Patents
Literature
2381 results about "Precondition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
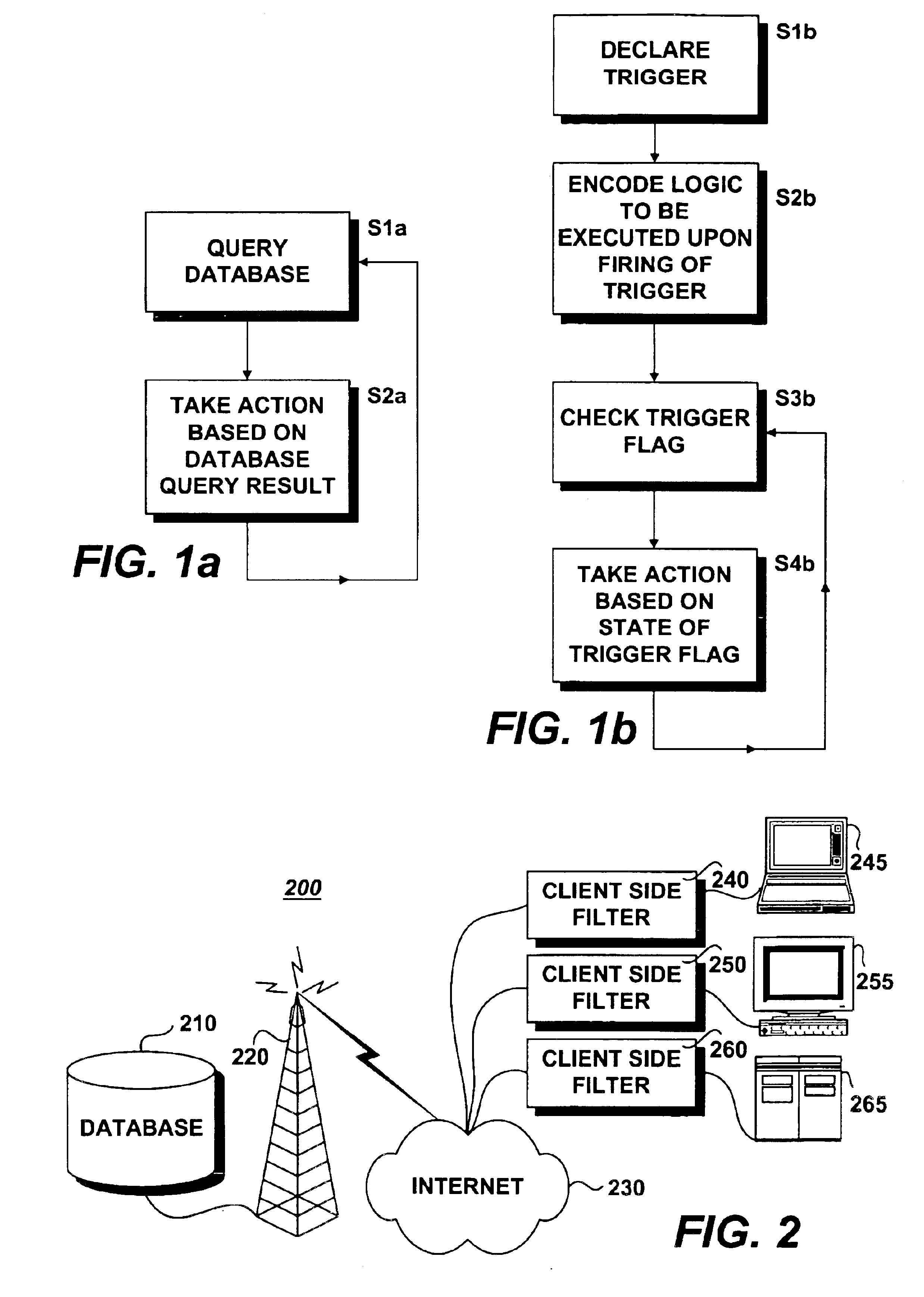
In computer programming, a precondition is a condition or predicate that must always be true just prior to the execution of some section of code or before an operation in a formal specification. If a precondition is violated, the effect of the section of code becomes undefined and thus may or may not carry out its intended work. Security problems can arise due to incorrect preconditions.
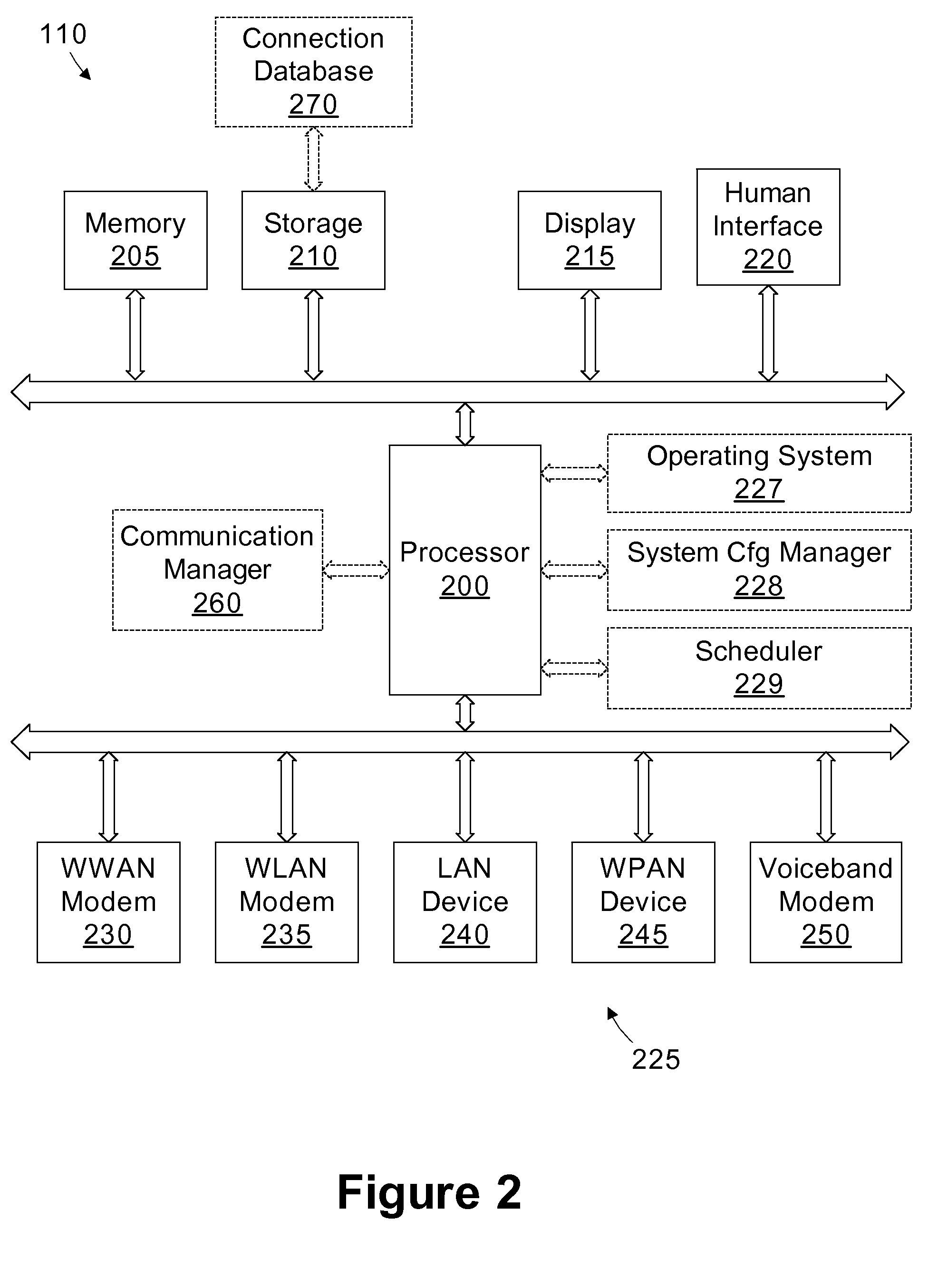
Method and apparatus for measuring reporting channel state information in a high efficiency, high performance communications system
InactiveUS6473467B1Efficient sharingInterference minimizationSpatial transmit diversityPolarisation/directional diversityChannel state informationCommunications system
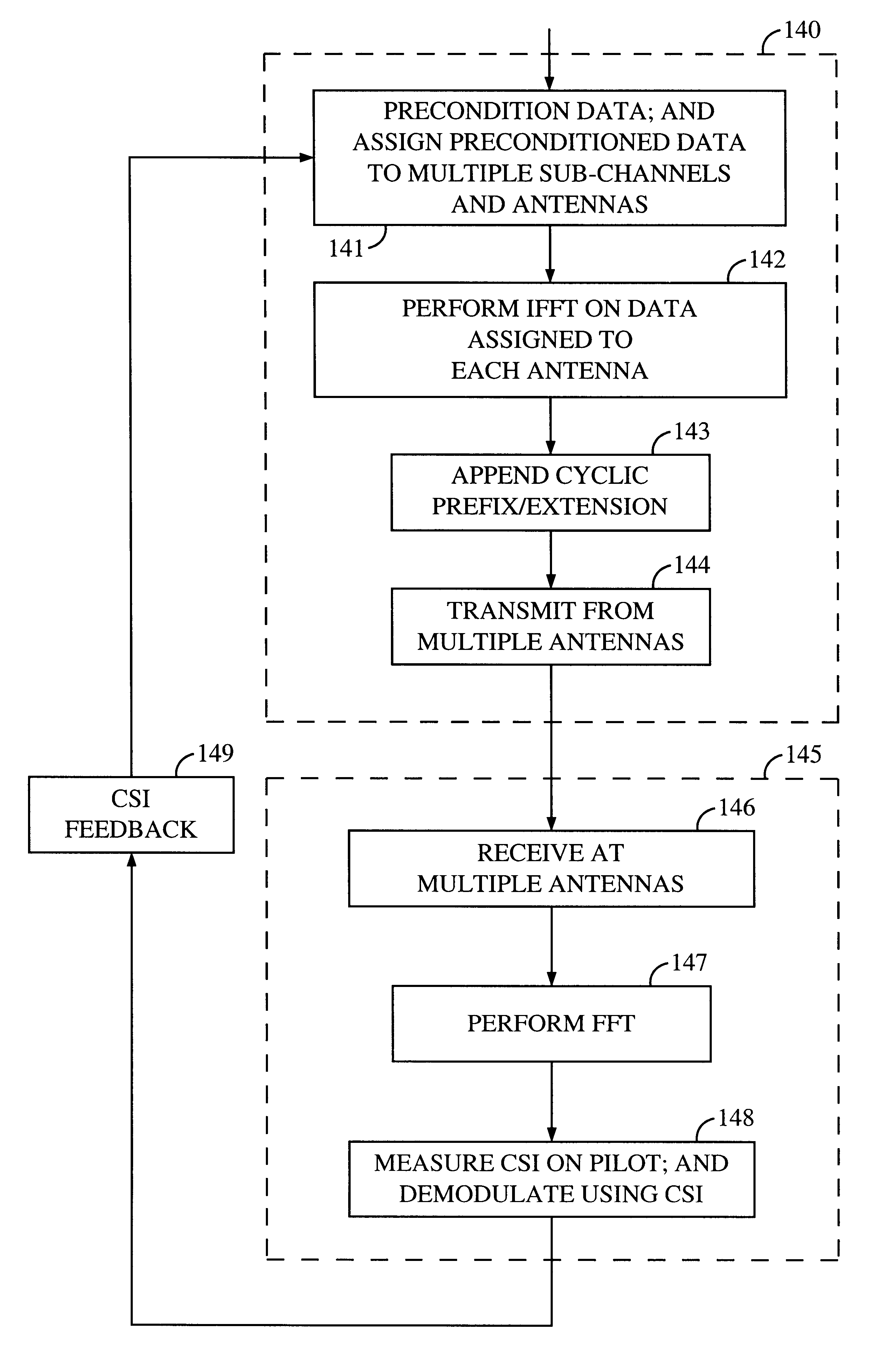
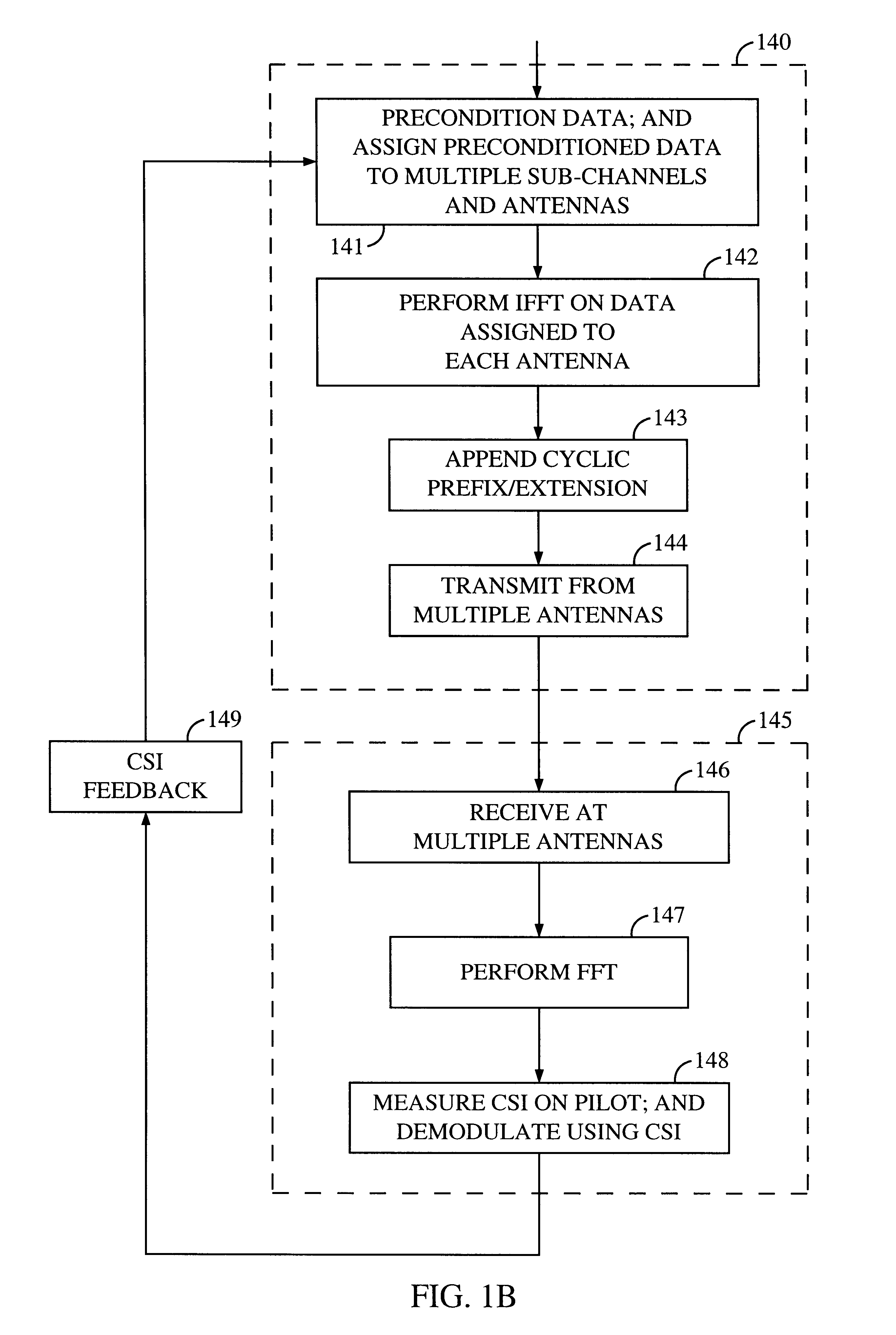
Channel state information (CSI) can be used by a communications system to precondition transmissions between transmitter units and receiver units. In one aspect of the invention, disjoint sub-channel sets are assigned to transmit antennas located at a transmitter unit. Pilot symbols are generated and transmitted on a subset of the disjoint sub-channels. Upon receipt of the transmitted pilot symbols, the receiver units determine the CSI for the disjoint sub-channels that carried pilot symbols. These CSI values are reported to the transmitter unit, which will use these CSI values to generate CSI estimates for the disjoint sub-channels that did not carry pilot symbols. The amount of information necessary to report CSI on the reverse link can be further minimized through compression techniques and resource allocation techniques.
Owner:QUALCOMM INC
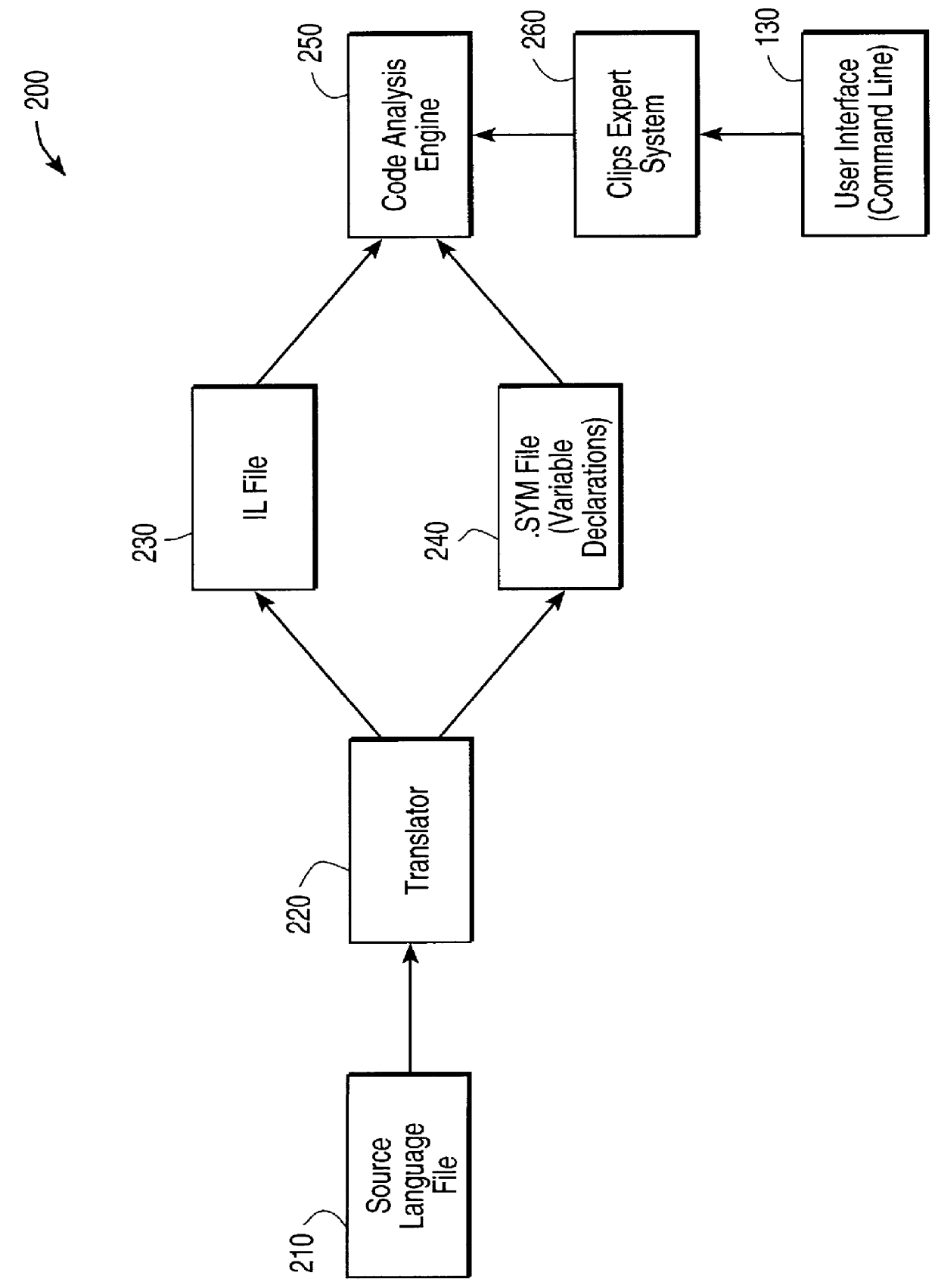
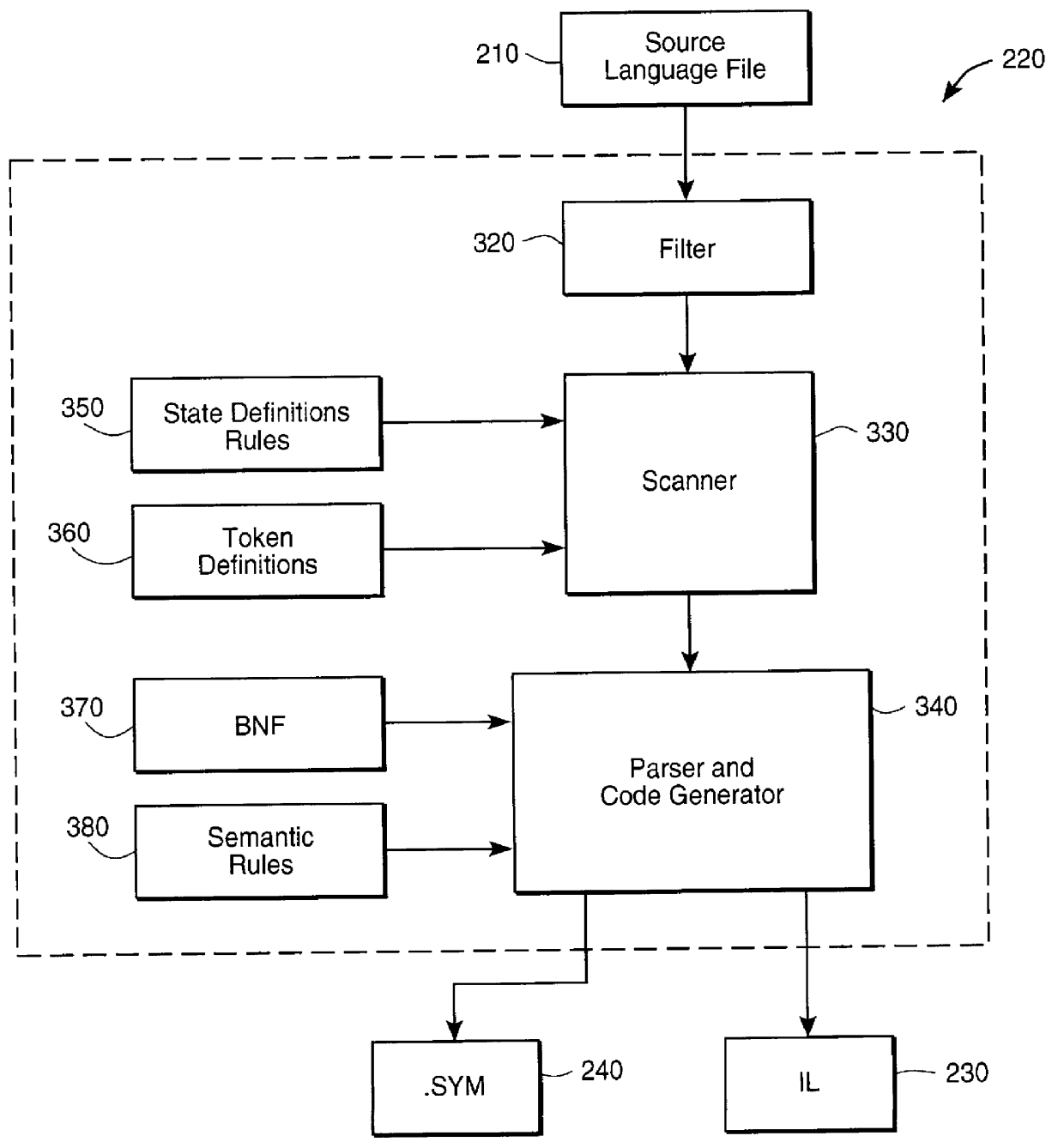
Method and apparatus for analyzing computer code using weakest precondition
An analyzer for maintaining and analyzing source code is disclosed. The analyzer includes a software translator for converting conventional source code into an intermediate language, slicing capability based upon weakest precondition determination, dual direction flow analysis and incorporation of a computational model to facilitate iterative code.
Owner:WELLS FARGO FOOTHILL
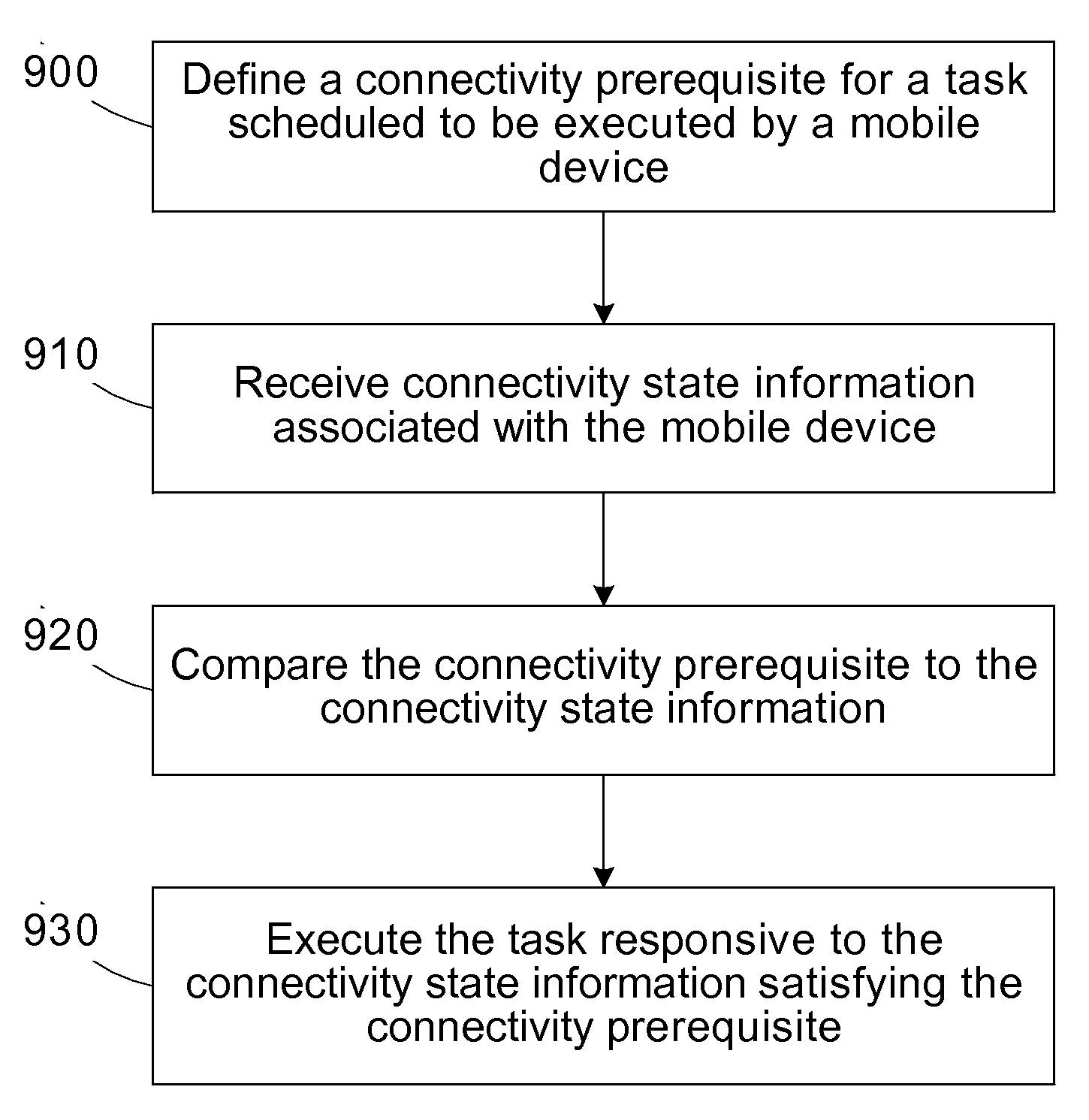
Task scheduler responsive to connectivity prerequisites
ActiveUS20080080411A1Well formedAssess restrictionDigital computer detailsMobile deviceDistributed computing
A method for scheduling tasks for execution by a mobile device is provided. A connectivity prerequisite is defined for a task scheduled to be executed by the mobile device. Connectivity state information associated with the mobile device is received. The connectivity prerequisite is compared to the connectivity state information. The task is executed responsive to the connectivity state information satisfying the connectivity prerequisite.
