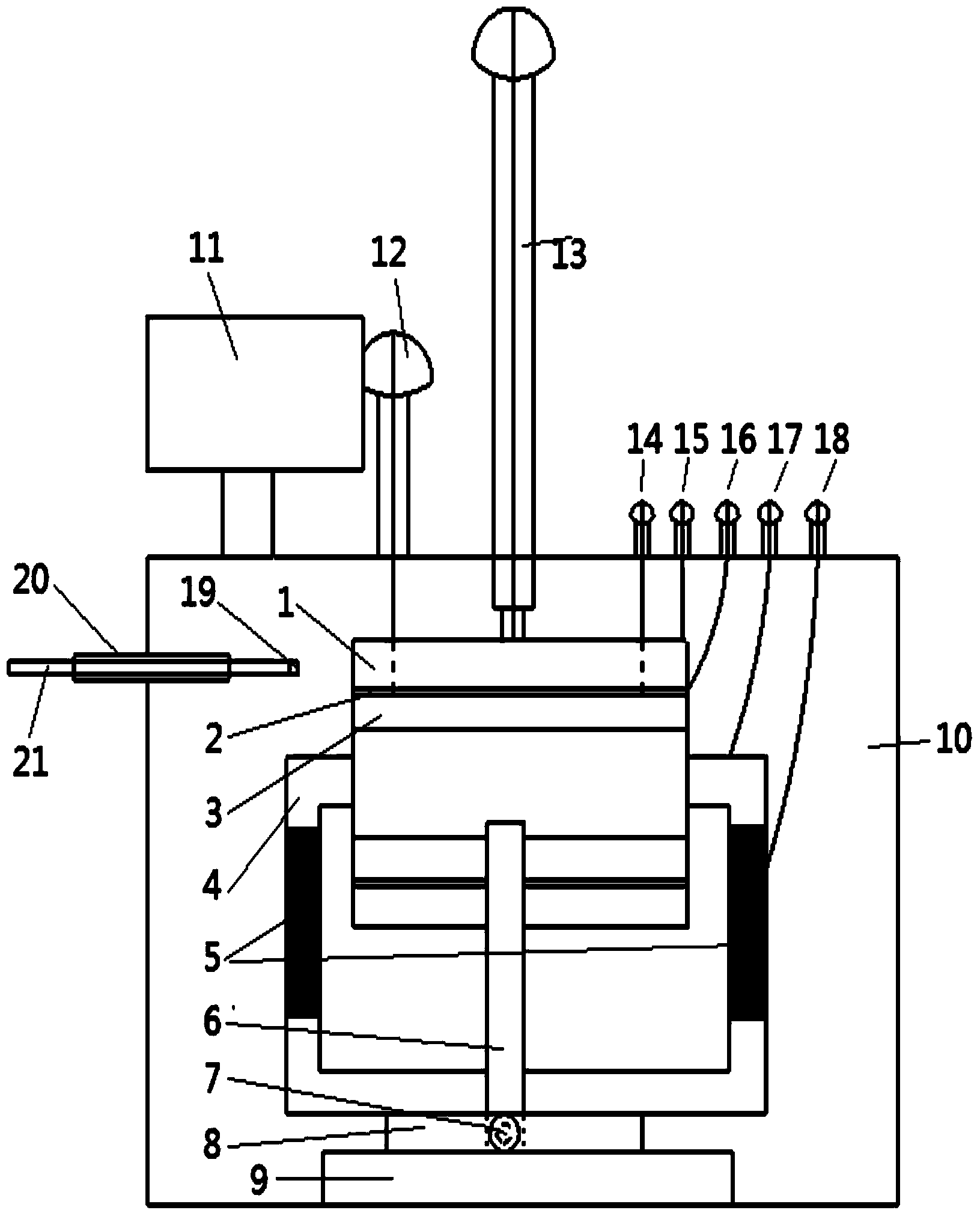
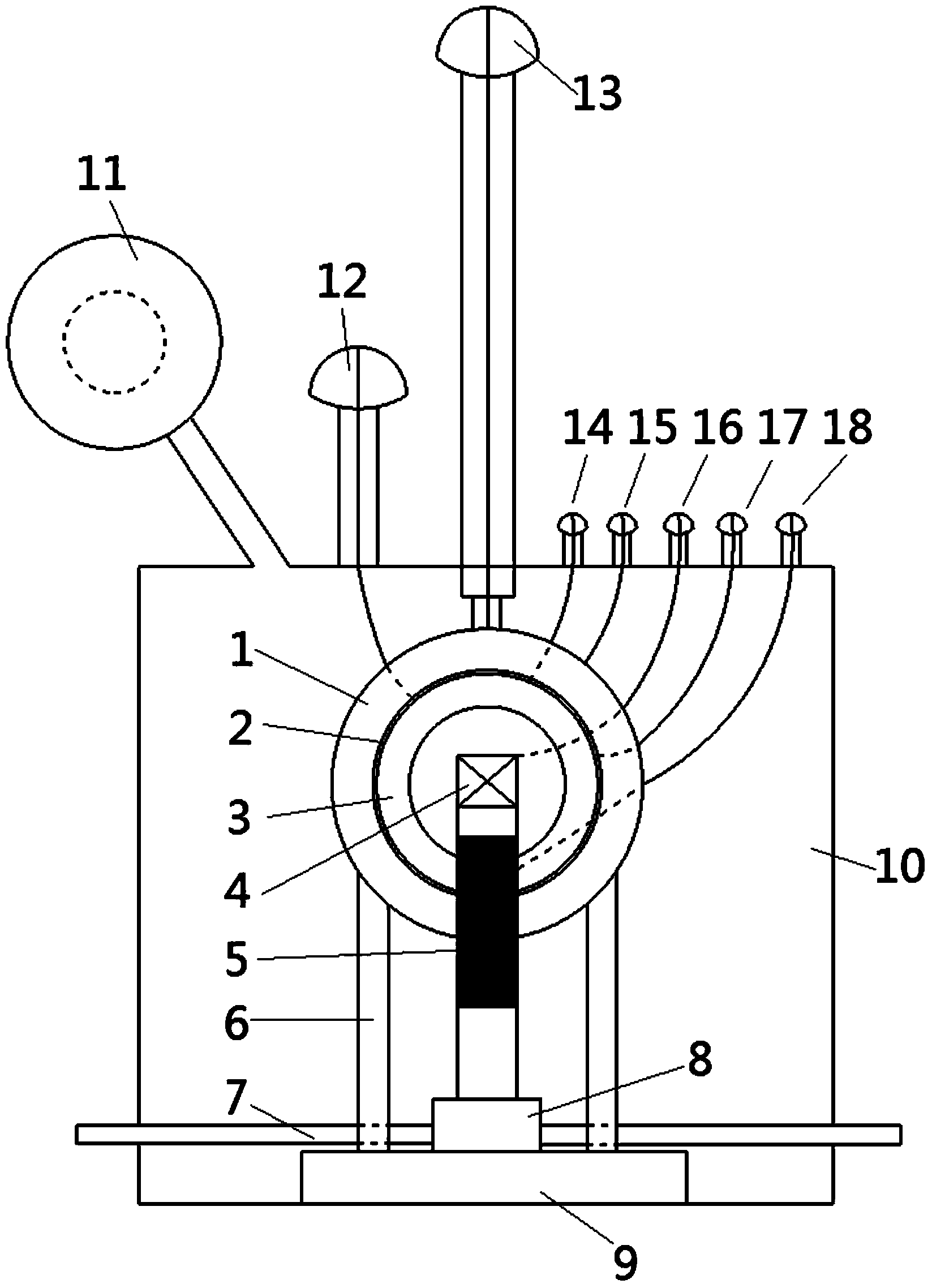
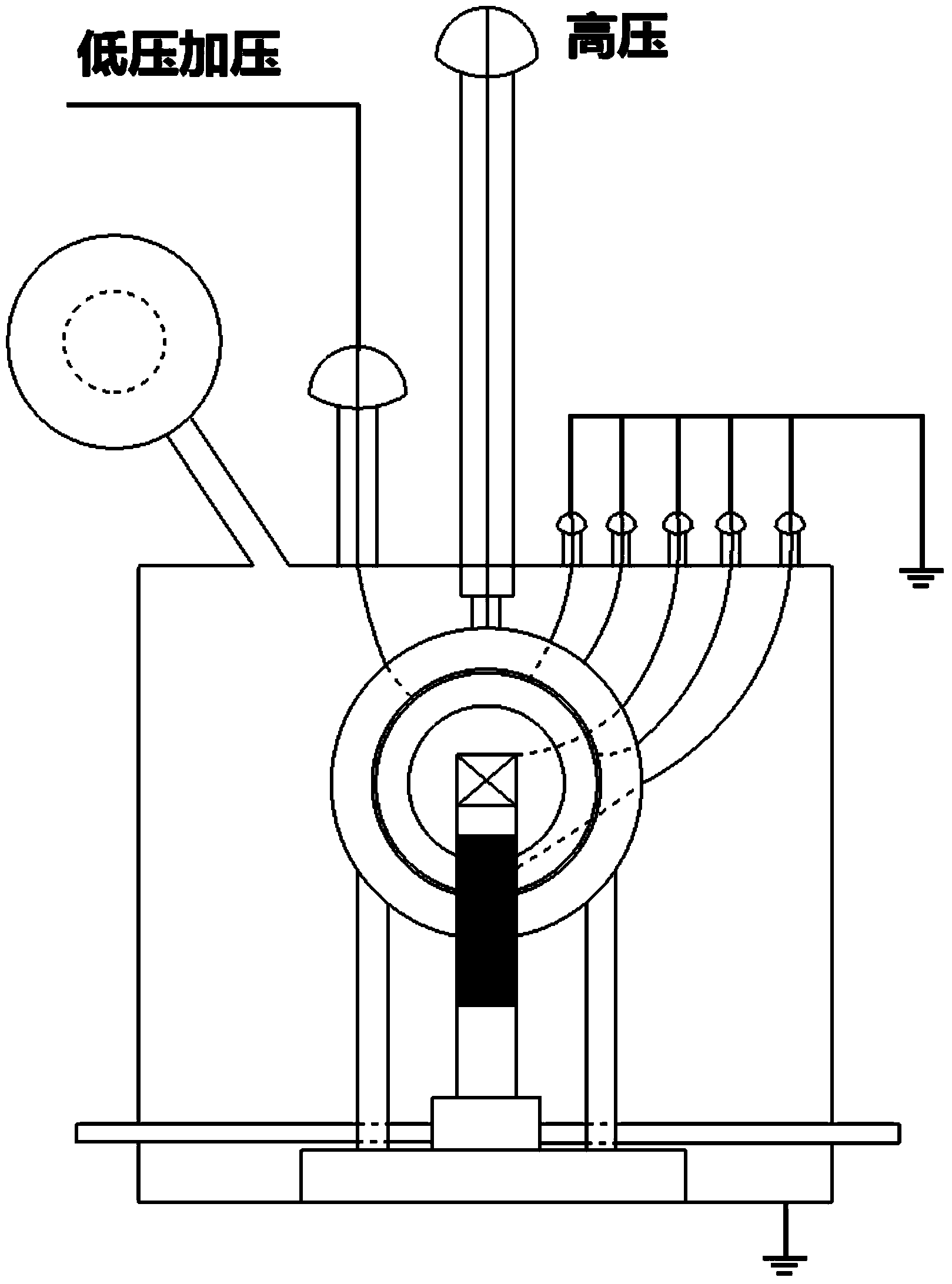
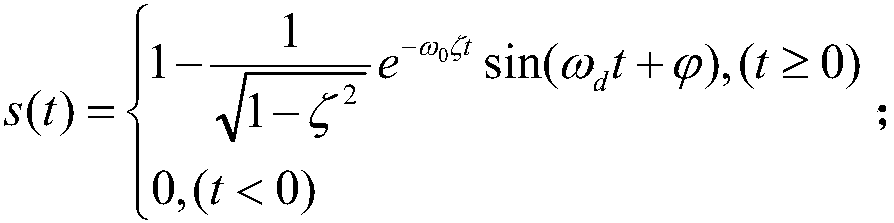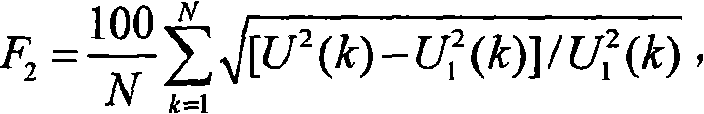Patents
Literature
1055 results about "Generation time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In population biology and demography, generation time is the average time between two consecutive generations in the lineages of a population. In human populations, generation time typically ranges from 22 to 33 years. Historians sometimes use this to date events, by converting generations into years to obtain rough estimates of time.
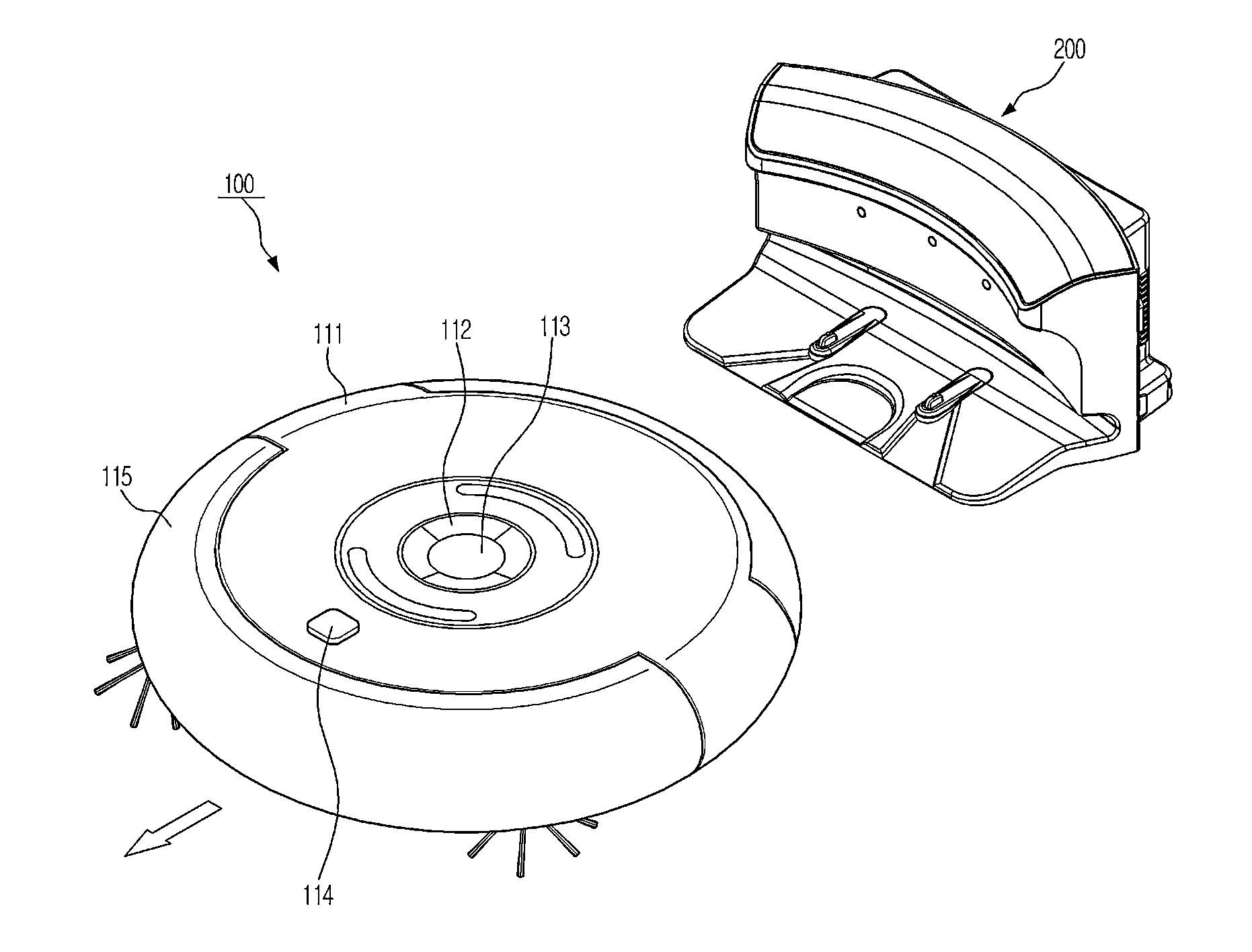
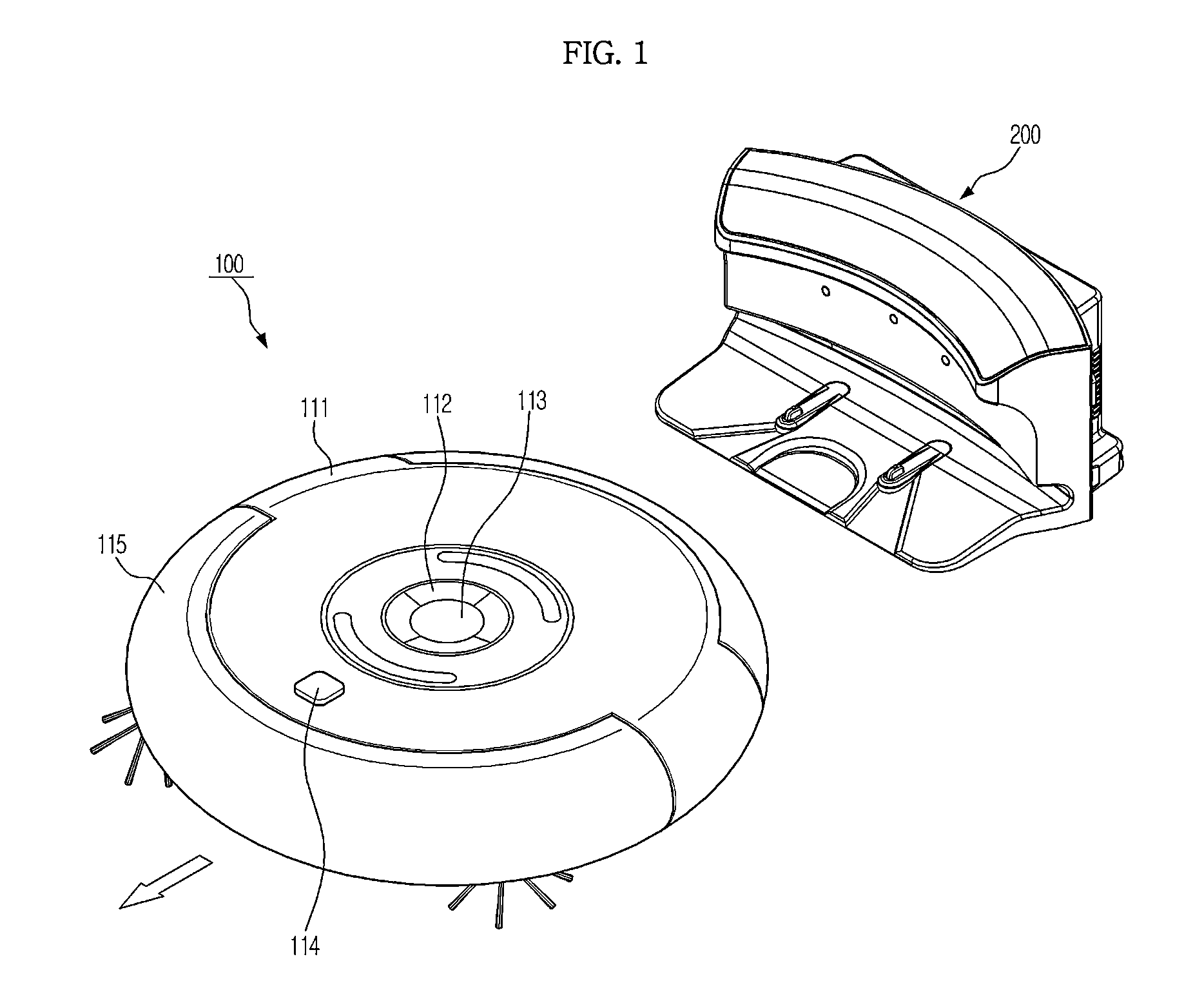
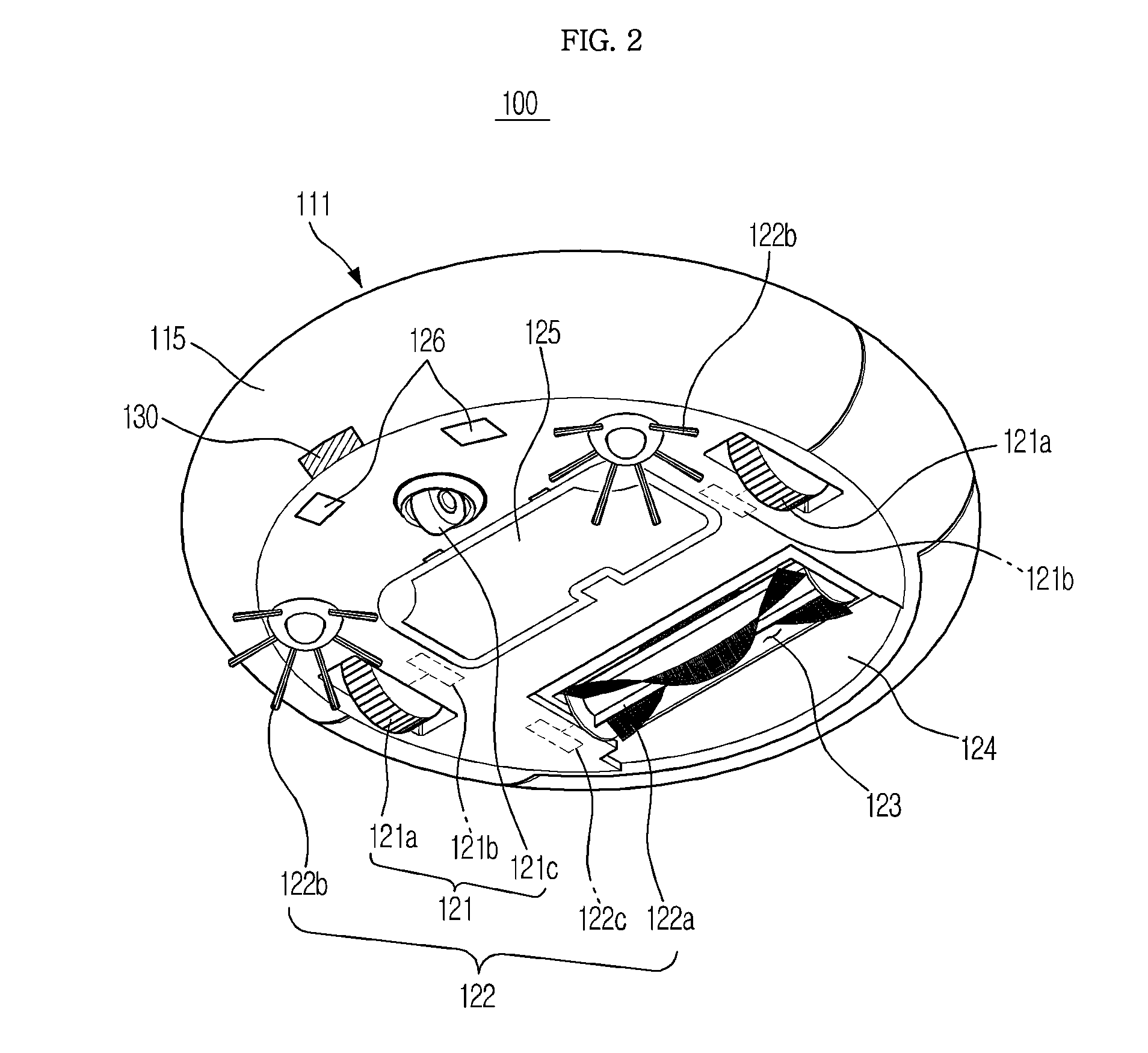
Robot cleaner and control method thereof
ActiveUS20140214205A1Accurate informationImprove receiver sensitivityProgramme-controlled manipulatorAutomatic obstacle detectionUltrasonic sensorReflected waves
A robot cleaner includes a main body, a traveling unit installed in the main body, to move the main body, an ultrasonic sensor to emit an oscillation wave, to receive a reflection wave reflected from an object surface, and to output vibration generated by the oscillation wave and vibration generated by the reception of the reflection wave as an electrical signal, a waveform analyzer to calculate a generation time period of the electrical signal output from the ultrasonic sensor, and a controller to determine information about the object surface based on the calculated generation time period of the electrical signal, and to control movement of the traveling unit based on the information about the object surface.
