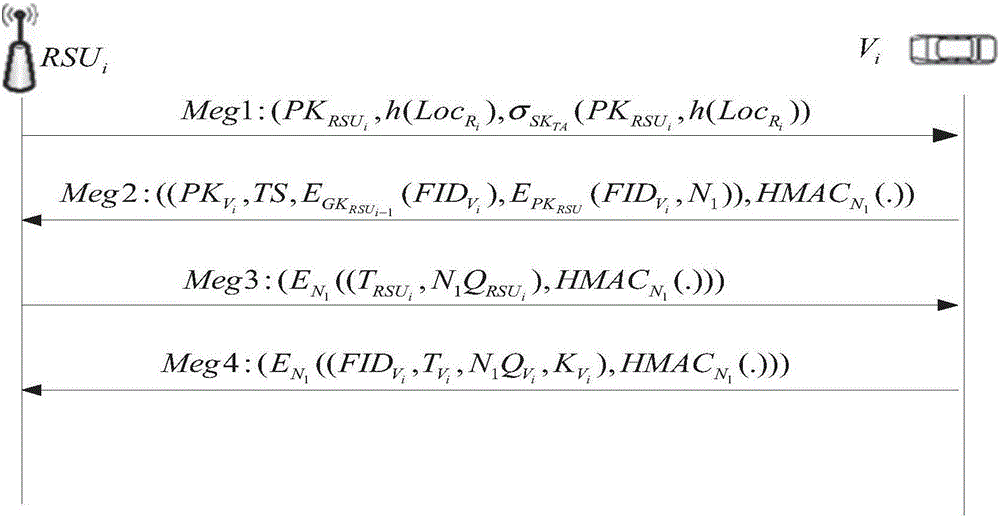Patents
Literature
306results about How to "Fast authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method, system and service for conducting authenticated business transactions
InactiveUS6957199B1Fast authenticationImprove securityComputer security arrangementsCommerceService provisionThe Internet
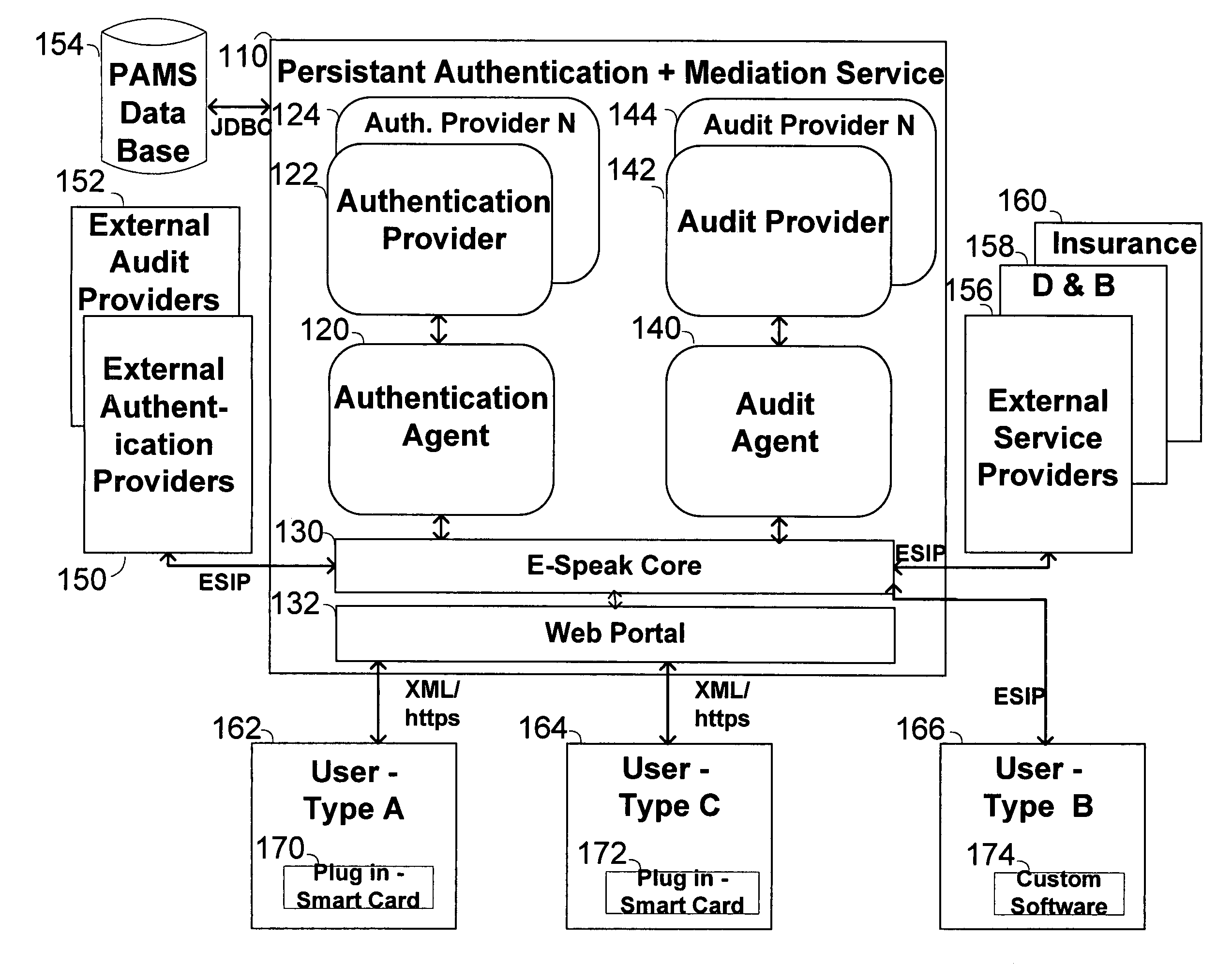
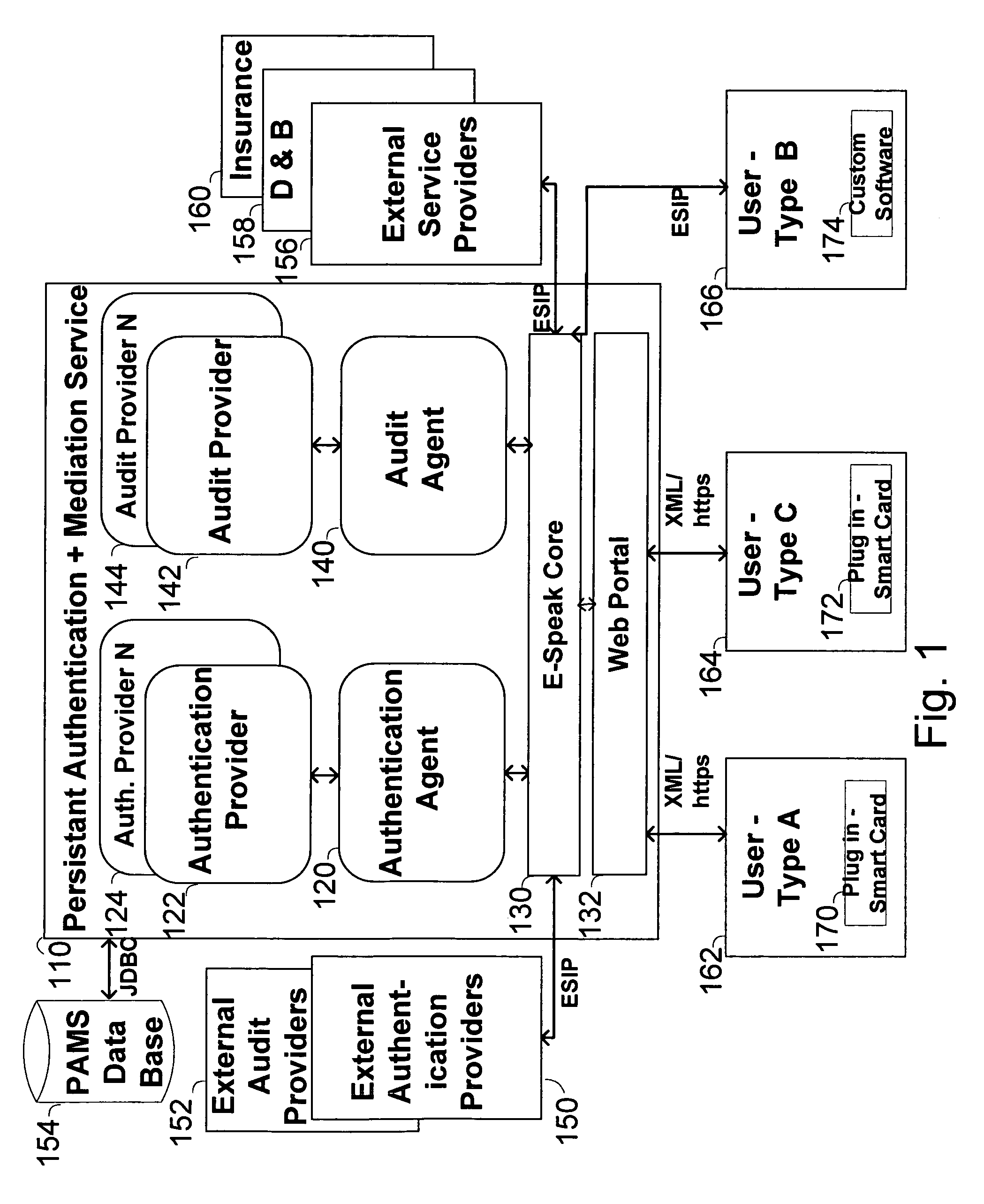
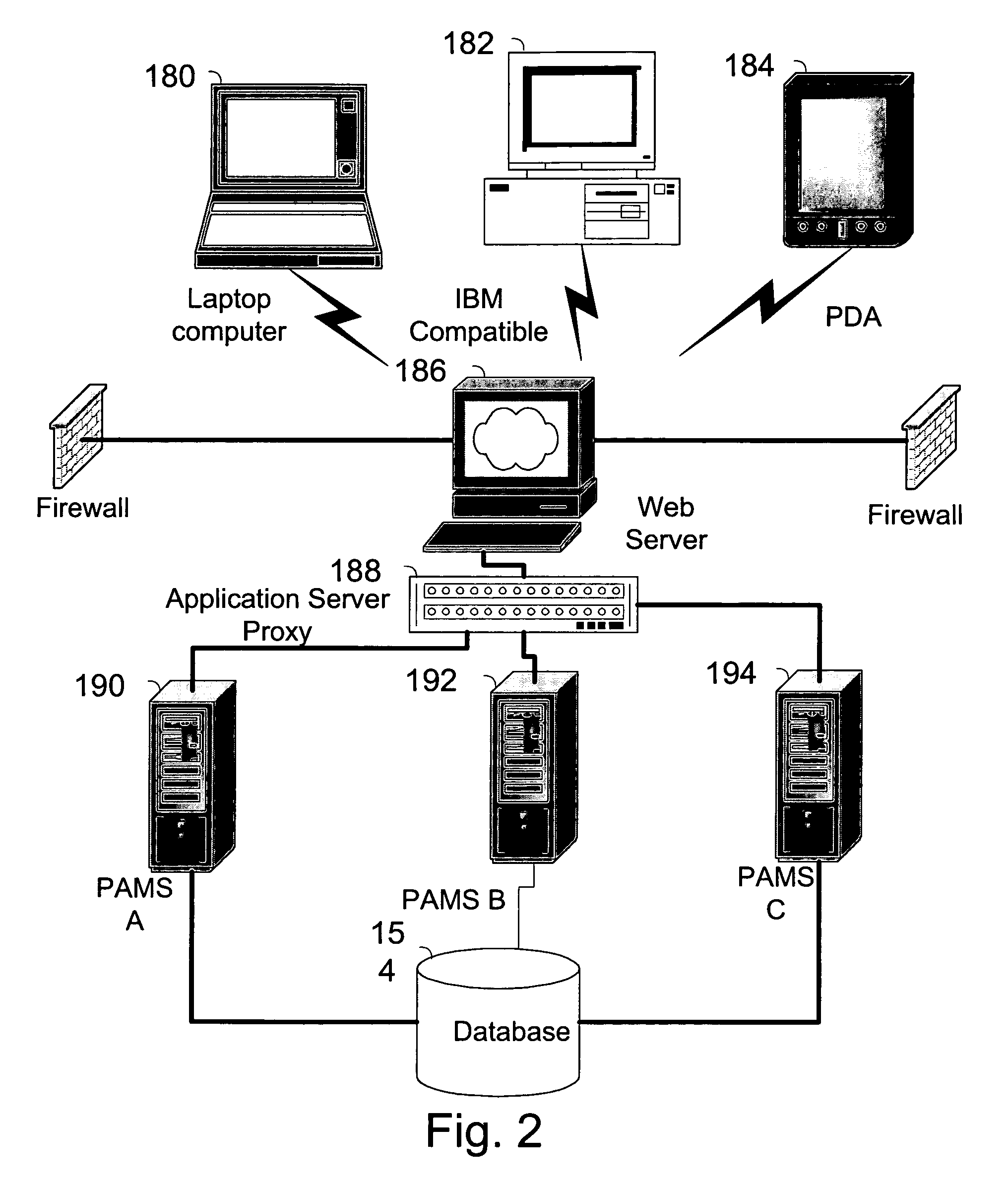
The invention pertains to a method, online service, and system, for creating partnerships based on trust relationships over a public network, authenticating trade partners, infrastructure providers and collaborators to each other, and providing users with an environment suitable for conducting transactions requiring a high level of trust. A service according to the invention is a persistent authentication and mediation service (PAMS) which is provided as an on-line service. One embodiment is a method for conducting authenticated business transactions involving microprocessor equipped devices over the Internet comprising:A. providing an on-line authentication service available on the distributed network;B. authenticating a plurality of users to said on-line authentication service using a closed authentication system to produce a plurality of authenticated users; andC. connecting a group of at least two of said plurality of authenticated users under persistent mediation of said on-line authentication service, producing a connected group of authenticated users.
Owner:FISHER DOUGLAS
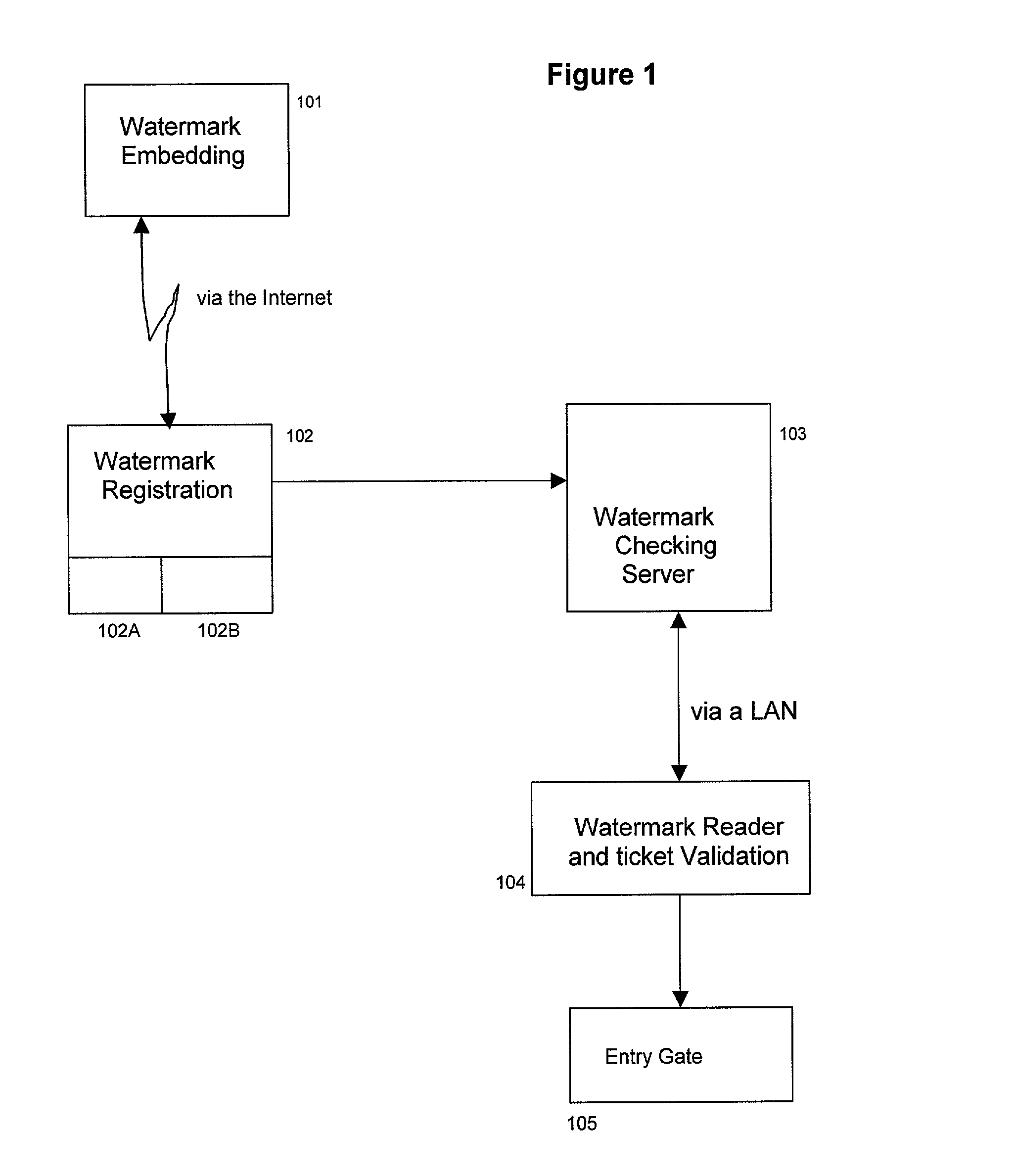
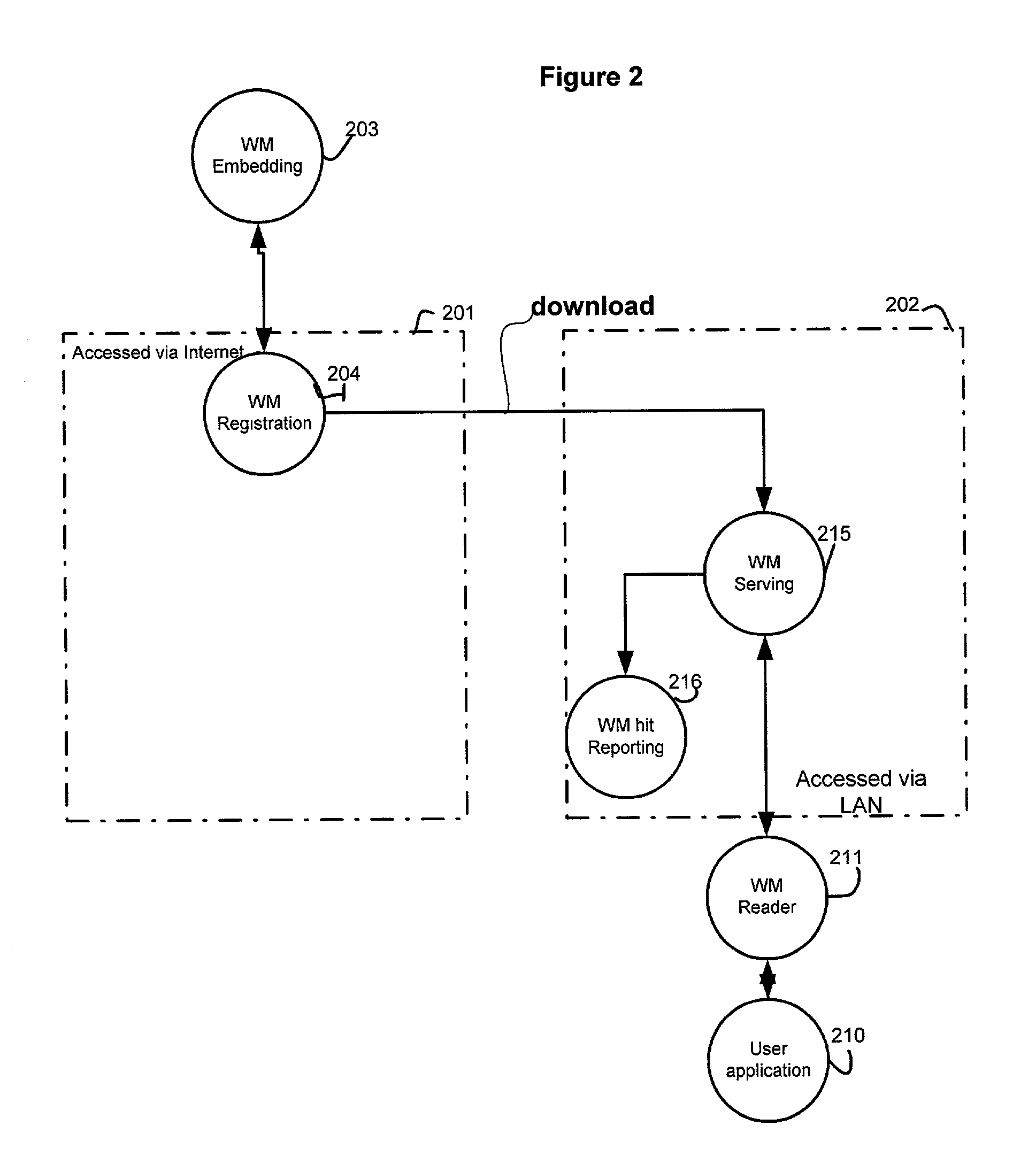
Distributed system for responding to watermarked documents
InactiveUS7111170B2Quick identificationFast authenticationOther printing matterUser identity/authority verificationData matchingThe Internet
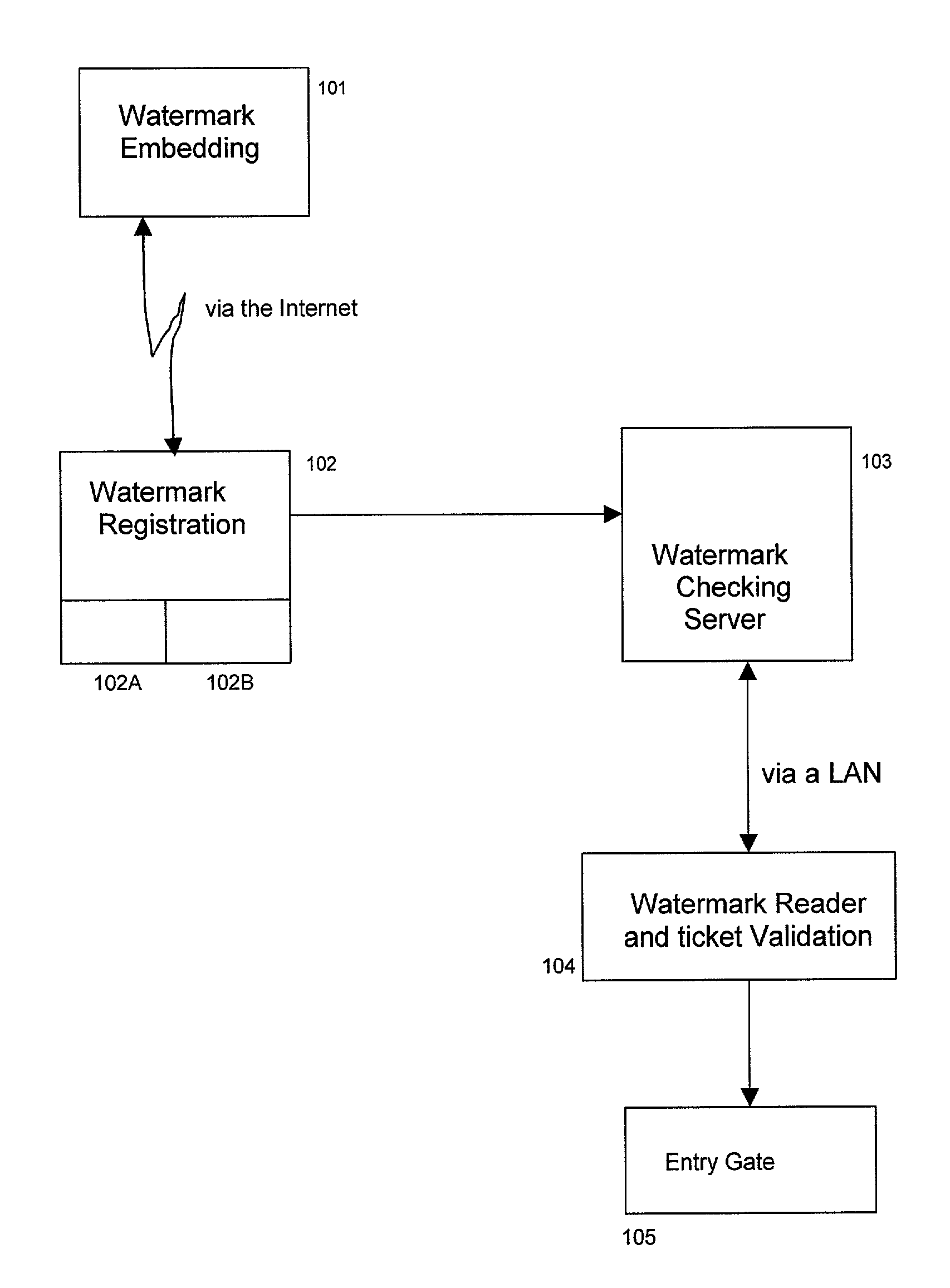
A method and system that registers data carried by a watermark with a server, reads watermark data from a document and generates an action string if a watermark read from a document matches registered data. In one embodiment the system includes two servers. Registration is done on one server via the internet the registration data is sent to a second server. The second server is interrogated via a local area network (LAN) to determine if particular watermark data is registered. The LAN allows data carried on documents such as tickets to be authenticated very quickly. In a second embodiment, there are multiple registration servers, each of which registers a different sets of watermark data. The compartmentalization of data increases security and privacy of data.
