optimal forwarding node through calculating distance of the nodes, analyzing situations of link status among the nodes and conditions of next-hop effective node density; and proposing a new connection probability calculating method according to a distance between a parameter node and a nearest node thereof. The self-adaptive routing method adopts a greedy opportunity forwarding (GOF) algorithm for designing routes, the greedy opportunity forwarding (GOF) algorithm shows good effects in terms of delivery ratio, average hop count, end-to-end time delay and the like when compared with the traditional greedy perimeterstateless routing algorithm (GPSR) and a self-adaptive link perception beaconless forwarding algorithm (SLBF), and the performance of the Internet-of-Vehicles is improved (wherein the delivery ratiois increased by 10%, the average hop count is decreased by 20%, and the end-to-end time delay is shortened by 10%).
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
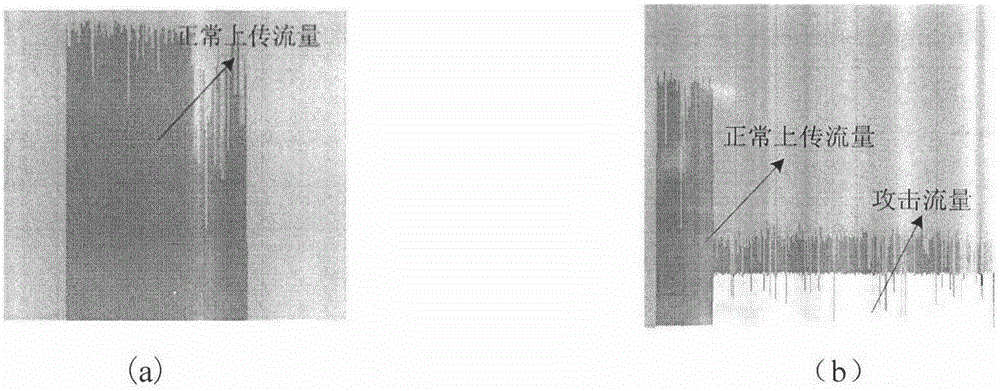
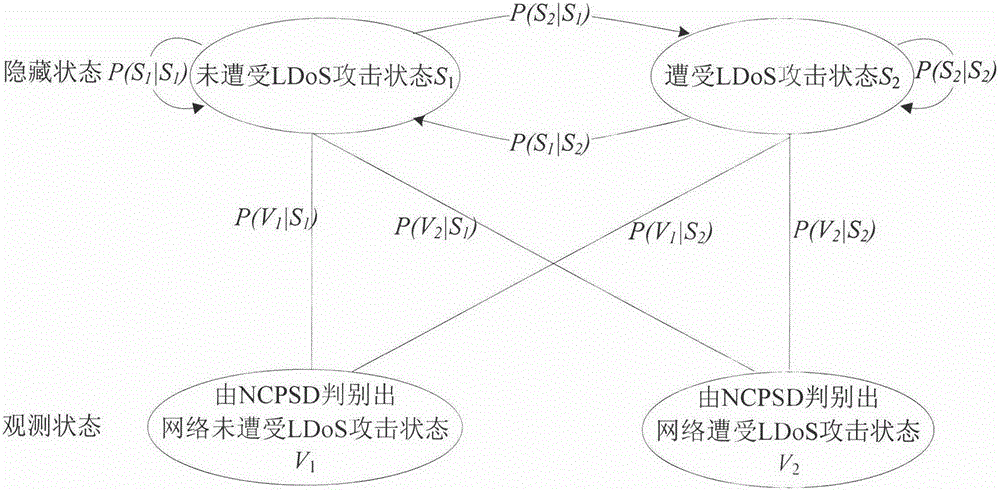
Method of using hidden Markov model to detect LDoS (Low-Rate Denial of Service) attack
A LDoS (Low-Rate Denial of Service) attack has features of low average rate and strong hidden performance. The traditional detection method does work. The invention provides a LDoS attack detection method based on the hidden Markov model for the LDoS attack. Firstly, the hidden Markov model is built for a network state, and a detection result in a NCPSD (Normalized Cumulative Power Spectrum Density) method serves as an observation value of the hidden Markov model; forward algorithm is used to obtain deviation of different observation value sequences in the model to serve as a detection basis; and in NS-2, the detection method is tested, experimental results show that the method can effectively detect the LDoS attack, and compared with other methods, the detection performance is better. The detection rate is 99.96% through hypothesis test, and the method has the advantages of high detection probability, low false alarm rate and low missed alarm rate.
Owner:CIVIL AVIATION UNIV OF CHINA
Data forwarding in hybrid mesh networks
ActiveUS8385345B2Improve service qualityNetwork traffic/resource managementNetwork topologiesStreaming dataForward algorithm
A system and method are disclosed for forwarding data in hybrid wireless mesh networks. The method includes configuring a number of mesh network nodes as Potential Relay Nodes (PRNs) in an overlay network associated with a hybrid wireless mesh network, streaming data packets from a source node to a destination node using a native data forwarding algorithm of the hybrid wireless mesh network, dynamically identifying Relay Nodes (RNs) among PRNs in the overlay network, creating secondary paths for sending data packets towards selected RNs in the overlay network, and relaying data packets from RNs to the destination node using the overlay network.
Owner:AT&T INTPROP I LP
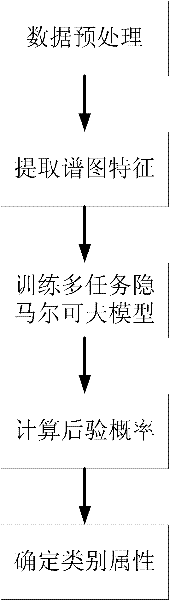
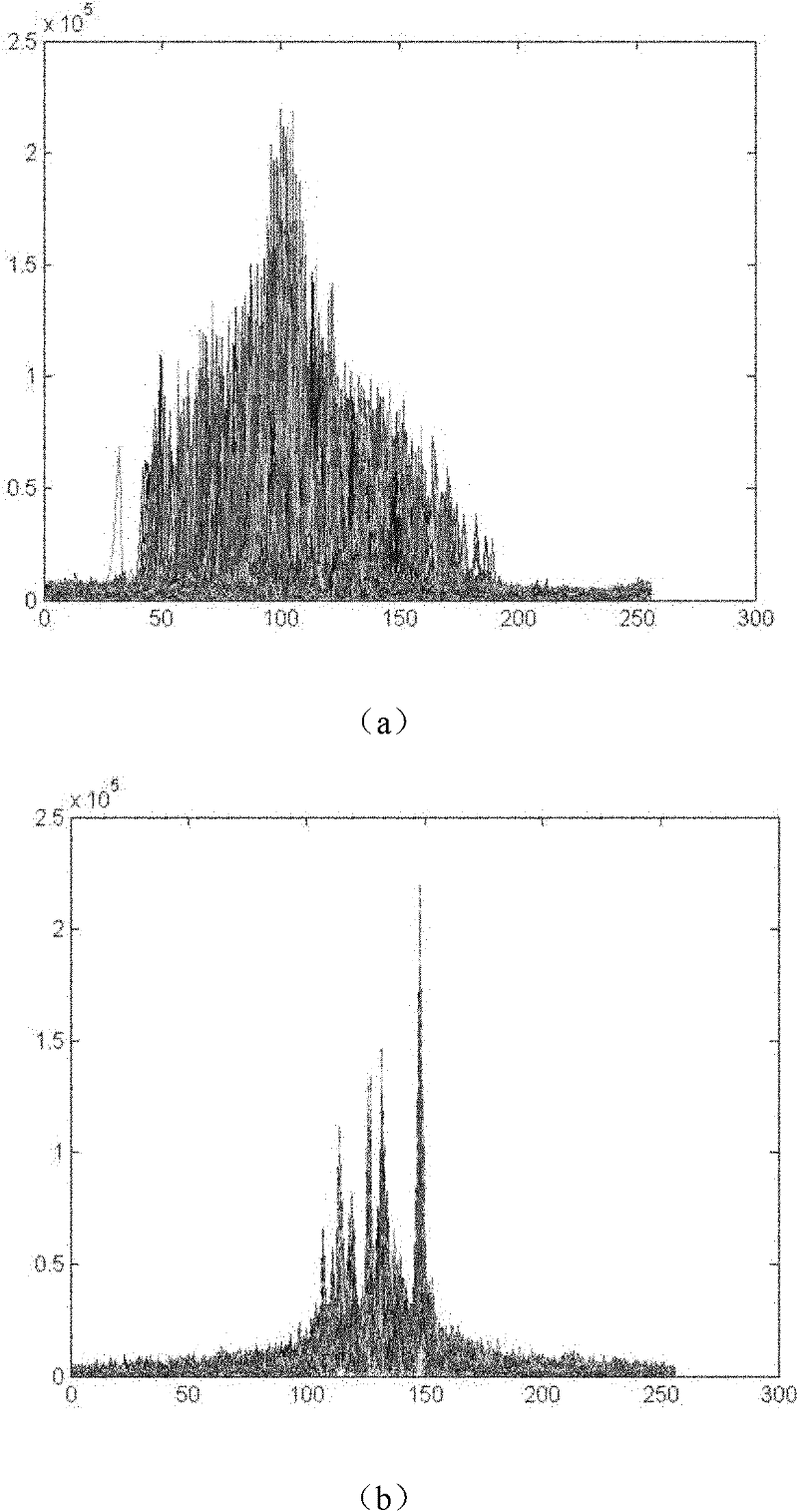
Spectrogram feature-based radar target high-resolution distance image identification method
ActiveCN102175999AEasy to identifyReduce demandWave based measurement systemsCharacter and pattern recognitionForward algorithmCategory attribute
The invention provides a spectrogram feature-based radar target high-resolution distance image identification method for mainly solving the problems of poor identification performance and high memory demand and calculated quantity in the conventional radar aircraft target identification technology. The method comprises the following processes of: preprocessing radar training target distance echo data; extracting spectrogram features from the preprocessed radar training target distance echo data and the radar test target distance; training a multi-task hidden Markov model for the spectrogram features of each frame of the radar training target echo data along the time dimensions of the spectrogram features, determining parameters of the model, and calculating the posterior probability values of the radar test target echo data by using a forward algorithm; and taking the category attribute of the radar training target echo data corresponding to the maximum posterior probability value as the category attribute of the radar test target echo data. The method has the advantages of high identification performance and low memory demand and calculation burden, and can be used for identification of an aircraft target.
