Multi-step attack detection method based on multi-source abnormal event correlation analysis
An abnormal event and correlation analysis technology, applied in the field of network security, can solve problems such as manual dependence of detection methods, and achieve the effect of shortening discovery time, reducing system security risks, and improving overall security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
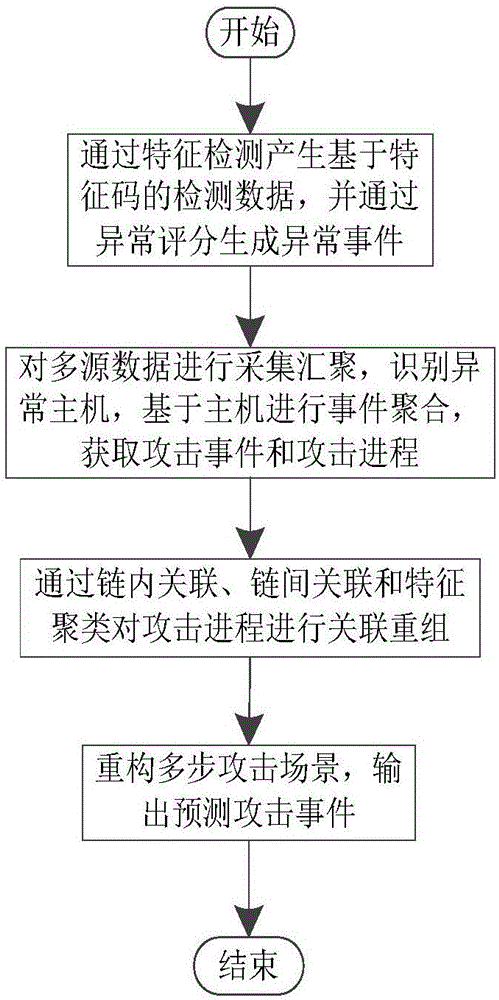
[0038] Embodiment one, see figure 1 As shown, a multi-step attack detection method based on multi-source abnormal event correlation analysis includes the following steps:
[0039] Step 1. Generate signature-based detection data through feature detection, and generate abnormal events through abnormal scoring;
[0040] Step 2. Collect and aggregate multi-source data, identify abnormal hosts, aggregate events based on hosts, and obtain attack events and attack processes;
[0041] Step 3. Reorganize the attack process through intra-chain association, inter-chain association and feature clustering;
[0042] Step 4. Reconstruct the multi-step attack scenario and output the predicted attack event.
[0043]By correlating and aggregating scattered and isolated security events, a relatively complete multi-step attack scenario is generated, which improves the security analysis capabilities of security managers, expands security perspectives, helps effectively deal with scattered multi-...
Embodiment 2
[0044] Embodiment two, see Figure 1-7 As shown, a multi-step attack detection method based on multi-source abnormal event correlation analysis includes the following content:
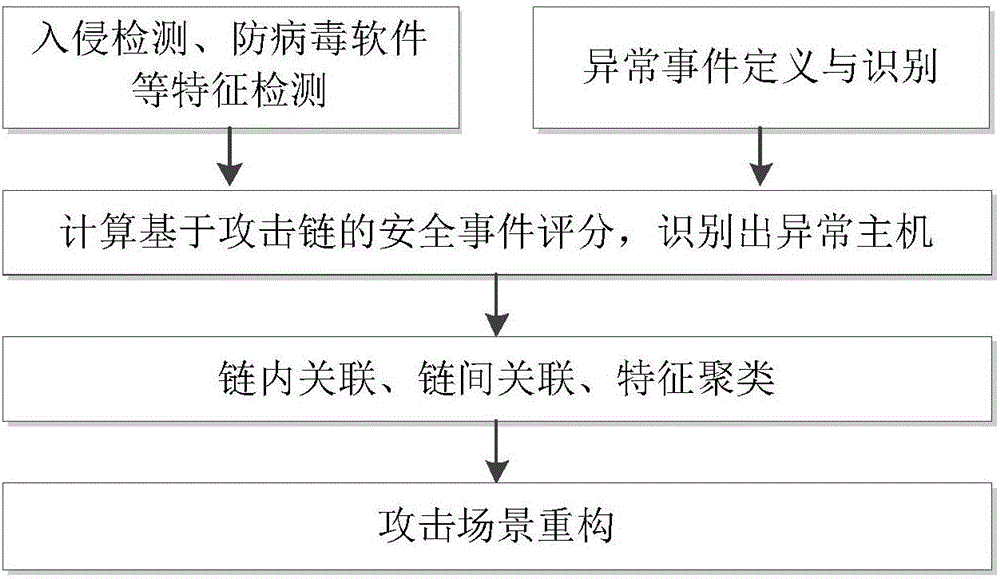
[0045] 1) Generate signature-based detection data through feature detection, and generate abnormal events through abnormal scoring.
