Patents
Literature
186 results about "Trusted system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In the security engineering subspecialty of computer science, a trusted system is a system that is relied upon to a specified extent to enforce a specified security policy. This is equivalent to saying that a trusted system is one whose failure would break a security policy (if a policy exists that the trusted system is trusted to enforce).
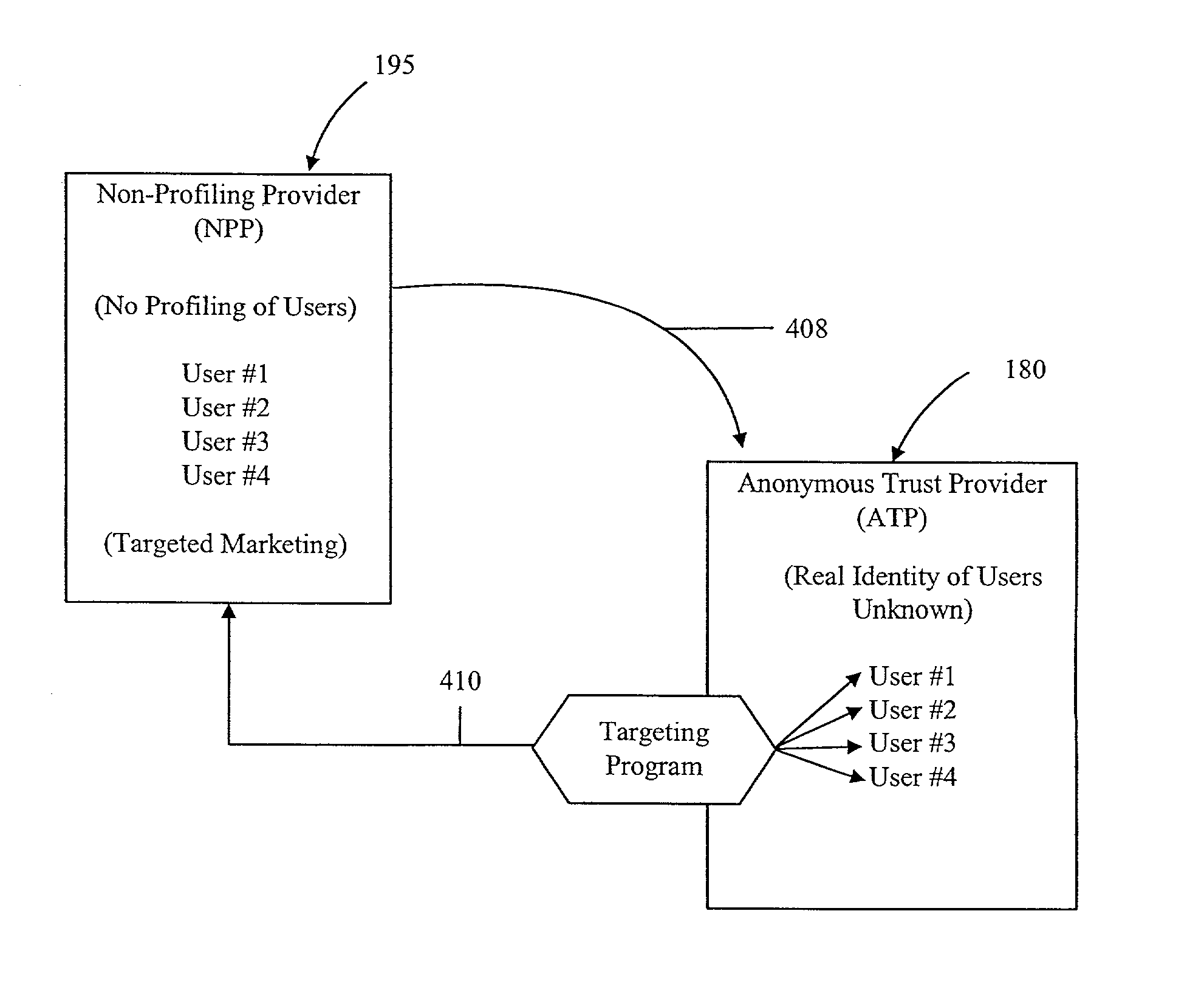
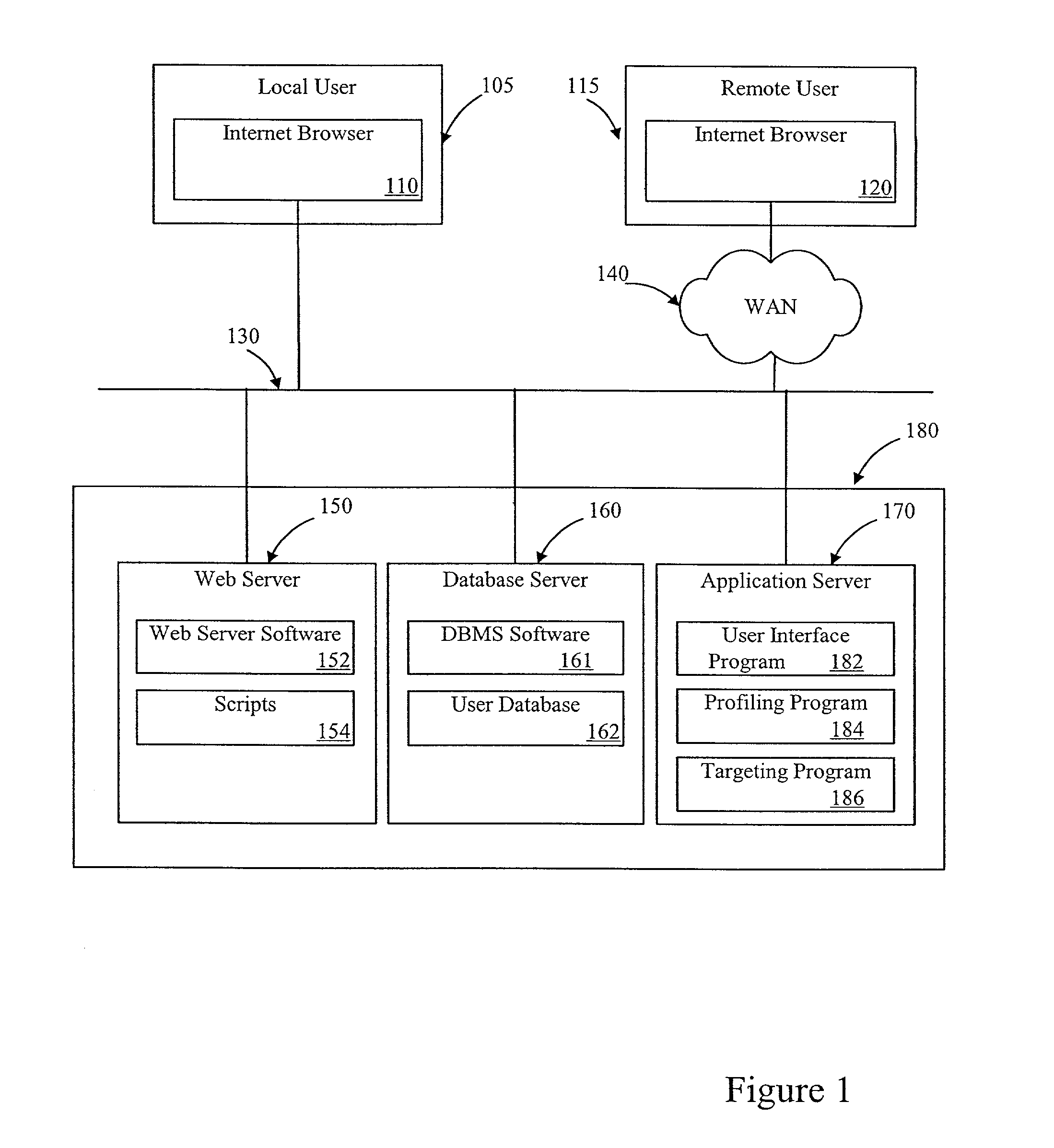
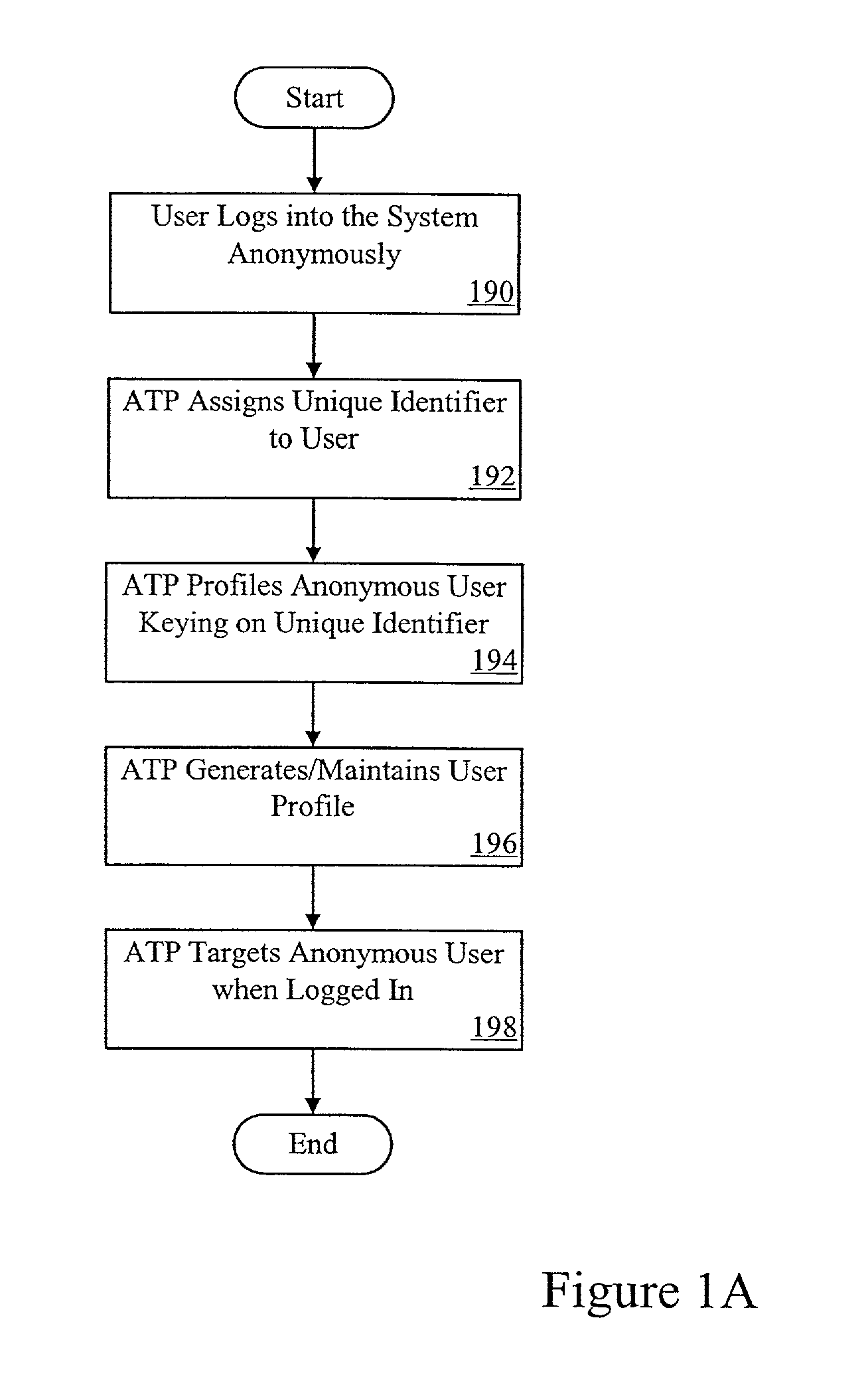
System and method for anonymous transaction in a data network and classification of individuals without knowing their real identity
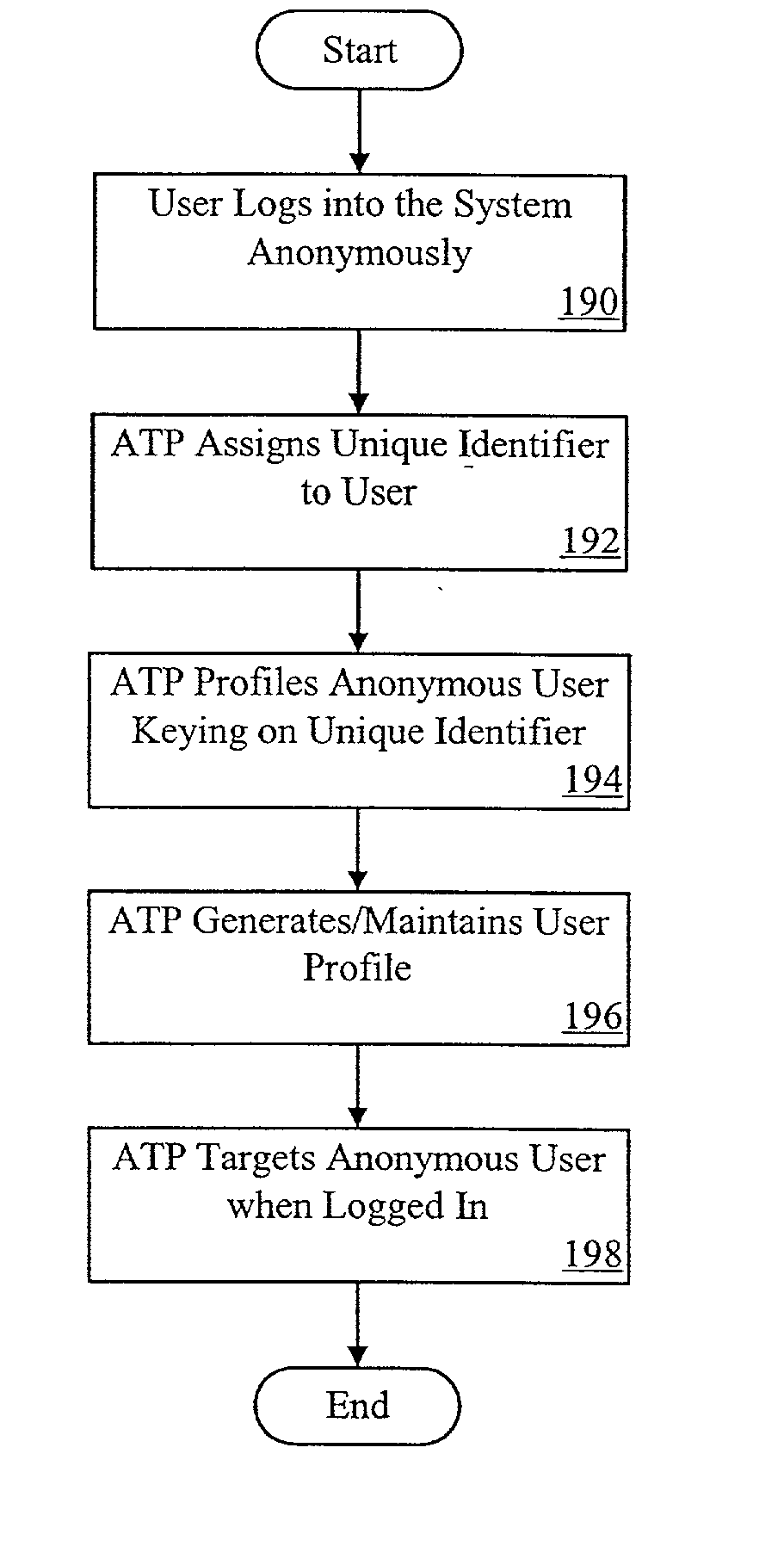
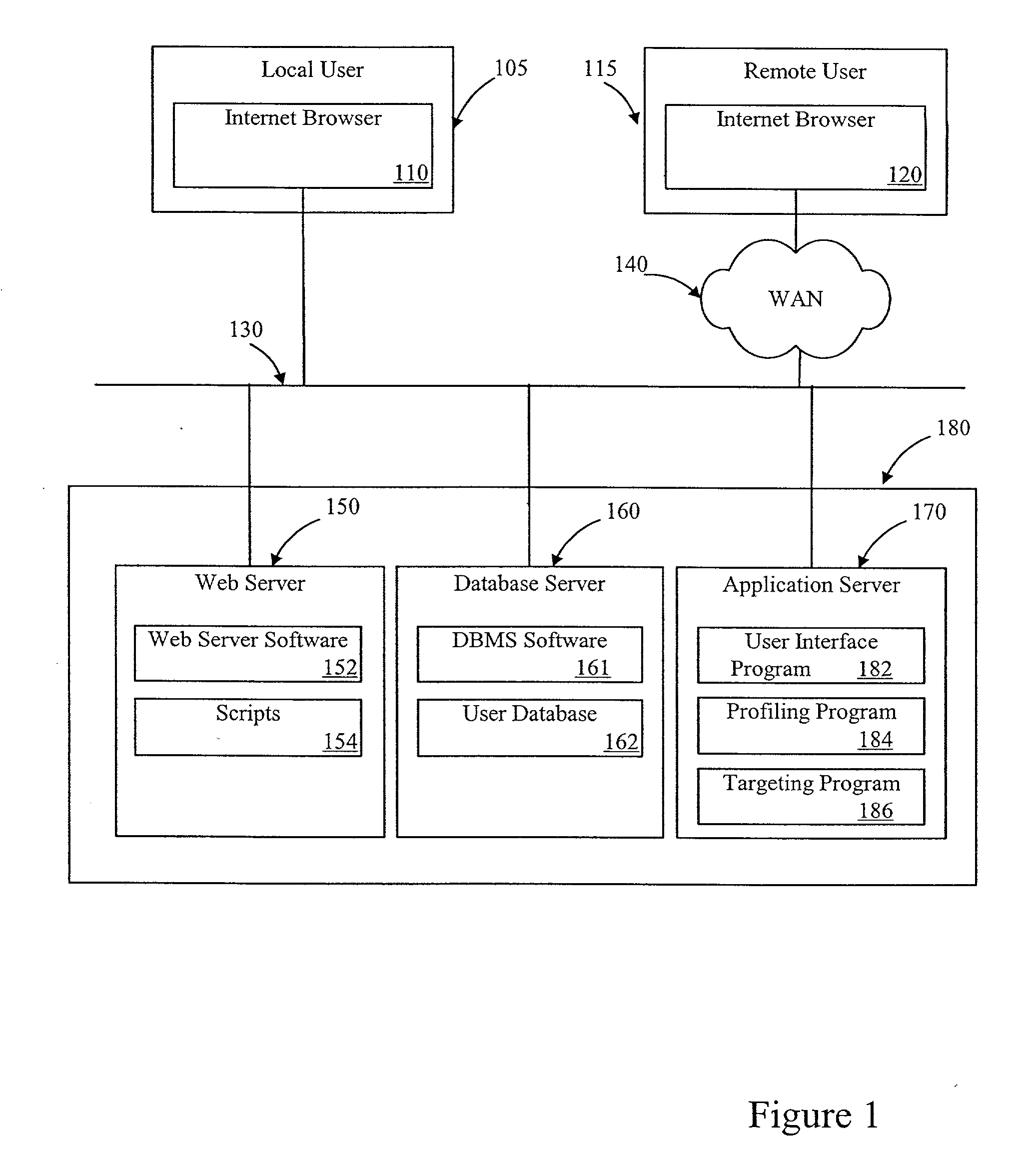
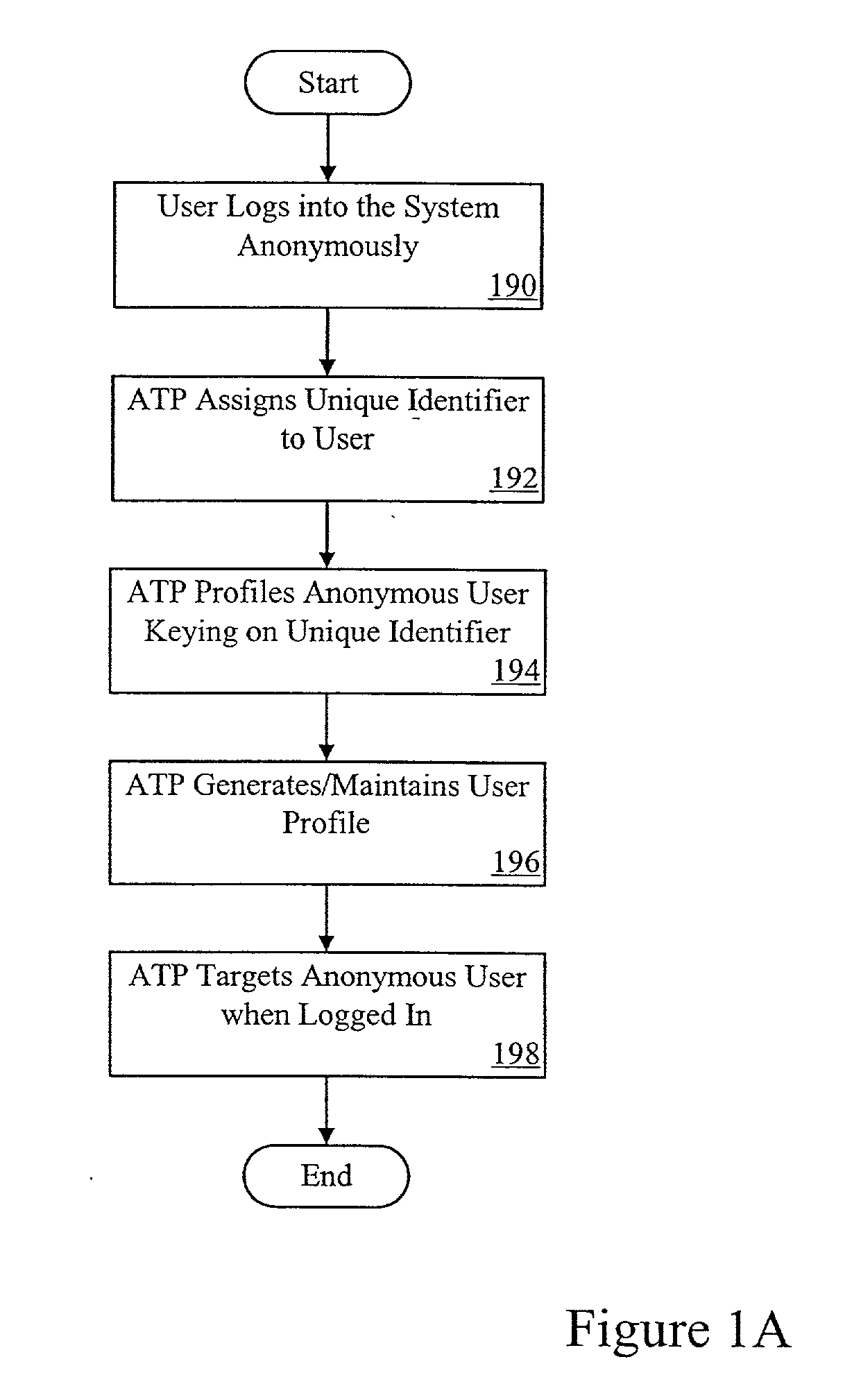
This invention relates generally to a computer-implemented method and system for having anonymous profiling of, and marketing to, anonymous users in a data network, particularly in the Internet. It enables an individual to surf the Internet anonymously as well as enabling third parties to use profiling information to target such anonymous users. The real identity of the individual is never known within the anonymous trust system.
