Patents
Literature
3698 results about "High availability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
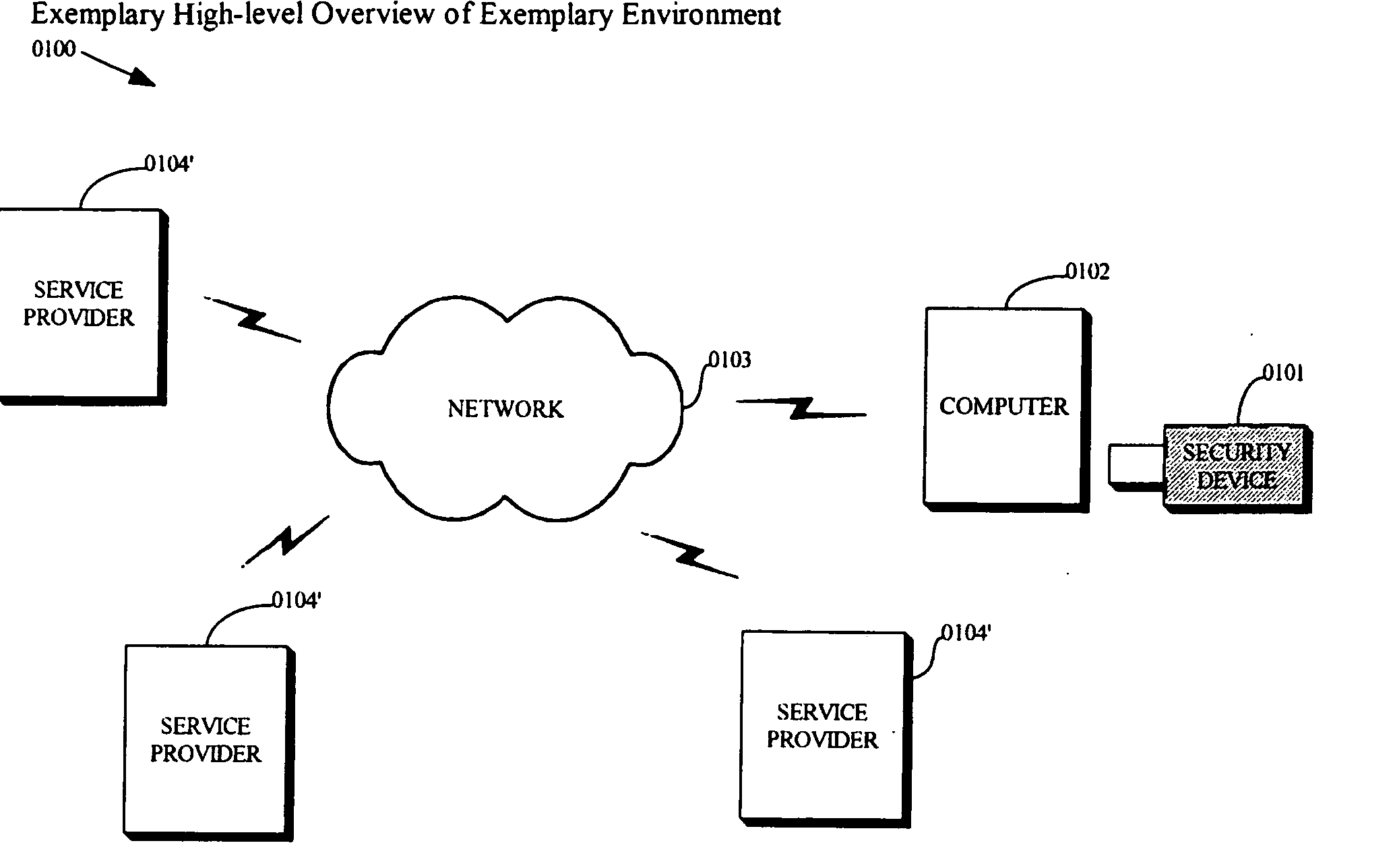
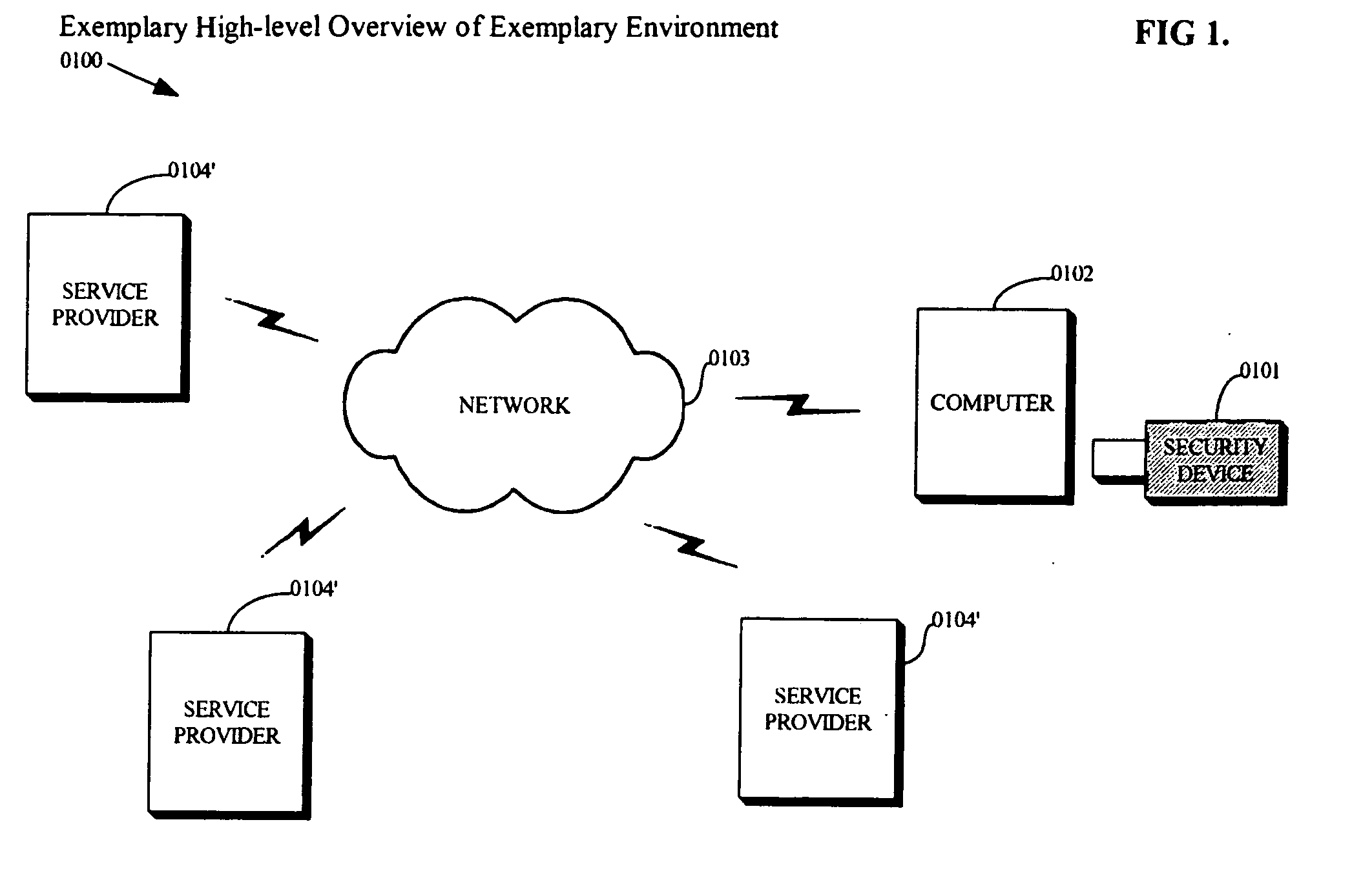
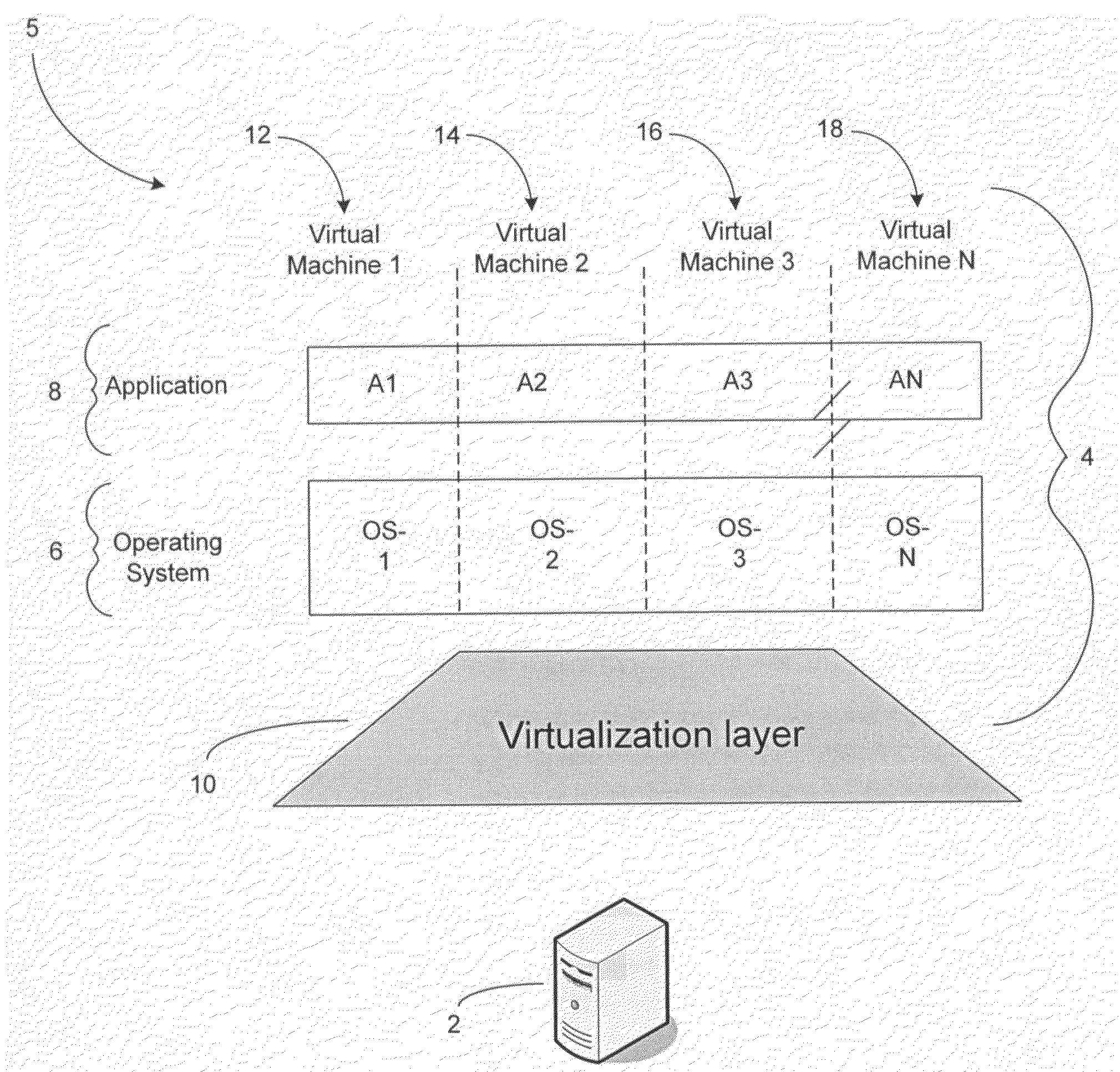
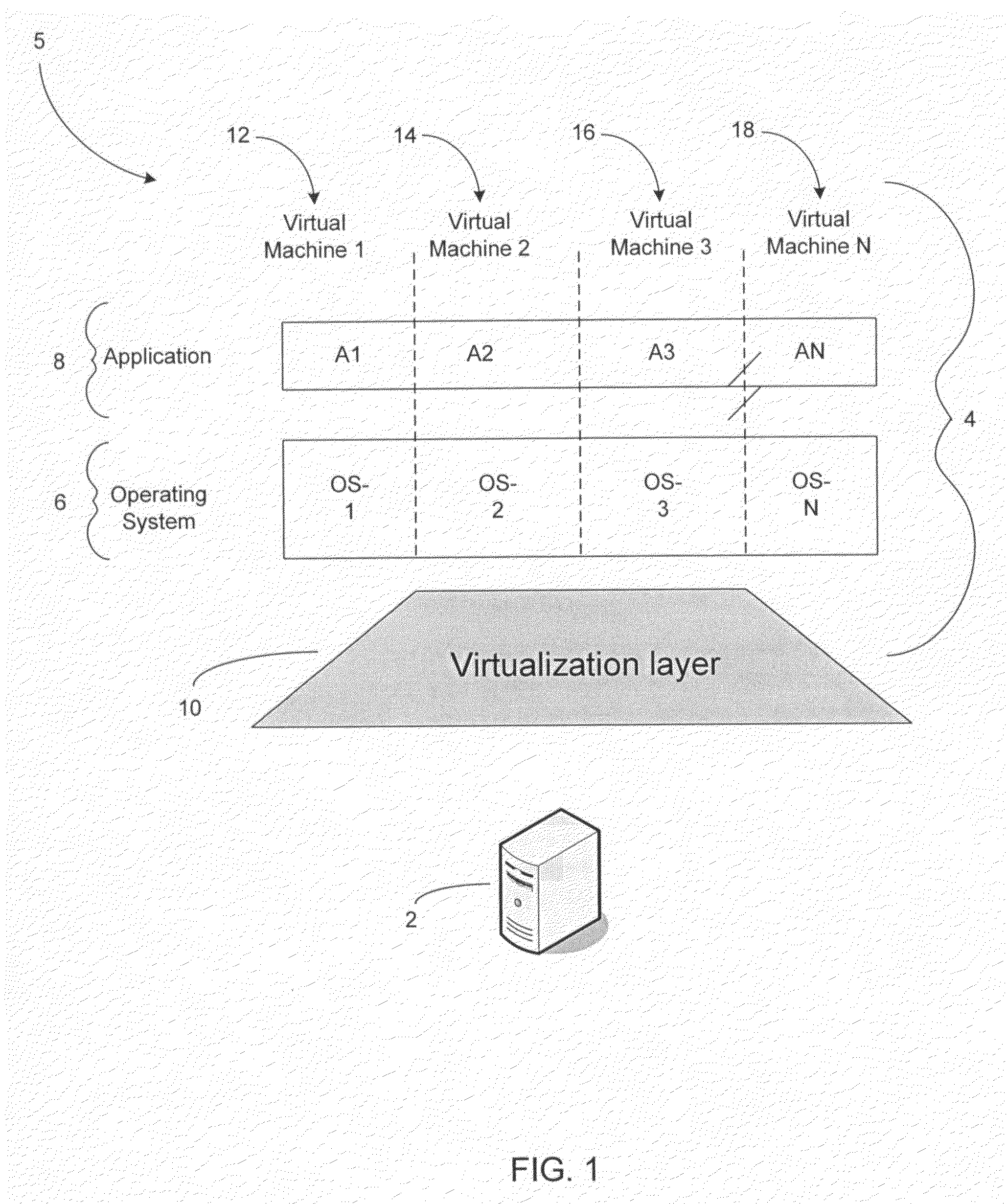
High availability (HA) is a characteristic of a system, which aims to ensure an agreed level of operational performance, usually uptime, for a higher than normal period. Modernization has resulted in an increased reliance on these systems. For example, hospitals and data centers require high availability of their systems to perform routine daily activities. Availability refers to the ability of the user community to obtain a service or good, access the system, whether to submit new work, update or alter existing work, or collect the results of previous work. If a user cannot access the system, it is – from the users point of view – unavailable. Generally, the term downtime is used to refer to periods when a system is unavailable.
Practical platform for high risk applications
InactiveUS20070180509A1Safe and reliable and easy to use practicalIncrease system complexityDigital data processing detailsUser identity/authority verificationSystem integrationComputer hardware
The present invention is a portable device that a computer can boot from, containing a prefabricated independent operating system environment which is engineered from the ground up to prioritize security while maximizing usability, in order to provide a safe, reliable and easy to use practical platform for high risk applications. An embodiment of the present invention may temporarily transform an ordinary computer into a naturally inexpensive logical appliance which encapsulates a turn-key functional solution within the digital equivalent of a military grade security fortress. This allows existing hardware to be conveniently leveraged to provide a self contained system which does not depend on the on-site labor of rare and expensive system integration and security experts.
Owner:SWARTZ ALON R +1
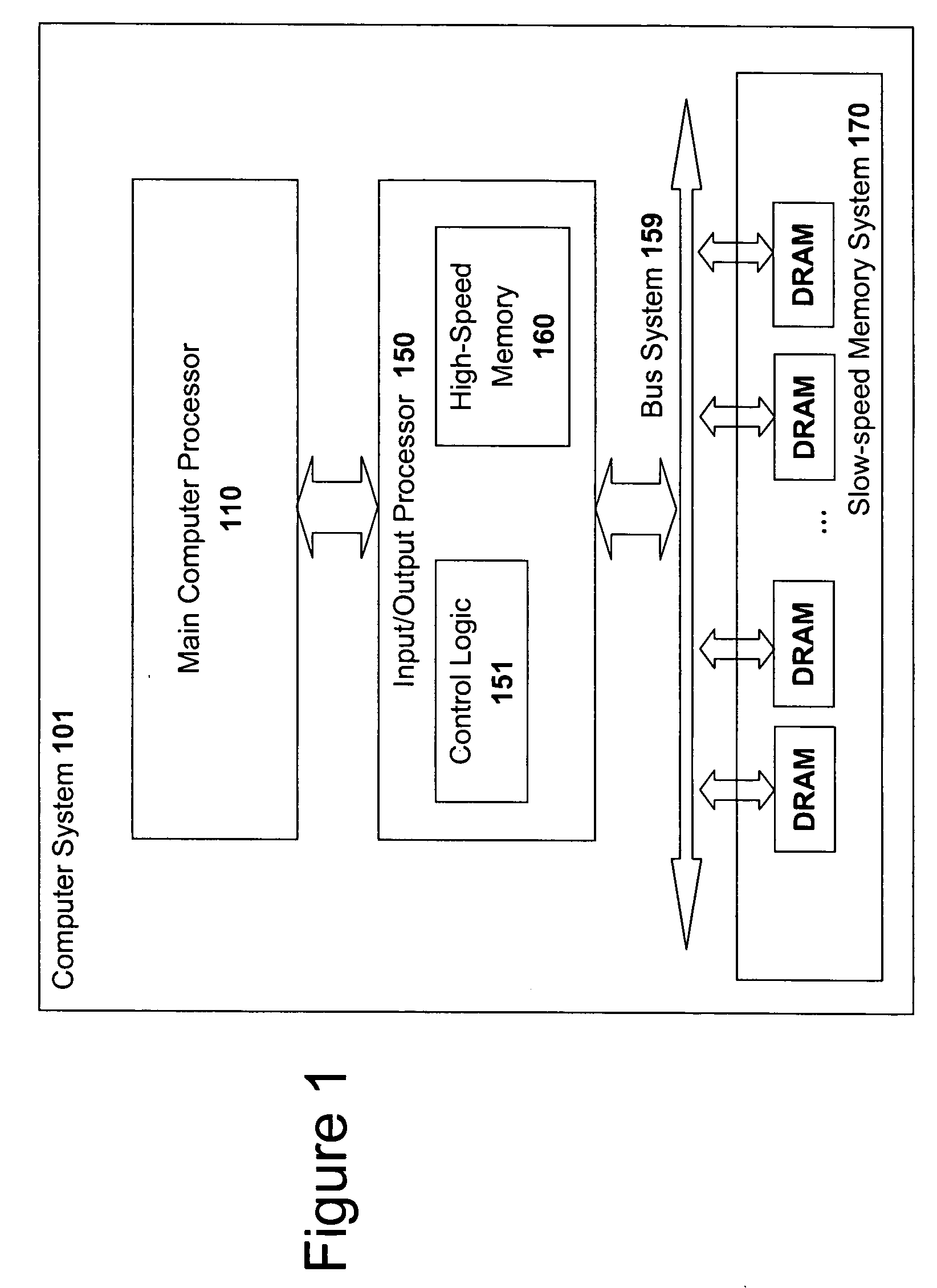
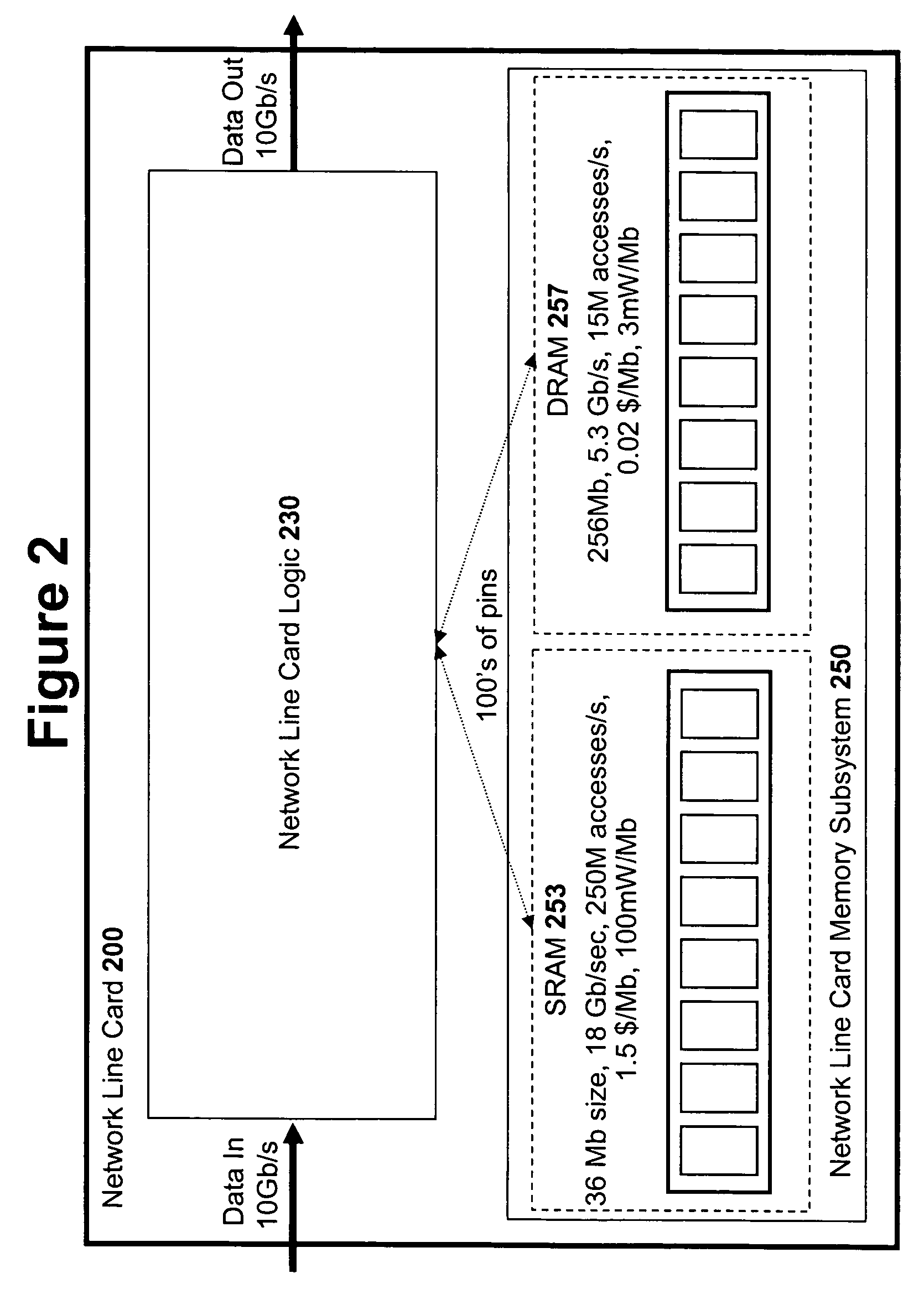
High speed memory control and I/O processor system
ActiveUS20050240745A1Easy to handleSimplify memory access taskMemory architecture accessing/allocationMemory adressing/allocation/relocationHigh speed memoryTailored approach
An input / output processor for speeding the input / output and memory access operations for a processor is presented. The key idea of an input / output processor is to functionally divide input / output and memory access operations tasks into a compute intensive part that is handled by the processor and an I / O or memory intensive part that is then handled by the input / output processor. An input / output processor is designed by analyzing common input / output and memory access patterns and implementing methods tailored to efficiently handle those commonly occurring patterns. One technique that an input / output processor may use is to divide memory tasks into high frequency or high-availability components and low frequency or low-availability components. After dividing a memory task in such a manner, the input / output processor then uses high-speed memory (such as SRAM) to store the high frequency and high-availability components and a slower-speed memory (such as commodity DRAM) to store the low frequency and low-availability components. Another technique used by the input / output processor is to allocate memory in such a manner that all memory bank conflicts are eliminated. By eliminating any possible memory bank conflicts, the maximum random access performance of DRAM memory technology can be achieved.
Owner:CISCO TECH INC
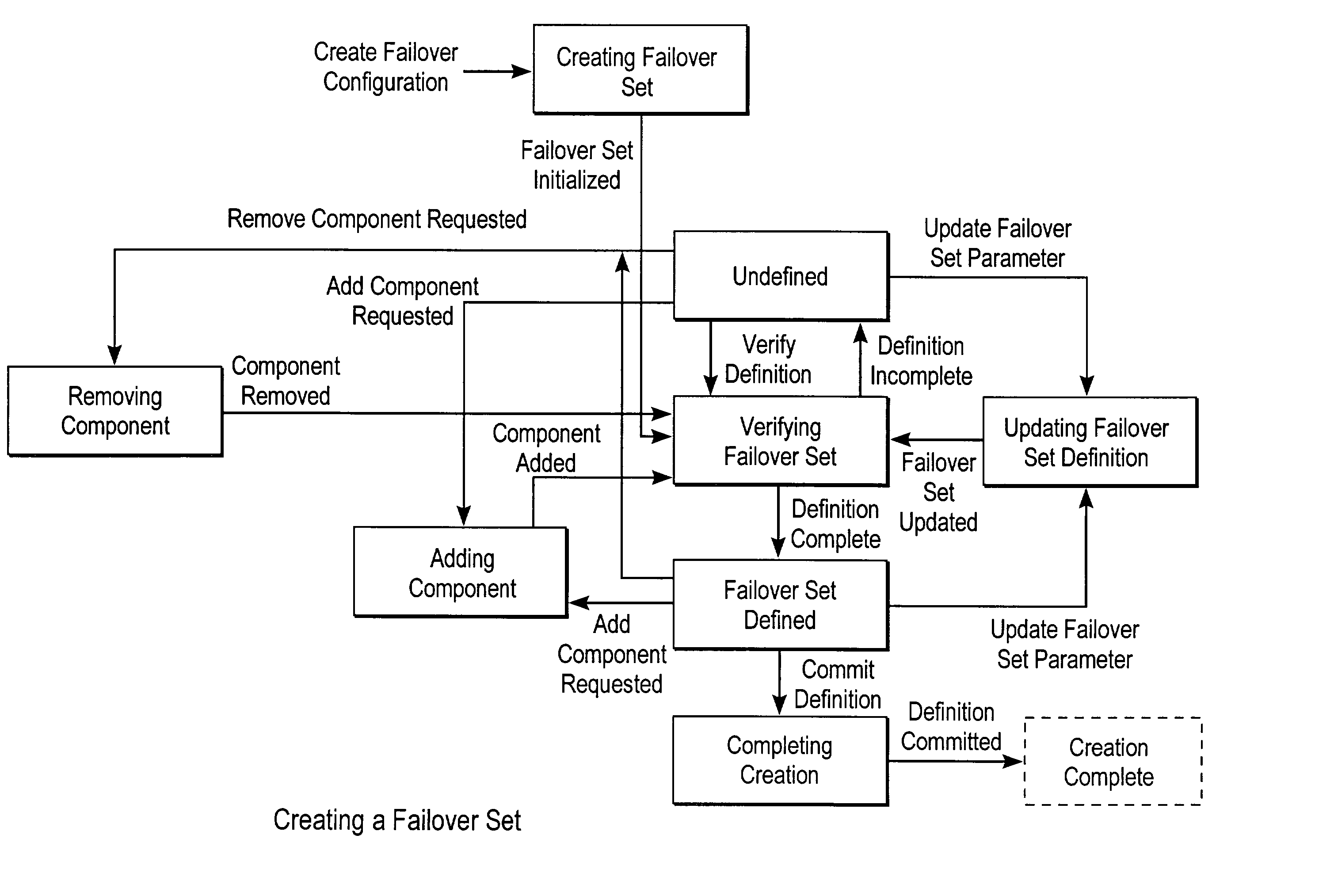
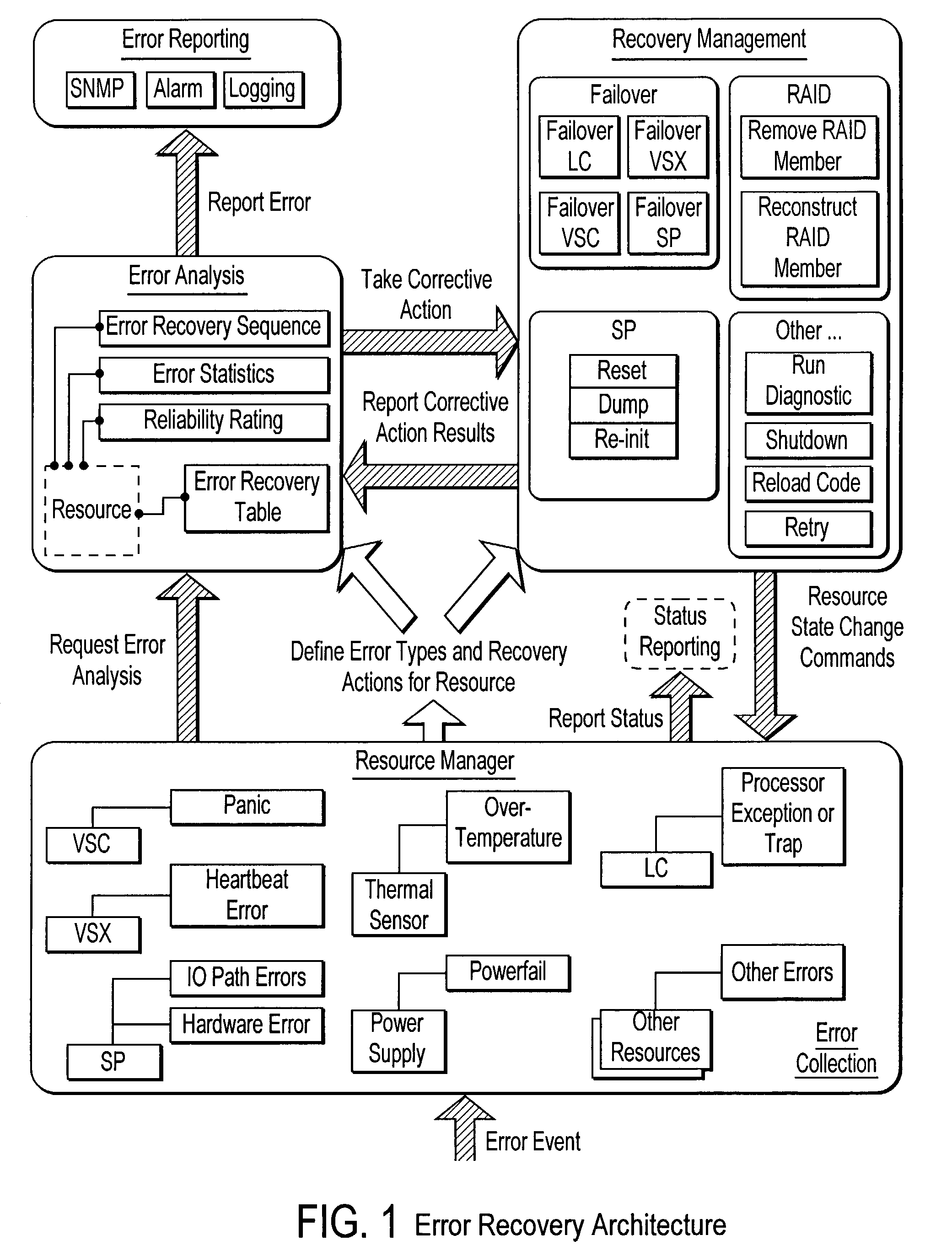
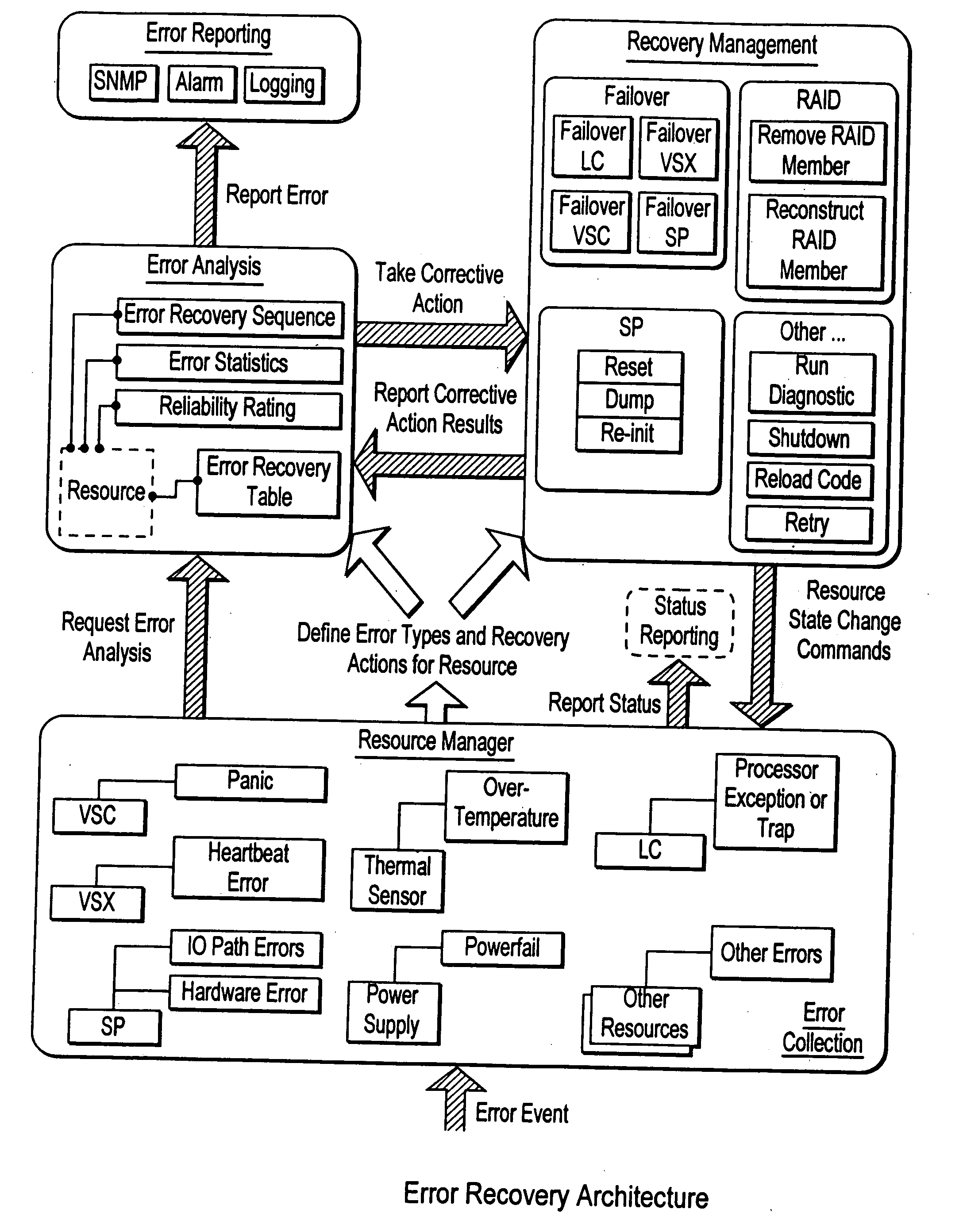
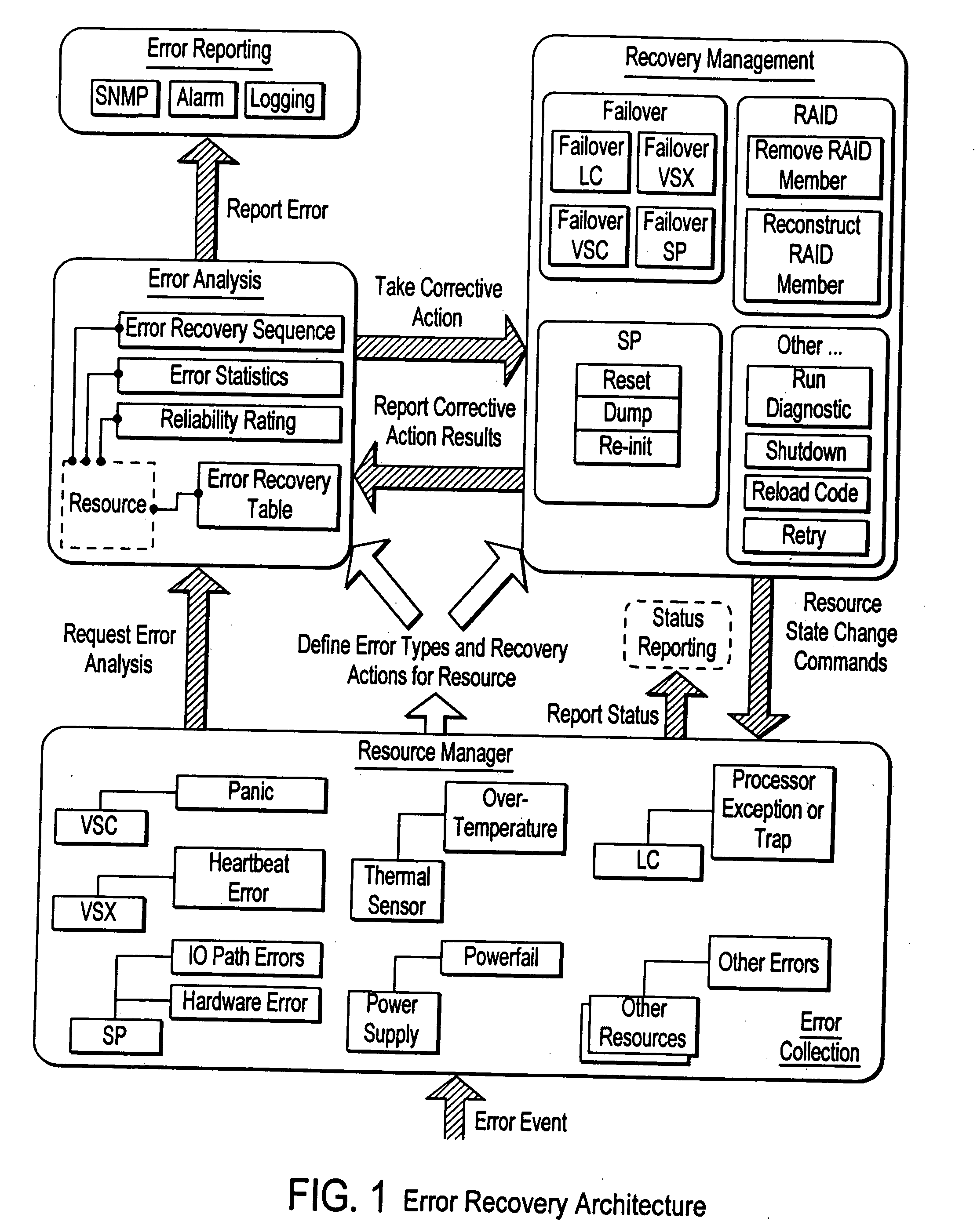
Failover processing in a storage system
InactiveUS7039827B2Improve usabilityInput/output to record carriersDigital data processing detailsFault toleranceFailover
Failover processing in storage server system utilizes policies for managing fault tolerance (FT) and high availability (HA) configurations. The approach encapsulates the knowledge of failover recovery between components within a storage server and between storage server systems. This knowledge includes information about what components are participating in a Failover Set, how they are configured for failover, what is the Fail-Stop policy, and what are the steps to perform when “failing-over” a component.
