Patents
Literature
5370results about How to "Good service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
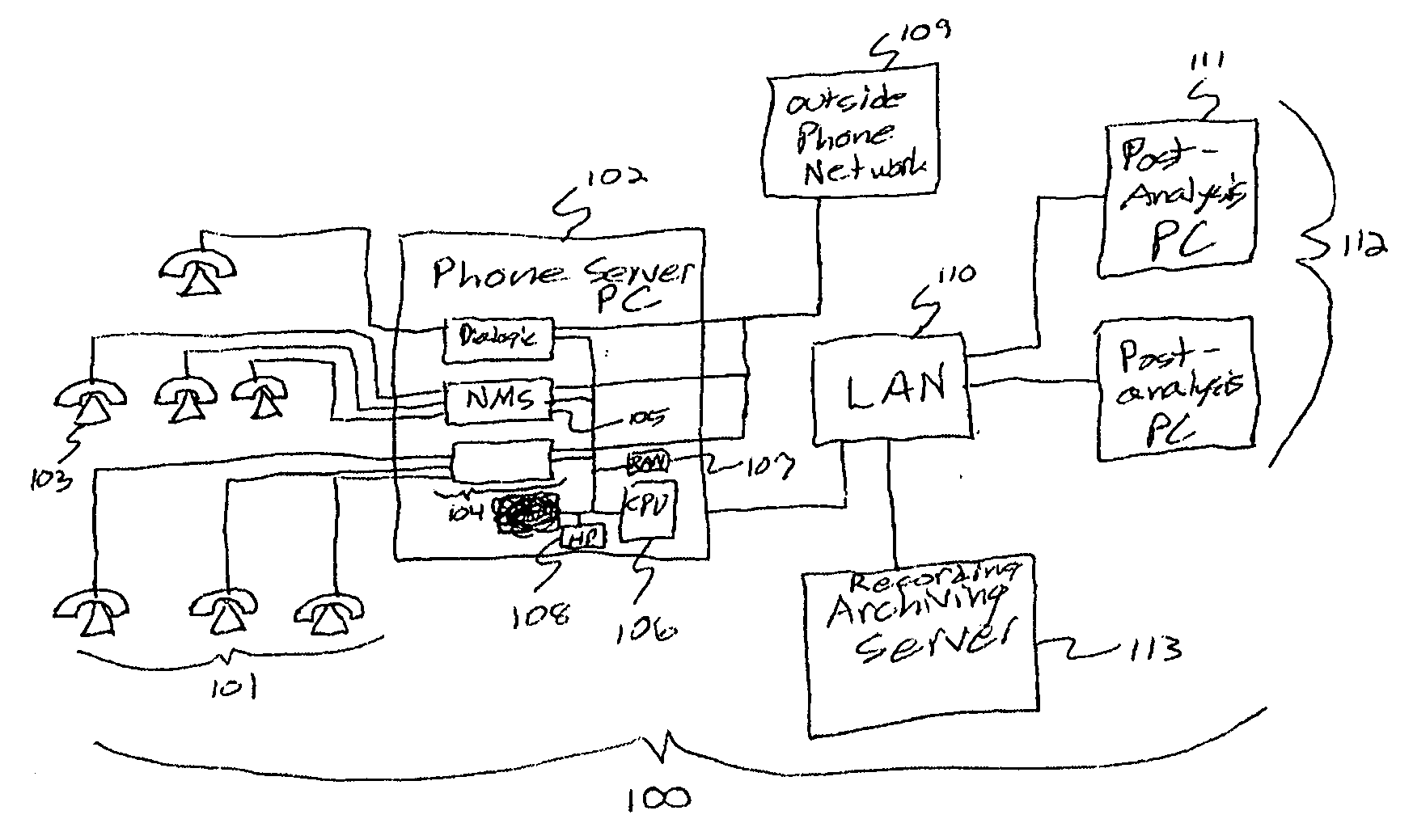
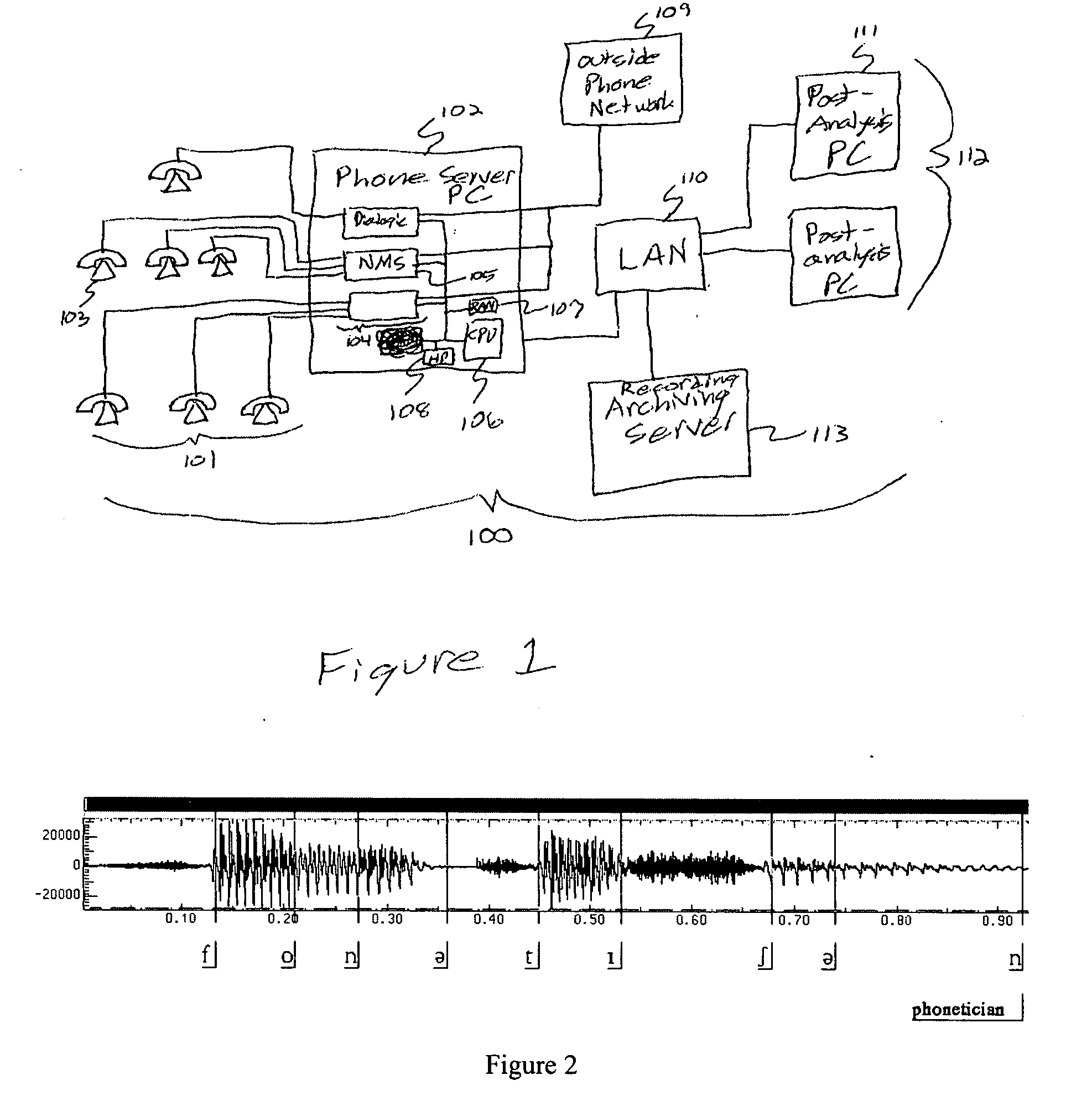
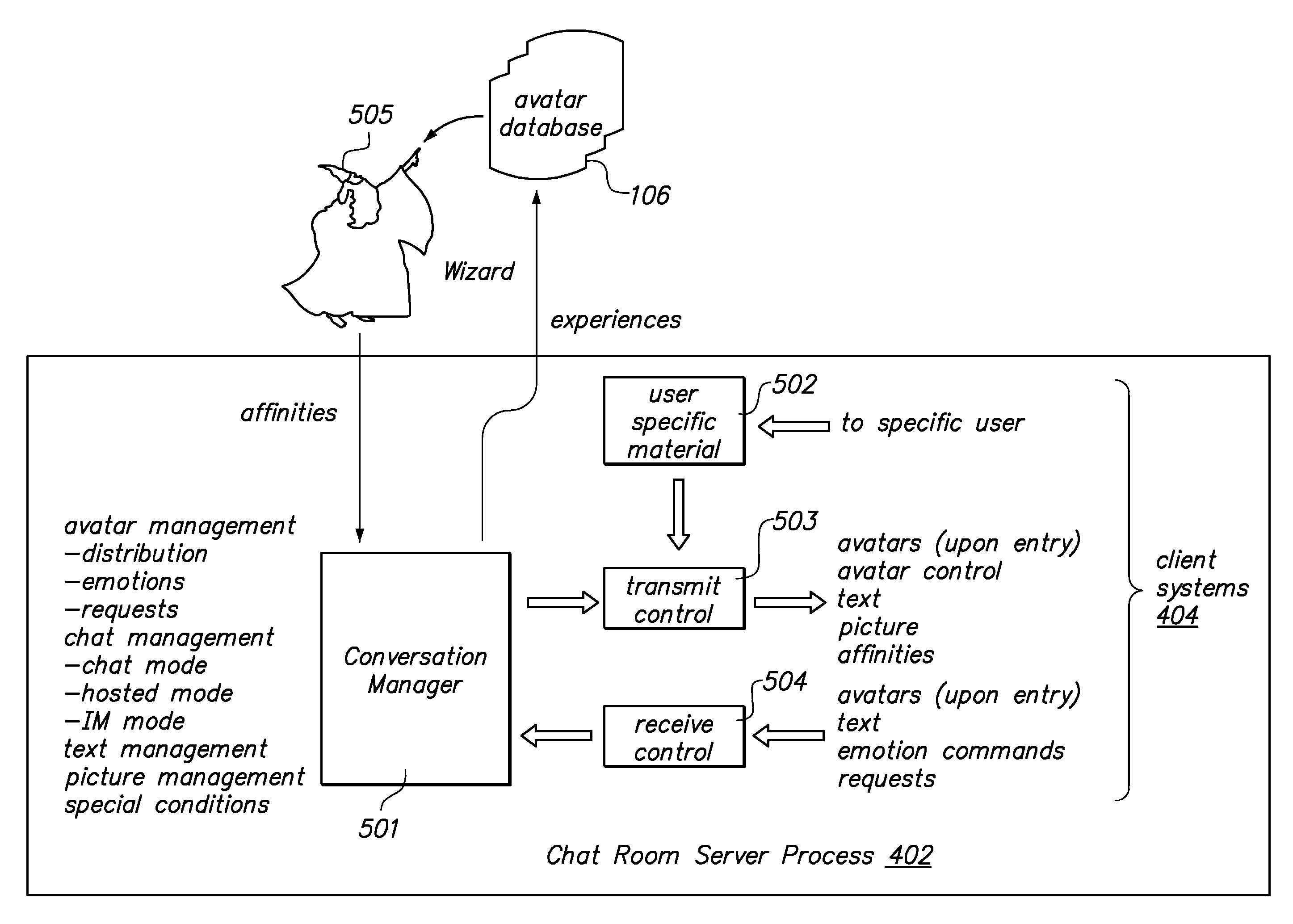
Multi-party conversation analyzer & logger
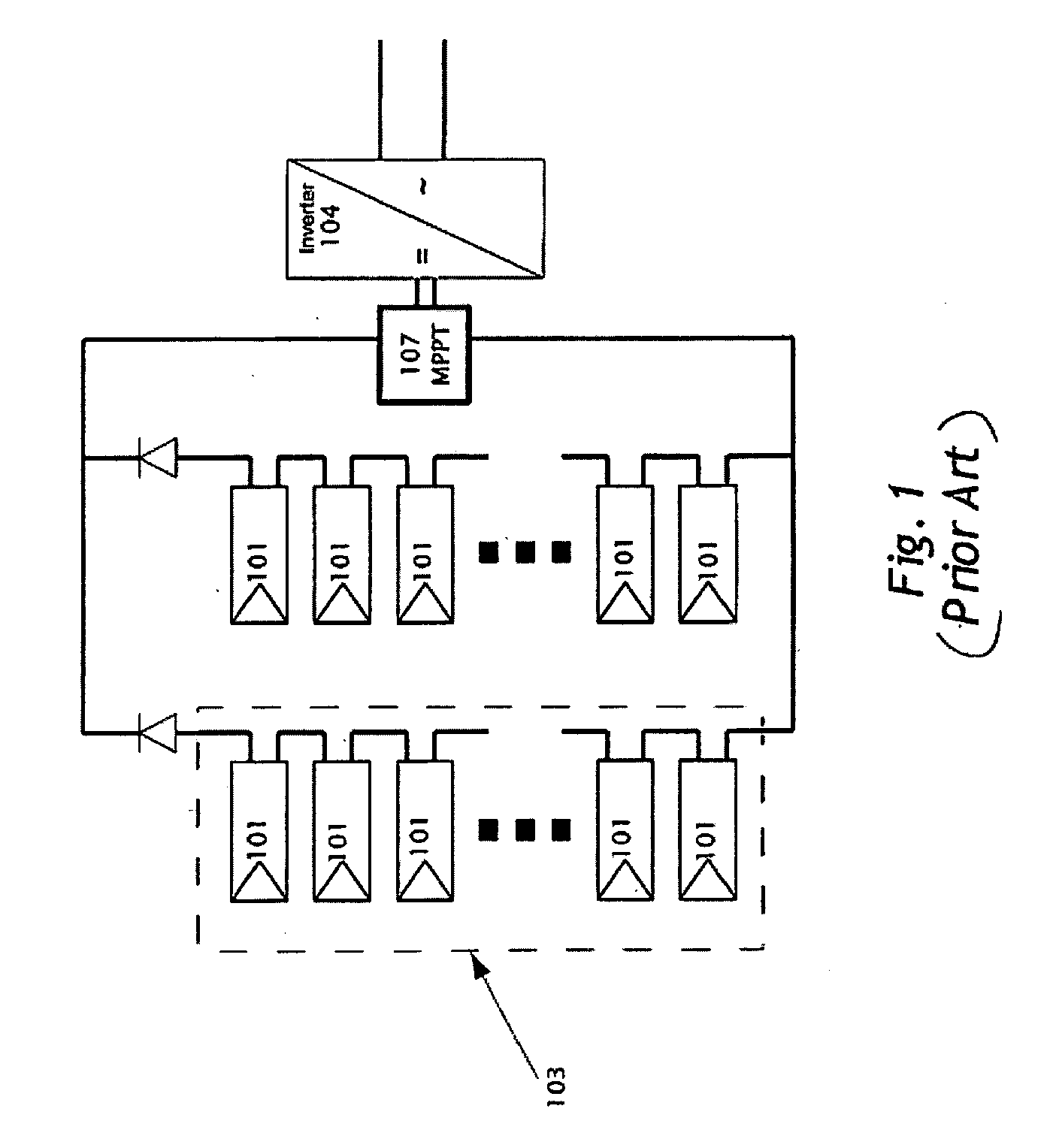
ActiveUS20070071206A1High precisionFacilitate interruptionInterconnection arrangementsSubstation speech amplifiersGraphicsSurvey instrument
A multi-party conversation analyzer and logger uses a variety of techniques including spectrographic voice analysis, absolute loudness measurements, directional microphones, and telephonic directional separation to determine the number of parties who take part in a conversation, and segment the conversation by speaking party. In one aspect, the invention monitors telephone conversations in real time to detect conditions of interest (for instance, calls to non-allowed parties or calls of a prohibited nature from prison inmates). In another aspect, automated prosody measurement algorithms are used in conjunction with speaker segmentation to extract emotional content of the speech of participants within a particular conversation, and speaker interactions and emotions are displayed in graphical form. A conversation database is generated which contains conversation recordings, and derived data such as transcription text, derived emotions, alert conditions, and correctness probabilities associated with derived data. Investigative tools allow flexible queries of the conversation database.
Owner:SECURUS TECH LLC
Advertising with video ad creatives
InactiveUS20070157228A1Good serviceAdvertisementsAnalogue secracy/subscription systemsRelevant informationThe Internet
The serving of advertisements with (e.g., on) video documents may be improved in a number of ways. For example, a system may (a) accept information defining at least one ad spot associated with at least one instance of an video document, (b) accept offers to have advertisements served in the ad spot(s), and (c) arbitrate among competing advertisements, using at least the offers, to determine at least one advertisement to be served in that ad spot(s). As another example, a system may (a) accept relevance information for an advertisement, (b) determine at least one video document using the accepted relevance information, (c) present information about the video document(s) to an advertiser associated with the advertisement, and (d) accept, from the advertiser, an offer to have its advertisement served with at least one of the video document(s) accepted. As yet another example, a system may (a) accept relevance information for an video document, (b) determine a plurality of advertisements relevant to the video document using the relevance information and serving constraints of the advertisements, and (c) select at least one of the determined relevant advertisements to be served with the video document. Examples of video documents include video files published on the Internet, television programs, live or recorded talk shows, video-voice mail, segments of an video conversation, etc.