Owner:ADVANCED MICRO DEVICES INC
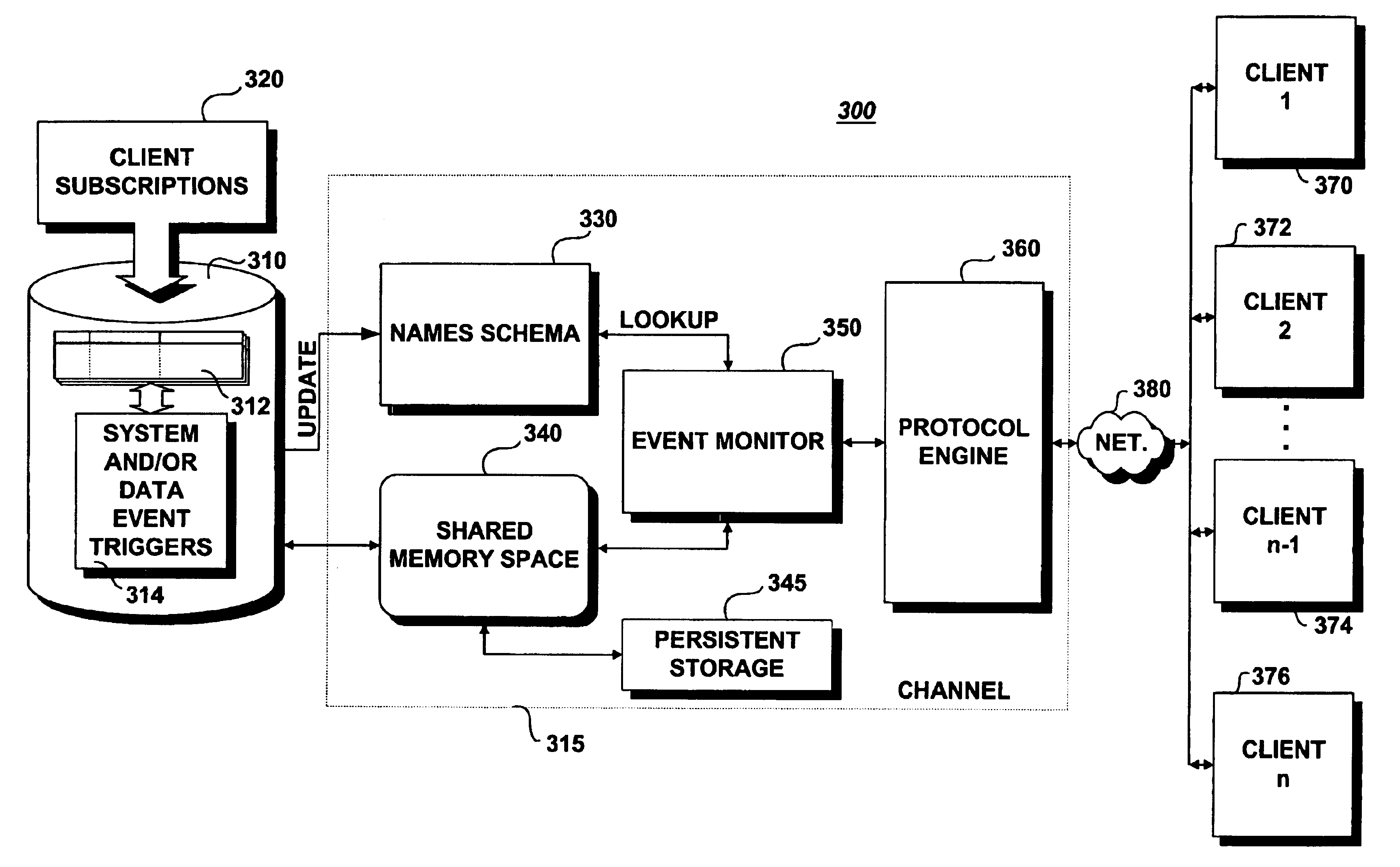
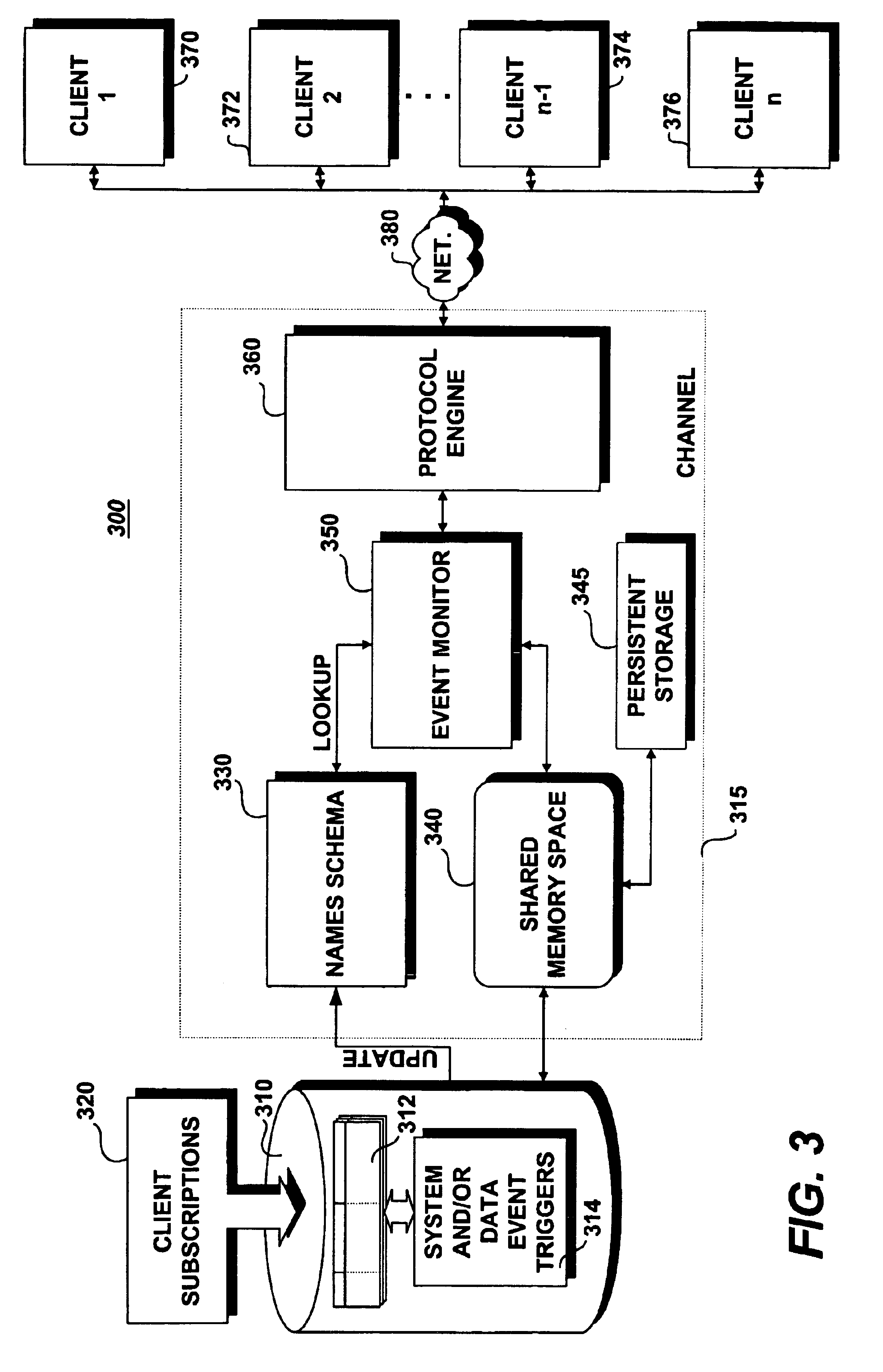
Methods and systems for asynchronous notification of database events
InactiveUS6910070B1Efficiently notifiedDigital data information retrievalData processing applicationsThe InternetApplication software
A method for asynchronously notifying an application client of a system or data event of interest within a database includes steps of receiving a subscription to an event name from a logical agent, the event name corresponding to the event of interest, and receiving a registration from the application client, the registration including delivery information indicating at least where and how a notification concerning the event is to be delivered. The occurrence of the event is then detected within the database, whereupon the notification of the detected event is published to a data structure referenced by the event name. The delivery information is then retrieved and the published notification is formatted according to the retrieved delivery information. The formatted notification is then asynchronously delivered to the application client over a network, such as the Internet. The application client may specify a rule, the satisfaction of which is a precondition to the delivery of the notification. The application client, in this manner, receives only the notification for which it has subscribed and receives the notifications substantially contemporaneously with the occurrence of the system or data event.
Owner:ORACLE INT CORP
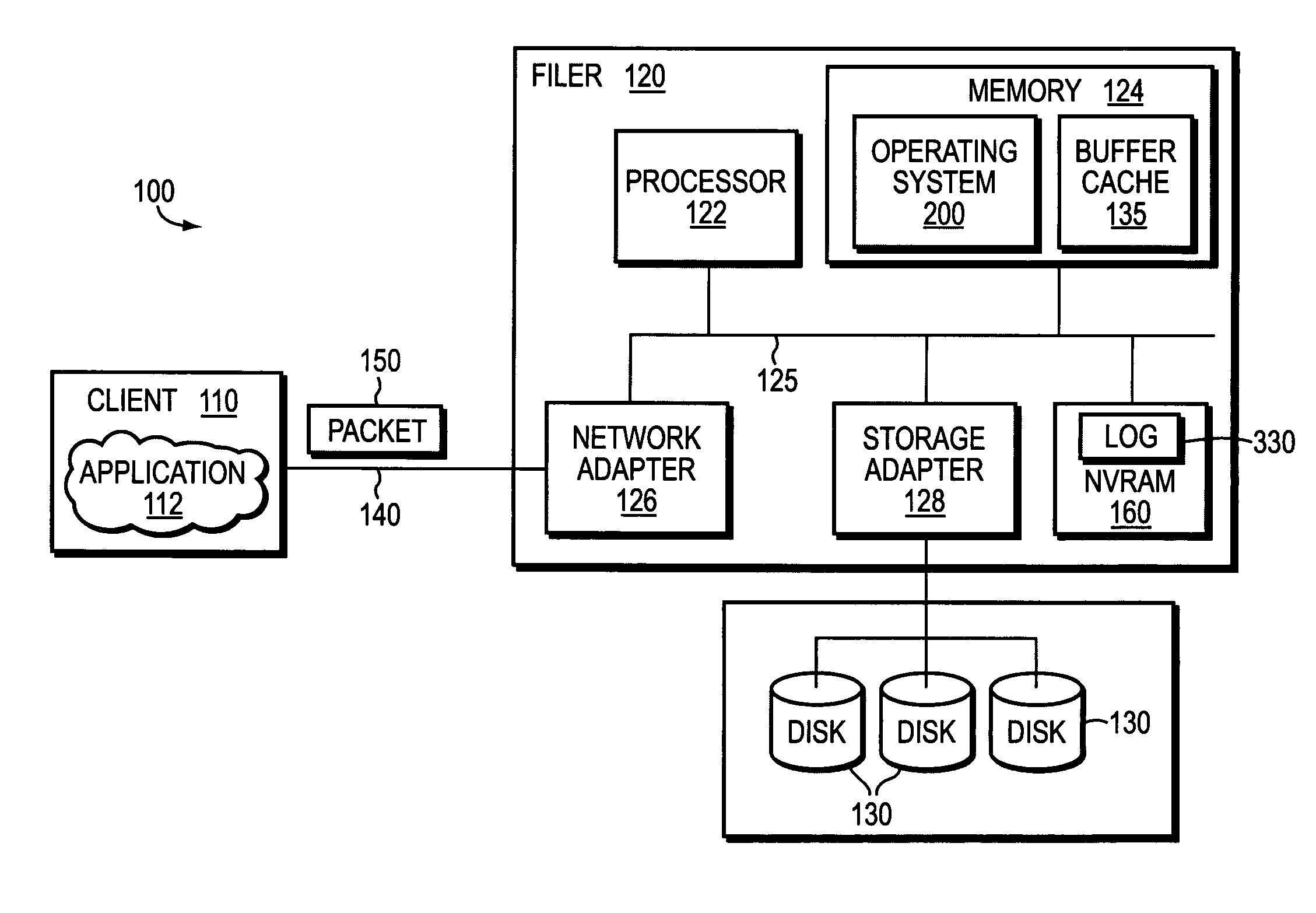
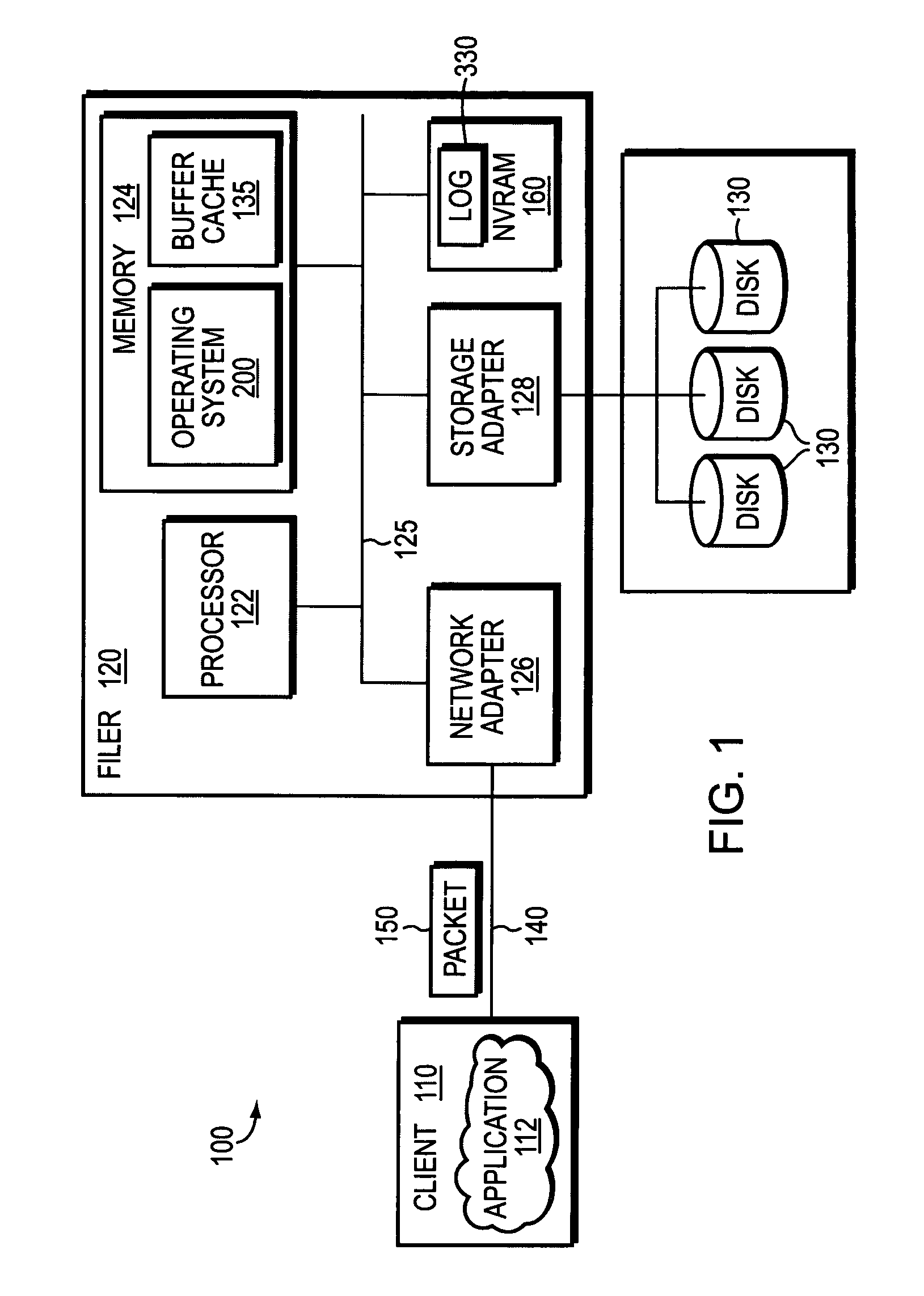
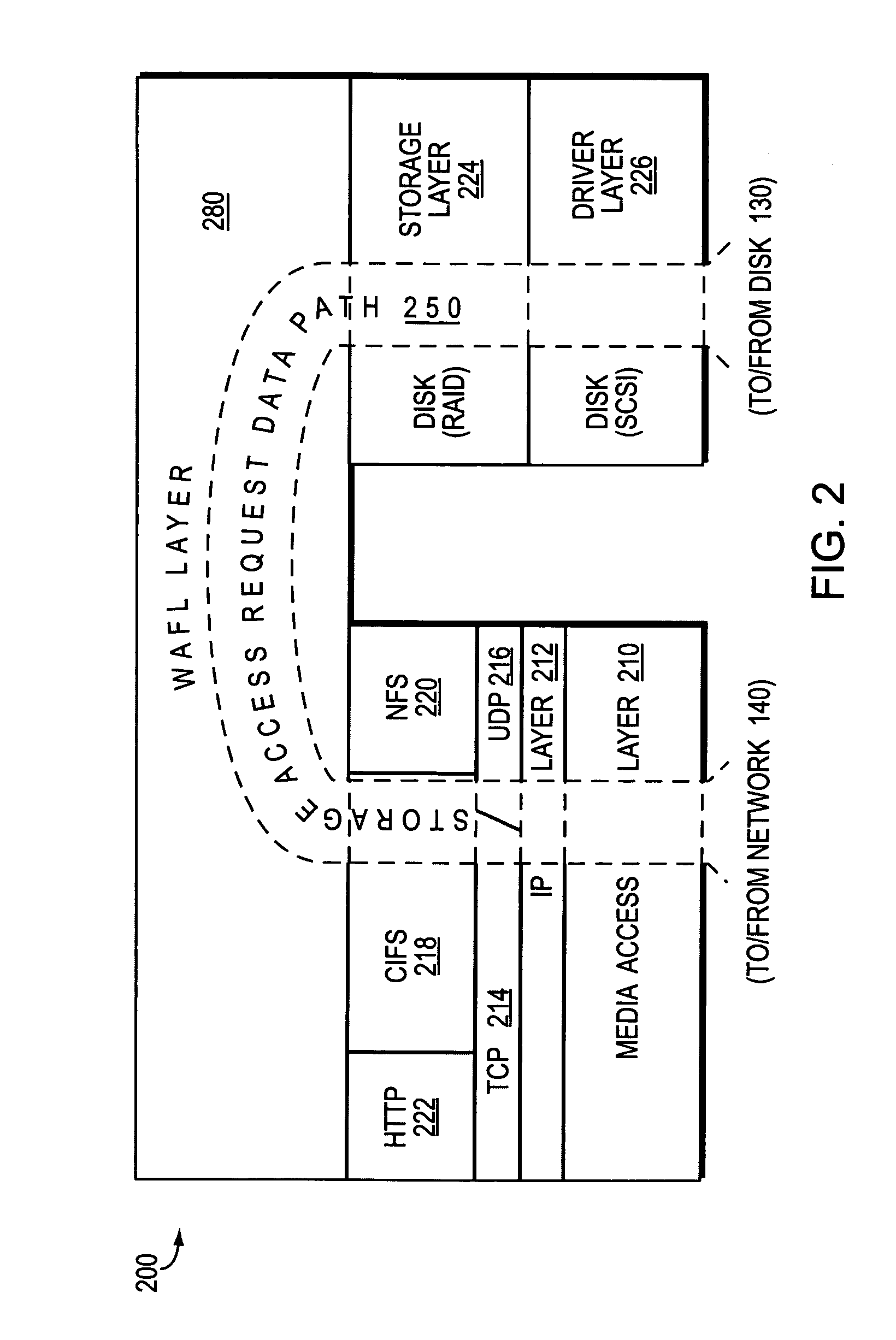
System and method for parallelized replay of an NVRAM log in a storage appliance
InactiveUS7249150B1Avoid mistakesError detection/correctionSpecial data processing applicationsFile systemClient-side
A system and method for enabling parallel replay of a backup memory log of client transaction request entries to a network storage appliance file system is provided. The backup memory is typically implemented as a non-volatile random access memory (NVRAM). An initiator establishes a swarm of messages with a plurality of transaction blocks pointing to logged request entries and related states associated therewith. The states represent the various phases of file system recovery and disk storage including a retrieval of disk information (data and meta-data), typically in the form of a LOAD, and a subsequent modify phase. The swarm is transferred to the file system for parallel disk information-retrieval in an interleaved process. Any transactions that cannot be performed due to a required prerequisite action (e.g. a prior file-create) are returned to the initiator for reloading once the prerequisite action has occurred.
Owner:NETWORK APPLIANCE INC
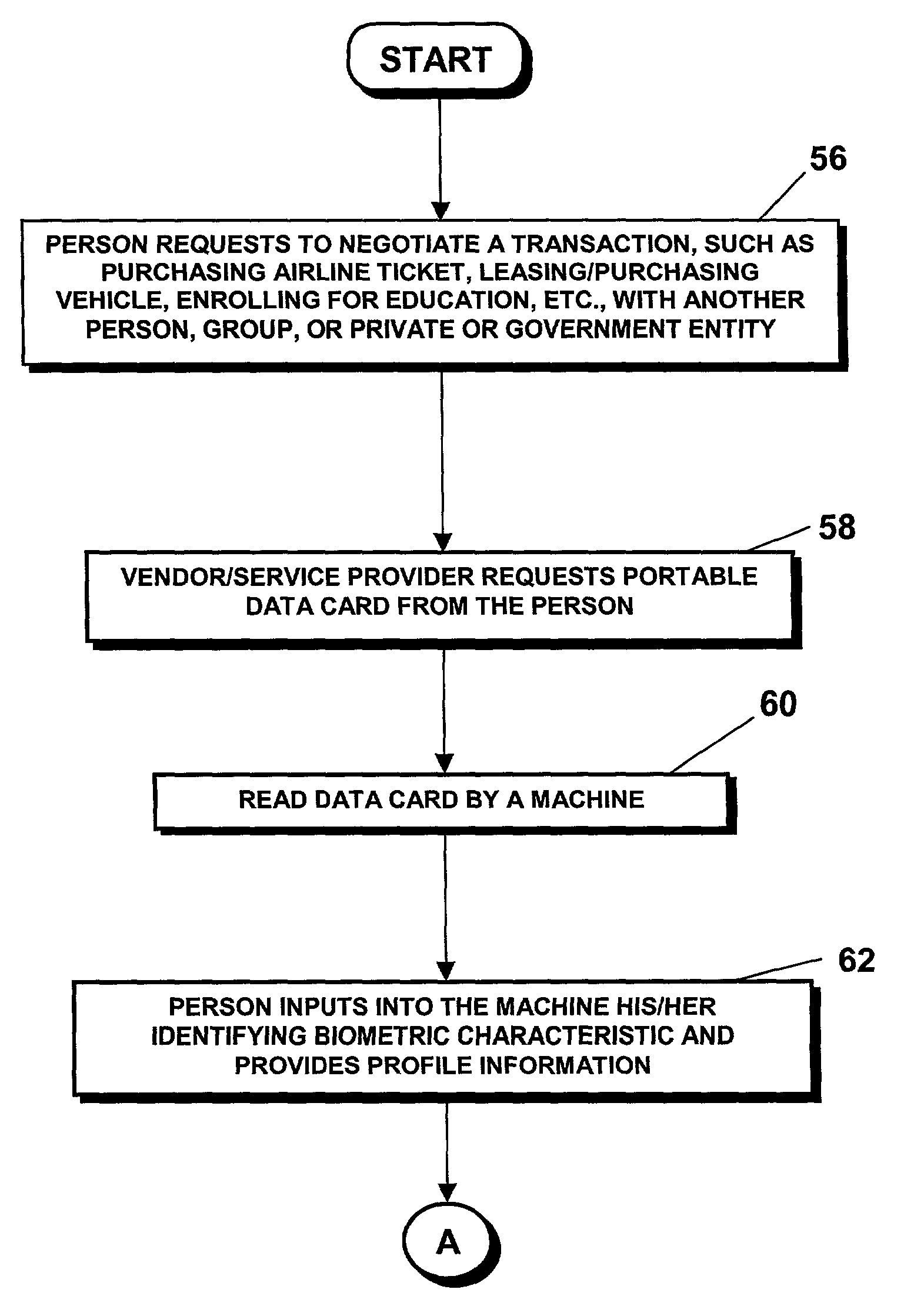
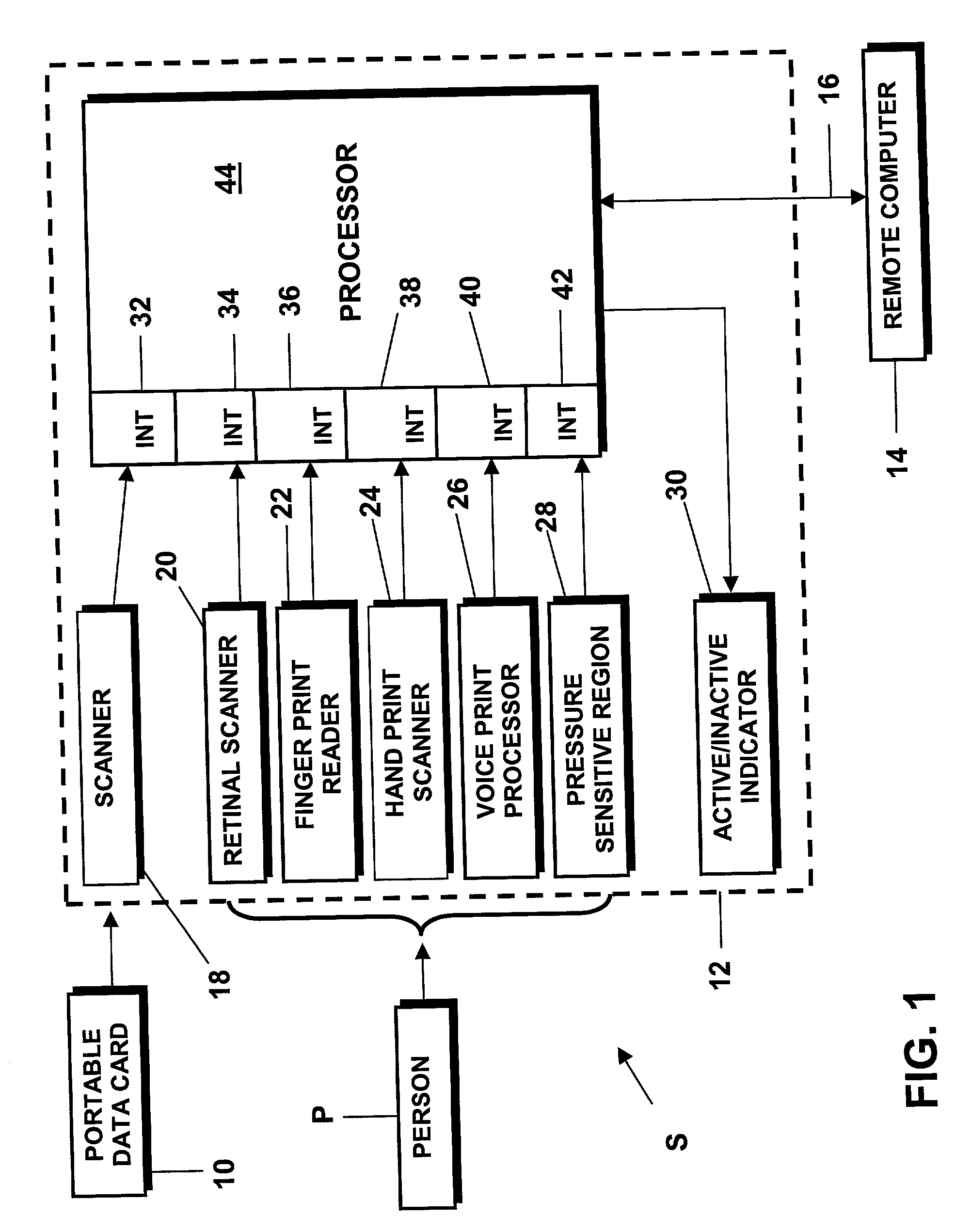
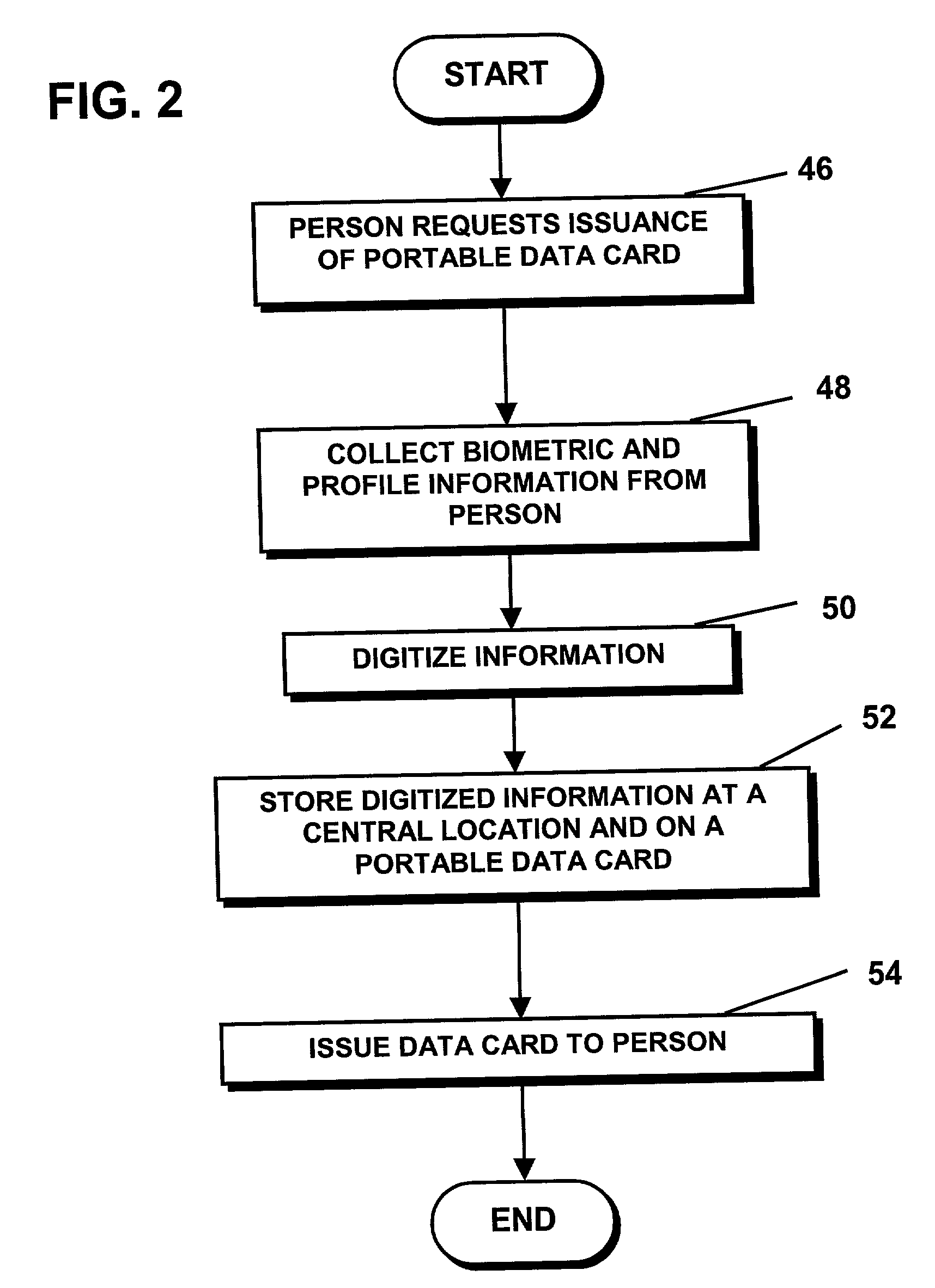
National identification card system and biometric identity verification method for negotiating transactions
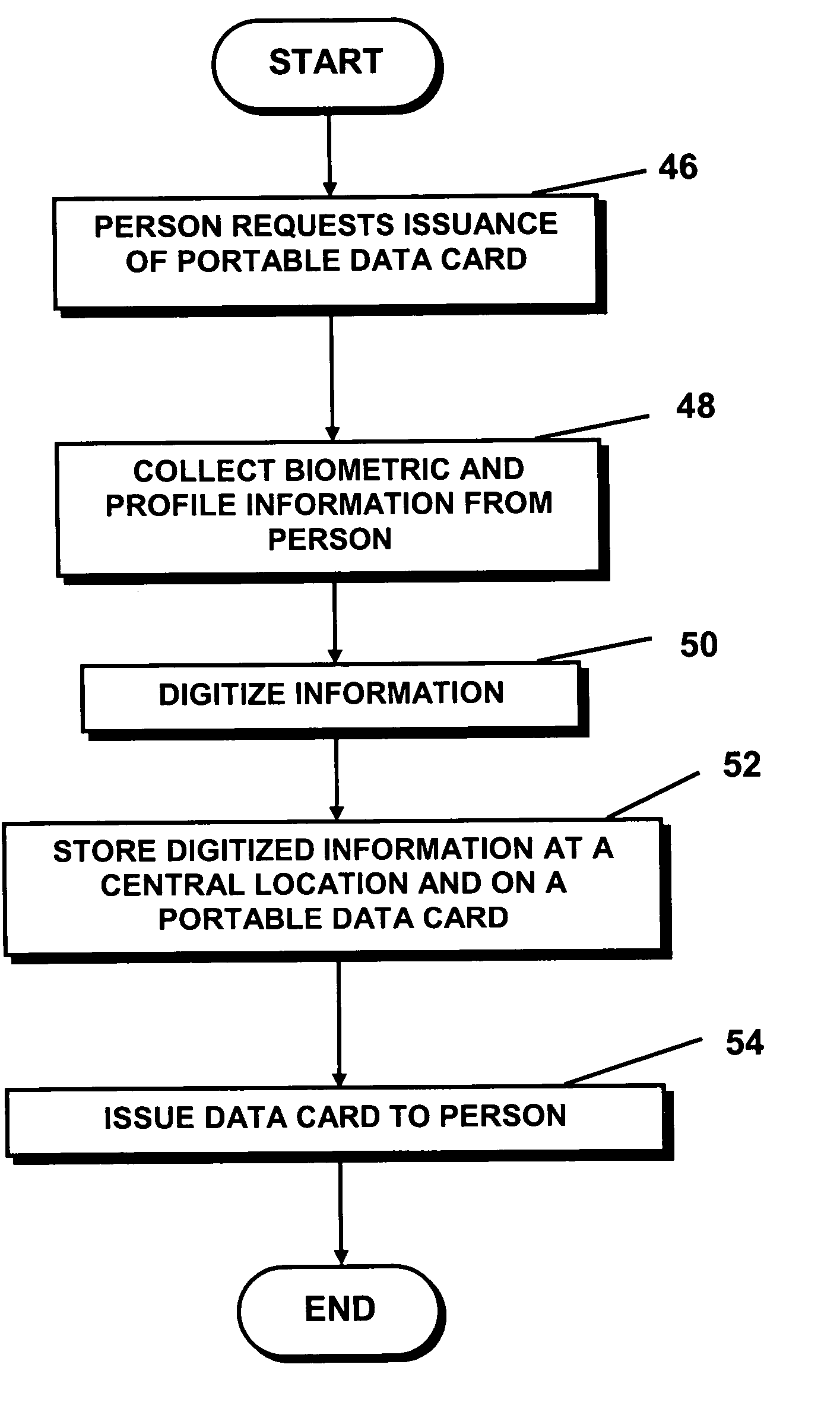
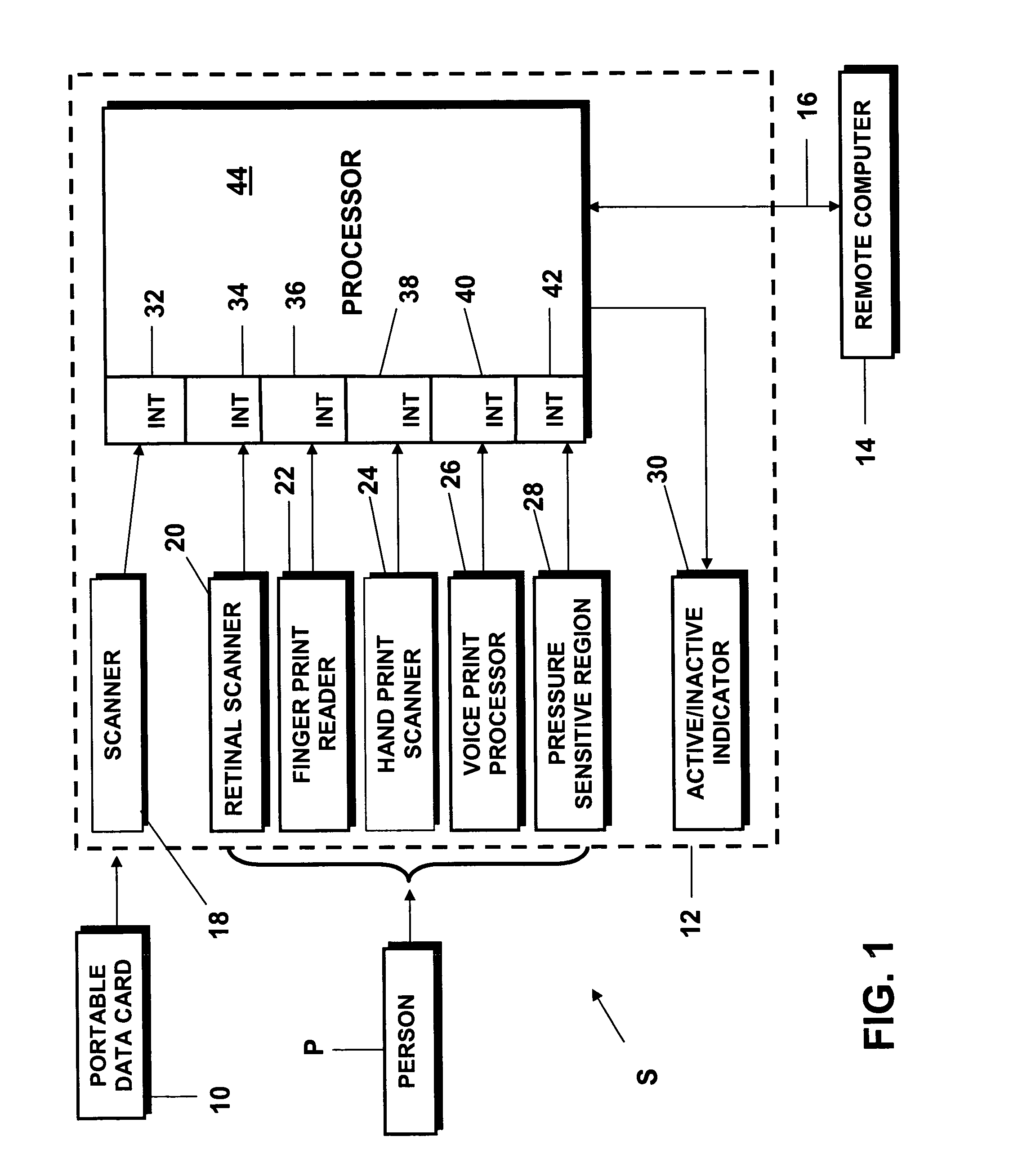
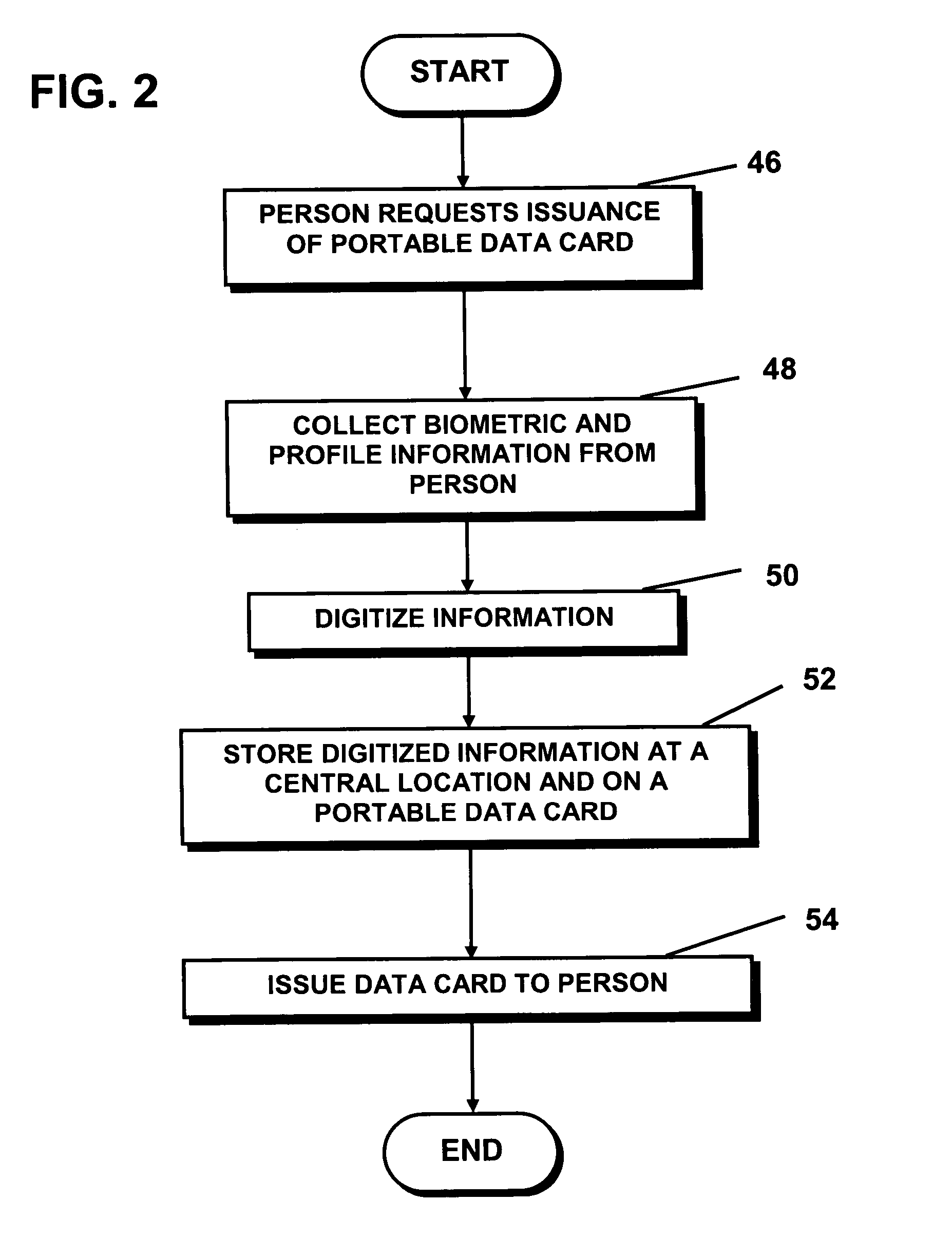