Owner:DIGIMARC CORP
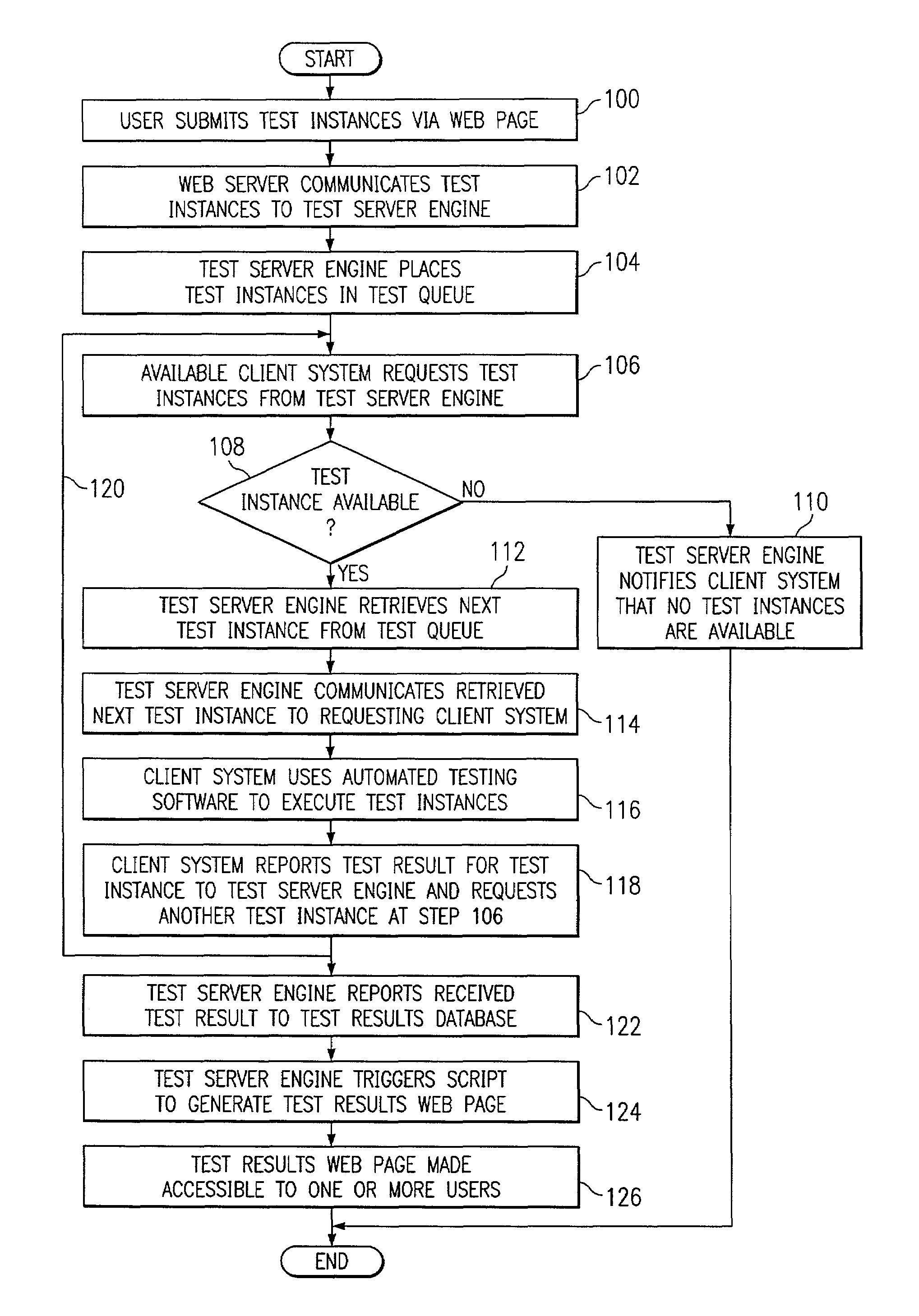
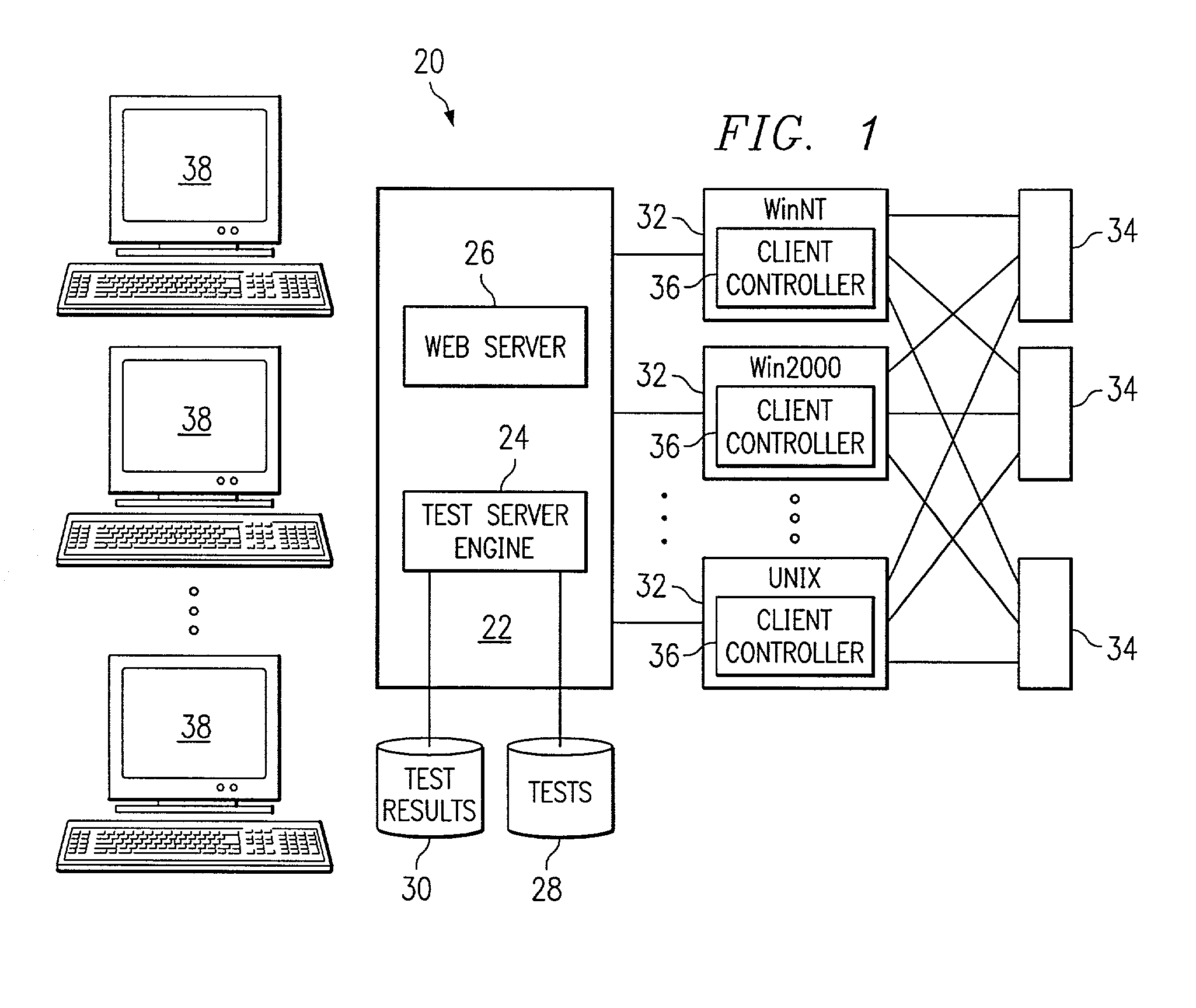
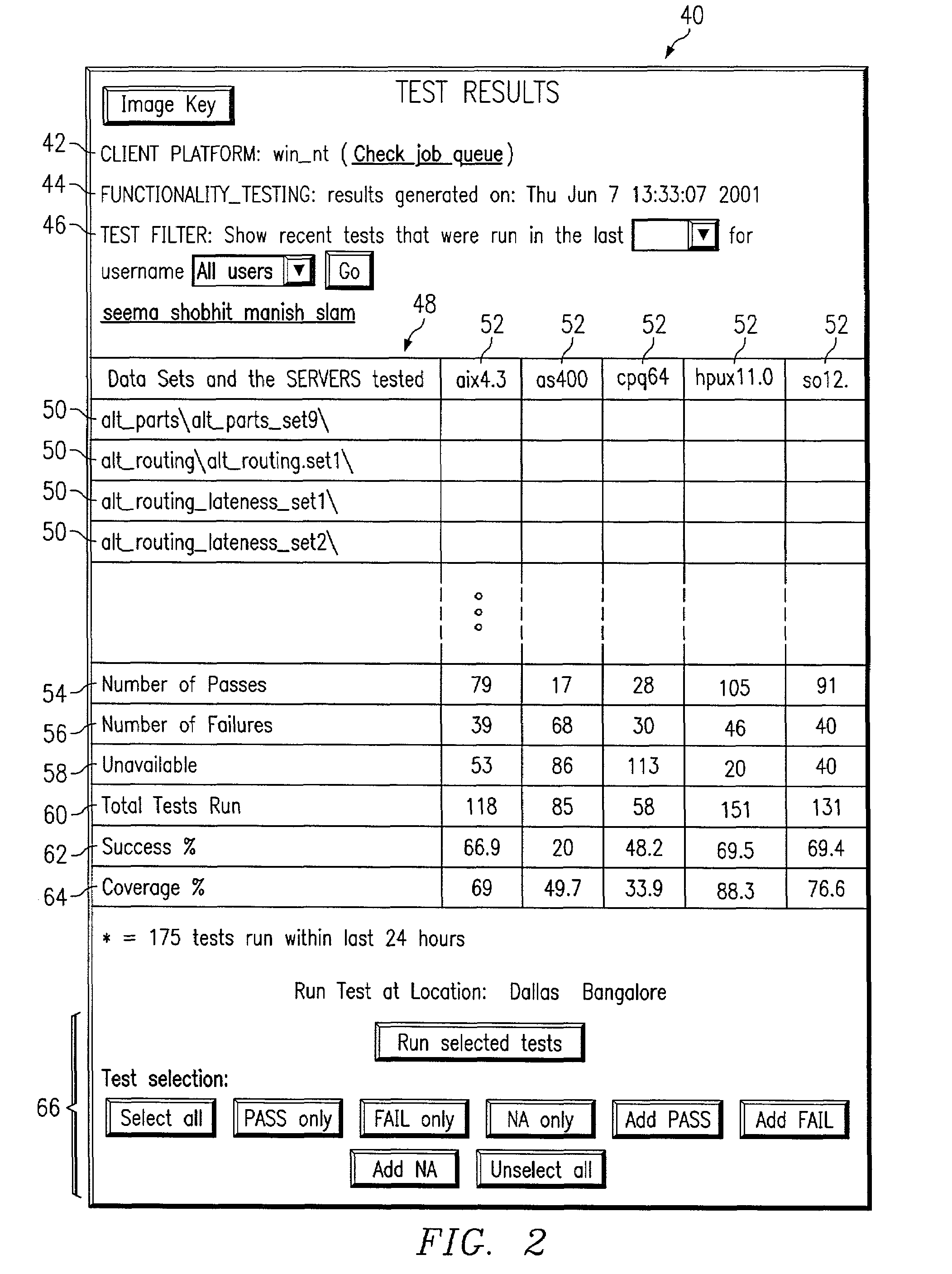
Distributed automated software graphical user interface (GUI) testing
InactiveUS7055137B2Disadvantages can be reduced eliminatedEfficient managementSoftware testing/debuggingSpecific program execution arrangementsGraphicsComputer hardware
Owner:JDA SOFTWARE GROUP
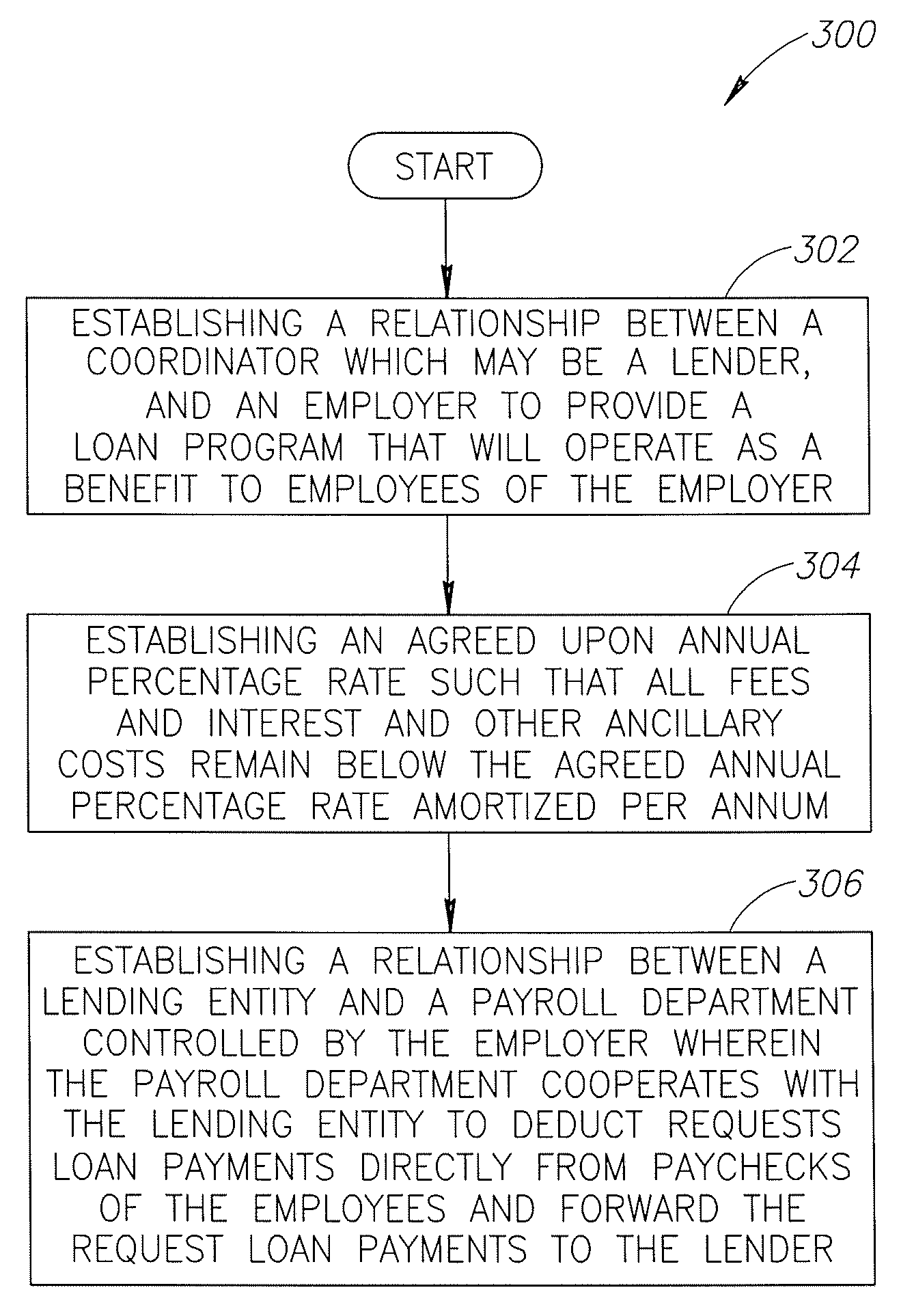
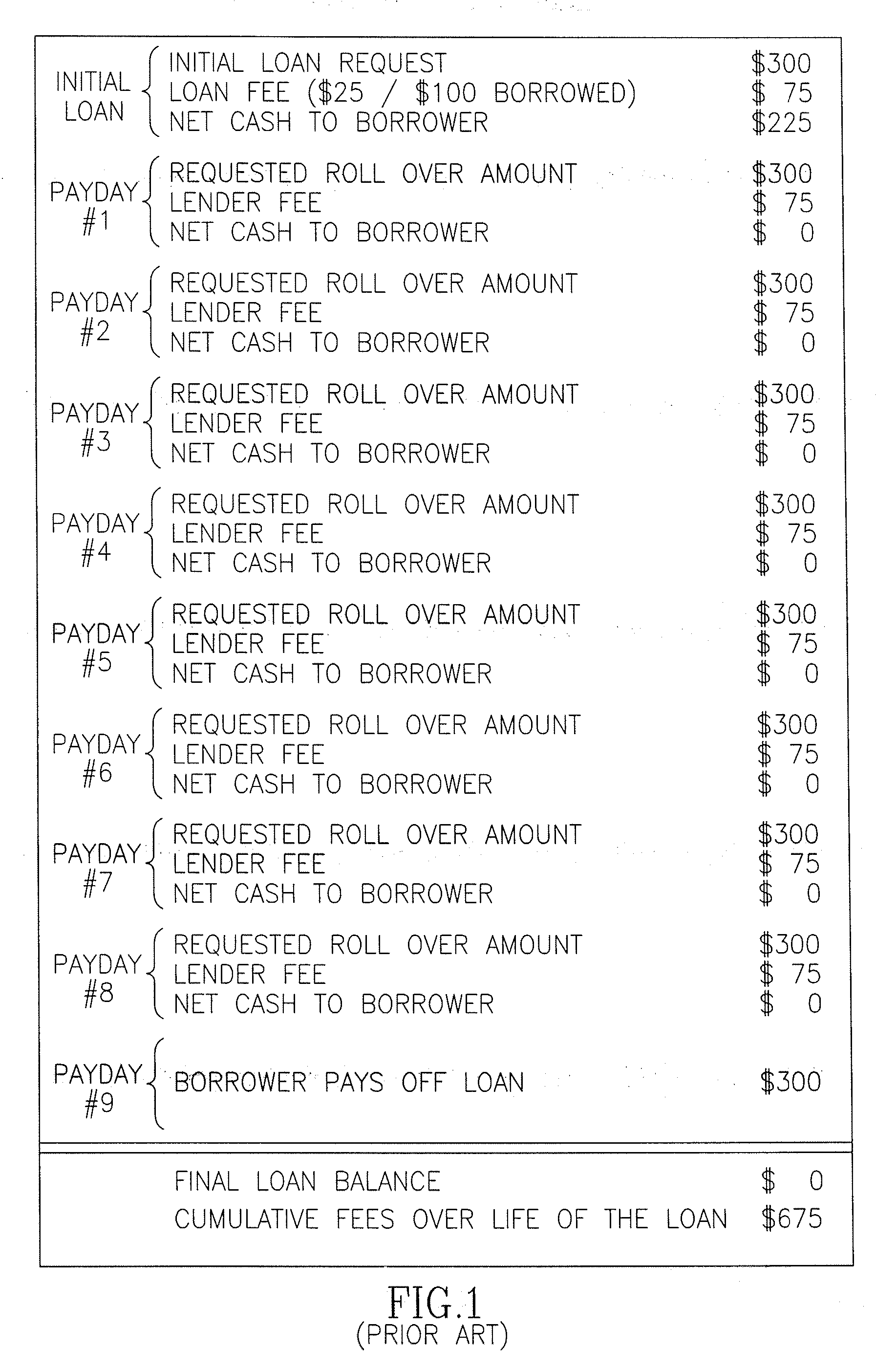
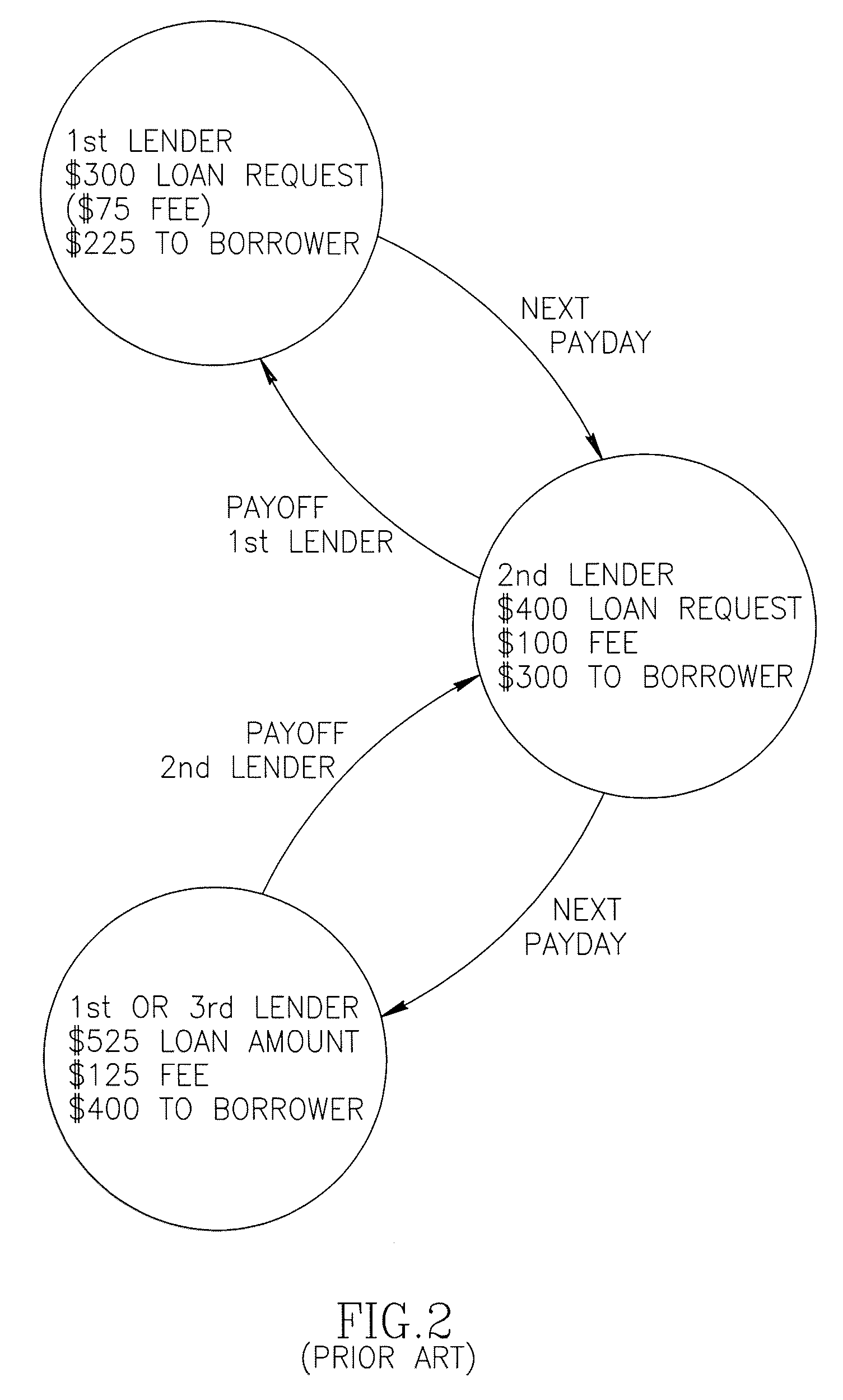
Loan program and process for transacting the same
ActiveUS20080005001A1Low costSave stepsFinancePayment architectureTelecommunicationsProgram planning
Owner:EMPLOYEE LOAN SOLUTIONS LLC
Apparatus and method for authenticating user for network access in communication system
InactiveUS20060070116A1Initial investment costReduce initial investment costDigital data processing detailsUser identity/authority verificationInternet service providerProtocol processing
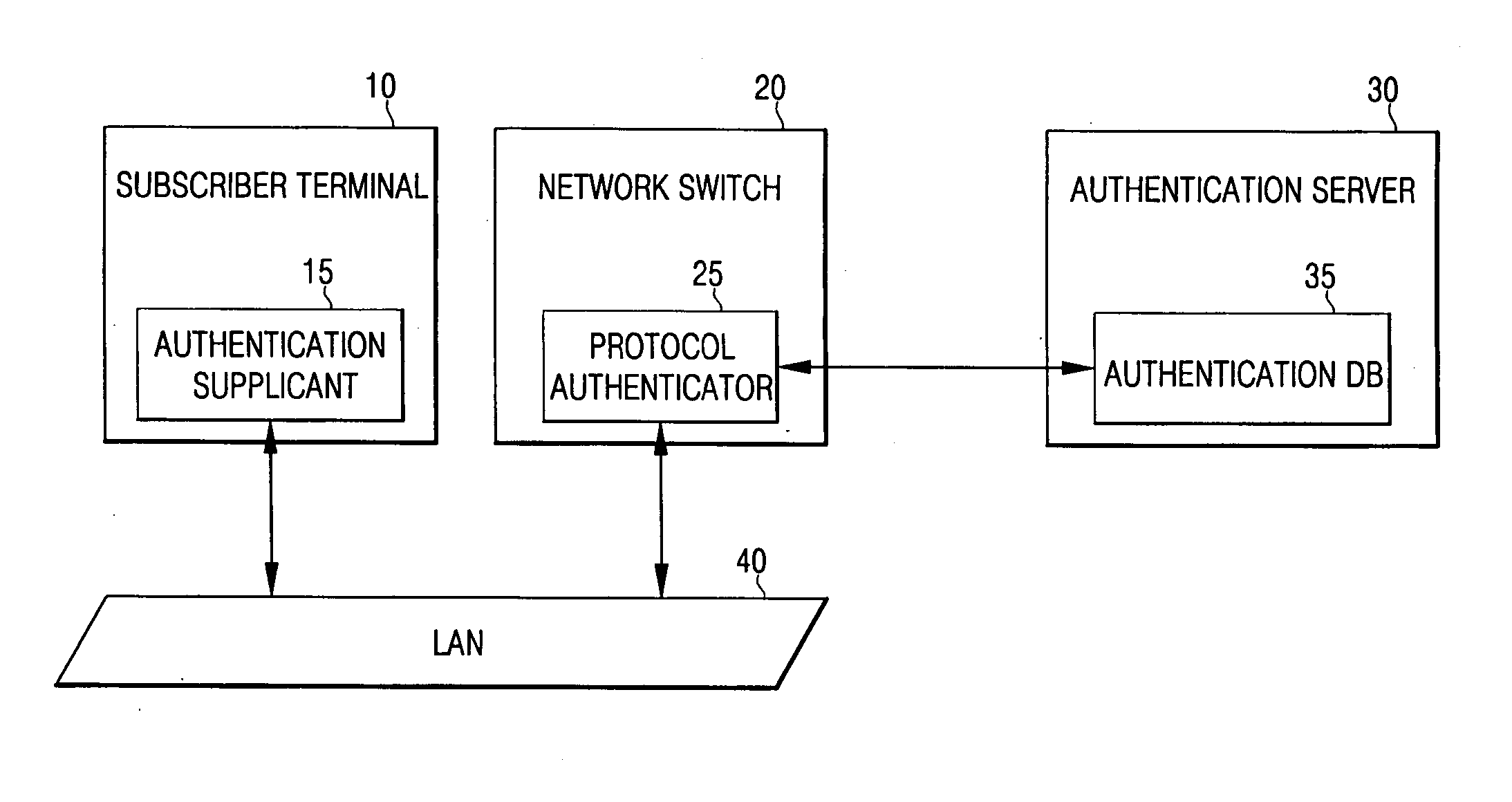
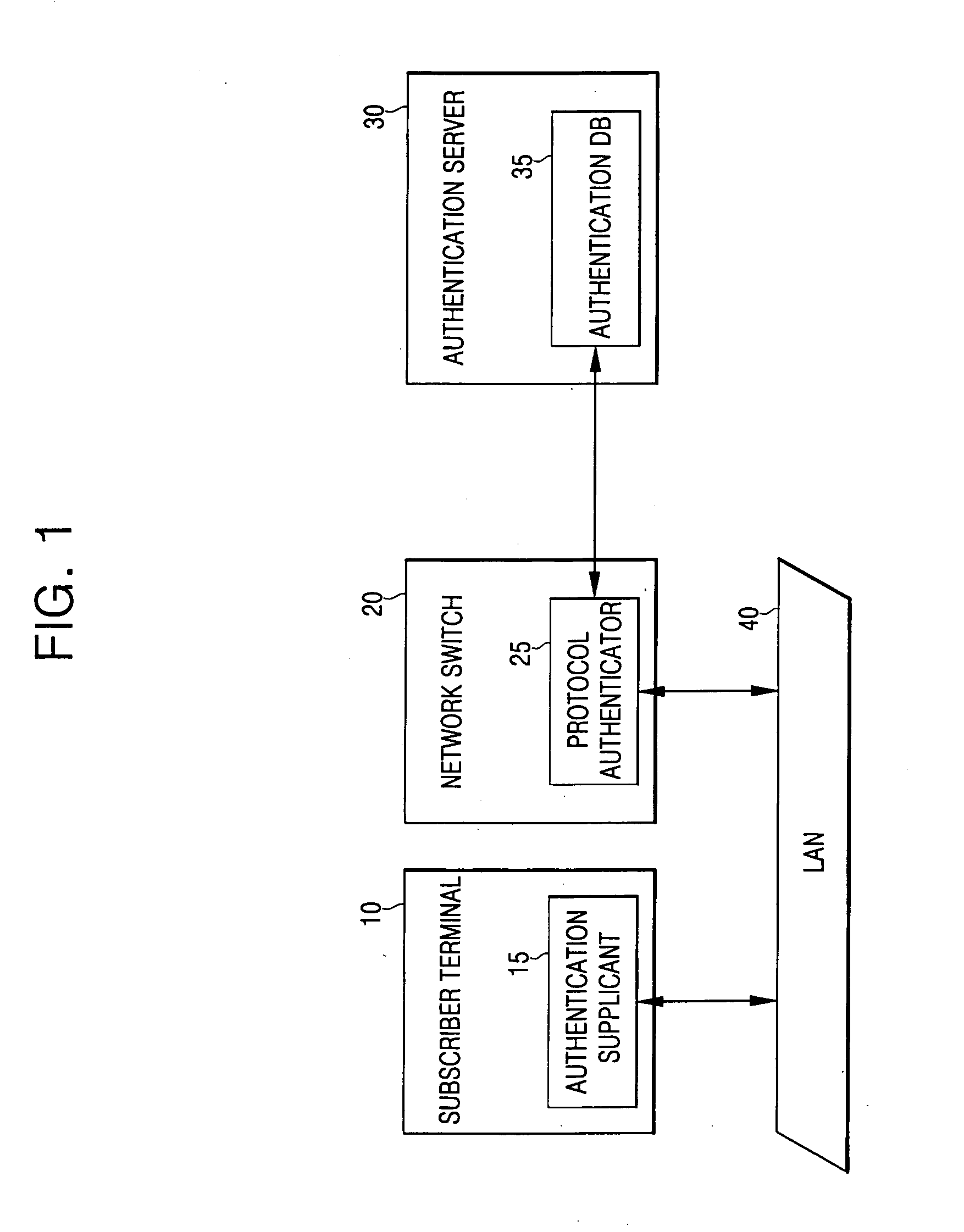
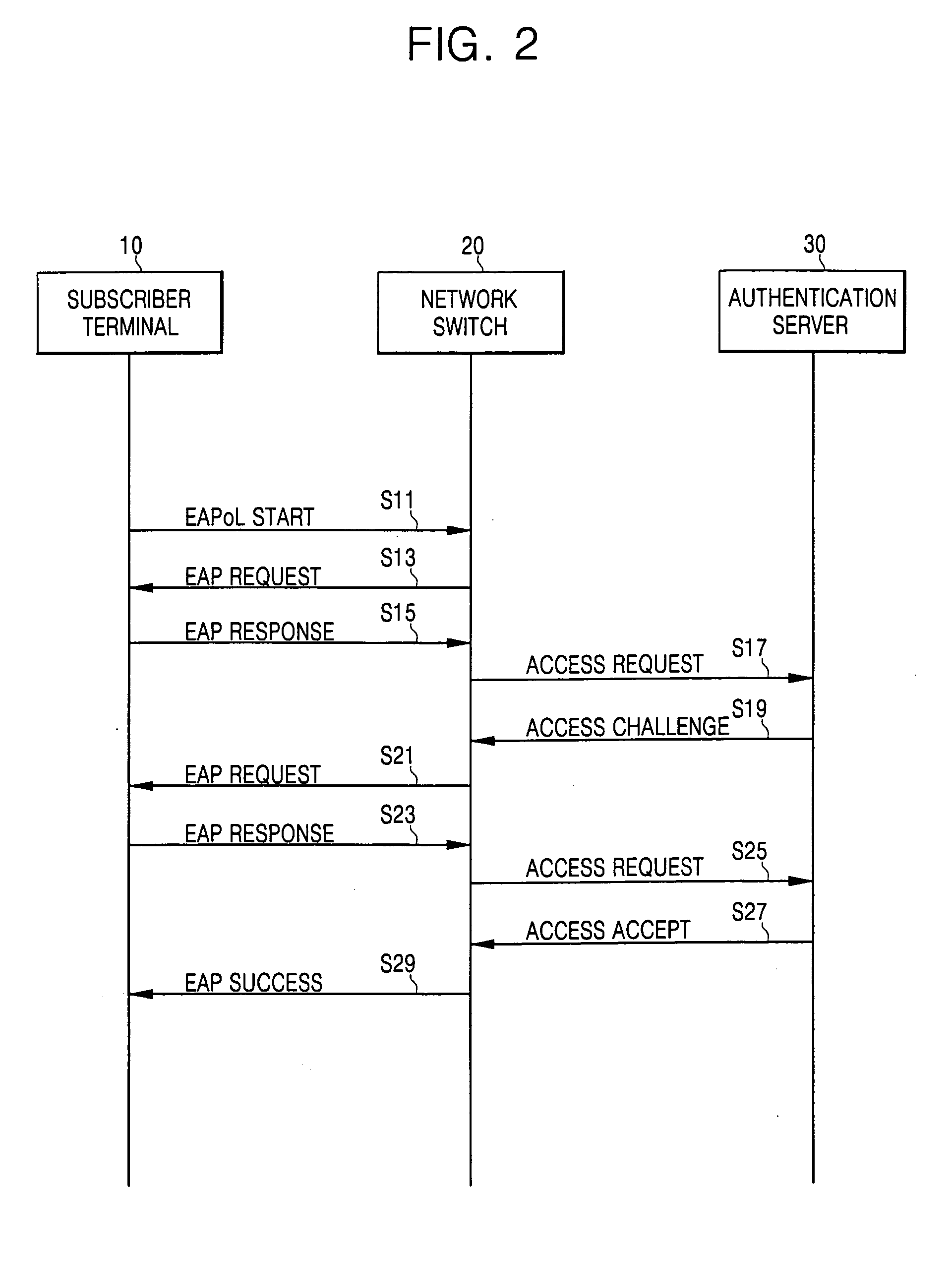
An apparatus for authenticating a user for network access in a communication system comprises: an input module contained in a subscriber terminal for receiving and transferring identification information and a password for network access from a user; an authentication supplicant contained in network equipment for requesting network access authentication for the identification information and password transferred from the input module; an authentication server for storing information related to the network access authentication, and for performing authentication to determine whether to permit the subscriber terminal to access a network in response to the authentication request; and a protocol authenticator for performing protocol processing between the authentication supplicant and the authentication server. A corresponding method is disclosed. Thus, it is possible to authenticate subscriber terminals for network access without the installation, by an Internet service provider, of specific software (e.g., a supplicant program) in all of the subscriber terminals.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for controlling access to a network resource
