Patents
Literature
368166results about "Transmission" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
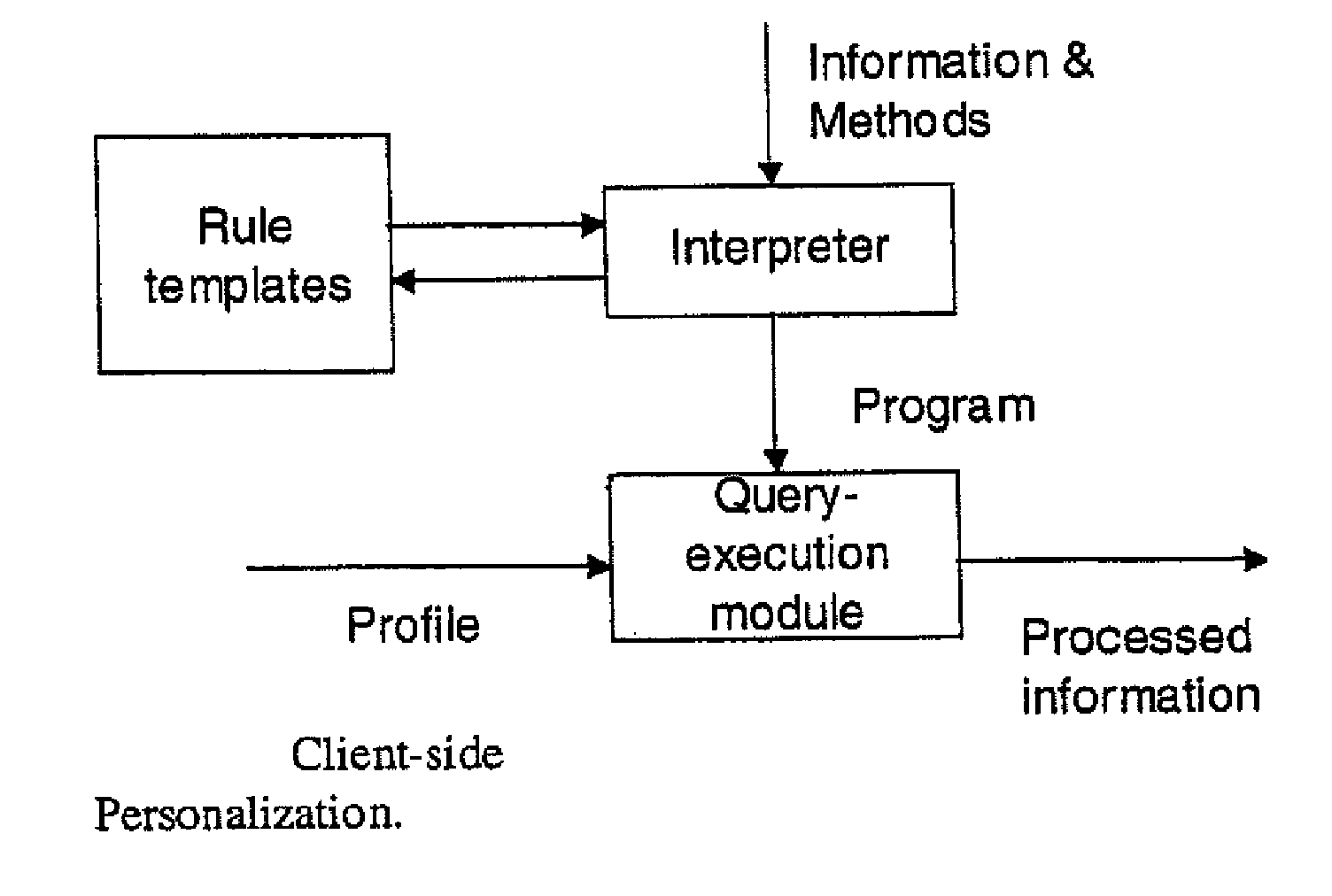
Secure data interchange
InactiveUS20090254971A1Improve privacyLimited accessDigital data processing detailsAnalogue secracy/subscription systemsInformation accessData interchange
A secure data interchange system enables information about bilateral and multilateral interactions between multiple persistent parties to be exchanged and leveraged within an environment that uses a combination of techniques to control access to information, release of information, and matching of information back to parties. Access to data records can be controlled using an associated price rule. A data owner can specify a price for different types and amounts of information access.
Owner:STRIPE INC
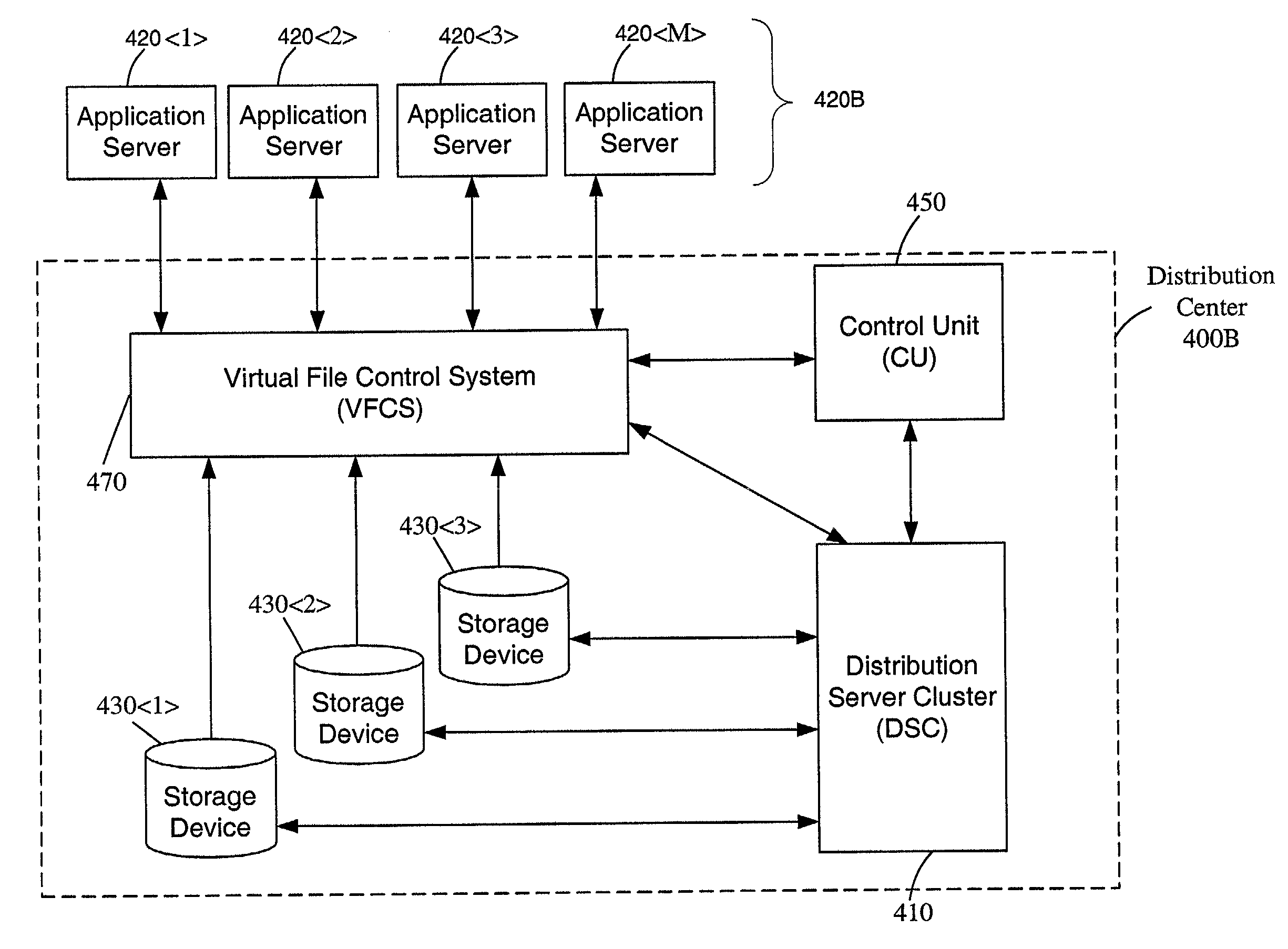
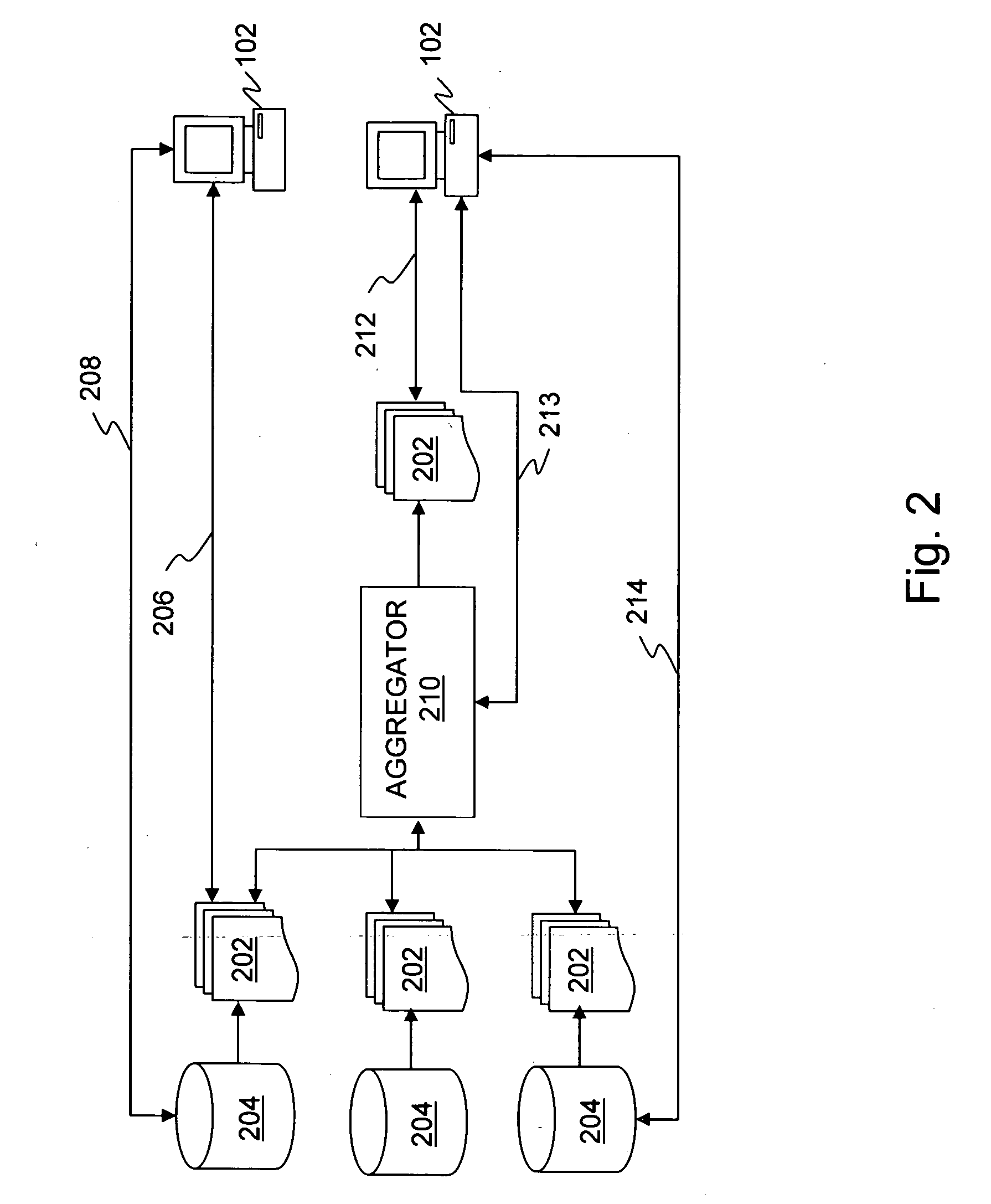
Method and system for managing distributed content and related metadata
InactiveUS7272613B2Reduce storage requirementsReduce amountData processing applicationsError detection/correctionControl systemFile system
The invention provides a method and system for creating an innovative file system that separates its directory presentation from its data store. The method and system include processing, division, distribution, managing, synchronizing, and reassembling of file system objects that does not delay the presentation of the content to the user, but also uses a reduced amount of storage space. The invention includes the ability to manage and control the integrity of the files distributed across the network, and the ability to serve and reconstruct files in real time using a Virtual File Control System.
Owner:PRISMEDIA NETWORK +1
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
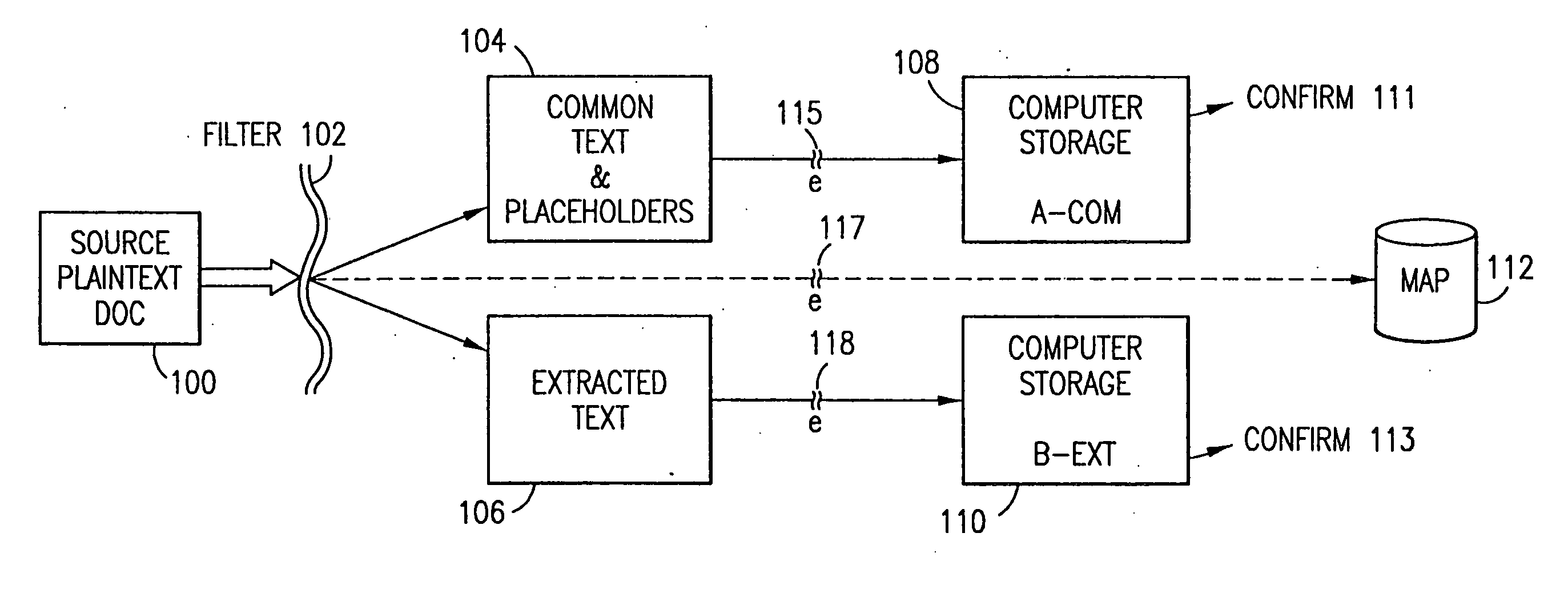
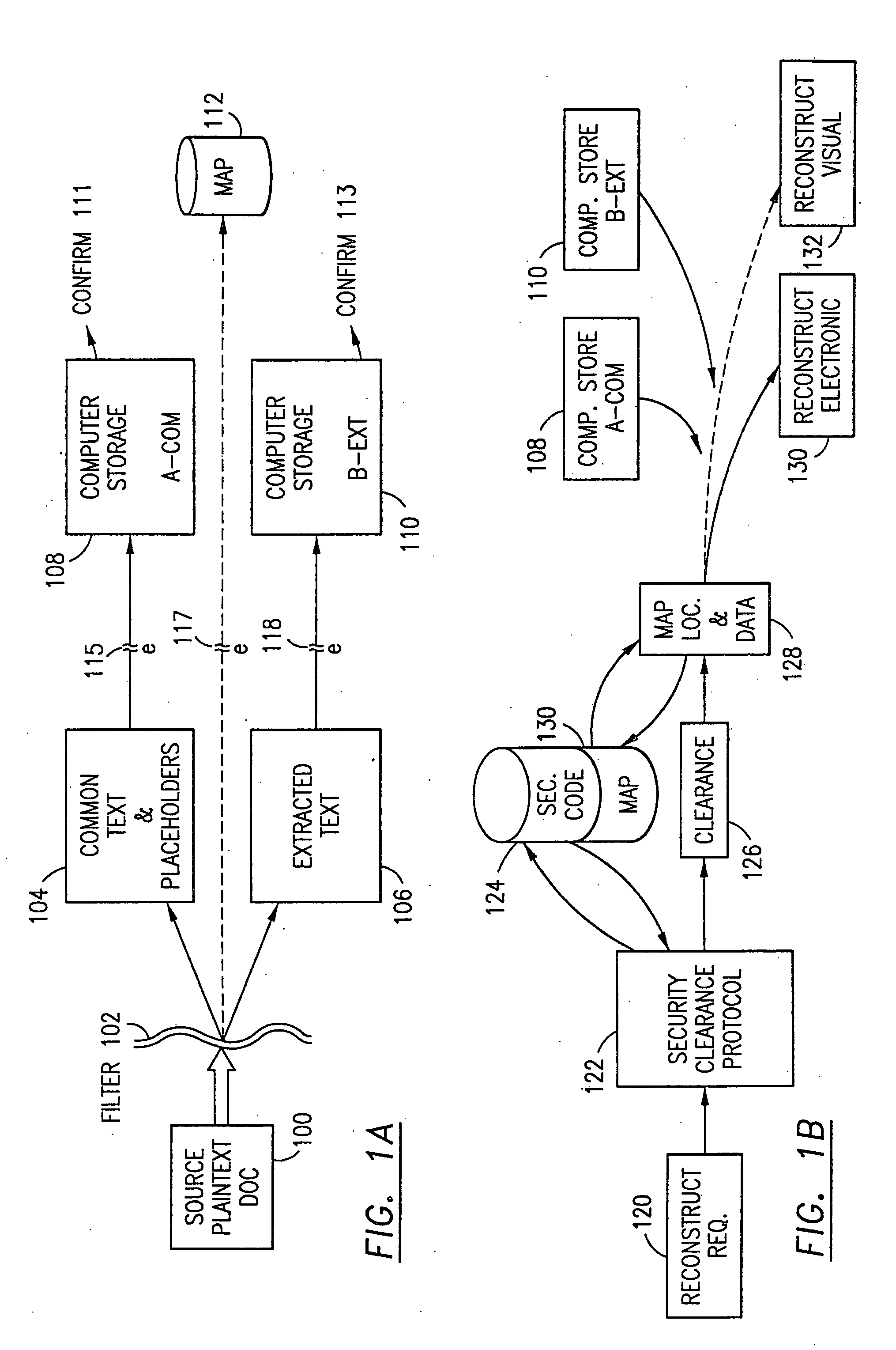
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
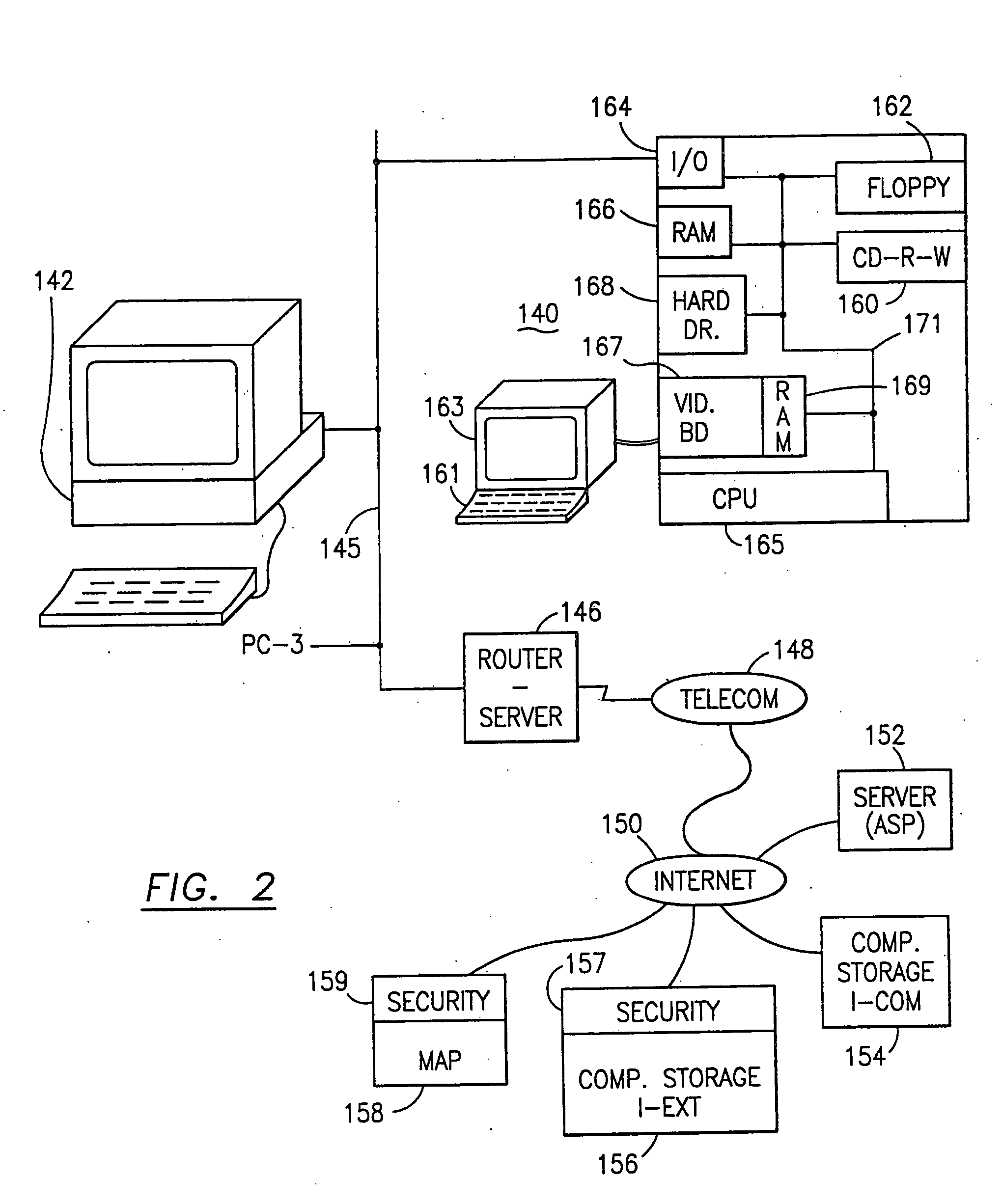
System, method, and computer program product for providing location based services and mobile e-commerce
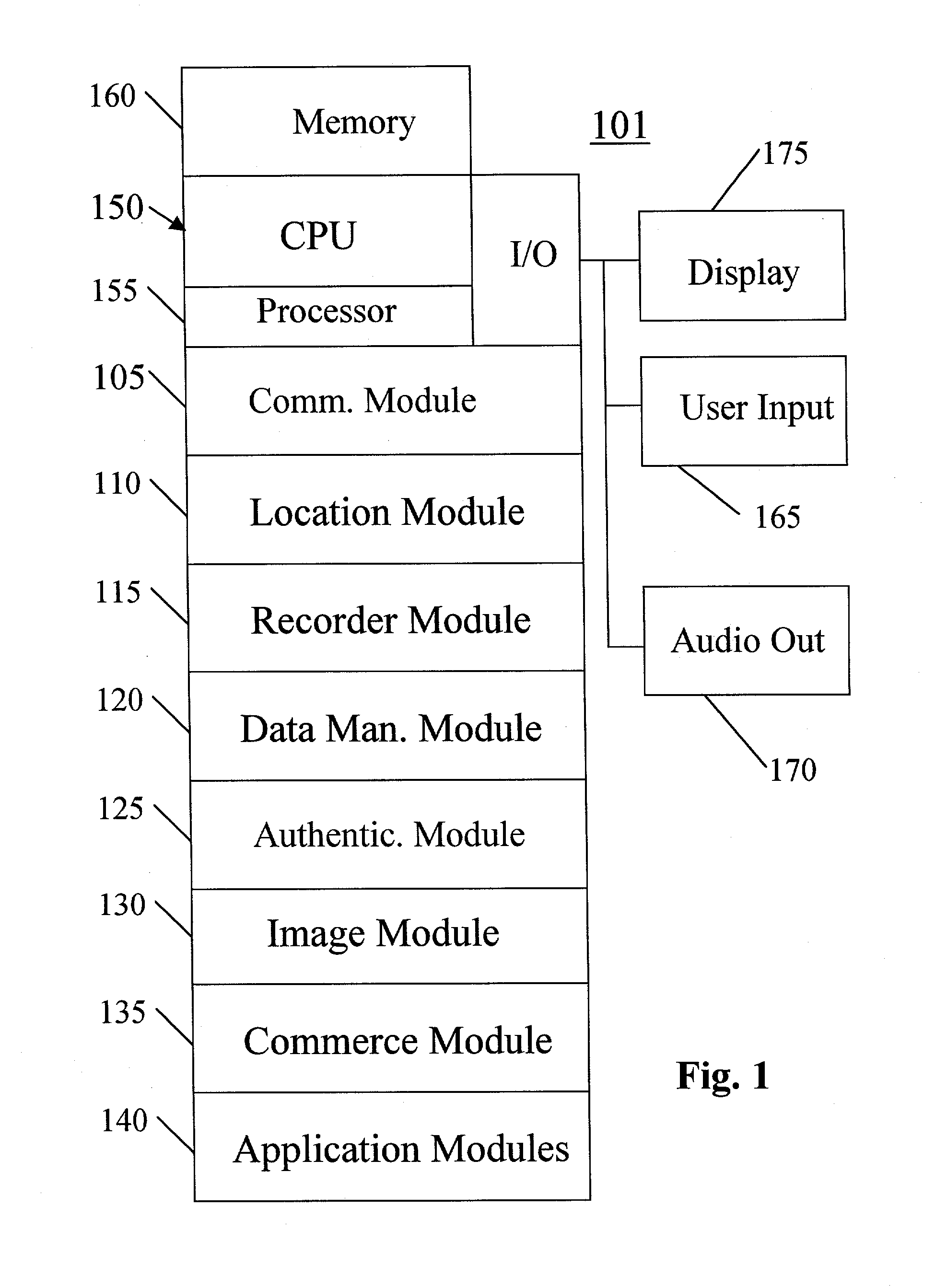
ActiveUS20030065805A1Facilitating localized e-commerceFacilitate communicationTelevision system detailsColor television detailsDisplay deviceData file
A system, method, apparatus and computer program product for providing location based functions and mobile e-commerce comprising a central processing unit including a processor, a storage device, and programming stored in the storage device, a display device, an audio input device, an audio output device, a communications module, a commerce module, an image module, and a location module. The programming controls the operation of the present invention to provide functions based on location data, to facilitate commercial exchanges by wirelessly exchanging payment and product information with venders, to identify services such as venders meeting selection criteria, to wirelessly exchange select information with other users and systems, to restrict and / or monitor the use of the device based on authorized user parameters, selecting one of a plurality networks through which to communicate, detecting a trigger for performing an action based on a change in location and sensed data, storing a voice annotation with a computer data file, determining service providers and associated communication parameters, contemporaneously maintaining a wireless voice and data link, providing a system for selecting and delivering mobile advertisements, and many other functions and services that are described herein.
Owner:GULA CONSULTING LLC
Systems and methods for establishing a cloud bridge between virtual storage resources
Methods and systems for establishing a cloud bridge between two virtual storage resources and for transmitting data from one first virtual storage resource to the other virtual storage resource. The system can include a first virtual storage resource or cloud, and a storage delivery management service that executes on a computer and within the first virtual storage resource. The storage delivery management service can receive user credentials of a user that identify a storage adapter. Upon receiving the user credentials, the storage delivery management service can invoke the storage adapter which executes an interface that identifies a second virtual storage resource and includes an interface translation file. The storage delivery management service accesses the second virtual storage resource and establishes a cloud bridge with the second virtual storage resource using information obtained from the second virtual storage resource and information translated by the storage adapter using the interface translation file.
