Patents
Literature
453 results about "Event correlation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
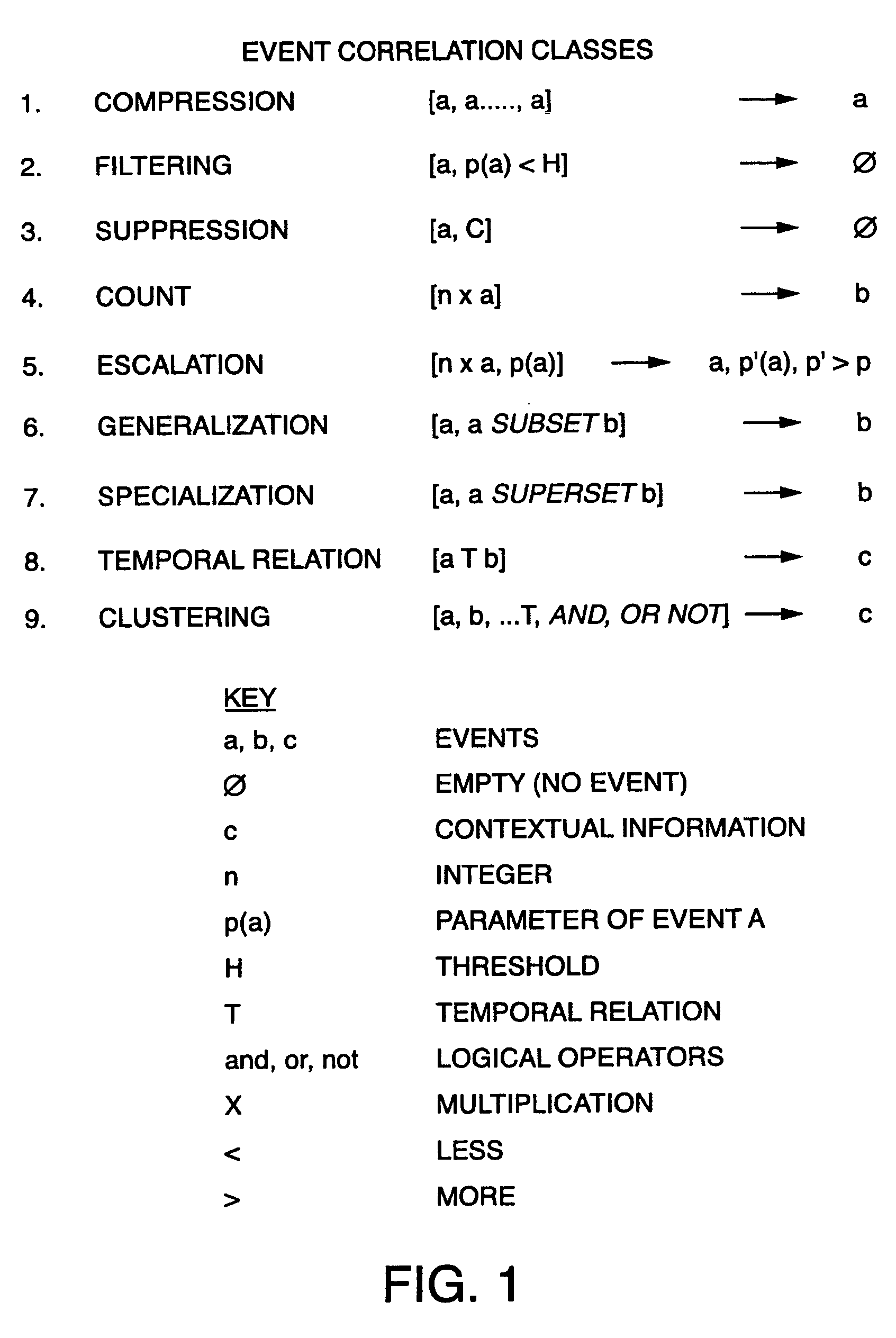
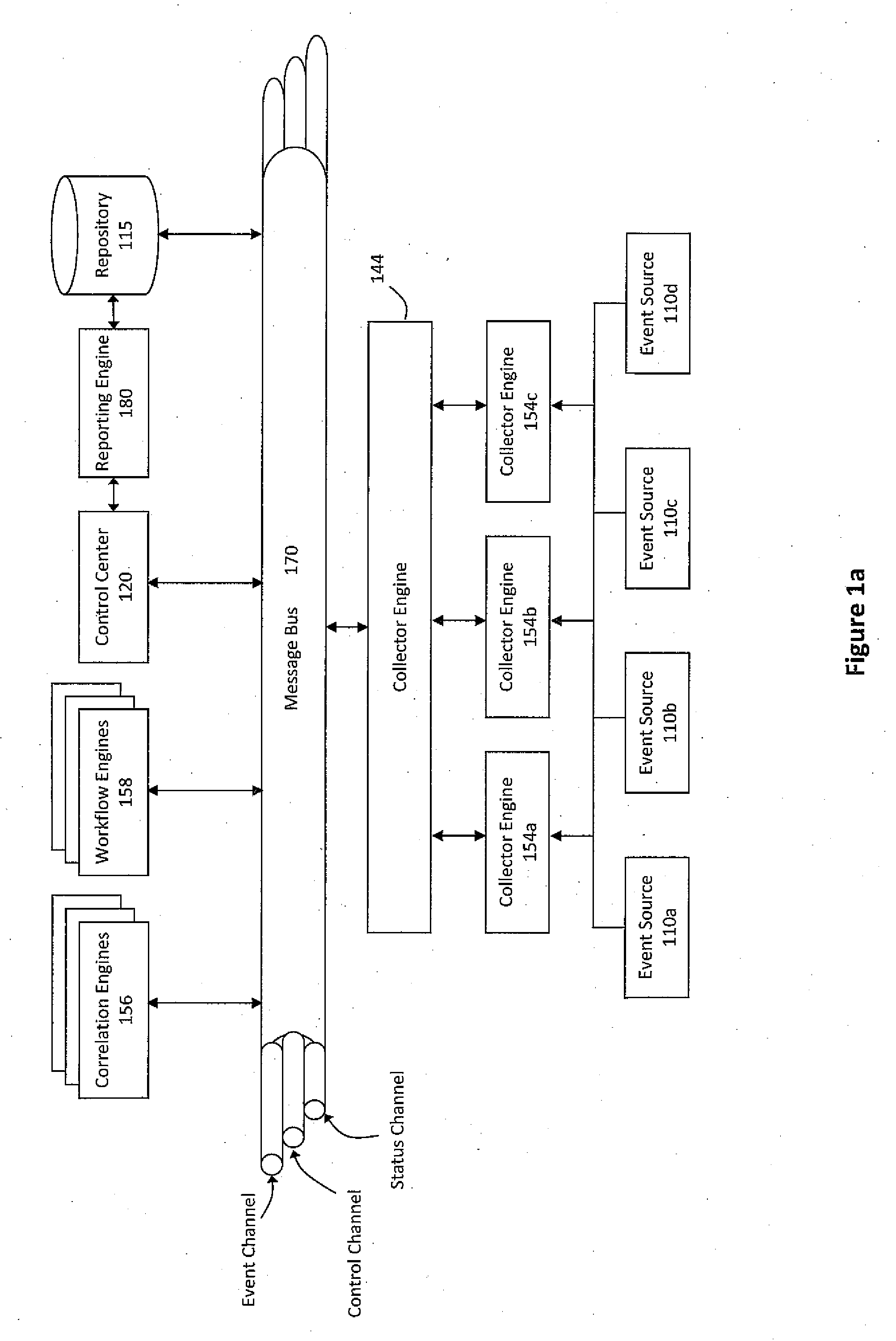
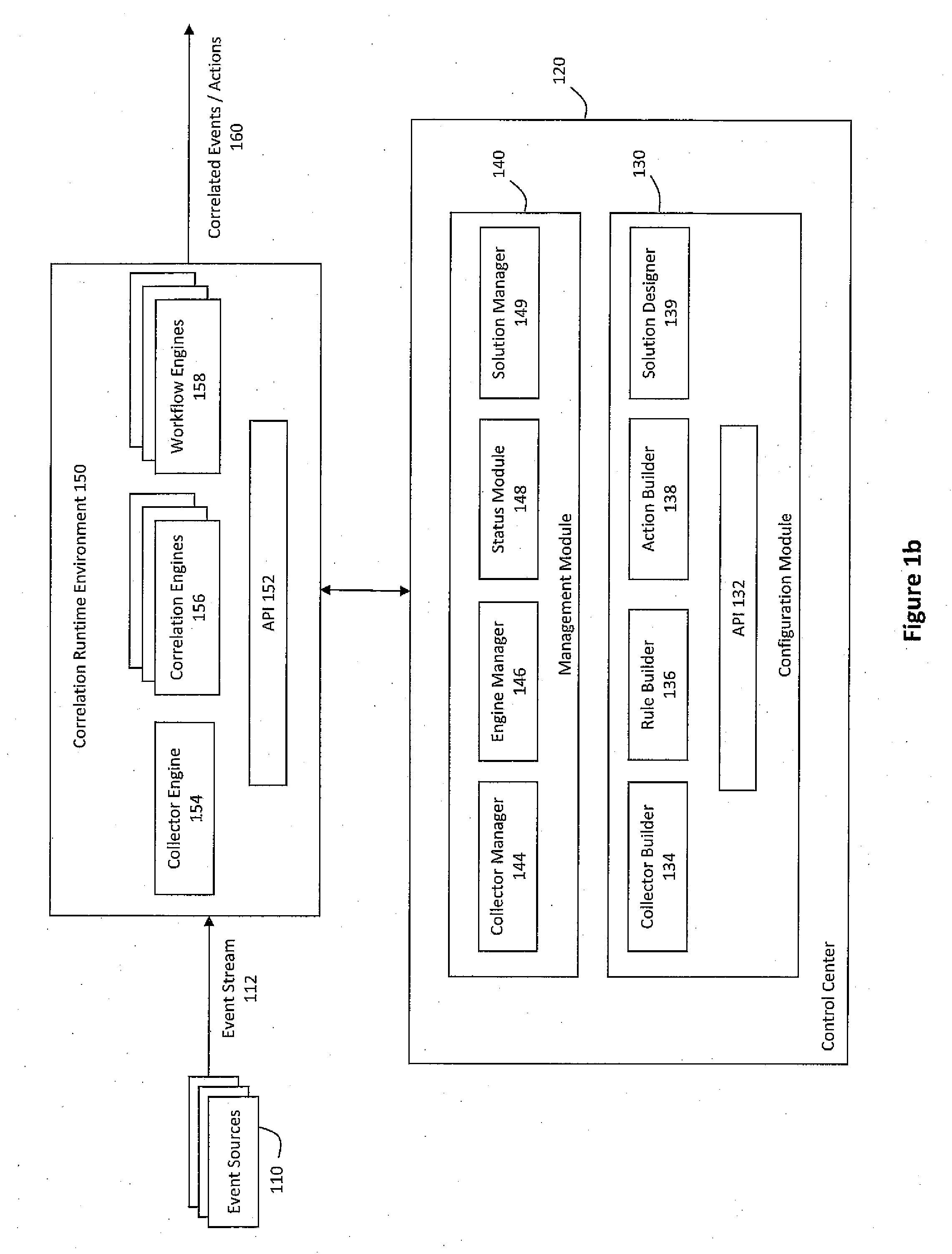
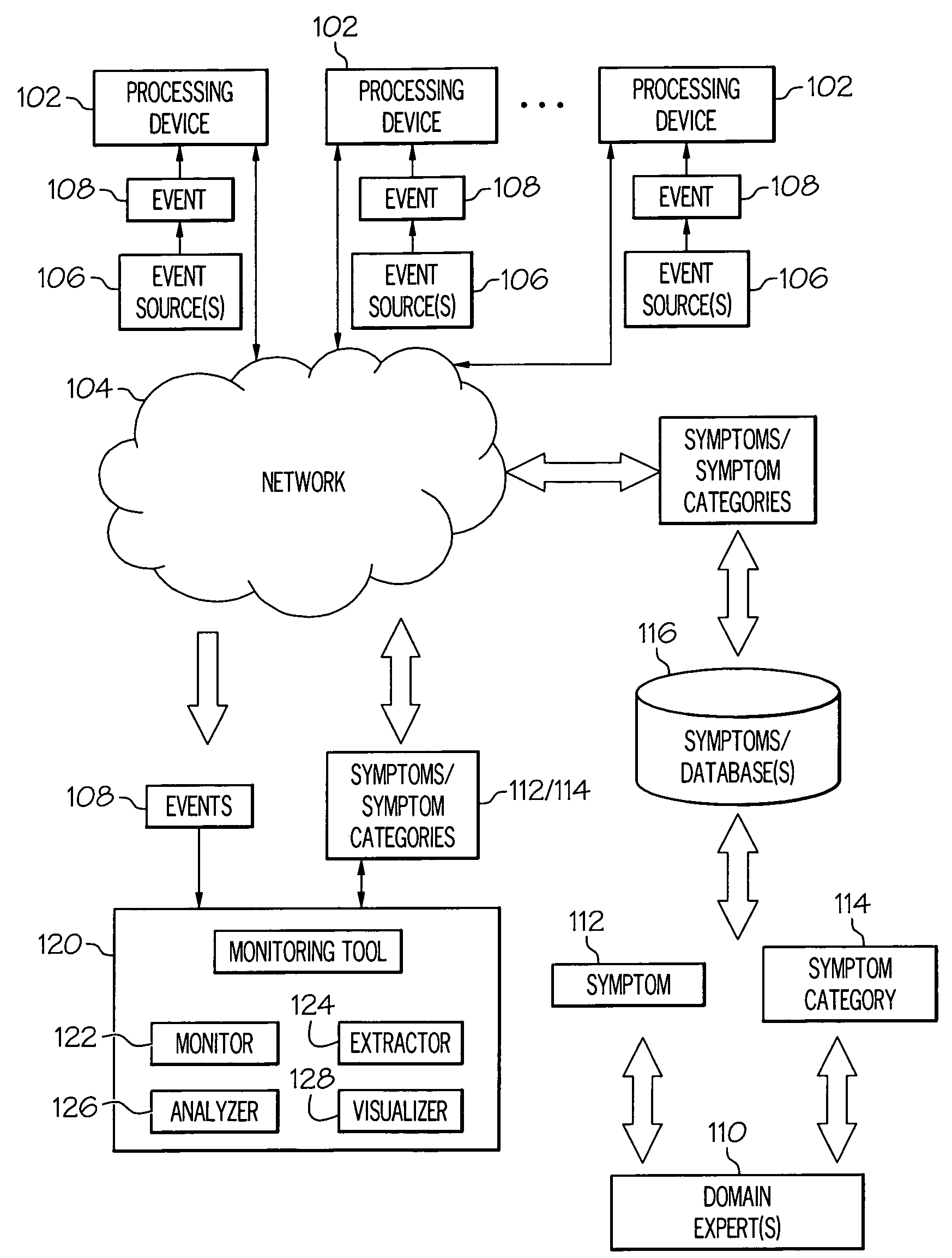
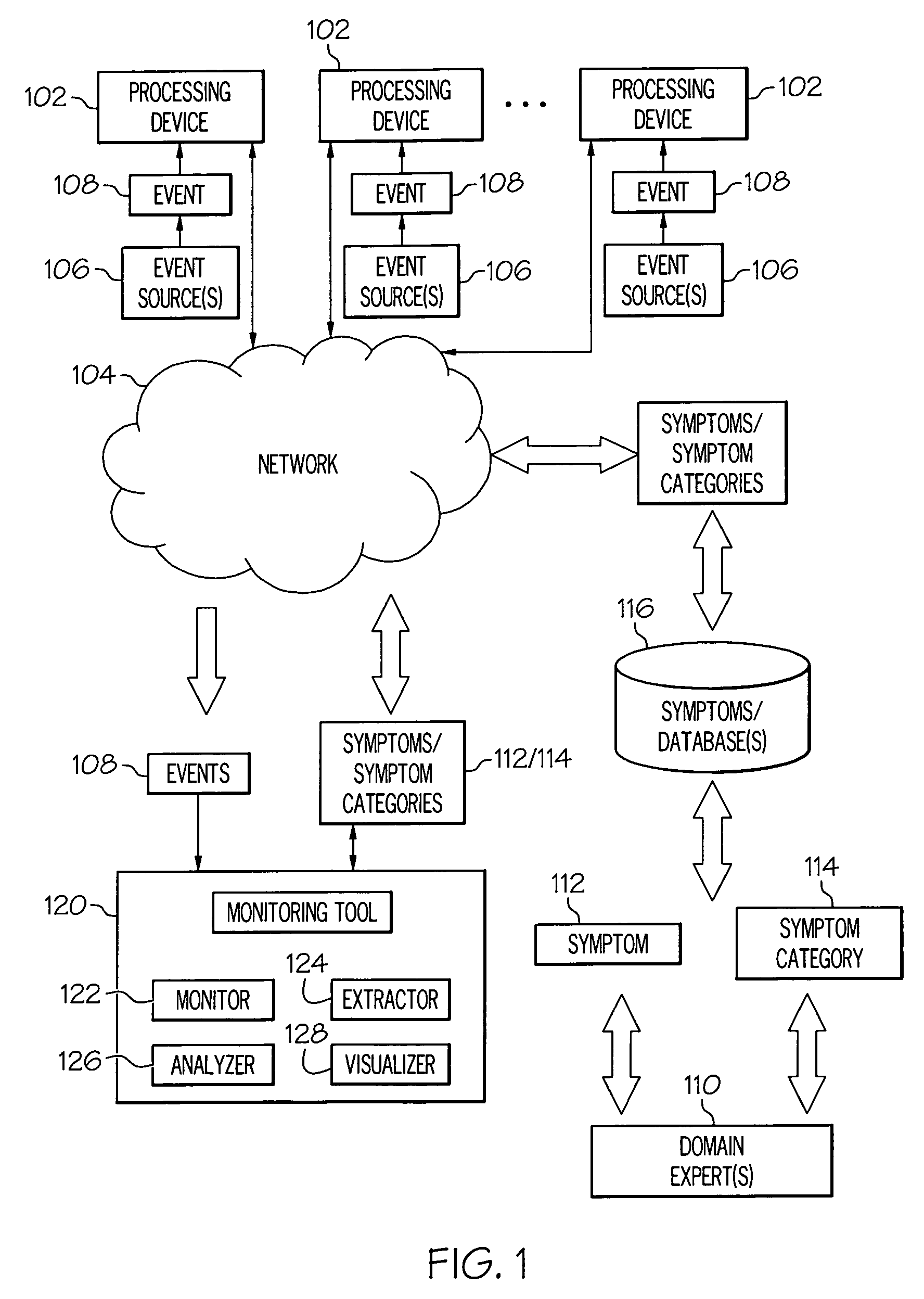
Event correlation is a technique for making sense of a large number of events and pinpointing the few events that are really important in that mass of information. This is accomplished by looking for and analyzing relationships between events.
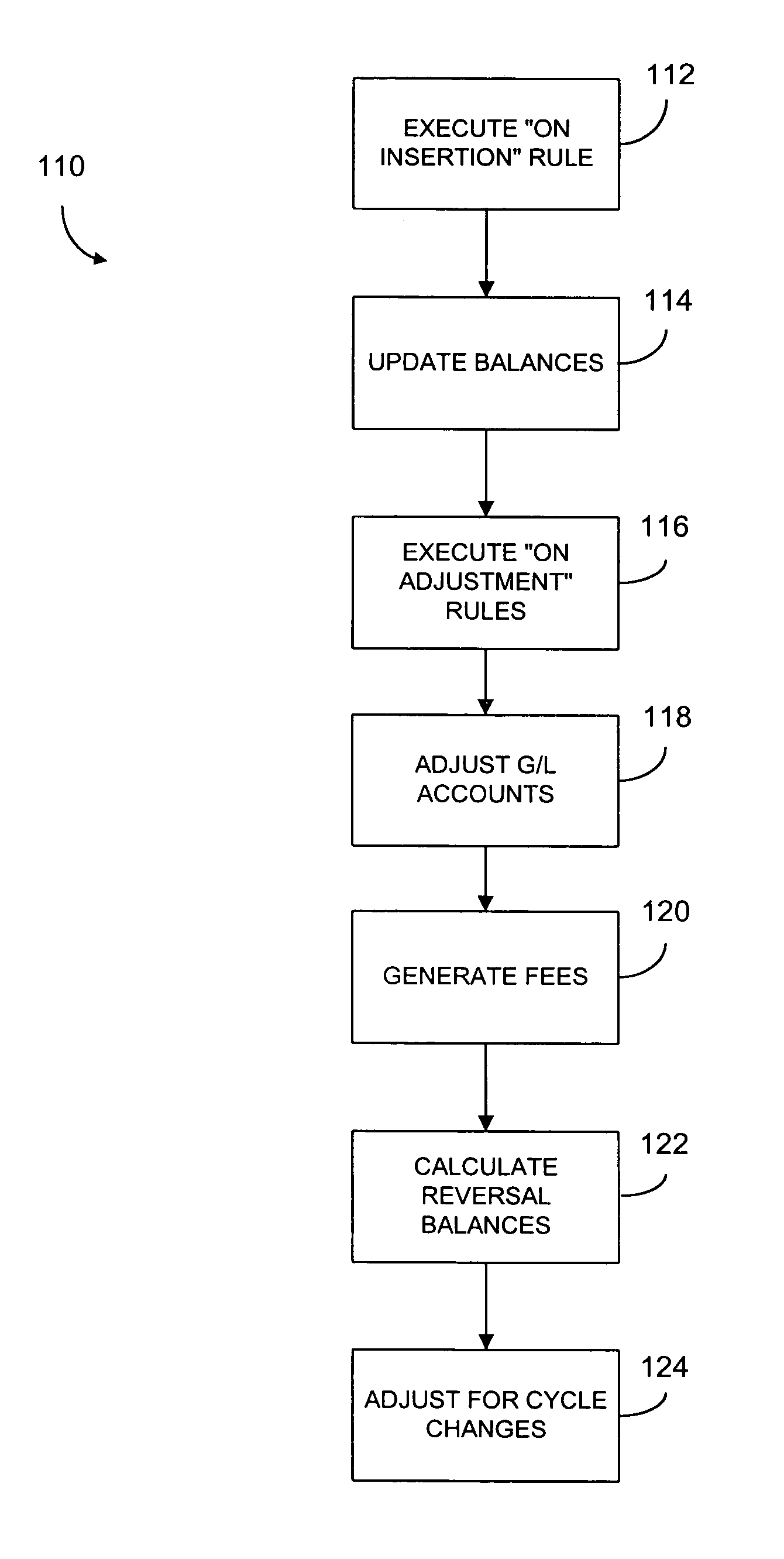
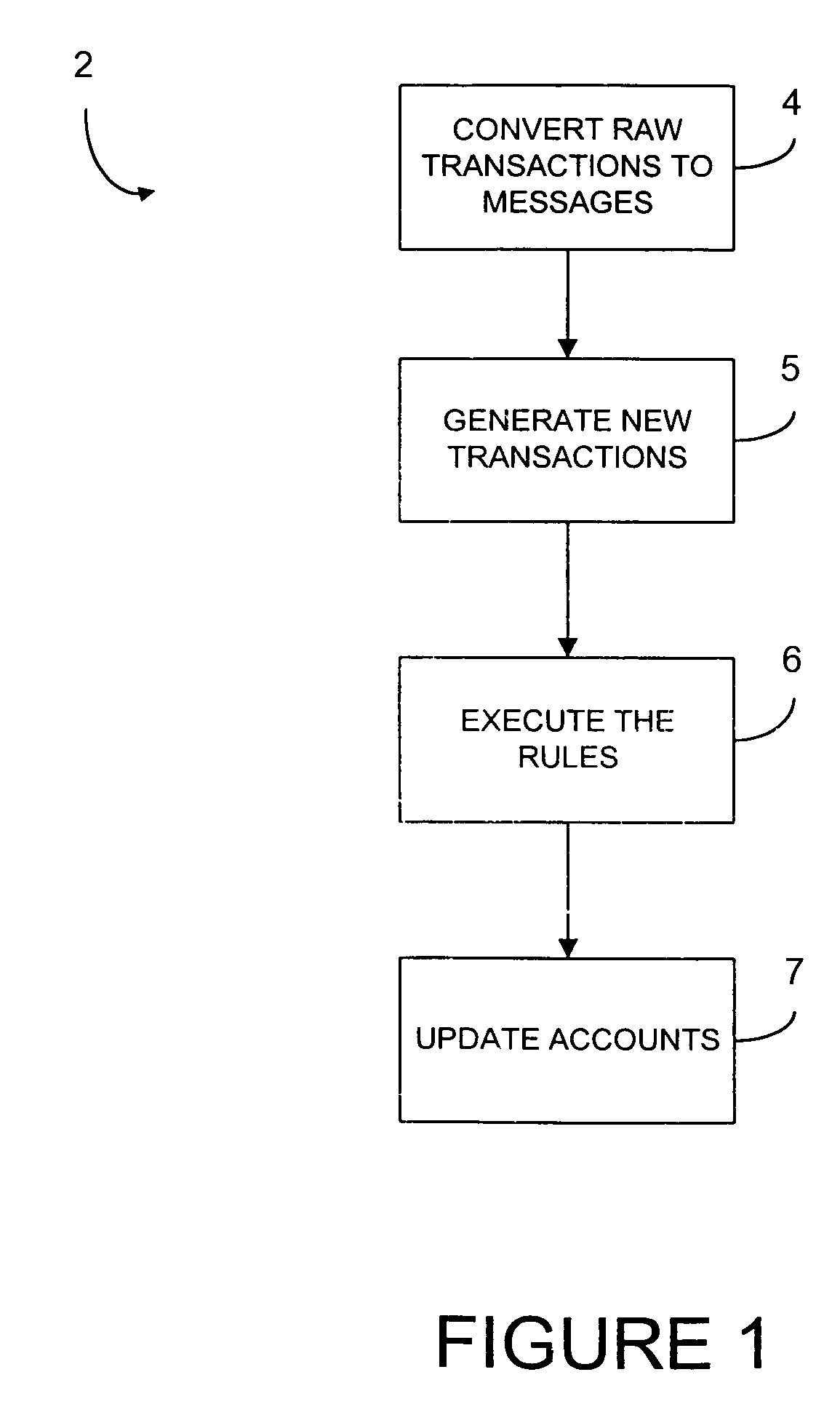
Methods and systems for managing financial accounts
InactiveUS7117172B1Useful managingReduce in quantityComplete banking machinesFinanceSource codeParameter control
Processing systems and methods receive events, such as a transaction to an account, and converts the events into messages. Each message then invokes one or more rules which are executed by a rules engine. The execution of these rules may invoke the execution of additional rules. After all rules have executed, the account associated with the event is updated, such as by projecting the account. The rules have their parameters defined in a repository so that the parameters can be easily changed without any need to recompile. The processing systems receive authorizations and other transactions and runs in real-time as transactions arrive. As a result, balances are updated continuously and accounts are read and updated only when there is activity. Hierarchy is user configurable, including multiple hierarchy to any depth. System operations are controlled by rules and their parameters and most modifications can be accomplished without access to source code.
