Internet of things device supply chain trust system management method, computer program, computer
A technology of IoT devices and management methods, which is applied in the fields of cyberspace security, blockchain, and the Internet of Things, can solve the problem that the effective link of the central server is difficult to guarantee, and the low power consumption and lightweight computing requirements of the Internet of Things devices cannot meet the processing requirements. Computational overhead of decryption, difficulty in adjustment and adaptation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0090] Embodiment 1, data storage method and data structure. The specific content is as follows:
[0091] (1) Overall design
[0092] In the ROM of the IoT device, store: the ID of the IoT device, the K of the IoT device itself R ,Security code.
[0093] In the SSD of the IoT device, store: the top-level public key of the owner of the IoT device, anti-counterfeiting code, and others.
[0094] In the RAM of the IoT device, store: the owner's top-level public key, the blockchain.
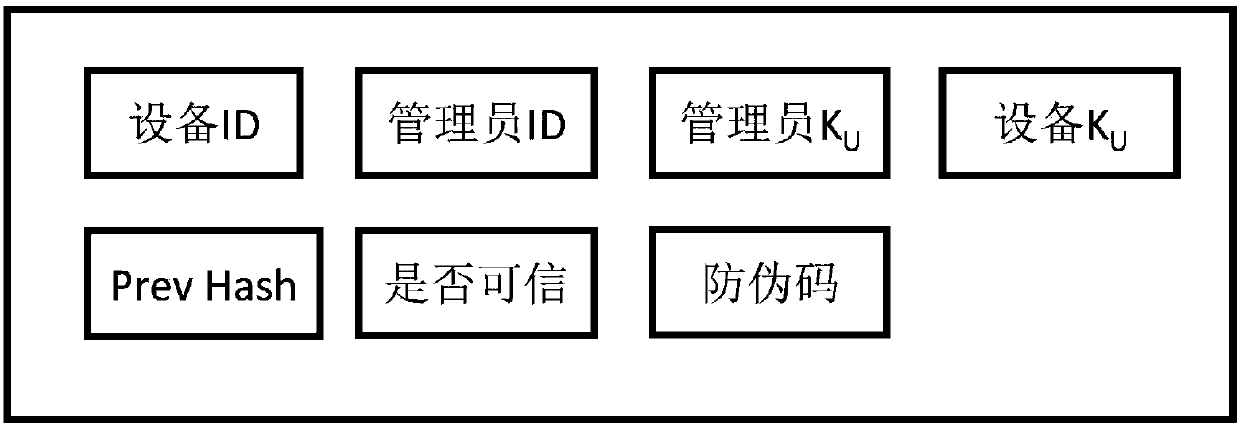
[0095] The structure of each block in the blockchain is as follows image 3 shown.
[0096] The description of each field in the block is as follows:
[0097] IoT Device ID: A unique identifier for an IoT device.
[0098] Administrator ID: Support multiple administrators to manage multiple IoT devices.
[0099] Administrator's public key: assign a public-private key pair to each administrator, and write the administrator's public key into the block. This field is used to establish trust betwe...
Embodiment 2
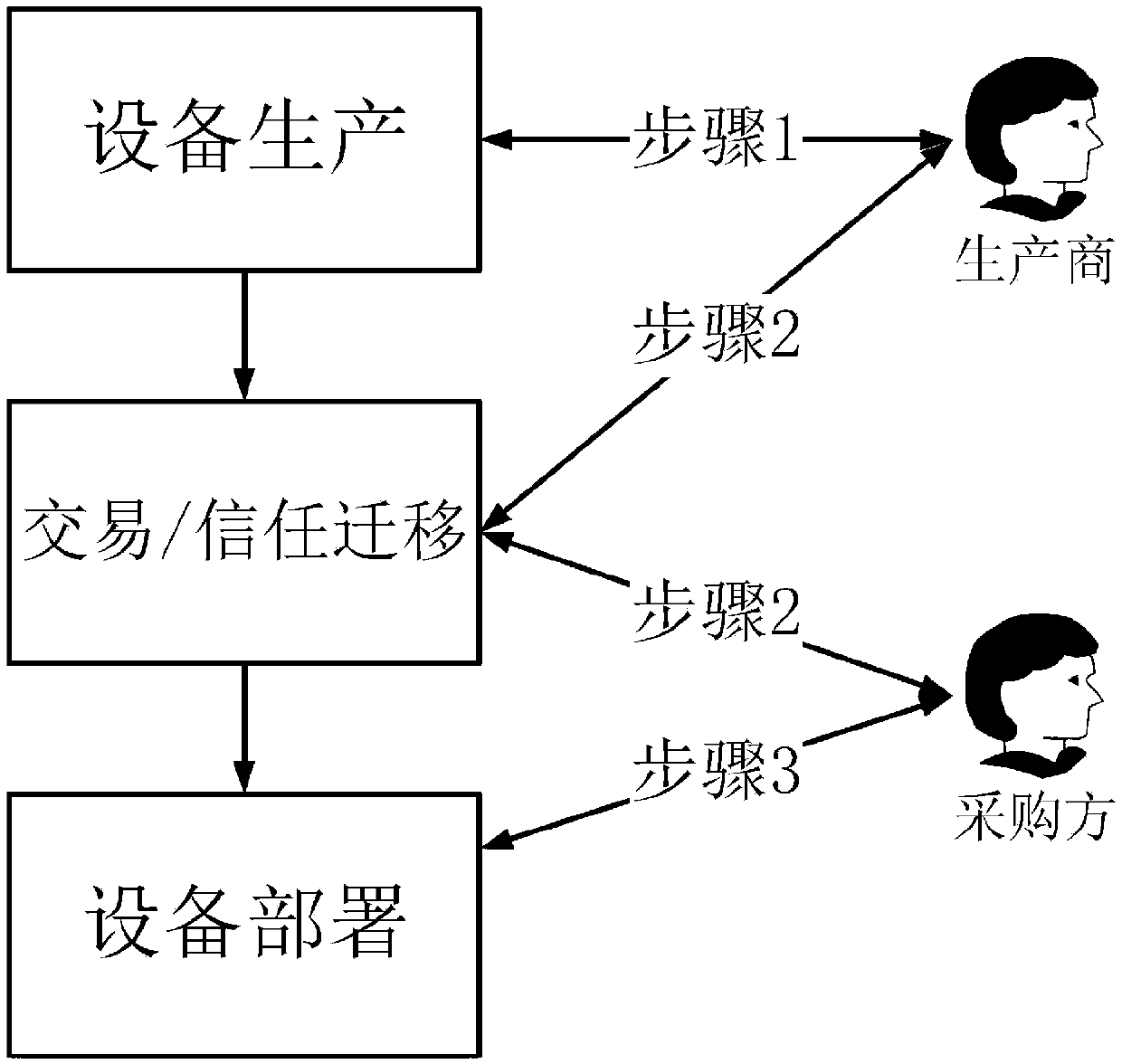
[0119] Embodiment 2, trust relationship migration. The specific content is as follows:
[0120] Trust migration occurs when the ownership of IoT devices changes, mainly when the manufacturer sells the IoT devices to the purchaser. The interactive process of trust relationship migration is as follows: Figure 4 shown.