Owner:SAMSUNG ELECTRONICS CO LTD
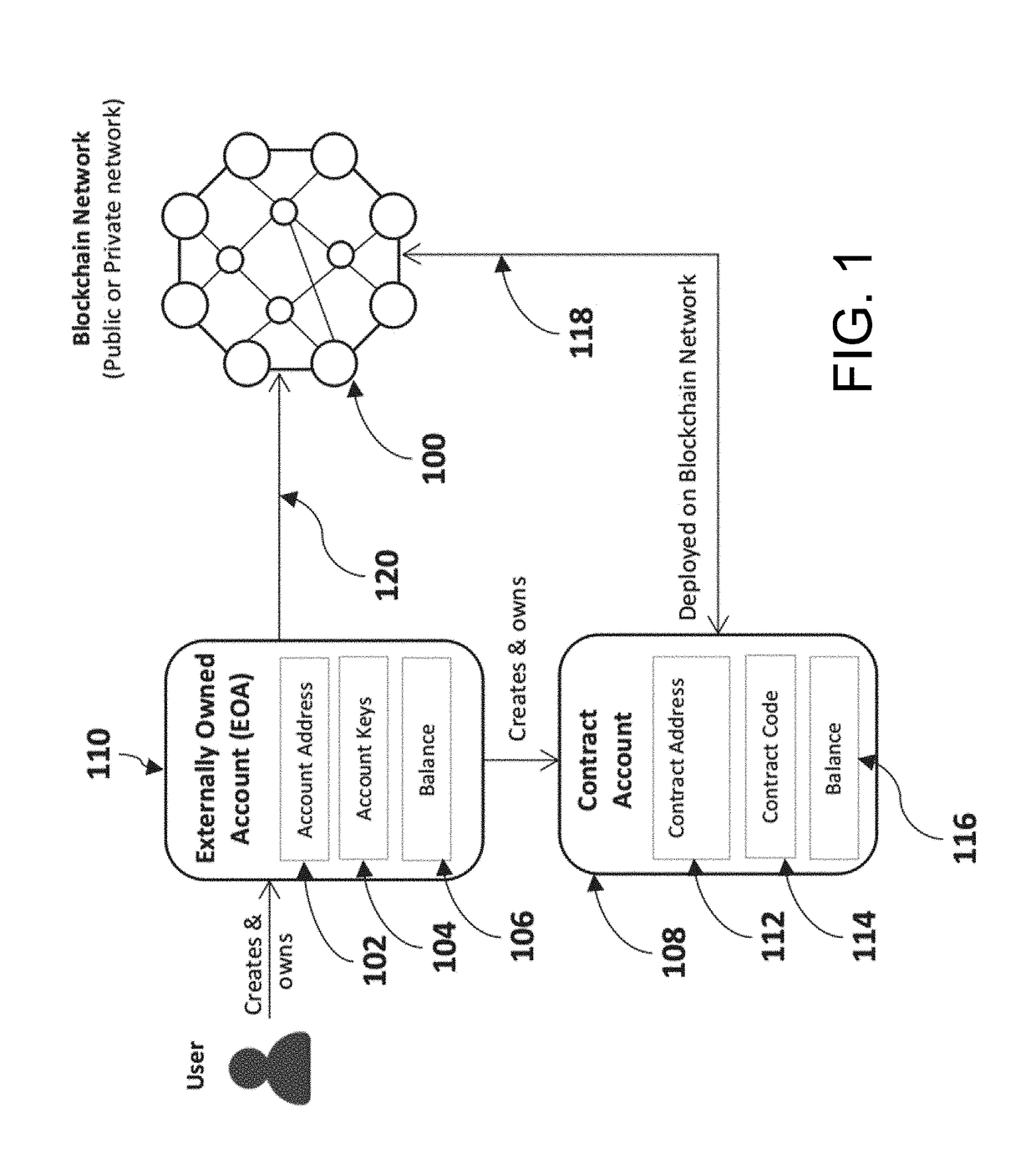
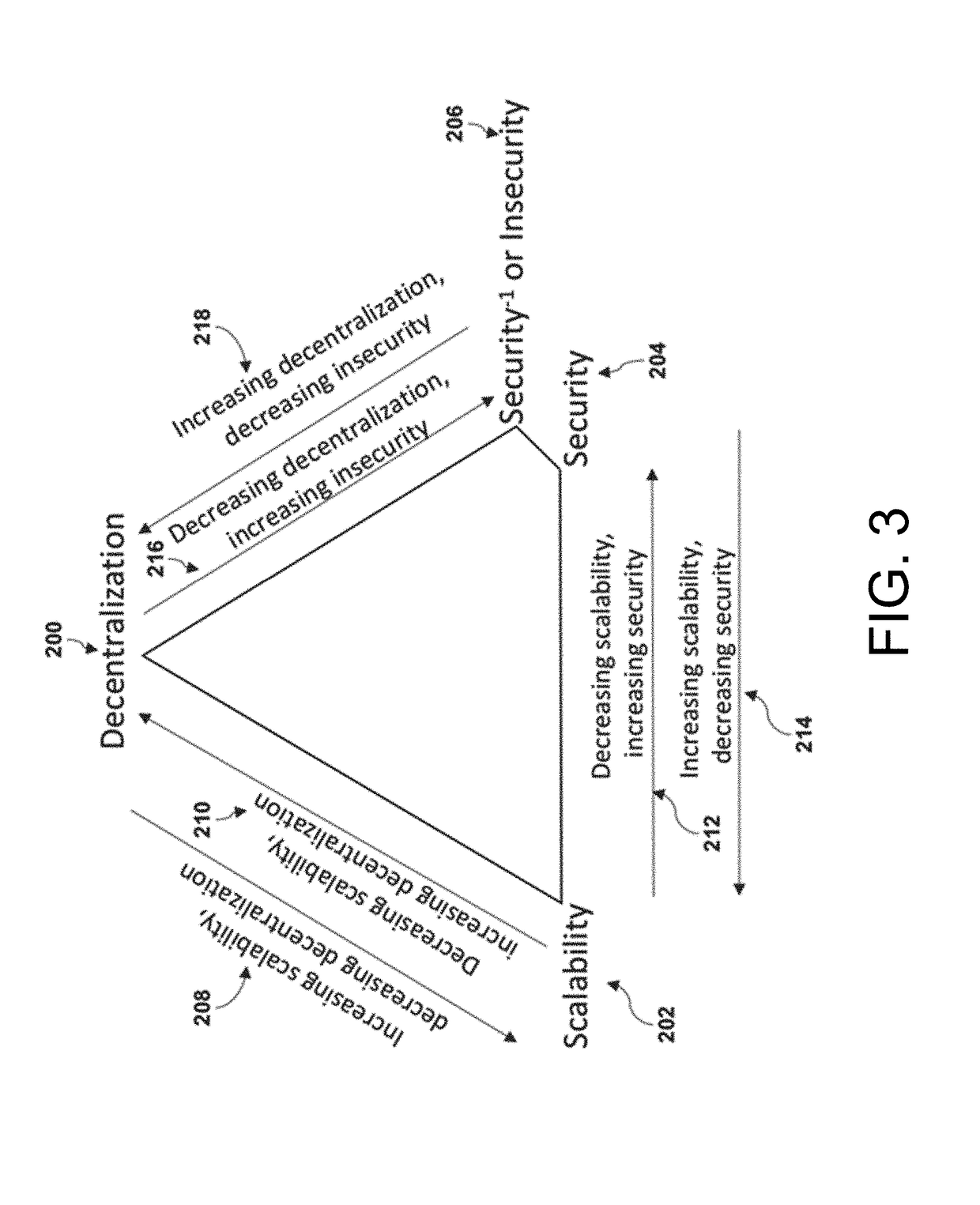
Method and System for Tuning Blockchain Scalability, Decentralization, and Security for Fast and Low-Cost Payment and Transaction Processing
ActiveUS20190018887A1Privacy protectionScalability issueSynchronising transmission/receiving encryption devicesEncryption apparatus with shift registers/memoriesPropagation delayPayment
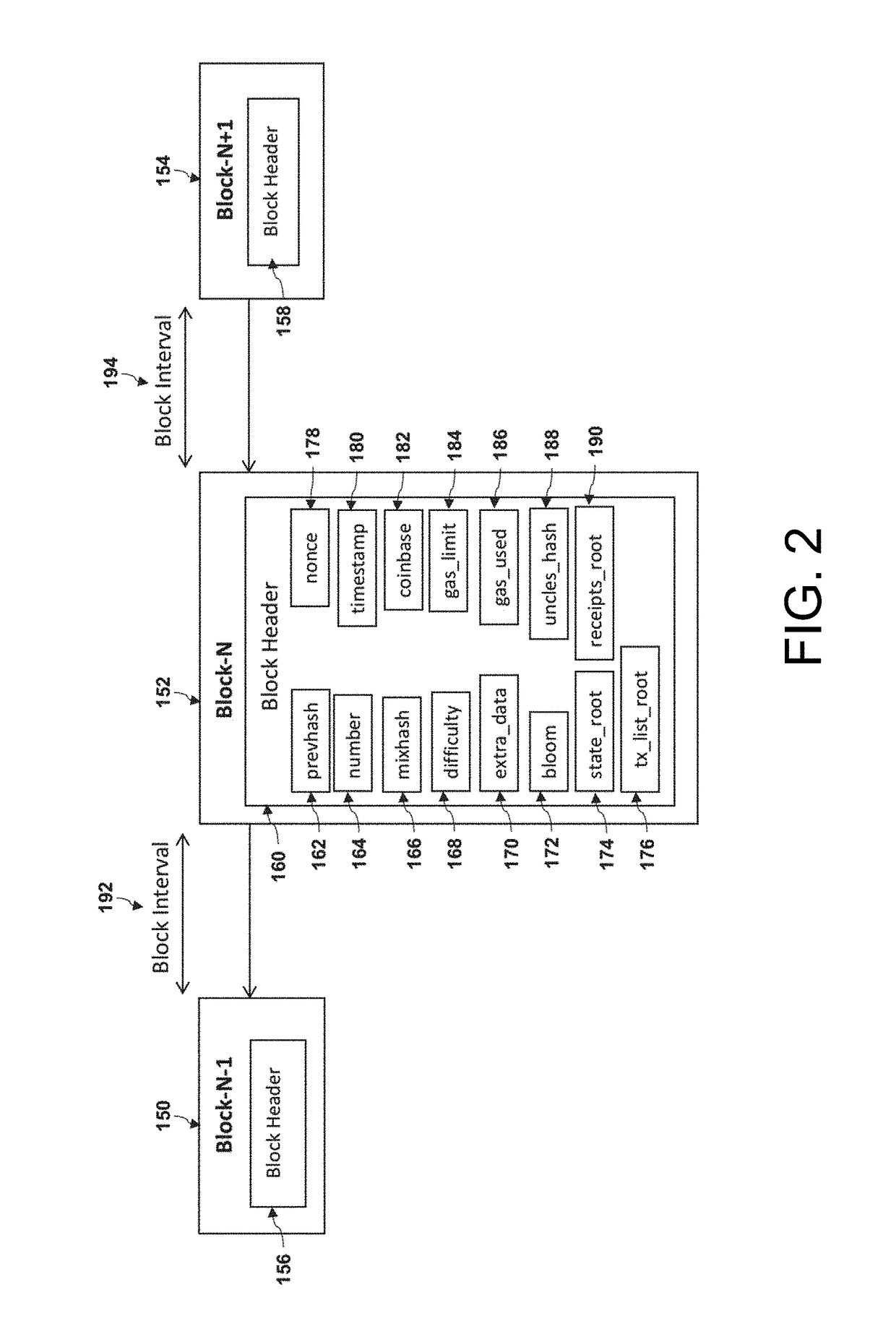
A method of processing and validating transactions on a multi-chain network including receiving first and second pluralities of transactions, recording the first and second pluralities of transactions to first and second blocks on a first blockchain in a multi-chain network, publishing the first and second plurality of transactions to a first managed topic associated with the multi-chain network on a first messaging server, defining a first published transactions, and transmitting the first published transactions to a first subscriber, defining a first transmitted transaction. Receipt of the first transmitted transaction initiates generation of a first merged block comprising the first published transactions and recording of the first merged block to a second blockchain on the multi-chain network. The first blockchain has a parameter difference from the second blockchain selected from the group consisting of block generation time, transaction throughput, transaction latency, stale block rate, block propagation delay and consensus algorithm used.
Owner:MADISETTI VIJAY K
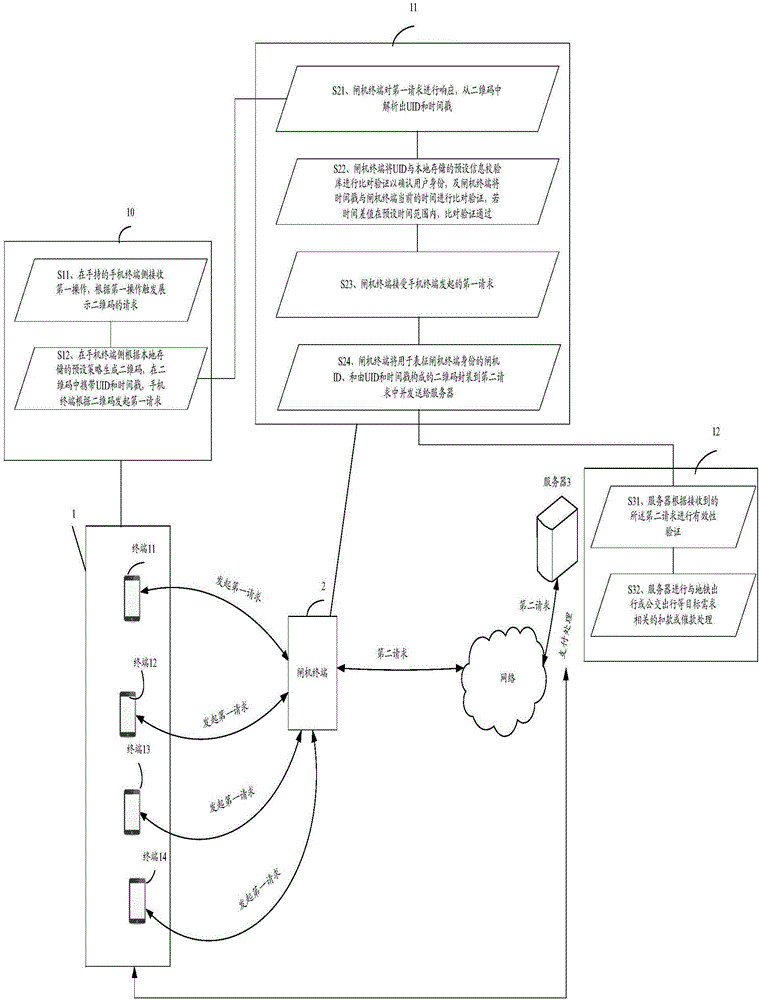
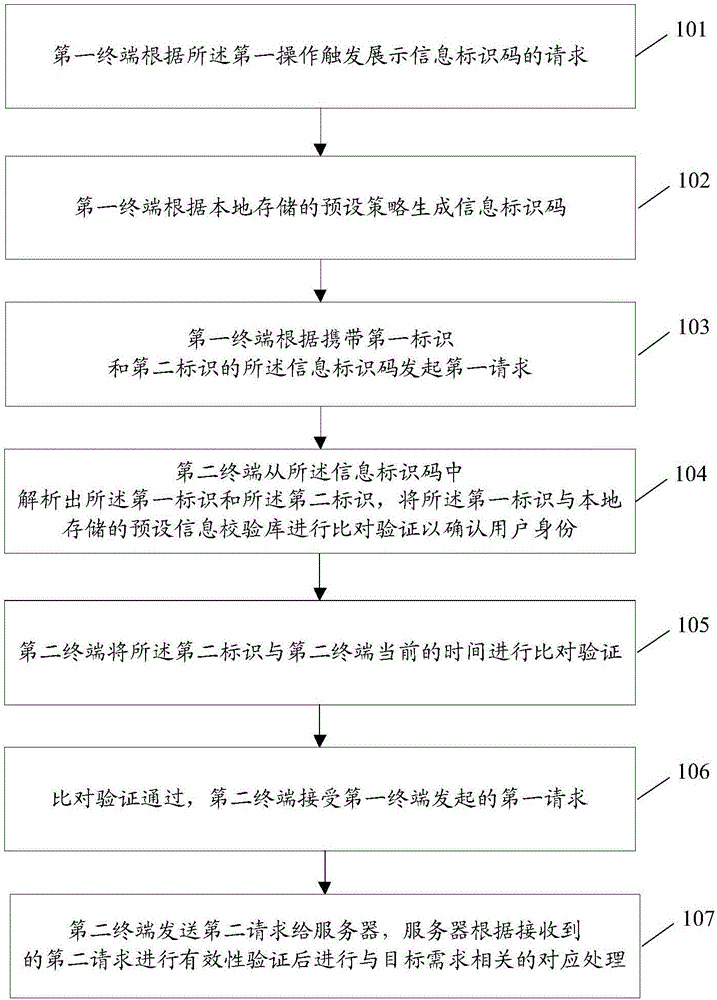
Method and system for information verification based on information identification code
ActiveCN106846506AMeets requirementsEasy to expand and developTicket-issuing apparatusCryptography processingTime rangeComputer terminal
The invention discloses a method and system for information verification based on an information identification code. The method includes the steps that according to a locally stored preset strategy, the information identification code is generated, and first identification used for representing the identity of a user and a second identification used for representing generation time of the information identification code are carried in the information identification code; a first terminal initiates a first request according to the information identification code to request that a second terminal verifies the identity of the user to meet a target requirement; the second terminal compares and verifies the first identification and a locally stored preset information verification library to determine the identity of the user; the second terminal compares and verifies the second identification and current time of the second terminal, if a time differential value is within a preset time range, comparison and verification are passed, the second terminal receives the first request initiated by the first terminal, and after a server carries out effective verification, corresponding processing related to the target requirement is carried out.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Methods and apparatus for encoding and decoding data transmitted over telephone lines
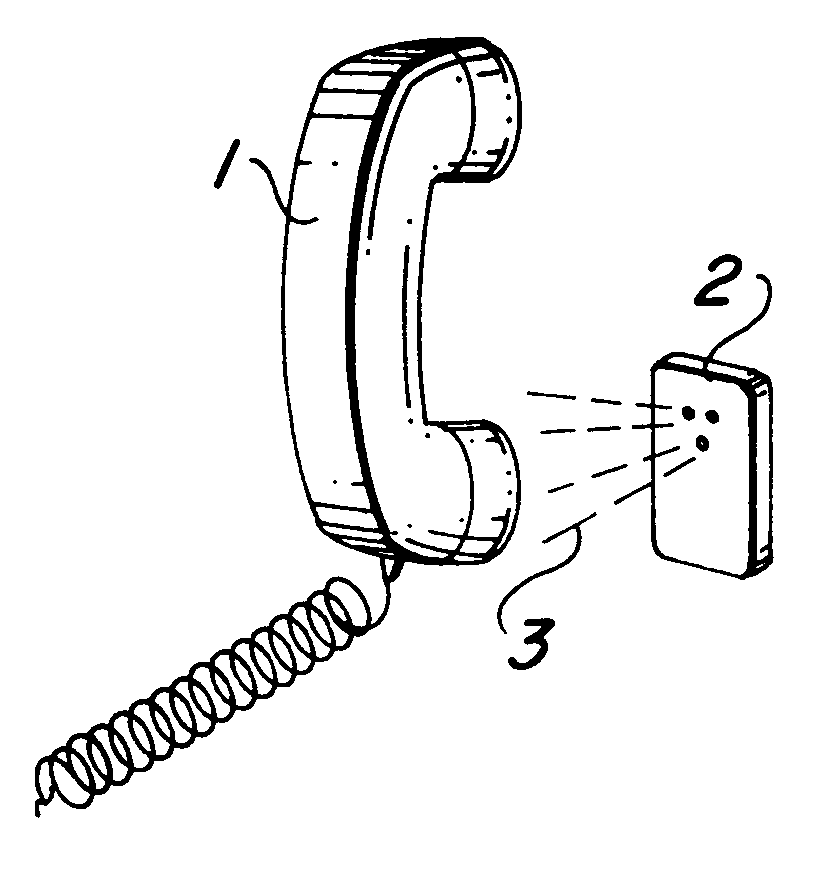
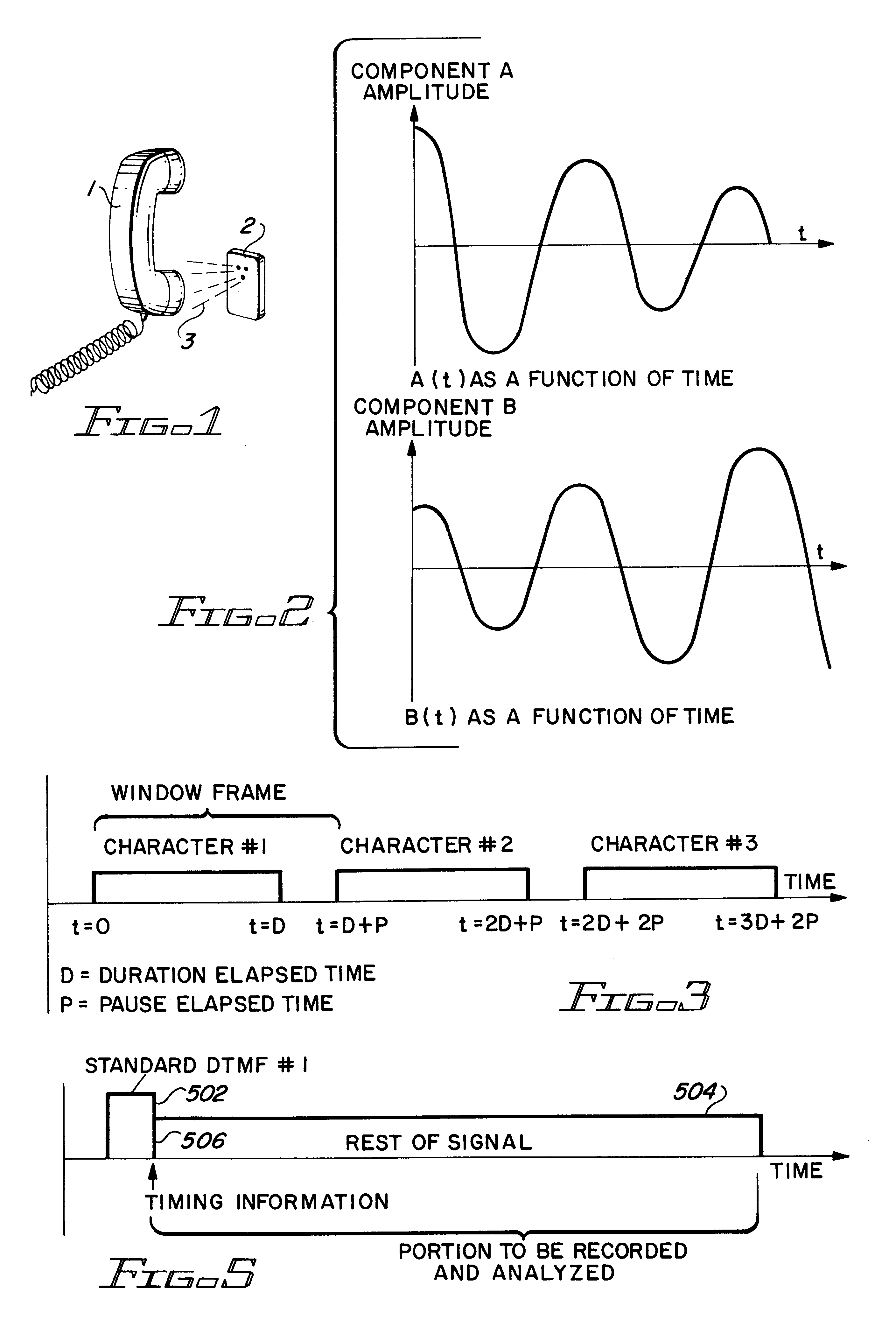
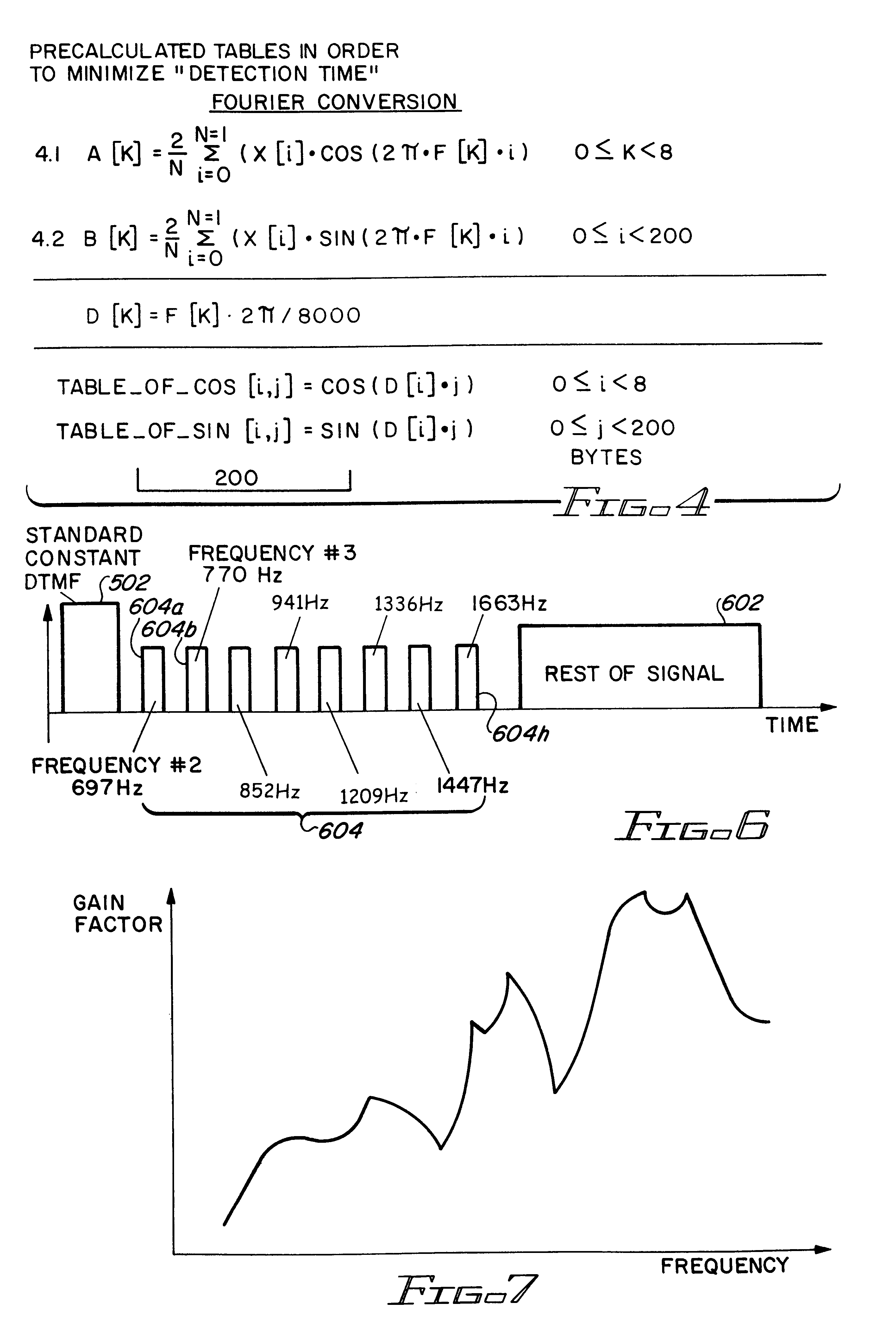
A method of generation and detection of acoustic signals carrying alpha-numeric data for reducing the effects of noise and thereby improving signal transmission without the need to boost the power of the signal. In accordance with one aspect of the invention, a special DTMF acoustic signal consisting of a combination of two frequencies will be generated for the representation of a particular alpha-numeric character that will be similar to the standard DTMF tone. The difference between the amplitudes of both frequencies varies during the time of generation of the DTMF tone in such a way that both signals will arrive at a final destination detector, i.e., an interactive voice response board, at least for a portion of the generation time, at a relatively similar amplitude, thereby substantially increasing the probabilities of being recognized as a DTMF signal.