Owner:XIAN CETC XIDIAN UNIV RADAR TECH COLLABORATIVE INNOVATION INST CO LTD
Time-domain-characteristic-based method for identifying high-resolution range profile of radar target
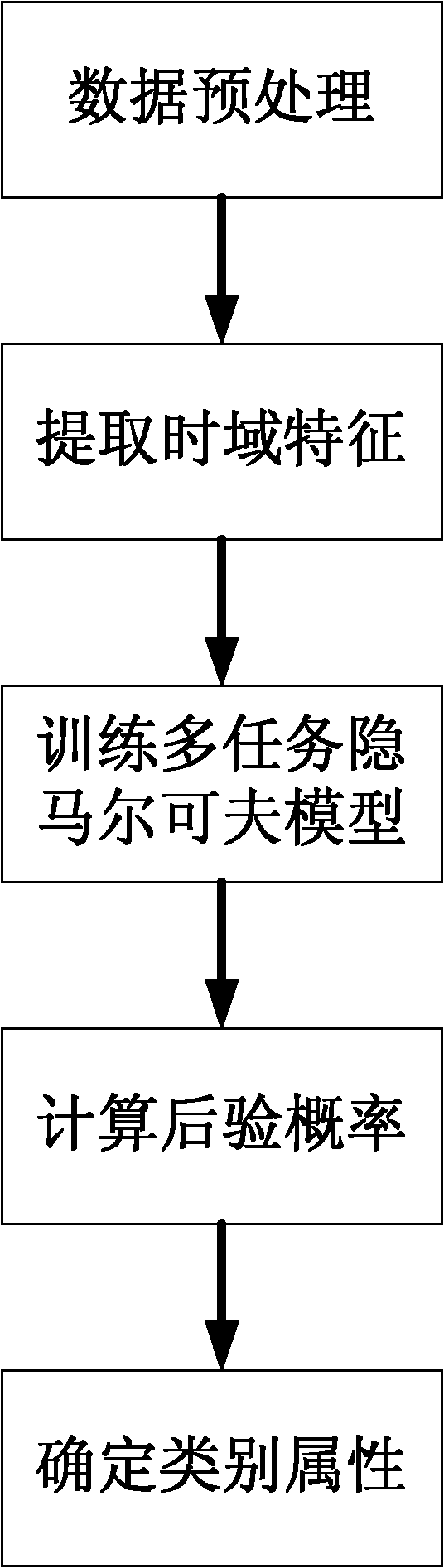
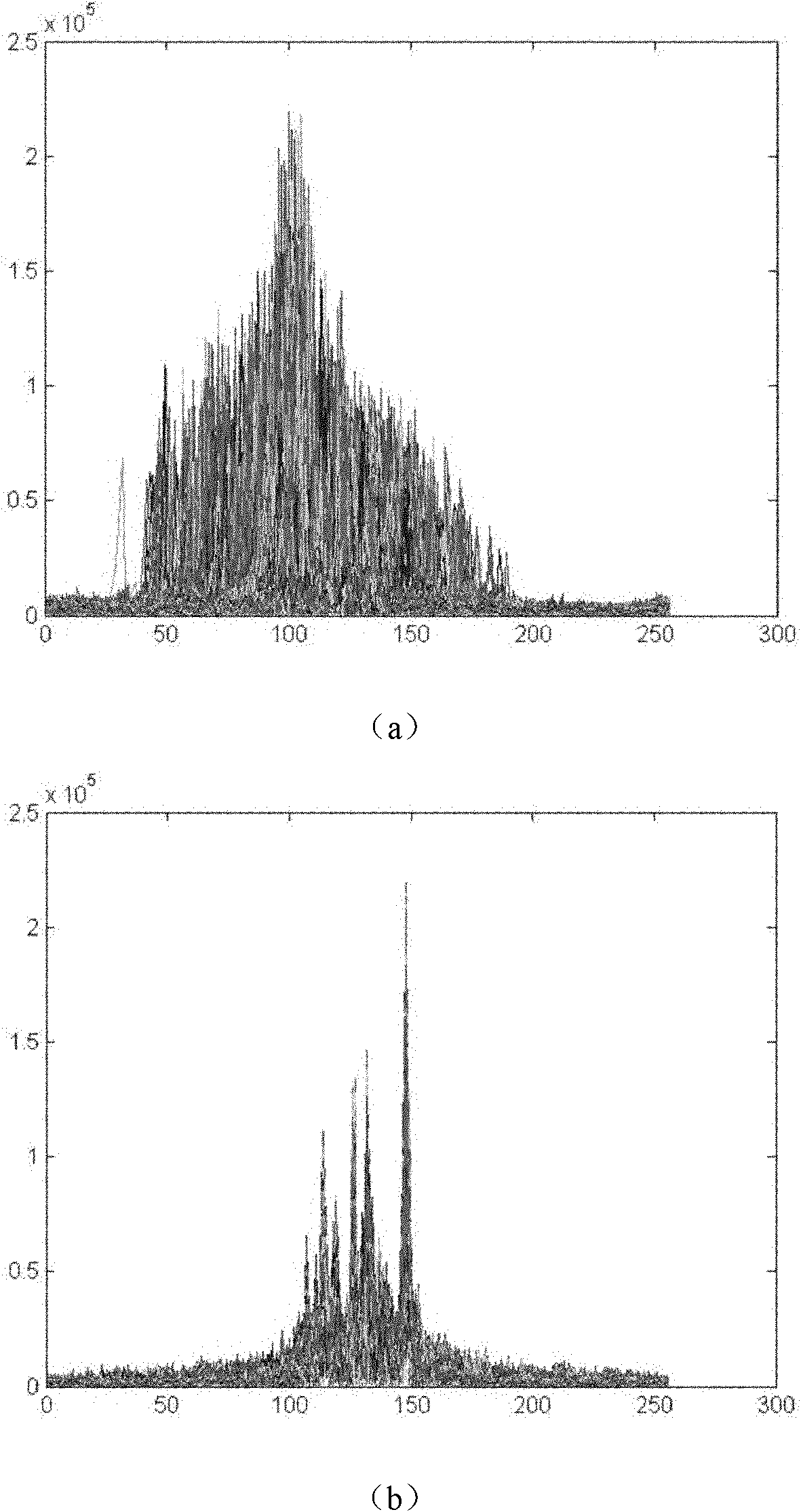
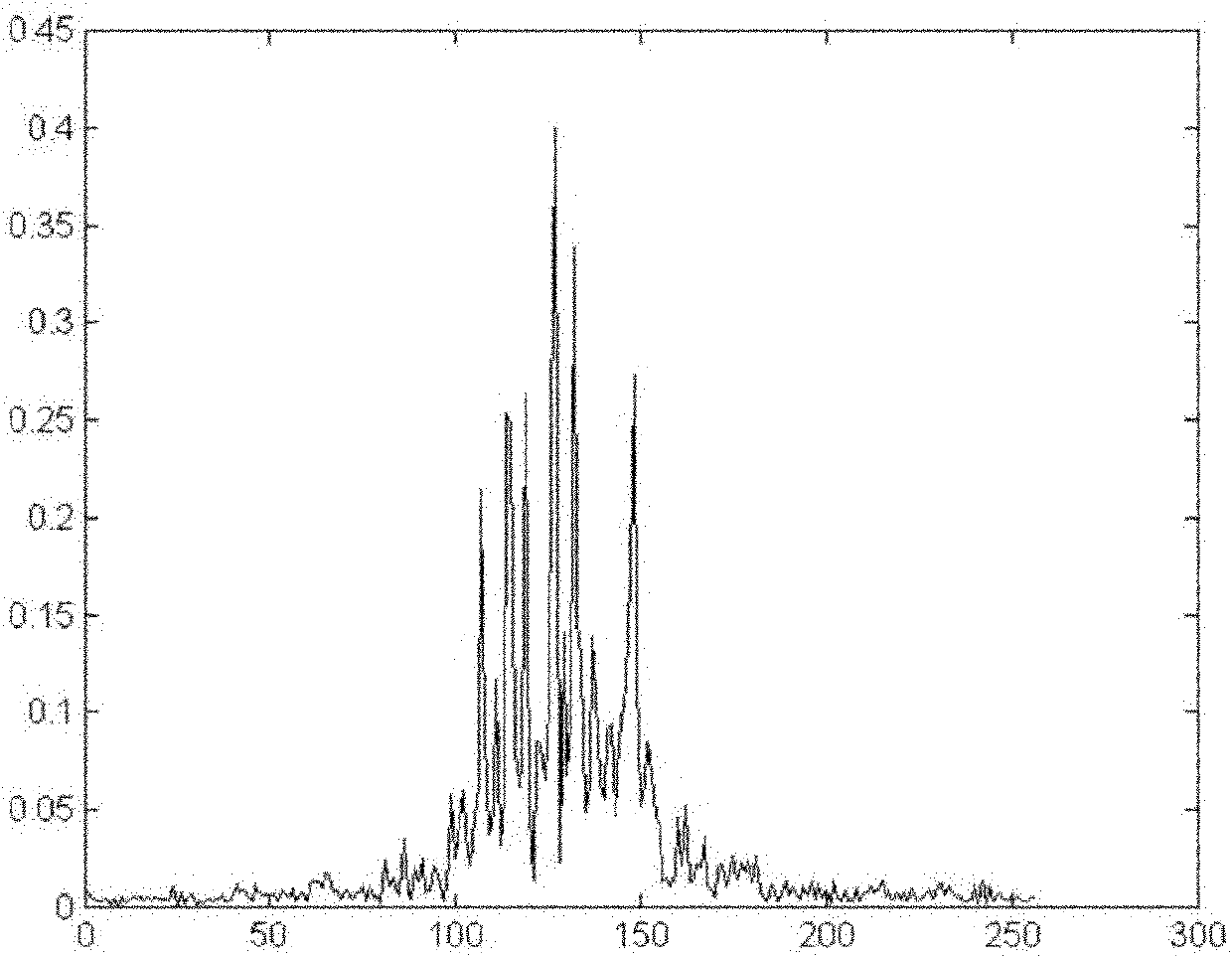
ActiveCN102169177AEasy to identifyReduce demandWave based measurement systemsInternal memoryForward algorithm
The invention provides a time-domain-characteristic-based method for identifying a high-resolution range profile of a radar target, mainly solving the problems of the traditional radar airplane target identification technology, such as poor identification performance and large internal memory requirement and calculation quantity. The method comprises the following implementation steps of: preprocessing radar training target range echo data; taking modulus from the preprocessed radar training target range echo data and radar testing target range echo data to obtain respective time domain characteristics; training a multitask hidden Markov model for the time domain characteristic of every frame of the radar training target echo data along an echo range unit to determine model parameters, and calculating posterior probability values of the radar testing target echo data by using a forward algorithm; and regarding the categorical attribute of the radar training target echo data corresponding to the maximum posterior probability value as the categorical attribute of the radar testing target echo data. The method disclosed by the invention has the advantages of high identification performance and small internal memory requirement and calculation quantity and can be used for identifying an airplane target.
Owner:XIDIAN UNIV
Workflow bidirectional scheduling method based on cloud computing
ActiveCN104834995ALow costMeet the individual needs of flexible schedulingResourcesForward algorithmPersonalization
The invention discloses a workflow bidirectional scheduling method based on cloud computing. The workflow bidirectional scheduling method comprises a step 1 of adopting a backward algorithm to begin distribution and scheduling from tail nodes of multiple task nodes of a workflow under a condition that the workflow can be timely completed at the deadline, so as to obtain a workflow subjected to the backward algorithm; and a step 2 of adopting a forward algorithm according to the earliest start time of the multiple task nodes to begin forward scheduling of each take node from head nodes of the multiple task nodes of the workflow subjected to the backward algorithm under a condition that the dependence relationship of the multiple task nodes is satisfied and the deadline of the workflow is not exceeded. The workflow bidirectional scheduling method based on cloud computing saves the cost of a user and meets customized demands for flexible scheduling of the user.
Owner:上海英拿信息技术有限公司
Method and Device to Manage Fluid Volumes in the Body
ActiveUS20150250427A1Mechanical/radiation/invasive therapiesMedical devicesForward algorithmMedicine
A system and method for determining the amount of fluid to be removed from a dialysis patient is disclosed. The system utilizes sensors and a computer. The computer obtains the input parameters from the sensors, along with information added directly by the user, and performs a forward algorithm to determine a recommended change in patient fluid level. As fluid is removed, the effect of the removal on the parameters is detected by the sensors and re-transmitted back to the computer. The computer then performs a backward algorithm to refine the variables used in the forward algorithm and obtain more accurate results. The system and method provide for changing the amount of fluid removed from the patient based on the results of the algorithm and the data received from the sensors.
Owner:MOZARC MEDICAL US LLC
Design method for PAC controller based on intelligent control algorithms
InactiveCN105759607AHigh control output precisionAvoid heavy computationAdaptive controlForward algorithmNetwork communication
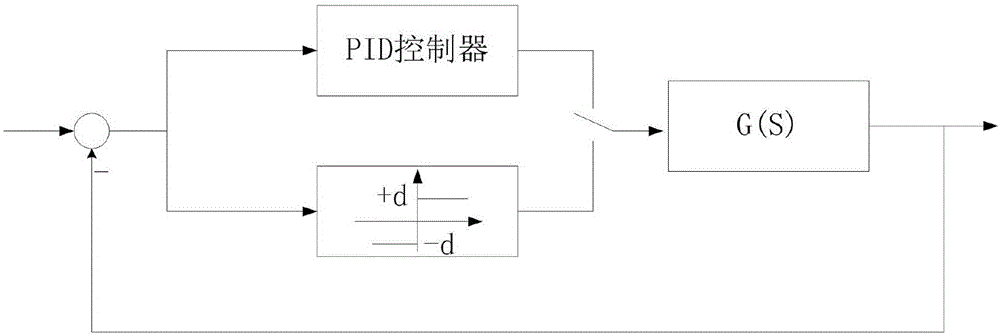
The invention discloses a design method for a PAC controller based on intelligent control algorithms. On the basis of a conventional PAC controller, the invention can improve the control accuracy and control response, and meet higher control requirements by using intelligent control algorithms such as an improved PID control algorithm, a variable universe fuzzy PID control algorithm, a PID control algorithm based on a neural network. In an aspect of network communication, the Ethernet, CAN bus and other means of communication are added on the basis of conventional serial ports 232 and 485, and Modbus-RTU, Modbus-TCP, CANopen, custom protocols and so forth are used for achieving network interconnection. An integral windup prevention algorithm, an algorithm for differentiation of control variables, a differential forward algorithm and the like are added on the basis of a conventional PID, the PID effect can be significantly improved, the response speed is increased, and the control overshoot is reduced.