Owner:RESOURCE CONSORTIUM LTD LLC
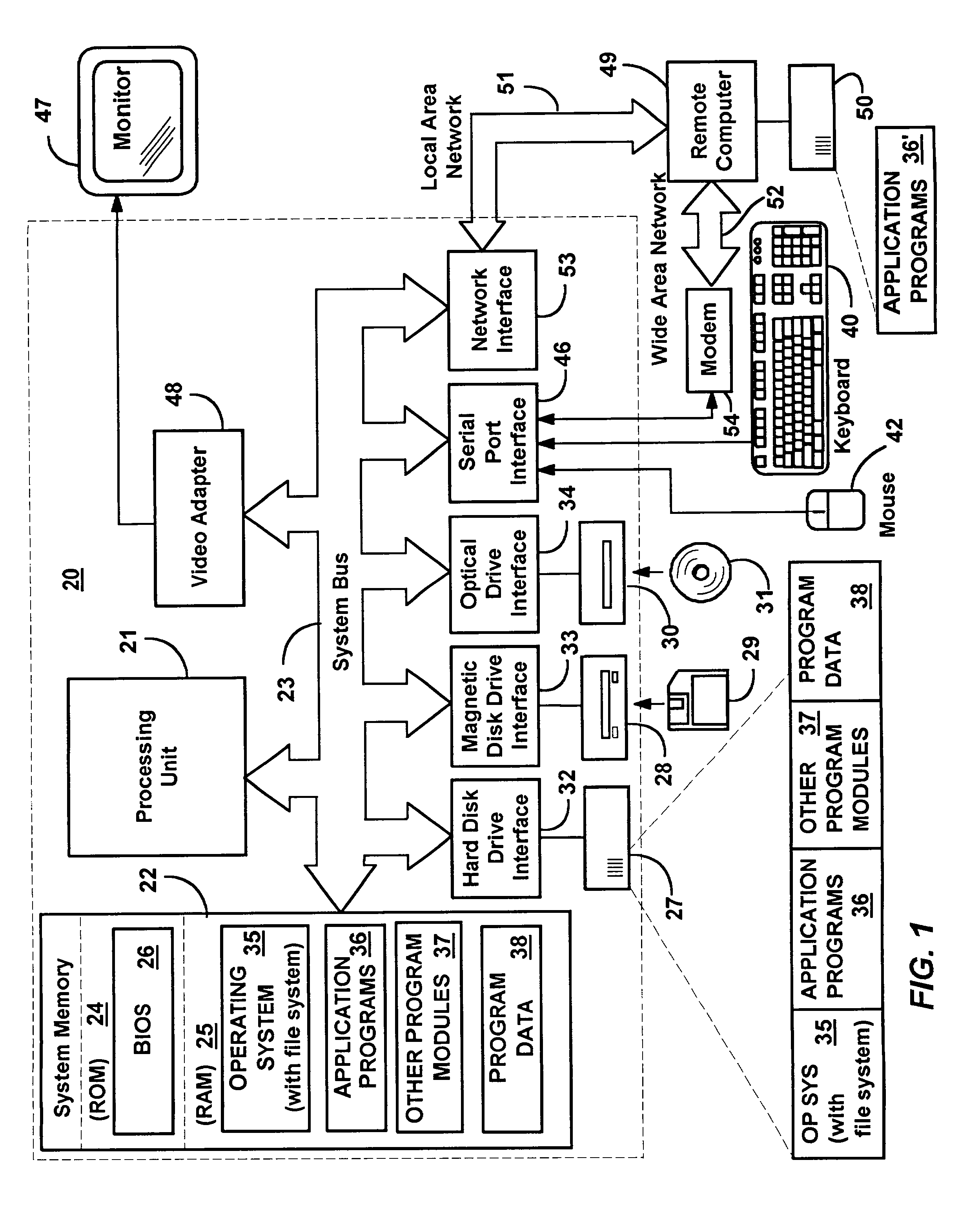
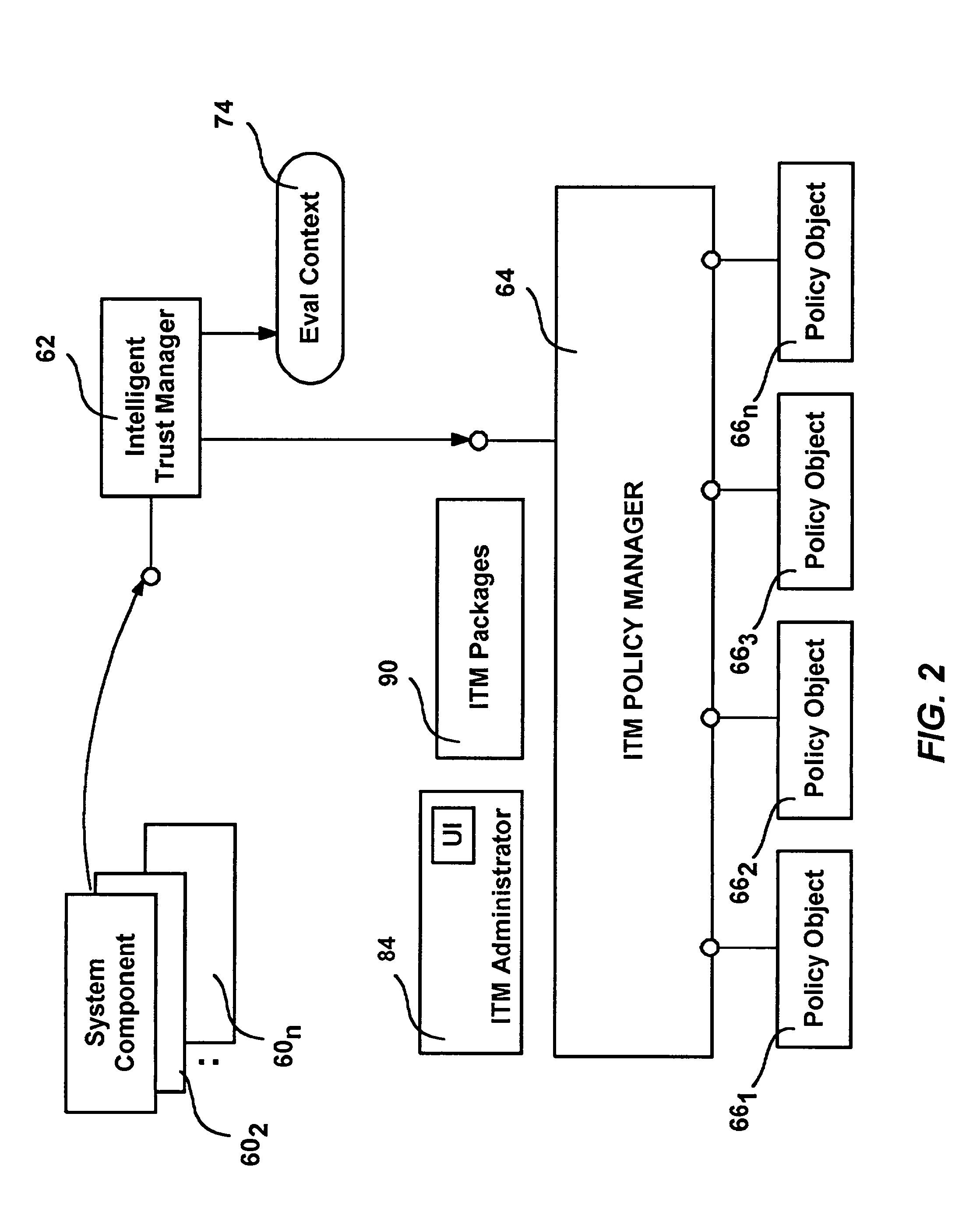
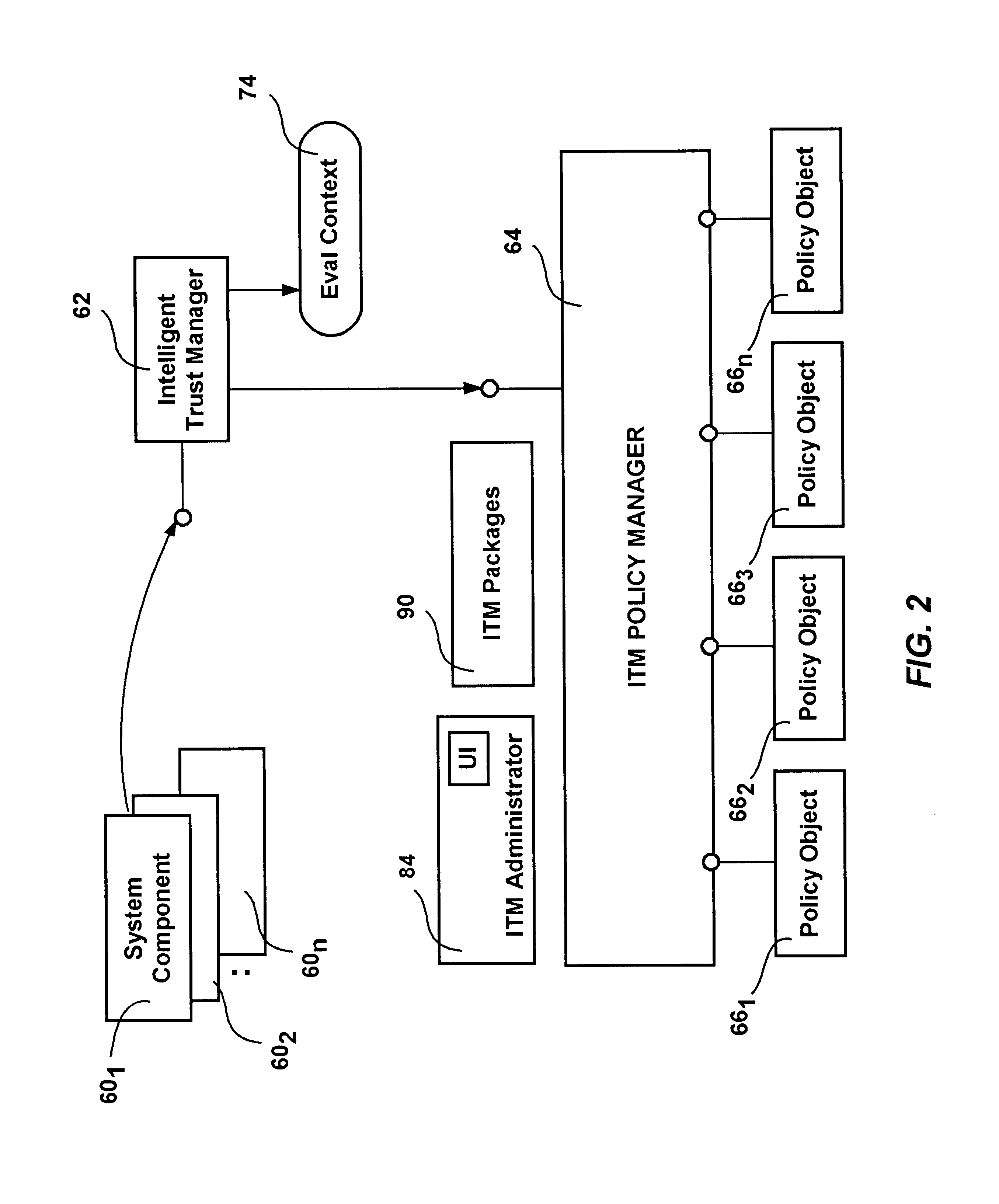
Intelligent trust management method and system
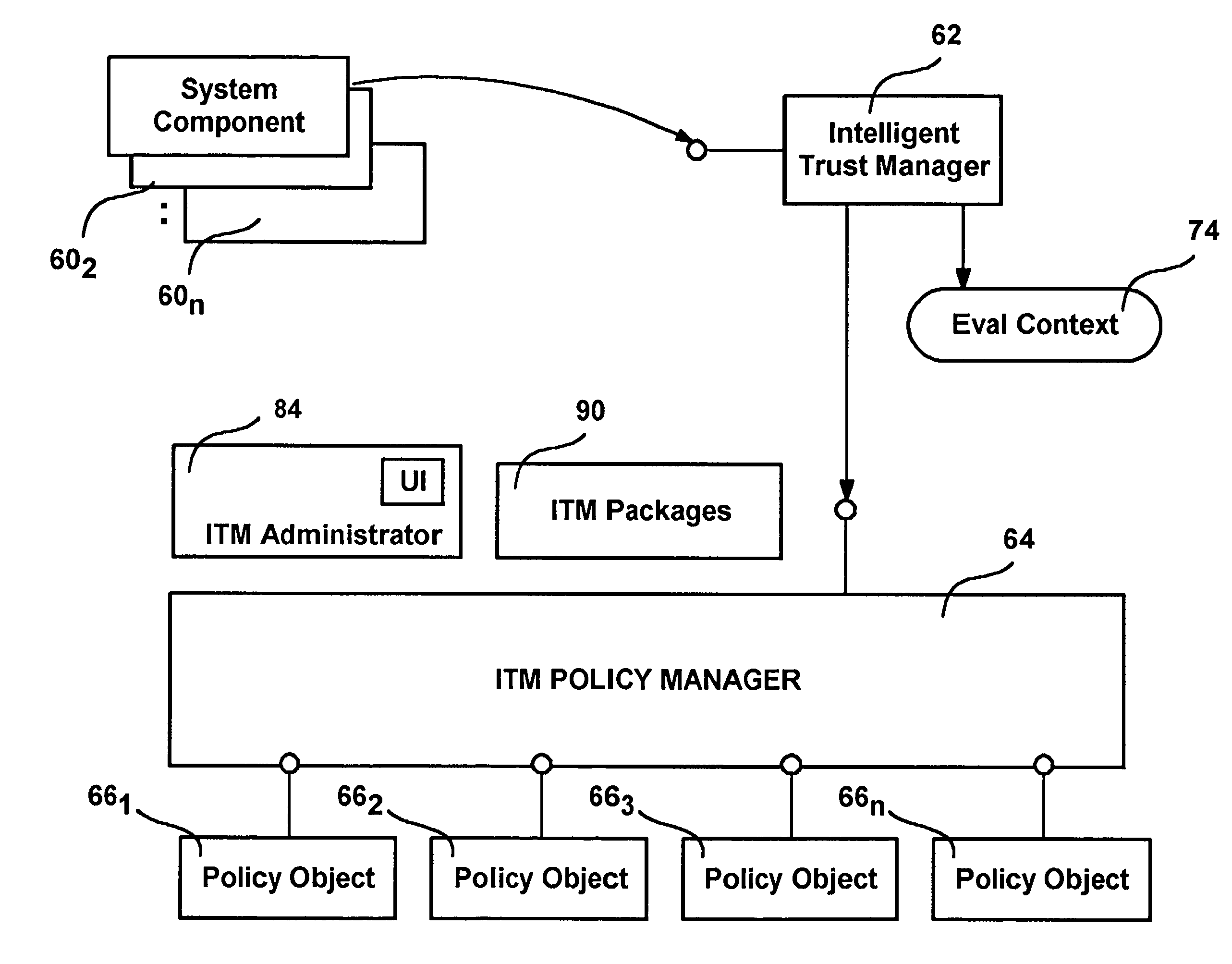
Intelligent Trust Management provides a centralized security facility that gives system components a flexible mechanism for implementing security policies. System components such as applications create a request describing an action that needs to be checked against an appropriate security policy. The request is given to a trust system that determines which policy object applies to the request, and may pass request arguments to the policy. The policy objects include executable code that uses any arguments along with dynamically obtained variable information to make a decision. The decision is returned to the system component, which then operates accordingly. Policy objects may maintain state and interface with the user independent of the system component in order to obtain information to make their decisions. Policy objects may call other policy objects and / or mathematically combine the results of other policy objects to make a decision.
Owner:MICROSOFT TECH LICENSING LLC
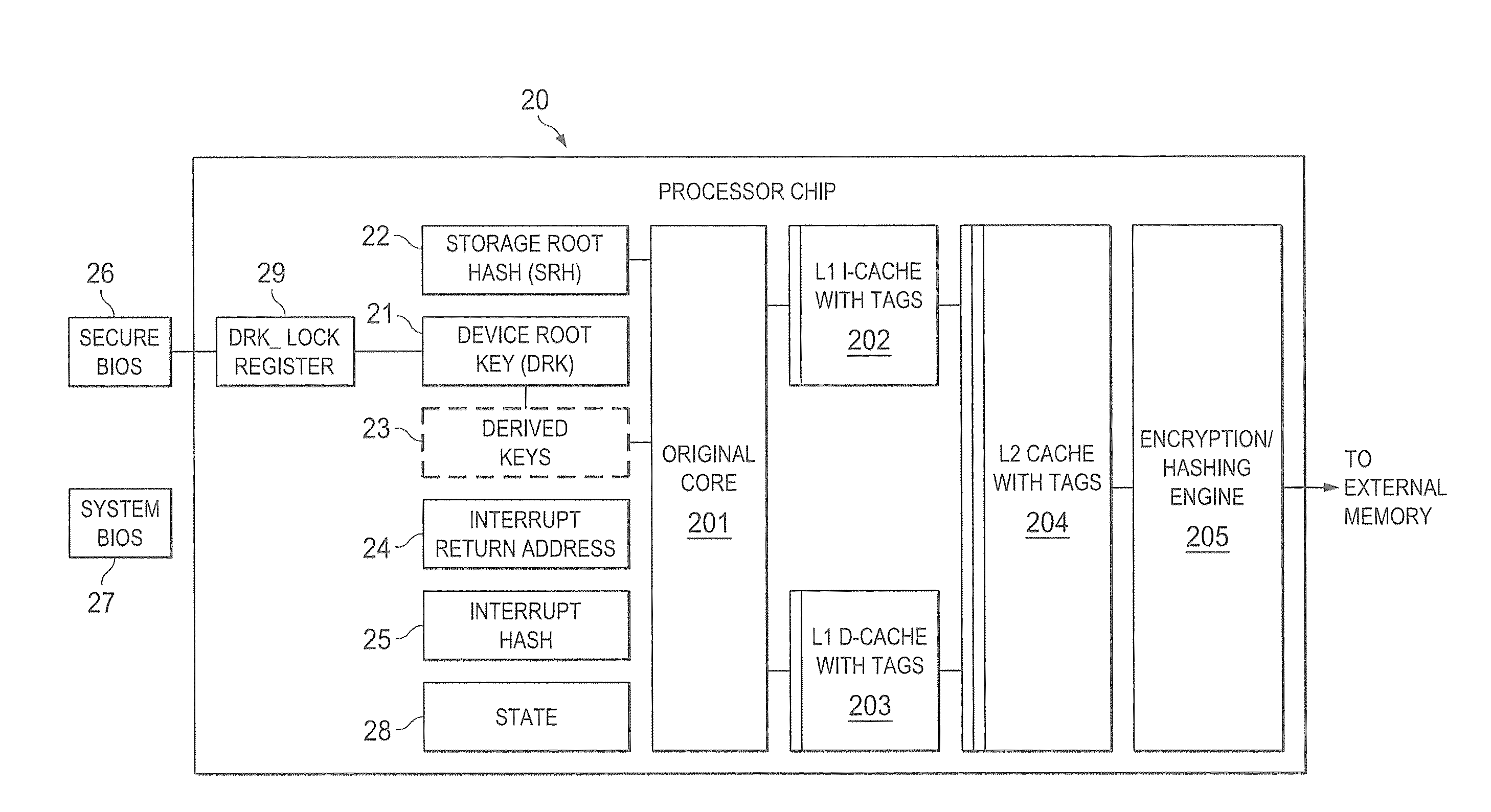
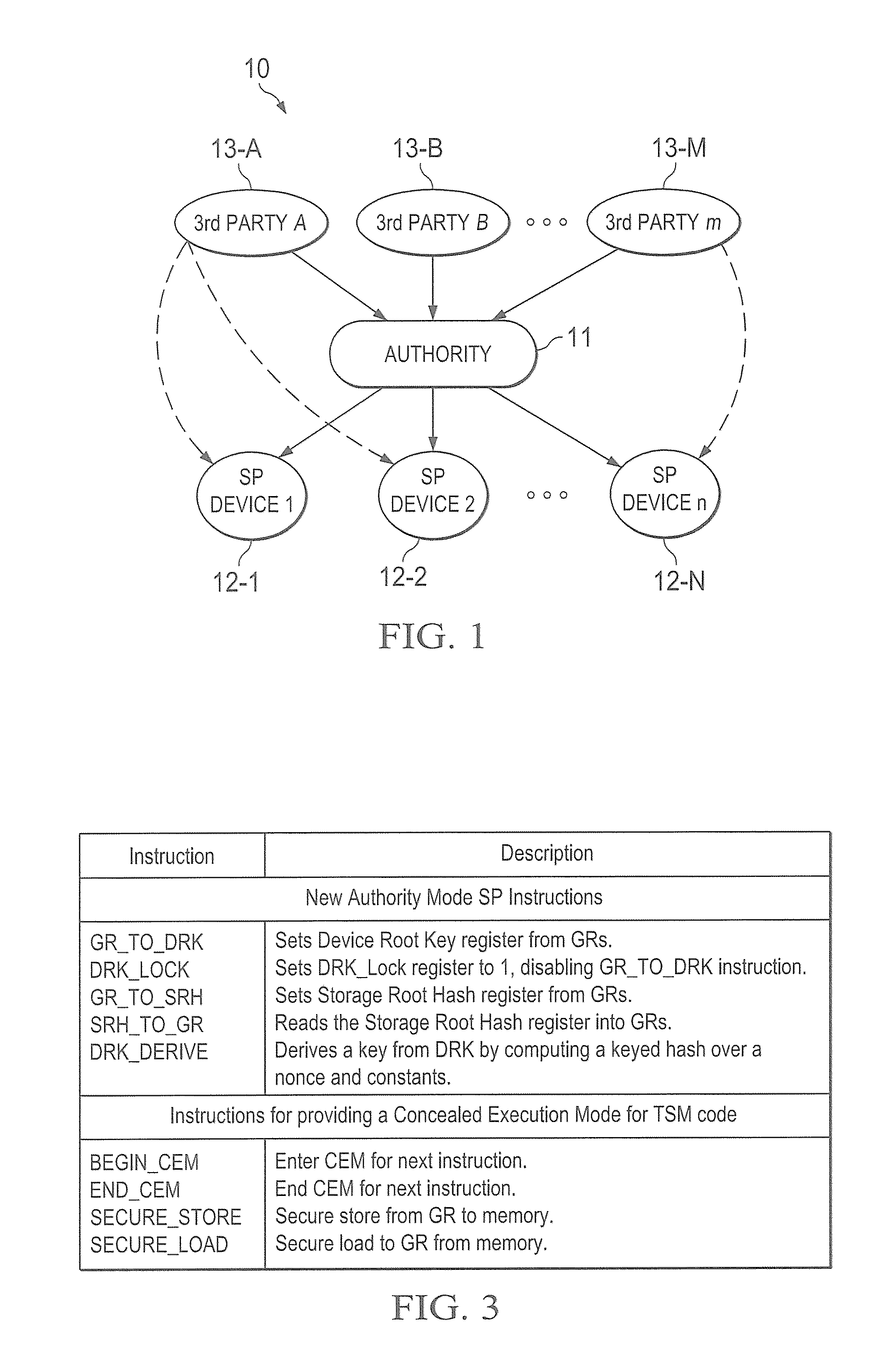
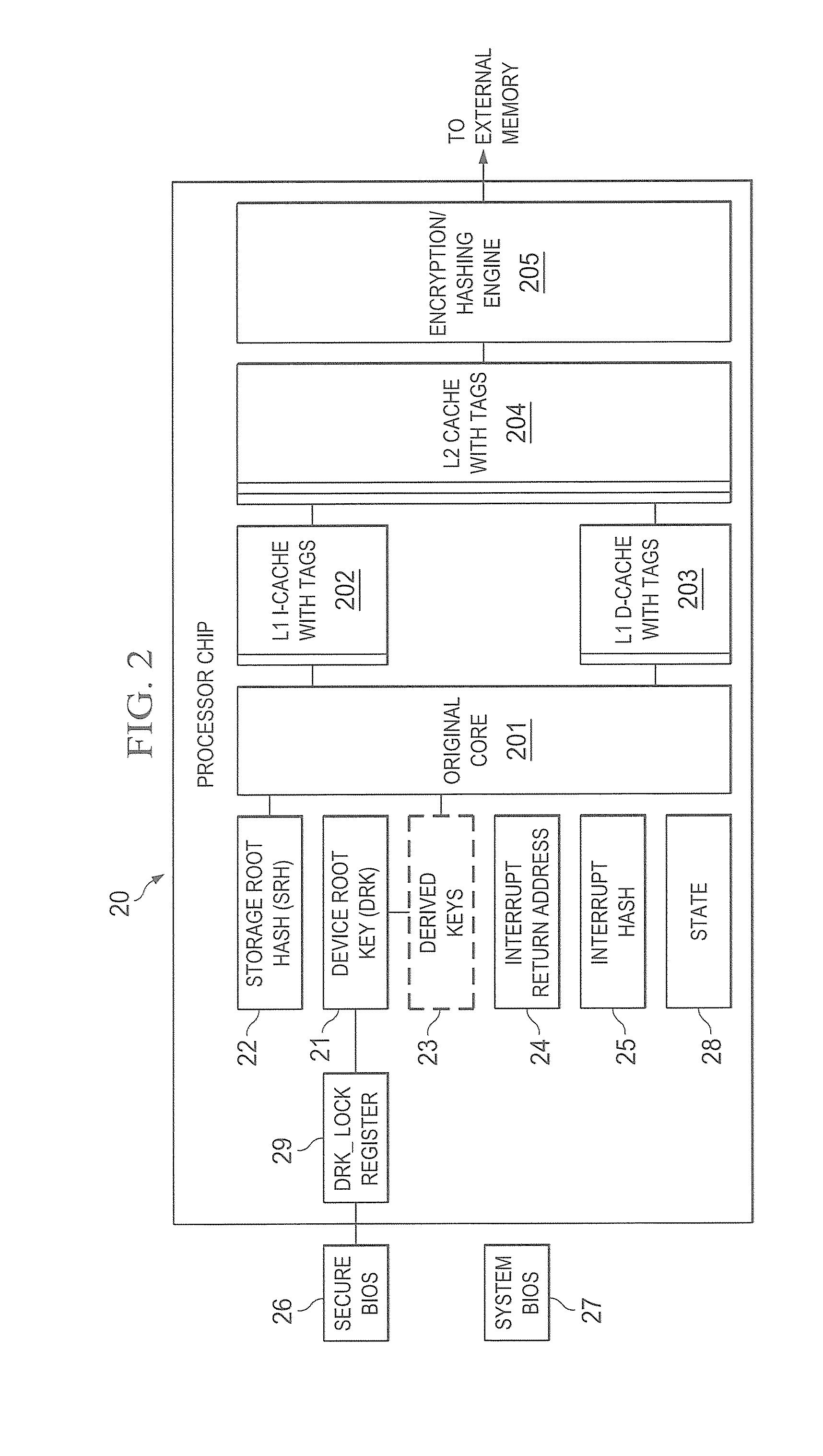
Hardware trust anchors in sp-enabled processors
ActiveUS20100042824A1User identity/authority verificationDigital computer detailsOperational systemConfidentiality
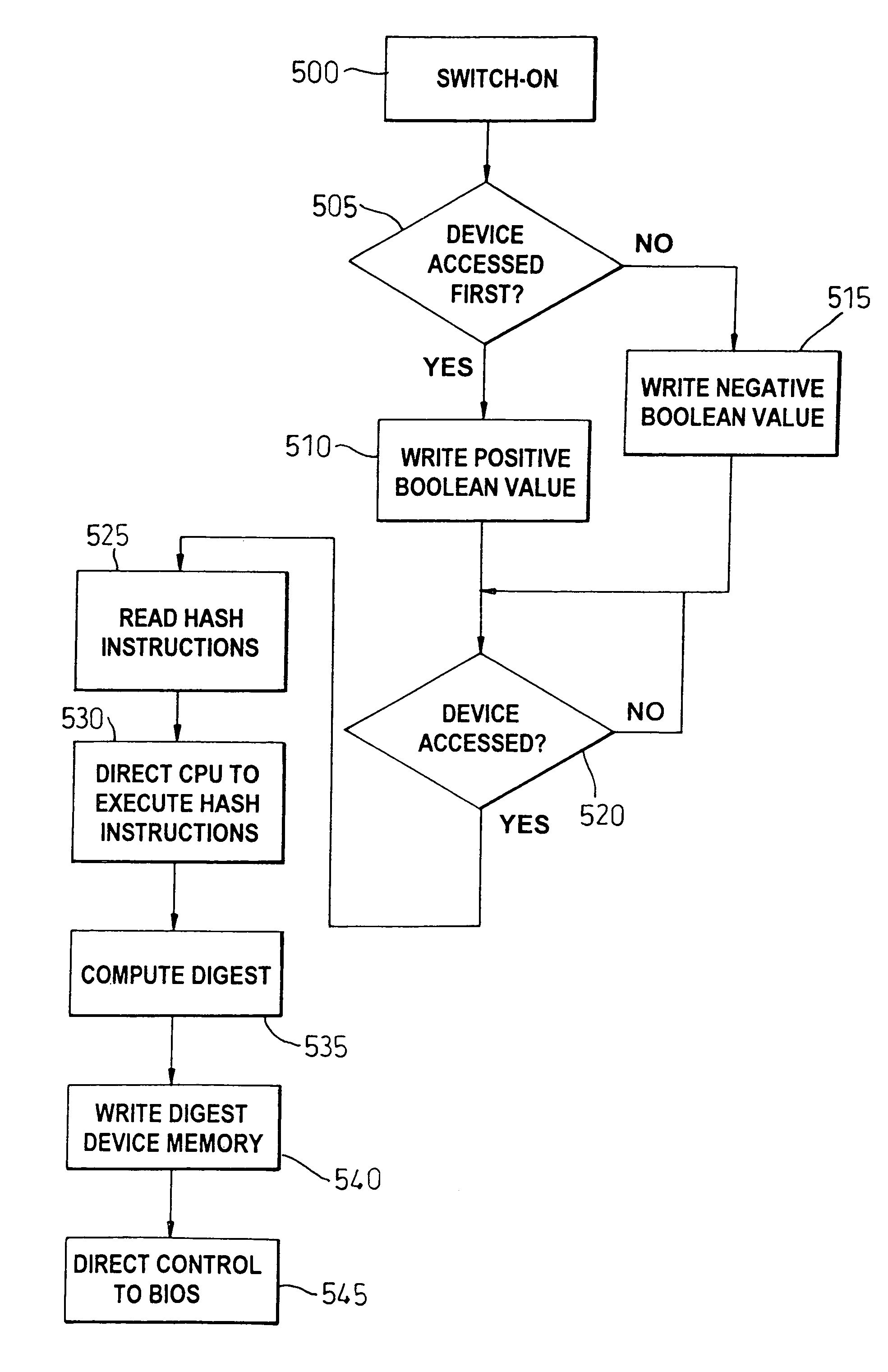
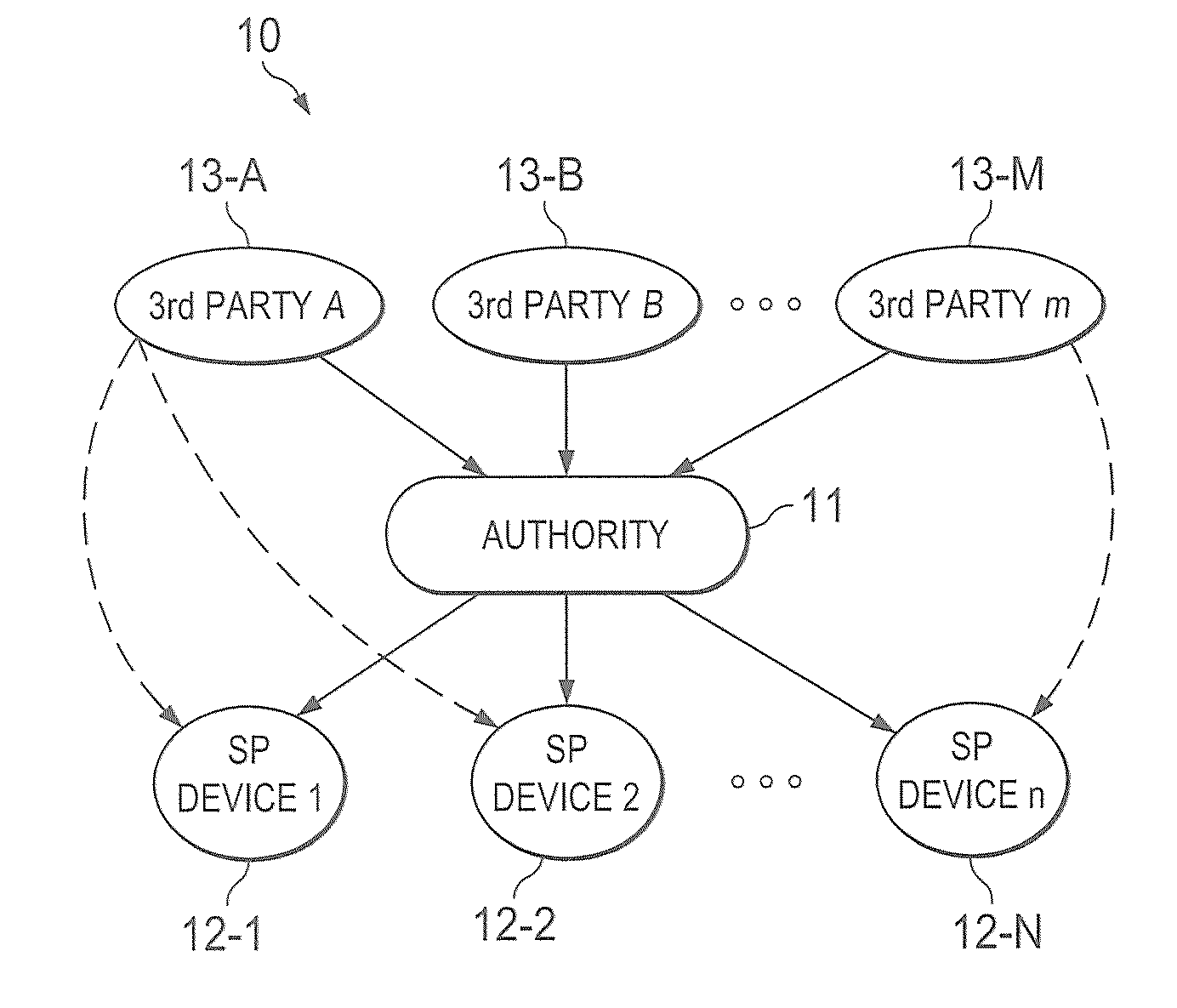
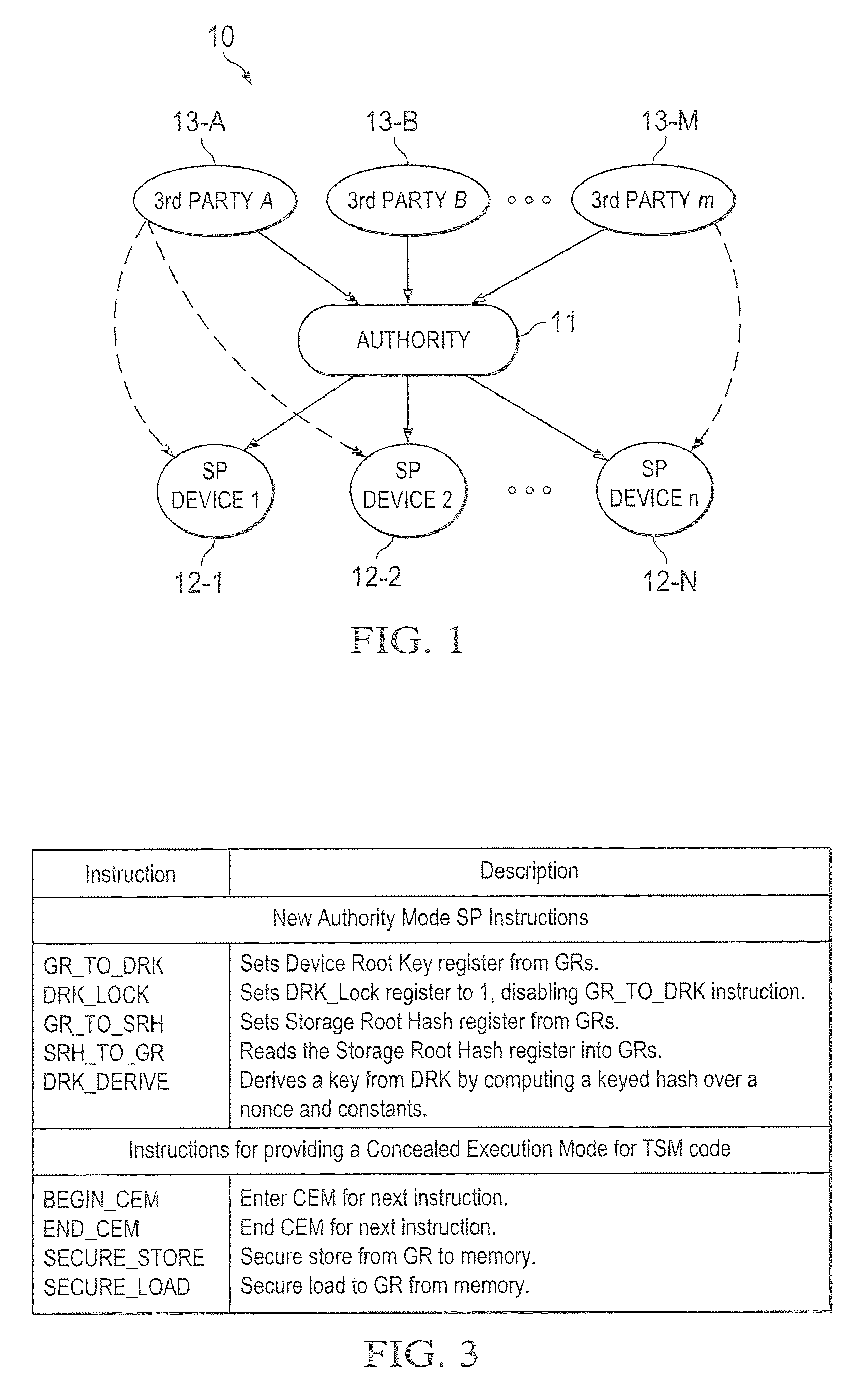
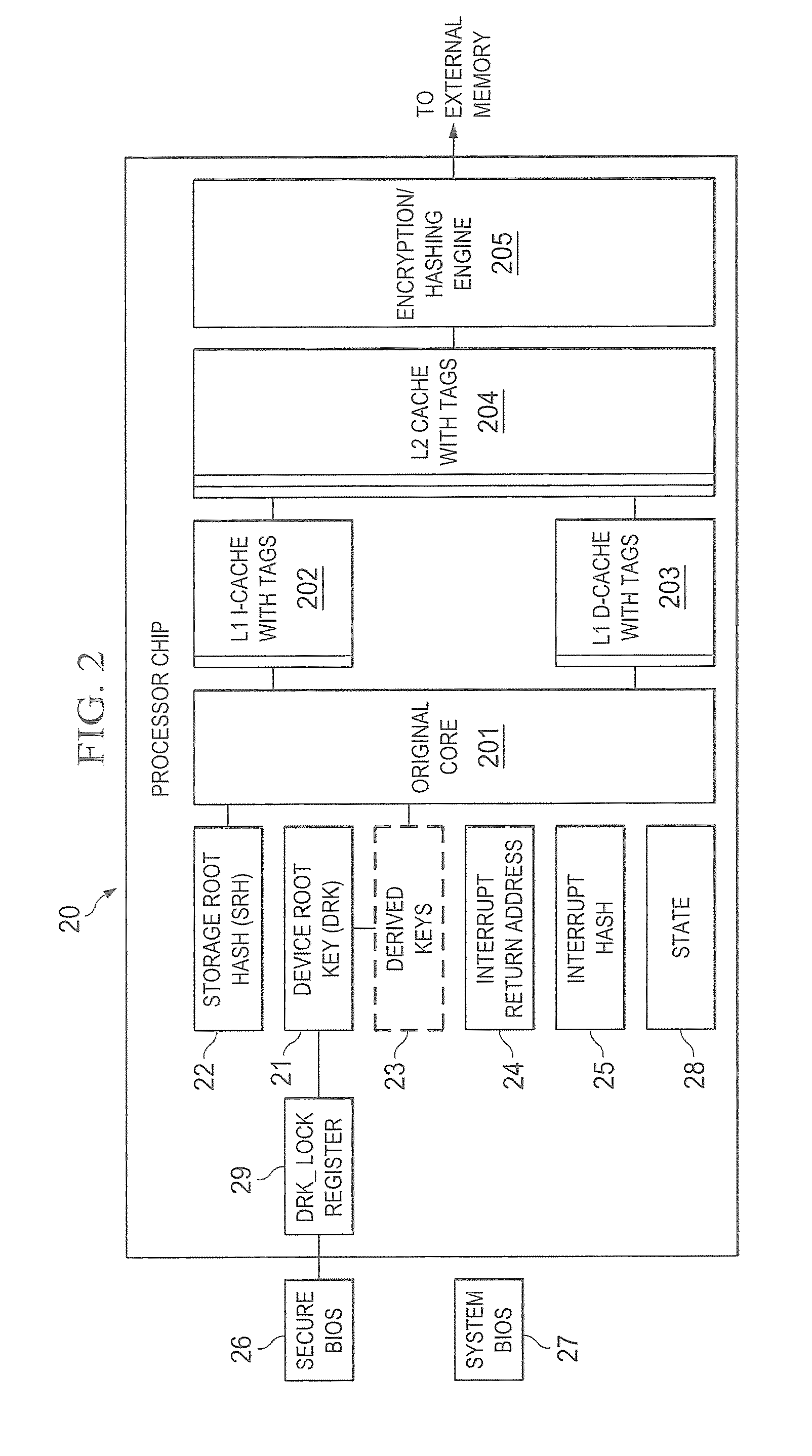
A trust system and method is disclosed for use in computing devices, particularly portable devices, in which a central Authority shares secrets and sensitive data with users of the respective devices. The central Authority maintains control over how and when shared secrets and data are used. In one embodiment, the secrets and data are protected by hardware-rooted encryption and cryptographic hashing, and can be stored securely in untrusted storage. The problem of transient trust and revocation of data is reduced to that of secure key management and keeping a runtime check of the integrity of the secure storage areas containing these keys (and other secrets). These hardware-protected keys and other secrets can further protect the confidentiality and / or integrity of any amount of other information of arbitrary size (e.g., files, programs, data) by the use of strong encryption and / or keyed-hashing, respectively. In addition to secrets the Authority owns, the system provides access to third party secrets from the computing devices. In one embodiment, the hardware-rooted encryption and hashing each use a single hardware register fabricated as part of the computing device's processor or System-on-Chip (SoC) and protected from external probing. The secret data is protected while in the device even during operating system malfunctions and becomes non-accessible from storage according to various rules, one of the rules being the passage of a certain time period. The use of the keys (or other secrets) can be bound to security policies that cannot be separated from the keys (or other secrets). The Authority is also able to establish remote trust and secure communications to the devices after deployment in the field using a special tamper-resistant hardware register in the device, to enable, disable or update the keys or secrets stored securely by the device.