A method and system for preventing or obstructing a person from negotiating a transaction with another person, group, or entity in a population, includes verifying and crosschecking the identity of the person and the status of the national identification card carried by the person, as a prerequisite to negotiating or entering into a transaction, such as purchasing an airline ticket. If an irregularity is found during the verification or crosscheck, or if the identification card is found to be invalid or expired, the person is prevented or obstructed from negotiating that or any subsequent transaction with any other person, group or entity in the population.
Owner:CROSSCHECK IDENTIFICATION SYST INT
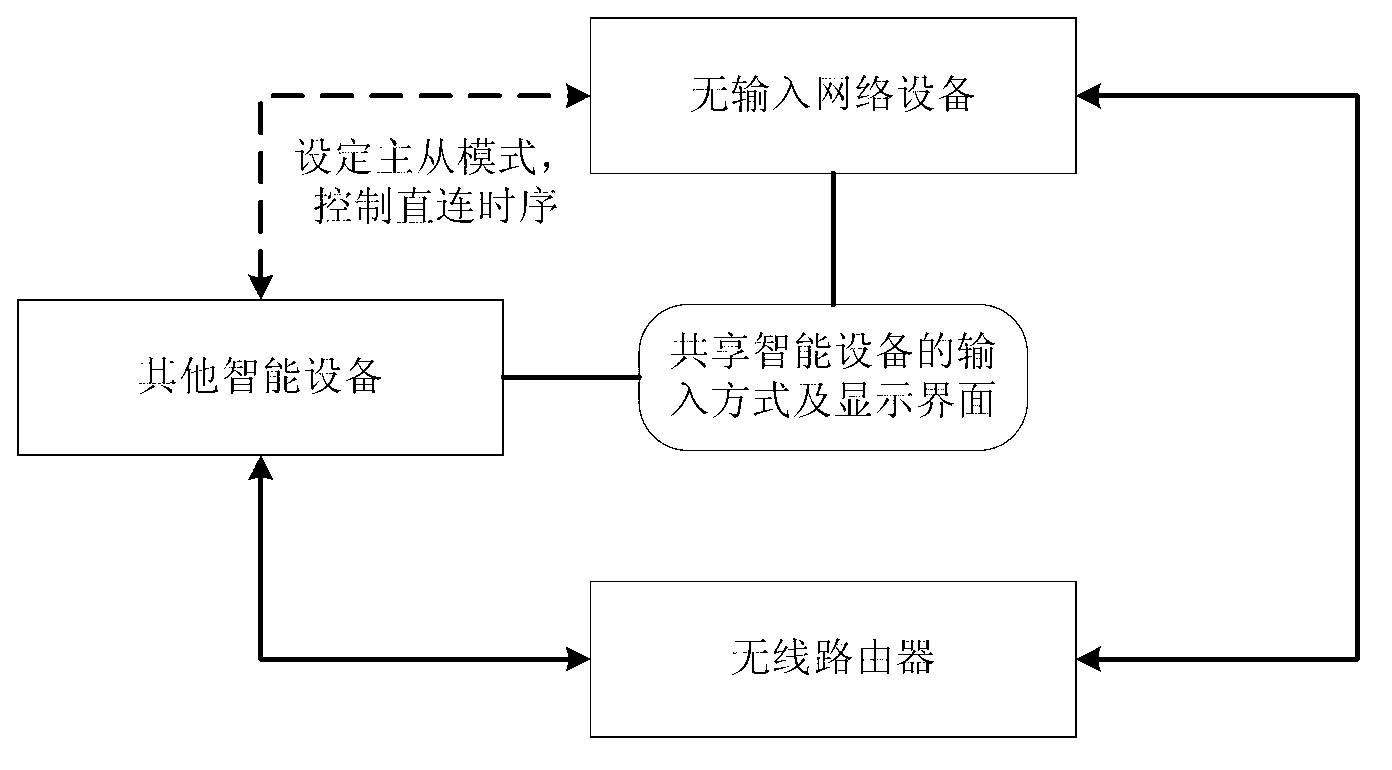
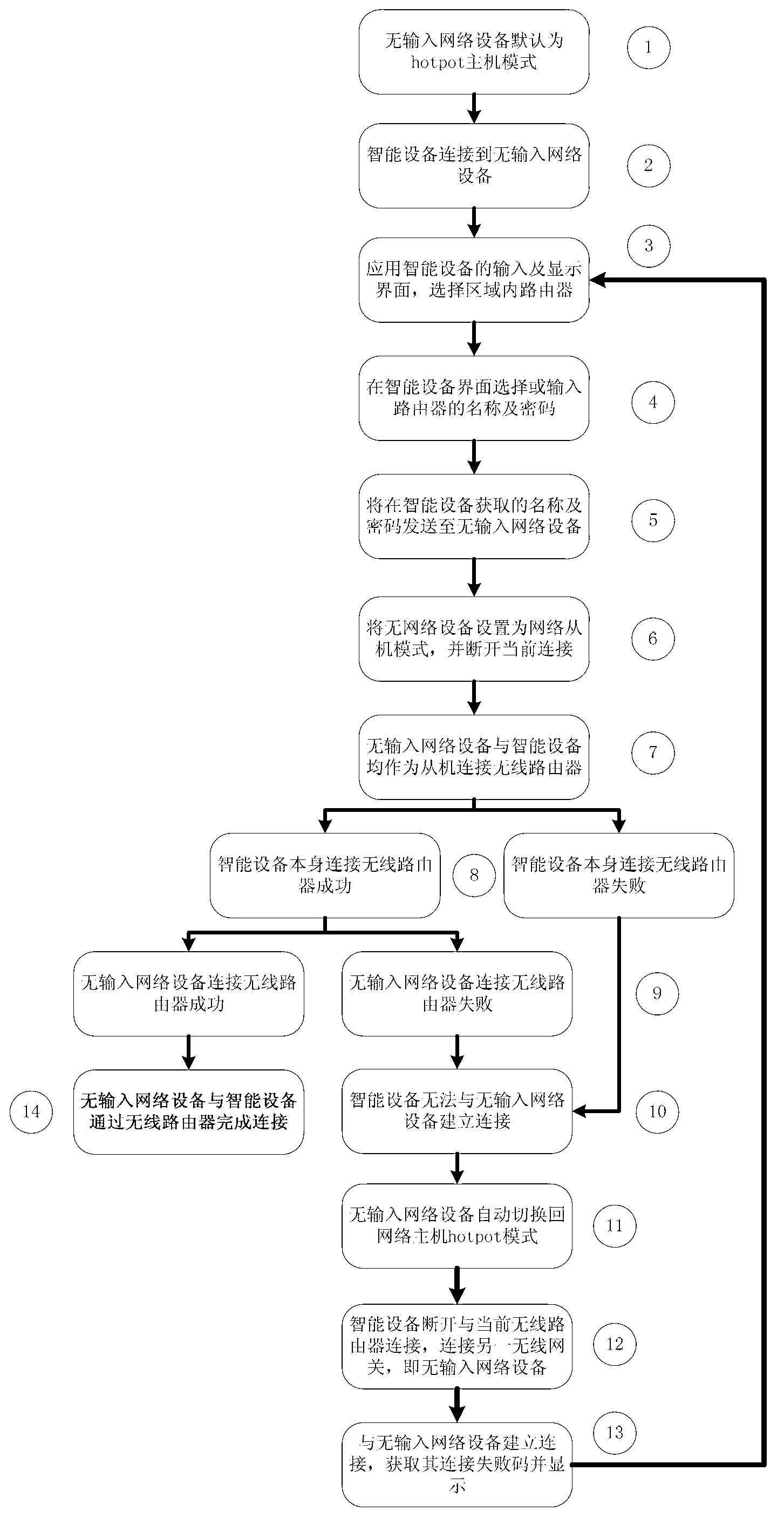
Method for accessing zero-input wireless equipment into network and zero-input wireless equipment
InactiveCN102711282ASolve the problem of not being able to access other gateway devices through the same wireless communication module at the same timeSolve functionConnection managementThe InternetNetwork communication
The invention belongs to the technical field of network communication, and discloses a method for accessing a piece of zero-input wireless equipment into network. By the method, network connecting information of a piece of target wireless gateway equipment can be transmitted to the zero-input wireless equipment through a piece of equipment which can be connected with the zero-input wireless equipment and provided with an input device, so that an aim of accessing the zero-input wireless equipment into a local area network in a form of a wireless network slave is realized in the precondition that the zero-input wireless equipment is not separately provided with the input device, and the technical effect that other equipment in the local area network can share the data or functions of the zero-input wireless equipment and can be interconnected with the other equipment or be accessed into the Internet through the gateway equipment is achieved.
Owner:尚喆
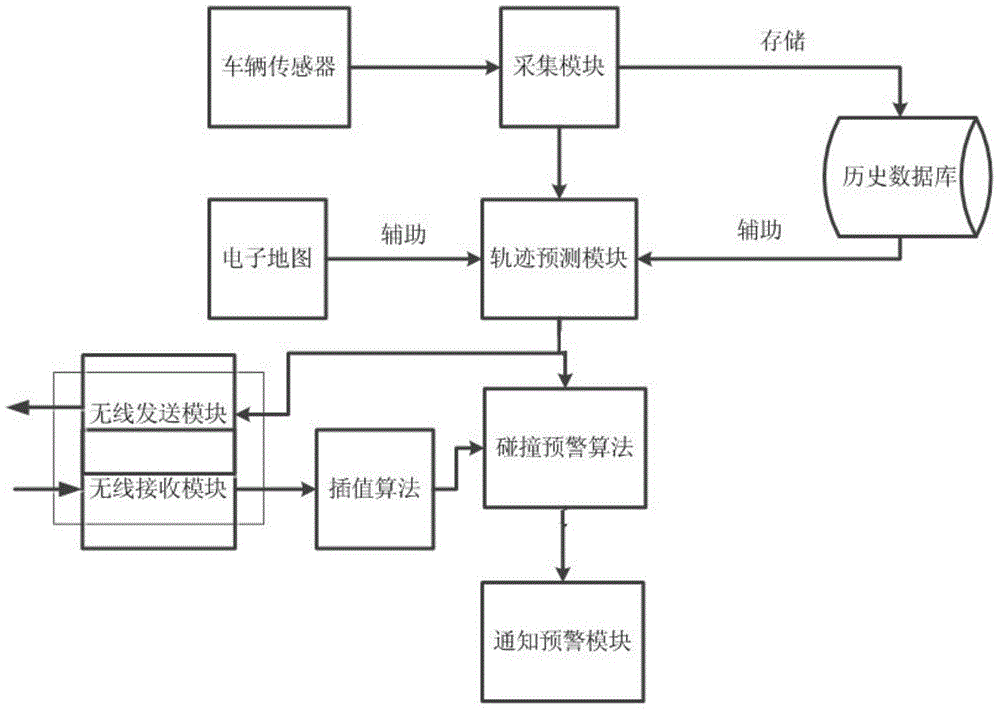
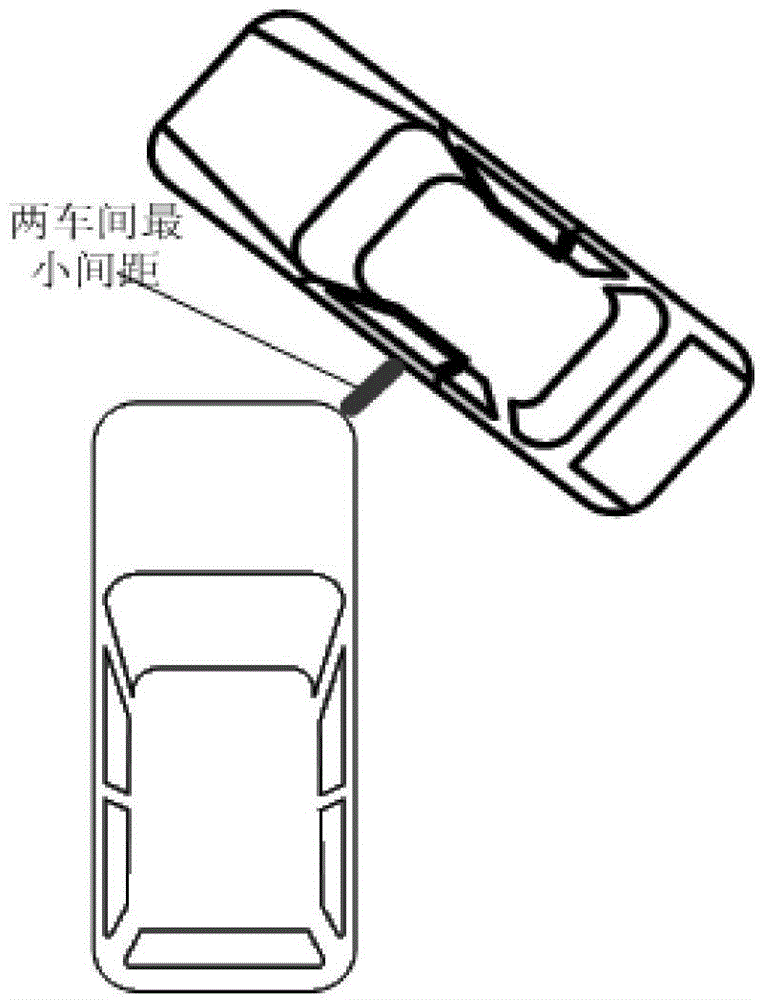
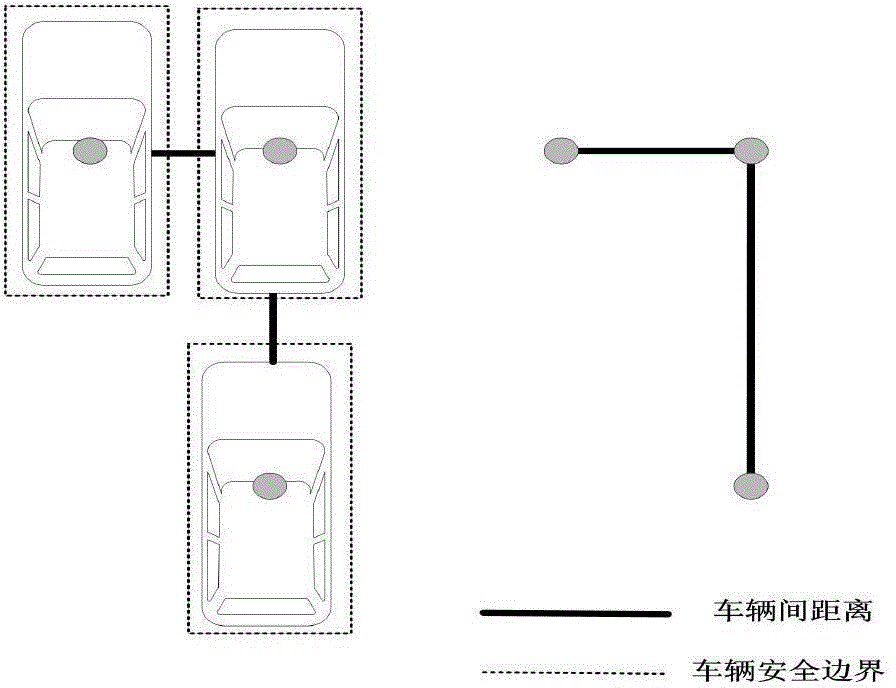
Crashing detecting and warning method based on vehicle network technology
InactiveCN104882025ASafe distance judgment is accurateReduce computational workloadAnti-collision systemsNetwork packetTracking model
The invention relates to a crashing detecting and warning method based on vehicle network technology. The method comprises the following steps: collecting vehicle information and driving information; establishing a track model with the assistance of historical driving data and an electronic map of a vehicle and according to current driving information of the vehicle for predicting the track of the vehicle in the future n seconds; and judging if there exists danger of crashing according to a security boundary of the vehicle at a moment in the future, and performing warning if the danger of crashing exists. Track information of surrounding vehicles is known through a wireless receiving-transmitting module for receiving and transmitting a vehicle network broadcast protocol dada packet. According to the invention, a driver can be warned in time to avoid the danger, and the driving efficiency with the precondition of ensured security is improved.
