Patents
Literature
29200 results about "Operational system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An operational system is a term used in data warehousing to refer to a system that is used to process the day-to-day transactions of an organization. These systems are designed in a manner that processing of day-to-day transactions is performed efficiently and the integrity of the transactional data is preserved.
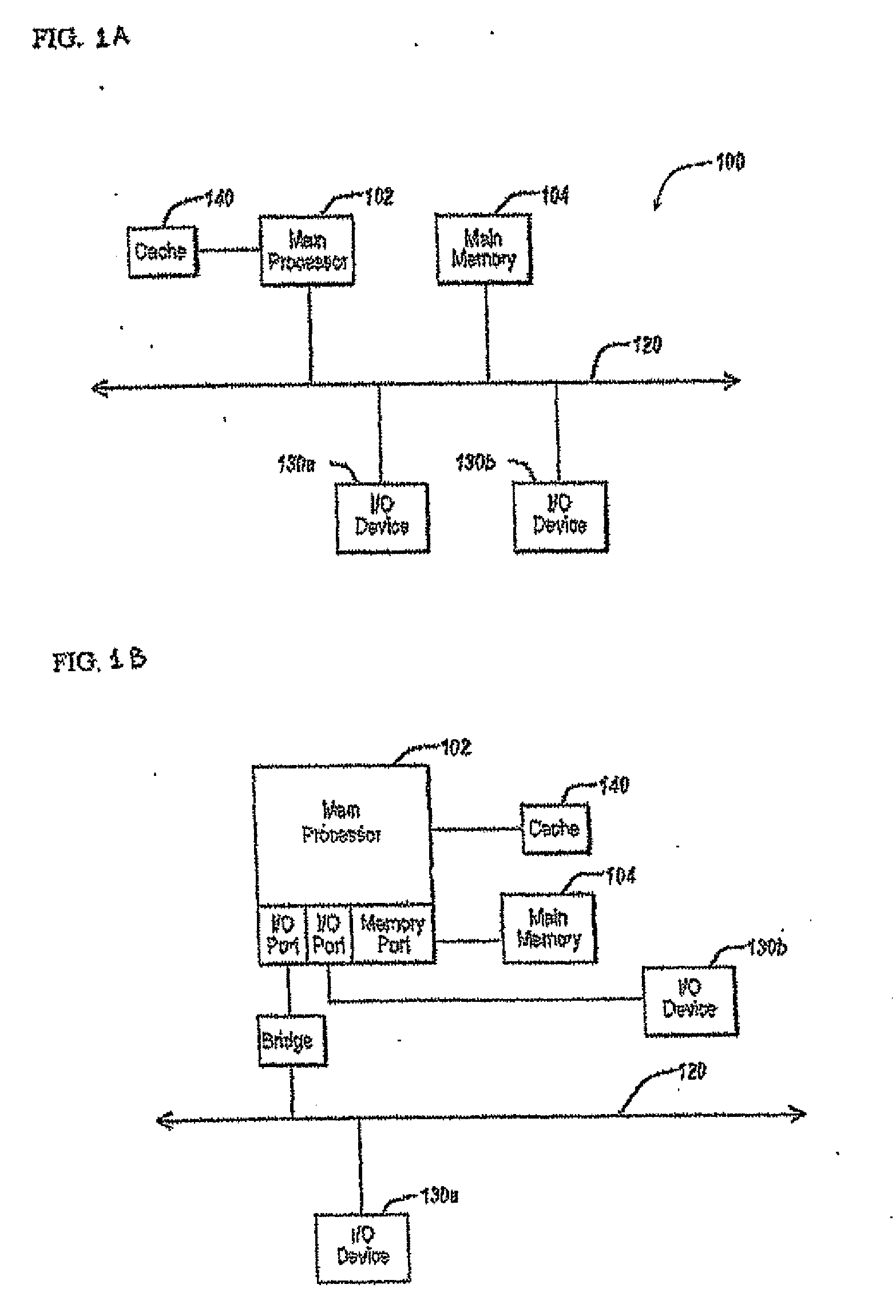
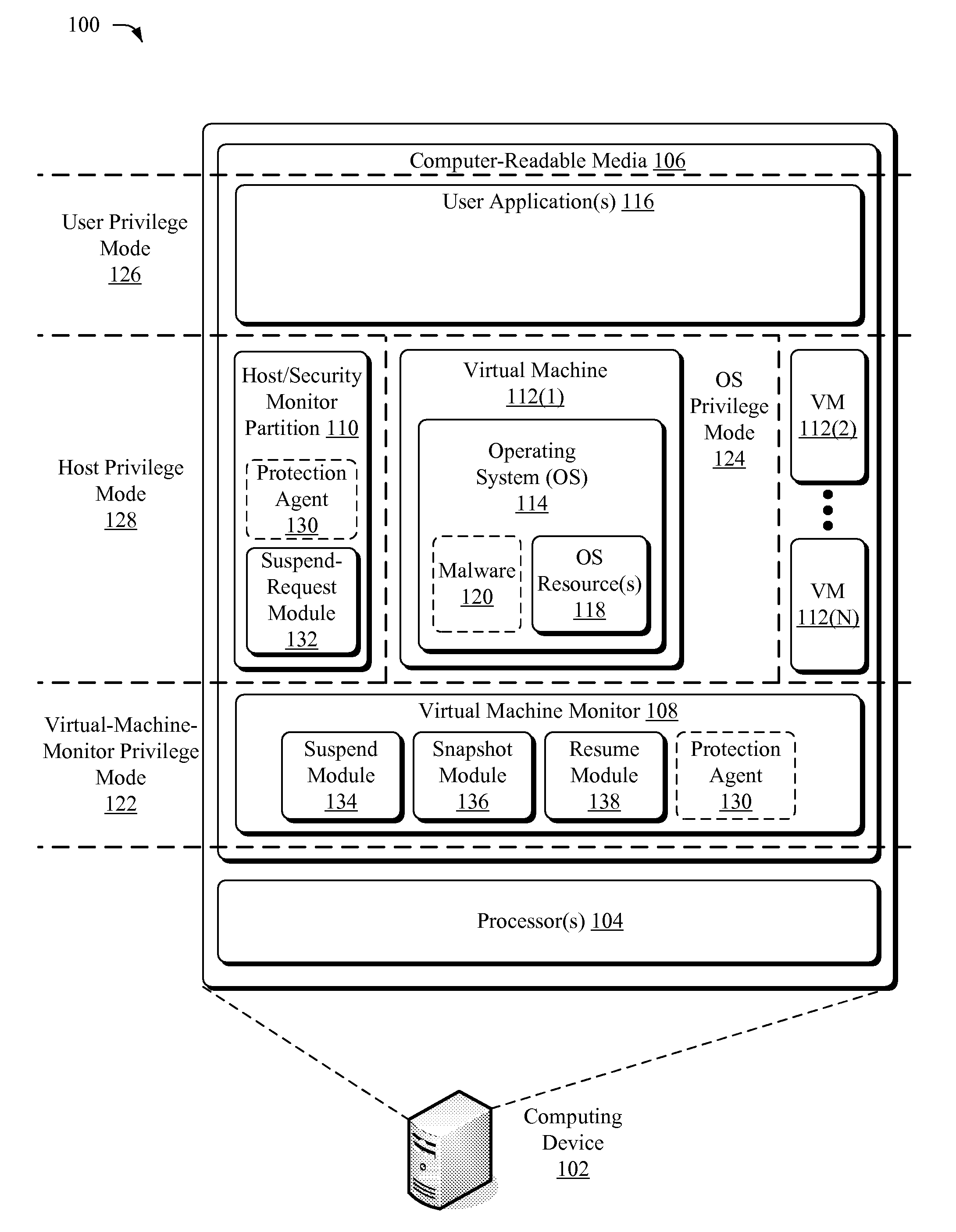
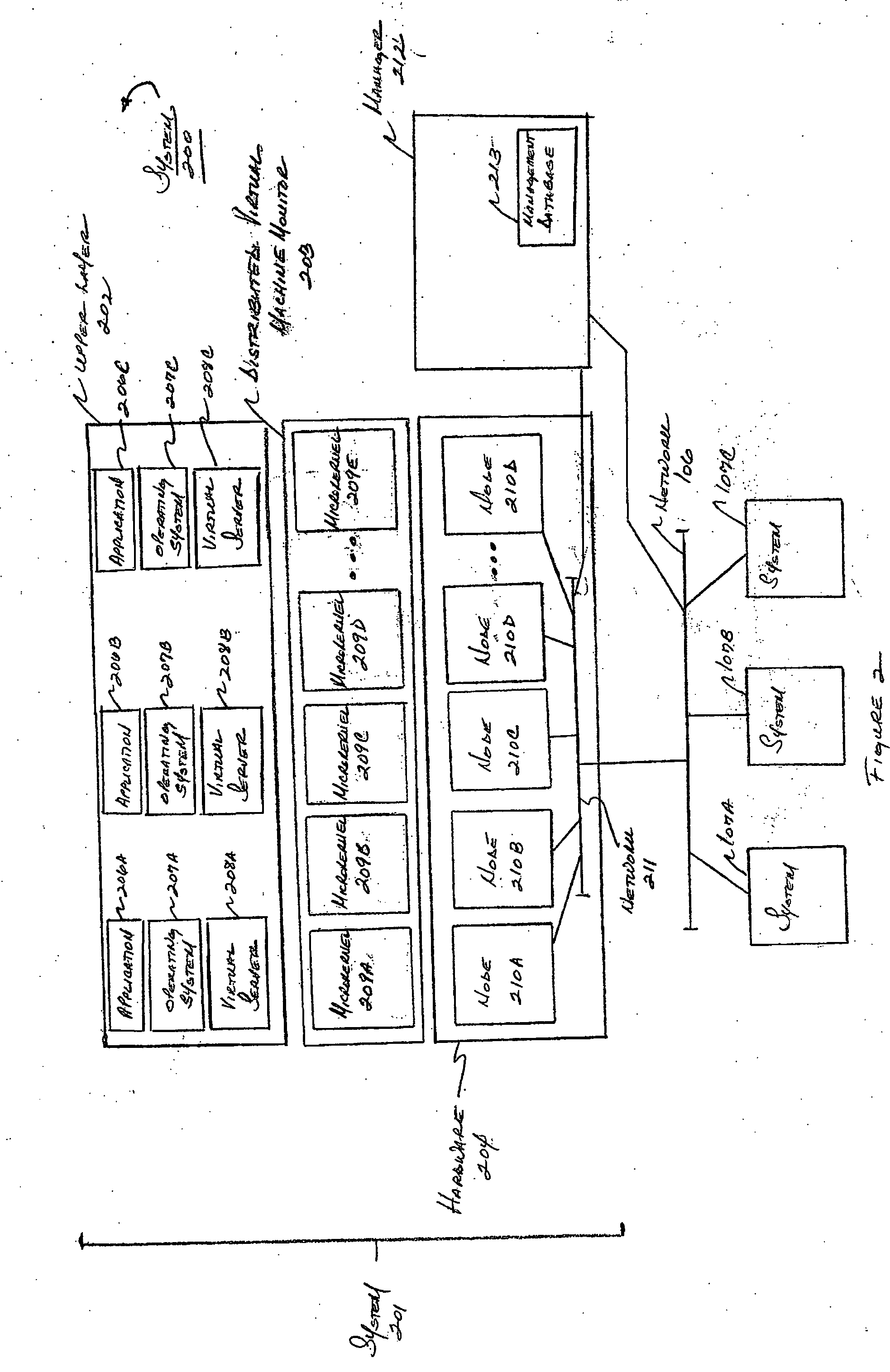
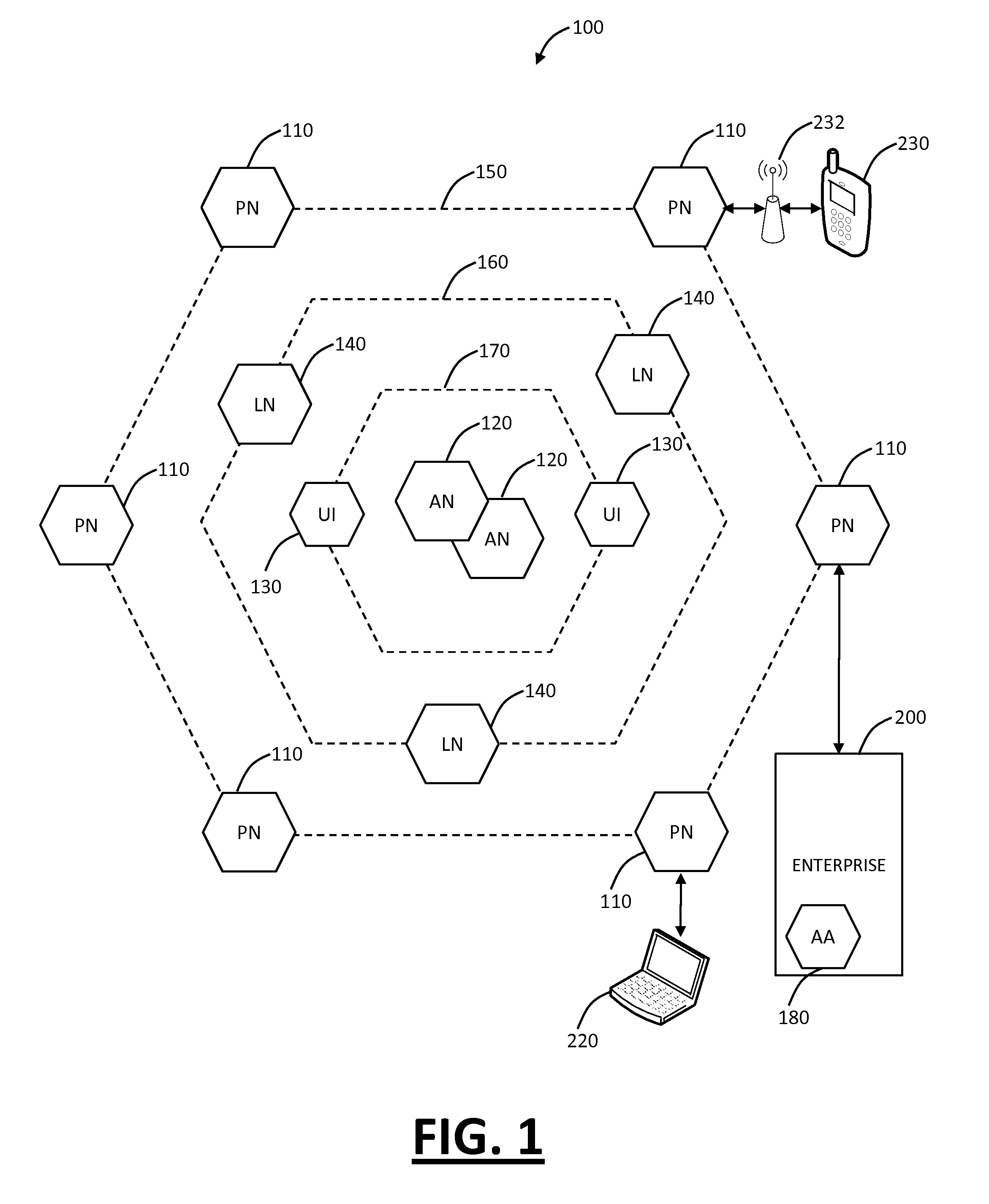
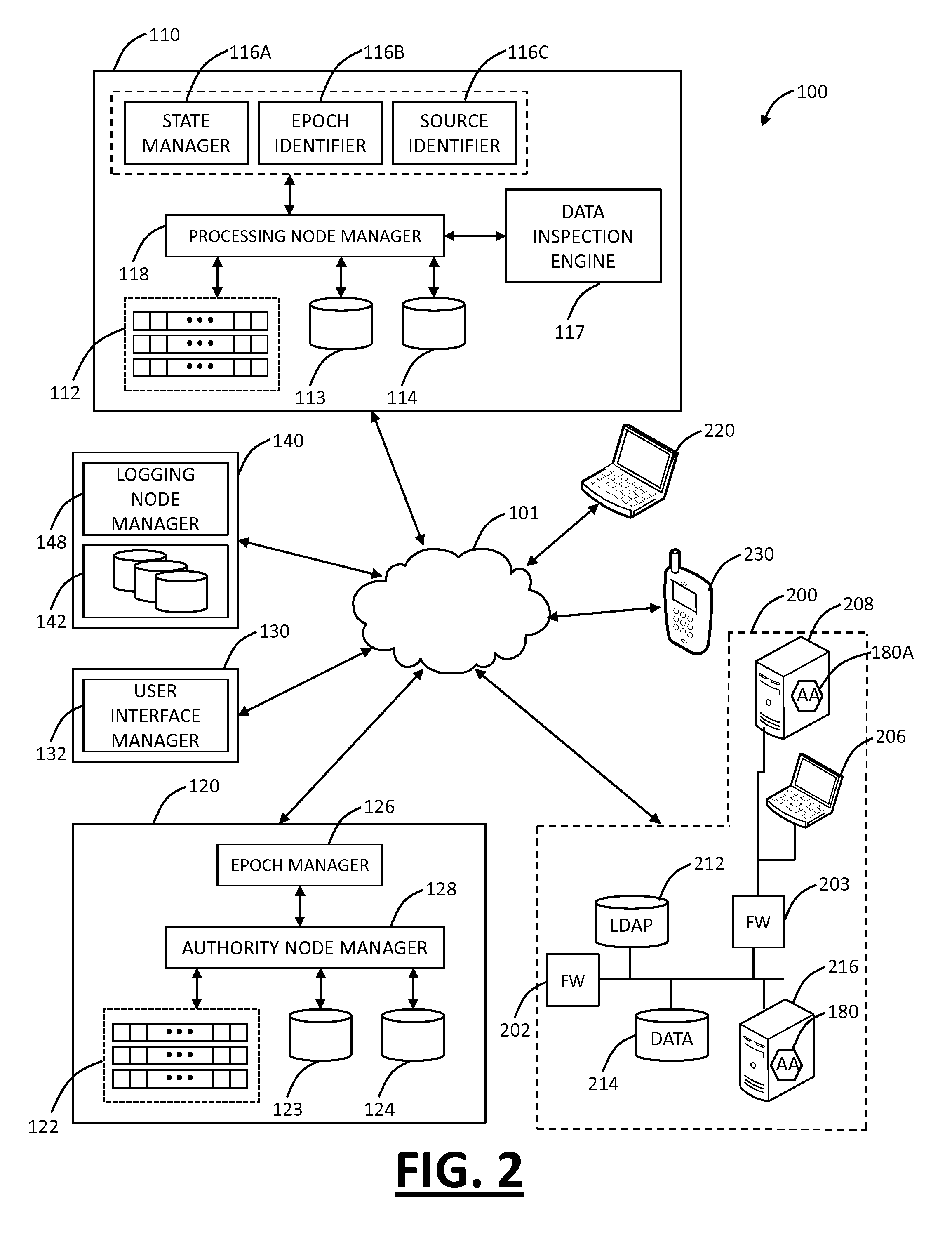
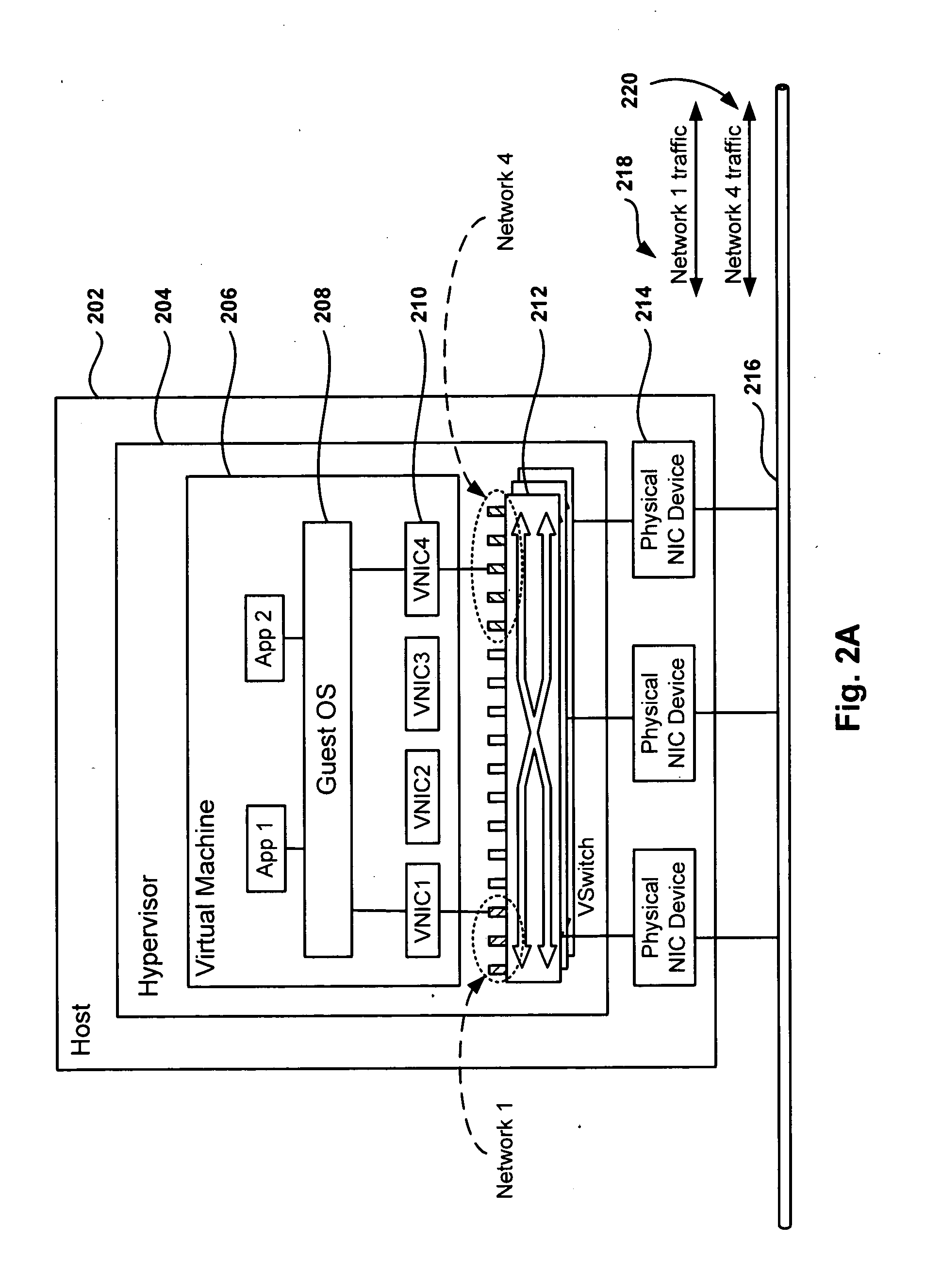
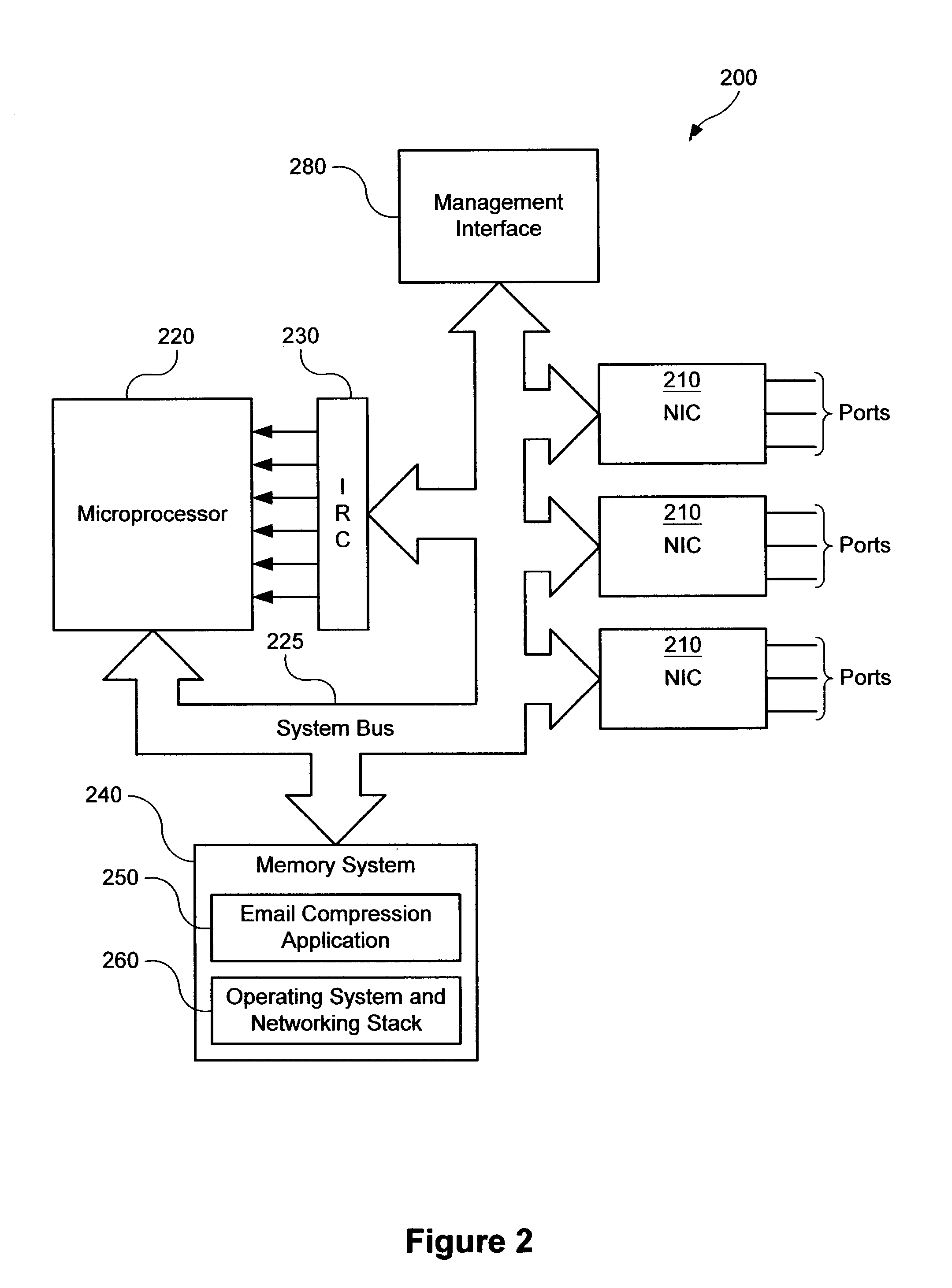
System and method for managing virtual servers
ActiveUS20050120160A1Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemPrimitive state
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes. A virtual computing platform is provided that allows for the creation, deletion, modification, control (e.g., start, stop, suspend, resume) and status (i.e., events) of the virtual servers which execute on the virtual computing platform and the management capability provides controls for these functions. In a particular example, such a platform allows the number and type of virtual resources consumed by a virtual server to be scaled up or down when the virtual server is running. For instance, an administrator may scale a virtual server manually or may define one or more policies that automatically scale a virtual server. Further, using the management API, a virtual server can monitor itself and can scale itself up or down depending on its need for processing, memory and I / O resources. For example, a virtual server may monitor its CPU utilization and invoke controls through the management API to allocate a new processor for itself when its utilization exceeds a specific threshold. Conversely, a virtual server may scale down its processor count when its utilization falls. Policies can be used to execute one or more management controls. More specifically, a management capability is provided that allows policies to be defined using management object's properties, events and / or method results. A management policy may also incorporate external data (e.g., an external event) in its definition. A policy may be triggered, causing the management server or other computing entity to execute an action. An action may utilize one or more management controls. In addition, an action may access external capabilities such as sending notification e-mail or sending a text message to a telephone paging system. Further, management capability controls may be executed using a discrete transaction referred to as a “job.” A series of management controls may be assembled into a job using one or management interfaces. Errors that occur when a job is executed may cause the job to be rolled back, allowing affected virtual servers to return to their original state.
Owner:ORACLE INT CORP
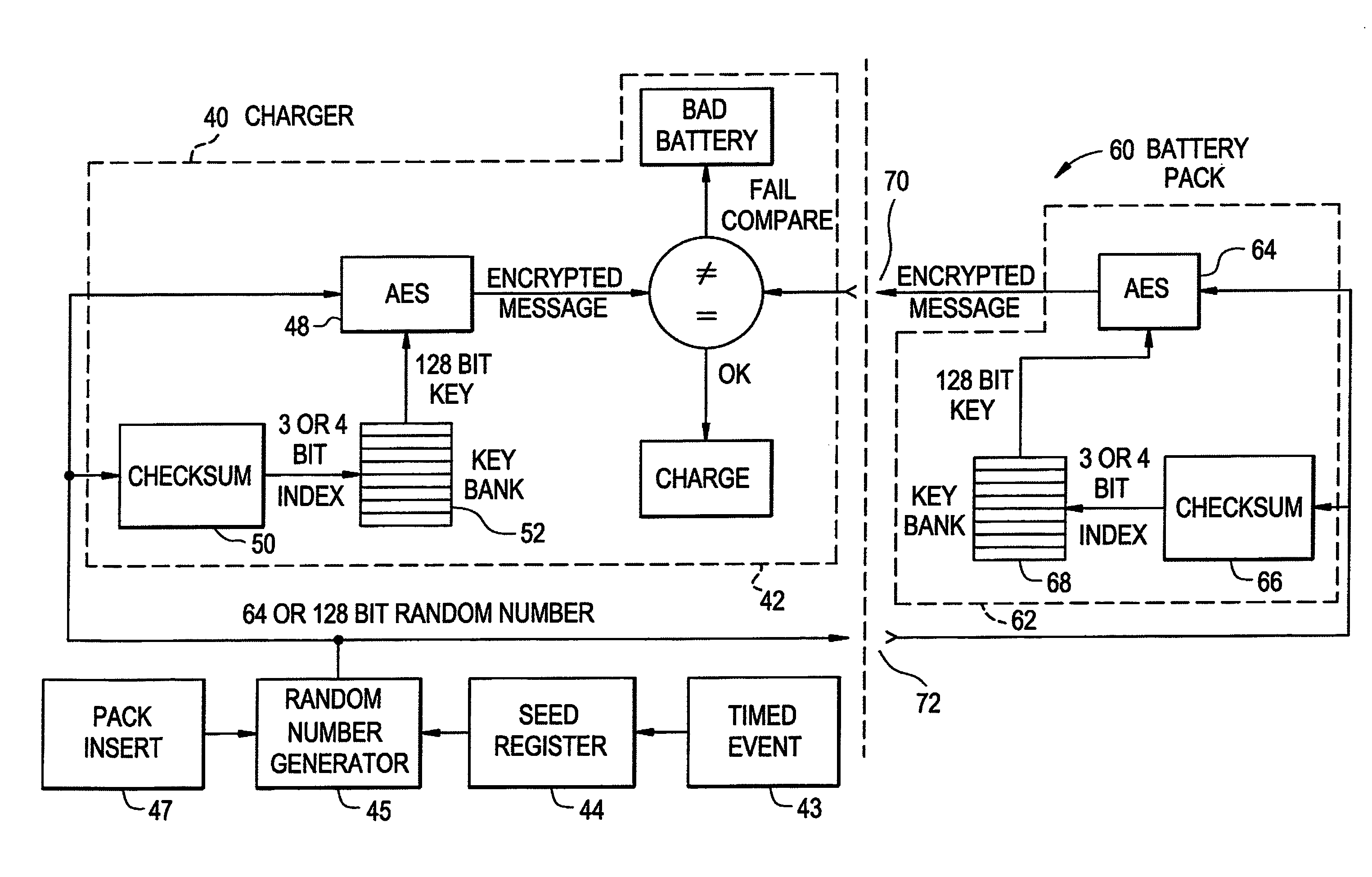
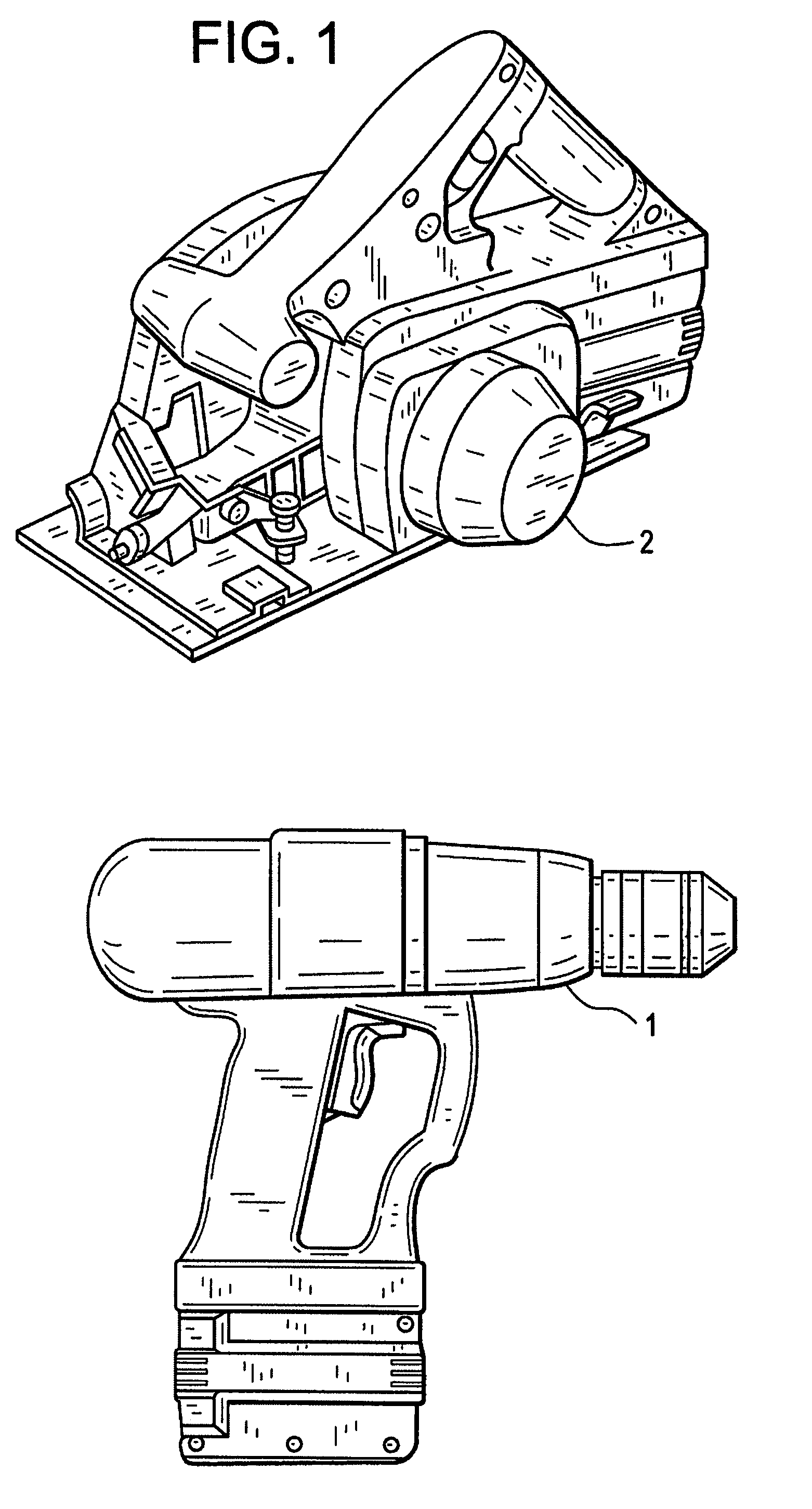
Rechargeable battery pack and operating system
InactiveUS7941865B2Data stream serial/continuous modificationVolume/mass flow measurementOperational systemData stream
A method and system for authenticating a smart battery having a smart battery and an electronic device. Both the device and the smart battery generate encrypted random strings using key material based by A / D noise bits as a seed value. A pseudo random number is generated from the A / D noise that is transmitted to both the electronic device and the smart battery. The pseudo random number is used by both devices as a key index to select one of a plurality of keys stored in separate key libraries. The keys, or key material, is used to execute an encryption algorithm. The two encryption data streams are then compared to authenticate the smart battery.
