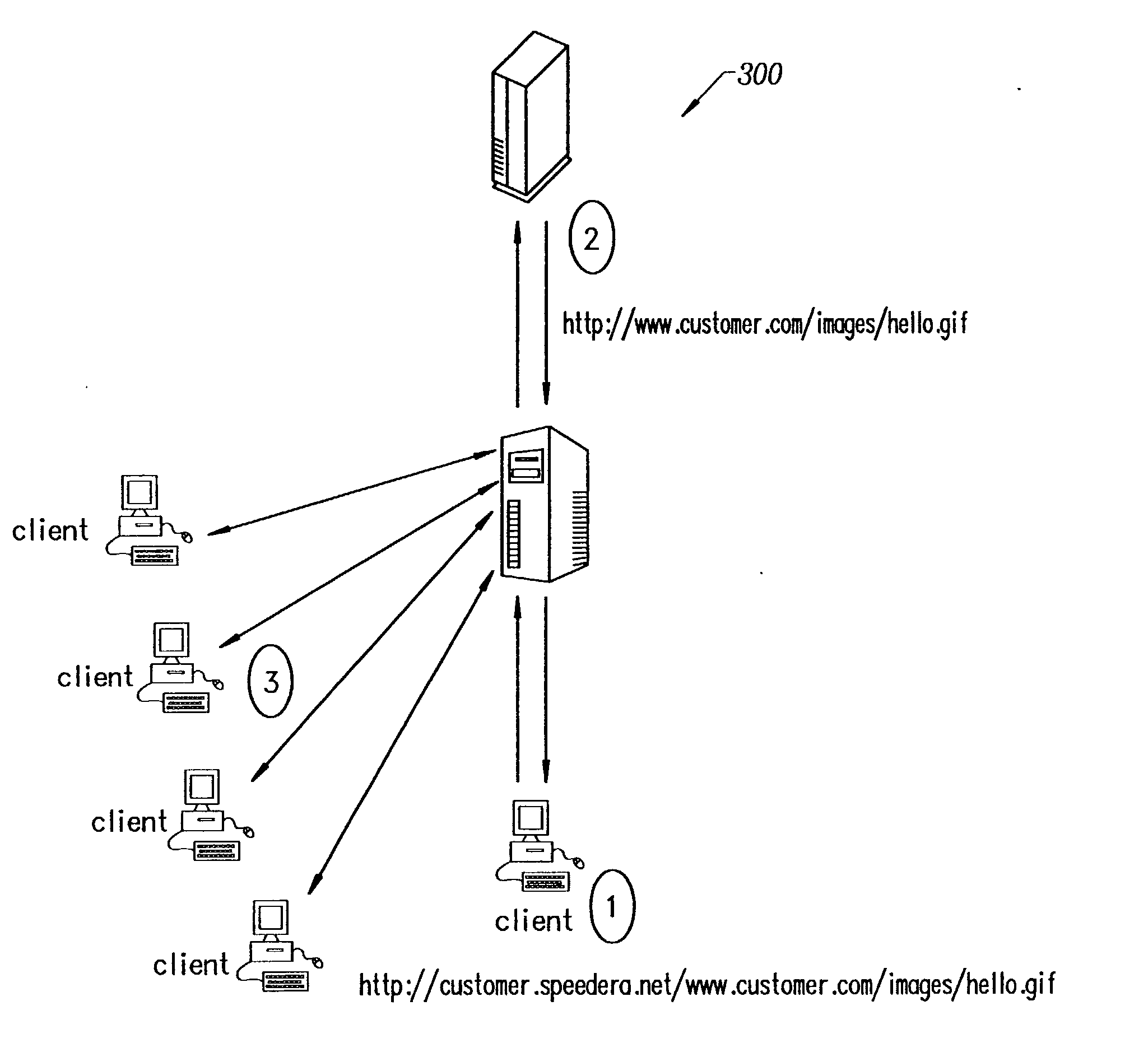
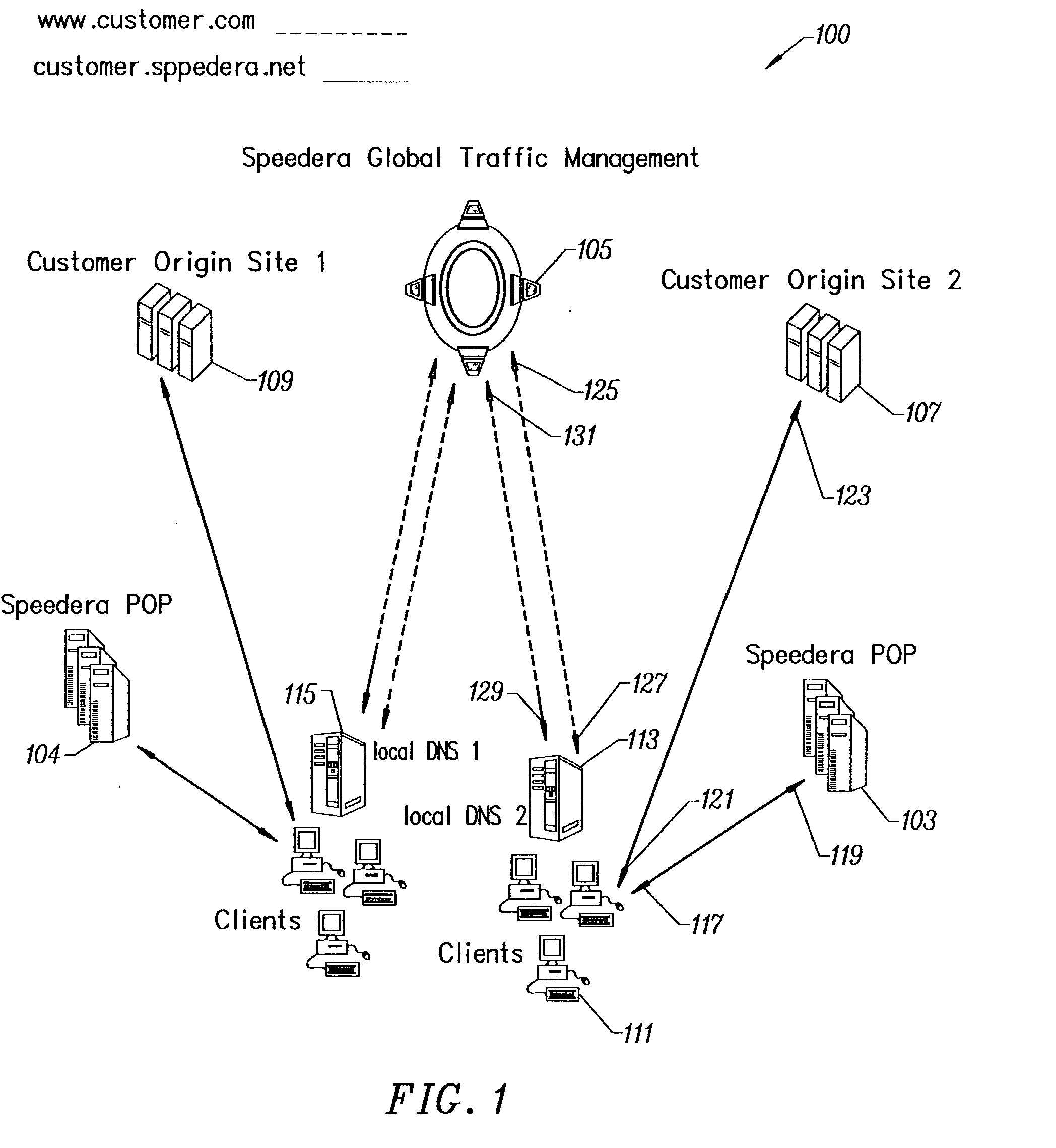
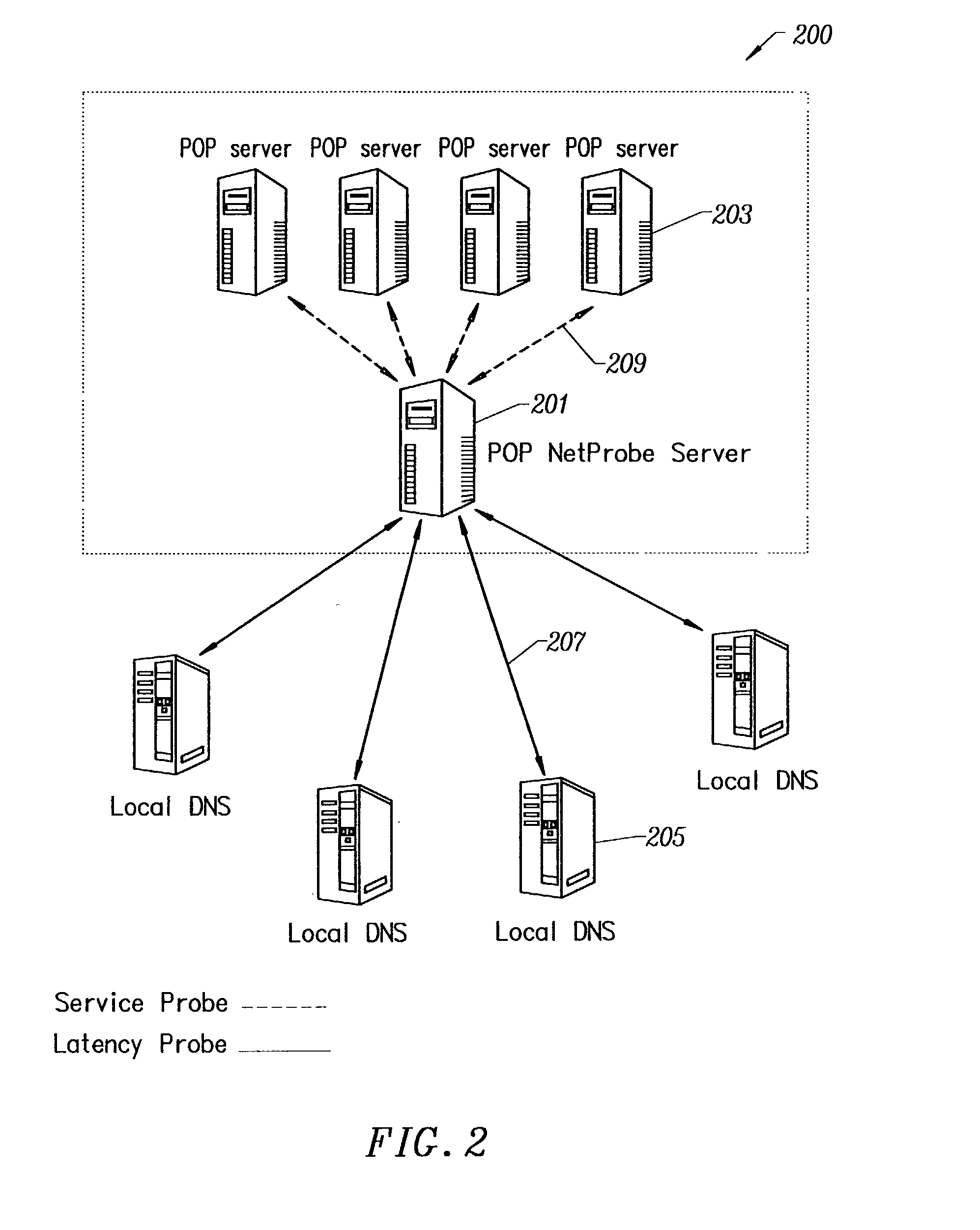
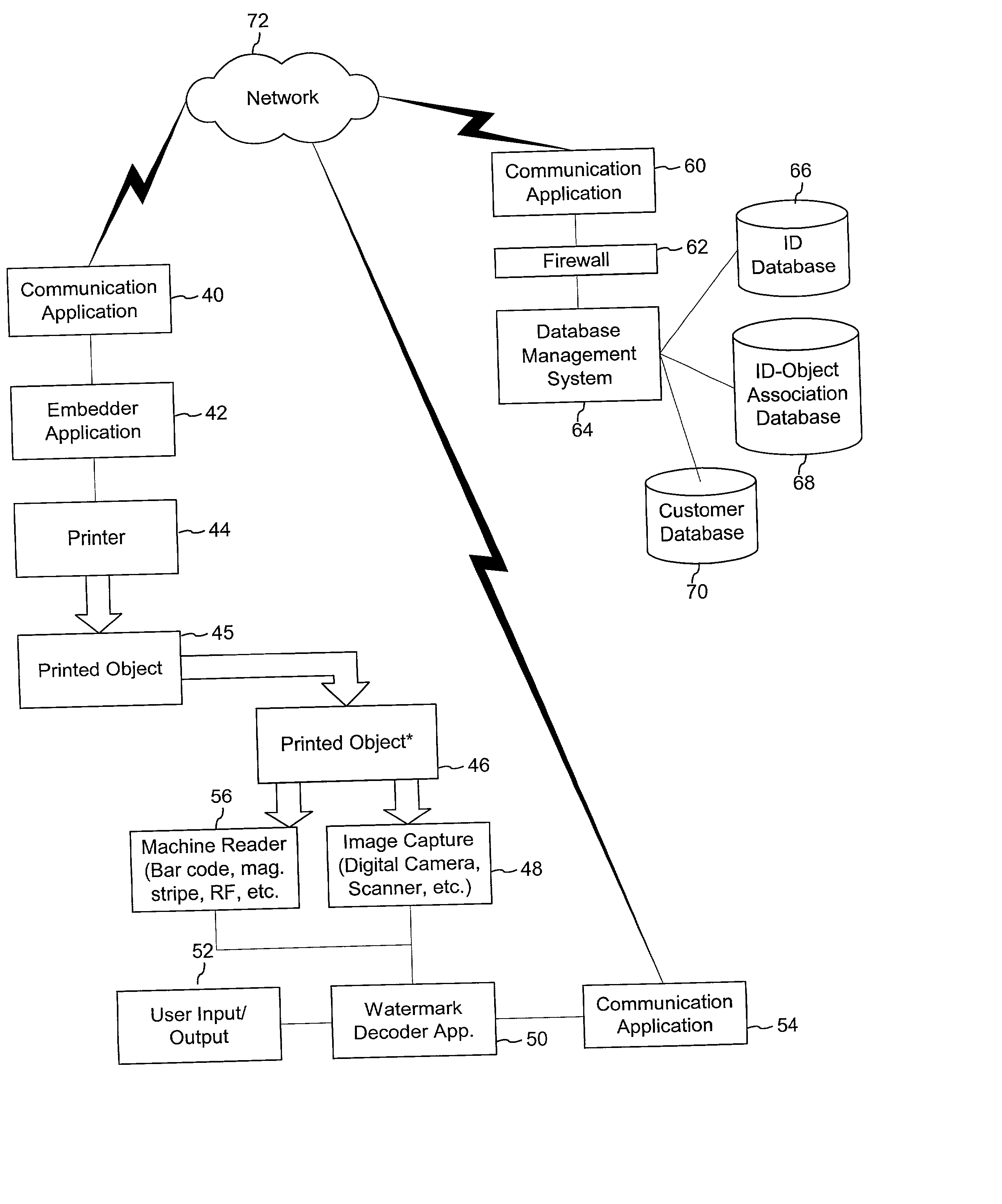
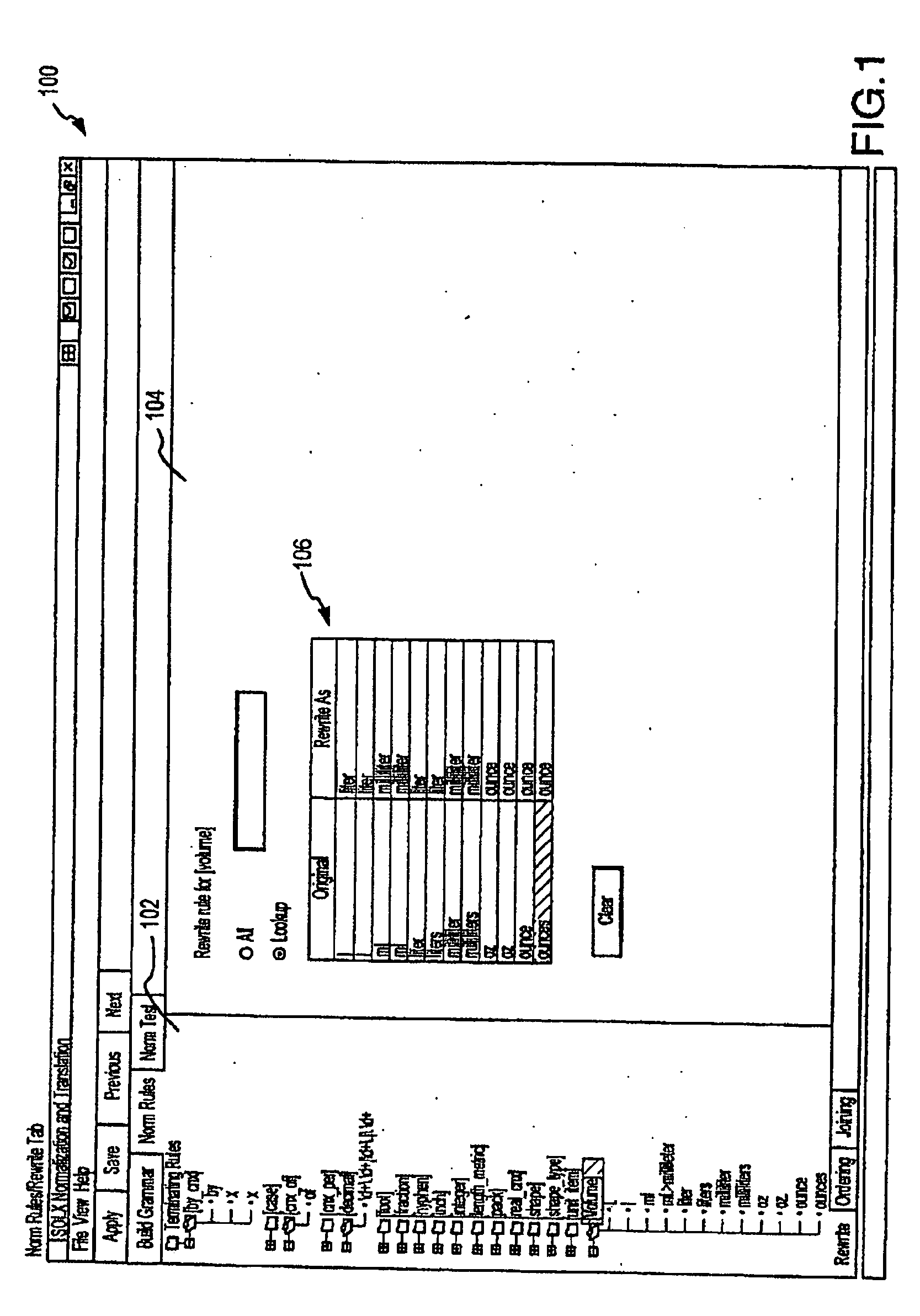
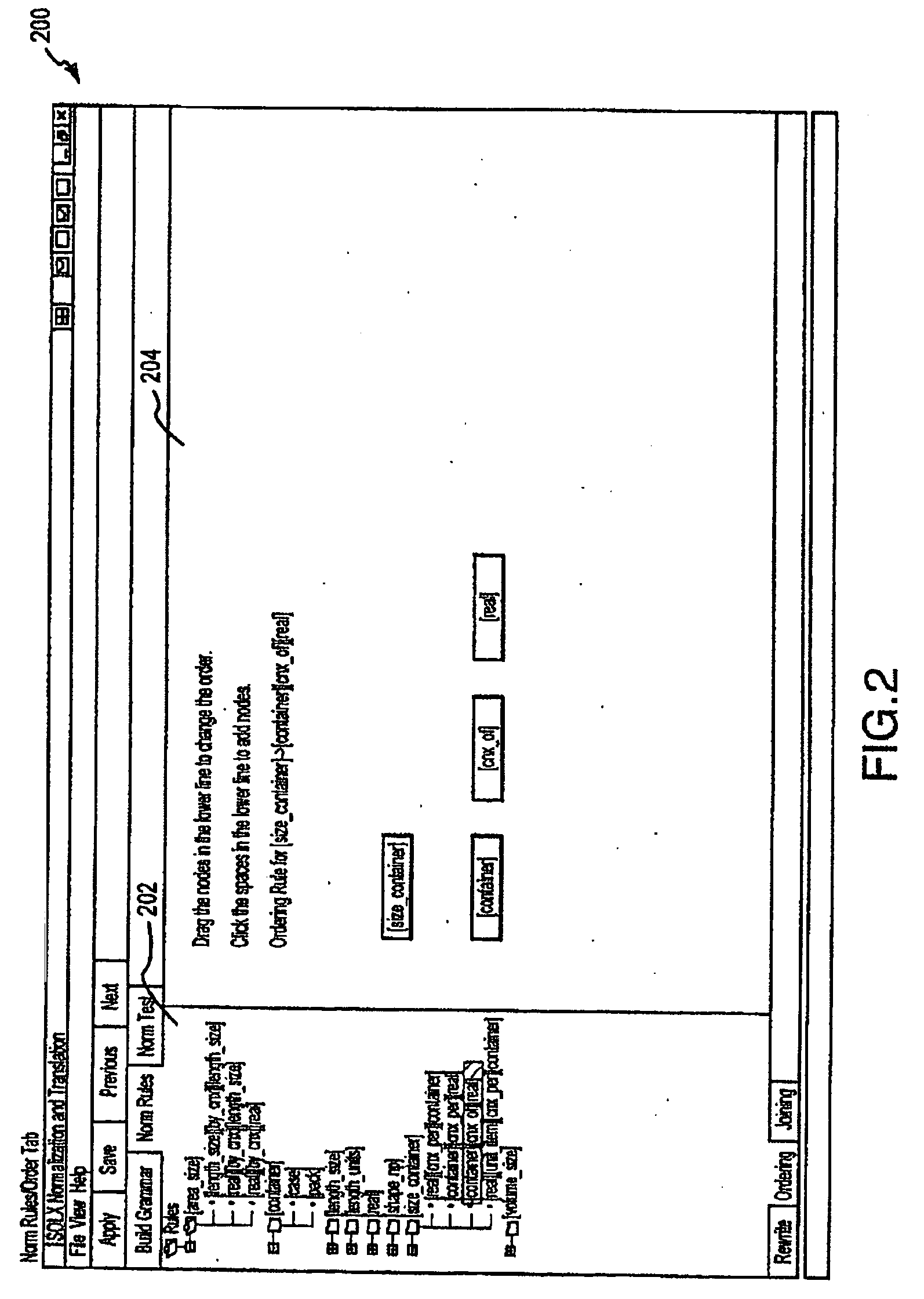
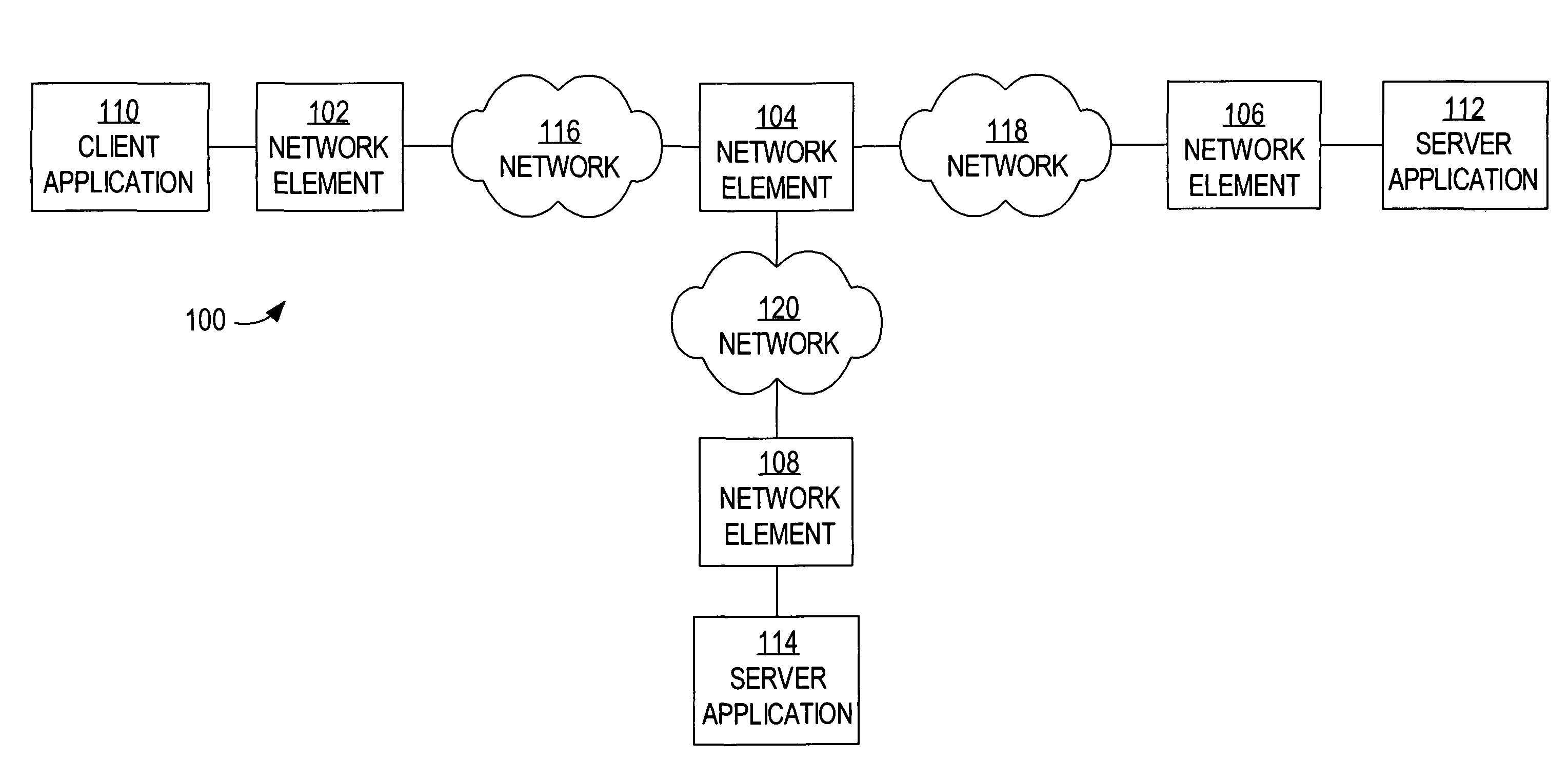
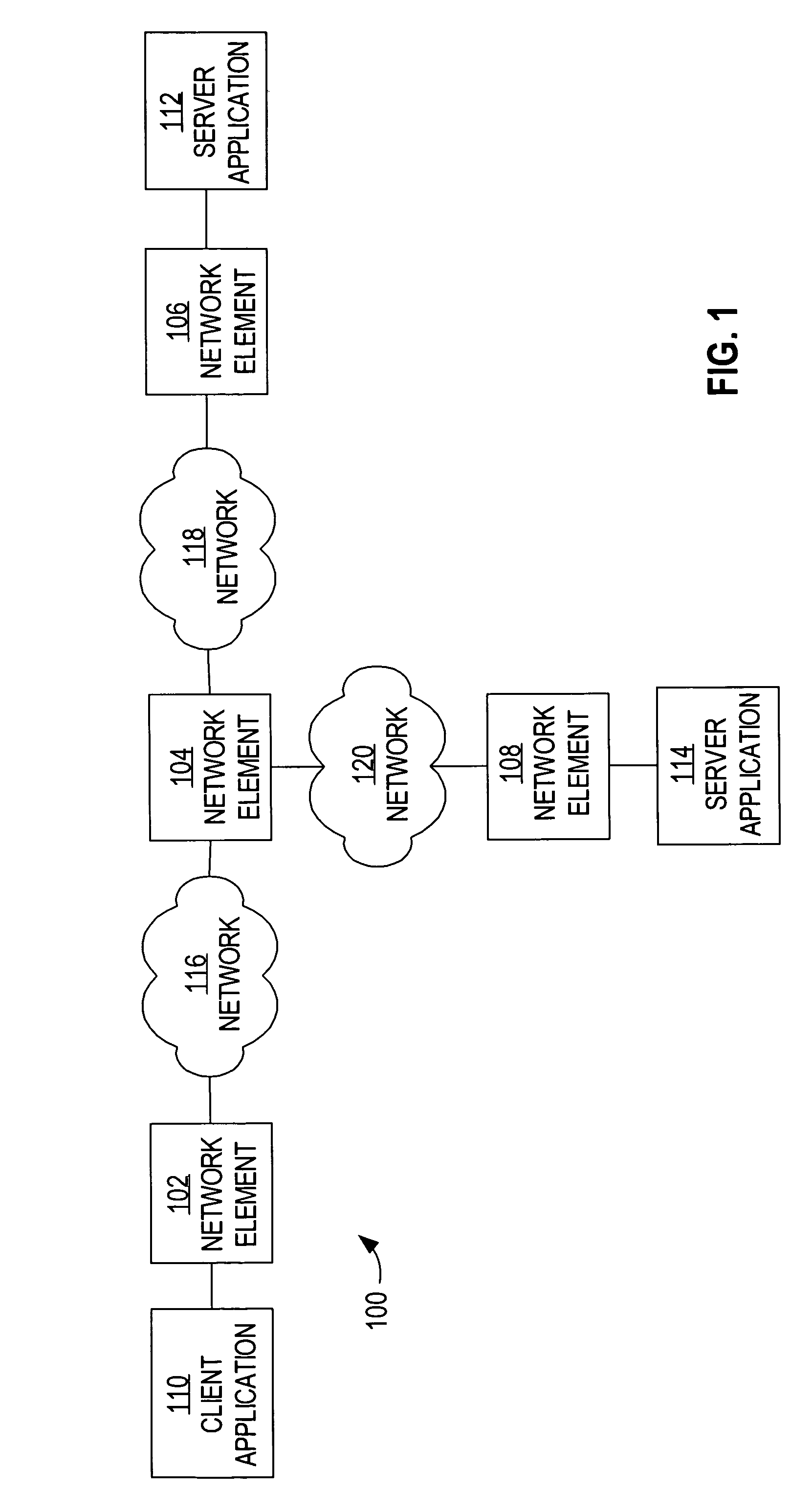
Patents
Literature
12991 results about "Relevant information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Relevant information. Data which is applicable to the situation or problem at hand that can help solve a problem or contribute to a solution.