Owner:NETWORK APPLIANCE INC
High-availability cluster virtual server system
InactiveUS6944785B2Minimize occurrenceImprove system performanceInput/output to record carriersData switching networksFailoverHigh availability
Systems and methods, including computer program products, providing high-availability in server systems. In one implementation, a server system is cluster of two or more autonomous server nodes, each running one or more virtual servers. When a node fails, its virtual servers are migrated to one or more other nodes. Connectivity between nodes and clients is based on virtual IP addresses, where each virtual server has one or more virtual IP addresses. Virtual servers can be assigned failover priorities, and, in failover, higher priority virtual servers can be migrated before lower priority ones. Load balancing can be provided by distributing virtual servers from a failed node to multiple different nodes. When a port within a node fails, the node can reassign virtual IP addresses from the failed port to other ports on the node until no good ports remain and only then migrate virtual servers to another node or nodes.
Owner:NETWORK APPLIANCE INC
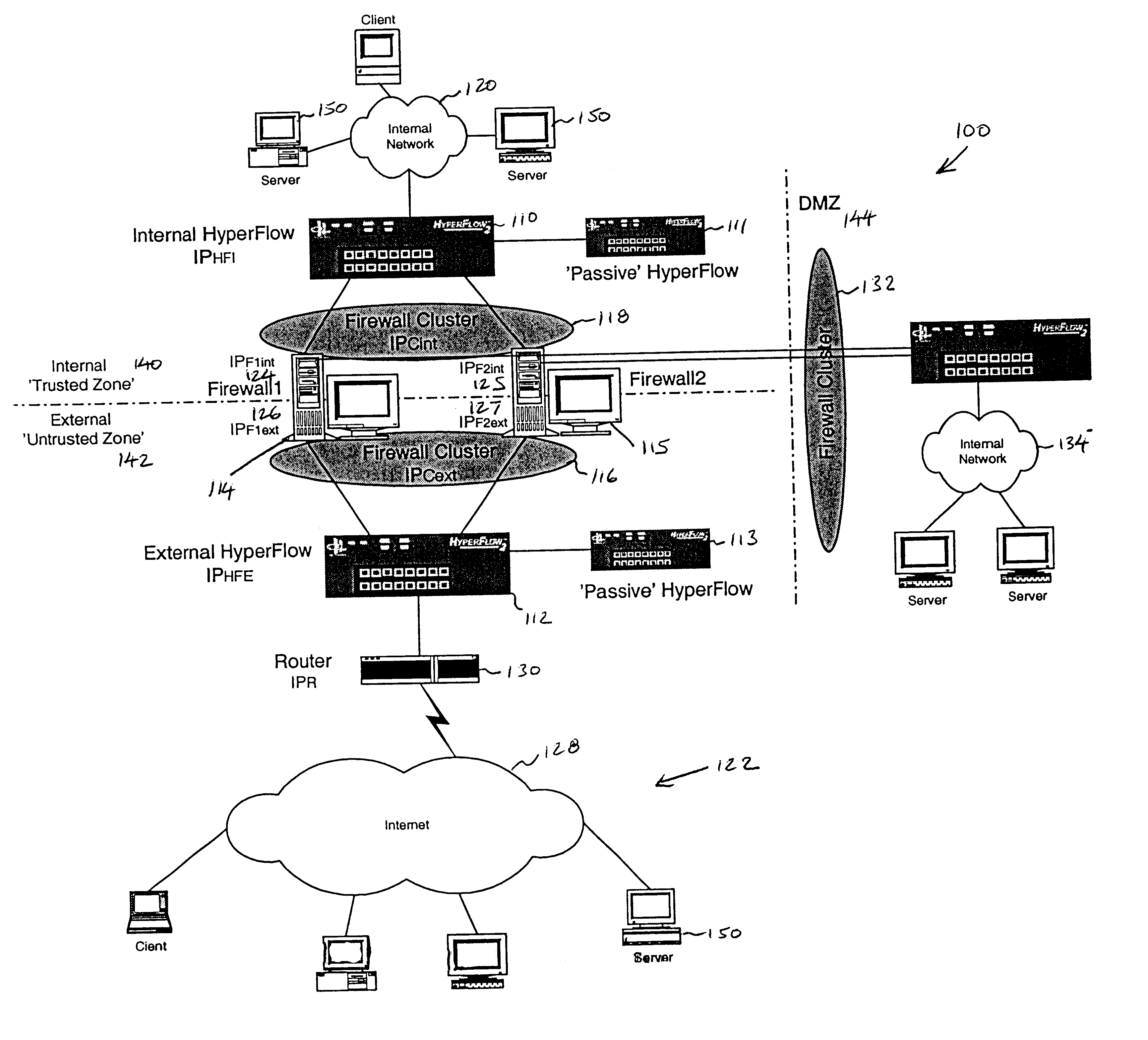
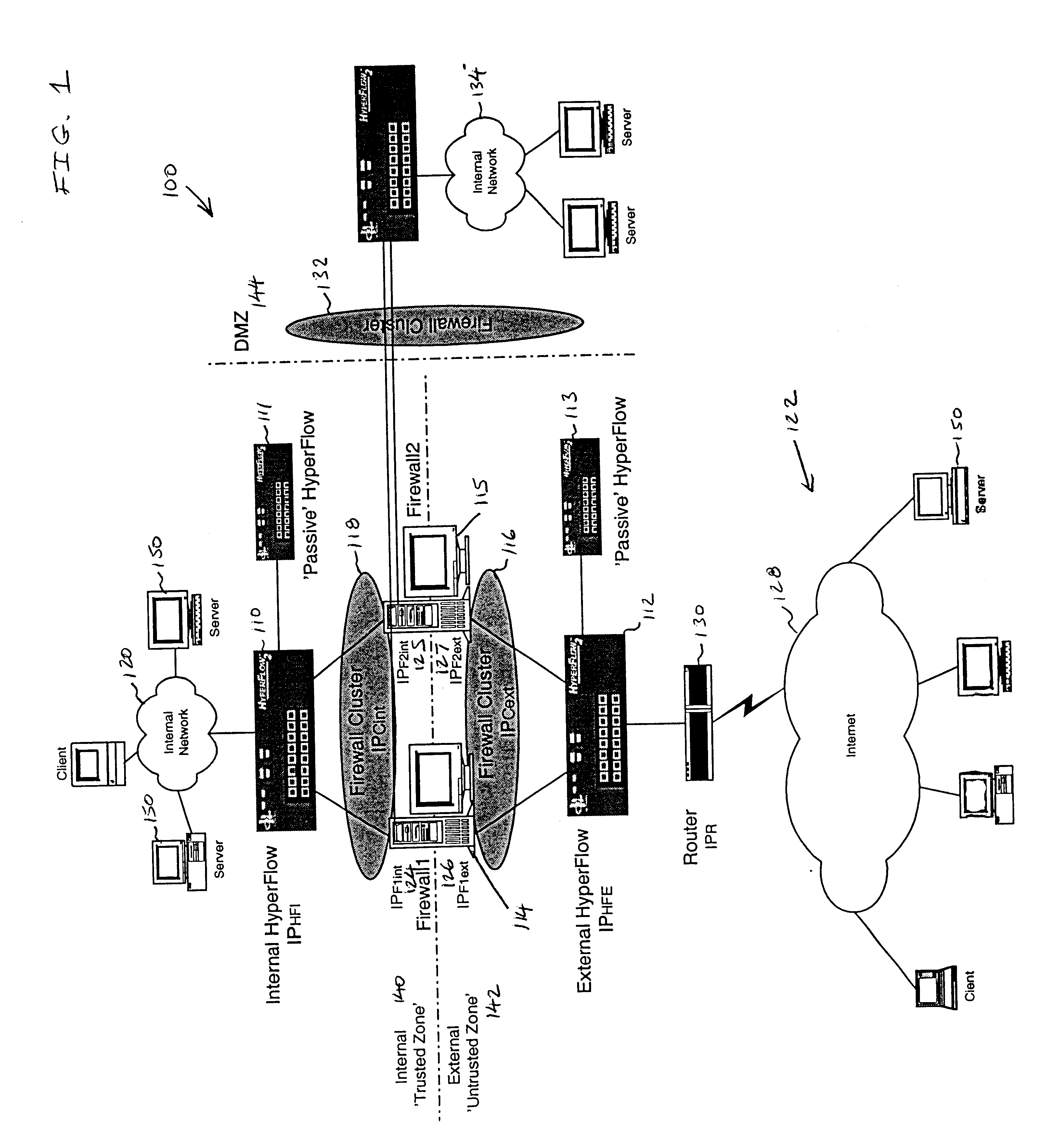
Firewall clustering for multiple network servers
InactiveUS6880089B1Increase capacityReduce calculationMultiple digital computer combinationsProgram controlTraffic capacityExtensibility
A firewall clustering system connects two or more firewalls between an internal network and an external network. The plurality of two or more firewalls are combined to supply high-availability and scaling of processing capacity. Firewalls maintain client-server state information. Flow controllers are connected to the firewalls and placed on both the internal “trusted” side and the external “untrusted” side of the firewalls. Flow controllers are placed on both sides of the firewalls to ensure that traffic for a given client-server session flows through the same firewall in both inbound and outbound directions. The firewalls perform filtering operations and / or network address translation (NAT) services. In both cases, the flow controllers supply high availability, scalability, and traffic distribution for the firewalls in the firewall cluster.
Owner:CITRIX SYST INC
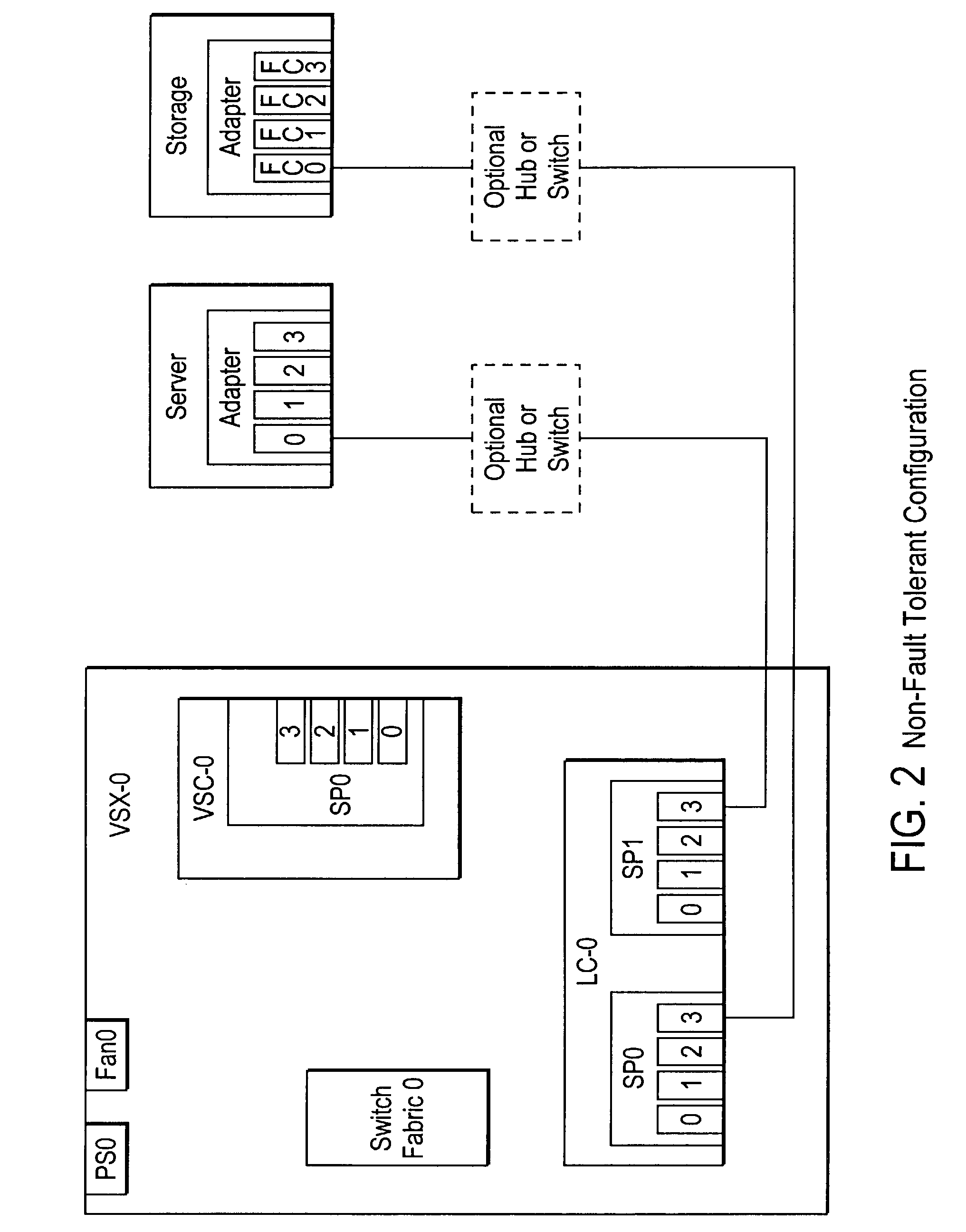
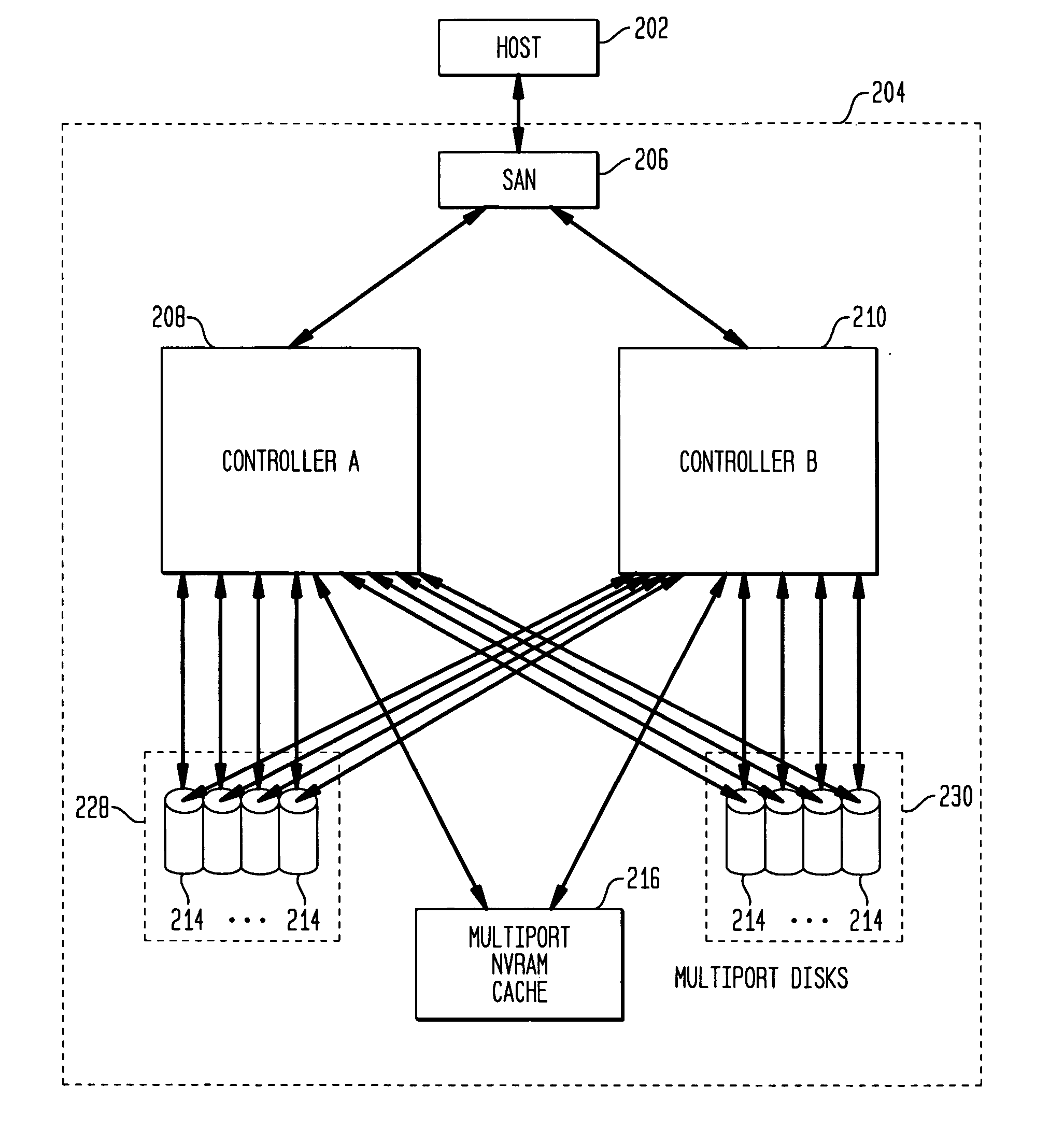
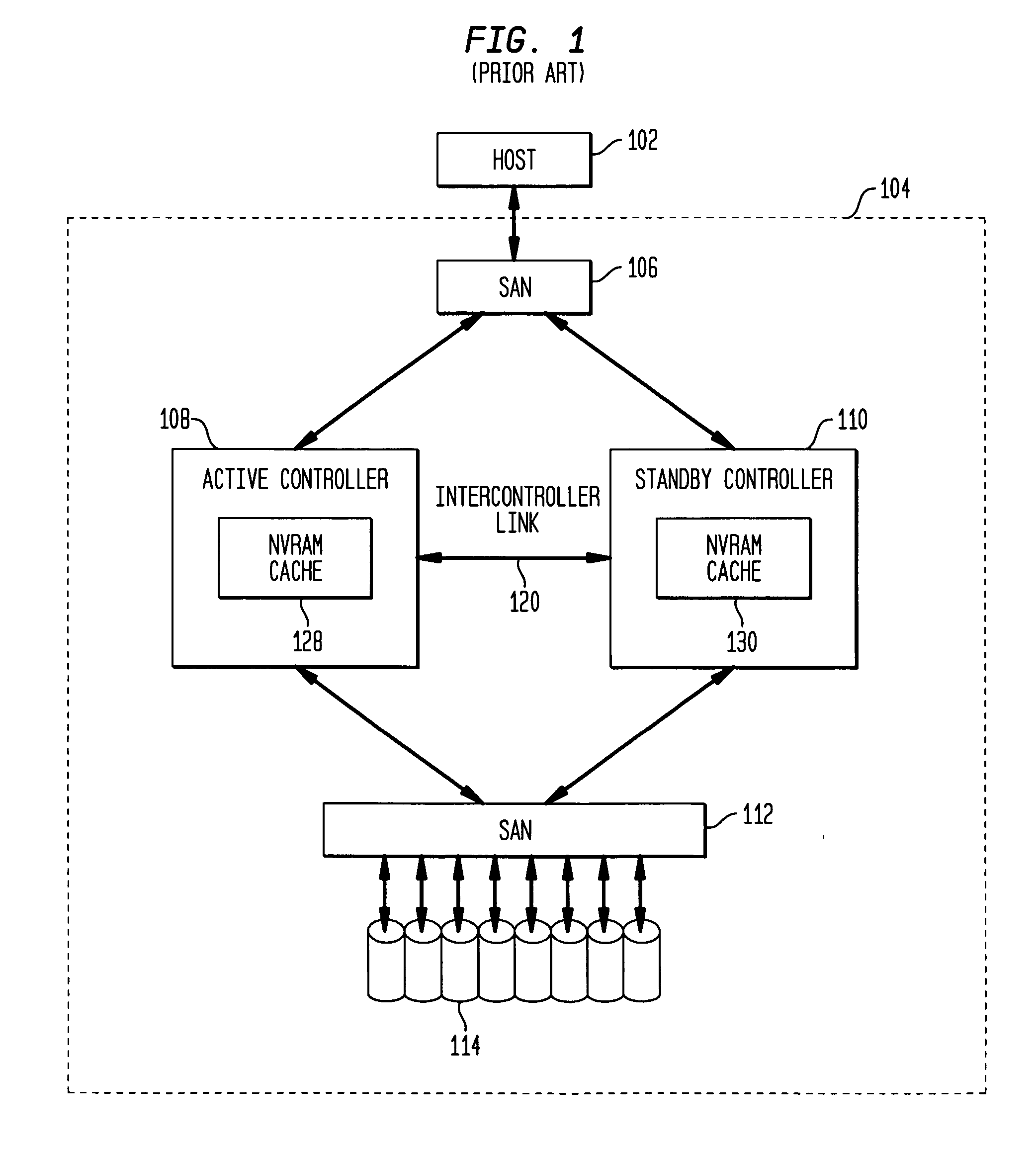
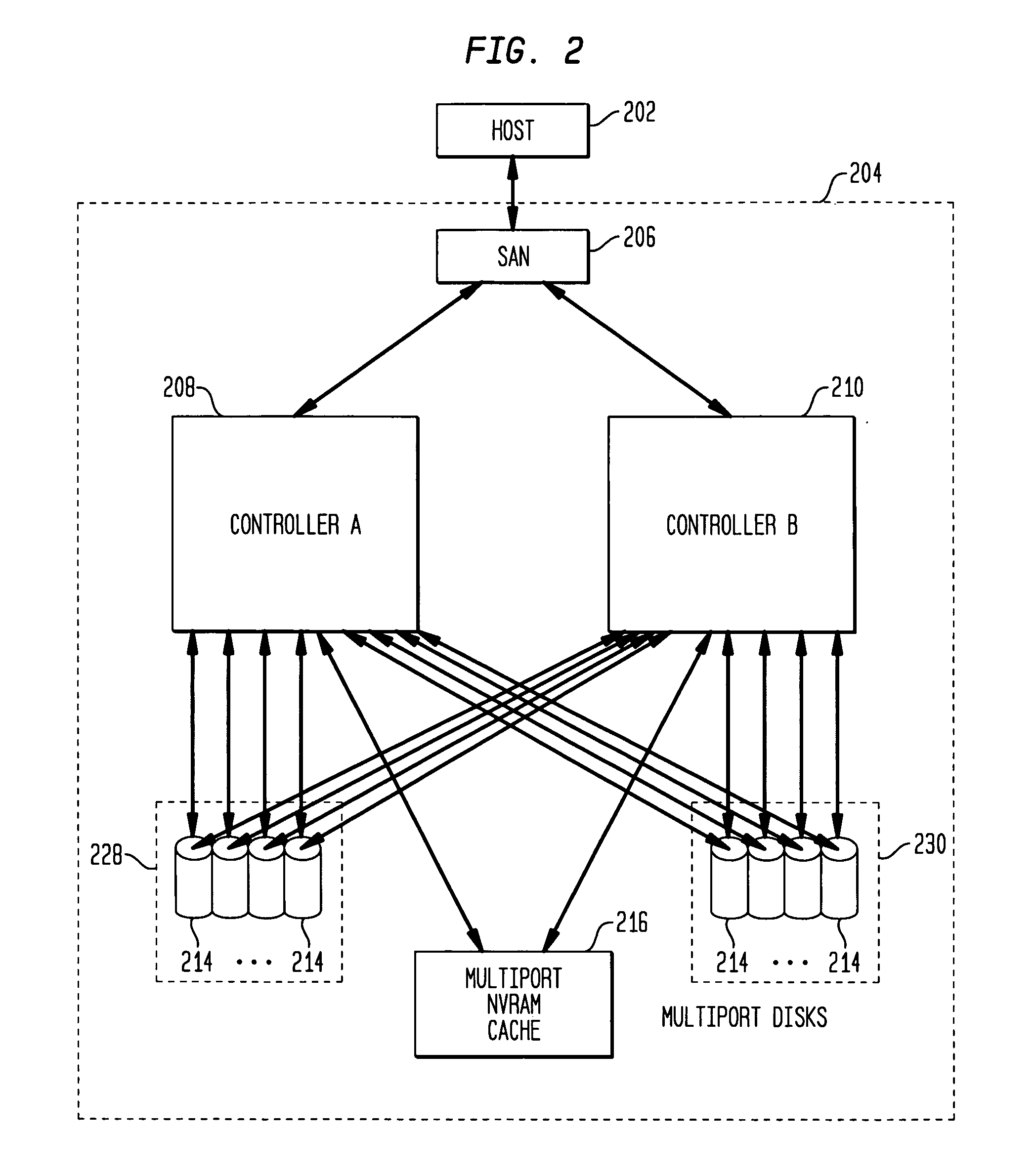
High availability storage system
Methods and systems are described for a storage system including at least two controllers configured to handle write requests and a non-volatile cache connected to both controllers that stores data received from the controllers. The non-volatile cache is accessible by the first and second controllers using an interface technology permitting two or more communication paths between a particular active controller and the non-volatile cache to be aggregated to form a higher data rate communication path. Additionally, a plurality of storage devices are each connected using the interface technology to each controller for storing data received from the controllers.