Owner:DONGHUA UNIV
Virtual reality psychophysiological conditioning medium
The instant invention provides a medium including a program operable within a virtual reality device which is designed for perfecting mental visualization within the mind of a subject sufficient alone to effect a desired neurological and / or physiological change within the body of the subject, even in the substantial absence of any physical movement by the subject. The program includes a dynamic scenario that is designed to communicate in chronological order: (I.) a condition which requires a remedy; (ii.) a mode for effecting the remedy; (iii.) the performance of the mode so as to effect the remedy; and, (iv.) rectification of the condition through the performance of the mode. The program is interspersed with audible, visual or combined audible / visual subliminal stimuli, designed to aid a subject in achieving the goal. It also provides the medium in combination with a virtual reality device and a method of using the same. The steps of the method include: operatively interfacing the program with the device and mounting the device on the subject; and, running the program. Optionally, the program can be designed to precondition of the subject's mind, such as inducing a state of meditation or hypnosis, or combinations thereof, and thereafter communicate a metaphoric or real, or combined real and metaphoric, scenario to the subject. The scenario of the program can be designed to exist in real time, real space, compressed time, compressed space, expanded time, expanded space, or any combination thereof, real or metaphoric or any combination of real and metaphoric. Optionally the program is further designed to enable (motor) interaction between the subject and / or an operator external to the preconditioning and the device.
Owner:SEVER JR FR
Fault tolerant rolling software upgrade in a cluster
A method and system are provided for conducting a cluster software version upgrade in a fault tolerant and highly available manner. There are two phases to the upgrade. The first phase is an upgrade of the software binaries of each individual member of the cluster, while remaining cluster members remain online. Completion of the first phase is a pre-requisite to entry into the second phase. Upon completion of the first phase, a coordinated cluster transition is performed during which the cluster coordination component performs any required upgrade to its own protocols and data structures and drives all other software components through the component specific upgrade. After all software components complete their upgrades and any required data conversion, the cluster software upgrade is complete. A shared version control record is provided to manage transition of the cluster members through the cluster software component upgrade.
Owner:IBM CORP
Storage systems and methods
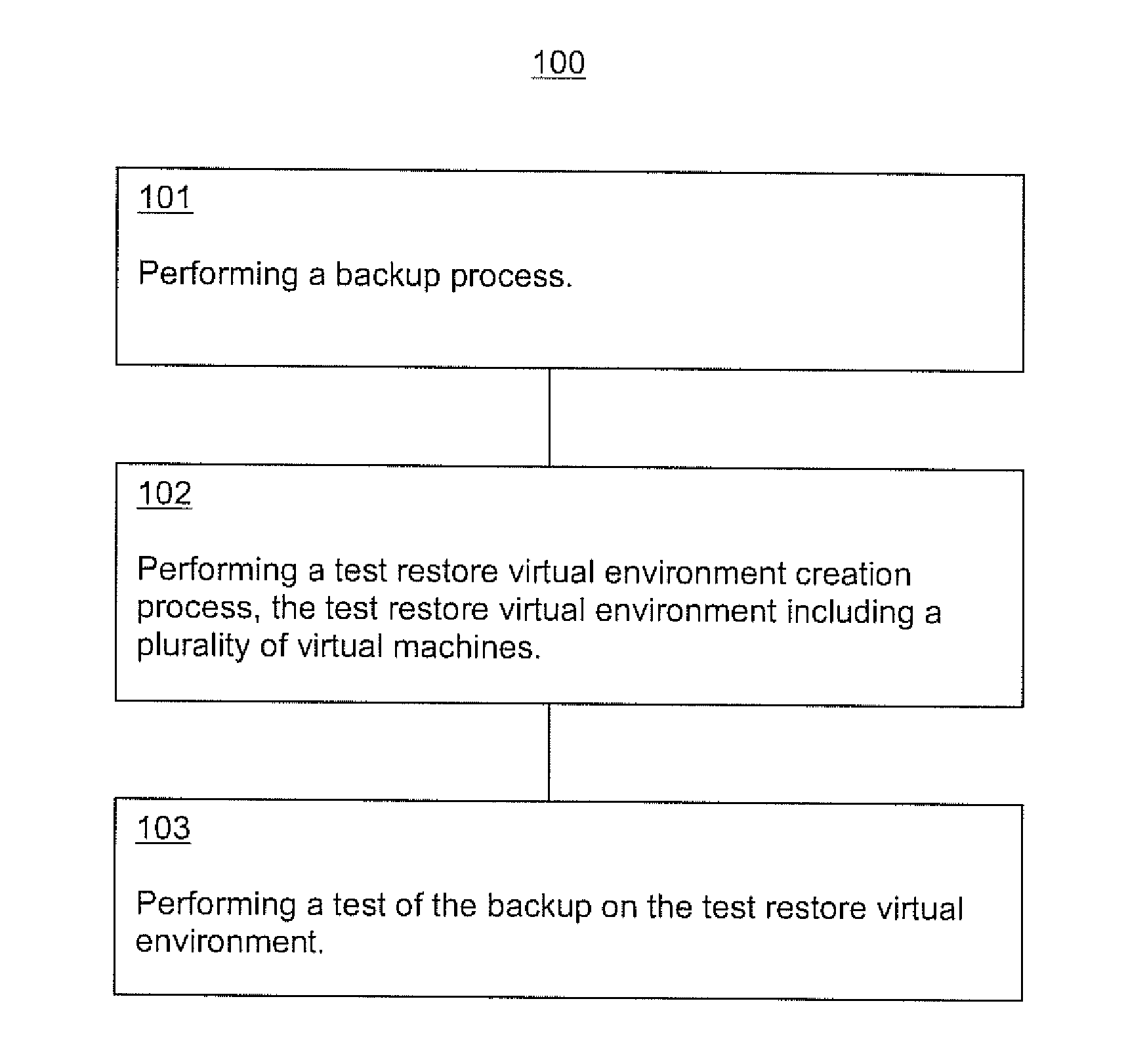
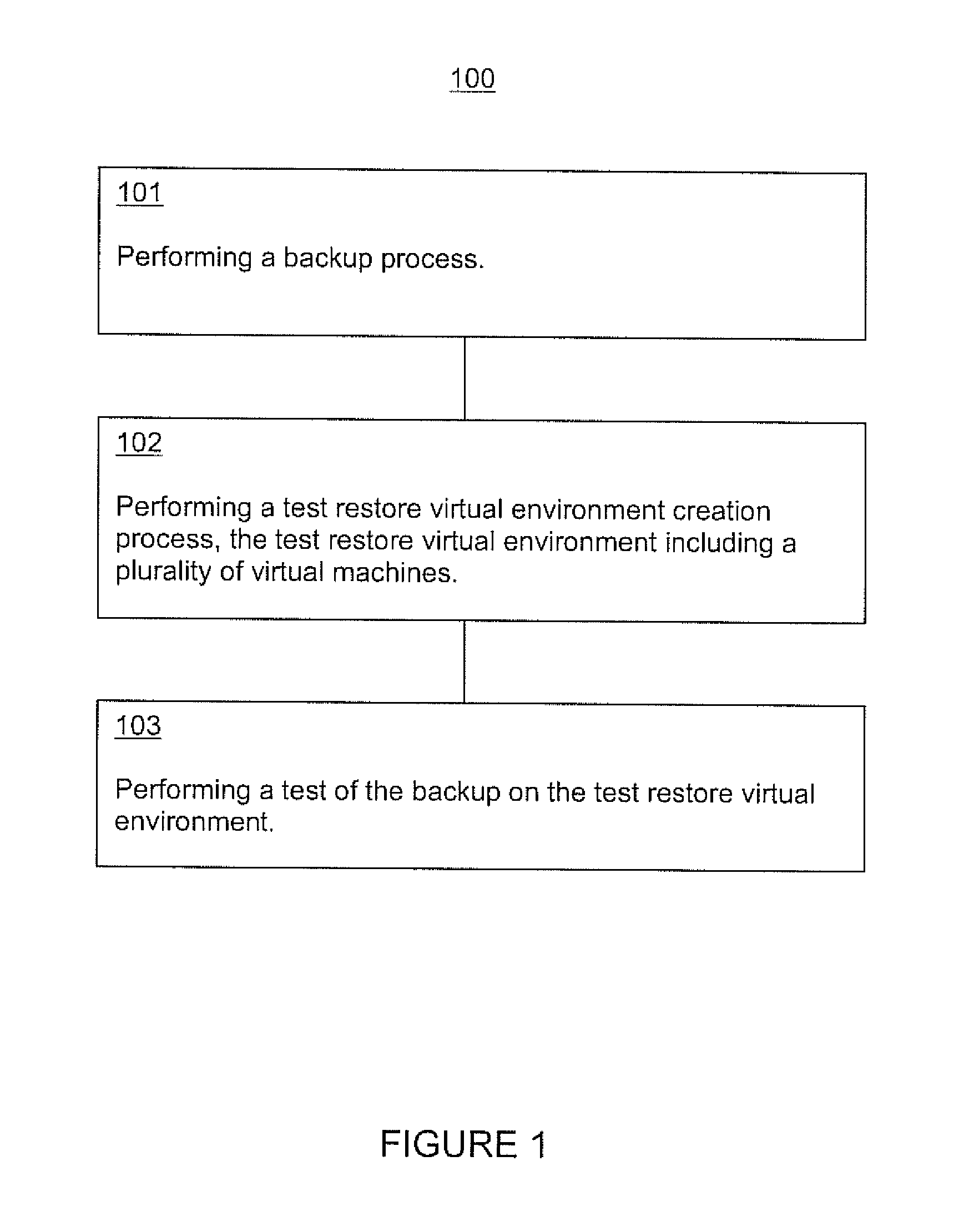
ActiveUS20110202734A1Memory loss protectionError detection/correctionHybrid storage systemVirtual machine
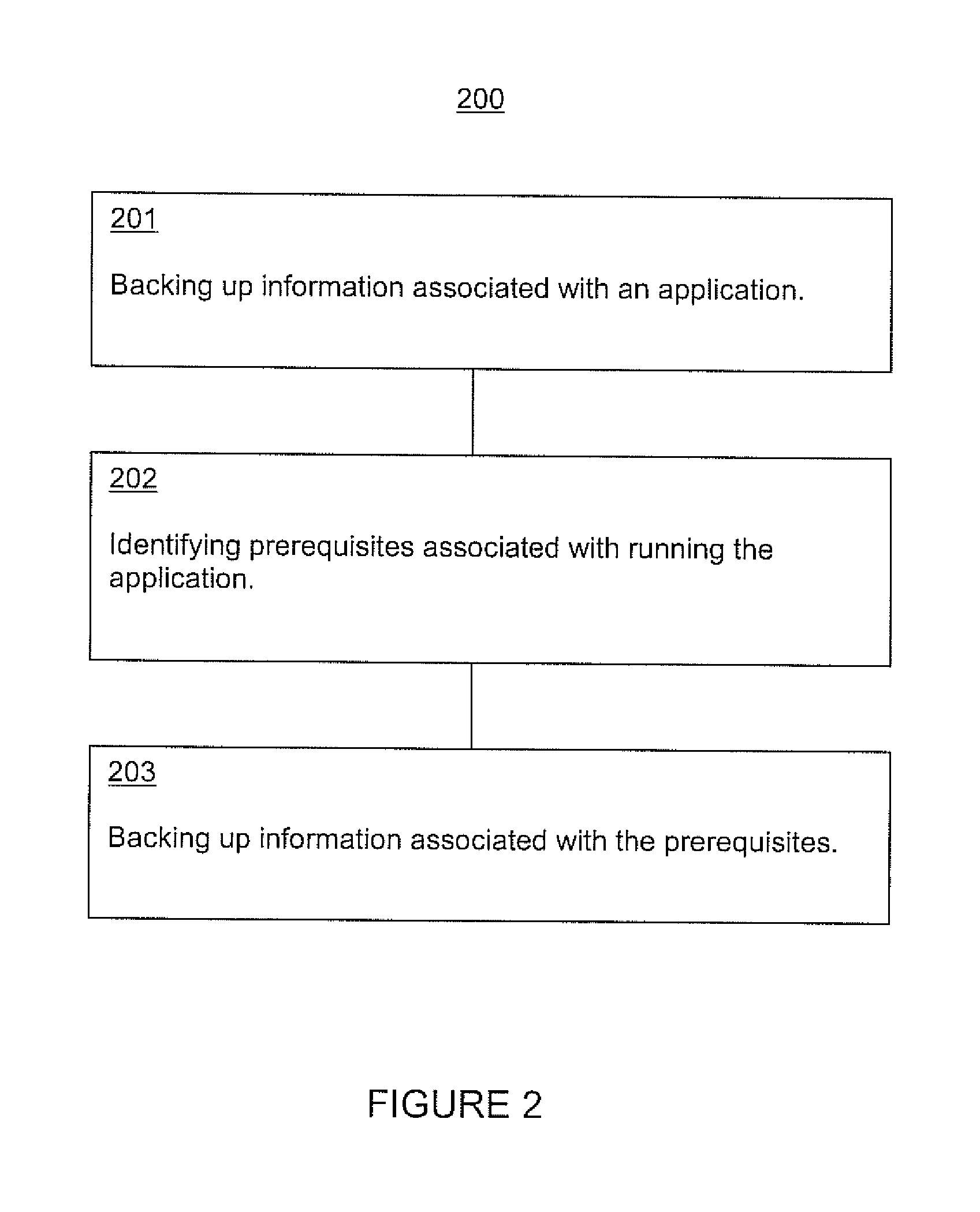
Systems and methods for backup test restore are presented. In one embodiment a backup restore test method includes performing a backup process; performing a test restore virtual environment creation process, the test restore virtual environment including a plurality of virtual machines; and performing a test of the backup on the test restore virtual environment. The backup process can include backing up information associated with an application; identifying prerequisites associated with running the application; and backing up information associated with the prerequisites. The test restore virtual environment creation process can include gathering information identifying the prerequisites associated with the application; creating the plurality of virtual machines, wherein the plurality of virtual machines includes virtual machines corresponding to physical machines the application and perquisites run on; and bringing up the plurality of virtual machines utilizing the information from the backup process.
Owner:VERITAS TECH
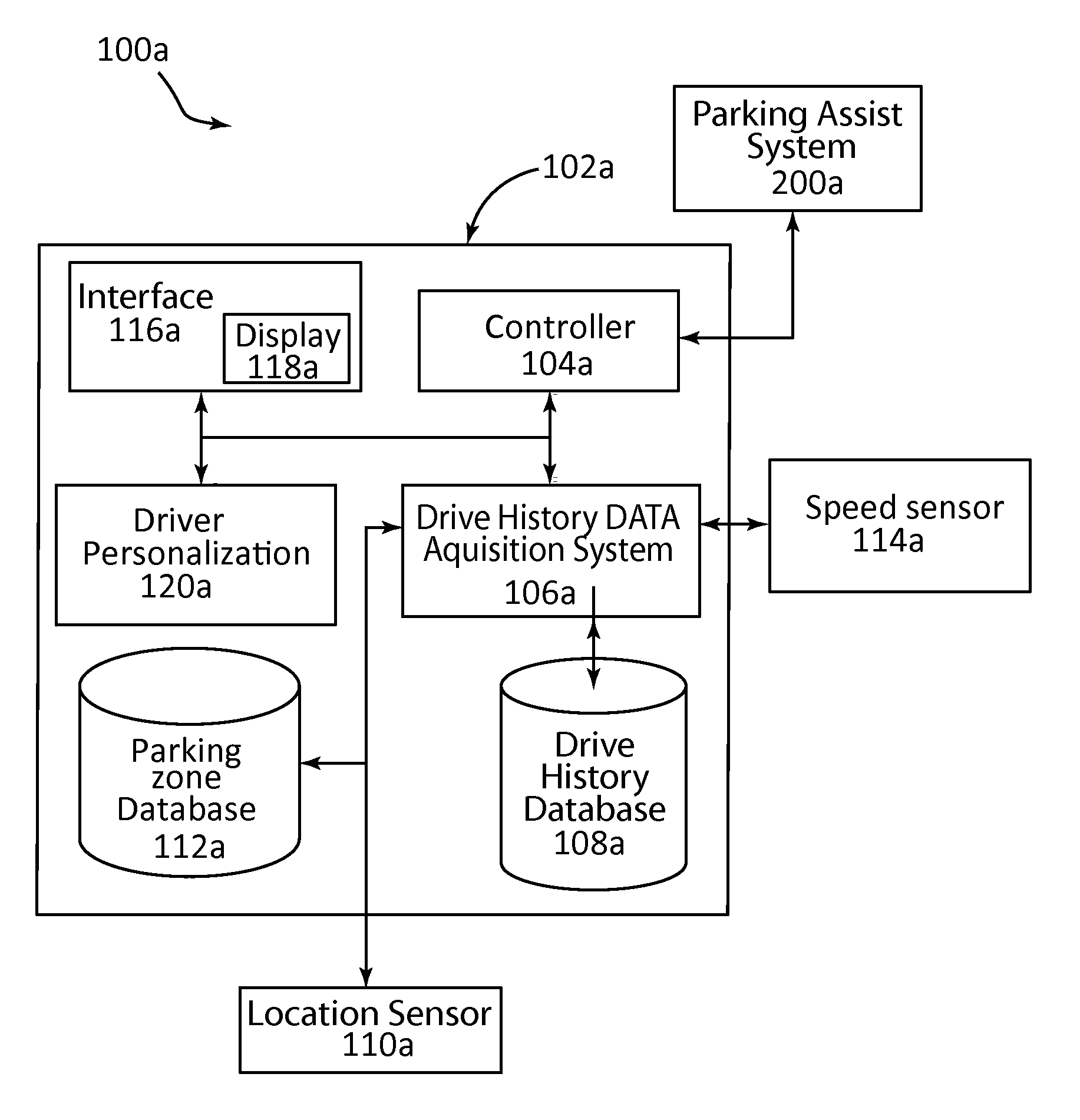
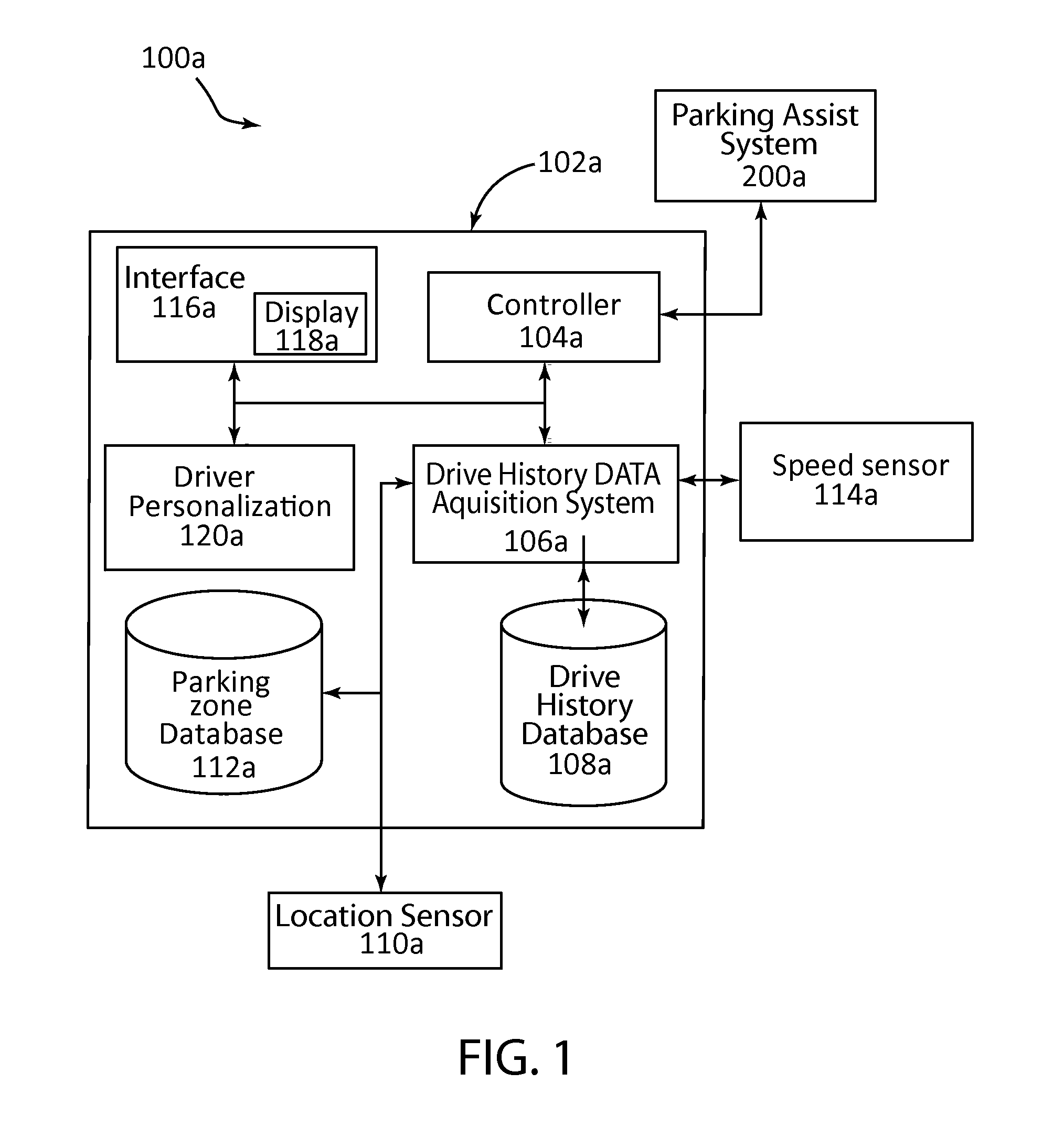
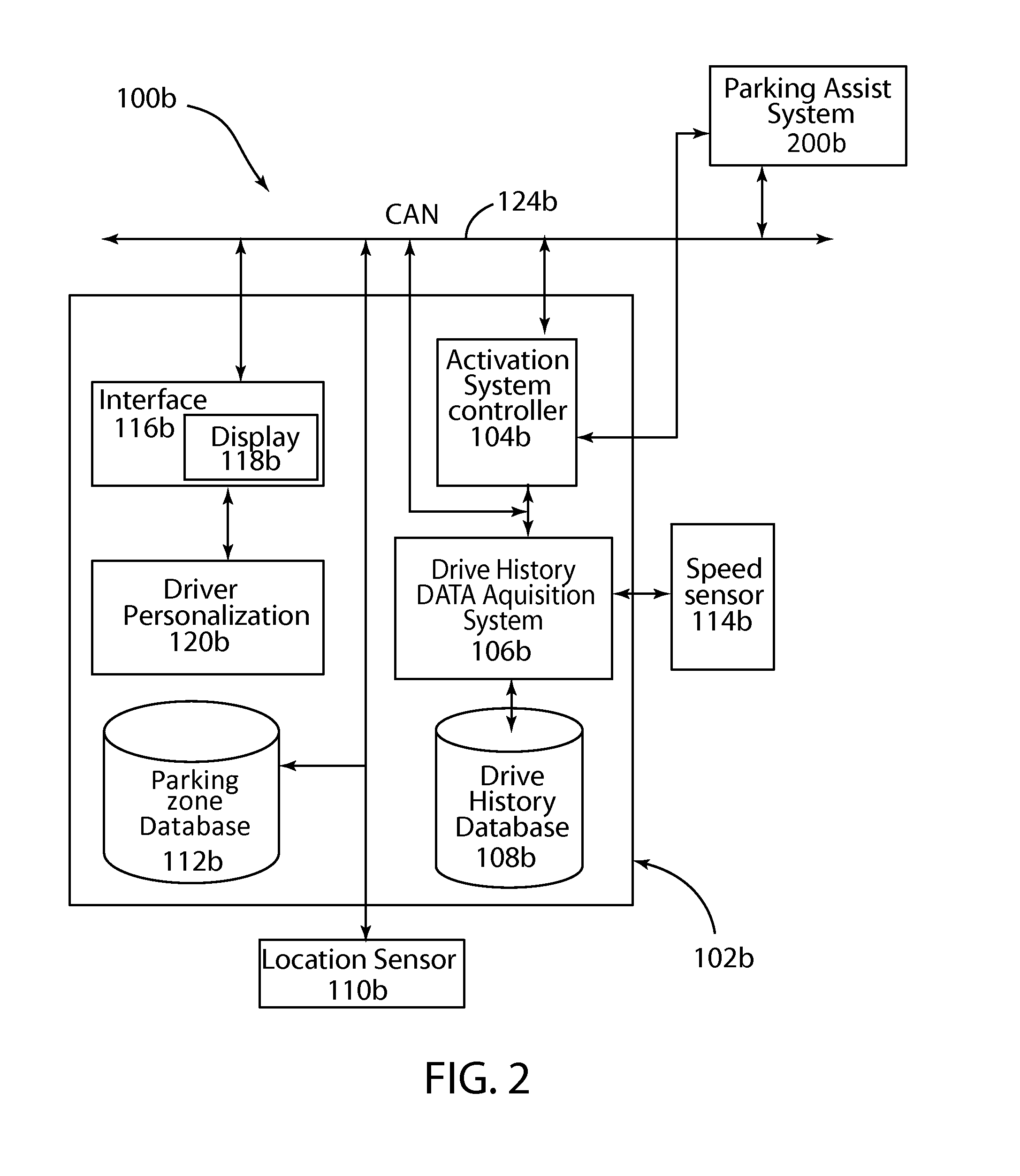
Automatic park and reminder system and method of use
A parking system adaptively controlling a vehicle during a parking maneuver using a park assist system, for example an active park assist (APA) or trailer backup assist (TBA). Control of the park assist system based on previous speed profiles at a geographic location where the same park assist system was previously activated. The parking system including an activation system that, based on vehicle speed and geographic location, activates the park assist system when preconditions for park assist system operation are met. The activation system may cooperate with the park assist system based on default or previously stored drive history profiles associated with the current geographic location.
Owner:FORD GLOBAL TECH LLC
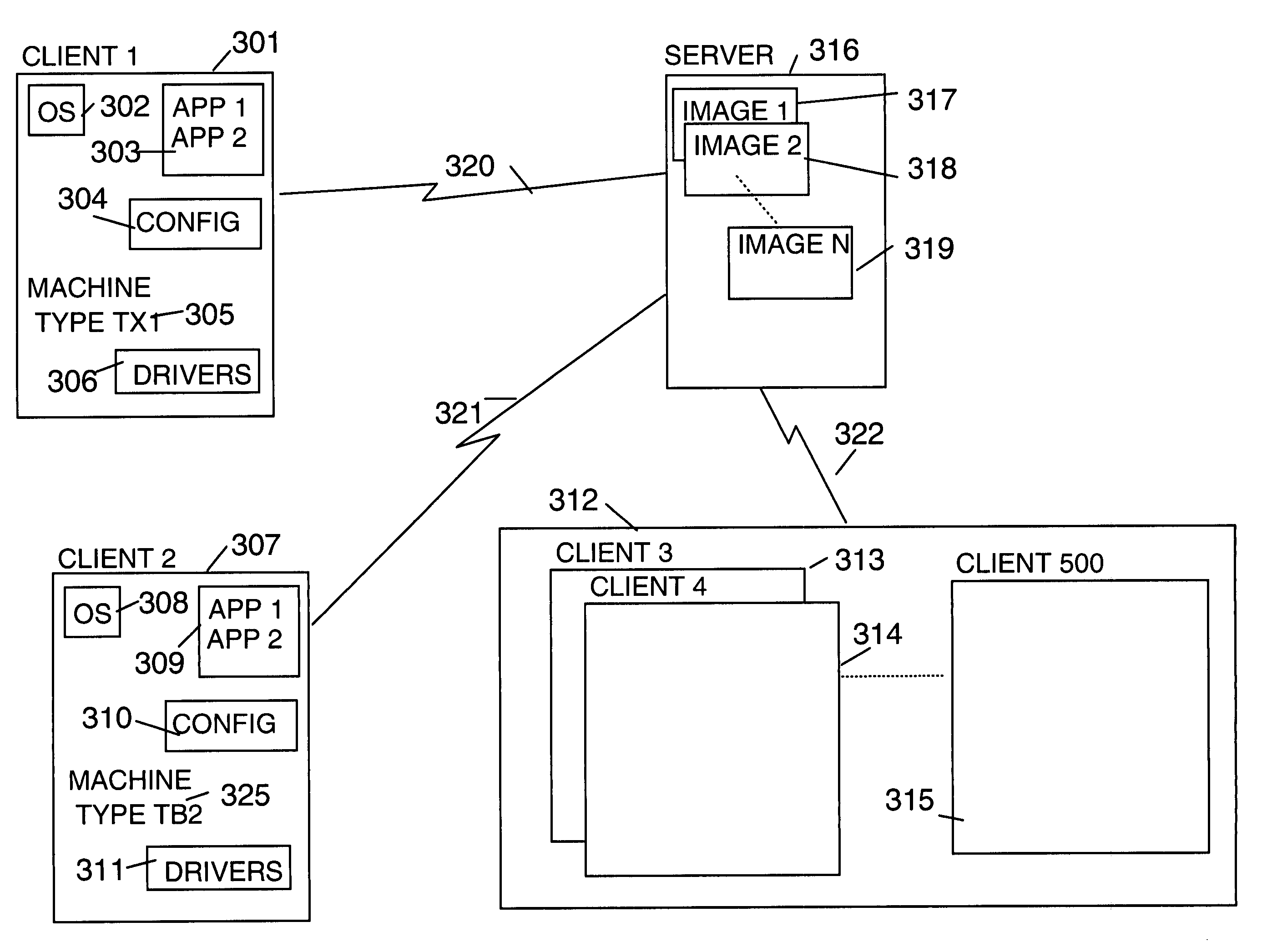
Build time determination and installation of drivers on cloned systems
InactiveUS20050027831A1Digital computer detailsProgram loading/initiatingComputerized systemApplication software
A clone (replica) image of a computer system is loaded to a target computer system being built. A detection program running on the target computer system detects configuration information and attached devices and provides this information to a build program. The build program provides needed program components, applications, prerequisites and device drivers for the target computer according to build rules defined for the target computer type / model. Optionally, the detection program further detects that there are updates required for the detection program and installs the updates before proceeding with the build process.