Owner:CITRIX SYST INC
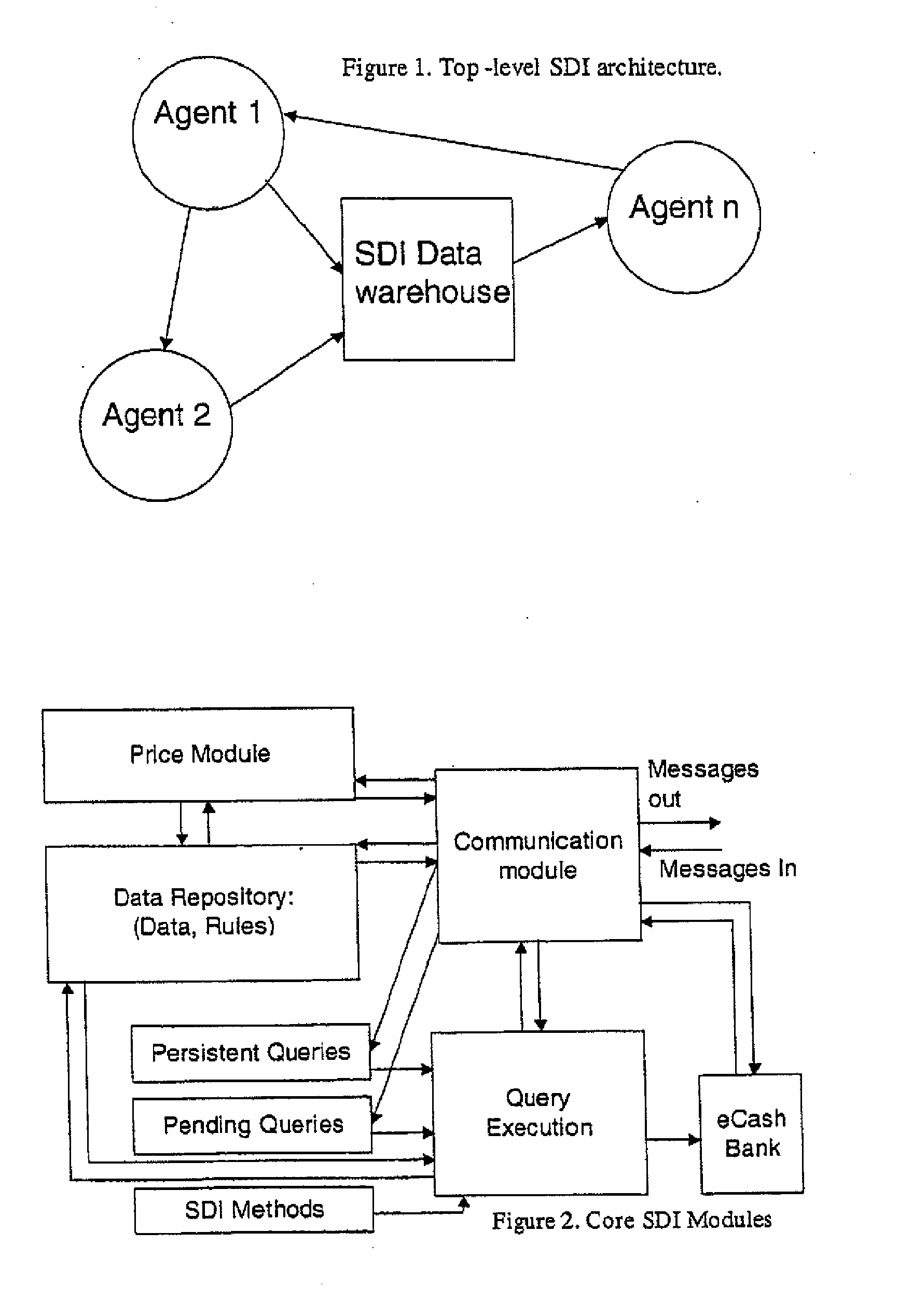
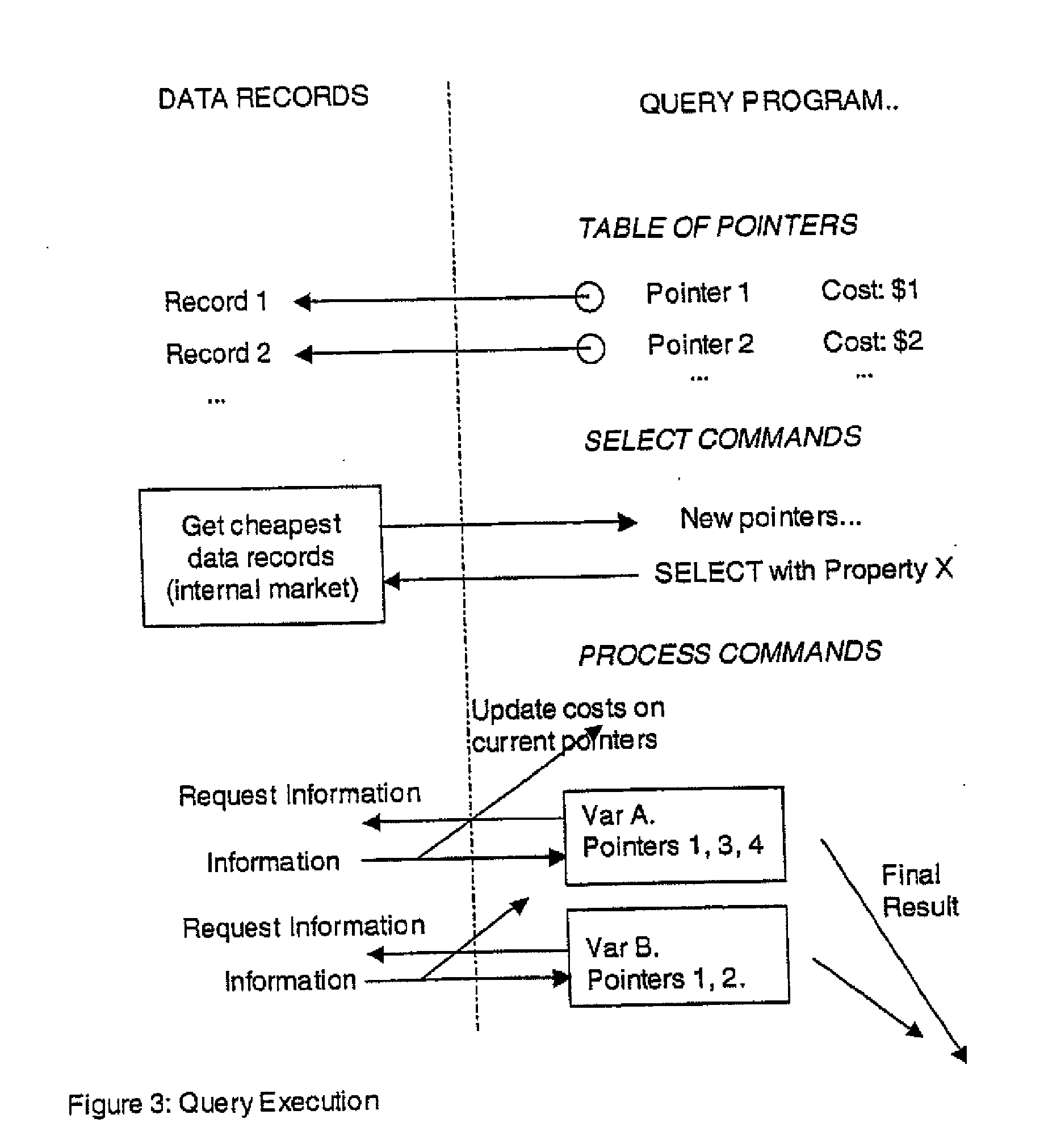
Secure data interchange
InactiveUS7630986B1Low pricePrivacy protectionMultiple digital computer combinationsOffice automationCommunications systemInternet privacy
A system for exchanging data includes a communication system, a first and a second party connected to the communication system, wherein each party has personal data, and each party has a disclosure policy to control dissemination of its data, and a secure intermediate party connected to the communication system, wherein the secure intermediate party exchanges data between the first and second parties in accordance with their respective disclosure policies.
Owner:STRIPE INC
Processing management information
InactiveUS8095413B1Readily availableOffice automationTransmissionManagement information systemsData science
Owner:VIRTUALAGILITY
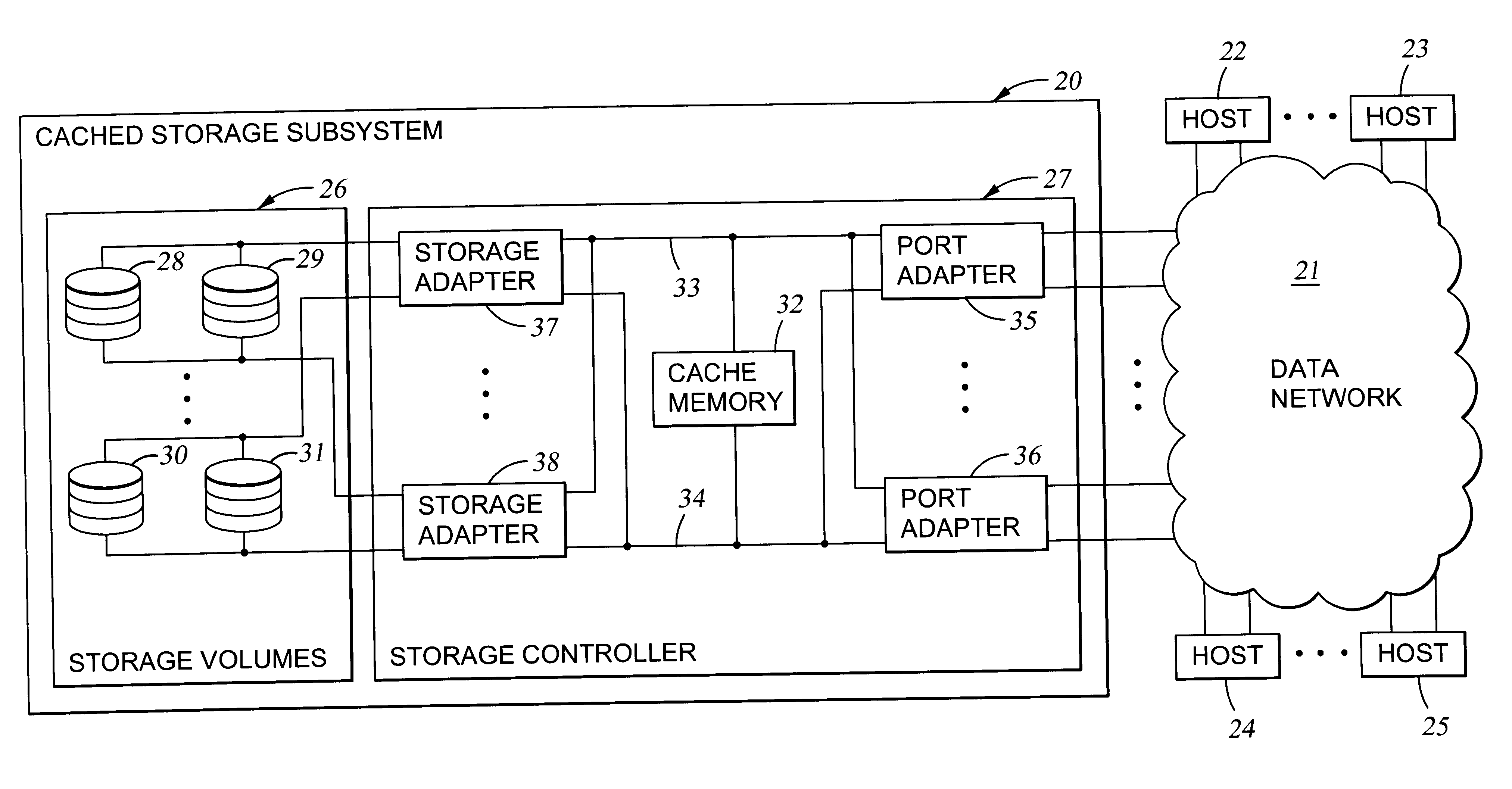
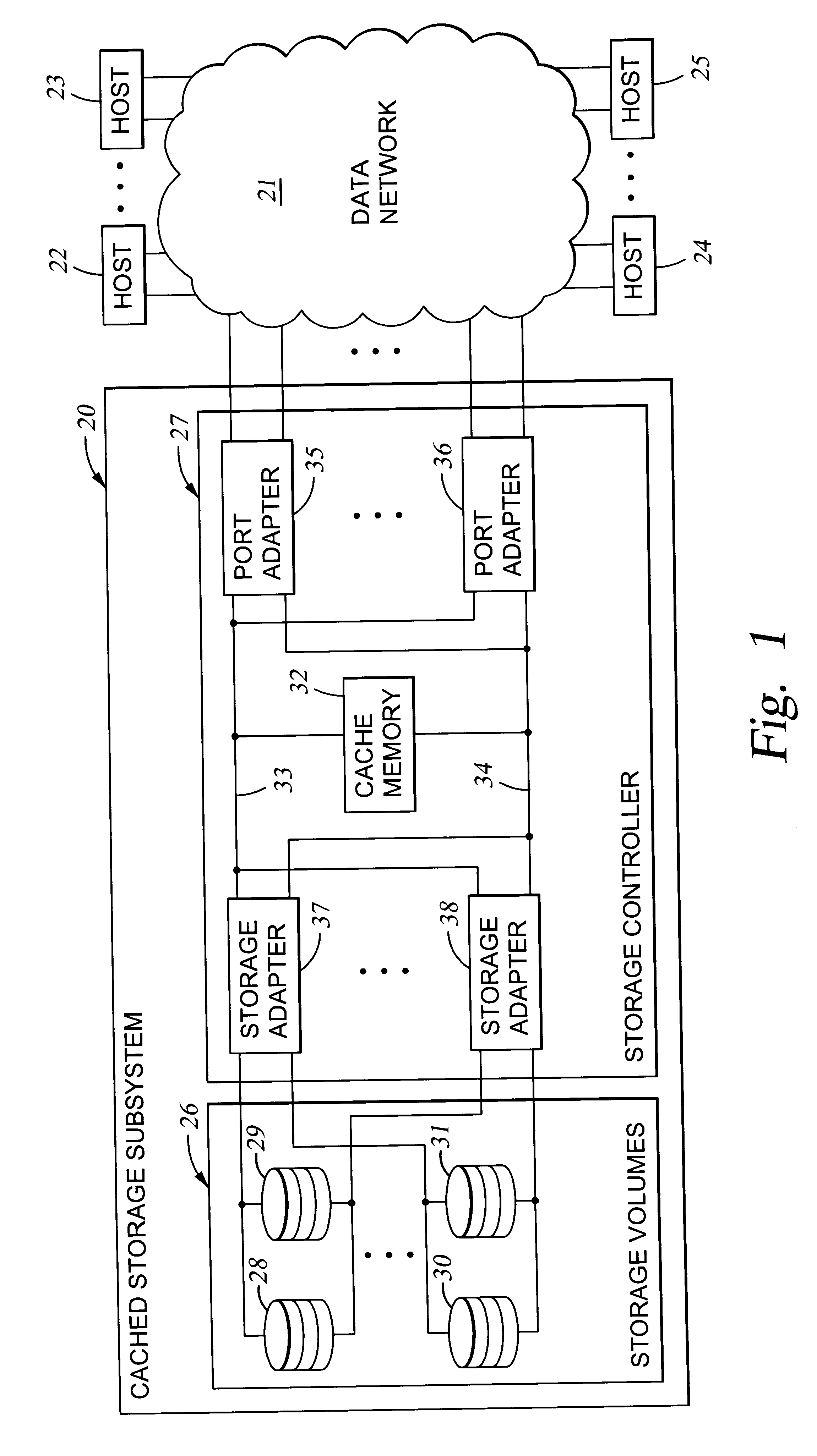
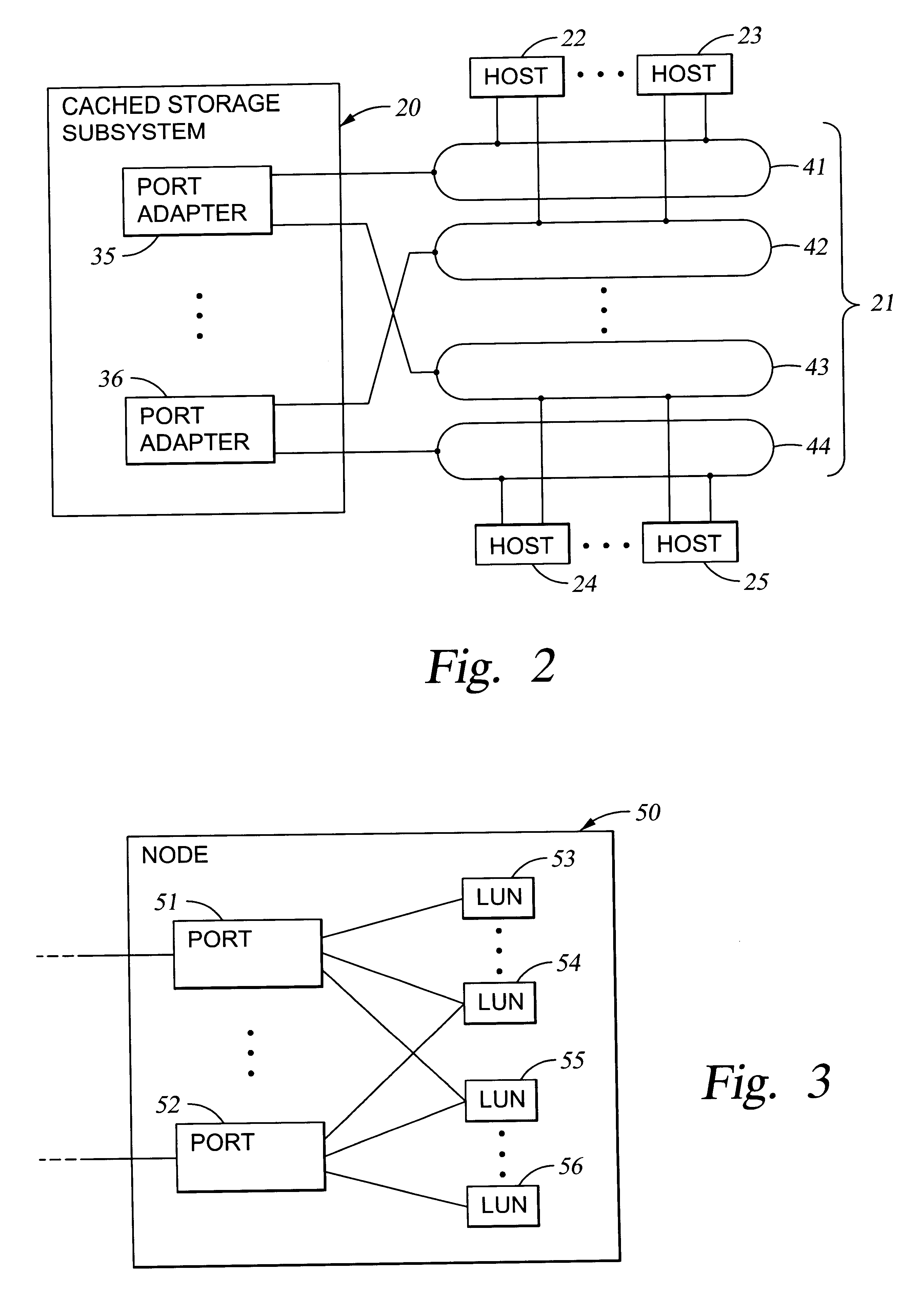
Virtual ports for data transferring of a data storage system
A storage controller has at least one physical data port for a data network including host processors. The storage controller is programmed to provide a plurality of virtual ports for access to storage, and a virtual switch for routing storage access requests from the physical port to the virtual ports. The virtual ports and the virtual switch are defined by software. The virtual ports appear to the hosts as physical ports in the data network. For example, in a Fiber-Channel network, the virtual ports have World Wide Names (WWNs) and are assigned temporary addresses (S_Ds), and the virtual switch provides a name server identifying the WWNs and S_IDs of the virtual ports. For convenient partitioning of storage among host processors, one or more virtual ports are assigned to each host, and a set of storage volumes are made accessible from each virtual port. A host can access storage at a virtual port only if the virtual port has been assigned to the host. Preferably, storage can be accessed through each virtual port by no more than one assigned host, although a shared volume may be accessible from more than one virtual port. The storage controller may provide a service for reporting to a host the virtual ports through which the host can access storage, and the storage volumes that are accessible to the host through each of the virtual ports.
Owner:EMC IP HLDG CO LLC
Managing user information on an e-commerce system
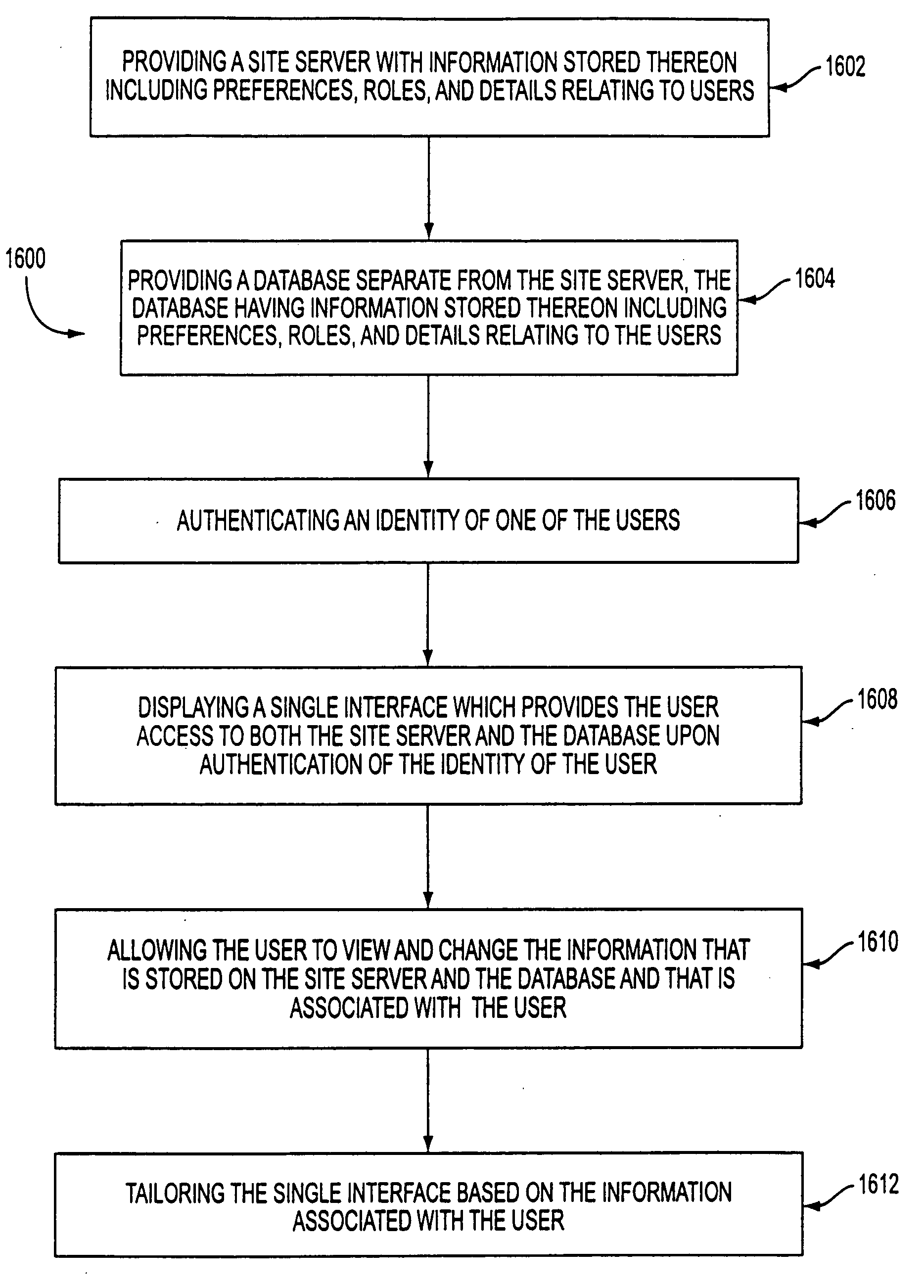
The present invention provides for the management of user information of both site server and regular web site users. A site server is provided with information stored thereon including preferences, roles, and details related to users. A database separate from the site server is also provided. The database has information stored thereon including preferences, roles, and details relating to the users. An identity of one of the users is authenticated. A single interface is displayed which provides the user access to both the site server and the database upon authentication of the identity of the user. The user is allowed to view and change the information that is stored on the site server and the database and that is associated with the user. The single interface is tailored based on the information associated with the user.
Owner:ACCENTURE GLOBAL SERVICES LTD
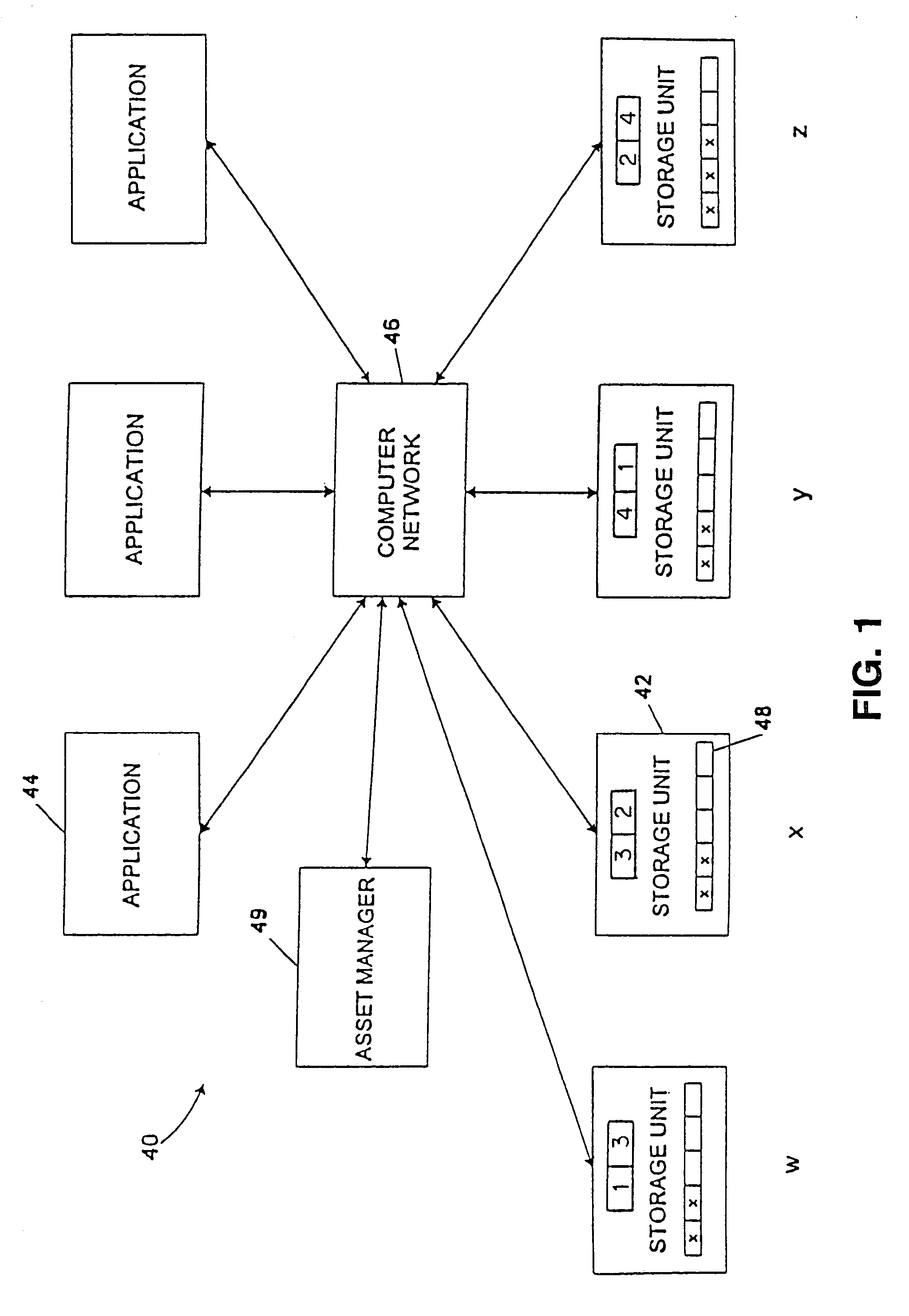
Computer system and process for transferring multiple high bandwidth streams of data between multiple storage units and multiple applications in a scalable and reliable manner
InactiveUS7111115B2Improve reliabilityImprove scalabilityInput/output to record carriersData processing applicationsHigh bandwidthData segment
Multiple applications request data from multiple storage units over a computer network. The data is divided into segments and each segment is distributed randomly on one of several storage units, independent of the storage units on which other segments of the media data are stored. At least one additional copy of each segment also is distributed randomly over the storage units, such that each segment is stored on at least two storage units. This random distribution of multiple copies of segments of data improves both scalability and reliability. When an application requests a selected segment of data, the request is processed by the storage unit with the shortest queue of requests. Random fluctuations in the load applied by multiple applications on multiple storage units are balanced nearly equally over all of the storage units. This combination of techniques results in a system which can transfer multiple, independent high-bandwidth streams of data in a scalable manner in both directions between multiple applications and multiple storage units.