Owner:CORECARD SOFTWARE
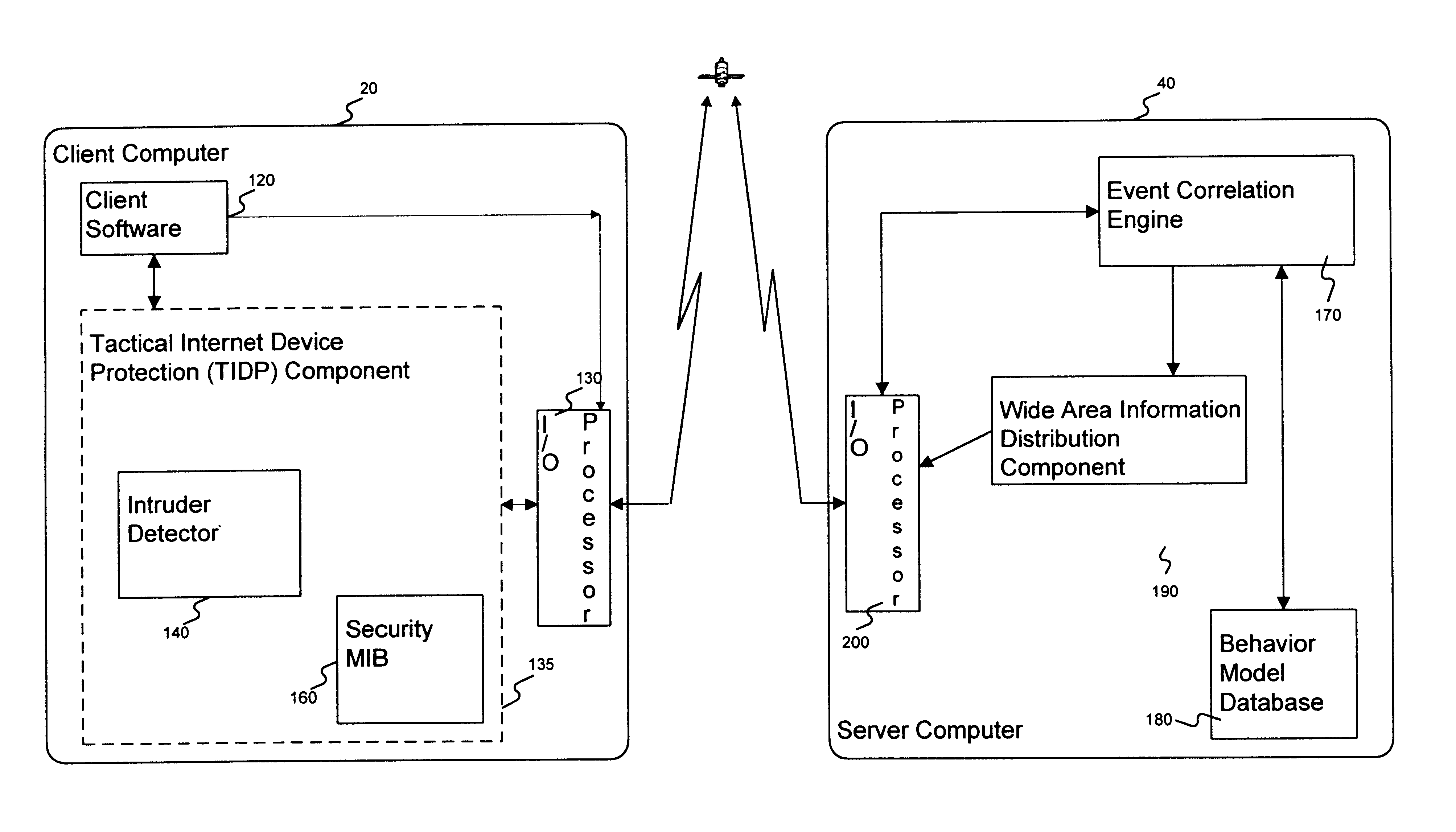
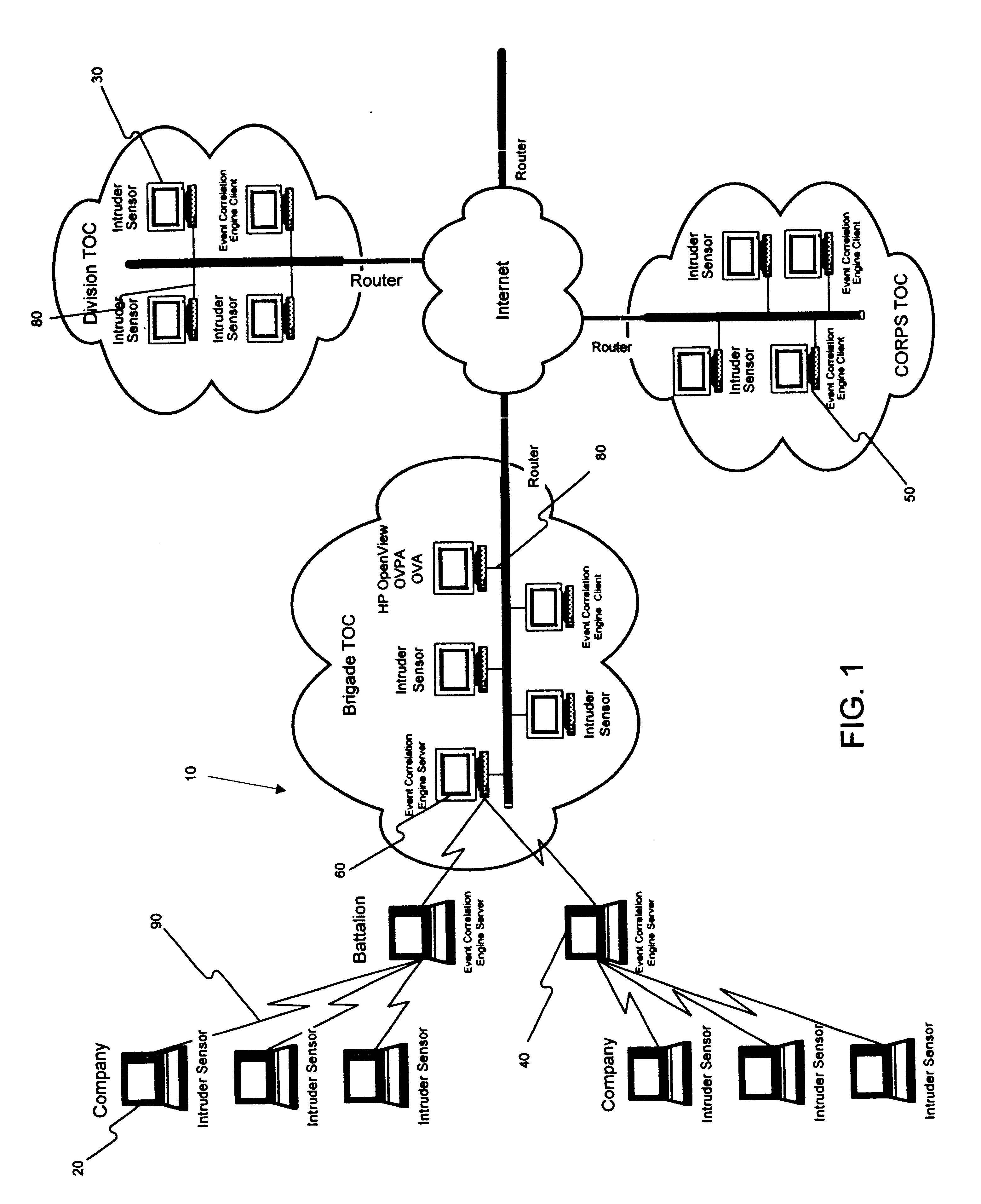
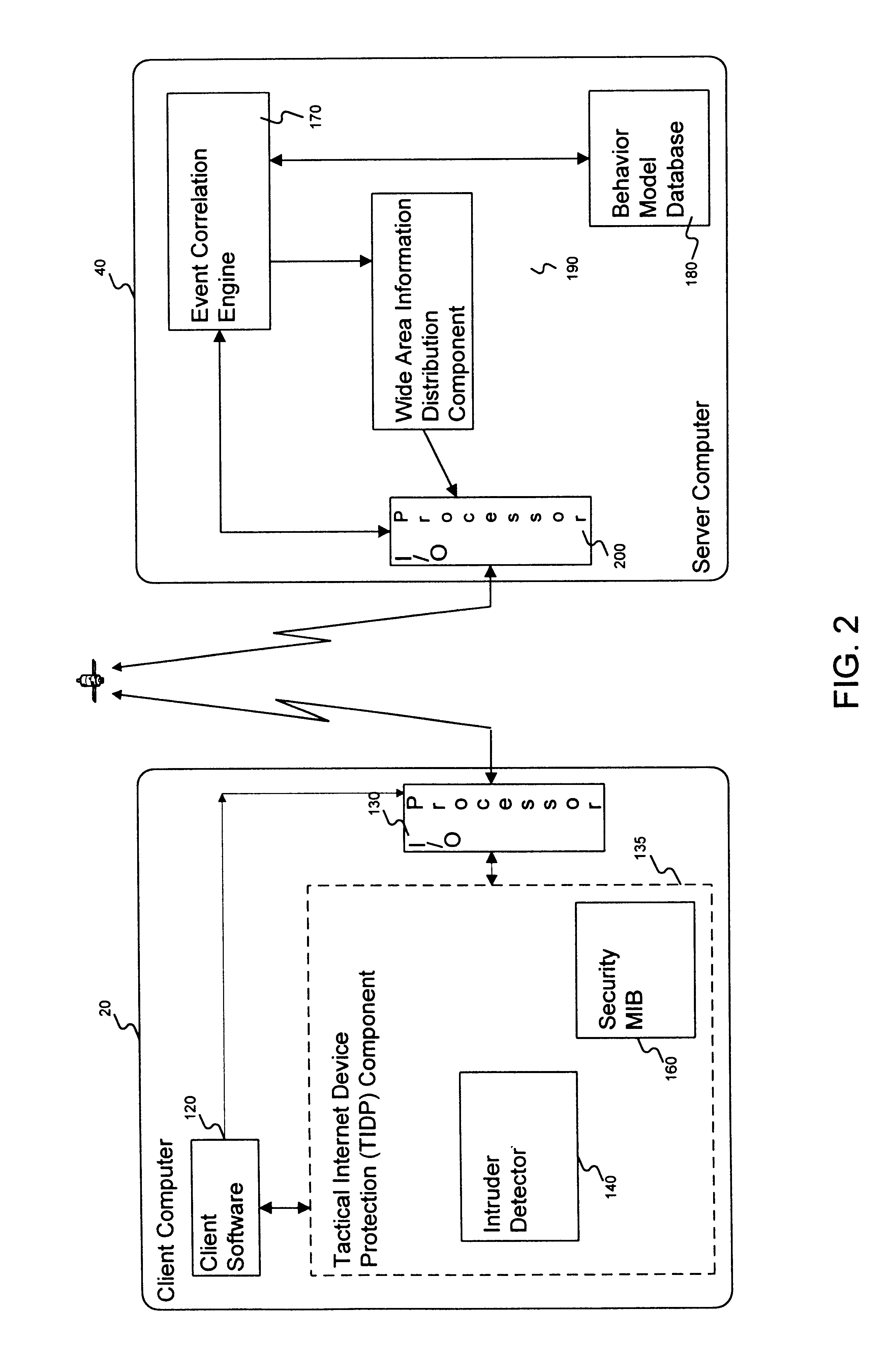
Method and apparatus for an intruder detection reporting and response system
InactiveUS6910135B1Improve securityWide rangeMemory loss protectionError detection/correctionThe InternetWorkstation
A method and apparatus is disclosed for improving the security of computer networks by providing a means operating passively on the network for detecting, reporting and responding to intruders. The system is comprised of a plurality of intruder sensor client computers and associated event correlation engines. Resident in the memory of the client computer and operating in the background is a Tactical Internet Device Protection (TIDP) component consisting of a passive intruder detector and a security Management Information Base (MIB). The passive intruder detector component of the TIDP passively monitors operations performed on the client computer and emits a Simple Network Management Protocol (SNMP) trap to an event correlation engine when it identifies a suspected intruder. The event correlation engine, through the use of a behavior model loaded in its memory, determines whether the user's activities are innocent or those of a perspective intruder. When the event correlation engine is unable to classify a user based on a single trap message, it can request historical information from the security MIB, a database of the operating history of the client computer including a chronology of the illegal operations performed on the client. Once the event correlation engine determines that an intruder is located at an associated client workstation, it generates a status message and transmits the message to all of its subscribers, informing them of the presence and location of a suspected intruder.
Owner:LEVEL 3 COMM LLC +2
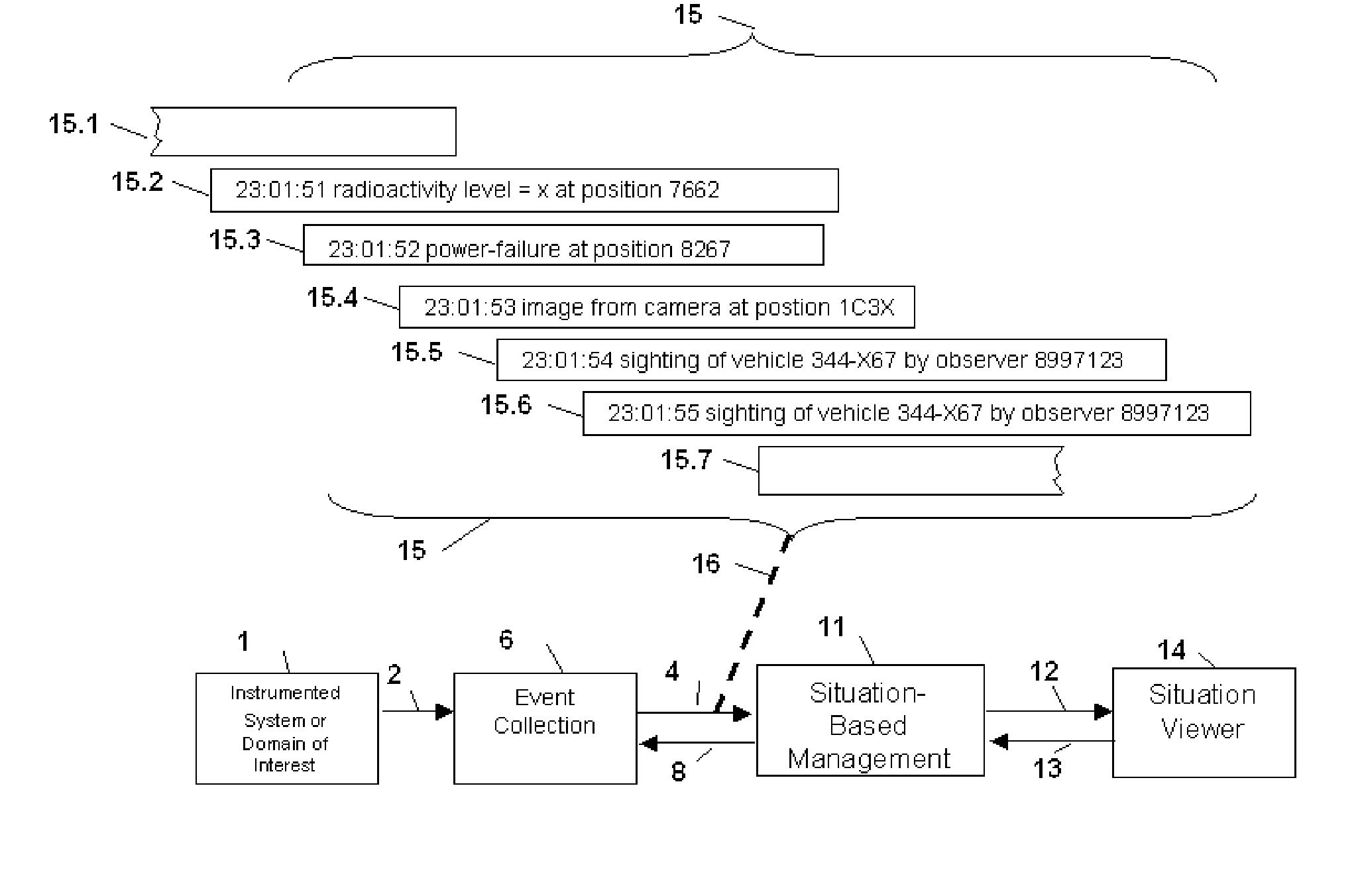
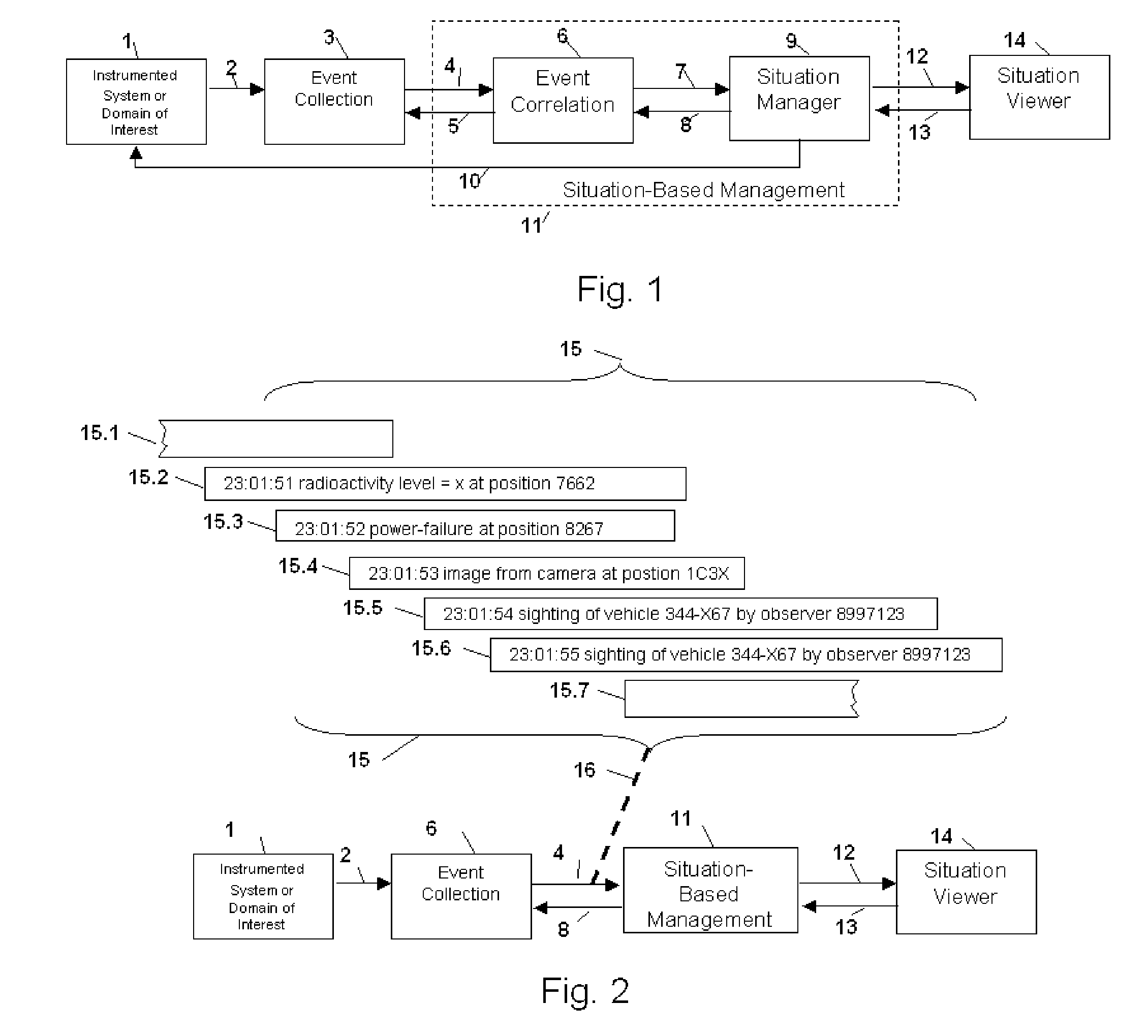
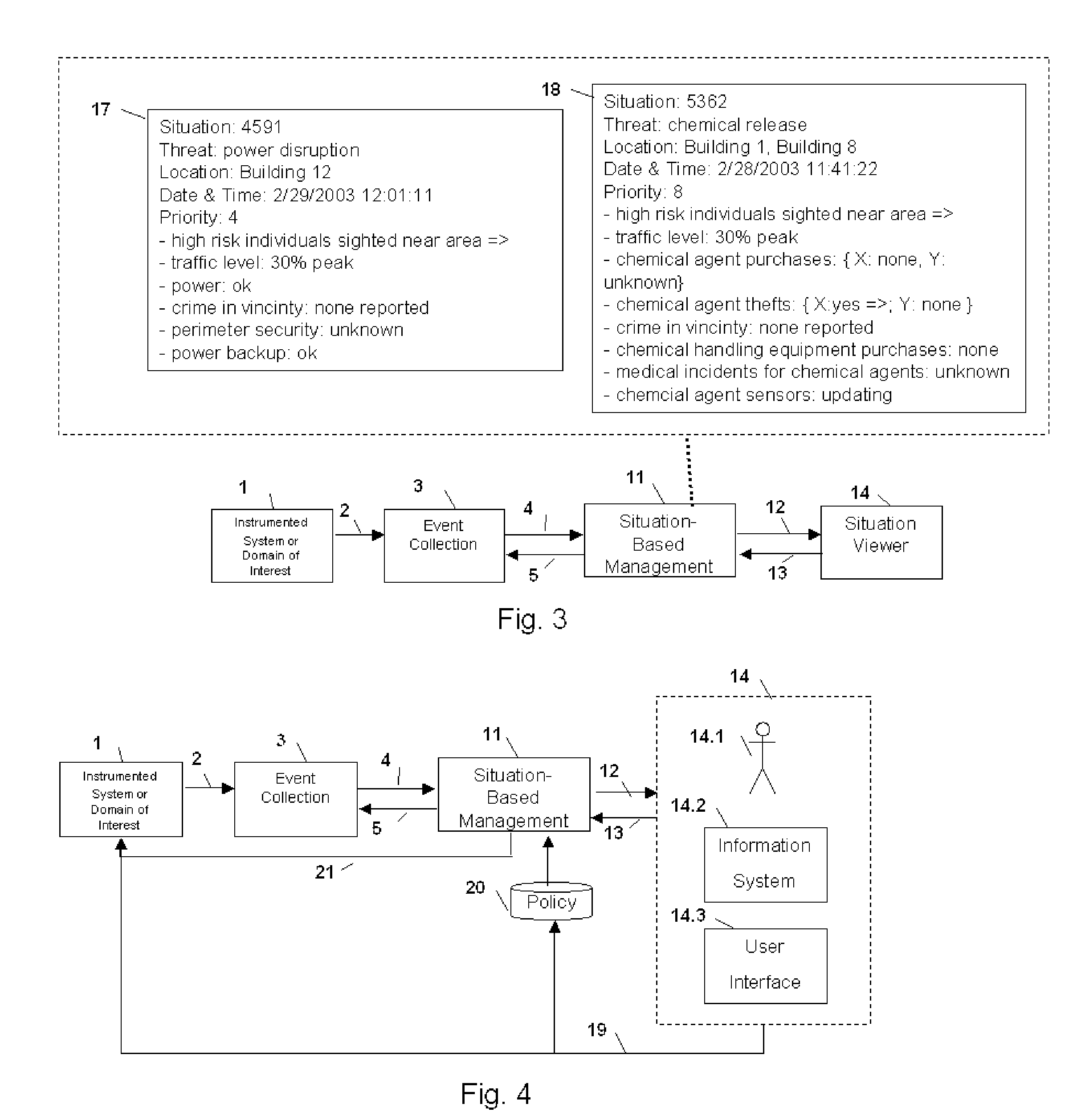
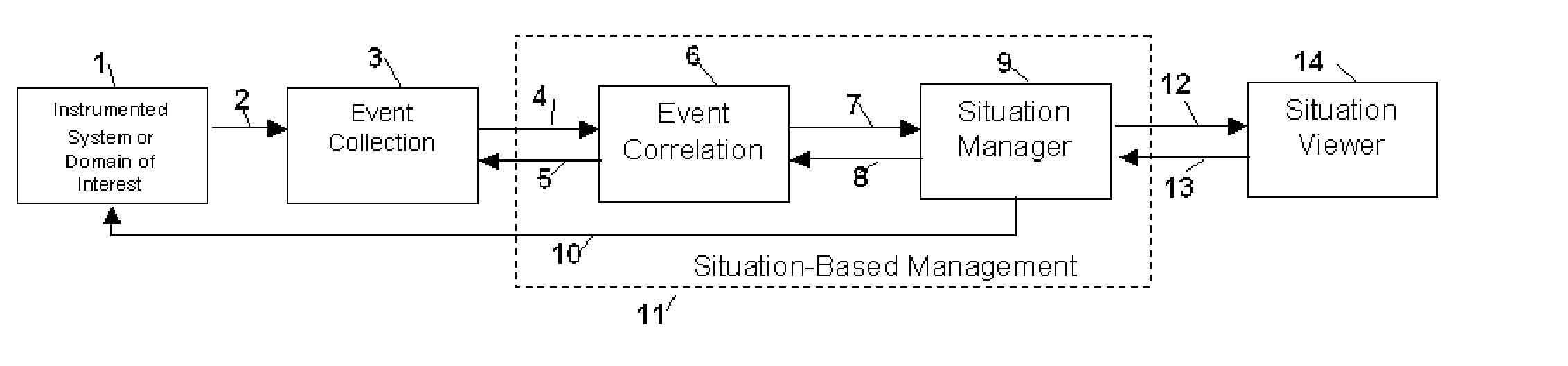
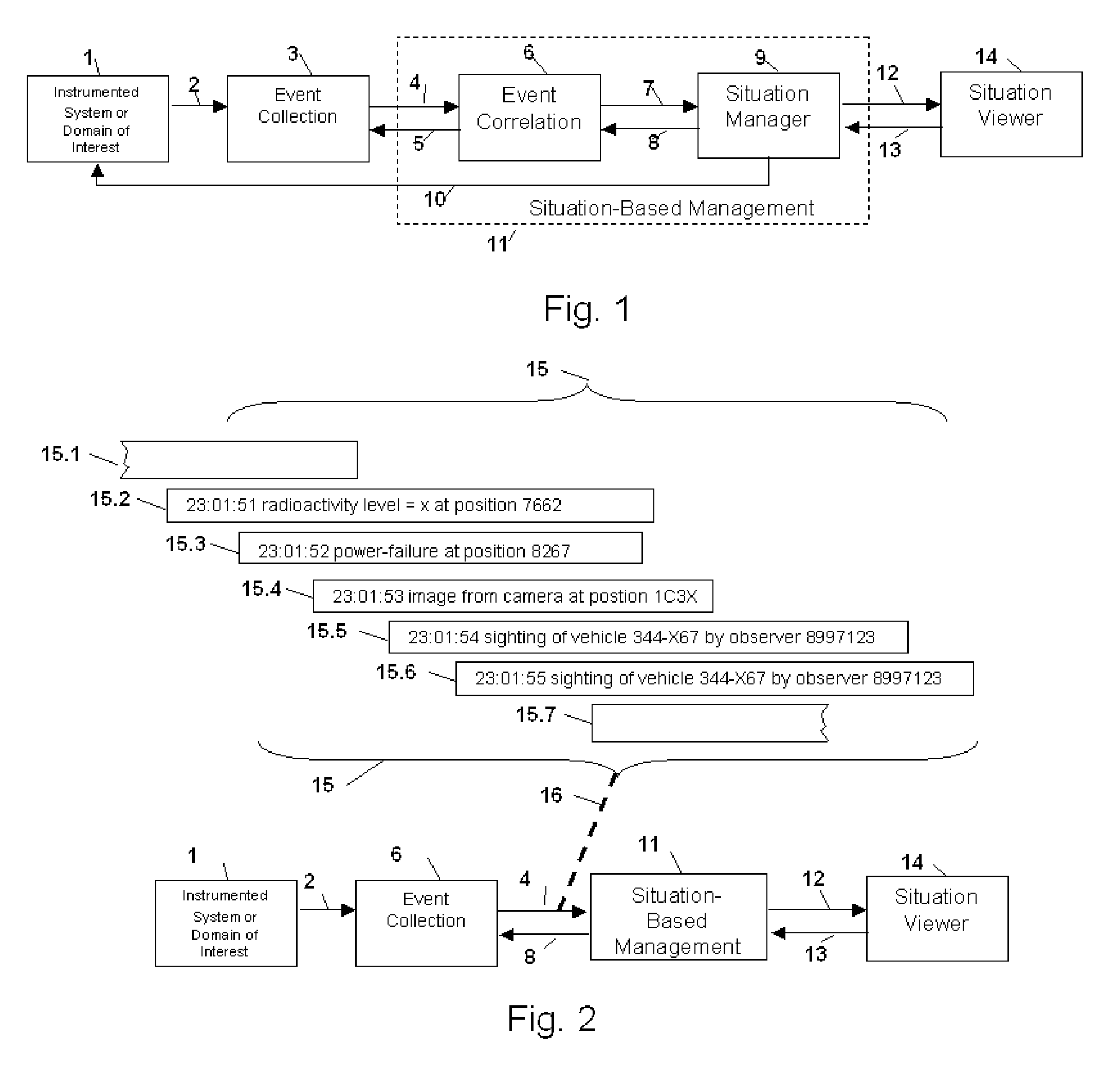
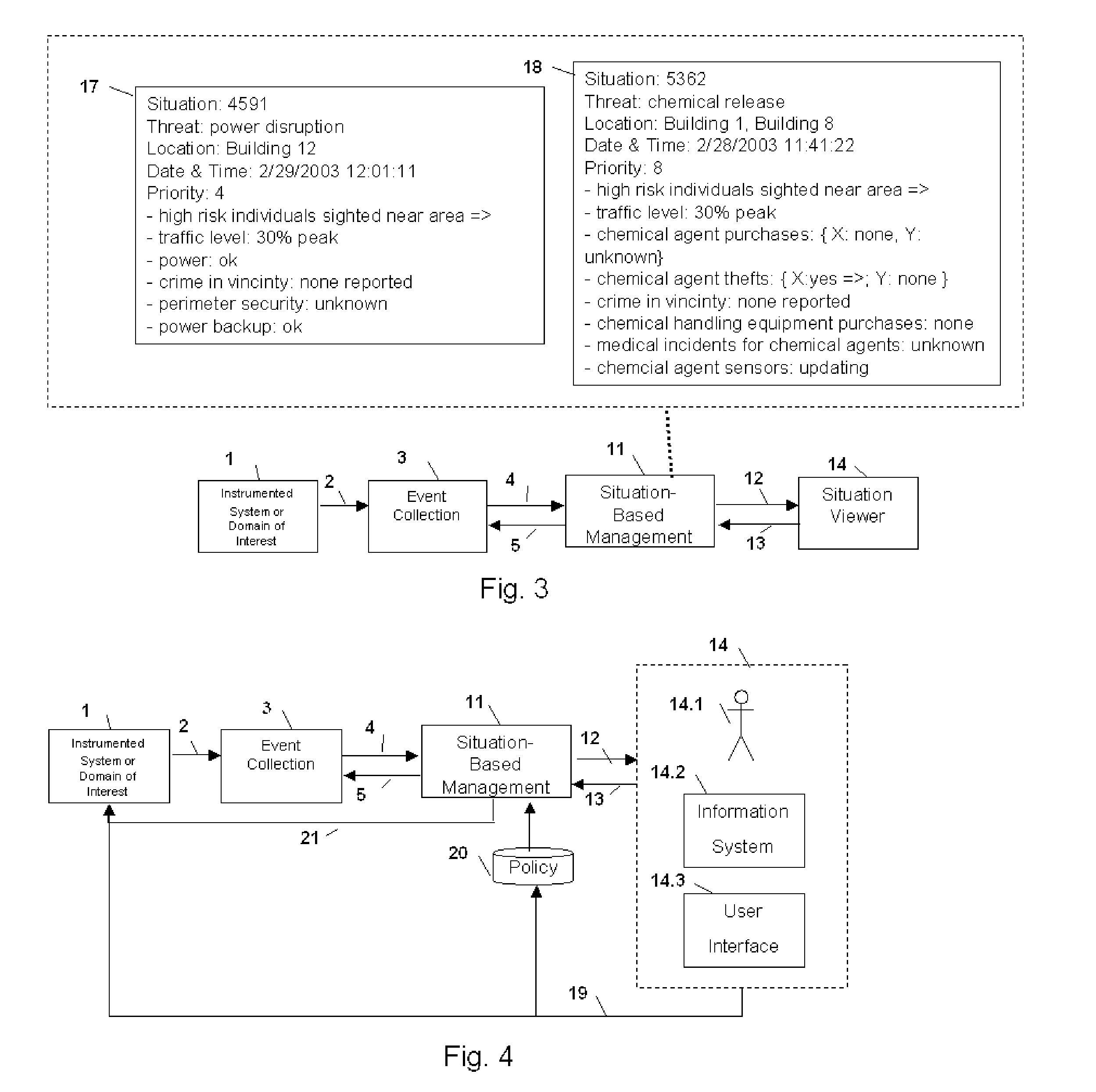
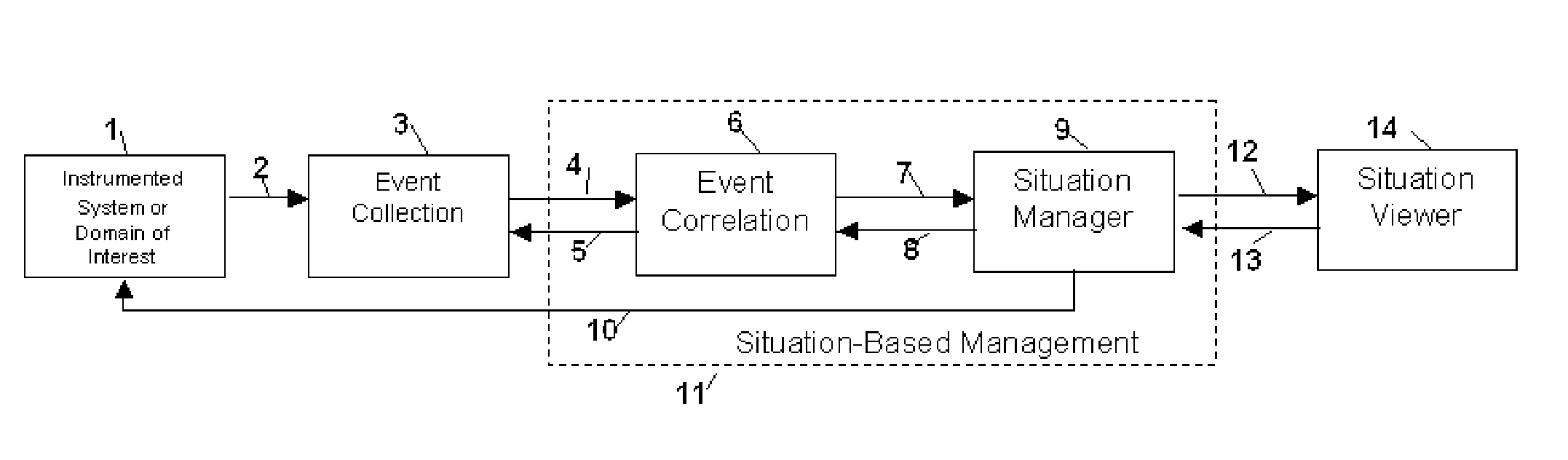
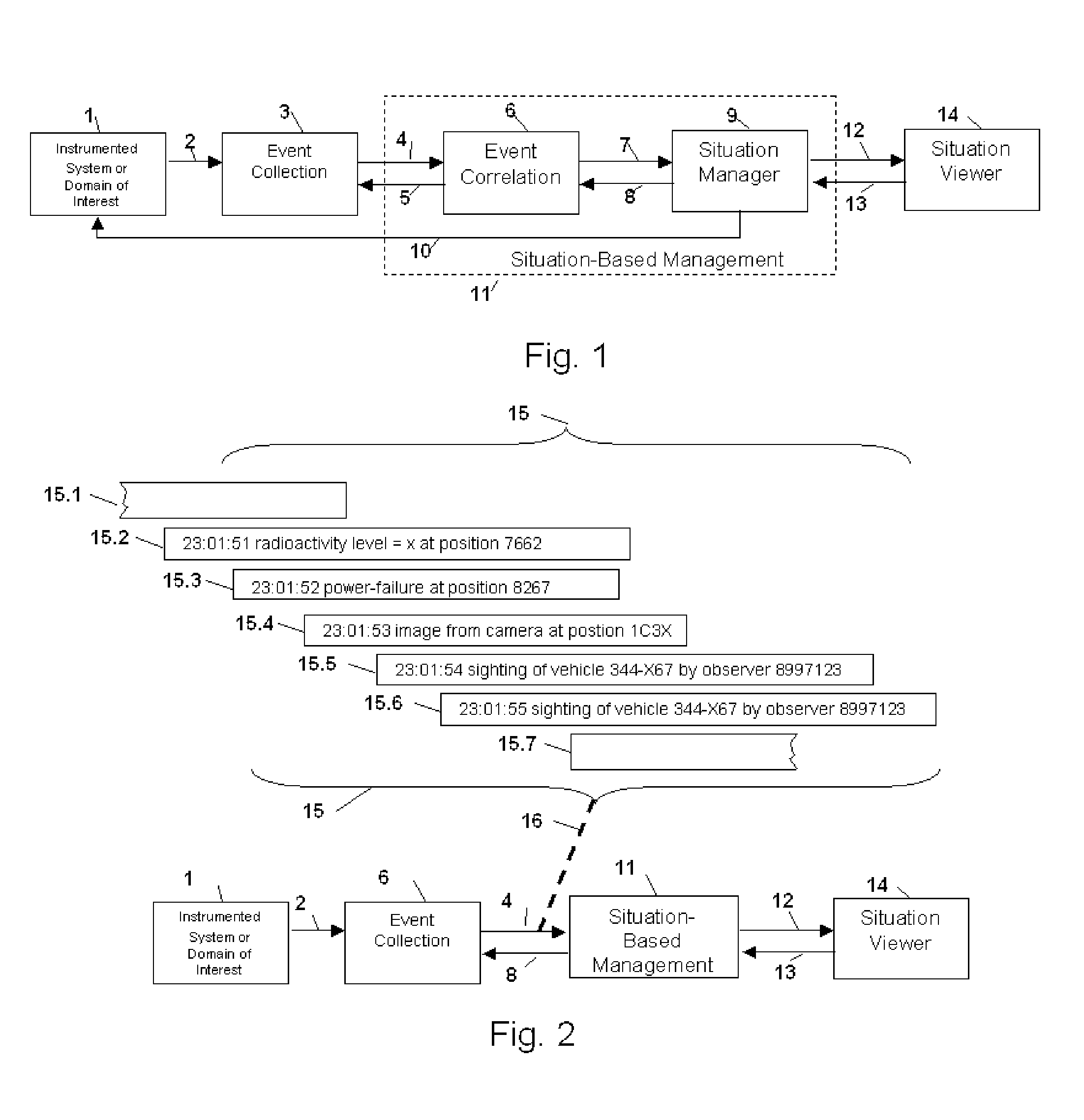
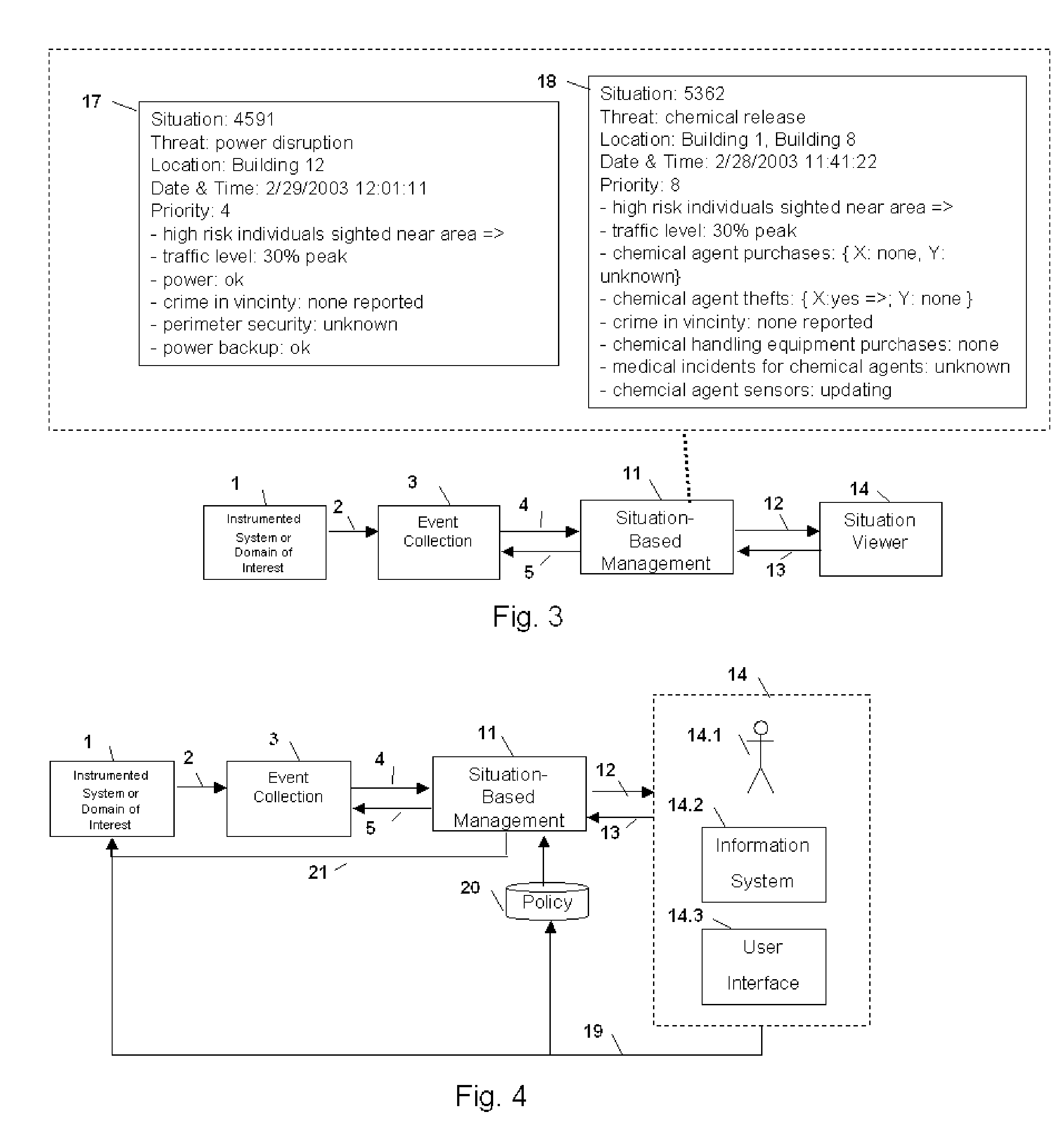
Method and Apparatus for Situation-Based Management
InactiveUS20050228763A1Guaranteed normal transmissionRemove redundant informationDigital computer detailsResourcesArtificial systemsComputer science
Method and apparatus for situation-based management of natural and artificial systems using event correlation and a situation manager. Input is provided from multiple sources in the form of a collection of events. A first level of processing performs event correlation over the collection of events and infers new events and new qualities of events. A second level of processing manages situations based on the collection of events, where situations are recognized, maintained, and given a degree of confidence. Situations are periodically updated based on incoming events. The assertion of a situation may call for information from external sources, provide information for external sources, and provide control instructions to external sources. Given a current situation, past, and possible future situations are inferred. Additionally, a method and apparatus for bi-directional communication between the event correlator and situation manager.