Owner:HEWLETT PACKARD DEV CO LP
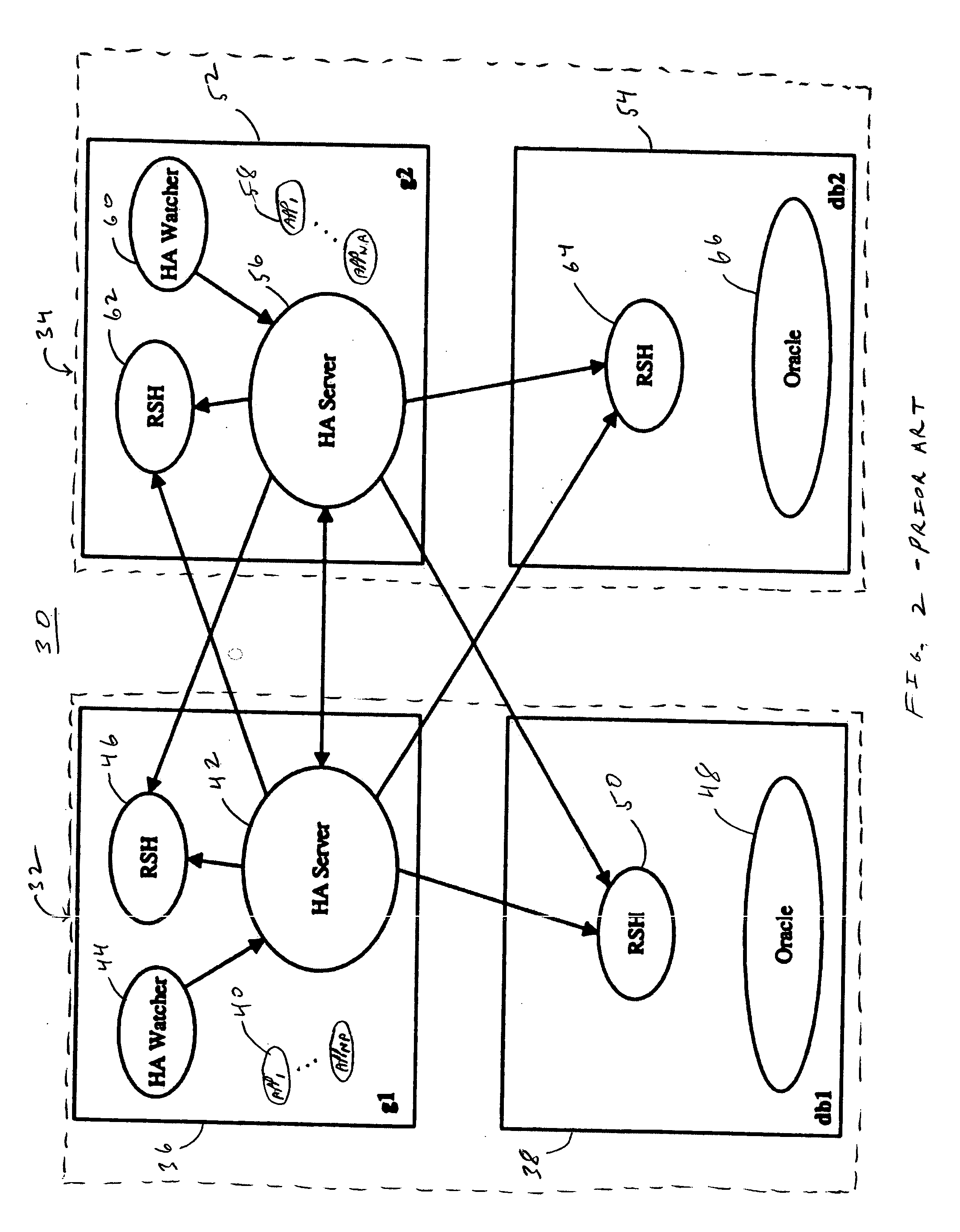
Method and system for achieving high availability in a networked computer system
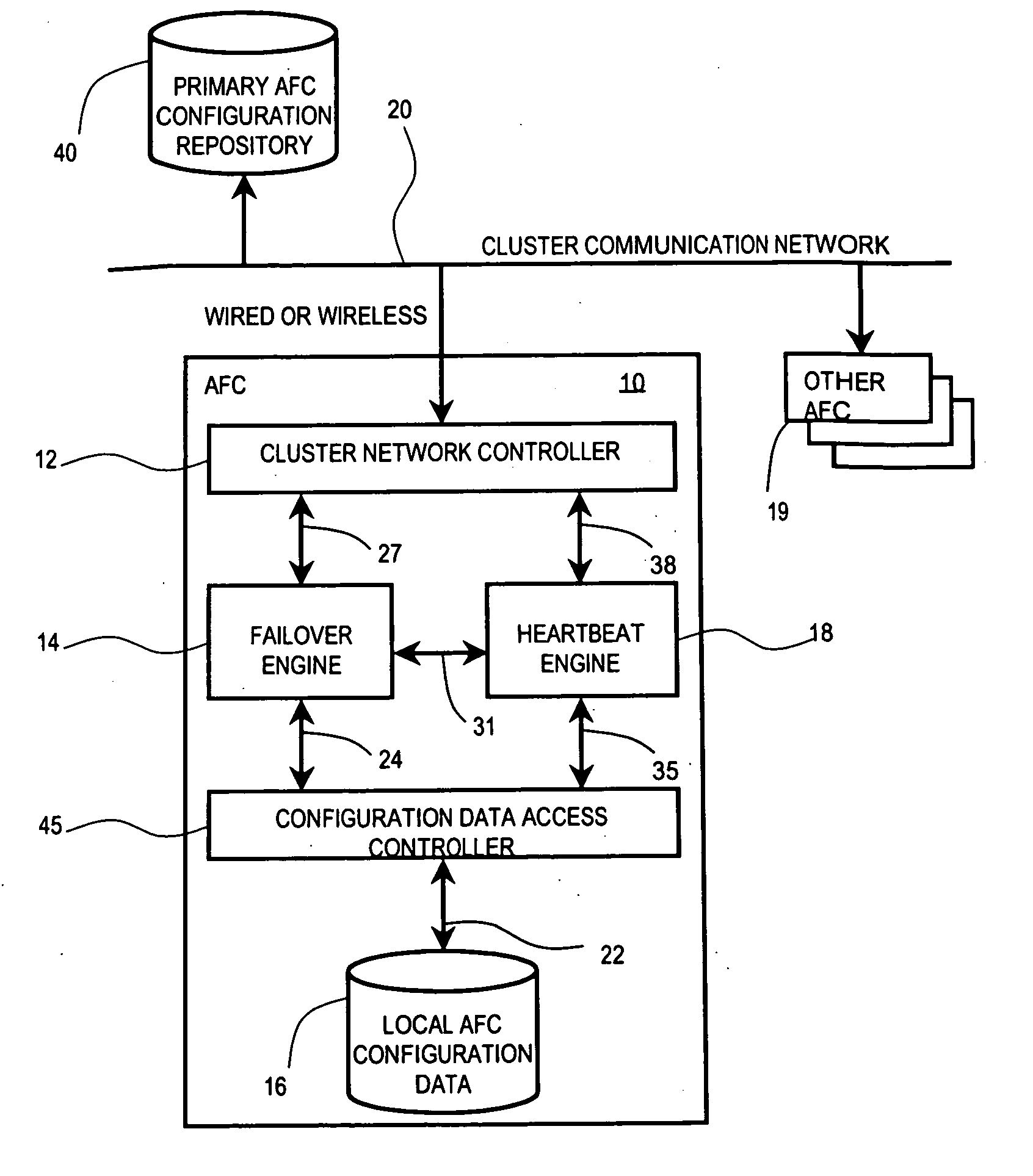
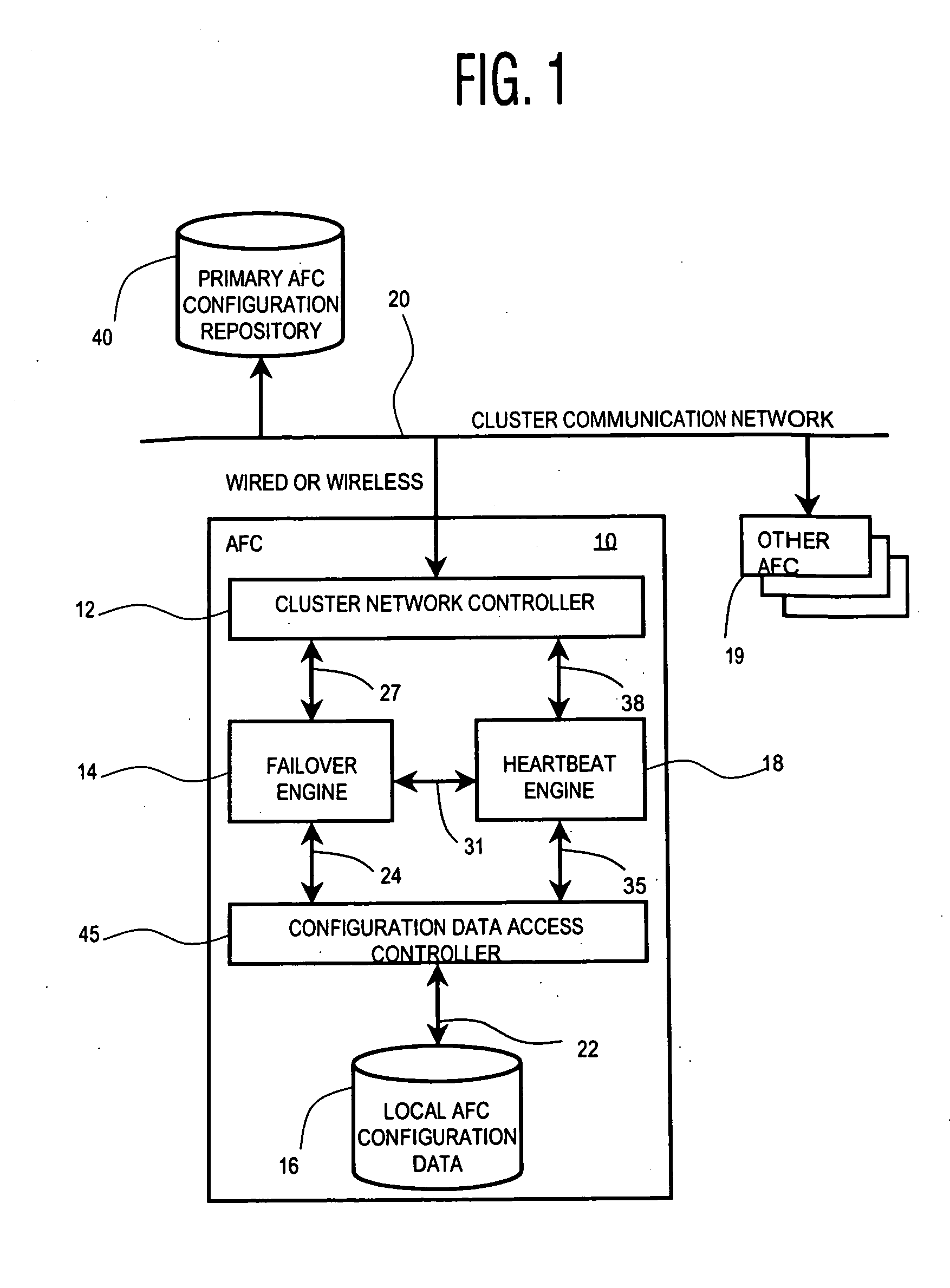
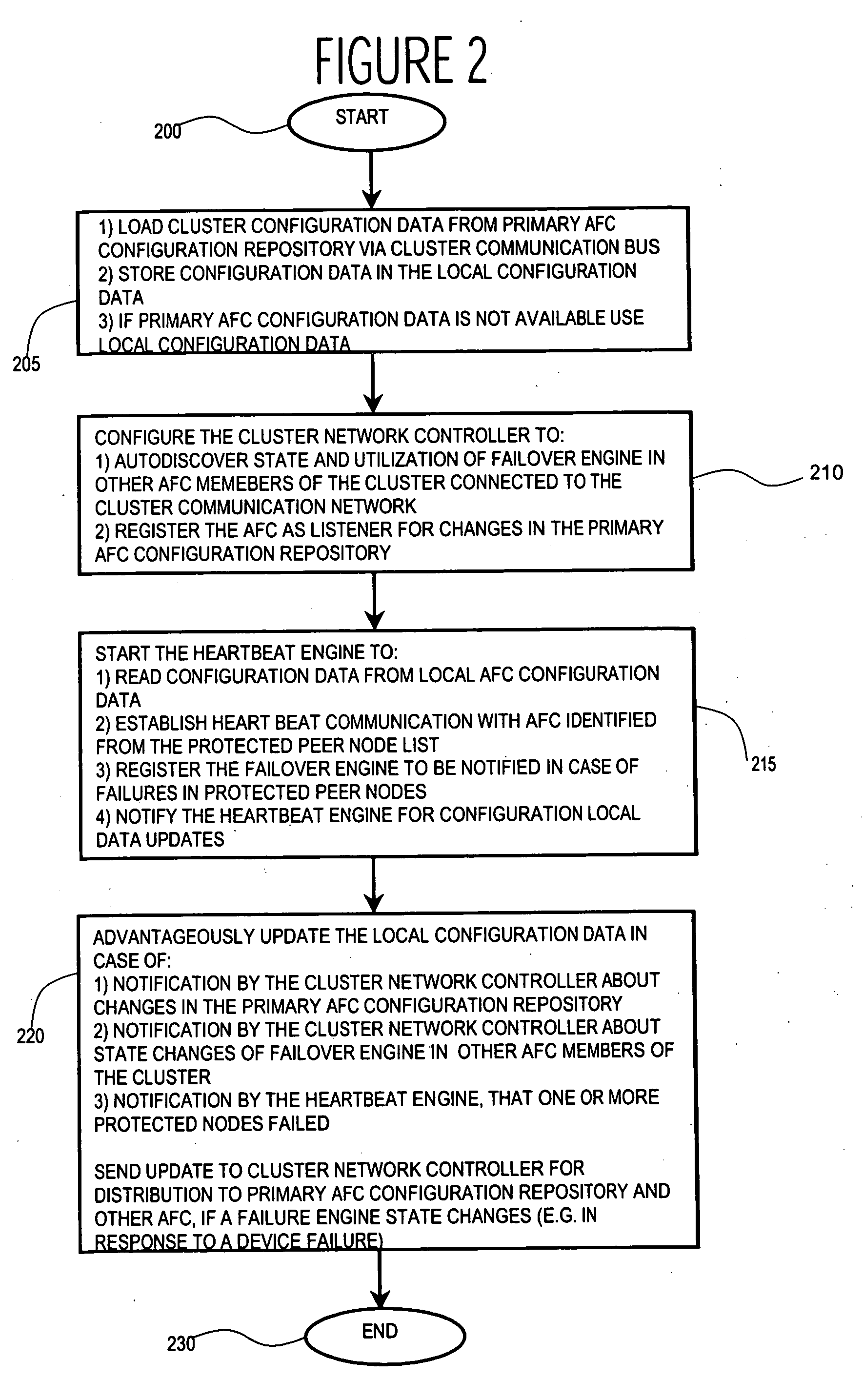
InactiveUS6854069B2Improve portabilityImprove reusabilityError detection/correctionData switching networksNetwork connectionHigh availability
The present invention describes a method and system for achieving high availability in a networked computer system. In particular, the method for achieving high-availability is executed in a networked computer system. The networked computer system includes nodes connected by a network. The method includes using high-availability-aware components to represent hardware and software in the networked computer system, managing the components to achieve a desired level of redundancy, and monitoring health of the networked computer system, including health of components and nodes. The method further includes detecting a failure in the networked computer system. Failures detected by the method include failures of a component and / or node. Finally, the method includes recovering from the failure by performing an appropriate failure recovery procedure.
Owner:ORACLE INT CORP
Virtual private network having automatic reachability updating
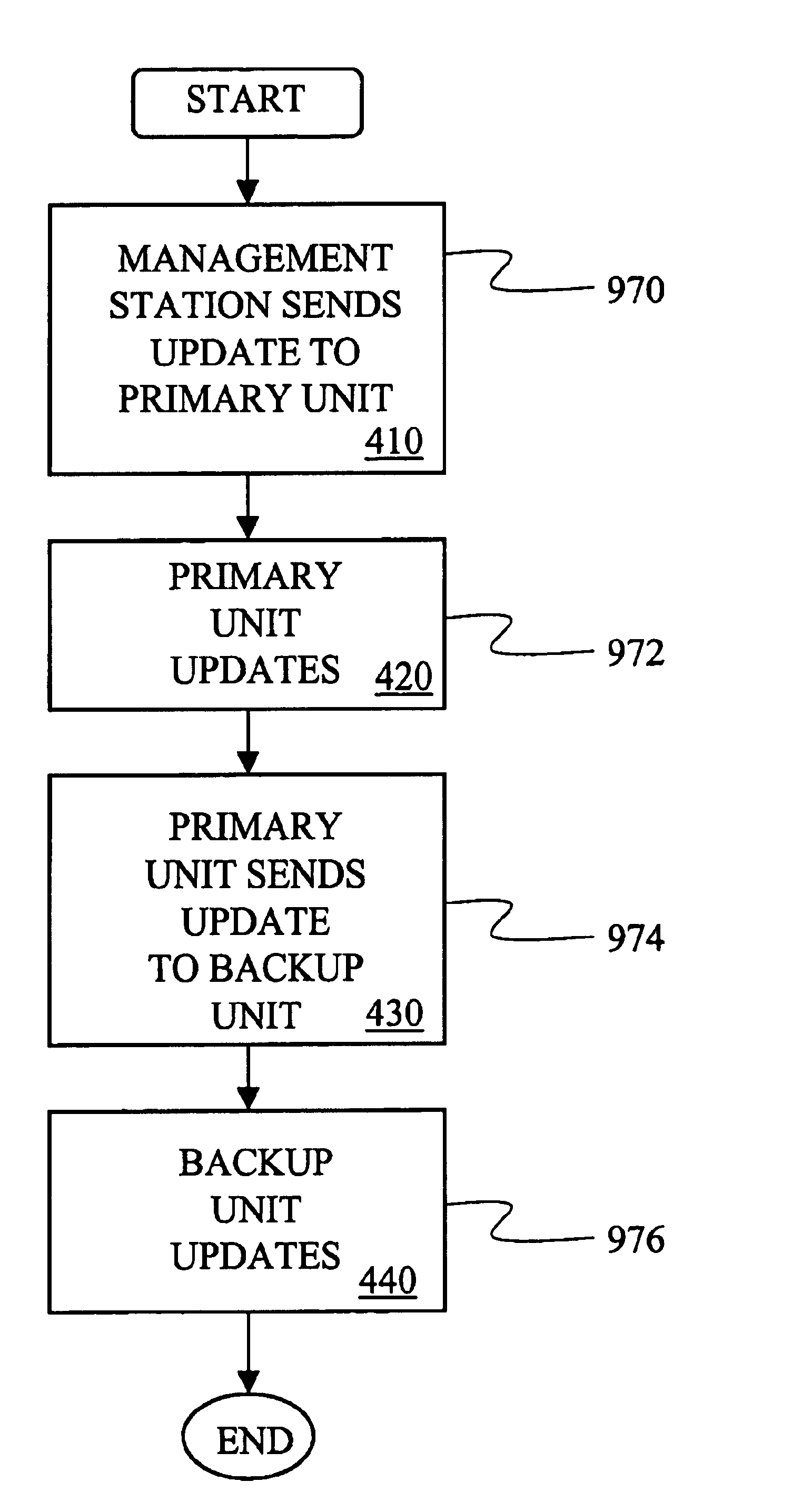
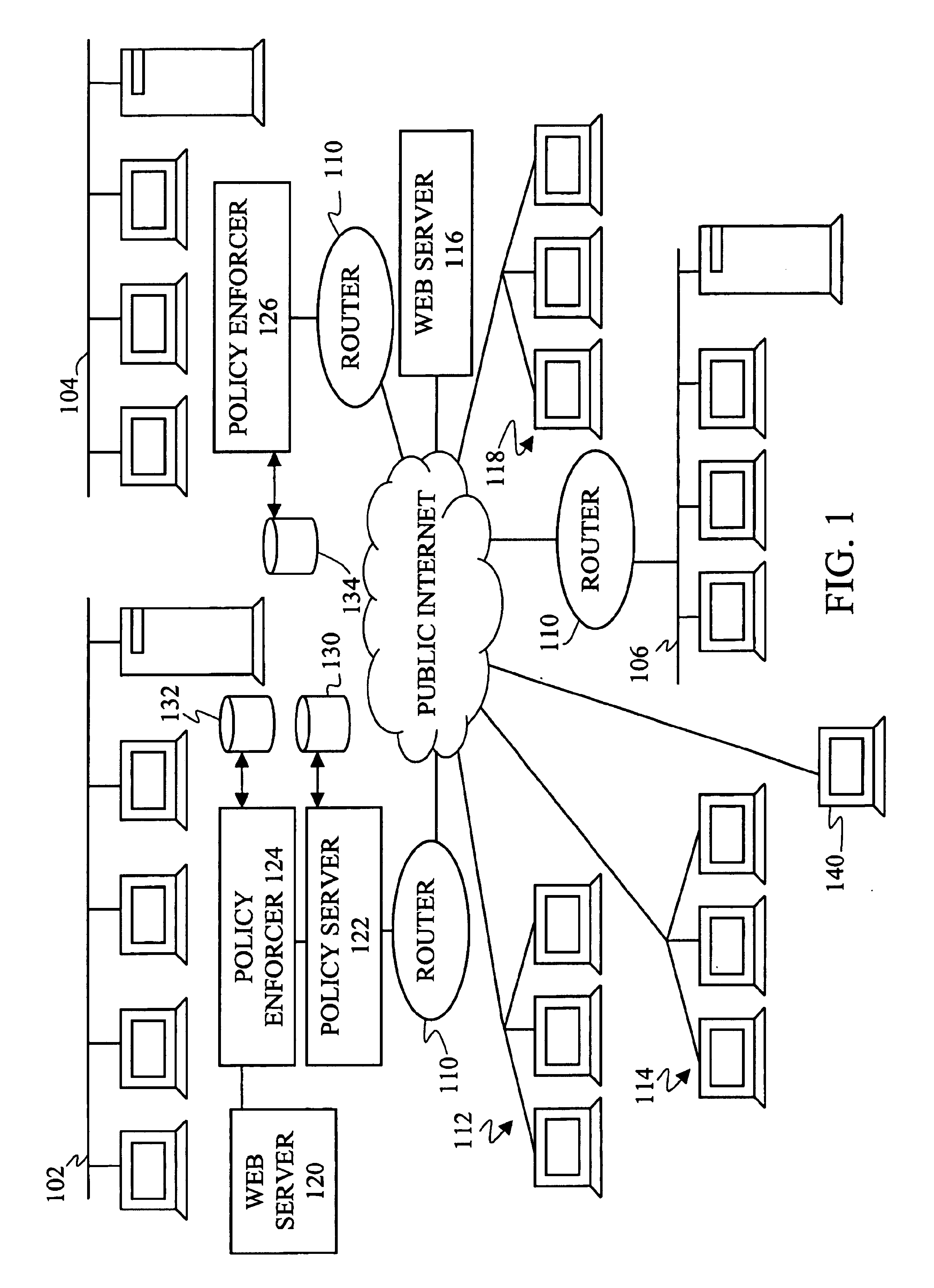
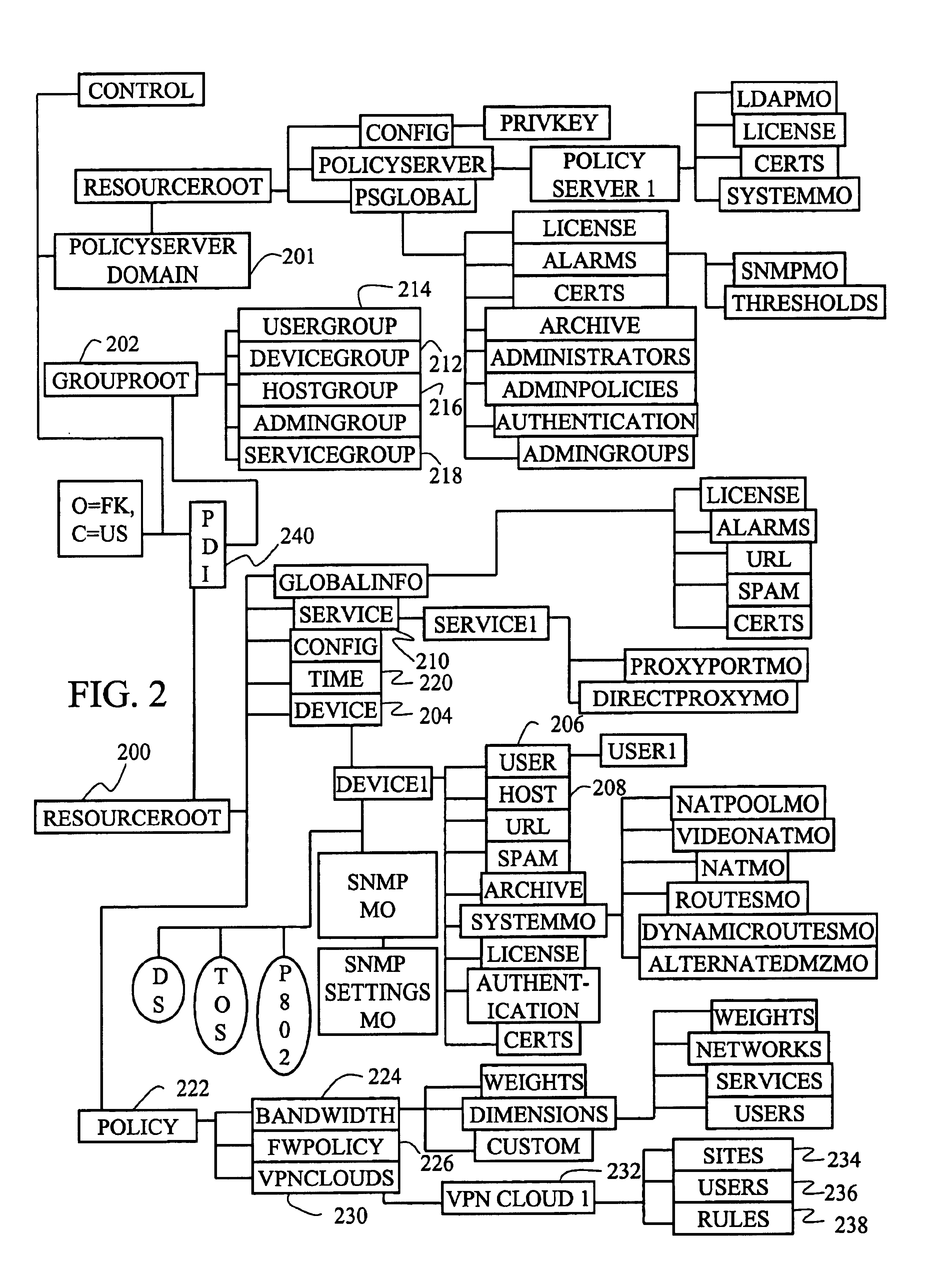
InactiveUS20050138204A1Easy to createCommunication securityEnergy efficient ICTDigital data protectionPrivate networkReachability
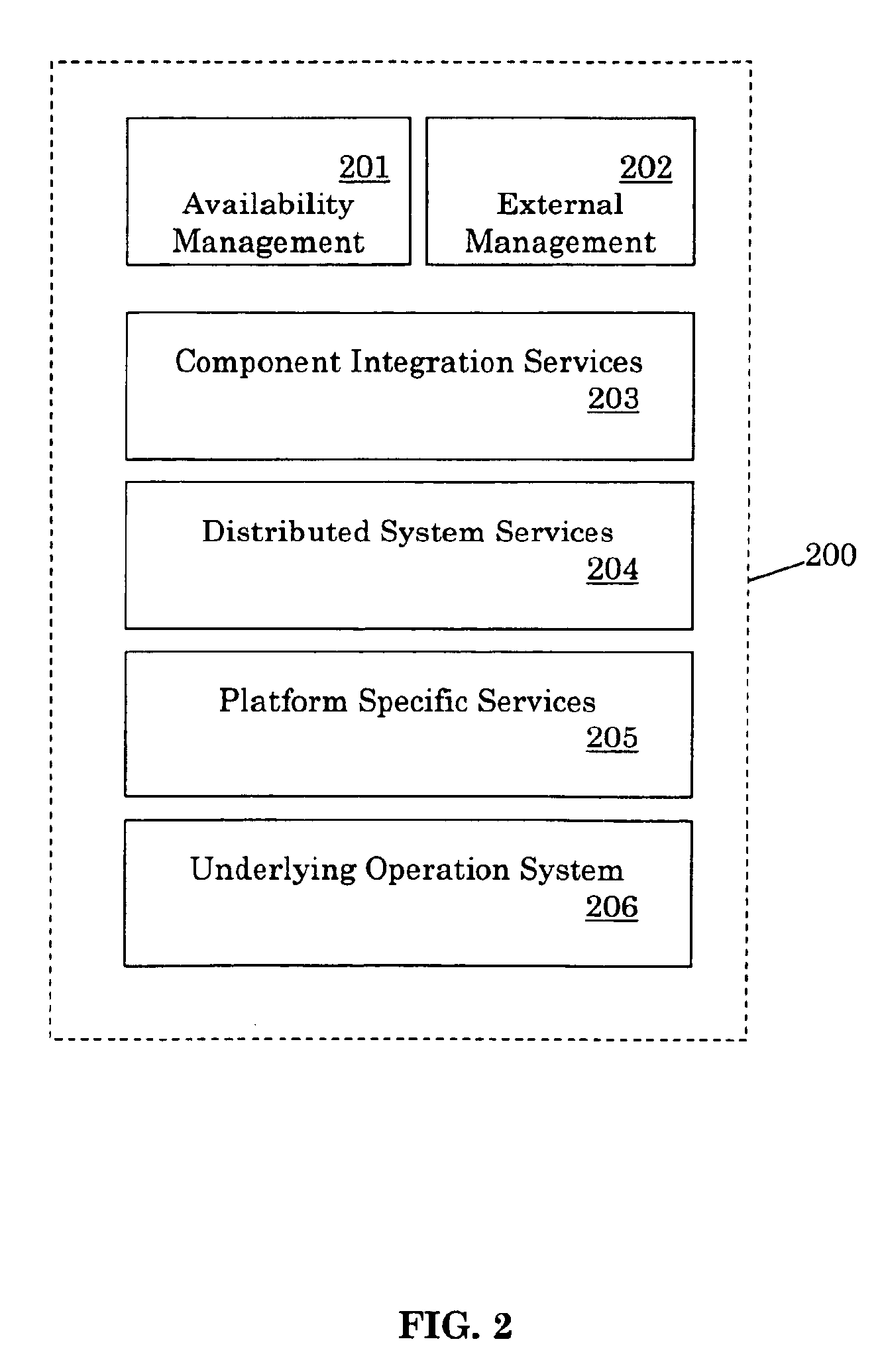
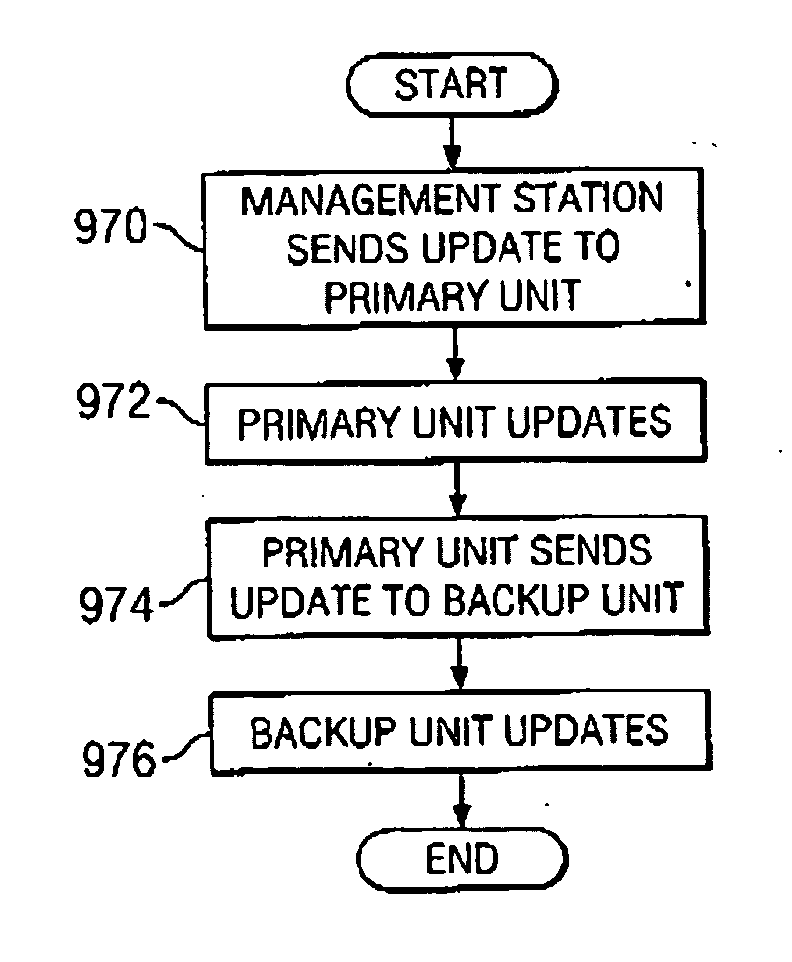
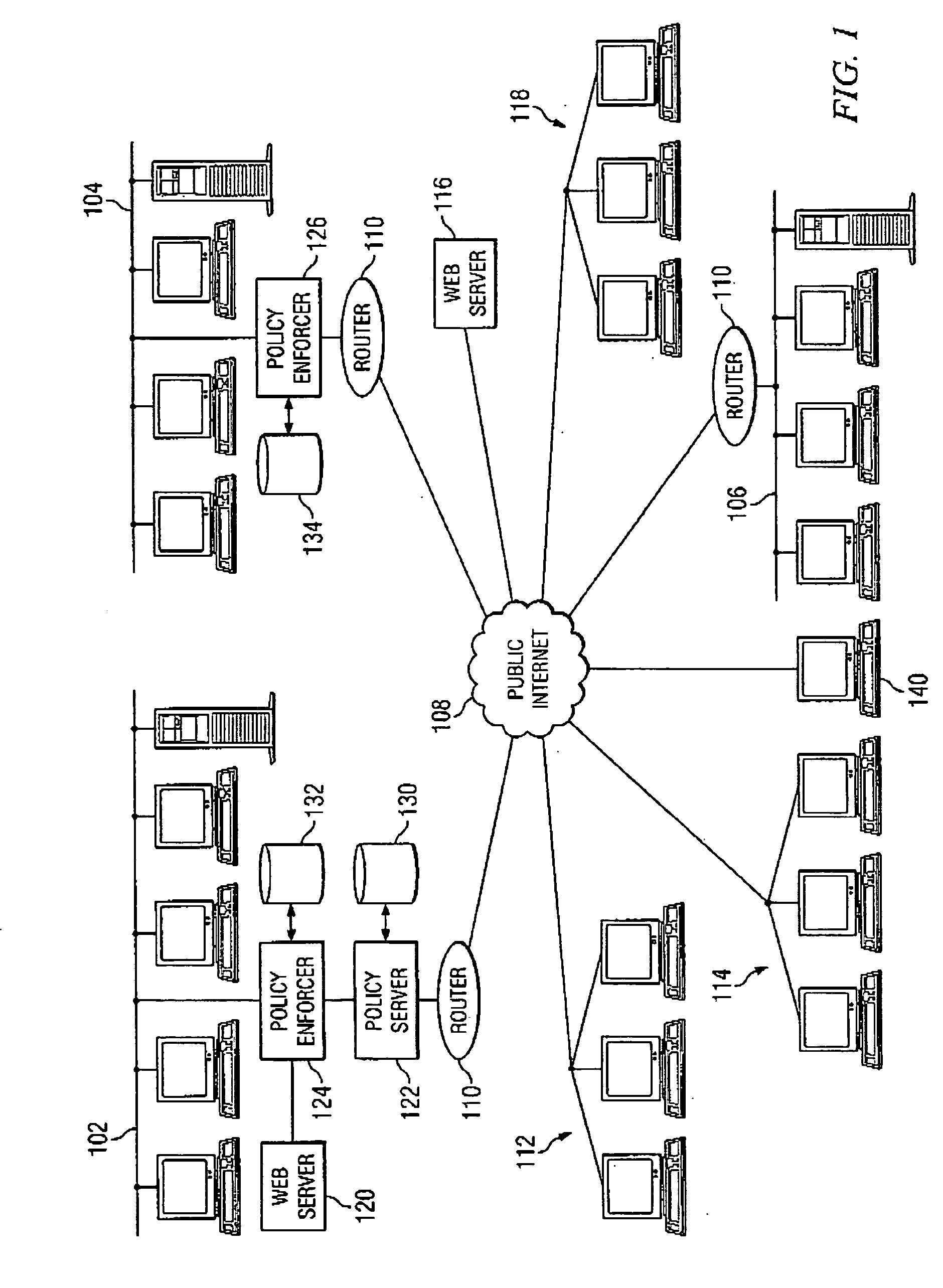
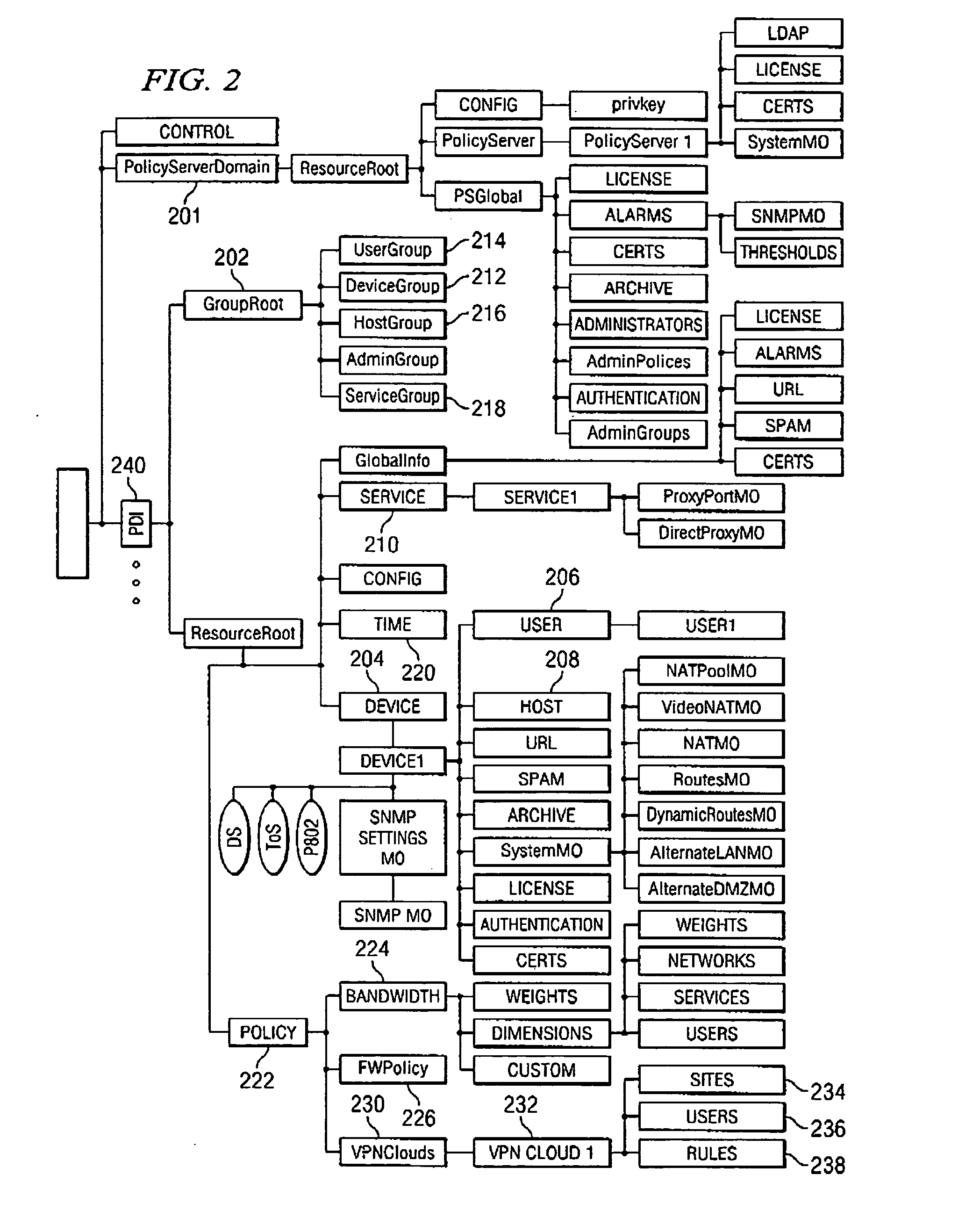
A unified policy management system for an organization including a central policy server and remotely situated policy enforcers. A central database and policy enforcer databases storing policy settings are configured as LDAP databases adhering to a hierarchical object oriented structure. Such structure allows the policy settings to be defined in an intuitive and extensible fashion. Changes in the policy settings made at the central policy server are automatically transferred to the policy enforcers for updating their respective databases. Each policy enforcer collects and transmits health and status information in a predefined log format and transmits it to the policy server for efficient monitoring by the policy server. For further efficiencies, the policy enforcement functionalities of the policy enforcers are effectively partitioned so as to be readily implemented in hardware. The system also provides for dynamically routed VPNs where VPN membership lists are automatically created and shared with the member policy enforcers. Updates to such membership lists are also automatically transferred to remote VPN clients. The system further provides for fine grain access control of the traffic in the VPN by allowing definition of firewall rules within the VPN. In addition, policy server and policy enforcers may be configured for high availability by maintaining a backup unit in addition to a primary unit. The backup unit become active upon failure of the primary unit.