Owner:BEIJING UNIV OF TECH
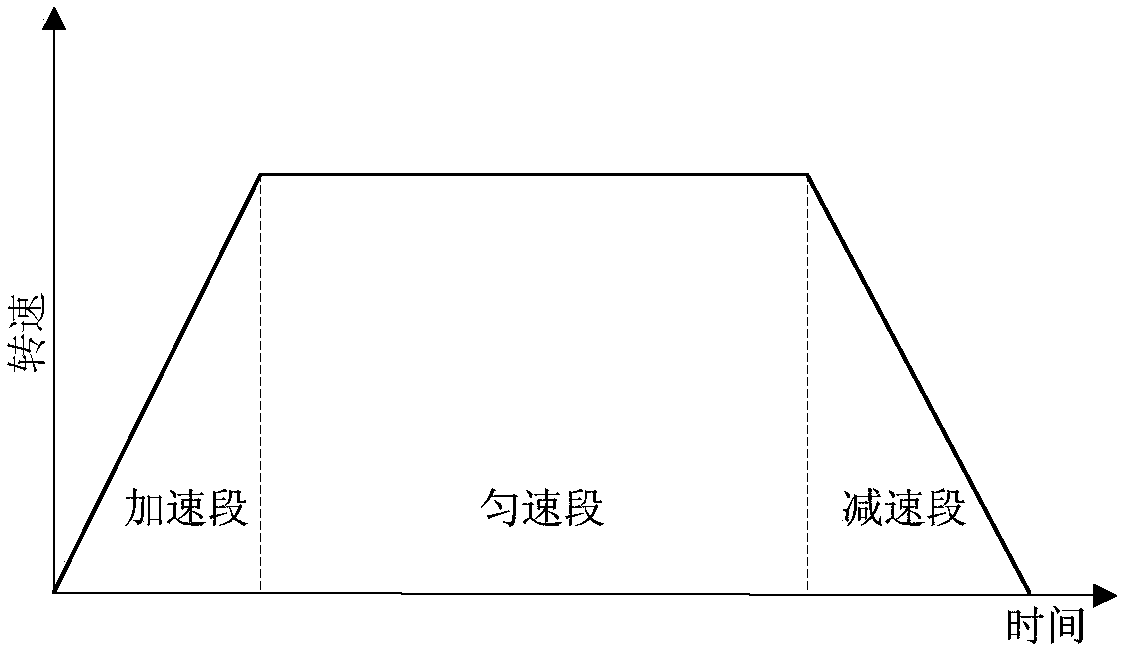
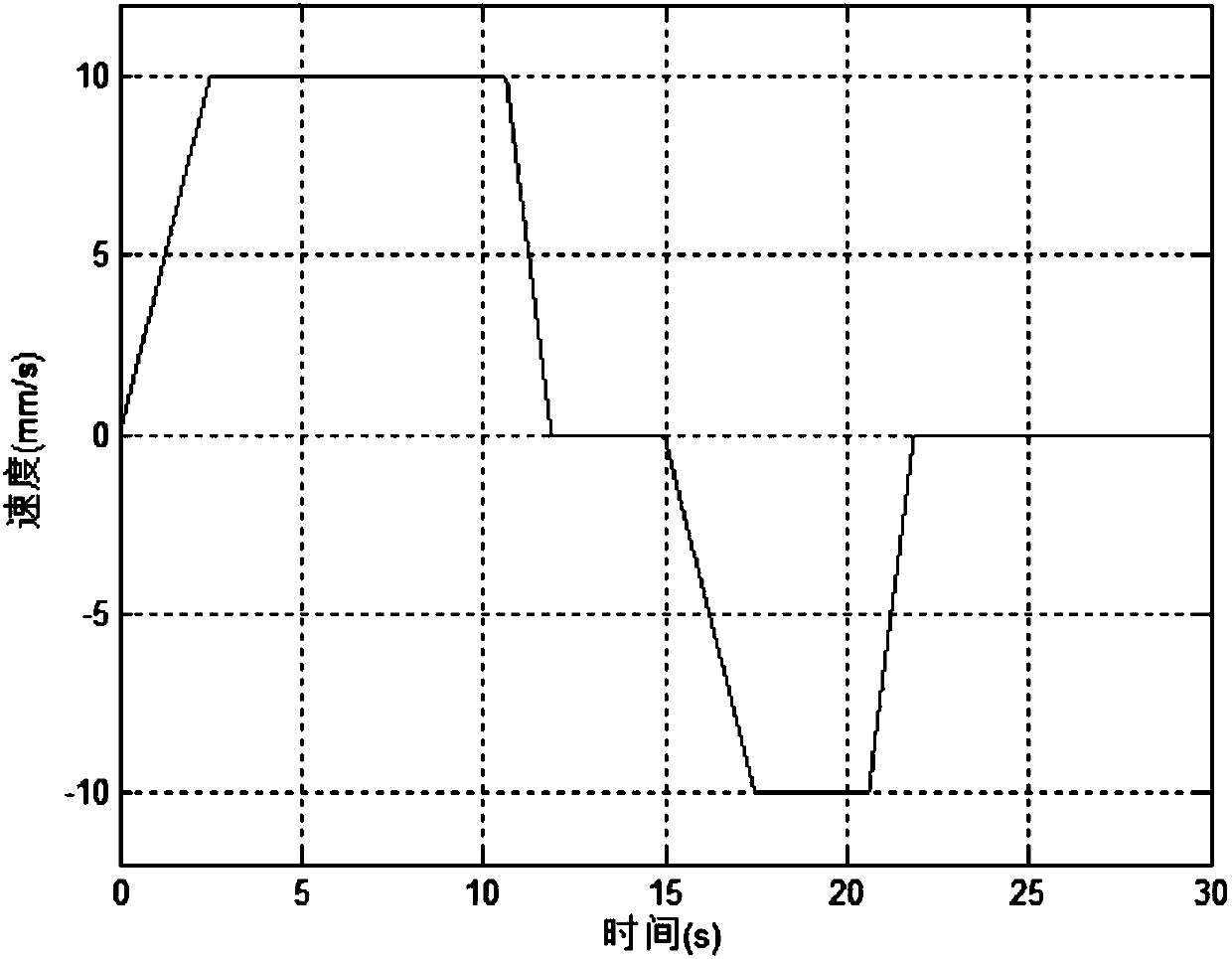
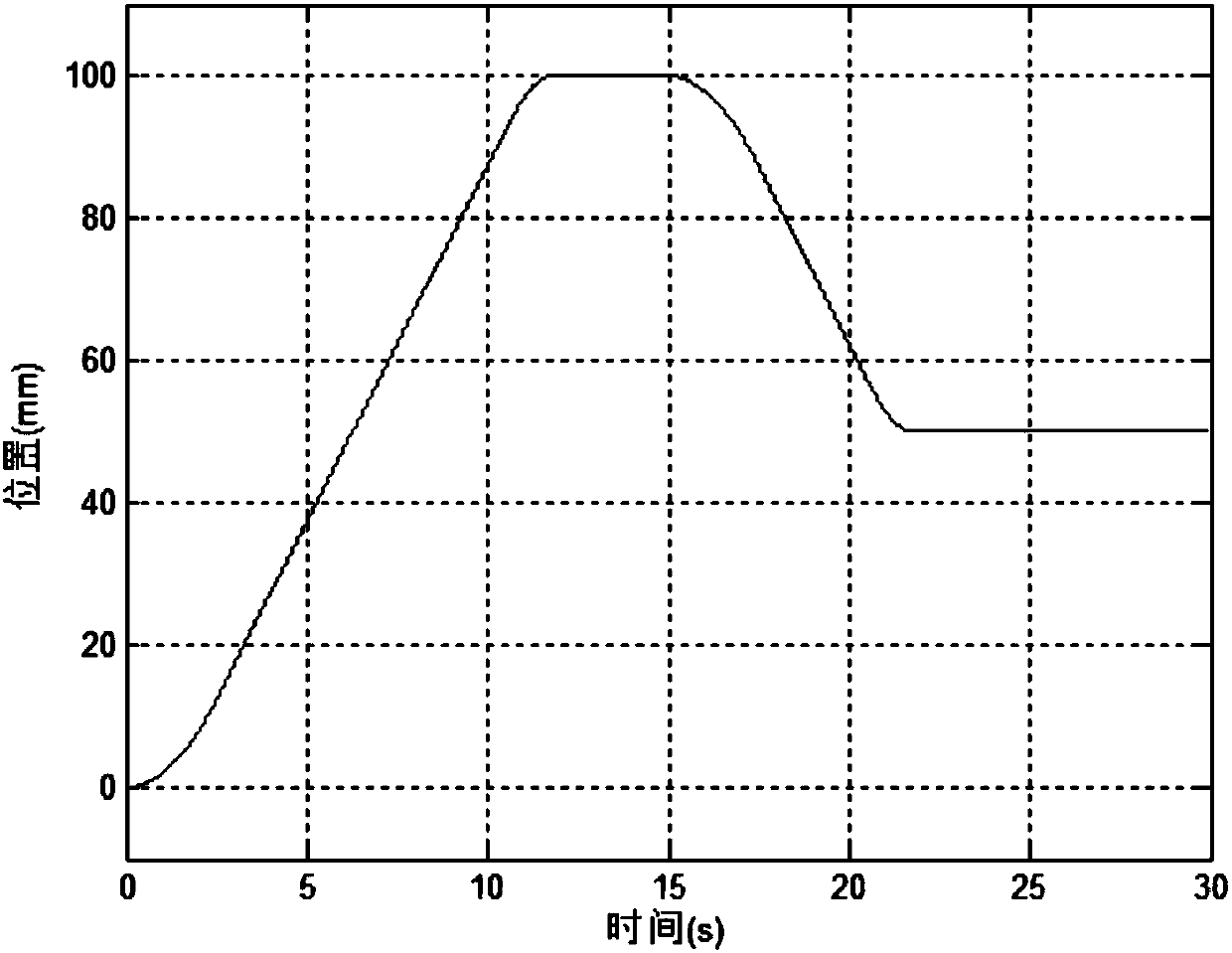
Motion curve discrete dynamic planning method
ActiveCN107844058AImprove Motion Control AccuracyImprove efficiencyAdaptive controlForward algorithmObject motion
The invention relates to a motion curve discrete dynamic planning method, which relates to the technical field of motion control. The motion curve discrete dynamic planning method is based on a discrete mathematical model of object motion, adopts a dynamic forwarding algorithm, calculates a speed value satisfying maximum deceleration of a subsequent position distance at first according to currentmotion information (position, speed), then calculates acceleration forwardly in an inverse mode, planning a curve by utilizing accelerated motion, decelerated motion and constant velocity motion, realizes trapezoidal accelerated and decelerated motion of an object, can ensure that a number of planned routes is an integral multiple of a discrete period and a speed is zero when a position destination is reached, and can plan the curve in real time according to varied target positions, so as to improve the motion control precision and efficiency.
Owner:BEIJING INST OF SPECIALIZED MACHINERY
Data forwarding in hybrid mesh networks
InactiveUS20130142108A1Improve service qualityFrequency-division multiplex detailsNetwork traffic/resource managementForward algorithmStreaming data
A system and method are disclosed for forwarding data in hybrid wireless mesh networks. The method includes configuring a number of mesh network nodes as Potential Relay Nodes (PRNs) in an overlay network associated with a hybrid wireless mesh network, streaming data packets from a source node to a destination node using a native data forwarding algorithm of the hybrid wireless mesh network, dynamically identifying Relay Nodes (RNs) among PRNs in the overlay network, creating secondary paths for sending data packets towards selected RNs in the overlay network, and relaying data packets from RNs to the destination node using the overlay network.
Owner:AT&T INTPROP I LP
Wifi and geomagnetism fused indoor positioning system and method based on HMM (Hidden Markov Model)
ActiveCN108521627AOvercoming the problem of low precisionHigh precisionParticular environment based servicesLocation information based serviceForward algorithmHide markov model
The invention discloses a wifi and geomagnetism fused indoor positioning system and method based on an HMM (Hidden Markov Model). The method comprises the following steps: matching a wifi signal acquired by a mobile terminal in real time with a pre-established wifi fingerprint library to obtain a local position area; initializing the position in the area to obtain an initial probability distribution matrix; obtaining a state transition probability matrix by using a position relationship of label points in the local position area; and fusing a geomagnetic signal with a pre-established geomagnetic fingerprint library to obtain an observation probability matrix, and estimating the position of a user according to a forward algorithm. When the user is positioned in the local position area determined by the wifi signal, the current real-time geomagnetic signal is used to update the observation probability matrix, and the position of the user is estimated by the observation probability matrixand the state transition matrix; otherwise, the wifi signal is introduced to re-establish the local position area, and the initial probability distribution matrix, the state transition probability matrix and the observation probability matrix are updated according to the preceding method. According to the wifi and geomagnetism fused indoor positioning method based on the provided by the invention, various information is effectively fused, and the positioning accuracy of the system is improved.
Owner:SOUTH CHINA UNIV OF TECH
Energy collection wireless sensor network routing algorithm based on geographical location
ActiveCN106211257AProcess stabilityUse energy balanceHigh level techniquesWireless communicationForward algorithmGeographic site
The invention discloses an energy collection wireless sensor network routing algorithm based on a geographical location. The algorithm comprises the steps of S1, changing a single-routing path mode of a greedy algorithm into a multi-routing path mode; S2, employing a new type border routing forwarding mode; S3, starting an energy level mechanism, starting a first step of a greedy mode, dividing a high energy level node set and a low energy level node set in a communication radius range of a to-be-forwarded node; S4, starting a second step of the greedy mode, selecting a next hop node from the node set on which energy level division screening is carried out through an improved layered self-adaptive greedy algorithm; and S5, entering a border routing forwarding algorithm for selection of the next hop node when greed is failed. According to the algorithm, with respect to the to-be-forwarded node, in the routing process, factors such as distance, an angle peripheral node density and residual energy between the next hop node and a destination node can be integrated, so that the routing path is converged to the optimum routing path to the greatest extent, and the node energy is utilized in balance.