Owner:GOOGLE LLC
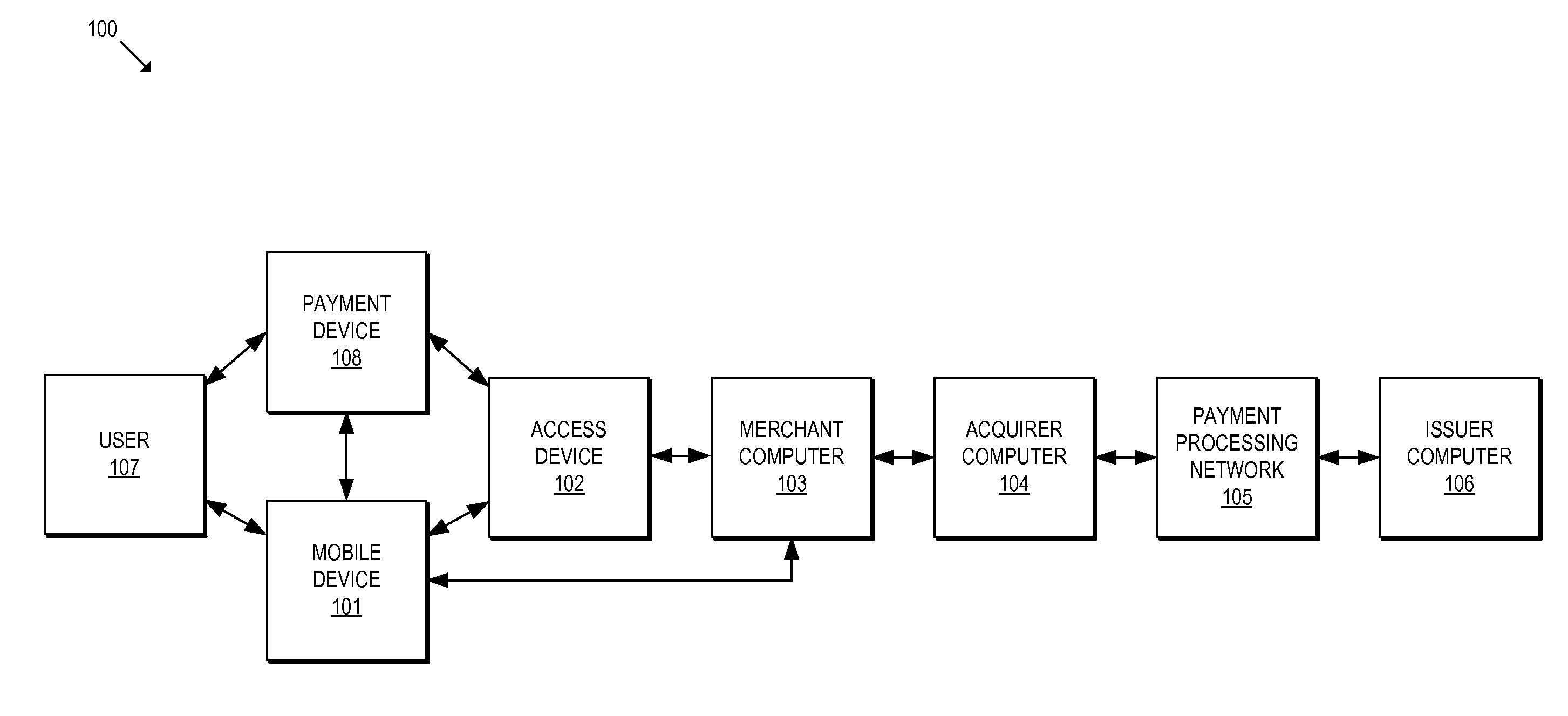
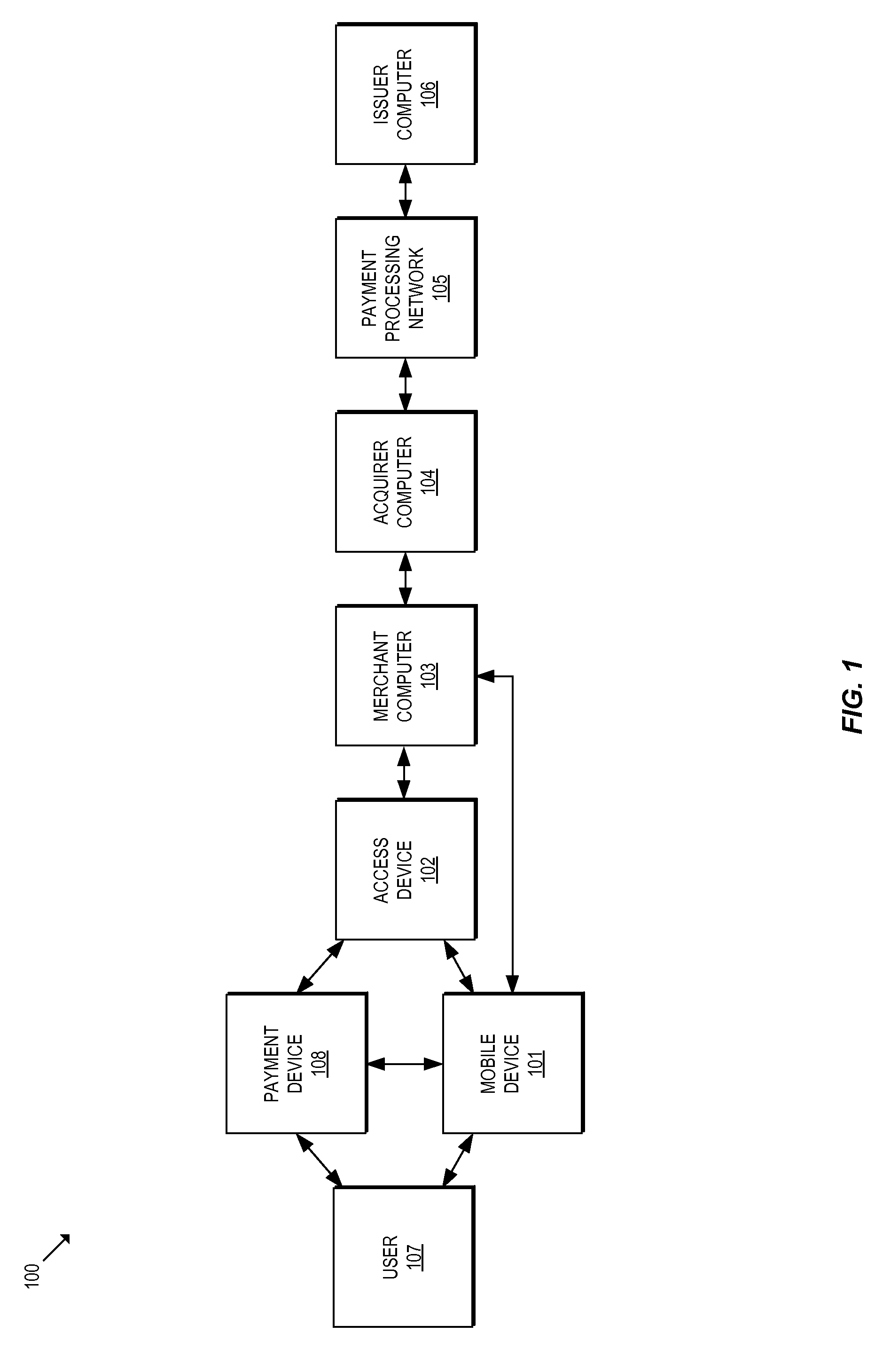
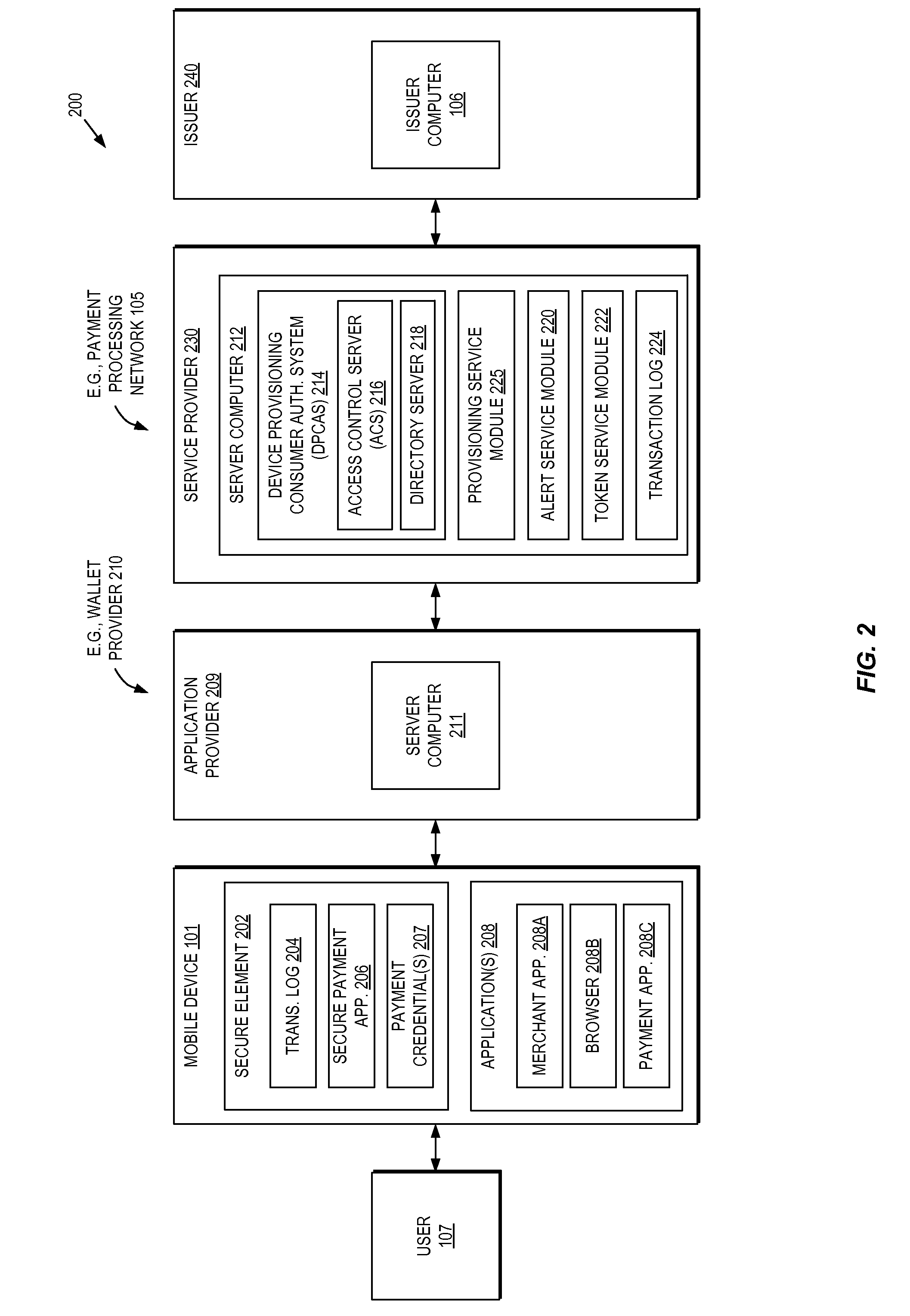
Methods and systems for provisioning mobile devices with payment credentials
ActiveUS20150046339A1Unnecessary delayProcessing speedFinanceElectronic credentialsPaymentMedium Risk
Embodiments are described that are directed to optimizing the provisioning of payment account credentials to mobile devices utilizing mobile wallets. In some embodiments, one of multiple provisioning schemes may be selectively chosen for payment account credential provisioning based upon a determined risk involved with a particular provisioning request. A low risk provisioning request leads to an immediate provisioning of a payment credential, whereas a provisioning request of high risk results in the provisioning request being denied. In some embodiments, medium risk provisioning requests will cause an additional user authentication to be performed before the payment account provisioning is finalized. The additional user authentication may occur using a separate communication channel than the channel in which the provisioning request was received.
Owner:VISA INT SERVICE ASSOC
System and method for matching users of a gaming application
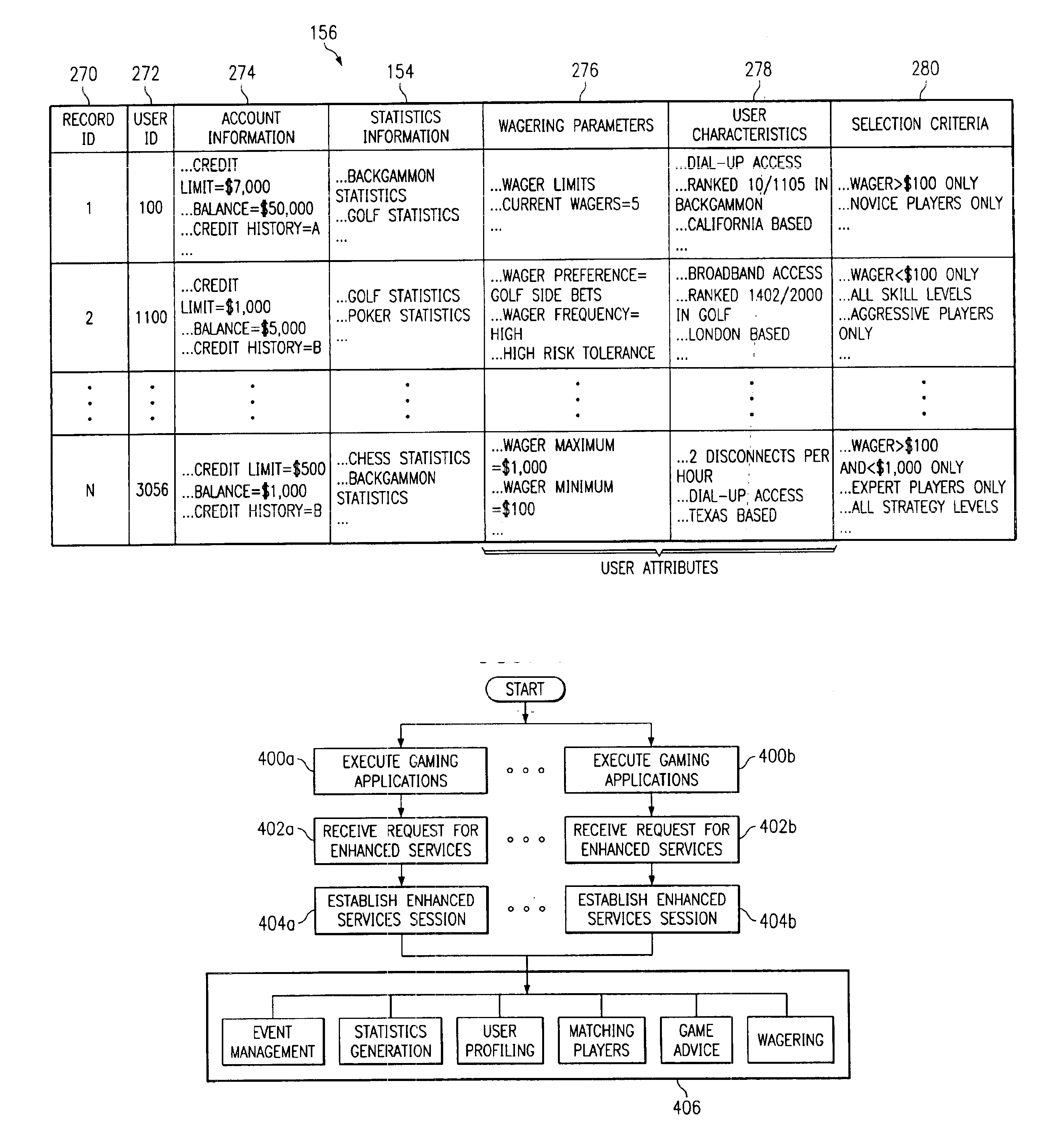
