Patents
Literature
605 results about "Virtual computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
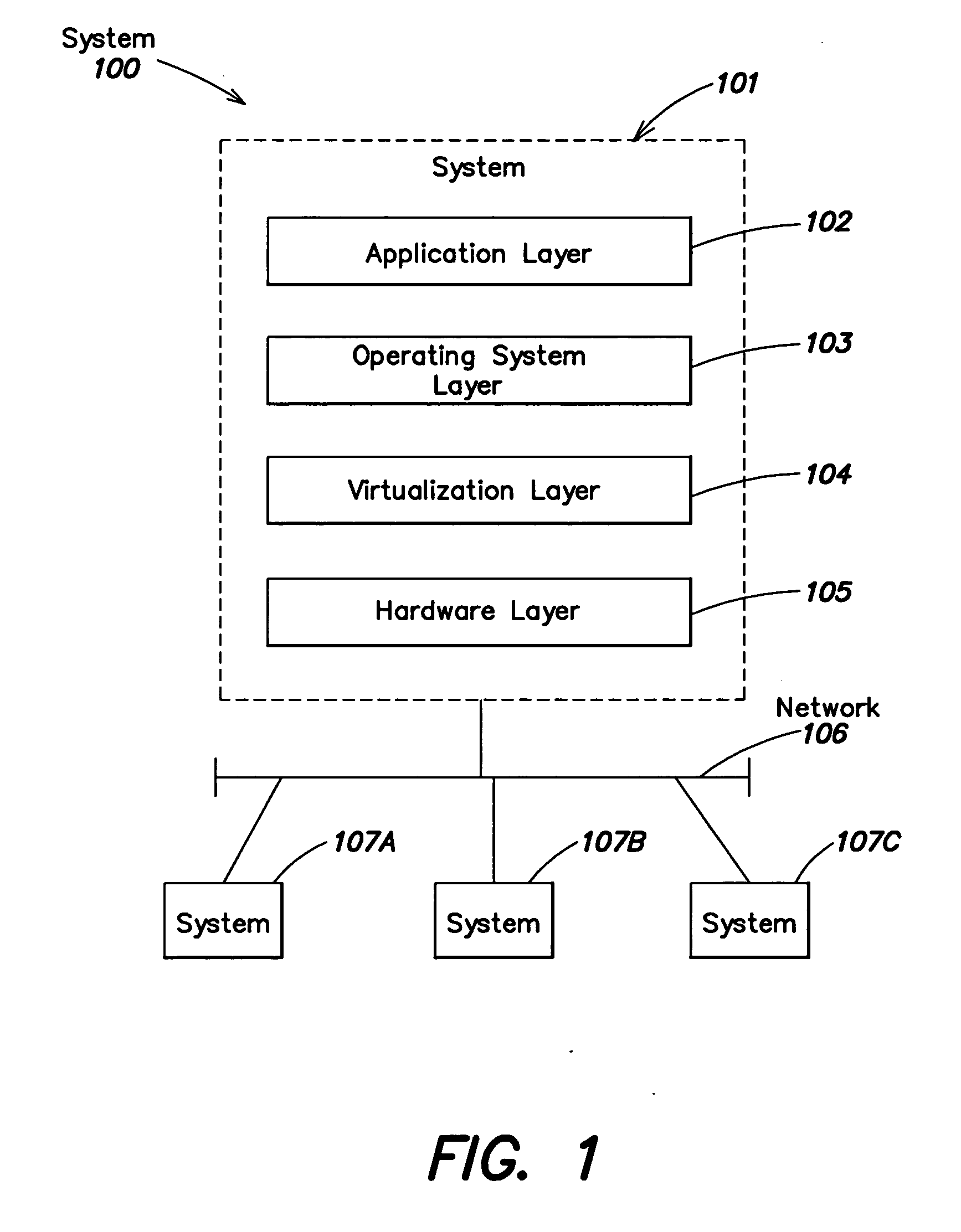
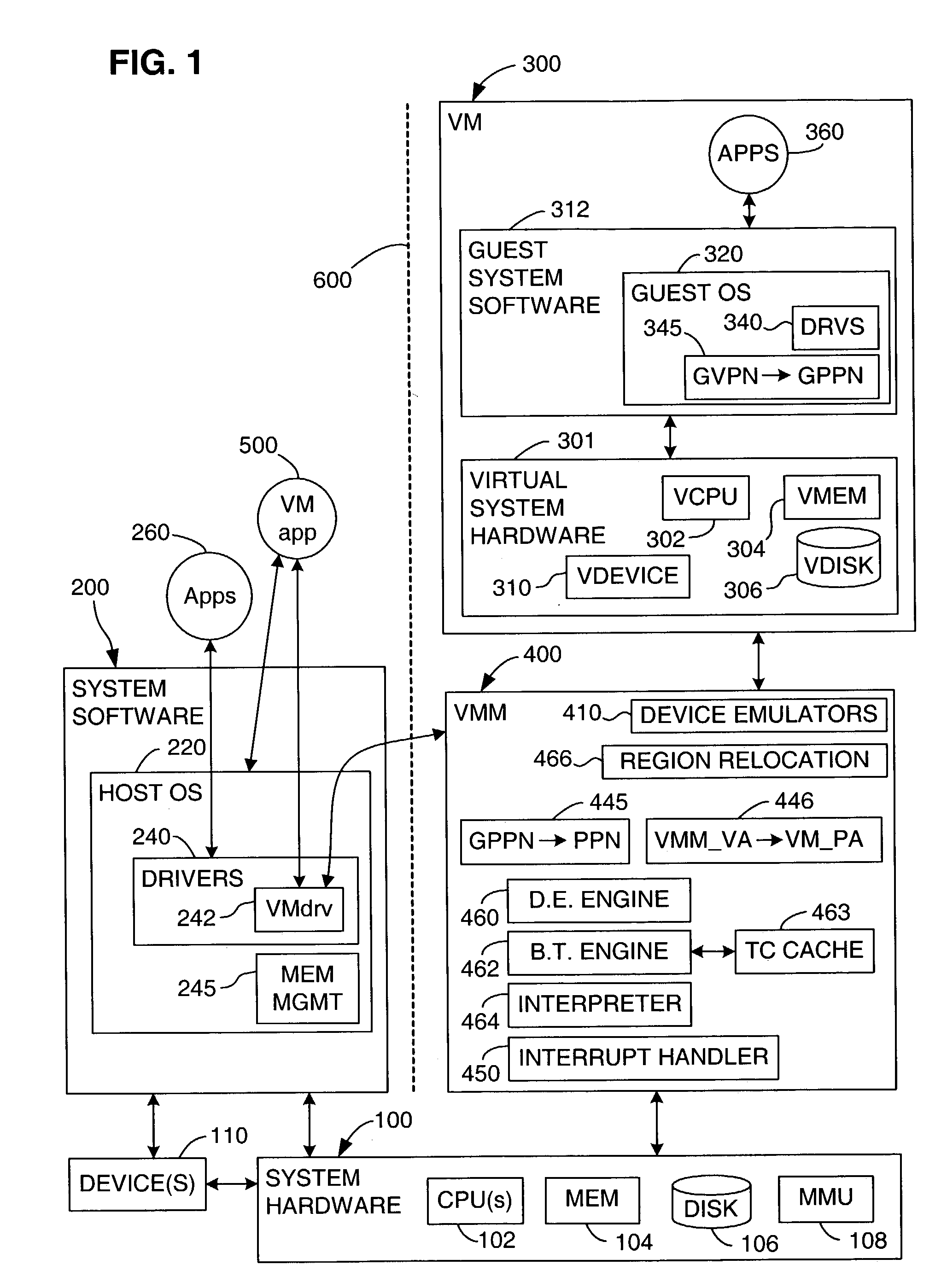
Virtual computing allows computer users remote access to software applications and processes when they need it. Users gain access via the Internet through a wireless or network server. For a fee, users can boost their computers' capabilities, size, performance, processes and/or software applications whenever they need it.
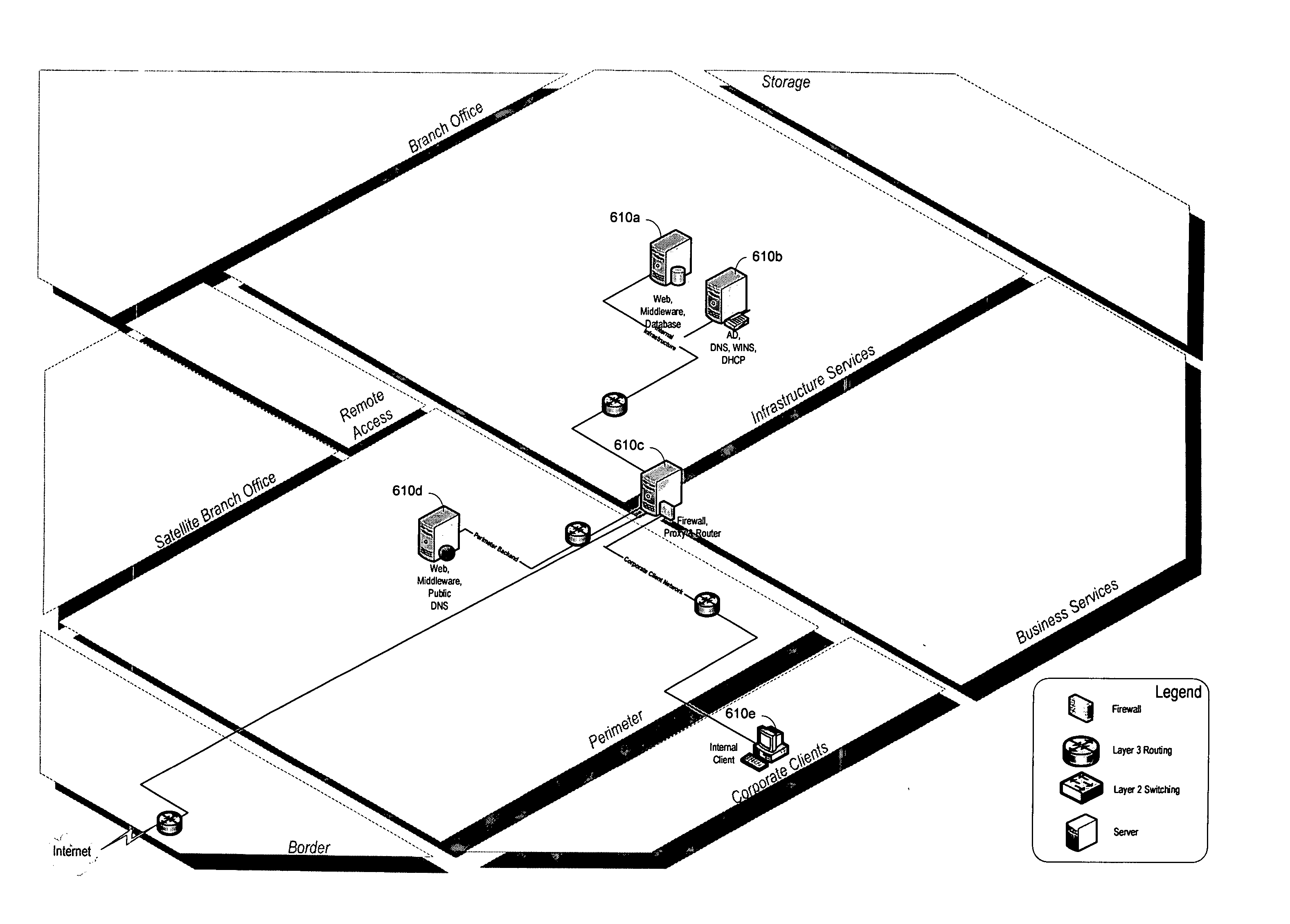
System and method for managing virtual servers
ActiveUS20050120160A1Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemPrimitive state
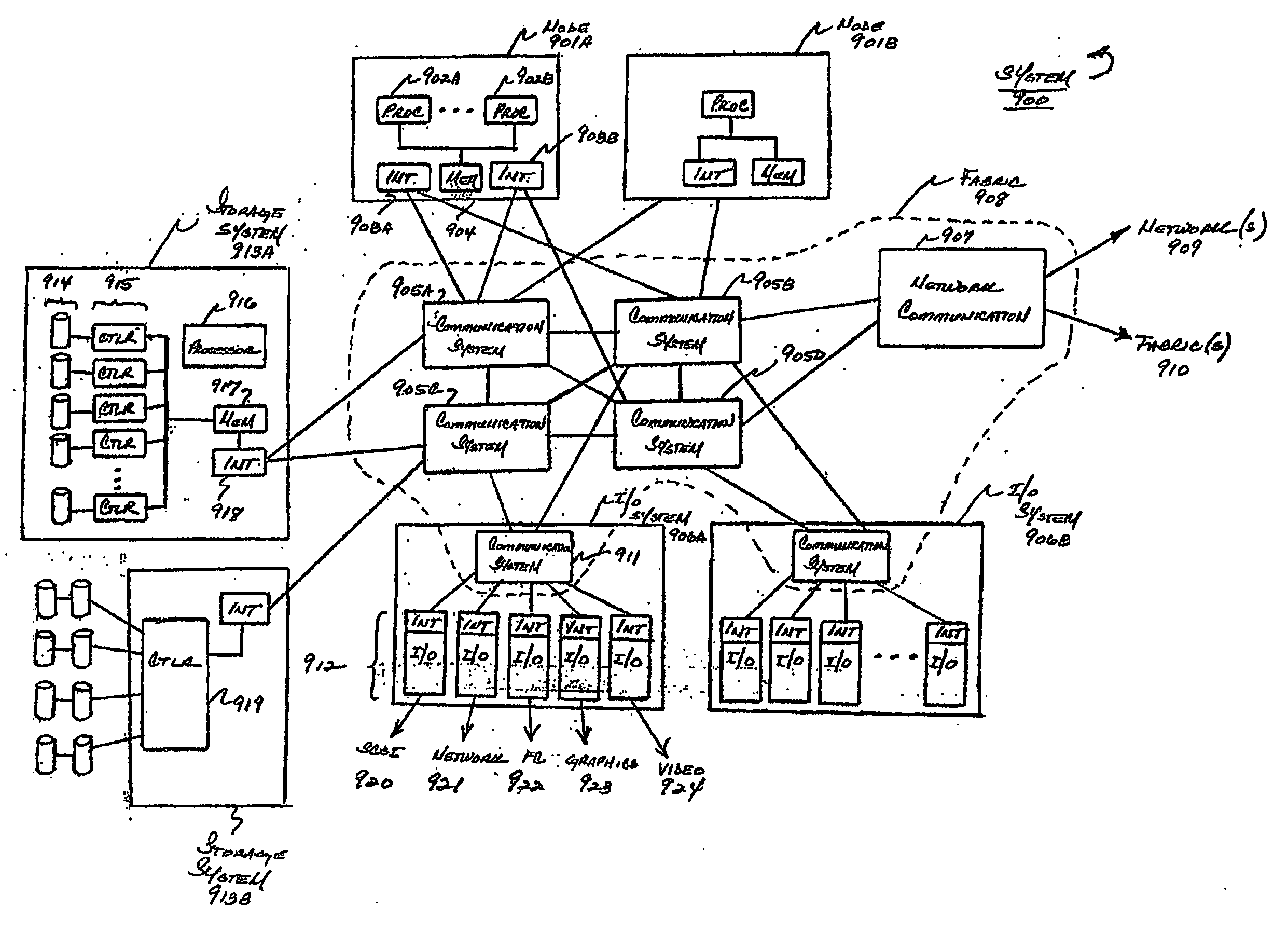
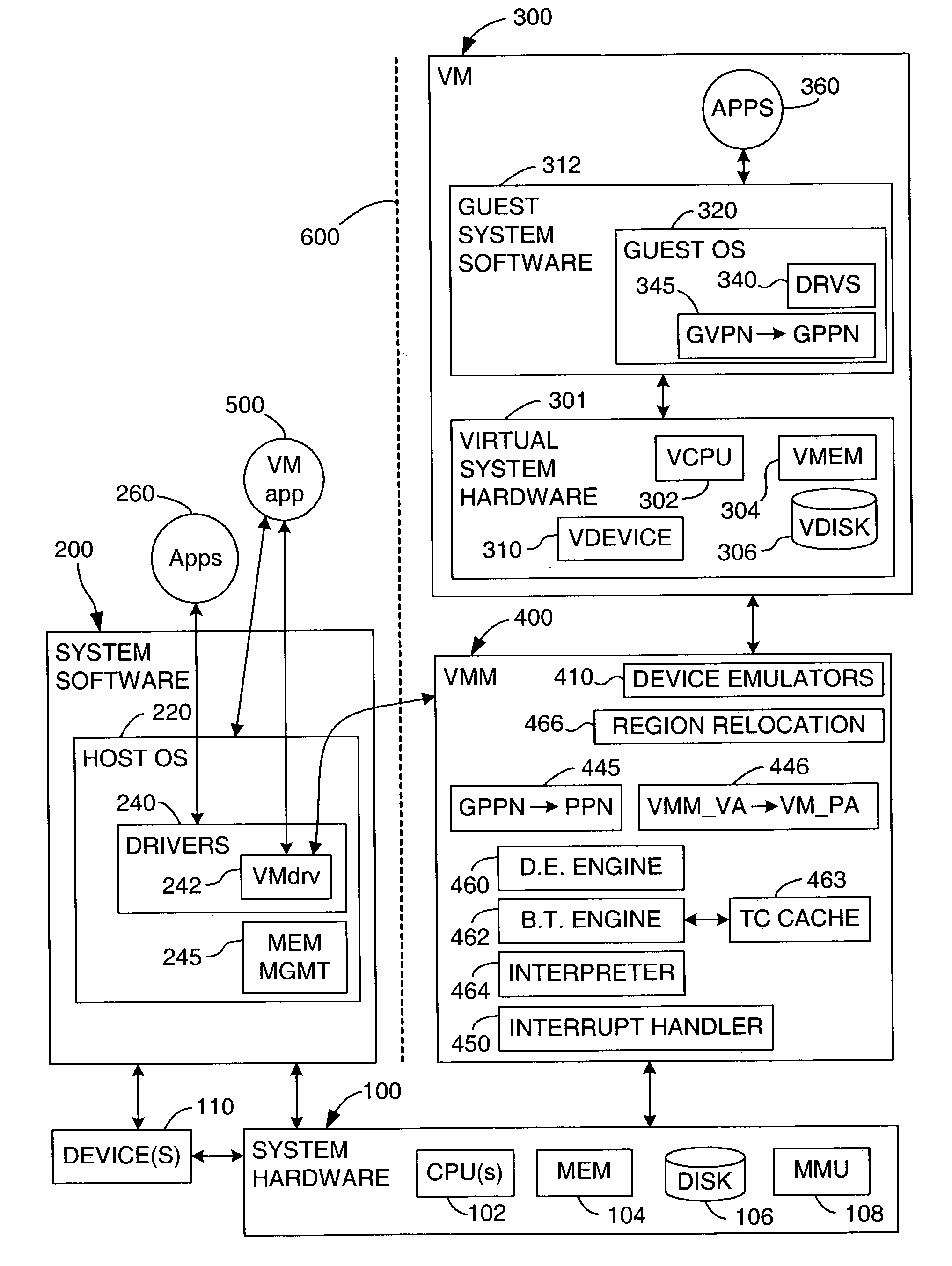
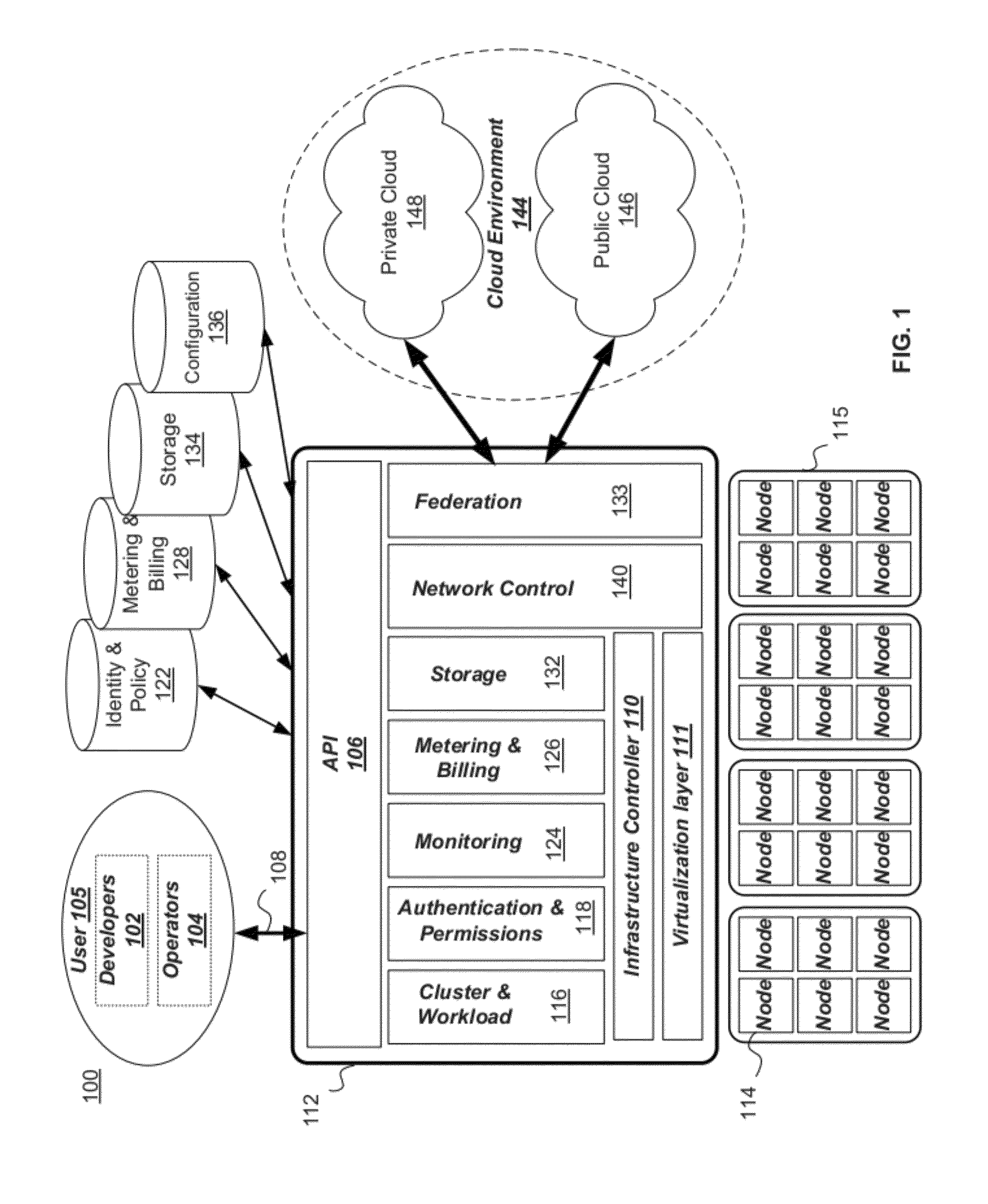
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes. A virtual computing platform is provided that allows for the creation, deletion, modification, control (e.g., start, stop, suspend, resume) and status (i.e., events) of the virtual servers which execute on the virtual computing platform and the management capability provides controls for these functions. In a particular example, such a platform allows the number and type of virtual resources consumed by a virtual server to be scaled up or down when the virtual server is running. For instance, an administrator may scale a virtual server manually or may define one or more policies that automatically scale a virtual server. Further, using the management API, a virtual server can monitor itself and can scale itself up or down depending on its need for processing, memory and I / O resources. For example, a virtual server may monitor its CPU utilization and invoke controls through the management API to allocate a new processor for itself when its utilization exceeds a specific threshold. Conversely, a virtual server may scale down its processor count when its utilization falls. Policies can be used to execute one or more management controls. More specifically, a management capability is provided that allows policies to be defined using management object's properties, events and / or method results. A management policy may also incorporate external data (e.g., an external event) in its definition. A policy may be triggered, causing the management server or other computing entity to execute an action. An action may utilize one or more management controls. In addition, an action may access external capabilities such as sending notification e-mail or sending a text message to a telephone paging system. Further, management capability controls may be executed using a discrete transaction referred to as a “job.” A series of management controls may be assembled into a job using one or management interfaces. Errors that occur when a job is executed may cause the job to be rolled back, allowing affected virtual servers to return to their original state.
