Patents
Literature
5267 results about "Public network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
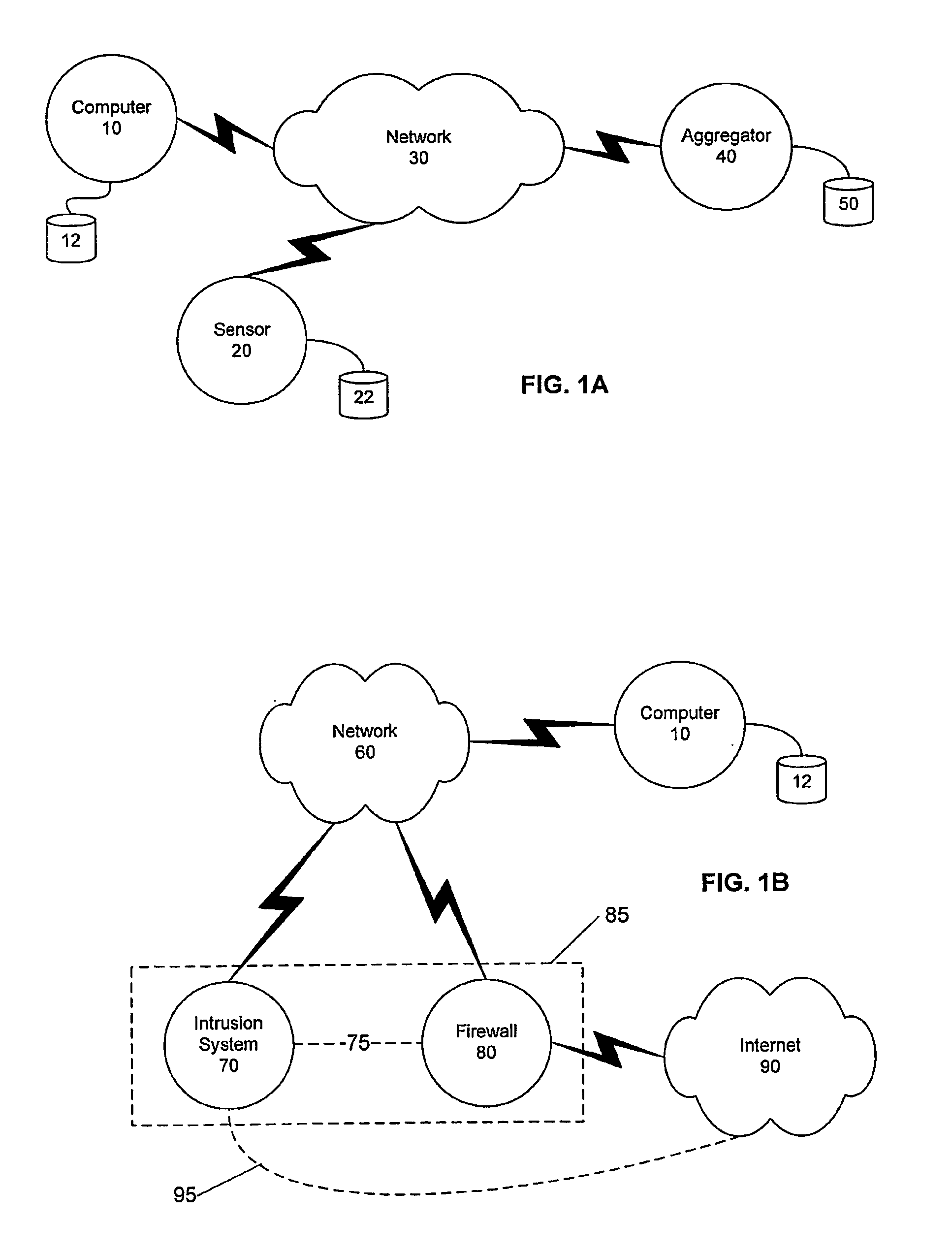
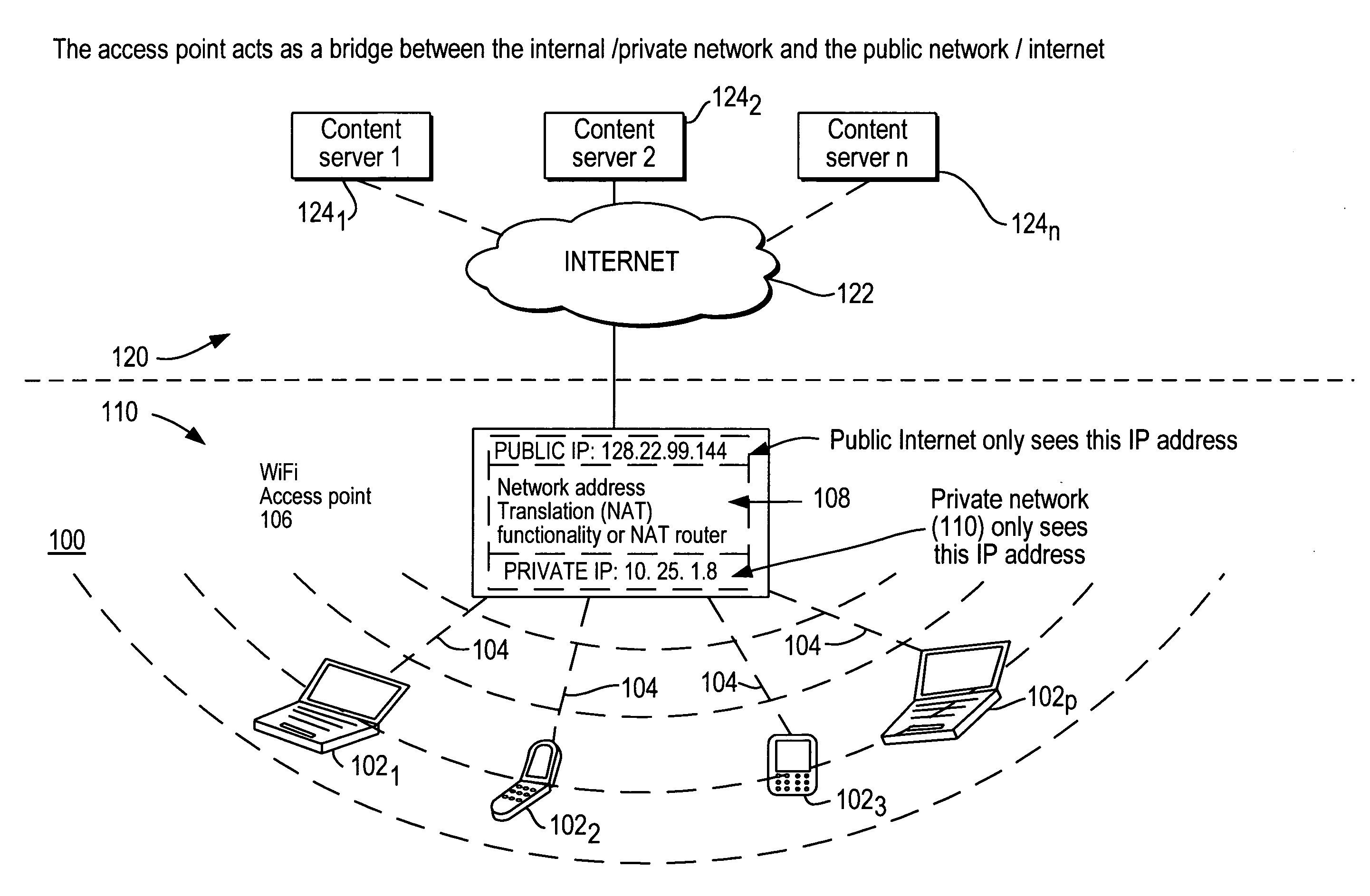
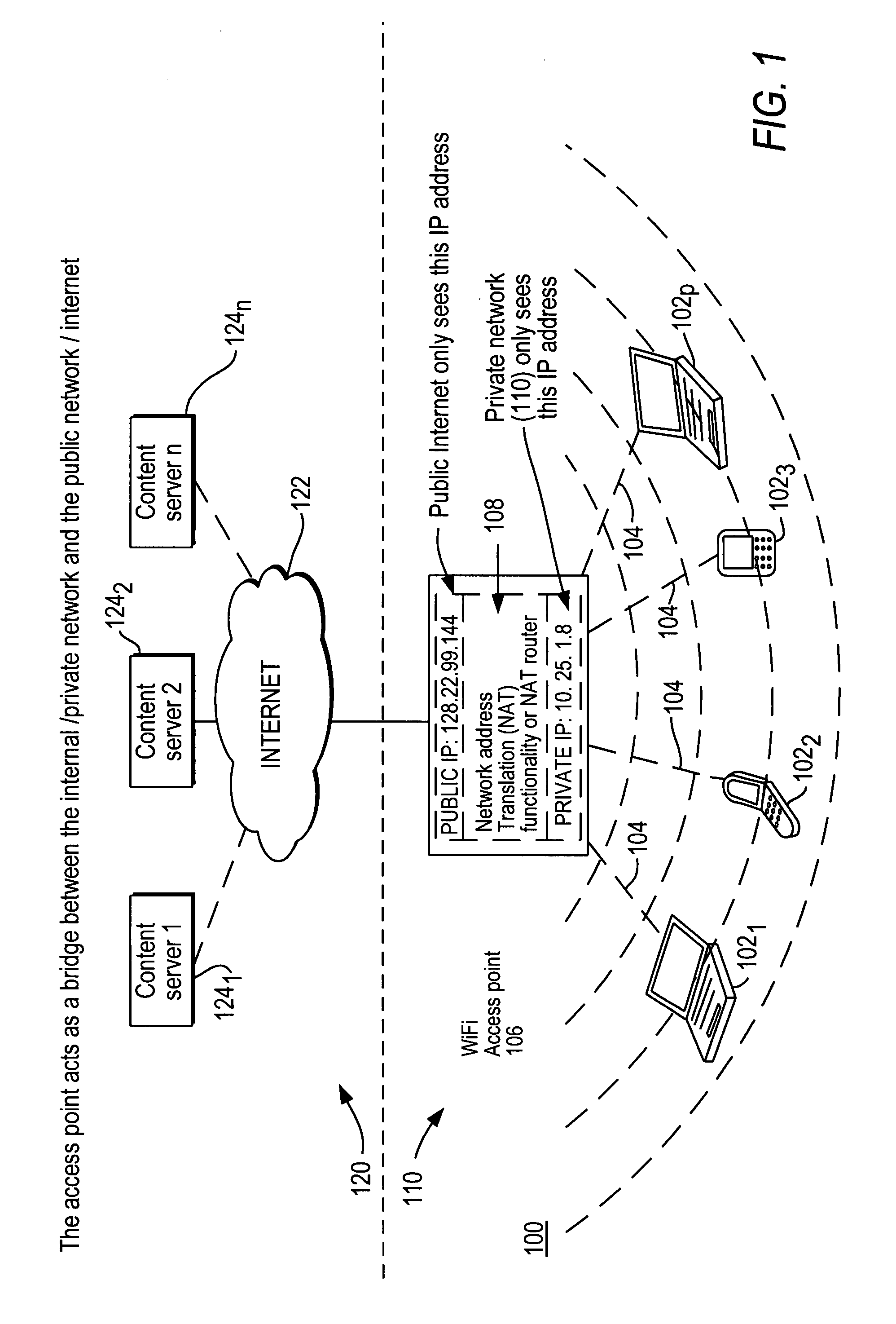
A public network is a type of network wherein anyone, namely the general public, has access and through it can connect to other networks or the Internet.
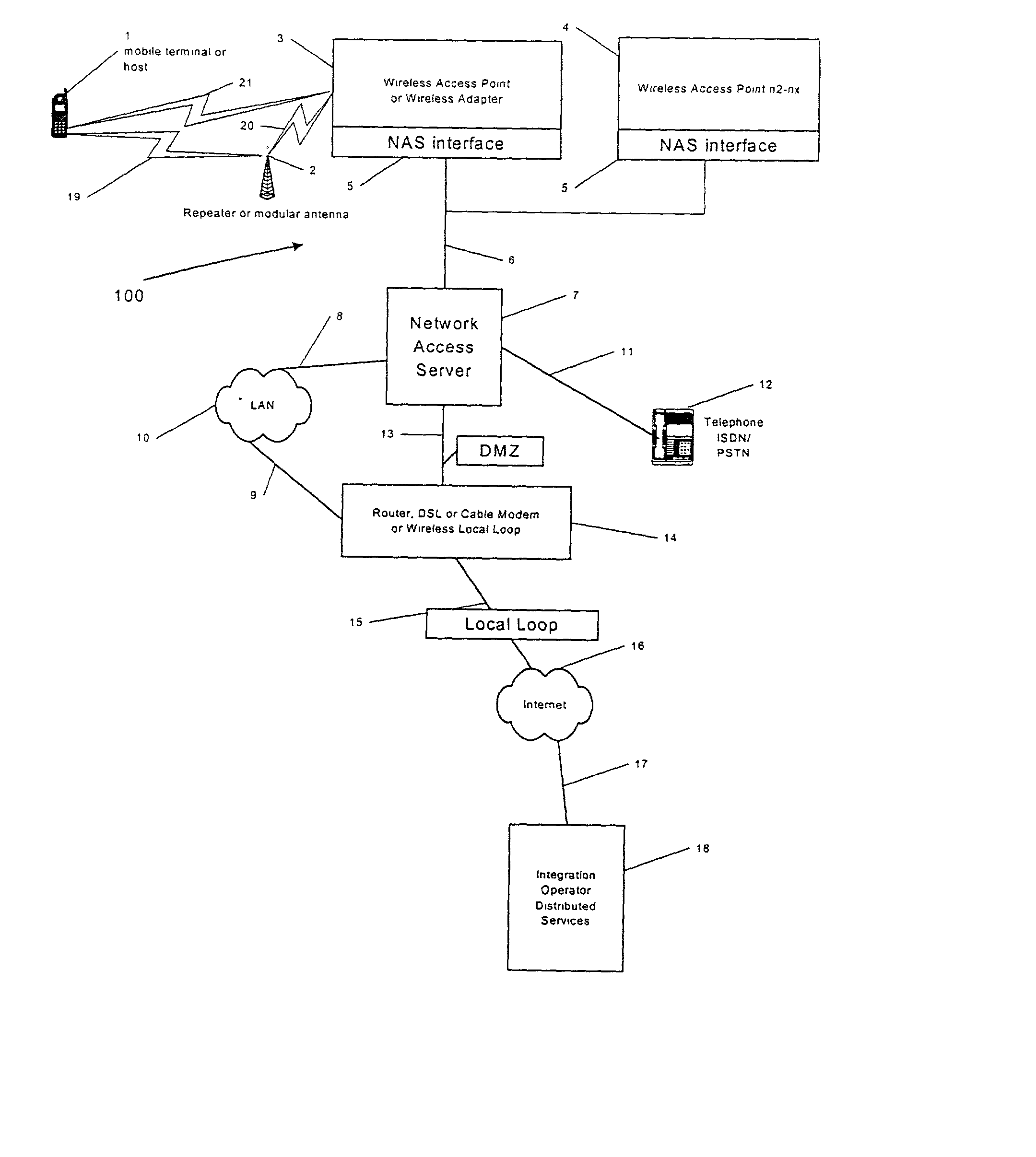
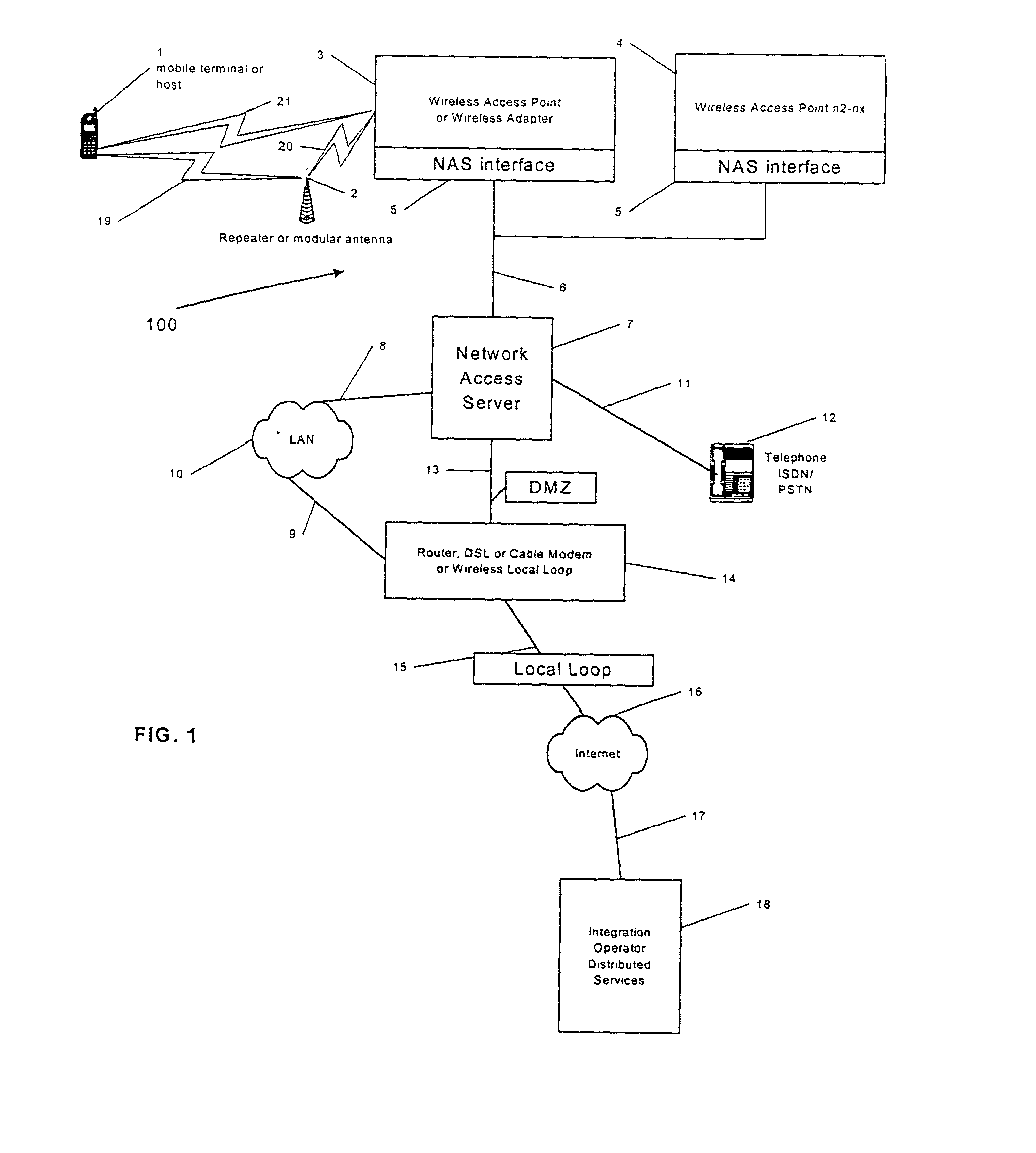
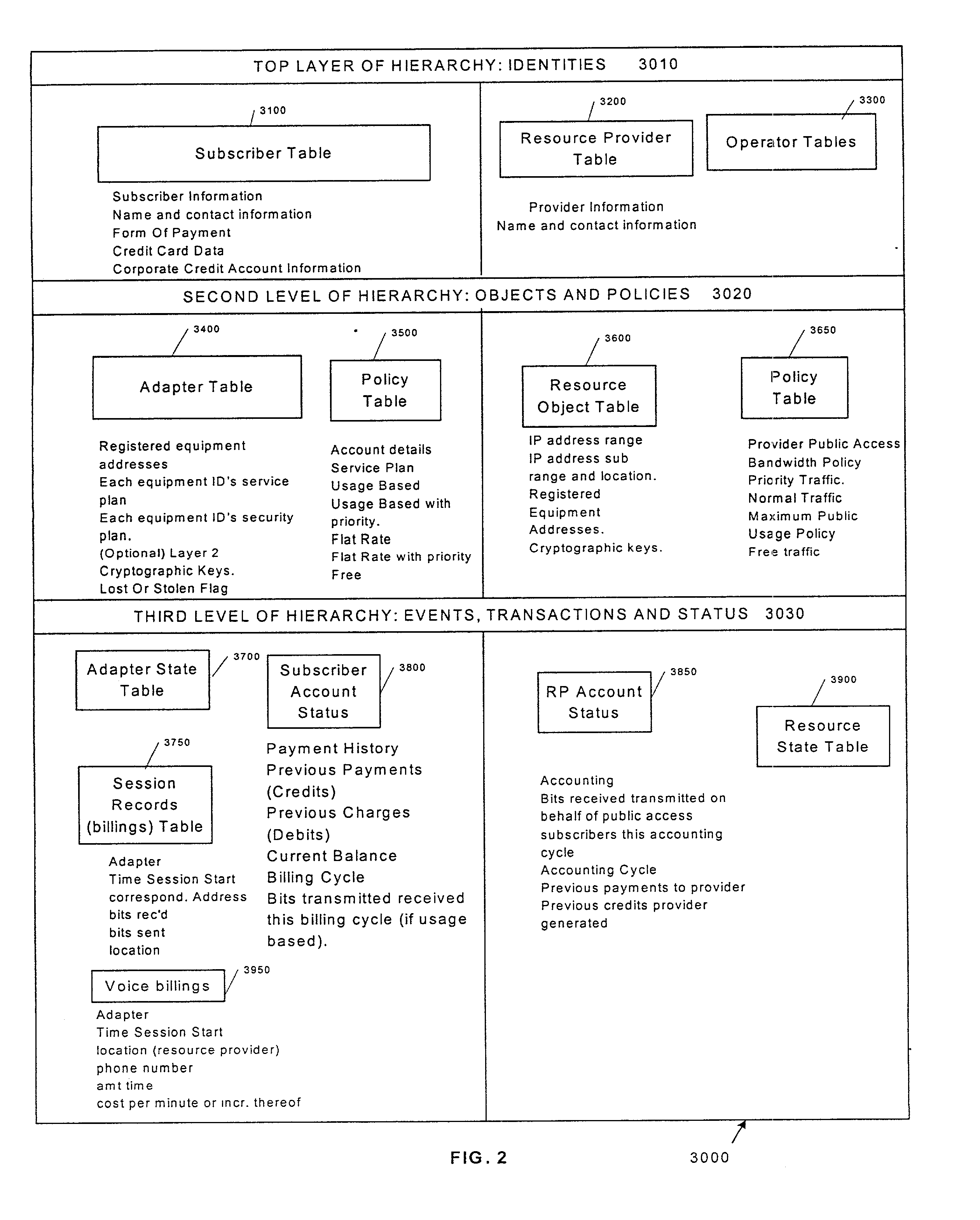
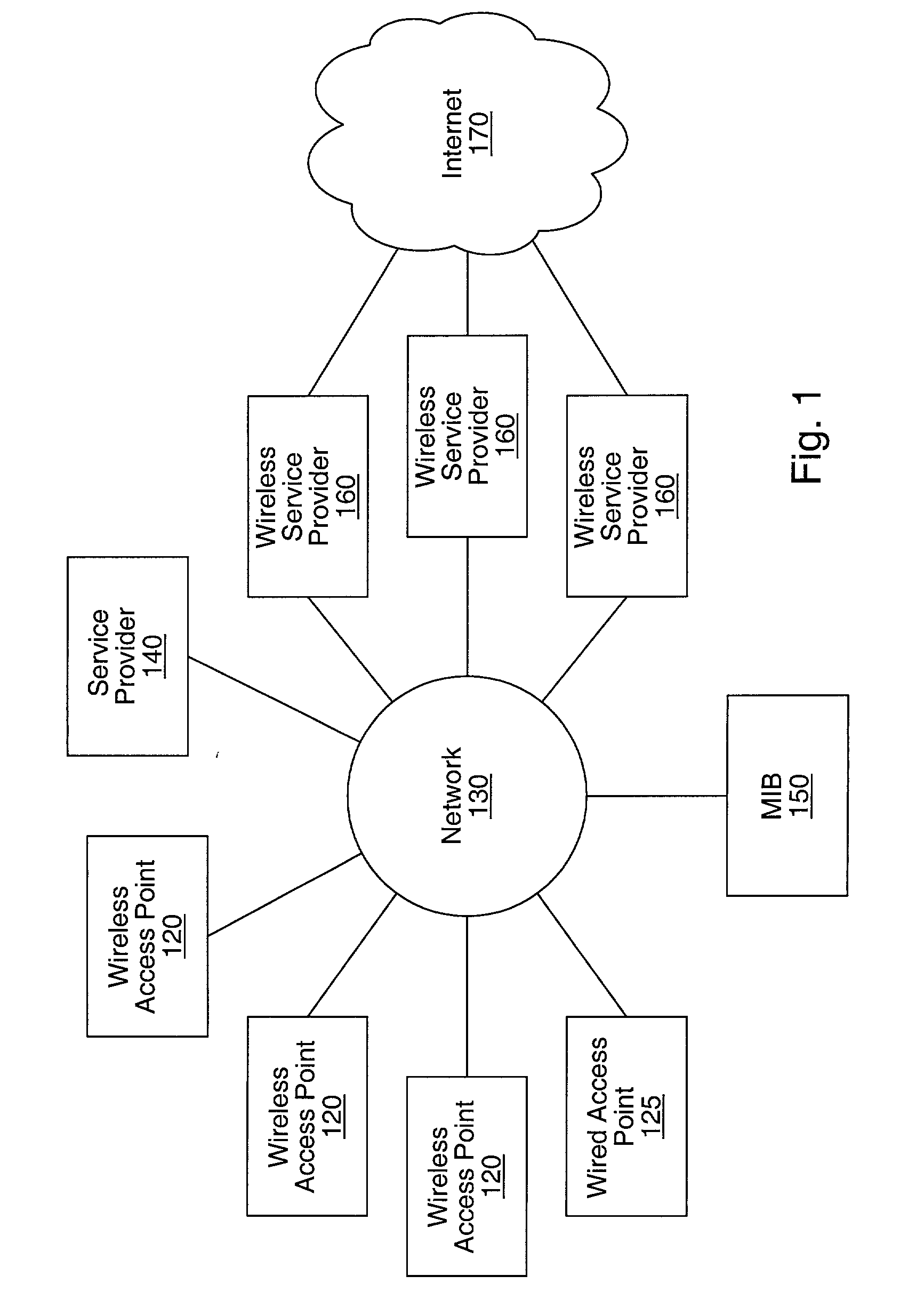
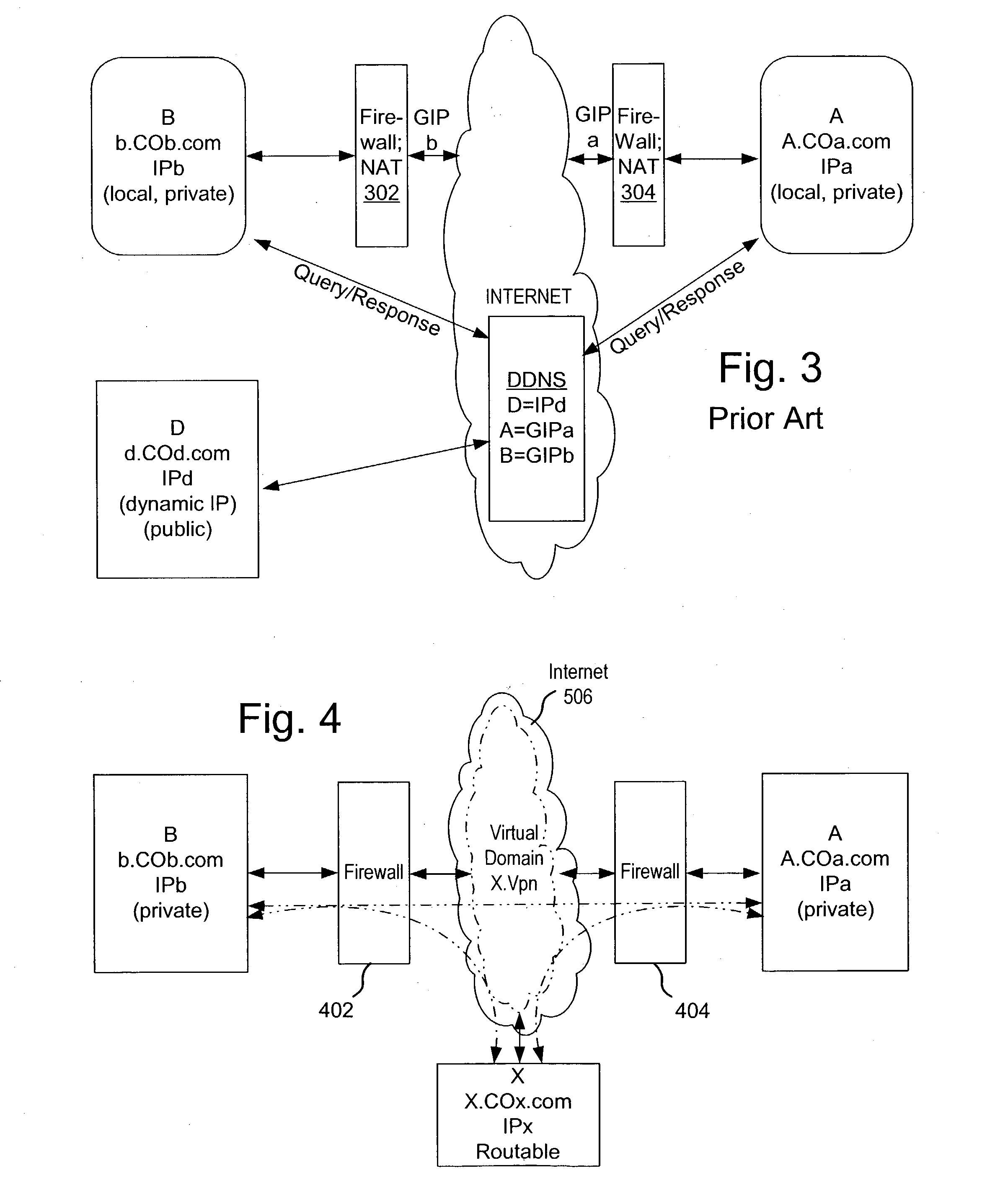
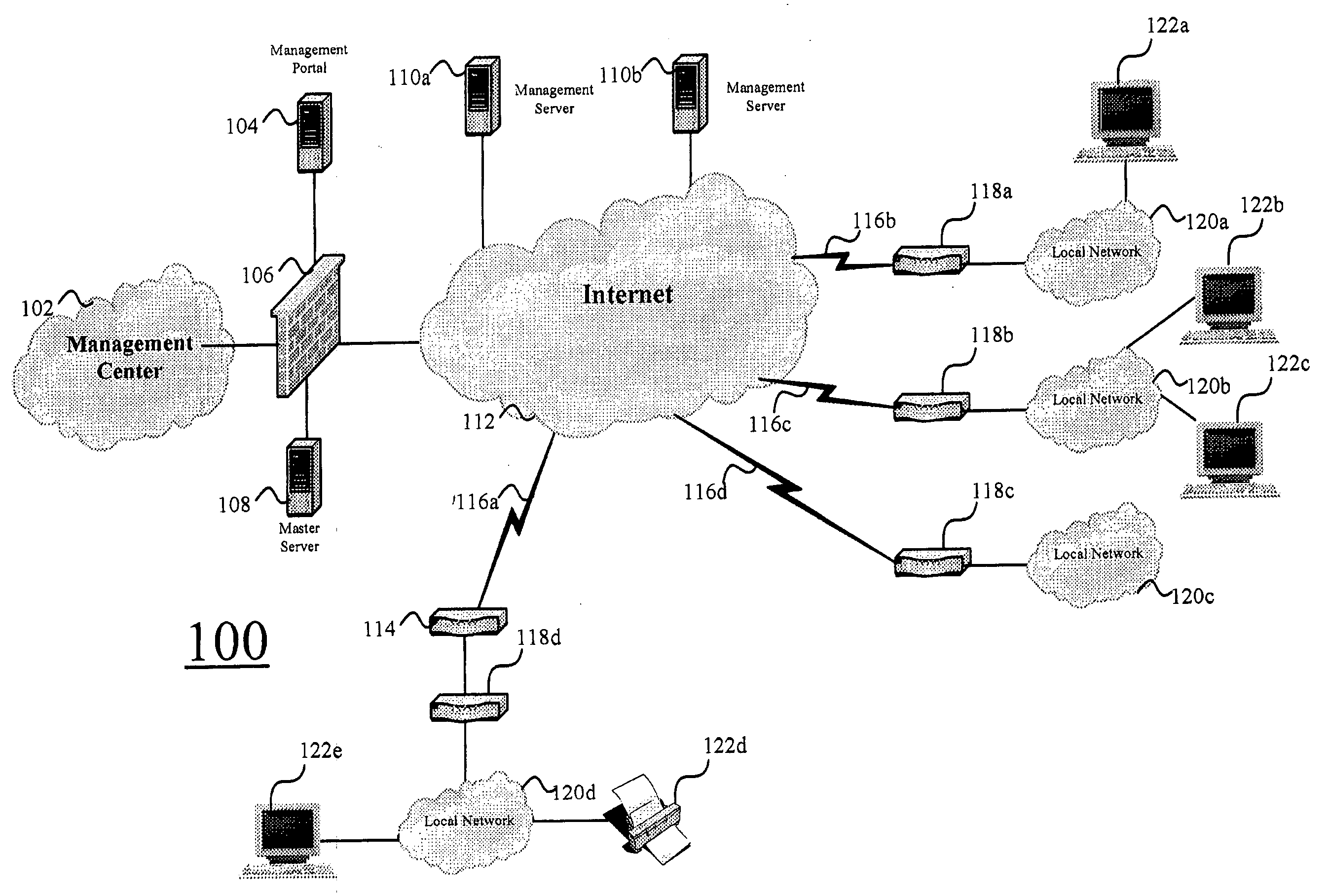
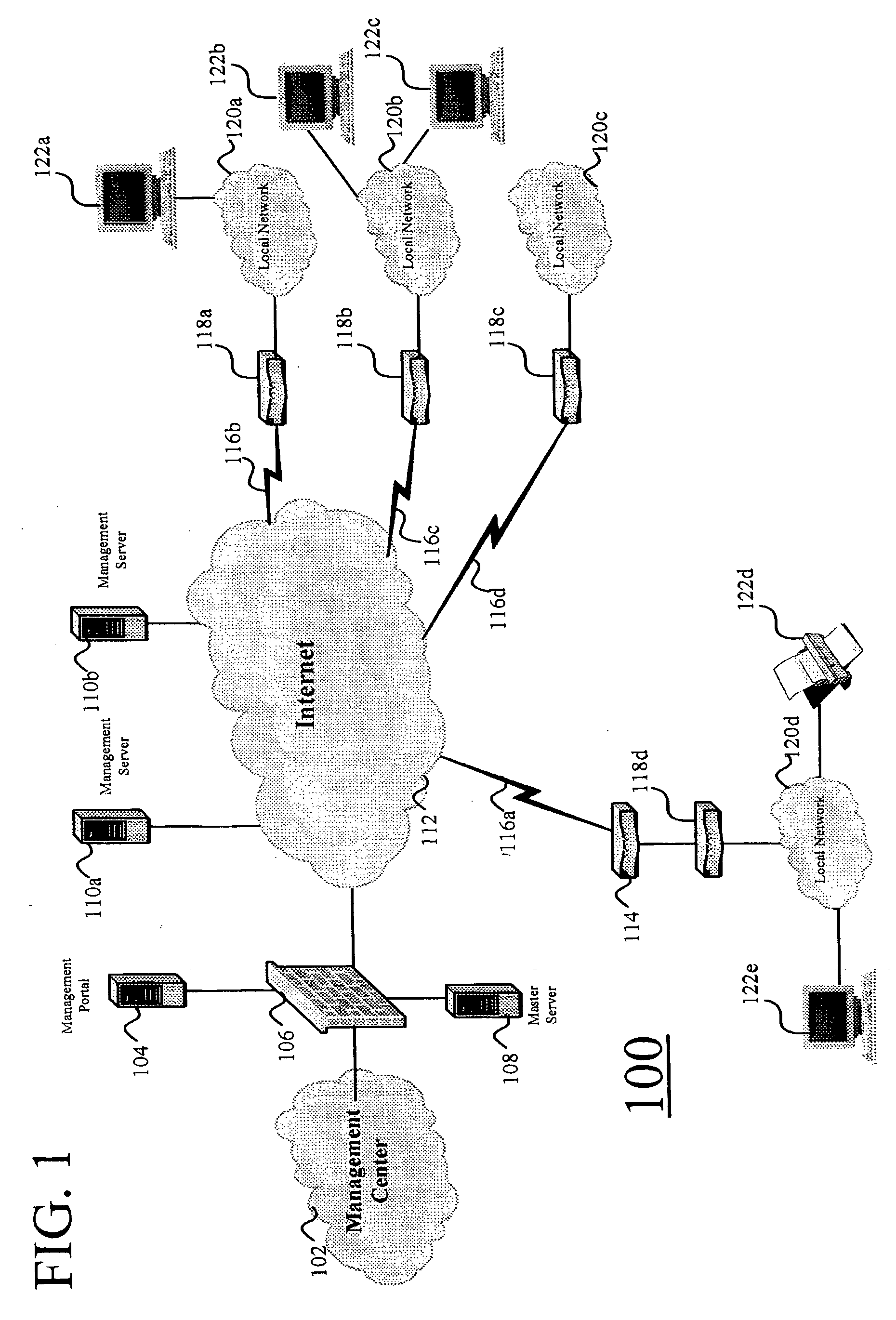
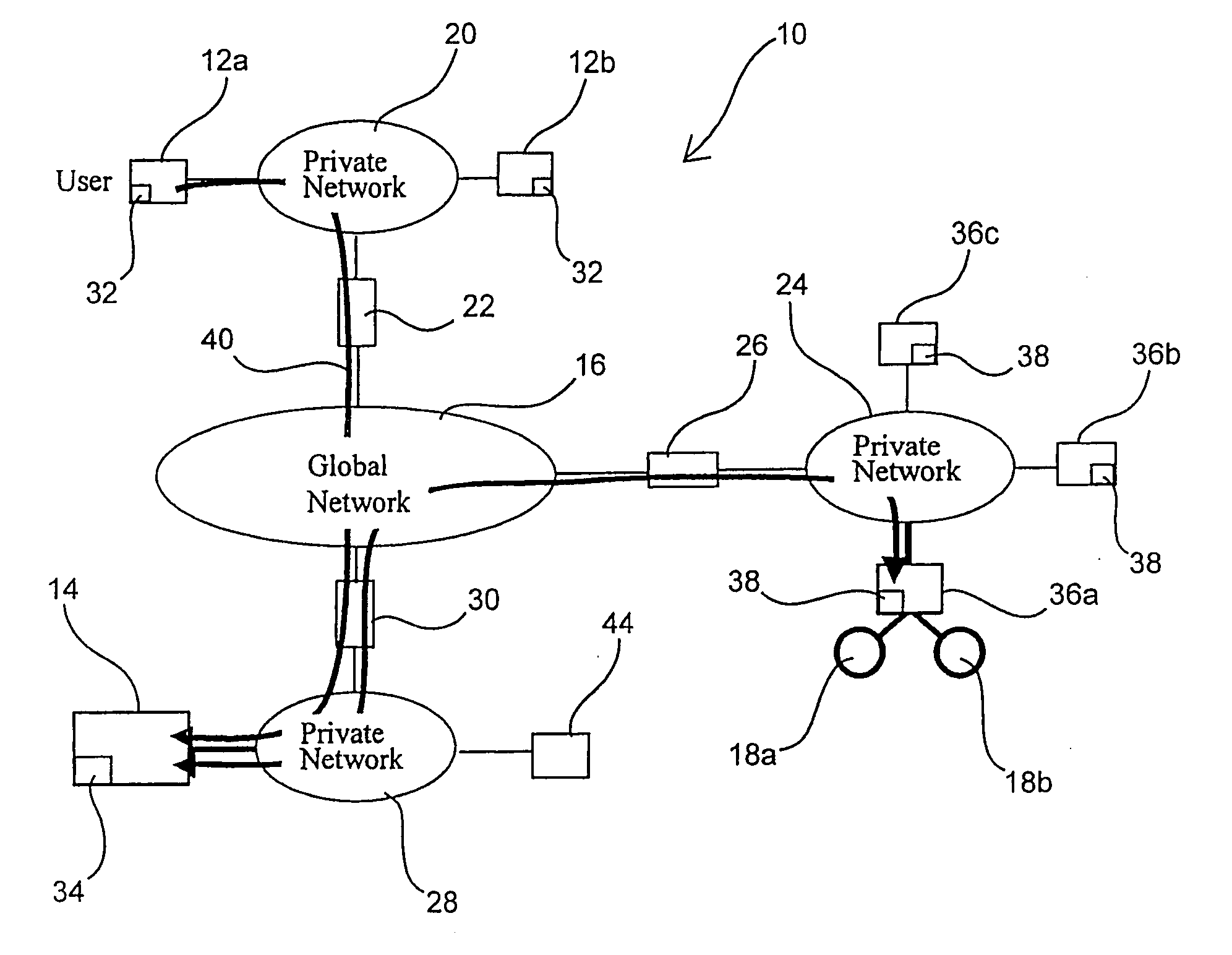
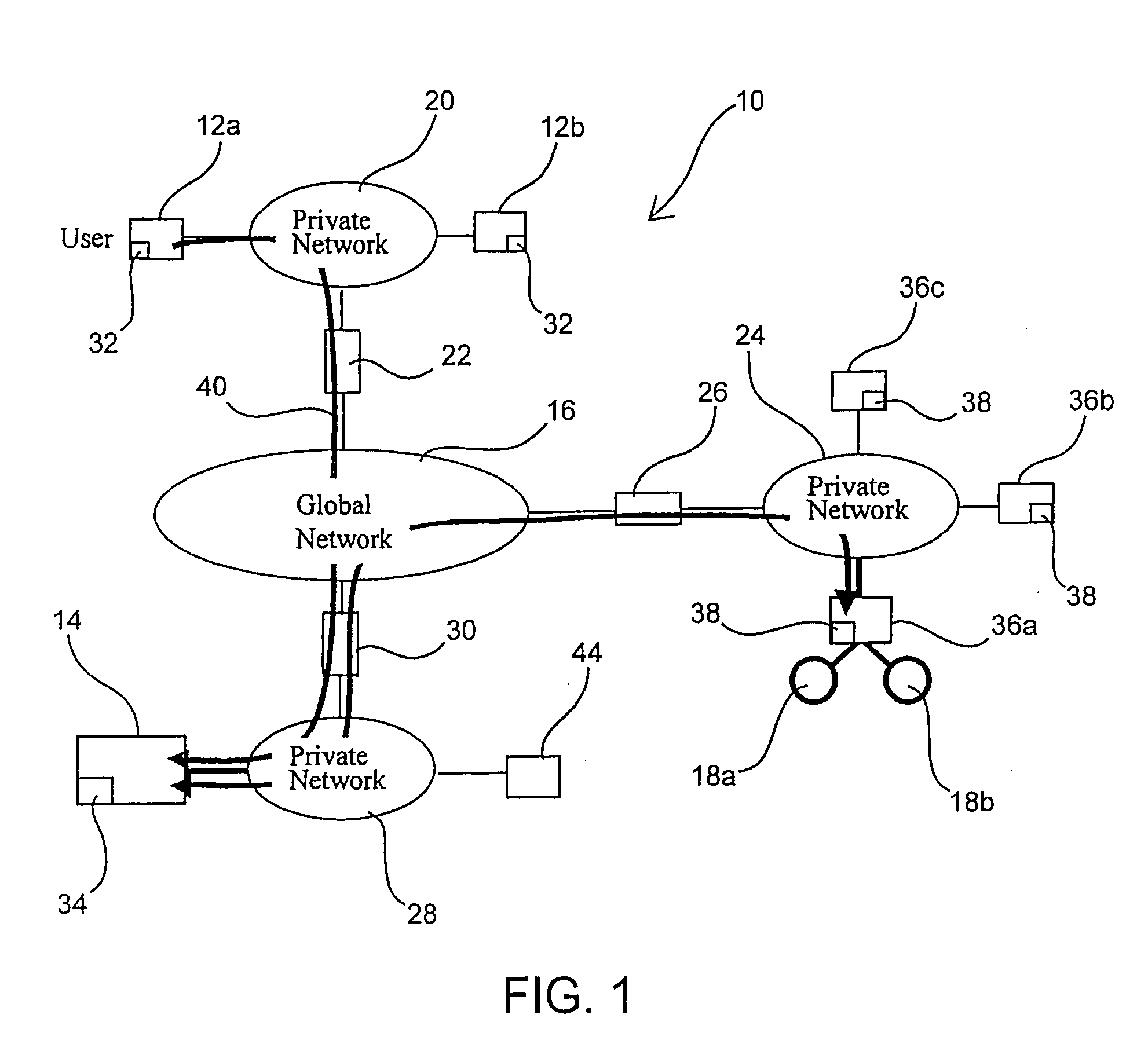
Integrating public and private network resources for optimized broadband wireless access and method
InactiveUS20020075844A1Network traffic/resource managementNetwork topologiesNetwork access serverPrivate network
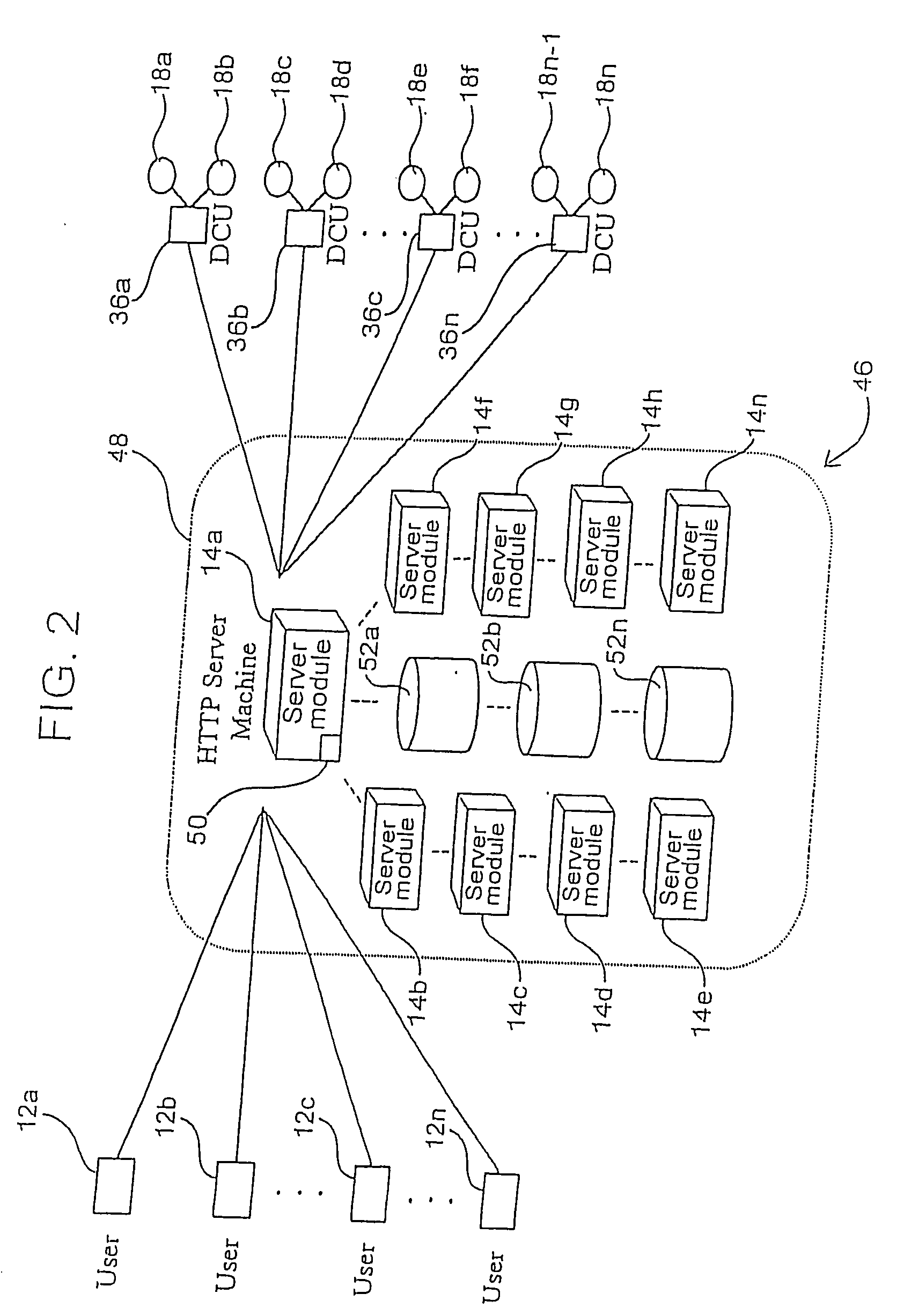
A system and method are disclosed for providing ubiquitous public network access to wireless, mobile terminals using private networks having private network access points and connections with the public network. The wireless, mobile terminals are permitted to use wireless, radio frequency communication devices comprising private network access points. A network access server (NAS) is associated with each wireless, radio frequency communication device and provides an interface between the wireless, mobile terminals and the private network. The NAS controls registration of wireless, mobile terminals as subscribers, and provides public network access to the mobile terminals through the private network's access point and public network connection. The NAS also restricts access by the mobile terminals to the private network, meters network useage by the mobile terminals, and controls use of bandwidth by the mobile terminals. The NAS also interfaces with integration operator distributed services over the public network. The integration operator services include databases and servers for storing and providing subscriber and network provider information for subscriber registration, network access and useage control, and accounting purposes. The NAS may be provided as a standalone element embodied in a computer, or may be integrated with the wireless radio frequency device and / or a network adaptor device for the private network.
Owner:NTT DOCOMO DCMR COMM LAB USA