Owner:GUANGZHOU UNIVERSITY
Fuzzy adaptive PID control method for fuel cell voltage
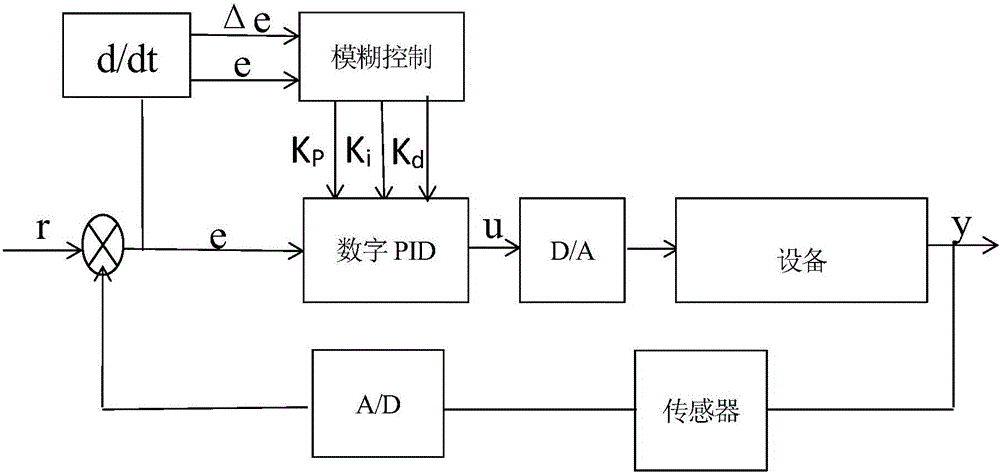
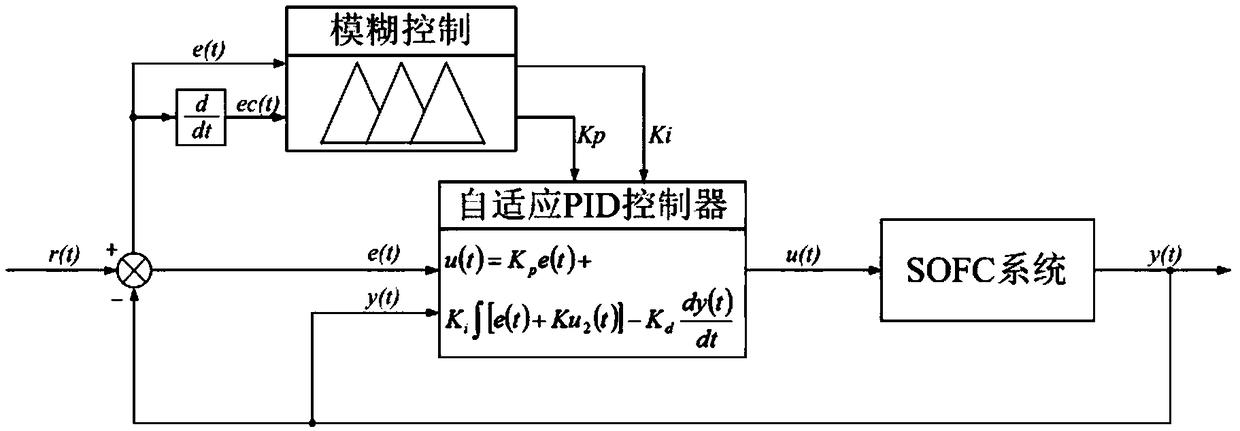
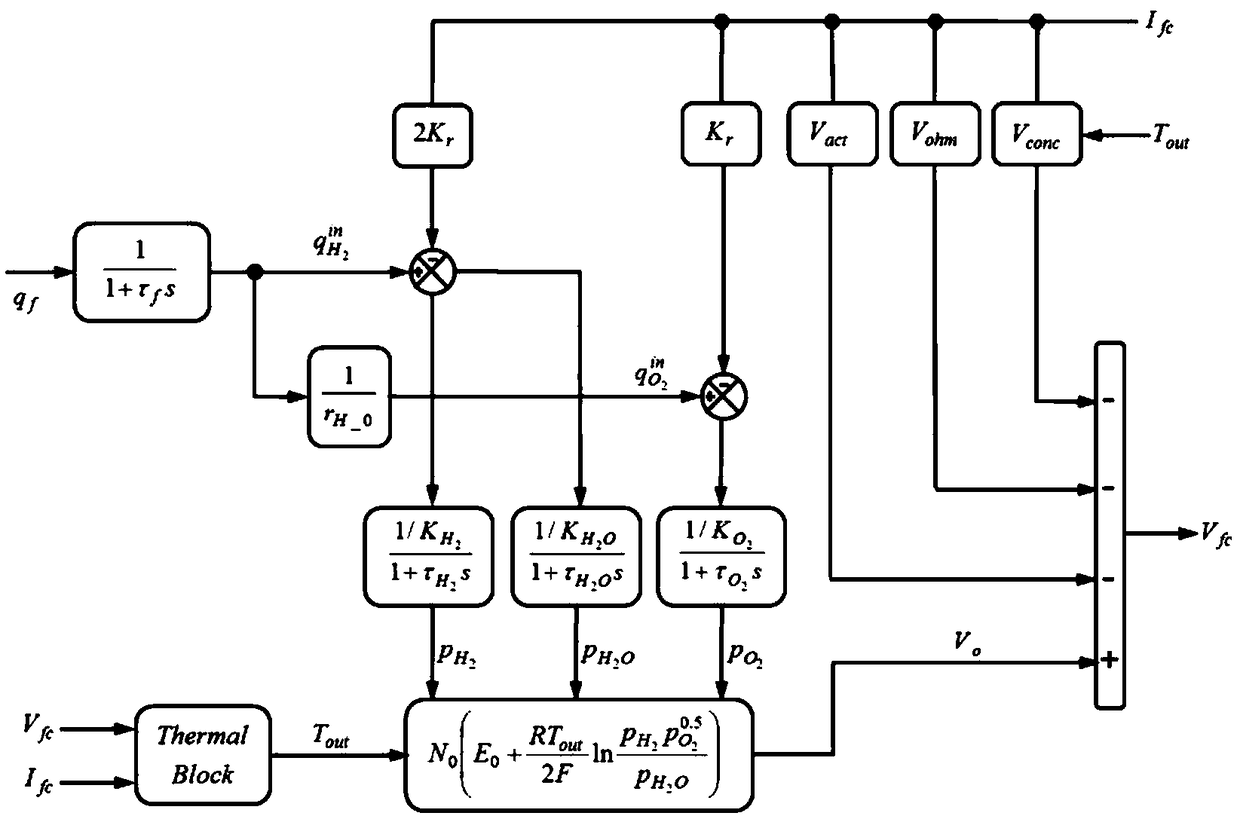
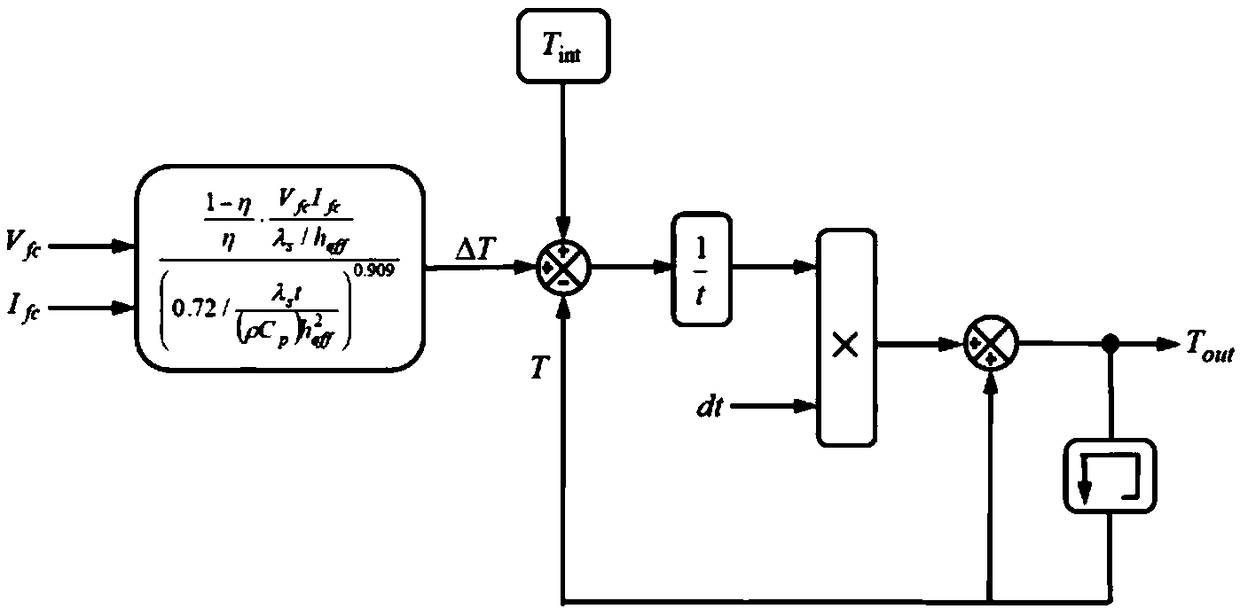
InactiveCN109240078ANo overshootQuick responseControllers with particular characteristicsForward algorithmFuzzy rule
The invention discloses a fuzzy adaptive PID control method for a fuel cell voltage. The method comprises the following steps of setting up a dynamic model of a fuel cell; carrying out a step responsetest on the dynamic model of the fuel cell, carrying out transfer function identification based on obtained response data through adoption of a least square method, and carrying out parameter settingof a PID controller through utilization of an identified model; and designing a fuzzy controller, carrying out fuzzification on the fuzzy controller according to a voltage error and a change rate ofthe voltage error, carrying out fuzzy reasoning and defuzzification according to a fuzzy rule, thereby obtaining correction parameters, and correcting a proportion coefficient and an integral coefficient, wherein differentiation action is realized according to a differentiation forward algorithm. According to the method, influence of fuel cell nonlinearity can be effectively suppressed, overshootis reduced, transition time is reduced, an integral saturation phenomenon and a jump phenomenon of differentiation action are overcome, and ideal control performance is achieved.
Owner:SOUTHEAST UNIV
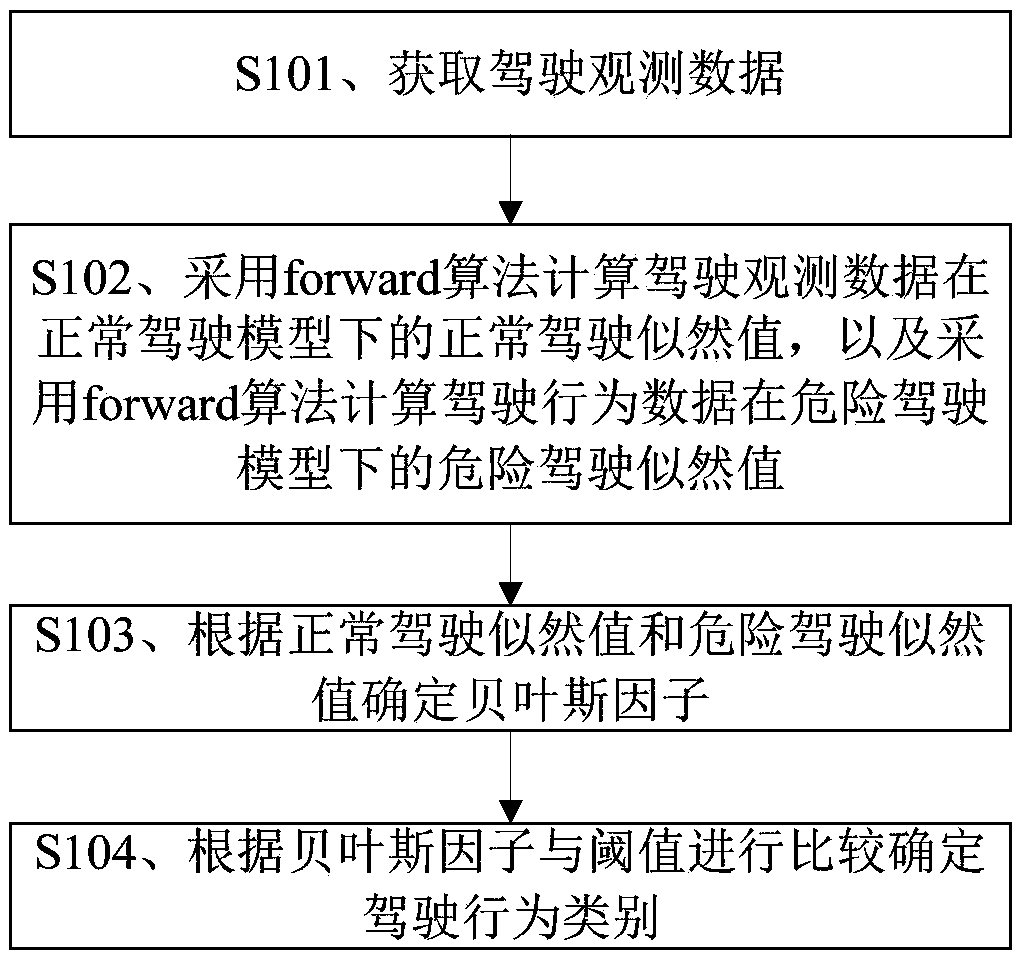
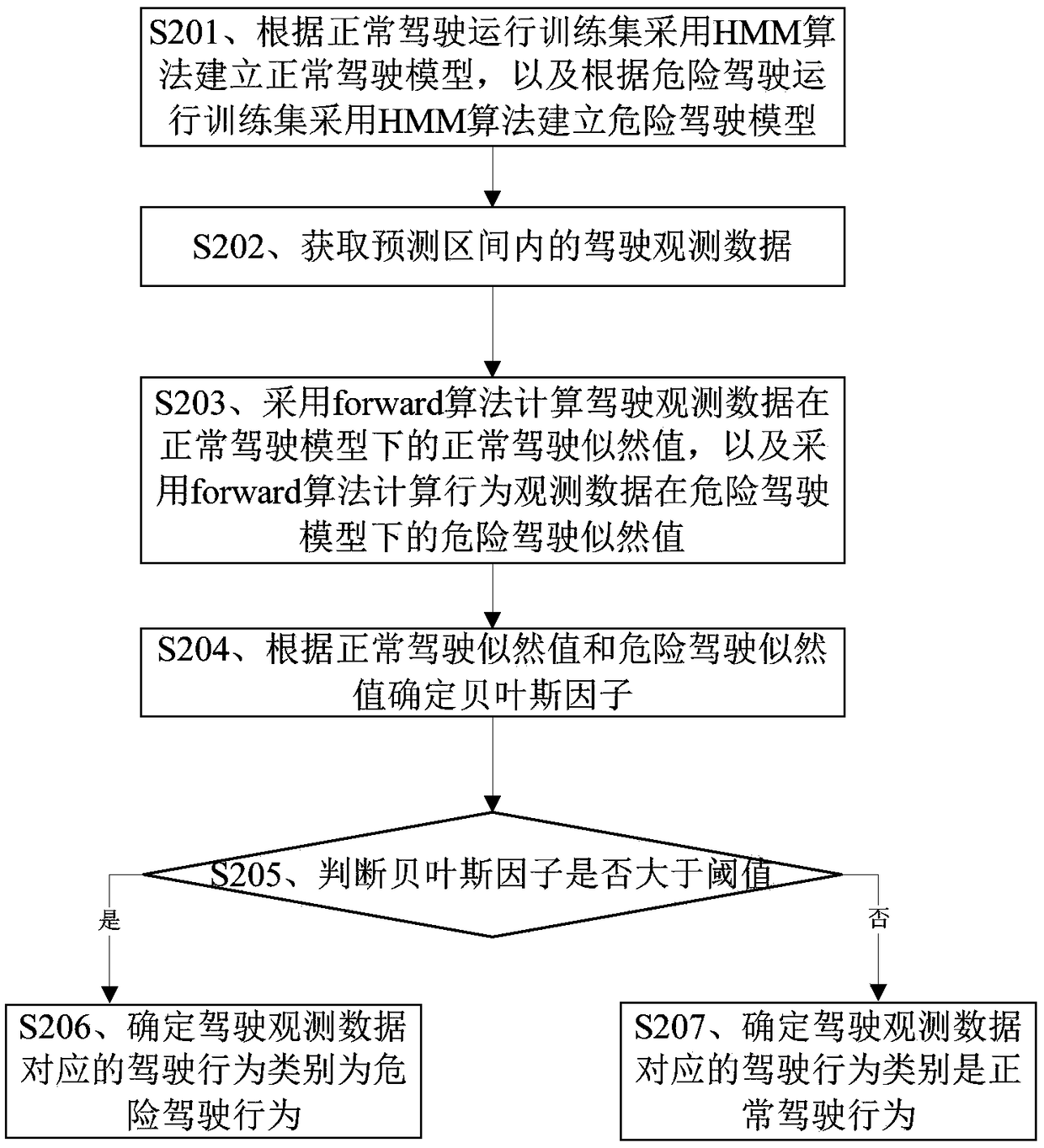
A driving behavior classification method and device based on an HMM algorithm
InactiveCN109447182AImprove accuracyImprove securityCharacter and pattern recognitionForward algorithmObservation data
The invention discloses a driving behavior classification method based on an HMM algorithm. The driving behavior classification method comprises the steps of obtaining driving observation data; calculating a normal driving likelihood value of the driving observation data under a normal driving model by adopting a forward forward algorithm, and calculating a dangerous driving likelihood value of the driving behavior data under the dangerous driving model by adopting the forward algorithm; determining a Bayesian factor according to the normal driving likelihood value and the dangerous driving likelihood value; and comparing the Bayesian factor with a threshold value to determine a driving behavior category. By implementing the method and the device, the accuracy of identifying the driving behavior can be improved.