Owner:ALTUSYS
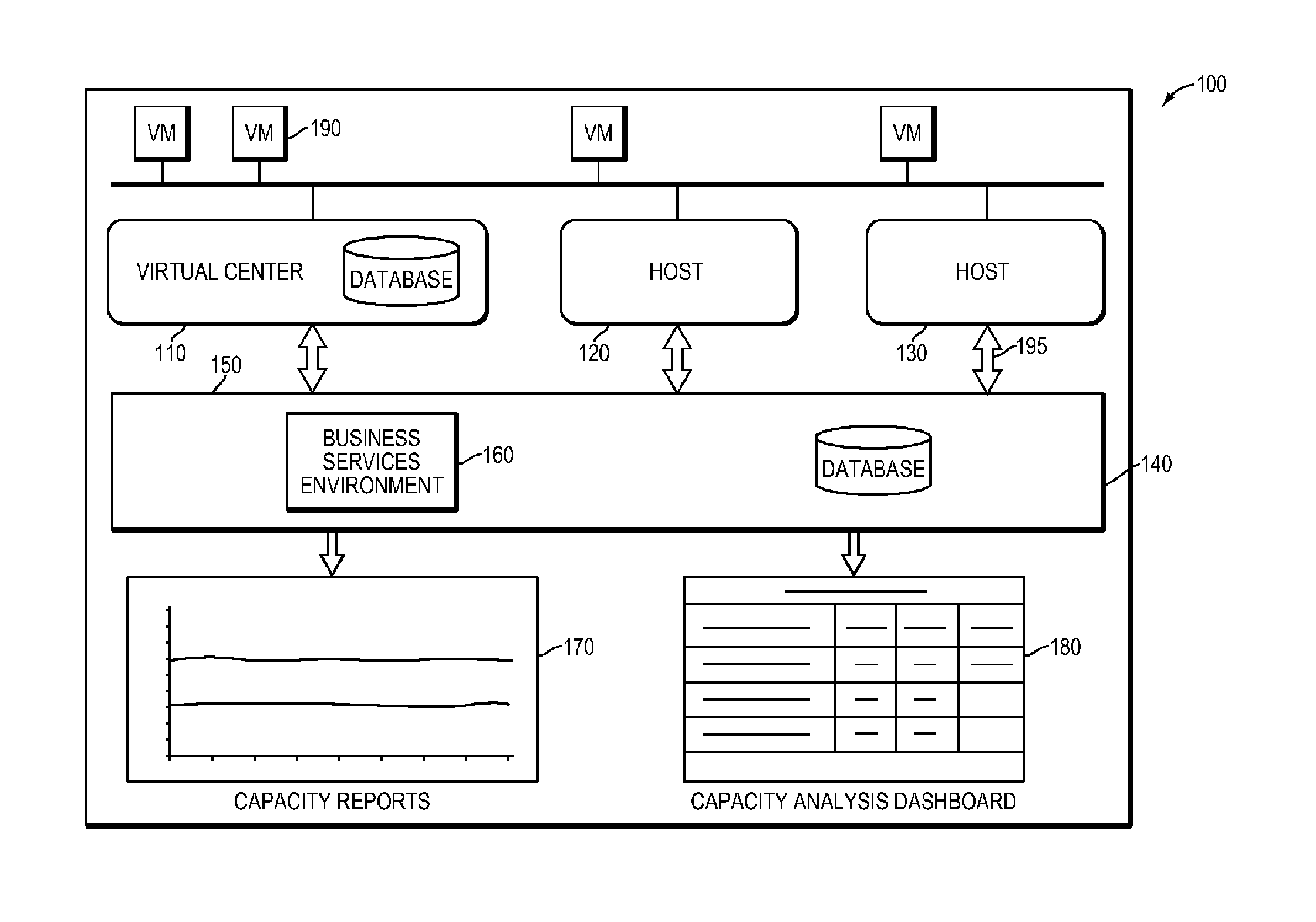
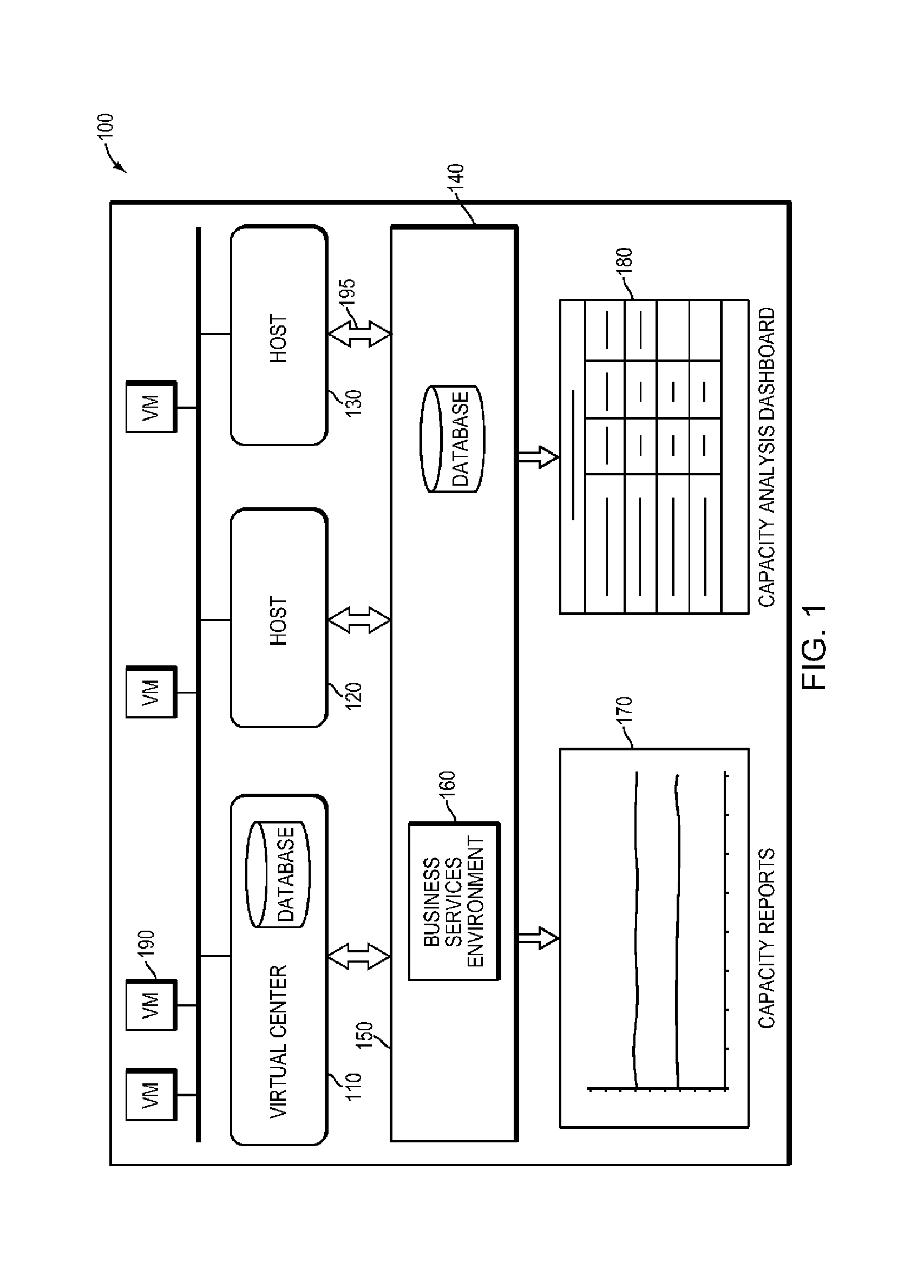
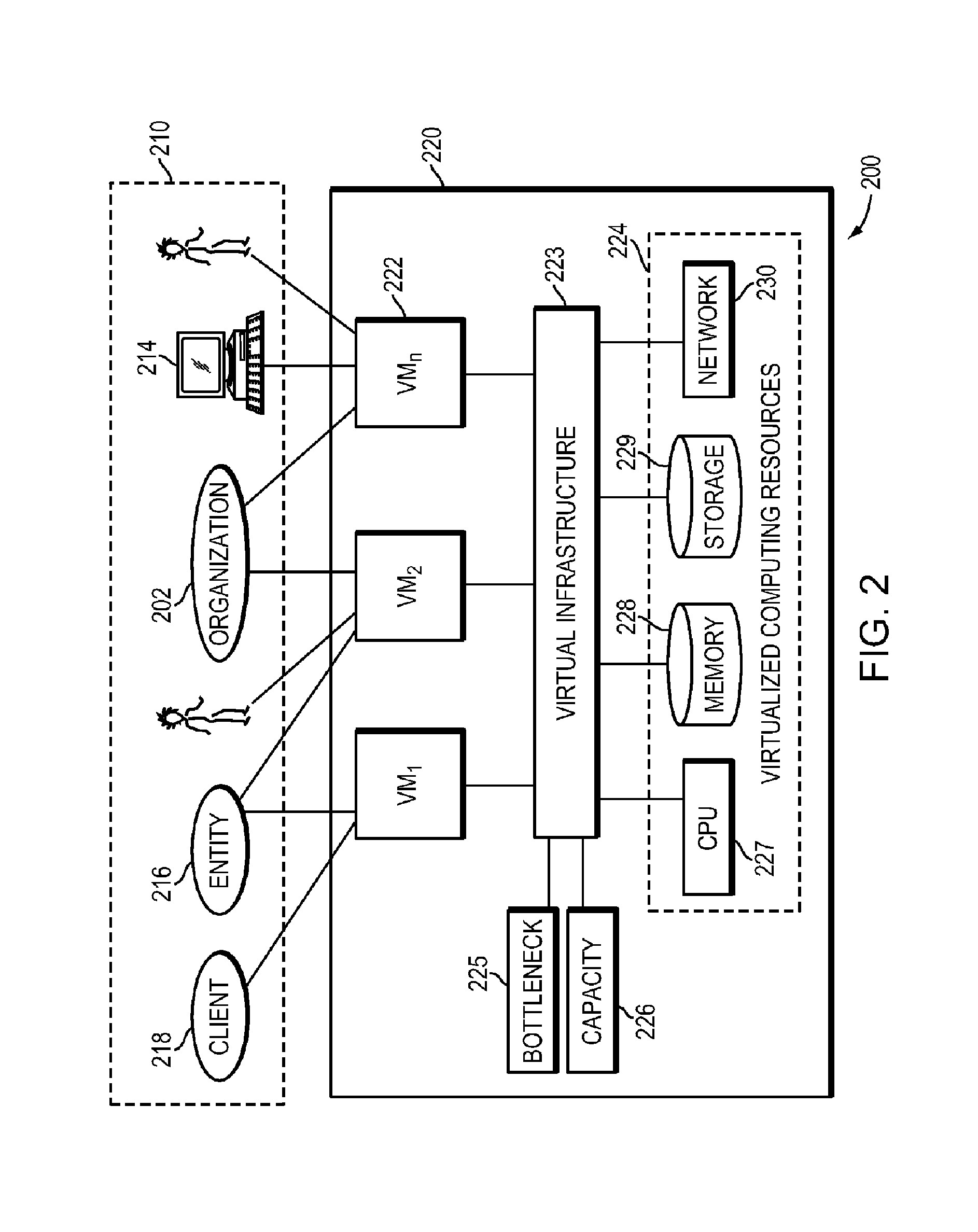
Systems and methods for real-time monitoring of virtualized environments
ActiveUS8738972B1Improve operationImprove performanceError detection/correctionSpecial data processing applicationsVirtualizationRoot cause
A method of root cause analysis in a virtual machine environment includes receiving a plurality of events from a system monitoring the virtualized environment. The events may include alarms or alerts, such as alarms or alerts associated with a resource reaching or exceeding a threshold. The capacity manager consumes these events and performs event correlation to produce a set of correlated events. The capacity manager performs a root cause analysis on the set of correlated events to identify one or more root causes. The capacity manager further performs an impact analysis to determine how the root cause impacts the system, such as other virtual machines, hosts or resource in the virtual environment. Based on the root cause and impact analysis, the capacity manager makes one or more recommendations to address issues with or to improve the operations and / or performance of the virtualized environment.
Owner:QUEST SOFTWARE INC
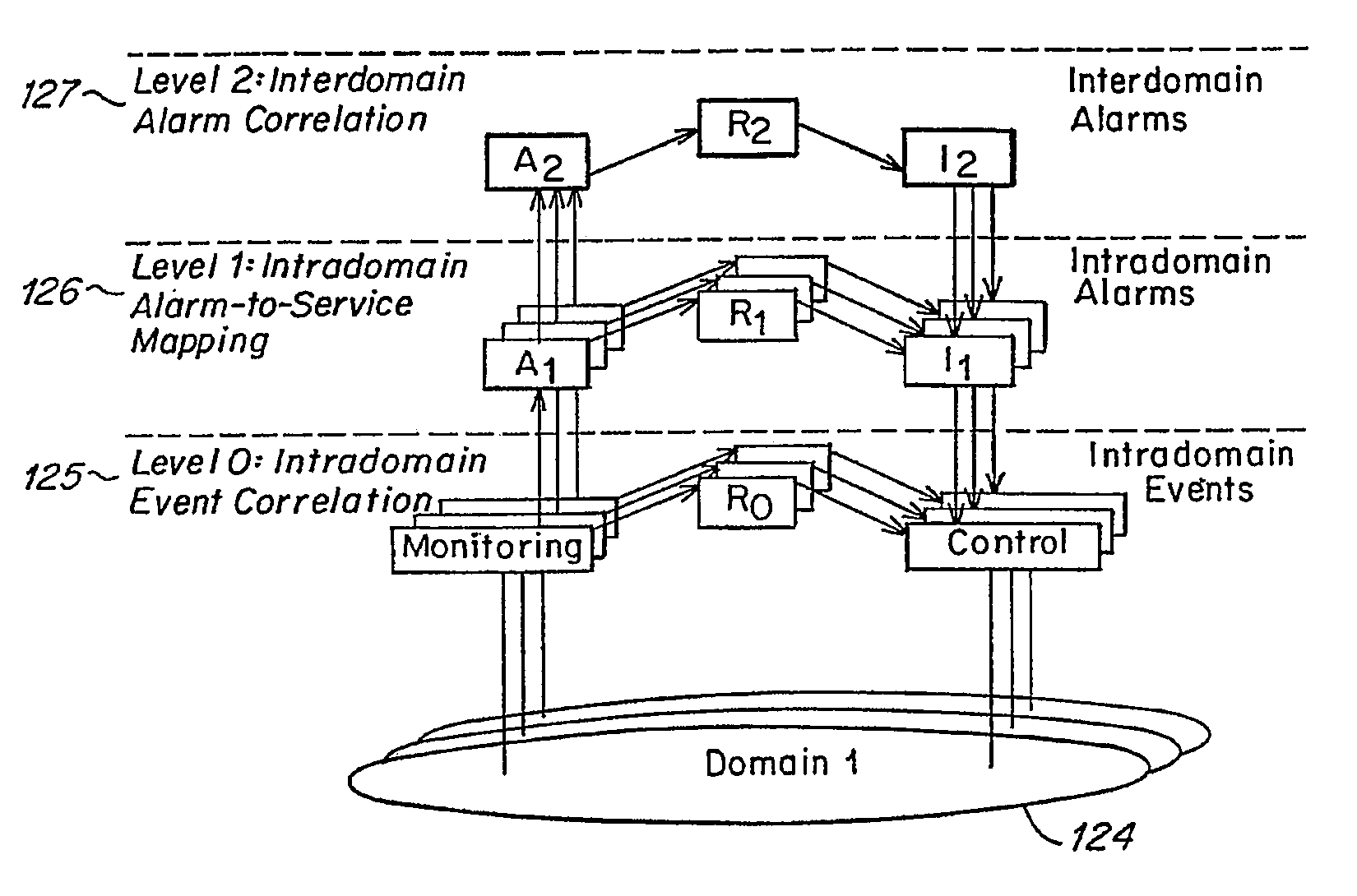
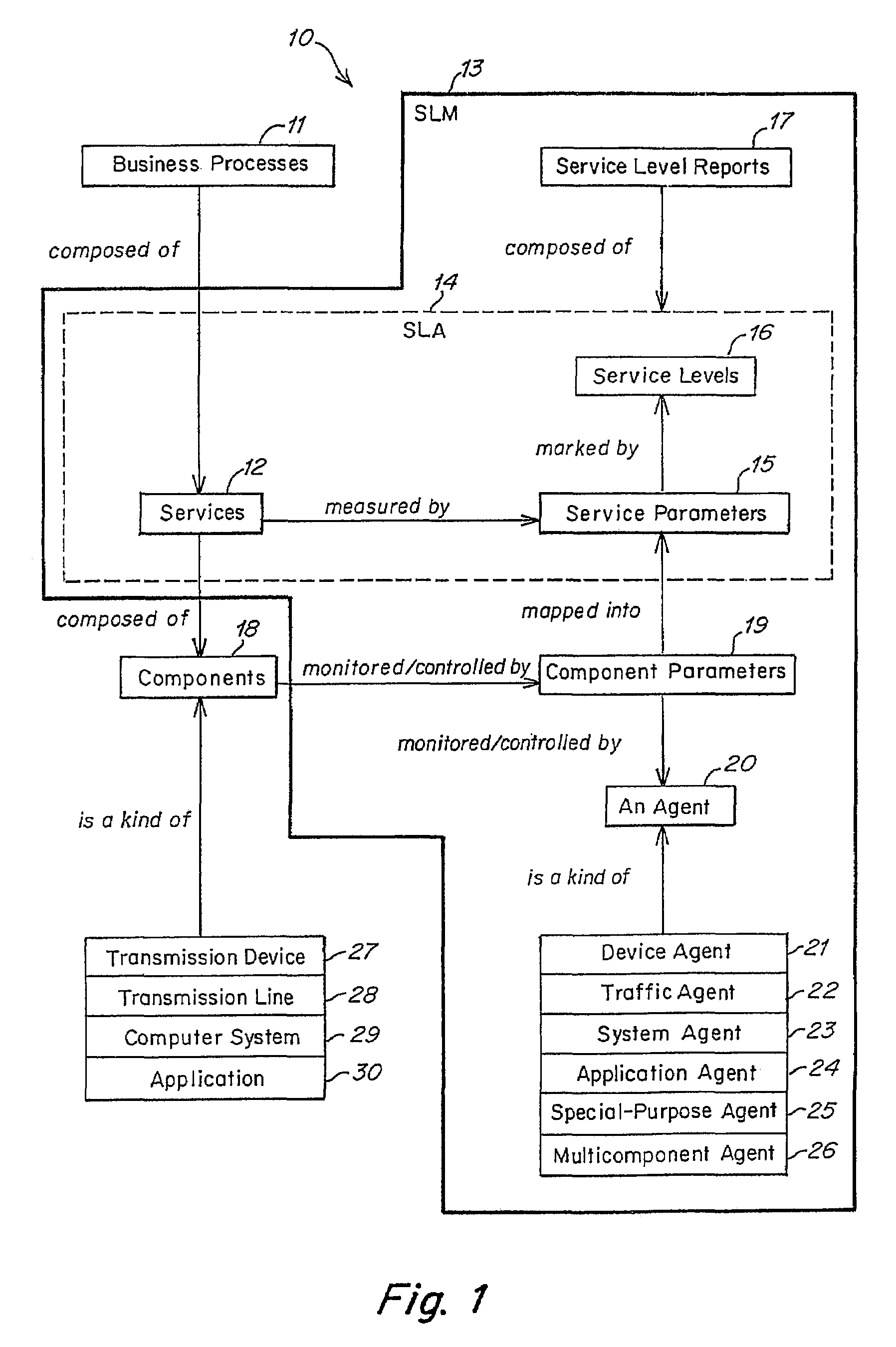
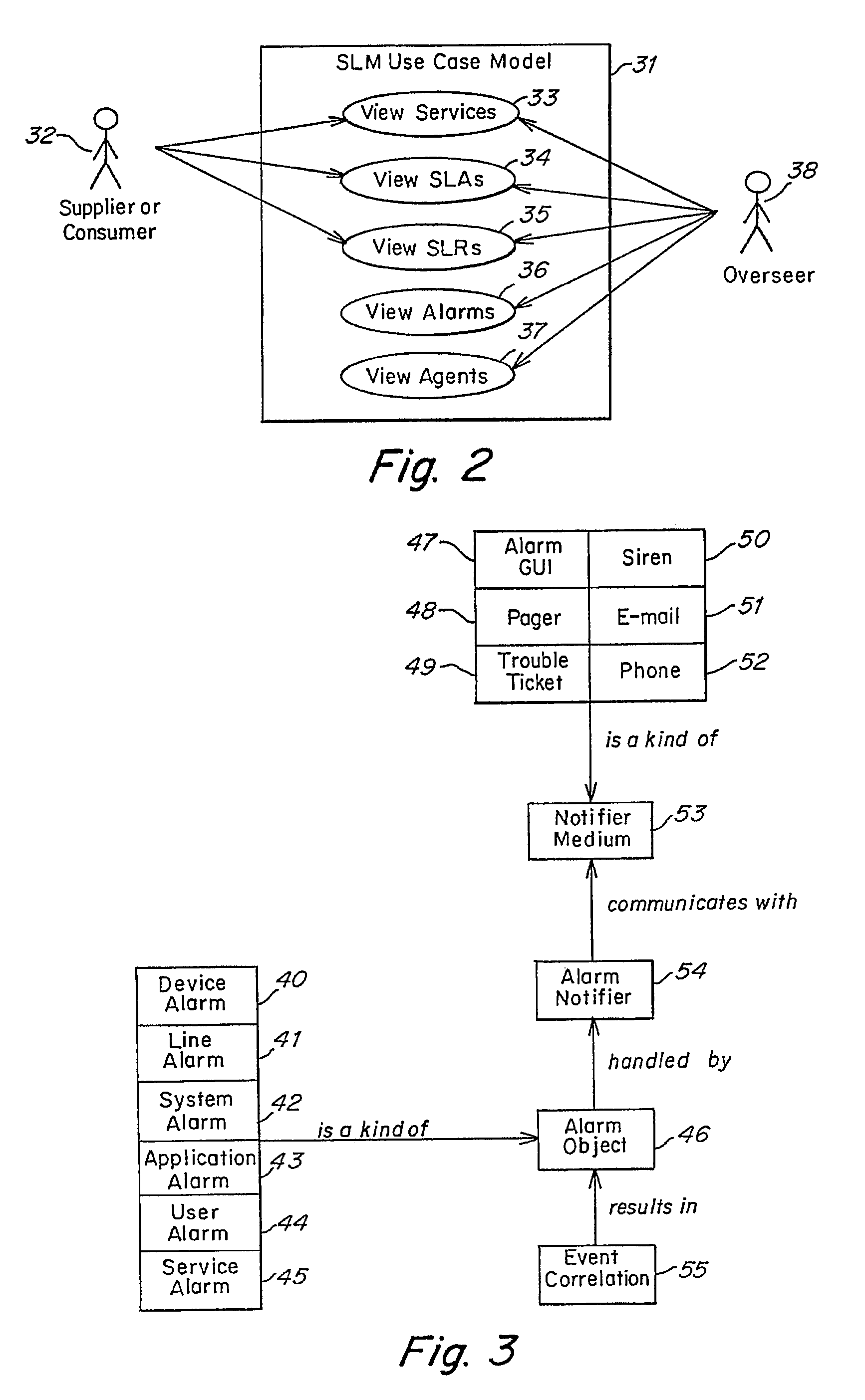
Method and apparatus for event correlation in service level management (SLM)
Method and apparatus for service level management, wherein business processes are composed of services. A state of the service is defined by one or more service parameters, and the service parameters depend upon performance of network components that support the service, e.g., component parameters. The state of the service may depend, for example, on a collection of service parameter values for availability, reliability, security, integrity and response time. A service level agreement is a contract between a supplier and a customer that identifies services supported by a network, service parameters for the services, and service levels (e.g., acceptable levels) for each service parameter.
Owner:COMP ASSOC THINK INC
Method and Apparatus for Context-Sensitive Event Correlation with External Control in Situation-Based Management
InactiveUS20050222811A1Efficient processingDigital computer detailsNuclear monitoringArtificial systemsTwo-way communication
Method and apparatus for situation-based management of natural and artificial systems using event correlation and a situation manager. Input is provided from multiple sources in the form of a collection of events. A first level of processing performs event correlation over the collection of events and infers new events and new qualities of events. A second level of processing manages situations based on the collection of events, where situations are recognized, maintained, and given a degree of confidence. Situations are periodically updated based on incoming events. The assertion of a situation may call for information from external sources, provide information for external sources, and provide control instructions to external sources. Given a current situation, past, and possible future situations are inferred. Additionally, a method and apparatus for bi-directional communication between the event correlator and situation manager.
