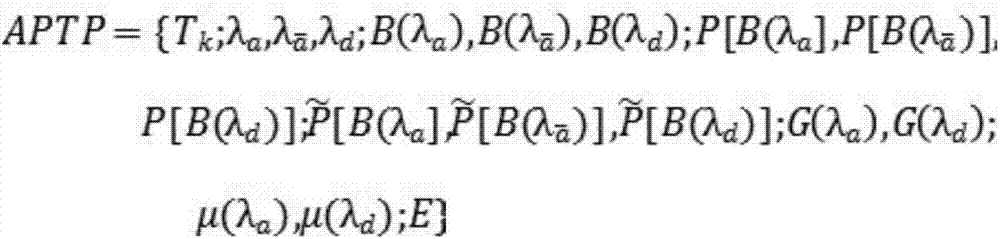Patents
Literature
100 results about "Advanced persistent threat" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An Advanced Persistent Threat (APT) is a stealthy computer network threat actor, typically a nation state or state-sponsored group, which gains unauthorized access to a computer network and remains undetected for an extended period . In recent times, the term may also refer to non-state sponsored groups conducting large-scale targeted intrusions for specific goals.
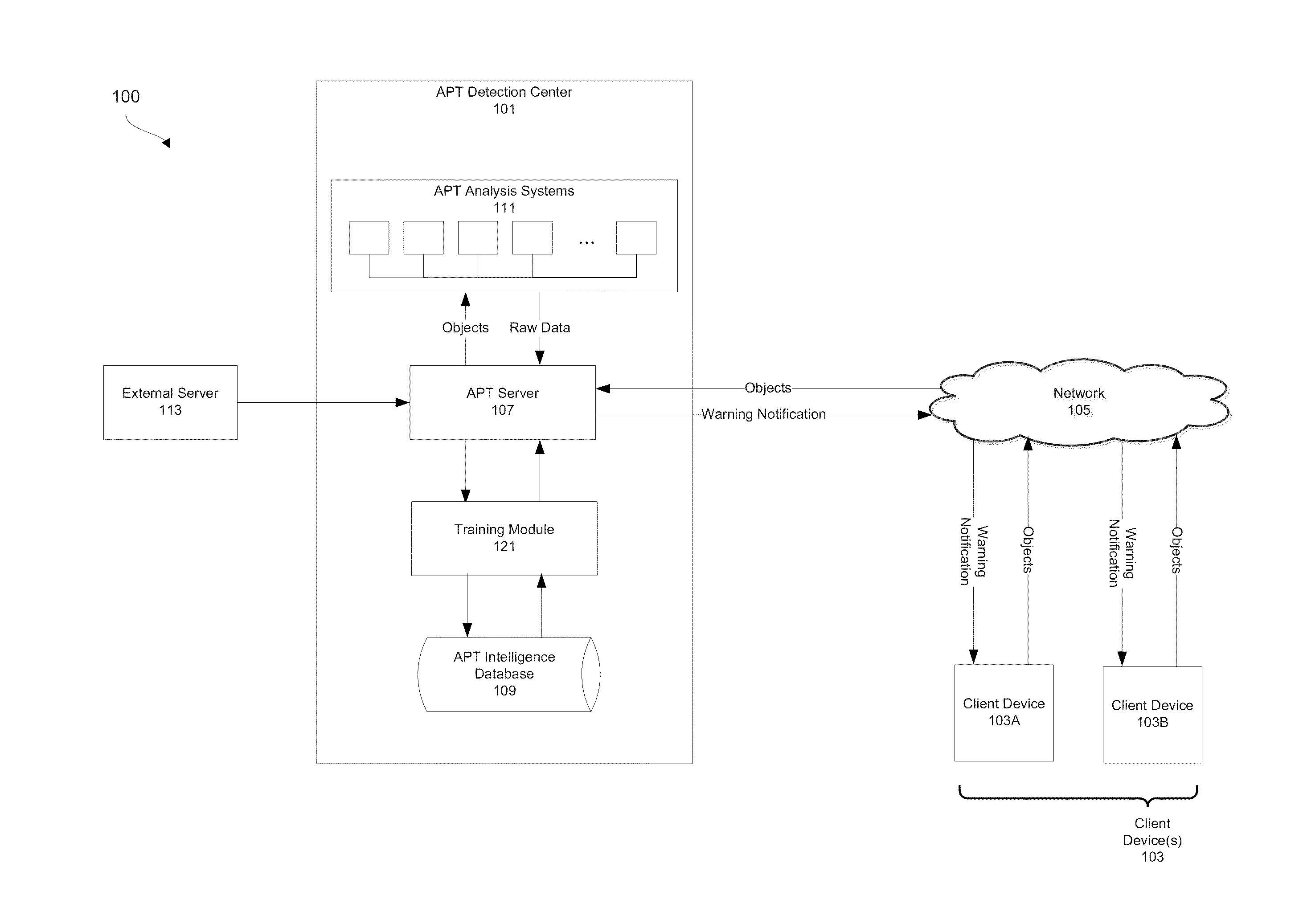
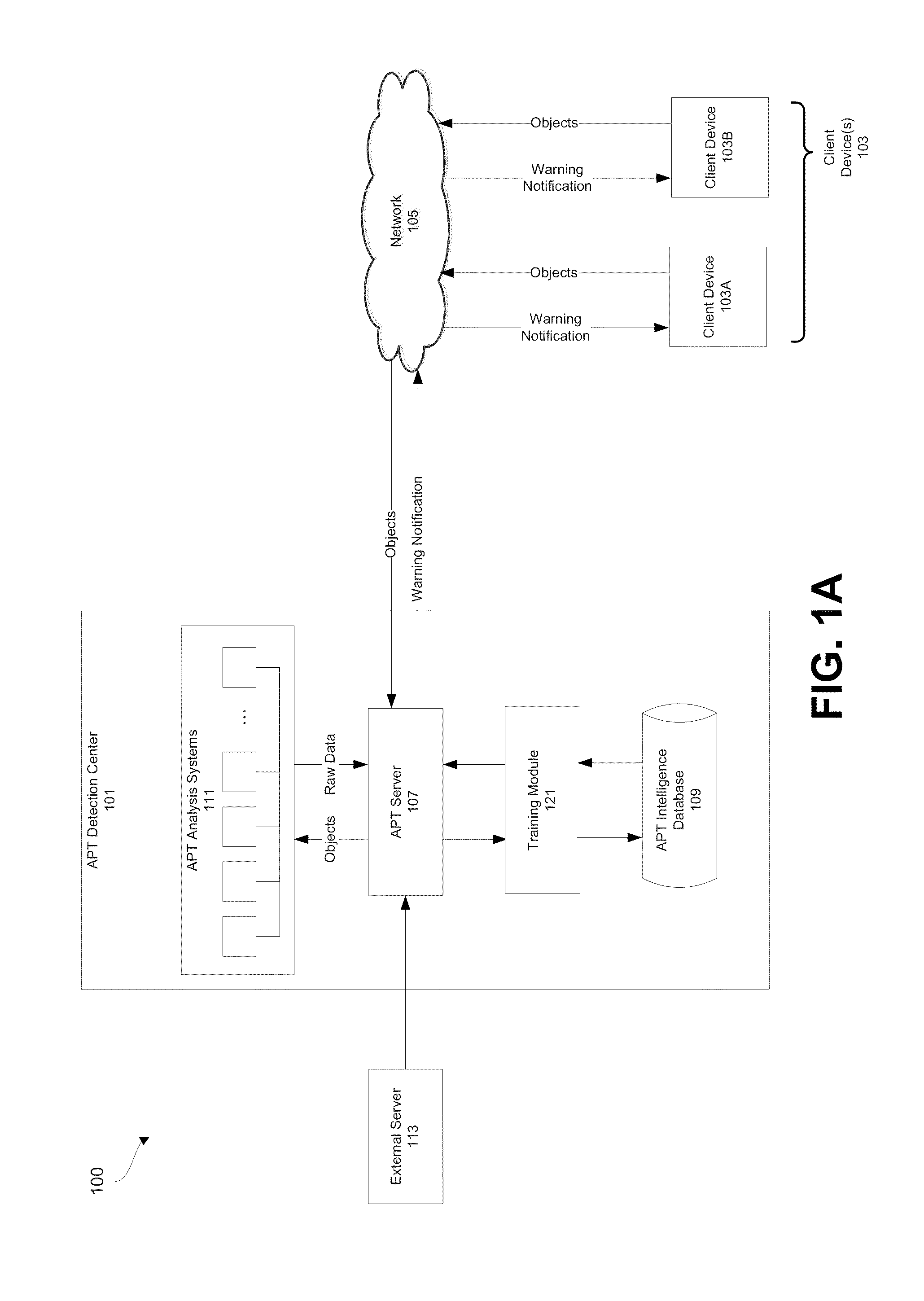
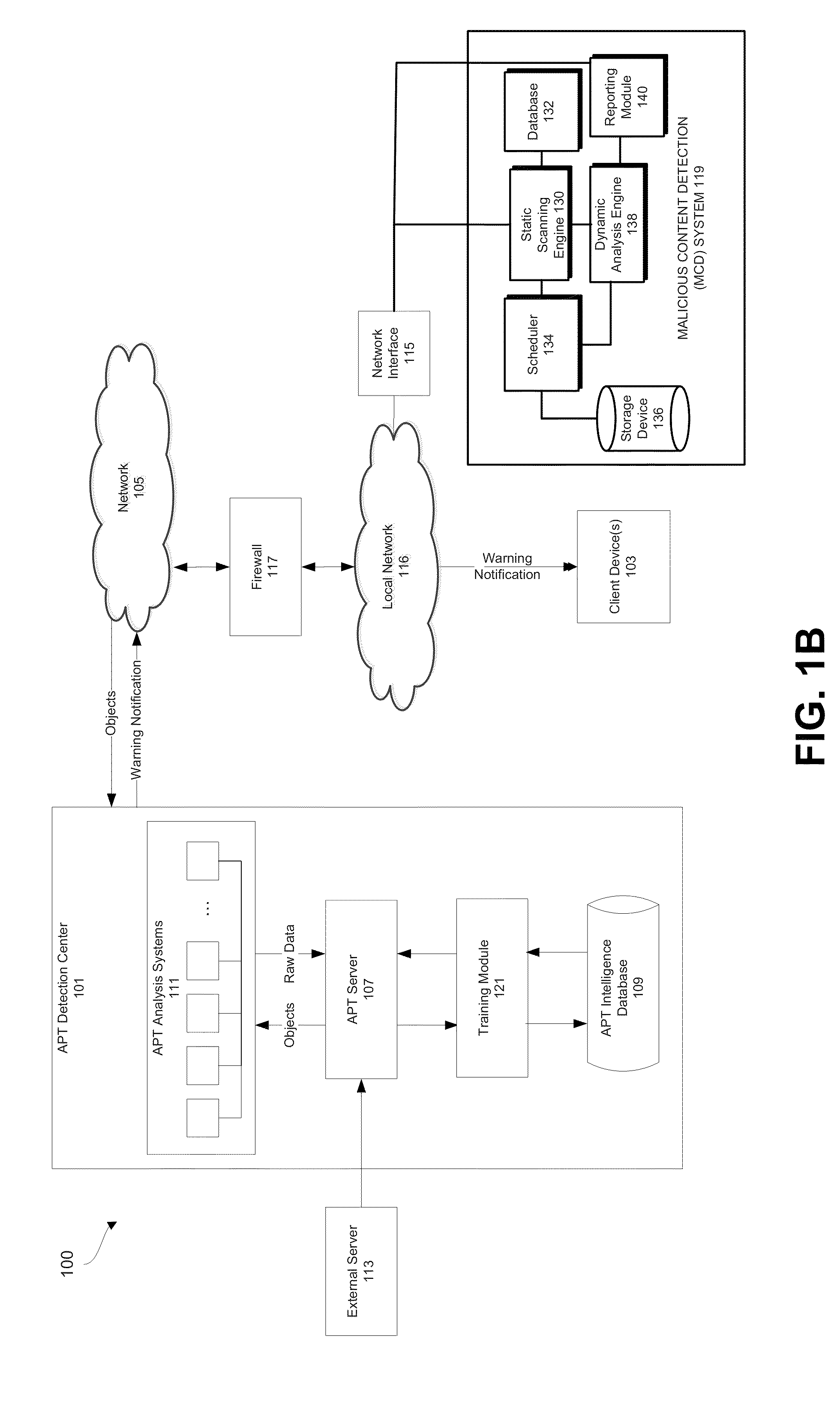
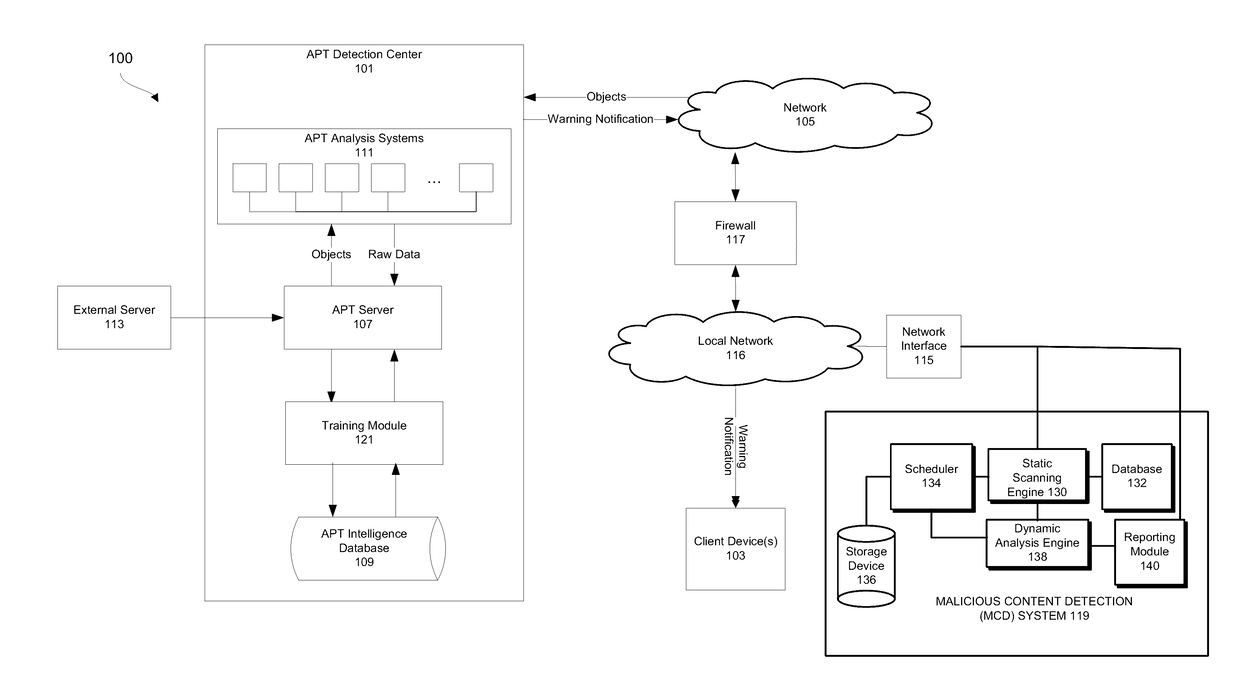
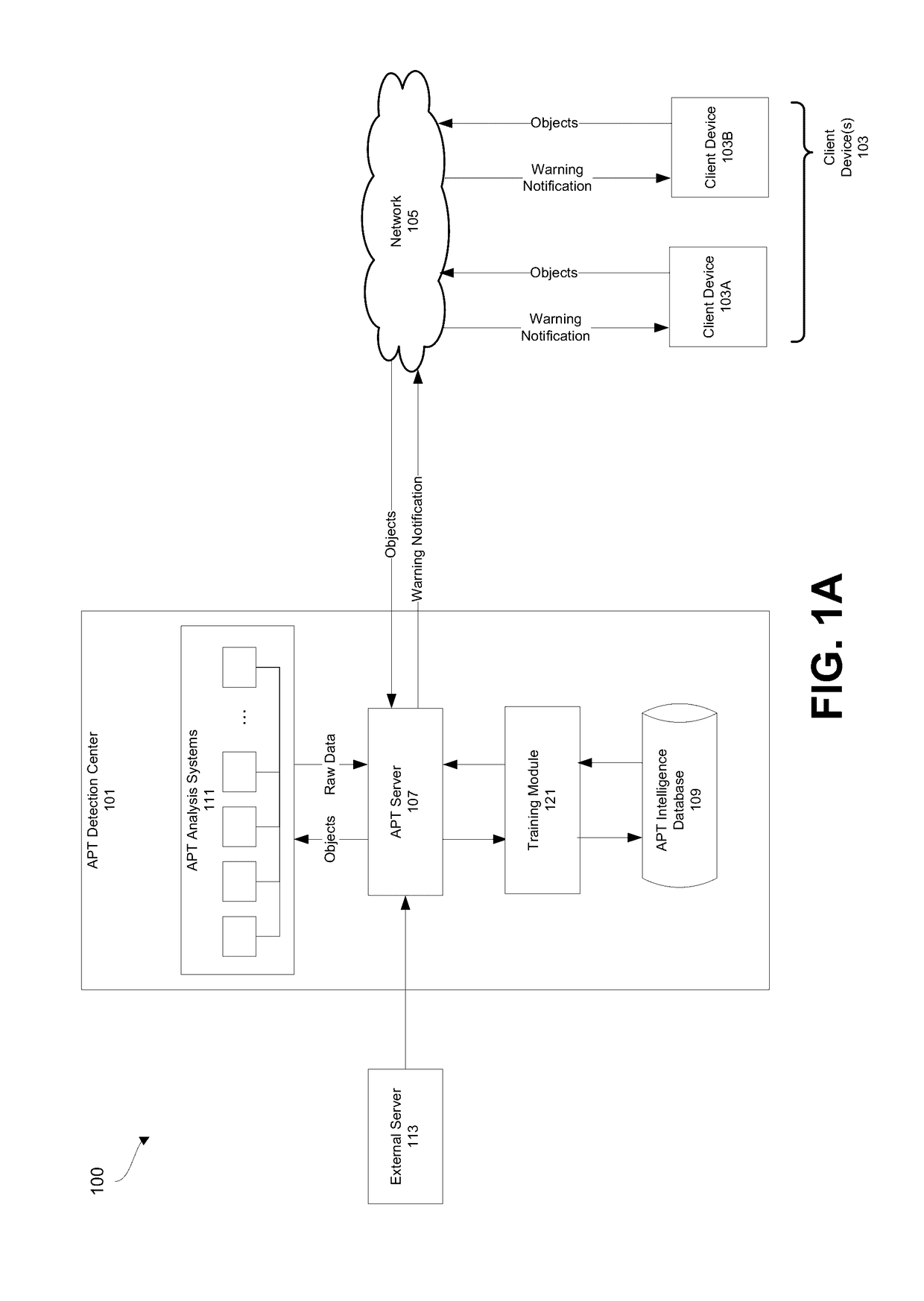
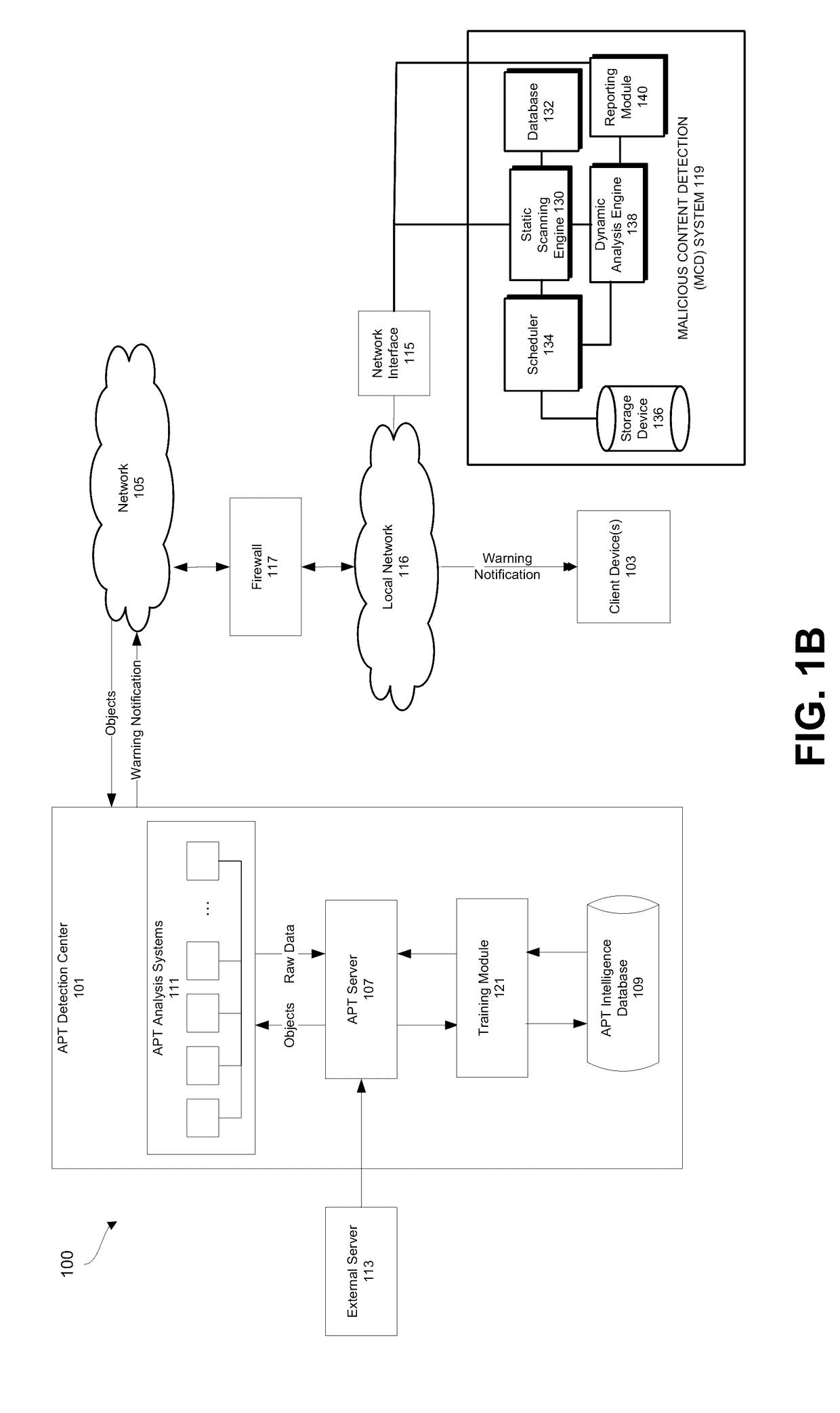
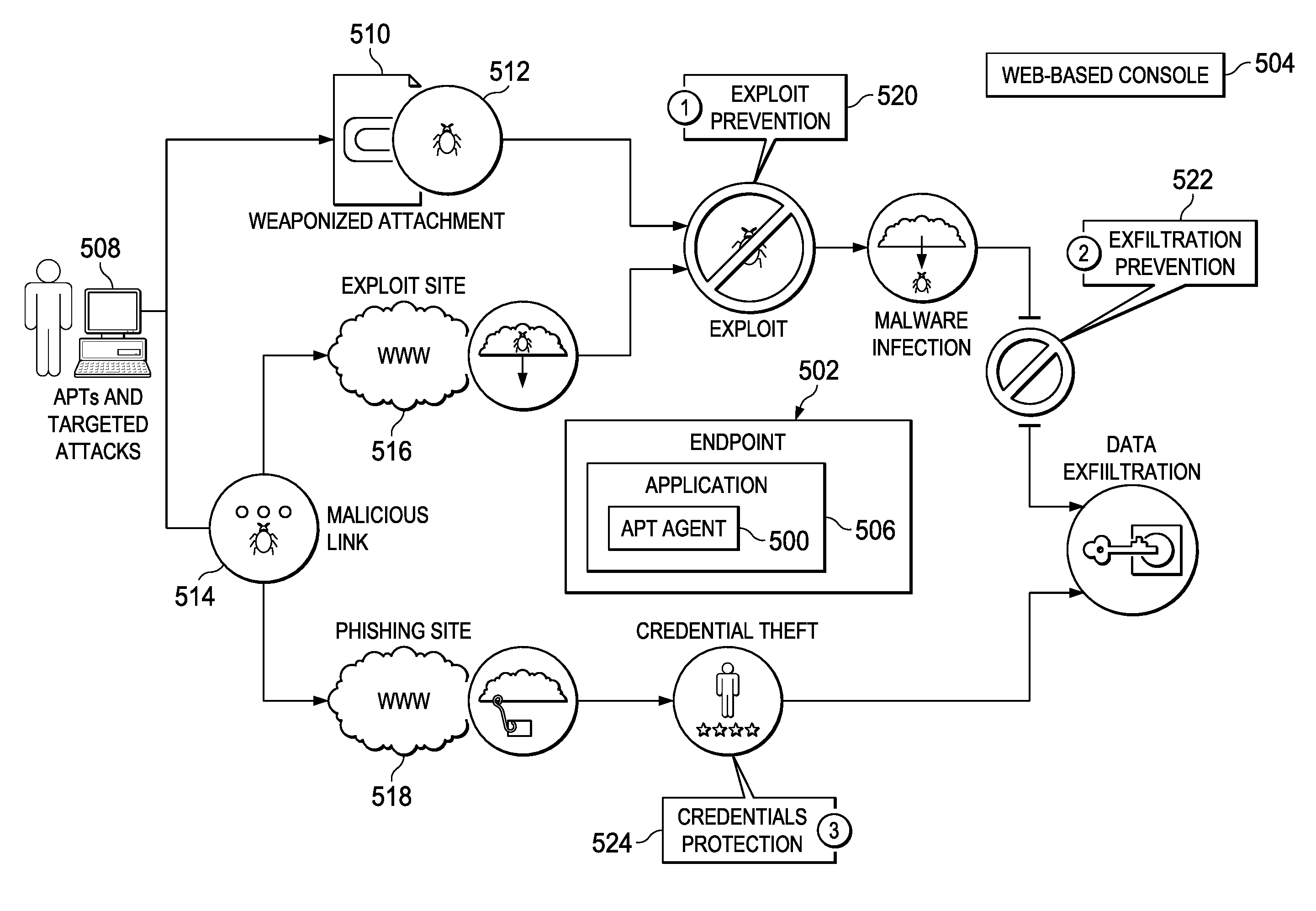
Advanced persistent threat (APT) detection center
ActiveUS20150096024A1Memory loss protectionError detection/correctionInternet privacyAdvanced persistent threat
A computerized method is described in which one or more received objects are analyzed by an advanced persistent threat (APT) detection center to determine if the objects are APTs. The analysis may include the extraction of features describing and characterizing features of the received objects. The extracted features may be compared with features of known APT malware objects and known non-APT malware objects to determine a classification or probability of the received objects being APT malware. Upon determination that the received objects are APT malware, warning messages may be transmitted to a user of associated client devices. Classified objects may also be used to generate analytic data for the prediction and prevention of future APT attacks.