Owner:IBM CORP
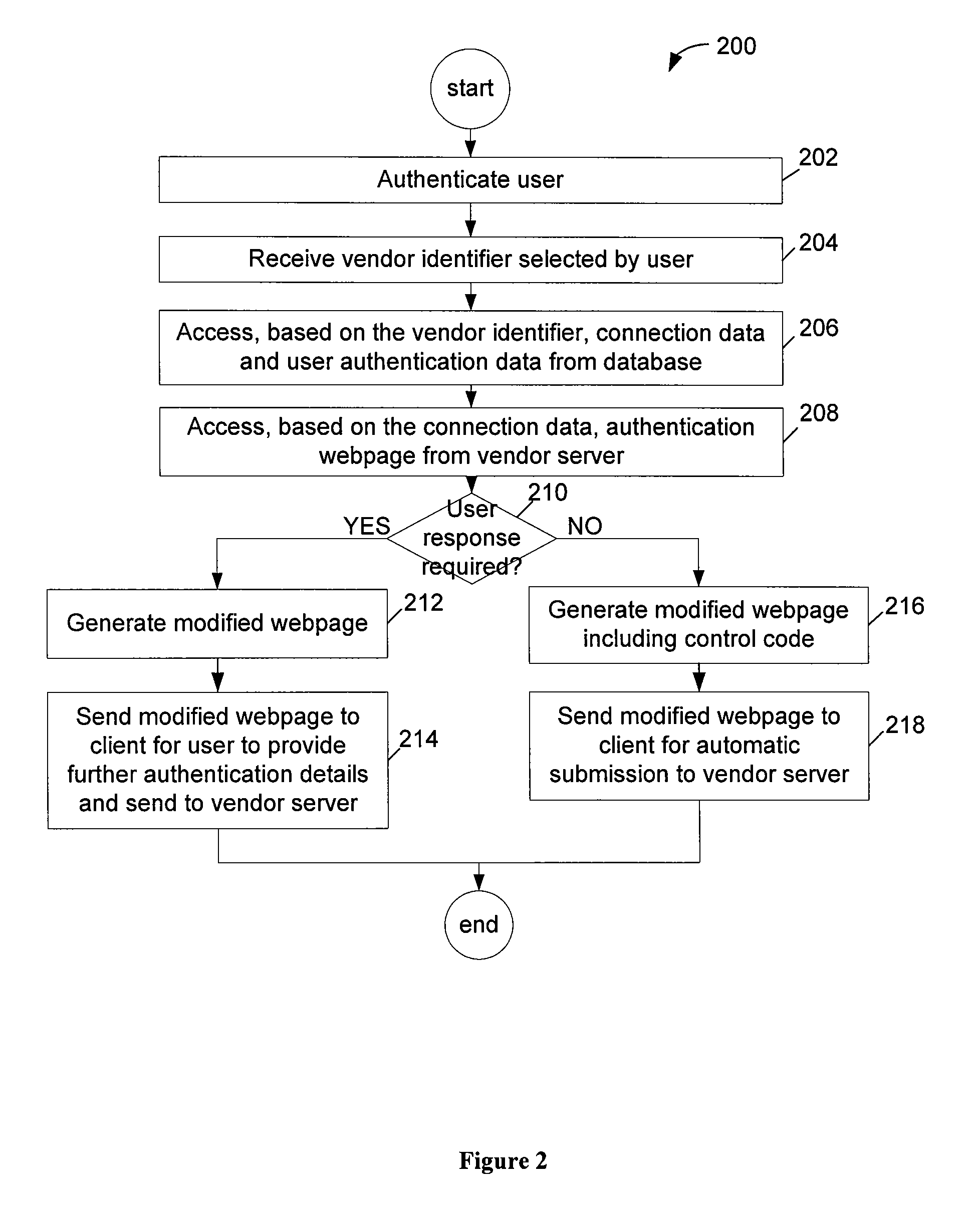
Secure authentication method and system
InactiveUS20070156592A1Computer security arrangementsBuying/selling/leasing transactionsNetwork connectionInternet privacy
An automated method for authenticating a customer with a vendor, the method including the steps of (a) the customer nominating a remote authentication agent, (b) the customer identifying themselves by transmission of customer credentials to the authentication agent via a network connection, (c) the vendor identifying themselves by transmission of vendor credentials to the authentication agent, and (d) the authentication agent providing credentials for the customer to the vendor so that the vendor can perform authentication as a prerequisite to permitting direct communication between the vendor and customer through the network.
Owner:REALITY ENHANCEMENT
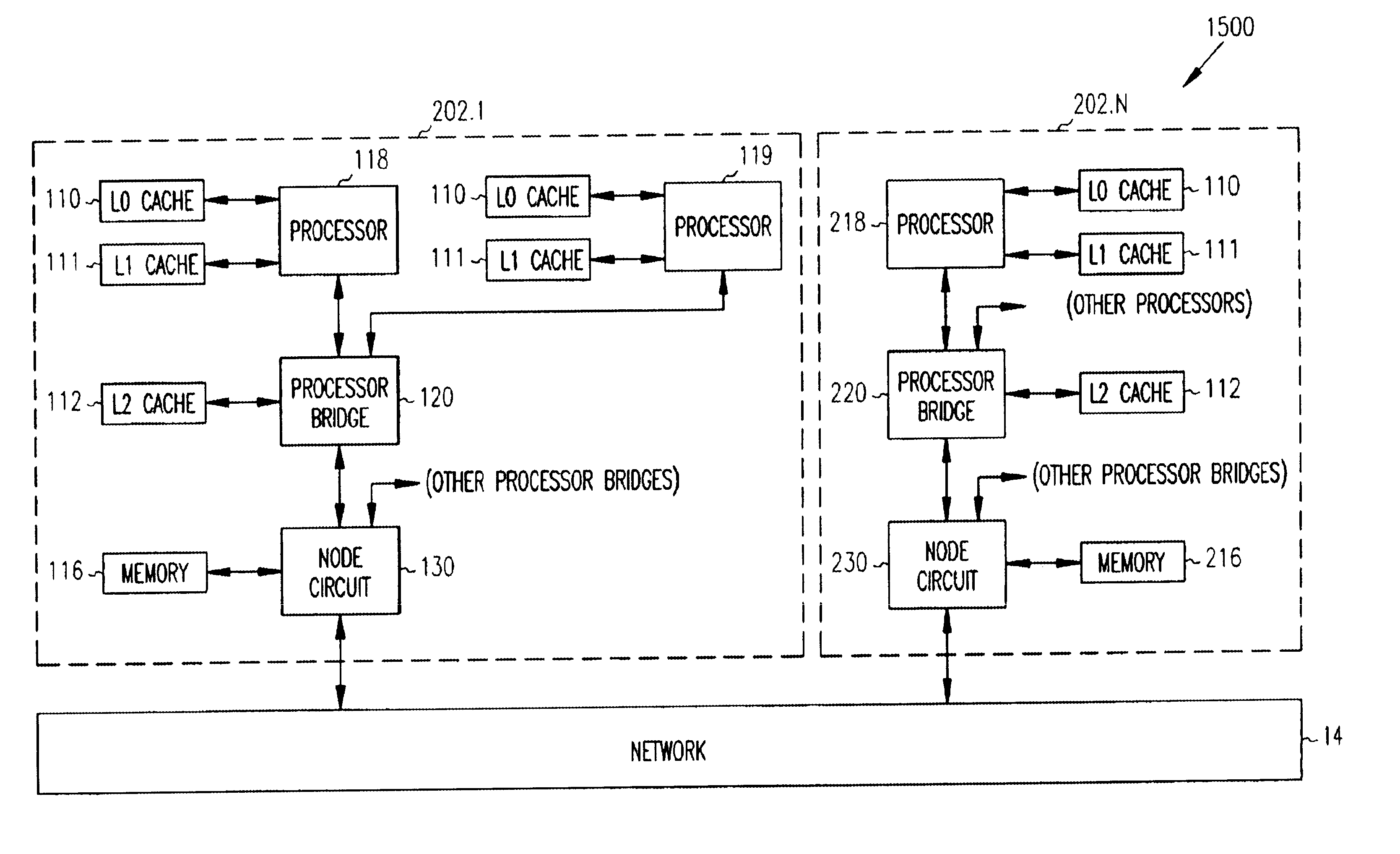
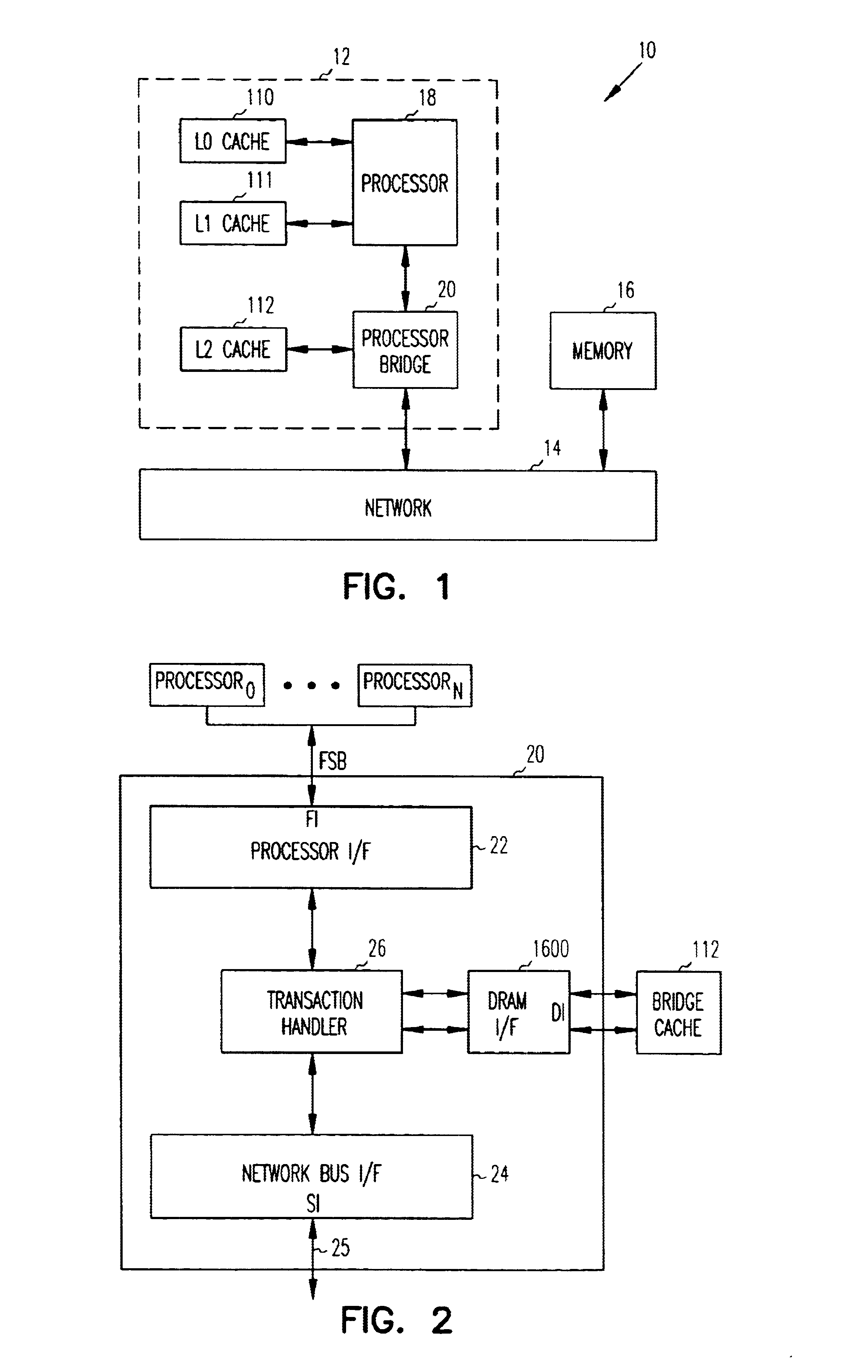
Method and cache-coherence system allowing purging of mid-level cache entries without purging lower-level cache entries
A method and apparatus for purging data from a middle cache level without purging the corresponding data from a lower cache level (i.e., a cache level closer to the processor using the data), and replacing the purged first data with other data of a different memory address than the purged first data, while leaving the data of the first cache line in the lower cache level. In some embodiments, in order to allow such mid-level purging, the first cache line must be in the "shared state" that allows reading of the data, but does not permit modifications to the data (i.e., modifications that would have to be written back to memory). If it is desired to modify the data, a directory facility will issue a purge to all caches of the shared-state data for that cache line, and then the processor that wants to modify the data will request an exclusive-state copy to be fetched to its lower-level cache and to all intervening levels of cache. Later, when the data in the lower cache level is modified, the modified data can be moved back to the original memory from the caches. In some embodiments, a purge of all shared-state copies of the first cache-line data from any and all caches having copies thereof is performed as a prerequisite to doing this exclusive-state fetch.
Owner:RPX CORP +1
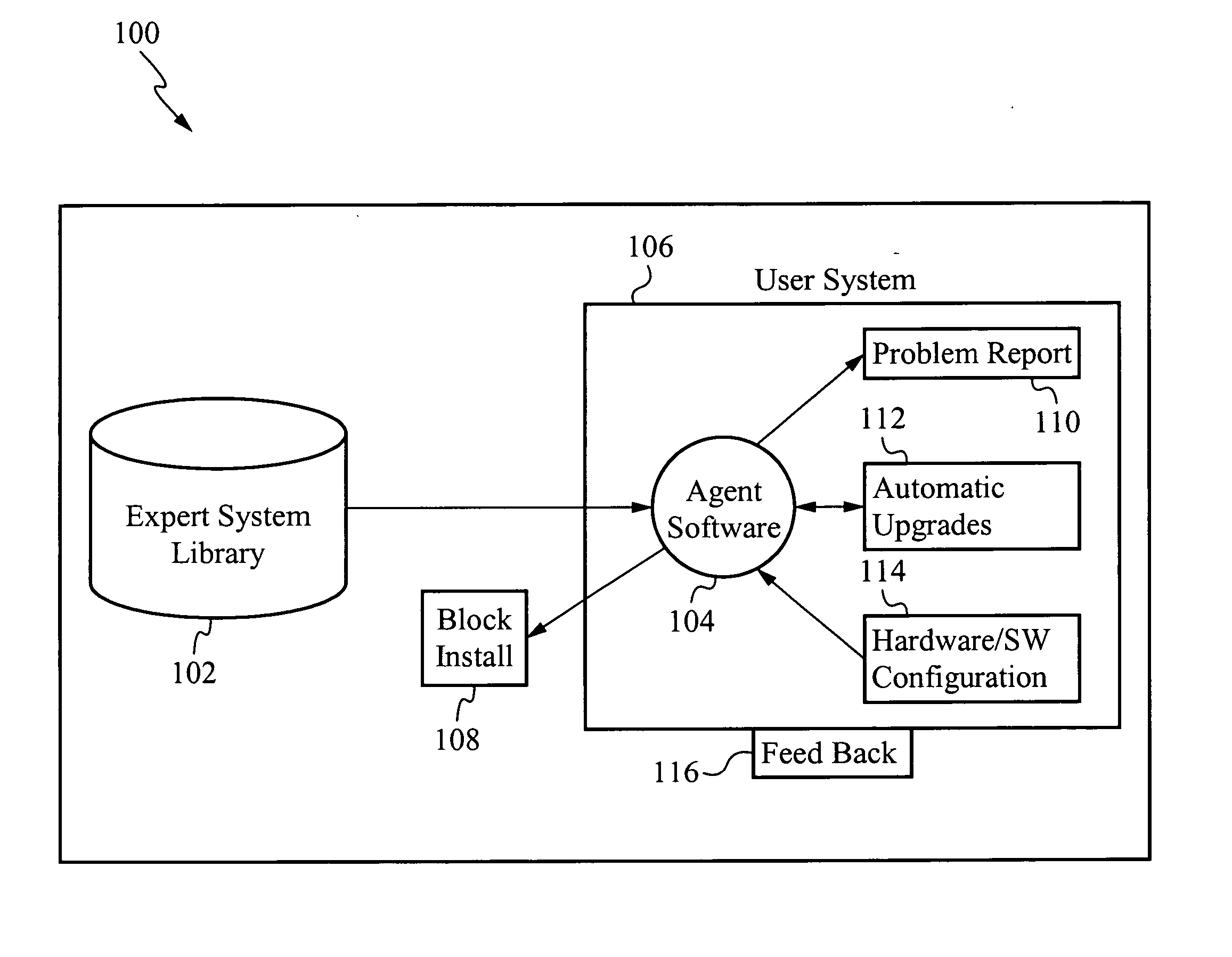
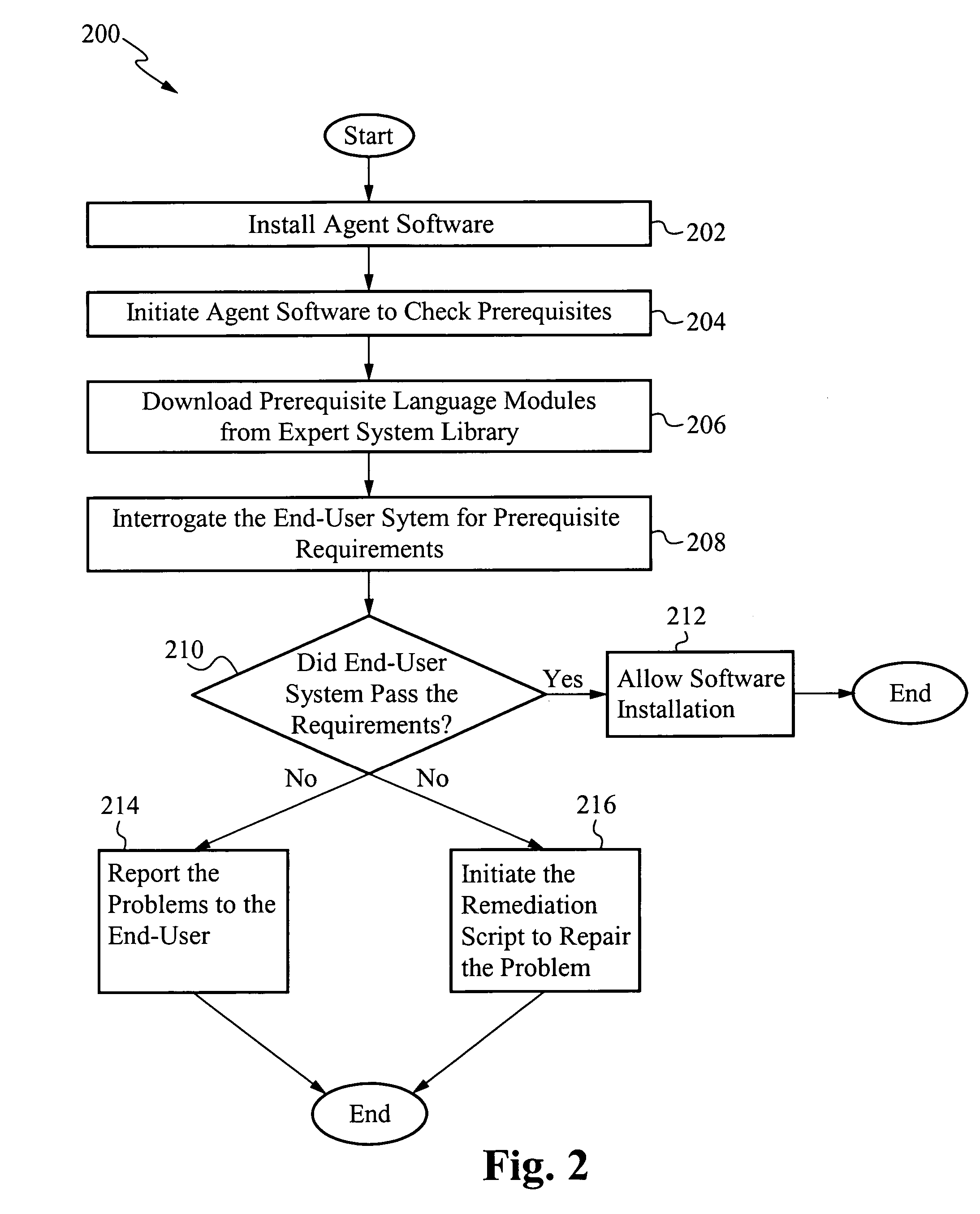
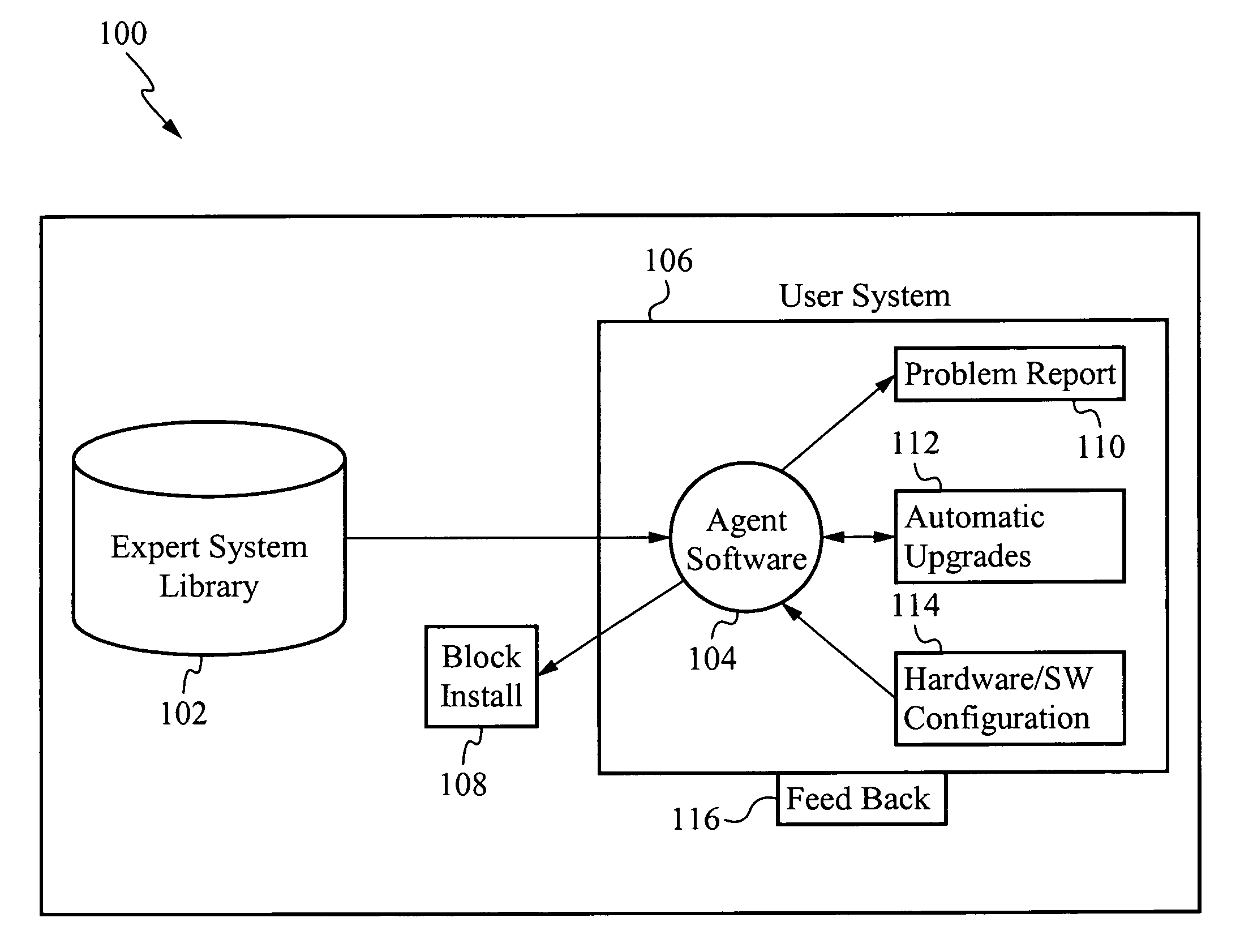
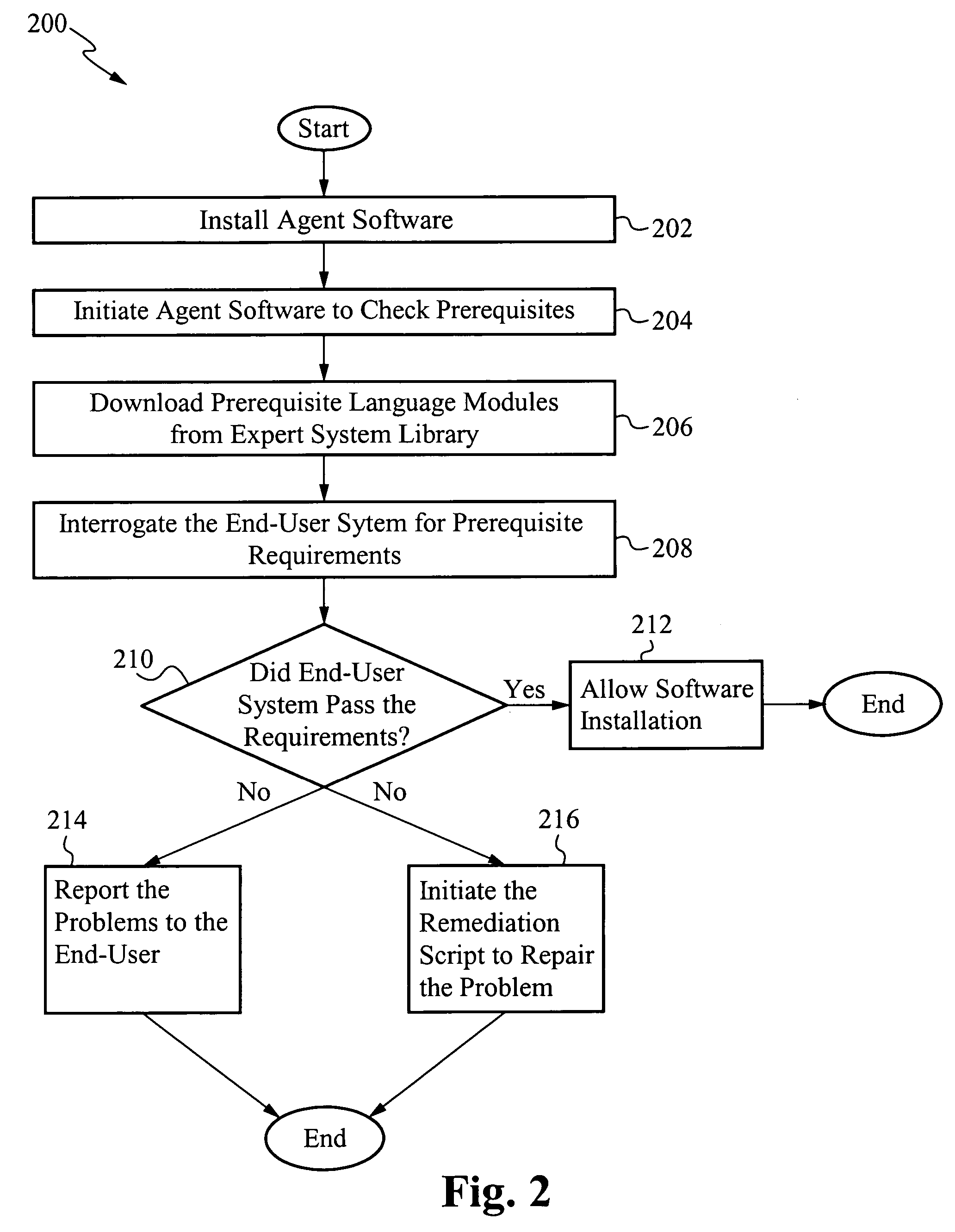
Pre-install compliance system
ActiveUS20060224544A1Accurate operationEasy to installMultiple digital computer combinationsDigital dataSoftwareExpert system
The present invention interrogates computer systems prior to software installations to ensure software installations operate correctly and do not conflict with existing hardware and software. An agent application is first installed on a user's system. When a new program is about to be installed on the user's system, the agent checks if certain prerequisite requirements are met. The prerequisite requirements are downloaded from an expert system library, and the agent interrogates the user's system to determine if it passes the downloaded requirements. If the system passes, then the software is installed. If the system does not pass, then a report is sent to the user and / or a remediation script is initiated to repair the problem. After software is installed, if errors arise that were not previously detected, a feedback mechanism sends the errors to the expert system library so future errors are detected preemptively.