Owner:AVID TECHNOLOGY
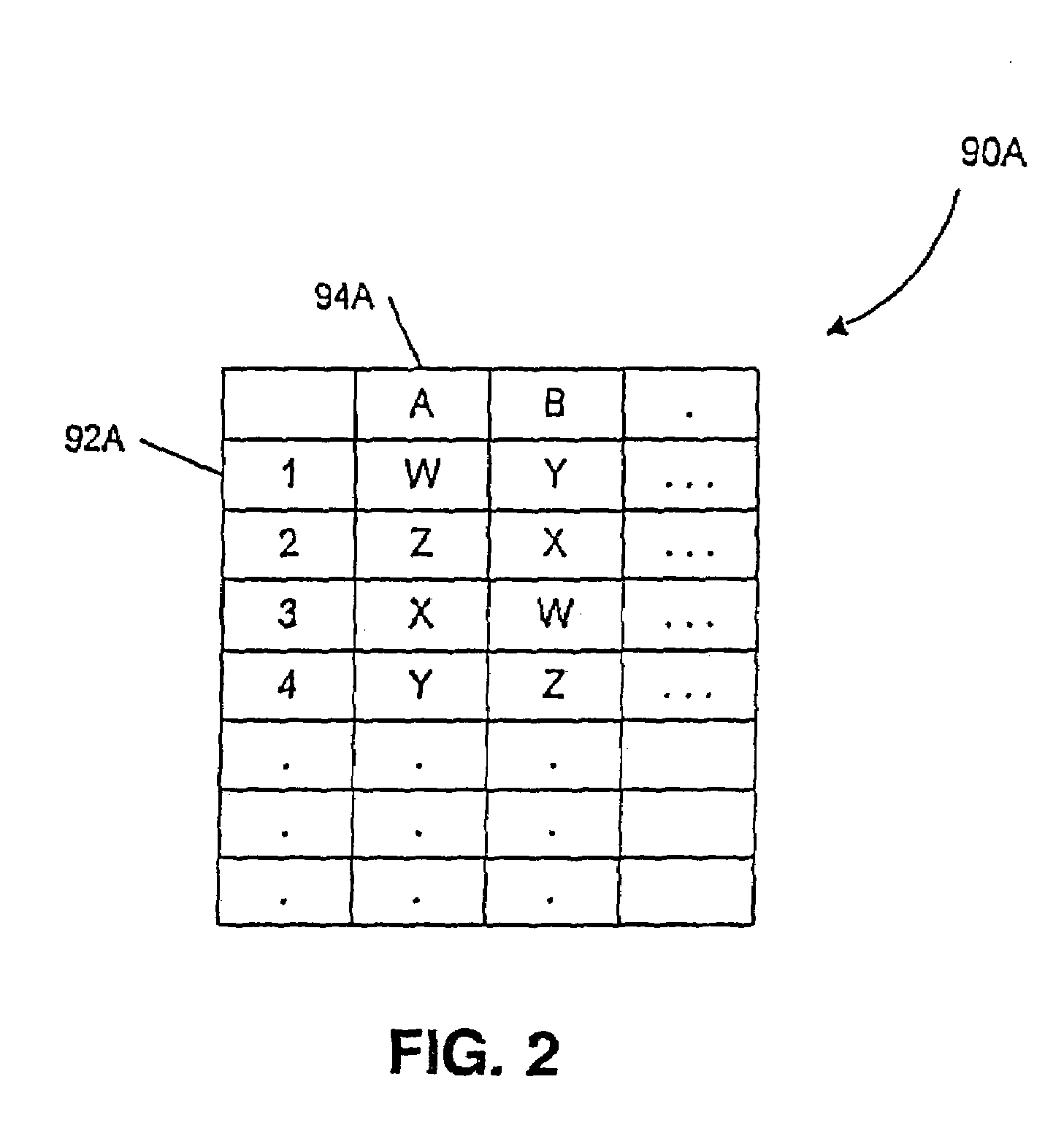
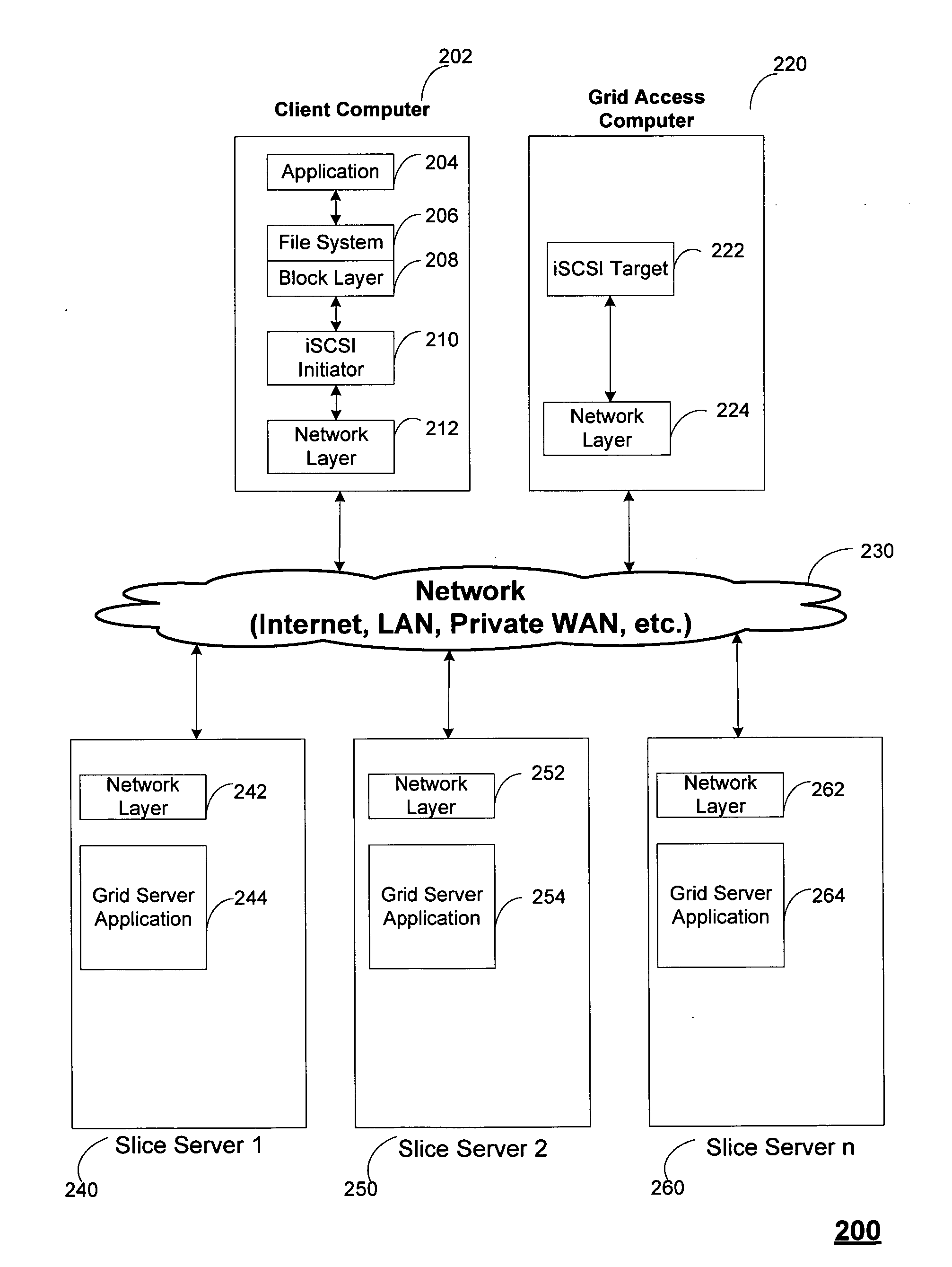
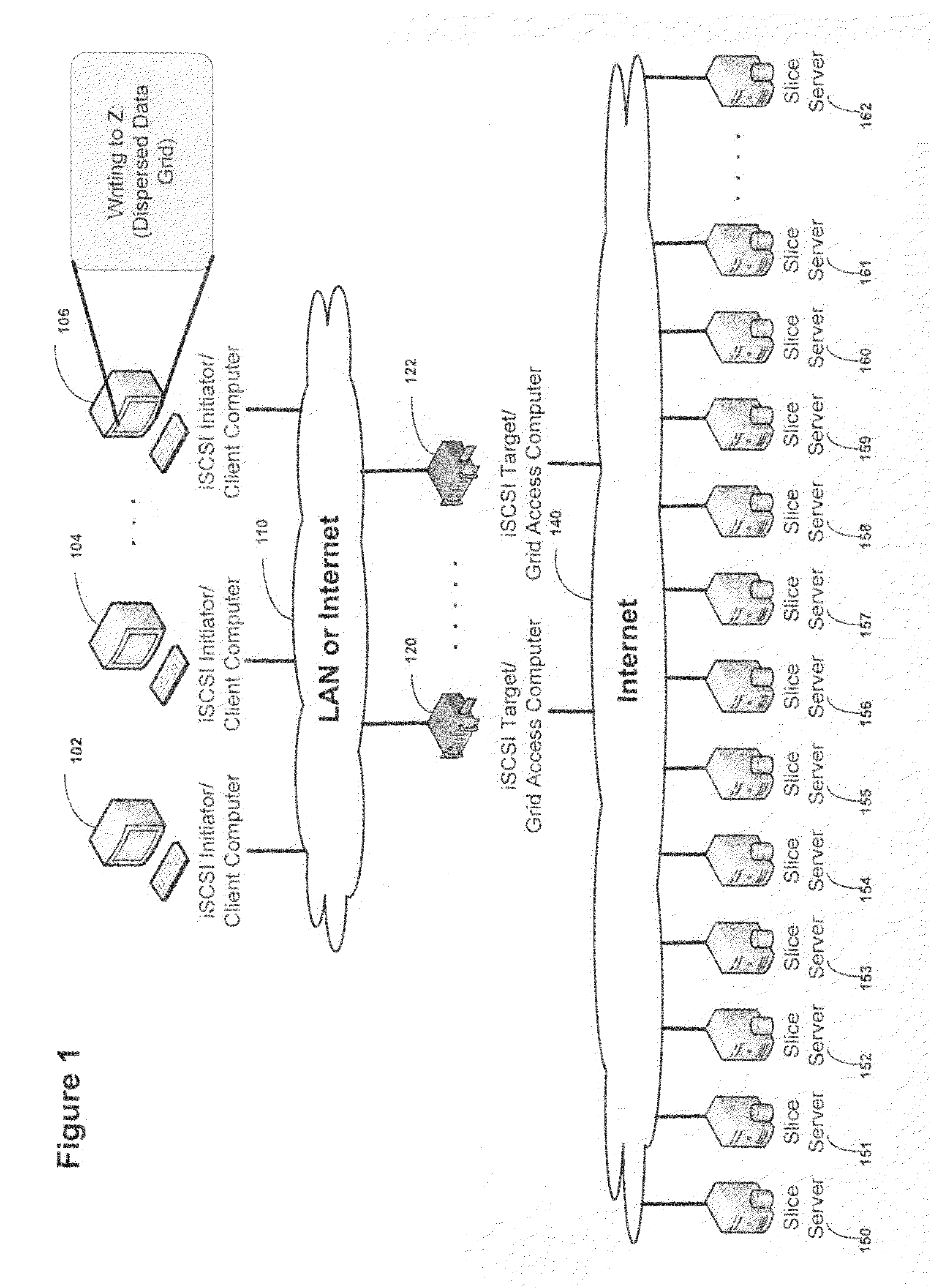
Block based access to a dispersed data storage network
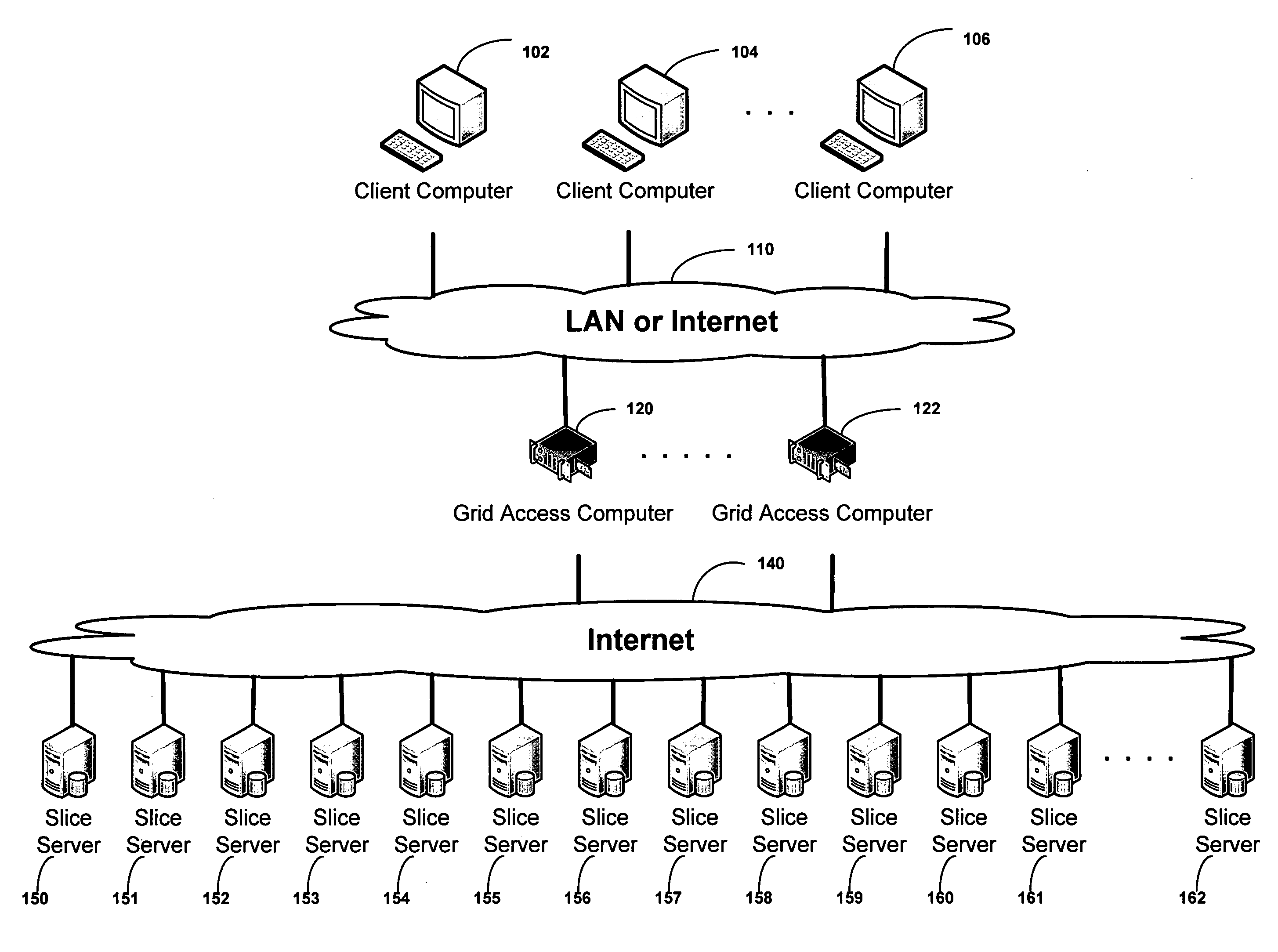
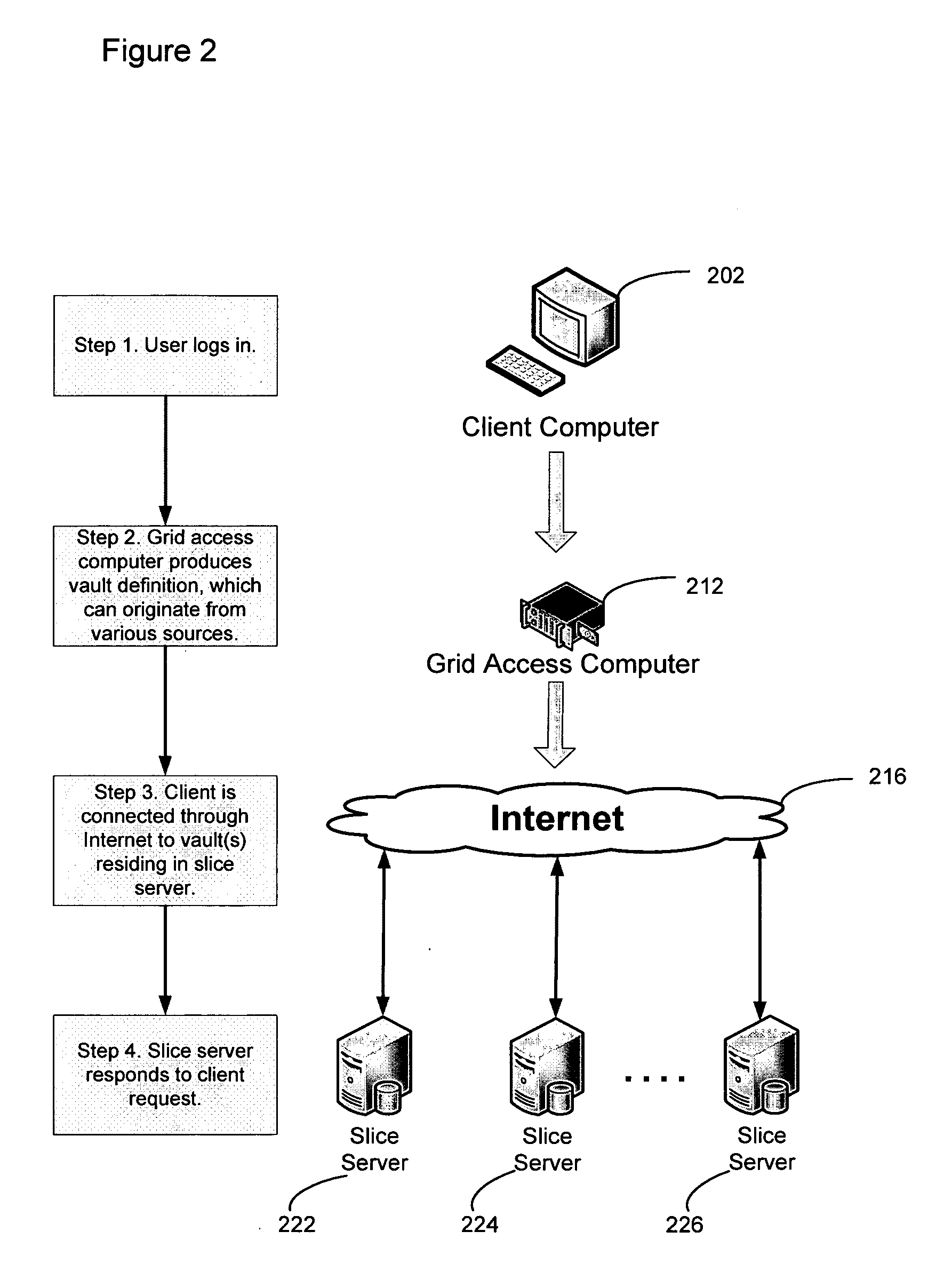
ActiveUS20100023524A1Simple methodDigital data processing detailsError detection/correctionFile systemData store
A block-based interface to a dispersed data storage network is disclosed. The disclosed interface accepts read and write commands from a file system resident on a user's computer and generates network commands that are forwarded to slice servers that form the storage component of the dispersed data storage network. The slice servers then fulfill the read and write commands.
Owner:PURE STORAGE
Storage system and a storage management system
InactiveUS20060047907A1Improve matchMemory loss protectionMultiple digital computer combinationsData packStorage management
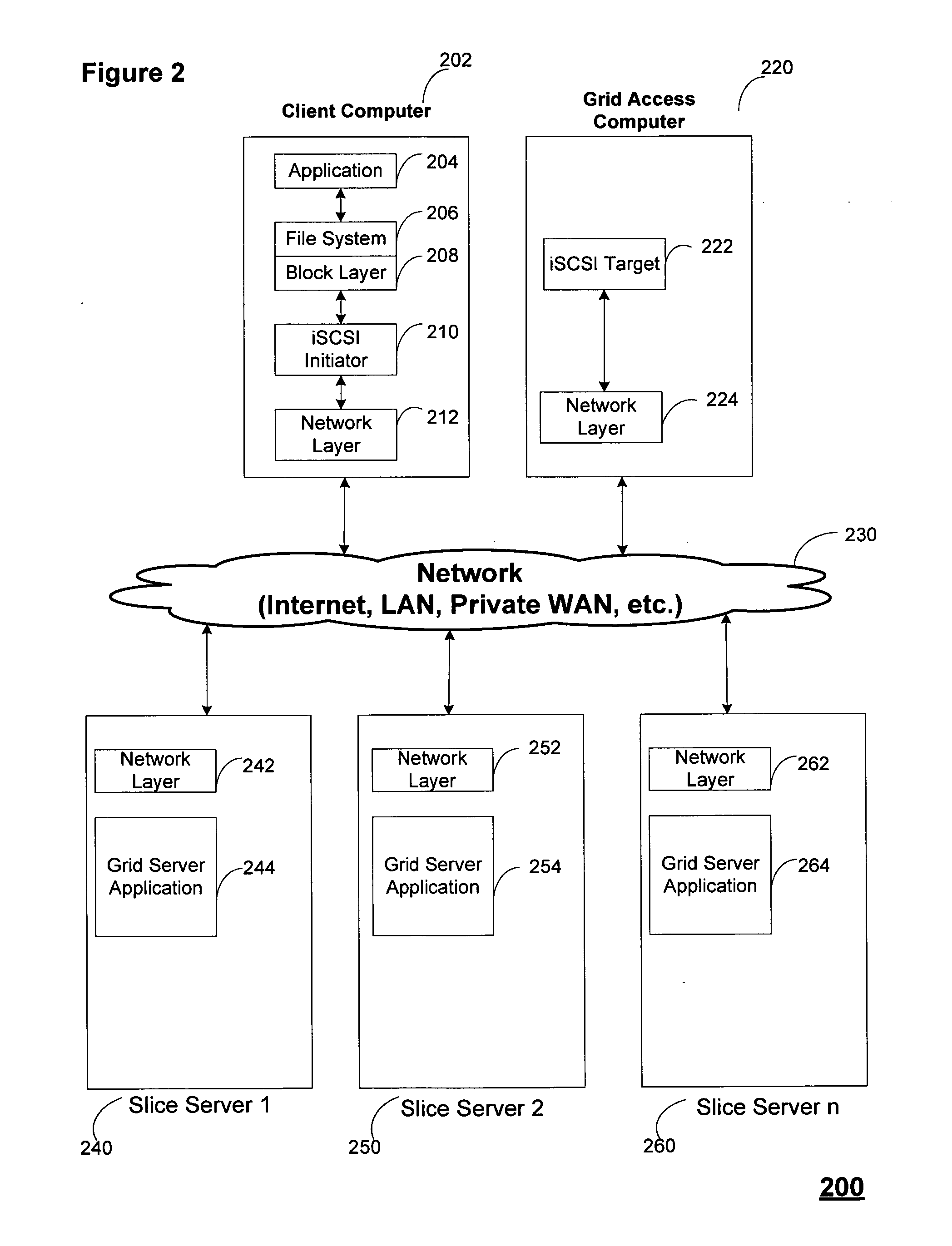
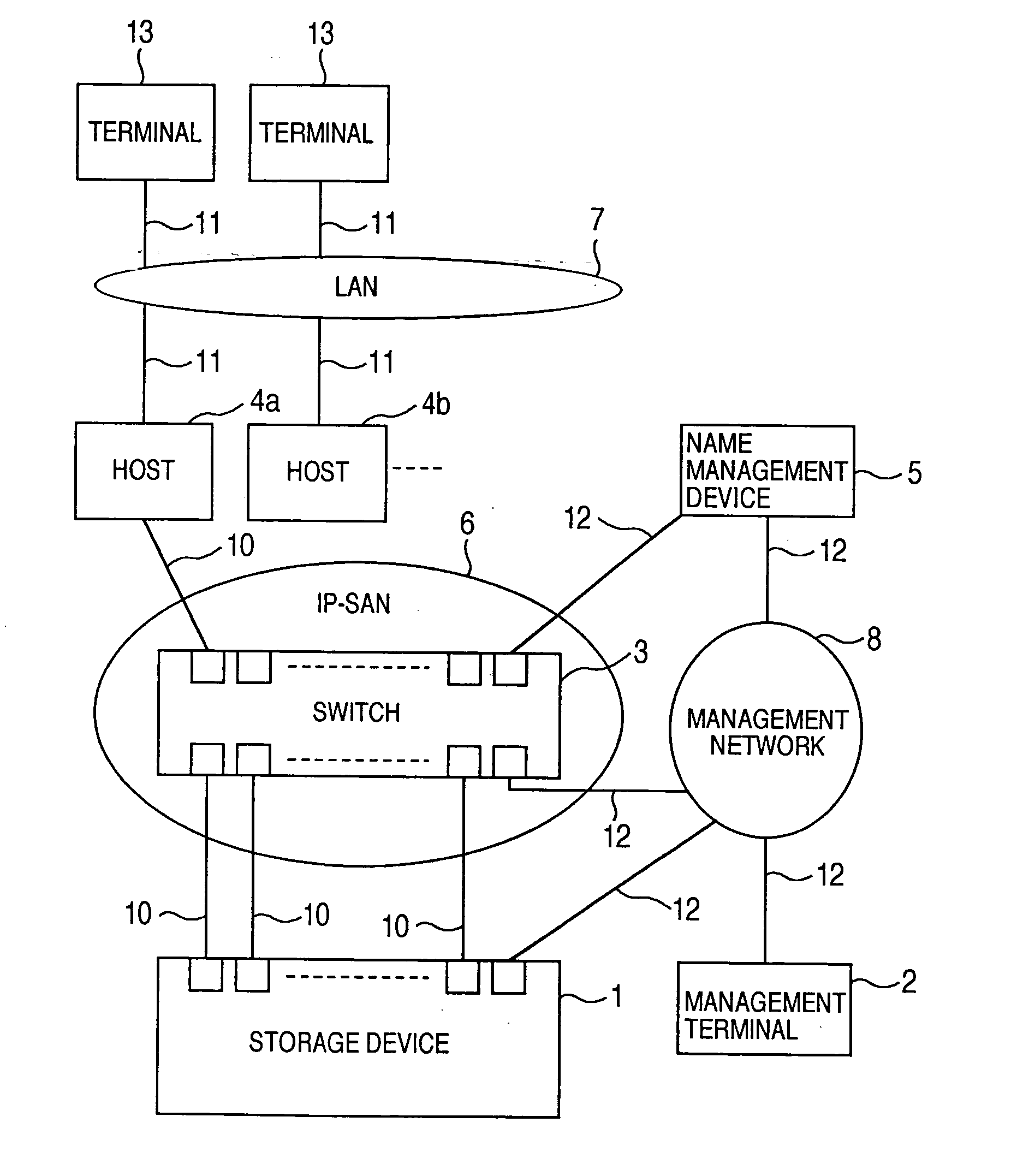
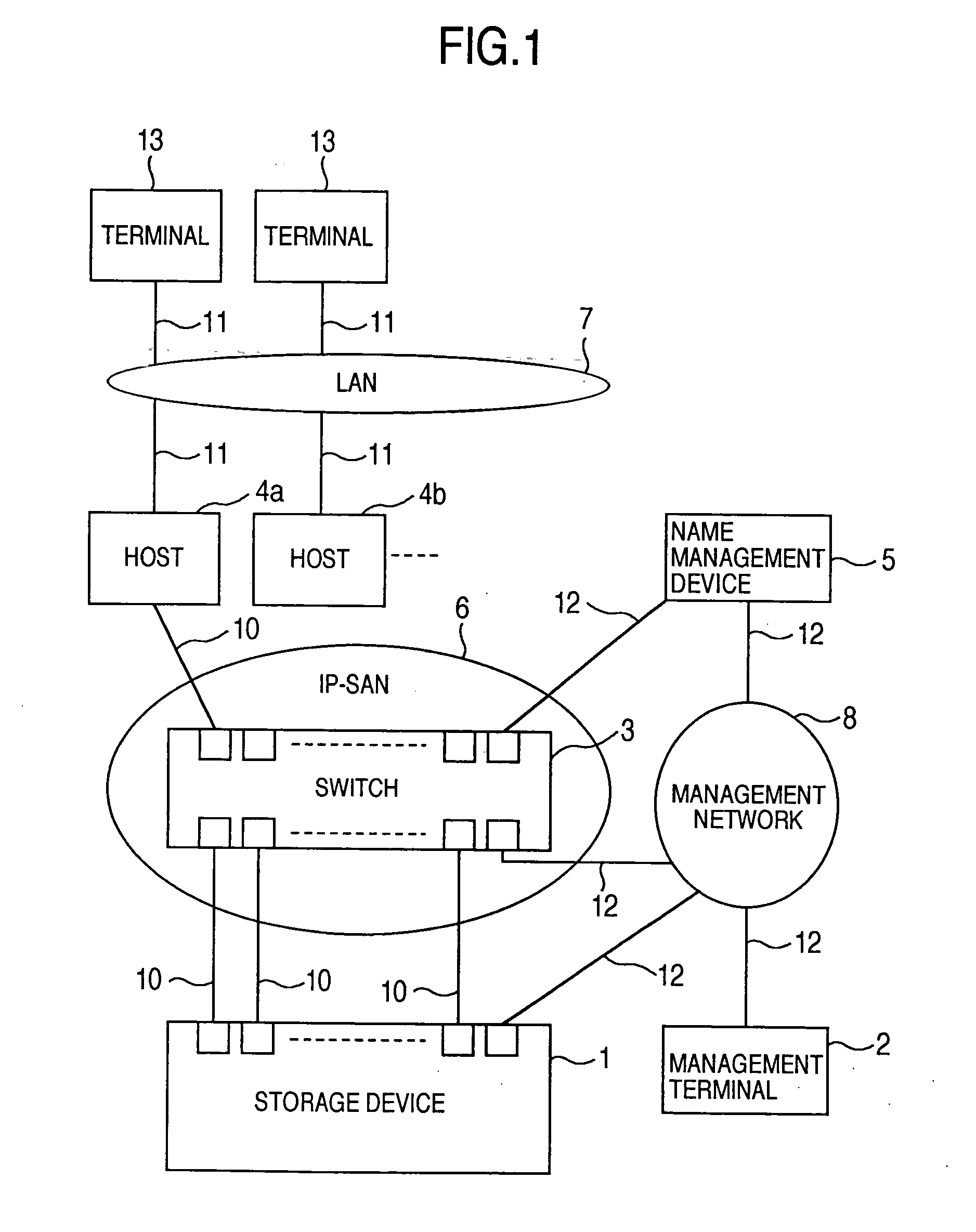
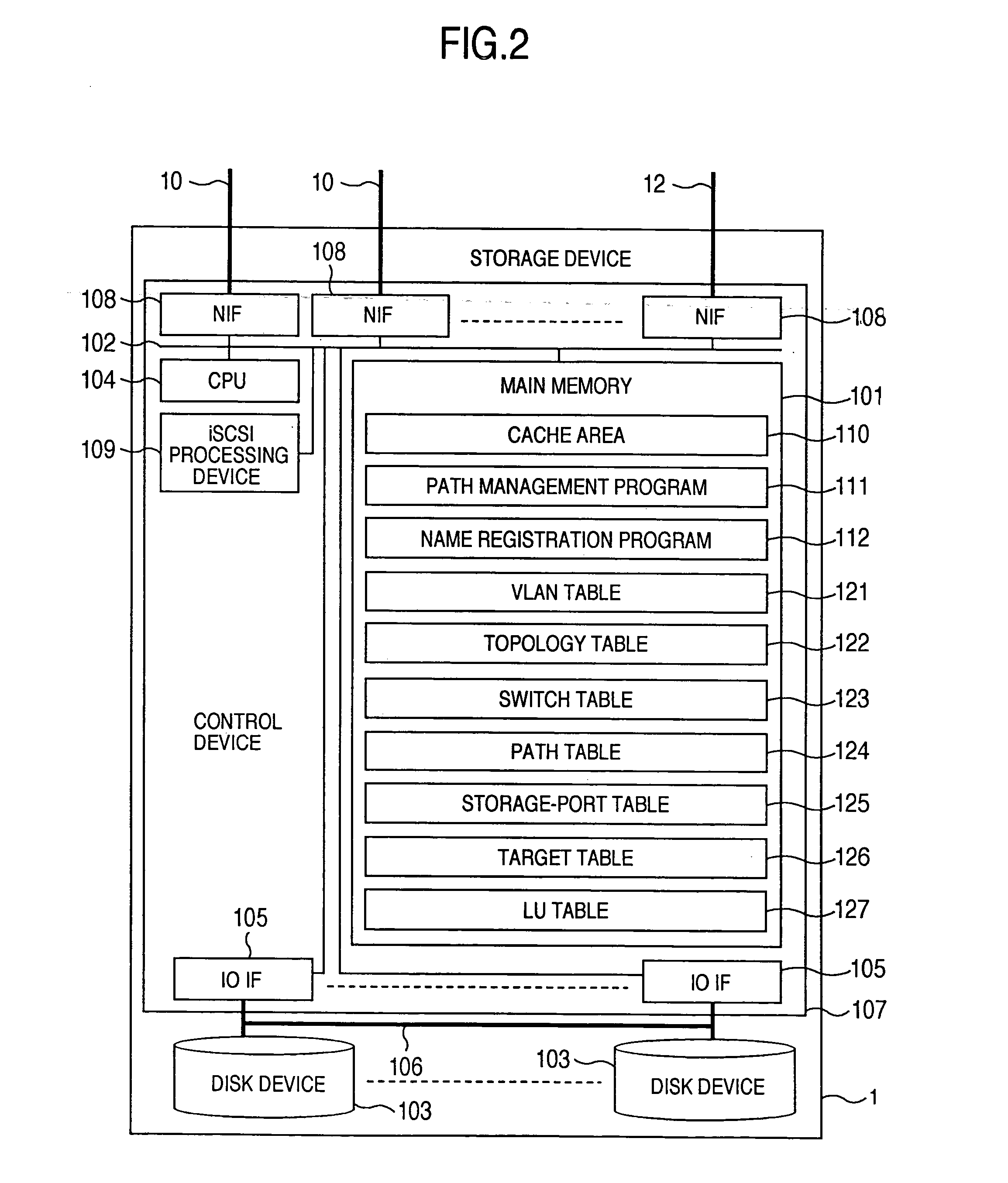
A storage device managing one or more logical volumes is connected with a name management device through an IP-SAN 6 composed of a switch. The storage device stores a topology table saving connecting relation among physical ports of host, physical ports of the storage device and physical ports of the switch, reads an identifier of the host and an identifier of the logical volume, selects a unused first physical port of the switch by referring to the topology table, selects a second physical port of the switch connected with the storage device, registers a group composed of the host and the logical volume with the name management device, and executes a configuration of allowing packets to be transferred between the first and the second physical ports with respect to the switch.