Owner:FIREEYE SECURITY HLDG US LLC +1
Advanced persistent threat (APT) detection center
A computerized method is described in which one or more received objects are analyzed by an advanced persistent threat (APT) detection center to determine if the objects are APTs. The analysis may include the extraction of features describing and characterizing features of the received objects. The extracted features may be compared with features of known APT malware objects and known non-APT malware objects to determine a classification or probability of the received objects being APT malware. Upon determination that the received objects are APT malware, warning messages may be transmitted to a user of associated client devices. Classified objects may also be used to generate analytic data for the prediction and prevention of future APT attacks.
Owner:FIREEYE SECURITY HLDG US LLC +1
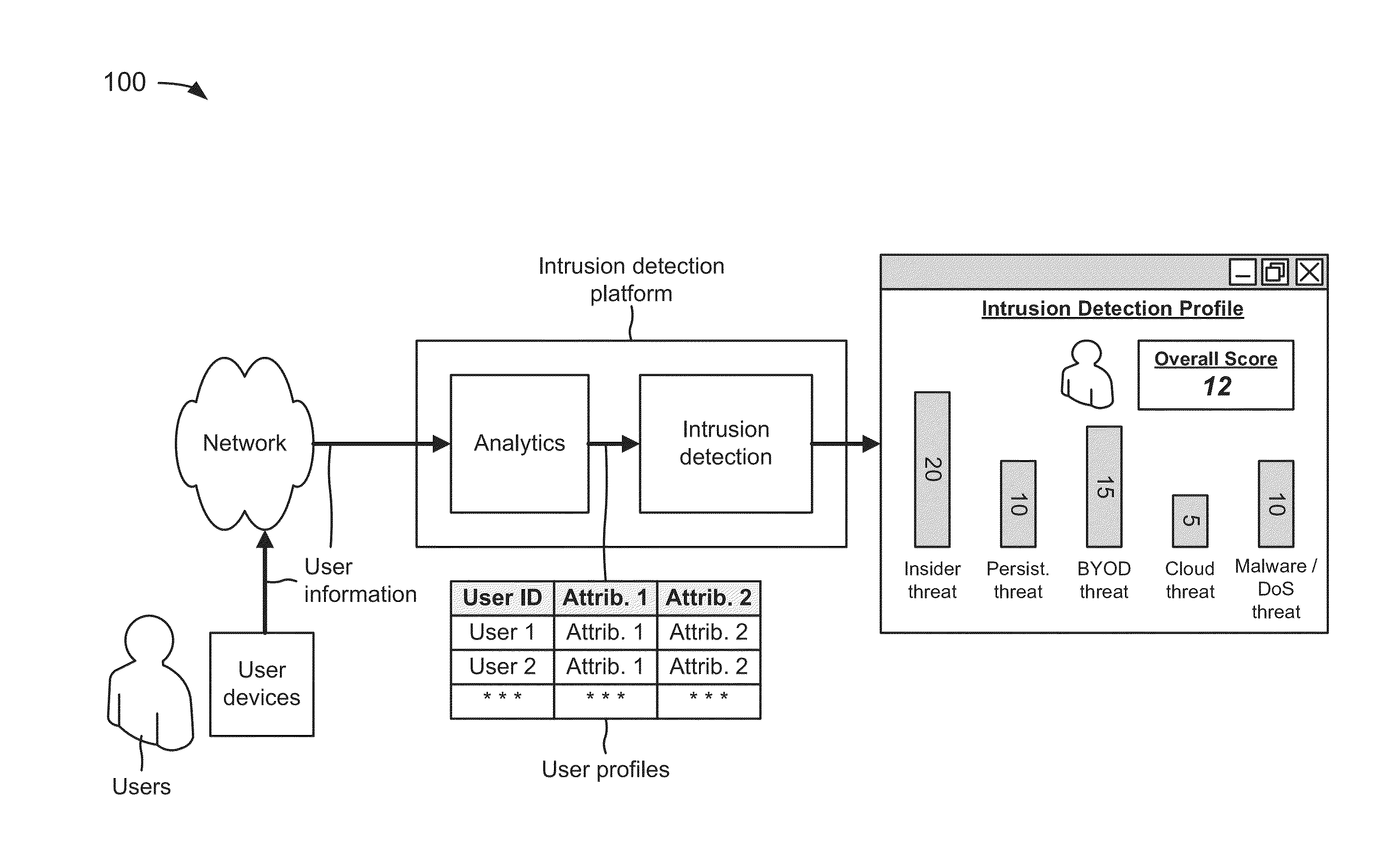
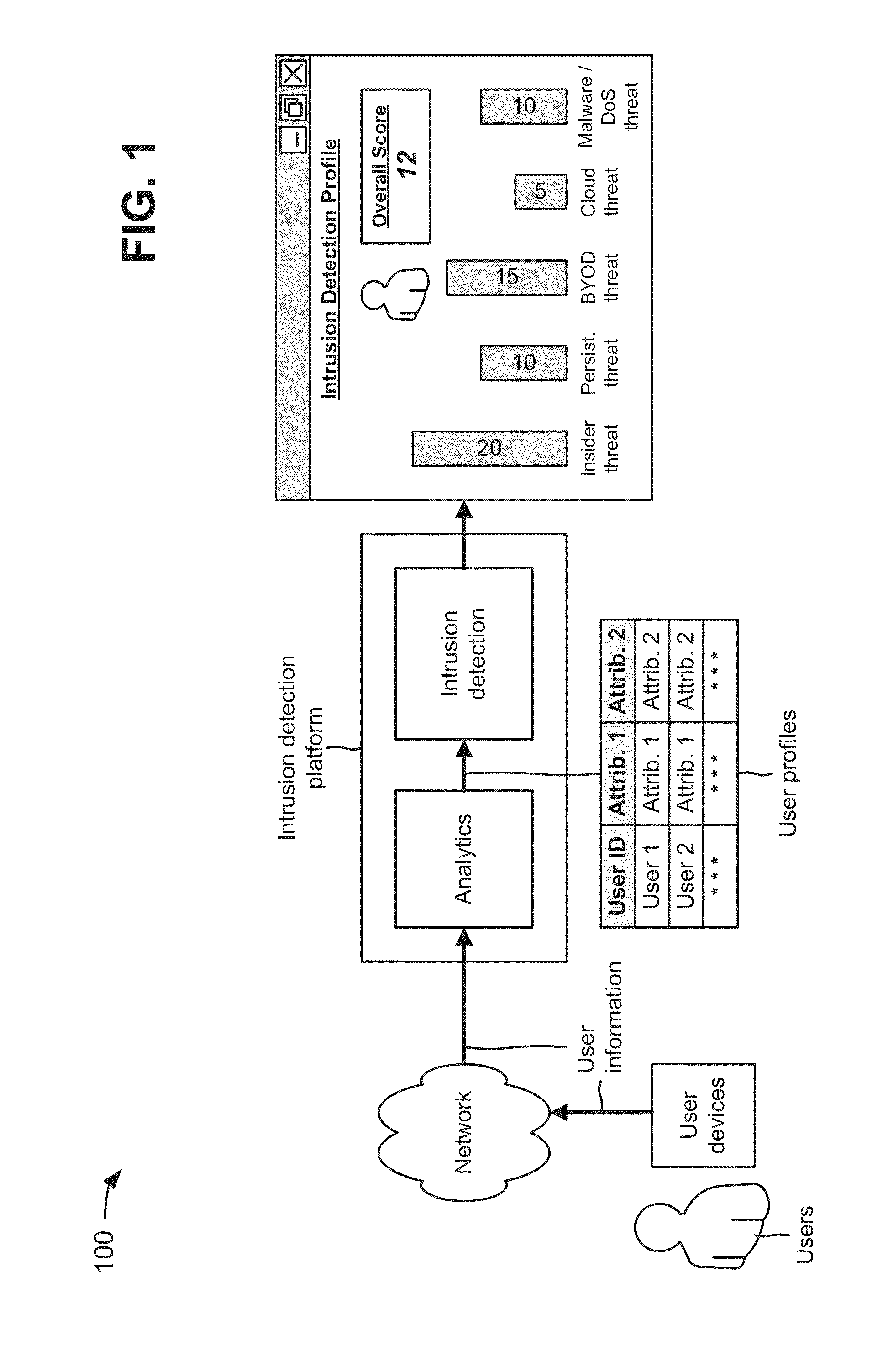
Intrusion detection platform
A device receives user information associated with a user of a user device that is associated with a network, and creates a user profile, associated with the user, based on the user information. The device determines threats to the network, by the user, based on the user profile. The threats to the network include insider threats, advanced persistent threats, bring your own device (BYOD) threats, cloud security threats, malware threats, and / or denial of service (DoS) threats. The device stores or presents, for display, information associated with the determined threats to the network by the user.
Owner:VERIZON PATENT & LICENSING INC
Systems and methods for tracking, predicting, and mitigating advanced persistent threats in networks
ActiveUS20160300227A1Increase network bandwidthGood serviceData switching networksProtocols using social networksComputer securityAdvanced persistent threat
Systems and methods for tracking, predicting, and mitigating Advanced Persistent Threat (APT) attacks in a network include detecting, from monitoring, events related to one or more subscribed entities, wherein the monitoring includes two or more of analyzing traffic flow, analyzing virtual currency transactions, and monitoring information related to the one or more subscribed entities on the Internet; analyzing the events to determine a likelihood of an attack on a specific subscribed entity of the one or more subscribed entities; and causing mitigation of the attack based on the determined likelihood, wherein the mitigation comprises one or more actions in the network relative to the specific subscribed entity.
Owner:CIENA
Multi-step attack detection method based on multi-source abnormal event correlation analysis
ActiveCN106790186AImprove Security Analysis CapabilitiesReduce time to discoveryTransmissionFeature extractionCorrelation analysis
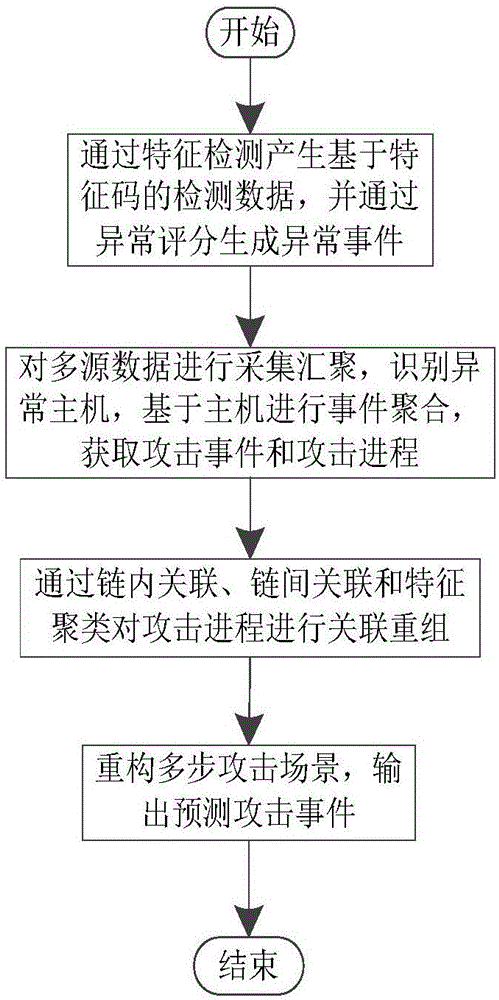
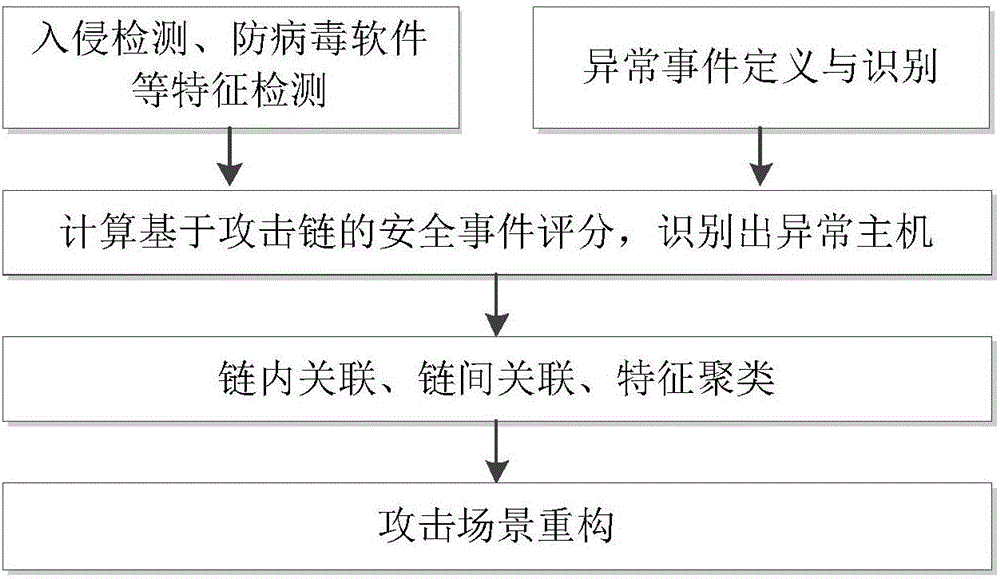
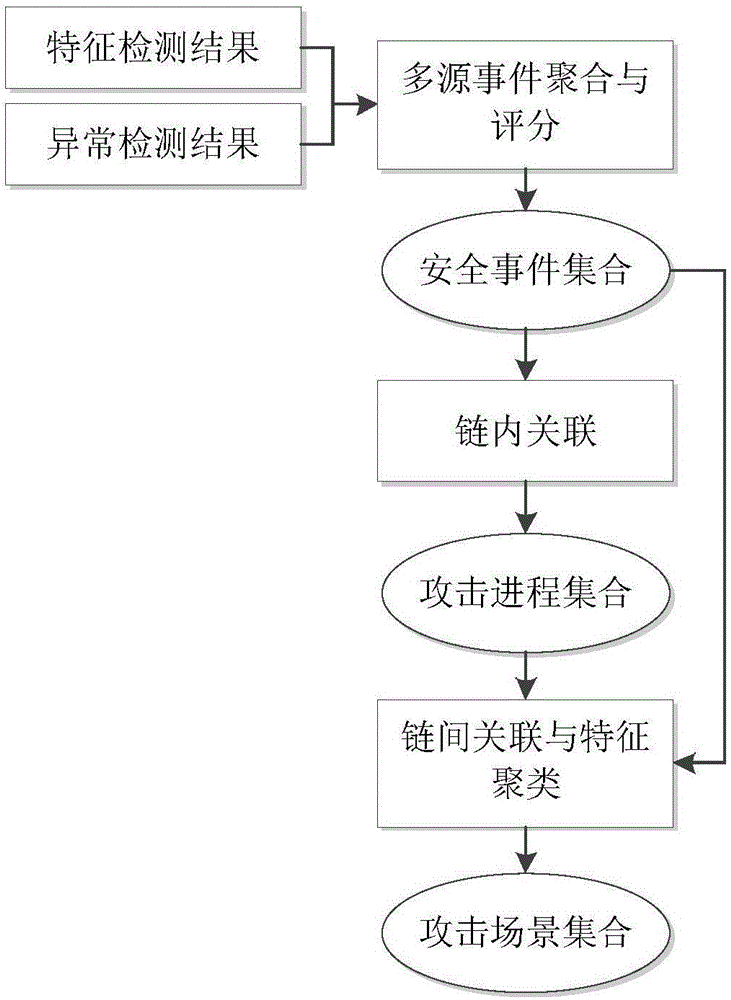
The invention relates to a multi-step attack detection method based on multi-source abnormal event correlation analysis. The multi-step attack detection method comprises the following steps: firstly, calculating a safety event score based on an attach chain through feature extraction and abnormal event definition and identification, identifying an abnormal host and clustering various types of events by taking an attacked host as a clue; secondly, carrying out correlated recombination on a suspected attack progress by utilizing means including intra-chain correlation, inter-chain correlation, feature clustering and the like; finally, reconstructing a multi-source attack scene and outputting a predicated attack event. According to the multi-step attack detection method provided by the invention, dispersed and isolated safety events are subjected to the correlation analysis to generate the relative complete multi-step attack scene; a safety analysis capability of safety managers can be improved and a safety view angle is expanded; distributed and scattered multi-step attack threats are effectively coped and the finding time of attack behaviors is shortened; an effective predication and defending solution is provided for high-grade attack means including APT (Advanced Persistent Threat) and the like; the safety risks of a system are reduced and the network information safety is effectively protected.
Owner:THE PLA INFORMATION ENG UNIV
APT (advanced persistent threat) detection method and system
InactiveCN103312679AEasy to detectAddressing Aggressive Behavior IssuesData switching networksAdvanced persistent threatComputer security
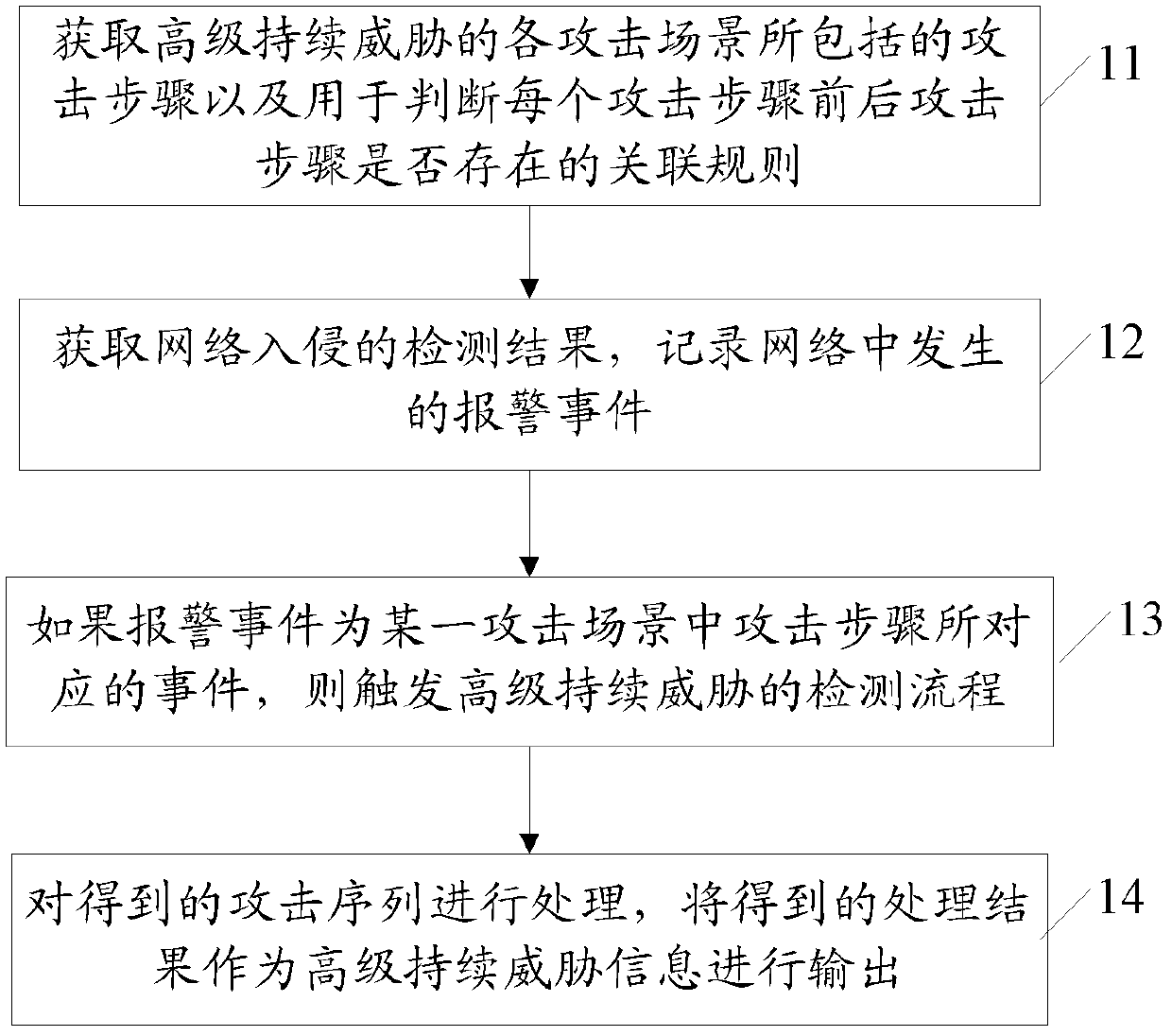
The invention provides an APT (advanced persistent threat) detection method and an APT detection system. The APT detection method comprises the following steps of obtaining attack steps included by each attack scene of the APT and an association rule which is used for judging whether a previous attack step and a later attack step of each attack step exist or not, wherein each attack step corresponds to a plurality of different events capable of realizing the attack steps; obtaining a detection result of network intrusion, and recording an alarm event generated in network; if the alarm event is taken as an event corresponding to the attack step of a certain attack scene, triggering a detection process of the APT, processing an obtained attack sequence and outputting the obtained process result as APT information.