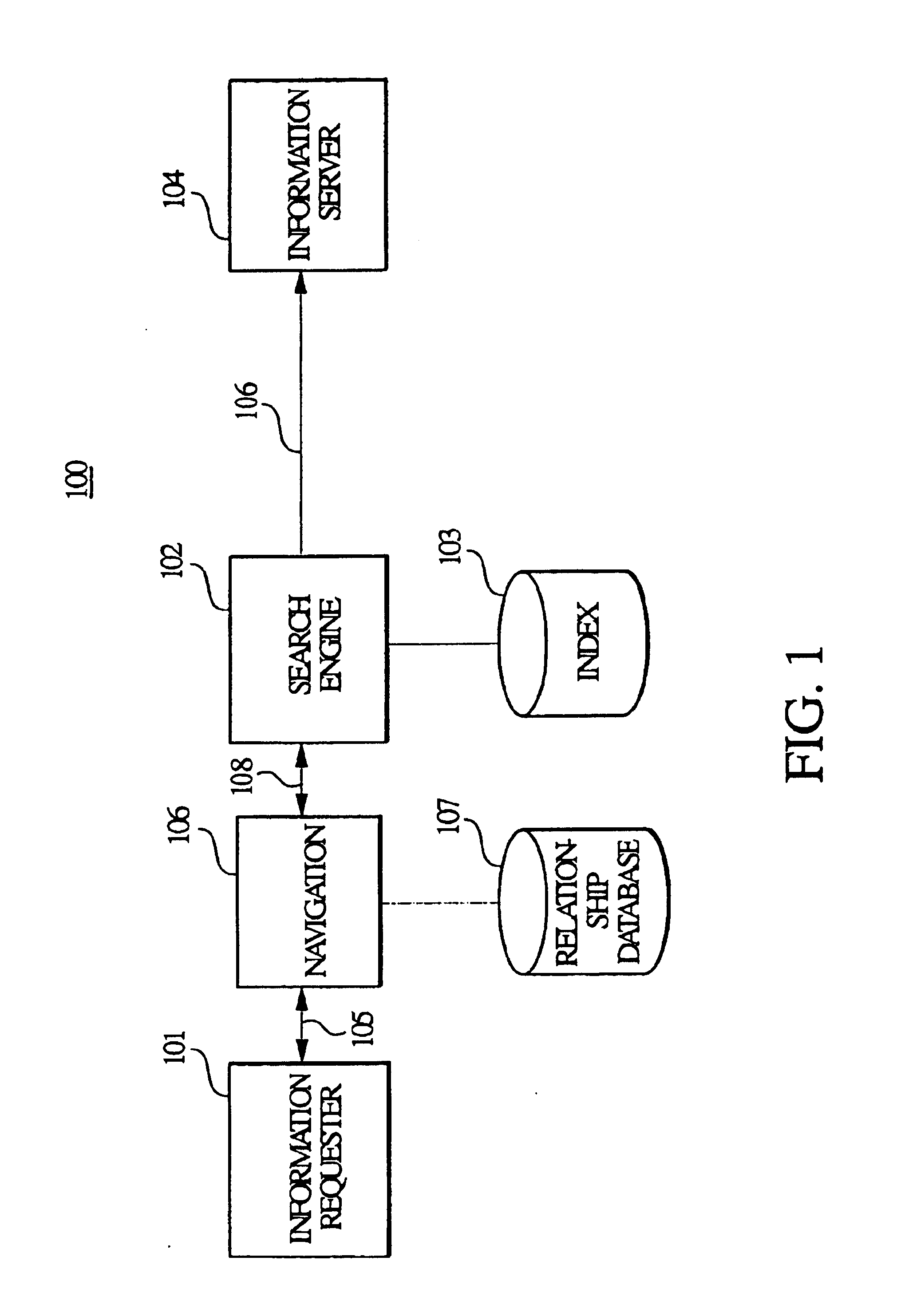
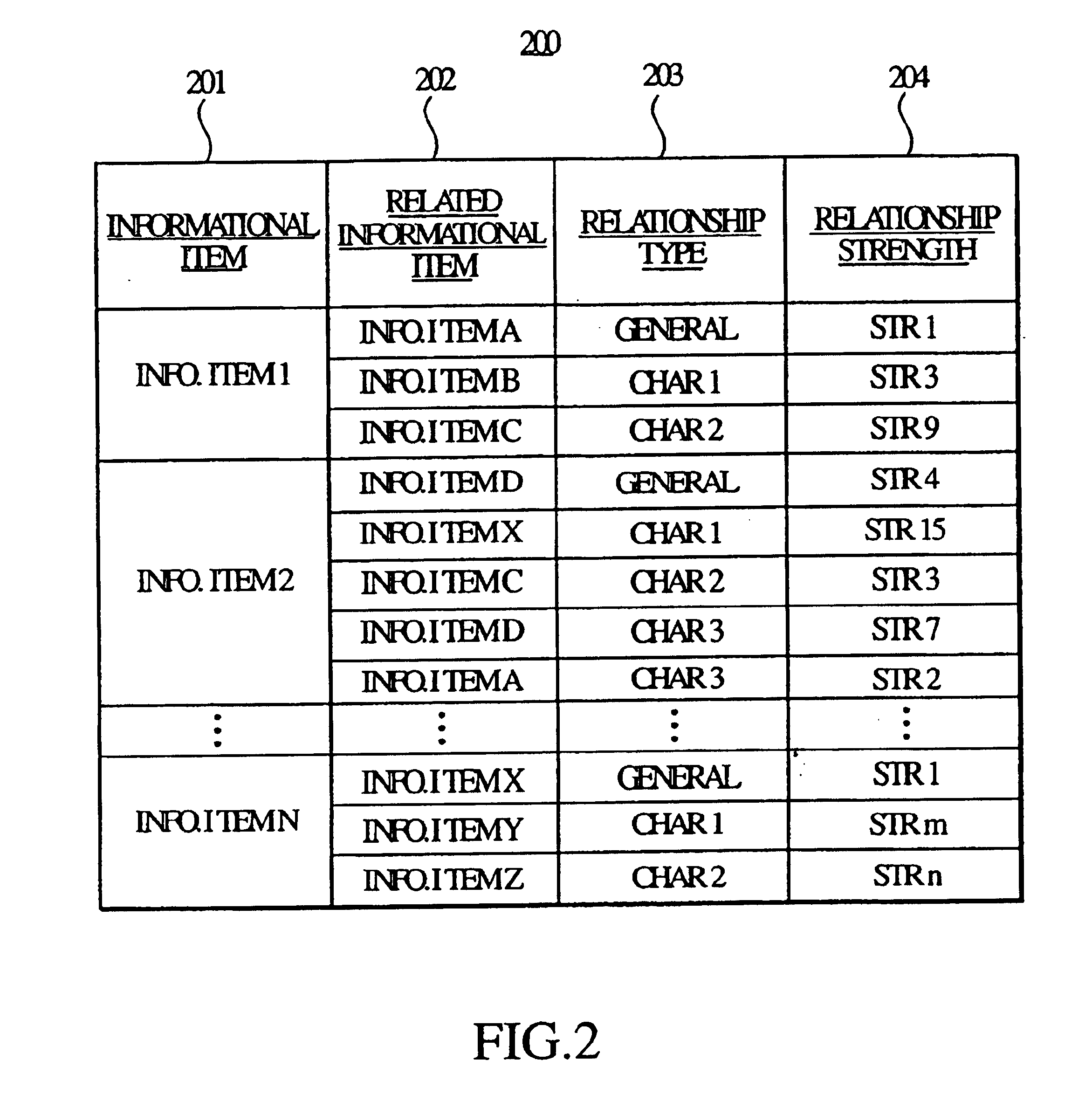
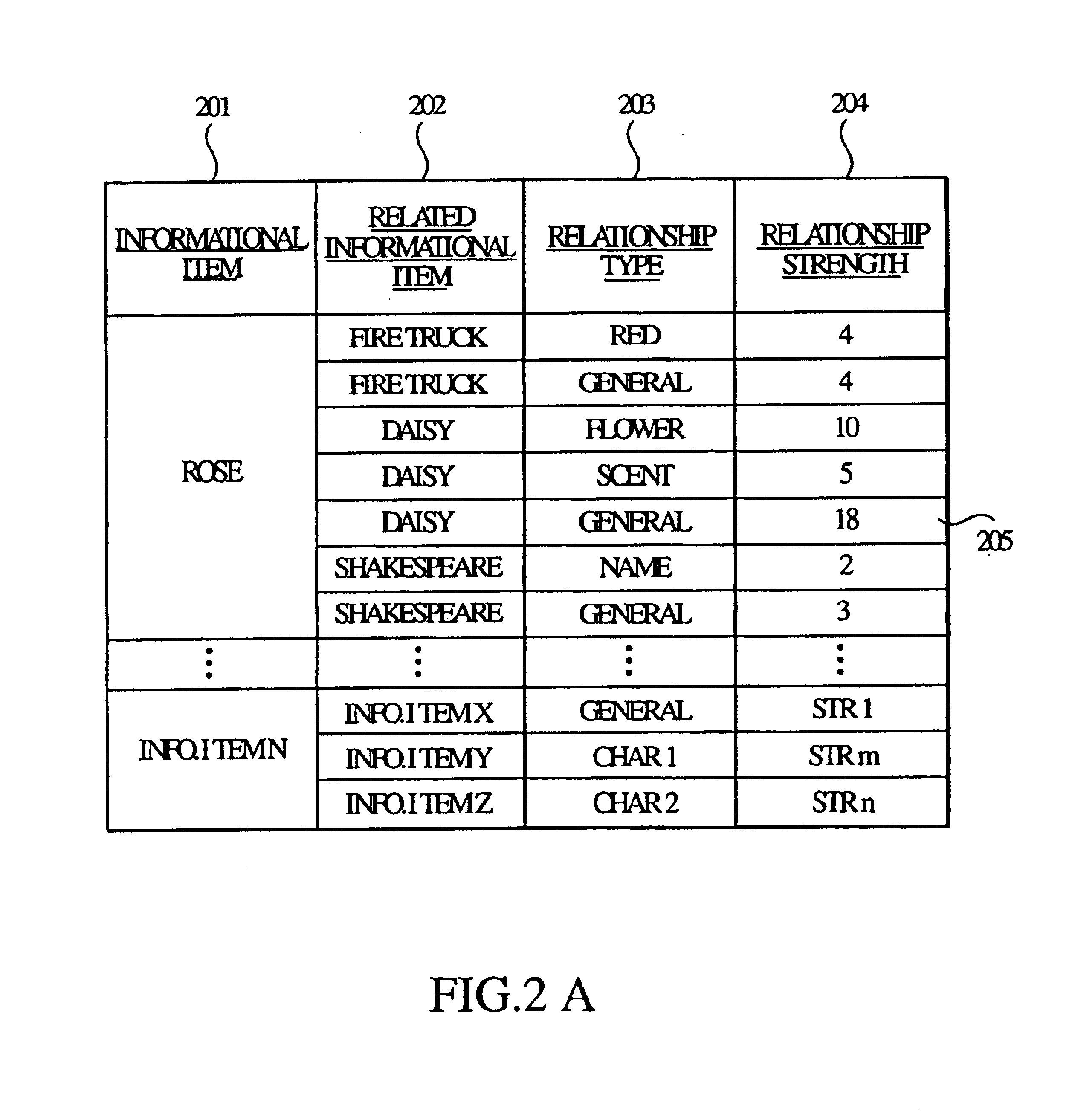
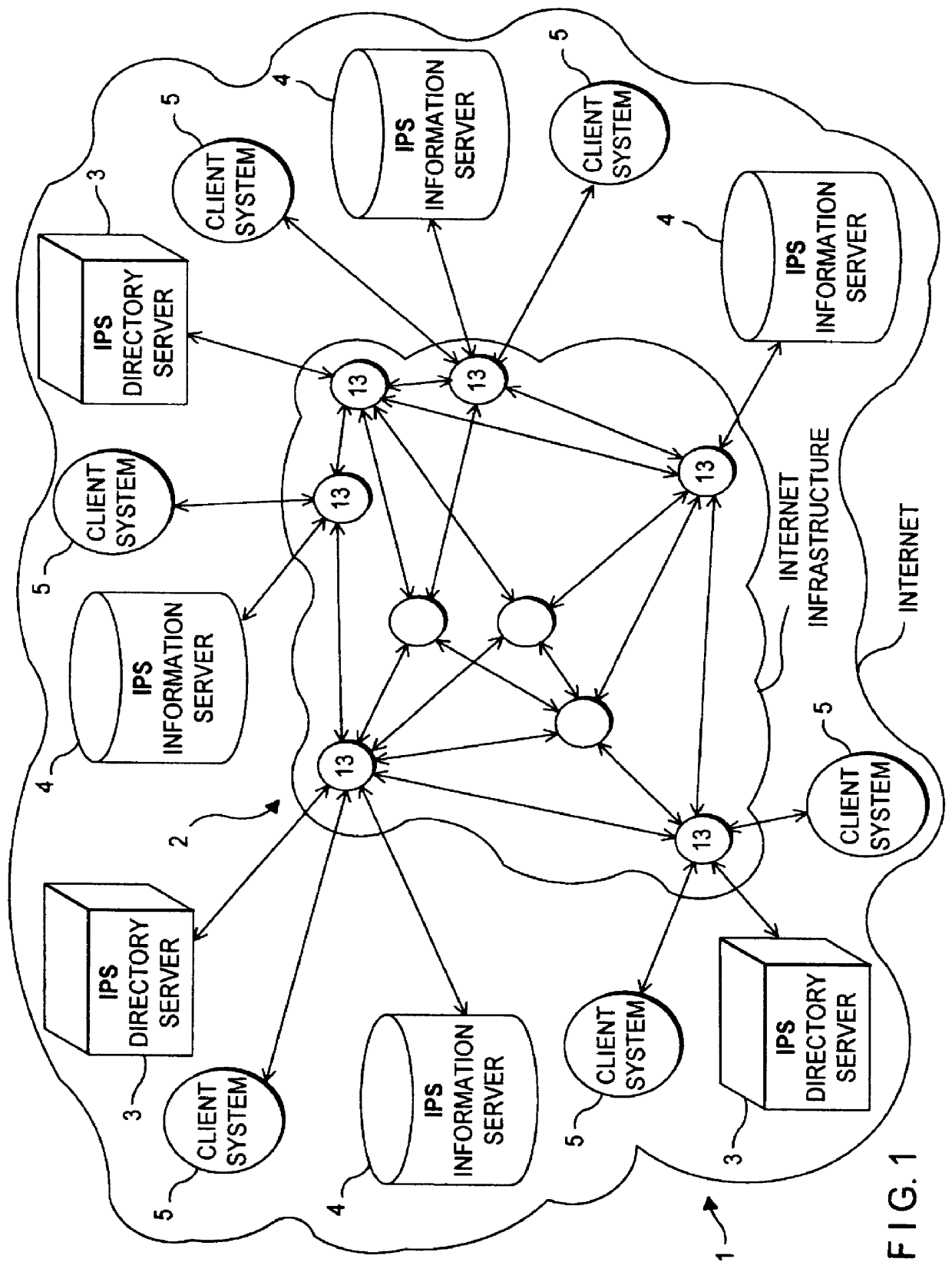
Usage based strength between related information in an information retrieval system
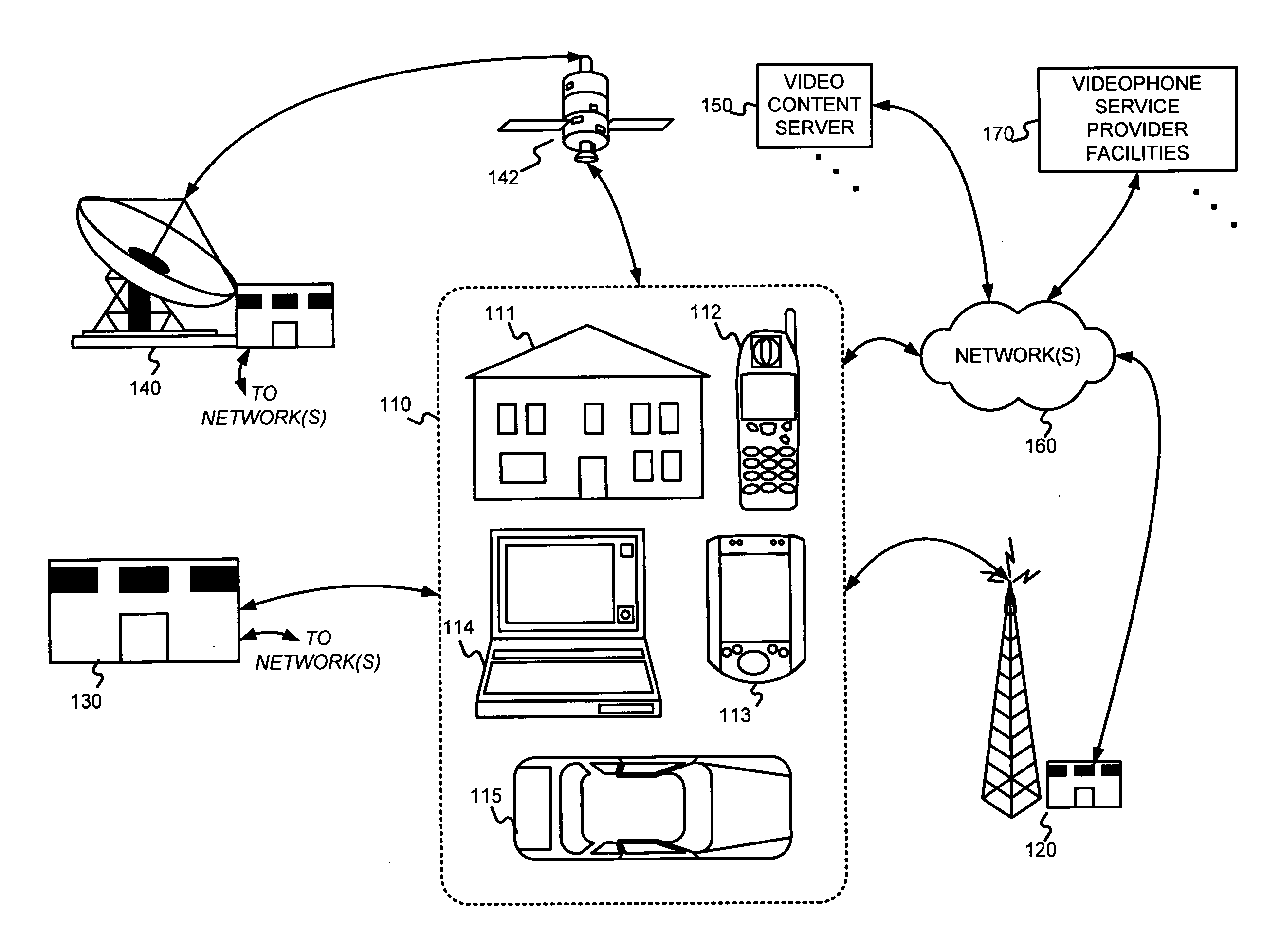
InactiveUS6842748B1Data processing applicationsDigital data processing detailsRelevant informationData library
An information retrieval system in accordance with the principles of the present invention maintains a database that defines a relational association between a plurality of informational items in the system. The relational association is based on historical navigational behavior of users of the information retrieval system, and includes a relationship type, which is based on the characteristic similarities between the informational items, and relationship strength, which is based on the historical frequency of any related informational items being selected by a user within the same information retrieval session. When a navigation from one informational item to another information item is detected, the relationship type and the relationship strength of the two informational items are determined and stored in the database. During a subsequent selection of an informational item, any related informational items related to the selected informational item are sorted based on the respective relationship types and relationship strengths, and are provided in a sorted list from which the user can select.
Owner:ORACLE OTC SUBSIDIARY
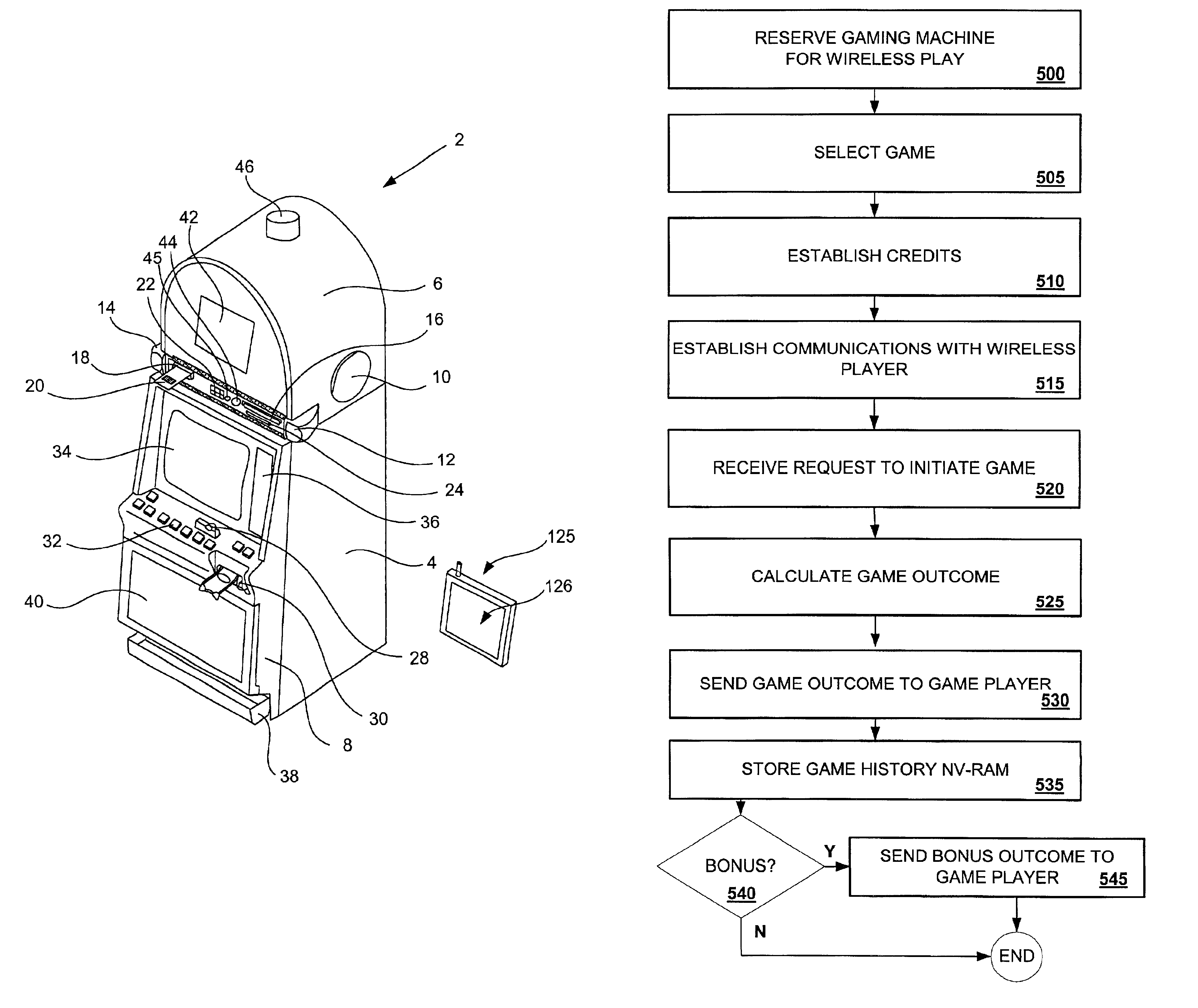
Wireless game player
InactiveUS6846238B2Apparatus for meter-controlled dispensingVideo gamesRelevant informationGame player
A disclosed gaming machine provides methods and apparatus for operating a wireless game player that presents a game of chance executed on a gaming machine in communication with the wireless game player. In one embodiment, the wireless game player is a hand-held mobile device, electronically linked to a licensed gaming machine via a wireless connection. All random number generation (RNG) events, game outcomes, meter information, game related information, and all cash transactions are maintained in the licensed (controlled) gaming machine and not the wireless game player. The wireless game player may be used anywhere within the legal areas of the casino and it has the capability of identifying who is using it. For example, a biometric input device, such as a finger print reader may be used on the wireless game player to identify the player. Thus, the issue of under-age or excluded players is addressed.
Owner:IGT
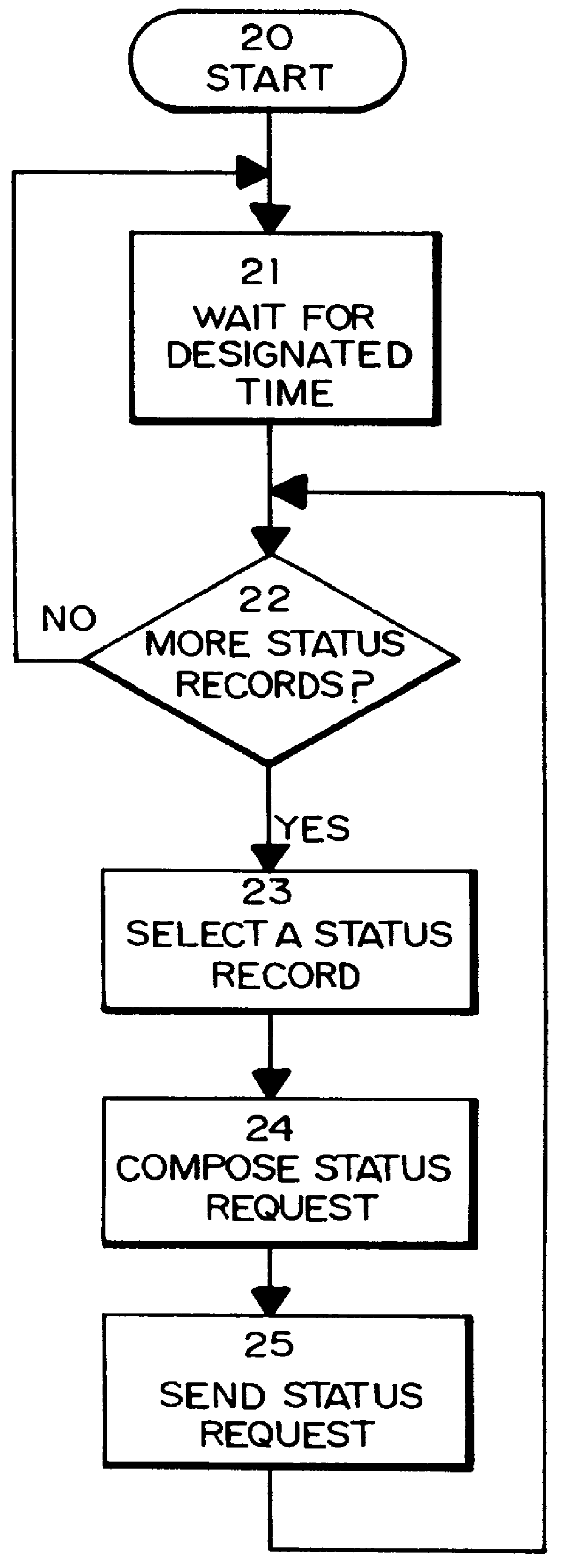
Method for supplying automatic status updates using electronic mail
A method is disclosed for automatically updating the status of customers' orders and shipments via electronic mail without using a human attendant to create and send the electronic mail messages. Preferably implemented in software, the updating method allows a large set of customers to be periodically updated over a computer or communications network via electronic mail. The method utilizes a database for maintaining order and shipping status and other relevant information.
Owner:EBAY INC
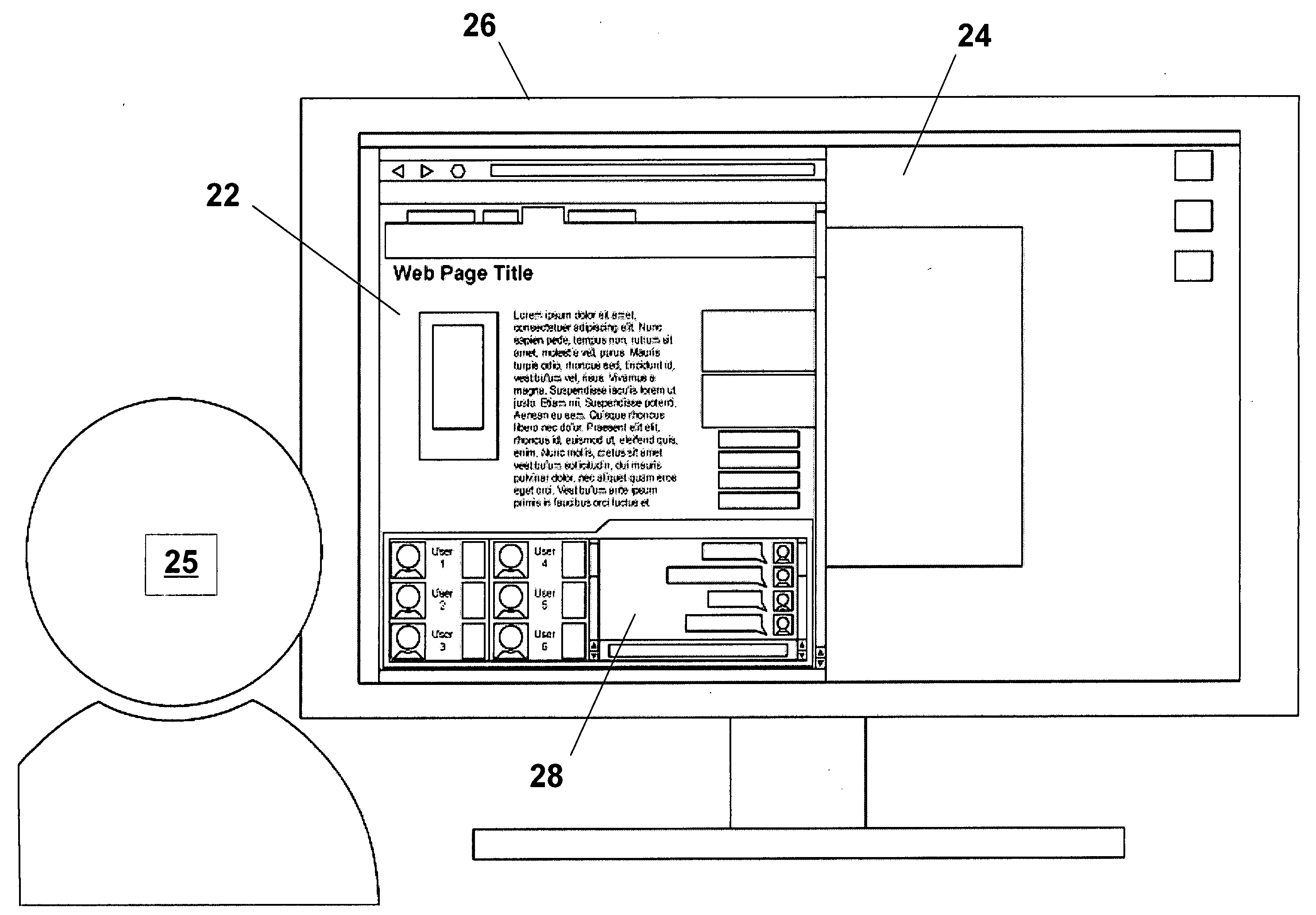
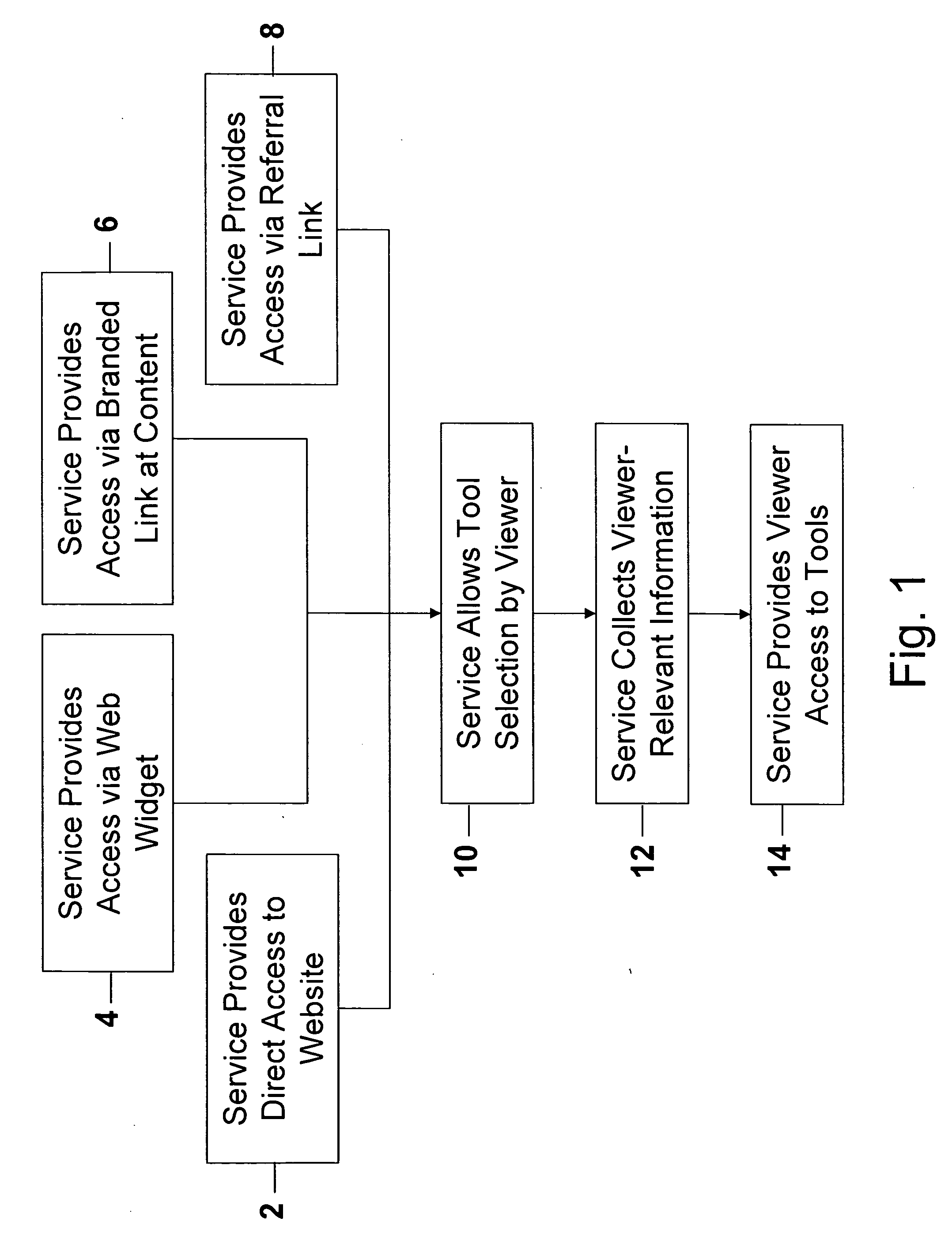
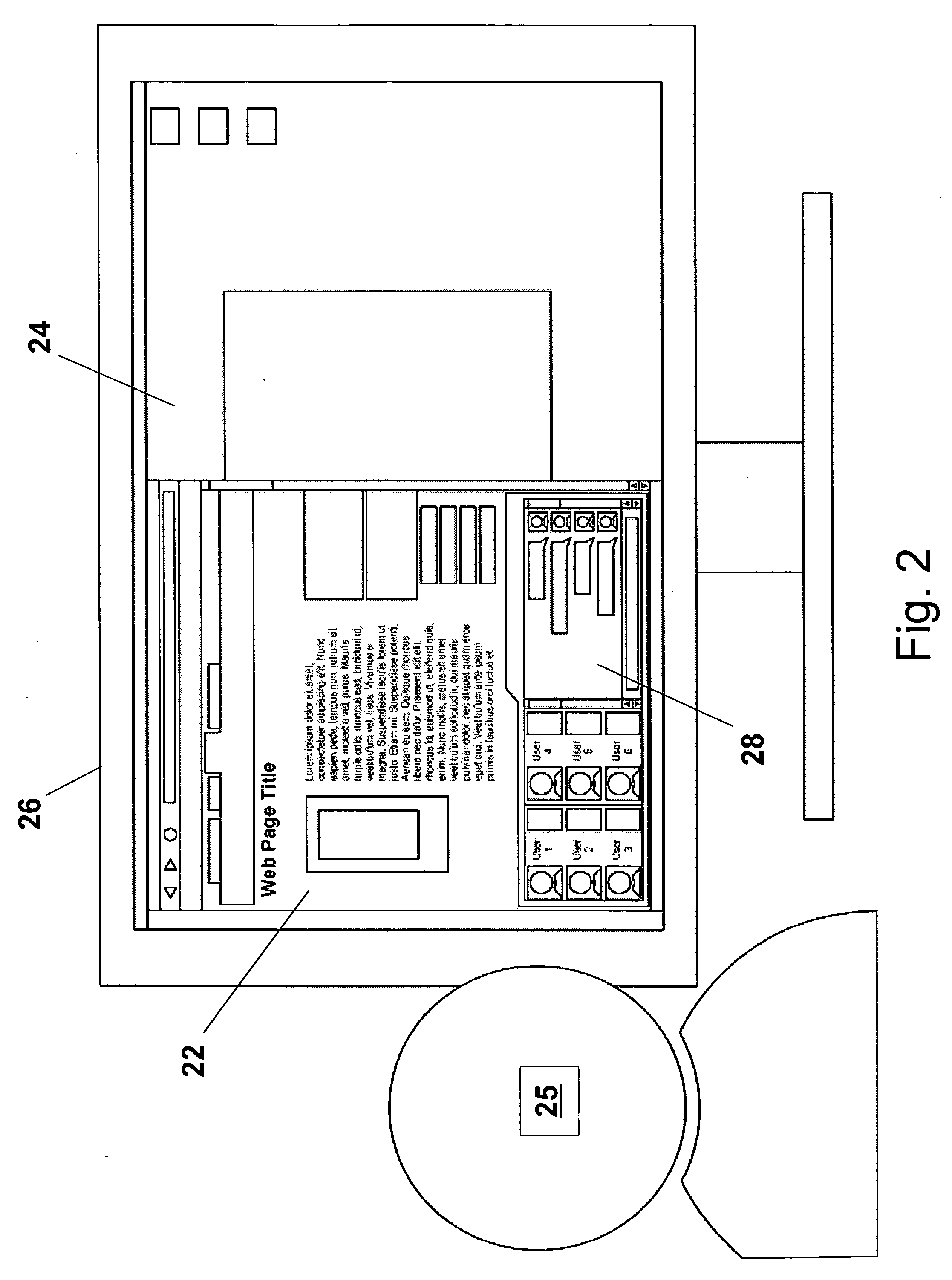
Dynamic information management system and method for content delivery and sharing in content-, metadata- & viewer-based, live social networking among users concurrently engaged in the same and/or similar content
Disclosed are tools, methods, and systems for establishing generally live, Content-based social networks, and for concurrently sharing Content and Content-relevant information within a social network. A Service registers Viewers and / or n-Users, and provides tools that enable a Viewer to identify n-Users concurrently viewing the same or similar Content, or having an interest in the same or similar Content. A Viewer can initiate or join a Content-based social network, and can share their Content with others, or view others' Content, and interact with n-Users via any of several methods. Service tools also enable a Viewer to define and selectively block or alter objectionable material so that it is no longer perceivable in its objectionable form. The described tools, methods, and systems also enable numerous innovative approaches to generate revenue for a Service, for providers of product and / or services, for Content providers, and others.