Owner:ORACLE INT CORP
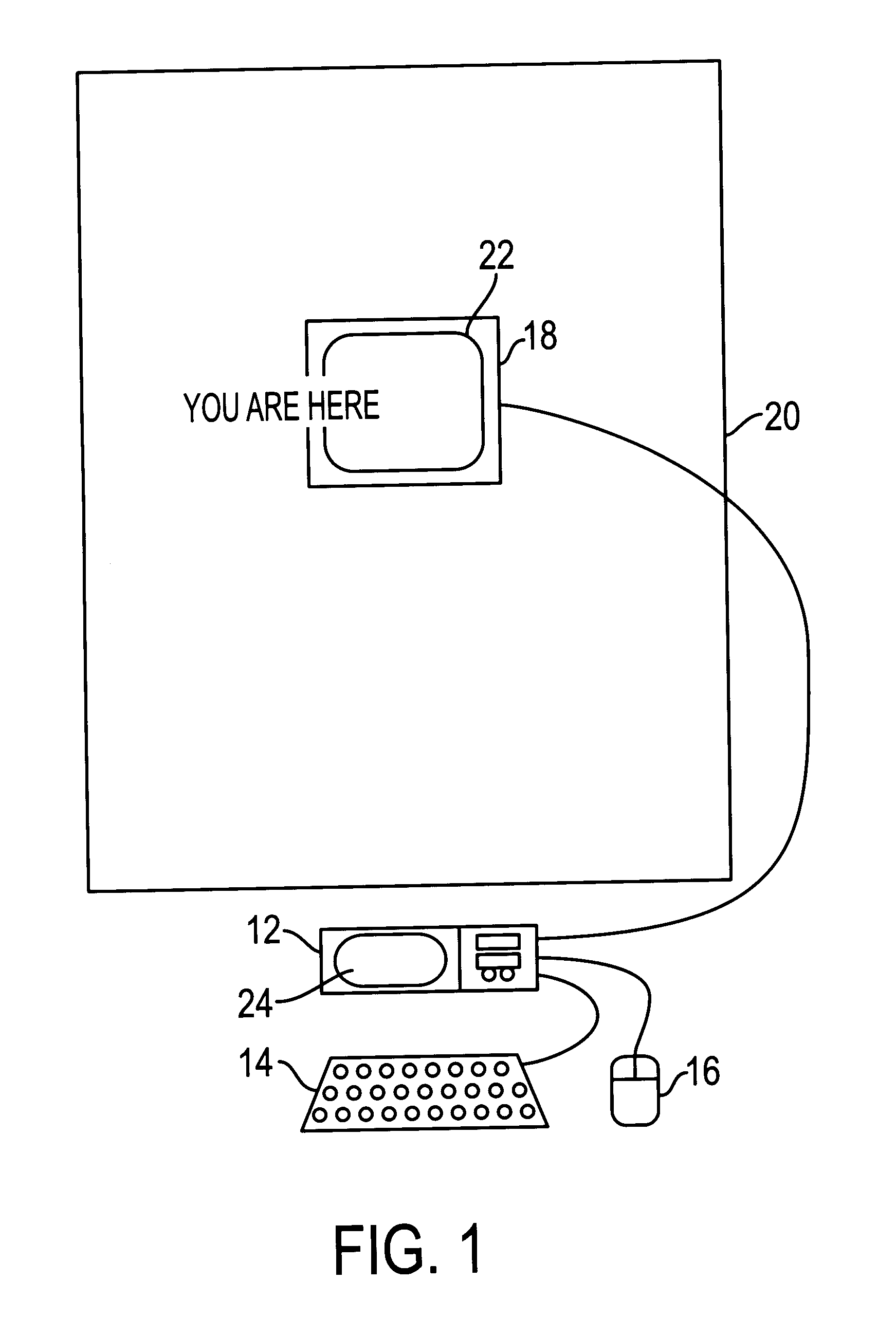
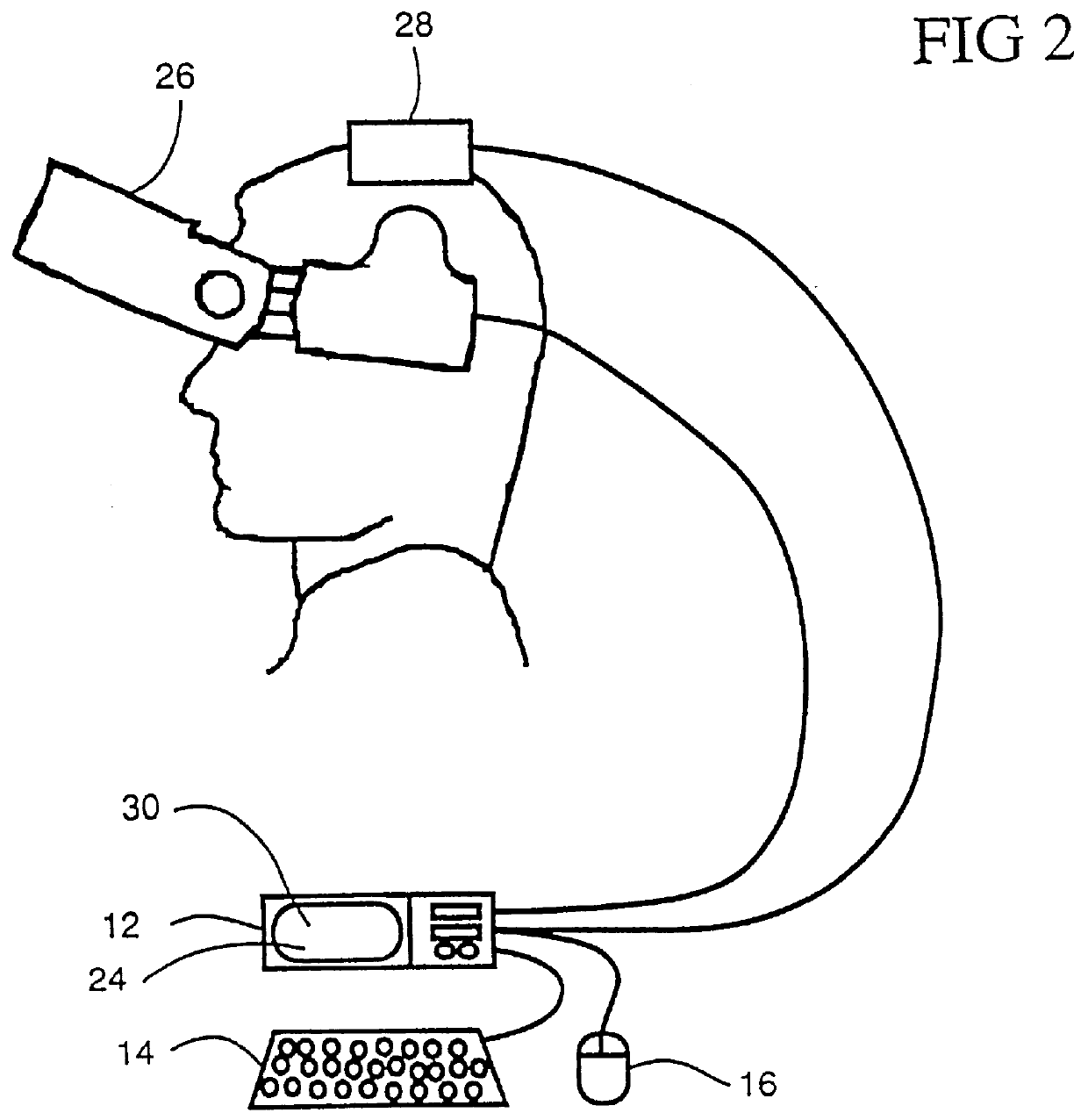
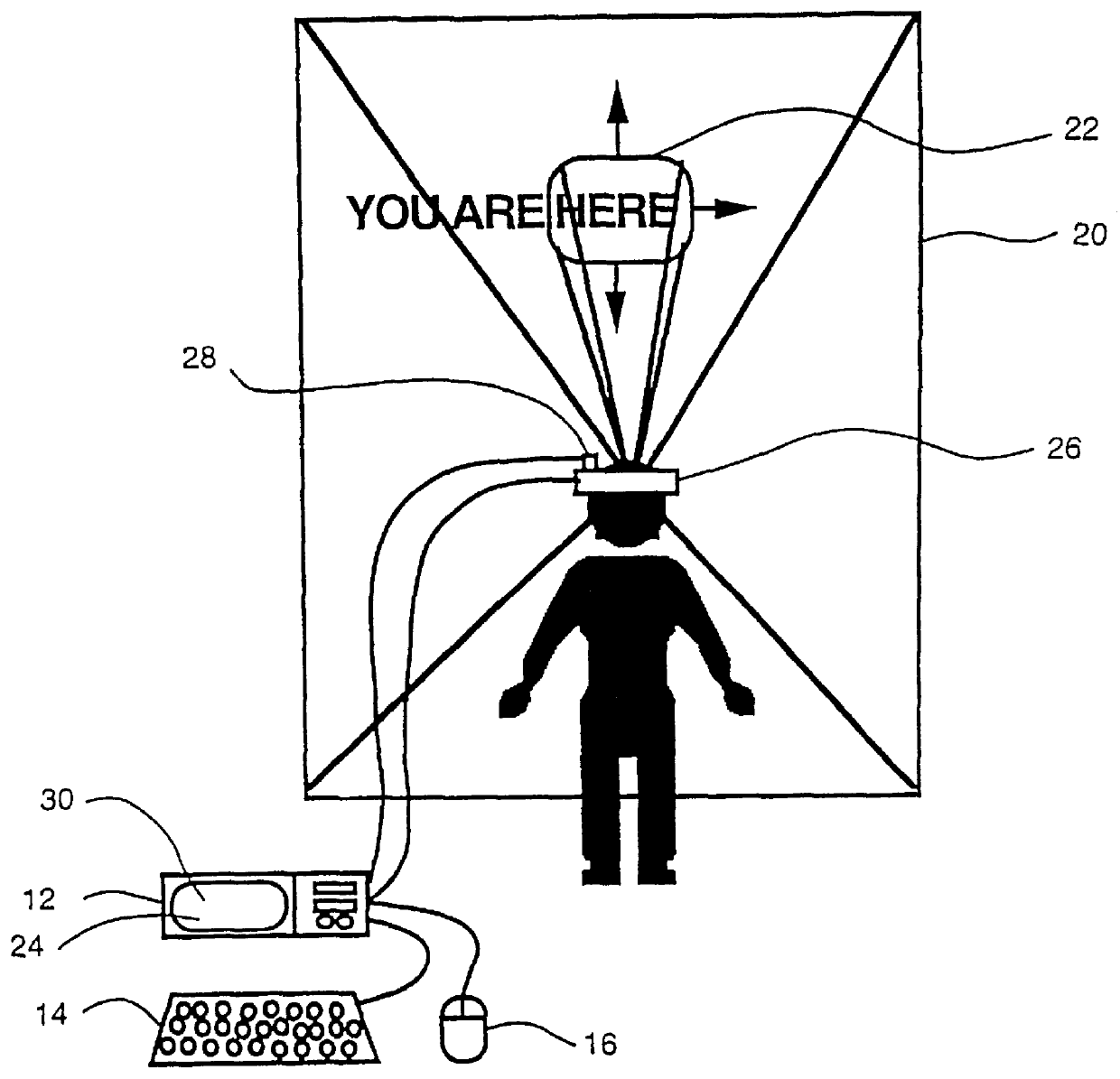
Intuitive control of portable data displays
InactiveUS6184847B1Reduce jitterInput/output for user-computer interactionCathode-ray tube indicatorsVisually impairedData display
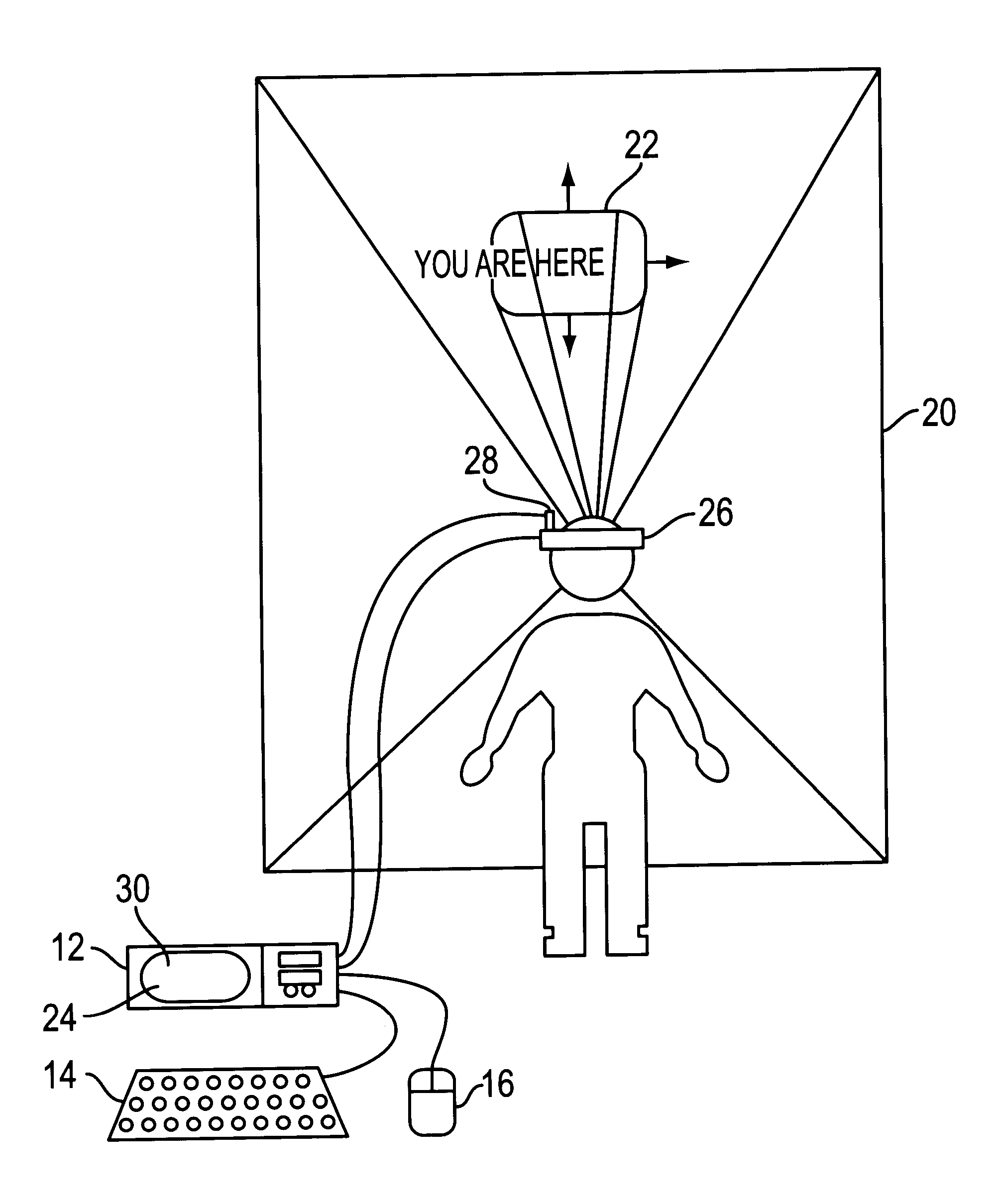
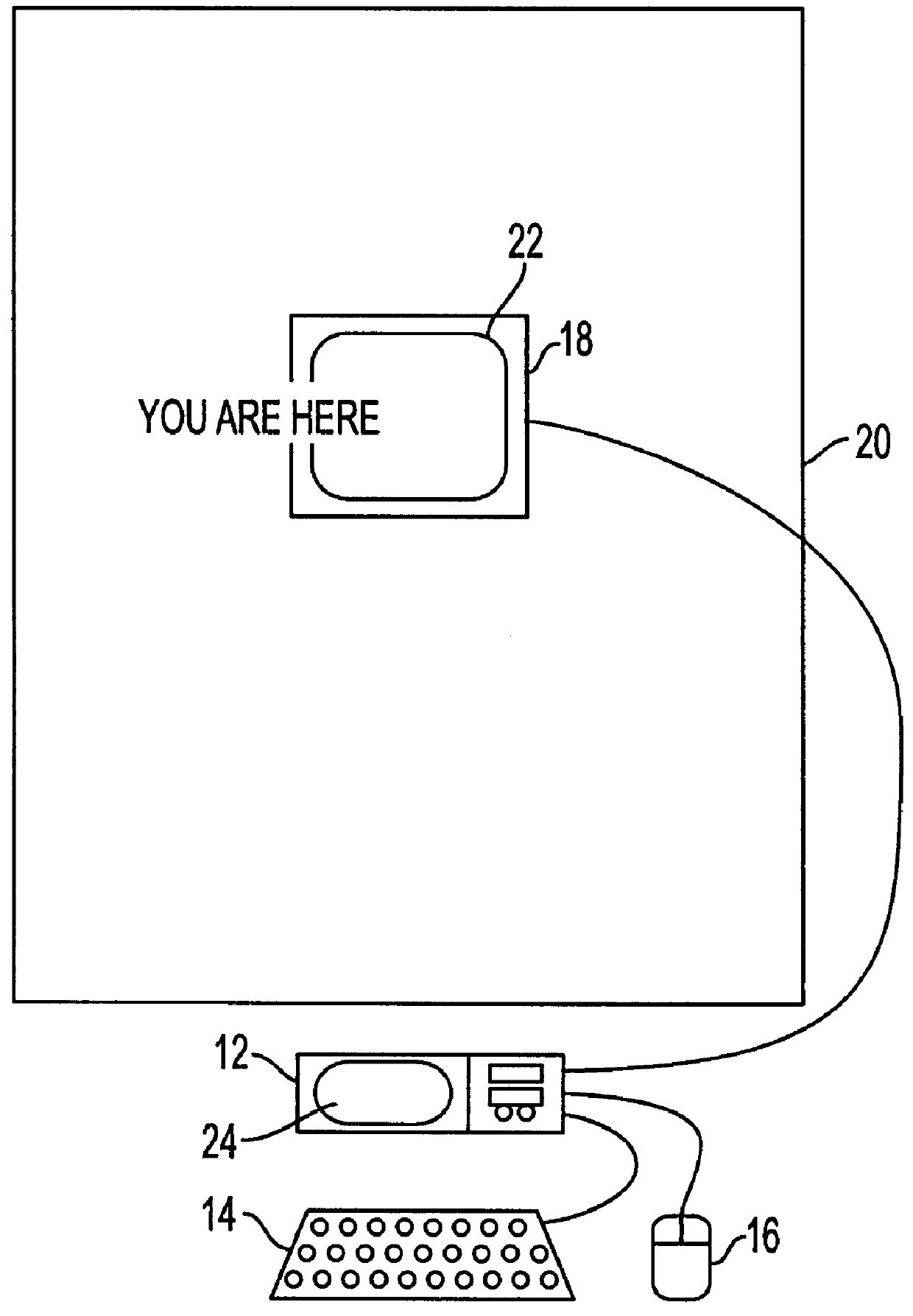
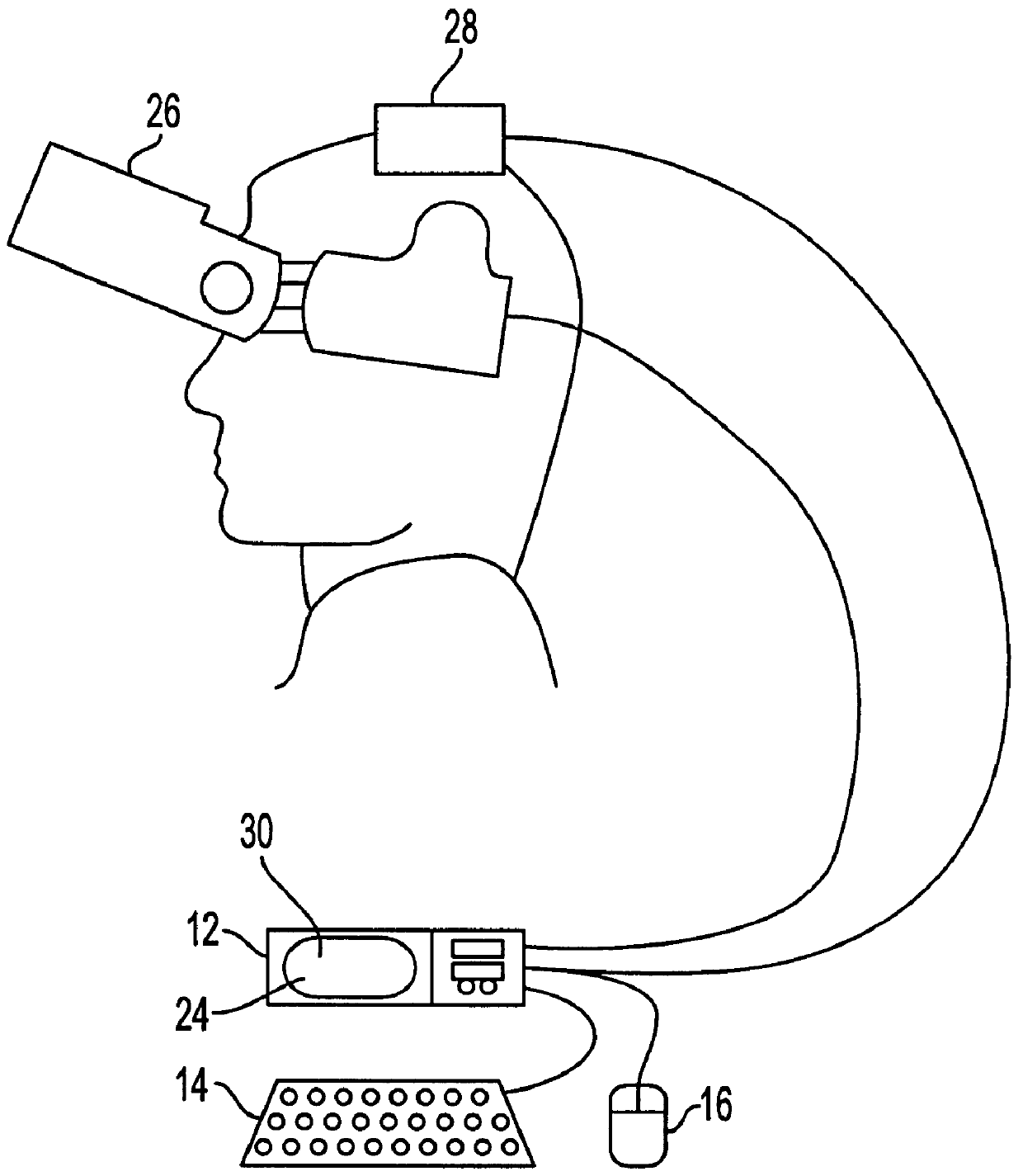
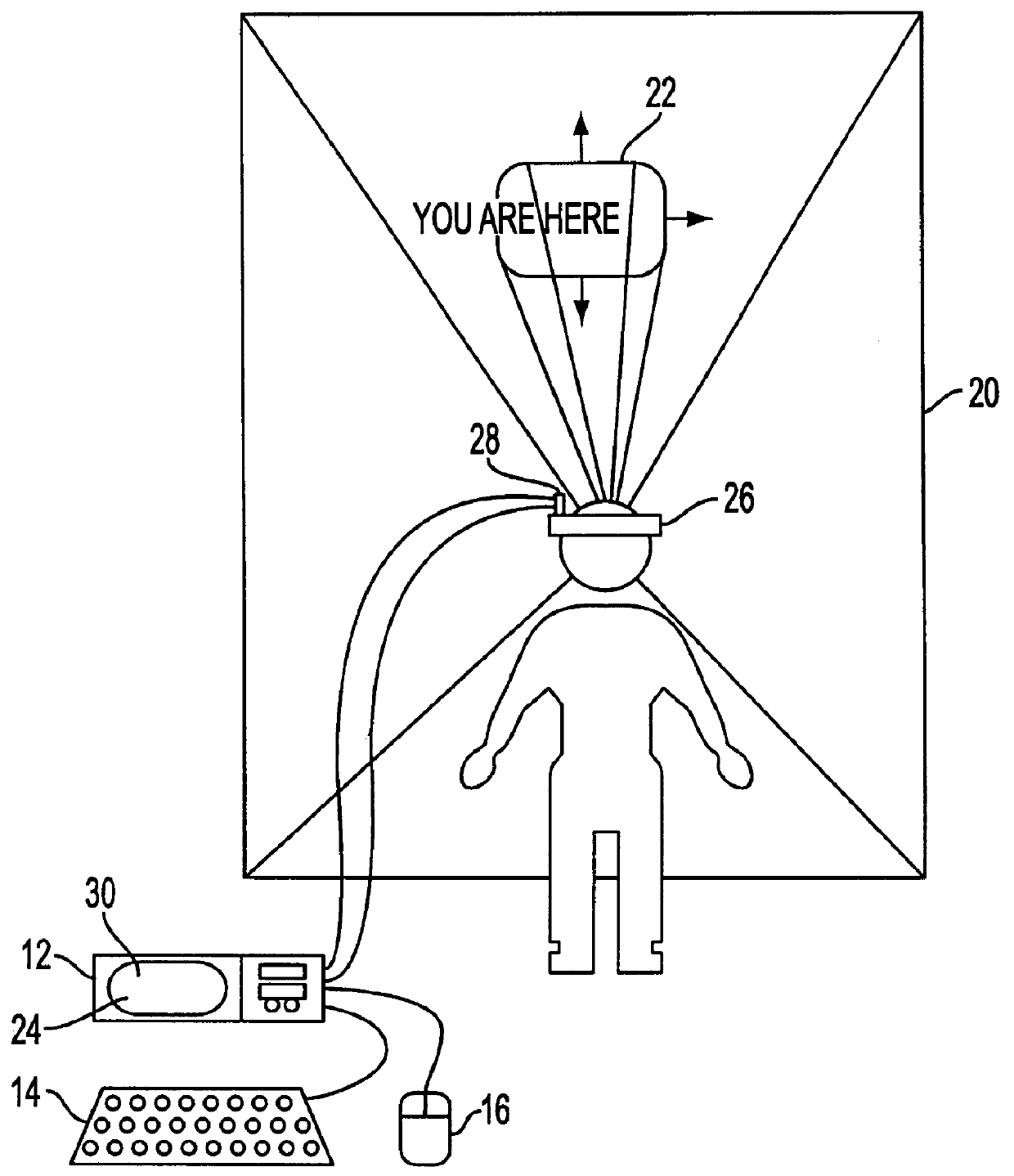
A virtual computer monitor is described which enables instantaneous and intuitive visual access to large amounts of visual data by providing the user with a large display projected virtually in front of the user. The user wears a head-mounted display or holds a portable display containing a head-tracker or other motion tracker, which together allow the user to position an instantaneous viewport provided by the display at any position within the large virtual display by turning to look in the desired direction. The instantaneous viewport further includes a mouse pointer, which may be positioned by turning the user's head or moving the portable display, and which may be further positioned using a mouse or analogous control device. A particular advantage of the virtual computer monitor is intuitive access to enlarged computer output for visually-impaired individuals.
Owner:META PLATFORMS INC +1
Method and apparatus for providing virtual computing services
InactiveUS20050044301A1Easy to manageLow costResource allocationMemory adressing/allocation/relocationVirtualizationOperational system
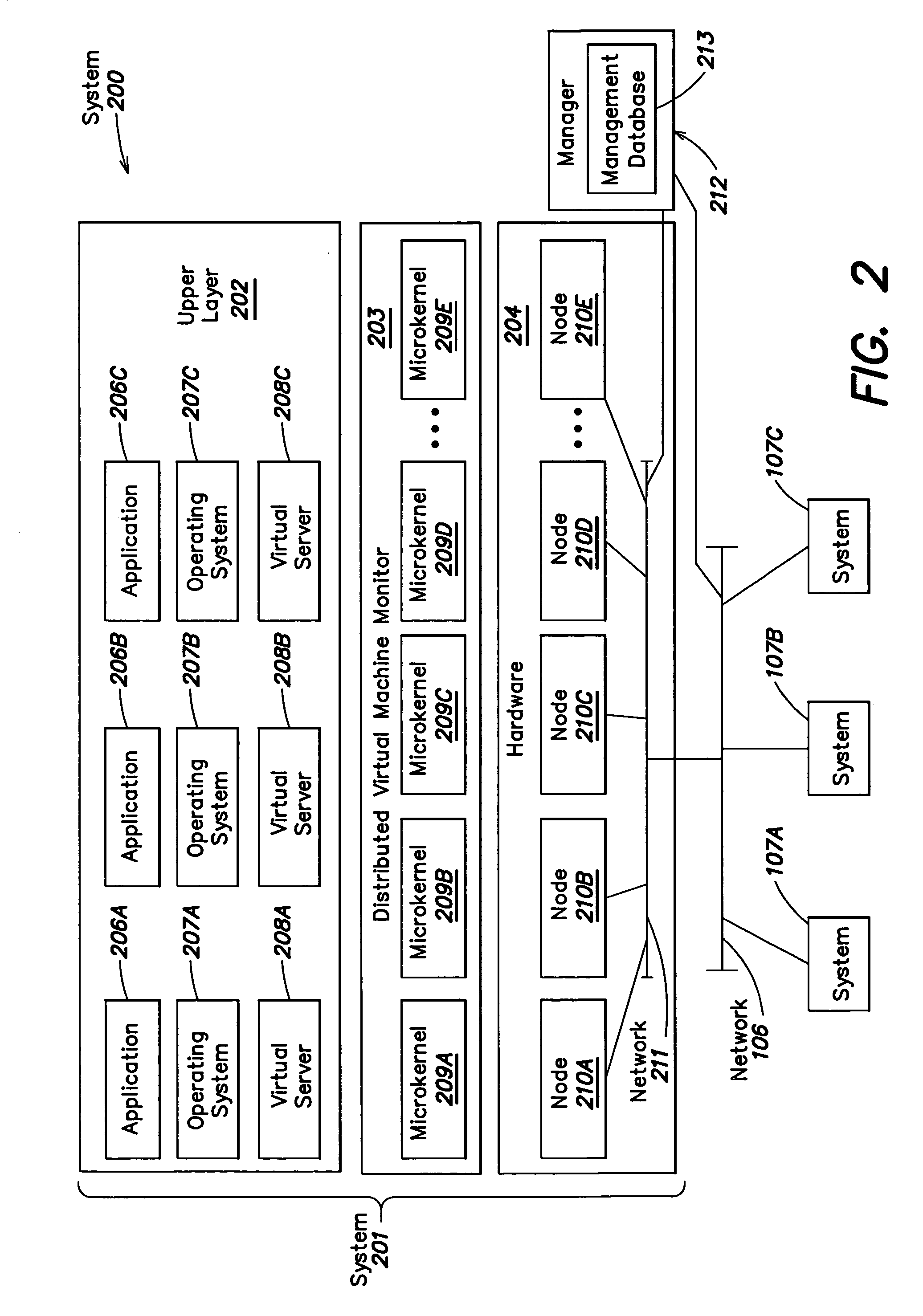
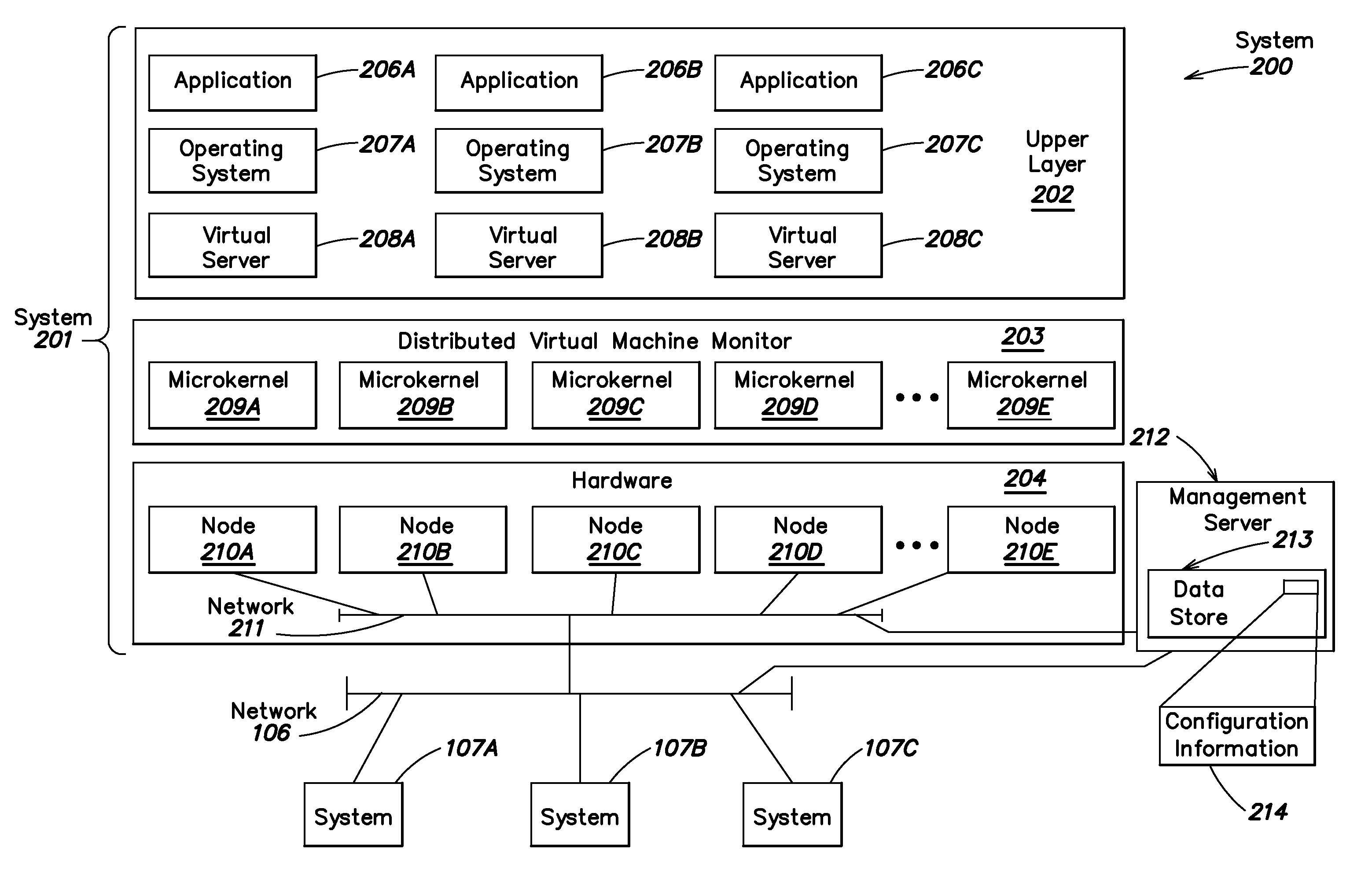
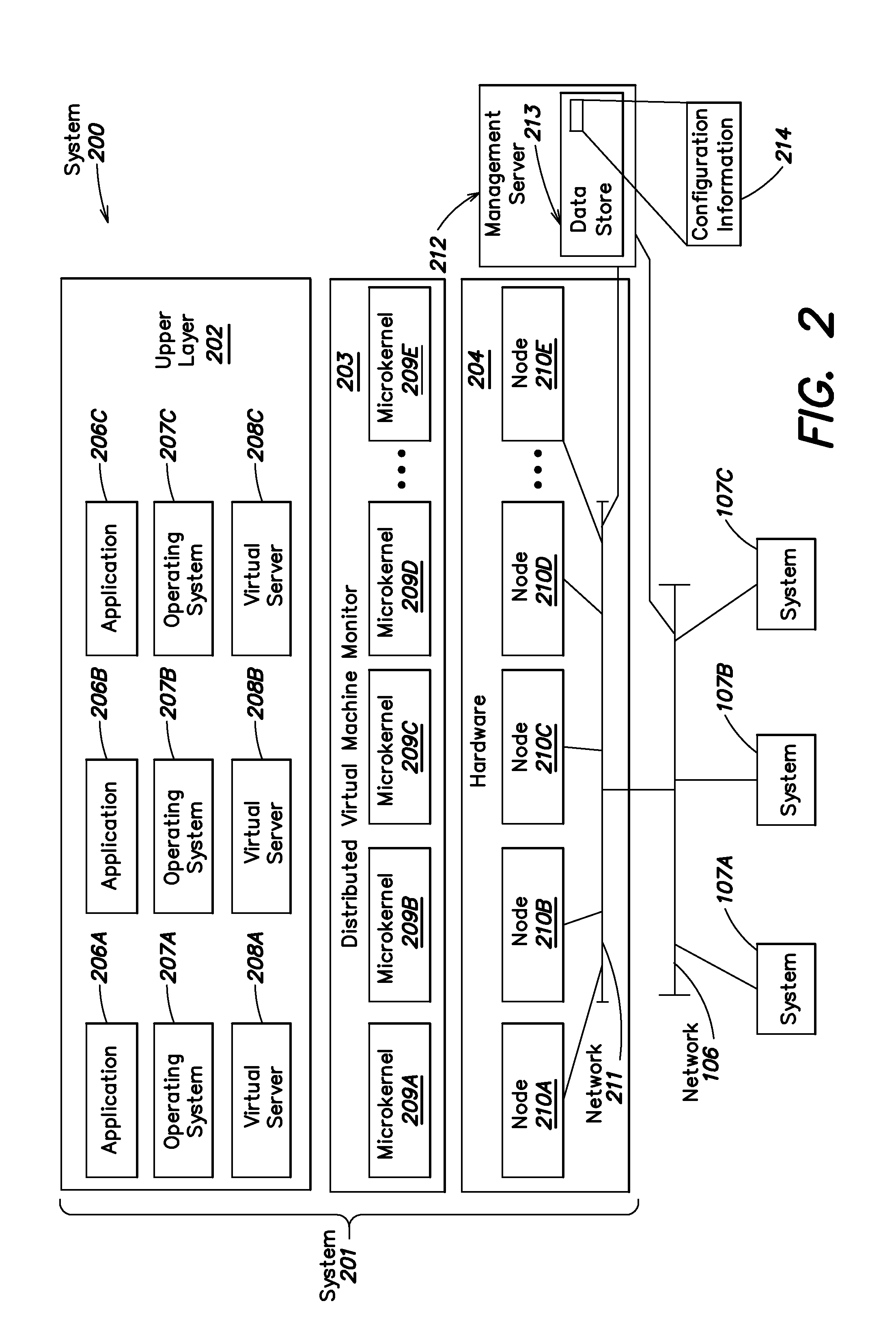
A level of abstraction is created between a set of physical processors and a set of virtual multiprocessors to form a virtualized data center. This virtualized data center comprises a set of virtual, isolated systems separated by a boundary referred as a partition. Each of these systems appears as a unique, independent virtual multiprocessor computer capable of running a traditional operating system and its applications. In one embodiment, the system implements this multi-layered abstraction via a group of microkernels, each of which communicates with one or more peer microkernel over a high-speed, low-latency interconnect and forms a distributed virtual machine monitor. Functionally, a virtual data center is provided, including the ability to take a collection of servers and execute a collection of business applications over a compute fabric comprising commodity processors coupled by an interconnect. Processor, memory and I / O are virtualized across this fabric, providing a single system, scalability and manageability. According to one embodiment, this virtualization is transparent to the application, and therefore, applications may be scaled to increasing resource demands without modifying the application.