Owner:CIDWAY TECH
Machine learning model training method, device, storage medium and computer device
ActiveCN109345302AImprove accuracyGood effectAdvertisementsCharacter and pattern recognitionFeature dataModel parameters
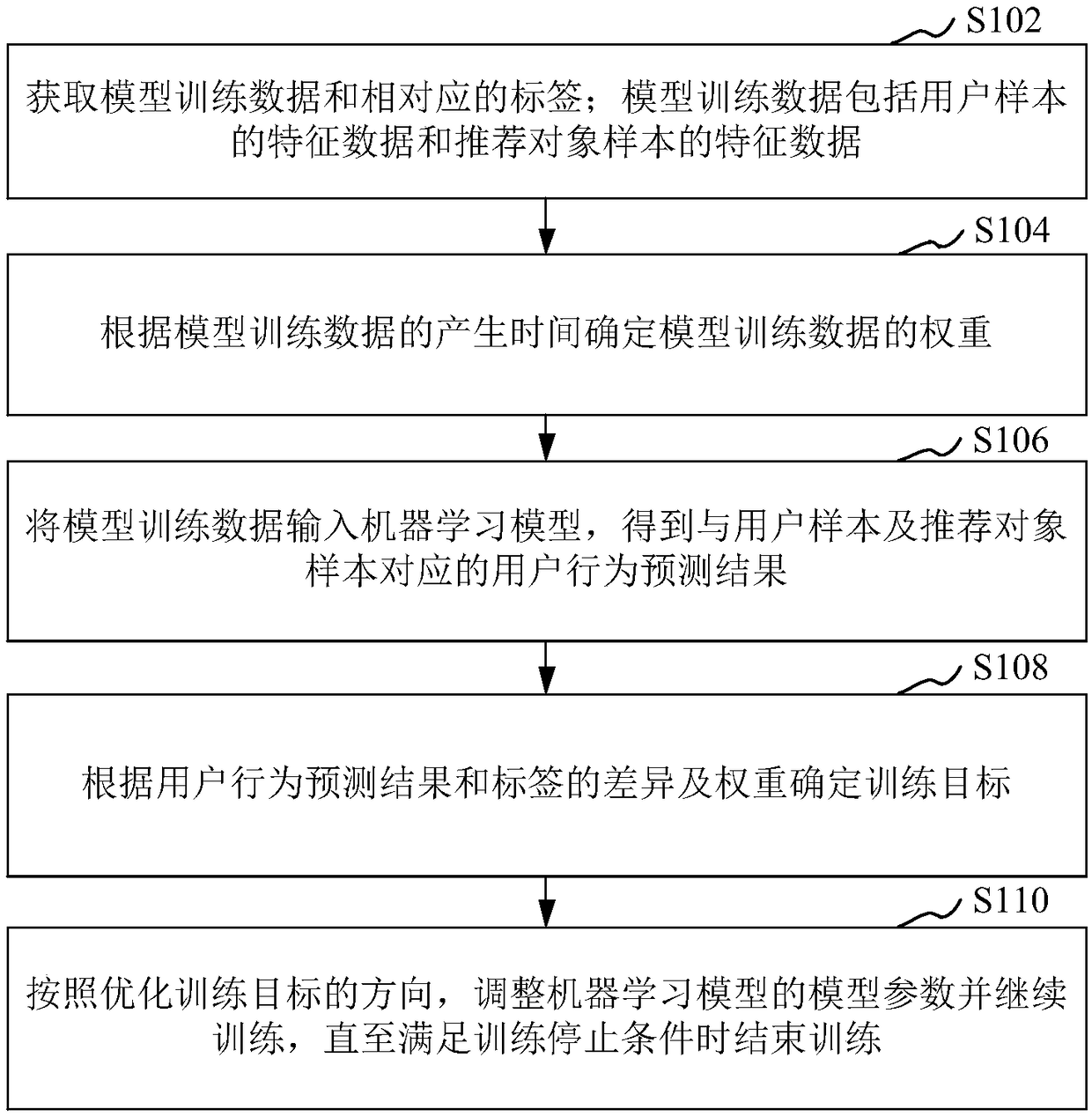
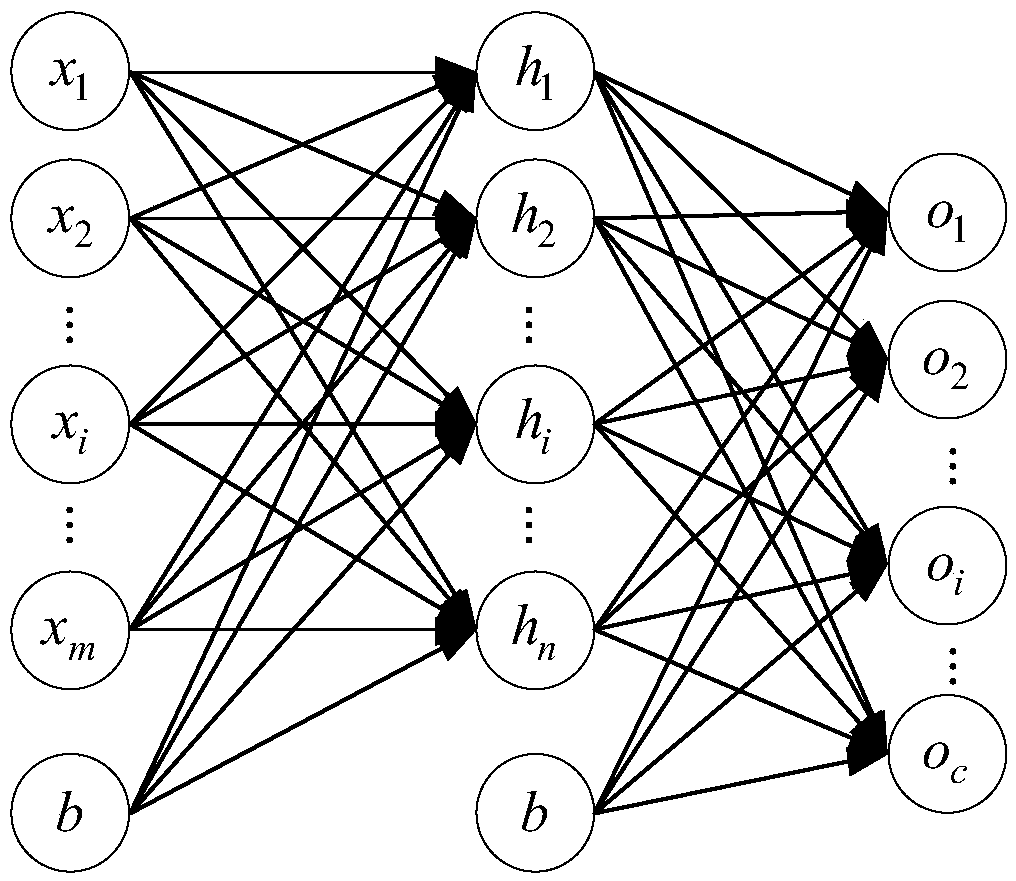
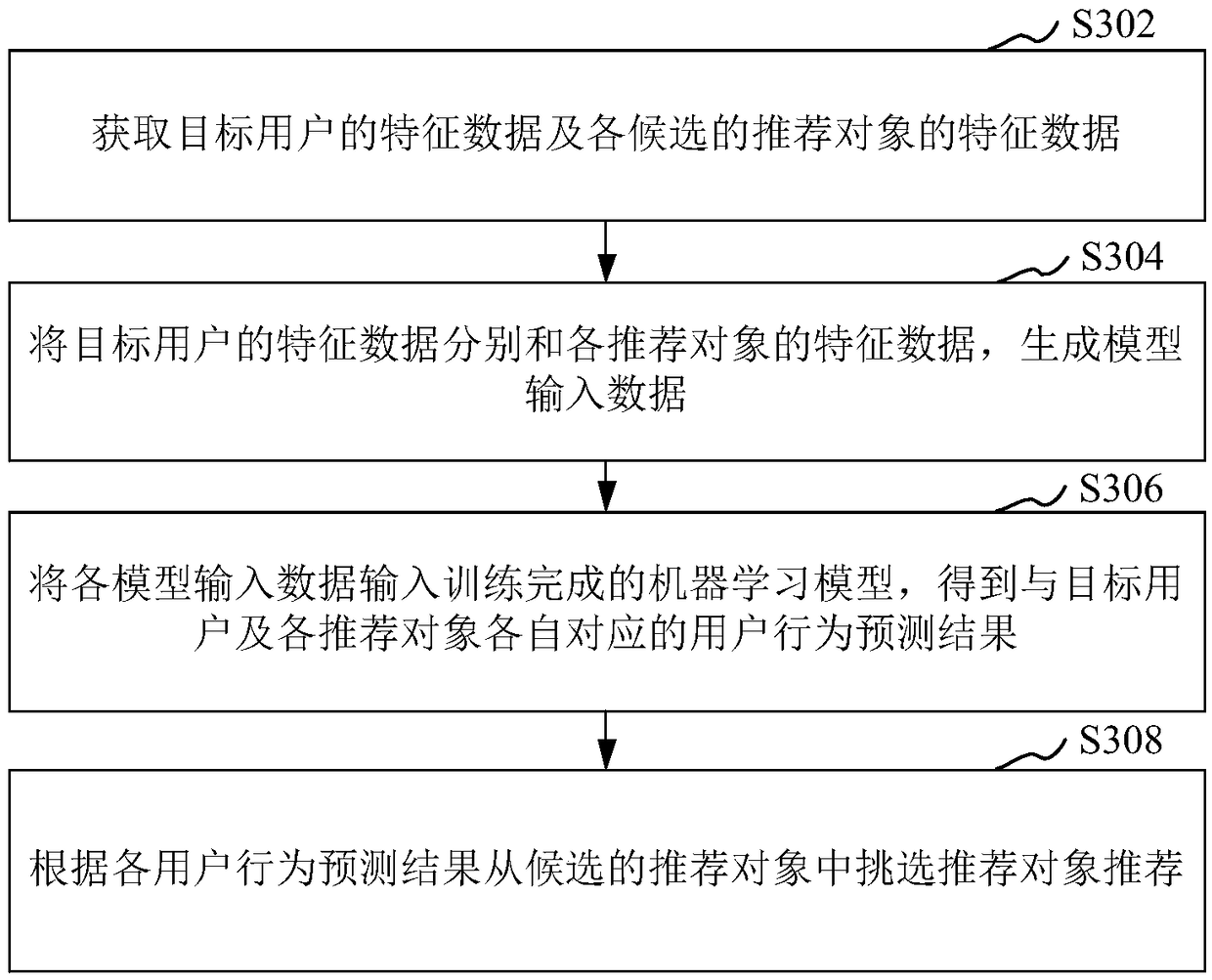
A machine learning model training method, apparatus, storage medium and compute device are disclosed. That method includes: obtaining model training data and correspond tag; The model training data includes feature data of a user sample and feature data of a recommended object sample; Determining a weight of the model training data according to a generation time of the model training data; Inputting the model training data into a machine learning model to obtain a user behavior prediction result corresponding to the user sample and the recommendation object sample; Determining a training target according to a difference between the user behavior prediction result and the tag and the weight; According to the direction of optimizing the training objective, the model parameters of the machinelearning model are adjusted and the training is continued until the training is finished when the training stopping condition is satisfied. The prediction effect of the machine learning model trainedby the scheme provided by the present application is good.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Relay wireless sensor network routing method based on energy balance and distance cooperation
InactiveCN101489275AData transmission is stableShorten the timeEnergy efficient ICTNetwork topologiesEnergy balancedInformation data
A wireless sensor network routing method based on energy equalization and distance cooperation relates to data fusion and routing technique of wireless sensor network, and is typically used for clustering routing technique. According to a given regulation, the sensor nodes in the wireless sensor network are divided to cluster head node, relay node and cluster member node. The energy consumption of whole wireless sensor network is fully equalized and the effective usage factor of energy is increased. An energy threshold LT is introduced for realizing the smooth transition of roles between nodes, saving the cluster generation time and reducing the energy consumption. Single-hop communication is adopted in the cluster. Direct sequence spread spectrum is applied. Each cluster uses a unique cluster spreading code. All nodes in the cluster use the unique cluster spreading code for transmitting data to the cluster head and the inter-cluster interference is effectively reduced. The method of the invention can obtain purpose of prolonging the survival time of network under the precondition that the information data is reliably, effectively and accurately transmitted to the base station.
Owner:SHANDONG UNIV
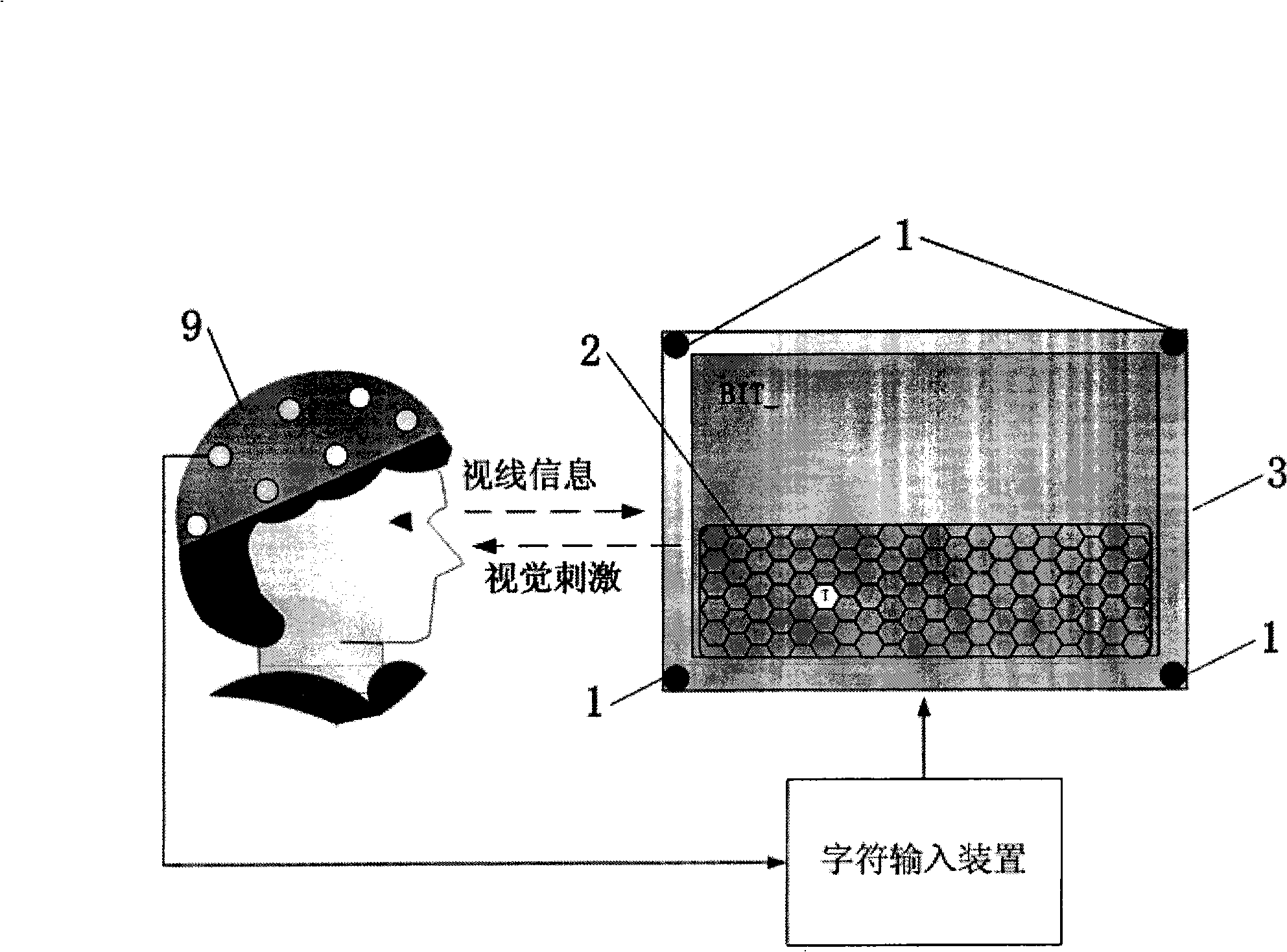
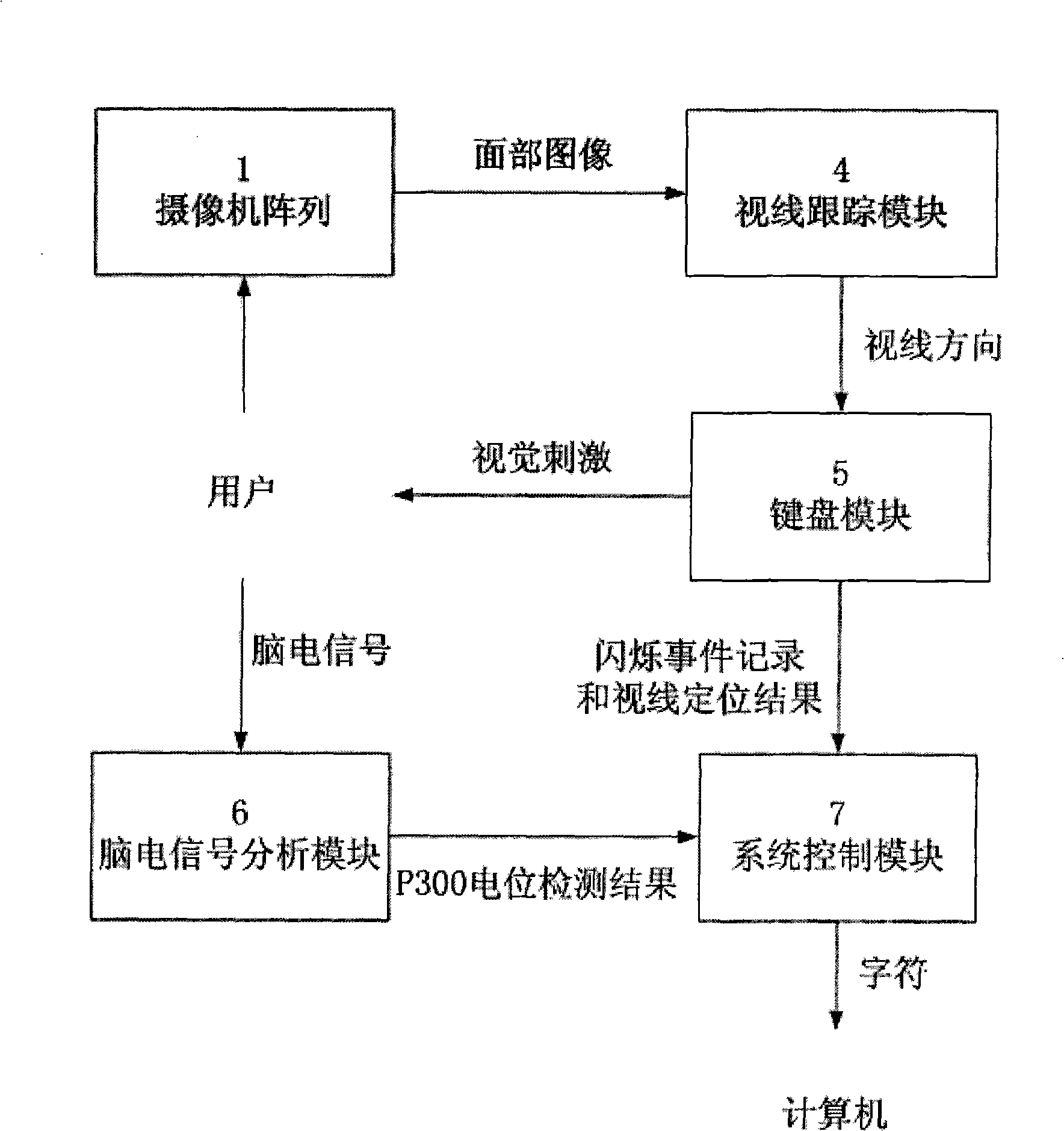
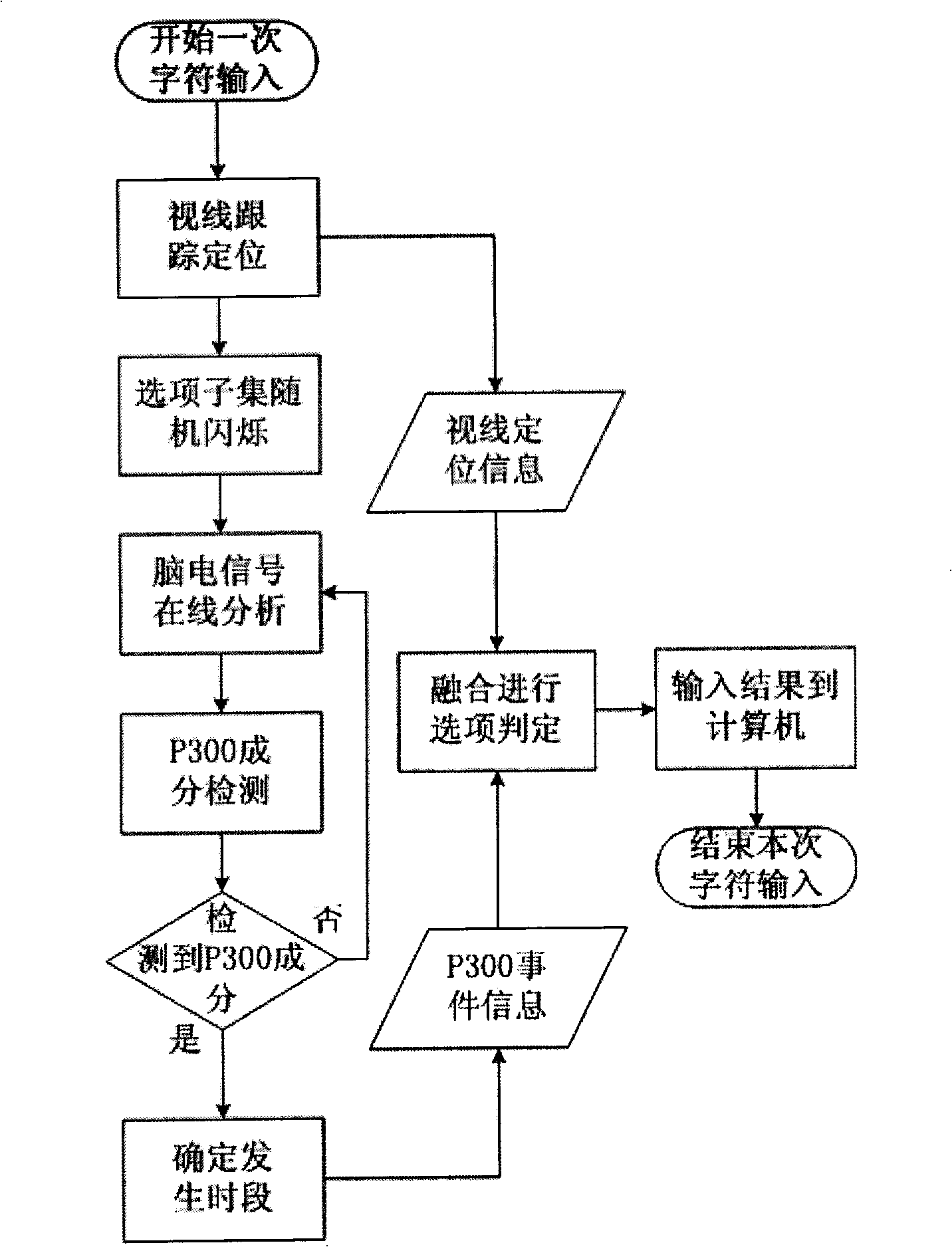
Character input device based on eye tracking and P300 electrical potential of the brain electricity
InactiveCN101515199AEasy to useInput/output for user-computer interactionCharacter and pattern recognitionHuman machine interactionInput device
The invention relates to a character input device based on eye tracking and P300 electrical potential of the brain electricity, which comprises a video camera array, an eye tracking module, a keyboard module, a brain electricity signal analyzing module and a system control module. The device combines the high spatial resolution of the eye tracking and the high time resolution of the P300 electrical potential detection of the brain electricity, firstly, determines an area where the keyboard is according to visual lines of a user, and then controls random flickers of all character keys in the area, arouses the P300 electrical potential of the brain electricity of the user, determines the character keys which the user wants to select according to the generation time of the electrical potential and the visual line location, thus realizing the input operation of characters. The invention provides a new human-machine interaction technique which does not need manpower to be involved and is not affected by the noise of the environment for use.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
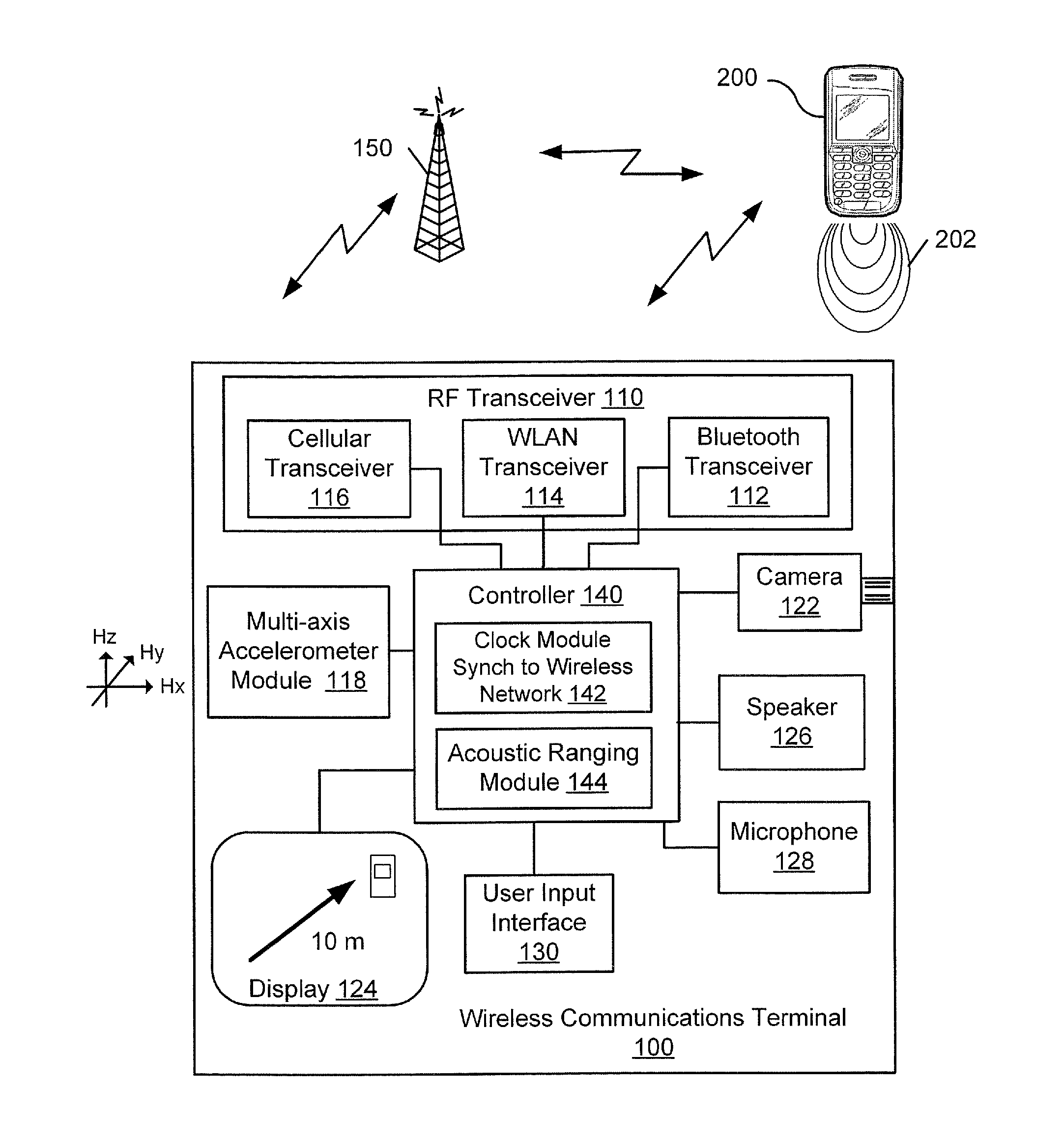
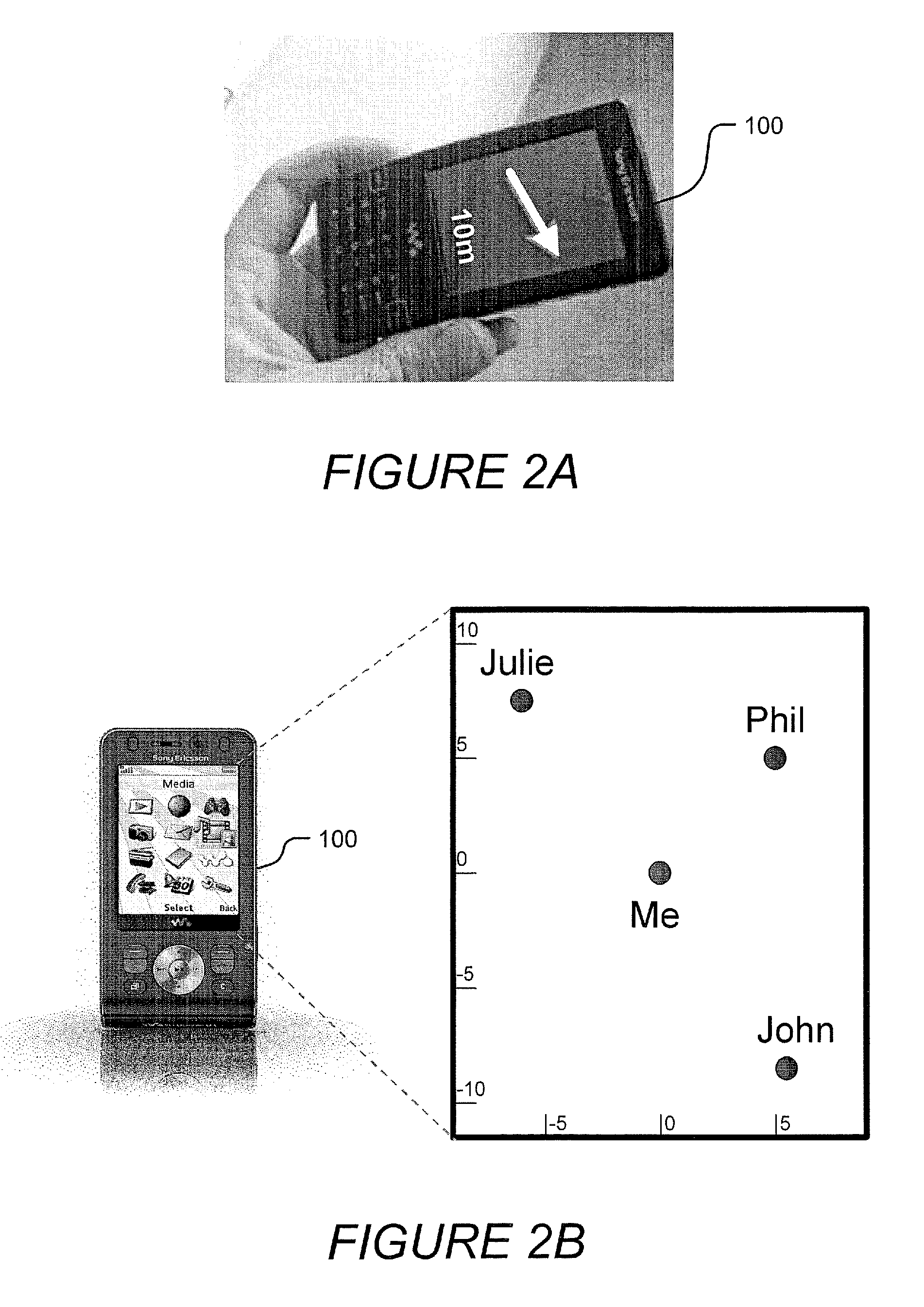
Wireless communication terminals and methods using acoustic ranging synchronized to RF communication signals
InactiveUS20090233551A1Synchronisation information channelsTransmission systemsTransceiverPropagation time
Wireless communication terminals and methods are disclosed that determine acoustic ranging synchronized to RF communication signals. A communication terminal can include a RF transceiver, a microphone, and a controller. The controller synchronizes a clock in response to known timing characteristics of received RF communication signals. The controller determines an acoustic signal generation time relative to the RF communication signal synchronized clock at which the other communication terminal will generate an acoustic signal. The controller determines an acoustic signal receipt time relative to the RF signal synchronized clock when the acoustic signal from the other communication terminal is detected in the microphone signal. The controller further determines a propagation time of the acoustic signal from the other communication terminal to the microphone based on a difference between the acoustic signal generation time and the acoustic signal receipt time, and determines a range to the other communication terminal in response to the propagation time of the acoustic signal.