Owner:IYER SHANKER V +3
System and method for storage takeover
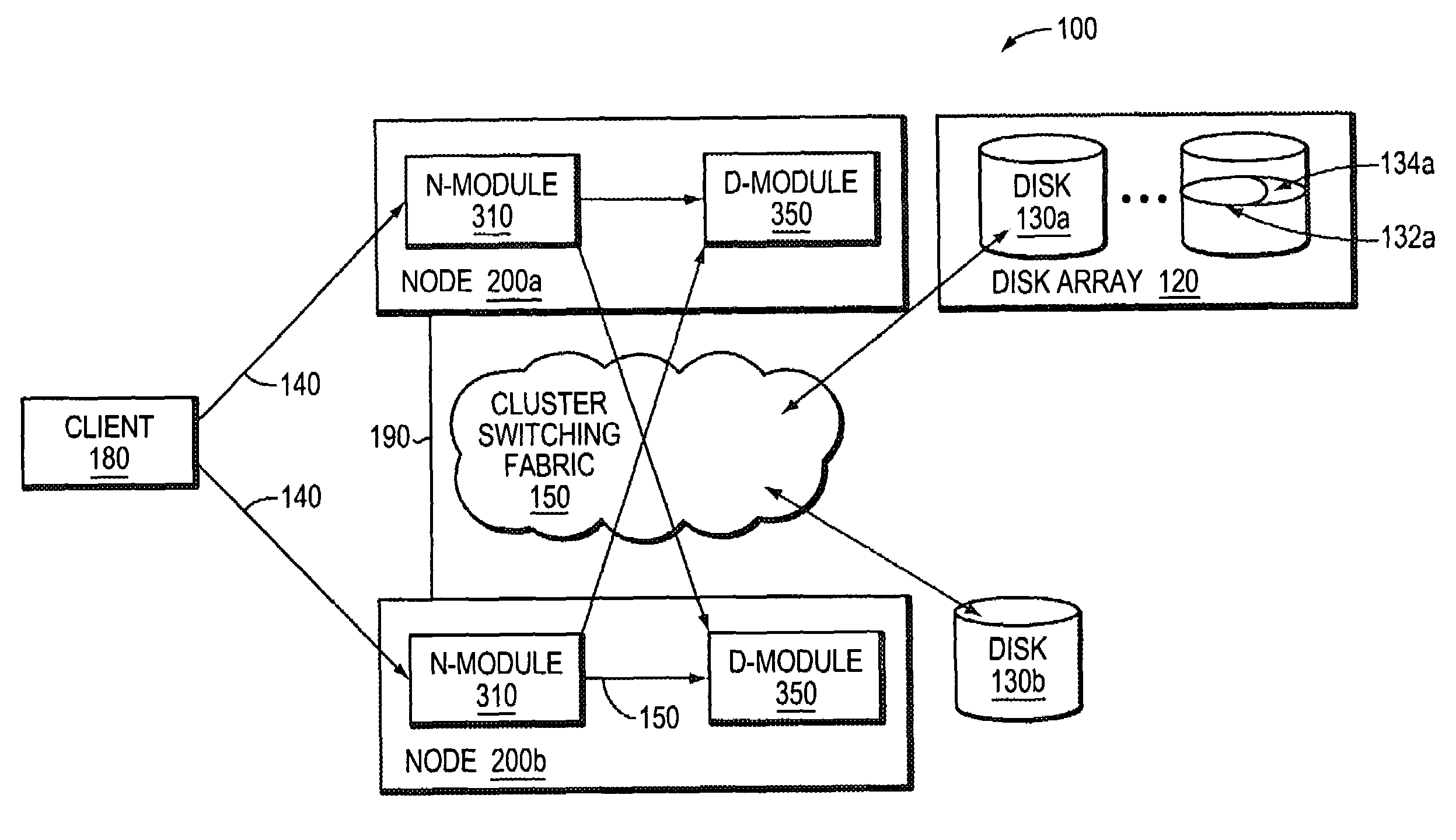
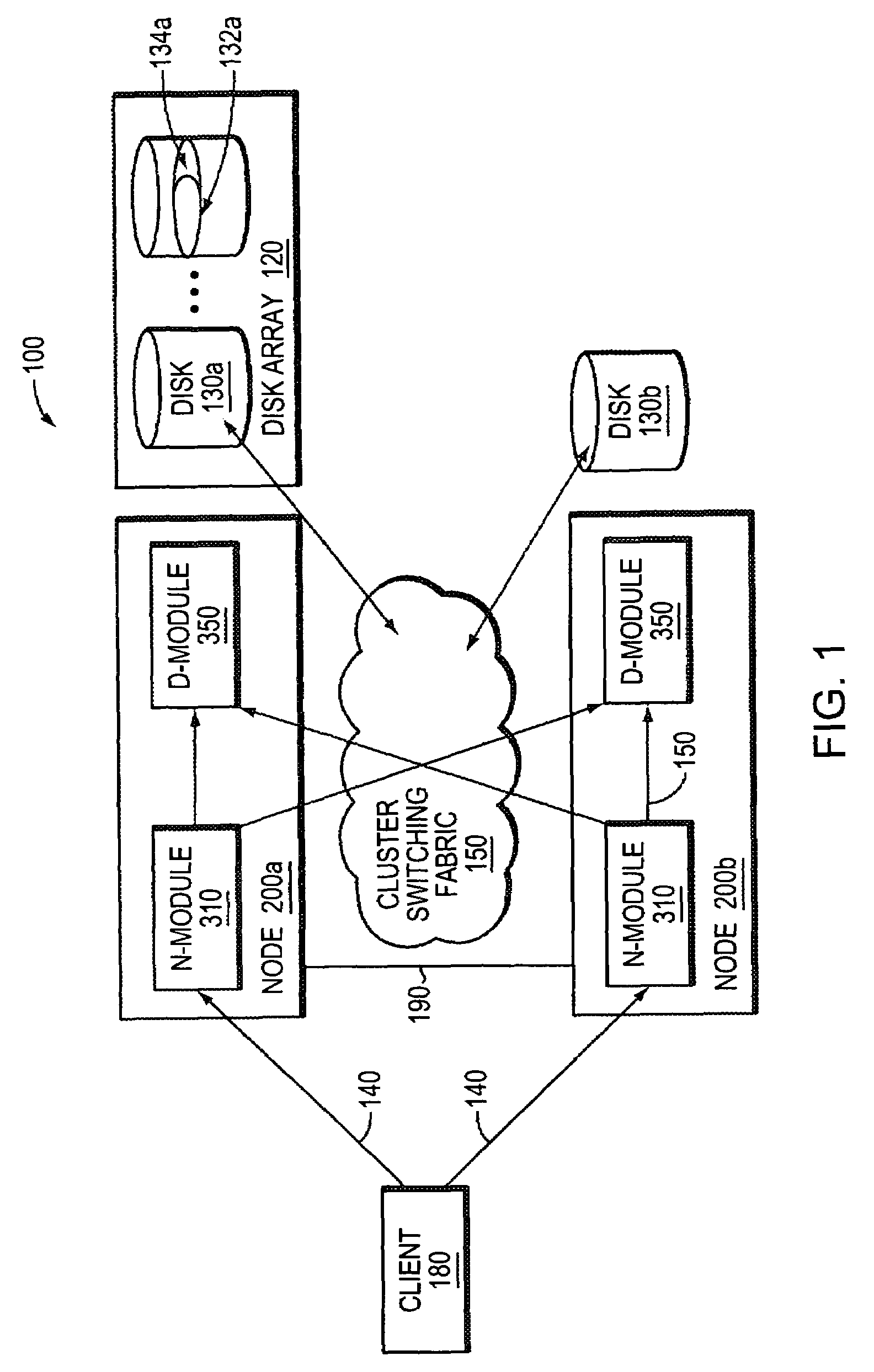
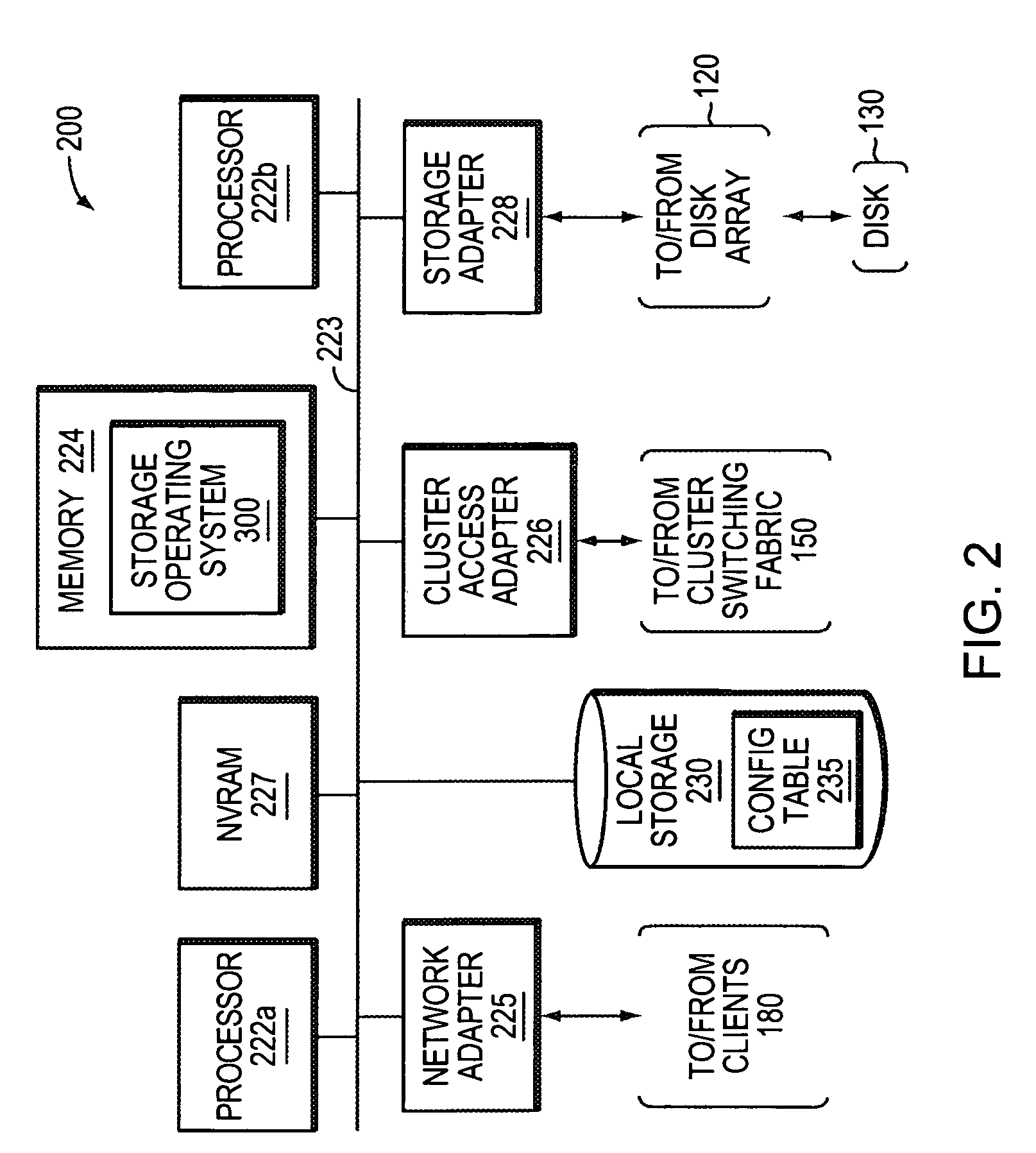
A takeover system and method for high availability in the face of component failures for a multiple-node storage system cluster is provided. When a takeover is triggered either through a loss of cluster heartbeat, or through a user-initiated command, the system of the present invention is configured such that one or more surviving nodes asserts ownership on one or more of the failed node's disks such that all of the disks become locally owned by one of the surviving nodes. An assimilation of the disks into one or more aggregates is performed, and any duplicated file system identification numbers are corrected to avoid errors. As the disks thus appear to be locally owned by the surviving nodes, one or more newly assimilated aggregates are thus exposed to any N-module that interfaces with the surviving nodes.
Owner:NETWORK APPLIANCE INC
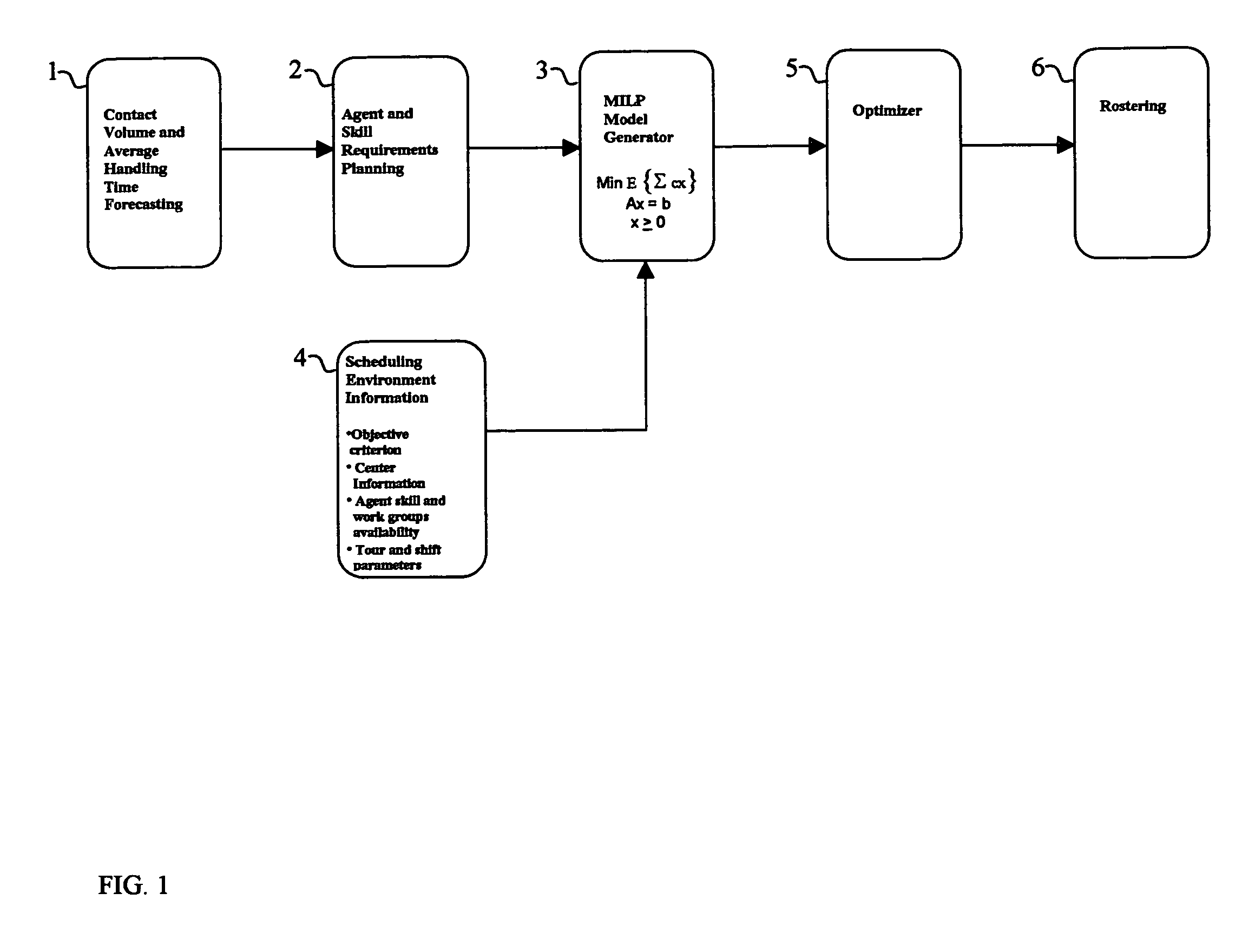
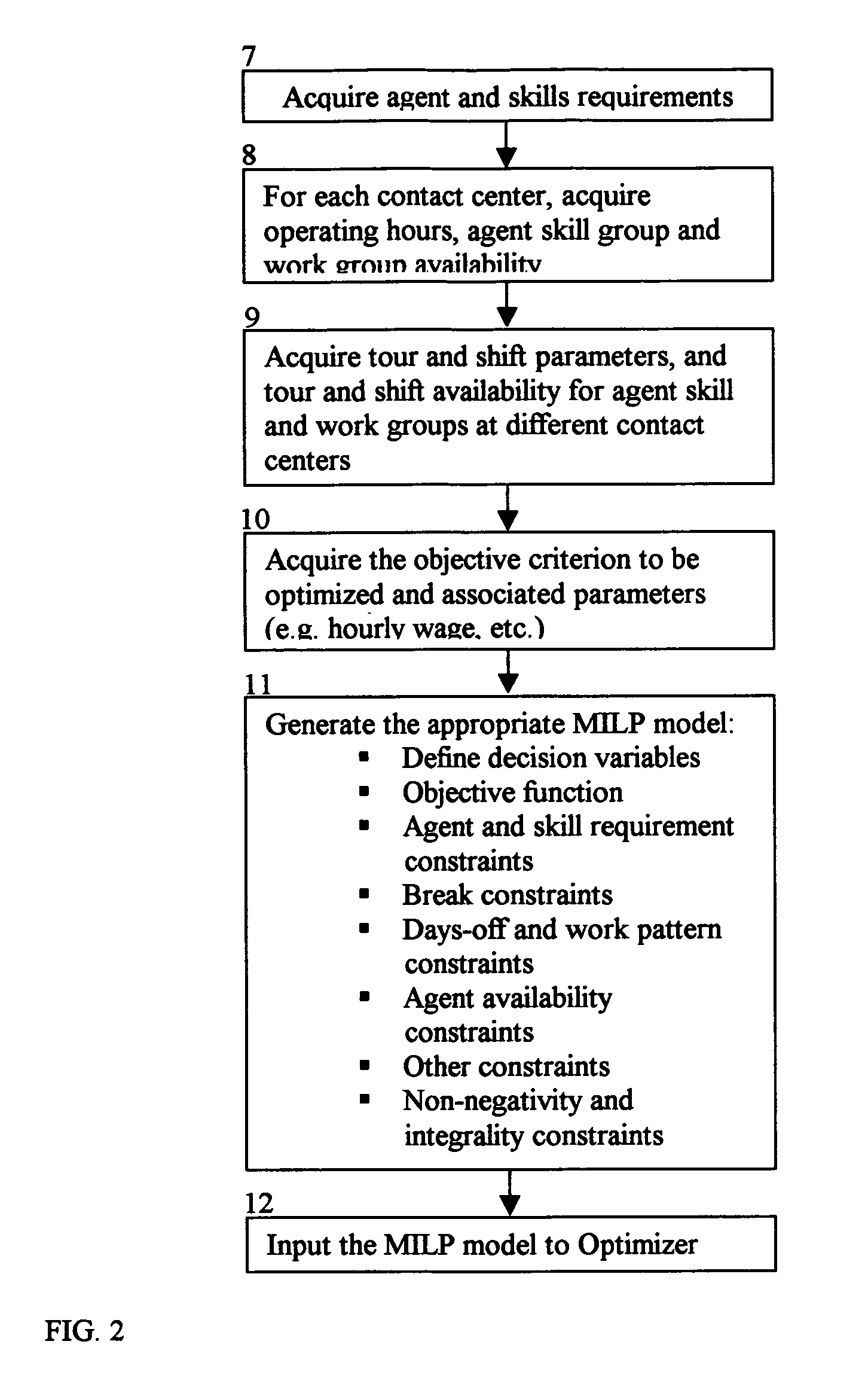
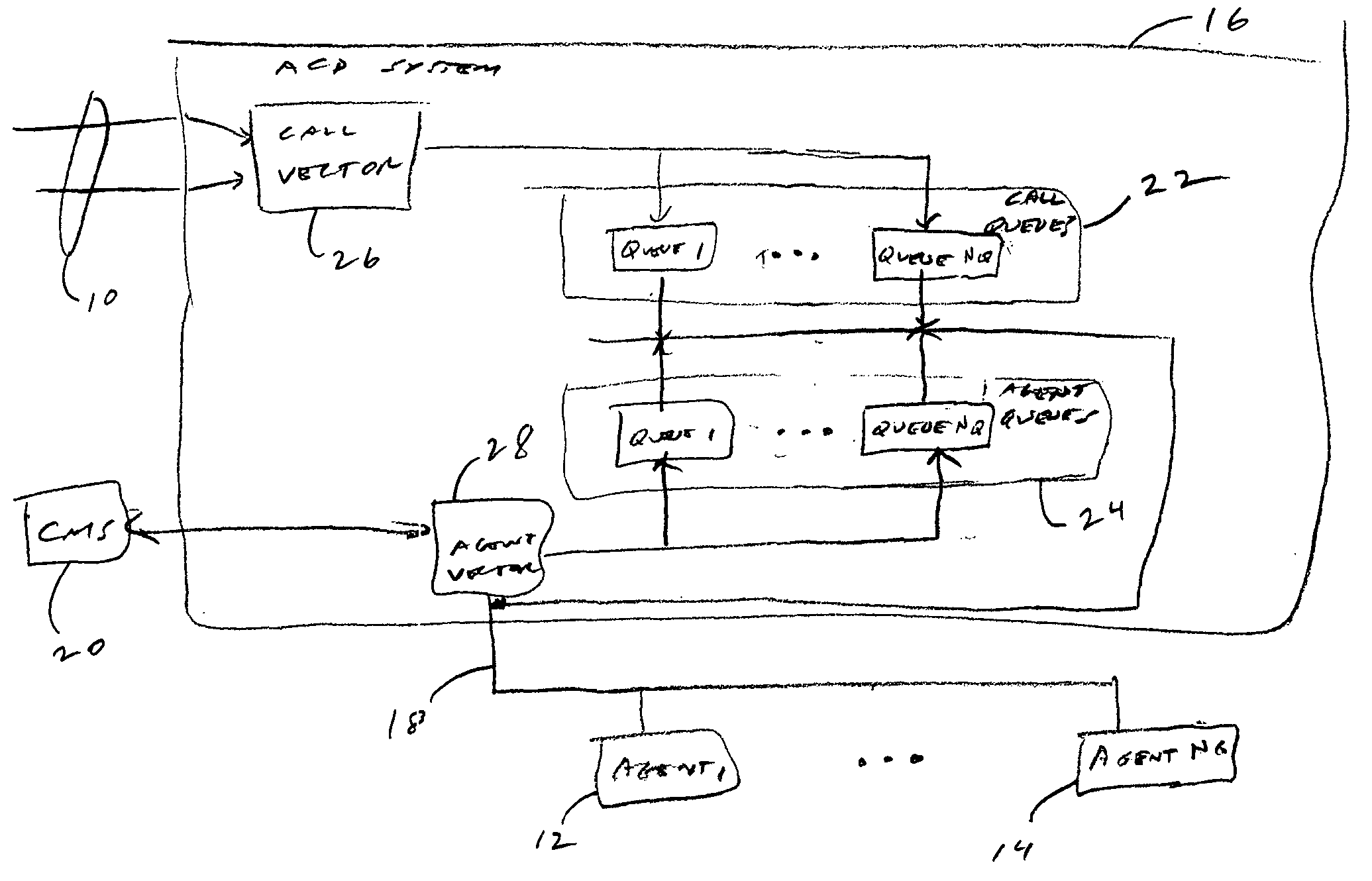
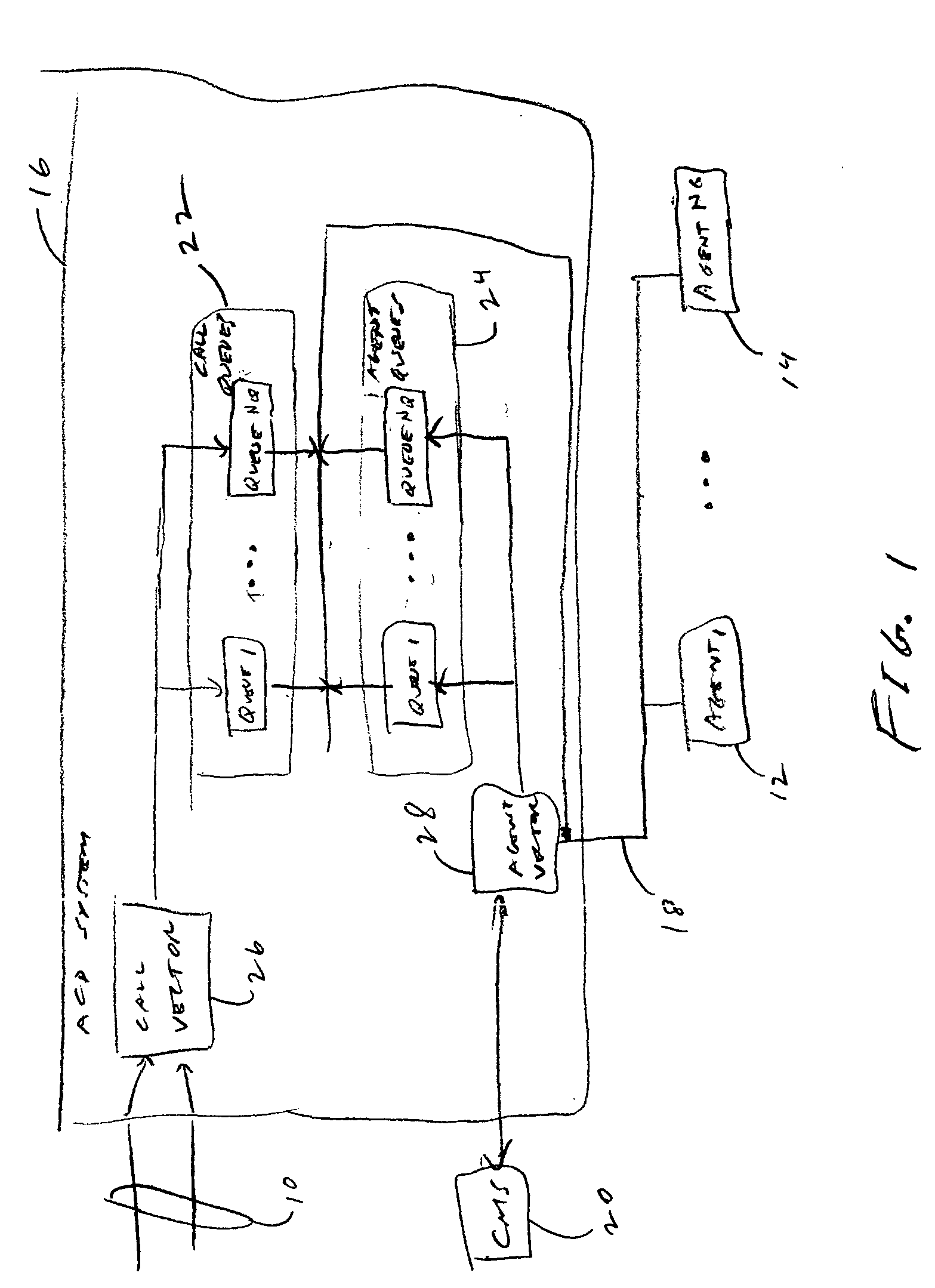
Contact center scheduling using integer programming
ActiveUS7725339B1Easy to solveFavorable objective valueOffice automationSpecial data processing applicationsContact centerWorkforce scheduling
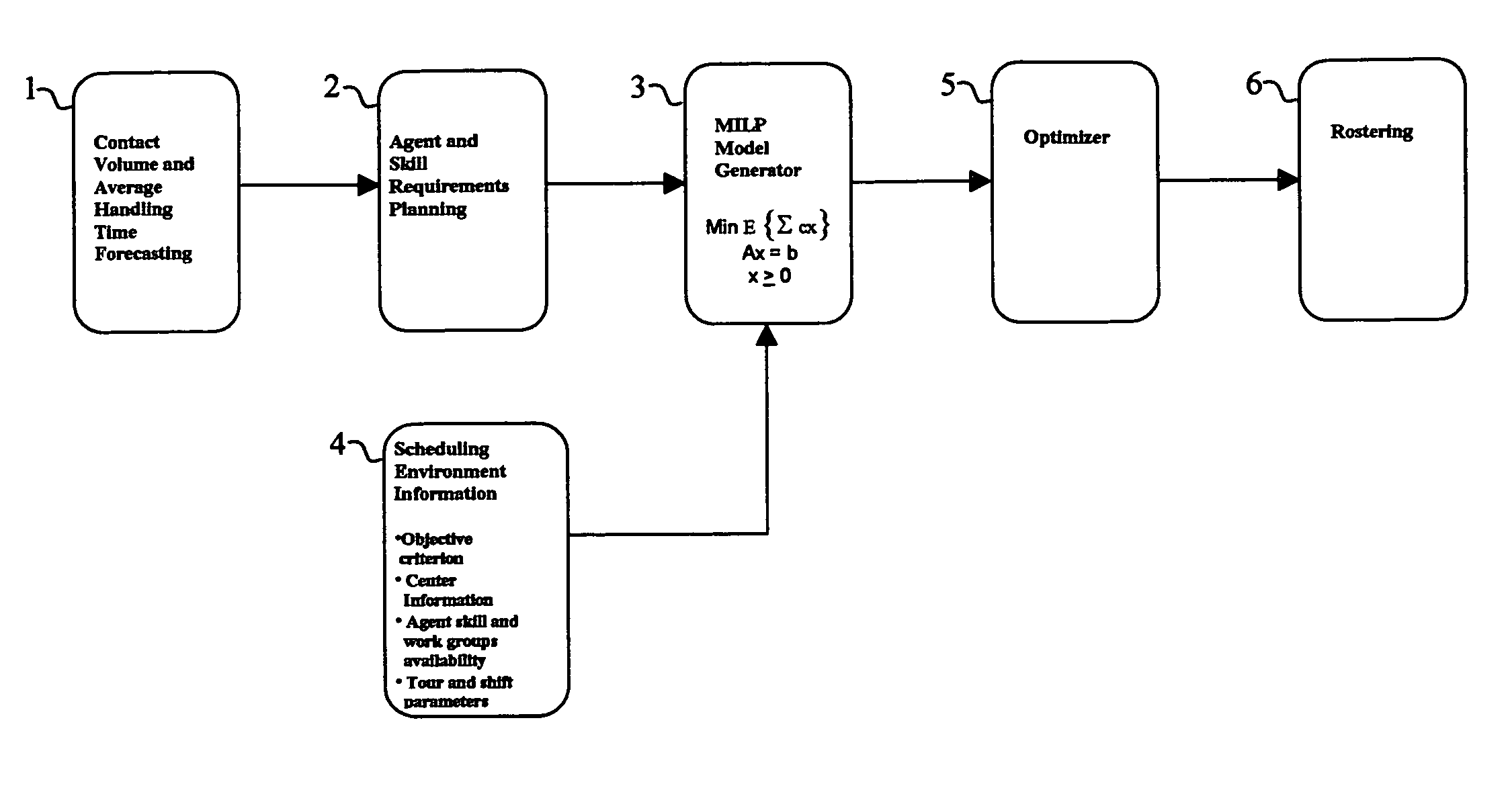
The present invention relates to a method for workforce scheduling in which workload and workload types vary during scheduling period. The method acquires agent and skill requirements for all periods and contact types; acquires the contact center information including agent skill groups, agent work groups, tour and shift scheduling rules, agent availability, objective criterion to be optimized and its parameters; develops a Mixed Integer Linear Programming (MILP) model for the scheduling environment; applied an optimization algorithm that uses the Branch and Bound algorithm with a Rounding Algorithm to improve performance; and locates a globally optimal or near optimal workforce schedule in total cost or paid time or agent satisfaction. Detailed schedules may be developed by assigning daily shifts to work patterns, and breaks scheduled to daily shifts.