Owner:GOOGLE LLC
Virtualized data storage vaults on a dispersed data storage network
ActiveUS20090094251A1Efficient managementData processing applicationsDigital data processing detailsInformation dispersalVirtualization
A system, method, and apparatus for implementing a plurality of dispersed data storage networks using a set of slice servers are disclosed. A plurality of information records are maintained, with each information record corresponding to a dispersed data storage network. The information record maintains what slice servers are used to implement the dispersed data storage network, as well as other information needed to administer a DDSN, such as the information dispersal algorithm used, how data is stored, and whether data is compressed or encrypted.
Owner:PURE STORAGE
Audio visual player apparatus and system and method of content distribution using the same
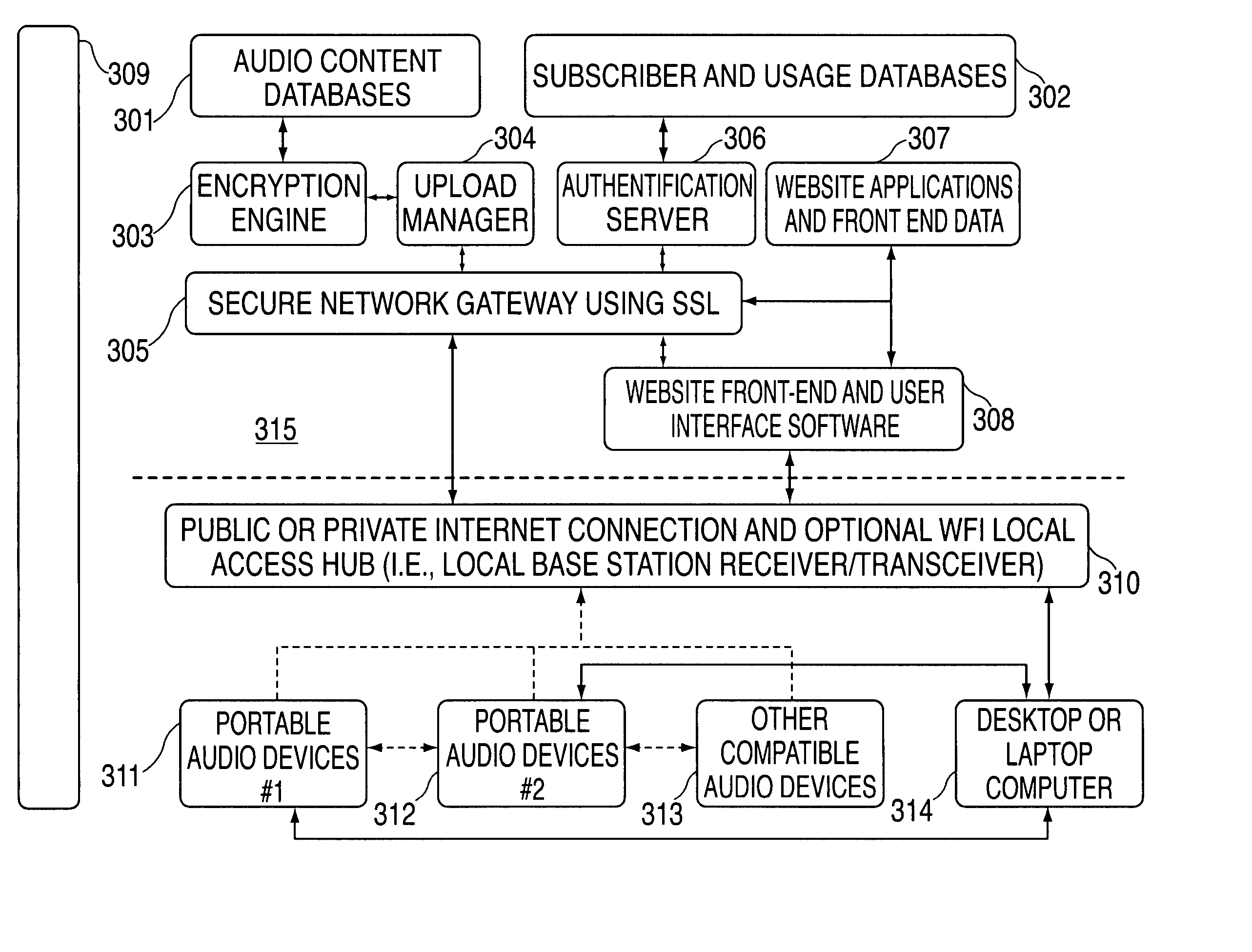
InactiveUS20060008256A1None of methods is secureTelevision system detailsColor television signals processingContent distributionVideo player
A portable wireless communications subscriber audio and / or video player apparatus and system and method for selecting, requesting, downloading, and playing audio and / or video data content files from an Internet-based database server. The wireless link is preferably implemented in accordance with the WiFi protocol, which allows connectivity to the Internet by being in proximity with a local base station or WiFi hotspot (i.e., publicly available local wireless access hub connected to the Internet). The portable wireless communications subscriber audio and / or video player apparatus and system preferably include a security means for monitoring and blocking unauthorized use of the player apparatus and system. The player apparatus further preferably has the capability to communicate with other neighboring player apparatus for the purpose of exchanging content data files, playlists and personal messages.
Owner:SANDISK TECH LLC
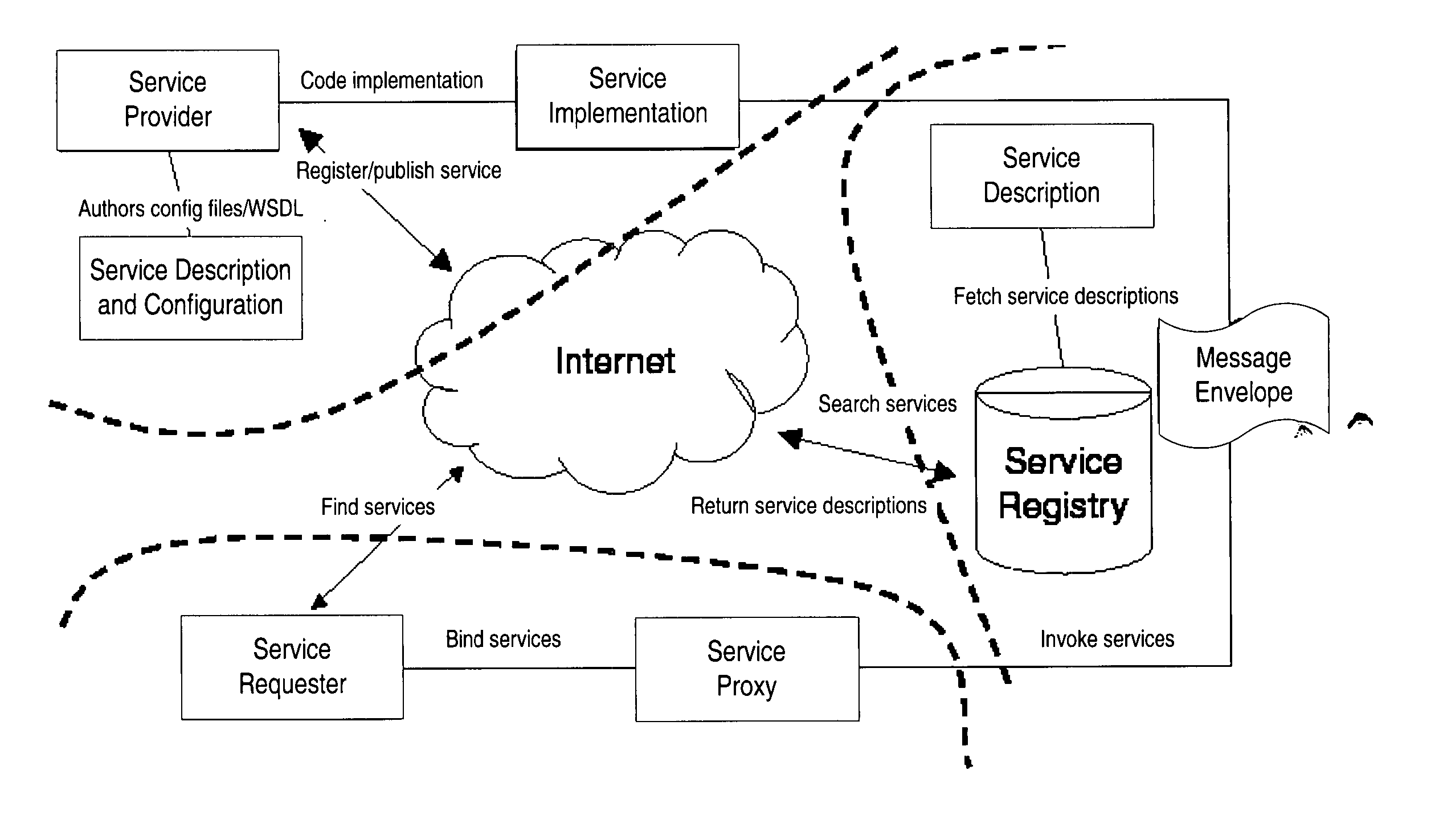
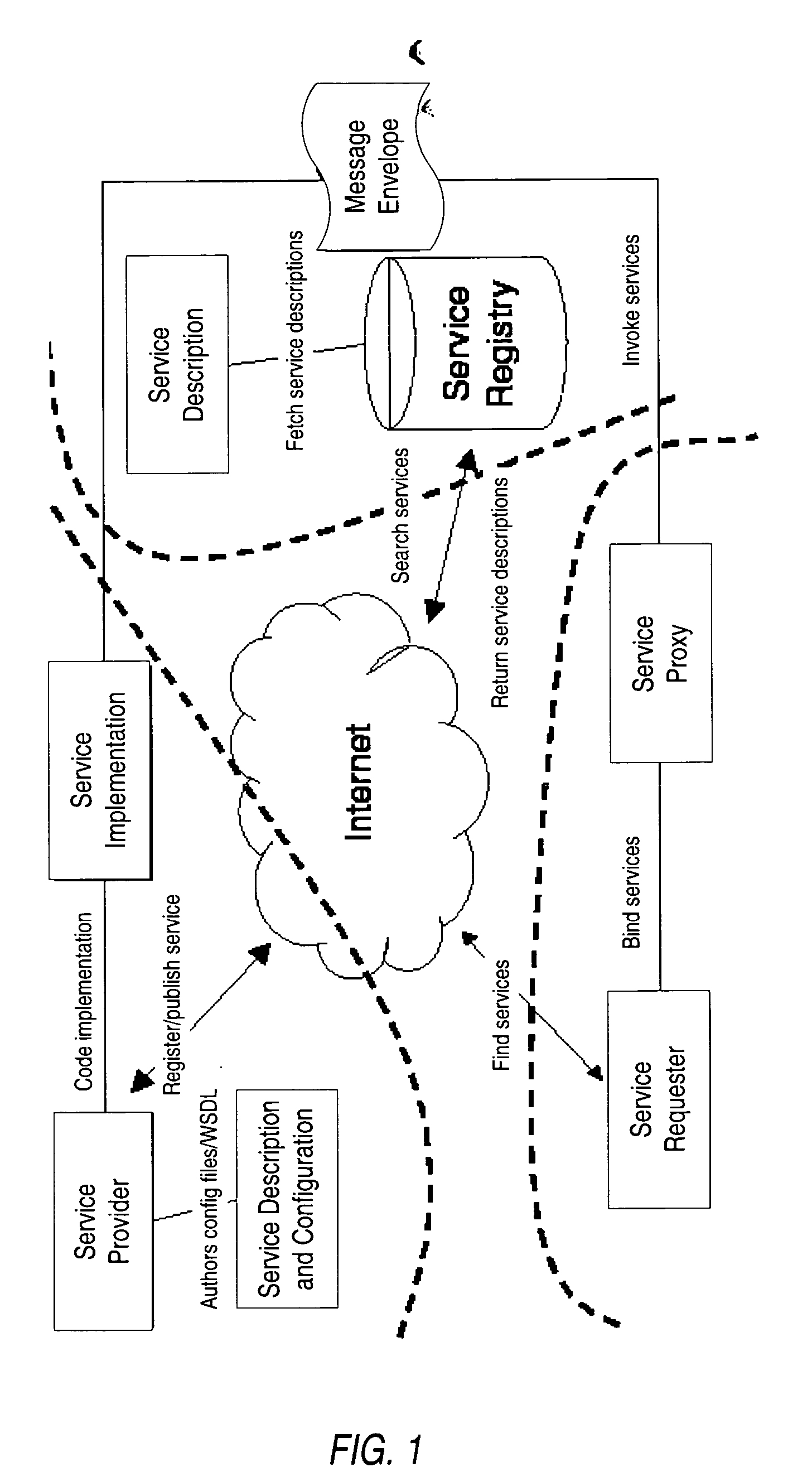
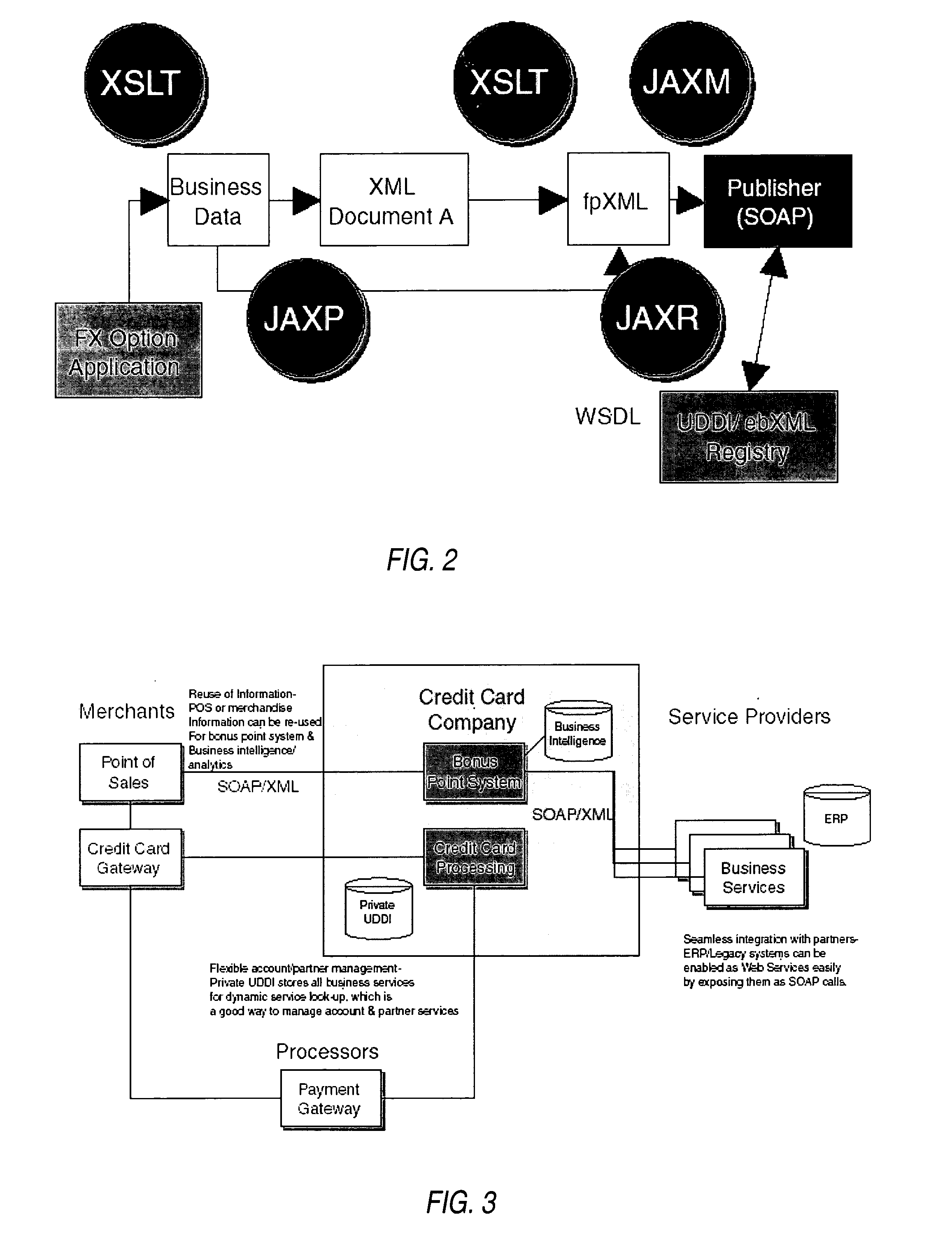
Structured methodology and design patterns for web services
ActiveUS20050044197A1Multiple digital computer combinationsDigital dataQuality of serviceBusiness-to-business
System and method for designing and implementing Web Services according to a structured methodology and design patterns. Embodiments may incorporate a structured methodology, best practices and design patterns that address reliability, availability and scalability of Web Services architecture. Embodiments may provide mechanisms for integrating heterogeneous technology components into Web Services. Embodiments may provide a vendor-independent Web Services architecture framework and reusable Web Services design patterns, which may be used in creating end-to-end solutions based on past experience and best practices. Embodiments may include design patterns and best practices for delivering Web Services solutions with Quality of Services. One embodiment may provide a Business-to-Business Integration (B2Bi) integration framework for Web Services. Embodiments may provide a Web Security framework and design patterns for designing end-to-end Web Services security.
Owner:ORACLE INT CORP
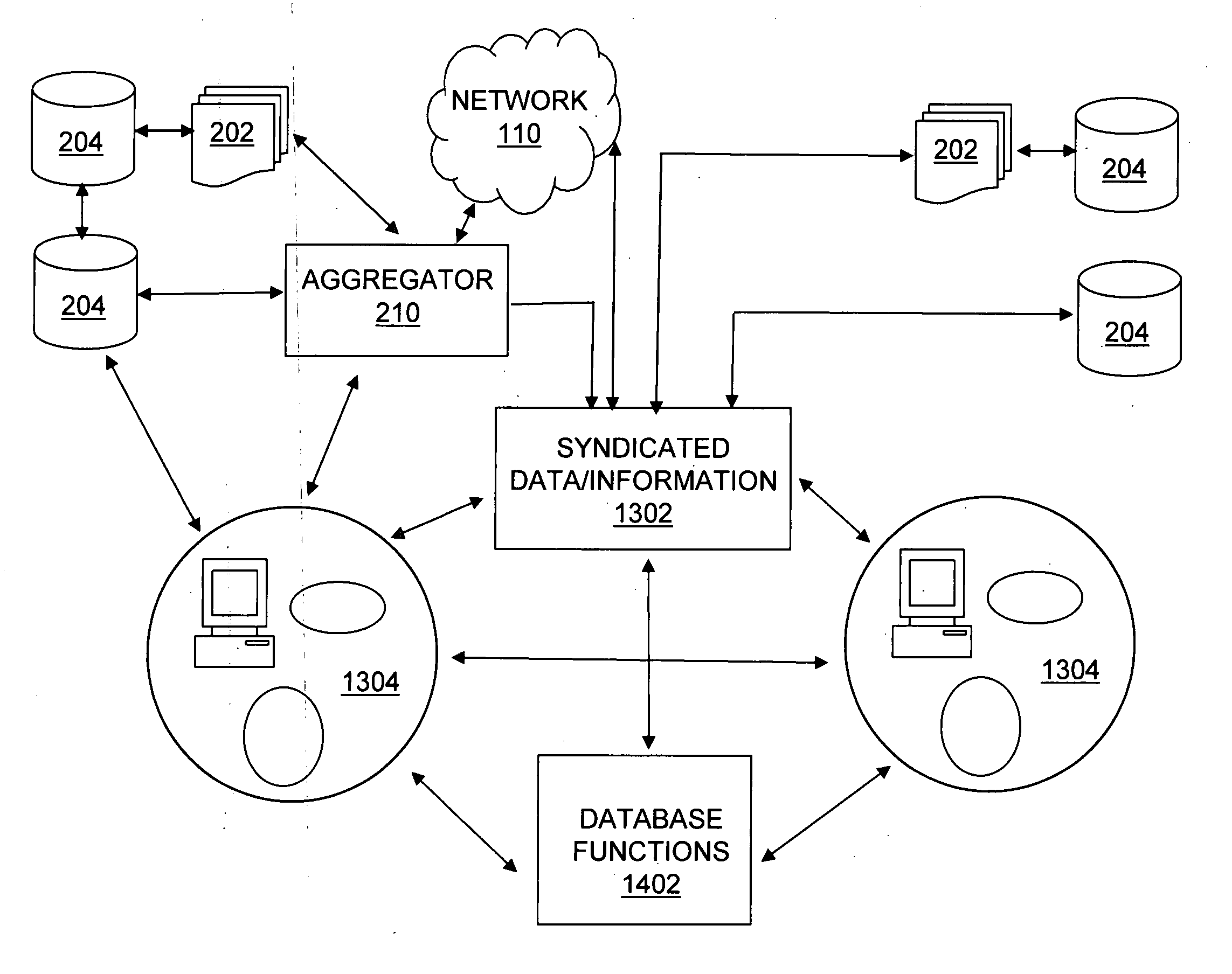
Enhanced syndication
InactiveUS20060173985A1Excellent ease of useRichly-functionedMechanical/radiation/invasive therapiesTechnology managementData feedData stream
A variety of tools and techniques are disclosed for managing, viewing, publishing, searching, clustering, and otherwise manipulating data streams. Data streams such as RSS data feeds may be searched, aggregated, and filtered into a processed feed. The processed feed, along with rules used to process the feed may be shared in a number of ways. A data feed management system may provide an integrated user interface through which a user may manage feeds, including searching for new feeds, managing and filtering current feeds, modifying a user profile, and sharing feeds and feed configuration data with other users. A server may provide a complementary search engine to locate new feeds and to store and / or index items or posts in known feeds. Together, these technologies may provide a richly-functioned feed management system and greater ease of use for individuals in managing large numbers of feeds and large amounts of data in feeds. Additional functional layers may provide for authentication, security, and privacy, metadata creation and management, and social networking features. Using the management tools and additional functionality, a syndicated data stream system may provide a platform for a wide array of useful consumer and business applications.
