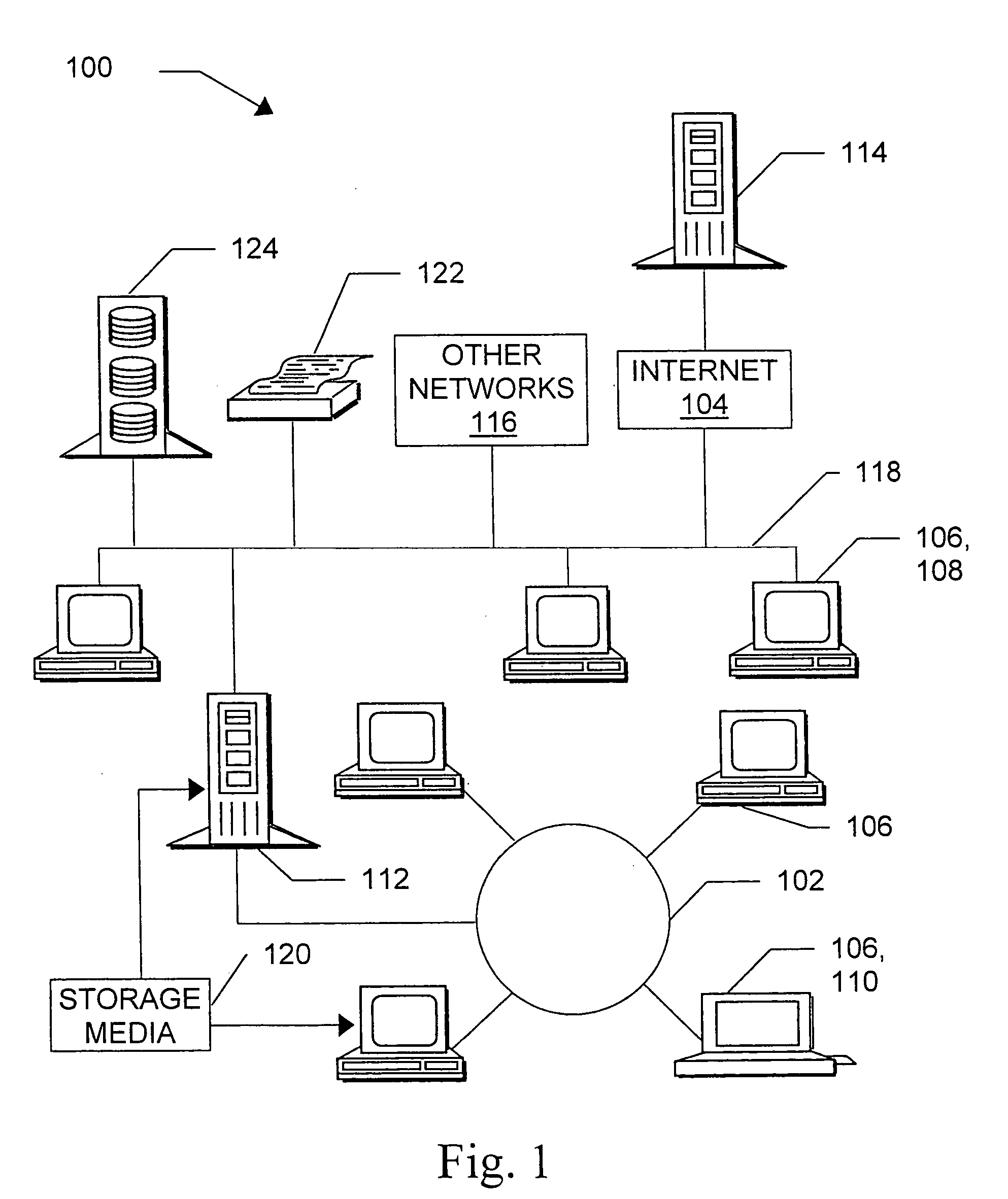
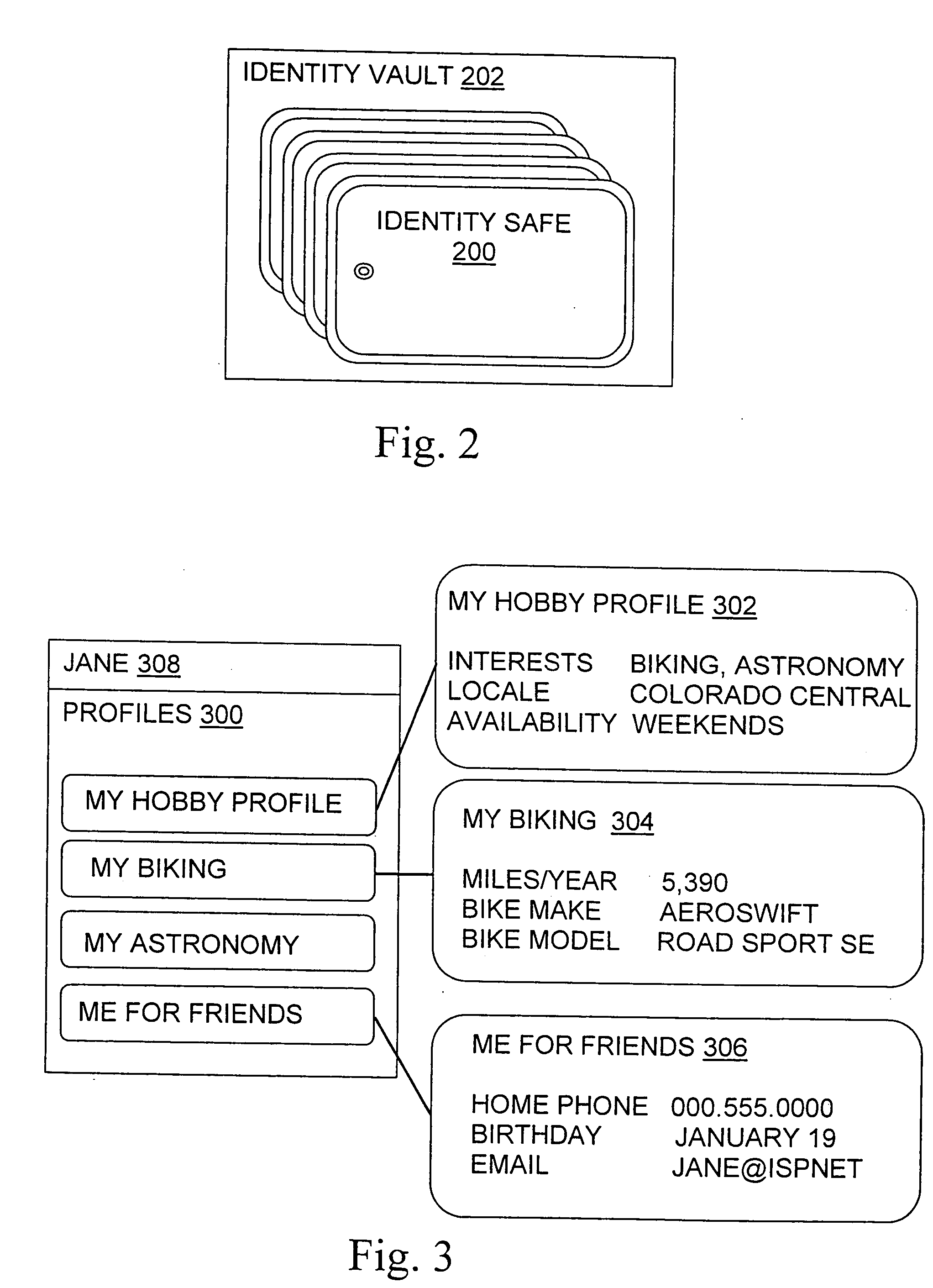
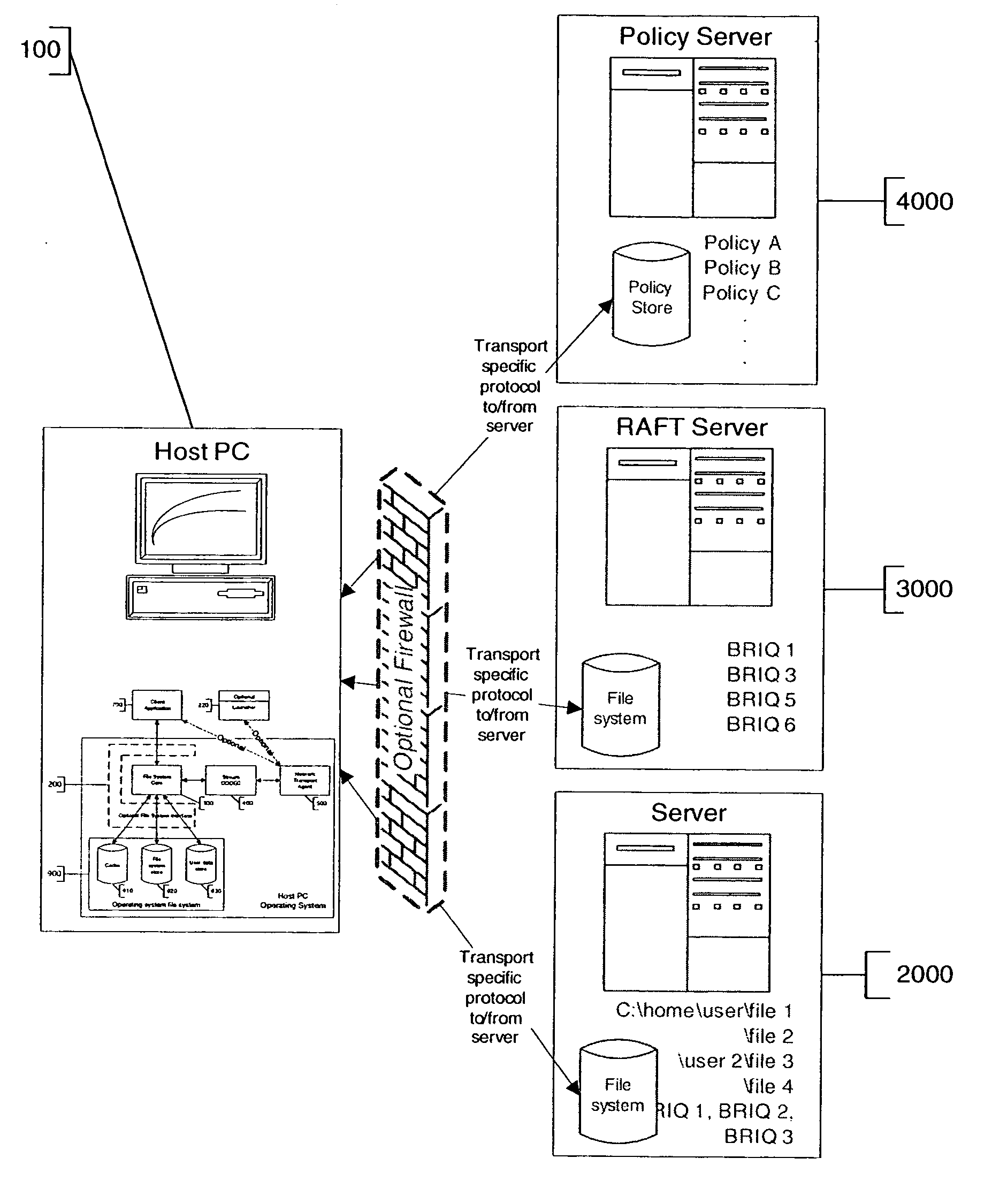
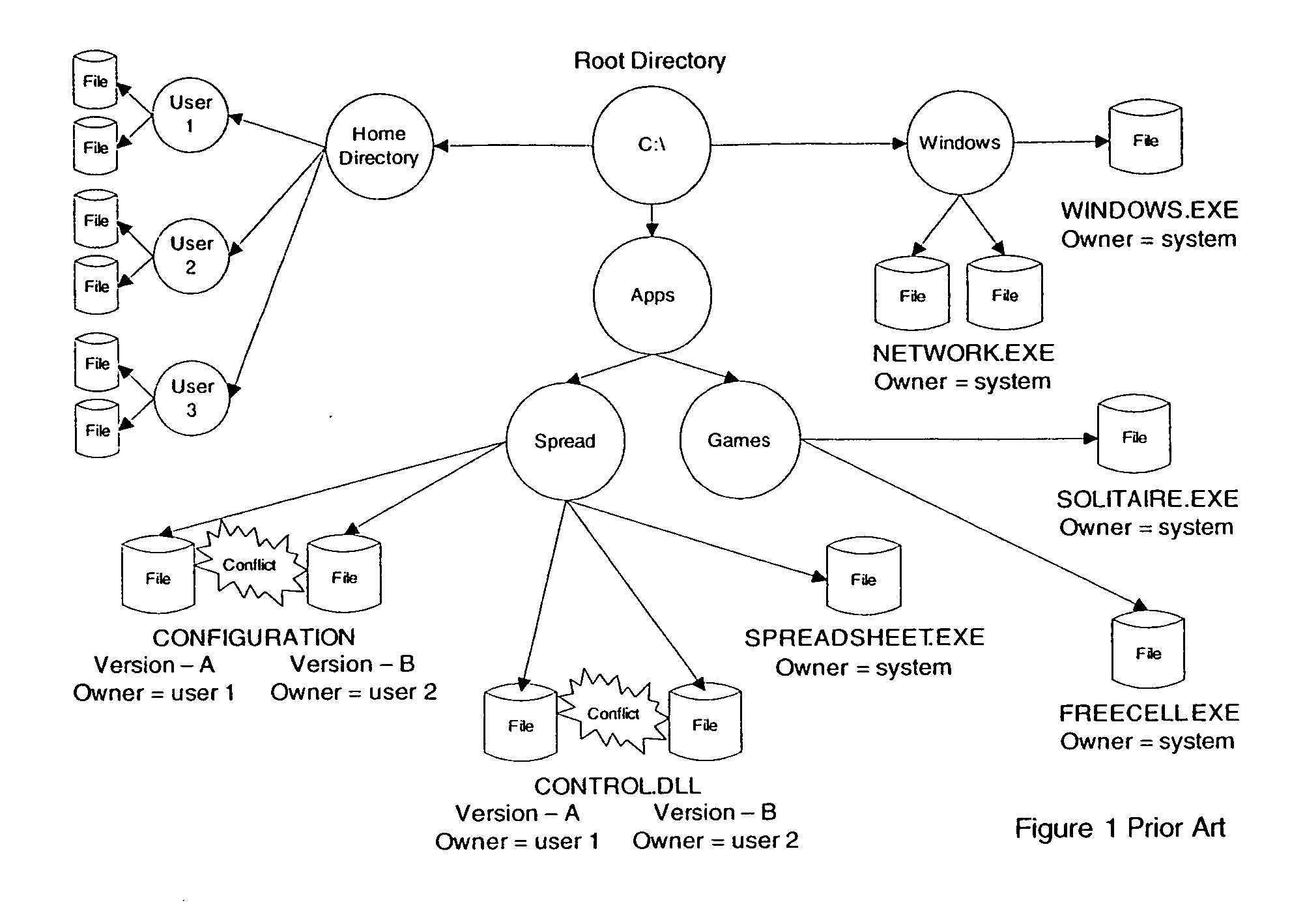
Patents
Literature
1025 results about "Configfs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
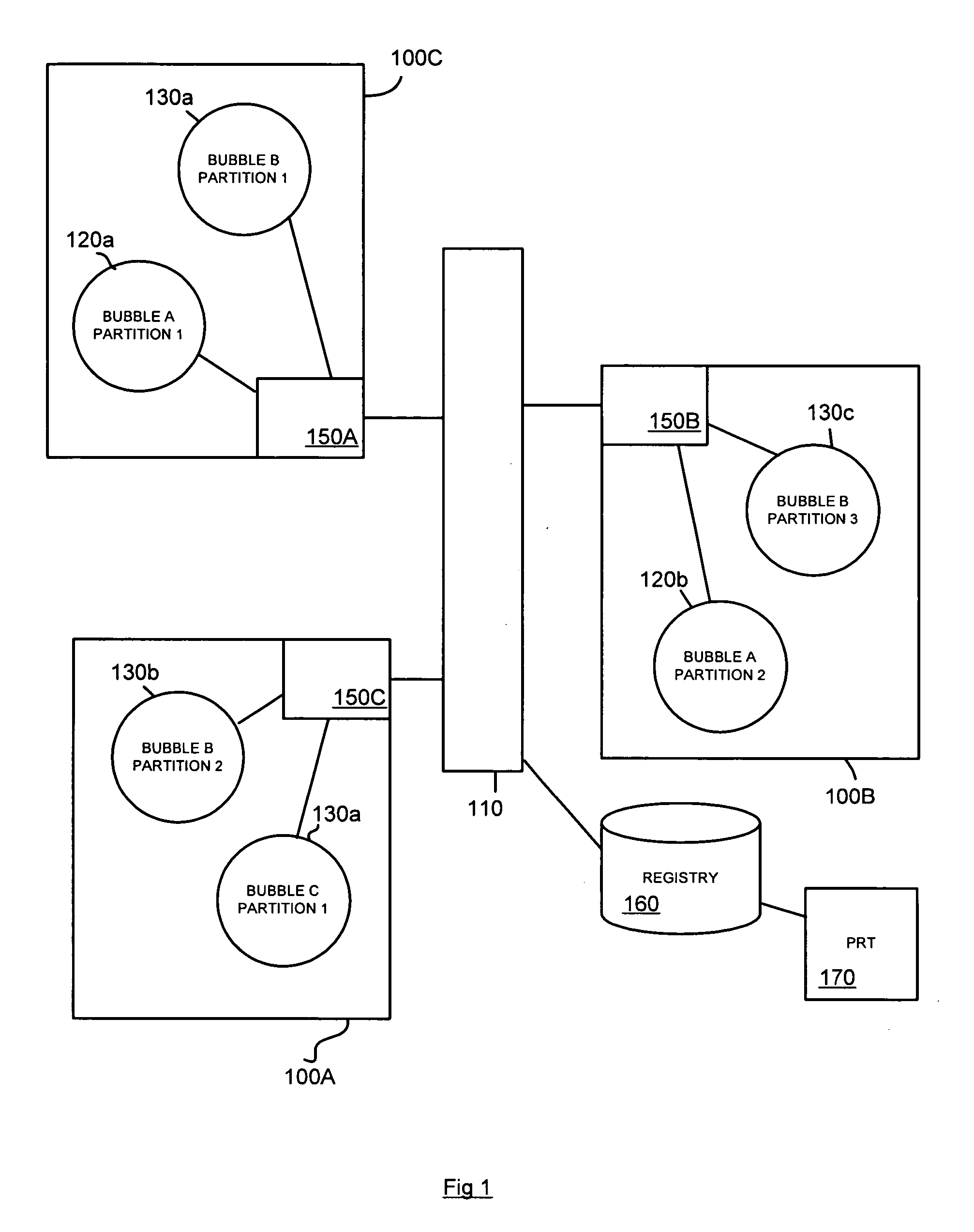
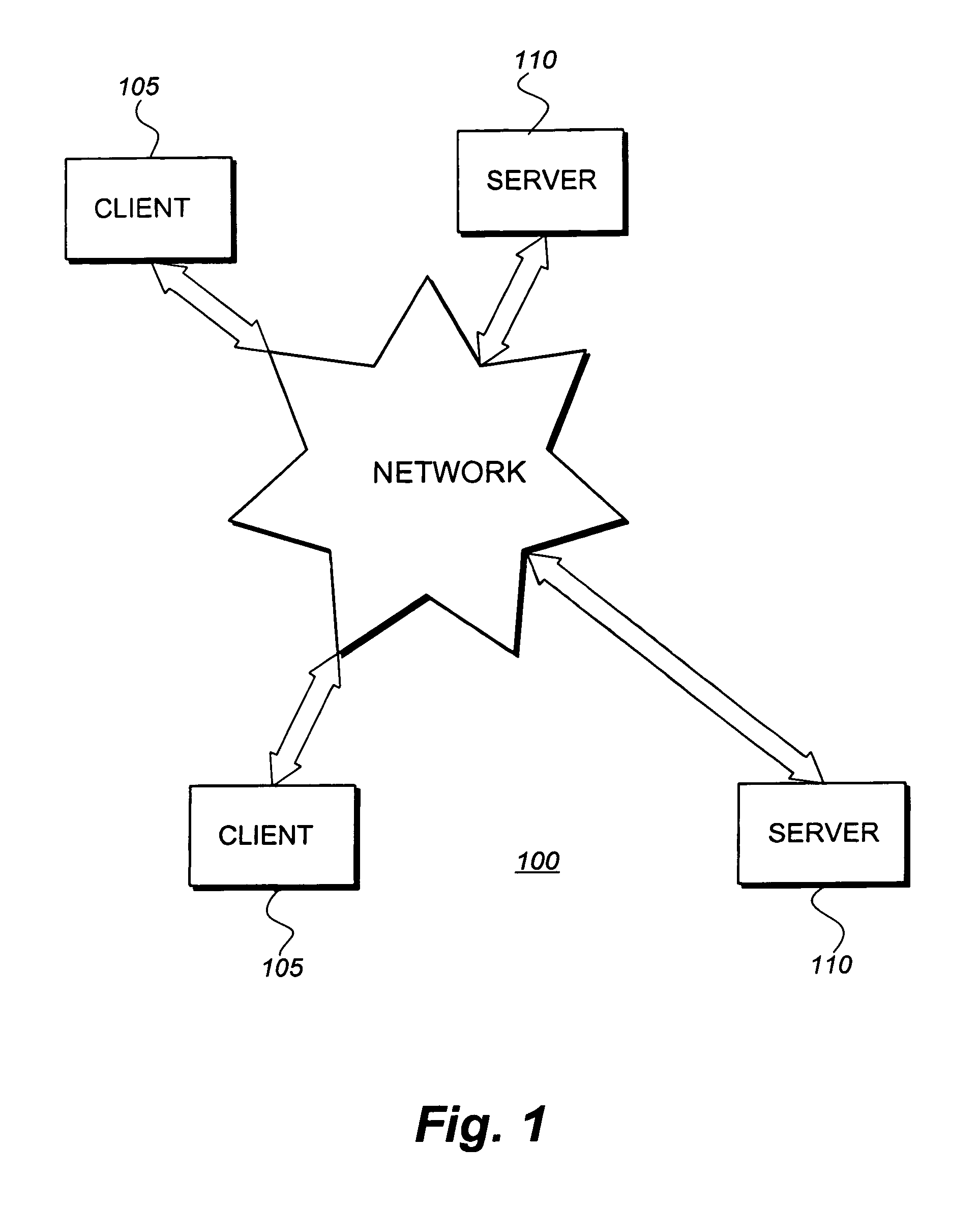
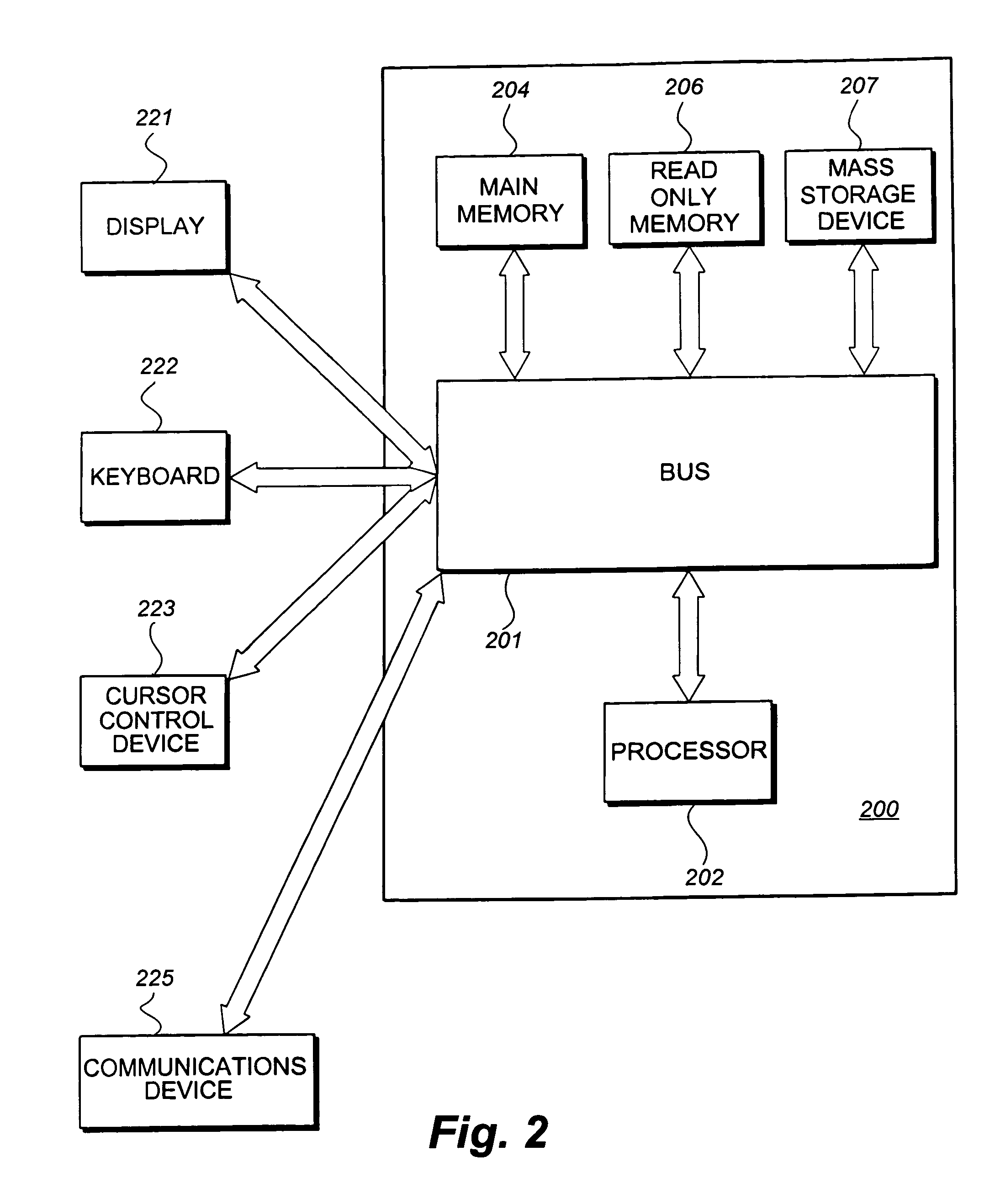
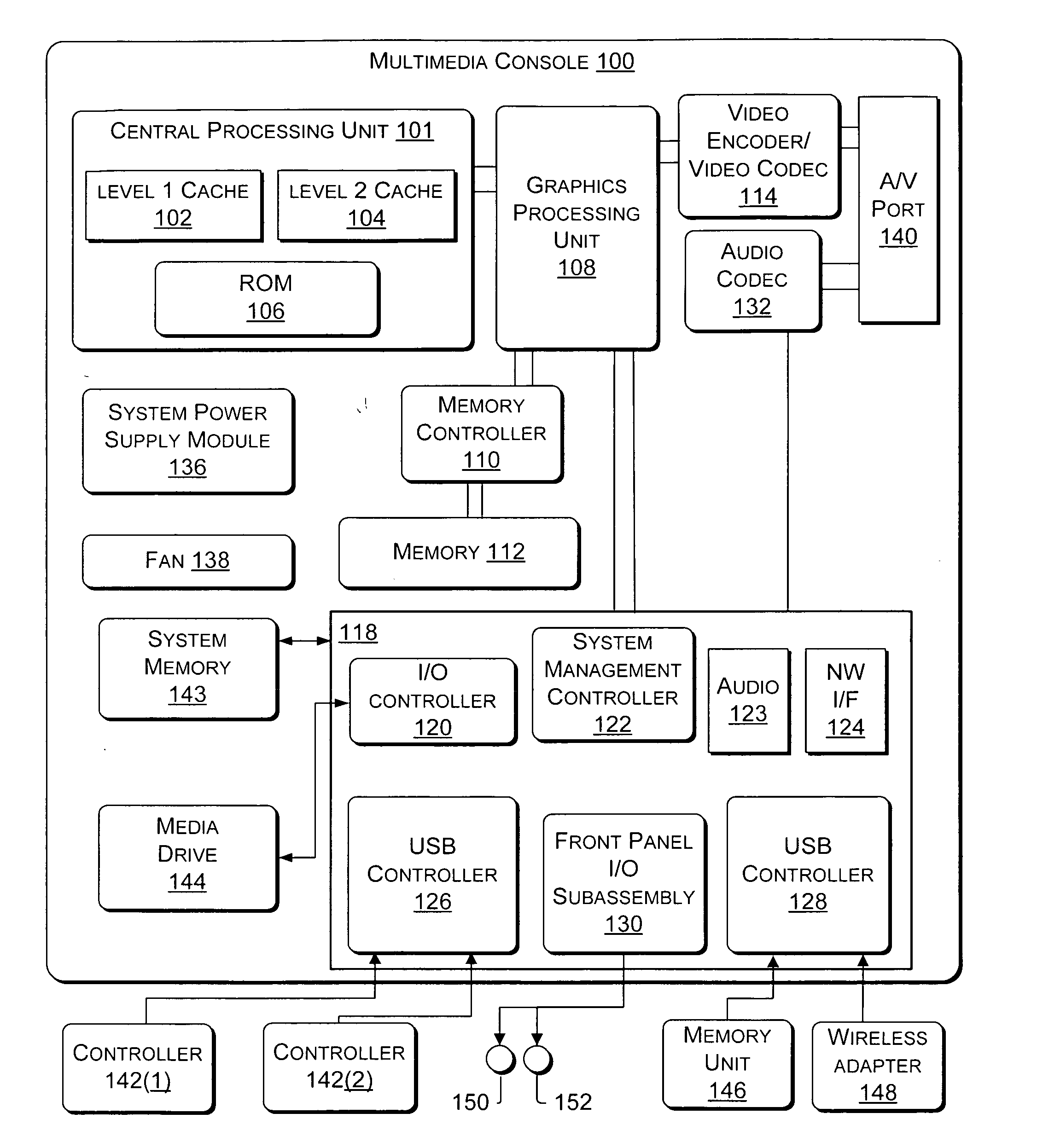
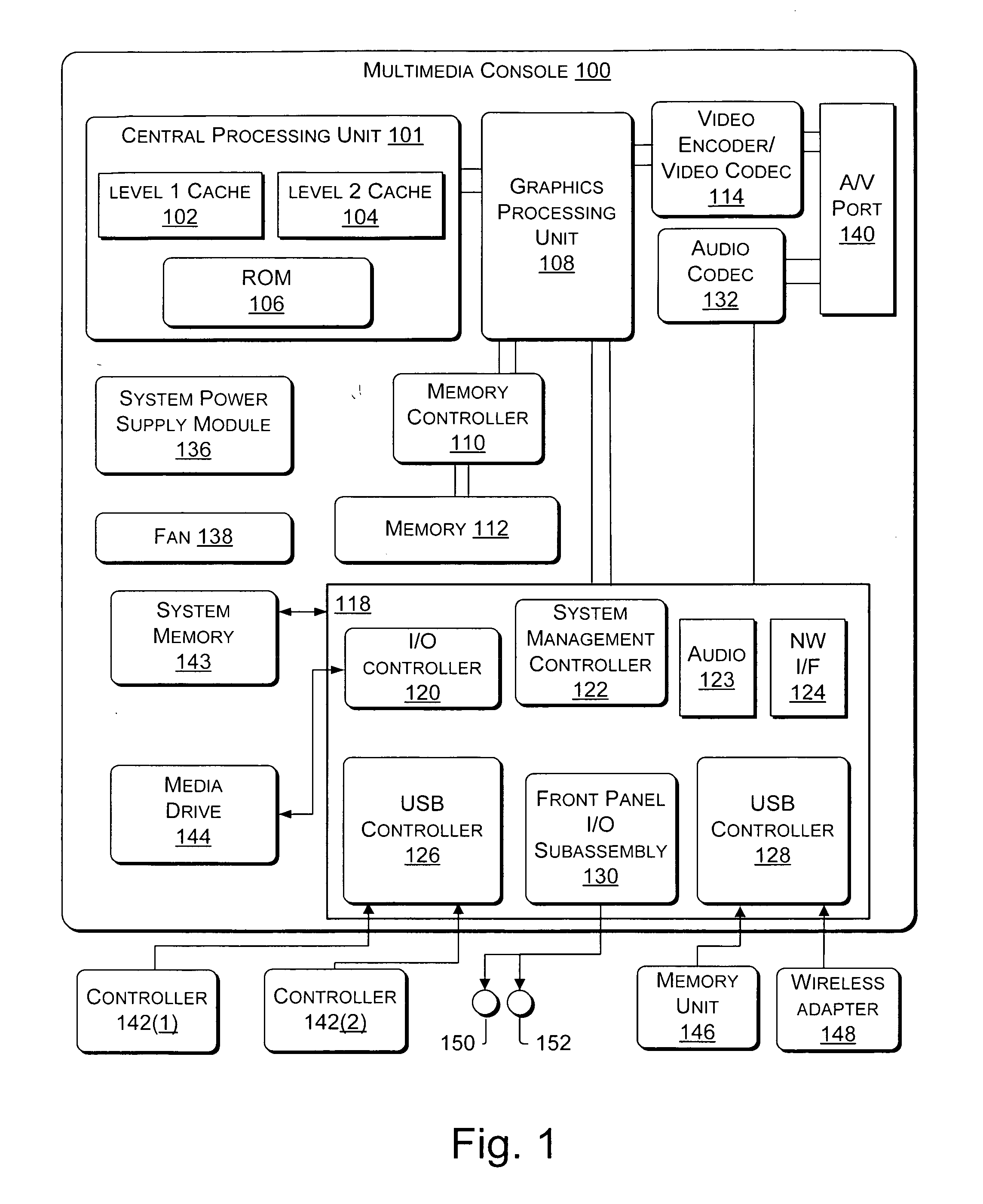
Configfs is a RAM-based virtual file system provided by the 2.6 Linux kernel.