Owner:LAUNCH TECH CO LTD
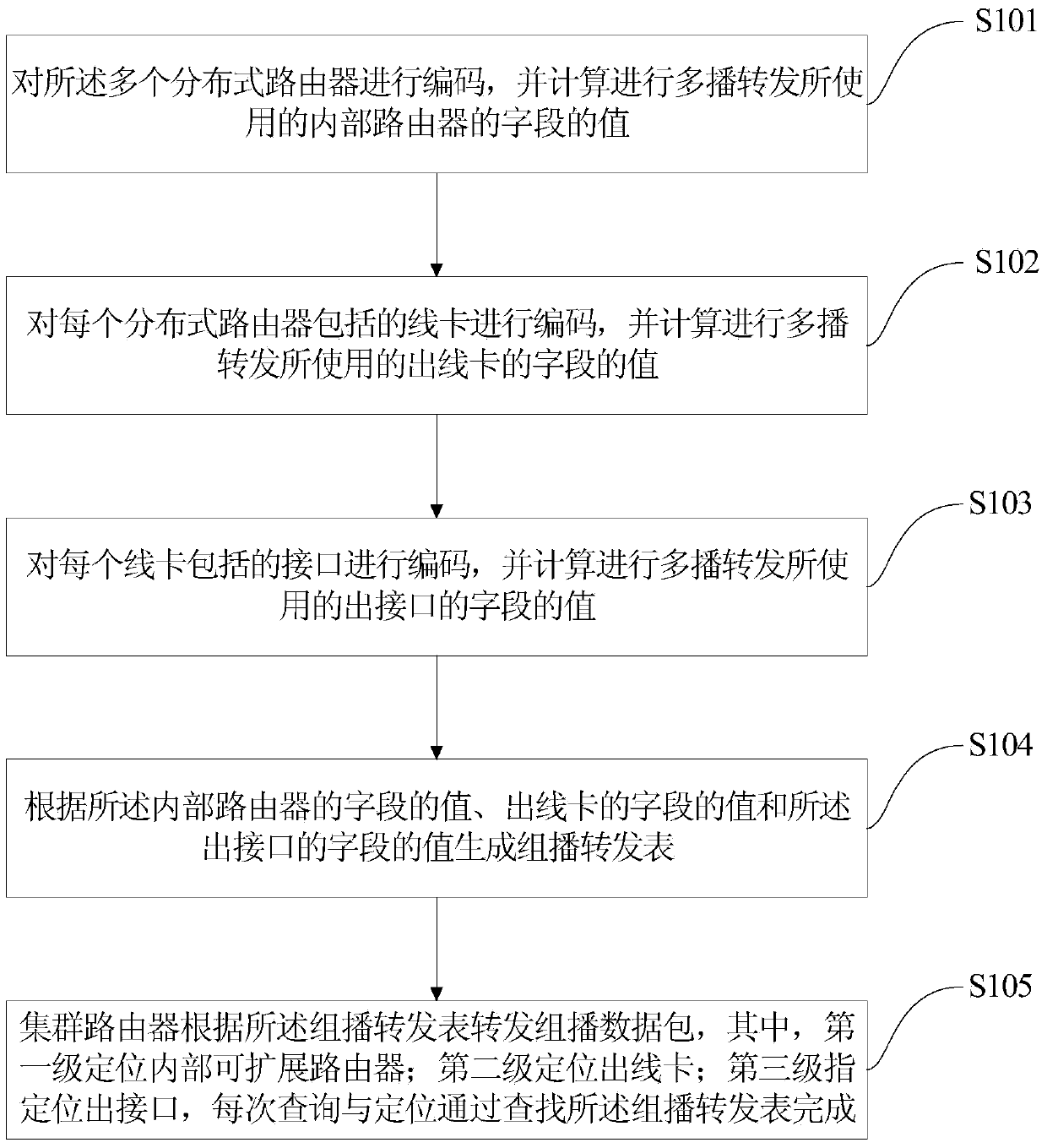
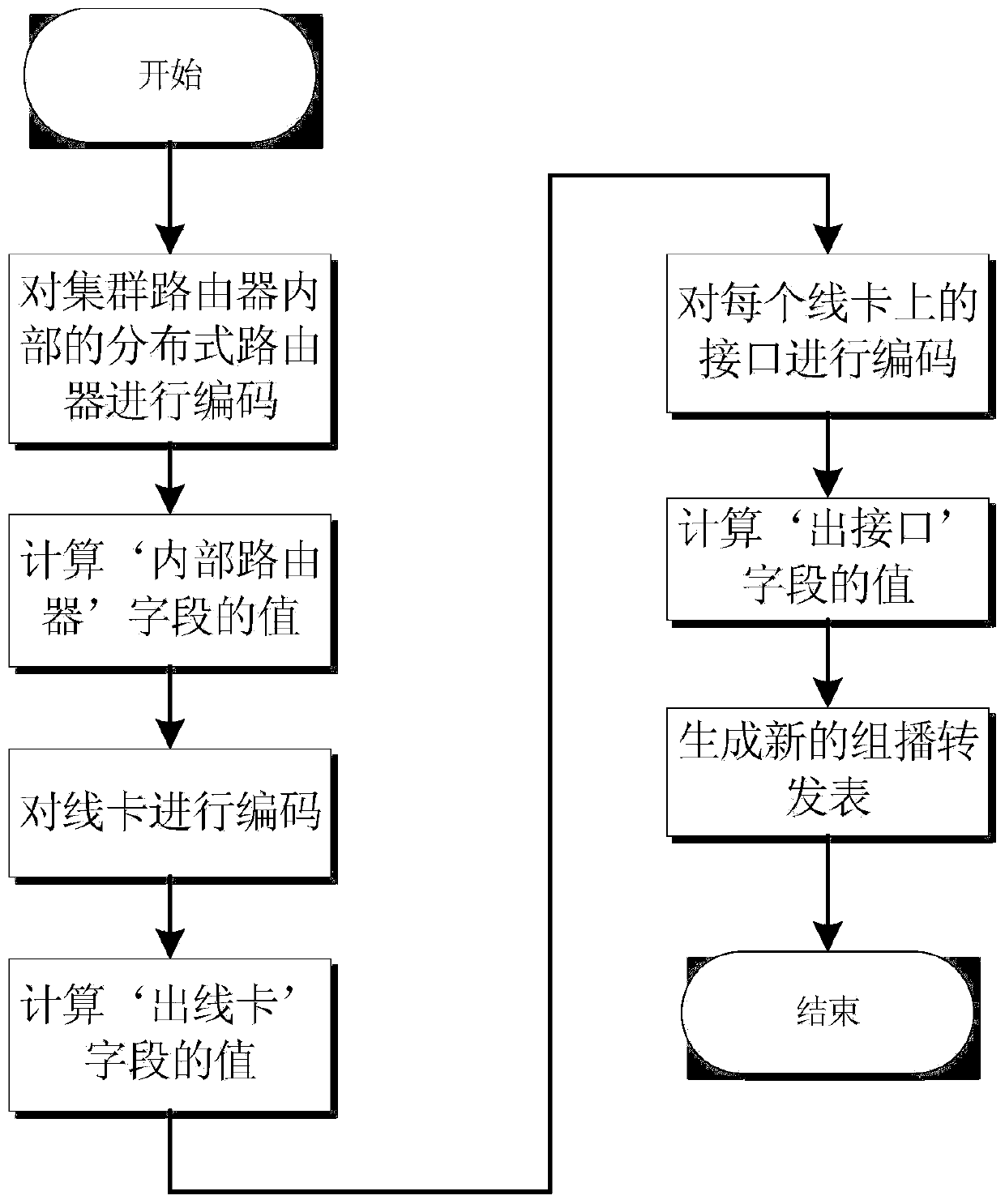
Cluster router multicast forwarding table designing and forwarding algorithm
InactiveCN104618248AReduce forwarding redundancyImprove forwarding efficiencyData switching networksMulticastForward algorithm
The invention discloses a cluster router multicast forwarding table designing and forwarding algorithm. The cluster router multicast forwarding table designing and forwarding algorithm comprises the steps of structuring a cluster router multicast forwarding table, wherein the steps include coding a plurality of distributed routers, and calculating the value of the field of an internal router, which is used for performing multicast forwarding; coding the line card of every distributed router, and calculating the value of the field of an outgoing line card used for performing the multicast forwarding; coding the interface of every line card, and calculating the value of the field of the outgoing interface used for performing the multicast forwarding; according to the value of the field of the internal router, the value of the field of the outgoing line card and the value of the field of the outgoing interface, generating the multicast forwarding table; according to the multicast forwarding table, performing three-stage multicast forwarding of multicast data packets. The cluster router multicast forwarding table designing and forwarding algorithm is applicable to cluster routers composed of multiple distributed routes and can reduce forwarding redundancy and forwarding time delay and achieve high forwarding efficiency.
Owner:CAPITAL NORMAL UNIVERSITY
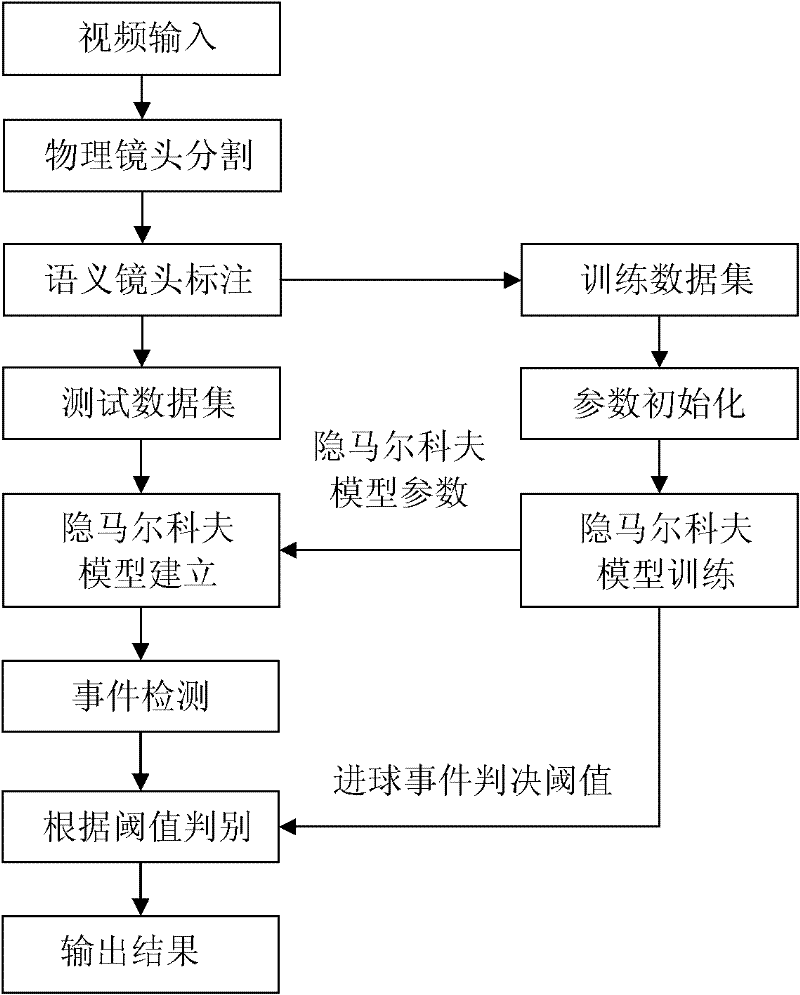
Method for detecting goal events in soccer video based on hidden markov model
InactiveCN102393909AEasy to detectSimplify the build processCharacter and pattern recognitionSpecial data processing applicationsForward algorithmData set
The invention discloses a method for detecting goal events in a soccer video based on a hidden markov model. By the method, the problems of complicated event detection system model and low detection rate in the prior art are solved. The method comprises the following steps of: firstly, performing physical shot segmenting and semantic shot labeling on a training video and a test video, and respectively forming a training data set and a test data set respectively by using acquired semantic shot sequences; secondly, calculating an initial parameter of the hidden markov model according to the training data set; thirdly, training an initial model by adopting a Baum-Welch algorithm and the training data set and establishing the hidden markov model for the goal events; fourthly, calculating a probability of the model for generating training data by adopting a forward algorithm and acquiring a judgment threshold value; and finally, calculating a probability of the model for generating test data and detecting the goal event in the test video according to the judgment threshold value. By the method, detection for semantic goal events can be realized accurately; and the method is applied to the field of semantic analysis, such as detection for wonderful events in the soccer video and the like.