Owner:SONY ERICSSON MOBILE COMM AB
Network anomaly traffic monitoring method and device
InactiveCN102957579AReduce false detection rateHigh precisionData switching networksTraffic capacityStreaming data
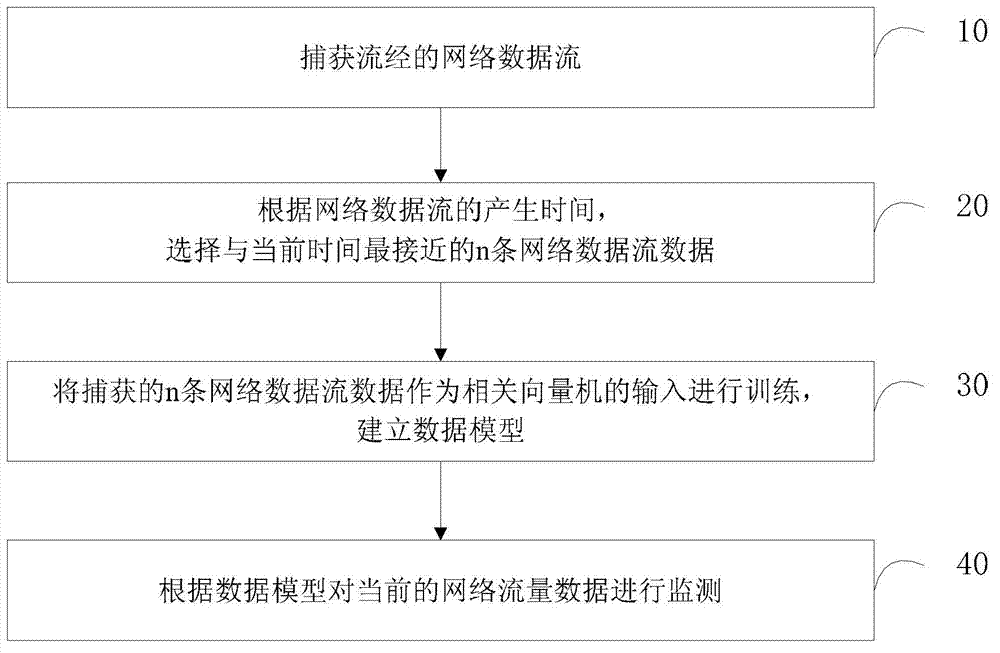
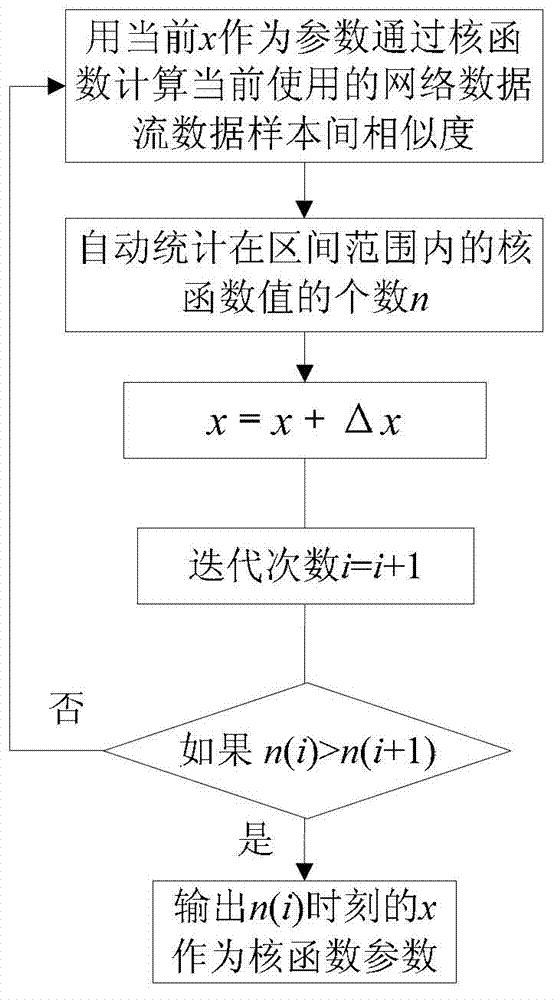
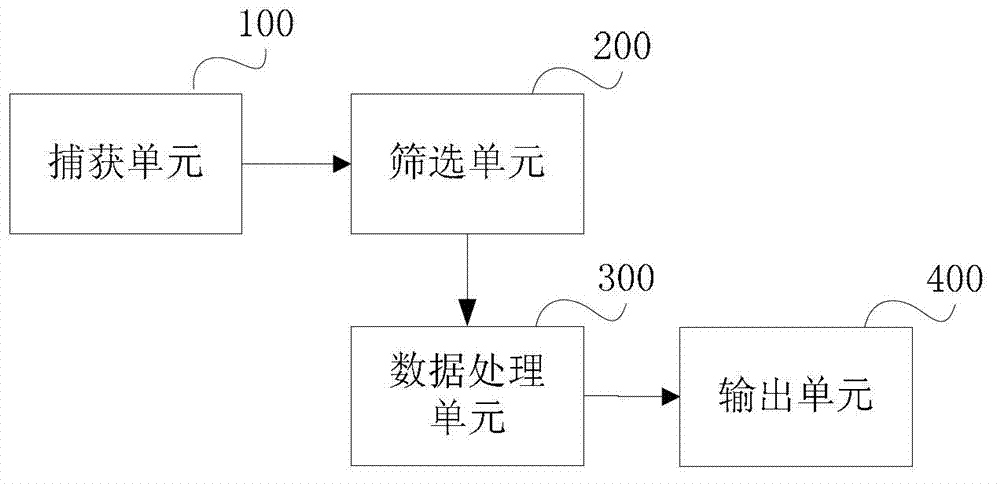
The invention discloses a network anomaly traffic monitoring method, belonging to the technical filed of information security. The network anomaly traffic monitoring method comprises the steps of: capturing a network data stream passing by; according to generation time of the network data stream, selecting n network data streaming data which are closest to the current time, wherein n is determined according to the calculating capacity of a system; training the captured n network data streaming data as input of a relevance vector machine, establishing a data model; and monitoring the current network traffic data according to the data model. By the method and the device, the classifying monitoring precision can be improved so that anomaly traffic is monitored more rapidly and effectively, and lower false drop rate and fallout ratio are ensured.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
Method for treating coking wastewater
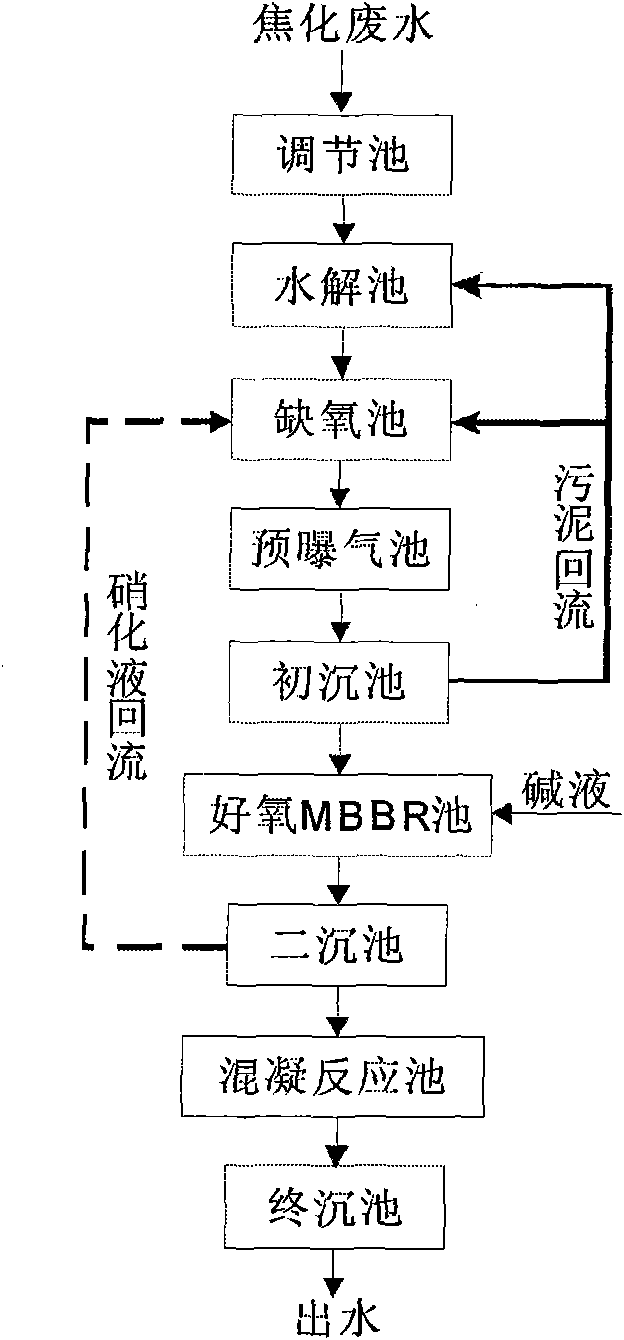
InactiveCN101602564AHigh activityNo reflow requiredTreatment with aerobic and anaerobic processesMultistage water/sewage treatmentHigh concentrationSludge
The invention discloses a method for treating coking wastewater, which belongs to the field of wastewater treatment. The method comprises the following steps that: wastewater of a coking plant enters a regulating reservoir for the adjustment of water quality and water amount, and orderly enters a hydrolytic tank, an anaerobic tank, a preaeration tank, a preliminary sedimentation tank, an aerobic tank, a secondary sedimentation tank and a coagulation reaction tank for treatment, wherein the hydrolytic tank and the preaeration tank are filled with a bio-cord filler; the sludge of the preliminary sedimentation tank refluxes into the hydrolytic tank and the anaerobic tank respectively; a clarifying solution of the secondary sedimentation tank refluxes into the anaerobic tank; and the aerobic tank adopts a moving bed bio-film reactor. The bio-cord filler adopted in the invention has short film formation time and high biomass, does not need repeated washing, and has strong shock resistance; and the moving bed bio-film reactor can fix a large amount of nitrobacteria with long generation time, and has no the problem of blocking. The method can remove high-concentration ammonia nitrogen and organic substances in the coking wastewater, and the COD and the ammonia nitrogen of treated effluent can synchronously achieve the primary standard of the national integrated wastewater discharge standard (GB9878-1996).
Owner:NANJING UNIV
Managing method of data of memorizer
InactiveCN1963814AQuick storageFast readSpecial data processing applicationsData managementData storing
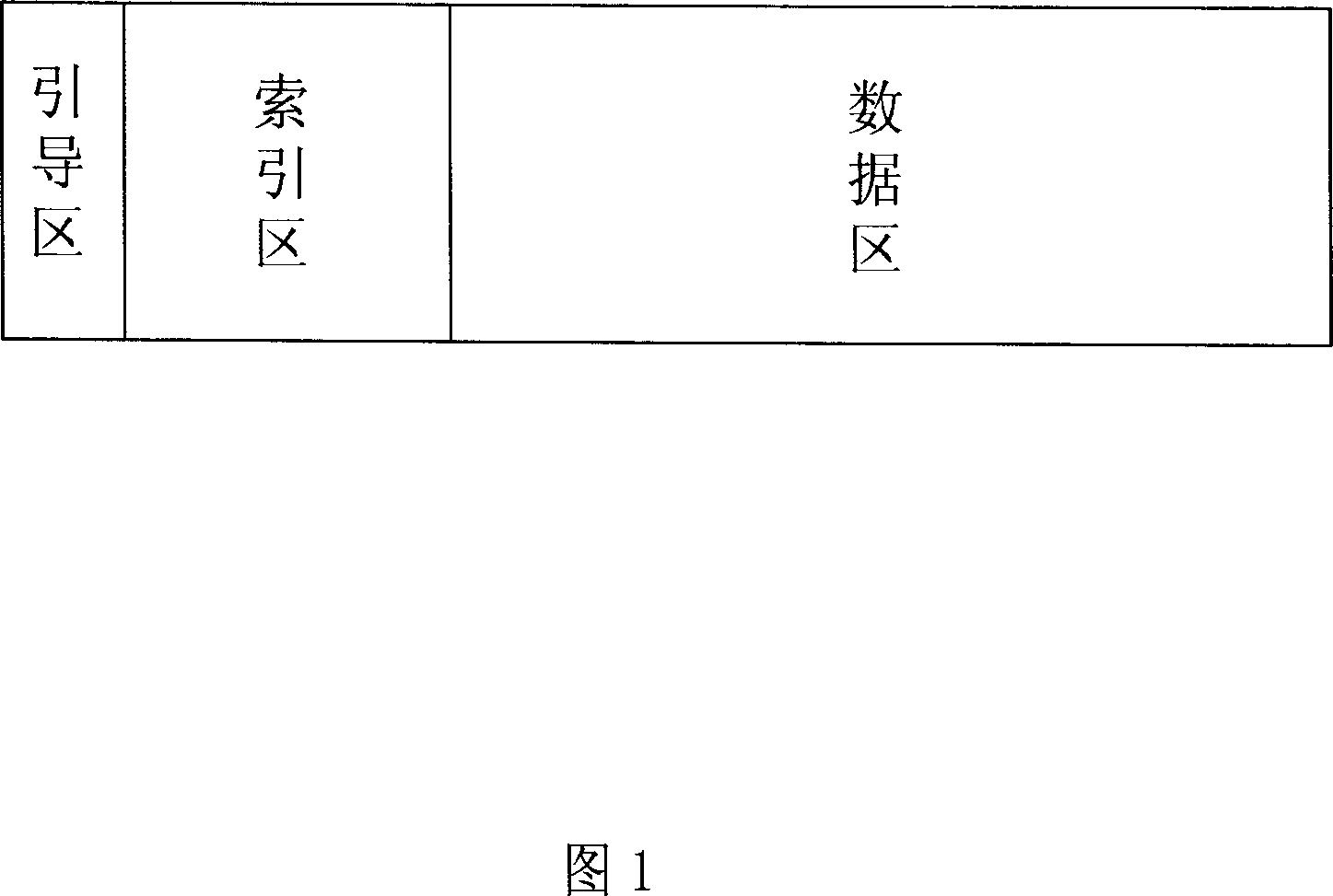
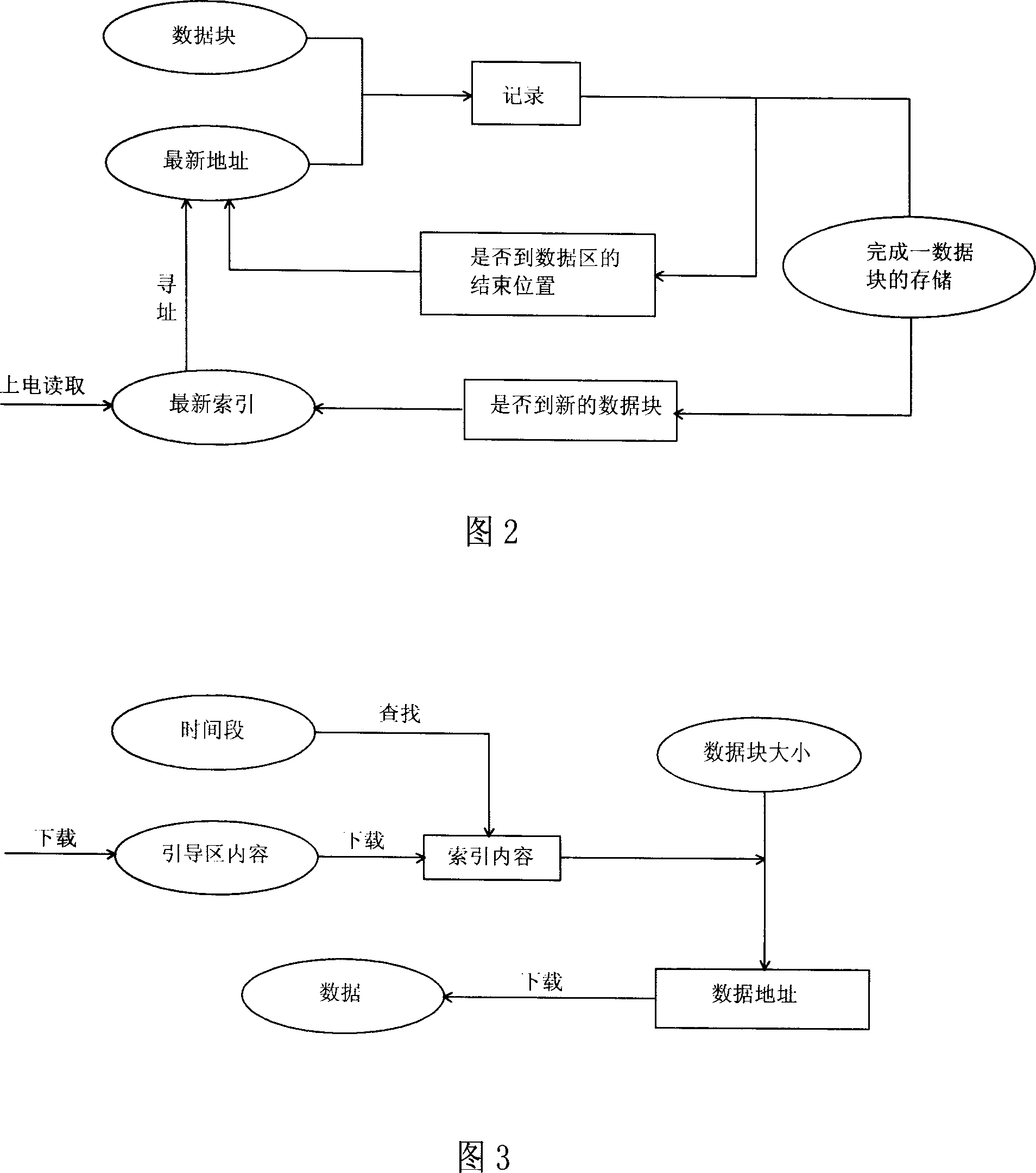
This invention relates to one memory data management method, which comprises steps of memory formatting and data storing and reading, wherein, the memory formatting is to divide memory into guide area, index area and data area; the guide area content comprises data area set property, index area set property, memory data block size, index size; the data area is to store several memory blocks; index area stores each data blocks relative index; each index content comprises data generation time and sum number.
Owner:珠海市泰德企业有限公司
Behavior characteristics-based network attack detection method and device
InactiveCN105471882AReduce in quantityImprove processing efficiencyTransmissionIp addressRule mining
The invention discloses a behavior characteristics-based network attack detection method and device, and relates to the technical field of information security. The technical points of the method comprise the following steps: step 1, collecting original security information output by various types of security equipment, and converting all security information into security events with the unified format; step 2, classifying all security events according to each field content; and step 3, sequencing all security events which have the same source IP address and the same destination IP address and occur within one monitoring period according to the sequence of event generation time to obtain security event combinations, and searching whether the same security event combination is stored in a security event correlation rule library or not, if yes, determining that a host corresponding to the destination IP address suffers from attacking and warning, or if not, storing all security events in an association rule mining database.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method and apparatus for transmitting and receiving status report in a mobile communication system
ActiveUS20070283032A1Timing errorError prevention/detection by using return channelMultiple digital computer combinationsAutomatic repeat requestMobile communication systems
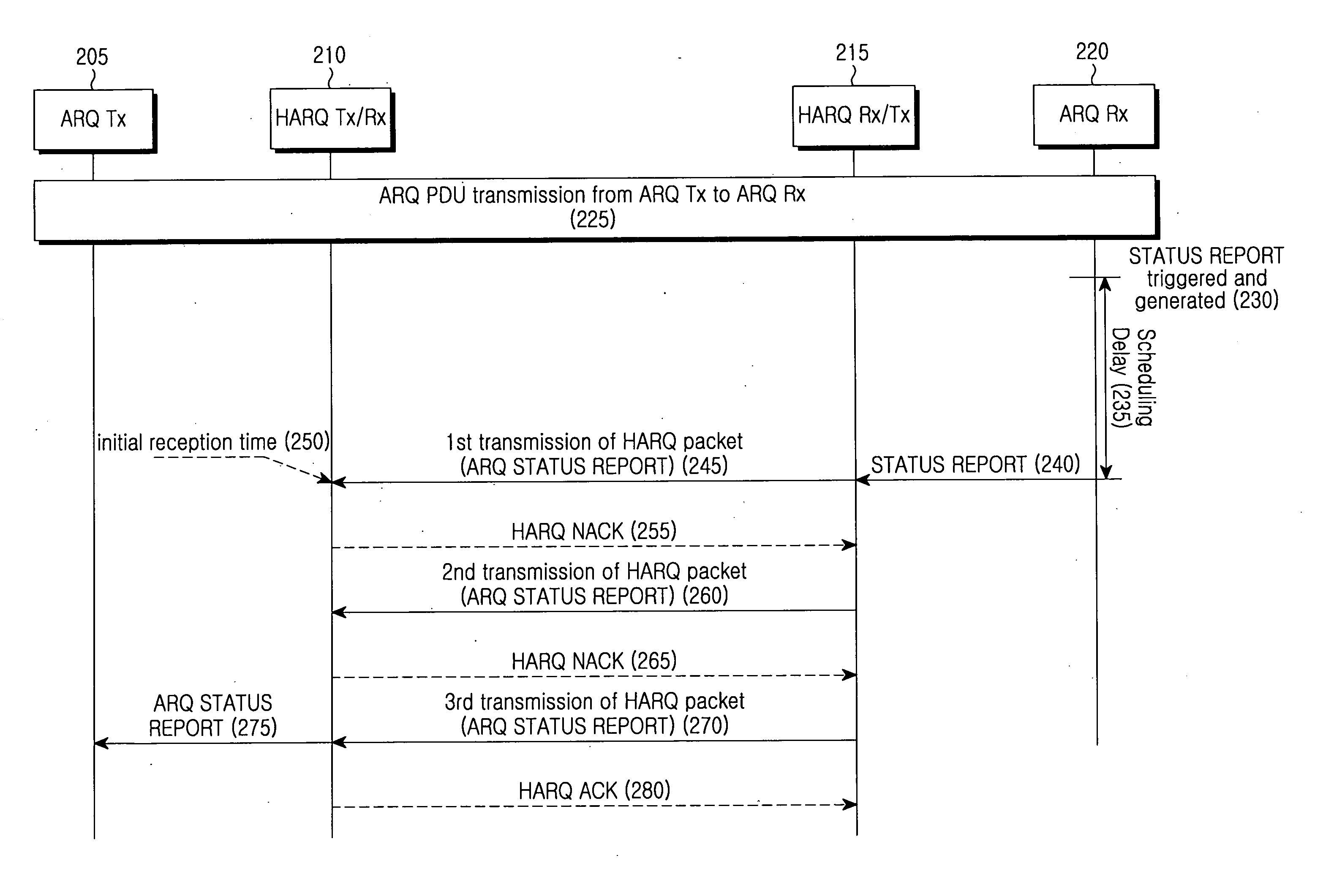
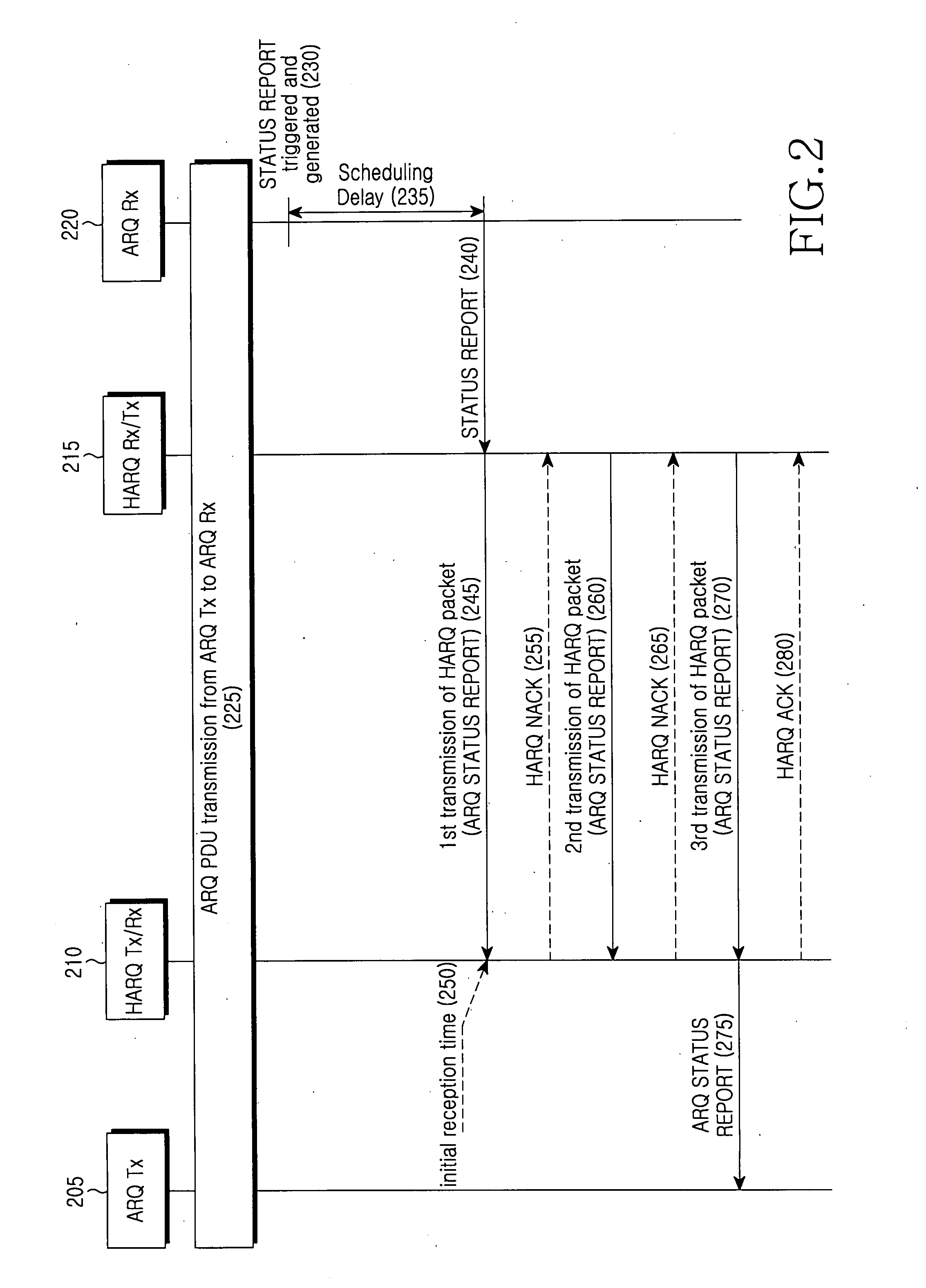
A method and apparatus for transmitting / receiving a status report in a mobile communication system where Automatic Repeat reQuest (ARQ) and Hybrid Automatic Repeat reQuest (HARQ) operate together. An ARQ receiving (Rx) entity determines whether transmission of the status report is permitted, if a predetermined status report generation condition is satisfied. If the transmission of the status report is permitted, the ARQ Rx entity generates a status report depending on a reception status of ARQ packets received up to the time the transmission of the status report is permitted, and transmits the generated status report to an ARQ transmitting (Tx) entity through an allocated transmission resource. The ARQ Tx entity determines an initial reception time of an HARQ packet including the status report as a generation time of the status report, and performs retransmission according to the status report.