Owner:NEONEKT LLC
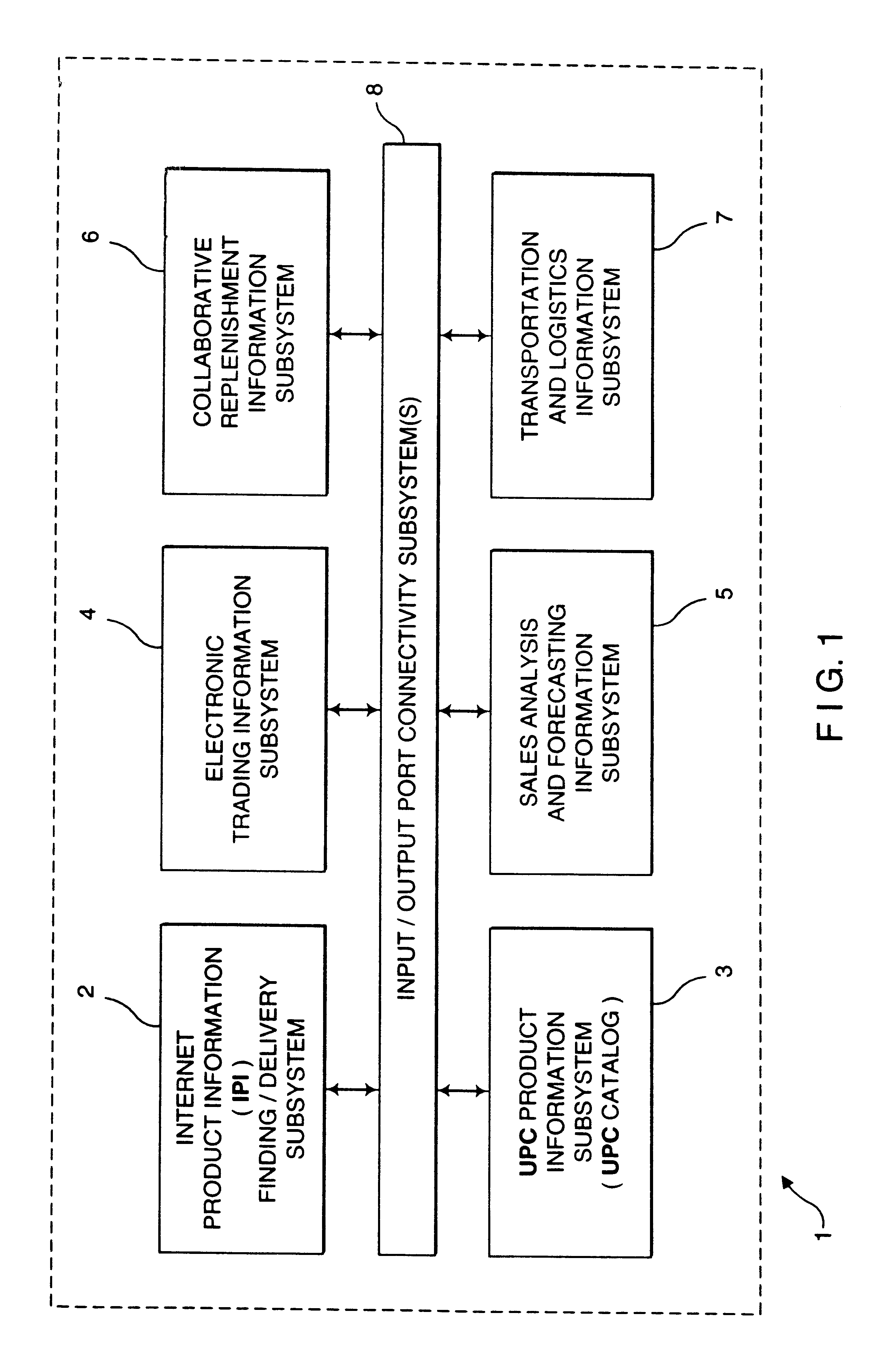
Method of and system for finding and serving consumer product related information over the internet using manufacturer identification numbers
InactiveUS6064979AHigh acceptanceMultiple digital computer combinationsApparatus for meter-controlled dispensingRelevant informationHome page
A method of and system for finding and serving consumer product-related information on the Internet comprising a database serving subsystem which stores: a plurality of manufacturer identification numbers (MINs) assigned to a plurality of manufacturers of consumer products; a plurality of home-page specifying URLs symbolically linked to the plurality of MINs; a plurality of universal product numbers (UPN) assigned to a plurality of consumer products made by the plurality of manufacturers; and a plurality of product-information specifying URLs symbolically linked to the plurality of UPNs. During operation, a client subsystem transmits to the database serving subsystem, a request for information which includes the UPN assigned to the consumer product on which product-related information is being sought. The database serving subsystem automatically compares the UPN against the stored plurality of MINs, and automatically returns to the client subsystem, one or more of URLs symbolically linked to the UPN, if URLs have been symbolically linked to the UPN within the database serving subsystem. However, if no URLs have been symbolically linked to the UPN, then the database serving subsystem automatically returns the home-page specifying URL symbolically linked to the MIN contained within the UPN in the request. By virtue of this novel MIN-based search mechanism embodied within the database serving subsystem, client subsystems are automatically provided with the home-page of the manufacturer's World Wide Web (WWW) site in situations where product-information specifying URLs have not yet been symbolically linked with the UPN on any one of the manufacturer's products.
Owner:PERKOWSKI THOMAS J
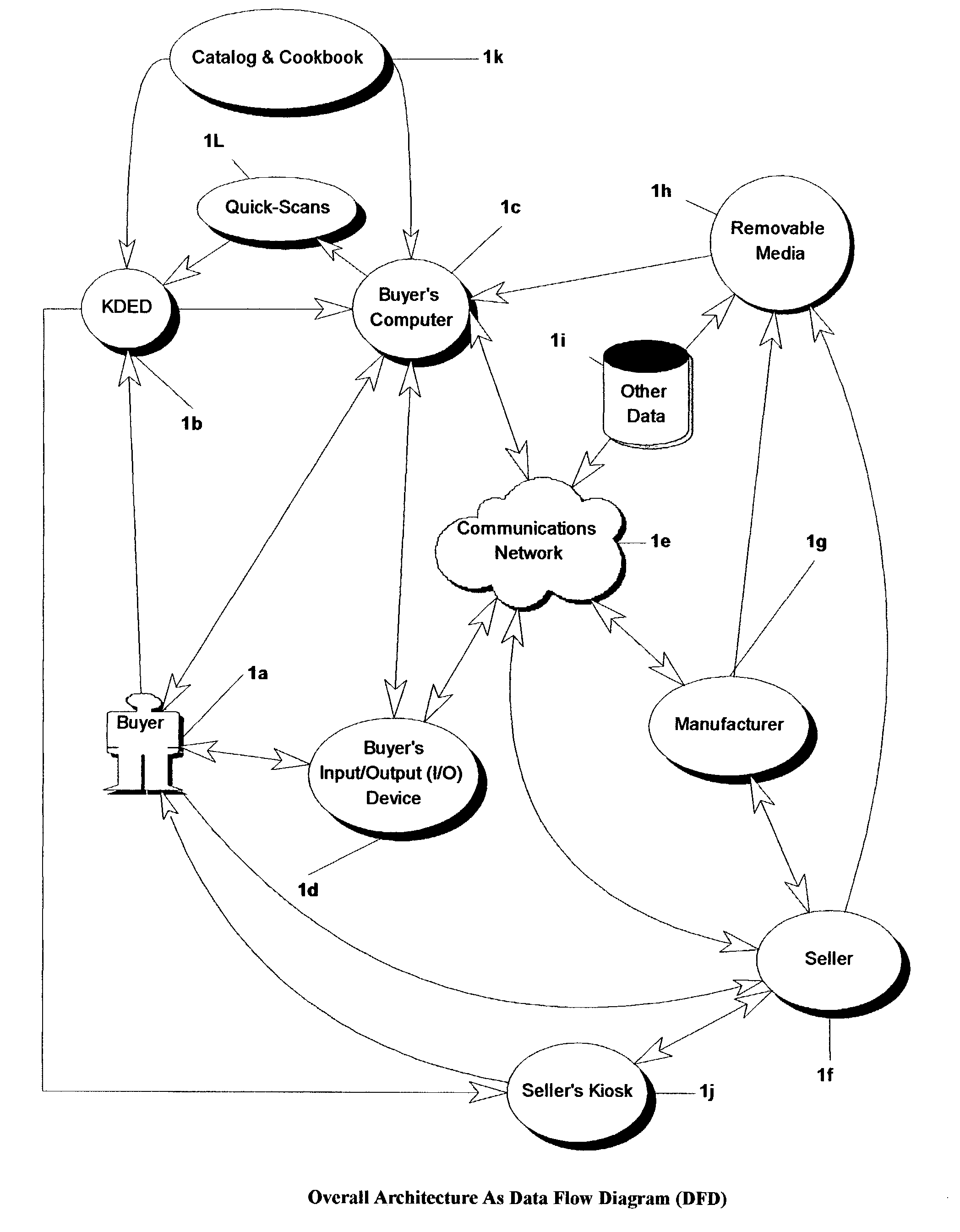
Distributed personal automation and shopping method, apparatus, and process
ActiveUS7797204B2Co-operative working arrangementsBuying/selling/leasing transactionsOff the shelfCommunications system
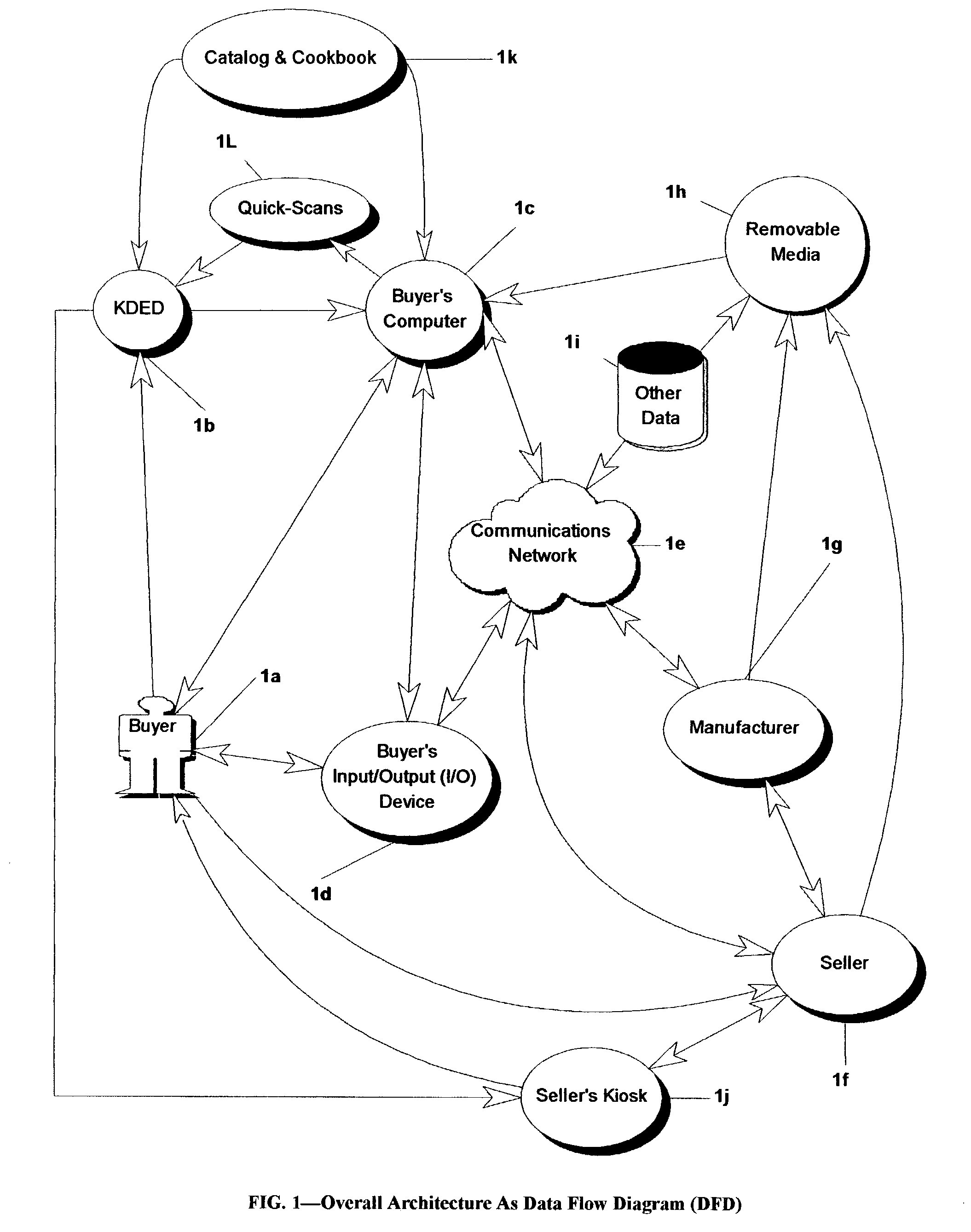
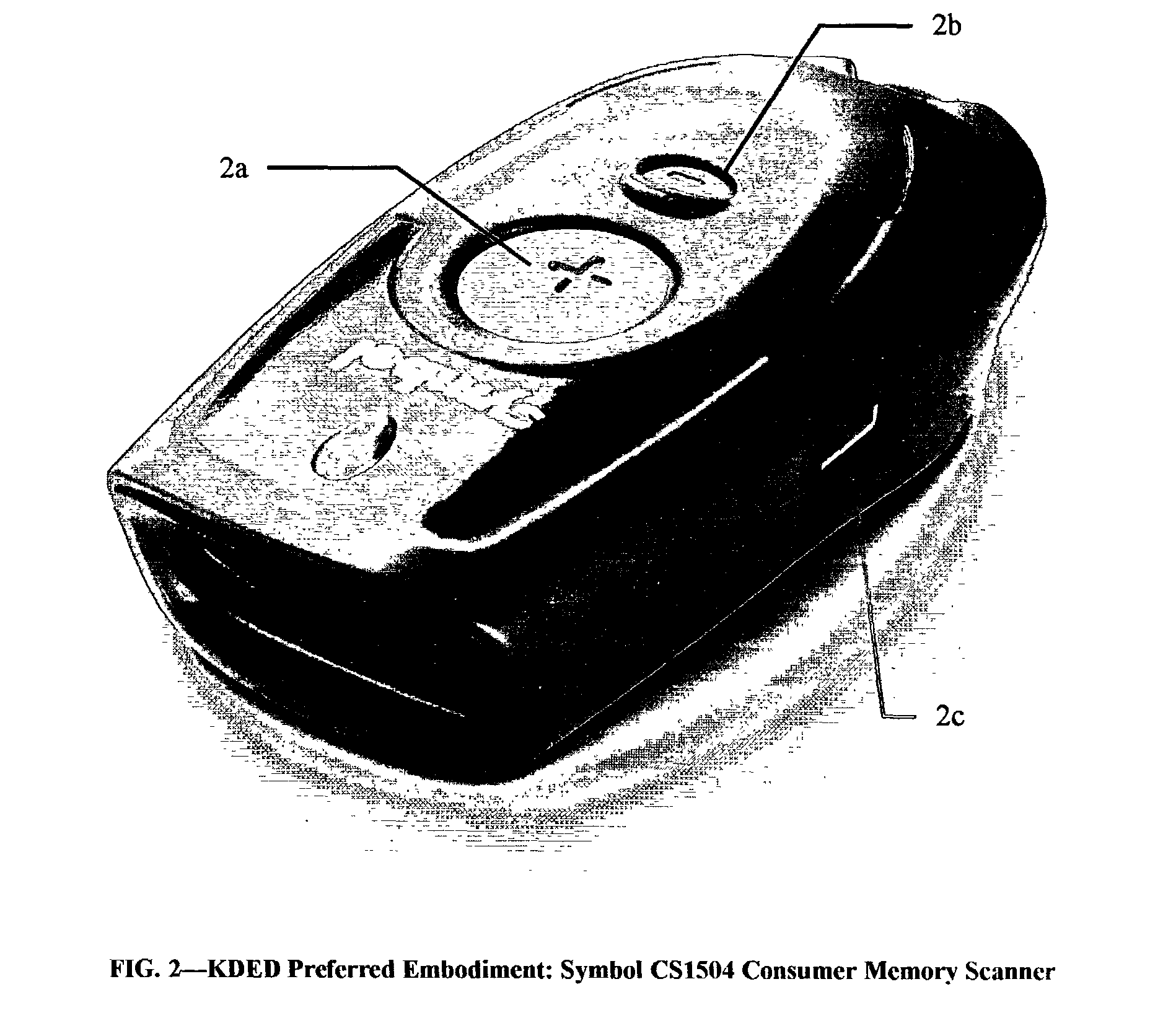
A business method utilizing a system comprising one or more distributed computers, application software, off-the-shelf peripheral components including keyboard-and-mouseless data entry (KDE) devices, business processes, human and KDE device readable data, related information on removable data storage media or available from external databases, and existing communications systems for speeding and improving: 1) personal or business automation, efficiency and productivity, goal attainment; 2) improving, speeding and automating the person-computer interface; 3) selection, acquisition, and tracking usage of items acquired from an existing supply chain; 4) marketing items and retaining customers buying the products, controlling their usage, and disseminating information about the products.
Owner:III HLDG 3
Methods and apparatus providing electronic messages that are linked and aggregated
InactiveUS7130885B2Promote collaborationAutomate quicklyMultiple digital computer combinationsOffice automationApplication softwareUser interface
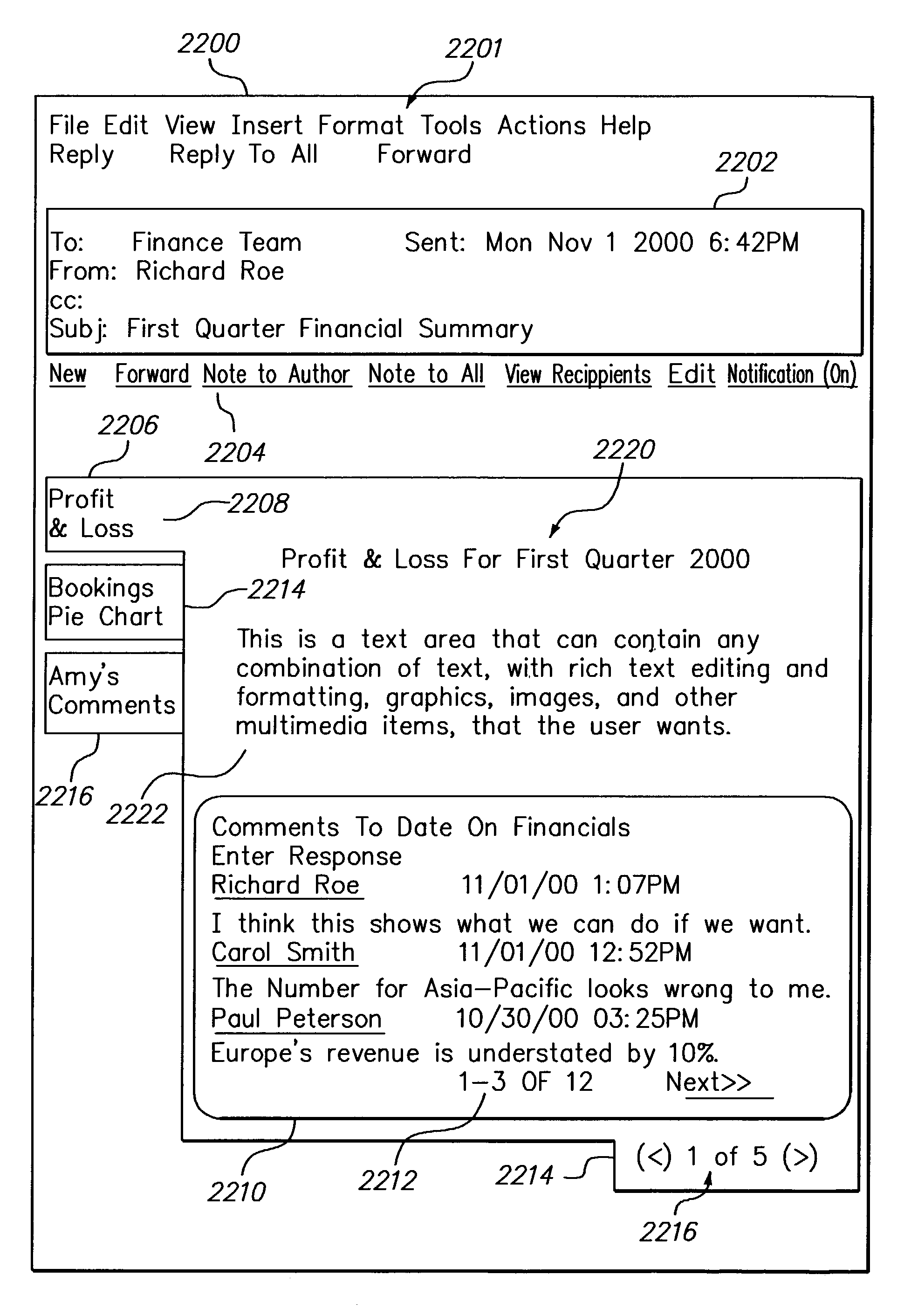
A method for associating related electronic messages in computer storage. A first transportable application is created and stored. User input requesting creation of a link from the first transportable application to another transportable application is received. User input that selects a second transportable application from among a plurality of previously created transportable applications is received. A link from the first transportable application to the second transportable application is created and stored. As a result, transportable application may be inter-related in complex message webs. The message webs may also be inter-related in message web rings. Links may be generated manually or automatically, based on context, workflow processes, or other known relationships among applications. Recipient lists and data may propagate among fields of linked transportable applications, directly or according to abstract business rules. Further, multiple-part electronic messages are disclosed. A graphical user interface of an electronic messaging system displays a message in the form of one or more header portions and one or more body portions. Each of the body portions has a selection region. While one body portion is visible at a given time, all the selection regions are continuously visible in the user interface to facilitate selection of any of the body portions at a particular time. Selecting a selection region of a non-displayed body portion causes a server to generate a refreshed user interface that includes the entirety of the selected body portion, and that hides the previously viewed body portion. As a result, a large amount of associated information may be combined in a single message in a way that is clearly organized and easily accessible.
Owner:METRICSTREAM
System and method for providing context sensitive recommendations to digital services
ActiveUS20040043758A1Reducing or minimizing the processing load and memoryReduces privacy concernInterconnection arrangementsDigital data information retrievalComputer networkRelevant information
A system and method is disclosed to provide recommendations to a wireless device, based on stored bookmark / short-cut data. When a wireless device accesses services, data pertaining to the service access, along with any context related information is transmitted within the wireless device, or to a remote server. The data is processed in conjunction with bookmarks / short-cuts specified within the device, and are organized and presented to the wireless device in accordance with preference instructions specified within the wireless device.
Owner:NOKIA TECHNOLOGLES OY
Advertising with video ad creatives
InactiveUS20070157228A1Good serviceAdvertisementsAnalogue secracy/subscription systemsRelevant informationThe Internet
The serving of advertisements with (e.g., on) video documents may be improved in a number of ways. For example, a system may (a) accept information defining at least one ad spot associated with at least one instance of an video document, (b) accept offers to have advertisements served in the ad spot(s), and (c) arbitrate among competing advertisements, using at least the offers, to determine at least one advertisement to be served in that ad spot(s). As another example, a system may (a) accept relevance information for an advertisement, (b) determine at least one video document using the accepted relevance information, (c) present information about the video document(s) to an advertiser associated with the advertisement, and (d) accept, from the advertiser, an offer to have its advertisement served with at least one of the video document(s) accepted. As yet another example, a system may (a) accept relevance information for an video document, (b) determine a plurality of advertisements relevant to the video document using the relevance information and serving constraints of the advertisements, and (c) select at least one of the determined relevant advertisements to be served with the video document. Examples of video documents include video files published on the Internet, television programs, live or recorded talk shows, video-voice mail, segments of an video conversation, etc.
Owner:GOOGLE LLC
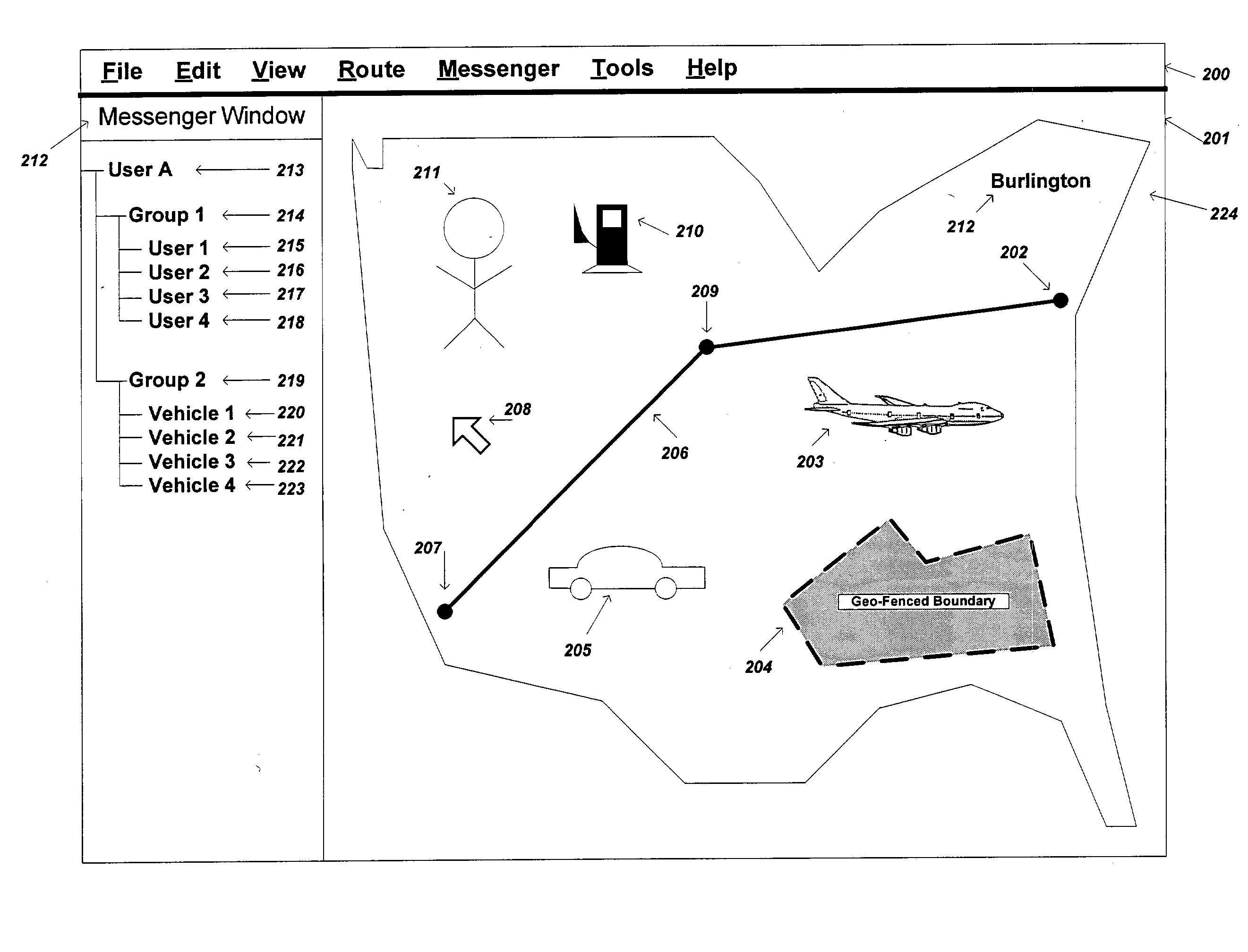
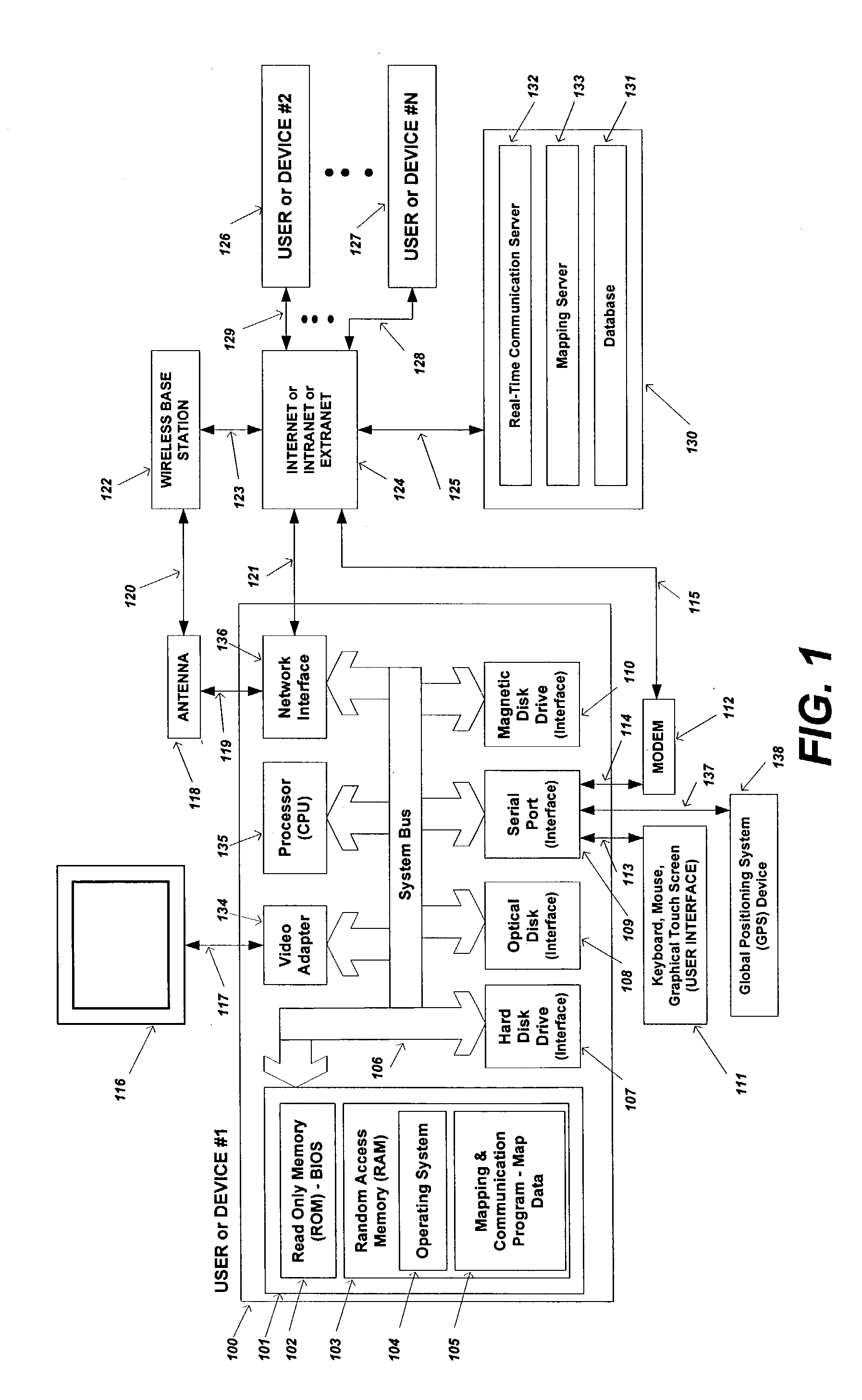
Method and apparatus for sending, retrieving and planning location relevant information
InactiveUS20040054428A1Improve user experienceLarge amount of informationInstruments for road network navigationNavigational calculation instrumentsNavigation systemCommunication device
The present invention is directed to a method and apparatus for sending and retrieving location relevant information to a user by selecting and designating a point of interest that is displayed on a graphical user interface and sending the location information associated with that point of interest to a receiver that is also selected using the graphical user interface. The location relevant information may also include mapped routes, waypoints, geo-fenced areas, moving vehicles etc. Updated location relevant information may also be continuously sent to the user while generating updated mapping information on the graphical user interface. The present invention may be practiced by using communication devices such as a personal computer, a personal digital assistance, in-vehicle navigation systems, or a mobile telephone.