Owner:BEIJING VENUS INFORMATION TECH +1
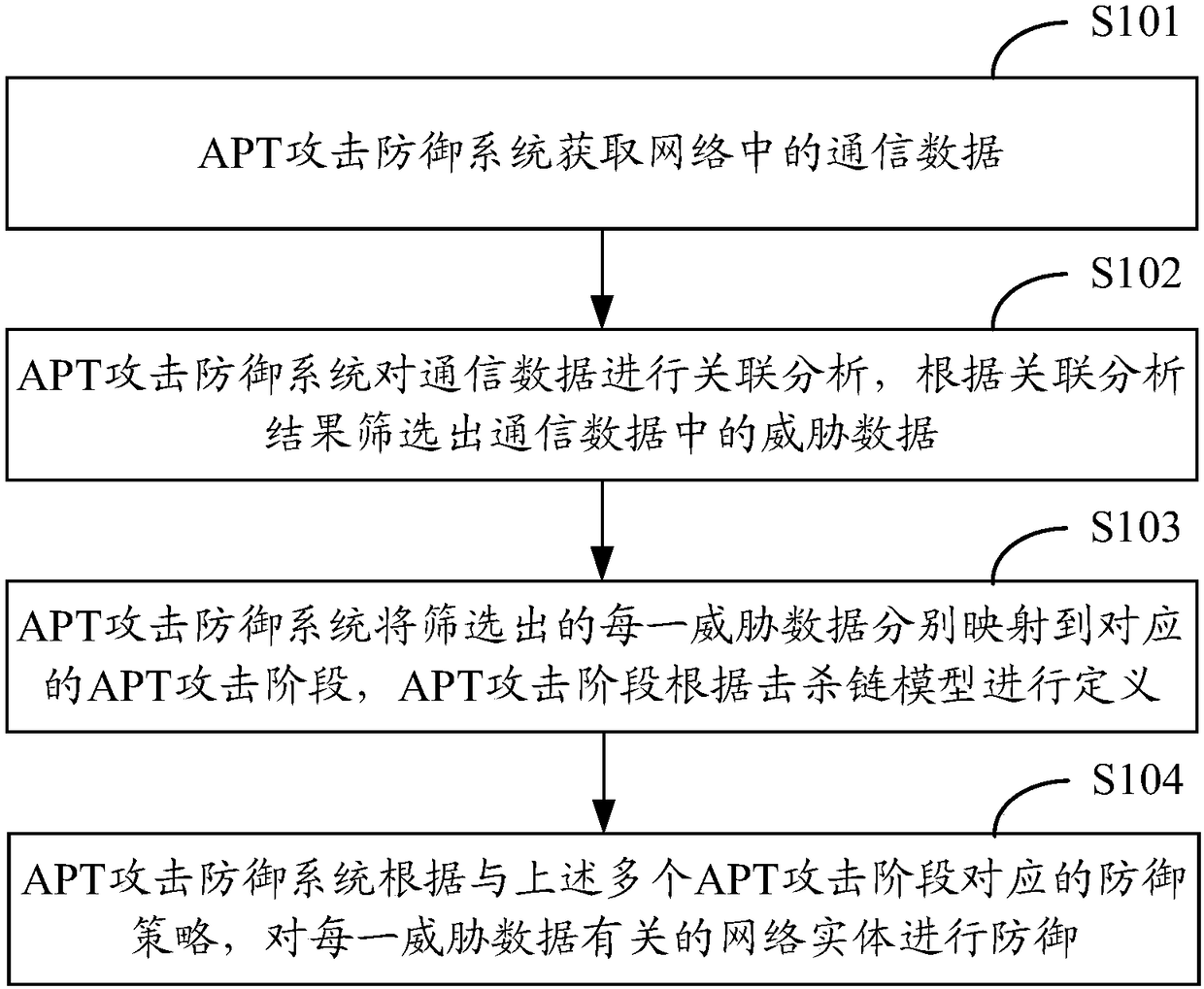
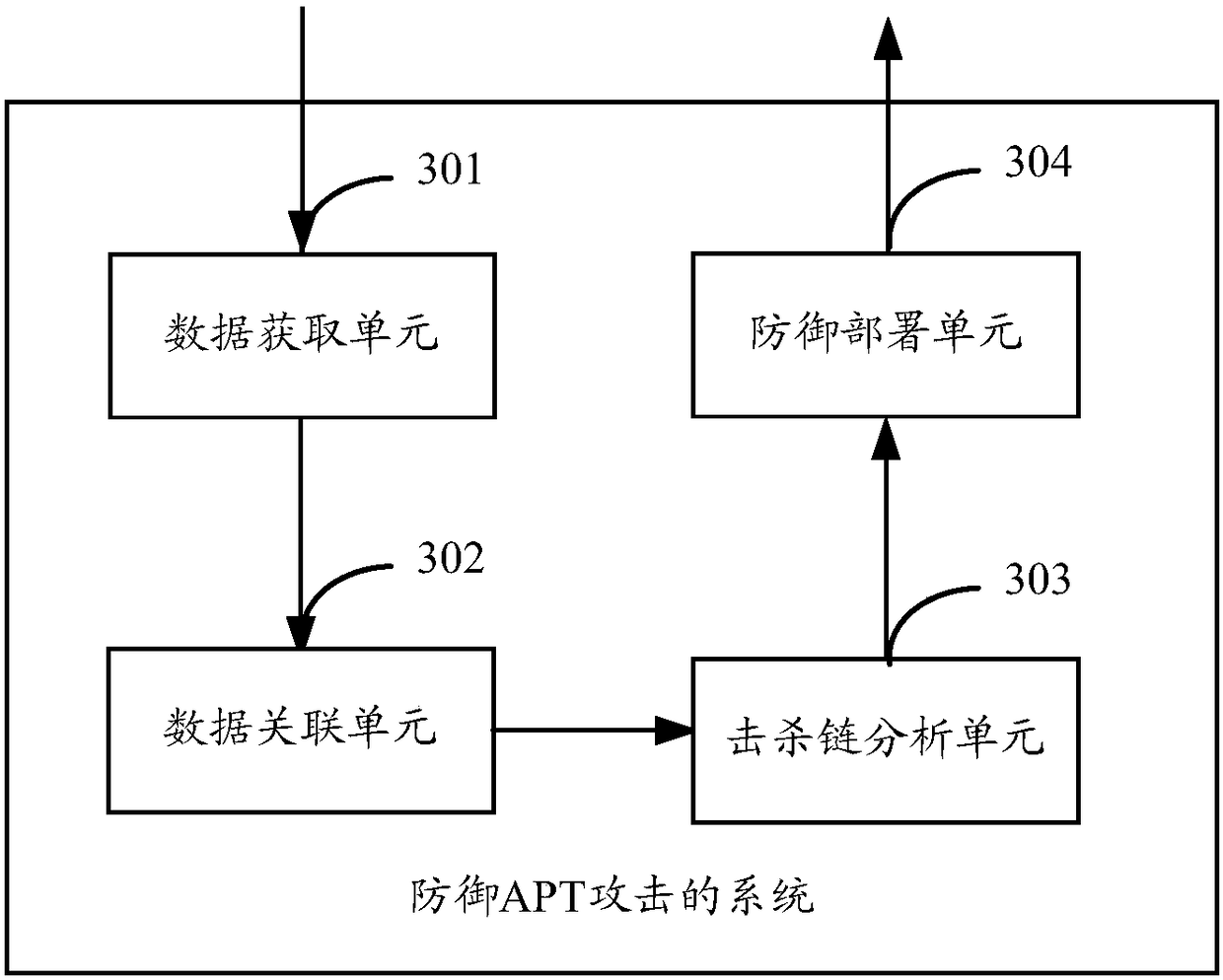
Method and system for defense against APT attacks
ActiveCN108259449AEffective detectionEffective defenseTransmissionAdvanced persistent threatKill chain
The application provides a method and system for defense against advanced persistent threat APT attacks. The method for defense against the advanced persistent threat APT attacks comprises the following steps: obtaining communication data in a network; performing association analysis on the communication data, and screening out the threat data in the communication data according to the results ofthe association analysis; mapping each piece of threat data to a corresponding APT attack stage separately, wherein the APT attack stage is defined according to the kill chain model; and performing defense on the network entity related to each piece of threat data according to the defense strategy corresponding to the plurality of APT attack stages. According to the method and system for defense against the advanced persistent threat APT attacks, the threat data is mapped to the corresponding APT attack stage, and corresponding defense strategies are taken for different APT attack stages, therefore, the APT attack processing is more targeted, and the APT attacks can be detected and defended more effectively.
Owner:NEW H3C TECH CO LTD
System, Method and Process for Protecting Data Backup from Cyberattack
System, method and process for securing and protecting data and data backups from cyberattack and implementing disaster recovery using machine learning and artificial intelligence. Embodiments learn and establish baseline parameters of routine, normal and non-compromised behavior and activity of virtual machines operative in cloud ecosystem, detect and recognize anomalous events related to advanced persistent threats to the instance, such as ransomware, and automatically implement preconfigured actions as determined by a user with the primary objective of protecting data and data backups.
Owner:CLOUD DADDY INC
APT (Advanced Persistent Threat) attack detection method and APT attack detection device based on malicious domain name detection
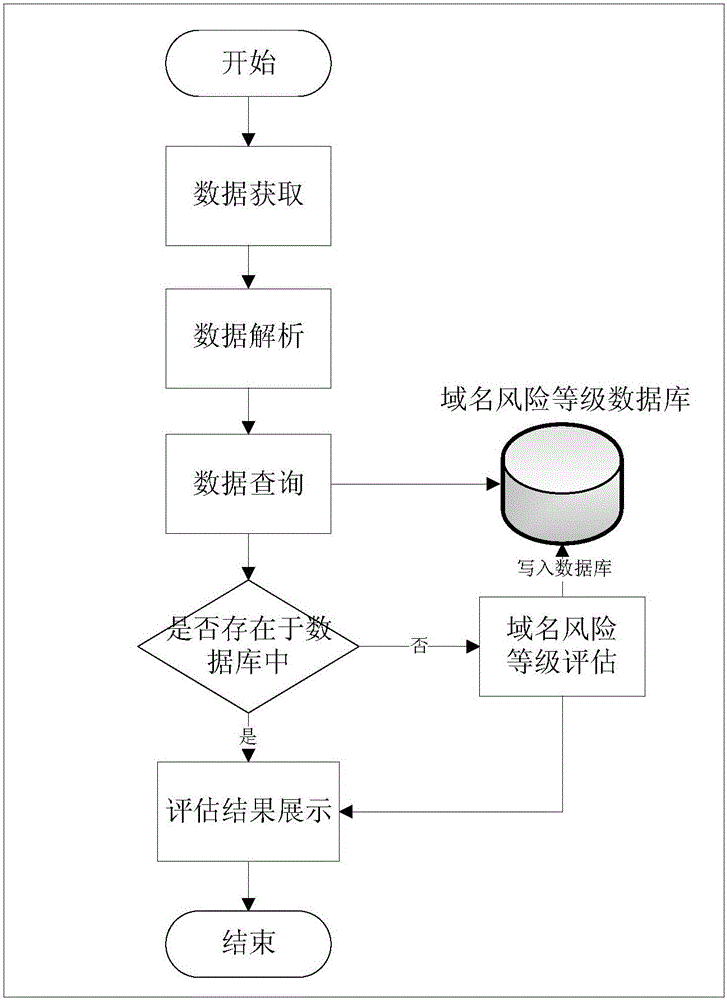
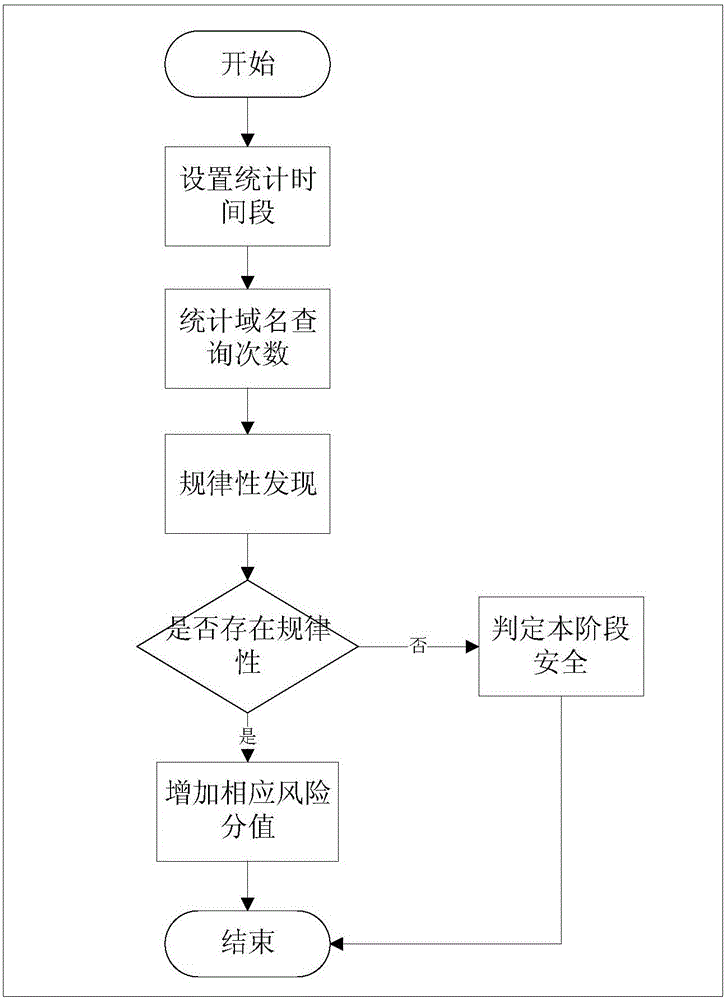
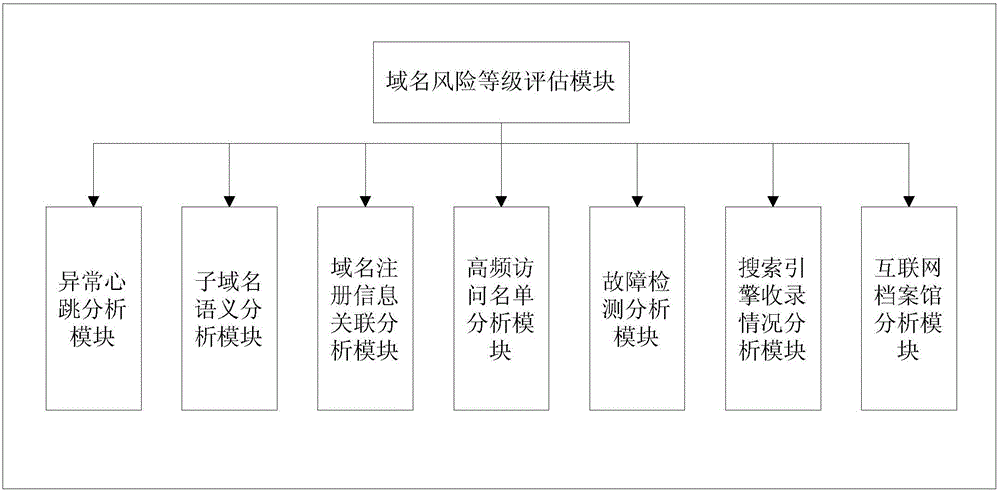
InactiveCN105141598AAccurate detectionMinimize consequencesTransmissionDomain nameAdvanced persistent threat
The invention provides an APT (Advanced Persistent Threat) attack detection method and an APT attack detection device based on malicious domain name detection. The APT attack detection method comprises the following steps: obtaining communication data in a network; analyzing the communication data so as to extract the IP (Internet Protocol) of a source host, a domain name inquired by the source host and the domain name inquiry time related in the communication data; inquiring a domain name risk grade database so as to determine whether the domain name inquired by the source host exists in the domain name risk grade database or not, if so, extracting and displaying a risk grade result corresponding to the domain name from the domain name risk grade database, and if not, evaluating the risk grade of the domain name and displaying a risk grade evaluation result so as to determine whether the source host is attacked by APT or not, wherein the risk grade evaluation result comprises abnormal heartbeat analysis and sub-domain name semantic analysis. The APT attack detection method and the APT attack detection device provided by the invention are capable of accurately detecting unknown malicious domain names; therefore, APT attacks can be detected in time; and consequences due to the APT attacks can be reduced.
Owner:COMMUNICATION UNIVERSITY OF CHINA
APT attack detection method based on deep belief network-support vector data description
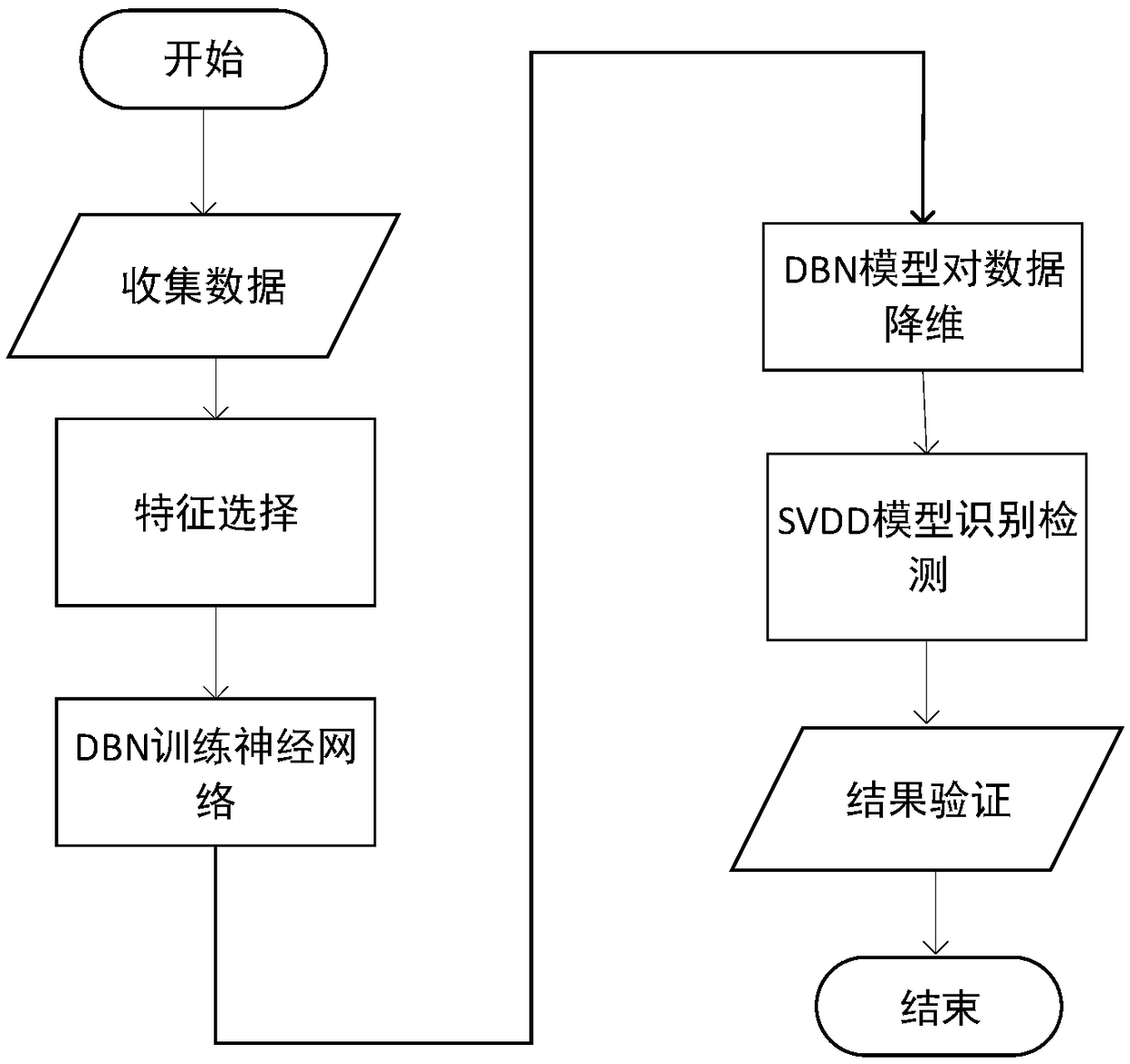
InactiveCN108848068AImplement attack detectionGood dimensionality reduction effectData switching networksRestricted Boltzmann machineFeature Dimension
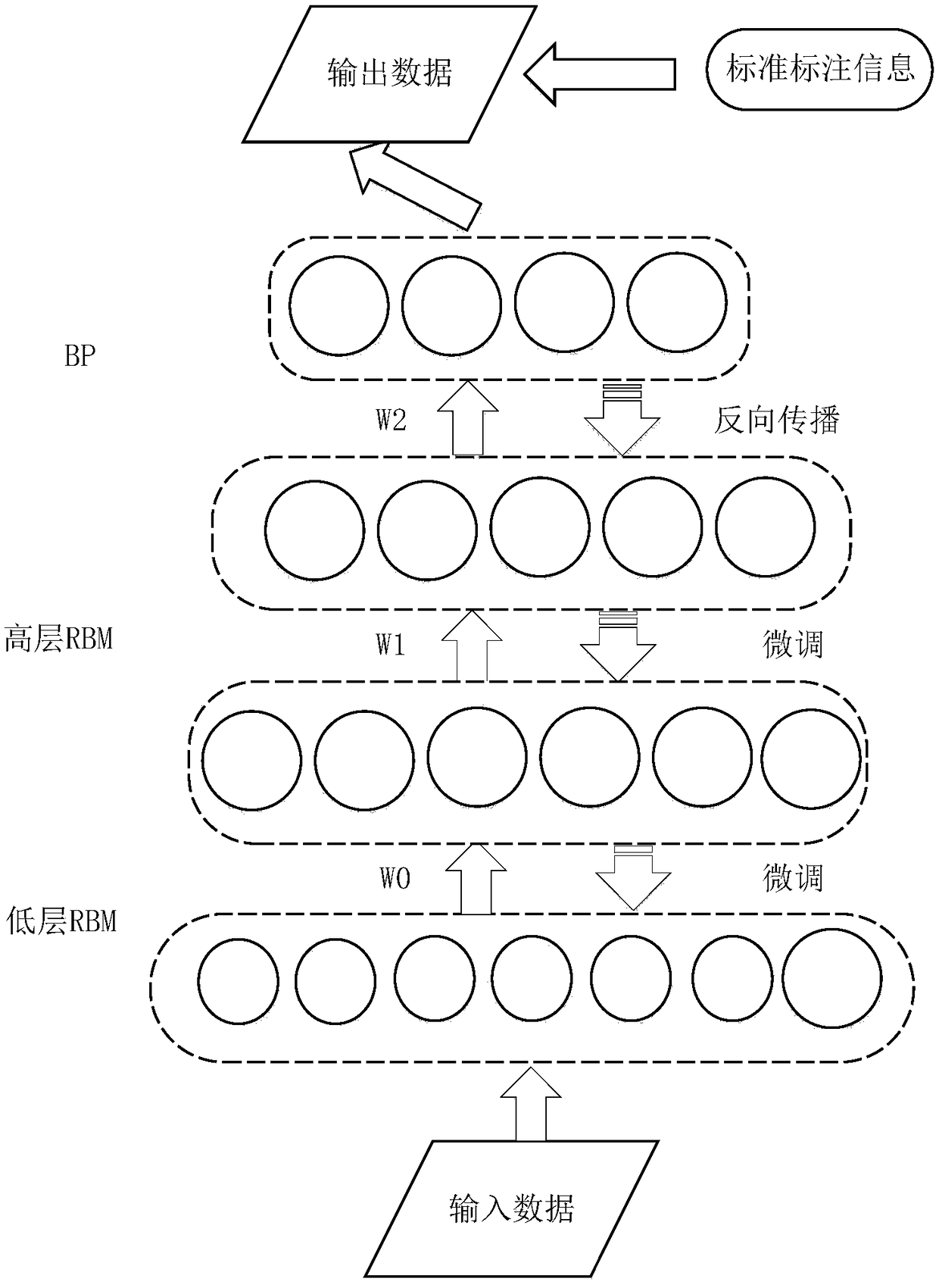
The invention discloses an advanced persistent threat (APT) attack detection method based on deep belief network-support vector data description. A deep belief network (DBN) is used for feature dimension-reduction and excellent feature vector extraction; and support vector data description (SVDD) is used for the data classification and detection. At a DBN training state, the feature dimension-reduction is performed by using the DBN model after obtaining a standard data set; a low-level restricted Boltzmann machine (RBM) receives simple representation transmitted from the low-level RBM by usingthe high-level RBM so as to learn more abstract and complex representation after performing the initial dimension-reduction, and back propagation of a back propagation (BP) neural network is used forrepeatedly adjusting a weight value until the data with excellent feature is extracted. The data processed by the DBN is divided into a training set and a testing set, and the data set is provided for the SVDD to perform training and identification detection, thereby obtaining the detection result. The attack detection method disclosed by the invention is suitable for the unsupervised attack datadetection with large data size and high-dimension feature, is fit for the APT attack detection and can obtain an excellent detection result.