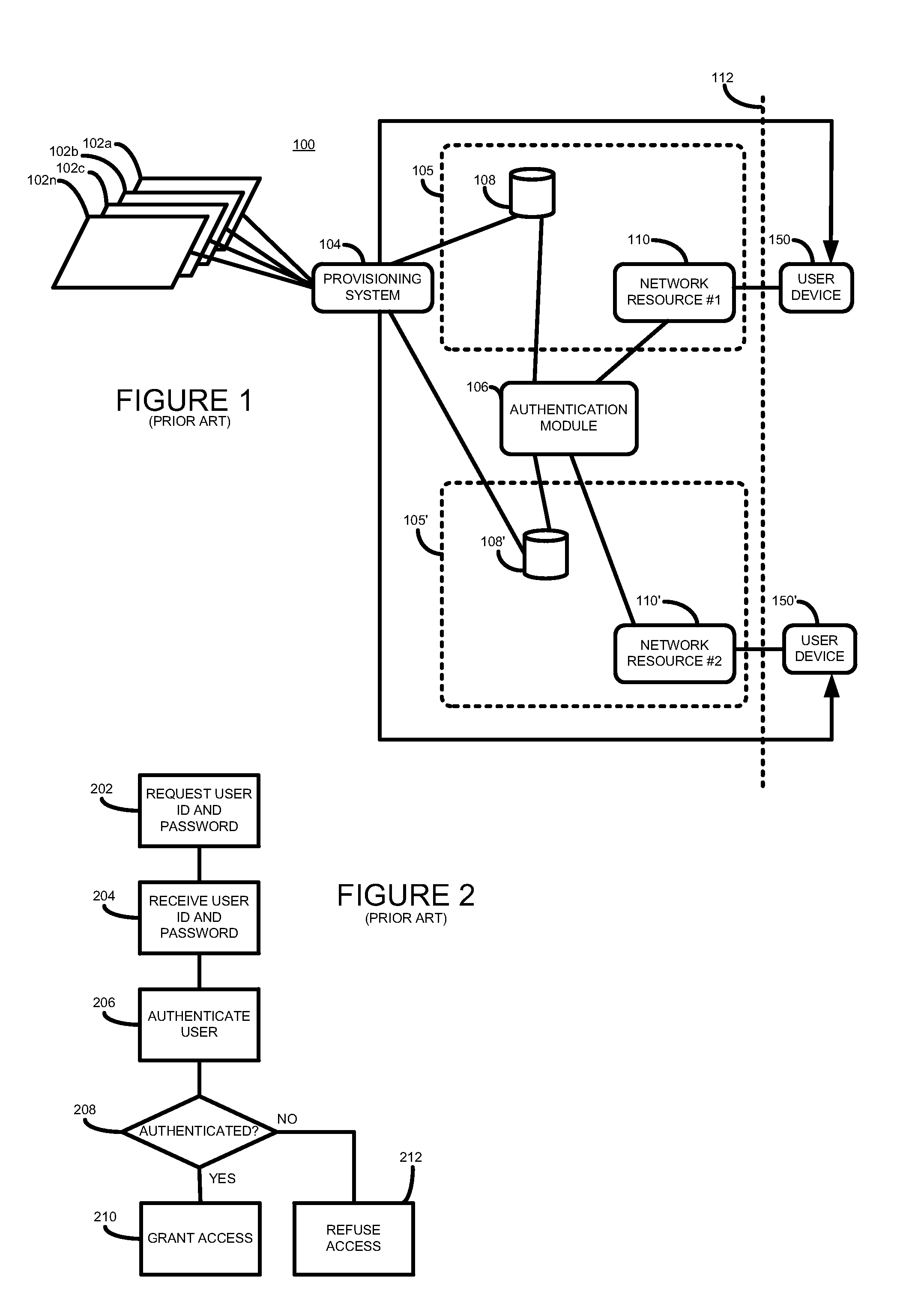
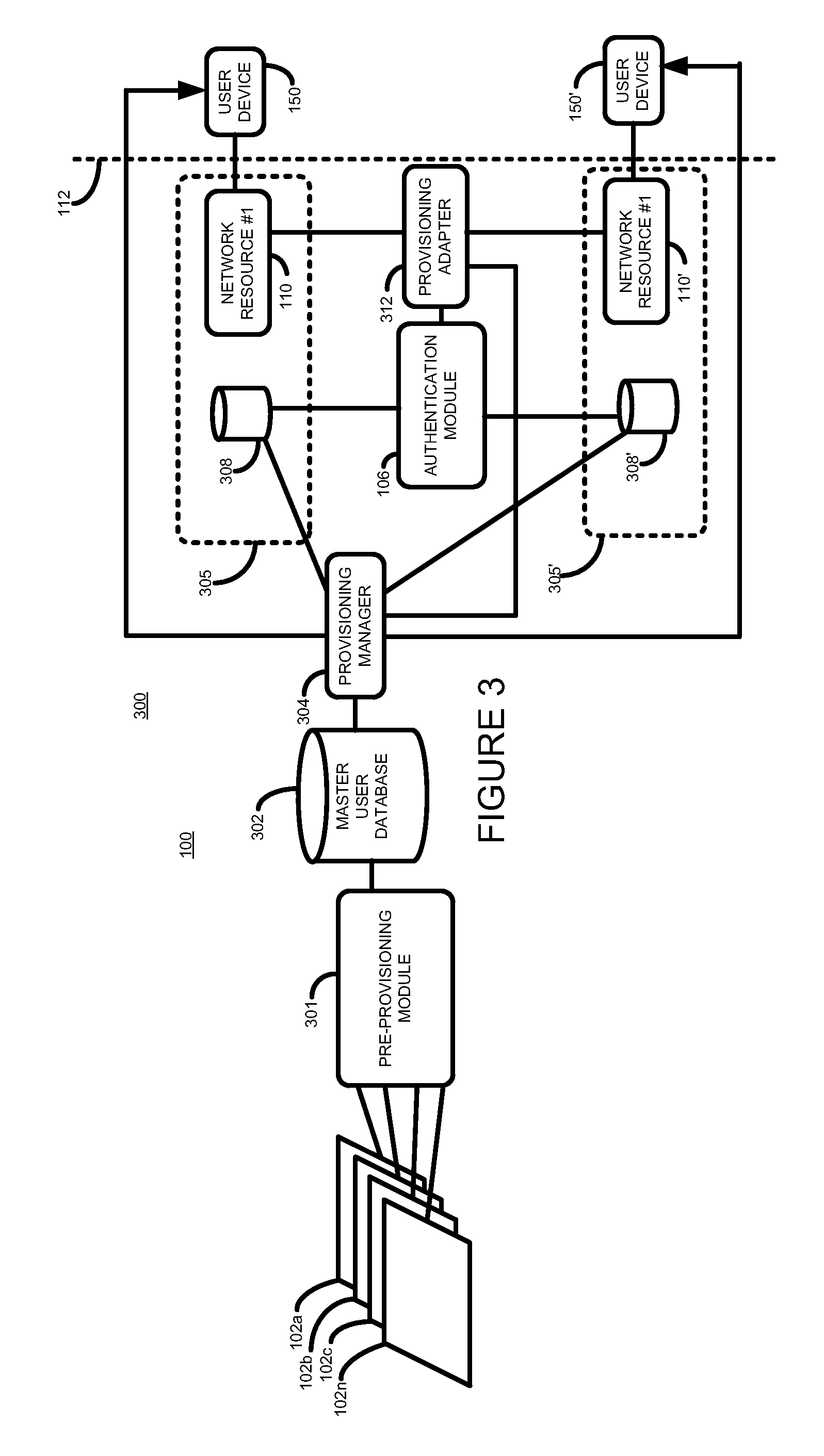
ActiveUS20110185403A1Low costImprove performanceDigital data processing detailsUser identity/authority verificationPasswordUser identifier
According to one aspect, there is provided a method of controlling access to a network resource. The method comprises receiving a request to grant a user access to the network resource, the request including a user identifier, determining whether the received user identifier is stored in a local user data store associated with the resource, and where it is not so determined determining, from user details stored in a master user data store, whether the user is authorized to access the resource, and where it is so determined obtaining a password, and storing the obtained password and user details in the local data store associated with the network resource.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Faster authentication with parallel message processing
InactiveUS7458095B2Fast authenticationLower Level RequirementsMemory loss protectionDigital data processing detailsCommunications systemMessage processing
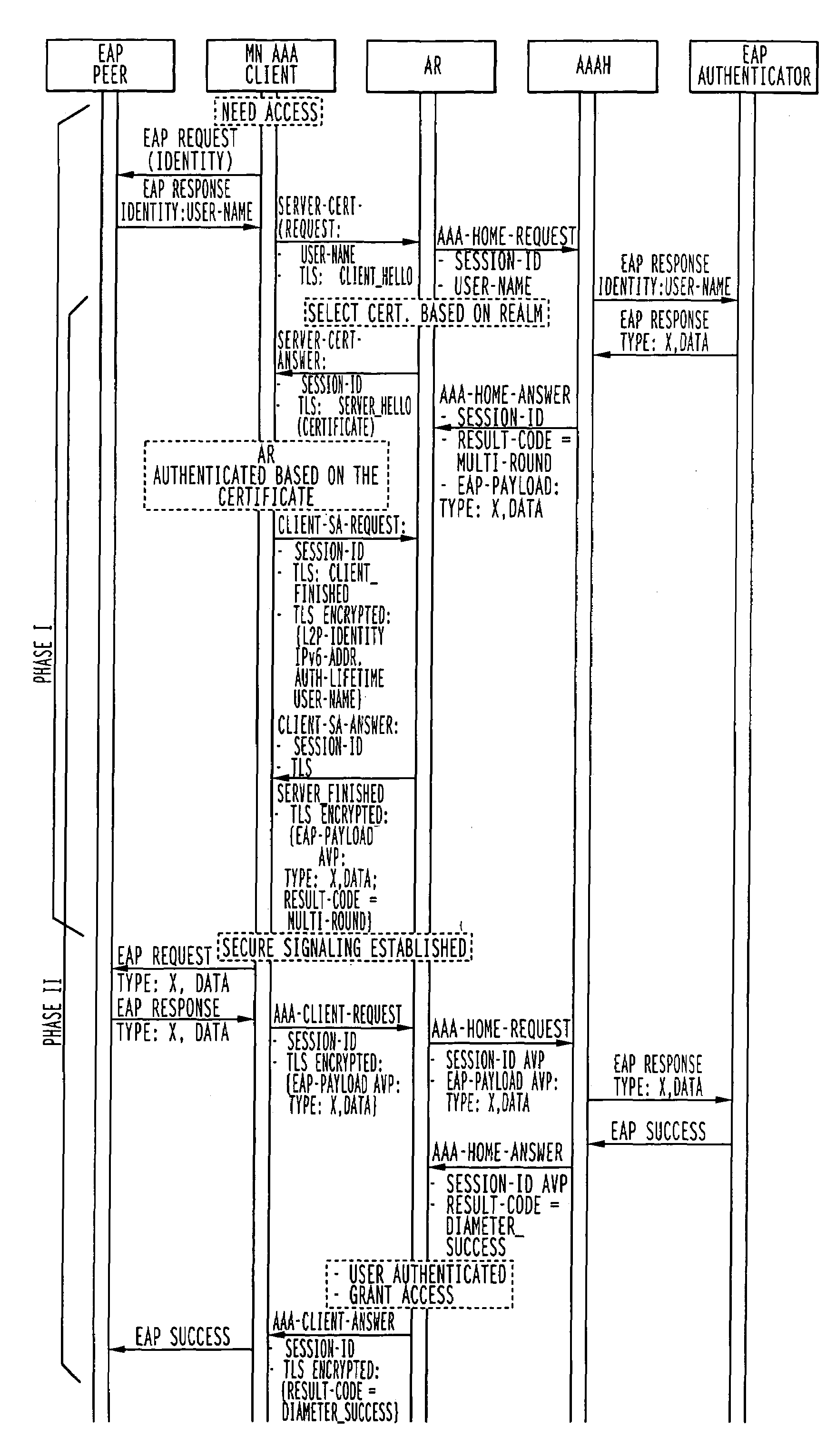
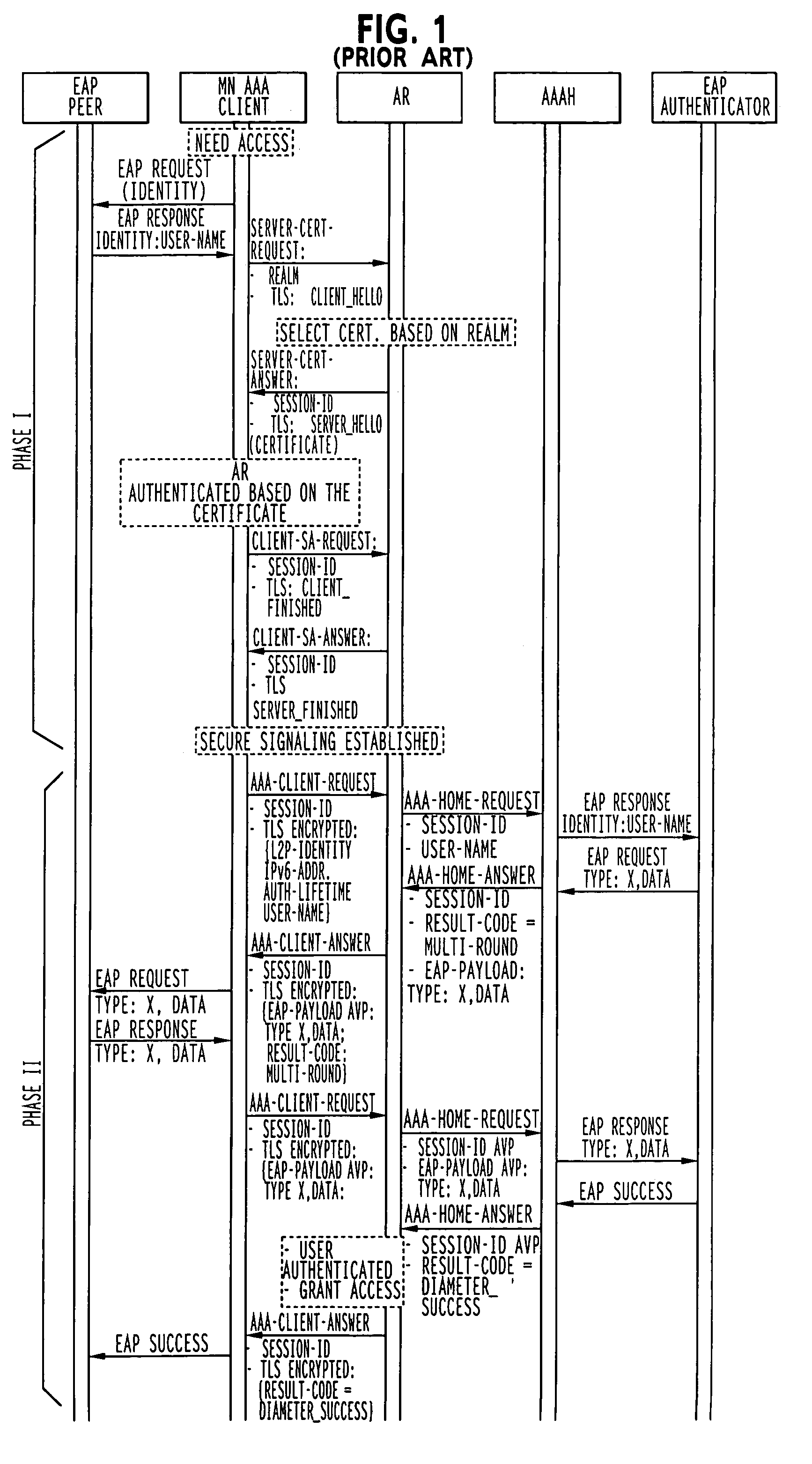
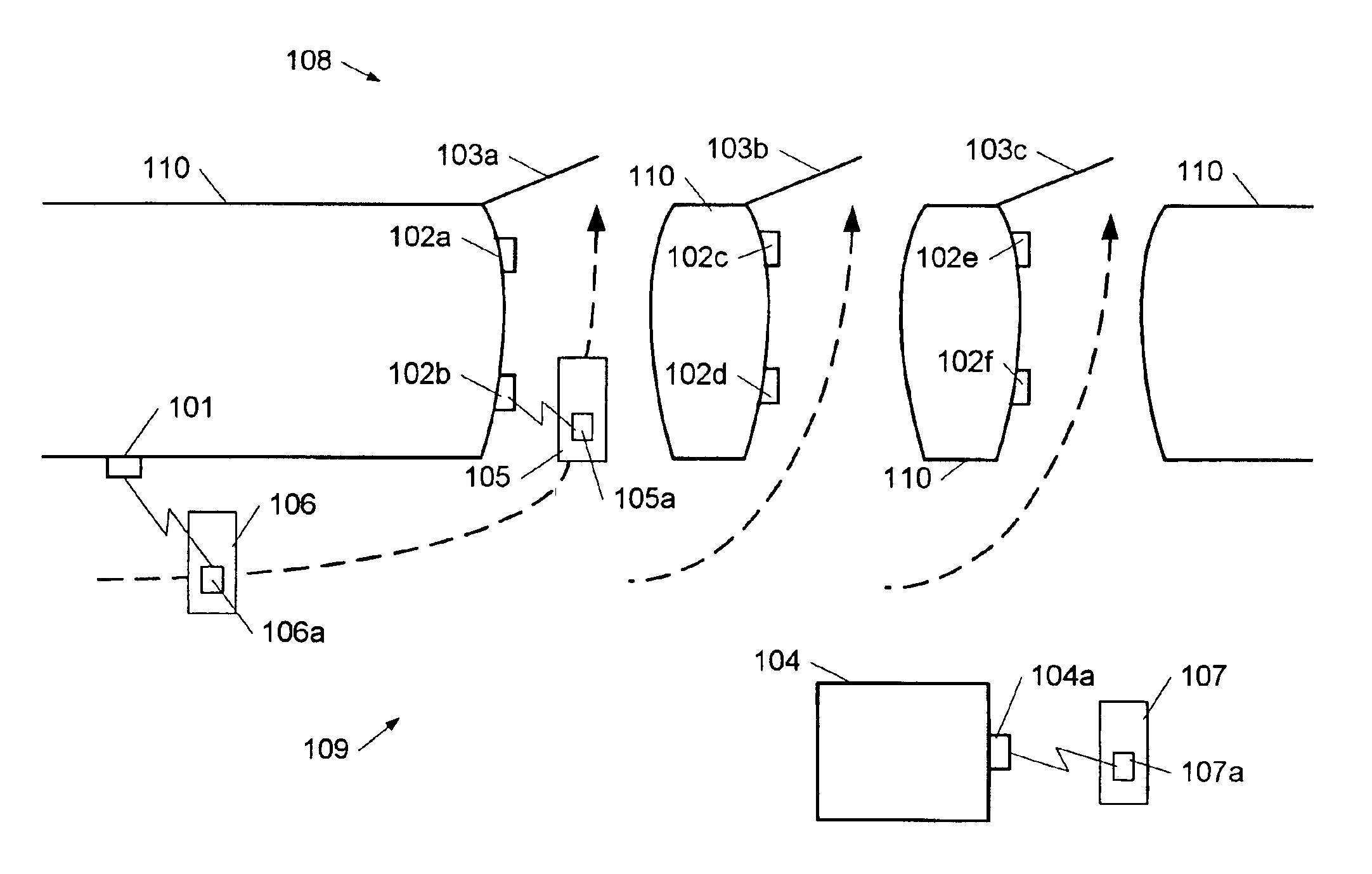
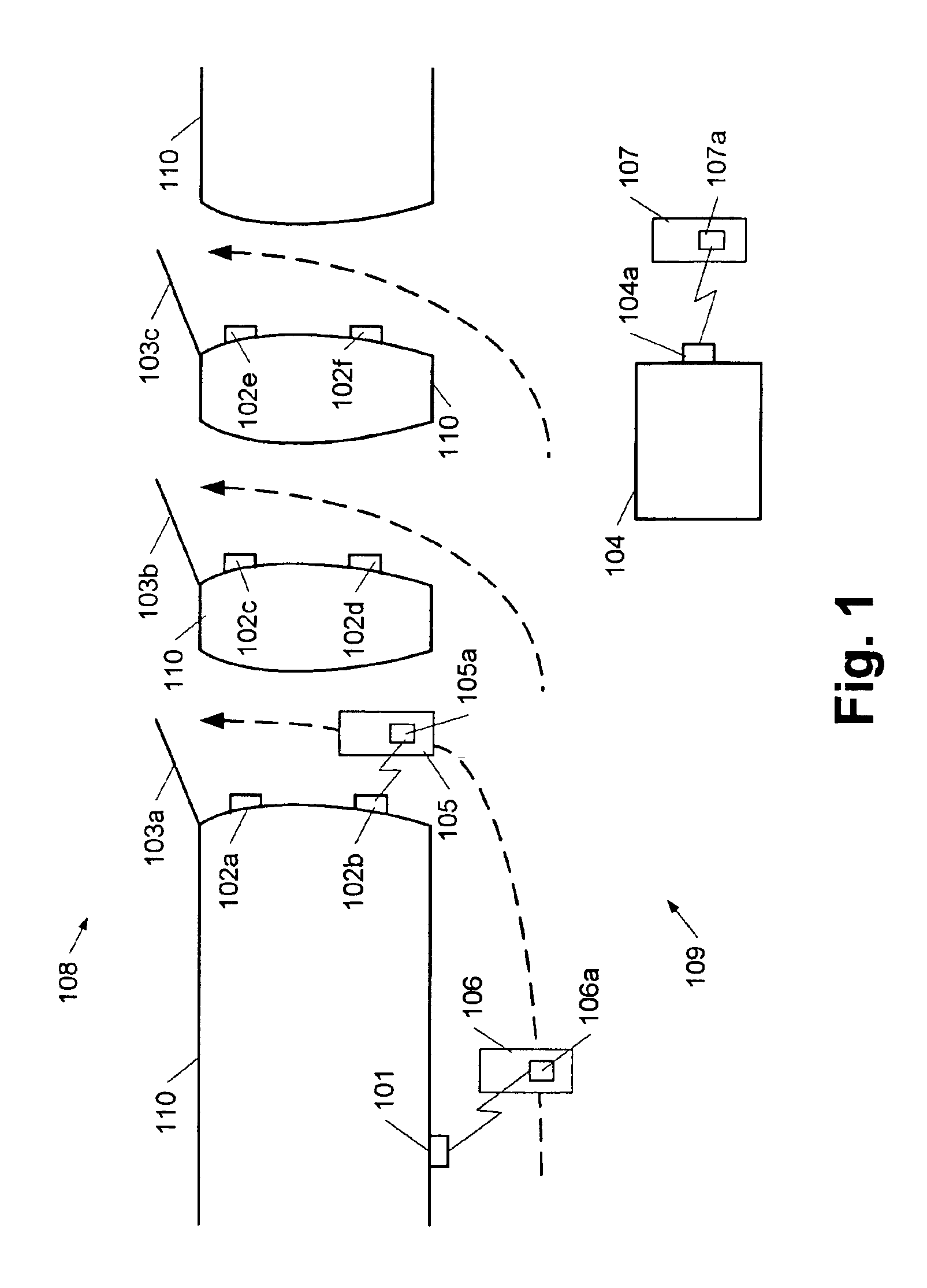
The invention is a method of connecting user equipment to at least one network, a communication system, and a user equipment. In a communication system comprising at least one network, including network entities which provide connectivity to user equipment, a method of connecting the user equipment to the at least one network in accordance with the invention includes establishing a secure tunnel which provides connection between the user equipment and one of the network entities; and authenticating the user equipment with another of the network entities; and wherein the authenticating of the user equipment with the another of the network entities occurs at least partially simultaneously with the establishing of the secure tunnel.
