Internet of Vehicles distributed authentication method based on controllable privacy
An authentication method, a technology of the Internet of Vehicles, which is applied in the field of vehicle network communication security, and can solve the problems of not achieving non-repudiation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
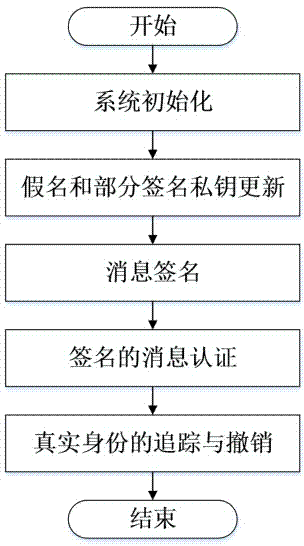
[0048] Such as figure 1 Shown, the present invention has 5 steps altogether, is respectively:
[0049] (1) System initialization: the authority selects public parameters and registers RSU and vehicles;
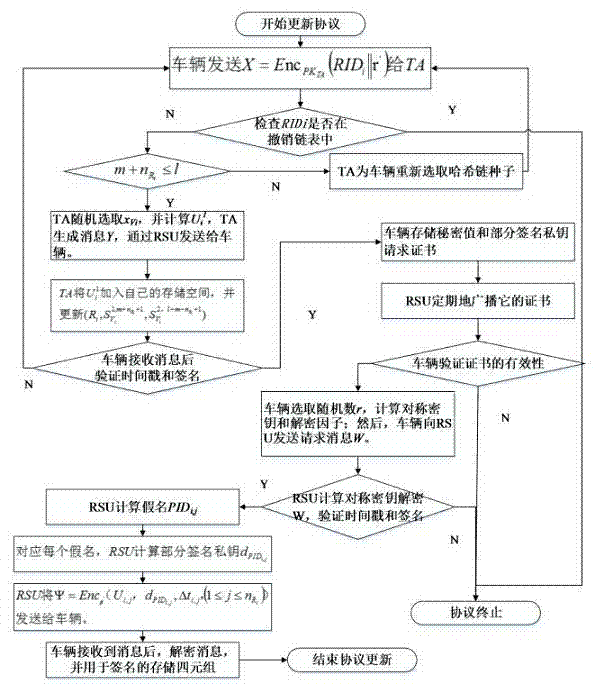
[0050] (2) Pseudonym and partial signature private key update: the authority authenticates the identity of the vehicle, issues a signature private key request certificate for the vehicle, and the vehicle obtains a batch of corresponding signature private keys from the RSU according to the signature private key request certificate;
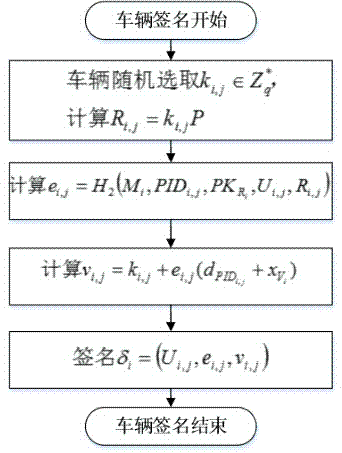
[0051] (3) Message signature: the vehicle uses the secret value issued by the authority and the signature private key obtained from the RSU to sign the message;
[0052] (4) Signed message authentication: The vehicle authenticates the signed message according to the received signed message sent by other vehicles;
[0053] (5) Tracking and revocation of the real identity: when the signed message is disputed, the authority will track the real ident...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com