Owner:SAMSUNG ELECTRONICS CO LTD
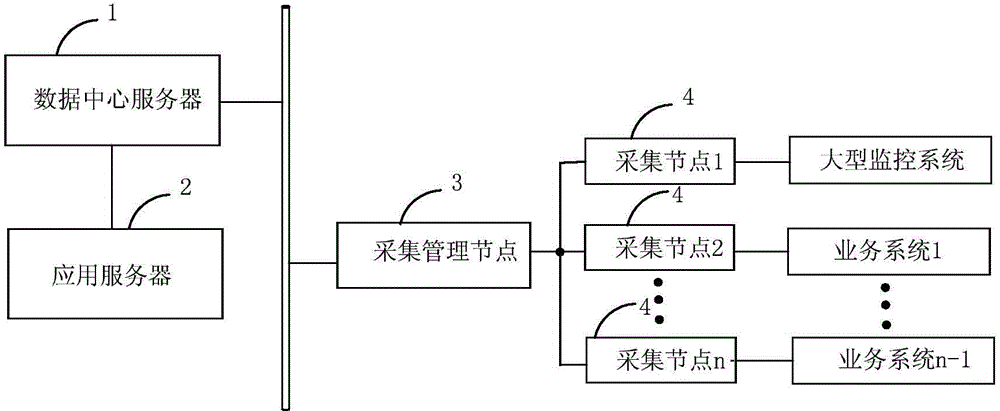
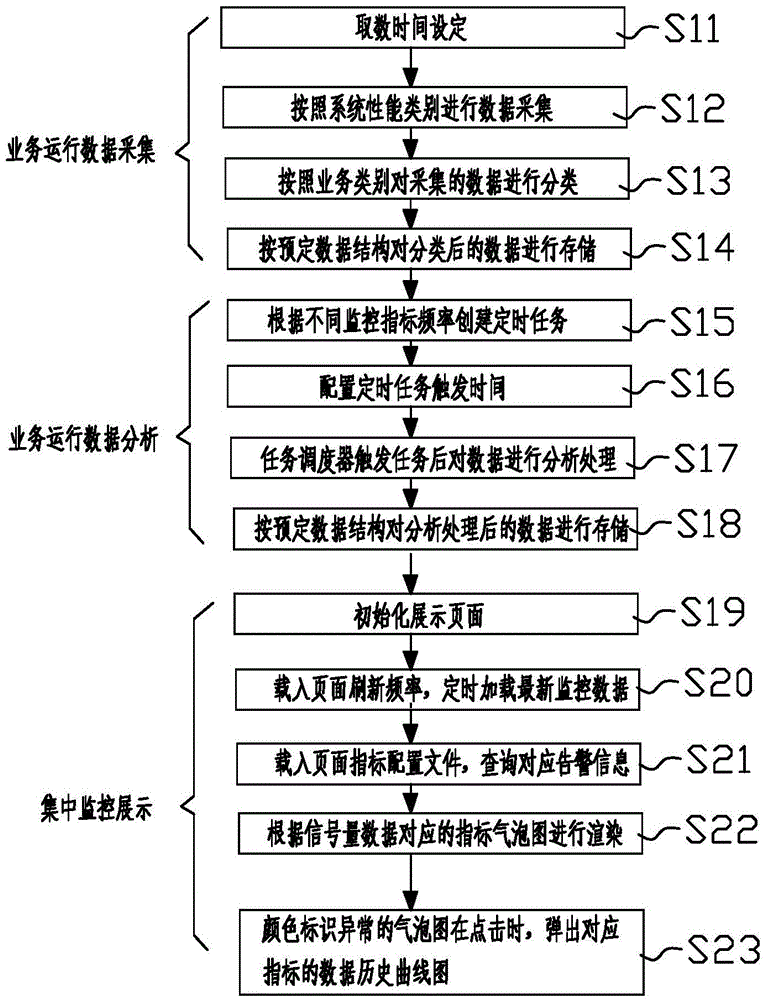
Centralized monitoring system and method based on data center
InactiveCN104407964ASmall scaleReduce Interaction ComplexityHardware monitoringTransmissionData centerMonitoring system
The invention provides a centralized monitoring system and a centralized monitoring method based on a data center. According to the system and the method disclosed by the invention, the data center is taken as an interface for data to flow in all steps, and thus seamless joint of all processing steps on data processing is realized; data acquisition time is preset according to generation time of system service data in bottom layer data acquisition; a data acquisition program is used for rapidly acquiring service operation data, including system state data, database and storage copy state, desk safety monitoring data, service processing data and the like; the data is stored in the data center in the form of a preset data structure; during data processing, the data can be screened, summated and compared according to a preset processing frequency by triggering a timed task according to a monitoring index frequency so as to generate fault alarming information; exhibition data such as fault alarming information, curve graph data and signal quantity data generated during an application exhibition use data processing process are exhibited to users in the forms of diagrams, sound, light and the like.
Owner:STATE GRID CORP OF CHINA +3
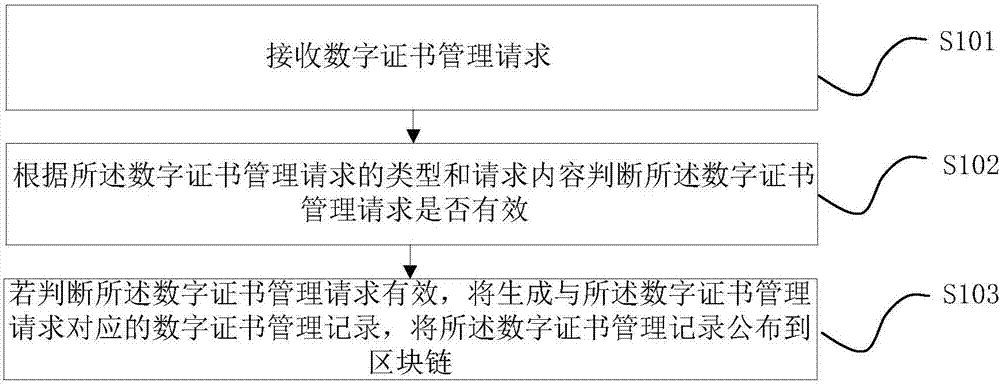
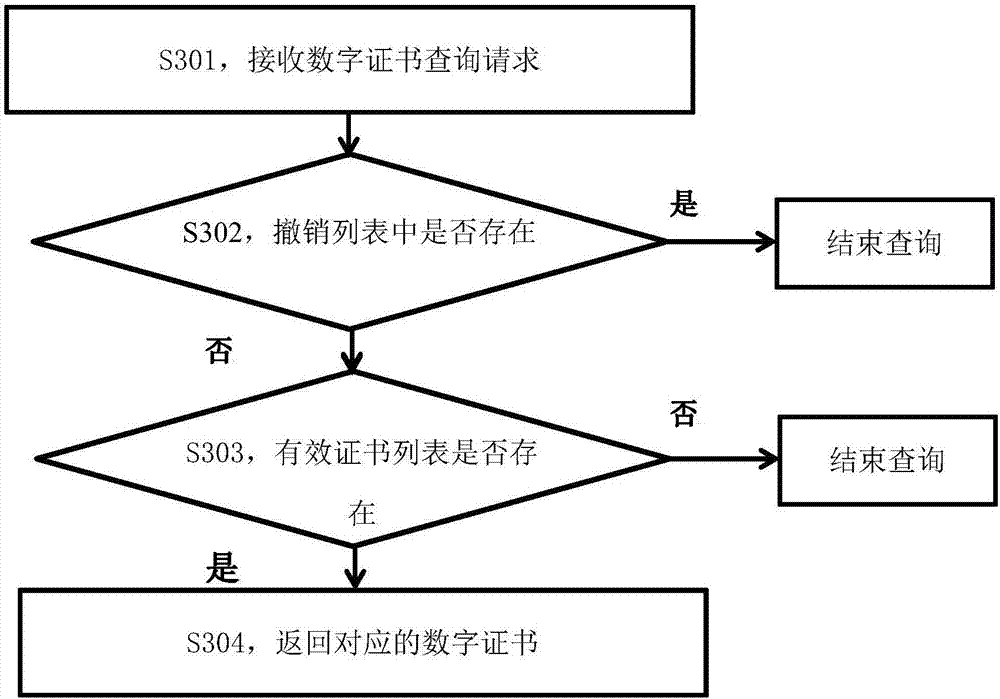
Digital certificate management method and system based on block chain
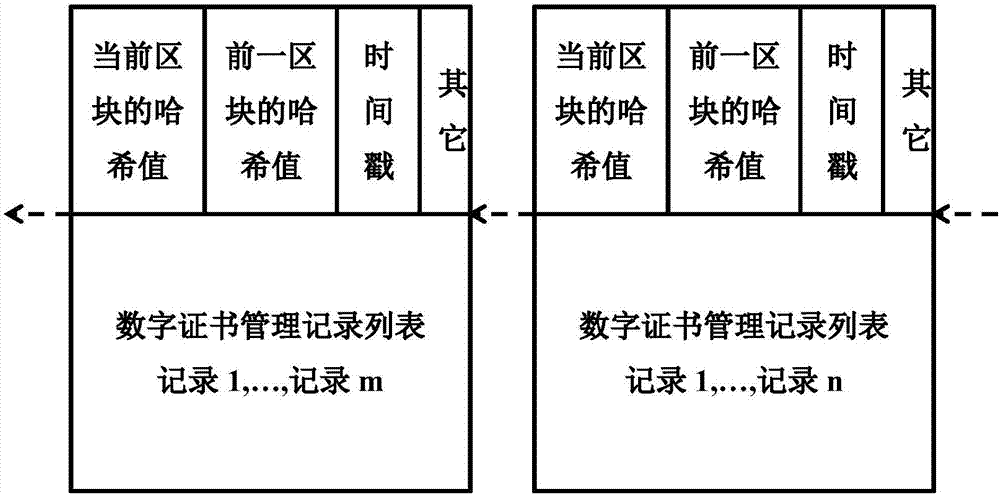
ActiveCN107425981AImprove distribution efficiencyImprove securityKey distribution for secure communicationUser identity/authority verificationDigital rights managementManagement system
The embodiment of the application provides a digital certificate management method and system based on a block chain. The method includes: receiving a digital certificate management request; determining whether the digital certificate management request is valid according to the type and request content of the digital certificate management request; and if yes, generating a digital certificate management record corresponding to the digital certificate management request, wherein the digital certificate management record is published to the block chain, the block chain is formed by link of a plurality of blocks in sequence according to the generation time, and each block comprises the generation time, a Hash value of the current block, a Hash value of a previous block, and one or more digital certificate management records. According to the method and system, the issuing efficiency of digital certificates and the stability of a digital certificate system can be effectively improved, faults of the digital certificate management system due to failure of a single node are prevented, and the security of the digital certificate management is effectively improved.
Owner:湖南岳麓山数据科学与技术研究院有限公司
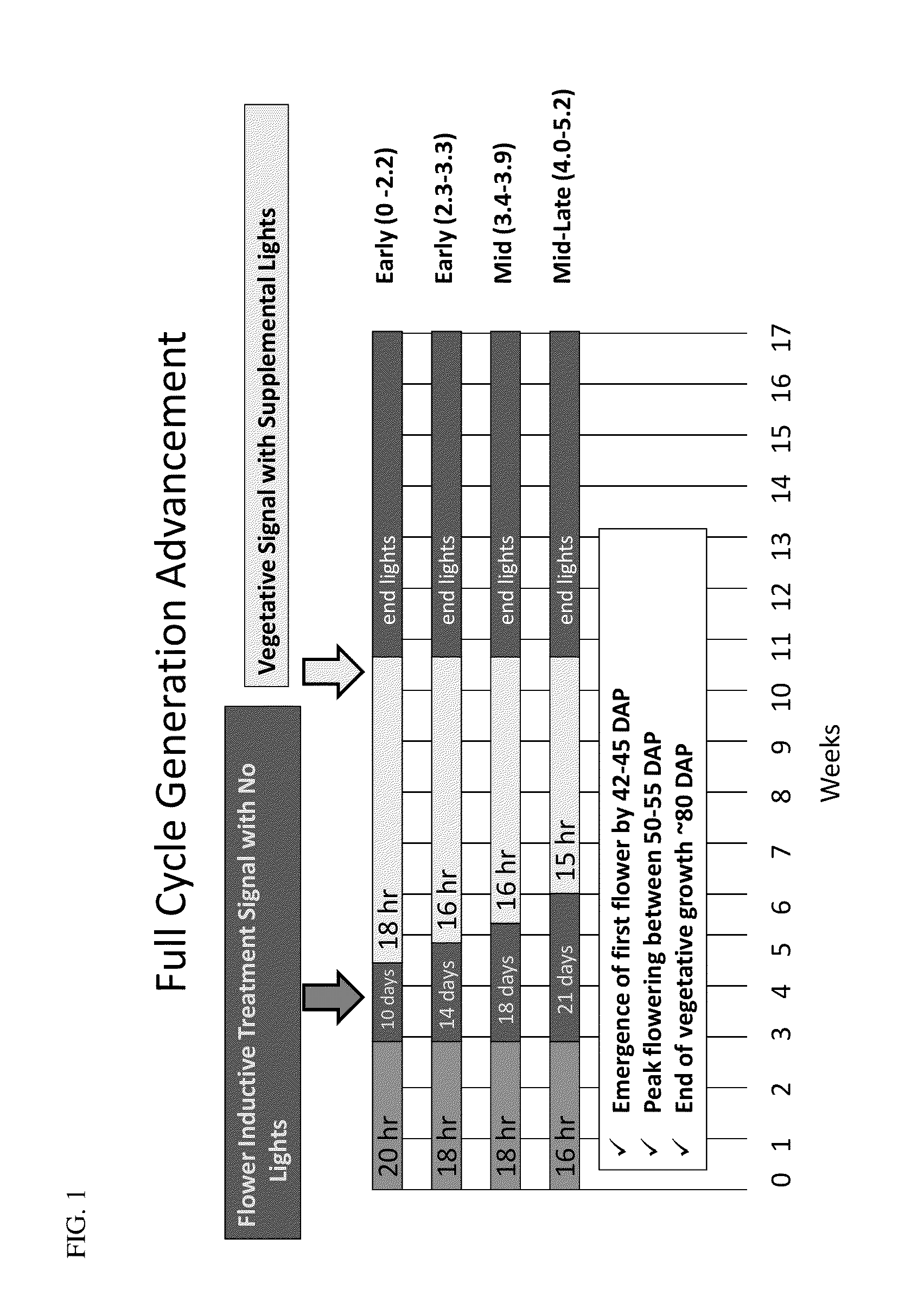
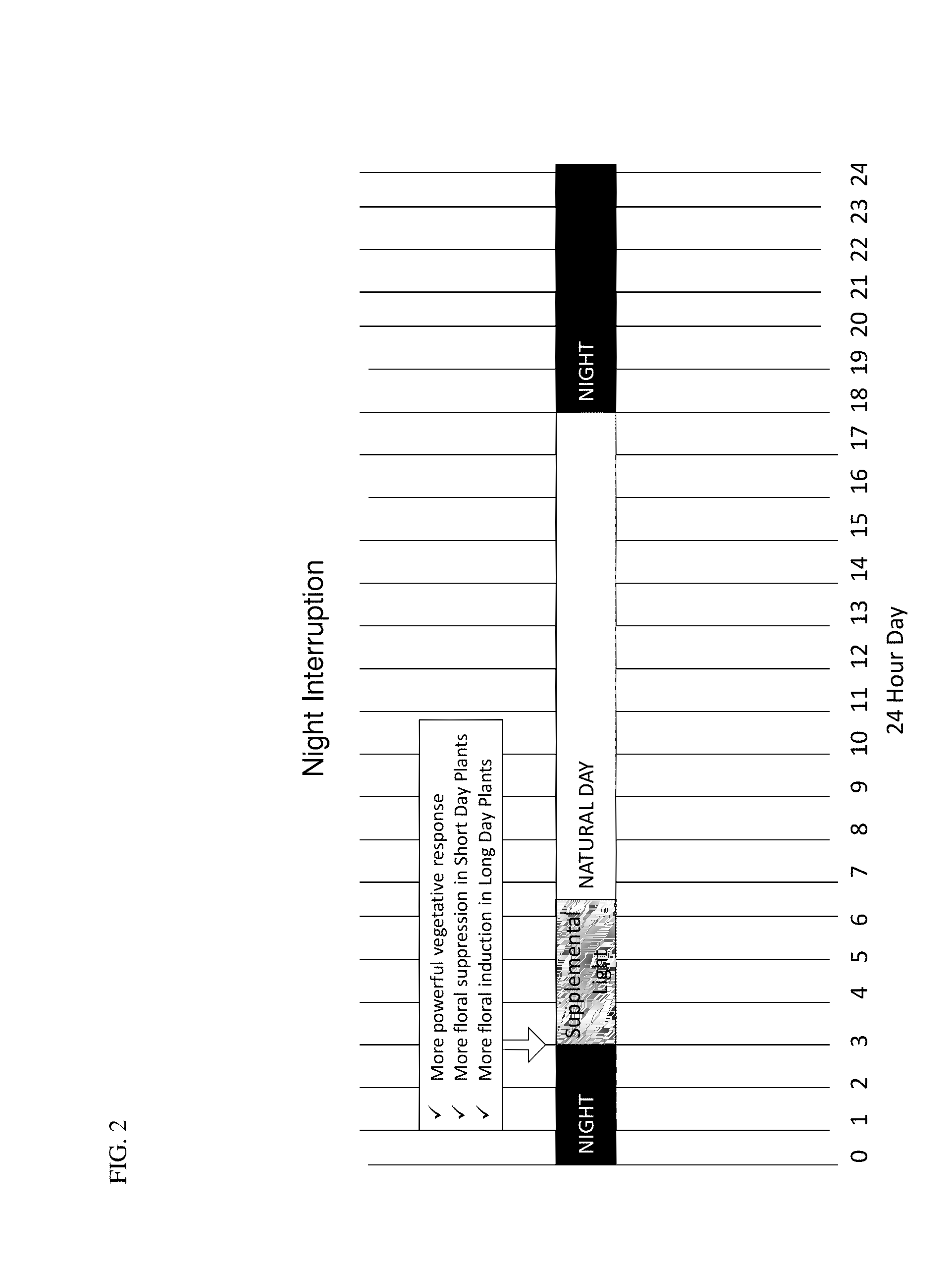
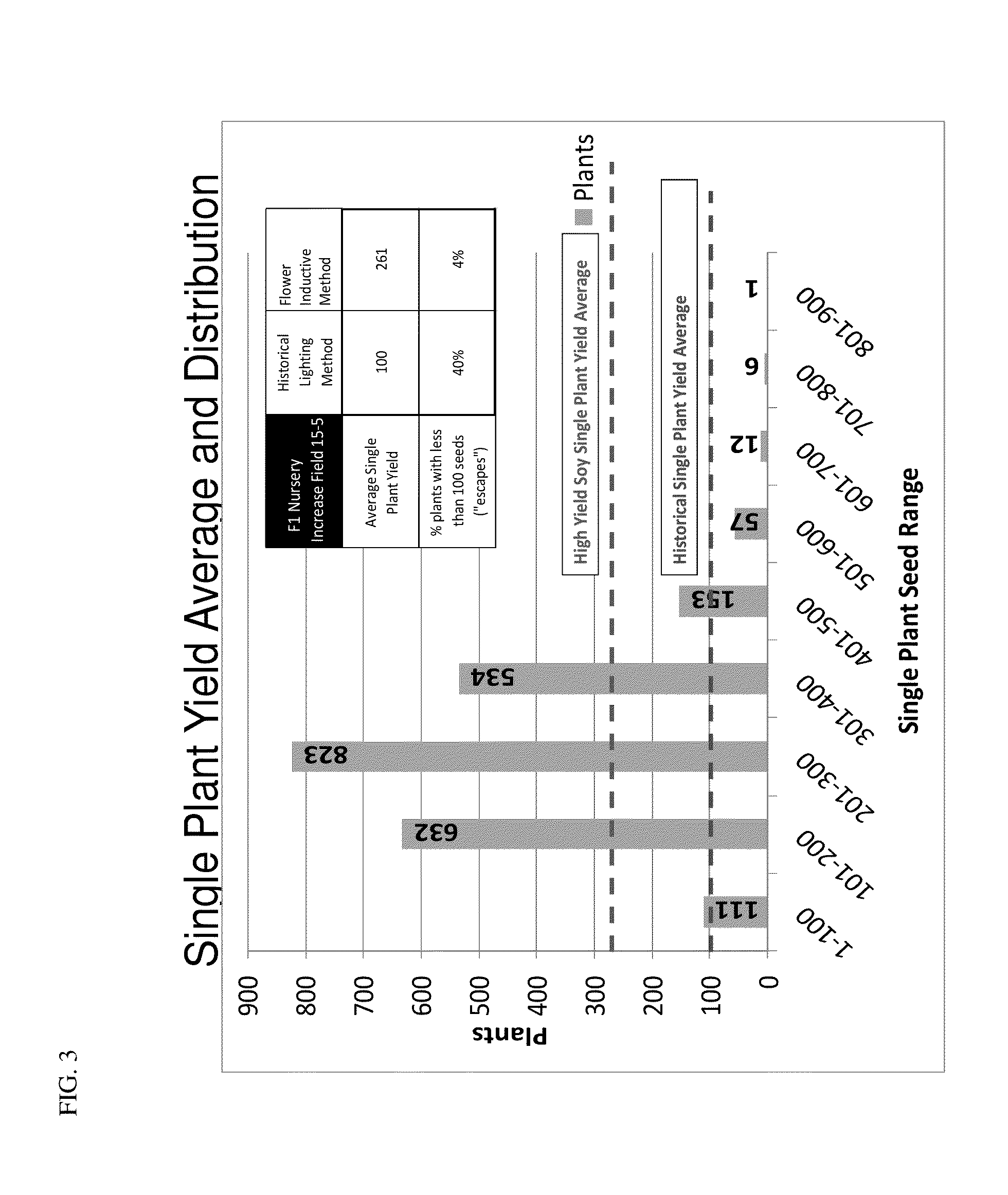
Methods for modifying flowering time and seed yield in field crops
Methods for manipulating yield and generation time of short day plants grown in a field environment are provided. The methods comprise manipulating external signals such as photoperiod in order to increase the per plant seed yield. Also provided are methods for synchronizing the flowering times of plants in different maturity groups.
Owner:MONSANTO TECH LLC
Method for simulating faults of power transformer
The invention discloses a method for simulating faults of a power transformer. According to a current mode and method for simulating the internal faults of the transformer, a returned transformer is commonly utilized to conduct fault simulation tests, or the fault stimulation tests are directly conducted in oil in the transformer, workload is large, fault modules need to be frequently replaced, and the simulation effect is poor. According to the method for simulating the faults of the power transformer, an electric power simulation transformer structure and a transformer fault model are used as the foundation, generation, disappearance and intensifying of transformer partial discharge faults and winding deformation faults are directly controlled outside a transformer body through an external regulation control method, and regulation can be safely conducted in the boosting process. By the adoption of the method for simulating the faults of the power transformer, the trouble of replacing the fault model in the fault simulating process is avoided, generation time and intensity of the faults in the boosting process can be conveniently regulated and controlled, and the method is accurate and efficient.
Owner:HANGZHOU XIHU ELECTRONICS INST
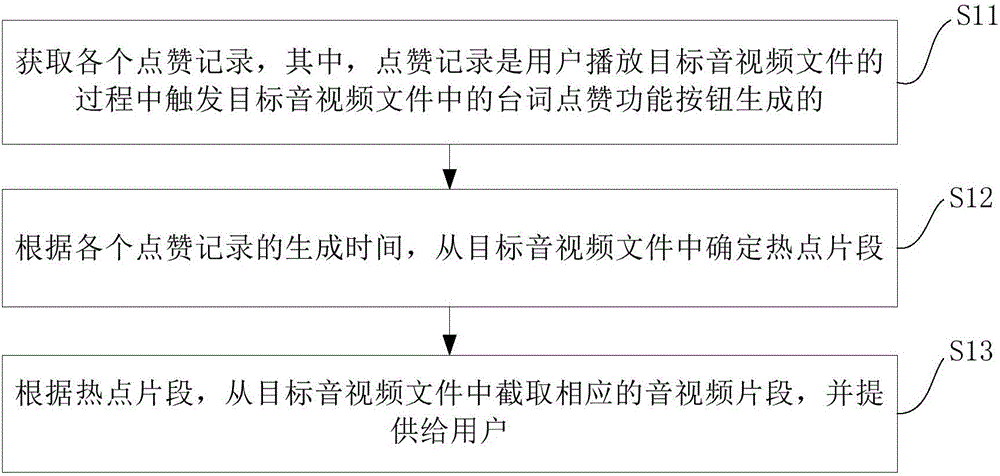
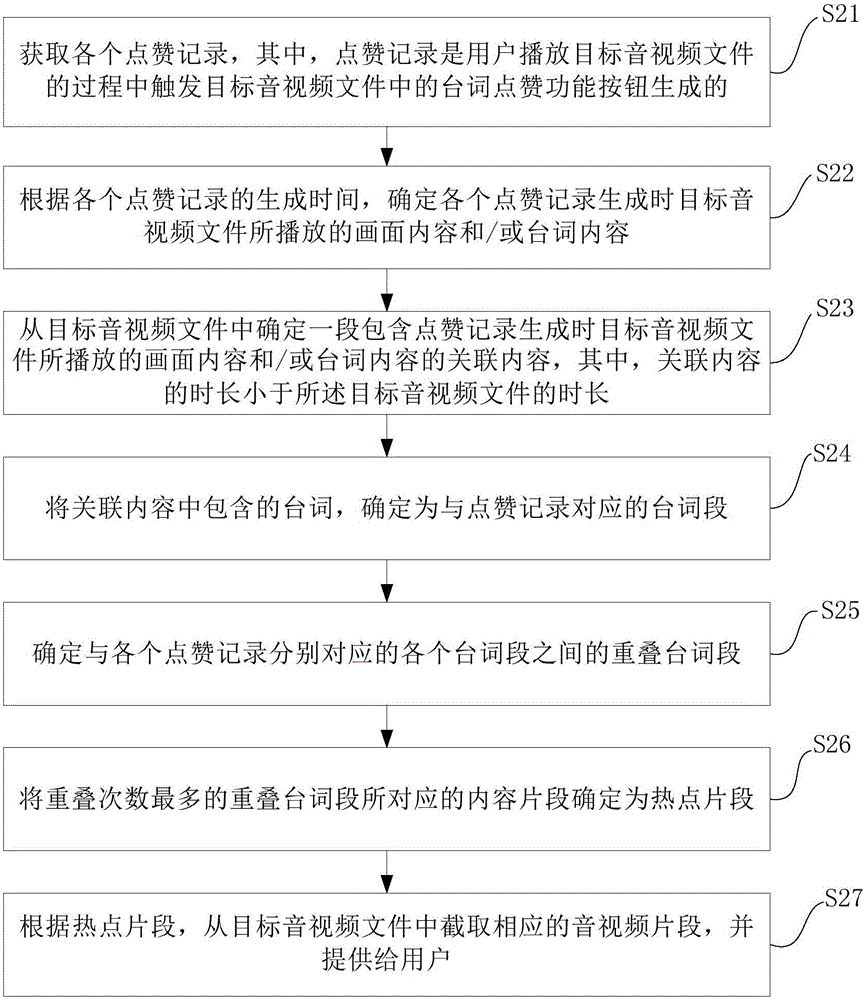
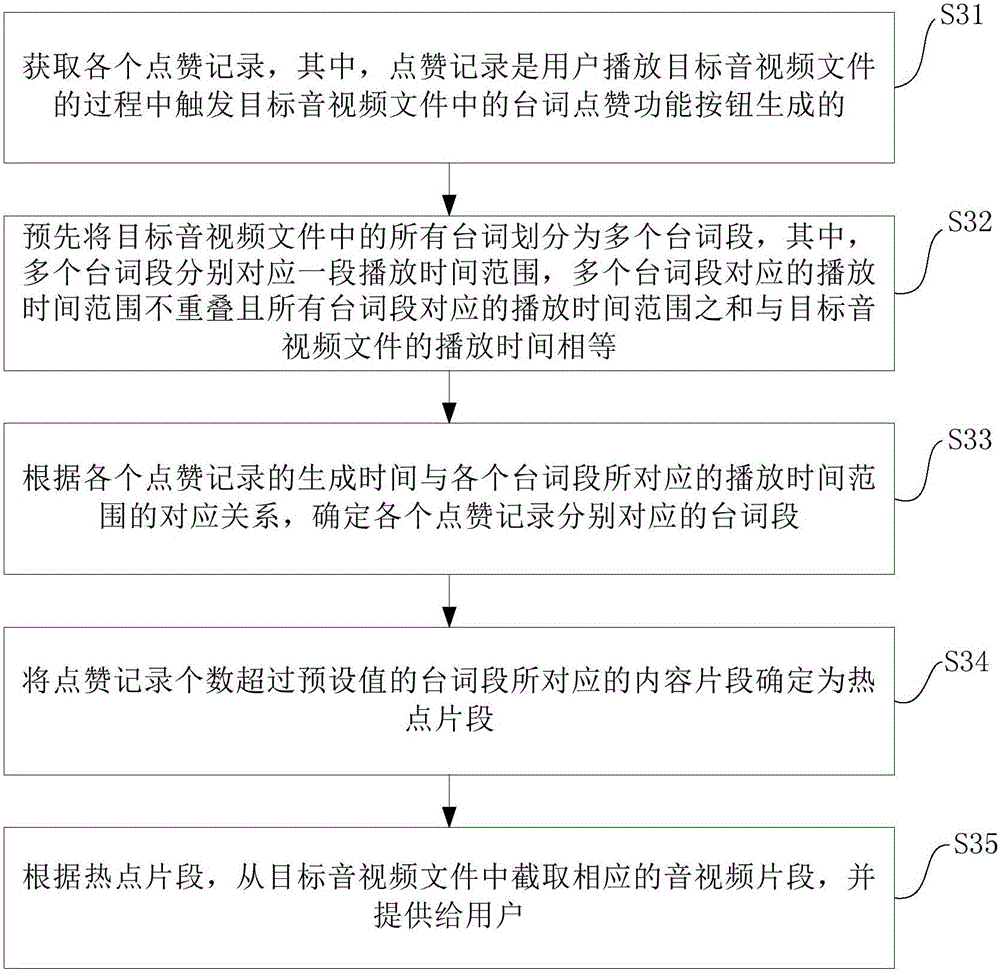
Audio/video segment providing method and device
The invention provides an audio / video segment providing method and device. The method comprises the following steps: acquiring each compliment record, wherein the compliment record is generated by a user by triggering a word compliment function button in a target audio / video file in a process of playing the target audio / video file; determining a hotspot segment from the target audio / video file according to a generation time of each compliment record; and intercepting a corresponding audio / video segment from the target audio / video file according to the hotspot segment, and providing the audio / video segment for the user. By adopting the audio / video segment providing method and device provided by the embodiment of the invention, the user can conveniently check wonderful fragments in the video.