Owner:NEWSILIKE MEDIA GROUP
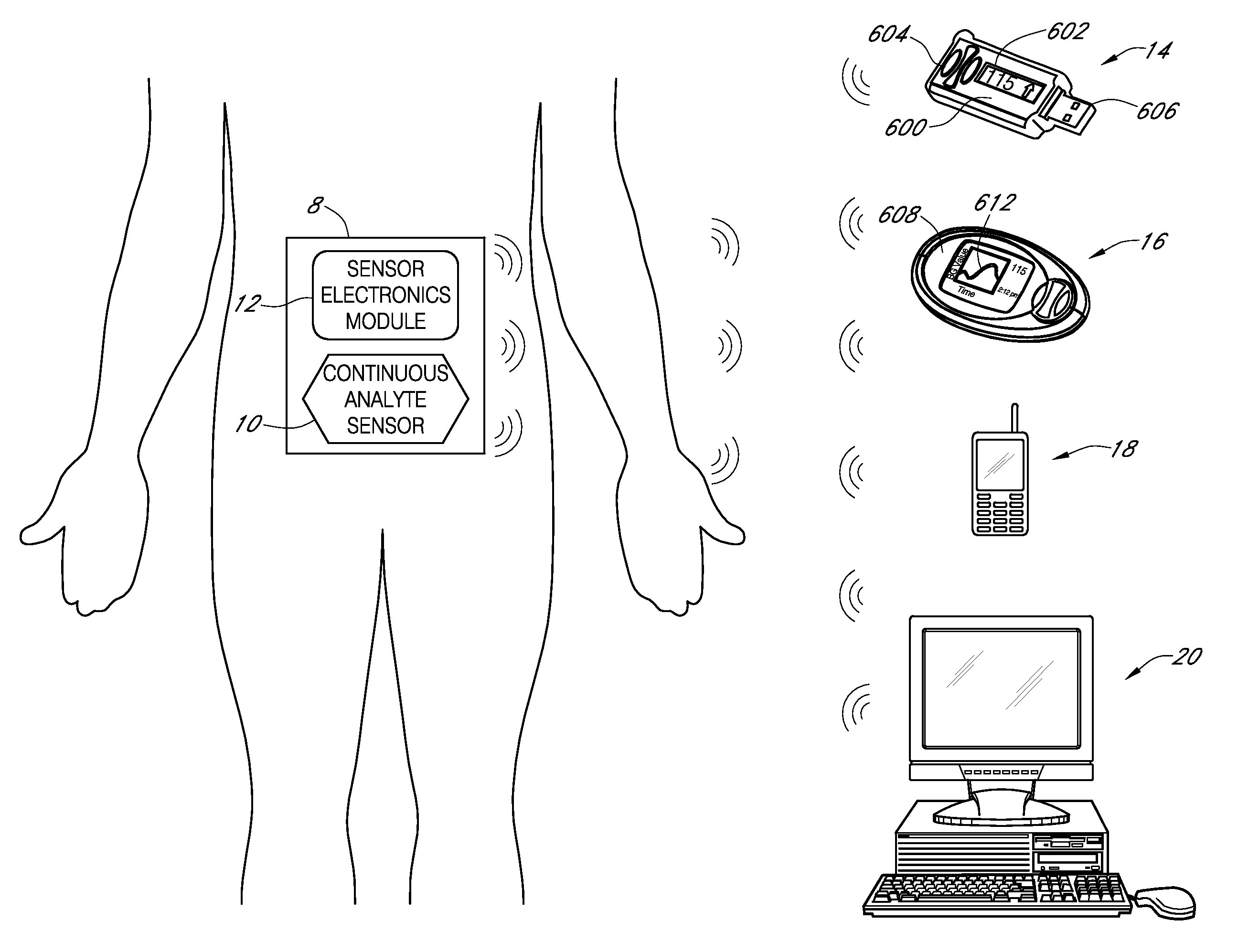
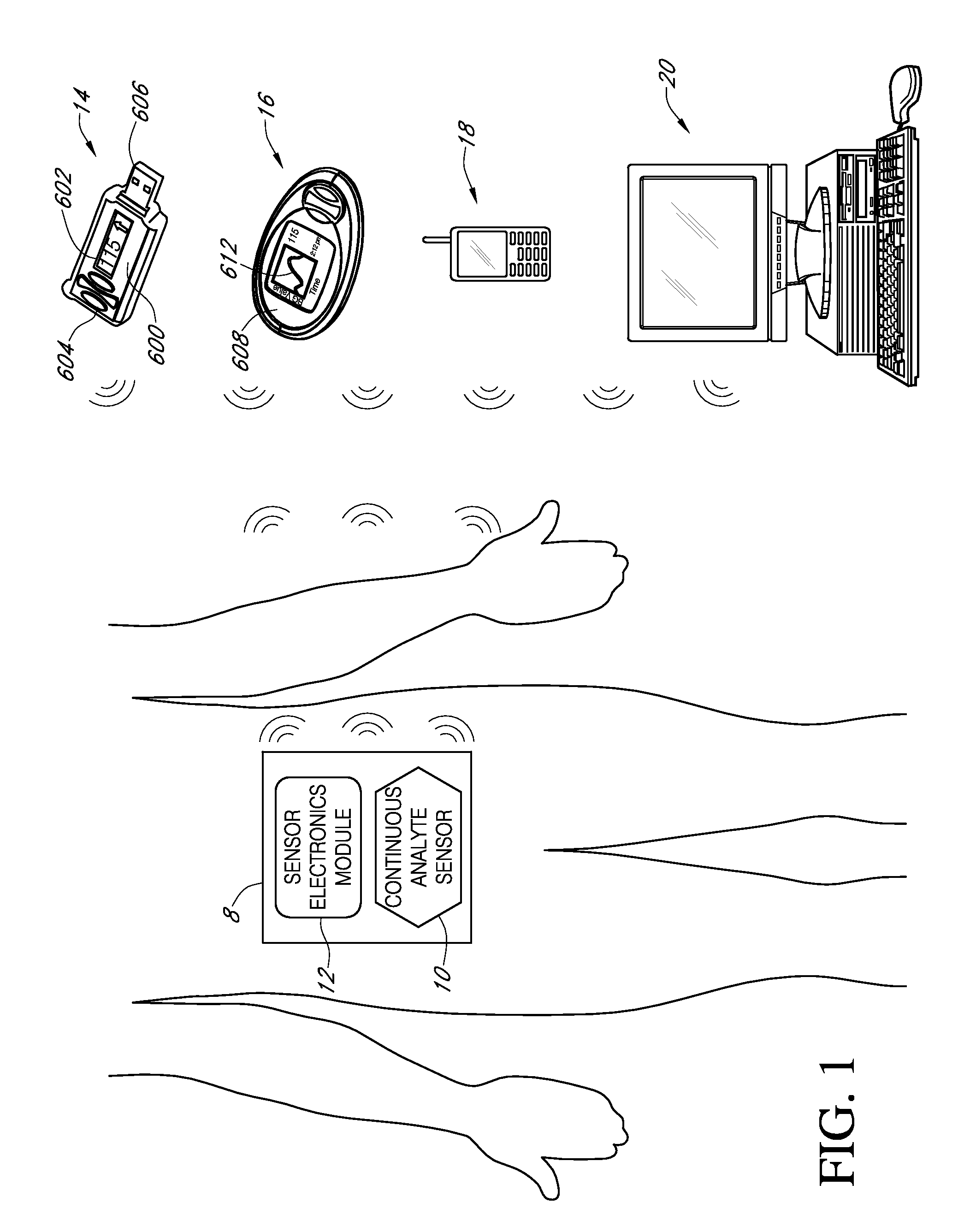
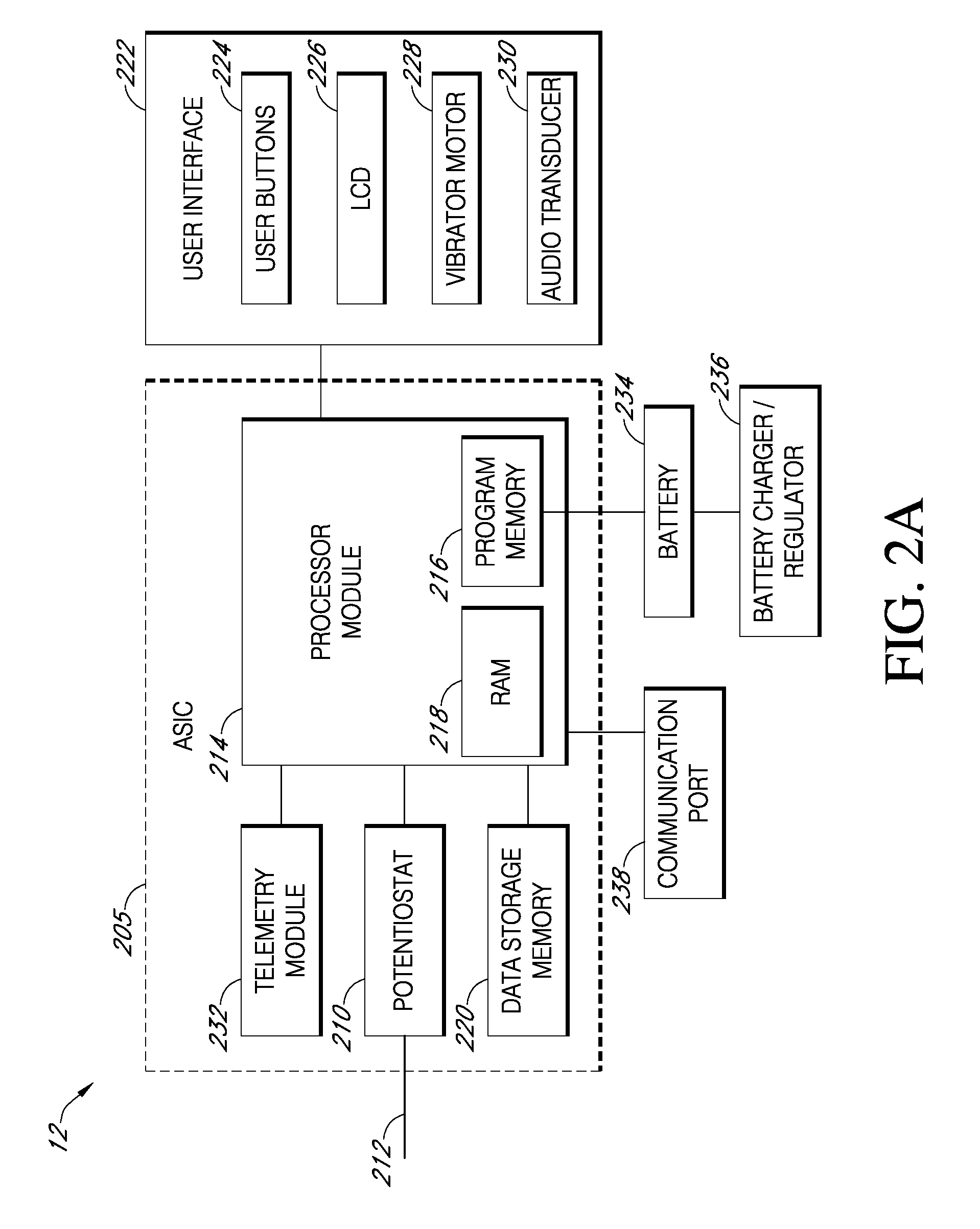
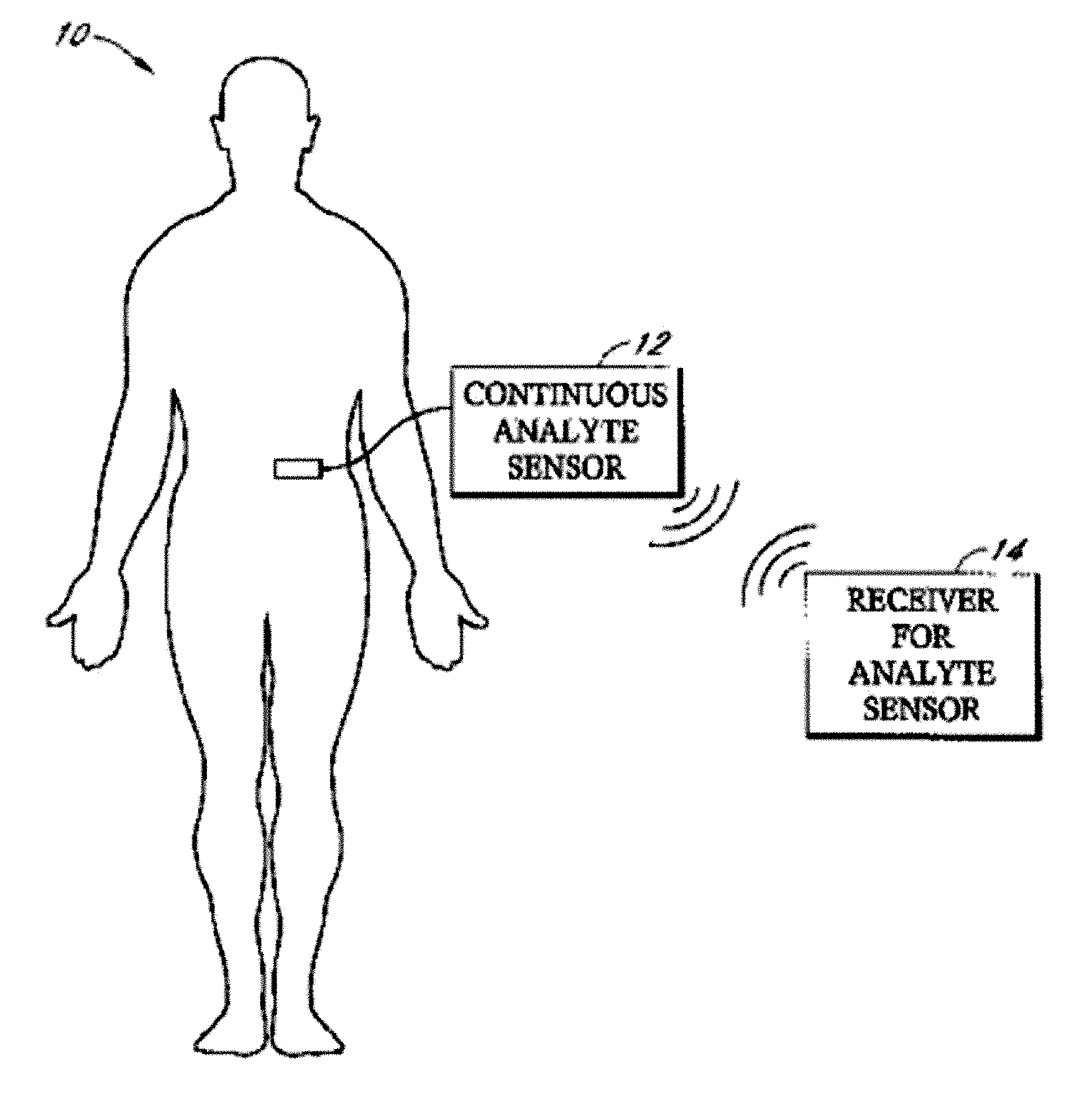
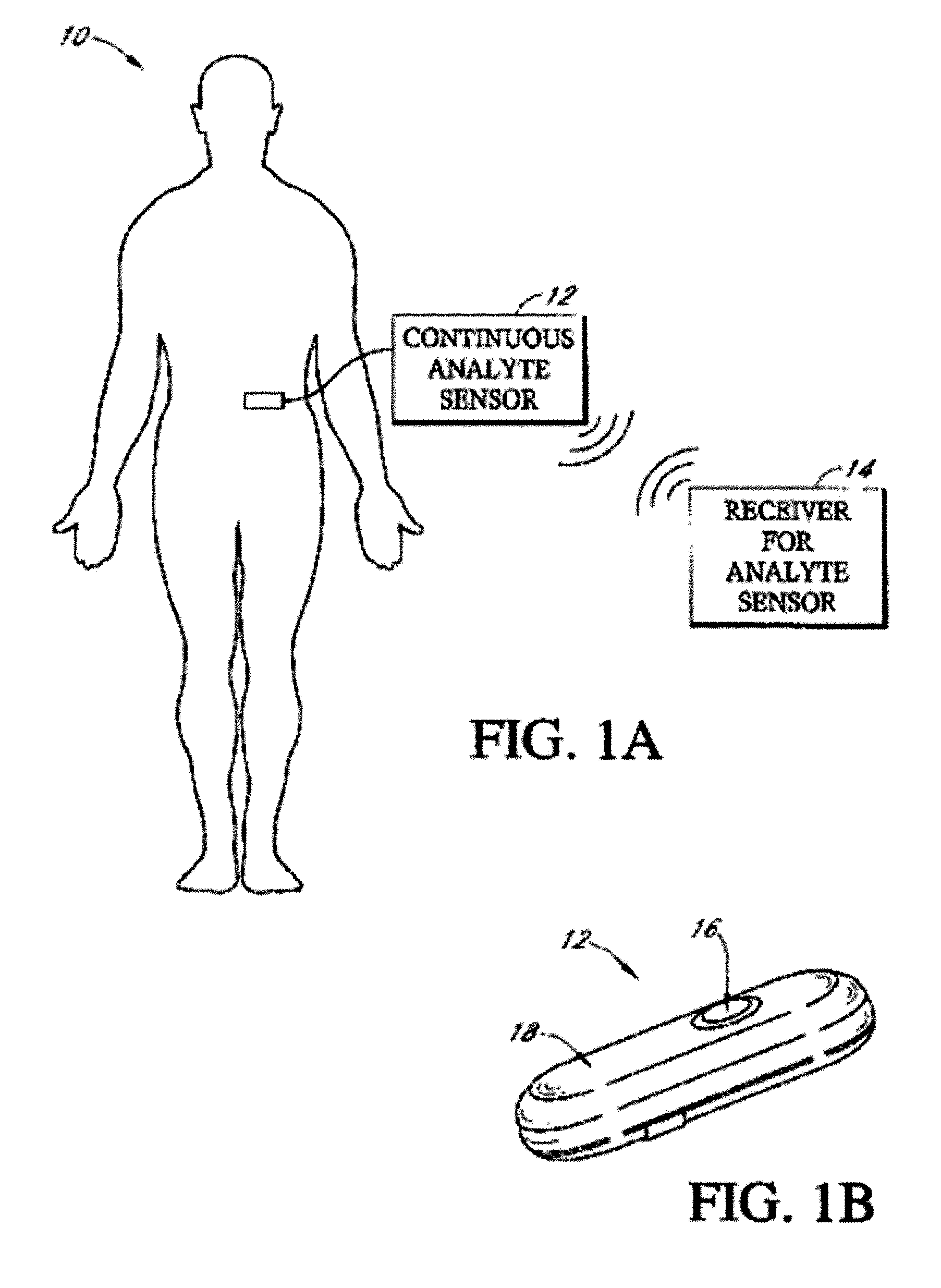
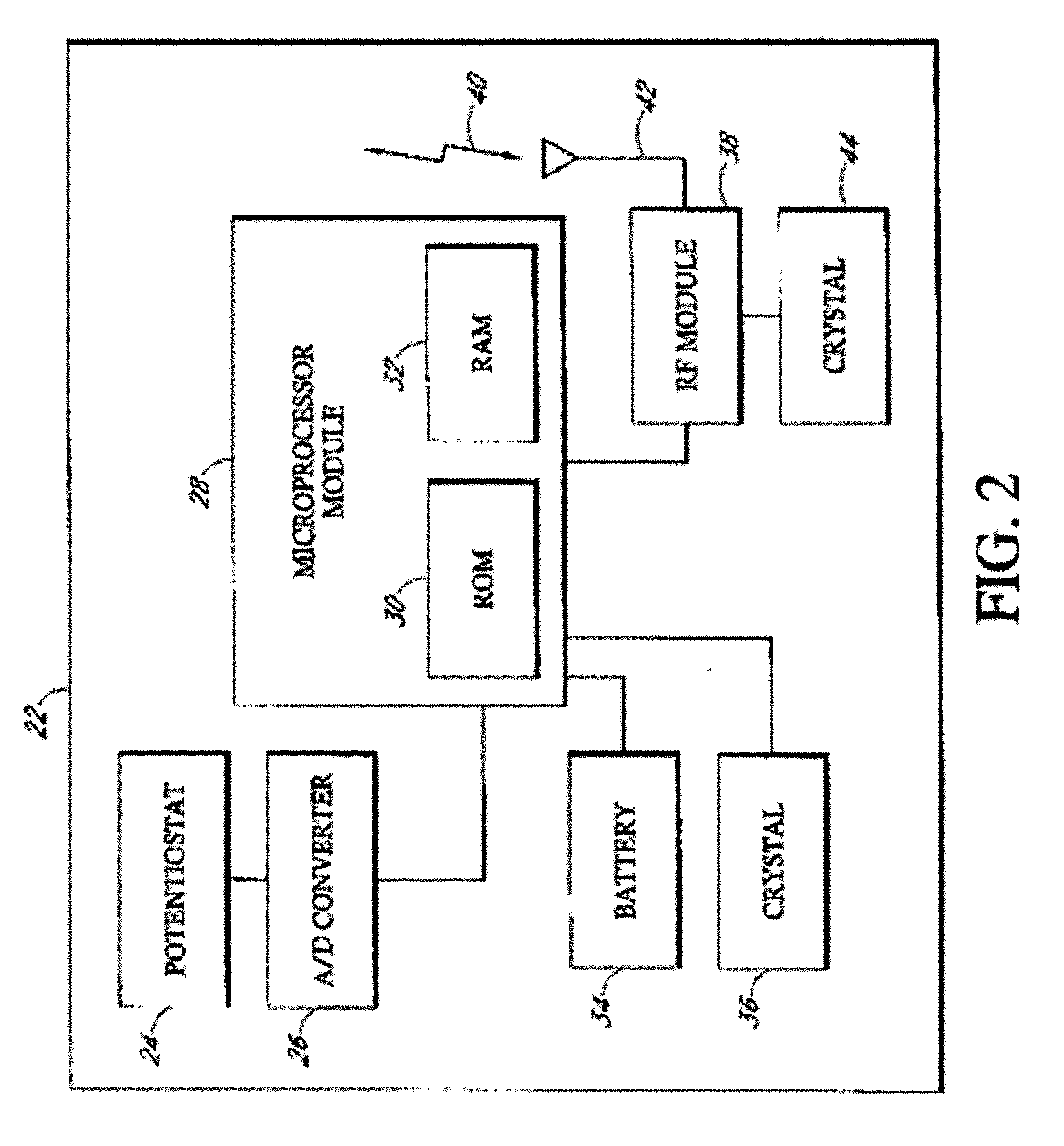
Systems and methods for processing, transmitting and displaying sensor data
Systems and methods for continuous measurement of an analyte in a host are provided. The system generally includes a continuous analyte sensor configured to continuously measure a concentration of analyte in a host and a sensor electronics module physically connected to the continuous analyte sensor during sensor use, wherein the sensor electronics module is further configured to directly wirelessly communicate displayable sensor information to a plurality of different types of display devices.
Owner:DEXCOM
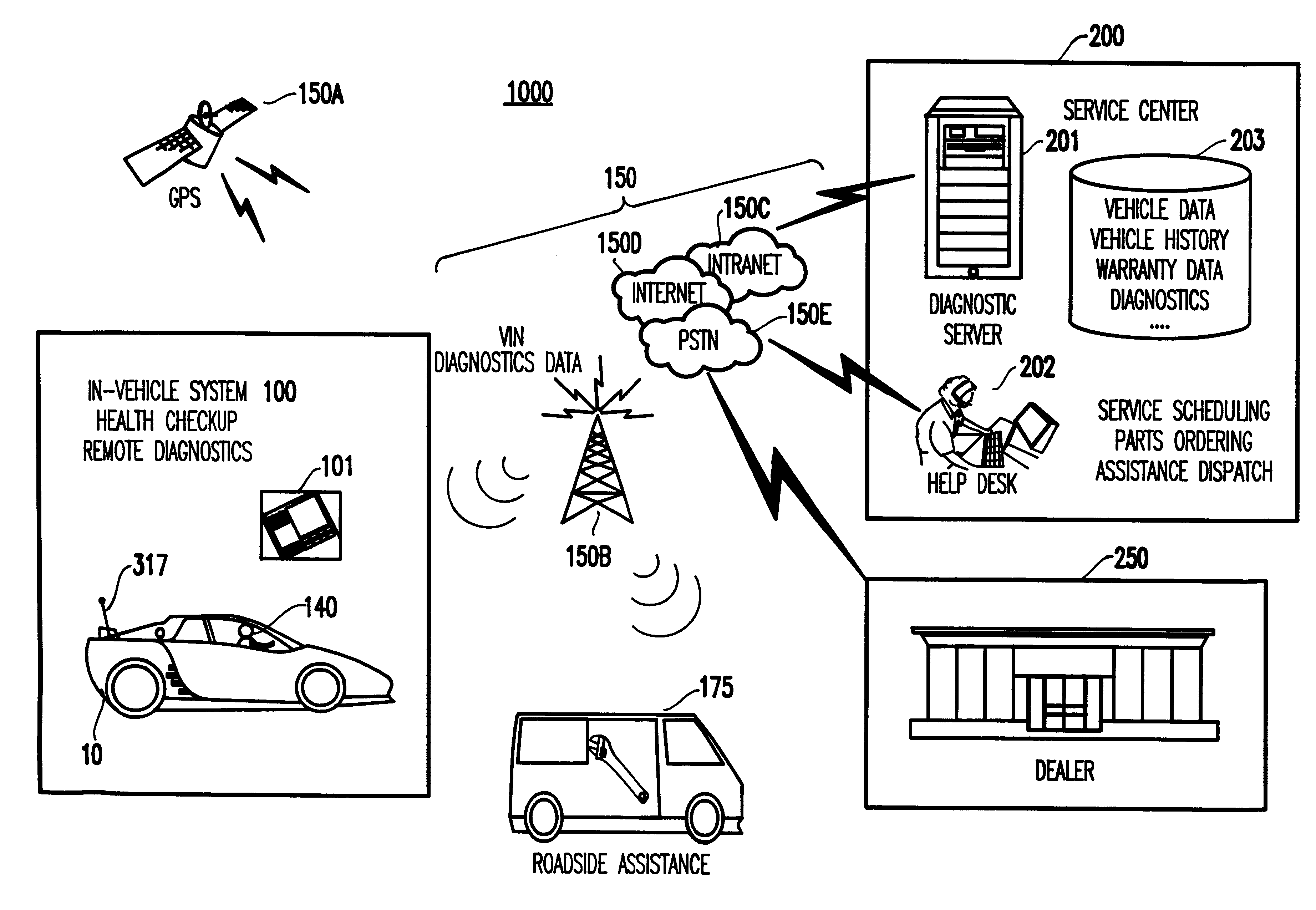
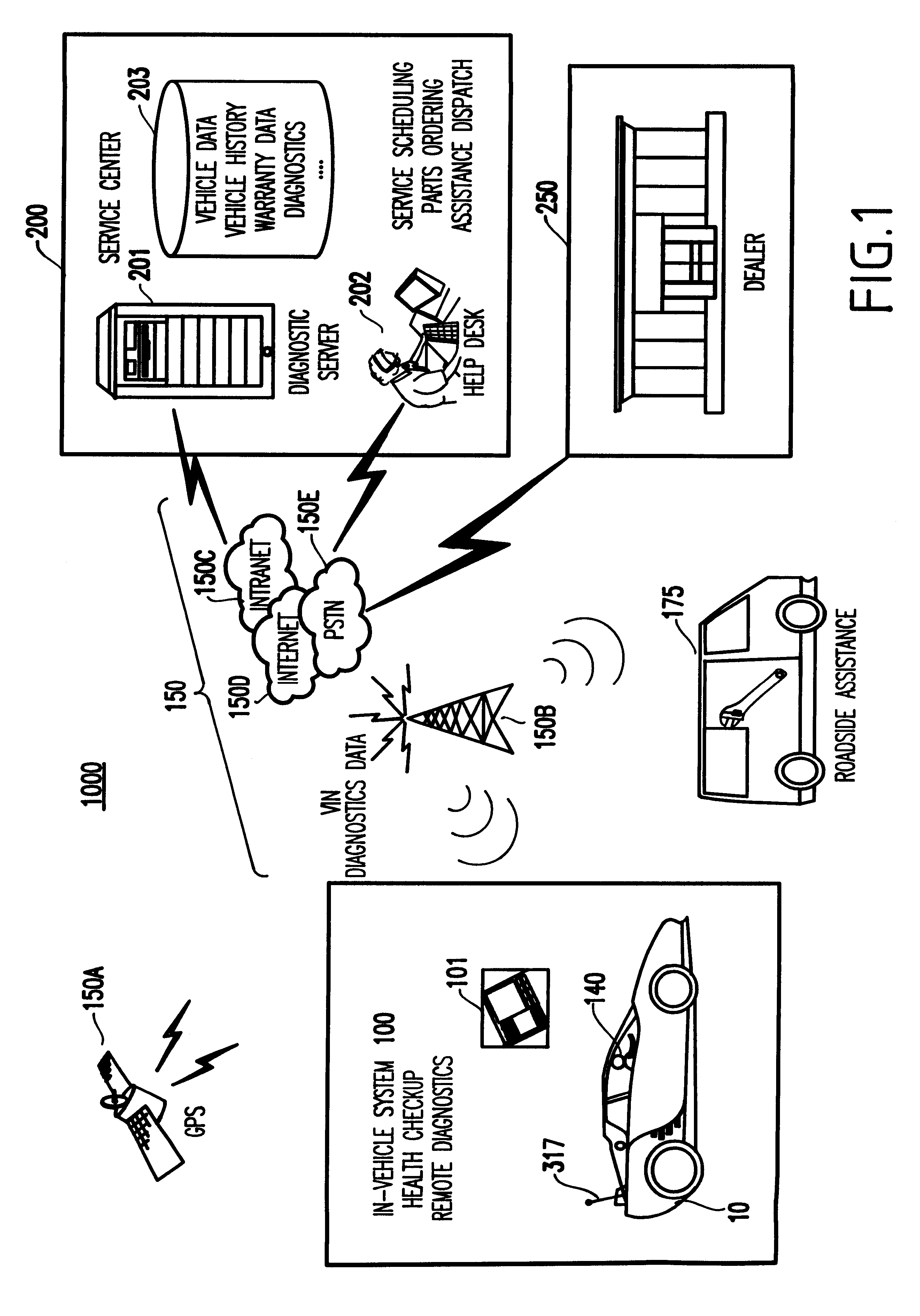
System and method for vehicle diagnostics and health monitoring
InactiveUS6330499B1Vehicle testingRegistering/indicating working of vehiclesSession managementCommunications system
A system and method for vehicle diagnostic and health monitoring includes a client computer device within the vehicle, coupled to the vehicle's monitoring systems, for data management, remote session management and user interaction, a communication system, coupled to the client computer device, for providing remote communication of data including data derived from internal monitoring systems of the vehicle, and a remote service center including a vehicle data store, a server computer, a diagnostic engine, and a communicator for communicating the results of analysis of vehicle information to the client computer device via the communication system.
Owner:CARRUM TECH LLC
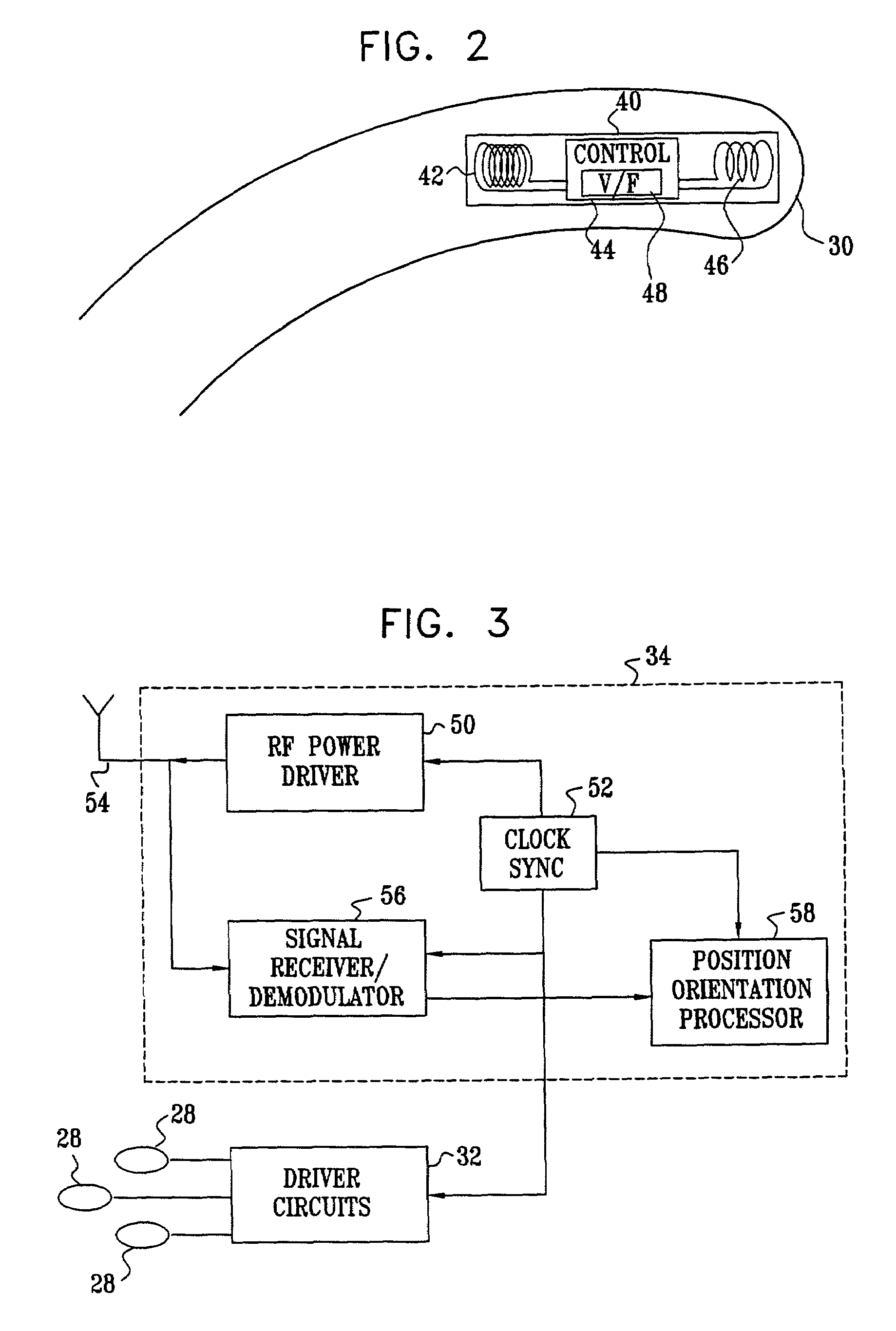
Wireless position sensor
Apparatus for tracking an object includes a plurality of field generators, which generate electromagnetic fields at different, respective frequencies in a vicinity of the object, and a radio frequency (RF) driver, which radiates a RF driving field toward the object. A wireless transponder is fixed to the object. The transponder includes at least one sensor coil, in which a signal current flows responsive to the electromagnetic fields, and a power coil, which receives the RF driving field and conveys electrical energy from the driving field to power the transponder. The power coil also transmits an output signal responsive to the signal current to a signal receiver, which processes the signal to determine coordinates of the object.