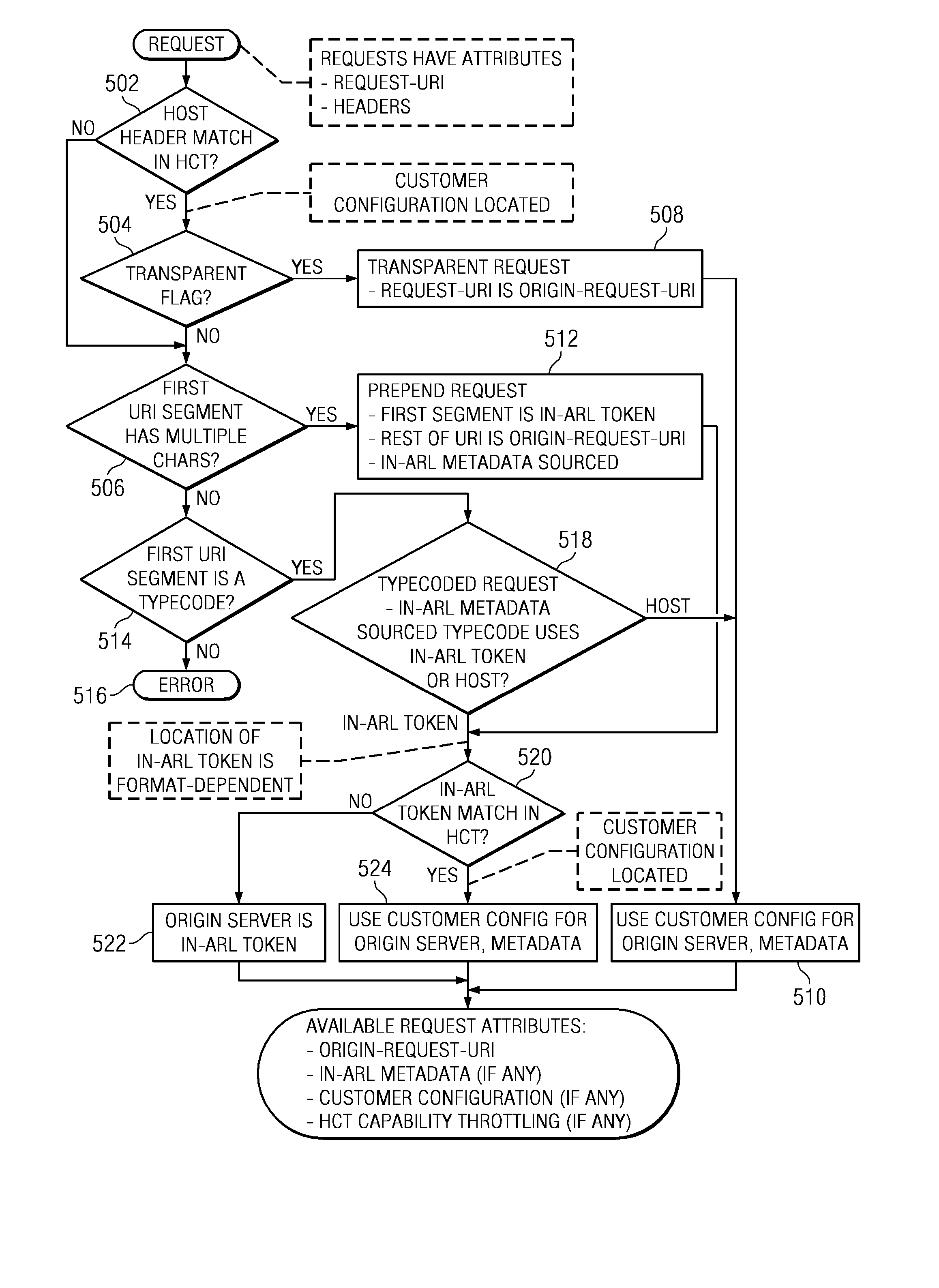
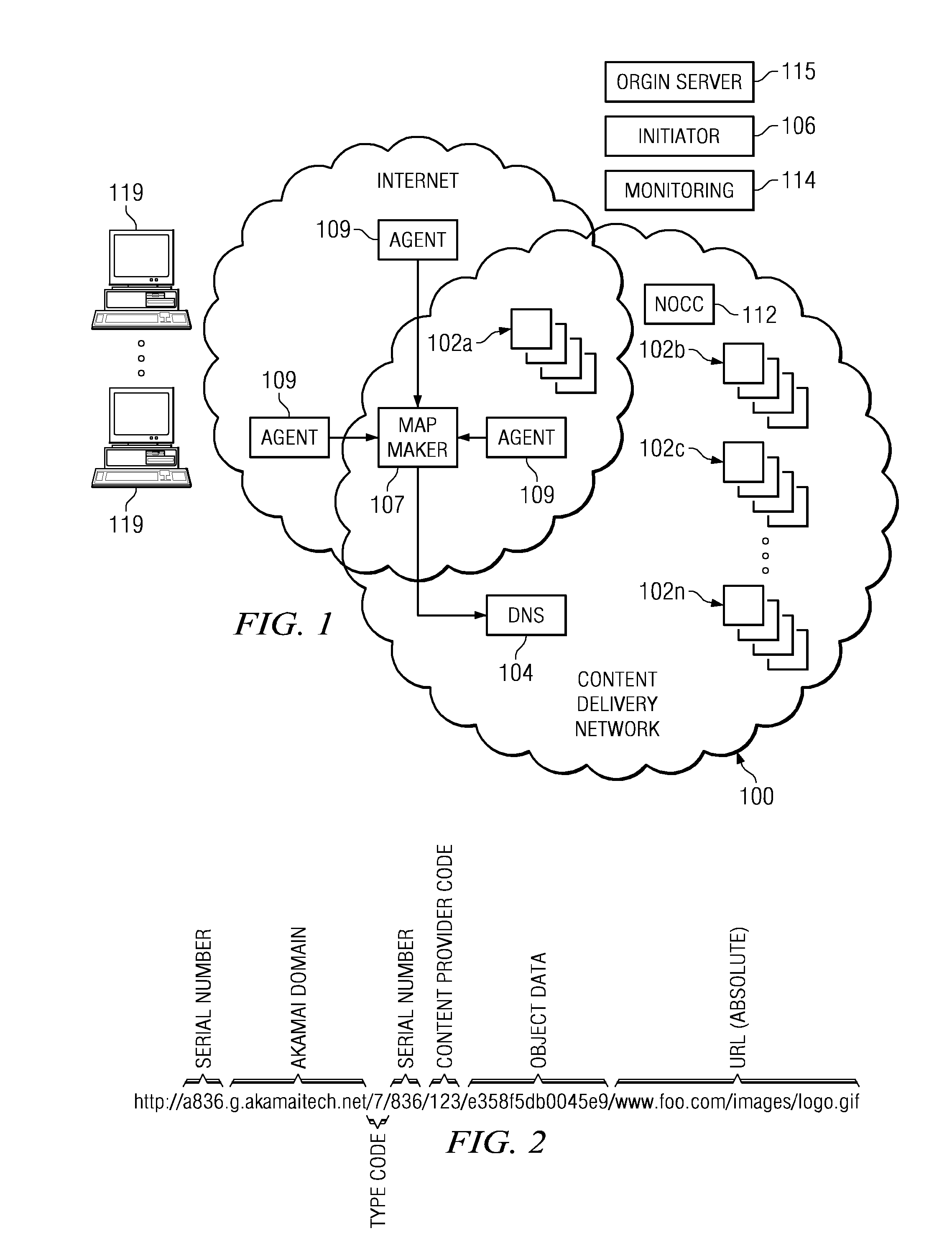
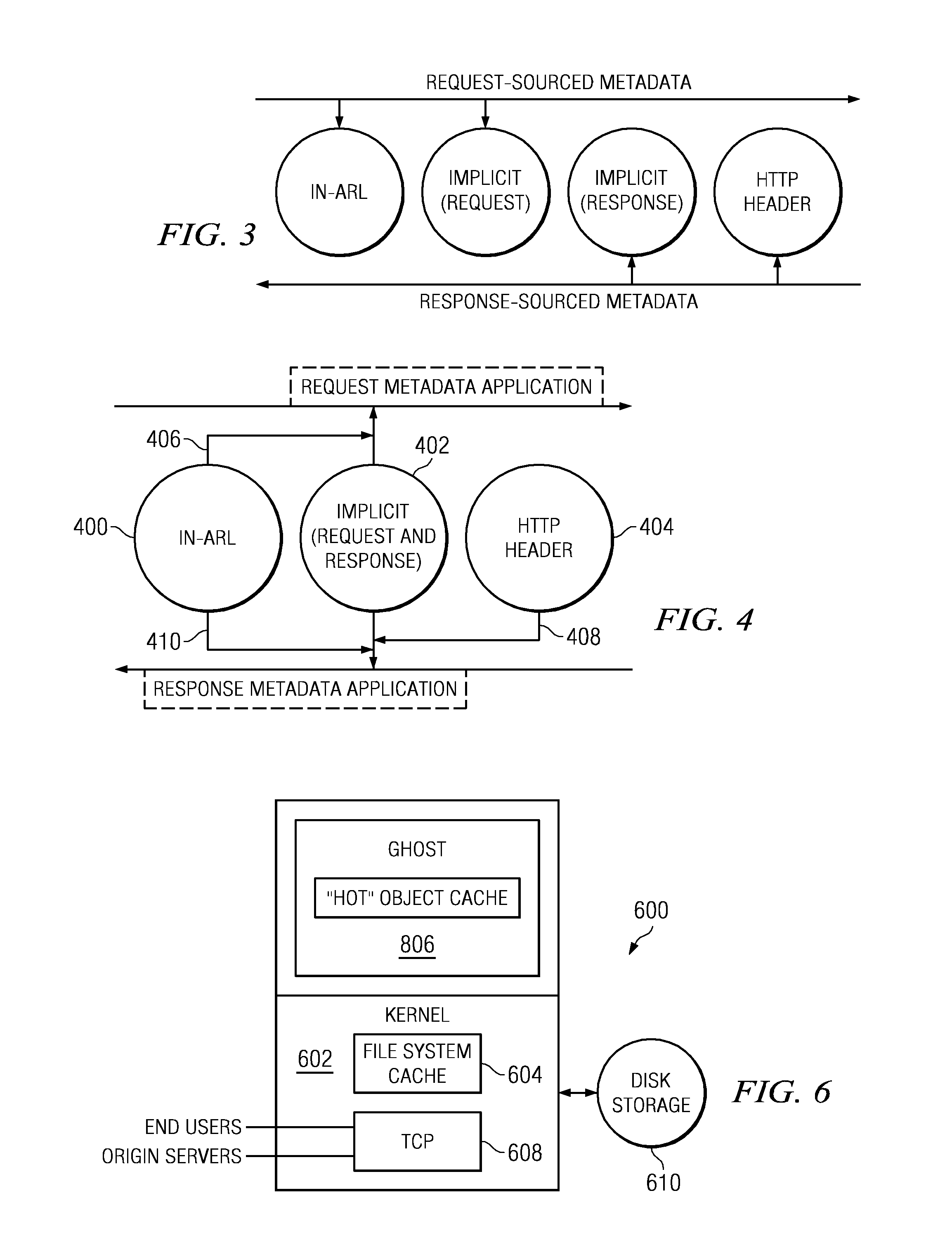
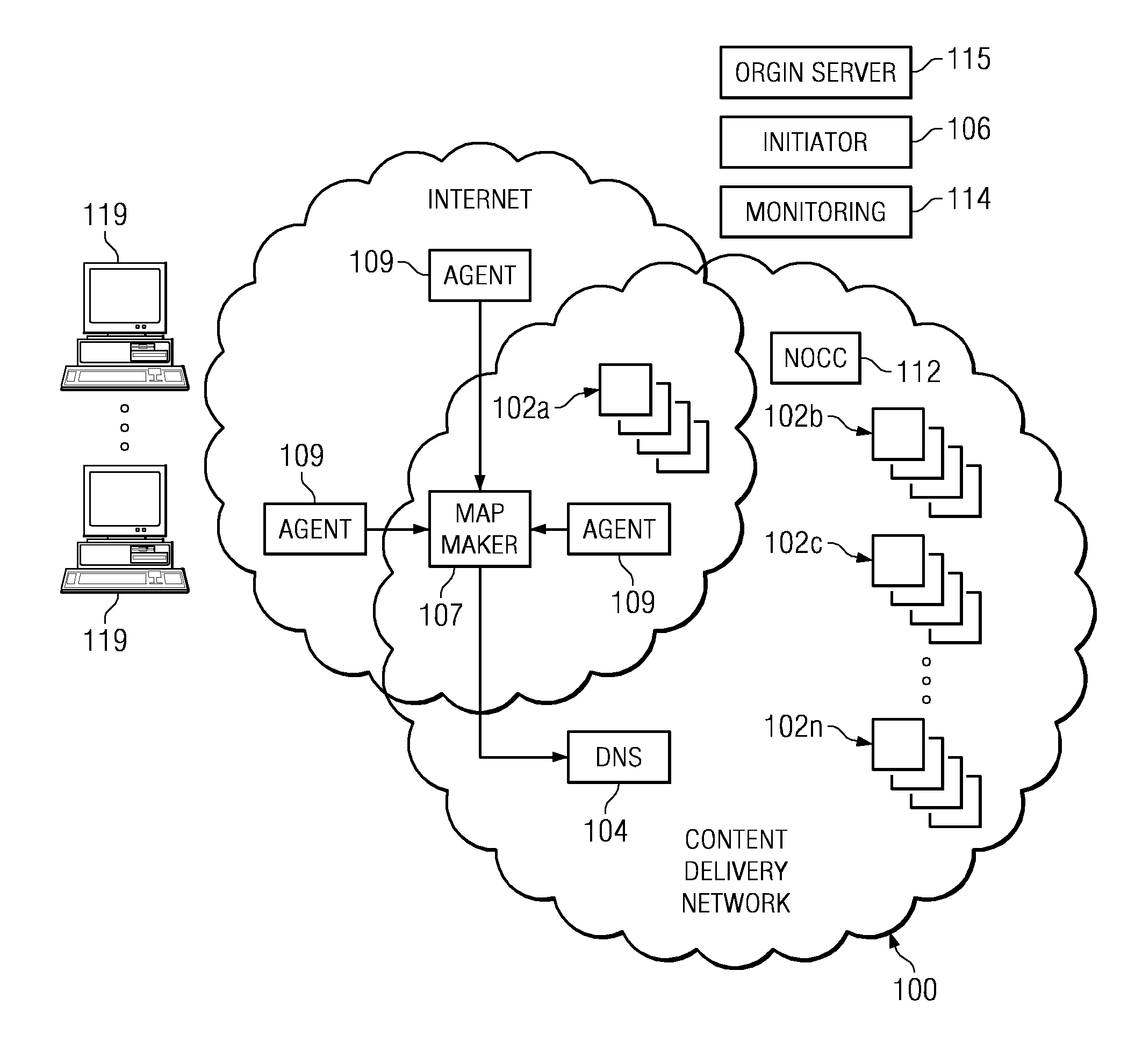
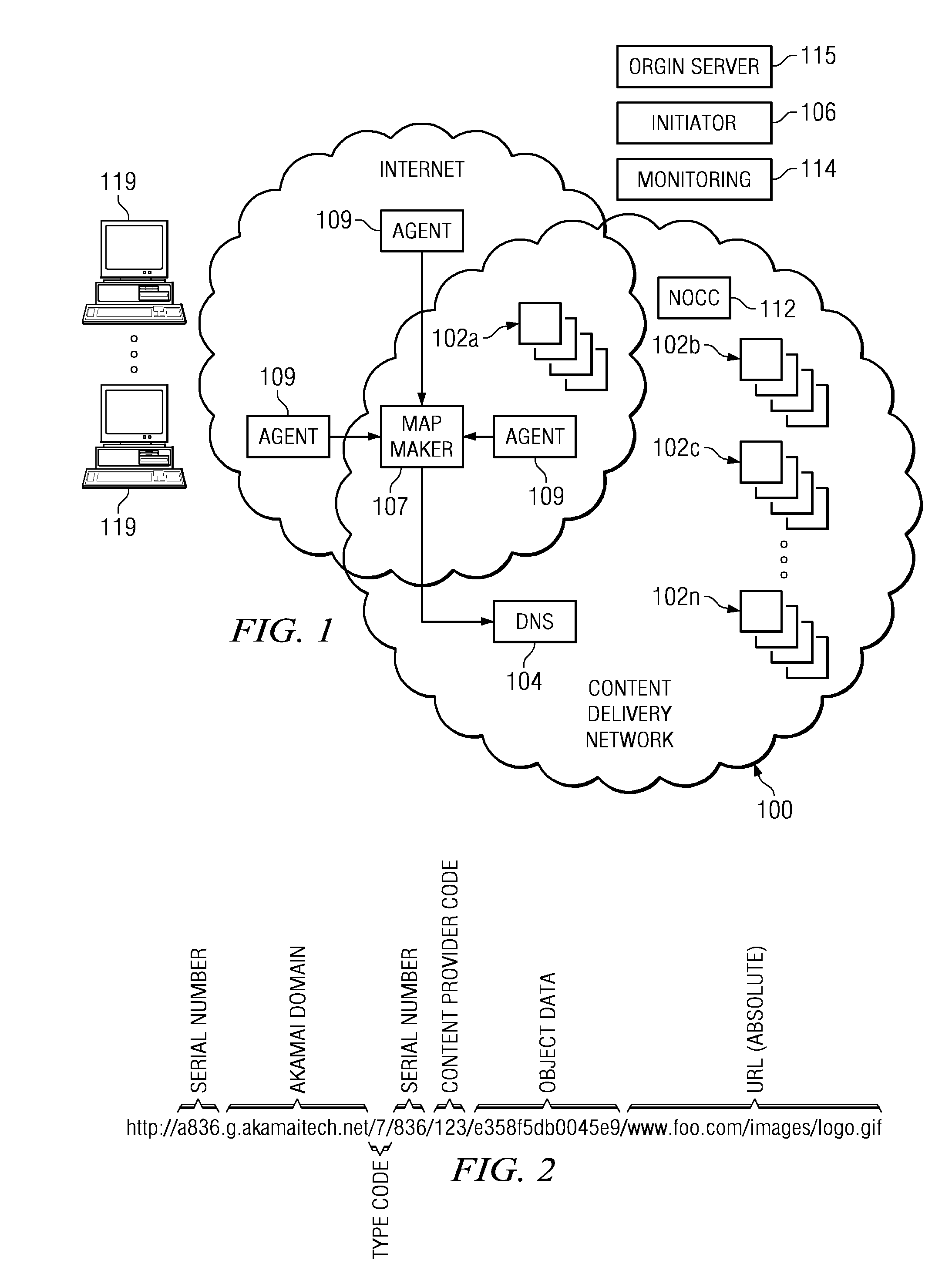
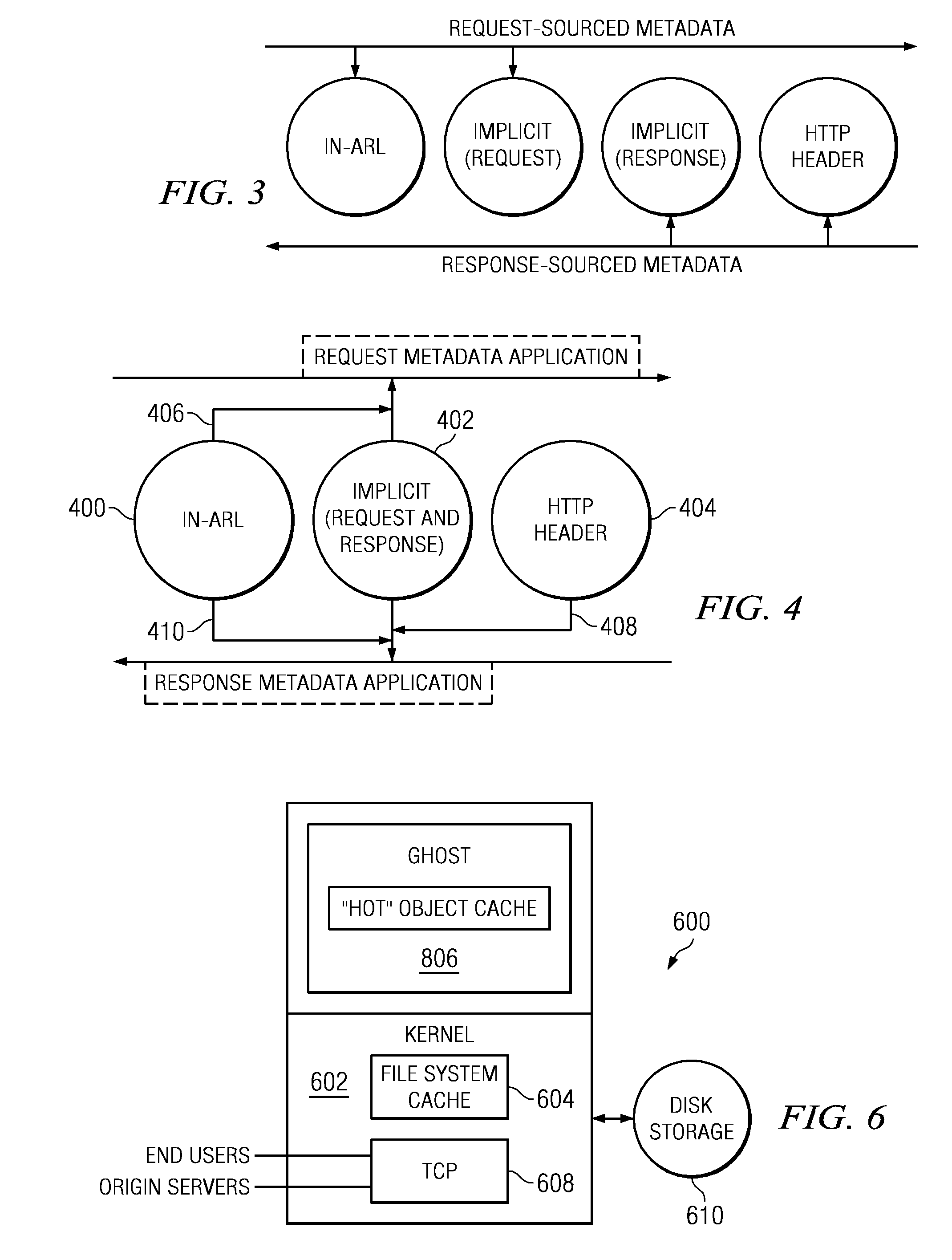
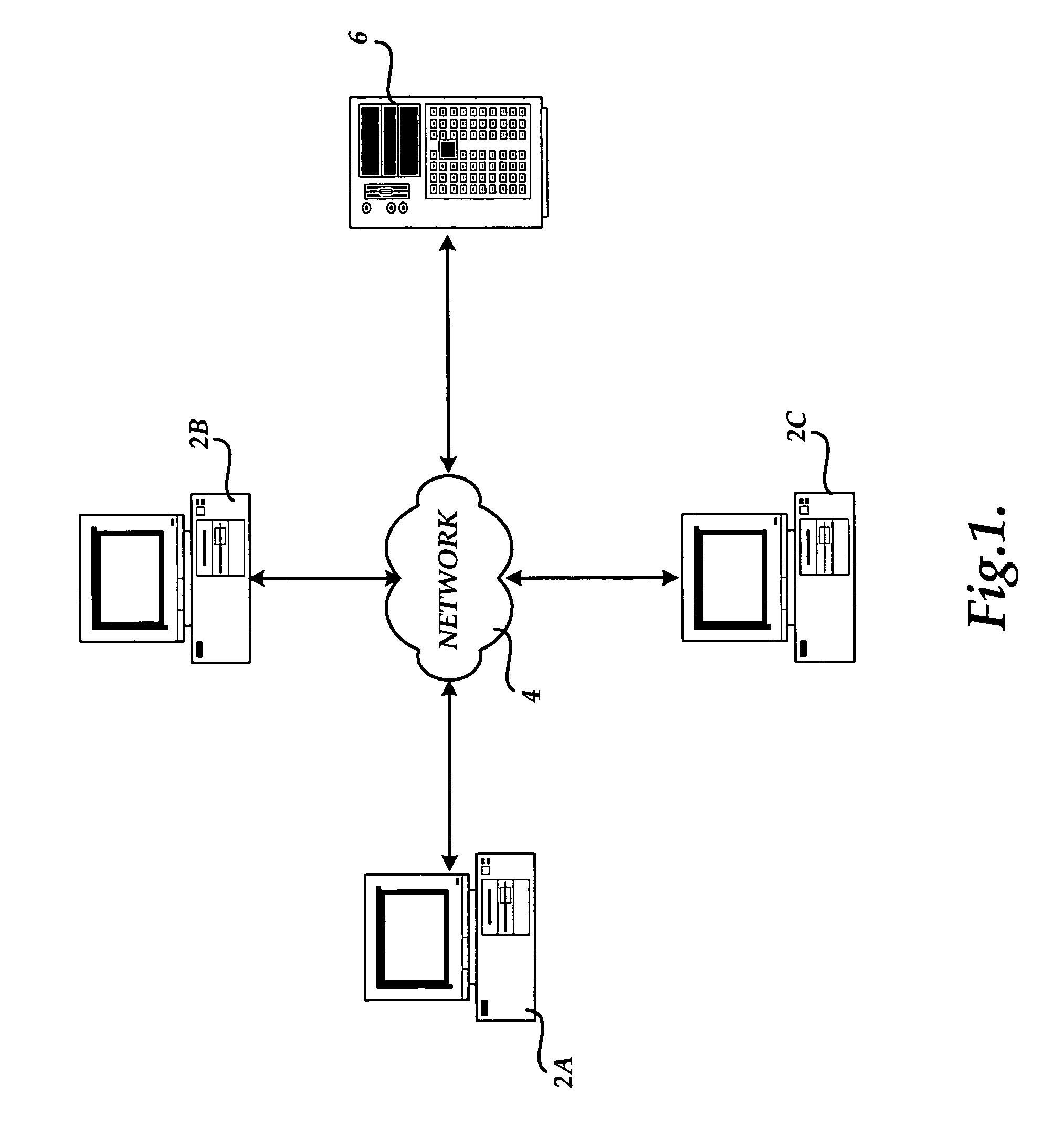
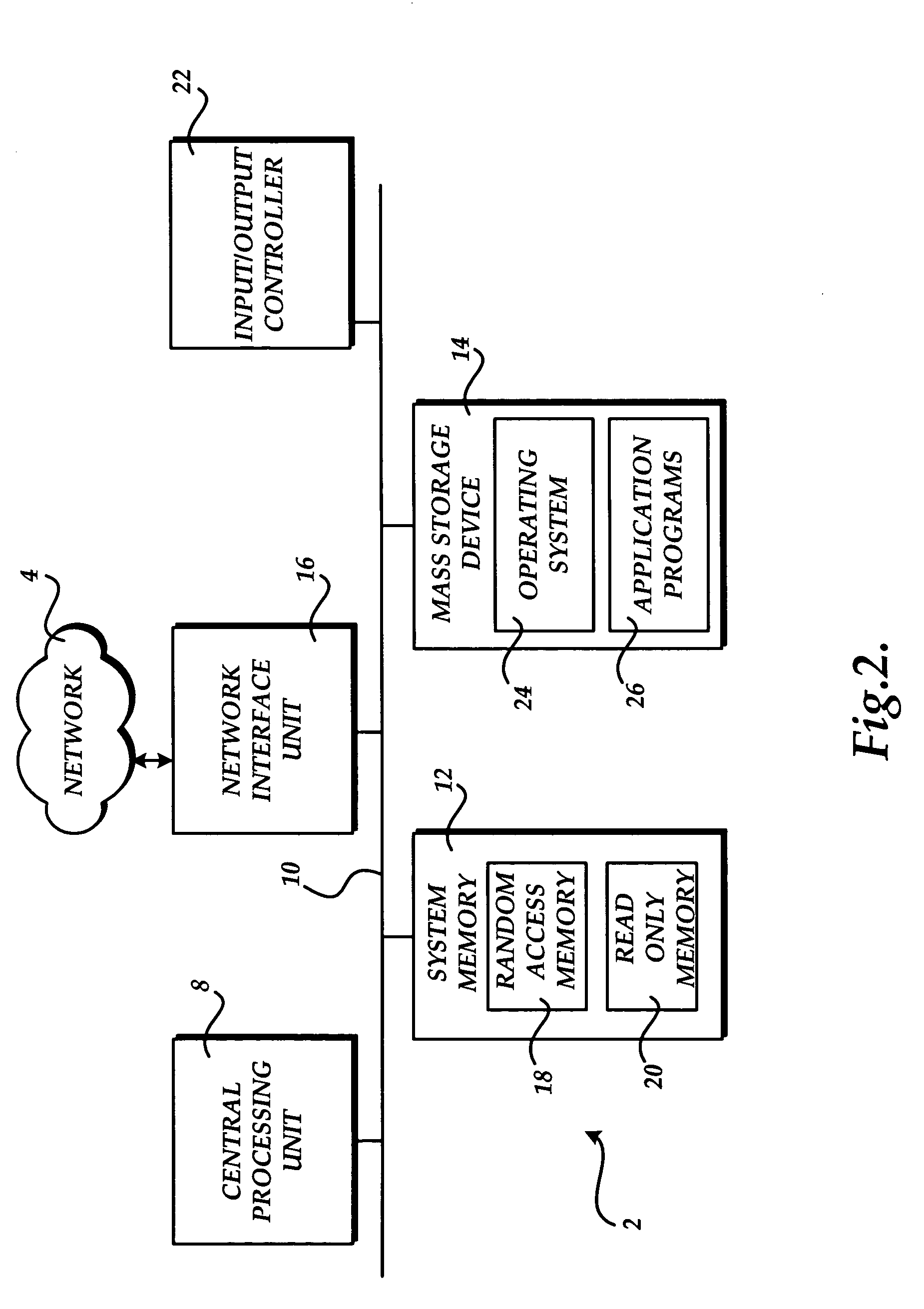
Content delivery network (CDN) content server request handling mechanism with metadata framework support
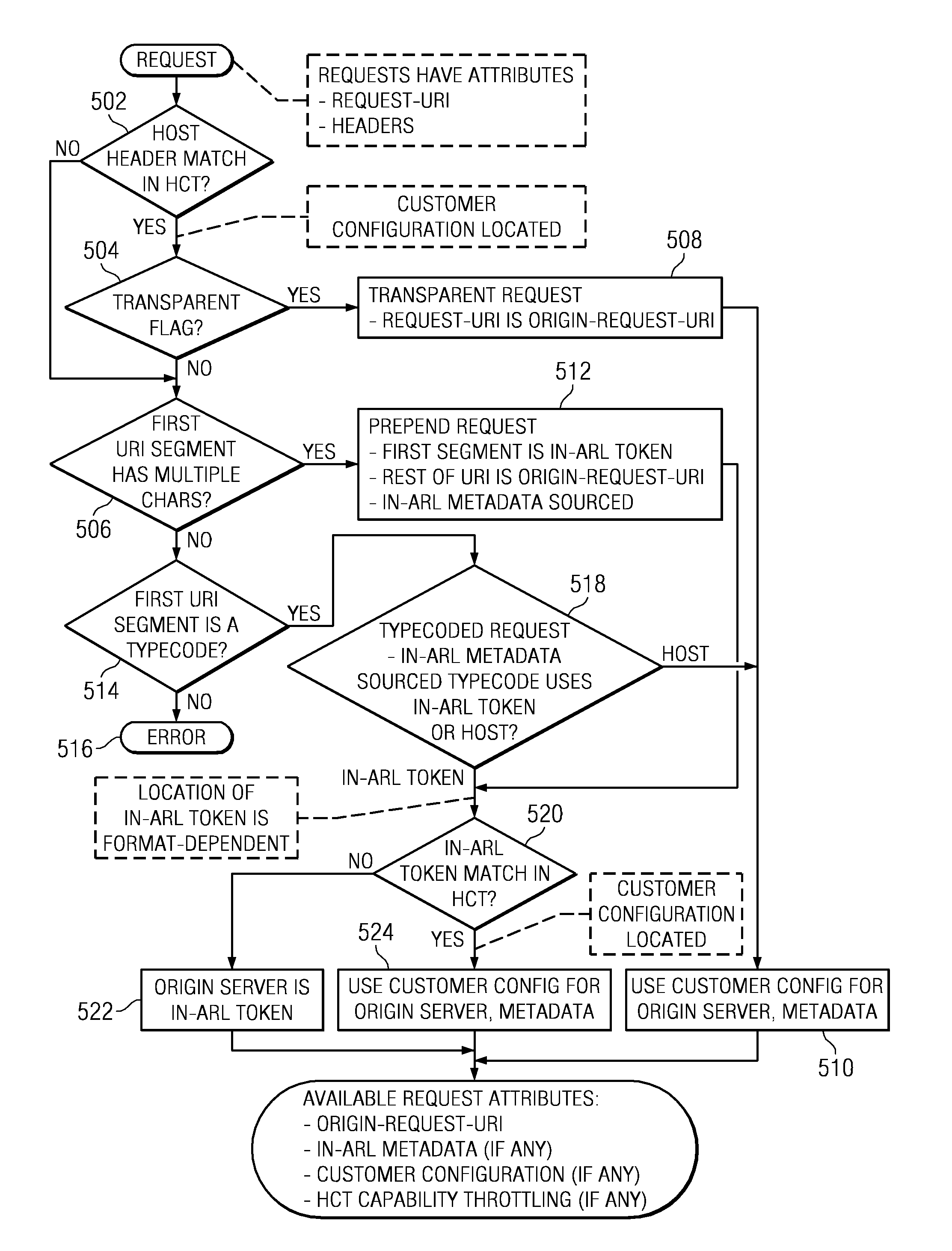
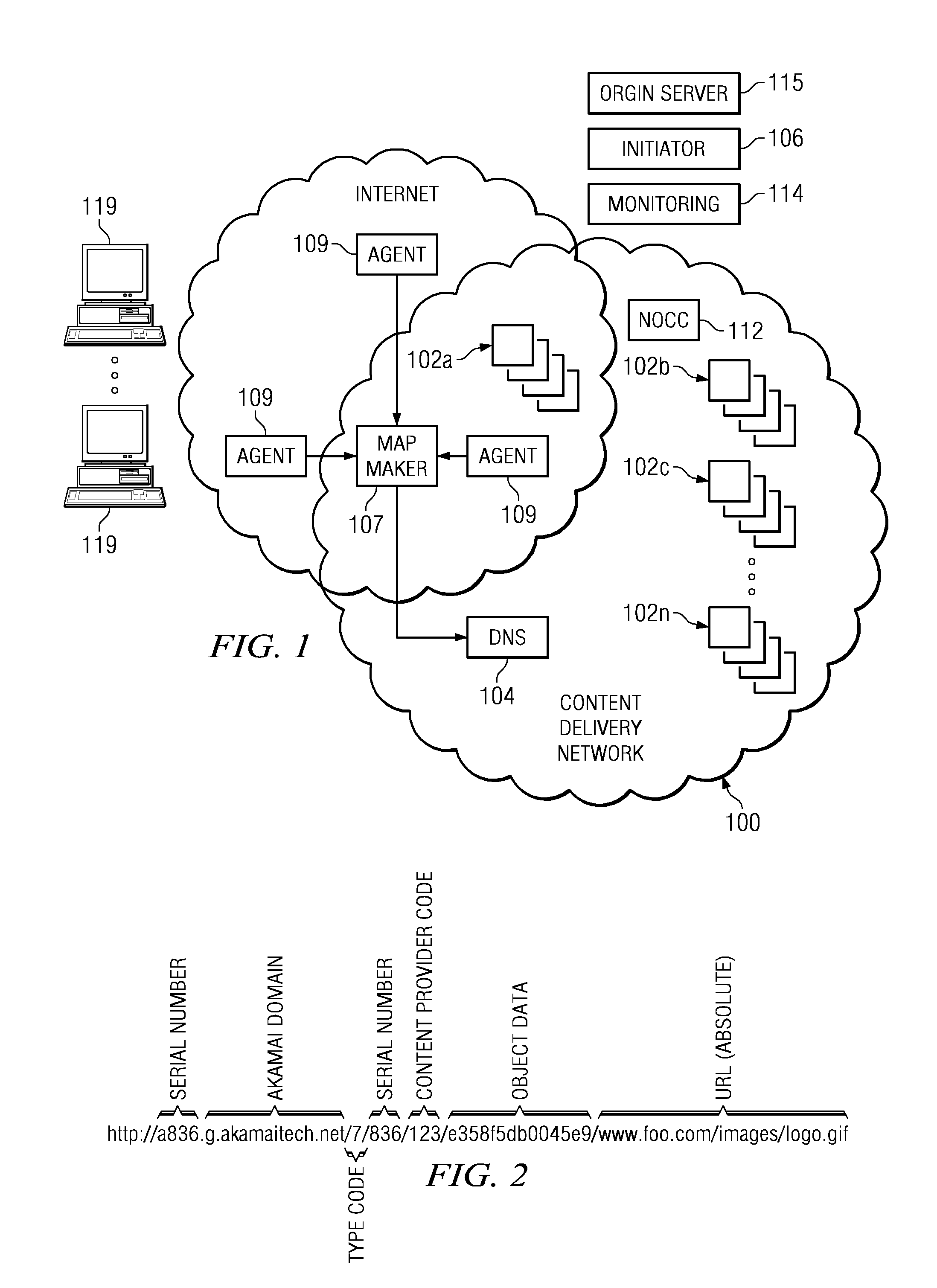
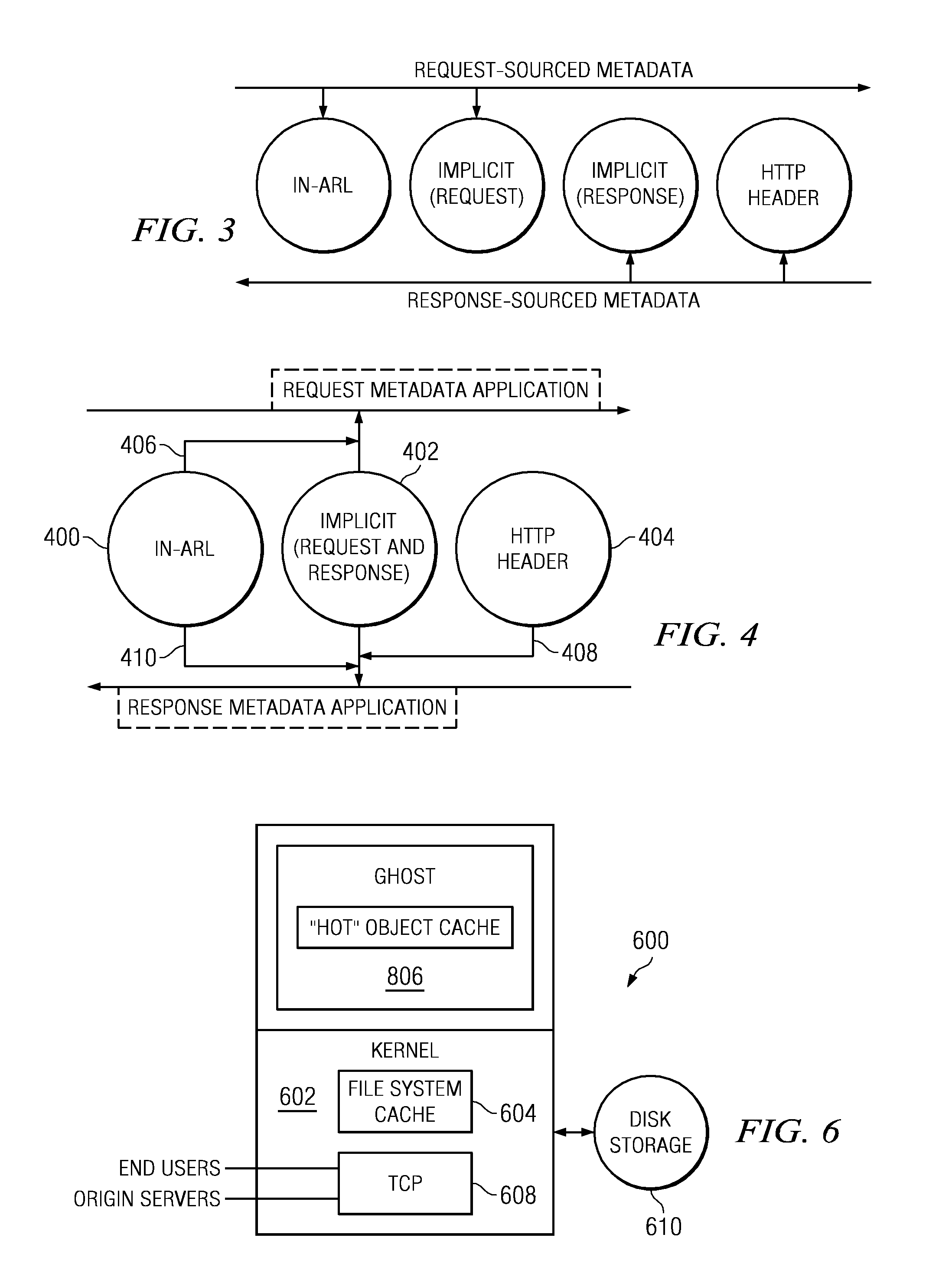
To serve content through a content delivery network (CDN), the CDN must have some information about the identity, characteristics and state of its target objects. Such additional information is provided in the form of object metadata, which according to the invention can be located in the request string itself, in the response headers from the origin server, in a metadata configuration file distributed to CDN servers, or in a per-customer metadata configuration file. CDN content servers execute a request identification and parsing process to locate object metadata and to handle the request in accordance therewith. Where different types of metadata exist for a particular object, metadata in a configuration file is overridden by metadata in a response header or request string, with metadata in the request string taking precedence.