Distributed network communication system which allows multiple wireless service providers to share a common network infrastructure
System and method for providing access to multiple wireless service providers (WSPs) on a shared network infrastructure. The system includes a plurality of access points (APs) coupled to a network which may be distributed in airports, mass-transit stations, businesses, etc. The network may couple to a wide area network, such as the Internet. Each AP may include a plurality of virtual APs (VAPs), each corresponding to a WSP. A portable computing device (PCD) of a user stores identification information indicating a WSP of a plurality of possible WSPs, and which may include an access level of the user. Each AP "listens for" or detects identification information associated with numerous WSPs. When the AP receives the identification information from the PCD, it determines the VAP / WSP for the PCD using the identification information. Network access is then provided to the PCD through the determined WSP at the determined access level.
Owner:CISCO TECH INC
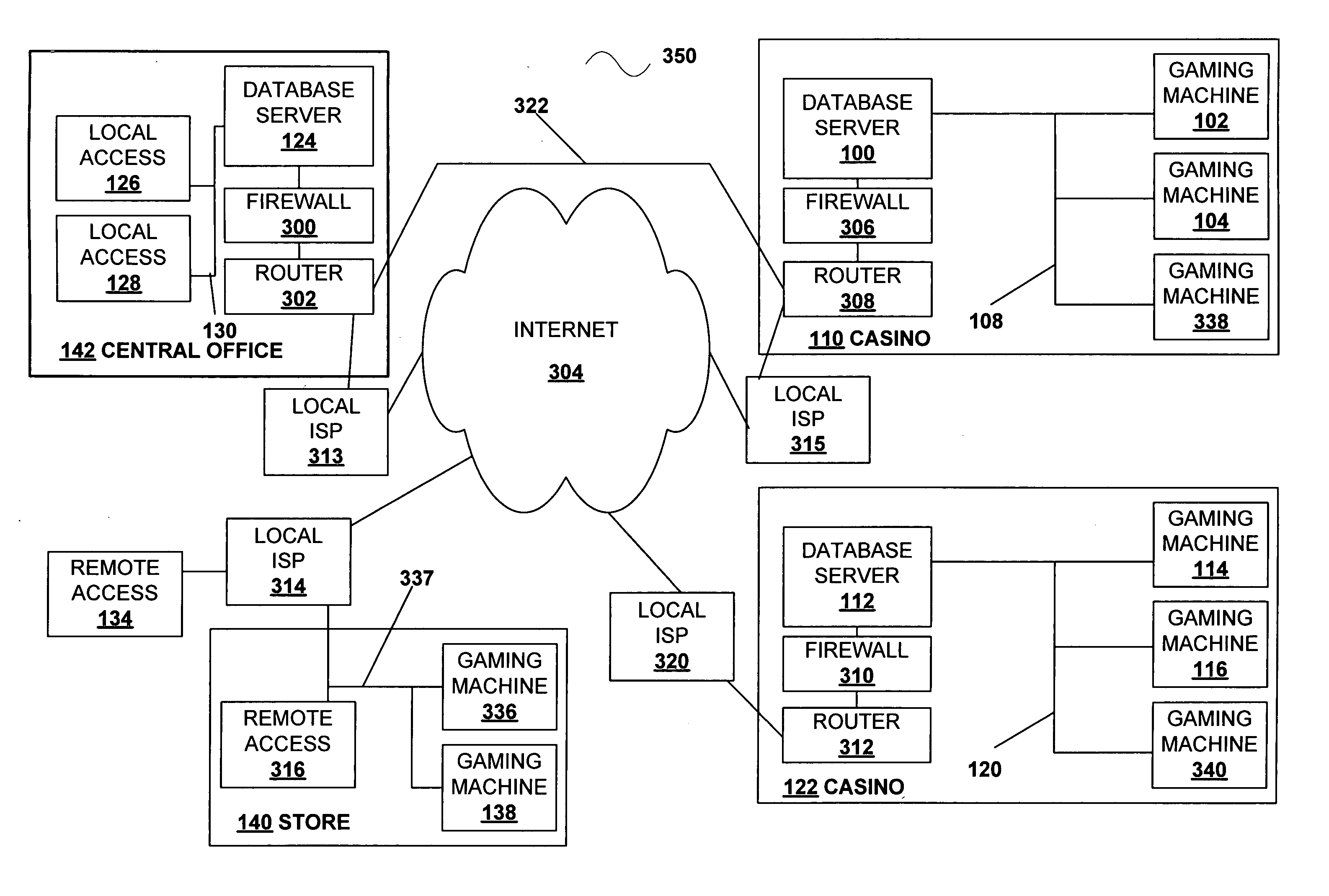
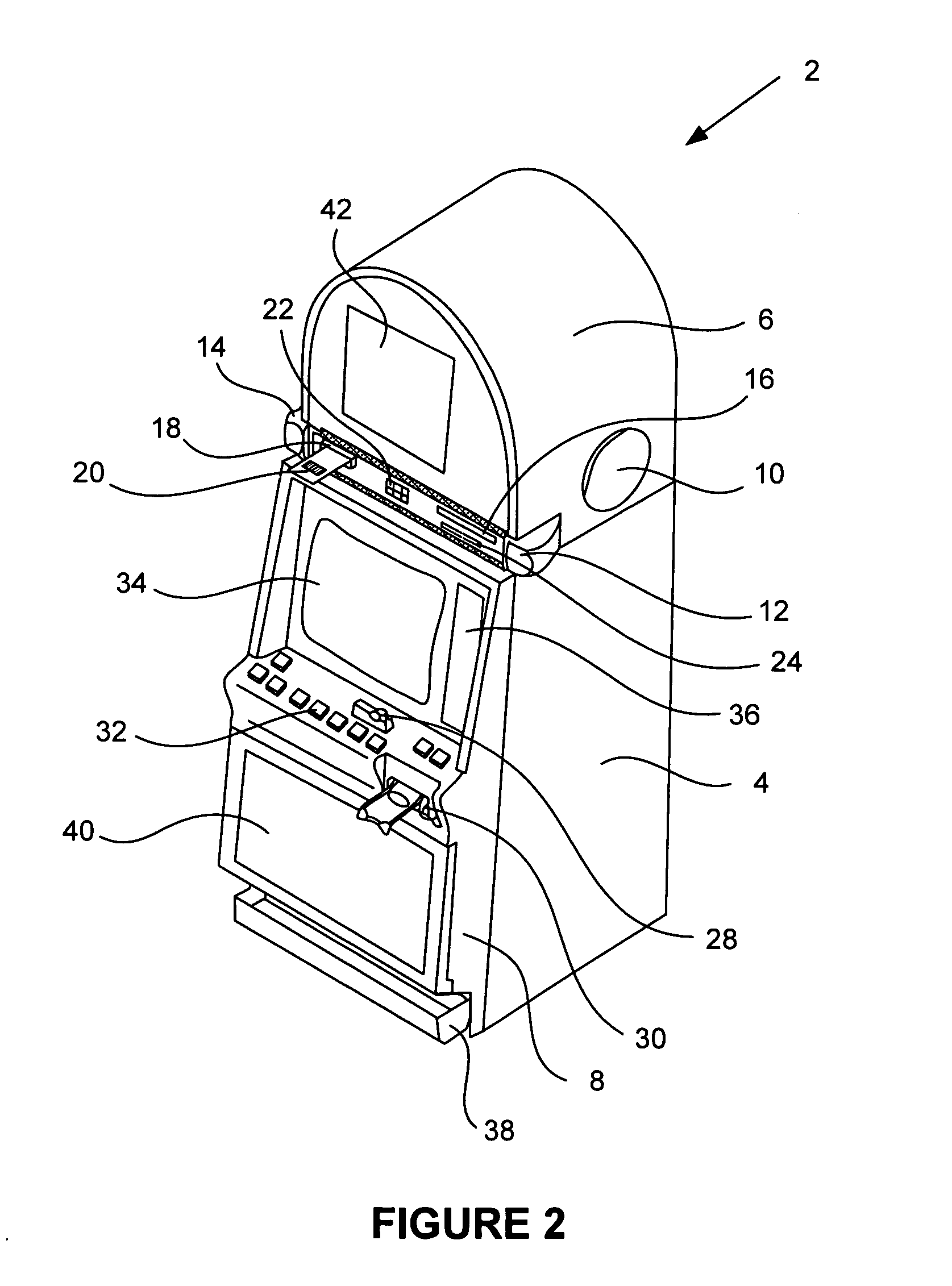
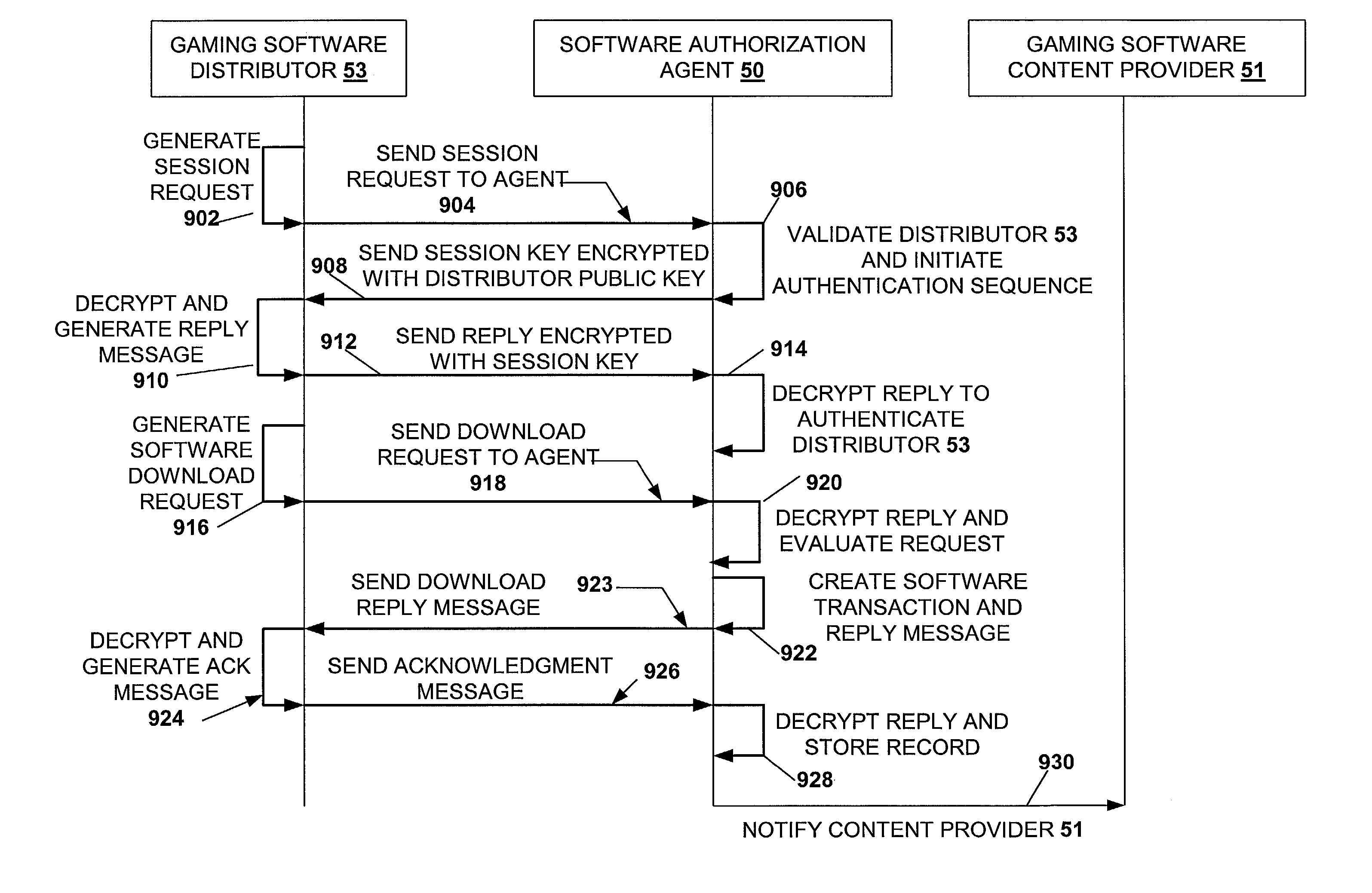
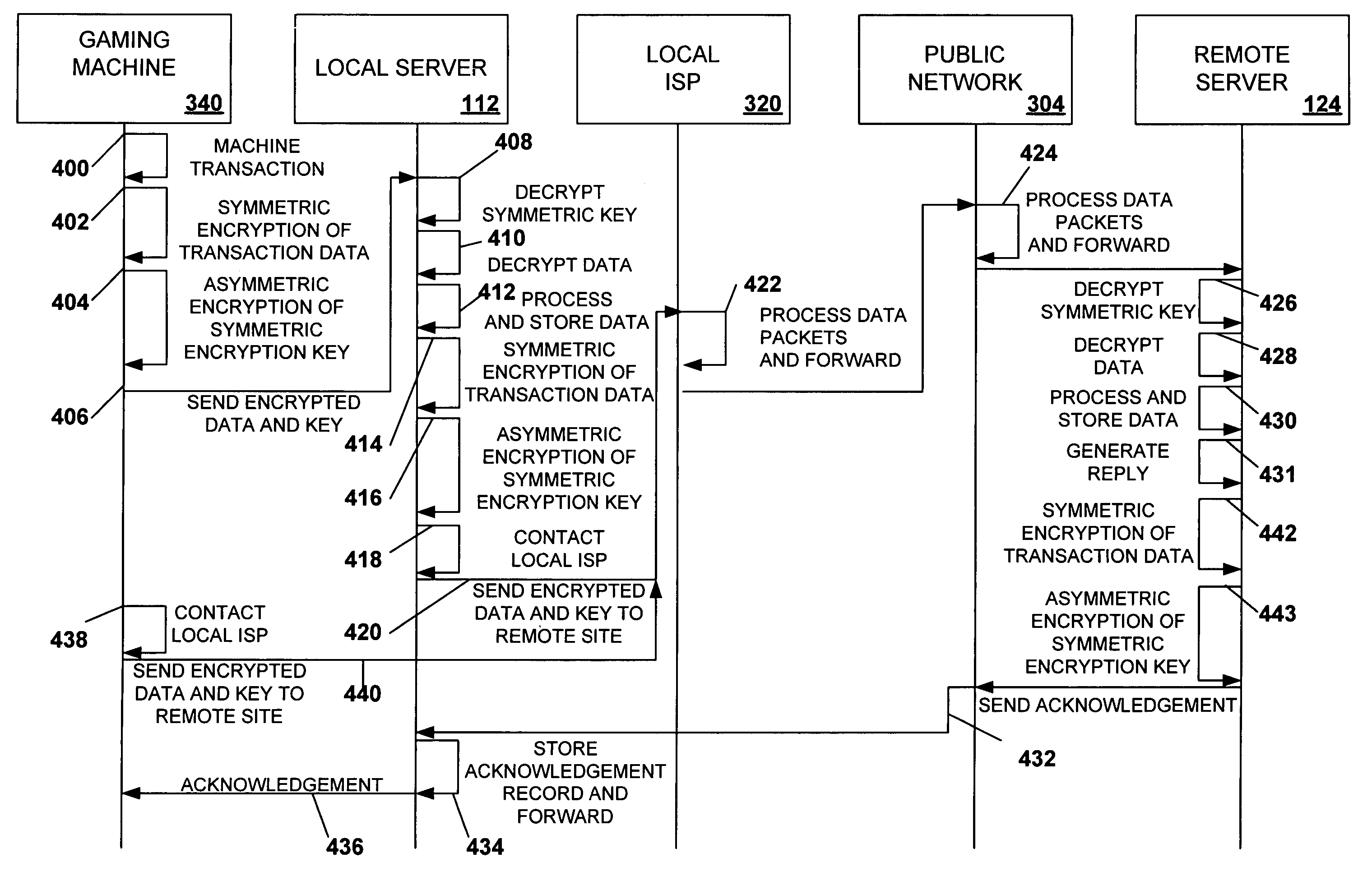
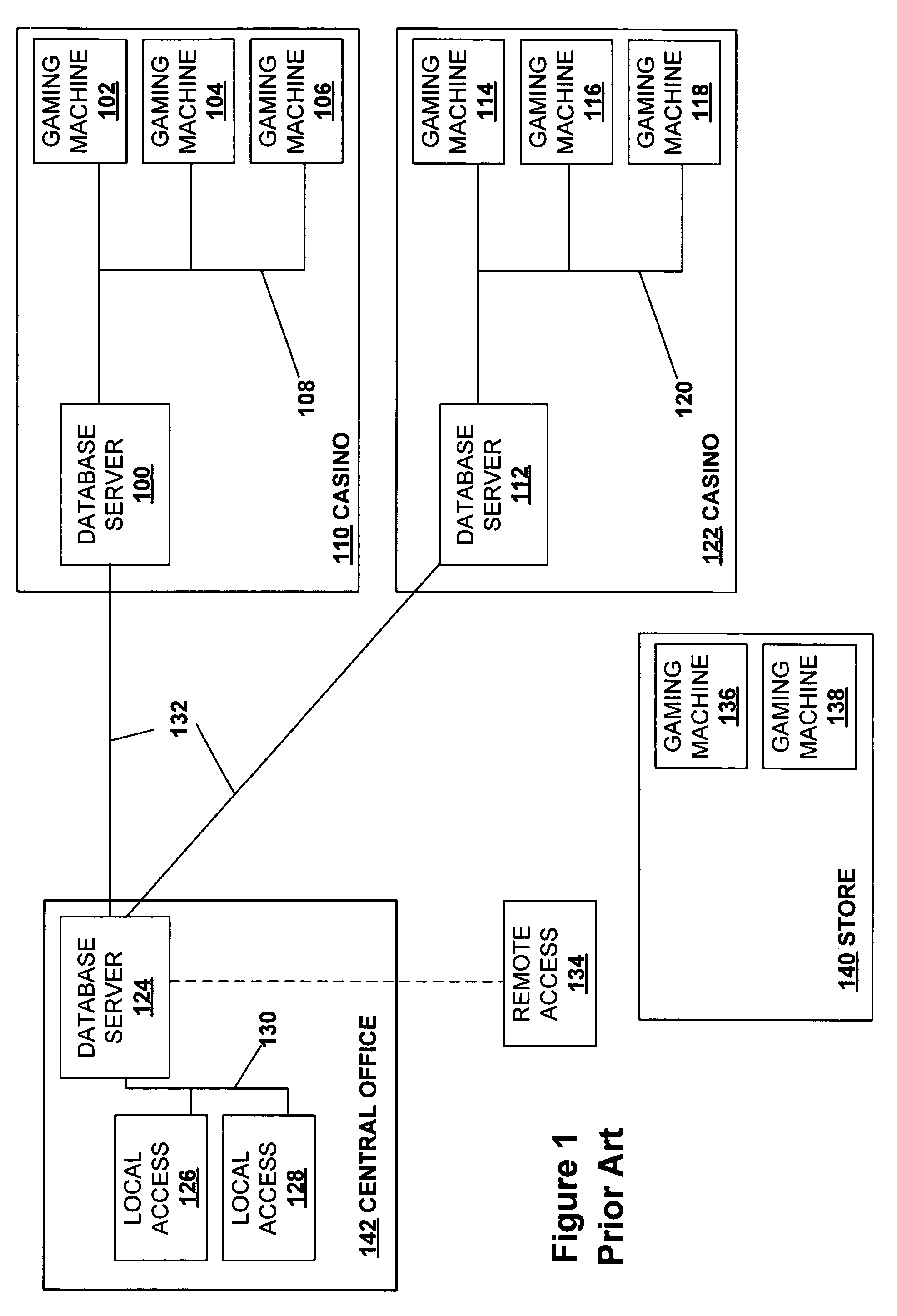
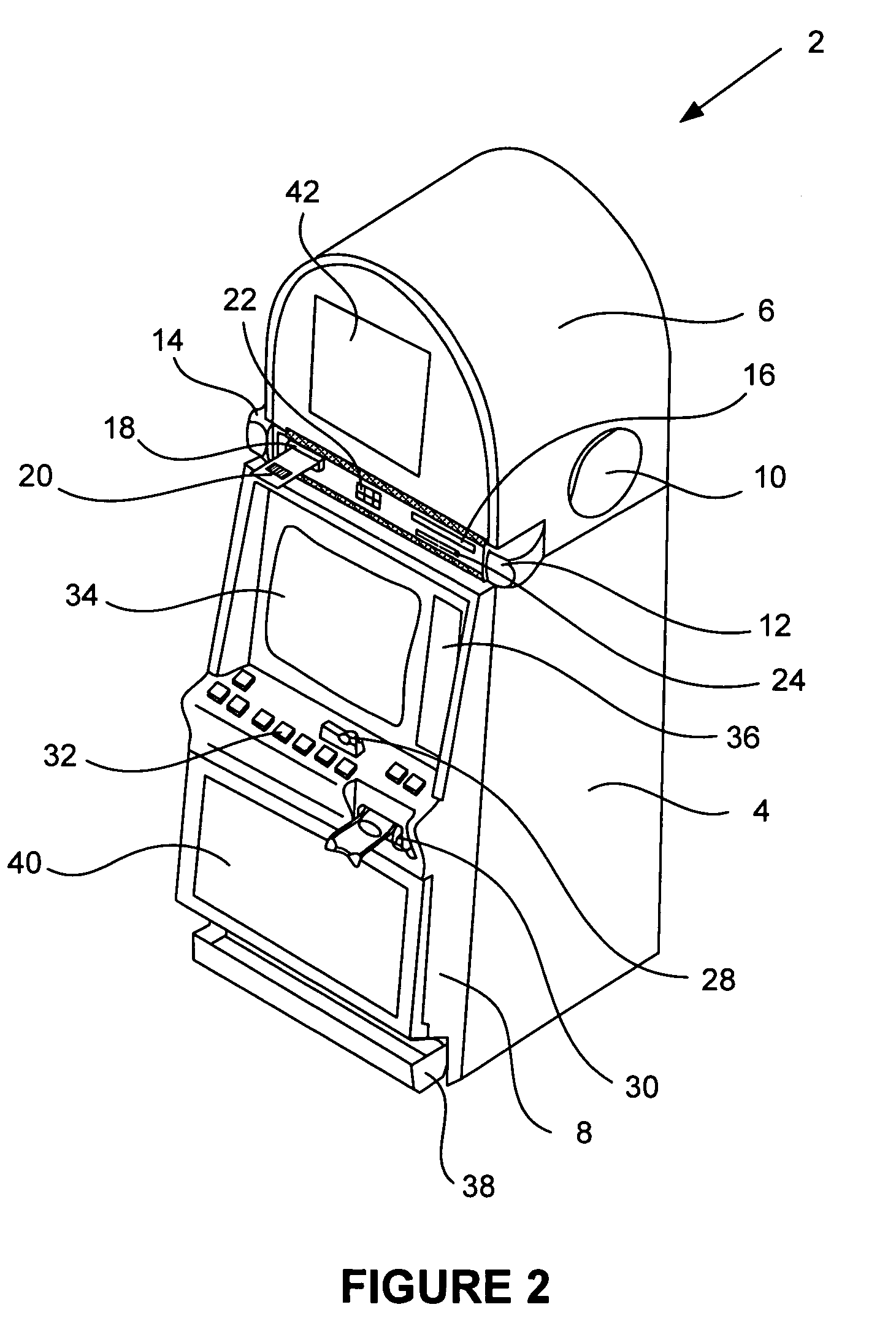
Secured virtual network in a gaming environment
InactiveUS20050192099A1Key distribution for secure communicationApparatus for meter-controlled dispensingSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
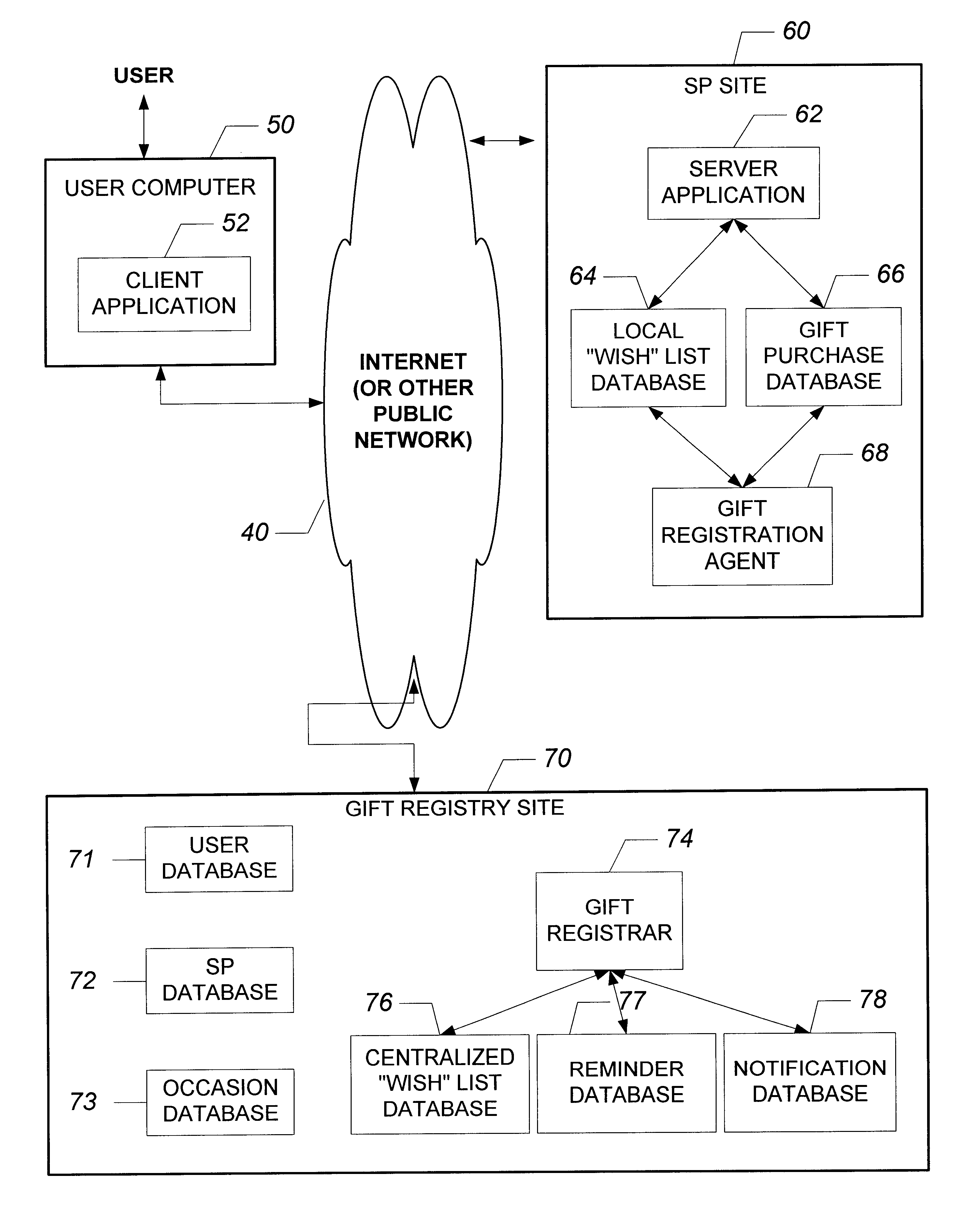
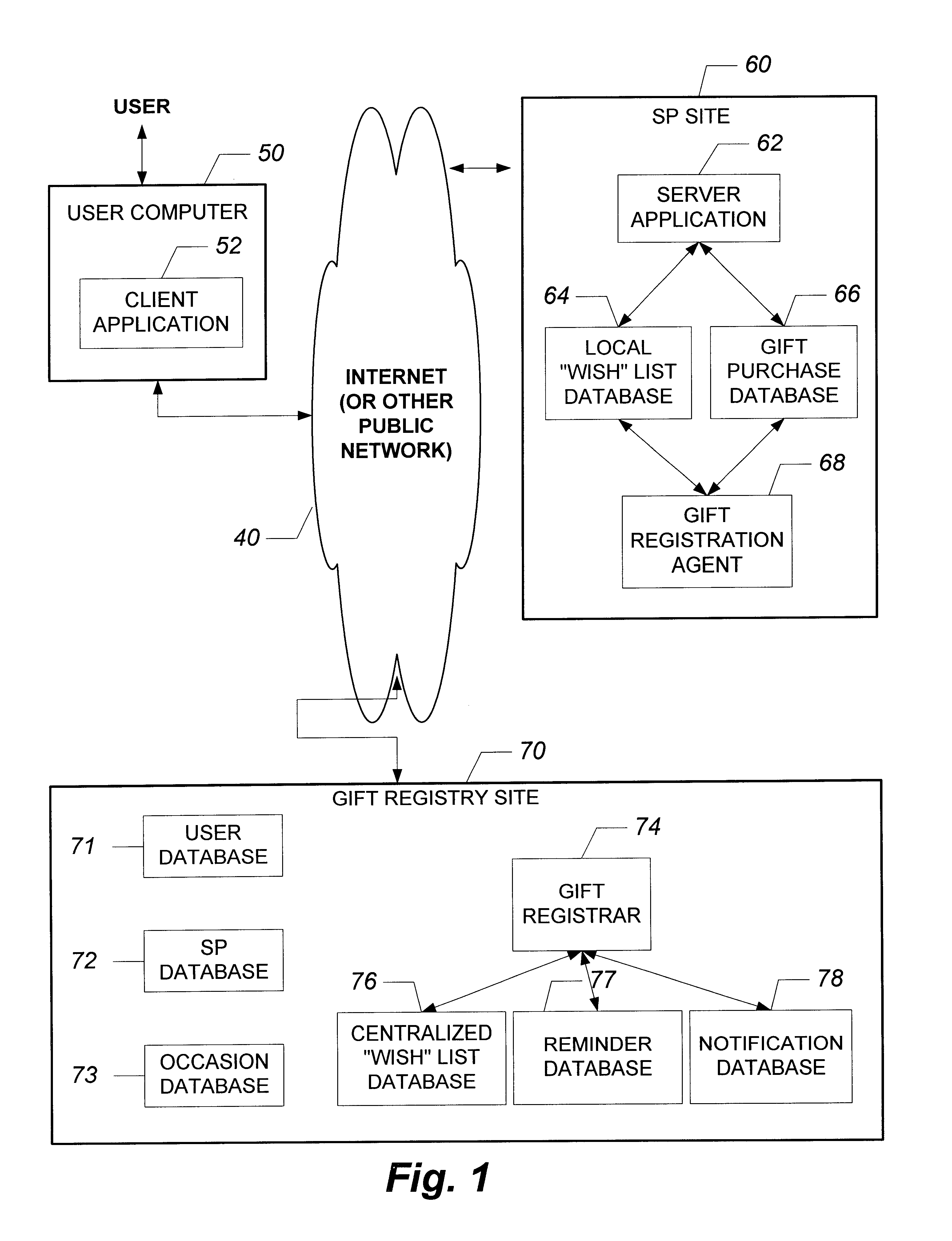
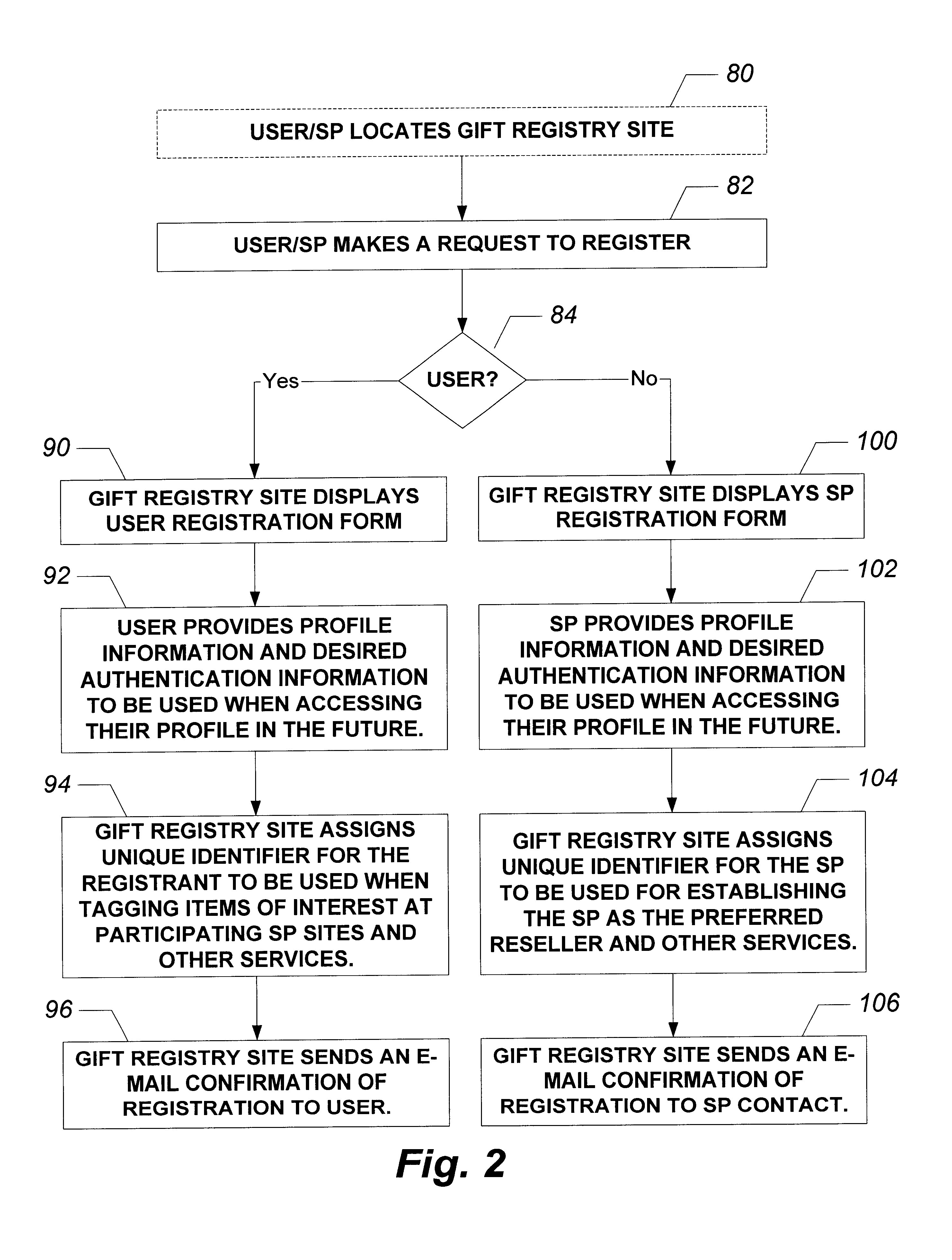
System and method for providing electronic multi-merchant gift registry services over a distributed network
InactiveUS6609106B1Minimal costMethod is fastReservationsBuying/selling/leasing transactionsWeb siteService provision
An online Gift Registry Service provides registration of information for a gift registrant and allows access to the registry by potential gift giver users. In addition, users can tag items of interest at participating Service Provider (SP) sites and the SP sites will register these items with the Gift Registry Service on the user's behalf. It further provides a streamlined checkout process for purchasing these gift items with the registered SP sites (e.g. World Wide Web sites) over a distributed public network. Users and Service Providers (SP) initially