Owner:PIECE FUTURE PTE LTD
Transmitting device, receiving device and transmitting/receiving system
InactiveUS20050027993A1Fast authenticationLow transmission rateTelevision system detailsKey distribution for secure communicationData memoryPlug and play
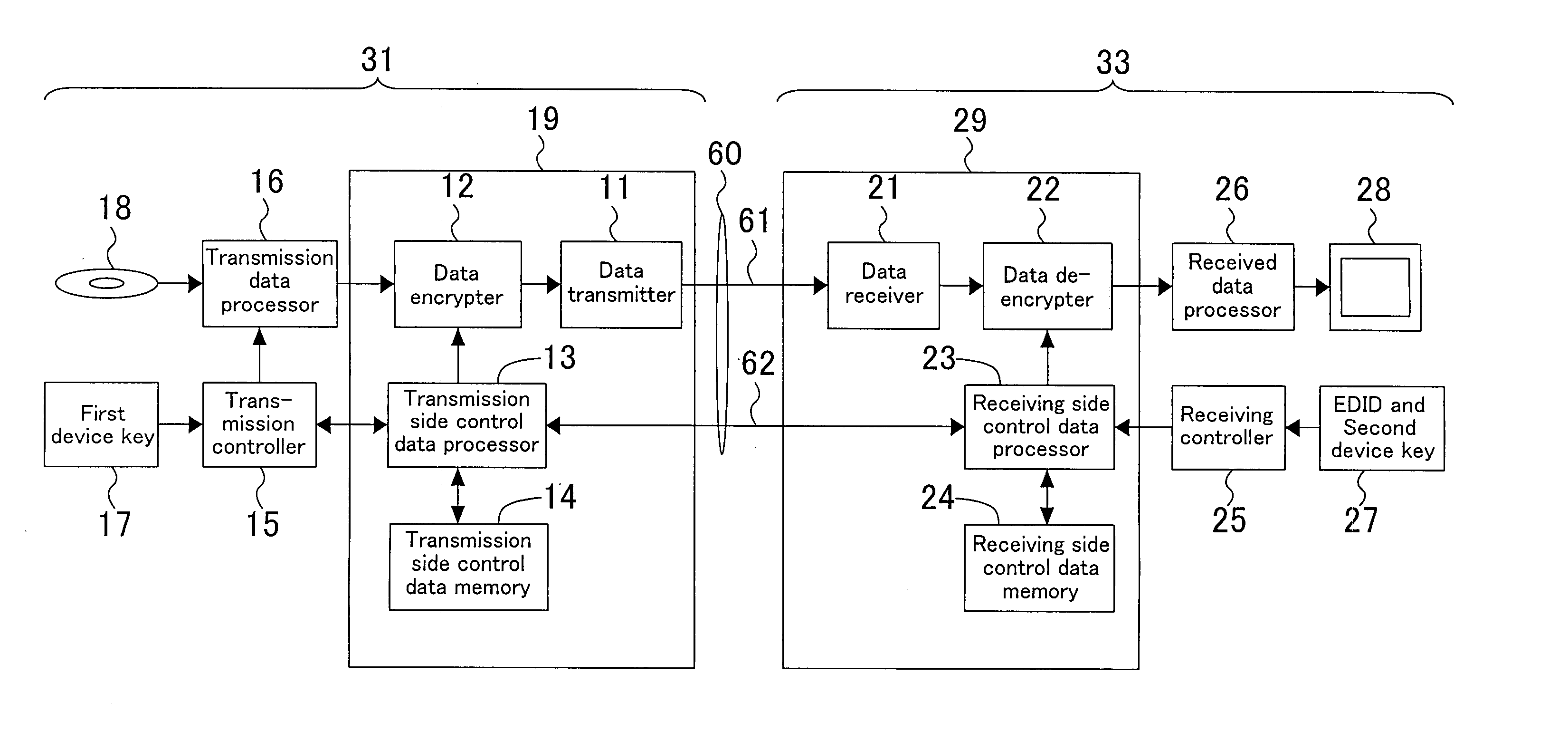
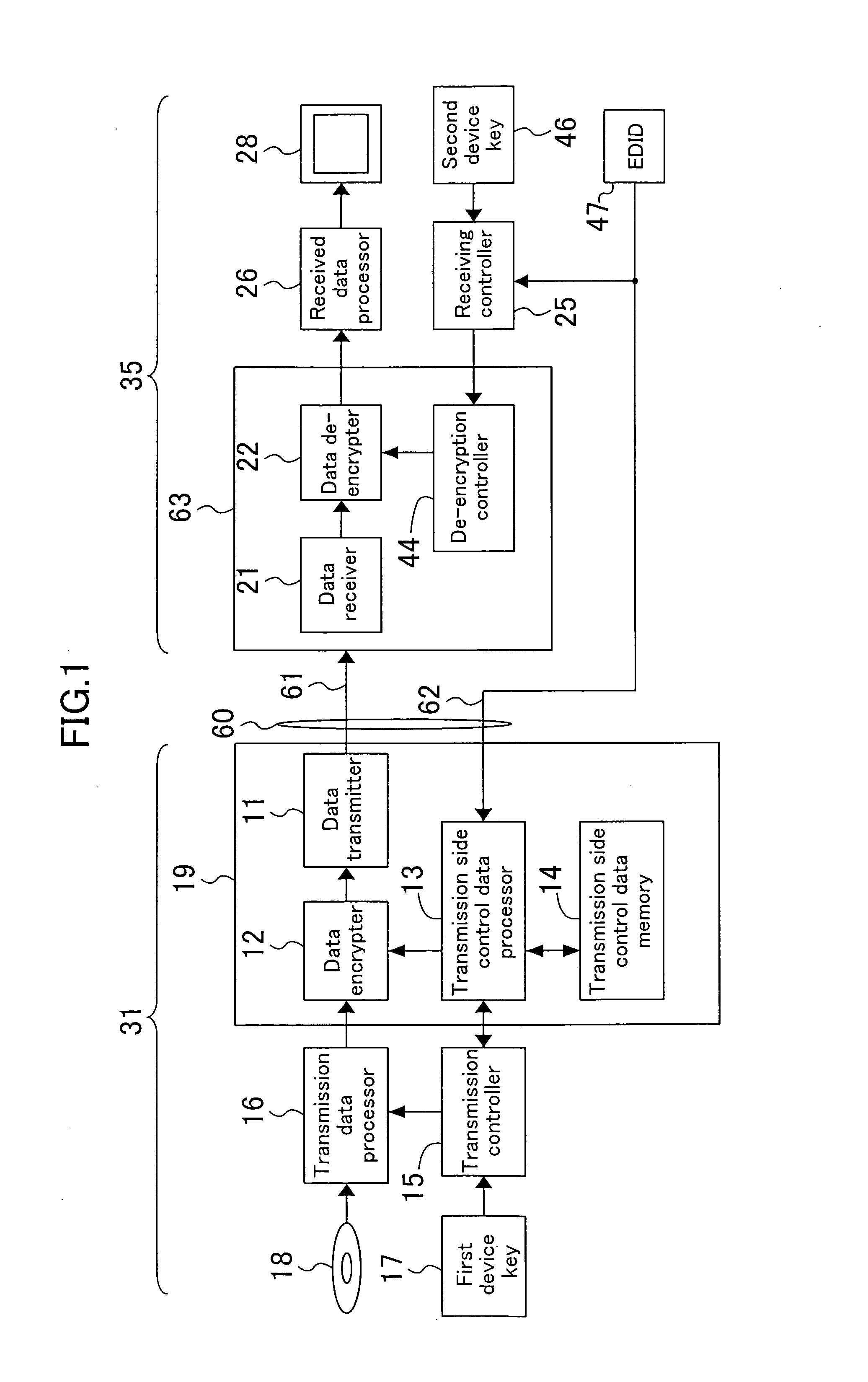
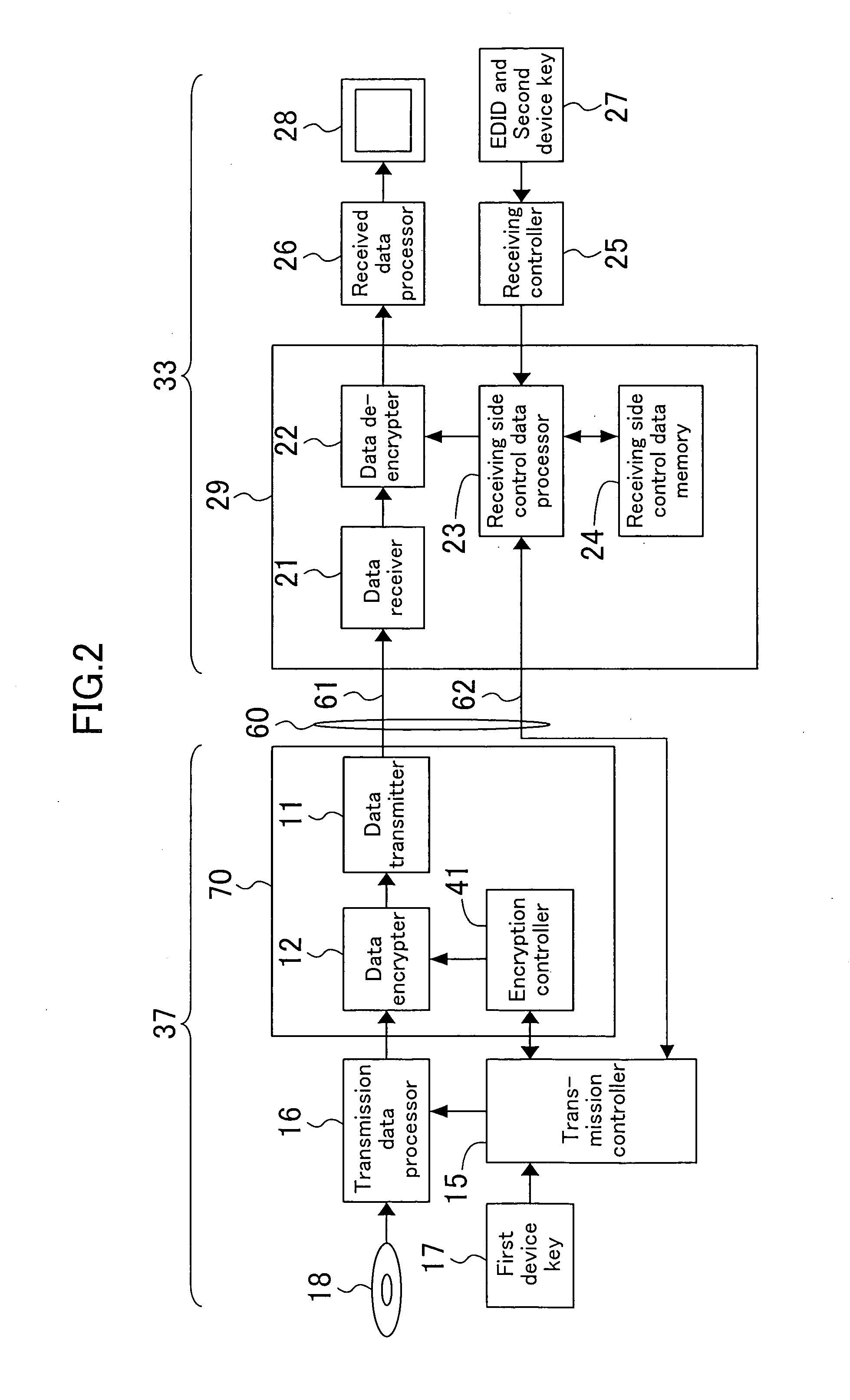
A transmitting device includes a transmission side control data memory. A receiving device includes a receiving side control data memory. In an operation state, EDID, a device key for and HDCP and the like are stored in the receiving side control data memory. Subsequently, the EDID and information necessary for HDCP authentication are copied from the receiving side control data memory to the transmission side control data memory through the DDC. A transmission controller accesses the transmission side control data memory and executes plug-and-play and HDCP authentication. The DDC realizes a one-to-one connection between the transmitting device and the receiving device. Thus, waveform distortion can be minimized and the length of a cable can be increased in a simple manner.
Owner:PANASONIC CORP
Method and system for authentication of units in a communications network
InactiveUS7020456B2Secure distributionSave capacityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemCommunication device
A method of granting, to a user communications device, access to a service provided by a plurality of service communications devices where an access key code is generated during an initial communications session between the user communications device and one of the service communications devices. The established access key code is subsequently stored in the user communications device and made available to the service communications devices for use in subsequent communications sessions between the user communications device and any one of the service communications devices. The invention further relates to a communications system and a user communications device.
Owner:TELEFON AB LM ERICSSON (PUBL)
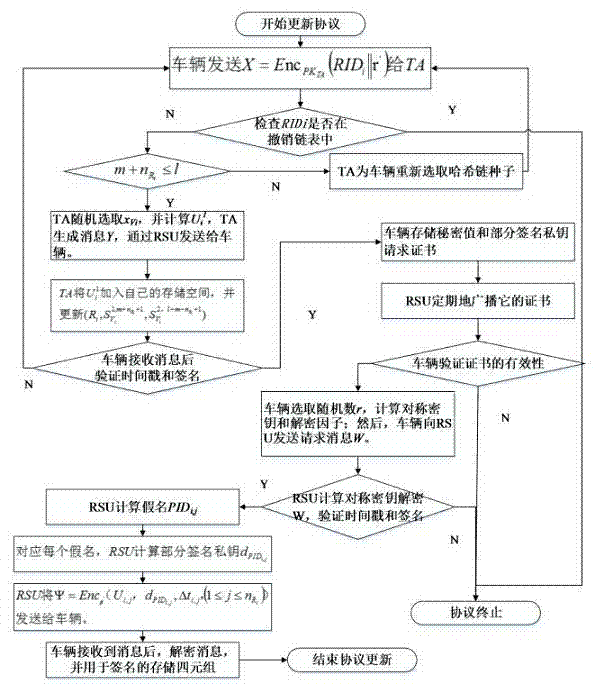
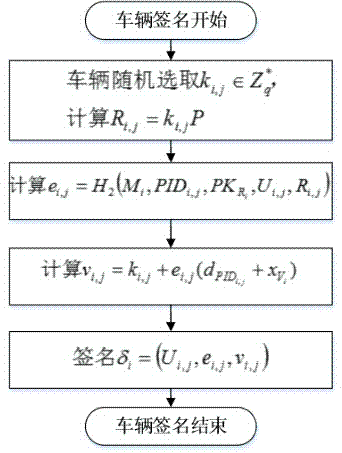
Internet of Vehicles distributed authentication method based on controllable privacy
InactiveCN104853351AReduce the burden onSolve the problem of non-repudiationSecurity arrangementTrusted authorityStructure of Management Information
The invention discloses an Internet of Vehicles distributed authentication method based on controllable privacy, relates to the field of vehicle network communication safety, and specifically relates to an Internet of Vehicles distributed authentication method based on controllable privacy. The method specifically includes five following steps: system initialization; private key update of fake names and a part of signatures; message signature; message authentication of signatures; and real identity tracking and revocation. According to the method, the double hash chain is employed to establish the fake names, the communication cost for invalidating a vehicle identity is irrelevant to the numbers of the fake names and a part of the signature private keys of the vehicle, a vehicle user can update multiple parts of signature private keys by the adoption of one authorization, and the burden of trusted authority (TA) and road-side units (RSU) is reduced; when a message with a controversial signature occurs, the TA can distinguish whether the signature is forged by the RSU according to re-signature of the message uploaded by the vehicle, and the problem of non-repudiation in the distributed environment is solved. According to the method, the security is high, the cost is low, and the method is applicable to node high-speed movement, topology structure volatility, and large-scale VANET network.
Owner:JIANGSU UNIV
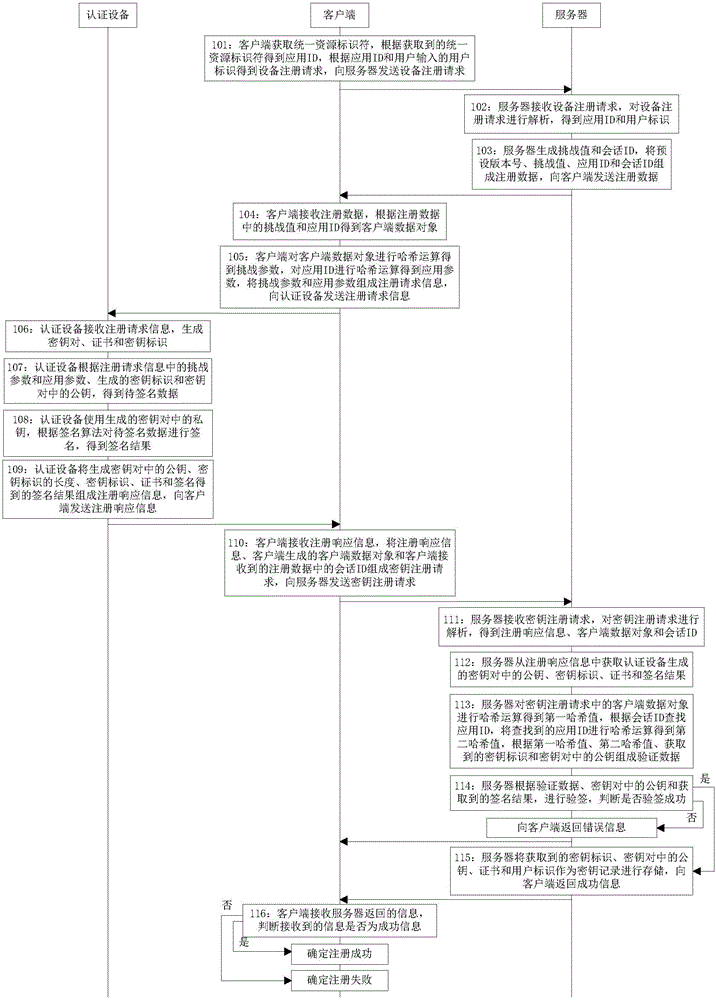
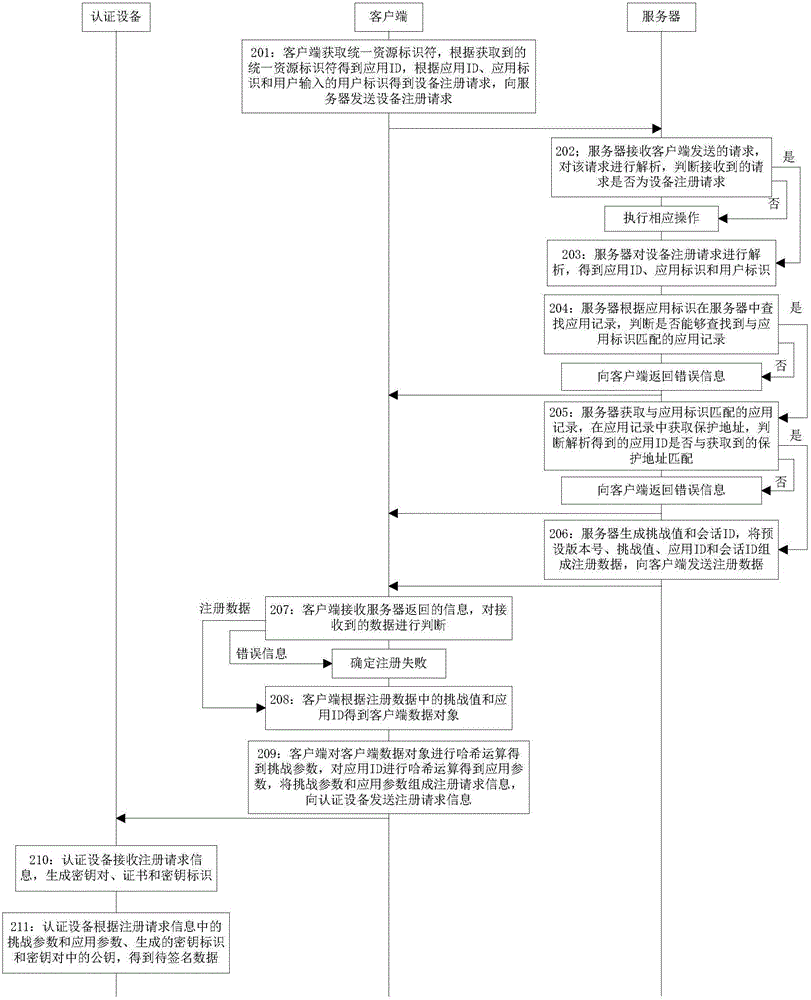
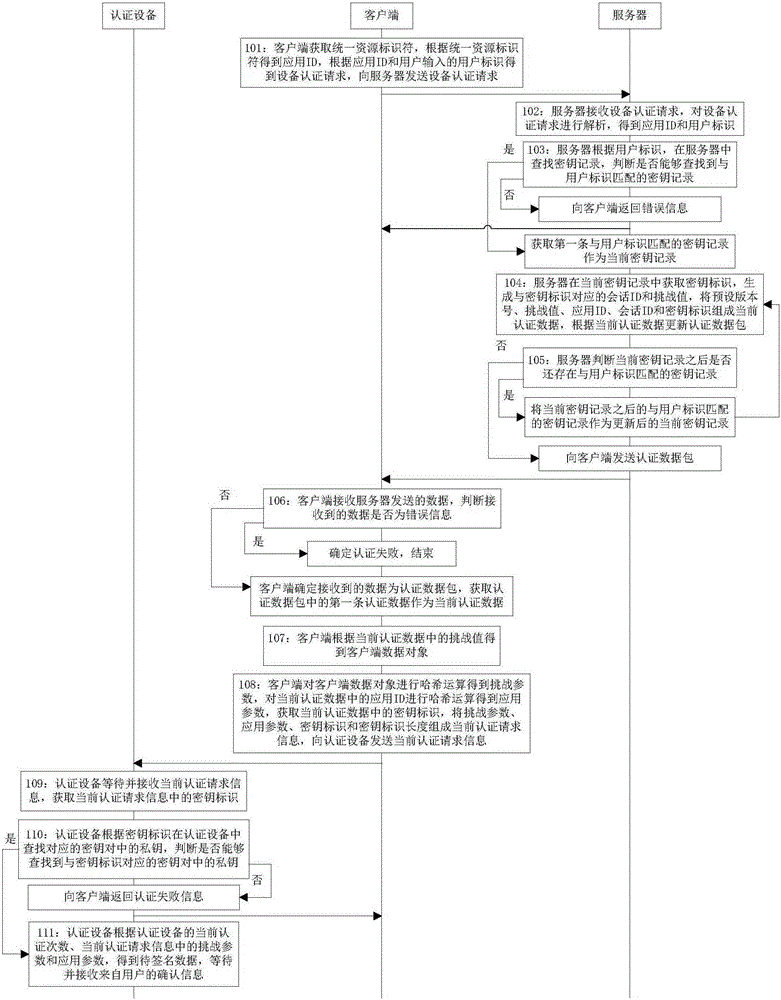
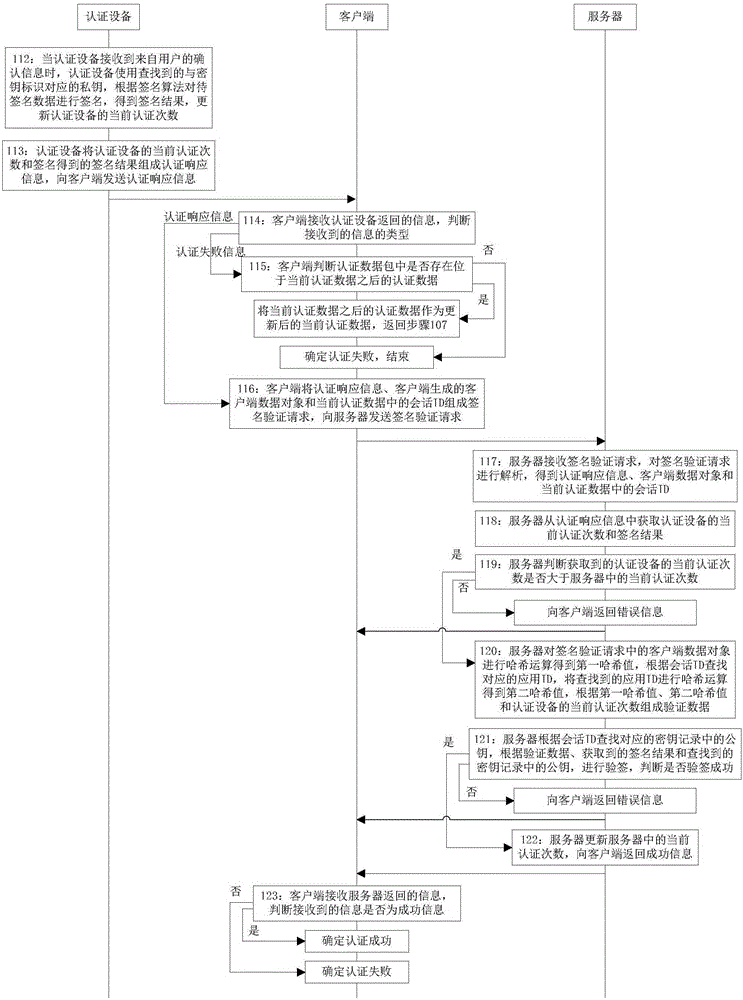
Method and equipment for performing registration based on authentication equipment
ActiveCN105162785AImprove securityFast authenticationUser identity/authority verificationUser inputInternet privacy
The invention discloses a method for performing registration based on authentication equipment. The method comprises the following steps: acquiring a uniform resource identifier by a client, acquiring an application ID according to the uniform resource identifier, and sending an equipment registration request obtained according to the application ID and a user identity input by a user to a server; receiving registration data returned by the server, and acquiring a client data object according to a challenge value in the registration data and the application ID; performing Hash operation on the client data object and the application ID respectively to obtain a challenge parameter and an application parameter, and transmitting registration request information consisting of the challenge parameter and the application parameter to the authentication equipment; receiving registration response information returned by the authentication equipment, and sending a key registration request consisting of the registration response information, the client data object and the registration data to the server; and receiving information returned by the server, judging whether the information is success information or not, if so, determining that the registration is successful, and otherwise determining that the registration fails.
Owner:FEITIAN TECHNOLOGIES
Authentication method and device based on authentication equipment
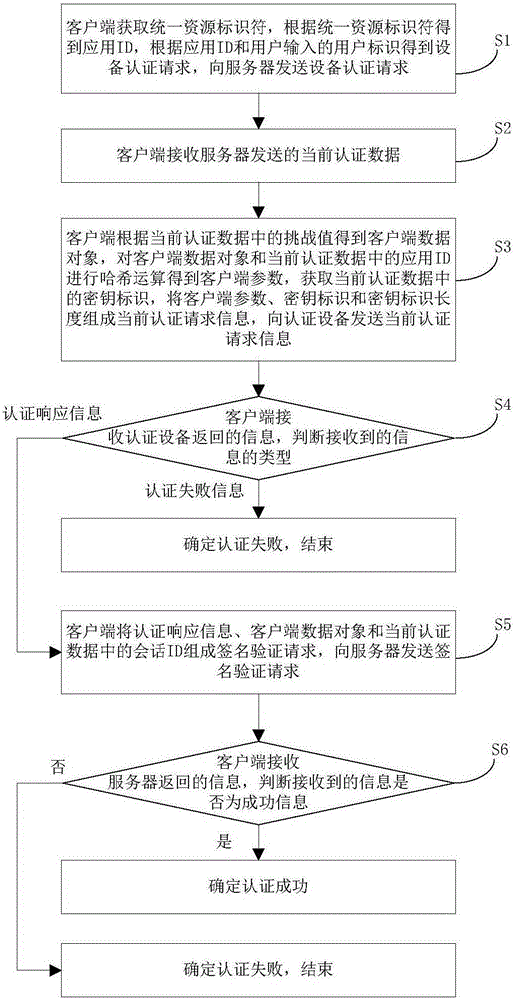
ActiveCN105187450AImprove securityFast authenticationSecurity arrangementSecuring communicationUniform resource identifierClient data
The invention discloses an authentication method and device based on authentication equipment. The method comprises: a client obtaining an application ID according to an obtained uniform resource identifier (URI), and sending an equipment authentication request obtained according to the application ID and the URI to a server; receiving the current authentication data sent by the server; obtaining a client data object according to the challenge value in the current authentication data, hashing the client data object and the application ID in the current authentication data to obtain client parameters, obtaining the key identifier in the current authentication data, and sending current authentication request information composed of the client parameters, the key identifier and a key identifier length to authentication equipment; receiving the authentication response information returned by the authentication equipment, and sending a signature verification request composed of the authentication response information, the client data object and the conversation ID in the current authentication data to the server; and receiving the information returned by the server, authentication being successful if successful information is returned, or else being failed.
Owner:FEITIAN TECHNOLOGIES
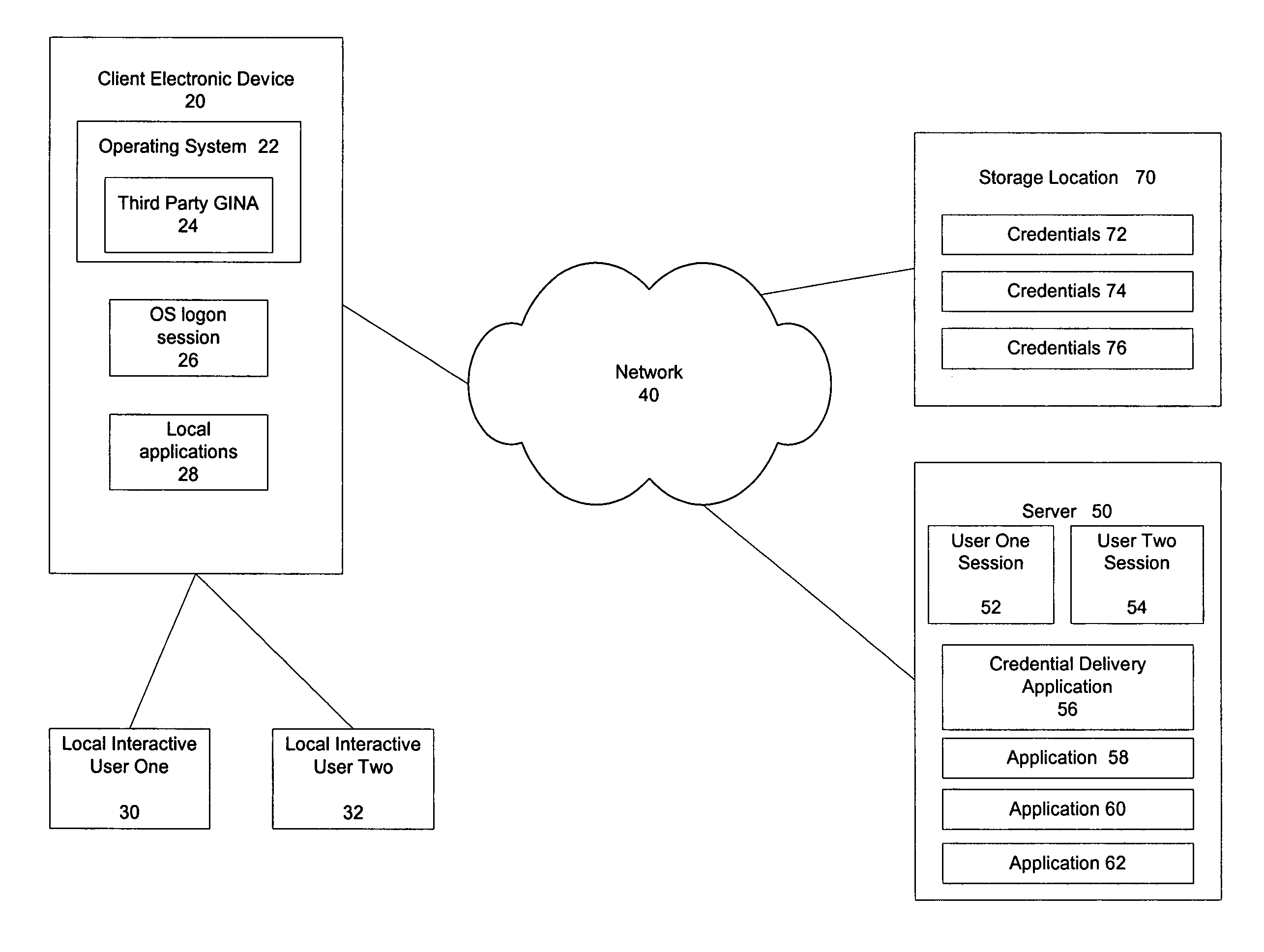
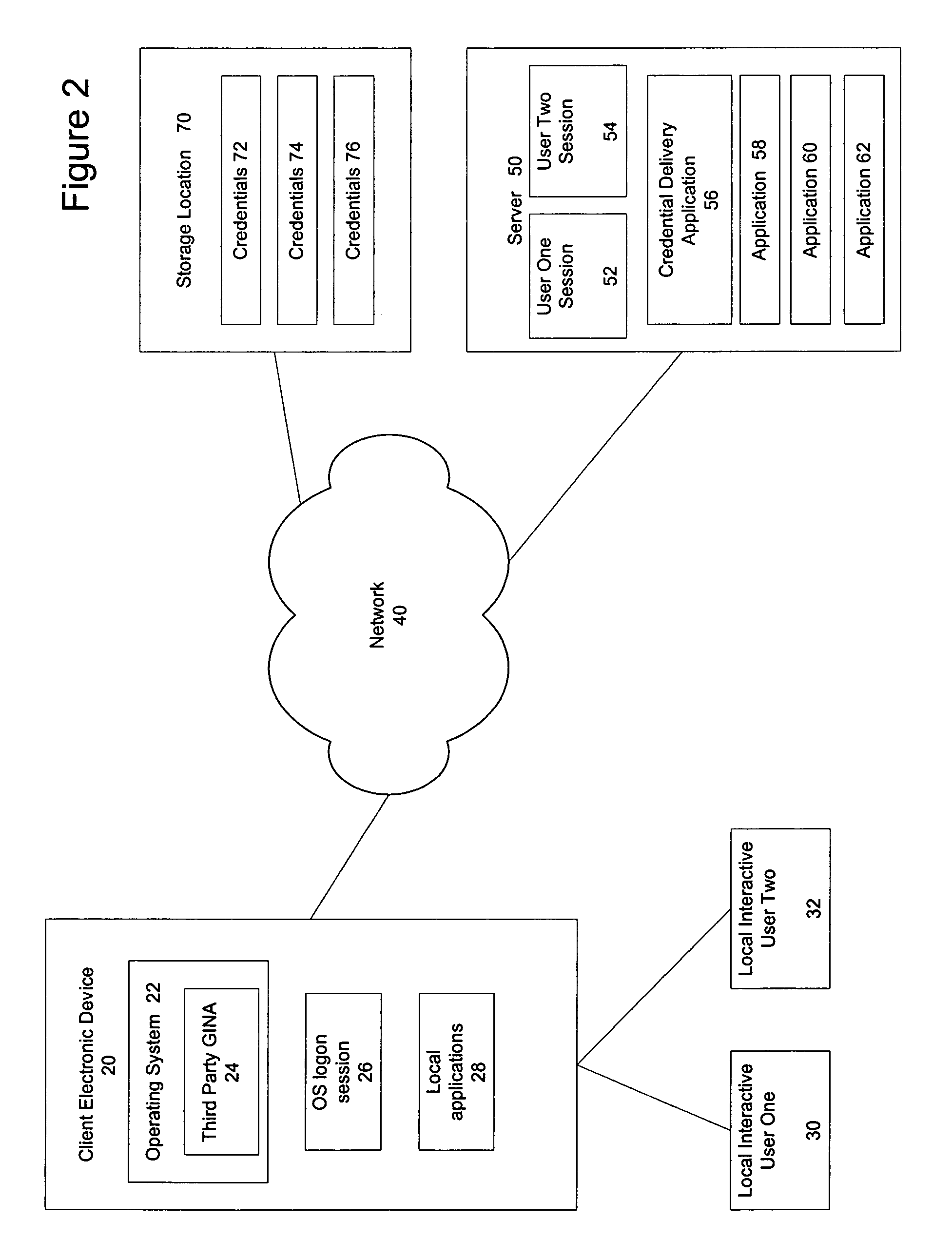
System and method for permission-based access using a shared account
ActiveUS7562226B2Quick switchFast authenticationDigital data processing detailsComputer security arrangementsOperational systemLocking mechanism
A mechanism for rapidly authenticating an interactive user in an operating system logon session based on a shared account by using a credential delivery application to enable permission-based access to a user's remote session from the shared account is disclosed. The present invention provides the ability to switch local interactive users, authenticate the new interactive user, and switch the remote session without requiring the client to first establish a new logon session tied to the new local interactive user. The present invention also alters the normal locking mechanism found in operating system logon sessions so as to restrict access to an interactive local user's applications (both local and remote) while still allowing the rapid switching of interactive users at the client device.