Owner:THE TRUSTEES FOR PRINCETON UNIV +1
System and method for anonymous transaction in a data network and classification of individuals without knowing their real identity
This invention relates generally to a computer-implemented method and system for having anonymous profiling of, and marketing to, anonymous users in a data network, particularly in the Internet. It enables an individual to surf the Internet anonymously as well as enabling third parties to use profiling information to target such anonymous users. The real identity of the individual is never known within the anonymous trust system.
Owner:RESOURCE CONSORTIUM LTD LLC
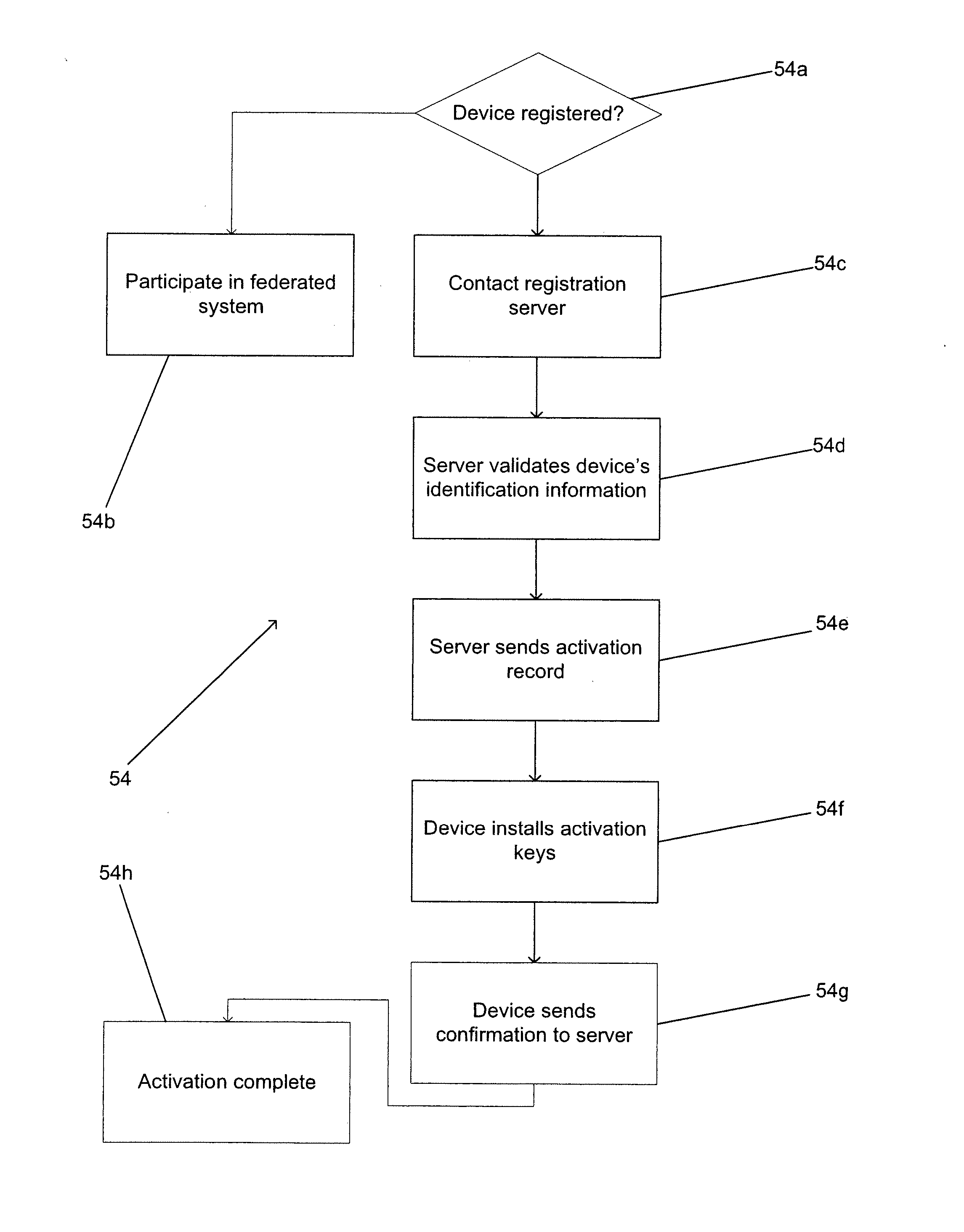
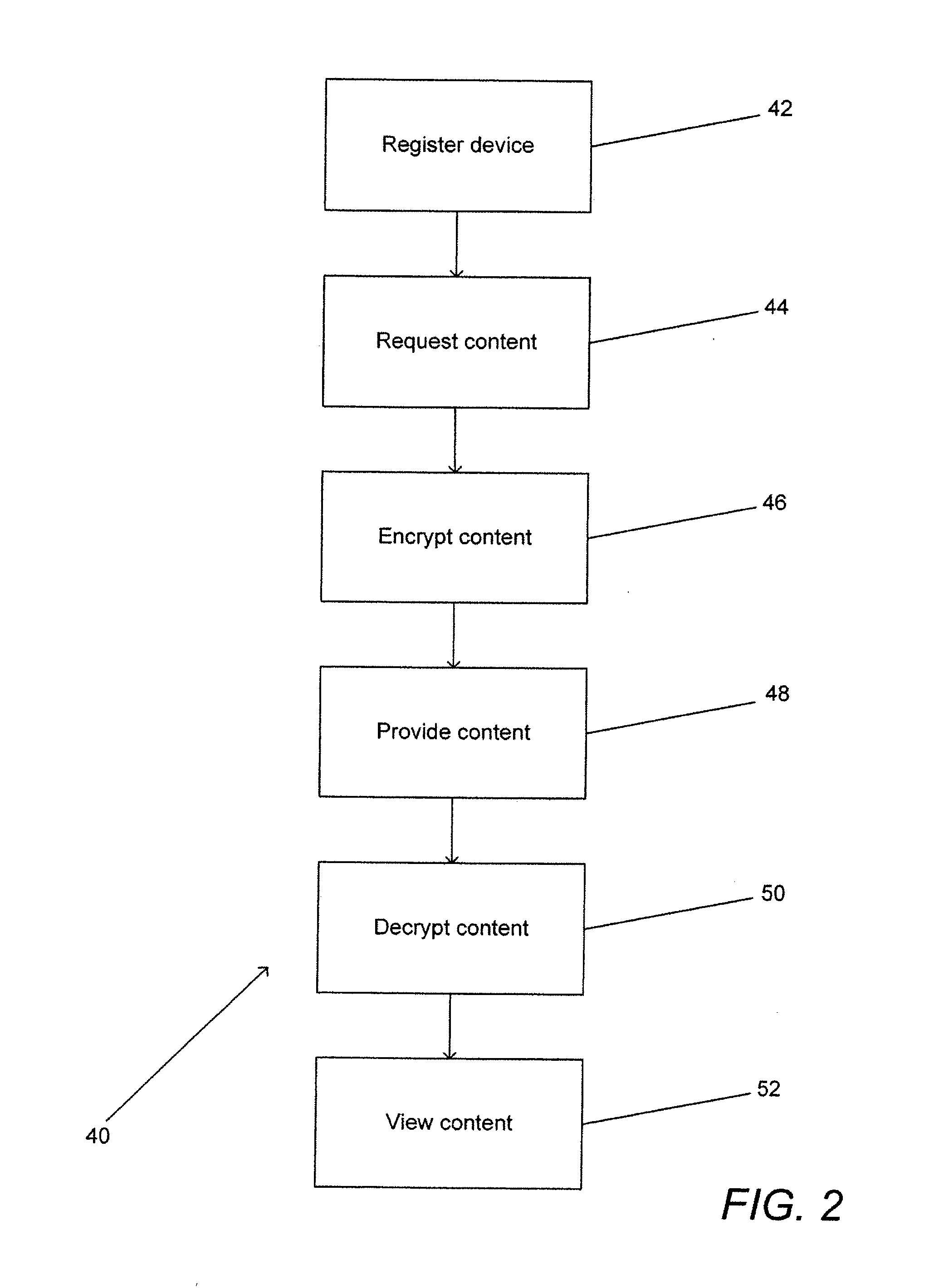
Federated digital rights management scheme including trusted systems
ActiveUS20080046718A1Multiple keys/algorithms usageDigital data processing detailsDigital rights managementBiological activation
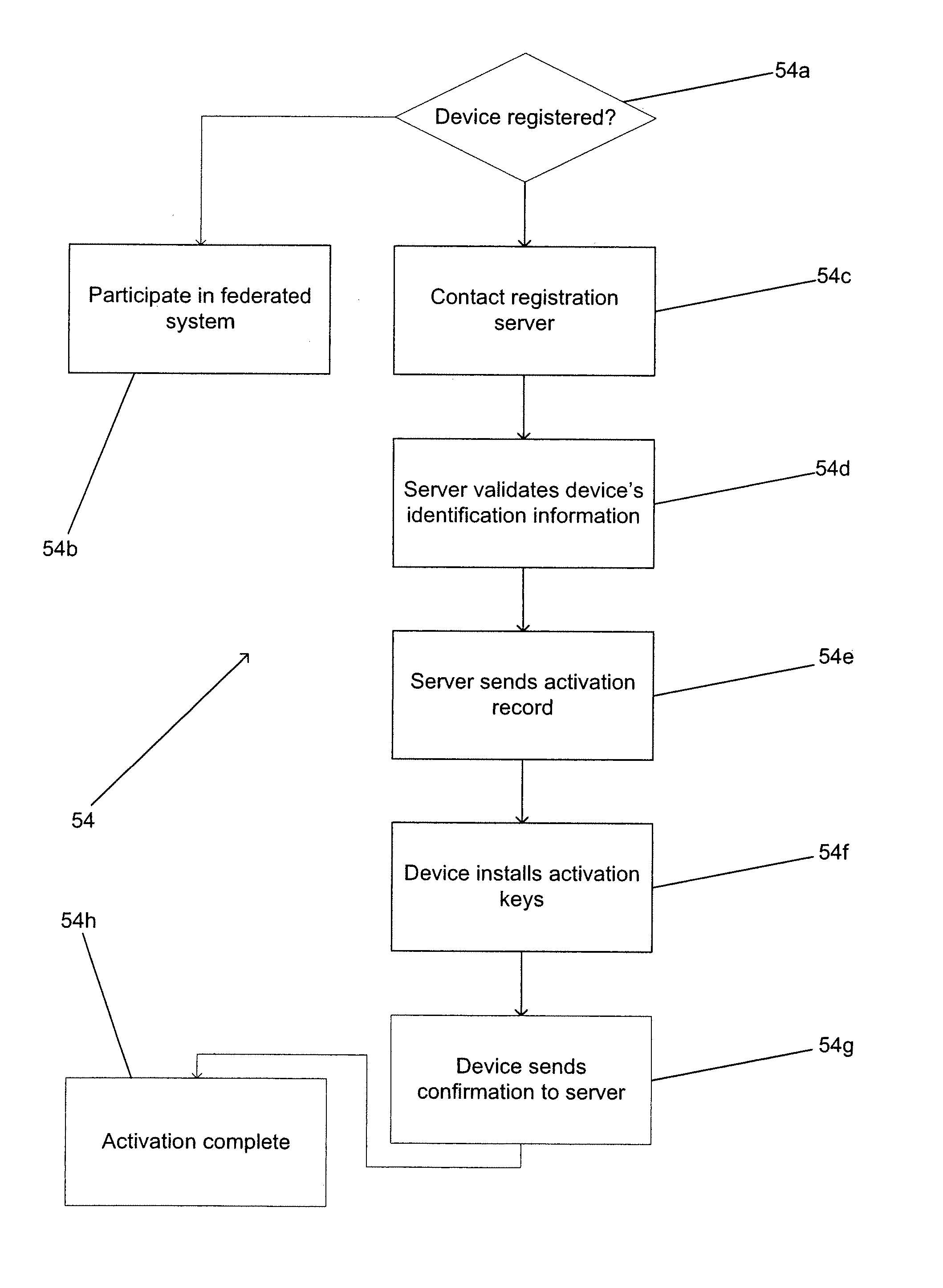
Federated systems for issuing playback certifications granting access to technically protected content are described. One embodiment of the system includes a registration server connected to a network, a content server connected to the network and to a trusted system, a first device including a non-volatile memory that is connected to the network and a second device including a non-volatile memory that is connected to the network. In addition, the registration server is configured to provide the first device with a first set of activation information in a first format, the first device is configured to store the first set of activation information in non-volatile memory, the registration server is configured to provide the second device with a second set of activation information in a second format, and the second device is configured to store the second set of activation information in non-volatile memory.
Owner:DIVX INC
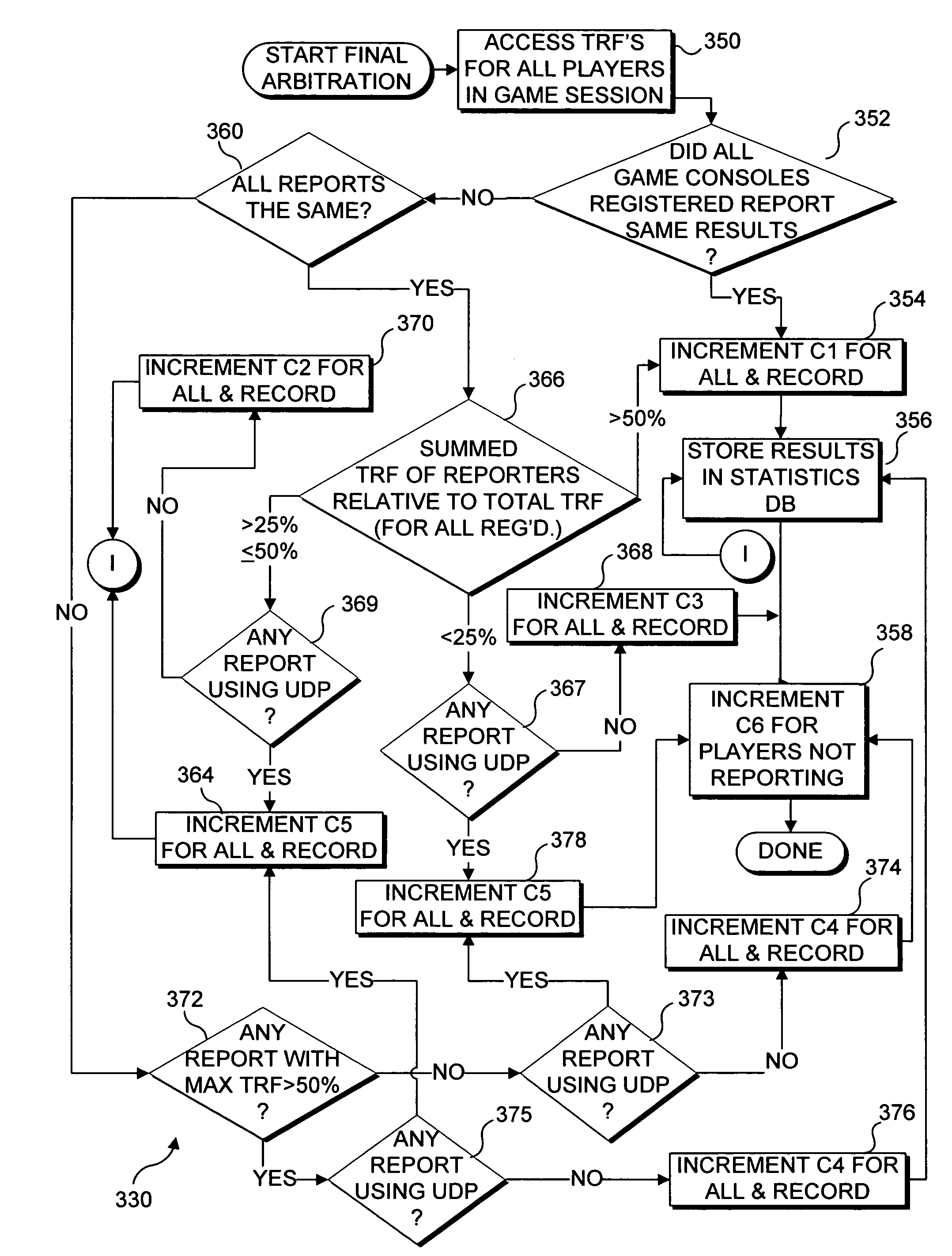
Player trust system and method
InactiveUS7367888B1Reduce probabilityIncrease ratingsDigital computer detailsVideo gamesTrusted systemMultimedia
Owner:MICROSOFT TECH LICENSING LLC
A government affair information resource sharing system based on a block chain
ActiveCN109787815AEnsure real-timeEnsure decentralizationData switching networksNon real timeExchange network
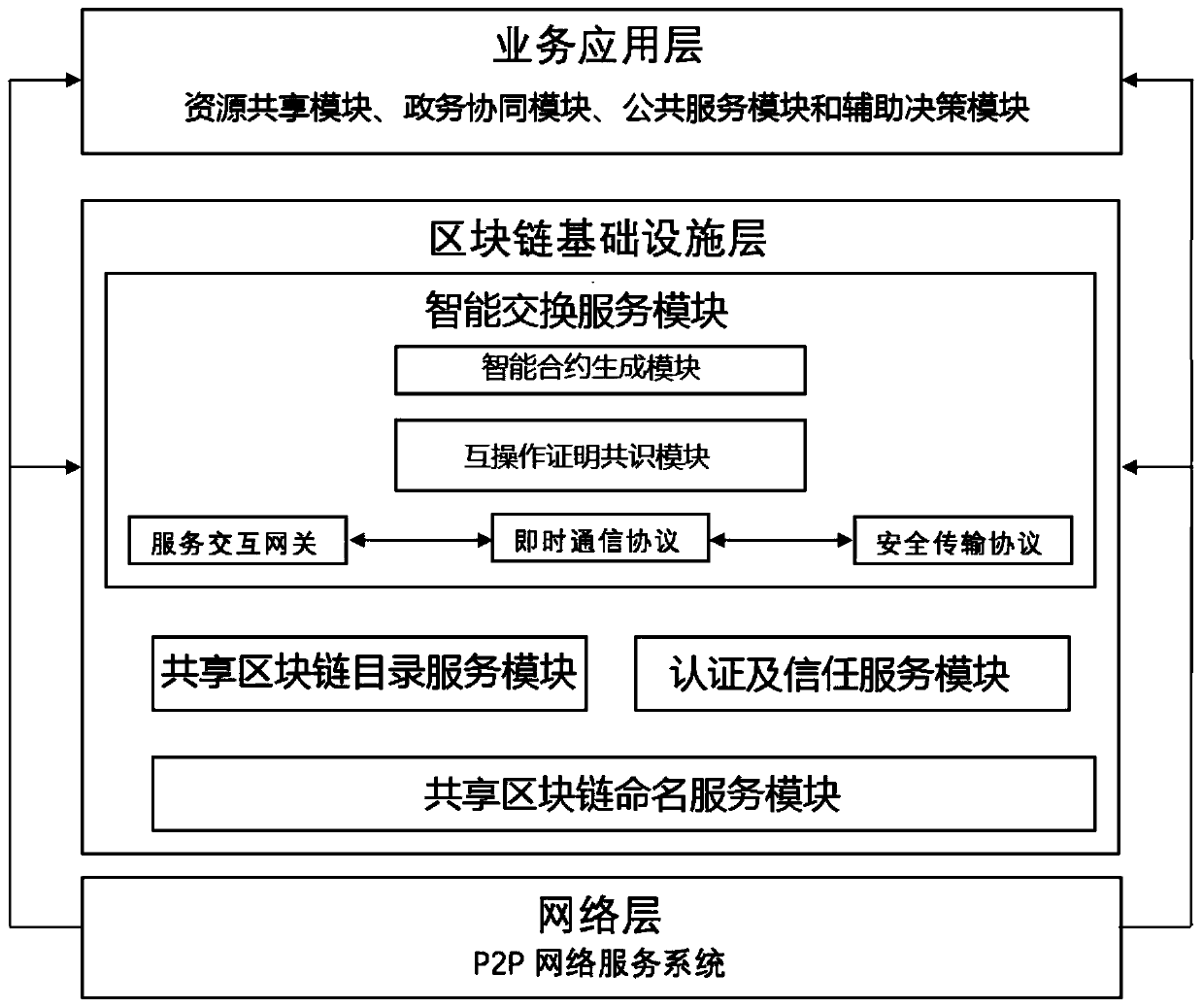
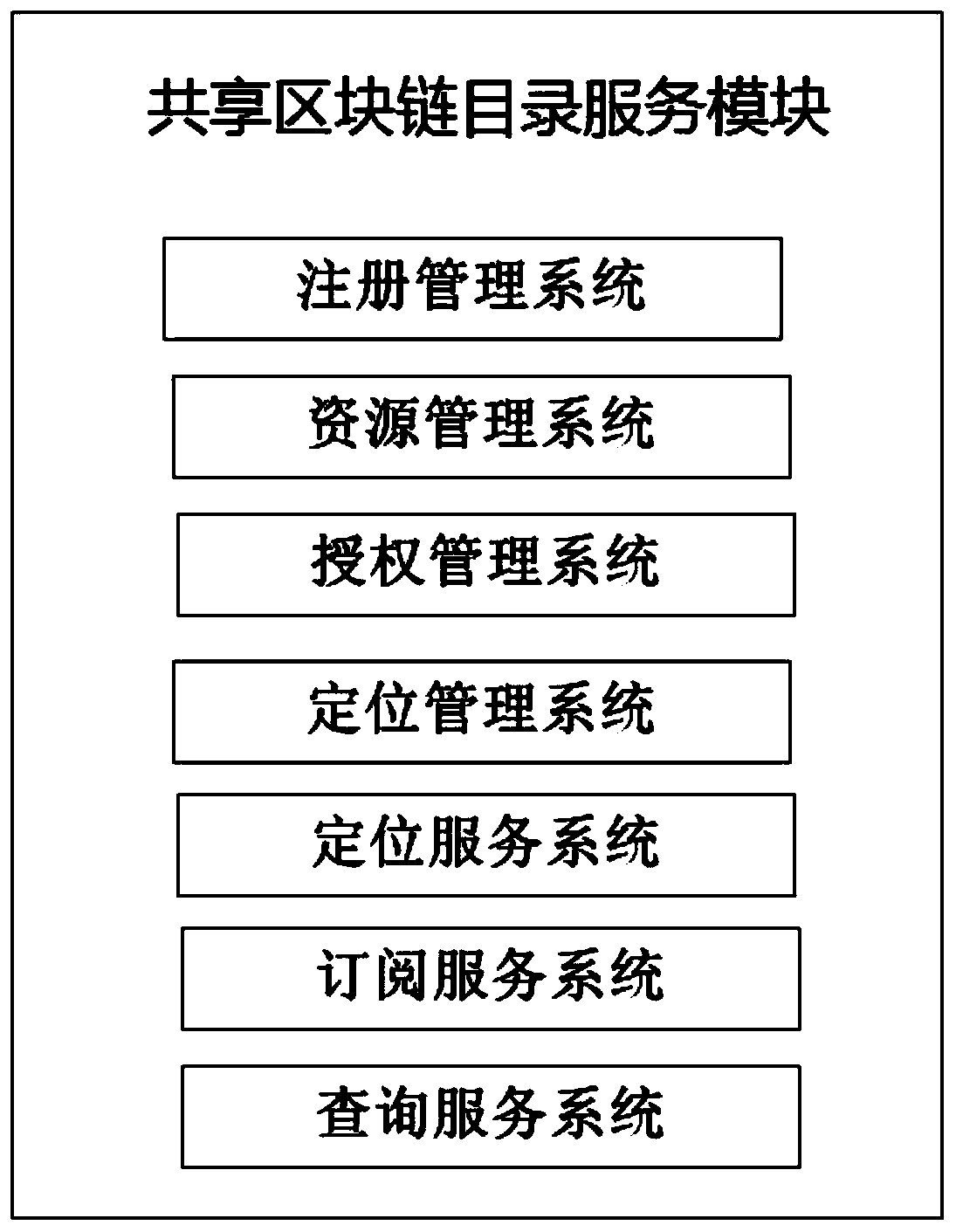
The invention discloses a government affair information resource sharing system based on a block chain, and belongs to the technical field of information sharing based on the block chain. By combiningP2P network, the cryptology and the artificial intelligence theory, the overall model architecture based on the block chain technology is provided, so that a government affair information resource sharing and exchange network system, a government affair information resource sharing and exchange block chain directory system, a certificate and trust system and an information resource sharing security intelligent exchange system are constructed. The government affair information sharing and exchanging system effectively solves the problems of trust islands, data ownership, peer-to-peer management, standard consistency, non-real-time exchange and the like in government affair information resource sharing application, and is high in safety, trustable, real-time exchange, data standard consistency, traceability and wide in sharing range.