[0121] Figure 4 The specific interaction content of the protocol shown is as follows:
[0122] ①: {IoT device ID, N A , transfer identifier, {△ 1} sig}.
[0123] ②: {IoT device ID, N B , transfer identifier} KP-制造商 .
[0124] ③: {N A N B ,KP-purchaser,{△ 2} sig} KP-物联网设备 .
[0125] Among them, N A , N B Both are random numbers; "KP-Purchaser" means the public key of the purchaser; △ 1 Indicates Hash (IoT device ID, N A , transfer identifier), that is, for {IoT device ID, N A , transfer identifier} for hash processing; △ 2 means Hash( KP-Purchaser), ie to { KP-Purchaser} for hash processing; {△} Sig means to sign △ with the private key o...
Embodiment 3
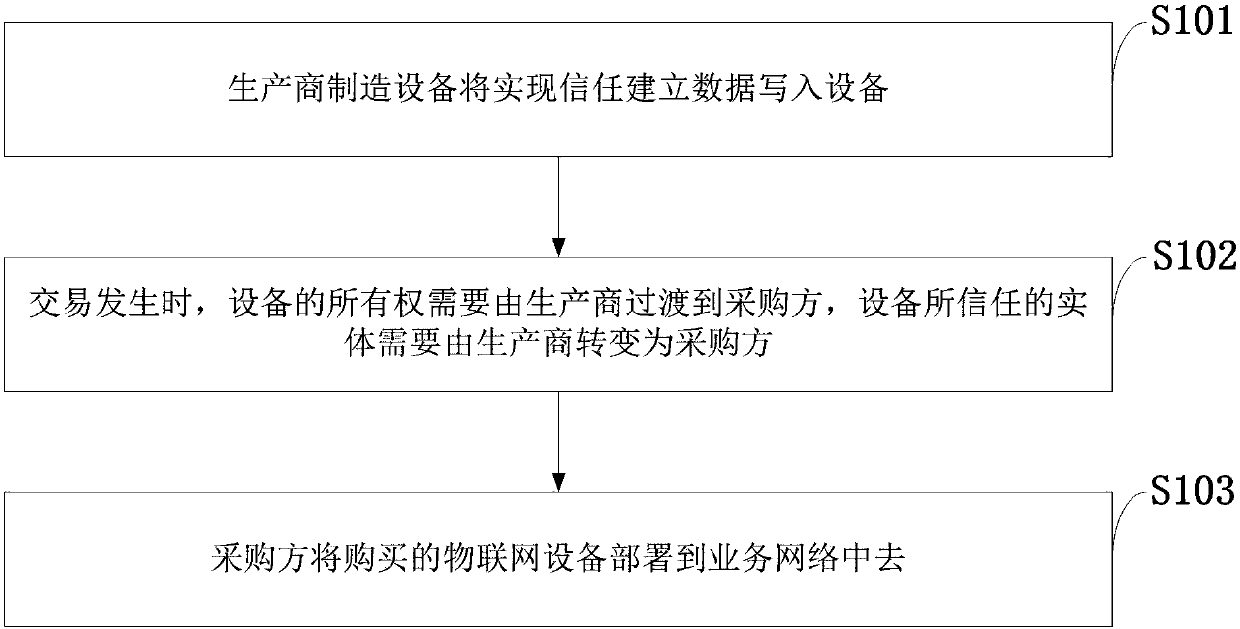
[0132] Embodiment 3, after purchasing the IoT device, the purchaser needs to deploy the IoT device to the service network. Deploying an IoT device means first writing the blockchain into the IoT device memory, as this is the carrier of trust. At this time, it is divided into two situations, corresponding to solving different problems.
[0133] (1) The applicable situation of the embodiment is that a large number of IoT devices are still in the base at this time and have not yet been deployed. To write the blockchain into the memory of the IoT device in this case, the blockchain can be generated by the server blockchain management module, and the server communication module is responsible for writing the blockchain into the memory of the IoT device.
[0134] combine image 3 Interpret each field in the blockchain block.
[0135] IoT device ID: directly read from the IoT device ROM;
[0136] Administrator ID: The purchaser can designate an administrator for the IoT device ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com