Owner:MICROSOFT TECH LICENSING LLC +1
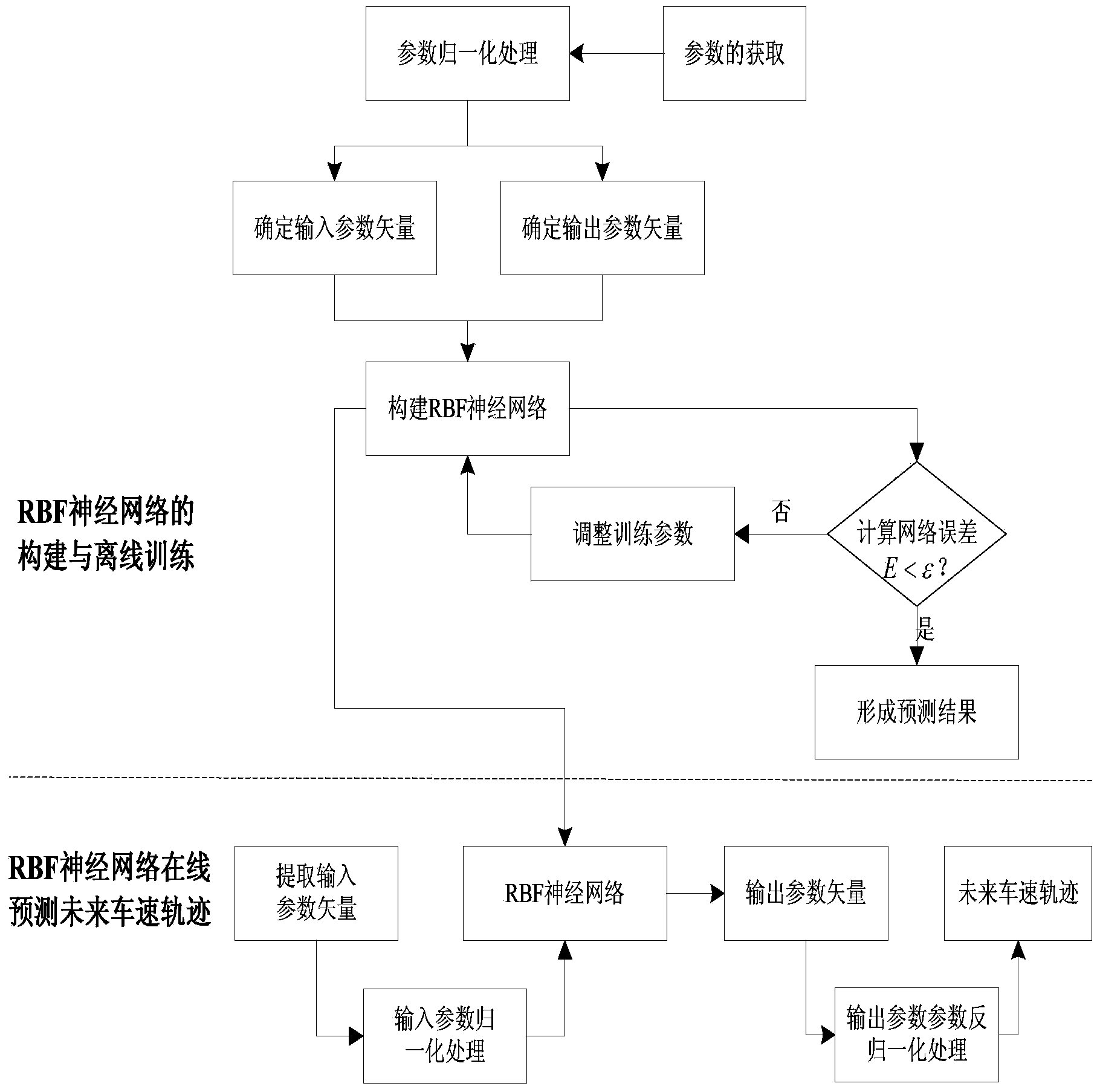
Method for predicting future speed trajectory of hybrid power bus
InactiveCN103914985AImprove accuracyRealize online predictionDetection of traffic movementNeural learning methodsDriver/operatorState parameter
The invention discloses a method for predicting the future speed trajectory of a hybrid power bus. The method includes the following steps that parameters are obtained and normalized; an input parameter vector and an output parameter vector of an RBF neural network are determined; the RBF neural network is offline trained; the future speed trajectory is online predicted. Based on online learning of the RBF neural network, prediction of the speed trajectory is studied under the precondition that global optimization of the control strategy of the hybrid power bus is achieved from the aspect of a people-bus-environment system, the method for predicting the bus future driving trajectory is provided and fully takes bus state parameters, driver driving styles and front road environment and traffic state parameters into consideration, and accuracy of prediction of the bus speed is improved. The influences of the people-bus-environment system on the future working condition is fully taken into consideration, accuracy of prediction of the working condition is improved while the bus has the precognition capacity, and a good foundation is laid for global optimization of the control strategy.
Owner:DALIAN UNIV OF TECH
National identification card system and biometric identity verification method for negotiating transactions
Owner:CROSSCHECK IDENTIFICATION SYST INT
System and Method to Facilitate Progress Forking
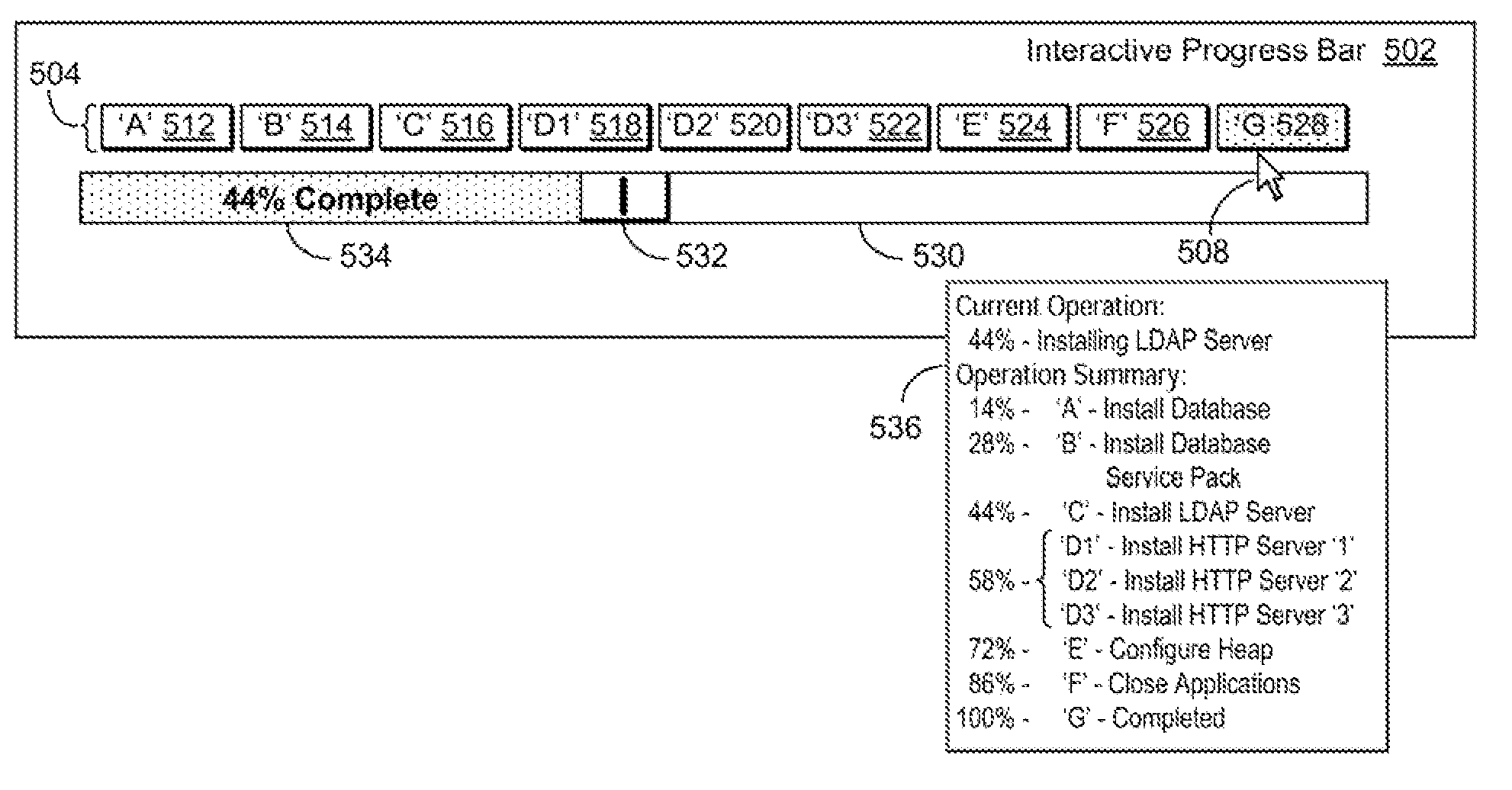
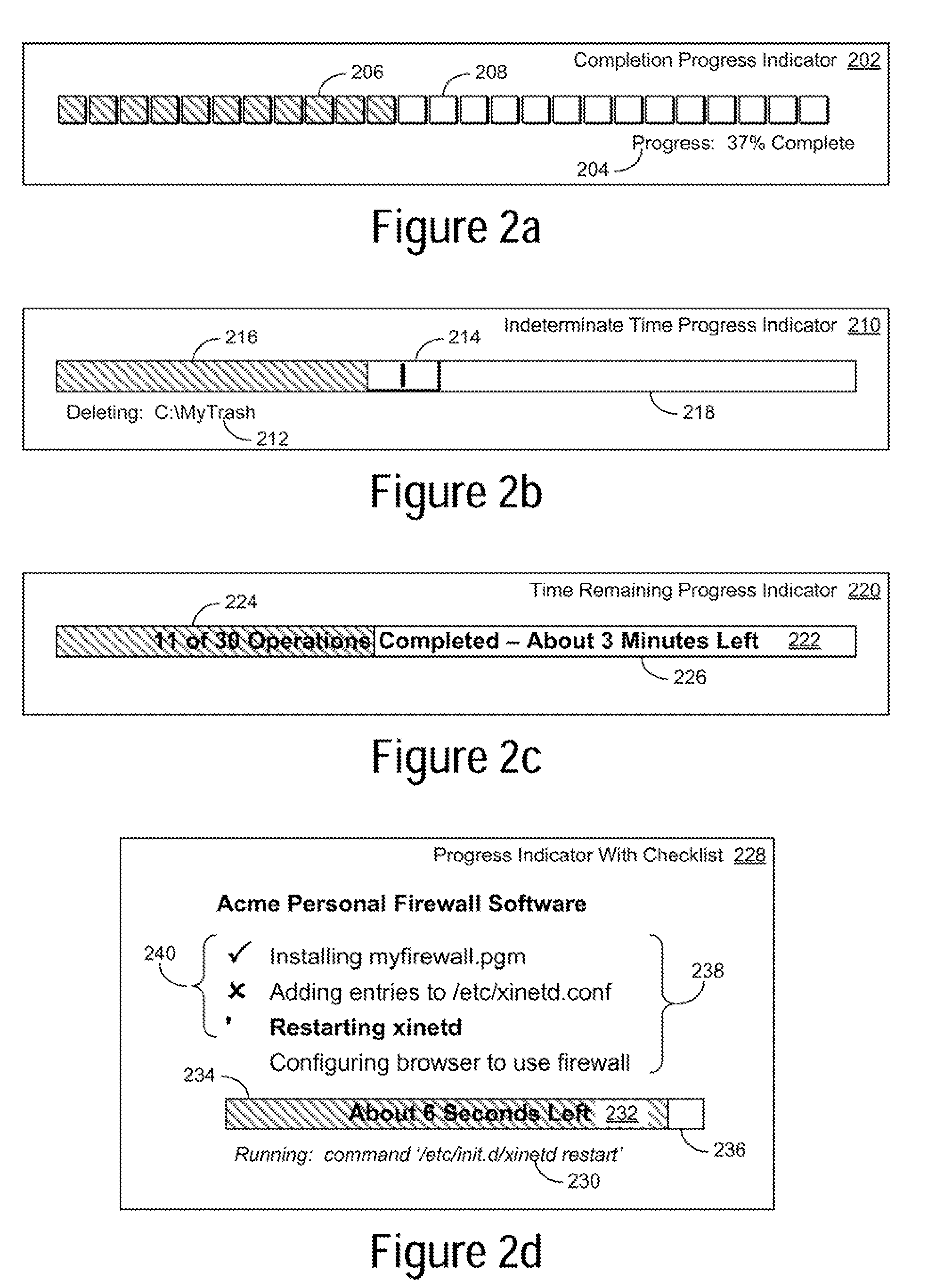
InactiveUS20090113334A1Insufficient resourceProgram loading/initiatingExecution for user interfacesCompletion StatusGraphics
A method, system and computer-usable medium are disclosed for providing graphical completion status information for the management of serial computer operations that are forked into parallel operations. A first interactive progress bar, comprising a plurality of progress indicator segments, is implemented to show the completion status of a composite application. A second progress bar is implemented for each element of the composite application as it is executed. Elements that are serially executed may require prerequisite or dependent operations. Forking operations are performed to execute elements in parallel. One or more progress indicator segments are selected to display information about their related computer operations. The user interacts with the information to pause, modify, reorder, reverse, retarget, or reverse the selected computer operations.
Owner:IBM CORP
Information feedback method and system based on space, time and frequency domain, customer equipment and base station
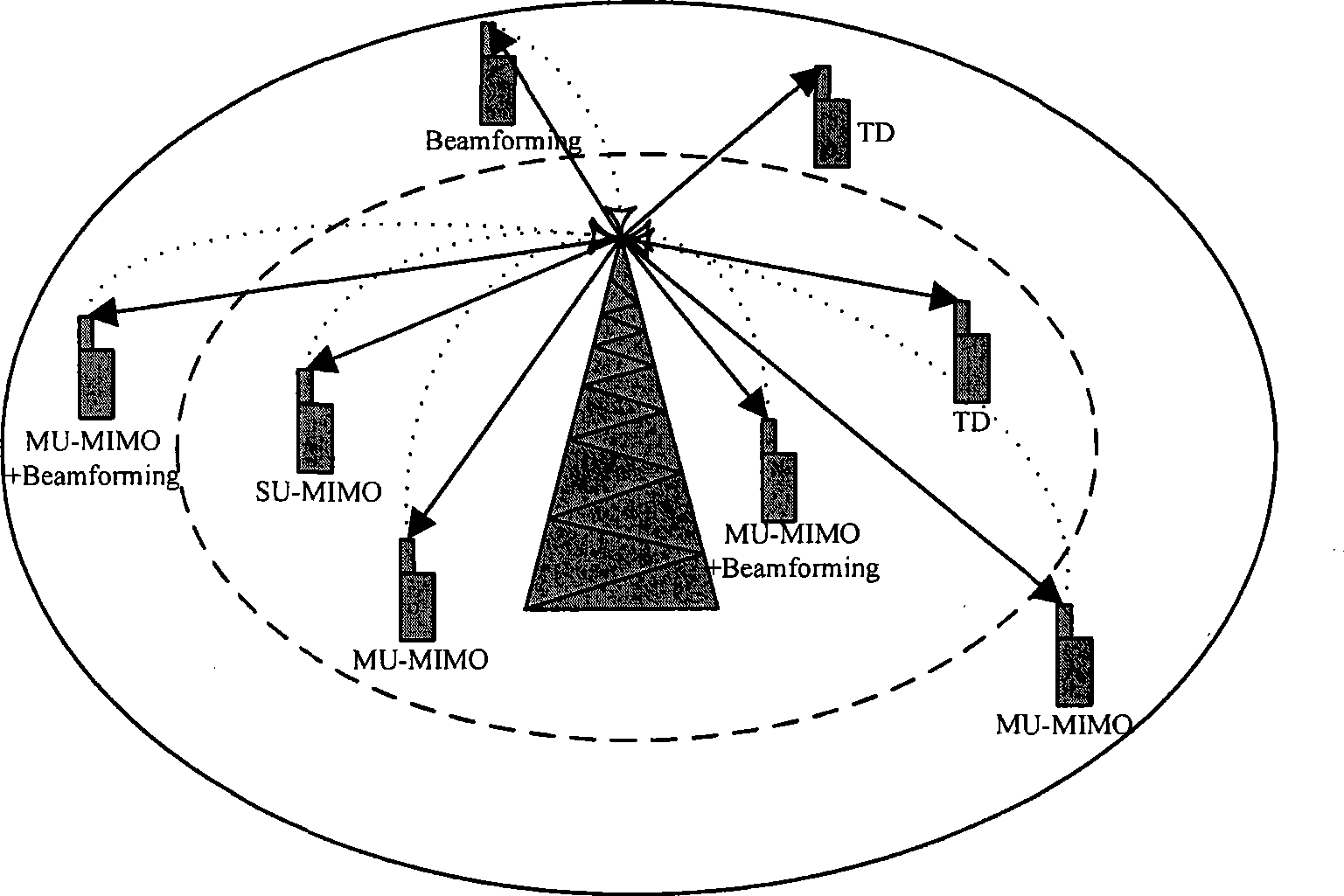
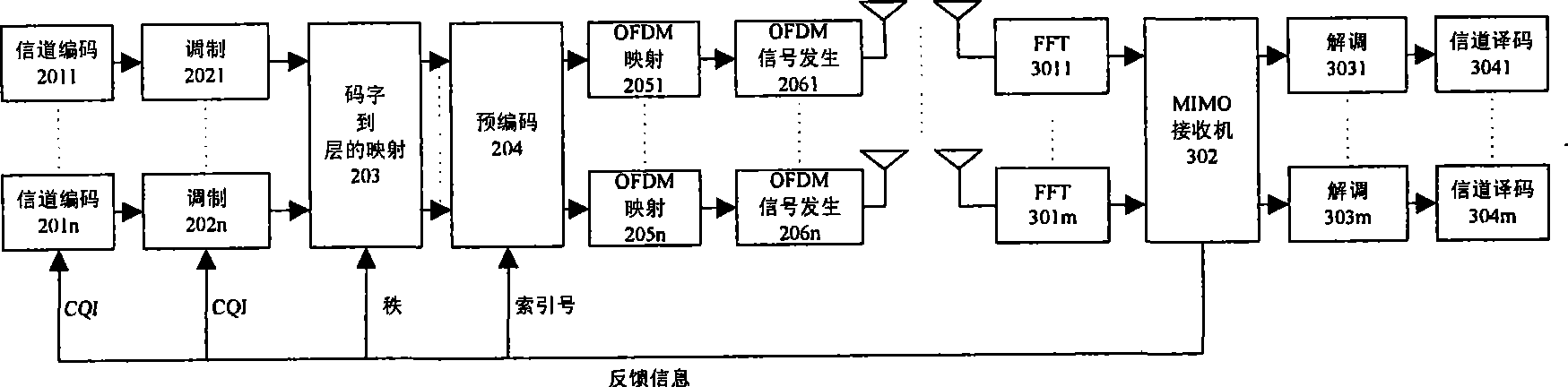
InactiveCN101388699AImprove spectrum utilizationImprove service qualitySpatial transmit diversityError prevention/detection by diversity receptionQuality of serviceUser equipment
The invention relates to a method for feeding information back on the basis of space time frequency domain, a system, a user device and a base station thereof, which are used in the technical field of wireless transmission, the user device in the invention measures and estimates the quality of a wireless transmission chain circuit of a downlink MIMO system, information such as order, pre-coding matrix key number, communication channel quality indication and the like of the downlink wireless transmission chain circuit is obtained, the selecting characteristics of the communication channel in three dimensional space of spatial domain, frequency domain and time domain are utilized to process the information of the downlink wireless transmission chain circuit in the spatial domain, the frequency domain and the time domain respectively, a feedback method which is used effectively and simply is used to transmit the information of the downlink chain circuit to the base station, the base station optimizes a transmitter according to the information which is fed back by the user device, and thereby the purpose of improving the whole data throughput of a wireless district and the data throughput of the district edge under the precondition that the service quality of the wireless district is considered is achieved.
Owner:SHARP KK
Mobile edge computing task unloading method in multi-user scene
ActiveCN108920279AGuaranteed service qualityEnsure fairnessProgram initiation/switchingResource allocationPersonalizationMobile edge computing
The invention discloses a mobile edge computing task unloading method in a multi-user scene, and relates to the processing technical field of mobile computing systems. The invention aims to reduce response time delay and energy consumption of a mobile device. The multi-user scene is multiple mobile devices and an MEC server which are connected. Each mobile device can select one of multiple channels between the mobile device and the MEC server to perform communication. The MEC server is connected with a center cloud server through a backbone network. The method specifically comprises the following steps: constructing a multi-user scene task unloading model; and performing a two-stage task unloading strategy based on a game theory: the first stage unloading strategy is as follows: determining whether unloading is executed on the mobile device or on the MEC server, and the second stage unloading strategy is as follows: while MEC server resources are insufficient, determining whether to wait on the MEC server or execute on the center cloud server. The method is capable of, under the precondition of guaranteeing service quality and fairness of a user, considering personal requirements of the user.
Owner:HARBIN INST OF TECH
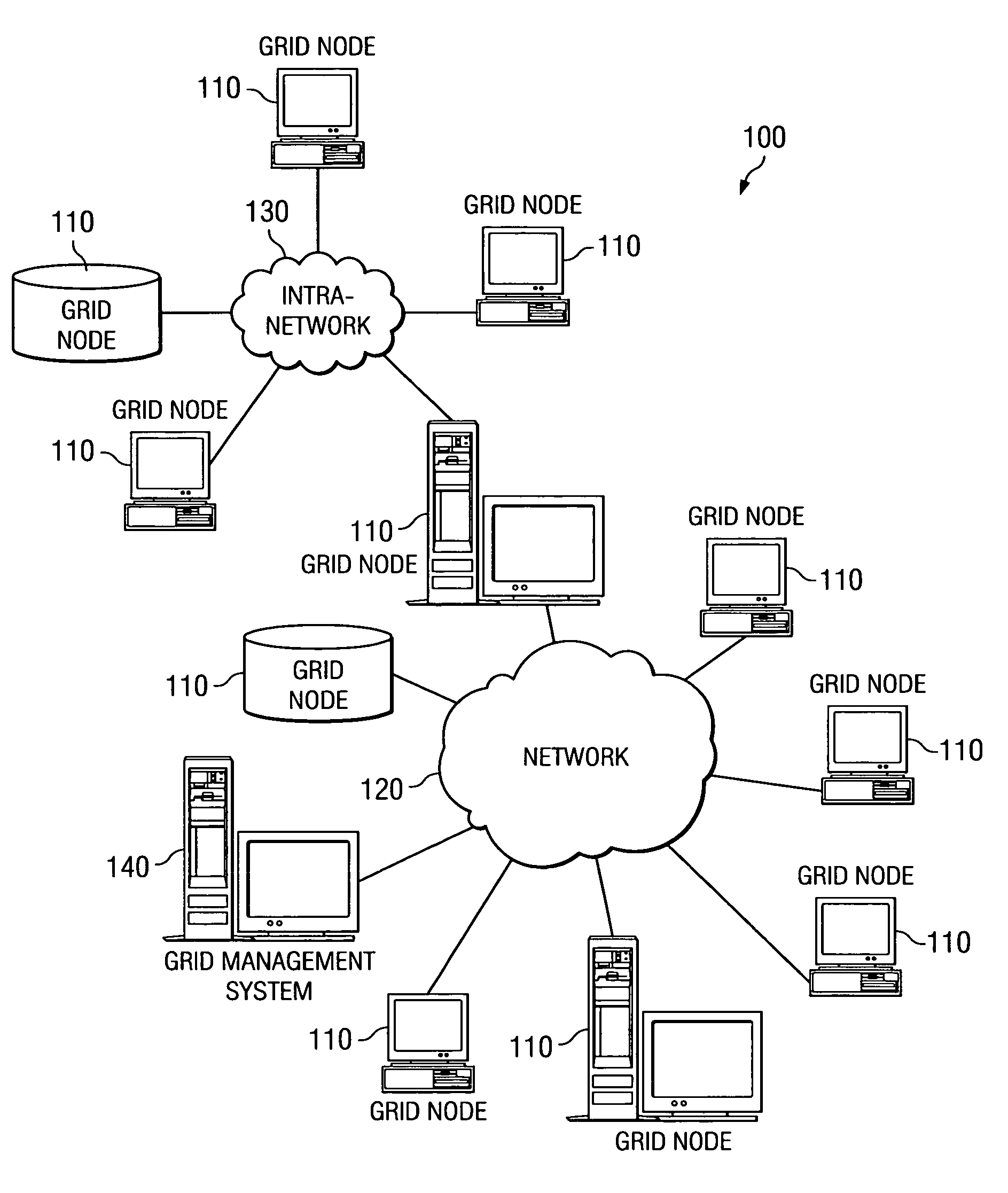
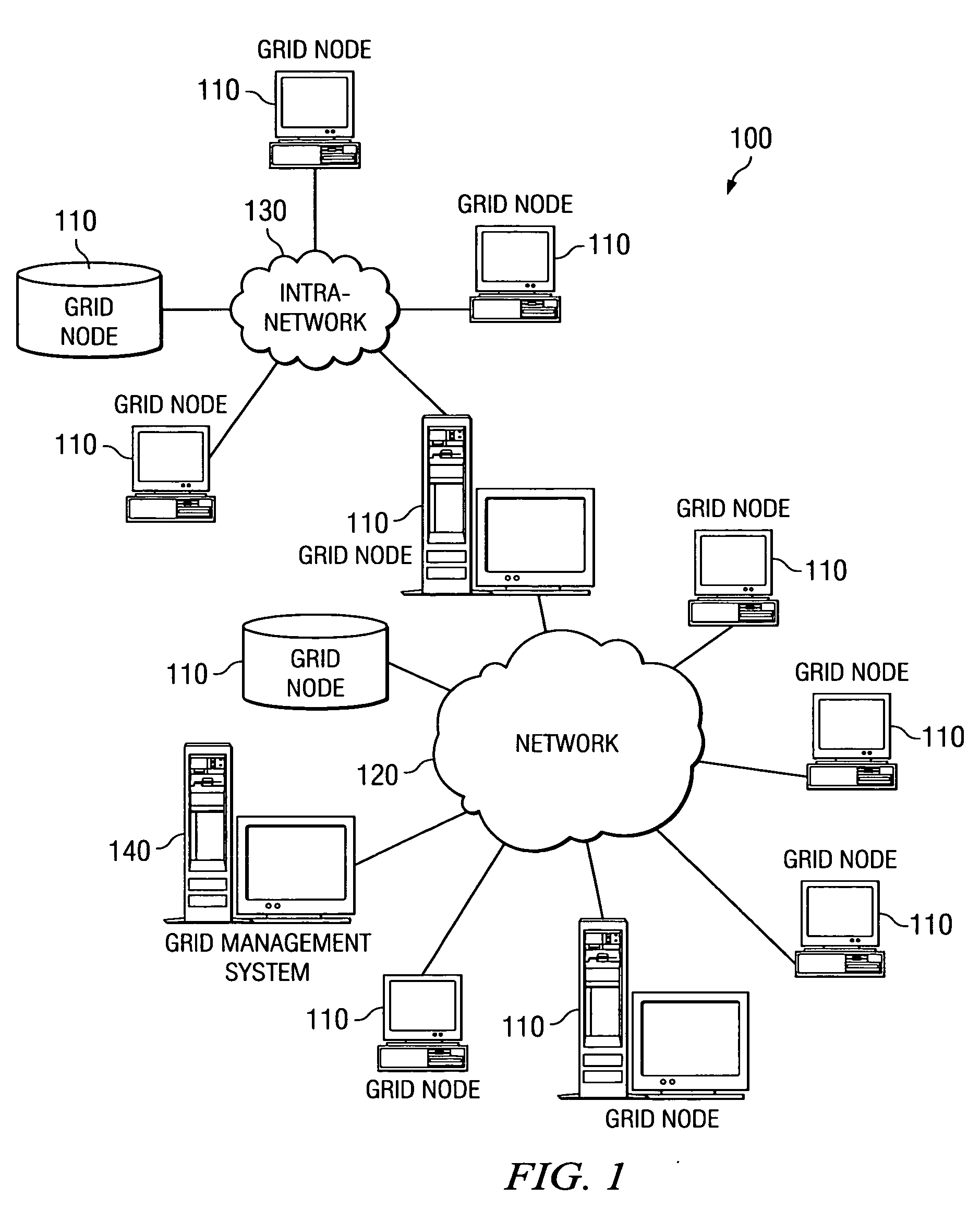
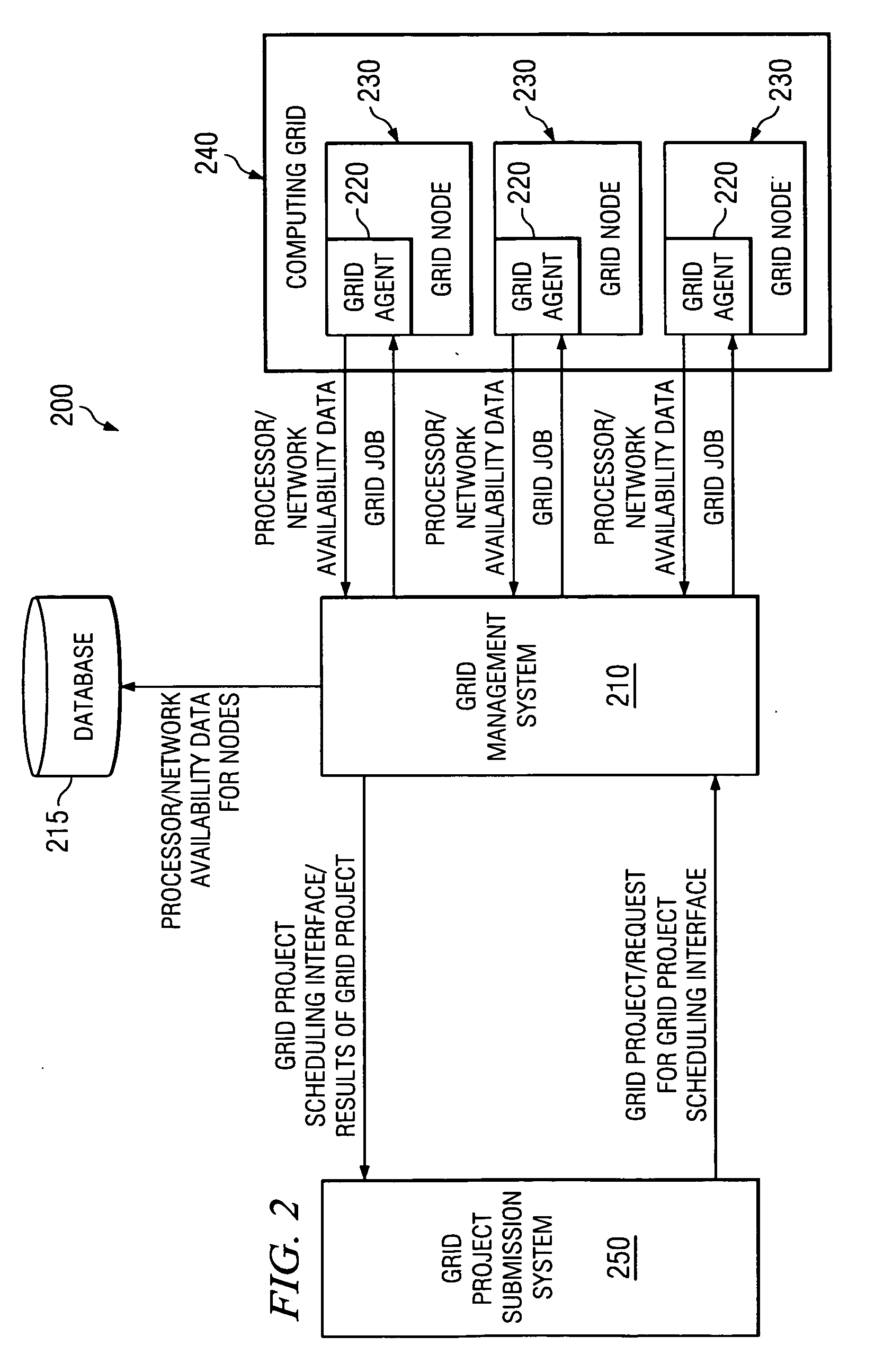
Method and apparatus for grid project modeling language
InactiveUS20070118839A1Digital computer detailsMultiprogramming arrangementsNetwork activityModeling language
A method and apparatus for modeling grid projects, such that their network and node resources may be readily determinable for simulation, scheduling, and control purposes. A model of a grid project is generated using a standardized grid project modeling language that sets forth a sequence of grid project phases. Within each phase, there may be any number of descriptions of parallel activities that need to be performed, such as, CPU processing, network activity, both, or even nested “sub” phases. Each of the descriptions specifies the properties of the described activities, such as the quantity of CPU required, network traffic expected, prerequisites, dependencies, activity splitting limits and characteristics, reliability actions, etc. The grid project model is parseable by the present invention to determine the various phases of a grid project and the various characteristics of each phase.