Owner:INCONTACT
Object model for network policy management
InactiveUS6944183B1Simplified managementEnergy efficient ICTDigital computer detailsNetwork managementAdaptive routing
Owner:ALCATEL-LUCENT USA INC
Failover processing in a storage system
InactiveUS20060117212A1Improve usabilityInput/output to record carriersDigital data processing detailsFault toleranceFailover
Failover processing in storage server system utilizes policies for managing fault tolerance (FT) and high availability (HA) configurations. The approach encapsulates the knowledge of failover recovery between components within a storage server and between storage server systems. This knowledge includes information about what components are participating in a Failover Set, how they are configured for failover, what is the Fail-Stop policy, and what are the steps to perform when “failing-over” a component.
Owner:NETWORK APPLIANCE INC
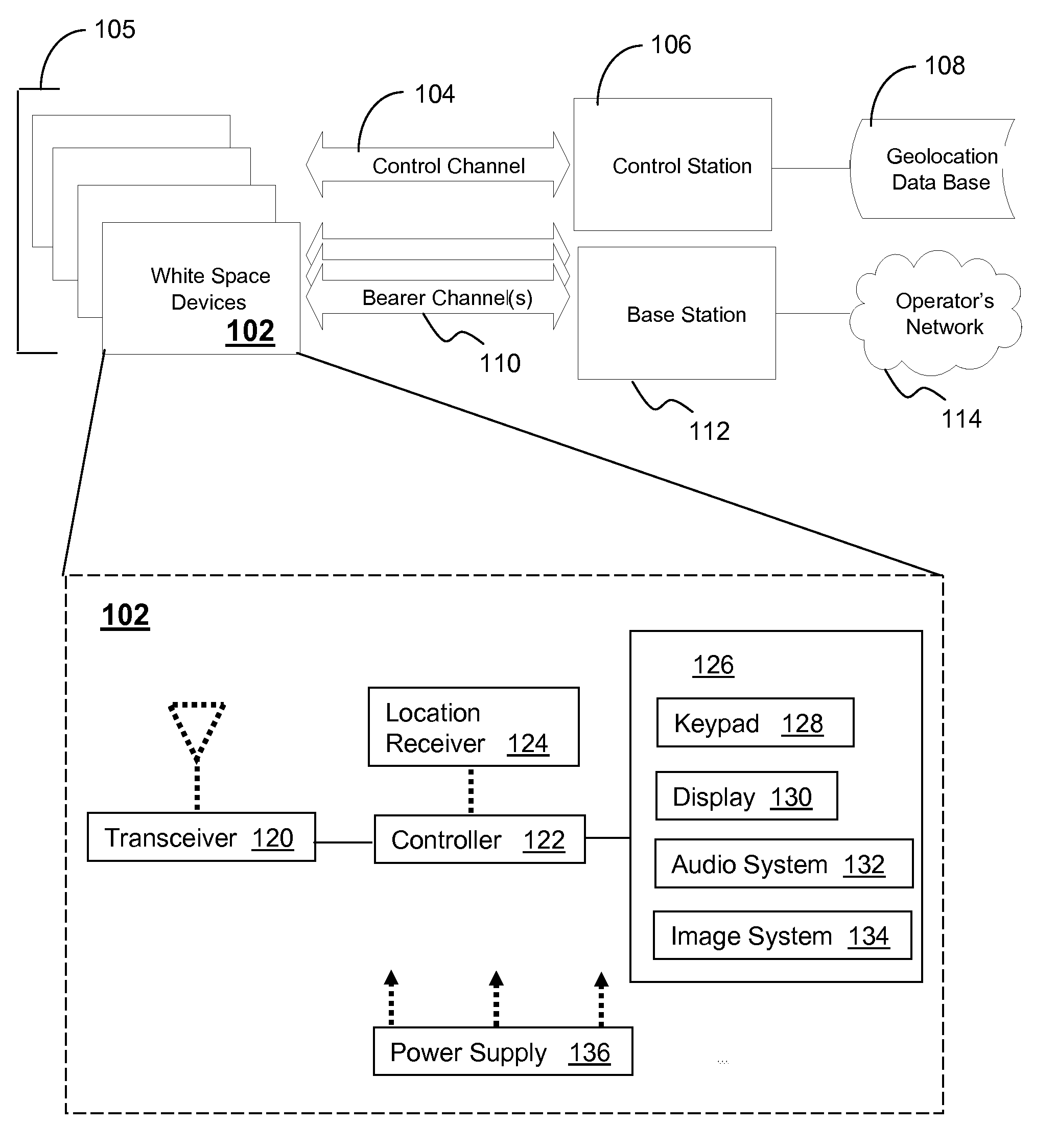
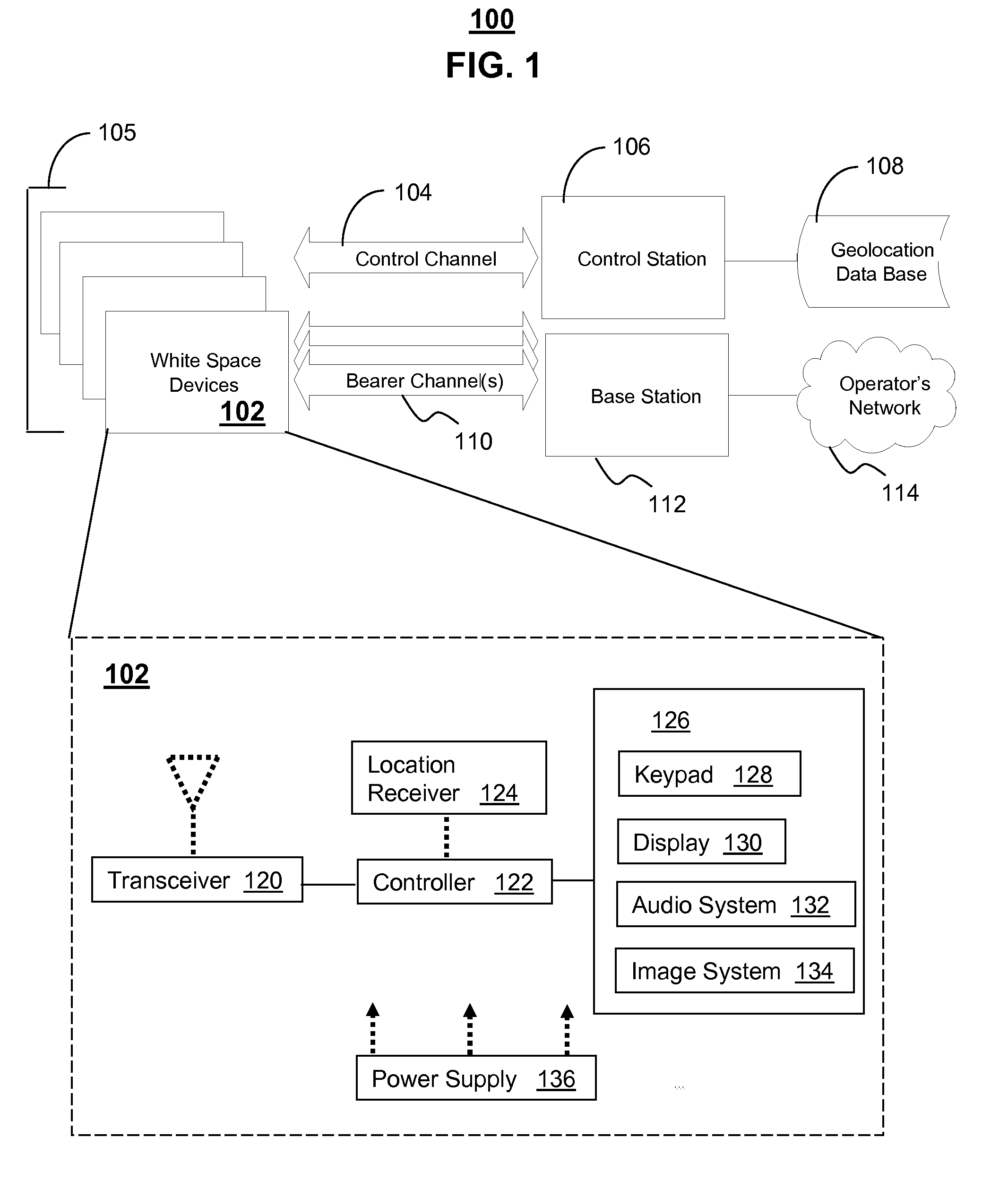
System and method for dynamic frequency assignment
White space devices (102) are unlicensed radiofrequency devices that must have certain capabilities in order to avoid harmful interference to licensed operations. In general, they must be location-aware, must be able to contact a geolocation database (108) and may not operate without receiving a positive control signal. A number of white space devices can use a control channel (104) to communicate with a control station (106). In addition to meeting the geolocation and positive control requirements given above, the control station coordinates the channels used by the white space devices so as to minimize (308) their aggregate interference. In one embodiment, a control channel uses a separate frequency band with high availability and reliability but low throughput. Embodiments optimize channel assignments where the potential interference depends on the mutual distances between the white space devices. Potential interference reductions of 20-30 dB have been found in simulations. Other embodiments are disclosed.
Owner:PROGENY LMS
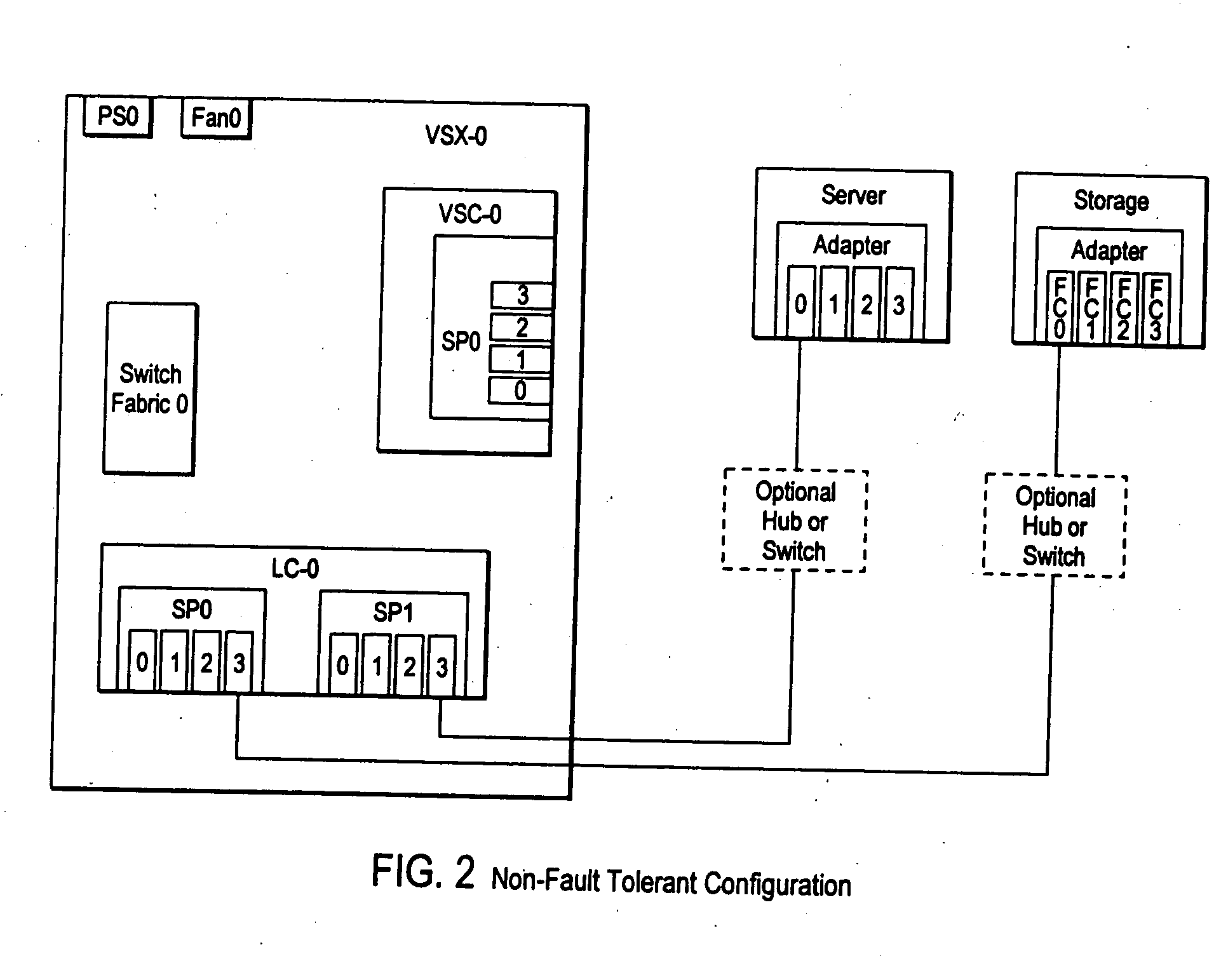
Fault tolerant shared system resource with communications passthrough providing high availability communications
InactiveUS6865157B1Improve usabilityError preventionTransmission systemsRouting tableHigh availability
A communications passthrough mechanism for high availability network communications between a shared system resource and clients of the system resource. The system resource includes a control / processing sub-system including multiple peer blade processors. A port of each blade processor is connected to each client / server network path and each client is connected to a corresponding port of each blade processor. Each blade processor includes a network fault detector exchanging beacon transmissions with other blade processors through corresponding blade processor ports and network paths. Each blade processor includes response generator responsive to a failure to receive a beacon transmission from a failed port of an other blade processor for redirecting the client communications to the failed port on the other blade processor to the corresponding port of the blade processor. A path manager in the blade processor is responsive to operation of the response generator for modifying the communications routing table to correspond with the redirection message to route the client communications to the failed port of the other blade processor to the other blade processor through the inter-processor communications link. Each blade processor may also include an inter-blade communications monitor for detecting a failure in the inter-processor communications link between the blade processor and another blade processor, reading the communications routing table to select a functional network communications path to a port of the other blade processor, and modifying the communications routing table to redirect inter-processor communications to the selected functional network communications path.
Owner:EMC CORP
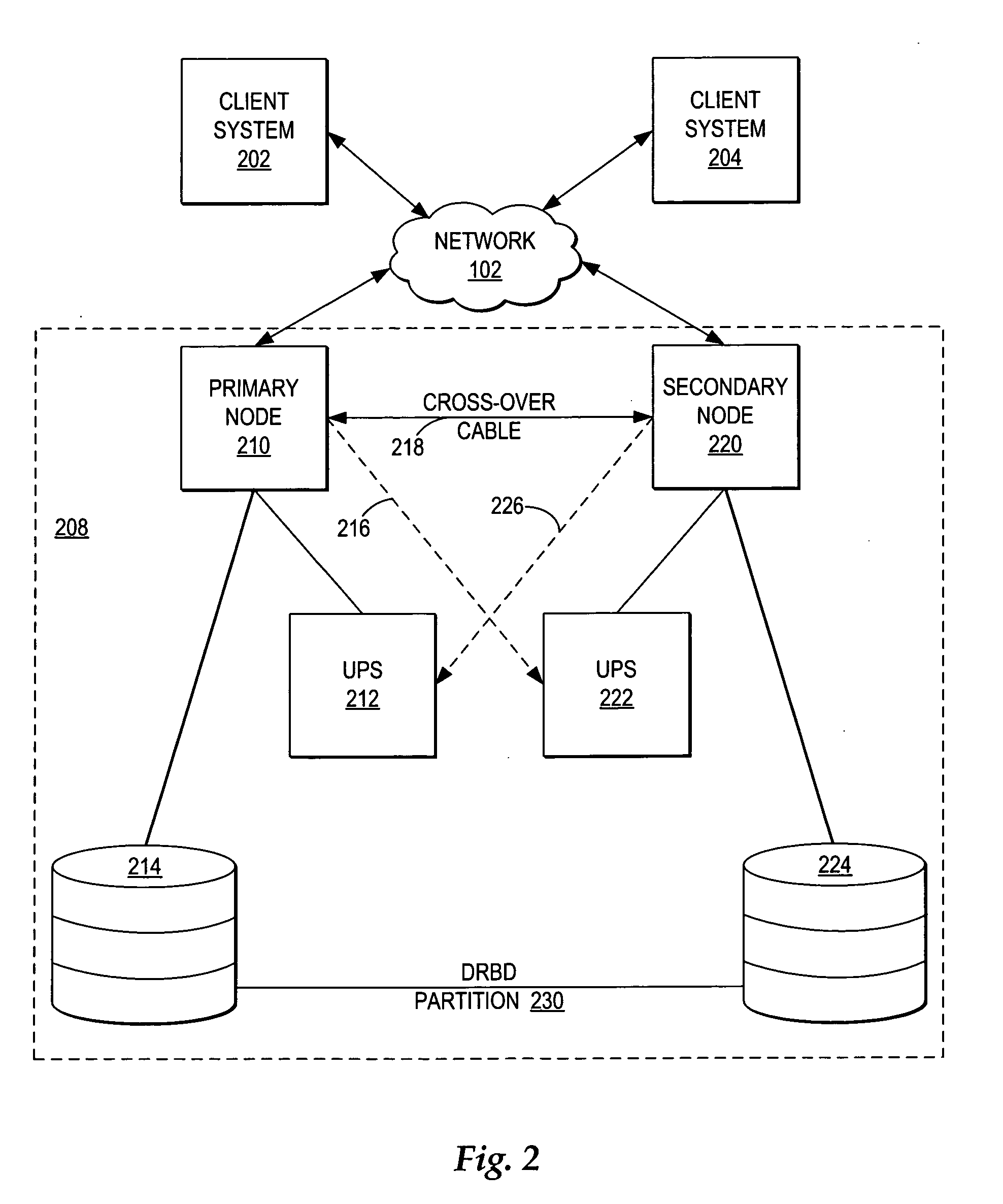
Managing failover of J2EE compliant middleware in a high availability system
InactiveUS20050172161A1Short recovery timeMinimal data lossRedundant hardware error correctionFailoverWeb application
A method, system, and program for managing failover of J2EE compliant middleware in a high availability system are provided. A primary node and a secondary node each run the same J2EE compliant middleware stack comprising layers including a load balancer, a web server, a web application server, a message control server, a monitoring server, and a database control server. In the primary node, all layers are active. In the secondary node, part of the layers are active and part of the layers are in standby. A data replication partition shared between the primary node and the secondary node includes persistent resource data accessible to a selection of the layers of the primary node. A heartbeat controller monitors each node, including the middleware stack, and upon detection of a failure, controls transfer of the services provided by the primary node to the secondary node by transferring virtual IP addresses from the primary node to the secondary node, remounting the data replication partition for access by the secondary node, and activating the standby layers which require access to the data in the data replication partition.
Owner:IBM CORP
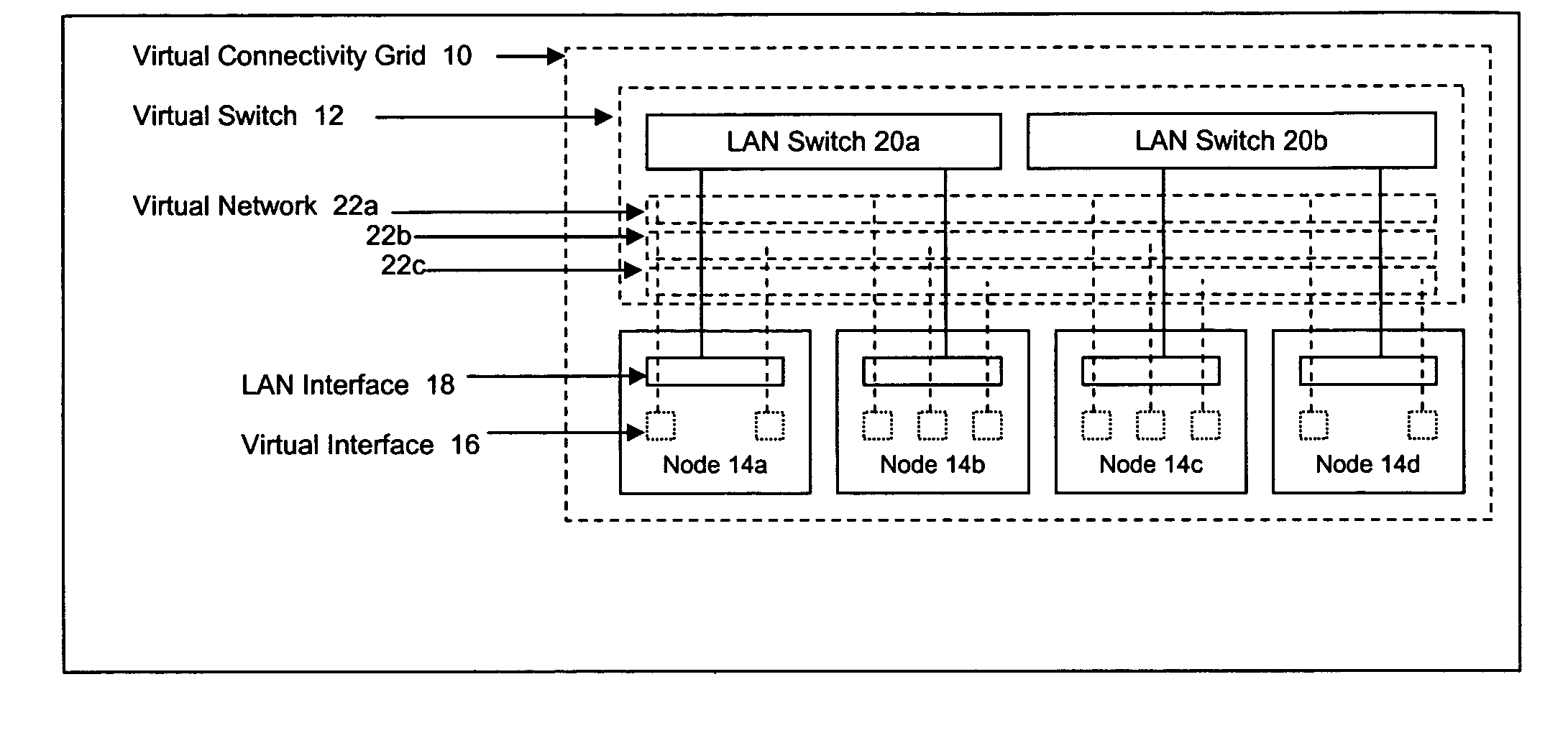
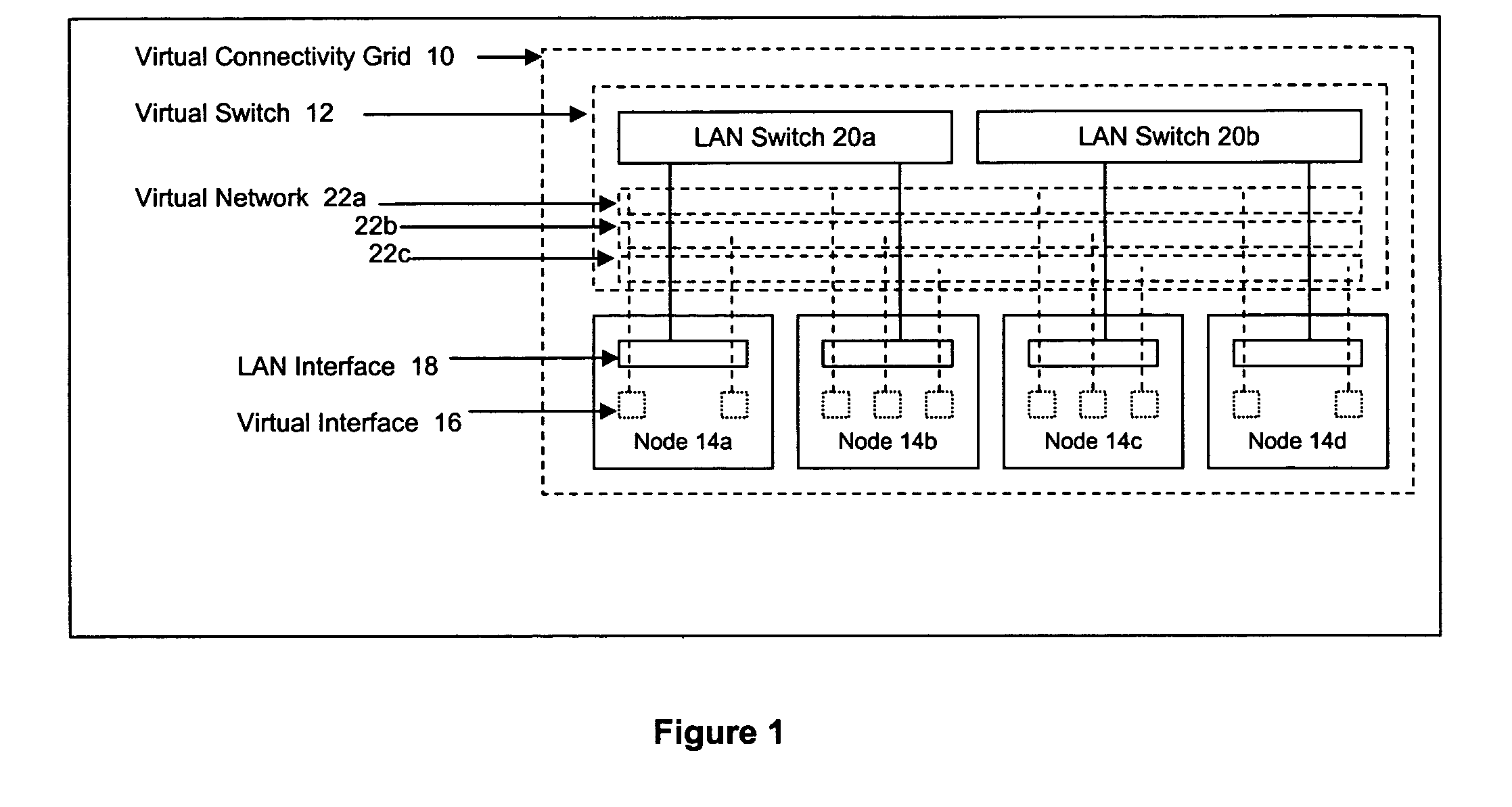
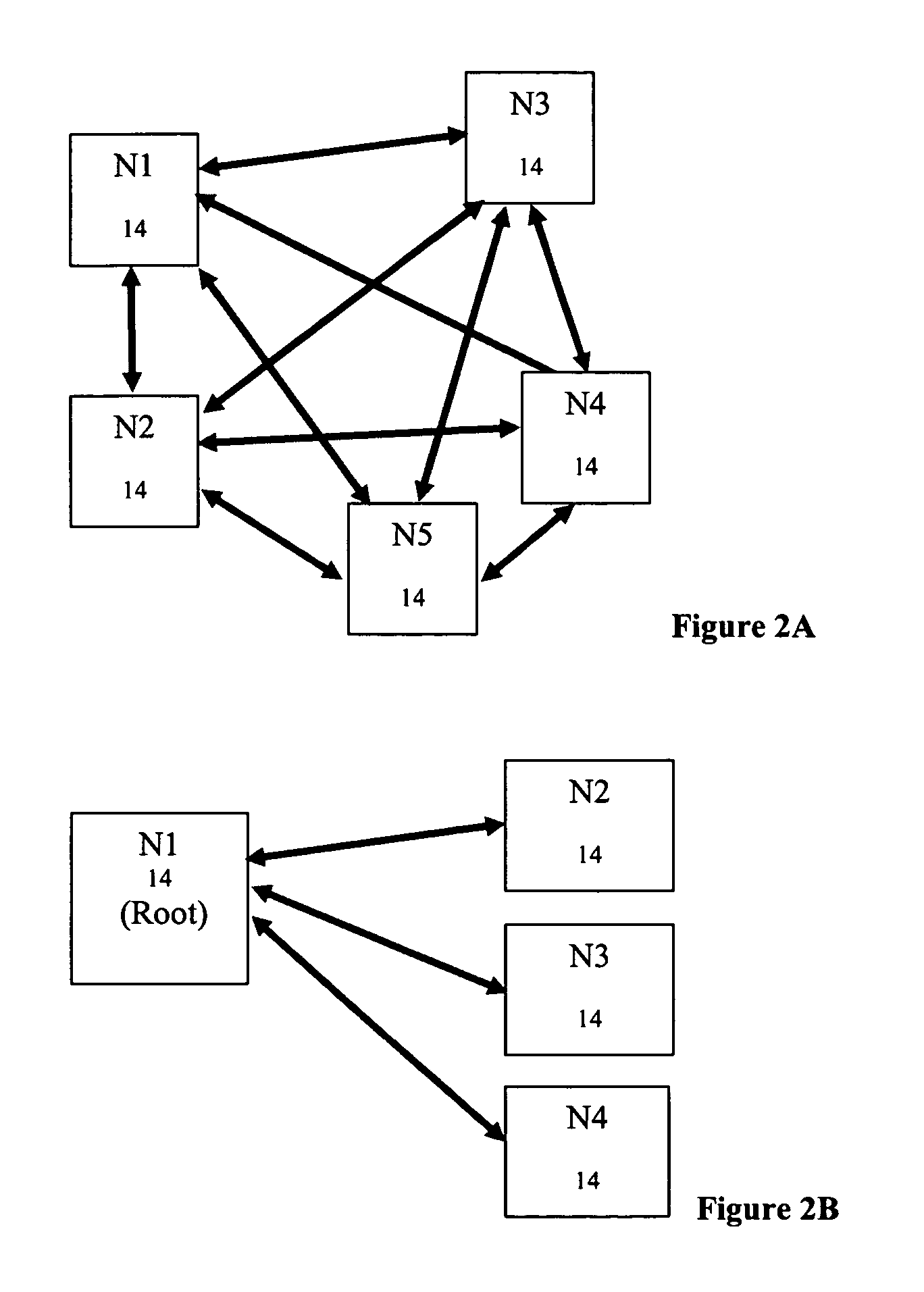
Method and apparatus for achieving dynamic capacity and high availability in multi-stage data networks using adaptive flow-based routing
ActiveUS20050091396A1Multiplex system selection arrangementsError preventionSystems managementHigh availability
Methods and systems for determining paths for flows within a multi-stage network made up of clusters of processing nodes. The flow paths may be determined without knowledge of whether or not packets of a particular flow will actually traverse specific ones of the clusters within the multi-stage network. In various implementations, the nodes of the multi-stage network may be coupled to one or more physical network switches through respective physical interfaces and a virtual connectivity grid superimposed thereon and configured through the use of a flow routing framework and system management framework to group the nodes into a number of clusters. The nodes of each cluster are configured to perform similar packet processing functions and the clusters are interconnected through virtual networks to which the nodes are communicatively coupled via virtual interfaces overlaid on top of the physical network interfaces.