Owner:YUNNAN UNIVERSITY OF FINANCE AND ECONOMICS
Transitive trust network
Methods, data structures, and systems by which entities can efficiently discover, extend, validate and establish business relationships over a digital network are disclosed. A transitive trust system can be utilized by any number of interconnected entities in which at least two of the entities are capable of sharing information. One or more entity trust lists contain, for at least two of the entities, at least one characteristic. Each characteristic can, for example, describe or pertain to the actual or perceived dependability, reliability and / or credibility of an entity. The system also includes at least one transactional trust list that contains at least one parameter relative to an exchange between at least two of the entities through at least one degree of separation between the entities. The transactional trust list can, for example, be a listing of any type of parameters that define or describe business exchanges within a particular industry segment. The transactional trust list can also list information about the types of transactional activities that can take place and proxy actions available to cooperating entities. The system retrieves information from the entity trust list and the transactional trust list in order to provide a framework for at least two of the entities to establish relationships with one another.
Owner:ACCENTURE GLOBAL SERVICES LTD
Intelligent trust management method and system
Owner:MICROSOFT TECH LICENSING LLC
Transitive trust network
Owner:ACCENTURE GLOBAL SERVICES LTD
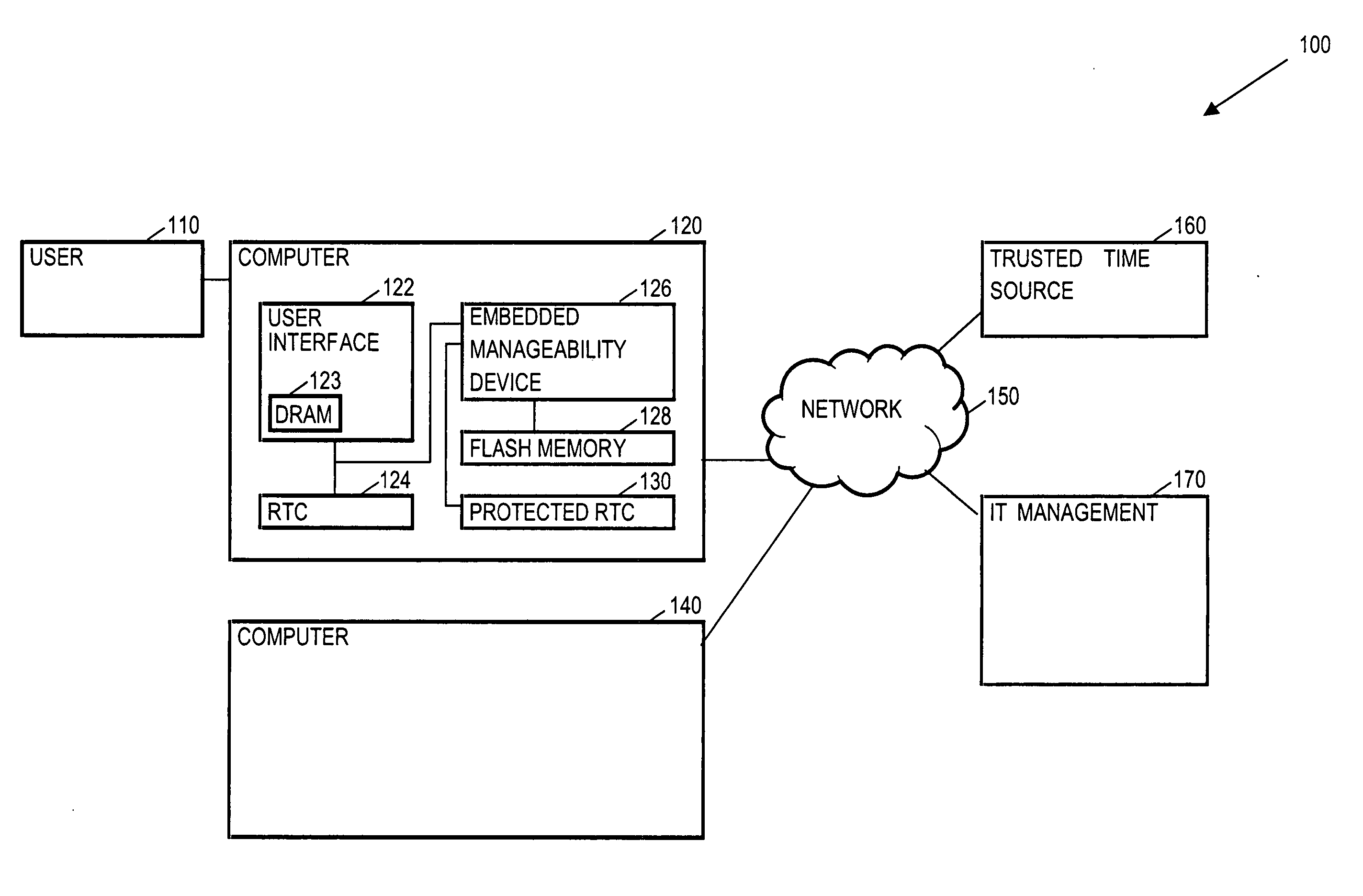
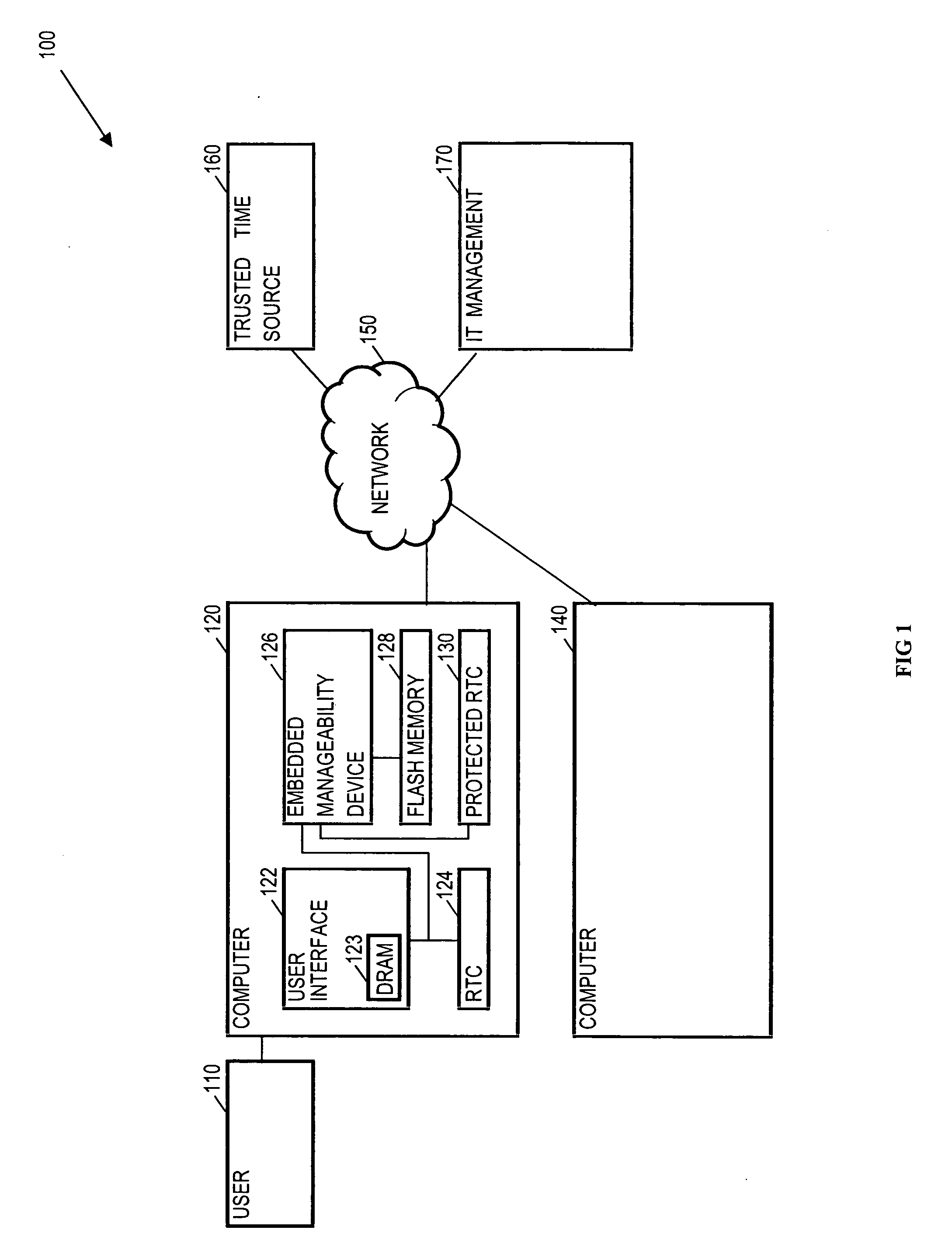
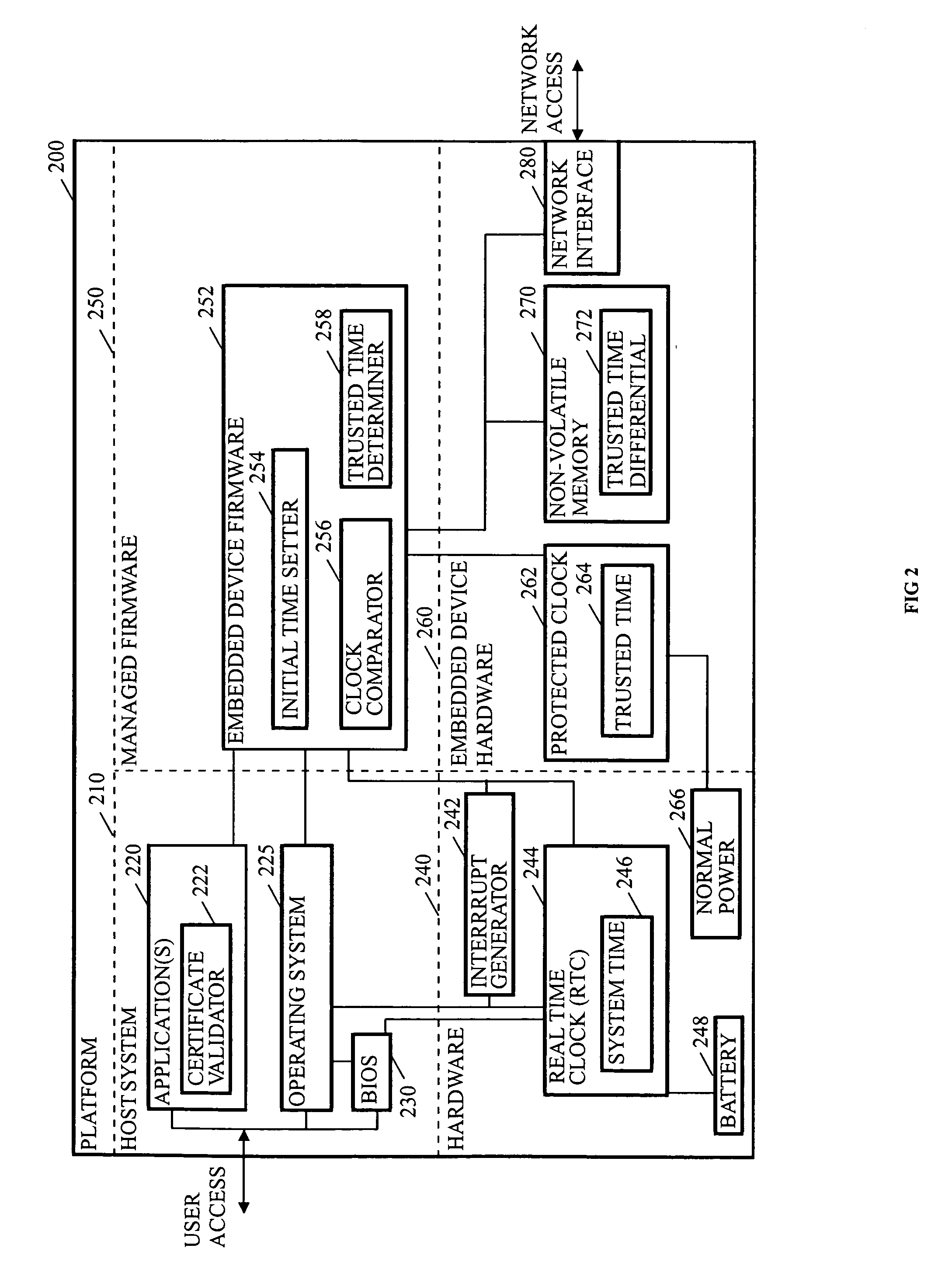
Protected clock management based upon a non-trusted persistent time source
InactiveUS20060294593A1Error detection/correctionVolume/mass flow measurementNetwork serviceTrusted system
Methods and arrangements to persist a trusted time for a protected clock based upon a non-trusted but persistent time source are disclosed. Embodiments may comprise an embedded device, which may be hardware, software, firmware, and / or other logic, to maintain a trusted time in a protected clock. The embedded device may initialize the protected clock by obtaining a trusted time from a trusted time source such as a network server. The embedded device then maintains the trusted time in the event of a power loss to the protected clock by monitoring a time differential between the protected clock and a non-trusted system clock. Many embodiments also employ the protected clock without a battery backup to advantageously save manufacturing costs and space, while maintaining the trusted time in the event of a power loss by relying on a battery backup for the non-trusted system clock. Other embodiments are disclosed and claimed.
Owner:INTEL CORP
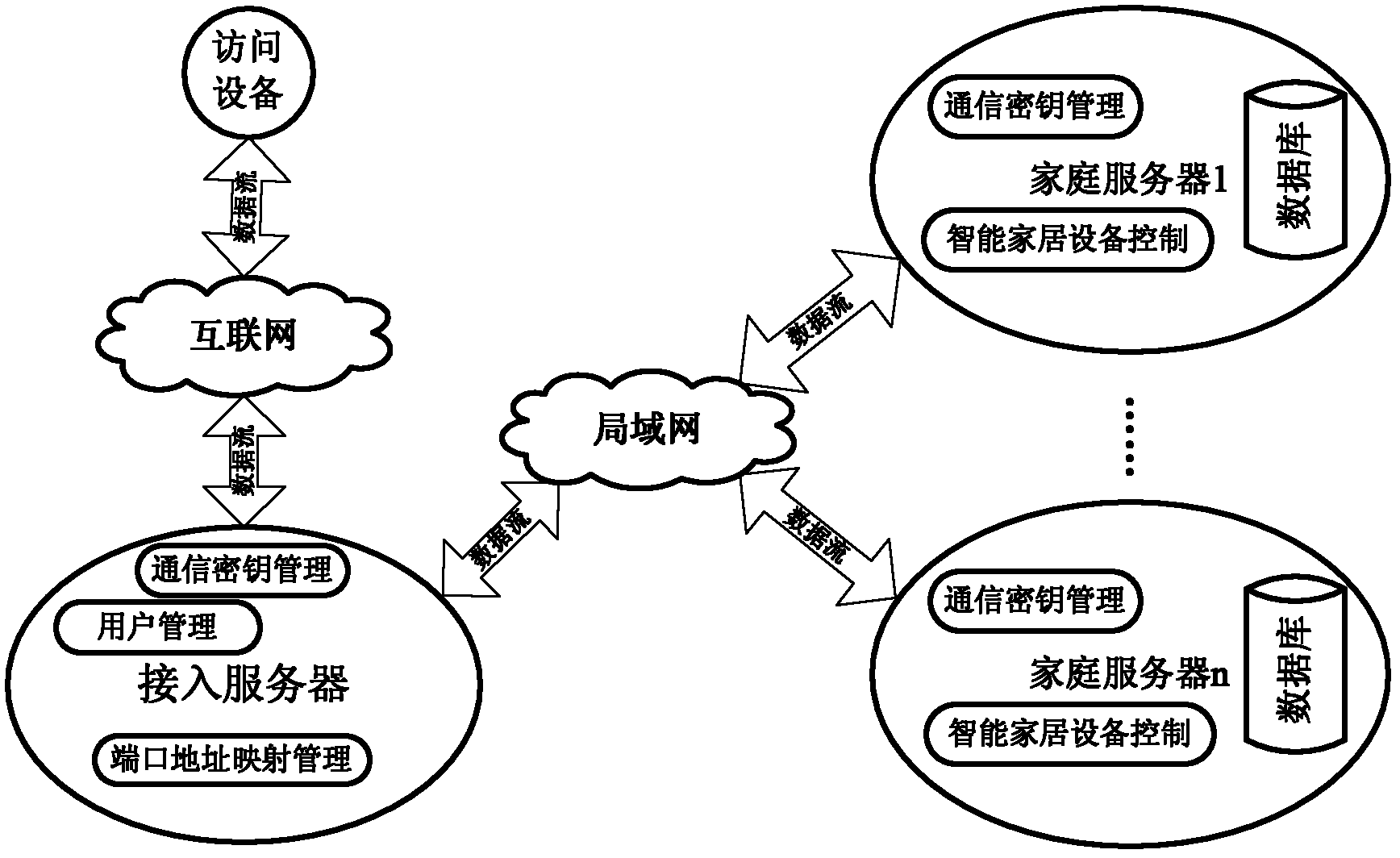
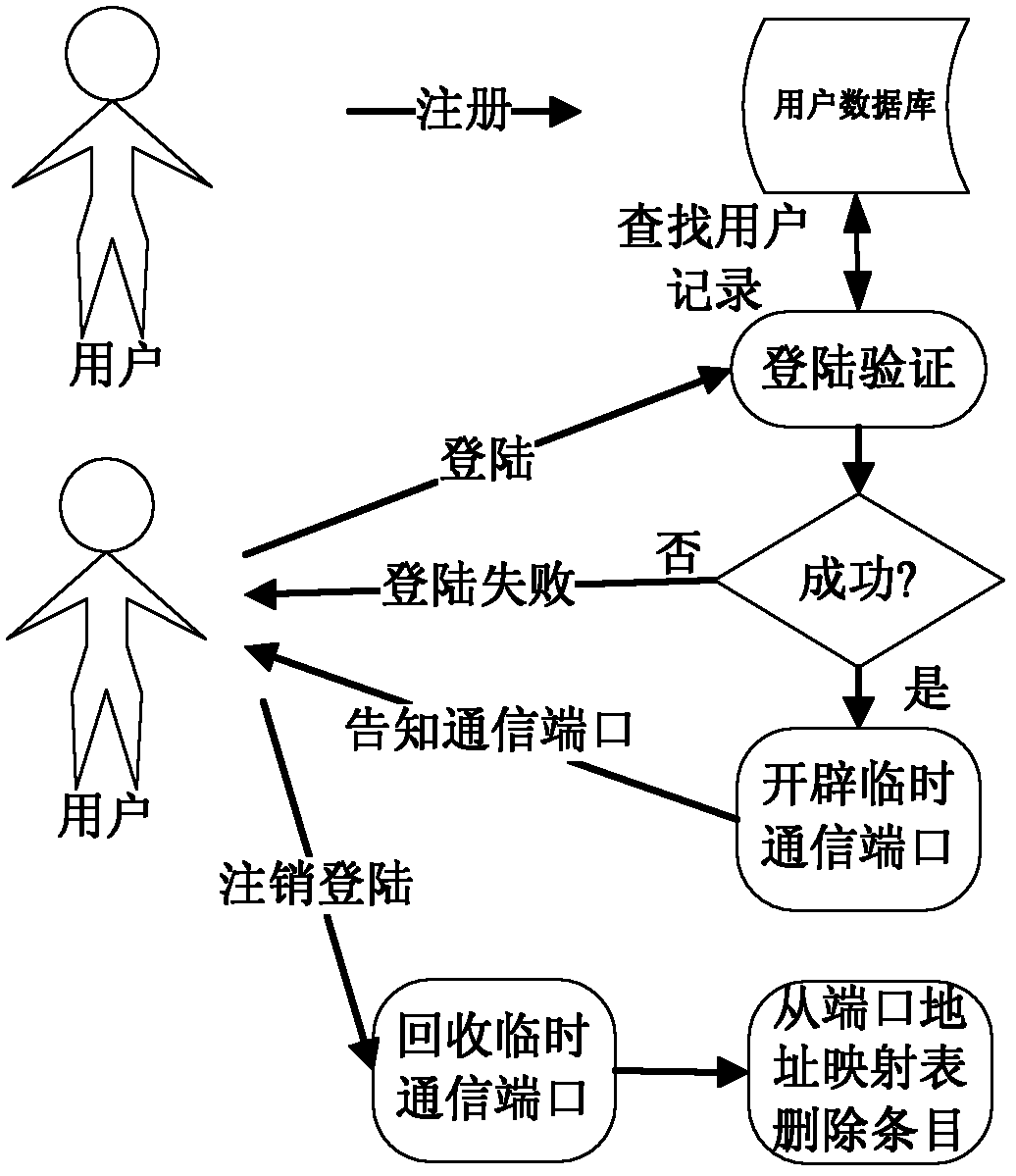
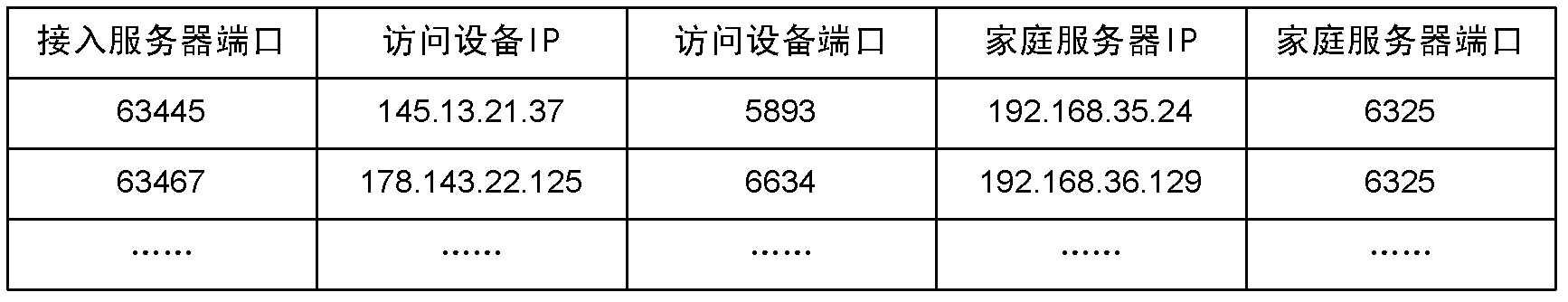
Trusted system for remote secure access of intelligent home
ActiveCN102594823AAvoid viewingPrevent tamperingKey distribution for secure communicationUser identity/authority verificationInternet privacyEngineering
The invention discloses a trusted system for remote secure access of intelligent home, which is designed into two parts, namely, 1, an address mapping part with login authentification, and 2, a communication key management part. According to the address mapping with login authentification, after a user logs in and accesses a server system, a mapping relation between a public network address and a LAN (local area network) address is established for the user; and according to the communication key management, a communication key for communication between an access device and a home server is consulted, and subsequent communication data is encrypted and decrypted by using the key, thereby ensuring that other people except the home server and the access device can not know the contents of the communication, and ensuring that after an access server as a middleman carries out malicious modification on communication data, the two communication parties can discover the malicious modification timely and then end up the communication. The system disclosed by the invention has high dependability to users and a property management company at which the access server is located. The system is suitable to be applied to the real scenes of intelligent home, thereby facilitating the social promotion of the intelligent home.