Owner:BLACK & DECKER INC
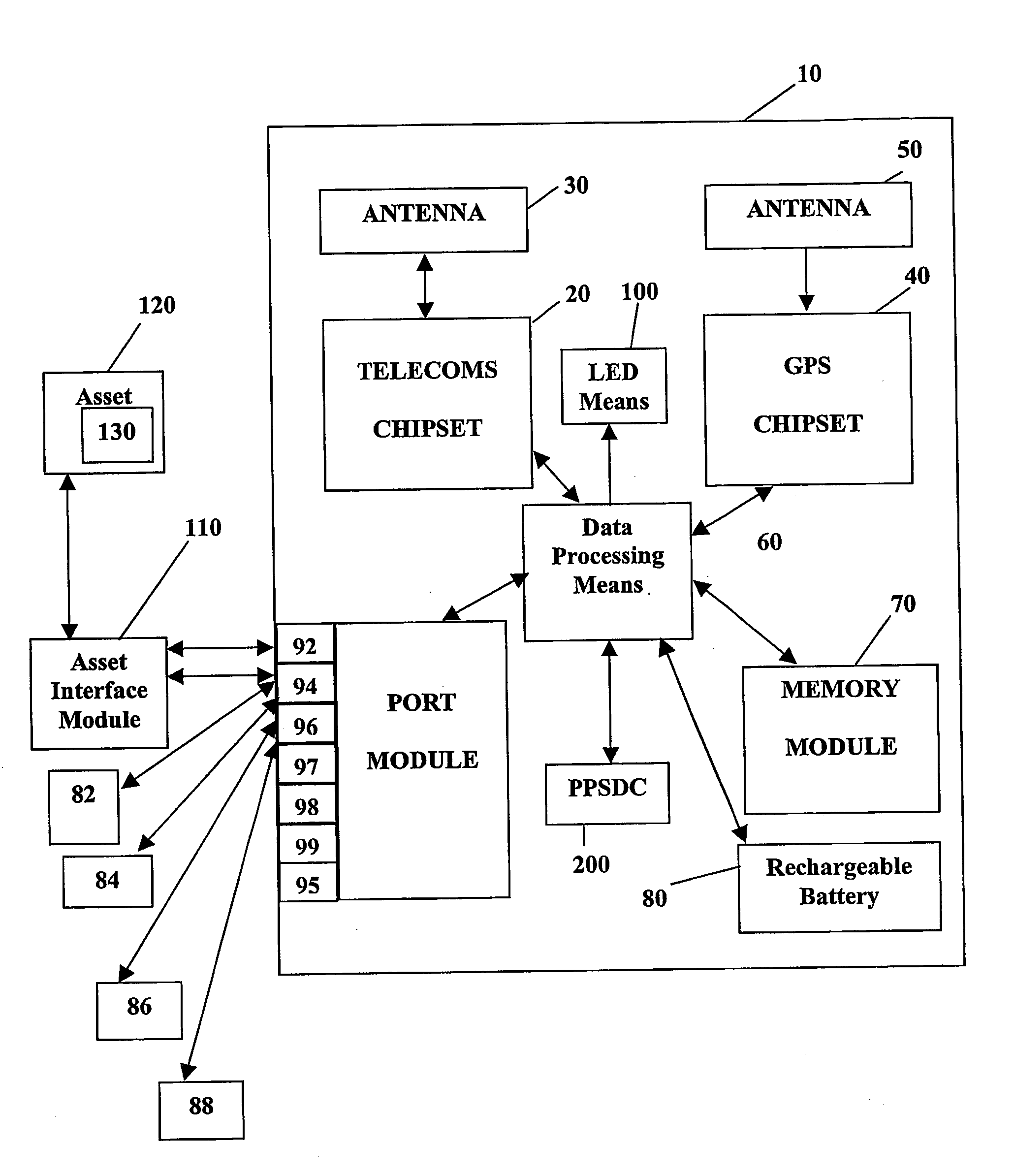
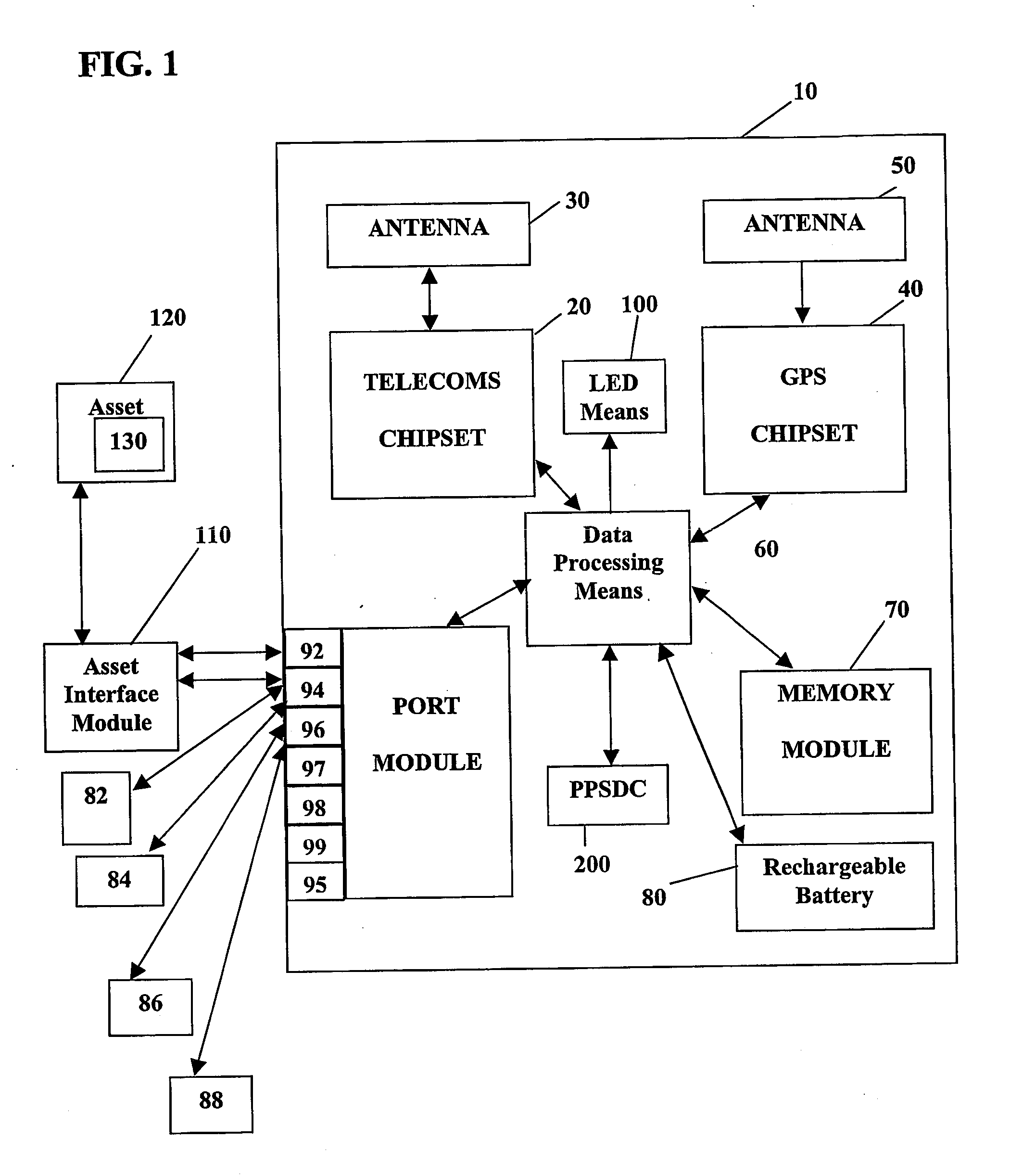
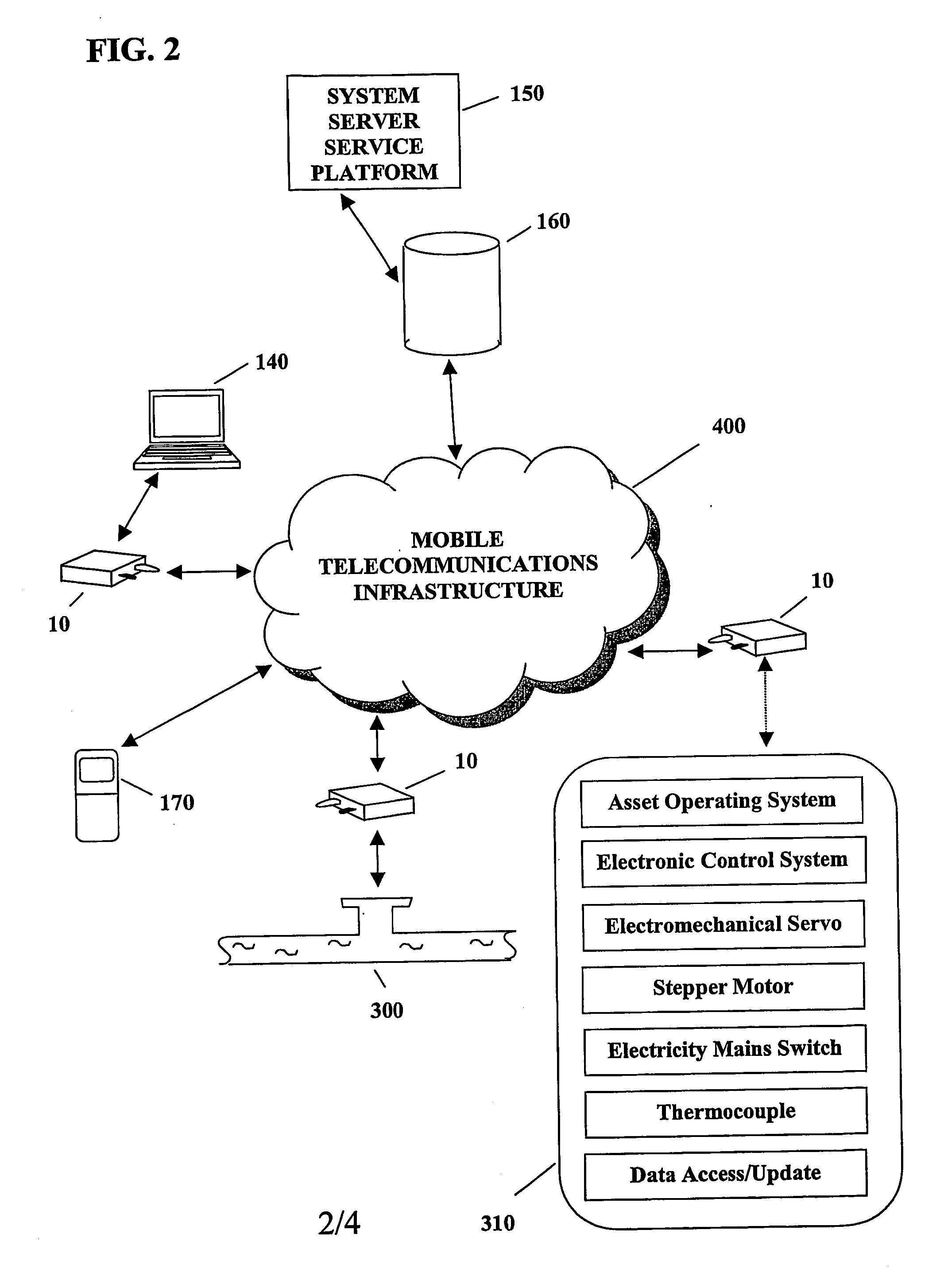
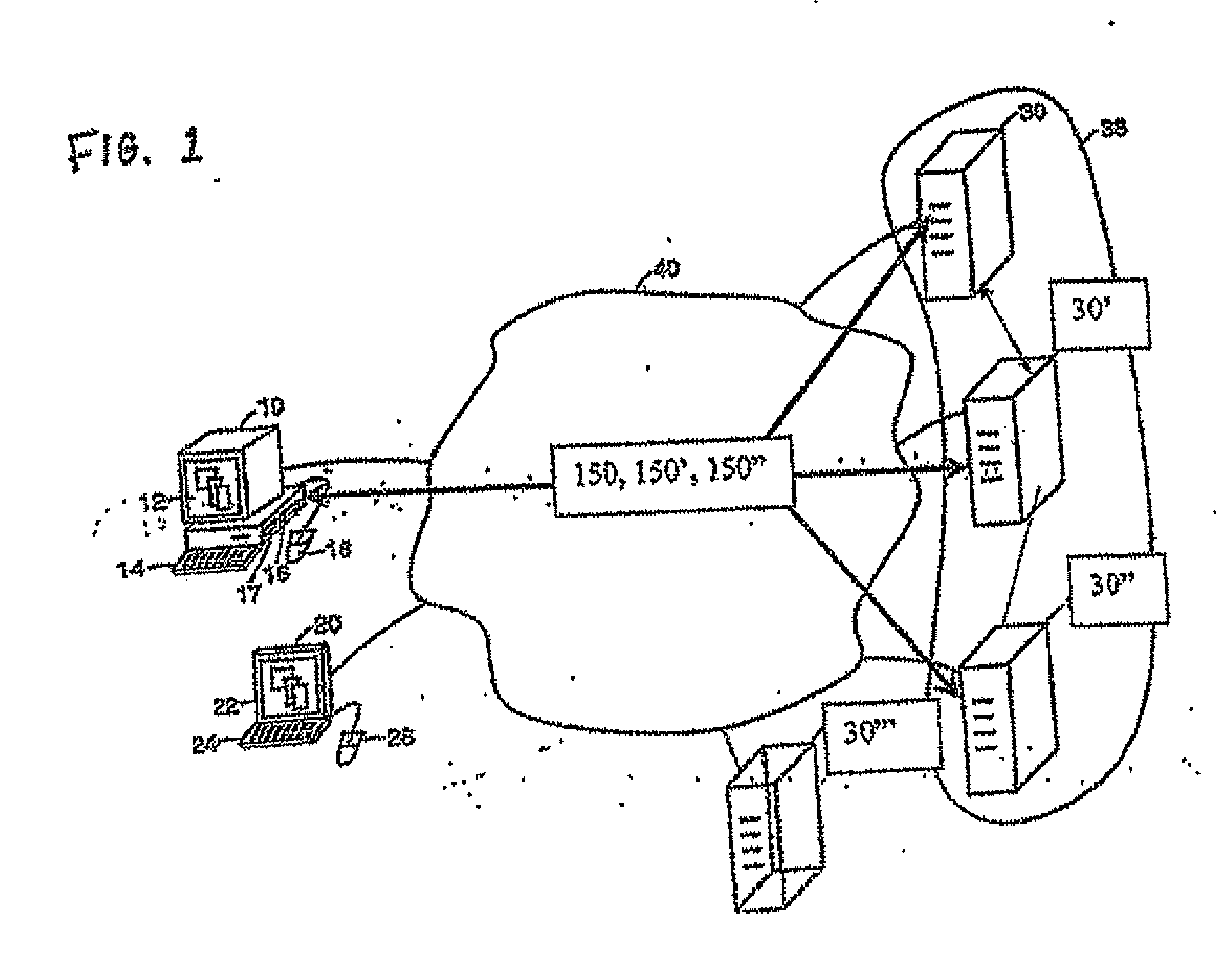
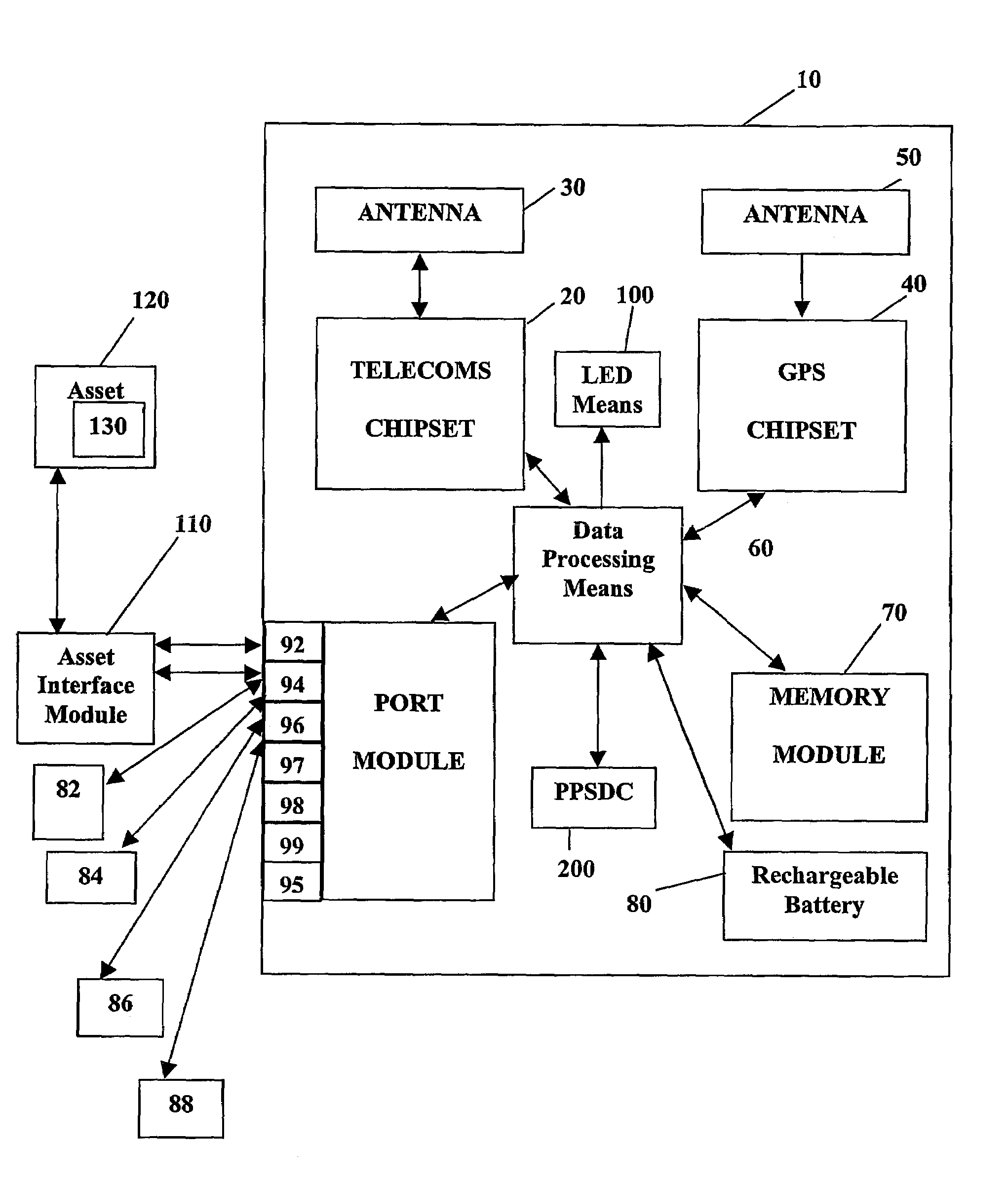
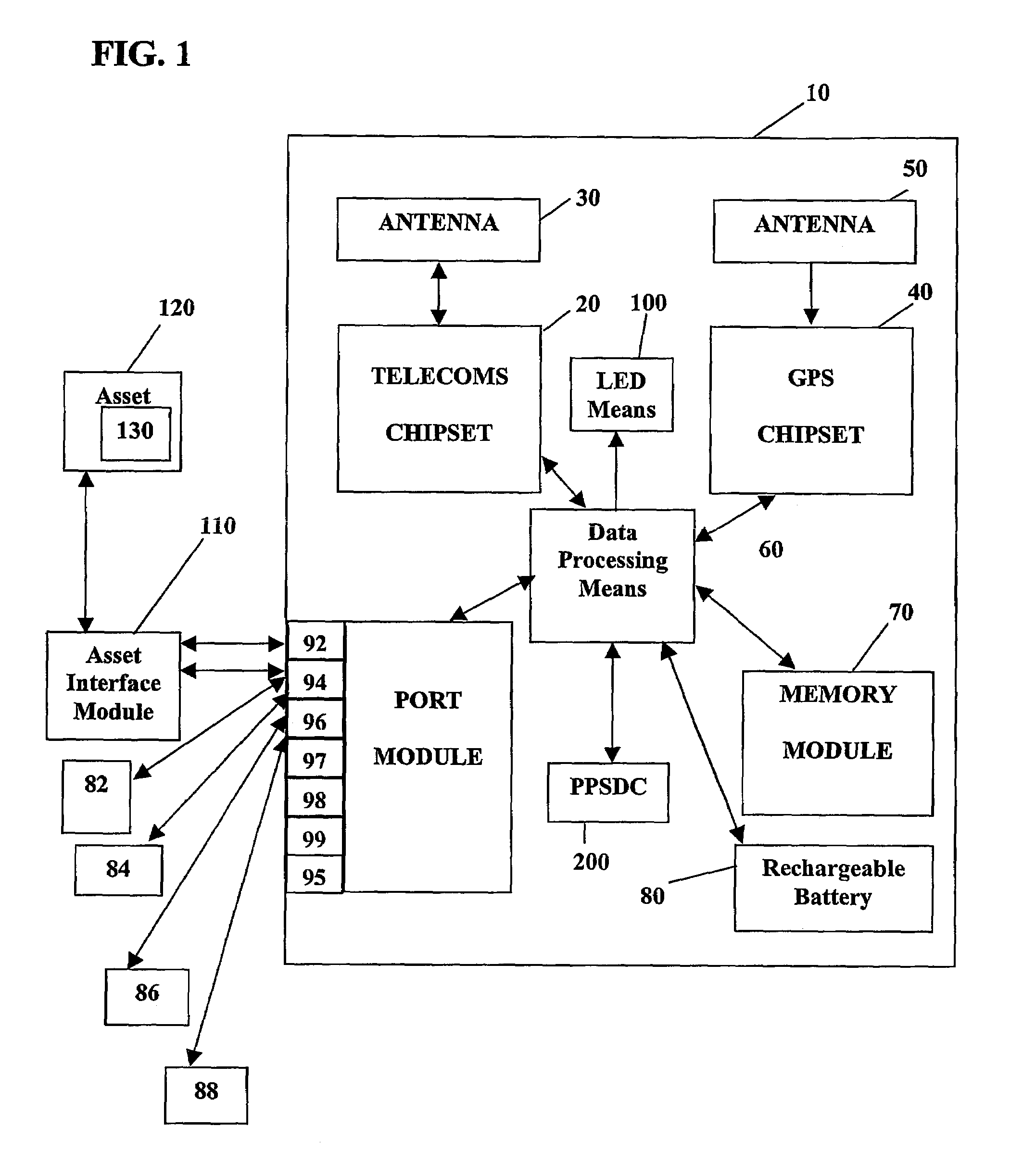
System and method for monitoring and control of wireless modules linked to assets
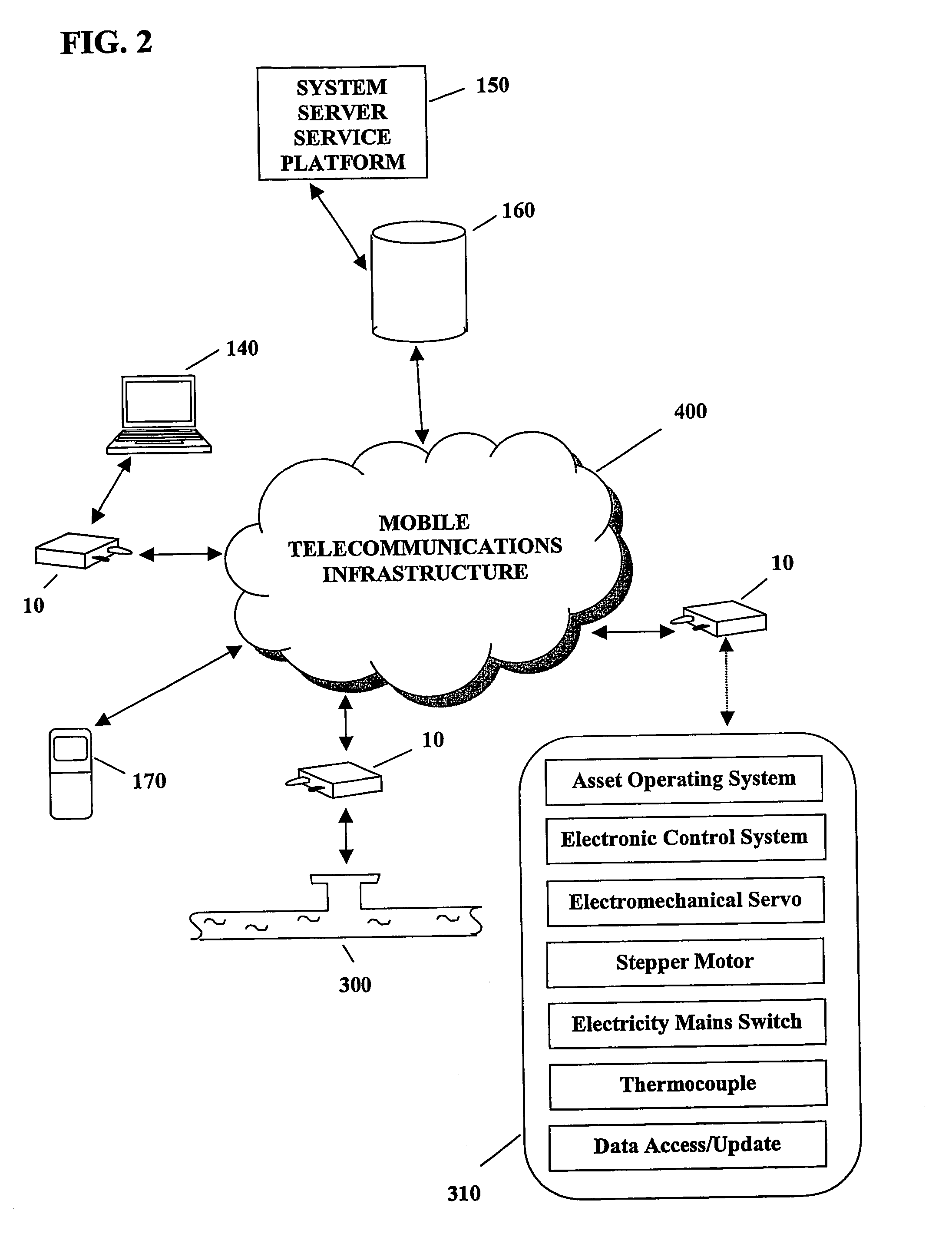
A system and method for remote asset management is described which can provide the basis for a diverse product group including an improved remote location monitoring system, a means for communicating with and for monitoring the status and or location of a plurality of diverse assets, as well as the means for communicating with said assets for the purpose of modifying the operational status of one or more of said assets according to one or more stored data parameters such as location, use, battery power, and such like. The remote asset management system comprise a wireless module, which is associated with at least one of the plurality of assets and which is interfaced with the operating system of said asset and or with an electromechanical control means, which may control one or more features of the operation of said assets. A supporting network-based, or internet-based service platform controls and manages the status of each of the plurality of assets, either automatically, or in response to received messages from fixed or wireless communication devices, and which is capable of selectively communicating data to said assets for changing the operational status of said assets according to pre-programmed conditions.