Owner:CITRIX SYST INC
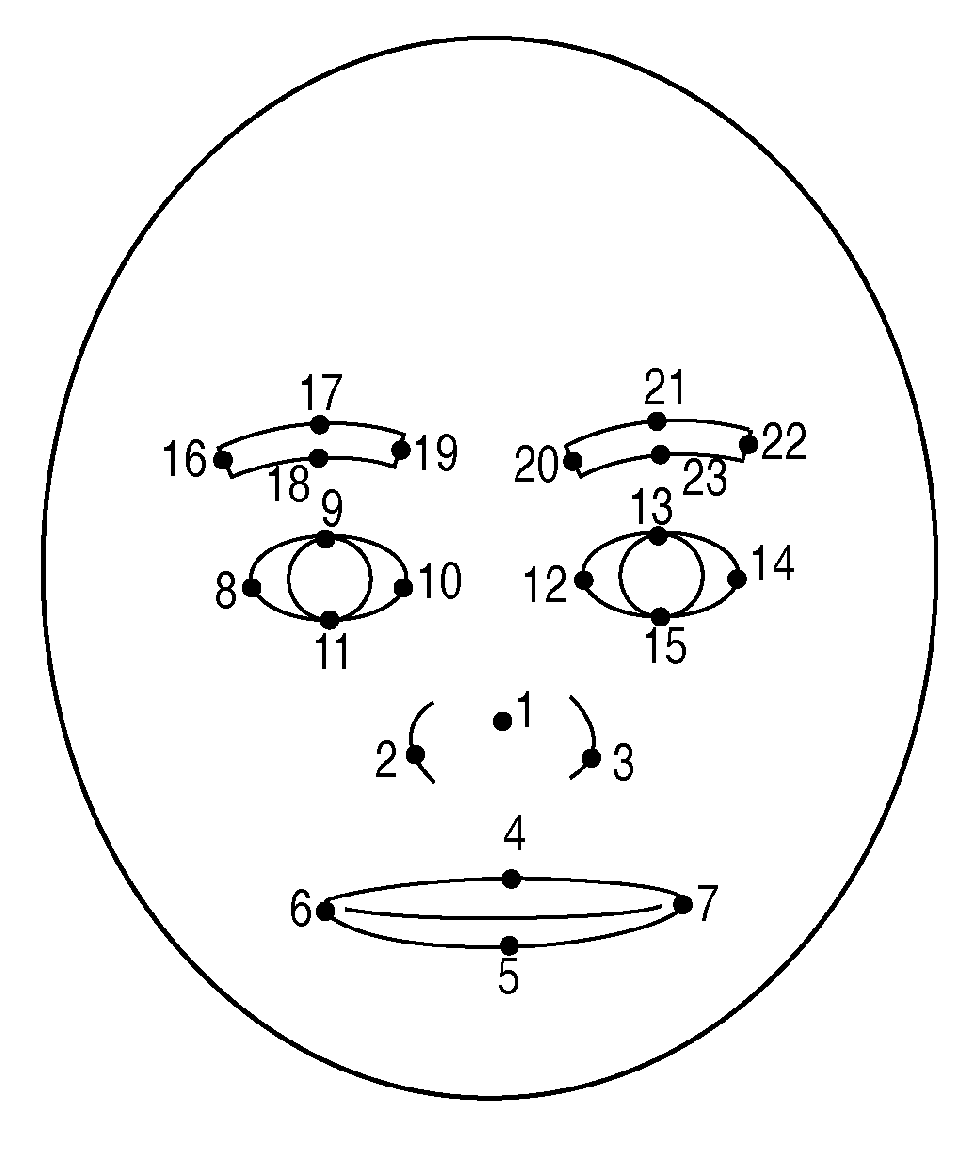
Personal authentication apparatus and personal authentication method
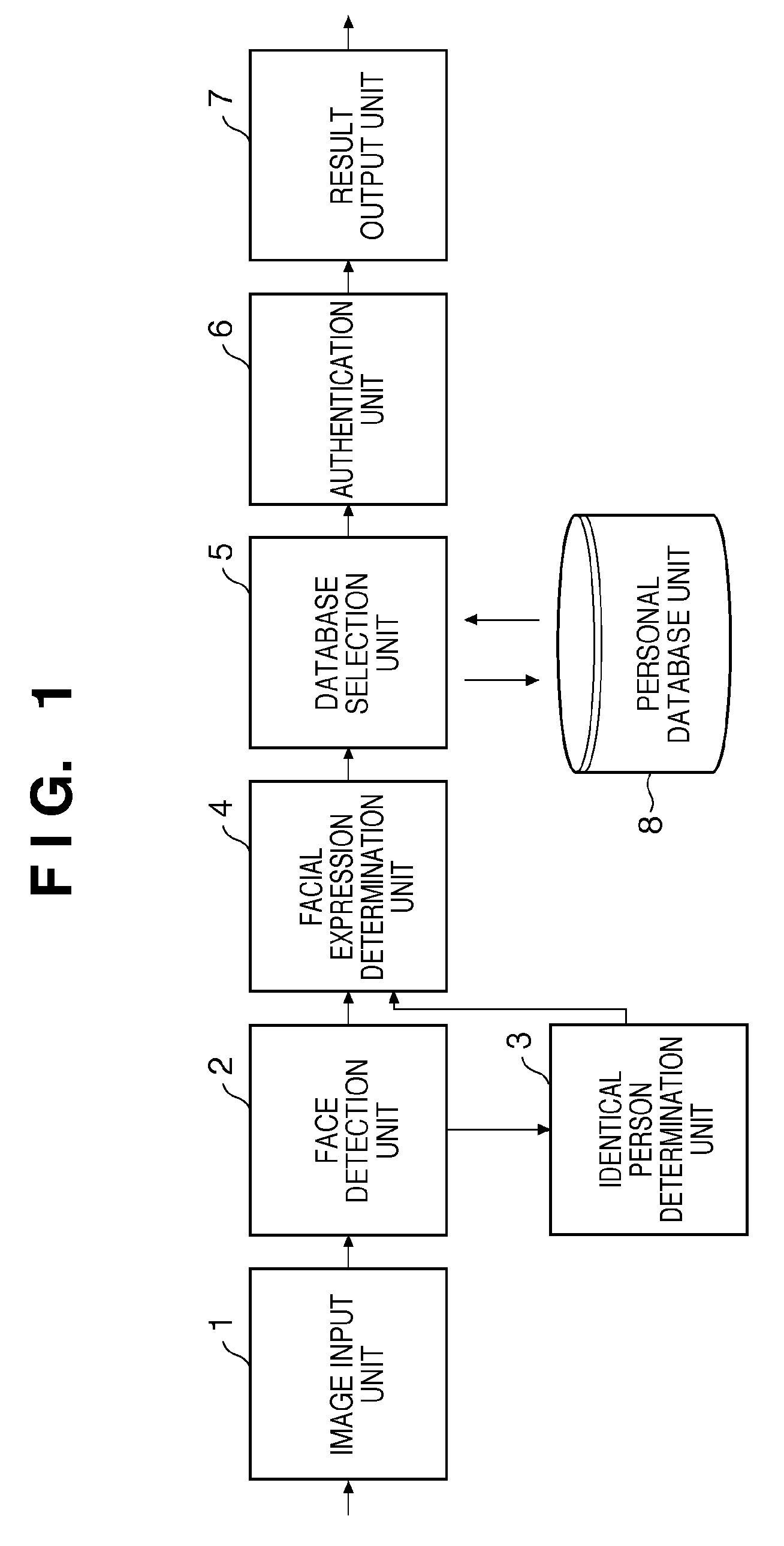
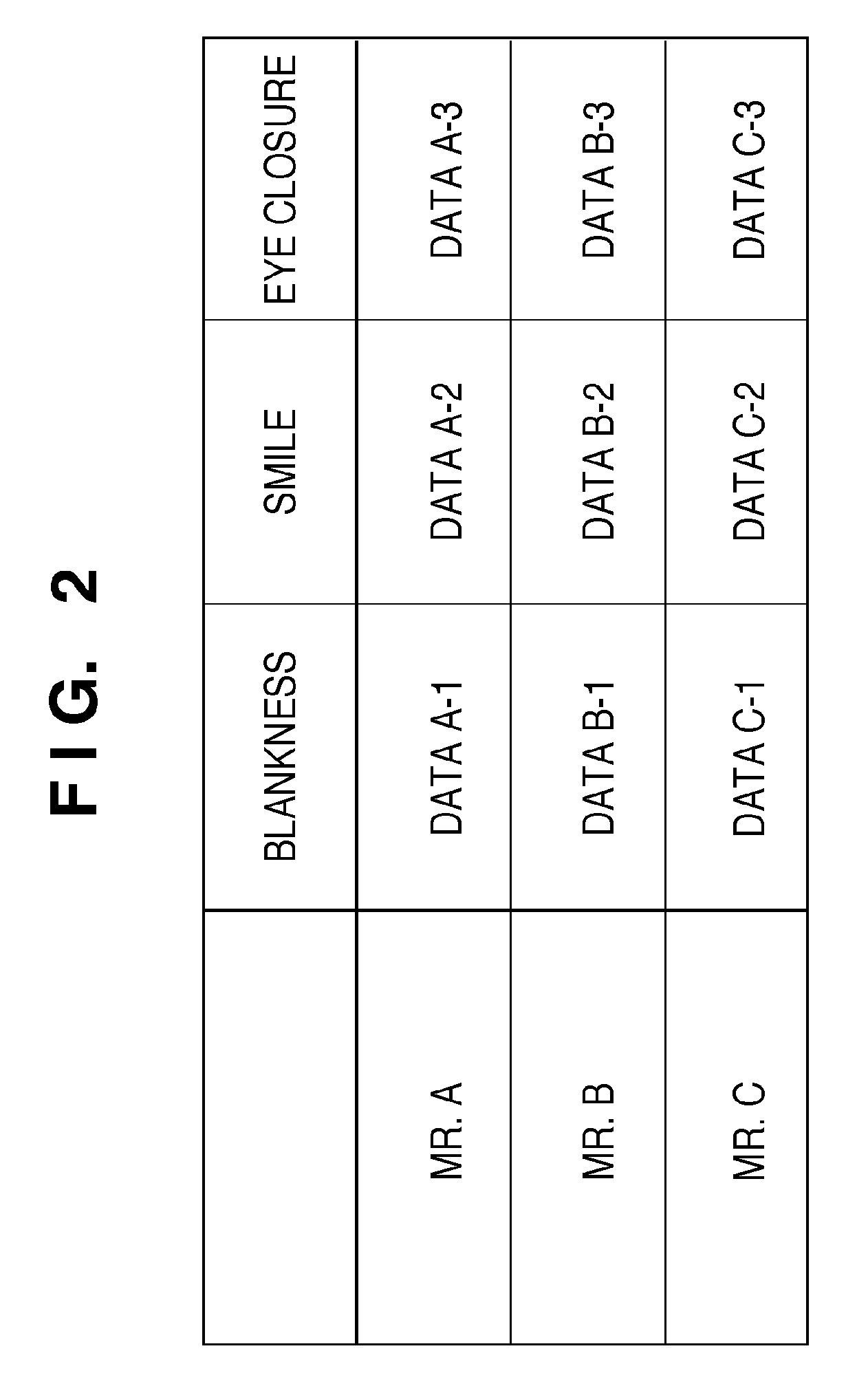
InactiveUS20090309702A1Fast authenticationImprove accuracyElectric signal transmission systemsImage analysisFace detectionFeature data
A personal authentication apparatus comprises an input unit configured to input image data; a face detection unit configured to detect a face region of a person included in the image data input by the input unit, and to detect feature data from the detected face region; a facial expression determination unit configured to determine a facial expression from the face region detected by the face detection unit; a storage unit configured to store feature data used to authenticate a person in correspondence with respective facial expressions of a plurality of faces; a selection unit configured to select feature data corresponding to the facial expression determined by the facial expression determination unit from the storage unit; and an authentication unit configured to authenticate a person by comparing the feature data of the face region detected by the face detection unit, and the feature data selected by the selection unit.
Owner:CANON KK
Method for designing vehicle network group negotiation communication protocol
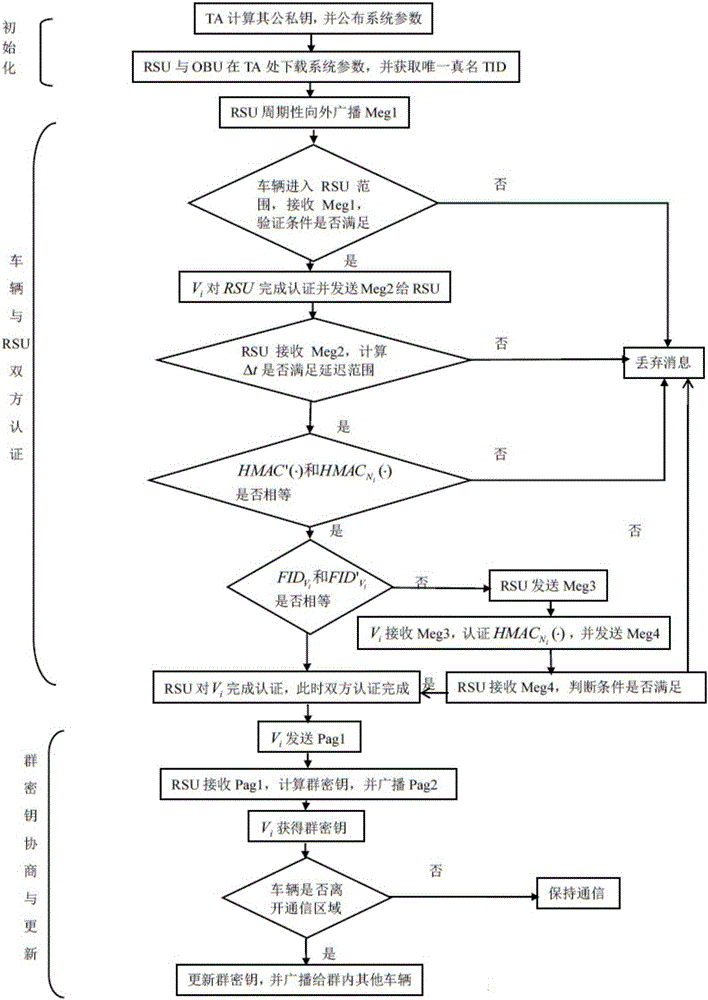
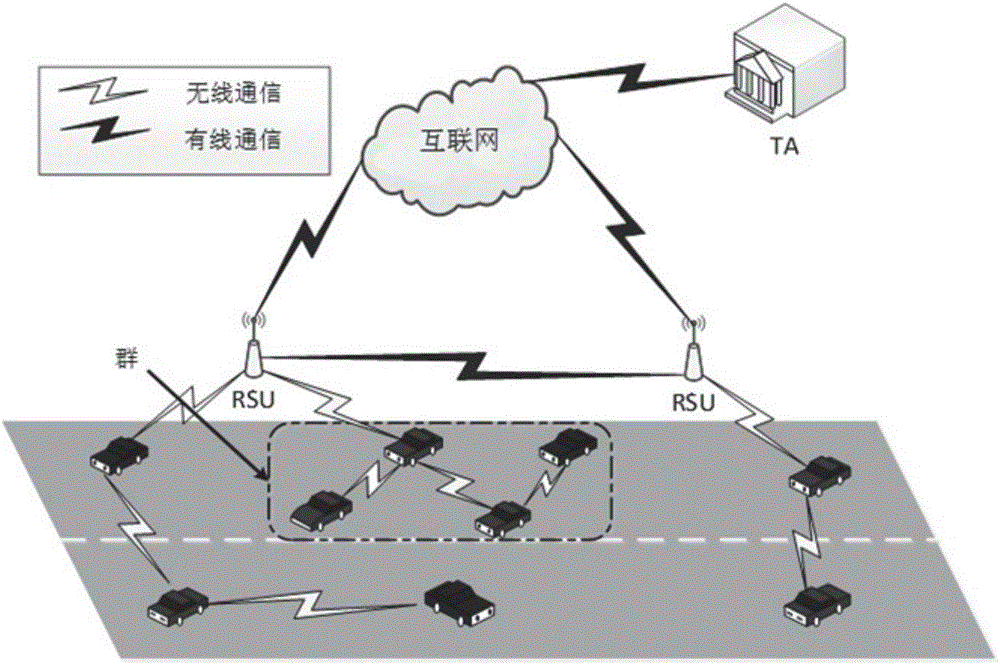
InactiveCN106027233ASolve the delay problemFast authenticationKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessVehicle networks
The invention discloses a method for designing a vehicle network group negotiation communication protocol, which includes the following steps: (1) first establish a system model; (2) system initialization; (3) both vehicle and roadside unit RSU authentication; ( 4) Negotiation and update of the group key; (5) Communication within the group mainly includes broadcast communication, communication between vehicles and RSUs, and one-to-one communication between vehicles. The present invention adopts a public key system without a certificate, and the communication process does not require the participation of a third-party TA, avoiding the time delay problem when the TA authenticates the certificate when the public key encryption system is used, and accelerates the authentication speed. Through the way of group key transmission, the number of authentications of legal vehicles is reduced. Using key agreement to generate keys instead of group leaders to distribute keys reduces the workload of group leaders and eliminates the possible single point of failure.
Owner:JIANGSU UNIV
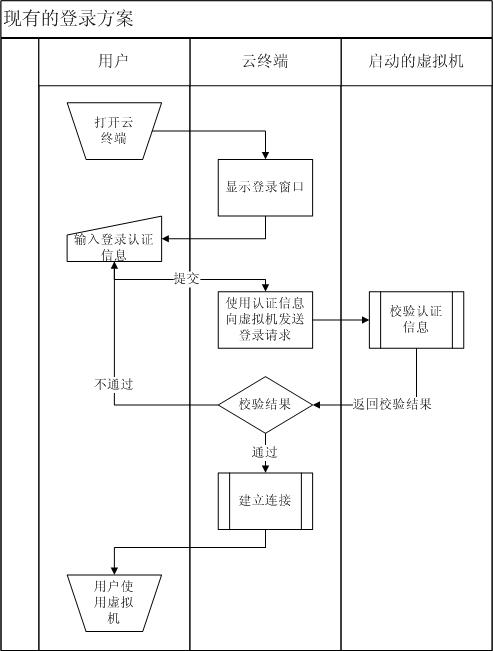
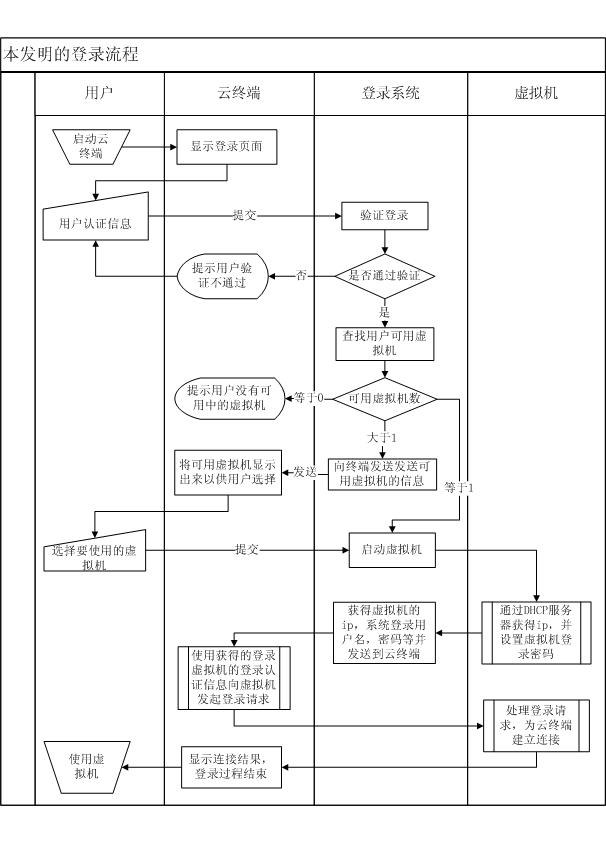
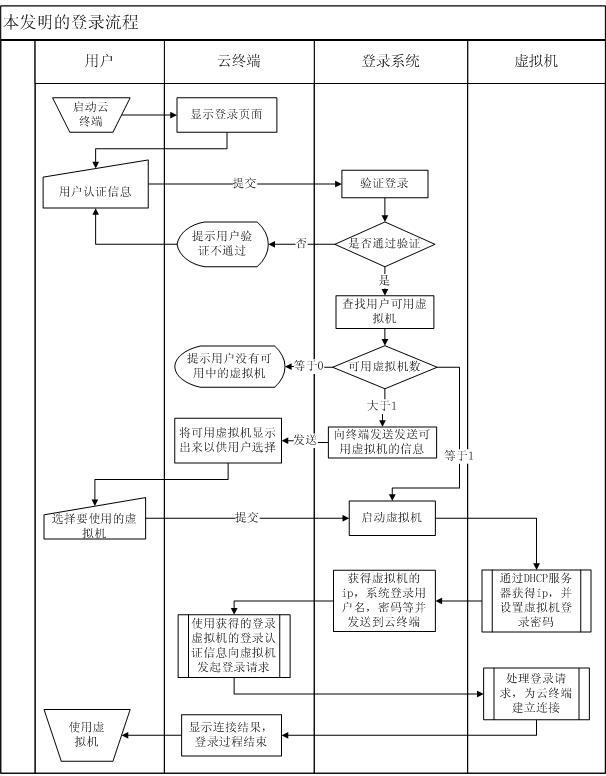
Method for mini-station to authenticate and log in virtual machine in cloud system and login system
The invention discloses a method for a mini-station to authenticate and log in a virtual machine in a cloud computing system and a login system. The method comprises the following steps that: (1) the mini-station logs in the cloud computing system by the login system; (2) the login system searches for the number of available virtual machines in the cloud computing system; (3) the login system starts the virtual machine in the cloud computing system according to virtual machine selection rules and executes steps (4) to (6) if the number of the available virtual machines is more than or equal to 1, otherwise returns information indicating that the cloud computing system does not have available resources to the mini-station, and the mini-station quits; (4) the virtual machine generates virtual machine login information, and transmits the virtual machine login information to the login system; (5) the login system transmits the virtual machine login information to the mini-station; and (6) the mini-station logs in the virtual machine. By the method and the login system, the mini-station can rapidly authenticate and log in the virtual machine, and the virtual machine is not required to be kept in a starting state so as to make safer the system and effectively save resources.
Owner:GCI SCI & TECH
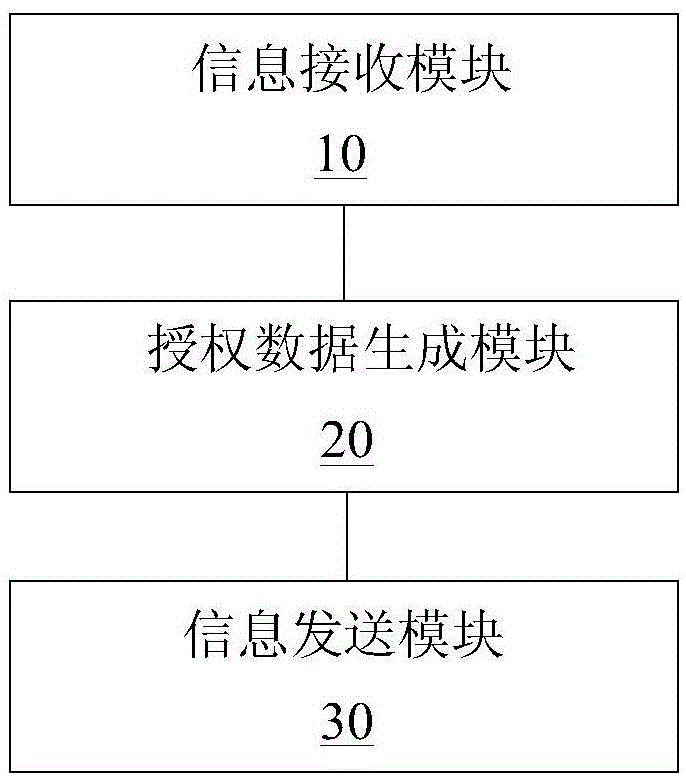
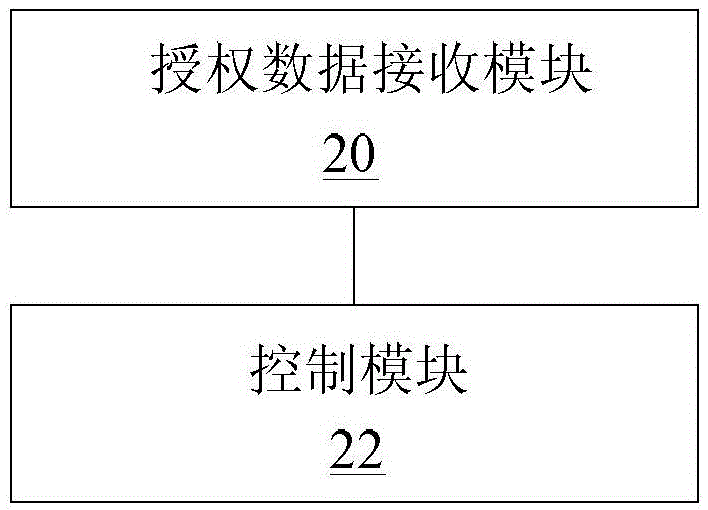
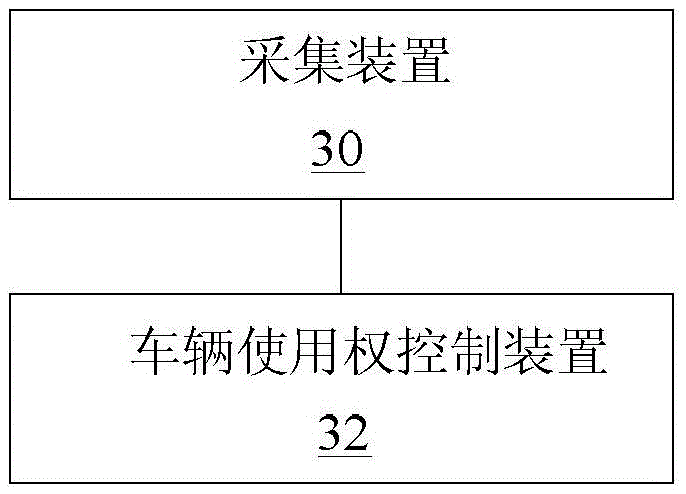
Automobile use right sharing device, control device and intelligent automobile
The invention discloses an automobile use right sharing device, a control device and an intelligent automobile. The automobile use right sharing device comprises an information receiving module, an authorization data generating module and an information transmitting module, wherein the information receiving module is used for receiving automobile use right application information of an automobile use right applicant and automobile authorization result information of an automobile owner; the authorization data generating module is used for associating pre-stored characteristic information of the automobile use right applicant with automobile information to generate authorization data after receiving the automobile authorization result information agreed by the automobile owner; and the information transmitting module is used for transmitting the automobile use right application information when identity information of the automobile use right applicant passes through the verification, transmitting the automobile authorization result information when the automobile authorization result information is received and transmitting the authorization data. According to the technical scheme provided by the invention, automobiles are rapidly and reliably shared, the traveling mode is optimized, the traveling experience is improved, the traveling efficiency is increased, the traveling cost is reduced, and social problems, such as automobile tail gas pollution, road congestion and the like, due to the increasing of the automobiles are solved.