Owner:SHANGHAI MARITIME UNIVERSITY
Multidimensional deep-level APT (Advanced Persistent Threat) attack detection method
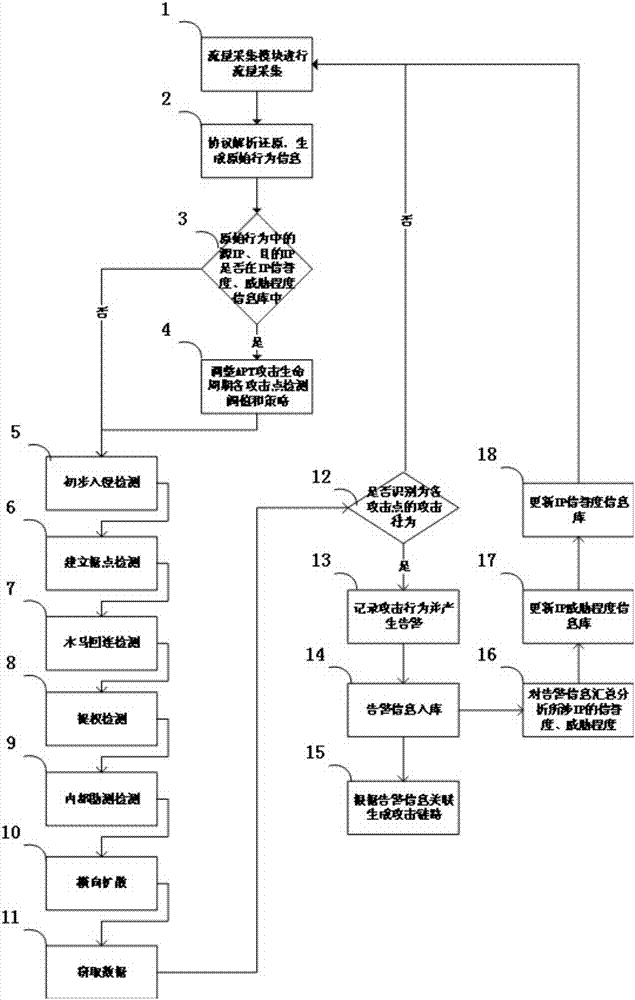
The invention relates to the field of APT attack detection and aims at providing a multidimensional deep-level APT (Advanced Persistent Threat) attack detection method. The method comprises steps: traffic collection and analytical reduction are carried out on common network application layer protocol data packets; acquired network application behaviors are analyzed and detected, an attack behavior is recorded and an alarm is given; the detection strategy and the mechanism for each attack point are further optimized; and an APT attack link is generated through correlation. Multidimensional deep-level analysis and detection can be carried out on possible attack points in each stage of an APT attack life cycle, an attack clue found in an attack stage can be used to further serve as the basis for the detection of other attack stages, the detection conclusion in each attack stage is used for further correlation, and an attack evidence with higher certainty is formed.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Real-time network abnormal behavior detecting system and method based on big data
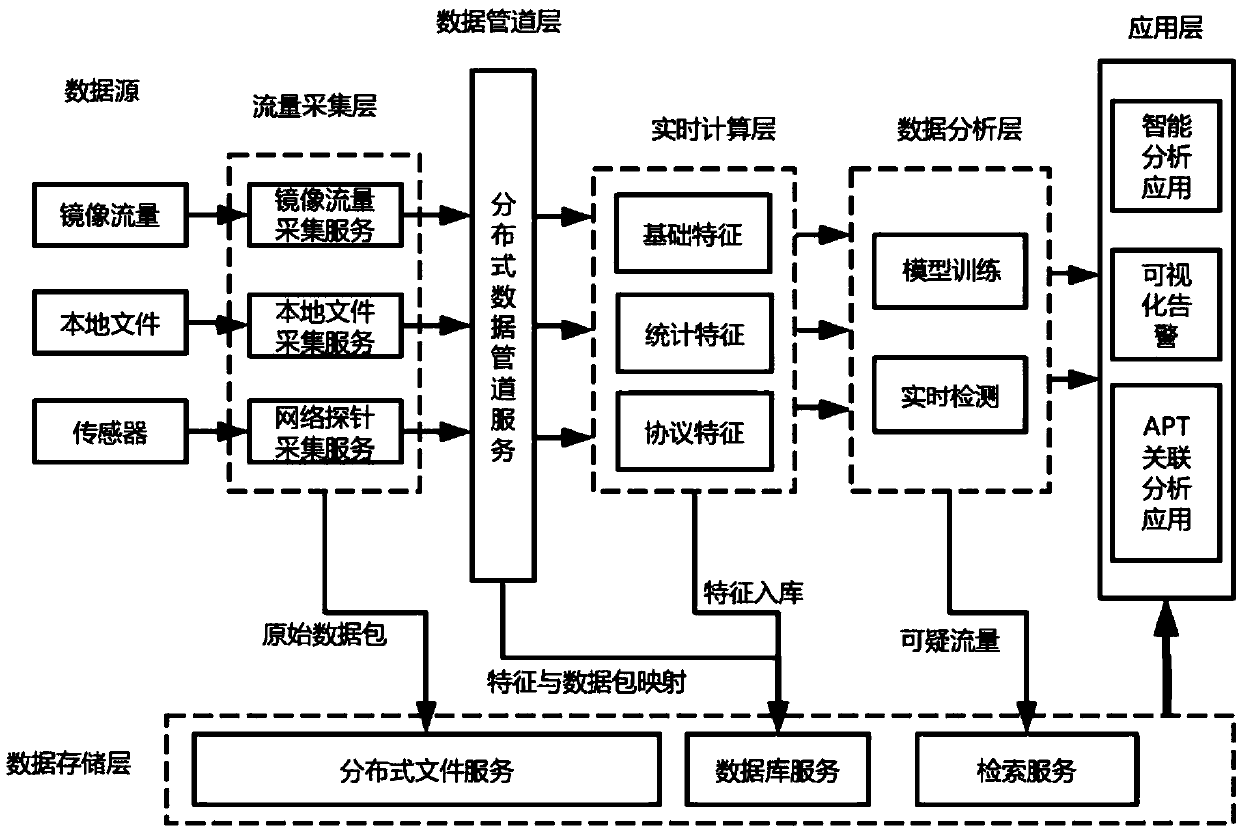
ActiveCN108040074ALittle performance dependencyImprove collection efficiencyMachine learningTransmissionData acquisitionFalse alarm
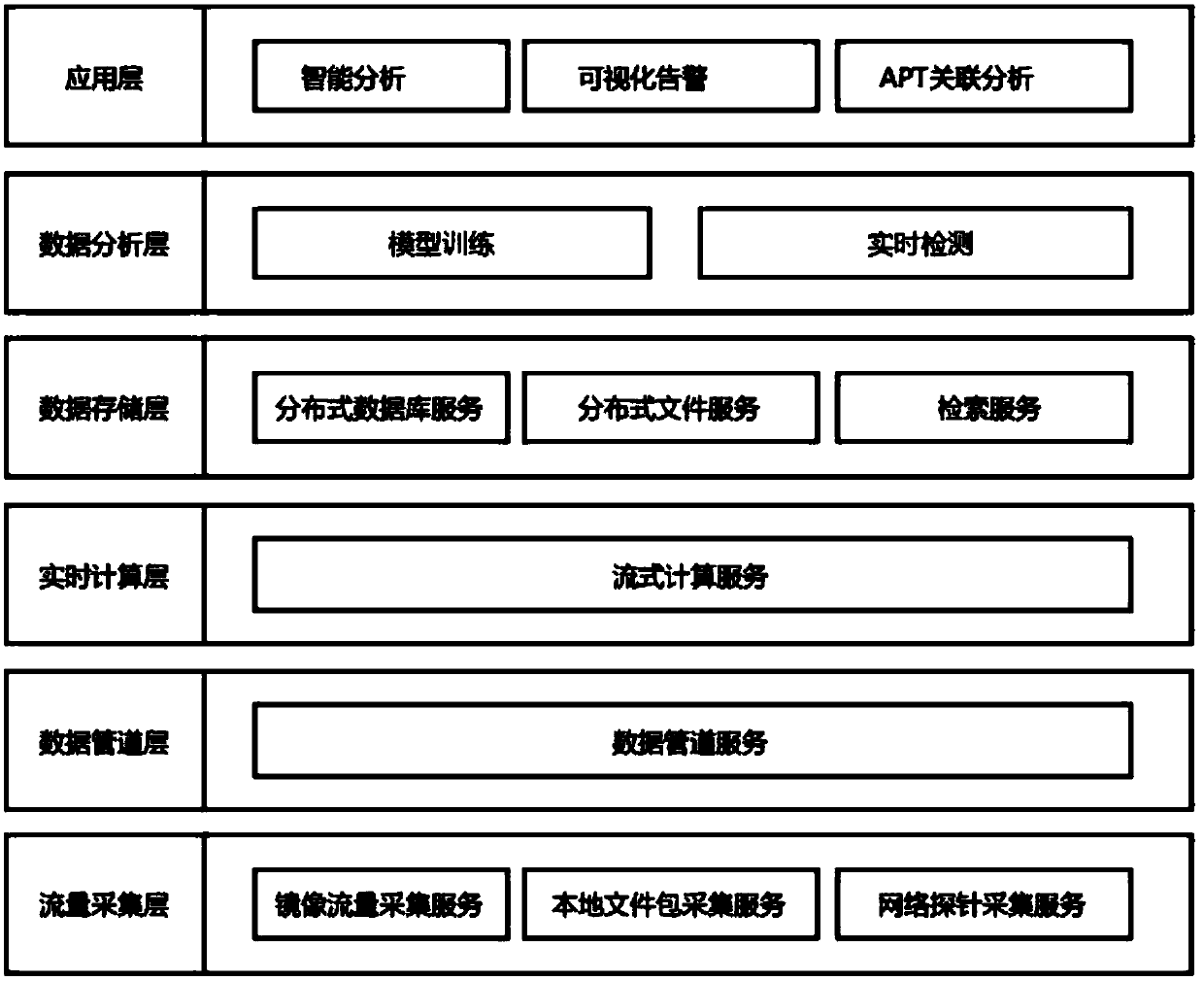
The invention provides a real-time network abnormal behavior detecting system based on big data. The real-time network abnormal behavior detecting system comprises a flow collecting layer, a data pipeline layer, a real-time calculation layer, a data storage layer, a data analysis layer and an application layer, wherein the flow collecting layer comprises a collecting device; the data pipeline layer comprises a data pipeline service module adopting a distributed message system; the real-time calculation layer comprises a stream-oriented computation module; the data storage layer comprises a distributed file service module, a distributed database module and an retrieval service module; the data analysis layer comprises a model training module and a real-time detection module; the applicationlayer comprises a visual warning module. The invention also discloses a real-time network abnormal behavior detecting method based on big data. The data collection efficiency is high; the data transmission is stable and reliable; the advanced persistent threat can be efficiently detected and analyzed; the traceability evidence can be realized; the retrieval by analysts is convenient; the model training efficiency is high; the false alarm rate is low.
Owner:SOUTH CHINA UNIV OF TECH
Detection of advanced persistent threat having evasion technology
ActiveUS9178900B1Volatile memory can be restoredError detection/correctionPlatform integrity maintainanceVirtual memoryAdvanced persistent threat
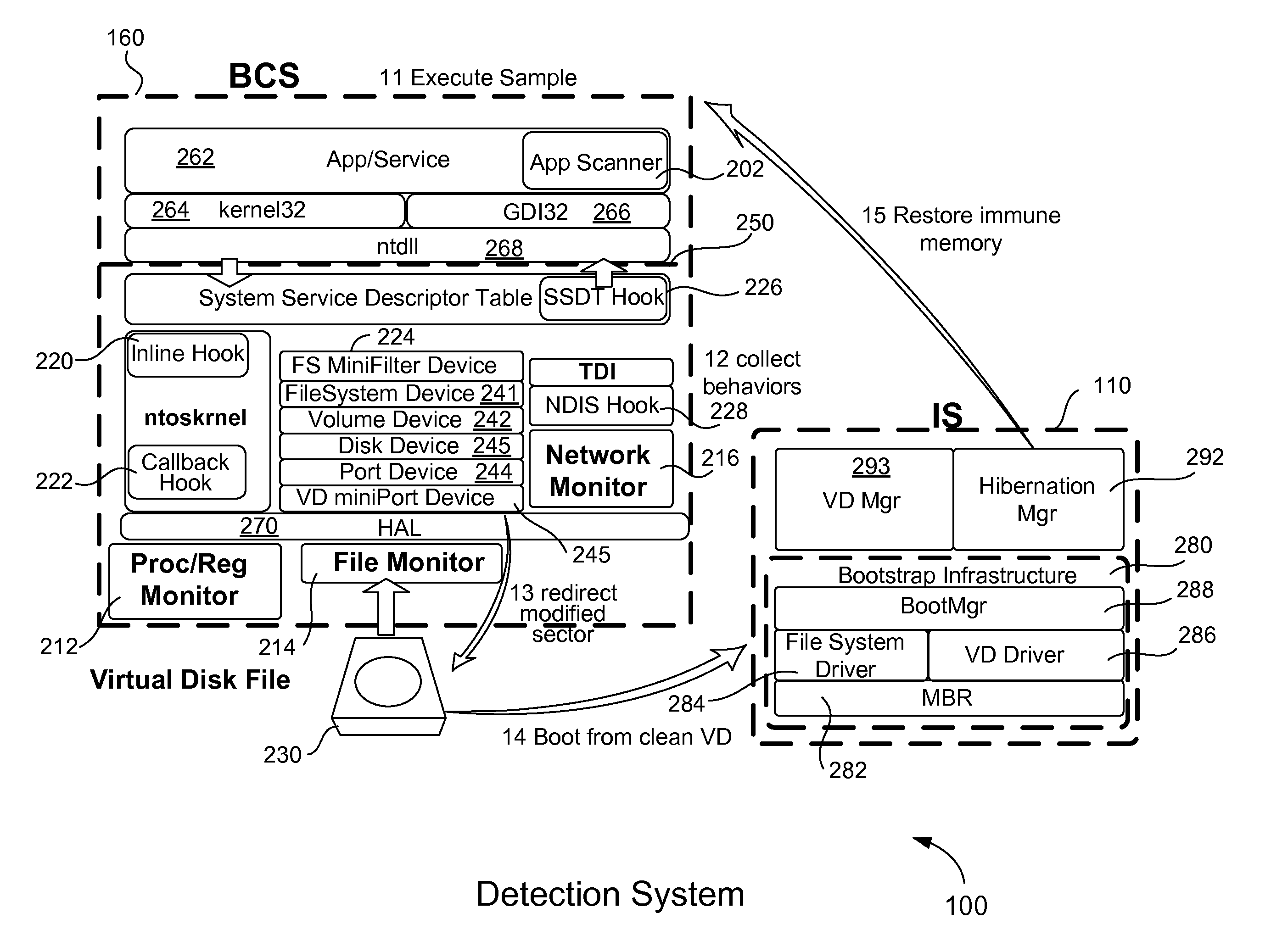
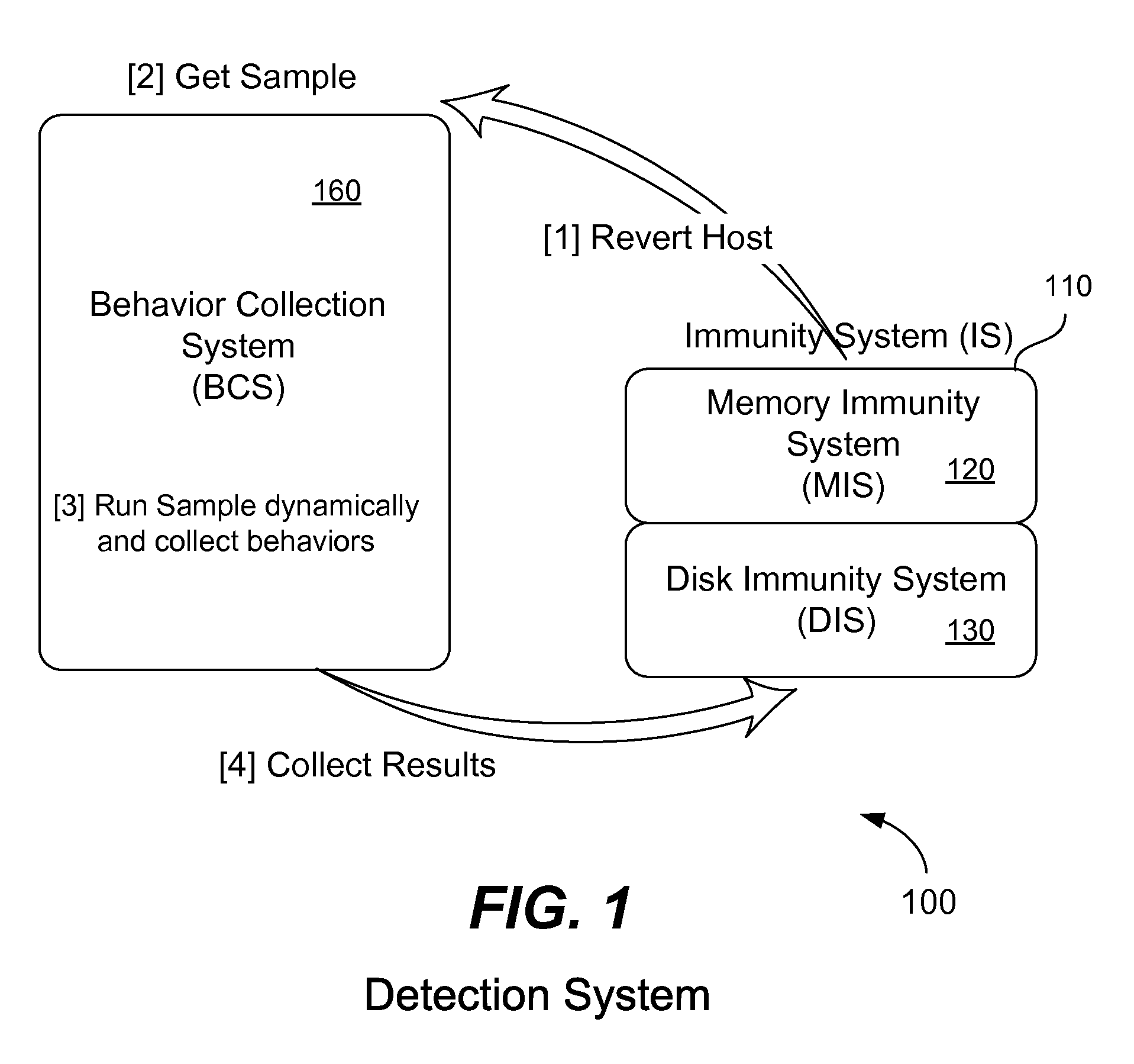
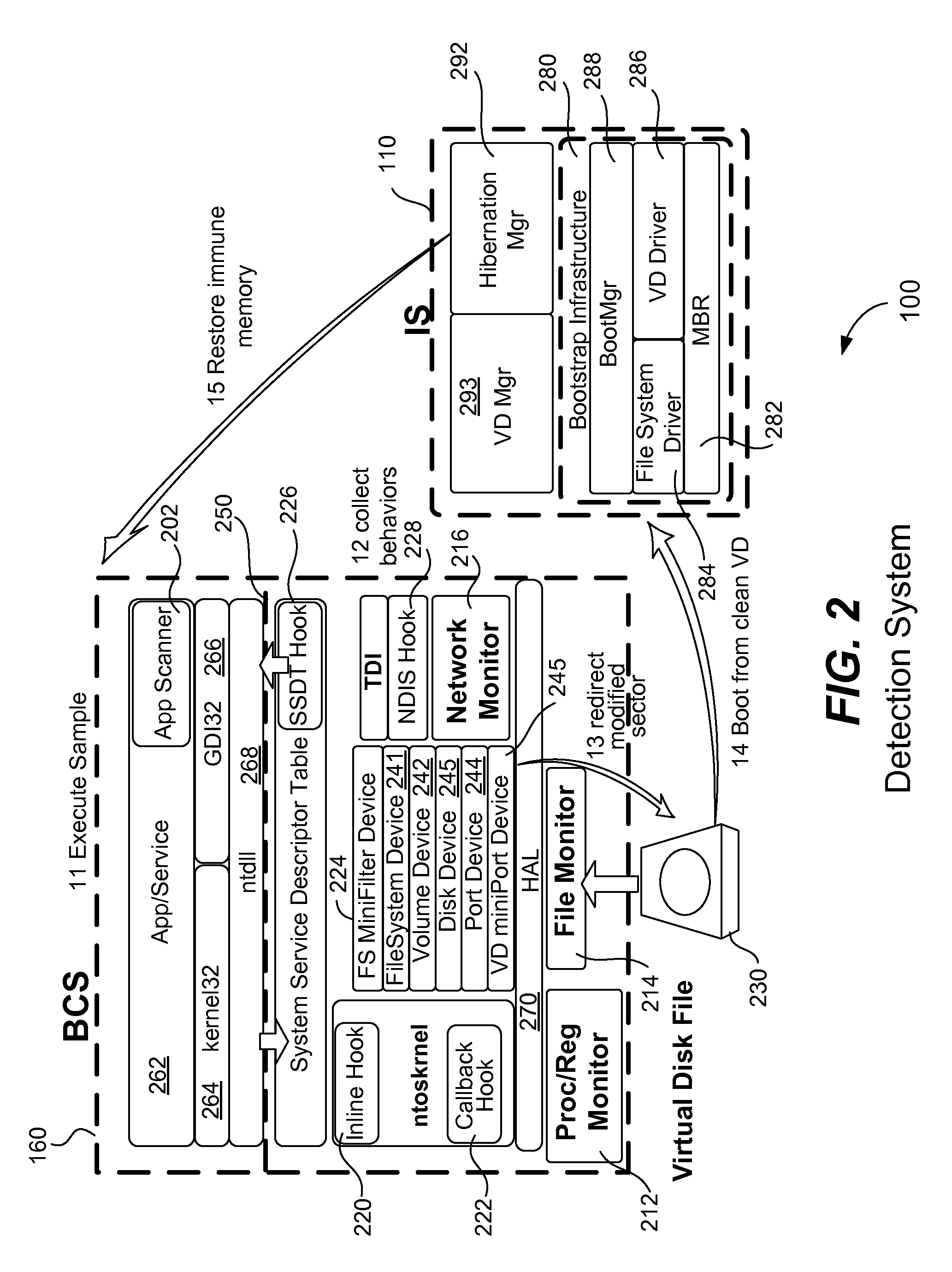
A computer executes a suspicious software sample directly on its CPU in order to detect if the software sample is malicious. The software sample does not execute within a sandbox or virtual machine. Before the sample executes, a memory state of the computer is saved and a virtual disk file is created to bootstrap the computer at a later time. Malicious behavior of the software sample is collected while it executes and a report is generated. Hard disk access requests are redirected to a virtual disk file. The software sample does not detect that it is being analyzed. After execution of the sample, the computer is reverts to a clean state by bootstrapping the computer from the saved virtual disk file and then restoring the computer's volatile and non-volatile virtual memory from the saved memory state. A new software sample may then be executed and analyzed on the clean computer.