Owner:BIOSENSE
Systems and Methods to Target Predictive Location Based Content and Track Conversions
ActiveUS20080248815A1Particular environment based servicesDevices with GPS signal receiverCommunications systemMobile device
Methods and systems that record the location of a user and transmit targeted content to a user based upon their current and past location information. A network is configured to include a server programmed with a database of targeted content, a database of location information, a database of user information, a database searching algorithm, and a wireless communication system capable of communicating with the user's mobile device. The location of the mobile device is ascertained and recorded. The location information is analyzed to determine the routes taken by the user, businesses visited by the user, and other behaviors of the user. Targeted content is sent to the mobile device of the user and whether the user visits the physical locations associated with the targeted content is monitored. Payment systems, phone exchange systems, and other features may also be integrated to provide detailed conversion tracking to producers of targeted content and business owners.
Owner:META PLATFORMS INC
Implantable analyte sensor
ActiveUS20050245795A1Improved patient convenienceConvenient careImmobilised enzymesBioreactor/fermenter combinationsAnalyteEngineering
Abstract of the DisclosureAn implantable analyte sensor including a sensing region for measuring the analyte and a non-sensing region for immobilizing the sensor body in the host. The sensor is implanted in a precisely dimensioned pocket to stabilize the analyte sensor in vivo and enable measurement of the concentration of the analyte in the host before and after formation of a foreign body capsule around the sensor. The sensor further provides a transmitter for RF transmission through the sensor body, electronic circuitry, and a power source optimized for long-term use in the miniaturized sensor body.
Owner:DEXCOM
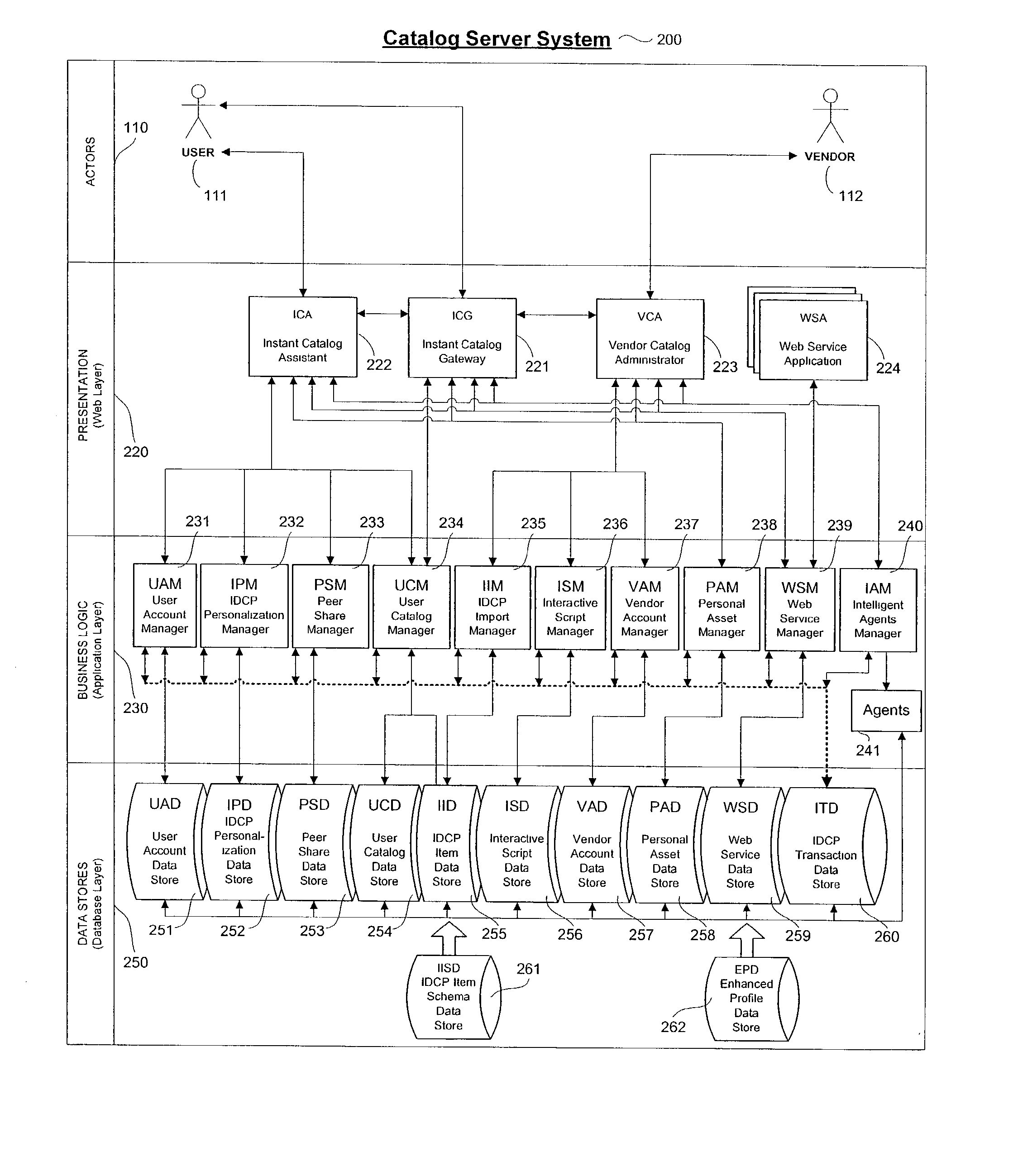
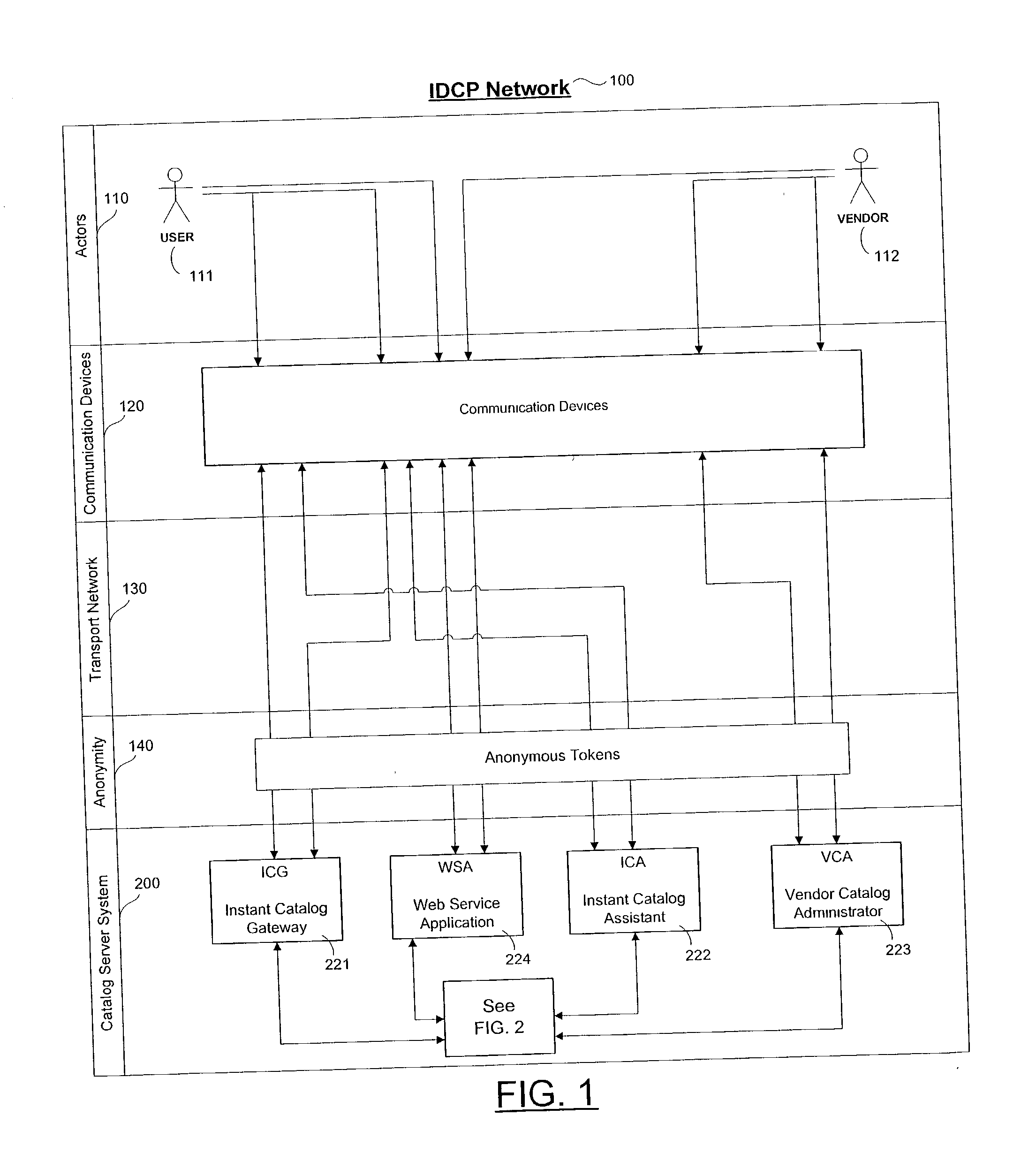
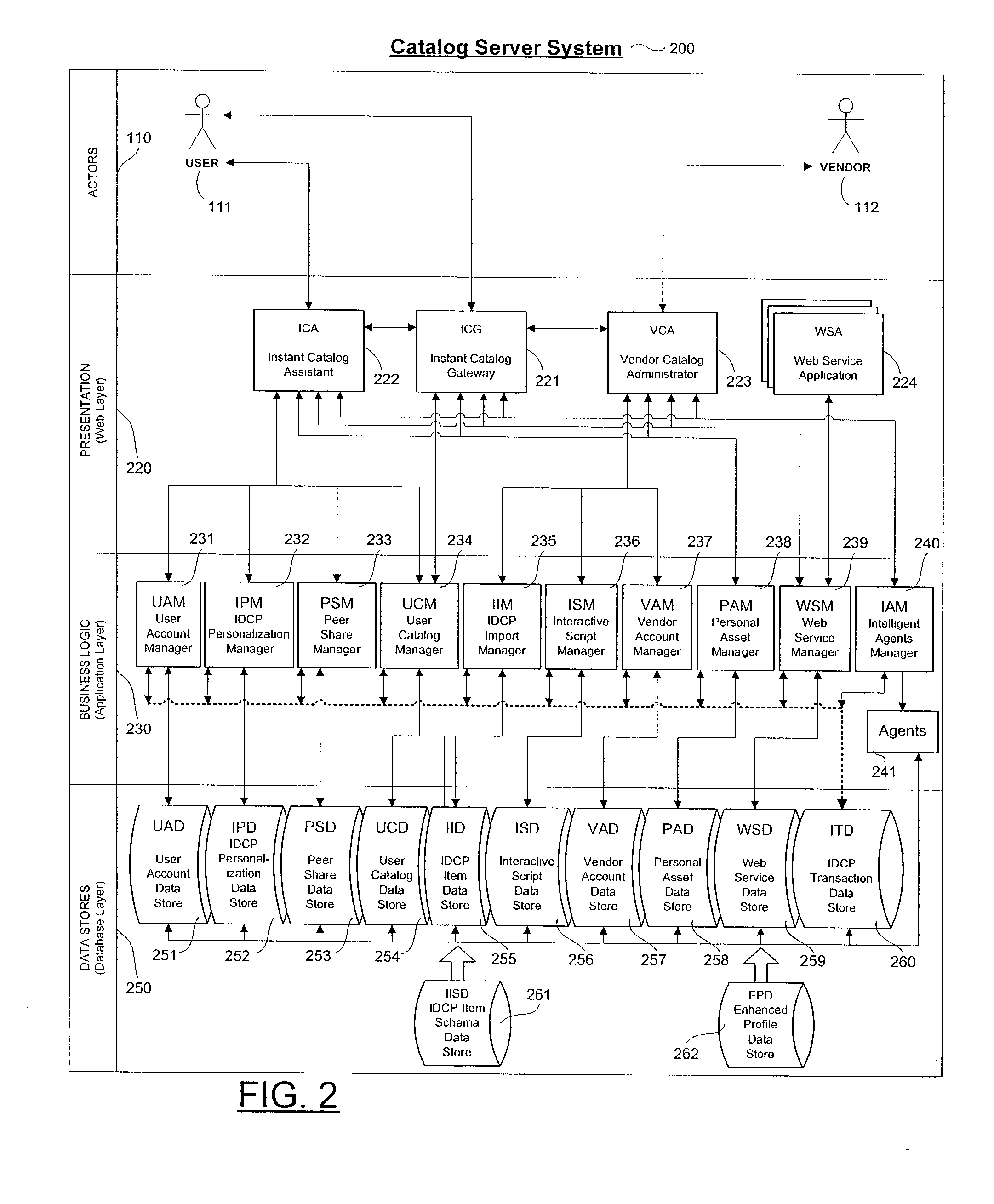
Personalized interactive digital catalog profiling
InactiveUS20030028451A1Facilitate transactionsReduce deliveryDigital data information retrievalComputer security arrangementsPersonalizationWeb browser
An interactive and enhanced digital Instant Catalog of products, services, and information that is personalized or personally profiled, to each unique user of the catalog. The catalog instantly and intelligently captures, stores, manages, and processes self-selected, reusable and "re-distributable" catalog groupings anonymously, for personalizing, enhancing, monitoring, tracking, and peer sharing through multiple mediums and platforms by intelligent agents for a variety of user and vendor specified purposes. The personally profiled cataloged information can be viewed instantaneously and simultaneously by each effected component or member of a supply chain, at the time the product or service has been cataloged, without identifying the cataloger. The user, who preferably employs a Web browser over the Internet, personalizes the interactively produced intelligent catalog content. Products, services, and information groupings are digitally captured and stored by an intelligent catalog agent for enhanced personalized interaction and networking through a peer sharing network, or through an open catalog exchange. The user has the ability to create their own individualized world of products, services, and information that is contextually tailored to each user's unique environment in real-time. Web services hosted within a personal Extranet can anonymously assist and facilitate a context specific task or service insightfully and spontaneously. Through the selective cataloging of multi-vendor products, services, and information, a user is able to fully control, personalize, enhance and share, any lifestyle interest captured from ITV, print, the World Wide Web, businesses, and peers.
Owner:INTENTIONIZE LLC
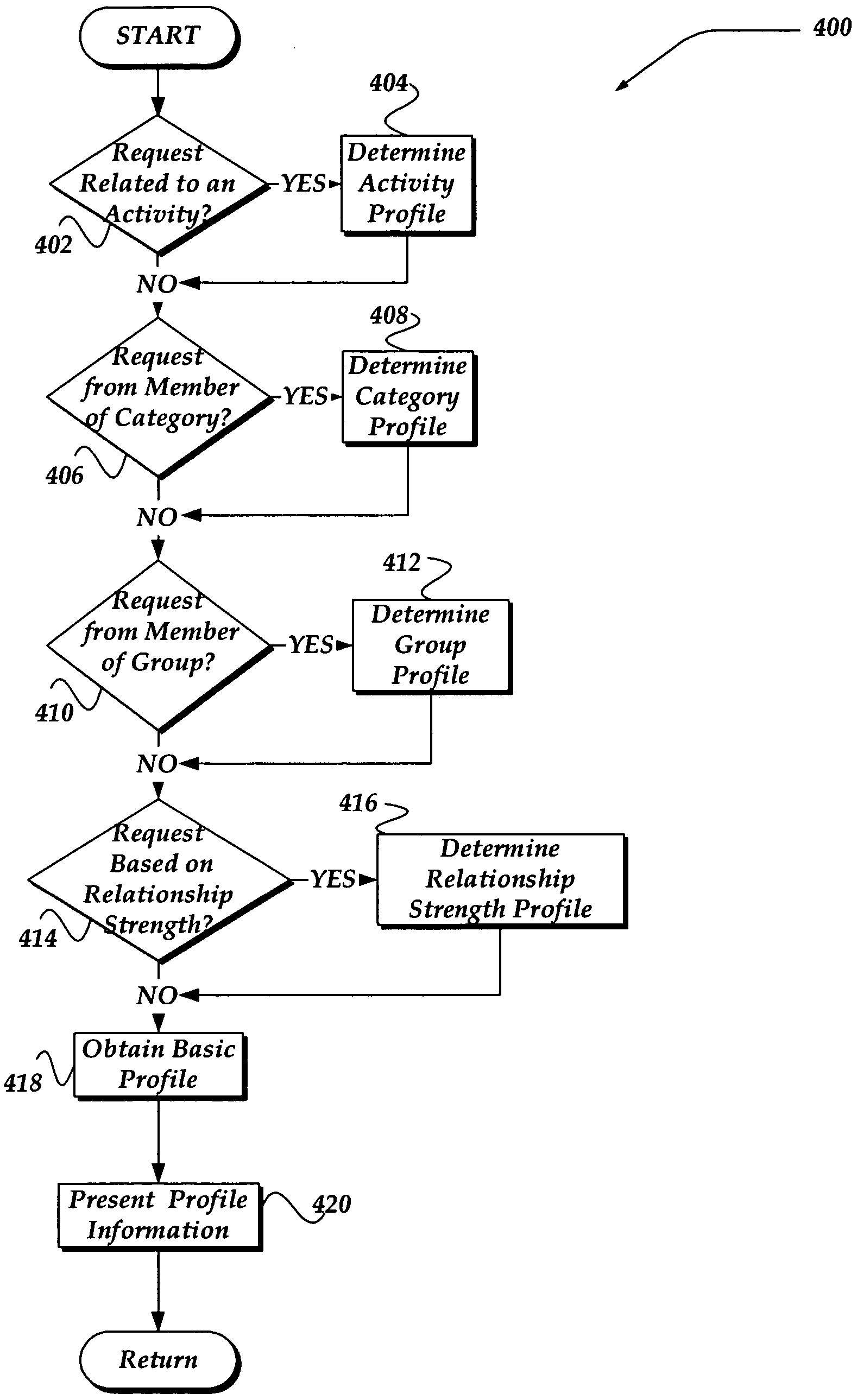
Method and system for customizing views of information associated with a social network user
A method, apparatus, and system are directed towards managing a view of a social network user's personal information based, in part, on user-defined criteria. The user-defined criteria may be applied towards a user's relationship with each prospective viewer. The user-defined criteria may include degrees of separation between members of the social network, a relationship to the prospective viewer, as well as criteria based, in part, on activities, such as dating, employment, hobbies, and the like. The user-defined criteria may also be based on a group membership, a strength of a relationship, and the like. Such user-defined relationship criteria may then be mapped against various categories of information associated with social network user to provide customized views of the social network user.
Owner:SLACK TECH LLC
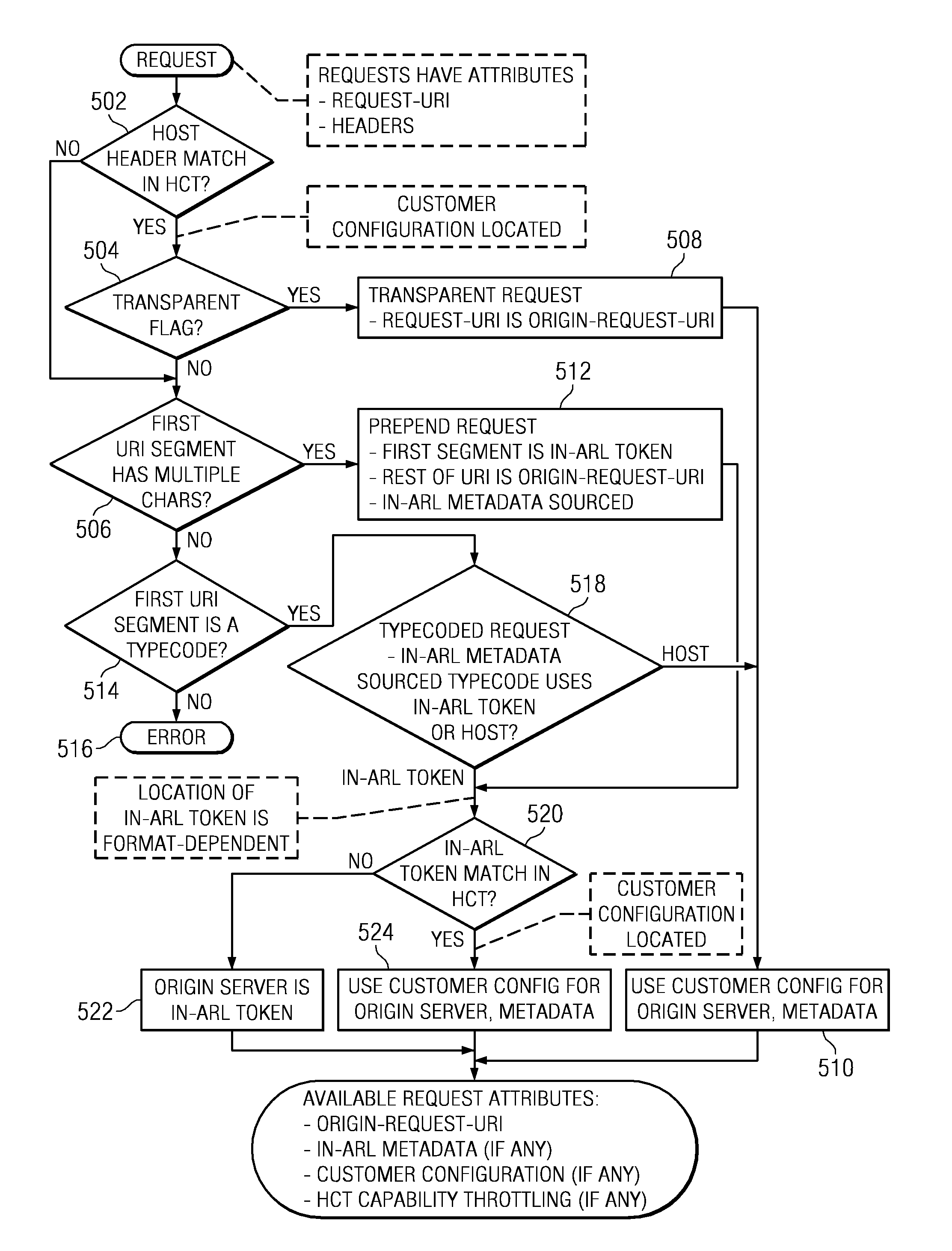
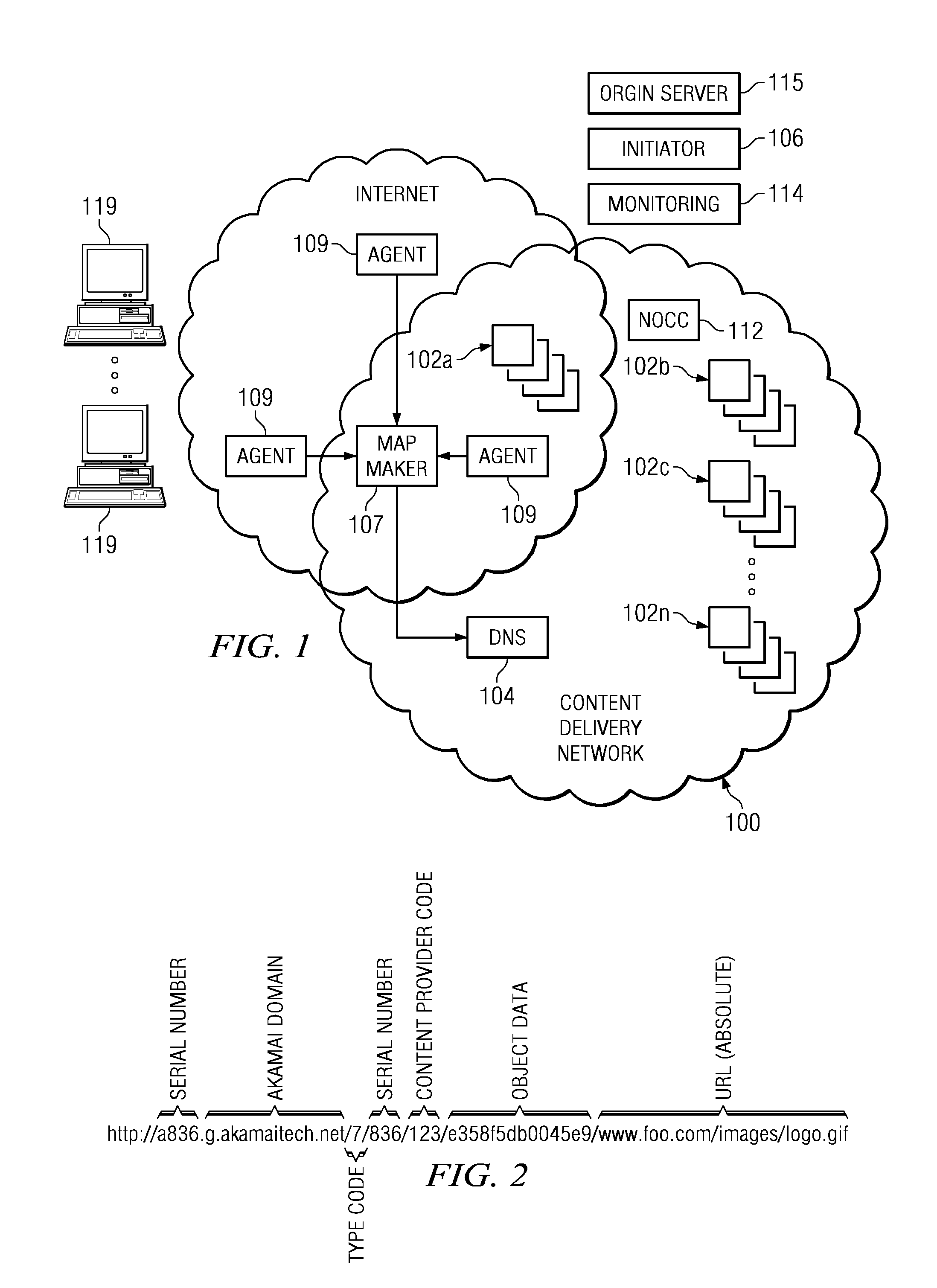
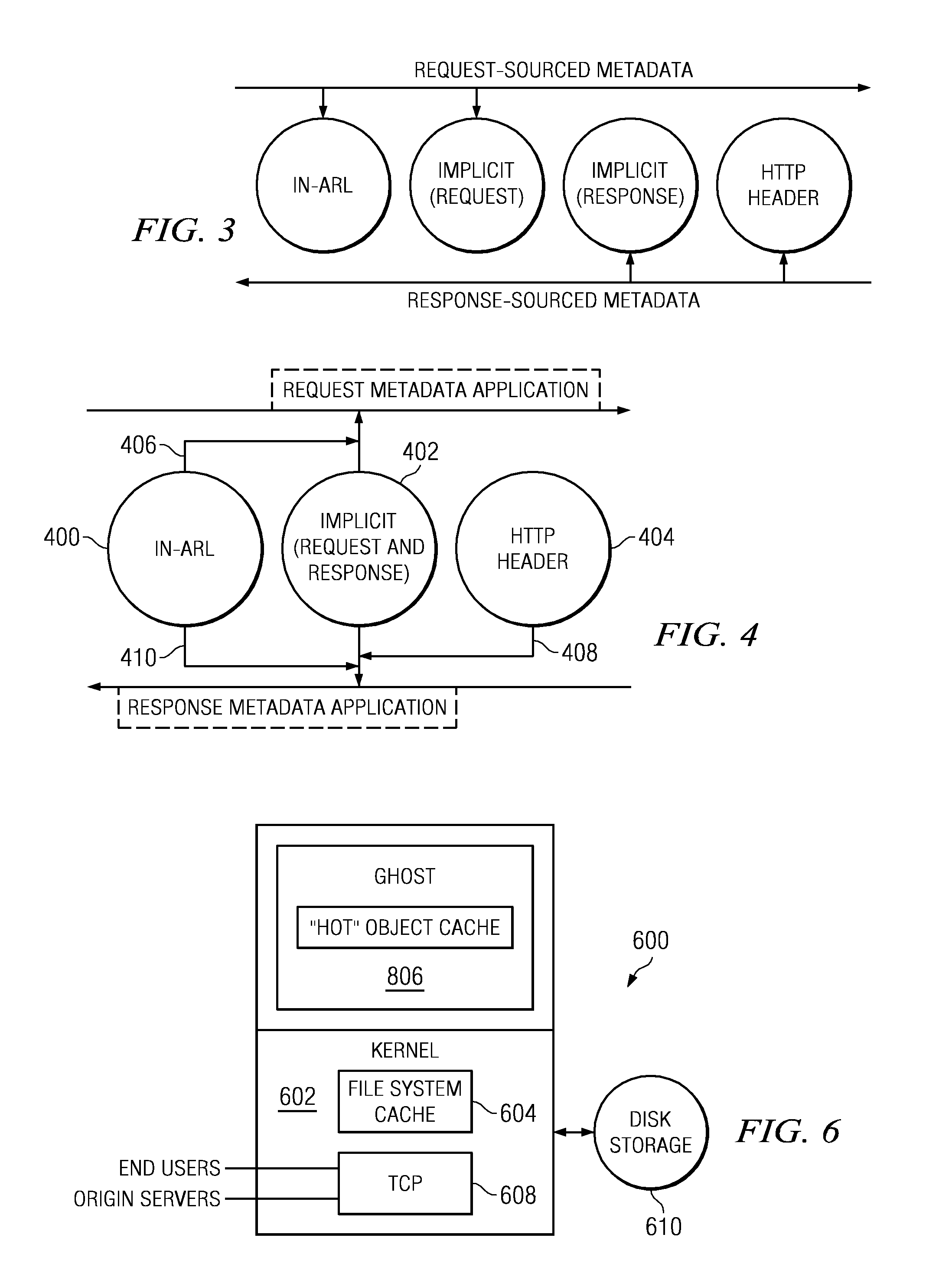
Content delivery network (CDN) content server request handling mechanism with metadata framework support
To serve content through a content delivery network (CDN), the CDN must have some information about the identity, characteristics and state of its target objects. Such additional information is provided in the form of object metadata, which according to the invention can be located in the request string itself, in the response headers from the origin server, in a metadata configuration file distributed to CDN servers, or in a per-customer metadata configuration file. CDN content servers execute a request identification and parsing process to locate object metadata and to handle the request in accordance therewith. Where different types of metadata exist for a particular object, metadata in a configuration file is overridden by metadata in a response header or request string, with metadata in the request string taking precedence.