Owner:TELECOMM SYST INC
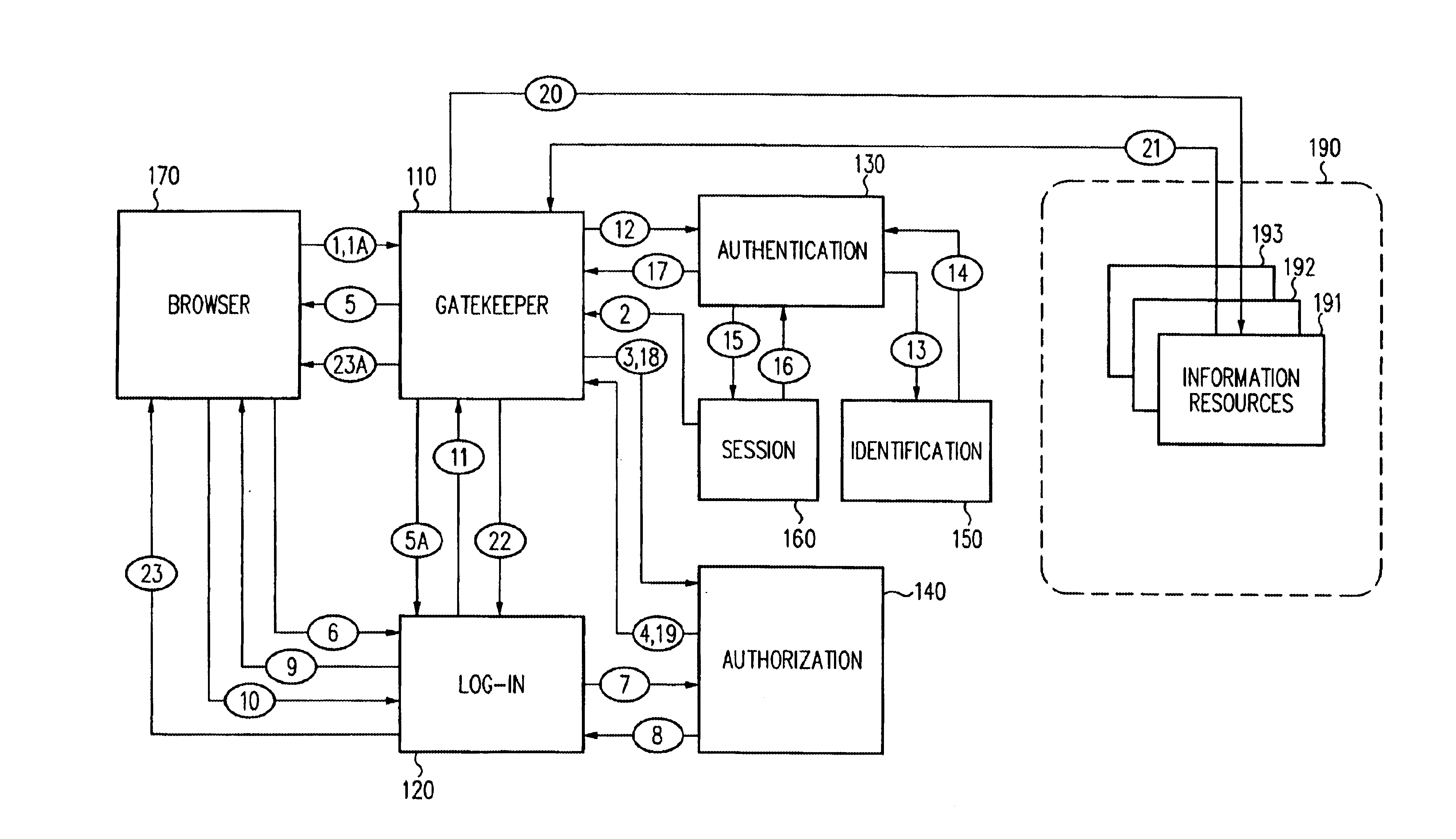
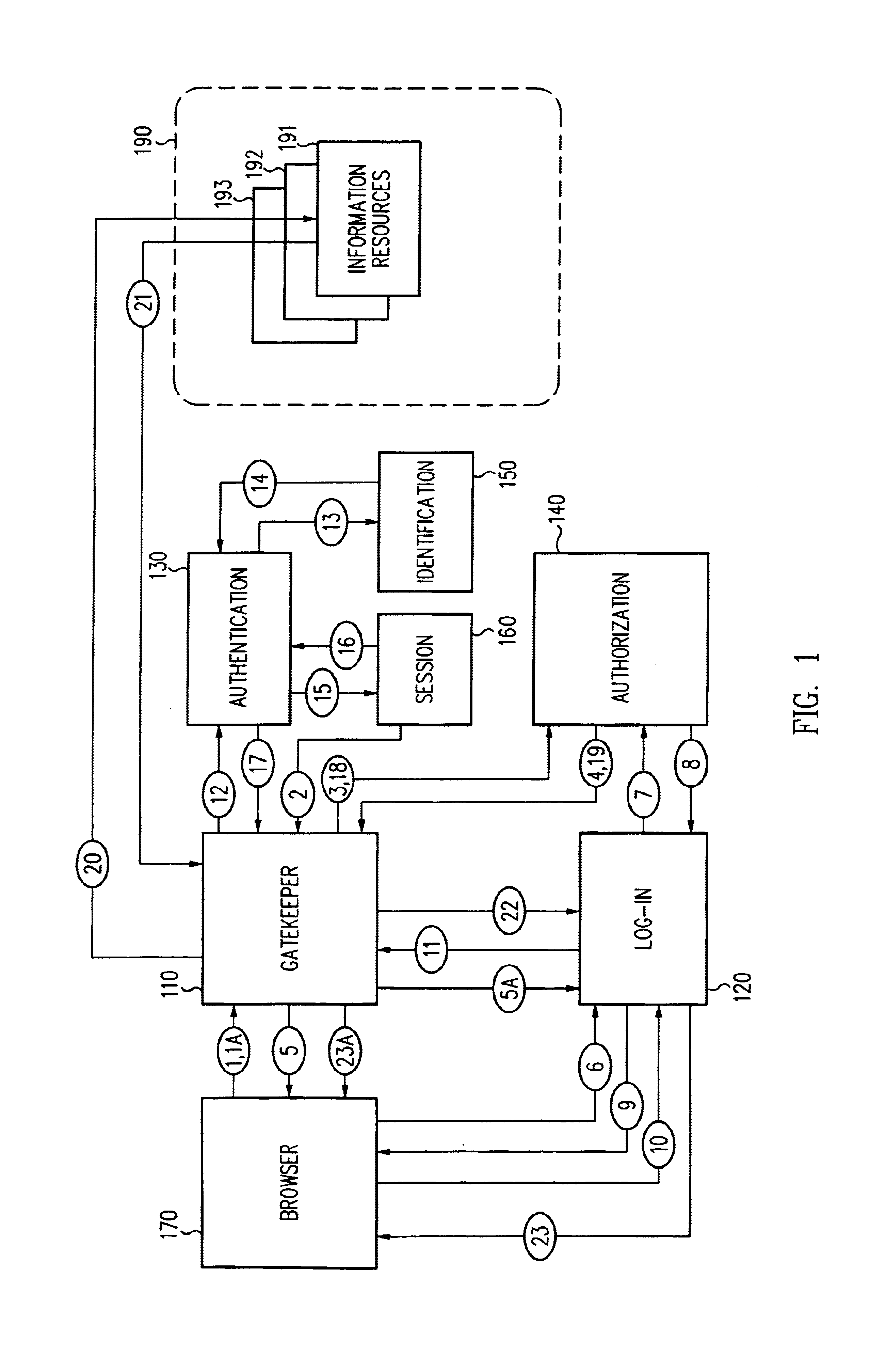
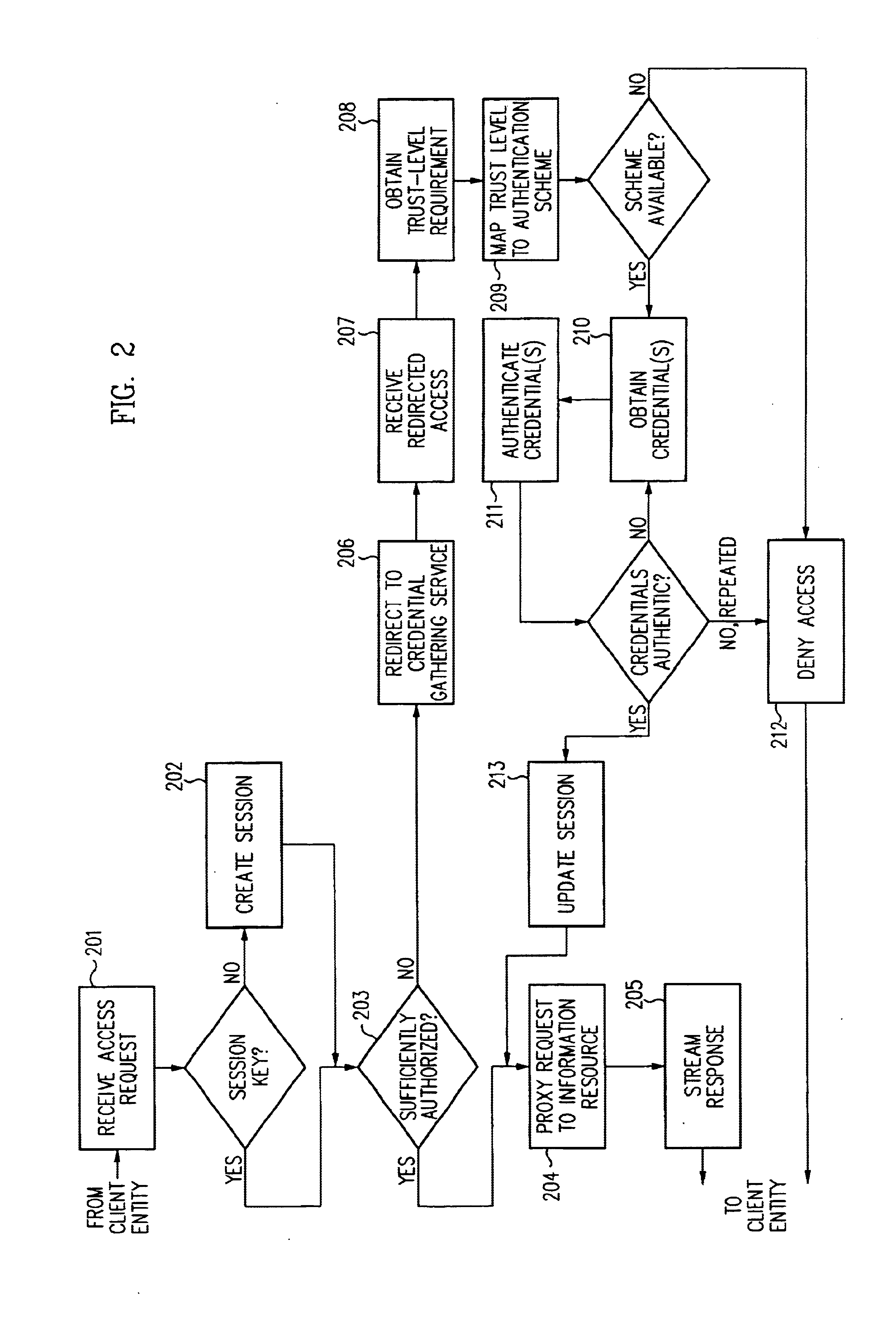
Security architecture with environment sensitive credential sufficiency evaluation
InactiveUS6691232B1Digital data processing detailsUnauthorized memory use protectionInformation resourceTrust level
By including environment information in a security policy, a security architecture advantageously allows temporal, locational, connection type and / or client capabilities-related information to affect the sufficiency of a given credential type (and associated authentication scheme) for access to a particular information resource. In some configurations, time of access, originating location (physical or network) and / or connection type form a risk profile that can be factored into credential type sufficiency. In some configurations, changing environmental parameters may cause a previously sufficient credential to become insufficient. Alternatively, an authenticated credential previously insufficient for access at a given trust level may be sufficient based on a changed or more fully parameterized session environment. In some configurations, the use of session tracking facilites (e.g., the information content of session tokens) can be tailored to environmental parameters (e.g., connection type or location). Similarly, capabilities of a particular client entity (e.g., browser support for 128-bit cipher or availablity of a fingerprint scanner or card reader) may affect the availability or sufficiency of particular authentication schemes to achieve a desired trust level.
Owner:ORACLE INT CORP
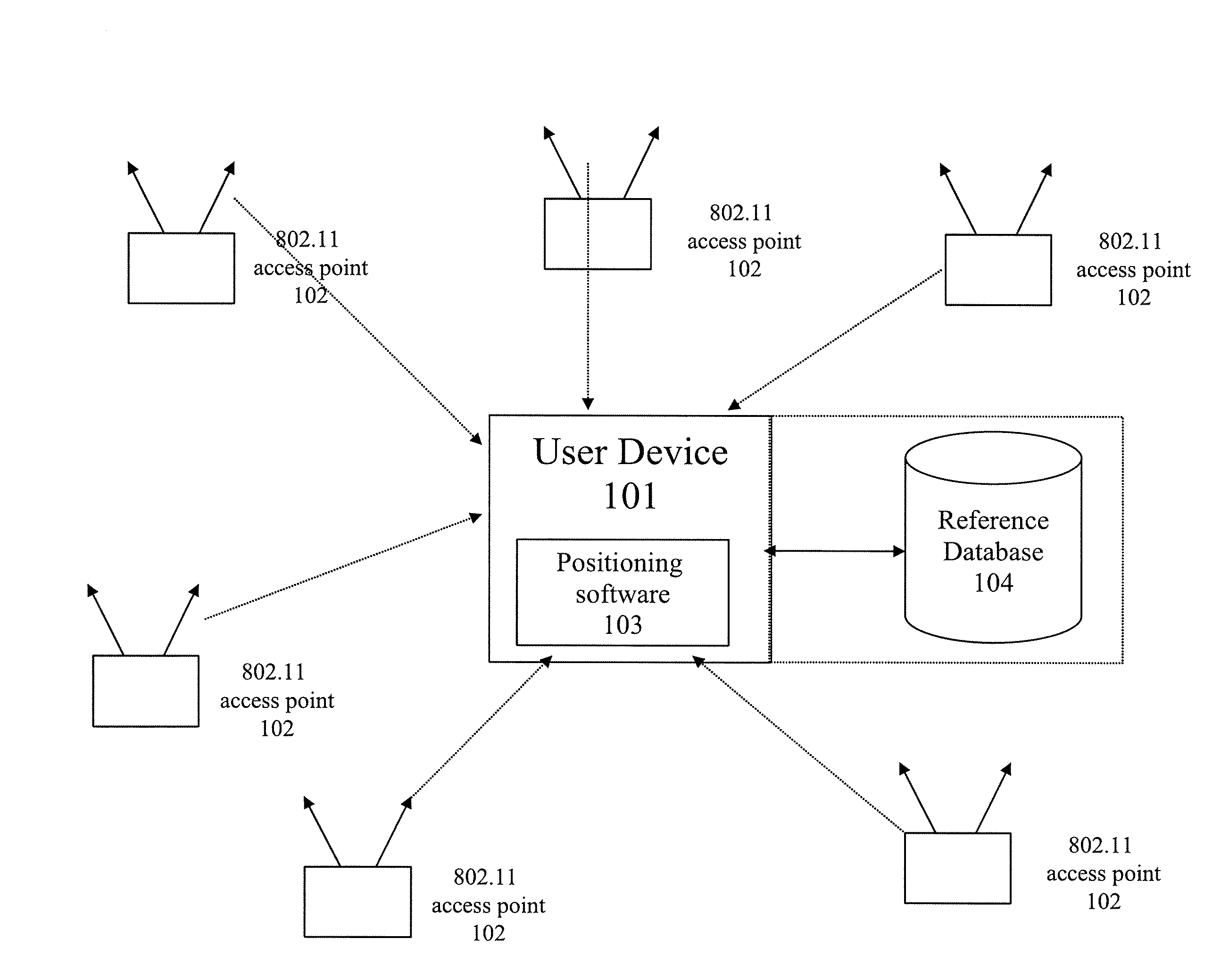
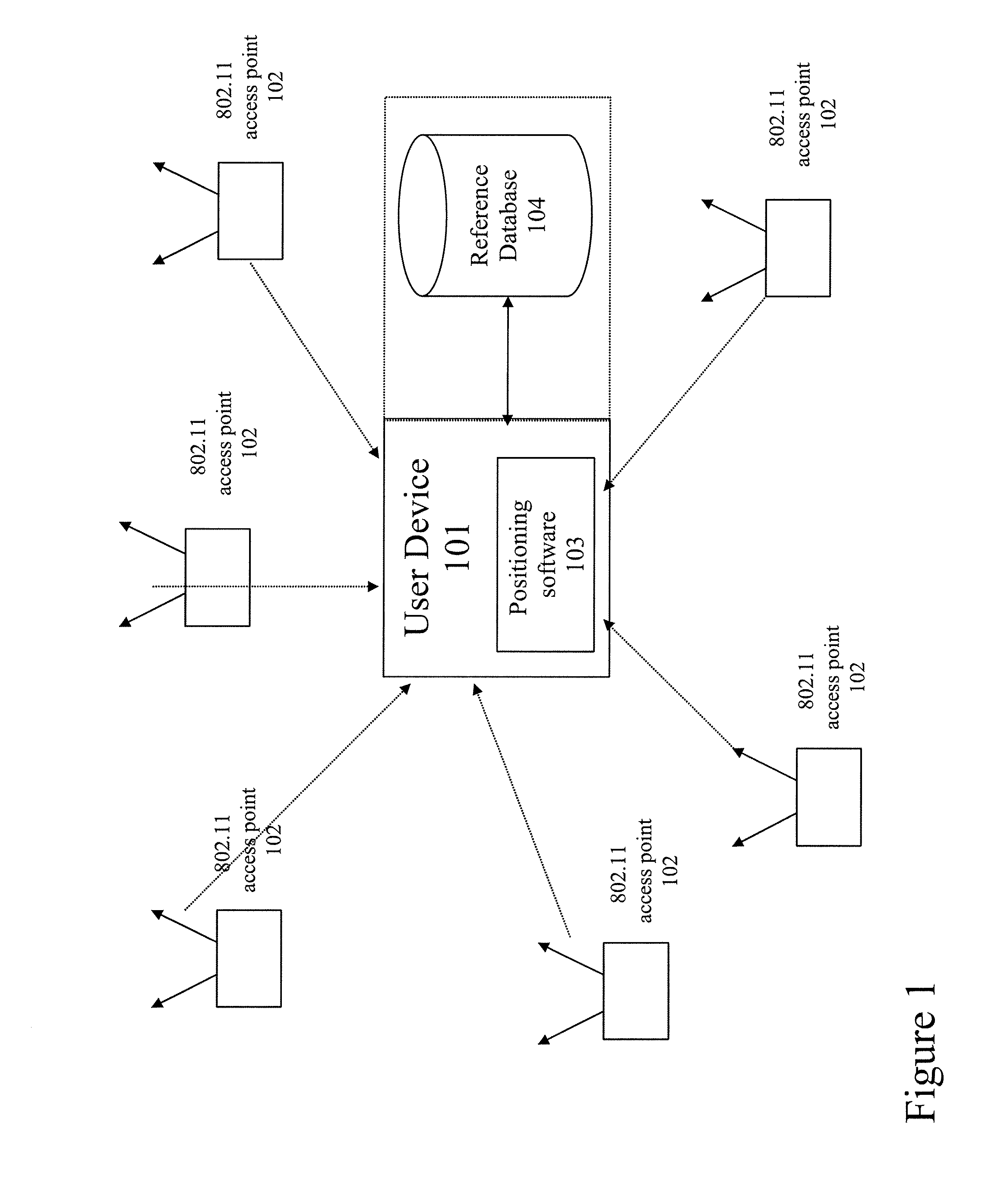
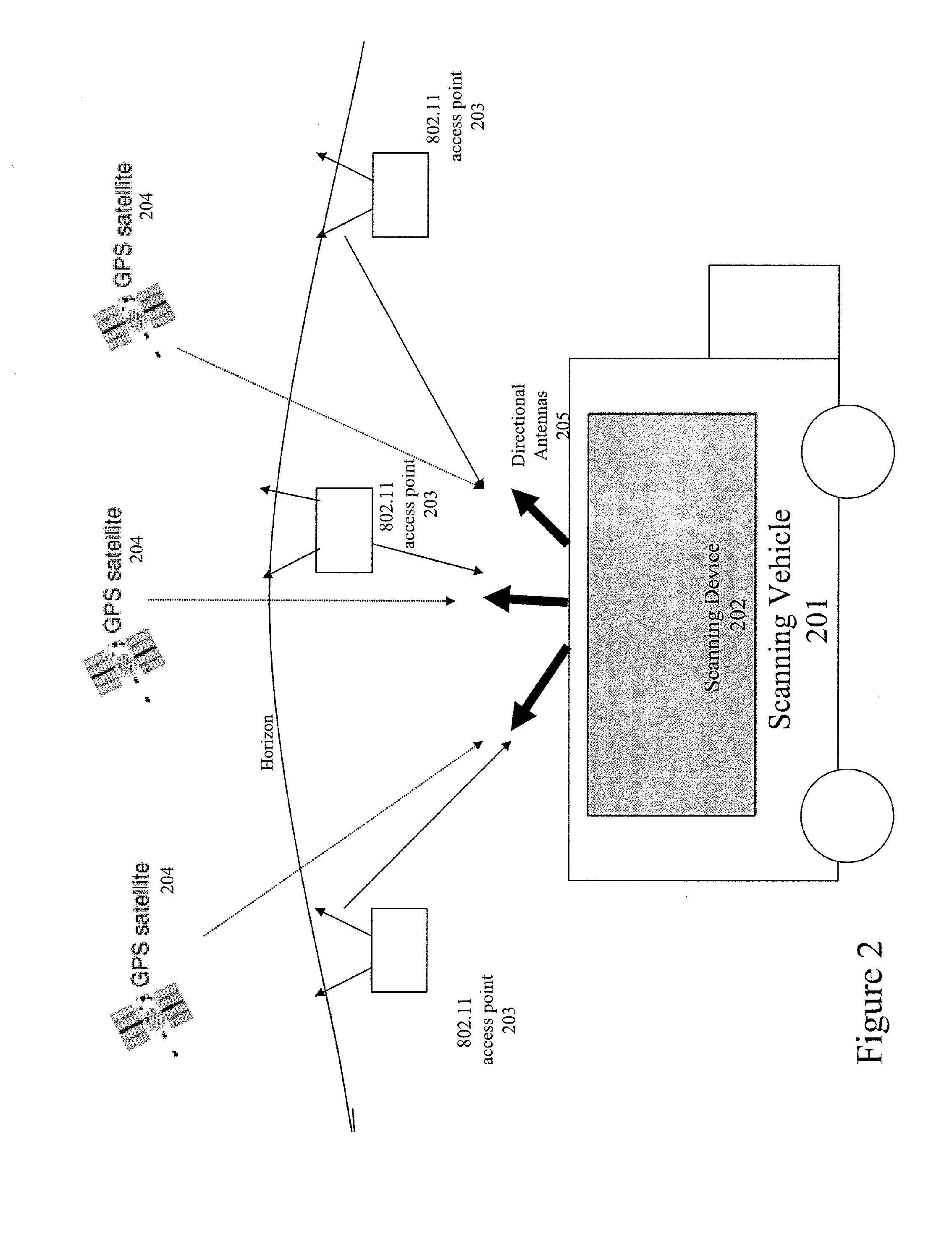
Method and system for selecting and providing a relevant subset of wi-fi location information to a mobile client device so the client device may estimate its position with efficient utilization of resources
Methods and systems for selecting and providing a relevant subset of Wi-Fi location information to a mobile client device so the client device may estimate its position with efficient utilization of resources.A method of providing a relevant subset of information to a client device is based in part on scanning for Wi-Fi access points within range of the client device, using a Wi-Fi database that covers a large target region to retrieve information about these access points, using this information to estimate the position of the mobile client device, selecting a limited region in the vicinity of the estimated location of the client device, and providing information about Wi-Fi access points within this limited region to the client. For efficient transfer and maintenance of data, the target region may be divided into a hierarchy of fixed geographical tiles.
Owner:SKYHOOK WIRELESS
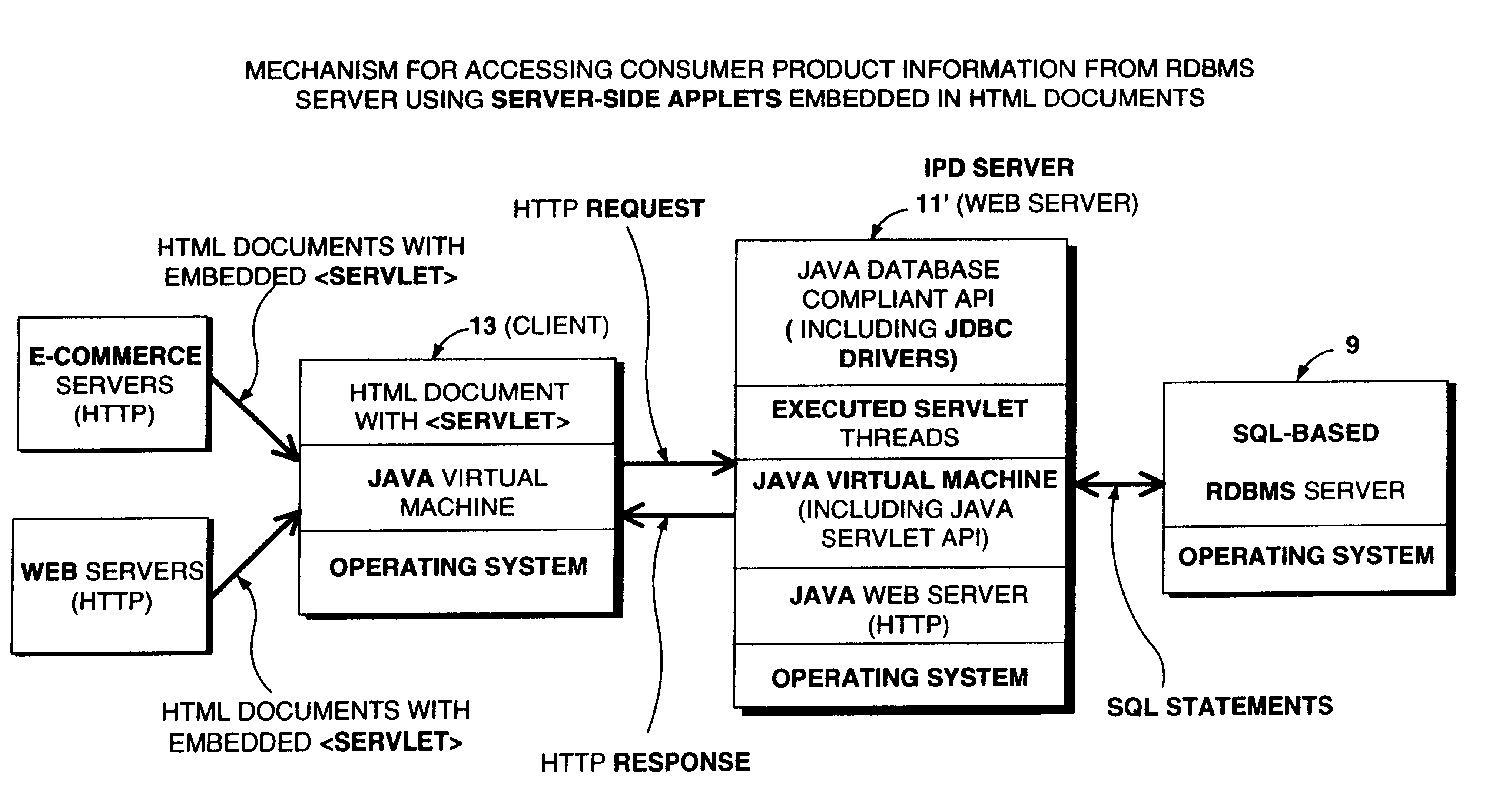
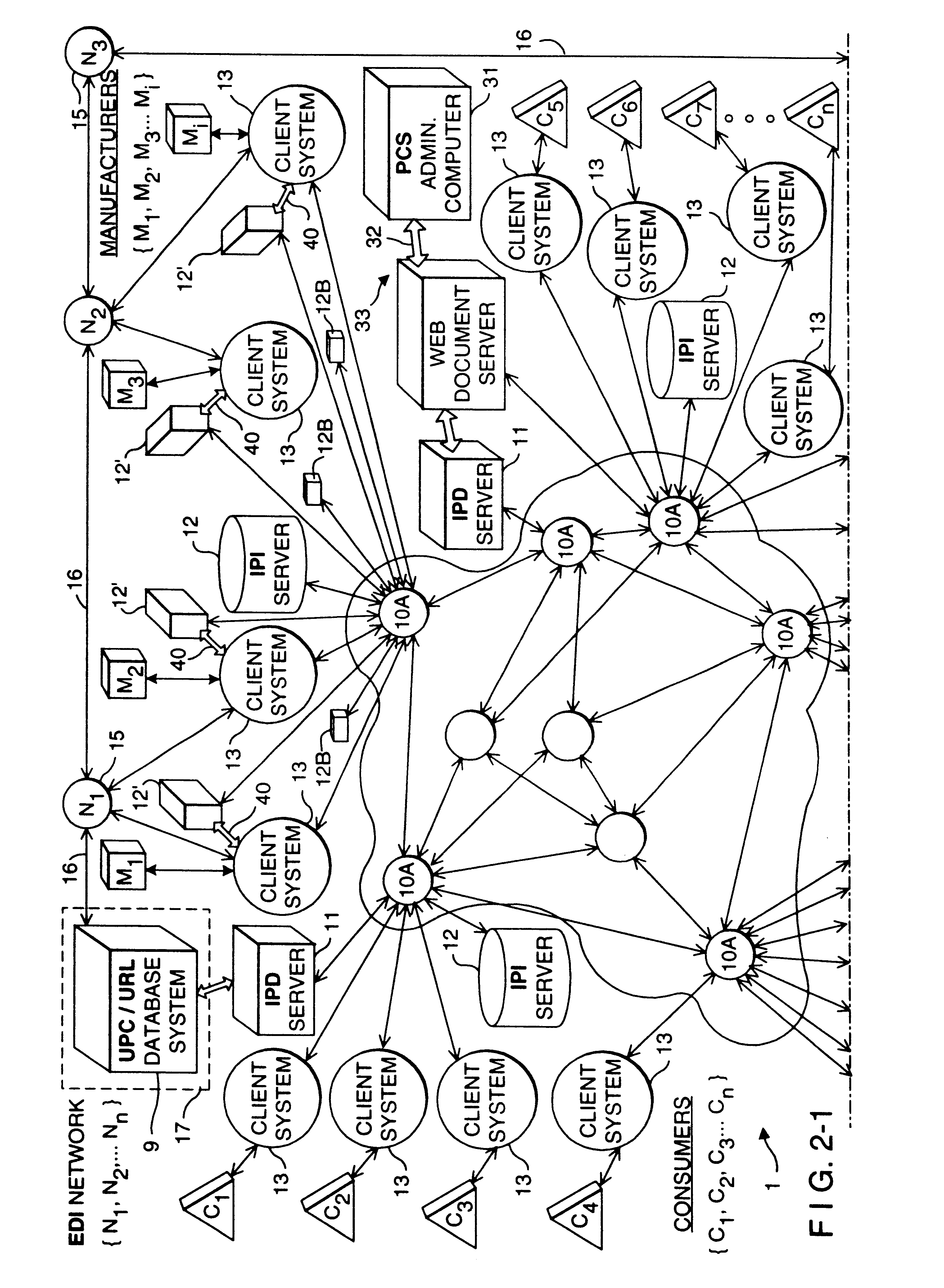
Method of and system for enabling the access of consumer product related information and the purchase of consumer products at points of consumer presence on the world wide web (WWW) at which consumer product information request (CPIR) enabling servlet tags are embedded within html-encoded documents
InactiveUS6625581B1Easy to readDigital data information retrievalAdvertisementsPoint of presenceAlternative technology
Method of and system for delivering consumer product related information to consumers over the Internet. The system and method involves creating an UPN-encoded Consumer Product Information (CPIR) enabling Applet for each consumer product registered within a manufacturer-managed UPN / URL database management system. Each CPIR-enabling Applet is encapsulated within an executable file and then stored in the UPN / URL database management system. Each CPIR-enabling Applet is searchable and downloadable by, for example, (1) retailers purchasing products from an electronic-commerce enabled product catalog, (2) advertisers desiring to link consumer product information to Web-based product advertisements, or (3) anyone having a legitimate purpose of disseminating such information within the stream of electronic commerce. After downloading and extraction from its encapsulating file, the CPIR-enabling Applet is embedded within an HTML-encoded document associated with, for example, an EC-enabled store, on-line auction site, product advertisement, Internet search engine or directory, and the like. Upon encountering such an Applet-encoded HTML document on the WWW, the consumer need only perform a single mouse-clicking operation to automatically execute the underlying CPIR-enabling Applet (on either the client or server side of the network), causing a UPN-directed search to be performed against the manufacturer-defined UPN / URL Database, and the results thereof displayed in an independent Java GUI, without disturbing the consumer's point of presence on the WWW. Preferably, the CPIR-enabling Applets are realized using Java(TM) technology, although it is understood that alternative technologies can be used to practice the system and methods of the present invention.