Owner:IBM CORP
System and method for scheduling software updates
InactiveUS20080201702A1Error detection/correctionSoftware engineeringData processing systemProgram planning
A system and method for scheduling software updates on data processing systems. In an embodiment, software updates are scheduled on a data processing system by identifying a list of software updates; scheduling at least one primary software update for execution within a scheduled outage time based on an estimated execution time and an estimated rollback time for the at least one primary software update; executing the at least one primary software update during the scheduled outage time; and ordering the list of software updates for possible execution of at least one secondary software update in any remaining outage time in dependence upon the estimated execution times and estimated rollback times for each of the remaining software updates. The list of software updates may also be ordered in further dependence upon evaluation of relative priorities between the software updates, any prerequisite software updates, and a performance scaling factor for the data processing system.
Owner:IBM CORP
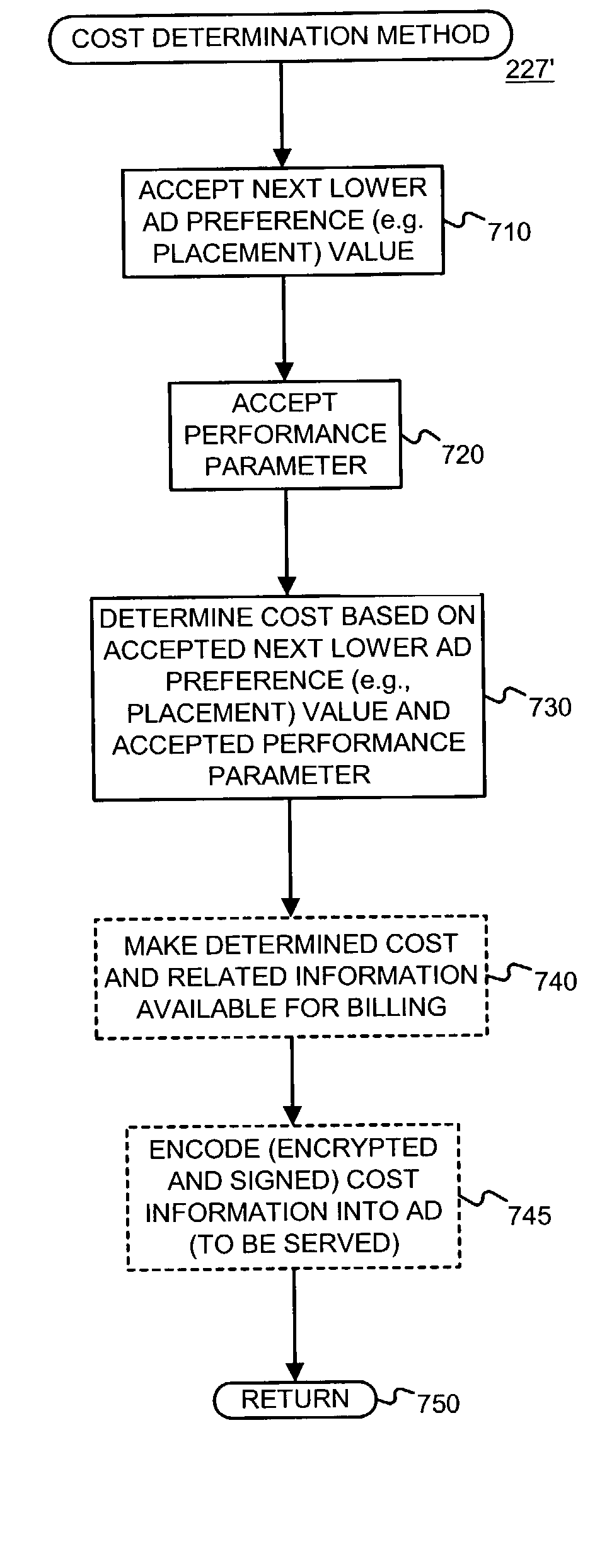
Automated price maintenance for use with a system in which advertisements are rendered with relative preferences
A cost maintenance scheme useful with an advertising system which orders ads in a manner that maximizes both their relevance and their economic value, and which provides a fair bidding process in which a winning bidder is assured of not having paid too much. Ordering may be done based on accepted maximum ad bid information and / or ad performance information. For example, this information may be used to determine a position value. Cost may be determined based on accepted maximum ad bid information and / or performance information. Billing the determined cost may be subject to a condition precedent.
Owner:GOOGLE LLC
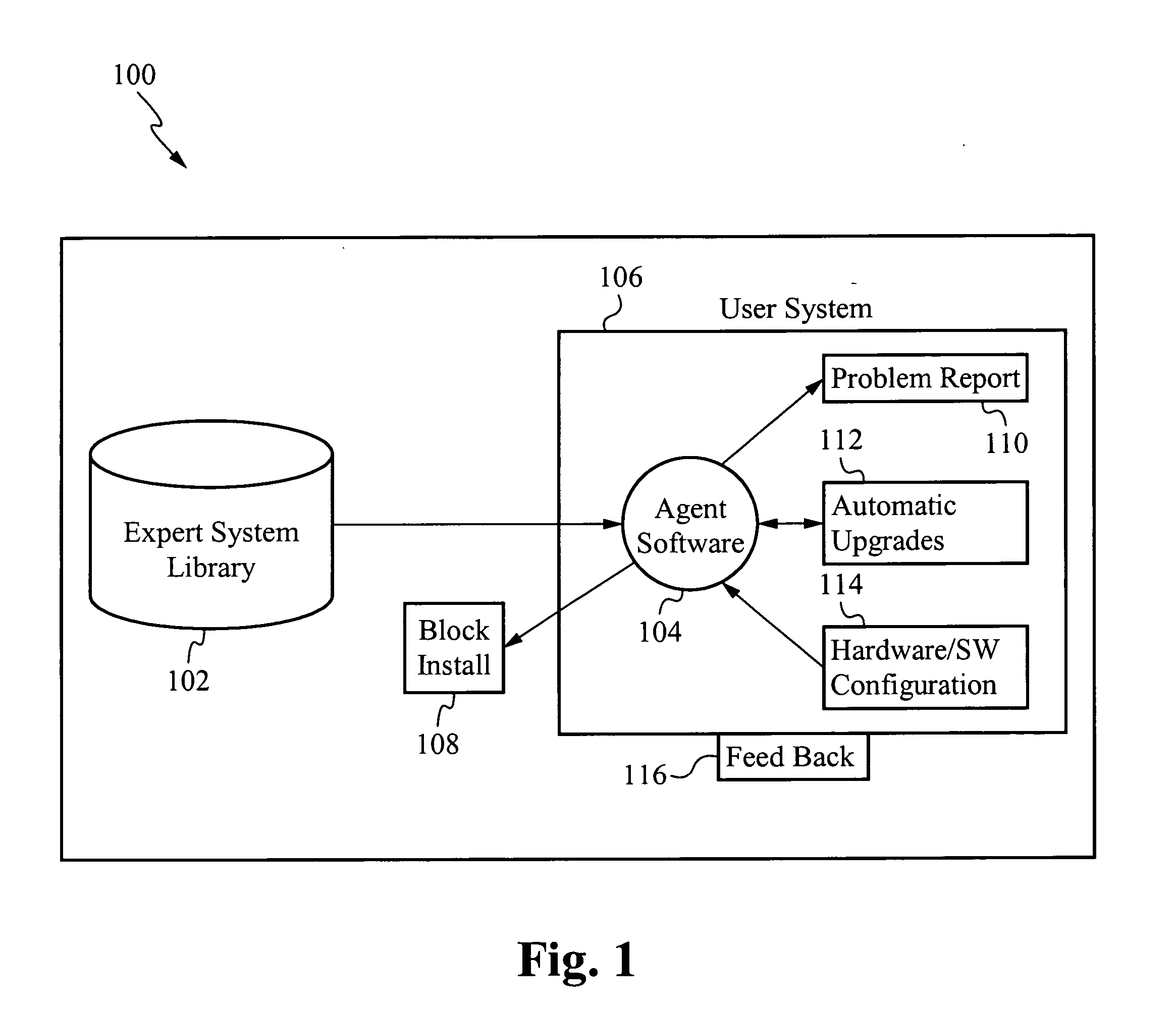
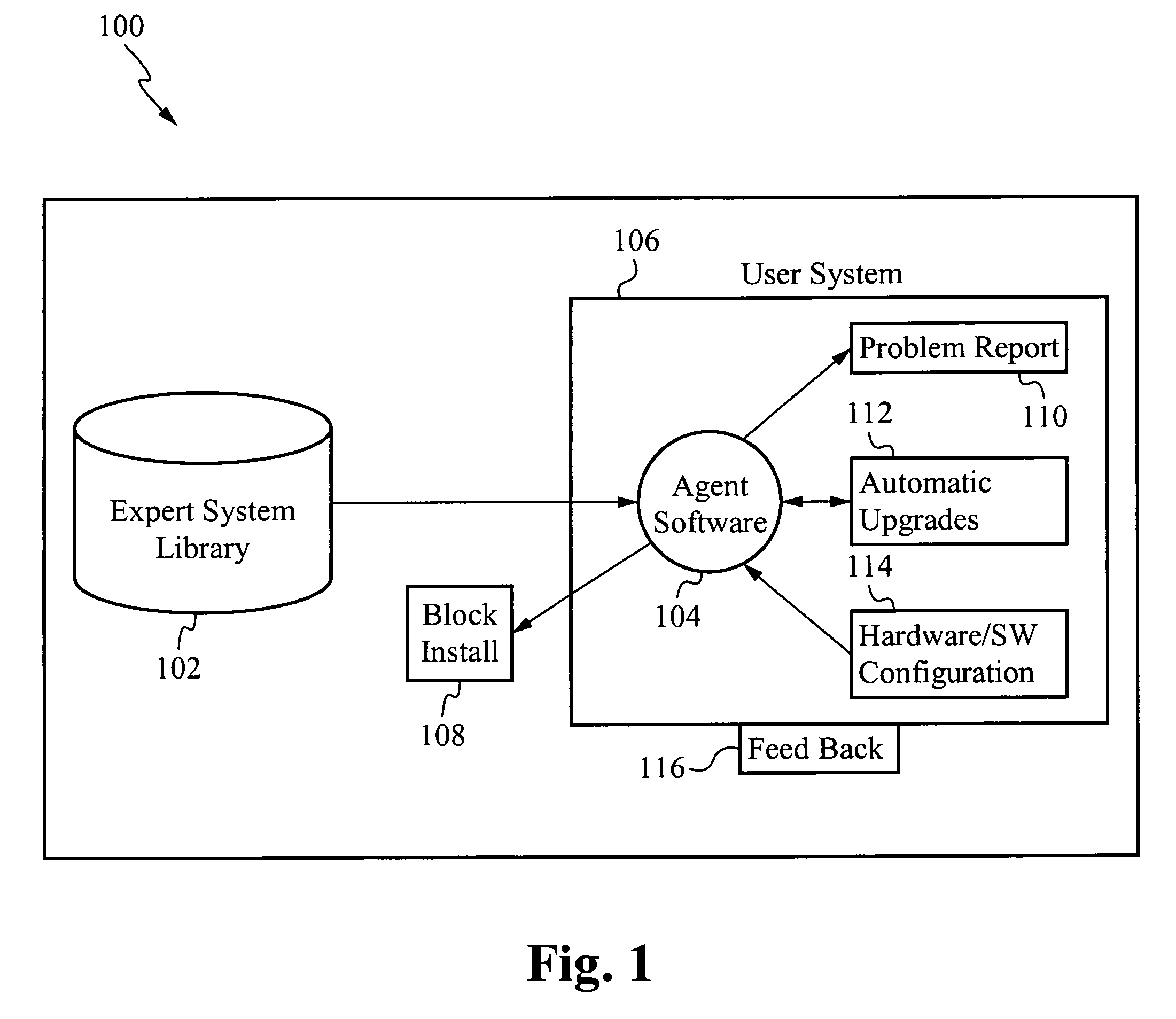
Pre-install compliance system
ActiveUS7624086B2Multiple digital computer combinationsDigital dataApplication softwareExpert system
The present invention interrogates computer systems prior to software installations to ensure software installations operate correctly and do not conflict with existing hardware and software. An agent application is first installed on a user's system. When a new program is about to be installed on the user's system, the agent checks if certain prerequisite requirements are met. The prerequisite requirements are downloaded from an expert system library, and the agent interrogates the user's system to determine if it passes the downloaded requirements. If the system passes, then the software is installed. If the system does not pass, then a report is sent to the user and / or a remediation script is initiated to repair the problem. After software is installed, if errors arise that were not previously detected, a feedback mechanism sends the errors to the expert system library so future errors are detected preemptively.
Owner:MICROSOFT TECH LICENSING LLC +1
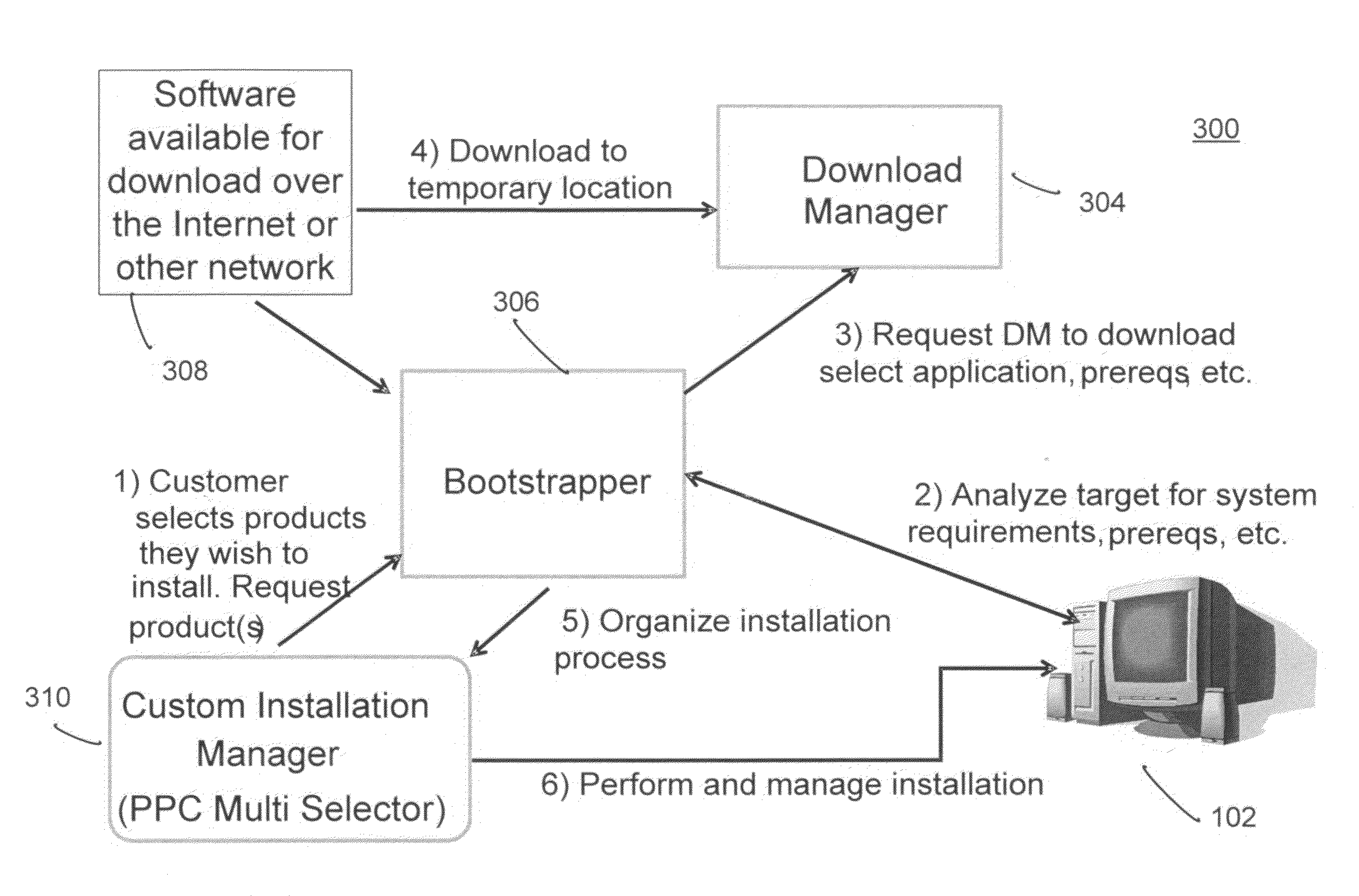
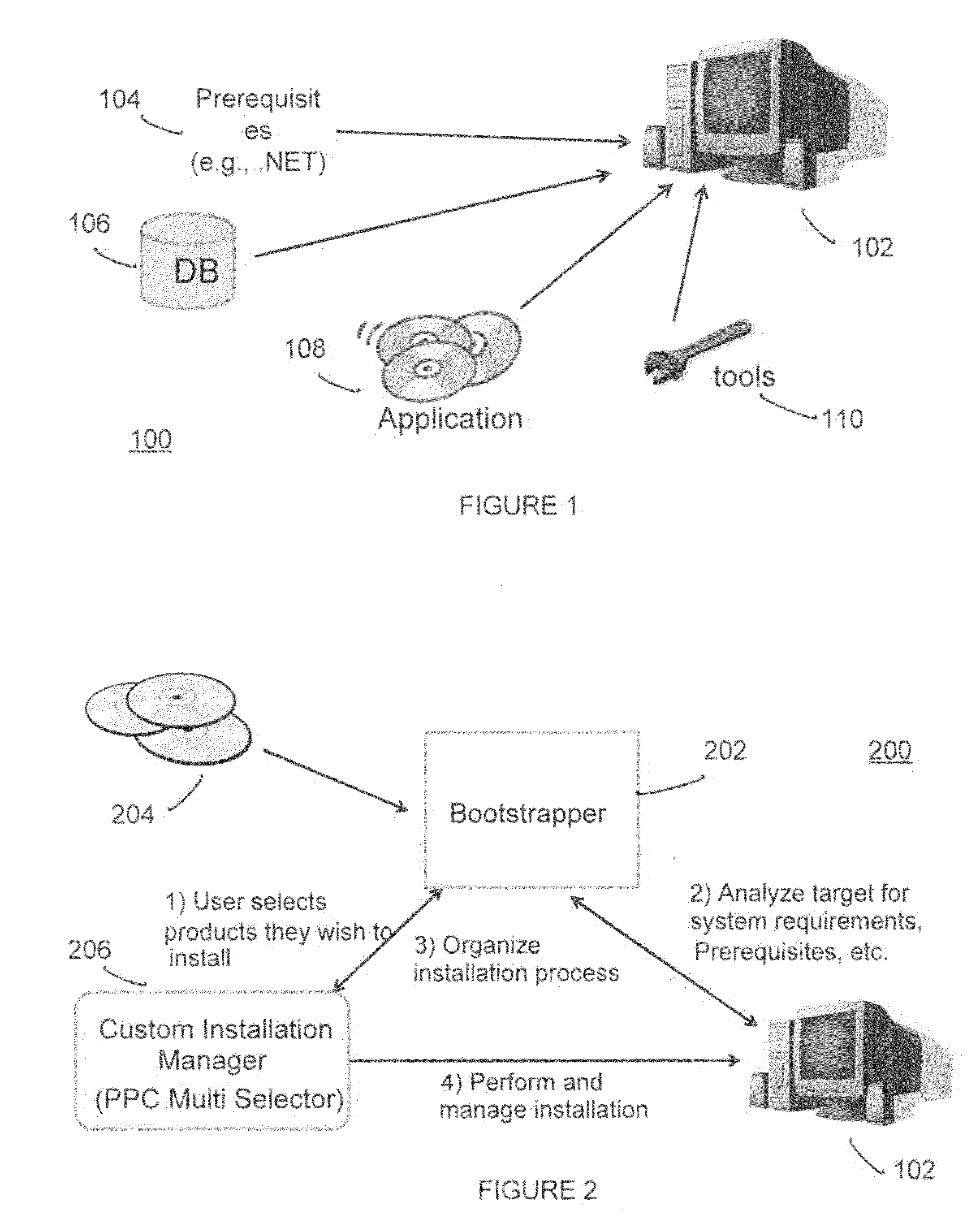
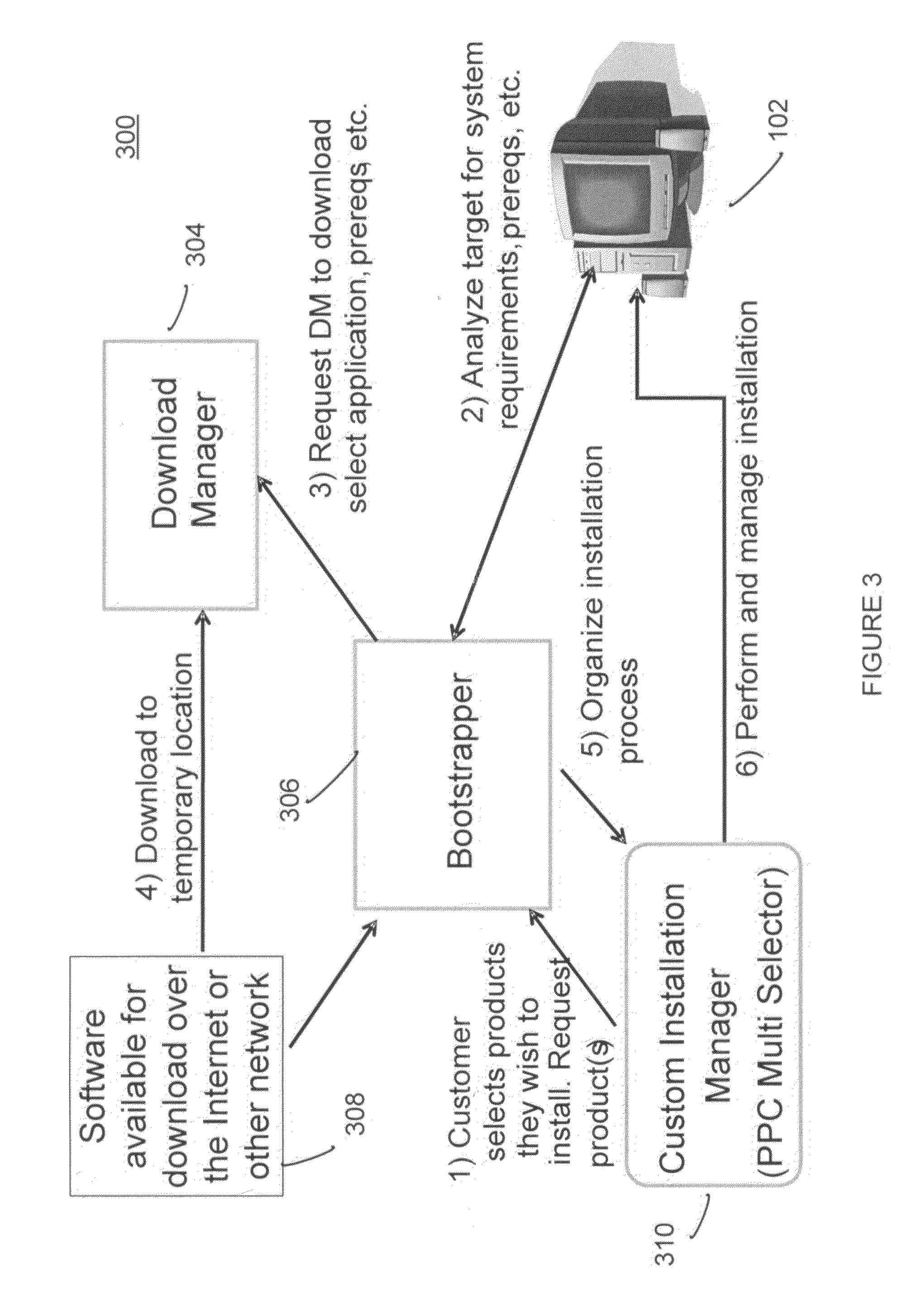
Bootstrapper and software download manager
ActiveUS20090064135A1Complete efficientlyAvoid componentsBootstrappingProgram loading/initiatingSystem requirementsUser interface
The present invention provides a bootstrapper and download manager for handling the download and installation of one or more software products to a computer. The invention determines system requirements and whether any prerequisite software is required by a software product to be downloaded. Any necessary prerequisite software is installed on the computer and if more than one software product has a shared prerequisite, then the invention recognizes that and prevents downloading multiple ones of the shared prerequisites. Also, in the event of an interruption or error during download, the invention can resume downloading or installation based on the download successfully stored on the local machine without requiring the download all over again. This saves considerable time during the download and install process and enhances user productivity and experience. A download manager provides a user interface to efficiently select from multiple software products for download and negotiate issues such as multiple and different product licenses.