Owner:ORACLE INT CORP
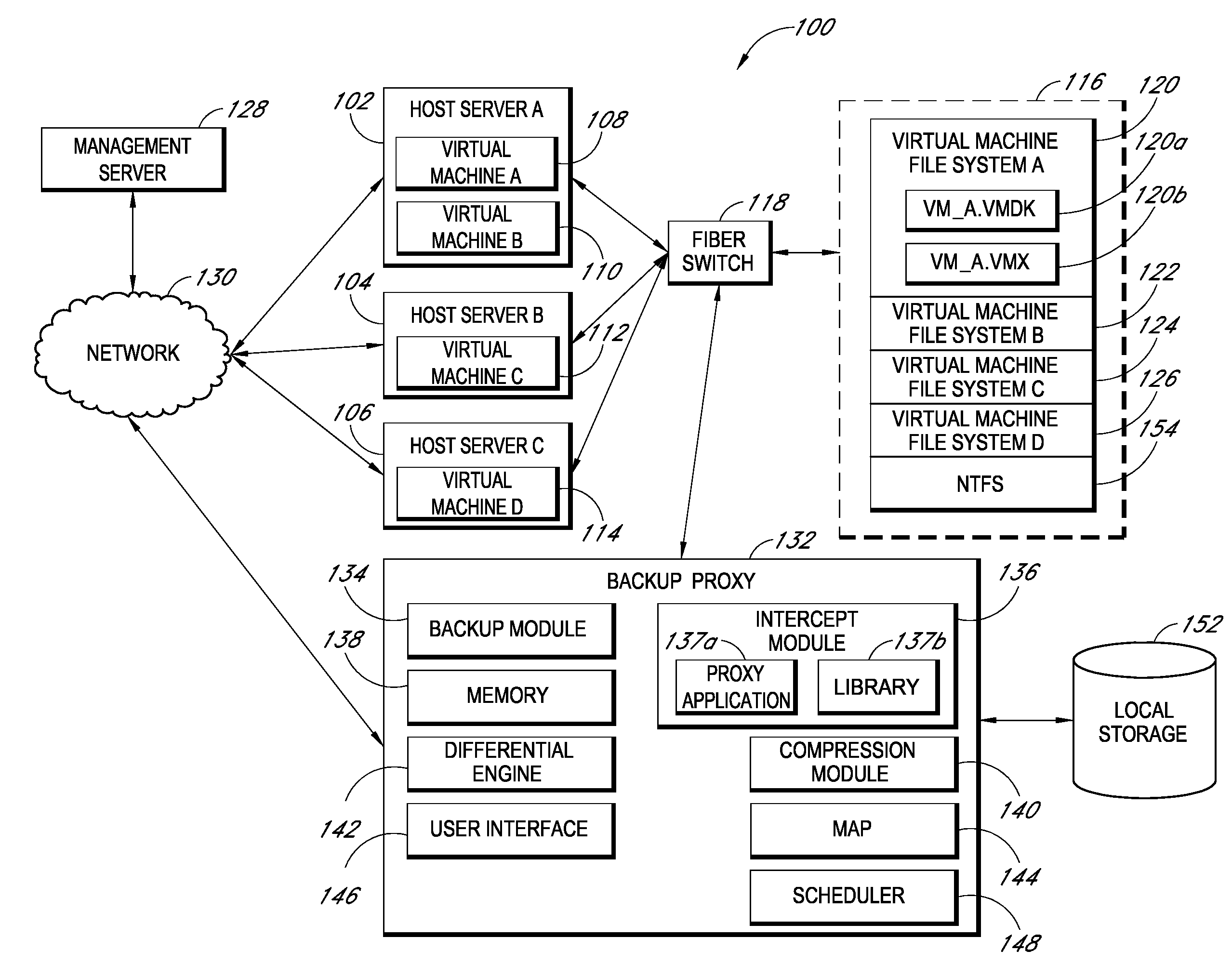
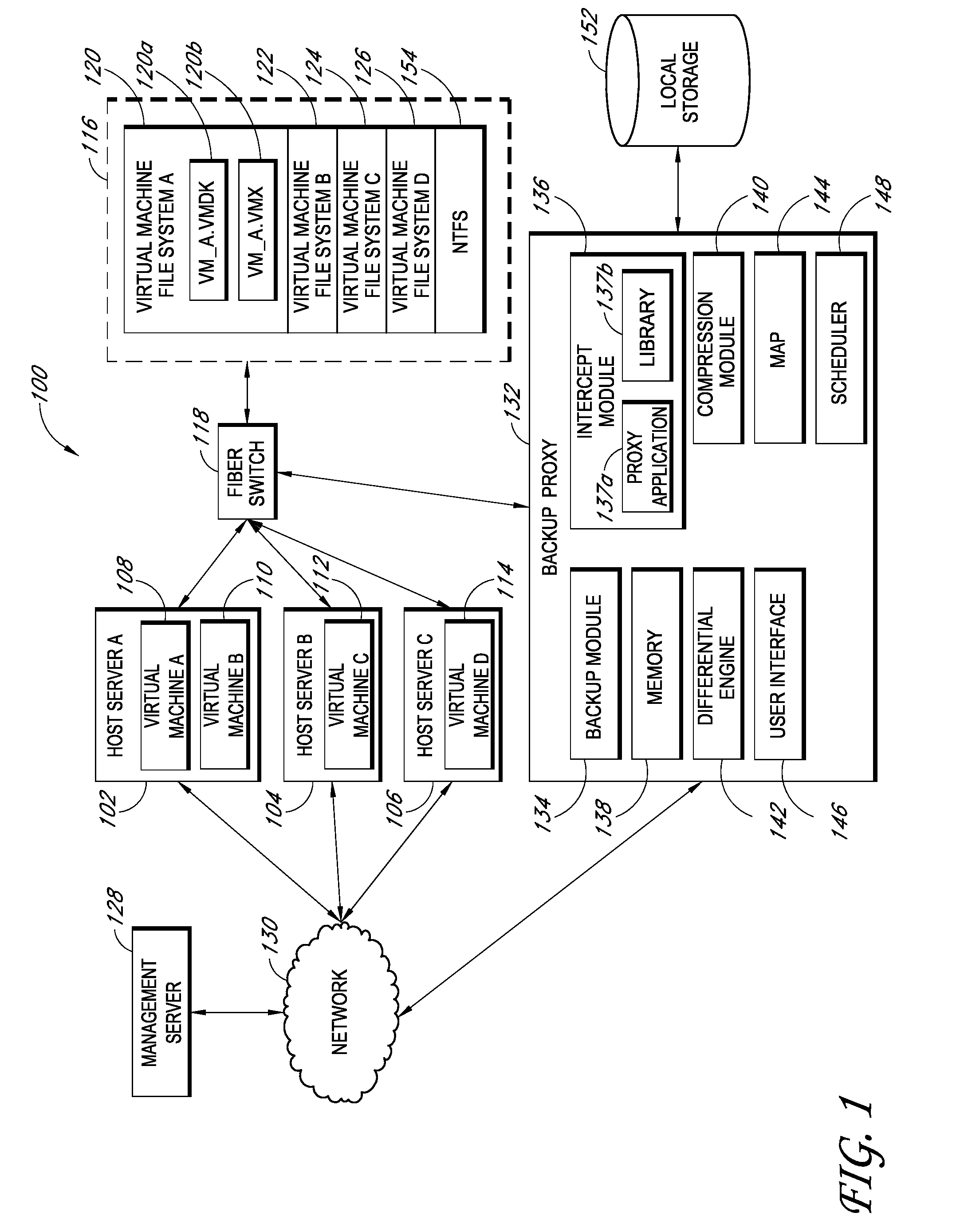
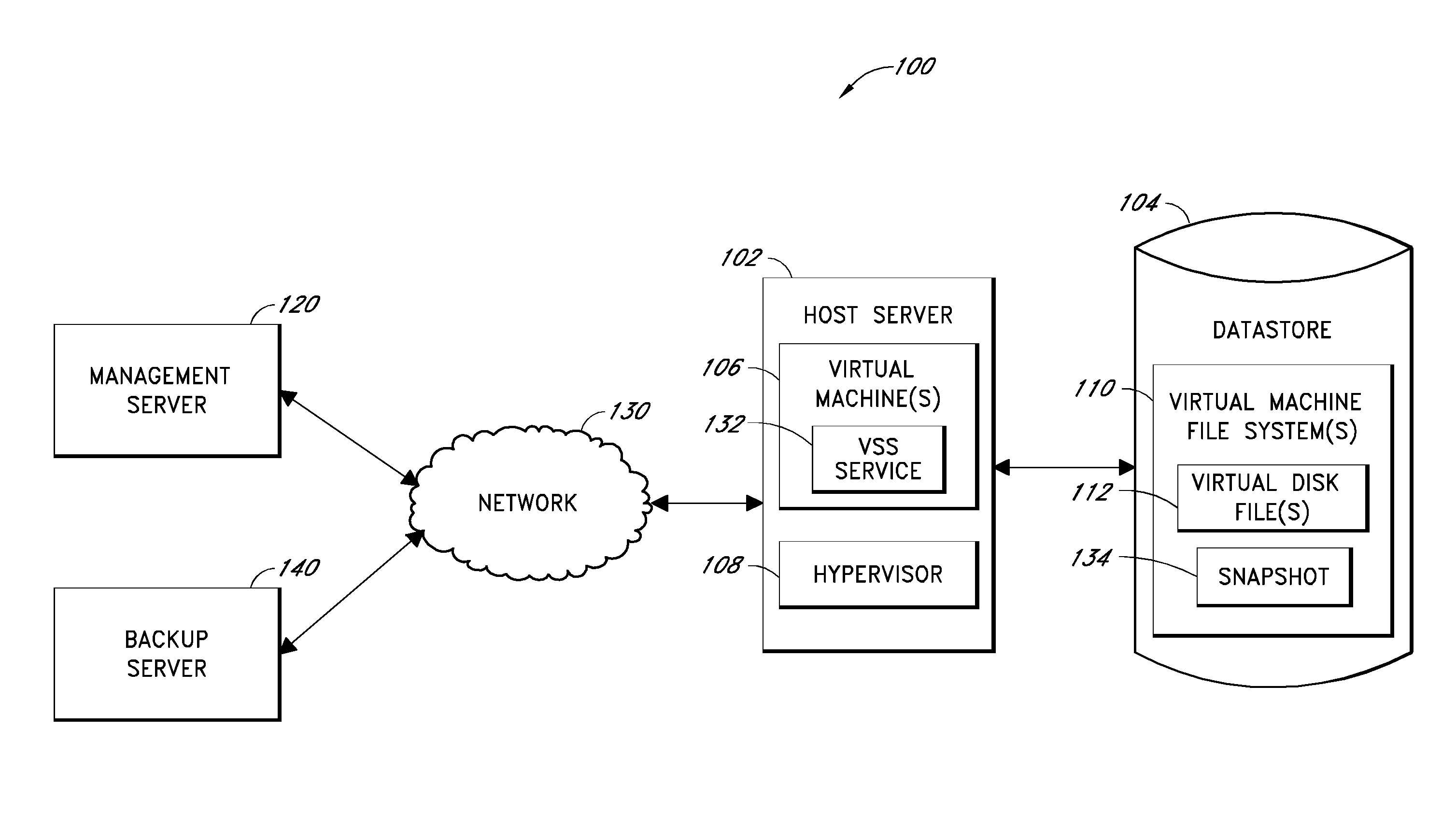
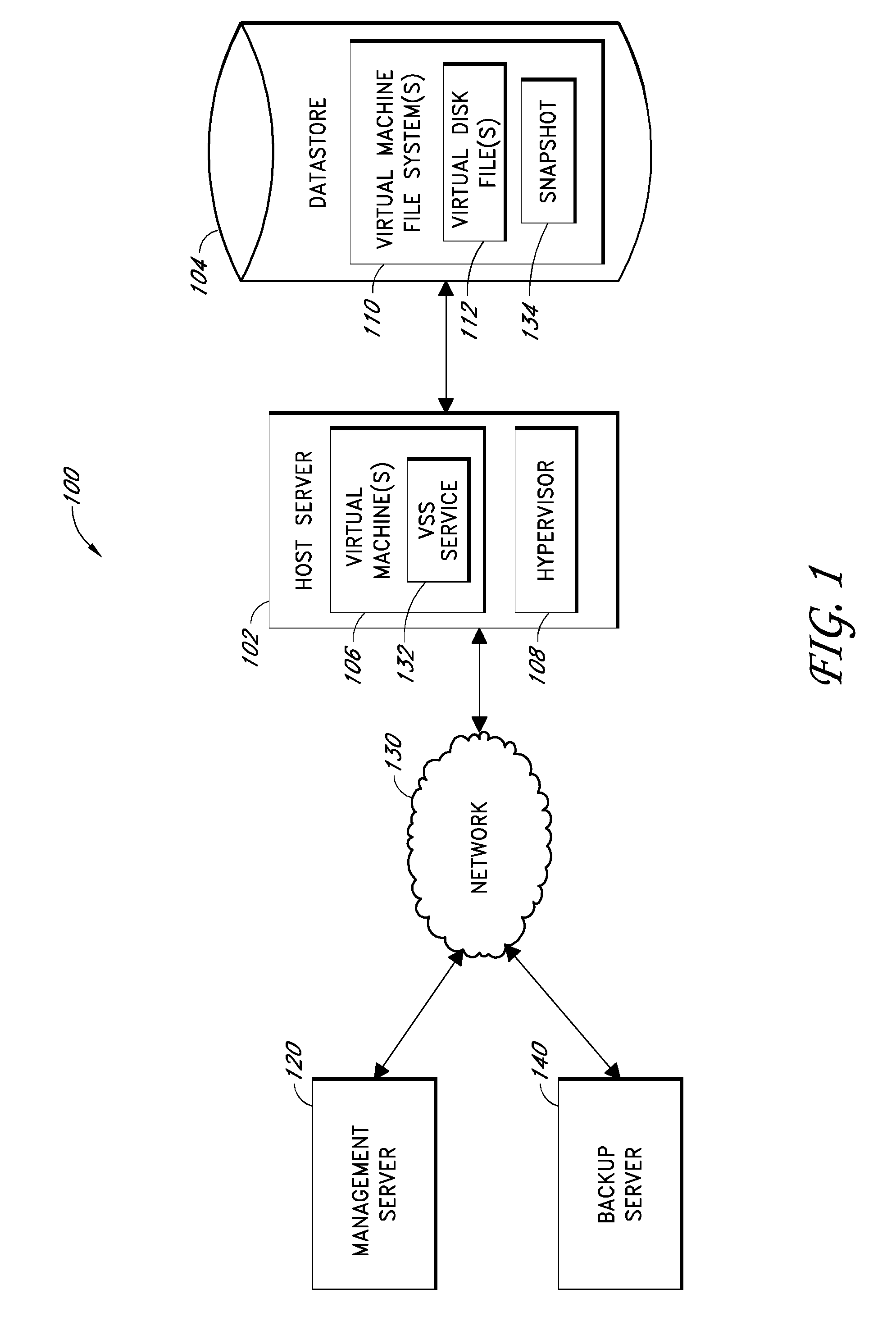
Systems and methods for performing backup operations of virtual machine files
ActiveUS20100011178A1Memory loss protectionError detection/correctionCommunications managementOperational system
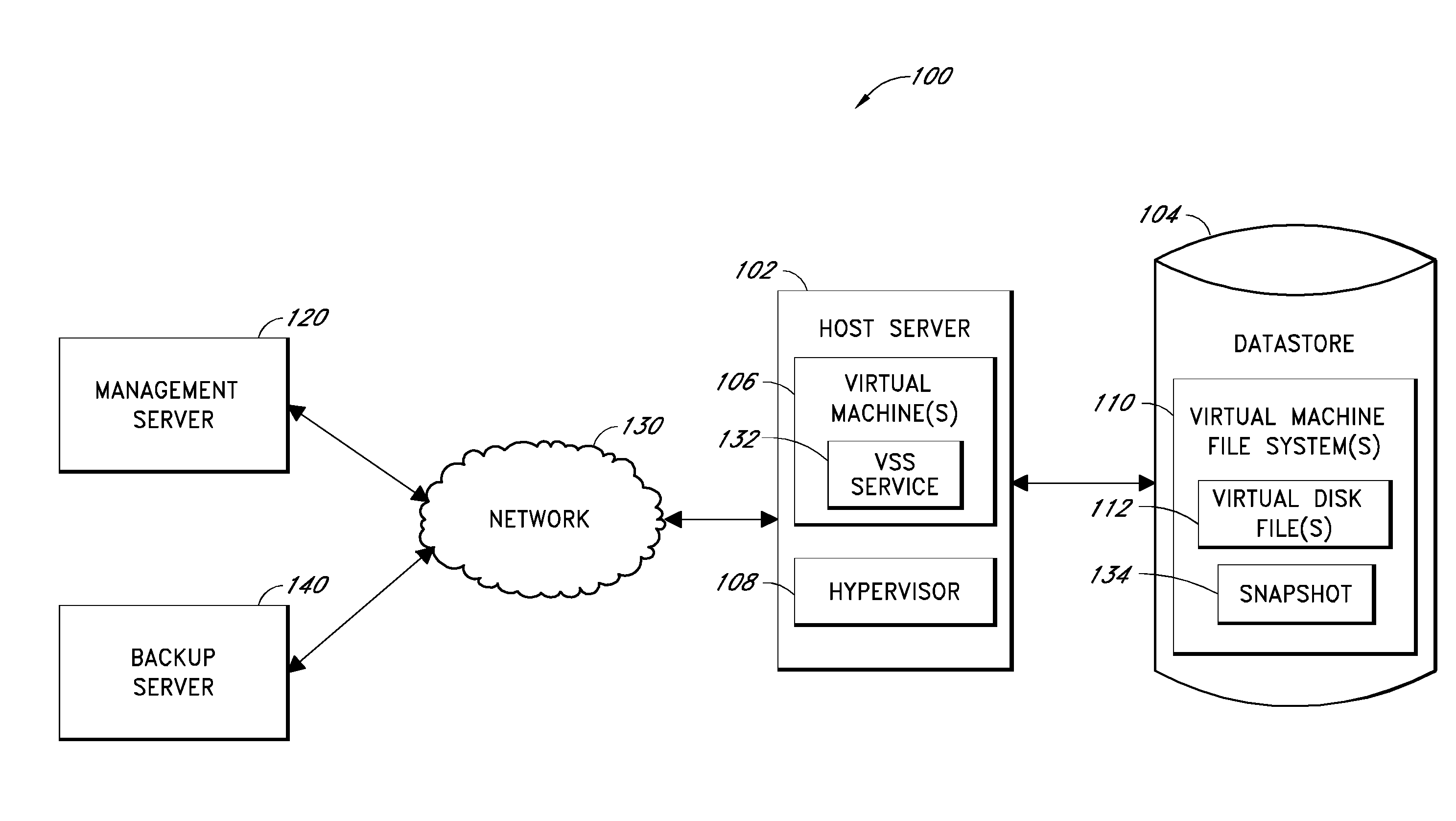
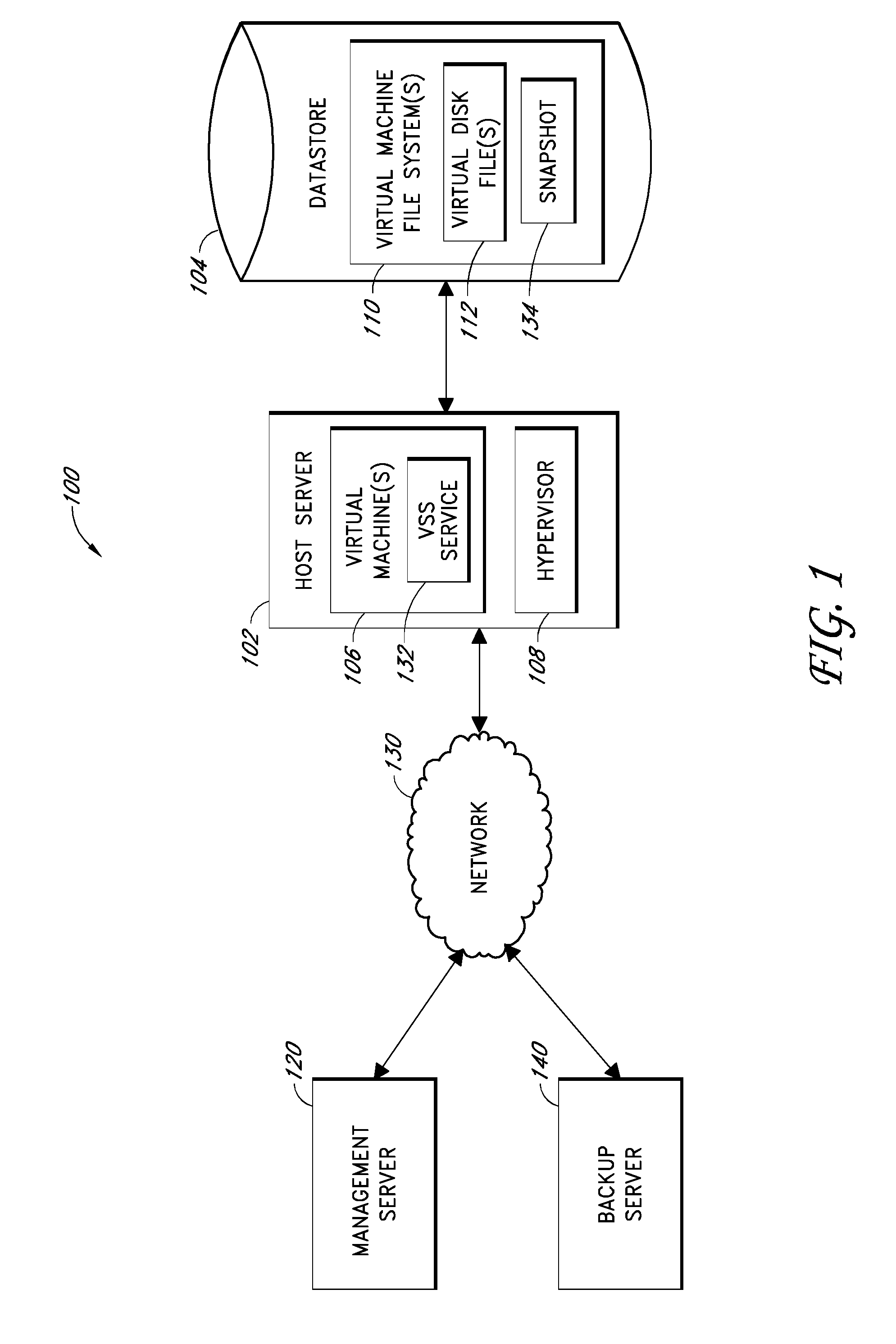
Backup systems and methods are disclosed for a virtual computing environment. Certain examples include a system having a backup management server that communicates with a host server having at least one virtual machine. The management server coordinates with the host server to perform backup copies of entire virtual machine disks from outside the guest operating system of the virtual machine. In certain examples, such backup systems further utilize a volume shadow copy service executing on the host server to quiesce virtual machine applications to put data in a consistent state to be backed up. The backup system then utilizes hypervisor snapshot capabilities of the host server to record intended changes to the virtual machine disk files while such files are being copied (e.g., backed up) by the host server. Such recorded changes can be later committed to the virtual machine disk files once the backup operation has completed.
Owner:QUEST SOFTWARE INC
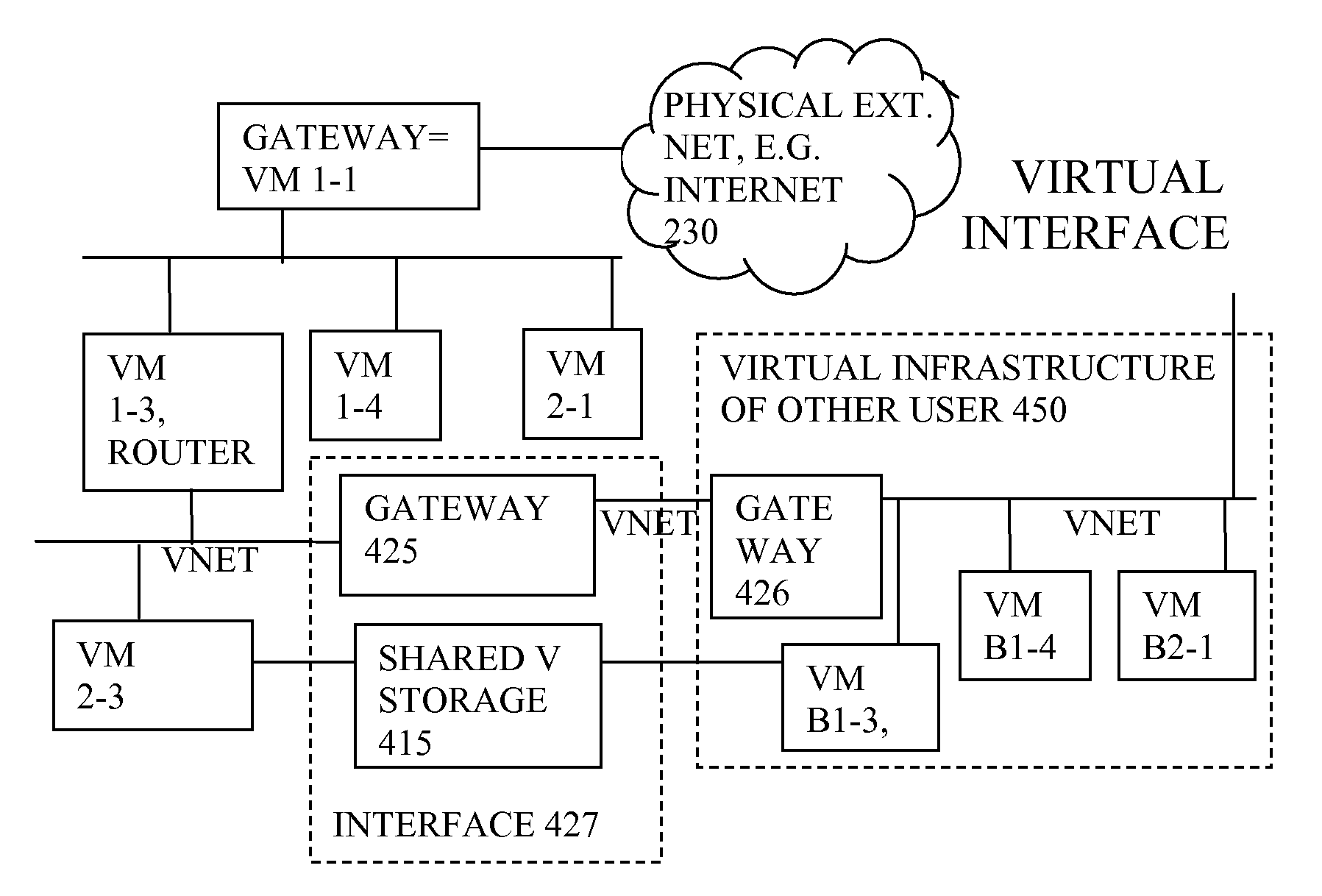
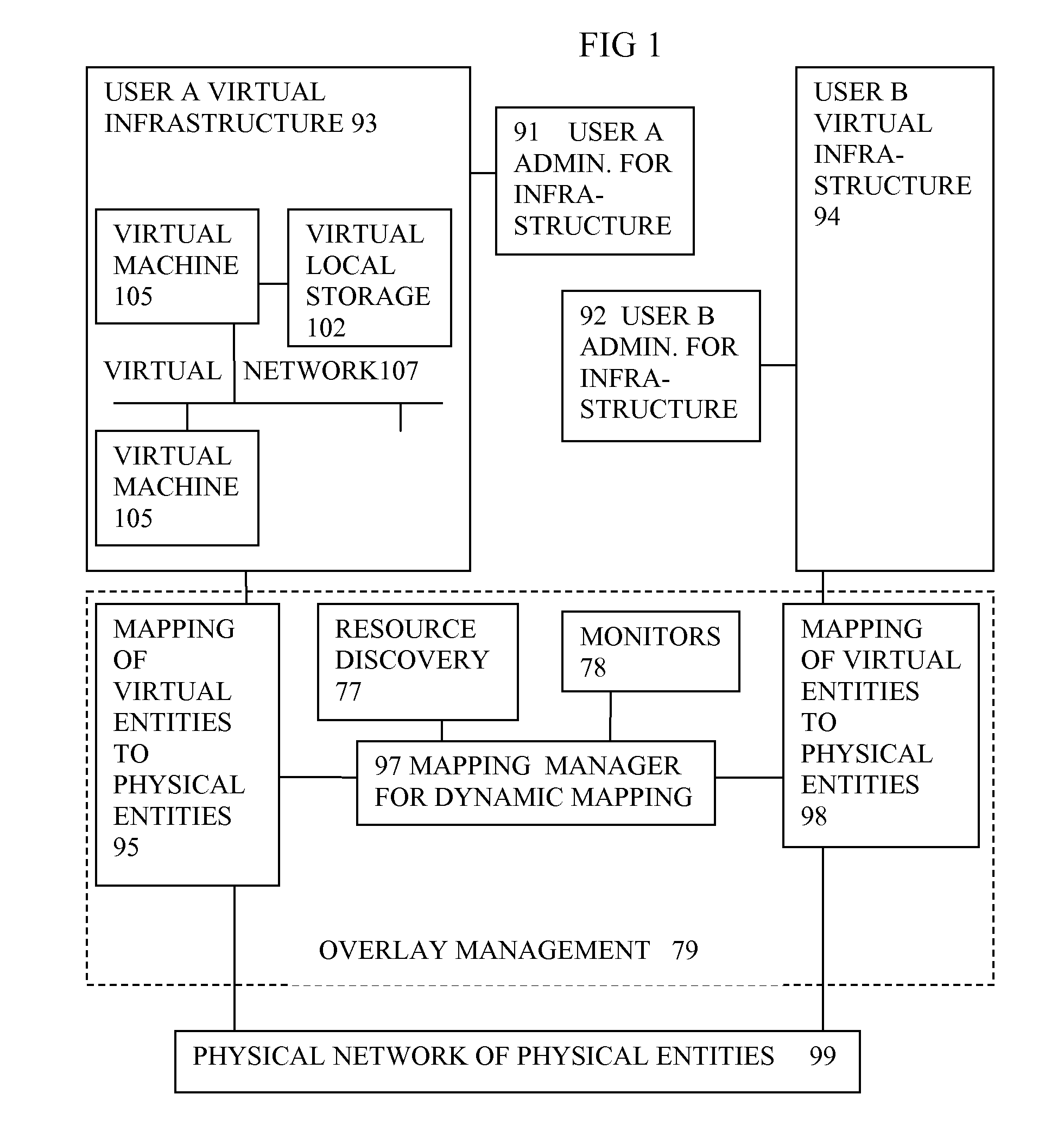
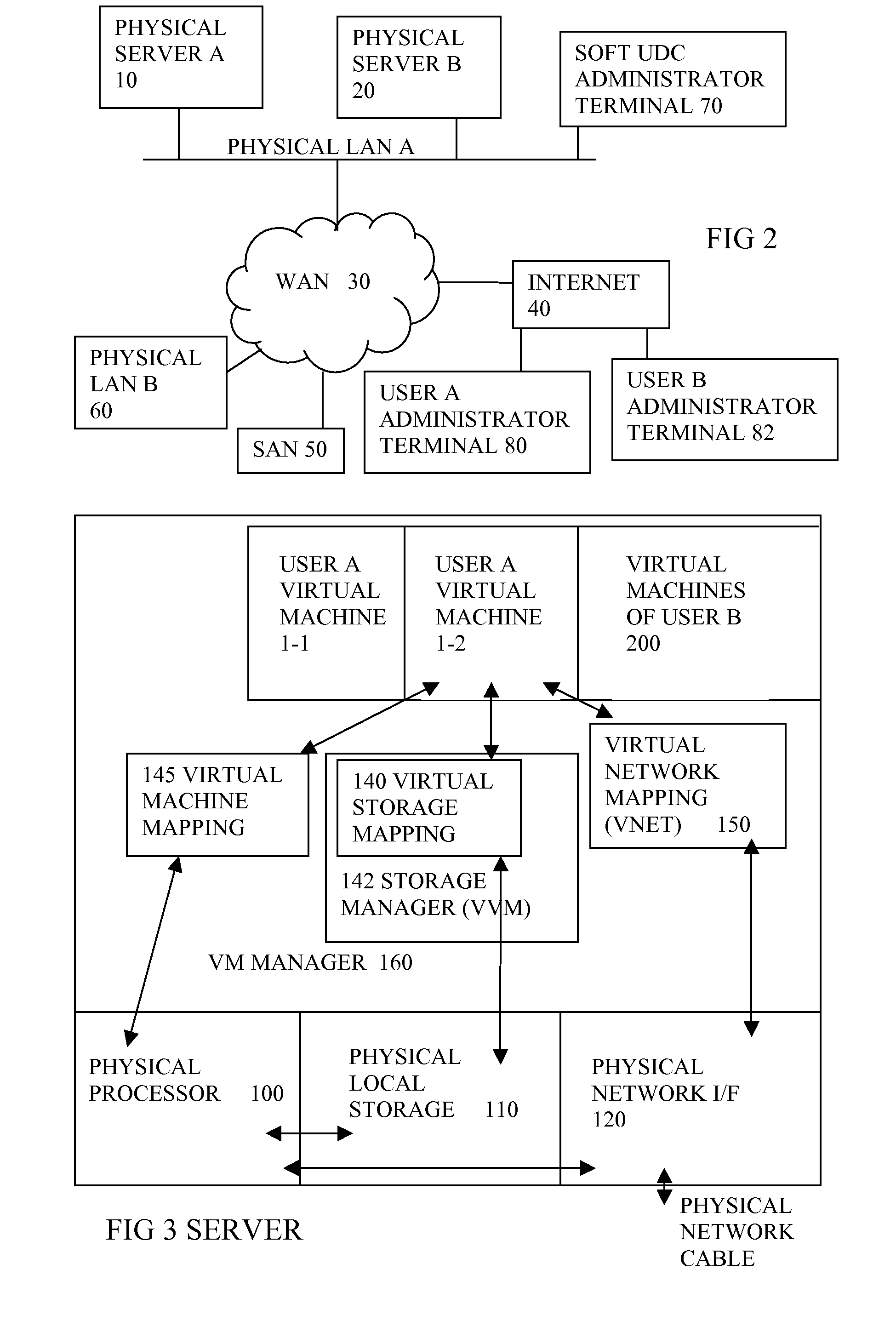
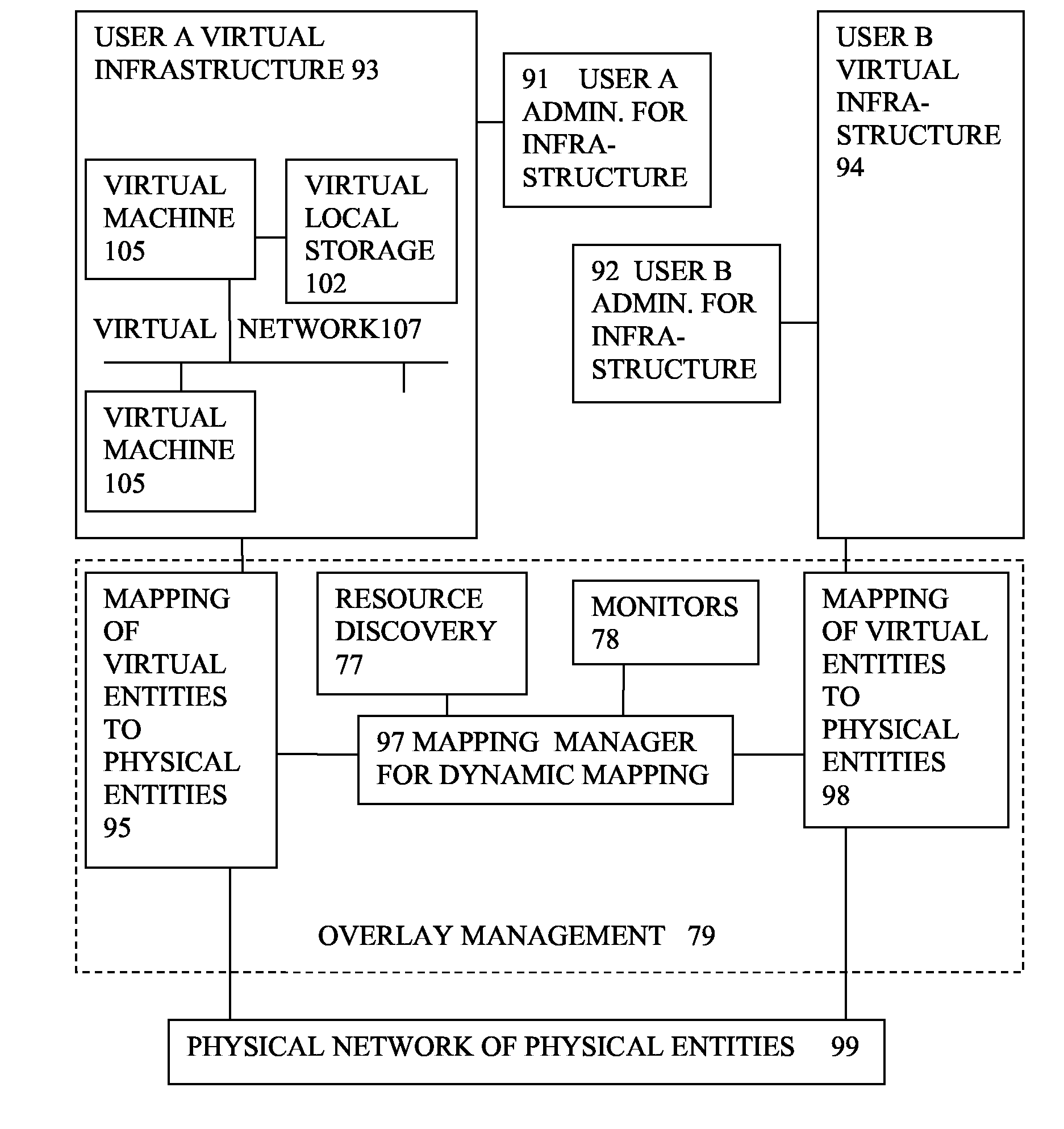
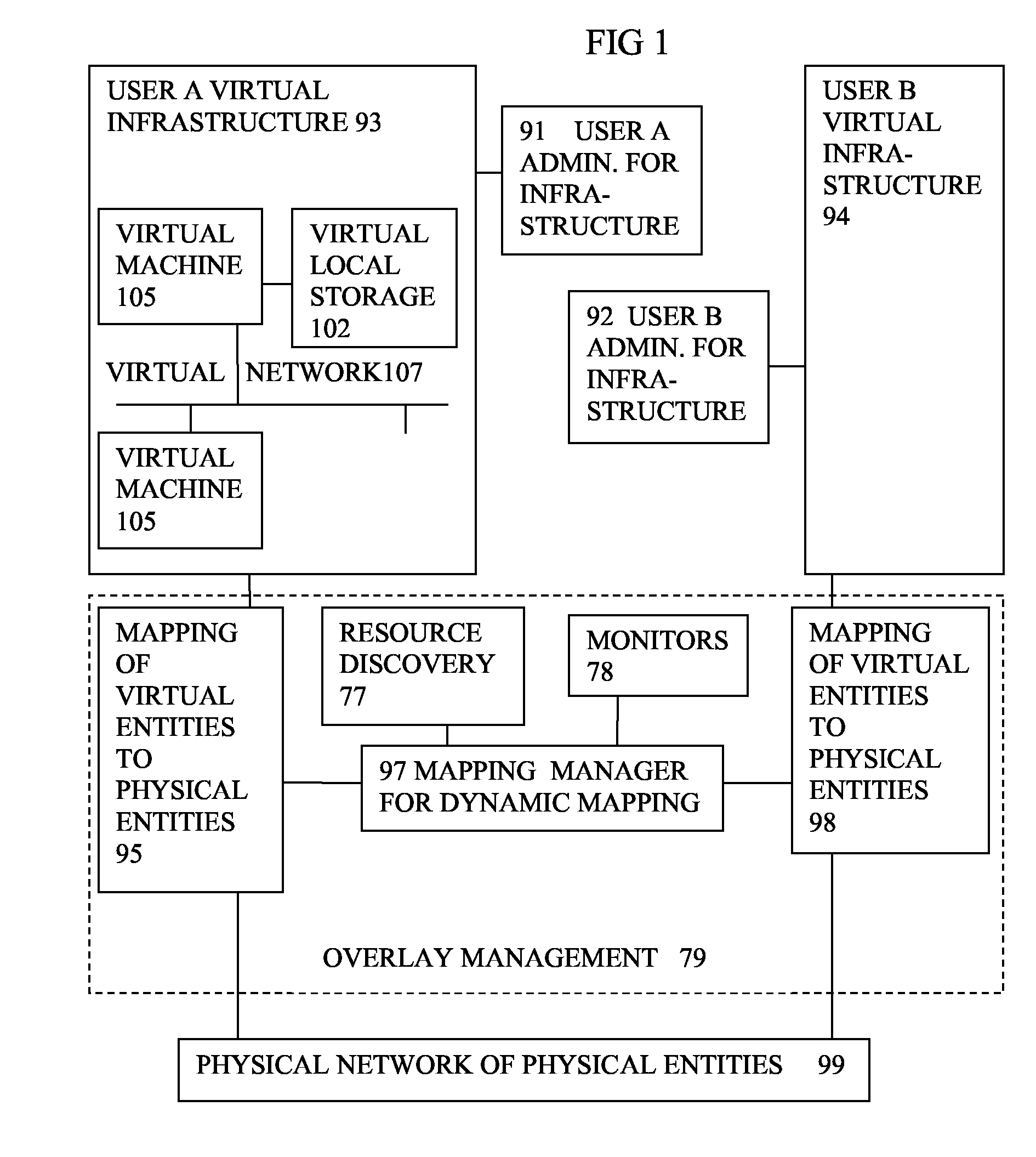
Virtual computing infrastructure
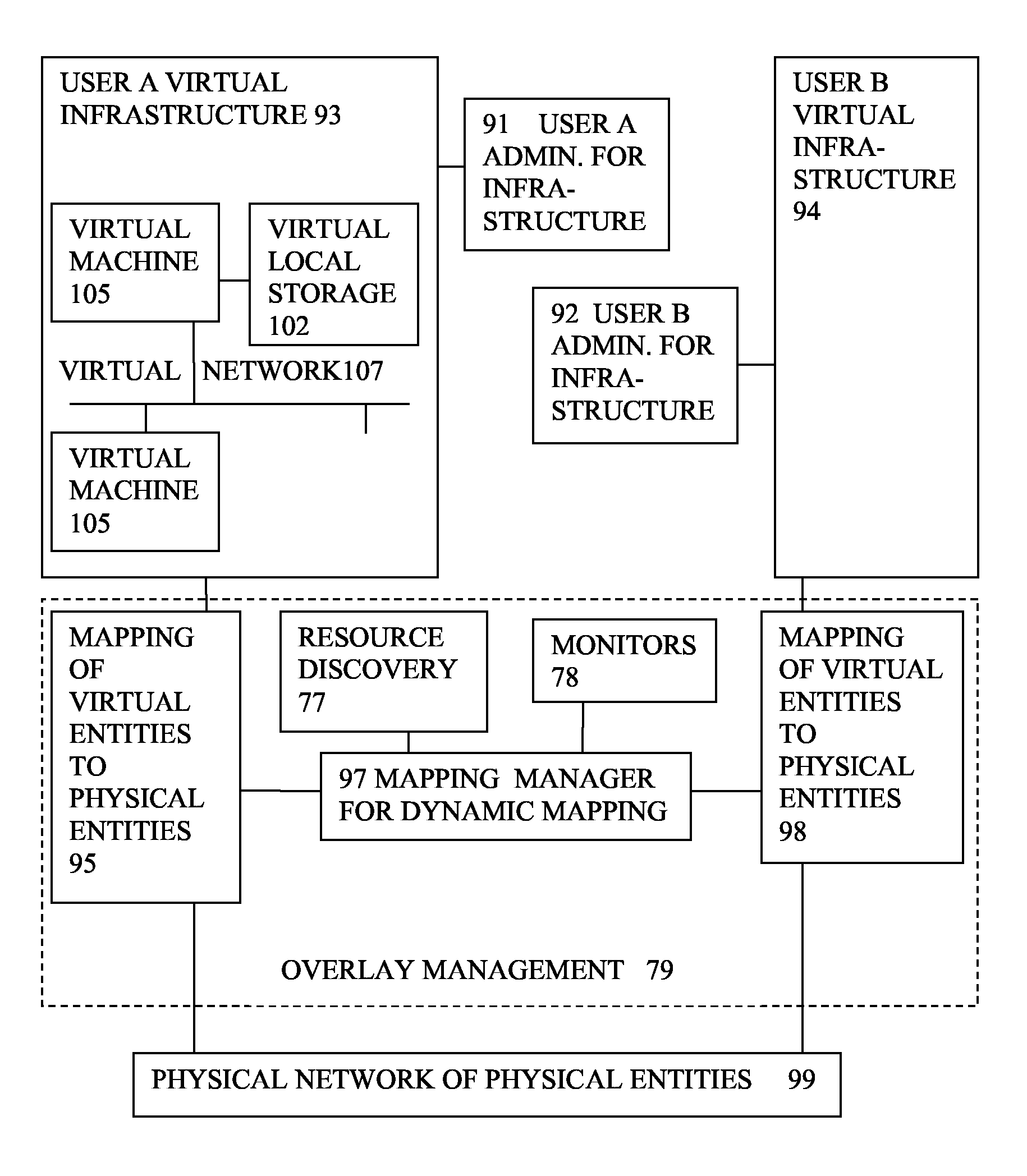
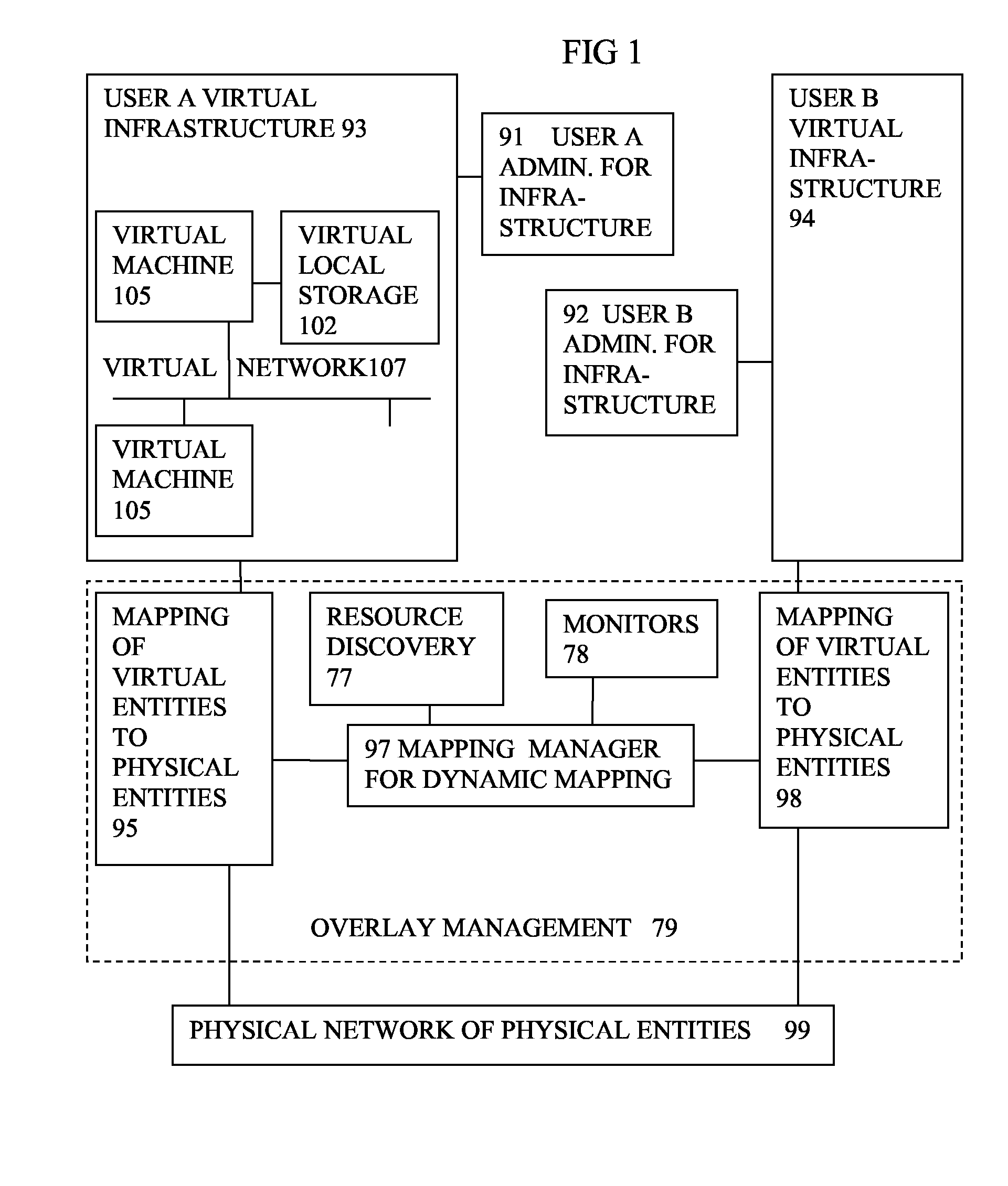
InactiveUS20090199177A1Overcome disadvantagesCritical applicationResource allocationTransmissionVirtualizationNetwork communication
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. The system has a mapping manager to dynamically alter the mapping for balancing, performance, and redundancy. There can be more independence from the underlying physical configuration, compared to known methods of virtualizing only some of the entities. The mapping manager can be distributed across a number of entities on different physical servers arranged to cooperate with each other.