Owner:LETV HLDG BEIJING CO LTD +1
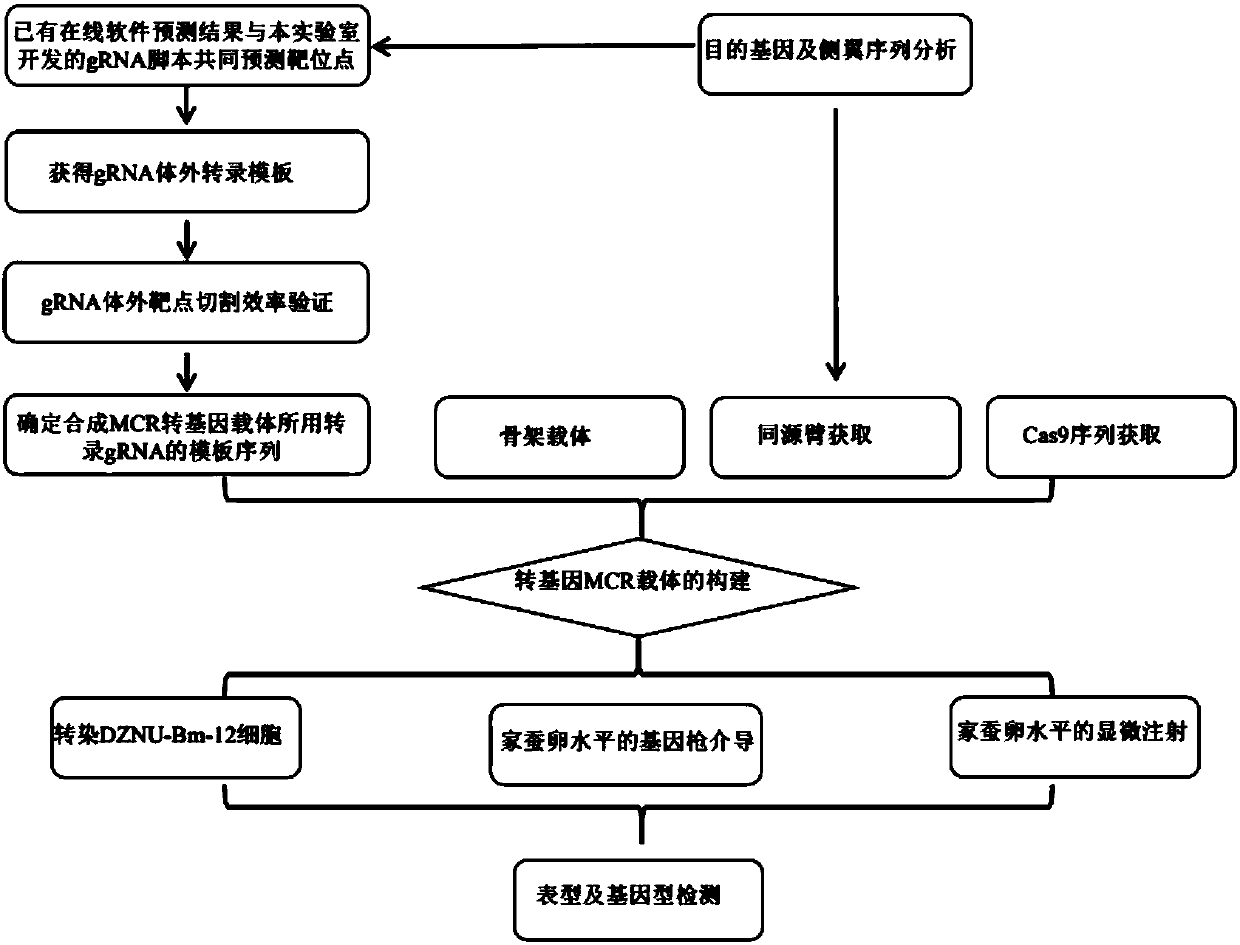
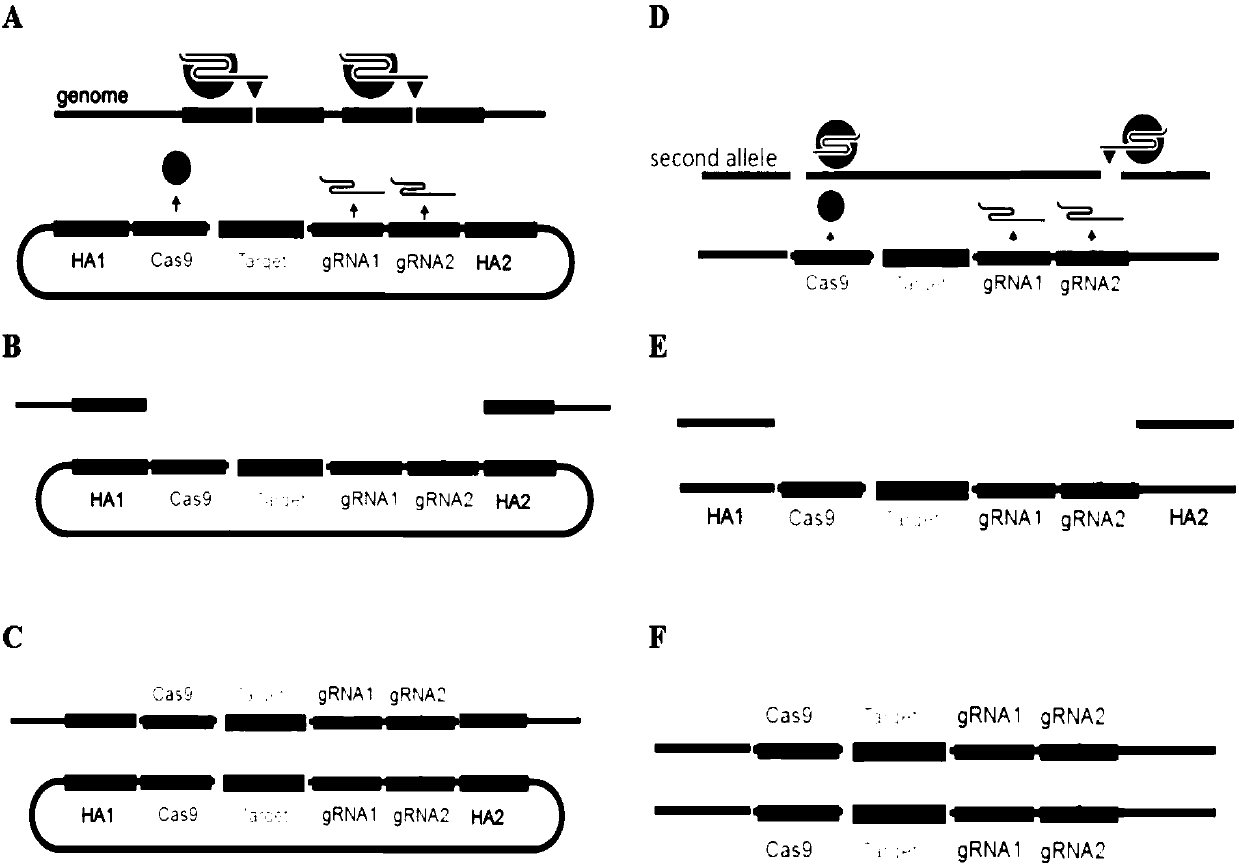
Precision and high-efficiency transgenic carrier as well as construction method and application thereof
ActiveCN107760715AReduce workloadReduce subsequent crossesStable introduction of DNAVector-based foreign material introductionA-DNACatalytic effect
The invention discloses a precision and high-efficiency transgenic carrier as well as a construction method and application thereof. The transgenic carrier is obtained by completely assembling a genecoding CRISPR / Cas9 proteins, a DNA template of gRNAs, a homologous arm of a target gene side wing and a target gene to be transferred into a same plasmid vector. By adopting the precision and high-efficiency transgenic carrier as well as the construction method and application thereof, the workload and the subsequent hybridization for operating the gene in a laboratory can be significantly reduced, the homozygote generation time can be shortened, and the transgenic efficiency can be significantly increased. Based on an MCR method, the external target gene and the Cas9 gene are jointly transferred into silkworm genome in the process for precisely modifying the gene by virtue of the catalytic effect of the Cas9, the homozygote can be generated in a G0 generation, i.e. the mutation generatedon one copy can be automatically propagated onto an allele.
Owner:山东菌胜生物科技有限责任公司
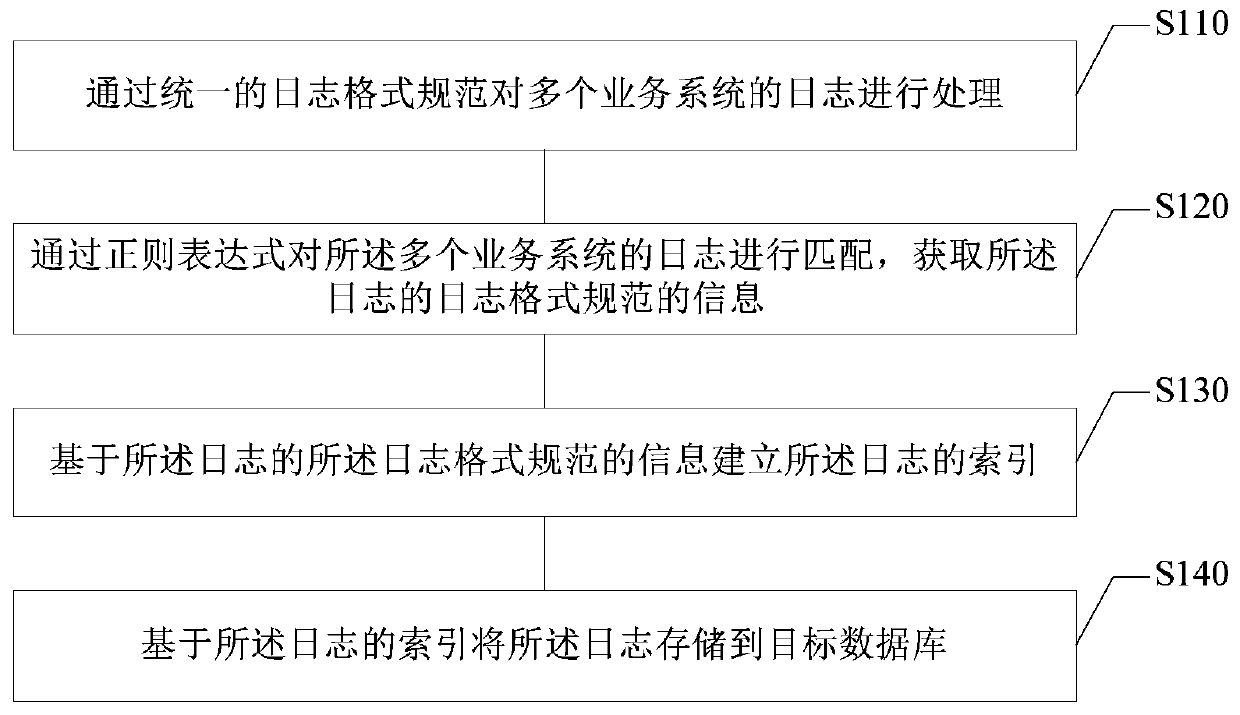
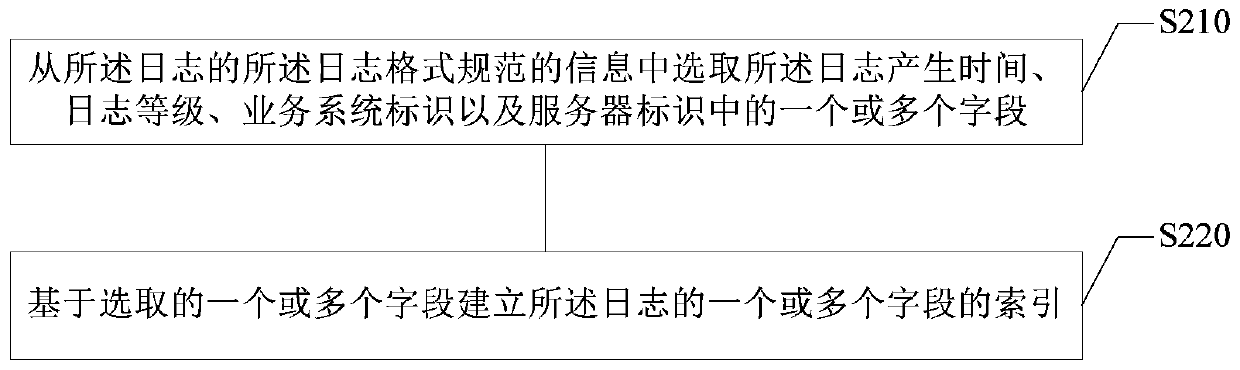
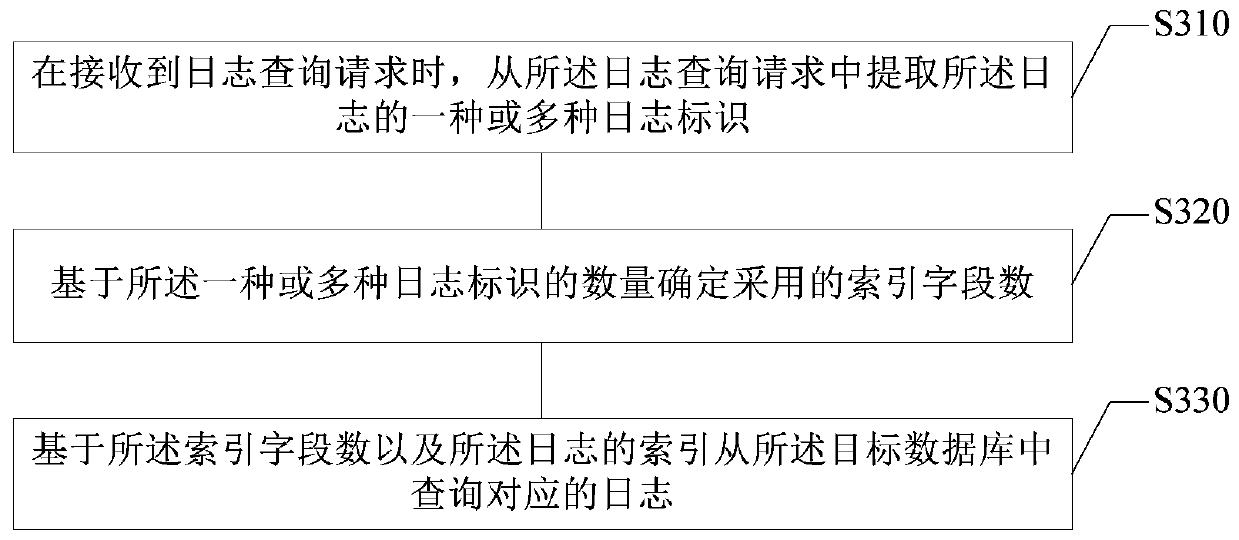
Log processing method and device, electronic equipment and storage medium
PendingCN109800223AEase of batch processingImprove query efficiencySpecial data processing applicationsDatabase indexingBatch processingRegular expression
The embodiment of the invention provides a log processing method and device, electronic equipment and a storage medium, and relates to the technical field of computers. The method comprises the following steps: processing logs of a plurality of business systems through a unified log format standard; matching the logs of the plurality of business systems through a regular expression to obtain log format specification information of the logs with the log format specification information comprising log generation time, log levels, business system identifiers and server identifiers; establishing an index of the log based on the information of the log format specification of the log; and storing the log into a target database based on the index of the log. According to the technical scheme provided by the embodiment of the invention, logs of various business systems can be unified, batch processing of the logs is facilitated, and the log query efficiency can be improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
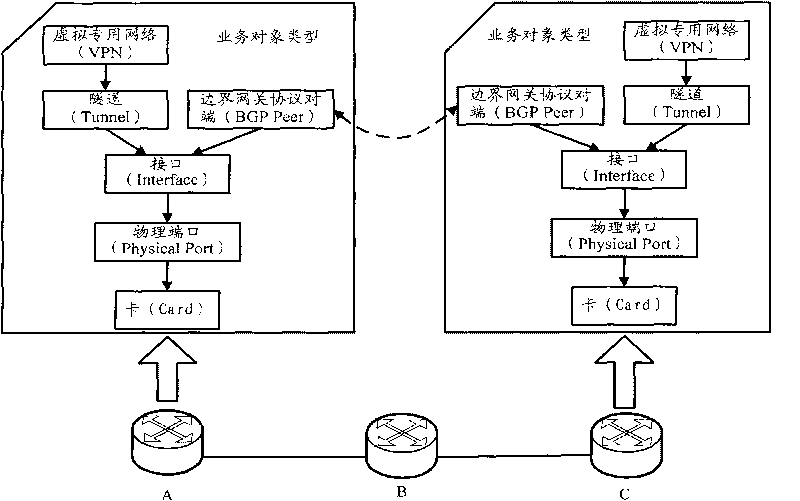
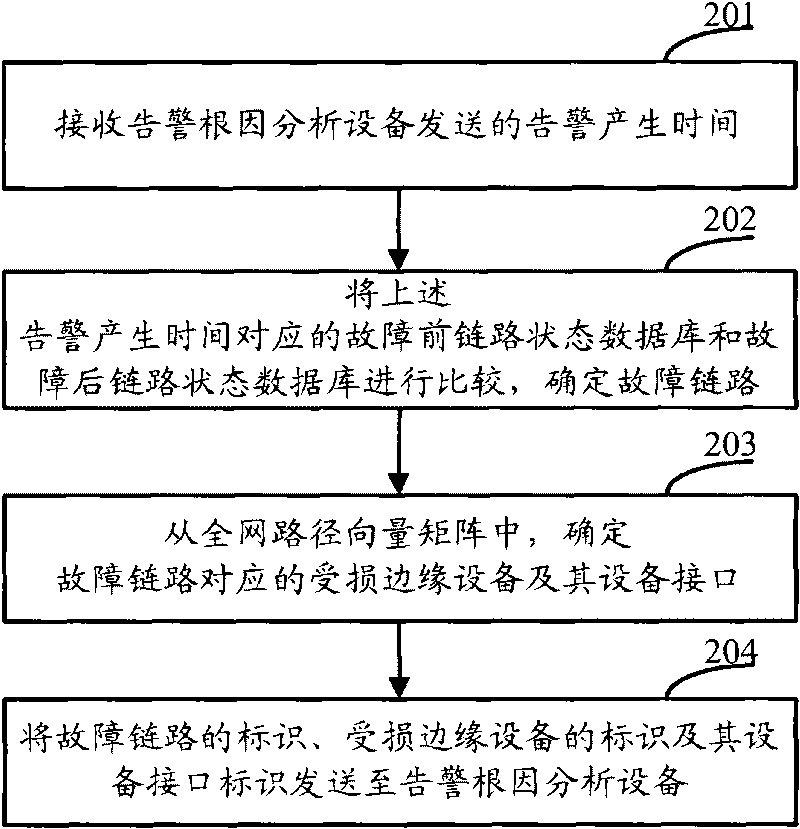
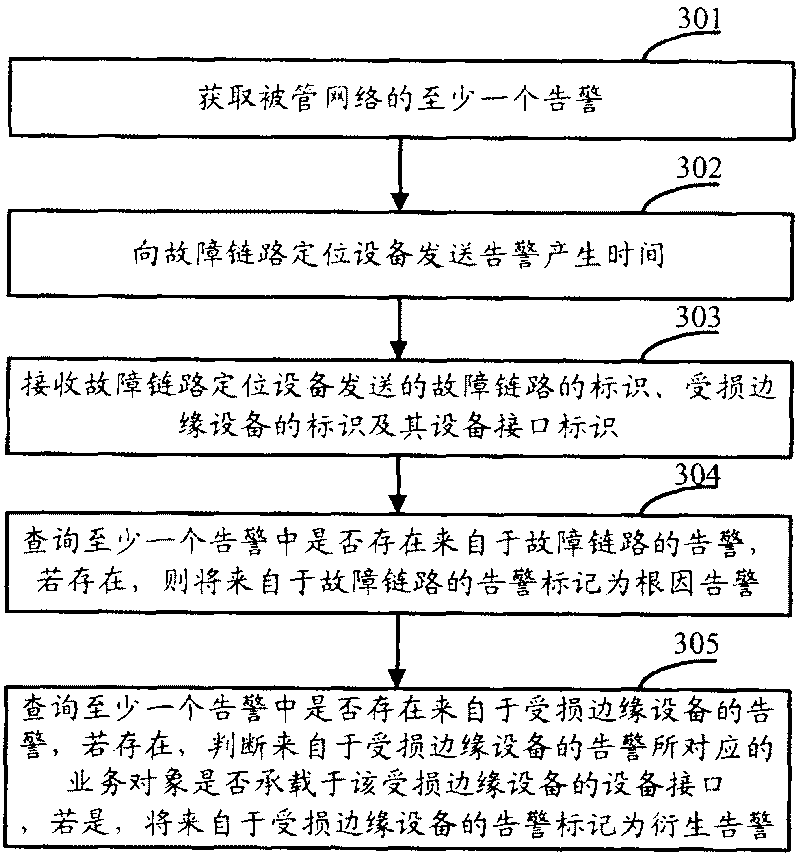
Positioning method of failed link and alarm root cause analyzing method, equipment and system
ActiveCN101707537AAvoid collectingReduce consumptionData switching networksRoot causeRoot cause analysis
The embodiment of the invention discloses a positioning method of a failed link as well as alarm root cause analyzing method, equipment and system, wherein the alarming root cause analyzing method comprises the steps of: acquiring at least one alarm of a managed network; sending alarm generation time to positioning equipment of the failed link; receiving a mark of the failed link, a mark of damaged edge equipment and an equipment interface mark of the damaged edge equipment, which are sent by the positioning equipment of the failed link; querying whether the at least one alarm contains the alarm from the failed link or not, if so, marking the alarm from the failed link as a root cause alarm; judging whether the alarm from the damaged edge equipment exists or not, if so, judging whether a service object corresponding to the alarm is loaded on an equipment interface of the damaged edge equipment or not, and if so, marking the alarm from the damaged edge equipment as a derivative alarm. The embodiment of the invention can realize the network-level alarm root cause analysis, prevent the route information of all equipment in the network from being acquired and reduce the network resource consumption.