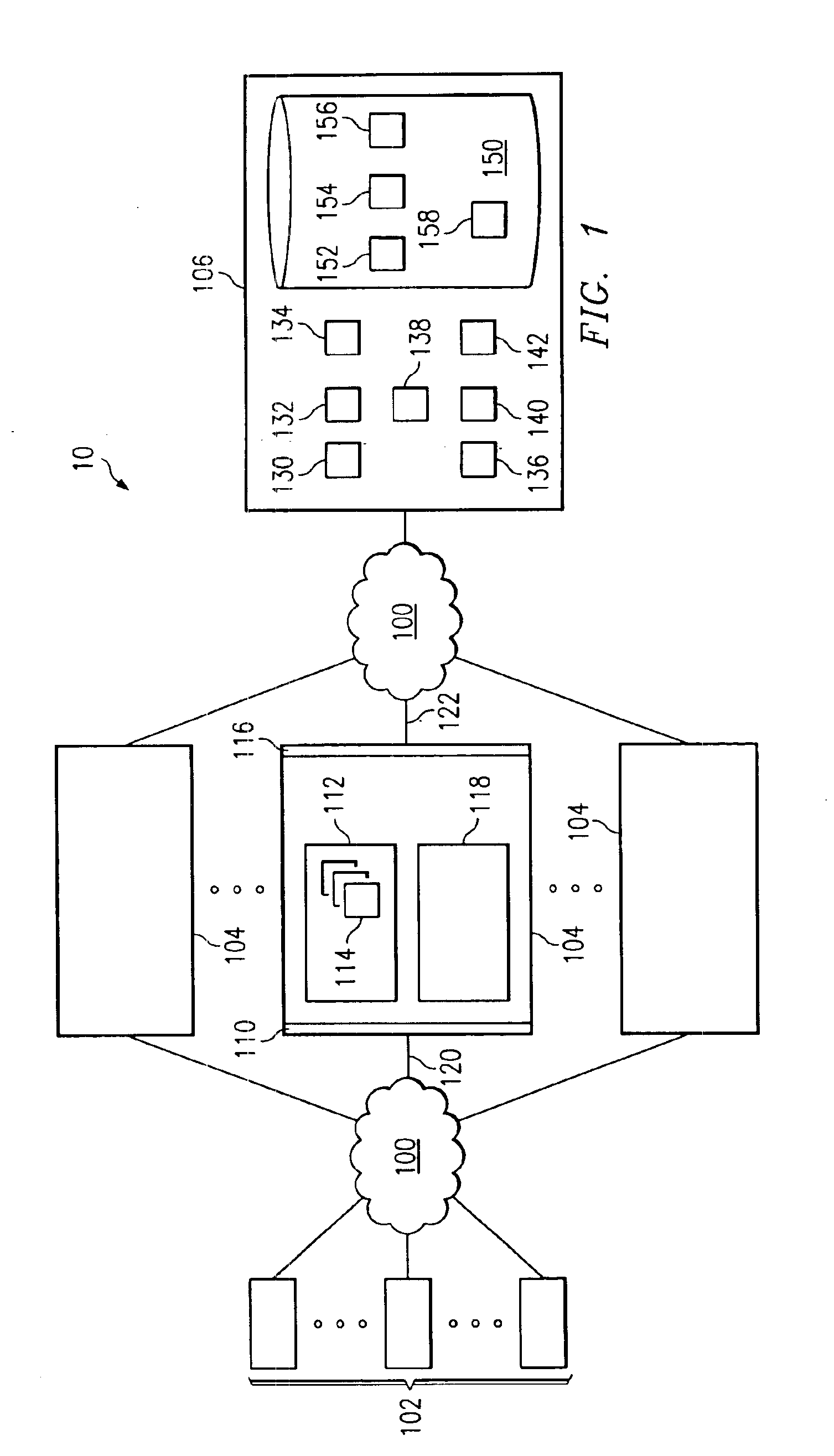
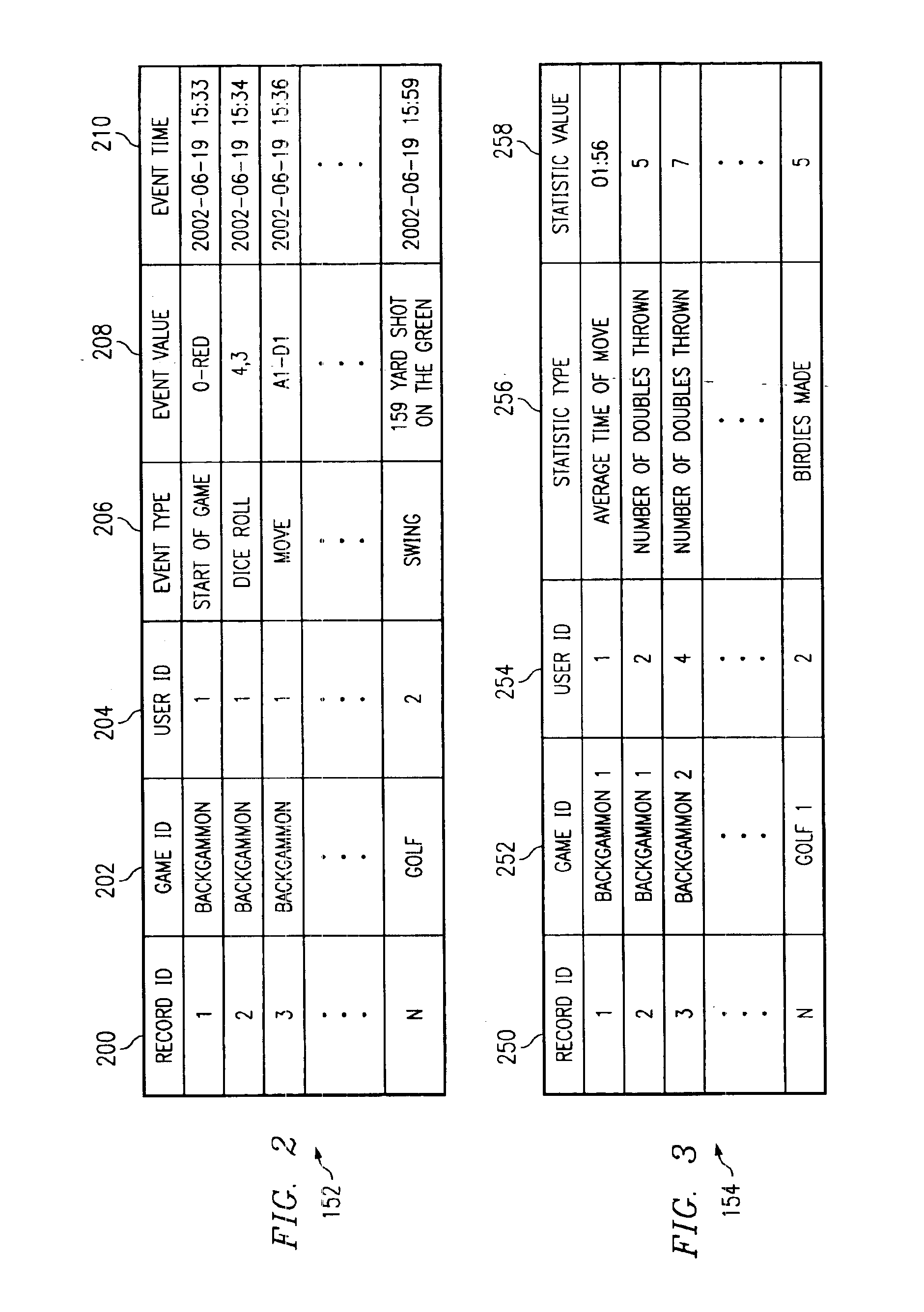
InactiveUS6887159B2Rich gaming experienceGood serviceApparatus for meter-controlled dispensingVideo gamesSelection criterionMultimedia
Owner:INTERACTIVE GAMES LTD
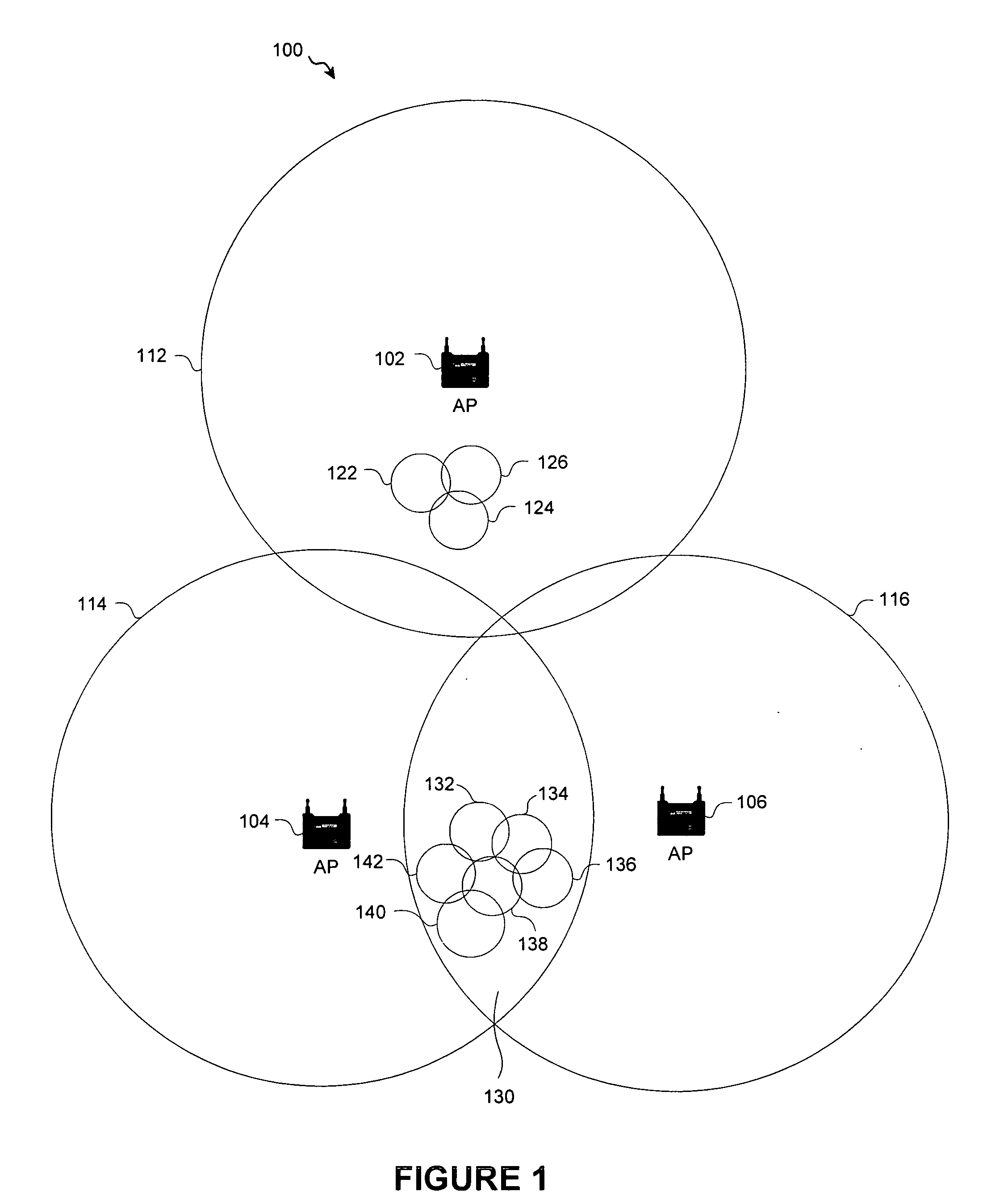
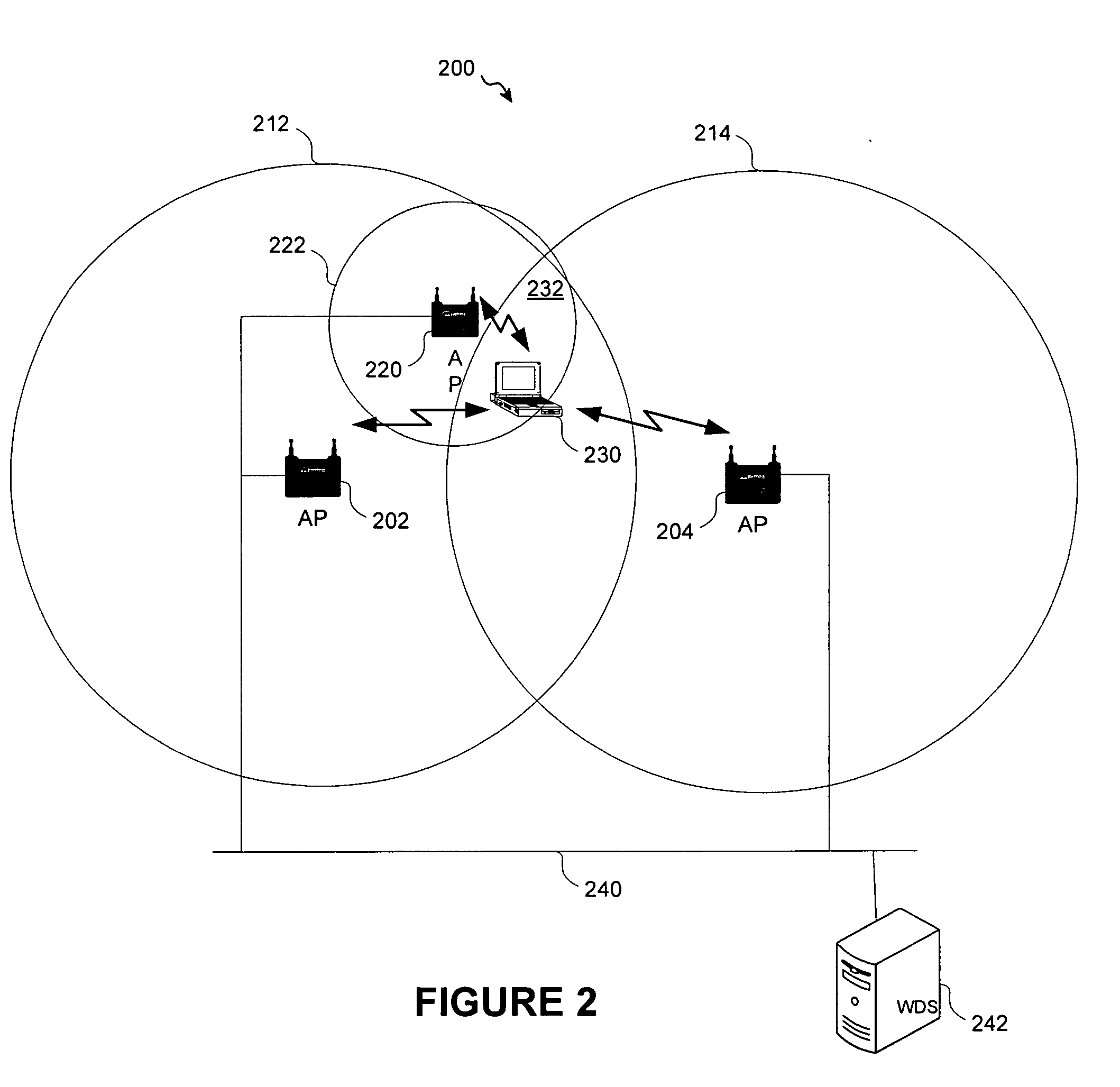
System and method for integrated WiFi/WiMax neighbor AP discovery and AP advertisement
ActiveUS20070140163A1Facilitate loadingLightly loadNetwork traffic/resource managementAssess restrictionTelecommunicationsWiMAX
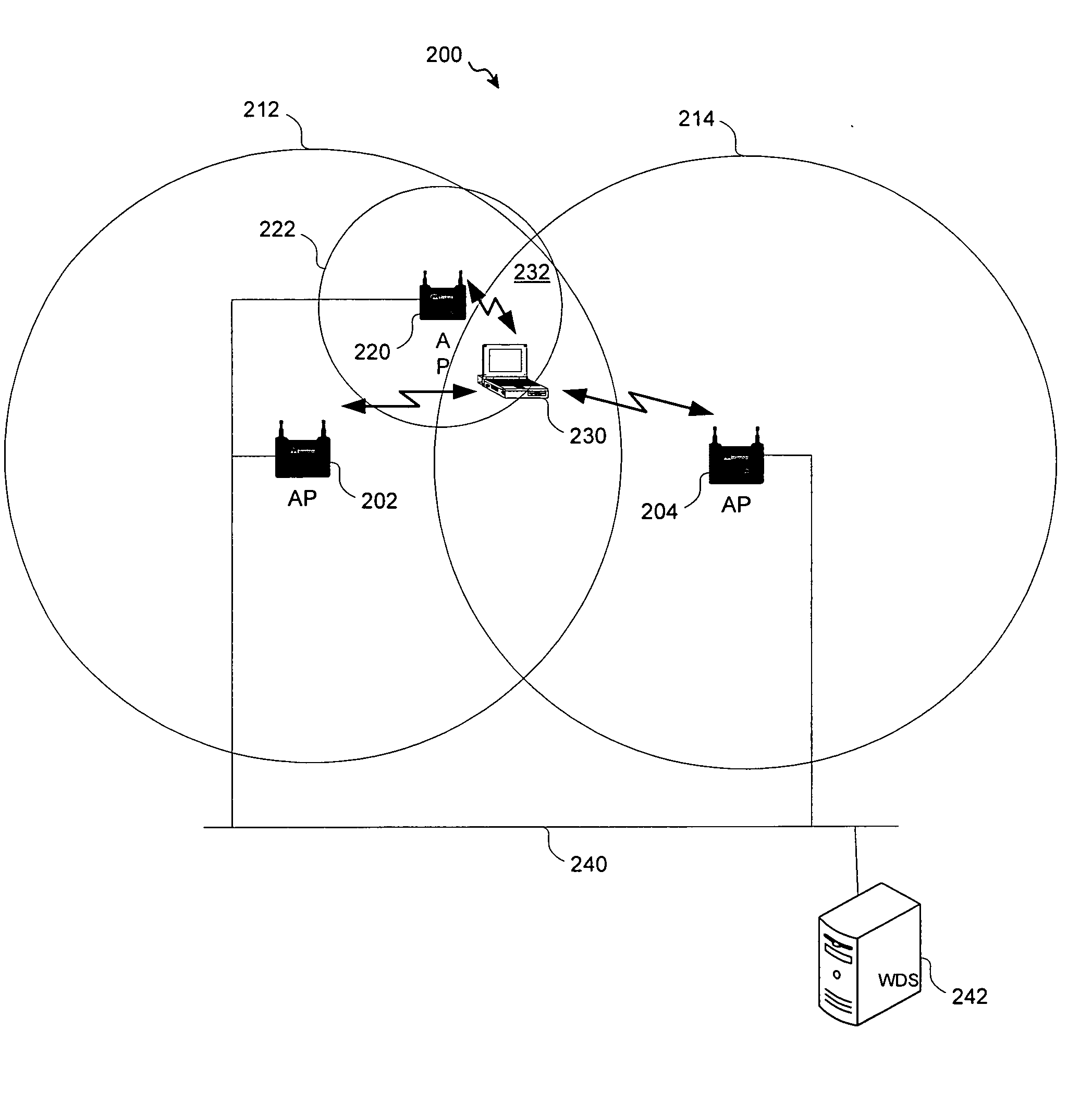
A system and method wherein mobile nodes scan both 802.16 and 802.11 radio channels for neighbor access points. A mobile node reports both WiMax and WiFi neighbor access points to its parent access point. A parent access point advertises both WiMax and WiFi neighbor access points to child mobile nodes to facilitate faster roaming and load balancing. A parent WiMax AP can direct a mobile node to roam to a neighbor WiFi access point that has a lighter load or offers enhanced services. As an option, a location tracking protocol is used to determine the location of a mobile node and the mobile node's parent AP advertises neighbor APs that offer services in the mobile node's location.