Owner:XIDIAN UNIV
Power abnormal fluctuation detection and prediction calculation method based on integrated algorithm
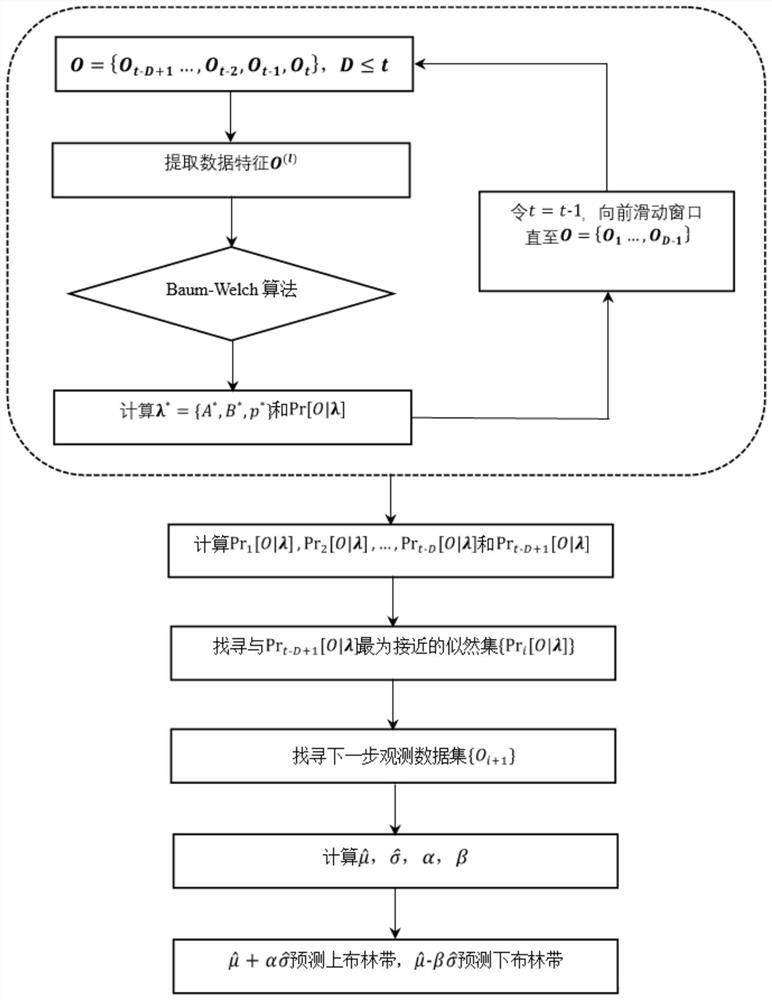
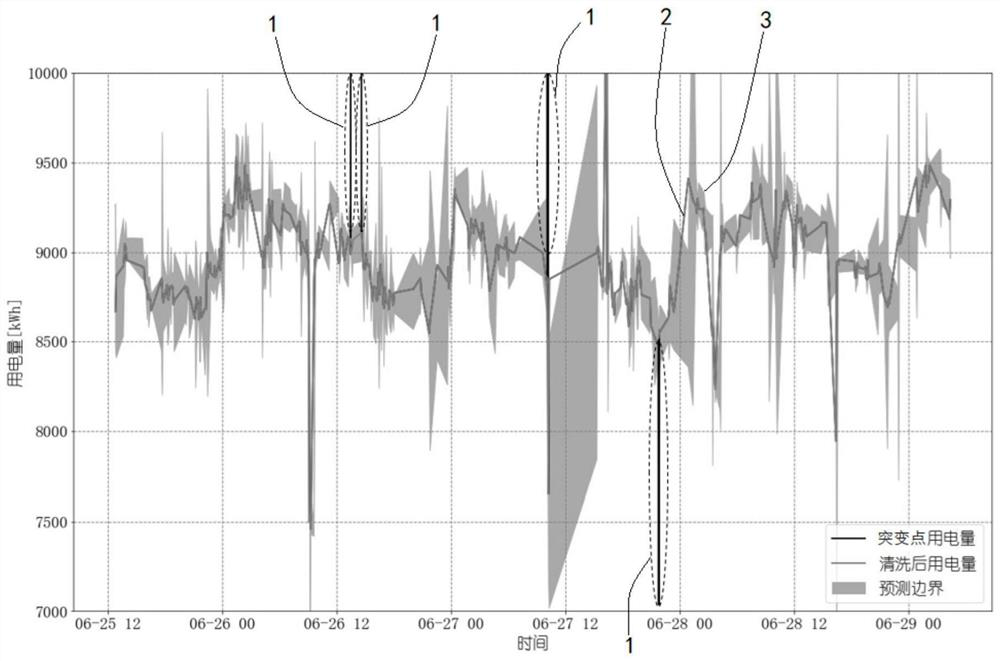
ActiveCN113505935AReal-time prediction of power consumptionAdapt to fully mining the problem of abnormal detection of power consumptionForecastingComplex mathematical operationsForward algorithmAlgorithm
The invention relates to power abnormal fluctuation detection and prediction calculation method based on mutational site analysis and a hidden Markov model integration algorithm. The method comprises the following steps of: acquiring power consumption data as data of a time sequence input for detection and prediction; mutational site analysis: realizing the mutational site analysis of abnormal fluctuation through Bayesian inference by using the collected electricity consumption data; mutational site data prediction: processing information with correlation in time by utilizing a hidden Markov model, processing information aiming at a time sequence, obtaining likelihood parameters by adopting a hidden Markov forward algorithm and a Baum-Welch algorithm, obtaining mutational site prediction data, and obtaining a maximum likelihood value corresponding to a sliding window through training features. The improvement is carried out based on abrupt change point analysis and a basic algorithm of a hidden Markov model, electric power consumption can be detected in real time, a reasonable range of an electric power consumption interval at a future moment can be predicted and calculated, and it is judged that the electric power consumption is abnormal if the range is exceeded.
Owner:上海东方低碳科技产业股份有限公司
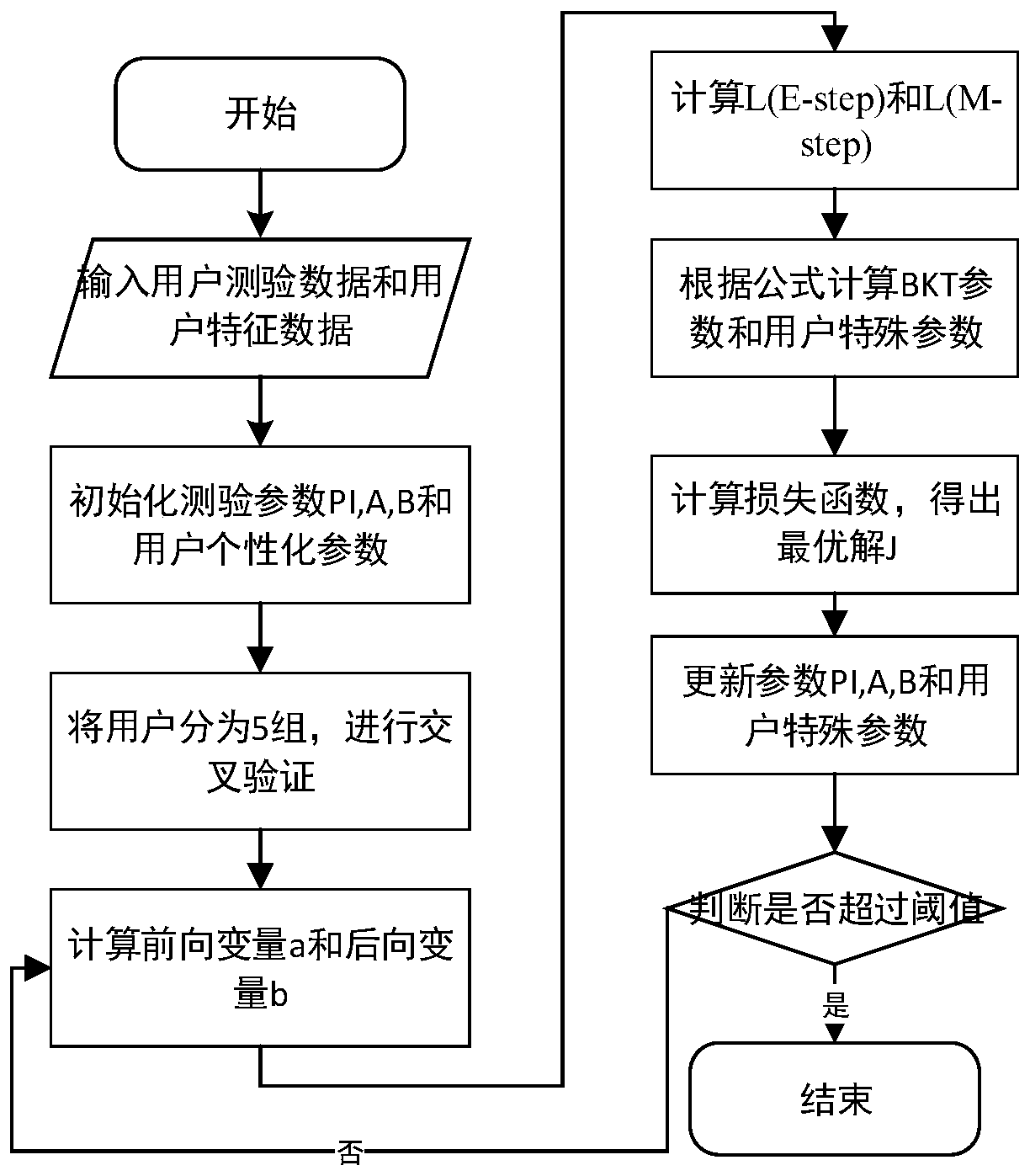
Method for constructing knowledge structure based on personalized Bayesian knowledge tracking model
InactiveCN110297817ASpecial data processing applicationsDatabase design/maintainancePersonalizationForward algorithm
The invention provides a method for constructing a knowledge structure based on a personalized Bayesian knowledge tracking model, and belongs to the technical field of education information model construction. The method comprises the steps: step 1, establishing an observation matrix and a state matrix; step 2, establishing a parameter model of the Bayesian knowledge tracking model; step 3, establishing a parameter fusion model for fusing personalized parameters of the learner into a traditional Bayesian knowledge tracking parameter model; step 4, completing the calculation problem definitionof the parameter model obtained in the step 3 by using a forward algorithm and a backward algorithm; step 5, performing maximum log-likelihood estimation on the parameter model to obtain a loss function, and updating parameters [theta] by utilizing the loss function; calculating parameters and weight parameters according to the loss function, to obtain a personalized Bayesian knowledge-based tracking model, and finally, completing the construction of a knowledge structure.
Owner:HARBIN INST OF TECH
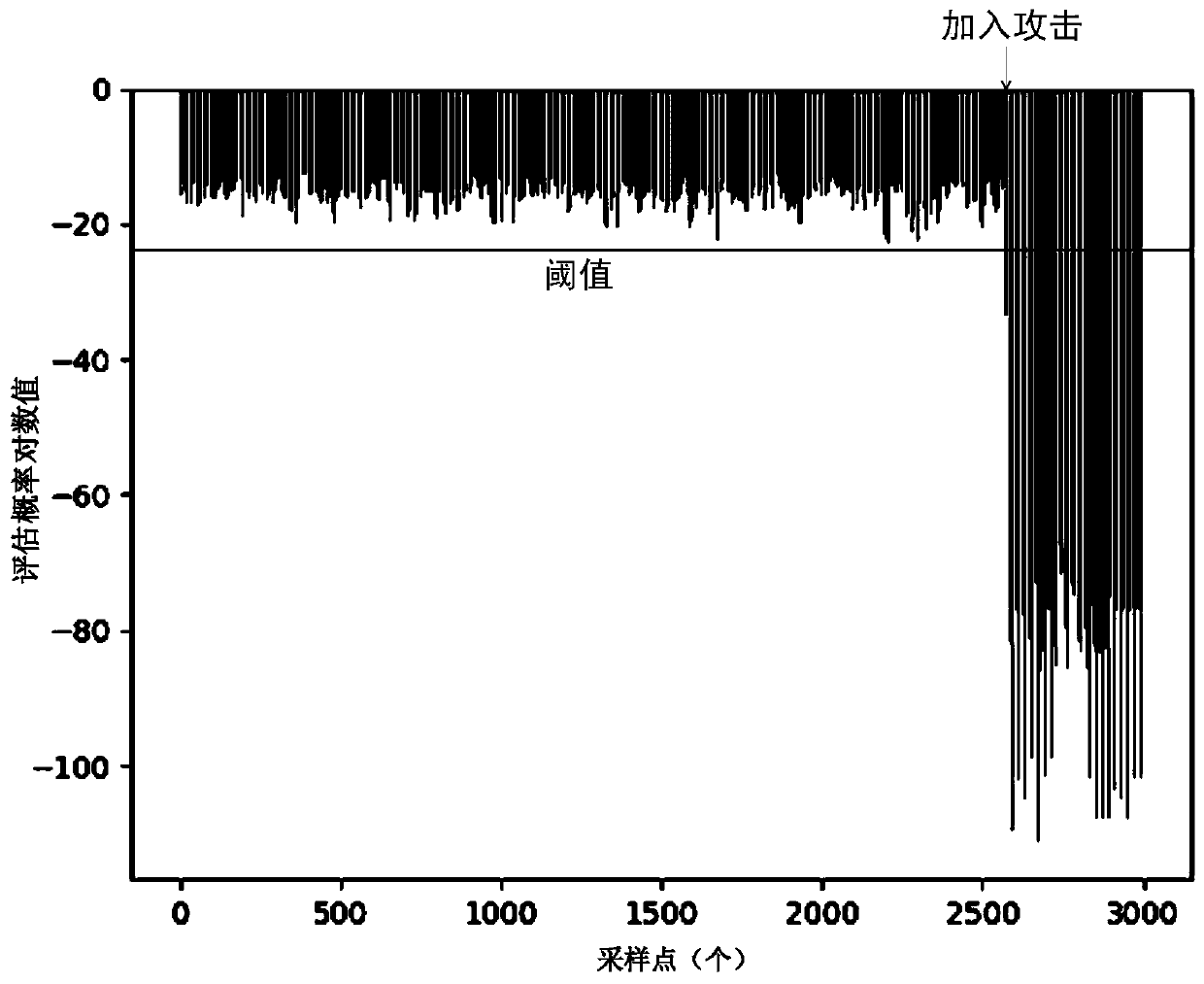