Owner:HUAWEI TECH CO LTD
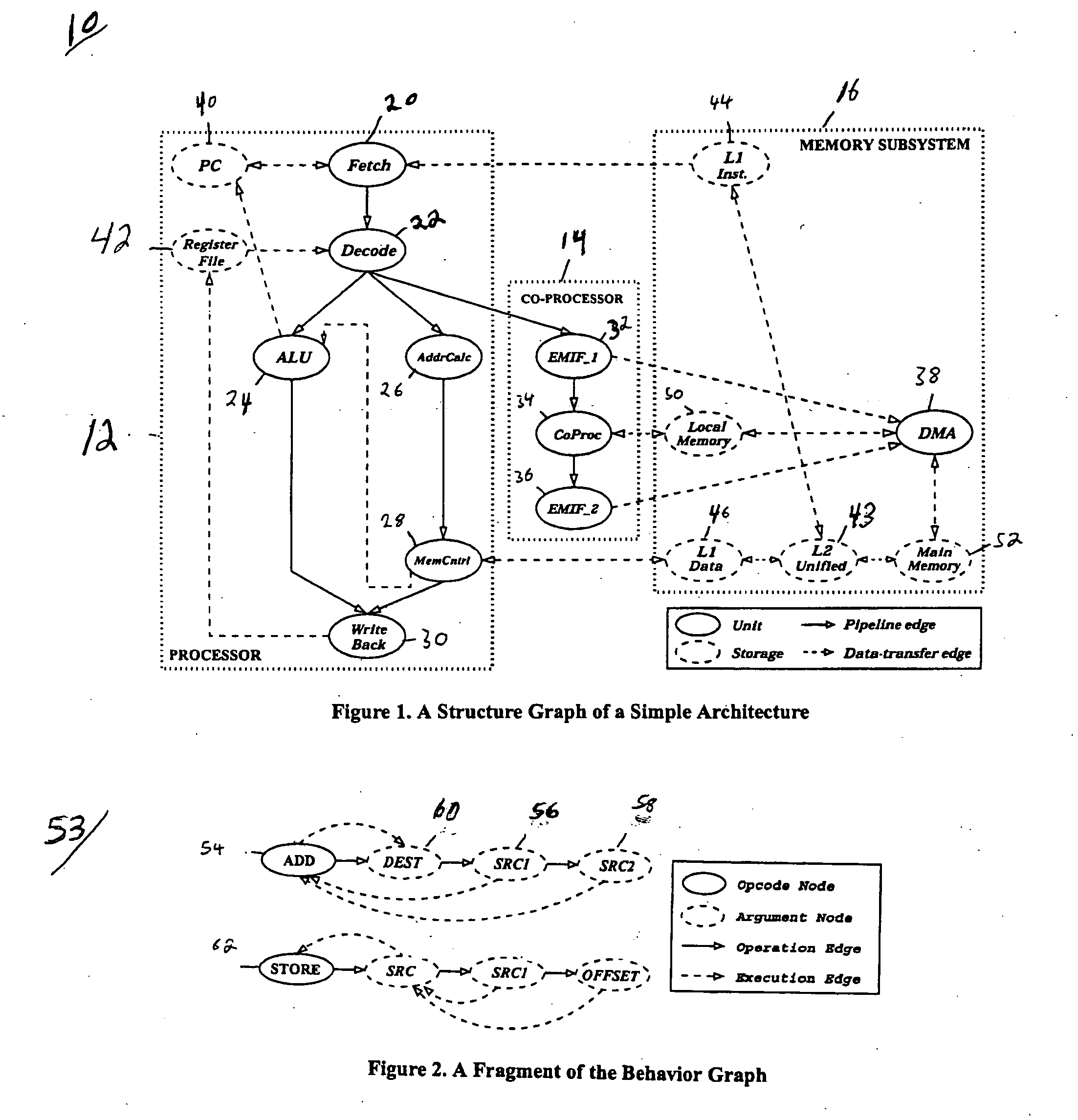
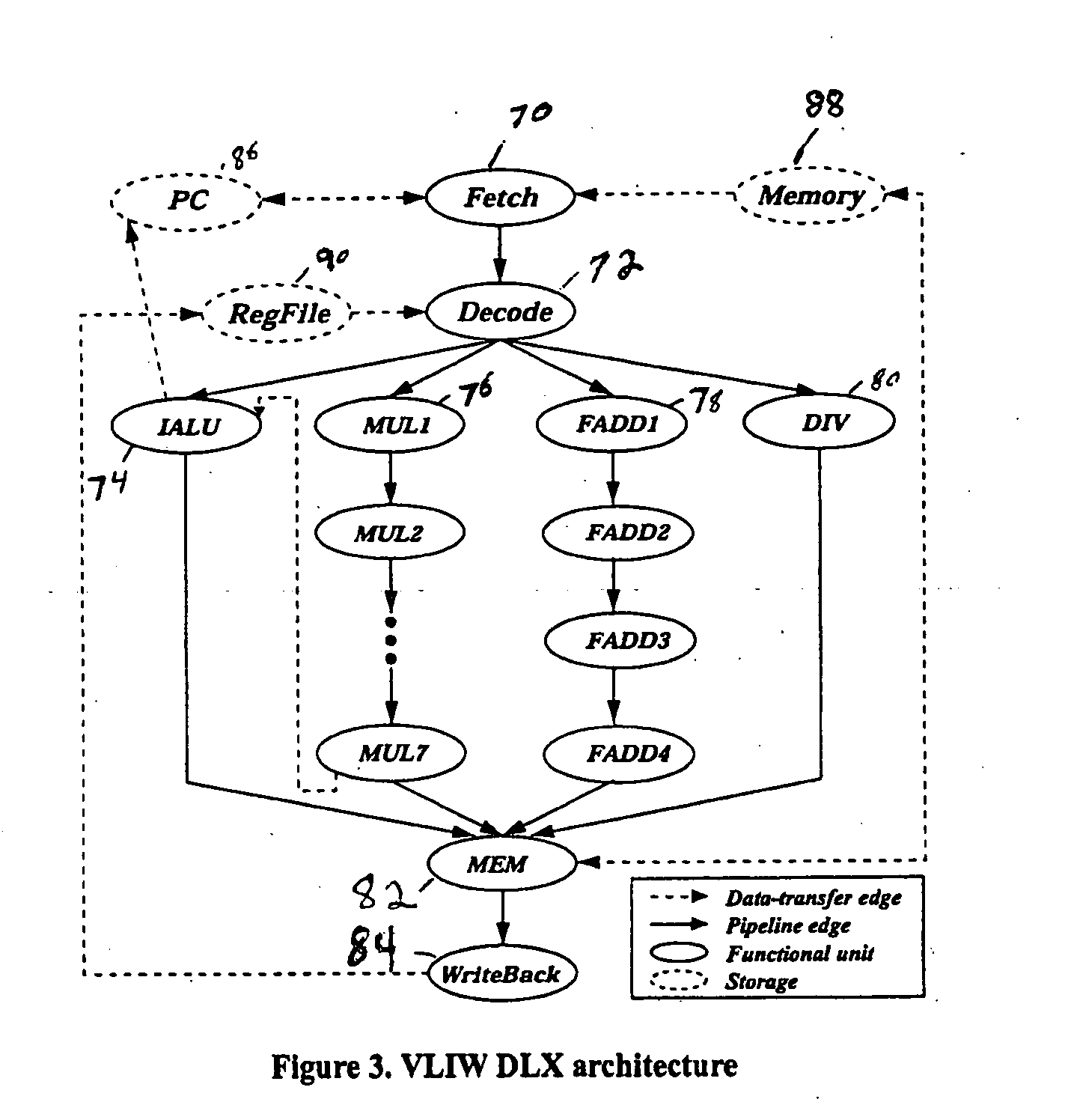
Functional coverage driven test generation for validation of pipelined processors
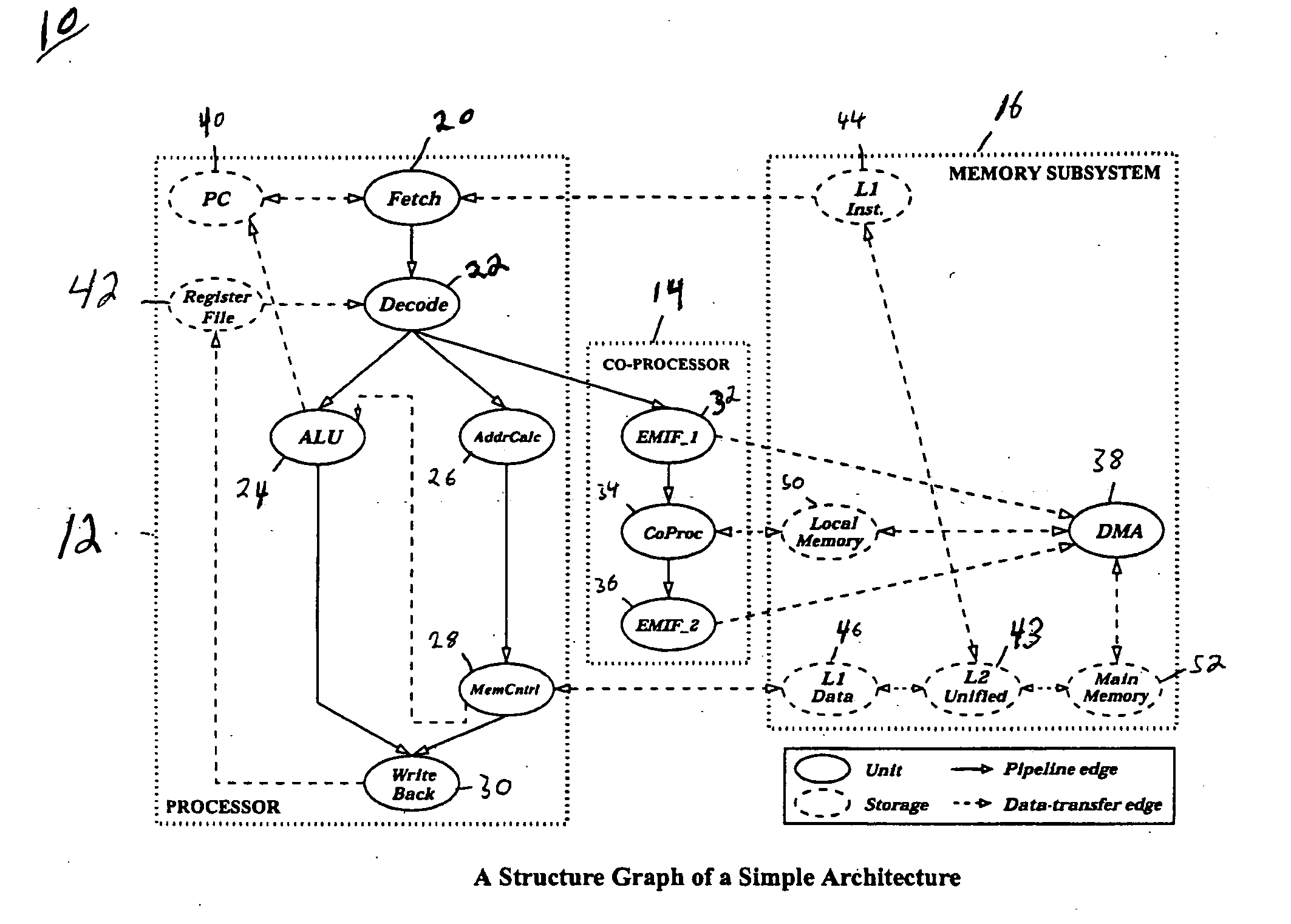
ActiveUS20060107158A1Handle large designReduce build timeElectronic circuit testingError detection/correctionGraphicsComputer architecture
A functional coverage based test generation technique for pipelined architectures is presented. A general graph-theoretic model is developed that can capture the structure and behavior (instruction-set) of a wide variety of pipelined processors. A functional fault model is developed and used to define the functional coverage for pipelined architectures. Test generation procedures are developed that accept the graph model of the architecture as input and generate test programs to detect all the faults in the functional fault model. A graph model of the pipelined processor is automatically generated from the specification using functional abstraction. Functional test programs are generated based on the coverage of the pipeline behavior. Module level property checking is used to reduce test generation time.
Owner:RGT UNIV OF CALIFORNIA
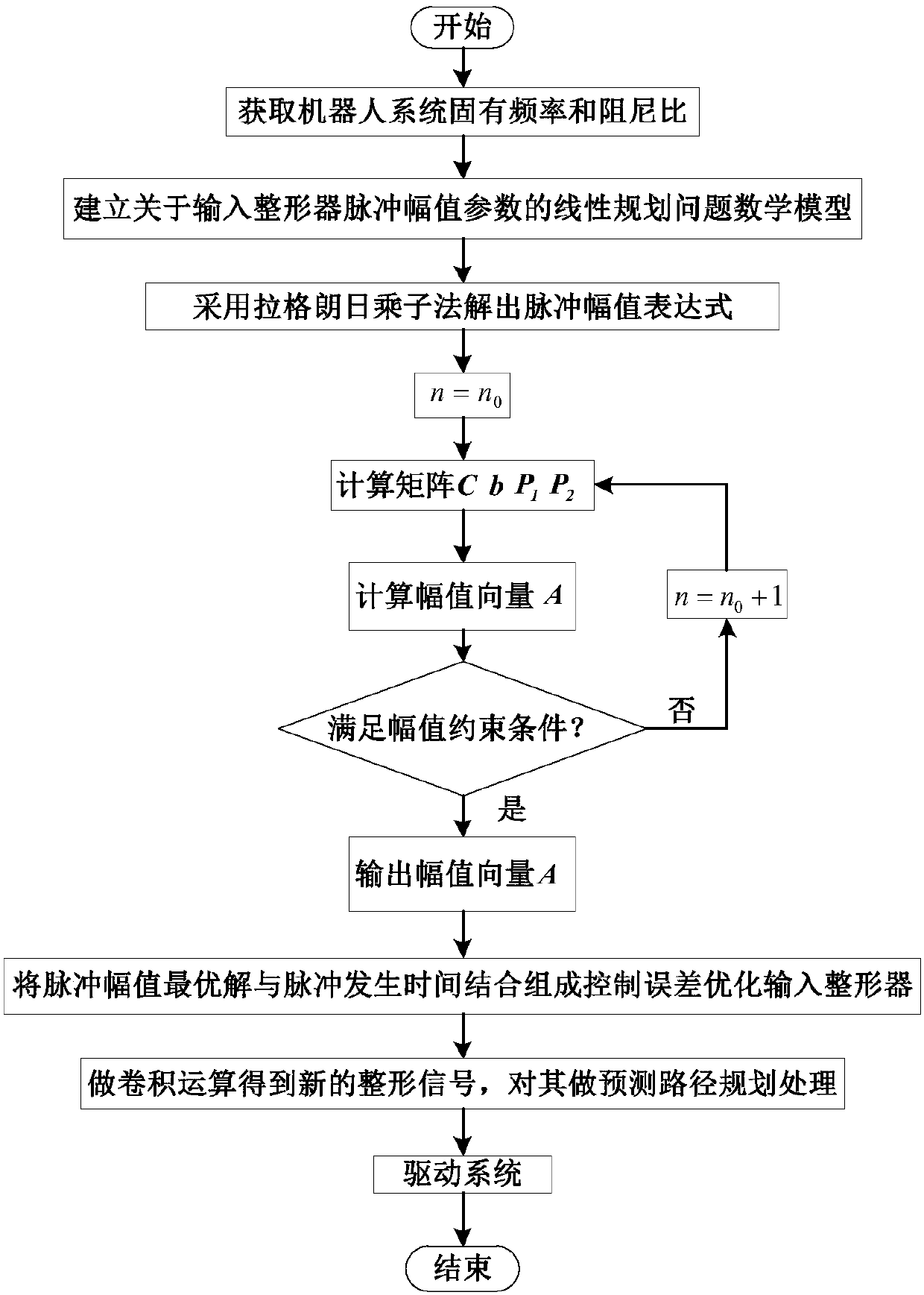
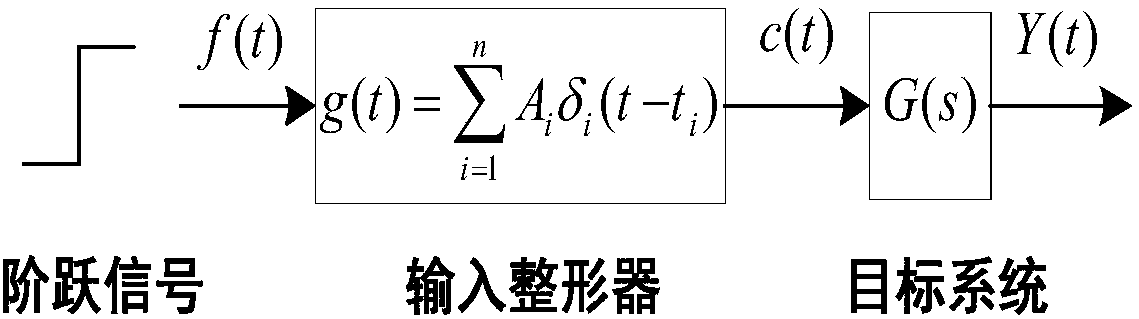
Robot joint tail end residual vibration restraining method based on input shaper
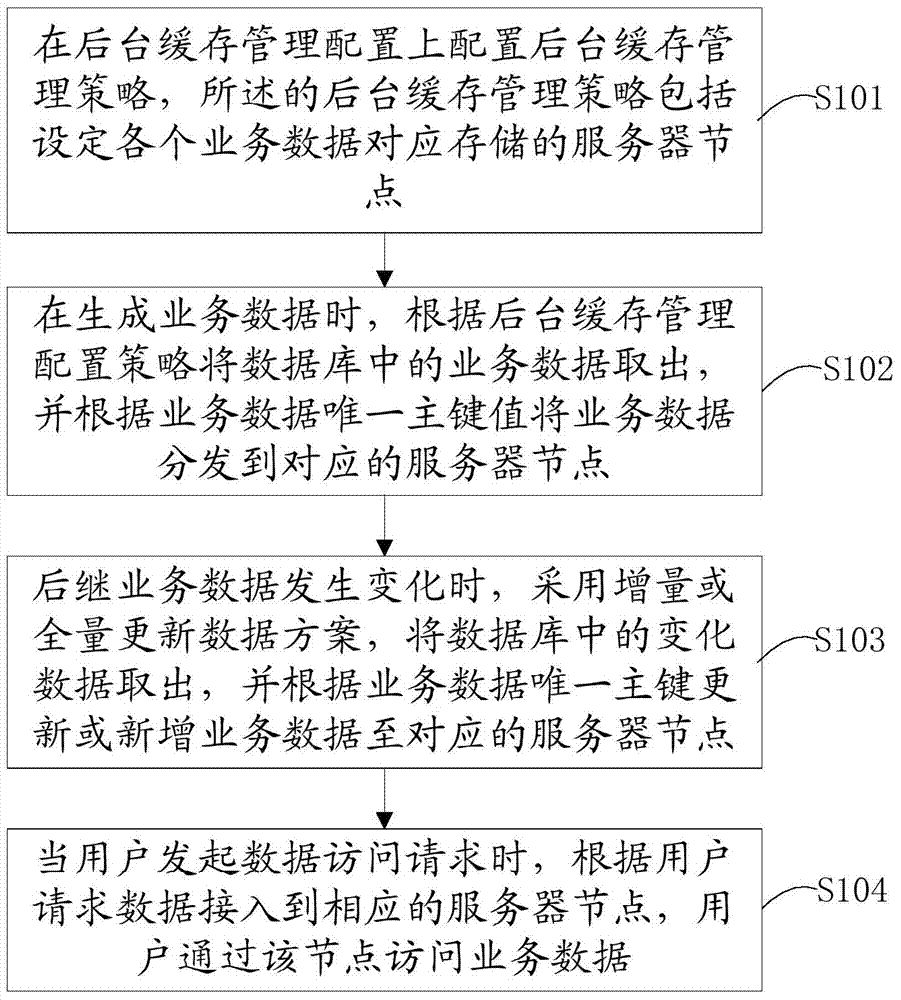
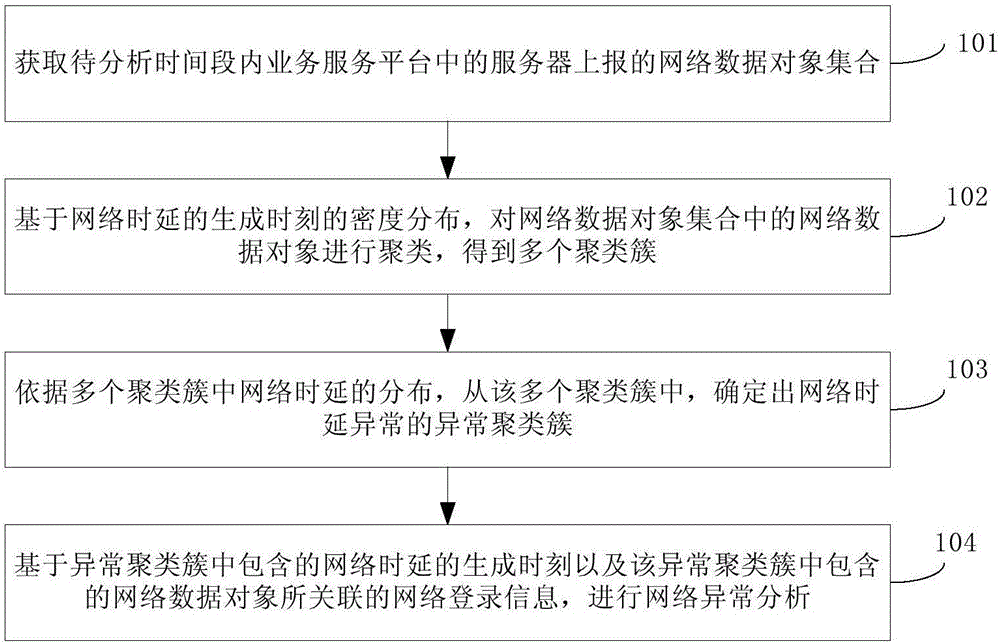
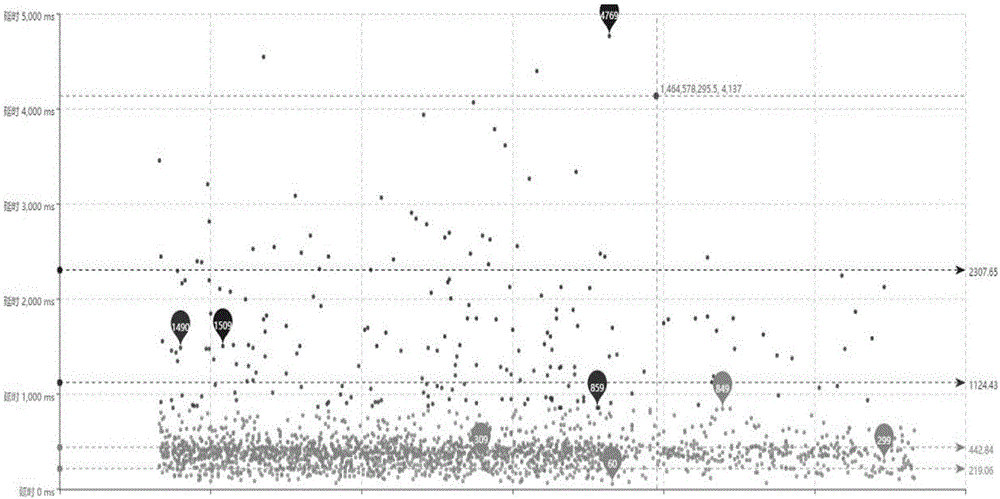
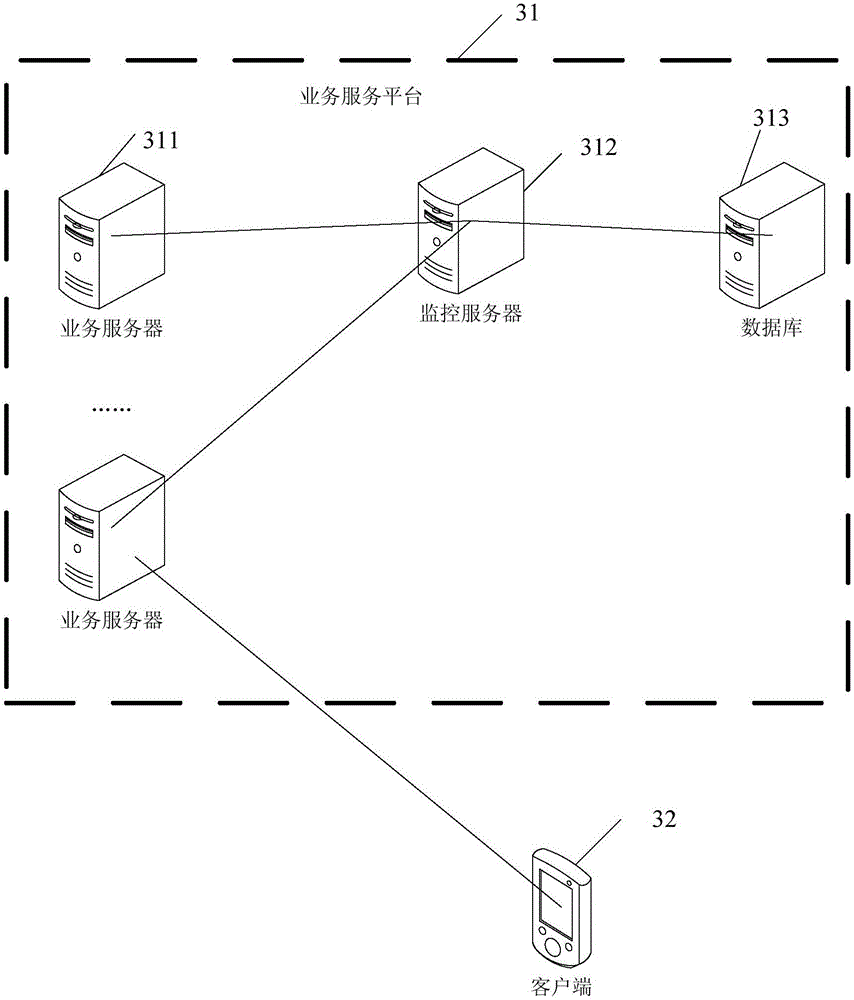
The invention discloses a robot joint tail end residual vibration restraining method based an input shaper. The robot joint tail end residual vibration restraining method based the input shaper comprises the steps that firstly, the undamped inherent frequency omega0 and the damping ratio zeta of a robot system are obtained; secondly, a linear programming problem mathematic model about the pulse amplitude parameter of the input shaper is established; thirdly, a pulse amplitude expression is solved through a lagrangian multiplier method, and the optimal solution of the pulse amplitude is workedout through iteration; fourthly, the optimal solution of the pulse amplitude and the pulse generation time are combined to form the control error optimization input shaper; and fifthly, a reference signal and the control error optimization input shaper are subjected to convolution operation, so that a novel shaping signal is obtained, and after a predicted path is planned for the novel shaping signal, the system is driven by the signal to restrain robot tail end residual vibration. According to the robot joint tail end residual vibration restraining method based the input shaper, the robustness of the input shaper is enhanced, and a process control error and a positioning error are minimized; and the predicted path is planned for the shaped signal, and thus the system lag time caused by input shaping is compensated and reduced.
Owner:SOUTH CHINA UNIV OF TECH
Method and equipment for obtaining node transmission information of transmission path
The invention provides a method and a device for acquiring node transmission information on a transmission path. The method comprises: network time of a source node and a target node are synchronized, when the source node transmits a Ping message to the target node, the transmission time of the message is recorded in the IP header option field of the Ping message; after the Ping message reaches the target node, at least one of the following information is recorded: the IP header option field which copies the transmission time to the Ping reply message, the time when the target node receives the Ping message, the time when the Ping reply message is generated, the time when the Ping reply message is transmitted, the CPU occupancy rate the memory occupancy rate, the interface type and MTU when the Ping reply is generated. At least one of the above information is transmitted to the source node; and according to the transmission time of the source node, the receiving time of the target node, the generation time and the transmission time, the delay information is calculated and CPU utilization rate, the memory occupancy rate, the interface type and the MTU are extracted. The invention can easily and effectively acquire relevant delay information system information and interface information of each node in the transmission path,.