Owner:M2M SOLUTIONS
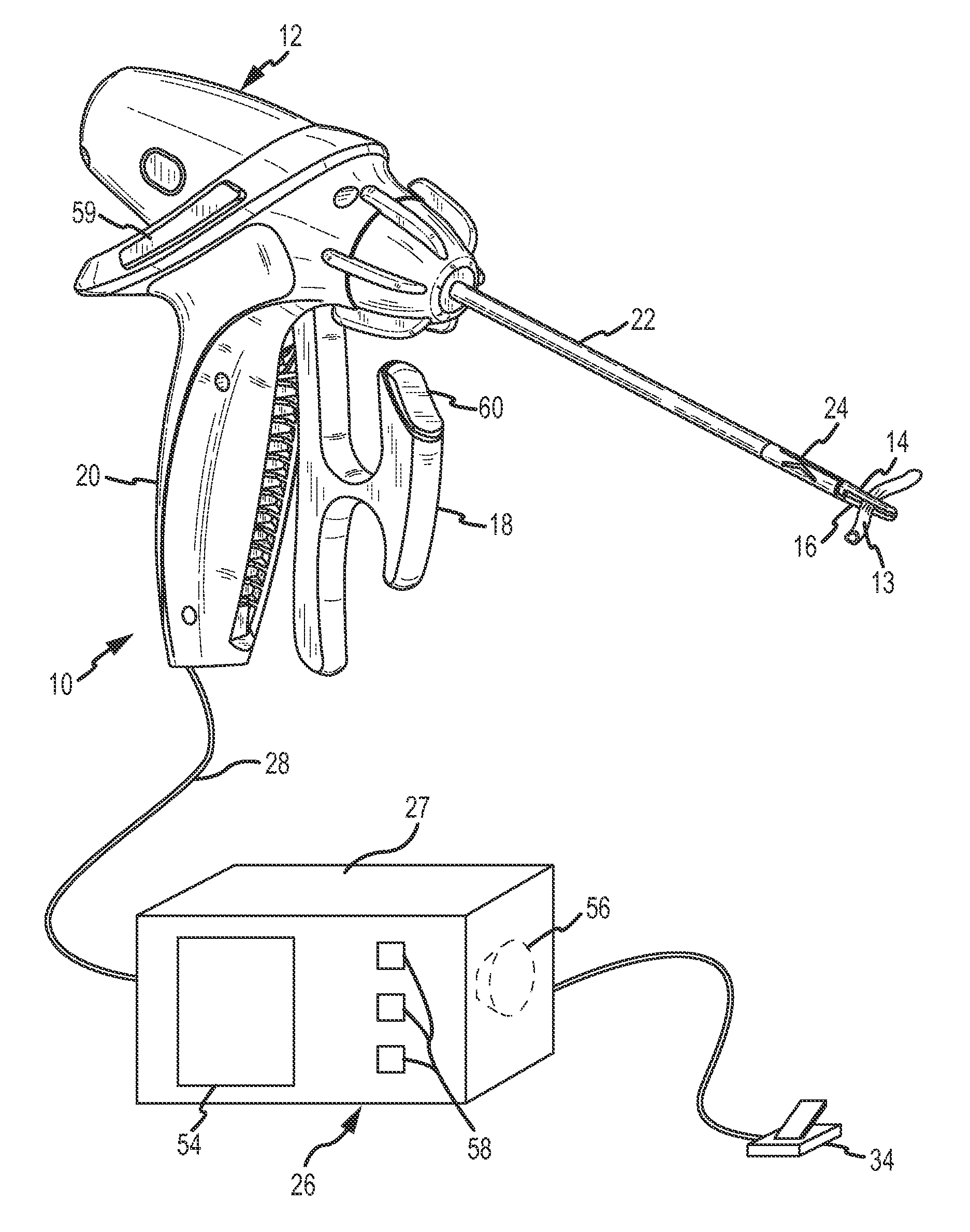
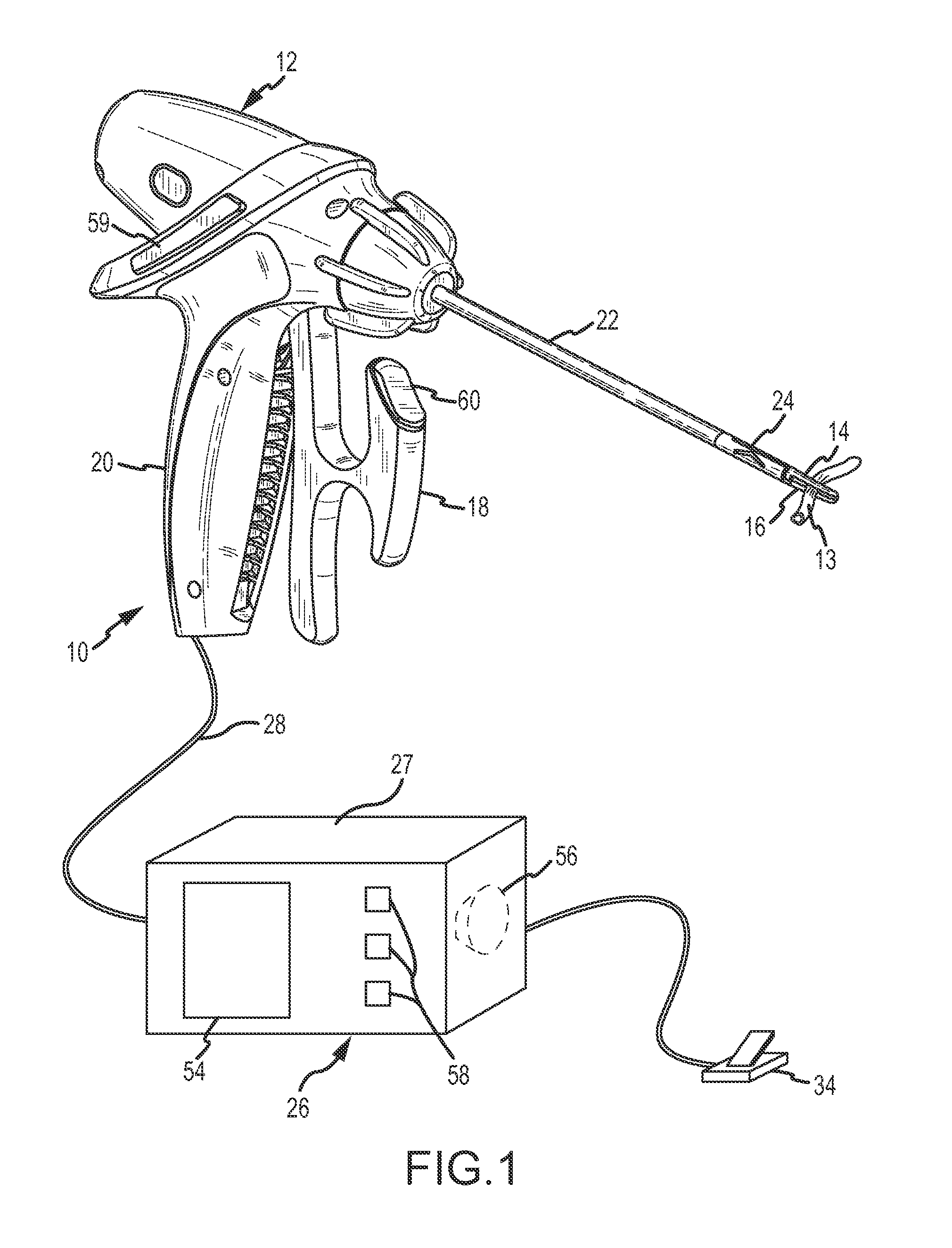
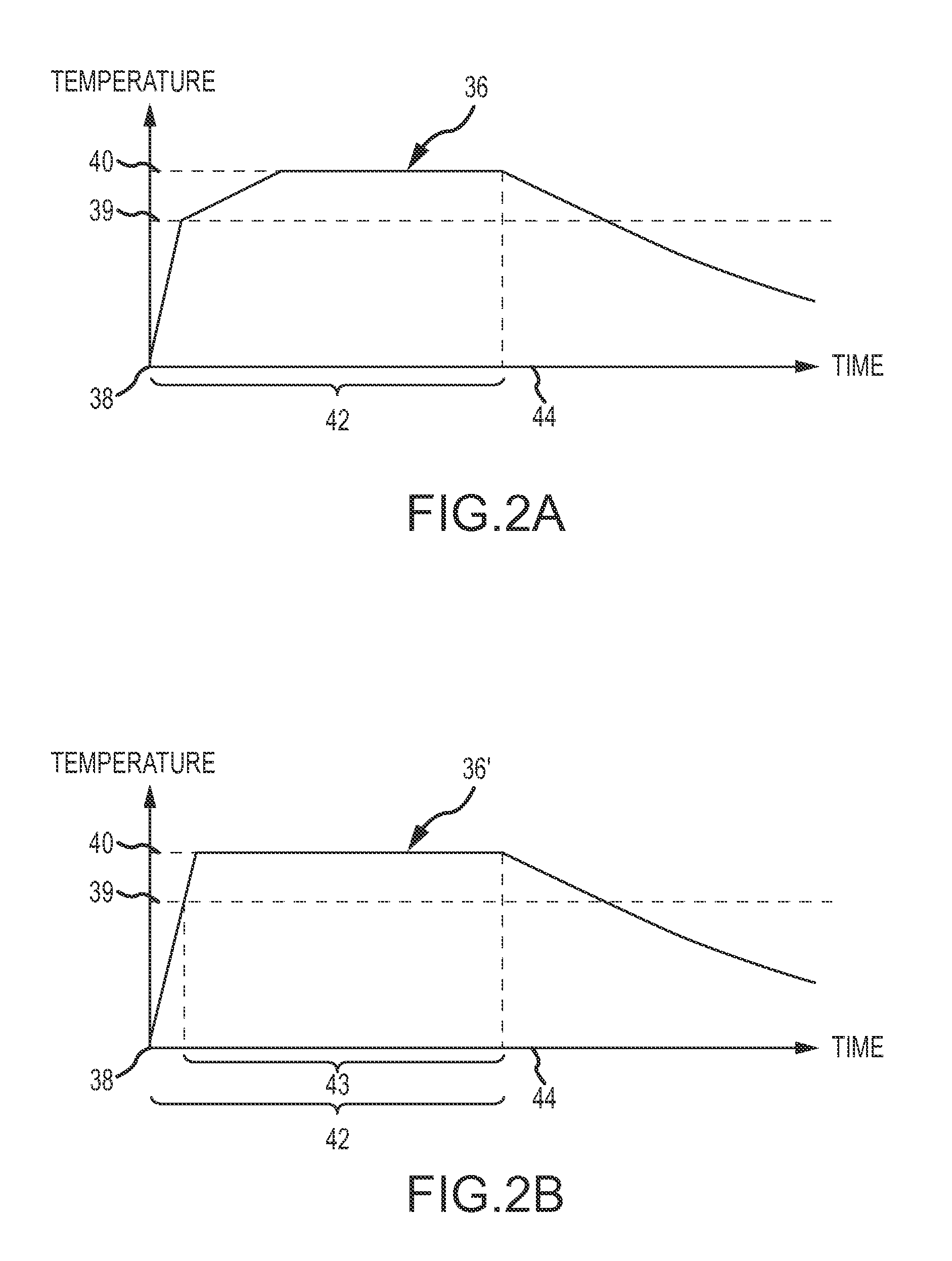
Tissue fusion system and method of performing a functional verification test
InactiveUS8840609B2Reduce traumaProlong surgery timeSurgical instruments for heatingSurgical forcepsElectrical resistance and conductanceOperational system
A jaw heating element of a handpiece of a thermal tissue operating system is tested on an ongoing basis by supplying a test heater power signal to the jaw heating element between individual thermal tissue operations. Voltage and current through the jaw heating element is sensed and the resistance of the jaw heating element is calculated. If the calculated resistance is outside a range of predetermined acceptable values, an error condition is indicated.
Owner:CONMED CORP
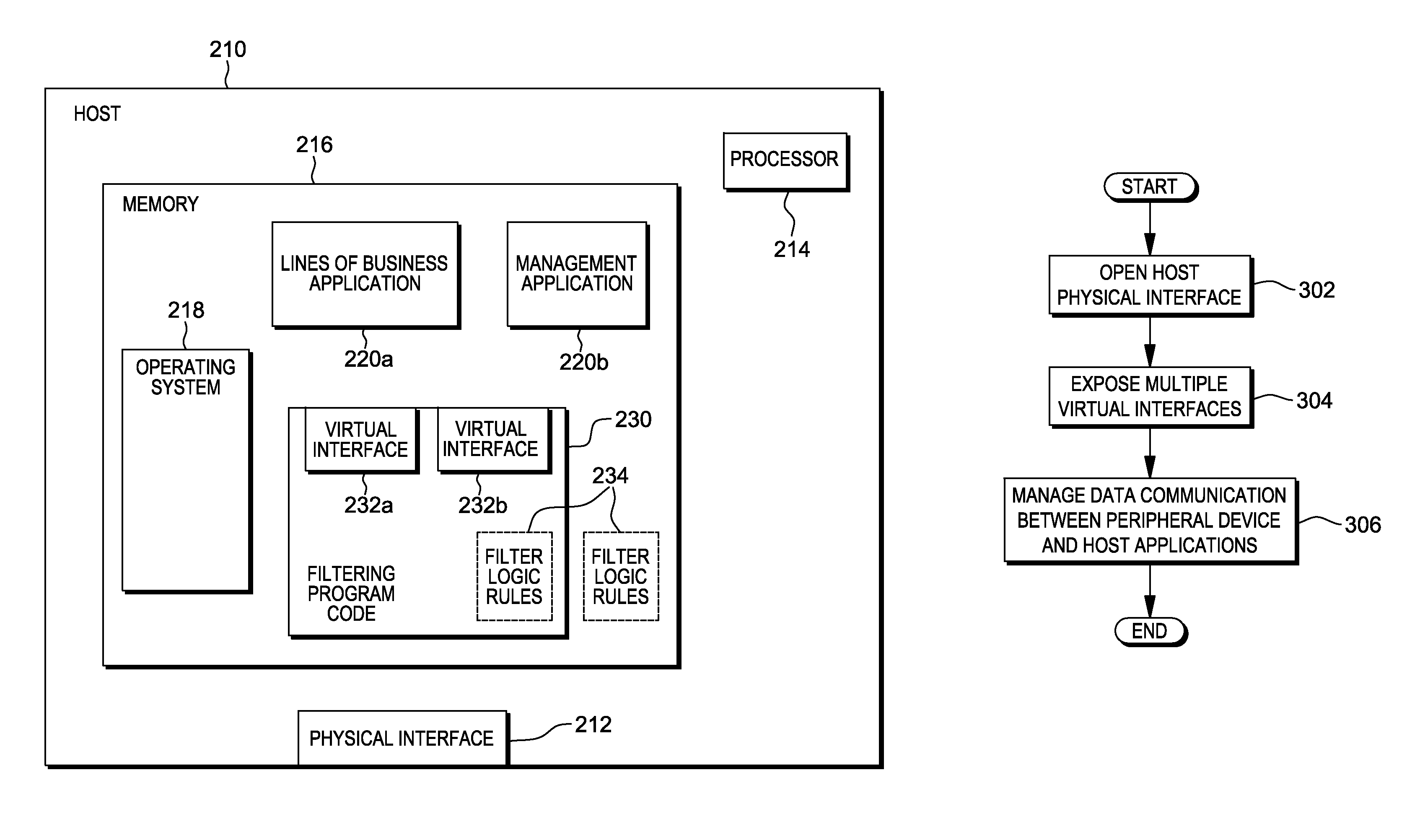
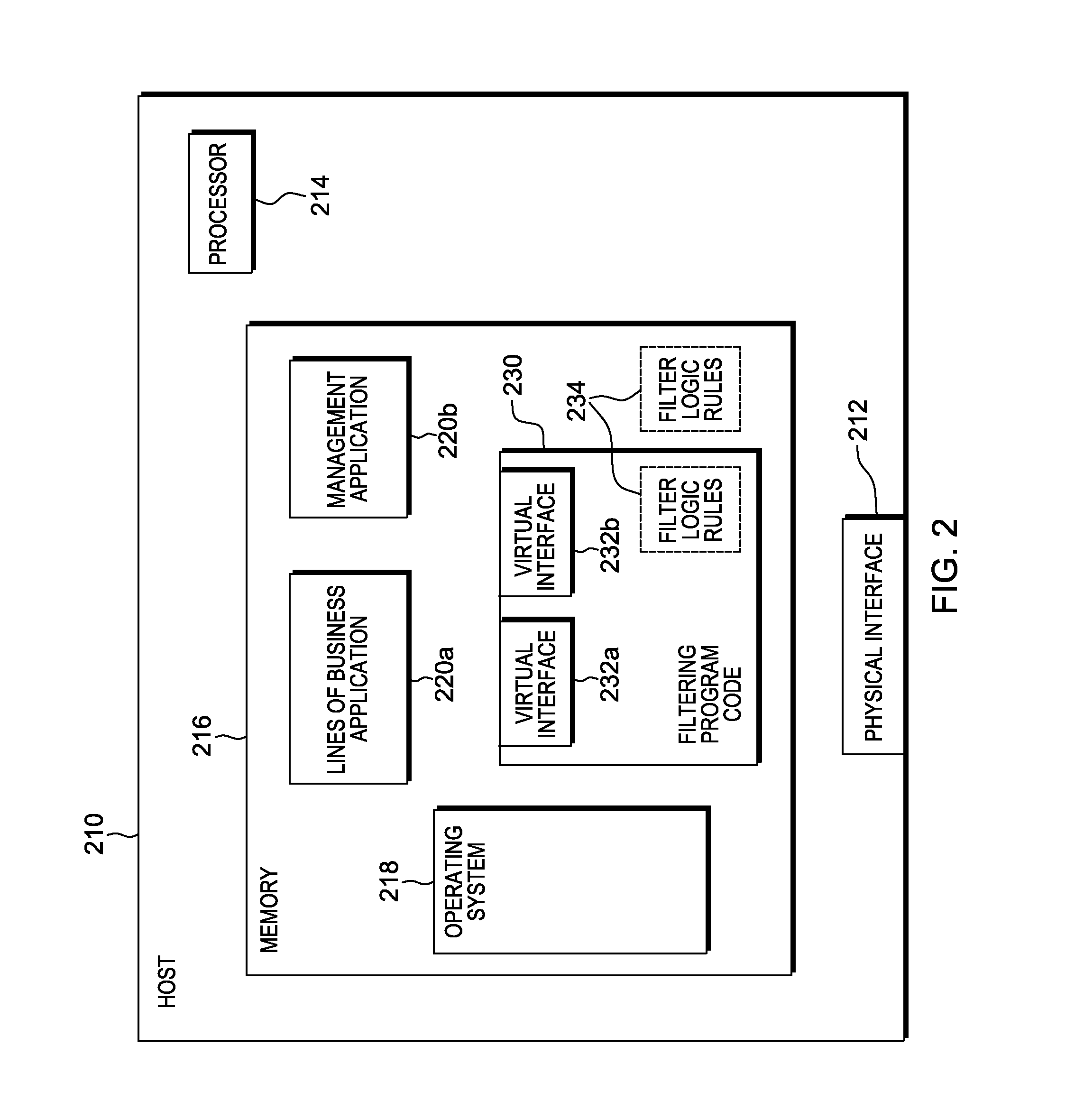
Device management using virtual interfaces
ActiveUS8621123B2Program controlInput/output processes for data processingOperational systemComputerized system
Management of data communication between a peripheral device and host computer system is provided. A physical interface for communicating data between a peripheral device and applications executing on the host is opened and controlled by a software module. First and second virtual interfaces of the software module are exposed to an operating system of the host, and the operating system exposes the first and second virtual interfaces to a first application and a second application executing on the host. The first virtual interface is used for communicating data between the peripheral device and the first application through the physical interface, and the second virtual interface is used for communicating data between the peripheral device and the second application through the physical interface. Management of data communication between the peripheral device and the first application and between the peripheral device and the second application is thereby provided.
Owner:HONEYWELL INT INC
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
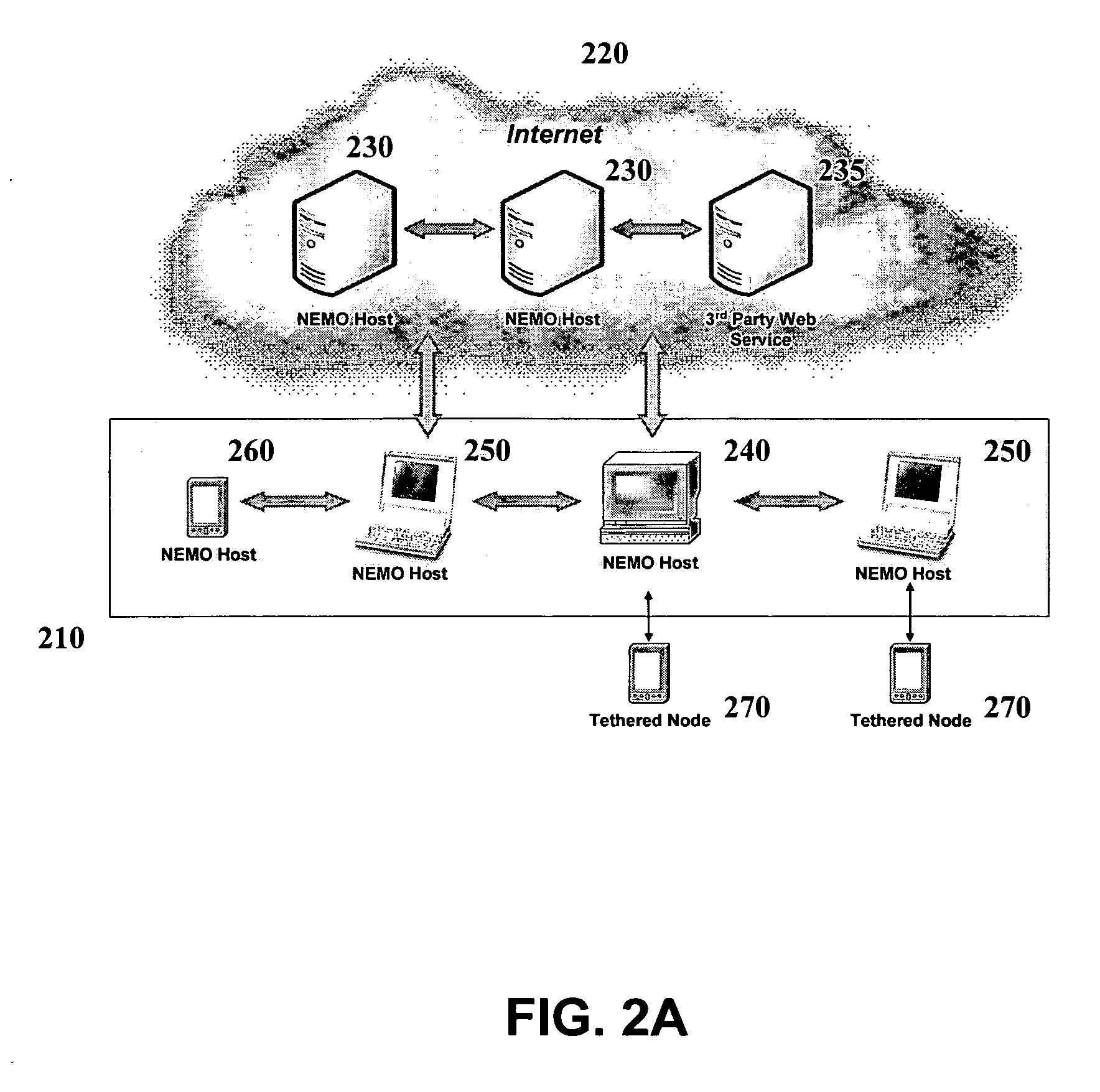
Multi-access terminal with capability for simultaneous connectivity to multiple communication channels
ActiveUS20060193295A1Improve reliabilityImprove behaviorNetwork traffic/resource managementTime-division multiplexTransceiverOperational system
An apparatus is disclosed for permitting a mobile terminal having multiple, heterogeneous network connections (e.g., multiple wired or wireless transceivers of various types) to set up and maintain virtual connections over multiple networks to either the same or to multiple destinations. The mobile terminal can “load-share” traffic, i.e., it can distribute segments of traffic over a full set of heterogeneous networks, significantly improving the reliability and availability of communications. In a first embodiment, a mobile terminal is configured with multiple radio frequency (RF) transceivers. Operating system software is provided for dynamically establishing and maintaining traffic flow for user applications over multiple communications paths, and for automatically adapting to variations in the networking environment, application traffic flow requirements, end user preferences, or mobility. In a second embodiment, a software-defined radio is used to implement the physical layer protocols for each desired network, eliminating the need for multiple transceivers.
Owner:TRUSTEES OF STEVENS INST OF TECH THE
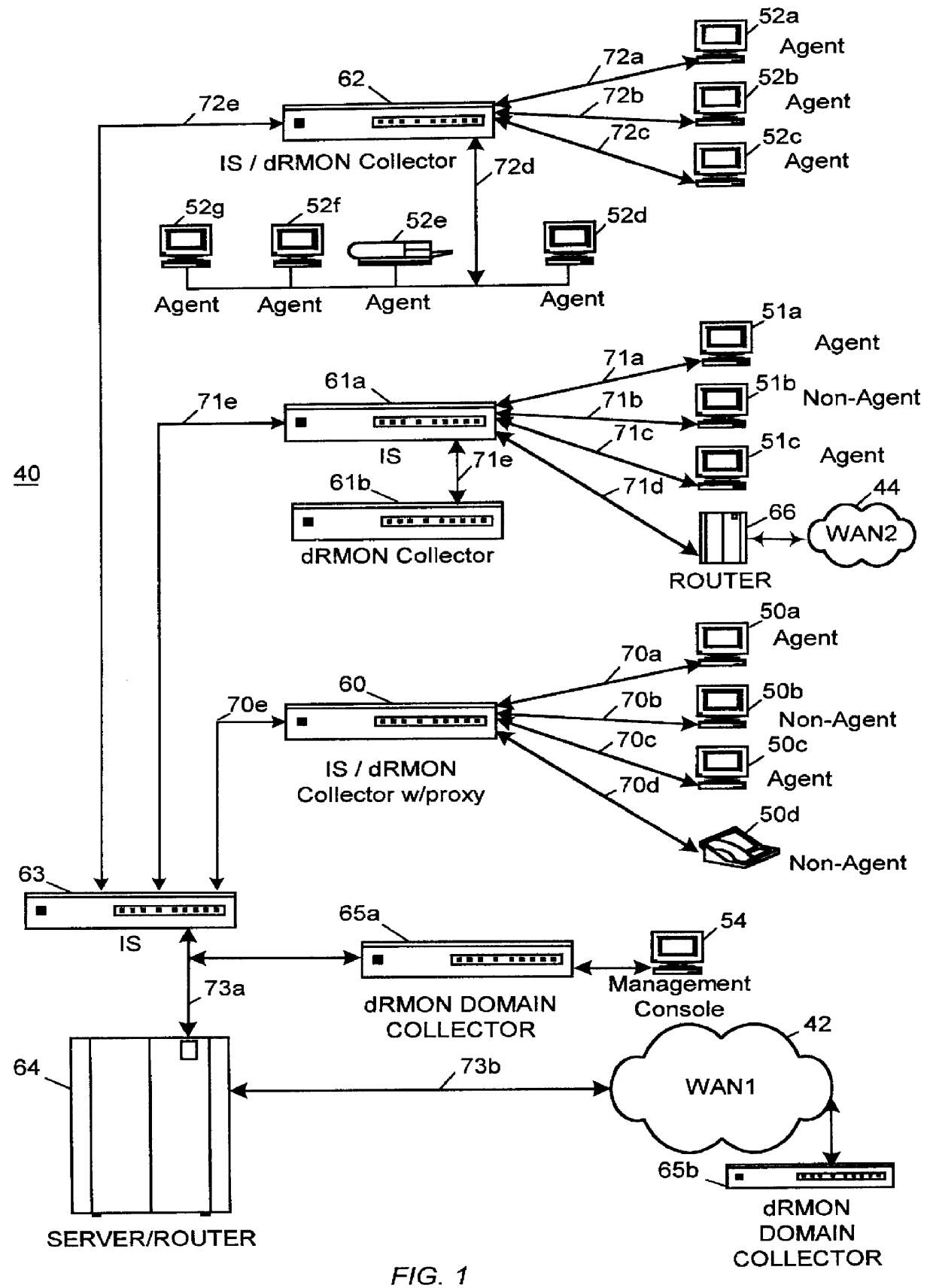
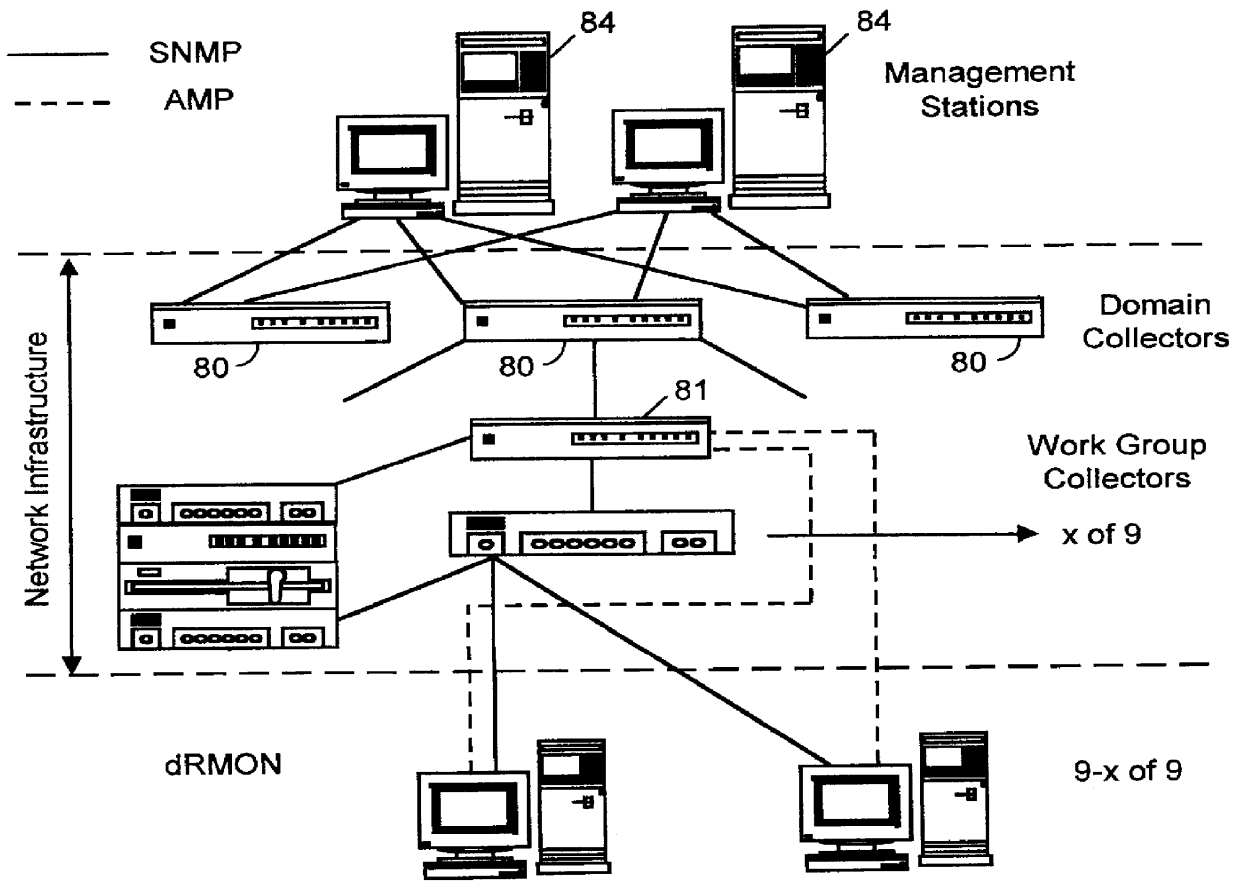
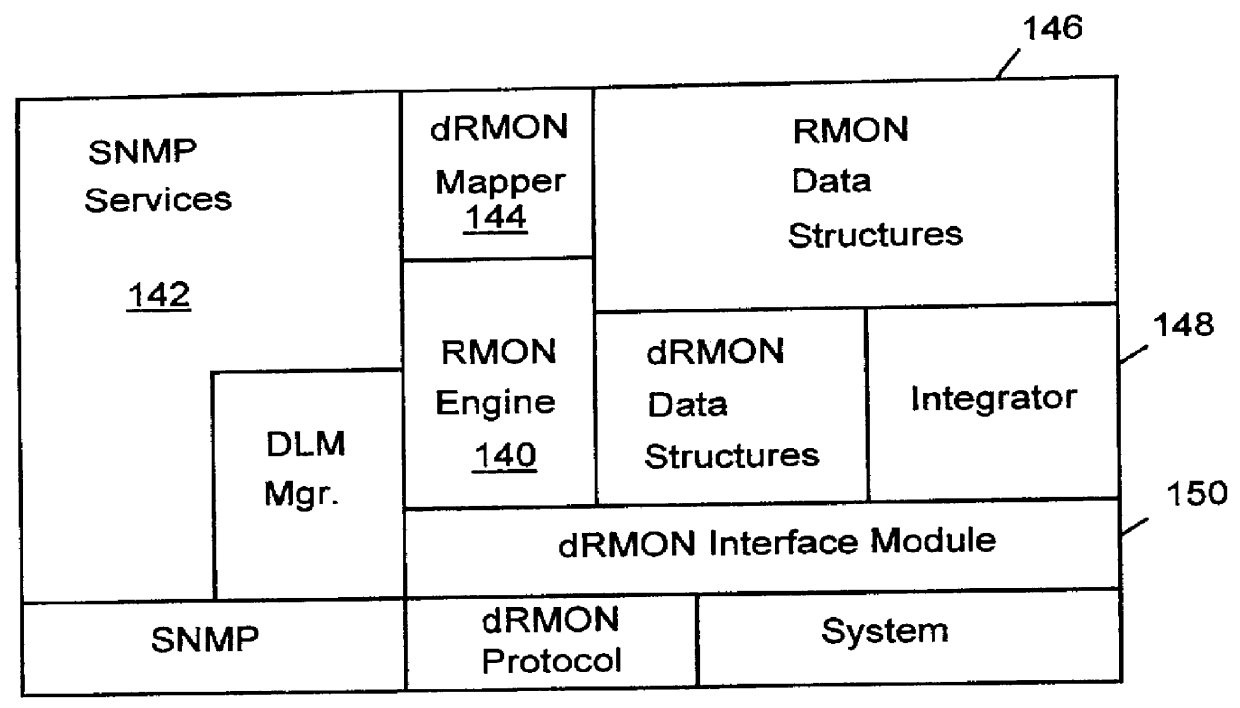
Distributed remote monitoring (dRMON) for networks
InactiveUS6108782AError preventionFrequency-division multiplex detailsNetwork operating systemOperational system
Distributed remote monitoring (dRMON) of network traffic and performance uses distributed nodes to collect traffic statistics at distributed points in the network. These statistics are forwarded to collectors which compile the statistics to create combined views of network performance. A collector may mimic a prior art, non-distributed, network probe and may interact with network management software as though it were a stand alone network probe thereby simplifying a user's interaction with the distributed system. The invention is designed to work in accordance with a variety of standard network management protocols including SNMP, RMON, and RMON2 but is not limited to those environments. The invention has applications in a variety of communication system environments including local area networks, cable television distribution systems, ATM systems, and advanced telephony systems. A specific embodiment of the invention solves is particularly optimized to work in LAN environments with end systems running under Windows-compatible network operating systems.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Methods and systems for interacting, via a hypermedium page, with a virtual machine executing in a terminal services session
ActiveUS20070171921A1Low costReduce difficultyDigital data information retrievalInterprogram communicationHyperlinkClient agent
A method for making a hypermedium page interactive, the hypermedium page displayed by a network browser, includes the step of selecting a hyperlink on the hypermedium page displayed on a client machine, the hyperlink identifying a desired computing resource. A hyperlink configuration file is retrieved, the hyperlink configuration file corresponding to the hyperlink and identifying a server machine. A client agent is started on the client machine. The client agent creates, via a terminal services session, a communication link to a virtual machine executing on the server identified by the hyperlink configuration file, the virtual machine executed by a hypervisor executing in the terminal services session provided by an operating system executing on the server. The client agent receives data from the virtual machine and displays, on the client machine, the received data without intervention by the network browser.