Owner:DELL PROD LP
High availability multi-tenant feature
InactiveUS20050025303A1Special service for subscribersDigital computer detailsConfigfsHigh availability
A multi-tenant call-center system and method of configuring and monitoring. The system includes a plurality of telephone lines, a plurality of agent positions, a call distribution system connecting the plurality of agent positions to the telephone lines, a call management system connected to the call distribution system. The call management system includes a storage system of storing database files, processes and configuration files, a memory system for processing the database files and configuration files and running selected processes stored on the storage system, a configuration server for reading the configuration file and starting selected processes according to multi-tenant inter-process dependencies and process priorities, and a monitor process for monitoring each of the started processes according to a respective monitor frequency in the configuration file.
Owner:ALCATEL-LUCENT USA INC +1
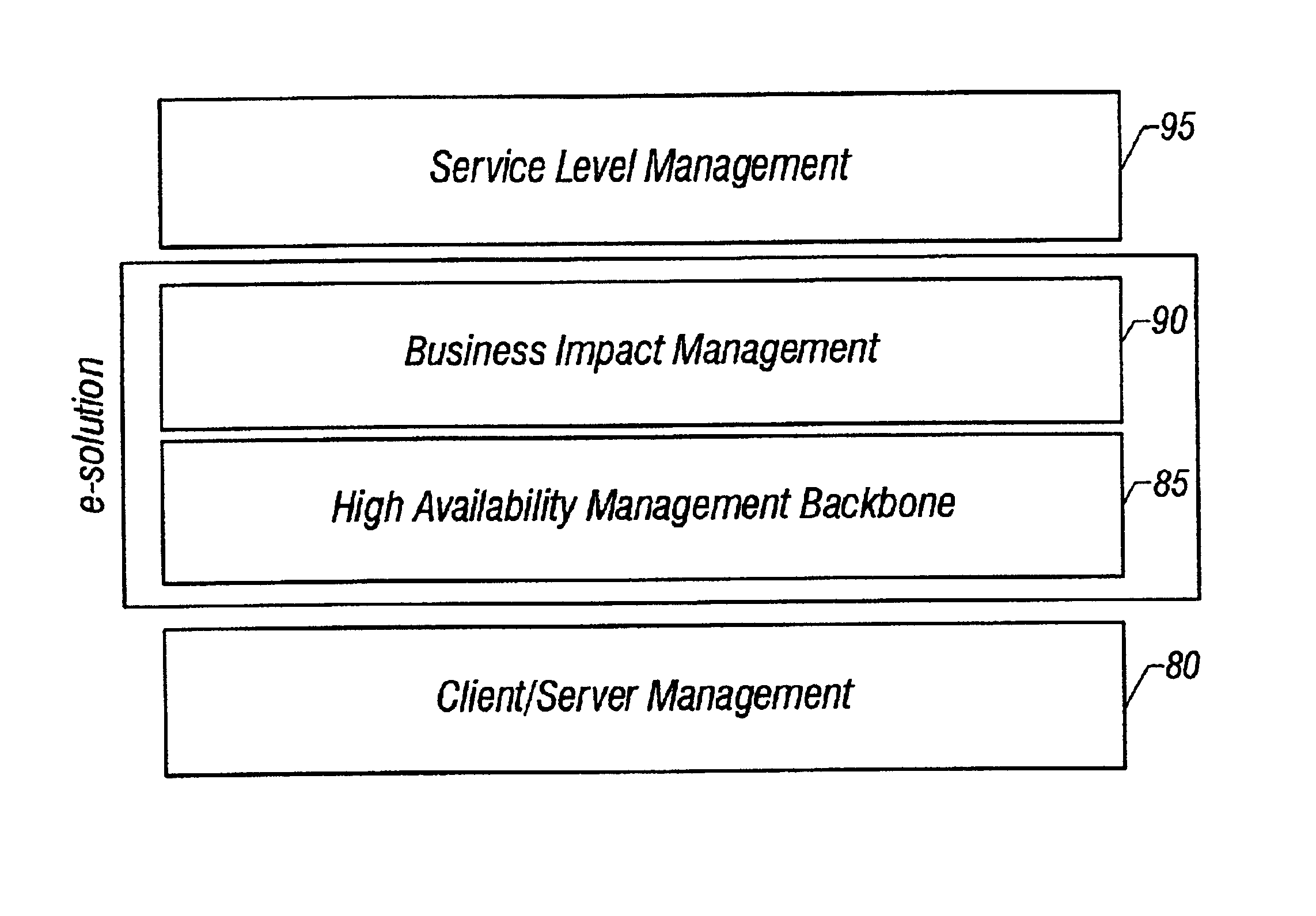
System and method of enterprise systems and business impact management
InactiveUS6983321B2Faster and accurate analysisAvoid lot of costDigital computer detailsPayment architectureBusiness managementPotential impact
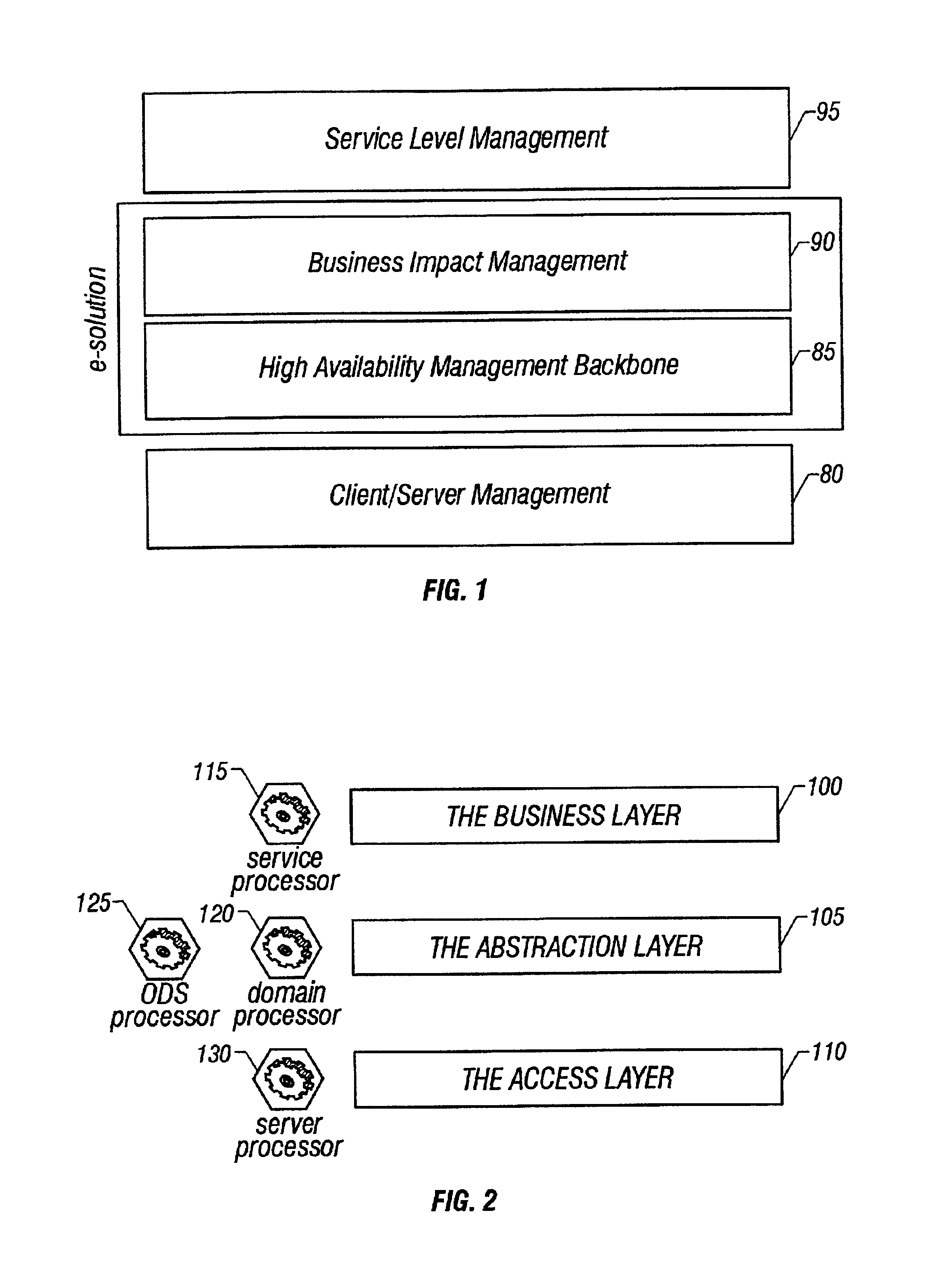
A system architecture and a method for management using a cellular architecture to allow multi-tier management of events such as the managing of the actual impact or the potential impact of IT infrastructure situations on business services. A preferred embodiment includes a high availability management backbone to frame monitoring operations using a cross-domain model where IT Component events are abstracted into IT Aggregate events. By combining IT Aggregate events with transaction events, an operational representation of the business services is possible. Another feature is the ability to connect this information to dependent business user groups such as internal end-users or external customers for direct impact measurement. A web of peer-to-peer rule-based cellular event processors preferably using Dynamic Data Association constitutes management backbone crossed by event flows, the execution of rules, and distributed set of dynamic inter-related object data rooted in the top data instances featuring the business services.
Owner:BMC SOFTWARE
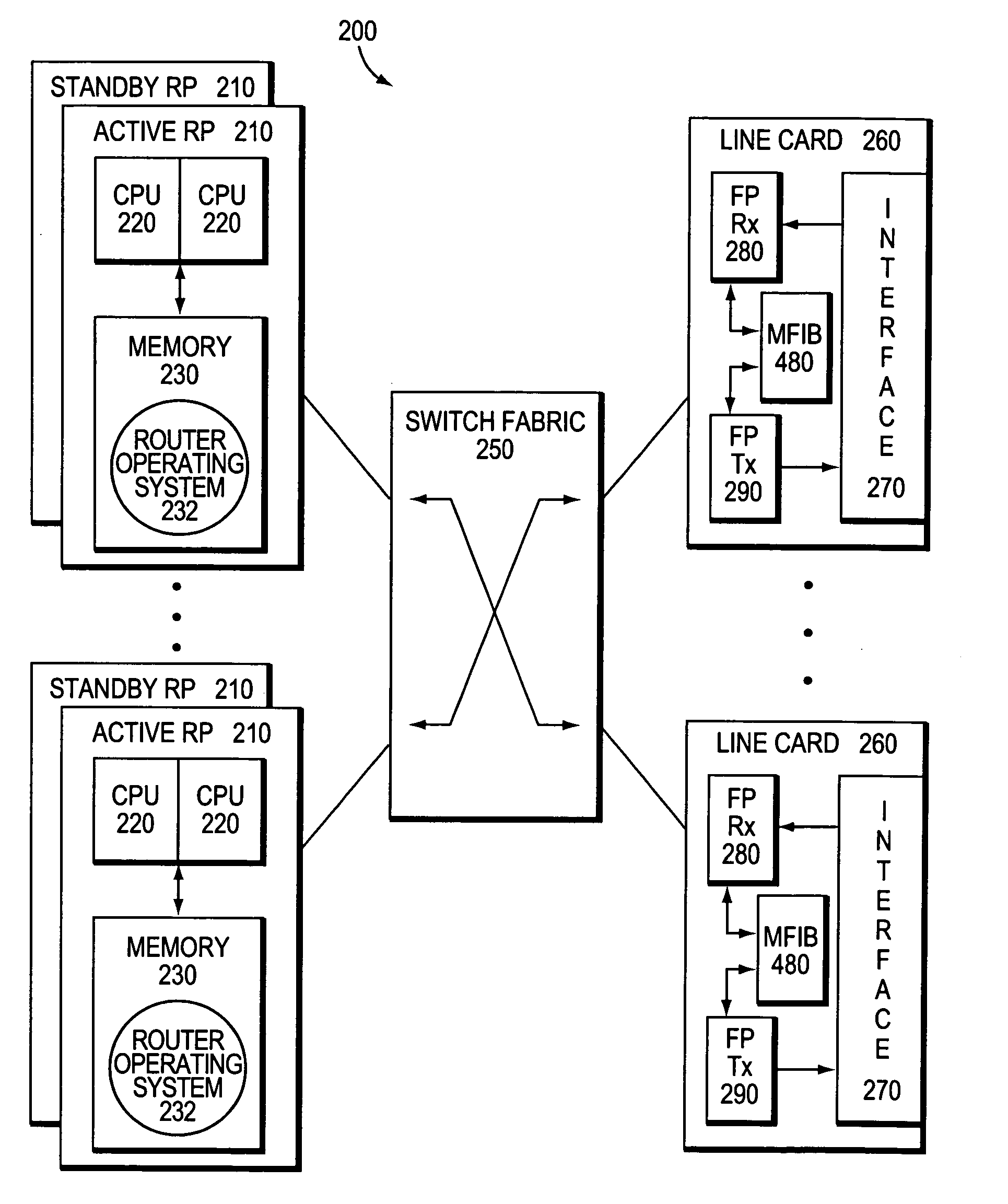
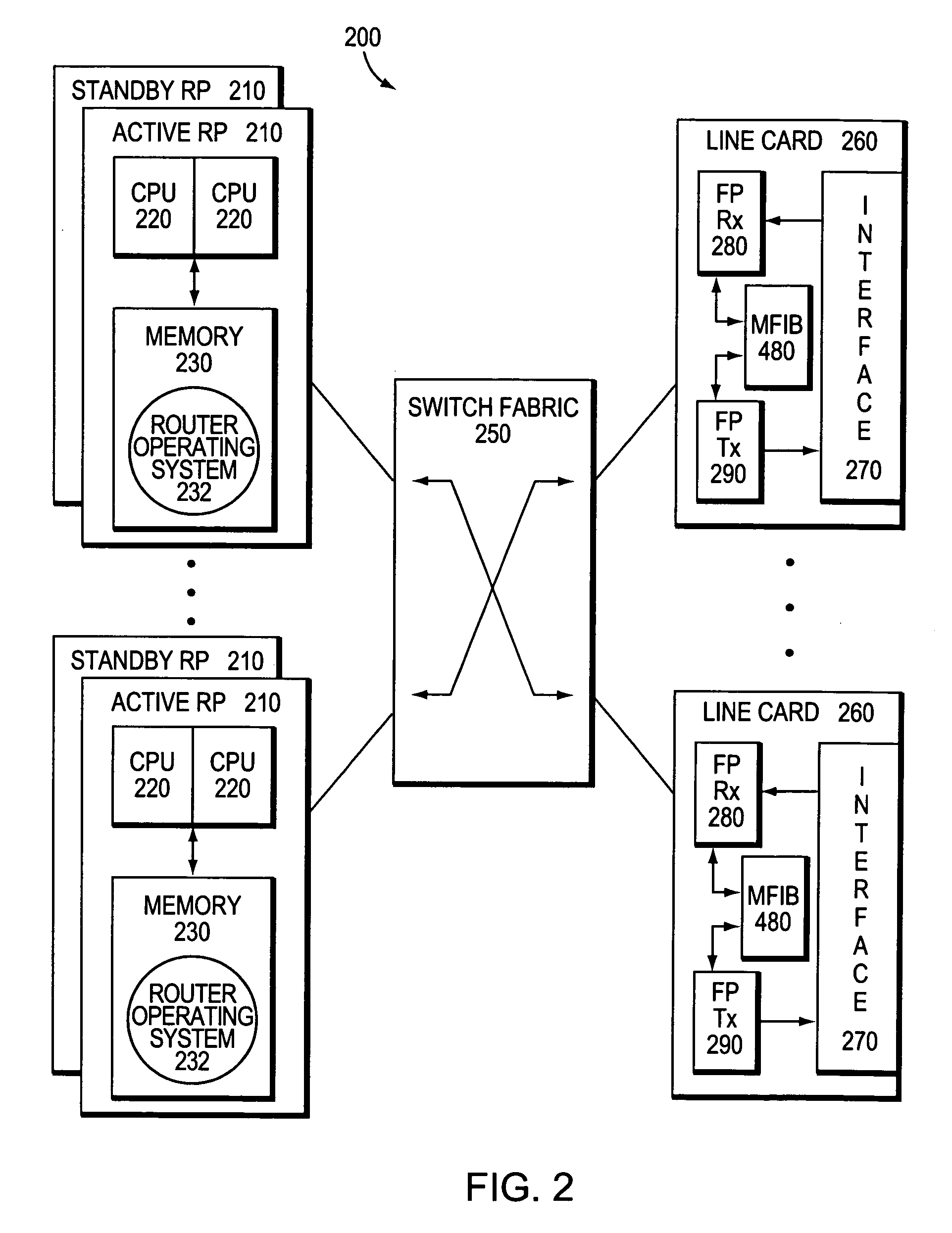
System and method for preserving multicast data forwarding during control failures in a router
ActiveUS20060018253A1Eliminate needImprove usabilityError preventionTransmission systemsData connectionHigh availability
A multicast non-stop forwarding (NSF) router architecture enhances high availability of a multicast router in a computer network. The router architecture further preserves multicast data forwarding through a data plane during NSF recovery of one or more failures in a control plane of the router. Various multicast components of the router cooperate to provide a checkpointing and recovery technique of the multicast NSF architecture that enables efficient restart and recovery of the control plane failures without loss of data connectivity.
Owner:CISCO TECH INC
Transactions Across Blockchain Networks
In asynchronous public network, synchronous leaderless Byzantine consensus protocol operating with guaranteed safety and time-bound termination of individual protocol rounds is enabled with nodes having clustered architecture and highly available data transactions, and implemented with algorithm that defuses the effect of stop-faulty processes and bypasses the partitioned network links. Utilizing the time-bound consensus, a protocol and architecture for cross-chain transactions accomplish safe interoperability across blockchain networks. Multiple cross-chain transacting networks interconnected in a federation overcome the limitations of blockchain networks with monolithic ledgers in regard to transaction latency, scalability of throughput, volume of managed data, and openness for further interoperability.
Owner:KLIANEV IVAN
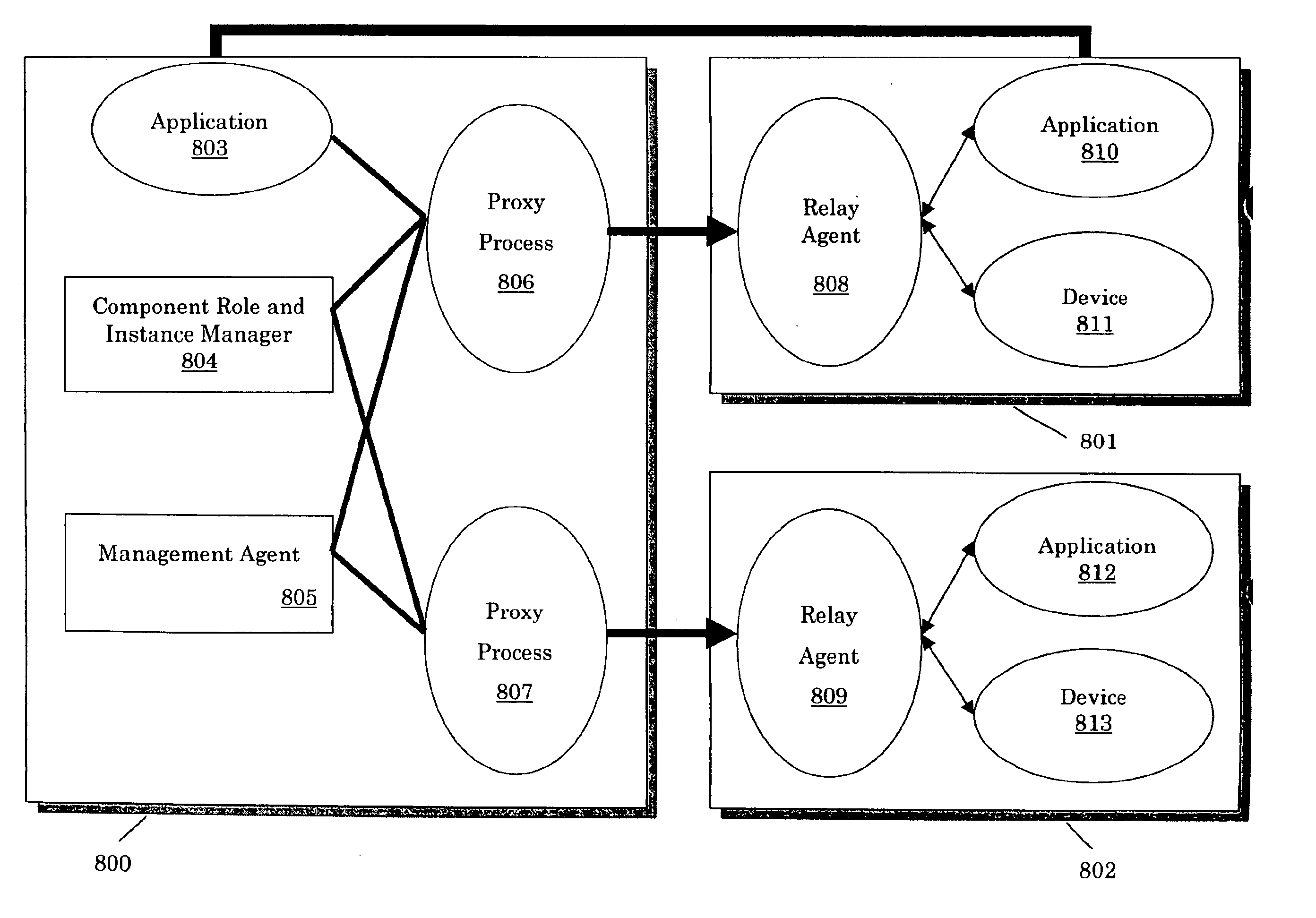
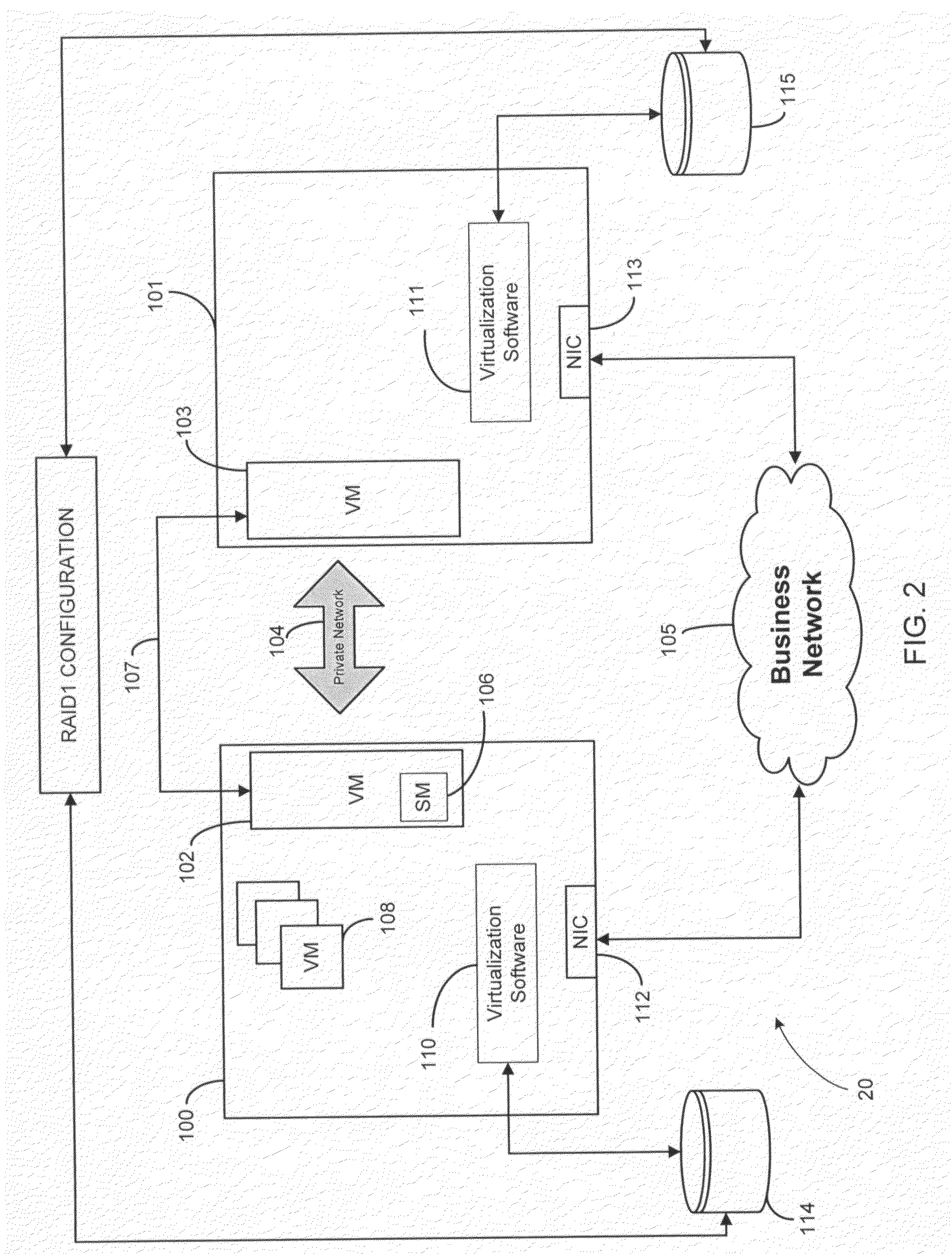
Systems and methods of high availability cluster environment failover protection
A transparent high-availability solution utilizing virtualization technology is presented. A cluster environment and management thereof is implemented through an automated installation and setup procedure resulting in a cluster acting as a single system. The cluster is setup in an isolated virtual machine on each of a number of physical nodes of the system. Customer applications are run within separate application virtual machines on one physical node at a time and are run independently and unaware of their configuration as part of a high-availability cluster. Upon detection of a failure, traffic is rerouted through a redundant node and the application virtual machines are migrated from the failing node to another node using live migration techniques.