Owner:HEWLETT PACKARD DEV CO LP
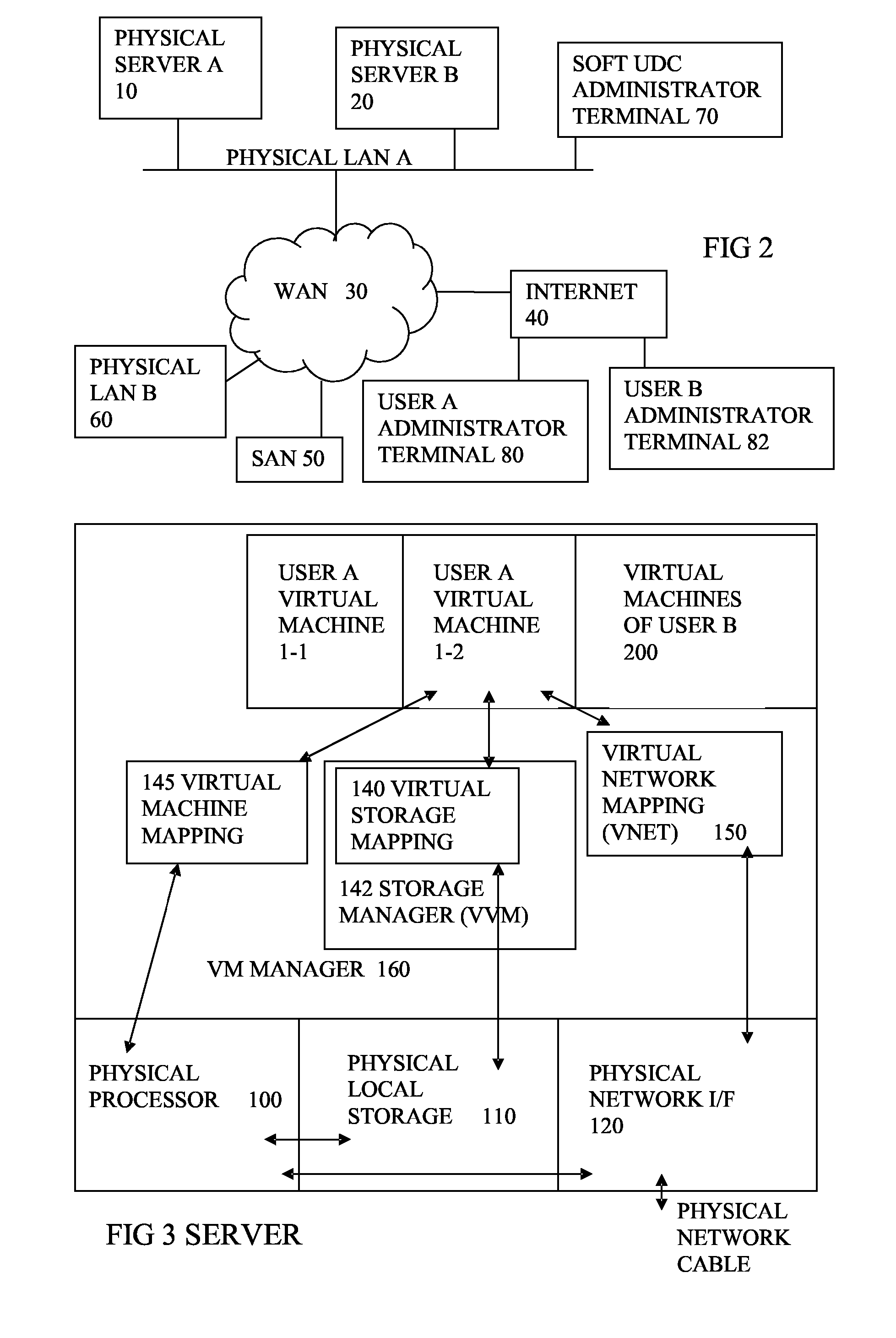
Virtual computing infrastructure
ActiveUS20110119748A1More separatedReduce hardware costsResource allocationComputer security arrangementsNetwork communicationApplication software
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. Virtual infrastructures of different users share physical resources but are isolated and have their own management entities. An interface between infrastructures allows controlled relaxation of the isolation, using a gateway between virtual nets, or shared virtual storage devices. This can allow businesses to share data or applications, while maintaining control of security.
Owner:RED HAT +1
Simulated computer system for monitoring of software performance
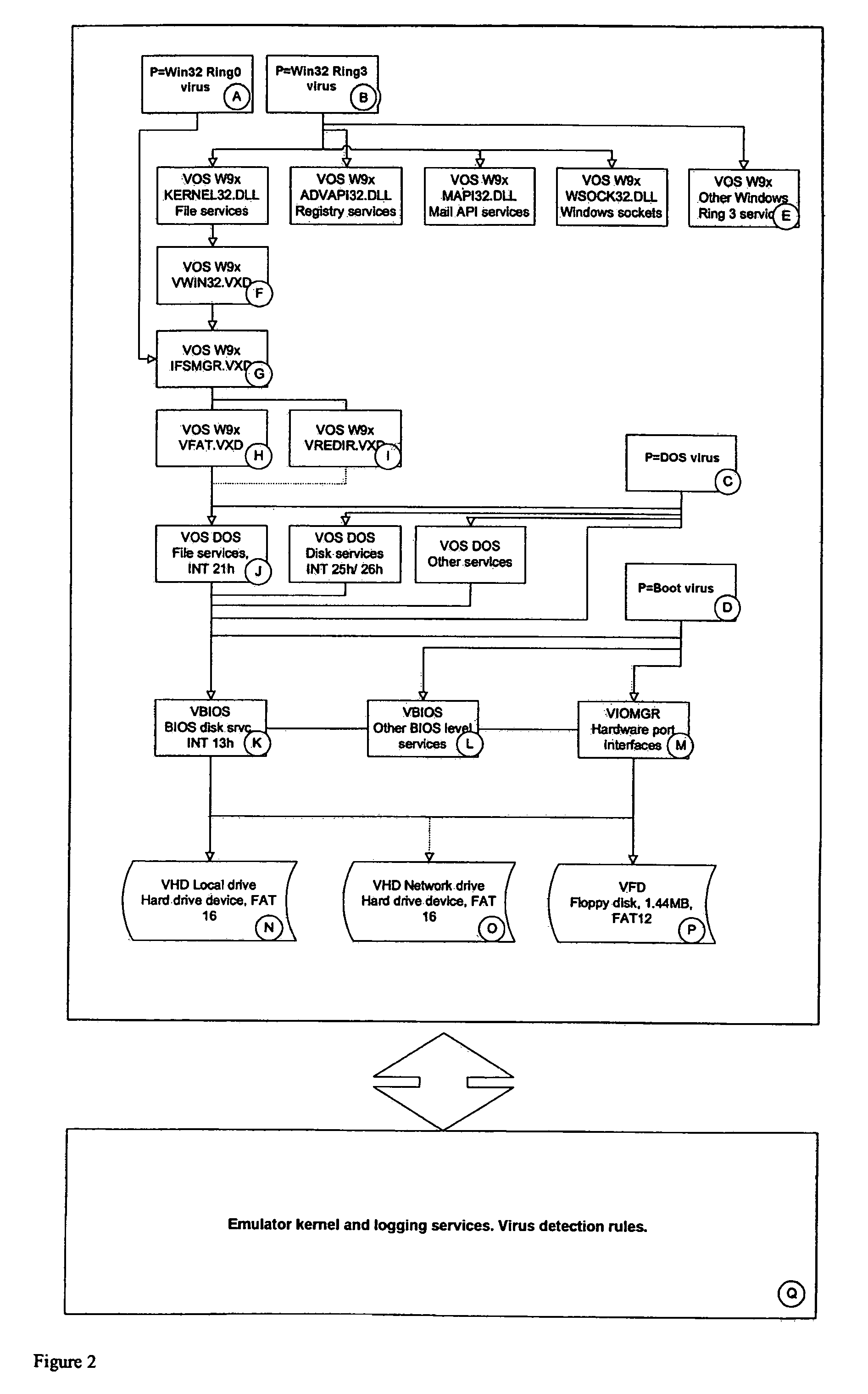
InactiveUS7356736B2Reduce riskMemory loss protectionError detection/correctionVery low riskOperational system
A system S is defined which is capable of simulating a computer (virtual computer, VC) for the purpose of software performance monitoring. The system is implemented as a set of software modules (SM) that can be exchanged to change the behavior of the VC. The VC is driven by a CPU emulator, and can run any operating system (virtual operating system, VOS) that is supported by the available SM's. The system is designed to log accesses to system resources and the nature of these accesses. The system is particularly useful for determining whether an executable or file contains an unknown virus, with a very low risk of false positives. Detected viruses include encrypted, polymorphic, metamorphic and other virus types.
Owner:CA TECH INC
Virtual computing infrastructure
ActiveUS20090300605A1More separatedReduce hardware costsResource allocationSoftware simulation/interpretation/emulationOperational systemNetwork communication
A system has a virtual overlay infrastructure mapped onto physical resources for processing, storage and network communications, the virtual infrastructure having virtual entities for processing, storage and network communications. Each virtual infrastructure can be passivated by suspending applications, stopping operating systems, and storing state, to enable later reactivation. This is simpler for a complete virtual infrastructure than for groups of virtual entities and physical entities. It enables cloned virtual infrastructure to be created for testing, upgrading or sharing without risk to the parent. On failure, reversion to a previous working clone is feasible.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
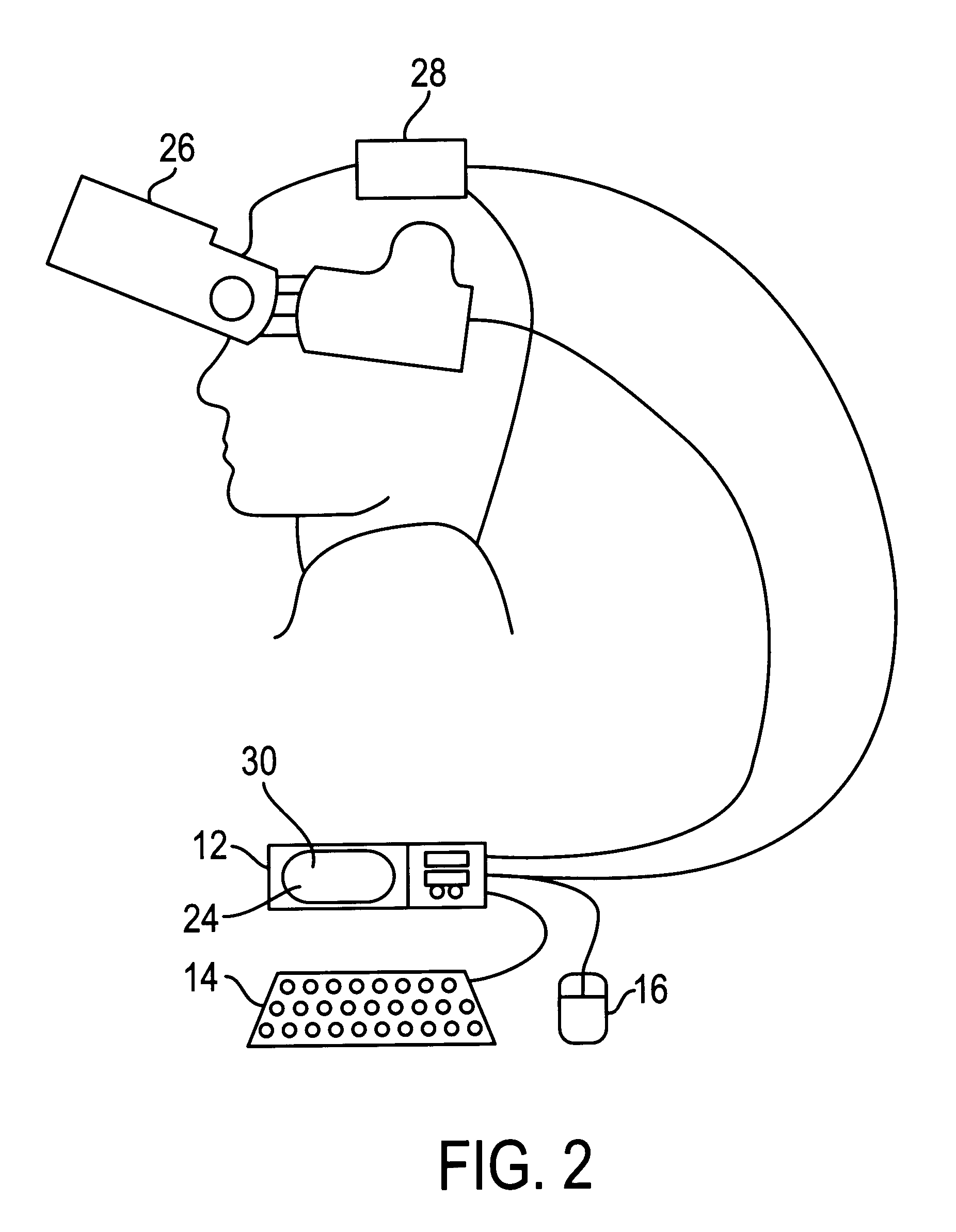
Wearable display and methods for controlling same
InactiveUS6127990AReduce jitterCosmonautic condition simulationsColor television detailsComputer monitorDisplay device
A virtual computer monitor is described which enables instantaneous and intuitive visual access to large amounts of visual data by providing the user with a large display projected virtually in front of the user. The user wears a head-mounted display containing a head-tracker, which together allow the user to position an instantaneous viewport provided by the head-mounted display at any position within the large virtual display by turning to look in the desired direction. The instantaneous viewport further includes a mouse pointer, which may be positioned by turning the user's head, and which may be further positioned using a mouse or analogous control device. A particular advantage of the virtual computer monitor is intuitive access to enlarged computer output for visually-impaired individuals.
Owner:REMBRANDT PORTABLE DISPLAY TECH LP
TLB miss fault handler and method for accessing multiple page tables
ActiveUS7111145B1Memory adressing/allocation/relocationComputer security arrangementsVirtual memoryError processing
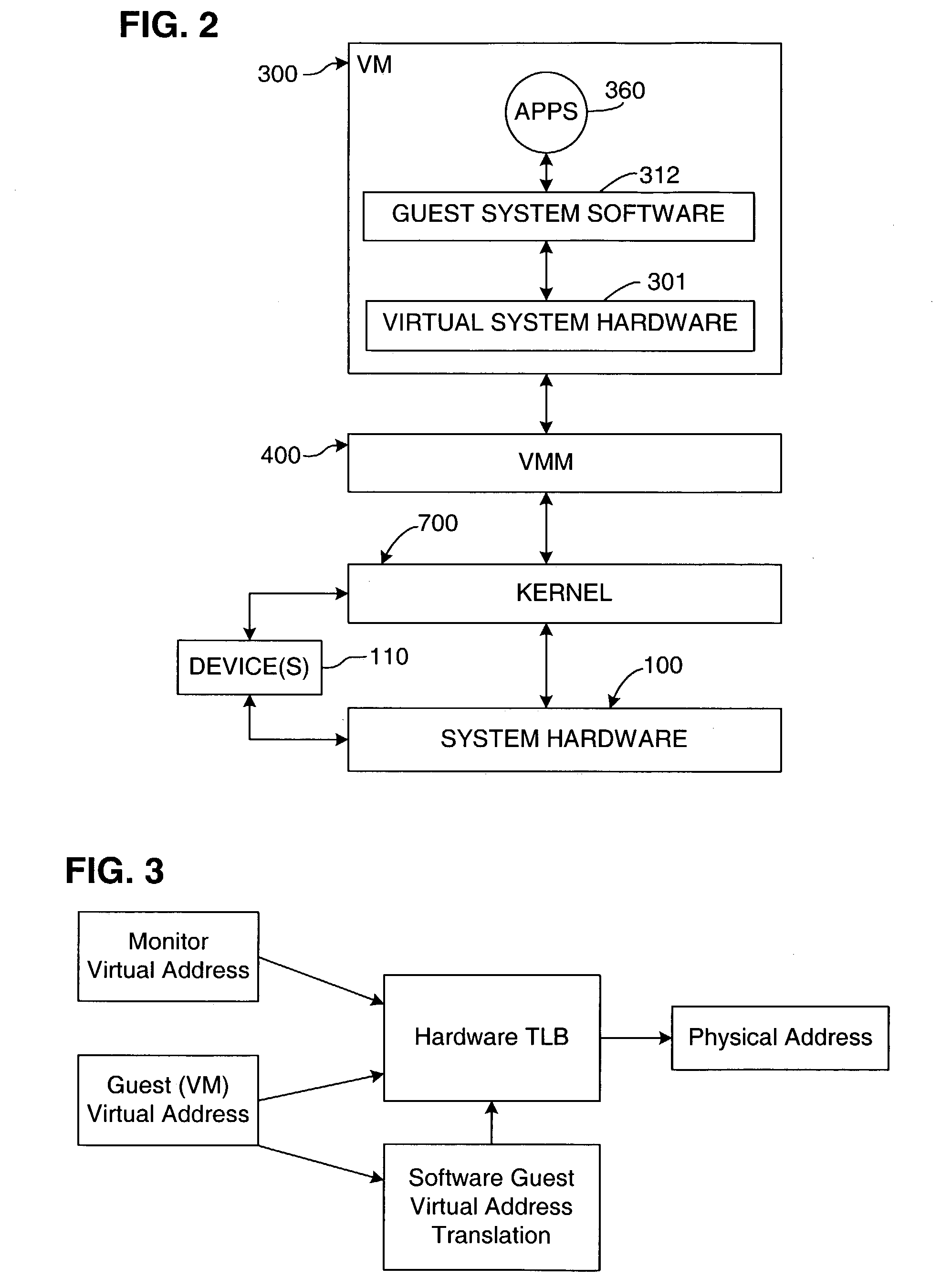
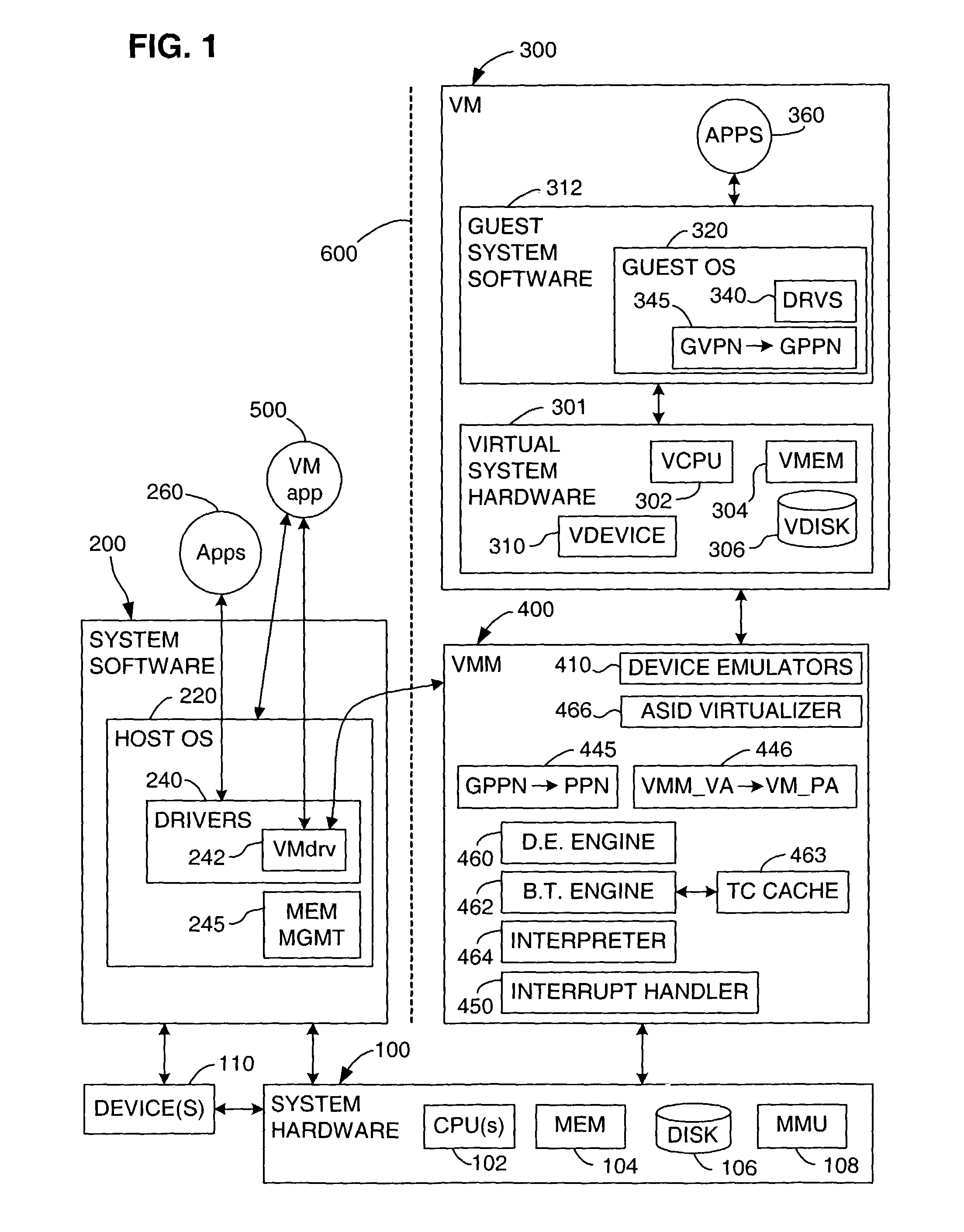
A virtual memory system implementing the invention provides concurrent access to translations for virtual addresses from multiple address spaces. One embodiment of the invention is implemented in a virtual computer system, in which a virtual machine monitor supports a virtual machine. In this embodiment, the invention provides concurrent access to translations for virtual addresses from the respective address spaces of both the virtual machine monitor and the virtual machine. Multiple page tables contain the translations for the multiple address spaces. Information about an operating state of the computer system, as well as an address space identifier, are used to determine whether, and under what circumstances, an attempted memory access is permissible. If the attempted memory access is permissible, the address space identifier is also used to determine which of the multiple page tables contains the translation for the attempted memory access.
Owner:VMWARE INC
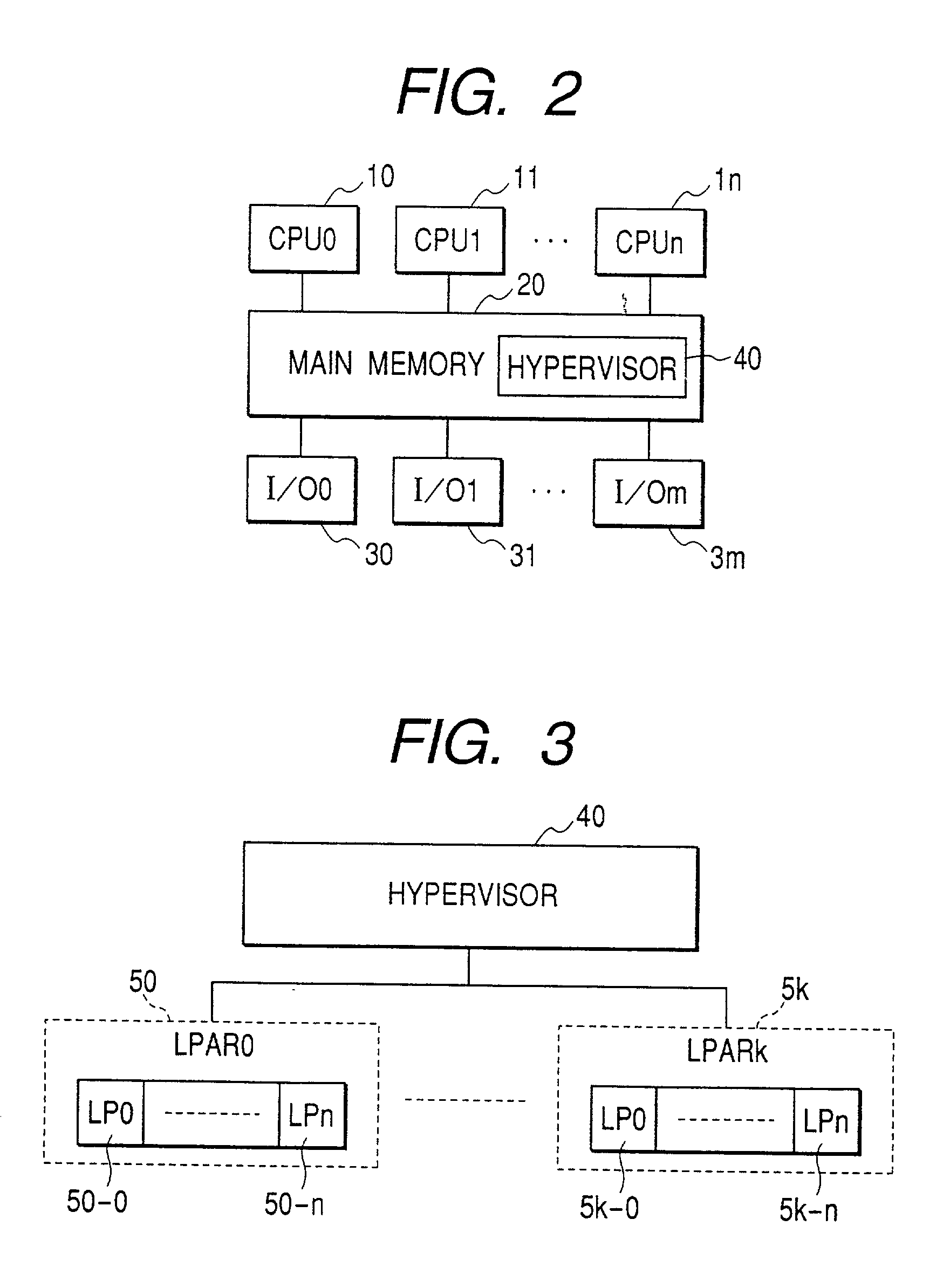
Virtual computer system with dynamic resource reallocation
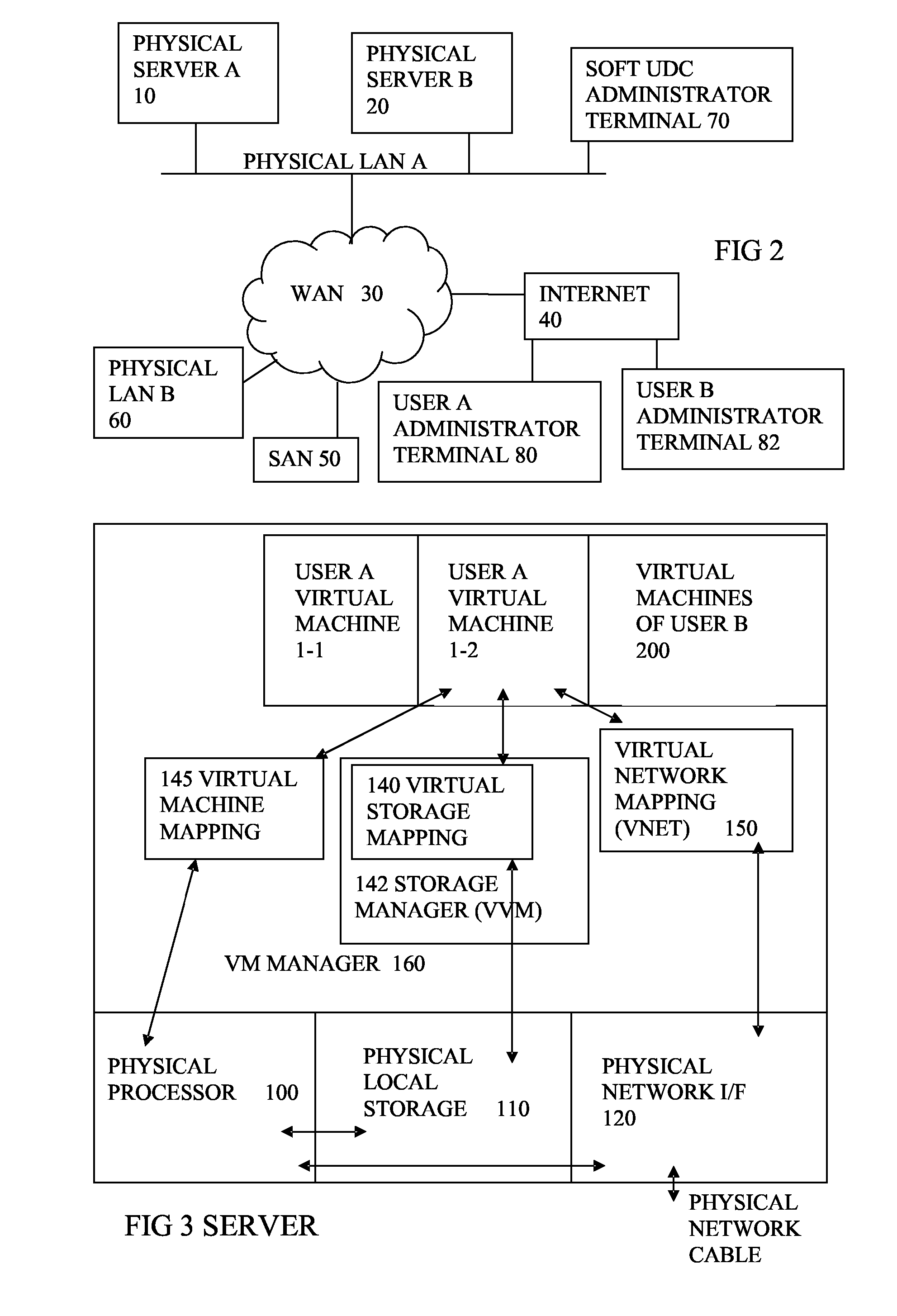
InactiveUS20020087611A1Resource allocationError detection/correctionDynamic resourceVirtual computing
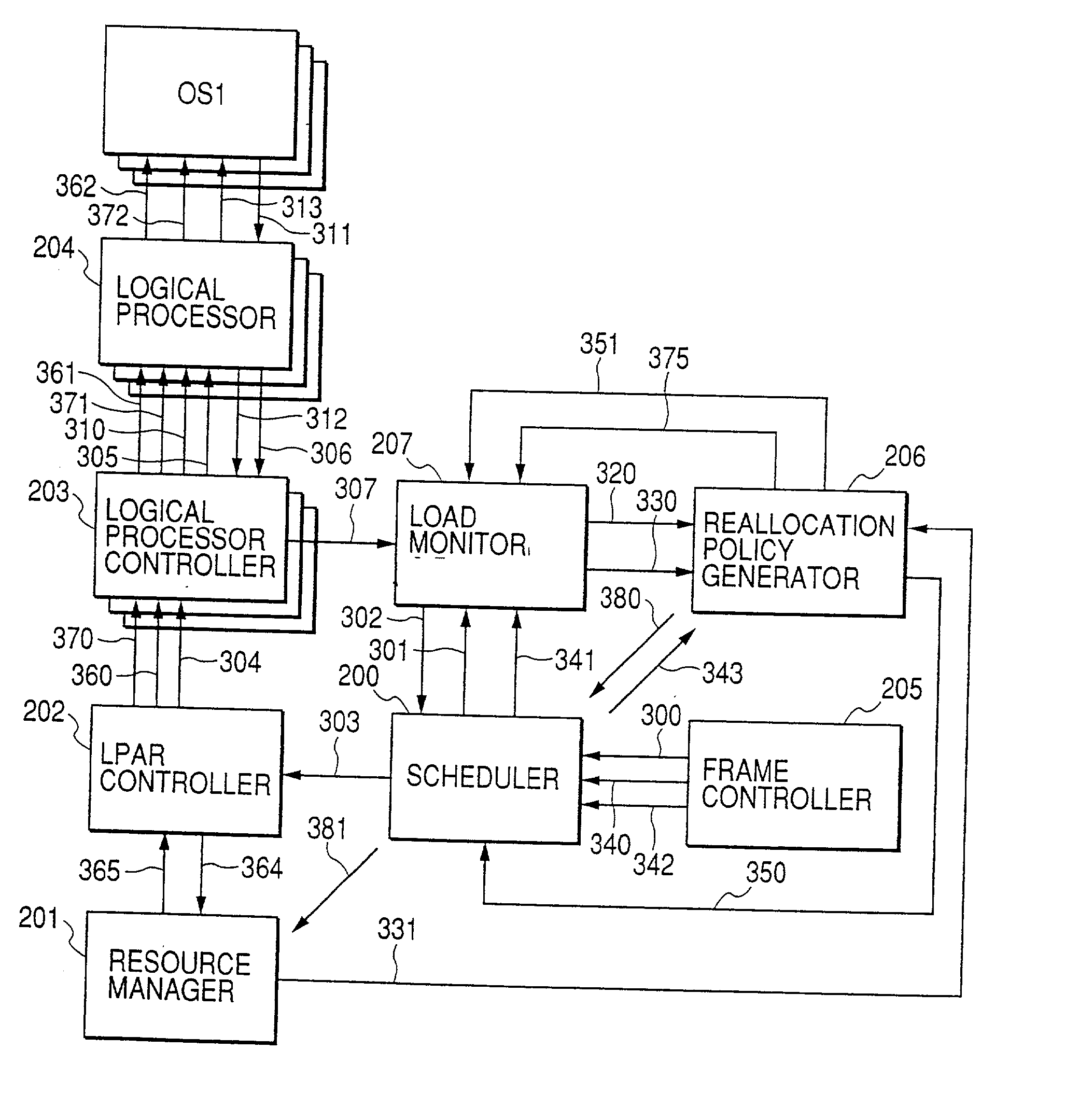
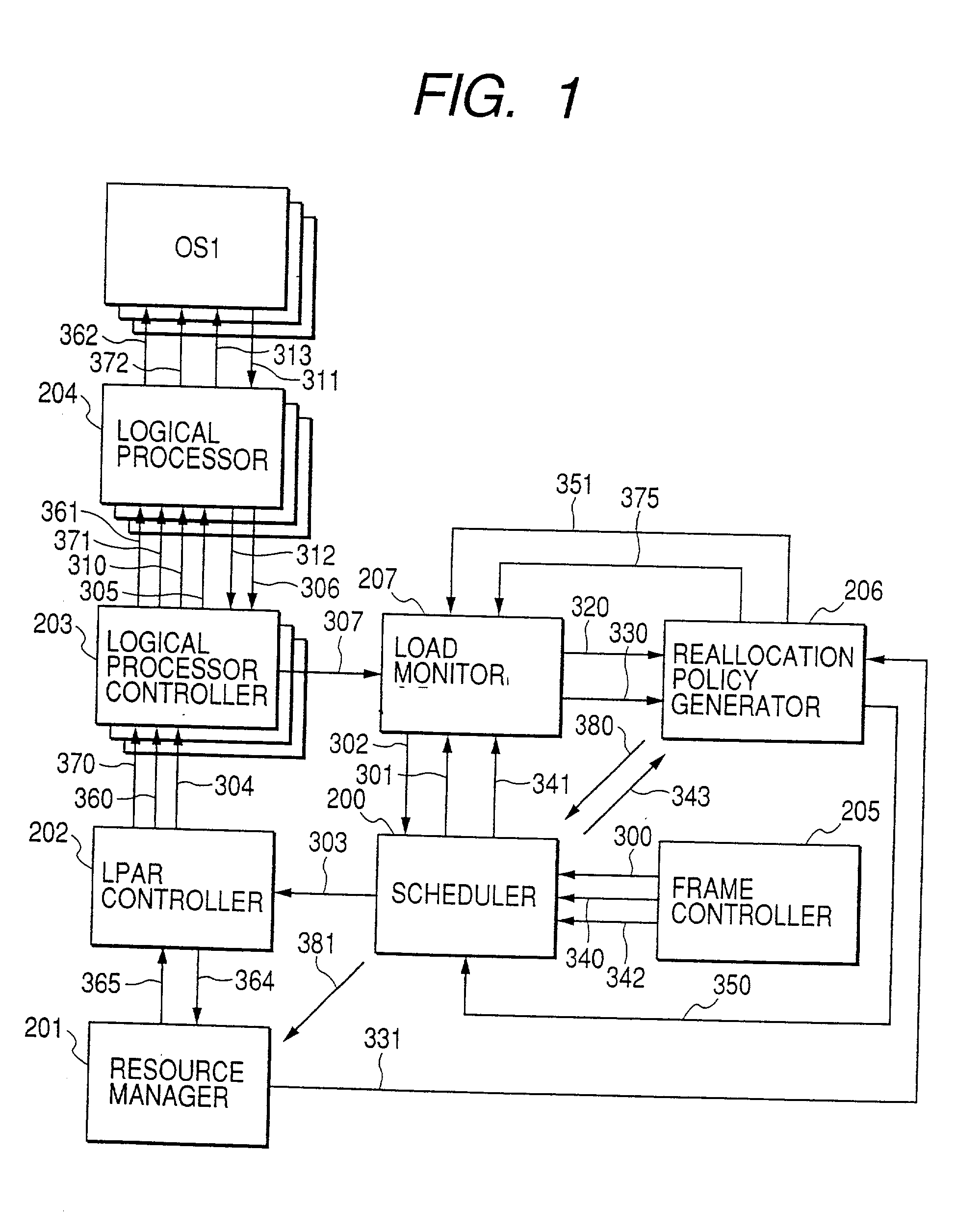
A virtual computer system including a reallocation means, in which a plurality of LPAR are operated by logically dividing physical resources composing a physical computer exclusively or in time dividing manner so as to dynamically change reallocation of physical resources among each of LPARs. Based on load conditions measured by an application or an OS of each LPAR, physical resource allocation to each LPAR is determined, thereby conducting reallocation of LPAR.