Owner:CHINA TELECOM CORP LTD
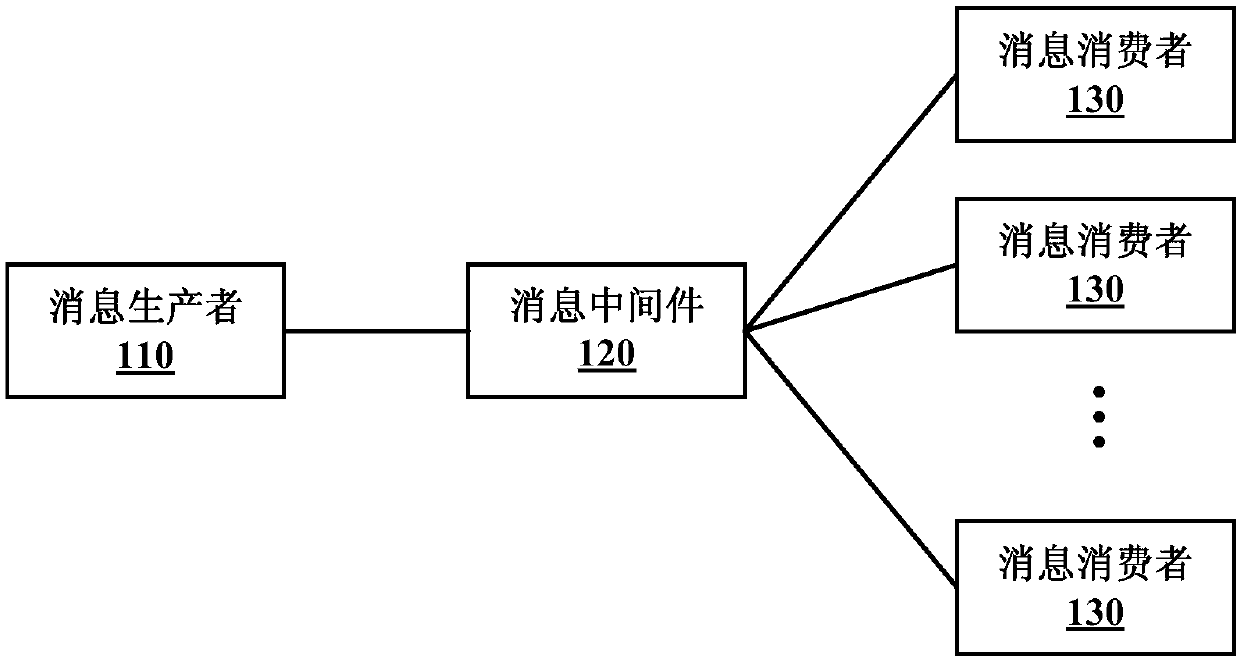
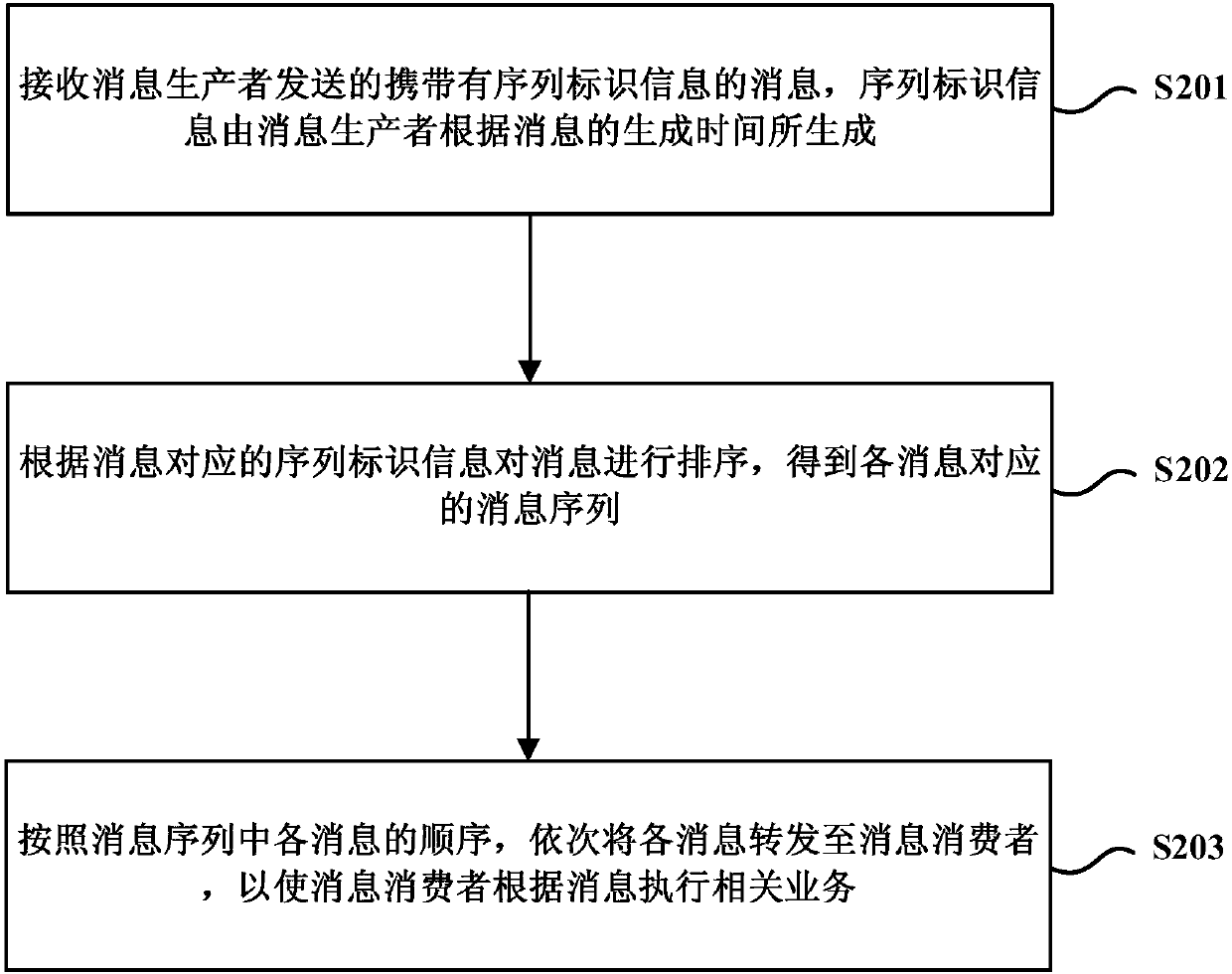
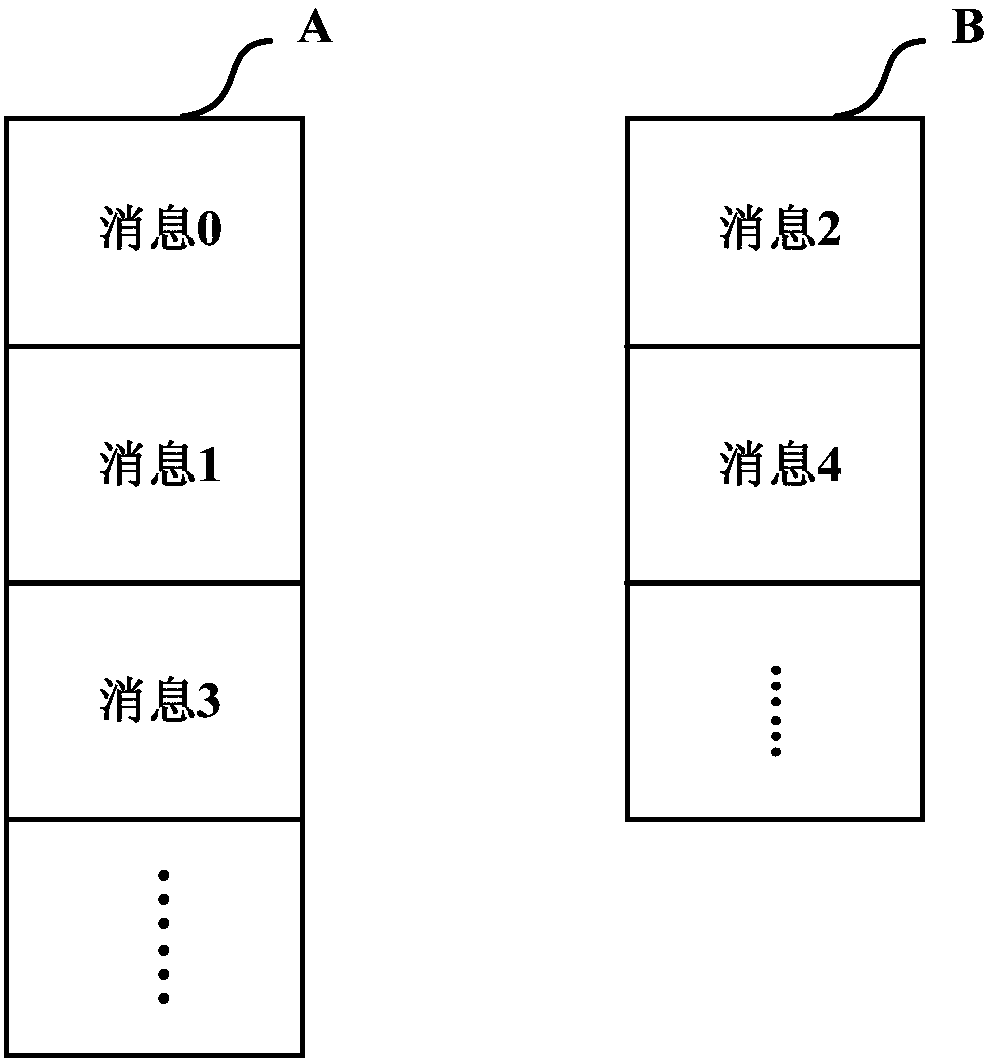
Message processing methods, message processing devices and message processing system
InactiveCN107656825AEnsure consistencyReliable deliveryInterprogram communicationHardware monitoringMessage processingMessage passing
The embodiment of the application discloses message processing methods, message processing devices and a message processing system, which are used for realizing reliable message passing among heterogeneous systems. The method includes: receiving messages which are sent by a message producer and carry sequence identification information, wherein the sequence identification information is generatedby the message producer according to generation times of the messages; sorting the messages according to the sequence identification information, which corresponds to the messages, to obtain a messagesequence corresponding to each message; and forwarding each message to a message consumer in sequence according to an order of each message in the message sequence to enable the message consumer to execute a related service according to the message. According to the technical solution, consistency of consumption and sending of the messages on orders is ensured, then reliable message passing amongthe heterogeneous systems is ensured, and a situation that related-service disruption is caused when the consumption order and the sending order of the messages are inconsistent is avoided.
Owner:SHANGHAI AILONG INFORMATION TECH
Method for monitoring traffic in packet switched network
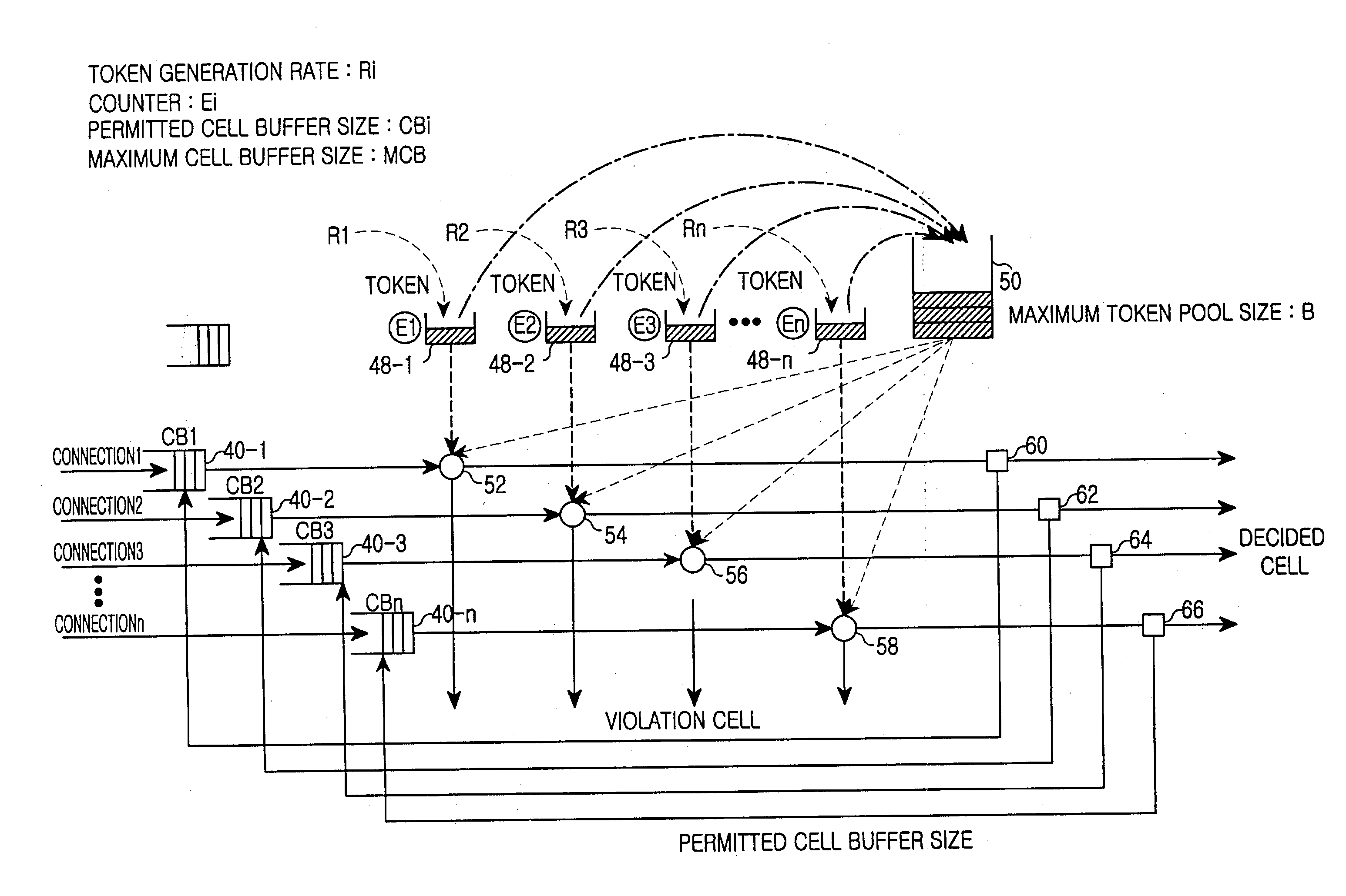
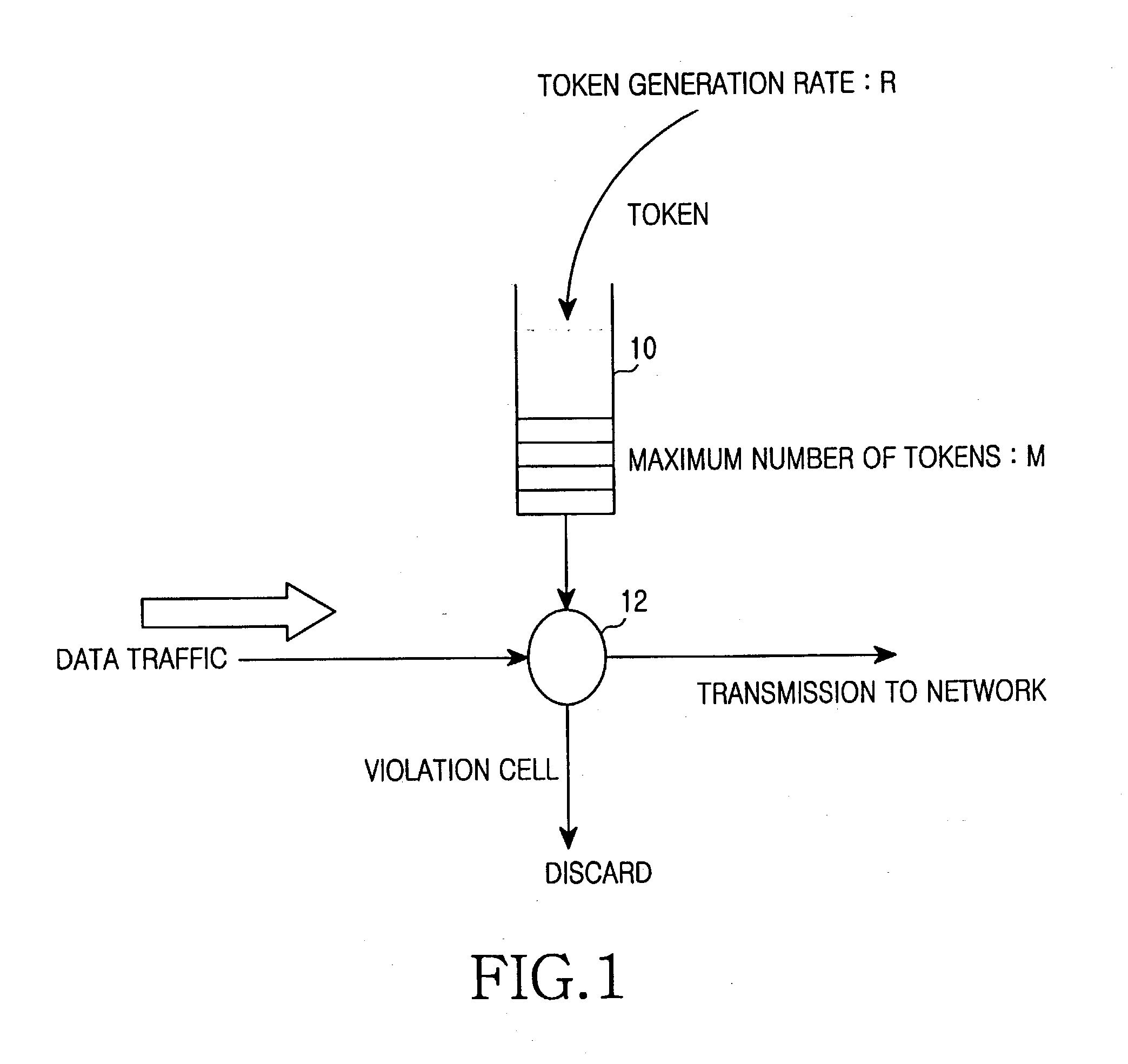
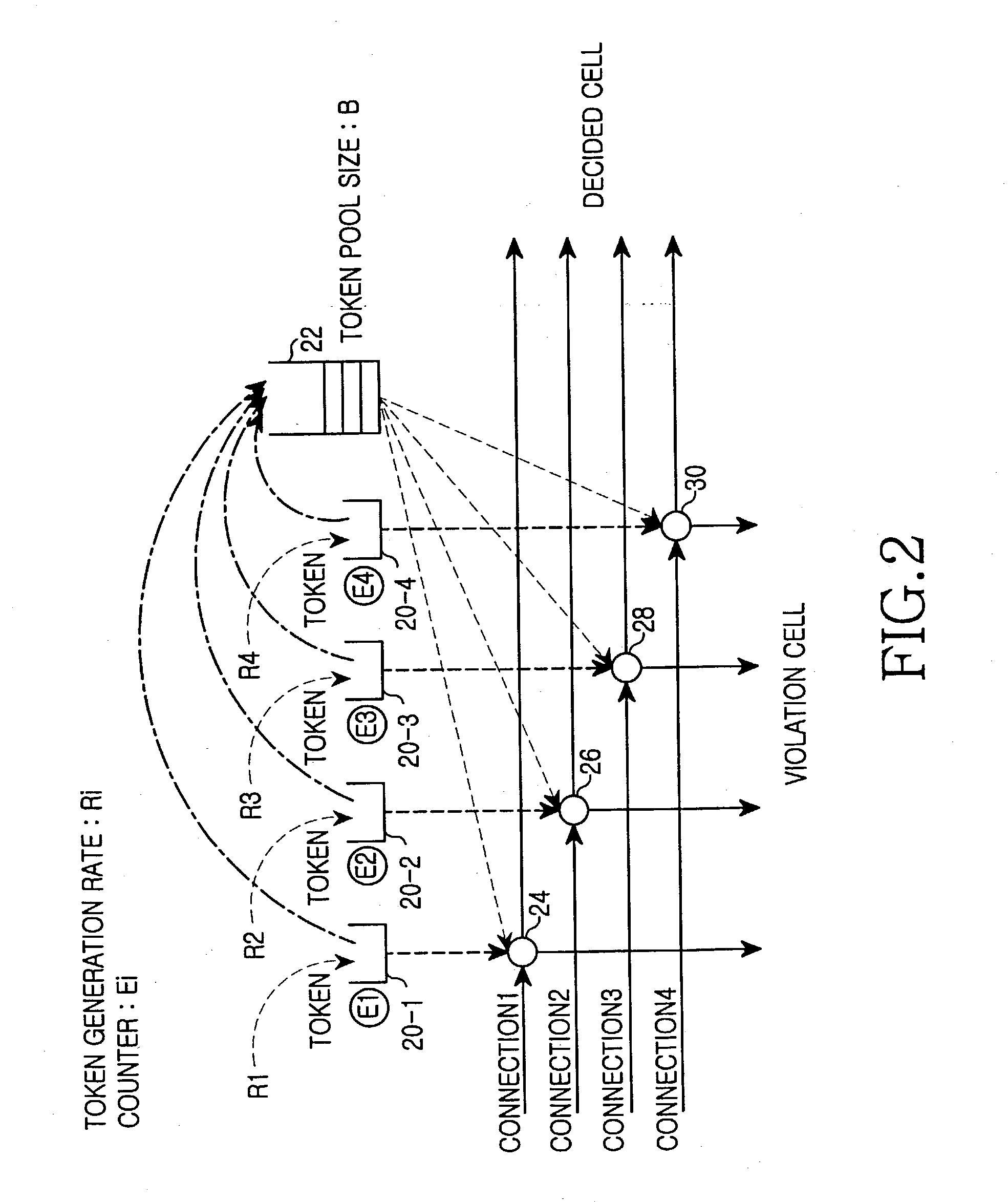
InactiveUS20040008625A1Improve bandwidth utilizationError preventionFrequency-division multiplex detailsGeneration rateExchange network
A method for monitoring traffic in a packet switched network. The packet switched network includes connections grouped in a single group; token buffers for respectively corresponding to the connections, and storing tokens generated at a predetermined token generation rate by the corresponding connection; a shared token pool for being shared among the connections, and storing the generated tokens therein when each token buffer of each connection is over a predetermined maximum size; and counters for respectively corresponding to the connections, and counting tokens stored in the shared token pool by a corresponding connection. The method for monitoring traffic in the packet switched network includes the steps of: a) providing data buffers for respectively corresponding to the connections and storing a packet of a contract-following connection in case of a temporary deficiency of a network resource; b) if a token buffer of a corresponding connection is over a predetermined maximum size and the shared token pool is over its own predetermined maximum size, storing tokens generated during a token generation time in the shared token pool, and controlling a count value of a corresponding counter; c) checking the count value of the corresponding counter, and selectively controlling a permitted buffer size of a data buffer of a corresponding connection upon receiving the checking result of the count value of the corresponding counter; and d) checking a token buffer of a corresponding connection and a shared token pool if a packet reaches the corresponding connection or is present in a data buffer of the corresponding connection, and selectively storing a received packet in a corresponding data buffer according to a count value of a corresponding counter if there is no token in the token buffer of the corresponding connection and the shared token pool.
Owner:SAMSUNG ELECTRONICS CO LTD
Monitoring and warning method, monitoring and warning device, monitoring and warning equipment and computer-readable storage medium
ActiveCN109688188AReduce workloadAlarm is accurateData switching networksSystem stabilityGeneration time
Owner:PING AN TECH (SHENZHEN) CO LTD
Distributed type caching method and system
InactiveCN103595776ASolve the problem of downtime data lossSolve the lossTransmissionDistributed cacheCache management
The invention provides a distributed type caching method and system. The method comprises the steps of configuring backstage cache management strategies on backstage cache management configuration, wherein the backstage cache management strategies comprise the step of setting server nodes in which service data are stored correspondingly, calling the service data in a database according to the backstage cache management strategies at service data generation time, and sending the service data to corresponding service nodes according to a unique primary key value of the service data. The method and system realize distributed cache of the service data, greatly reduce pressure of server nodes, and avoid loss of the service data and blocking of service nodes I / O.
Owner:FUJIAN NETDRAGON WEBSOFT
Network anomaly monitoring method and device
Owner:TENCENT TECH (SHENZHEN) CO LTD
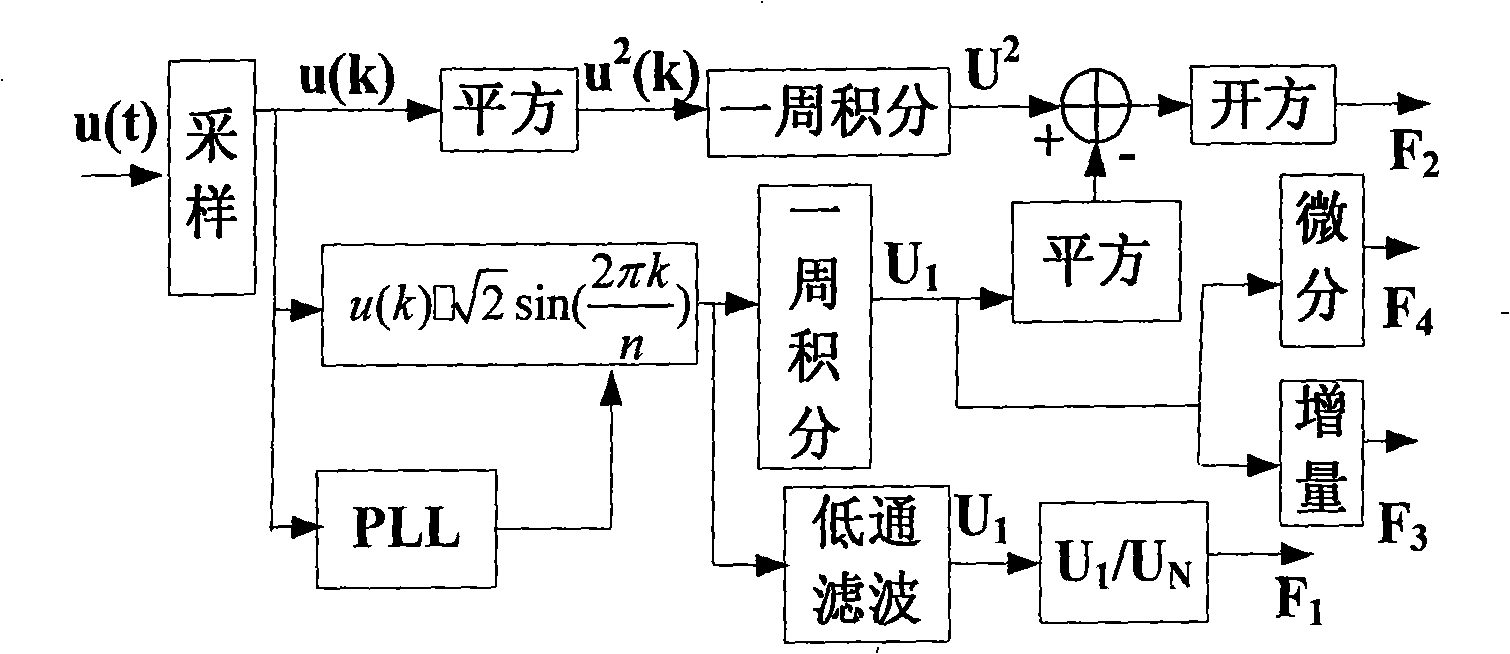
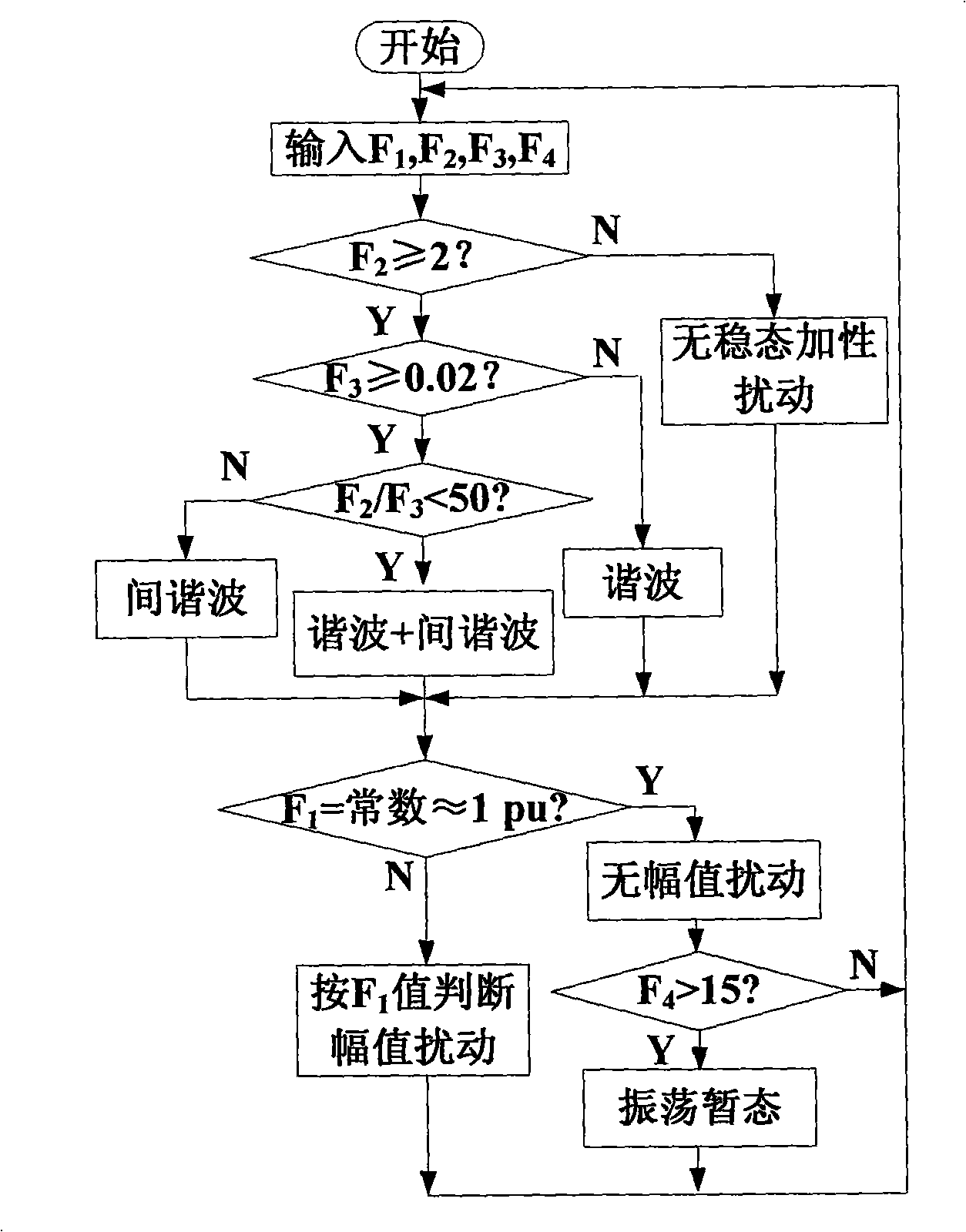
Voltage quality monitoring and perturb automatic classification method based on analysis in time-domain
InactiveCN101339208ASmall amount of calculationCurrent/voltage measurementElectrical testingOvervoltageBusbar
Time-domain characteristic of voltage signal is analyzed due to the methods of voltage quality monitoring based on time-domain analysis and automatic classification method of disturbance; four characteristic quantities used for classifying disturbing signal of electric power quality are extracted; an automatic classification method for disturbance of electric power quality is given out based on the four characteristic quantities. The method can conclusively and automatically identify the disturbing signals of electric power, such as a harmonic wave, an inter-harmonic wave, a wave and flickering, under voltage, overvoltage, oscillation transient voltage, voltage swell and sag, momentary interruption, and the like, and mixing disturbing signals from voltage signals. The generation time can be identified and strength of the disturbing signals can be evaluated. The method is little in calculated amount, which can be realized with single chip DSP, thus especially being applicable to on-line monitoring of voltage quality. Disturbing signal of various electric power qualities and the mixing disturbing signals can be automatically identified from a plurality of recorder data of substation busbar voltage, the generation time can be identified and the strength of the disturbing signals can be evaluated.
Owner:CHINA UNIV OF MINING & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com