Owner:AKAMAI TECH INC
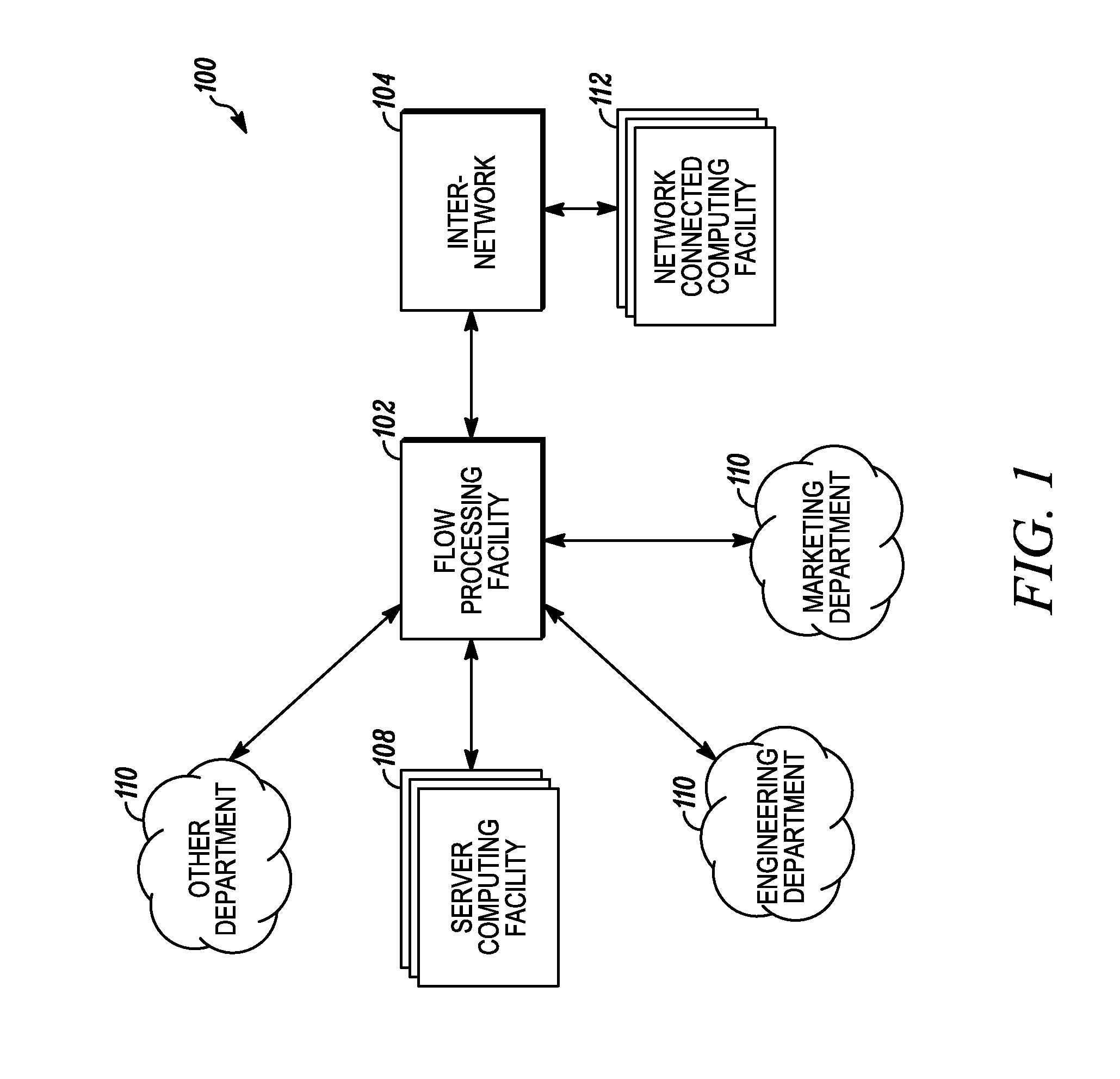
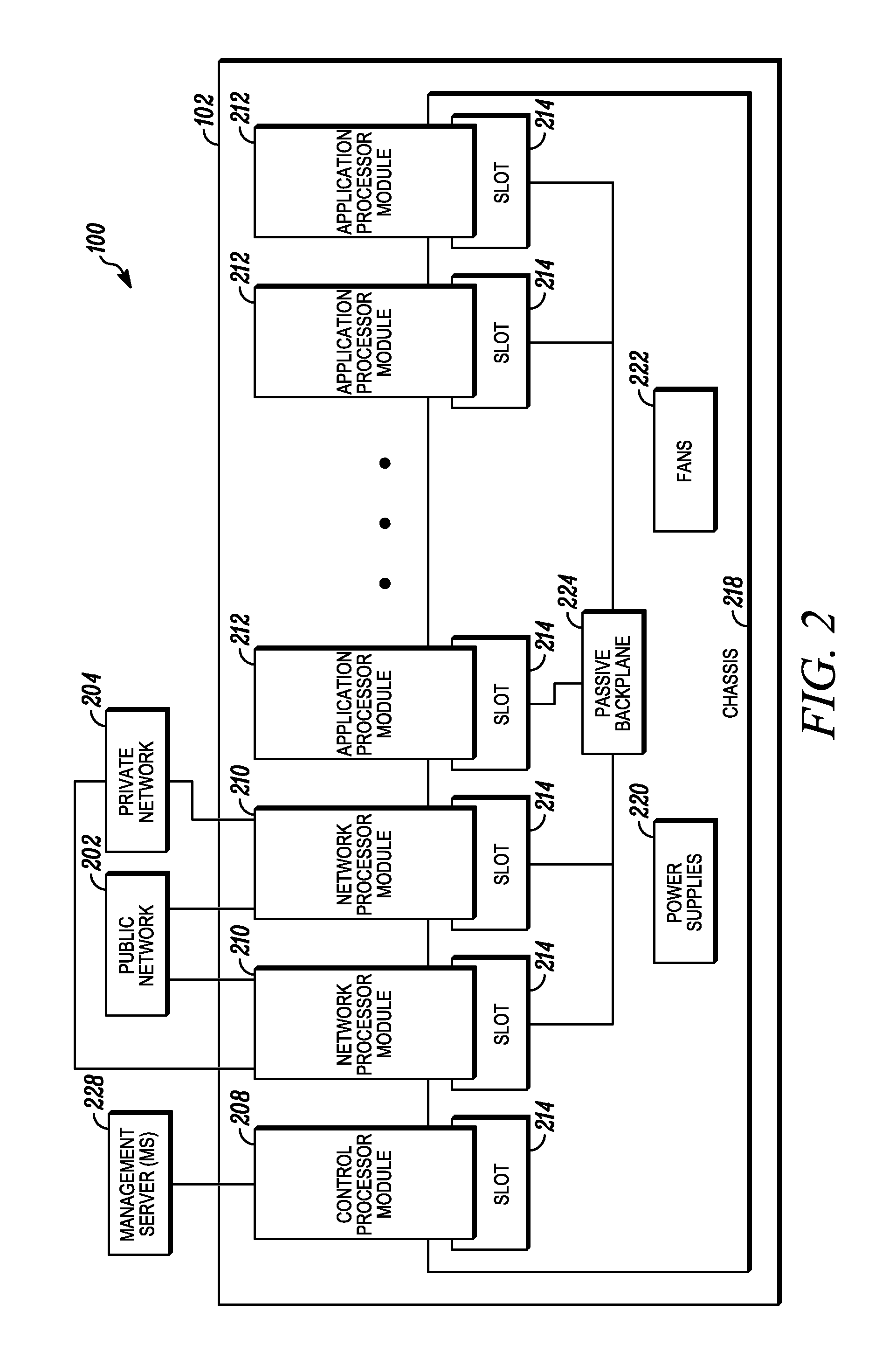
Processing data flows with a data flow processor
InactiveUS20110238855A1Increased complexityAvoid problemsMultiple digital computer combinationsPlatform integrity maintainanceData controlConfigfs
An apparatus and method to distribute applications and services in and throughout a network and to secure the network includes the functionality of a switch with the ability to apply applications and services to received data according to respective subscriber profiles. Front-end processors, or Network Processor Modules (NPMs), receive and recognize data flows from subscribers, extract profile information for the respective subscribers, utilize flow scheduling techniques to forward the data to applications processors, or Flow Processor Modules (FPMs). The FPMs utilize resident applications to process data received from the NPMs. A Control Processor Module (CPM) facilitates applications processing and maintains connections to the NPMs, FPMs, local and remote storage devices, and a Management Server (MS) module that can monitor the health and maintenance of the various modules.
Owner:BLUE COAT SYSTEMS
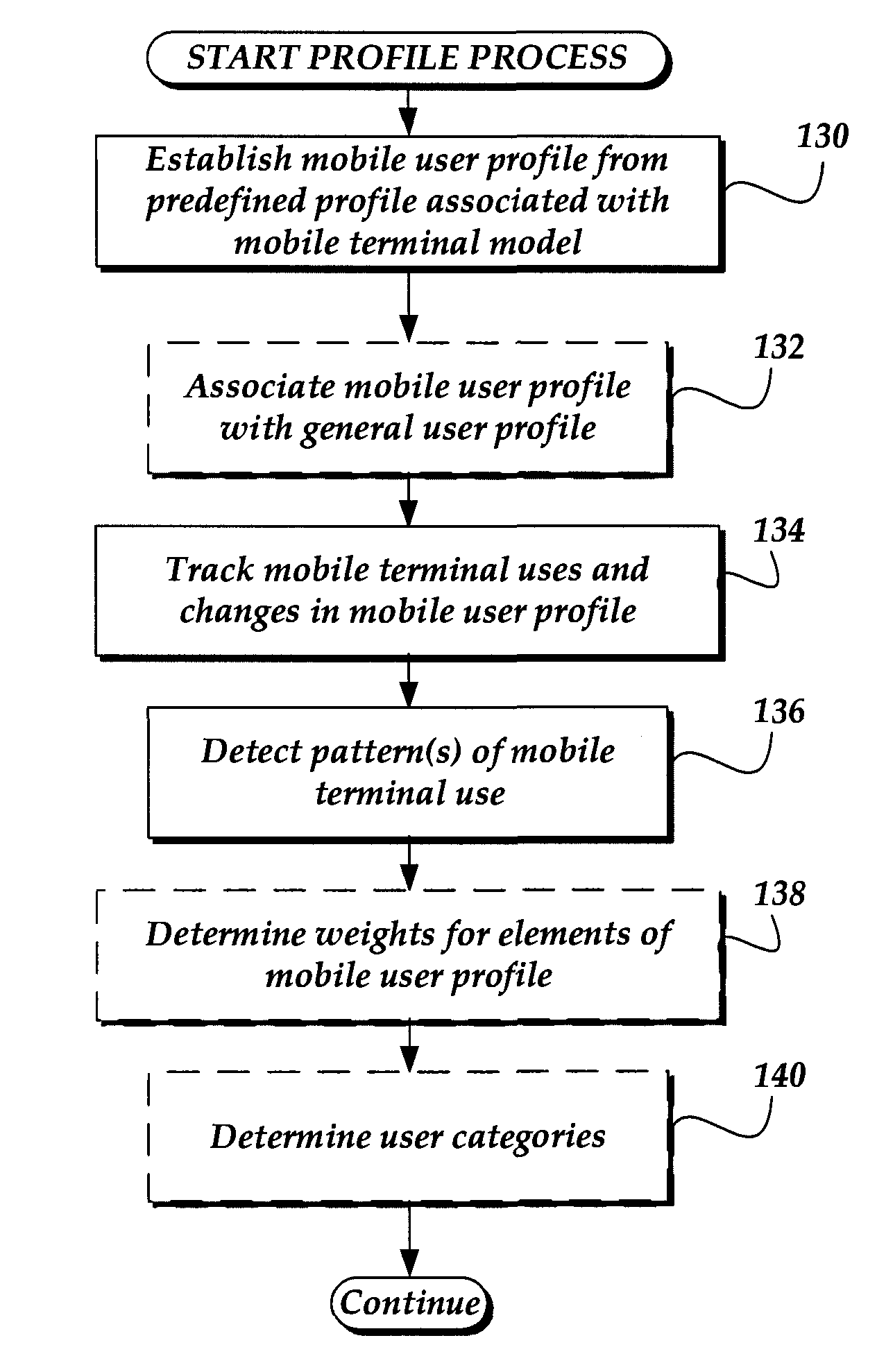
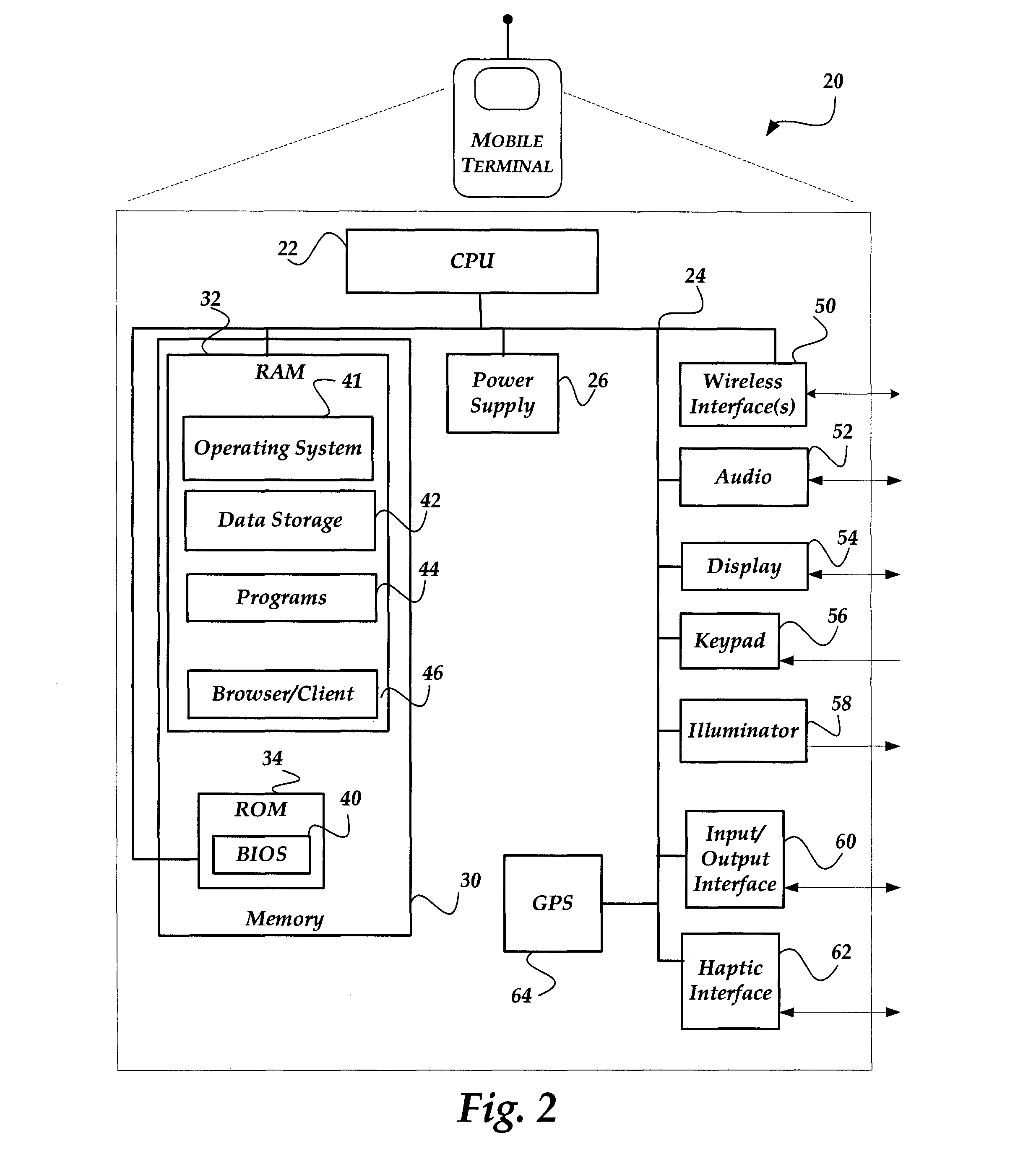
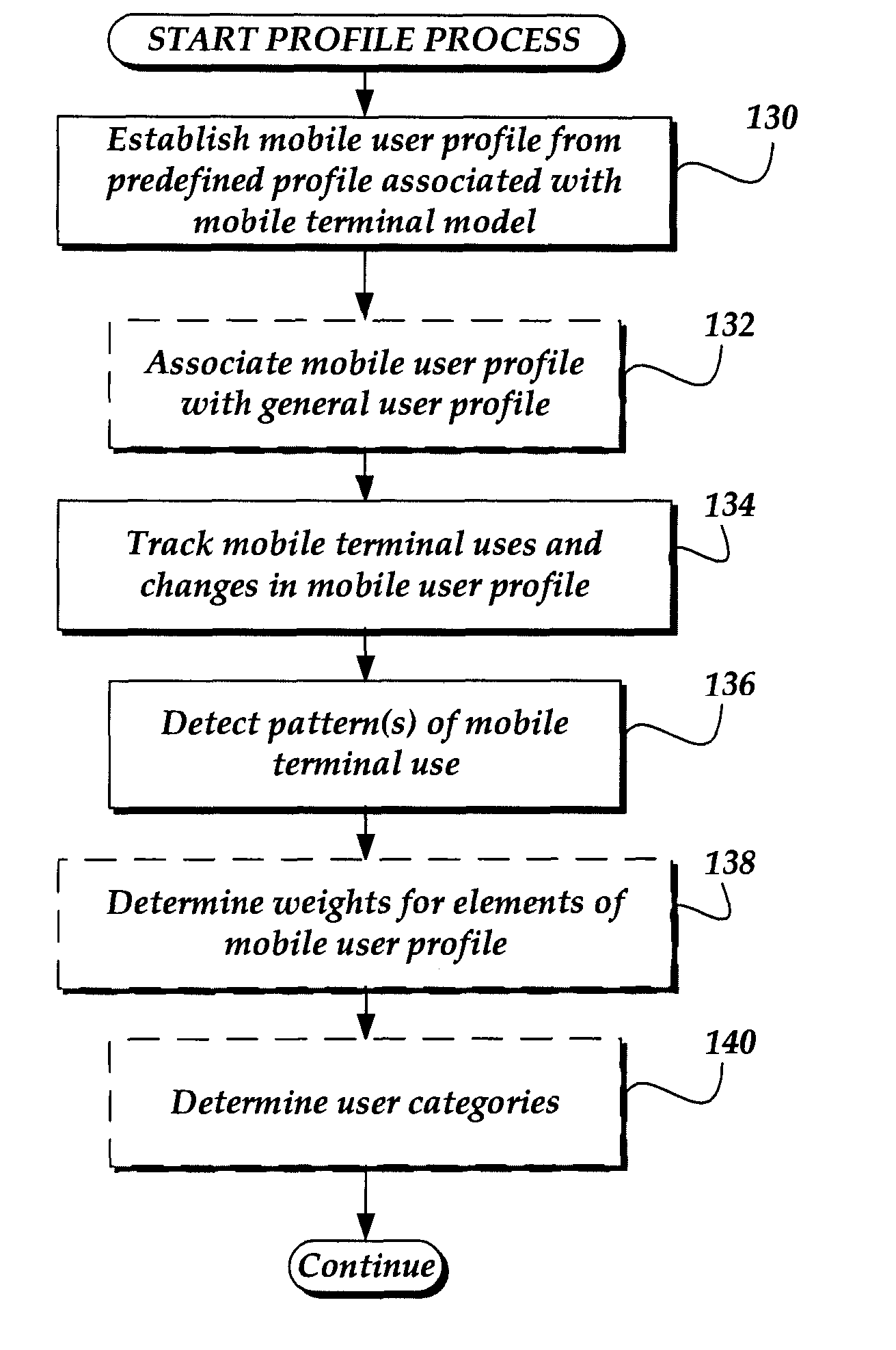
Prefetching content based on a mobile user profile
InactiveUS20060277271A1Network topologiesMultiple digital computer combinationsConfigfsService provision
A system and method are directed towards prefetching content for a mobile terminal based on characteristics of, and tracked usage of the mobile terminal to request content through an online portal service, which provides access to content in multiple subject areas. A mobile user profile is created from the characteristics and patterns of the tracked usage. The tracked usage information includes the time, location, frequency at which the content was requested. Based on the mobile user profile information, content similar to previously requested content is prefetched and cached in anticipation of the mobile terminal making a similar request. Prefetching may also occur based on a trigger event such as the mobile terminal returning to a location from which certain content was previously requested. Prefetching may further be based on a related general user profile that indicates usage of an alternate electronic device to access content through the portal.
Owner:OATH INC
Content delivery network (CDN) content server request handling mechanism with metadata framework support
To serve content through a content delivery network (CDN), the CDN must have some information about the identity, characteristics and state of its target objects. Such additional information is provided in the form of object metadata, which according to the invention can be located in the request string itself, in the response headers from the origin server, in a metadata configuration file distributed to CDN servers, or in a per-customer metadata configuration file. CDN content servers execute a request identification and parsing process to locate object metadata and to handle the request in accordance therewith. Where different types of metadata exist for a particular object, metadata in a configuration file is overridden by metadata in a response header or request string, with metadata in the request string taking precedence.
Owner:AKAMAI TECH INC
Method for determining metrics of a content delivery and global traffic management network
ActiveUS7523181B2Efficient executionMetering/charging/biilling arrangementsError preventionData packConfigfs
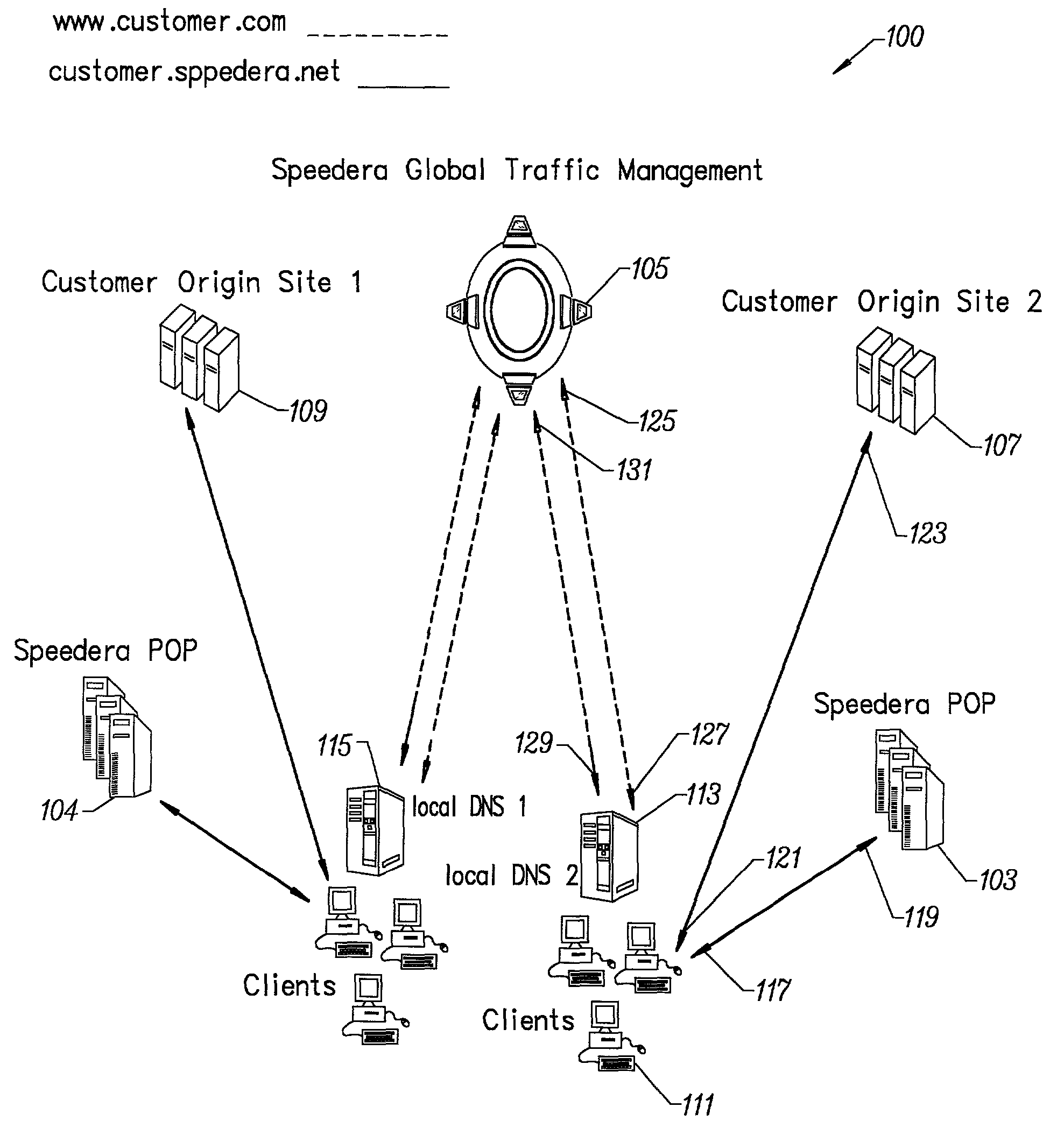
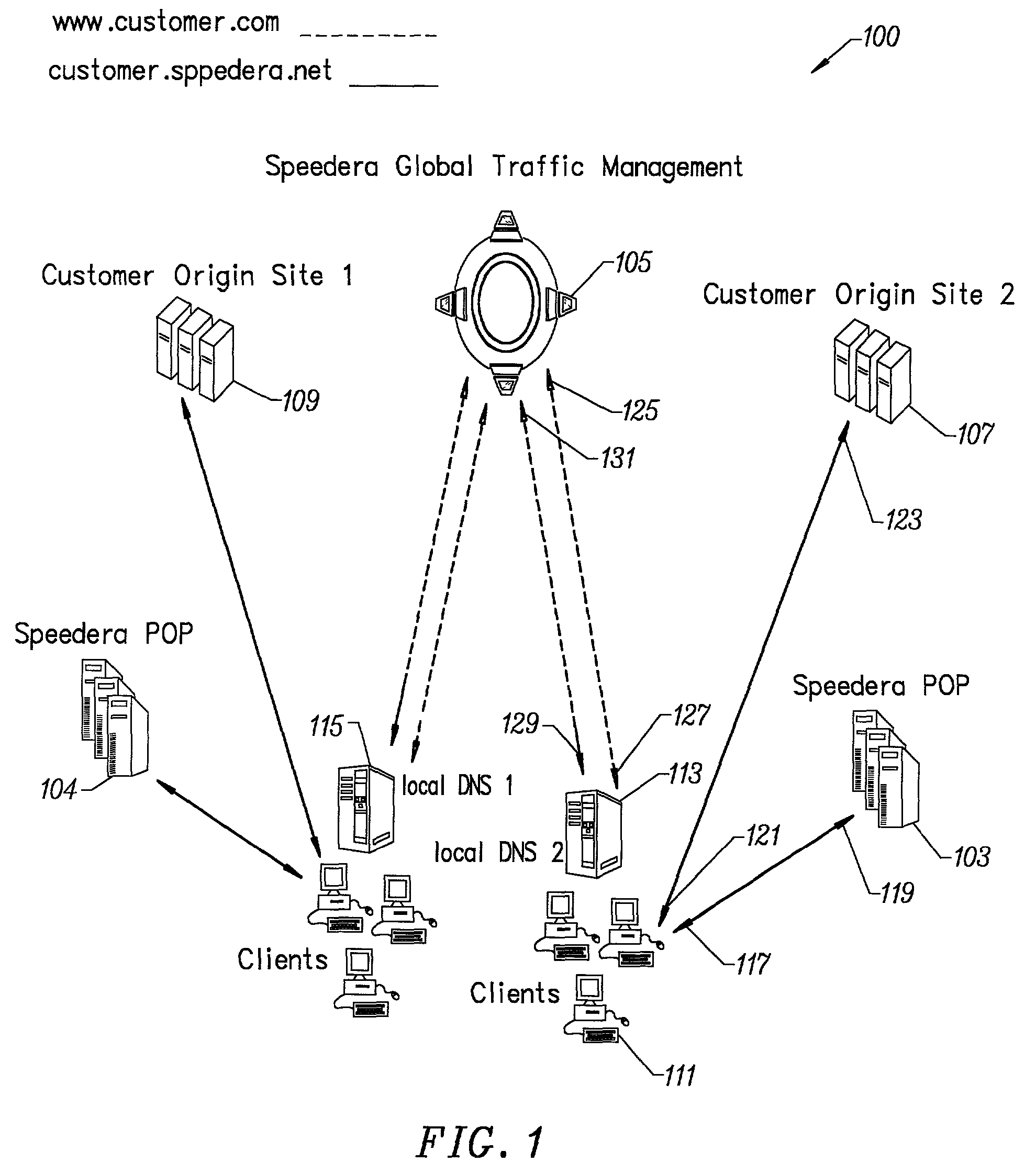
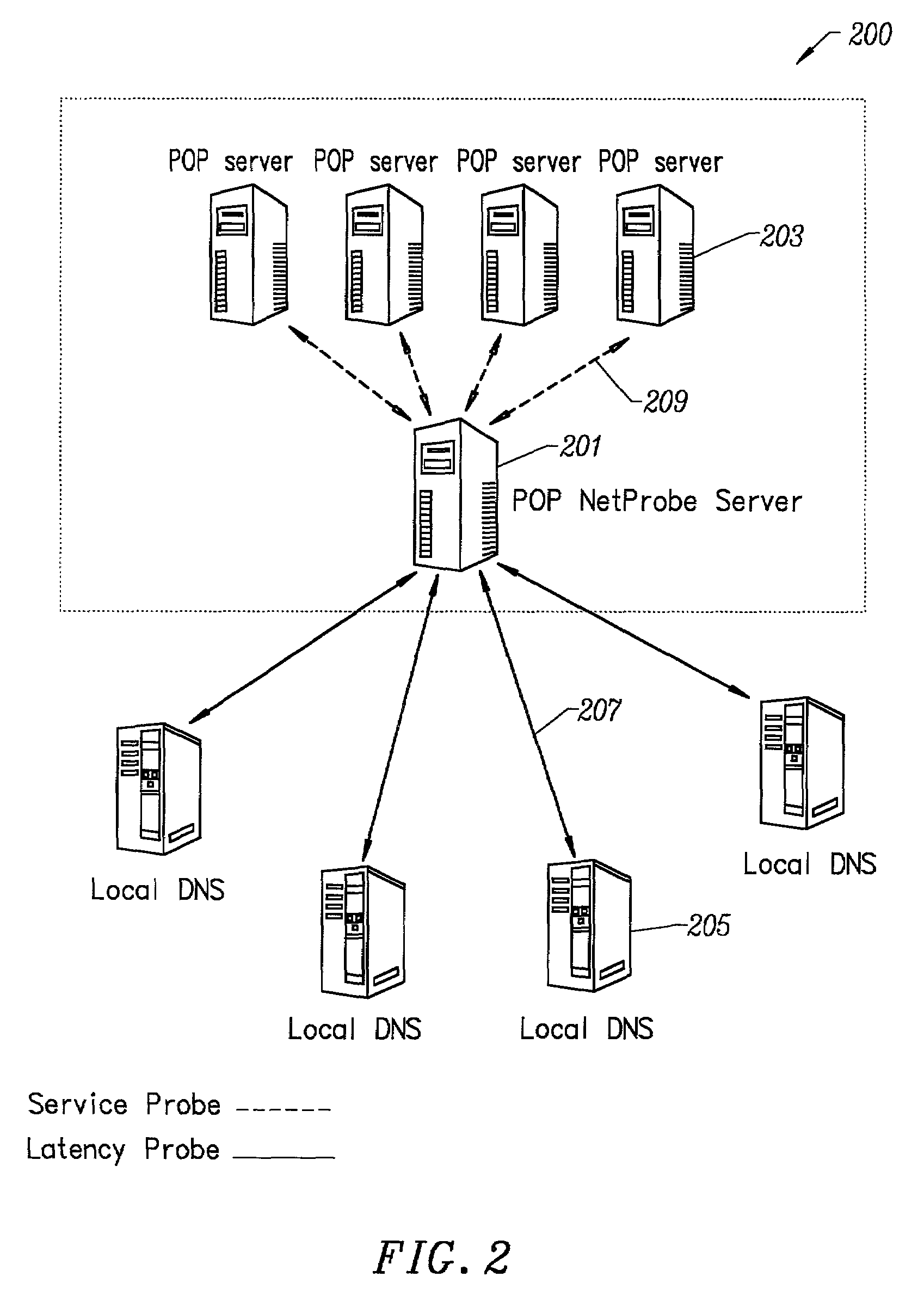
A method for determining metrics of a content delivery and global traffic management network provides service metric probes that determine the service availability and metric measurements of types of services provided by a content delivery machine. Latency probes are also provided for determining the latency of various servers within a network. Service metric probes consult a configuration file containing each DNS name in its area and the set of services. Each server in the network has a metric test associated with each service supported by the server which the service metric probes periodically performs metric tests on and records the metric test results which are periodically sent to all of the DNS servers in the network. DNS servers use the test result updates to determine the best server to return for a given DNS name. The latency probe calculates the latency from its location to a client's location using the round trip time for sending a packet to the client to obtain the latency value for that client. The latency probe updates the DNS servers with the clients' latency data. The DNS server uses the latency test data updates to determine the closest server to a client.