Owner:HITACHI LTD
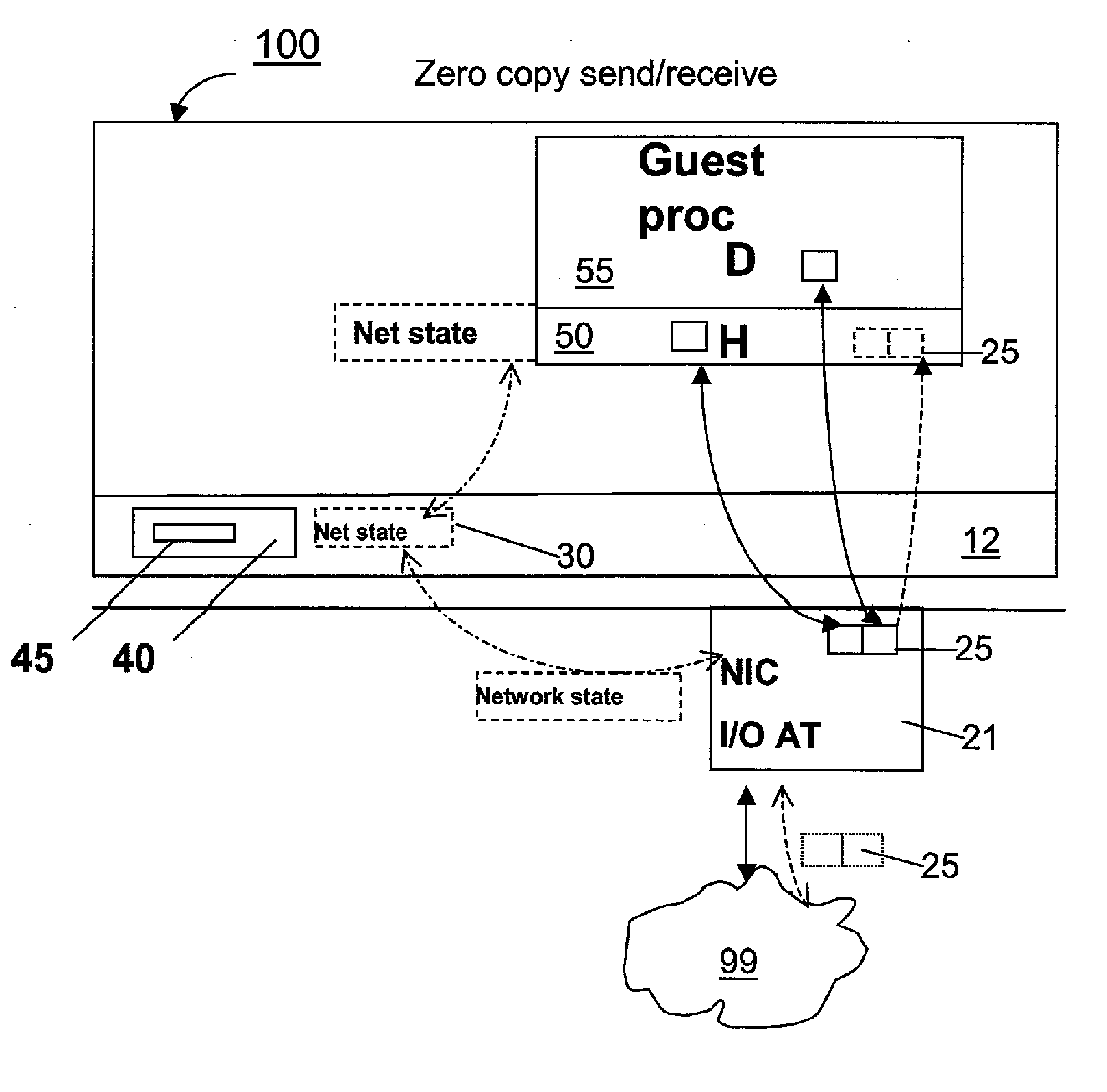
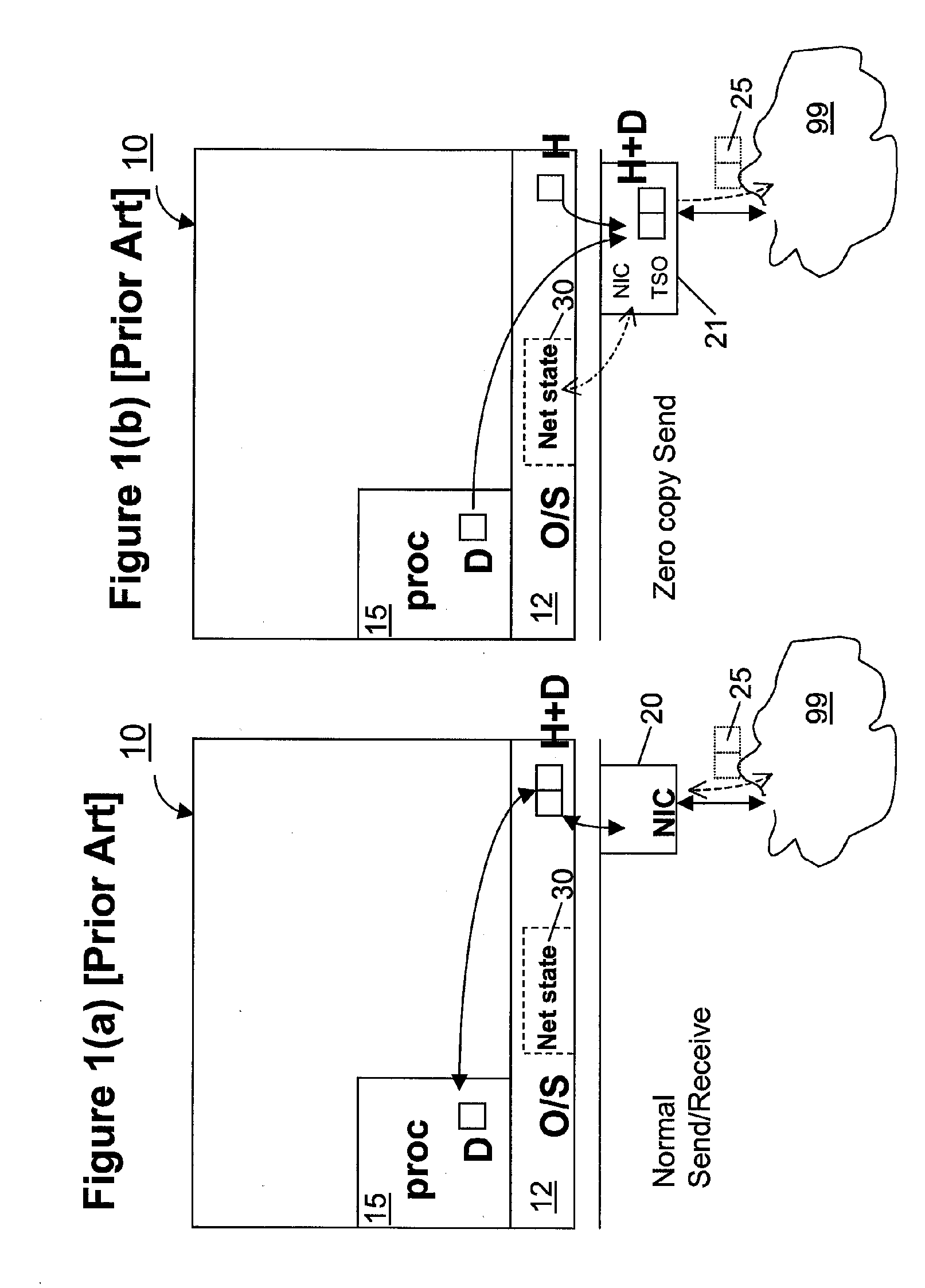
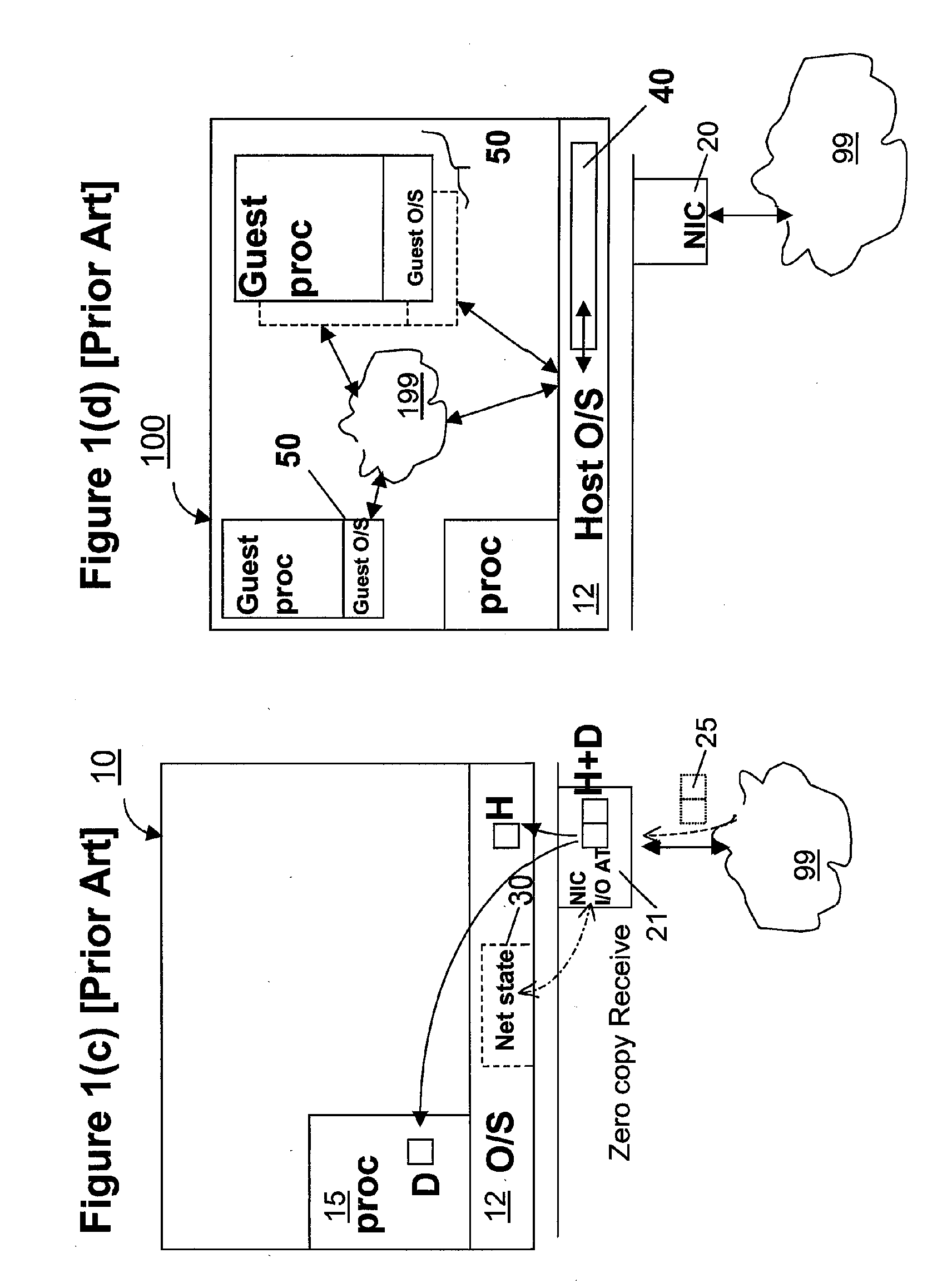
Zero-copy network I/O for virtual hosts
ActiveUS20070061492A1Eliminate the problemSolve excessive overheadDigital computer detailsTransmissionData packVirtualization
Techniques for virtualized computer system environments running one or more virtual machines that obviate the extra host operating system (O / S) copying steps required for sending and receiving packets of data over a network connection, thus eliminating major performance problems in virtualized environment. Such techniques include methods for emulating network I / O hardware device acceleration-assist technology providing zero-copy I / O sending and receiving optimizations. Implementation of these techniques require a host O / S to perform actions including, but not limited to: checking of the address translations (ensuring availability and data residency in physical memory), checking whether the destination of a network packet is local (to another virtual machine within the computing system), or across an external network; and, if local, checking whether either the sending destination VM, receiving VM process, or both, supports emulated hardware accelerated-assist on the same physical system. This optimization, in particular, provides a further optimization in that the packet data checksumming operations may be omitted when sending packets between virtual machines in the same physical system.
Owner:RED HAT
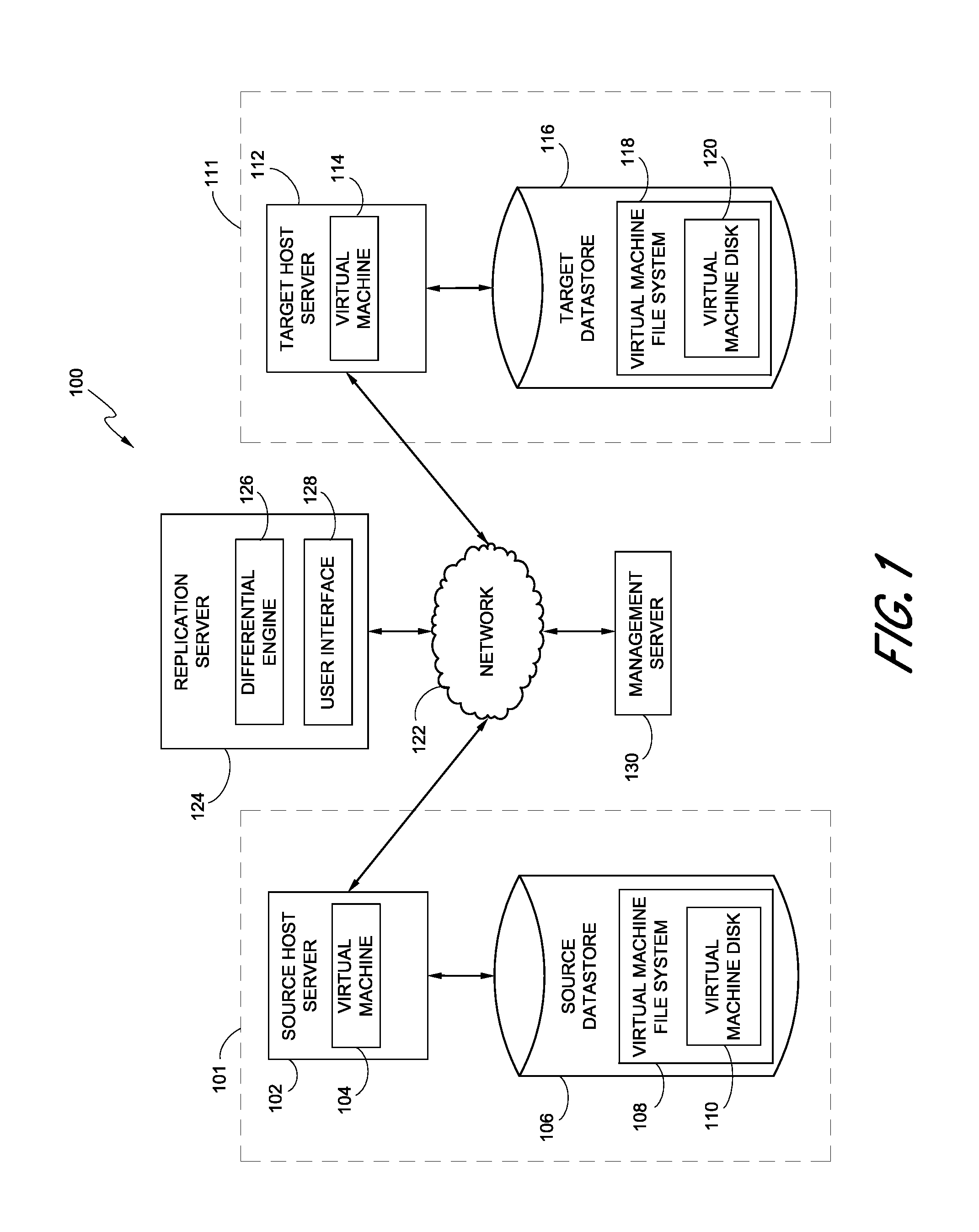
Replication systems and methods for a virtual computing environment
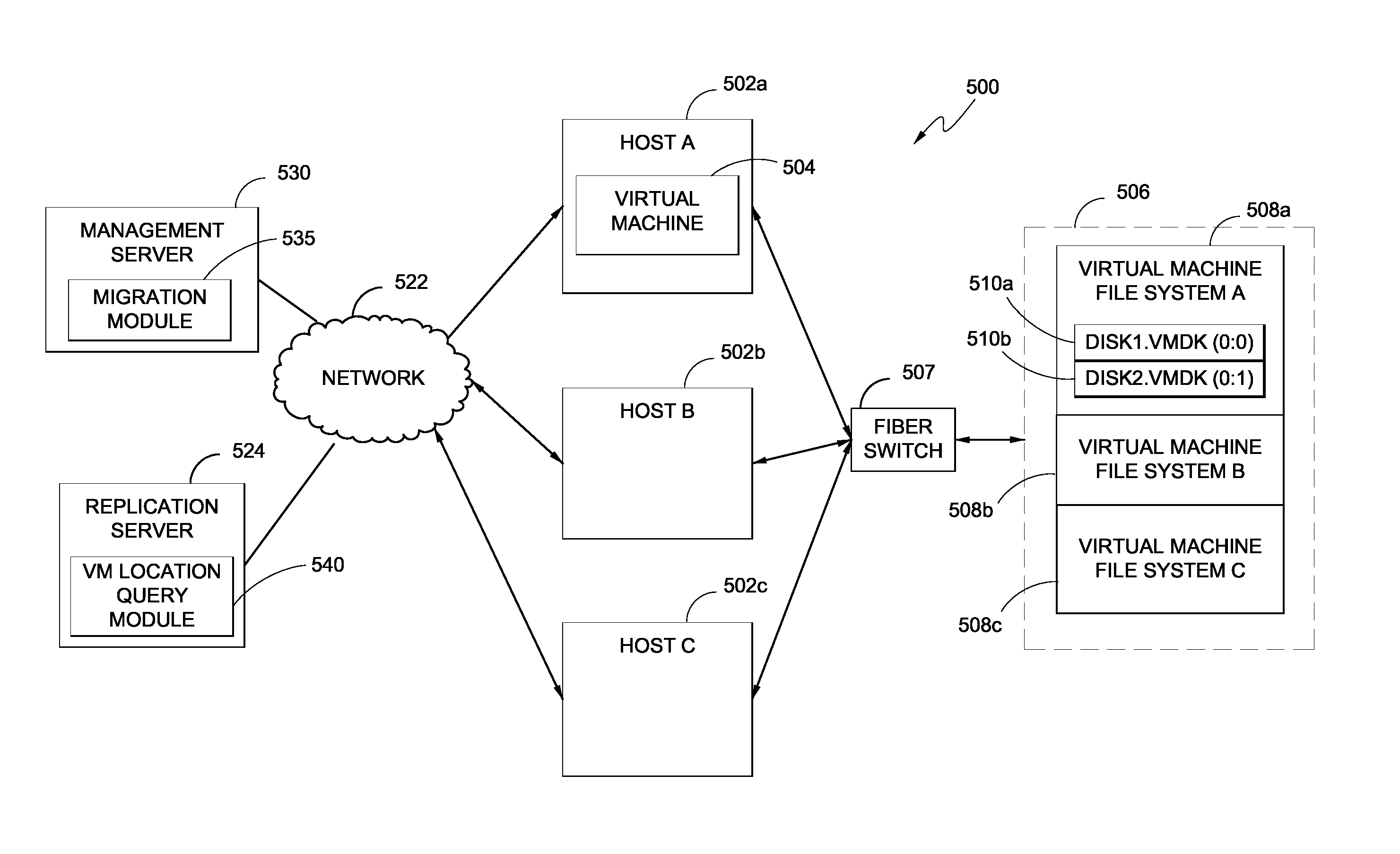
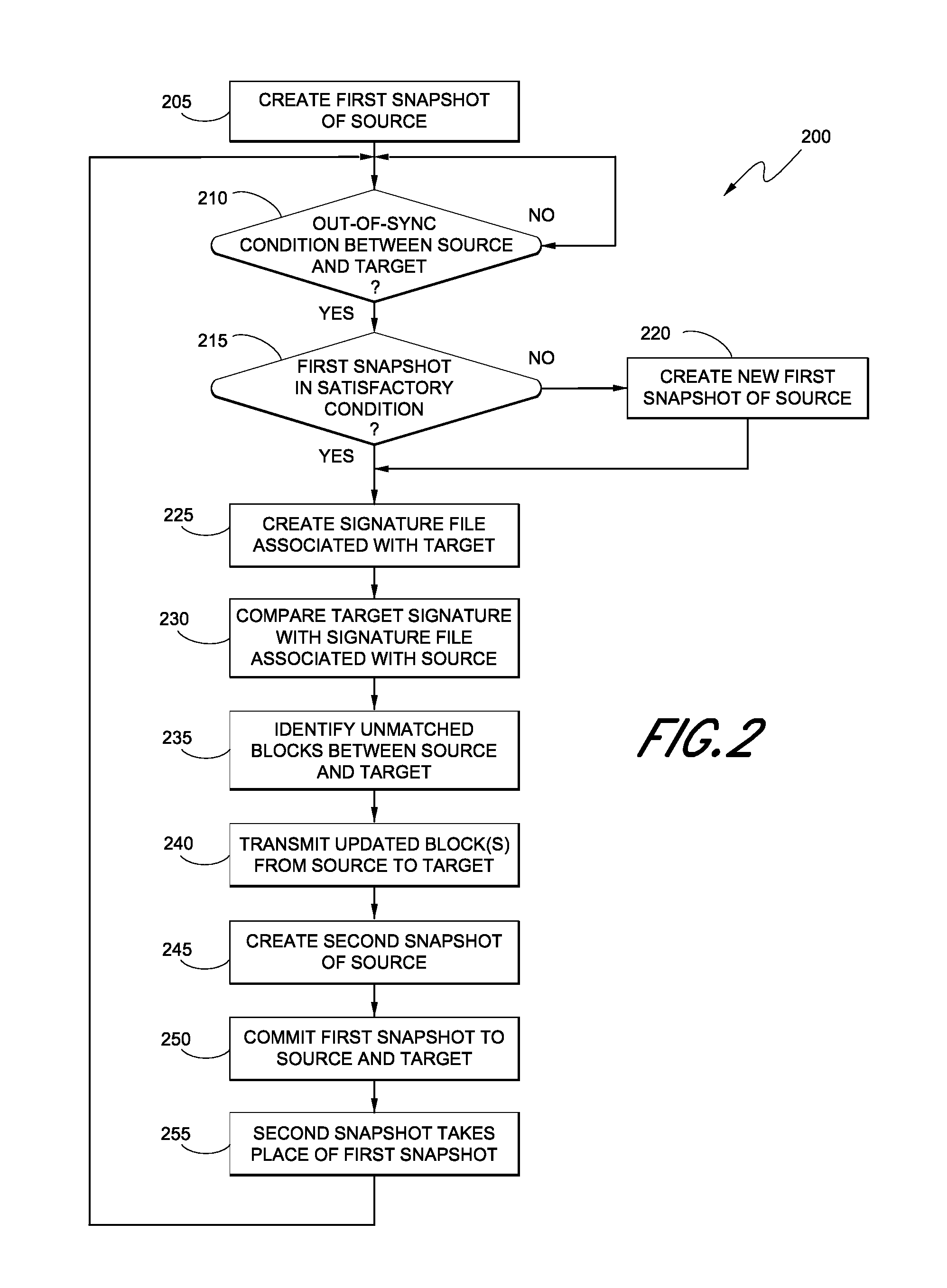
Hybrid replication systems and methods for a virtual computing environment utilize snapshot rotation and differential replication. During snapshot rotation, data modifications intended for a source virtual machine disk (VMDK) are captured by a primary snapshot. Once a particular criterion is satisfied, the data modifications are redirected to a secondary snapshot while the primary snapshot is committed to both source and target VMDKs. The secondary snapshot is then promoted to primary, and a new secondary snapshot is created with writes redirected thereto. If the VMDKs become out-of-sync, disclosed systems can automatically perform a differential scan of the source data and send only the required changes to the target server. Once the two data sets are synchronized, snapshot replication can begin at the previously configured intervals. Certain systems further provide for planned failover copy operations and / or account for migration of a virtual machine during the copying of multiple VMDKs.
Owner:QUEST SOFTWARE INC
Virtual computer monitor
InactiveUS6084556AReduce jitterCosmonautic condition simulationsCathode-ray tube indicatorsComputer monitorDisplay device
A virtual computer monitor is described which enables instantaneous and intuitive visual access to large amounts of visual data by providing the user with a large display projected virtually in front of the user. The user wears a head-mounted display containing a head-tracker, which together allow the user to position an instantaneous viewport provided by the head-mounted display at any position within the large virtual display by turning to look in the desired direction. The instantaneous viewport further includes a mouse pointer, which may be positioned by turning the user's head, and which may be further positioned using a mouse or analogous control device. A particular advantage of the virtual computer monitor is intuitive access to enlarged computer output for visually-impaired individuals.