Owner:ALTUSYS
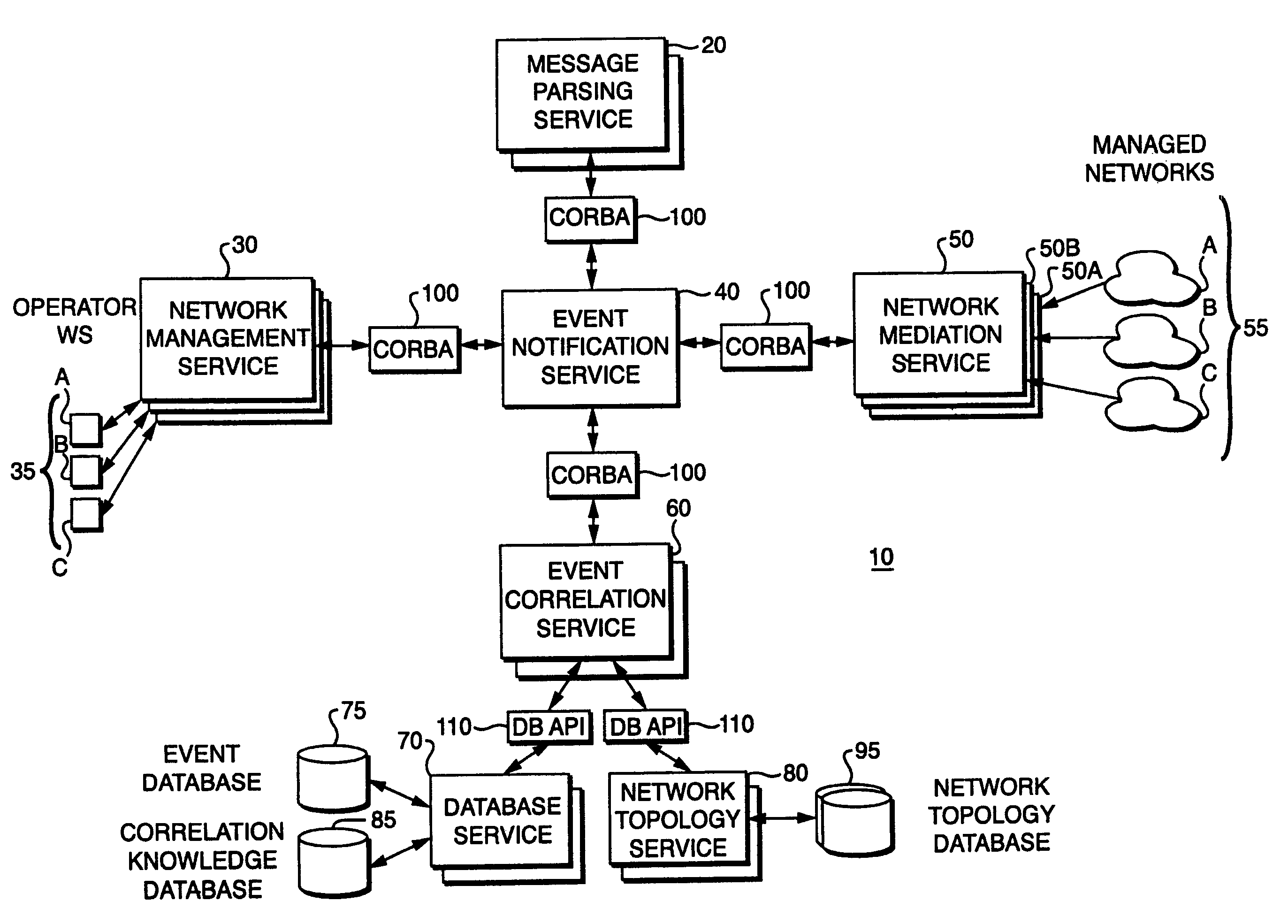
System and method for providing a global real-time advanced correlation environment architecture
InactiveUS6941557B1Easy to replaceFacilitate communicationDigital computer detailsMultiprogramming arrangementsData processing systemNetwork management
A method and system are disclosed for efficiently correlating network events within a data processing system and then transmitting messages to various network entities in response to an occurrence of a particular network event. According to the present invention, a network mediation service receives raw message streams from one or more external networks and passes the streams in real-time to the event notification service. The event notification service then passes the message to the message parsing service for processing. After the message has been parsed by the message parsing service, it is passed back to the event notification service which passes the message along an event channel to the network management service. The message is also passed to the event correlation service for event correlation. A knowledge-based database of message classes that define how to interpret the message text are used by the event correlation service to match correlation rule conditions to the observed events. After event correlation service processes the parsed event, it is passed to the network management service for resolution.
Owner:VERIZON LAB
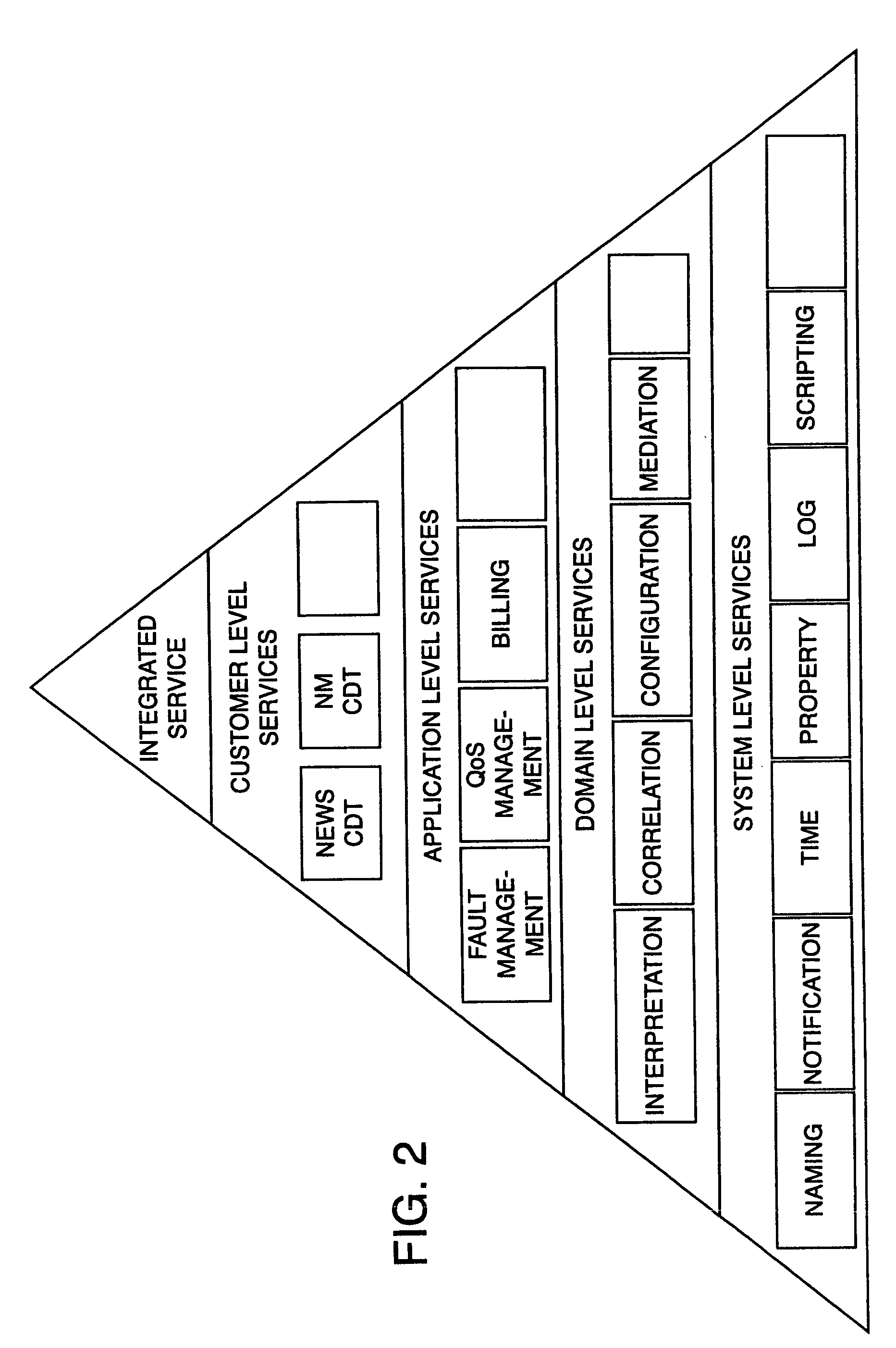
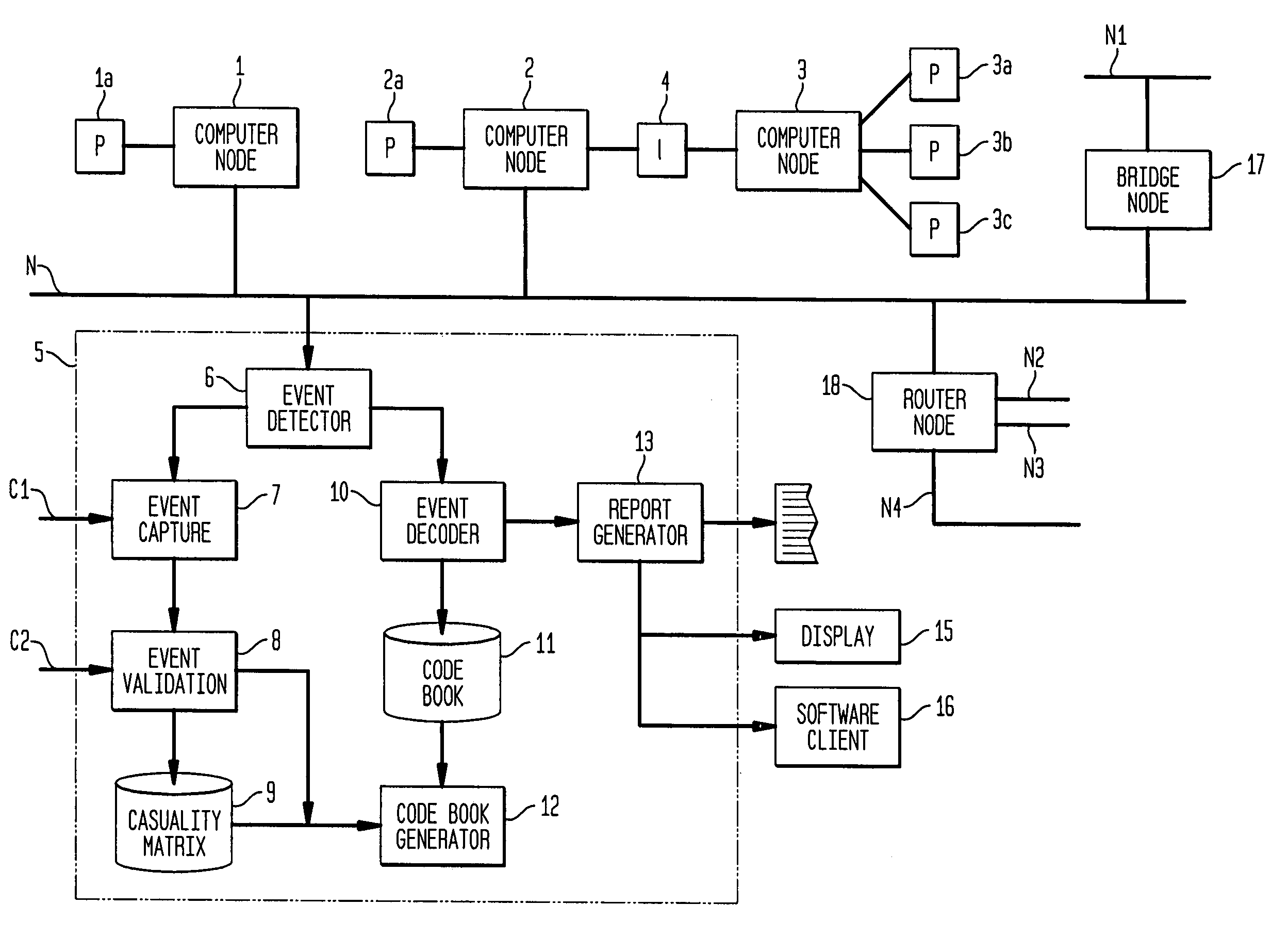
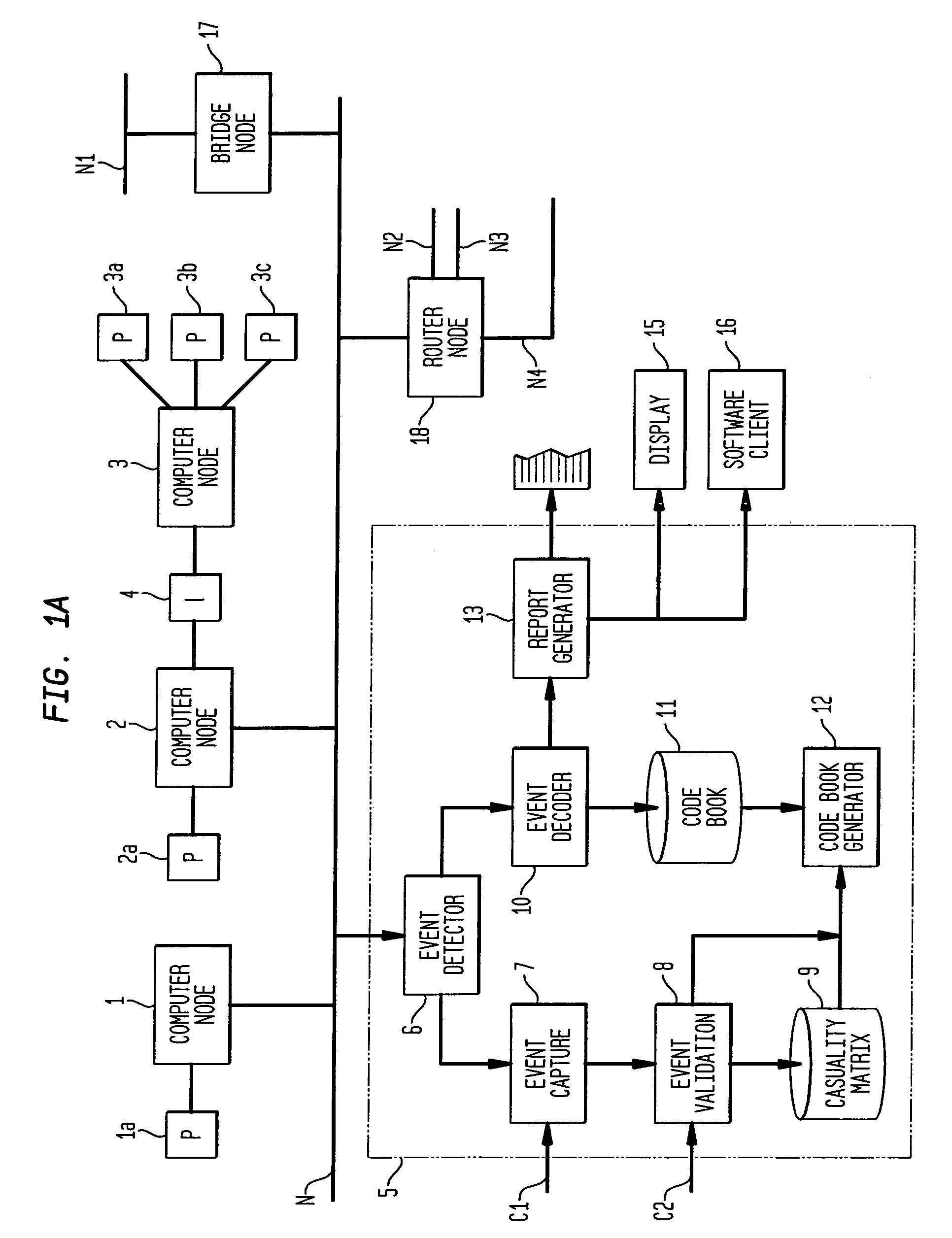
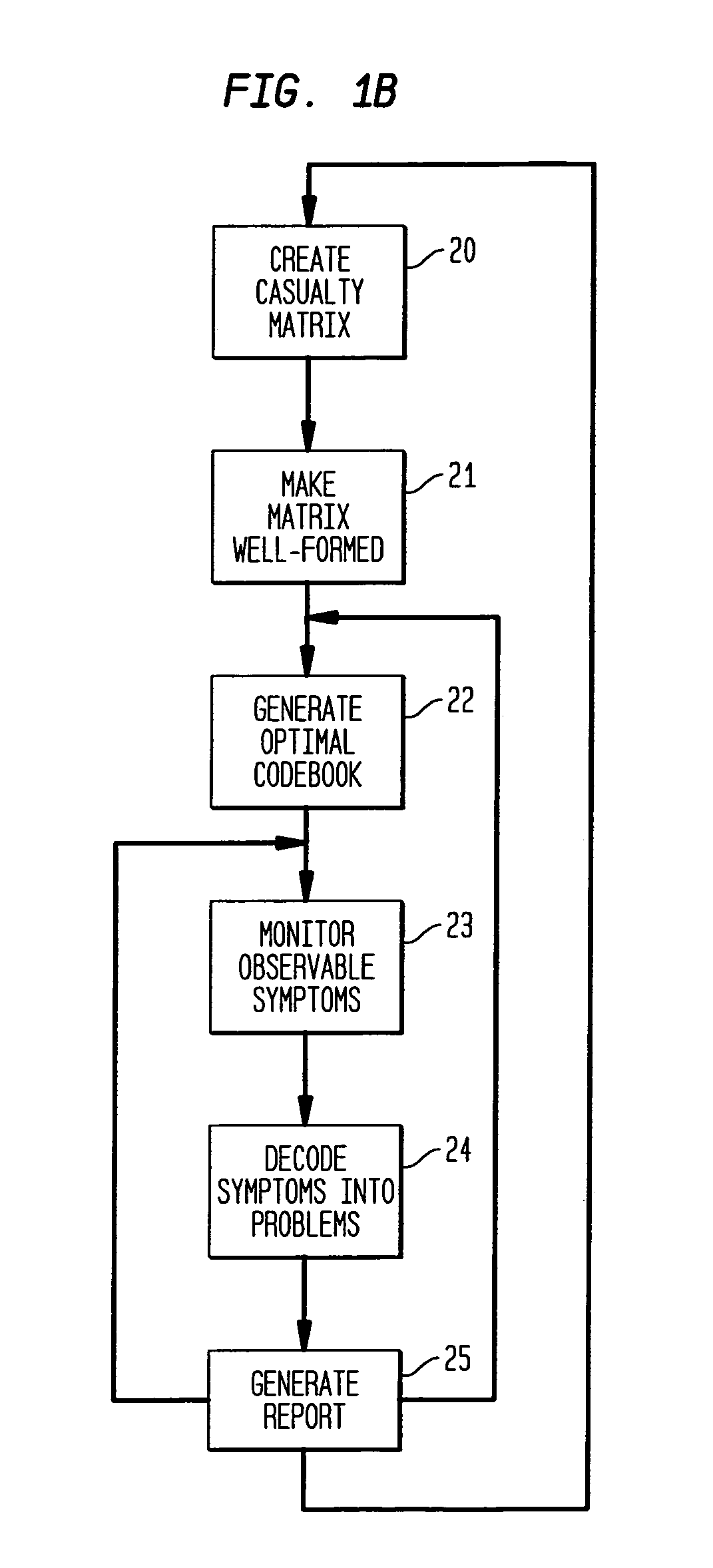
Apparatus and method for event correlation and problem reporting
InactiveUS7107185B1Effective monitoringImprove efficiencyNuclear monitoringDigital computer detailsComplex systemComputer science
A computer implemented method on a computer readable media is provided for determining the source of a problem in a complex system of managed components based upon symptoms. The problem source identification process is split into different activities. Explicit configuration non-specific representations of types of managed components, their problems, symptoms and the relations along which the problems or symptoms propagate are created that can be manipulated by executable computer code. A data structure is produced for determining the source of a problem by combining one or more of the representations based on information of specific instances of managed components in the system. Computer code is then executed which uses the data structure to determine the source of the problem from one or more symptoms.
Owner:VMWARE INC
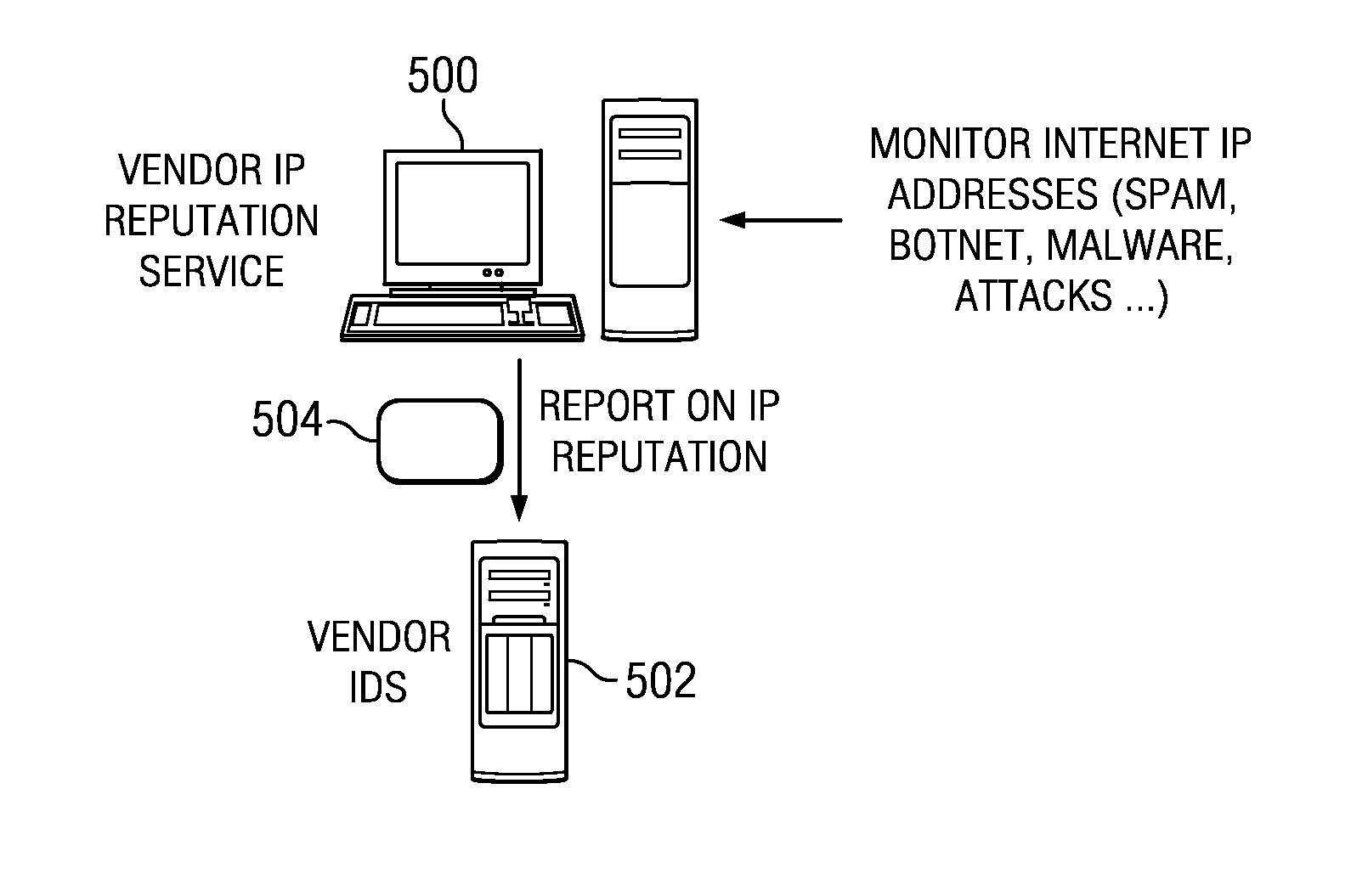
Cooperative intrusion detection ecosystem for IP reputation-based security
ActiveUS20140059683A1Easy to operateImprove system response timeMemory loss protectionError detection/correctionPattern matchingContinuous data
An intrusion detection system (IDS) is enhanced to operate in a cluster of such systems, and IDSs organized into a cluster cooperate to exchange IP reputation influencing events information between or among the cooperating systems in real-time to enhance overall system response time and to prevent otherwise hidden attacks from damaging network resources. An IDS includes an IP reputation analytics engine to analyze new and existing events, correlate information, and to raise potential alerts. The IP reputation analytics engines may implement an algorithm, such as a pattern matching algorithm, a continuous data mining algorithm, or the like, to facilitate this operation. Clustering IDS endpoints to share IP reputation influencing events, using the cluster-wide view to determine IP reputation, and feeding the cluster-wide view back to the IDS endpoints, provides for enhanced and early detection of threats that is much more reliable and scalable as compared to prior art techniques.
Owner:IBM CORP
System and method for auditing governance, risk, and compliance using a pluggable correlation architecture
ActiveUS20100198636A1Promote repairDrawback can be addressedFinanceComputer security arrangementsEvent correlationEnforcement
Described herein is a system and method for auditing governance, risk, and compliance using an event correlation architecture. In particular, the event correlation architecture may include a solution designer for defining a solution pack that enforces one or more specific governance, risk, or compliance controls, and a solution manager for deploying the solution pack within the event correlation architecture to configure the architecture for enforcement of the one or more controls. Thus, a collection of content defined in the solution pack may be used to enrich one or more events received at the event correlation architecture, and a correlation engine may then correlate the events using the content in the solution pack to enforce the one or more governance, risk, or compliance controls.
Owner:ORACLE INT CORP
Incremental detection and visualization of problem patterns and symptoms based monitored events
A computer system includes a symptoms database having symptoms that relate to problems, where each symptom includes an event correlation rule having corresponding predicates. To identify a root cause of a problem, collected events are correlated with symptoms based upon their associated event correlation rule(s). For each symptom at least partially matched to an event, visualization information is associated with corresponding events based upon the visualization attribute of the symptom, and textual information is associated with event based upon the recommendation of the symptom. Moreover, recommendations may be provided to an operator, such as based upon information associated with the symptom. The event and symptom data is analyzed by grouping events in the set of events based upon their associated visualization information and presenting the textual information associated with an operator-selected event.