Owner:CISCO TECH INC
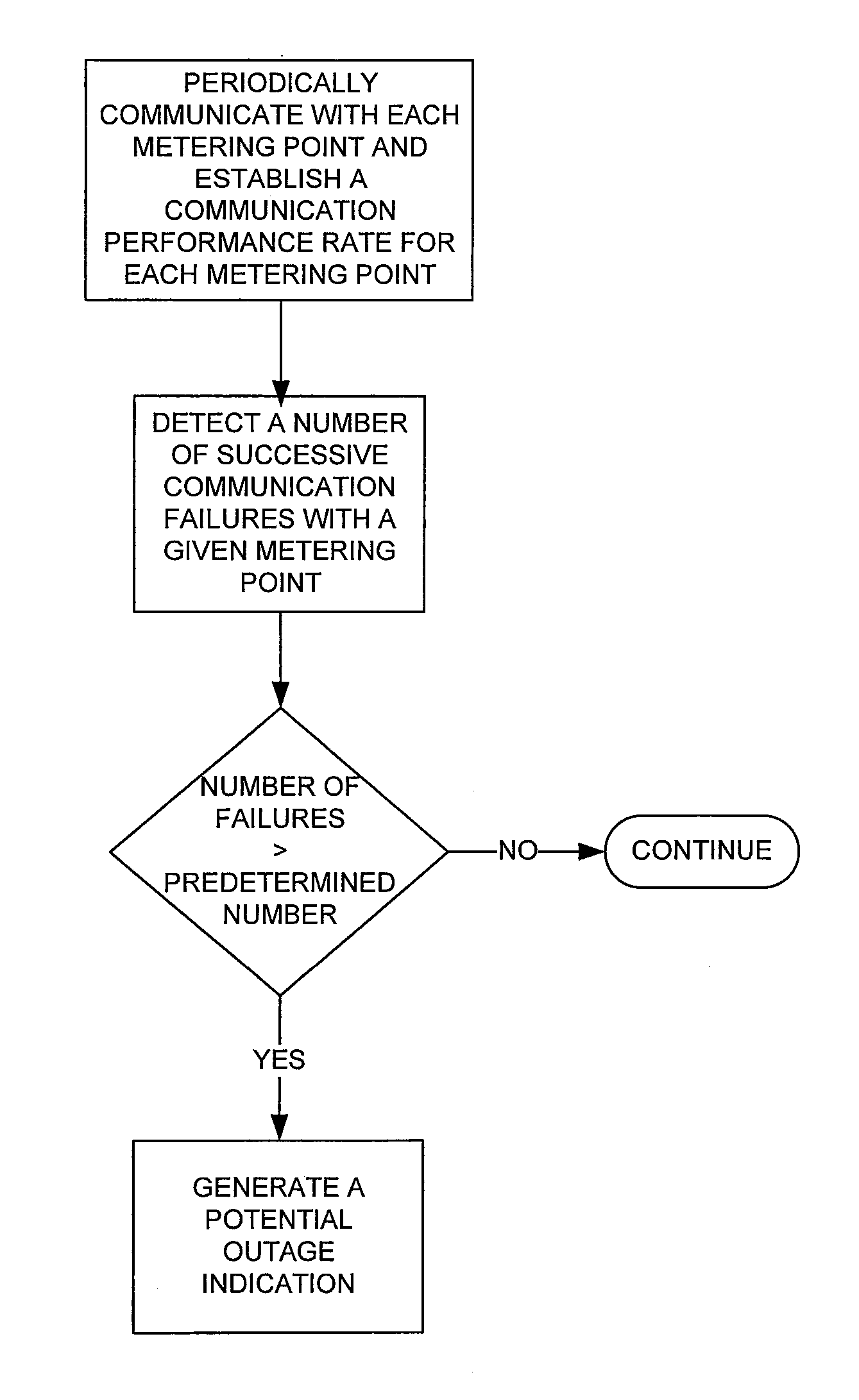
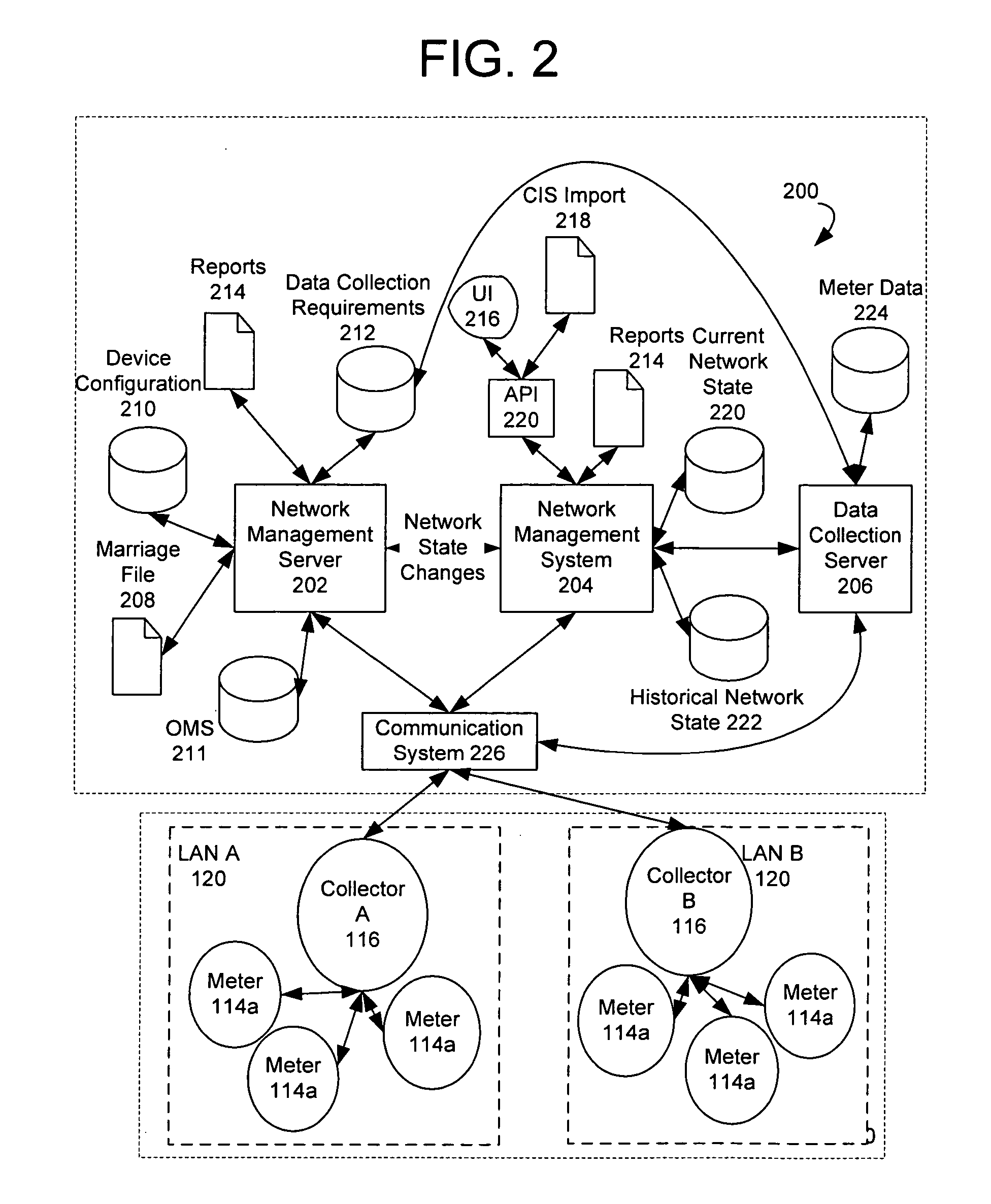
Using a fixed network wireless data collection system to improve utility responsiveness to power outages
ActiveUS7308370B2Good serviceElectric signal transmission systemsElectrical testingCollection systemWireless data
A system for determining service outages and restorations includes an outage management server (OMS) that generates reports of outages and restoration information for metering endpoints. The outages may be caused by faults at various locations in the distribution network. The metering endpoint may include a transmitter having a battery backup that transmits the outage information upon a failure to detect a voltage at the endpoint. The transmission of the information may be filtered based on configurable criteria. The metering endpoints may also inform the OMS when power is restored.
Owner:ELSTER ELECTRICTY LLC
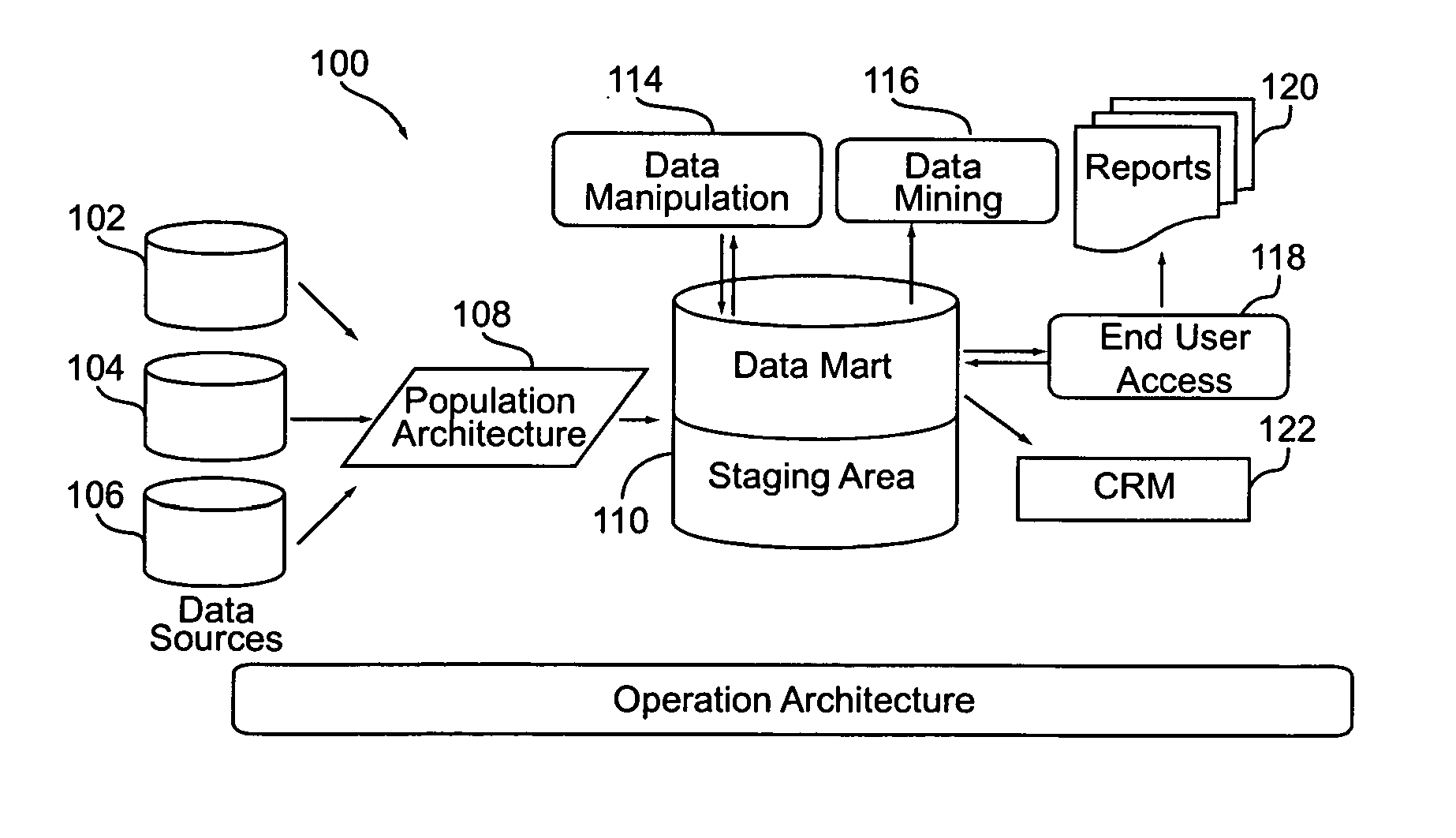
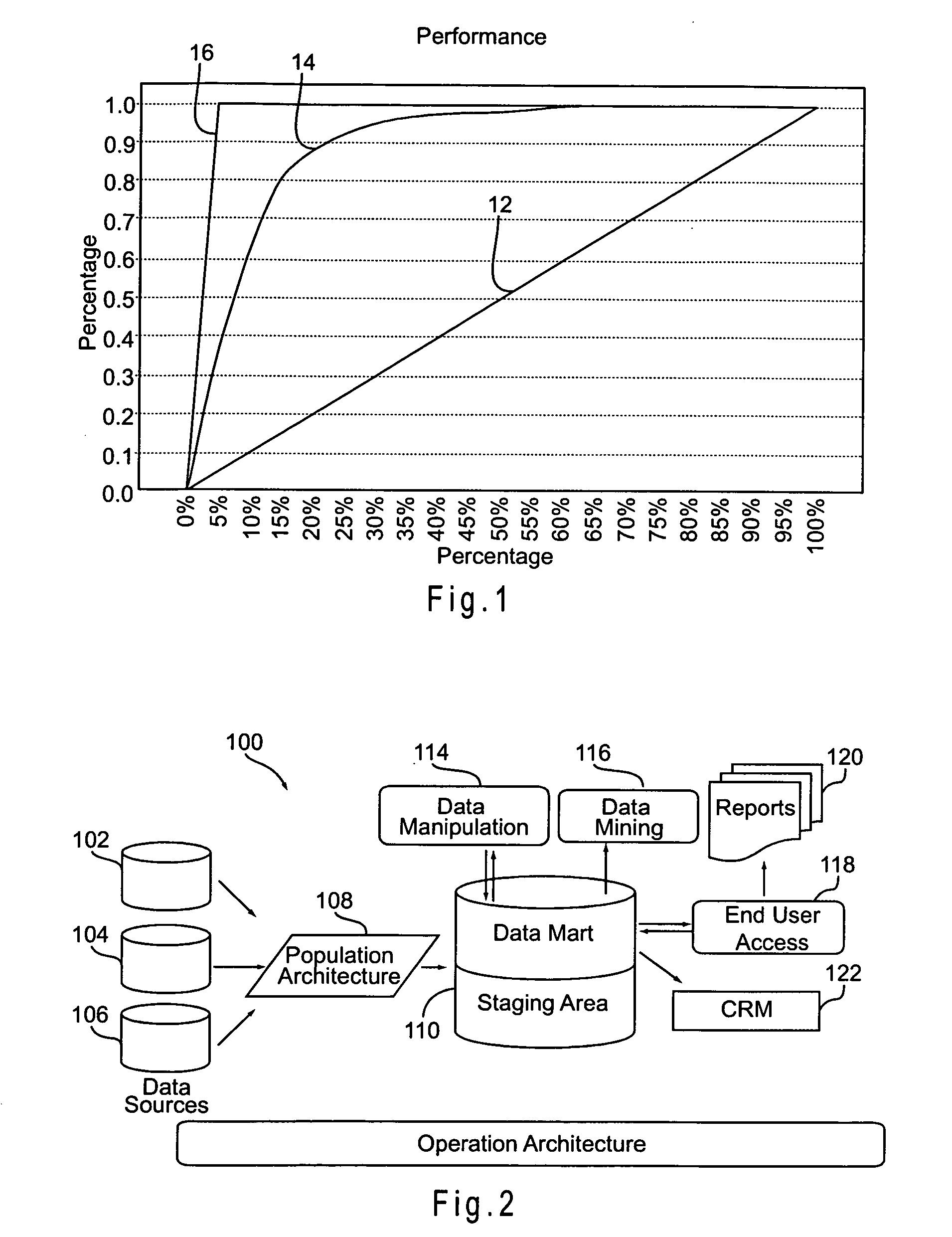
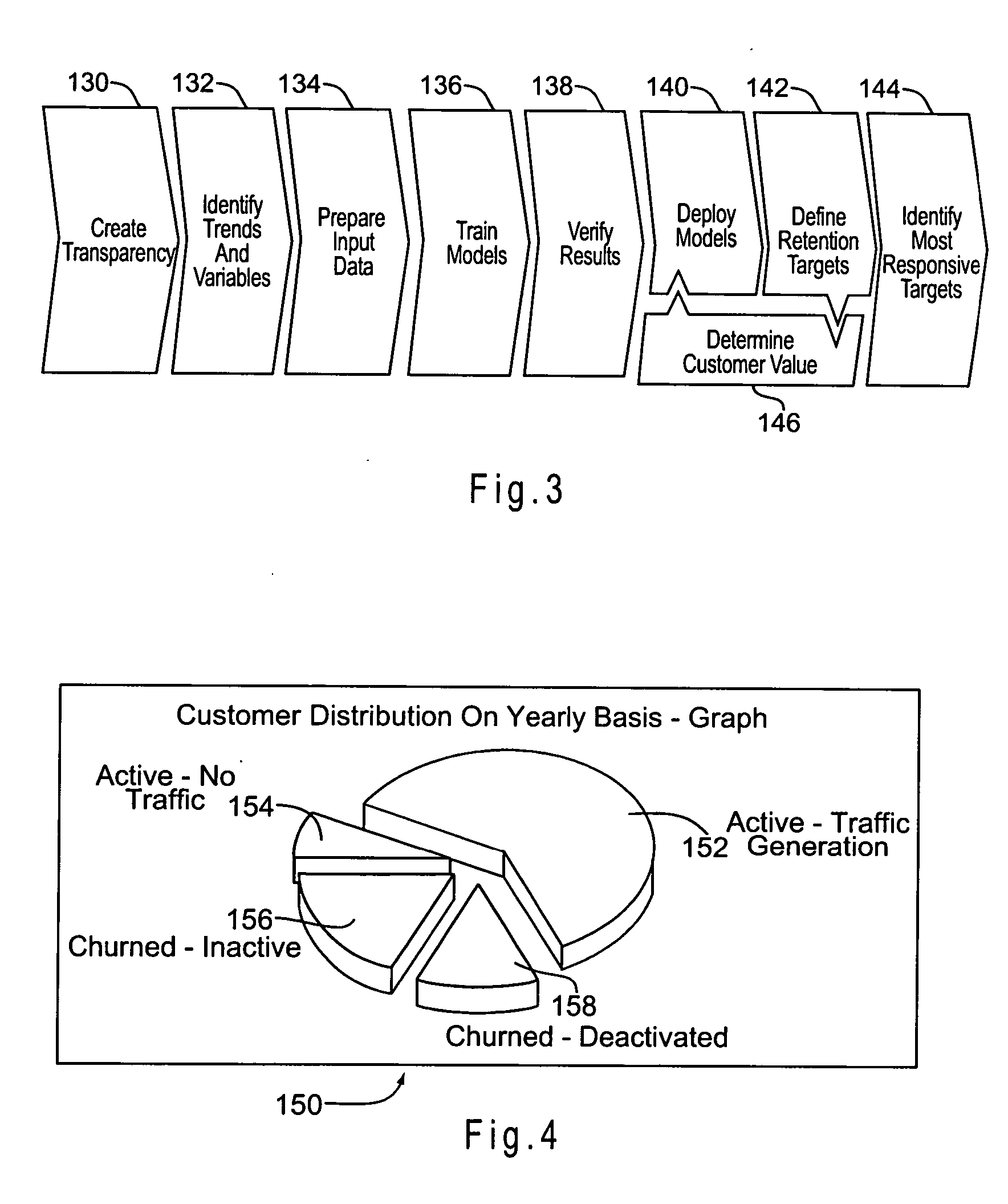
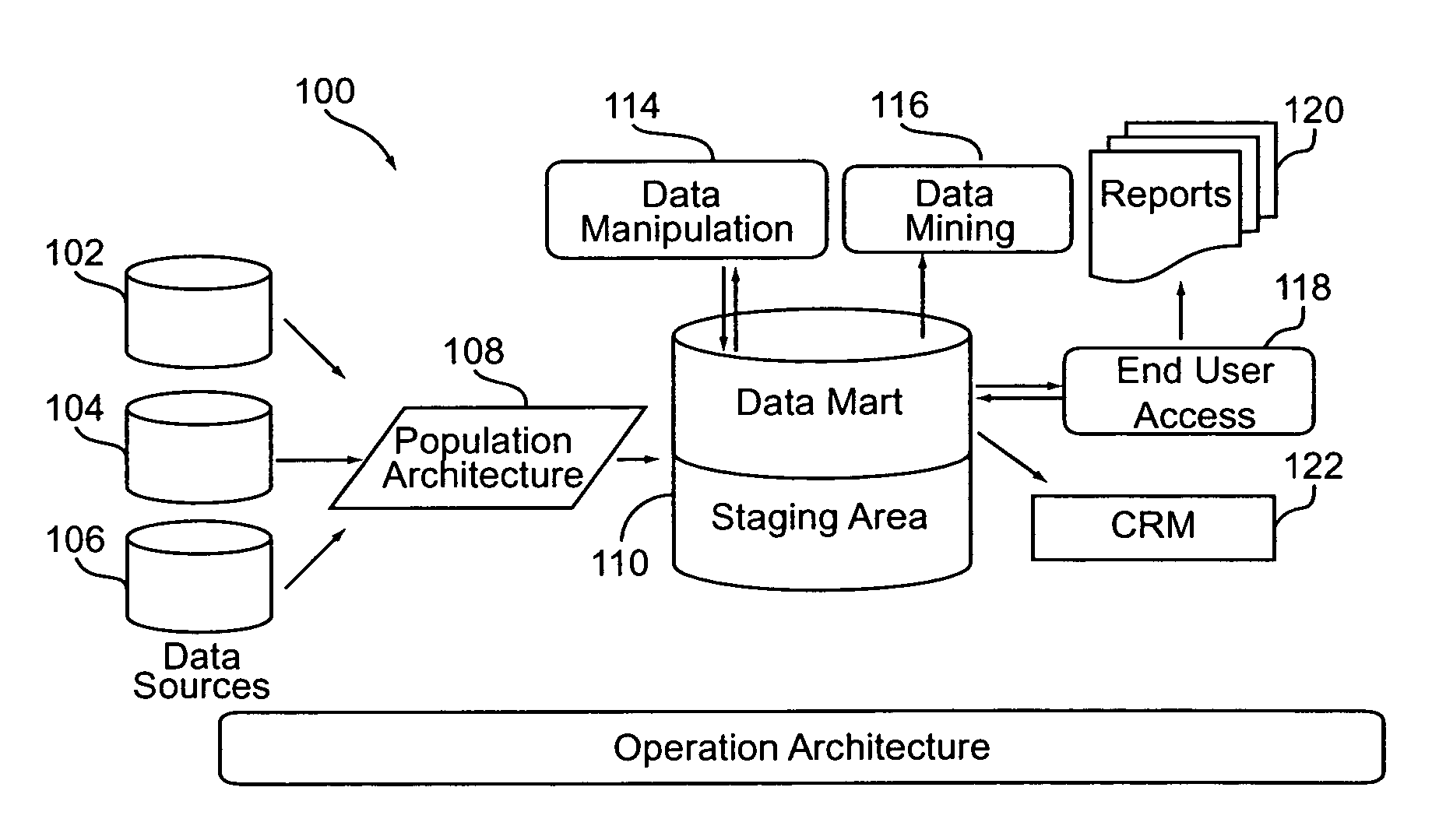
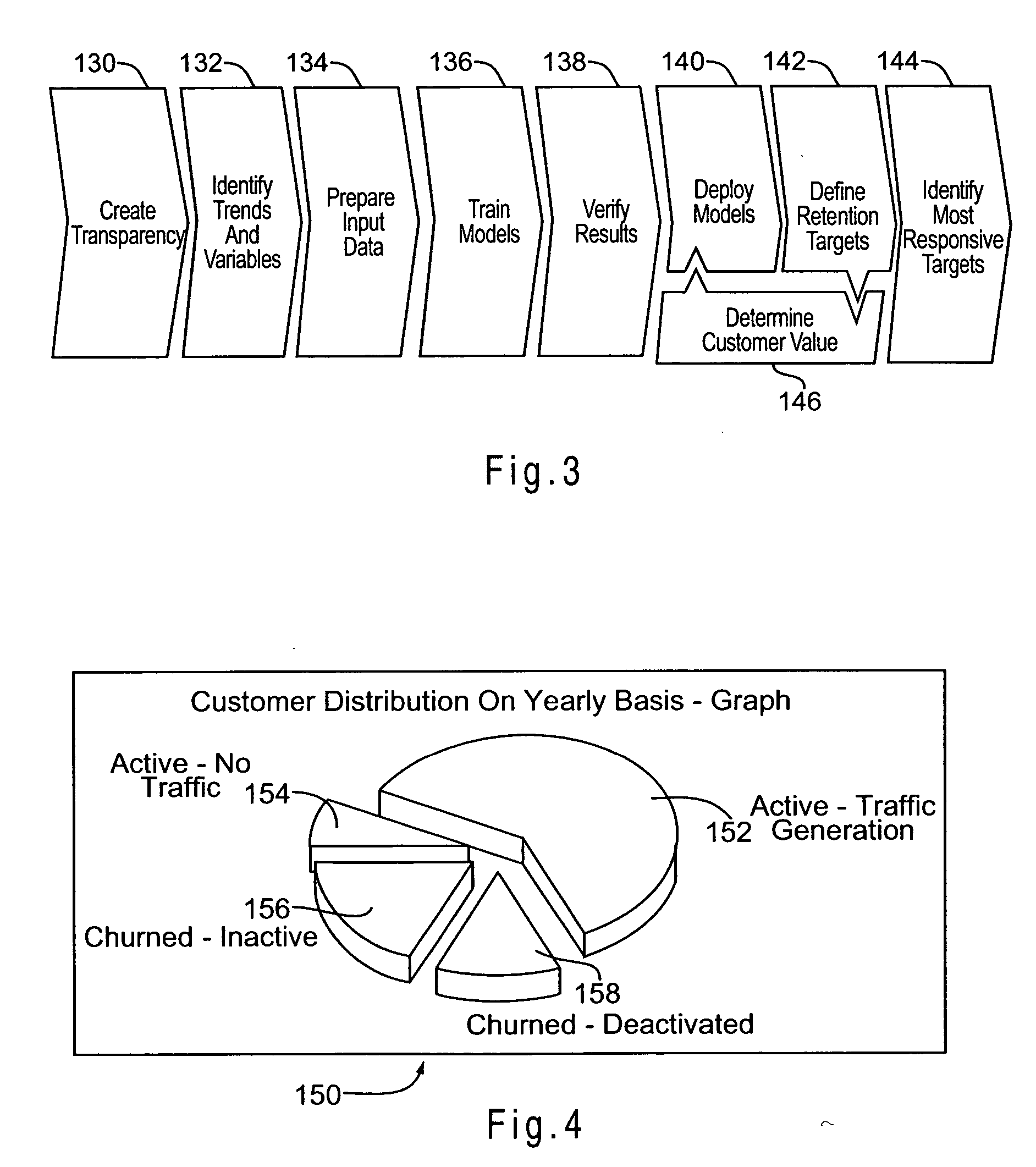
Churn prediction and management system
ActiveUS20070156673A1Avoid erosionFacilitates efforts to retain high profitability customersSpecial data processing applicationsMarketingCustomer attritionData operations
A system and method for managing churn among the customers of a business is provided. The system and method provide for an analysis of the causes of customer churn and identifies customers who are most likely to churn in the future. Identifying likely churners allows appropriate steps to be taken to prevent customers who are likely to churn from actually churning. The system included a dedicated data mart, a population architecture, a data manipulation module, a data mining tool and an end user access module for accessing results and preparing preconfigured reports. The method includes adopting an appropriate definition of churn, analyzing historical customer to identify significant trends and variables, preparing data for data mining, training a prediction model, verifying the results, deploying the model, defining retention targets, and identifying the most responsive targets.
Owner:ACCENTURE GLOBAL SERVICES LTD
Optimizing Distributed Computer Networks
ActiveUS20120089664A1Uniform applicationIncrease flexibility and efficiency and accelerationMultiple digital computer combinationsProgram controlClient-sideNetwork service
In one general embodiment, a computer-implemented method for managing a distributed computer network performed by one or more processors includes the steps of: receiving a request from a client in the distributed computer network for a network service; optimizing a delivery of the requested network service to the client from a server in the distributed computer network; and monitoring an execution of the delivery of the network service.