Owner:META PLATFORMS INC
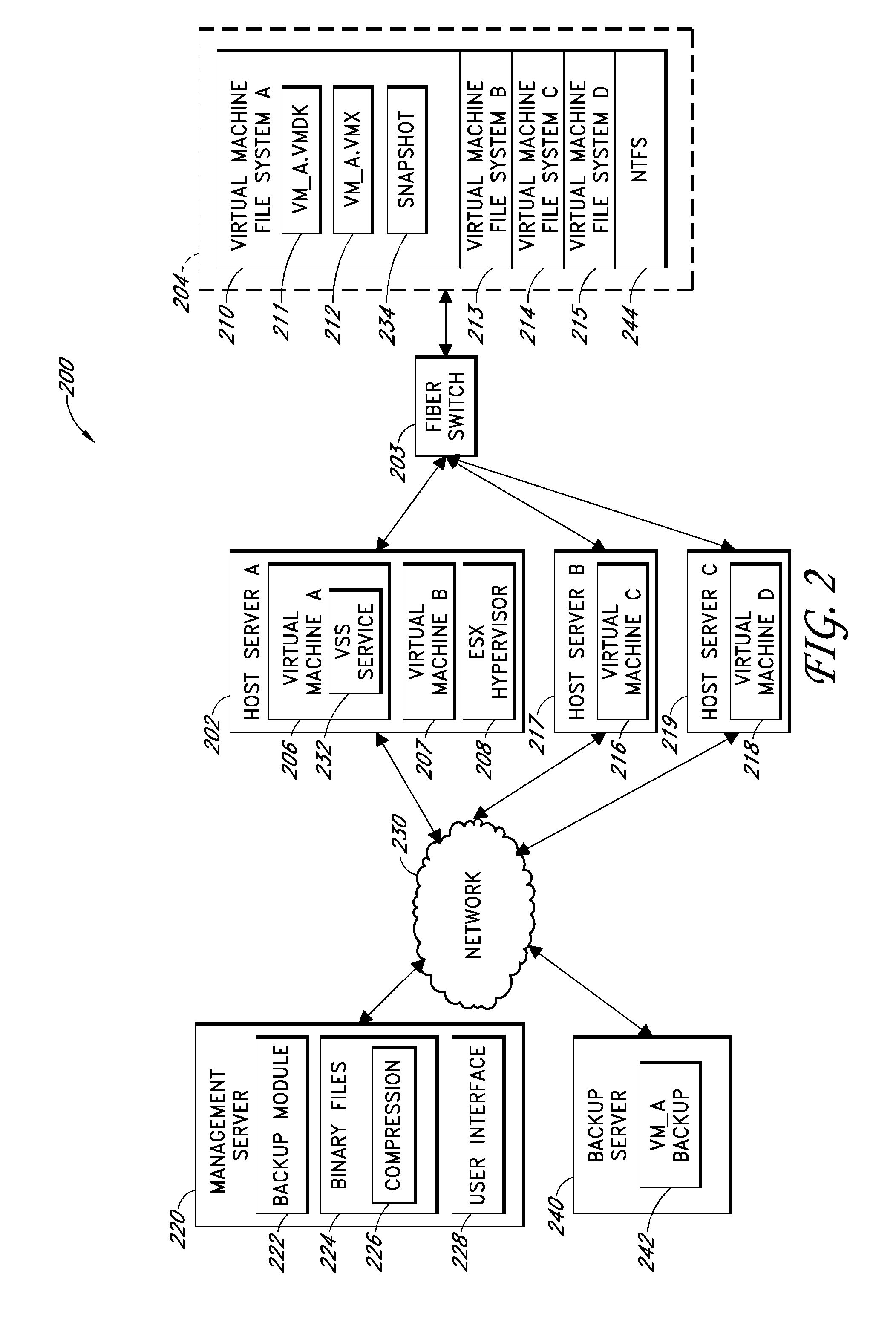
Backup systems and methods for a virtual computing environment
ActiveUS8060476B1Reduce the amount requiredReduce image sizeError detection/correctionDigital data processing detailsApplication programming interfaceApplication software
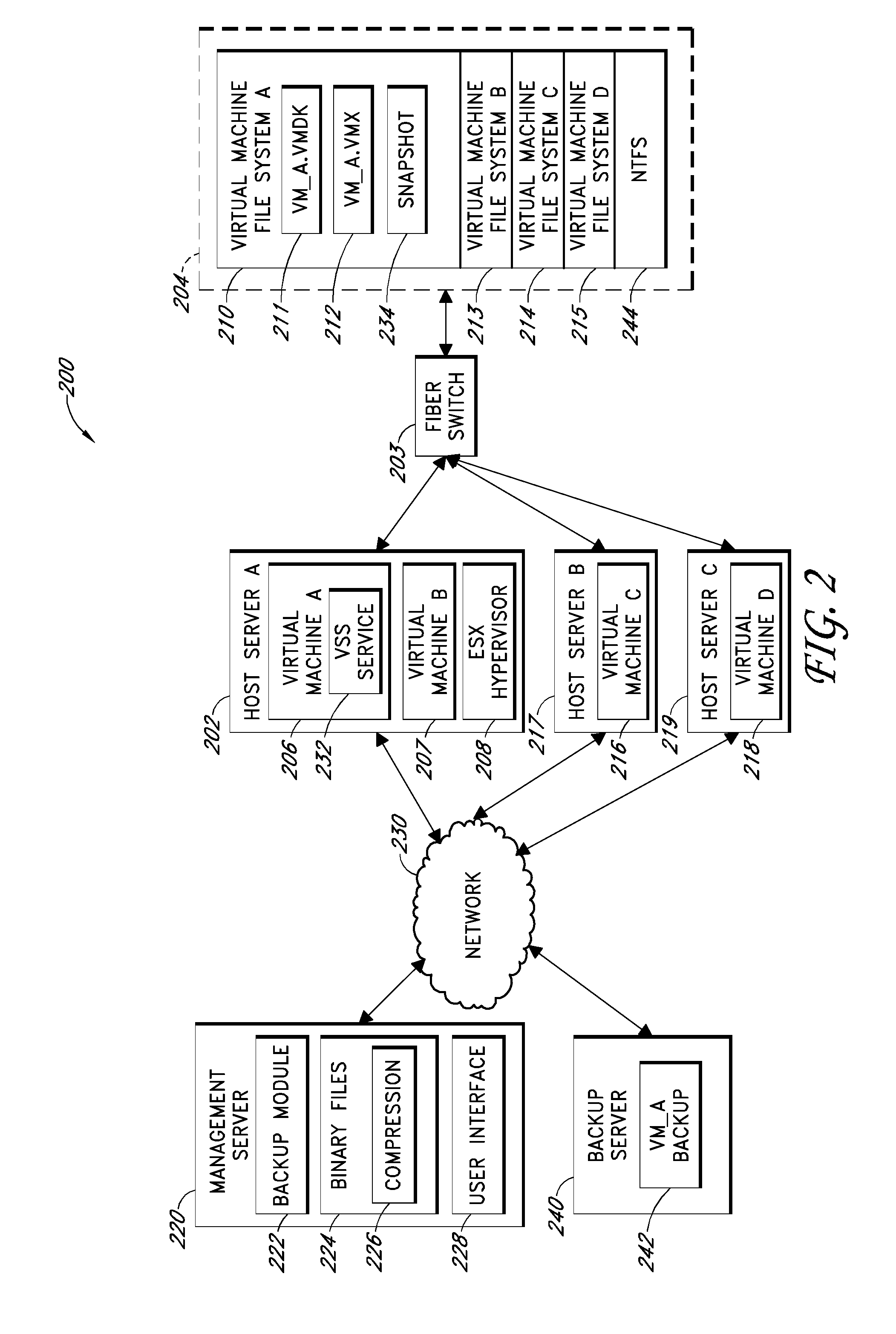
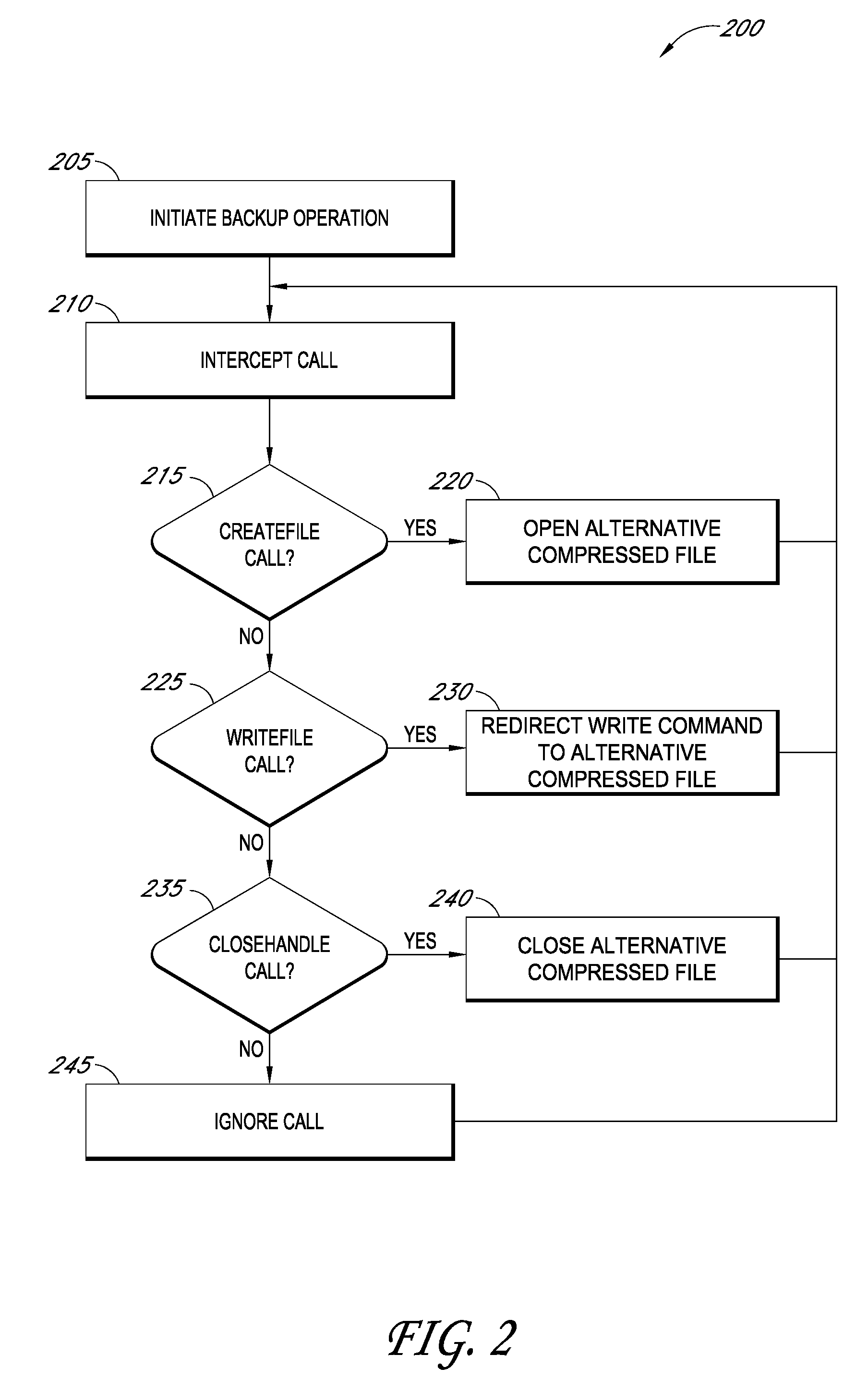
Improved backup and storage operations are disclosed for virtual computing environments using a backup proxy server to perform storage operations on one or more virtual machine disks. The proxy server can include a module that intercepts application programming interface (API) calls, for writing backup data to a first location, prior to the data arriving on the proxy disk. During the intercept process, the data can be compressed in memory pages of the proxy server and redirected to an alternative backup disk location. The proxy server can also include a differential engine that identifies changes to the virtual machine disk at the block level since the last full backup. The differential engine can advantageously leverage memory pages of the proxy server to compare differences between signatures of blocks of the last full backup with signatures of new blocks. Subsequently, only blocks with non-matching signatures are processed for backup.
Owner:QUEST SOFTWARE INC
System and Method for Securing Information in a Virtual Computing Environment
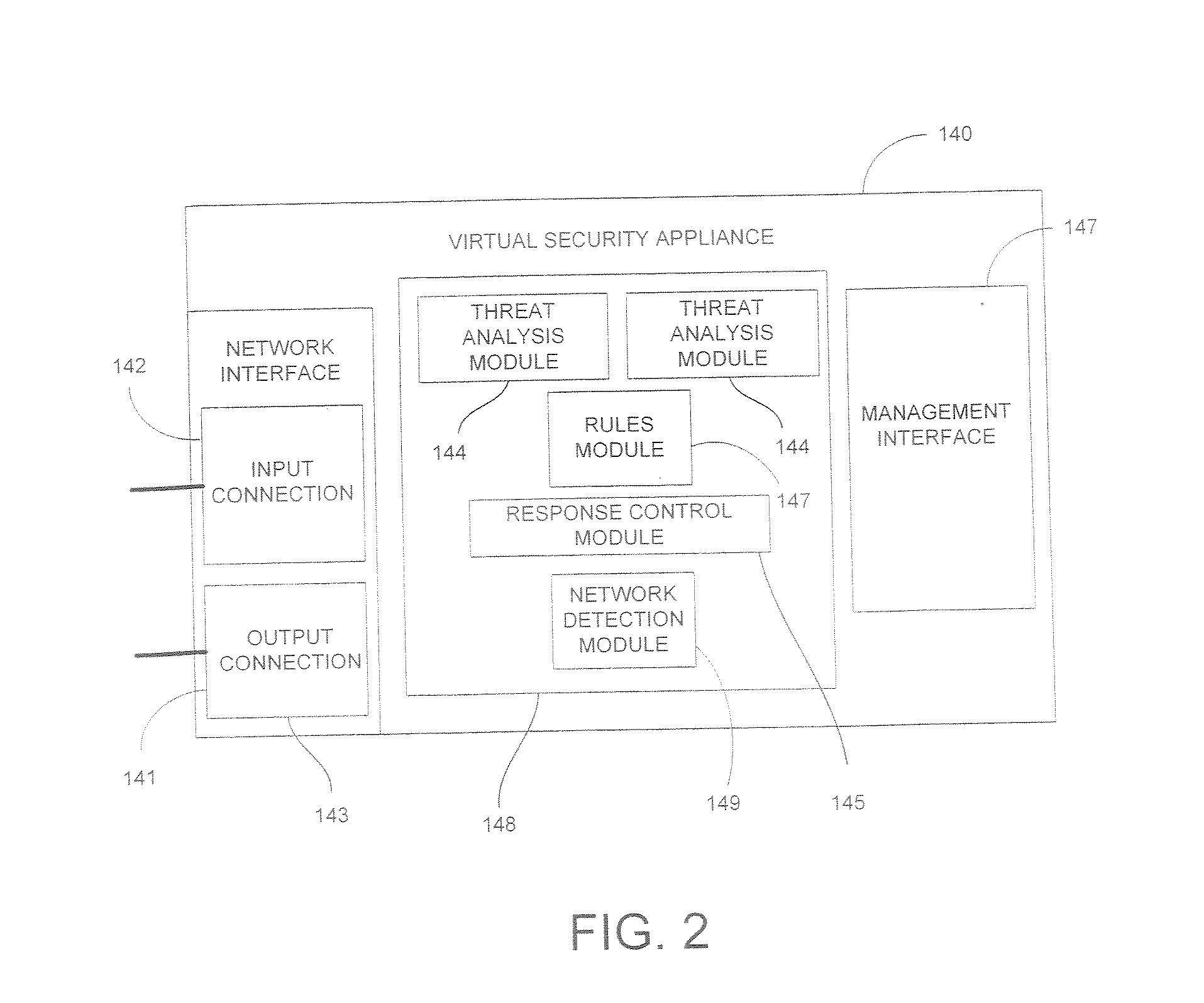
InactiveUS20070266433A1Improve employee productivityIncrease the challengeMultiple digital computer combinationsPlatform integrity maintainanceVirtual computingHost machine
A virtual security appliance is provided for disposition in a virtual network having at least one other virtual network device, the virtual network residing on a host data processing machine. The virtual security appliance comprises an interface configured for receiving a data communication directed to the at least one other virtual network device and a security function module adapted for initiating a security function responsive to said data communication meeting predetermined criteria.
Owner:STRATACLOUD
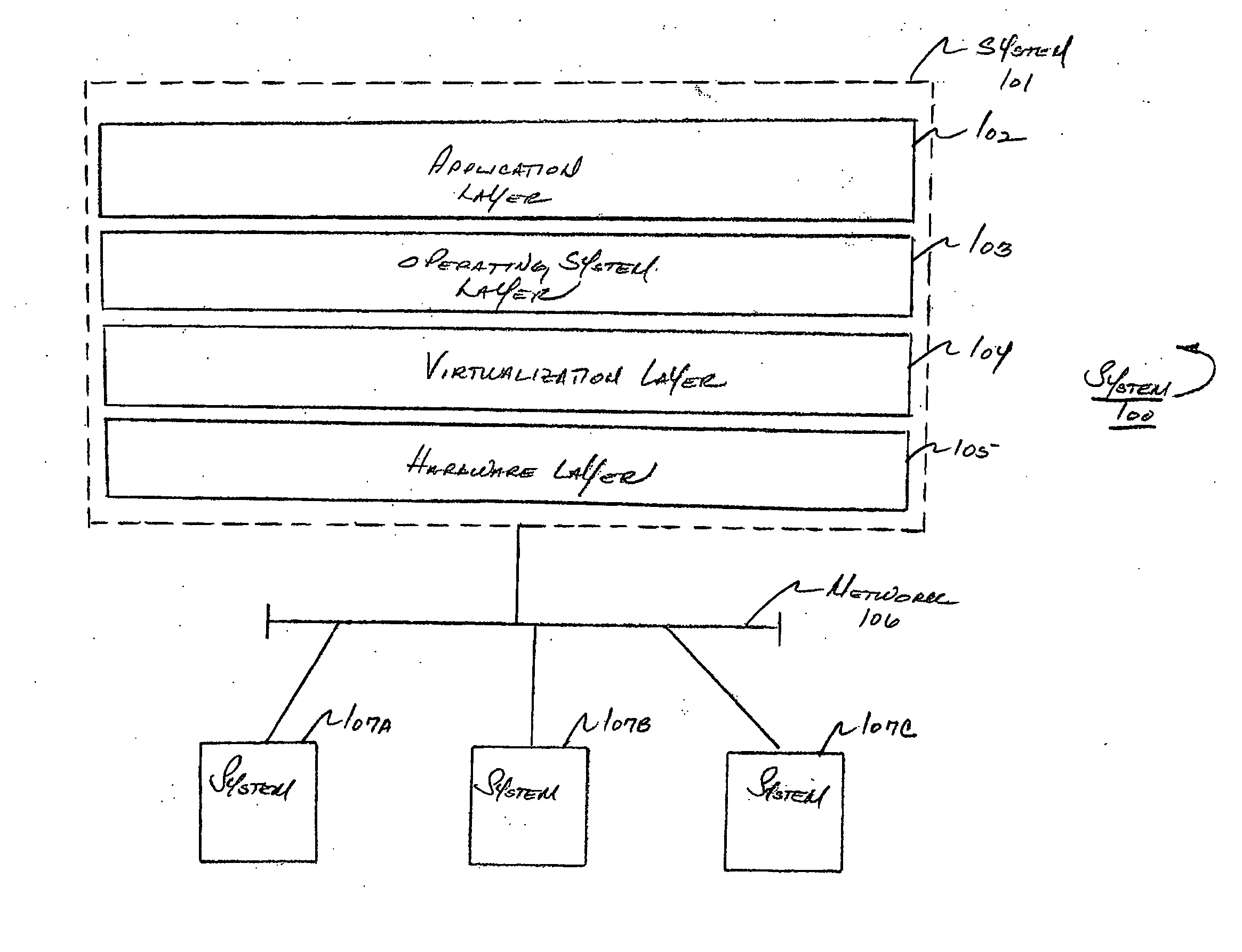
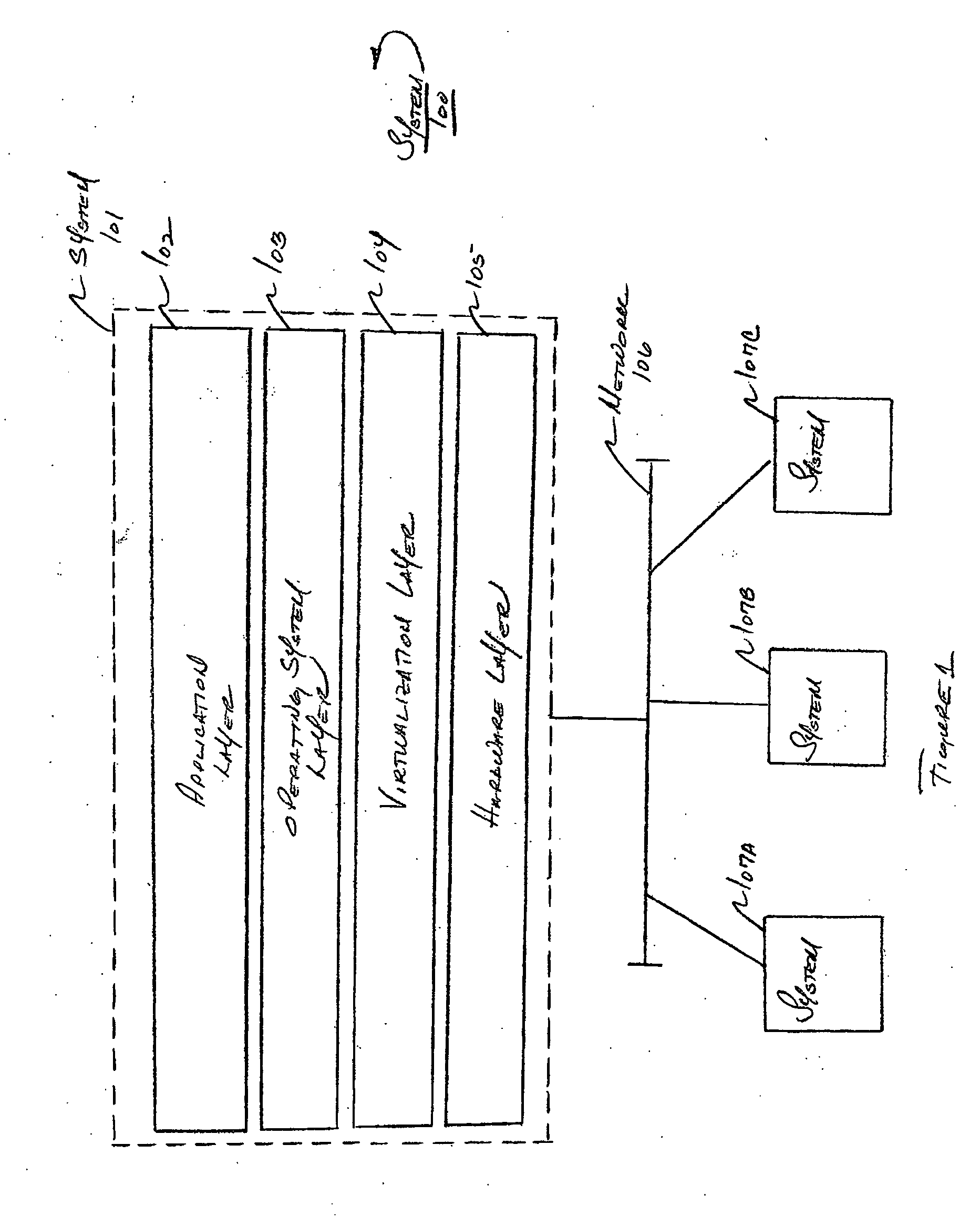
Methods and apparatus for implementing a virtualized computer system
InactiveUS20060090136A1Error detection/correctionDigital computer detailsVirtualizationVirtual computing
In one aspect, a method of creating a virtualized computer environment that represents a real world computer environment is provided. The real world computer environment comprises a plurality of components, the plurality of components comprising a plurality of computer devices and at least one network device that implements a network that interconnects the plurality of computer devices, the real world computer environment comprising at least one security facility that implements at least one security function in the real world computer environment. The method comprises acts of including in the virtualized computer environment a virtualized representation of at least one of the plurality of computer devices in the real world computer environment and implementing the at least one security function in the virtualized computer environment. In another aspect, a virtualized representation of the at least one network device is provided. In another aspect, software is executed in the virtual computer environment.
Owner:MICROSOFT TECH LICENSING LLC
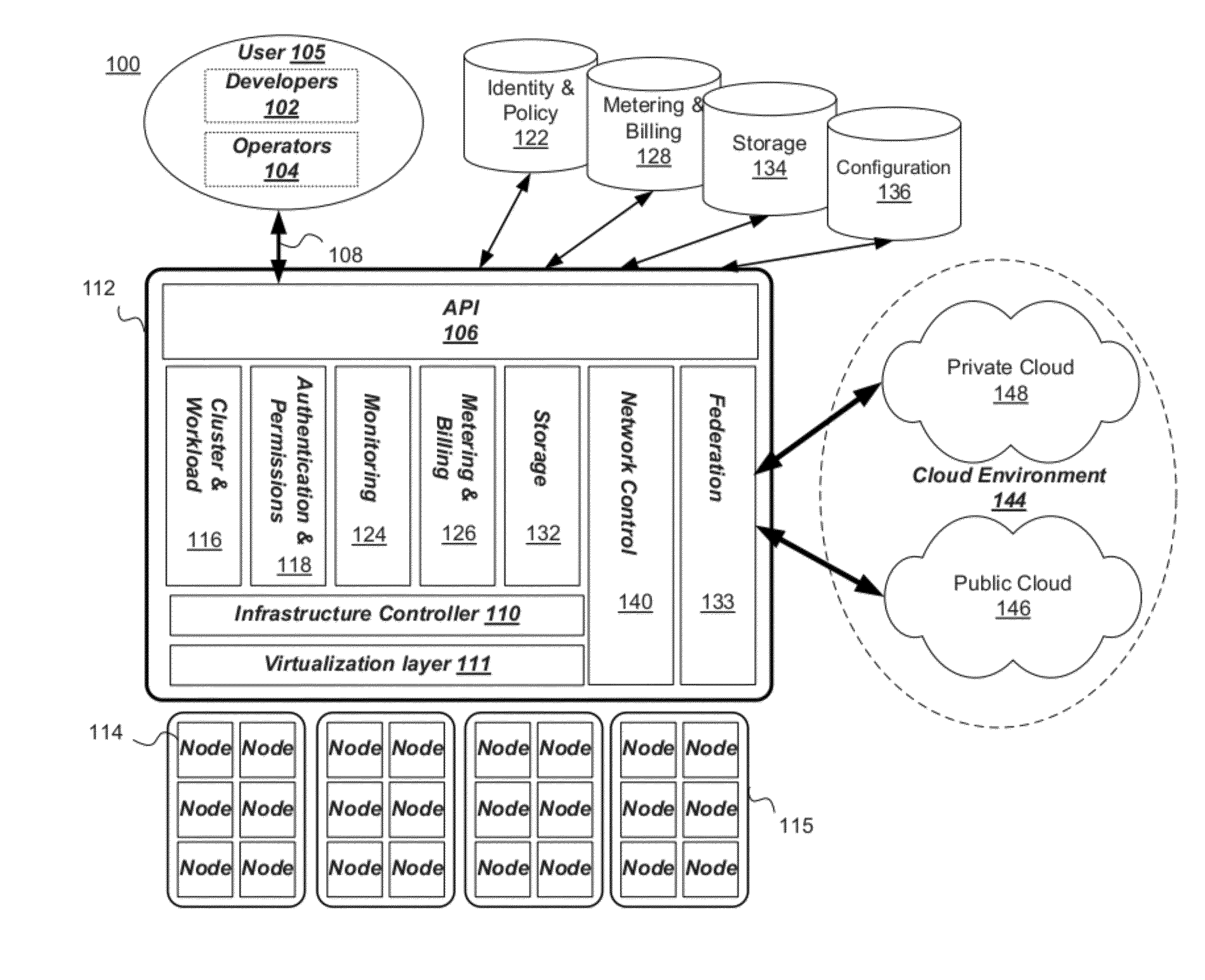
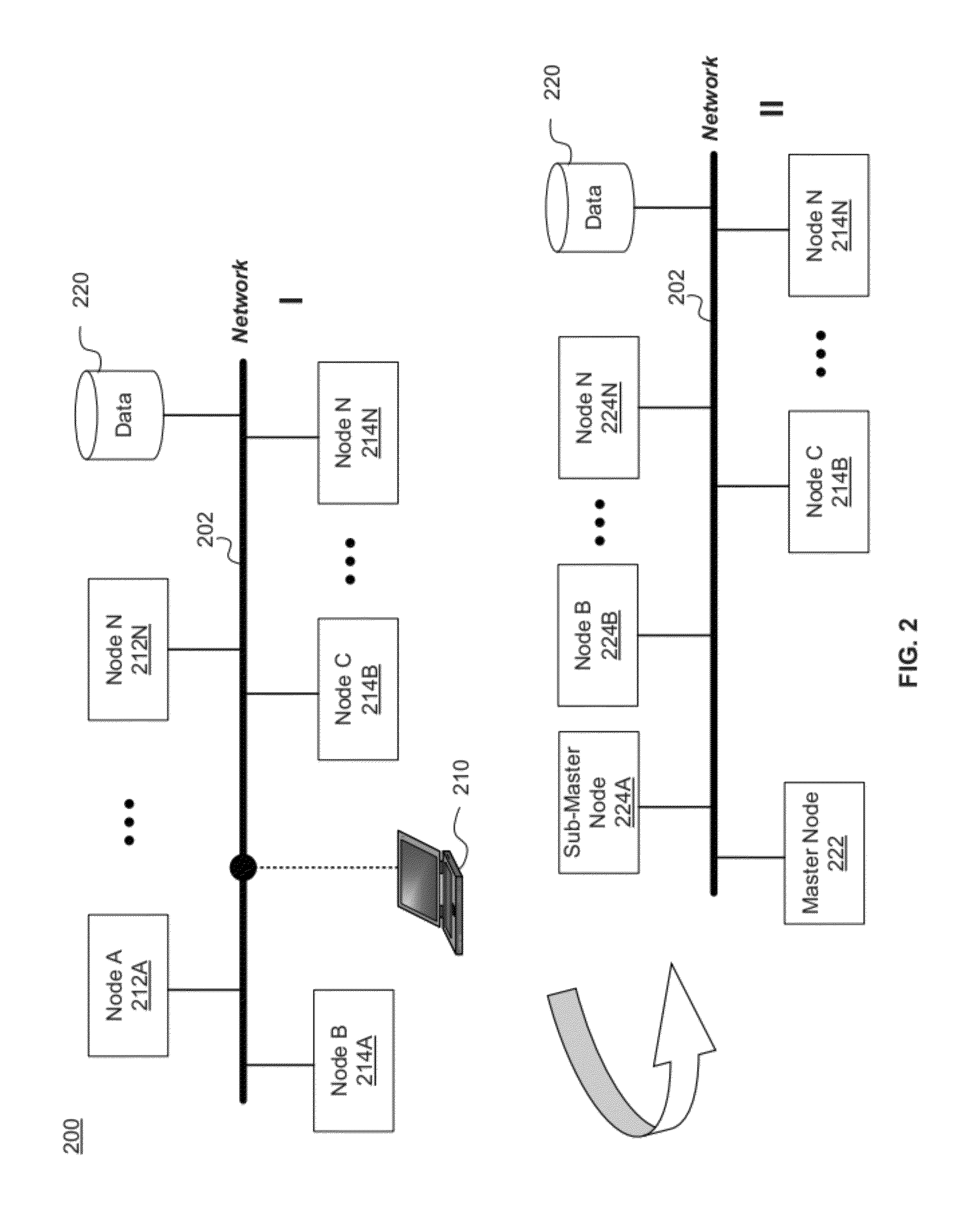
Building a Cloud Computing Environment Using a Seed Device in a Virtual Computing Infrastructure
ActiveUS20120110055A1Improve functionalityFacilitate communicationFinanceTelephonic communicationVirtual computingManagement system
A cloud computing environment having a plurality of computing nodes is described. A seed device is connected to a network. From the seed device, a launching of a cloud computing management configuration is initiated. The seed device includes a repository of software. From the seed device, software is installed on one of the plurality of computing nodes to run a cloud computing management system. The software is loaded from one of the plurality of computing nodes onto each of the plurality of nodes. A computing node is selected from the plurality of computing nodes, to designate as a master node. Operations of the cloud computing management system is controlled from the master node.
Owner:ORACLE INT CORP
Distributed virtual machine monitor for managing multiple virtual resources across multiple physical nodes
ActiveUS8776050B2Grow and shrink capabilityMaximize useResource allocationMemory adressing/allocation/relocationOperational systemGNU/Linux
A management capability is provided for a virtual computing platform. In one example, this platform allows interconnected physical resources such as processors, memory, network interfaces and storage interfaces to be abstracted and mapped to virtual resources (e.g., virtual mainframes, virtual partitions). Virtual resources contained in a virtual partition can be assembled into virtual servers that execute a guest operating system (e.g., Linux). In one example, the abstraction is unique in that any resource is available to any virtual server regardless of the physical boundaries that separate the resources. For example, any number of physical processors or any amount of physical memory can be used by a virtual server even if these resources span different nodes.
Owner:ORACLE INT CORP
Systems and Methods for Graphical User Interface Interaction with Cloud-Based Applications
ActiveUS20130246932A1Small sizeExecution for user interfacesInput/output processes for data processingVirtualizationGraphics
Systems and methods may: execute a virtualized application instance in a virtual computing environment; receive from a remote client device first object data relating to a first set of user interactions received with respect to a client-side graphical use interface (GUI) object at the remote client device, the client-side GUI object representing a GUI object of the virtualized application instance; translating the first object data to second object data relating to the GUI object of the virtualized application instance, the second object data executing a command when applied to the GUI object of the virtualized application instance; and synchronizing the GUI object of the virtualized application instance with the client-side GUI object by applying the second object data to the GUI object of the virtualized application instance.
Owner:CLOUDON
Systems and methods for performing backup operations of virtual machine files
ActiveUS8046550B2Error detection/correctionSoftware simulation/interpretation/emulationOperational systemApplication software
Backup systems and methods are disclosed for a virtual computing environment. Certain examples include a system having a backup management server that communicates with a host server having at least one virtual machine. The management server coordinates with the host server to perform backup copies of entire virtual machine disks from outside the guest operating system of the virtual machine. In certain examples, such backup systems further utilize a volume shadow copy service executing on the host server to quiesce virtual machine applications to put data in a consistent state to be backed up. The backup system then utilizes hypervisor snapshot capabilities of the host server to record intended changes to the virtual machine disk files while such files are being copied (e.g., backed up) by the host server. Such recorded changes can be later committed to the virtual machine disk files once the backup operation has completed.
Owner:QUEST SOFTWARE INC
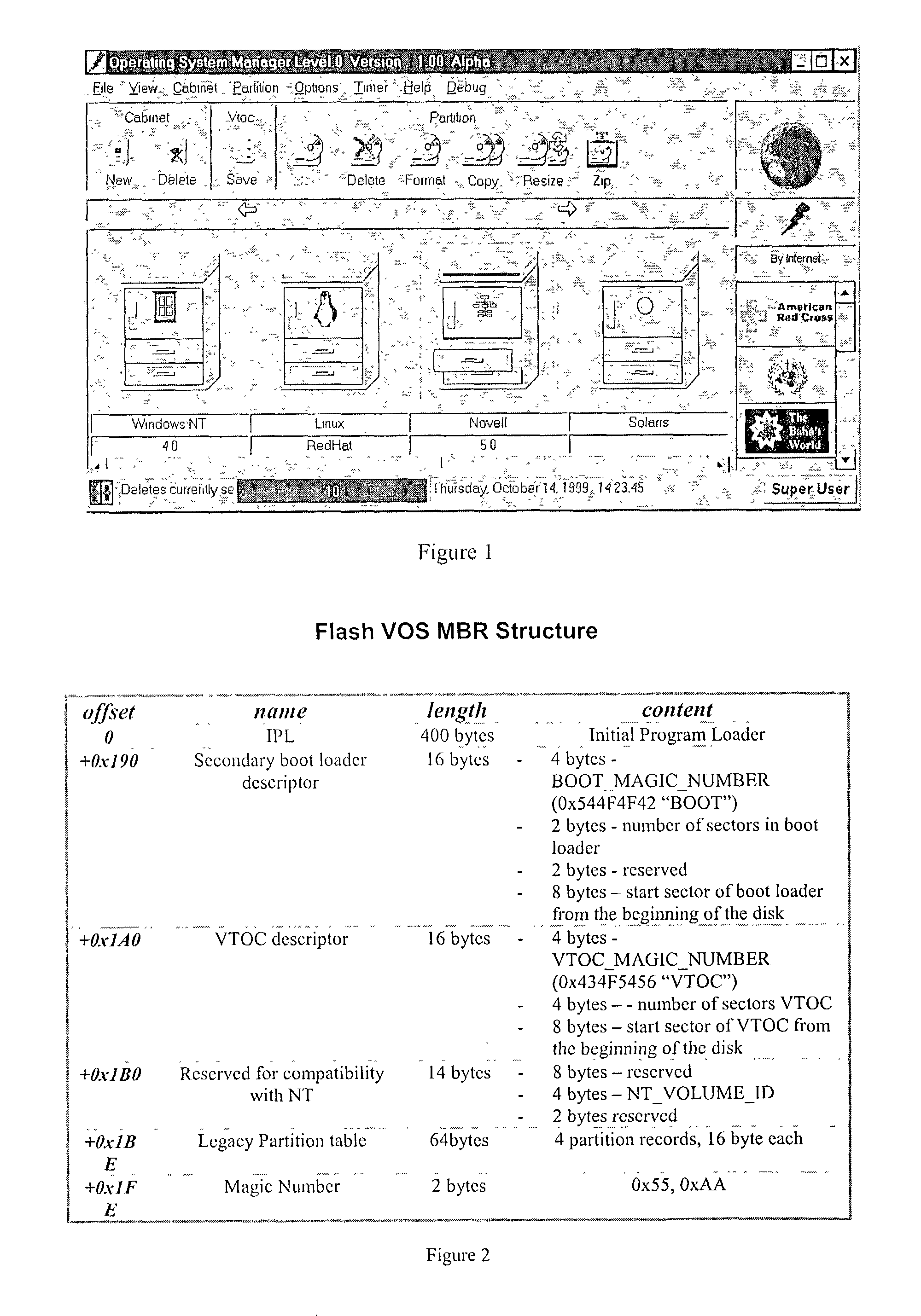
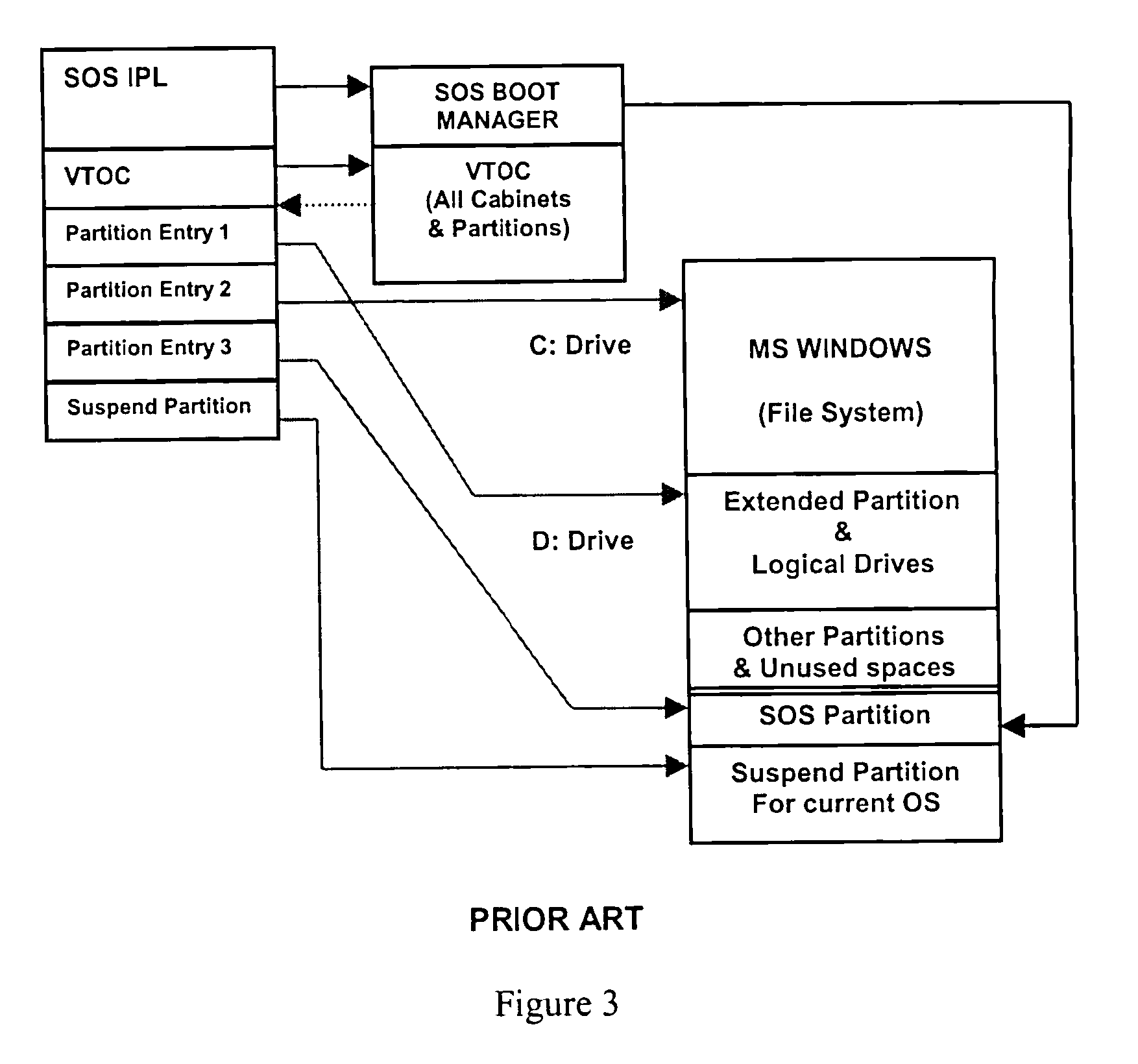
Computer system capable of fast switching between multiple operating systems and applications
ActiveUS7356677B1Fast transferFast shutdownDigital data processing detailsDigital computer detailsApplication program softwareOperational system
A method and apparatus is presented that allows rapid switching between multiple operating system environments on a single computer, through the use of a Super Operating System operating between the computer system's firmware level and a plurality of bootable operating systems and applications. Relevant data, such as hardware controls, bootable operating systems, and applications software, are grouped onto physical partitions in physical memory. Combinations of compatible partitions can be assigned to a cabinet to create a virtual computer system. A given partition is assignable to multiple cabinets. By operating above the virtual computer systems, the Super Operating System uses the suspend and resume functions of the power management support functions to suspend and hybernate one operating virtual computer system, while activating and operating an alternate virtual computer system on the same computer.