register with the Gift Registry Service and are provided additional functionality. For users, a reminder service is provided to notify individuals automatically upon the trigger of certain events, such as important dates or product sales from online merchants. In addition, there are various occasion planning services available such as distribution lists, discussion groups, and other related resources for multiple events including weddings, baby showers, etc. These other resources include sending out announcements, reserving halls, and contracting services of related businesses for the occasion. A distinct advantage of this system is that users can perform all the planning for the event online in the comfort of their home or office. Service Providers on the other hand, can register system notification messages to be triggered on pre-determined events. In addition, Service Providers can obtain marketing information to tailor their products and services.
Owner:ROBERTSON STEVEN C
Secured virtual network in a gaming environment
InactiveUS7168089B2Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
Method, system and service for conducting authenticated business transactions
InactiveUS6957199B1Fast authenticationImprove securityComputer security arrangementsCommerceService provisionThe Internet
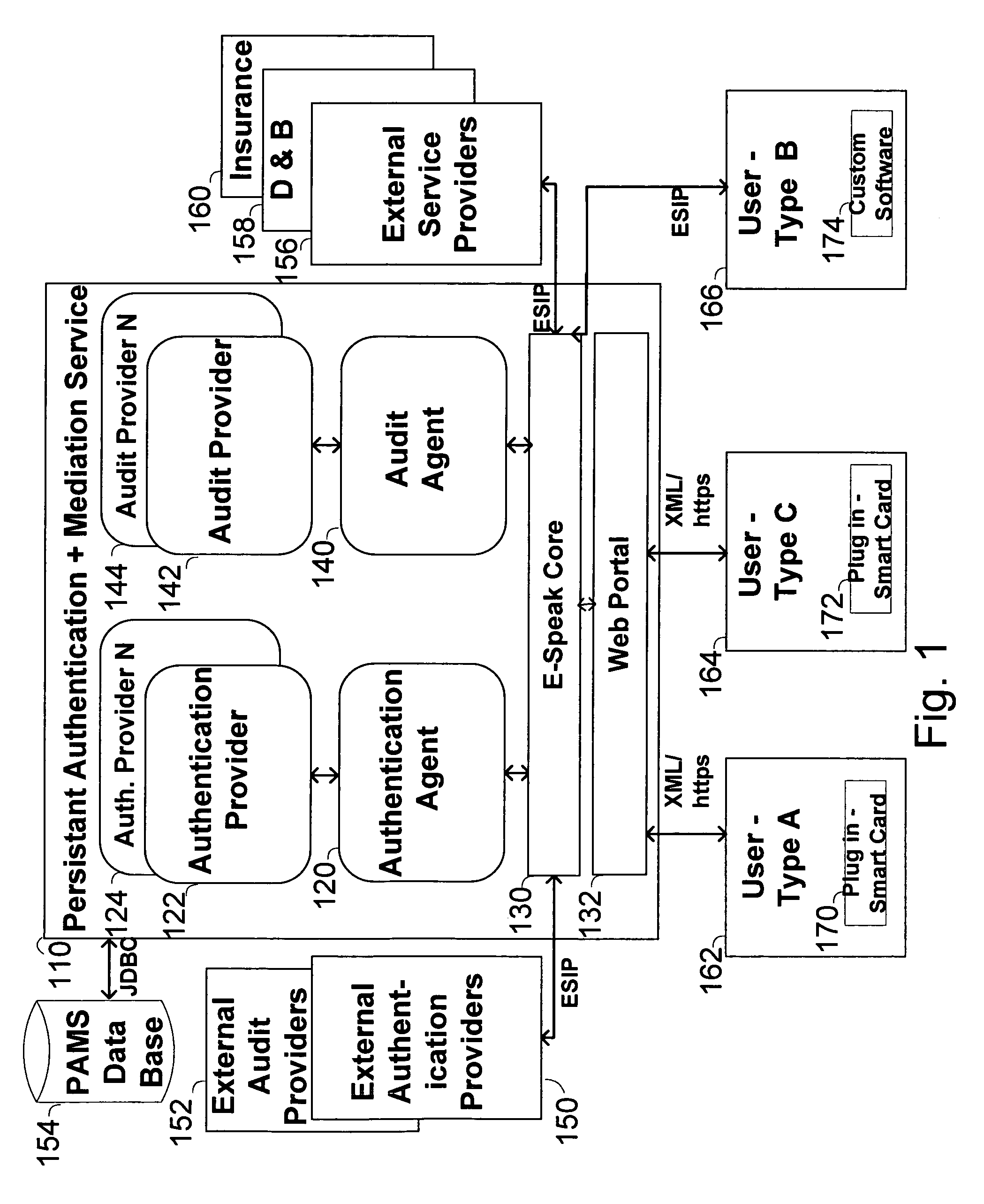
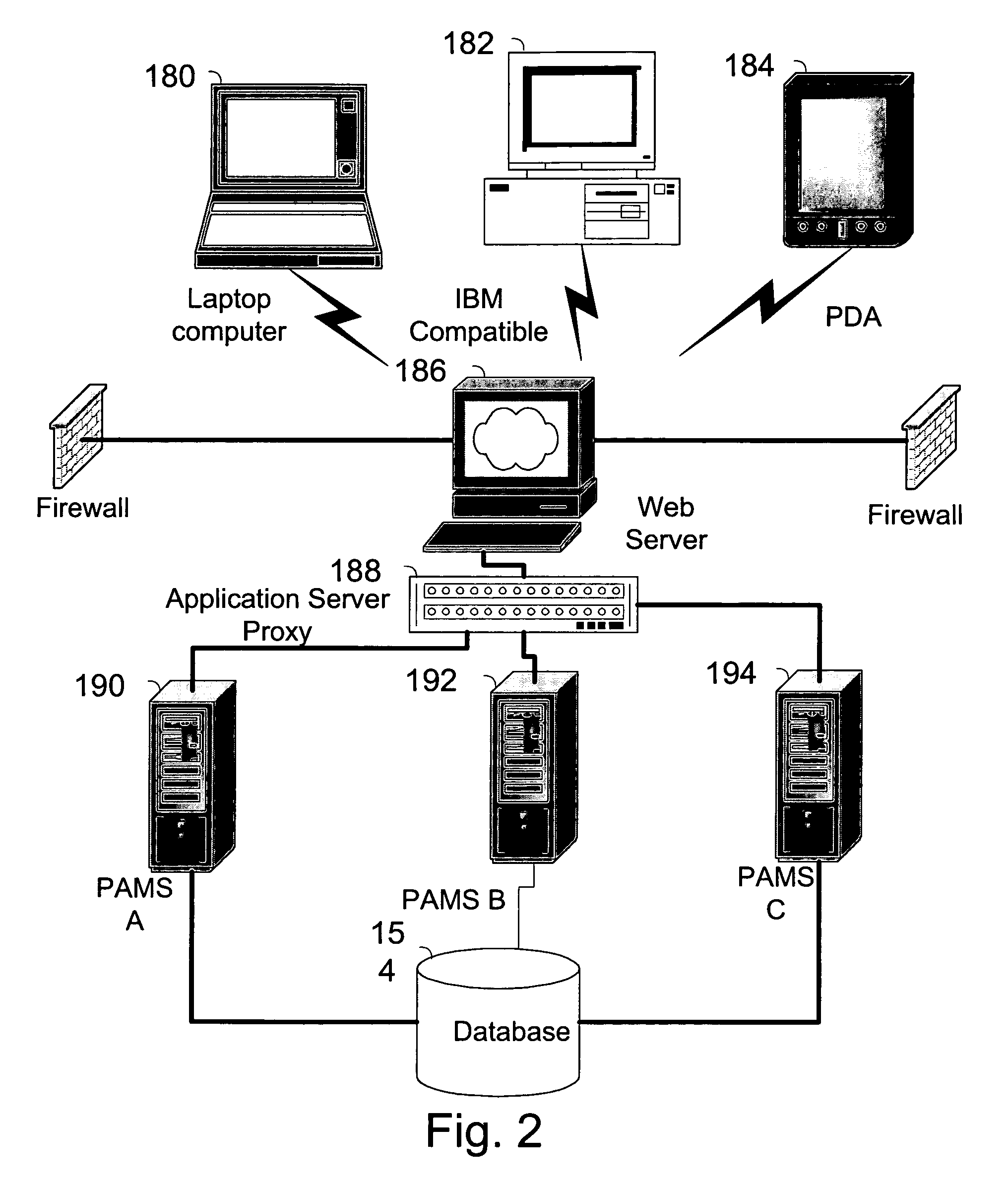
The invention pertains to a method, online service, and system, for creating partnerships based on trust relationships over a public network, authenticating trade partners, infrastructure providers and collaborators to each other, and providing users with an environment suitable for conducting transactions requiring a high level of trust. A service according to the invention is a persistent authentication and mediation service (PAMS) which is provided as an on-line service. One embodiment is a method for conducting authenticated business transactions involving microprocessor equipped devices over the Internet comprising:A. providing an on-line authentication service available on the distributed network;B. authenticating a plurality of users to said on-line authentication service using a closed authentication system to produce a plurality of authenticated users; andC. connecting a group of at least two of said plurality of authenticated users under persistent mediation of said on-line authentication service, producing a connected group of authenticated users.