Owner:安徽奇点智能新能源汽车有限公司
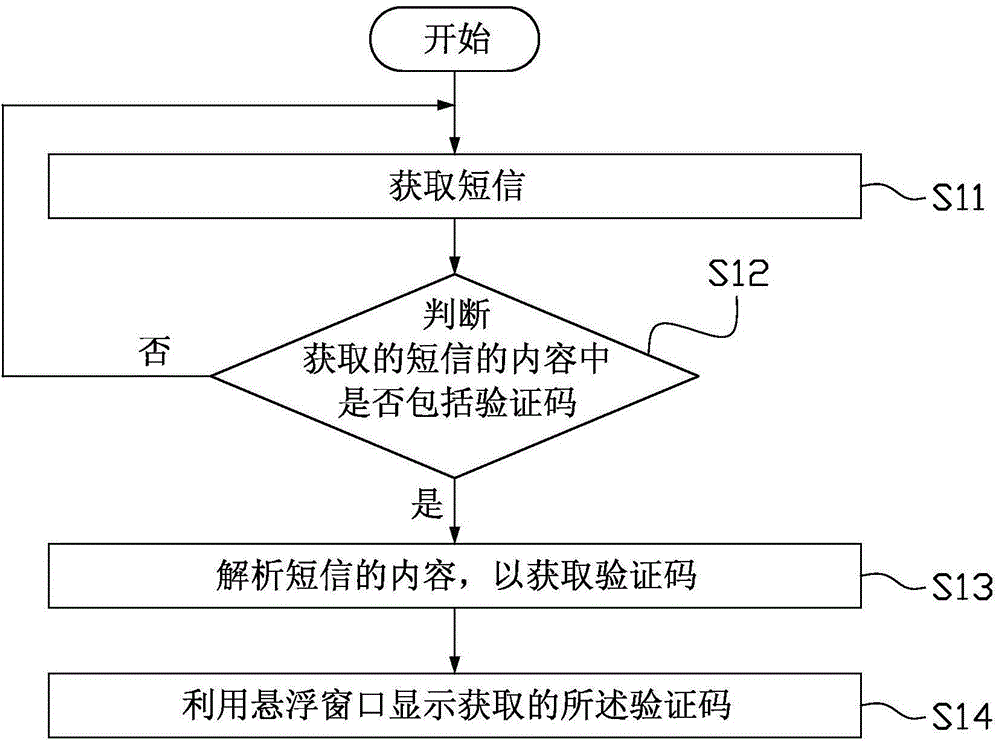
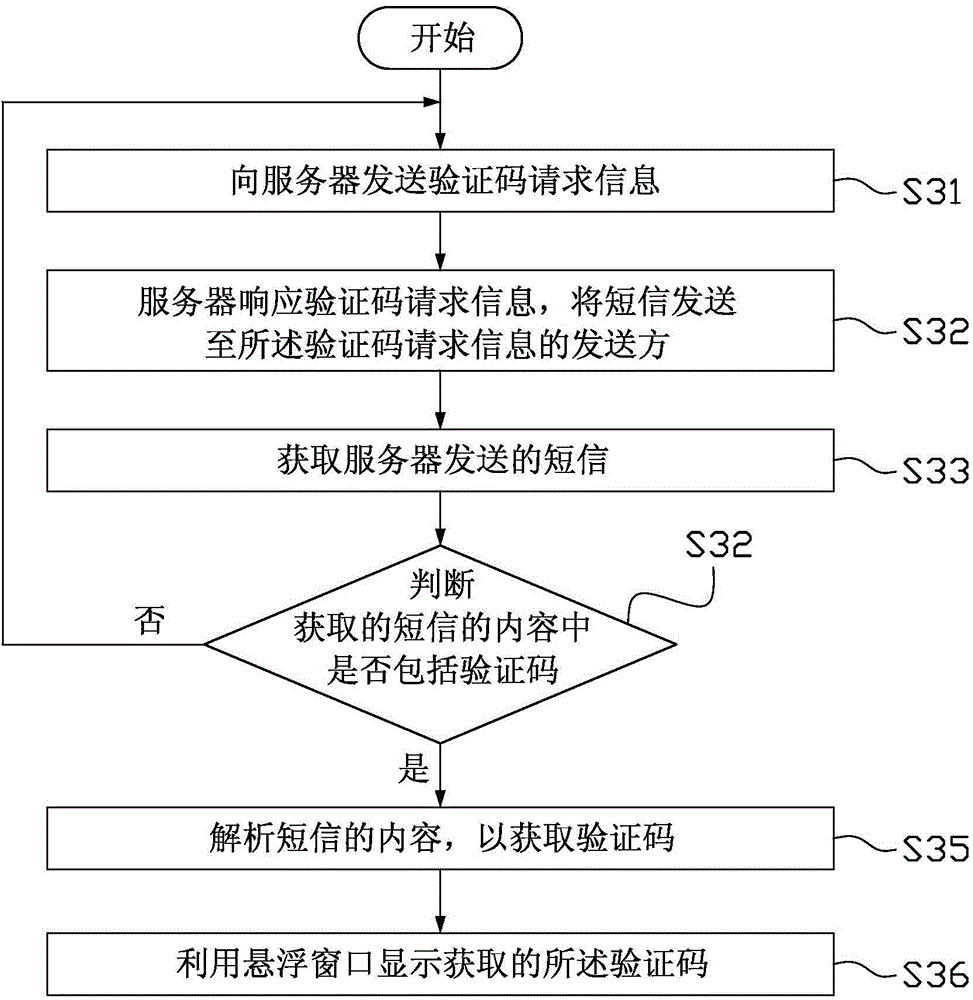
Verification code display method, verification code display device and mobile terminal
InactiveCN104935744AFast authenticationImprove experienceSubstation equipmentDisplay deviceComputer terminal
The invention provides a verification code display method. The verification code display method comprises the steps as follows: obtaining a short message; judging whether the content of the short message contains a verification code or not, and returning to the step of obtaining the short message if the content of the short message does not contain the verification code; analyzing the content of the short message if the content of the short message contains the verification code so as to obtain the verification code; and using a floating window to display the obtained verification code. The invention further provides a verification code display device and a mobile terminal. The verification code display method, the verification code display device and the mobile terminal of the invention could automatically analyze the verification code from the content of the short message and use the floating window to display the obtained verification code without needing a user to manually extract and record the verification code in the short message such that the user could perform identity authentication quickly by using the short message. The verification code display method, the verification code display device and the mobile terminal of the invention provide excellent user experience.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Hardware module-based authentication in intra-vehicle networks
ActiveUS20190104149A1Minimal latencyImprove securityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesElectronic control unitVehicle networks
A secure hardware-based module or Security Electronic Control Unit (SECU) for a Controller Area Network (CAN) prevents an attacker from sending malicious messages through the CAN bus to take over control of a vehicle. The SECU shares a unique key and counter with each ECU on the CAN bus. When a legitimate ECU sends a message, it first compresses the message and then generates a MAC of the counter and a secret key. The counter is increased by one for each transmitted message. The ECU then fits the compressed message and the MAC into one CAN frame and sends it onto the CAN bus. The SECU performs the message verification on behalf of the intended receiver(s) of the message. If the verification passes, the receiver(s) simply decompress the message and use it as a normal CAN message. If the verification fails, the SECU will corrupt the CAN frame before it is fully received by the intended receiver(s). The corrupted CAN frame will be ignored by the intended receiver(s) as if it was never received. Therefore, a malicious message generated by an attacker will inflict no damage on the system.
Owner:GEORGE MASON UNIVERSITY
An Internet of Things authentication method and device based on a block chain
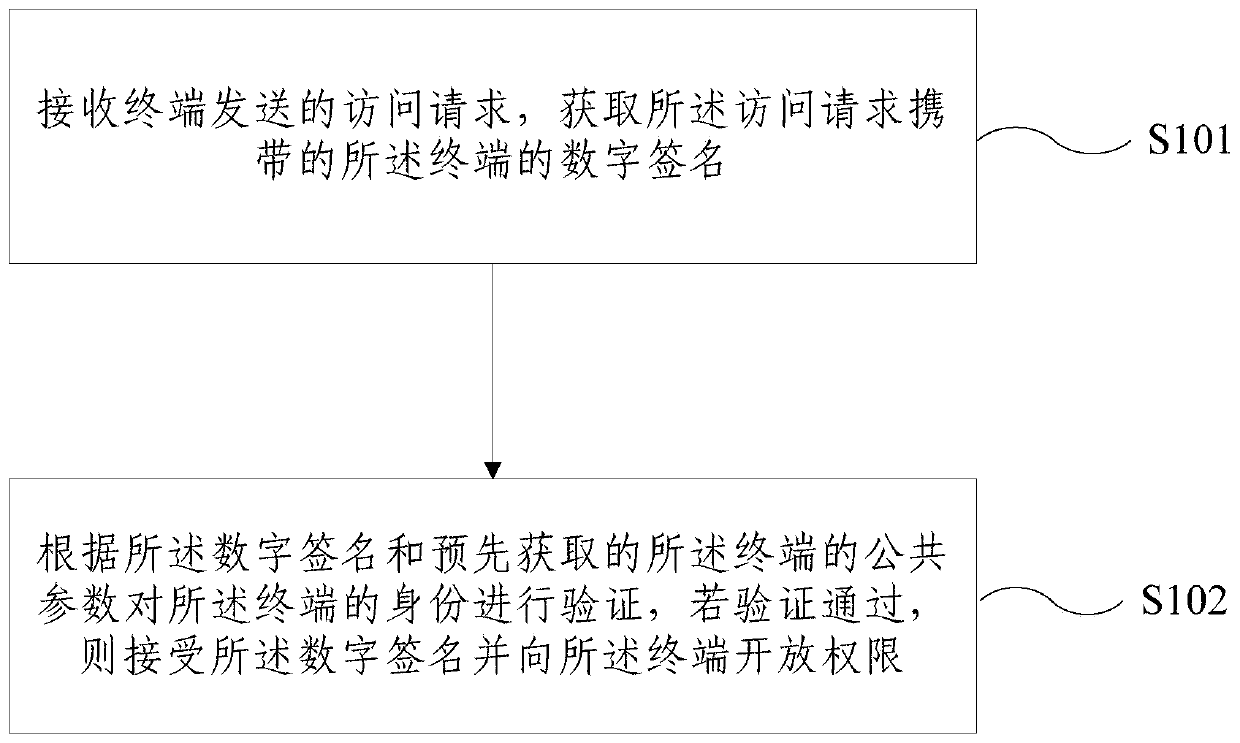
ActiveCN109714173APrivacy protectionSecure the EdgeUser identity/authority verificationData switching networksDigital signatureComputer terminal
The embodiment of the invention provides an Internet of Things authentication method and device based on a block chain. The method comprises the following steps: receiving an access request sent by aterminal, and obtaining a digital signature of the terminal carried by the access request; Verifying the identity of the terminal according to the digital signature and pre-acquired public parametersof the terminal, and if the verification is passed, receiving the digital signature and opening the authority to the terminal; Wherein the public parameter is obtained according to a message broadcasted by the first node; And the first node is an edge node for registering the terminal to a block chain edge layer used on the block chain. The embodiment of the invention provides an Internet of Things authentication method and device based on a block chain. By combining the decentralized authentication of the block chain and the advantage that the computing and storage capacity is lowered to be close to the network edge device, the edge node can directly authenticate, the privacy of the terminal can be effectively protected, the edge security of the terminal can be protected, and the authentication speed can be increased.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Method, system and apparatus for authenticating user identity
InactiveUS20140351596A1Operational securitySimple software installationDigital data processing detailsUser identity/authority verificationPaymentInternet privacy
The present invention relates to a method and system for authenticating user identity with a user terminal, authentication front-end computer system, and authentication server. In a first scheme, the user terminal transmits an authentication instruction comprising an authentication message to the authentication front-end computer system. Then, the authentication front-end computer system transmits an authentication request comprising the authentication message to a specific authentication server. In a second scheme, the user terminal transmits an authentication request comprising an authentication message to a specific authentication server. In any schemes, after receiving the authentication request, the authentication server authenticates a user's identity according to the authentication message. Preferably, the authentication server transmits an authentication result to the authentication front-end computer system. When a user pays a certain amount of money to an operator, the authentication server transfers the specific amount from a specific user payment account to a specific operator account after successful authentication.
Owner:CHAN KK
Method and apparatus for WLAN initial link setup
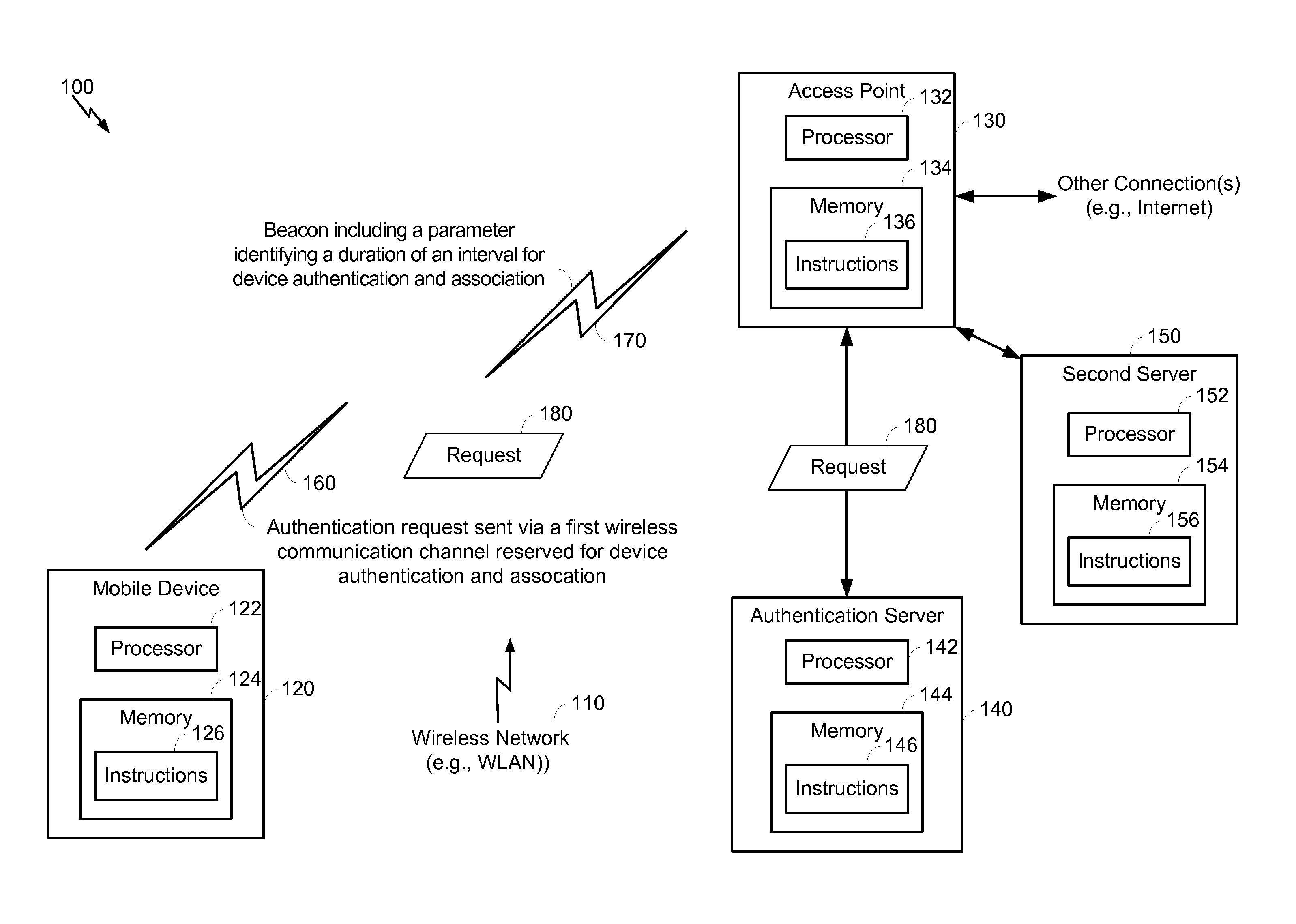
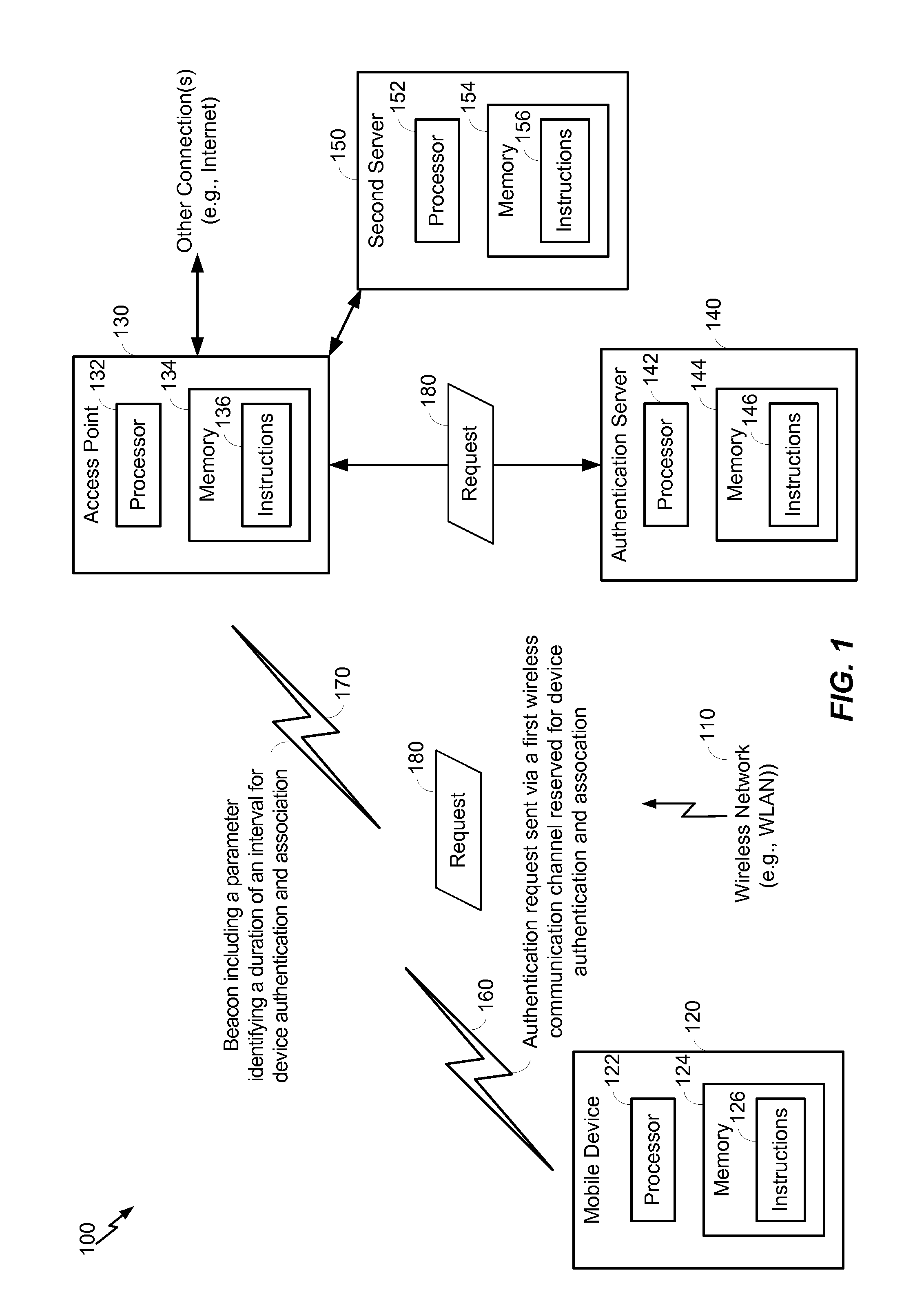
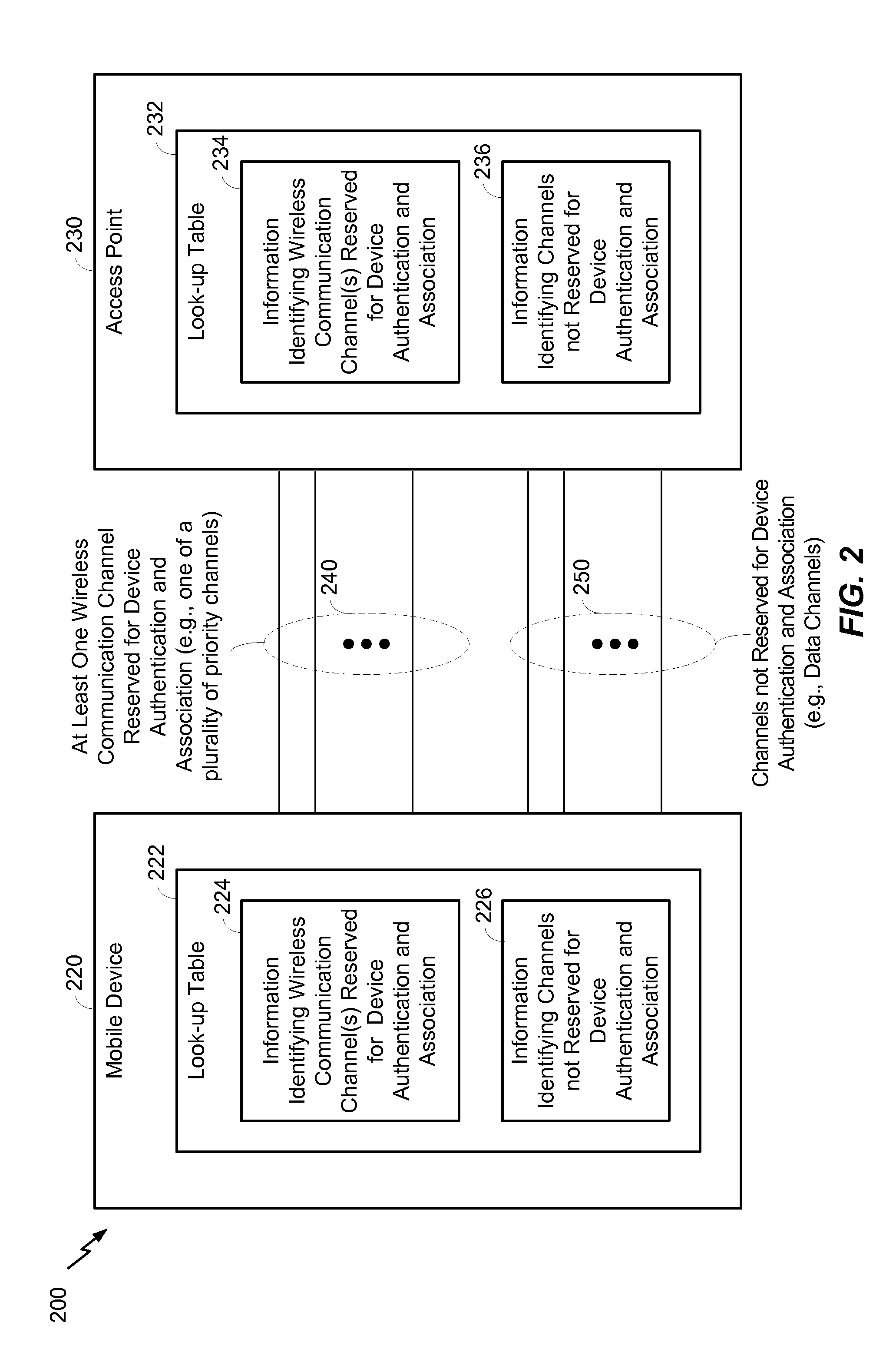
ActiveUS20130336240A1Fast initial setup of wireless connectionReduce delaysError preventionNetwork traffic/resource managementMobile deviceAuthentication
In a particular embodiment, a method includes scanning, by a mobile device, for a first wireless communication channel that is reserved for device authentication and association. The mobile device sends an authentication request to an access point via the first wireless communication channel. The method further includes receiving a reply to the authentication request from the access point.
Owner:QUALCOMM INC
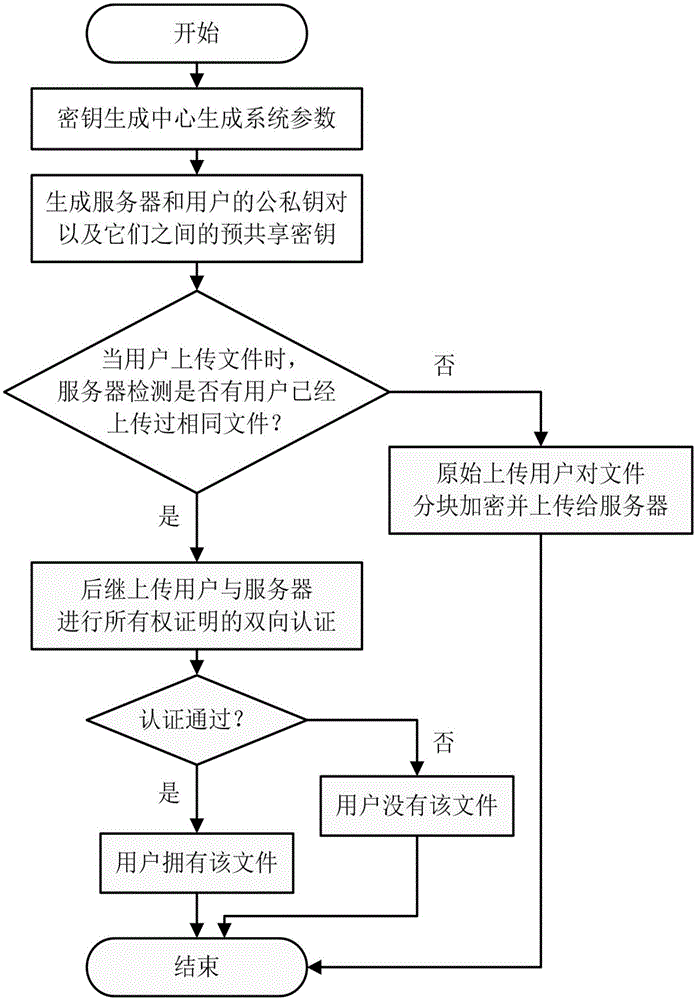
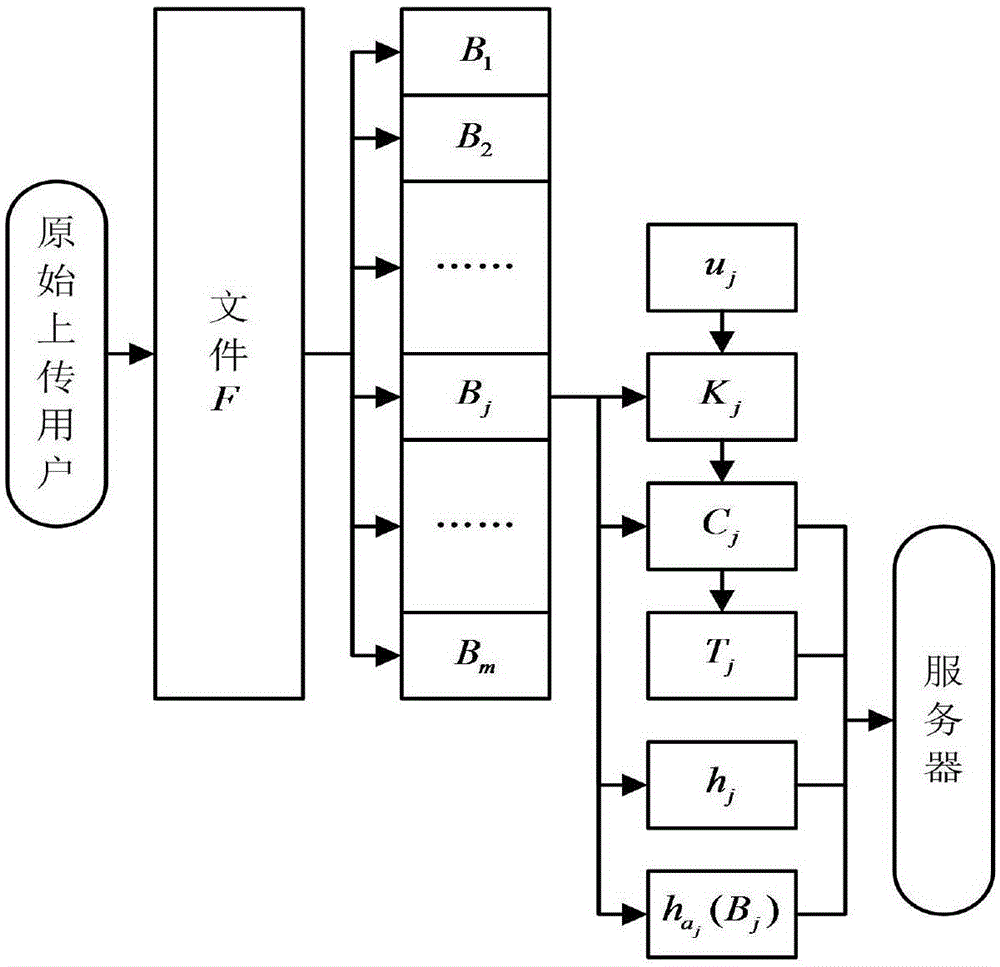
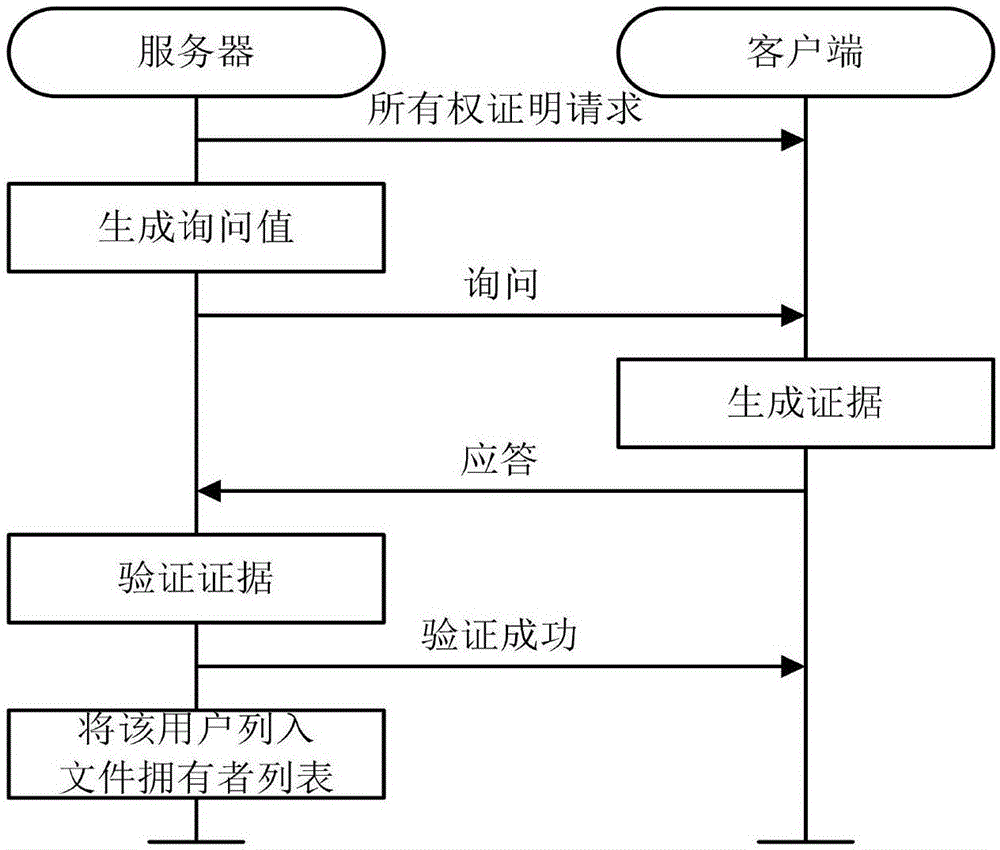
File ownership proof method based on convergence encryption
InactiveCN105141602AResist attackPrevent leakageUser identity/authority verificationOriginal dataClient data
The invention discloses a file ownership proof method based on convergence encryption, which mainly solves the problem in the prior art that the security of taking a hash value as an ownership evidence is bad. The implementation steps are as follows: step 1 of generating a system parameter, a server key and a user key by a key generation center; step 2 of detecting whether the user is a first user that uploads files by the server; step 3 of performing block encryption on the files by the first uploading user and uploading the files; step 4 of issuing an ownership proof request by the server, generating an inquiry value and transmitting the inquiry value to the client; step 5 of performing ownership proof the client receives the inquiry value; step 6 of performing ownership verification after the server receives a reply by the server, and after that, continuing to upload a bidirectional authentication between the user and the client. According to the file ownership proof method based on the convergence encryption provided by the invention, a signature of an original data block is adopted as an evidence of owning the files, thus the security of the evidence can be improved, the network upload bandwidth and cloud server storage overhead can be reduced, and the method can be used for supporting a cloud storage system across client data deduplication.