Repeated machining process concealment attack detection method based on hidden Markov model
ActiveCN110290118AHigh precisionEasy quantizationTransmissionComplex mathematical operationsForward algorithmAlgorithm
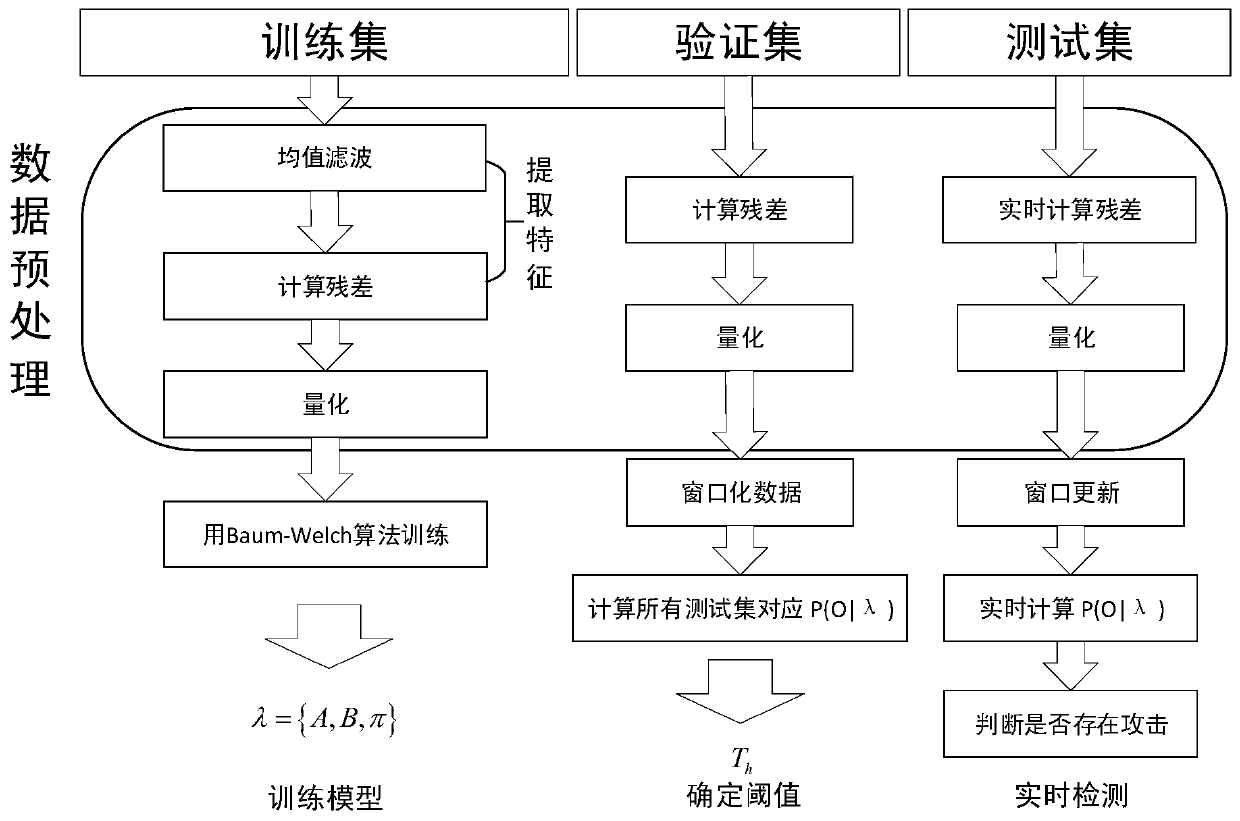
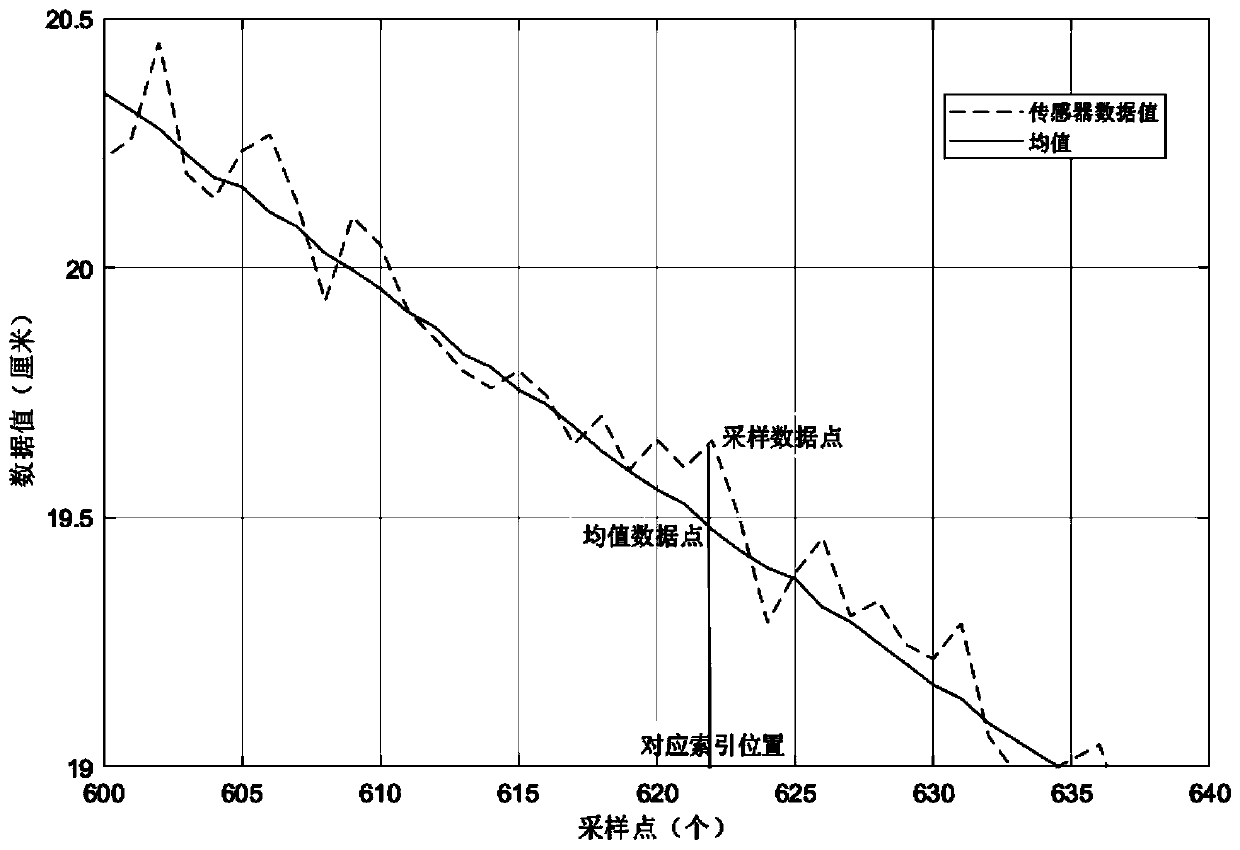
A repeated machining process concealment attack detection method based on a hidden Markov model is divided into a model training stage, a threshold determination stage and an intrusion detection stage, and each stage needs to be subjected to data preprocessing operation; in order to retain useful information and prevent distortion, a mean filtering method is proposed to obtain a theoretical mean value, then a residual error is calculated, namely the mean value is substracted from a sampling value, and an absolute value is taken to obtain a residual error value sequence; after data preprocessing, Baum-Welch algorithm is used for training to obtain model parameters, a forward algorithm is used for estimating a probability value, a threshold value is determined, and finally whether an attack exists or not is judged by judging the affinity of a real-time observation sequence and a model. According to the method, disturbance and attacks can be extracted, concealment attacks can be effectively detected, adjustment can be conducted according to specific data in the aspects of a quantification method and a final judgment decision, and the application range is wide.
Owner:ZHEJIANG UNIV OF TECH
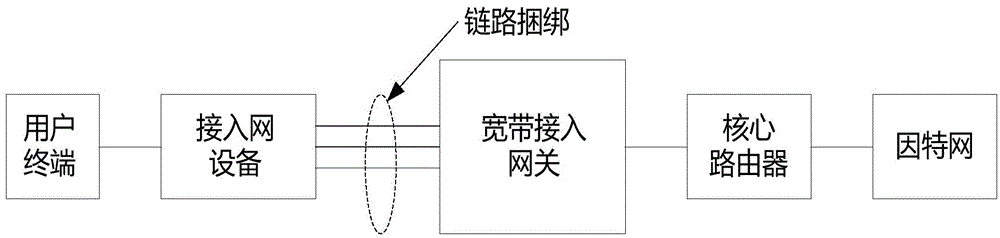
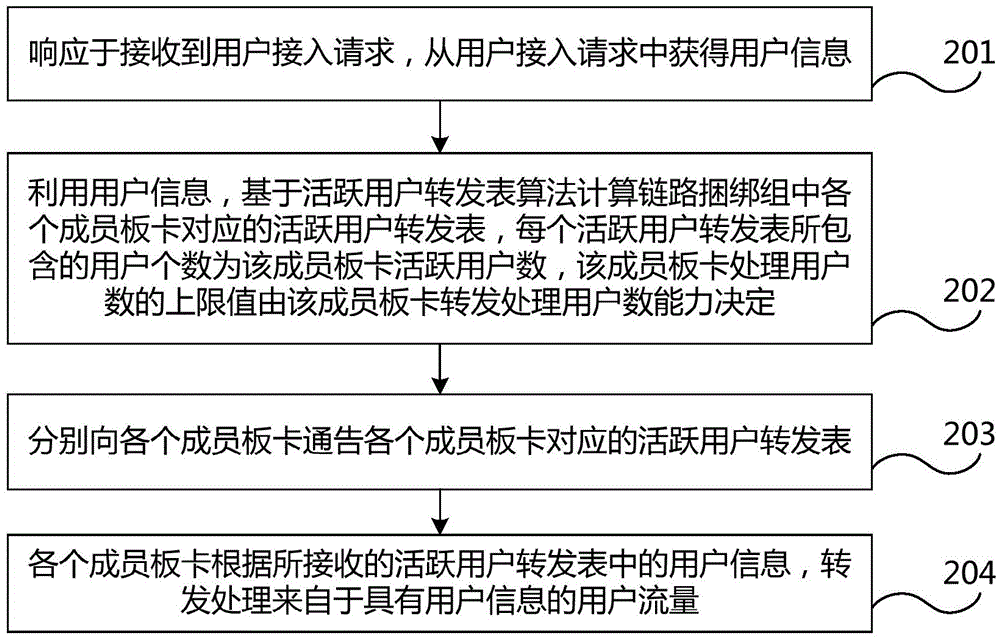
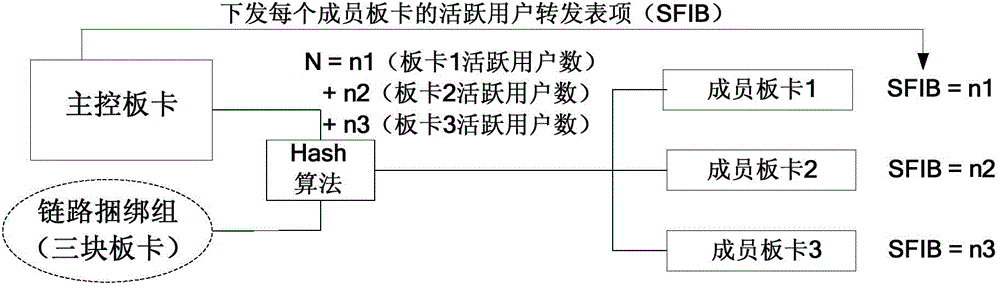
Broadband access gateway user access method and apparatus, and broadband access gateway
ActiveCN104426686AHigh speed switchingIncrease the number ofNetwork connectionsTraffic capacityForward algorithm
The invention discloses a broadband access gateway user access method and apparatus, and a broadband access gateway. The method comprises the following steps: obtaining user information from a user access request in response to the received user access request; calculating an active user forwarding list corresponding to each member board in a link binding group on the basis of an active user forwarding algorithm by use of the user information, wherein the user number include in each active user forwarding list is the active user number of the corresponding member board, and the upper limit value of the corresponding member board in processing the user number is determined by the capability of the member board in forwarding and processing the user number; respectively notifying each member board of the active user forwarding list corresponding to each member board; and each member board, according to the user information in the received active user forwarding list, forwarding and processing user flow with the user information. According to the technical scheme provided by the invention, the user number of broadband access gateway users accessing into link binding is increased, and the performance of accessing into the link binding by the broadband access gateway users is improved.