Owner:PERKOWSKI THOMAS J
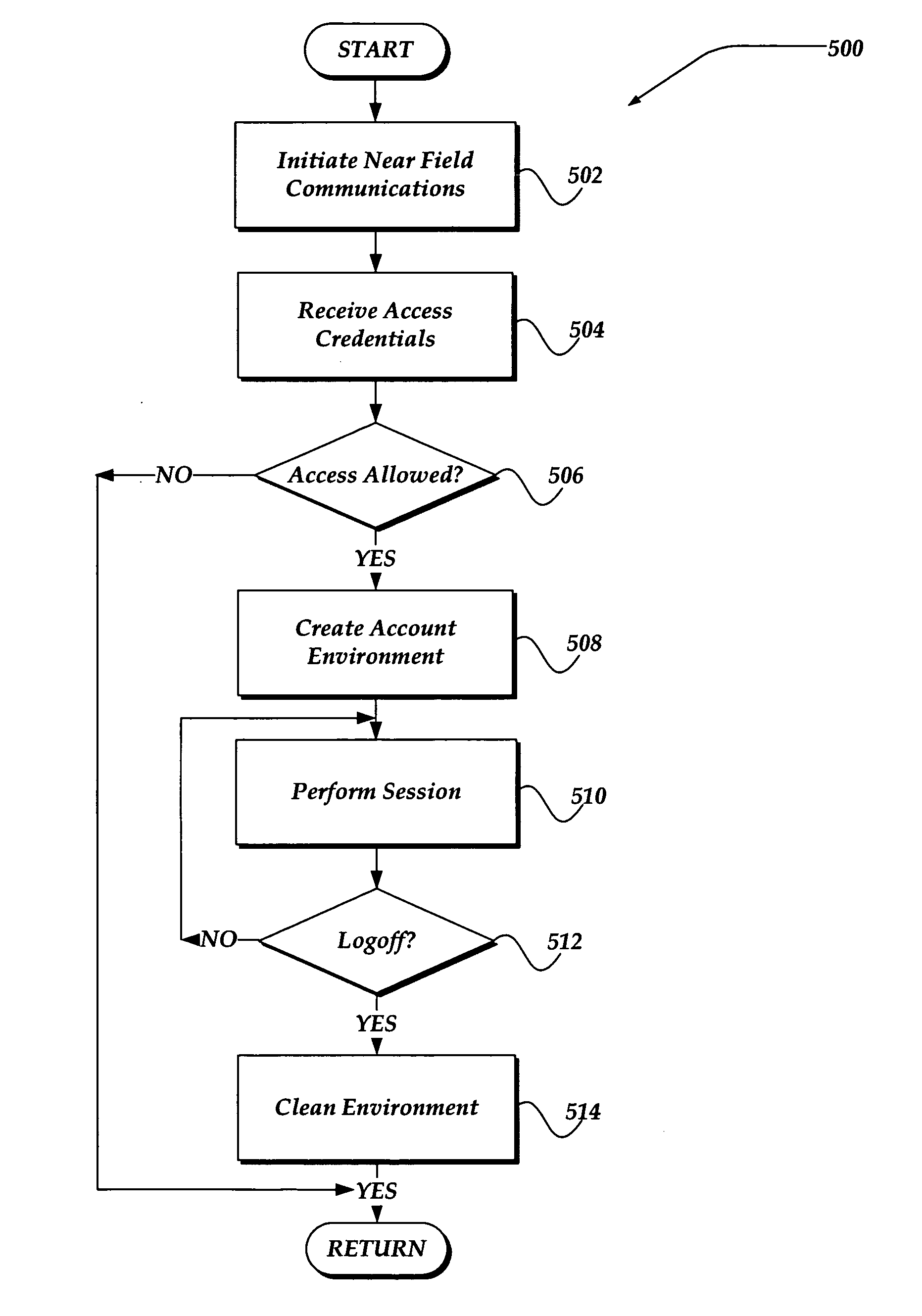
Managing an access account using personal area networks and credentials on a mobile device
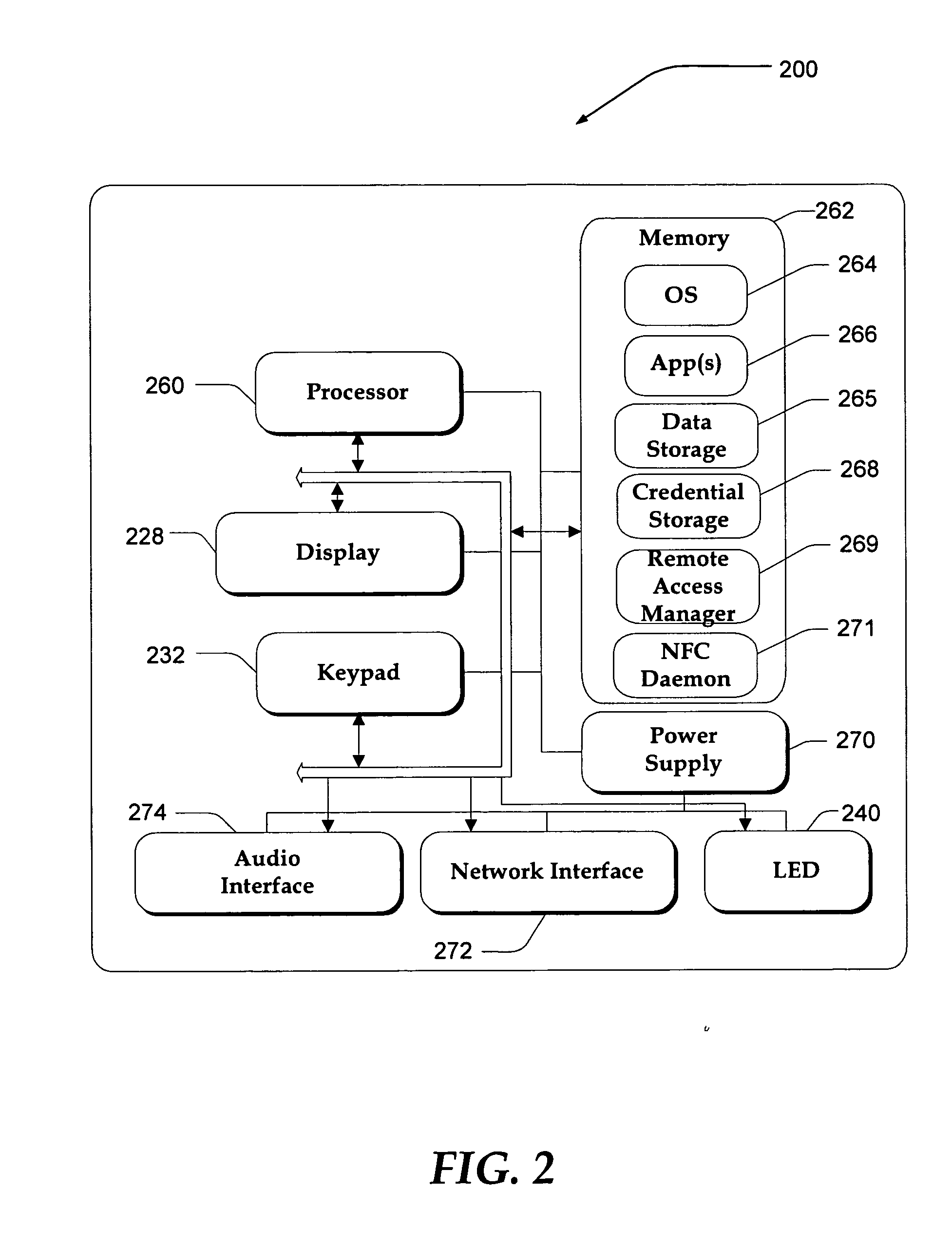
InactiveUS20060183462A1Near-field transmissionUnauthorised/fraudulent call preventionAccess networkRelevant information
A system, apparatus, and method are directed towards automatically managing an access account at an access point using near field communications and credentials stored on a mobile device. The mobile device receives, out-of-band, information for use in creating an account for accessing network resources from the access point. As the mobile device is brought into proximity with the access point, a wireless network connection is established using a near field communication (NFC) protocol. The information, which may include a user credential, account information, and so forth, is communicated to the access point. The access point employs the information to establish an account and create an environment from which access to the network resources may be obtained. Upon termination, the access point removes from itself any user specific data. The access point may provide also session related information useable in billing the user of the mobile device.
Owner:NOKIA CORP
Method and system for facilitating electronic dispute resolution
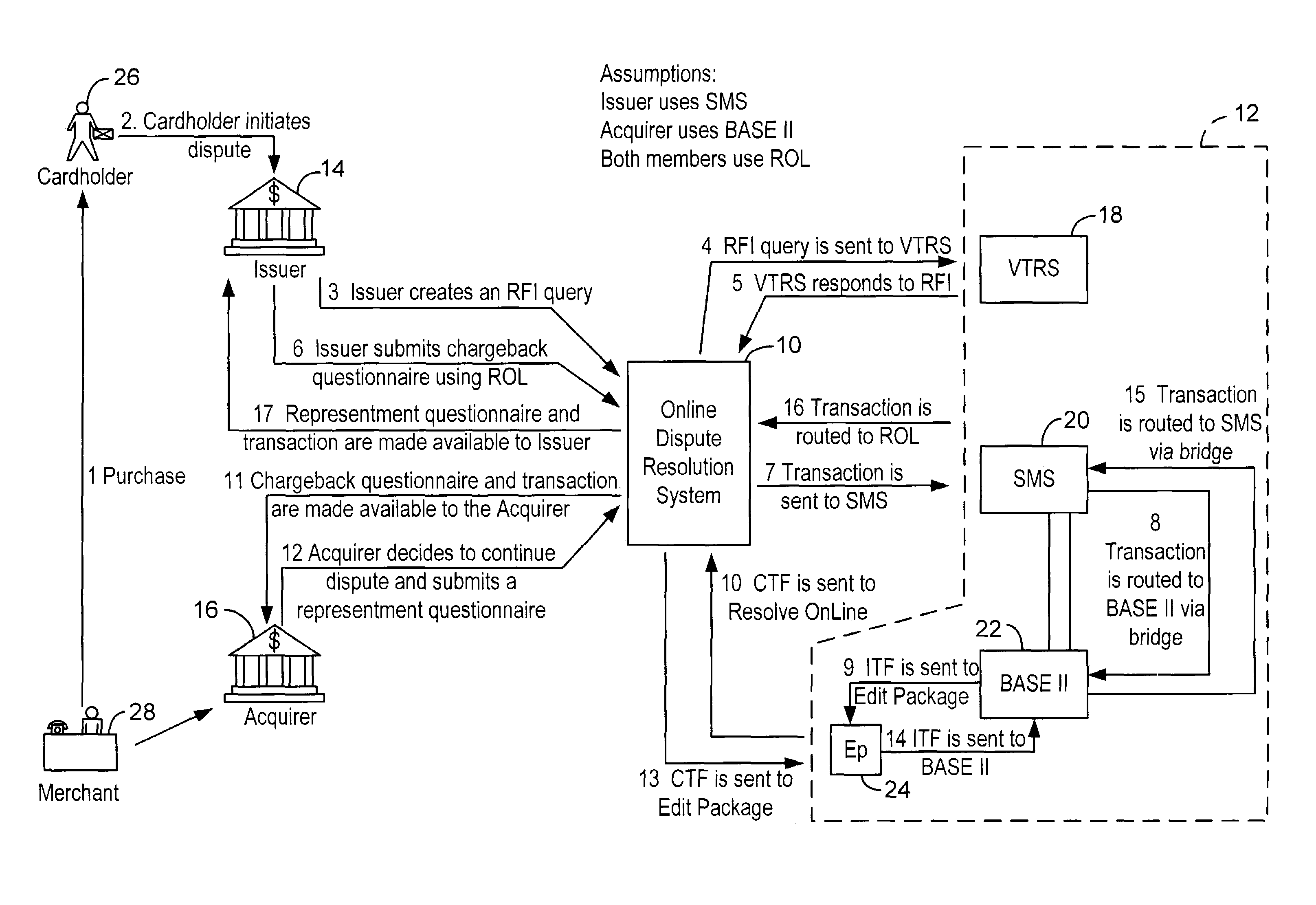
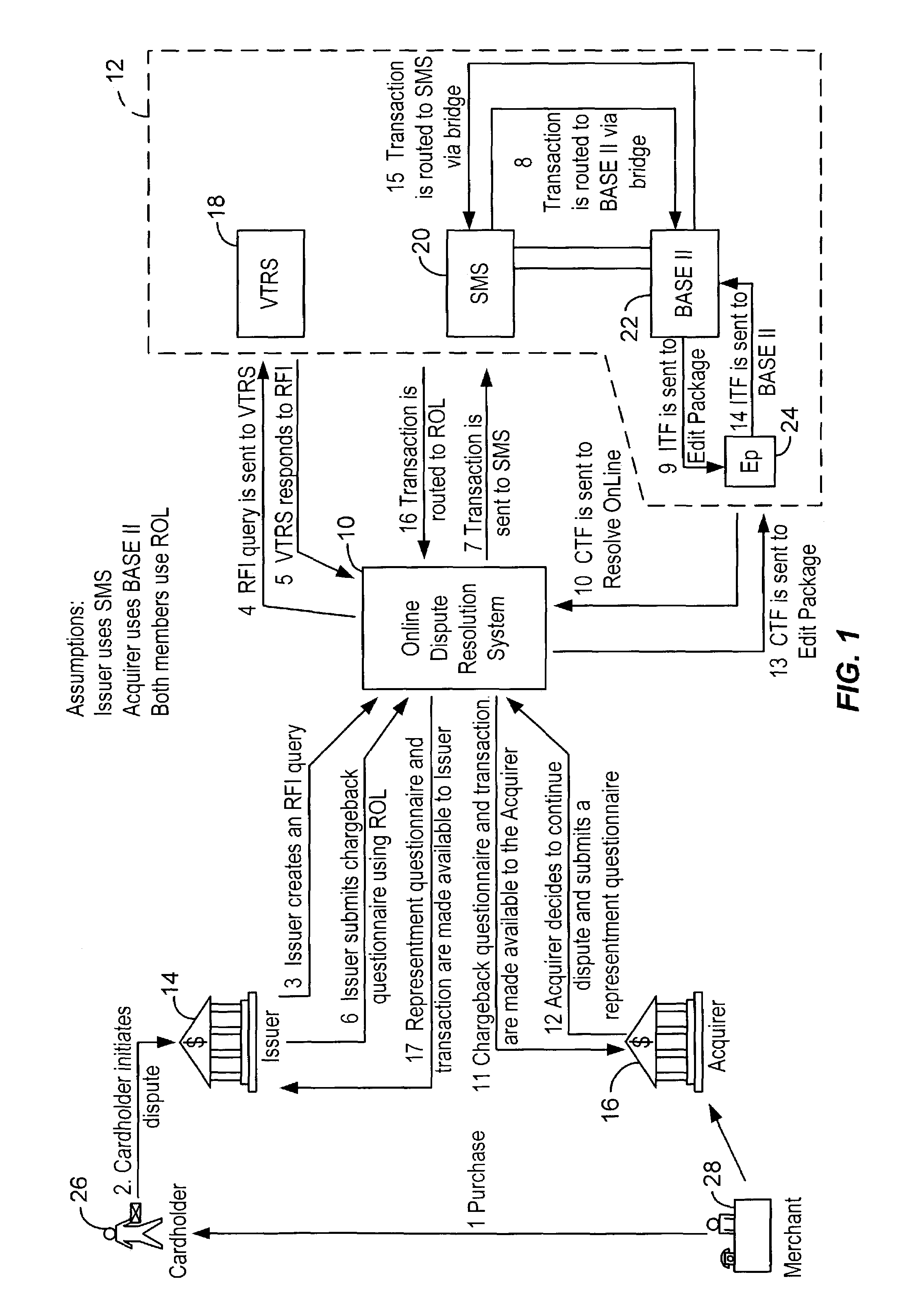
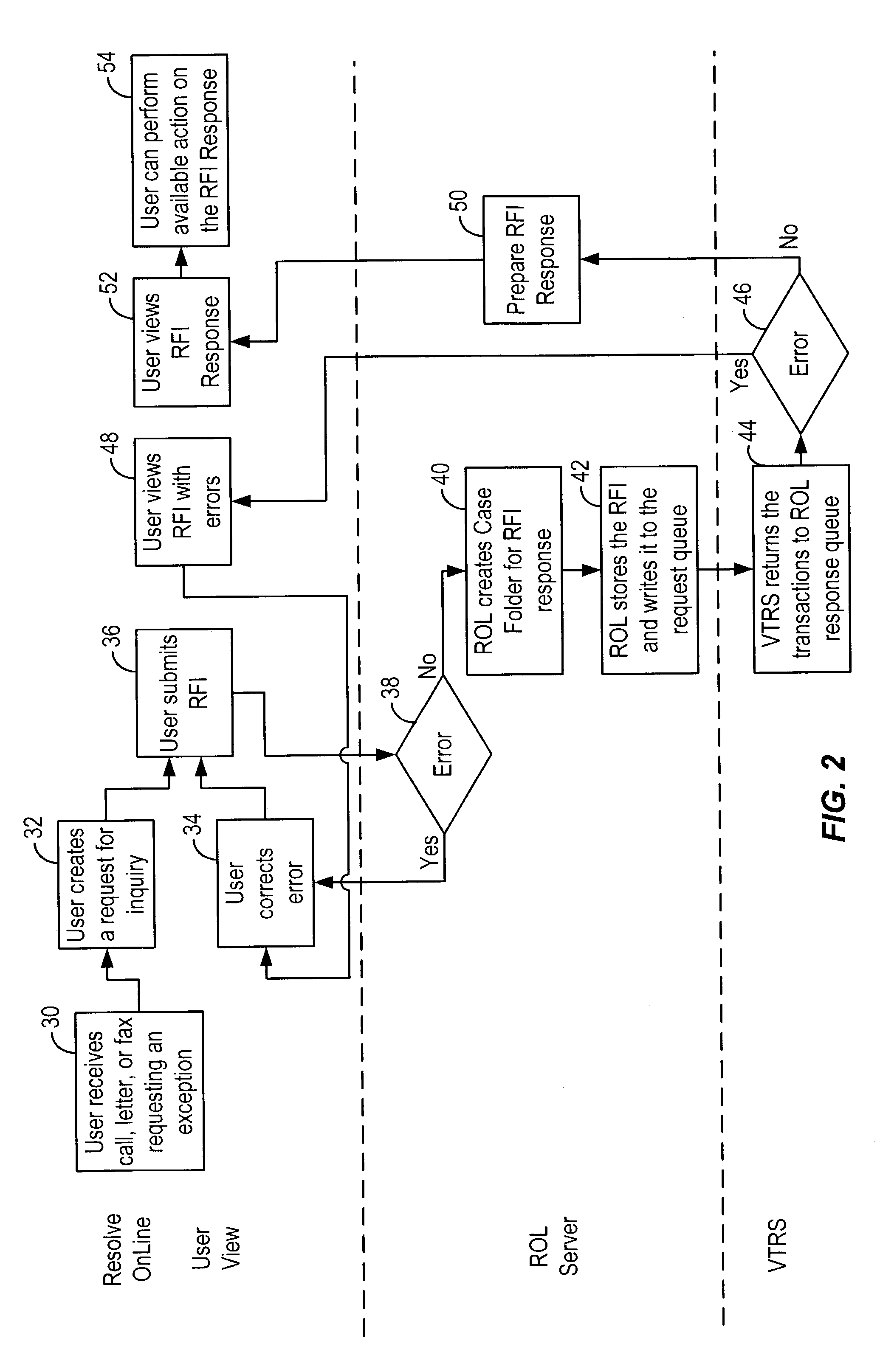
A system for facilitating payment transaction disputes is provided. According to one aspect of the system, a user, such as an issuer, is allowed to use the system to resolve a disputed transaction. Based on information provided by a cardholder, the issuer is able to use the system to retrieve transactional information relating to the disputed transaction reported by the customer for review. When the issuer uses the system to retrieve information relating to the disputed transaction, a case folder is created. The case folder is a repository for storing all the relevant information and documentation relating to the disputed transaction. Using the information retrieved by the system, the issuer then determines whether to initiate a dispute. Alternatively, the system can also be used by an acquirer to respond to a dispute, usually on behalf of one of its merchant. If a dispute is responded to, a questionnaire is then created by the system. Alternatively, the issuer may decline to initiate a dispute and either seek additional information from the cardholder or deny the cardholder's inquiry. The case folder and the questionnaire are created for a specific disputed transaction. The questionnaire is designed to capture information from the cardholder and / or the issuer relating to the disputed transaction. The questionnaire may be pre-populated with previously retrieved transactional information which is stored in the case folder. Relevant documents in support of the disputed transaction may also be attached as part of the questionnaire. Various parties to the dispute may then provide relevant information (including supporting documentation) to the system. The relevant information provided by the parties is maintained in the case folder. The system then keeps track of the relevant timeframes for the case folder to ensure that each party to the dispute is given the correct period of time to respond during the processing of a dispute. Prior to filing the dispute for arbitration or compliance, the system permits the parties to resolve the dispute amongst themselves without the help of an arbiter through pre-arbitration and pre-compliance. If the parties to the dispute are unable to resolve the dispute on their own, the system also permits the parties to resolve the dispute via arbitration or compliance with the help of an arbiter. The system provides the arbiter with access to the case folder to allow the arbiter to render an informed decision on the dispute.
Owner:VISA USA INC (US)
Delivery and presentation of content-relevant information associated with frames of audio-visual programs
InactiveUS20050193425A1Efficient deliveryTelevision system detailsDisc-shaped record carriersThird partyRelevant information
A method for delivery and presentation of content-relevant information associated with frames in an AV program enables TV viewers to retrieve information on the contents (for example, objects, items, concepts and the like) associated with a frame or a set of frames (video segments) when they watch TV or video programs. The information relevant to frame(s) is delivered to a STB or DVR by third-party service providers through back channels such as the Internet if the information of how to accurately access the frames pointed by STB users are delivered to the service providers, and the content-relevant information may be presented in the form of a GUI for the TV viewer.
Owner:SULL SANGHOON +3
System and method for trading complex energy securities
InactiveUS20100218108A1Input/output for user-computer interactionData processing applicationsCommunication interfaceRelevant information
A system for presentation and management of energy-related information and securities, comprising a digital exchange, a client system comprising a plurality of display and input modalities, a communications interface software adapted to allow communications between the client system and the digital exchange, and a control interface within the client system adapted to drive the display and input modalities, wherein the control interface, on receiving input from a user, causes data from the digital exchange to be retrieved and displayed in one or more of the display modalities to the user, and upon receipt of a request from the user via an input modality of the client system after the user has retrieved and reviewed data from the digital exchange, an order to execute a transaction is transmitted to the digital exchange by the client system, and on receipt of an order to execute a transaction from a client system, the digital exchange combines the ordered transaction with other similar transactions from a plurality of users and thereby creates or modifies a marketable security visible to at least one other user via the digital exchange, is disclosed.
Owner:CRABTREE JASON +4
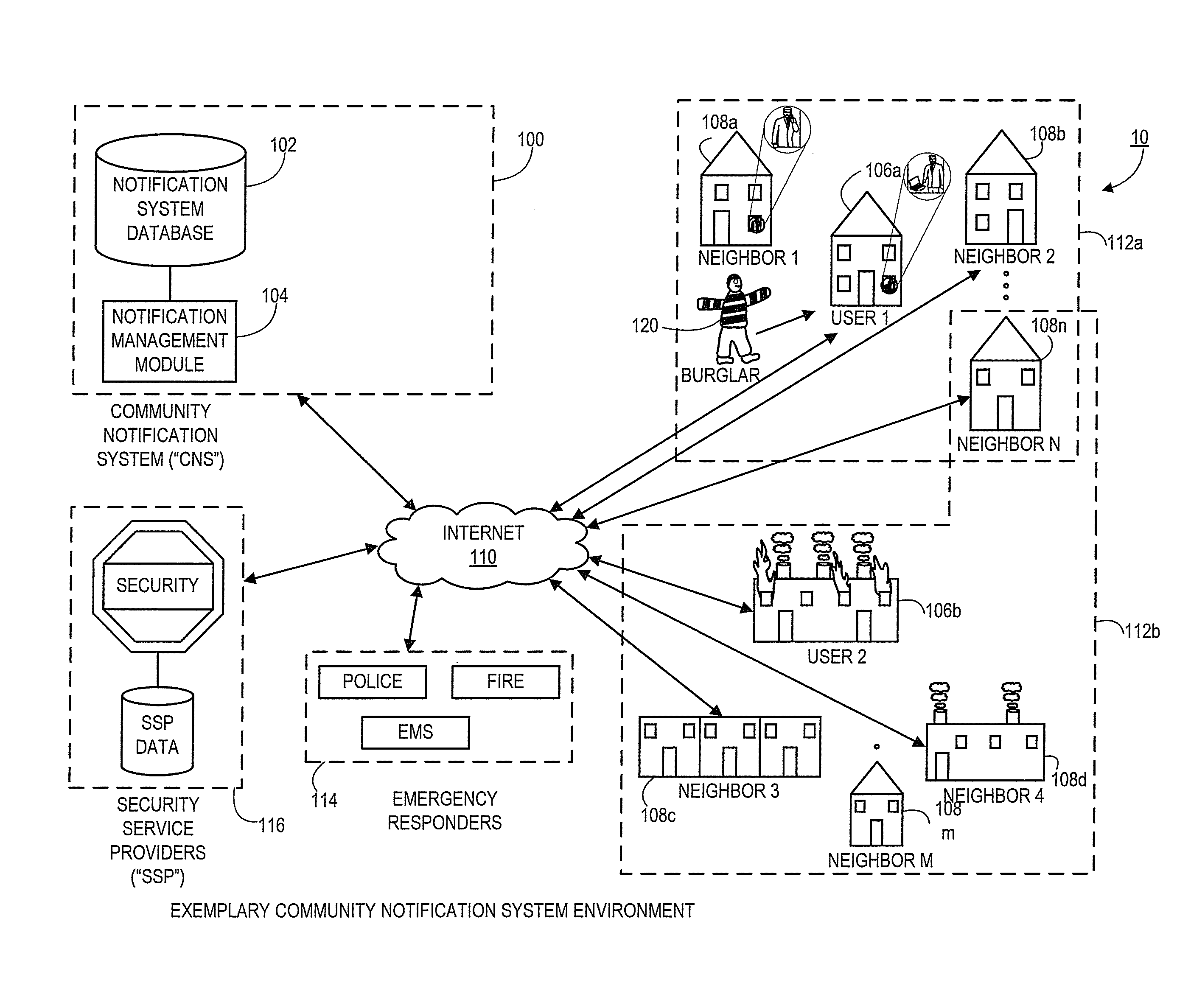
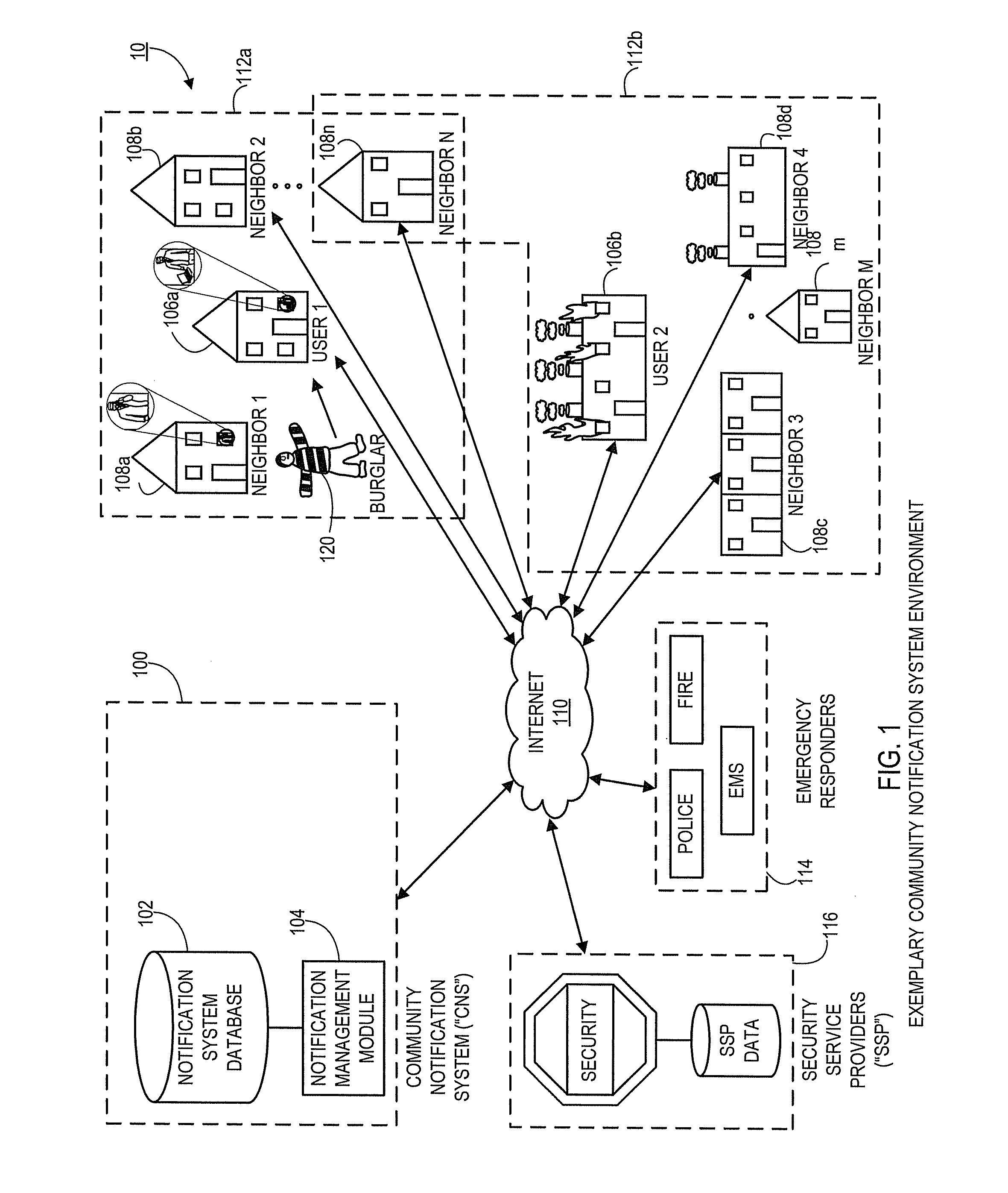
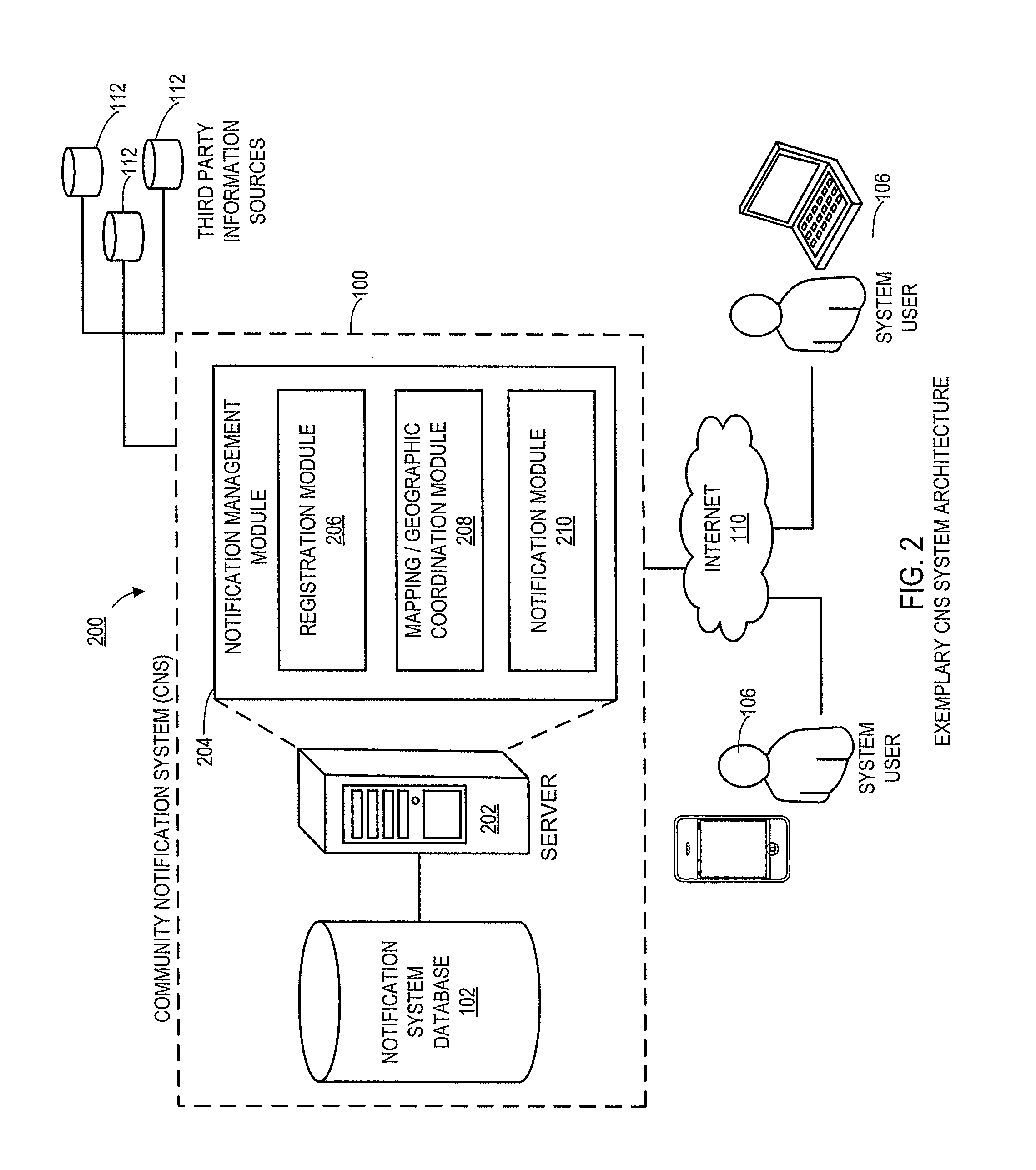
Systems and methods for notifying proximal community members of an emergency or event
Aspects of the present disclosure generally relate to systems and methods for an automated community notification system (“CNS”) that is configured to notify certain individuals with relevant information relating to occurrence of an event or emergency at a given geographical location. Generally, aspects of the system include operative connections to one or more security system providers (“SSPs”) to identify events / emergencies at properties. In alternate embodiments, system users provide event information to the CNS via users' electronic devices. According to one aspect, system users register with the CNS and provide user information, preferences, geographic information, etc., and the CNS subsequently utilizes that information (in connection with other third party information sources) to establish “neighborhood networks” for system users. Typically, members of in the same neighborhood network are notified and provided with relevant information when an emergency occurs at the property or geographic location of another user in the members' network.