Owner:TREND MICRO INC
APT attack detection method
ActiveCN106817248AGuaranteed detection accuracyImprove generalization abilityData switching networksFeature extractionData set
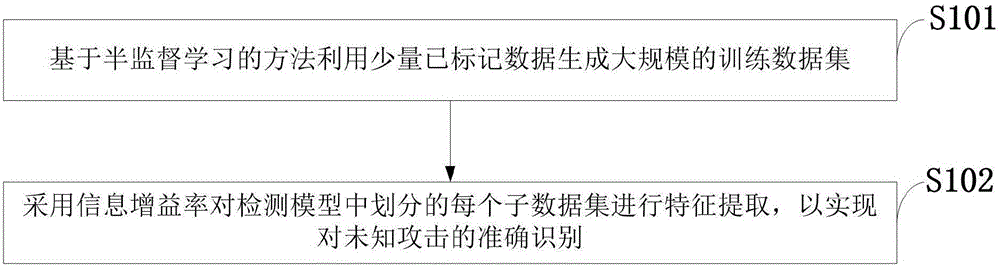
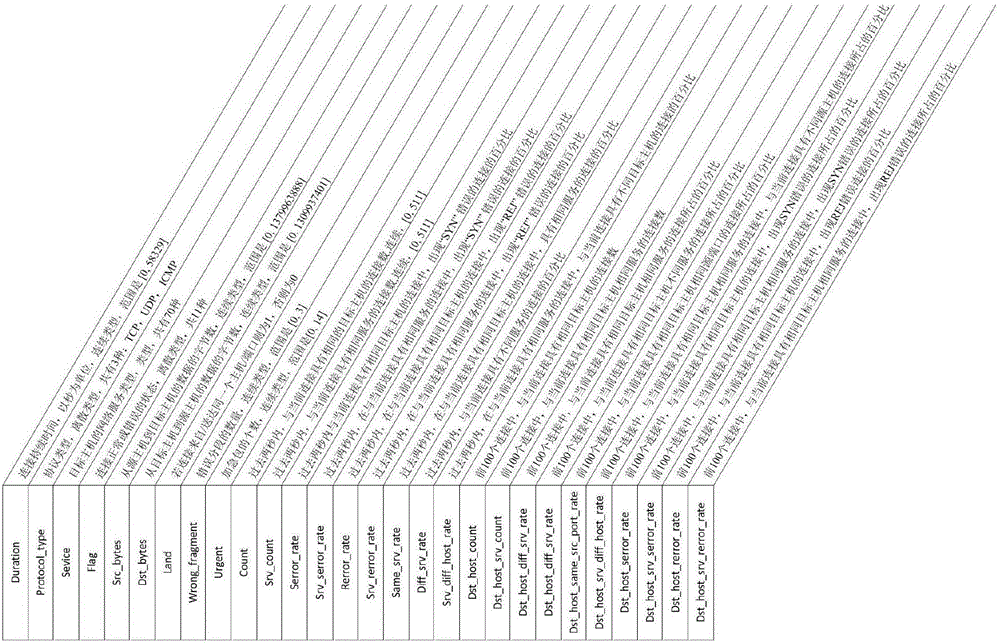
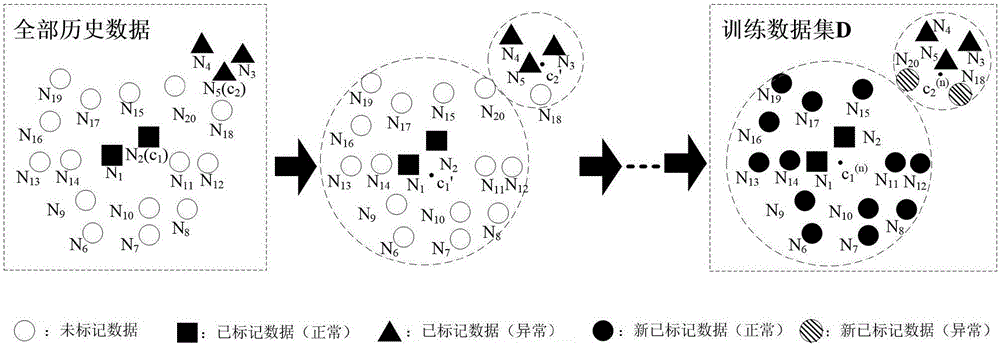
The invention discloses an advanced persistent threat APT attack detection method. A semi-supervised learning algorithm is used to mark data having similar characteristics, and a small quantity of marked data are used to generate a large-scale training data set, and then an information gain ratio is introduced to determine the degrees of the influences of the different characteristics on detection. The information gate ratio is used for characteristic extraction of every sub-data set in a detection model, and accurate identification of unknown attacks is realized. An improved k-means algorithm is used to mark the data having the similar characteristics, and on the basis of the small quantity of marked data, the accurate marking of a lot of training data sets is realized, and therefore the detection accuracy of the model is guaranteed; and by introducing the information gain ratio in the model, the degrees of the influences of the different characteristics on the detection are determined, and influences of redundancy and noise characteristics in the data are reduced, and therefore important flow characteristics are selected, the generalization capability of the detection model is improved to detect the unknown attacks.
Owner:XIDIAN UNIV
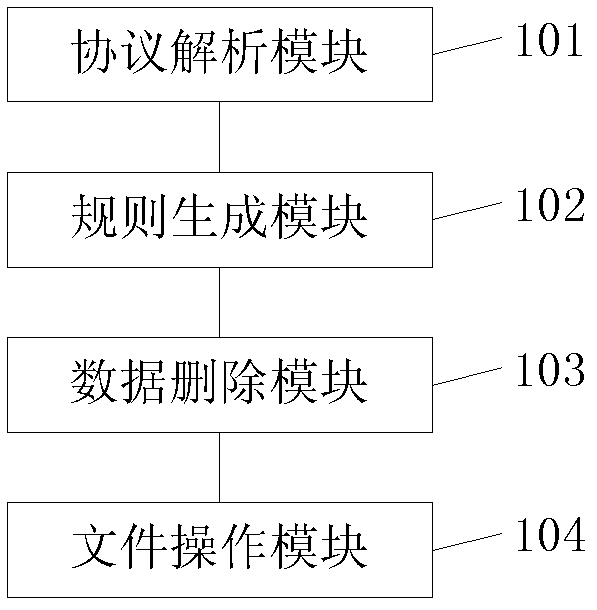
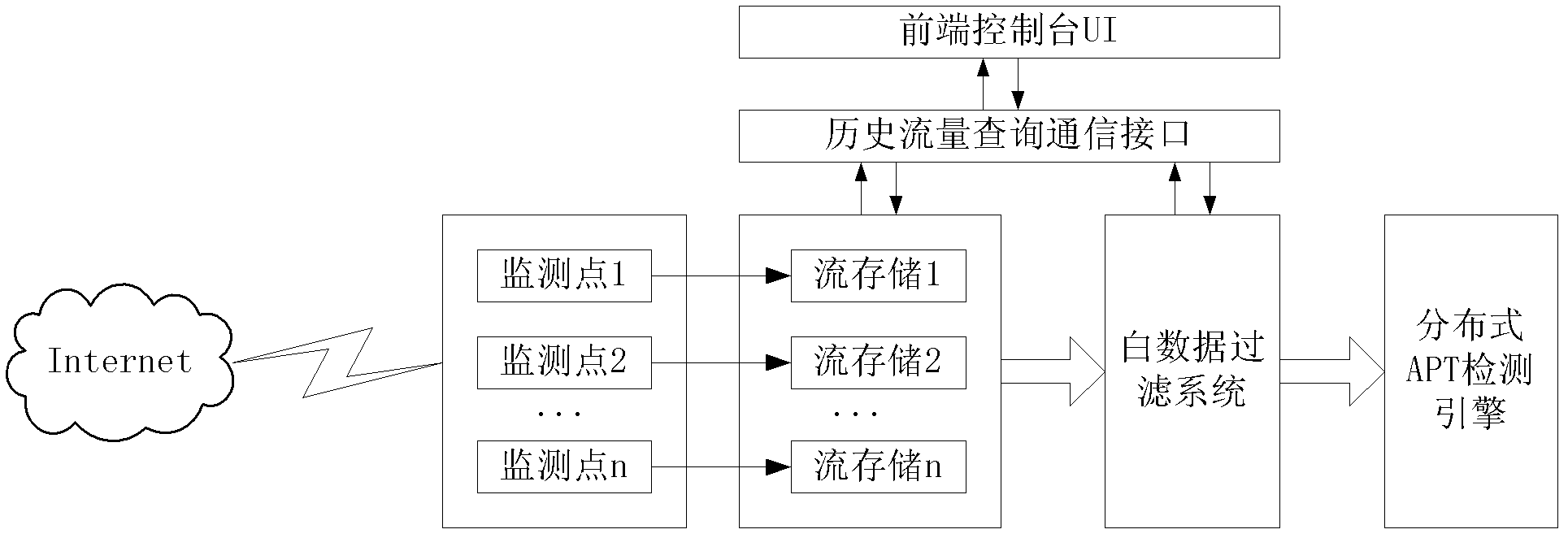
White data filter method and system in APT (Advanced Persistent Threat) intelligent detection and analysis platform
InactiveCN102594625AClean up in timeSolve the degradabilityData switching networksTraffic capacityNetwork packet
The invention discloses a white data filter method and system in an APT (Advanced Persistent Threat) intelligent detection and analysis platform. The white data filter method comprises the following steps of: performing protocol analysis on each packet capturing library Pcap data packet in the stored historical flow data, so as to obtain the control information and data of the Pcap data packet; generating a filter criteria according to a predetermined white data filter condition; matching the analyzed control information of each Pcap data packet with the filter criteria, if the control information of one Pcap data packet satisfies the filter criteria, then deleting the control information and data of the Pcap data packet; after deleting the control information and data, re-packaging and encapsulating the other data and control information into a Pcap data packet and then transmitting the Pcap data packet to an APT search engine. The white data filter method and system in the APT intelligent detection and analysis platform, disclosed by the invention, can rationally degrade the filtered and stored historical data.
Owner:BEIJING VENUS INFORMATION TECH +1
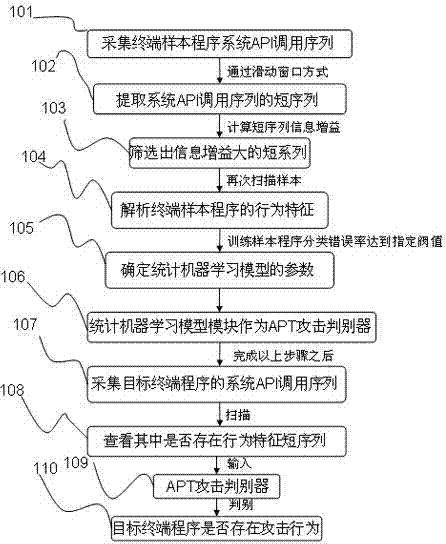
Discrimination method for advanced persistent threat attack
The invention relates to a discrimination method for advanced persistent threat attack. The discrimination method comprises the following steps: collecting an API (Application Program Interface) calling sequence of a terminal sample program system; extracting the API calling short sequence of the terminal sample program system through a MapReduce module, then, calculating the information gain of the short sequence, and screening program behavior characteristics with huge information gain; scanning the API calling sequence of the terminal sample program system again to obtain the behavior characteristics of a terminal sample program; using the behavior characteristics of each sample program as input by a statistical machine learning model module, training the statistical machine learning model module until the classification correction rate of the training sample program by the statistical machine learning model module is above 90%, determining a model parameter, and taking the model parameter as an APT (Advanced Persistent Threat) attack discriminator; collecting the system calling sequence of a target terminal program; and after the API calling sequence of the target program is collected and the behavior characteristics of the target program are extracted, judging whether the target program has attack behaviors. The discrimination method is high in APT attack detection capability and shortens the extraction time of program behavior characteristics.
Owner:BEIJING VRV SOFTWARE CO LTD
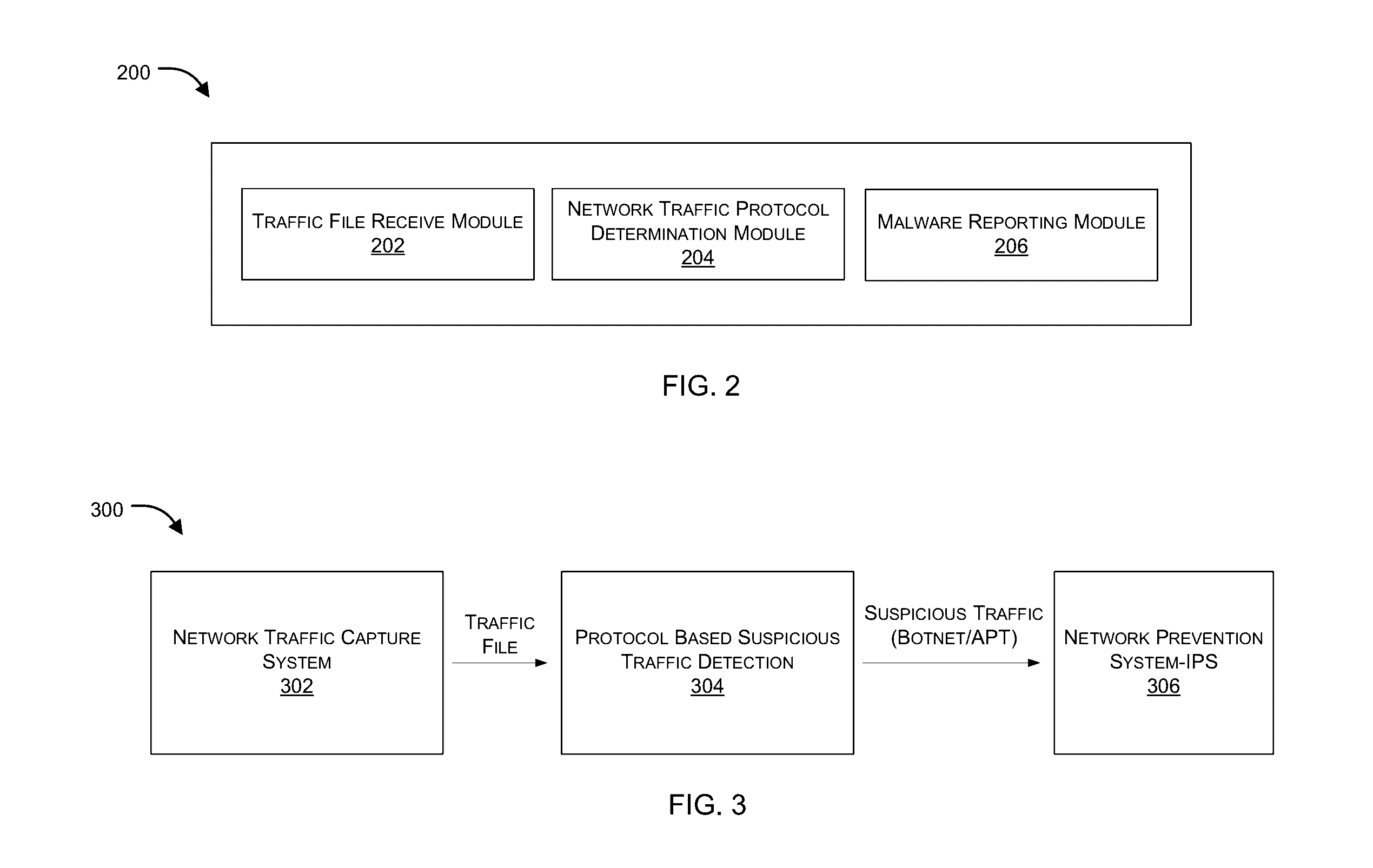
Protocol based detection of suspicious network traffic
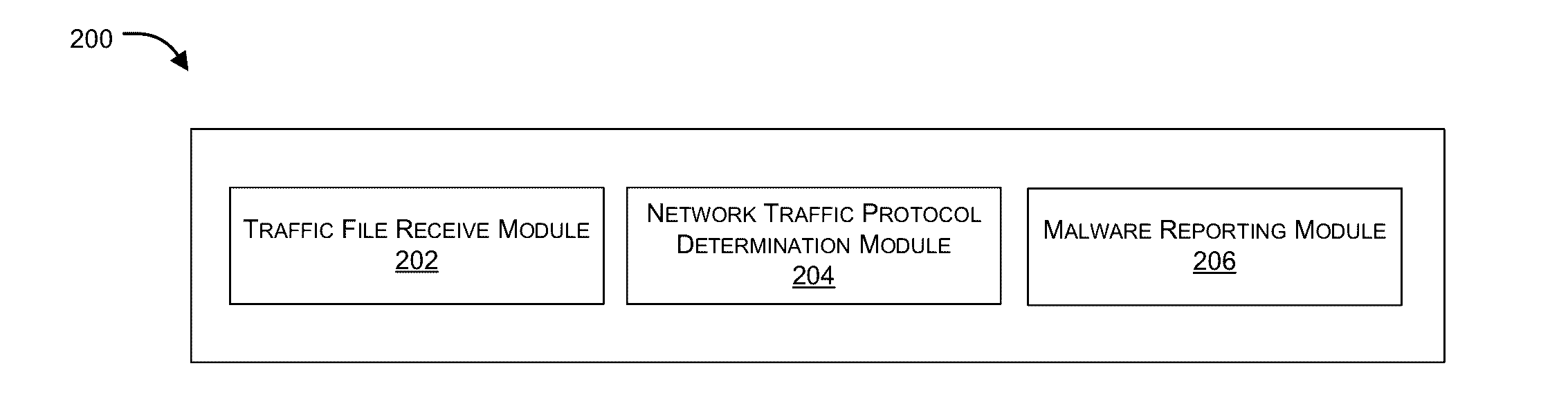
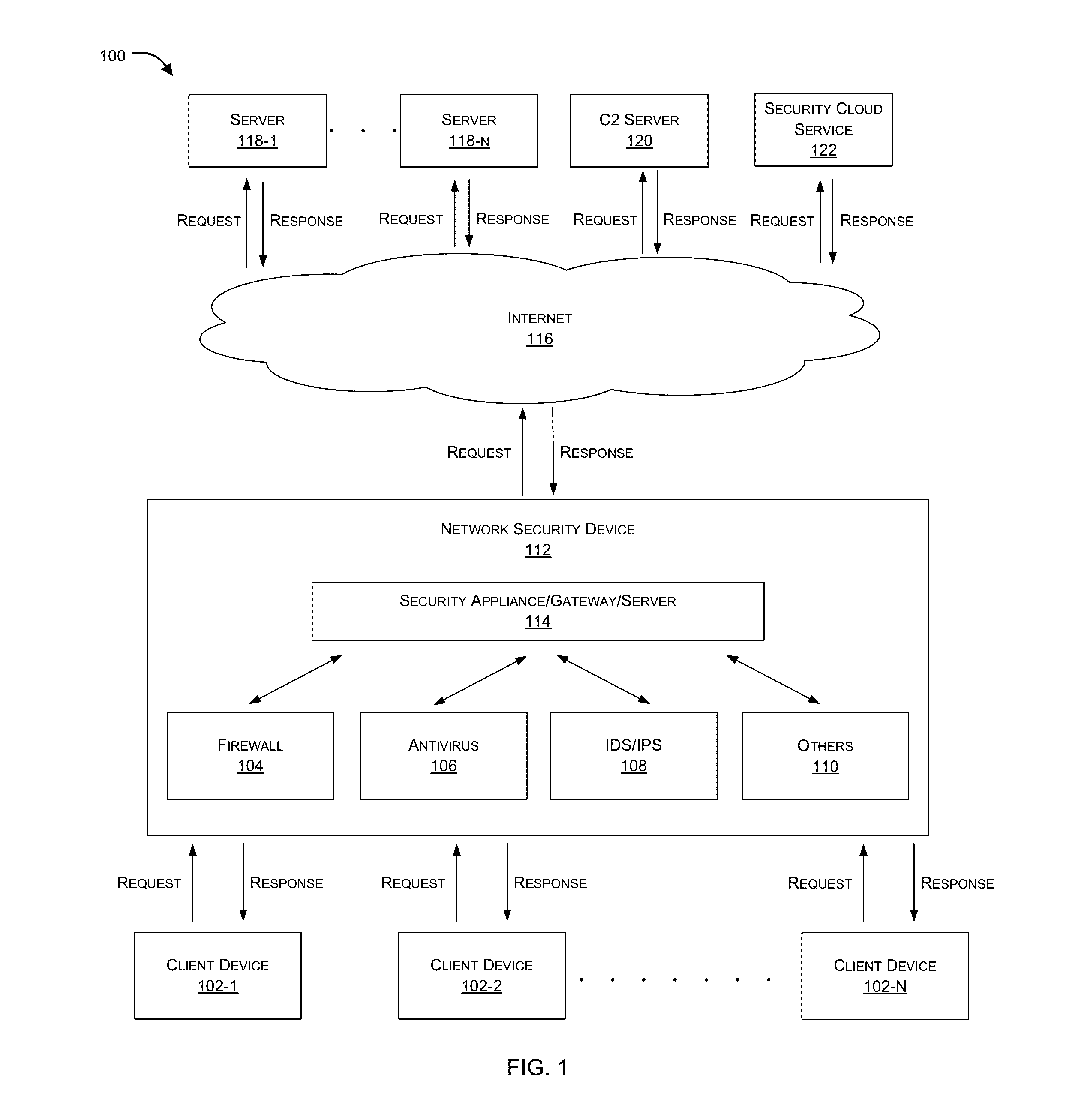
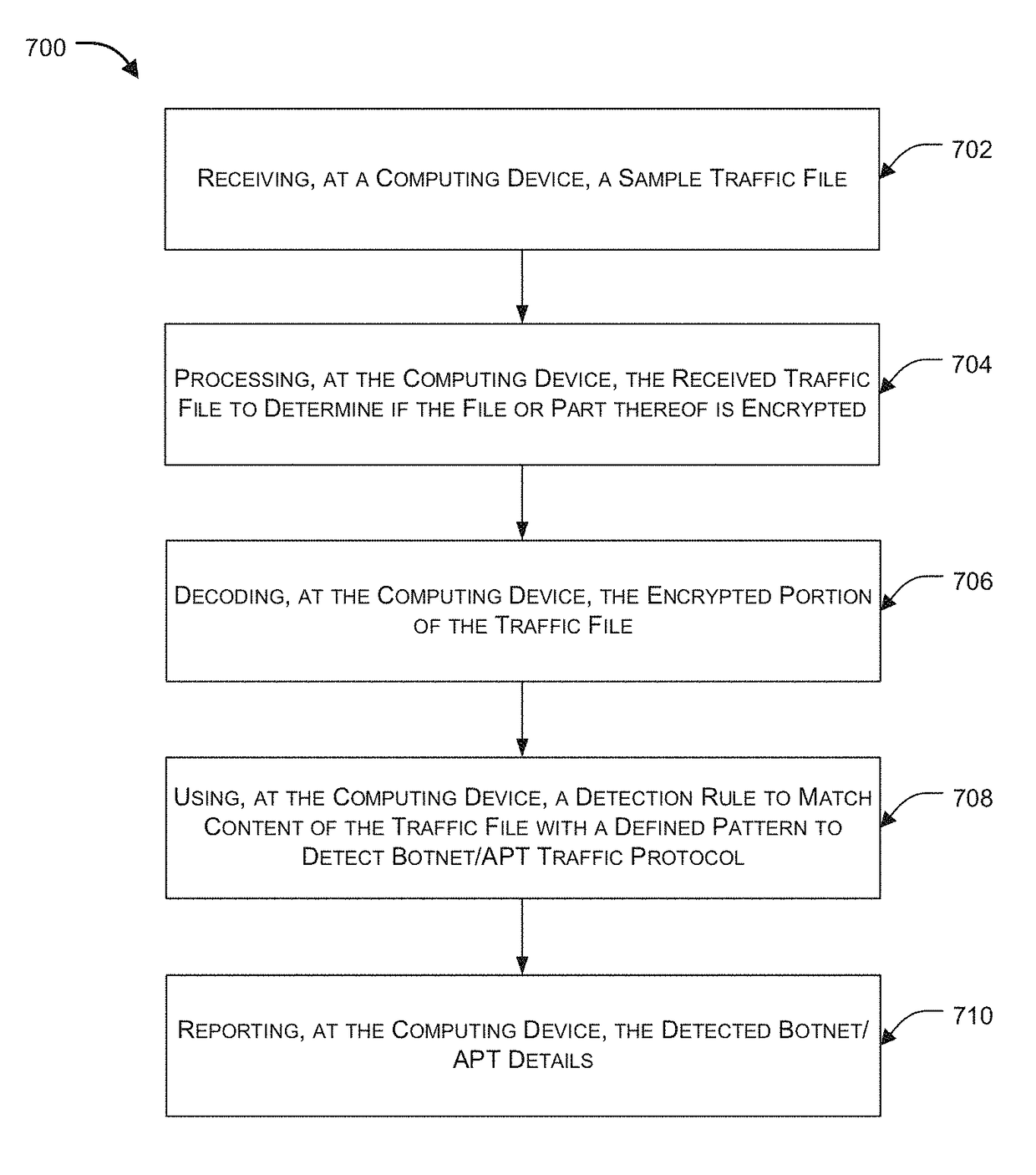
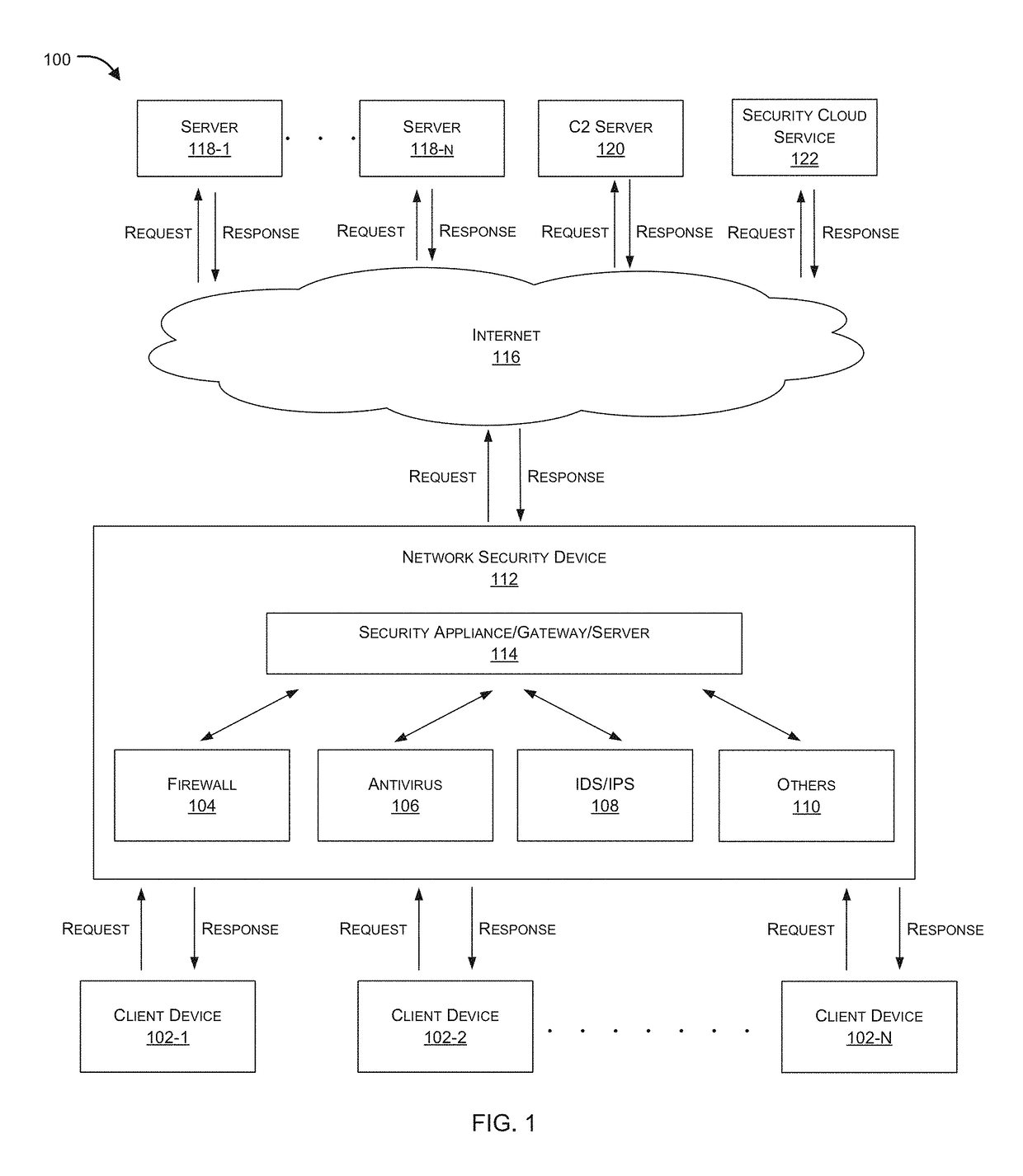
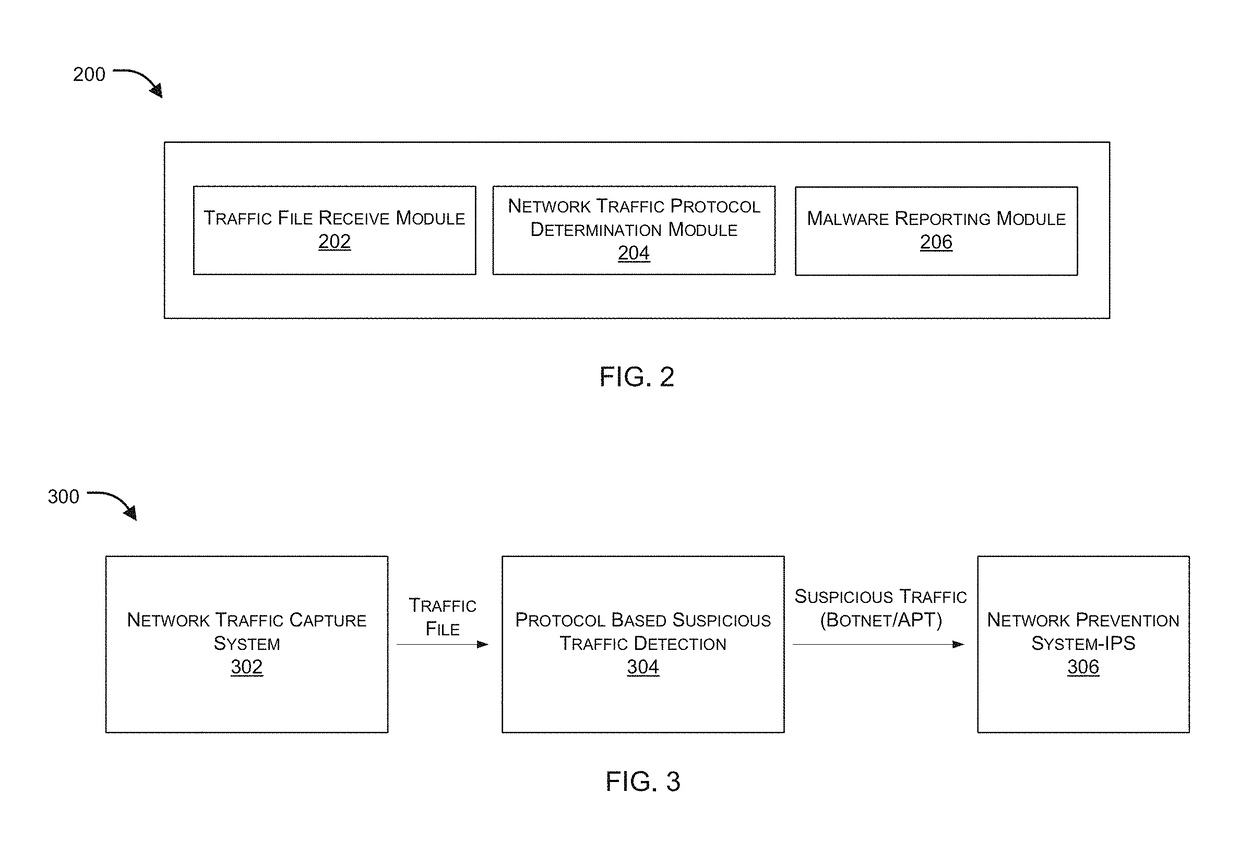
ActiveUS20160381070A1Memory loss protectionError detection/correctionNetworking protocolInternet traffic
Embodiments of the present invention relate to identification of suspicious network traffic indicative of a Botnet and / or an Advanced Persistent Threat (APT) based on network protocol of such traffic. According to one embodiment, a traffic file is received at a network security device that is protecting a private network. The traffic file contains therein network traffic associated with the private network that has been captured and stored. The received traffic file is processed by the network security device to determine whether the network traffic relates to a network protocol that is indicative of existence of a network security threat within the private network. When existence of the network security threat is detected, then the network security device reports details regarding the network security threat.