Owner:IBM CORP
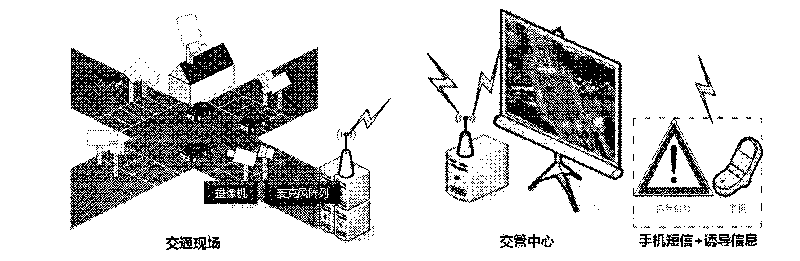
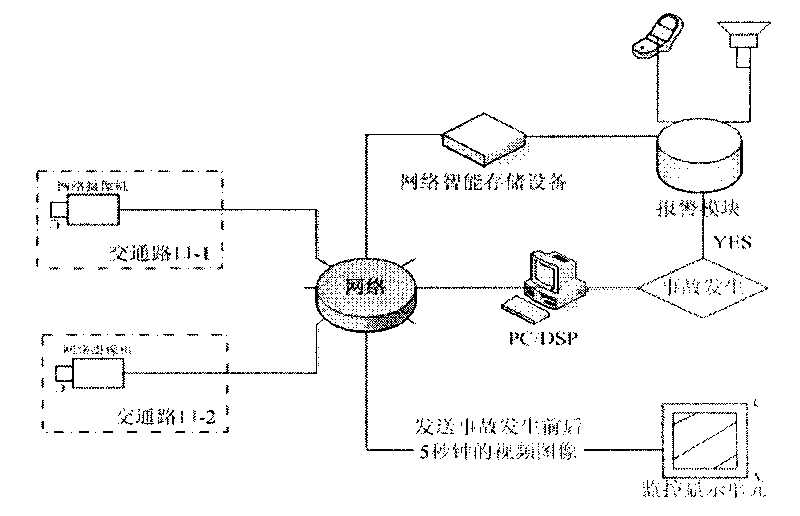
Crossroad traffic event automatic detection system based on multi-source information fusion
InactiveCN101751782AOvercome limitationsReal-time acquisitionDetection of traffic movementClosed circuit television systemsElevation angleInformation analysis
The invention discloses a crossroad traffic event automatic detection system based on multi-source information fusion. The invention aims at urban crossroad traffic management, establishes audio-video traffic information acquisition, traffic information analytical processing and traffic event automatic alarming three subsystems. The invention mainly comprises: designing and realizing an acquisition subsystem of multi-source traffic information (traffic audio information, traffic video information, multi-angle video information, elevation angle video information); realizing a traffic parameter automatic extractive technique based on traffic audio and traffic video; realizing a traffic event (car crash, illegal parking, jam and retrograde motion) automatic detection technique based on the multi-source information fusion; and realizing a software system for traffic event report, traffic event associated video information transmission, and traffic control center display and processing, and forming an integrated crossroad traffic event automatic detection system.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL
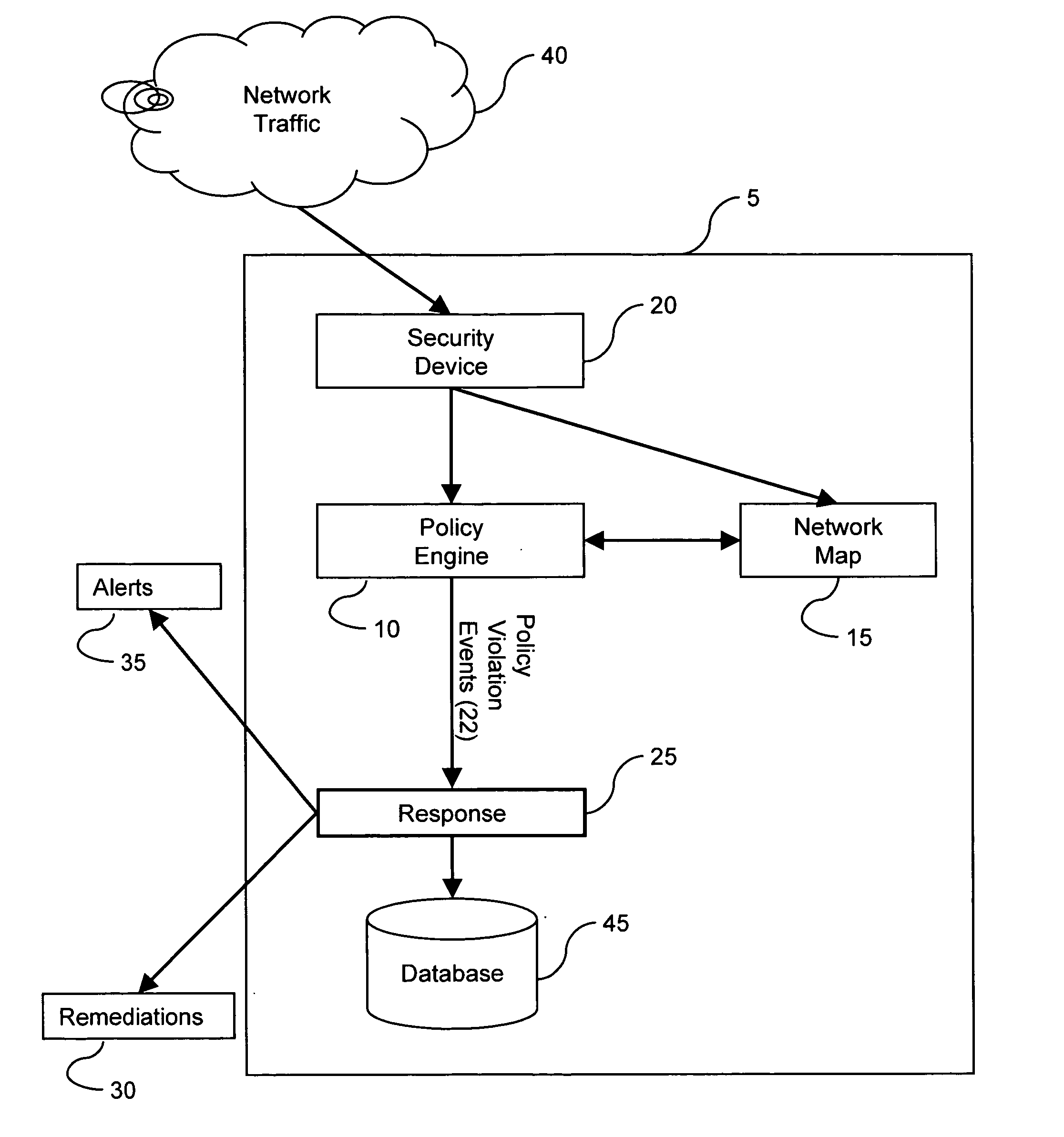
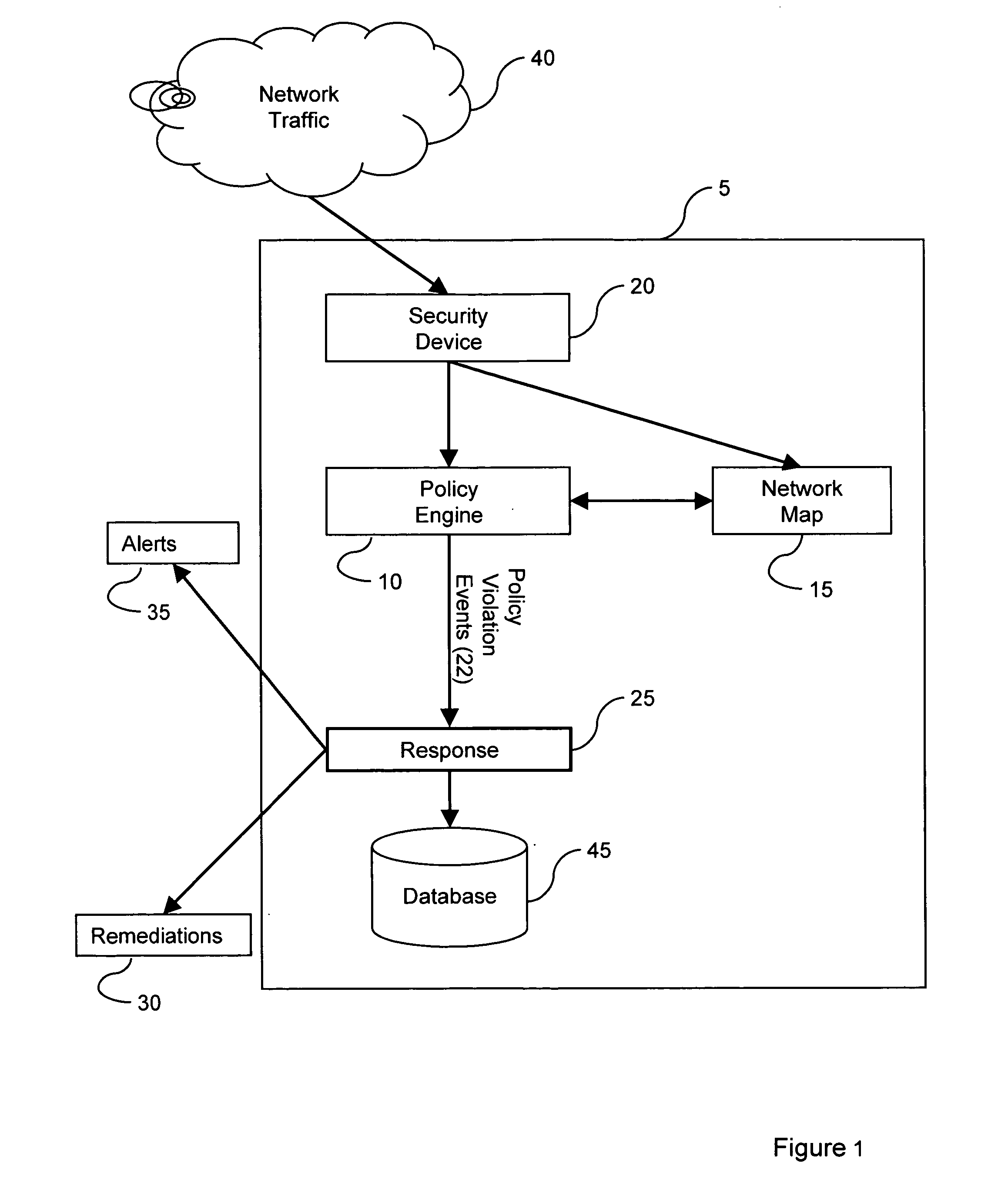
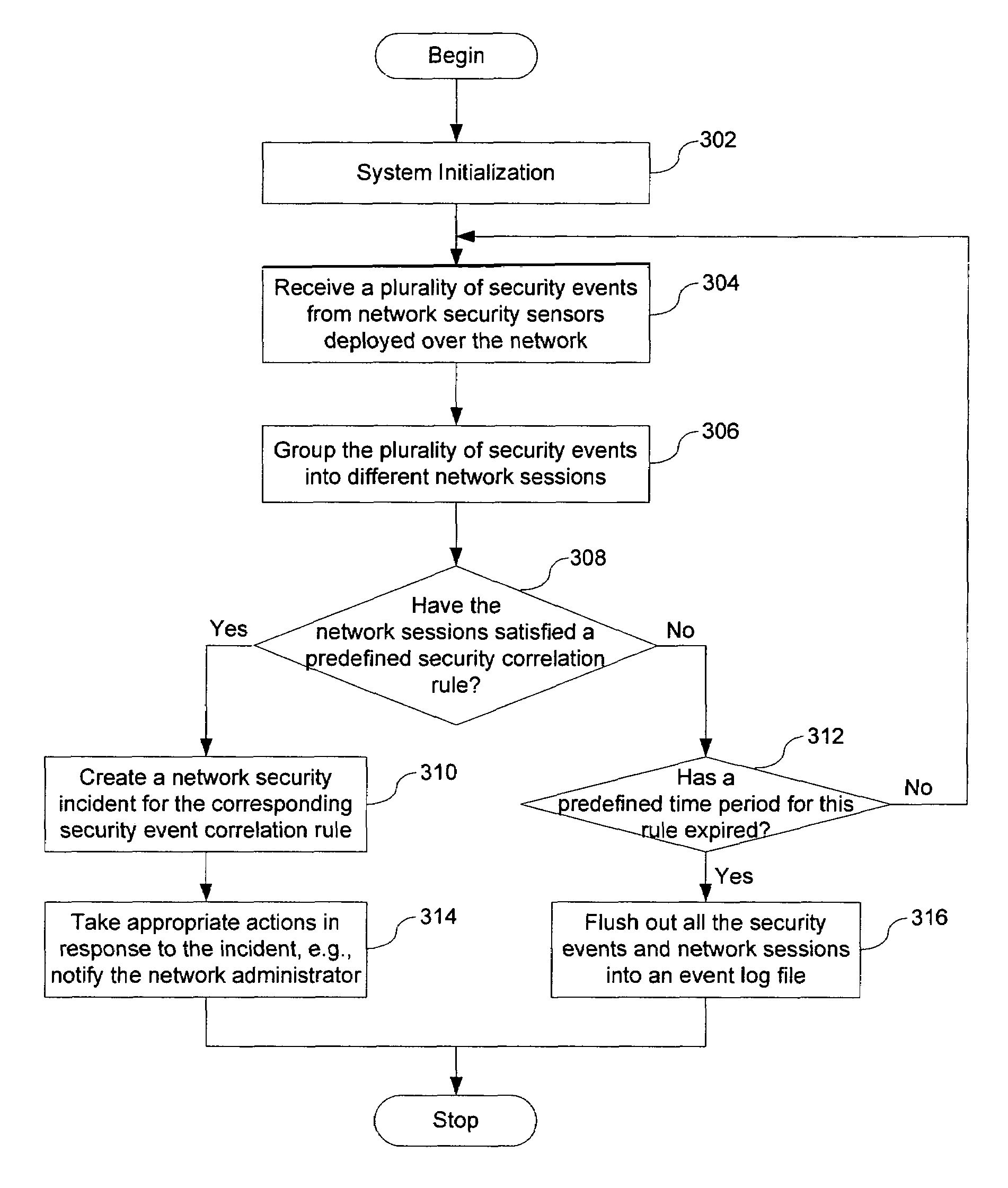
Method and system for displaying network security incidents
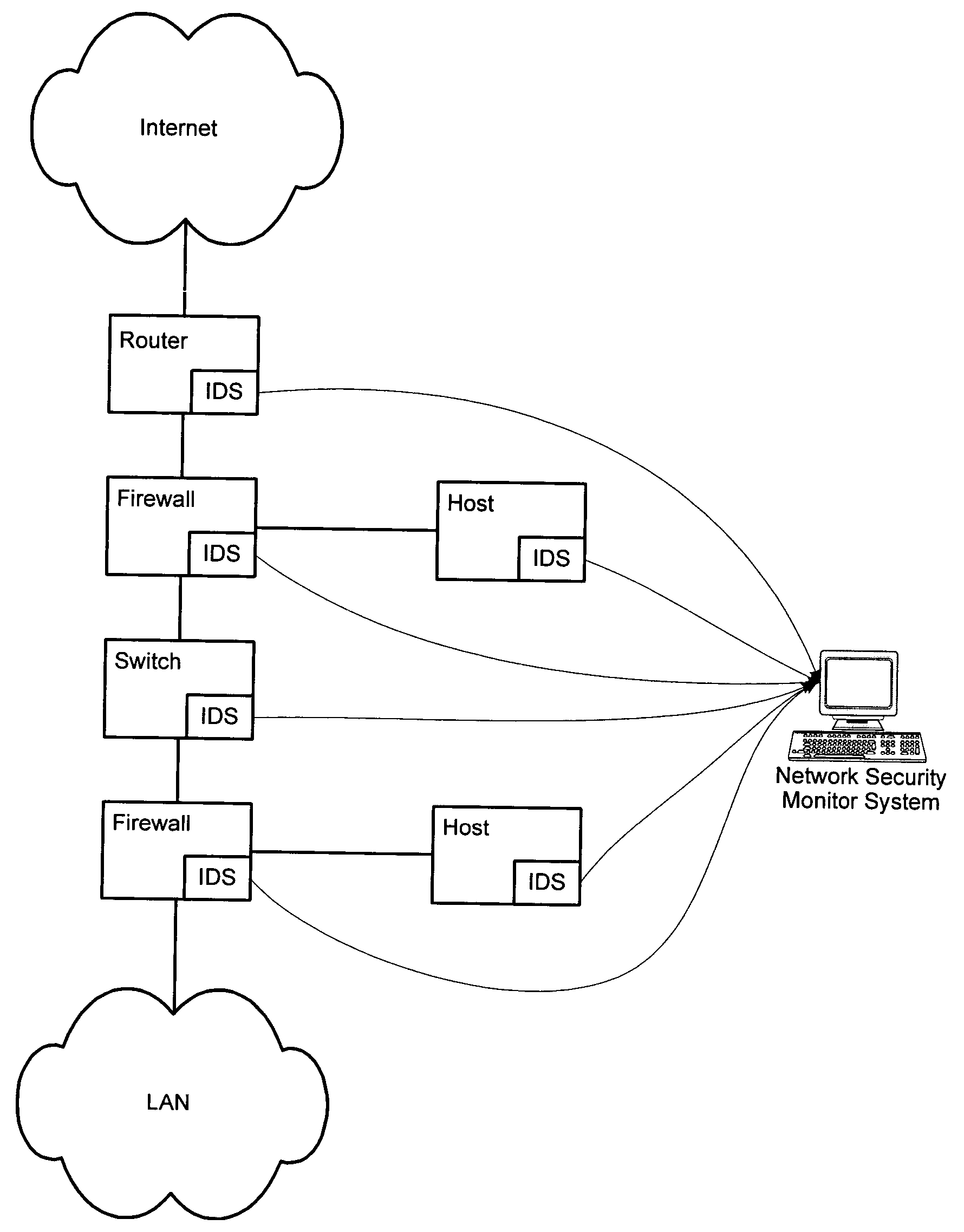
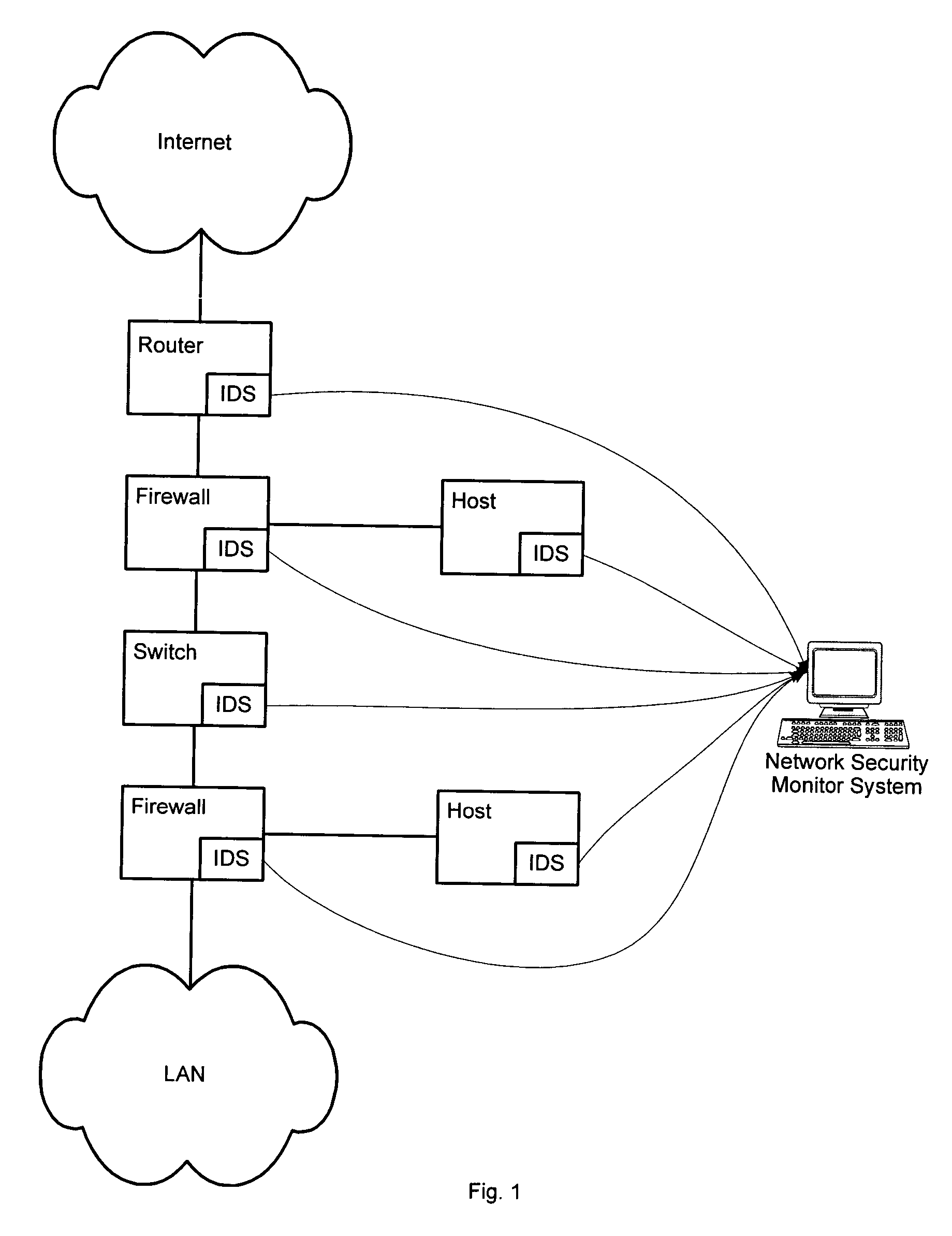
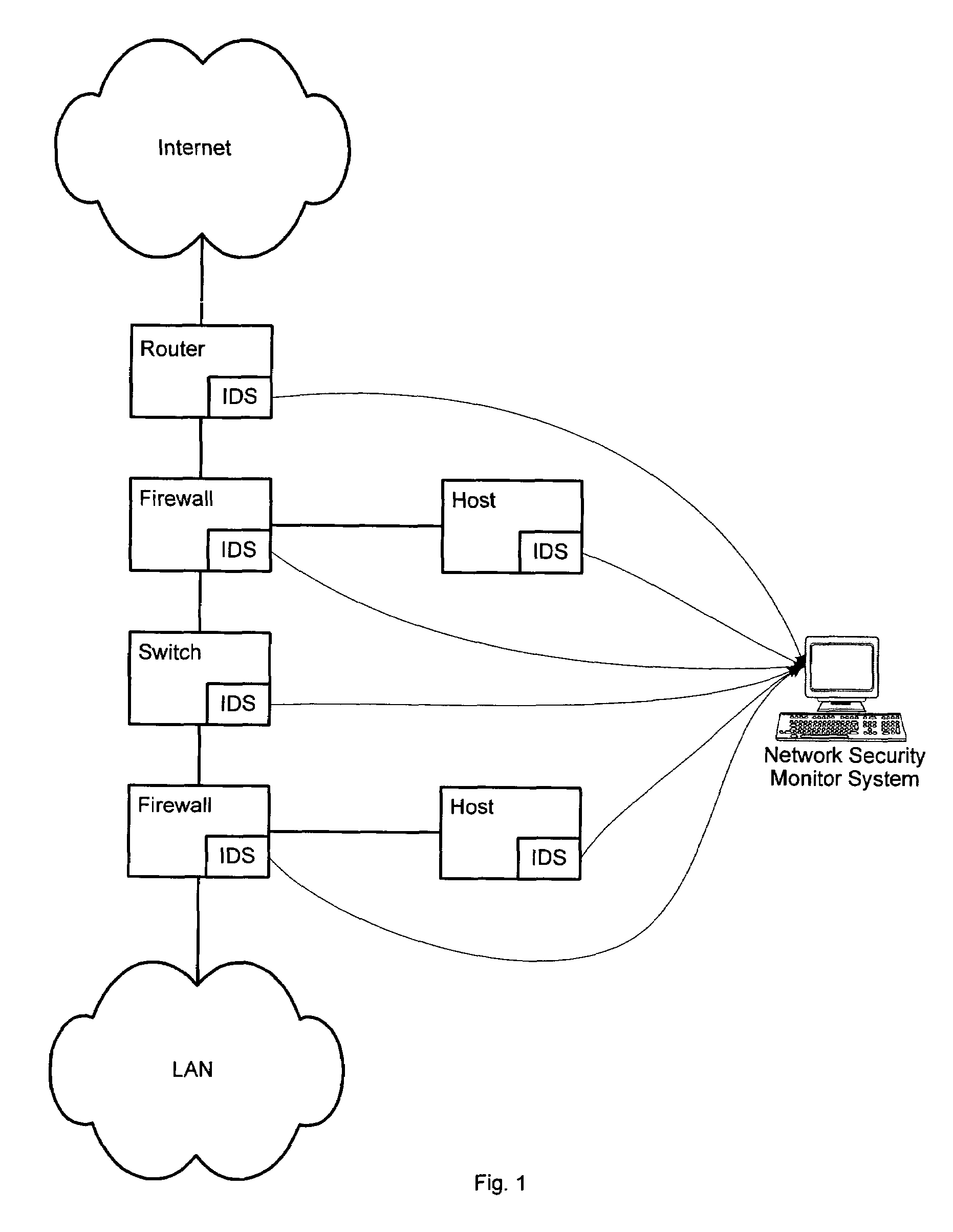
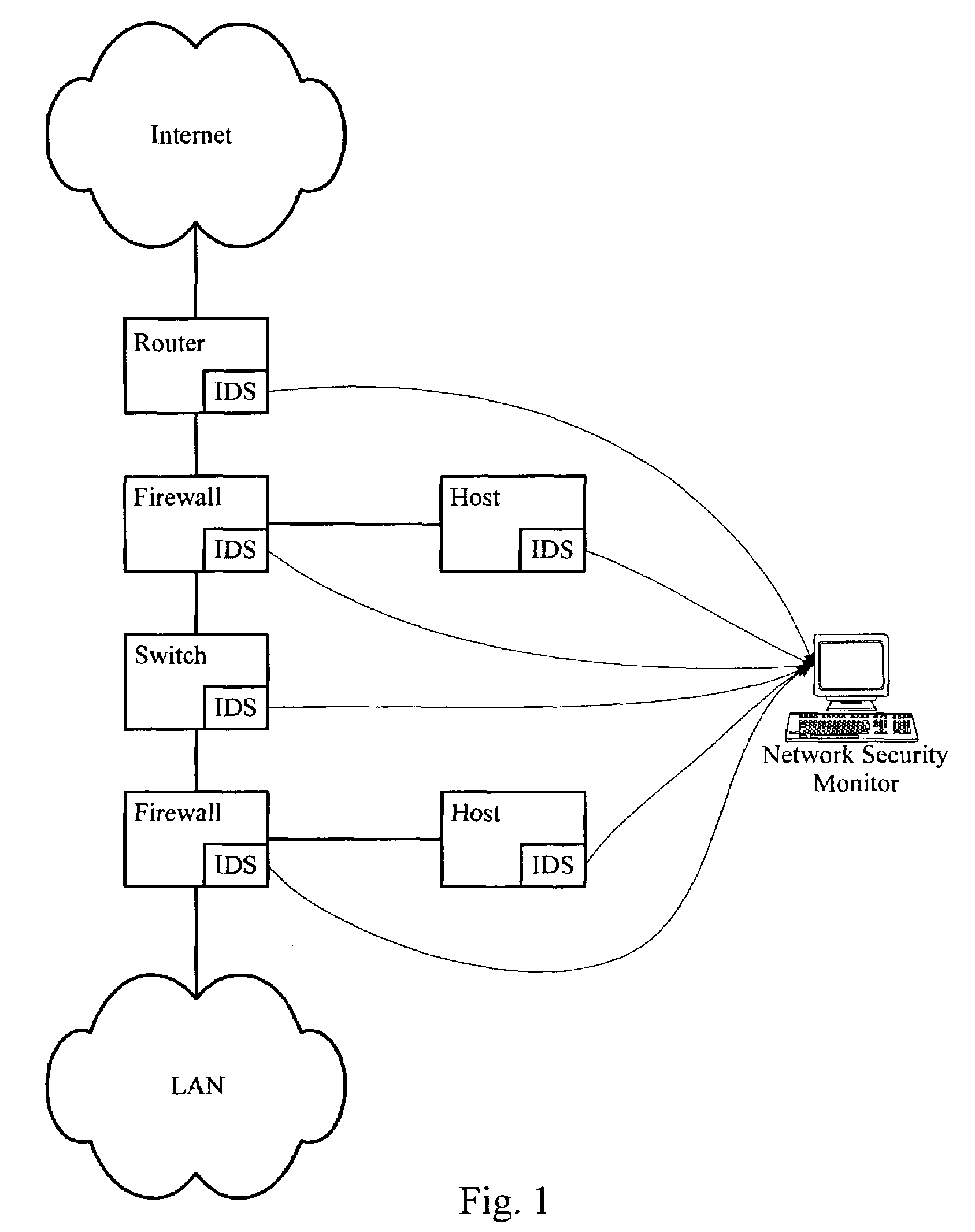
InactiveUS20050060562A1Digital data processing detailsDigital computer detailsNetwork attackSafety monitoring
A network security monitor system groups a plurality of security events into network sessions, correlates the network sessions according to a set of predefined network security event correlation rules and generates a security incident for the network sessions that satisfy one of the network security event correlation rules. The system then presents the information of the network sessions and security incidents to a user of the system in an intuitive form. The user is able to not only learn the details of a possible network attack, but also creates new security event correlation rules intuitively, including drop rules for dropping a particular type of events.
Owner:CISCO TECH INC
Network attack scene generating method based on multi-source alarm logs
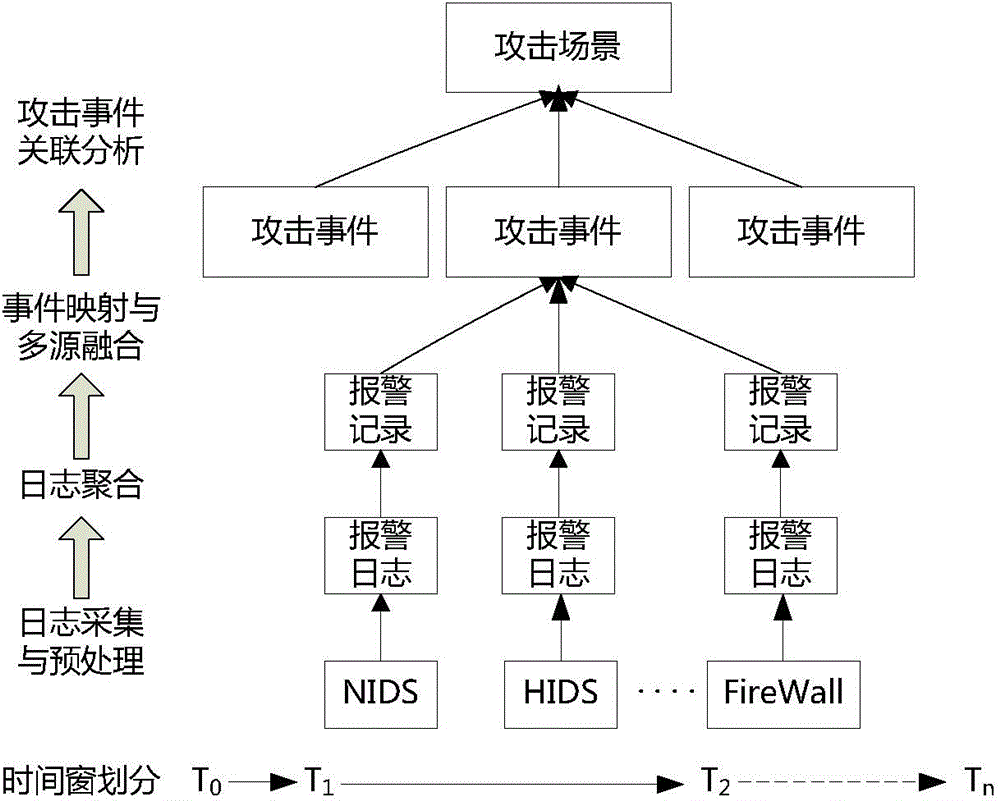
InactiveCN104539626AReflects security threat statusShow intentData switching networksCorrelation analysisNetwork attack
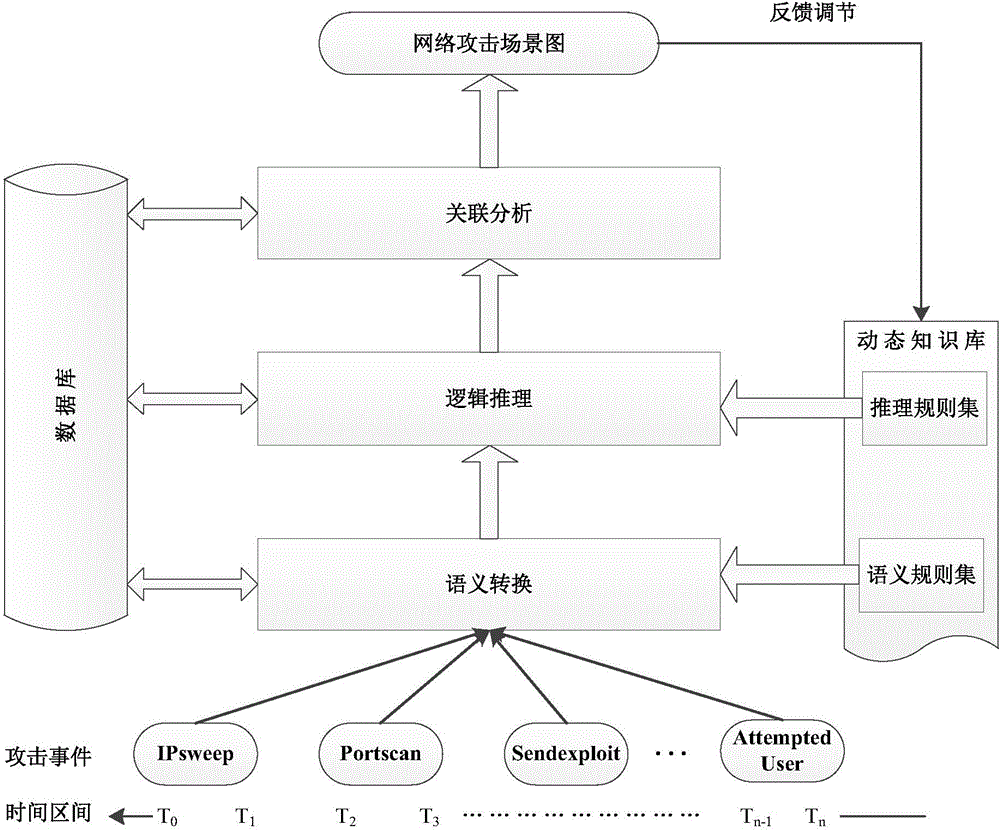
The invention relates to a network attack scene generating method based on multi-source alarm logs. The network attack scene generating method includes the steps that firstly, the alarm logs generated by multiple network security protection devices are collected, effective alarm log data are extracted through preprocessing, and noise, redundancy or ineffective logs are removed; for the effective alarm logs acquired by one device, log format differences of different devices are shielded through single-source log aggregation and mapping, and attack event information is analyzed and extracted; attack events extracted from different sources are fused and analyzed, and network attack events with high credibility are generated; then through correlation analysis of the attack events, a network attack scene graph is generated, and the whole attack process of one attack operation is analyzed. Due to the fact that the multi-source logs are fused, the analyzed attack event information can more completely and more reliably depict attacks to which a network is subject, attack scenes are acquired through correlation analysis of the attack events, the intentions of attackers can be more clearly shown, and the security threat state of the network can be more clearly reflected.