Owner:FISHER DOUGLAS
Secure virtual community network system
ActiveUS20040249911A1Convenient introductionMultiple digital computer combinationsOffice automationPrivate networkPublic network
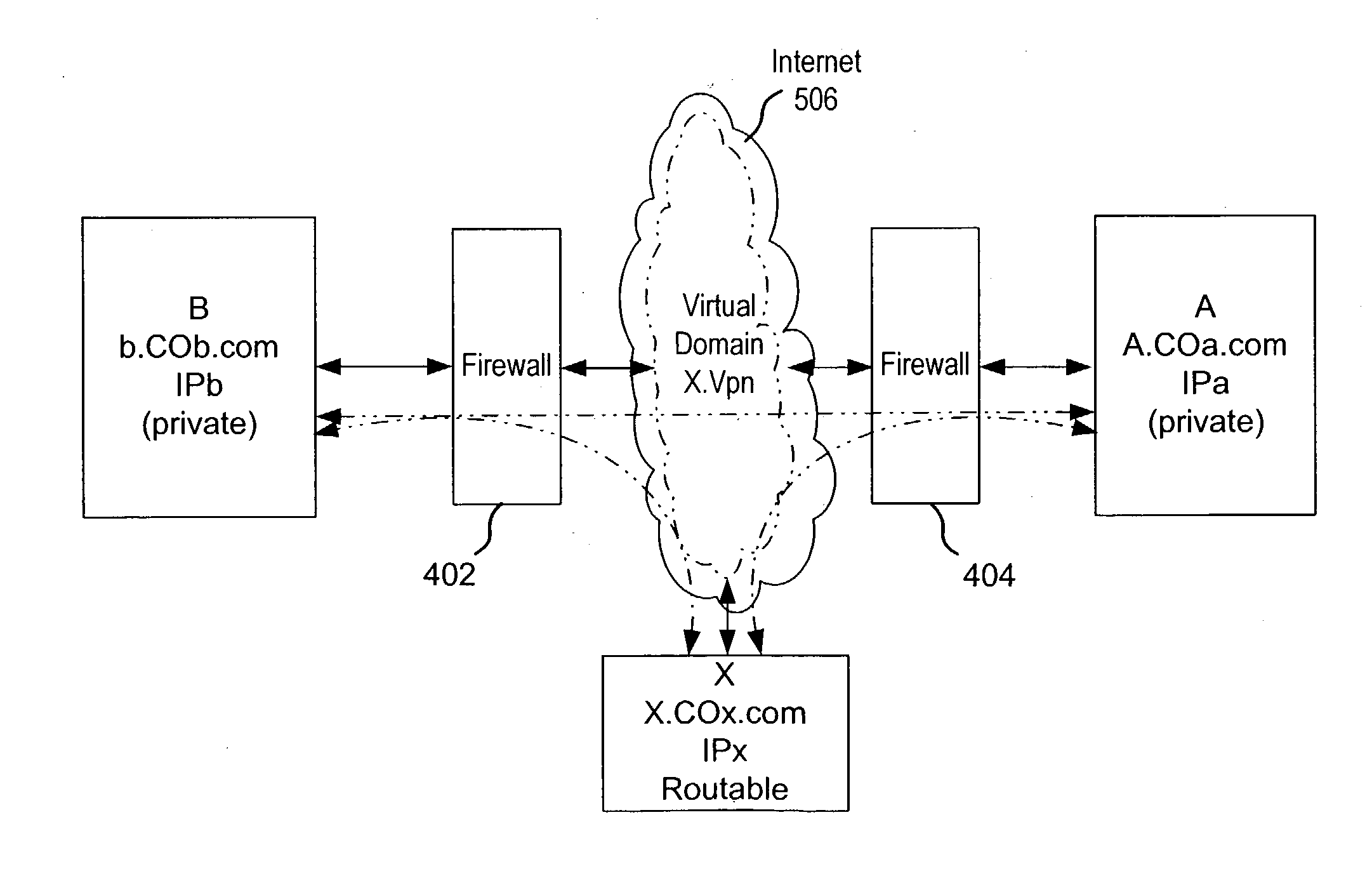
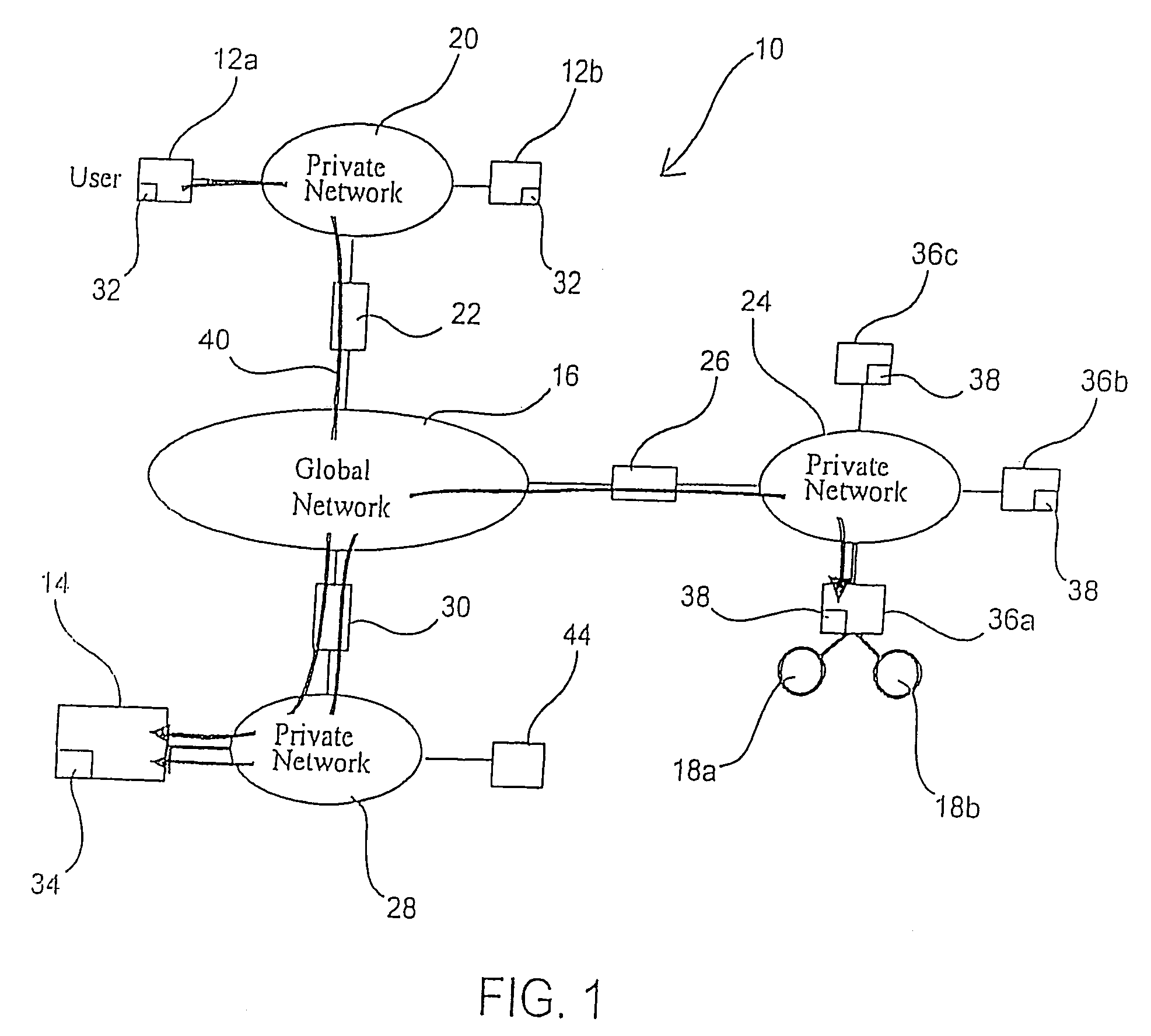
A private virtual dynamic network is provided for computing devices coupled to public networks or private networks. This enables computing devices anywhere in the world to join into private enterprise intranets and communicate with each other. In one embodiment, the present invention provides a separate private virtual address realm, seen to each user as a private network, while seamlessly crossing public and private network boundaries. One implementation of the present invention uses an agent to enable an entity to participate in the network without requiring the member to add new hardware or software.
Owner:F POSZAT HU
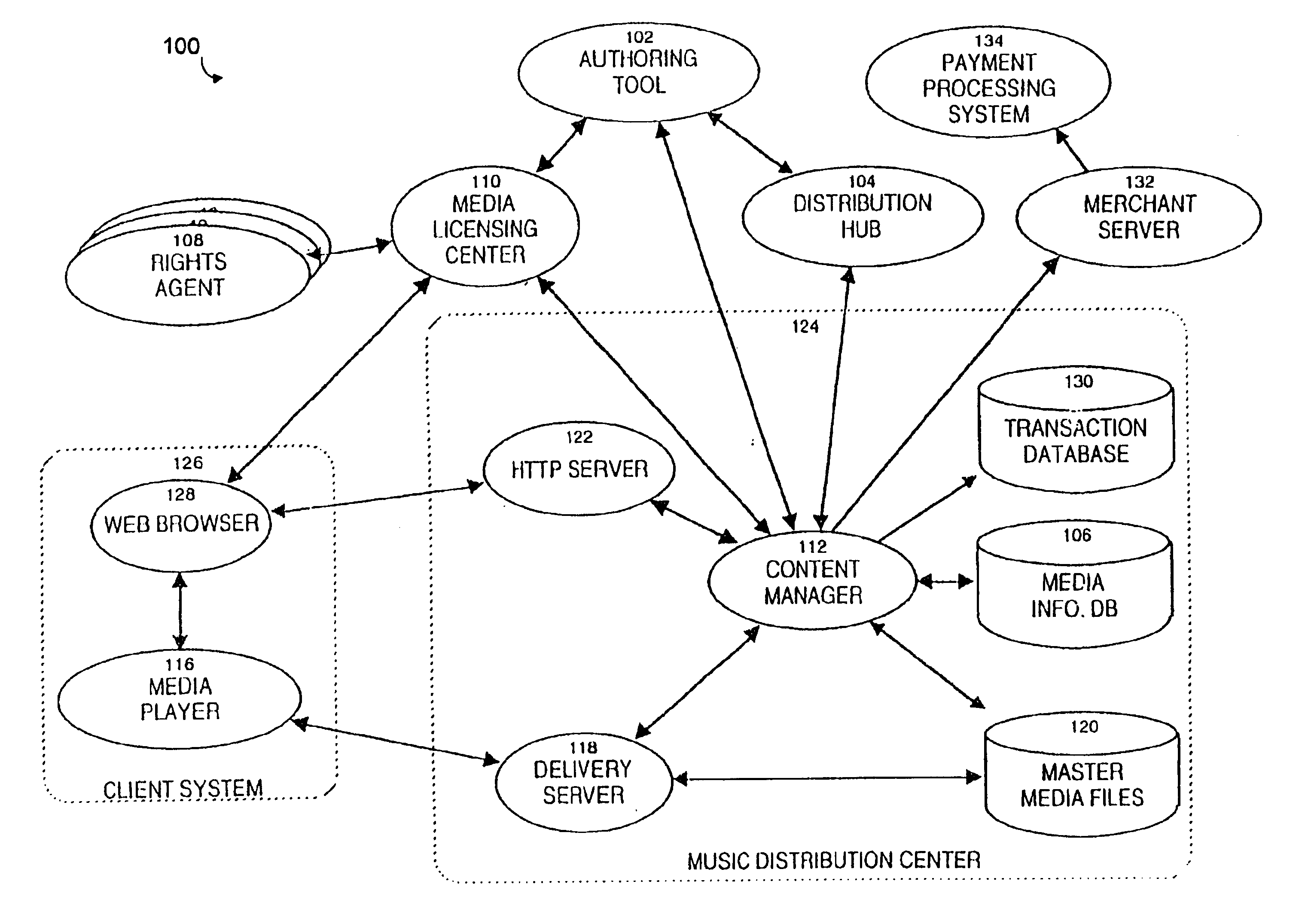
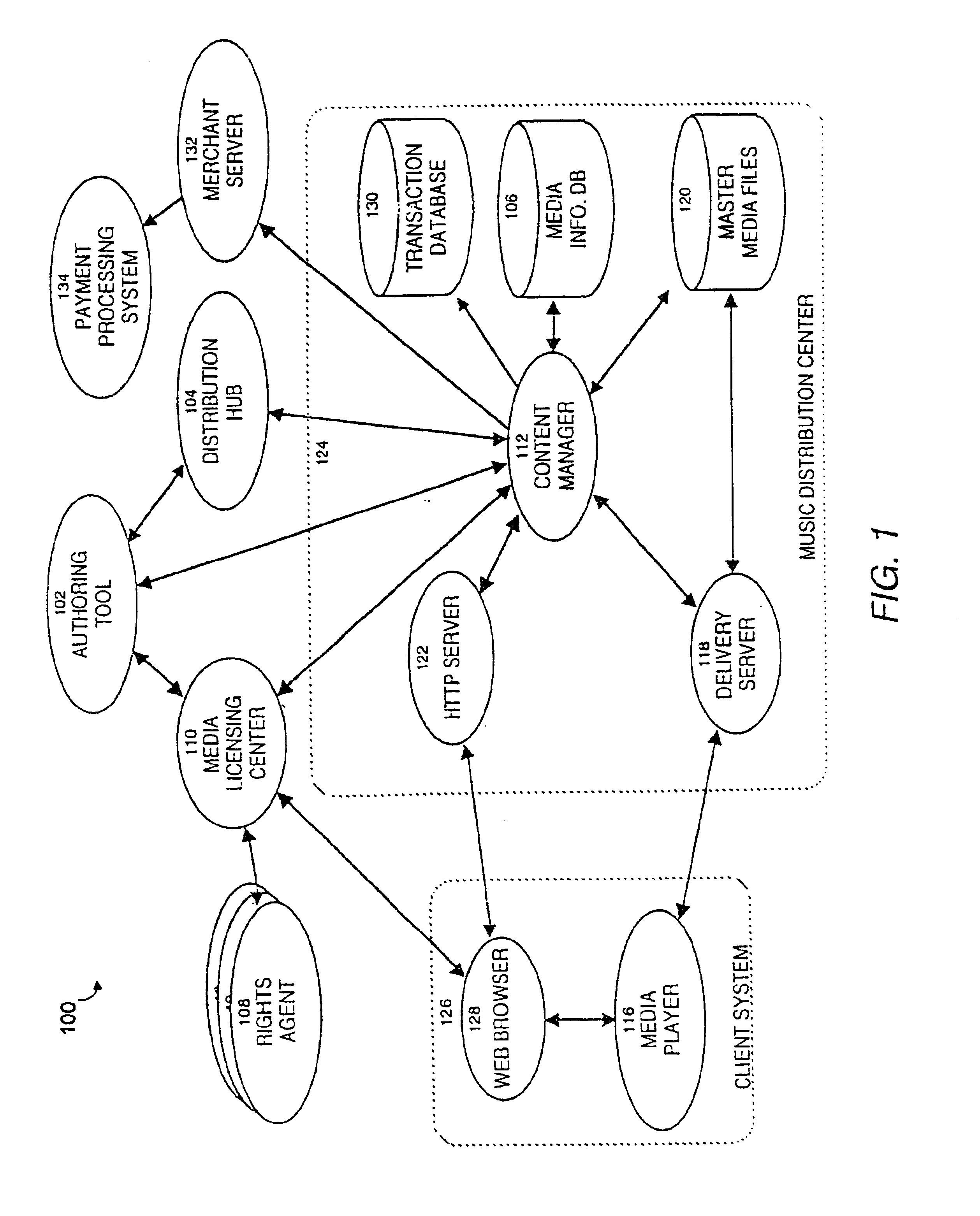
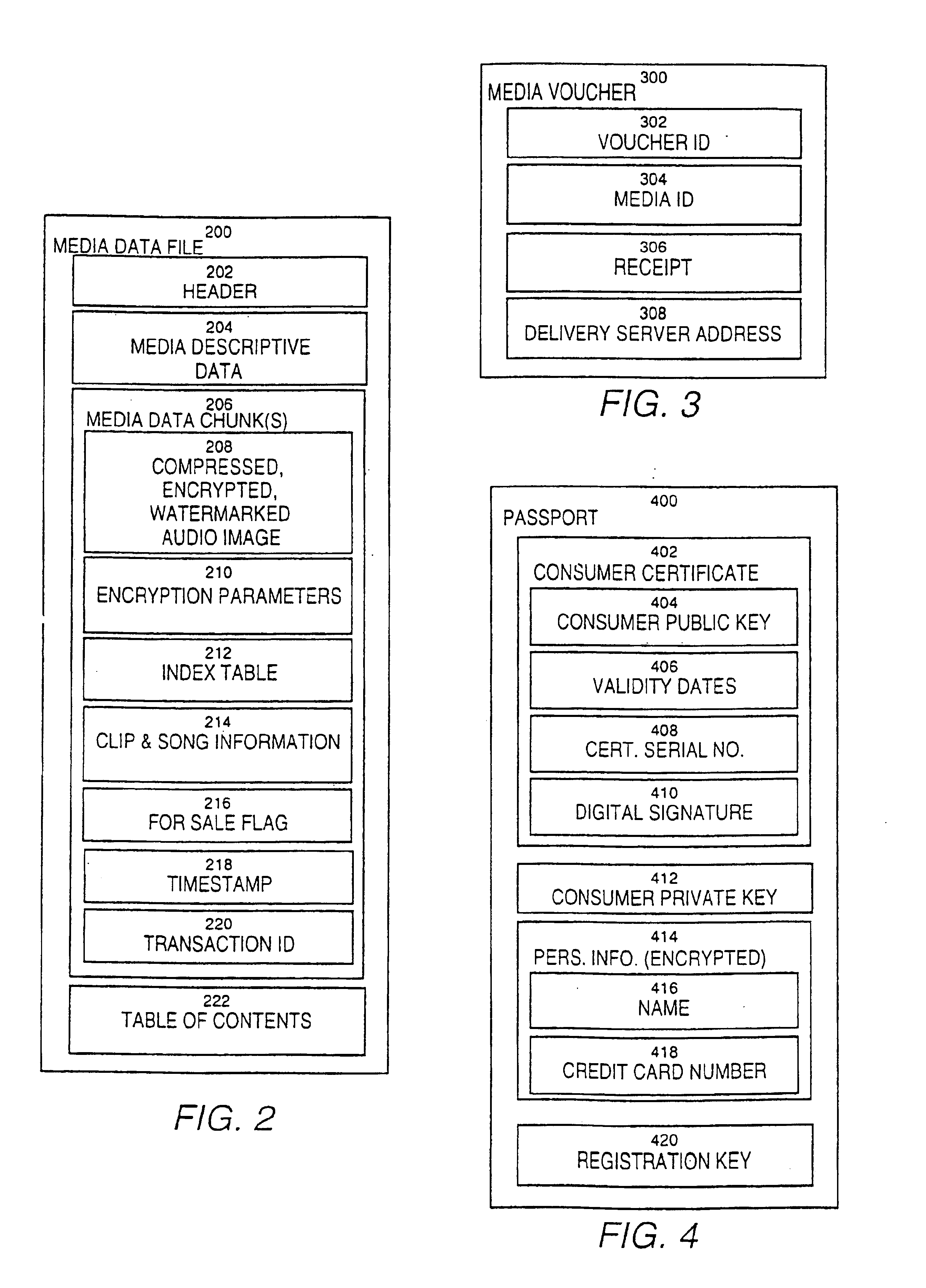
Secure online music distribution system
InactiveUS6868403B1Ease of useFlexibilityReservationsPayment architectureCredit cardClient server systems
A computer implemented online music distribution system provides for the secure delivery of audio data and related media, including text and images, over a public communications network. The online music distribution system provides security through multiple layers of encryption, and the cryptographic binding of purchased audio data to each specific purchaser. The online music distribution system also provides for previewing of audio data prior to purchase. In one embodiment, the online music distribution system is a client-server system including a content manager, a delivery server, and an HTTP server, communicating with a client system including a Web browser and a media player. The content manager provides for management of media and audio content, and processing of purchase requests. The delivery server provides delivery of the purchased media data. The Web browser and HTTP server provide a communications interface over the public network between the content manager and media players. The media player provides for encryption of user personal information, and for decryption and playback of purchased media data. Security of purchased media data is enhanced in part by the use of a personal, digital passport in each media player. The digital passport contains identifying information that identifies the purchaser, along with confidential information, such as credit card number, and encryption data, such as the media player's public and private keys. The media player encryption data is used to encrypt purchased media data, which is decrypted in real time by the media player. The media player also displays confidential information, such as the purchaser's credit card number, during playback.
Owner:MICROSOFT TECH LICENSING LLC
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050149481A1Reduce bandwidth requirementsDigital data processing detailsMultiple digital computer combinationsData accessRemote computer
Applications, systems and methods for efficiently accessing and controlling data of devices among multiple computers over a network. Peer-to-peer exchanges of data between private computers is made possible while providing seamless, firewall-compliant connectivity. Such functionality is available even among private users over a public network, and even when multiple firewalls must be passed through. A firewall compliant connection may be established between a local computer and at least one remote computer; at least one file on a storage device associated with one of the computers is selected, and securely sent to at least one other computer over the secure connections. Computers may be connected over a wide area network with or without a connection server, with or without a VPN.
Owner:WESTERN DIGITAL TECH INC
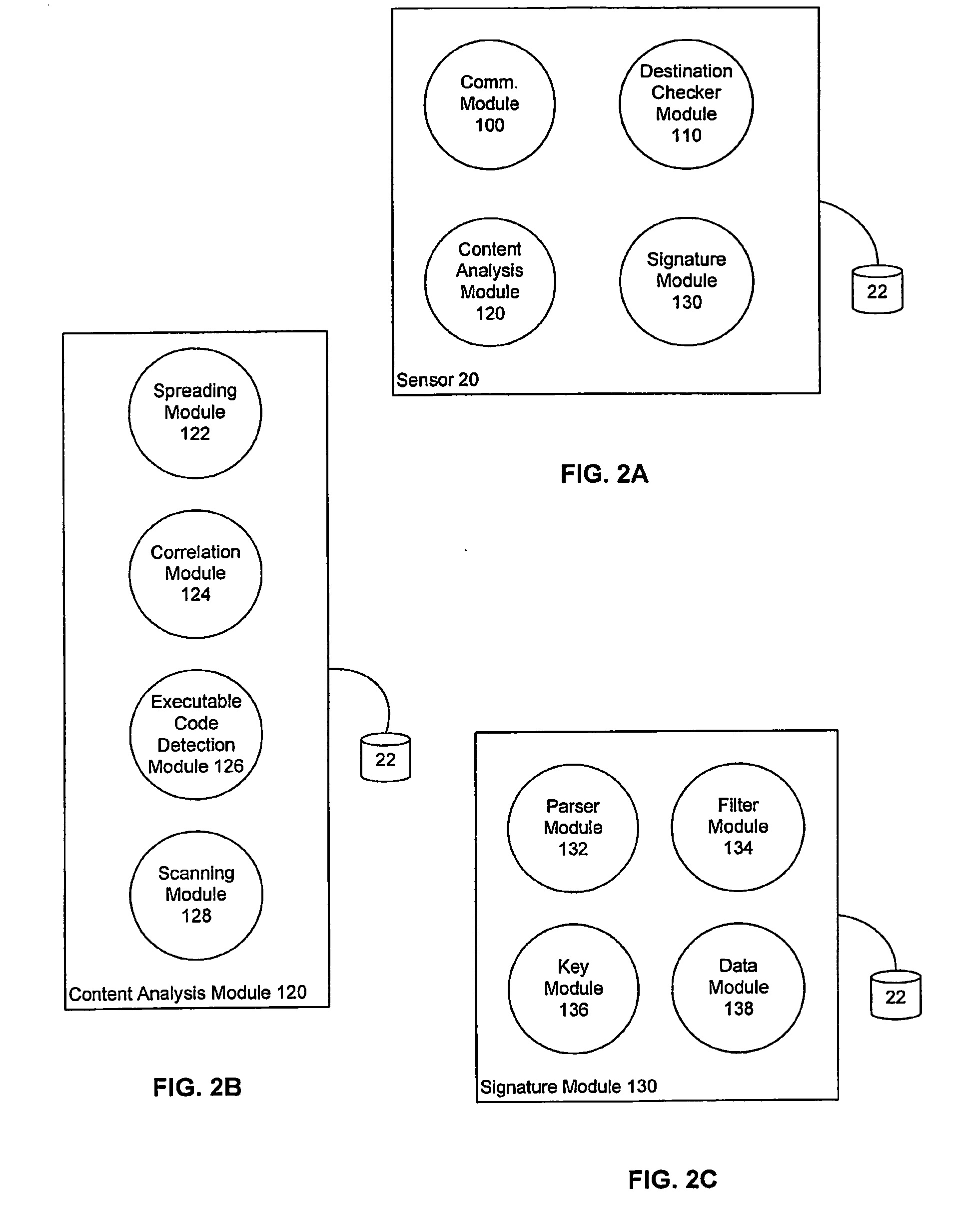
Detecting Public Network Attacks Using Signatures and Fast Content Analysis
ActiveUS20080307524A1Memory loss protectionUser identity/authority verificationComputer hardwarePrivate network
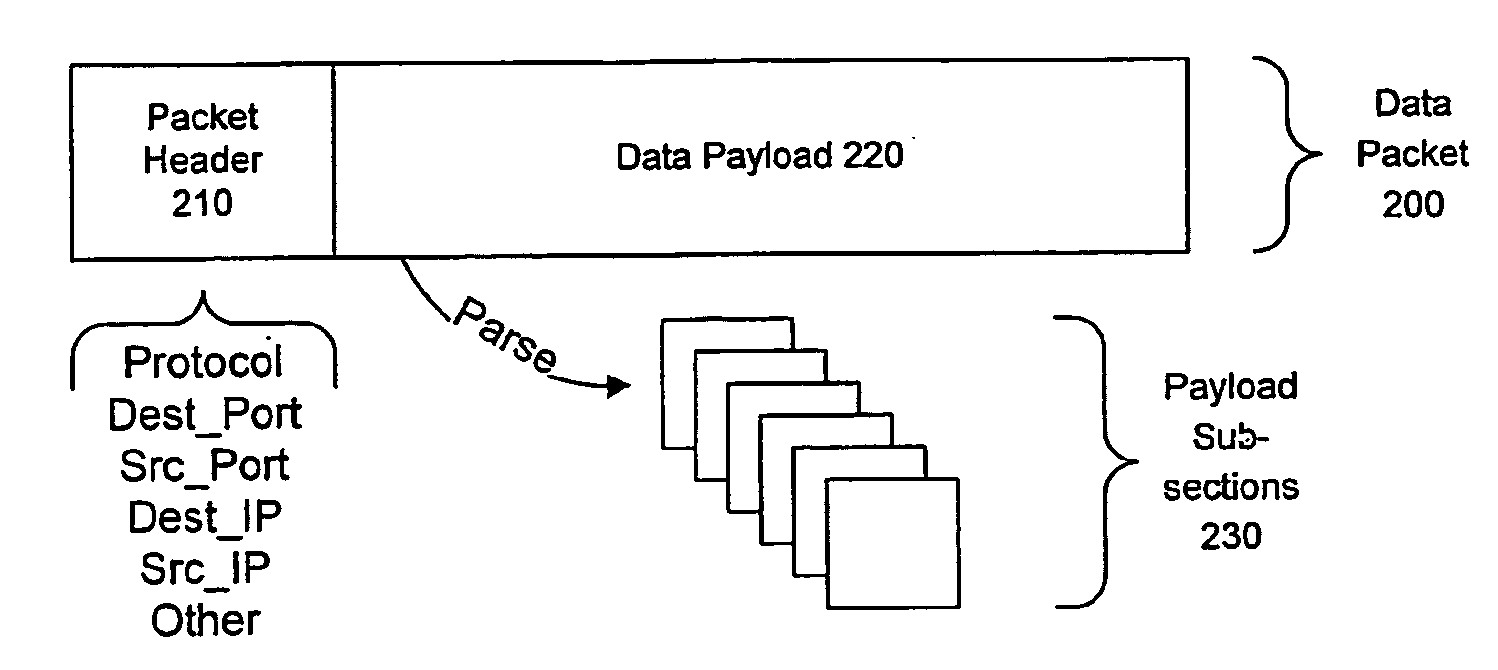
Network worms or viruses are a growing threat to the security of public and private networks and the individual computers that make up those networks. A content sifting method if provided that automatically generates a precise signature for a worm or virus that can then be used to significantly reduce the propagation of the worm elsewhere in the network or eradicate the worm altogether. The content sifting method is complemented by a value sampling method that increases the throughput of network traffic that can be monitored. Together, the methods track the number of times invariant strings appear in packets and the network address dispersion of those packets including variant strings. When an invariant string reaches a particular threshold of appearances and address dispersion, the string is reported as a signature for suspected worm.
Owner:RGT UNIV OF CALIFORNIA
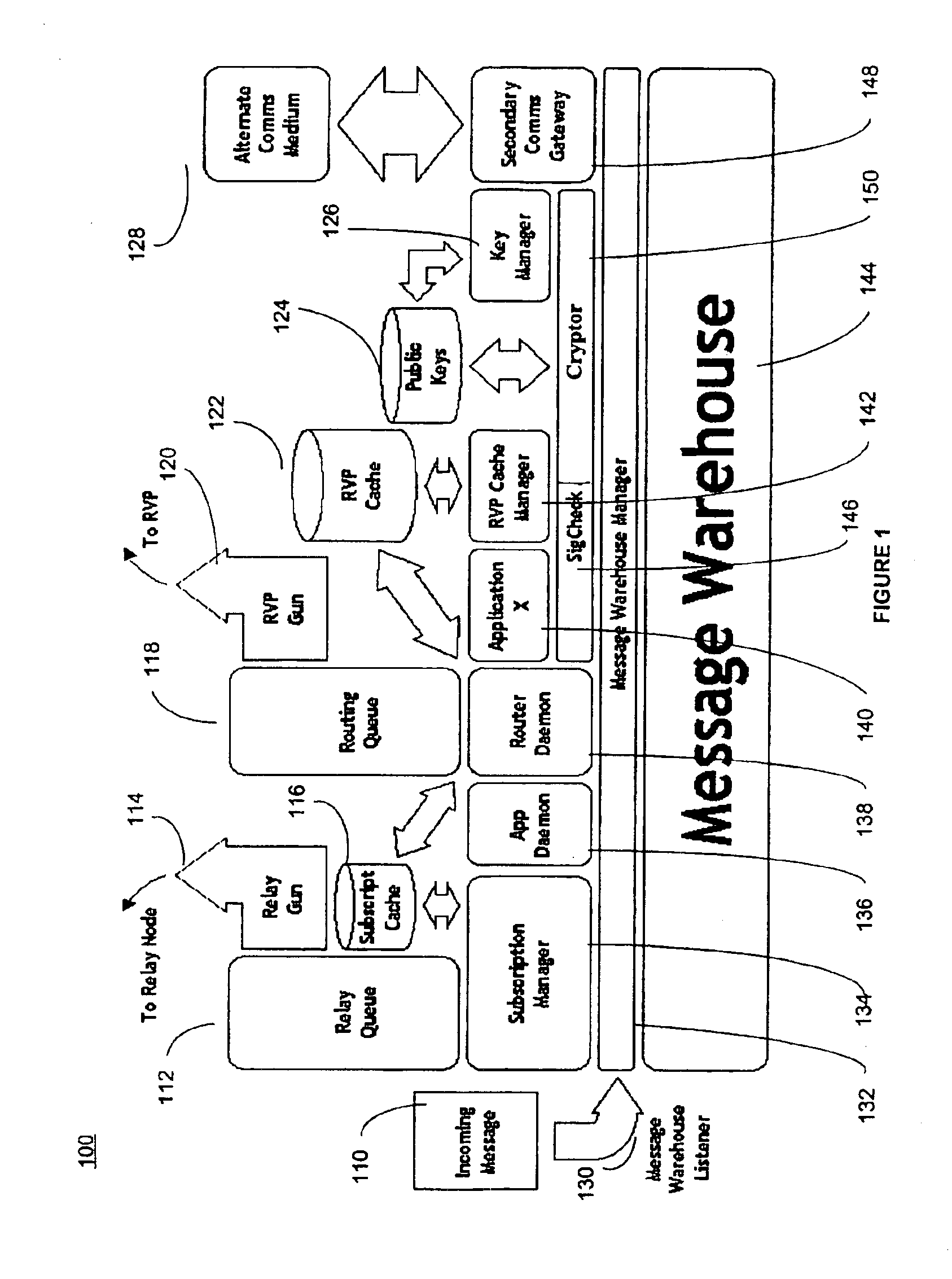
System and method for secure message-oriented network communications
InactiveUS6959393B2Minimize threatFacilitate and control accessKey distribution for secure communicationDigital data processing detailsSecurity MeasureNetwork communication
The present invention provides a message-oriented middleware solution for securely transmitting messages and files across public networks unencumbered by intervening network barriers implemented as security measures. It also provides a dynamic, dedicated, application level VPN solution that is facilitated by the message-oriented middleware. Standard encryption algorithms are used to minimize the threat of eavesdropping and an Open-Pull Protocol (OPP) that allows target nodes to pull and verify the credentials of requestors prior to the passing of any data. Messaging can be segregated into multiple and distinct missions that all share the same nodes. The security network's architecture is built to resist and automatically recover from poor, slow, and degrading communications channels. Peers are identifiable by hardware appliance, software agent, and personally identifiable sessions. The security network provides a dynamic, private transport for sensitive data over existing non-secure networks without the overhead and limited security associated with traditional VPN solutions.
Owner:THREATGUARD
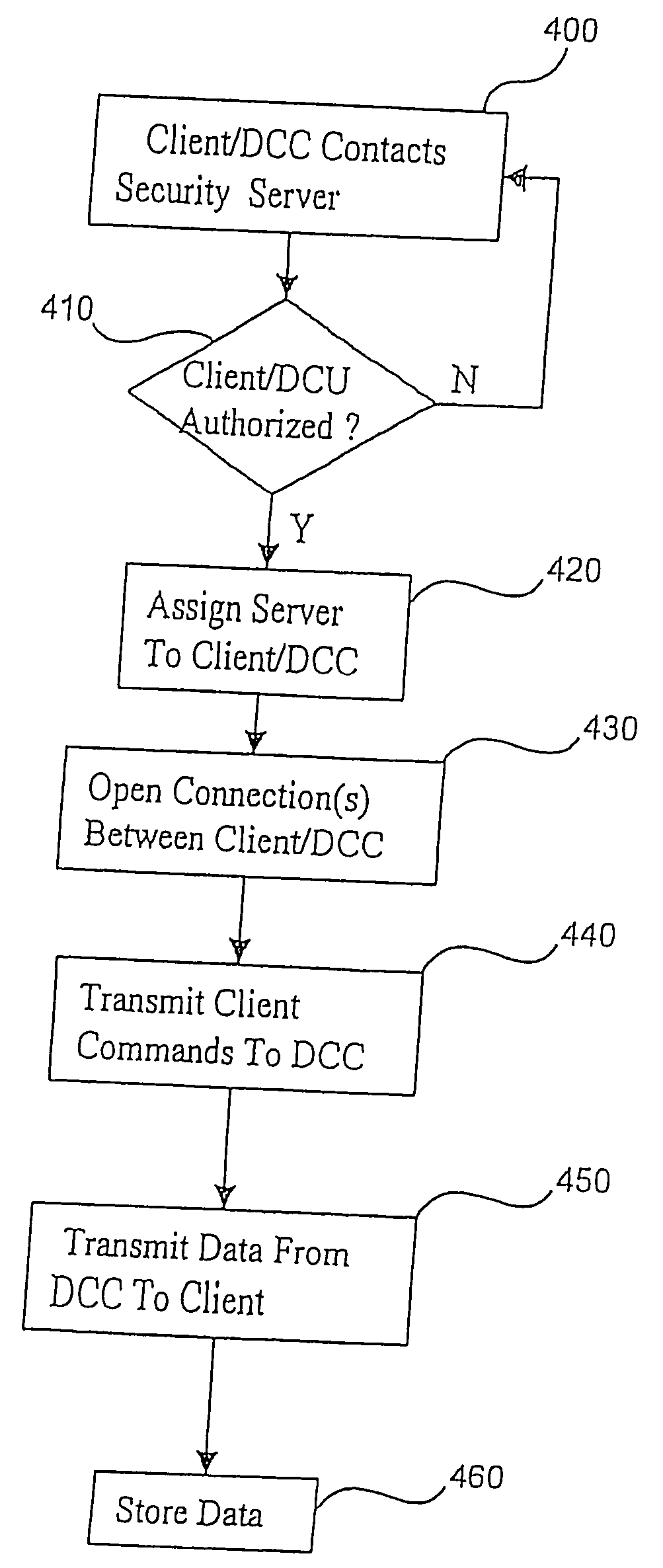
Configuring a user device to remotely access a private network
InactiveUS20090129301A1Network traffic/resource managementRadio transmissionPrivate networkPublic network
Configuring a mobile device to remotely access a private network involves determining, via the private network, first network parameters that enable the mobile device utilize to a computing service of the private network. The device also determines, via a gateway coupled to the private network, second network parameters that allow the mobile to utilize the computing service via a public network. The first and second network parameters are stored on the mobile device. A request is received from a user of the mobile device to access the computing service. It is determined that the mobile device is not on the private network. In response to determining that the mobile device is not on the private network, the second network parameters are utilized to access the computing service via the gateway in response to the request.