[0046] 2) Collect and aggregate multi-source data, identify abnormal hosts, aggregate events based on hosts, and obtain attack events and attack processes.
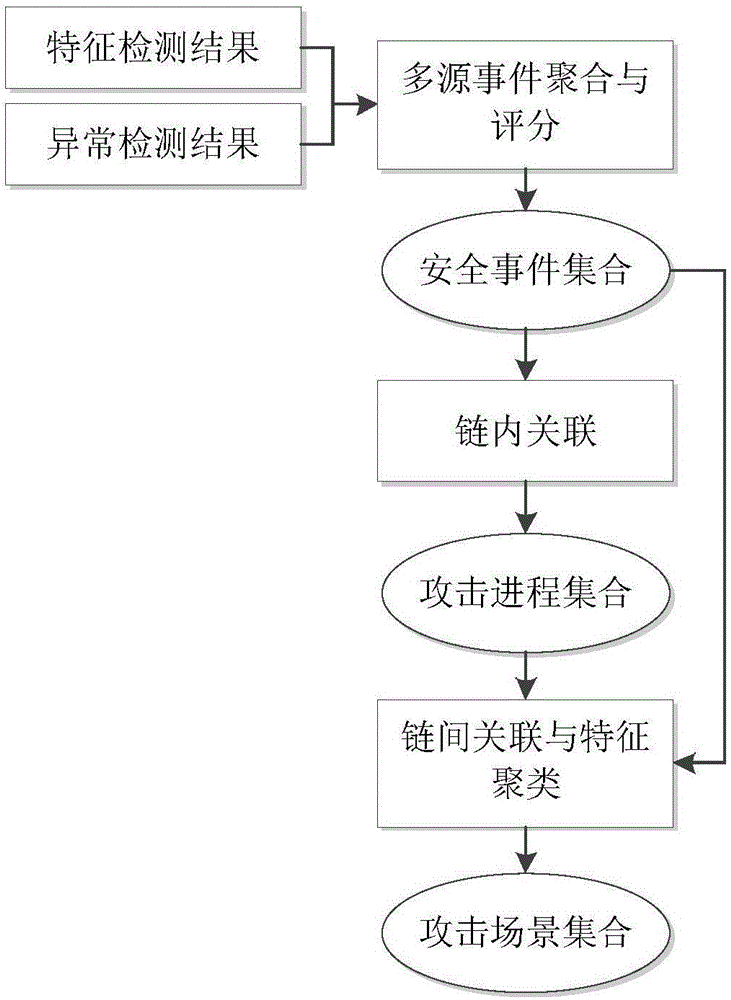
[0047] The attack chain scoring method is used to quantify the attack event and attack process to form an attack chain attack event. The attack event includes: source and destination host identification, event type, event mark, attack stage, start and end time, and security score; Event groups satisfying the logical characteristics of an attack chain form an attack process. Identify abnormal hosts, aggregate events based on victim hosts, and extract events involving the same host into the same collection.
[0048...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com