Owner:STRATUS TECH IRELAND LTD
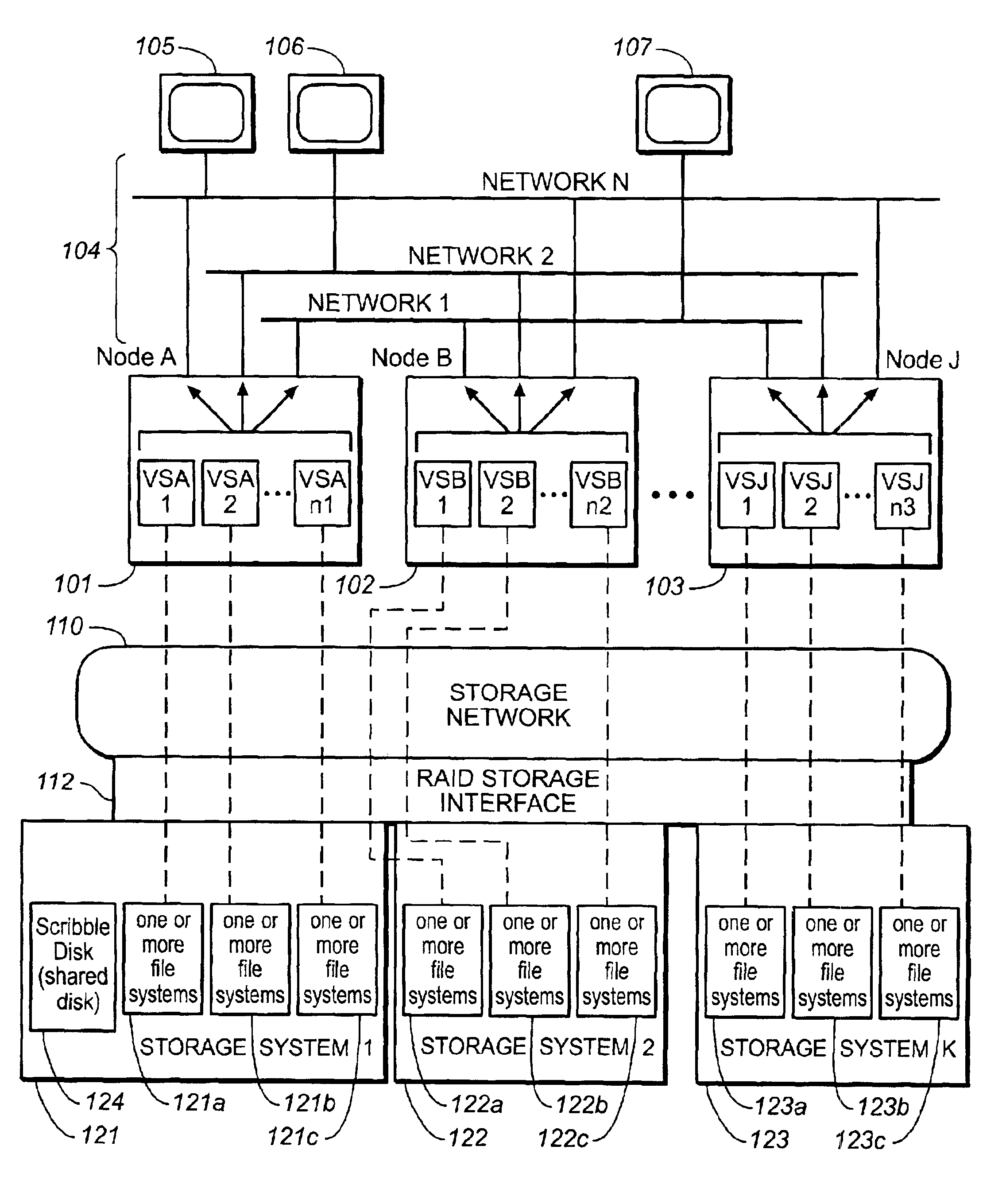
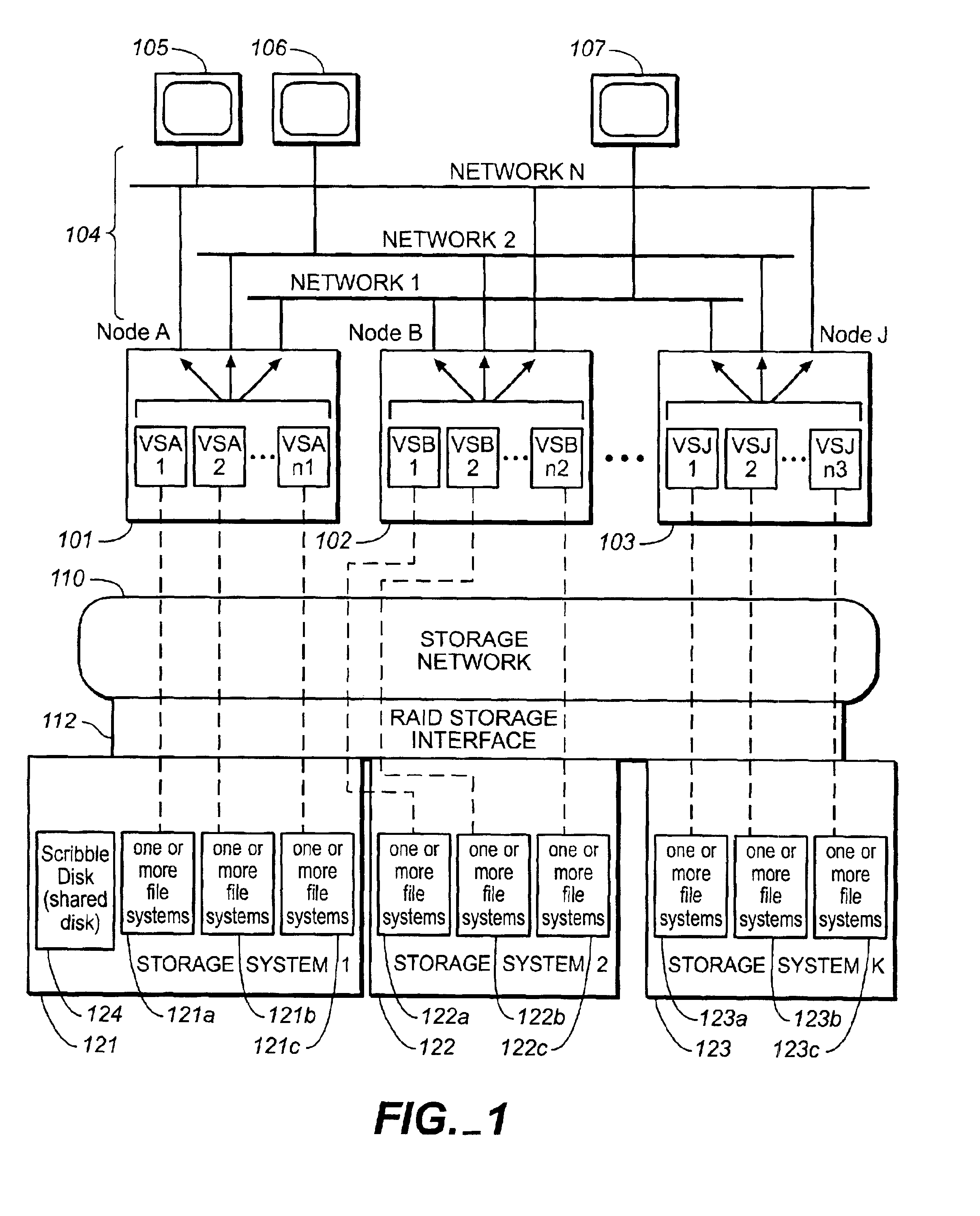
Dynamic network based storage with high availability
ActiveUS7546354B1Error detection/correctionMultiple digital computer combinationsTraffic capacityApplication server
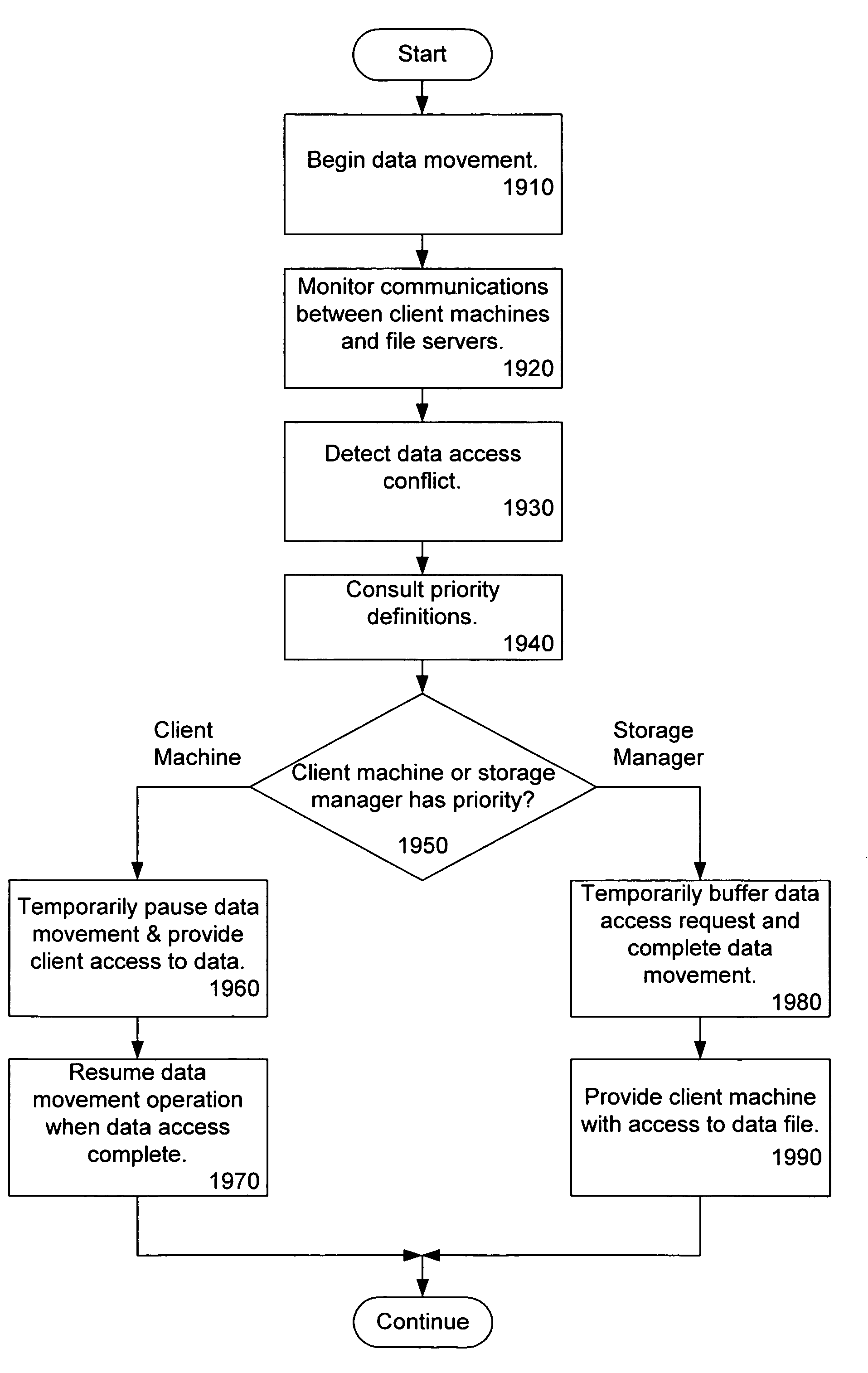
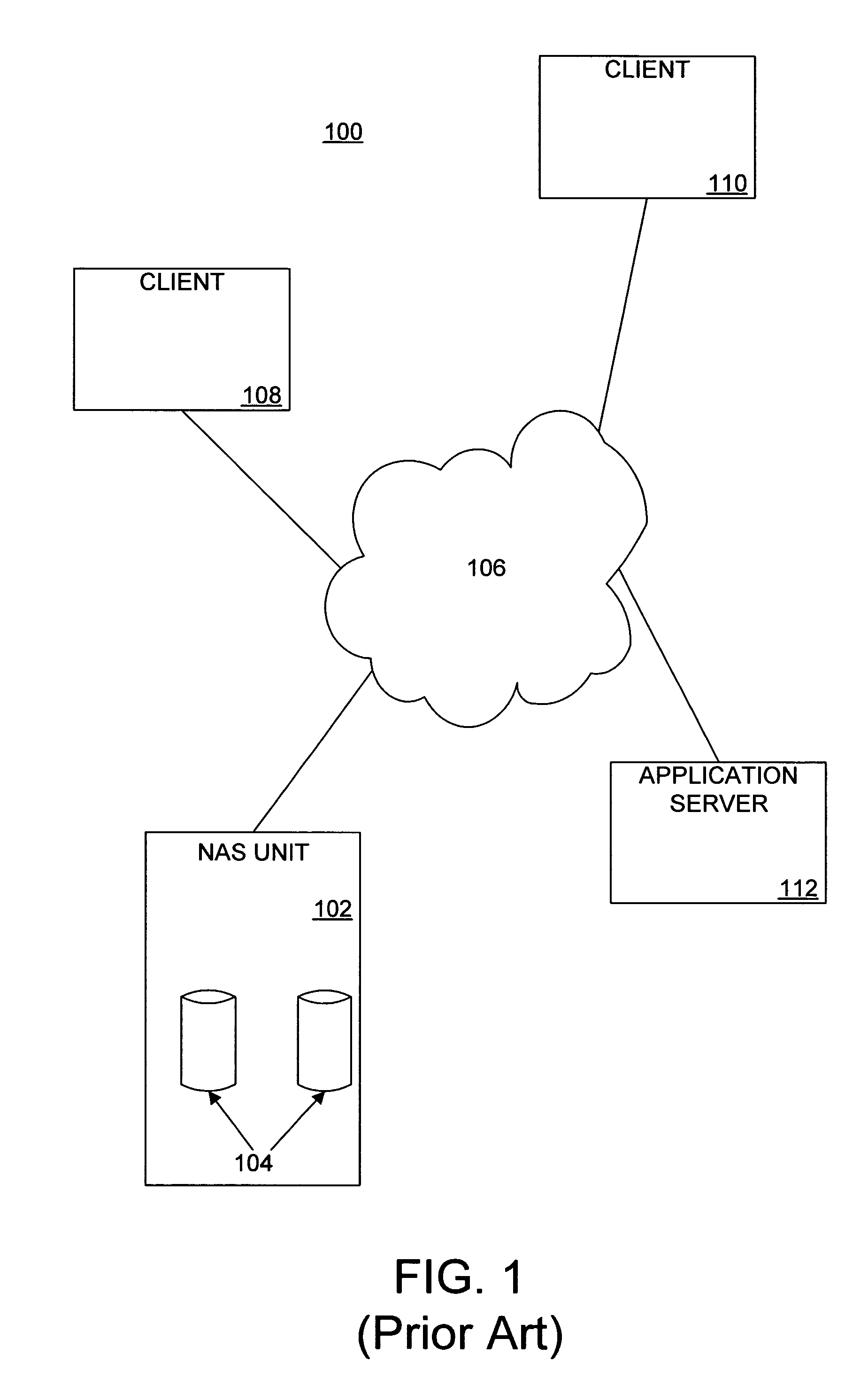
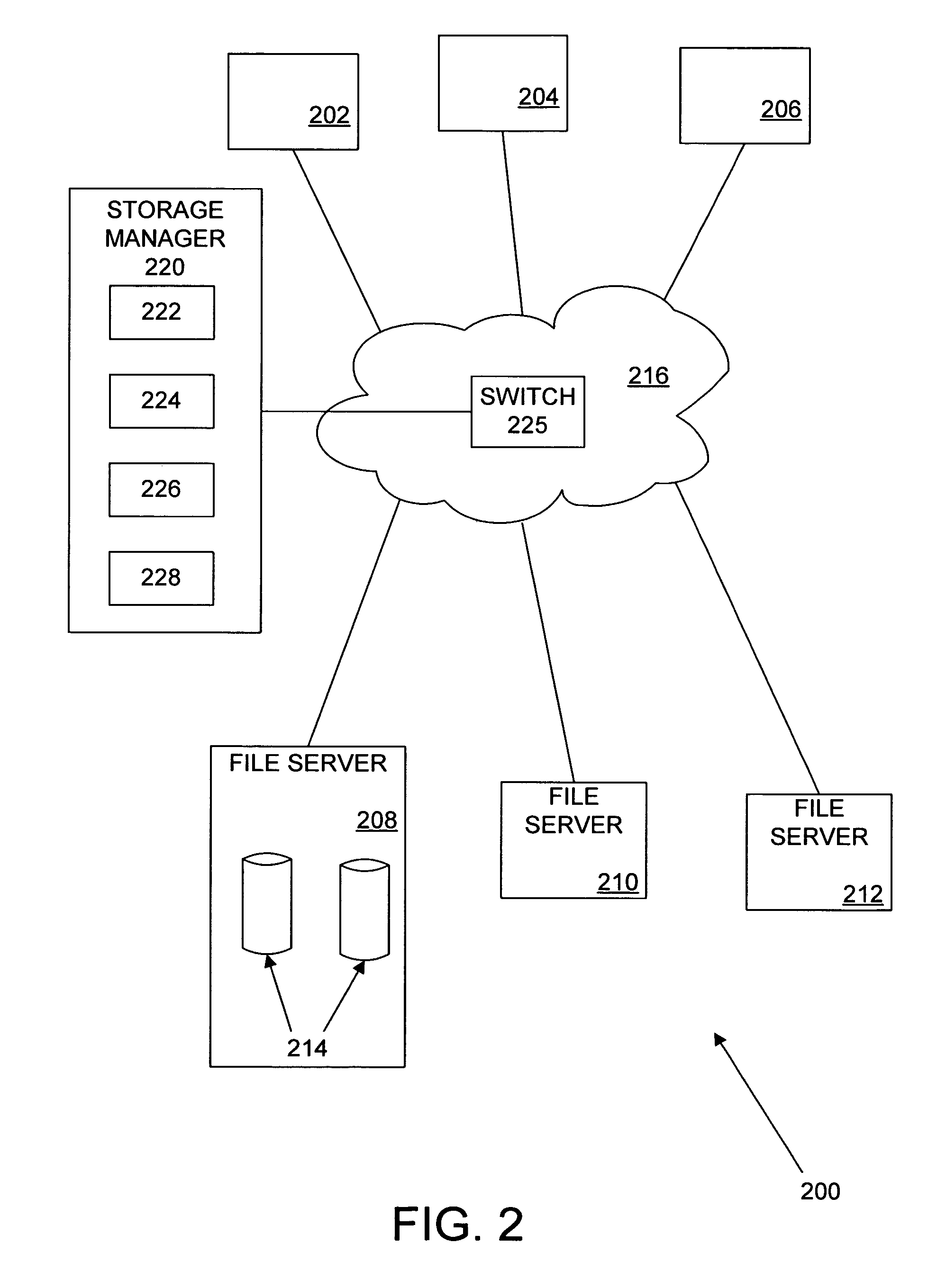
The present invention provides a scalable, highly available distributed network data storage system that efficiently and reliably provides network clients and application servers with access to large data stores, such as NAS units, and manages client and server requests for data from the data stores, thereby comprising a distributed storage manager. A storage manager constructed in accordance with the invention can receive and process network requests for data at a large, aggregated network data store, such as a collection of NAS units, and can manage data traffic between the network clients and NAS units.
Owner:EMC IP HLDG CO LLC
Distributed traffic controller for network data
InactiveUS7299294B1Improve availabilityEnsure availabilityComputer security arrangementsMultiple digital computer combinationsNetwork availabilityBack end server
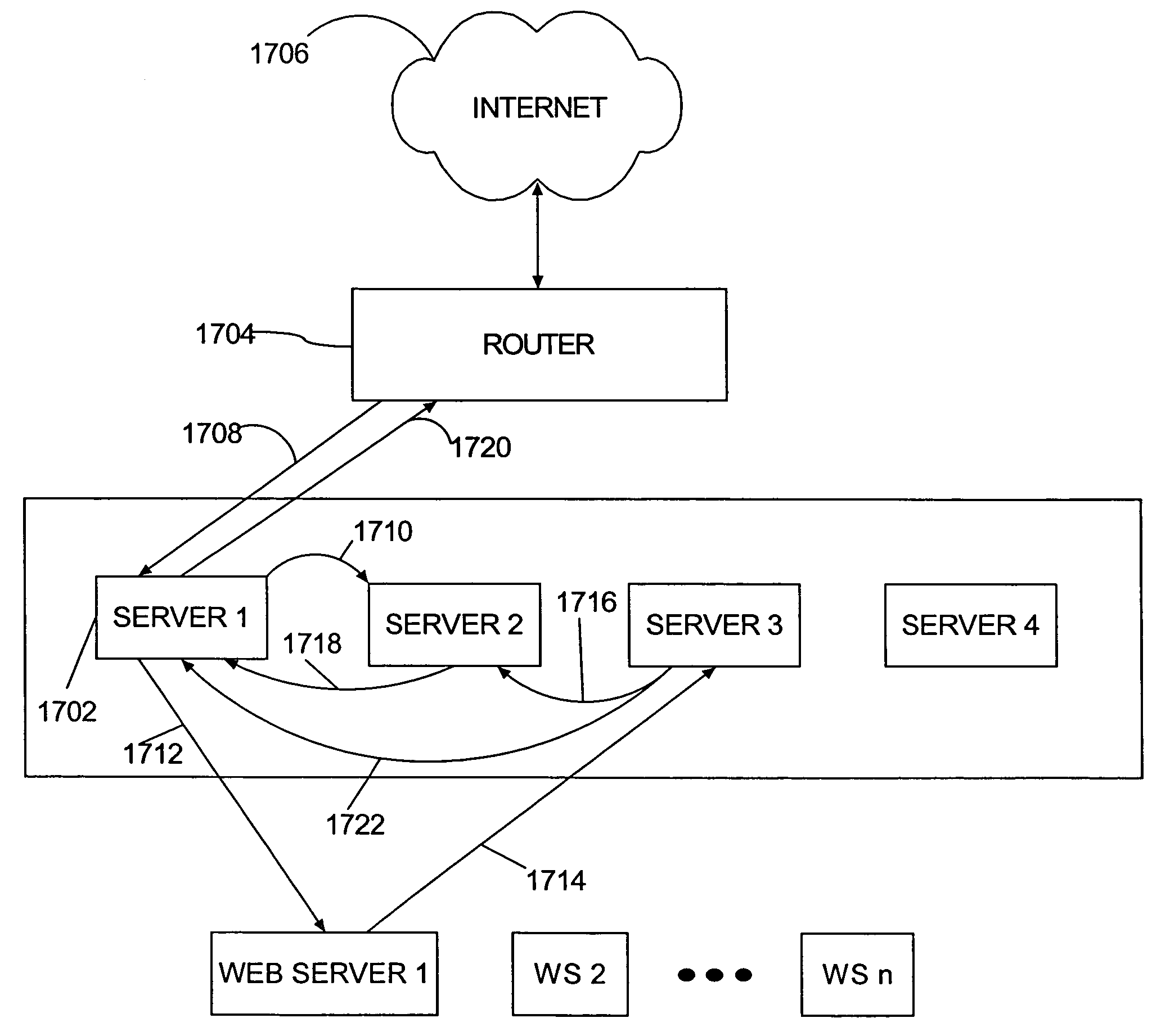
A distributed gateway for controlling computer network data traffic dynamically reconfigures traffic assignments among multiple gateway machines for increased network availability. If one of the distributed gateway machines becomes unavailable, traffic assignments are moved among the multiple machines such that network availability is substantially unchanged. The machines of the distributed gateway form a cluster and communicate with each other using a Group Membership protocol word such that automatic, dynamic traffic assignment reconfiguration occurs in response to machines being added and deleted from the cluster, with no loss in functionality for the gateway overall, in a process that is transparent to network users, thereby providing a distributed gateway functionality that is scalable. Operation of the distributed gateway remains consistent as machines are added and deleted from the cluster. A scalable, distributed, highly available, load balancing network gateway is thereby provided, having multiple machines that function as a front server layer between the network and a back-end server layer having multiple machines functioning as Web file servers, FTP servers, or other application servers. The front layer machines comprise a server cluster that performs fail-over and dynamic load balancing for both server layers.
Owner:EMC IP HLDG CO LLC
Method and system for remote load balancing in high-availability networks
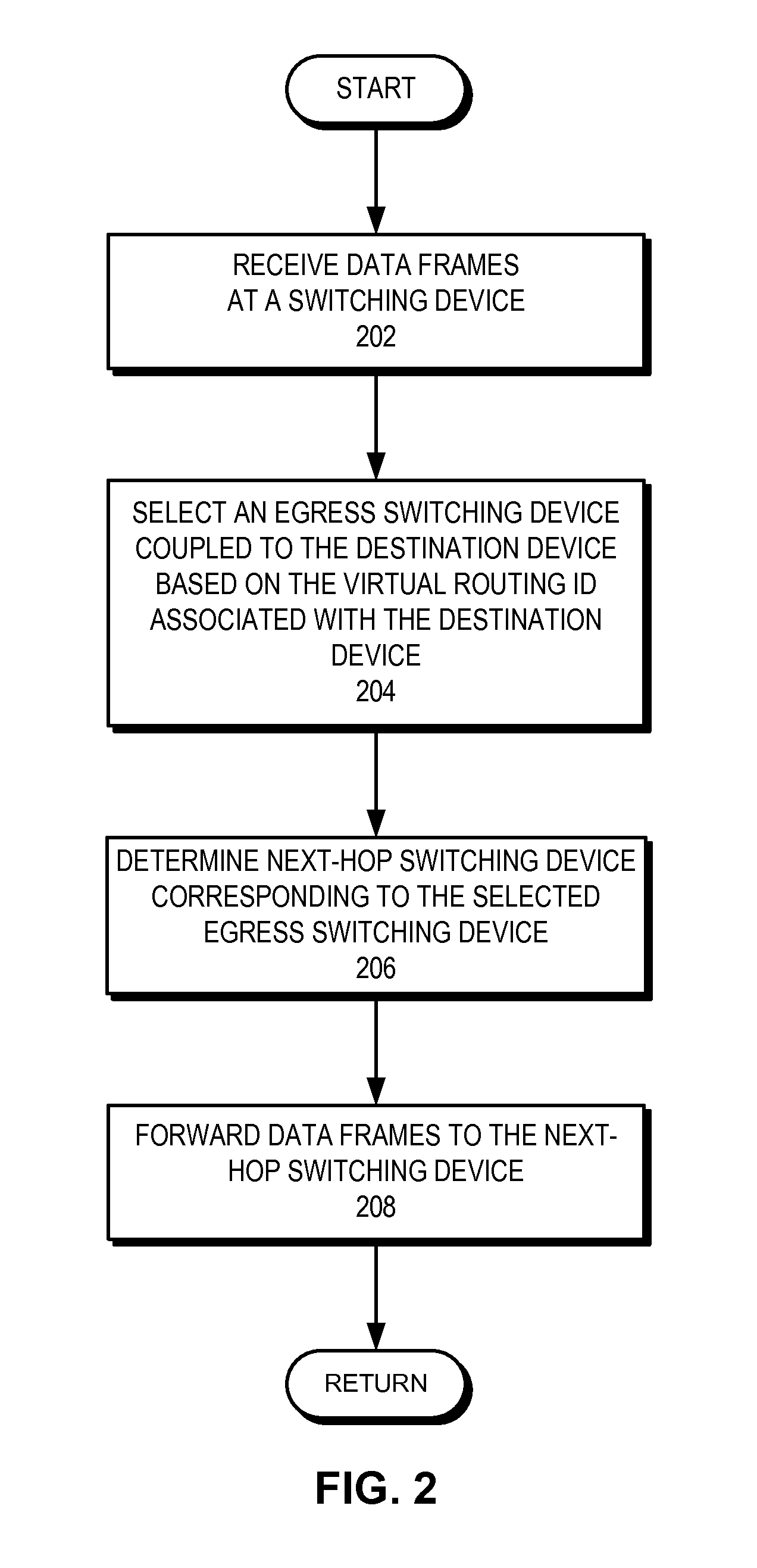
InactiveUS20120163164A1To achieve load balancingFacilitating remote load balancingError preventionFrequency-division multiplex detailsHigh availabilityDatapath
A system is provided for facilitating remote load balancing in a high-availability network. During operation, the system receives a plurality of data frames destined for a destination device, wherein the destination device is coupled to a network via a trunk link, the trunk link coupling the destination device to at least two separate egress switching devices. The system then forwards the data frames via at least two data paths, each of which leads to a respective egress switching device.
Owner:AVAGO TECH INT SALES PTE LTD
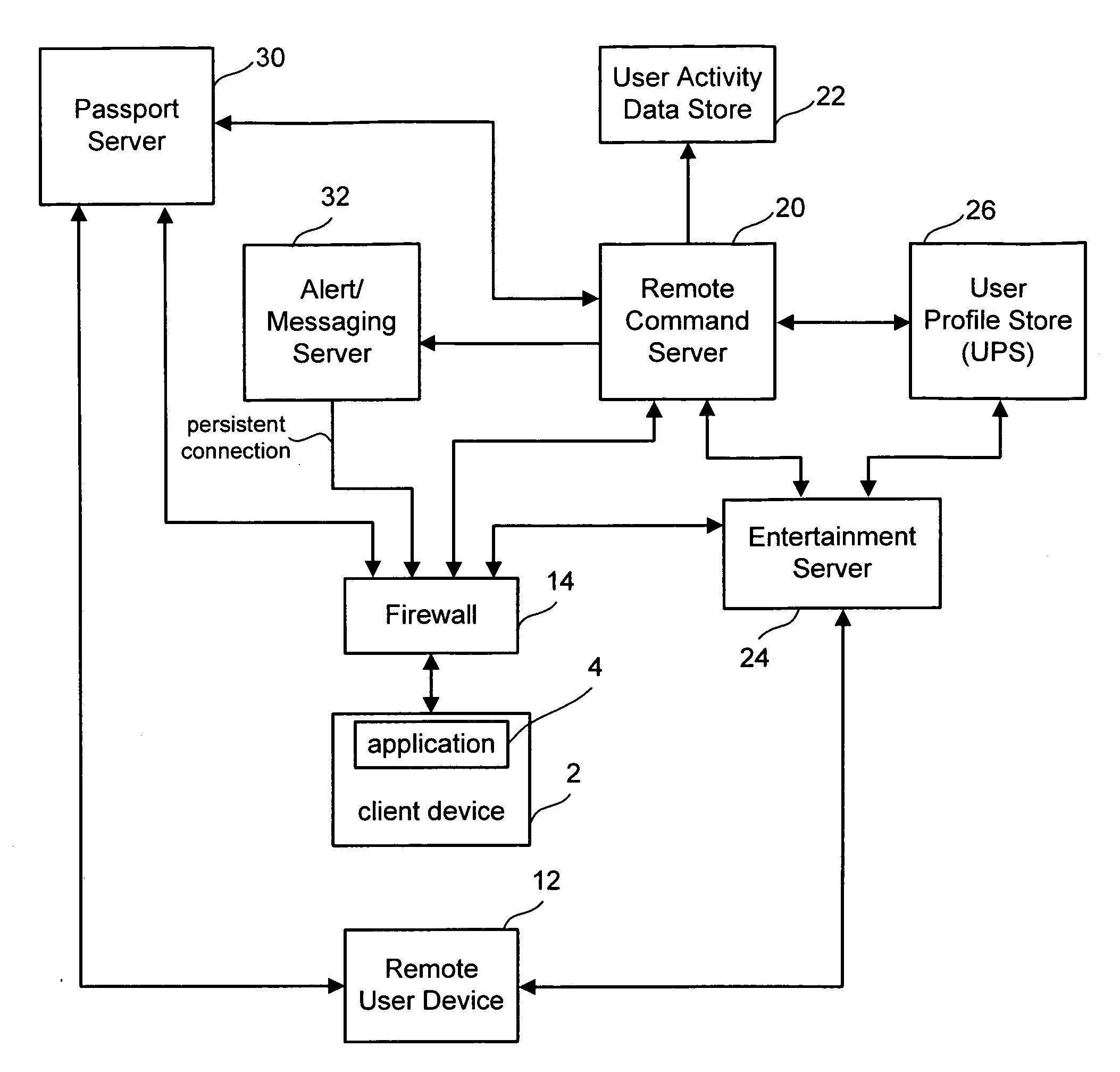
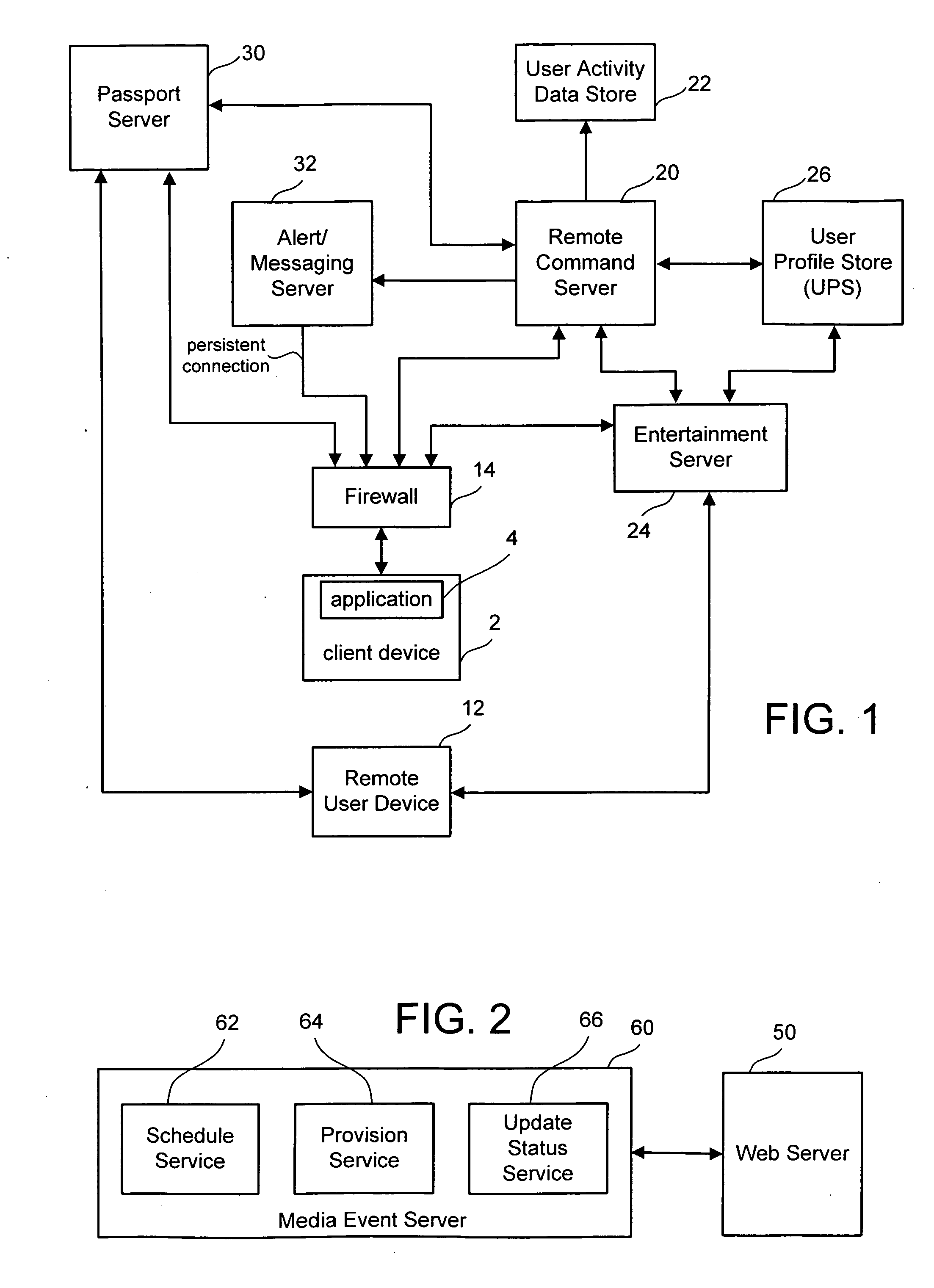
Remote command framework for devices
ActiveUS20060161662A1Improve protectionMemory loss protectionError detection/correctionThe InternetHigh availability
A robust device messaging framework is disclosed that enables a user to send commands to a device. A provisioning service is used to provision unique device identities and maps user web identities to device identities. The provisioning service also limits device per day provisioning attempts to limit denial of service attacks. A command service allows remote users to issue commands to a device, synchronize outgoing commands with incoming results, receive accurate feedback about whether a command was received, and maintain state information about the device. A device layer encrypts and stores device identities, authenticates itself with the command service, establishes a high-availability Internet connection to receive alerts that a command has issued, and reports results to the server-based command service.