Owner:NOKIA CORP
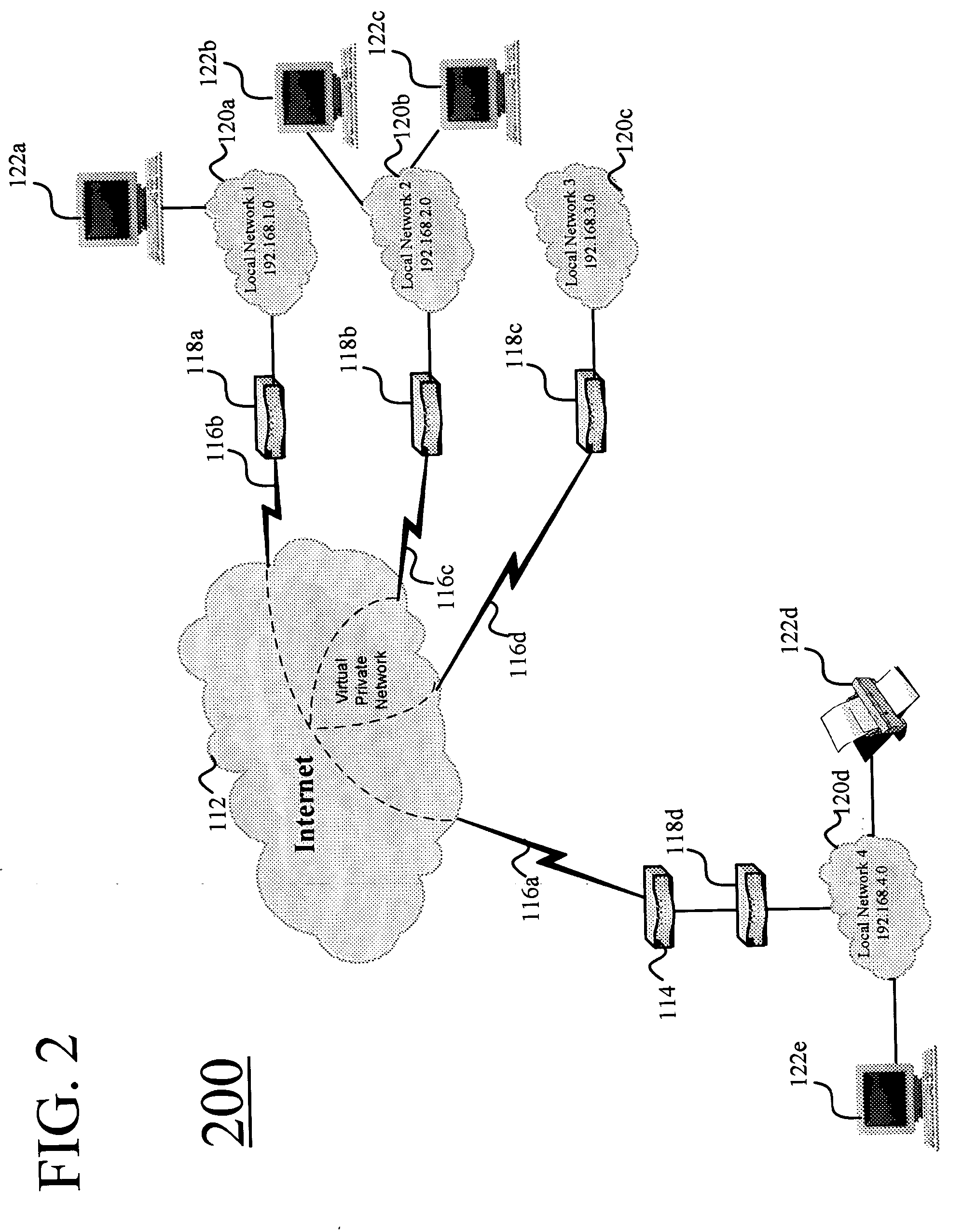
Systems and methods for automatically configuring and managing network devices and virtual private networks
ActiveUS20060236095A1Multiple digital computer combinationsSpecial data processing applicationsComputer hardwareGraphics
Systems and methods are disclosed for automatically configuring, managing, and maintaining a network device or VPN using a public network such as the Internet. Initial configuration of a network device or VPN occurs upon a user entering minimal information via a simple HTML page. After receipt of this minimal information, the present invention automatically configures the network device or VPN without user intervention. Thereafter, a user may modify the network device or VPN configuration via an easy-to-use and easy-to-understand graphical user interface. Parameters are presented such that a user simply checks and unchecks boxes, or clicks on radio buttons, to configure network device parameters. Upon completion of the selection, the user clicks on save, and the configuration is automatically modified. In addition, upon a significant change to any network device, the changed network device automatically initiates reconfiguration of the network device or VPN with zero input from a user.
Owner:ANXEBUSINESS
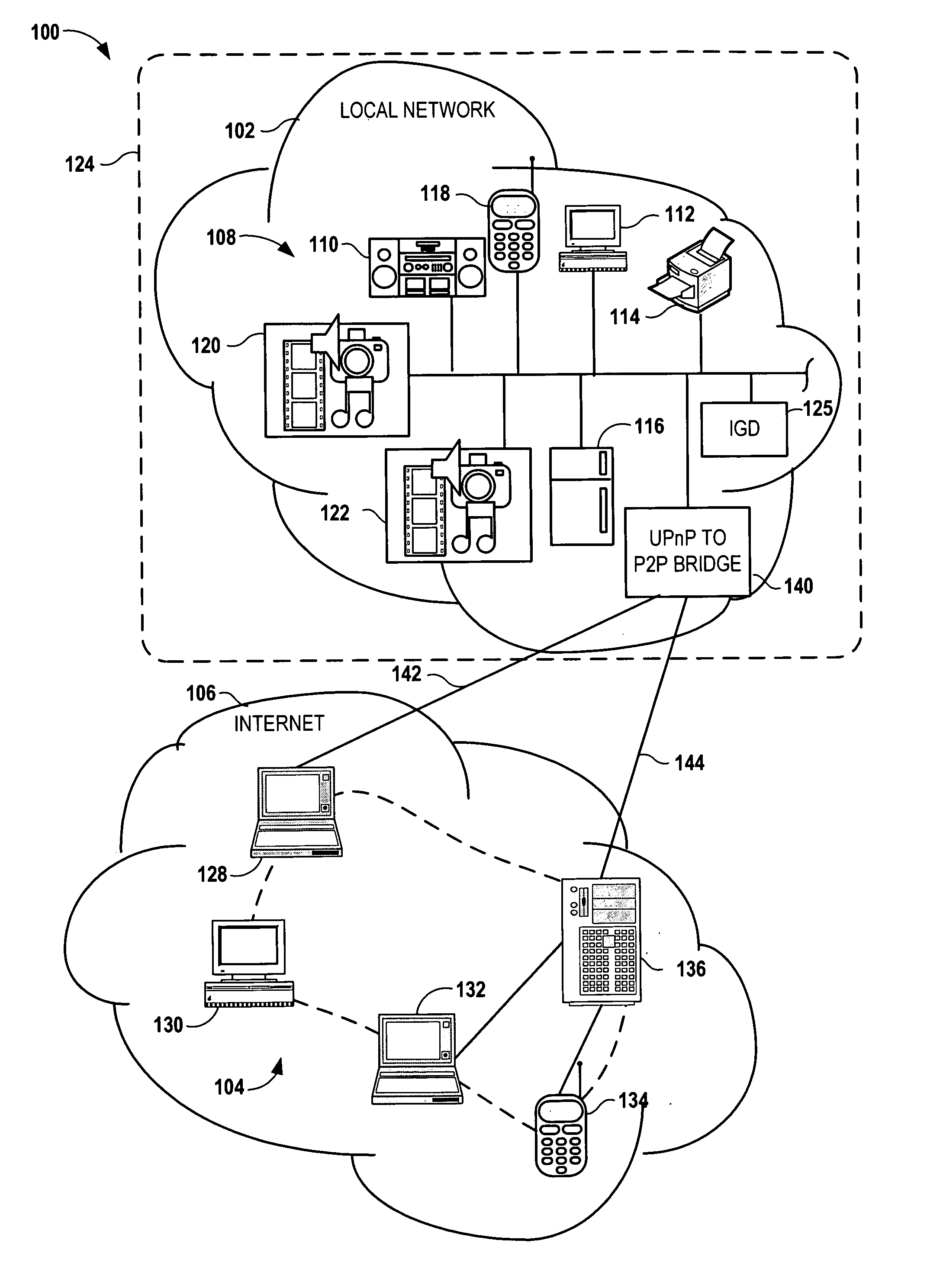
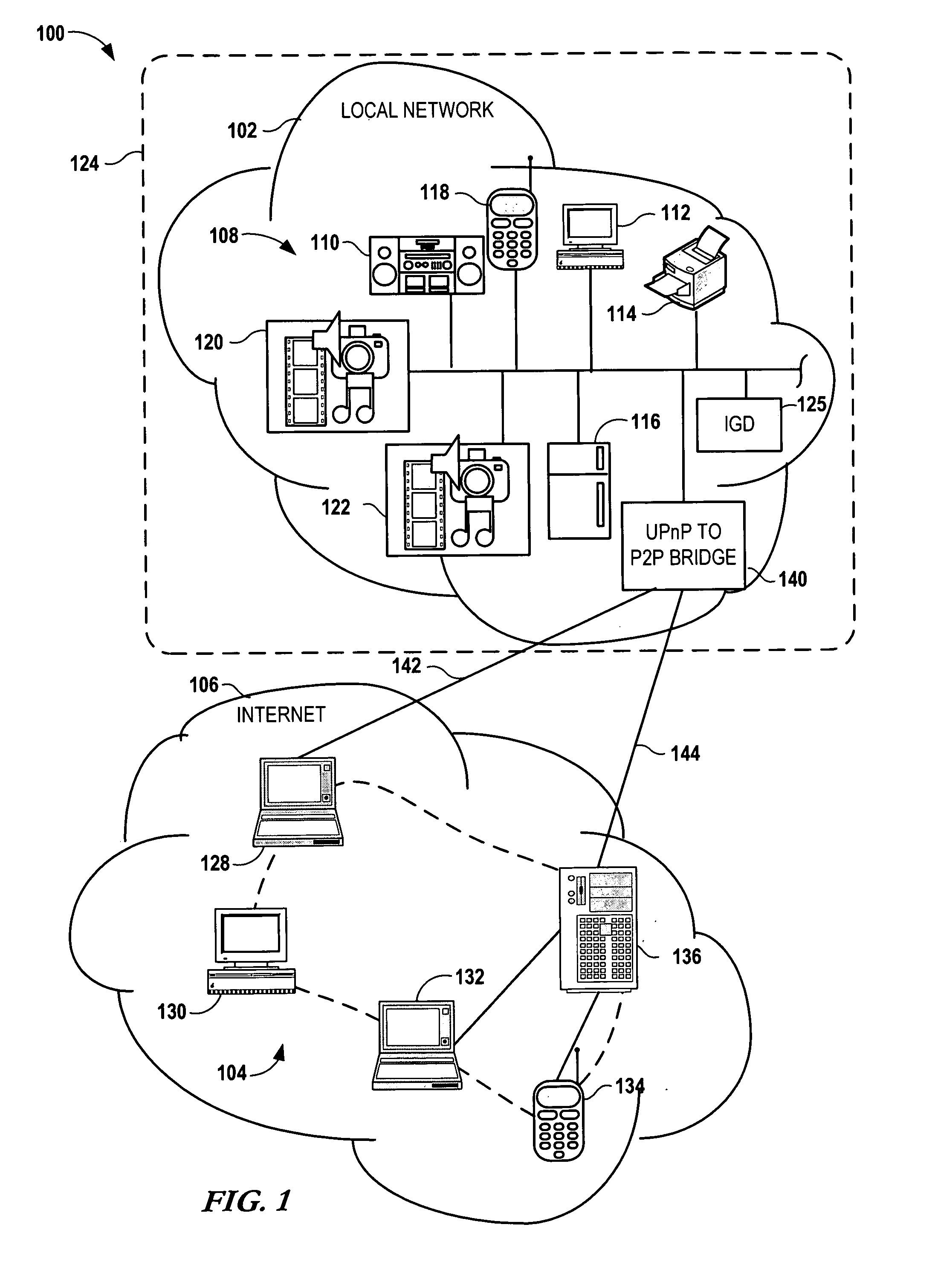
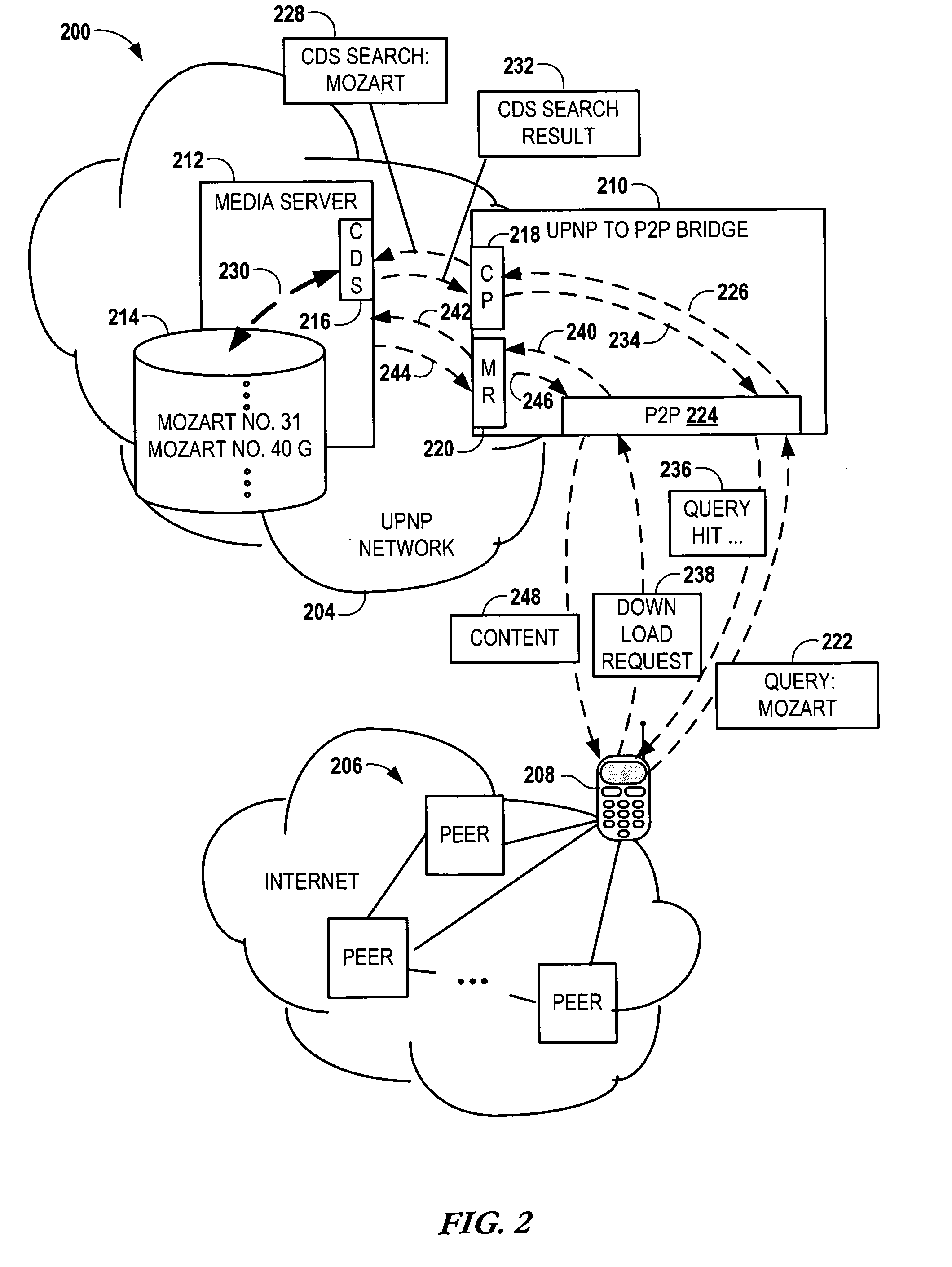
Bridging between AD HOC local networks and internet-based peer-to-peer networks
ActiveUS20070274327A1Easy to downloadFacilitate downloading the mediaData switching by path configurationMultiple digital computer combinationsNetworking protocolTTEthernet
Bridging between ad hoc local networks and Internet based peer-to-peer networks involves coupling a bridge device to a local network using an ad-hoc, peer-to-peer protocol used for exchanging data between consumer electronics devices. The bridge device is coupled to a public network using an Internet-based peer-to-peer networking protocol. In one arrangement, metadata related to media accessible from a media server of the local network is determined via the bridge device, and the metadata is transformed via the bridge device to enable peer-to-peer devices of the public network to discover the media via the bridge device using the Internet-based peer-to-peer networking protocol. In another arrangement, metadata related to media accessible from the public network is determined via the peer-to-peer networking protocol, and the metadata is transformed via the bridge device to enable a device of the local network to discover the media via the bridge device using the ad-hoc, peer-to-peer protocol.
Owner:CONVERSANT WIRELESS LICENSING LTD
Managed peer-to-peer applications, systems and methods for distributed data access and storage
InactiveUS20050114711A1Digital data processing detailsUser identity/authority verificationPrivate communicationDisplay device
Applications, systems and methods for securely and remotely operating a remote computer from a local computer over a network while providing seamless, firewall-compliant connectivity. Secure and remote operation includes authenticating at least one remote computer for connection to at least one computer over the network and / or at least one local computer for connection to at least one remote computer over the network; establishing a secure connection between the at least one local computer and the at least one remote computer over the network; and integrating a desktop of at least one remote computer on a display of at least one local computer. The connections may be made over a public network, as well as through multiple firewalls without loss of functionality. A method of accessing and using at least one remote computer from a local computer over a public network may include centrally authenticating, at a location having a public address, a first computer having a first, firewall protected private address; creating a first firewall compliant connection between a publicly addressed connection server and the first computer upon authentication of the first computer; establishing a second firewall compliant connection between the publicly addressed connection server and a second computer having a second firewall protected private address; establishing a private-to-public-to-private communications tunnel, wherein the connection server routes communications from the first computer through the first firewall compliant connection and the second firewall compliant connection to the second computer, and from the second computer through the second firewall compliant connection and the first firewall compliant connection to the first computer; and performing at least one further step selected from the group consisting of: integrating a file structure of accessible files accessed at the second or first computer, into a file structure contained at the first or second computer, respectively; at least one of integrating a desktop of the second computer on a display of the first computer and integrating a desktop of the first computer on a display of the second computer; and directly operating the second computer from the first computer or the first computer from the second computer, wherein the computer that is directly operated is selected from the group consisting of: home appliances, video equipment, audio equipment, printers, fax machines, office equipment, medical devices, vehicles, cameras, RFID equipment, laboratory equipment, manufacturing machinery, GPS equipment, and devices having one or more embedded microprocessors.
Owner:WESTERN DIGITAL TECH INC
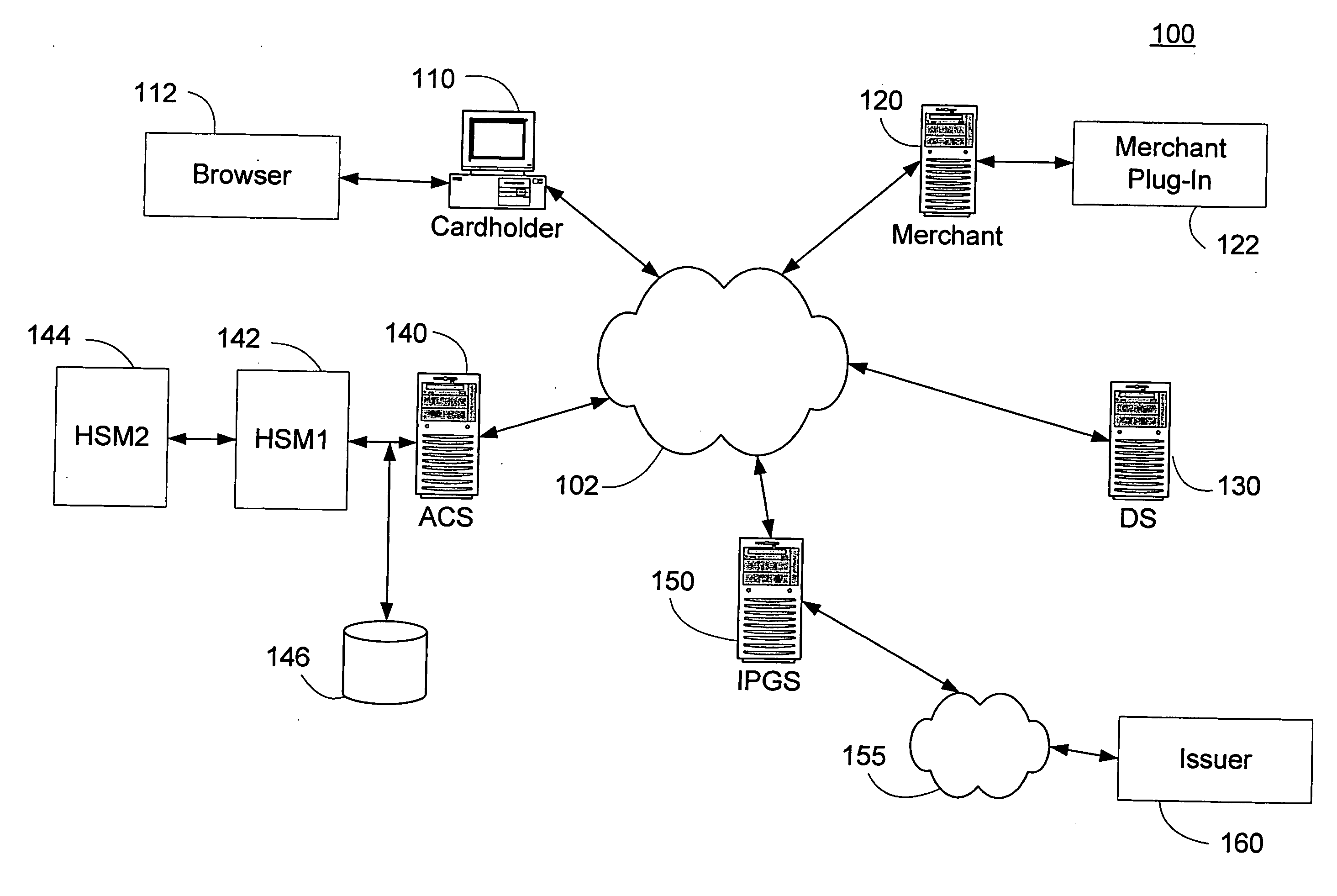
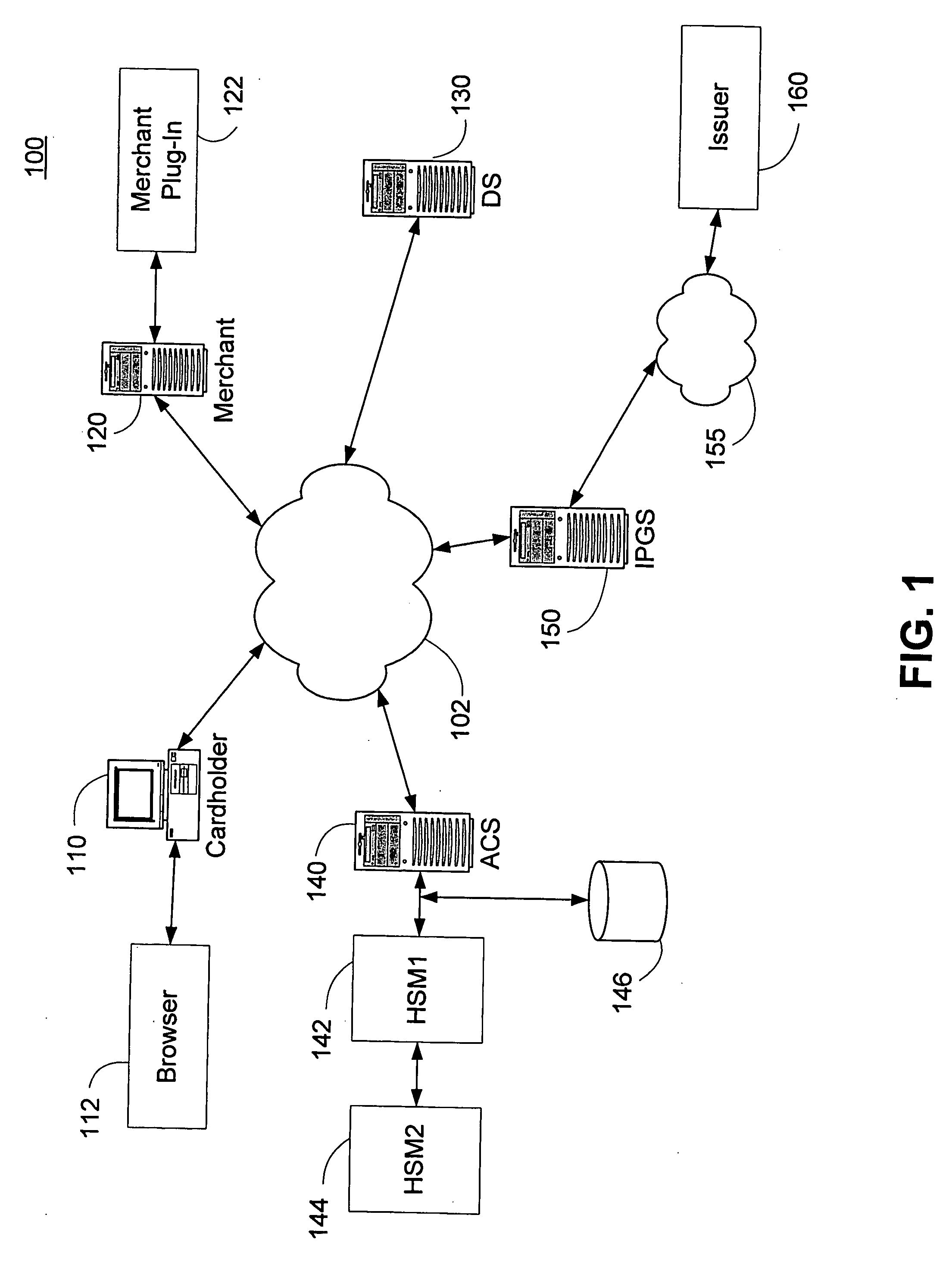
Persistent dynamic payment service
The invention comprises online methods, systems, and software for improving the processing of payments from financial accounts, particularly credit and debit card payments made from consumers to merchants in online transactions. The preferred embodiment of the invention involves inserting a trusted third party online service into the payment authorization process. The trusted third party authenticates the consumer and authorizes the proposed payment in a single integrated process conducted without the involvement of the merchant. The authentication of the consumer is accomplished over a persistent communication channel established with the consumer before a purchase is made. The authentication is done by verifying that the persistent channel is open when authorization is requested. Use of the third party services allows the consumer to avoid revealing his identity and credit card number to the merchant over a public network such as the Internet, while maintaining control of the transaction during the authorization process.
Owner:FISHER DOUGLAS C
Generalized policy server
InactiveUS7272625B1Easy to handleMultiple digital computer combinationsTransmissionPolicy decisionTrust level
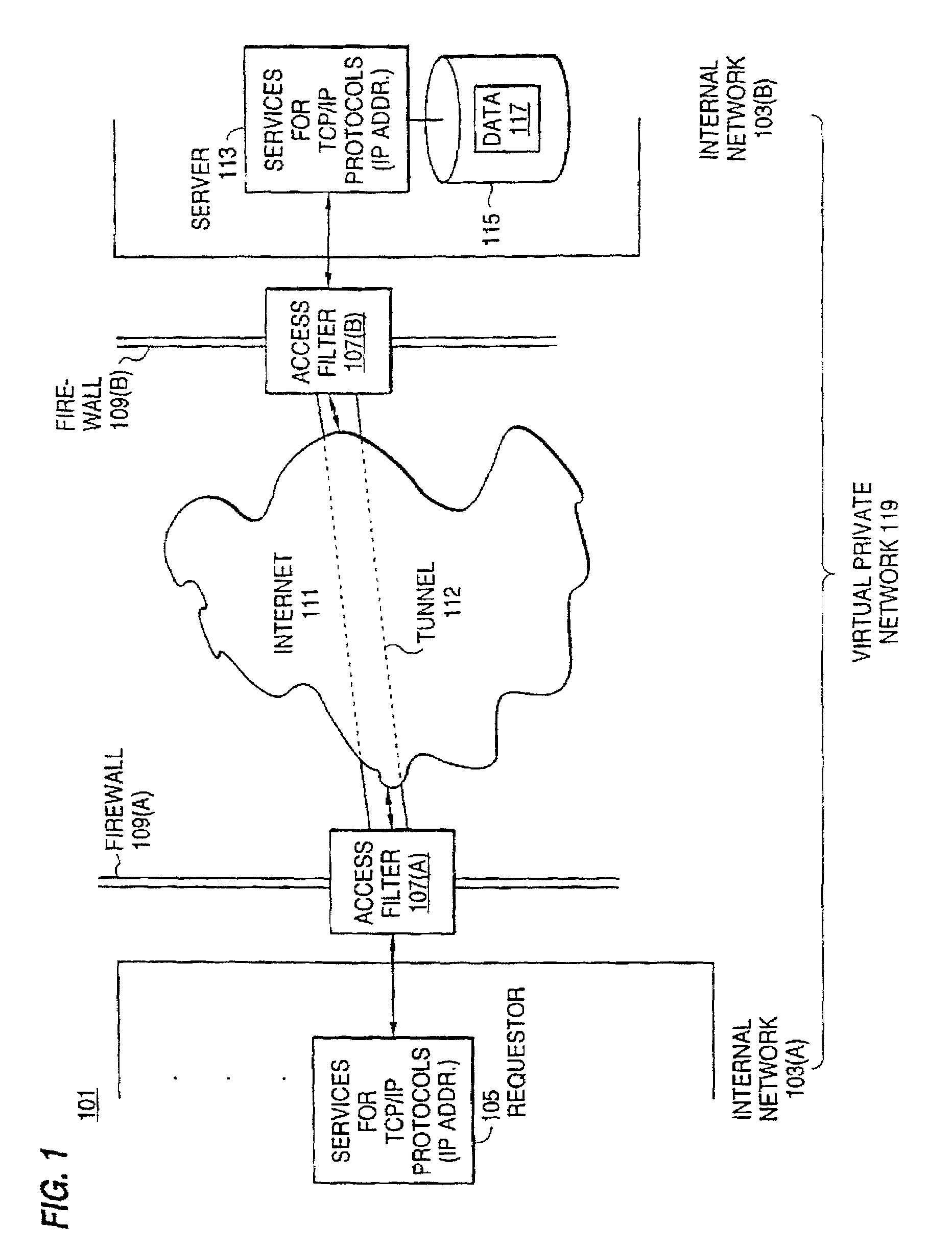
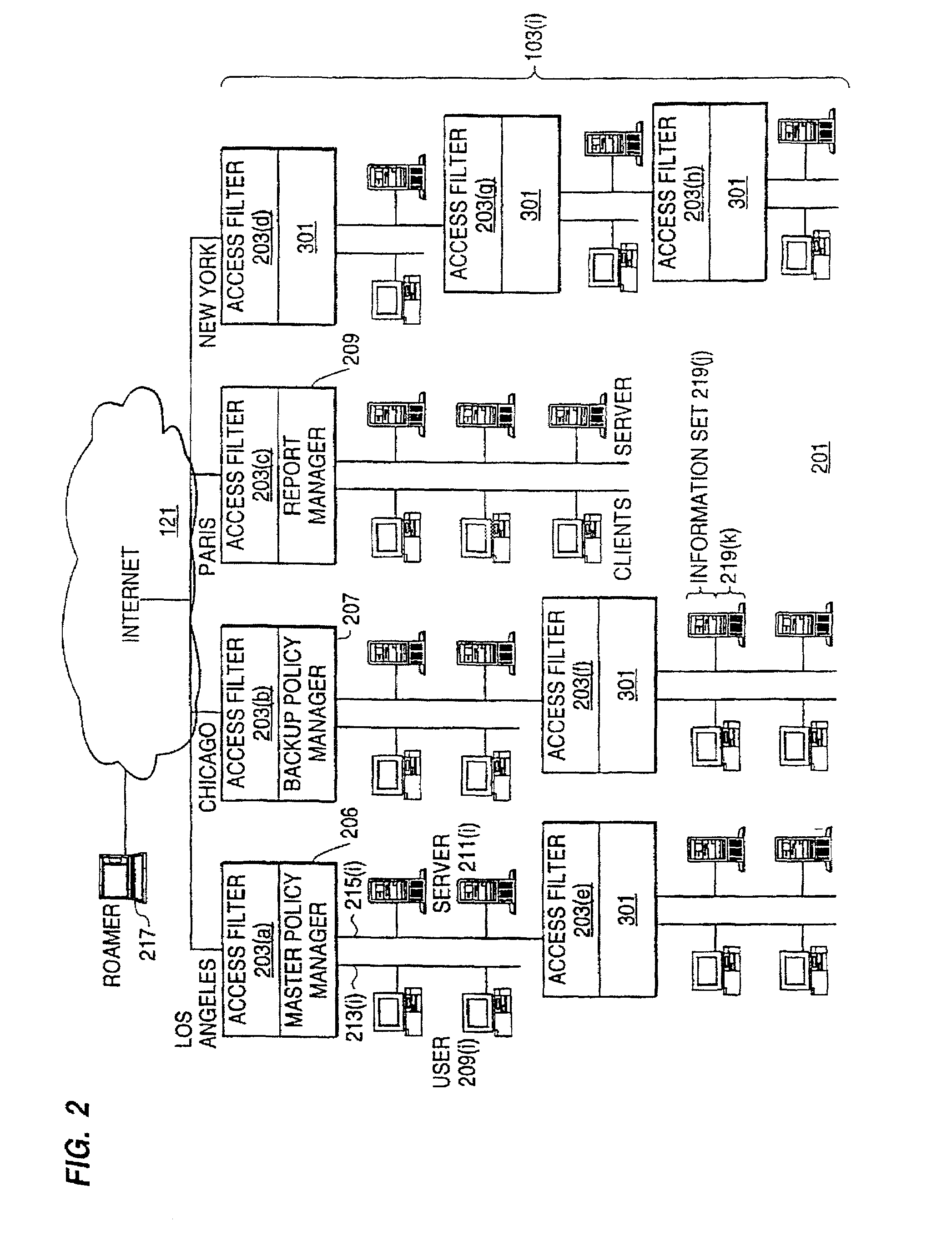
A policy system includes the policy server (2617); a policy database (2619) which located at policy decision point (2723); the access / response entity (2603); resource server (2711); policy message (2725) and policy enforcement point (2721). System connected through public network (2702) or internal network (103). The access filter (107, 203, 403) control access by use a local copy of an access control data base to determine whether an access request made by a user. Changes made by administrators in the local copies are propagated to all of the other local copies. Access is permitted or denied according to of access policies (307) which define access in terms of the user groups (FIGS. 9-12) and information sets (FIGS. 13A-18). The rights of administrators are similarly determined by administrative policies (FIGS. 23A-C). Access is further permitted only if the trust levels of the network by which is made by the sufficient access (FIGS. 25-29). A policy server component of the access filter has been separated from the access filter and the policies have been generalized to permit administrators of the policy server to define new types of actions and new types of entities. Policies may now further have specifications for time intervals during which the policies are in force and the entities may be associated with attributes that specify how the entity is to be used when the policy applies.