Owner:FORTINET
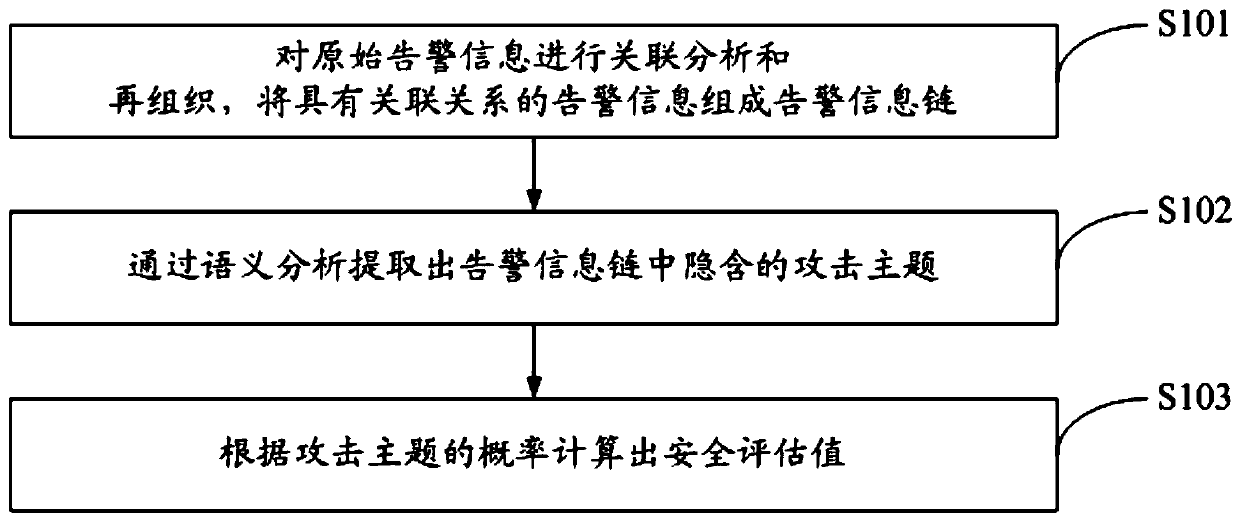
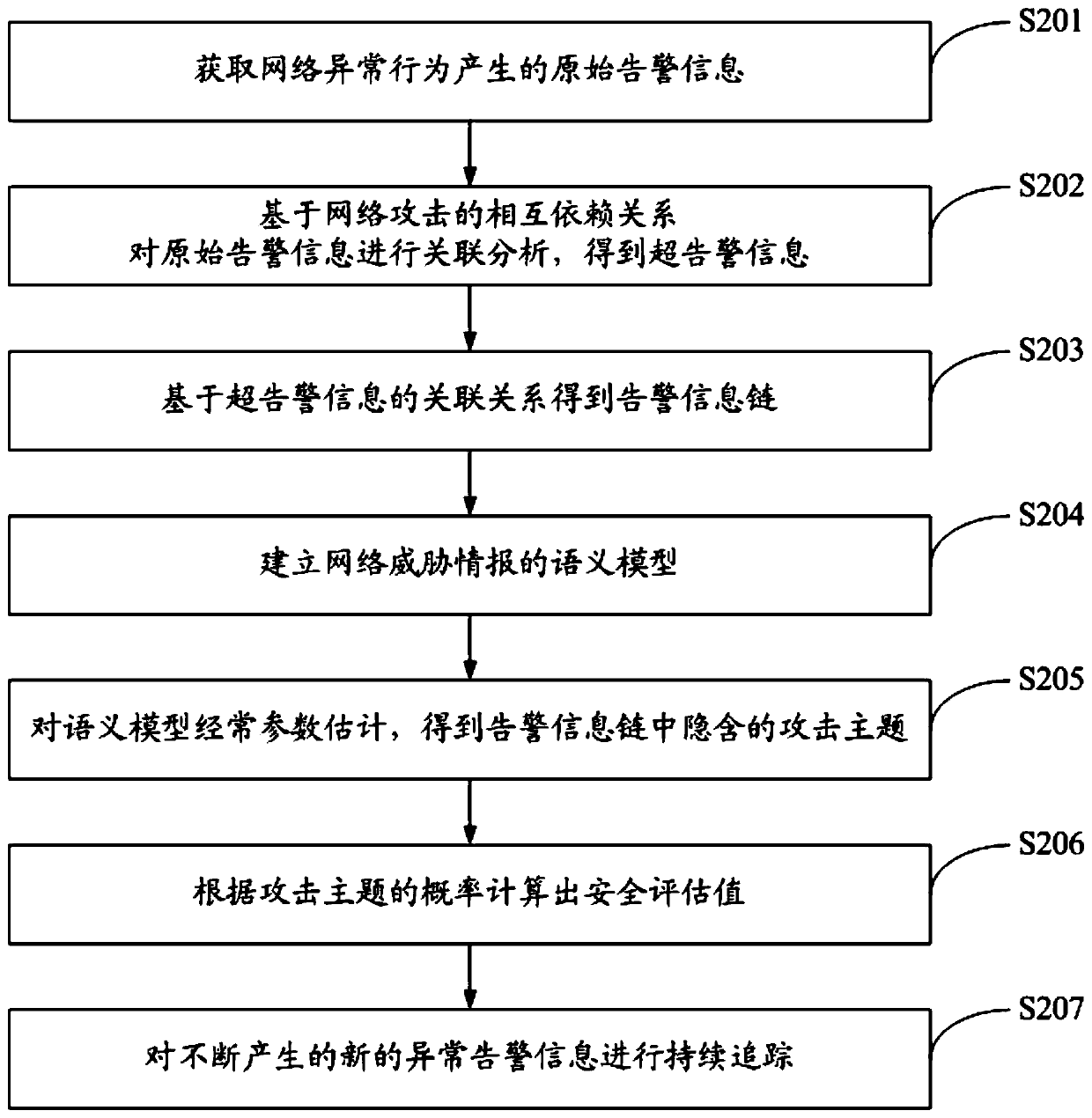
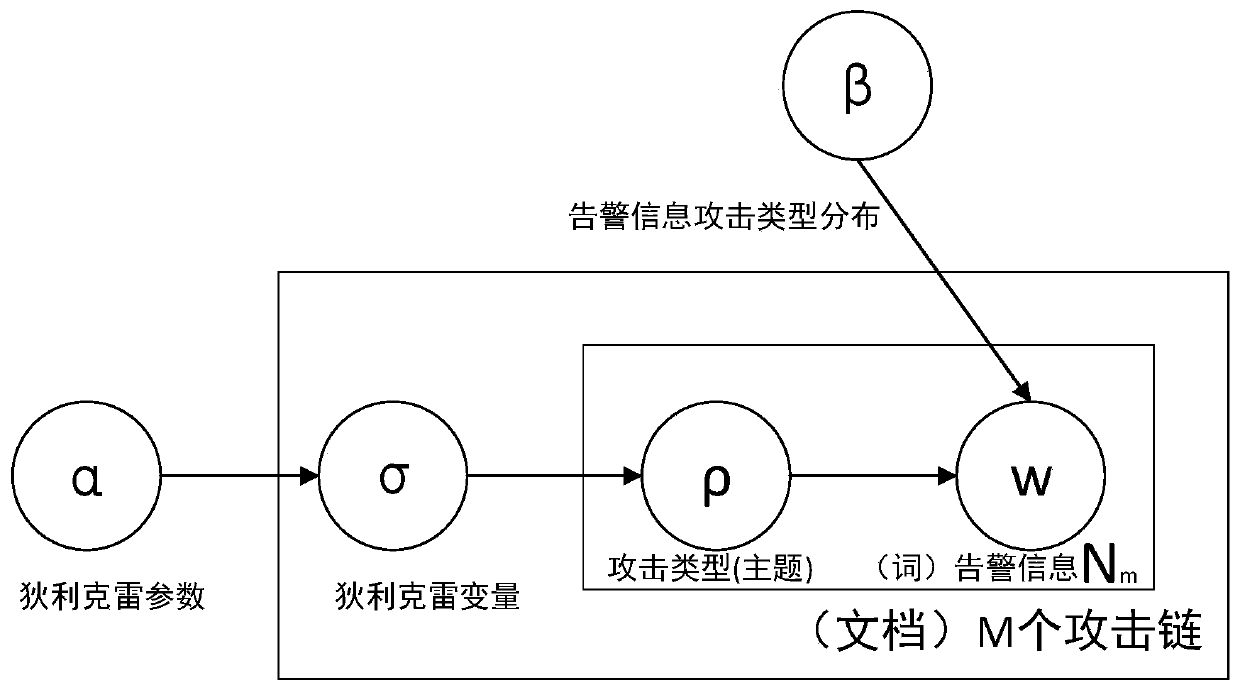
A multidimensional association analysis method and system for advanced persistent threats
ActiveCN109922069AEnable security posture assessmentImplement attack correlation assessmentData switching networksSpecial data processing applicationsPotential impactData mining
The invention discloses a multidimensional association analysis method and system for advanced persistent threats, and the method comprises the steps: carrying out the association analysis and reorganization of original alarm information, and enabling the alarm information with an association relationship to form an alarm information chain; extracting an attack theme hidden in the alarm information chain through semantic analysis; and calculating a security evaluation value according to the probability of the attack theme. According to the invention, attack correlation assessment can be realized, and potential influence of each attack stage of network threats on the security situation is discovered, so that the whole network security situation assessment is realized.
Owner:UNIV OF SCI & TECH OF CHINA
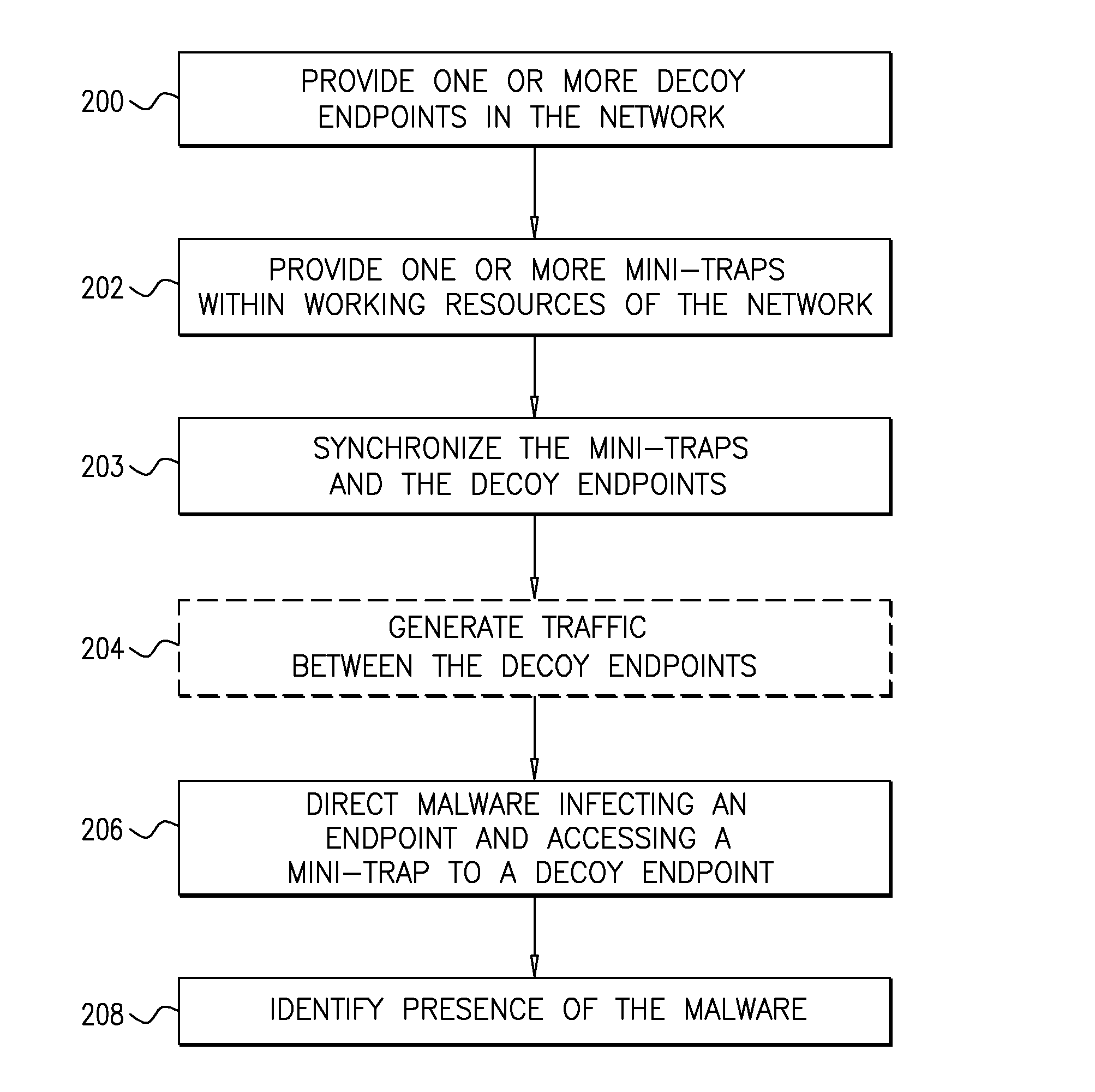
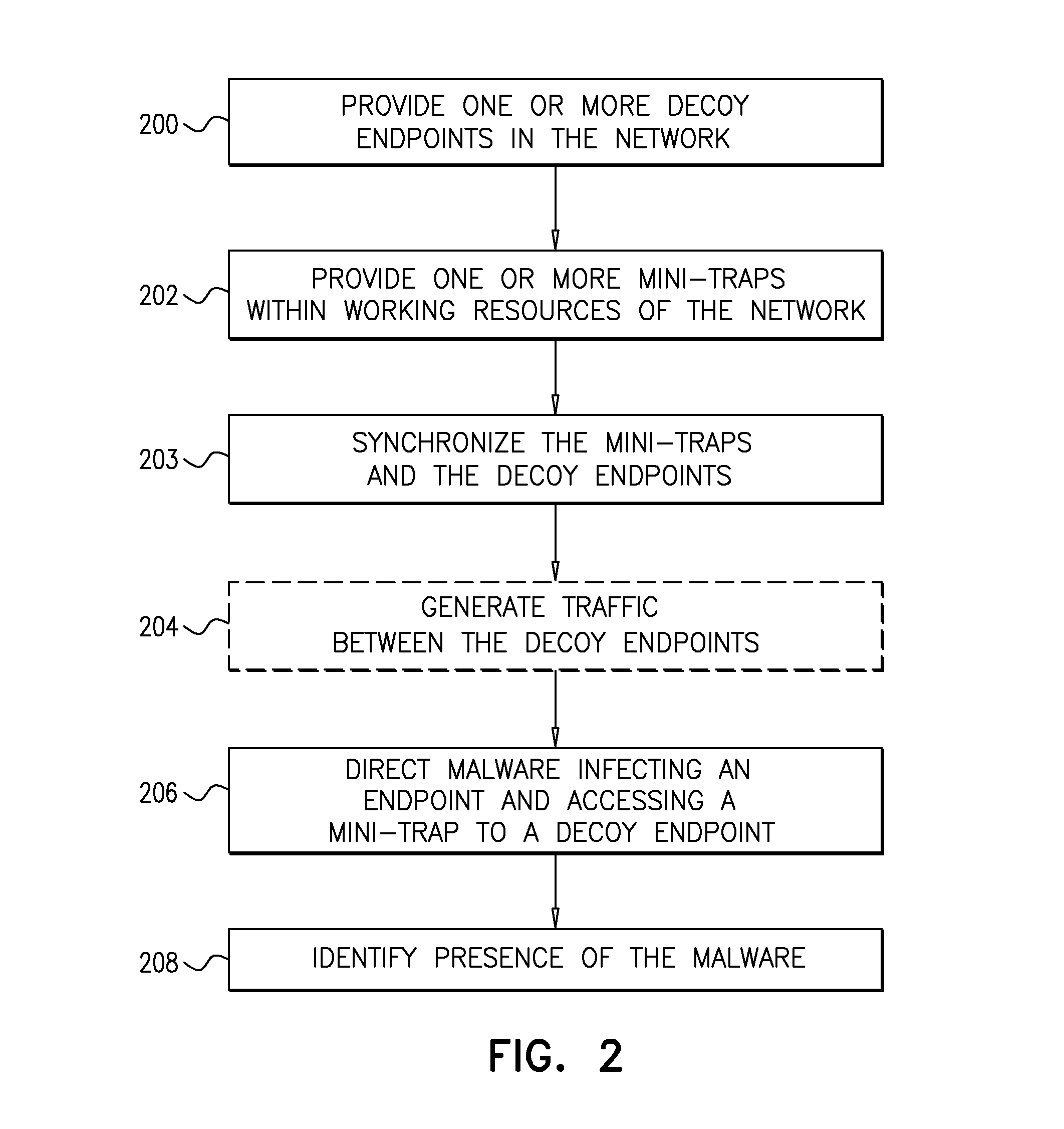
System and a Method for Identifying the Presence of Malware Using Mini-Traps Set At Network Endpoints
ActiveUS20160072838A1Memory loss protectionError detection/correctionSoftwareAdvanced persistent threat
A system for identifying the presence of advanced persistent threats on a network including a plurality of resources, interconnected to form a network, at least one decoy resource, at least one mini-trap installed on at least one of the plurality of resources and functionally associated with at one of the at least one decoy resource, the at least one mini-trap comprising deceptive information directing malware accessing the at least one mini-trap to the decoy resource associated therewith, and a manager node forming part of the network, locally or remotely, and configured to manage placement of the at least one mini-trap on the at least one of the plurality of resources and association between the at least one mini-trap and the decoy resource associated therewith.