Owner:THE PLA INFORMATION ENG UNIV
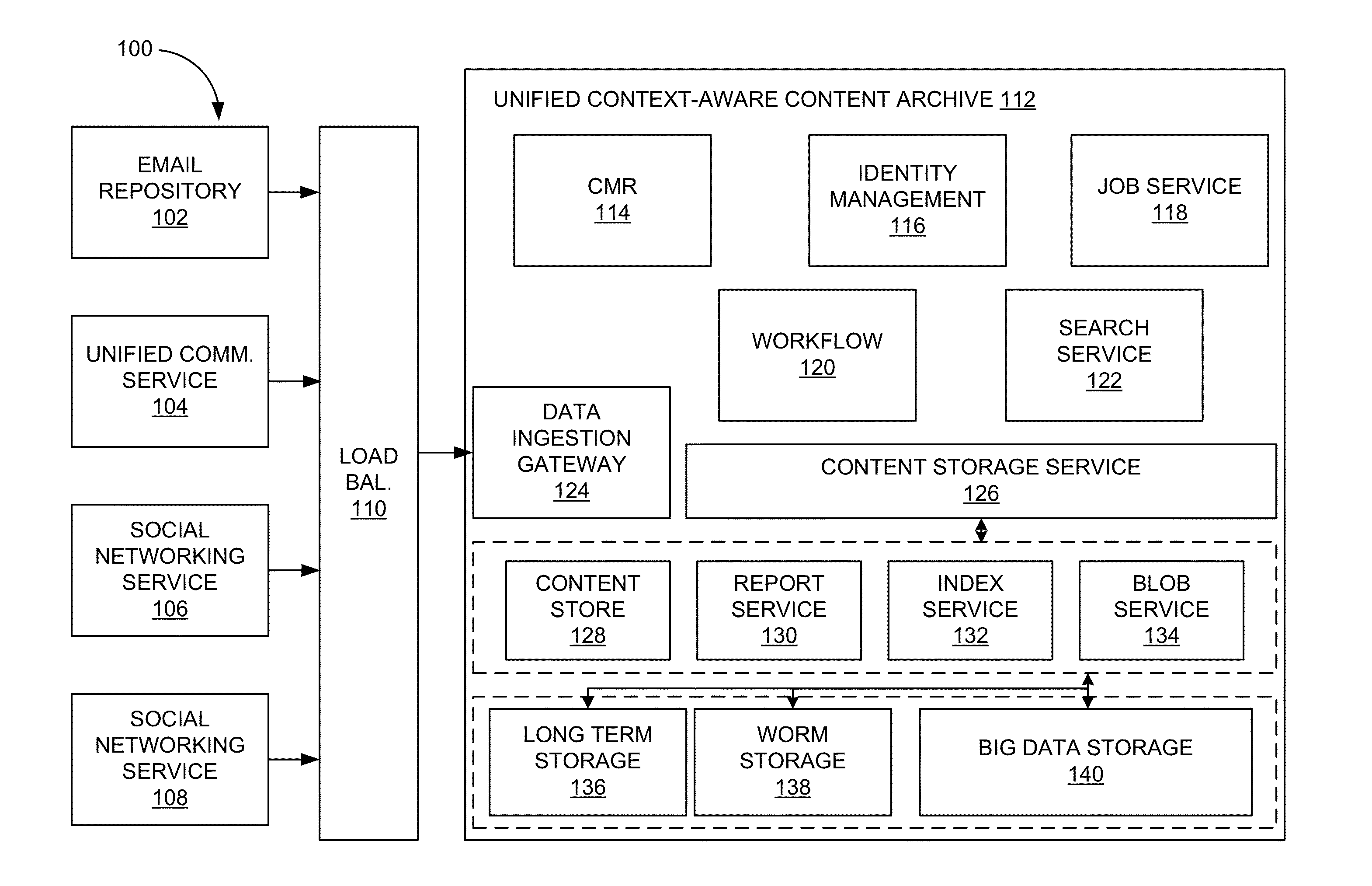
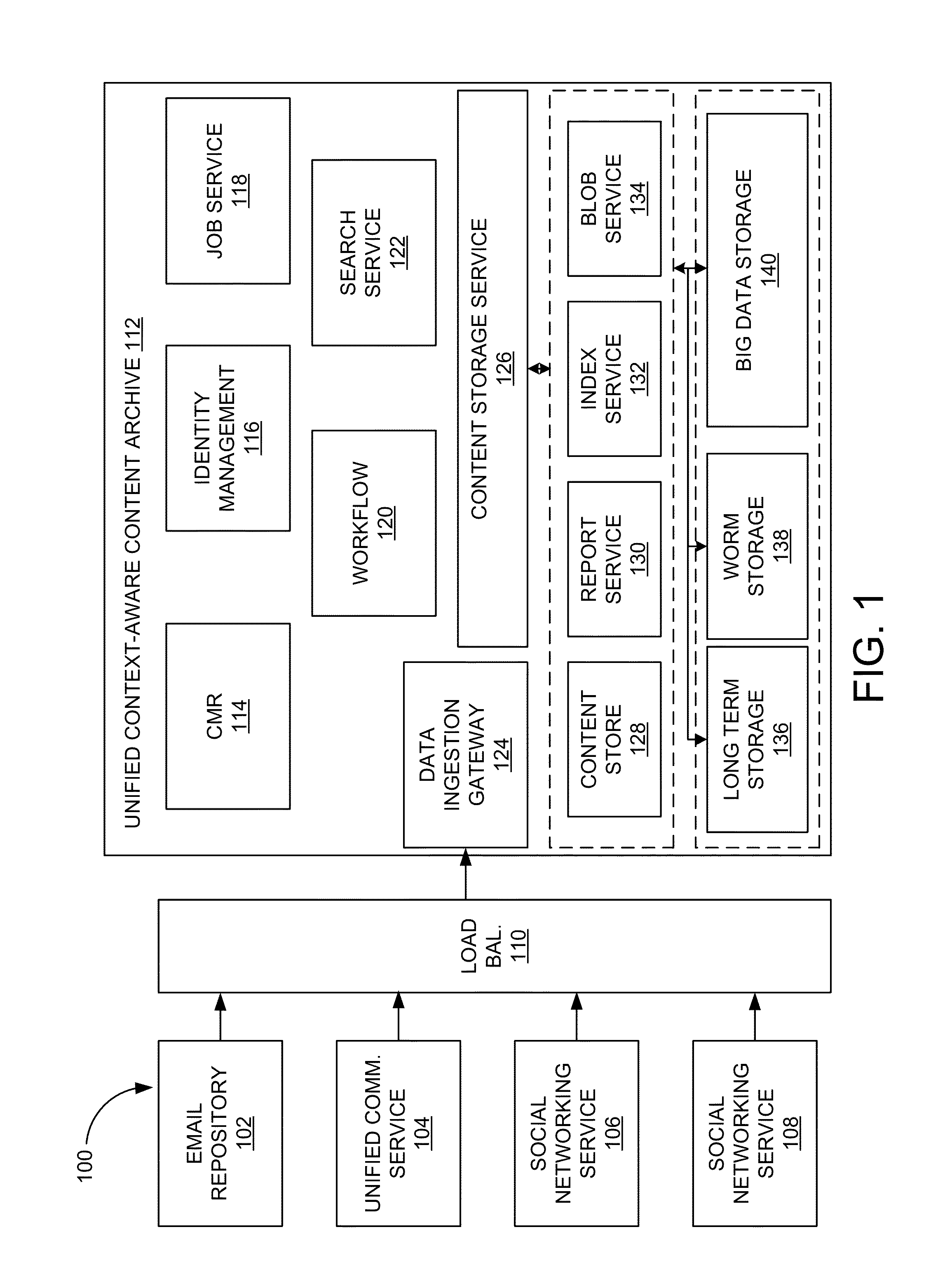
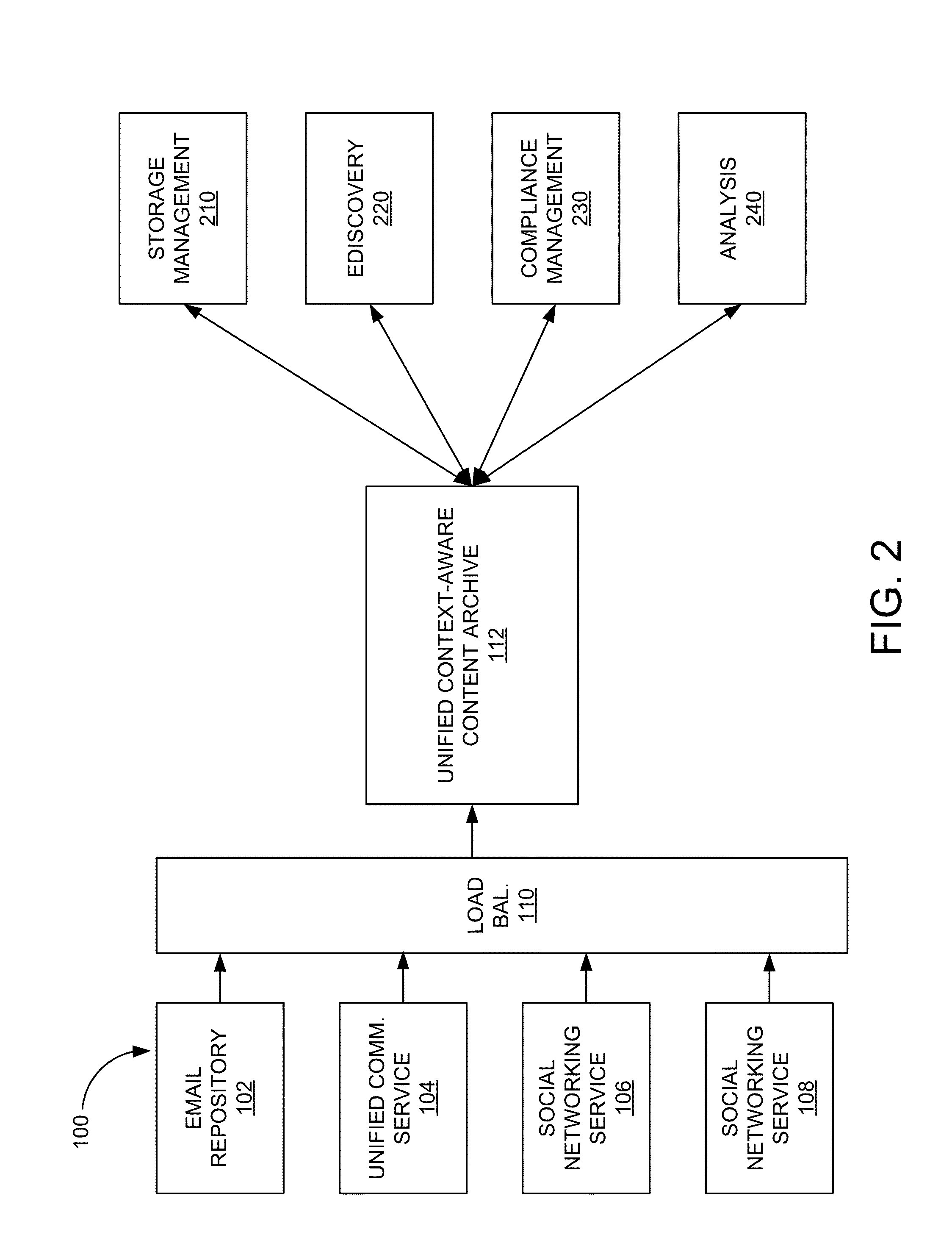
Unified context-aware content archive system
ActiveUS20150039565A1Digital data processing detailsRelational databasesBusiness managementTemporal succession
A unified context-aware content archive system allows enterprises to manage, enforce, monitor, moderate, and review business records associated with a variety of communication modalities. The system may store an information infoset derived or inferred from one or more documents representing communications according to the variety of communication modalities as interaction transcripts. An interaction transcript represents interactions between participants through the documents rather than the documents themselves allowing for derivation or inference of communication events, chronologies, and mappings to be stored in a common data structure. In one aspect, events correlation is provided between participants of communications that can be established by general time series analysis for the purposes of extracting meaningful statistics and interaction contexts and other characteristics of data. In another aspect, chronological mappings are provided of conversations between an established start and end time frame.
Owner:ACTIANCE
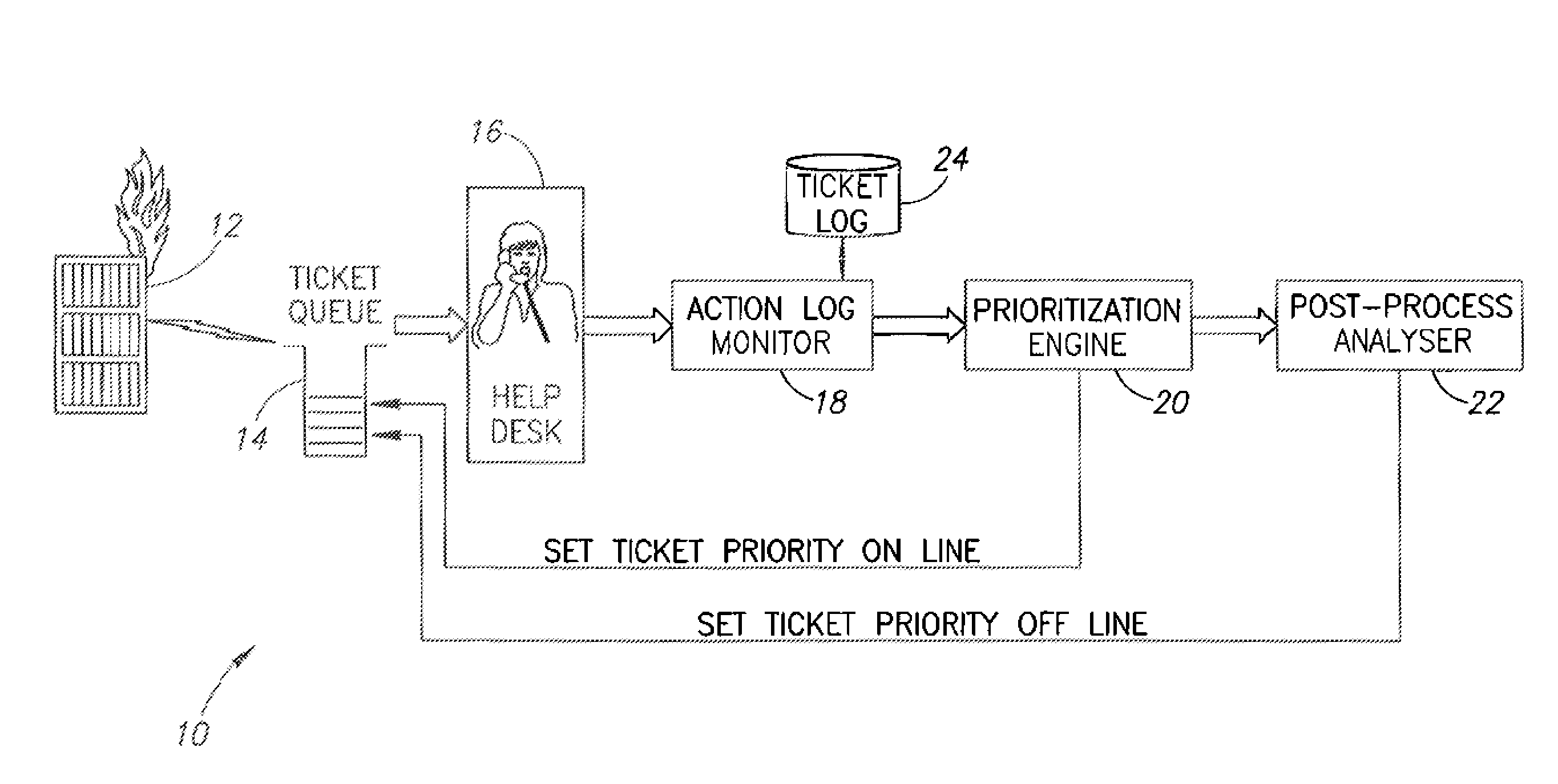
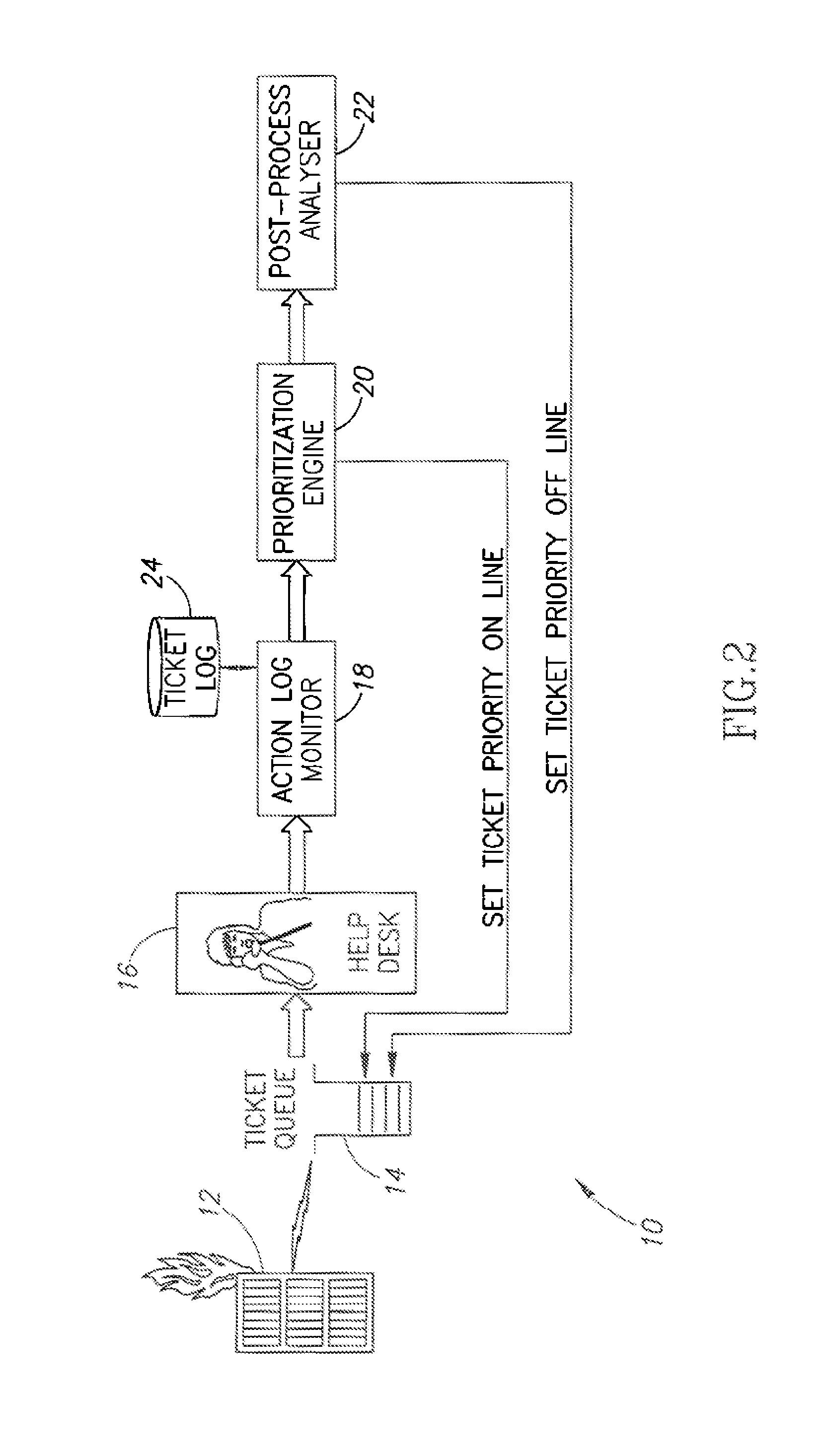
Event correlation based trouble ticket resolution system incorporating adaptive rules optimization
InactiveUS20080155564A1Reduce impactHigh degree of automationDigital computer detailsForecastingGood practiceProblem resolution
A system and method for event correlation and adaptive rules optimization in the context of a trouble ticket resolution system. The adaptive rules optimizer incorporates learning principles that achieve a high degree of automation while leaving control in the hands of an operator. To mitigate the effects of possible errors, the adaptive rules optimizer switches from hard decisions to soft decisions. The tickets in the queue and their related events are prioritized to mimic the best practices introduced by the support team handling the given problem, to take into account the business impact so that at each point in time the operator's work provides maximum overall benefit and to provide all auxiliary information that may be instrumental in the problem resolution process.
Owner:IBM CORP
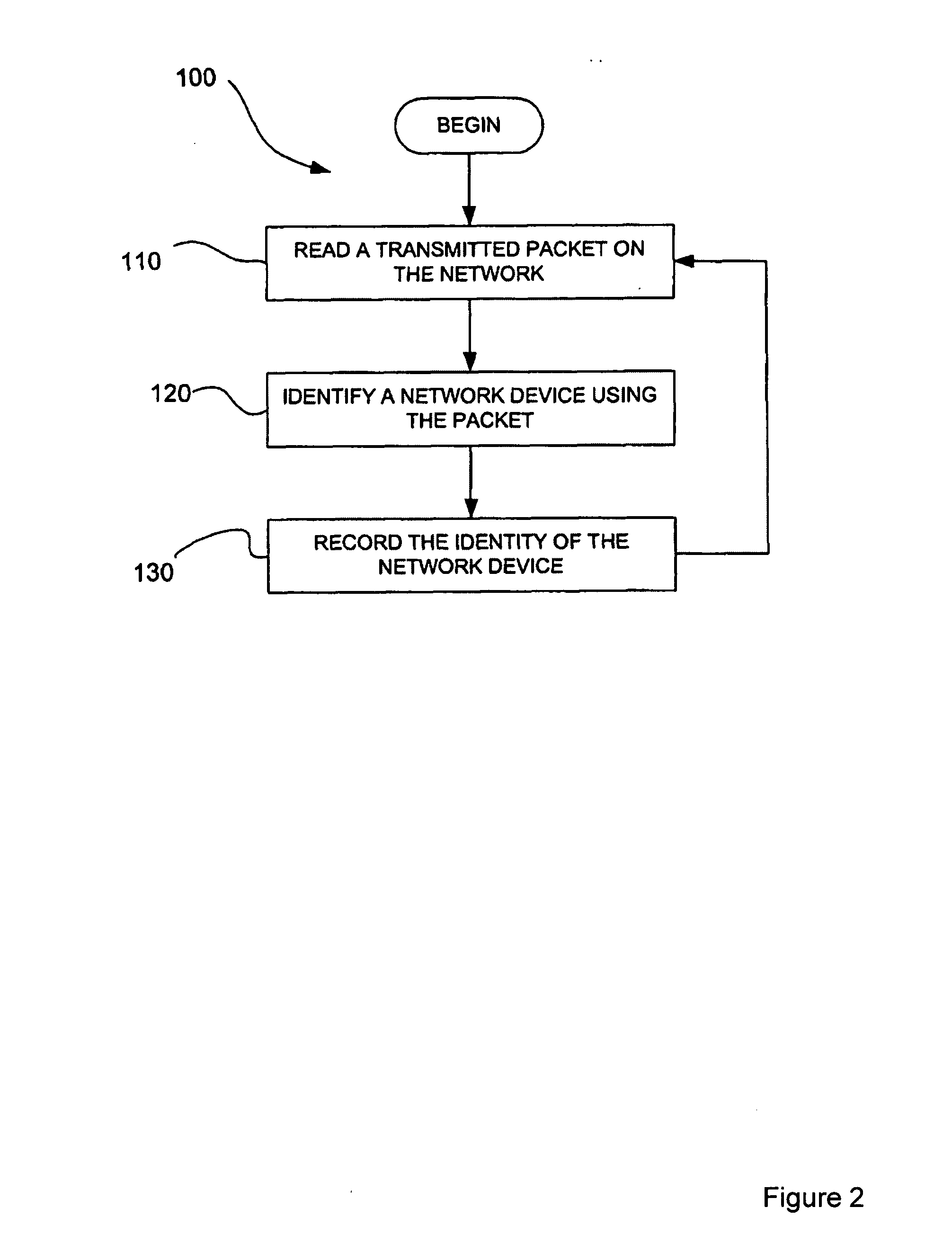
Intrusion event correlation with network discovery information
ActiveUS20080244741A1Minimize false positiveMinimize false positivesMemory loss protectionError detection/correctionNetwork topologyNetwork mapping
A policy component comprises policy configuration information. The policy configuration information contains one or more rules. Each rule and group of rules can be associated with a set of response actions. As the nodes on the monitored networks change or intrusive actions are introduced on the networks, network change events or intrusion events are generated. The policy component correlates network change events and / or intrusions events with network map information. The network map contains information on the network topology, services and network devices, amongst other things. When certain criteria is satisfied based on the correlation, a policy violation event may be issued by the system resulting in alerts or remediations.
Owner:CISCO TECH INC
Method and system for displaying network security incidents
InactiveUS7644365B2Digital data processing detailsDigital computer detailsNetwork attackEvent correlation
A network security monitor system groups a plurality of security events into network sessions, correlates the network sessions according to a set of predefined network security event correlation rules and generates a security incident for the network sessions that satisfy one of the network security event correlation rules. The system then presents the information of the network sessions and security incidents to a user of the system in an intuitive form. The user is able to not only learn the details of a possible network attack, but also creates new security event correlation rules intuitively, including drop rules for dropping a particular type of events.
Owner:CISCO TECH INC
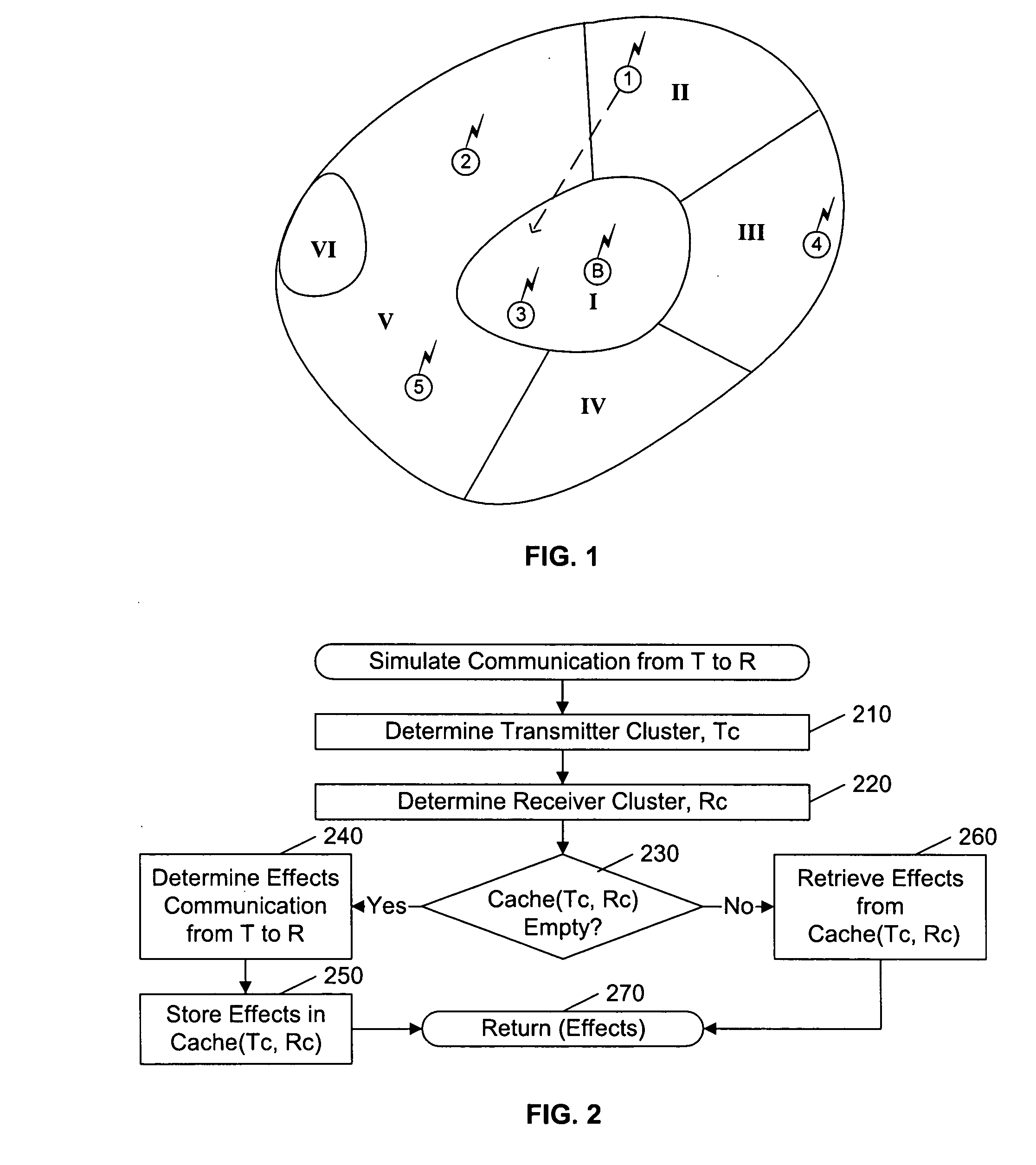
Wireless link simulation with generic caching
ActiveUS20050048964A1Shorten the timeRadio/inductive link selection arrangementsTransmission monitoringTransceiverGeographic area
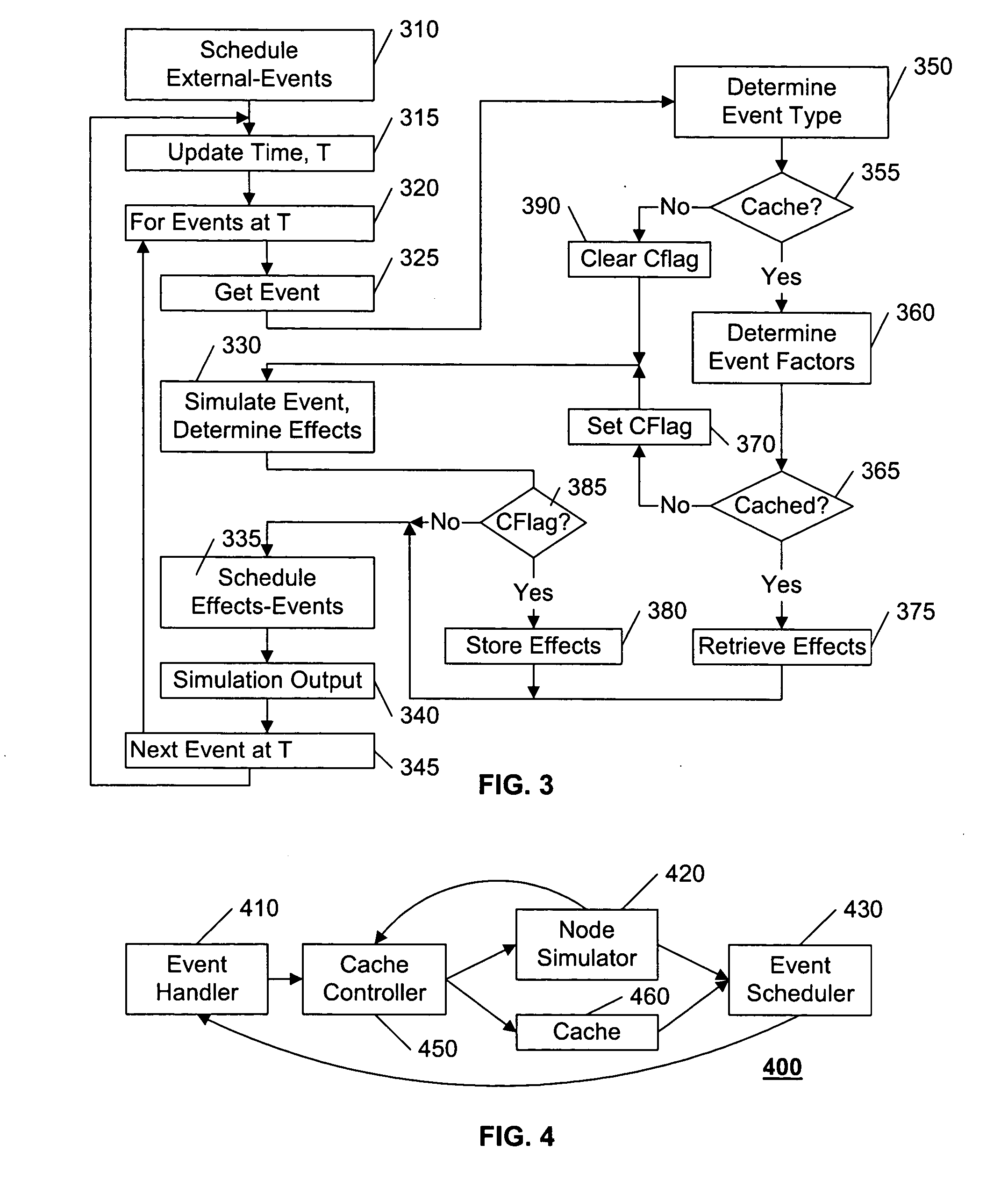
A simulation system includes a cache structure that stores determined characteristics related to the propagation of an event. If a similar event occurs, and the factors affecting the determination of these characteristics have not changed, the characteristics associated with the new event are retrieved from the cache, rather than being re-determined from the underlying factors. In the example of mobile transceivers, if multiple transceivers share a common set of underlying factors, the determined characteristics of one transceiver can be shared among all of the other transceivers. If the underlying factors are dependent upon geographic area, mobile transceivers that enter a geographic area having associated cached characteristics can use the cached characteristics of other transceivers that are, or had been, in the area. Because the cache process is structured to intercept a call to the routine that determines the characteristics, the modifications to a simulation system to incorporate this caching feature should be minimal.