Owner:MARSHMAN RES +1
Secured virtual network in a gaming environment
InactiveUS7515718B2Mosaic printer telegraph systemKey distribution for secure communicationSecure communicationThe Internet
A disclosed gaming machine may securely communicate with devices over a public network such as the Internet. The gaming machine utilizes a combination of symmetric and asymmetric encryption that allows a single gaming machine to securely communicate with a remote server using a public network. The secure communication methods may be used to transfer gaming software and gaming information between two gaming devices, such as between a game server and a gaming machine. For regulatory and tracking purposes, the transfer of gaming software between the two gaming devices may be authorized and monitored by a software authorization agent.
Owner:IGT
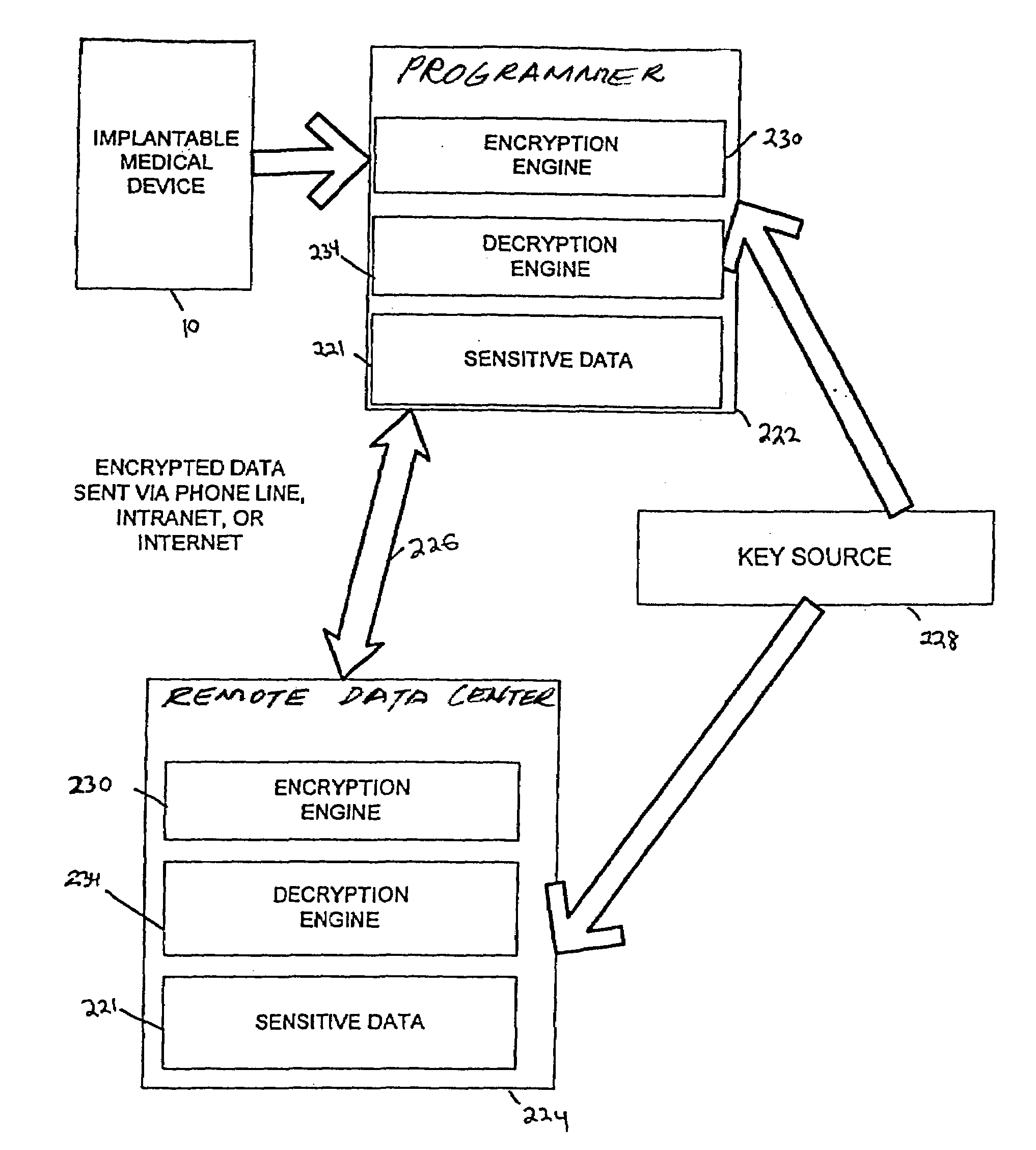
Method and apparatus to secure data transfer from medical device systems
InactiveUS7039810B1Key distribution for secure communicationElectrotherapyCommunications systemData center
Sensitive data such as patient records are securely transferred between a programmer and a data encryption. A database residing on the programmer contains patient information obtained by at least one implantable medical device. A key source provides the programmer with a first key and the remote expert data center with a second key to be used in the encryption / decryption process. An encryption engine residing within the programmer encrypts the sensitive patient information contained within the database, using the first key. The programmer transmits the encrypted patient information to the remote expert data center via a data communications system such as a public network. A decryption engine residing within the remote expert data center decrypts the encrypted sensitive patient information using the second key.
Owner:MEDTRONIC INC
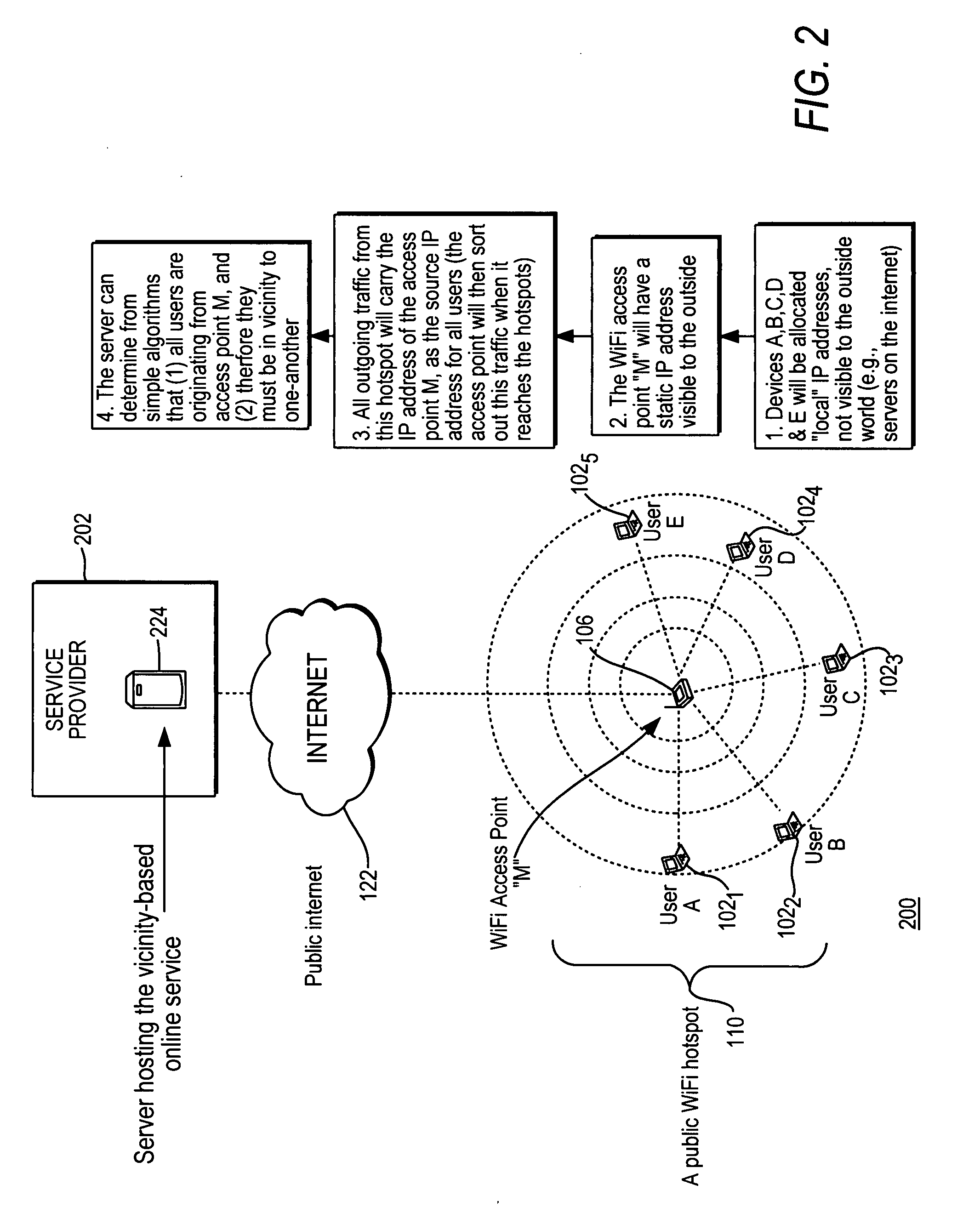
Vicinity-based community for wireless users
InactiveUS20080113674A1Network topologiesBroadcast service distributionCommunity basedPublic network
A method and apparatus for providing vicinity-based community services at a wireless access location by a public network service provider. The method includes the steps of receiving over a public network, at least one request for vicinity-based community services from at least one end-user accessing the wireless access point, grouping end-users accessing common wireless access points, and providing the vicinity-based community services in real time to end-users accessing the public network service provider from the wireless access point. The apparatus includes devices for carrying out the method described above.
Owner:BAIG MOHAMMAD FAISAL
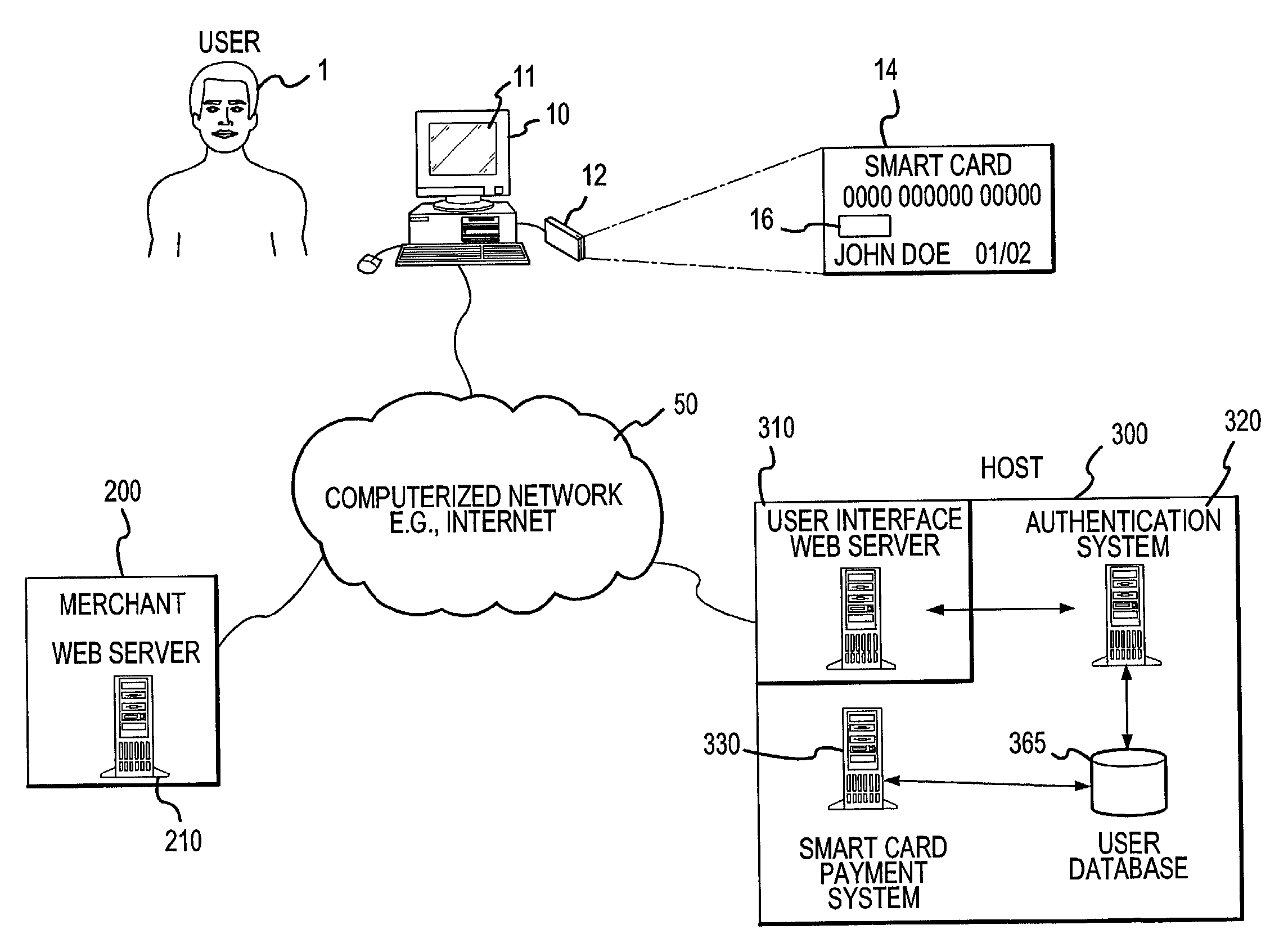
Online card present transaction
InactiveUS7292999B2Easy to optimizeRemove the burdenSecret communicationBuying/selling/leasing transactionsThe InternetPublic network
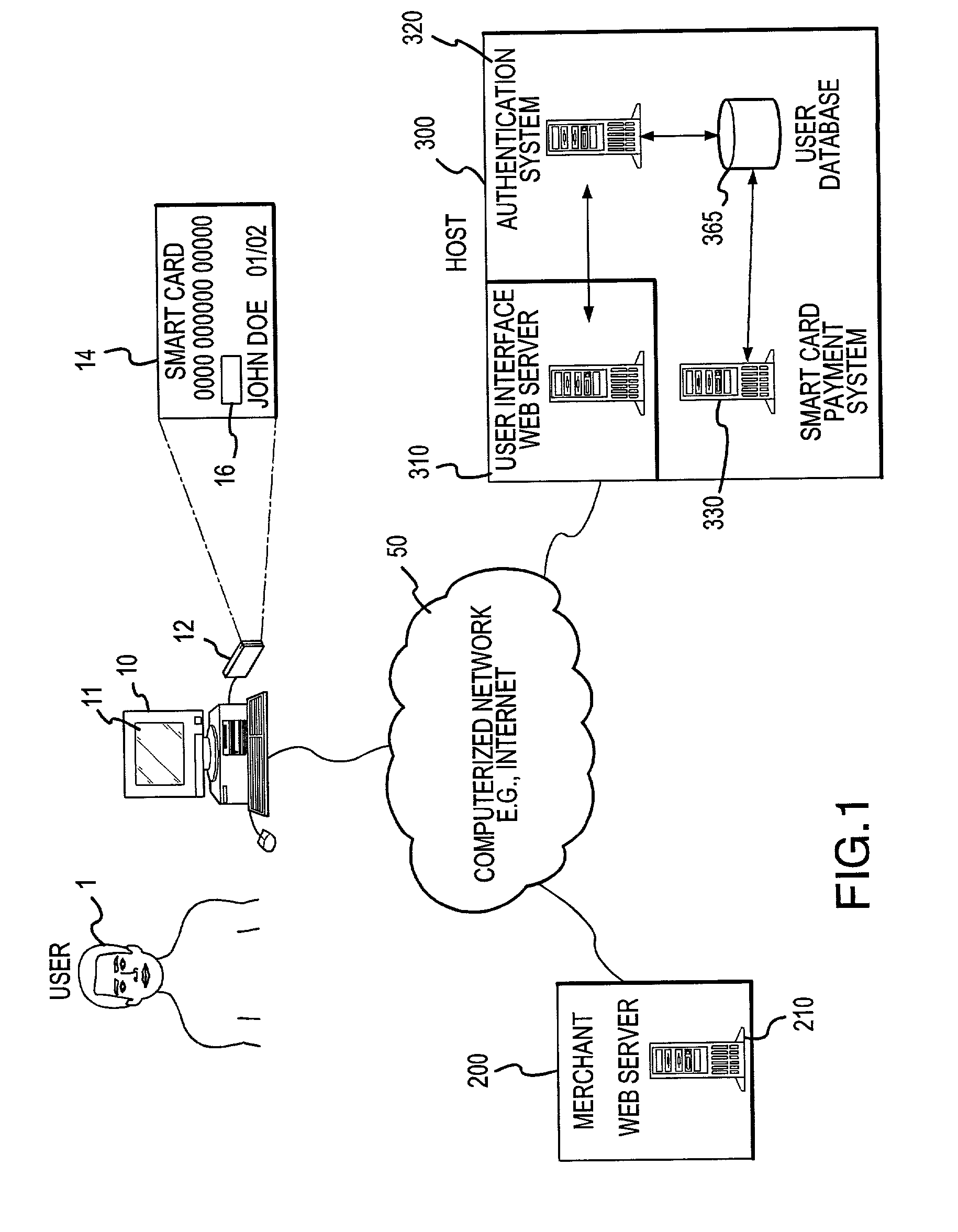
An online card-present transaction system facilitates card-present type transactions with a merchant over a public network. A host system is configured to accept authentication data from a user via an authentication device. The host system, after authenticating a user is configured to retrieve the user's account information from a user database system and translate a user account number into a temporary transaction number. The temporary transaction number is then transmitted directly from the host system to the merchant, thereby eliminating the need for the user to send to the merchant over the internet, the user's transaction account number.
Owner:LIBERTY PEAK VENTURES LLC
Network-based content distribution system
InactiveUS20090037388A1Maximize potential return-on-investmentMinimal burdenDigital data processing detailsUser identity/authority verificationContent distributionPublic network
Owner:VERIMATRIX INC
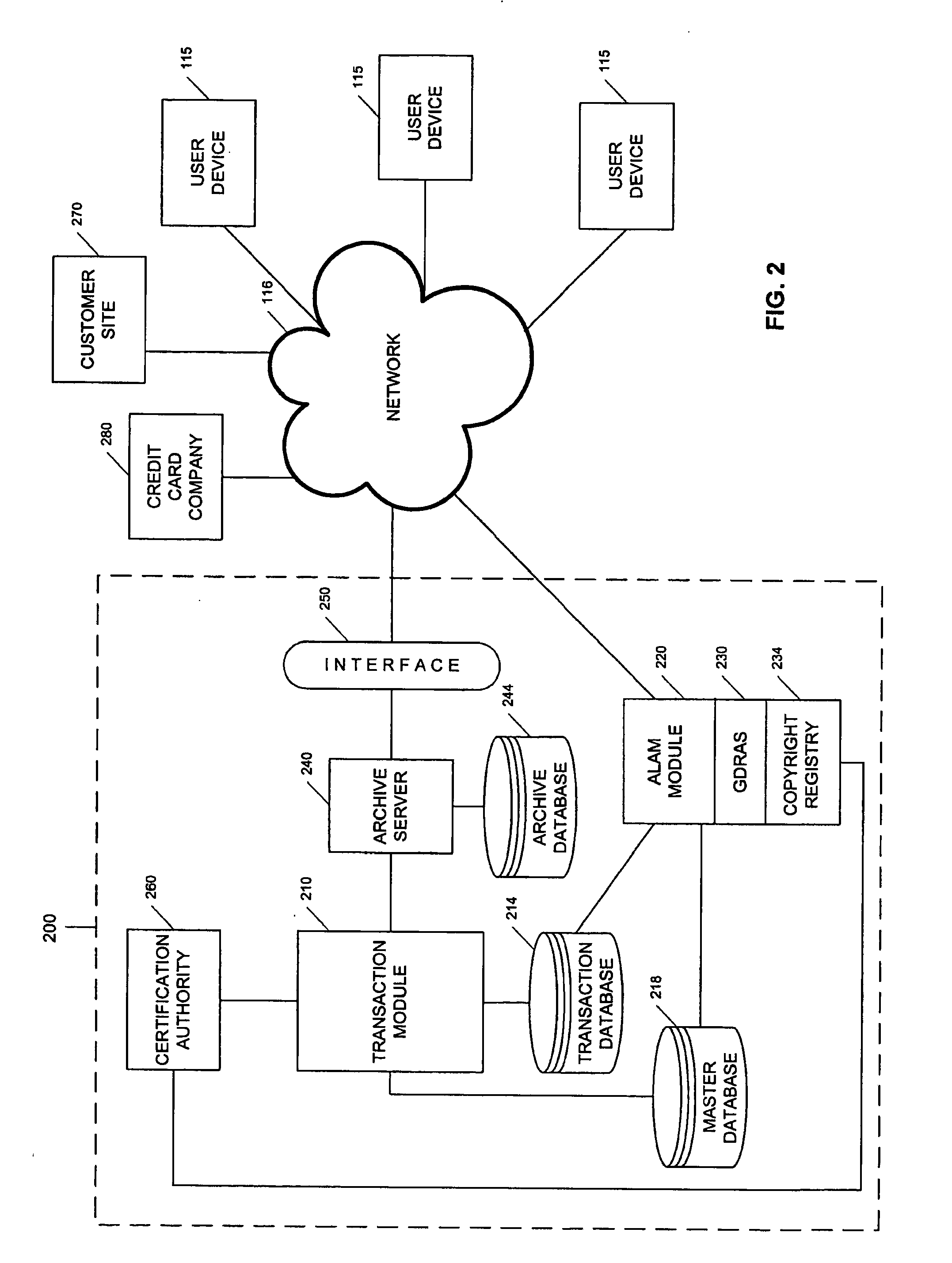
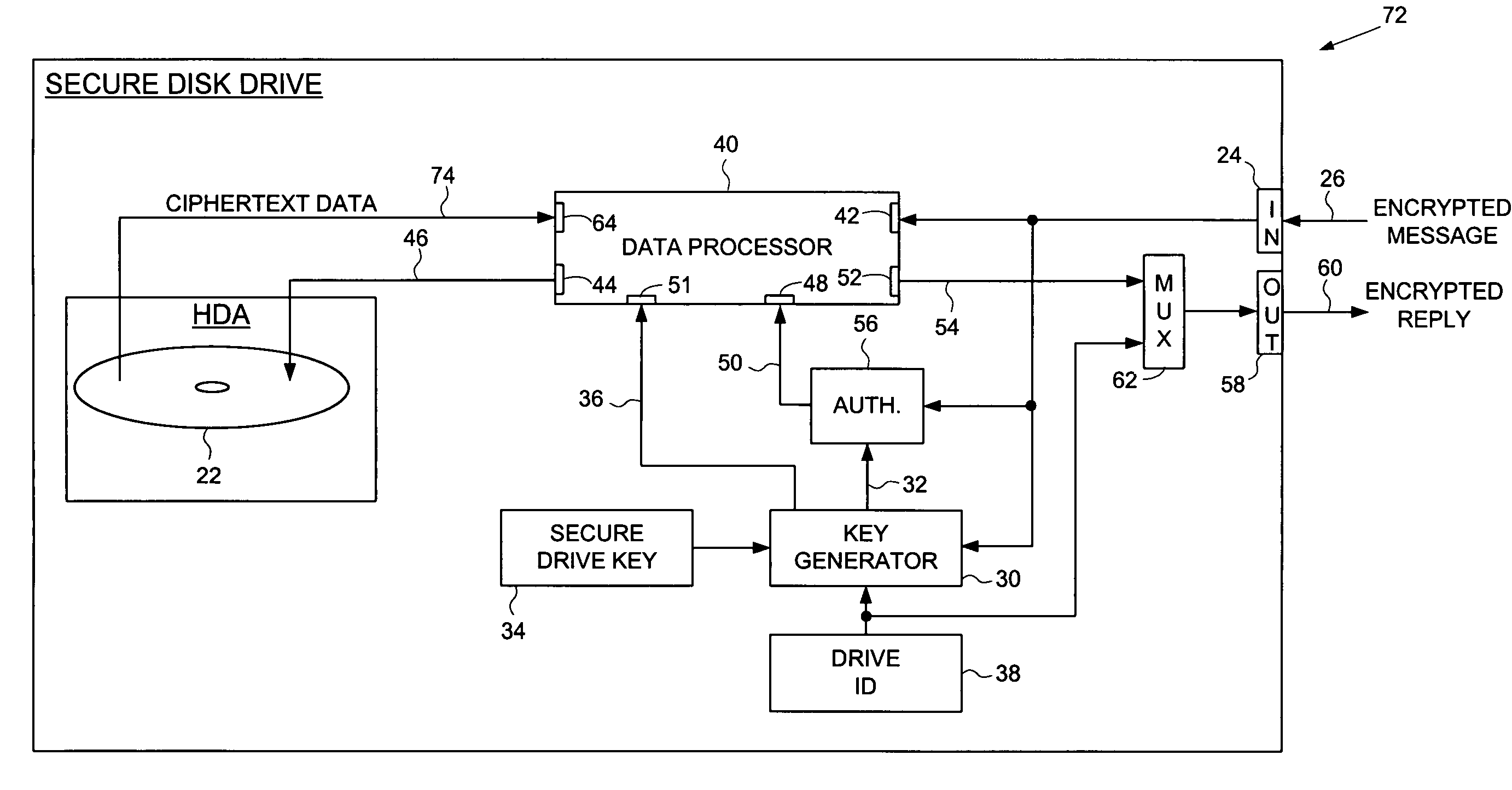
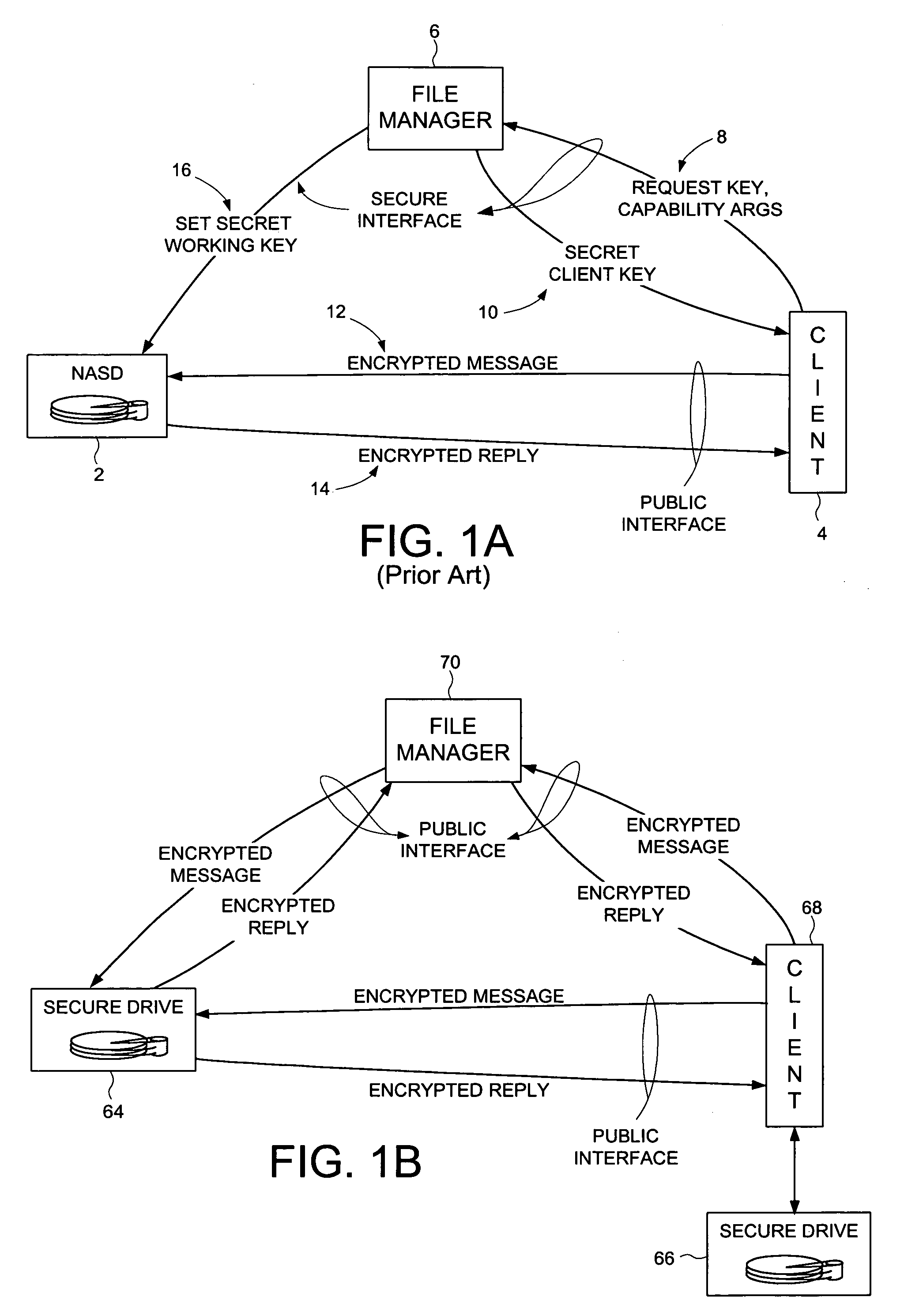
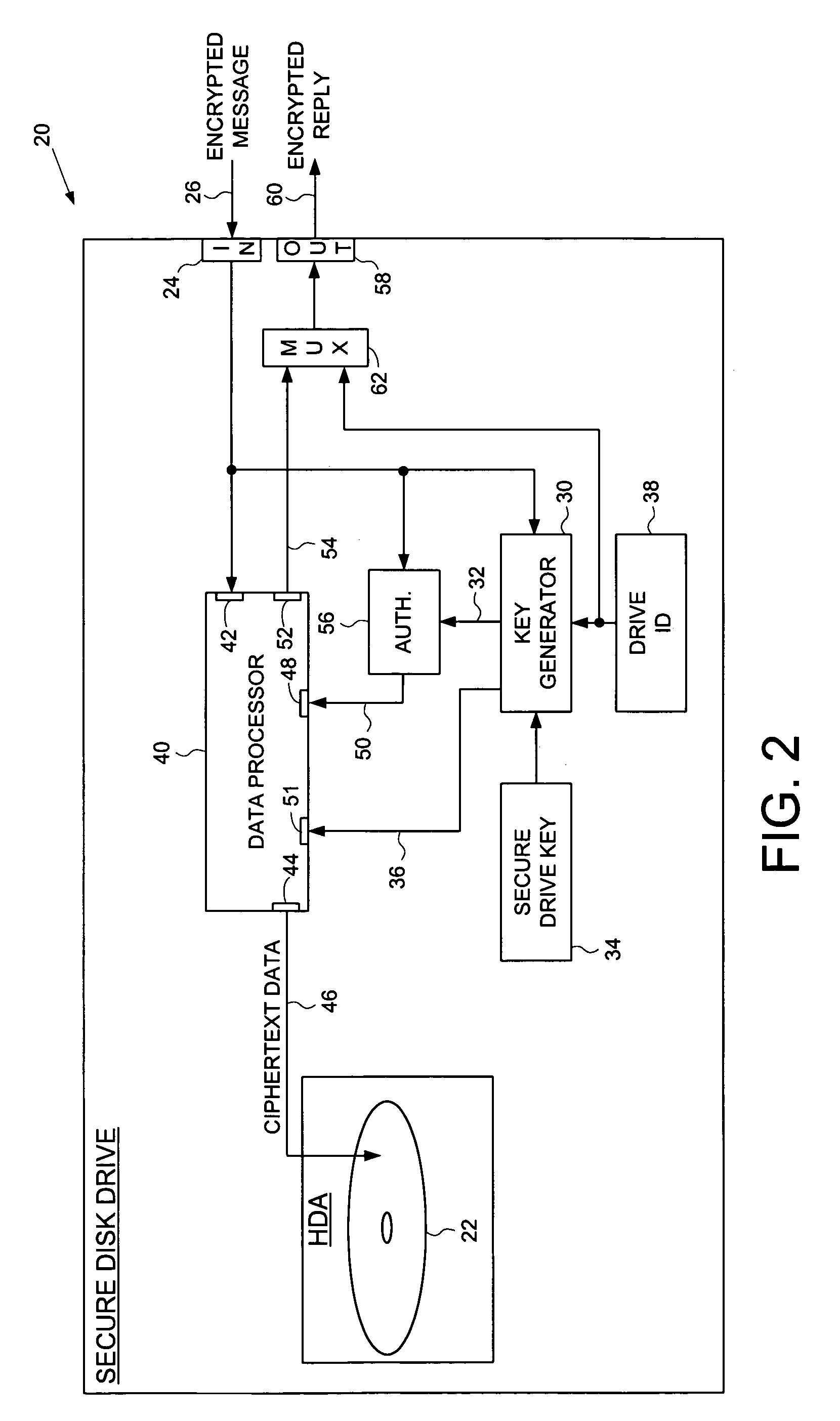
Secure disk drive comprising a secure drive key and a drive ID for implementing secure communication over a public network
InactiveUS7215771B1Volume/mass flow measurementUser identity/authority verificationSecure communicationCiphertext
A secure disk drive is disclosed comprising a disk for storing data, and an input for receiving an encrypted message from a client disk drive, the encrypted message comprising ciphertext data and a client drive ID identifying the client disk drive. The secure disk drive comprises a secure drive key and an internal drive ID. A key generator within the secure disk drive generates a client drive key based on the client drive ID and the secure drive key, and an internal drive key based on the internal drive ID and the secure drive key. The secure disk drive further comprises an authenticator for verifying the authenticity of the encrypted message and generating an enable signal, the authenticator is responsive to the encrypted message and the client drive key. The secure disk drive further comprises a data processor comprising a message input for receiving the encrypted message from the client disk drive, and a data output for outputting the ciphertext data to be written to the disk. The data processor further comprises an enable input for receiving the enable signal for enabling the data processor, and a key input for receiving the internal drive key, the internal drive key for use in generating a message authentication code. The data processor outputs reply data comprising the message authentication code. The secure disk drive outputs a reply to the client disk drive, the reply comprising the reply data and the internal drive ID.