Owner:苏州普康智慧养老产业科技有限公司
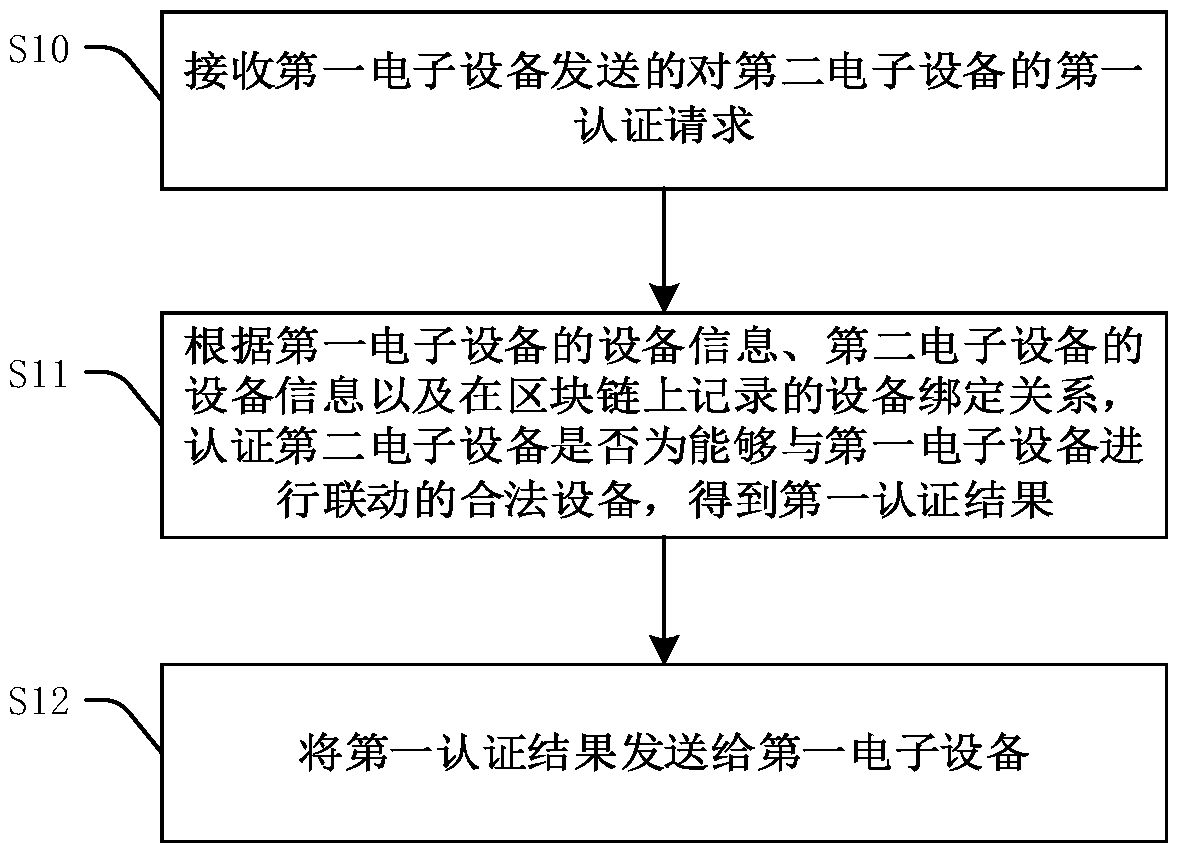
Authentication method, blockchain node and storage medium
The invention relates to the technical field of the Internet of Things, and provides an authentication method, a blockchain node and a storage medium. The authentication method is applied to the blockchain node, and specifically comprises the following steps: receiving a first authentication request sent by a first electronic device to a second electronic device, wherein the first authentication request carries the device information of the first electronic device and the device information of the second electronic device; authenticating, according to the first authentication request and a device binding relationship recorded on the blockchain, whether the second electronic device is a legal device capable of being linked with the first electronic device, and obtaining a first authentication result; and transmitting the first authentication result to the first electronic device, wherein the first authentication result is used to indicate whether the first electronic device authorizes the second electronic device to be linked with the first electronic device. The above method establishes a blockchain-based security trust system between electronic devices, which effectively protectsthe security of devices and IoT networks.
Owner:SICHUAN PANOVASIC TECH
Systems, methods, and apparatus for secure transactions in trusted systems
InactiveUS20080216172A1Accurate authenticationDigital data processing detailsUnauthorized memory use protectionTrusted systemChallenge response
Systems, methods, and software for protecting the identities of individuals, groups, and organizations are provided. In one embodiment, the systems, methods, and software provided by the present invention include a challenge-response architecture based upon entity-specific knowledge for verification of identity. In one aspect, a method for authenticating a first entity to at least one other entity includes creating an authenticator effective to authenticate said first entity to said at least one other entity; providing said authenticator or a substantially secure derivative thereof to an intermediary authentication service configured to interrogate said first entity; receiving a response to an identity interrogation from said first entity at said intermediary; and comparing at said intermediary the content of said response, or a derivative of said content, to said authenticator or said substantially secure derivative thereof to generate an estimation as to whether said first entity is authentic at said intermediary.
Owner:DIALSAFE
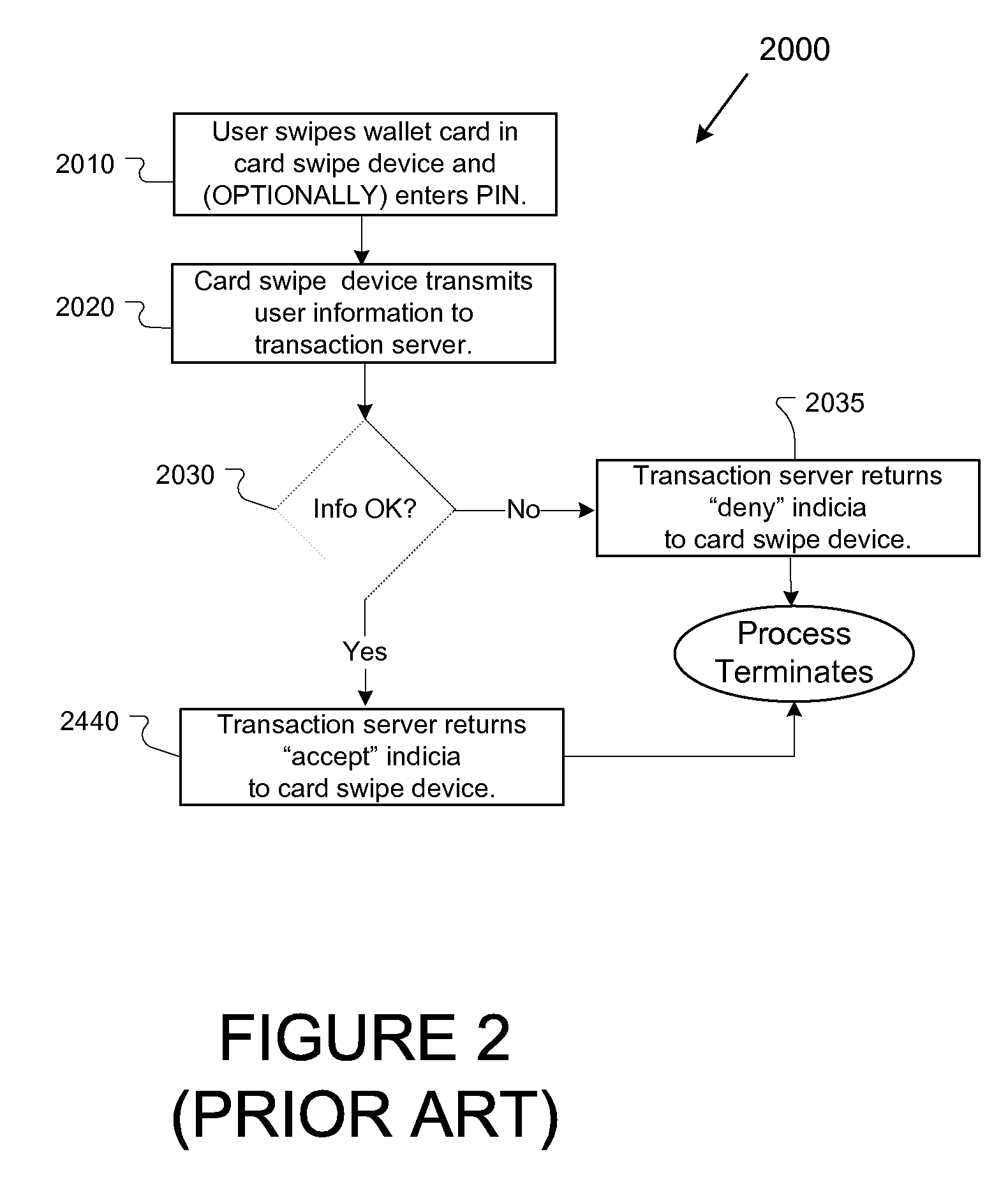
Trusted system
ActiveUS7275160B2Increase credibilityIncreased trust and confidenceFinanceUser identity/authority verificationTrusted systemElectronic systems
A method for allowing a financial transaction to be performed using a electronic system, the method comprising interrogating an electronic transaction terminal with an electronic security device to obtain an integrity metric for the electronic financial transaction terminal; determining if the transaction terminal is a trusted terminal based upon the integrity metric; allowing financial transaction data to be input into the transaction terminal if the transaction terminal is identified as a trusted terminal.
Owner:HEWLETT PACKARD DEV CO LP
Hardware trust anchors in SP-enabled processors
ActiveUS9317708B2Key distribution for secure communicationUser identity/authority verificationOperational systemConfidentiality
A trust system and method is disclosed for use in computing devices, particularly portable devices, in which a central Authority shares secrets and sensitive data with users of the respective devices. The central Authority maintains control over how and when shared secrets and data are used. In one embodiment, the secrets and data are protected by hardware-rooted encryption and cryptographic hashing, and can be stored securely in untrusted storage. The problem of transient trust and revocation of data is reduced to that of secure key management and keeping a runtime check of the integrity of the secure storage areas containing these keys (and other secrets). These hardware-protected keys and other secrets can further protect the confidentiality and / or integrity of any amount of other information of arbitrary size (e.g., files, programs, data) by the use of strong encryption and / or keyed-hashing, respectively. In addition to secrets the Authority owns, the system provides access to third party secrets from the computing devices. In one embodiment, the hardware-rooted encryption and hashing each use a single hardware register fabricated as part of the computing device's processor or System-on-Chip (SoC) and protected from external probing. The secret data is protected while in the device even during operating system malfunctions and becomes non-accessible from storage according to various rules, one of the rules being the passage of a certain time period. The use of the keys (or other secrets) can be bound to security policies that cannot be separated from the keys (or other secrets). The Authority is also able to establish remote trust and secure communications to the devices after deployment in the field using a special tamper-resistant hardware register in the device, to enable, disable or update the keys or secrets stored securely by the device.
Owner:THE TRUSTEES FOR PRINCETON UNIV +1
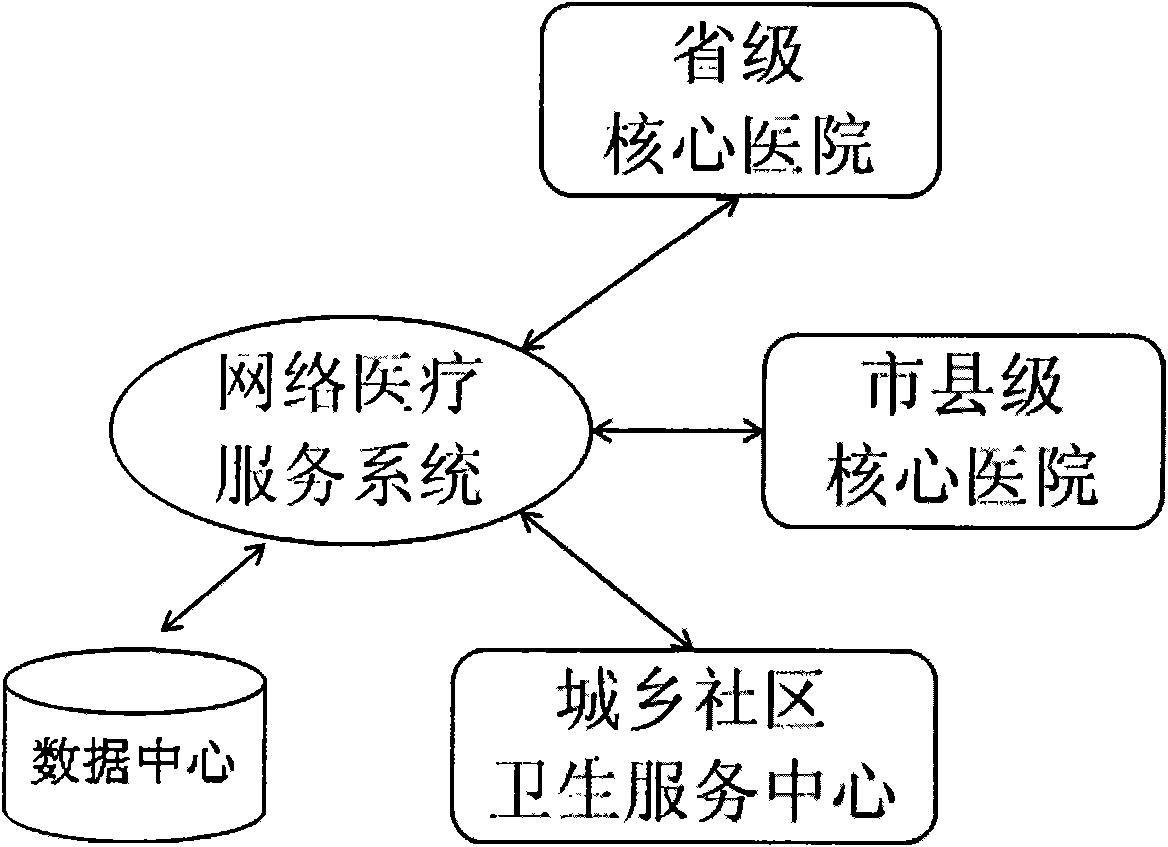
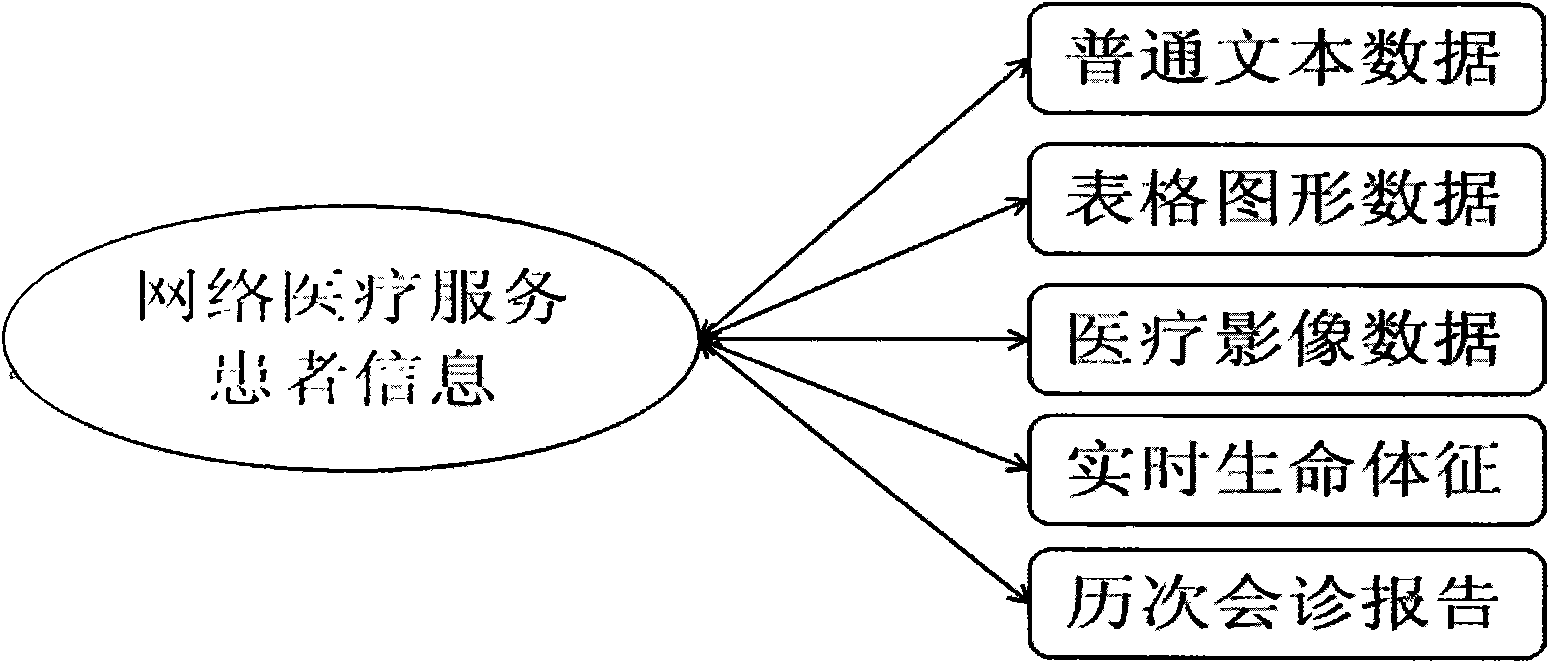
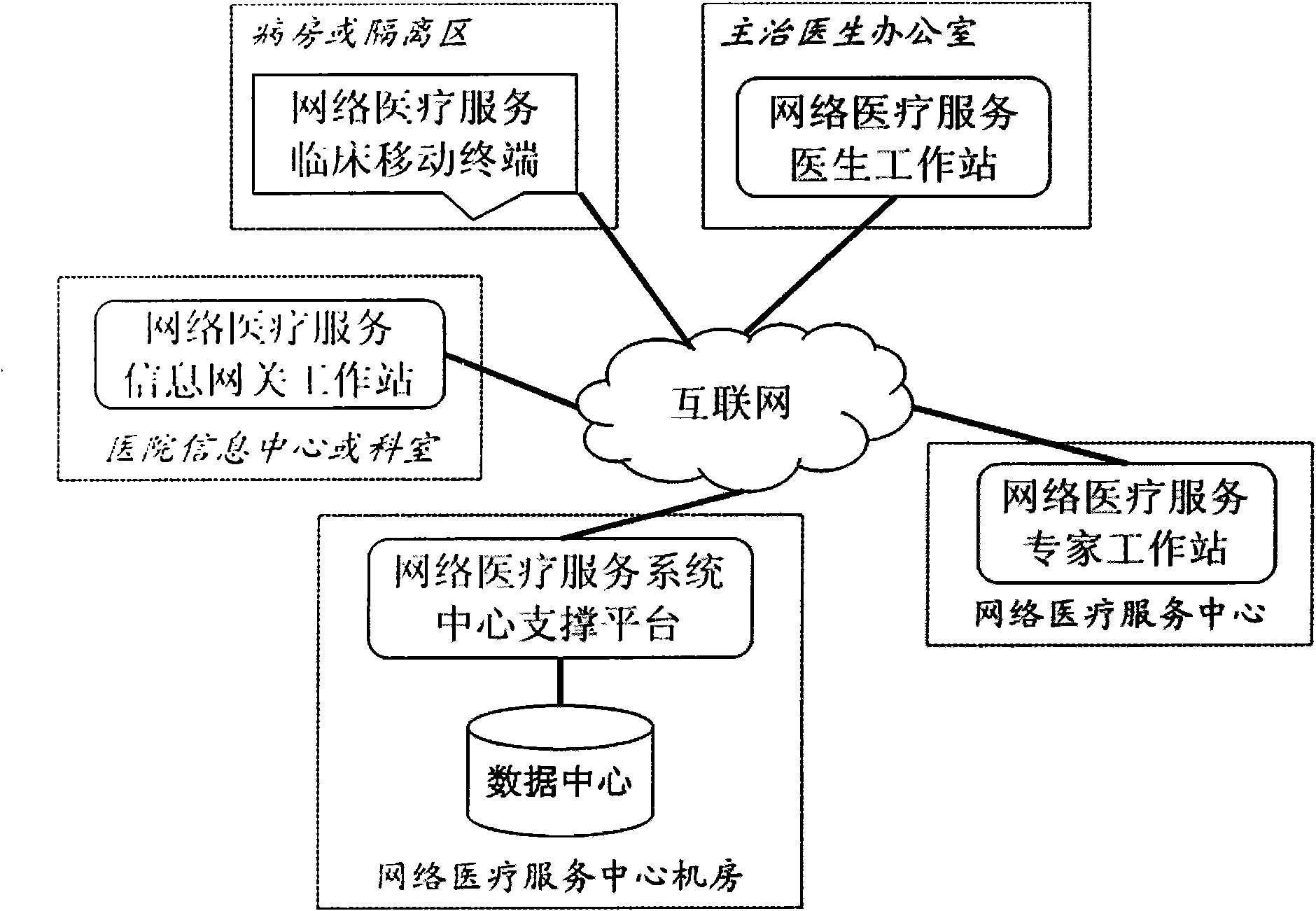
Multi-point interactive network medical service system
InactiveCN101655887AComprehensive diagnosis basisBasis for accurate diagnosisSpecial data processing applicationsData centerVideo record
The invention relates to a multi-point interactive network medical service system, which is characterized by taking the internet as a main communication mode, adopting streaming media and network communication technology, integrating real-time audio and video and data of various medical information platforms and apparatuses, and realizing the network-based interactive medical service cooperation between various stages of medical mechanisms. The multi-point interactive network medical service system has the advantages of acquiring all information on clinical diagnosis and real-time dynamic vital signs of a patient at a remote terminal through technology for integrating the various medical information platforms and apparatus, constructing a network trust system through uniform identify authentication and information security assurance technology, accessing all previous data, reports and process video records of the network medical service of the patient, performing further data mining and intelligent analysis on the data of the patient by constructing a data centre, and realizing audio video interaction-based diversified interactive network medical service integrated with clinic, teaching and research of remote intensive consultation, remote intensive care, remote outpatient consultation, two-way referral, teaching ward round, academic discussion, continuation education, cooperative research and the like.
Owner:杭州邦泰科技有限公司
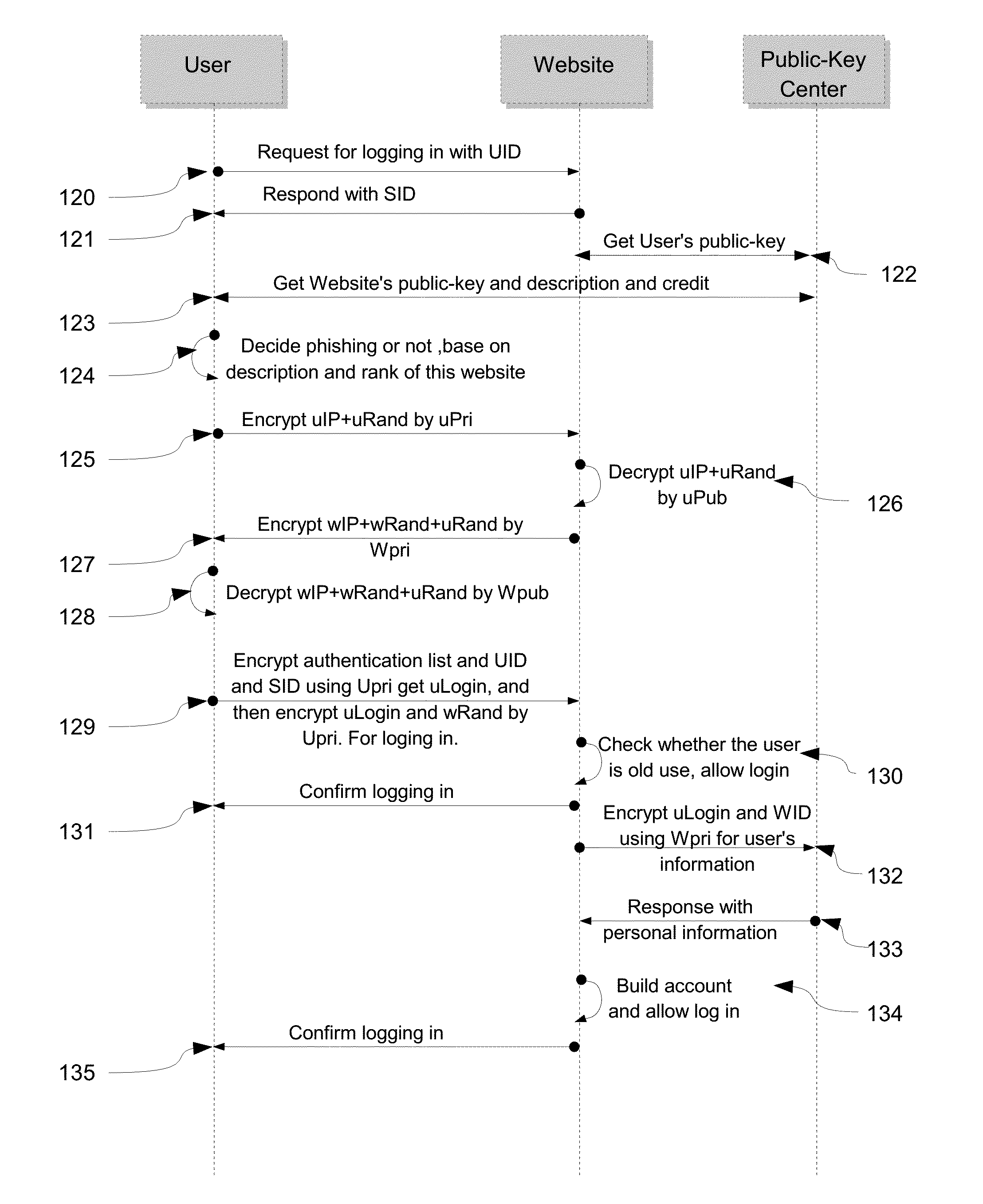
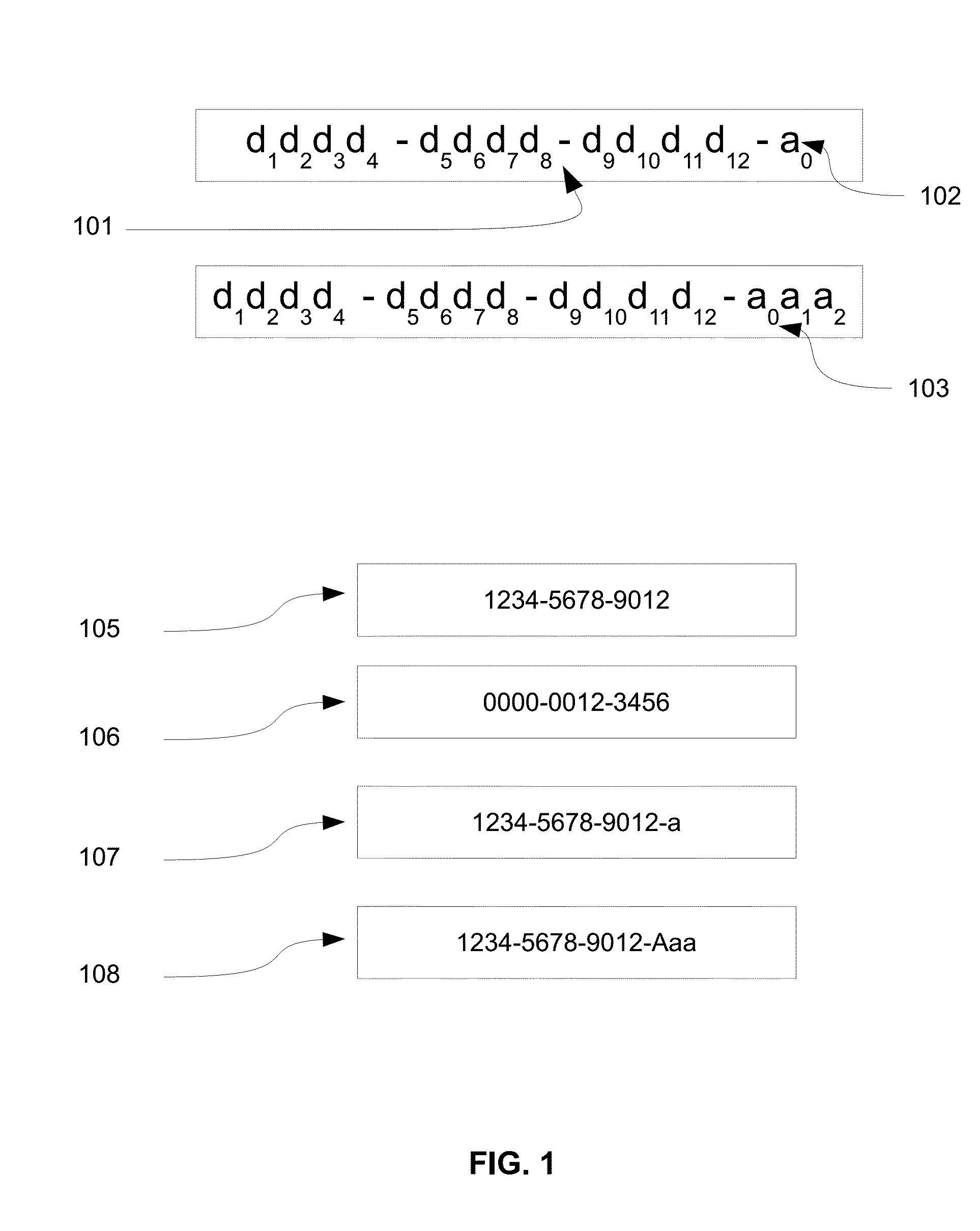
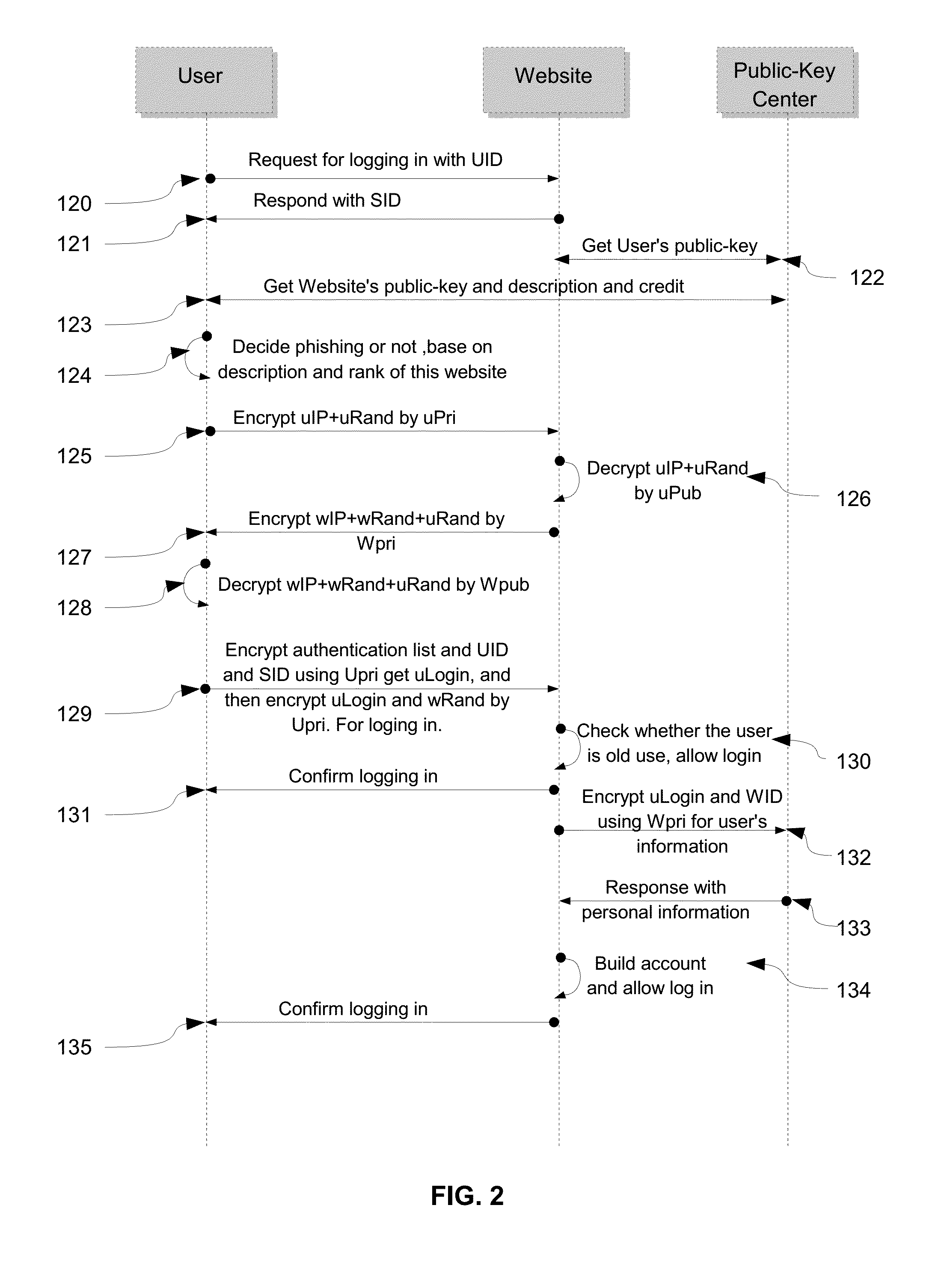
Secure way to build internet credit system and protect private information
InactiveUS20160192194A1Simple wayProtect their moneyUser identity/authority verificationSecurity arrangementCredit systemWeb site
A method includes building trust system among internet users, signing up in websites without password and protecting personal data in mobile device. Global Unique Identifier (GUID) is used to identify and accumulate internet credit for users and websites. First, user applies for GUID together with asymmetric-key, then the internet credit of this GUID can be accumulated based on transactions. Also, user can sign on or log in websites via GUID without using password and user name. In addition, dual data encryption and unpredictable random number is presented to anti-surveillance of communication. The personal information in mobile device are protected by asymmetric-key pairs and destroyed automatically after being stolen and mobile device's device-ID is used to chasing the stolen devices. In summary, the present invention is a securer way to build a trust system among internet users and protect data in mobile device.