Owner:CLIMOTE
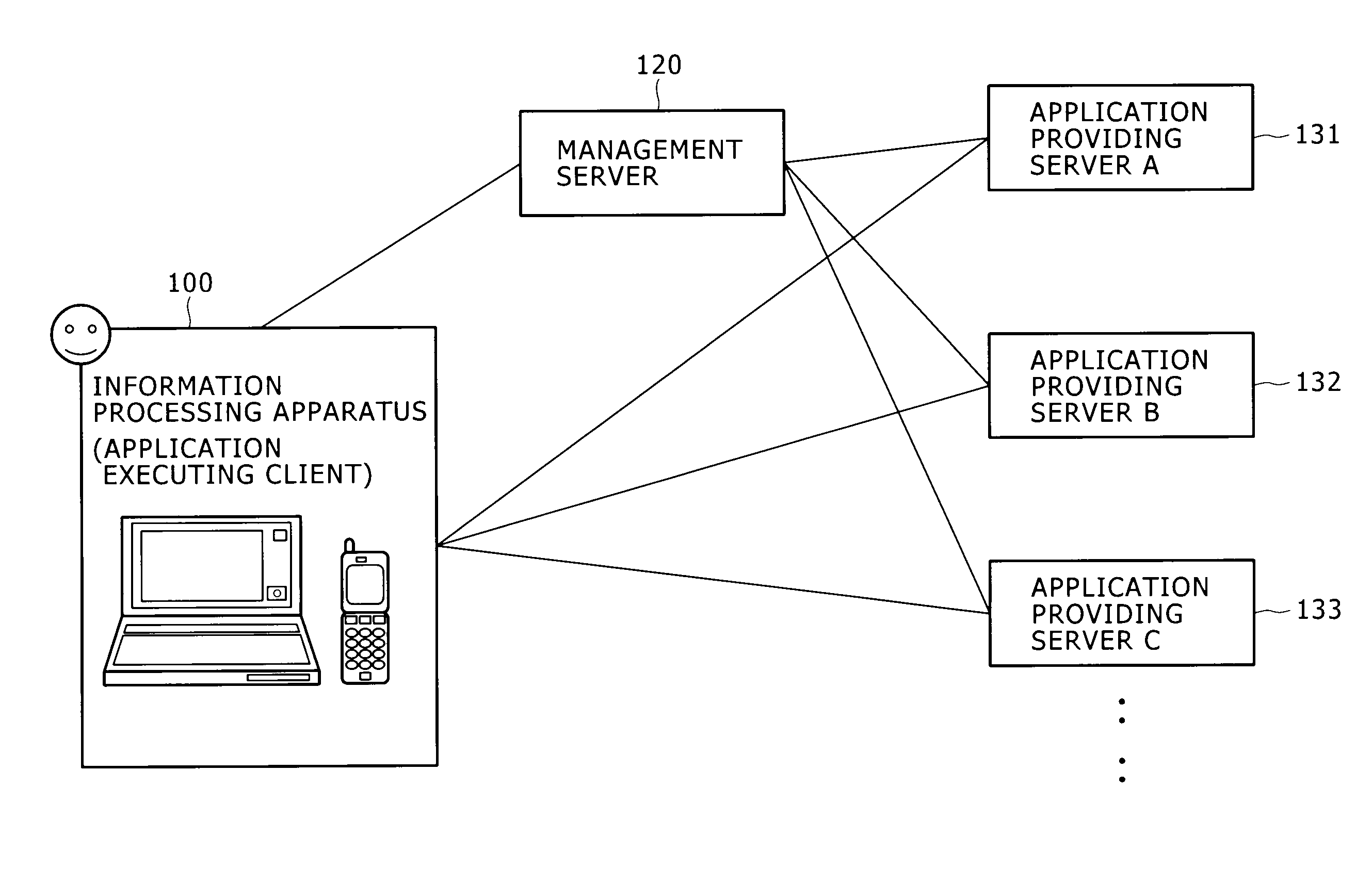
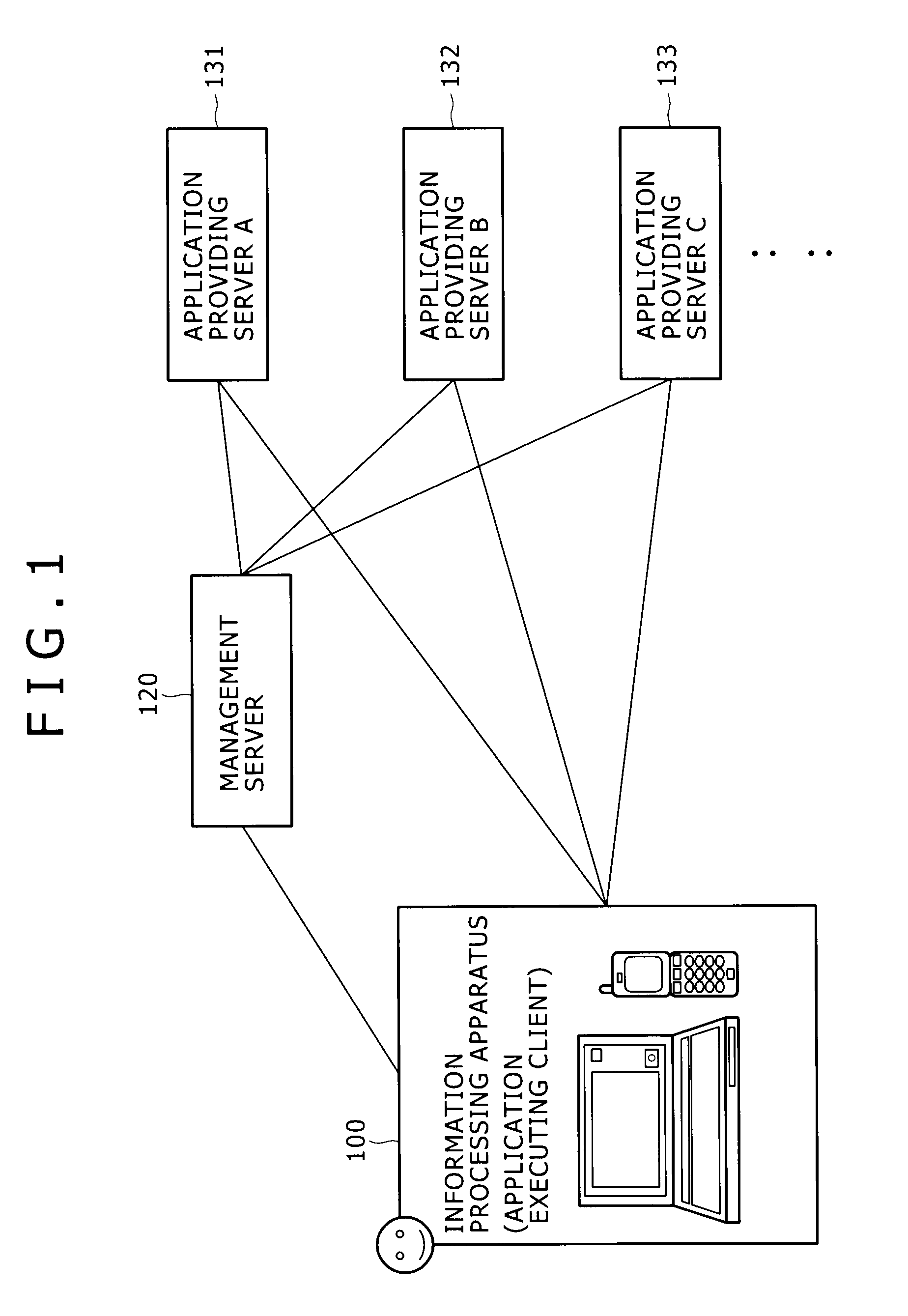
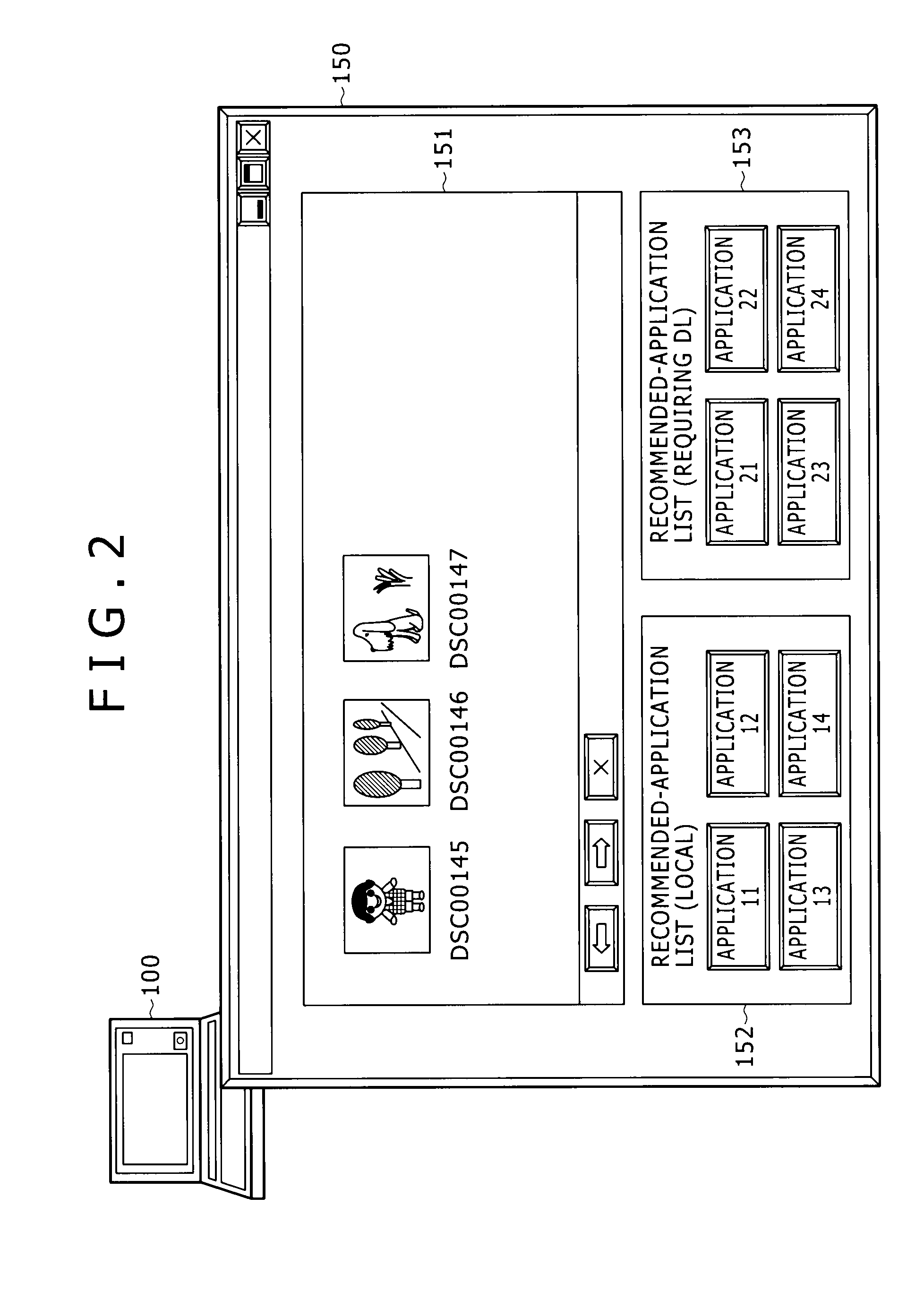
Information processing apparatus and information processing method
ActiveUS20100146442A1Easy to getMultiple digital computer combinationsOffice automationInformation processingRelevant information
Disclosed herein is an information processing apparatus including: a communication section configured to acquire application programs from external apparatus; a memory used for storing at least an application program and information relevant to the application program; an application execution section configured to execute the application program stored in the memory; and a control section configured to determine other application programs to be recommended in the course of execution of the application program in the application execution section, wherein information stored in the memory as the information relevant to the application program includes first relevant information and second relevant information which are used for determining the other application programs to be recommended in the course of execution of the application program in the application execution section
Owner:SONY CORP
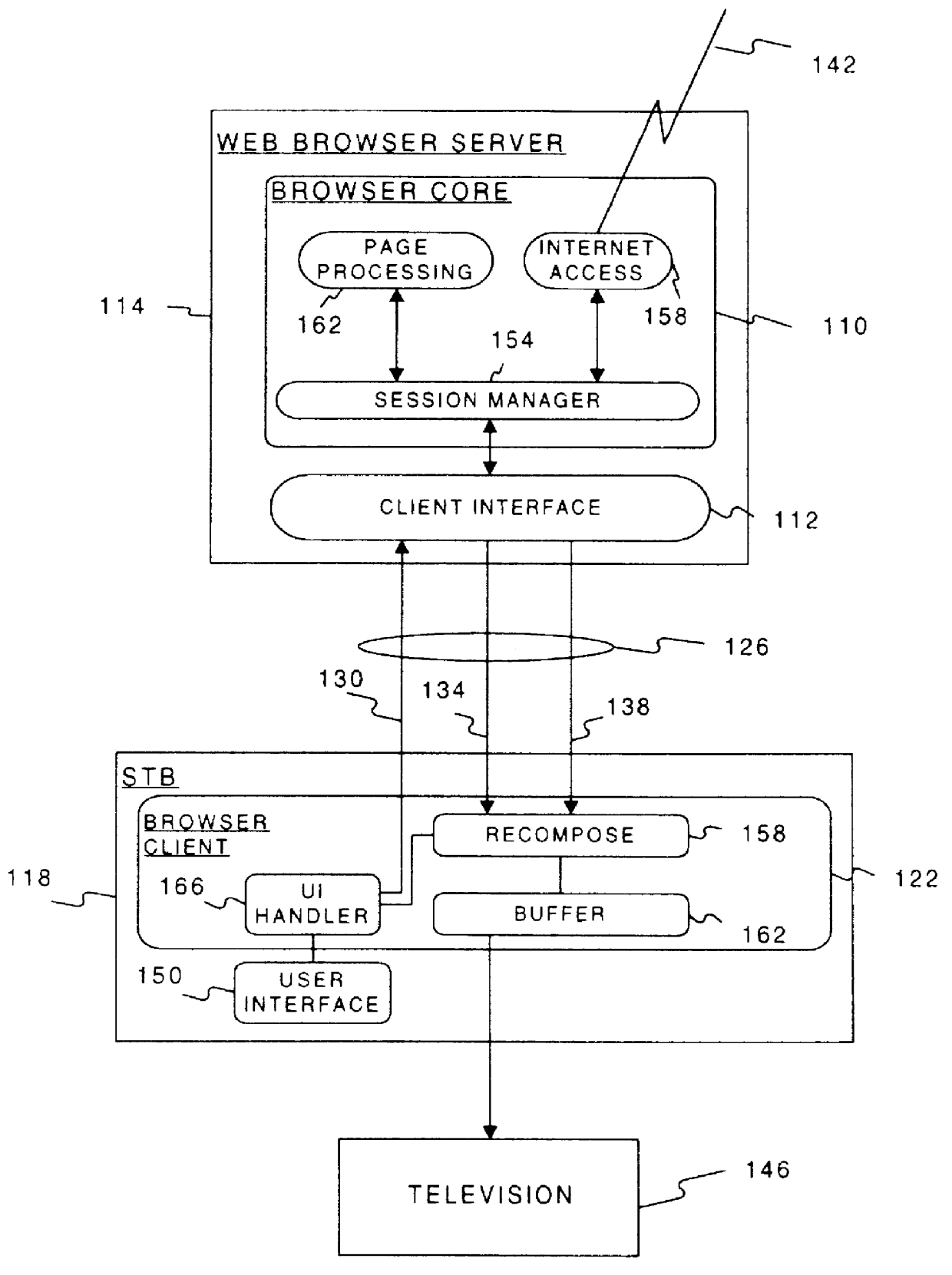
System for transmitting network-related information where requested network information is separately transmitted as definitions and display information
InactiveUS6049831ADigital data information retrievalDigital data processing detailsRelevant informationUser device
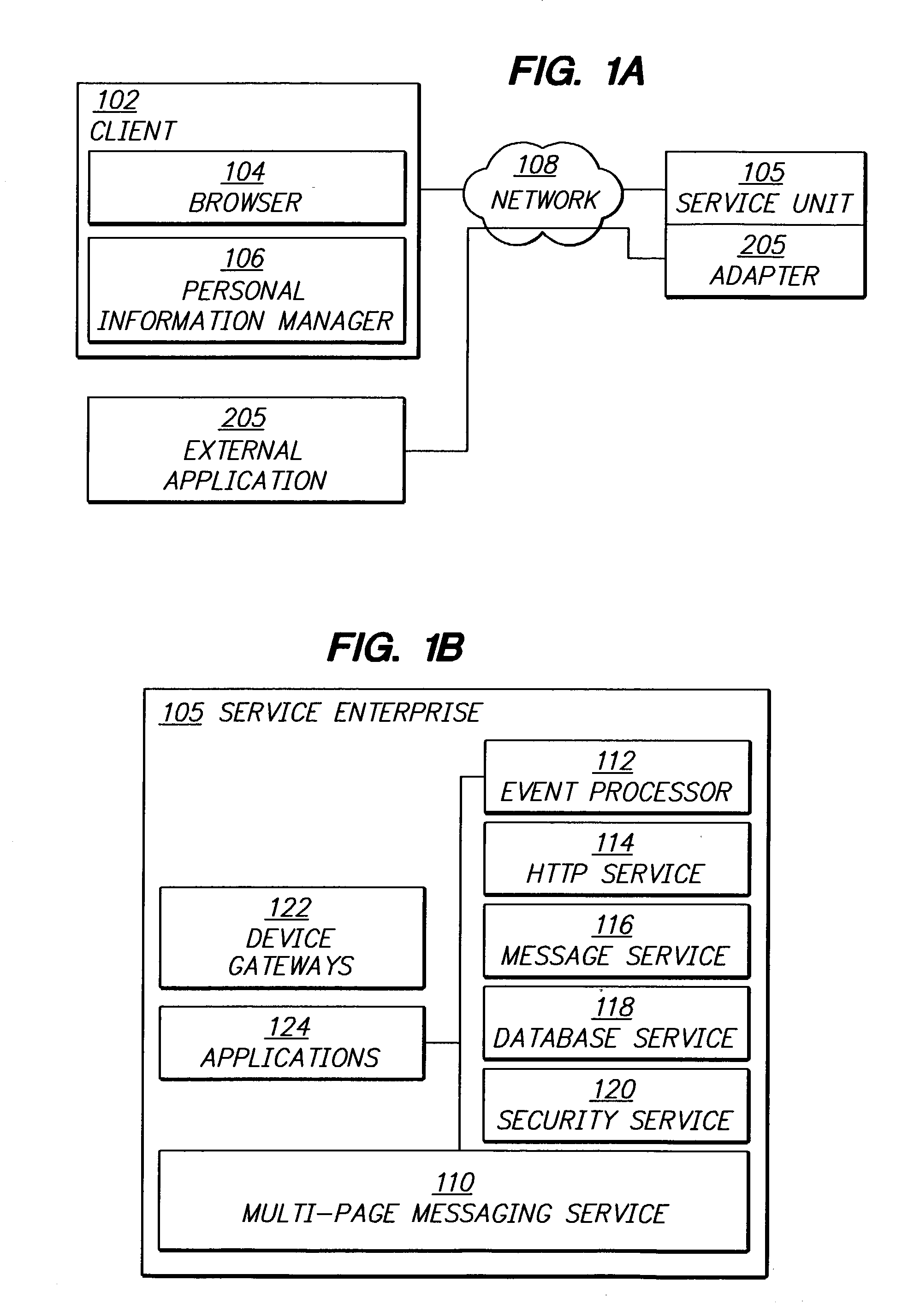
Web pages retrieved by a browser core are translated into user interface component definitions and page information. The definitions and page information are transmitted to a user device which recomposes the definitions and page information into a format for presentation to a user on a user device. Transmitting the definitions and page information includes translation of the definitions and page information into a format appropriate for both the particular communications media on which the information is transmitted, and the device to which the information is transmitted. The device includes a browser client which performs the recomposition. The browser client also receives user input, and may respond by altering the information locally at the user device, and sending information related to the user selection back to the browser core for further processing. The browser core also tracks user sessions, thus allowing a user to access the network from several devices, and capture session information for each access from each device. This allows users to switch devices, and start a new session at the point where a previous session ended.
Owner:LEVEL 3 COMM LLC
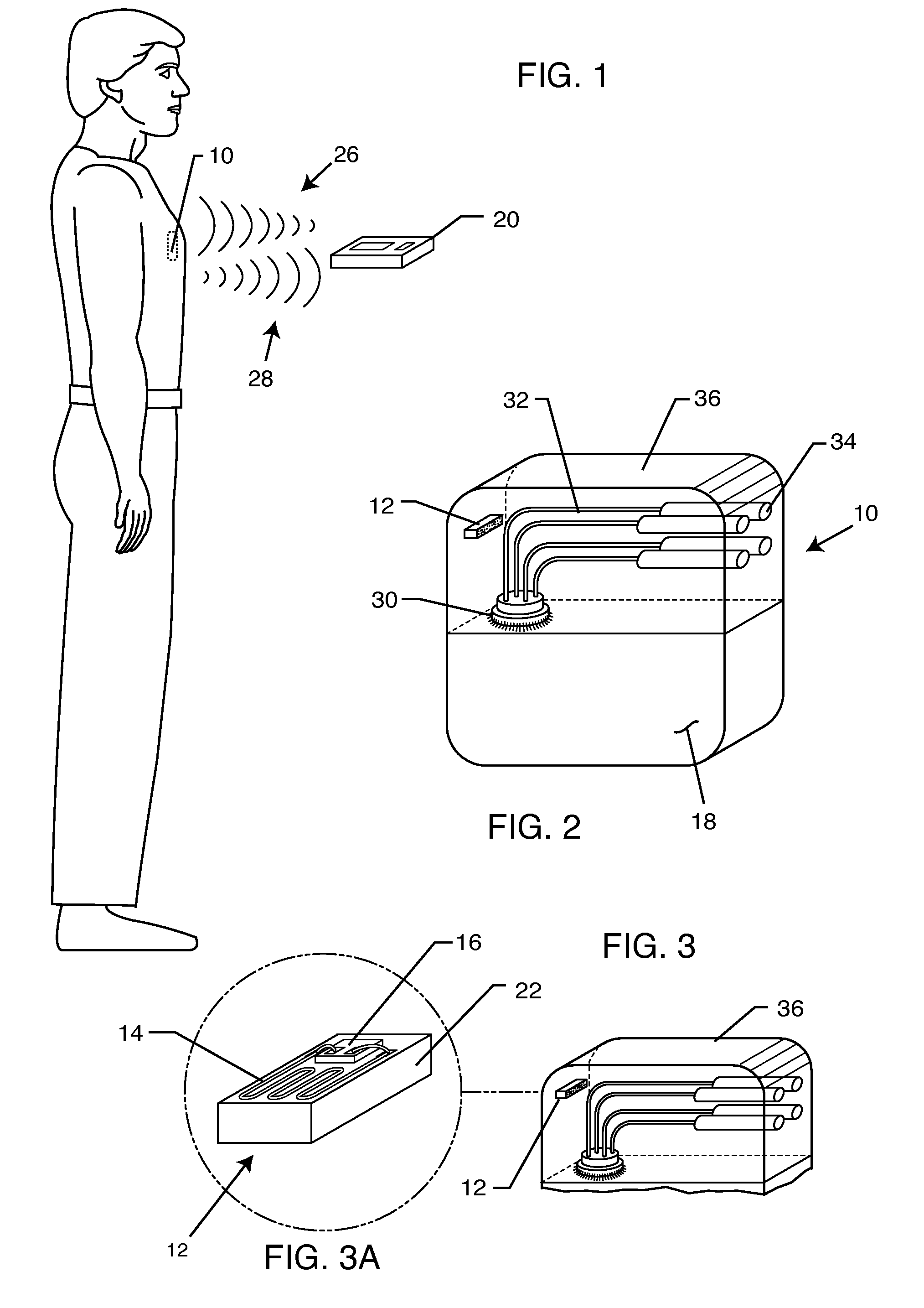
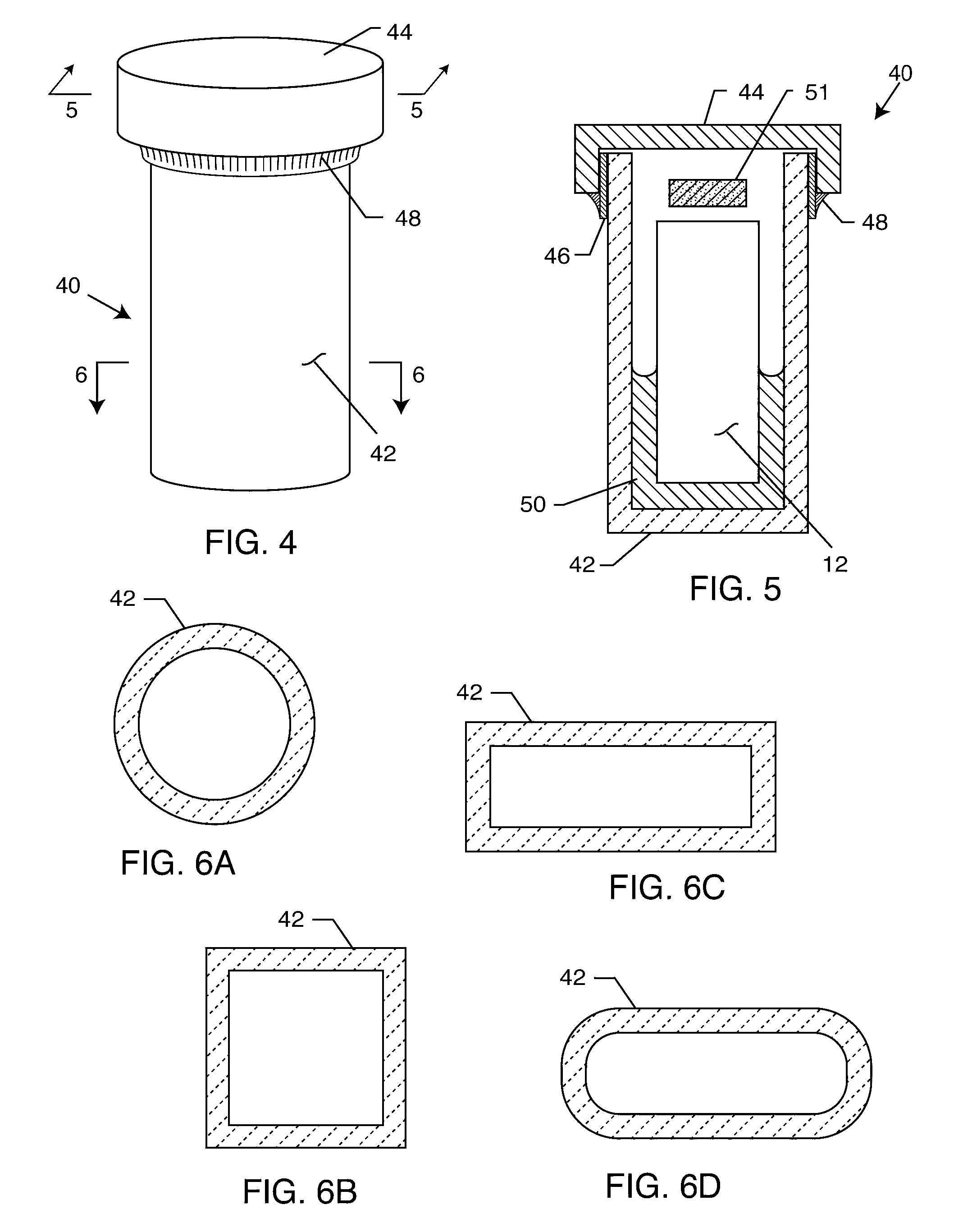
RFID detection and identification system for implantable medical devices
A radio frequency identification (RFID) system for use with active implantable medical devices (AIMD) implanted in a patient comprises an interrogator and an RFID tag comprising a substrate, an RFID chip, and an antenna. The RFID is typically enclosed in a biocompatible and hermetically sealed container comprising a ceramic housing, an end cap and an encapsulant. The RFID tag or sealed container may be affixed to an AIMD or surgically implanted in a patient adjacent to an AIMD. Alternatively, the sealed container may be injected into body tissue by a large needle syringe. The RFID tag may store information about an AIMD including manufacturer, model number and serial number. The RFID tag may also store information about a treating physician and / or patient including the treating physician's name and contact information, the patient's name, contact information, medical condition, treatment and other relevant information.