Owner:CITRIX SYST INC
System and method for monitoring and control of wireless modules linked to assets
InactiveUS7027808B2Wireless commuication servicesElectric/magnetic detectionOperational systemComputer module
A system and method for remote asset management is described which can provide the basis for a diverse product group including an improved remote location monitoring system, a means for communicating with and for monitoring the status and or location of a plurality of diverse assets, as well as the means for communicating with said assets for the purpose of modifying the operational status of one or more of said assets according to one or more stored data parameters such as location, use, battery power, and such like. The remote asset management system comprises a wireless module, which is associated with at least one of the plurality of asset and which is interfaced with the operating system of said assert and or with an electromechanical control means, which may control one or more features of the operation of said assets. A supporting network-based, or internet-based service platform, controls and manages the status of each of the plurality of assets, either automatically, or in response to received messages from fixed or wireless communication devices, and which is capable of selectively communicating data to said assets for changing the operational status of said assets according to pre-programmed conditions.
Owner:M2M SOLUTIONS
Multiple platform support system and method
InactiveUS9010641B2Software simulation/interpretation/emulationSpecial data processing applicationsSupporting systemData terminal
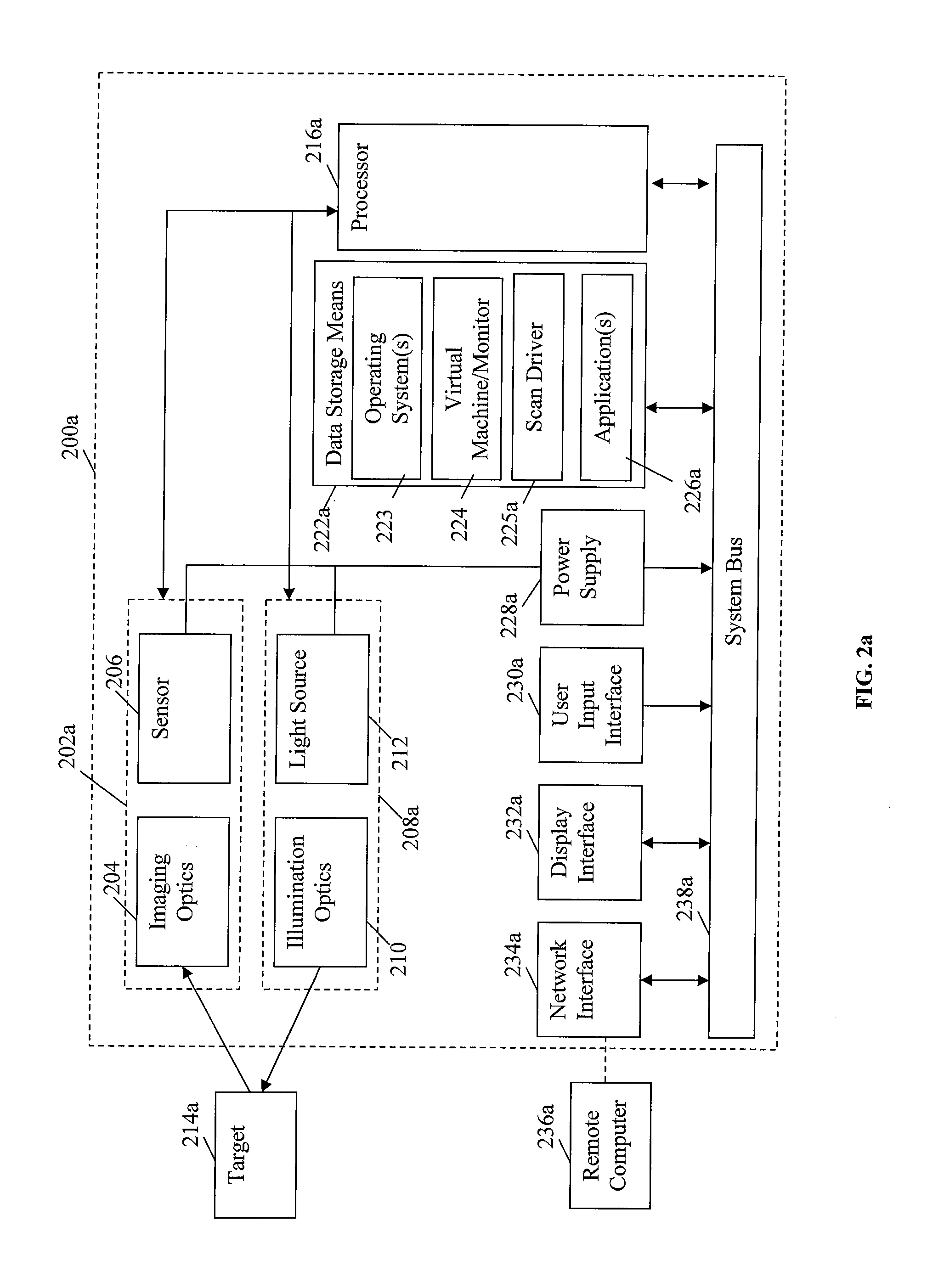
A portable data terminal including a processor having an instruction set architecture and data storage means configured to store a plurality of operating systems and a virtual machine monitor application program configured to receive at least one instruction from each operating system, communicate with the processor according to the instruction set architecture, and switch operating system access to the processor upon receipt of an electrical signal representing an event.
Owner:HAND HELD PRODS
Interoperable systems and methods for peer-to-peer service orchestration
InactiveUS20050027871A1Facilitating commercial exchangeIncrease flexibilityWeb data indexingCryptography processingOperational systemWeb service
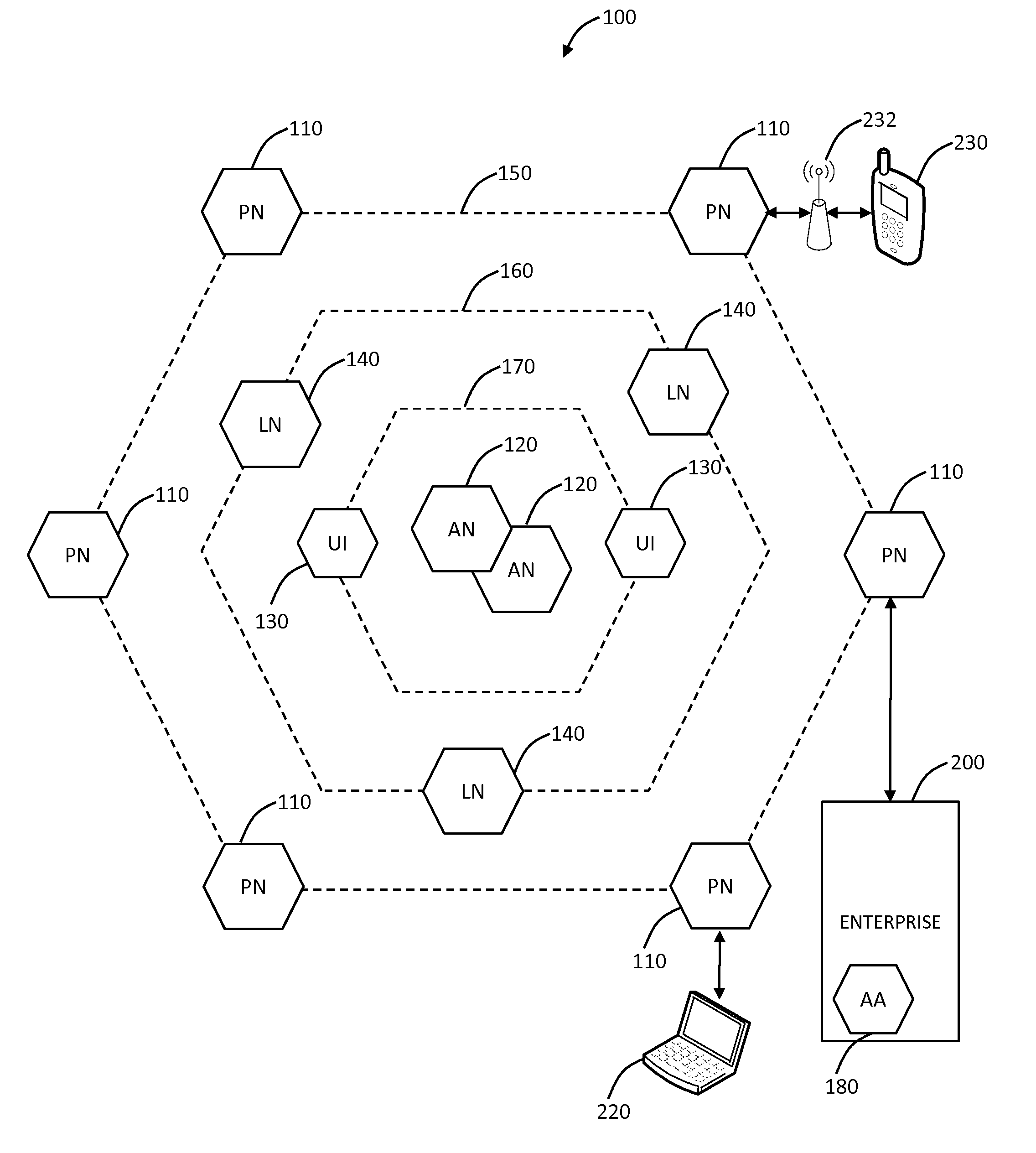
Systems and methods are described for performing policy-managed, peer-to-peer service orchestration in a manner that supports the formation of self-organizing service networks that enable rich media experiences. In one embodiment, services are distributed across peer-to-peer communicating nodes, and each node provides message routing and orchestration using a message pump and workflow collator. Distributed policy management of service interfaces helps to provide trust and security, supporting commercial exchange of value. Peer-to-peer messaging and workflow collation allow services to be dynamically created from a heterogeneous set of primitive services. The shared resources are services of many different types, using different service interface bindings beyond those typically supported in a web service deployments built on UDDI, SOAP, and WSDL. In a preferred embodiment, a media services framework is provided that enables nodes to find one another, interact, exchange value, and cooperate across tiers of networks from WANs to PANs.
Owner:INTERTRUST TECH CORP
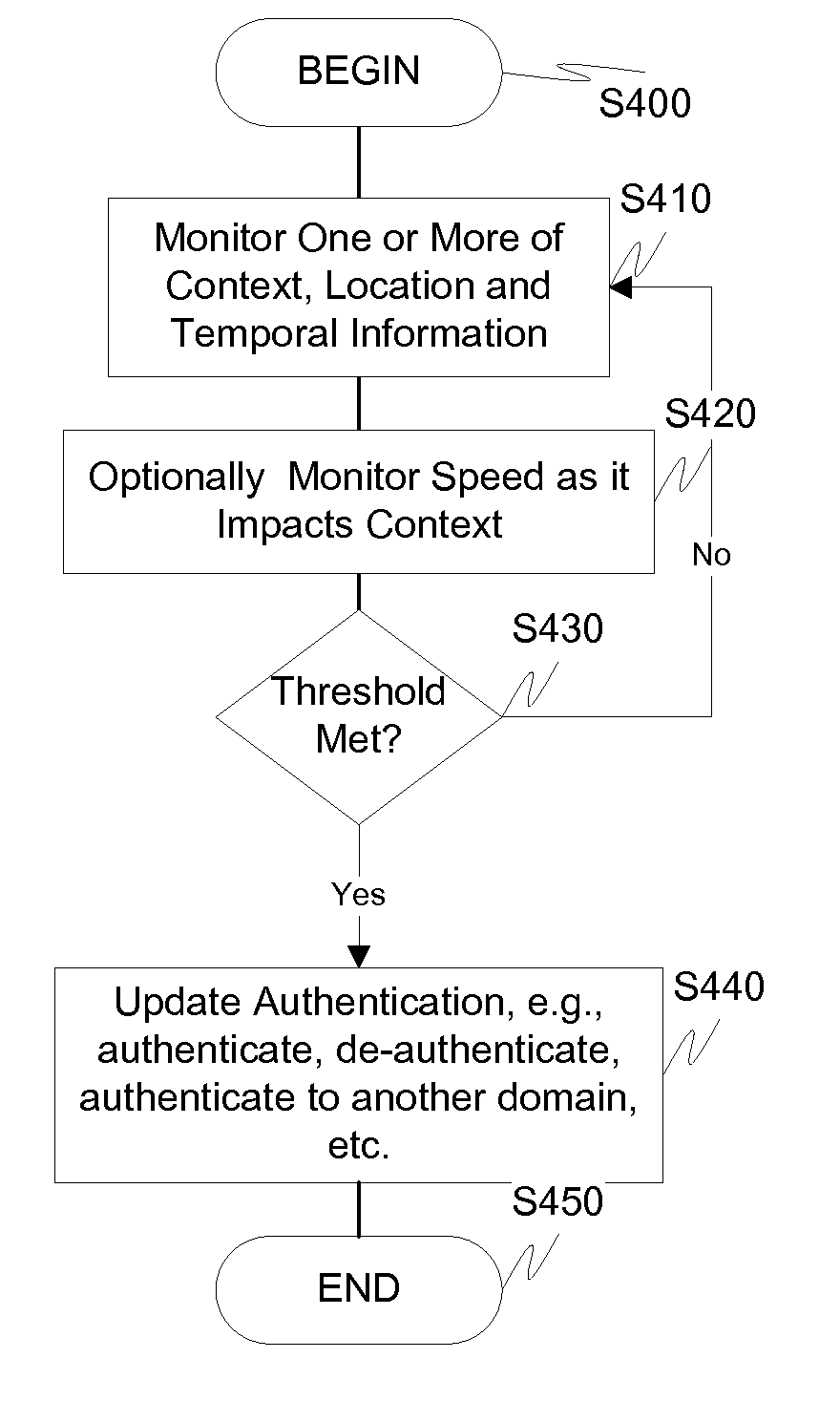
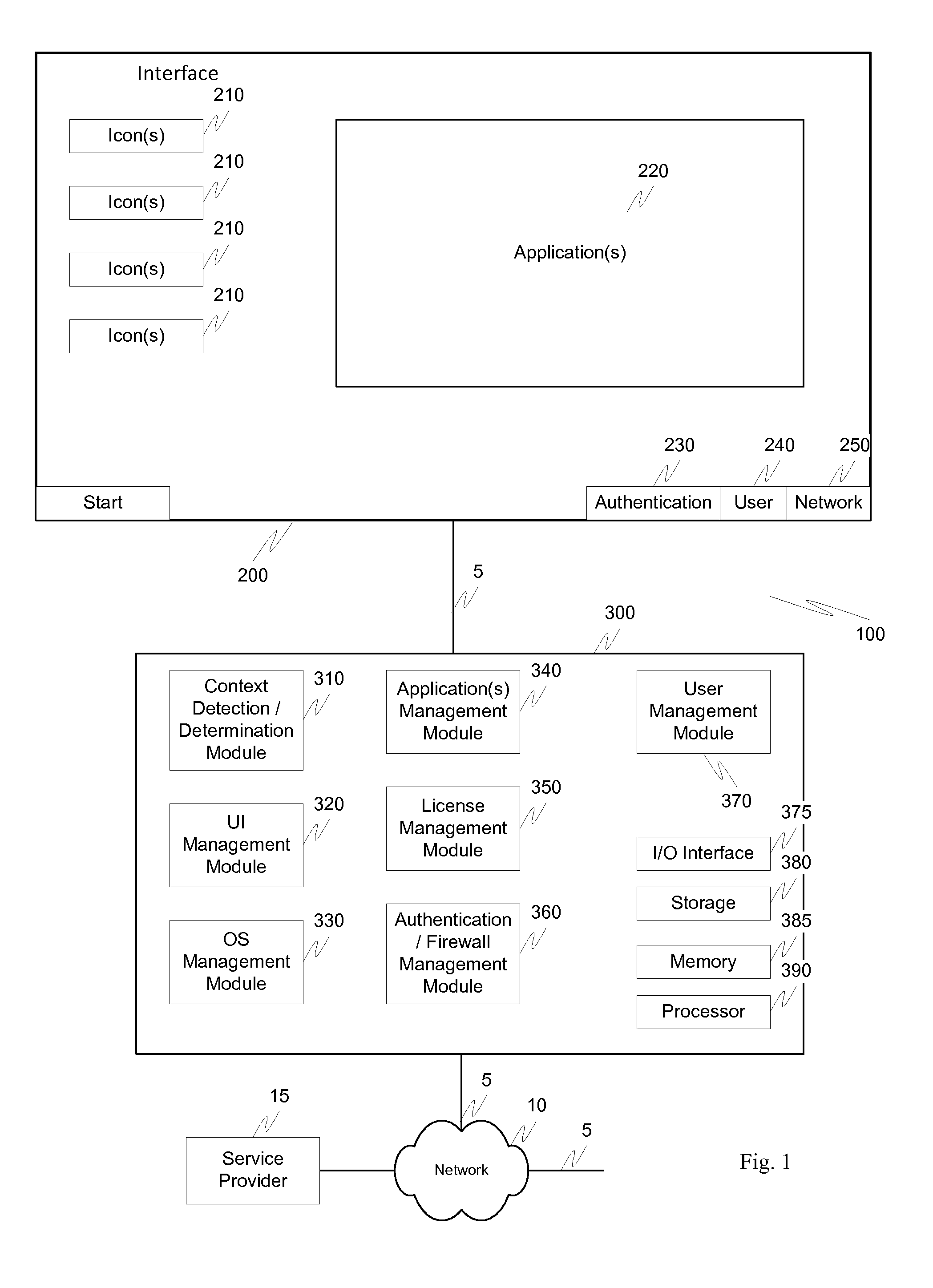
Screen icon manipulation by context and frequency of use
ActiveUS20110072492A1More user confidenceDigital data processing detailsMultiple digital computer combinationsTemporal informationOutbound communication
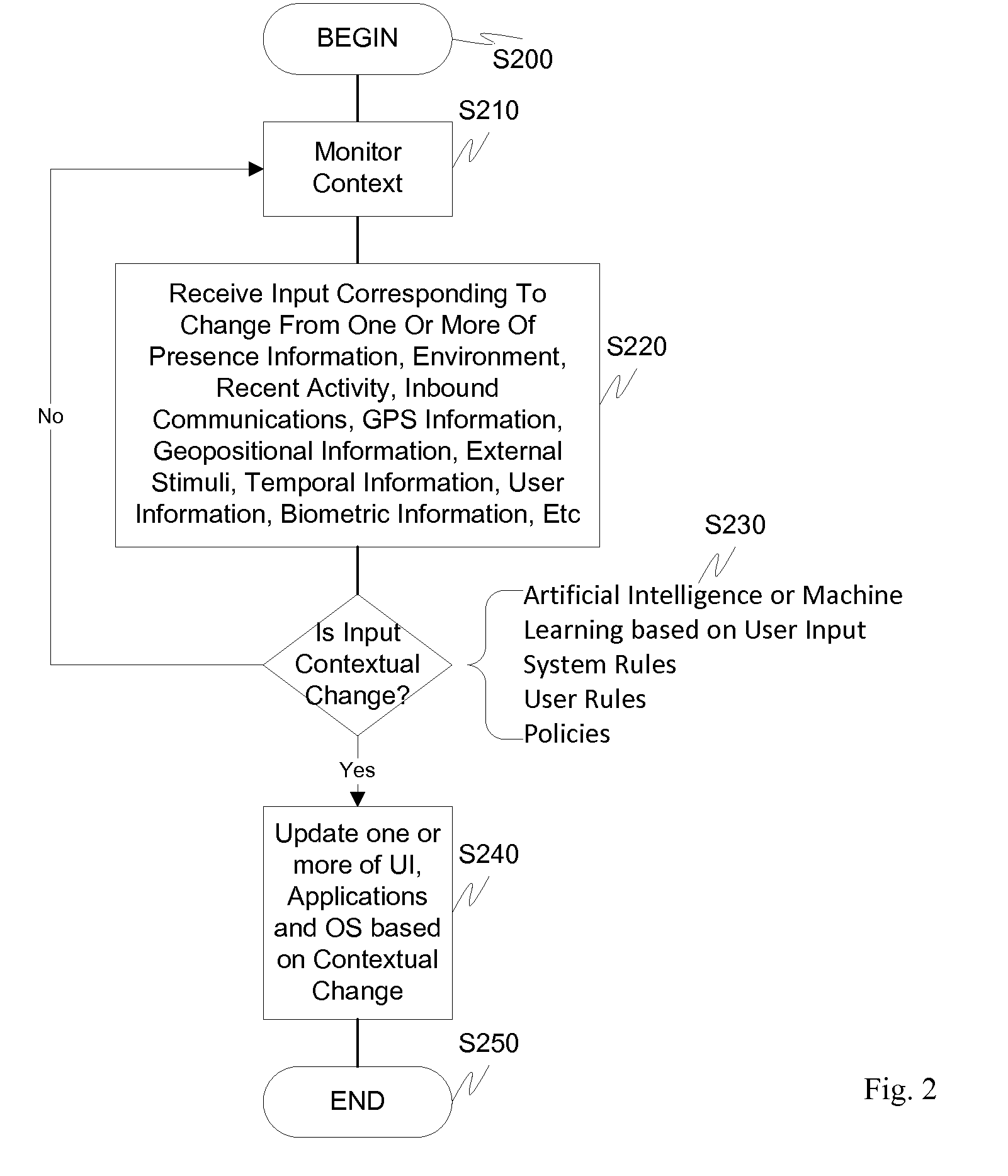
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
Detecting unauthorized use of computing devices based on behavioral patterns
InactiveUS20090199296A1Efficiently definedMemory loss protectionError detection/correctionSupporting systemOperational system
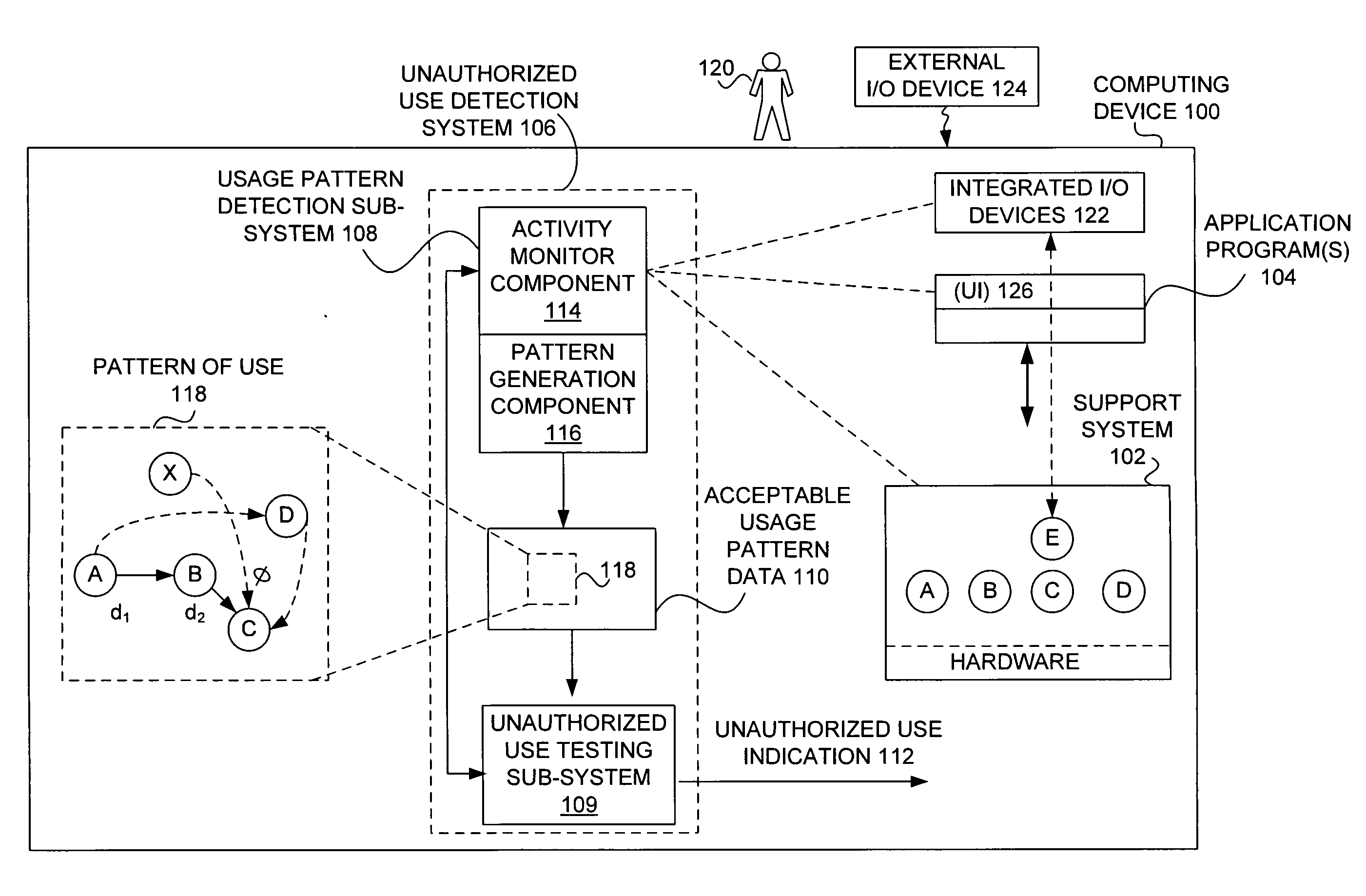
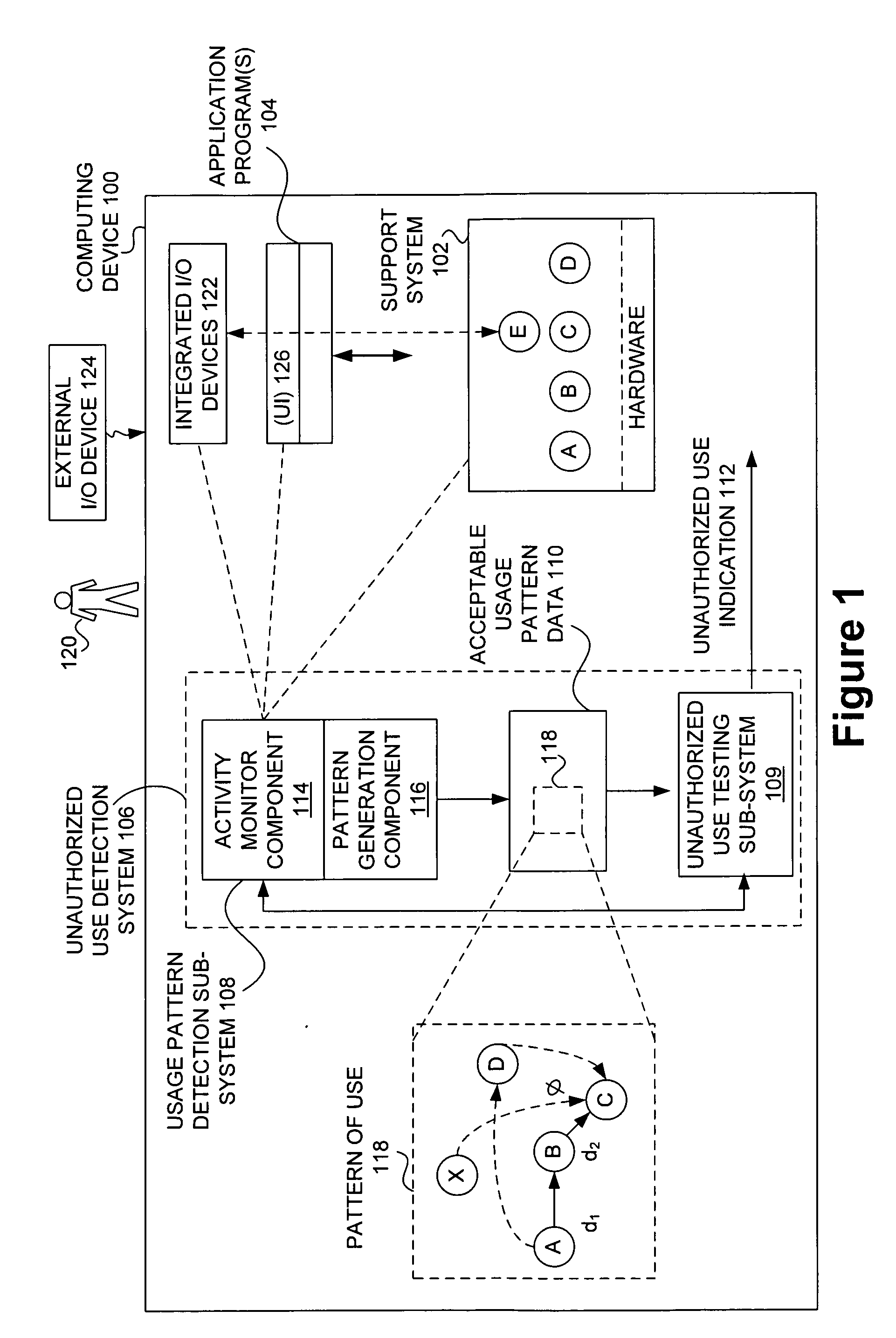
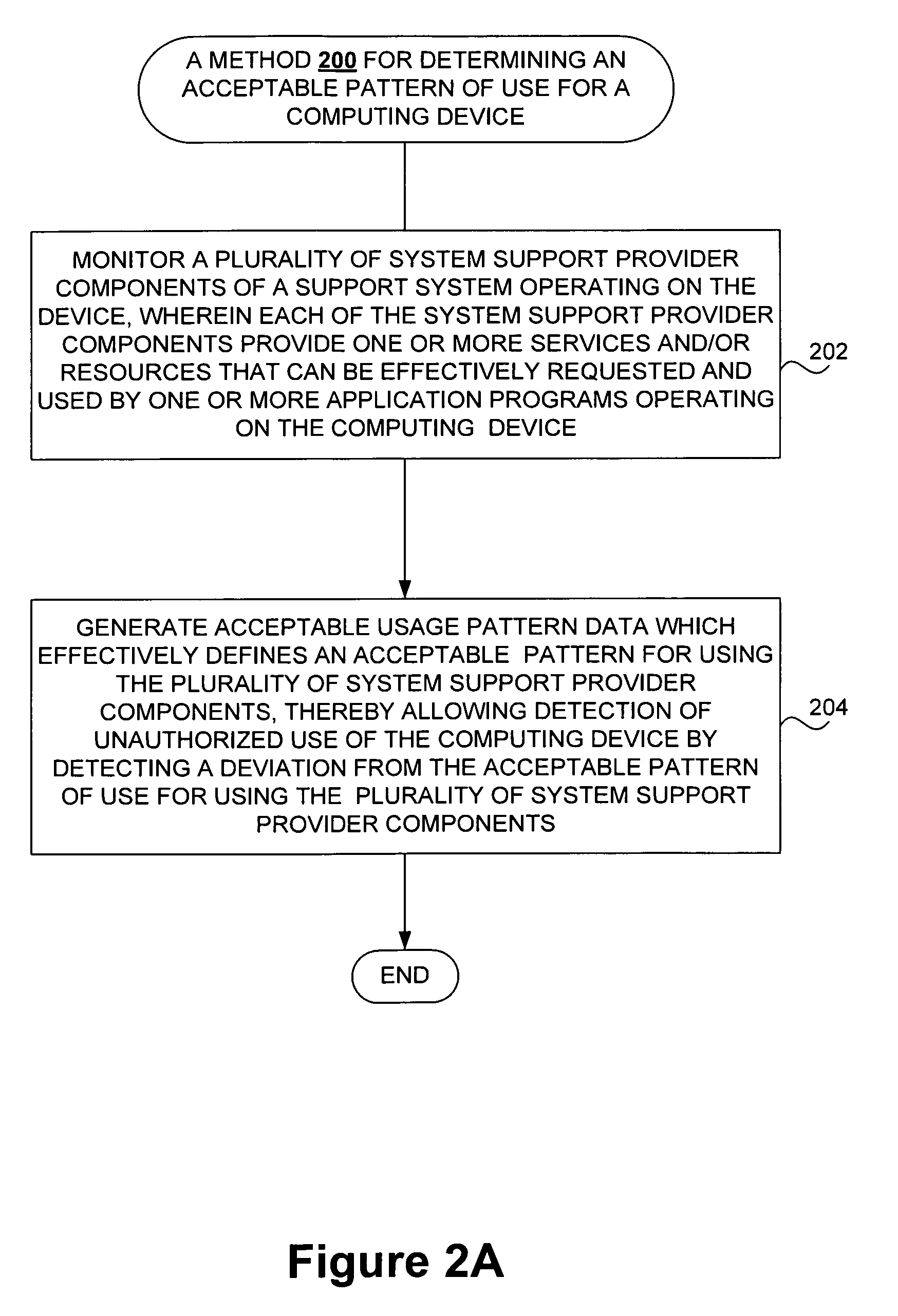
Techniques for detecting unauthorized use (e.g., malicious attacks) of the computing systems (e.g., computing devices) are disclosed. Unauthorized use can be detected based on patterns of use (e.g., behavioral patterns of use typically associated with a human being) of the computing systems. Acceptable behavioral pattern data can be generated for a computing system by monitoring the use of a support system (e.g., an operating system, a virtual environment) operating on the computing system. For example, a plurality of system support provider components of a support system (e.g., system calls, device drivers) can be monitored in order to generate the acceptable behavioral pattern data in a form which effectively defines an acceptable pattern of use (usage pattern) for the monitored system support provider components, thereby allowing detection of unauthorized use of a computing system by detecting any deviation from the acceptable pattern of use of the monitored system support provider components.