Owner:RIVERBED TECH LLC
Automatic correction of past position errors for location and inventory tracking
ActiveUS20100332125A1Few or no effectsAccurate descriptionPosition fixationNavigation instrumentsPosition errorComputer science
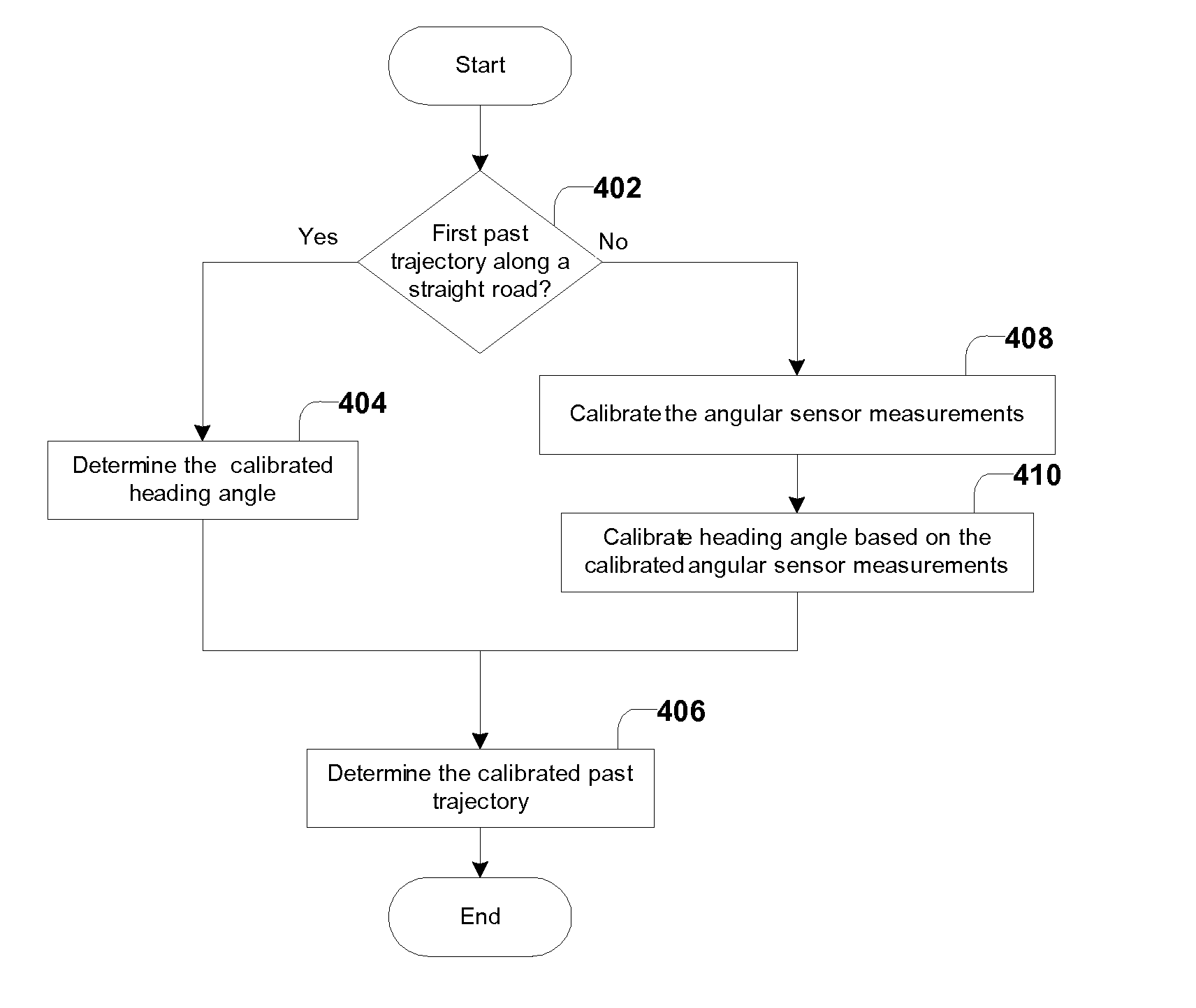
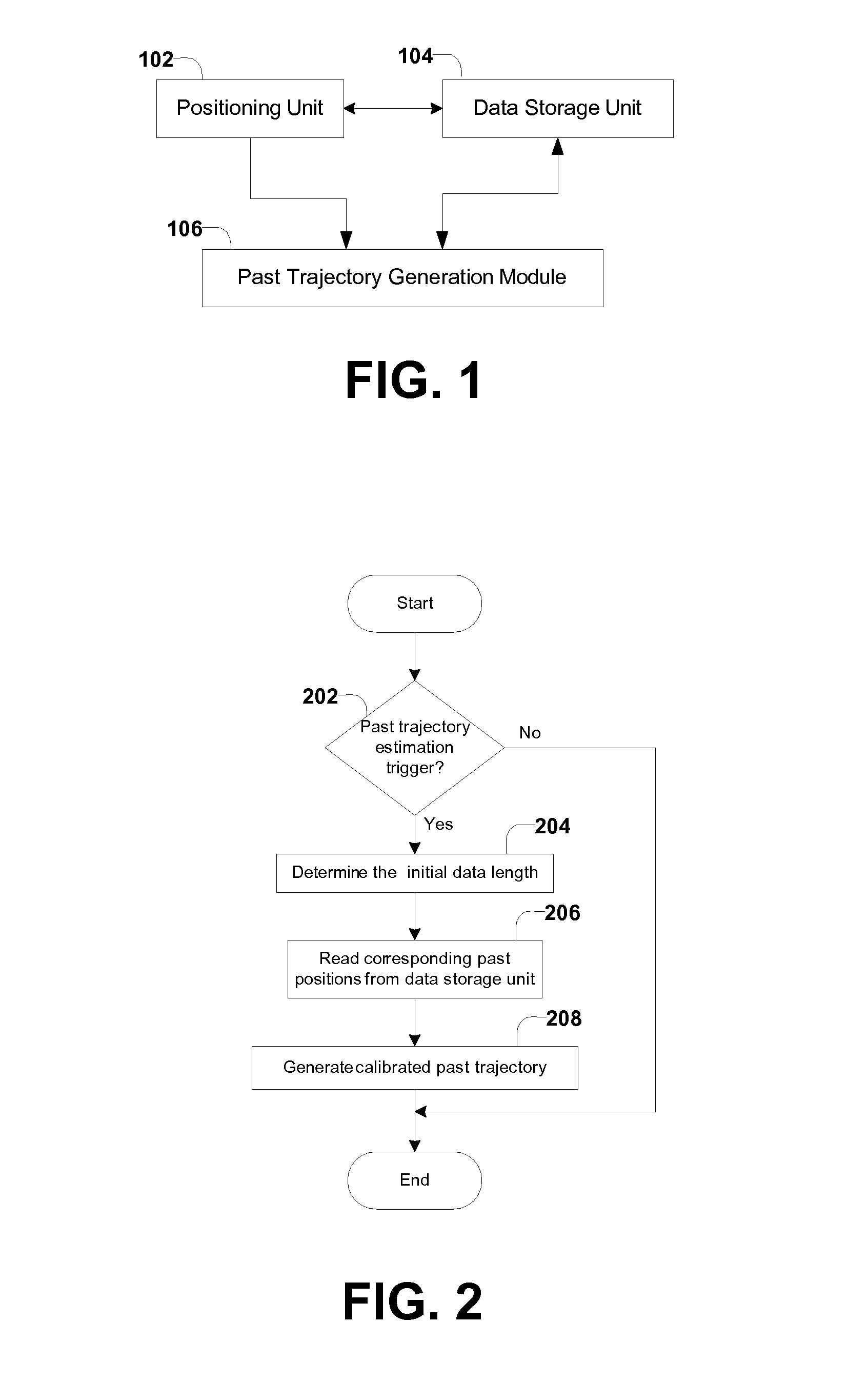
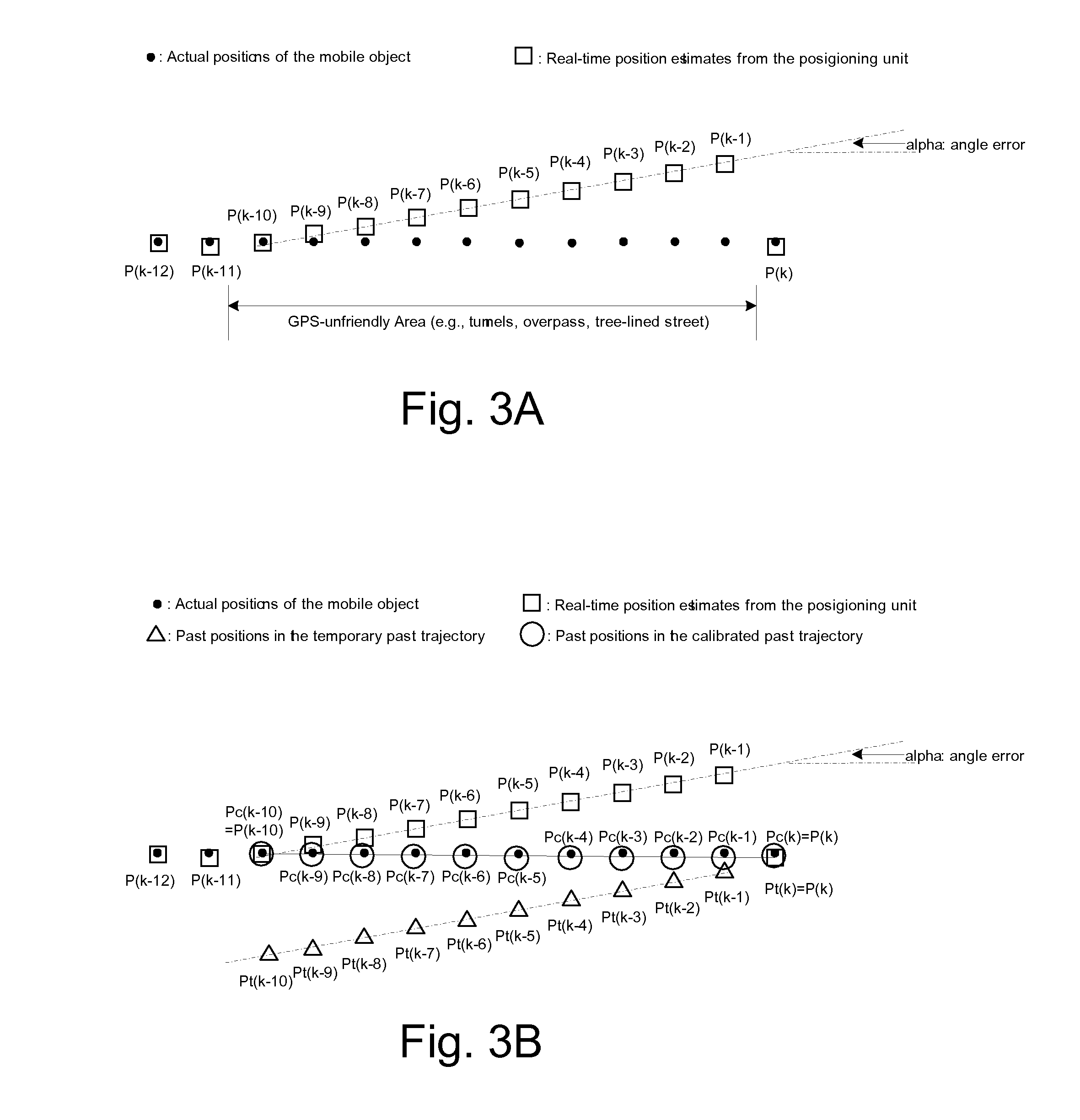
A method is provided for calibrating past position estimates from a positioning system that provides real-time position estimates of a mobile object. The method first stores the real-time position estimates, which as time goes by become past position estimates and naturally form a first past trajectory depicting the past movement of the mobile object. Subsequently, a calibrated past trajectory is determined, which includes calibrated past position estimates that correspond to the same time instances as the past positions in the first past trajectory. When real-time positions have low qualities, this method calibrates them at a later time by using (higher-quality) real-time positions both before and after them. Errors in the past positions are then corrected based on the calibrated past trajectory. When used with event detectors that indicate inventory transactions, this method can correct position errors associated with inventory events so as to improve the performance of inventory tracking.
Owner:MI JACK PRODS
Network security monitoring system
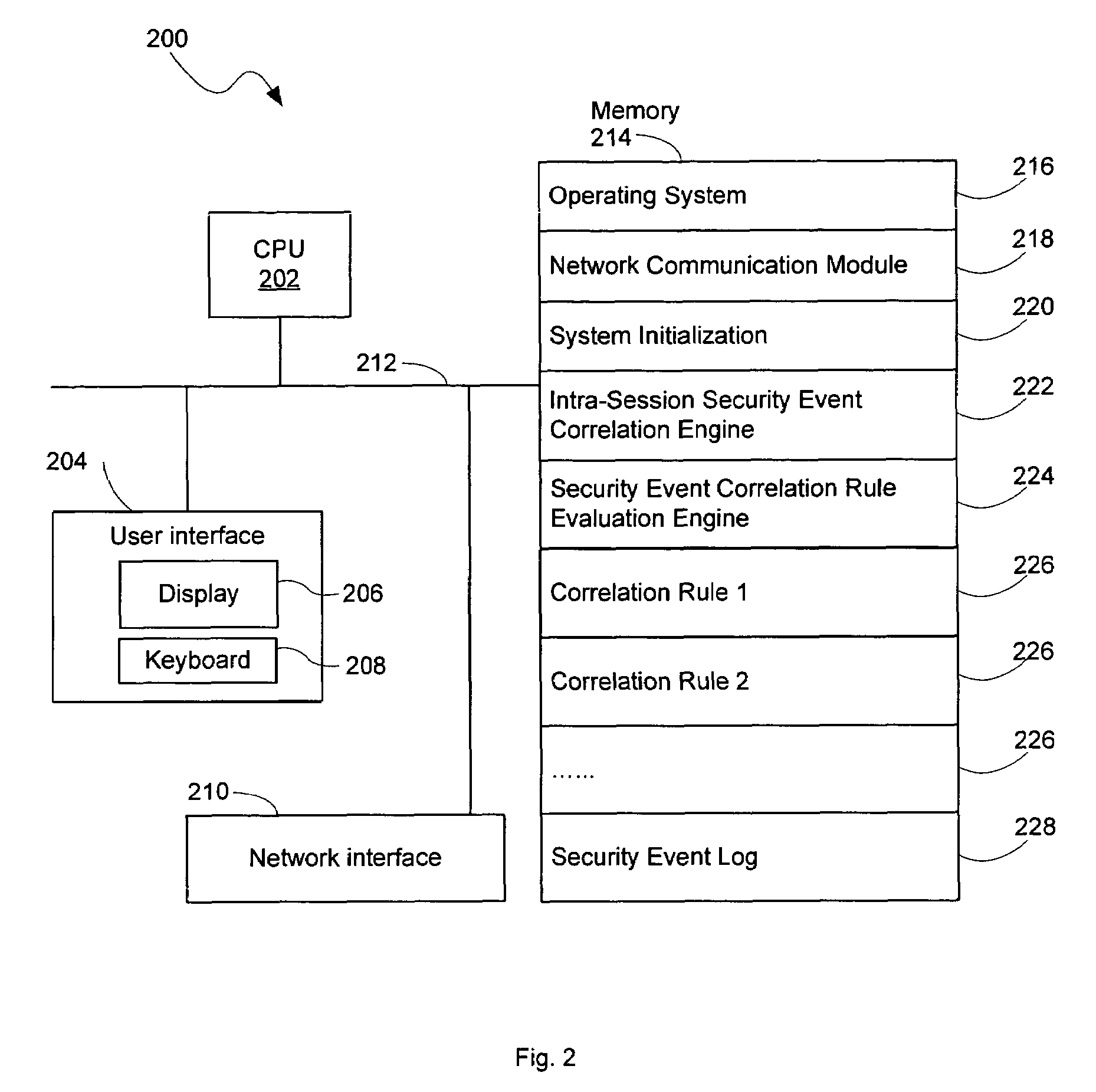
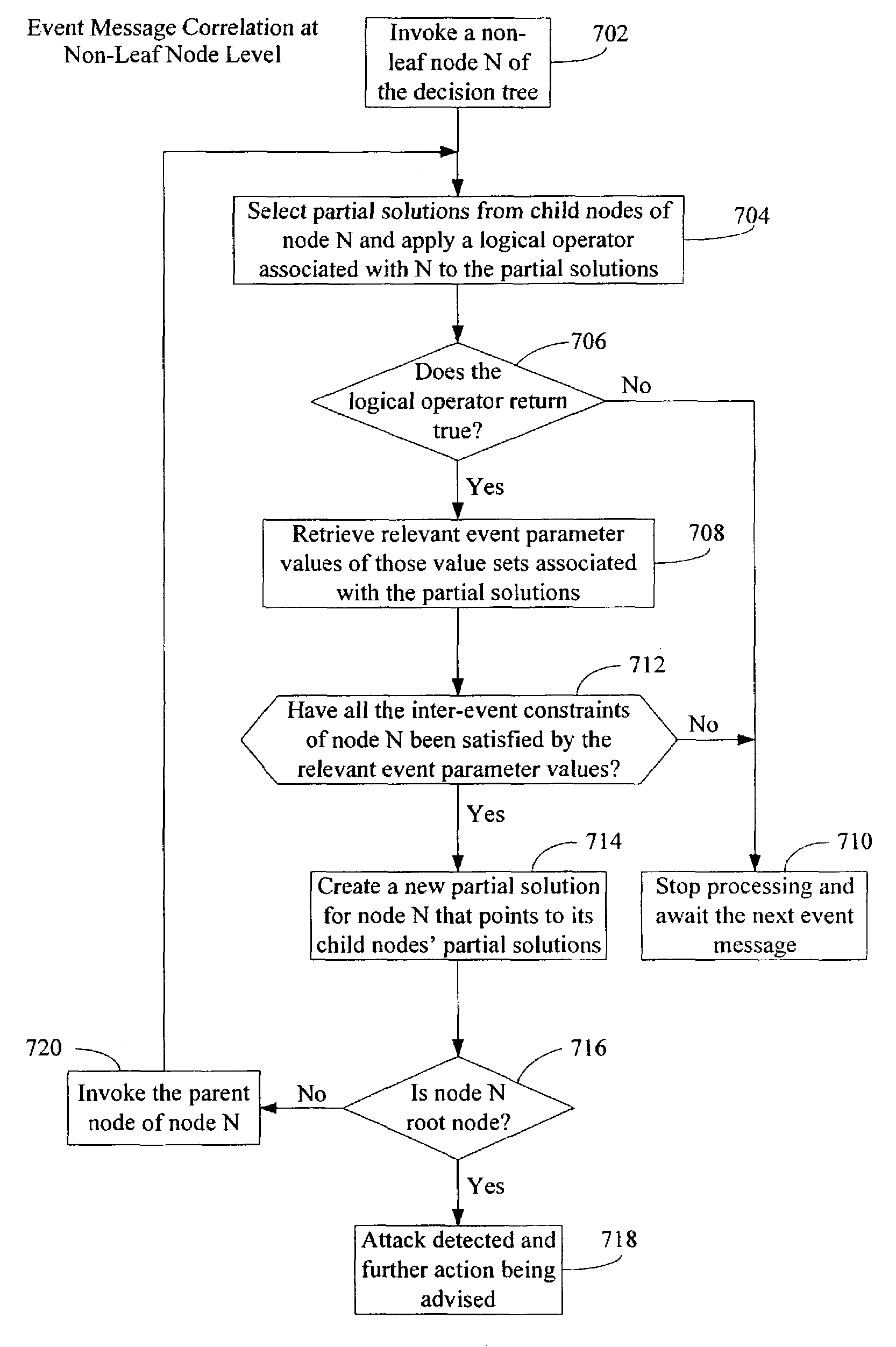
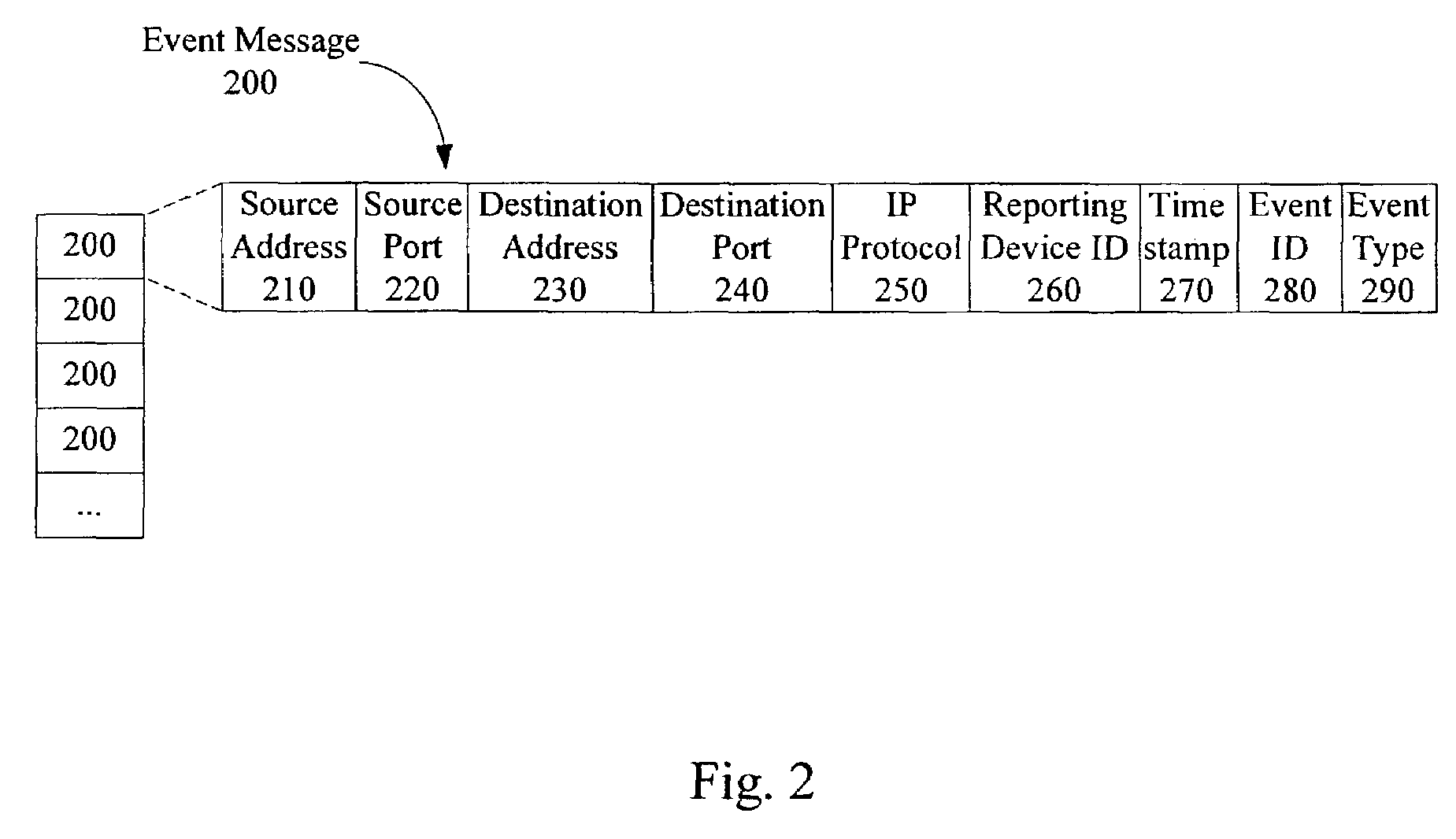
InactiveUS7483972B2Memory loss protectionError detection/correctionMonitoring systemPartial solution
A security monitoring system processes event messages related to computer network security in real time, evaluating inter-event constraints so as to identify combinations of events that are partial solutions to a predefined event correlation rule, and furthermore evaluating combinations of the partial solutions do determine if they together satisfy the predefined event correlation rule. A decision tree is formed based on the rule. Event messages are categorized into groups at leaf nodes of the tree in accordance with a plurality of intra-event constraints, and then the messages are correlated in accordance with a plurality of inter-event constraints at non-leaf nodes of the tree. When the inter-event constraint at a root node of the tree has been satisfied, a network attack alert is issued and protective actions may be taken.
Owner:CISCO TECH INC
Method and Apparatus for Coordination of a Situation Manager and Event Correlation in Situation-Based Management
InactiveUS20050222810A1Guaranteed normal transmissionRemove redundant informationNuclear monitoringDigital computer detailsArtificial systemsData science
Method and apparatus for situation-based management of natural and artificial systems using event correlation and a situation manager. Input is provided from multiple sources in the form of a collection of events. A first level of processing performs event correlation over the collection of events and infers new events and new qualities of events. A second level of processing manages situations based on the collection of events, where situations are recognized, maintained, and given a degree of confidence. Situations are periodically updated based on incoming events. The assertion of a situation may call for information from external sources, provide information for external sources, and provide control instructions to external sources. Given a current situation, past, and possible future situations are inferred. Additionally, a method and apparatus for bi-directional communication between the event correlator and situation manager.
Owner:ALTUSYS
People searches by multisensor event correlation
A data indexing system and method includes acquiring activity data in a context and indexing the activity data in accordance with contextual conditions. The activity data is stored in accordance with indices. An event is correlated with the activity data by using the indices to review the activity data in the context.
Owner:IBM CORP
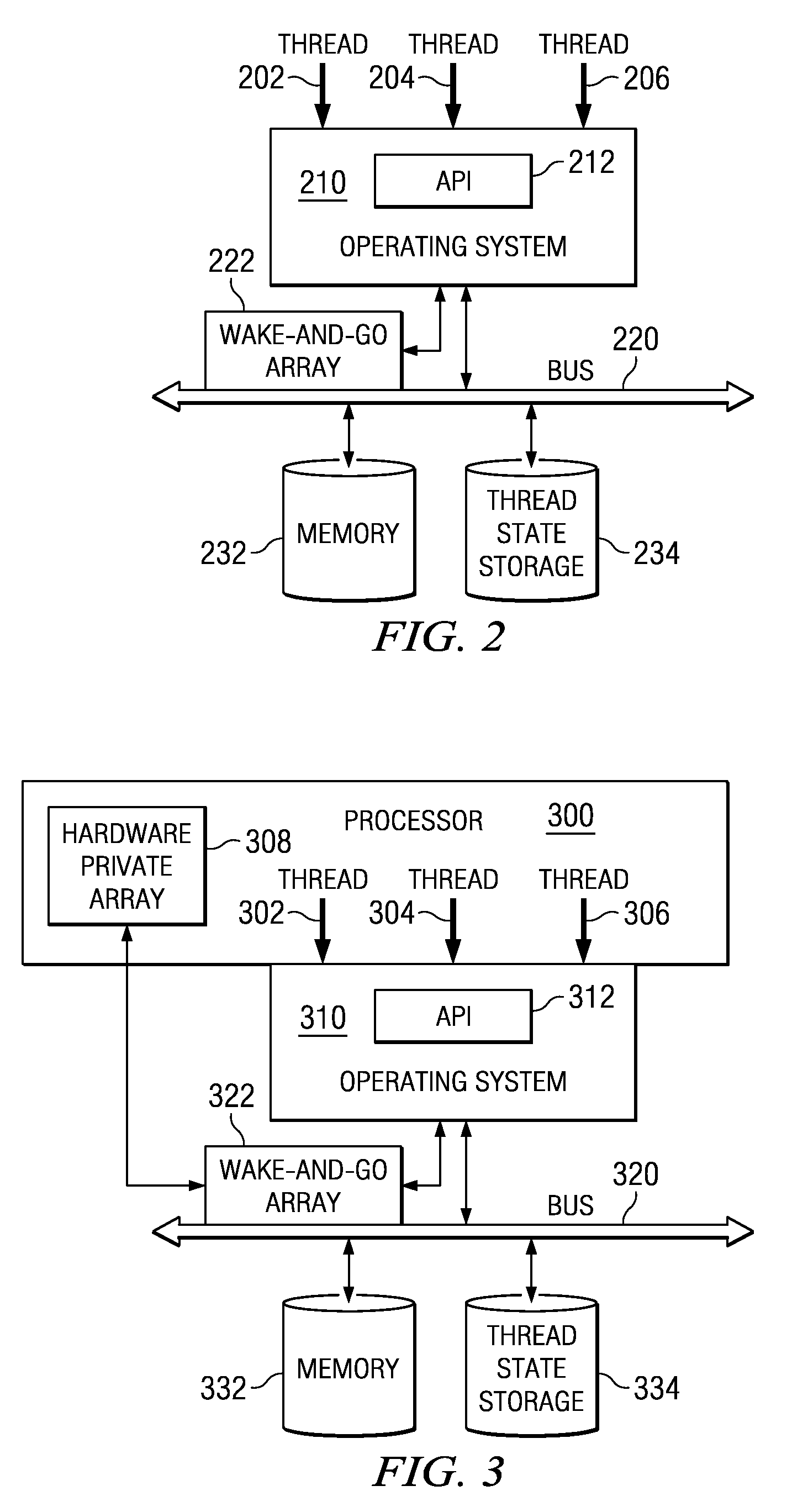
Wake-and-Go Mechanism with Data Monitoring
ActiveUS20090199029A1Energy efficient ICTVolume/mass flow measurementOperational systemArray data structure
A wake-and-go mechanism is provided for a data processing system. The wake-and-go mechanism recognizes a programming idiom, specialized instruction, operating system call, or application programming interface call that indicates that a thread is waiting for an event. The wake-and-go mechanism updates a wake-and-go array with a target address, expected data value, and comparison type associated with the event. The thread then goes to sleep until the event occurs. The wake-and-go array may be a content addressable memory (CAM). When a transaction appears on the symmetric multiprocessing (SMP) fabric that modifies the value at a target address in the CAM, logic associated with the CAM performs a comparison based on the data value being written, expected data value, and comparison type.