Owner:WILSON GREATBATCH LTD
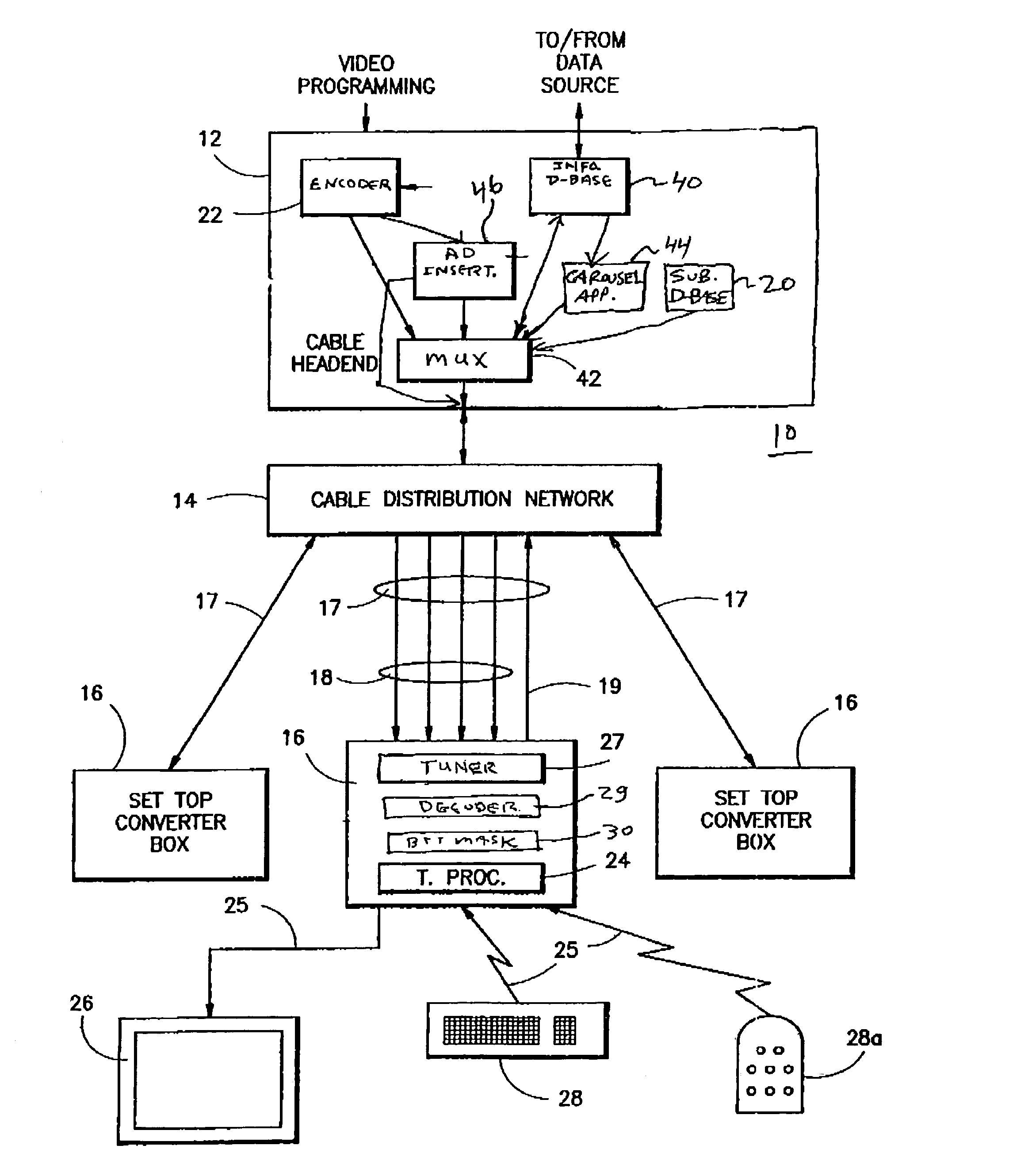
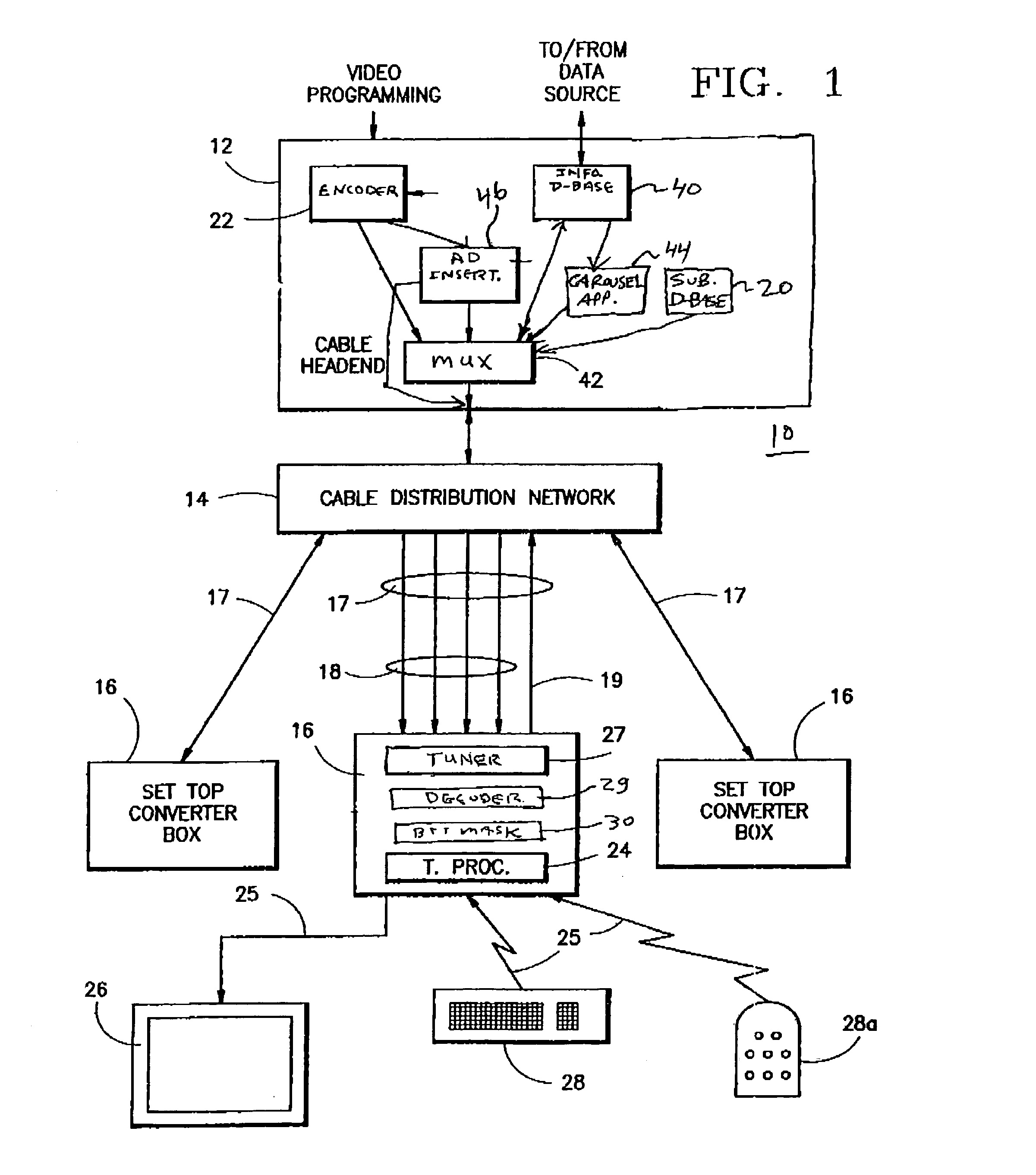
System and method for transmitting and displaying targeted infromation
InactiveUS7100183B2Improve advertising effectivenessAnalogue secracy/subscription systemsTwo-way working systemsRelevant informationDemographic data
A system and method for transmitting and displaying information in a television distribution system (10), or the like, transmits information that is targeted to a viewer matching particular demographic data. The results of a viewer completed demographic survey are used to generate a database known as a bit mask (30) that is made up of the viewer's demographic data. The bit mask (30) is used to control the particular advertising or other related information that is received by each system viewer. In a first technique, the transmission signal carrying the program or advertisement displayed to all viewers is embedded with one or more codes. These codes are compared to the bit mask to determine whether the viewer fits the desired demographic profile, and should be provided with additional information. In a second technique, multiple ads for demographic selective receipt by each viewer are simultaneously transmitted, and are automatically selected for viewing, depending on the viewer's stored demographic data.
Owner:COX COMMUNICATIONS
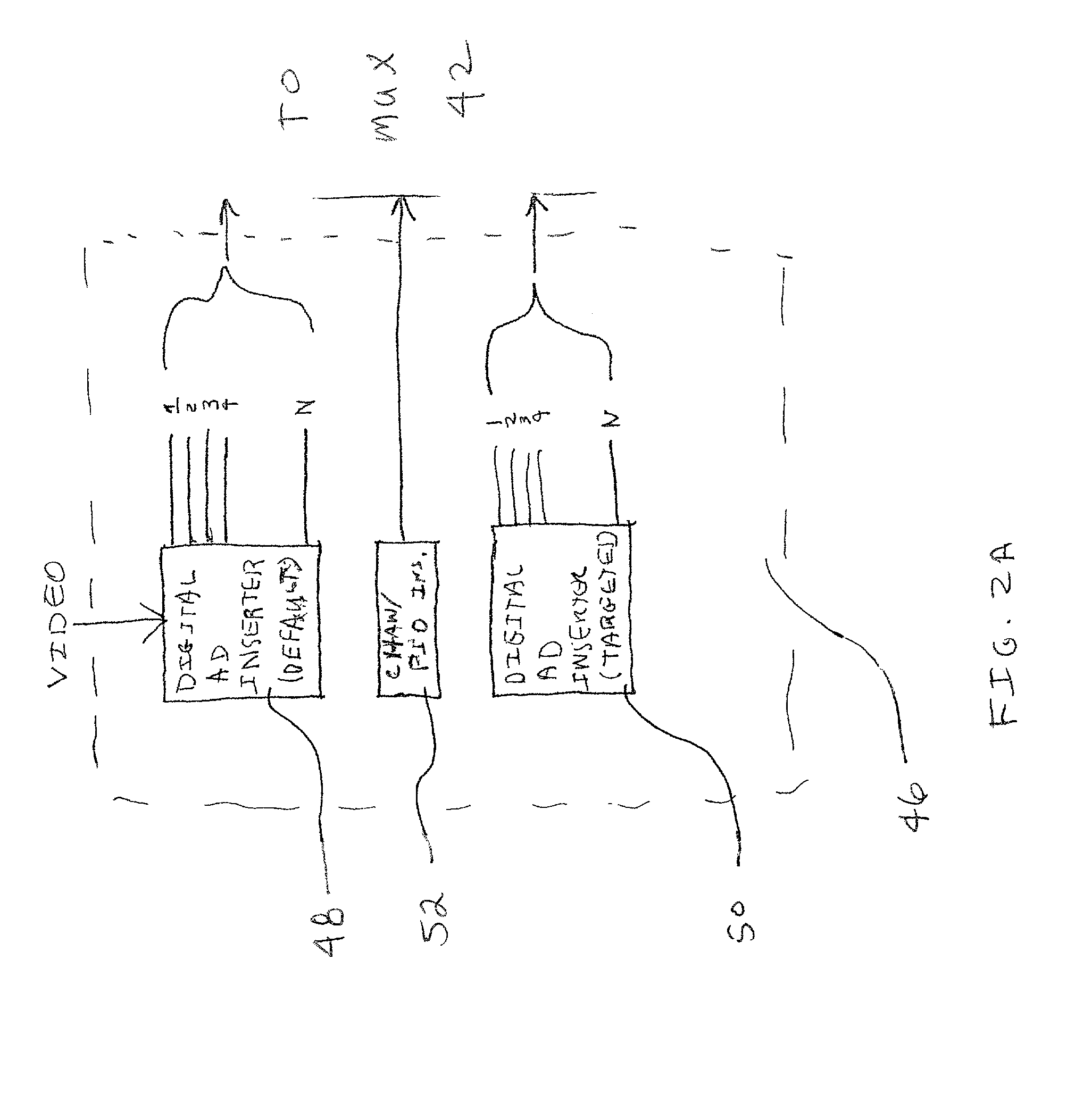
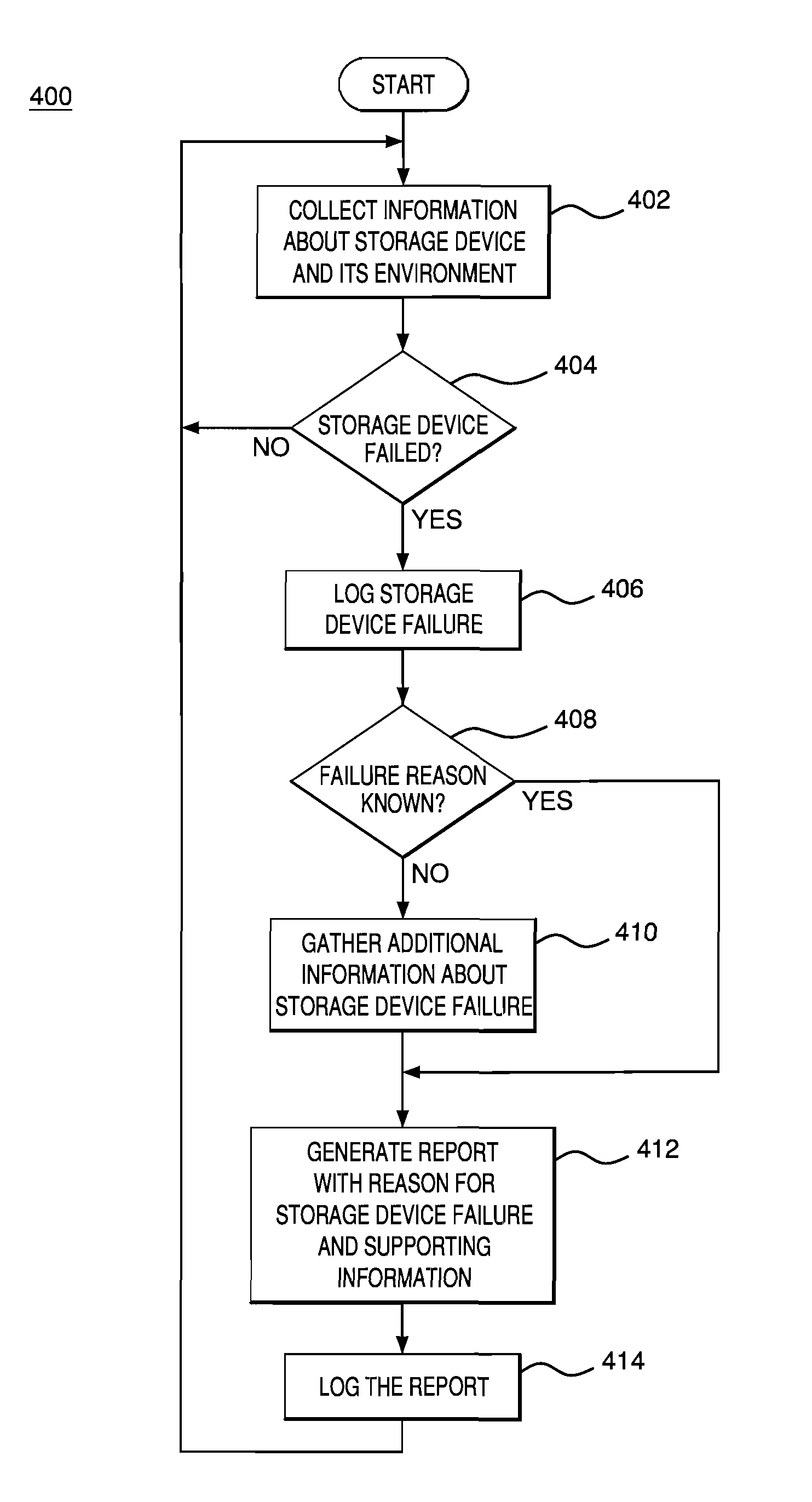
Creating environmental snapshots of storage device failure events
InactiveUS8949863B1Interprogram communicationNon-redundant fault processingRelevant informationDevice failure
A storage device failure in a computer storage system can be analyzed by the storage system by examining relevant information about the storage device and its environment. Information about the storage device is collected in real-time and stored; this is an on-going process such that some information is continuously available. The information can include information relating to the storage device, such as input / output related information, and information relating to a storage shelf where the storage device is located, such as a status of adjacent storage devices on the shelf. All of the relevant information is analyzed to determine a reason for the storage device failure. Optionally, additional information may be collected and analyzed by the storage system to help determine the reason for the storage device failure. The analysis and supporting information can be stored in a log and / or presented to a storage system administrator to view.
Owner:NETWORK APPLIANCE INC
Secure content delivery system
InactiveUS20030097564A1Metering/charging/biilling arrangementsUser identity/authority verificationExpiration TimeRelevant information
A secure streaming content delivery system provides a plurality of content servers connected to a network that host customer content that can be cached and / or stored, e.g., images, video, text, and / or software. The content servers respond to requests for customer content from users. The invention load balances user requests for cached customer content to the appropriate content server. A user makes a request to a customer's server / authorization server for delivery of the customer's content. The authorization server checks if the user is authorized to view the requested content. If the user is authorized, then the authorization server generates a hash value using the authorization server's secret key, the current time, a time-to-live value, and any other information that the customer has configured, and embeds it into the URL which is passed to the user. A content server receives a URL request from the user for customer content cached on the content server. The request is verified by the content server creating its own hash value using the customer server's secret key, the current time, a time-to-live value, and any other related information configured for the customer. If the hash value from the URL matches the content server's generated hash value, then the user's request is valid and within the expiration time period and the content server delivers the requested content to the user.
Owner:AKAMAI TECH INC
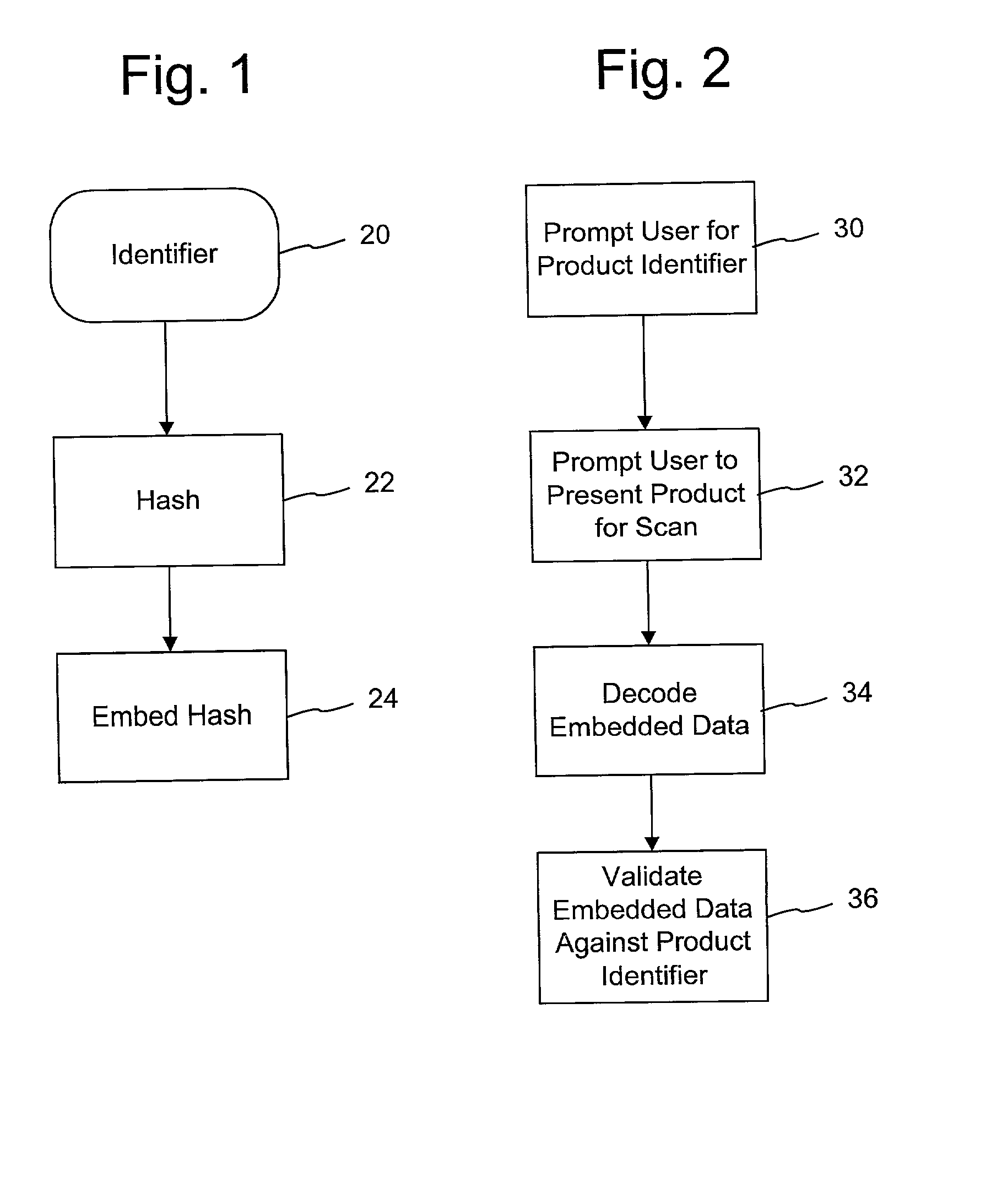
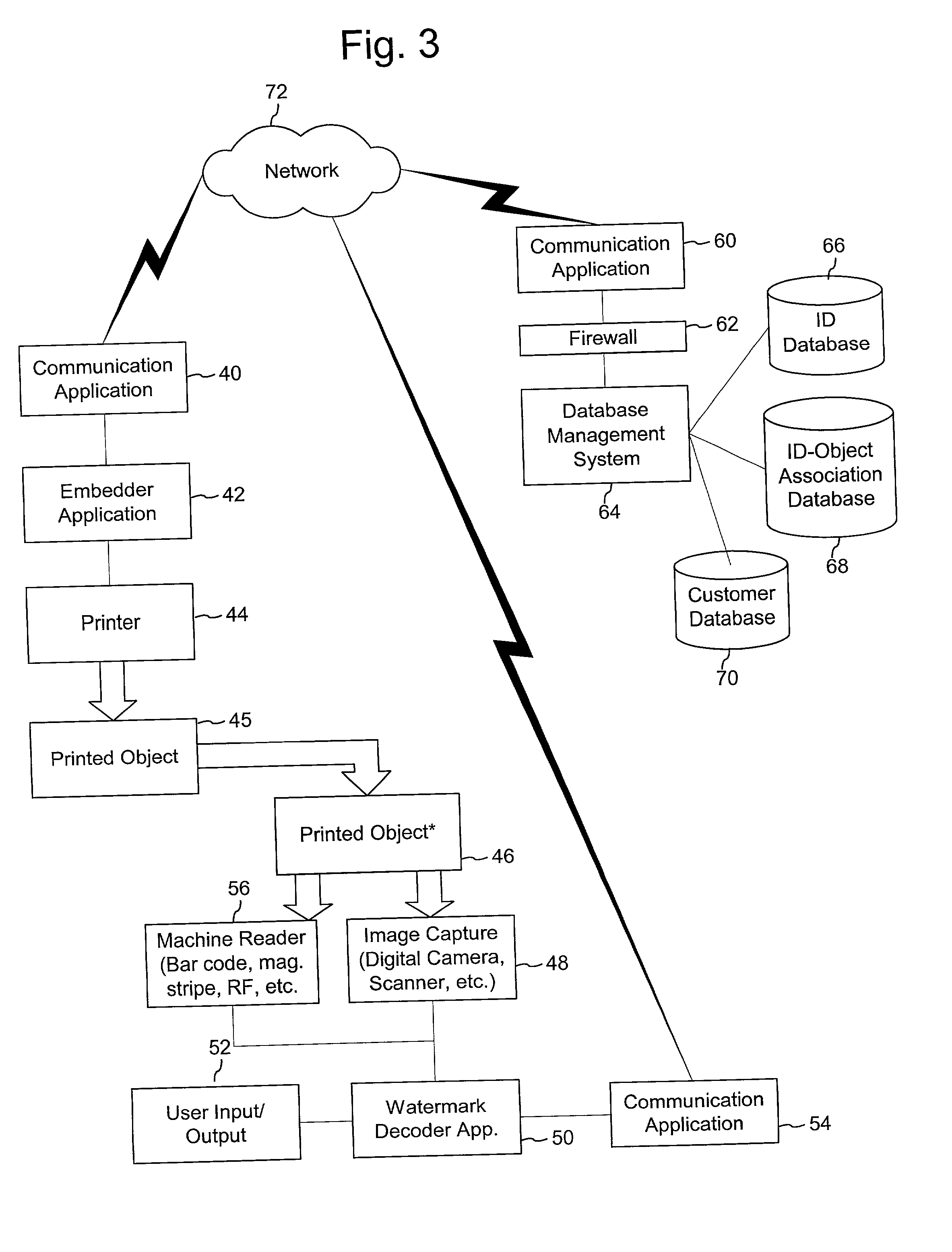
Authentication watermarks for printed objects and related applications
InactiveUS20020012445A1Correct Geometric DistortionMore dataOther printing matterPaper-money testing devicesRelevant informationCopy detection
The disclosure describes systems for creating and authenticating printed objects using authentication and copy detection watermarks. For example, one verification system includes a watermark decoder and a verification module. The watermark decoder detects a copy detection watermark in a printed object to determine whether the printed object has been reproduced. The verification module processes a message decoded from an authentication watermark on the printed object to authenticate the printed object or bearer of the printed object. The authentication and copy detection watermarks may be implemented as the same or different watermarks. For example, the copy detection watermark may be a fragile watermark that carries the message and that degrades in response to a reproduction operation, such as photocopying or scanning and then reprinting the object. Alternatively, the authentication and copy detection watermarks may be separate watermarks embedded in an image that is printed on the object. The authentication watermark, in some applications, includes an identifier that links the object to a database entry with related information about the object. This related information can be used to check the bearer of the object by comparing it with attributes of the bearer (such as a user ID or photo) or the validity of the object by comparing it with attributes that are visible or machine readable on the object.
Owner:INTUIT INC
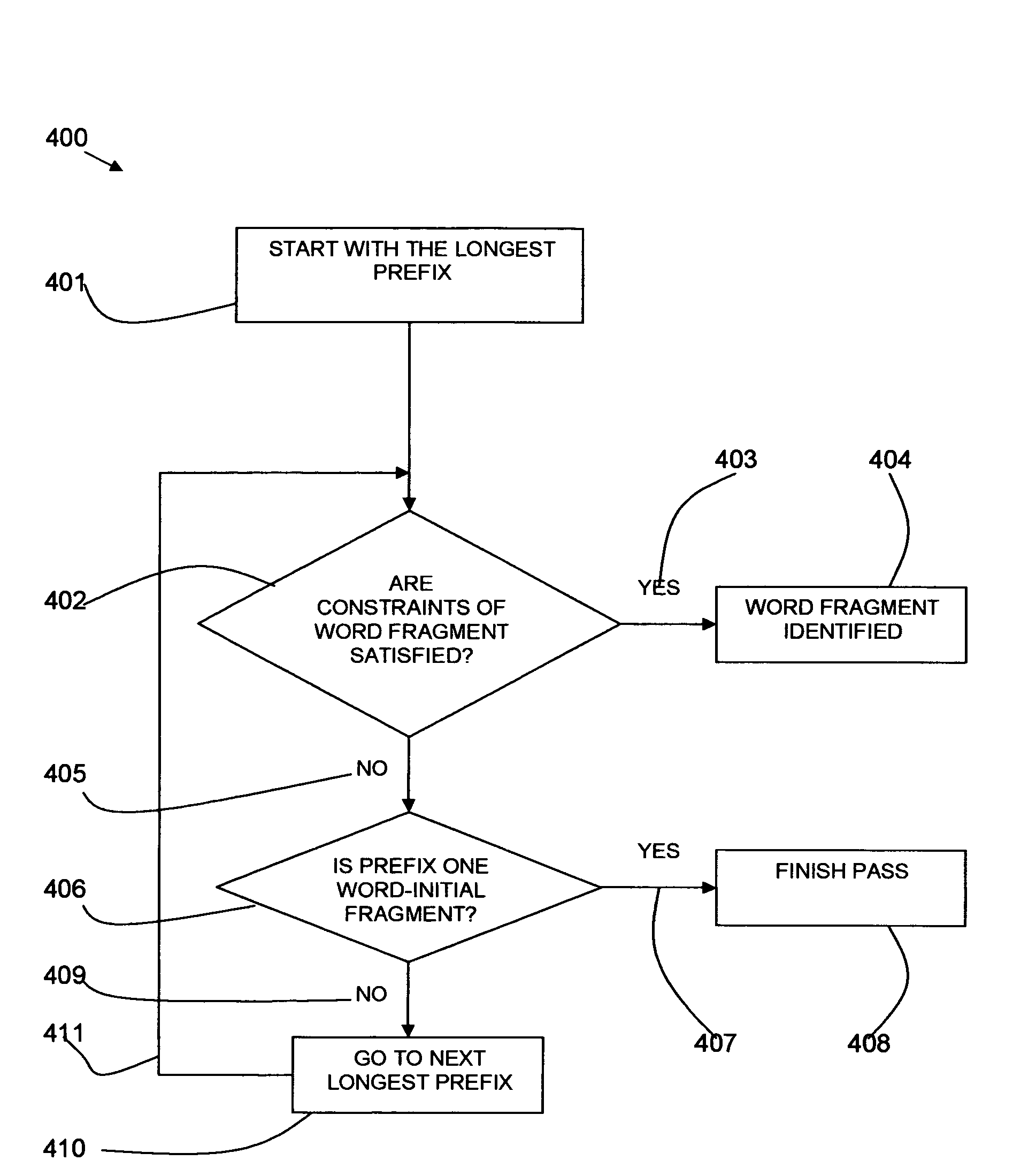
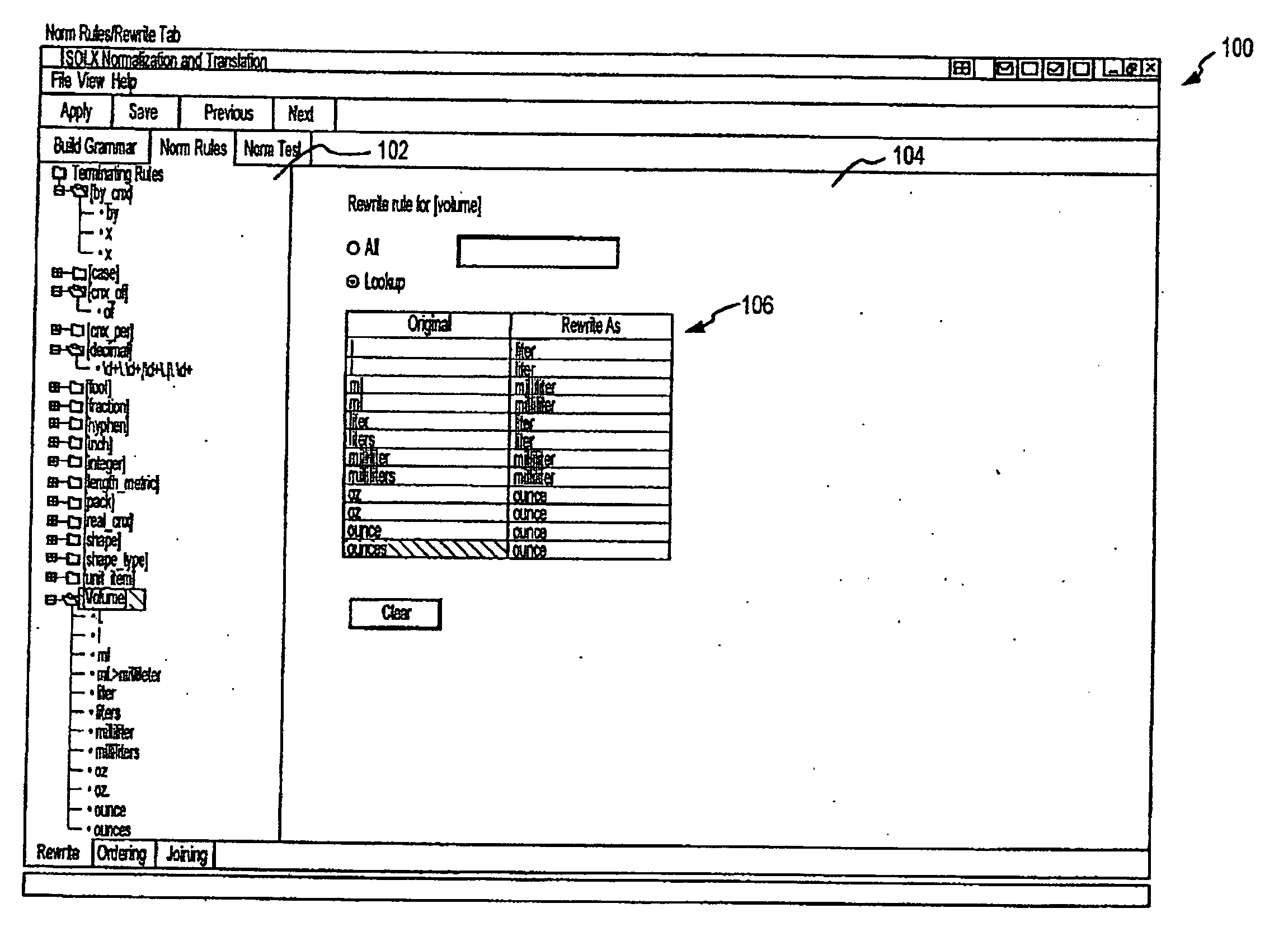
Method and system for language identification
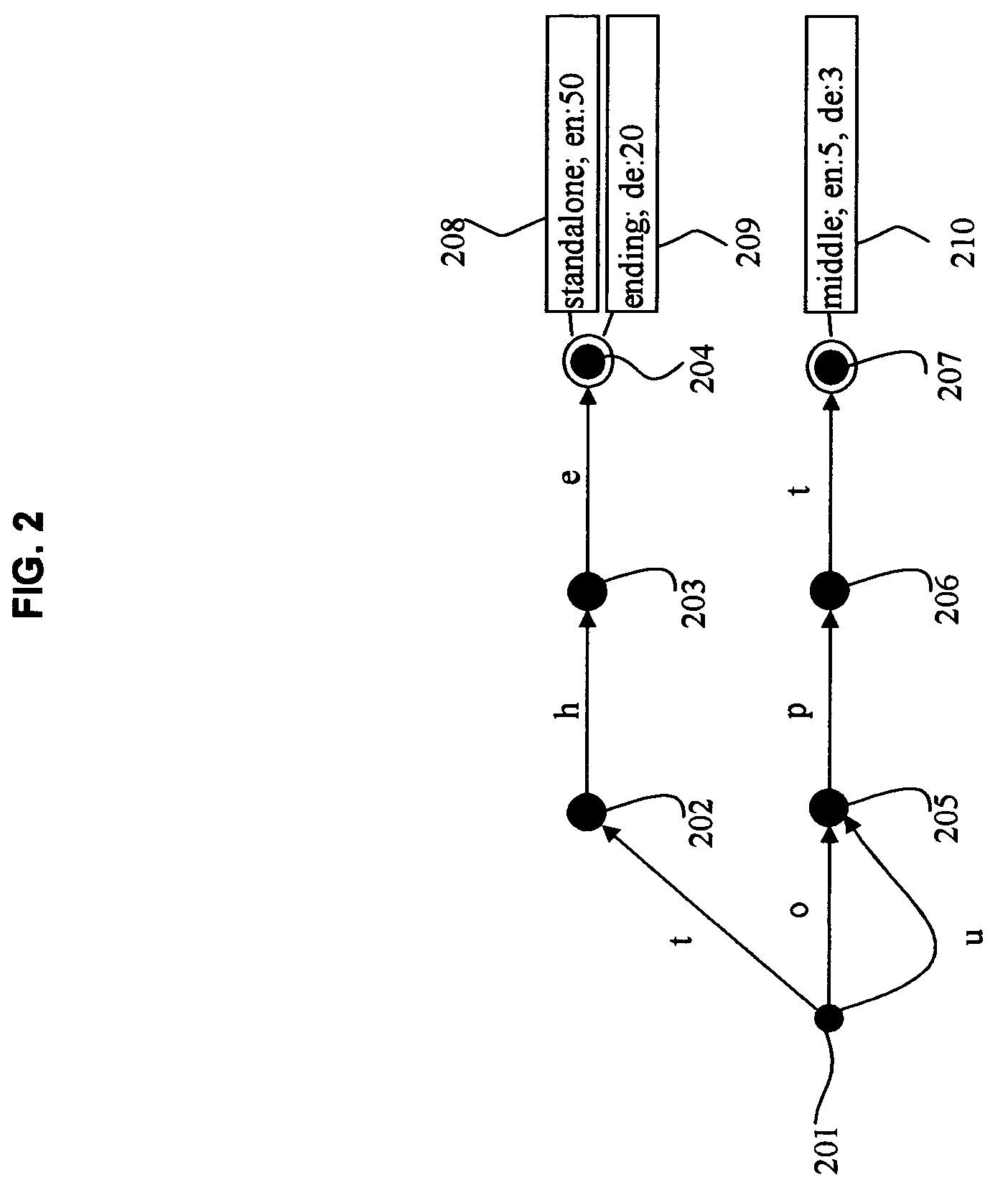
InactiveUS7818165B2Computationally efficientNatural language data processingSpecial data processing applicationsFeature setRelevant information
A method and system for language identification are provided. The system includes a feature set of a plurality of character strings of varying length with associated information. The associated information includes one or more significance scores for a character string for one or more of a plurality of languages. Means are provided for detecting character strings from the feature set within a token from an input text. The system uses a finite-state device and the associated information is provided as glosses at the final nodes of the finite-state device for each character string. The associated information can also include significance scores based on linguistic rules.