Owner:AKAMAI TECH INC
Managing digital identity information
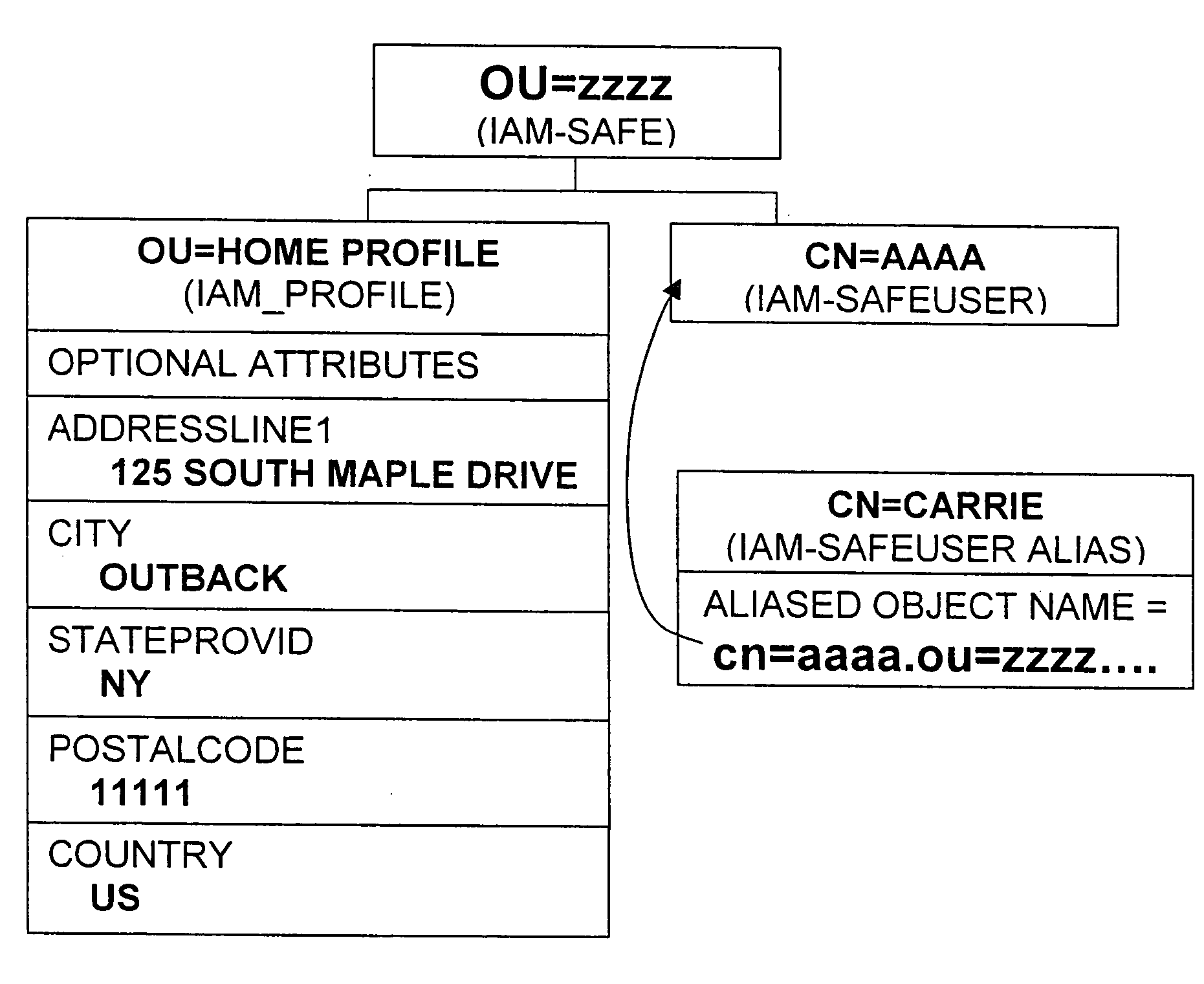
ActiveUS20050044423A1Maintain the integrity of relationshipsAdvanced technologyDigital data processing detailsMultiple digital computer combinationsDigital identityPassword
A basic architecture for managing digital identity information in a network such as the World Wide Web is provided. A user of the architecture can organize his or her information into one or more profiles which reflect the nature of different relationships between the user and other entities, and grant or deny each entity access to a given profile. Various enhancements which may be provided through the architecture are also described, including tools for filtering email, controlling access to user web pages, locating other users and making one's own location known, browsing or mailing anonymously, filling in web forms automatically with information already provided once by hand, logging in automatically, securely logging in to multiple sites with a single password and doing so from any machine on the network, and other enhancements.
Owner:EMC IP HLDG CO LLC
Policy based composite file system and method
InactiveUS20060259949A1Digital data information retrievalSpecial data processing applicationsFile systemConfigfs
A policy configurable file system includes a computer system upon which the policy configurable file system operates, a policy source for providing the configuration policies, and one or more file servers. The computer system includes software for enforcing one or more configuration policies. The policy source is typically either a policy server such that the policy is derived from the policy server, or a policy configurable file system, such that the policy is embedded in the policy configurable file system. The one or more file servers each uses a protocol, wherein the protocols of the one or more file servers are not all the same. In one case, the one or more of the configurable policies are separable from the policy configurable file system. In another case, the one or more configurable policies are downloadable to the computer system.
Owner:MICROSOFT TECH LICENSING LLC
Network apparatus and method for preview of music products and compilation of market data
InactiveUS20050267819A1Electrophonic musical instrumentsDisc-shaped record carriersCompact discWeb site
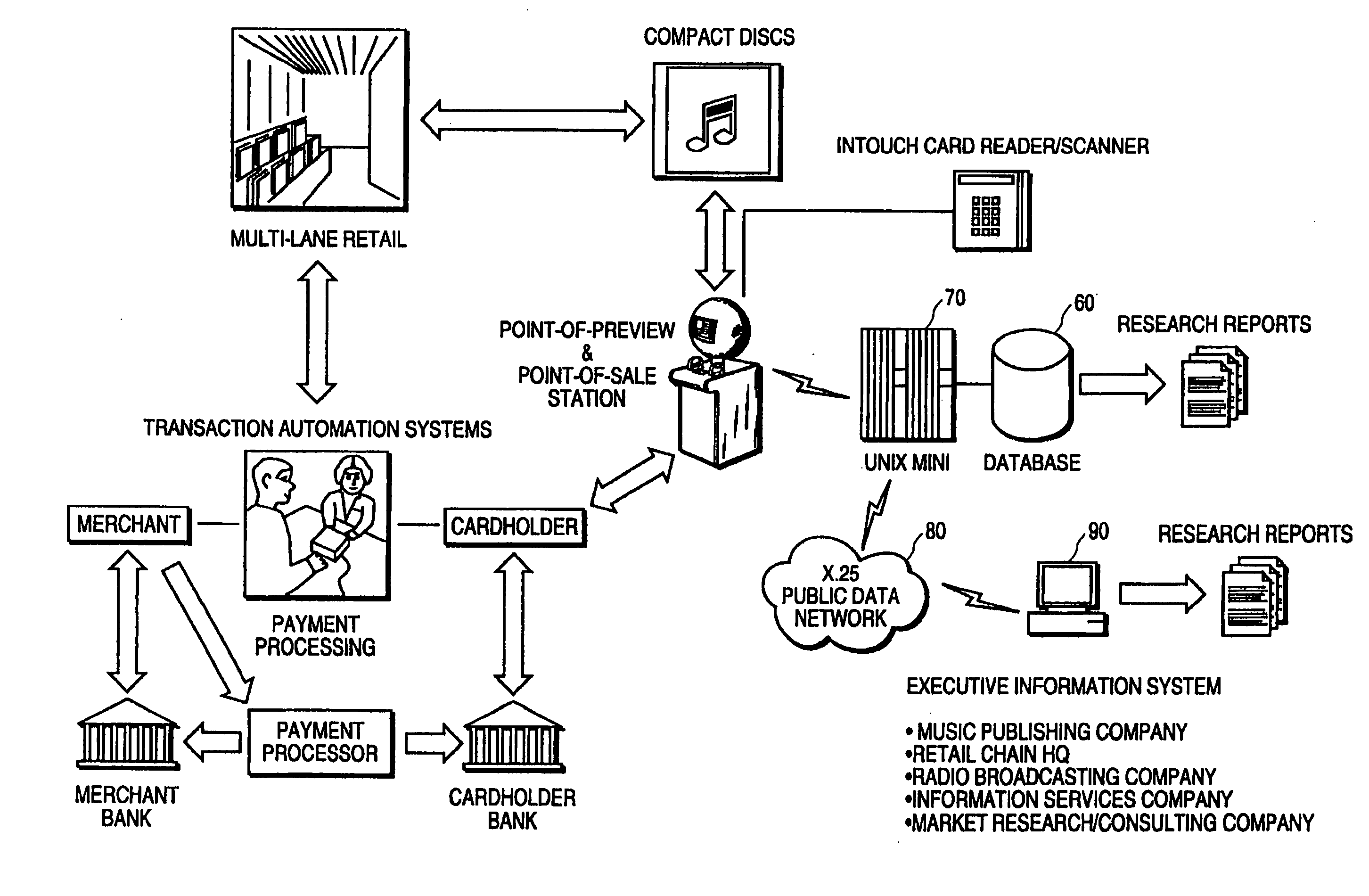
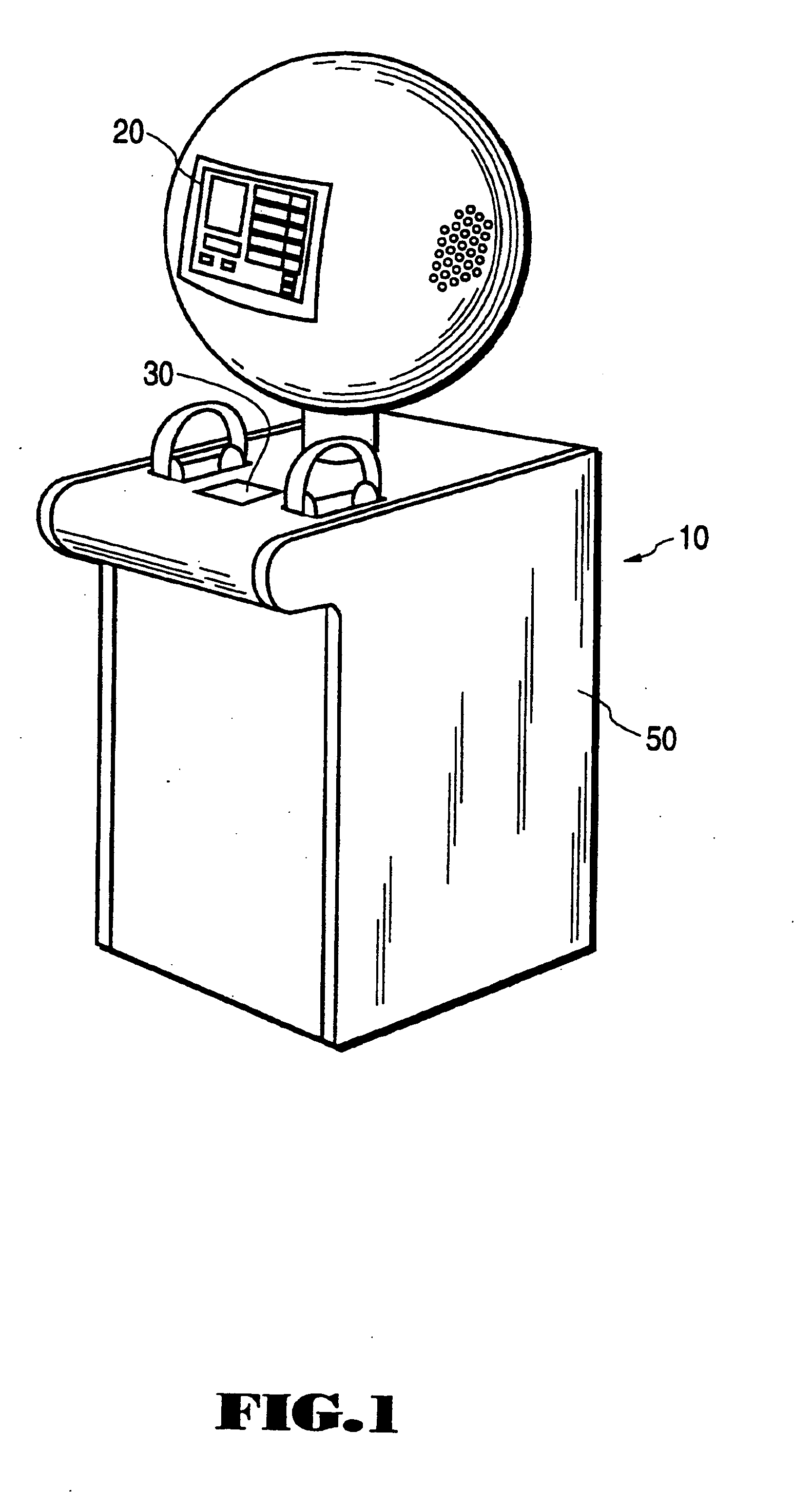
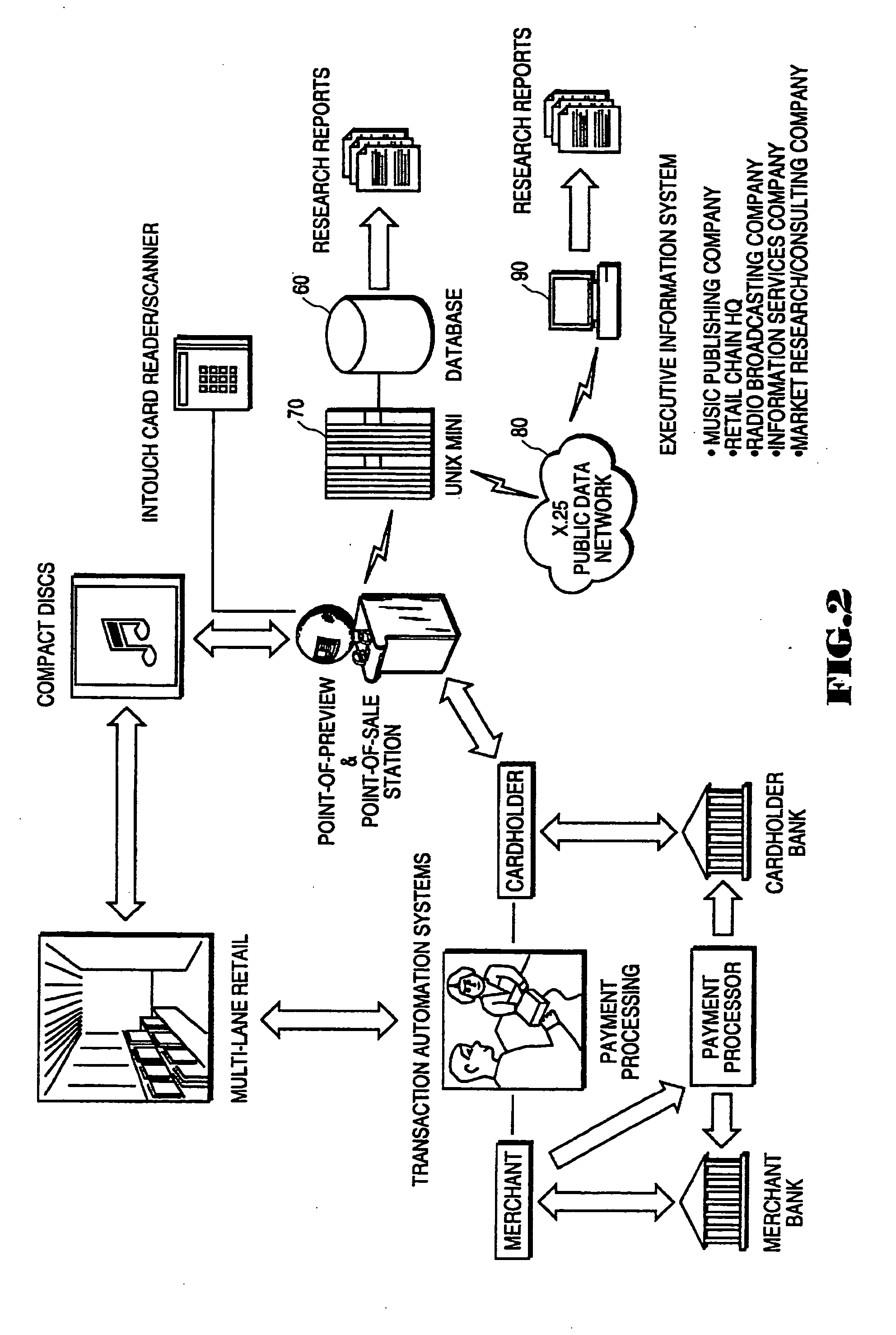
A system for on-line user-interactive multimedia based point-of-preview. The system provides for a network web site and accompanying software and hardware for allowing users to access the web site over a network such as the internet via a computer. The user is uniquely identified to the web site server through an identification name or number. The hardware associated with the web site includes storage of discrete increments of pre-selected portions of music products for user selection and preview. After user selection, a programmable data processor selects the particular pre-recorded music product from data storage and then transmits that chosen music product over the network to the user for preview. Subscriber selection and profile data (i.e. demographic information) can optionally be collected and stored to develop market research data. Since the system provides for multiple embodiments, the system contemplates previewing of audio programs such as music on compact discs, video programs such as movies and text from books and other written documents. Furthermore, it is contemplated that the network web site can be accessed from a publicly accessible kiosk, available, e.g. at a retail store location, or from a desk top computer.
Owner:KAPLAN JOSHUA D
Content delivery network (CDN) content server request handling mechanism
InactiveUS20070288588A1Digital data processing detailsMultiple digital computer combinationsConfigfsDatabase
To serve content through a content delivery network (CDN), the CDN must have some information about the identity, characteristics and state of its target objects. Such additional information is provided in the form of object metadata, which according to the invention can be located in the request string itself, in the response headers from the origin server, in a metadata configuration file distributed to CDN servers, or in a per-customer metadata configuration file. CDN content servers execute a request identification and parsing process to locate object metadata and to handle the request in accordance therewith. Where different types of metadata exist for a particular object, metadata in a configuration file is overridden by metadata in a response header or request string, with metadata in the request string taking precedence.
Owner:AKAMAI TECH INC
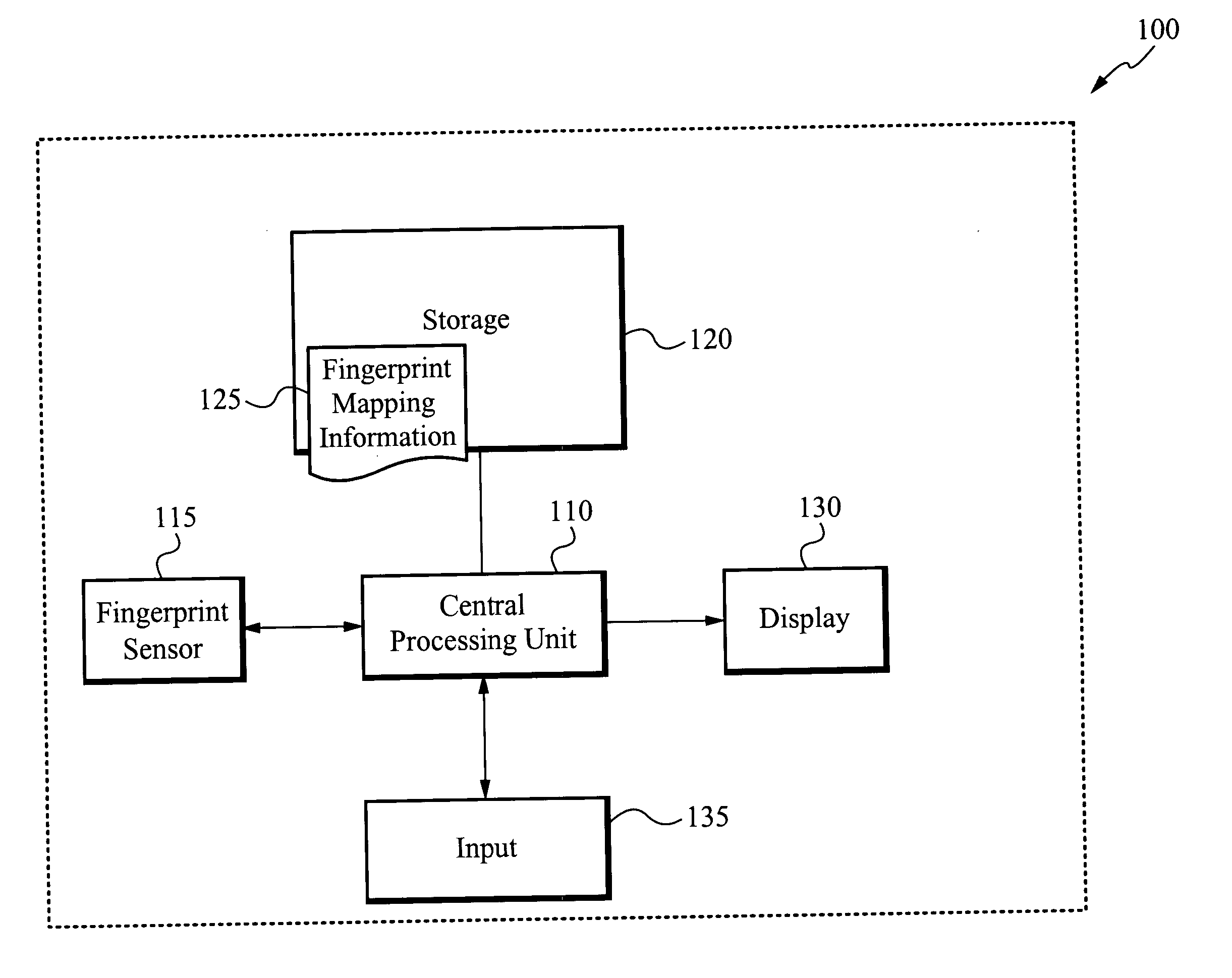
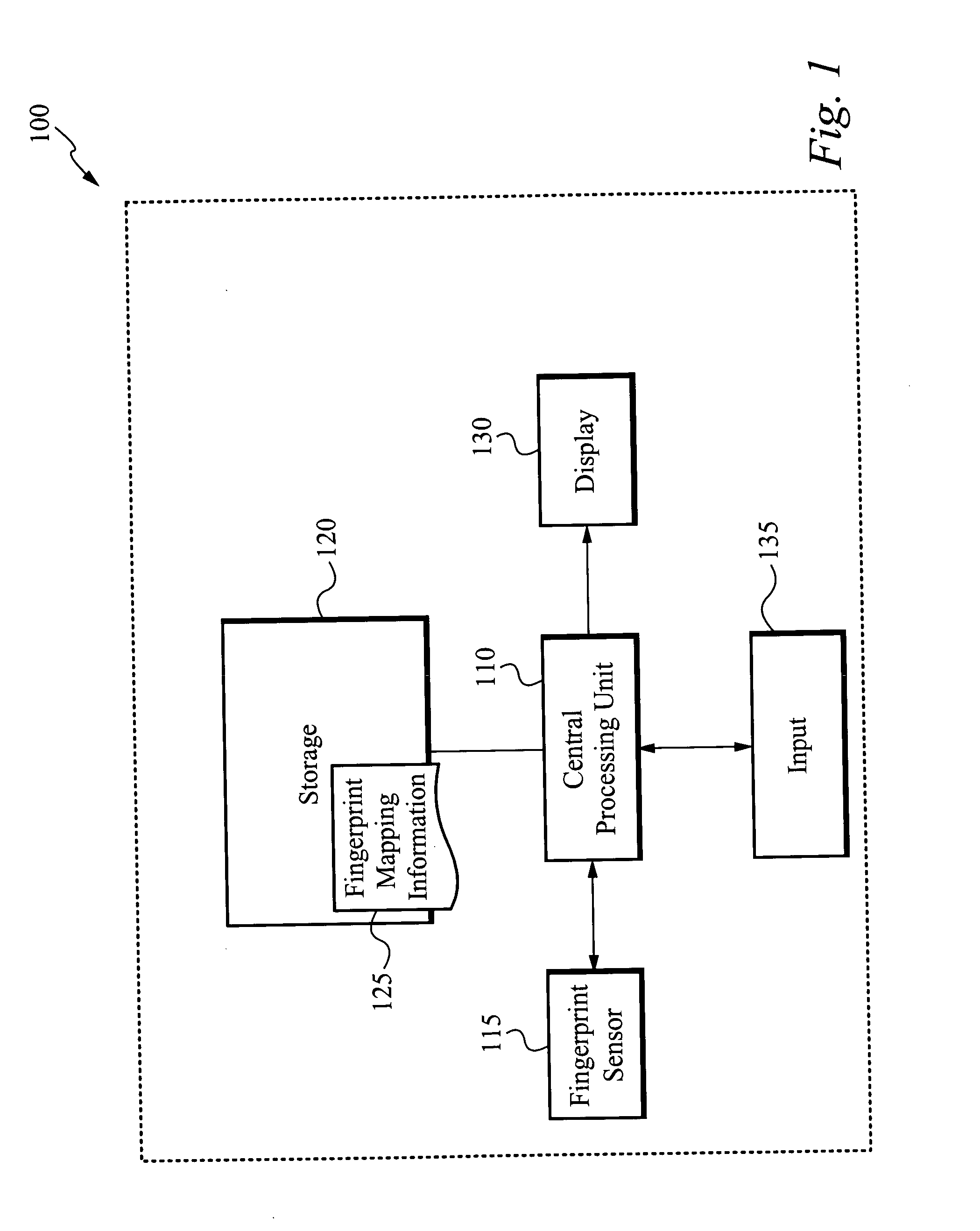
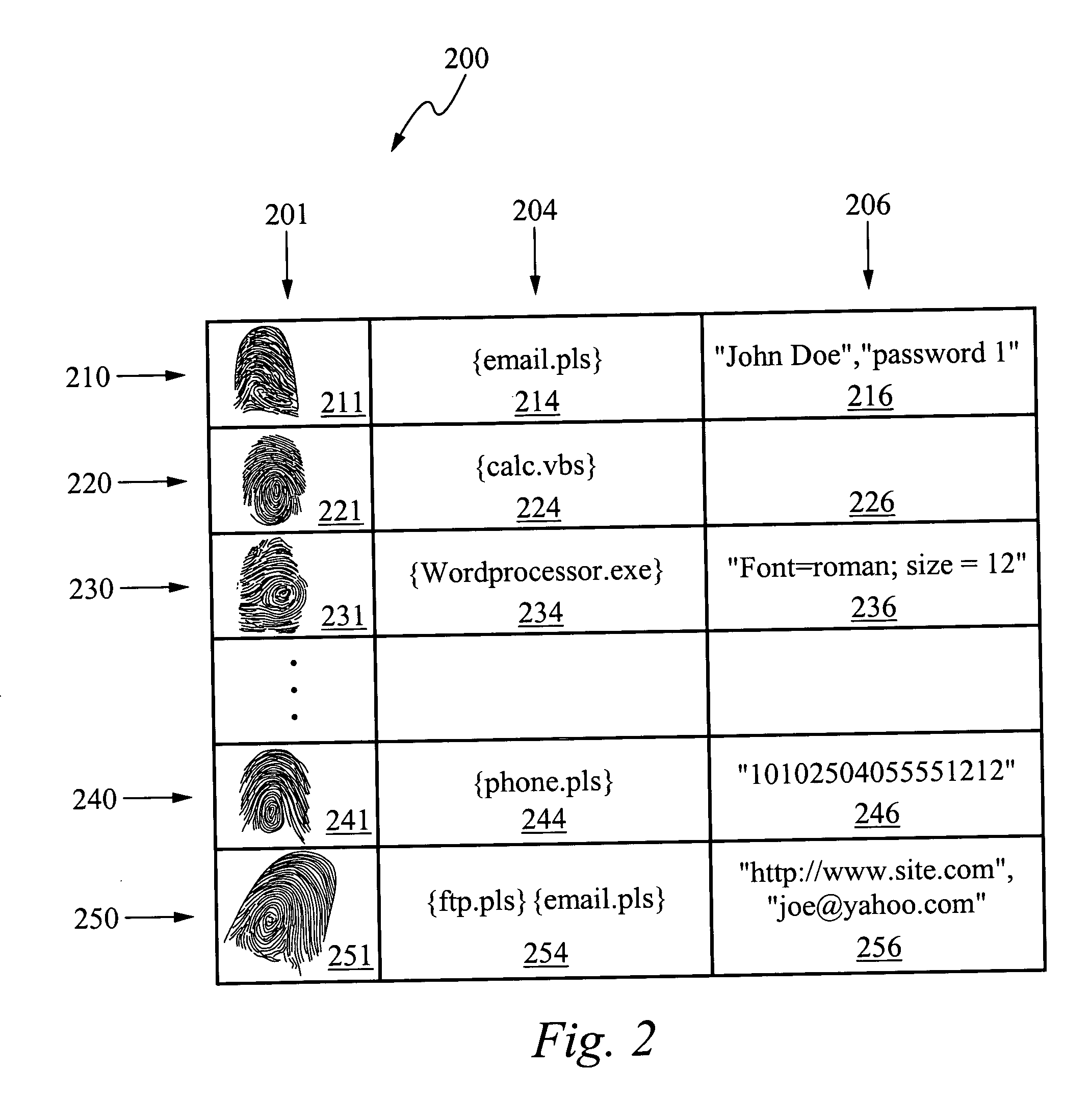
System for and method of finger initiated actions
InactiveUS20050169503A1Input/output for user-computer interactionElectric signal transmission systemsConfigfsRemote control
A device for and method of performing a task associated with fingerprint data is disclosed. The method comprises reading fingerprint data, matching the read fingerprint data to stored fingerprint data, the stored fingerprint data having an associated task, and performing the task. The associated task is part of a chain of tasks that are automatically executed when the read fingerprint data is matched to the stored fingerprint data. Preferably, at least one task has associated user profile data that is used to perform the task. An electronic device that can be controlled in accordance with the present invention includes, but is not limited to, a telephone, a personal computer, a personal digital assistant, and a remote controlled device.
Owner:APPLE INC
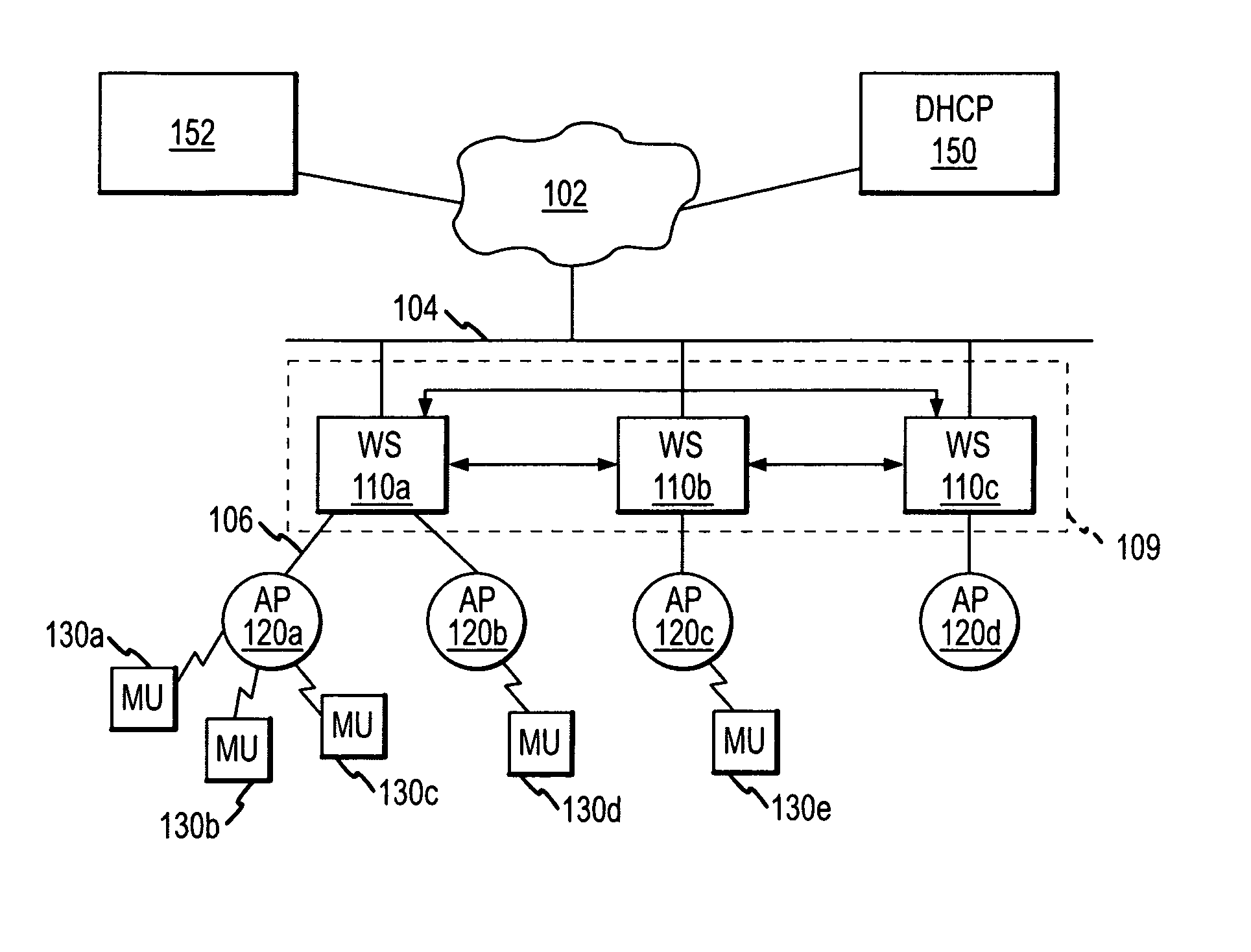
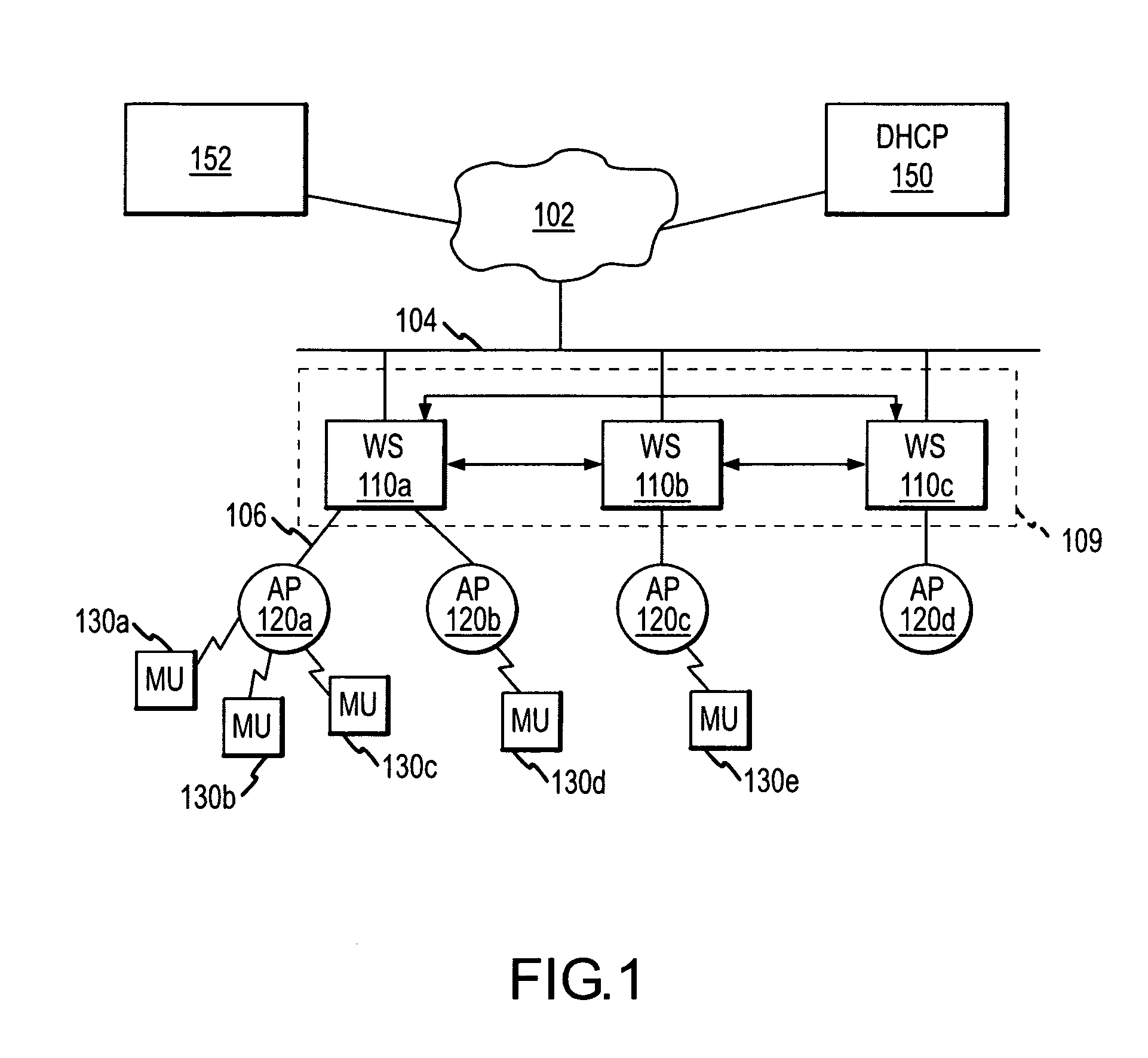
Methods and apparatus for cluster management using a common configuration file
InactiveUS20070230415A1Network traffic/resource managementWireless network protocolsIp addressConfigfs
Wireless switches in a cluster are managed by providing a configuration server for storing common configuration files and a DHCP server for storing cluster-specific configuration files corresponding to each cluster. A method for configuring the wireless switches then includes requesting, from the DHCP server, an IP address for the wireless switch; receiving, from the DHCP server, the IP address and the cluster-specific configuration file; receiving, from the configuration server, the common configuration file; and executing, at the wireless switch, the cluster-specific configuration file and the common configuration file.