Owner:ONE WORLD LED PTY LTD
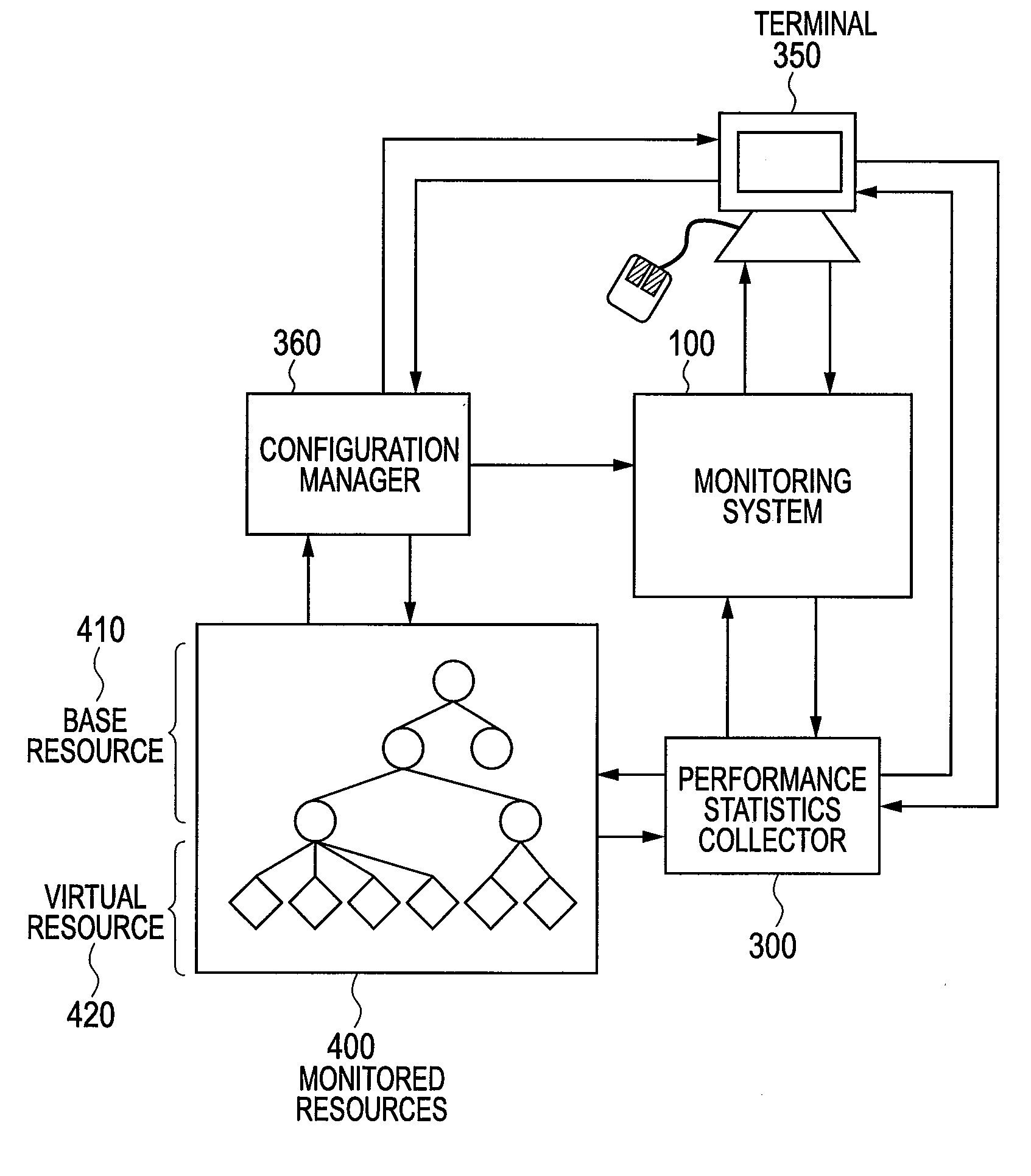
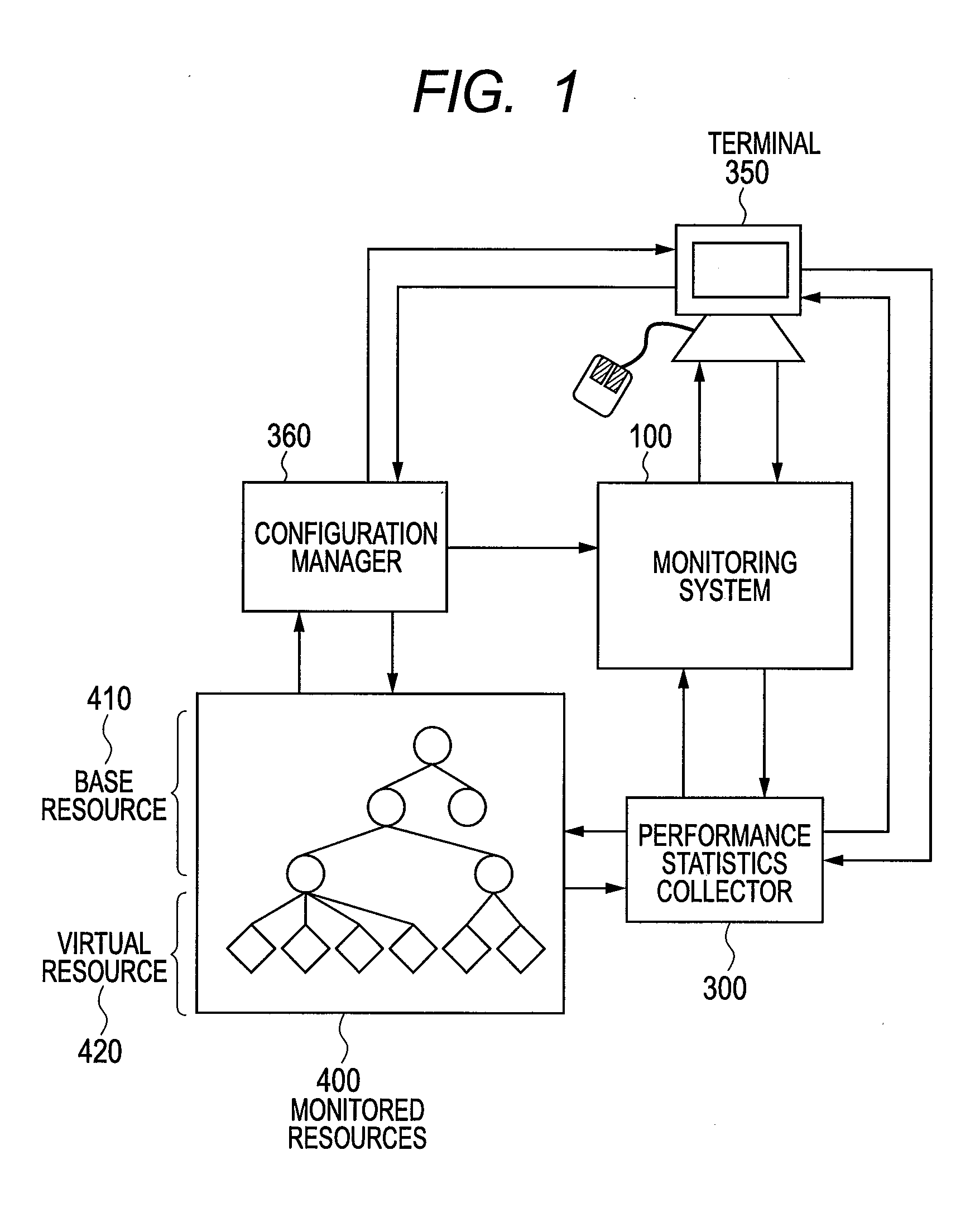
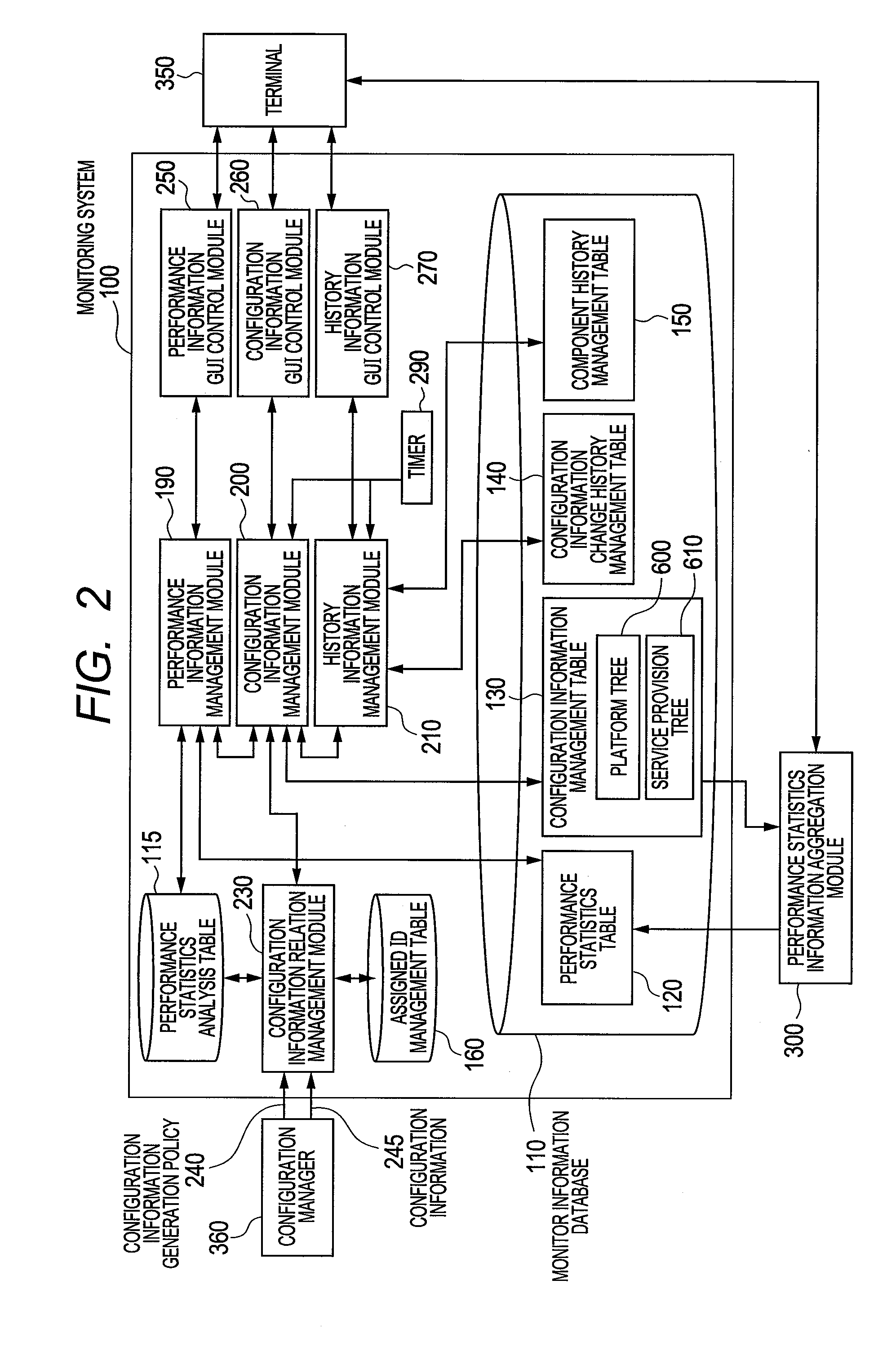
Monitoring system of computer and monitoring method
InactiveUS20120117226A1Low costEasy to analyzeDigital computer detailsProgram controlVirtualizationComputer resources
There is provided a monitoring system capable of representing relationships of computer resources that virtual servers use in a tree structure and aggregating the performance statistics of the virtual resources sharing physical resources. The monitoring system has: a virtualization module that makes virtual computers operate; and a monitoring module for monitoring the physical computers and components of the virtual computers. The monitoring module designates the physical computer and the components of the virtualizing module as base resources, manages the components of the virtual computers as virtual resources, generates a platform tree by extracting a tree structure from the virtual resources and the components of the base resources for predetermined platforms, generates a service provision tree by extracting a tree structure having the base or virtual resources as starting points, and establishes a reference relationship for the components contained in the platform tree and also contained in the service provision tree.
Owner:HITACHI LTD
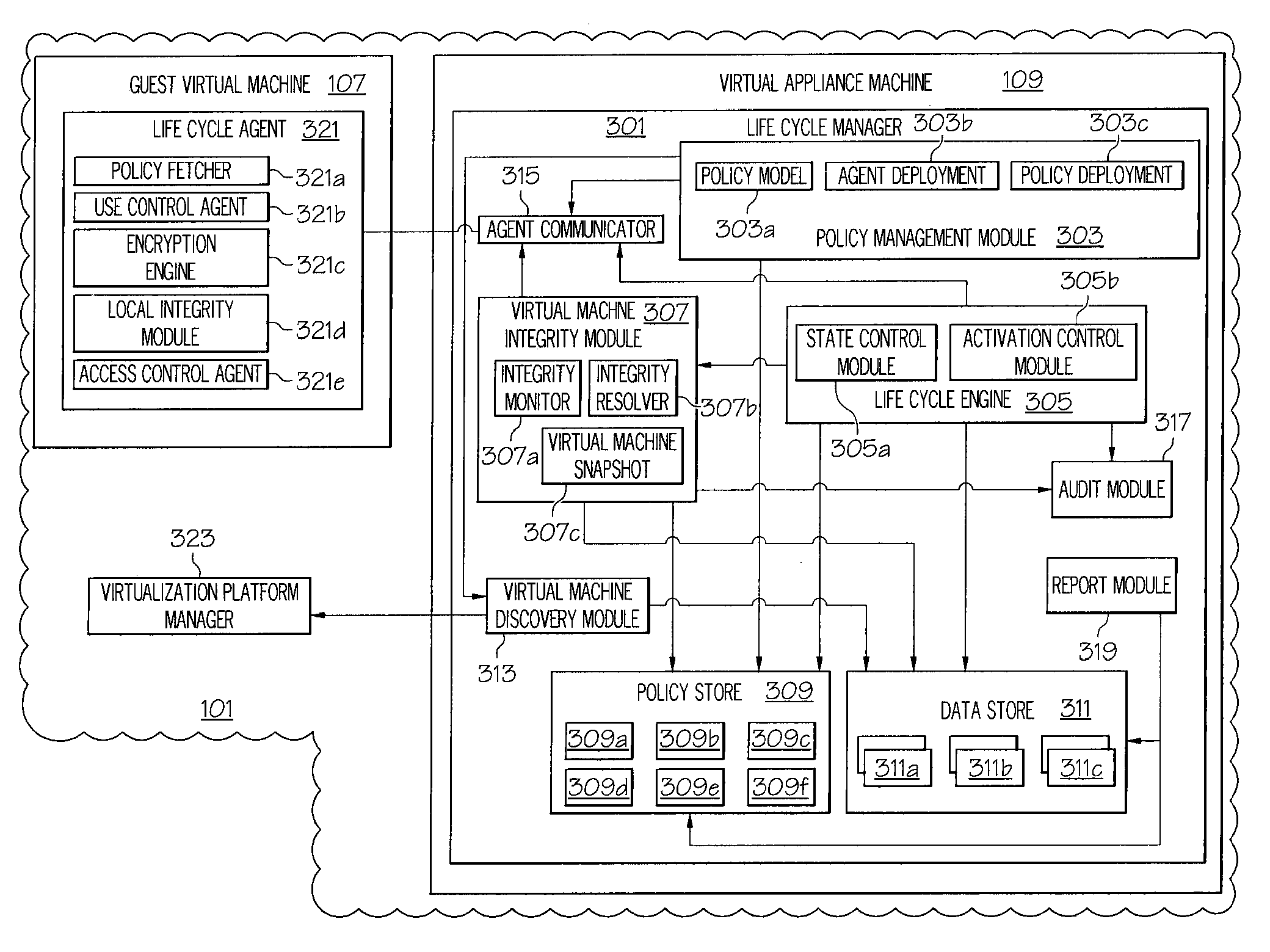
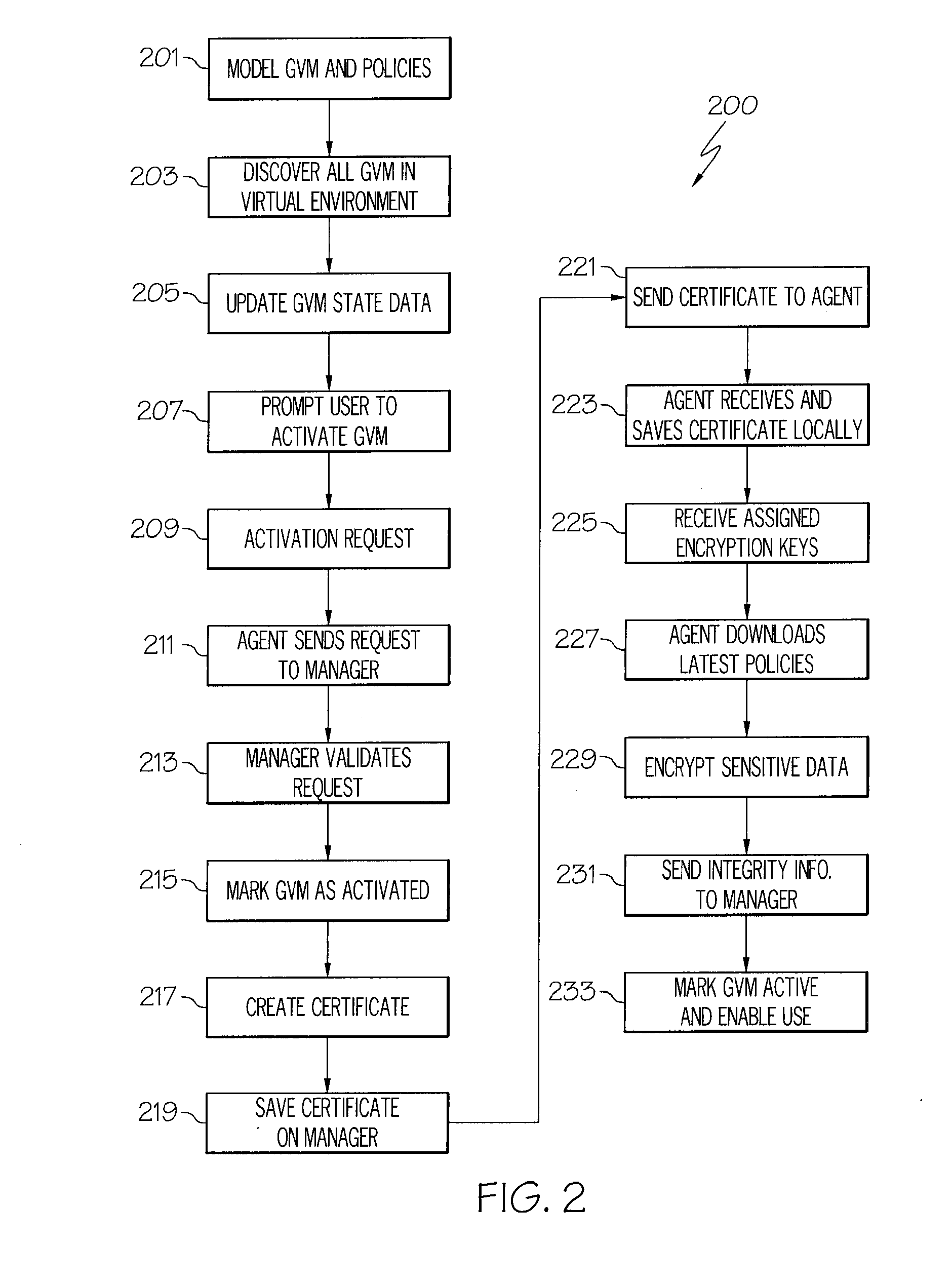
System and method for enforcement of security controls on virtual machines throughout life cycle state changes
ActiveUS20140096134A1Improve securityStrong security policyPlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtual computingData storing
Systems and methods associated with virtual machine security are described herein. One example method includes instantiating a guest virtual machine in a virtual computing environment. The method also includes installing a life cycle agent on the guest virtual machine, assigning an identifying certificate, a set of policies, and an encryption key to the guest virtual machine, and providing the certificate, policies, and encryption key to the guest virtual machine. The certificate, policies, and encryption key may then be used by the guest virtual machine to authenticate itself within the virtual computing environment and to protect data stored on the guest virtual machine.
Owner:CA TECH INC
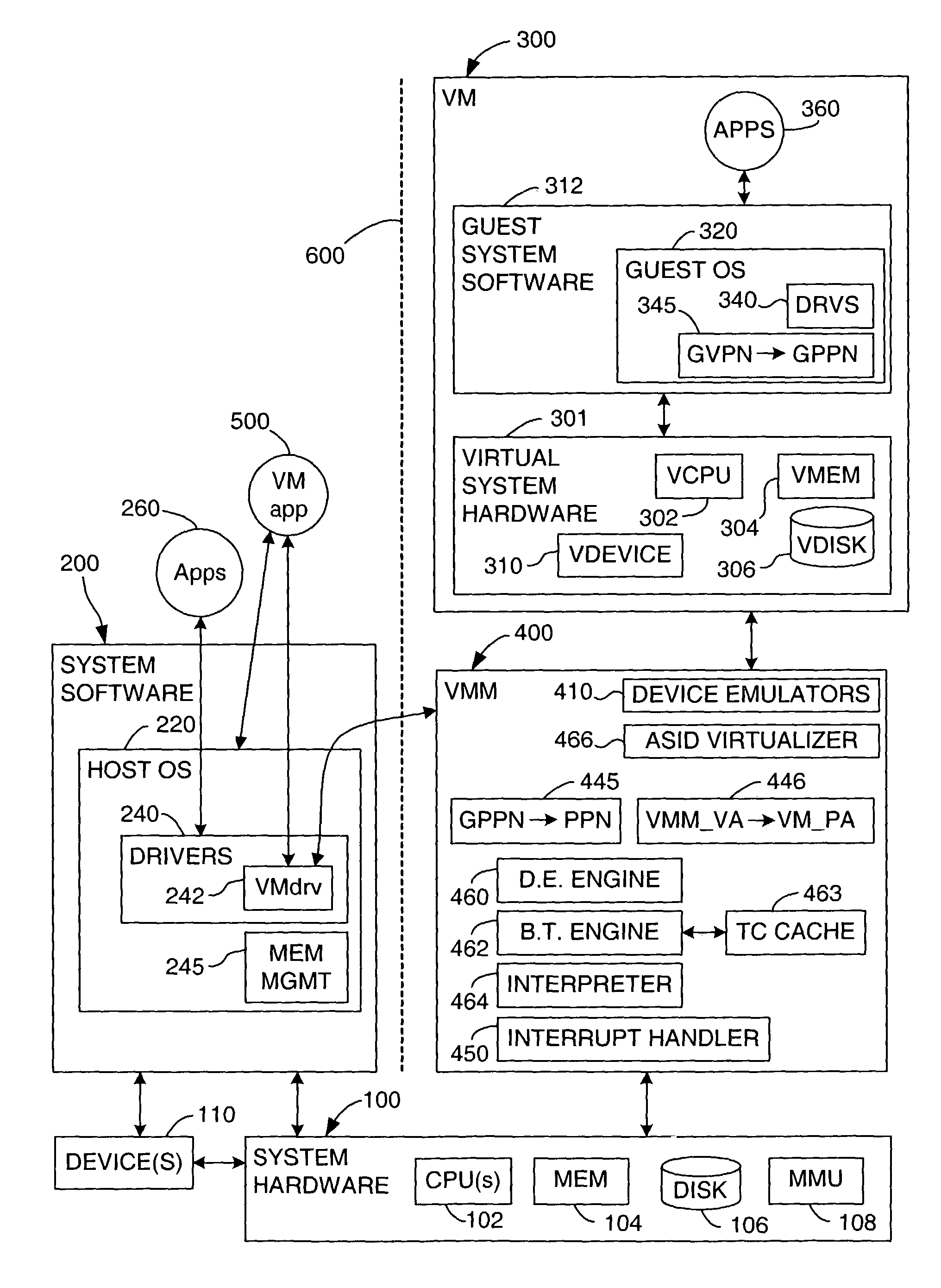
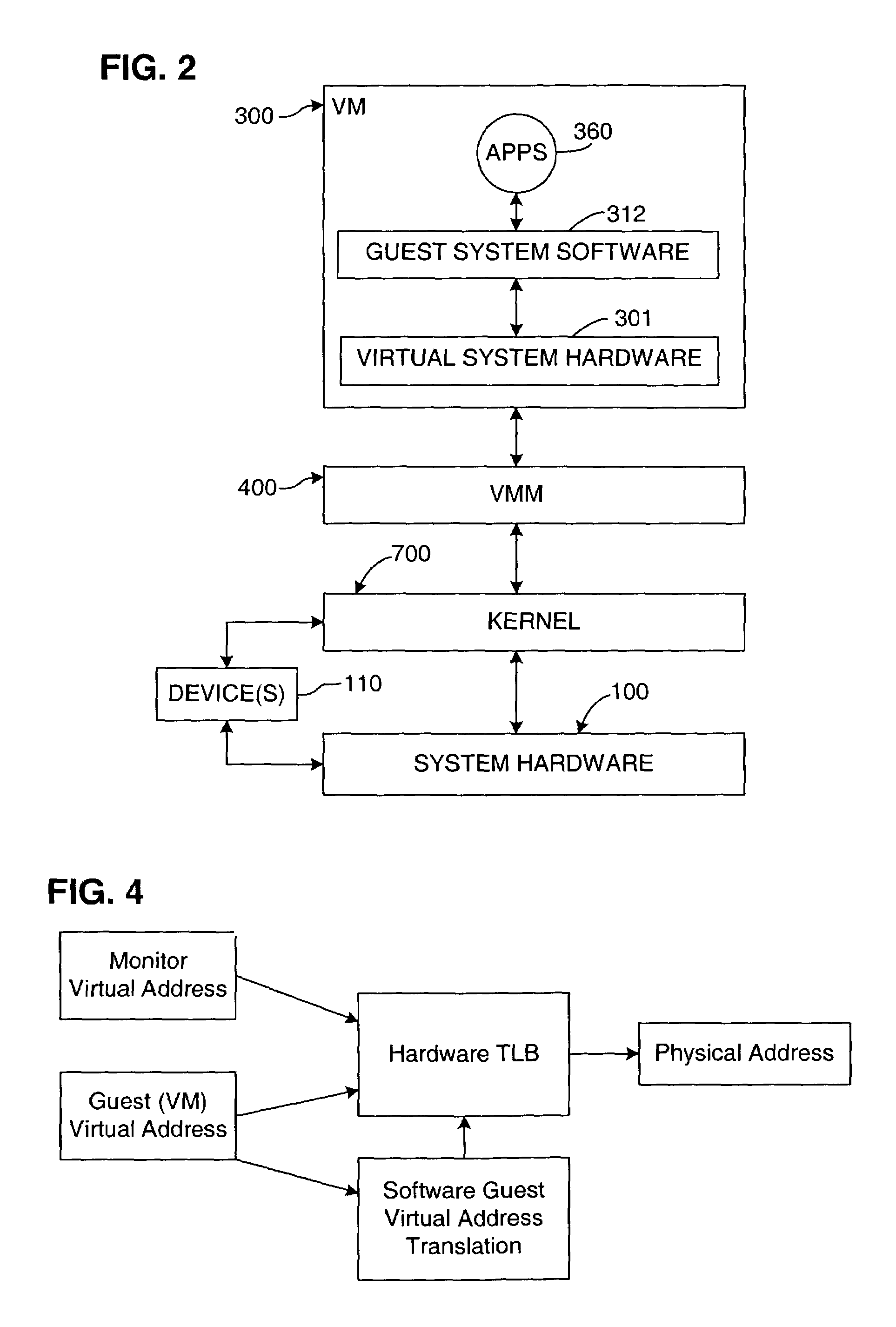
Virtualization system for computers that use address space indentifiers
A virtual computer system including multiple virtual machines (VMs) is implemented in a physical computer system that uses address space identifiers (ASIDs). Each VM includes a virtual translation look-aside buffer (TLB), in which guest software, executing on the VM, may insert address translations, with each translation including an ASID. For each ASID used by guest software, a virtual machine monitor (VMM), or other software unit, assigns a unique shadow ASID for use in corresponding address translations in a hardware TLB. If a unique shadow ASID is not available for a newly used guest ASID, the VMM reassigns a shadow ASID from a prior guest ASID to the new guest ASID, purging any entries in the hardware TLB corresponding to the prior guest ASID. Assigning unique shadow ASIDs limits the need for TLB purges upon switching between the multiple VMs, reducing the number of TLB miss faults, and consequently improving overall processing efficiency.
Owner:VMWARE INC
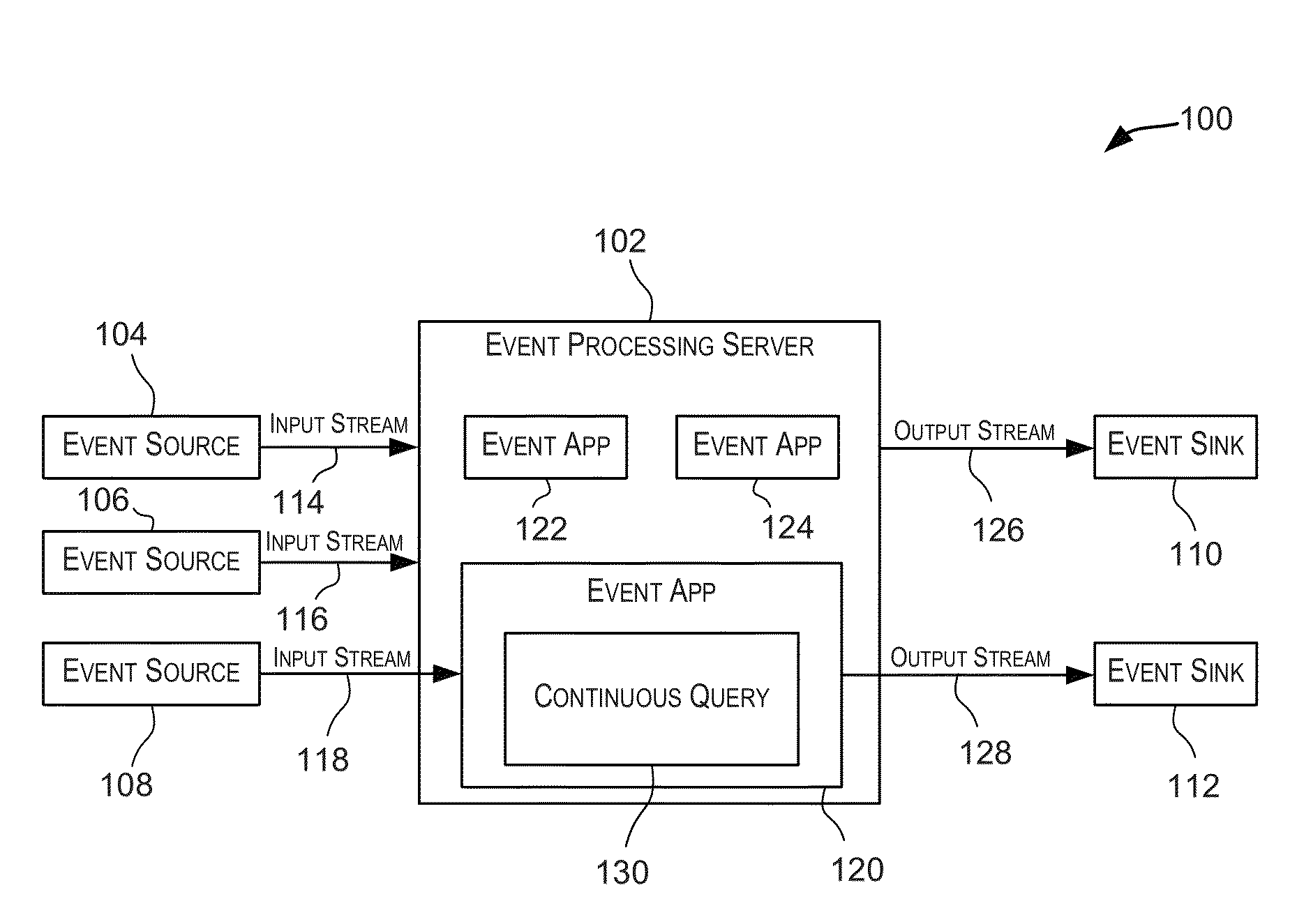
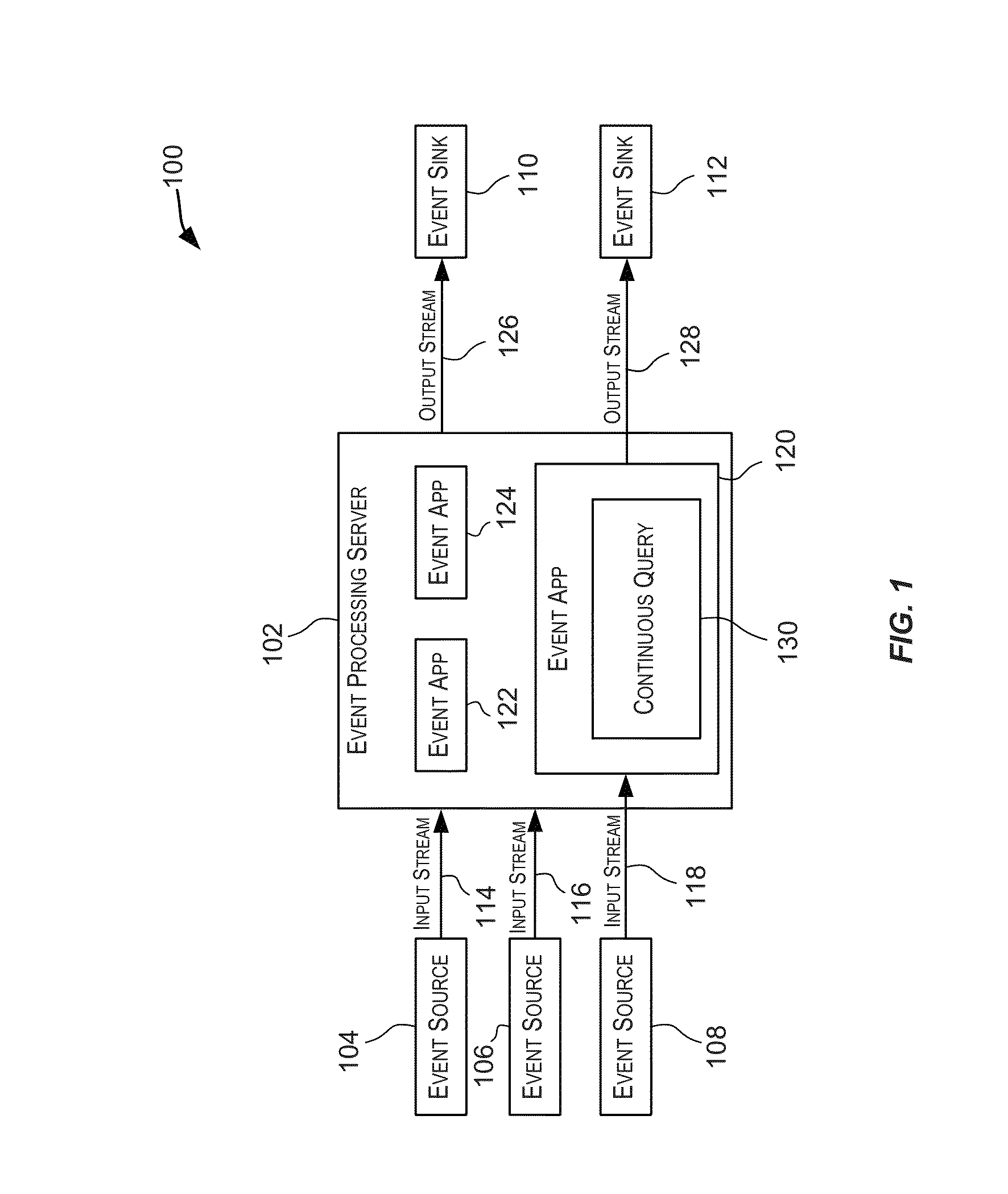
Scaling event processing using distributed flows and map-reduce operations
Some event ordering requirements can be determined based on continuous event processing queries. Other event ordering requirements can be determined based on distribution flow types being used to distribute events from event streams to node executing the queries. Events from event streams can be ordered according to ordering semantics that are based on a combination of all of these event ordering requirements. Additionally, virtual computing nodes can be associated with constraints, and computing processors can be associated with capabilities. Virtual computing nodes for processing event streams can be assigned to execute on various computing processors based on both these constraints and capabilities. Additionally, for each of several events in an event stream, a ratio between a total latency and a communication latency can be for determined. Based on an average of these ratios, a quantity of reducing nodes that will be involved in a map-reduce operation can be selected.