Owner:XIDIAN UNIV
Method for mutual authentication of user identities based on elliptic curve passwords
ActiveCN104639329AReduce verification timesReduce storage overheadPublic key for secure communicationUser identity/authority verificationInteraction timeMan-in-the-middle attack
The invention relates to a method for mutual authentication of user identities based on elliptic curve passwords. The characteristics of storage capability, calculation capability and limited bandwidth of an Ad Hoc network are considered, and a self-authentication public key system and the intractability of an elliptic curve discrete logarithm problem are utilized, so as to reduce the interaction times of the user identity authentication process, and accelerate the authentication speed. The method comprises the following steps of system initializing, user registering, and mutual authentication of the user identities. The method has the advantages that while the mutual authentication of the user identities is guaranteed, the function of session key negotiation is realized, the storage expense, communication expense and calculation expense are all less, the replay attack, man-in-the-middle attack, counterfeiting and tampering attack, and key disclosure counterfeiting attack can be resisted, a generated one-time session key has the advancing security and backward security, and the security is higher.
Owner:ZHEJIANG UNIV
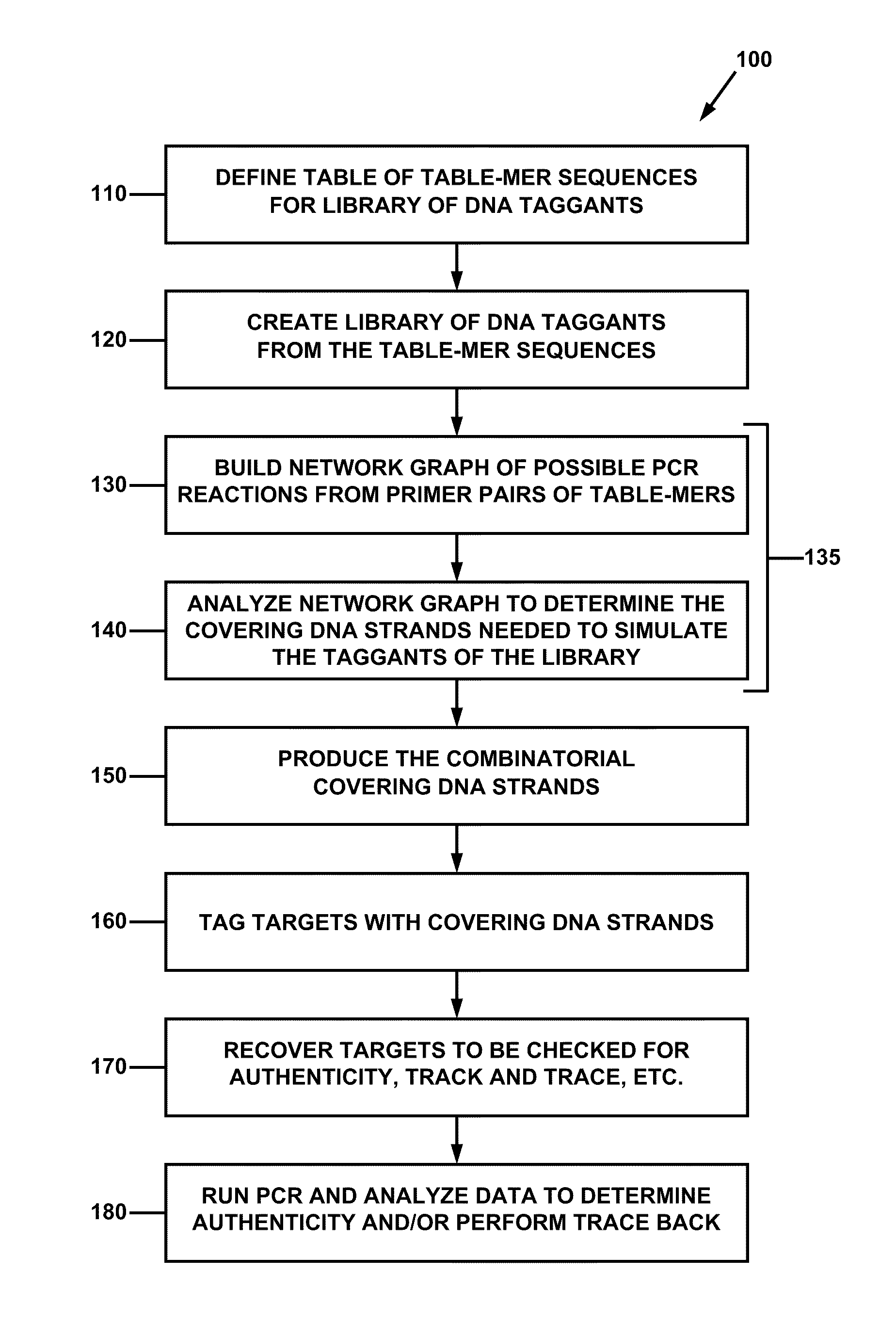
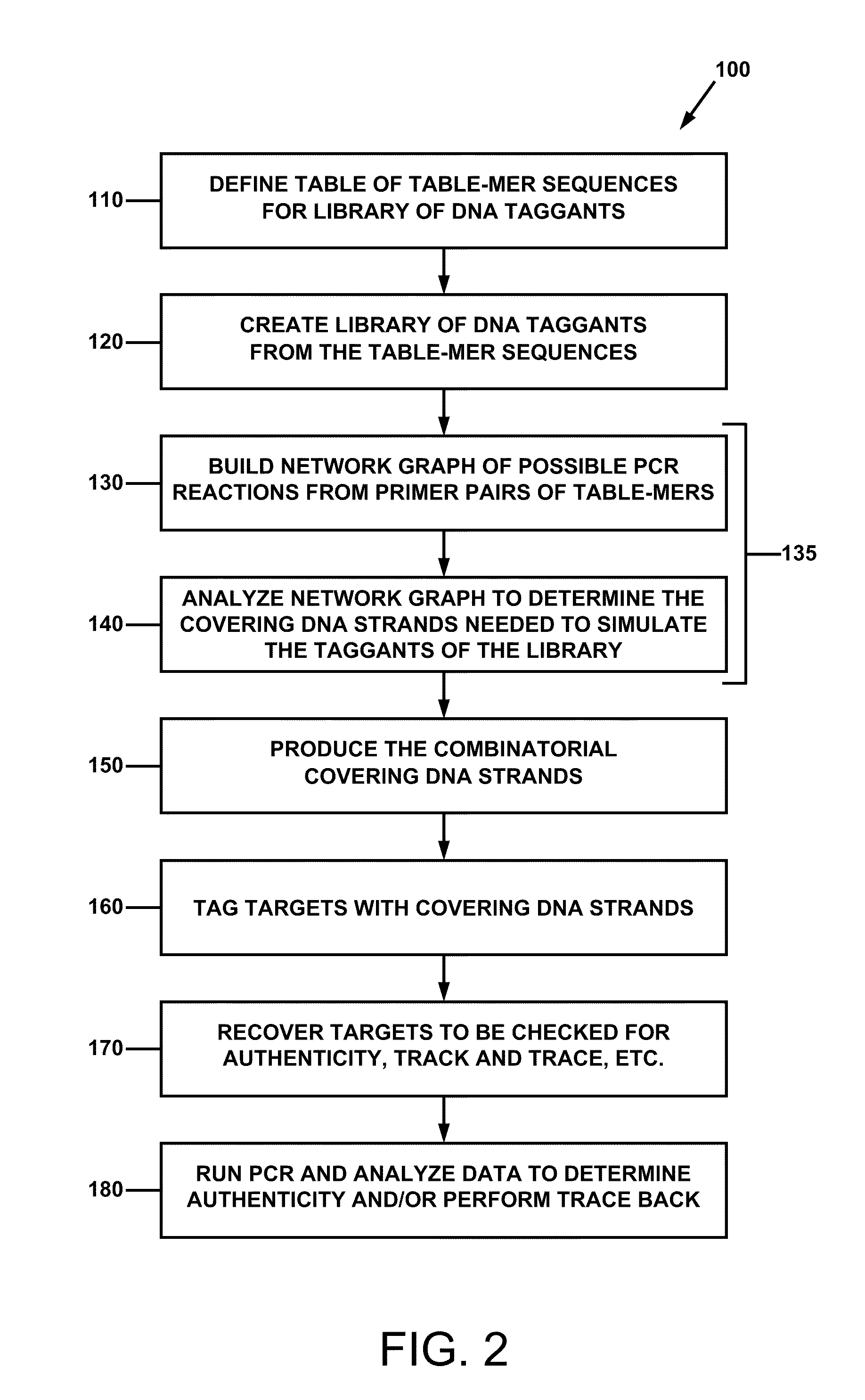
Combinatorial DNA taggants and methods of preparation and use thereof
ActiveUS20110165569A1Prevent counterfeitingAuthentication processSugar derivativesMicrobiological testing/measurementNucleotide sequencingBiology
DNA taggants in which the nucleotide sequences are defined according to combinatorial mathematical principles. Methods of defining nucleotide sequences of the combinatorial DNA taggants, and using such taggants for authentication and tracking and tracing an object or process are also disclosed.
Owner:PATENT INNOVATIONS
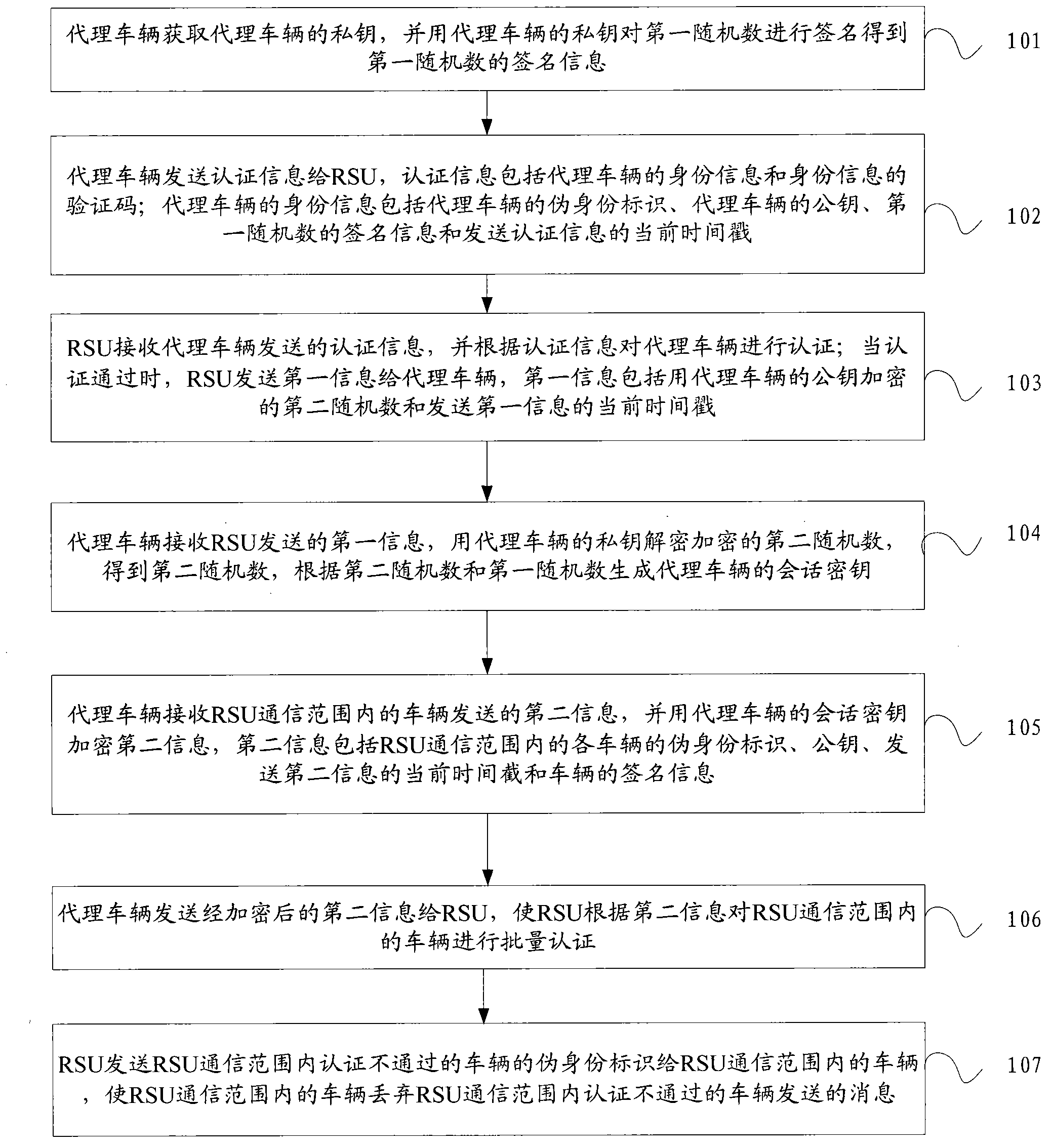
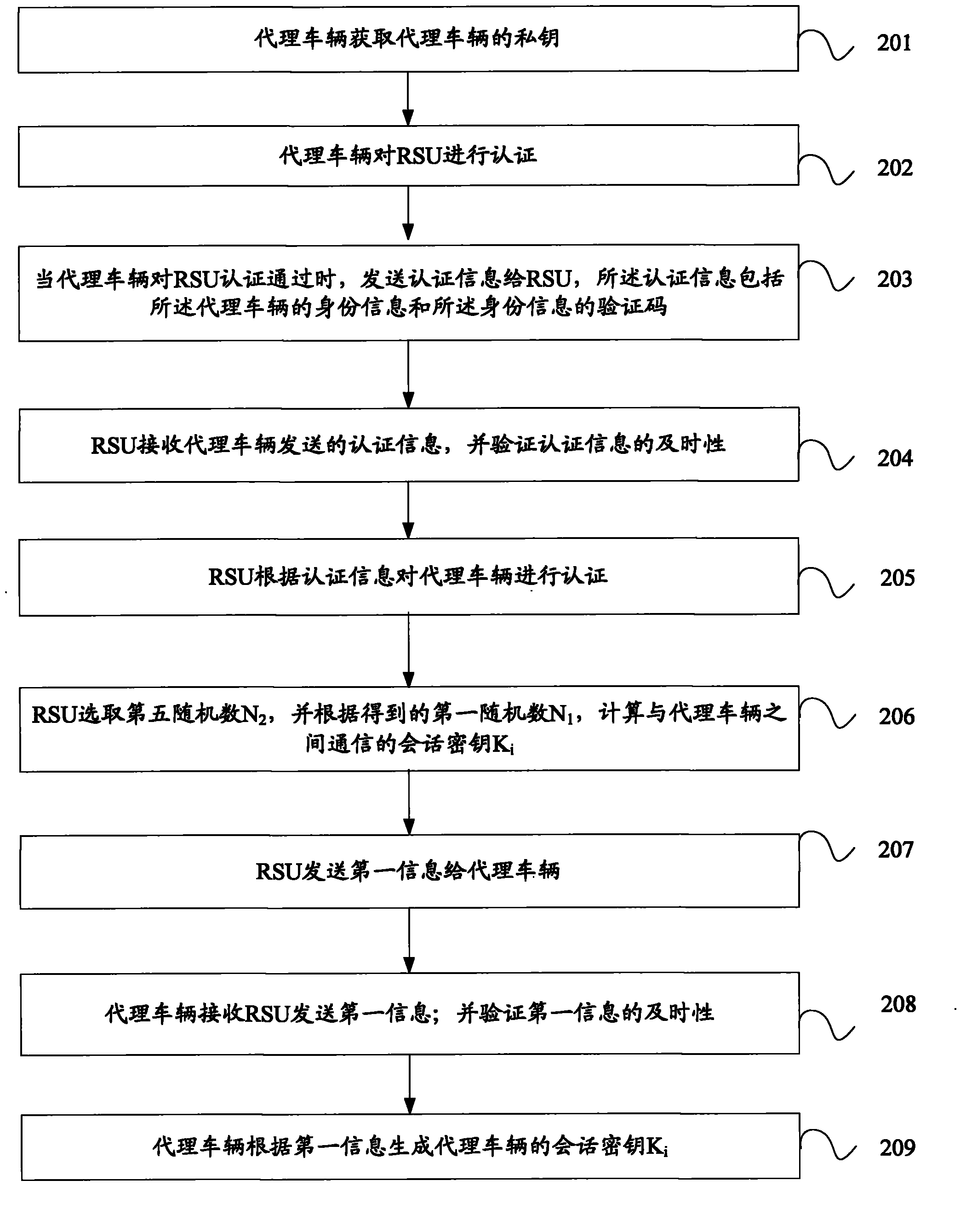
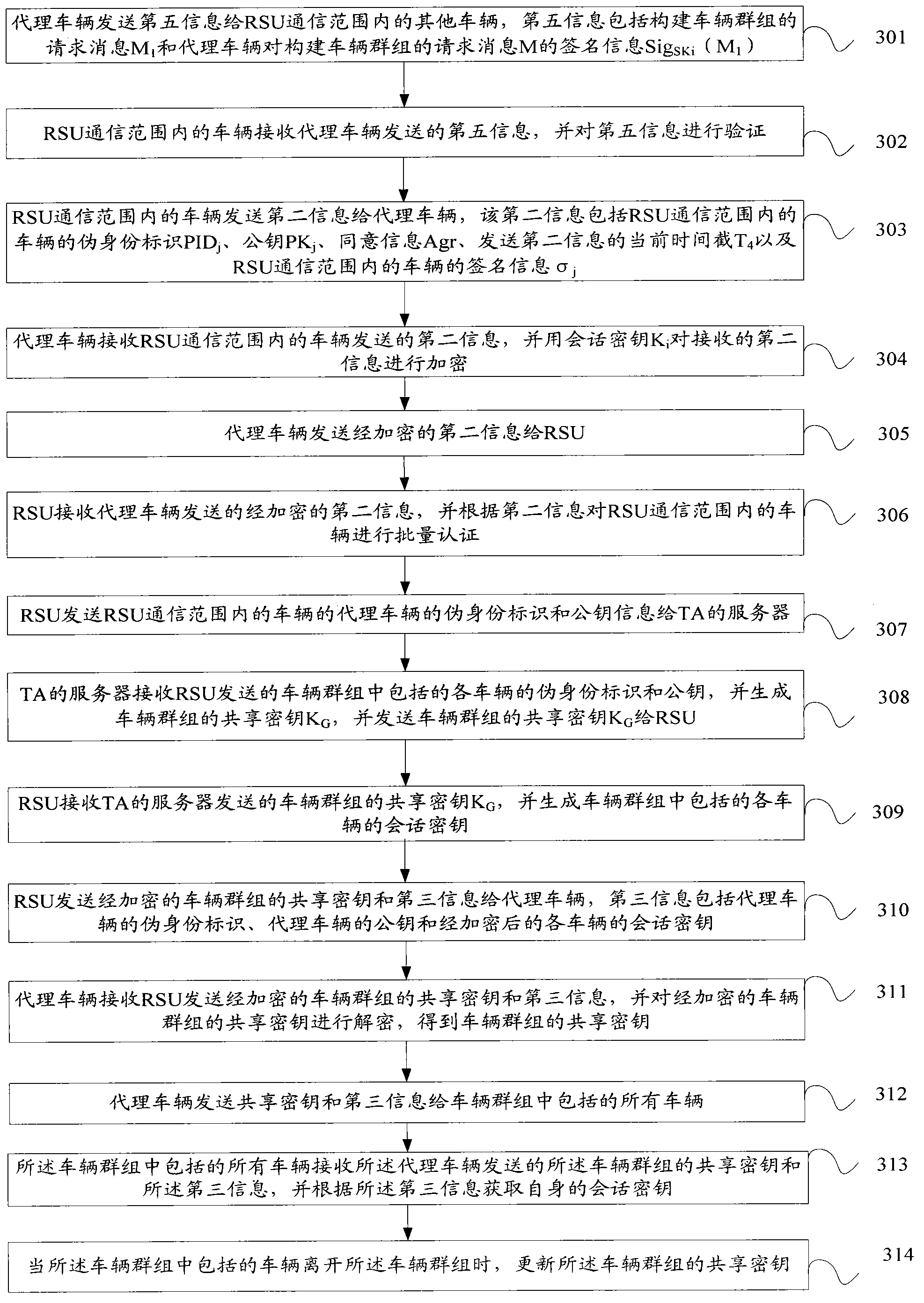
A method and system for certificating vehicle identity
InactiveCN104219663AFast authenticationAvoid key escrow issuesUser identity/authority verificationNetwork topologiesKey escrowSession key
The present invention discloses a method and system for certificating a vehicle identity, and belongs to the field of mobile communication. The method includes: a road side unit RSU certificates an agent vehicle and acquires a session key of the agent vehicle when the certification is passed; the agent vehicle constitutes a vehicle group, and receives second information sent by vehicles within the RSU communication scope; the second information is sent to the RSU after encrypted using the session key of the agent vehicle, so that the RSU certificates the vehicles in the RSU communication scope in a batch according to the second information; and the RSU sends a false identity identification of the vehicle which does not pass the certification within the RSU communication scope to the vehicles in the RSU communication scope. The system includes: an acquiring module, a sending module, a certification module, a generating module and an encryption module. The present invention acquires a private key of the agent vehicle through the agent vehicle, which avoids the problem of secret key hosting; moreover, the RSU sends the false identity identification of the vehicle which does not pass the certification to the vehicles in the RSU communication scope, which considers revocation for illegal vehicles.