Owner:YANG GONGMING
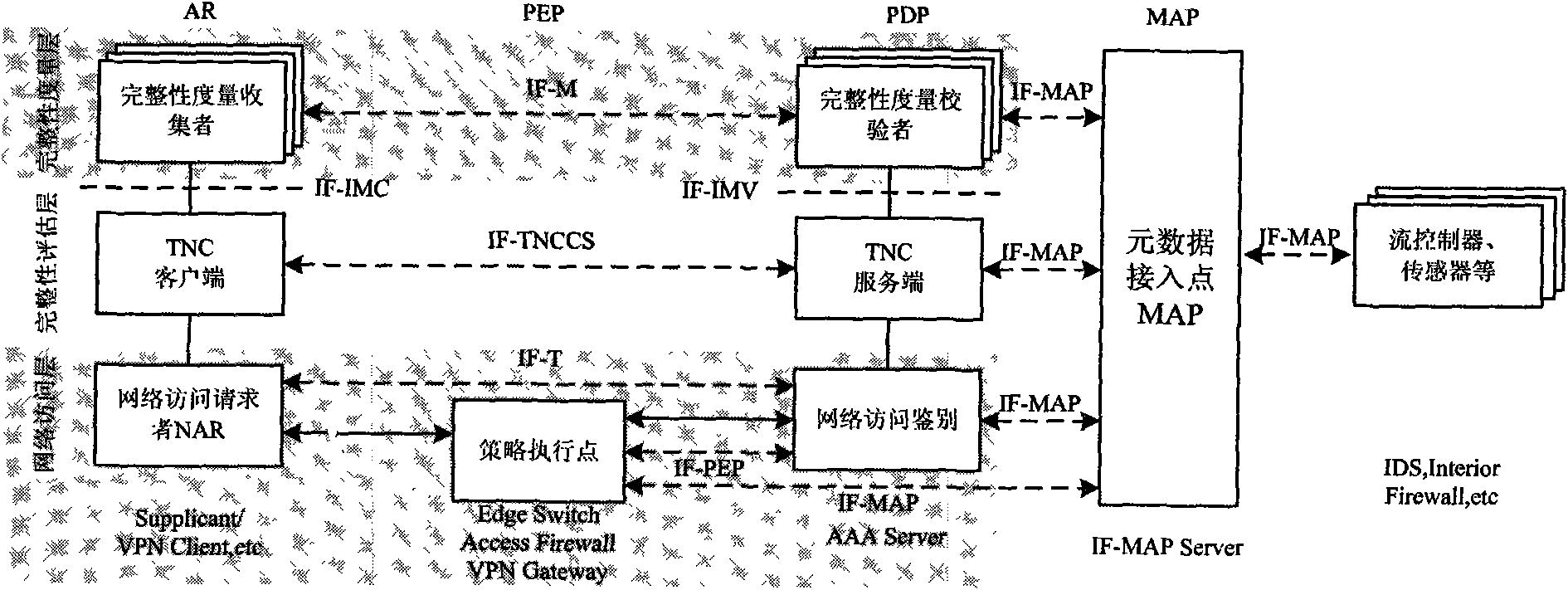
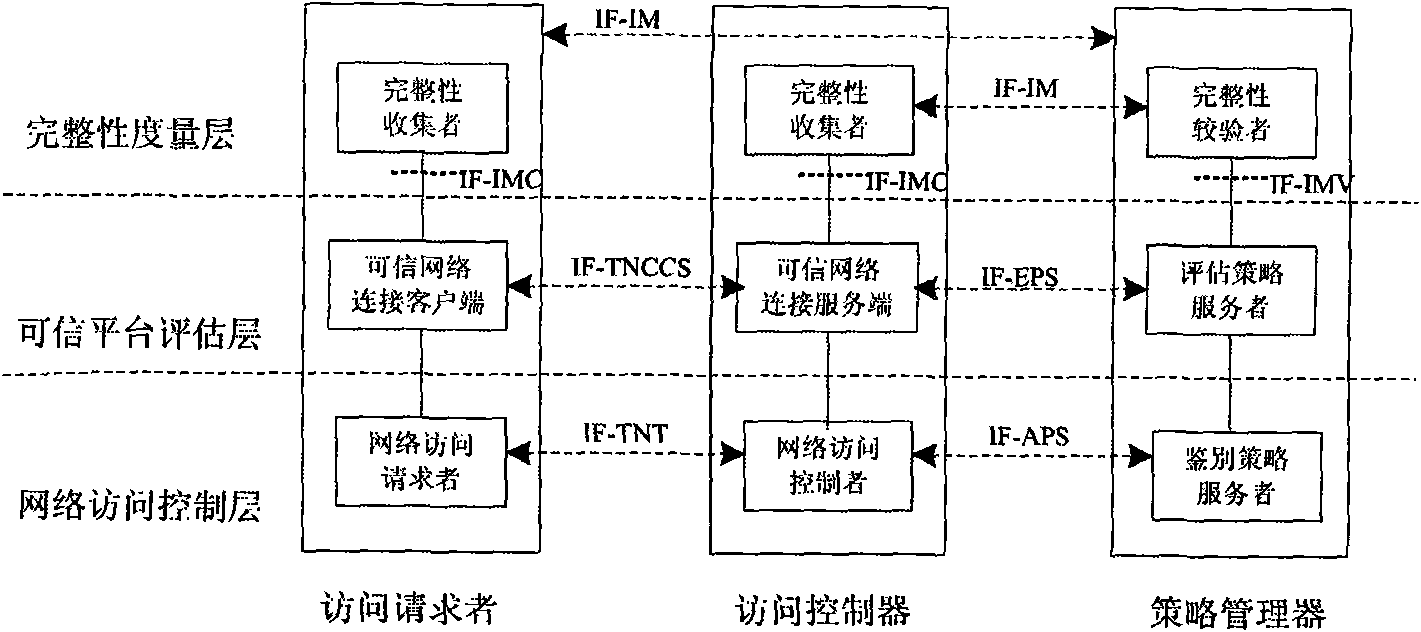
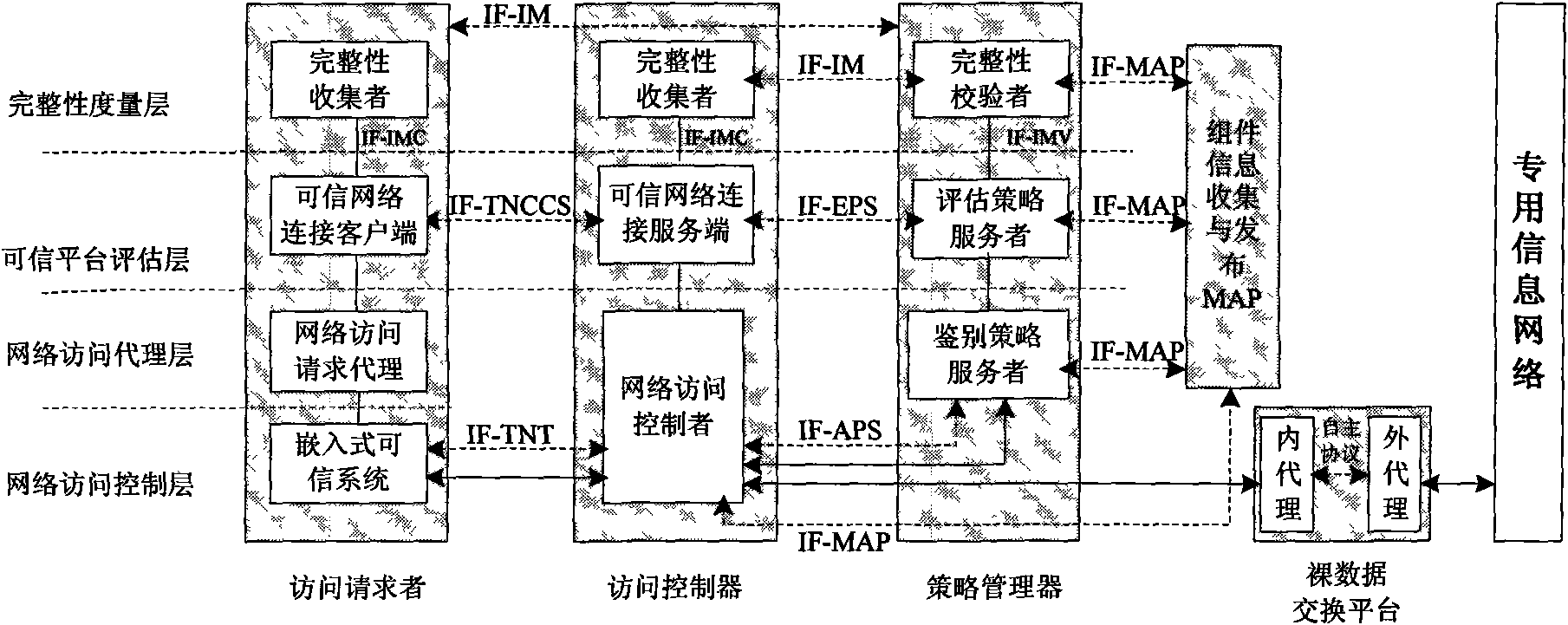
Architecture accessing trusted network for tolerating untrusted components and access method thereof
ActiveCN101778099AWork around the lack of TPM module supportWill not cause substantial security damageTransmissionSecurity arrangementOperational systemAccess method
The invention relates to a network connection method, in particular to architecture for trusted network connection of a terminal with TPM function and a computer network, and an access method thereof. The architecture consists of five parts, namely a trusted terminal for tolerating untrusted components, a trusted access gateway, an authentication policy management server, a component information collecting and publishing node MAP and a secure data exchange platform; an embedded trusted system layer additionally arranged in the trusted terminal is an independent and integral system on chip SOC, and is not influenced or controlled by an upper-layer operating system, so that the architecture has better realizability; the trusted access gateway and the trusted terminal adopt bidirectional nonequivalent trusted evaluation; and a data exchange platform is arranged additionally between the trusted terminal and the trusted access gateway, and can only realize data exchange with uniform format and transparent structure at raw data level so as to prevent protocol defect-based attacks; therefore, the invention provides a higher security protection mechanism for protecting the network.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Federated digital rights management scheme including trusted systems
ActiveUS7515710B2Digital data processing detailsUser identity/authority verificationDigital rights managementBiological activation
Federated systems for issuing playback certifications granting access to technically protected content are described. One embodiment of the system includes a registration server connected to a network, a content server connected to the network and to a trusted system, a first device including a non-volatile memory that is connected to the network and a second device including a non-volatile memory that is connected to the network. In addition, the registration server is configured to provide the first device with a first set of activation information in a first format, the first device is configured to store the first set of activation information in non-volatile memory, the registration server is configured to provide the second device with a second set of activation information in a second format, and the second device is configured to store the second set of activation information in non-volatile memory.
Owner:DIVX INC
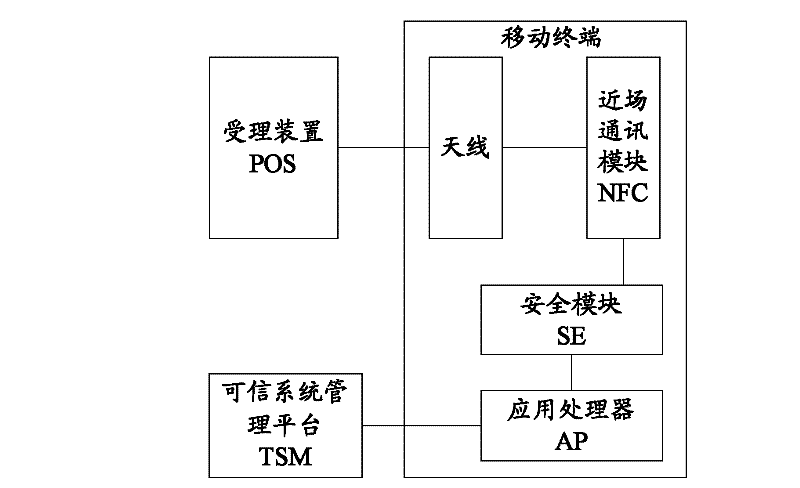
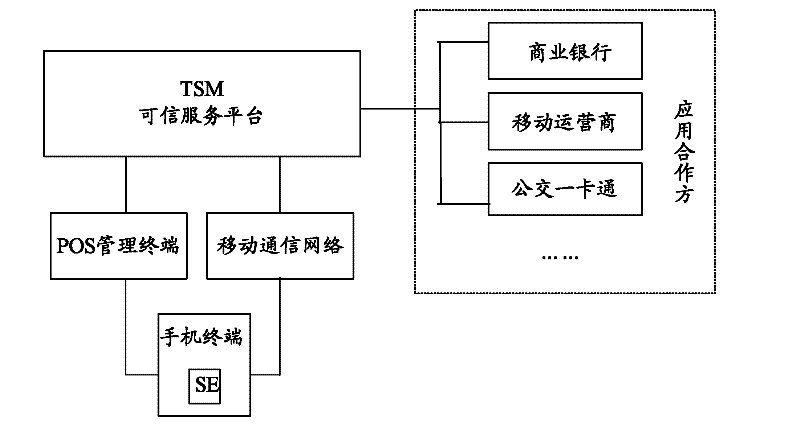
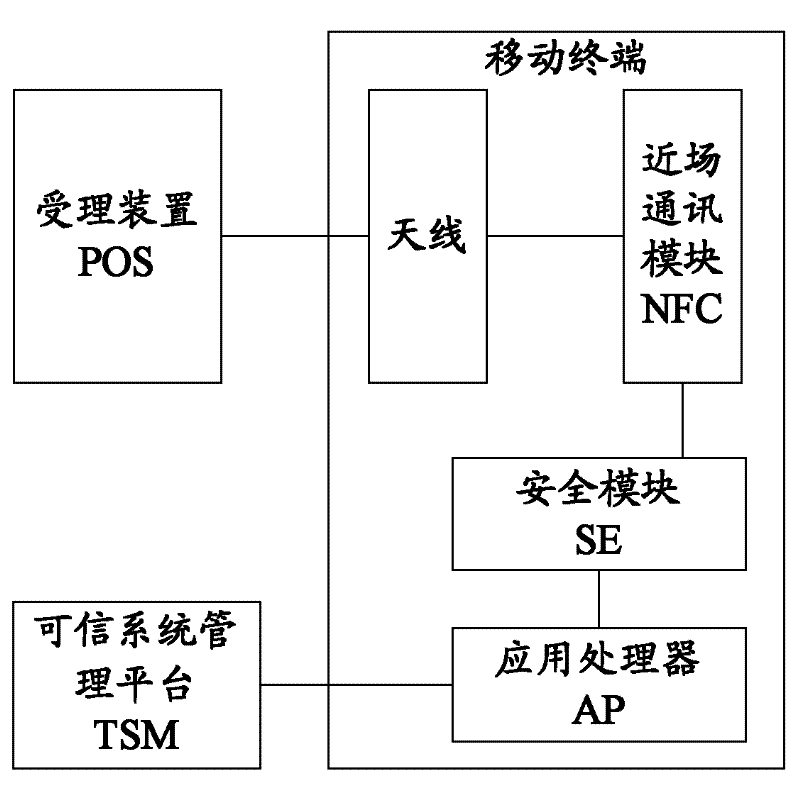
Mobile terminal
The invention provides a mobile terminal which comprises an application processor, a security module, a near field communication (NFC) chip and an antenna, wherein the application processor is used for downloading application information of various near field payment services from a trusted system manager (TSM) and storing the downloaded application information into the security module, the security module is used for completing a pavement procedure together with a handling device after receiving external trigger and starting a corresponding application, the antenna is used for forwarding signals between the near filed communication chip and the handling device, and the near field communication chip is used for receiving a radio frequency signal from the handling device, demodulating the received radio frequency signal and forwarding the demodulated command to the security module, as well as modulating a command response returned by the security module and forwarding the modulated signal to the handling device.
Owner:DATANG MICROELECTRONICS TECH CO LTD
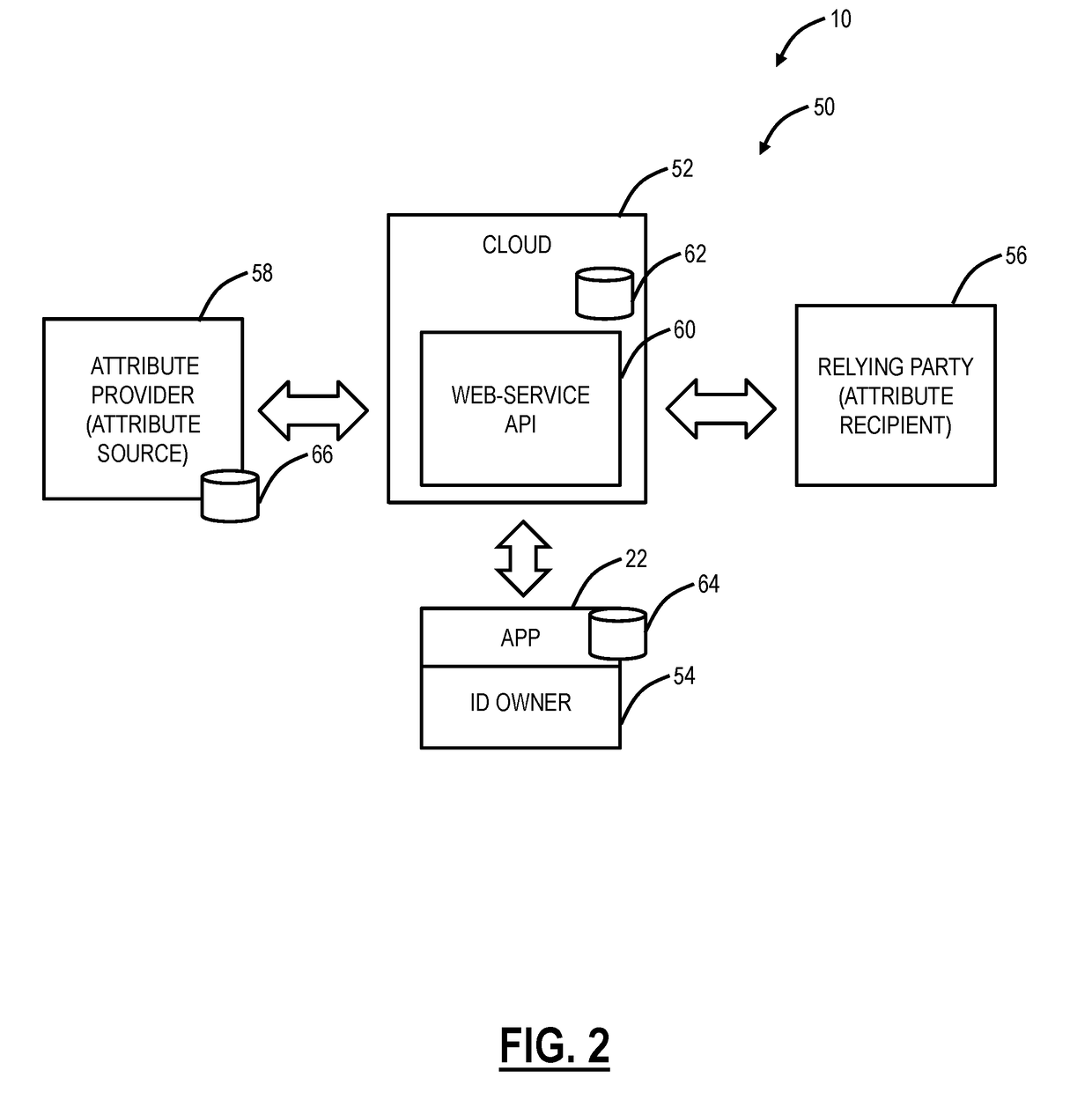
Identity binding systems and methods in a personal data store in an online trust system
ActiveUS20170237717A1Key distribution for secure communicationUser identity/authority verificationInternet privacyTrusted system
A computer-implemented method for managing a personal data store is described for binding one or more identities of different types associated with a user. The computer-implemented method is implemented in a trust system including one or more processing devices communicatively coupled to a network. The computer-implemented method includes receiving one or more self-asserted first attributes by the user and second attributes asserted by an Attribute Provider; utilizing one or more of the first attributes and the second attributes as inputs to obtain and / or produce one or more cryptographically signed attributes signed by an associated Attribute Provider; storing the first attributes, the second attributes, and the one or more cryptographically signed attributes in a personal data store associated with the user; and utilizing one or more of the first attributes, the second attributes, and the one or more cryptographically signed attributes to respond to a request from a Relying Party.