Owner:SAMSUNG ELECTRONICS CO LTD
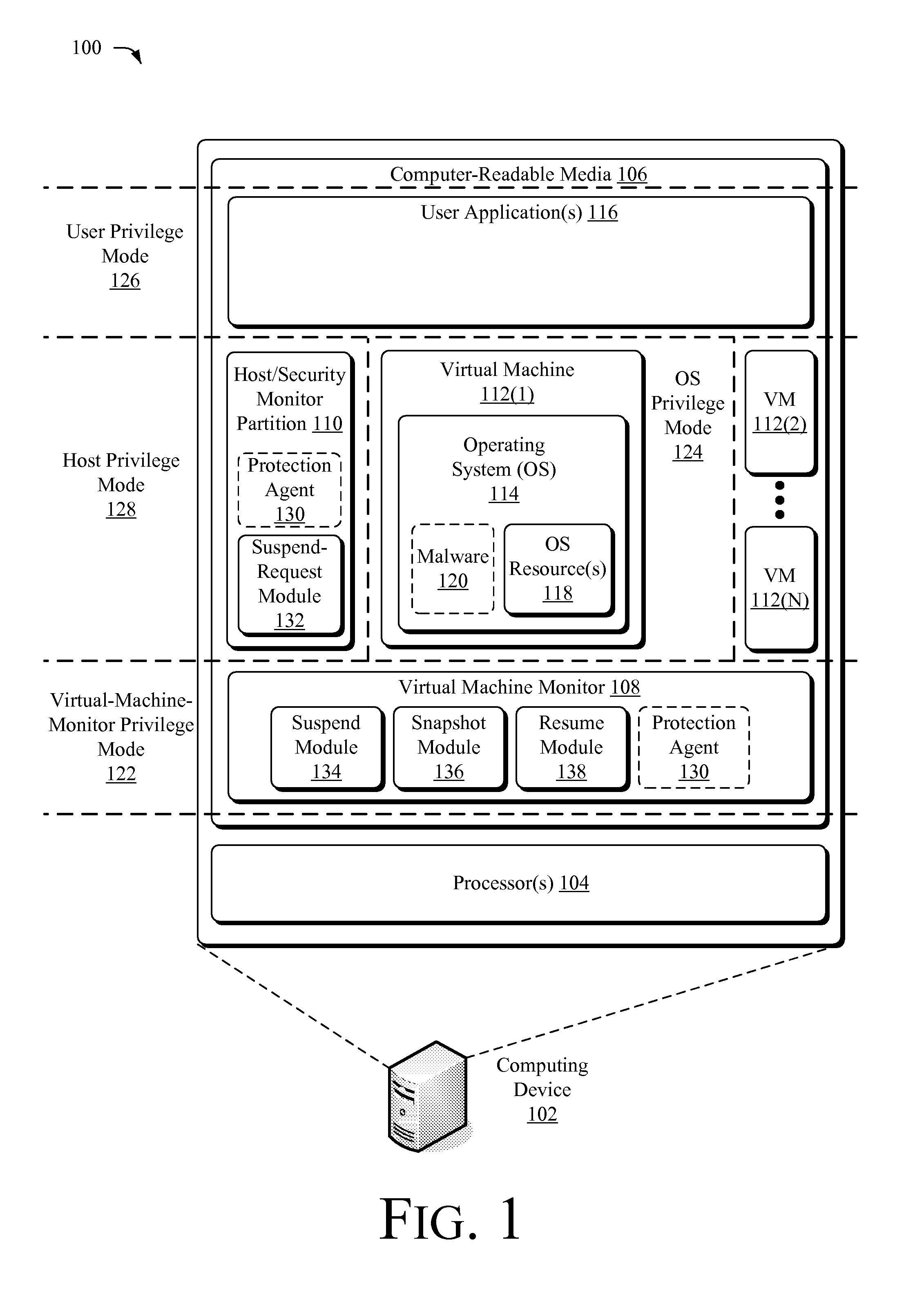
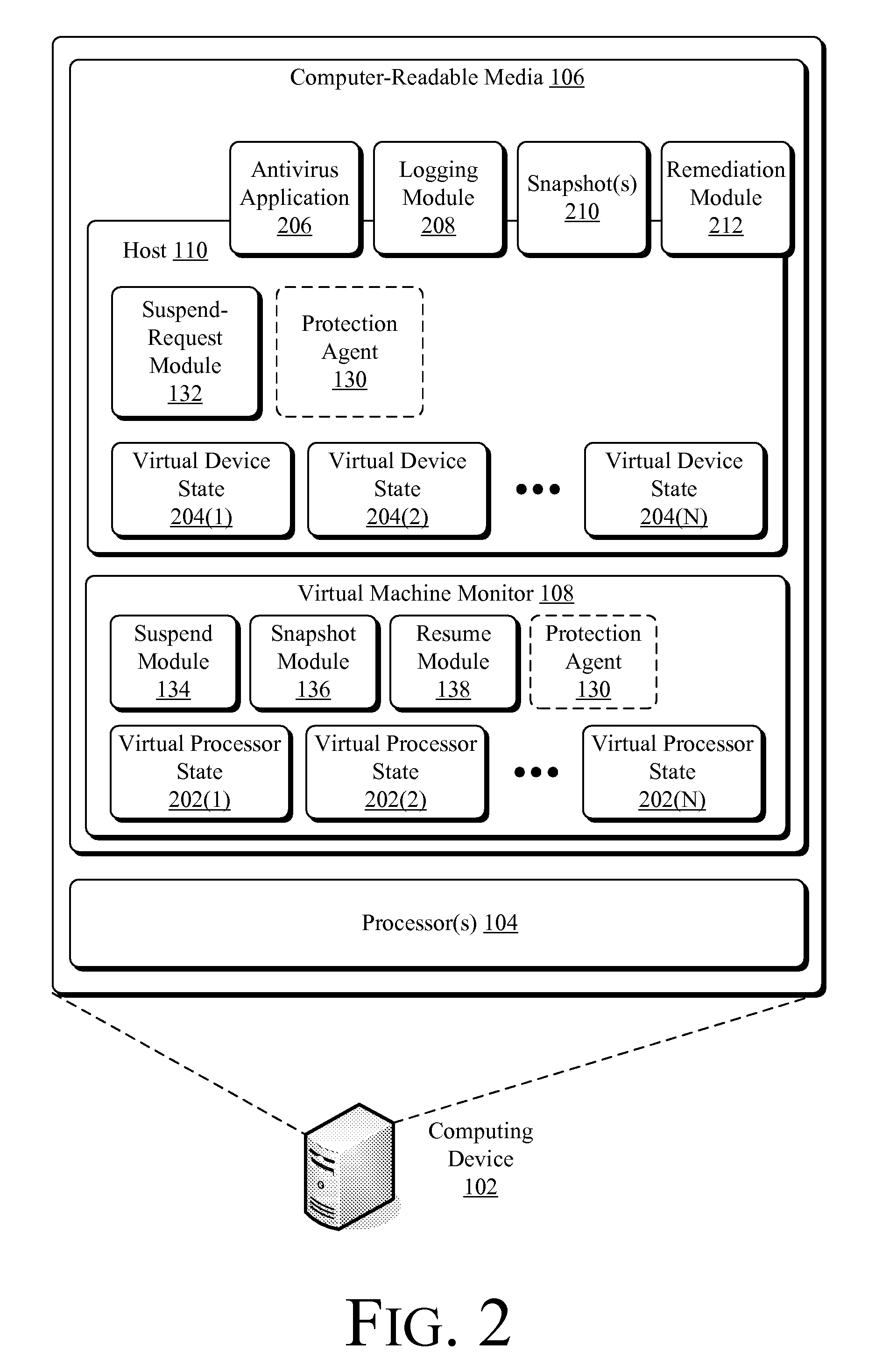
Suspending a Running Operating System to Enable Security Scanning
InactiveUS20090007100A1Well formedUser identity/authority verificationPlatform integrity maintainanceOperational systemRemedial action
Techniques described herein enable virtualizing a processor into one or more virtual machines and suspending an operating system of one of the virtual machines from outside of the operating system environment. Once suspended, these techniques capture a snapshot of the virtual machine to determine a presence of malware. This snapshot may also be used to determine whether an unauthorized change has occurred within contents of the virtual machine. Remedial action may occur responsive to determining a presence of malware or an unauthorized change.
Owner:MICROSOFT TECH LICENSING LLC
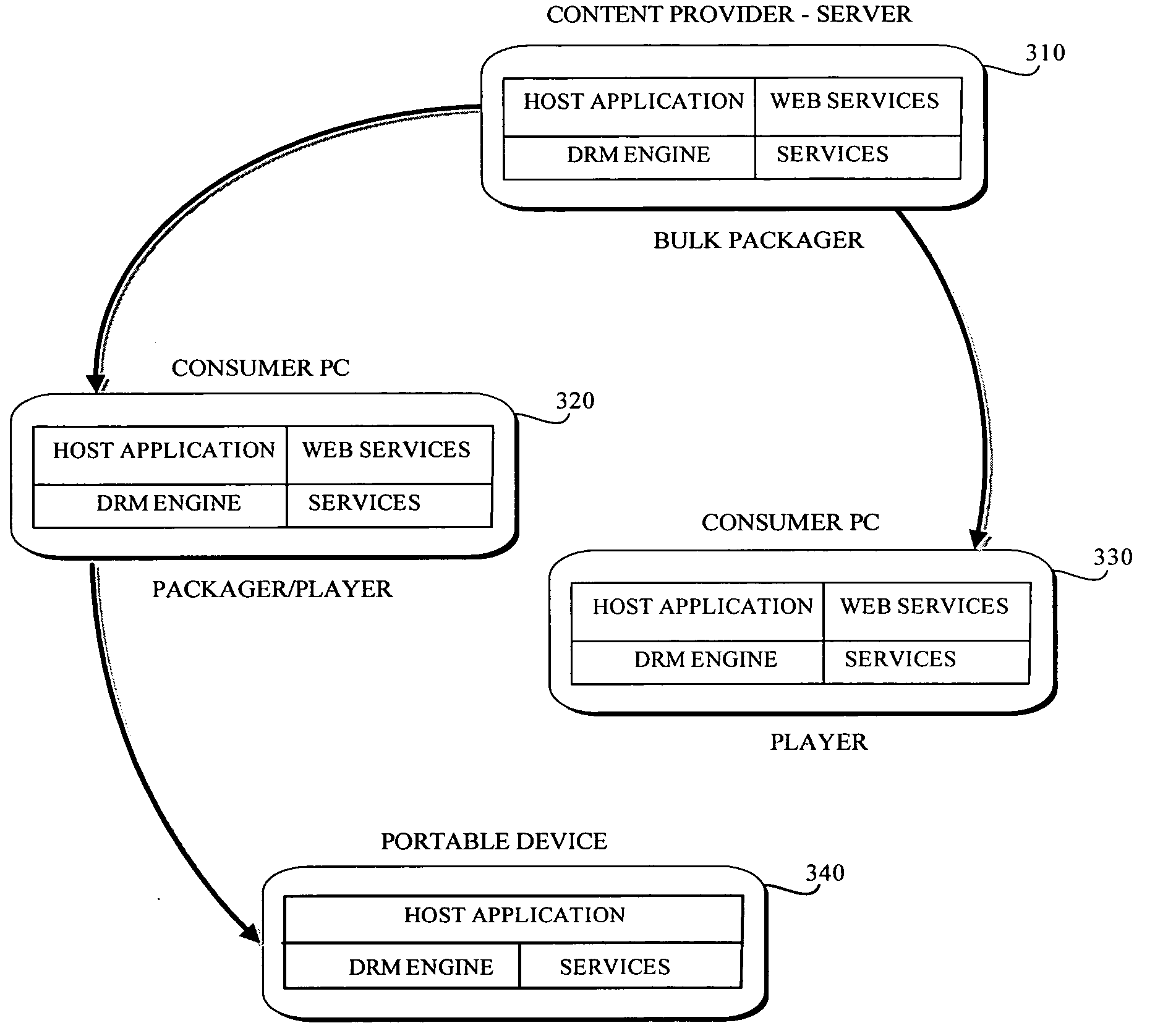
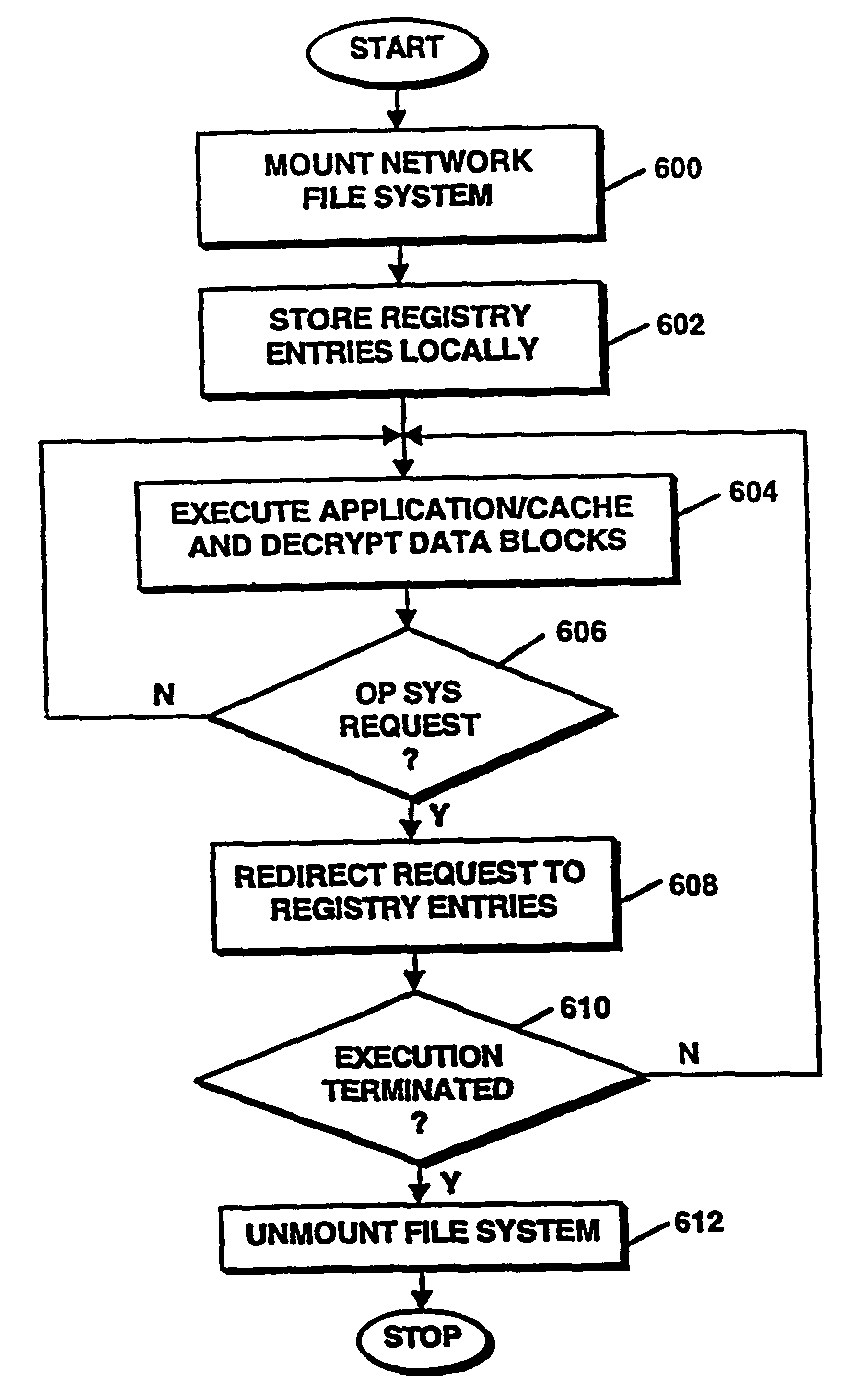
Method and apparatus for installation abstraction in a secure content delivery system
InactiveUS6374402B1Expand accessAvoid leverageTelevision system detailsBroadband local area networksOperational systemNetwork addressing
A system for secure delivery of on-demand content over broadband access networks includes a client application executing on a user's local computer system. The client application interacts with a content server on which a plurality of selectable titles are stored and further interacts with an access server which provides the network address of a title and keying data necessary for to the client process access and execute the title. The client process utilizes an installation abstraction which enables a title to be executed on the local computer system without ever being installed. The abstraction is achieved by mounting a network file system and storing a set of registry entries related to the title on the local computer system. Portions of the title are retrieved from the content server and executed by the local operating system. During title execution, requests from the local operating system are intercepted and redirected to the set of registry entries, as applicable. The times at which the client process may retrieve the title data from the content server are defined by the access server through use of an activator and token.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for providing virtual computing services
InactiveUS20050044301A1Easy to manageLow costResource allocationMemory adressing/allocation/relocationVirtualizationOperational system
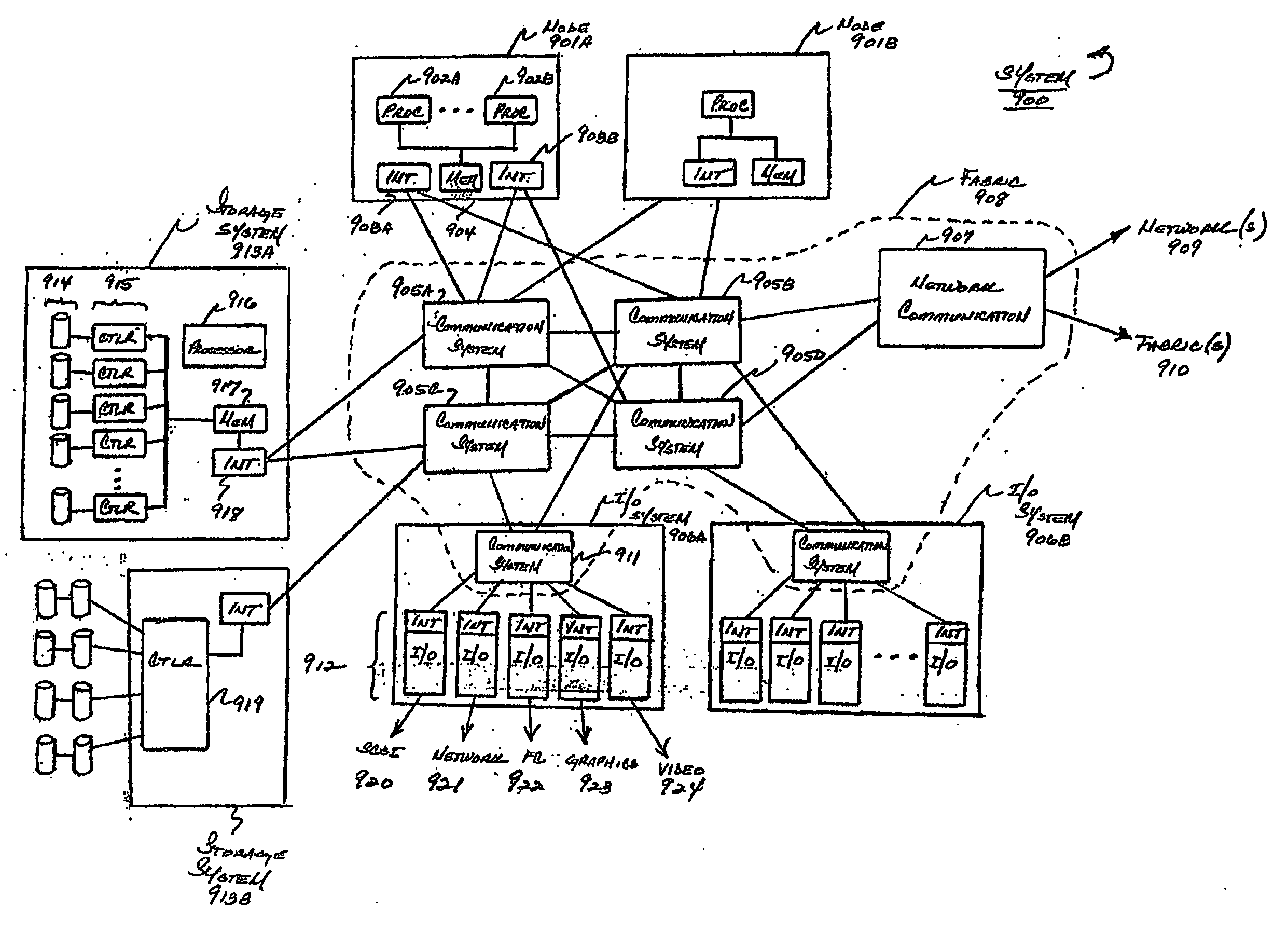
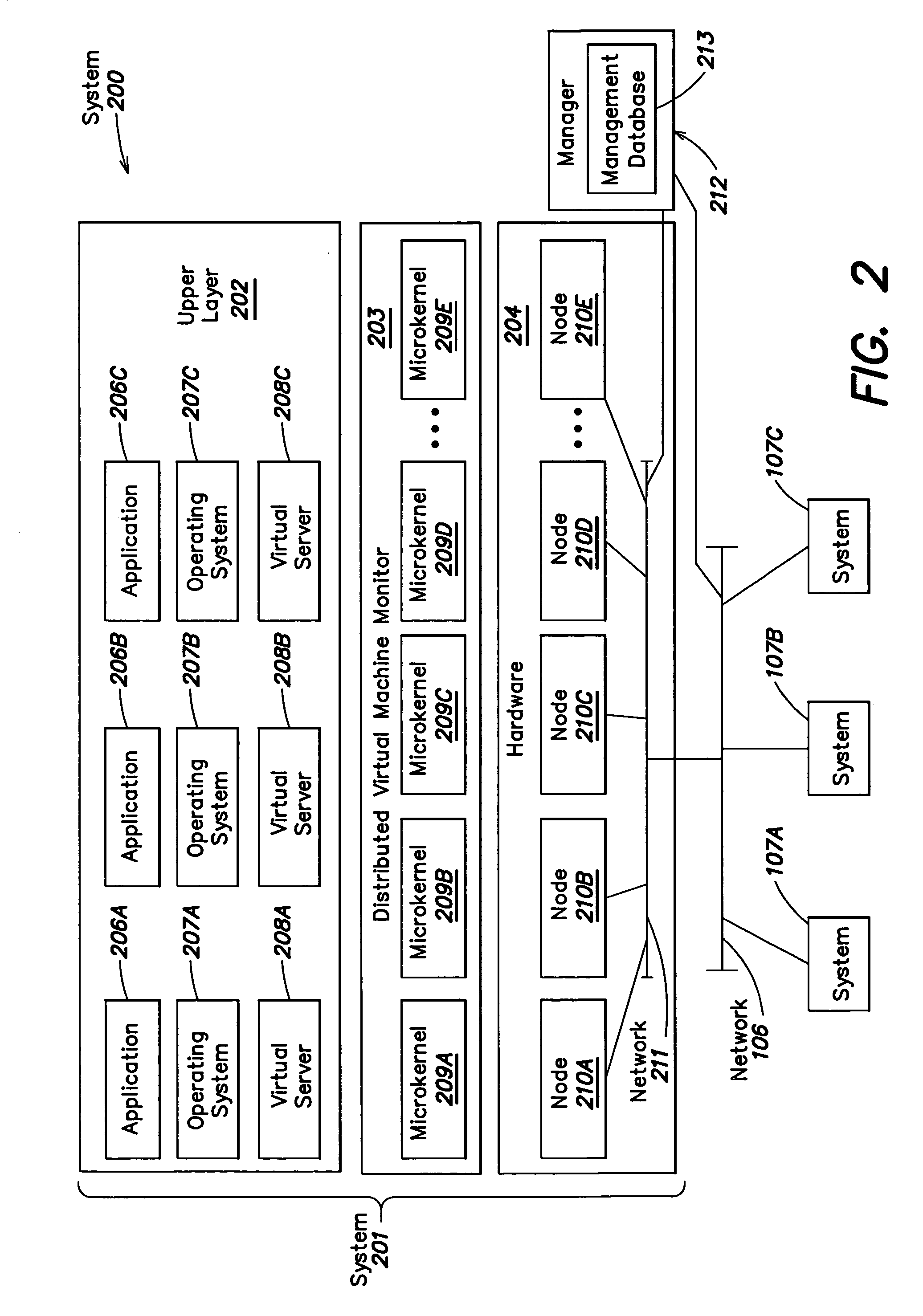
A level of abstraction is created between a set of physical processors and a set of virtual multiprocessors to form a virtualized data center. This virtualized data center comprises a set of virtual, isolated systems separated by a boundary referred as a partition. Each of these systems appears as a unique, independent virtual multiprocessor computer capable of running a traditional operating system and its applications. In one embodiment, the system implements this multi-layered abstraction via a group of microkernels, each of which communicates with one or more peer microkernel over a high-speed, low-latency interconnect and forms a distributed virtual machine monitor. Functionally, a virtual data center is provided, including the ability to take a collection of servers and execute a collection of business applications over a compute fabric comprising commodity processors coupled by an interconnect. Processor, memory and I / O are virtualized across this fabric, providing a single system, scalability and manageability. According to one embodiment, this virtualization is transparent to the application, and therefore, applications may be scaled to increasing resource demands without modifying the application.