Owner:SYMBOL TECH INC
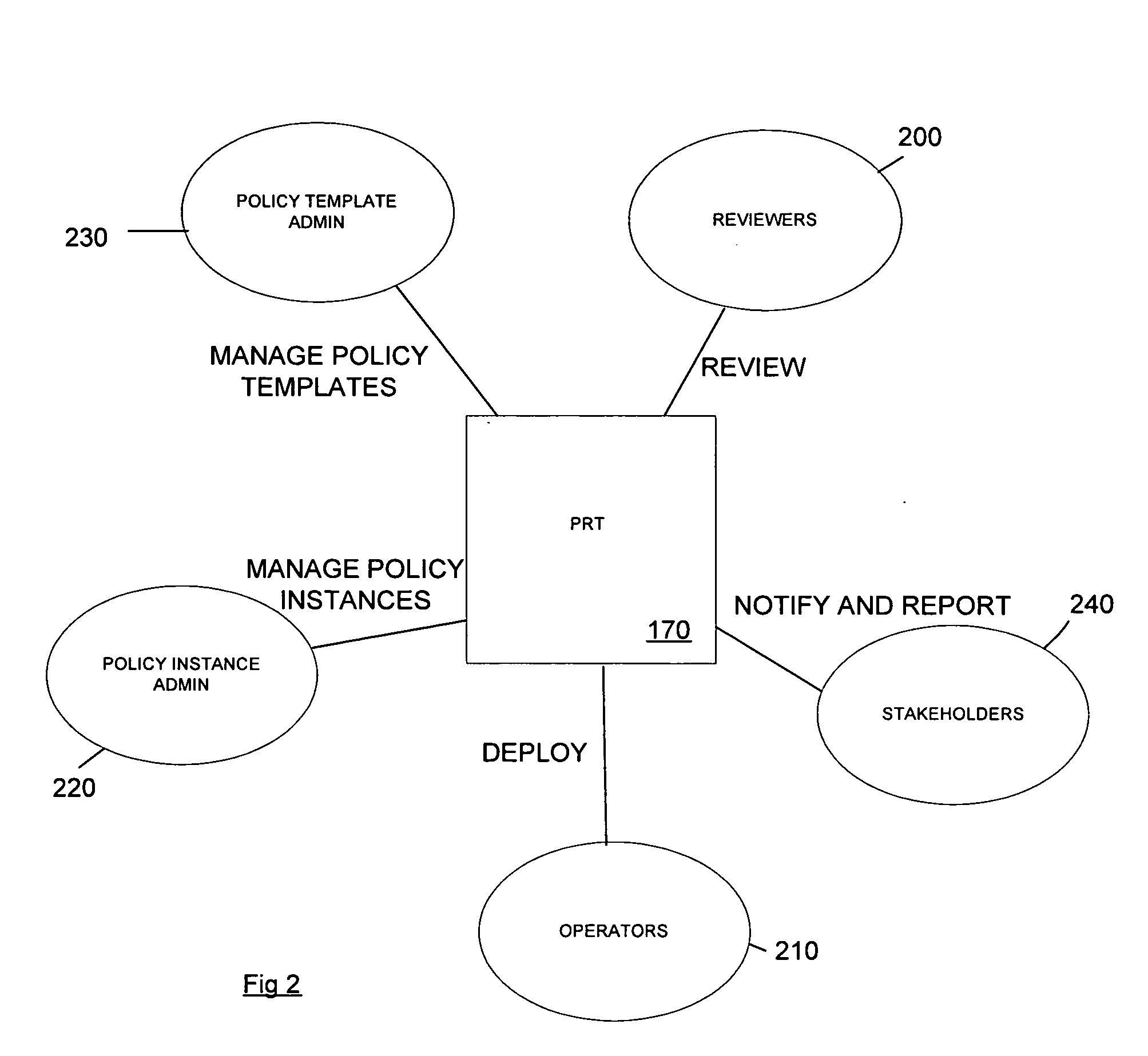
Method and apparatus for role-based security policy management
ActiveUS20050257244A1User identity/authority verificationUnauthorized memory use protectionConfigfsSecurity policy management
A method and corresponding tool are described for security policy management in a network comprising a plurality of hosts and at least one configurable policy enforcement point. The method, comprises creating one or more policy templates representing classes of usage control models within the network that are enforceable by configuration of the policy enforcement points; creating one or more policy instances, each based on one of the templates and instantiating the template for identified sets of hosts within the network to which the usage control model is to be applied, deploying the policy instances by generating and providing one or more configuration files for provisioning corresponding policy enforcement points within the network. Access to the templates and policy instances is controlled so that the policy templates are only modifiable by a first predeterminable user group, the policy instances are only modifiable by the first or a second predeterminable user group and the policy instances are only deployable by a third predeterminable user group.
Owner:VALTRUS INNOVATIONS LTD +1
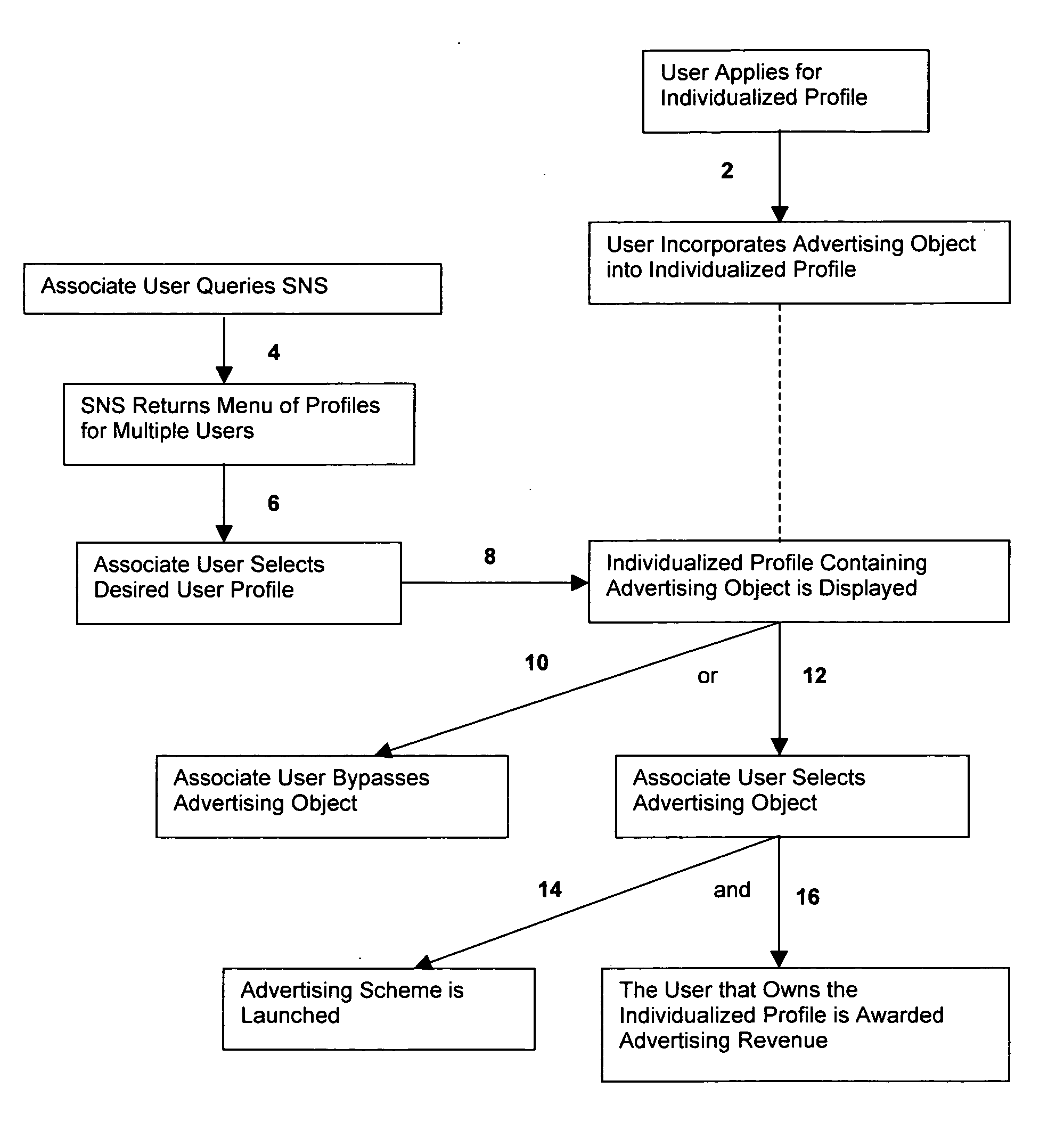
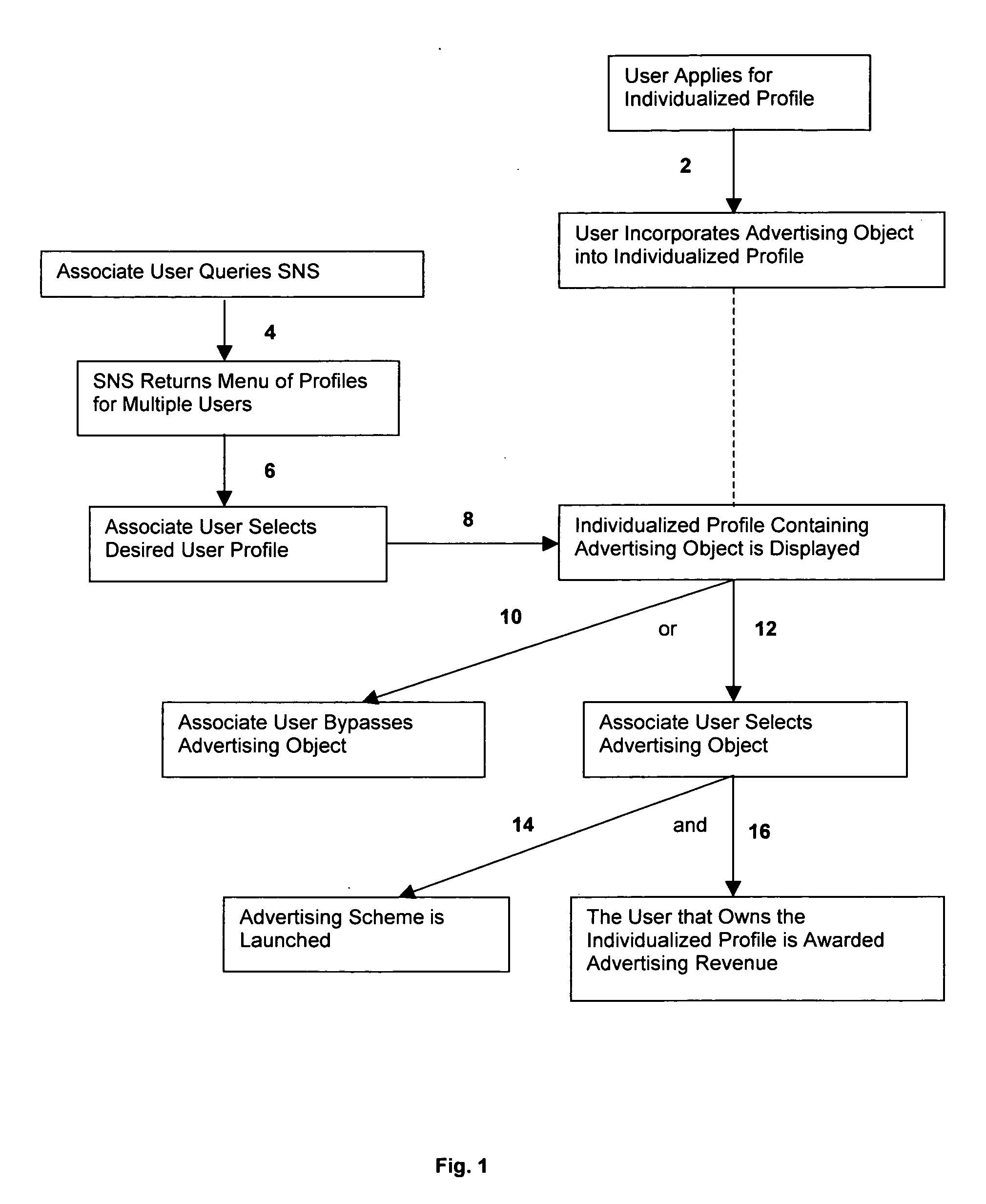
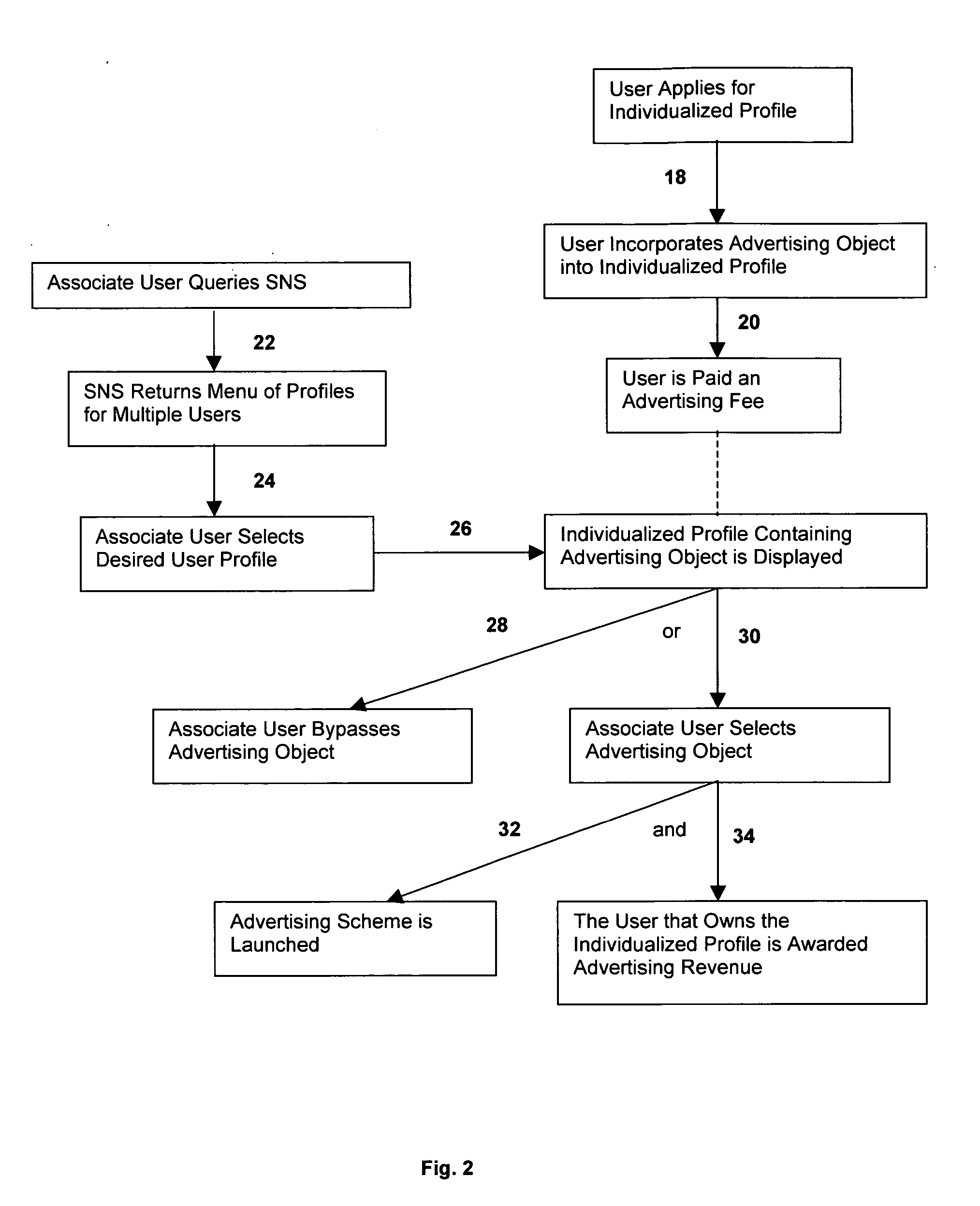
Social network e-commerce and advertisement tracking system
The present invention relates to methods of advertising, social networking systems, and individualized profiles located within social networking systems. According to a first aspect of the present invention, a method of advertising within a Social Networking System is provided, which is carried out by providing a group of users with access to a Social Networking System, wherein the Social Networking System provides each of its users with individualized profiles. The method further includes providing at least one “Social Network E-Commerce and Advertisement Tracking System” (referred to herein as “SNEATS” or “SNEATS server”), wherein the SNEATS server provides each user of the Social Networking System with the ability to access and incorporate one or more advertising objects into his or her individualized profile. In other embodiments, the SNEATS server provides third party vendors with the ability to access and incorporate one or more advertising objects into a user's individualized profile, provided such advertising objects are acceptable to such user. Upon incorporating an advertising object into an individualized profile, users of the Social Networking System may activate such advertising object, which causes an advertising scheme to be launched (e.g., an image, flash file, or secondary website) that promotes a particular good or service. The invention provides that, upon activating such advertising object, the user affiliated with the individualized profile that contains such advertising object is awarded advertising revenue.
Owner:WANTRZ
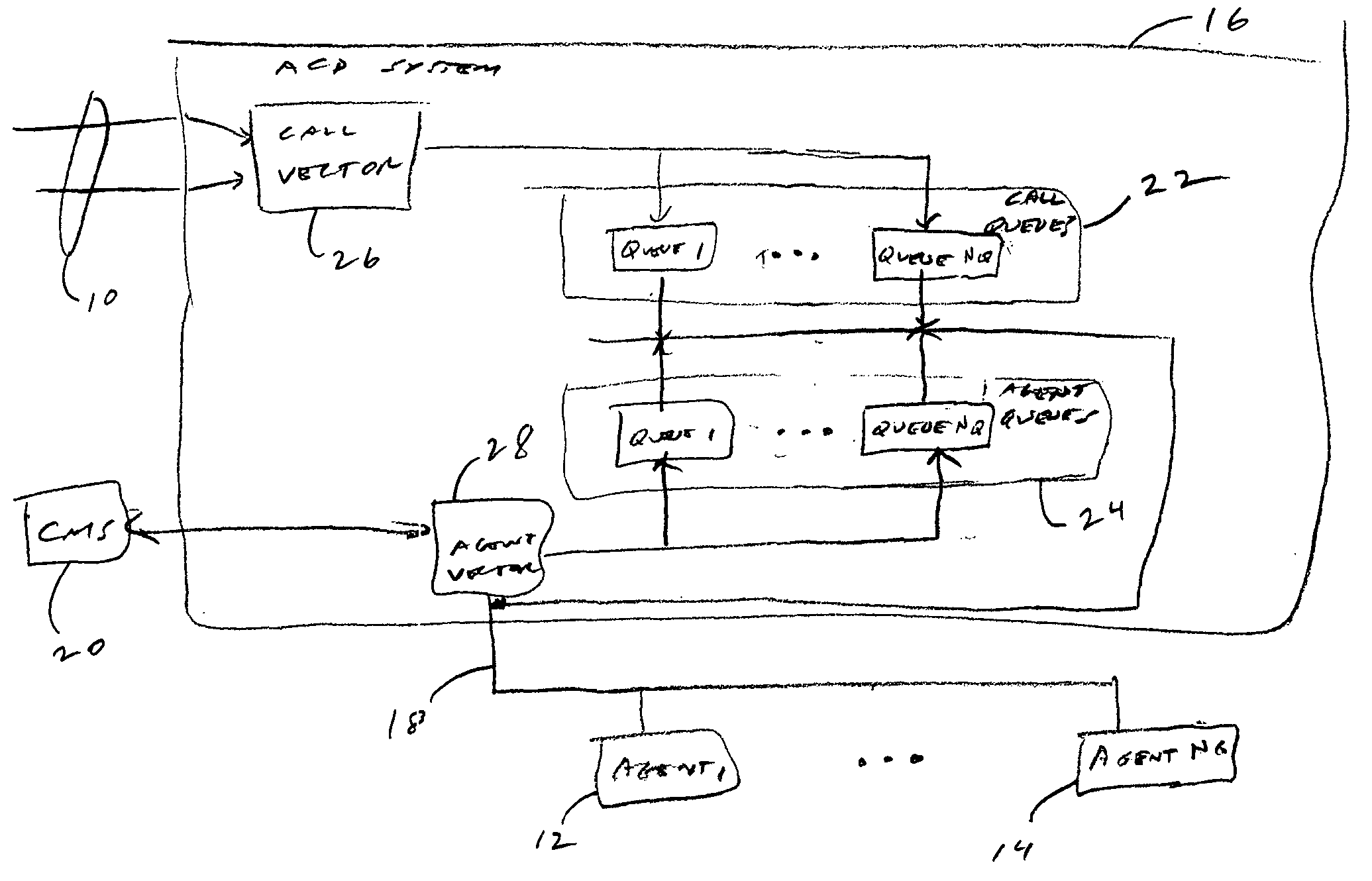
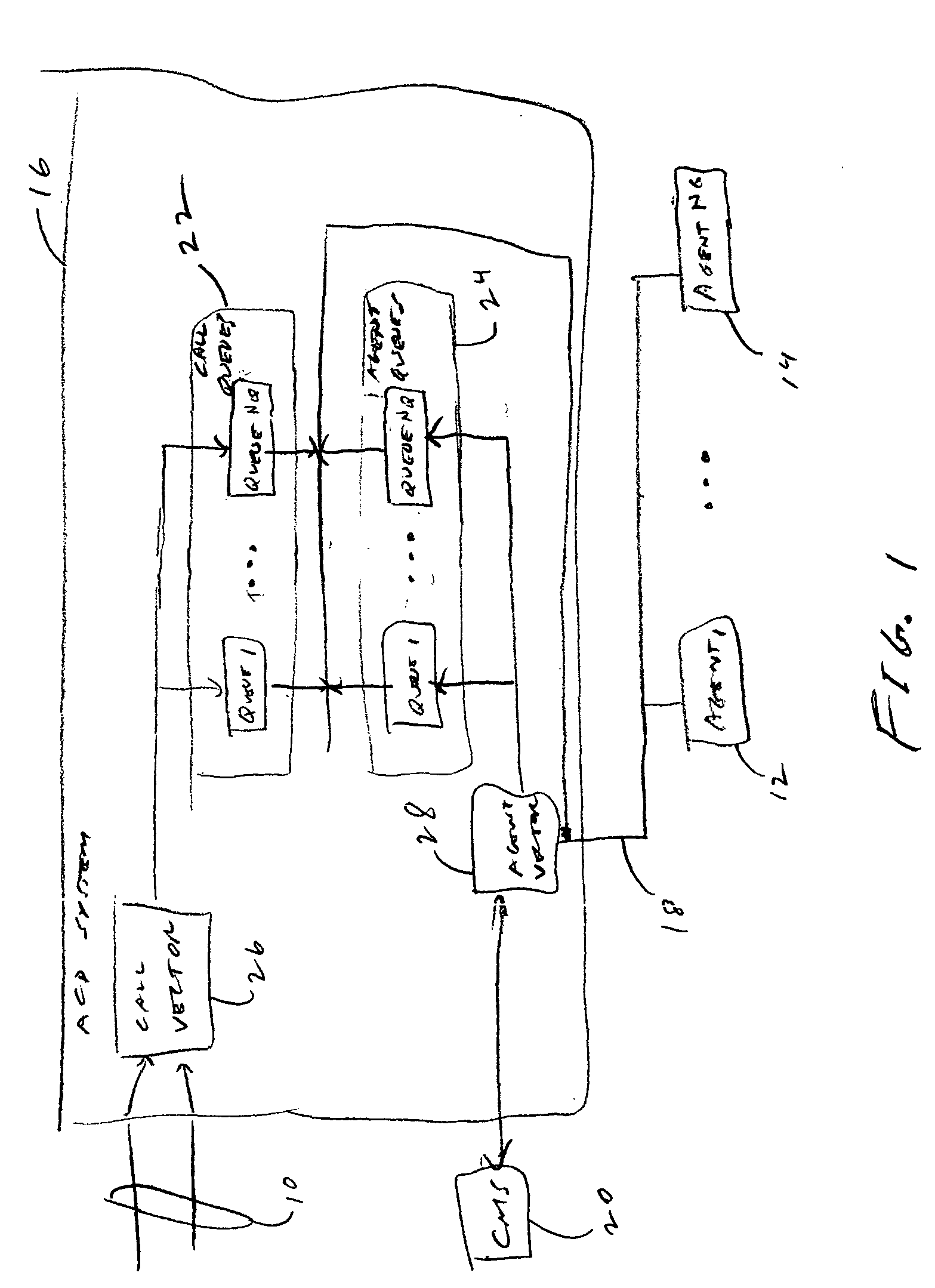
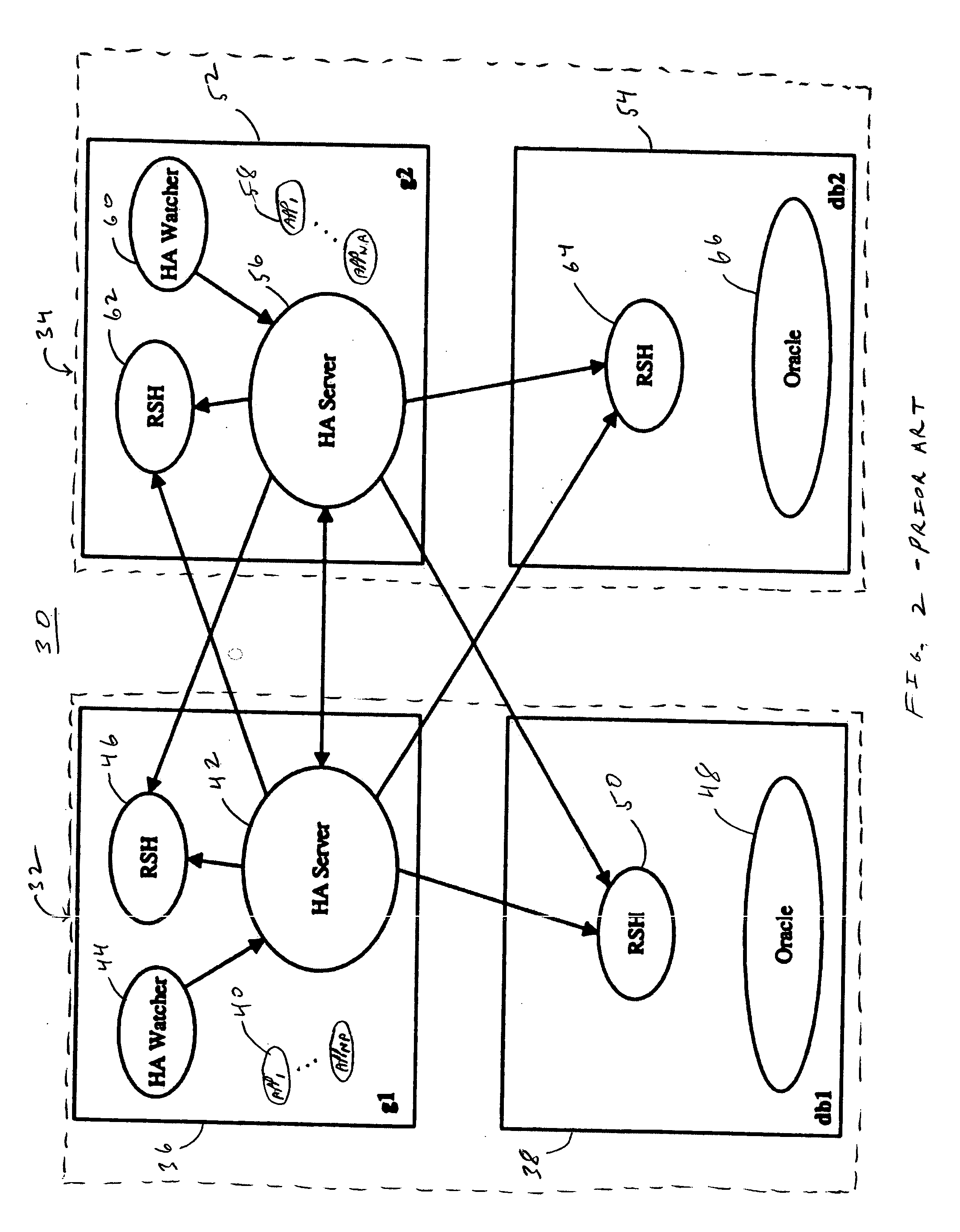
High availability multi-tenant feature
InactiveUS20050025303A1Special service for subscribersDigital computer detailsConfigfsHigh availability
A multi-tenant call-center system and method of configuring and monitoring. The system includes a plurality of telephone lines, a plurality of agent positions, a call distribution system connecting the plurality of agent positions to the telephone lines, a call management system connected to the call distribution system. The call management system includes a storage system of storing database files, processes and configuration files, a memory system for processing the database files and configuration files and running selected processes stored on the storage system, a configuration server for reading the configuration file and starting selected processes according to multi-tenant inter-process dependencies and process priorities, and a monitor process for monitoring each of the started processes according to a respective monitor frequency in the configuration file.