Owner:REFINITIV US ORG LLC
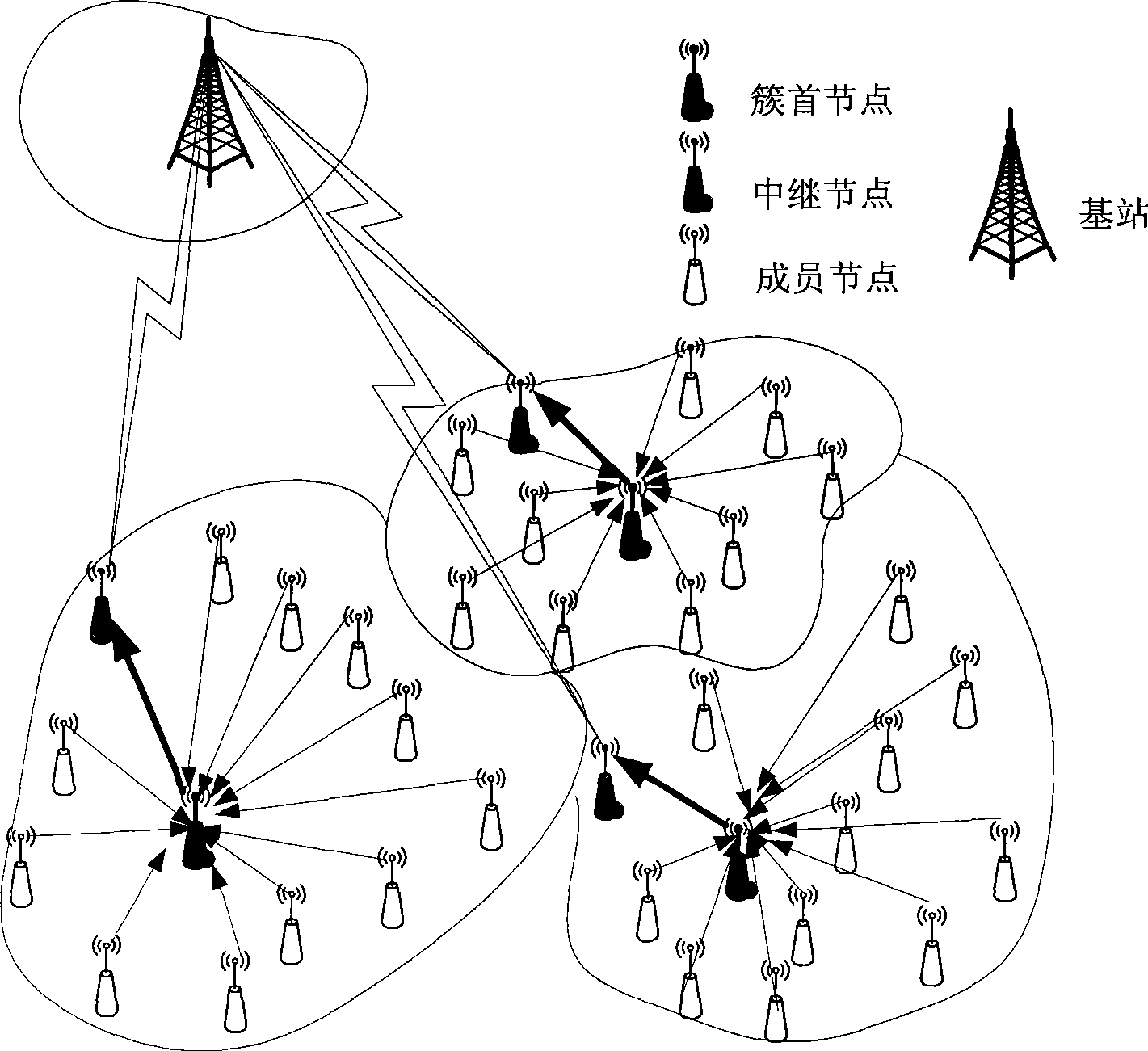
Relay wireless sensor network routing method based on energy balance and distance cooperation
InactiveCN101489275AData transmission is stableShorten the timeEnergy efficient ICTNetwork topologiesEnergy balancedInformation data
A wireless sensor network routing method based on energy equalization and distance cooperation relates to data fusion and routing technique of wireless sensor network, and is typically used for clustering routing technique. According to a given regulation, the sensor nodes in the wireless sensor network are divided to cluster head node, relay node and cluster member node. The energy consumption of whole wireless sensor network is fully equalized and the effective usage factor of energy is increased. An energy threshold LT is introduced for realizing the smooth transition of roles between nodes, saving the cluster generation time and reducing the energy consumption. Single-hop communication is adopted in the cluster. Direct sequence spread spectrum is applied. Each cluster uses a unique cluster spreading code. All nodes in the cluster use the unique cluster spreading code for transmitting data to the cluster head and the inter-cluster interference is effectively reduced. The method of the invention can obtain purpose of prolonging the survival time of network under the precondition that the information data is reliably, effectively and accurately transmitted to the base station.
Owner:SHANDONG UNIV
Mechanism for handling input parameters
InactiveUS20050091420A1Easy to specifyProgram loading/initiatingInput/output processes for data processingTheoretical computer sciencePaper document
The present mechanism provides a grammar for specifying required prerequisites (e.g., number and type of input parameters) that an object must possess in order for processing to occur on the object. The mechanism allows programmers and non-programmers to easily specify these prerequisites. The prerequisites may be associated directly or indirectly with a data structure. For a direct specification, the data structure comprises a parameter declaration for each expected input parameter. For an indirect specification, the data structure comprises a parameter definition that references an external description, such as in an XML document. The data structure also providing a mechanism that identifies a corresponding parameter within an input source for each expected input parameter based on its declaration. The input source does not include live objects. The mechanism further populates each expected input parameter with information associated with the corresponding parameter when the data structure becomes instantiated into an object.
Owner:MICROSOFT TECH LICENSING LLC
High-performance low-power-consumption embedded processor based on command dual-transmission
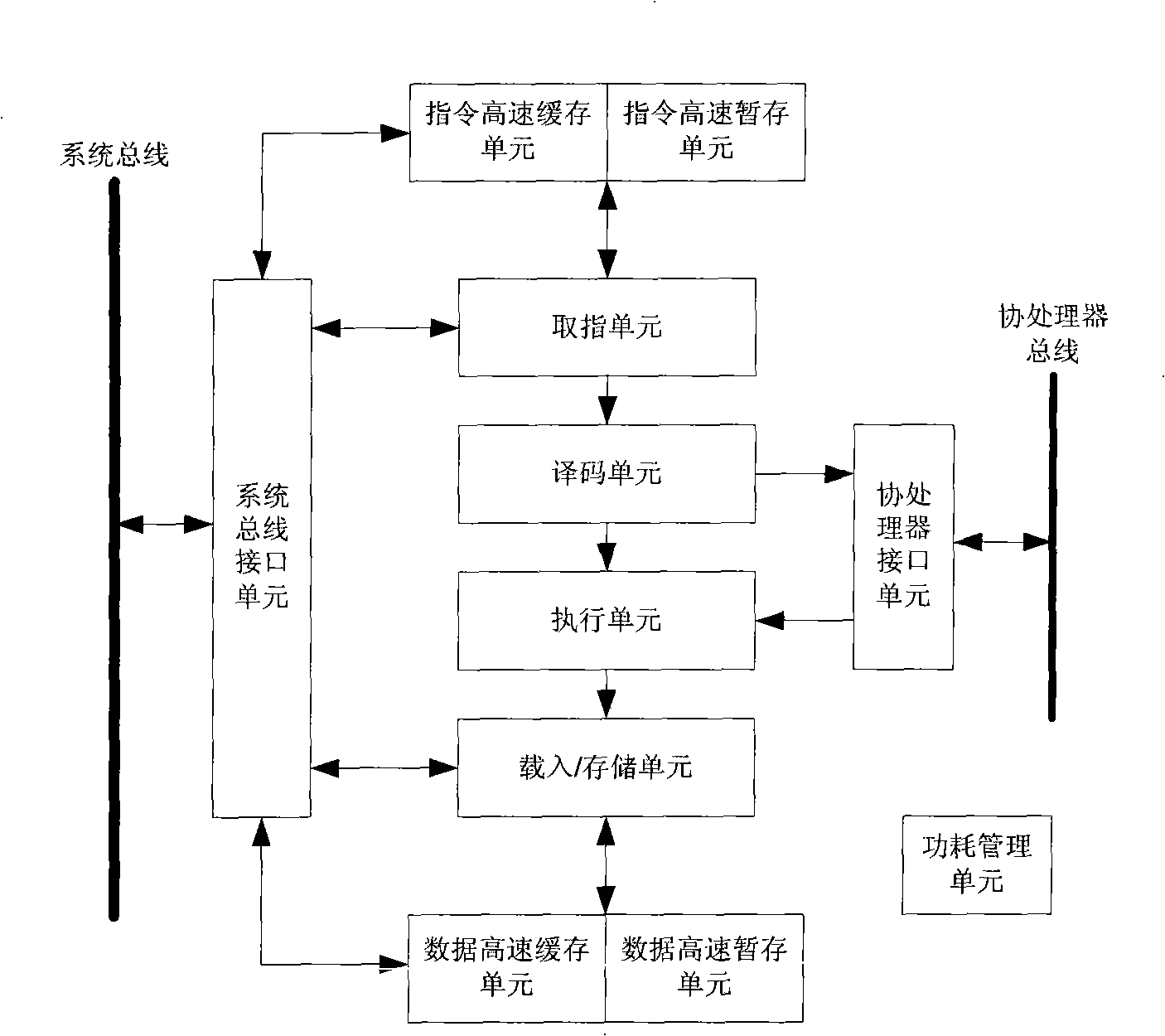
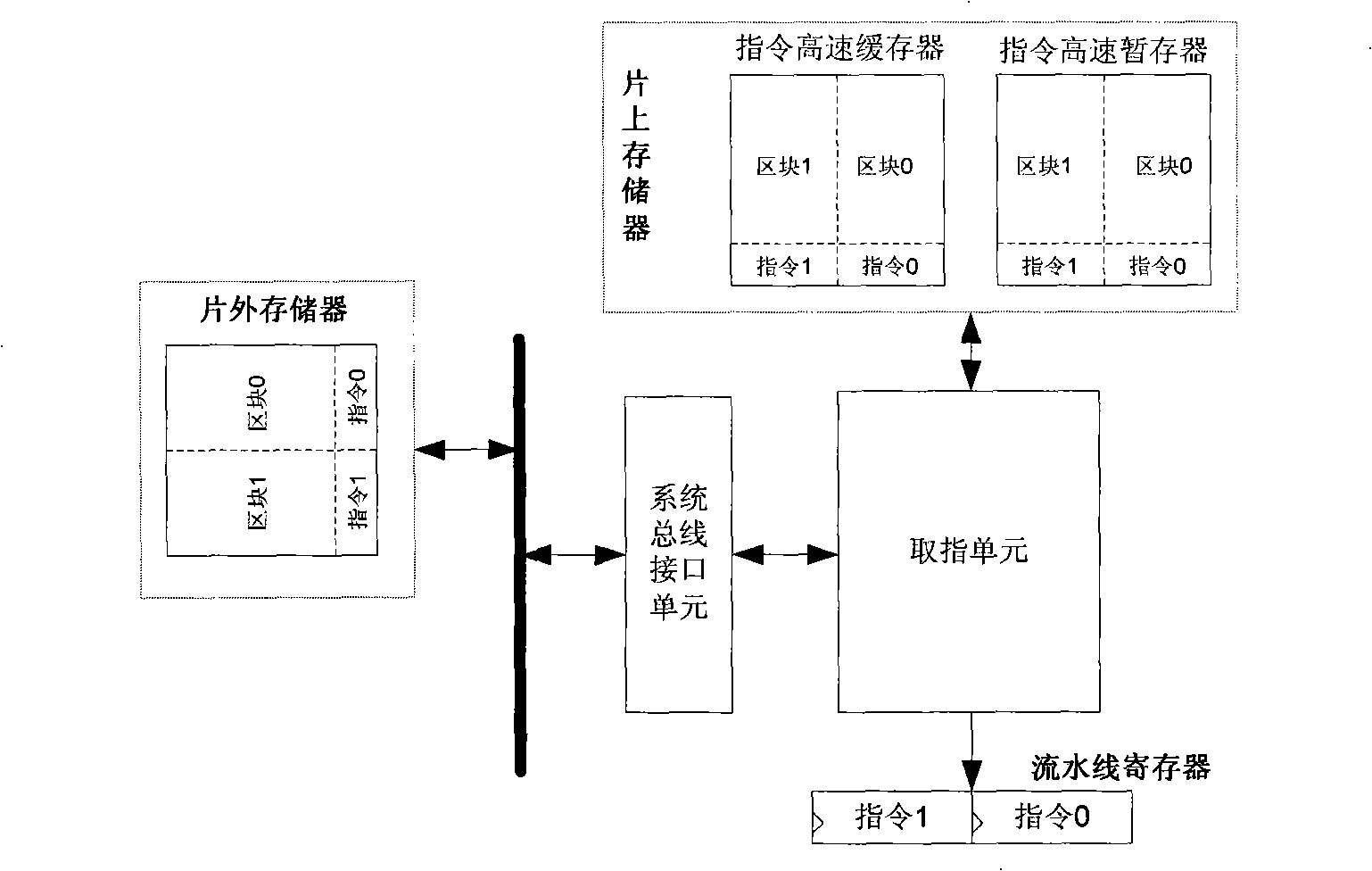
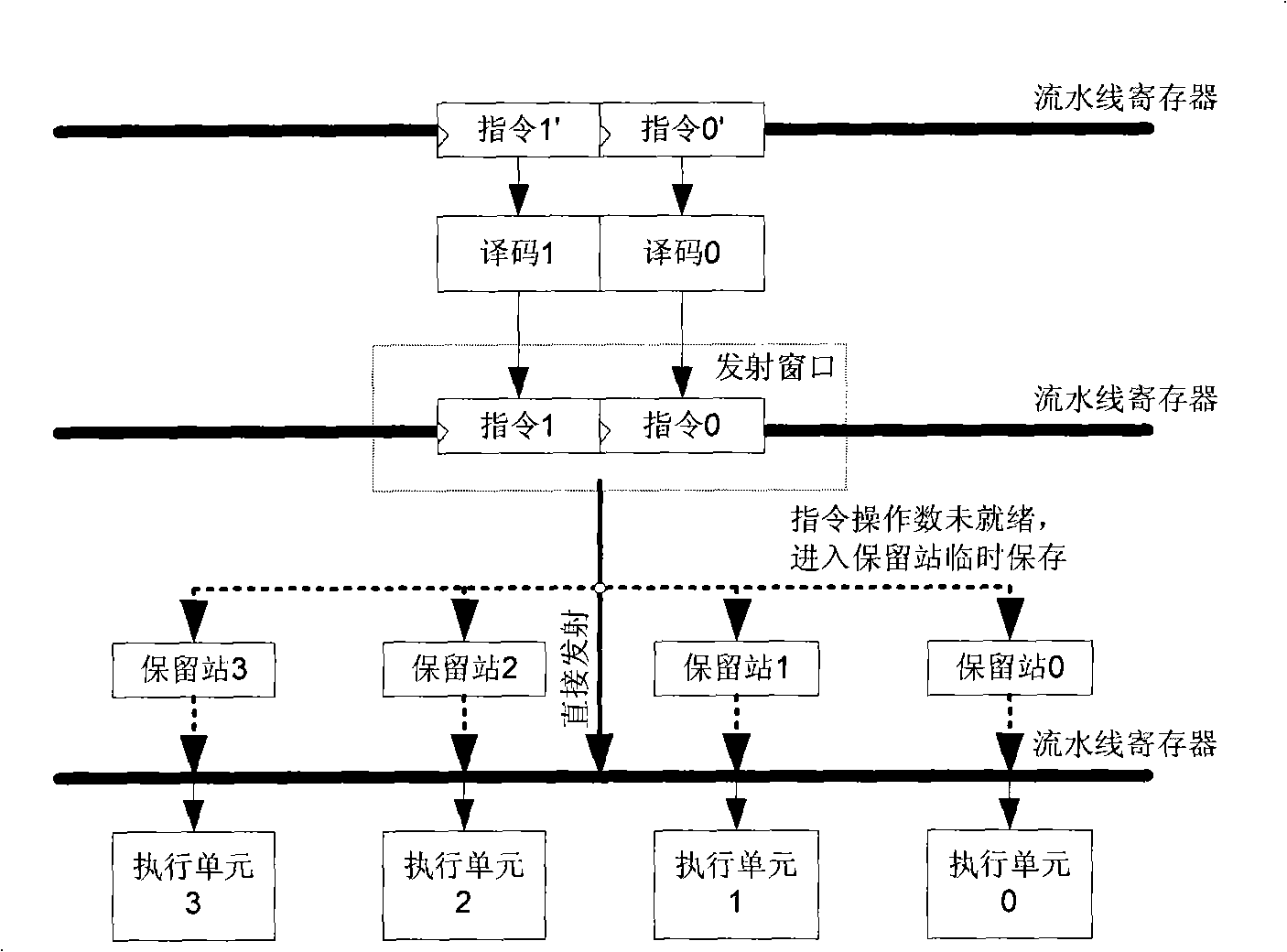
ActiveCN101526895AImprove parallel processing capabilitiesAchieve leapfrog developmentConcurrent instruction executionPower supply for data processingAssembly lineExecution control
The invention provides a high-performance low-power-consumption embedded processor based on command dual-transmission, comprising a command fetching unit, a two-way decoding unit, a transmitting unit, a command dispatch execution control unit, a command executing unit and a loading / storing unit; wherein the command fetching unit is used for pre-fetching two commands in a single clock cycle and sending the commands into an assembly line; the two-way decoding unit is used for parallelly decoding the two commands in the single clock cycle; the transmitting unit is used for parallelly transmitting the two commands in the single clock cycle; the command dispatch execution control unit is used for dynamically adjusting the command dispatch according to the computing load and controlling execution according to an out-of-order execution mechanism; the command executing unit is used for computing the results of the commands; and the loading / storing unit is used for ensuring that when the commands are absent, sequent commands can successfully occupy the assembly line and visit the data memory on the disc and the data memory outside the disc. The invention can improve the performance of the embedded processor and reduce the cost under the precondition of low power consumption.
Owner:C SKY MICROSYST CO LTD
Method and device for implementing entropy decoder based on H.264
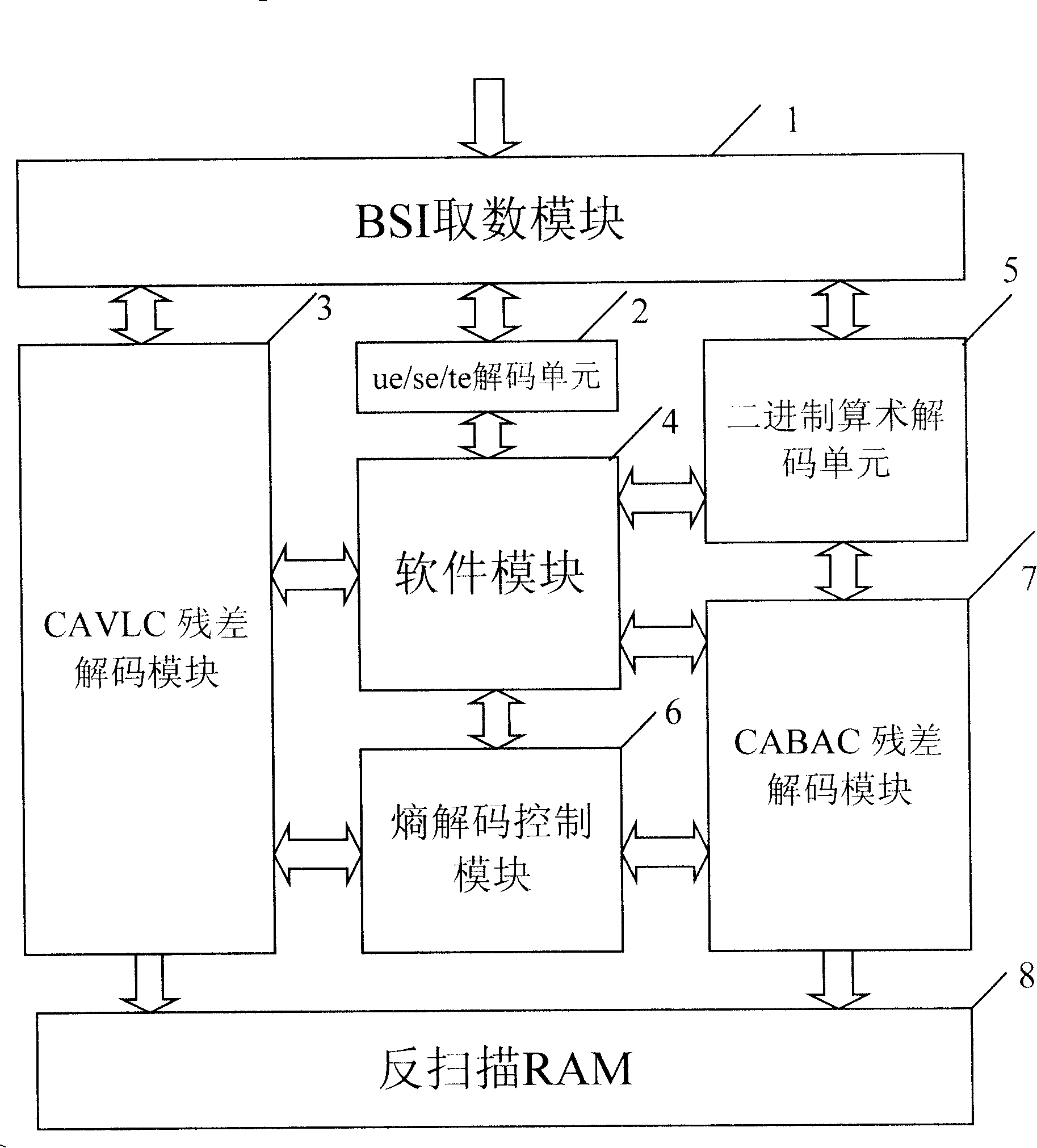
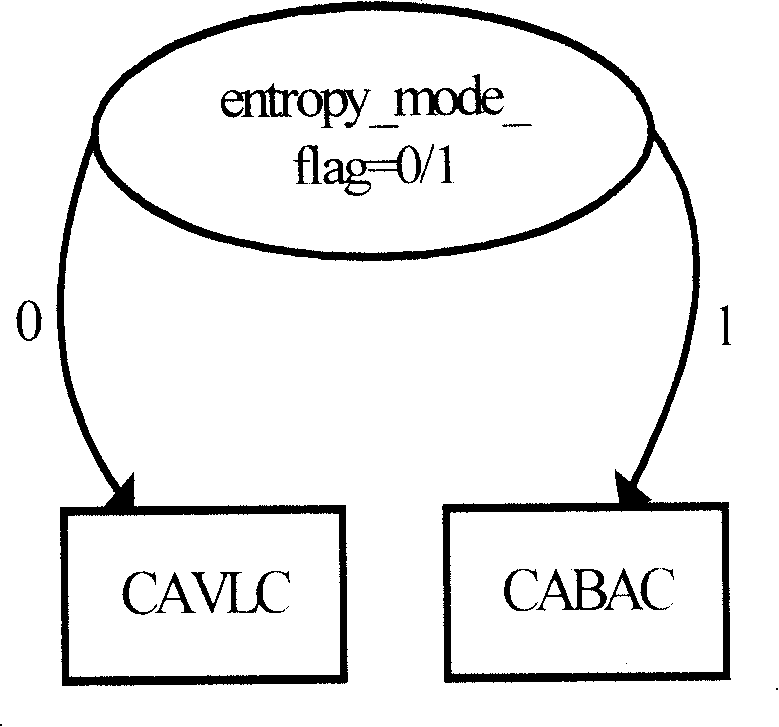
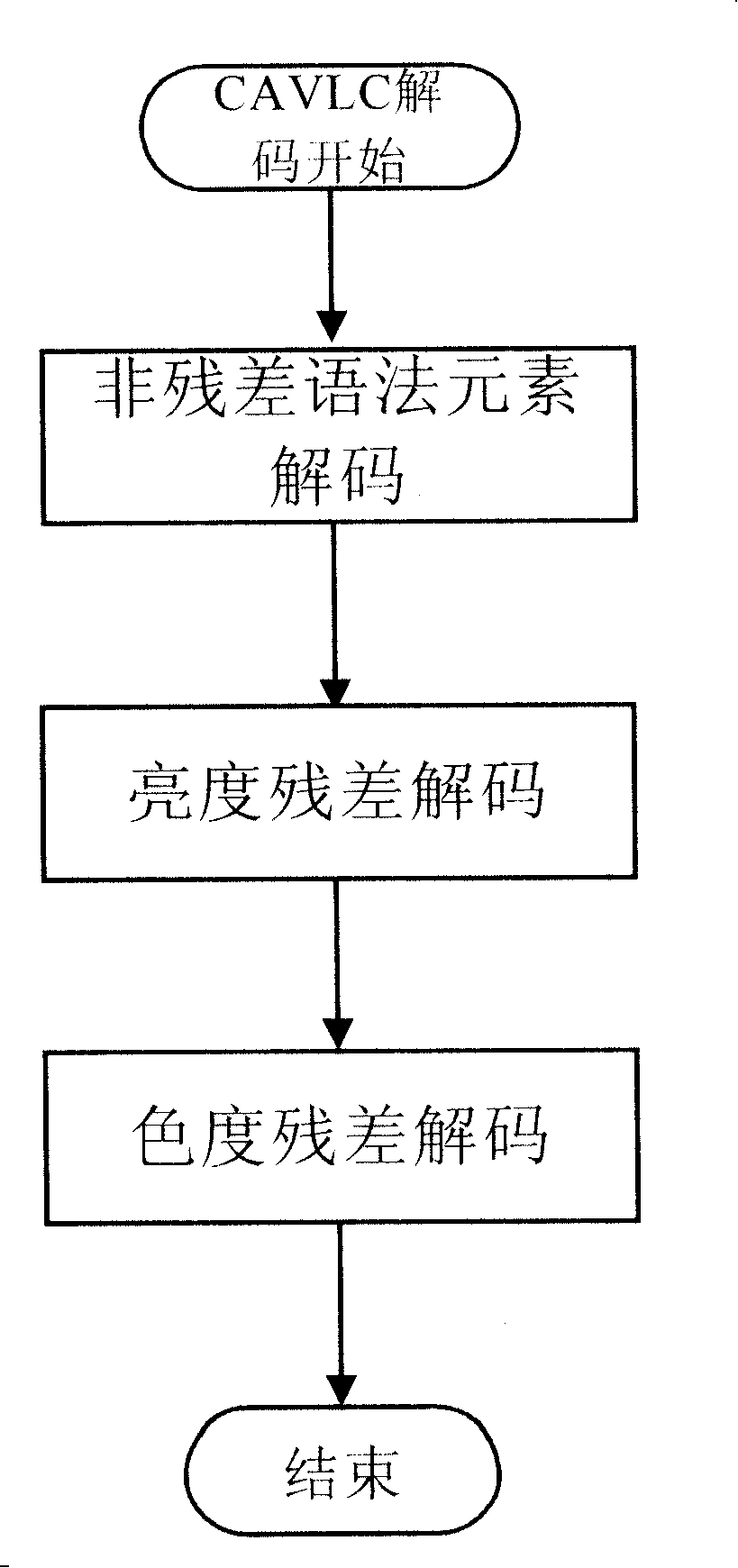
InactiveCN101198051AIncrease the difficultyImplement decodingTelevision systemsDigital video signal modificationComputation complexitySoftware modules
The invention discloses a method for decoding entropy coding residual data and so on which is specially used in an H.264 decoding MAE and a device. Because the method of the invention adopts collaborative work of software and hardware, parts which occupy a large number of resources during the decoding process are realized by means of a software method. The software program method is that: by the means of utilizing an embedded cpu to replace hardware circuits for operation, structural complexity and computation complexity are greatly reduced under the precondition that reliable decoding efficiency and decoding quality of an entropy decoder are guaranteed to be obtained, thereby the contradiction between structure and efficiency is effectively solved and decoding of CAVLC and CABAC entropy coding bit streams is smoothly realized. The entropy decoder comprises a BSI access module, a ue / se / te decoding unit, a CAVLC residual decoding module, a software module, a binary arithmetic decoding unit, an entropy decoding control module, a CABAC residual decoding module and an anti-sweep RAM.
Owner:ARKMICRO TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com