Owner:SAP PORTALS ISRAEL
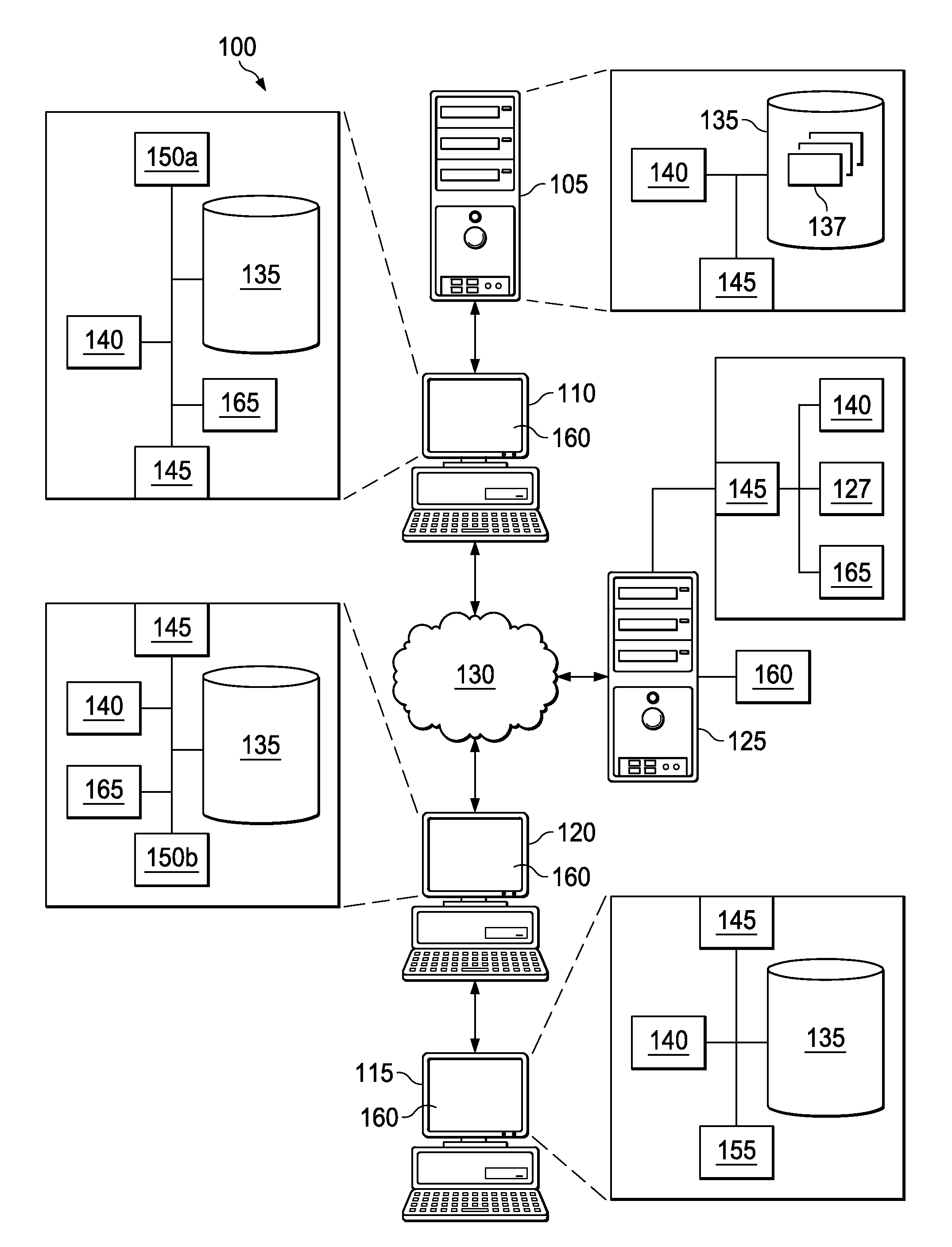
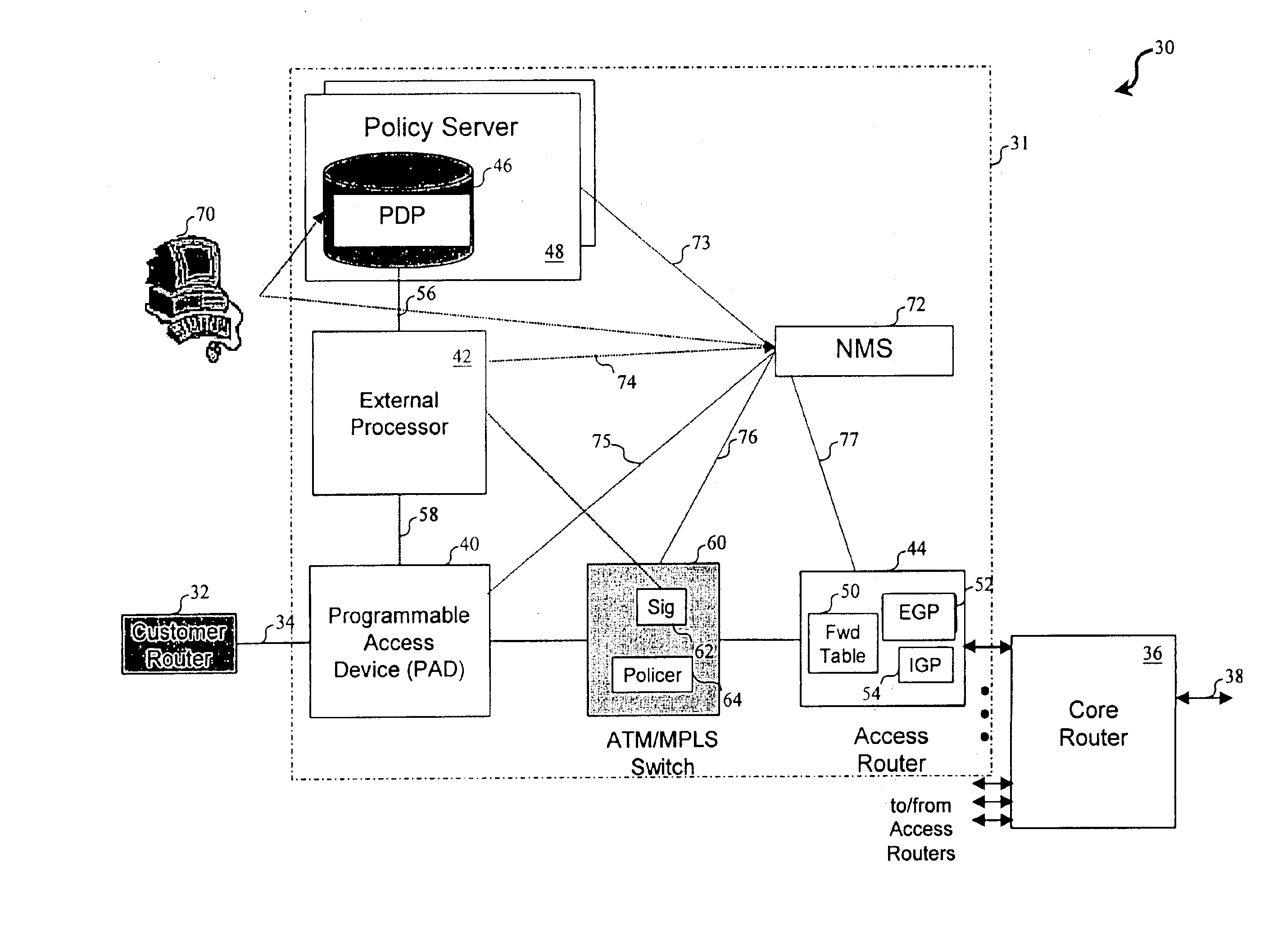
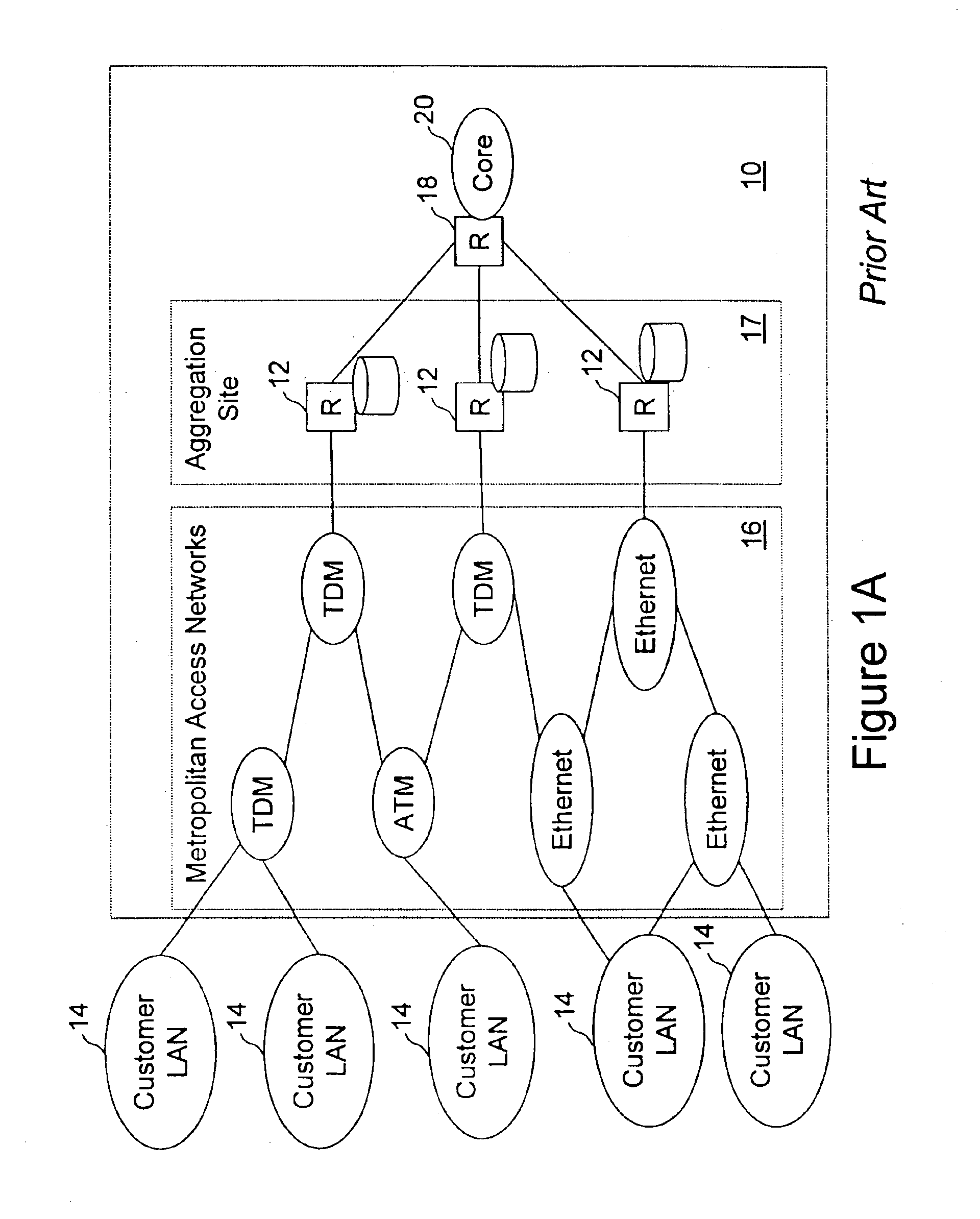
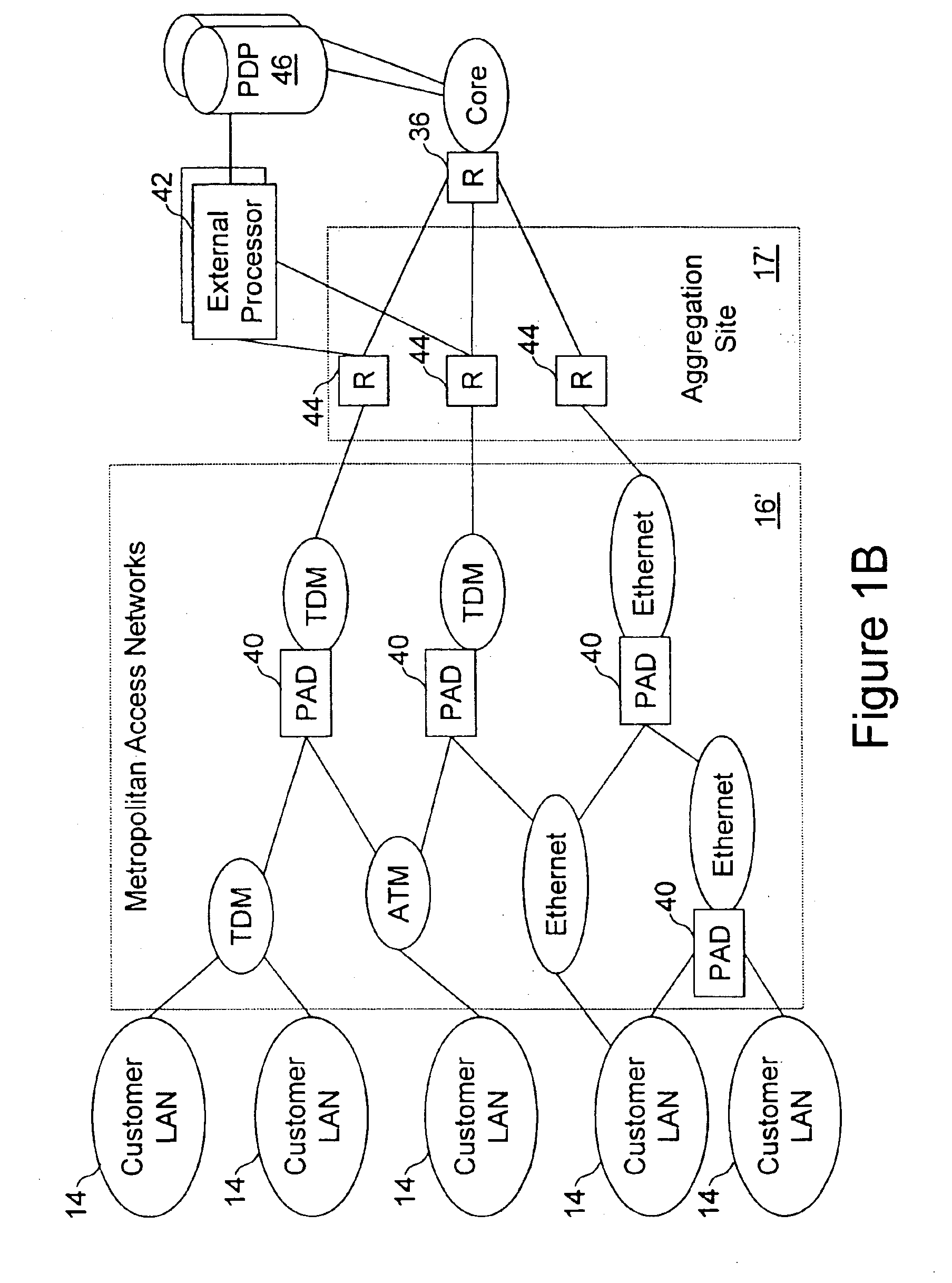
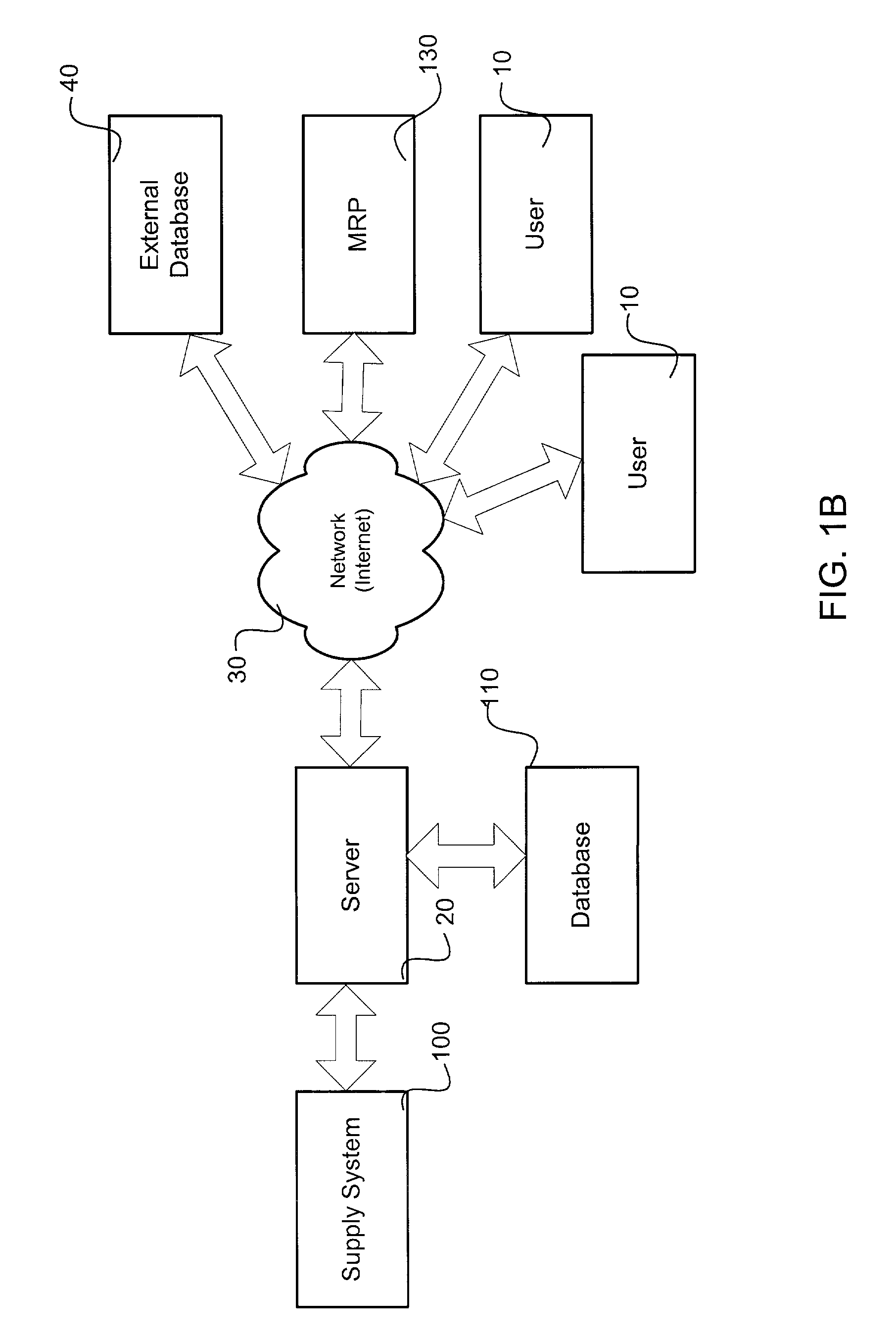
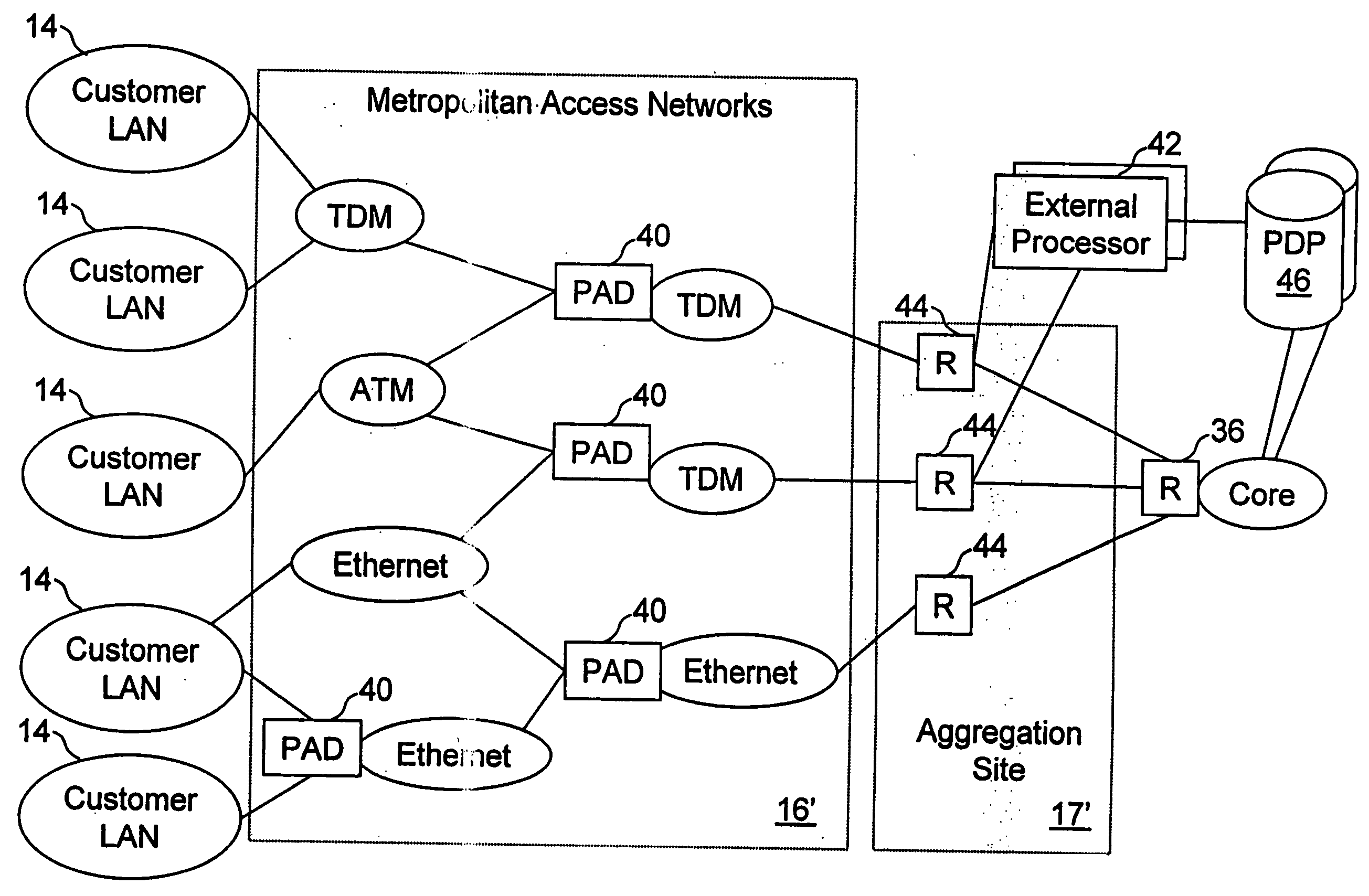
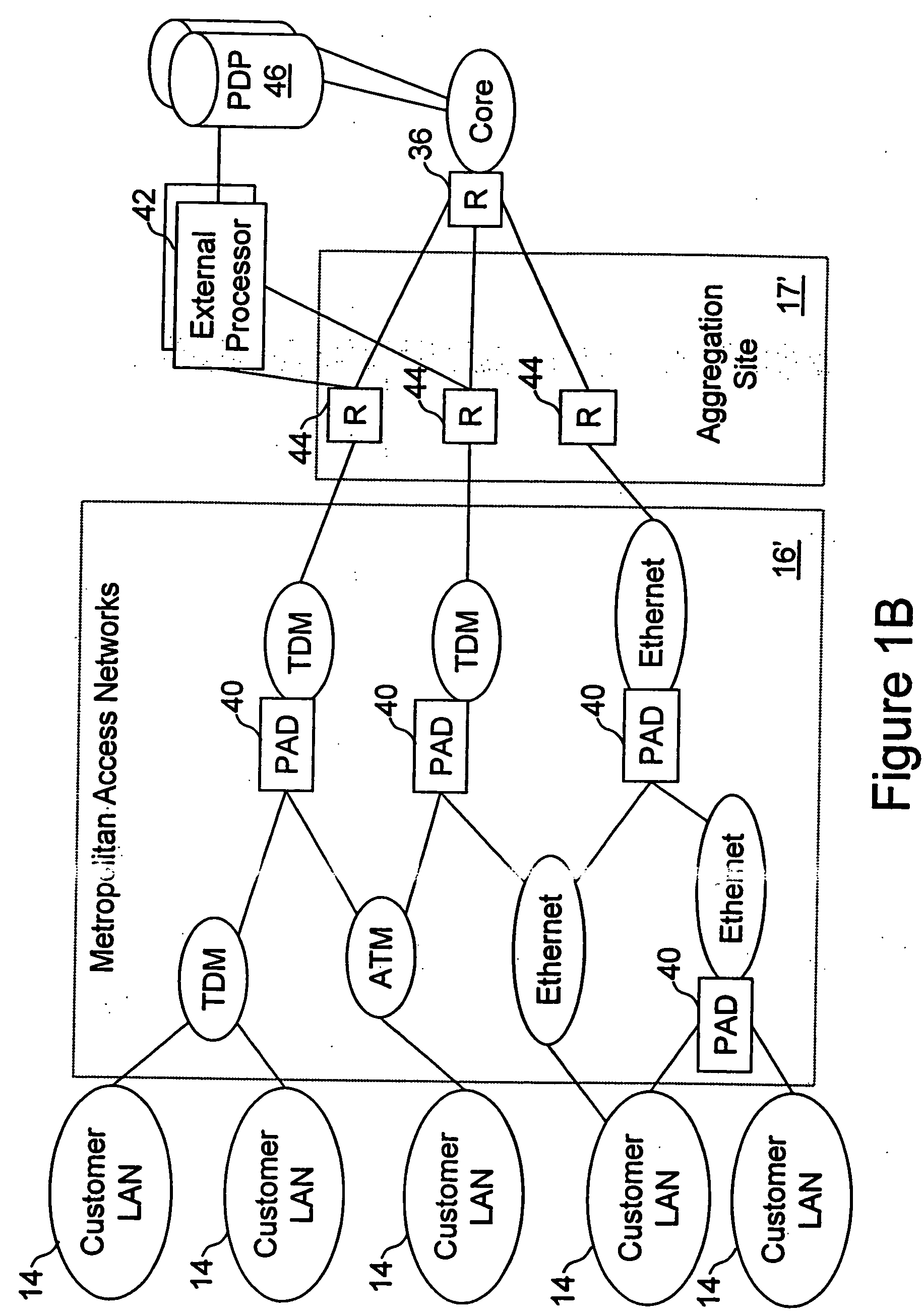
Network access system including a programmable access device having distributed service control
InactiveUS7046680B1Good extensibilityIncrease flexibilityData switching by path configurationMultiple digital computer combinationsProgrammable logic deviceMessage Passing Interface
A distributed network access system in accordance with the present invention includes at least an external processor and a programmable access device. The programmable access device has a message interface coupled to the external processor and first and second network interfaces through which packets are communicated with a network. The programmable access device includes a packet header filter and a forwarding table that is utilized to route packets communicated between the first and second network interfaces. In response to receipt of a series of packets, the packet header filter in the programmable access device identifies messages in the series of messages upon which policy-based services are to be implemented and passes identified messages via the message interface to the external processor for processing. In response to receipt of a message, the external processor invokes service control on the message and may also invoke policy control on the message.