Owner:ORACLE INT CORP
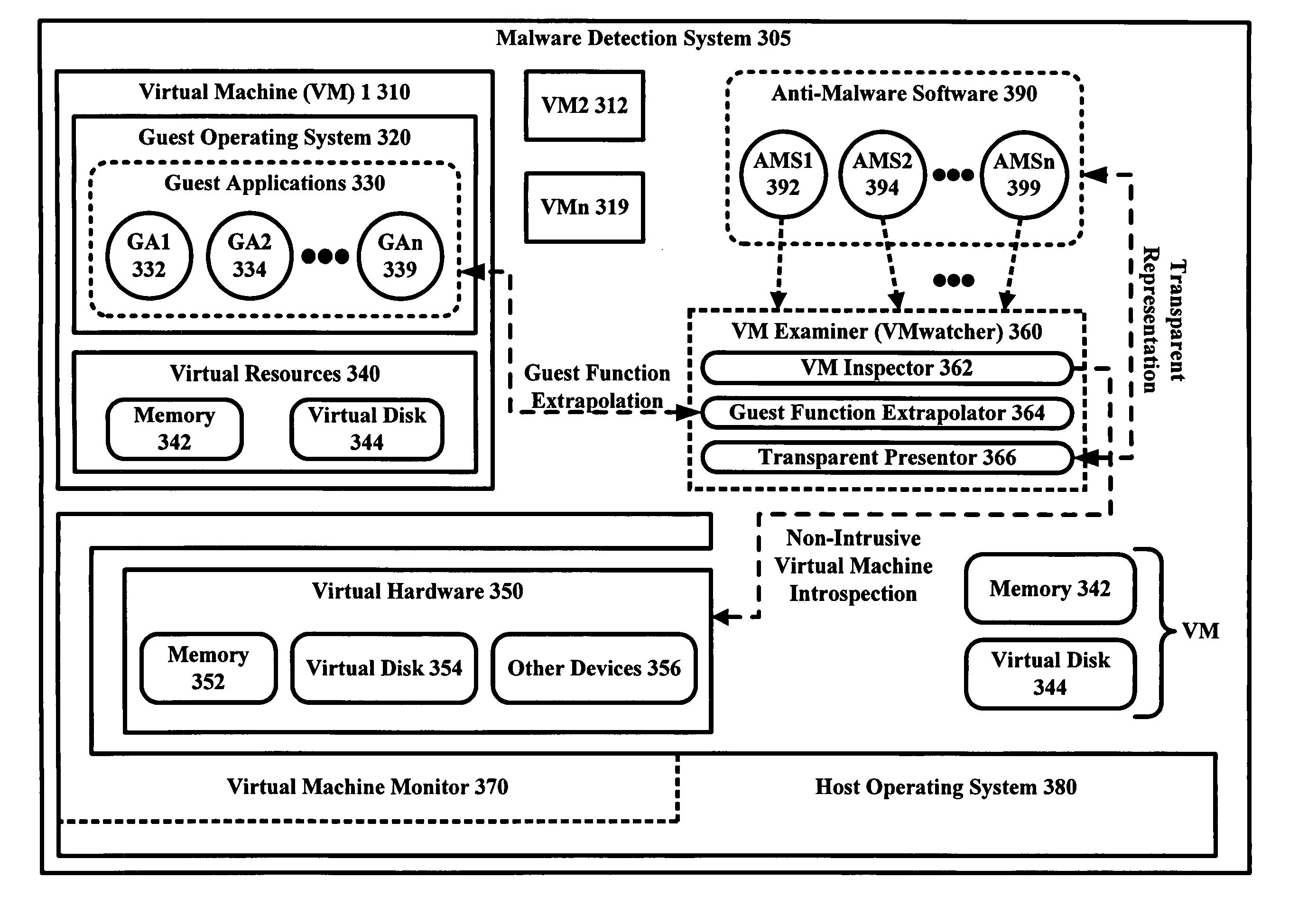
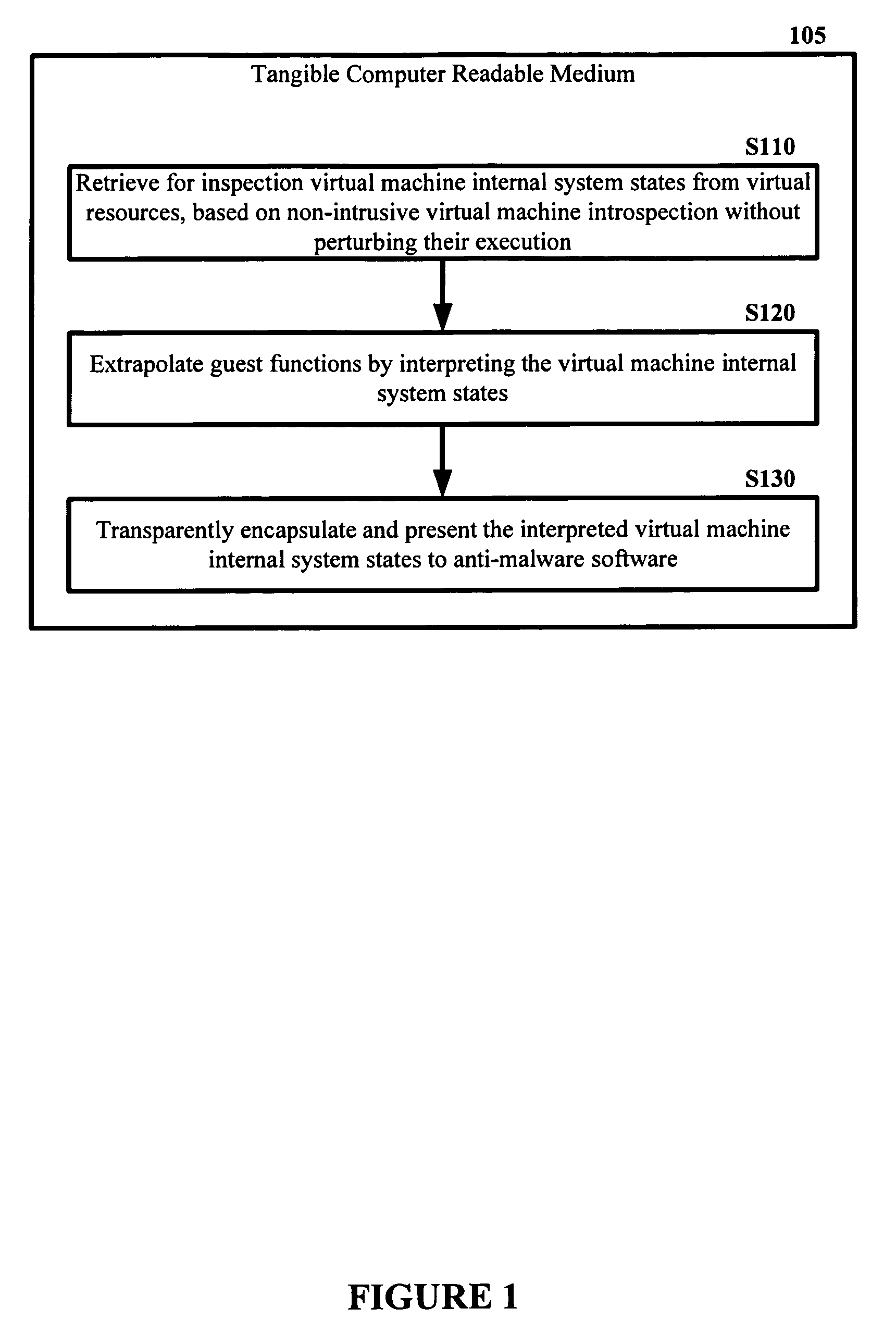
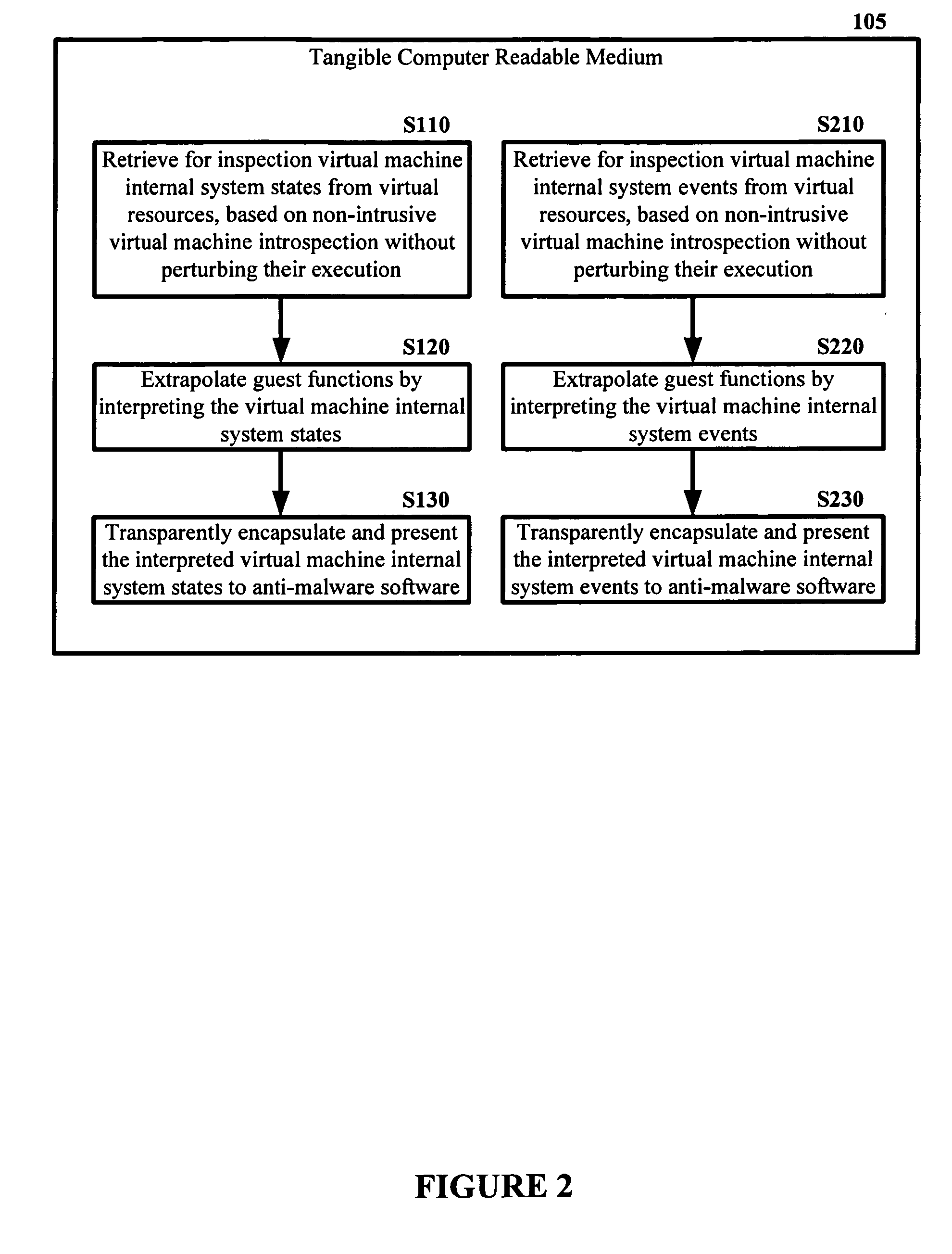
Malware Detector
InactiveUS20080320594A1Memory loss protectionError detection/correctionVirtual memoryOperational system
The malware detection system enables out-of-the box, tamper-resistant malware detection without losing the semantic view. This system comprises at least one guest operating system and at least one virtual machine, where the guest operating system runs on the virtual machine. Having virtual resources, the virtual machine resides on a host operating system. The virtual resources include virtual memory and at least one virtual disk. A virtual machine examiner is used to examine the virtual machine. With a virtual machine inspector, a guest function extrapolator, and a transparent presenter, the virtual machine examiner resides outside the virtual machine. The virtual machine inspector is configured to retrieve virtual machine internal system states and / or events. The guest function extrapolator is configured to interpret such states and / or events. The transparent presenter is configured to present the interpreted states and / or events to anti-malware software. The anti-malware software is configured to use the interpreted states and / or events to detect any system compromise.
Owner:GEORGE MASON INTPROP INC
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
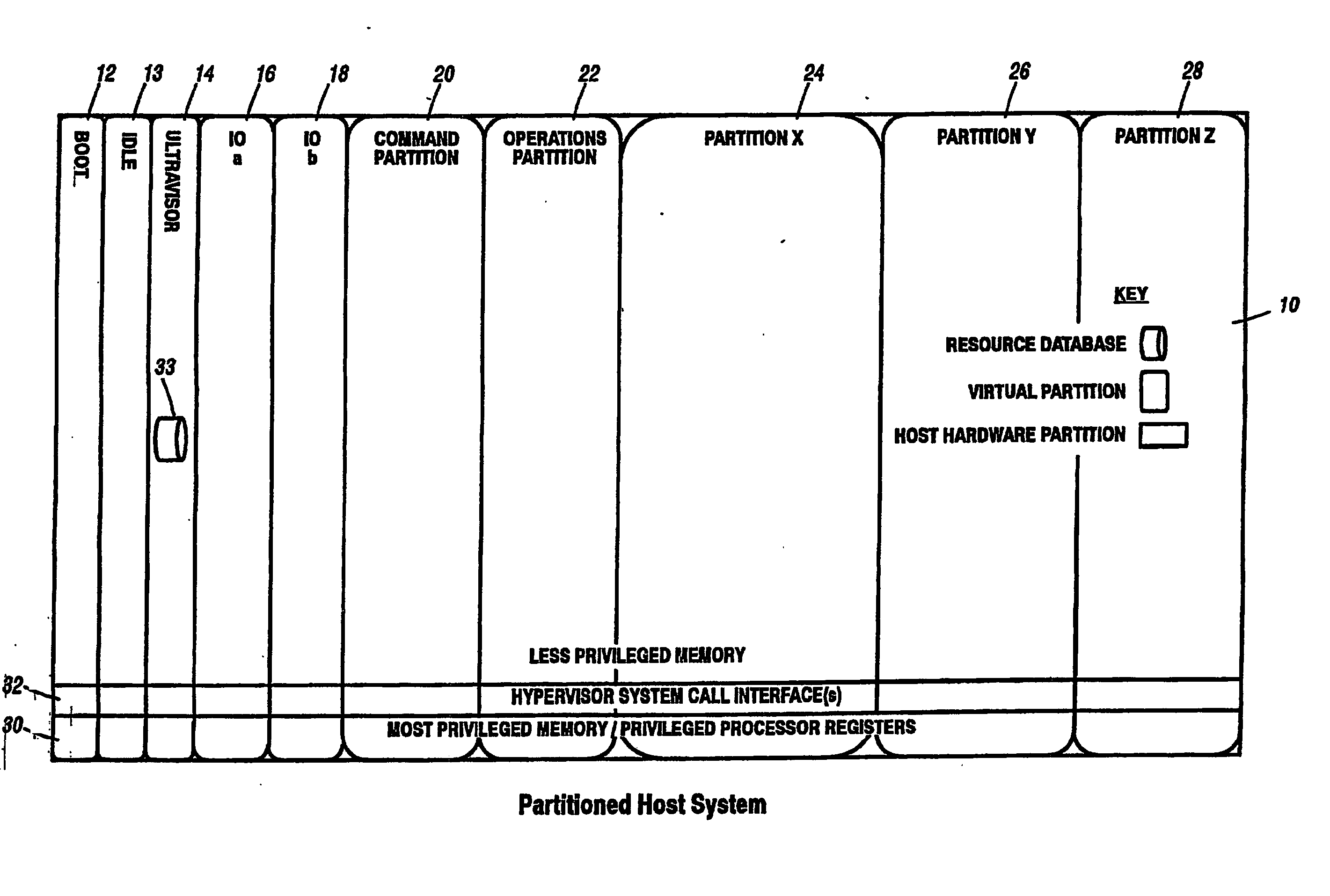
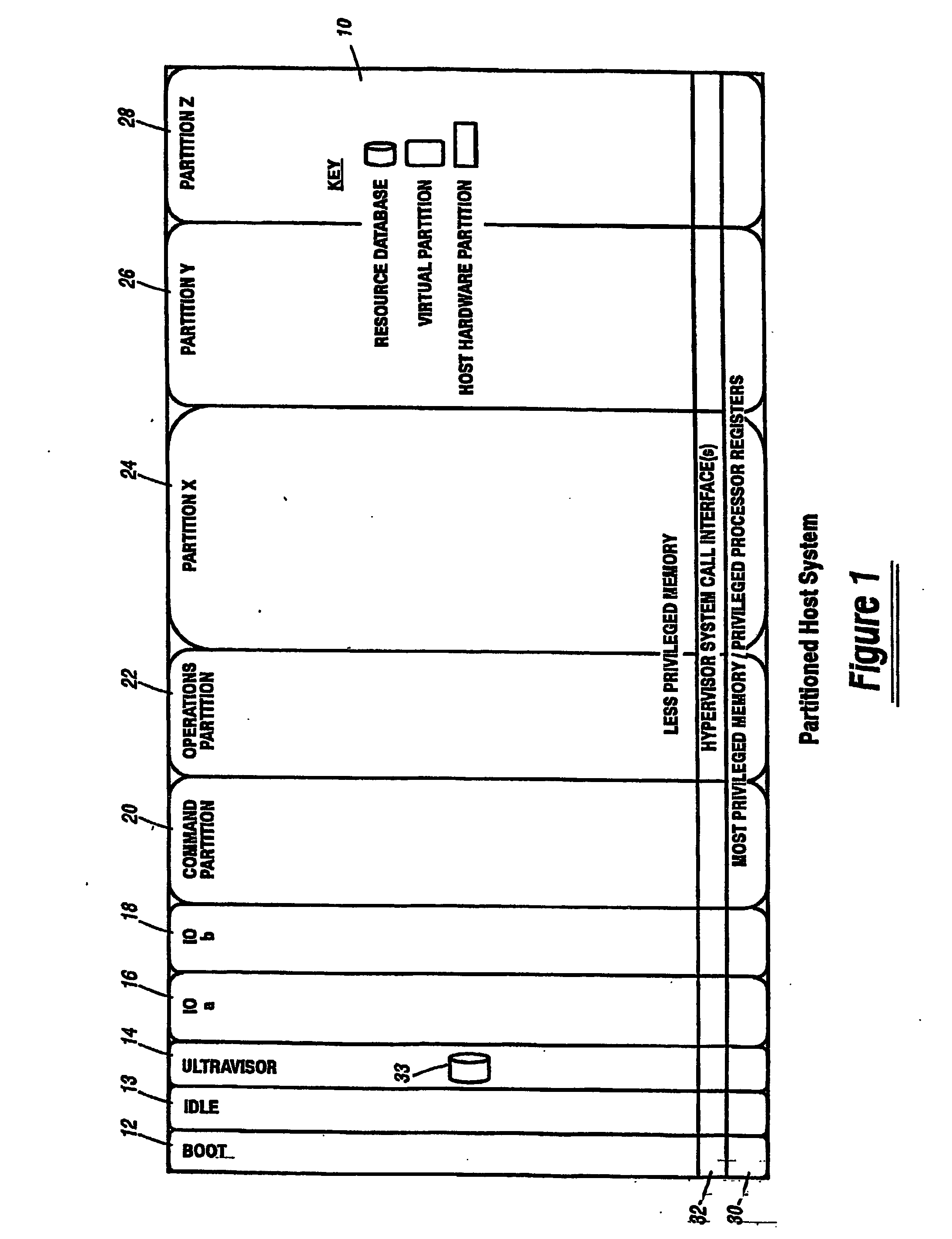
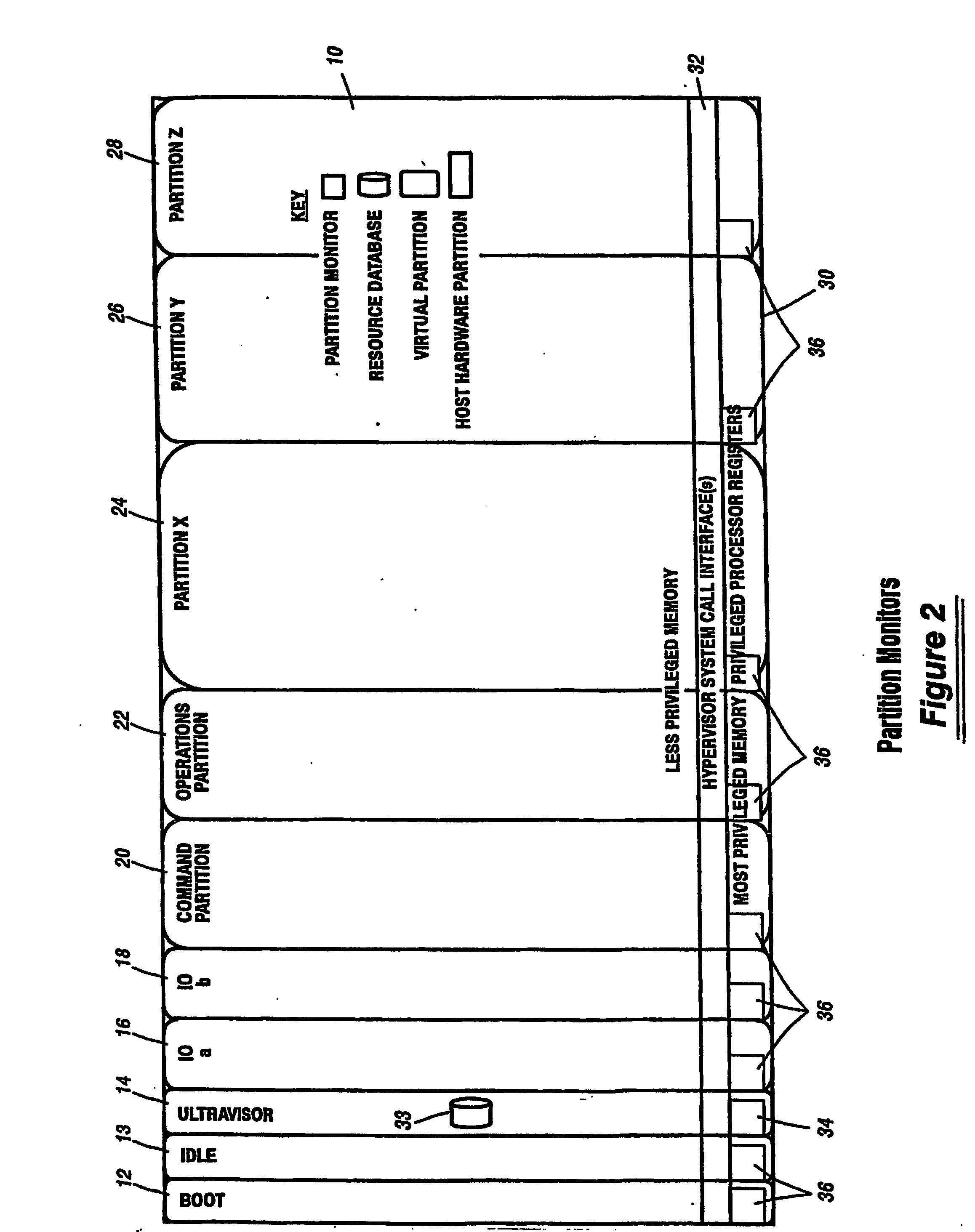
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
Cloud based mobile device security and policy enforcement
ActiveUS20120240183A1Computer security arrangementsMobile application execution environmentsTablet computerOperational system
The present disclosure relates to cloud based mobile device security and policy systems and methods to use the “cloud” to pervasively enforce security and policy on mobile devices. The cloud based mobile device security and policy systems and methods provide uniformity in securing mobile devices for small to large organizations. The cloud based mobile device security and policy systems and methods may enforce one or more policies for users wherever and whenever the users are connected across a plurality of different devices including mobile devices. This solution ensures protection across different types, brands, operating systems, etc. for smartphones, tablets, netbooks, mobile computers, and the like.
Owner:ZSCALER INC
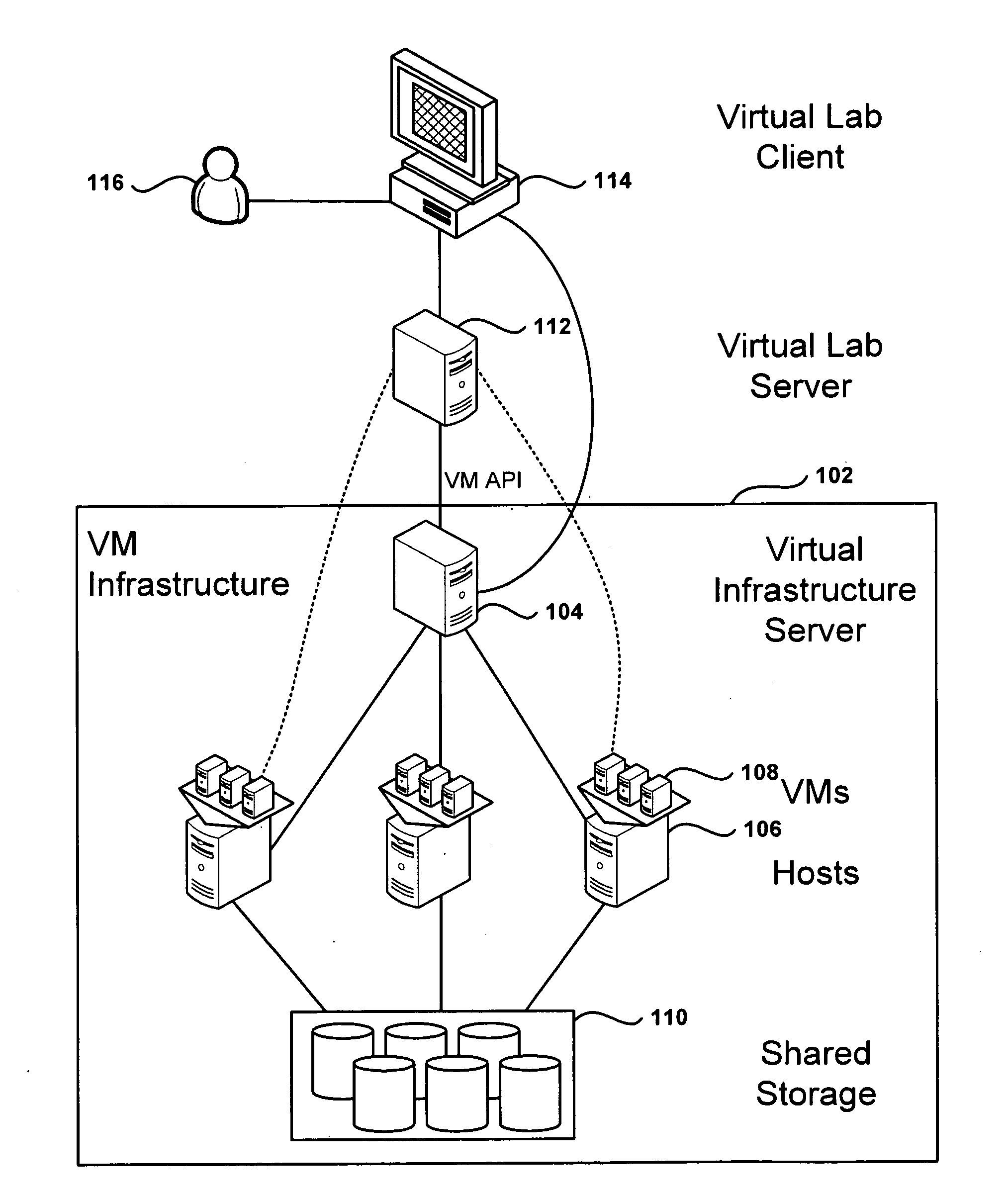
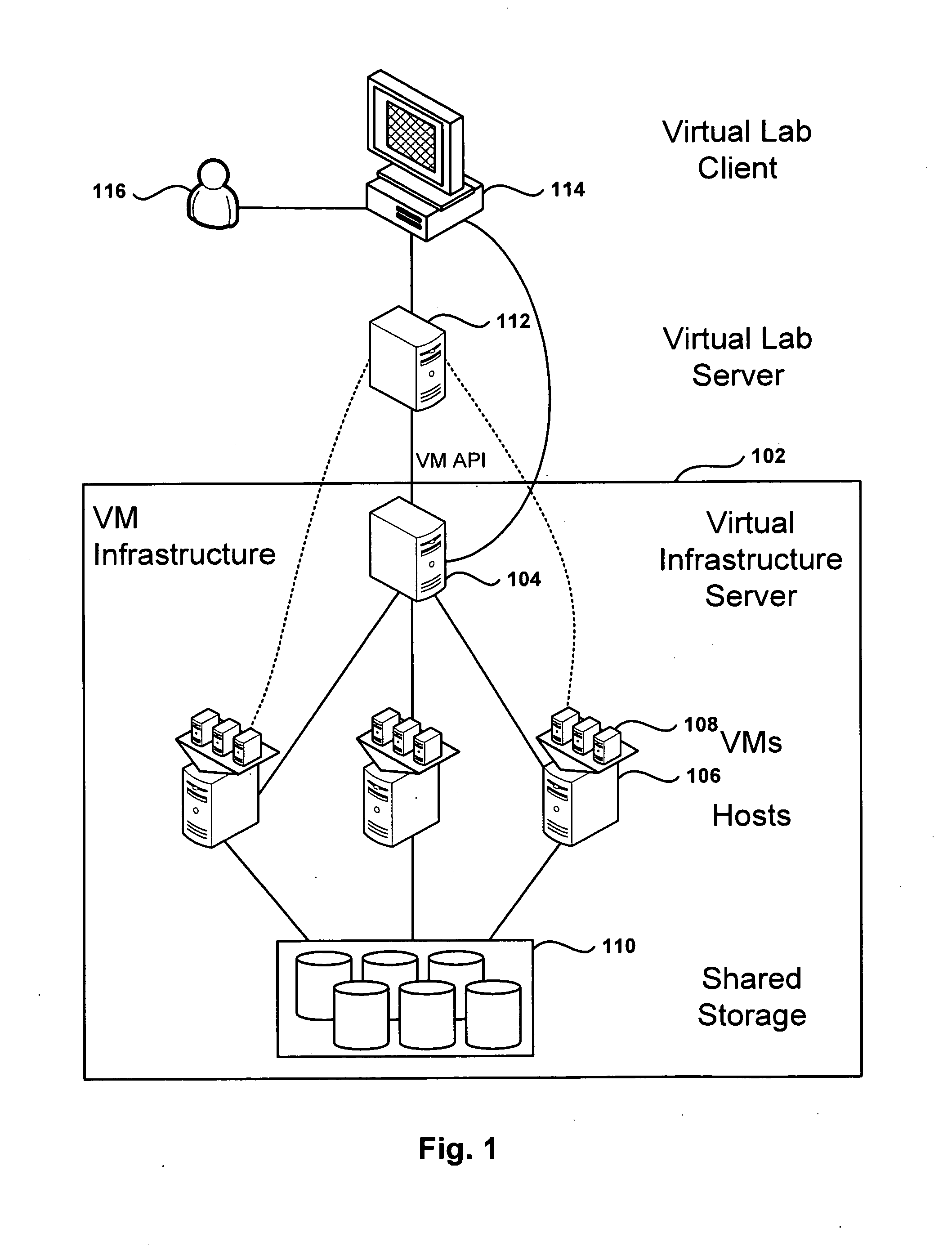
Management and Implementation of Enclosed Local Networks in a Virtual Lab
Methods, systems, and computer programs for creating isolated environments that include virtual machines (VM) and networks in a virtual infrastructure are presented. The method includes an operation to define a configuration of a virtual system which includes VMs, virtual network interface cards (VNIC) in the VMs, and configuration local networks (CLN). Further, the method associates each VNIC with one of the CLNs and transmits instructions to the virtual infrastructure for deploying the configuration. Deploying the configuration includes instantiating VMs and CLNs in the virtual infrastructure. Each VM is instantiated in a host monitored by a virtual lab server, and the CLNs are instantiated in the same hosts where the VMs have been instantiated. Only VMs from the configuration can connect to the instantiated CLNs. The method further transmits instructions to the virtual infrastructure to customize the VMs by executing the customization instructions in the guest operating systems of the VMs to configure the VMs' VNICs.