Owner:MICROSOFT TECH LICENSING LLC
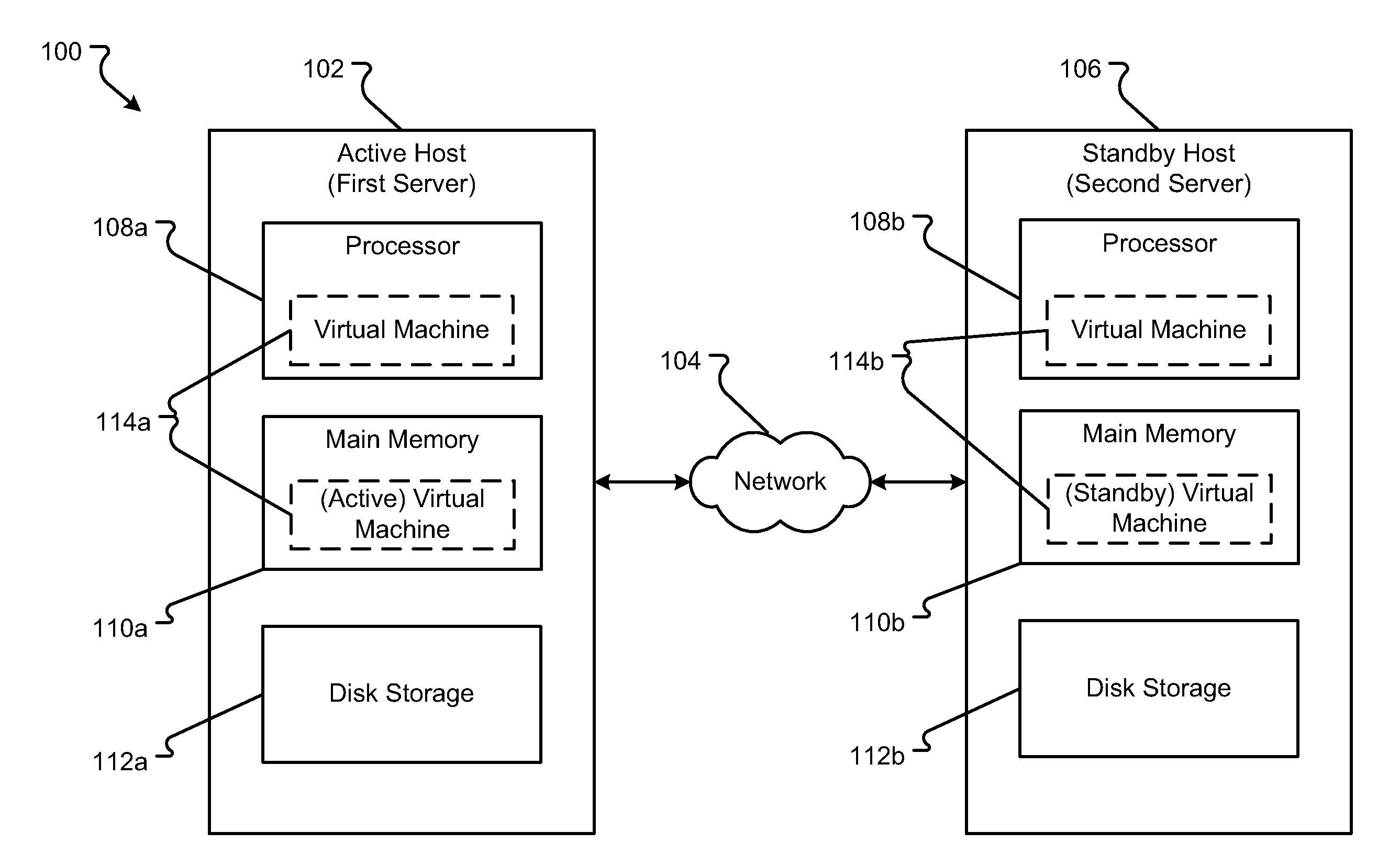
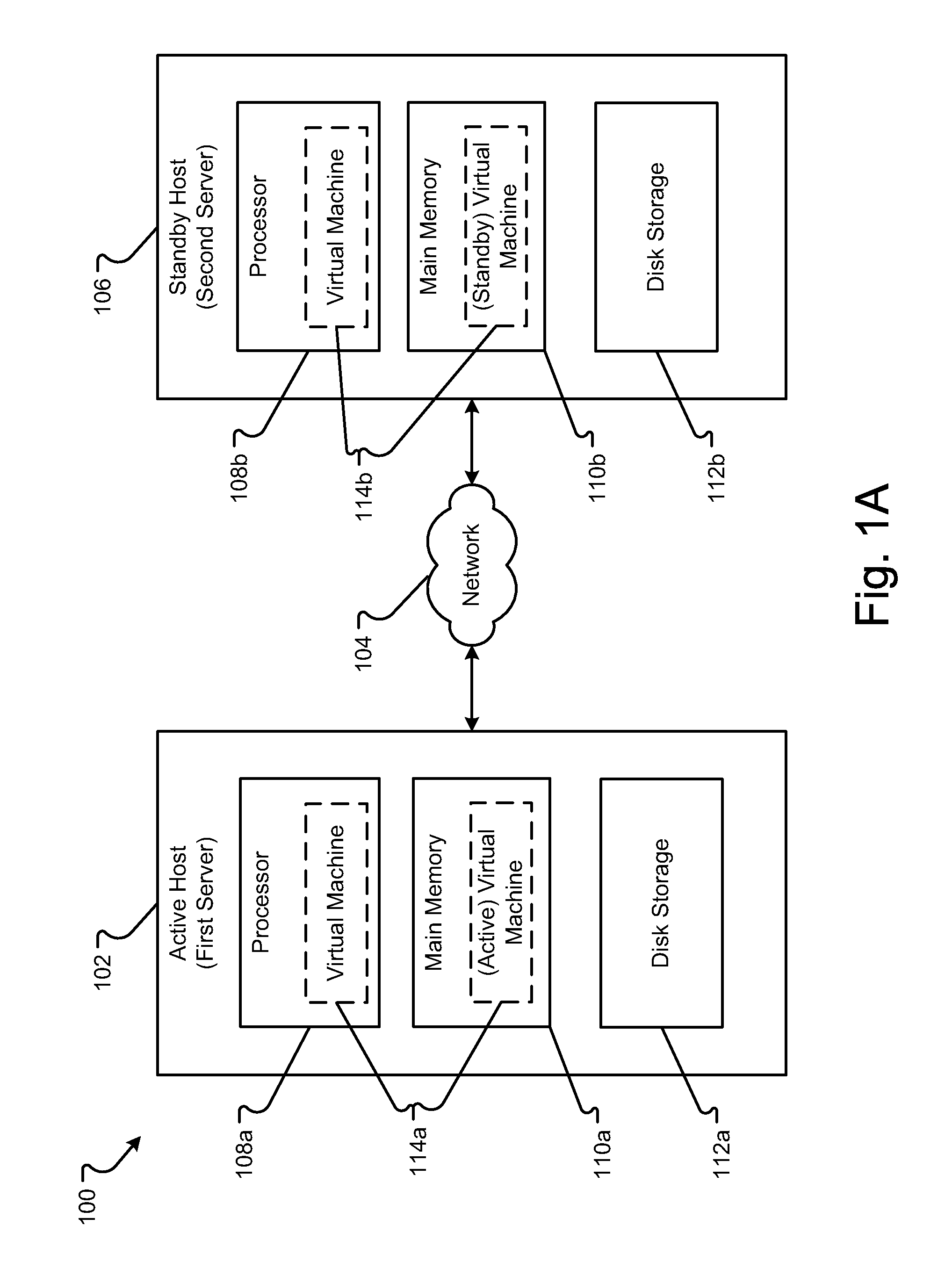
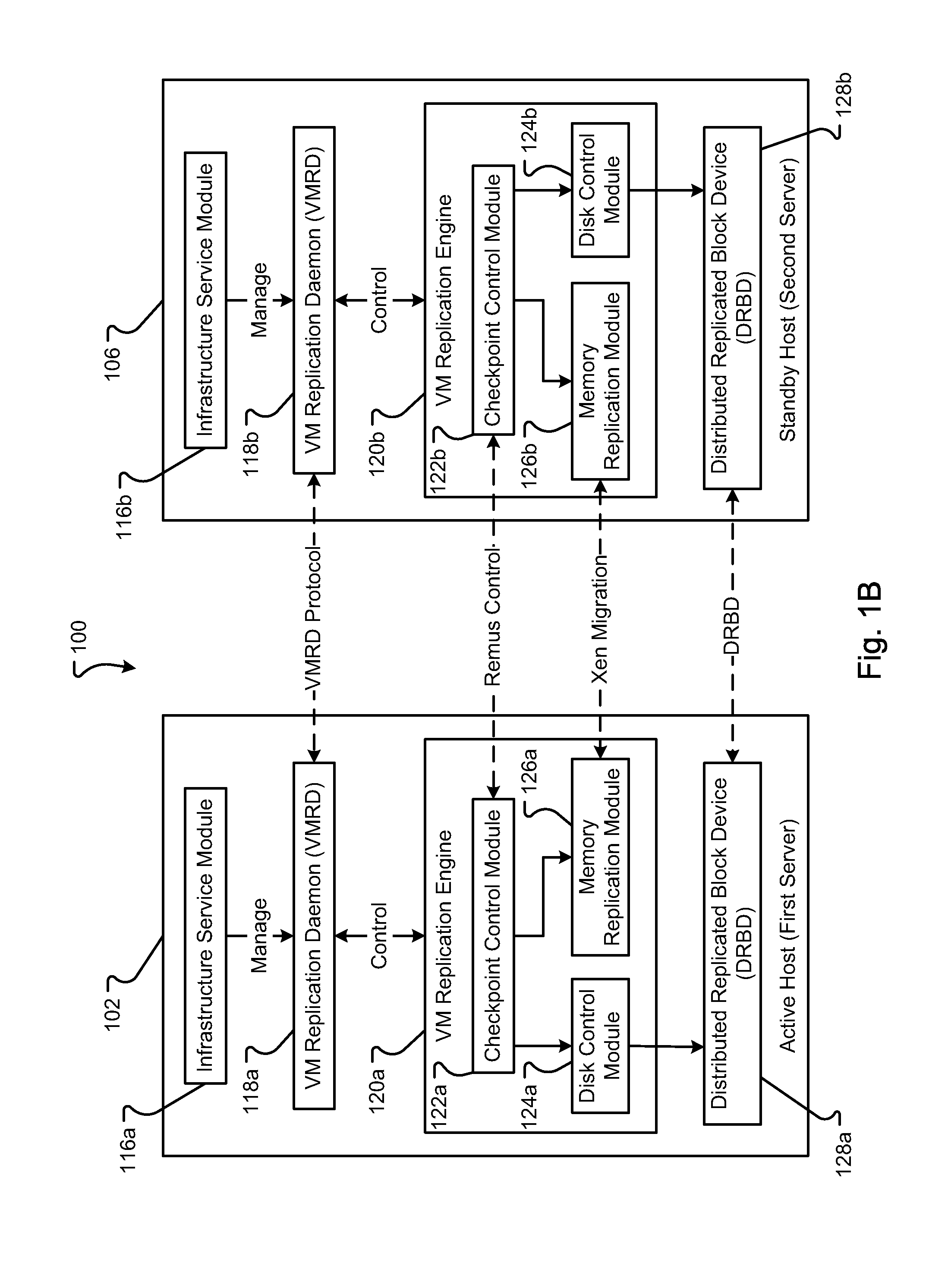
Method and Apparatus for Efficient Memory Replication for High Availability (HA) Protection of a Virtual Machine (VM)
ActiveUS20120084782A1Prevents buffer overflowSmall bufferMemory architecture accessing/allocationError detection/correctionDirty pageBuffer overflow
High availability (HA) protection is provided for an executing virtual machine. At a checkpoint in the HA process, the active server suspends the virtual machine; and the active server copies dirty memory pages to a buffer. During the suspension of the virtual machine on the active host server, dirty memory pages are copied to a ring buffer. A copy process copies the dirty pages to a first location in the buffer. At a predetermined benchmark or threshold, a transmission process can begin. The transmission process can read data out of the buffer at a second location to send to the standby host. Both the copy and transmission processes can operate substantially simultaneously on the ring buffer. As such, the ring buffer cannot overflow because the transmission process continues to empty the ring buffer as the copy process continues. This arrangement allows for smaller buffers and prevents buffer overflows.
Owner:AVAYA INC
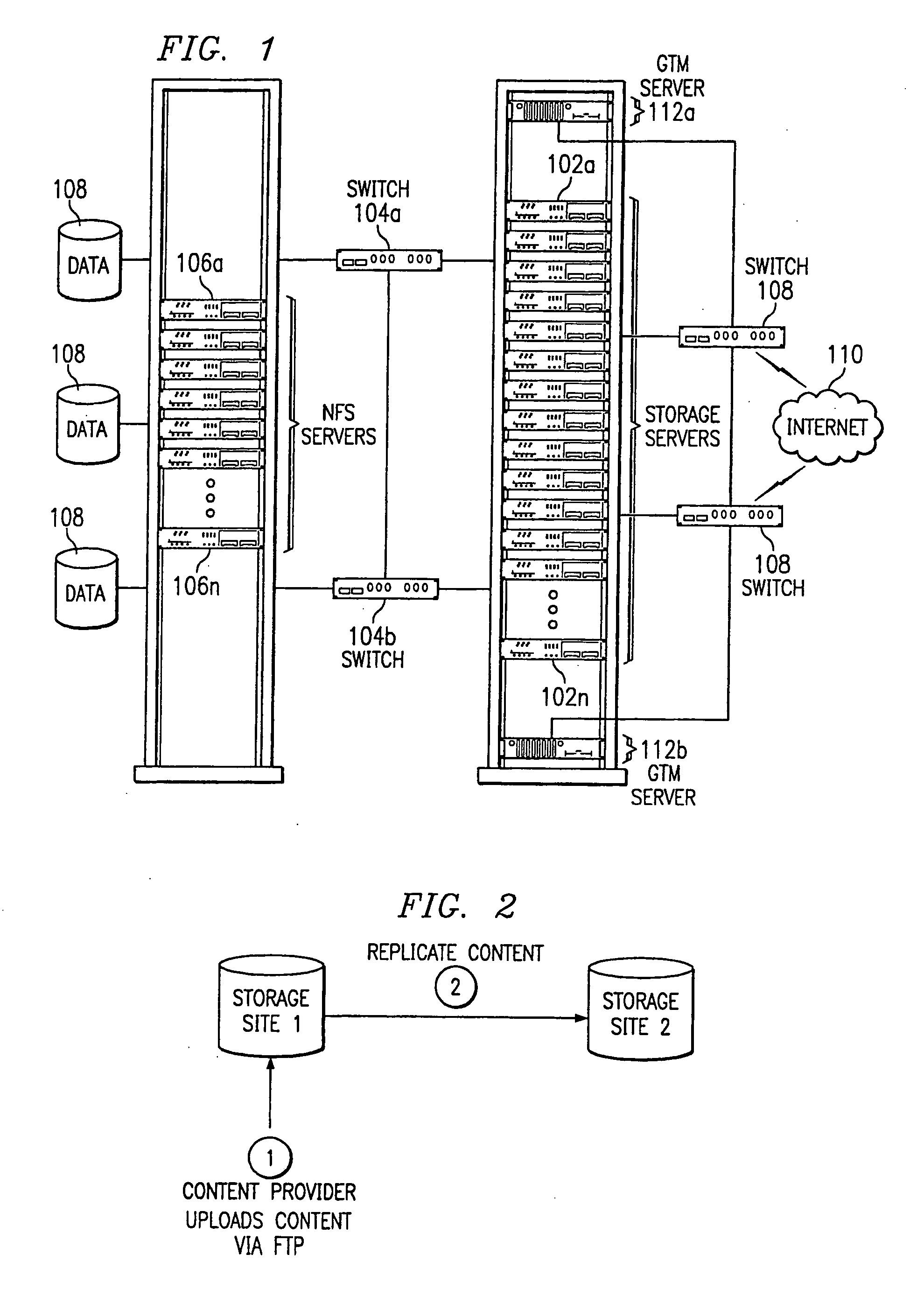
Scalable, high performance and highly available distributed storage system for Internet content
InactiveUS20070055765A1Infinite sequenceHigh degreeMultiple digital computer combinationsWebsite content managementInternet contentEdge server
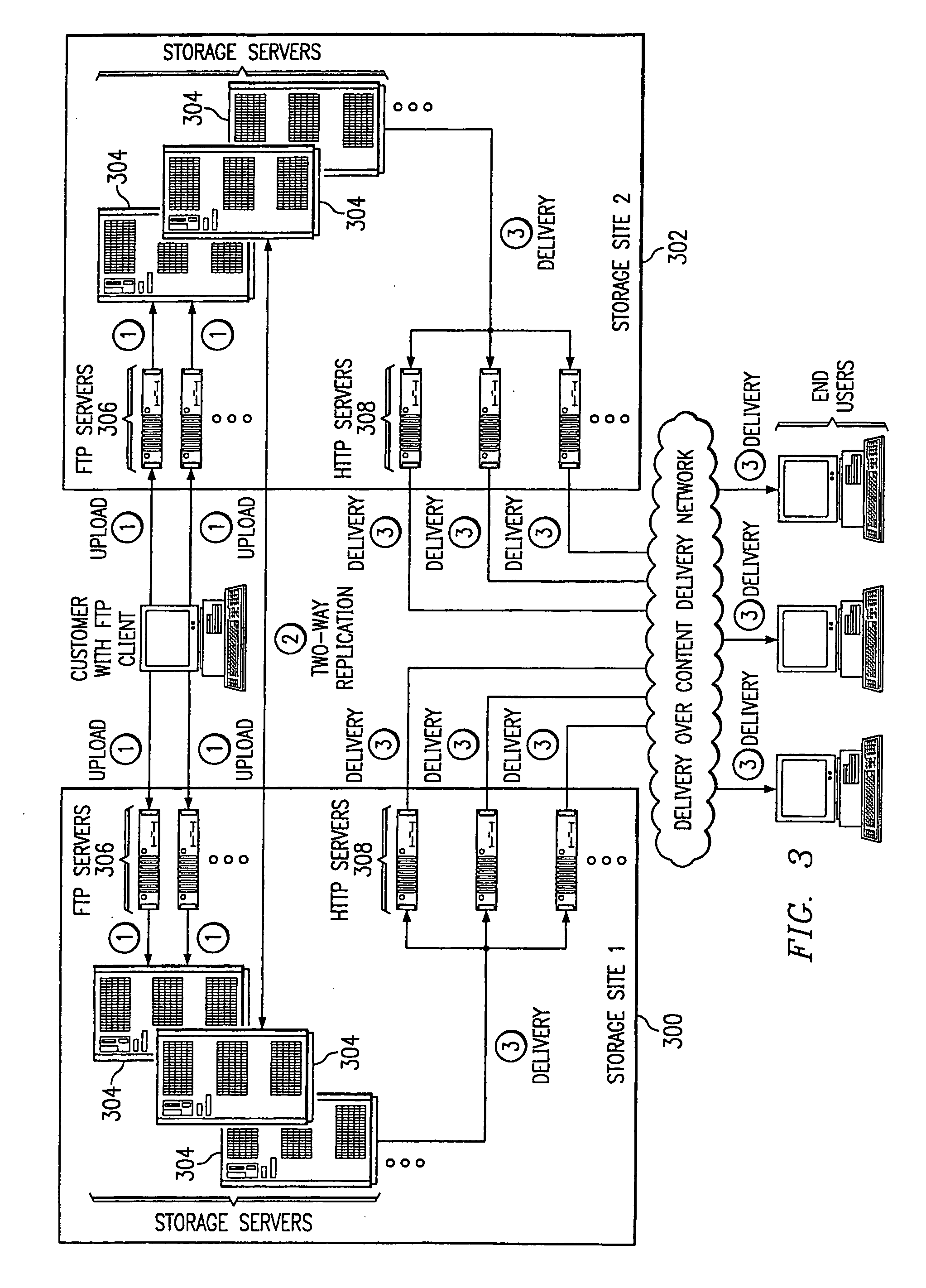
A method for content storage on behalf of participating content providers begins by having a given content provider identify content for storage. The content provider then uploads the content to a given storage site selected from a set of storage sites. Following upload, the content is replicated from the given storage site to at least one other storage site in the set. Upon request from a given entity, a given storage site from which the given entity may retrieve the content is then identified. The content is then downloaded from the identified given storage site to the given entity. In an illustrative embodiment, the given entity is an edge server of a content delivery network (CDN).
Owner:AKAMAI TECH INC
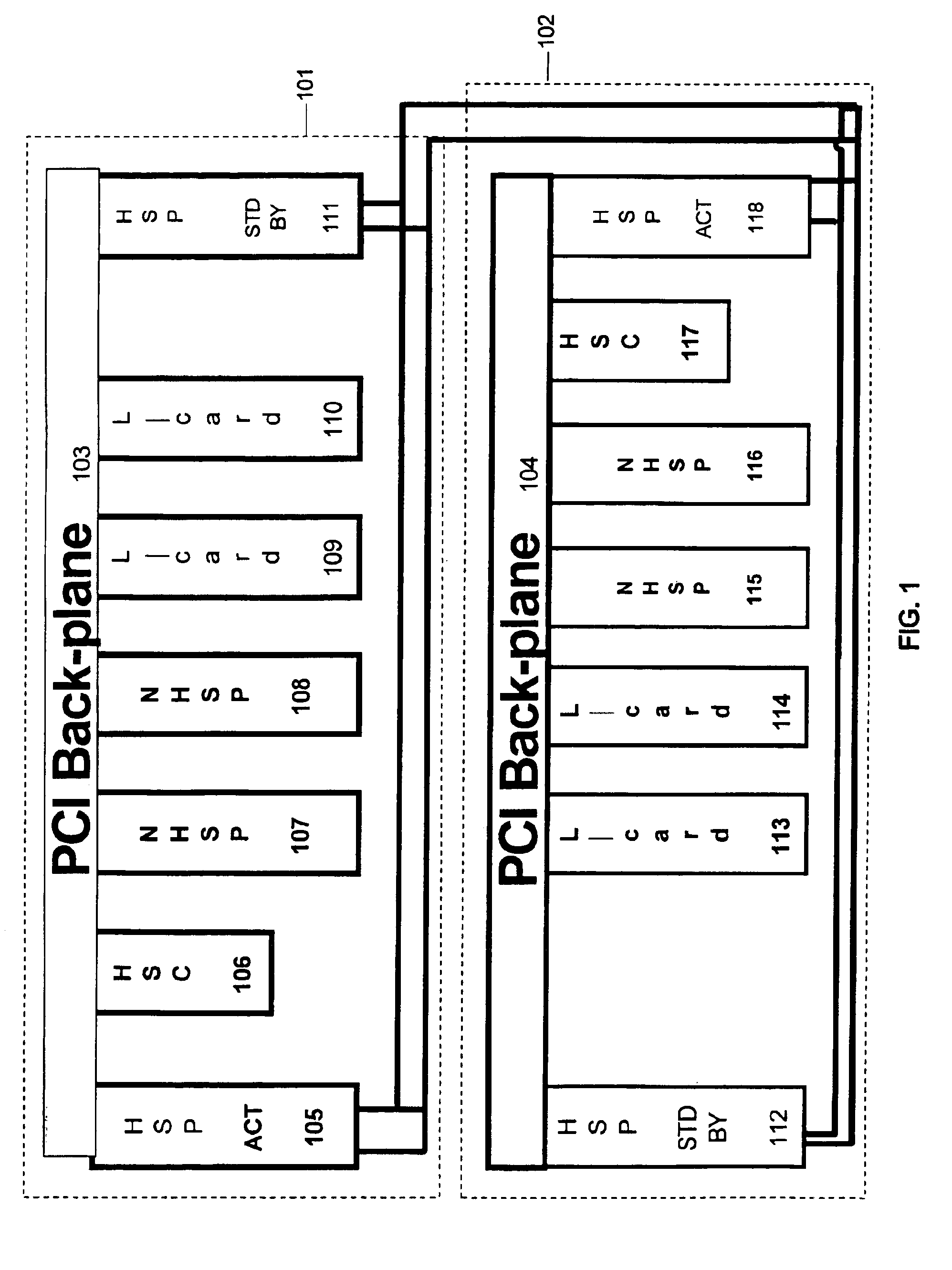
Processing device management system
ActiveUS20050138517A1Improve usabilityLow costError preventionTransmission systemsFailoverHigh availability
A system automatically adaptively modifies a fail-over configuration priority list of back-up devices of a group (cluster) of processing devices to improve availability and reduce risks and costs associated with manual configuration. A system is used by individual processing devices of a group of networked processing devices, for managing operational failure occurrences in devices of the group. The system includes an interface processor for maintaining transition information identifying a second processing device for taking over execution of tasks of a first processing device in response to an operational failure of the first processing device and for updating the transition information in response to a change in transition information occurring in another processing device of the group. An operation detector detects an operational failure of the first processing device. Also, a failure controller initiates execution, by the second processing device, of tasks designated to be performed by the first processing device in response to detection of an operational failure of the first processing device.
Owner:III HLDG 3
Multi-service queuing method and apparatus that provides exhaustive arbitration, load balancing, and support for rapid port failover
InactiveUS7151744B2Efficient multicastingEasy to handleError preventionTransmission systemsTraffic capacityFailover
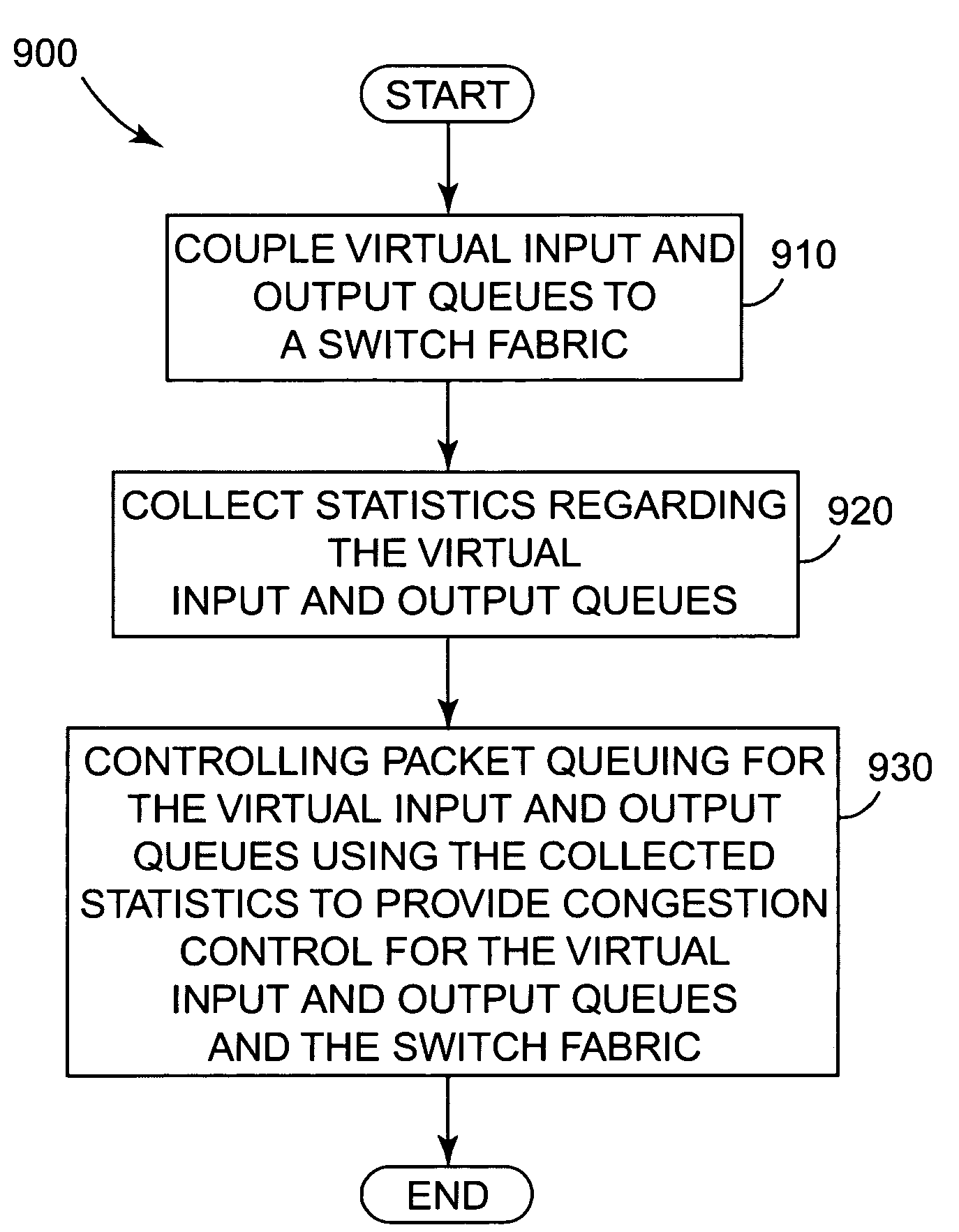
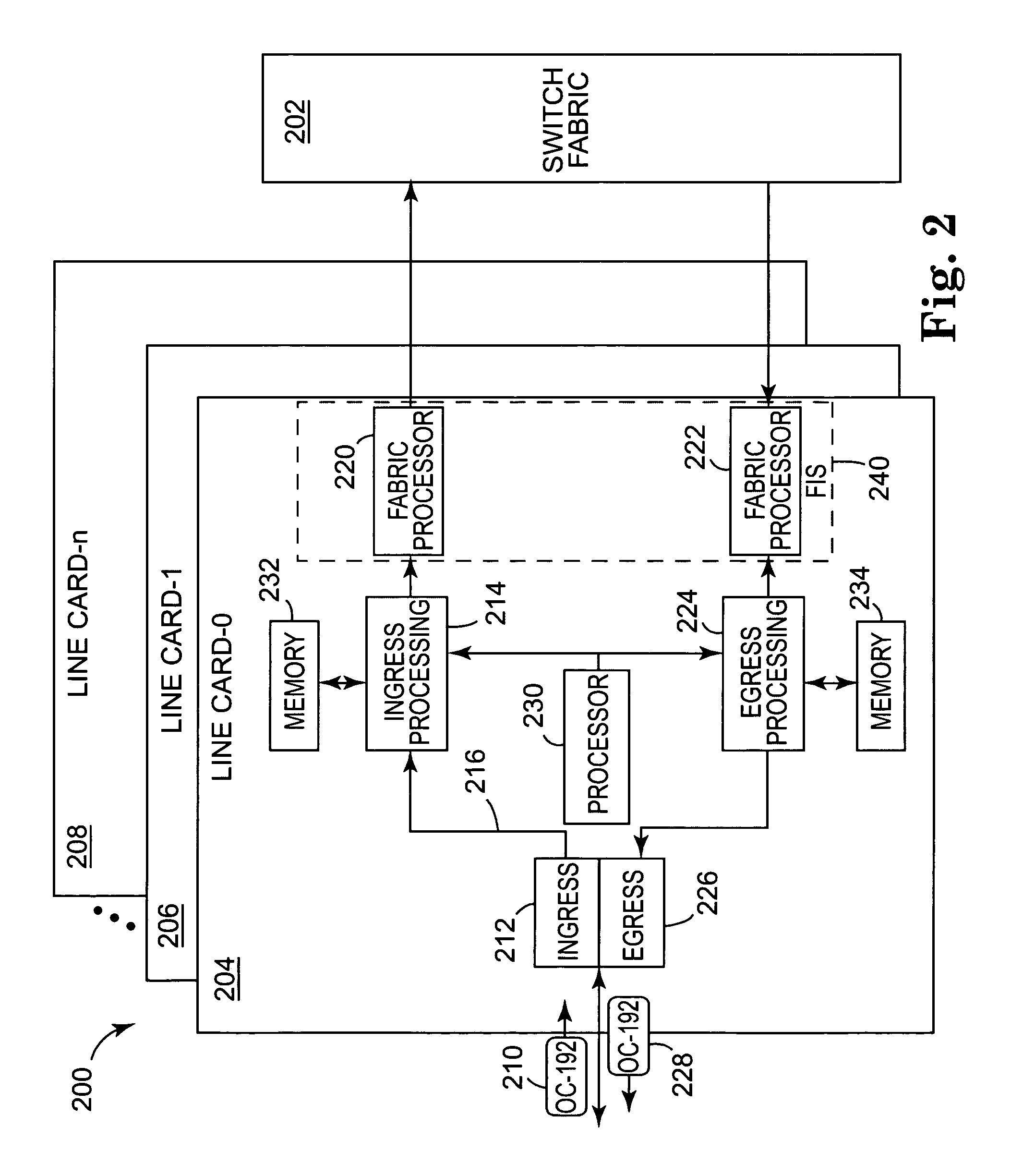
The present invention provides a multi-service queuing method and apparatus that provides exhaustive arbitration, load balancing, and support for rapid port failover. Routers and switches according to the present invention can instantaneously direct the flow of traffic to another port should there be a failure on a link, efficiently handle multicast traffic and provide multiple service classes. The fabric interface interfaces the switch fabric with the ingress and egress functions provided at a network node and provides virtual input and output queuing with backpressure feedback, redundancy for high availability applications, and packet segmentation and reassembly into variable length cells. The user configures fixed and variable-length cells. Virtual input and output queues are coupled to a switch fabric. Statistics regarding the virtual input and output queues are collected and packet queuing for the virtual input and output queues is controlled using the collected statistic to provide congestion control for the virtual input and output queues and the switch fabric.
Owner:RPX CORP
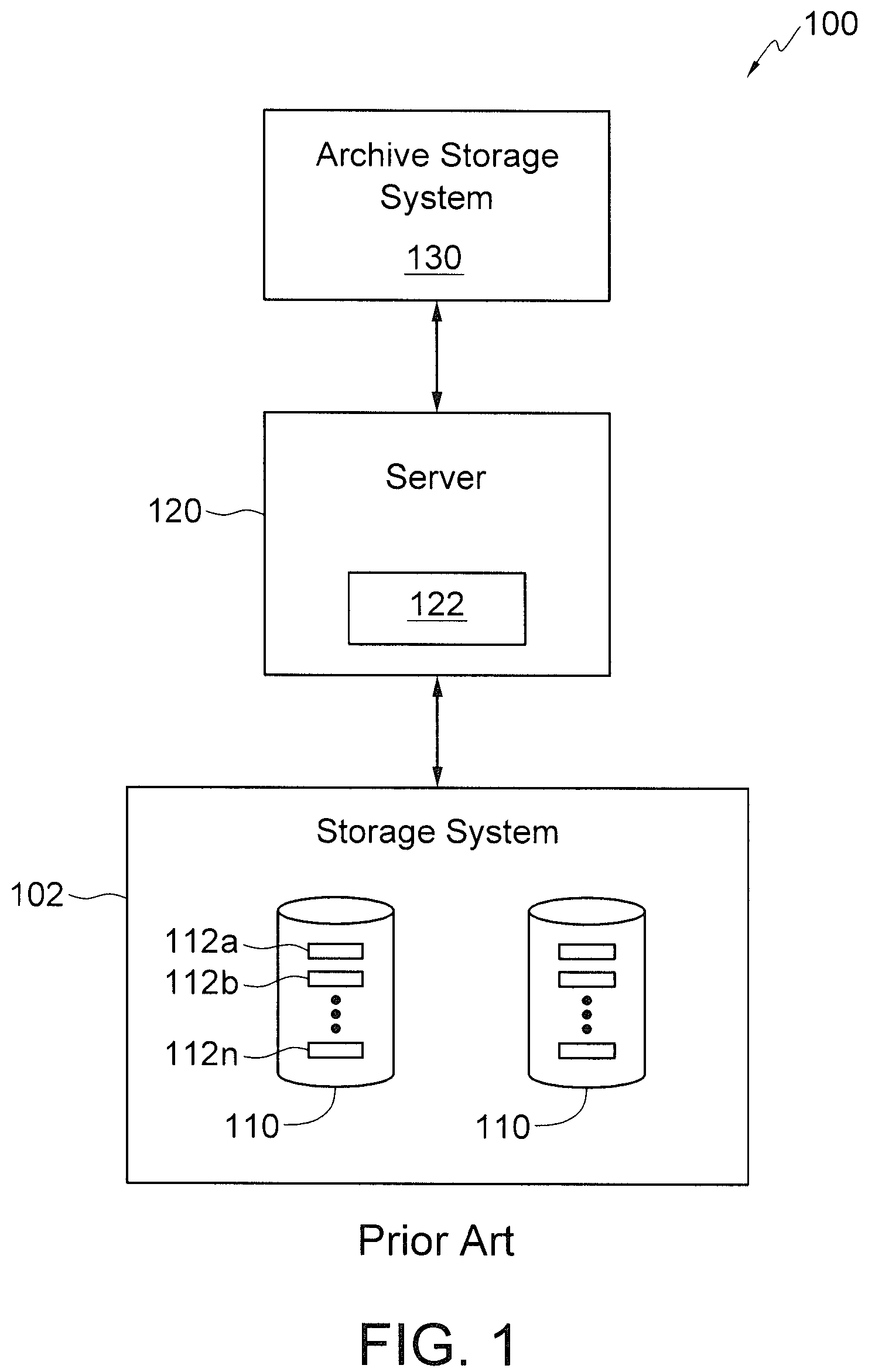
High-availability file archiving
ActiveUS8326805B1Digital data information retrievalError detection/correctionWide areaHigh availability
Computer file archiving systems and techniques are described. Various aspects include wide area high-availability file archiving, volume-level management capabilities of archiving systems, and methods and systems for storing file archiving metadata. The methods and systems described can be used individually or in combination.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com