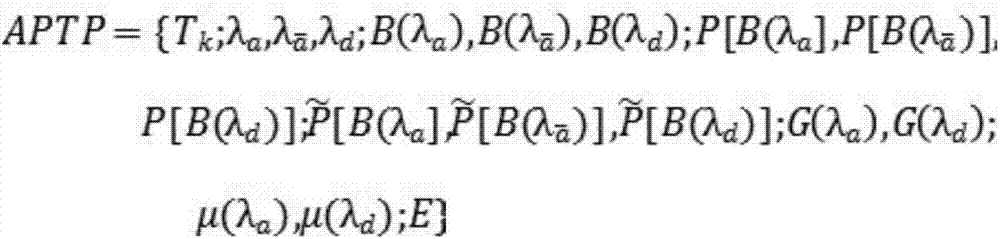Dynamic Bayesian game-based advanced persistent threat (APT) attack prediction method
A predictive method and dynamic technology, applied in the field of network security, can solve problems such as reducing system security performance, and achieve the effect of ensuring effectiveness and rationality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
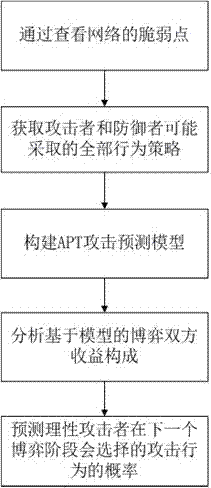
[0021] Attached below Figure 1-2 , the technical solution of the present invention is described in detail.
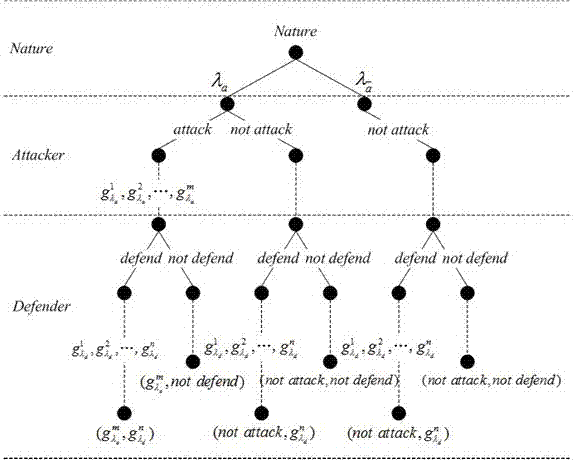
[0022] The most critical idea of the present invention is: in the dynamic Bayesian game system, each attacker and defender are rational participants, and do not violate the principle of game equilibrium, that is, they are based on the principle of maximizing their own interests. The benefits of attackers and defenders are used to predict the behaviors that attackers and defenders will take in the next game stage. Each game process will include multiple game stages, and each game stage is a one-time game, that is, after the two parties choose a strategy, they will not change their respective strategies until the end of the game stage.
[0023] Such as figure 1 As shown, the described APT attack prevention method based on dynamic Bayesian game is:
[0024] By viewing the vulnerable points of the network, obtain all possible behavior strategies of attackers and defen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com