Owner:AKAMAI TECH INC
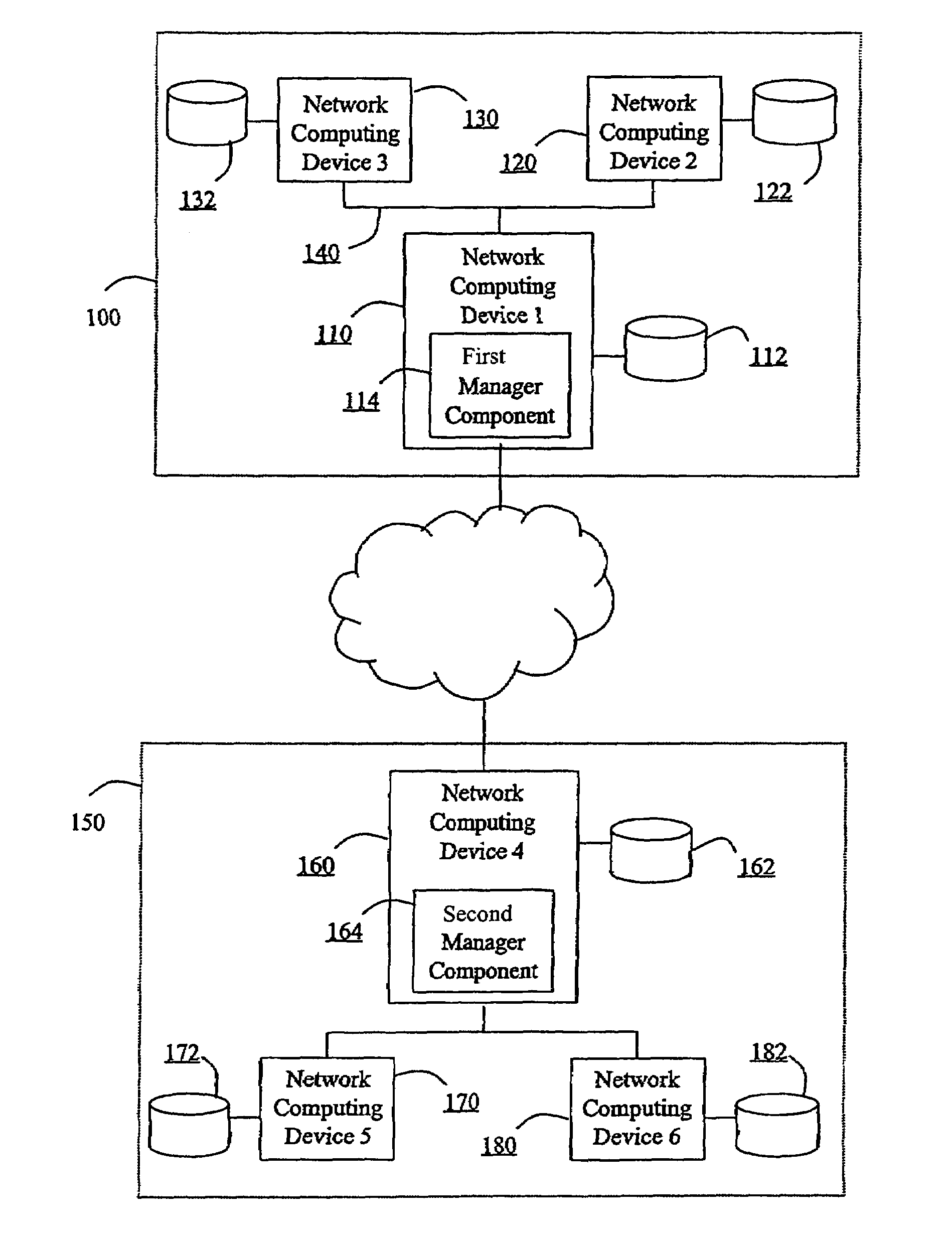
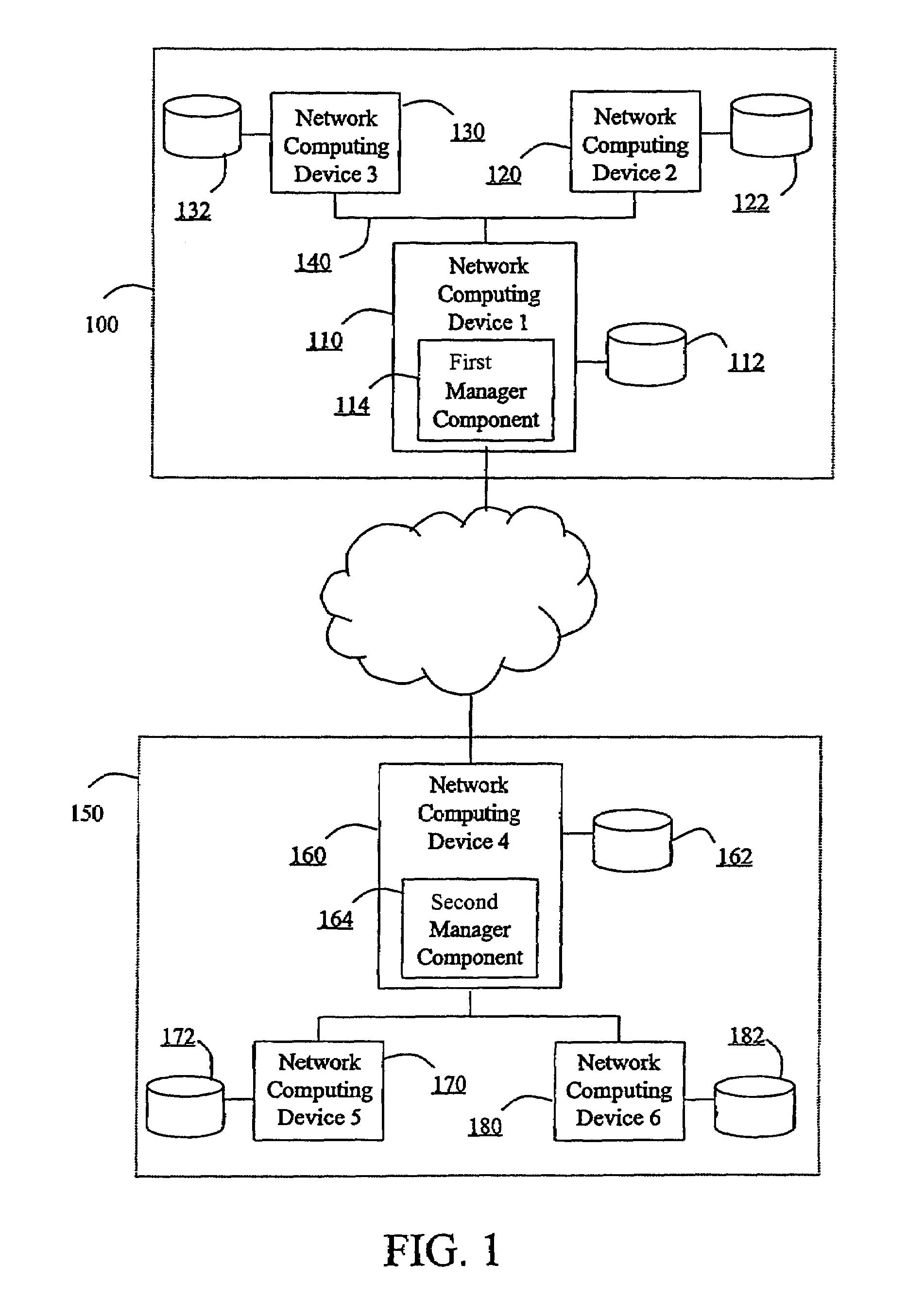
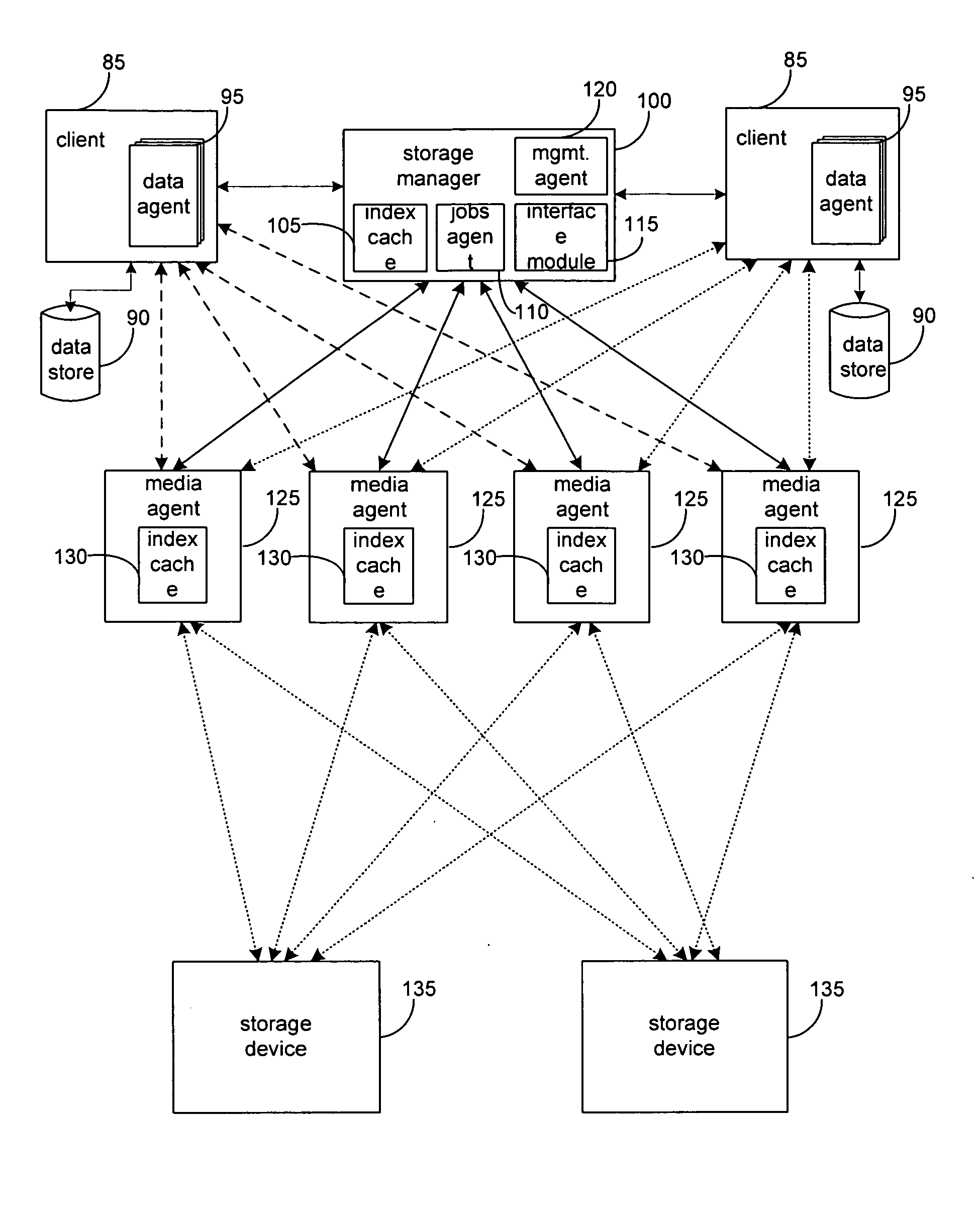
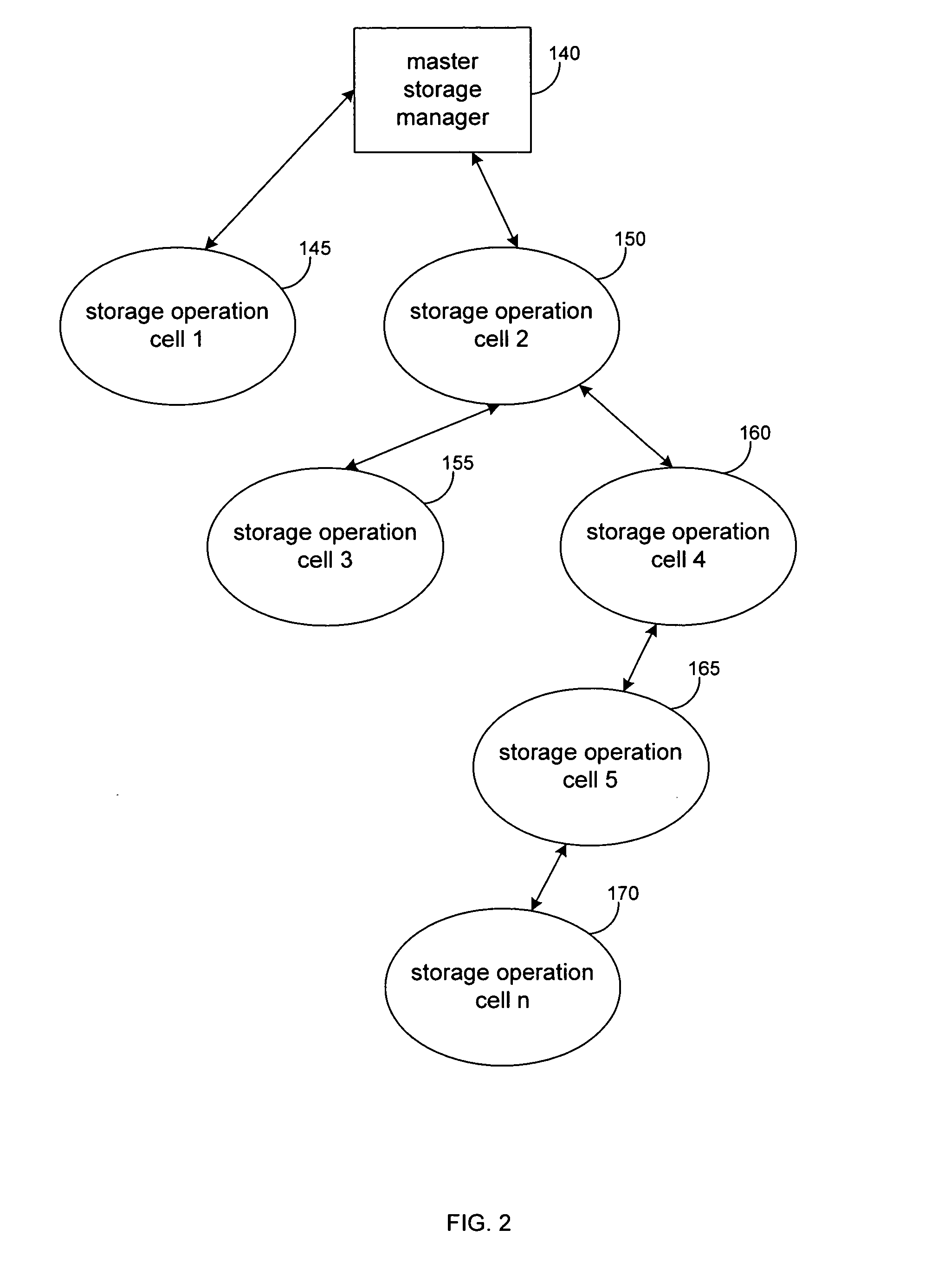
Hierarchical backup and retrieval system
InactiveUS7395282B1Data processing applicationsDigital data processing detailsSoftware agentAdministrative controls
The invention is a hierarchical backup system. The interconnected network computing devices are put into groups of backup cells. A backup cell has a manager software agent responsible maintaining and initiating a backup regime for the network computing devices in the backup cell. The backups are directed to backup devices within the backup cell. Several backup cells can be defined. A manager software agent for a particular cell may be placed into contact with the manager software agent of another cell, by which information about the cells may be passed back and forth. Additionally, one of the software agents may be given administrative control over another software agent with which it is in communication.
Owner:COMMVAULT SYST INC
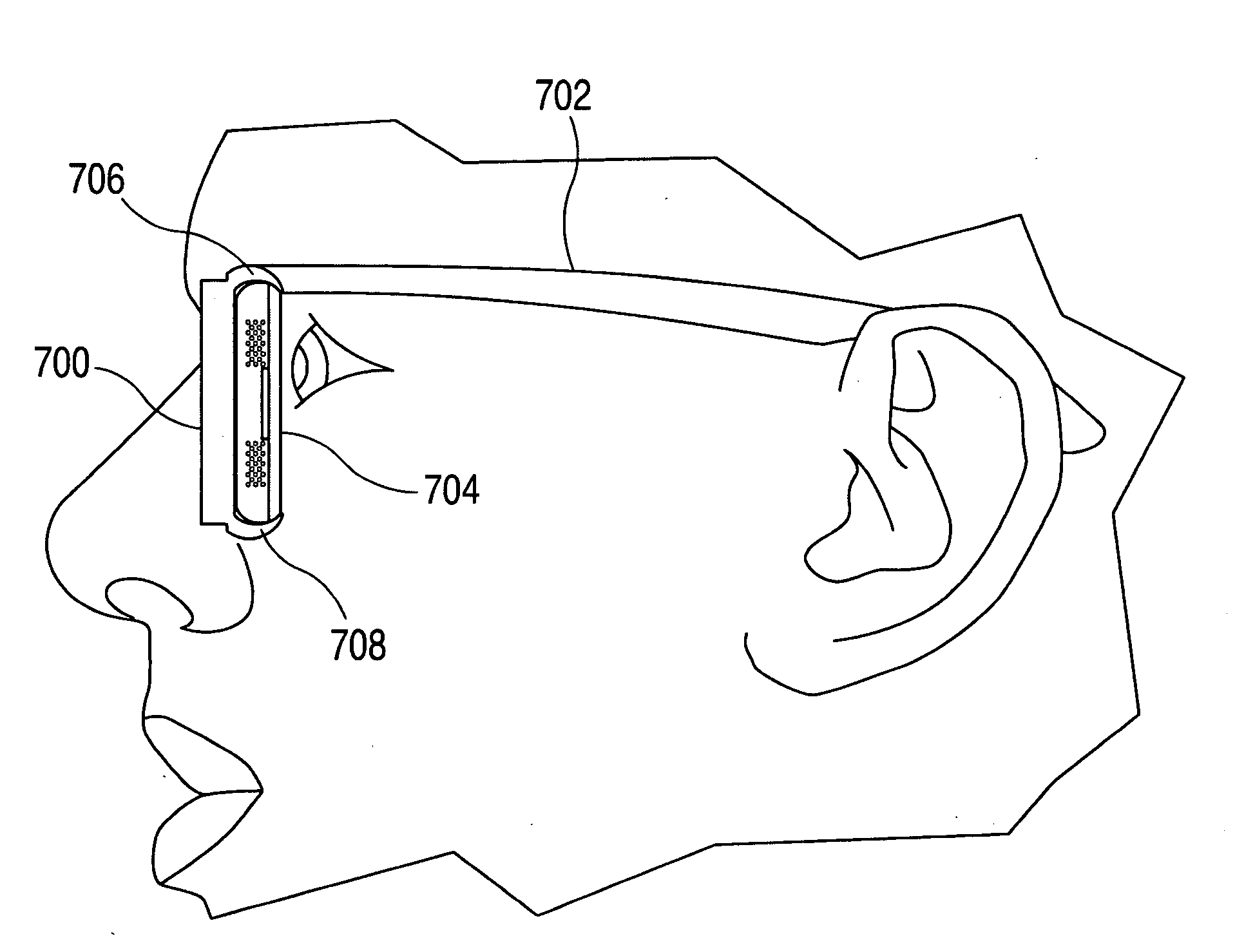
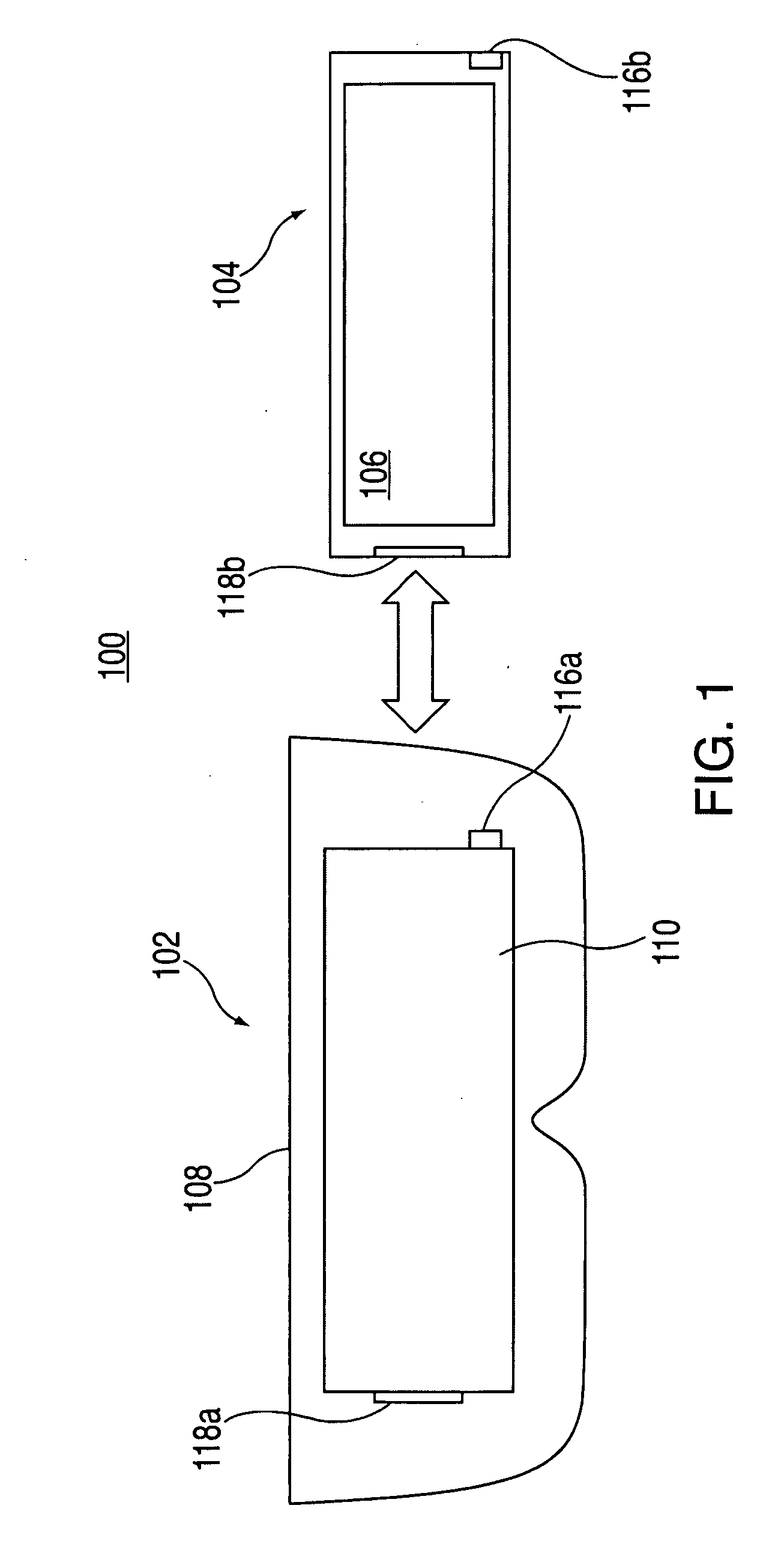
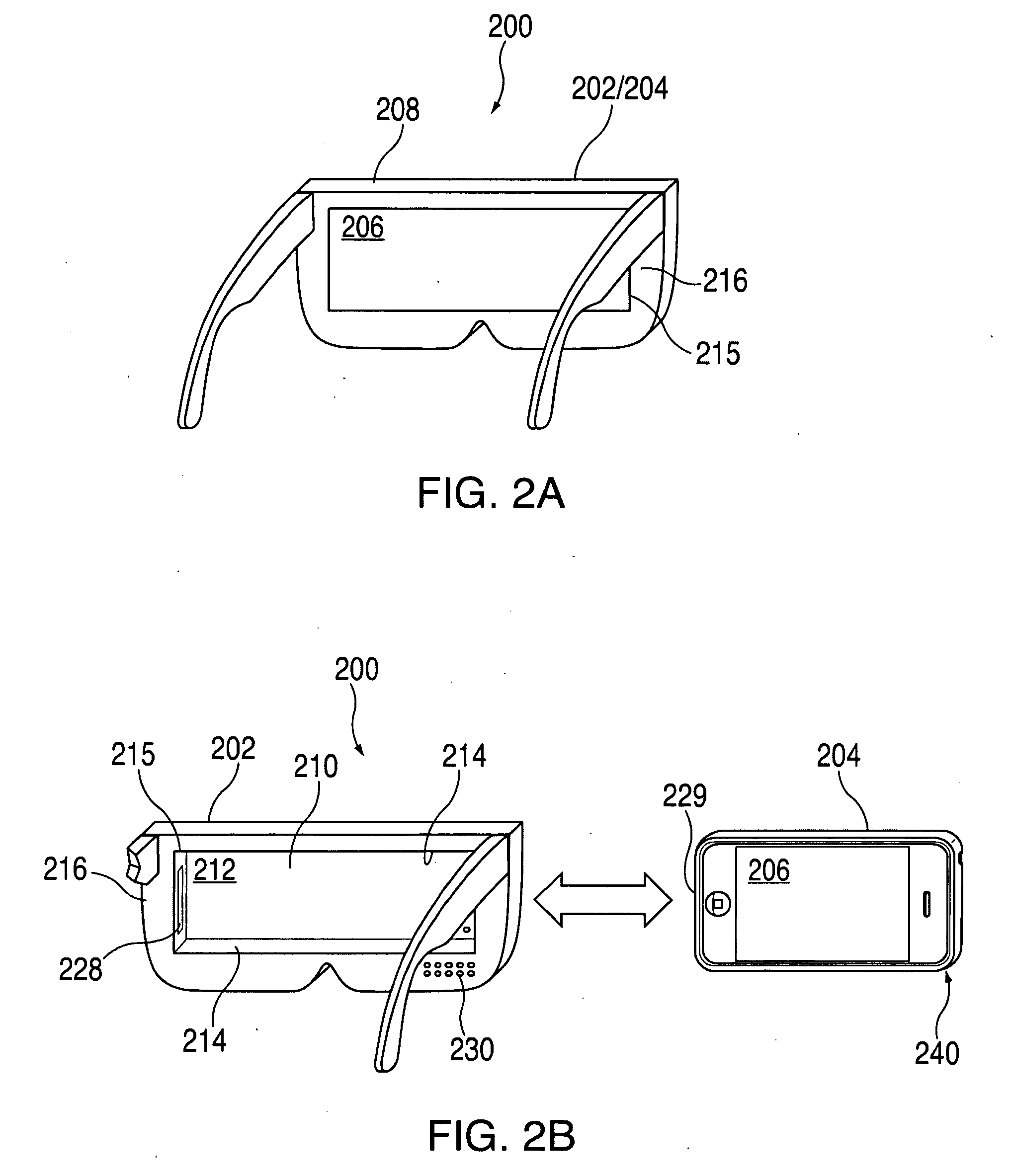
Head-mounted display apparatus for retaining a portable electronic device with display
Owner:APPLE INC
Automatic, personalized online information and product services
InactiveUS6981040B1Improve performanceManage efficiently enormousDigital data information retrievalMultiple digital computer combinationsLearning machinePersonalized search
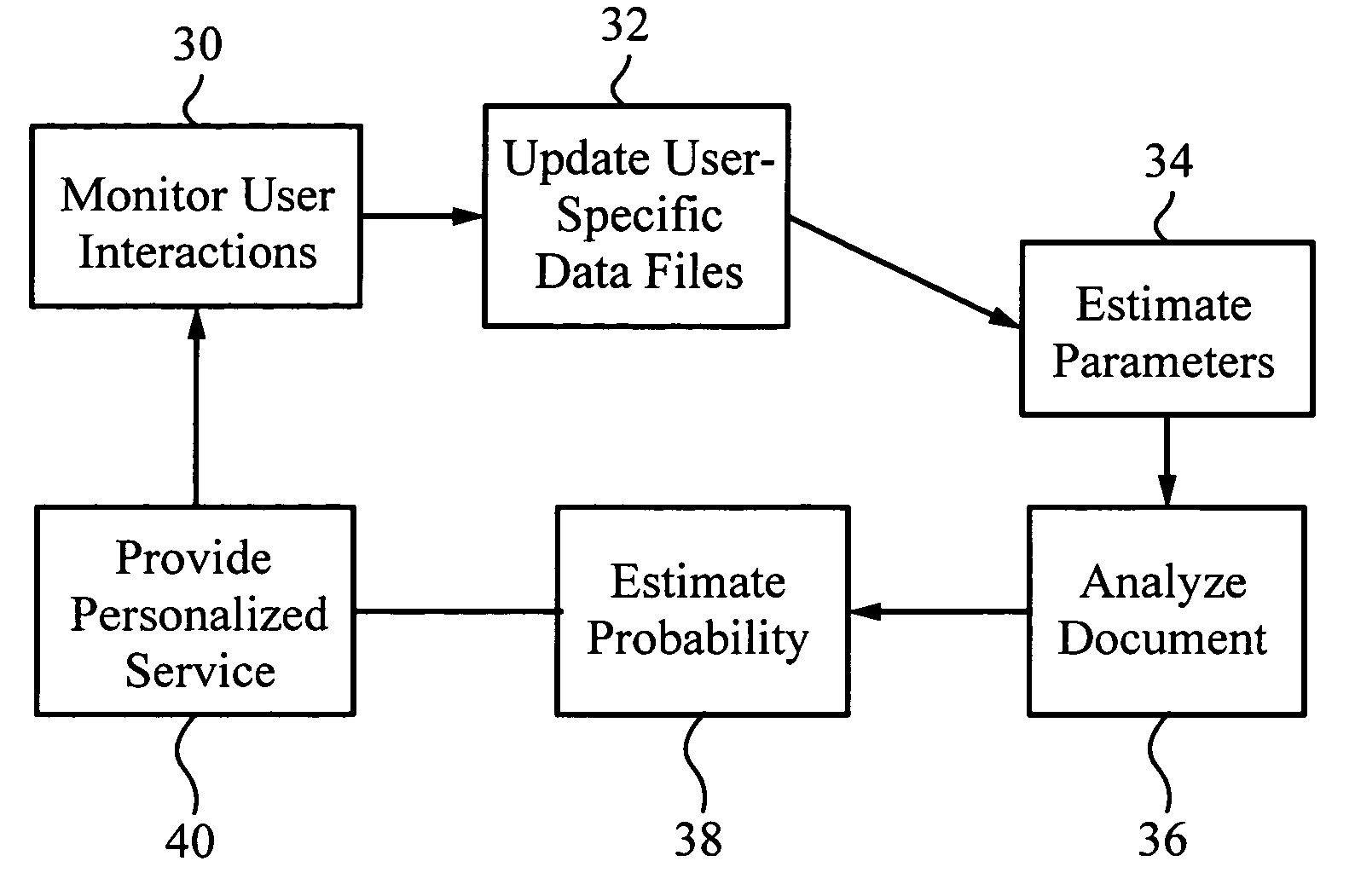
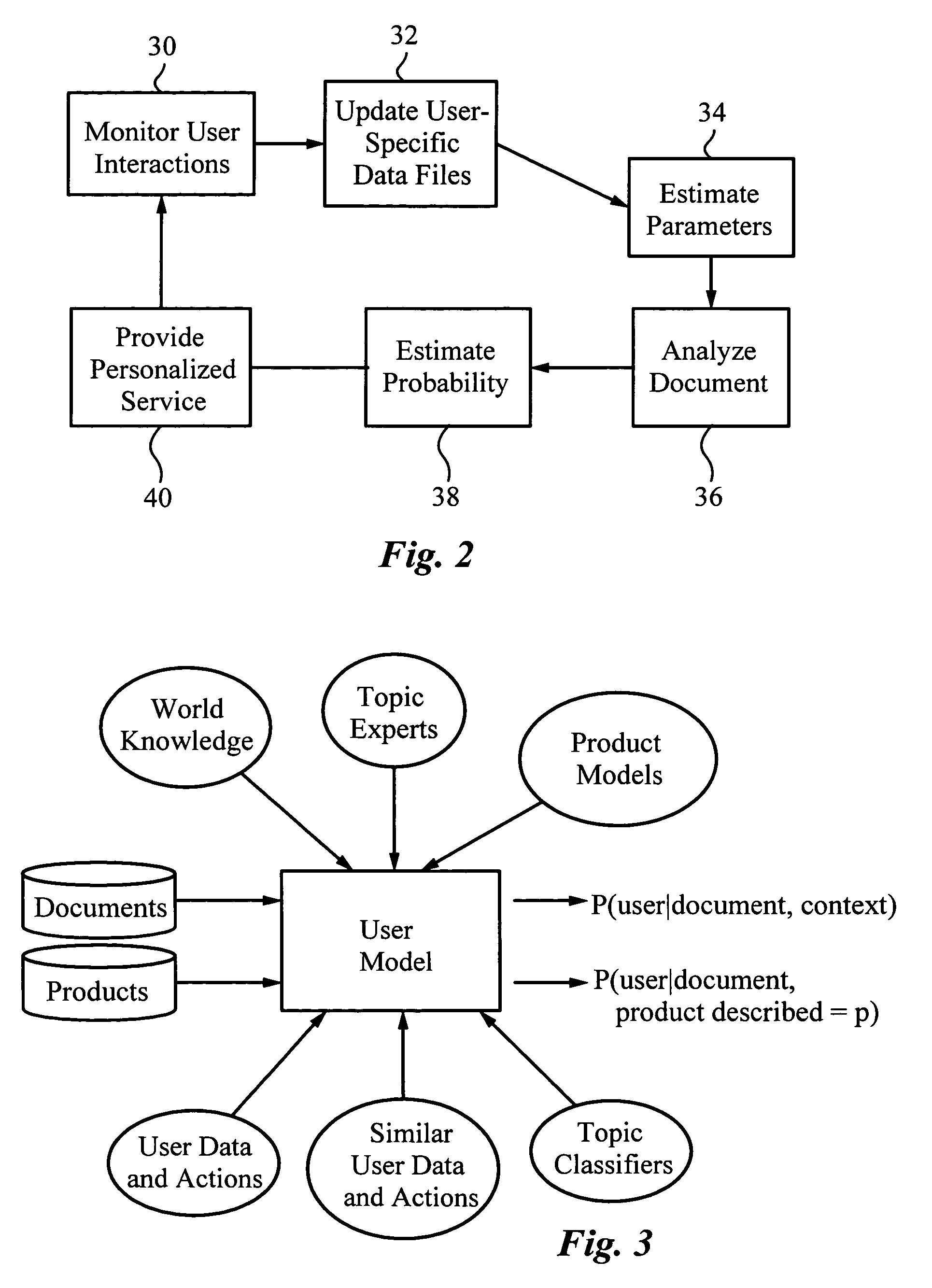
A method for providing automatic, personalized information services to a computer user includes the following steps: transparently monitoring user interactions with data during normal use of the computer; updating user-specific data files including a set of user-related documents; estimating parameters of a learning machine that define a User Model specific to the user, using the user-specific data files; analyzing a document to identify its properties; estimating the probability that the user is interested in the document by applying the document properties to the parameters of the User Model; and providing personalized services based on the estimated probability. Personalized services include personalized searches that return only documents of interest to the user, personalized crawling for maintaining an index of documents of interest to the user; personalized navigation that recommends interesting documents that are hyperlinked to documents currently being viewed; and personalized news, in which a third party server customized its interaction with the user. The User Model includes continually-updated measures of user interest in words or phrases, web sites, topics, products, and product features. The measures are updated based on both positive examples, such as documents the user bookmarks, and negative examples, such as search results that the user does not follow. Users are clustered into groups of similar users by calculating the distance between User Models.
Owner:PERSONALIZED USER MODEL PUM
Geographic based communications service