Owner:IBM CORP
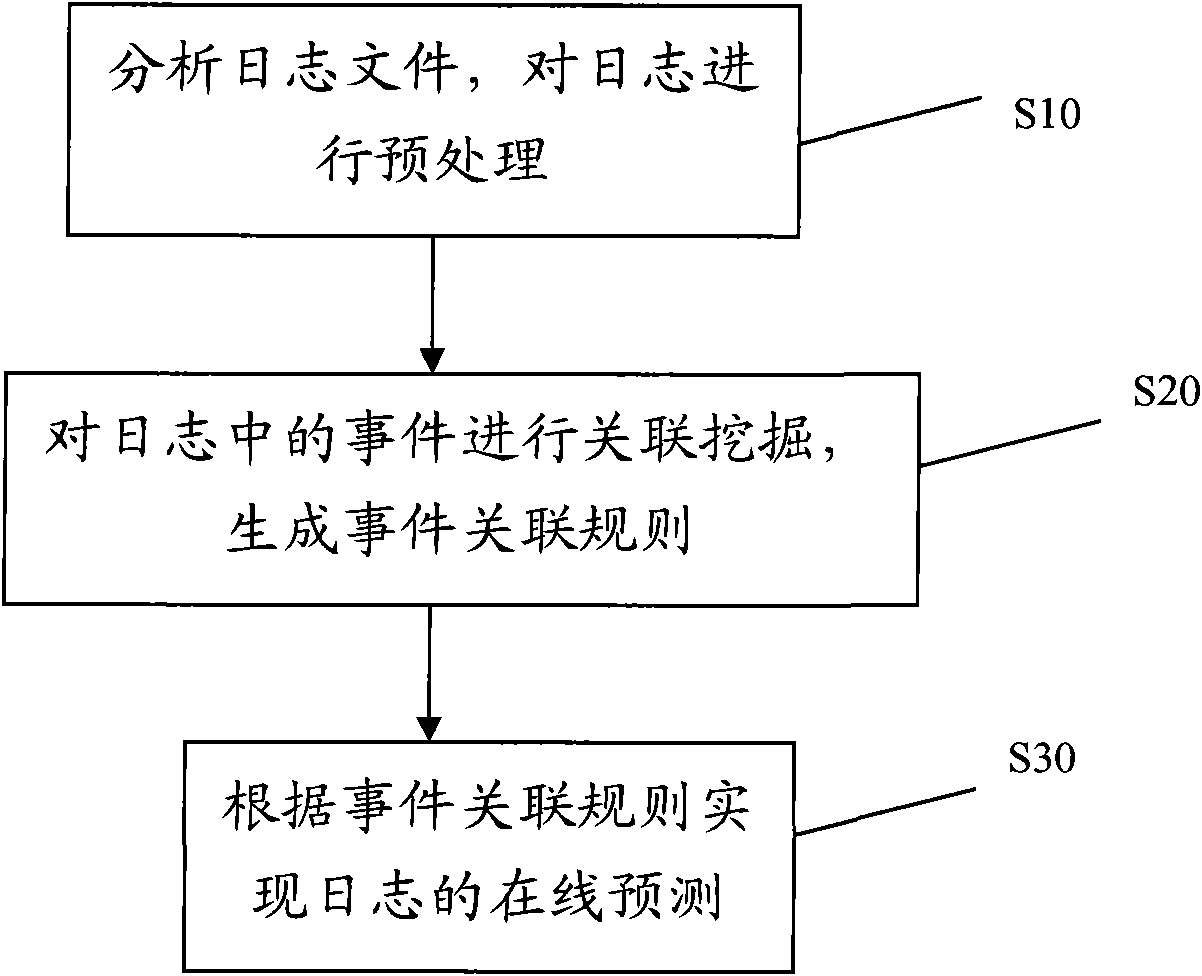
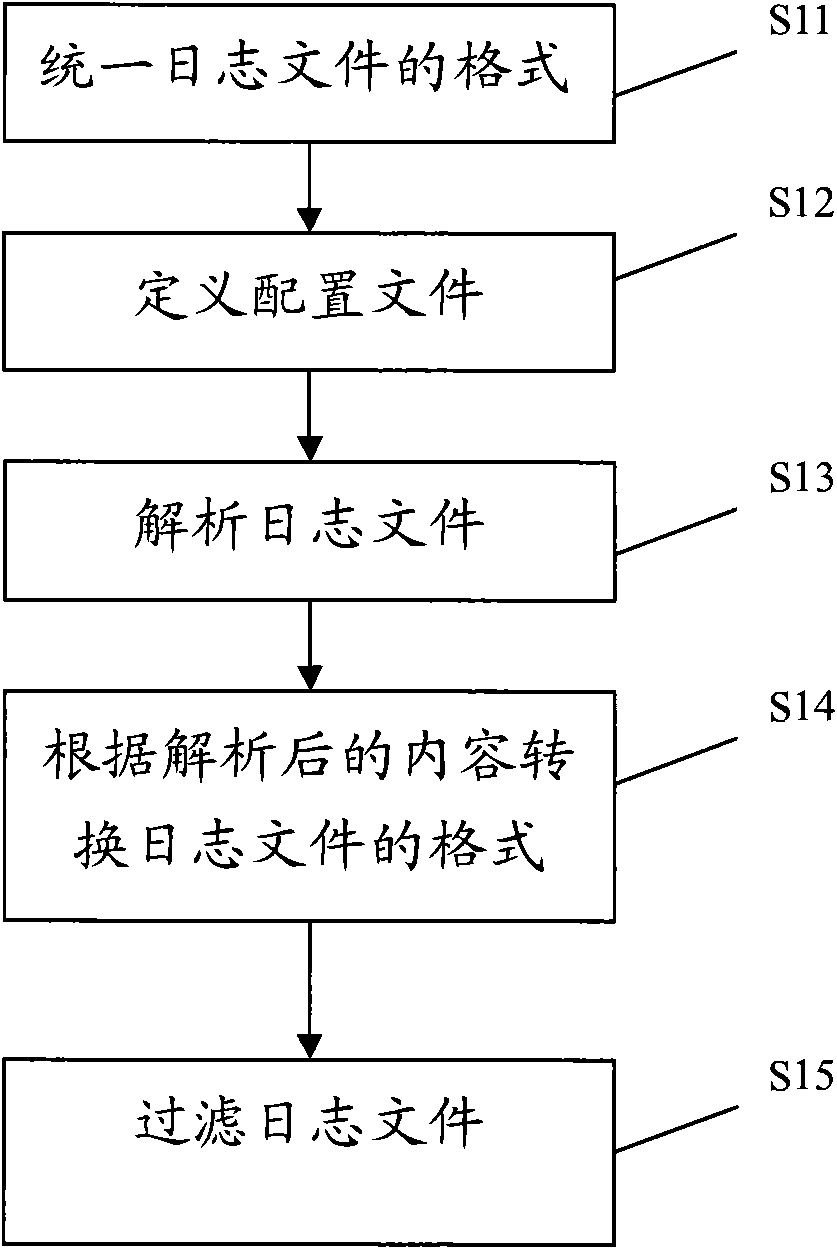
Online log analysis method
InactiveCN101888309AImprove behaviorImprove productivityData switching networksCluster systemsApproximate computing
The invention provides an online log analysis method, which comprises the following steps of: acquiring a log file from each node of a cluster system on line; defining an event sequence and an event correlation rule according to the log file, counting unitary event sequences, searching out a frequent unitary event sequence set, and obtaining a binary frequent event sequence candidate set C (2); performing statistics on support degree counting and posterior degree counting of the candidate binary frequent event sequence in the C (2), and calculating the degree of confidence and posterior degree; generating a binary frequent event sequence set F (2) and a binary rule set R (2); repeating the process until F(k) and R(k) are obtained, performing join operation on k-element frequent event sequences in the F(k), and generating an F(k+1)-element frequent event sequence set; performing approximate calculation on attribute values of elements which are not in R(k+1) but in F(k+1), until all frequent event sequences are generated; finding the event correlation rule according to the frequent event sequences; and predicting events in the log according to the event correlation rule on line.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
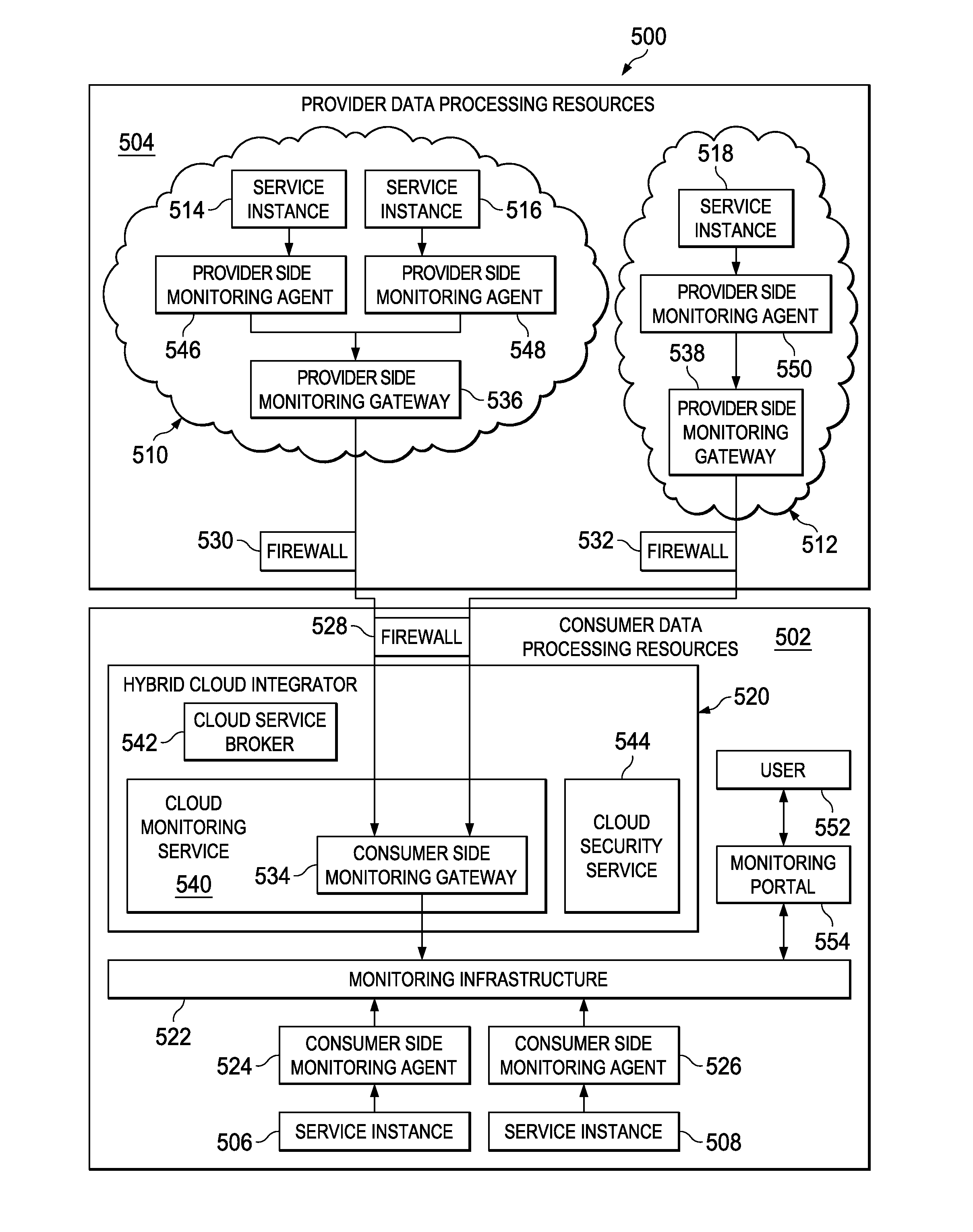
Data Processing Environment Event Correlation
InactiveUS20120272249A1Error detection/correctionMultiprogramming arrangementsWorkloadSoftware framework
A system and method for correlating events in data processing resources processing a workload. An event correlation service comprising an event correlation service software framework is provided on a processor unit. The event correlation service is configured, using the event correlation service software framework, for correlating the events from monitored data for the workload, wherein the workload is processed using the data processing resources provided by a provider of the data processing resources. The event correlation service receives monitored data for the workload as the workload is being processed. The monitored data is processed by the event correlation service to identify an occurrence of an event of interest for the workload as the workload is being processed. An output is provided in response to identifying the occurrence of the event of interest.
Owner:IBM CORP
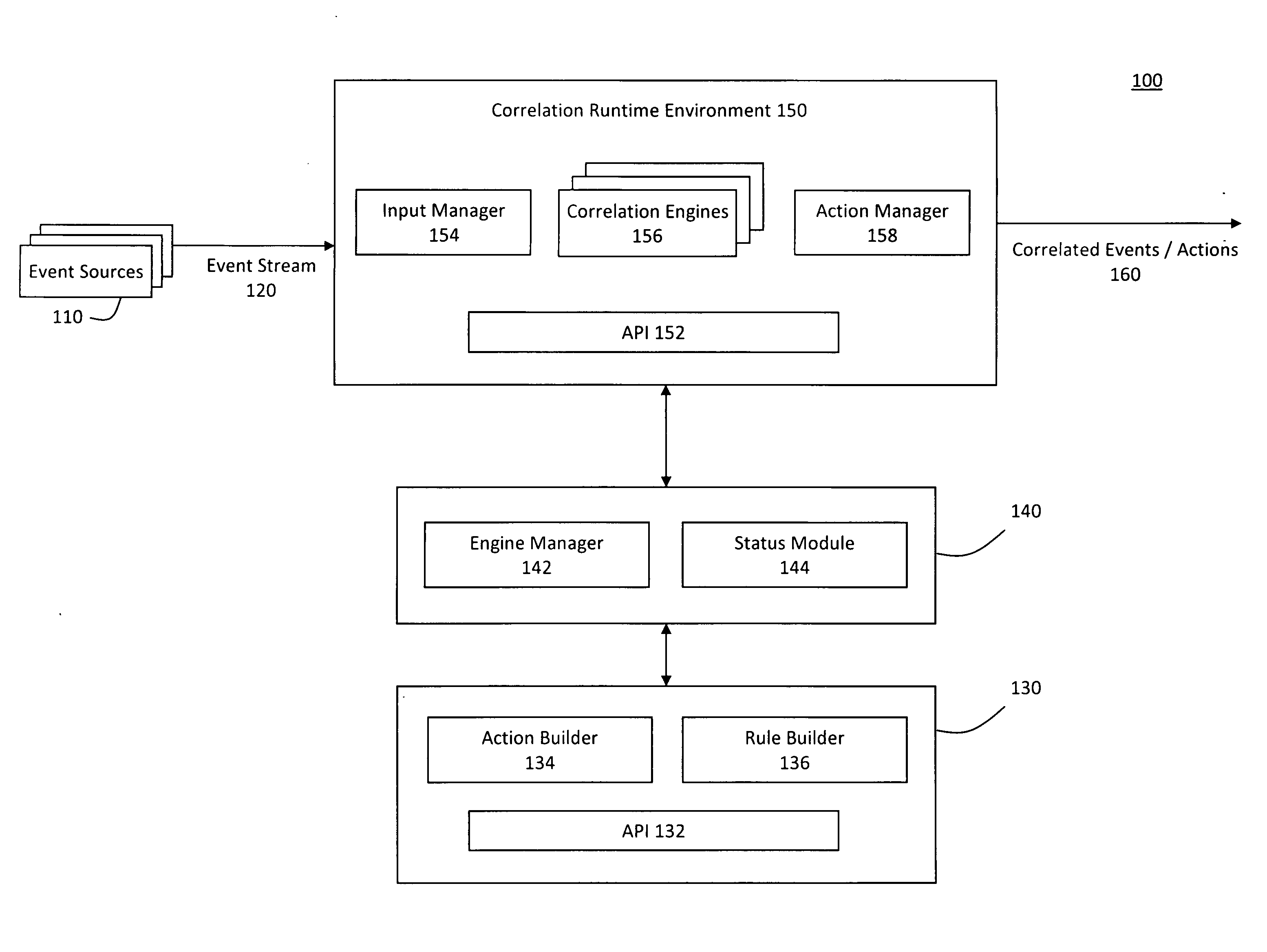
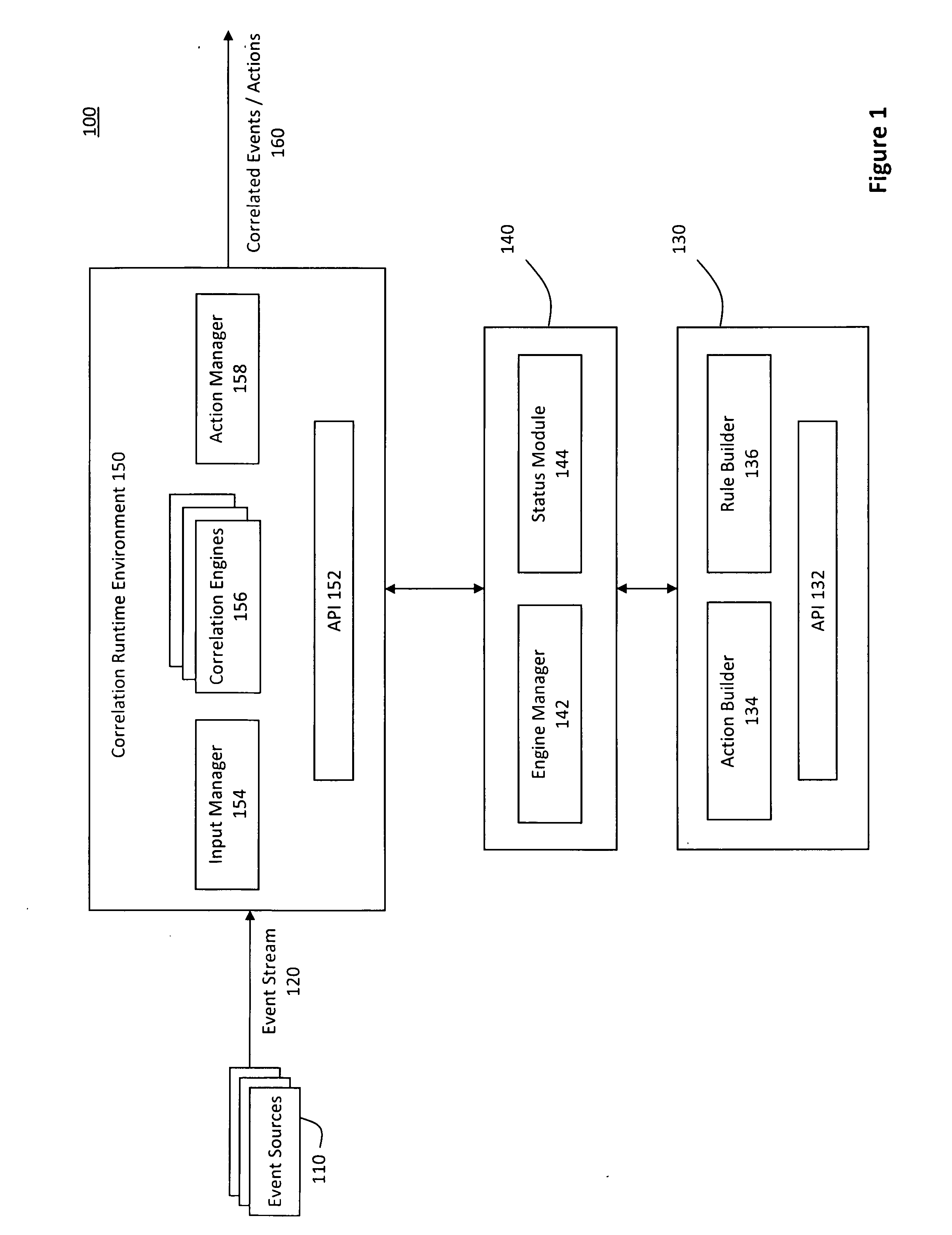
System and method for correlating events in a pluggable correlation architecture
ActiveUS20090265288A1Improve incident managementImprove remediationKnowledge representationSpecial data processing applicationsRemedial actionEvent triggered
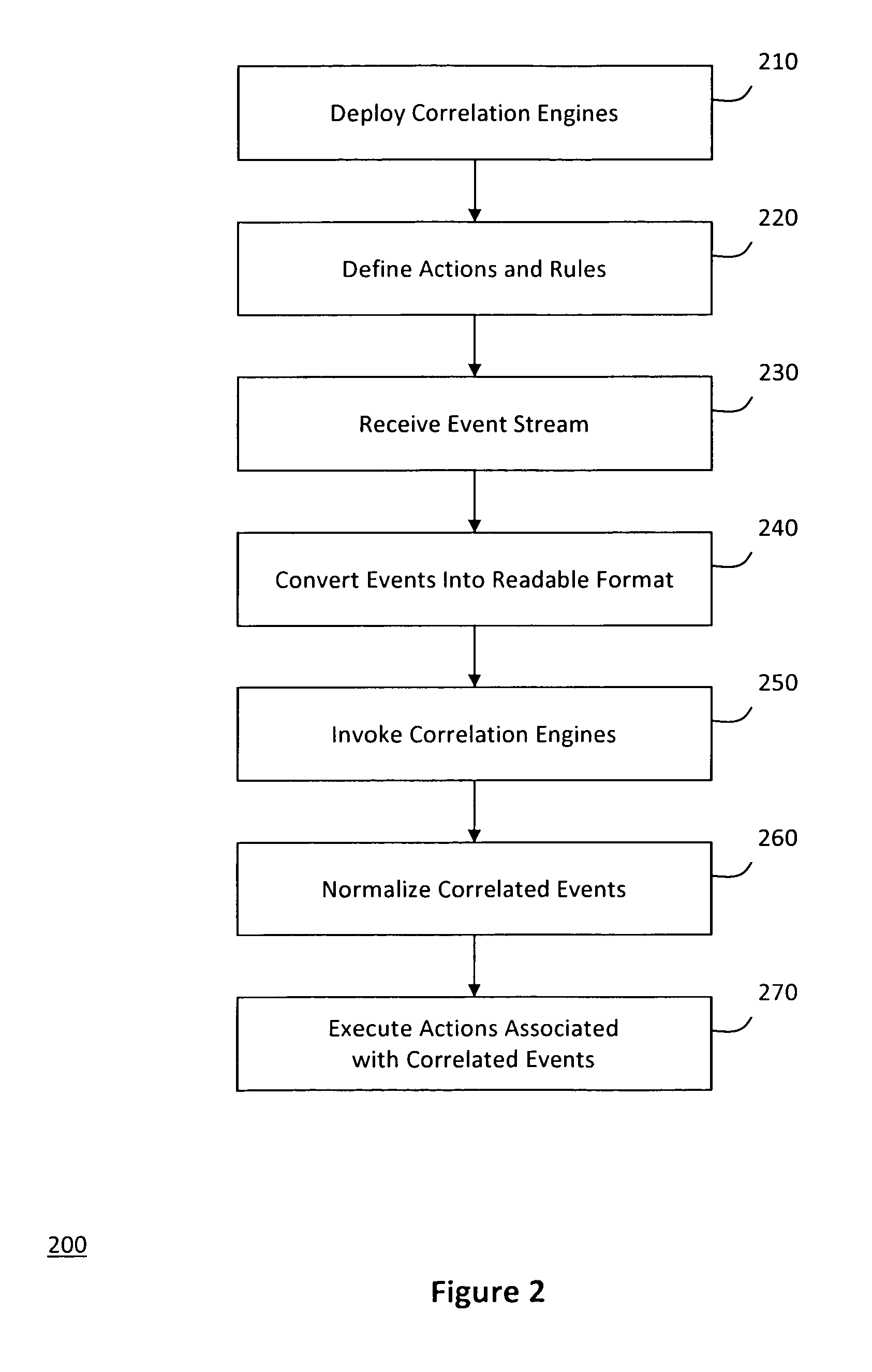
A system for pluggable event correlation may include an input manager that receives a plurality of events and converts the events into a format compatible with one or more of a plurality of correlation engines. The correlation engines may then evaluate the converted events using various rules and generate correlated events when the evaluated events trigger at least one of the rules. An action manager may execute remedial actions when the correlation engines generate the correlated events. Moreover, extensibility may be provided by enabling a user to define rules to be triggered when events occur in a predetermined pattern, and actions to be executed when a predetermined rule triggers a correlated event. Further, to plug a new correlation engine into the system, adapters may be deployed to handle input and output, while the user-defined rules may be validating according to semantic requirements of the new correlation engine.
Owner:EMC IP HLDG CO LLC
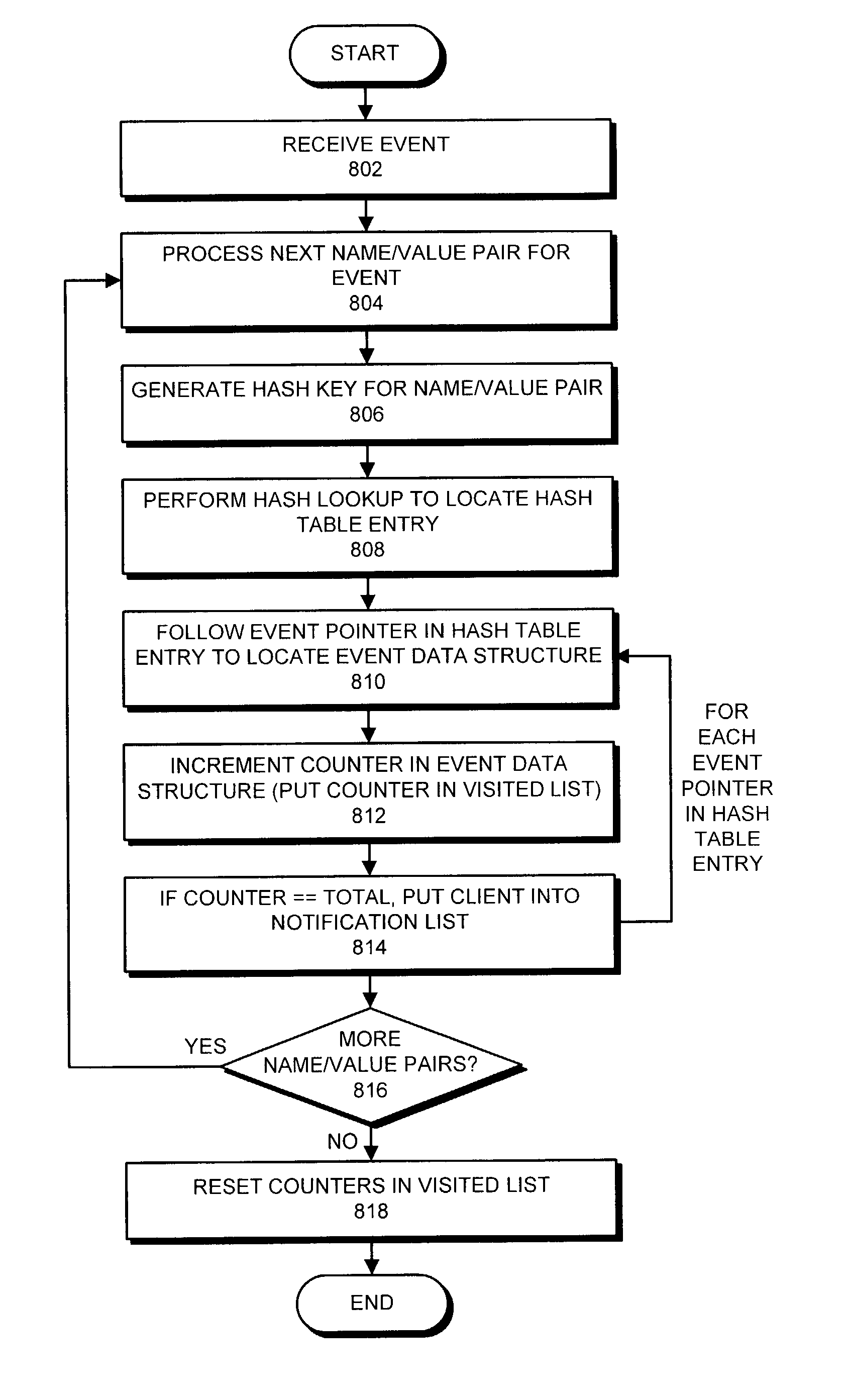
Facilitating event notification through use of an inverse mapping structure for subset determination
One embodiment of the present invention provides a system that performs event notification in a distributed computing system. During operation, the system receives an event that was generated at a node in the distributed computing system, wherein the event includes a set of name / value pairs associated with the event. Next, the system compares the event against a set of client event registrations to determine a set of clients to be notified of the event, wherein each client event registration identifies a client and a target set of name / value pairs, wherein the client is to be notified of the event if the target set of name / value pairs matches a subset of the set of name / value pairs associated with the event. Finally, the system sends a notification of the event to the set of clients to be notified of the event.
Owner:ORACLE INT CORP
Computer-implemented method and system for security event correlation
InactiveUS7673335B1Lower requirementFacilitate reducing memory requiredUnauthorized memory use protectionComputer security arrangementsEvent correlationNetwork security
A system and method for analyzing events from devices relating to network security, includes a device interface(s), for receiving events from devices. One or more processors, responsive to the event received pursuant to the device interfaces, evaluate the event in accordance with rules, wherein the rules define, inter alia, an operation the system is to take to evaluate the event and an action to be taken under specified conditions. Also, the processor can determine, responsive to the received event, whether the event is of interest, and if not, discarding the event. The processor can provide a correlation corresponding to the at least one event, for the rules.
Owner:APPLE INC
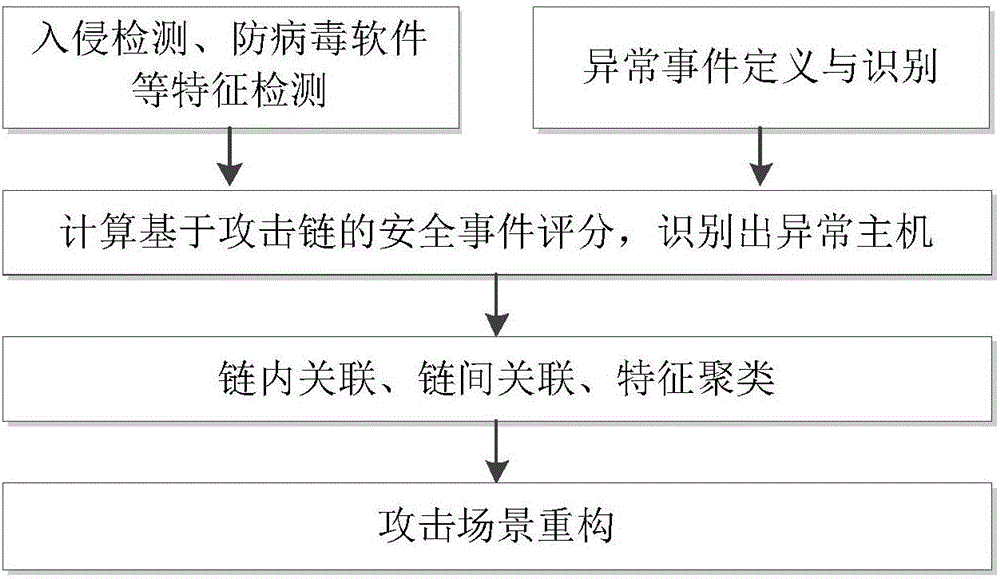
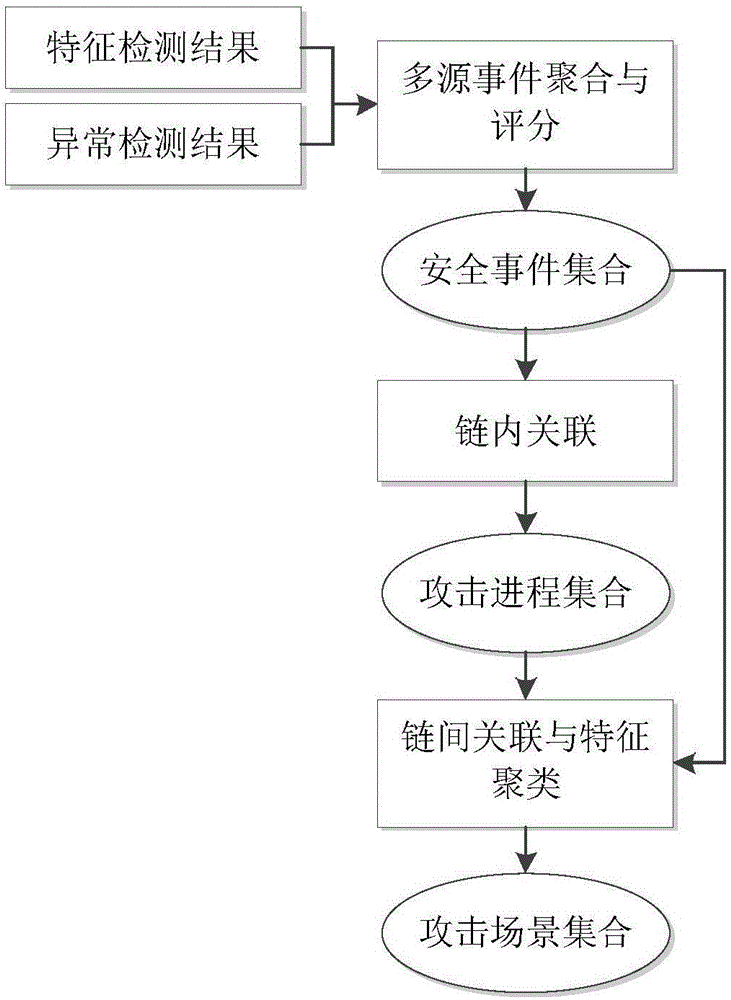
Multi-step attack detection method based on multi-source abnormal event correlation analysis
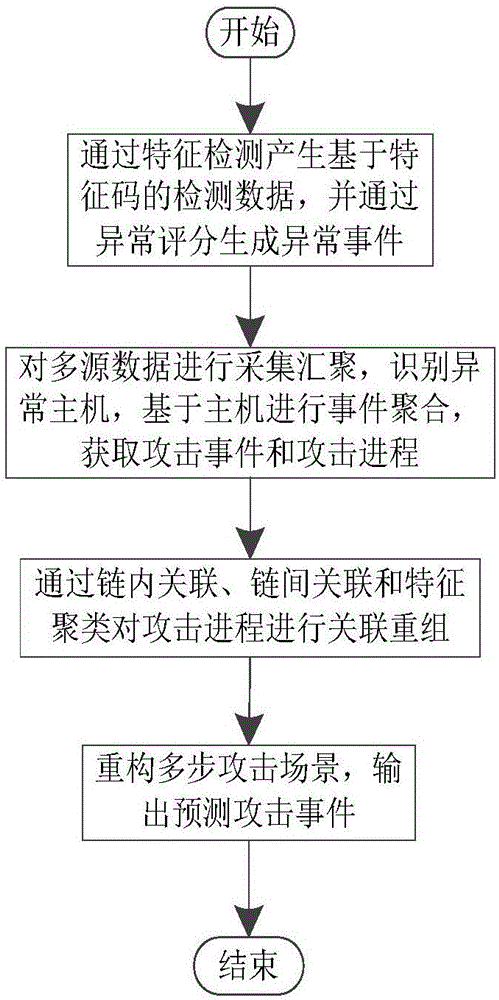
ActiveCN106790186AImprove Security Analysis CapabilitiesReduce time to discoveryTransmissionFeature extractionCorrelation analysis
The invention relates to a multi-step attack detection method based on multi-source abnormal event correlation analysis. The multi-step attack detection method comprises the following steps: firstly, calculating a safety event score based on an attach chain through feature extraction and abnormal event definition and identification, identifying an abnormal host and clustering various types of events by taking an attacked host as a clue; secondly, carrying out correlated recombination on a suspected attack progress by utilizing means including intra-chain correlation, inter-chain correlation, feature clustering and the like; finally, reconstructing a multi-source attack scene and outputting a predicated attack event. According to the multi-step attack detection method provided by the invention, dispersed and isolated safety events are subjected to the correlation analysis to generate the relative complete multi-step attack scene; a safety analysis capability of safety managers can be improved and a safety view angle is expanded; distributed and scattered multi-step attack threats are effectively coped and the finding time of attack behaviors is shortened; an effective predication and defending solution is provided for high-grade attack means including APT (Advanced Persistent Threat) and the like; the safety risks of a system are reduced and the network information safety is effectively protected.
Owner:THE PLA INFORMATION ENG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com