Owner:EVIDENT ID INC
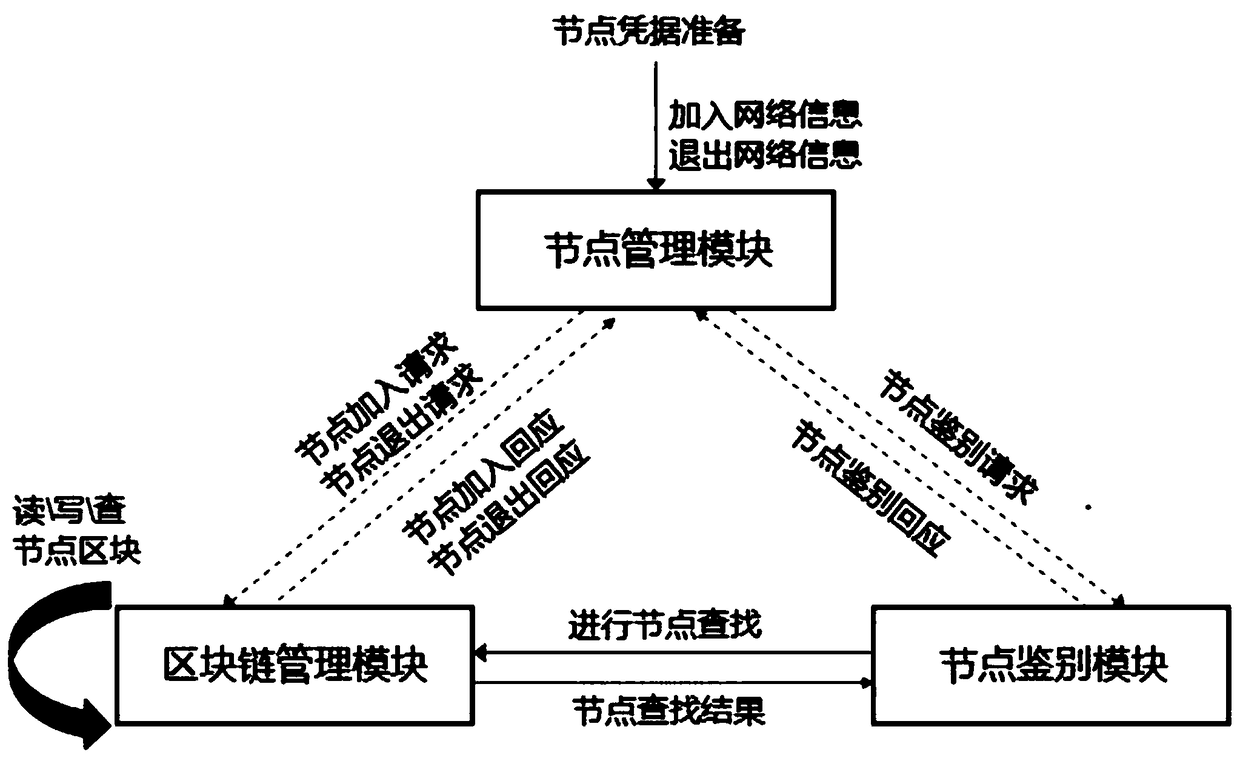
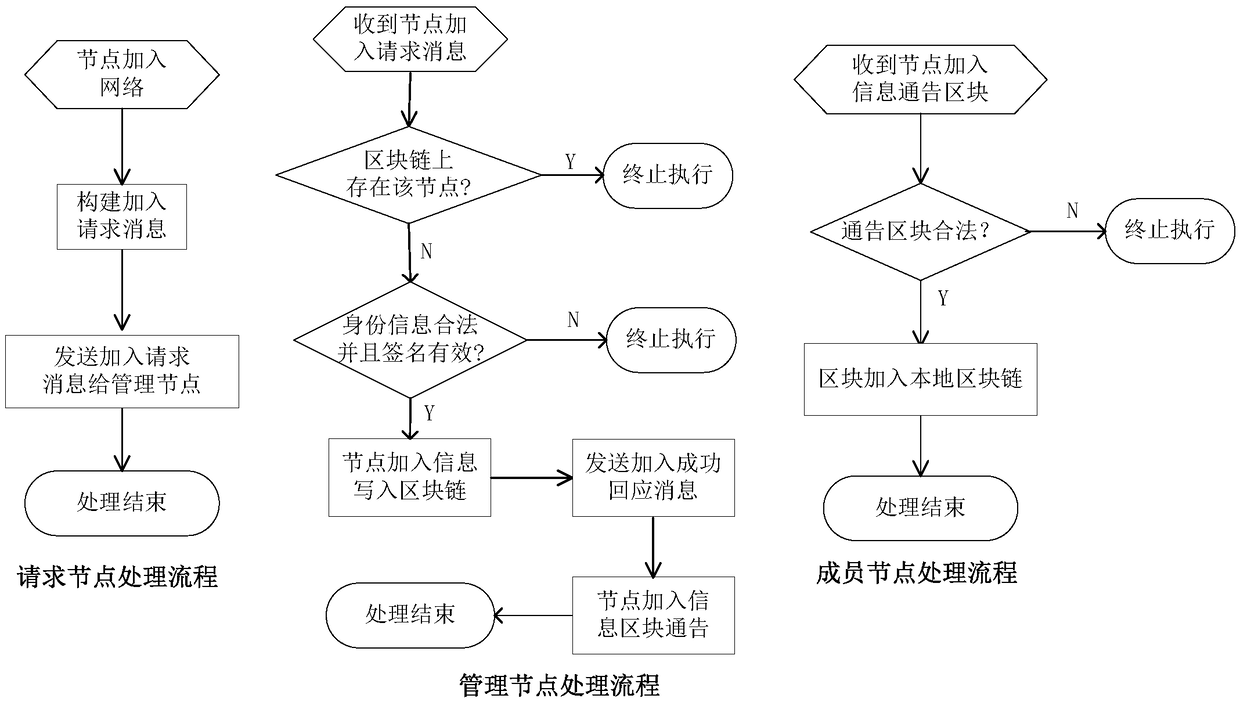
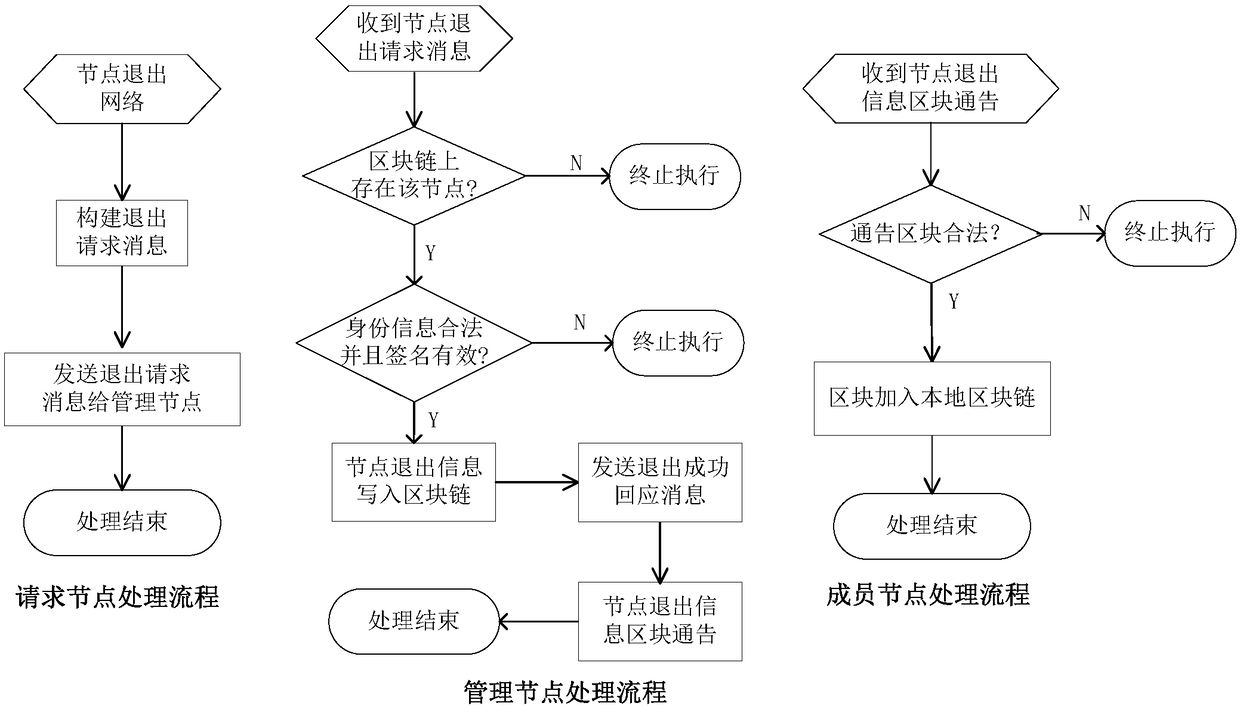
System and method for constructing trusted node network
ActiveCN109104415AImprove flexibilityIncrease elasticityUser identity/authority verificationTrusted systemNode authentication
The invention relates to a system for constructing a trusted node network. The system comprises a block chain management module, a node management module and a node identification module. Block chainmanagement module is responsible for the management of node member information on the block chain, that is, read, write, look up the node information of the block chain, as well as the read and writeprivileges management of the node block chain; the node management module is responsible for the joining and exiting of the node members on the block chain and the information management of the node network members. The node authentication module is responsible for authenticating the trustworthiness of other nodes on the block chain communicating with the node. The technical scheme is a decentralized trust system and peer-to-peer identity authentication mechanism based on block chain and public key technology, which is used to construct a trusted and controlled node network, and solve the security problems of single point failure, DoS attack, forgery and tampering in the centralized mechanism. There is no centralized trust and authority center in the technical scheme. What the new technical scheme establishes is a decentralized, distributed trust system and admittance mechanism maintained by the network node group.
Owner:JIANGSU FEIBO SOFTWARE TECH
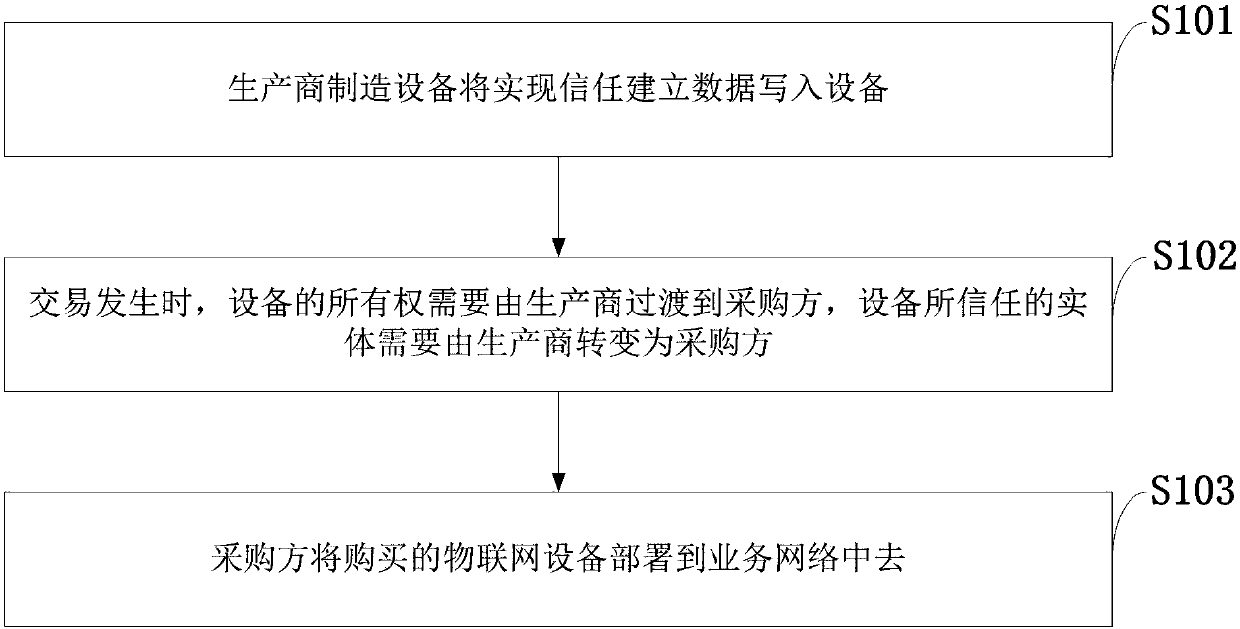
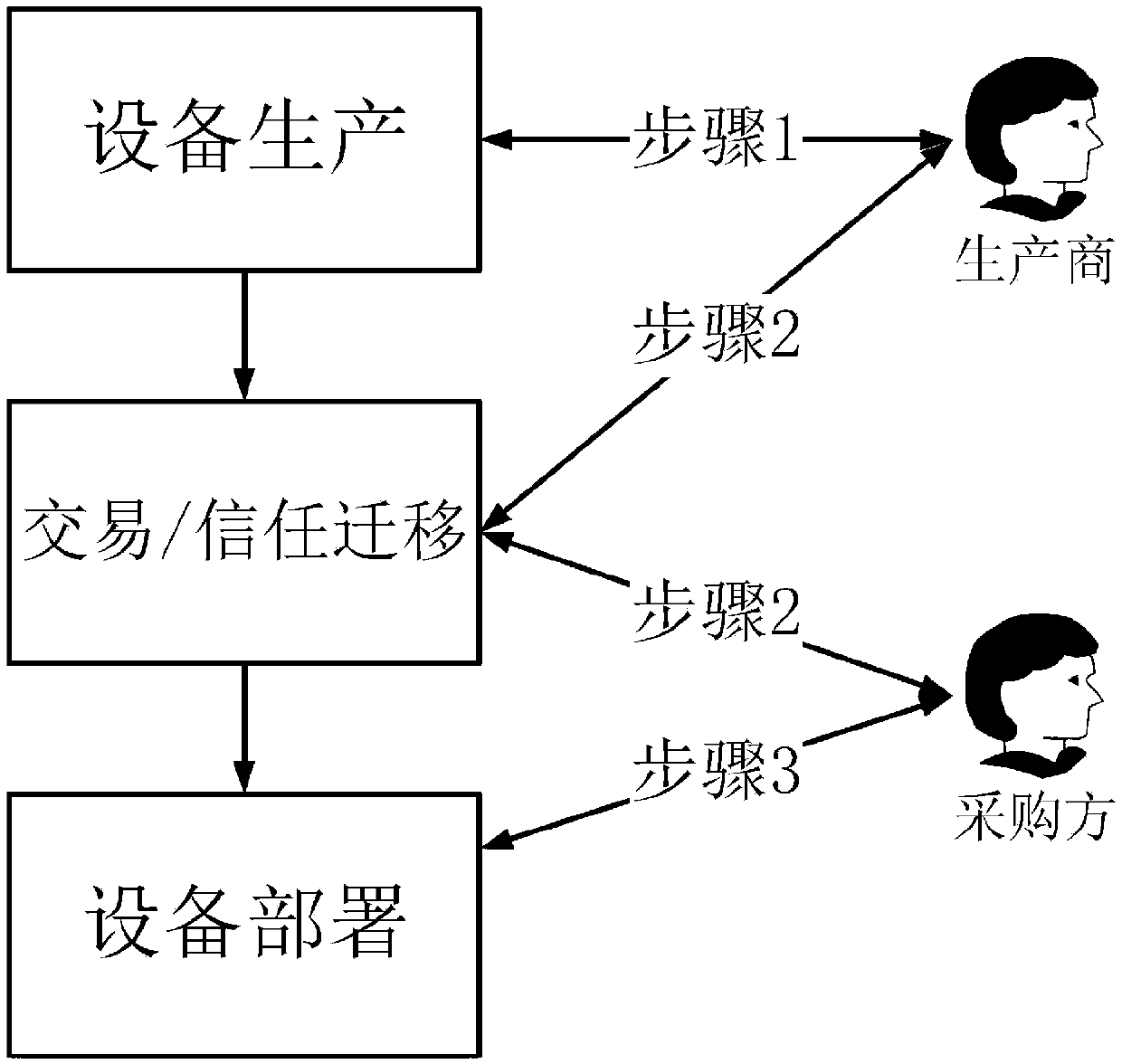
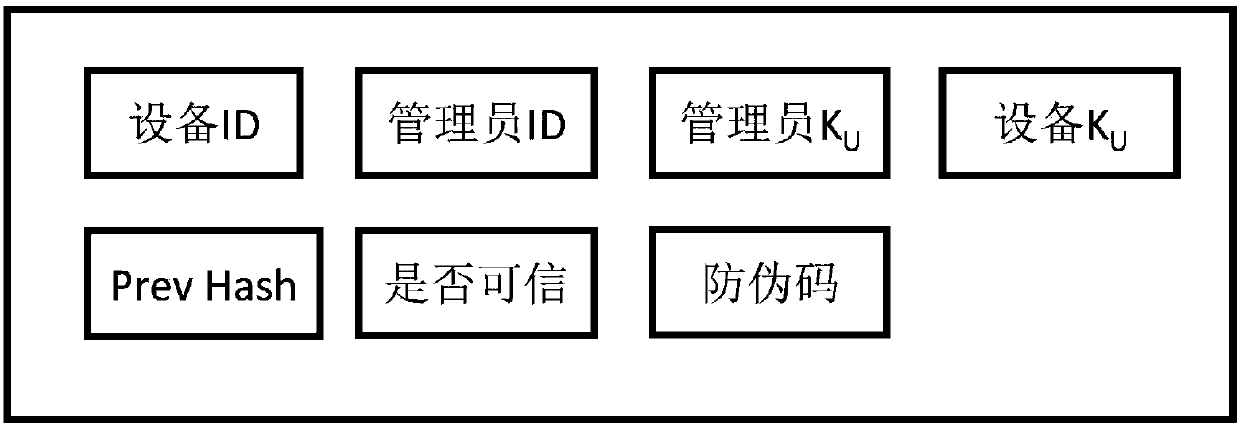
Internet of things device supply chain trust system management method, computer program, computer
ActiveCN107895111AIncrease flexibilityLess communication interactionDigital data authenticationTransmissionSecure communicationThe Internet
The invention belongs to the technical field of internet of things, block-chain and cyberspace security, and discloses a internet of things device supply chain trust system management method, a computer program and a computer. The production phase of an internet of things device, wherein internet of things device manufacturers interact with internet of things devices to write necessary informationinto the internet of things devices; internet of things device transaction phase, wherein the transfer of trust relationships between the internet of things devices and different internet of things device owners is completed; and internet of things device deployment phase, wherein the internet of things device owners deploy the internet of things devices to business networks. The method providessupports for secure communications between the internet of things devices; when the block-chain occupies a large storage space, a server relaxes the capacity of the block-chain in the internet of things device networks; the method achieves the identity authentication between an administrator and a plurality of internet of things devices, achieves the mutual trust between the internet of things devices, and supports a plurality of administrators to manage different internet of things devices; and the computing and storage costs of the internet of things devices are relatively low.
Owner:XIDIAN UNIV
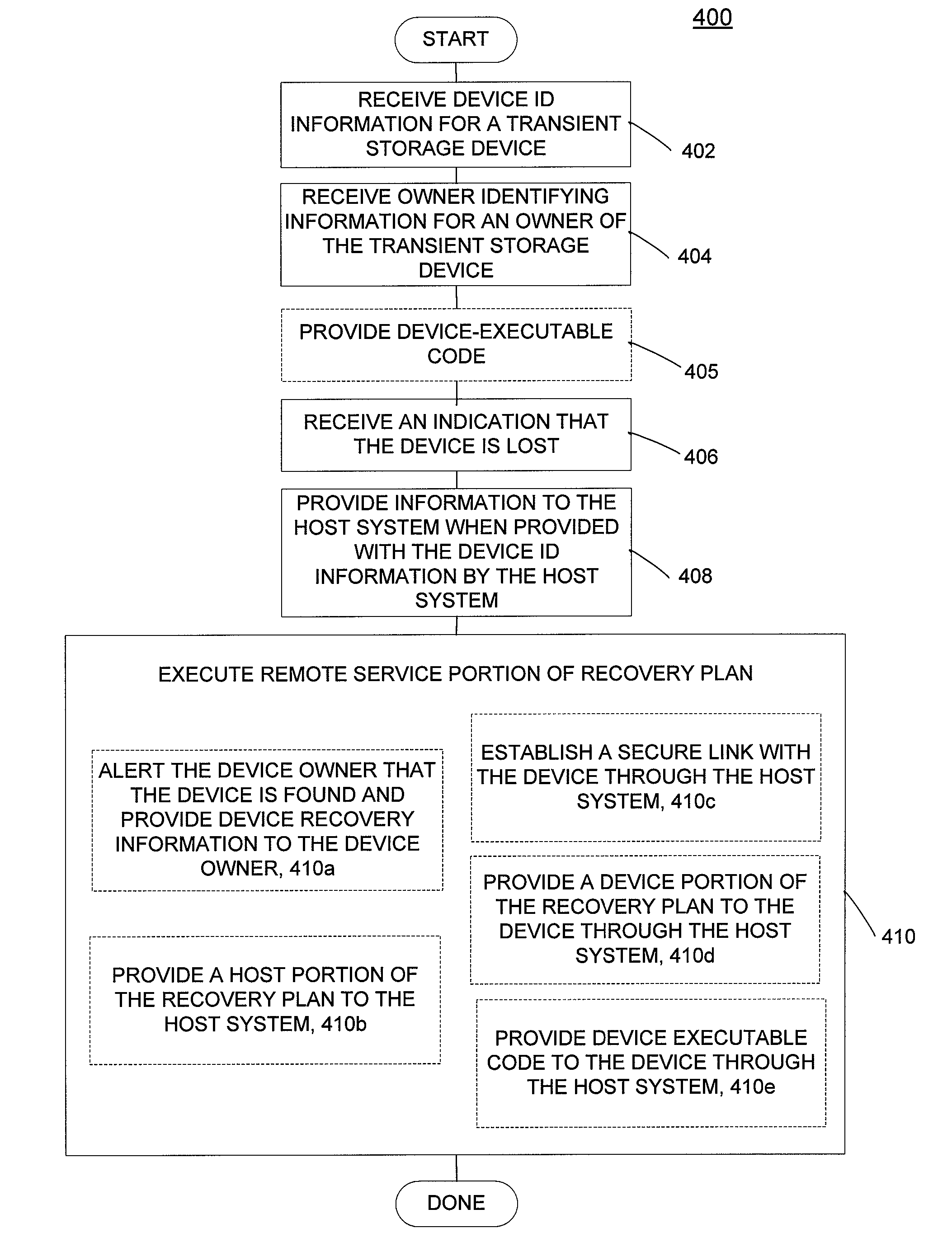
Systems for finding a lost transient storage device
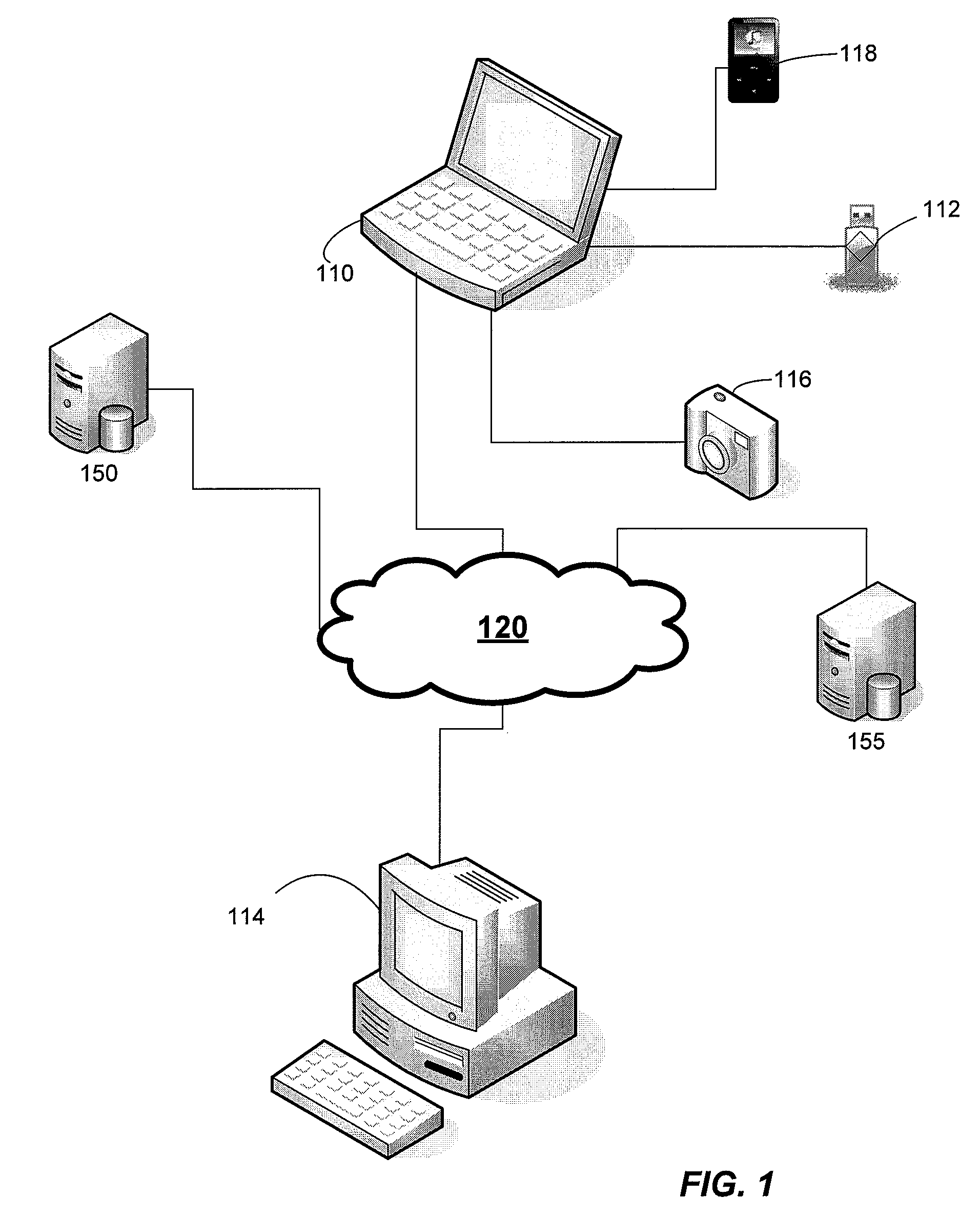
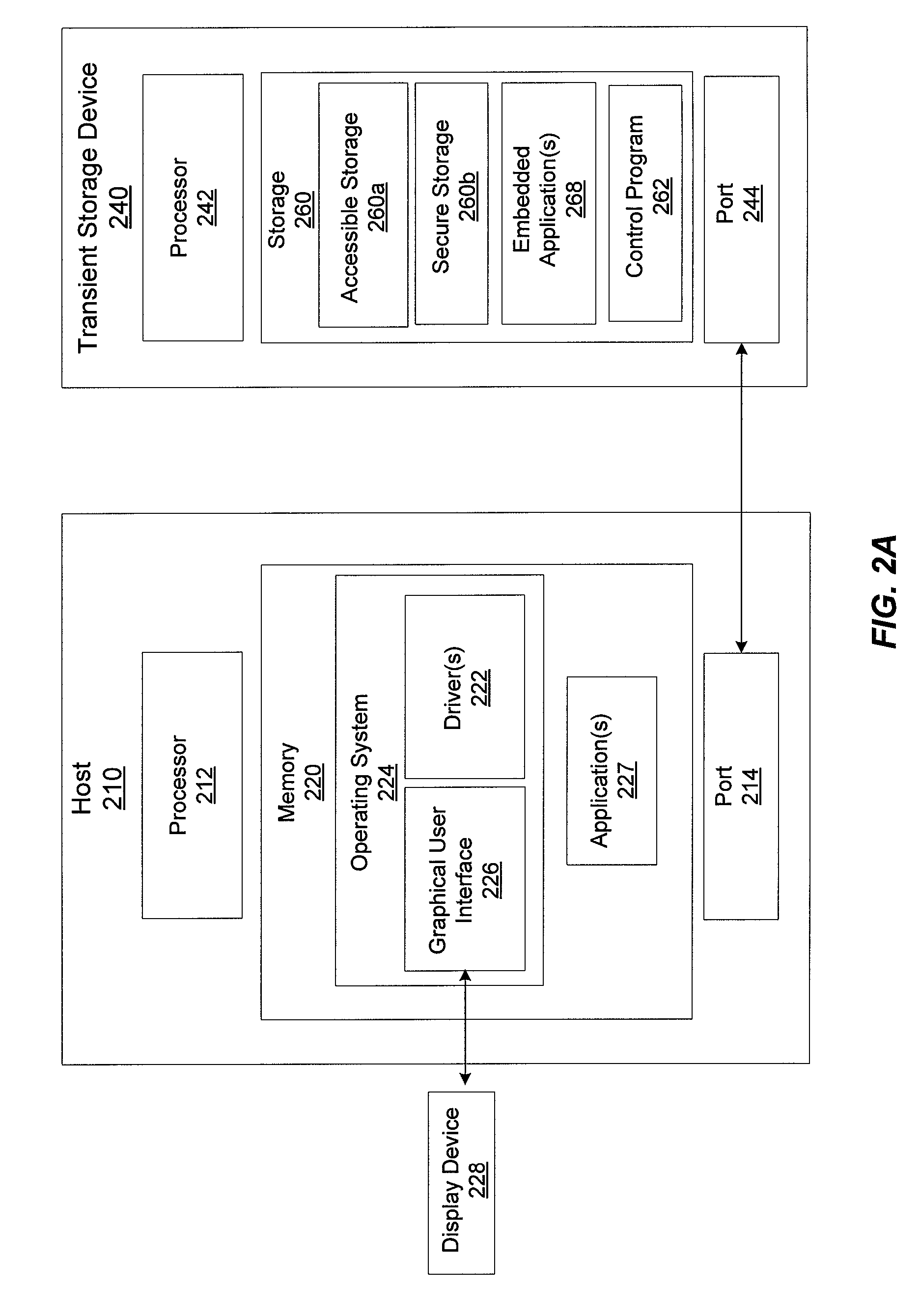
ActiveUS20090228991A1Volume/mass flow measurementPower supply for data processingProgram planningInformation device
Processes for identifying and recovering a lost transient storage device are provided. In some processes, information regarding the owner of the device is obtained. The device ownership information may be stored on a remote service with which the device is registered and / or may be stored on the device itself. In one process, the remote service provides the device with customized device-executable code when the device is registered. The device may also contain information regarding trusted systems. The process includes obtaining status information indicating whether a device is lost when the device is connected to a host system. In some processes, the status is determined by a remote service. In other processes, the status is determined by the device. If the device is lost then a device recovery plan is executed. Portions of a device recovery plan may be executed on the remote service, the host system, and / or the device.