Owner:ALCATEL-LUCENT USA INC +1
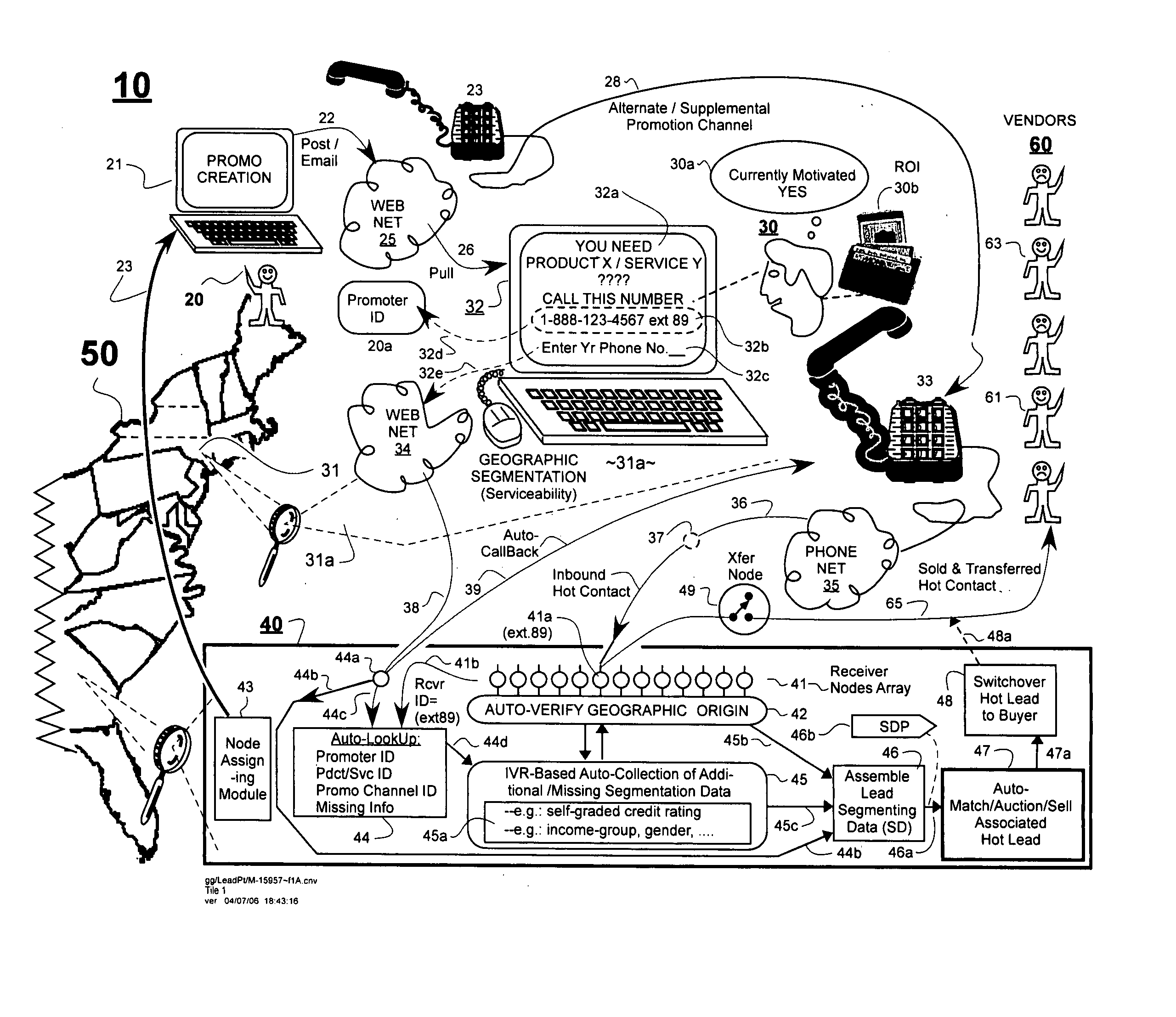
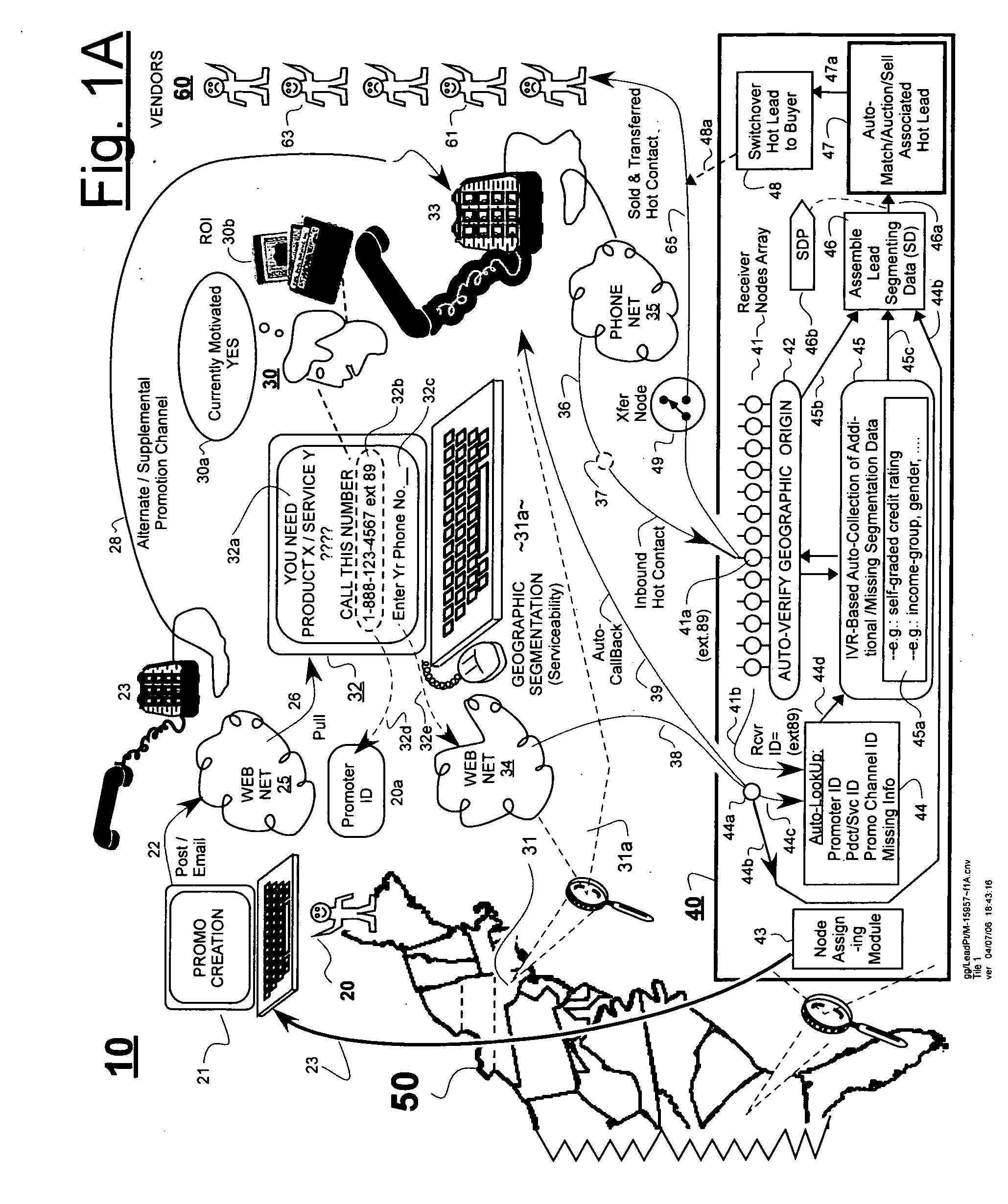
Automated attachment of segmentation data to hot contact leads for facilitating matching of leads to interested lead buyers
ActiveUS20060265259A1Reduce probabilityWaste timeFinanceSpecial data processing applicationsLive voiceWeb site
In an automated leads-and-bids matching system, bid profiles are defined to describe desires of lead buyers. Received leads are matched to active ones of the bid profiles whose specifications the leads substantially match. Lead segmentation data is captured on-the-fly for example by inducing potential consumers to navigate their way through tree-organized web sites that categorize the consumers according to their geographic location, income / revenue range, class of products desired and / or other attributes. Live voice or other telecommunication connections to the pre-classified consumers are coupled to corresponding, pre-classified telecommunication nodes of a call processing system. The call processing system deduces the segmentation data of the consumers from the identities of the pre-classified nodes through which their connections pass. The deduced segmentation data is passed to an automated matching system or auctioning subsystem that finds the highest bids for each given lead. A quality rating database rates the quality of leads provided by different sellers. A price discounting engine discounts the amount paid to sellers who are hot-rated as sources of inferior leads.
Owner:LEADPOINT
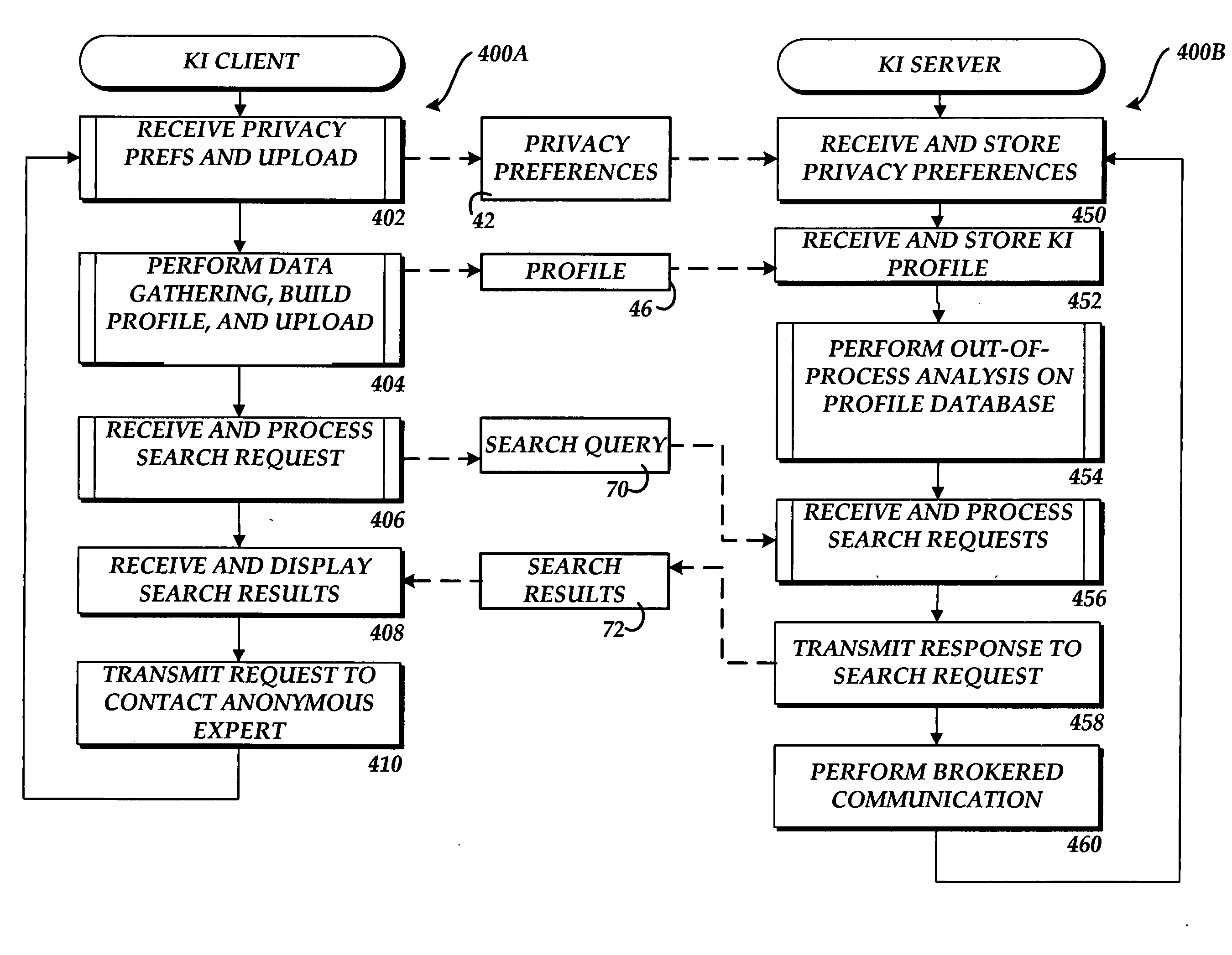
Method, system, and apparatus for creating a knowledge interchange profile
ActiveUS20060064431A1Increase weightDigital data processing detailsDigital computer detailsNoun phraseConfigfs
A method, system, and apparatus are provided for creating a knowledge interchange (“KI”) profile for a user that identifies the interests of the user, the individuals with which the user has communicated, and the topics on which the communication with the user was made. In order to create the KI profile, items of interest are gathered at the client computer by monitoring the interaction between a user and programs executing on the client computer. Once the items of interest have been identified, the KI profile is created by performing a social network analysis, an interest analysis, and a noun phrase analysis. Once the KI profile has been created, it may be uploaded to a server computer where it is aggregated with KI profiles created for other users.
Owner:MICROSOFT TECH LICENSING LLC
Providing relevant non- requested content to a mobile device
A system and method are directed towards providing non-requested content to a mobile terminal based on characteristics of, and tracked usage of the mobile terminal to request content through an online portal service, which provides access to content in multiple subject areas. A mobile user profile is created from the characteristics and patterns of the tracked usage. The tracked usage information includes the time, location, frequency at which the content was requested. Based on the mobile user profile information, content related to previously requested content is provided to the mobile terminal upon a trigger that is related to the requested content. The trigger event may include the mobile terminal returning to a location from which certain content was previously requested. The non-requested content may further be based on a related general user profile that indicates usage of an alternate electronic device to access content through the portal.
Owner:YAHOO ASSETS LLC
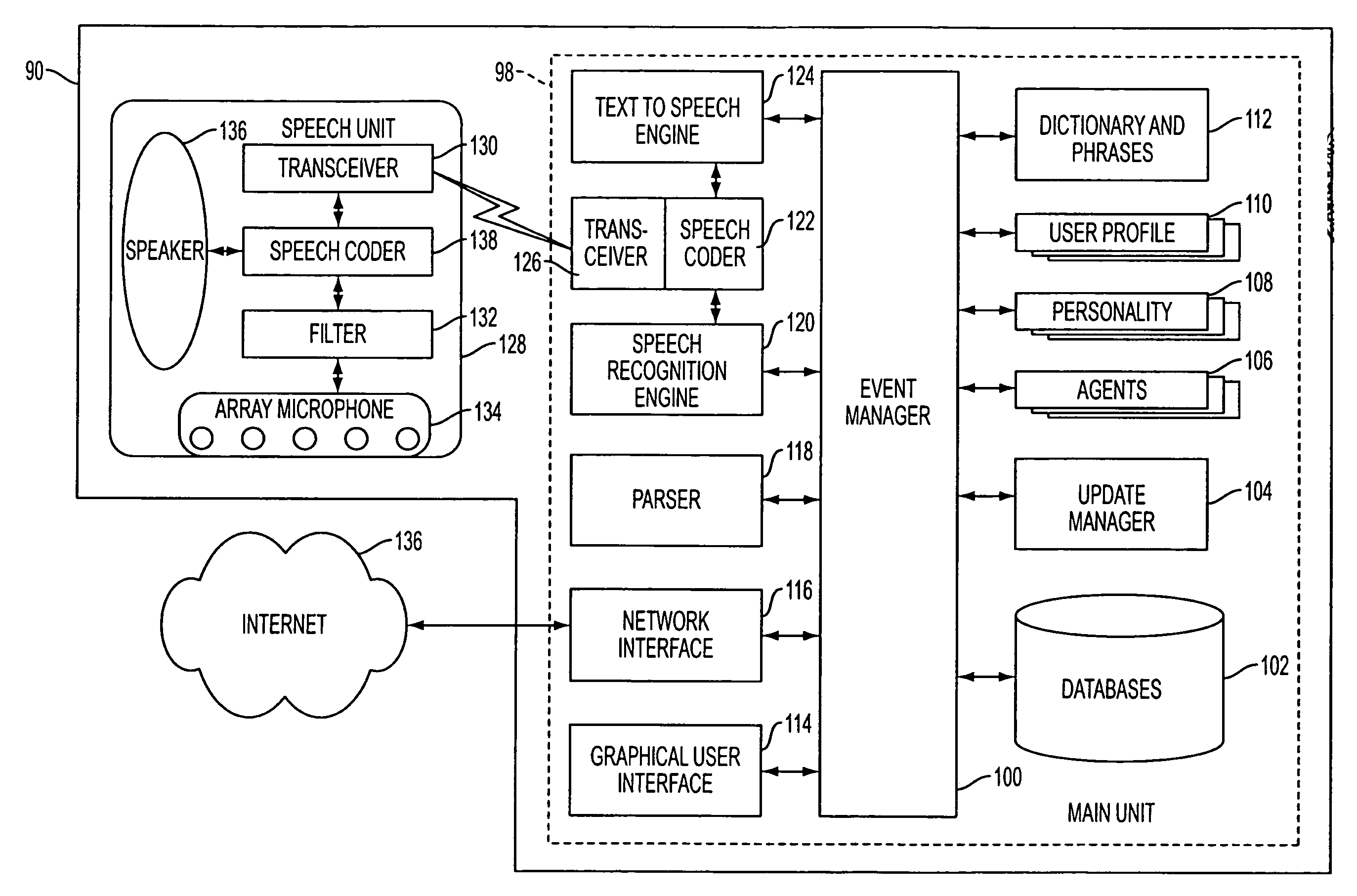
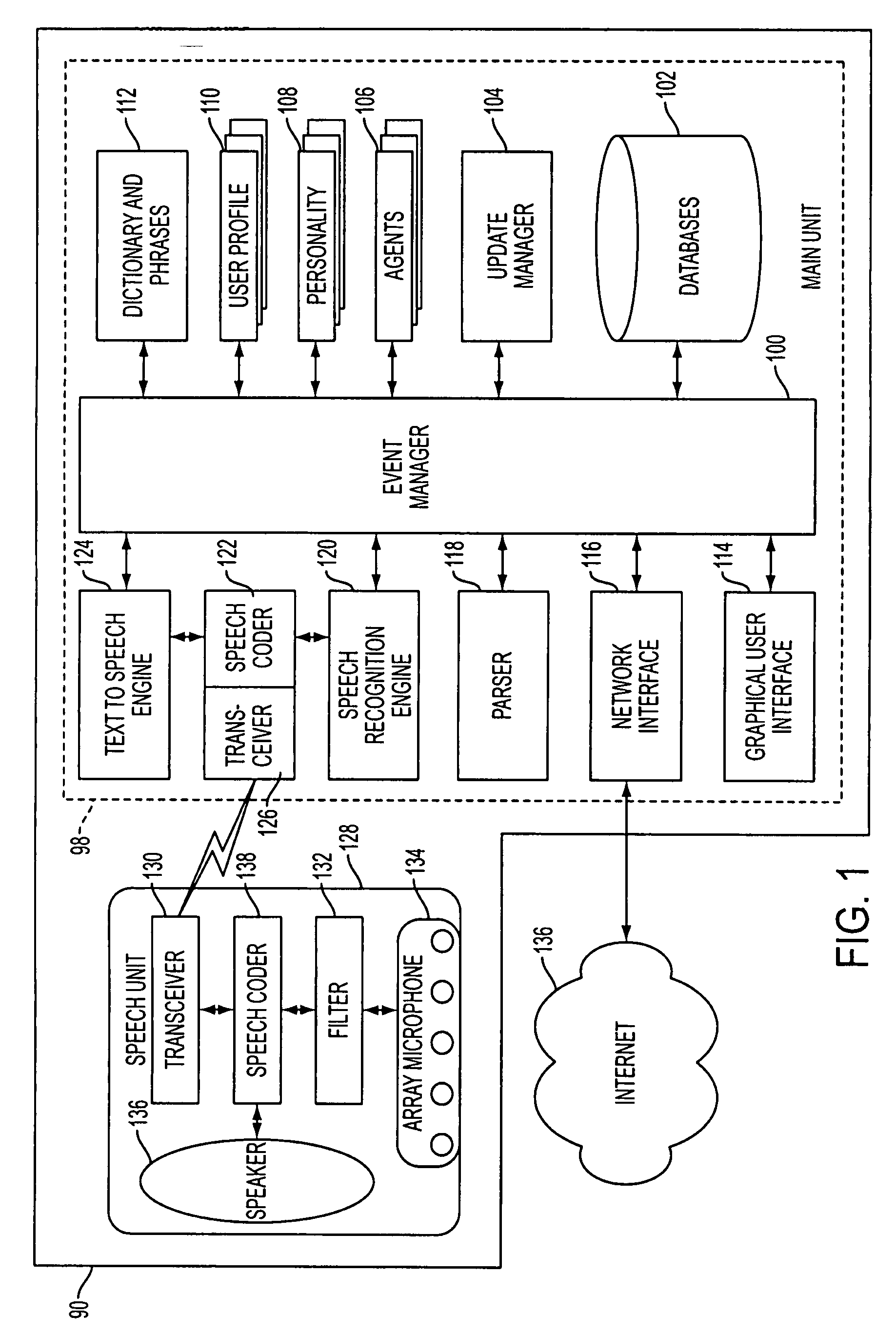
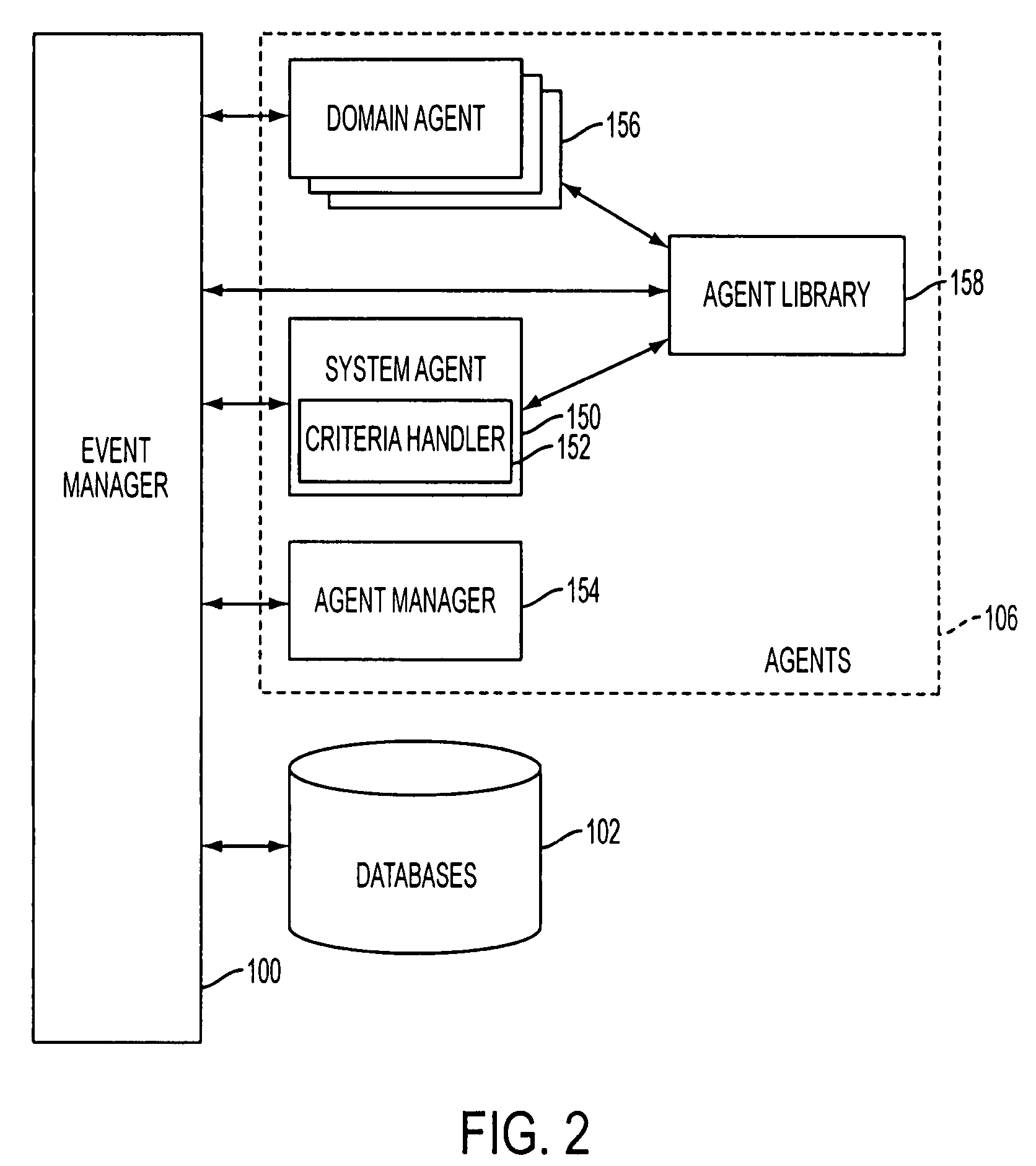
Systems and methods for responding to natural language speech utterance
InactiveUS20070265850A1Disseminate their knowledgeImprove system performanceData processing applicationsNatural language data processingPrior informationConfigfs
Systems and methods for receiving natural language queries and / or commands and execute the queries and / or commands. The systems and methods overcomes the deficiencies of prior art speech query and response systems through the application of a complete speech-based information query, retrieval, presentation and command environment. This environment makes significant use of context, prior information, domain knowledge, and user specific profile data to achieve a natural environment for one or more users making queries or commands in multiple domains. Through this integrated approach, a complete speech-based natural language query and response environment can be created. The systems and methods creates, stores and uses extensive personal profile information for each user, thereby improving the reliability of determining the context and presenting the expected results for a particular question or command.
Owner:DIALECT LLC
Linking of personal information management data
A system and method for linking information of one user to other users via a data aggregation server is provided. Various security settings govern the linking of information. Various methodologies for initiating a link of PIM data are also provided including automatic linking, targeted linking and requested linking. Implementations utilizing group profiles are also provided.
Owner:SEVEN NETWORKS INC
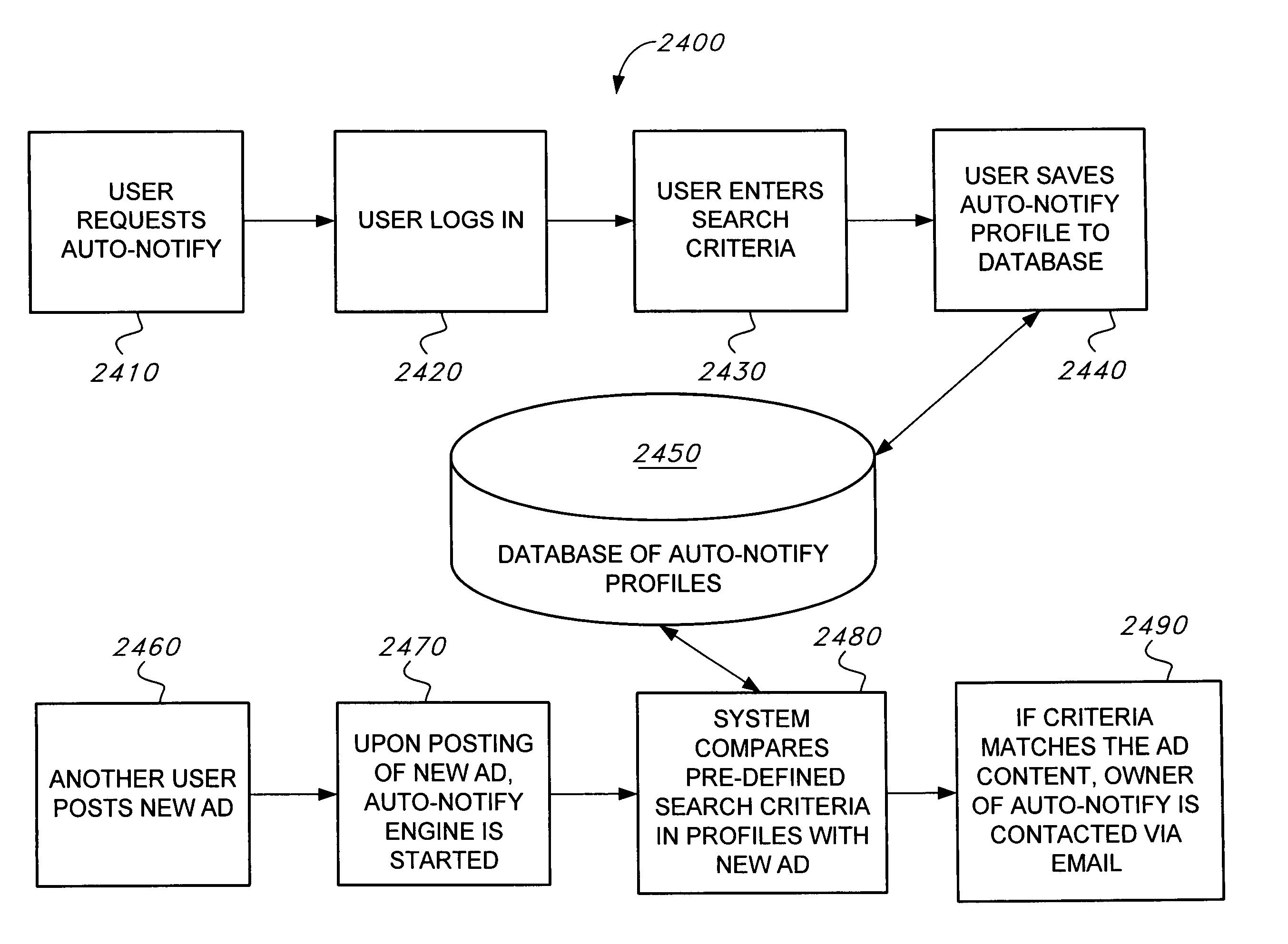
System and computerized method for classified ads
A system and / or computerized method for classified ads. The system is used for updating an ad profile, setting system variables, general variables, appearance variables, ad banner variables and multimedia variables, establishing a fee based ad arrangement, registering a user, setting up maintenance options and setting up a backup manager, a visibility options manager and a priority ranking options manager and setting up an affiliated Web site and an auto-notify function.
Owner:HAGEN PHILIP A
User interface for viewing aggregated game, system and personal information
A user interface for displaying a user profile in a gaming console that communicates to a remote service. A “Gamer Profile” is created that serves as a building block for services and applications that aim to create a social community of garners and grow relationships among players. In accordance with the present invention, the Gamer Profile is the entirety of information (e.g., metadata) related to a specific user. The Gamer Profile is developed from a set of services that collect and expose this information in a meaningful way to the community. Feedback information may be included that is provided by other users to further enhance the profile. The Gamer Profile also provides for personalization such that users can customize their gaming experience.
Owner:MICROSOFT TECH LICENSING LLC
Method of adding a device to a network
InactiveUS20060009861A1Low-cost implementationComputer controlSimulator controlLonWorksHome environment
A method of adding a device to an existing or new electrical or electronic automation or multimedia network. The invention facilitates adding a device to the network that can communicate using various protocols such as LonWorks, CEBus, X-10, etc. over media such as AC power line, IR, RF, twisted pair, optical fiber, etc. The method is a mechanism for adding a device to a system that can be used by an ordinary user of network capable electrical devices. The method comprises the steps an installer would perform including the handshaking that needs to occur between devices to accomplish the binding process. A Functional Profile for LonWorks networks is given as an example. This includes a Home Device profile that employs an automated explicit type messaging for all devices intended for use in a home environment. The invention includes adding to the device an install button and a visual indicator for status such as an LED. Alternatively, existing buttons and LEDs on the device may be used for installed and binding purposes. Other methods of binding can be employed by the use of wired or wireless handheld tools, remote controls, etc. Other interfaces and user feedback can be used such as touch screen, personal computers, cellular phones, PDAs, etc which can offer simple ‘virtual’ binding by the press of an icon versus the physical button on the device. The binding can be performed locally or remotely such as via LAN, WAN, Internet, etc.