InactiveUS6259405B1Direction finders using radio wavesBeacon systems using radio wavesGeographic regionsGeolocation
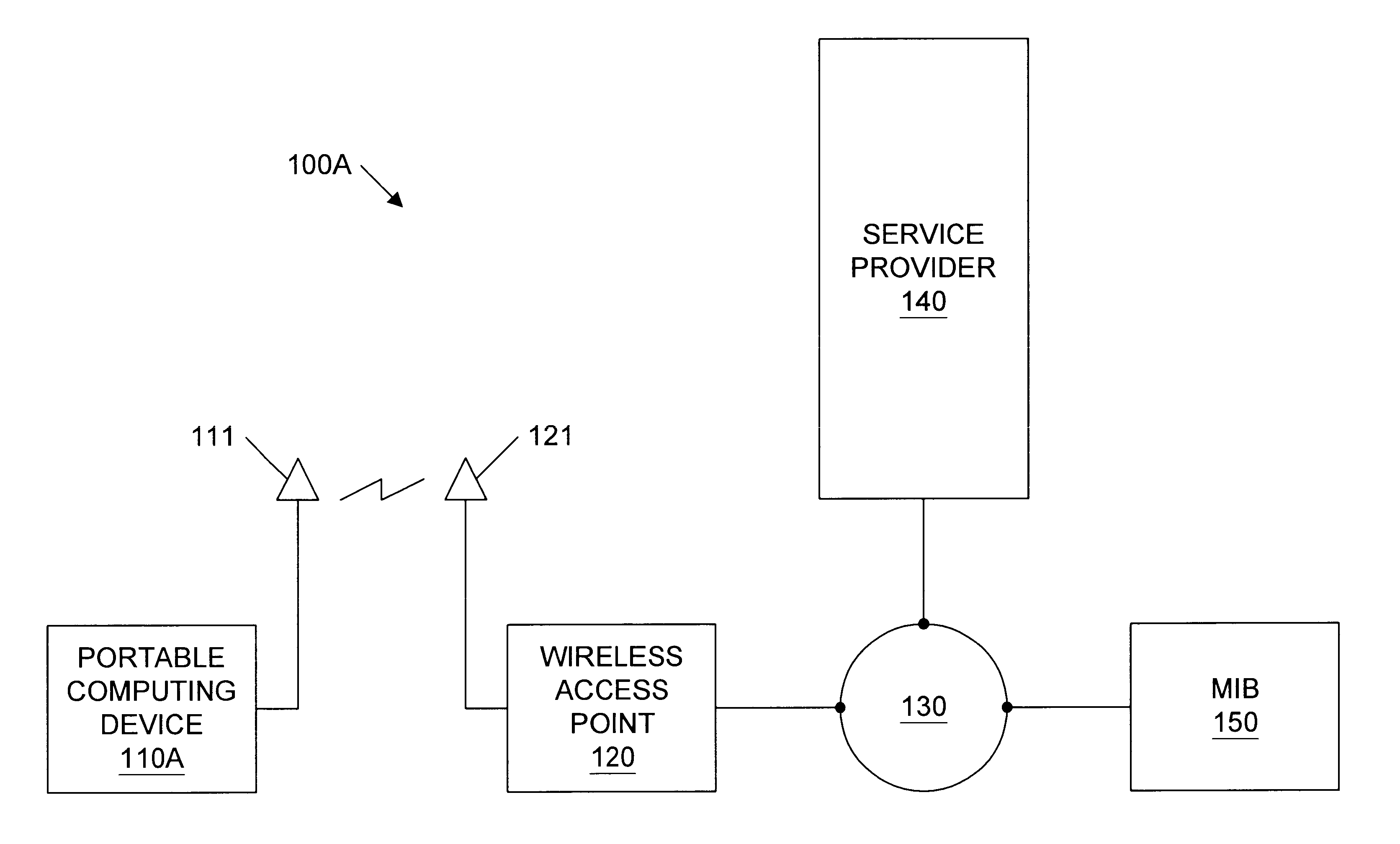
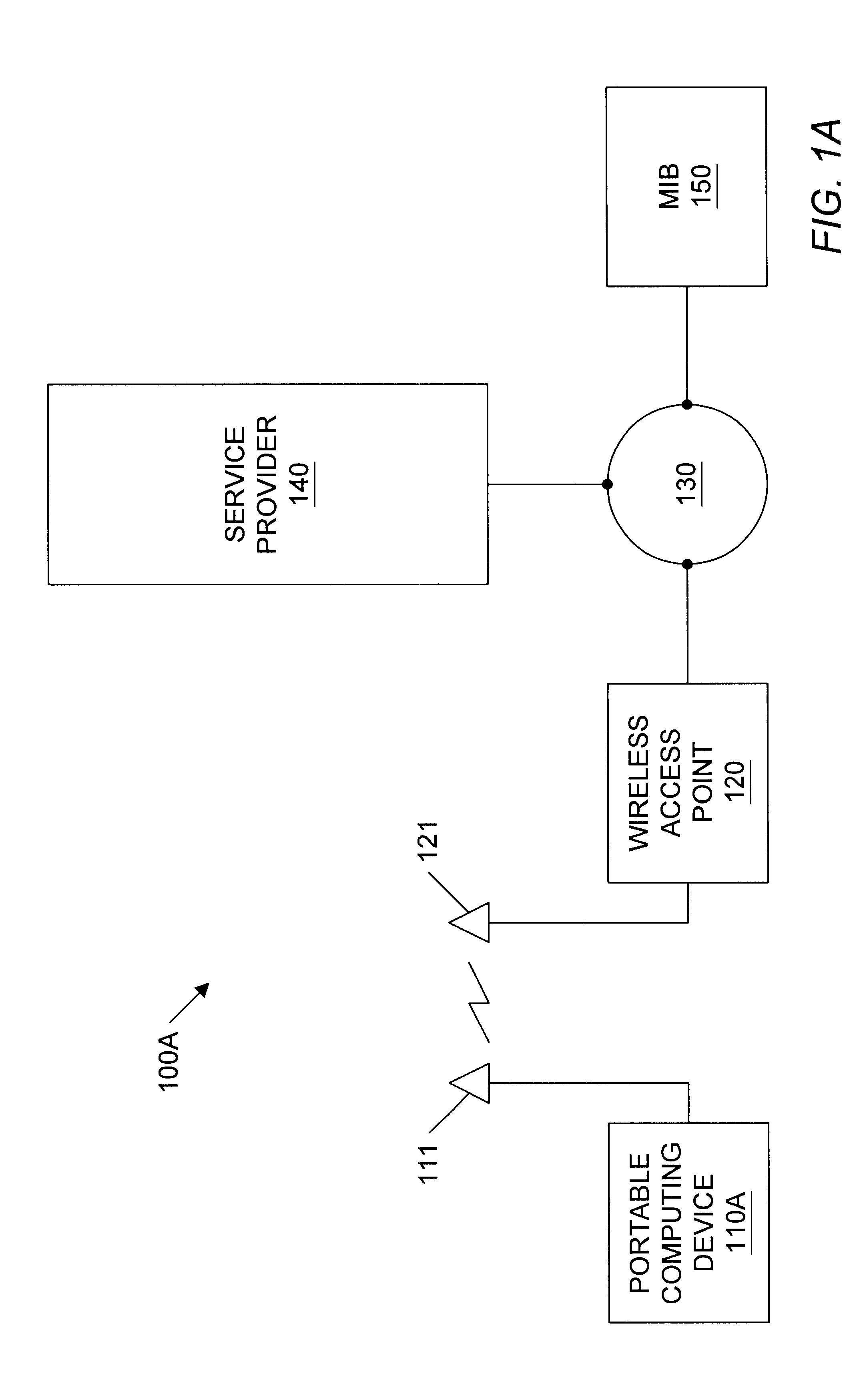
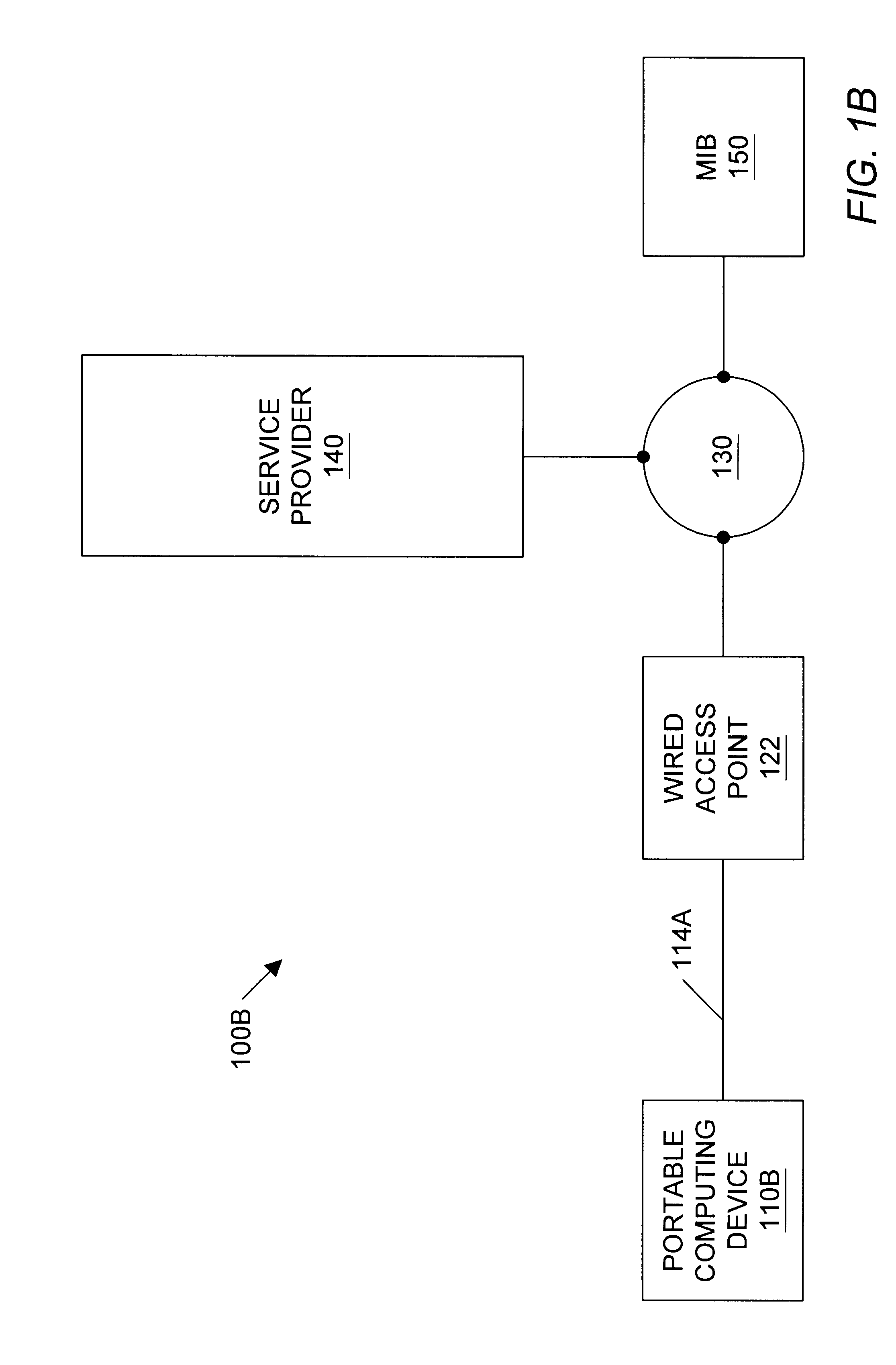
A geographic based communications service system that includes a network and a plurality of access points connected to the network and arranged at known locations in a geographic region. One or more service providers or information providers may be connected to the network to provide services or information on the network. A mobile user (MU) may use a portable computing device (PCD) to connect to the network and access information or services from the network. The PCD may be configured to transmit a signal indicating a presence of the PCD as well as identification information indicating the mobile user. Upon detection of the wireless signal by a first access point in proximity to the PCD, and upon receipt of the identification information indicating the user of the PCD, the first access point may transmit the identification information, as well as the known geographic location of the first access point, to one or more providers on the network. The known geographic location of the first access point indicates the approximate location of the PCD of the mobile user. A first information provider may receive this information and provide content information or services to the mobile user. For example, the first information provider may select content information dependent upon the known geographic location of the first access point and demographic information or past activities of the mobile user of the PCD. The first information provider may then provide the selected content information through the network and through the first access point to the PCD of the mobile user.
Owner:WAYPORT
Management of health care data
InactiveUS20070061393A1Mechanical/radiation/invasive therapiesTechnology managementUnstructured dataMedical device
Owner:NEWSILIKE MEDIA GROUP
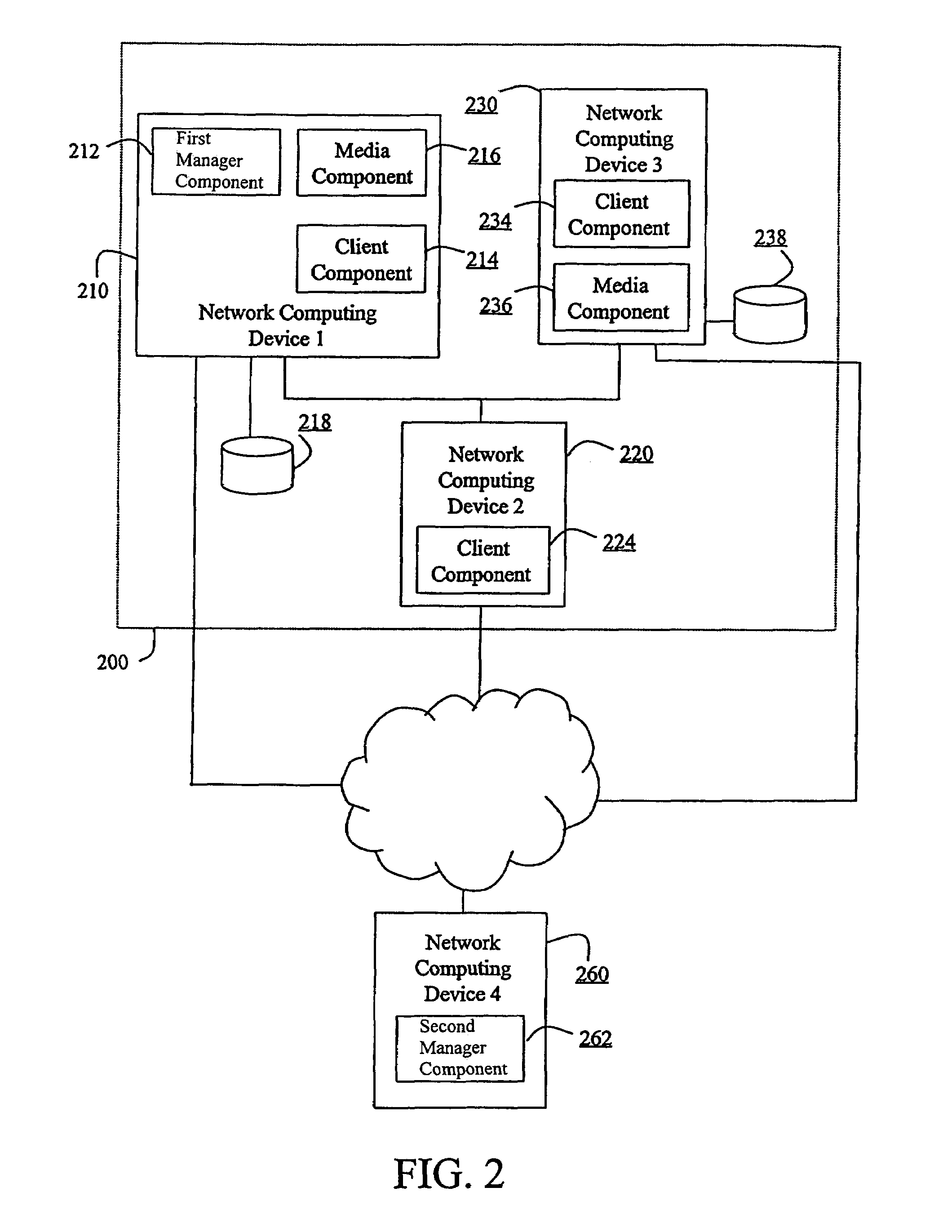
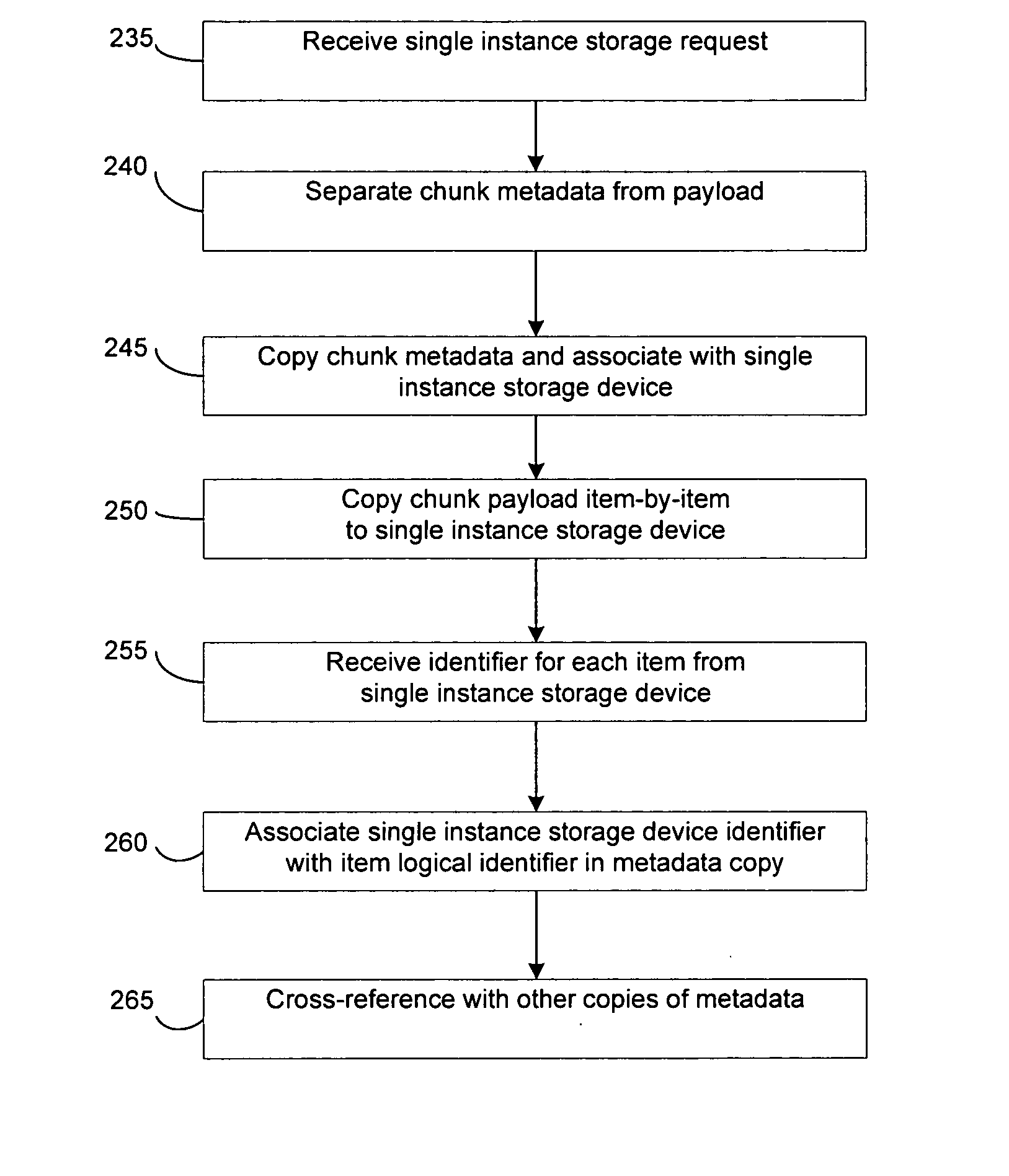
System and method to support single instance storage operations
Systems and methods for single instance storage operations are provided. Systems constructed in accordance with the principals of the present invention may process data containing a payload and associated metadata. Often, chunks of data are copied to traditional archive storage wherein some or all of the chunk, including the payload and associated metadata are copied to the physical archive storage medium. In some embodiments, chunks of data are designated for storage in single instance storage devices. The system may remove the encapsulation from the chunk and may copy the chunk payload to a single instance storage device. The single instance storage device may return a signature or other identifier for items copied from the chunk payload. The metadata associated with the chunk may be maintained in separate storage and may track the association between the logical identifiers and the signatures for the individual items of the chunk payload which may be generated by the single instance storage device.
Owner:COMMVAULT SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com