Owner:MICROSOFT TECH LICENSING LLC
Security terminal reinforcing model and reinforcing method of tolerable non-trusted component
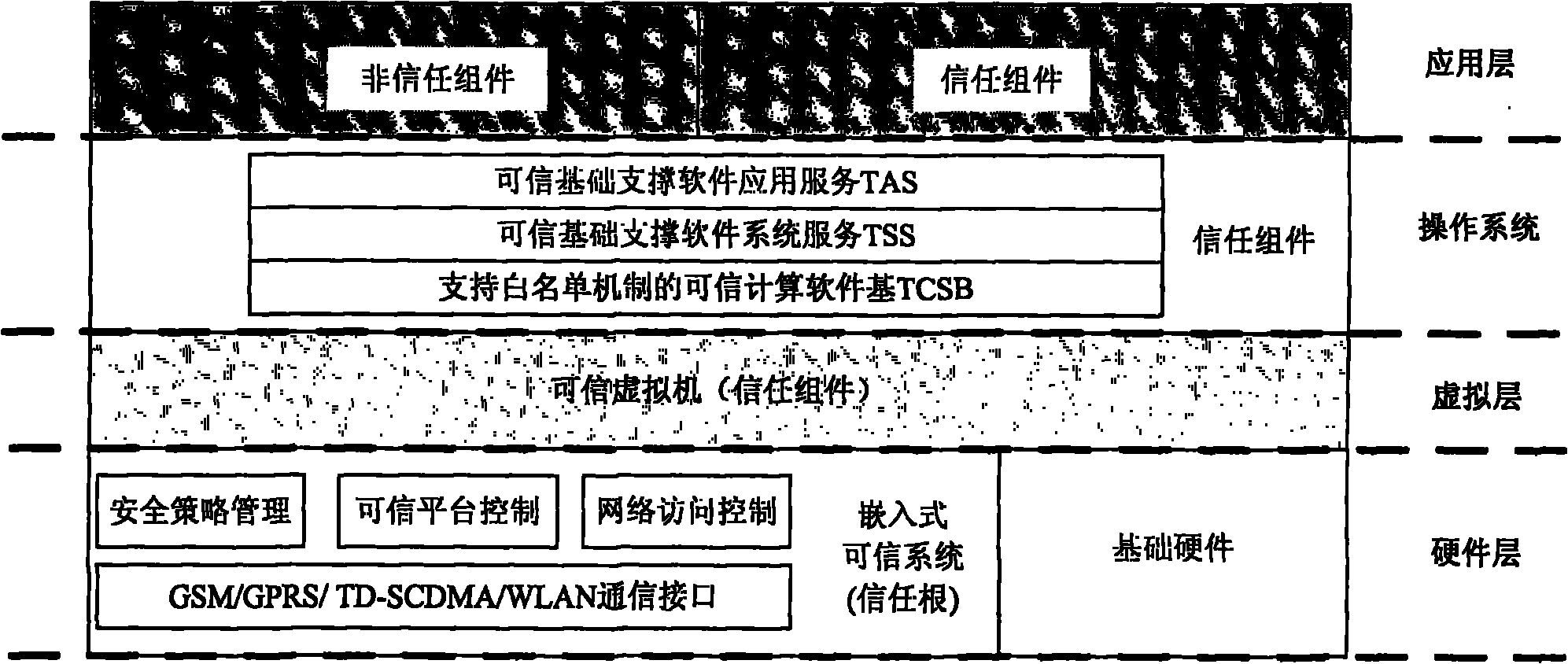
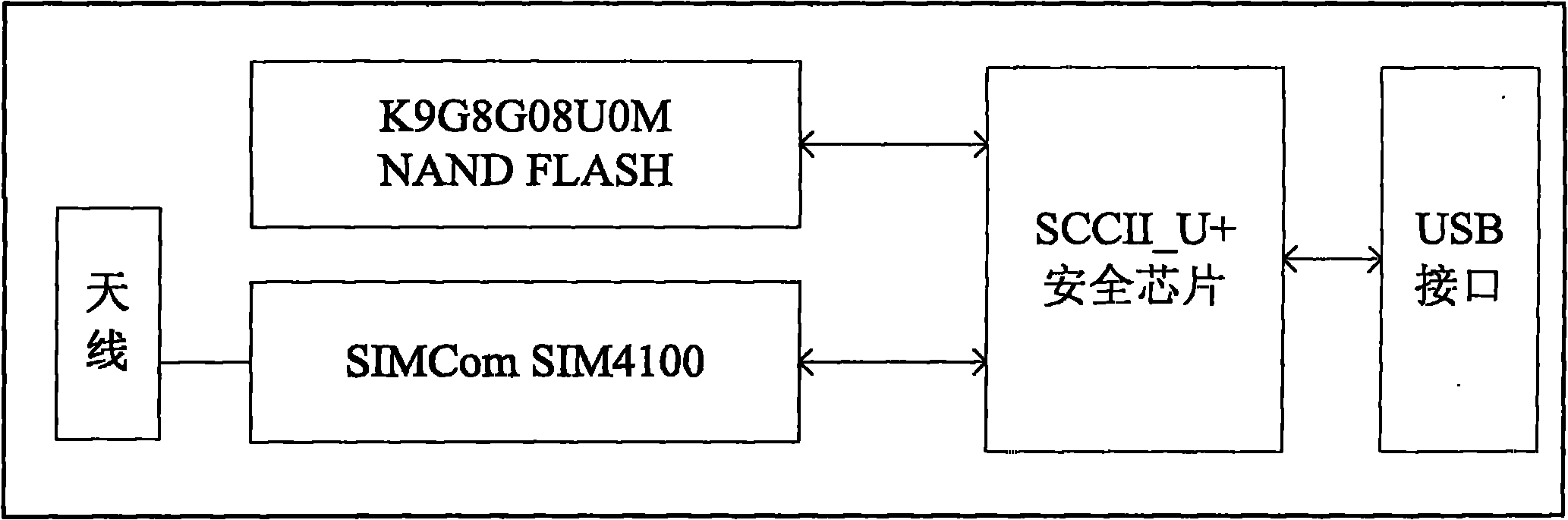
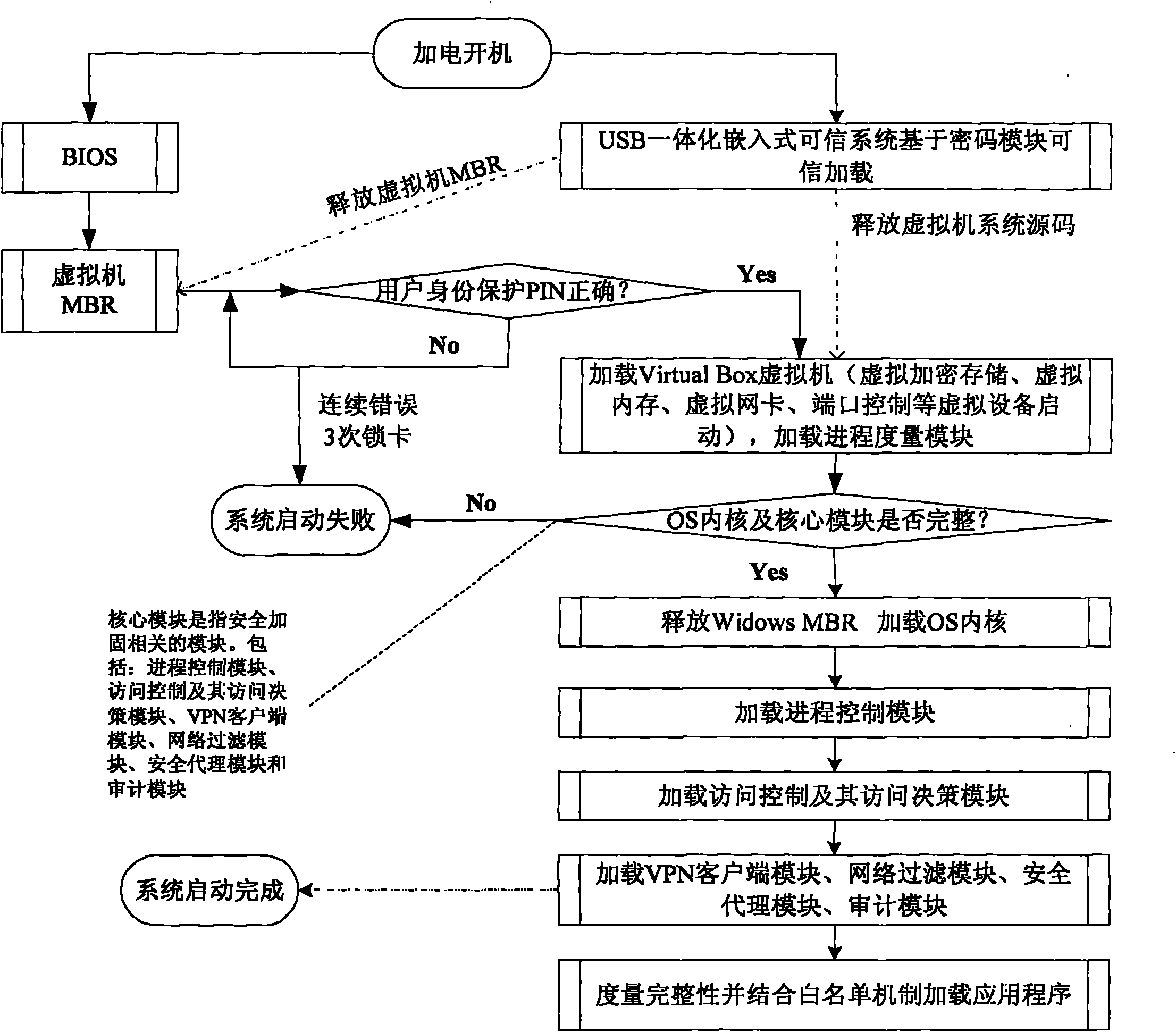
ActiveCN102004876APrevent leakageUniqueness guaranteedDigital data protectionPlatform integrity maintainanceAccess networkConfidentiality
The invention relates to a security terminal reinforcing model and reinforcing method of a tolerable non-trusted component, which can ensure the security of the computing environment of the terminal equipment in an access network. A universal serial bus (USB) integrated embedded trusted system is used as a trusted root of a terminal; the behavior control of the non-trusted component is realized based on a virtual machine; the trusted computing software supporting a white list mechanism ensures that services and applications listed in the white list mechanism can be started without integrity measurement to tolerate the loading and the running of the non-trusted component; and especially, under the condition that the component running on the terminal is not trusted, the predictability and the controllability of the final result are ensured, the confidentiality of the related information when the access terminal accesses the network is ensured, and the confidentiality and the integrity of the local information of the terminal are ensured. The invention is matched with the existing trusted computing and other information security technologies to construct a terminal computing environment with a predictable security result.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
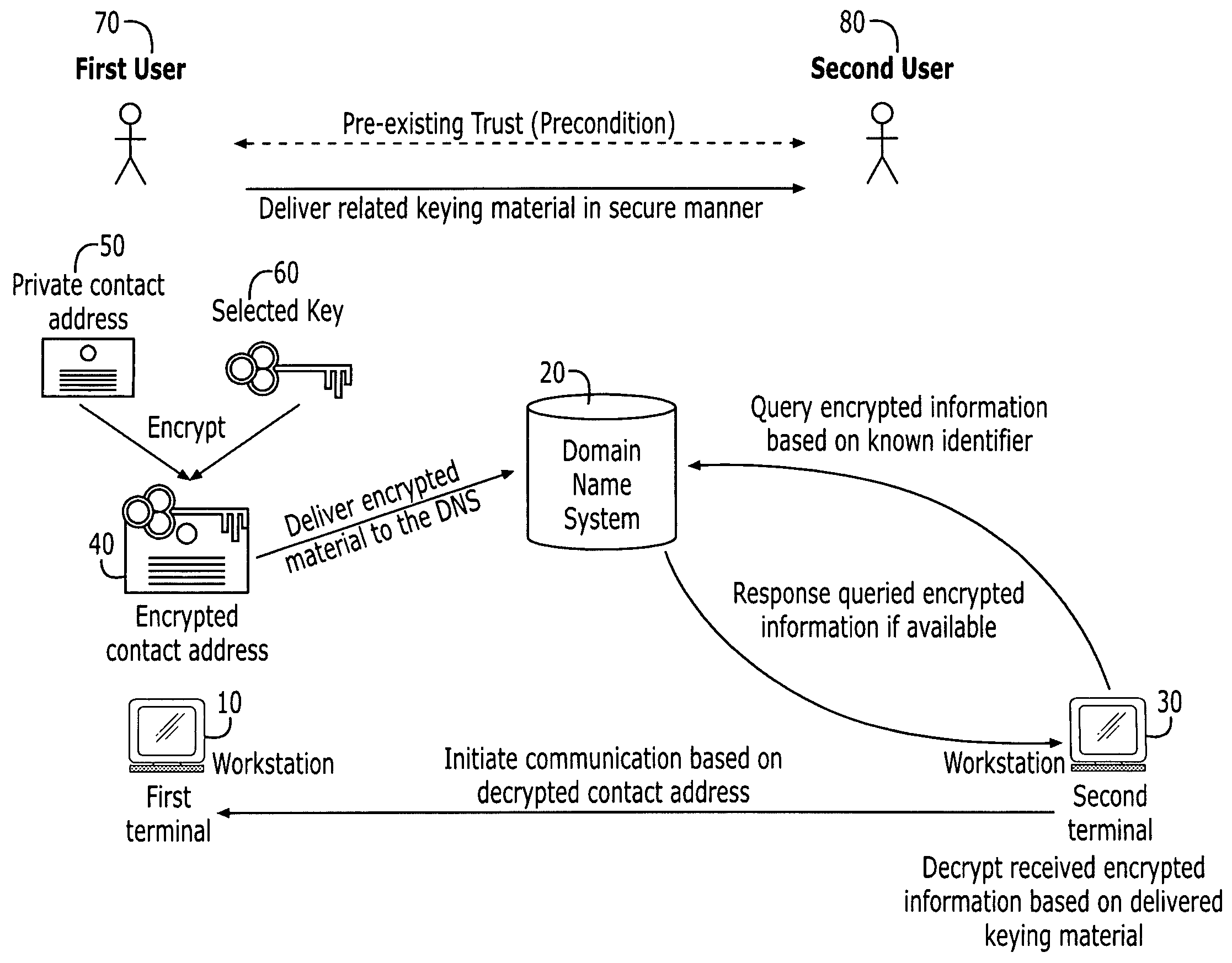
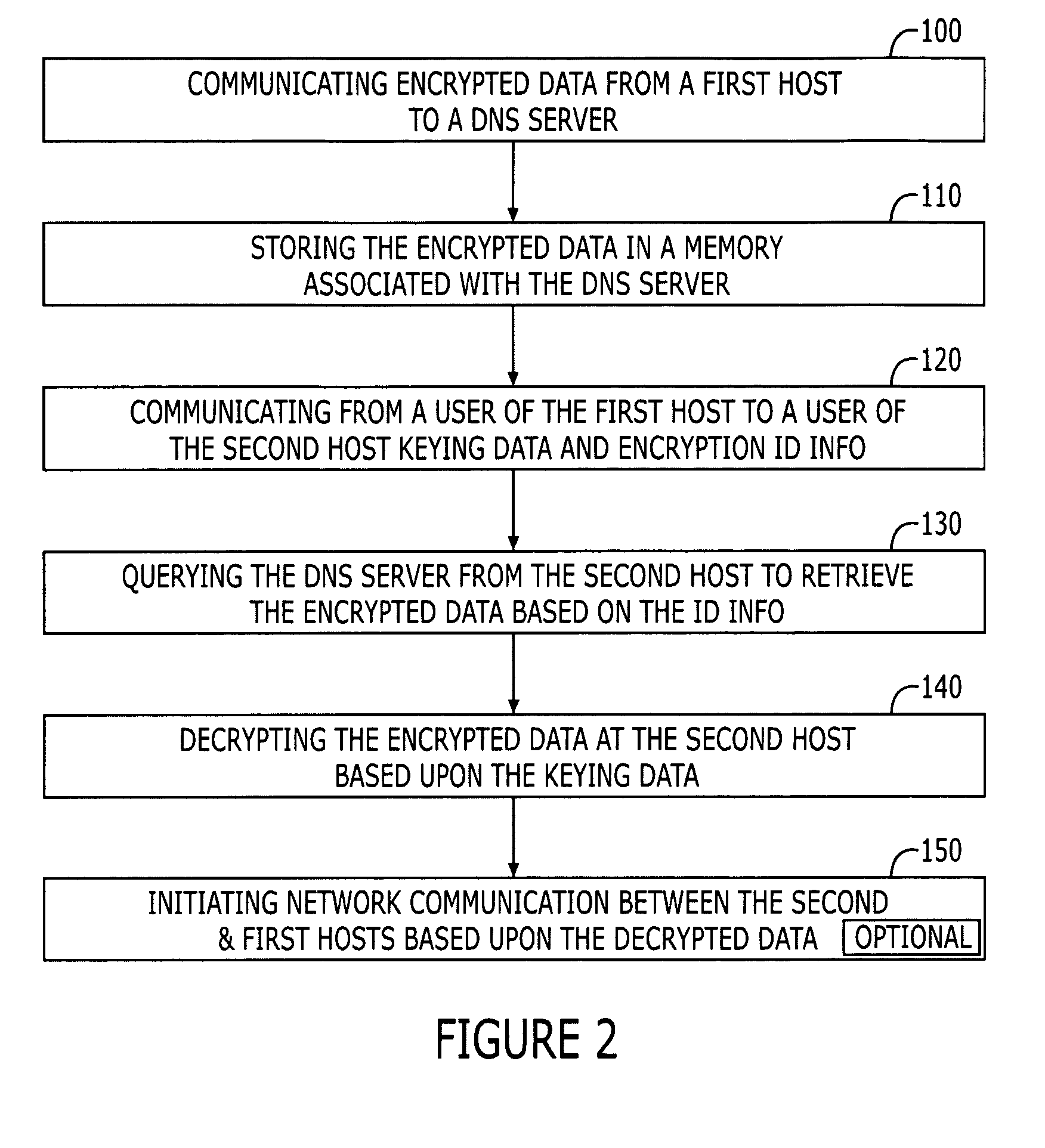
Systems and methods for secured domain name system use based on pre-existing trust
Systems, devices and methods are presented for providing controlled use of information stored publicly within the domain name system (DNS). Controlled use is established by storing encrypted data at the DNS servers and establishing trust, in the form of transfer of keying material, with requisite parties. The invention provides backward compatibility with existing DNS servers, in that, it provides for storage of encrypted data in existing resource records. The invention benefits from allowing storage in the DNS to be divided into both public and private classification, such that a user can identify and store certain public information that is available to all parties that have access to the DNS, while other information that has been classified as private is only available to parties which have established a trust.
Owner:NOKIA TECH OY
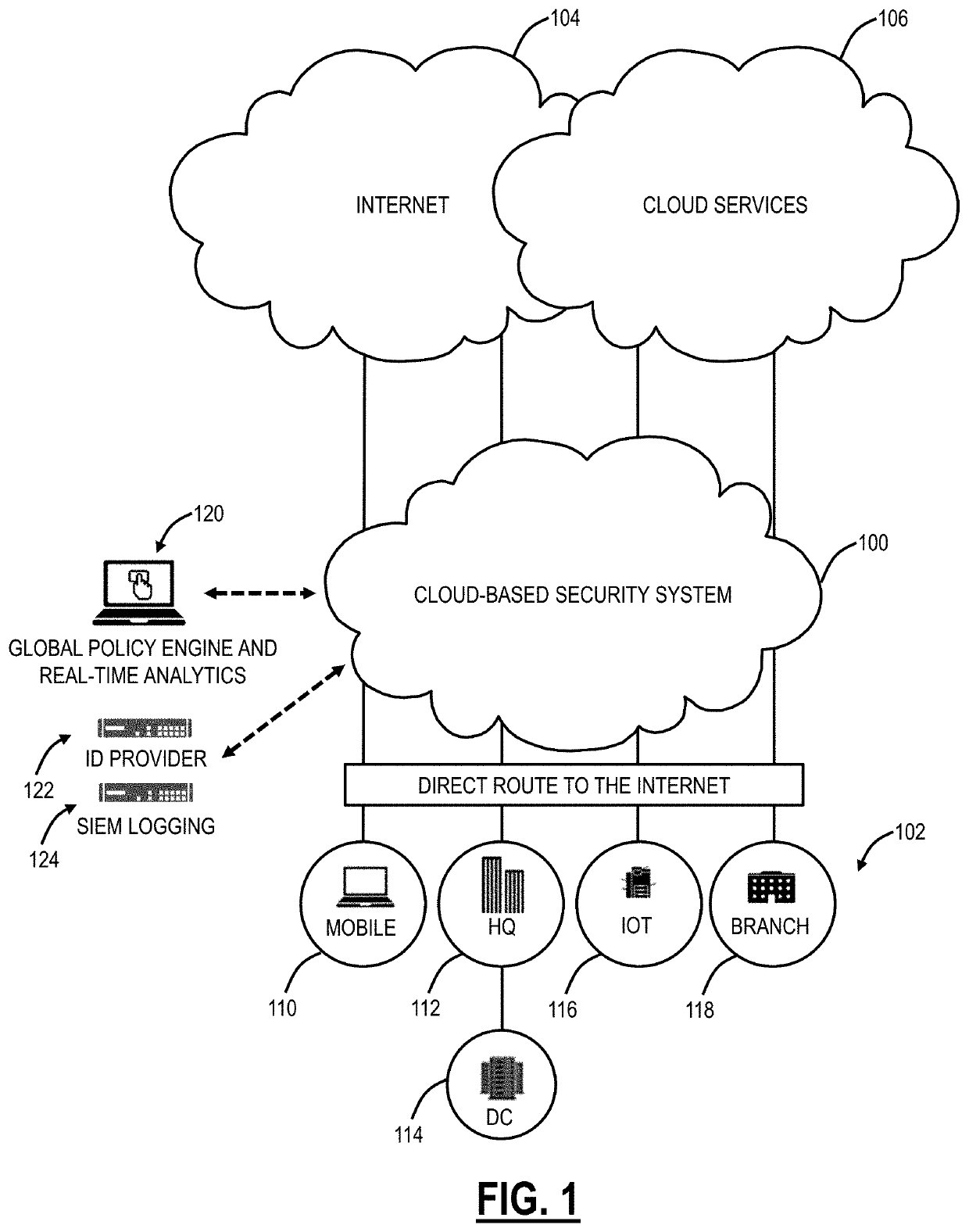
Cloud policy enforcement based on network trust
PendingUS20210029119A1Lower latencyMaking safeTransmissionSecurity arrangementComputer networkEngineering
Systems and methods include obtaining trusted network rules for a plurality of networks, wherein the trusted network rules include whether a network is untrusted or one of a plurality of trusted networks; obtaining policy configurations for each of the trusted network rules, wherein the policy configurations define configurations for a cloud-based system to use with a user device based on a corresponding network where the user device is connected; communicating with the user device and determining which network of the plurality of network the user device is connected; and applying the configurations in the cloud-based system for the user device based on the network the user device is connected. The steps can further include obtaining forwarding policies for each of the plurality of networks; and providing the forwarding policies to a connector application executed on the user device.
Owner:ZSCALER INC
Controlled parking of autonomous vehicles
InactiveCN104680835AIndication of parksing free spacesPayment architectureParking areaControl system
Systems and methods for controlled parking of autonomous vehicles are provided. In one embodiment, a method includes sending a request from a vehicle to park within a parking area controlled by a parking control system using a bi-directional trust system employing a digital authentication certificate, receiving at the vehicle a parking space assignment from the parking control system indicating an assigned parking space within the parking area using the bi-directional trust system, and autonomously controlling the vehicle to drive the vehicle to the assigned parking space within the parking area.
Owner:GM GLOBAL TECH OPERATIONS LLC
Identity-based wireless sensor network security trust method
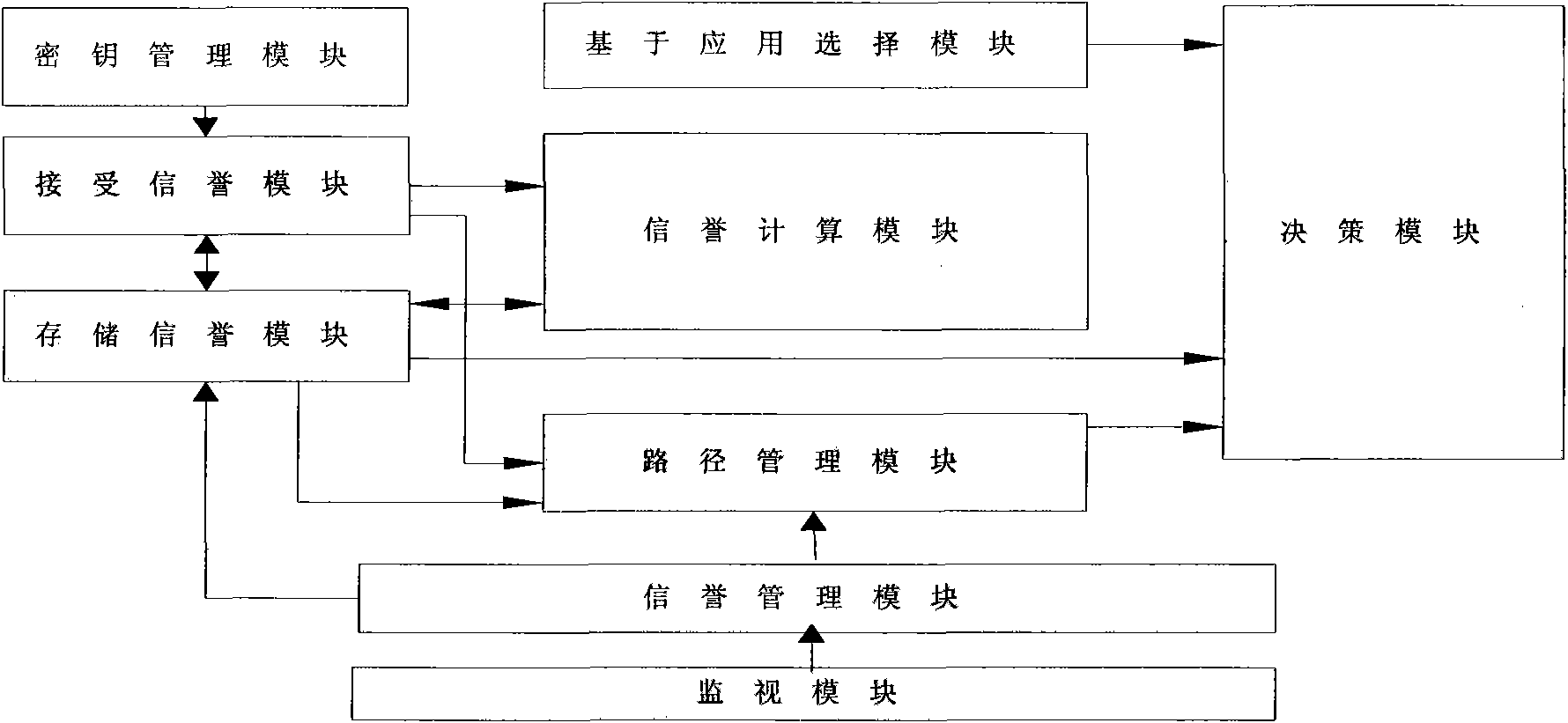
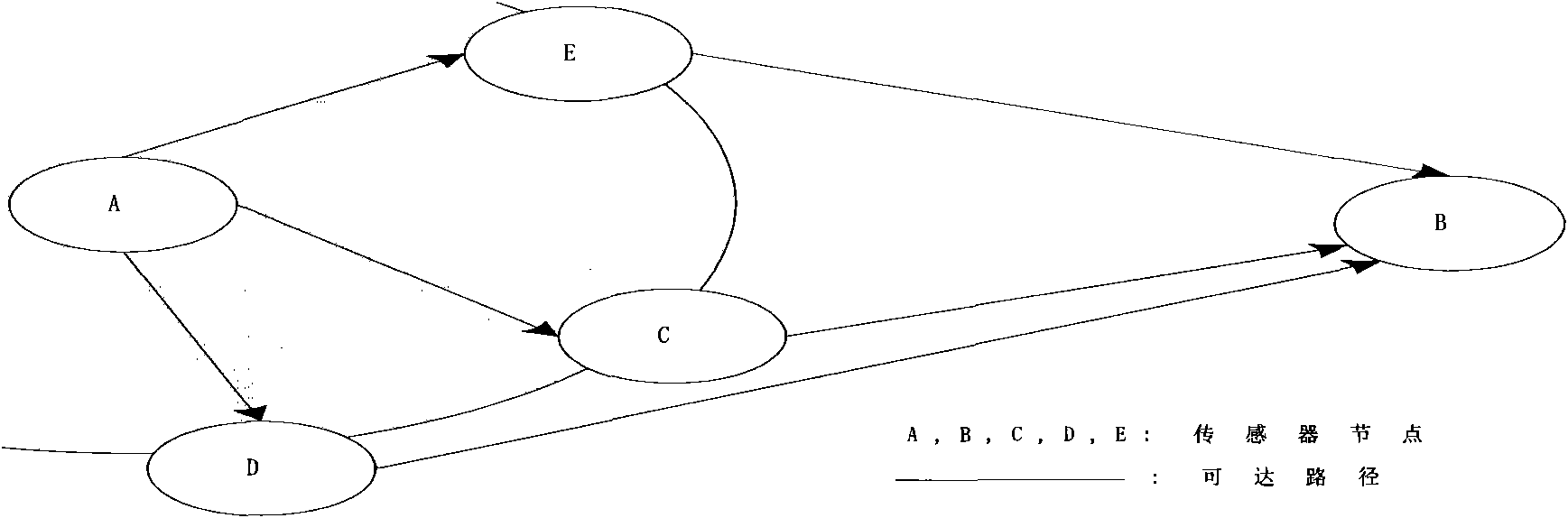
InactiveCN101600198AExchangeImplement encryptionNetwork topologiesSecurity arrangementTrusted systemAuthentication
The invention discloses an identity-based wireless sensor network security trust method. In the method, firstly each node in the network is loaded with a trust management structure; wherein the trust management structure is composed of a secret key management module, a receiving credit module, a storage credit module, a credit calculating module, an application selecting module, a route management module, a decision making module, a credit management module and a monitoring module. On the basis of the trust management structure, a trust communication network is established by broadcasting query node information among nodes, receiving query respond and updating node credit and by identity-based public key password encryption and authentication among nodes, so as to realize safe communication of credit information among nodes. The invention reduces complexity of credit calculation in the wireless sensor network, improves security of communication of the wireless sensor network trust system, solves communication problem of a source node and a destination node under multi-hop condition, and can meet the requirement of large-scale self-organized network application.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com