Owner:VMWARE INC
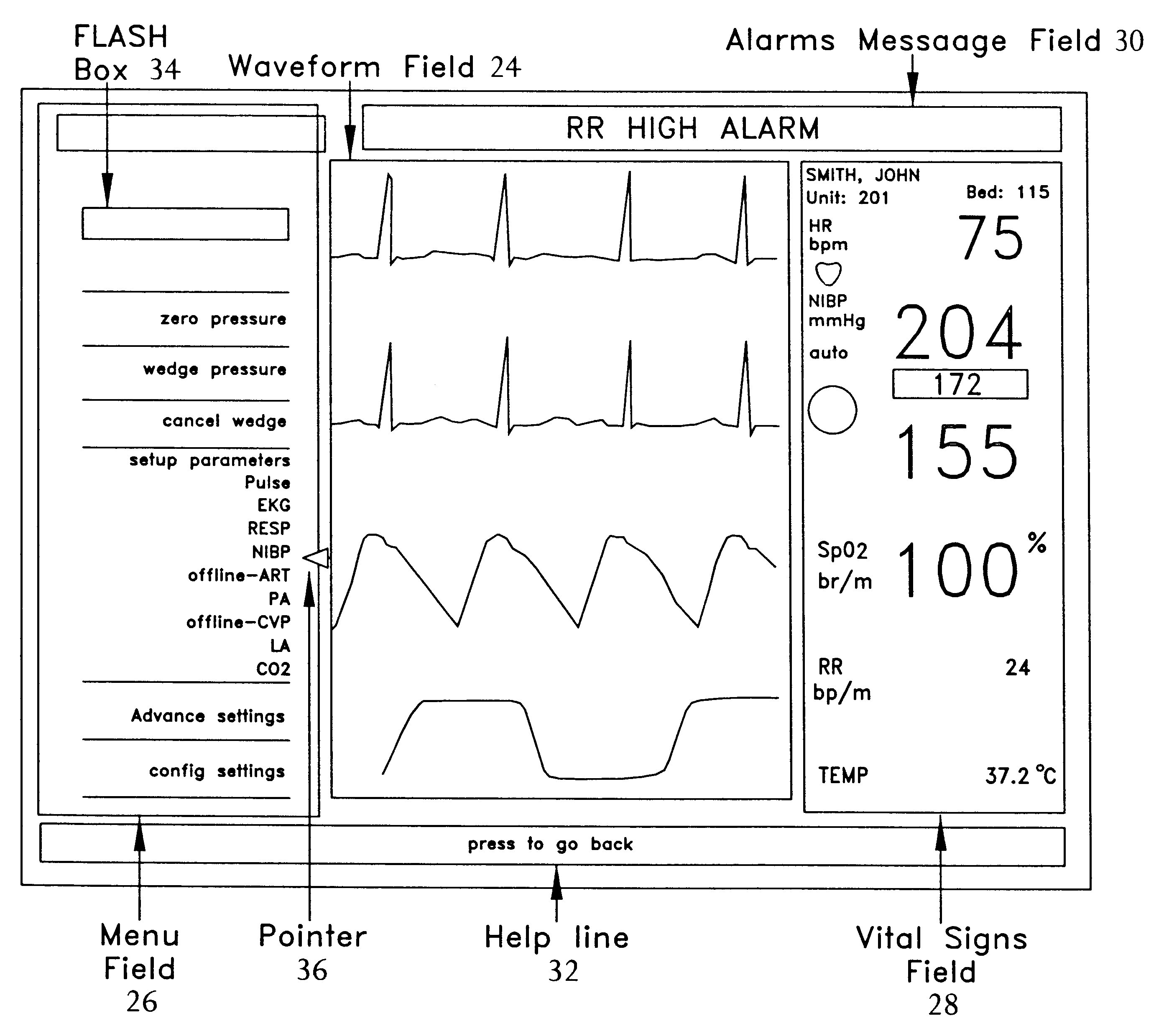
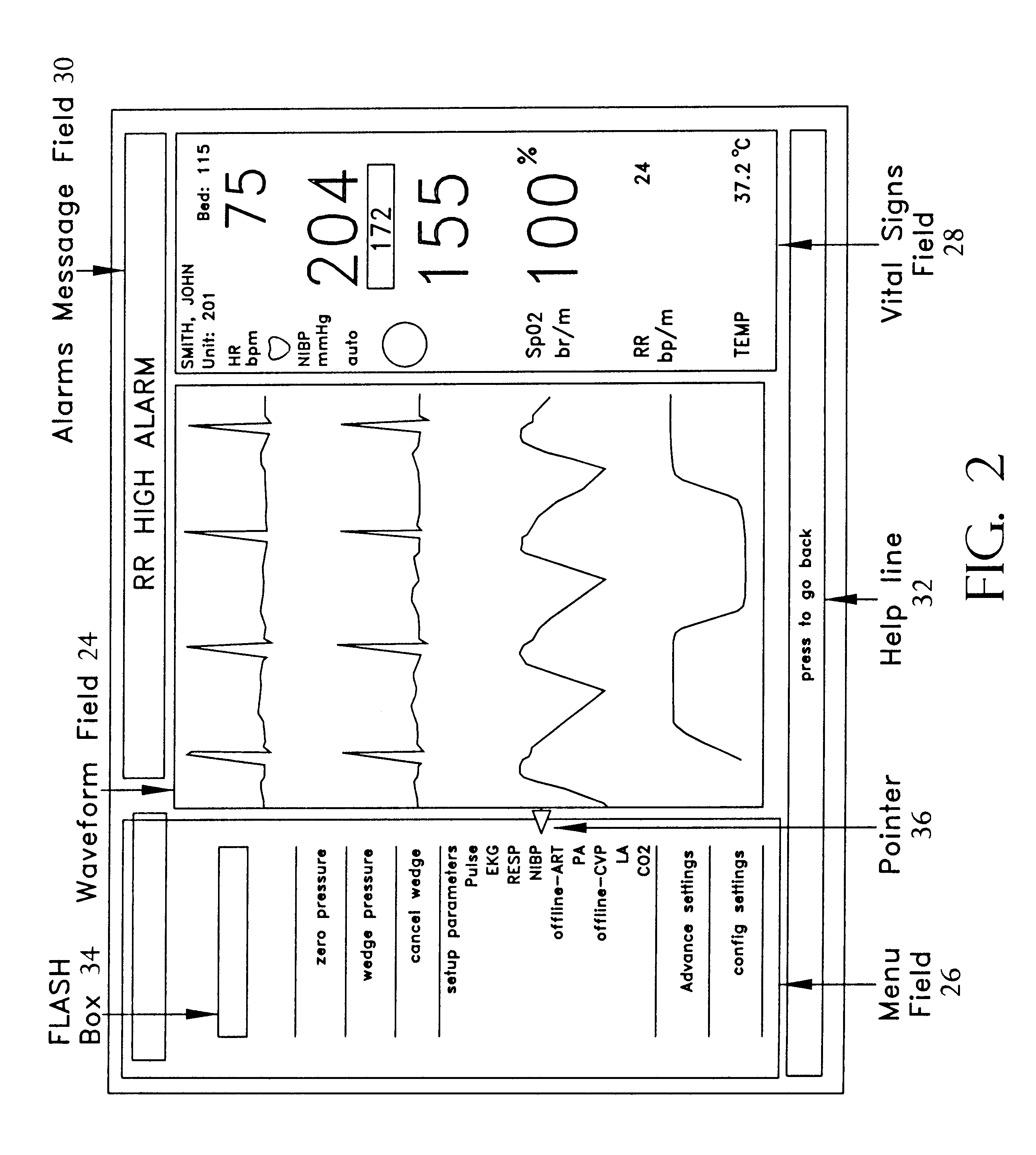
Reconfigurable user interface for modular patient monitor
InactiveUS6188407B1Maximize useMinimizing navigationData processing applicationsElectrocardiographyOperational systemModularity
A reconfigurable user interface for a modular patient monitor which selectively populates menus for operator selection based on the parameters which are available at any given time. Due to event processing, when a parameter module is added or removed from the system, the reconfigurable user interface is updated immediately to reflect the addition or subtraction of the associated parameter. A flash box in each menu provides shortcuts to the most likely menu option in response to asynchronous events such as alarms and the like. The flash box also assists the operator with the particular steps that must be followed to properly setup or operate a particular feature of the system. Since the menus are not modal, an operator may navigate the menus without making any selections or changing the state of the device.
Owner:GE MEDICAL SYST INFORMATION TECH
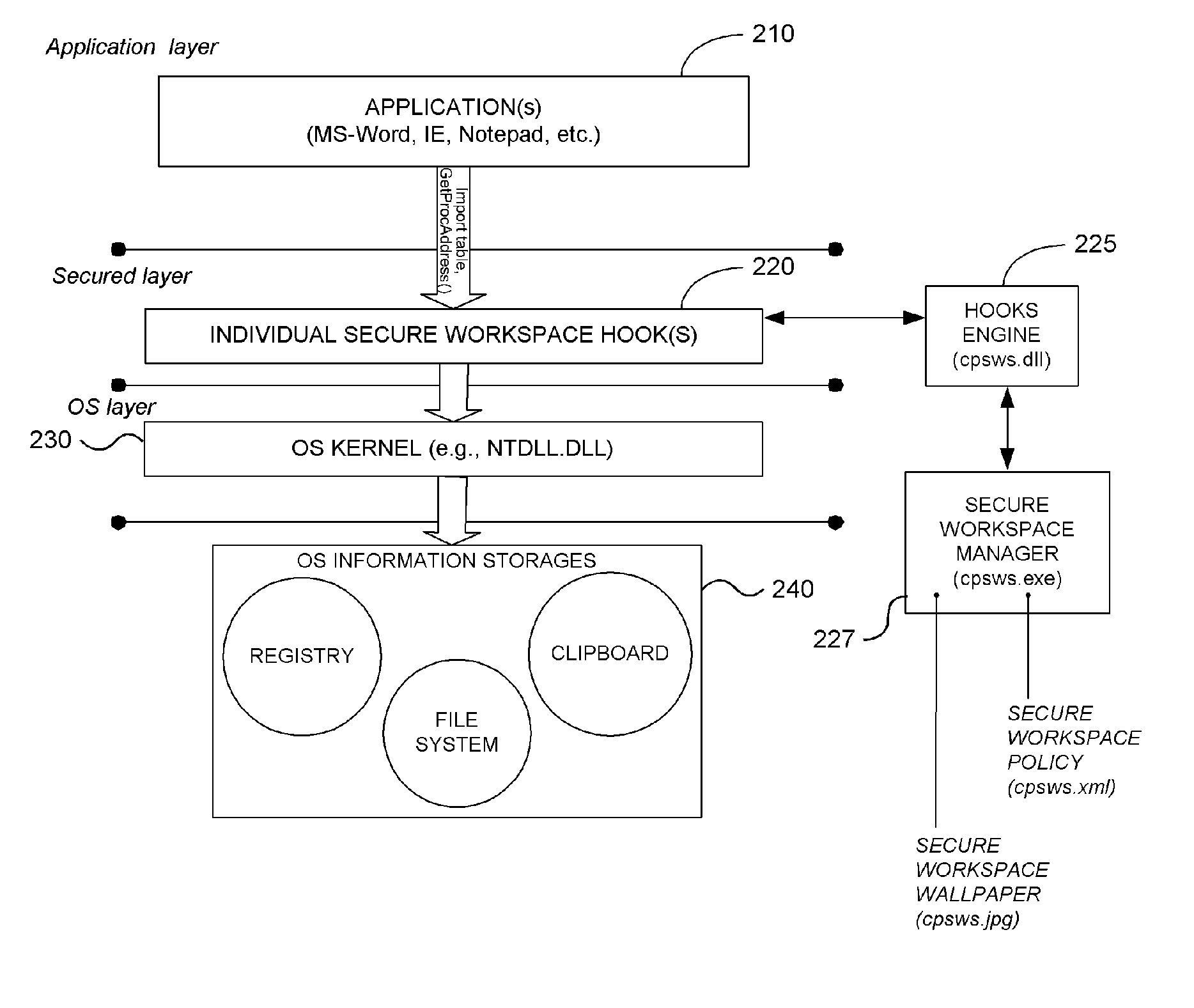
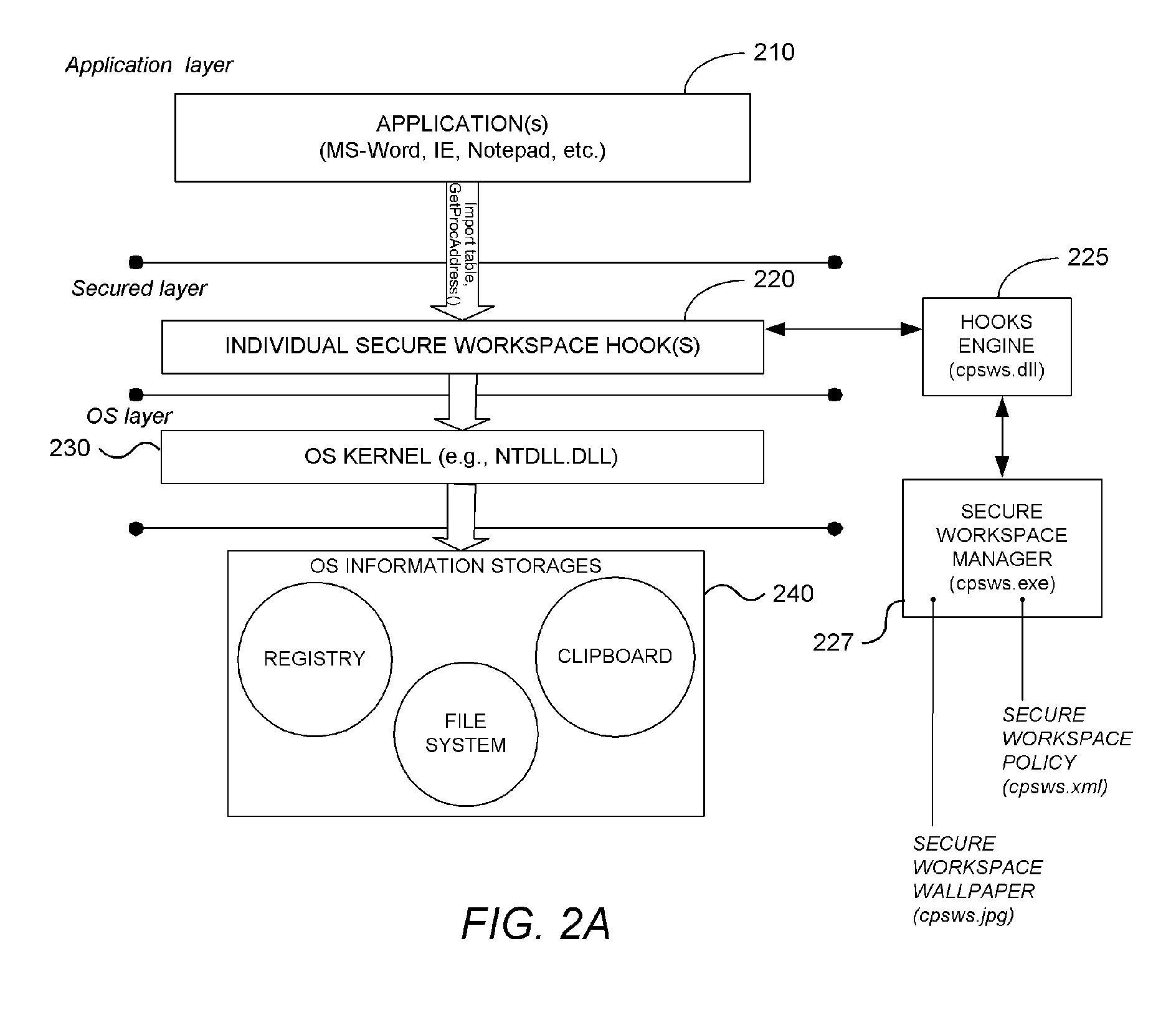
System and Methodology Providing Secure Workspace Environment
ActiveUS20070101435A1Avoid violationsUser identity/authority verificationAnalogue secracy/subscription systemsOperational systemWorkspace
System and methodology providing a secure workspace environment is described. In one embodiment, for example, in a computer system, a method is described for creating a secured workspace within an existing operating system for allowing users to run applications in a secured manner, the method comprises steps of: creating a policy for configuring the secured workspace, the policy specifying how information created during operation of the applications may be accessed; hooking particular functions of the operating system in order to obtain control over the information created during operation of the applications; during operation of the applications, encrypting the information to prevent unauthorized access; in response to a request for access to the information, determining whether the request complies with the policy; and if the request complies with the policy, satisfying the request by providing access to a decrypted copy of the information.
Owner:CHECK POINT SOFTWARE TECH INC
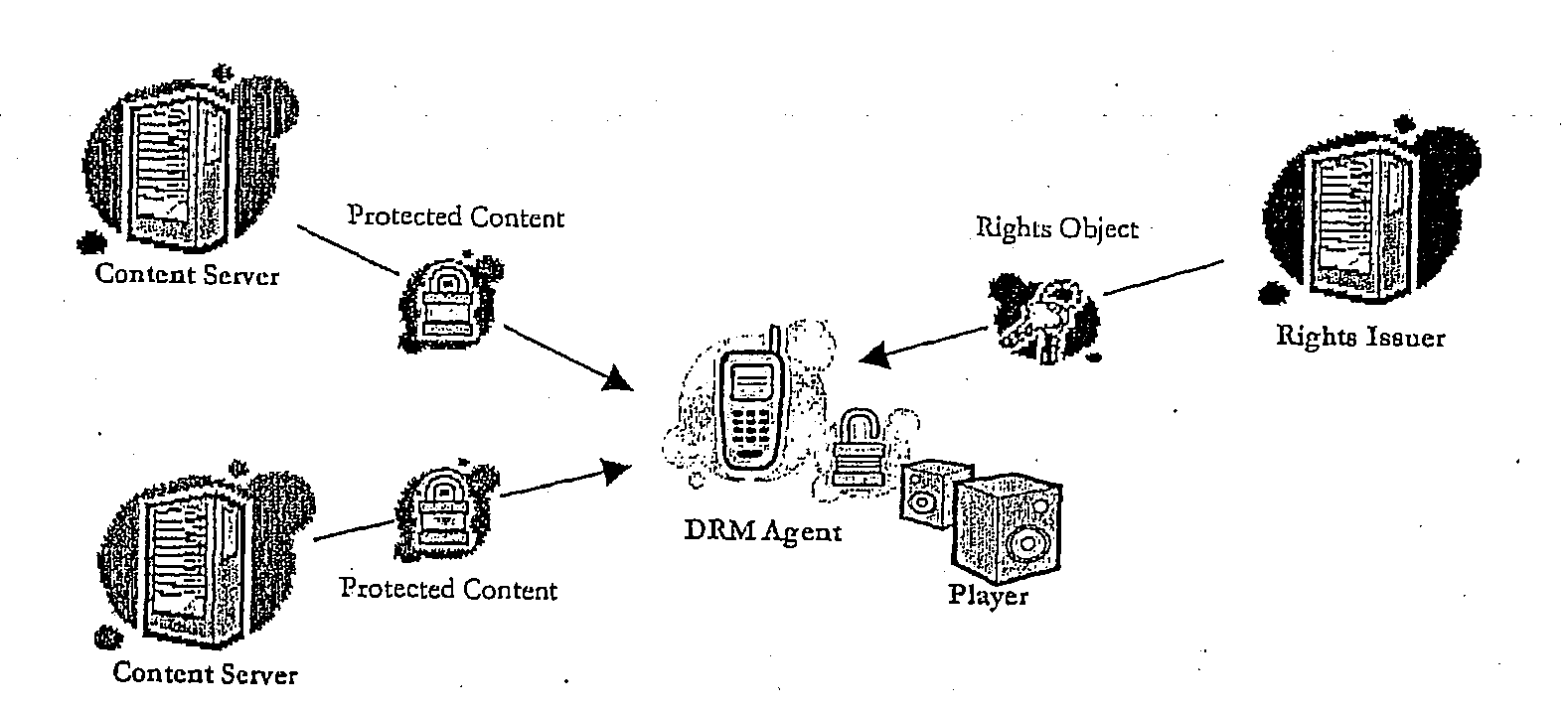
Method of Providing Digital Rights Management for Music Content by Means of a Flat-Rate Subscription
ActiveUS20100031366A1Reliable and goodEasy to manageMetering/charging/biilling arrangementsDigital data processing detailsOperational systemComputer network
The invention enables digital music content to be downloaded to and used on a portable wireless computing device. An application running on the wireless device has been automatically adapted to parameters associated with the wireless device without end-user input (e.g. the application has been configured in dependence on the device OS and firmware, related bugs, screen size, pixel number, security models, connection handling, memory etc. This application enables an end-user to browse and search music content on a remote server using a wireless network; to download music content from that remote server using the wireless network and to playback and manage that downloaded music content. The application also includes a digital rights management system that enables unlimited legal downloads of different music tracks to the device and also enables any of those tracks stored on the device to be played so long as a subscription service has not terminated.
Owner:TIKTOK PTE LTD
Practical platform for high risk applications
InactiveUS20070180509A1Safe and reliable and easy to use practicalIncrease system complexityDigital data processing detailsUser identity/authority verificationSystem integrationComputer hardware
The present invention is a portable device that a computer can boot from, containing a prefabricated independent operating system environment which is engineered from the ground up to prioritize security while maximizing usability, in order to provide a safe, reliable and easy to use practical platform for high risk applications. An embodiment of the present invention may temporarily transform an ordinary computer into a naturally inexpensive logical appliance which encapsulates a turn-key functional solution within the digital equivalent of a military grade security fortress. This allows existing hardware to be conveniently leveraged to provide a self contained system which does not depend on the on-site labor of rare and expensive system integration and security experts.
Owner:SWARTZ ALON R +1
Systems and methods for performing backup operations of virtual machine files
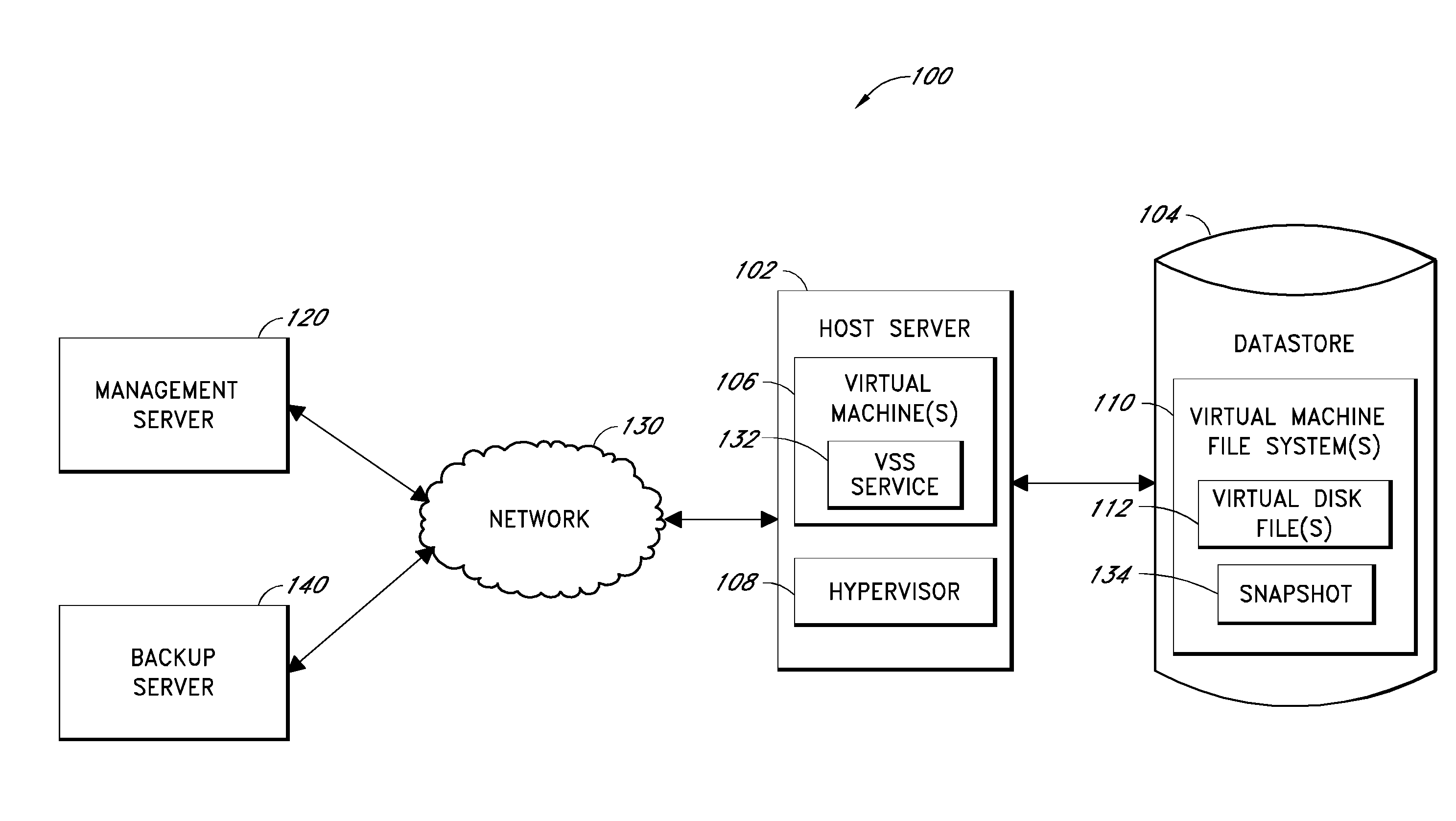
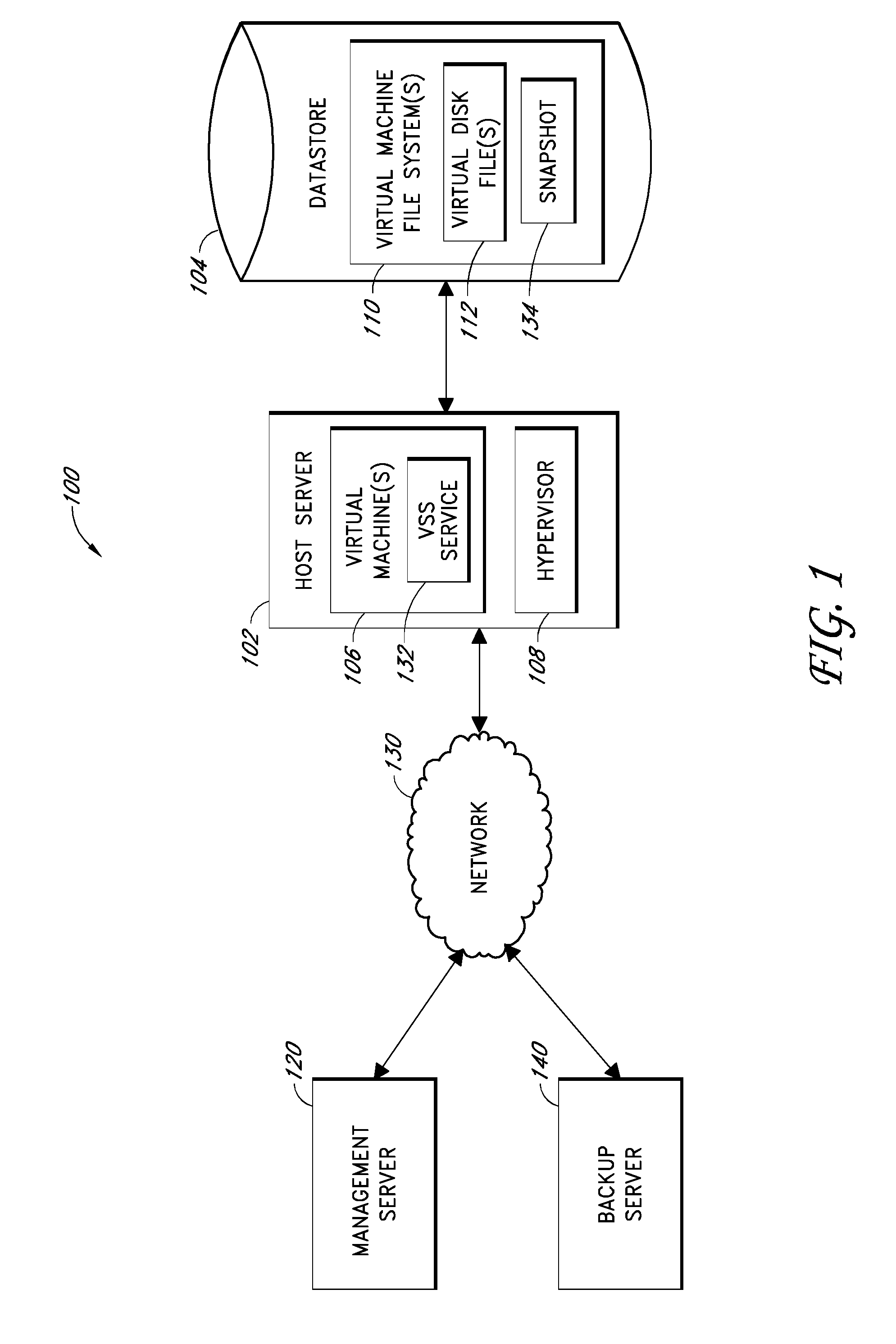
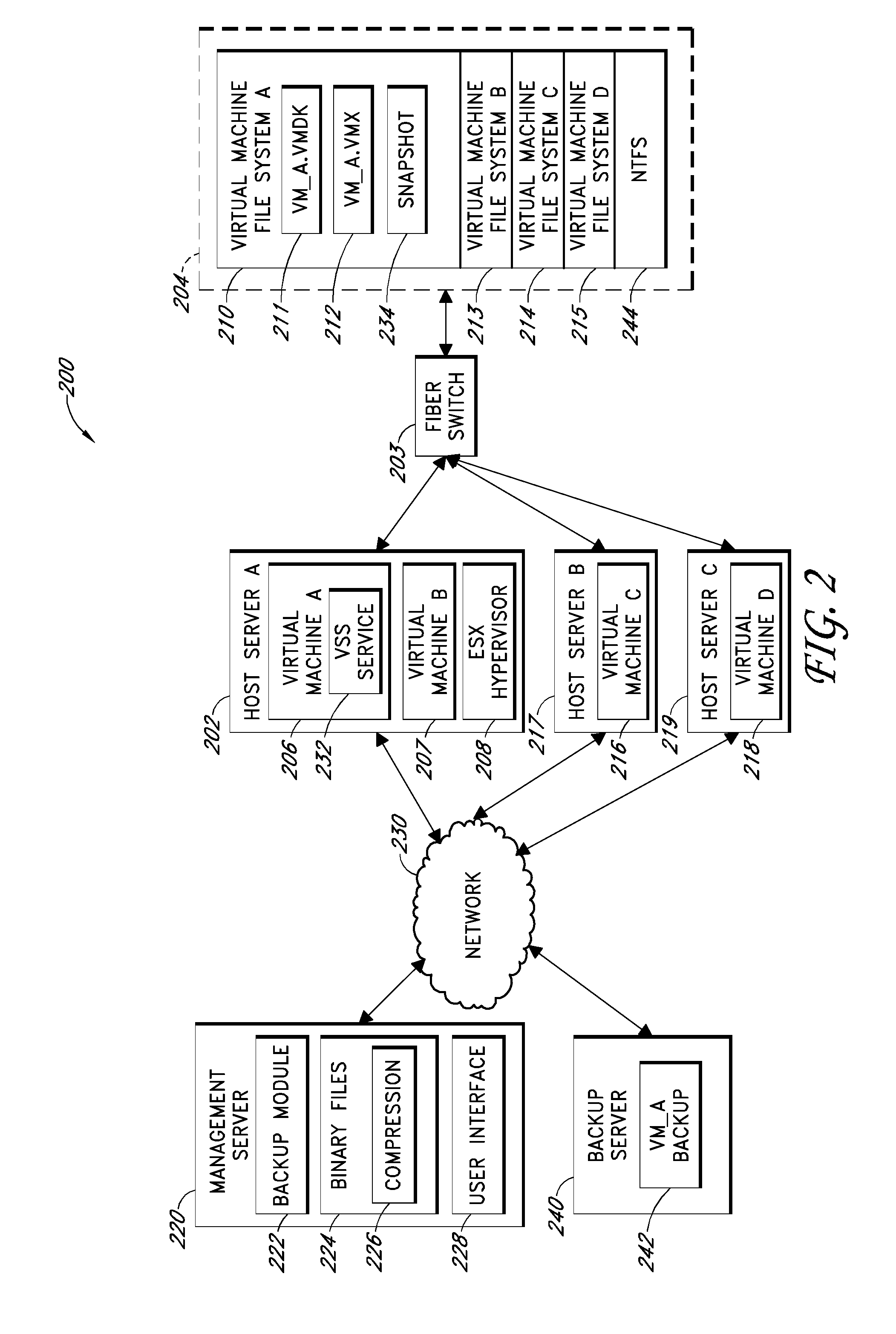
ActiveUS20100011178A1Memory loss protectionError detection/correctionCommunications managementOperational system
Backup systems and methods are disclosed for a virtual computing environment. Certain examples include a system having a backup management server that communicates with a host server having at least one virtual machine. The management server coordinates with the host server to perform backup copies of entire virtual machine disks from outside the guest operating system of the virtual machine. In certain examples, such backup systems further utilize a volume shadow copy service executing on the host server to quiesce virtual machine applications to put data in a consistent state to be backed up. The backup system then utilizes hypervisor snapshot capabilities of the host server to record intended changes to the virtual machine disk files while such files are being copied (e.g., backed up) by the host server. Such recorded changes can be later committed to the virtual machine disk files once the backup operation has completed.