Owner:CHINA TELECOM CORP LTD
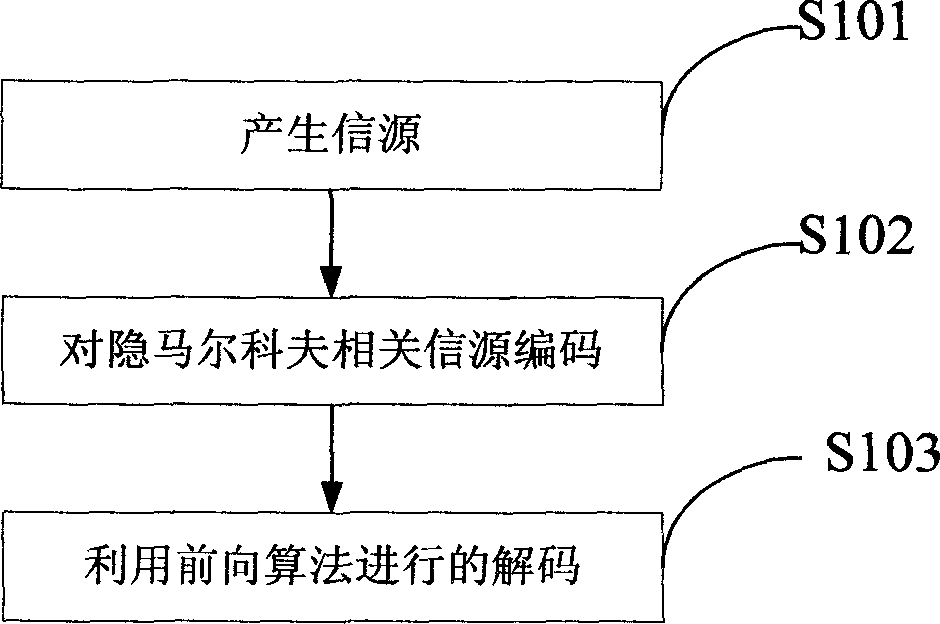
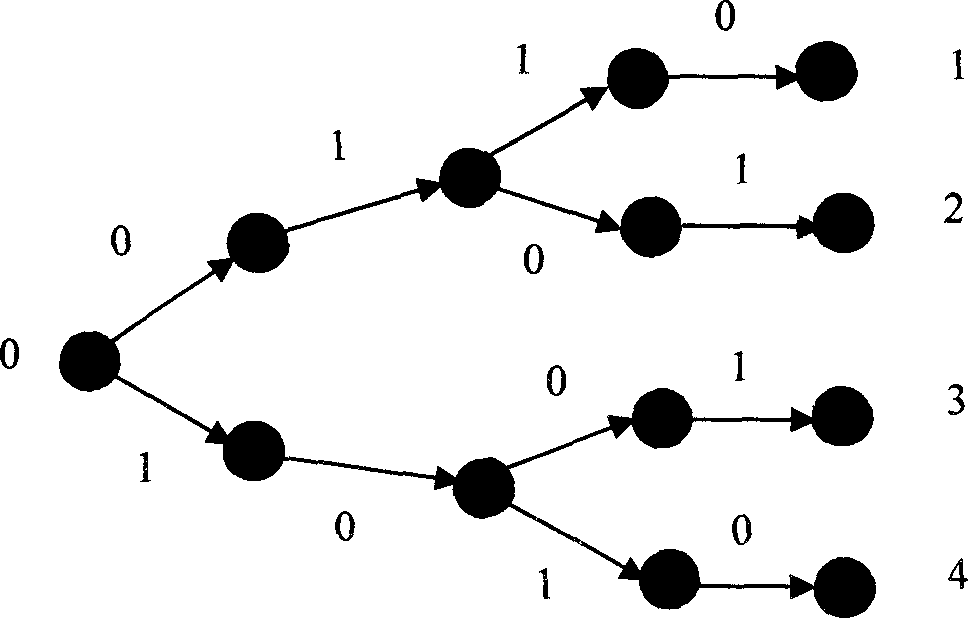
Hidden Markov related source coding method based on distributed arithmetic coding
The invention discloses a hidden Markov related source coding method based on distributed arithmetic coding. The hidden Markov related source coding method includes the following steps of generating sources, coding the Markov related sources, and decoding the Markov related sources by utilizing a forward algorithm. According to the hidden Markov related source coding method, the sources related to memory are compressed through a DAC. In the concrete realization process, the dependency among the sources is modeled to be one hidden Markov process. Experimental results show that execution results of the new scheme are close to the Slepian-Wolf theory bound, and the problems that ambiguous code words can exist on decoding ends and an SWC is asymmetrical after areas are overlapped in the existing SWC technology based on entropy coding are well solved. According to the hidden Markov related source coding method, the existing technology is well utilized, experimental results are good, and good application value is possessed.
Owner:NORTHWEST A & F UNIV
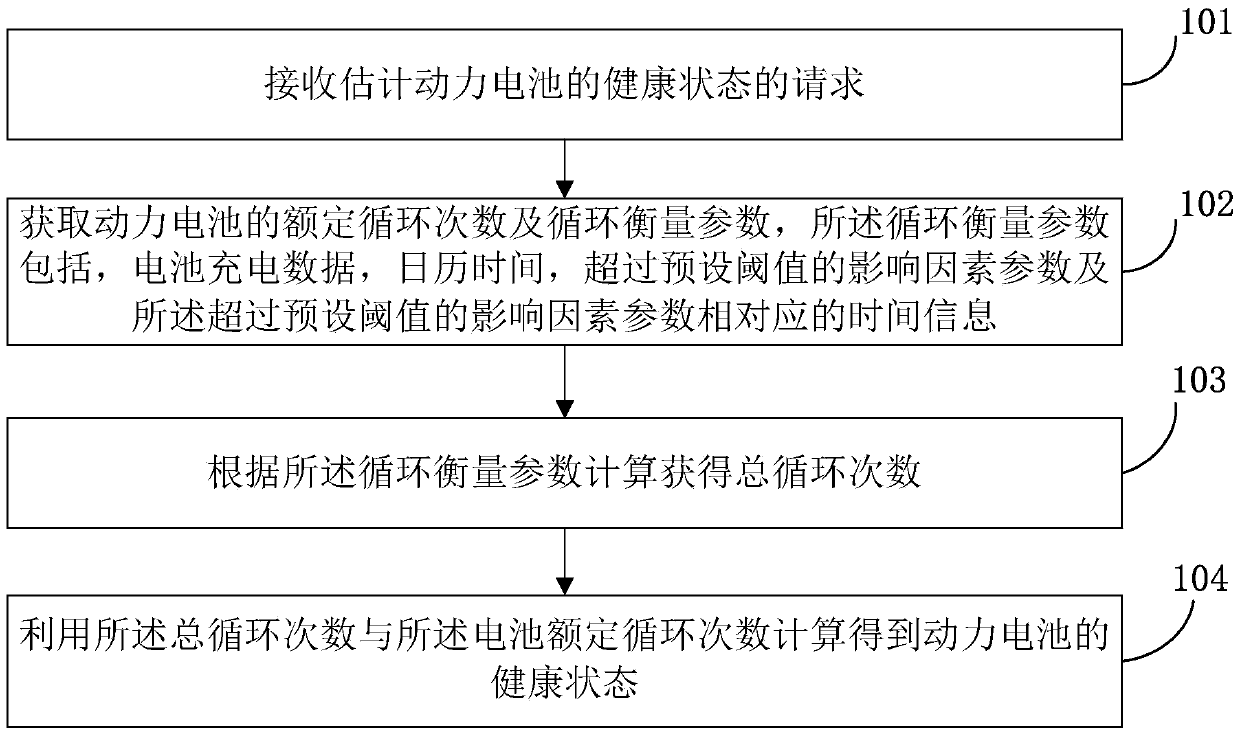
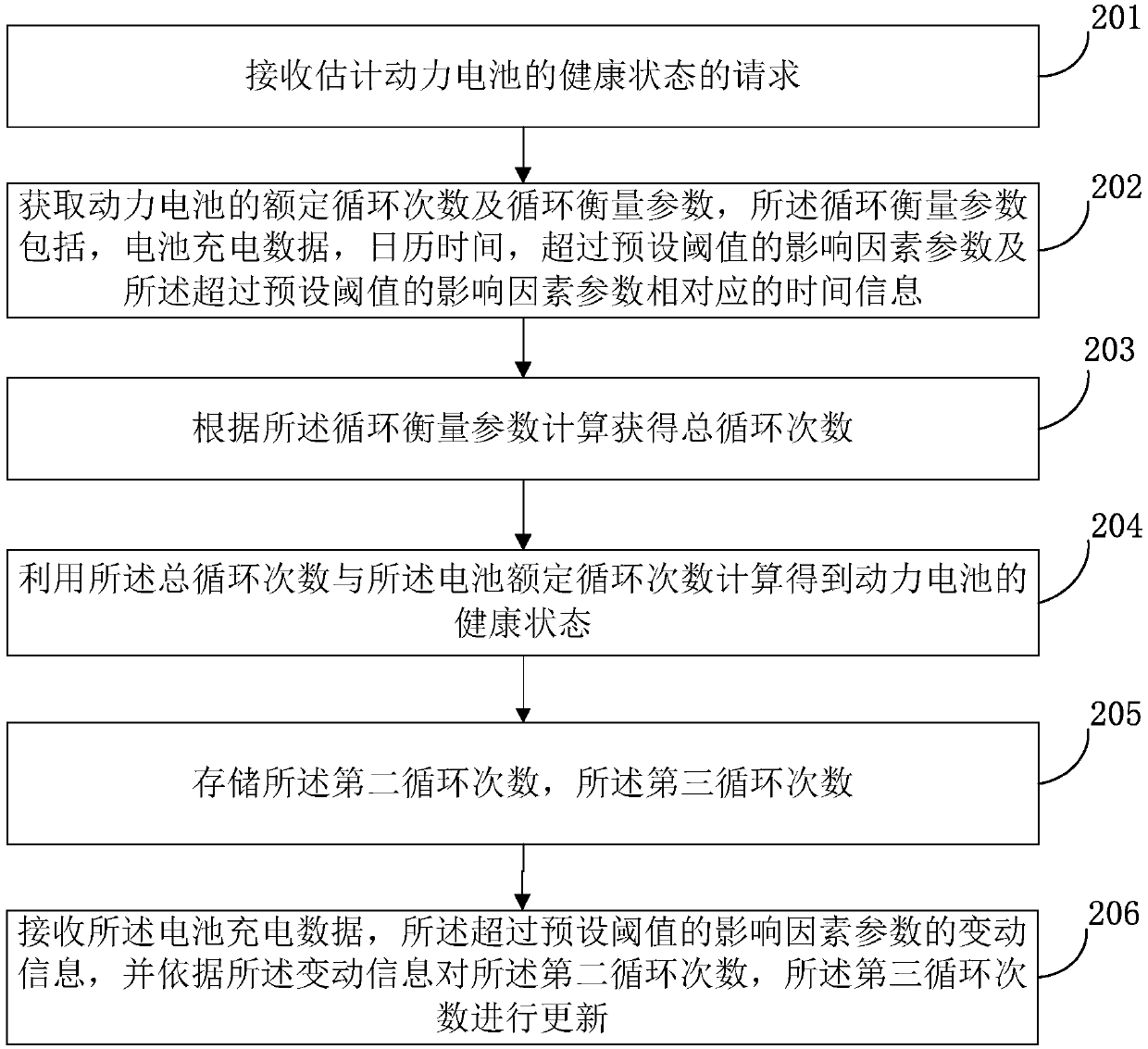
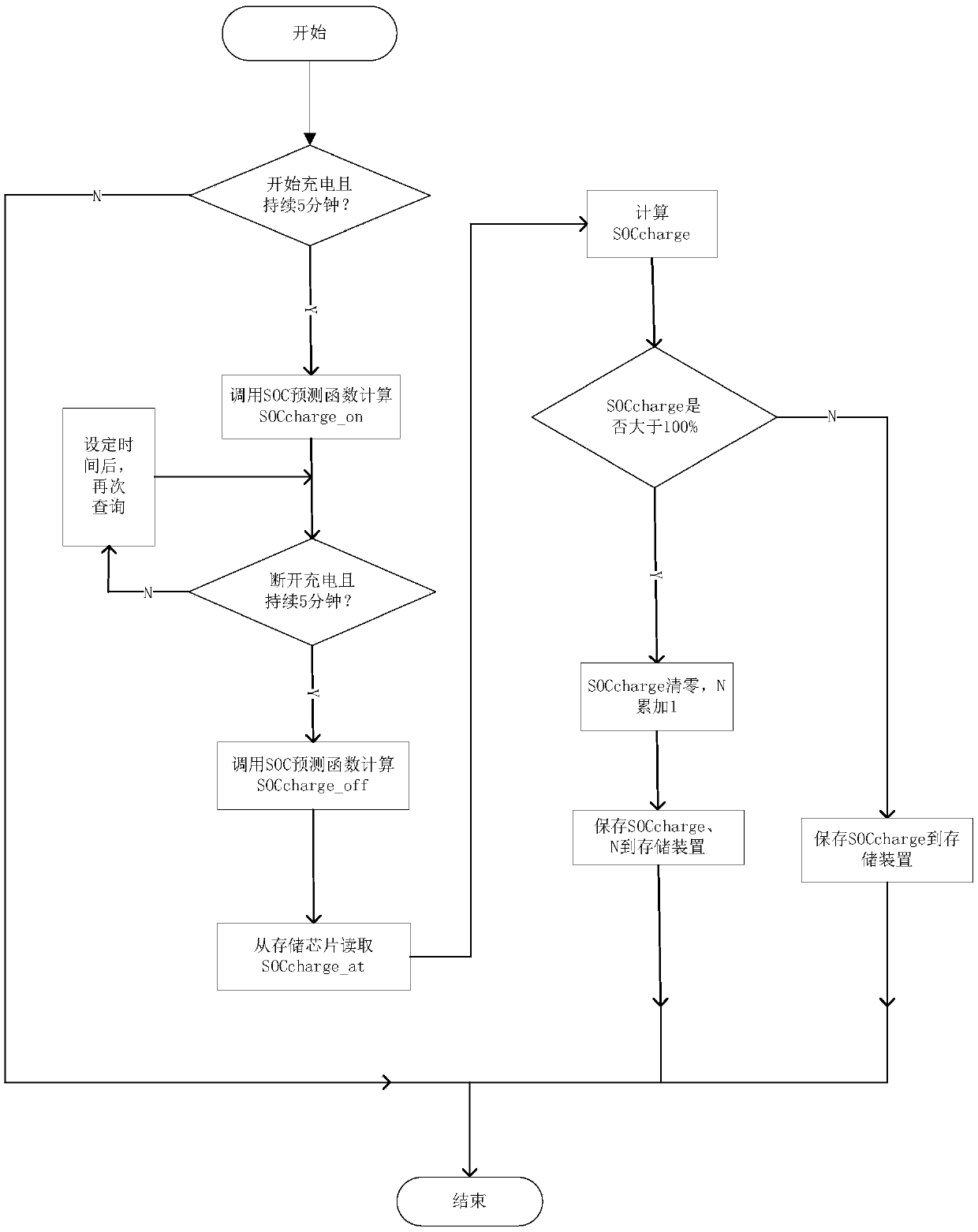
Method and device for estimating health state of power battery
The invention provides a method and device for estimating the health state of a power battery. The method for estimating the health state of the power battery comprises the steps that a request for estimating the health state of the power battery is received; rated cycle times and cycle measurement parameters of the power battery are obtained, wherein the cycle measurement parameters comprise battery charging data, calendar time, influence factor parameters exceeding a preset threshold value and time information corresponding to the influence factor parameters exceeding the preset threshold value; the total cycle times are calculated and obtained according to the cycle measurement parameters; the health state of the power battery is calculated and obtained by using the total cycle times and the rated cycle times of the battery. By introducing a cumulative charge metering algorithm and a quantitative forwarding algorithm, the efficiency, accuracy and operability of estimating the healthstate of the power battery are significantly improved.
Owner:SVOLT ENERGY TECHNOLOGY CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com