Owner:WESTERN DIGITAL TECH INC
Secure sockets layer proxy architecture
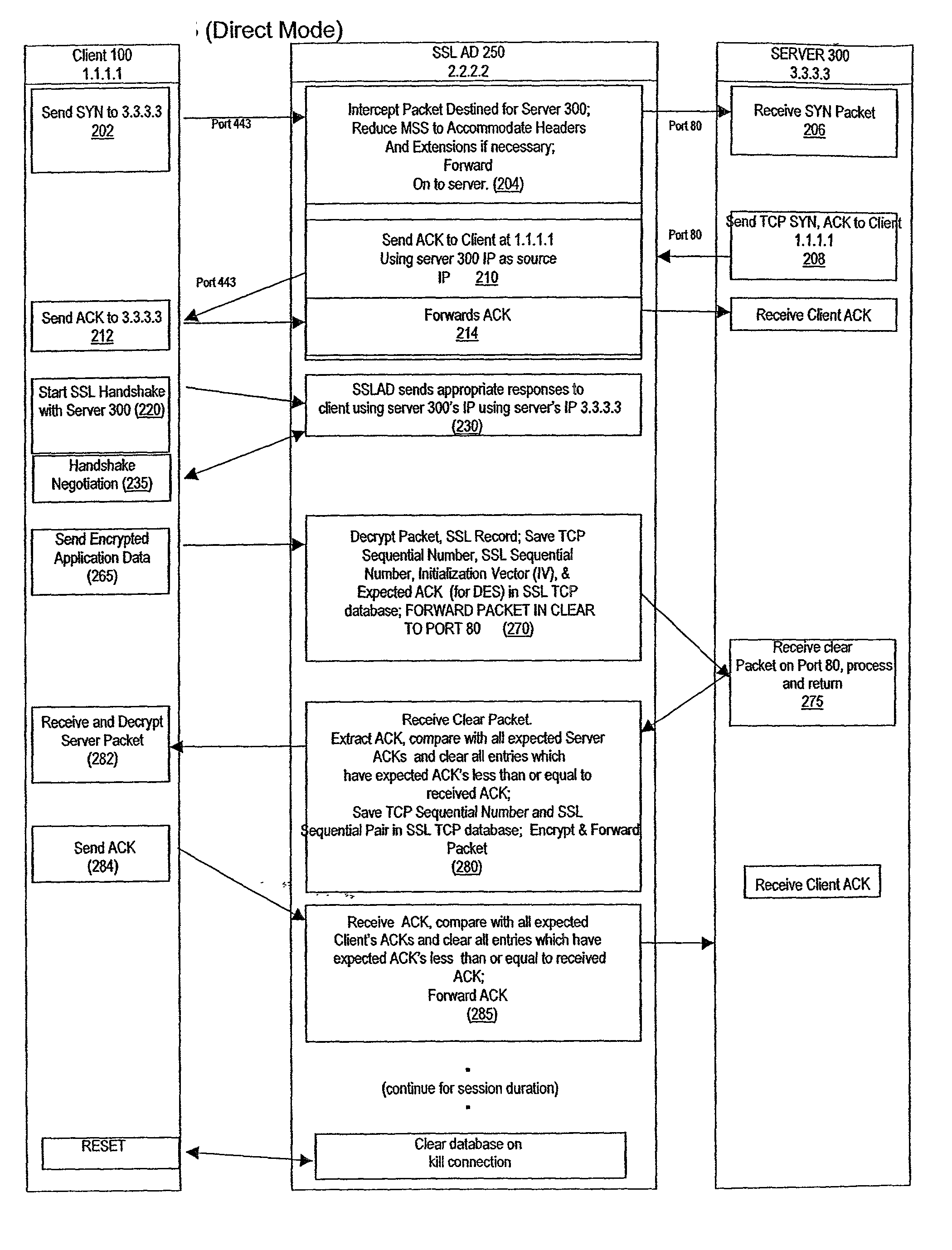
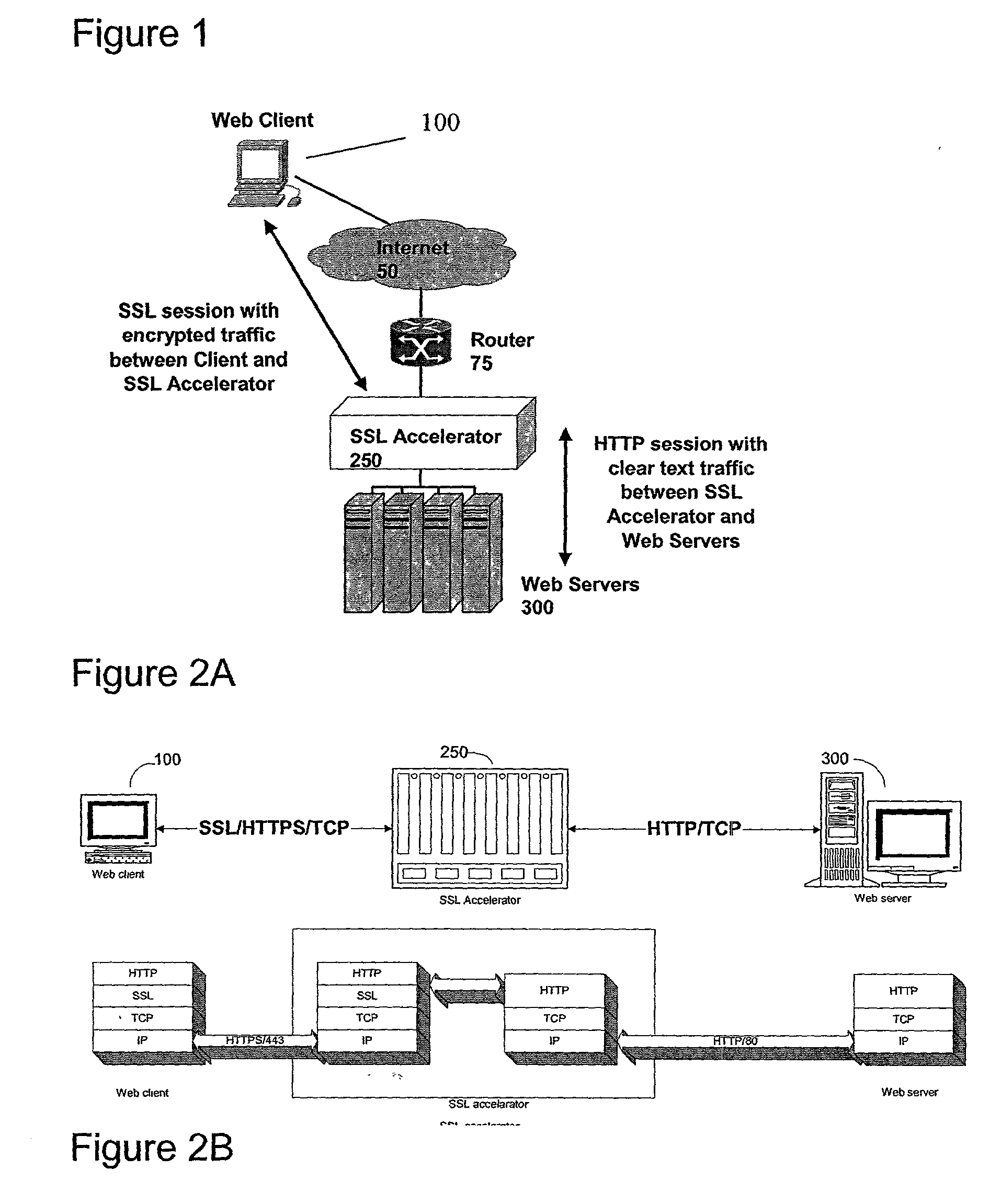
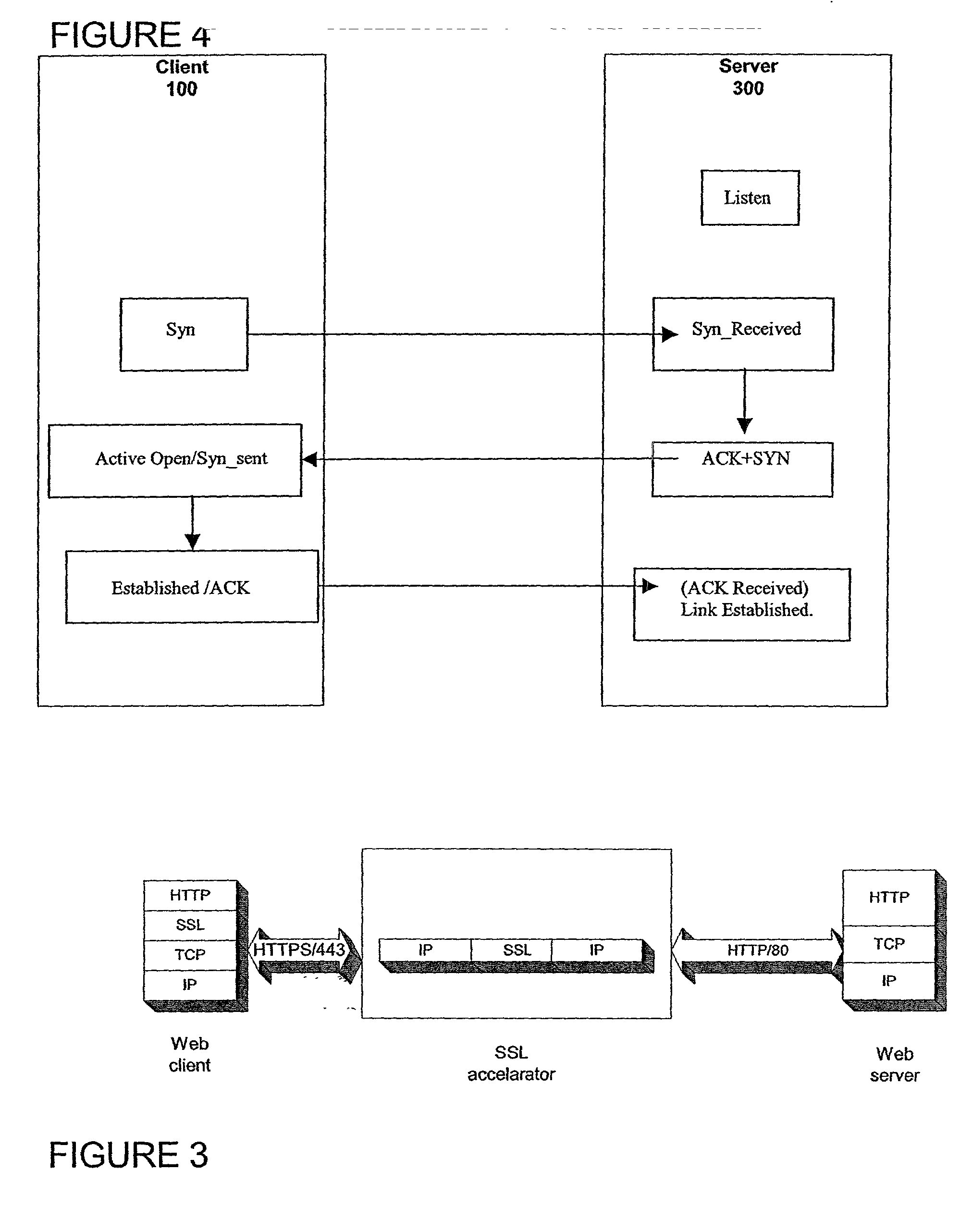
ActiveUS20030014628A1Low hardware requirementsLower latencyError detection/correctionMultiple digital computer combinationsSecure communicationChannel coupling
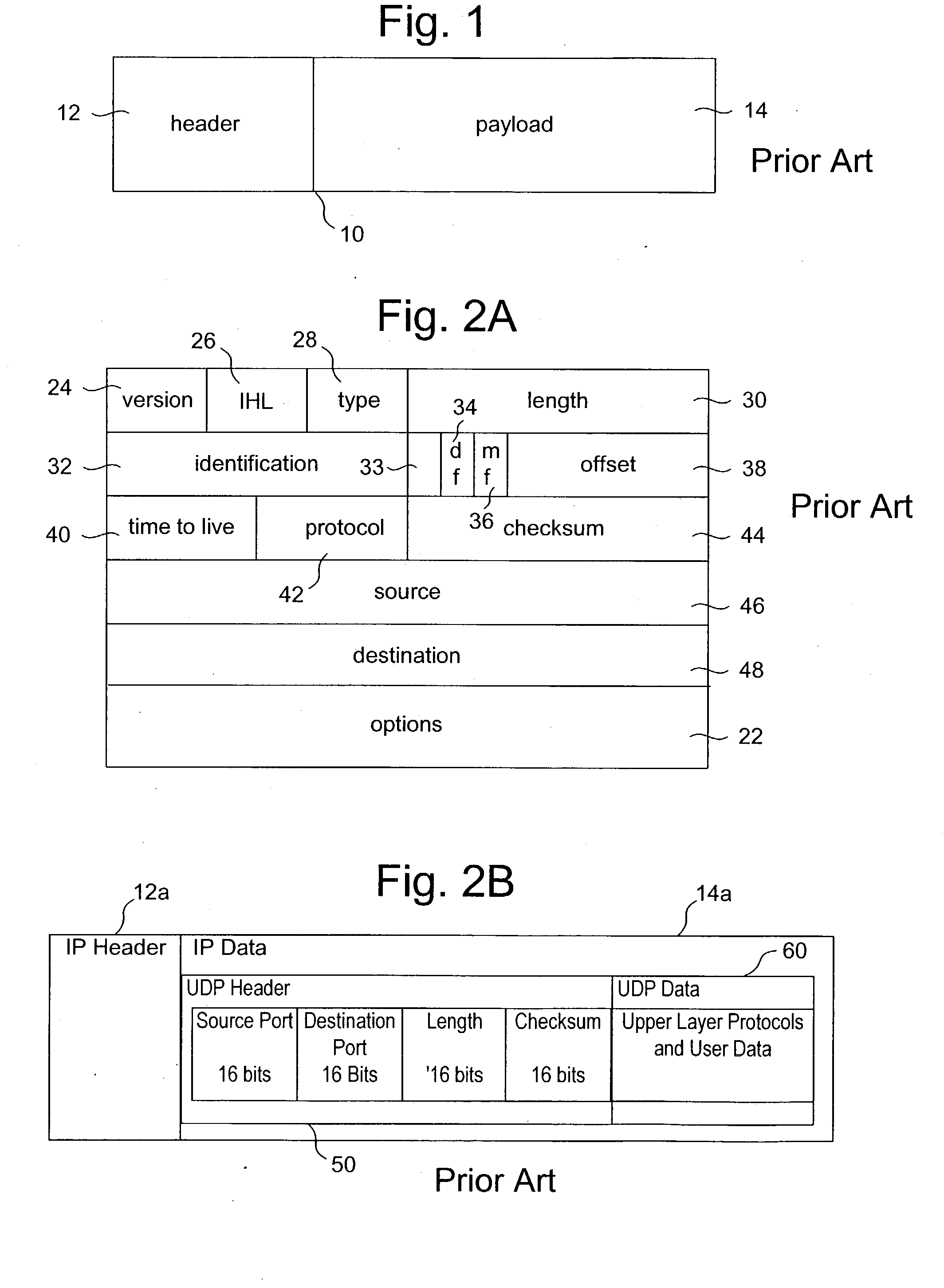
A method for secure communications between a client and one of a plurality of servers performed on an intermediary device coupled to the client and said plurality of servers. In one aspect, the method comprises: establishing an open communications session between the intermediary device and the client via an open network; negotiating a secure communications session with the client; establishing an open communications session with said one of said plurality of servers via a secure network; receiving encrypted data from the client via the secure communications session; decrypting encrypted application data; forwarding decrypted application data to the server via the secure network; receiving application data from the server via the secure network; encrypting the application data; and sending encrypted application data to the client. In a further aspect, an apparatus including a network interface communicating with the public network and the secure network at least one processor, programmable dynamic memory addressable by the processor, and a communications channel coupling the processor, memory and the network communications interface is provided. The apparatus further includes a proxy TCP communications engine, a proxy SSL communications engine, a server TCP communications engine; and a packet data encryption and decryption engine.
Owner:NEXSI SYST
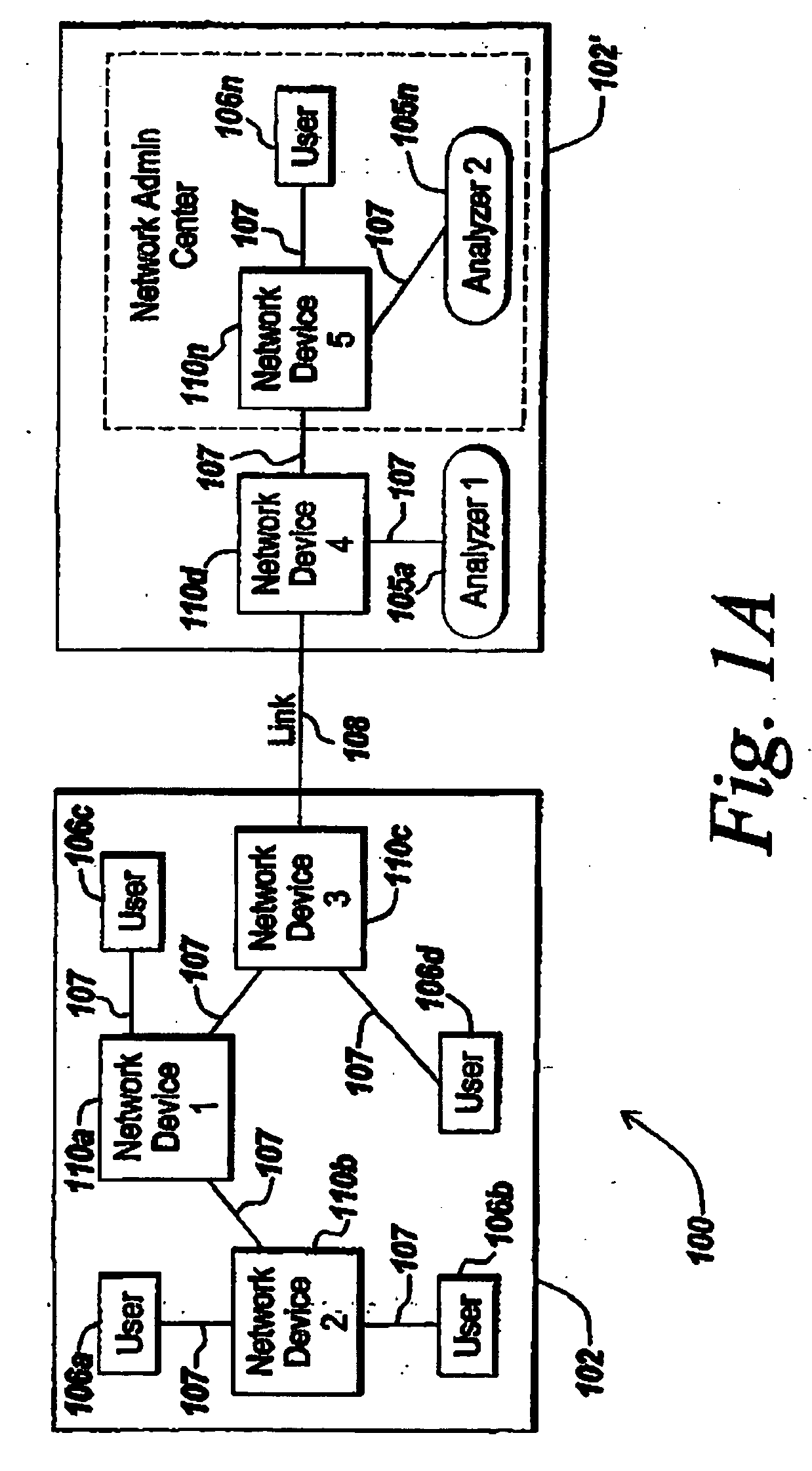
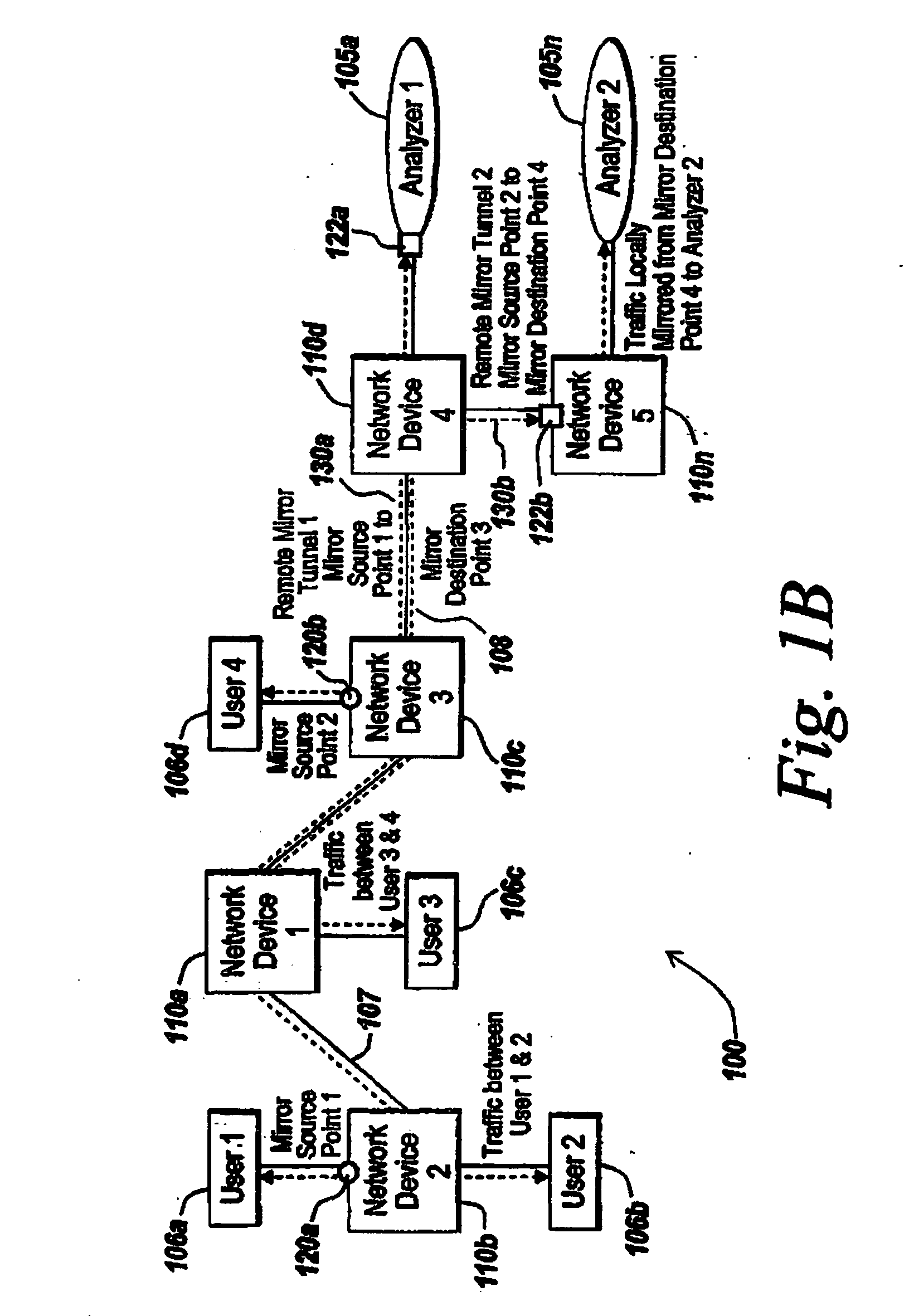
System, method and apparatus for traffic mirror setup, service and security in communication networks
ActiveUS20060059163A1Data switching networksSpecial data processing applicationsInternet networkPrivate network
The present invention provides method and systems for dynamically mirroring network traffic. The mirroring of network traffic may comprise data that may be considered of particular interest. The network traffic may be mirrored by a mirror service portal from a mirror sender, referred to as a mirror source, to a mirror receiver, referred to as a mirror destination, locally or remotely over various network segments, such as private and public networks and the Internet. The network traffic may be mirrored to locations not involved in the network communications being mirrored. The present invention provides various techniques for dynamically mirroring data contained in the network traffic from a mirror source to a mirror destination.