Owner:QUEST SOFTWARE INC
System and method for launching a resource in a network
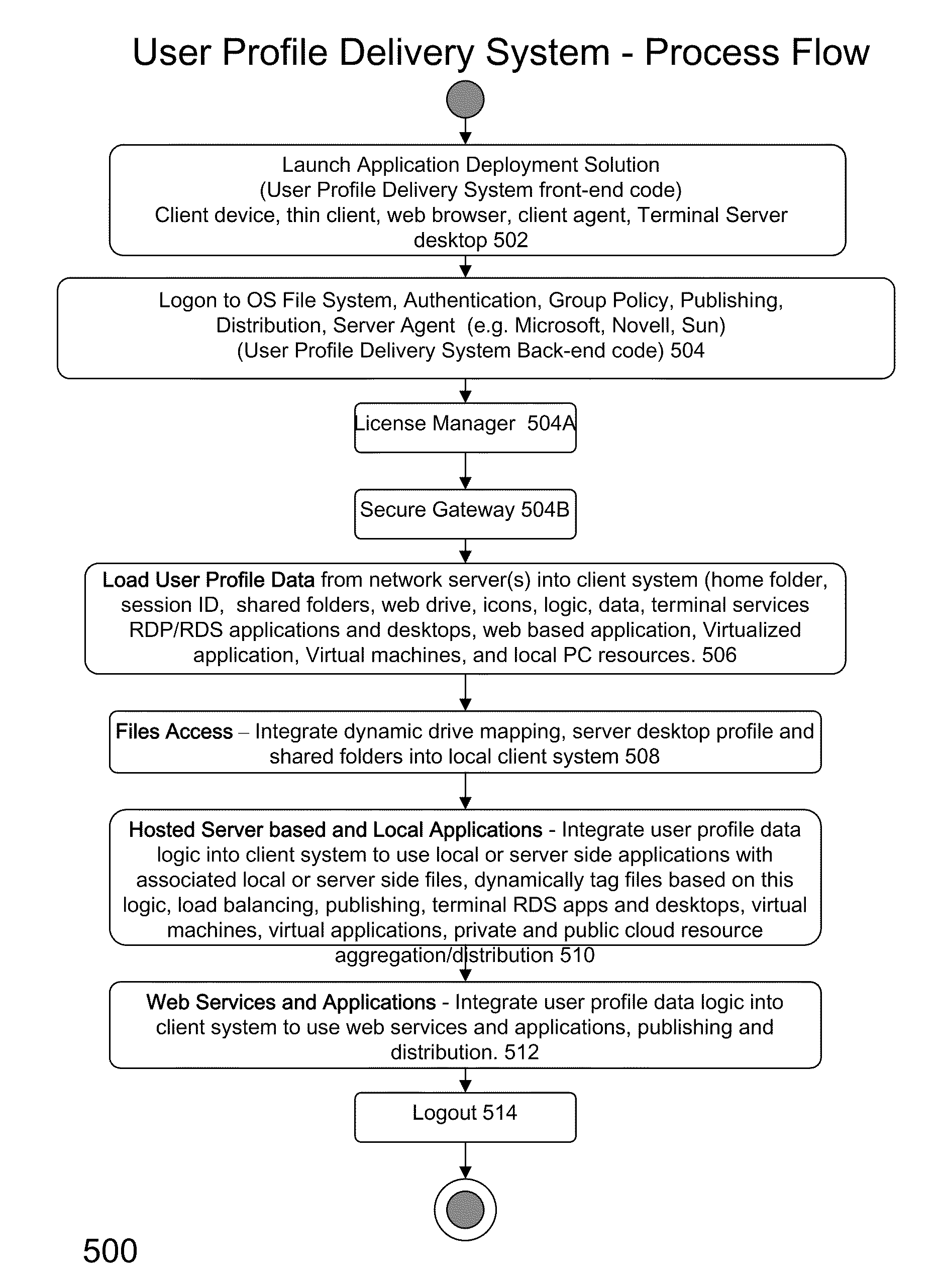
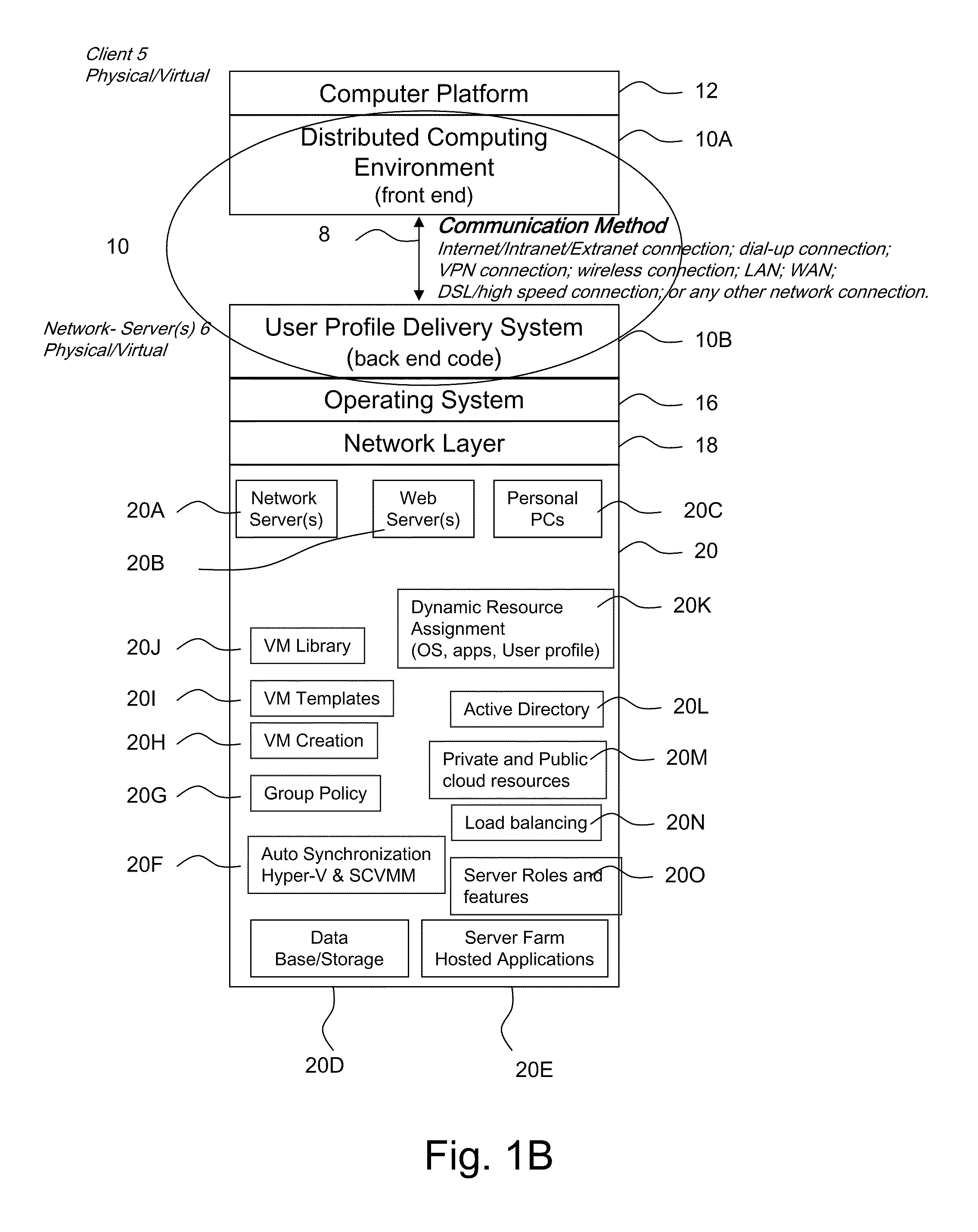
ActiveUS20110251992A1Provide controlDigital data processing detailsWireless commuication servicesOperational systemDirectory structure
The disclosure provides a system and method for a client connected to a server to a resource in a network. For the system a virtual machine module is provided to access a library and to create virtual machine templates and to create virtual machines from the virtual machine templates. The virtual machine module provides to a host machine in the network access to machines, user profile settings and instances of an application in the network and to multiple operating systems. The client has: access to an instance of the resource; an access module to provide the client with communication to access to the server using load balancing algorithms to access the file using Remote Desktop Protocol (RDP) commands; and an authentication module providing access to a directory structure accessed by the server using Microsoft Group Policy Objects (GPOs) and Active Directory (AD) services to authenticate the client with the server.
Owner:DESKTOPSITES
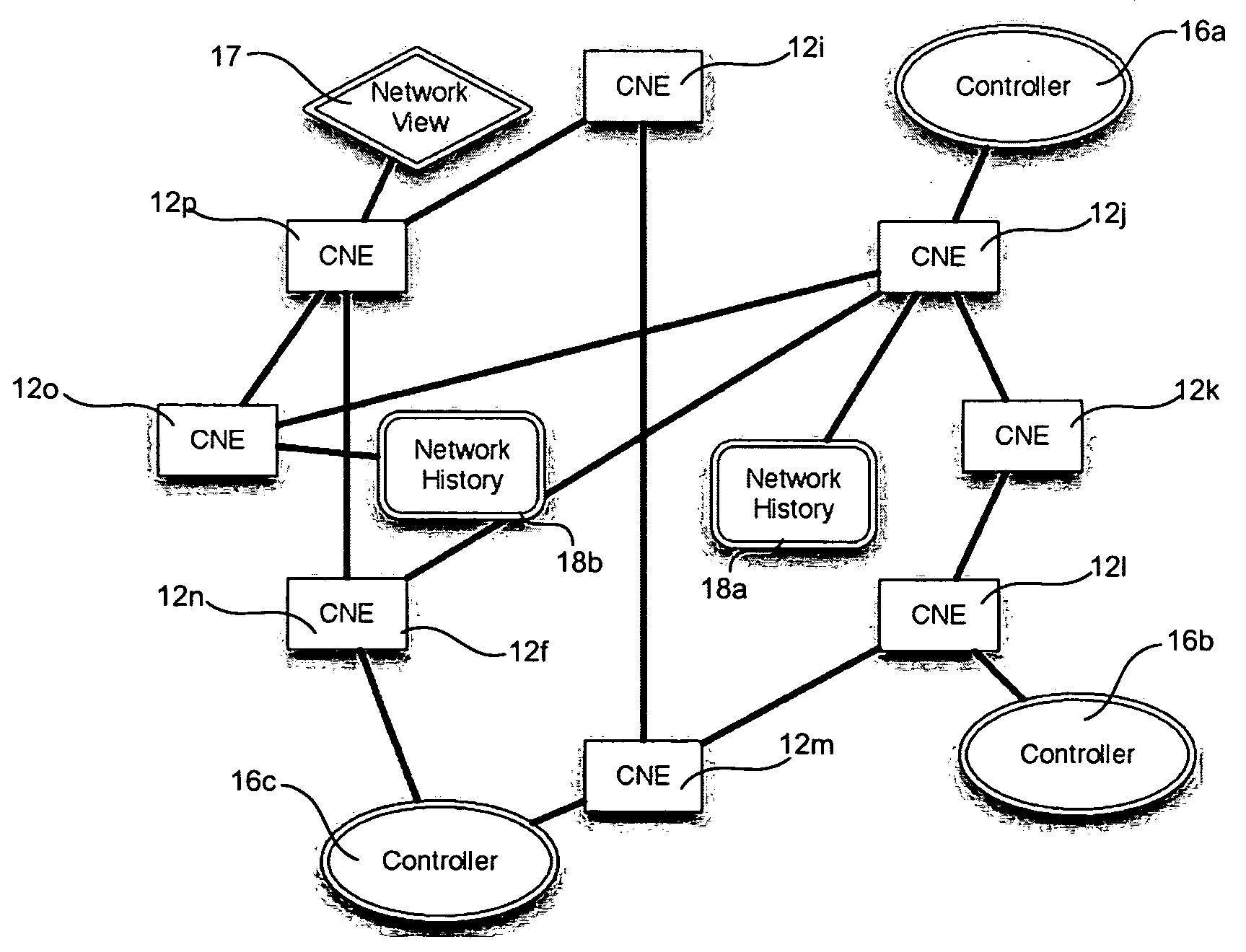
Network operating system for managing and securing networks
ActiveUS20090138577A1Reduced power modeDigital computer detailsTransmissionTraffic capacityAuto-configuration
Systems and methods for managing a network are described. A view of current state of the network is maintained where the current state of the network characterizes network topology and network constituents, including network entities and network elements residing in or on the network. Events are announced that correspond to changes in the state of the network and one or more network elements can be configured accordingly. Methods for managing network traffic are described that ensure forwarding and other actions taken by network elements implement globally declared network policy and refer to high-level names, independently of network topology and the location of network constituents. Methods for discovering network constituents are described, whereby are automatically configured. Routing may be performed using ACL and packets can be intercepted to permit host to continue in sleep mode. The methods are applicable to virtual environments.
Owner:NICIRA
Service-based compression of content within a network communication system
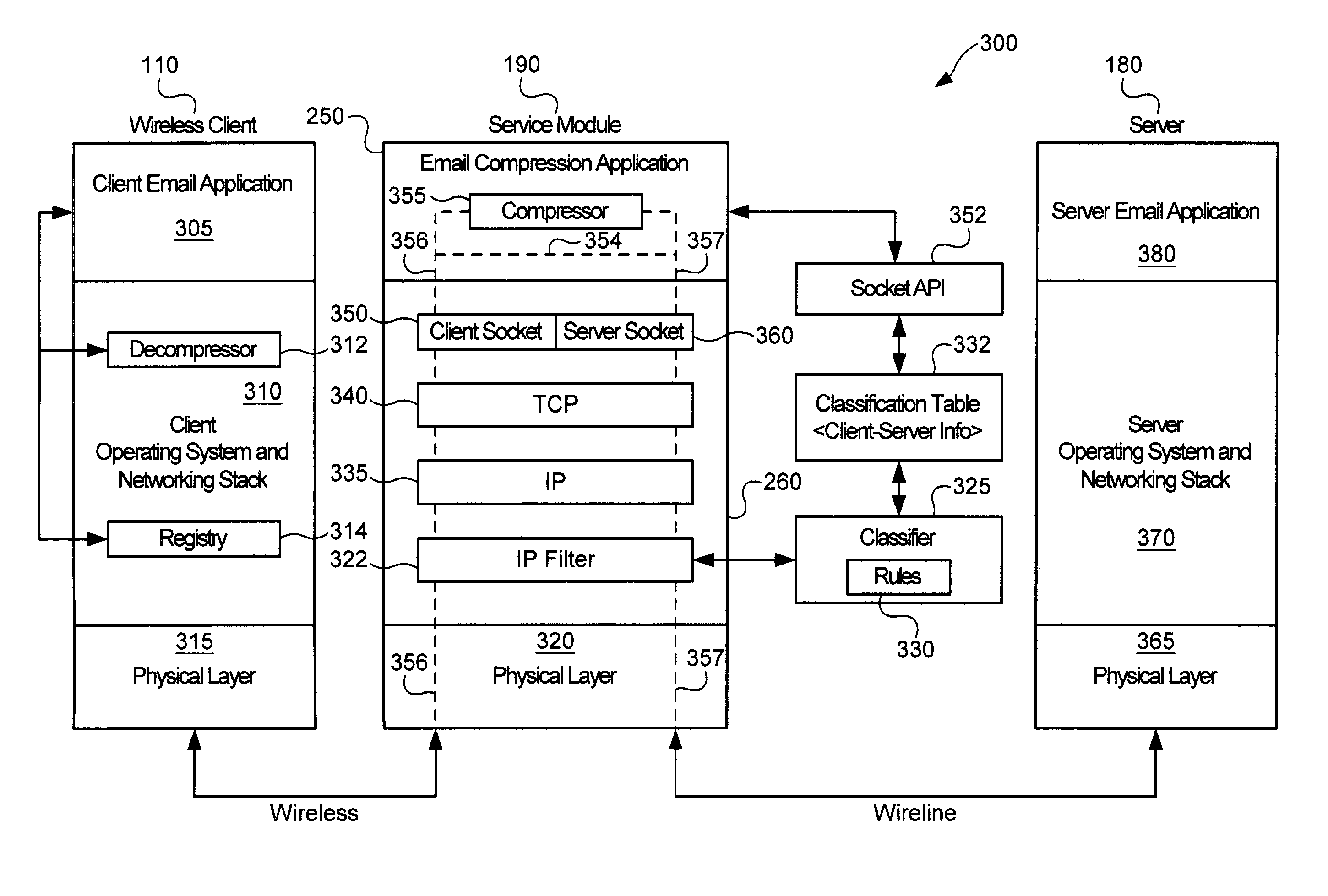
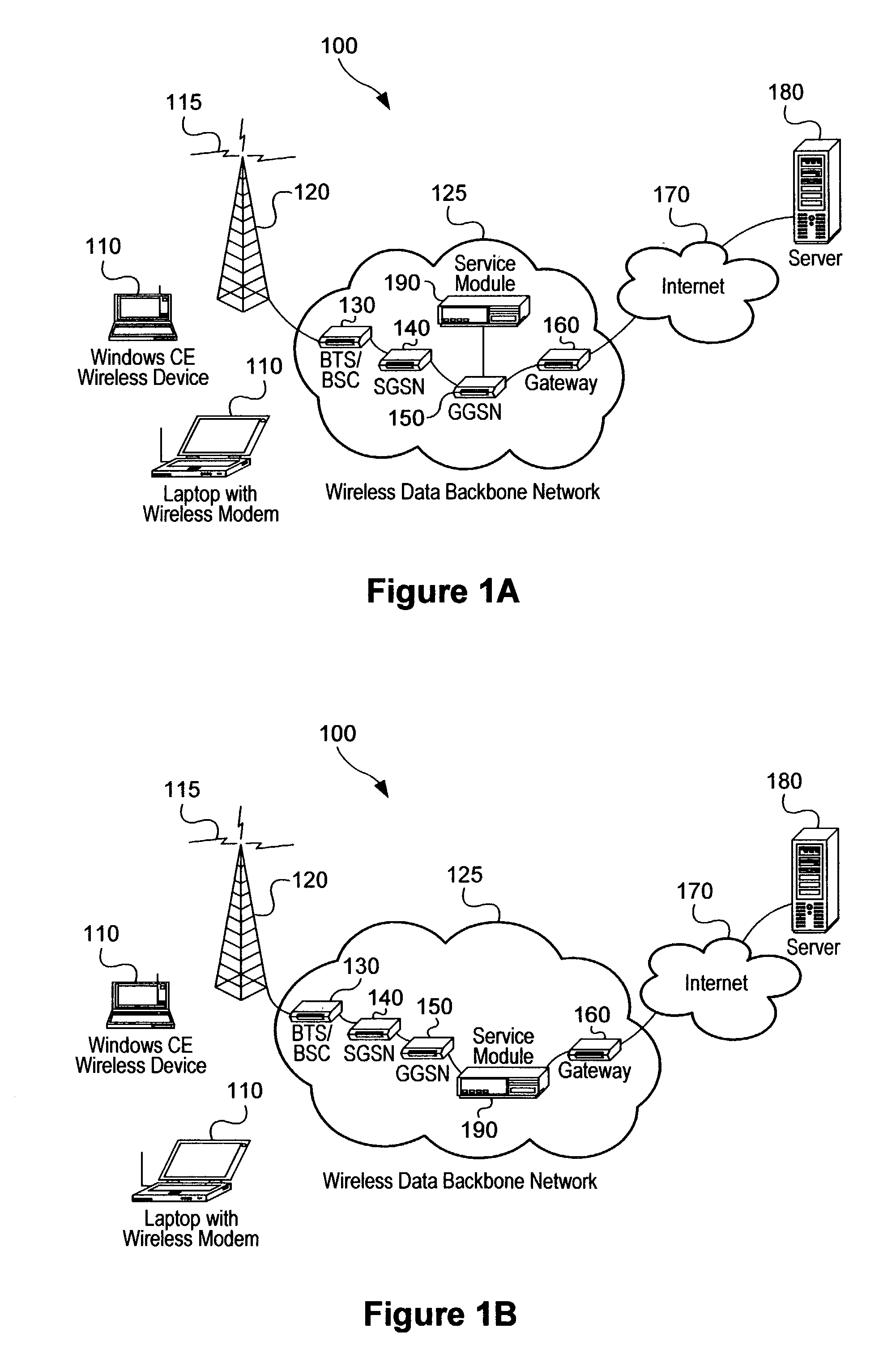
ActiveUS7024460B2Easy to decompressMultiple digital computer combinationsData switching networksOperational systemData stream
A service module incorporated within the network infrastructure intercepts packets communicated between a client and a server to determine whether the connection corresponds to an email service. If so, the service module breaks the connection by terminating the connection with the client at the service module and opening a separate connection between the service module and the server. Packets communicated between the client and the server may then be redirected to an email compression application that monitors messages communicated between the client and the server and processes the messages in accordance with the state of the email session. For messages corresponding to connection establishment, user authentication and other protocol-specific messages, for example, the email compression application may be configured to forward the messages to the originally intended destination. Messages corresponding to an email message data, however, are buffered within the email compression application. Once the entire message has been received, the email compression application may strip the message headers and any protocol-specific data, compress the data and attach new message headers corresponding to the compressed email message. The compressed and reformatted email message is then reinserted into the data stream for transmission to the intended destination. Because compression may occur between the server and client, compression may be performed without requiring special processing by the server before email messages are sent. Furthermore, because the email messages may be compressed in a format that can be readily decompressed using decompression libraries incorporated within the operating system of client devices, such as the CAB format or GZIP format, the client may decompress received email messages utilizing software already incorporated within the operating system of the client device, without requiring download or installation of special decompression software and / or coordination of compression / decompression of email messages with the server or sending party.
Owner:OPTIMORPHIX INC
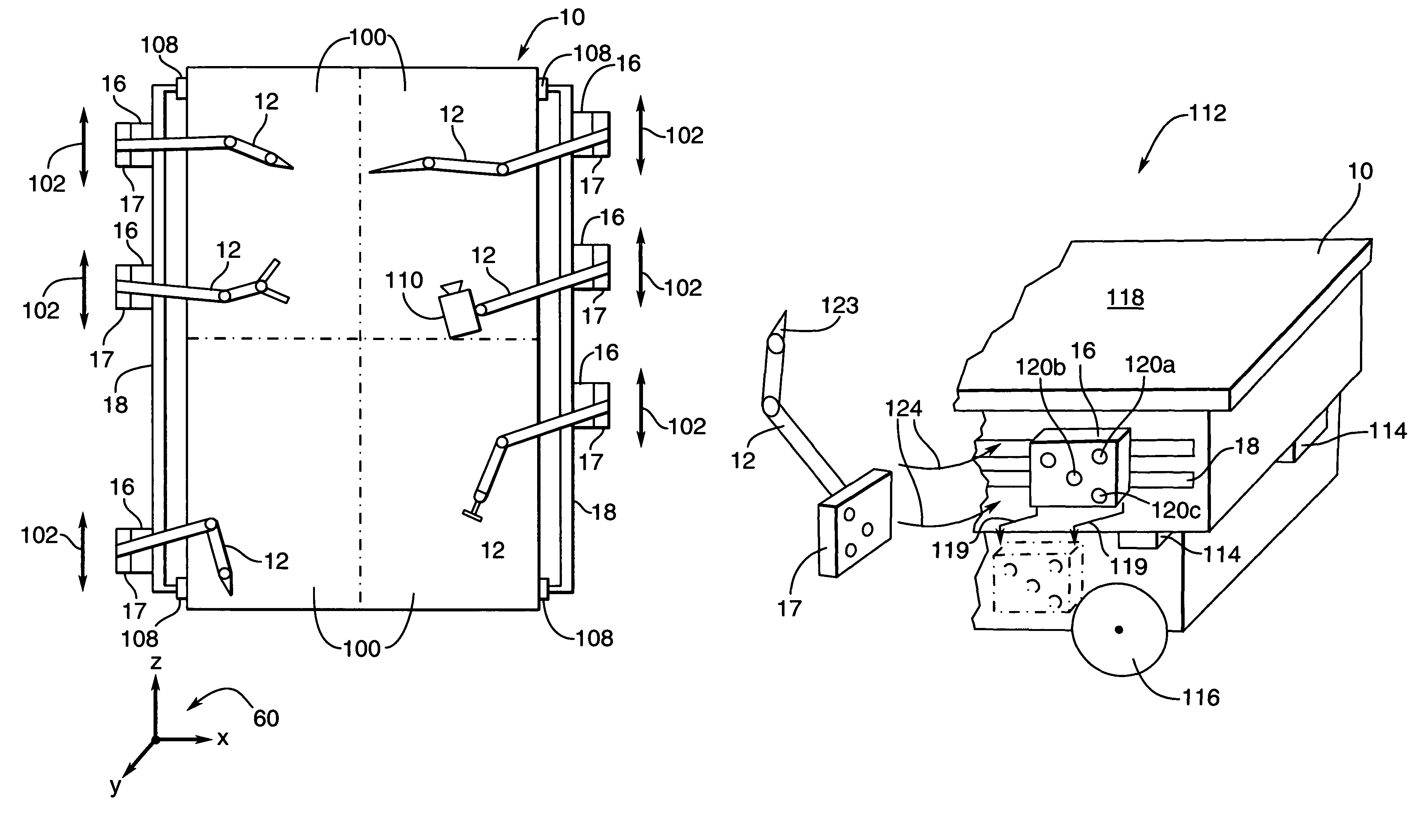
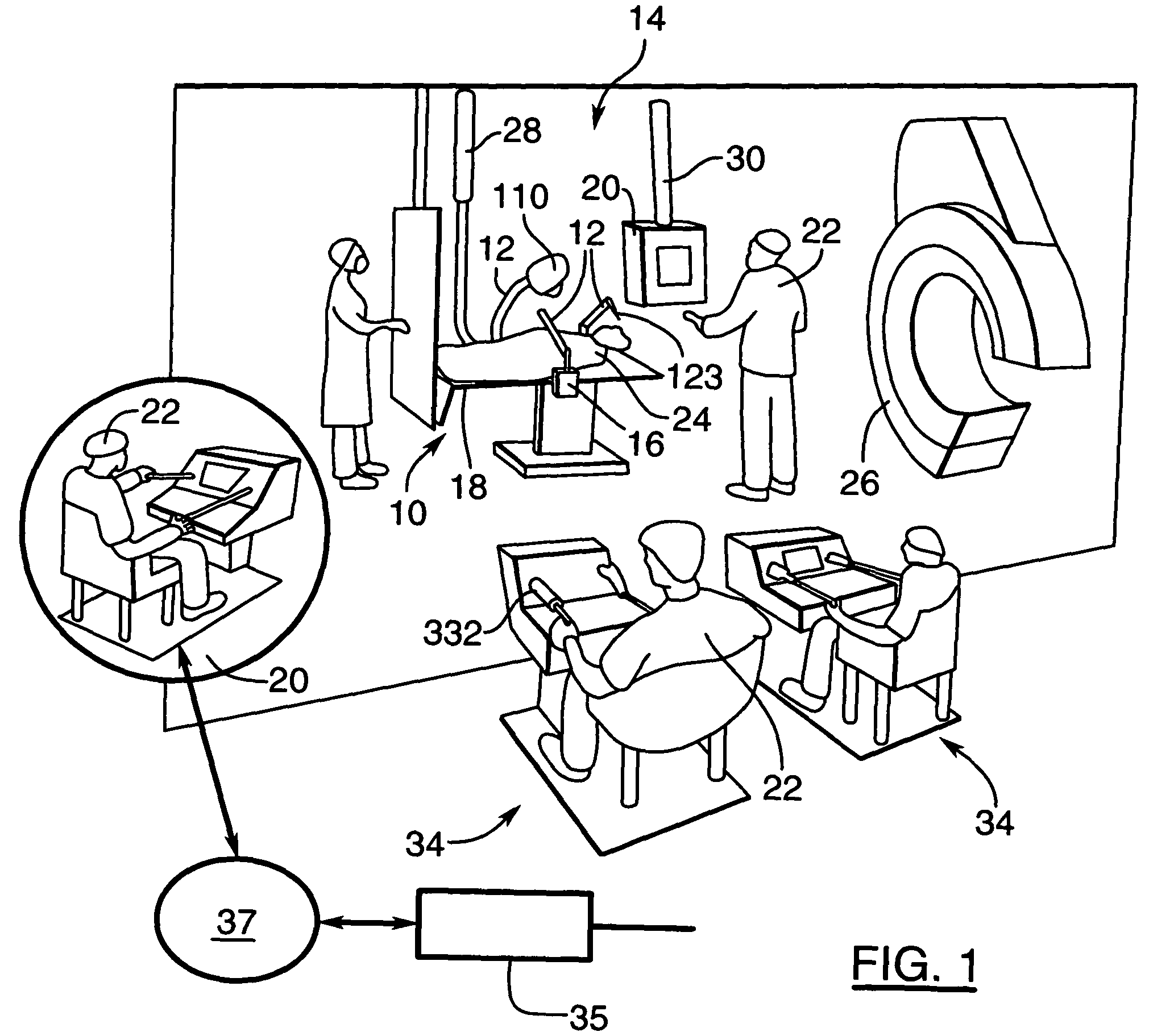
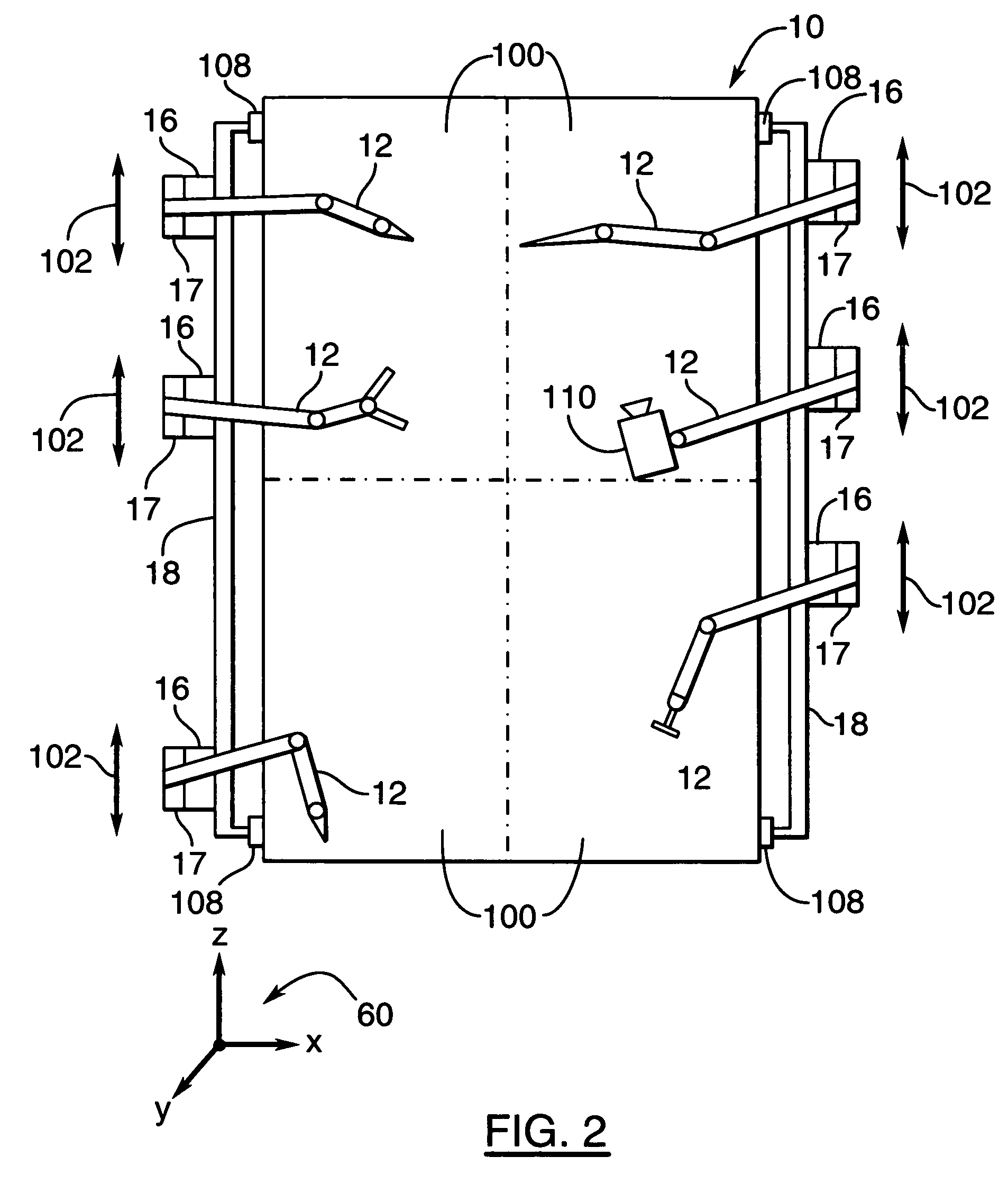
Multi-purpose robotic operating system and method
ActiveUS7979157B2Stable operating platformEasy to installProgramme-controlled manipulatorDiagnosticsSurgical operationRobotic systems
A dynamically configurable robotic system and method for performing surgical operations using a plurality of robotic arms remotely controlled by at least one operator console. The system comprises a track system configured for mounting to a patient support table, such that the track system provides a stable operating platform for the robotic arms and for facilitating placement of a proximal end of each of the arms at a selected position about a periphery of the patient support table. the system and method also have a plurality of base stations for operatively coupling each of the robotic arms to the track system, such that each of the base stations include a housing, a first connector for coupling the housing to the track system, the first connector configured for facilitating movement of the housing along the track system while coupled thereto, and a second connector for coupling the housing to the proximal end of at least one of the robotic arms, the second connector configured for providing at least one of power supply, control signalling, and data communication with respect to the coupled robotic arm. The system and method also have a control unit for coupling to at least two of the base stations and configured for dynamically connecting operative remote control between the coupled base stations and a first operator console of the at least one operator console.
Owner:CENT FOR SURGICAL INVENTION & INNOVATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com