Owner:FIDELIS SECURITY SYSTEMS
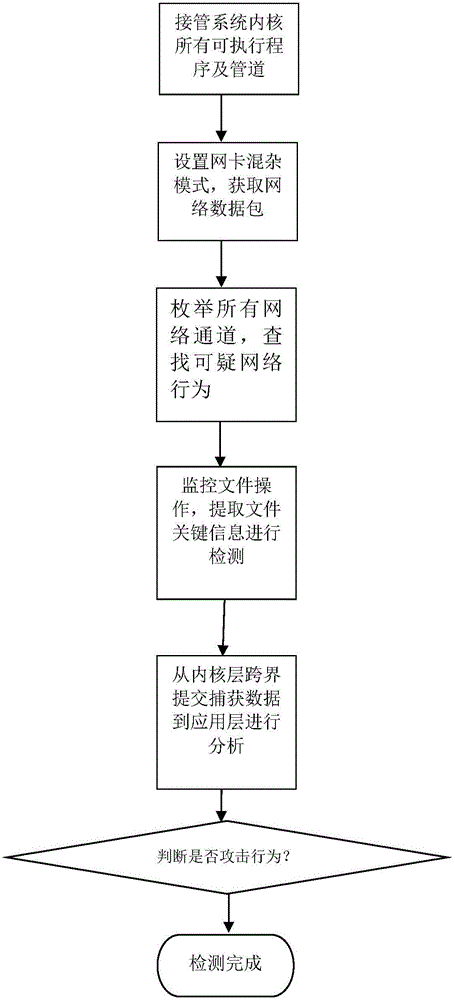
Advanced persistent threat detection method based on aggressive behavior analysis
The invention provides an advanced persistent threat detection method based on aggressive behavior analysis. The advanced persistent threat detection method comprises the steps that 1, all system kernel program execution pipelines are taken over; 2, a network card is set to be in a confusion mode, network data packets are acquired, local port analysis behaviors are combined as characteristics, and a system gives an alarm if malicious operating instructions of network attack behaviors are contained; 3, all network channels are enumerated, and the system gives an alarm if the malicious operating instructions of the network attack behaviors are contained; 4, file operation is monitored, key information is judged, and the system gives an alarm if the requirements are not met; 5, captured software API information are submitted to an application layer from a kernel layer in a trans-boundary mode so as to be submitted to a behavior analysis engine, whether the behaviors are attack behaviors or not is judged, if so, an alarm is given, and if not, the step 2 repeated. The advanced persistent threat detection method can detect advanced persistent threats, is high in detection efficiency and more comprehensively analyzes the situations of the behaviors performing attacking at a system level.
Owner:SHANGHAI JIAO TONG UNIV
Using source taint analysis to reduce false positives in an advanced persistent threat (APT) protection solution
ActiveUS9530016B1Reduce false positiveDigital data protectionPlatform integrity maintainanceData streamRemote system
In response to a local Advanced Persistent Threat (APT) agent identifying a potential data exfiltration attack, the binary identified in the attack is sent to a static analysis tool for further analysis. The agent also identifies a source and a sink involved in the potential data exfiltration. The static analysis tool decompiles the binary, and then runs the de-compiled code through a static analysis to identify data flows between the source and the sink, e.g., a data flow from the source that is the method used to read sensitive information, and a data flow to the sink that is the method used to write to the remote system. If there are such data flows, the activity reported by the agent is likely a true exfiltration attack. Based on this flow determination, the static analysis tool returns a response to the agent validating that the activity is an attack.
Owner:FINJAN BLUE INC
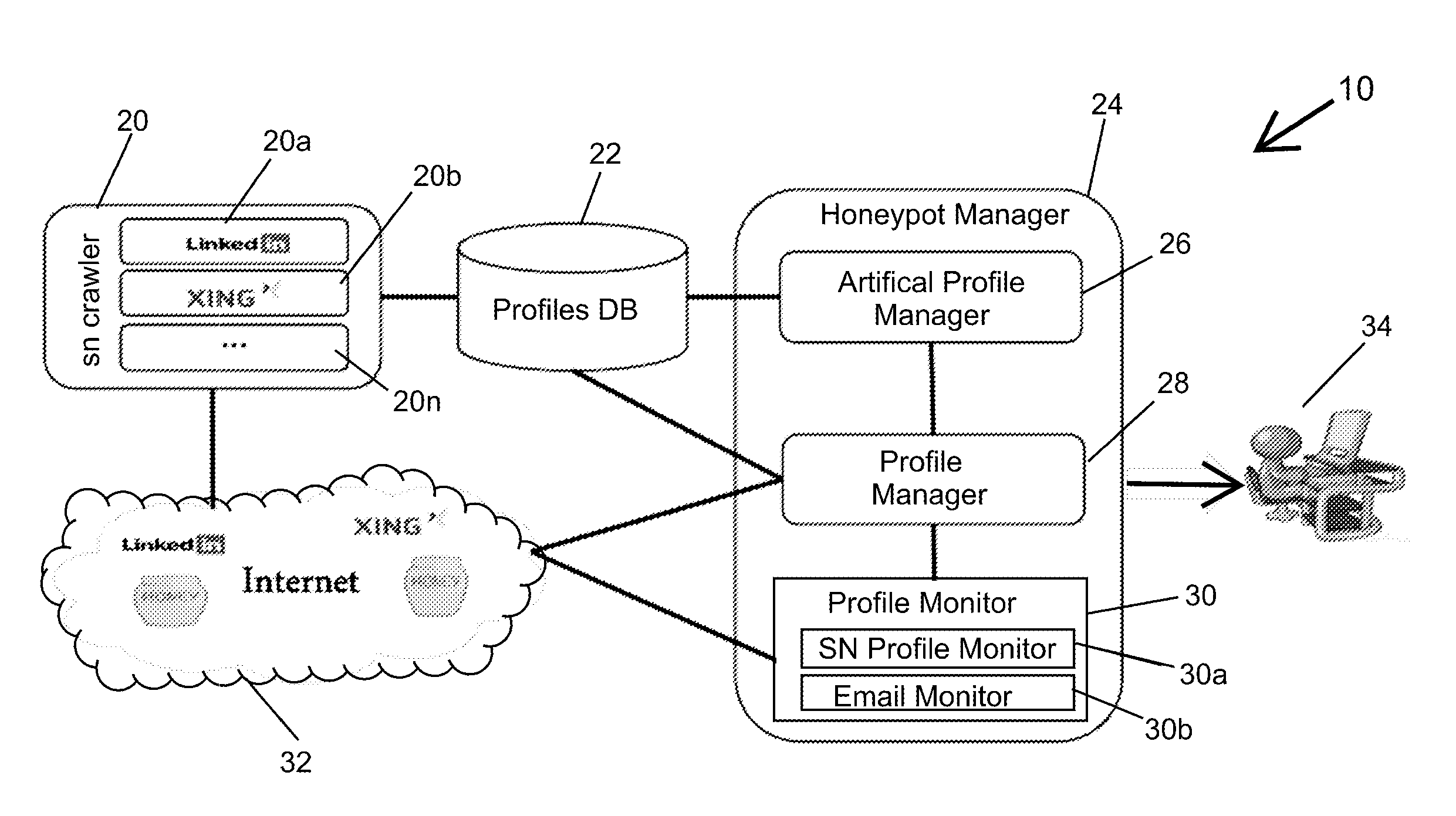
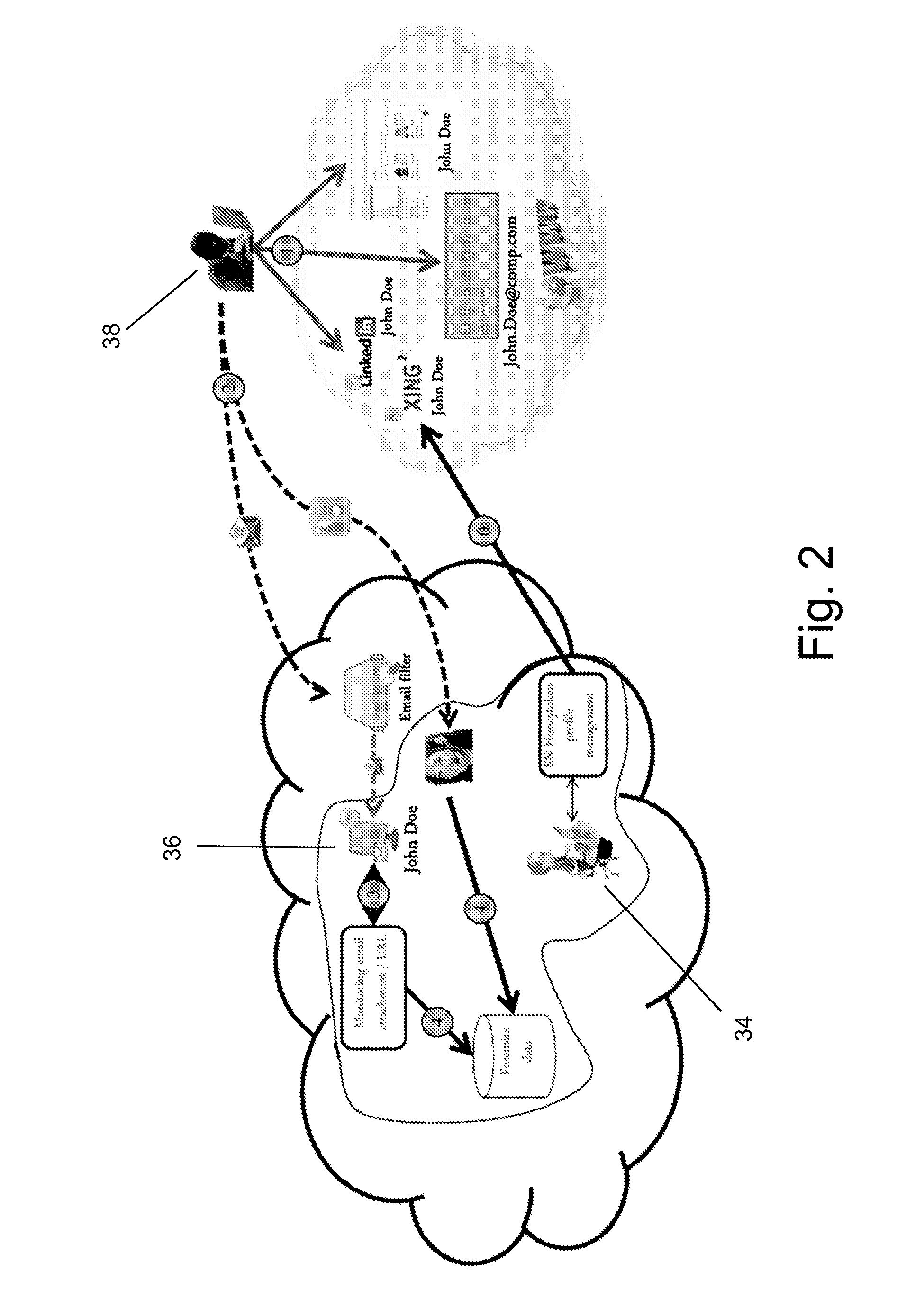
Social network honeypot
The invention is a method and system for detecting attackers that are interested in attacking an organization's infrastructure during the reconnaissance phase of an Advanced Persistent Threat (APT). APTs are very sophisticated attacks and incorporate advanced methods for evading current security mechanisms. Therefore, the present invention uses an innovative social network honeypot.
Owner:DEUTSCHE TELEKOM AG
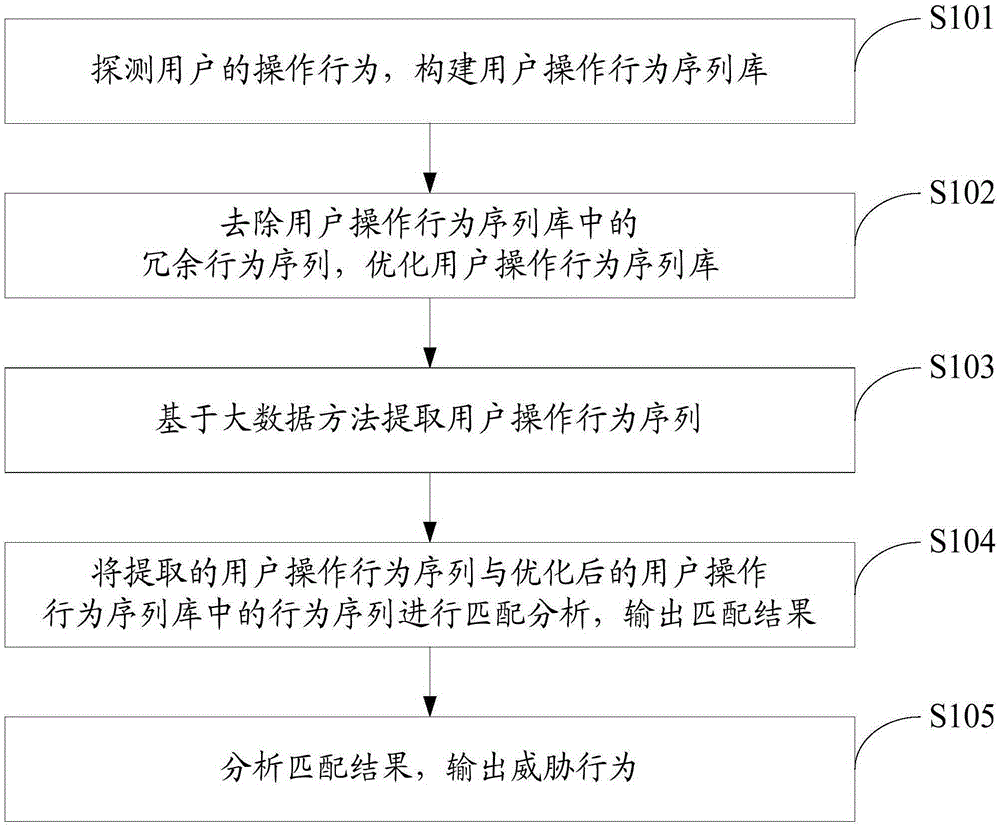
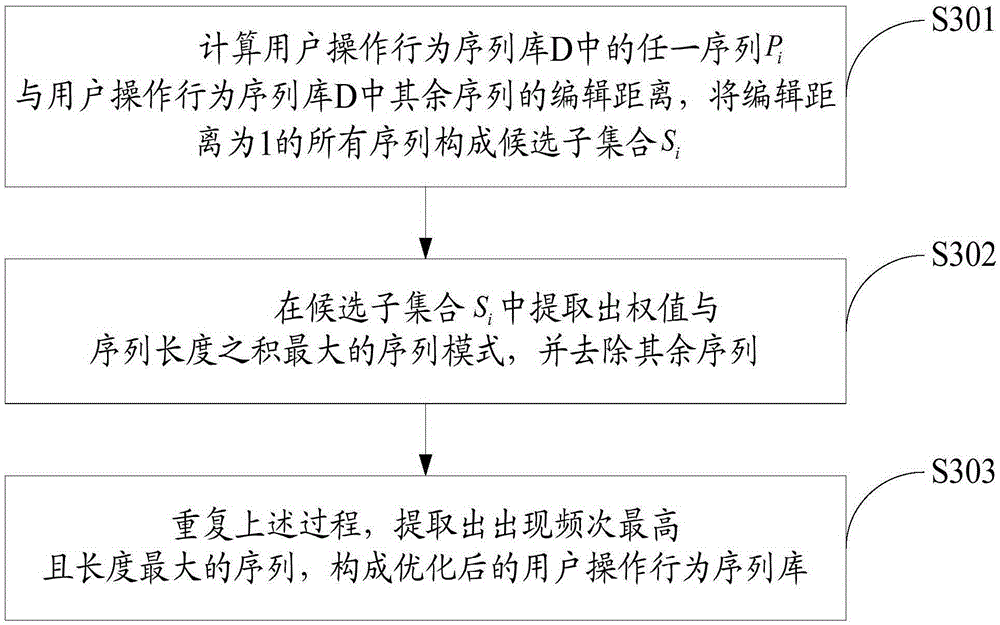
APT (Advanced Persistent Threat) attack detection method based on big data behavior sequence analysis
The invention discloses an APT (Advanced Persistent Threat) attack detection method based on big data behavior sequence analysis. The method comprises the following steps of detecting an operation behavior of a user, and constructing a user operation behavior sequence database; optimizing the user operation behavior sequence database; extracting a user operation behavior sequence based on a big data method; performing matching analysis on the extracted user operation behavior sequence and a behavior sequence in the user operation behavior sequence database, and outputting a matching result; and analyzing the matching result and outputting a threatening behavior. The APT attack detection method based on the big data behavior sequence analysis provided by the invention can improve the accuracy of threat detection, so as to construct a safe and efficient network active defense system, and effectively overcome the threat of APT attacks on network security.
Owner:THE PLA INFORMATION ENG UNIV
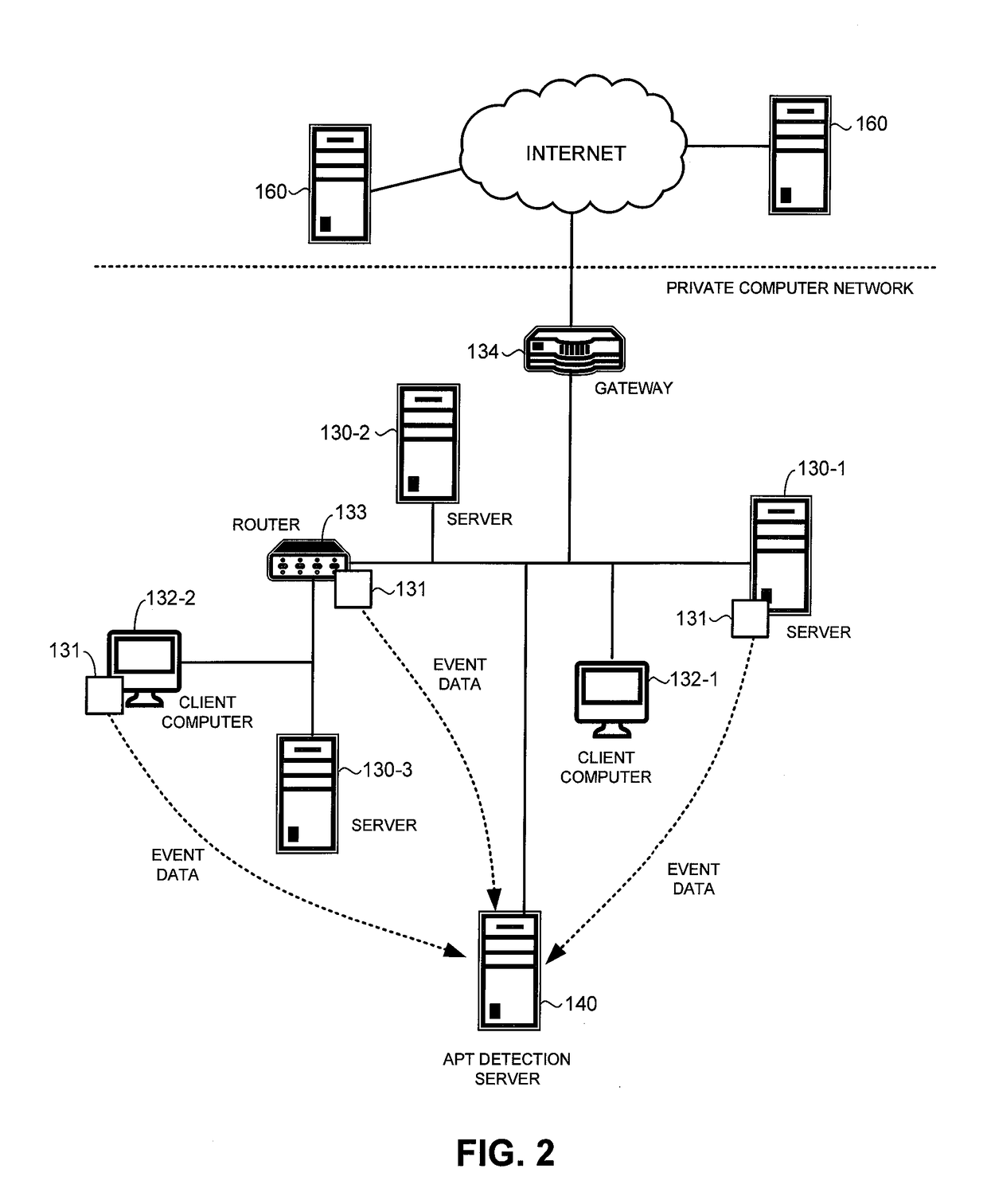
Detection of advanced persistent threat attack on a private computer network
A system for detecting an advanced persistent threat (APT) attack on a private computer network includes hosts computers that receive network traffic and process the network traffic to identify an access event that indicates access to a critical asset of an organization that owns or maintains the private computer network. The critical asset may be a computer that stores confidential data of the organization. Access events may be stored in an event log as event data. Access events indicated in the event log may be correlated using a set of alert rules to identify an APT attack.
Owner:TREND MICRO INC
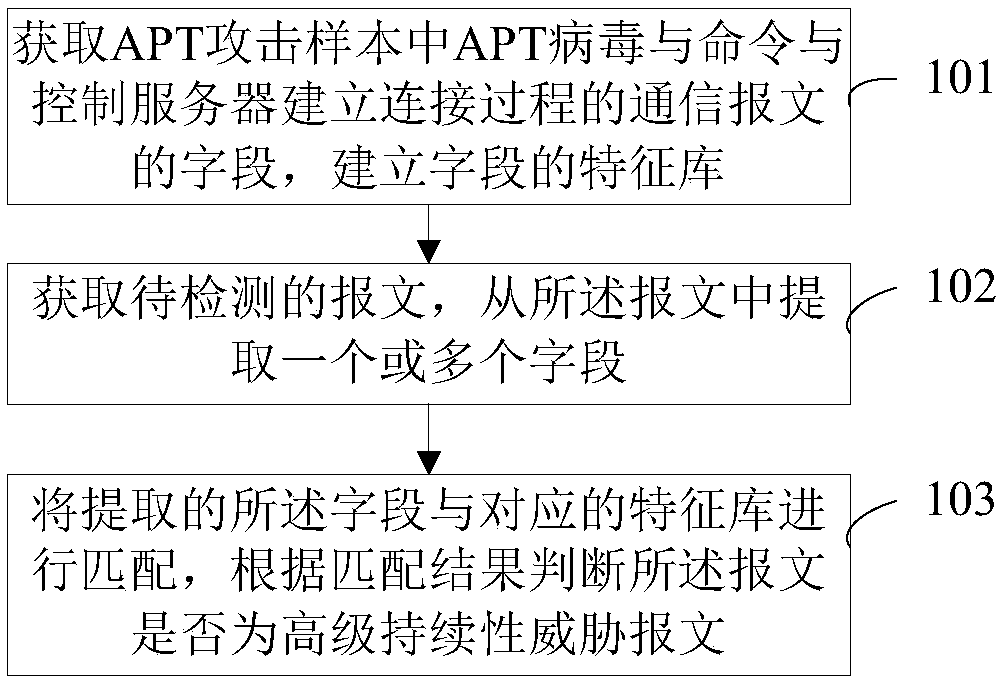
Advanced persistent threat attack detection method and device
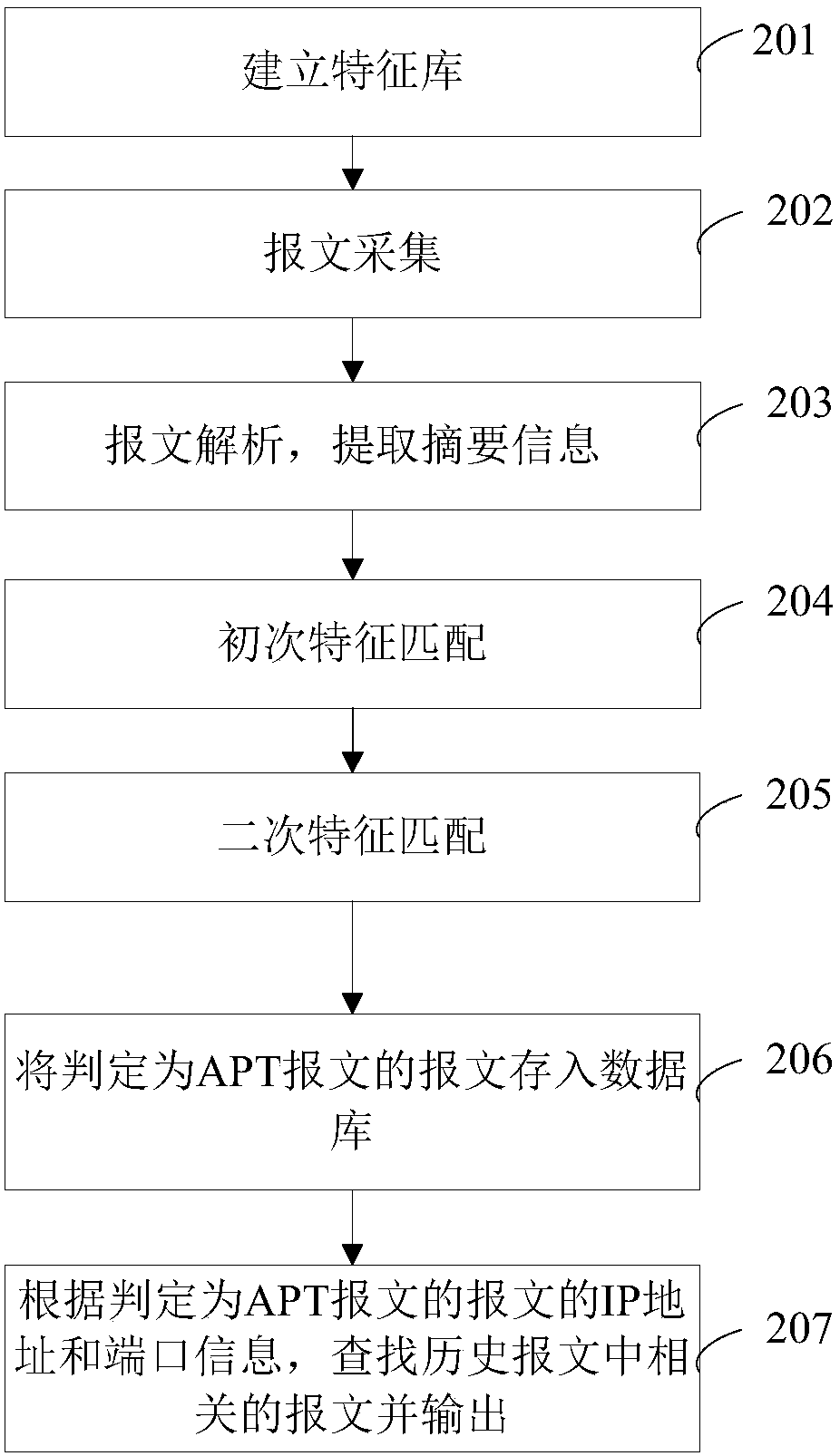
The invention discloses an advanced persistent threat attack detection method and device. The method comprises the steps of obtaining advanced persistent threat viruses in advanced persistent threat attack samples, establishing a communication message in a connection phase with a command and control server, and establishing feature libraries of fields according to the fields in the communication messages; obtaining a to-be-detected message, and extracting one or more fields from the message; and matching the extracted field with the corresponding feature library thereof, and judging whether the message is an advanced persistent threat message or not according to a matching result. According to the embodiment of the invention, the samples are analyzed, the feature libraries are established,and the to-be-detected message is matched with the feature library to judge whether the message is the advanced persistent threat message or not, so the message can be effectively detected. Two timesof matching operation: fuzzy matching and accurate matching are employed, so the detection efficiency and accuracy are greatly improved.