Owner:LINKEDIN
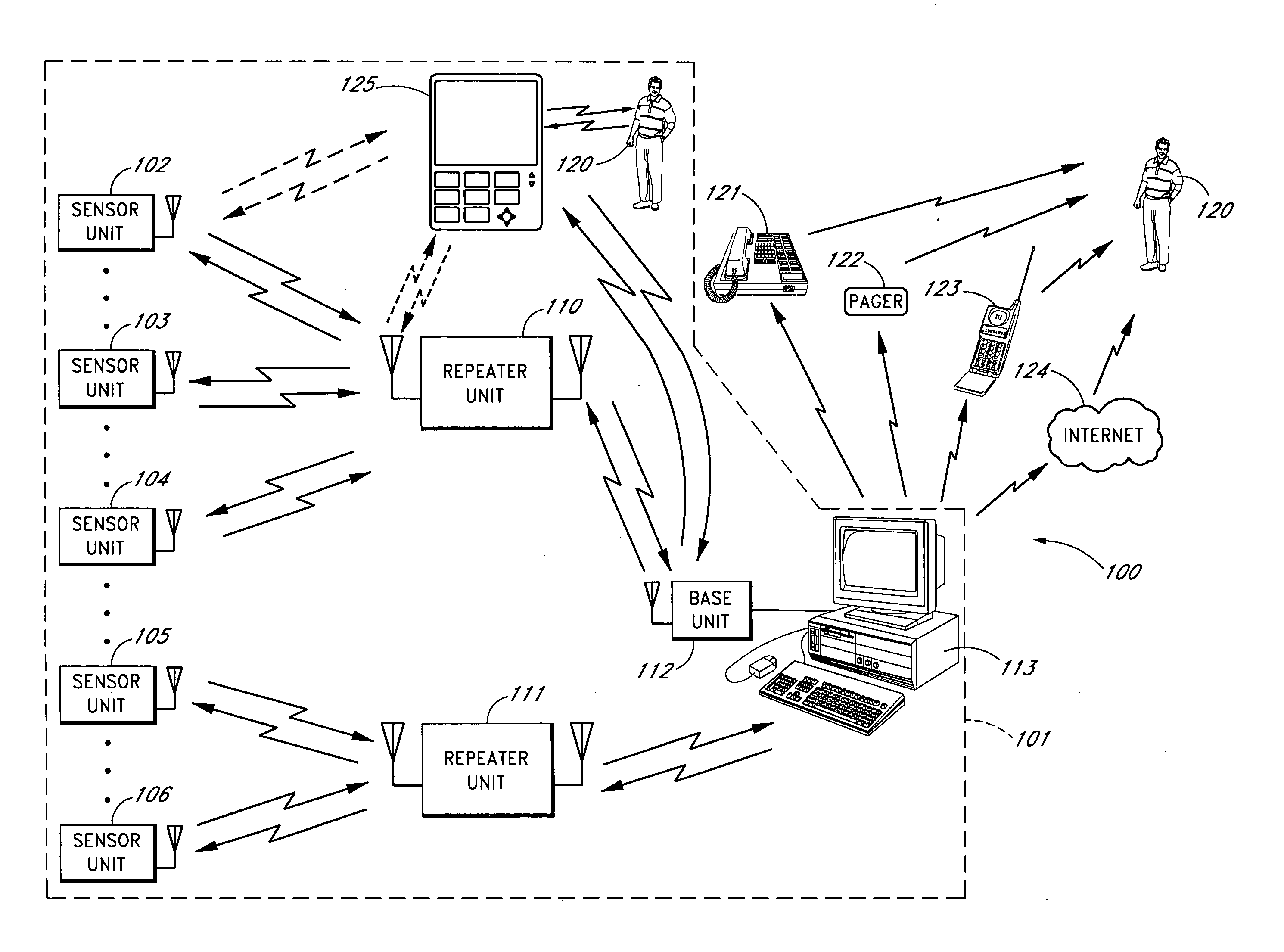
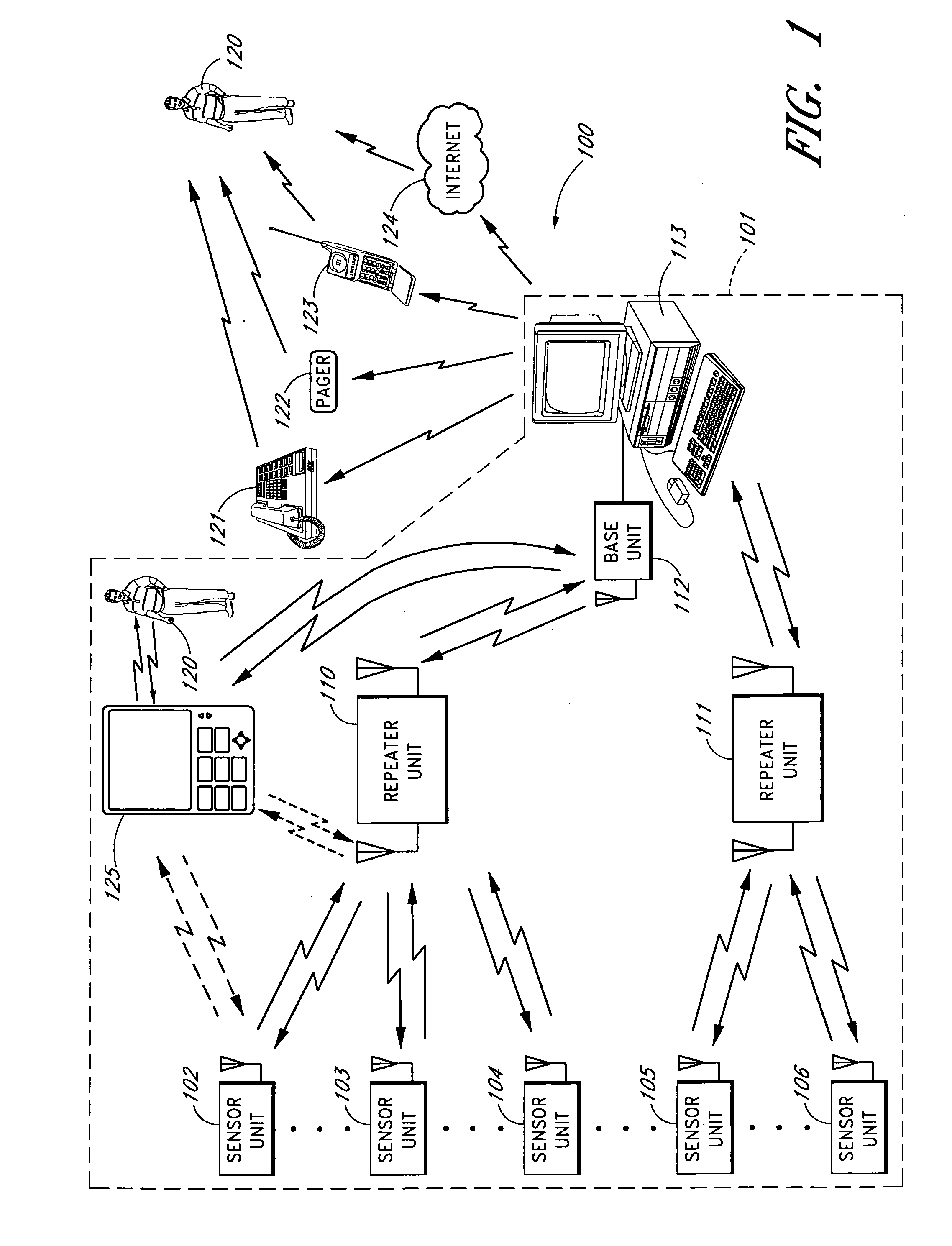
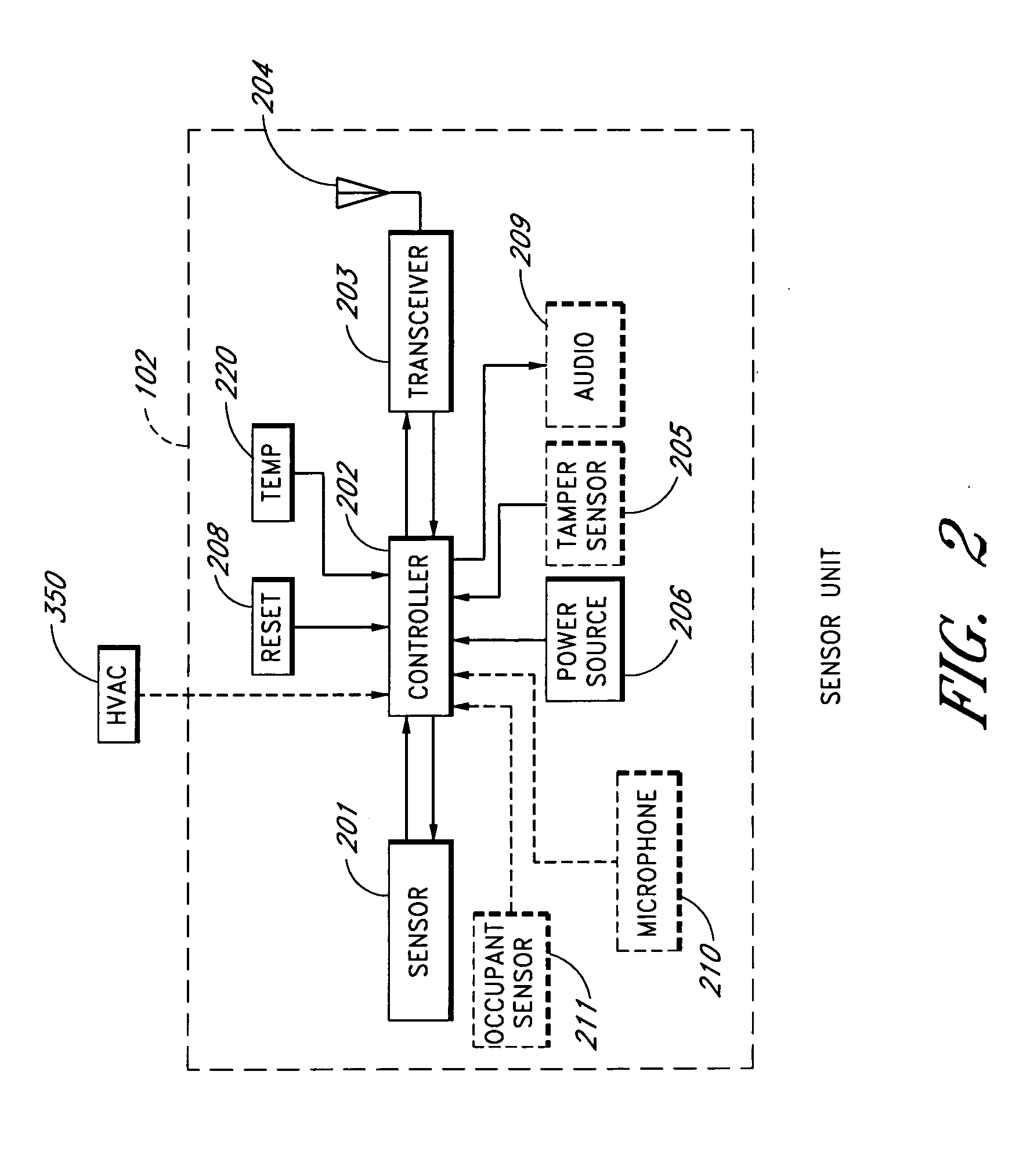
Portable monitoring unit
ActiveUS20070139183A1Quickly apprisedReduce harmSub-station arrangementsTransmission systemsMonitoring siteTransceiver
A sensor system that provides an adjustable threshold level for the sensed quantity is described. The adjustable threshold allows the sensor to adjust to ambient conditions, aging of components, and other operational variations while still providing a relatively sensitive detection capability for hazardous conditions. The adjustable threshold sensor can operate for extended periods without maintenance or recalibration. A portable monitoring unit working in communication with the sensor system provides immediate communication of conditions detected by the sensors. The portable monitoring unit allows building or complex management to be in communication with a sensor system at all times without requiring someone to be physically present at a monitoring site. The portable monitoring unit can be equipped with an auditory device for alerting management or a screen for displaying pertinent information regarding an occurring situation so that management can quickly identify and resolve the problem. In addition, the portable monitoring unit can also be equipped with function keys that allow the portable monitoring unit to send instructions back to the sensor system. In one embodiment, the portable monitoring unit also includes a second transceiver for communications over a short wave radio frequency, or with a cellular phone system.
Owner:GOOGLE LLC
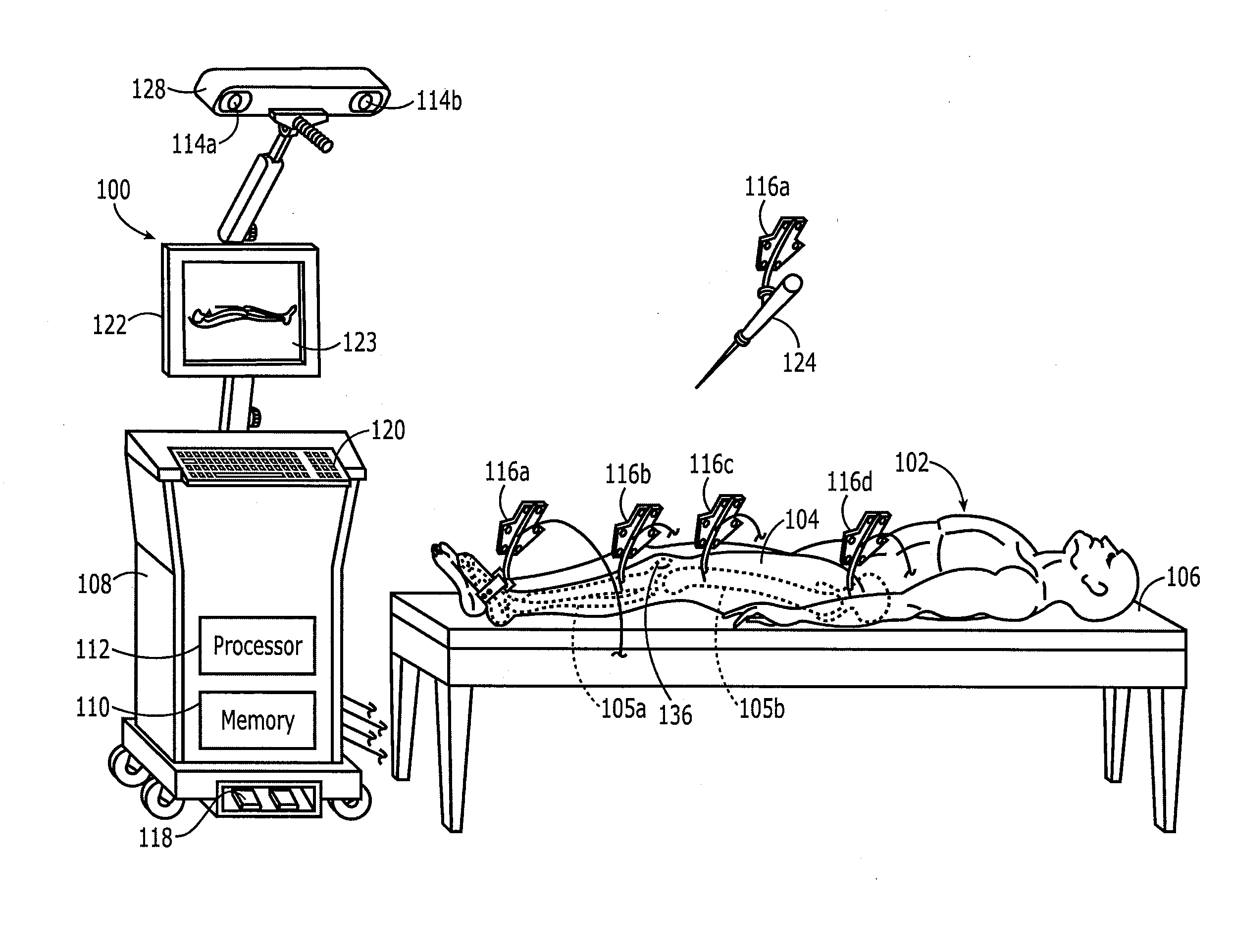
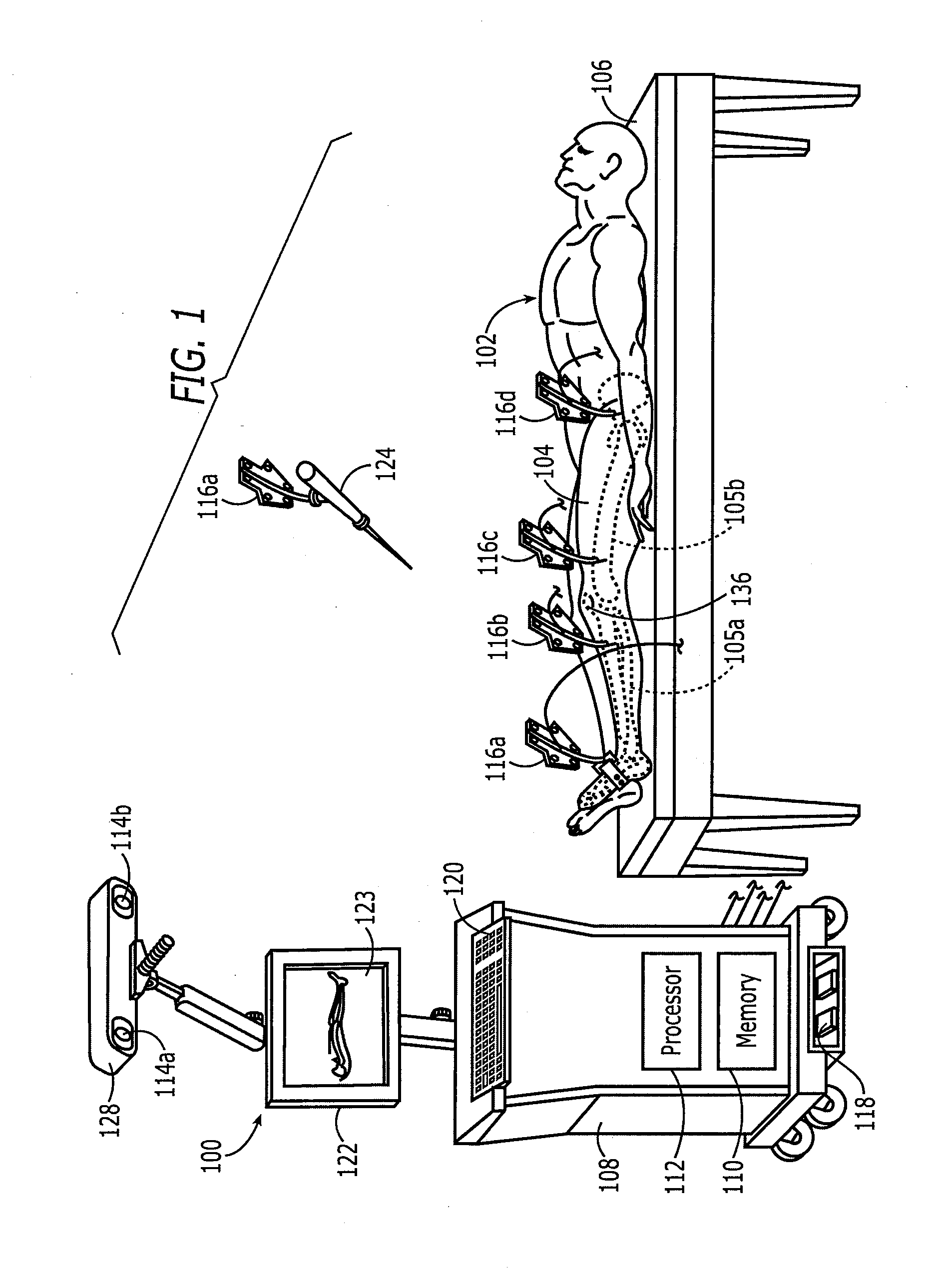
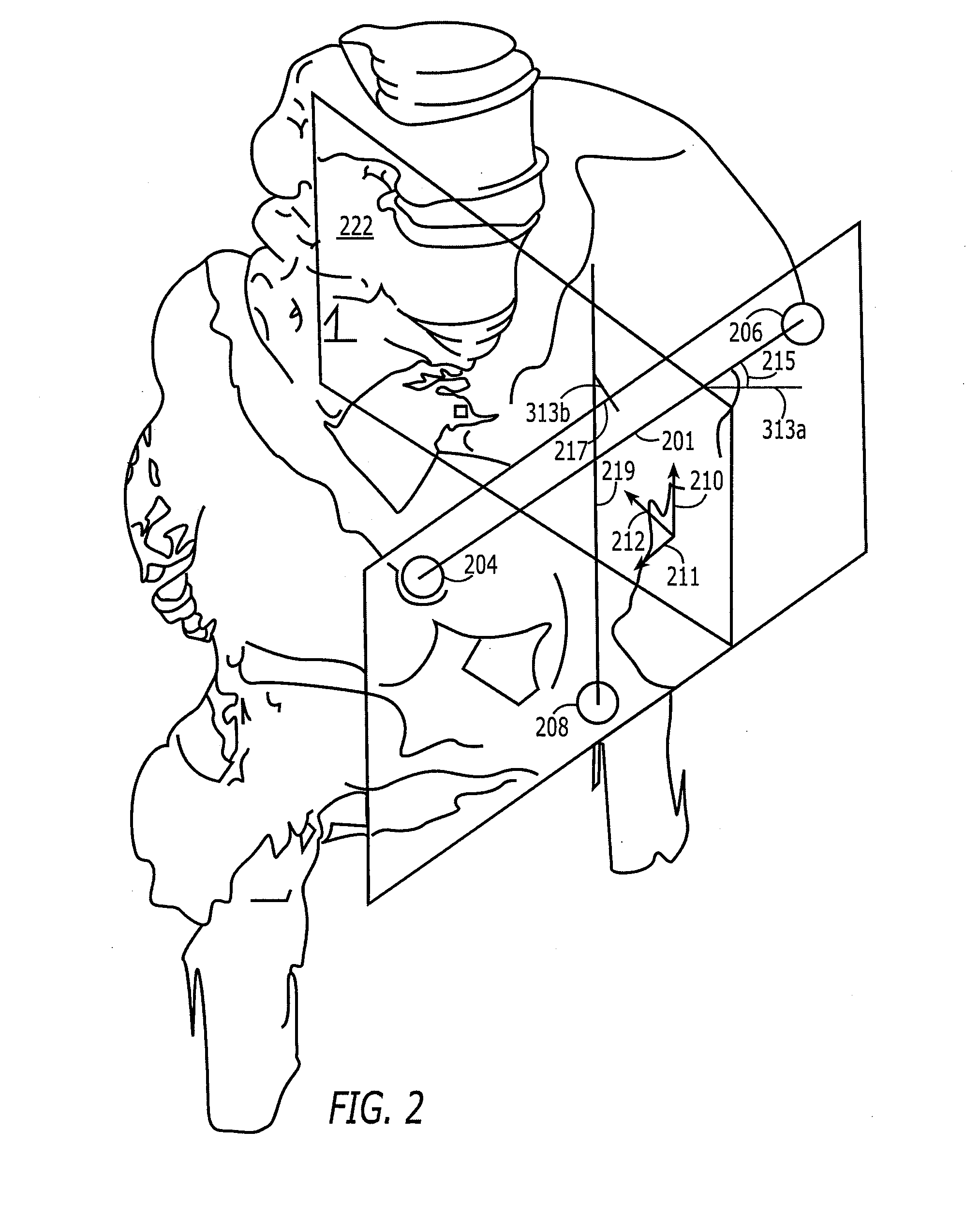
Method and apparatus for positioning a bone prosthesis using a localization system
InactiveUS20080051910A1Surgical navigation systemsSurgical systems user interfaceLocalization systemCoxal joint
Methods and apparatus using a surgical navigation system to position the femoral component of a prosthetic hip during hip joint replacement surgery without separately affixing a marker to the femur. The navigation system acquires the center of rotation of the hip joint as well as at least one point on the femur in the pelvic frame of reference. From these two points, the navigation system calculates the position and length of a first line between the center of rotation of the hip joint and the point on the femur. Optionally, a second point on the femur that is not on the first line is palpated. The system can calculate the position and length of a second line that is perpendicular to the first line and that runs from the first line to the second palpated point on the femur. The prosthetic cup is implanted and its center of rotation is recorded. A tool for forming the bore within which the stem of the femoral implant component will be placed is tracked by the navigation system. While the tool is fixed to the femur, the surgeon re-palpates the same point(s) on the femur that were previously palpated. The navigation system calculates the position and length of a first line between the center of rotation of the prosthetic cup and the re-palpated first point. If a second point on the femur was re-palpated, the navigation system also calculates the position and length of a perpendicular line between the first line and the second point. The surgical navigation system uses this information to calculate and display to the surgeon relevant information about the surgery, such as change in the patient's leg length and / or medialization / lateralization of the joint.
Owner:AESCULAP AG
Subject matter context search engine
ActiveUS20050289168A1Raise the possibilityEasy retrievalWeb data indexingRelational databasesRelevant informationSubject matter
A search system associates contextual metadata with search terms and / or stored terms to facilitate identification of relevant information. In one implementation, a search term is identified (4304) from a received search request. The search term is then rewritten (4306) in standard form and the standard form term is then set (4308) as the current search parameter. A source database is then searched (4310) using the current search parameter. If any results are obtained (4312) these results may be output (4320) to the user. If no results are obtained, a parent classification of the search term is set (4316) as the current search parameter and the process is repeated. The invention thereby provides the ease of use of term searching with the comprehensiveness of category searching.
Owner:ORACLE INT CORP
Method and apparatus for generating a network topology representation based on inspection of application messages at a network device
ActiveUS7996556B2Multiple digital computer combinationsProgram controlRelevant informationContext based
A method is disclosed for generating a network topology representation based on inspection of application messages at a network device. According to one aspect, a network device receives a request packet, routes the packet to the destination, and extracts and stores correlation information from a copy of the request packet. When the network device receives a response packet, it examines the contents of a copy of the response packet using context-based correlation rules and matches the response packet with the appropriate stored request packet correlation information. It analyzes recorded correlation information to determine application-to-application mapping and calculate application response times. Another embodiment inserts custom headers that contain information used to match a response packet with a request packet into request packets.
Owner:CISCO TECH INC
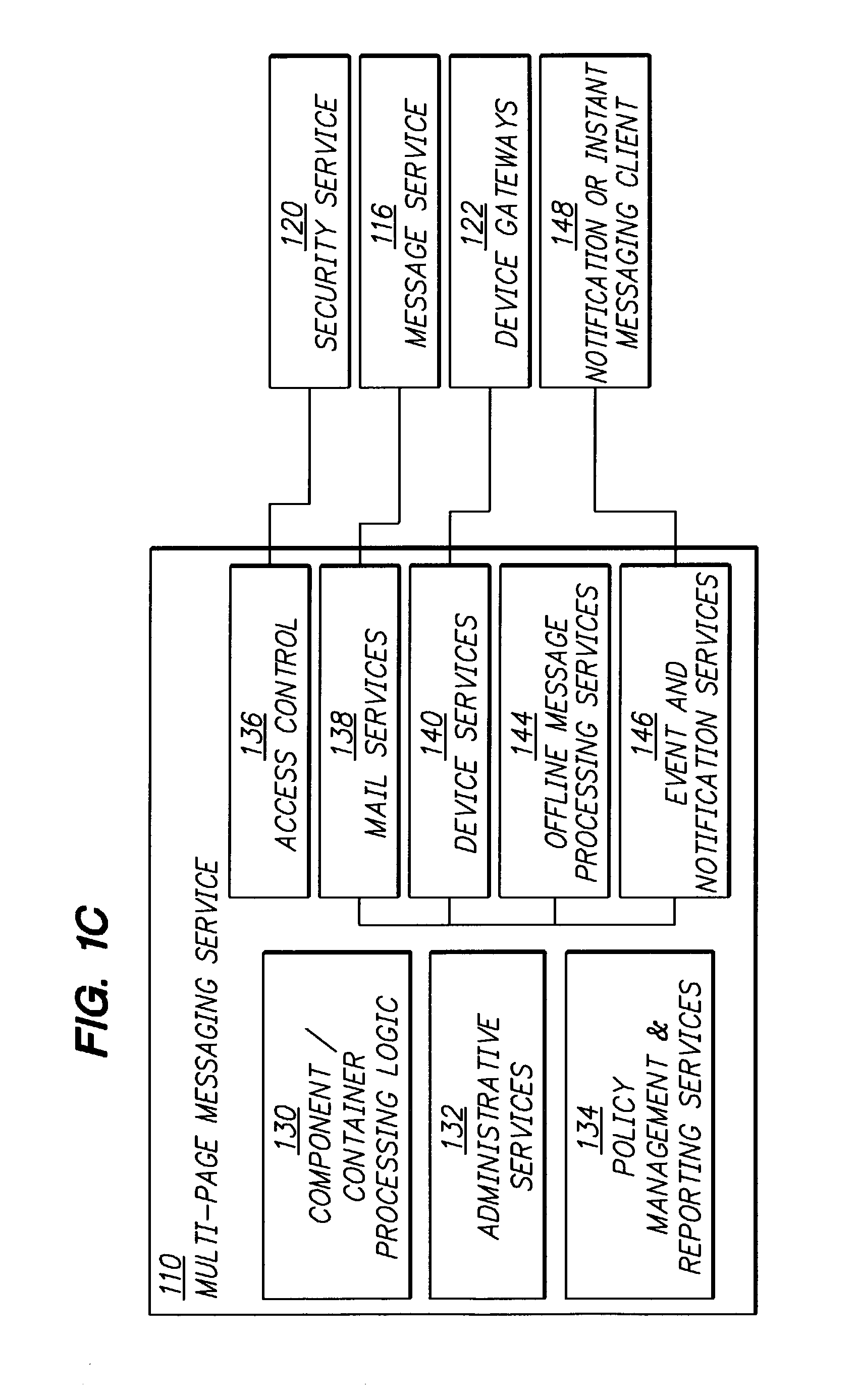
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com