Owner:ORACLE INT CORP
Virtual computing management systems and methods
InactiveUS20090164994A1Easy to transportSoftware simulation/interpretation/emulationMemory systemsOperational systemPersonal computer
Embodiments deliver an operating system and software applications to a personal computer. The operating system and software applications may be managed and configured at a central location prior to delivery. Data that is created or modified on the personal computer may, from time to time, be stored at the central location. When a user switches from one personal computer to another, any and all of the data may be transferred from the central location to the user's current computer. Additionally, the user's current computer may receive suitable versions of the operating system and applications from the central location. In any case, the operating system and software applications may run with a domain of execution that is provided by a hypervisor. Thus, the operating system and software applications may operate within a virtualized machine, perhaps alongside and in isolation from other operating systems and software applications.
Owner:VIRTUAL COMP +1
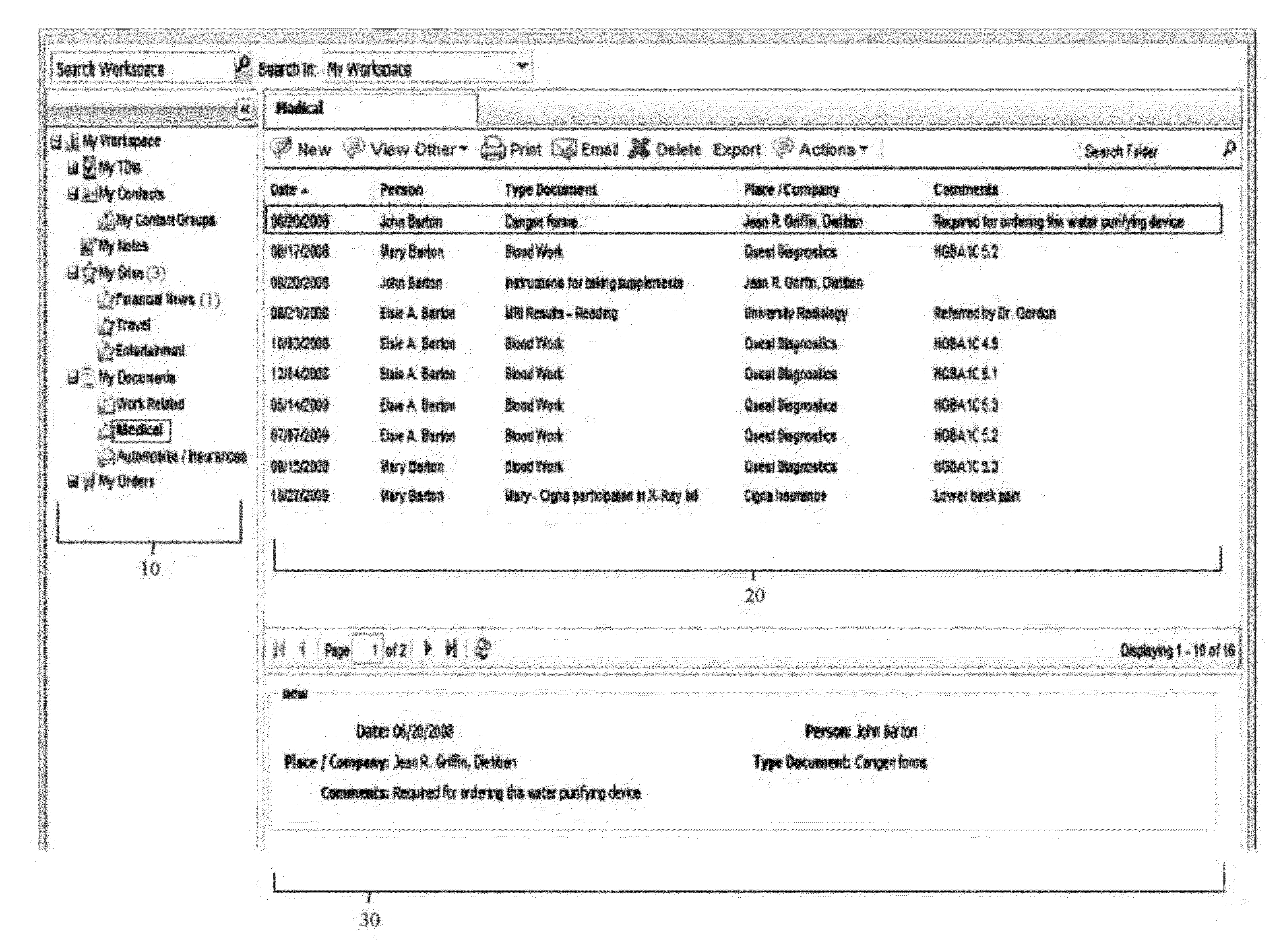
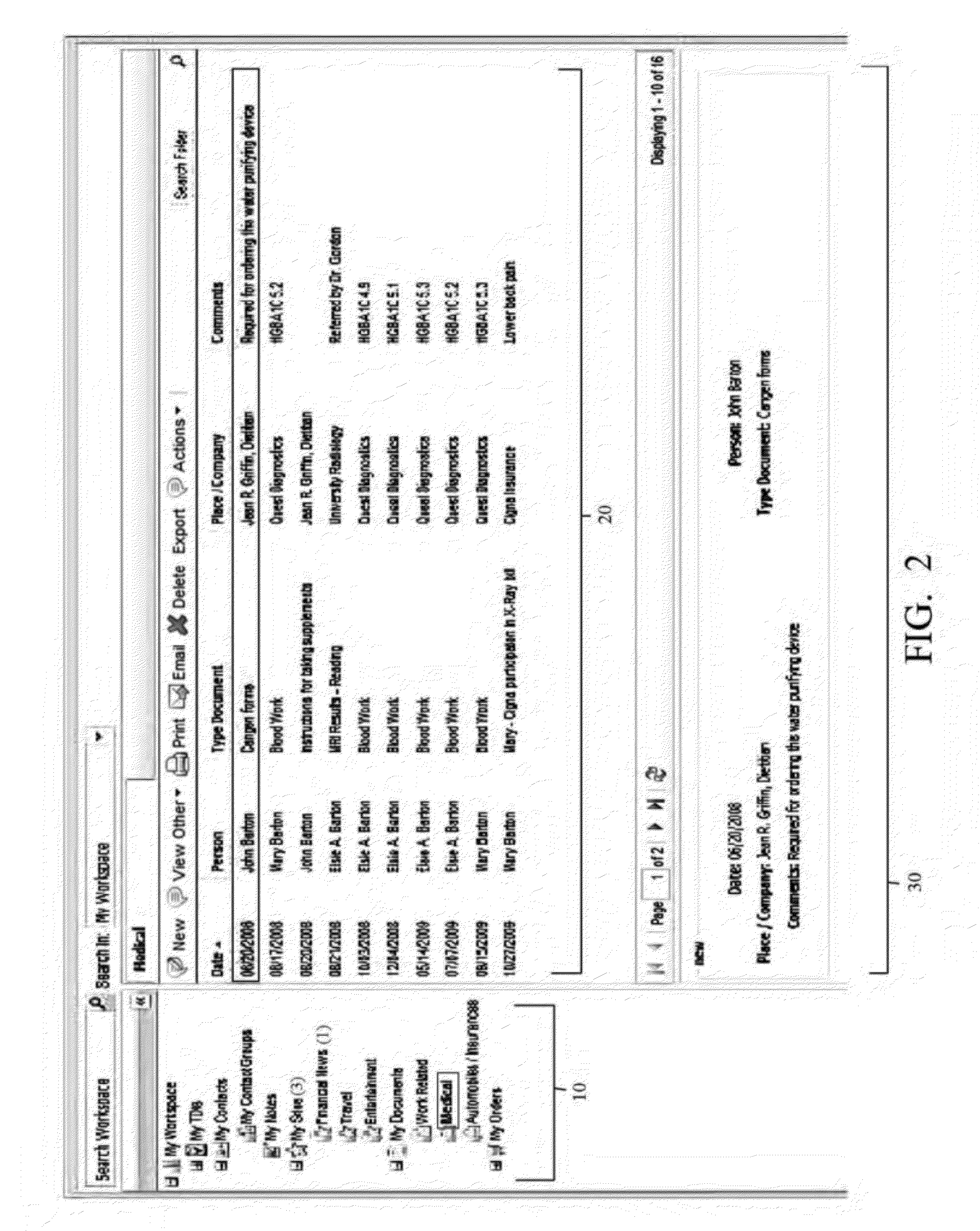
Integrated web-based workspace with curated tree-structure database schema
InactiveUS20120096389A1Streamlining actionStreamlining flowWebsite content managementSpecial data processing applicationsDocumentation procedureDocument preparation
A virtual web-based computing platform combining a particular network database hierarchy, graphical user interface, and integrated suite of computational tools accessible on demand, by which users gain access to an integrated Virtual Workspace for organizing emails, contacts, bookmarks, tasks, documents, notes, and all other relevant information. The network database hierarchy employs unique data structure and methods, allowing the user to centrally store and manage all data, regardless of type, as well as activities (actions taken and documented by the user). Nevertheless, the interface to said database offers a familiar folder / sub-folder “look and feel” using a tree data hierarchy, which gives a common, centralized and unified approach for storing, managing, displaying, and various types of data, regardless of object- and data-types.
Owner:IQTELL COM
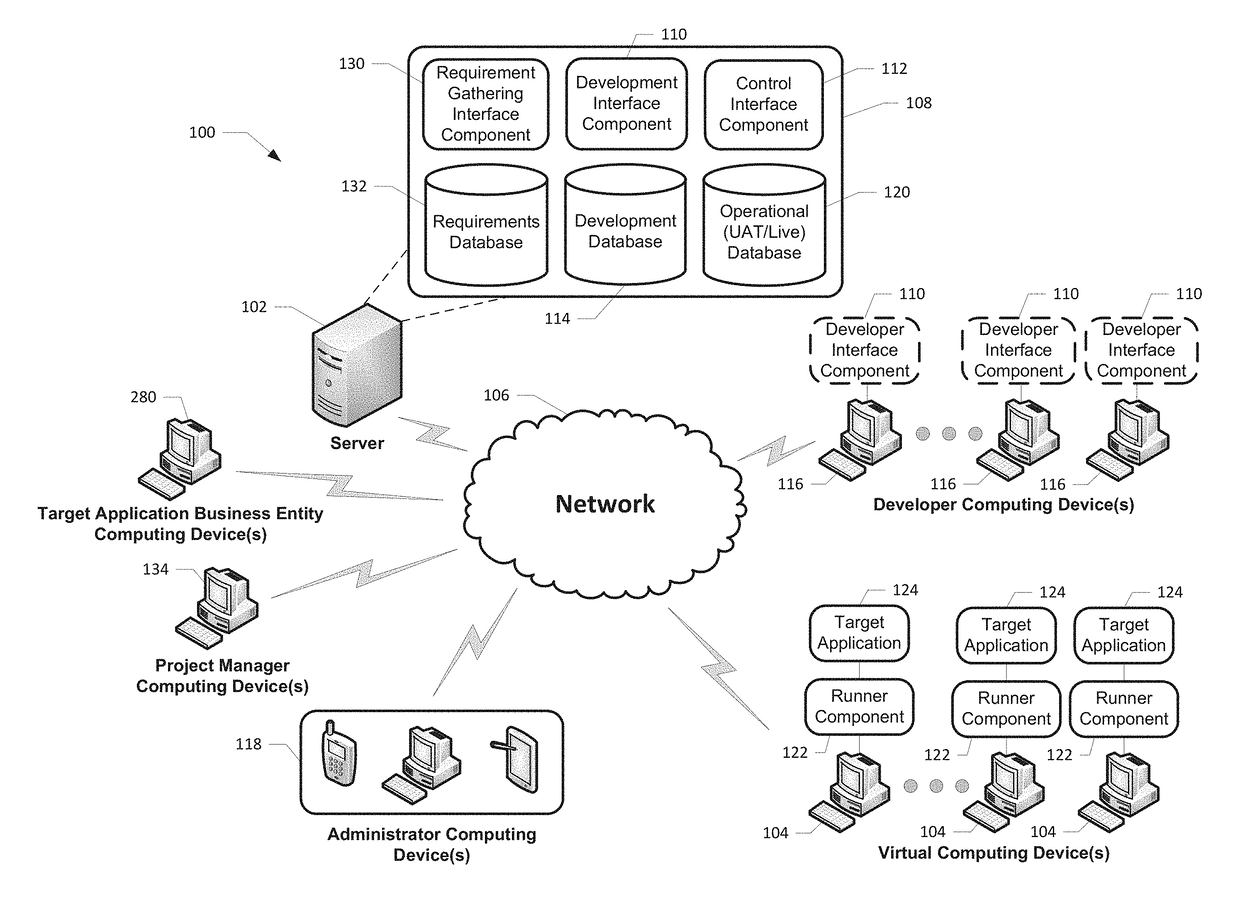
Robotics process automation platform
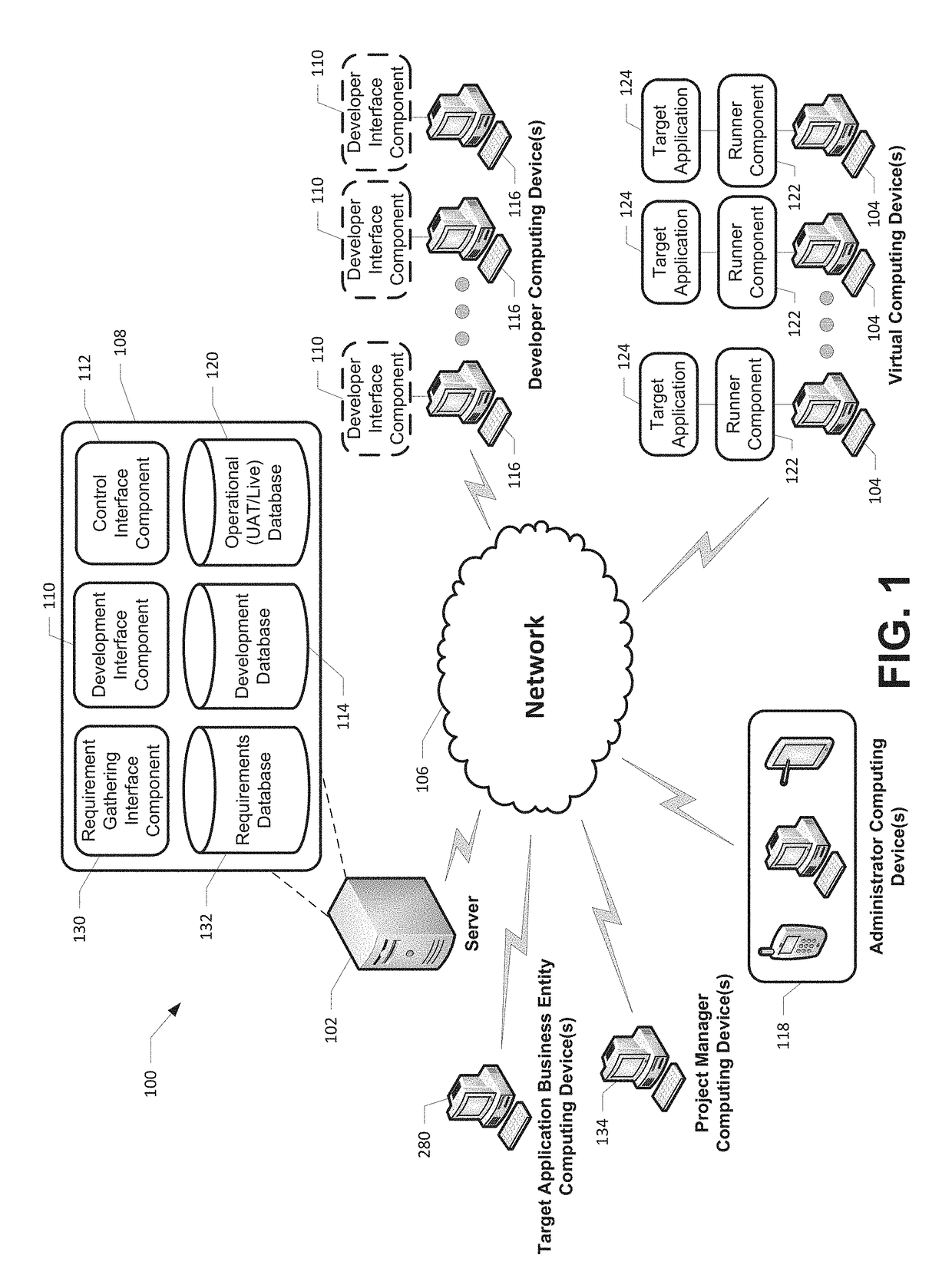
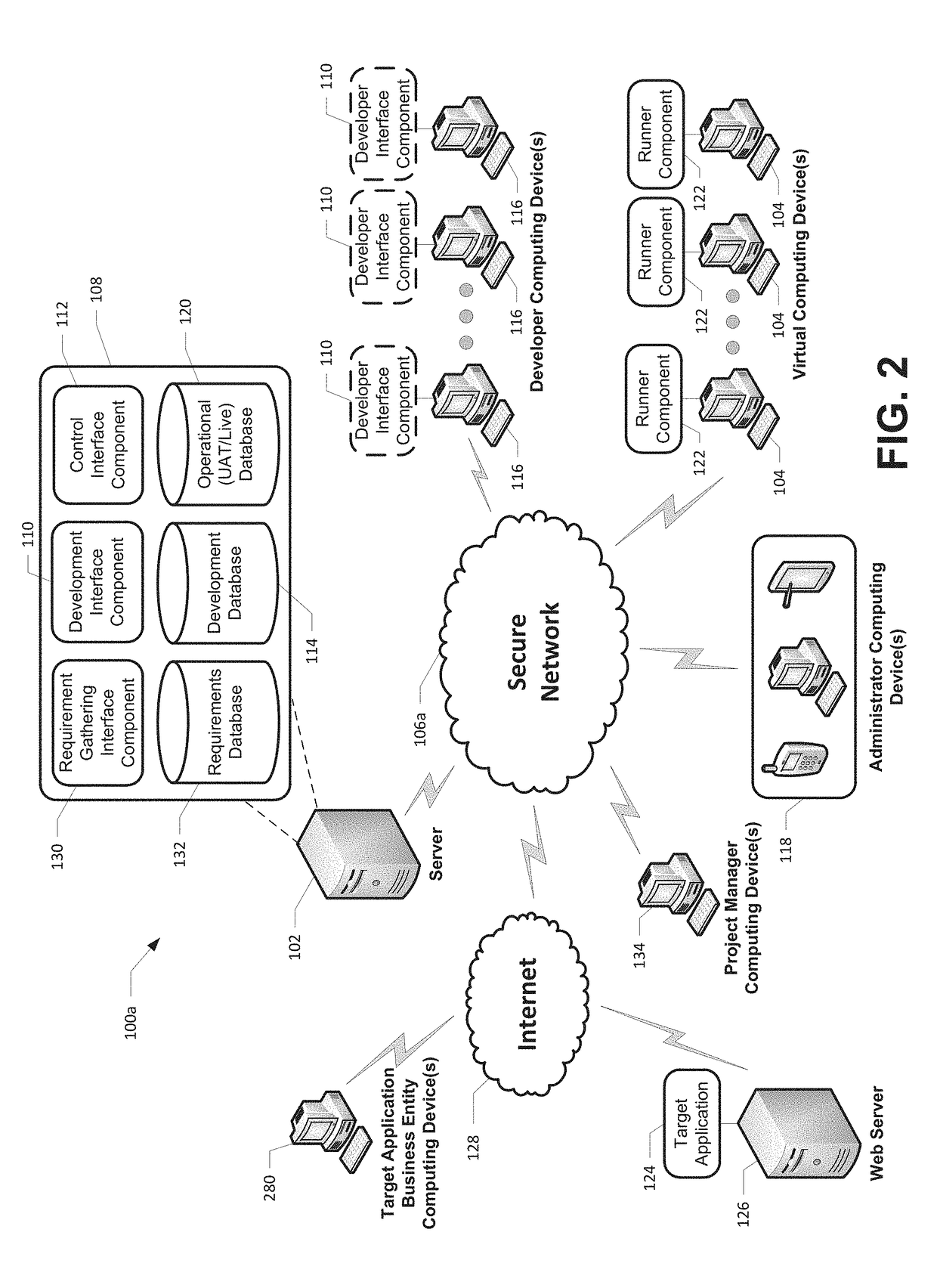
A robotics process automation platform for developing and managing a workflow is provided. The platform includes development and operational databases stored in a memory, a development interface component, a control interface component, and a runner component. The development interface component is configured for creating a workflow and storing the workflow in the development database. The control interface component is configured for selecting the workflow stored in the development database and storing a copy of the workflow in the operational database. The runner component is configured for receiving instructions from the control interface component to store a copy of the workflow stored in the operational database in a memory of a virtual computing device, and downloading the workflow in the second memory. The runner component is also configured for instructing the virtual computing device to execute the workflow in association with the target application.
Owner:SUTHERLAND GLOBAL SERVICES
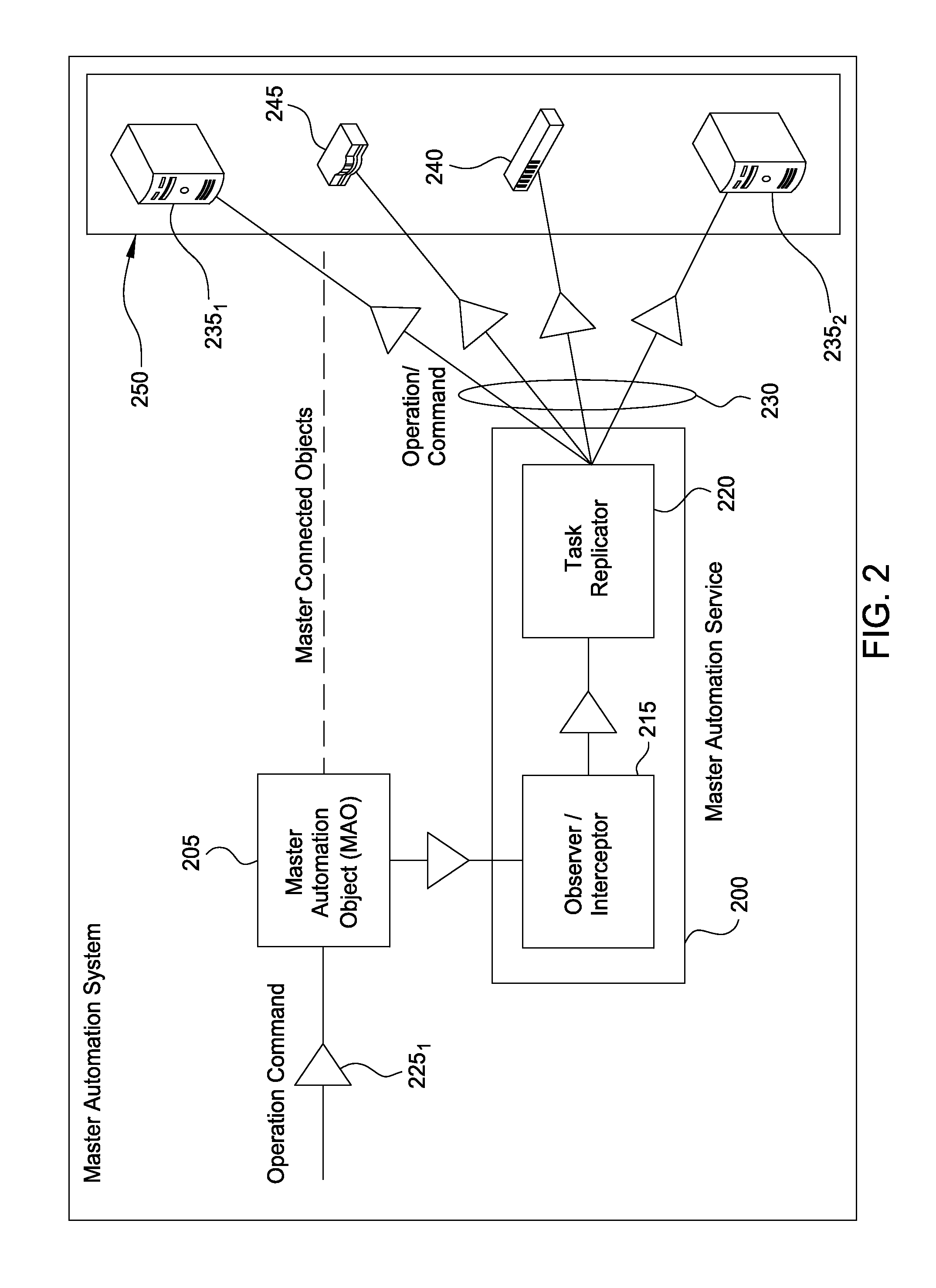
Master automation service
ActiveUS20140201735A1Software simulation/interpretation/emulationMemory systemsData centerVirtual computing
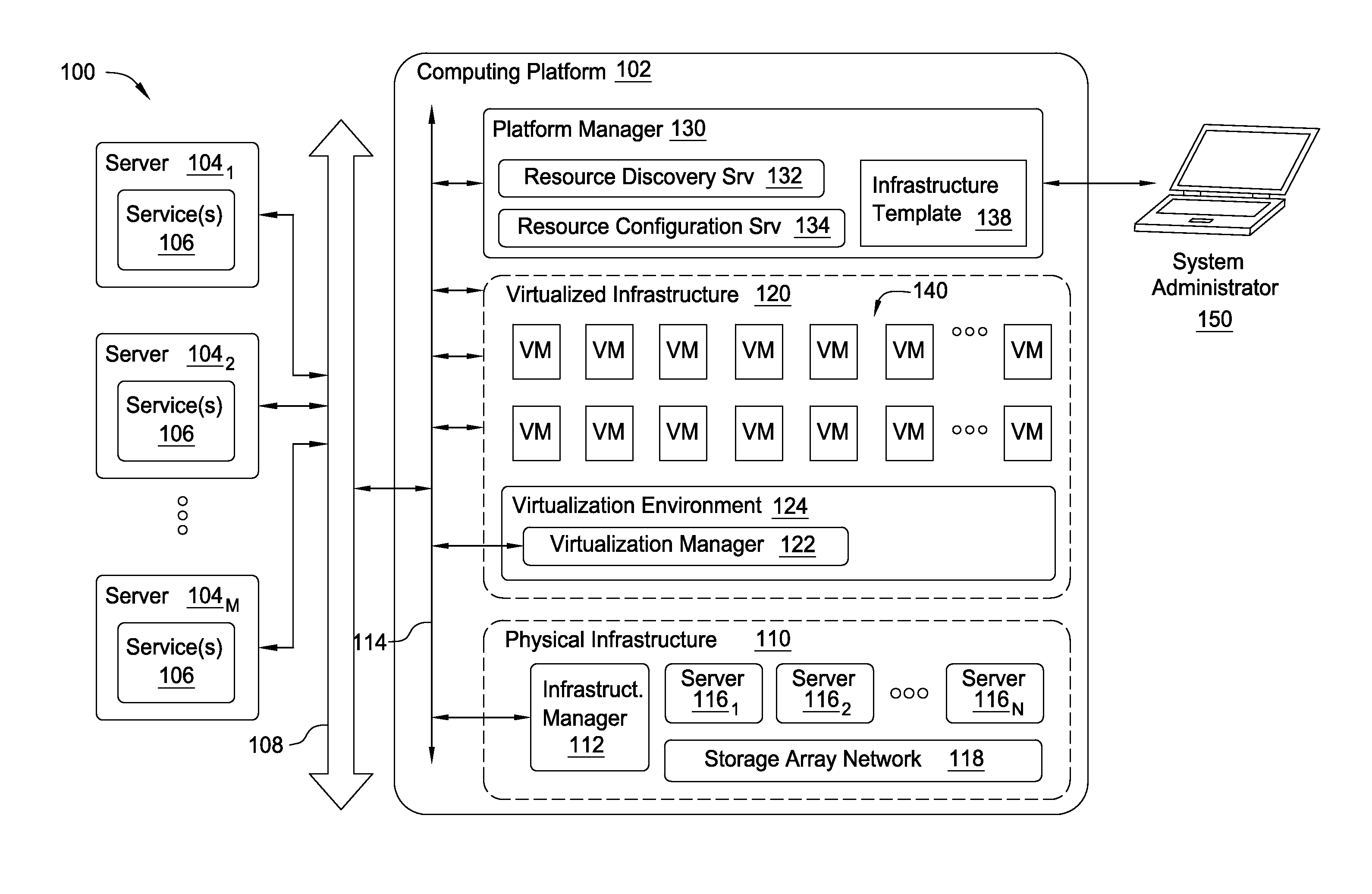
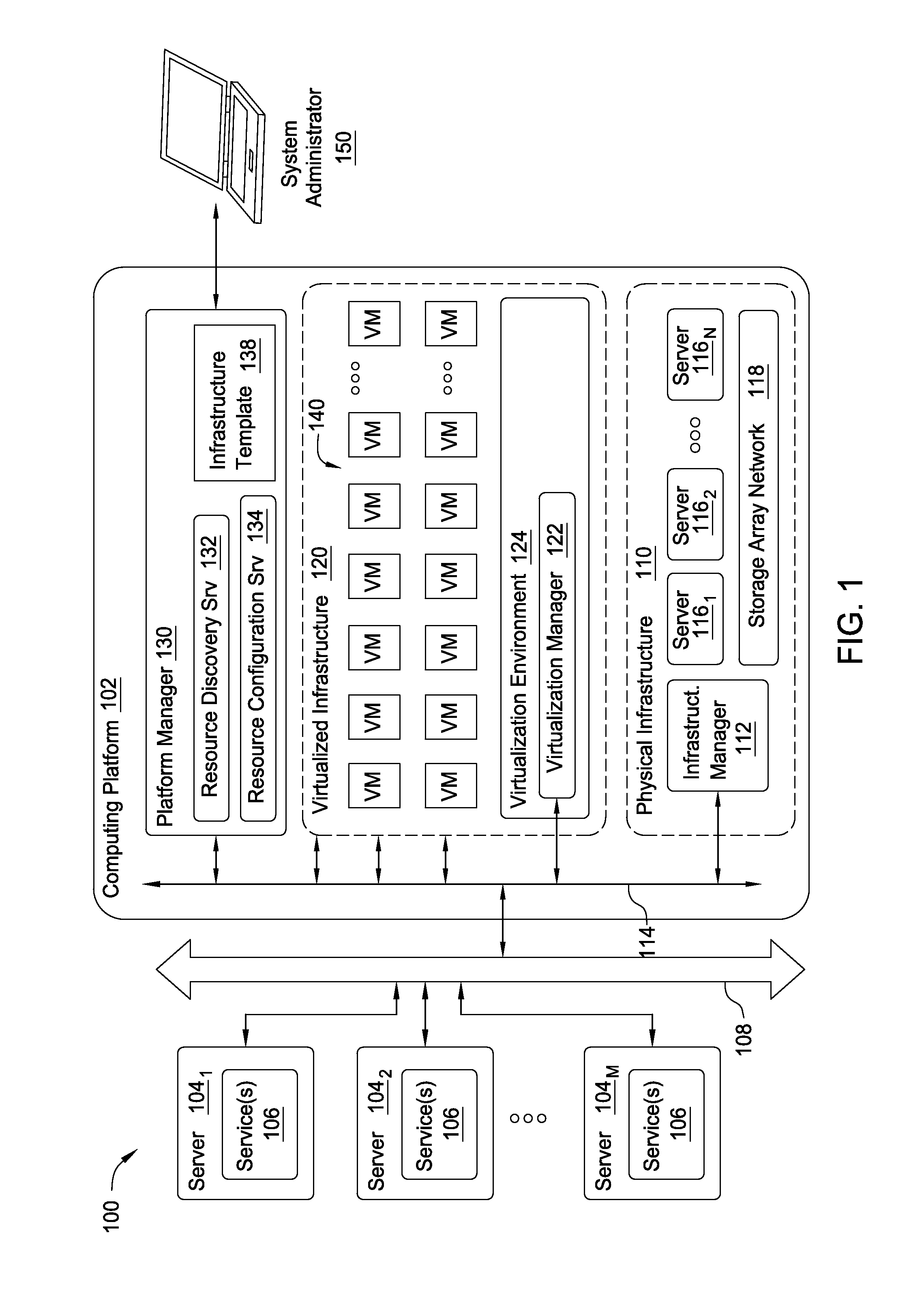
A method and system is provided for managing virtual machine instances (VMs) and other computing and network infrastructure within a data center. A user designates a computing device or resource (whether physical or virtual) as a master automation object (e.g., a virtual machine instance may be designated as a virtual template for command replication). The user then establishes an association between the master object and a set of physical and / or virtual computing resources that should replicate a set of designated commands sent to the master object. An automation service then intercepts / observes commands sent to the master object and sends the intercepted / observed commands to each computing device linked to the master object.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com