Owner:LEVITON MFG
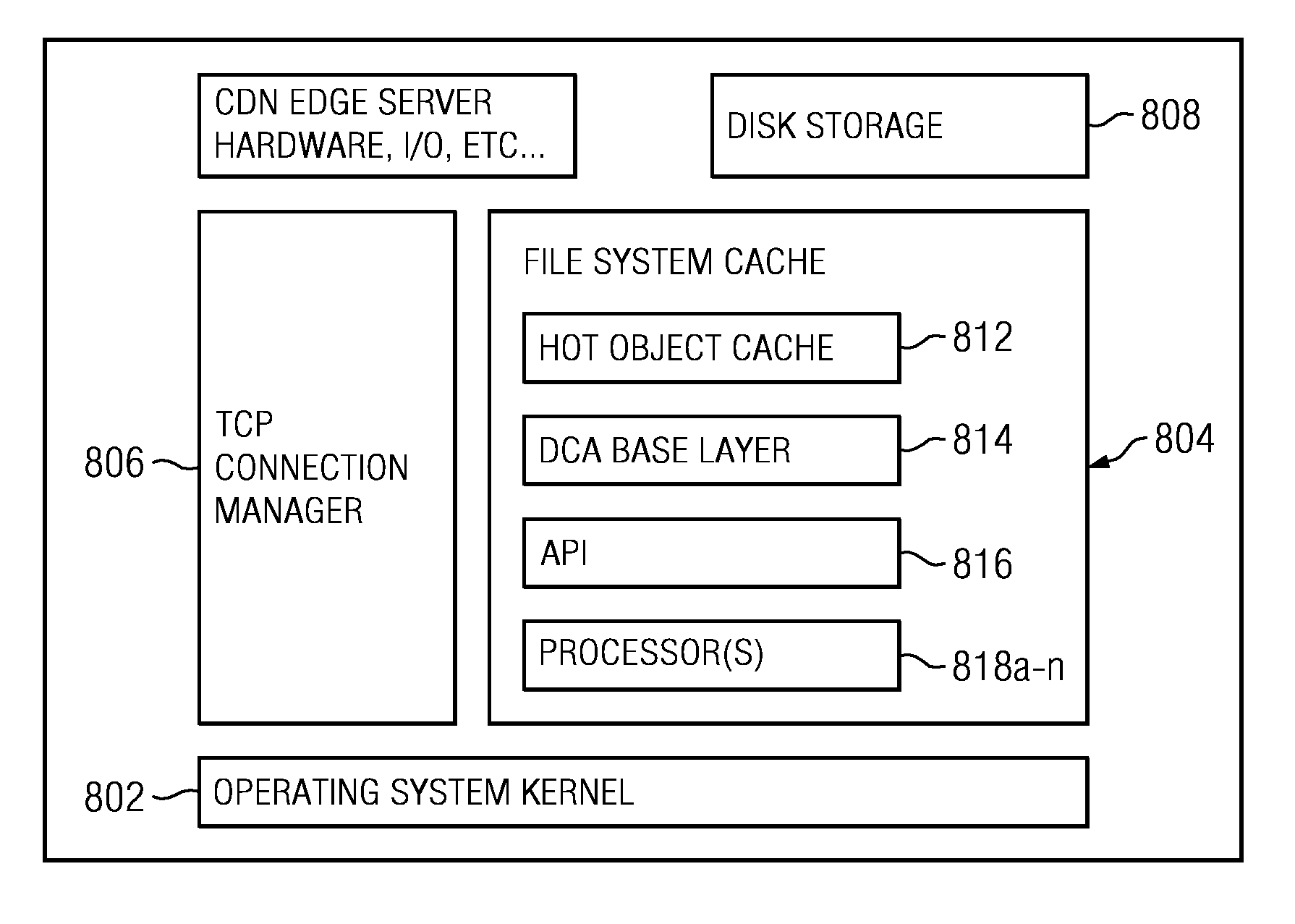
Dynamic content assembly on edge-of-network servers in a content delivery network
ActiveUS7752258B2Improve performanceFast loadingDigital data information retrievalMultiple digital computer combinationsEdge serverData center
Owner:AKAMAI TECH INC
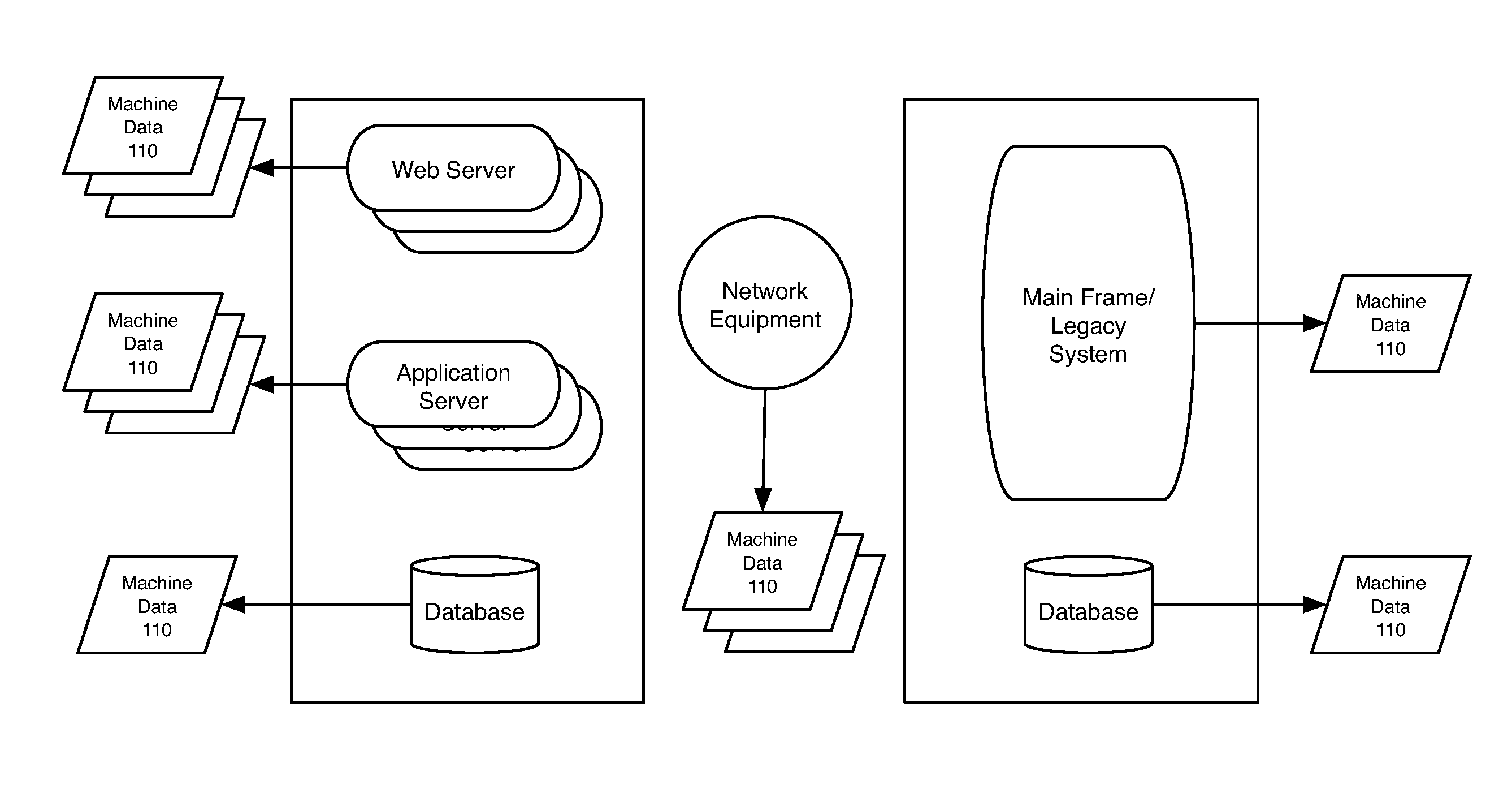
Machine Data Web
ActiveUS20070118491A1Preserve integrityError detection/correctionInterprogram communicationInformation processingConfigfs
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
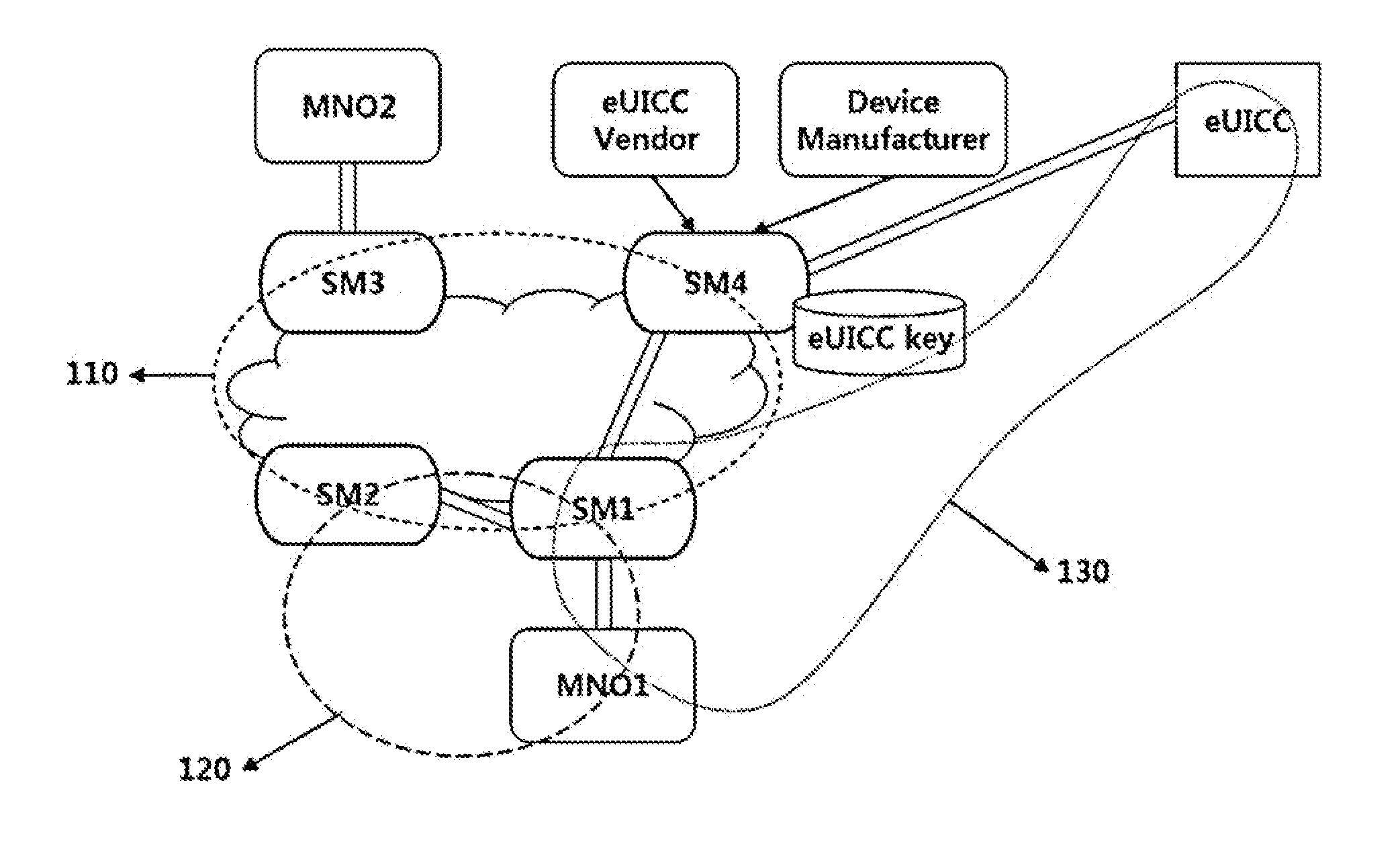
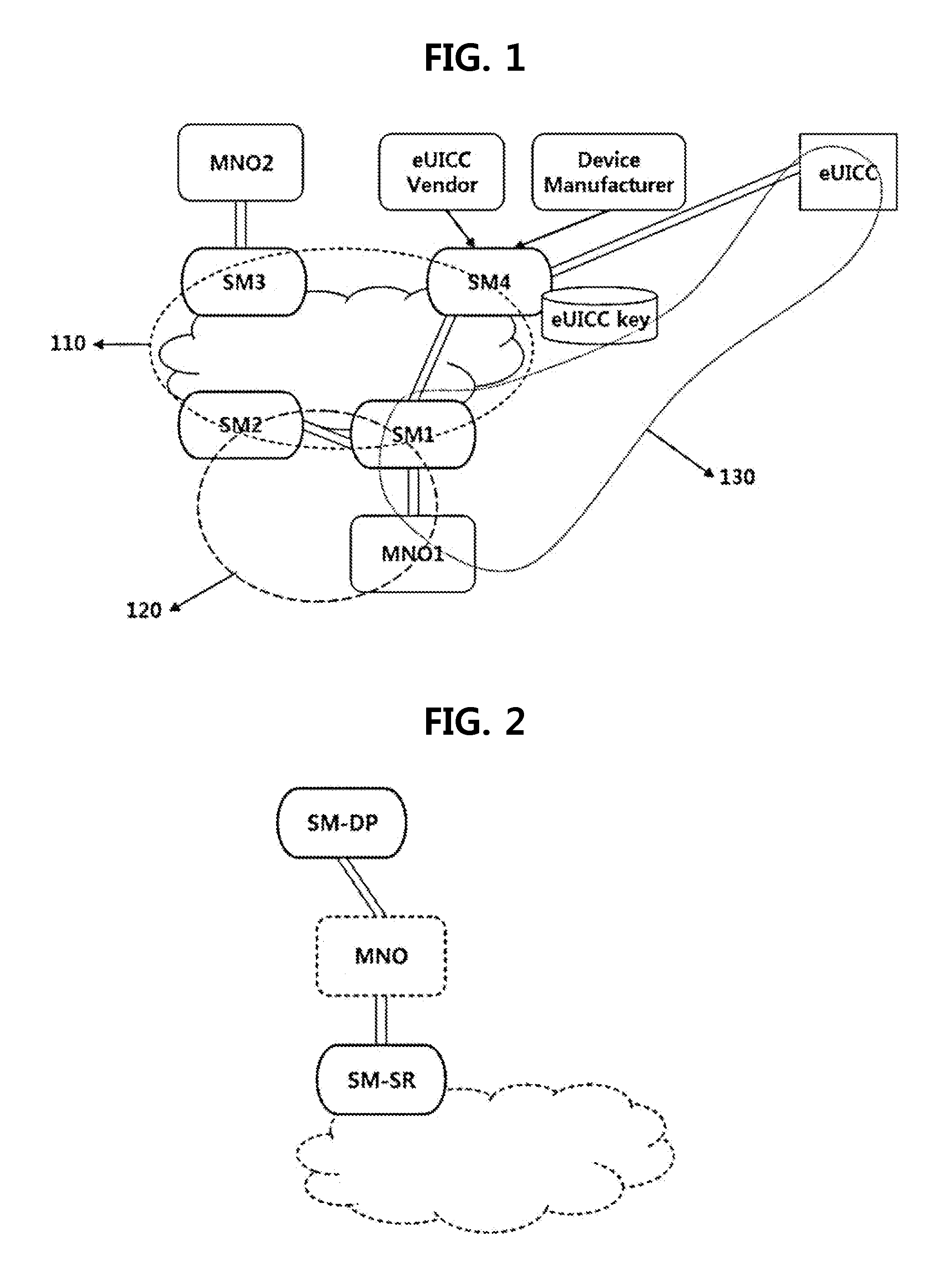
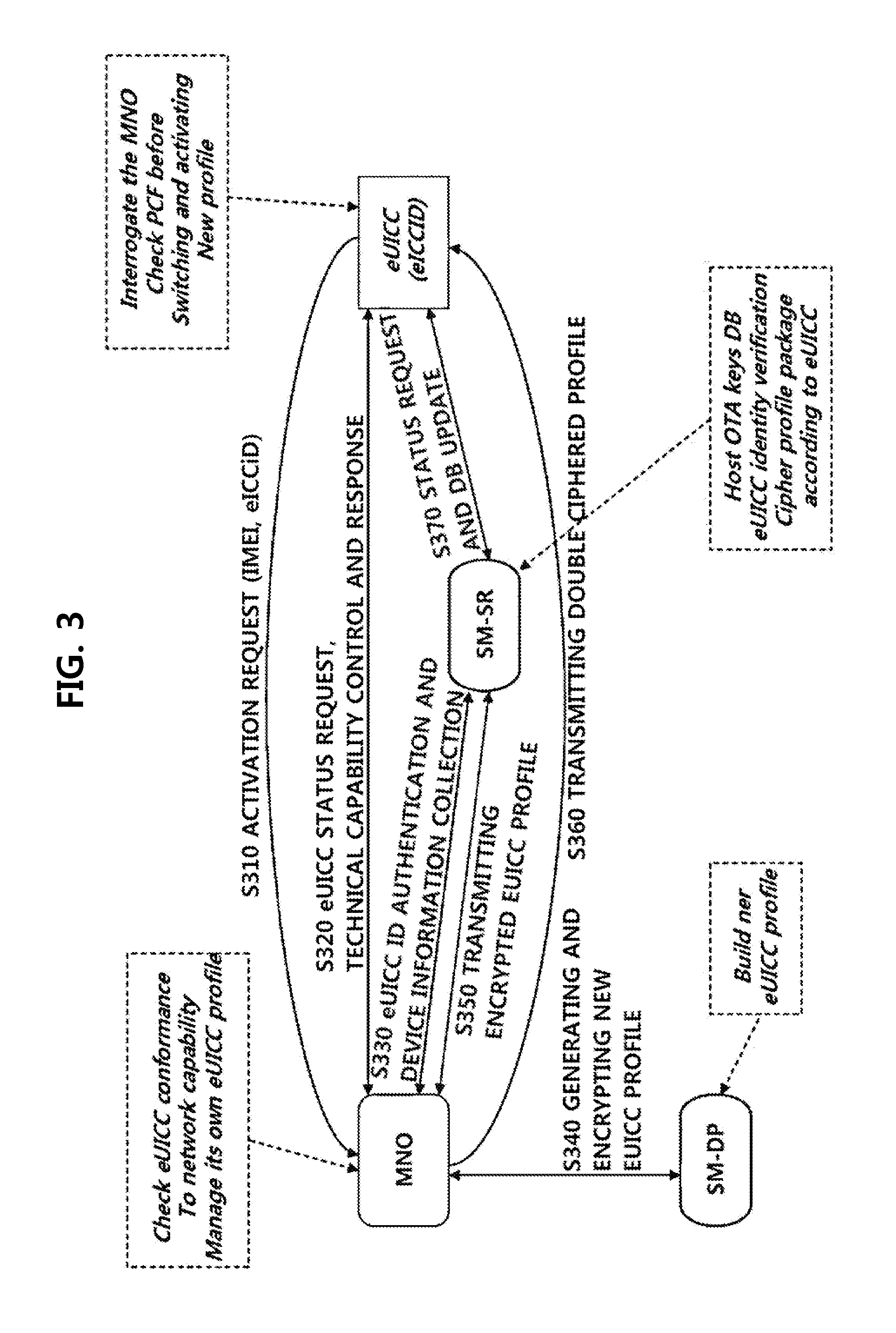
Method for managing profile of embedded uicc, and embedded uicc, embedded uicc-equipped terminal, provision method, and method for changing mno using same
The present invention provides a method wherein an MNO receives a secret key allocated to a corresponding embedded UICC (eUICC) through SM-SR (secure routing) in an environment where SM is divided and implemented as SM-SR and SM-DP (data preparation), that is, provided is a method wherein the MNO dynamically acquires the secret key (public key or the like) from the corresponding eUICC through the SM-SR and uses the acquired secret key. In addition, the present invention allows the eUICC to receive an encrypted profile from the MNO or the SM and decrypts the encrypted profile using profile access credential information (a secret key corresponding to an eUICC public key) stored in the eUICC to use the decrypted profile, thereby securely transmitting important data such as operation profiles, and blocking external entities such as a device or terminal from accessing the important data.
Owner:SAMSUNG ELECTRONICS CO LTD
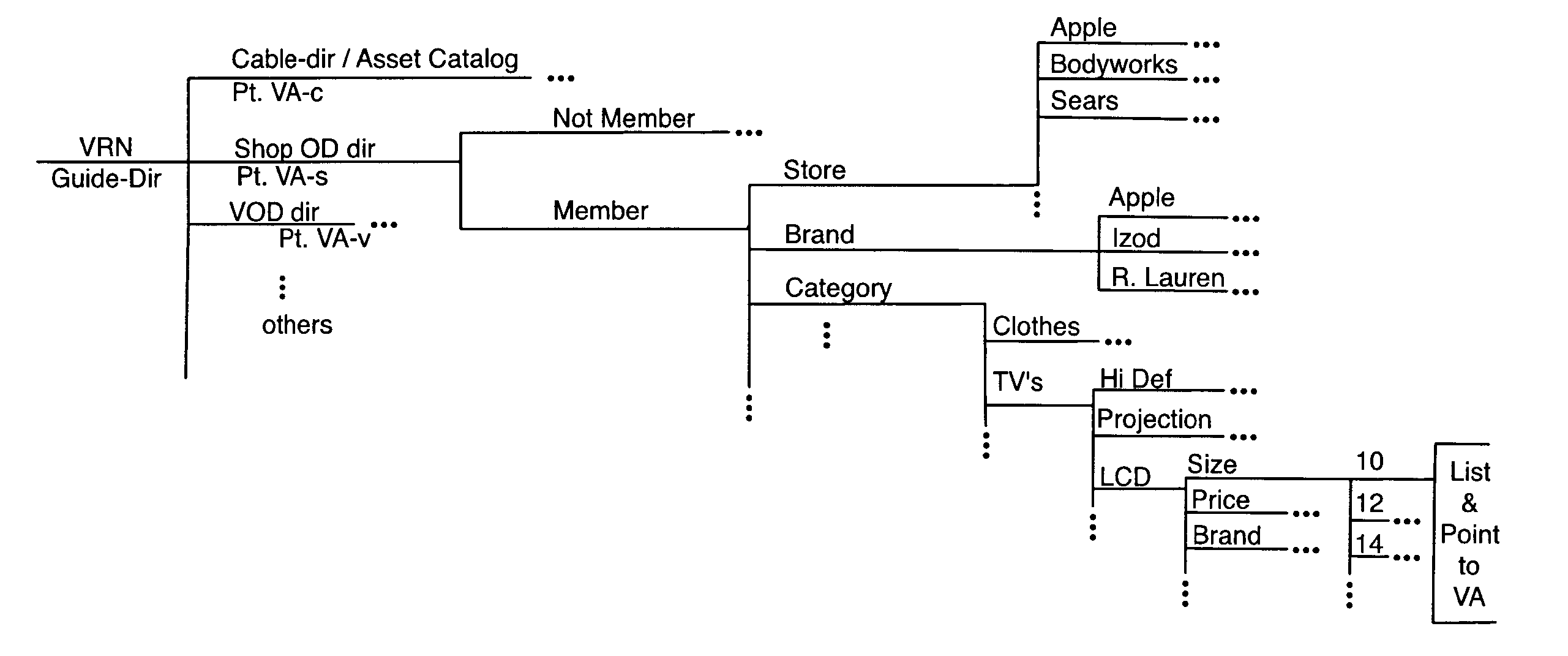
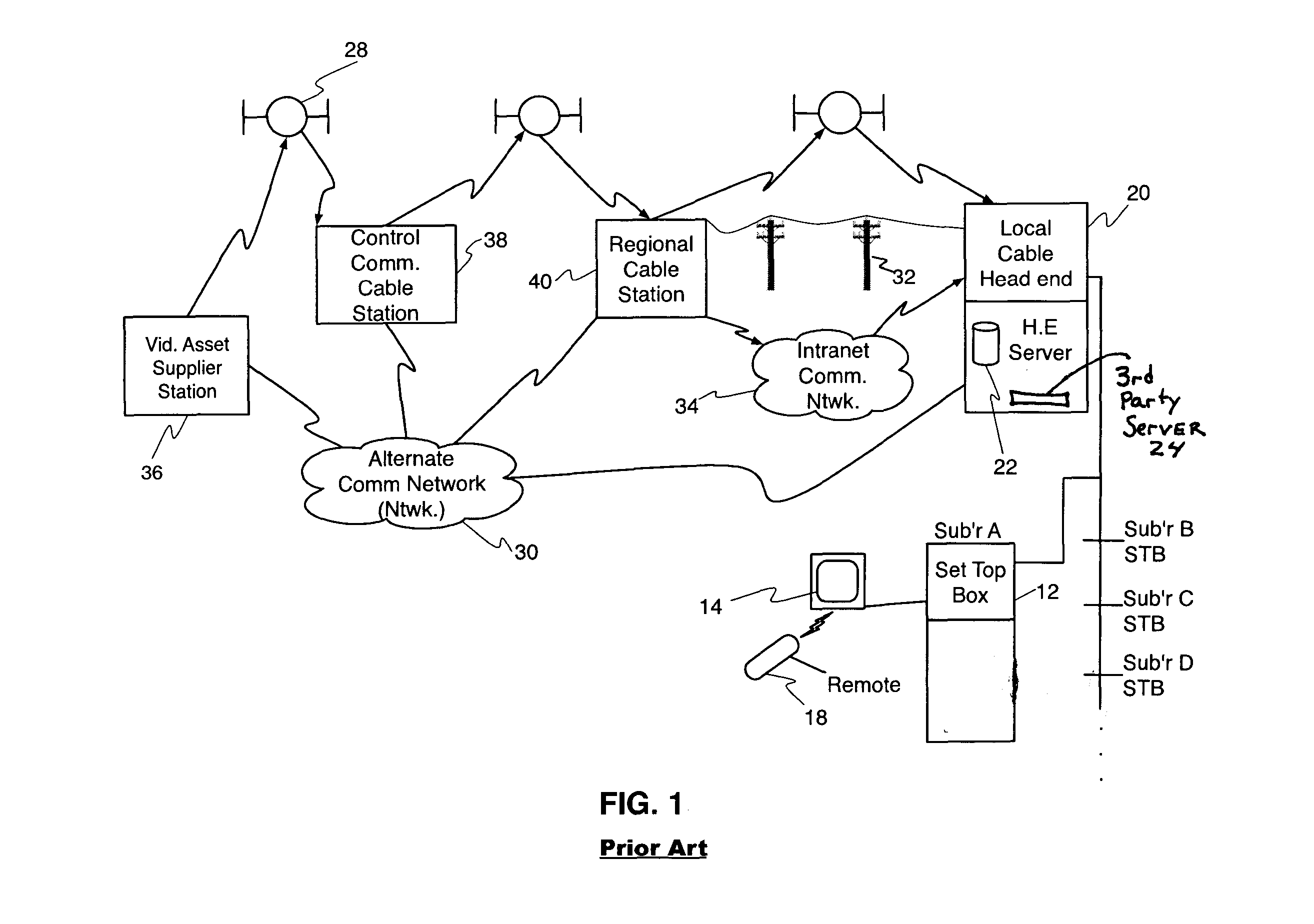
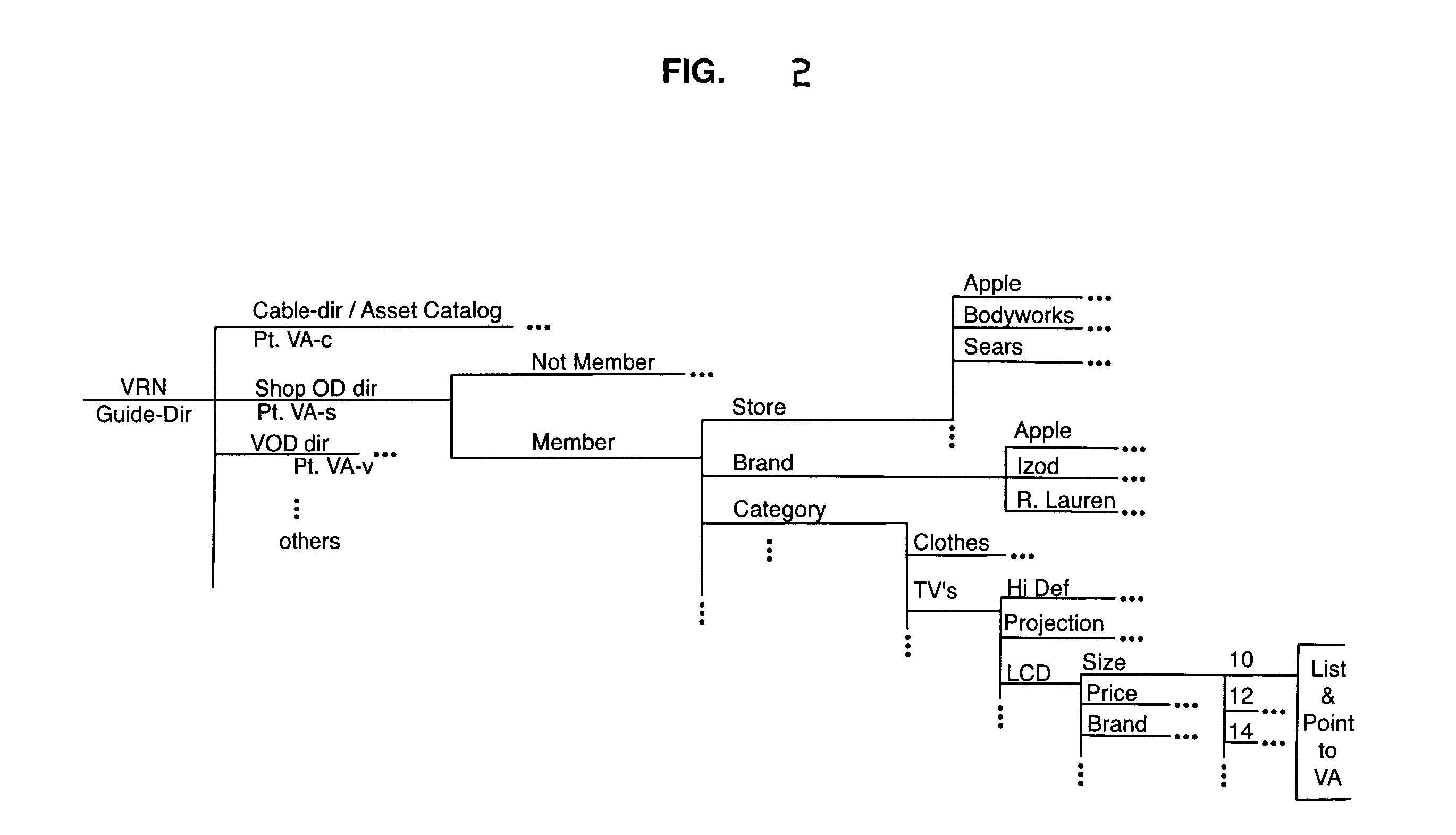
Interactive Multiple Channel User Enrollment, Purchase Confirmation Transactional System with Fulfillment Response Feature for Video On Demand Cable Systems
InactiveUS20070107016A1Television system detailsFrequency-division multiplex detailsComputer hardwareThe Internet
A multi-channel process enrolls user-viewers via VOD inputs and supplemental communications channels (cell phone, VoIP, land-line telephone, Internet or fax). Goods are advertised for the shop on-demand (OD) process via user's interactive TV (STB enabled TV set). A buy-now command is sent with the STB-ID code to the cable head end (HE) and shop OD client application operative thereat and to the shop OD computer server. If the set ID code matches the approved list at the HE, a purchase-confirmation is sent to the user via the STB-TV from the cable HE. One methodology sends a local confirm via metadata or specially configured VA asset. Supplemental communications channels handle supplemental confirms to the user. If not enrolled, supplemental communications network gathers user-viewer profile data. The profile lists user-selectable supple-comm message format (email, voice, text, fax). Non-enrollees may be given discounts to enroll. PINs are also used to control purchasing processes.
Owner:ON DEMAND SHOPPING
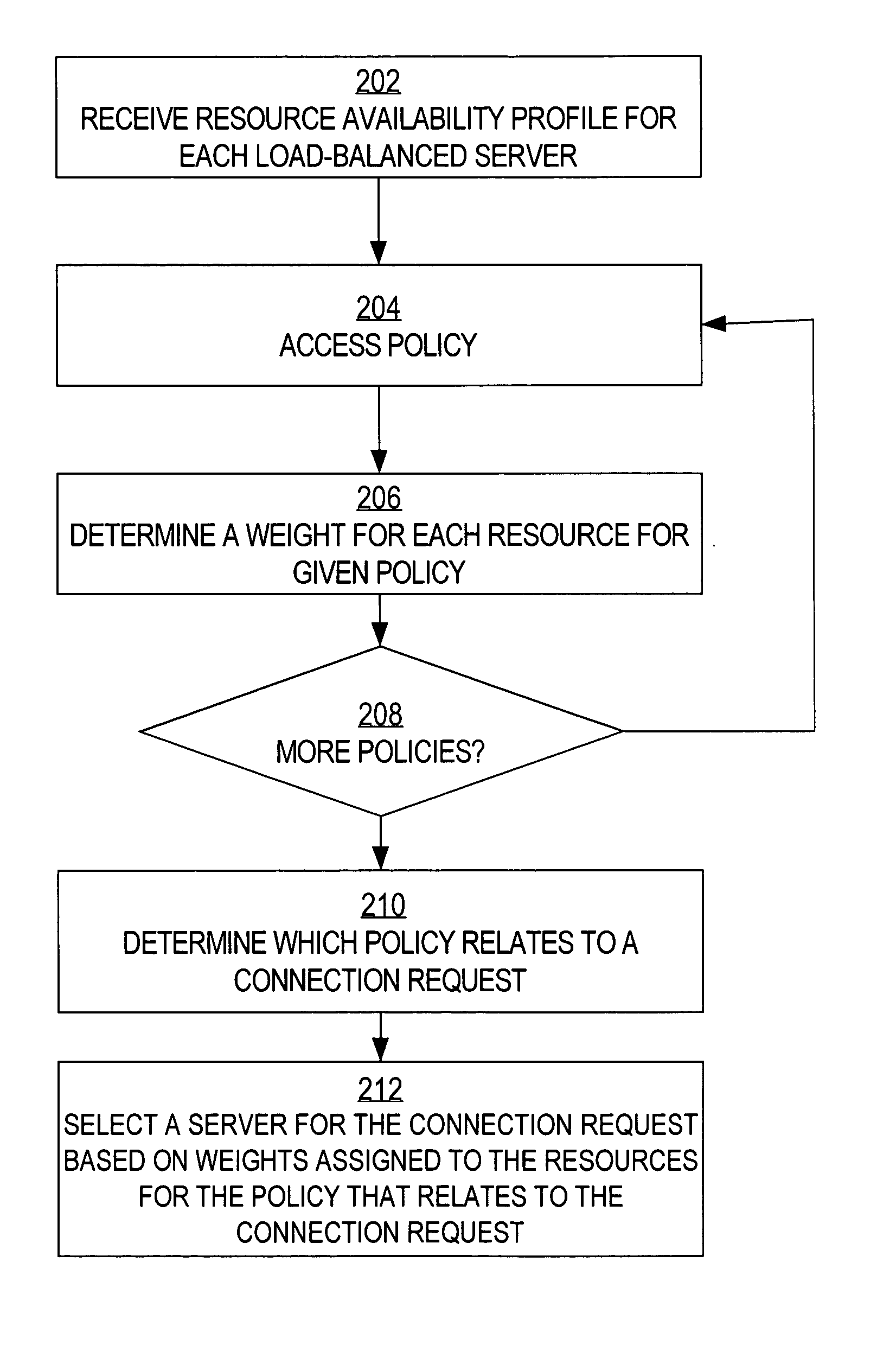
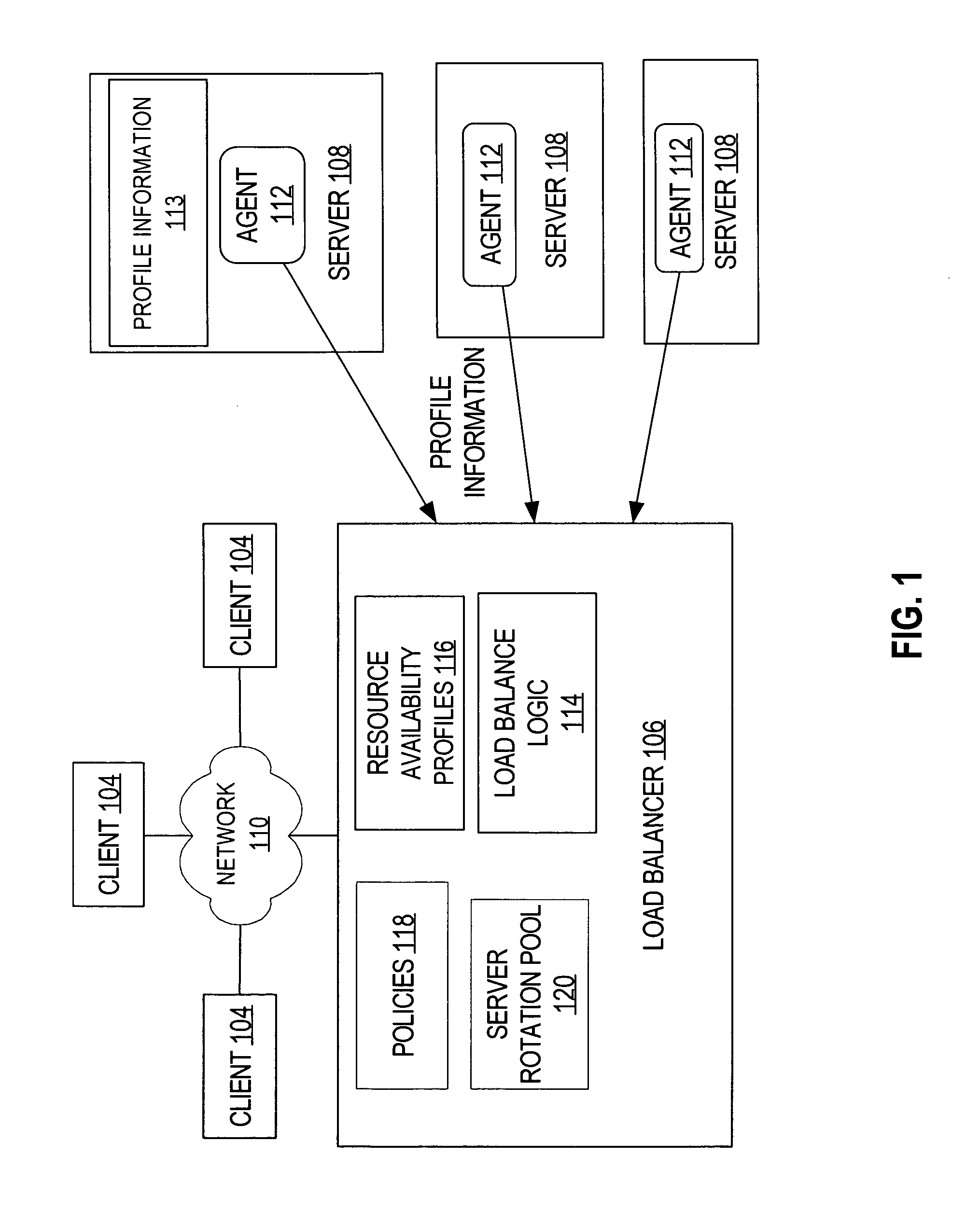
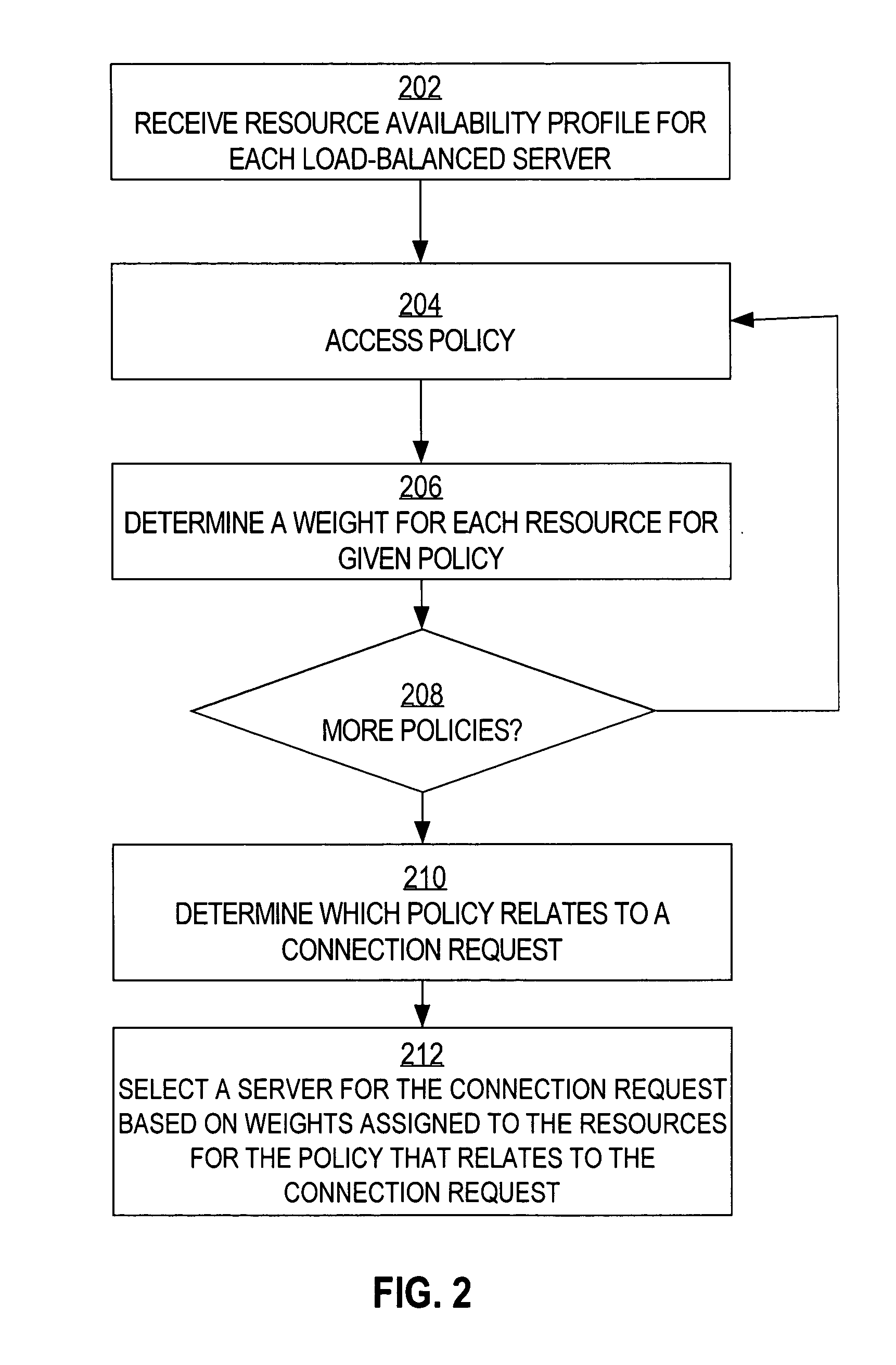
Load balancing mechanism using resource availability profiles
ActiveUS20060106938A1Reliability/availability analysisMultiprogramming arrangementsLoad SheddingConfigfs
Resource availability profiles are received, wherein each resource availability profile describes a resource associated with a server. Each resource is assigned a plurality of weights corresponding to a plurality of policies. The weights are determined by, for each of the plurality of the policies, determining a weight for each resource based a given policy and selected information in the resource availability profiles corresponding to the resources. The method further comprises determining a policy from the plurality of the policies corresponding to a given a context associated with a connection request. A first of the load-balanced servers is selected for the connection request based on the weights assigned to the plurality of resources for the policy for the given context.