Owner:VERIZON PATENT & LICENSING INC
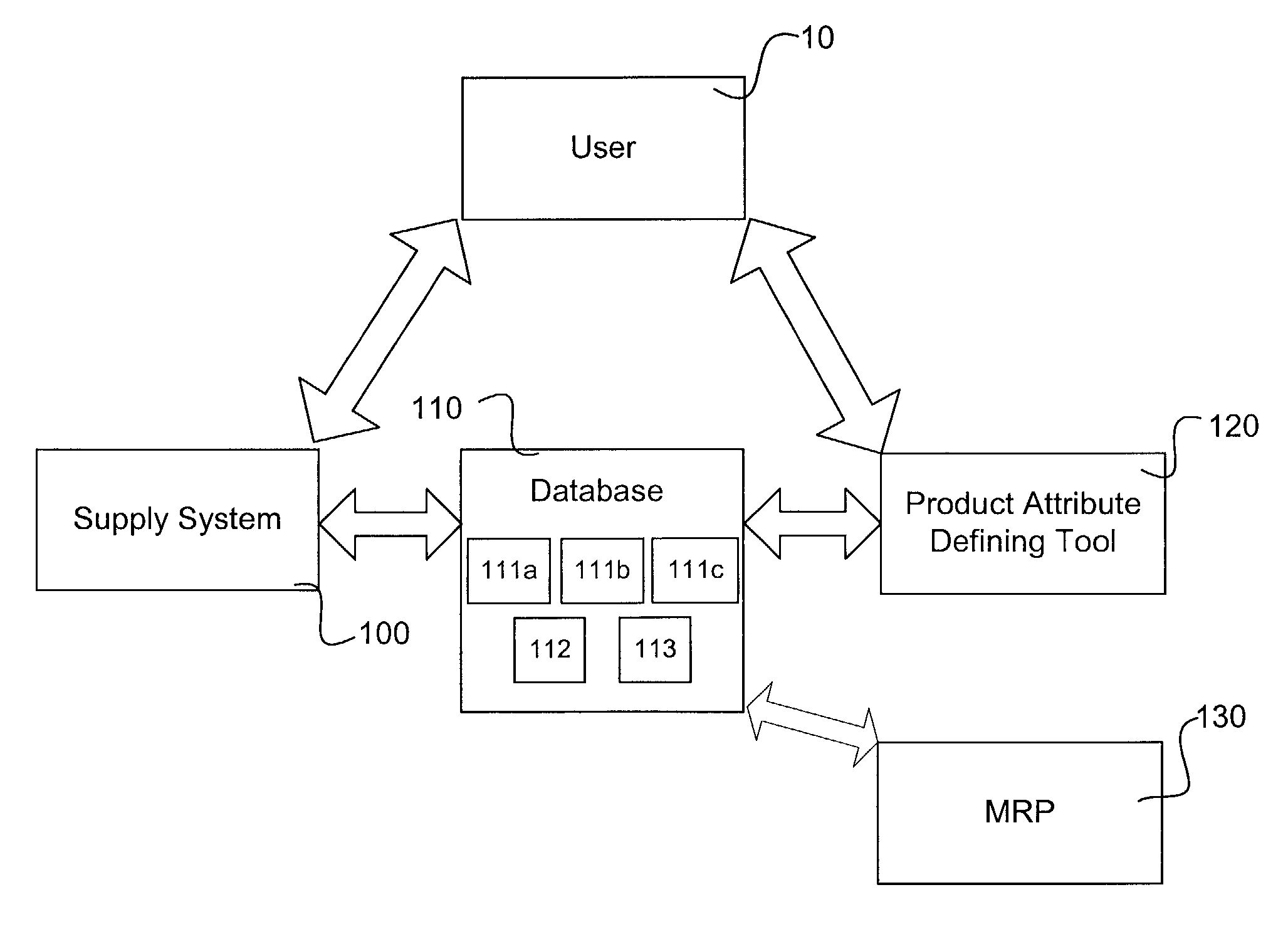
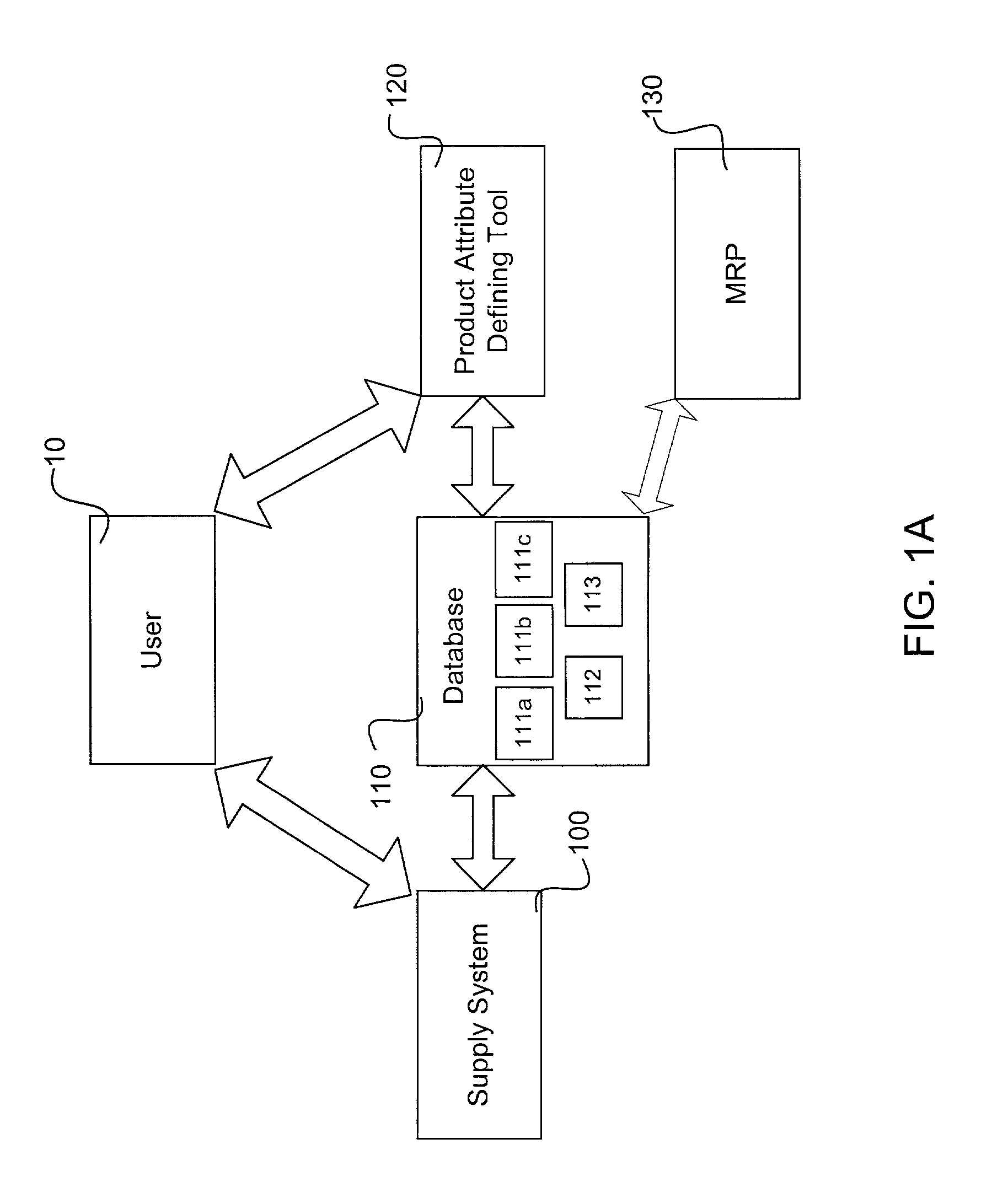
System and method for allocating the supply of critical material components and manufacturing capacity
InactiveUS7058587B1Improve responsivenessMaximize inventory useResourcesSpecific program execution arrangementsProgram planningChange analysis
The present invention allocates the supply of critical components and manufacturing capacity by optimizing critical material planning decisions and dynamically allocating constrained materials using advanced substitution logic that considers alternate suppliers and supports product life cycle from design through end-of-life. The present invention may utilize unique synchronized allocations and matched sets logic. The synchronized allocations ensure that all materials necessary for production are available in the appropriate time-phased allocation before beginning production to minimize wasted production capacity and materials. The supply system may include various combination of components, including a Supply Planner, a Resource Optimizer, a Constraint Based Master Planner, a Product Change Analyzer, a Comparer, a Resource Requirements Planner, a Finite Resource Planner, a Customer Promiser, and an Interactive Master Scheduler. Another embodiment of the supply system includes a tool that allows users to define products using engineering specifications.
Owner:BLUE YONDER GRP INC
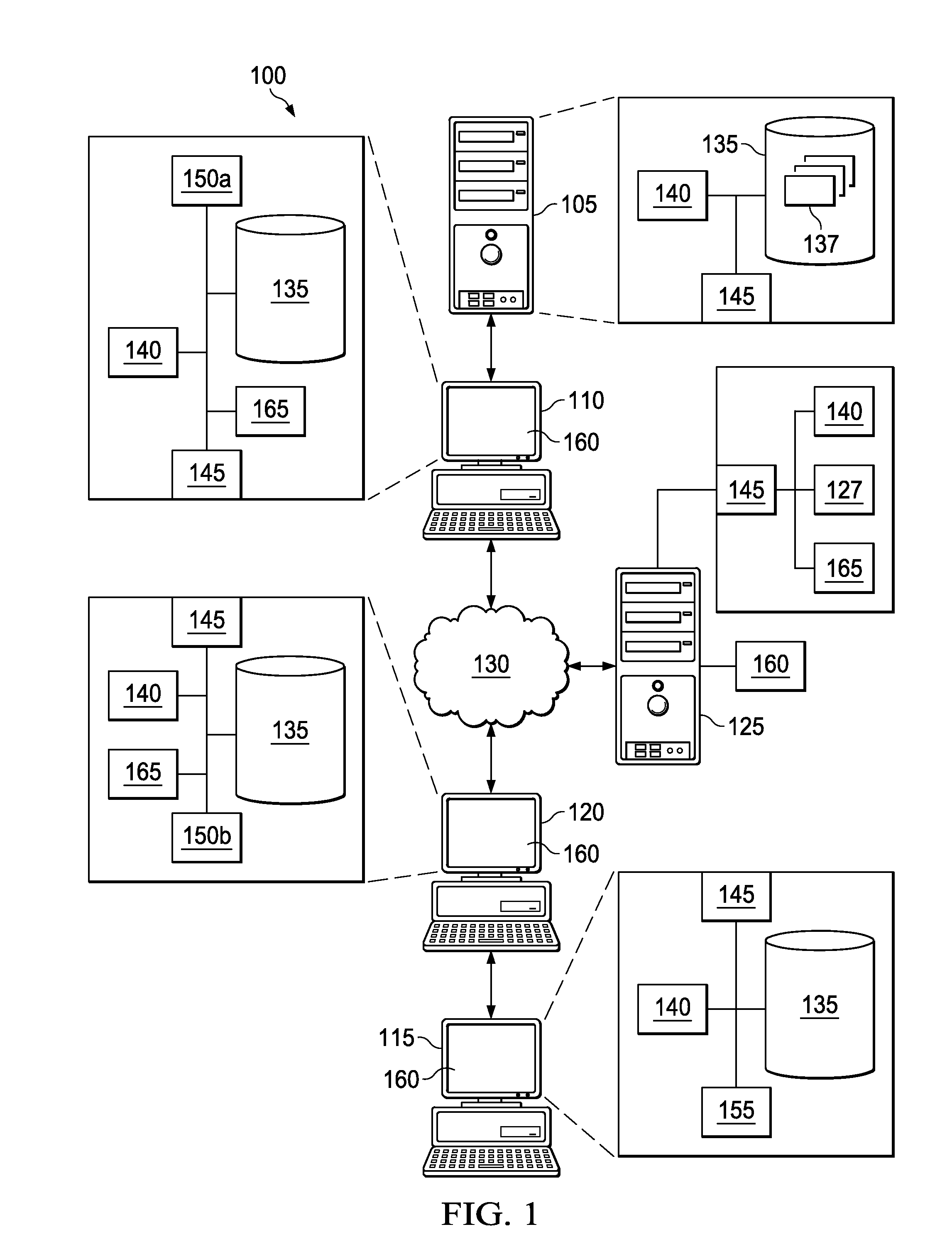
Network access system including a programmable access device having distributed service control
InactiveUS20050117576A1Good extensibilityIncrease flexibilityData switching by path configurationPacket communicationService control
A distributed network access system in accordance with the present invention includes at least an external processor and a programmable access device. The programmable access device has a message interface coupled to the external processor and first and second network interfaces through which packets are communicated with a network The programmable access device includes a packet header filter and a forwarding table that is utilized to route packets communication between the first and second network interfaces. In response to receipt of a series of packets, the packet header filter in the programmable access device identifies messages in the series of messages upon which policy-based services are to be implemented and passes identified messages via the message interface to the external processor for processing. In response to receipt of a message, the external processor invokes service control on the message and may also invoke policy control on the message.