Owner:ZTE CORP +1
Protocol based detection of suspicious network traffic
Embodiments of the present invention relate to identification of suspicious network traffic indicative of a Botnet and / or an Advanced Persistent Threat (APT) based on network protocol of such traffic. According to one embodiment, a traffic file is received at a network security device that is protecting a private network. The traffic file contains therein network traffic associated with the private network that has been captured and stored. The received traffic file is processed by the network security device to determine whether the network traffic relates to a network protocol that is indicative of existence of a network security threat within the private network. When existence of the network security threat is detected, then the network security device reports details regarding the network security threat.
Owner:FORTINET
Overflow vulnerability detection method and system for advanced persistent threat
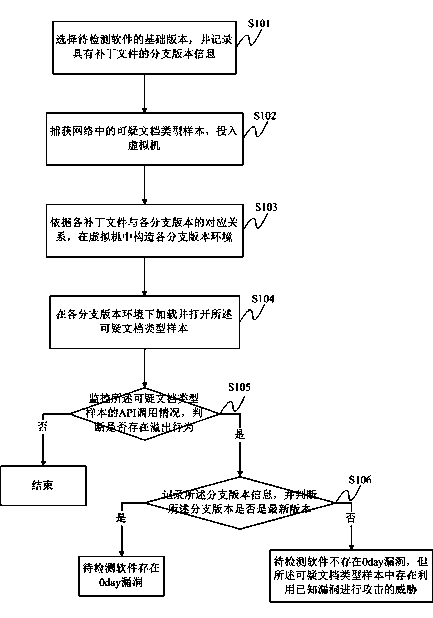
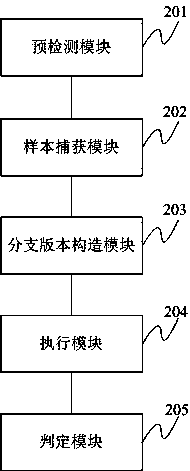
ActiveCN103902914AEfficient detectionPlatform integrity maintainanceDocumentationAdvanced persistent threat
The invention discloses an overflow vulnerability detection method and system for advanced persistent threat. Firstly, a basic version of software to be detected is selected, and branch version information containing patch files is recorded; the basic version is one or more important versions of the software to be detected; a suspicious file type sample in a network is captured and input into a virtual machine; according to corresponding relations of the patch files and branch versions, branch version environment is constructed in the virtual machine; the suspicious file type sample is loaded and opened in the branch version environment; API calling situations of the suspicious file type sample are monitored to judge whether overflow behaviors exist, and whether the branch versions are updated versions, and accordingly whether a 0day loophole capable of being used by the advanced persistent threat exists. Besides, known loopholes of the software to be detected can be effectively detected, and whether the 0day loopholes exist in the software to be detected can be found.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
Method and device for detecting threat attack, equipment and storage medium
InactiveCN109995736AImprove efficiencyResolve detectionTransmissionNetwork Access ControlAdvanced persistent threat
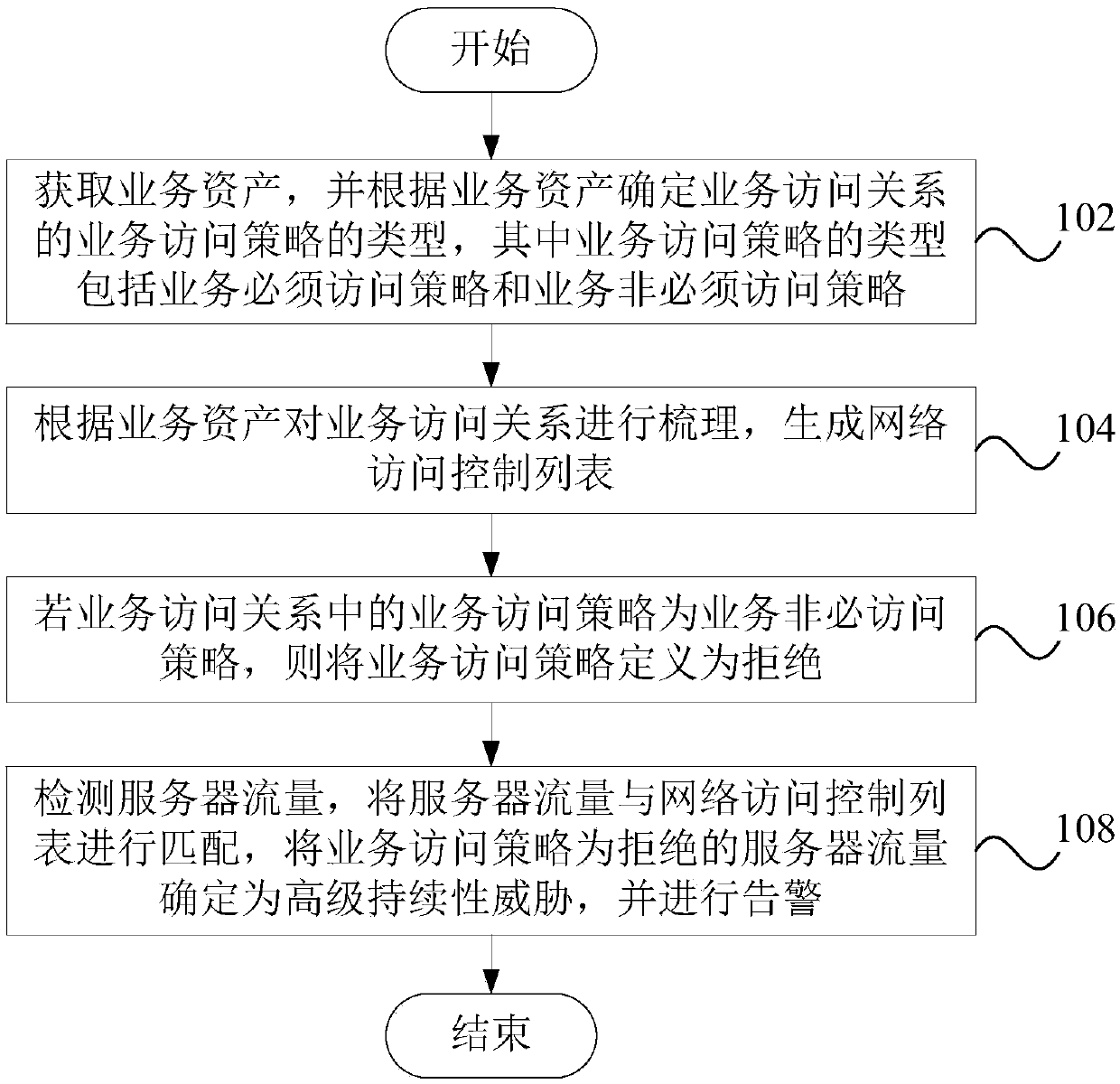
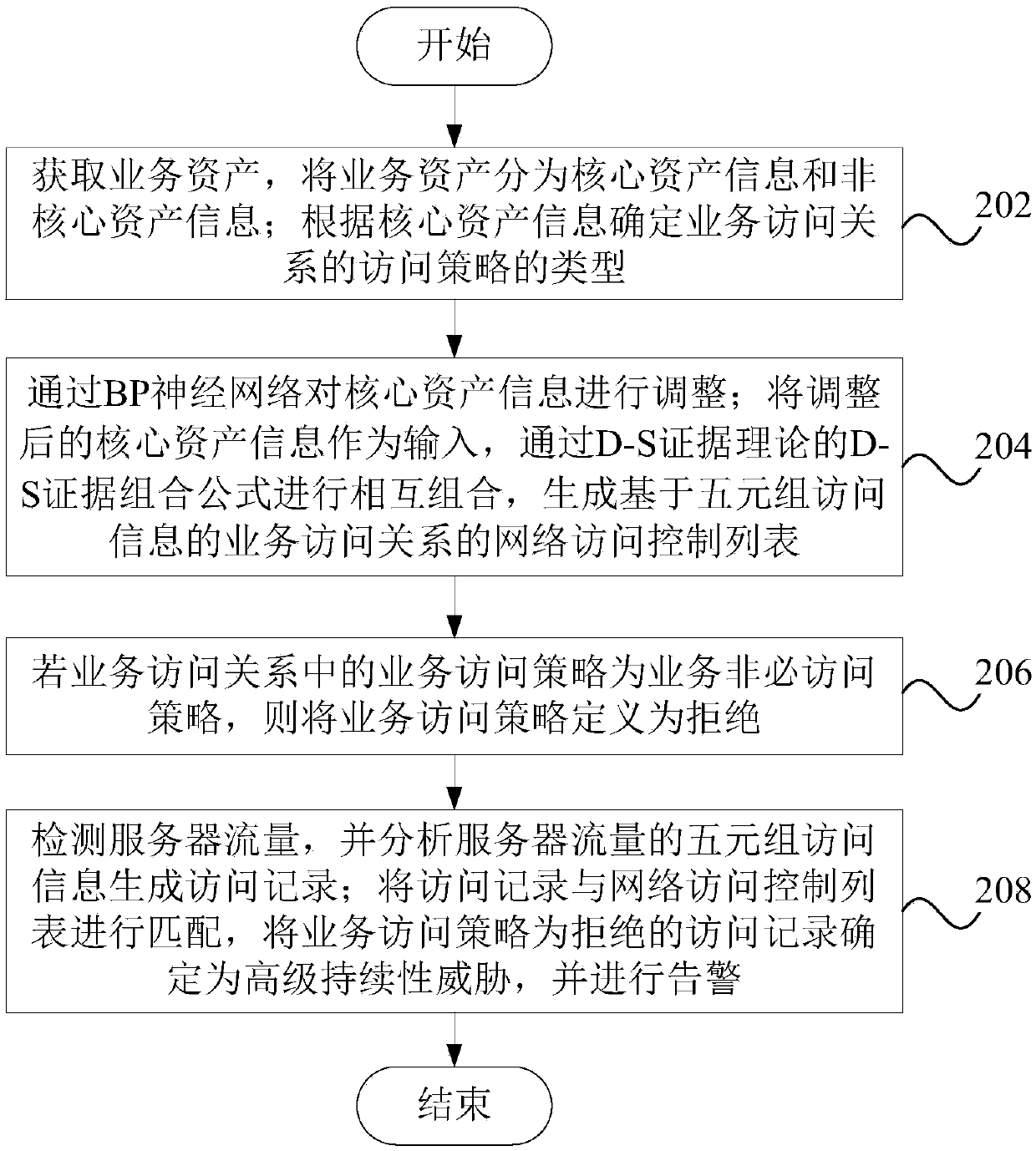
The embodiment of the invention discloses a method and device for detecting advanced persistent threat attacks by utilizing an access relation, computer equipment and a readable storage medium. The method comprises the steps that acquiring business assets, determining the type of a business access strategy of a business access relation according to the business assets, wherein the type of the business access strategy comprises a business necessary access strategy and a business unnecessary access strategy; according to the service assets, sorting the service access relationship to generate a network access control list; if the service access strategy in the service access relationship is a service non-necessity access strategy, defining the service access strategy as rejection; detecting the flow of the server, matching the flow of the server with the network access control list, determining the flow of the server of which the service access strategy is rejected as an advanced persistent threat, and giving an alarm. The advanced persistent threat attack is restrained from the path from organizing the service characteristics of the system, and the efficiency of safety management work and the effect of safety operation and maintenance are improved.
Owner:CHINA MOBILE GROUP SICHUAN +1
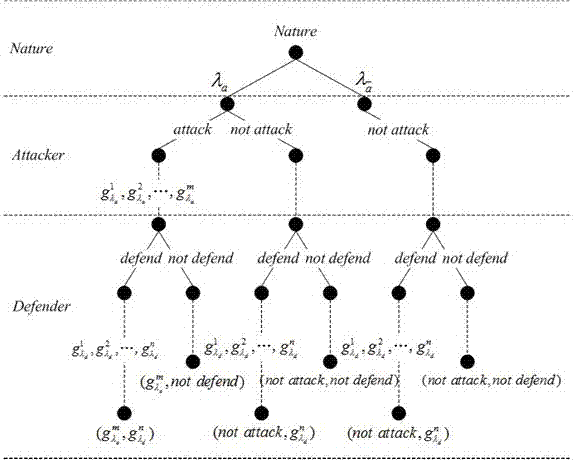
Dynamic Bayesian game-based advanced persistent threat (APT) attack prediction method
ActiveCN107070956AGuaranteed validityGuaranteed reasonablenessData switching networksPhases of clinical researchNetwork topology
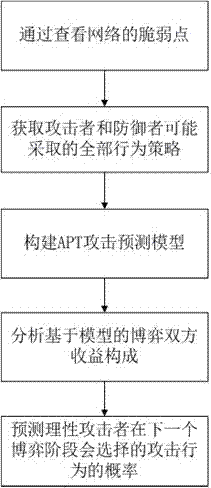
The present invention relates to a dynamic Bayesian game-based APT attack prediction method. The game two parities predict the to-be-taken behaviors of the opposite party by the currently obtained information, adopt the solutions by taking the self-interest maximization as the objective, and utilize the Bayesian game equalization to guarantee the prediction validity and rationality. The method of the present invention comprises the steps of checking the vulnerability of a network and obtaining all behavior strategies that an attacker and a defender possibly adopt according to a network topology structure; constructing an APT attack prediction model in a dynamic Bayesian game system, and analyzing the model-based composition of earnings of the game two parties; predicting the probability of the attack behaviors that are selected by the rational attacker at the next game stage by analyzing the earnings of the two parties of the attacker and the defender. The dynamic Bayesian game equalization of the present invention guarantees the prediction validity and rationality.
Owner:福建中信网安信息科技有限公司
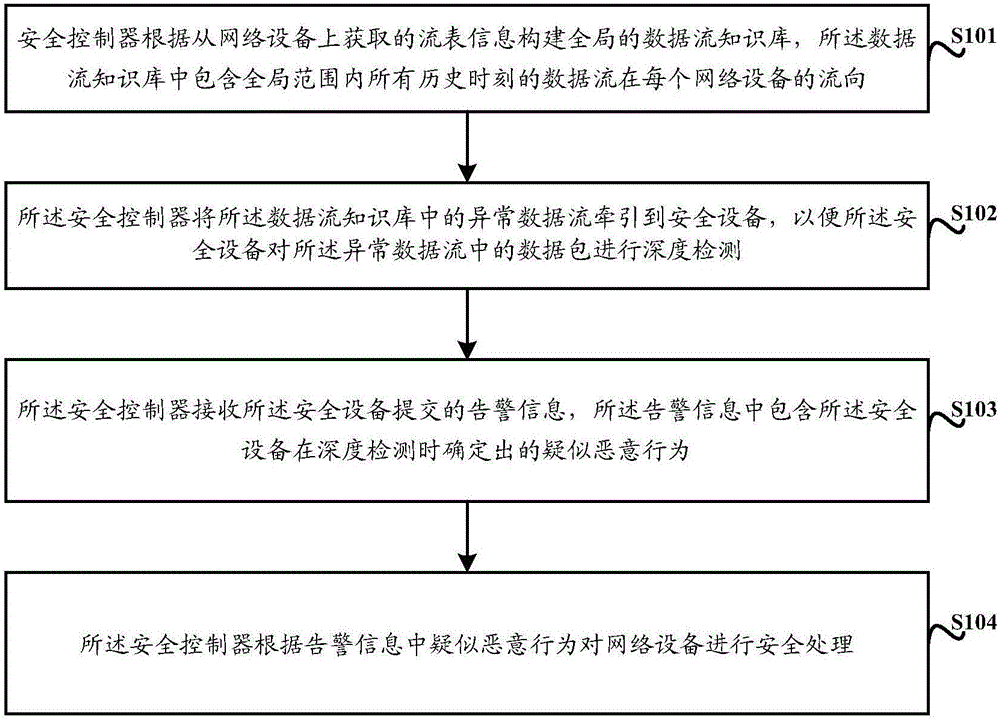
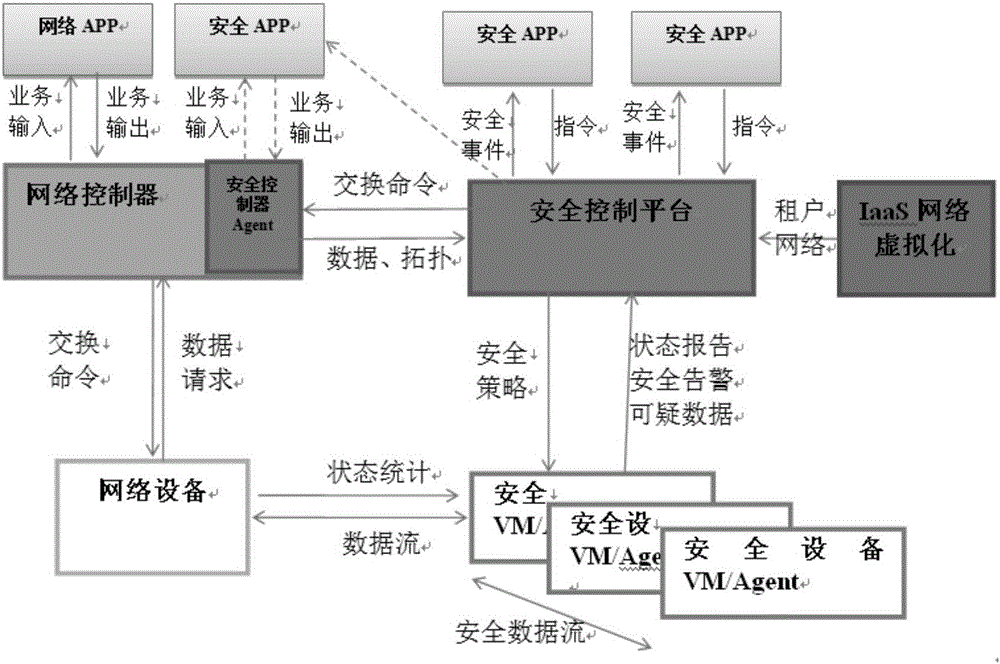
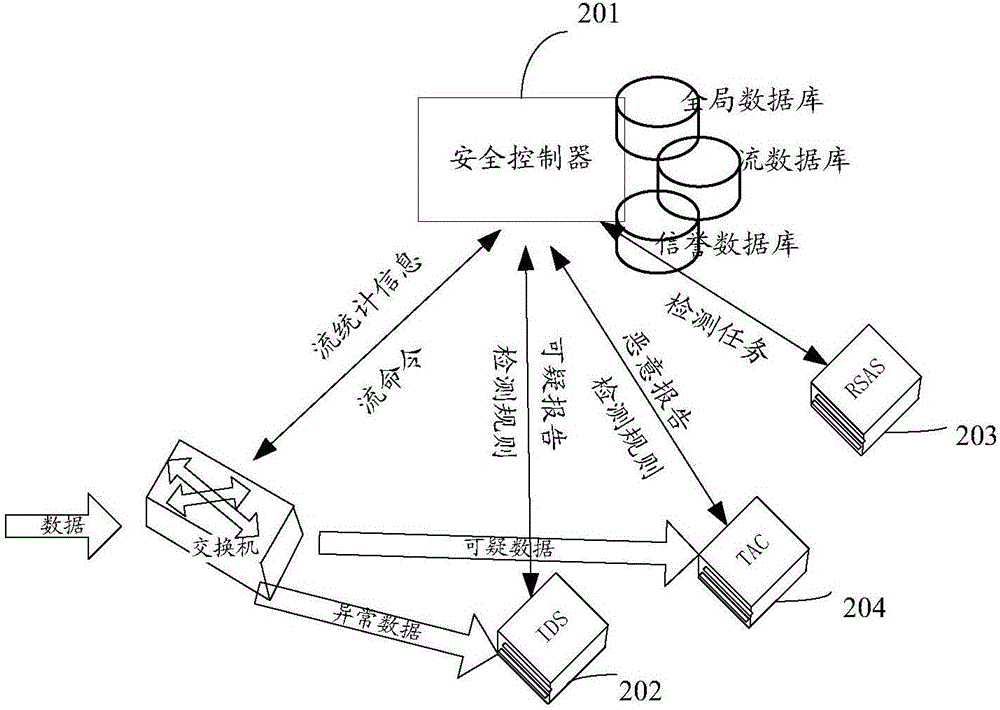
Method for defending APT attack and safety controller
InactiveCN106341426AReduce the burden onAvoid detecting blind spotsTransmissionData streamNetwork packet
The invention discloses a method for defending an advanced persistent threat (APT) attack and a safety controller. The method comprises: a safety controller constructs a global data stream knowledge base according to flow table information obtained from a network device, wherein the data stream knowledge base includes flow directions of data streams in all network devices at all historical times in a global range; the safety controller directing an abnormal data stream in the data stream knowledge base to a safety device, so that the safety device can carry out depth detection on a data packet in the abnormal data stream conveniently; the safety controller receives warning information submitted by the safety device, wherein the warning information includes a suspected malicious behavior that is determined by the safety device during depth detection; and the safety controller carries out safety processing on the network devices based on the suspected malicious behavior in the warning information. The invention provides a novel method for defending an APT attack, so that an APT attack can be defended effectively.
Owner:CHINA SOUTHERN POWER GRID COMPANY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com