Owner:CISCO TECH INC
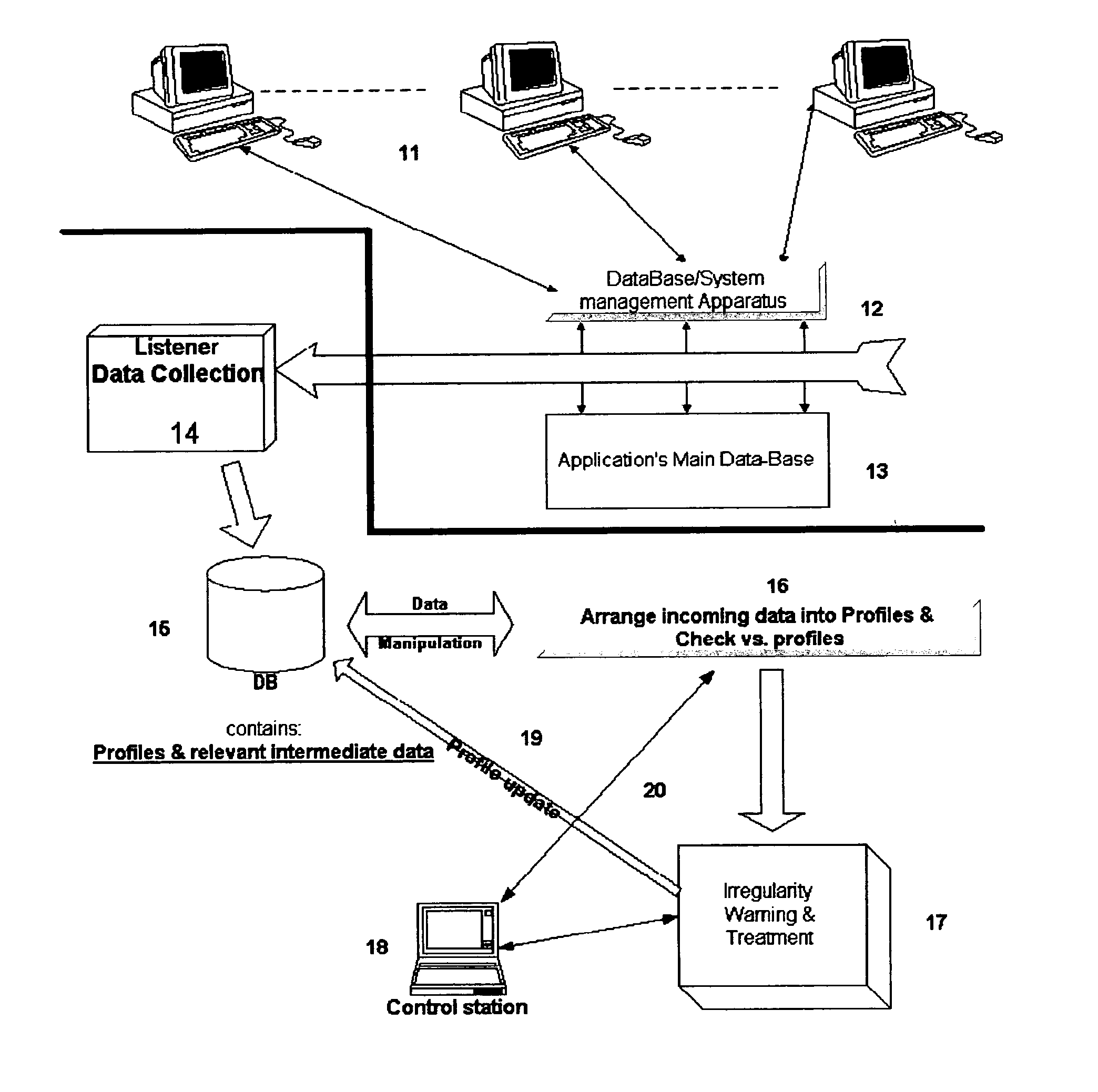
Detection of misuse or abuse of data by authorized access to database
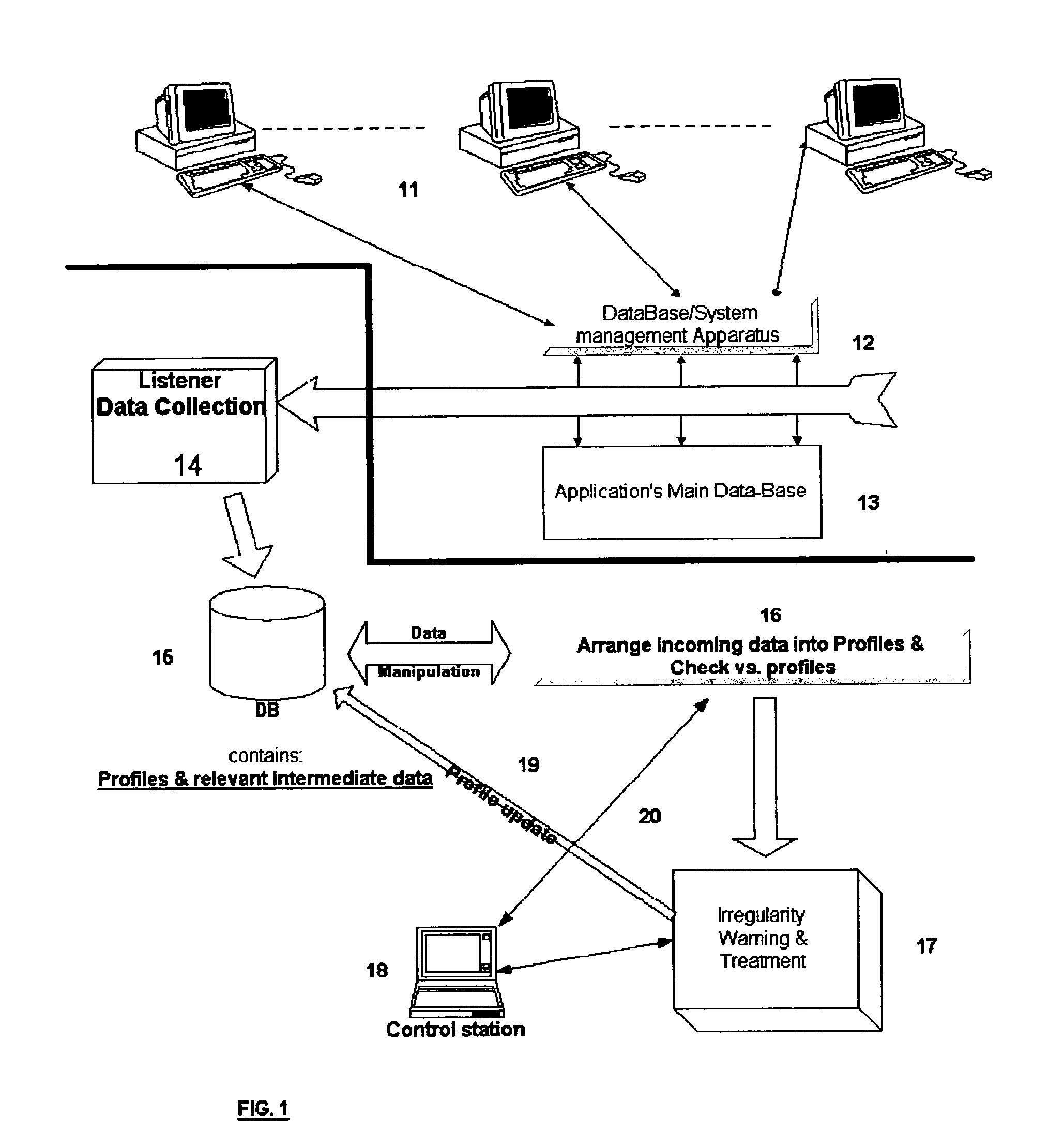
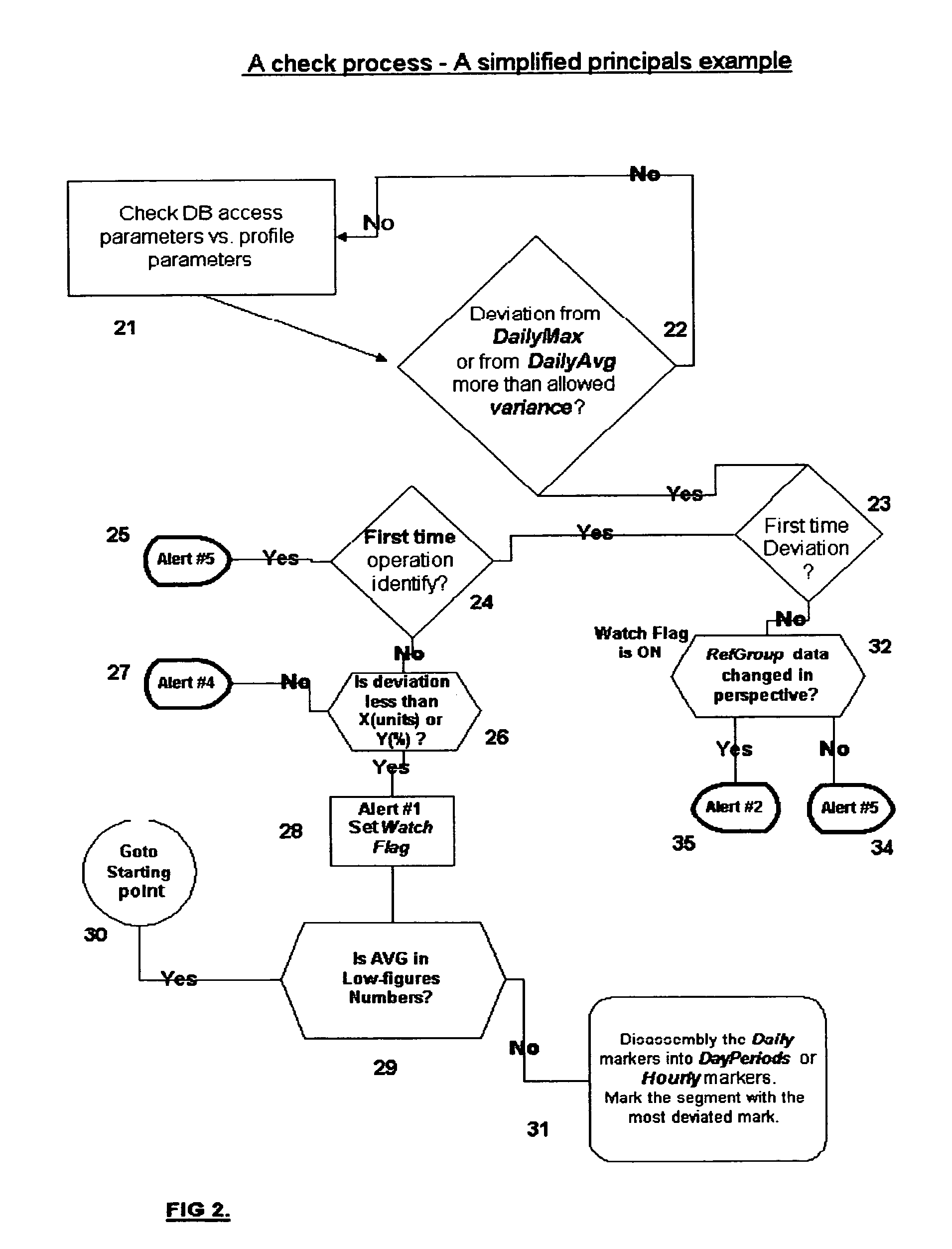
InactiveUS20050086529A1Raise the possibilityEasy to detectDigital data processing detailsHardware monitoringConfigfsData content
The present invention relates to a system for detecting misuse and / or abuse of data related to database done by a user with authorized access to a data system and its database. User behavior is monitored as to its nature of database access, analyzed to create, and compare to, a specific profile. No understanding for the meaning of data content is needed. Each deviation from normal pattern, stored in the profile, is checked in various parameters and ranked, reporting to a system owner.
Owner:IDOT COMP
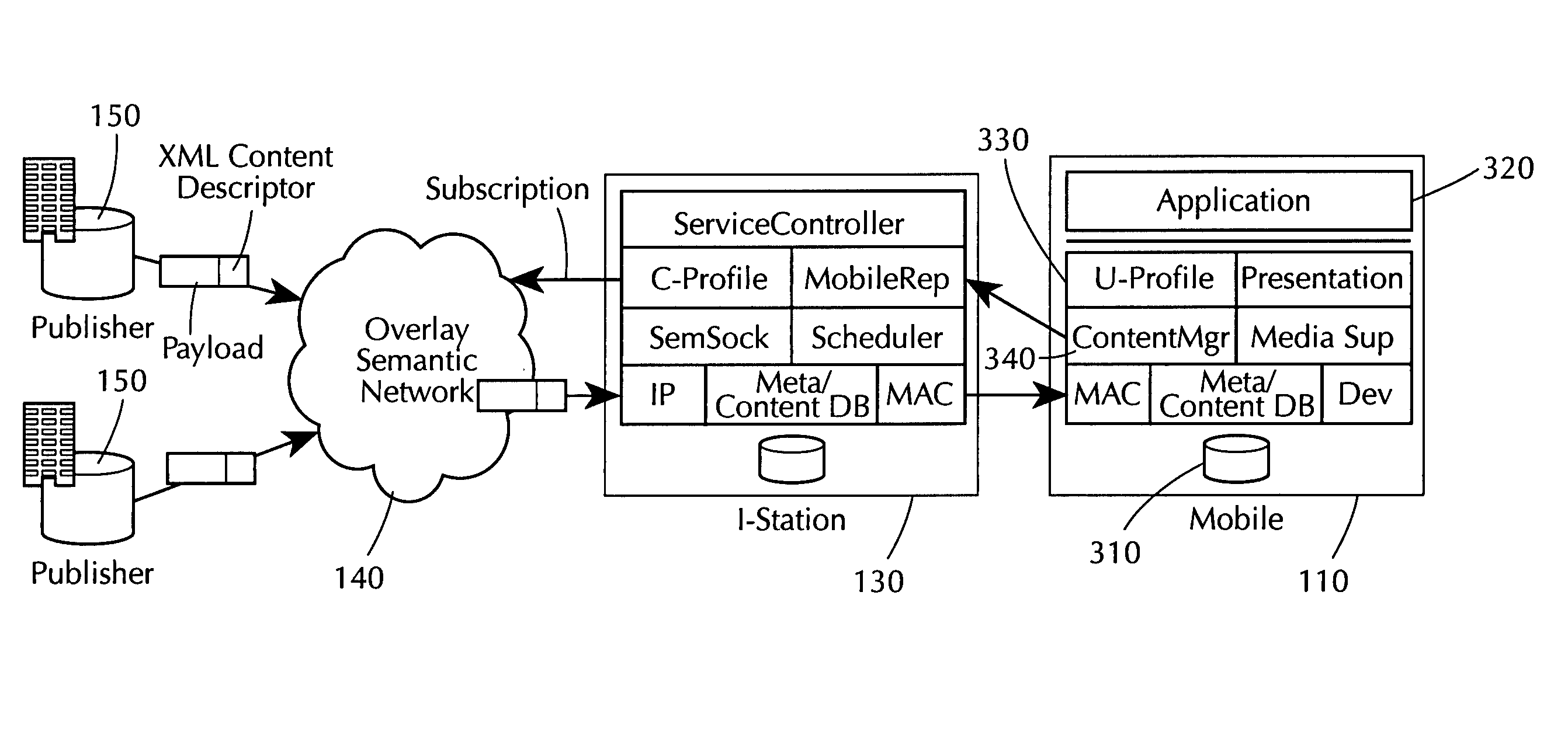
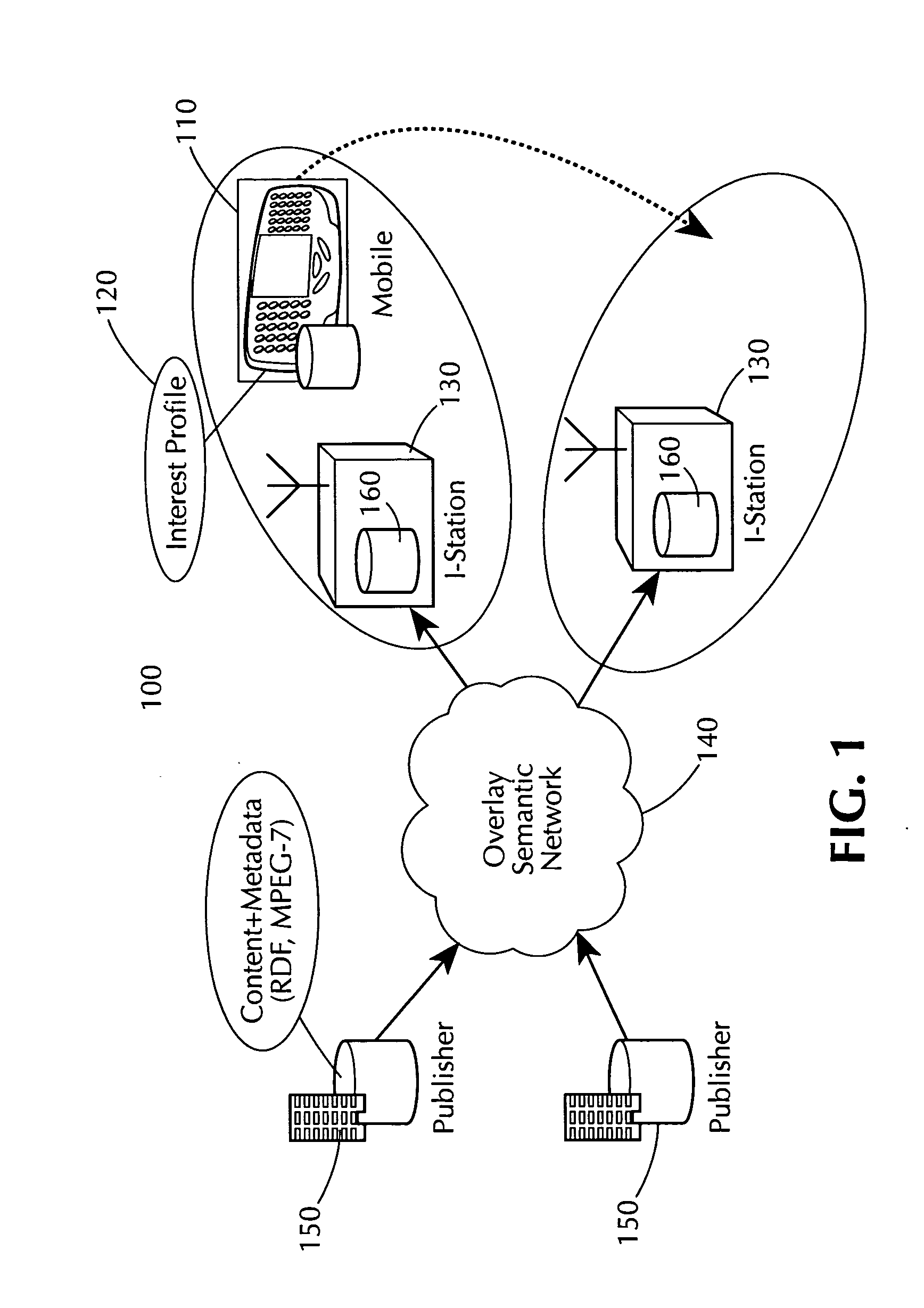
Method and apparatus for using wireless hotspots and semantic routing to provide broadband mobile serveices
InactiveUS20050128995A1Network traffic/resource managementTime-division multiplexCost effectivenessHigh bandwidth
A system and method for providing cost-effective broadband mobile services using a hybrid wireless network consisting of wide-area cellular (“3G”) supplemented by hotspot caches are provided. The proposed architecture uses opportunistic access of high-bandwidth wireless hotspot to dramatically reduce the cost per MB of media delivered to mobile end-users. The system also uses a “semantic multicast routing” approach to caching and delivering media based on individual user profiles.
Owner:OTT MAXIMILIAN A +2
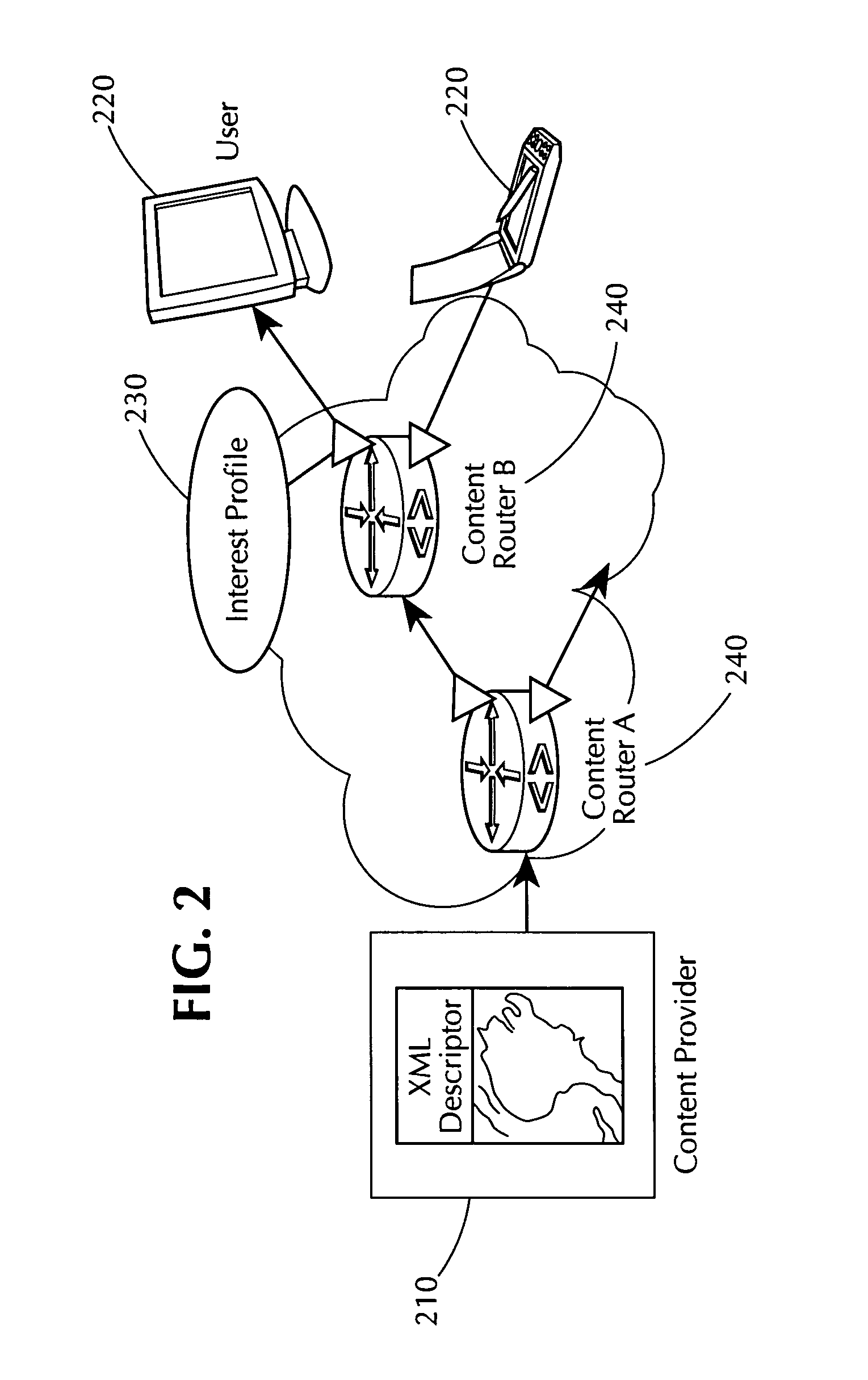
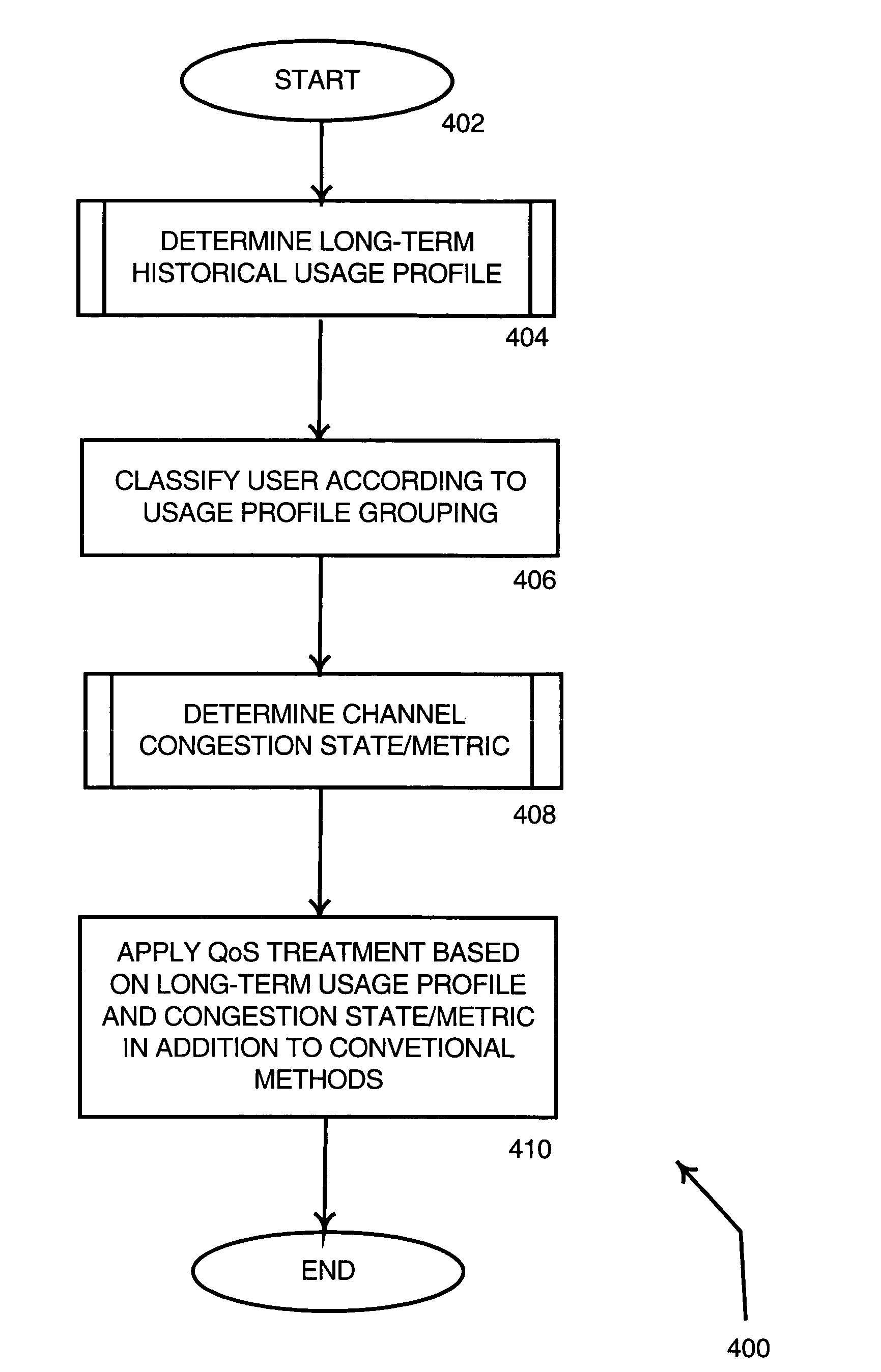
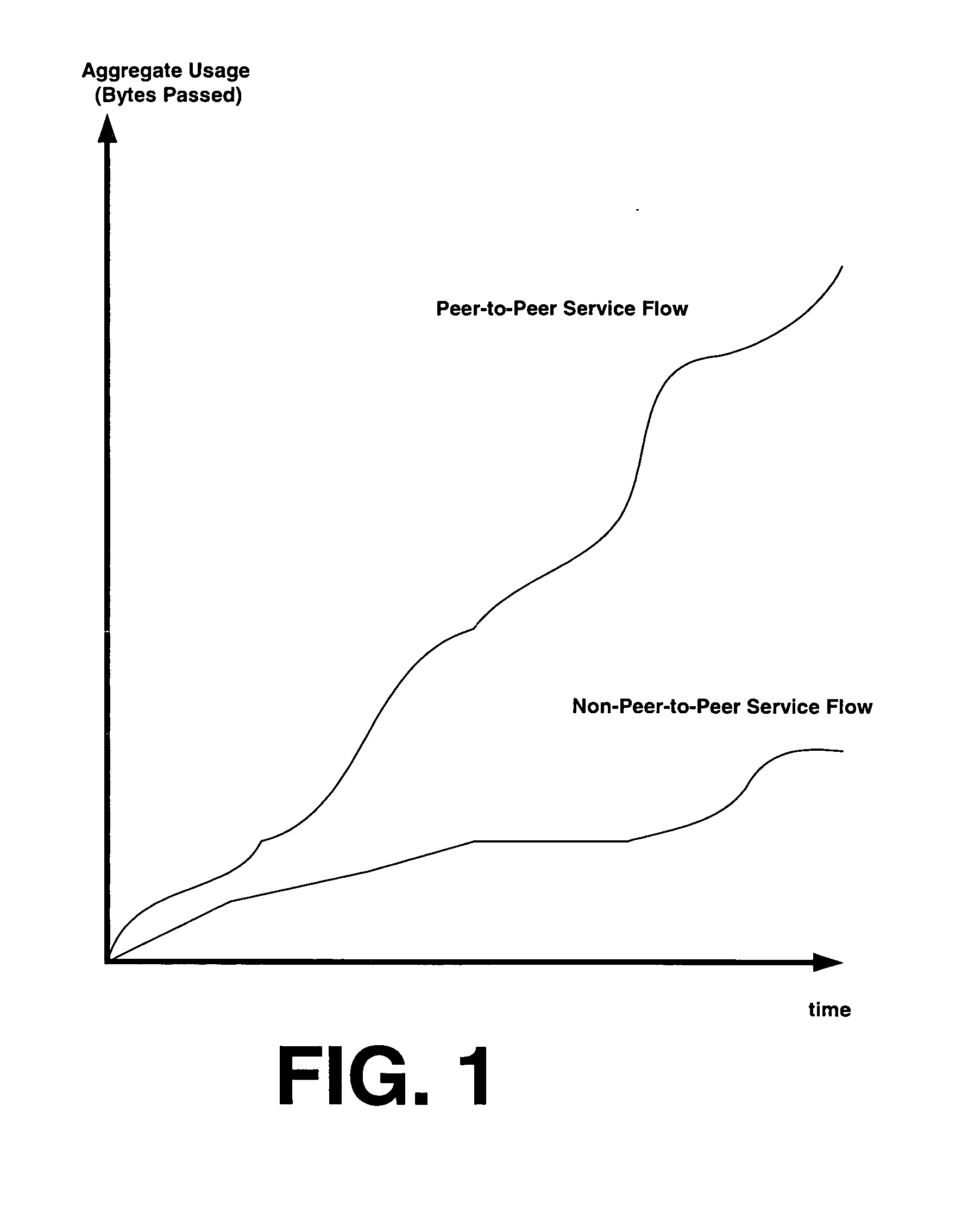
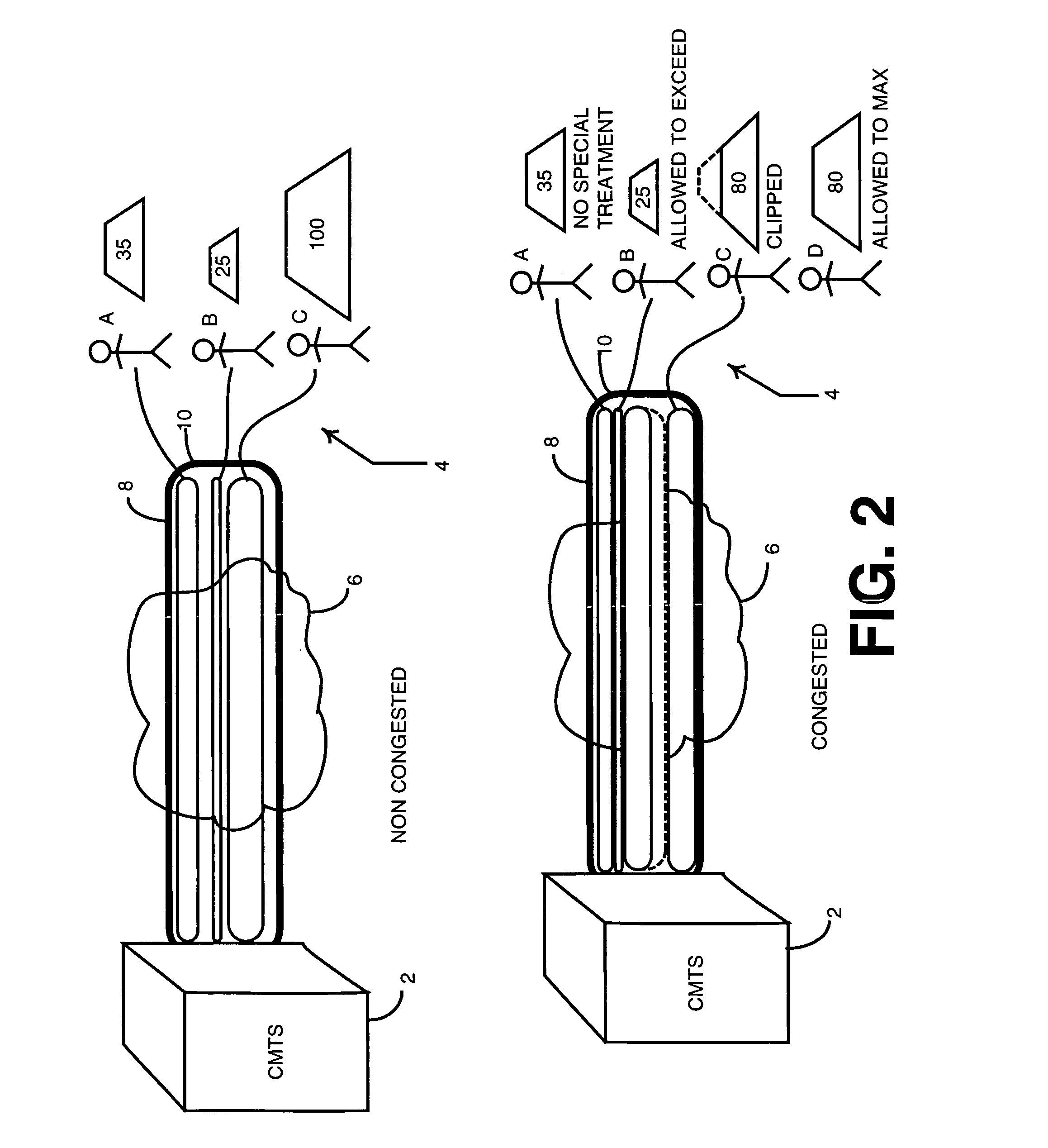
Method and system for dynamically managing cable data bandwidth based on channel congestion state and subscriber usage profile
A long-term usage profile and a congestion state metric are used to determine QoS treatment to apply to packets corresponding to a given network user. A user's historical long-term use, measured over one or more periods of time, is used to generate a profile that is compared to one or more predetermined usage threshold level(s). If the usage profile, either singular or composite corresponding to whether one or more than one measurement is used respectively, exceeds the threshold(s), QoS treatment is applied to service flow bytes according to the comparison results during times of network channel congestion. Congestion metrics are determined based on a count of the number of bytes dropped during a congestion measurement window. Either the count itself or the count rate of change combined with the count are compared to a congestion threshold. If the measured / derived values exceed a congestion threshold, the channel is deemed congested.
Owner:ARRIS INT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com