Owner:EXTREME NETWORKS INC
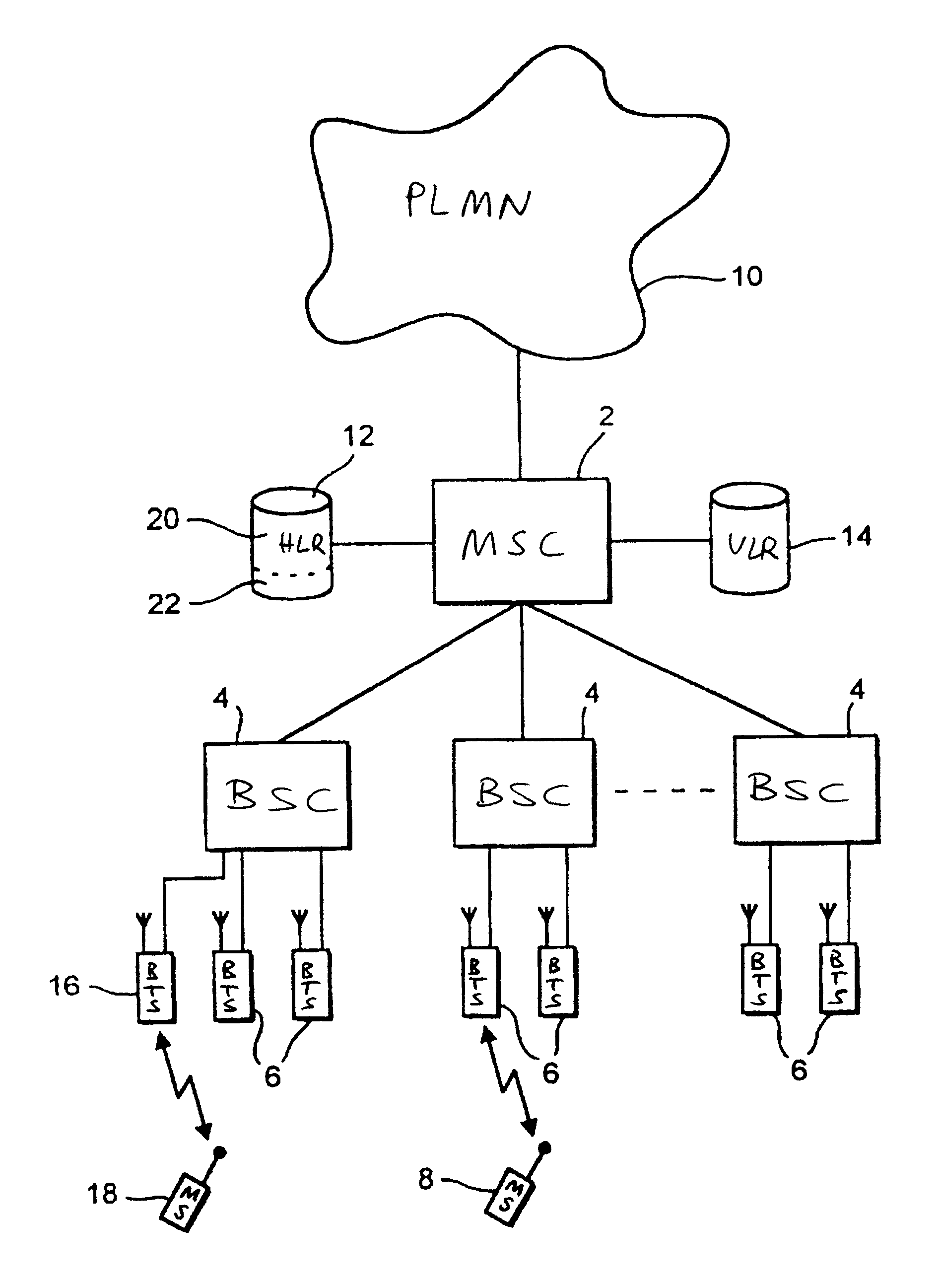
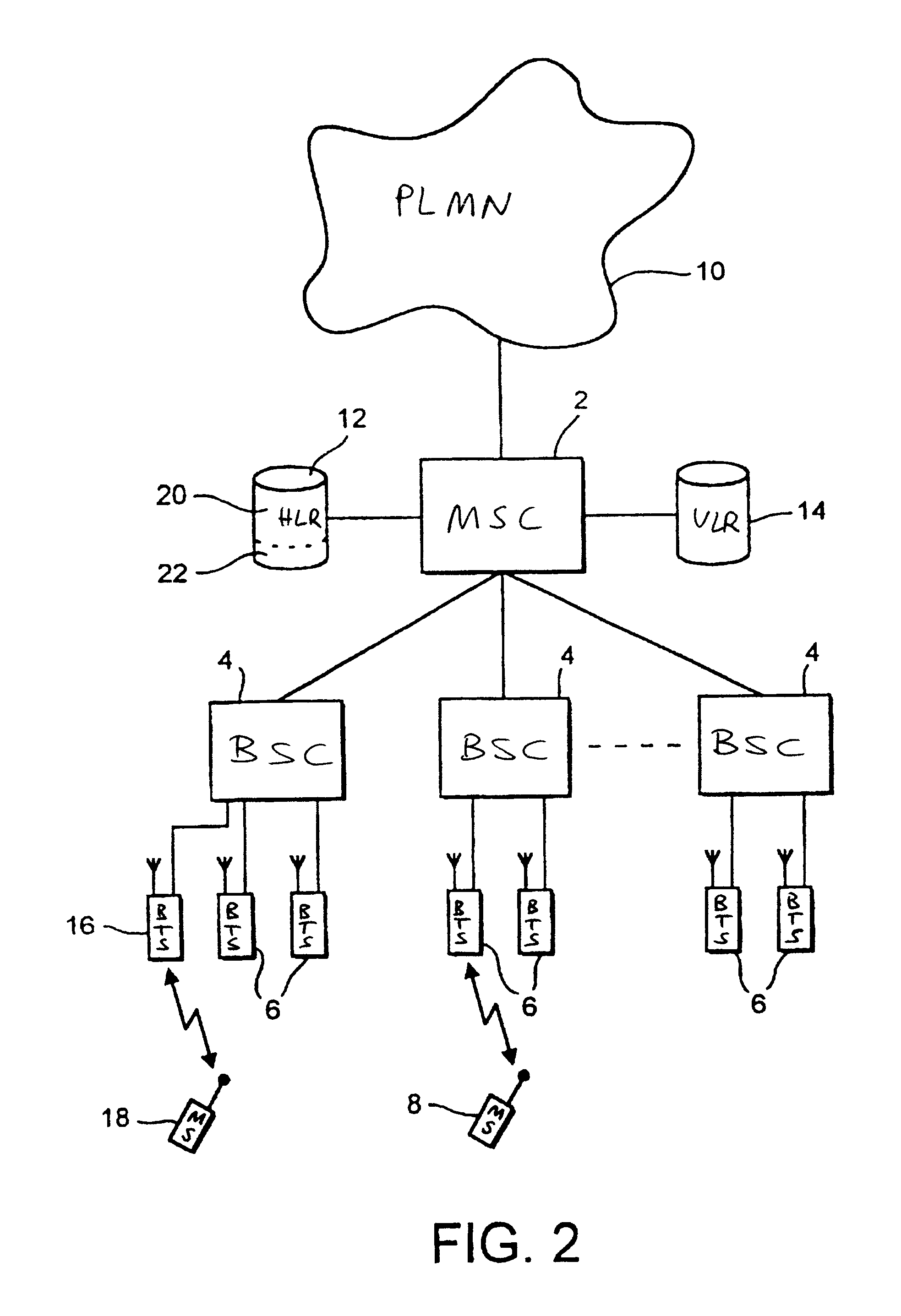
Mobile communications system having a cellular communications network comprising a public network portion and a private network portion using a common radio interface protocol
InactiveUS6826414B1Easy to distinguishReduce congestionAssess restrictionNetwork topologiesCommunications systemPrivate network
A public mobile communications network is configured in accordance with an established protocol which includes a private network portion to which only a selected set of mobile stations have access. The selected set of mobile stations has a private network identity code which is different from a public network identity code. A base transceiver station of the private network portion broadcasts the private network identity code on its broadcast control channel. A mobile switching center prevents public subscriber mobile stations from registering via the private network portion, while the private subscriber mobile stations are allowed to register over the entire network.
Owner:FRANCE TELECOM SA
Method and system for secure authentication
ActiveUS20050036611A1Digital data processing detailsMultiple digital computer combinationsPaymentTelecommunications link
A system and method configured to provide secure Personal Identification Number (PIN) based authentication is disclosed. A passcode or PIN associated with a customer value card can be securely authenticated by an issuer prior to authorizing payment. An Access Control Server (ACS) can receive the PIN or passcode from a customer via a secure connection over a public network. The ACS can generate an encrypted PIN and can communicate the encrypted PIN to a remote issuer for authentication. The ACS can use one or more hardware security modules to generate the encrypted PIN. The hardware security modules can be emulated in software or implemented in hardware. The system can be configured such that the PIN is not exposed in an unencrypted form in a communication link or in hardware other than the originating customer terminal.
Owner:VISA USA INC (US)
Method and apparatus for distributing content
InactiveUS8412707B1Metadata text retrievalDigital data processing detailsPrivate networkThe Internet
Owner:USTRINGER
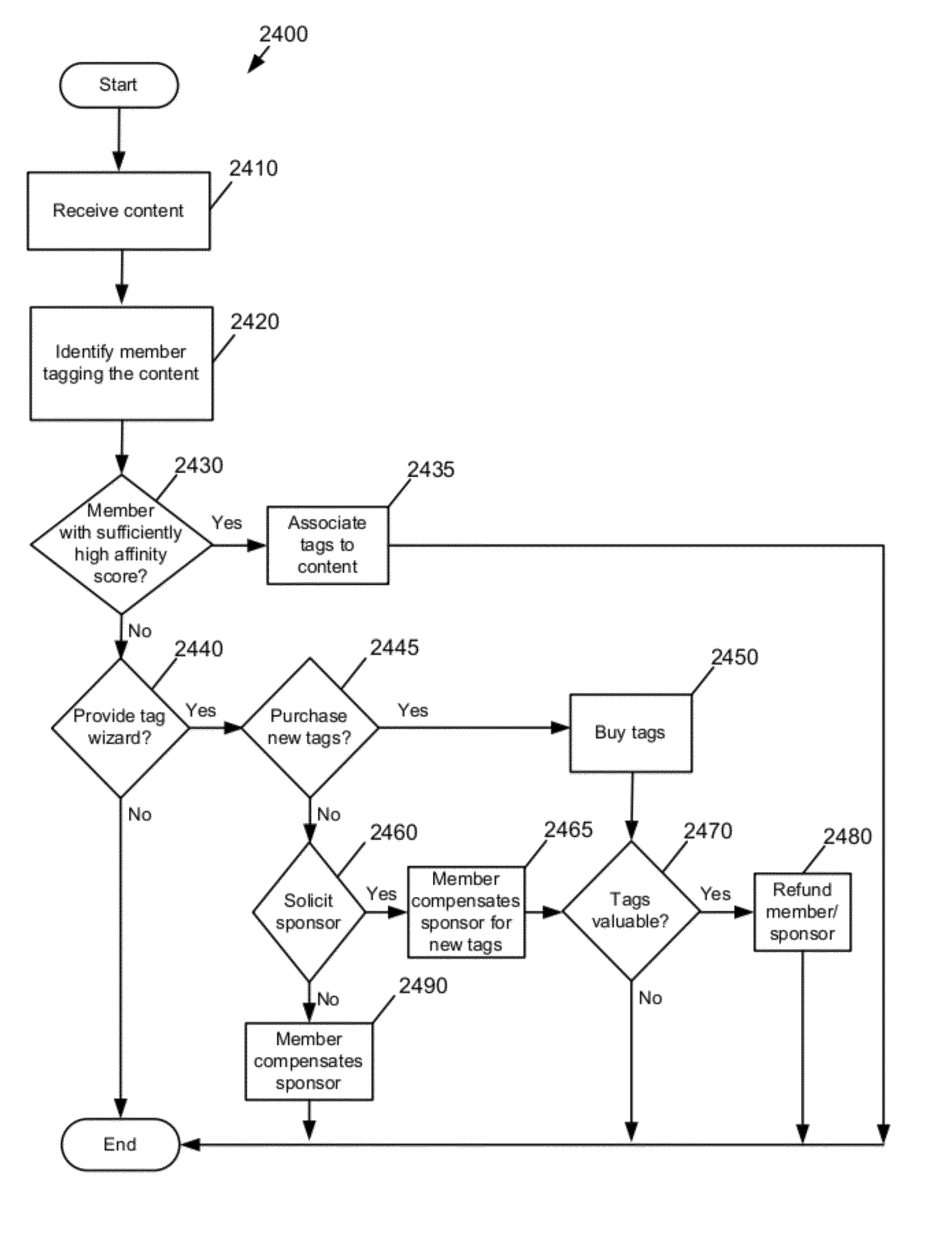
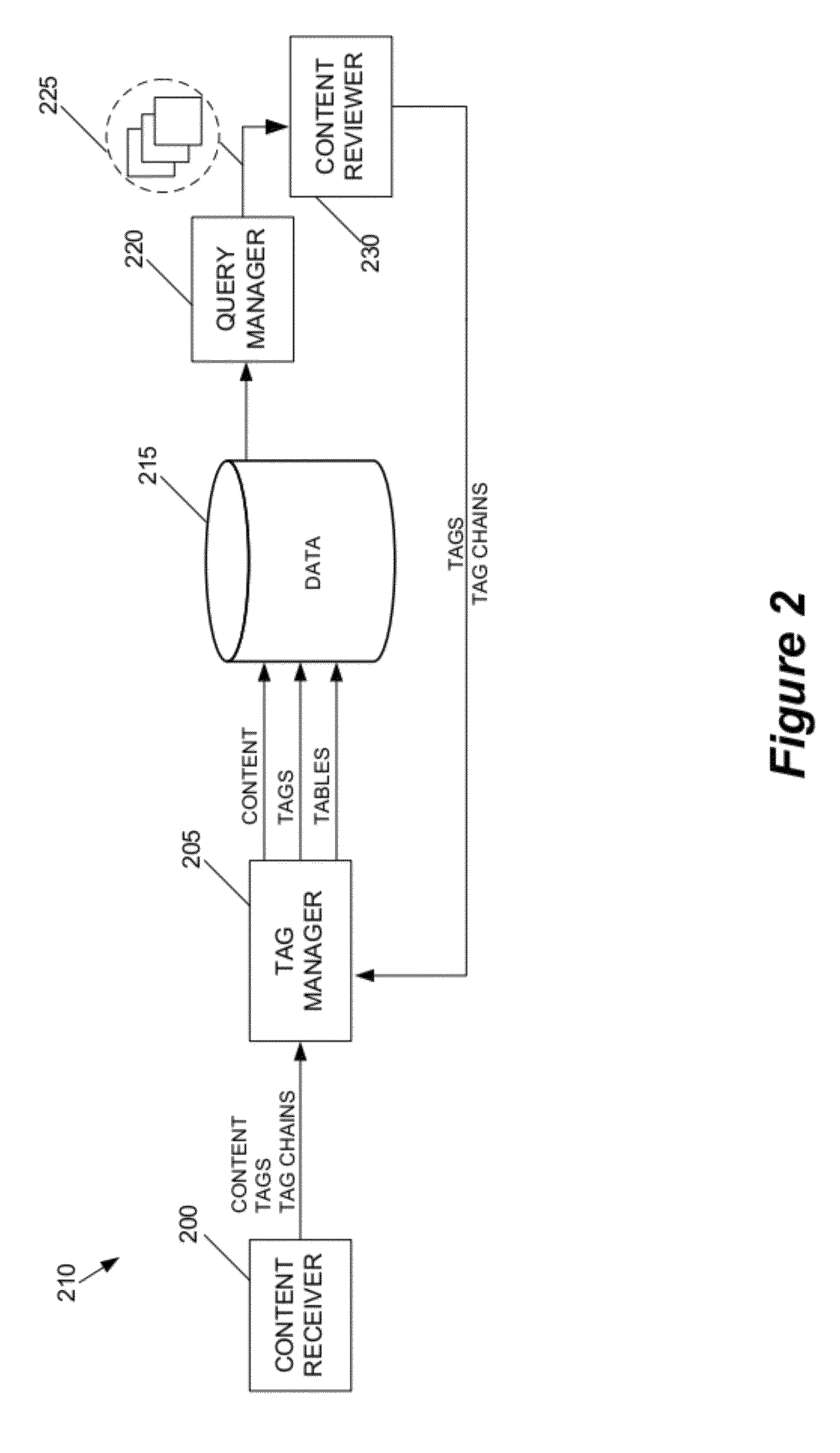
Method and apparatus for distributing content
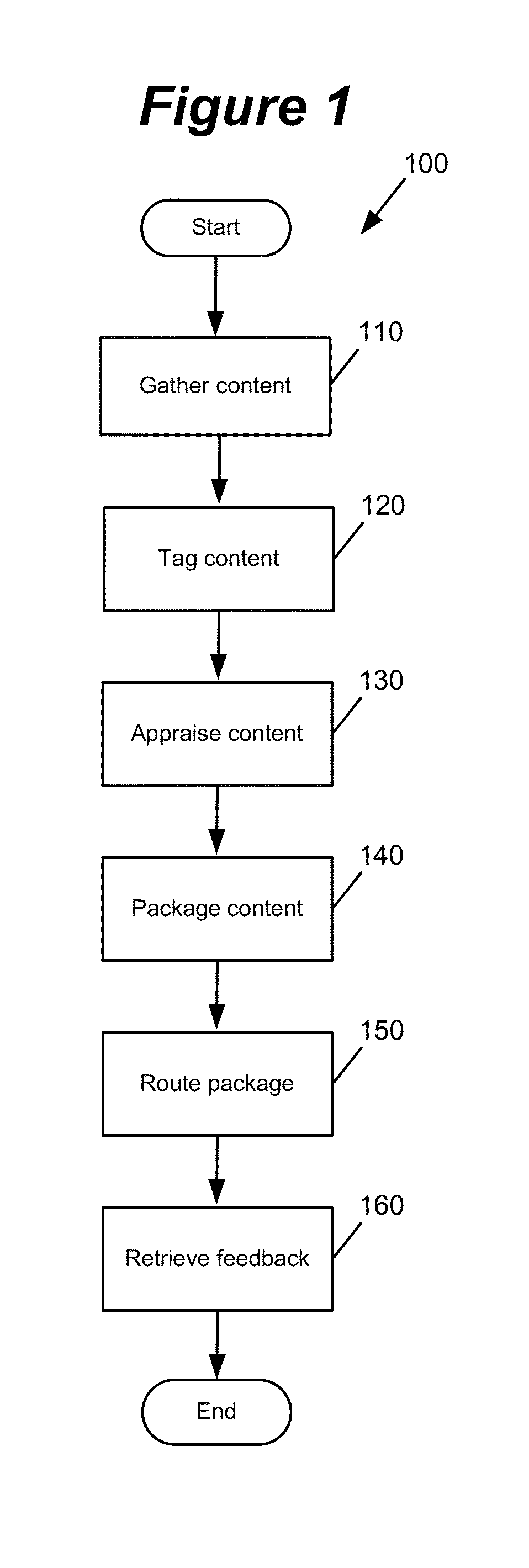
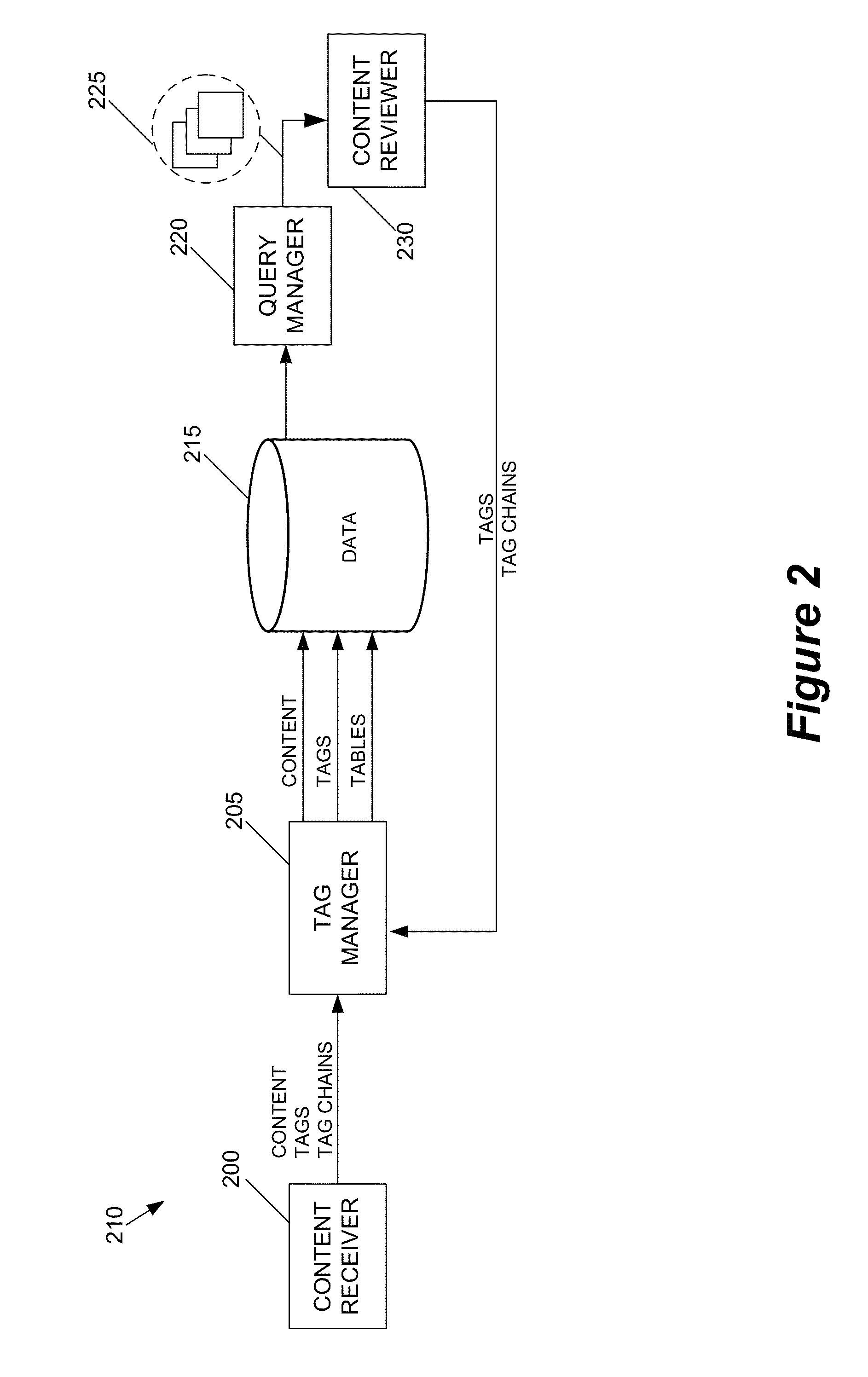
InactiveUS8452790B1Metadata text retrievalDigital data processing detailsPrivate networkThe Internet
Some embodiments provide a system that provides a UI for delivering content to a content reviewer. The UI includes (i) a first UI tool for receiving a user query and for searching a set of content items based on the user query, (ii) a second UI tool for retrieving a set of tags associated with each particular content item, and (iii) a third UI tool for generating a list of content items based on the retrieved tags. In some embodiments, each tag in the set of tags is associated with a computed metric. The tags are sorted based on this metric in some embodiments. The metric of some embodiments is based at least partly on a user type. User types include content provider, content retriever, and content evaluator. In some embodiments, the UI also includes a UI tool for receiving content or presenting the list of content items through a communications network. In various embodiments, the communications network may be a network of networks (e.g., the Internet), a private network, a public network, a wireless cellular network, etc.
Owner:USTRINGER
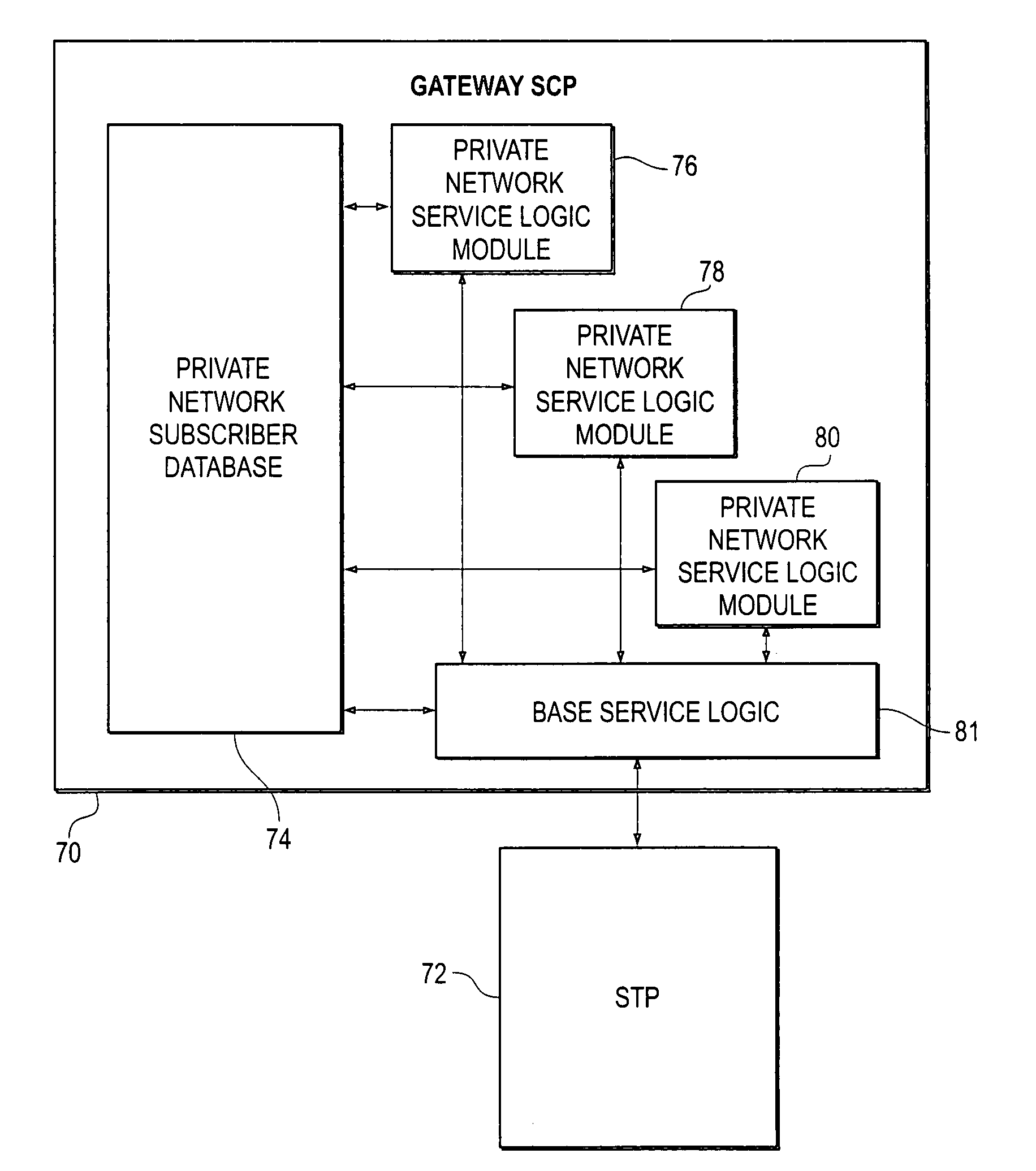
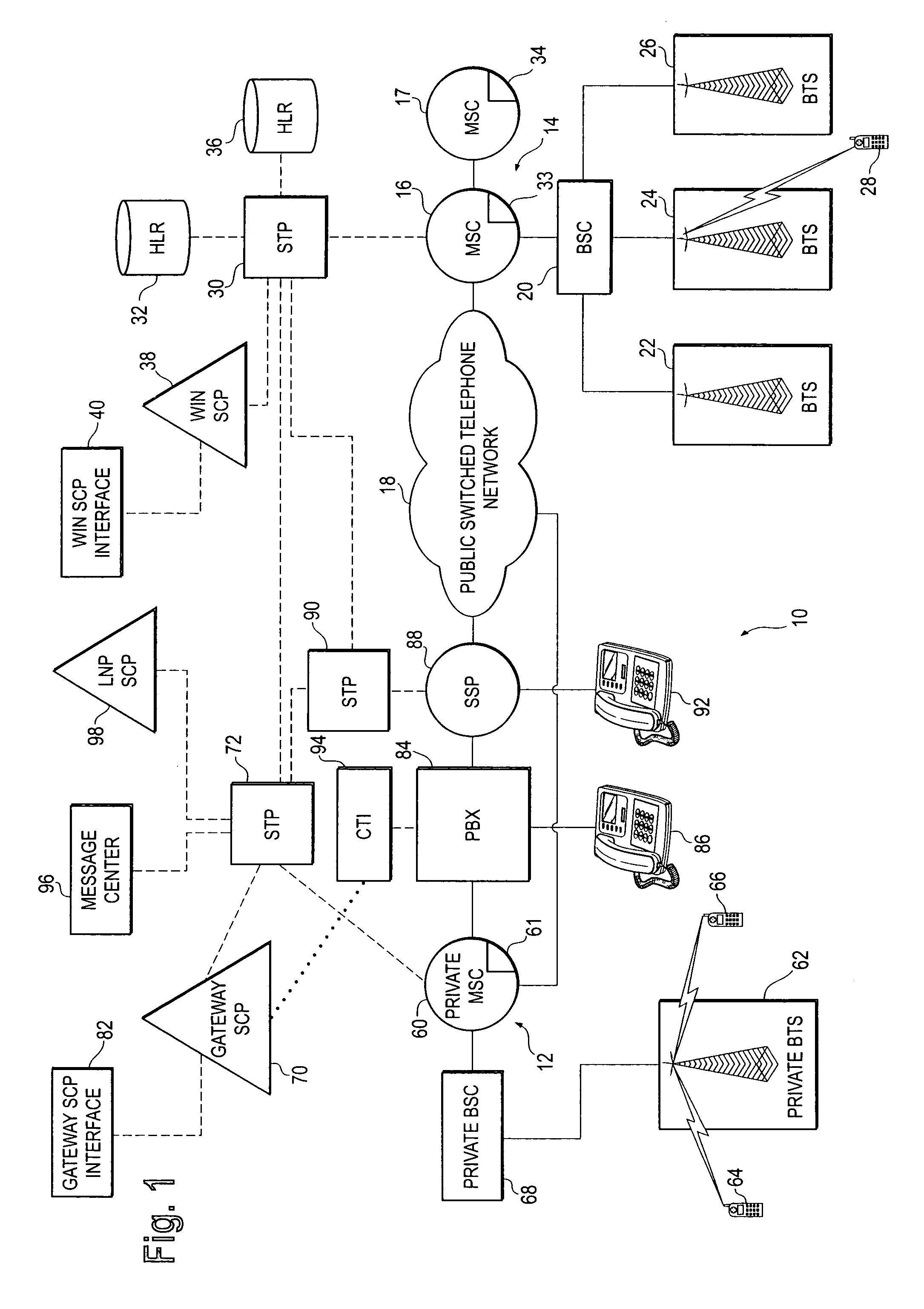
Private wireless network integrated with public wireless network
InactiveUS6970719B1Multiplex system selection arrangementsInterconnection arrangementsService profilePrivate network
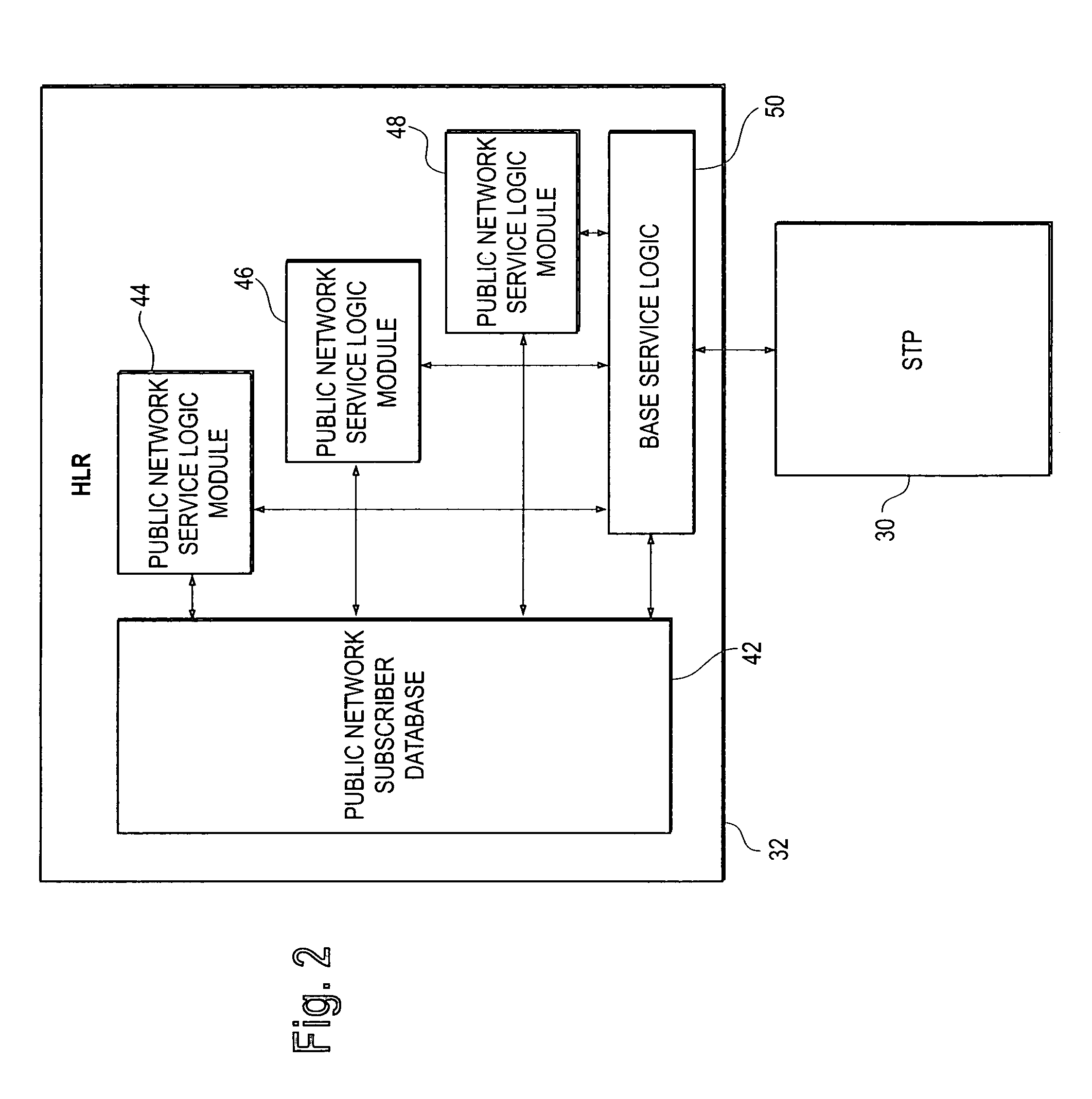
A private wireless network is able to provide wireless telecommunication services to subscriber mobile stations that also subscribe to a public wireless network. The private wireless network includes a private base transceiver station (BTS), a private mobile switching center (MSC), and a gateway service control point (SCP). The private BTS provides a private network wireless coverage area within which the mobile station can communicate with the base transceiver station over an air interface. The gateway SCP has a private network database containing private network data records for subscribing mobile stations. A private network data record includes a private network service profile and a private network locator address. The public wireless network has a home location register (HLR) with a public network database containing public network data records for subscribing mobile stations. A public network data record includes a public network service profile and a public network locator address. When a subscriber mobile station is active on the private wireless network, the private network locator address identifies the private MSC, and the public network locator address identifies the gateway SCP. By providing the private network wireless coverage area so that it overlaps the public network's wireless coverage area, the subscriber mobile station may be handed off between the private and public wireless networks.
Owner:SPRINT SPECTRUM LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com