Owner:JIANGSU UNIV
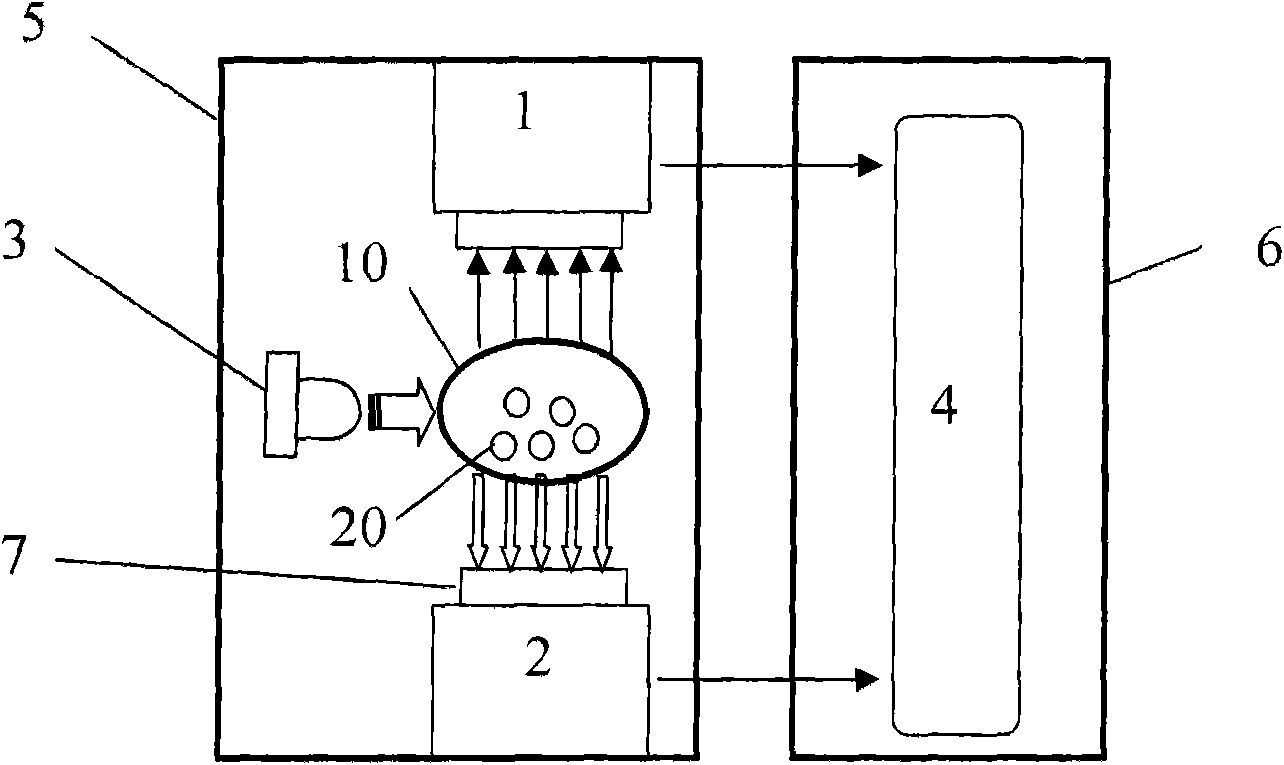
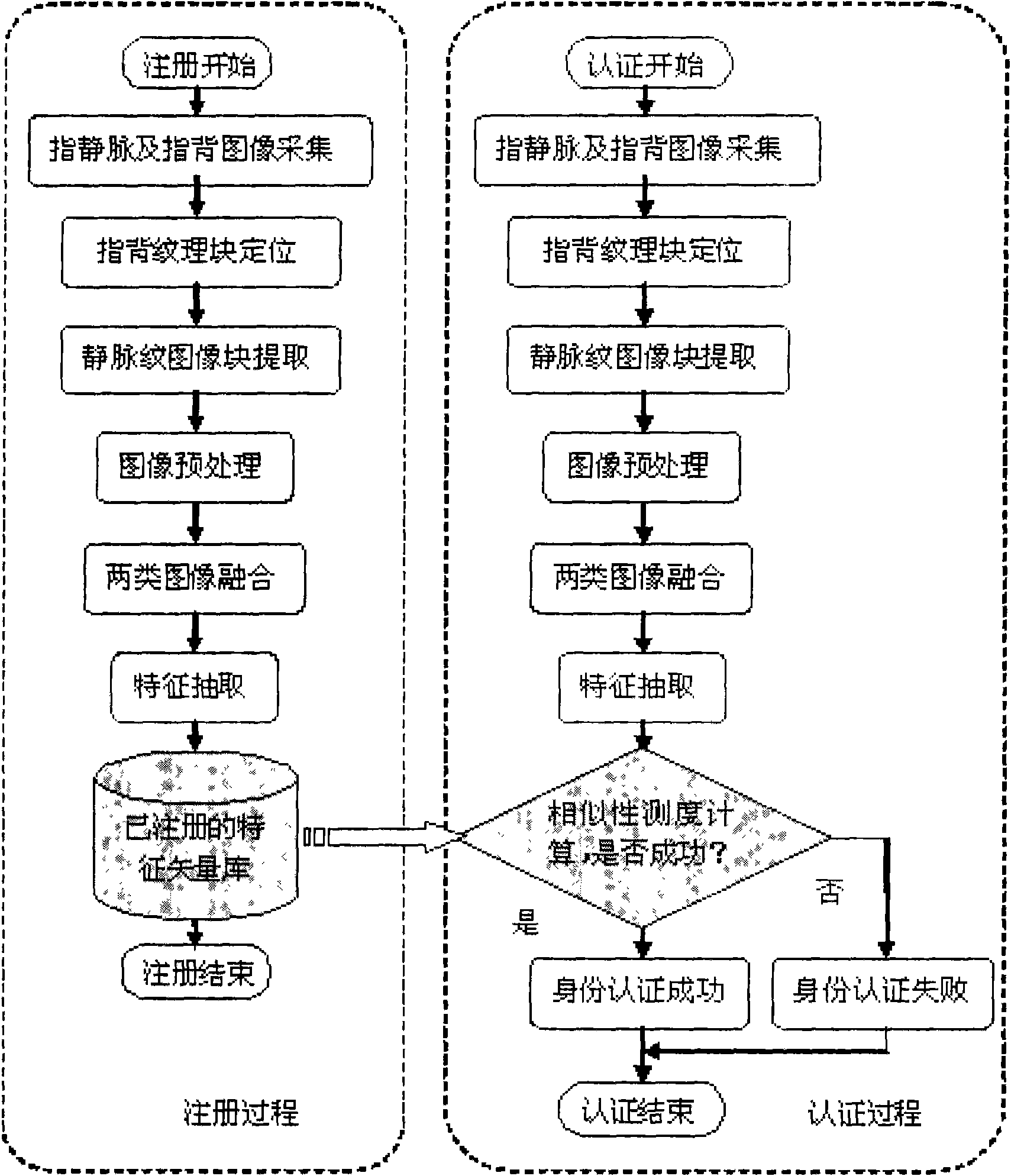
Imaging device based on vein pattern and backside pattern of finger and multimode identity authentication method
ActiveCN101539995AImprove stabilityImprove applicabilityCharacter and pattern recognitionVeinBiometrics
The invention discloses an imaging device based on vein pattern and backside pattern of a finger and a multimode identity authentication method, wherein the imaging device comprises an acquisition support on which a concave finger putting area is arranged; a visible light imaging device which is arranged at one side of the concave finger putting area of the acquisition support and used for acquiring the back picture of the finger; a near infrared imaging device which is arranged at the other side of the concave finger putting area of the acquisition support and opposite to the visible light imaging device, and used for acquiring the vein picture of the finger by the irradiation of a near infrared light supply; and the bar-shaped near infrared light supply which is arranged on the acquisition support and used for irradiating near infrared light to the finger from the side of the finger. The identity authentication method comprises a logon procedure and an authentication procedure, and the adopted biological features thereof comprise the backside pattern and vein pattern of the same finger. The invention also relates to identity authentication equipment comprising the imaging device, which has better anti-counterfeit performance, and can effectively improve the stability and applicability of a biometrics identification system.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
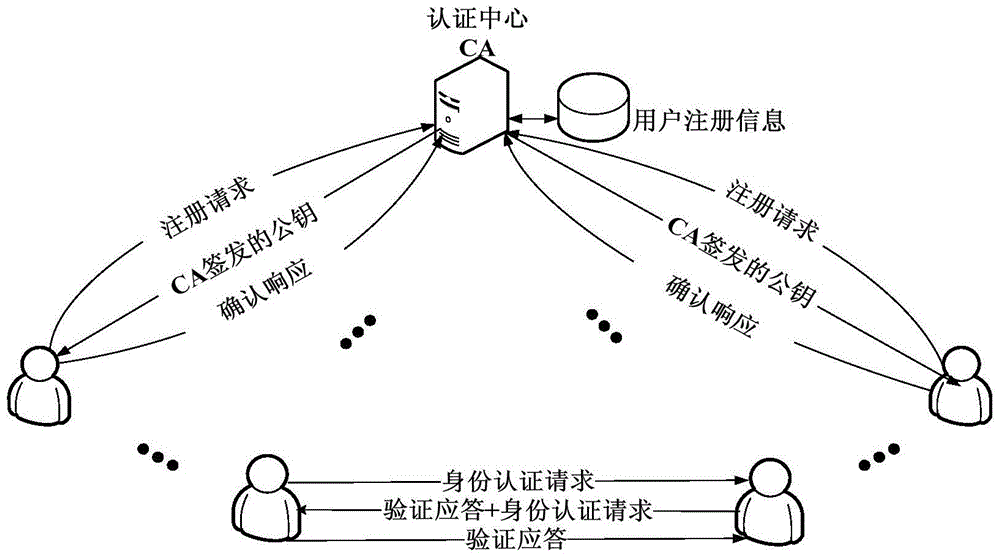
Network real-name system implementing method
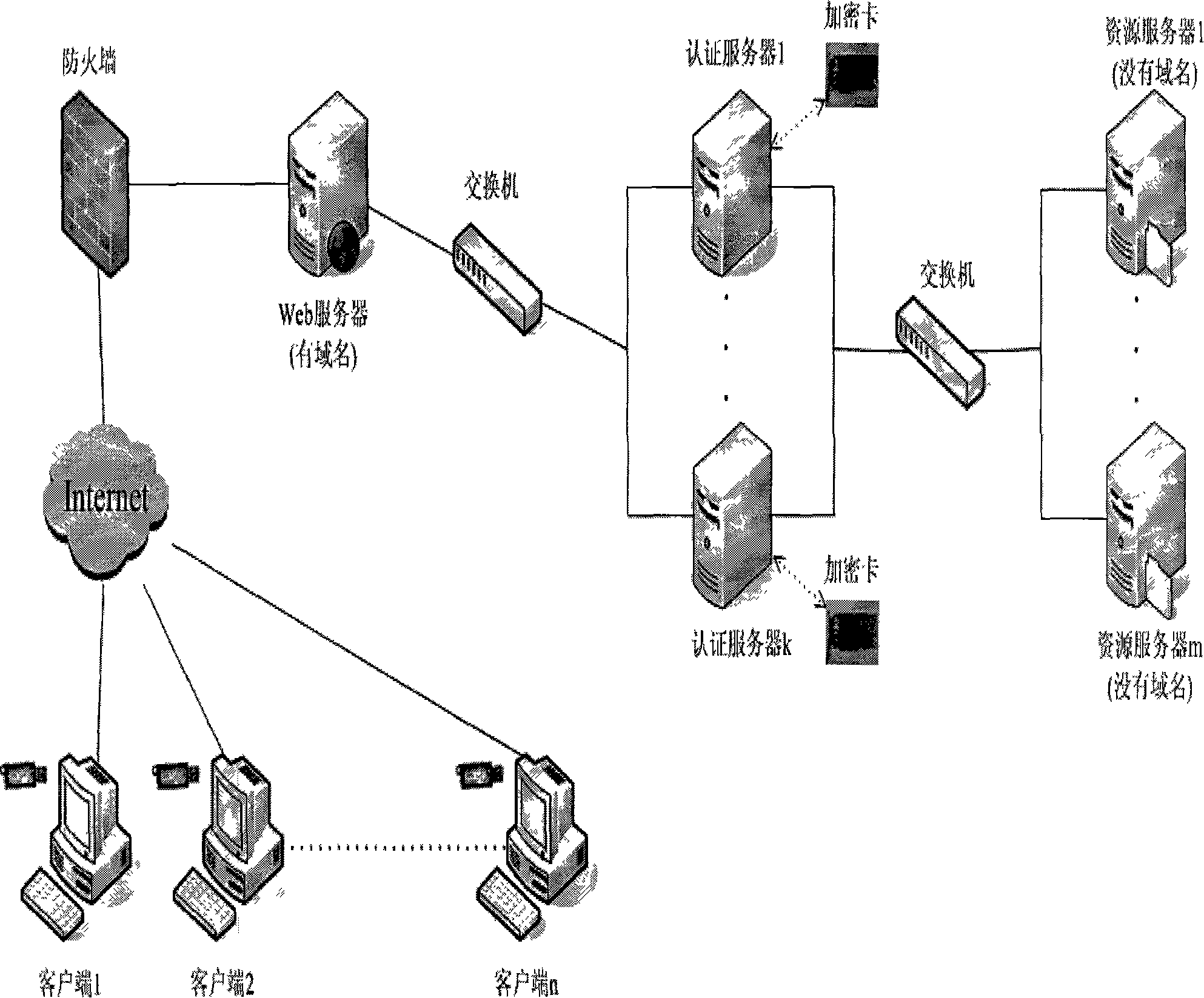
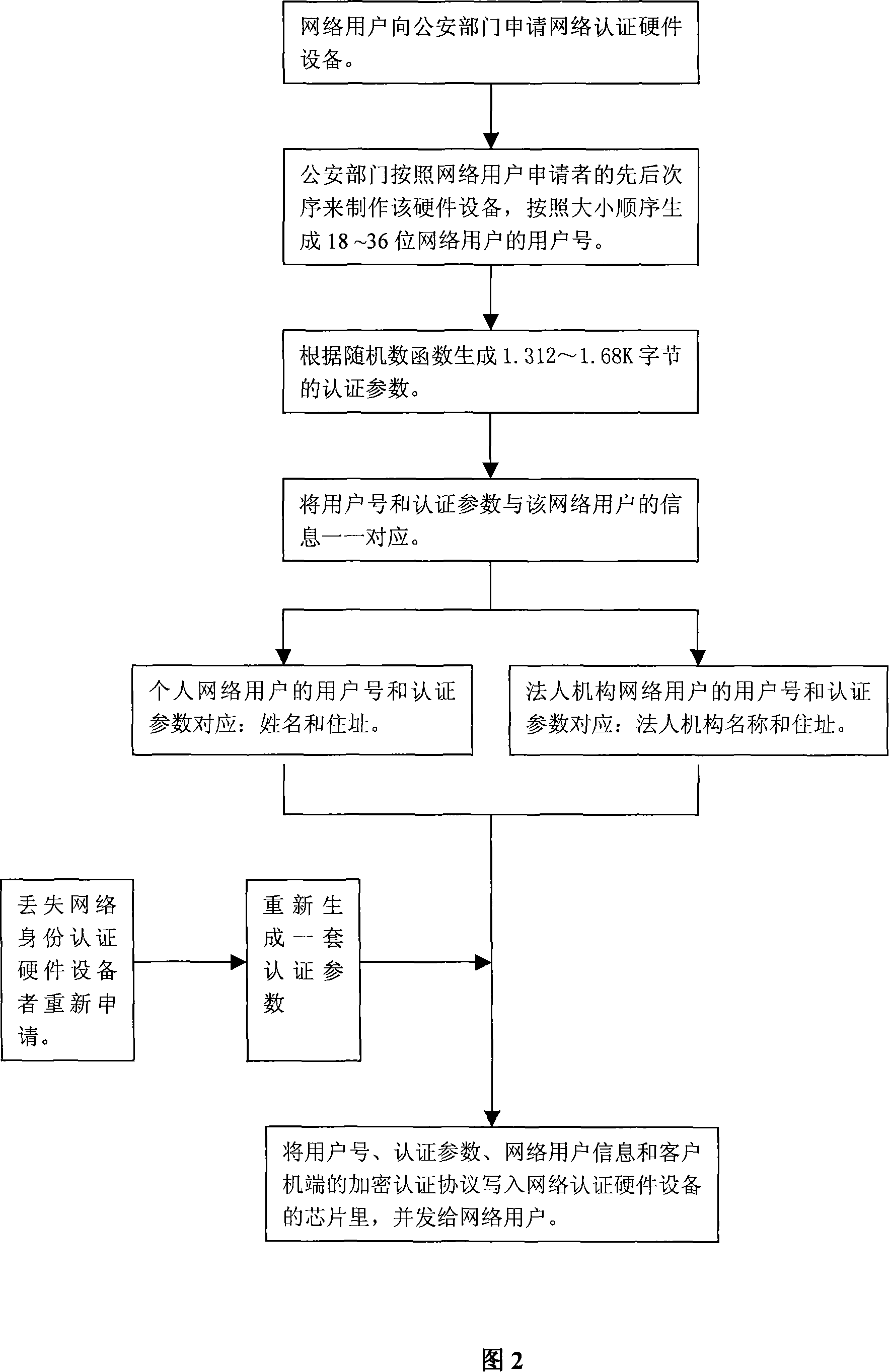
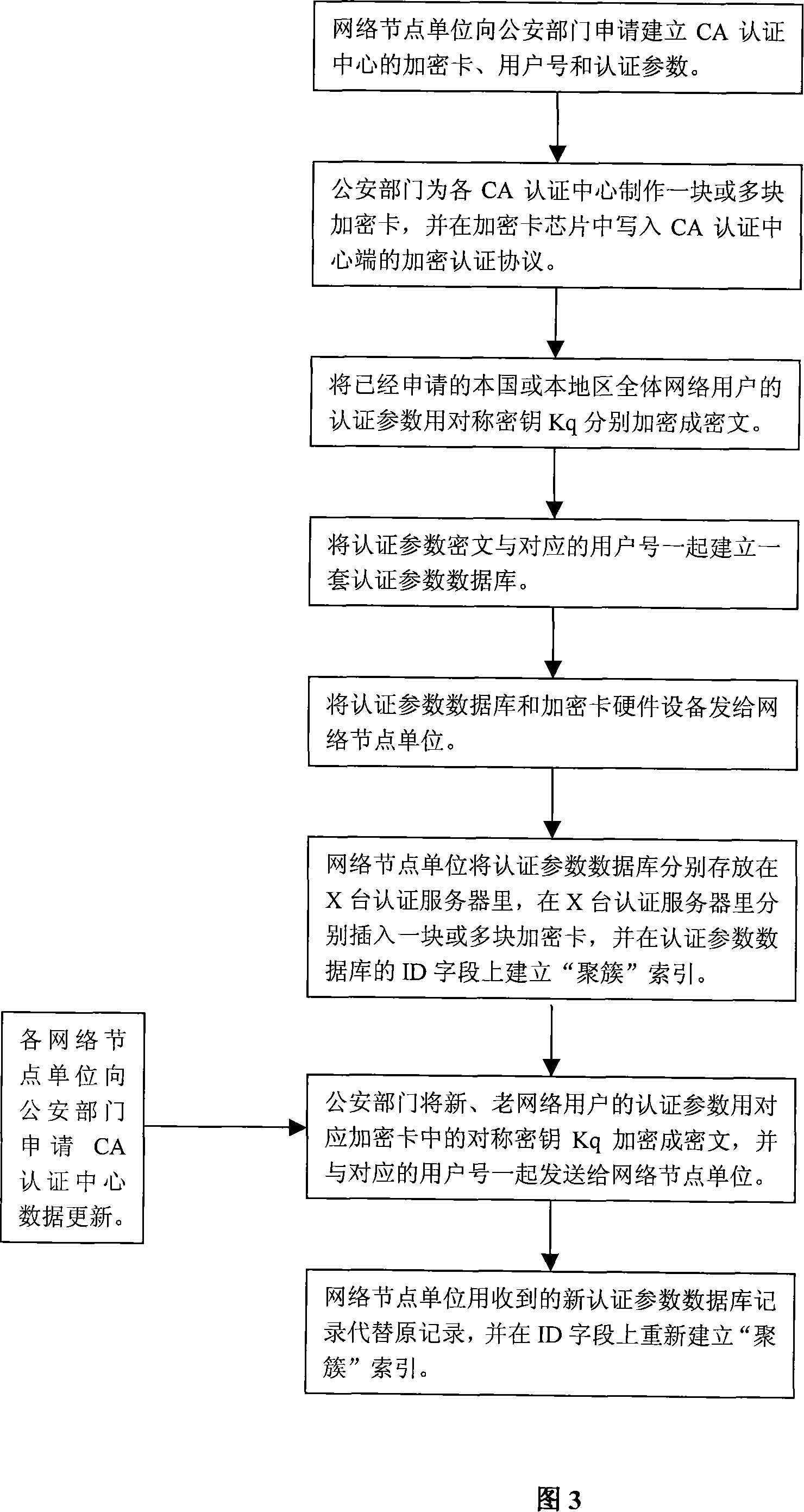
InactiveCN101136750AImprove authentication efficiencyImprove security levelUser identity/authority verificationApplication serverWeb authentication
The implement method for real name system establishes center of authentication (CA) respectively for network nodes i.e. WEB server as unit. The method connects WEB server with CA and network resources or application servers (AS) in series mode. Identifiers and authentication parameters of overall network users in homeland or local area are stored in AS of CA in advance. Protocol of cryptographic authentication based on algorithm of symmetric cryptography and technique of combined symmetric cryptographic key are built in hardware chips at two ends of client and CA. all CAs in each network node can provide authentication of network ID for overall network users in homeland or local area. Each network user holds hardware device for network authentication. Through authentication of CA in each network node, resources or application server in each network node logs on network. Thus, the method implements management on networks in homeland or local government through real name system.
Owner:BEIJING JINAOBO DIGITAL INFORMATION TECH
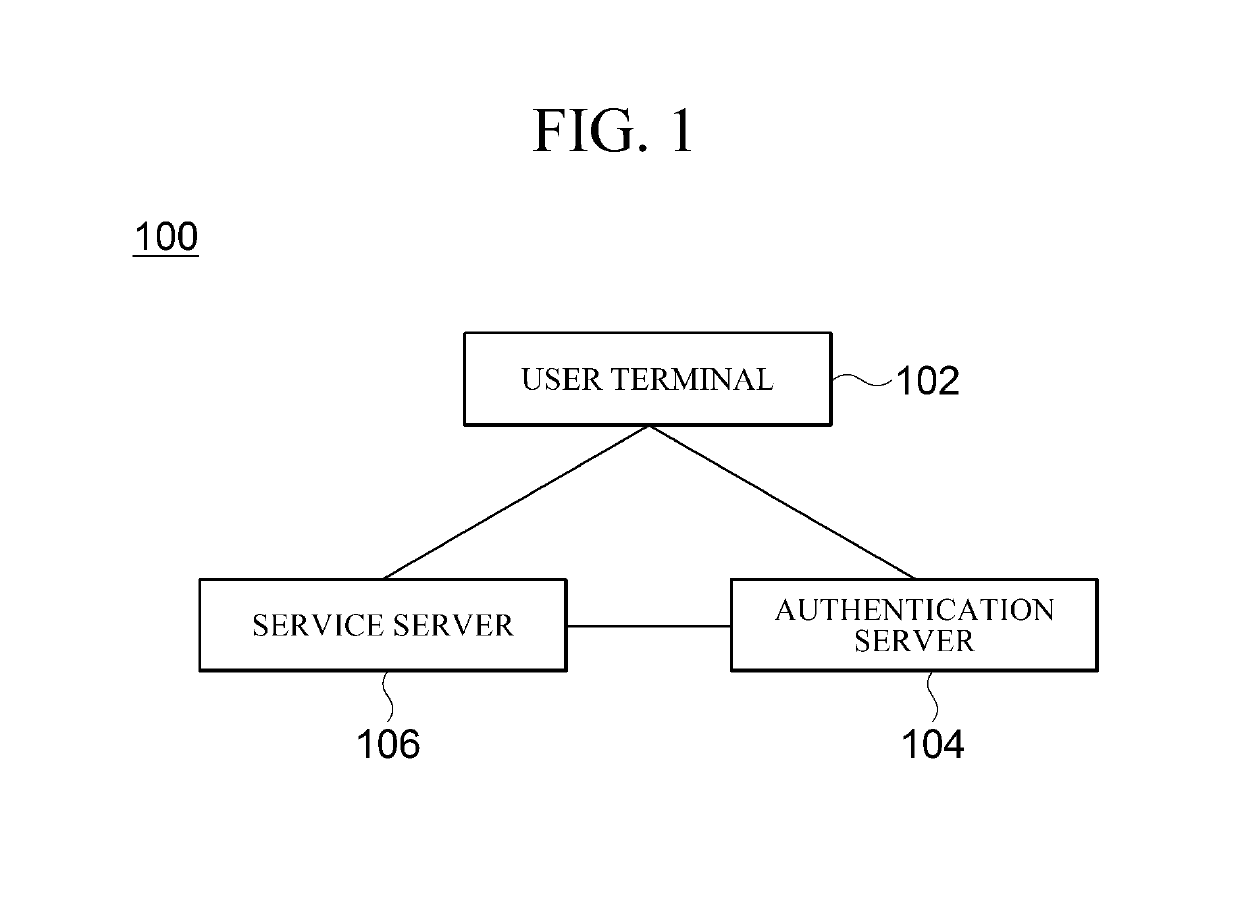
Authentication system and method, and user equipment, authentication server, and service server for performing same method
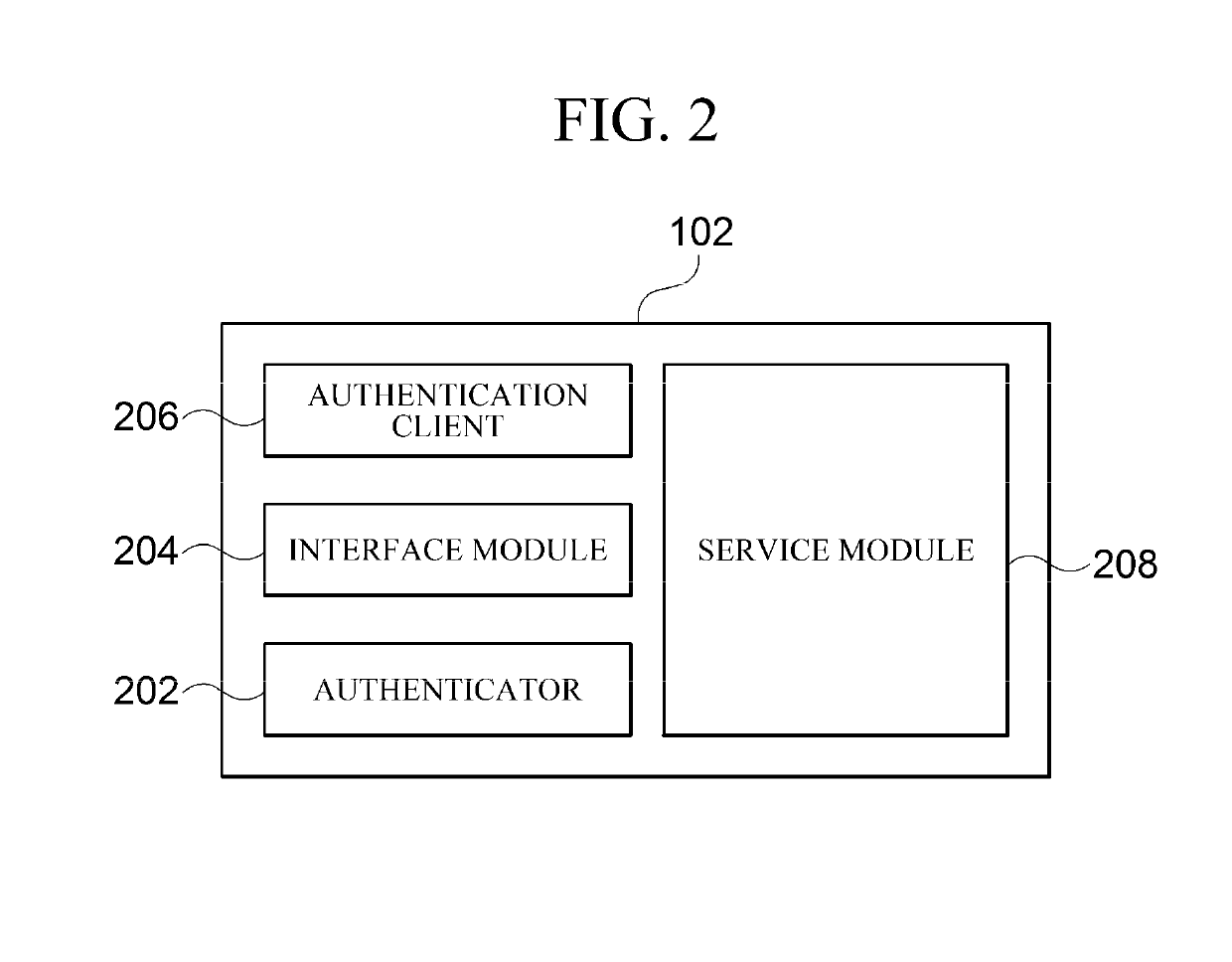
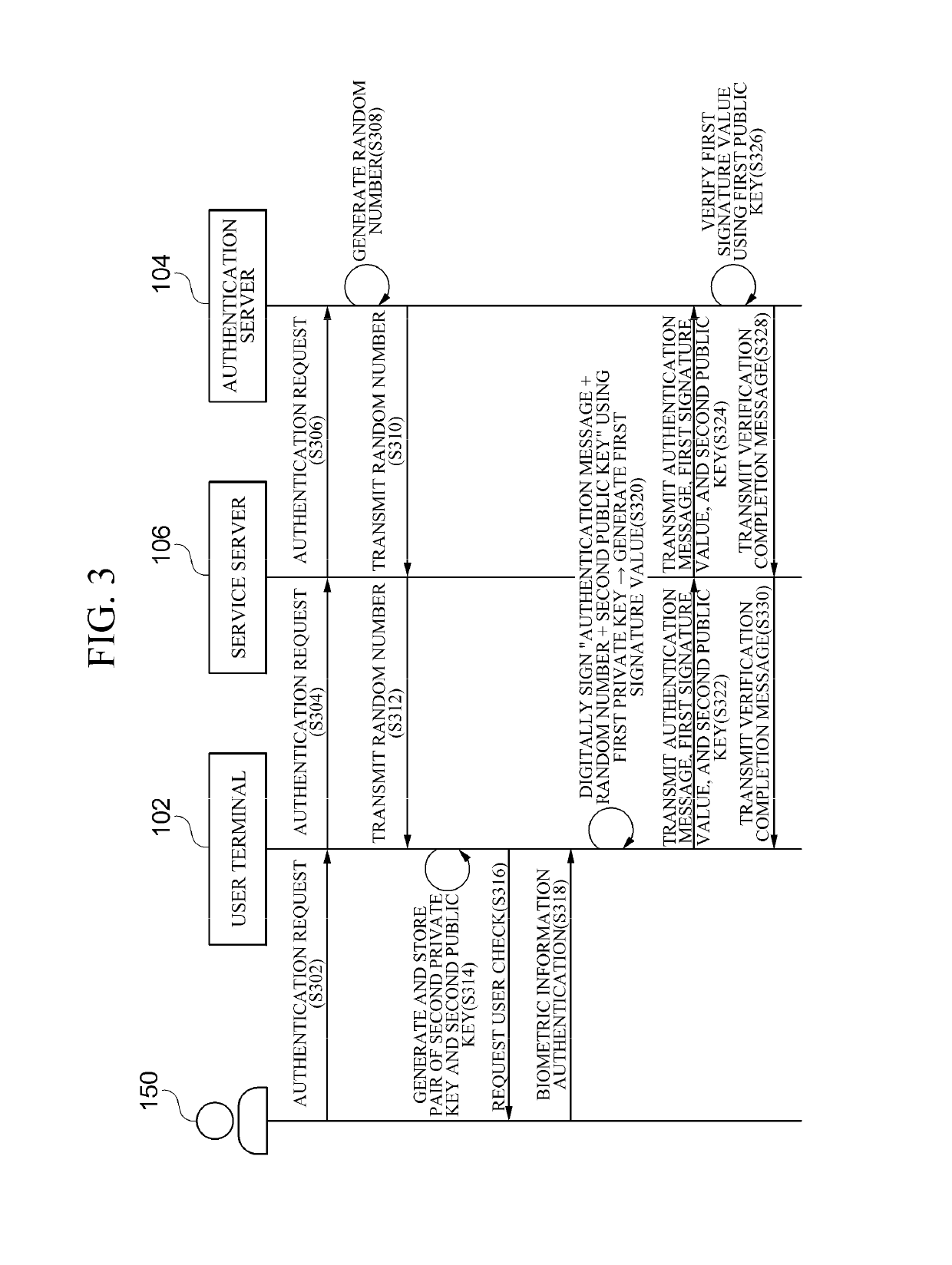
InactiveUS20190190723A1Authentication procedure is simplifiedFast authenticationKey distribution for secure communicationPublic key for secure communicationAuthentication serverAuthentication system
Provided are an authentication system and method, and a user terminal, an authentication server, and a service server for performing the authentication method. According to embodiments of the present invention, a complex authentication procedure carried out in the conventional FIDO authentication technology is simplified using a second public key of which the integrity has been checked, so that a transaction occurring in an authentication procedure can be minimized. Such an authentication method is advantageously suitable to provide a service requiring fast authentication, such as security buying and selling or futures trading.
Owner:SAMSUNG SDS CO LTD
Information processing device, information processing method
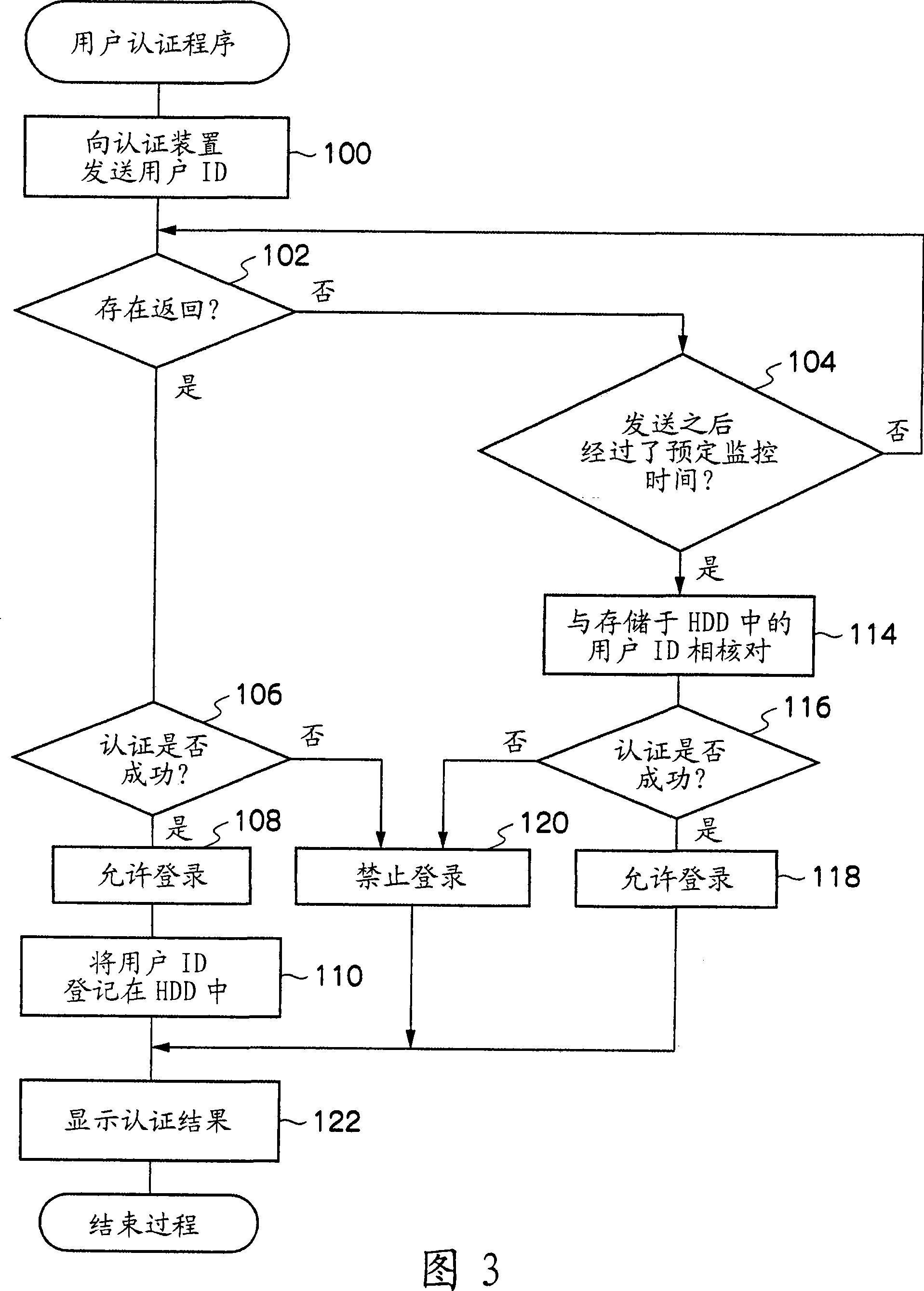
ActiveCN101431594ASuppression of Registered JobsImprove securityDigital data authenticationPictoral communicationComputer hardwareInformation processing
The information processing device includes, a communication portion that communicates with a certification device which performs certification of whether or not a user has usage permission, a reception portion that receives input identification information for identifying the user, a storage portion that stores previously registered identification information, a certification portion that performs user certification, when the reception portion receives the input identification information and the communication portion requests certification of a user by sending the identification information to the certification device, based on result information, when result information is obtained from the certification device indicating a certification result, and based on whether or not the identification information is stored in the storage portion, when the result information is not obtained, and a registration portion that registers the certified identification information in the storage portion, when certification that a user has usage permission is obtained based on the result information.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com