Owner:VERIZON PATENT & LICENSING INC
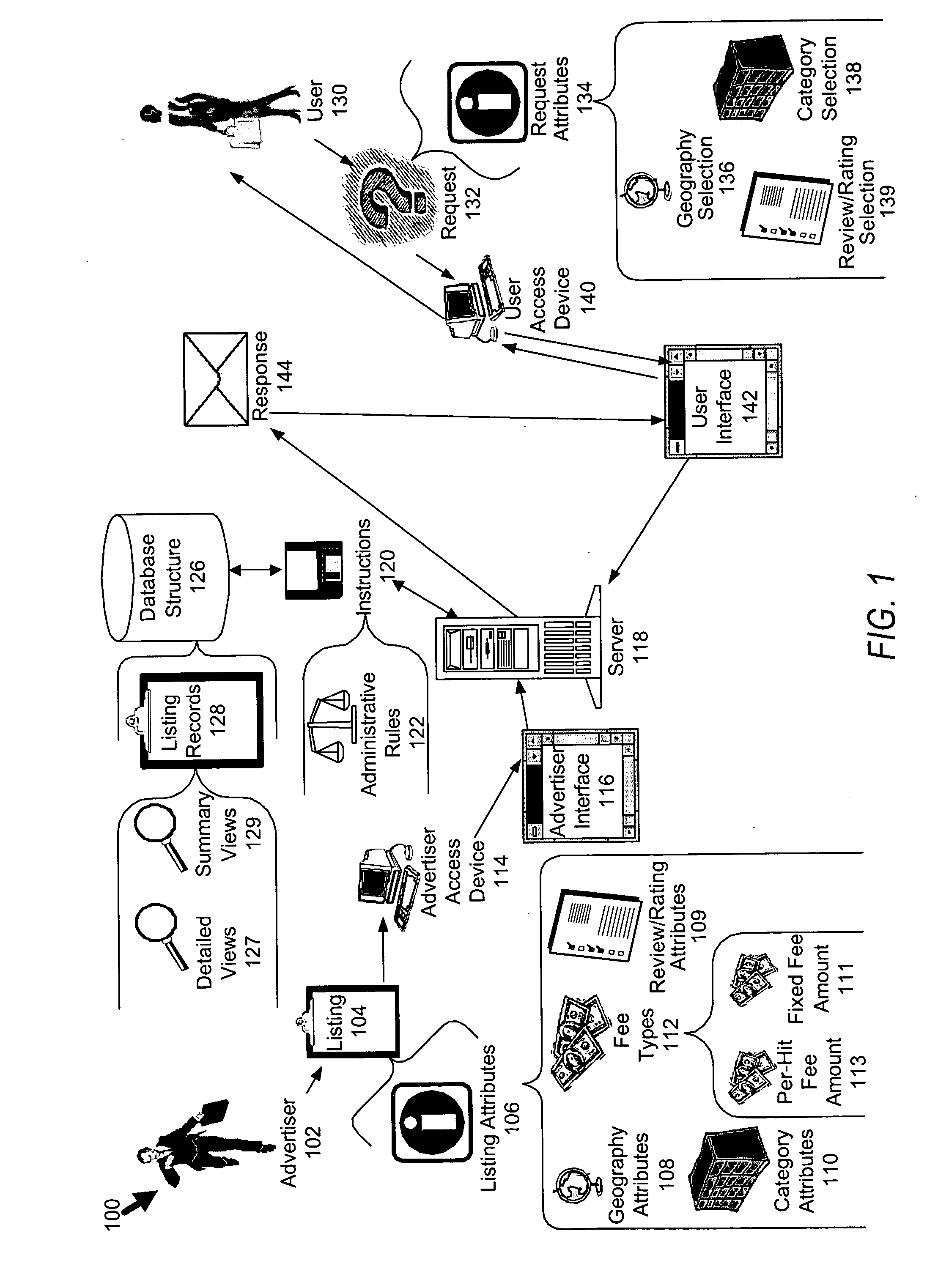
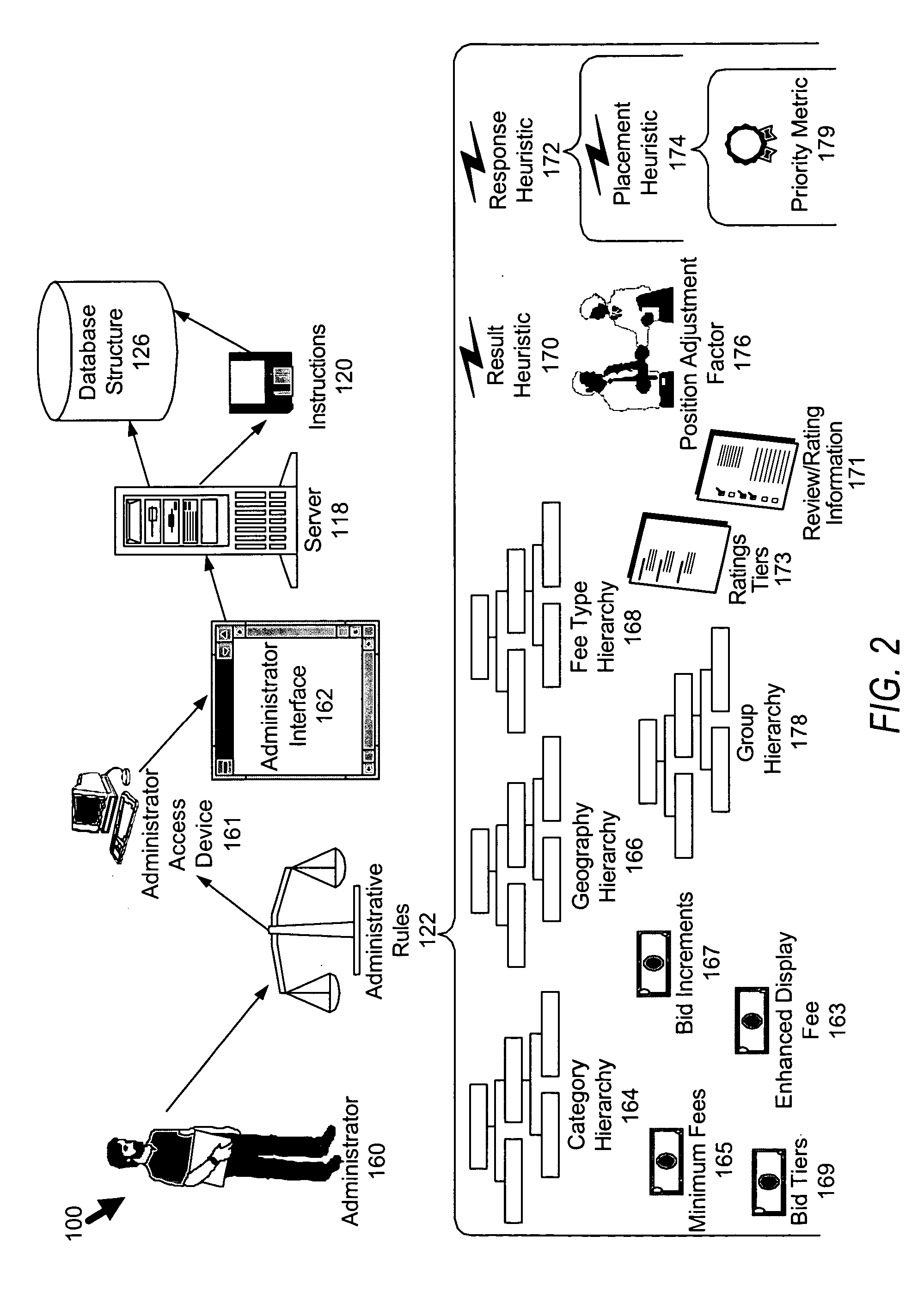
Business rating placement heuristic
ActiveUS20050065811A1Enhance priority metricImprove abilitiesFinanceAdvertisementsData miningSystem administrator
A system and method for distributing information (collectively the “system”) is disclosed. The system includes category-based, geography-based, and ratings-based attributes to better “focus” the information distributed by the system. In the processing of listing-based attributes (e.g. attributes limited to a particular listing), the system can also be influenced by relationship-based attributes (e.g. attributes between the administrator of the system and the advertisers, and even potentially users).
Owner:THRYV INC
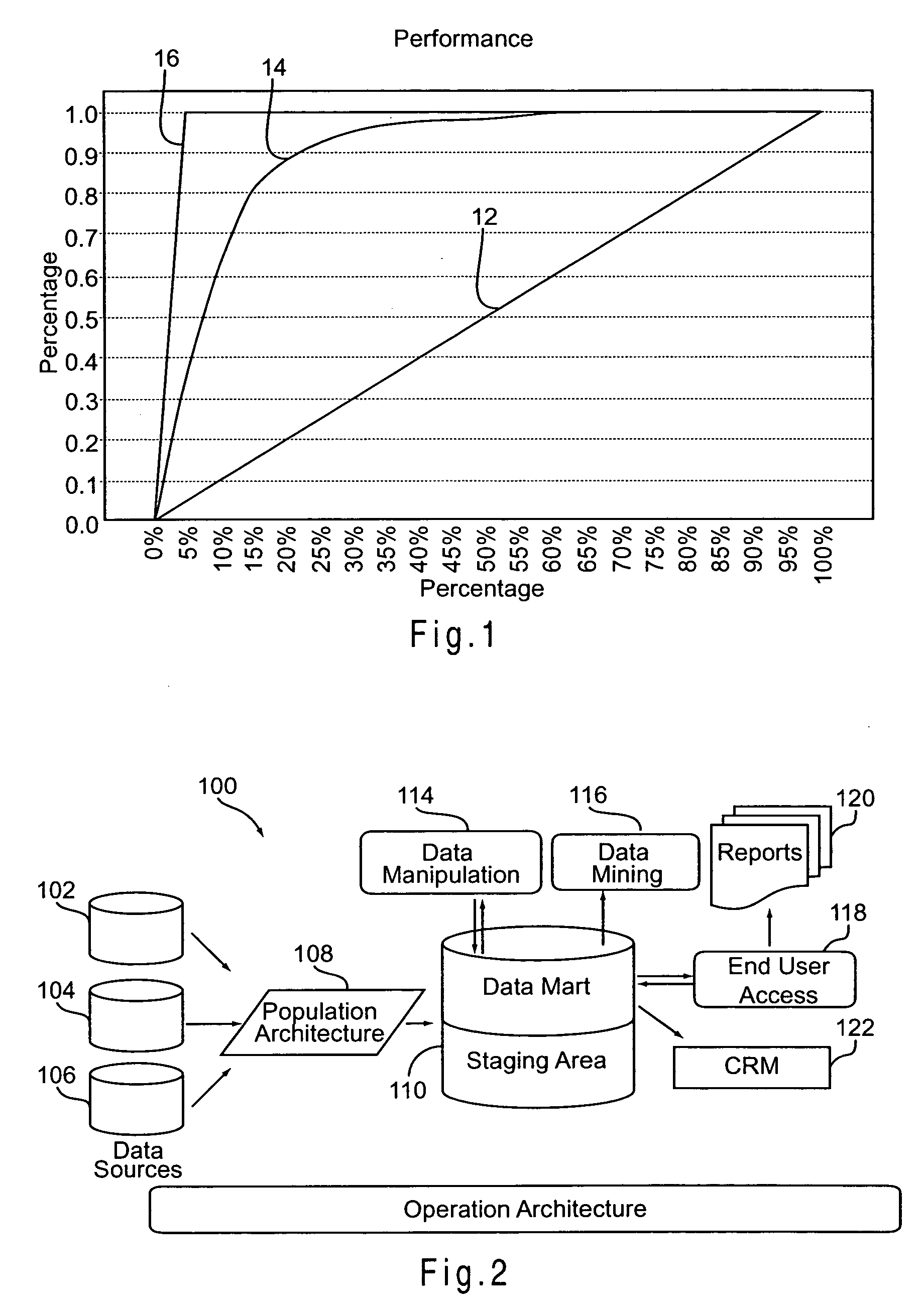
Statistical modeling methods for determining customer distribution by churn probability within a customer population
InactiveUS20070185867A1Avoid erosionFacilitates efforts to retain high profitability customersDatabase queryingMarketingData dredgingCustomer attrition
A system and method for managing churn among the customers of a business is provided. The system and method provide for an analysis of the causes of customer churn and identifies customers who are most likely to churn in the future. Identifying likely churners allows appropriate steps to be taken to prevent customers who are likely to chum from actually churning. The system included a dedicated data mart, a population architecture, a data manipulation module, a data mining tool and an end user access module for accessing results and preparing preconfigured reports. The method includes adopting an appropriate definition of churn, analyzing historical customer to identify significant trends and variables, preparing data for data mining, training a prediction model, verifying the results, deploying the model, defining retention targets, and identifying the most responsive targets.
Owner:ACCENTURE GLOBAL SERVICES LTD
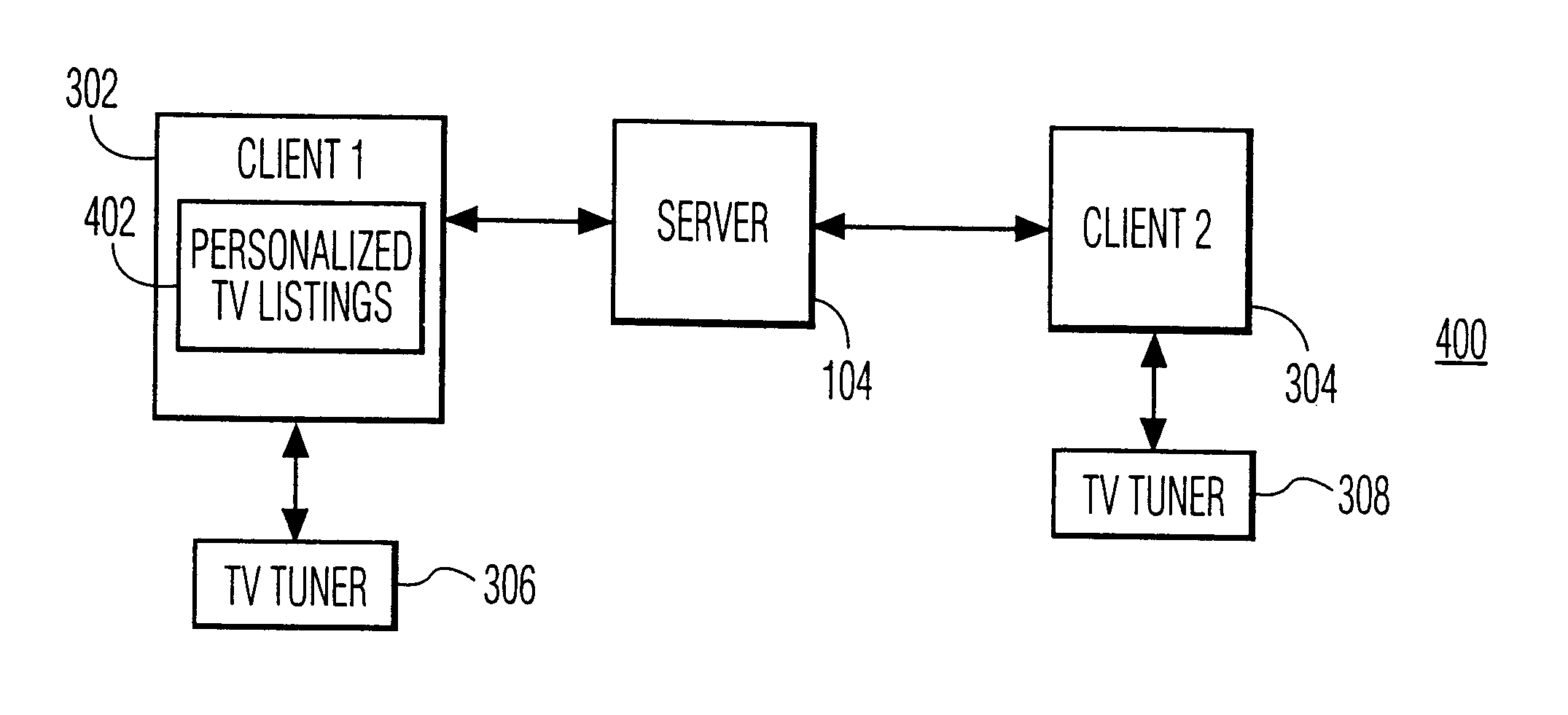
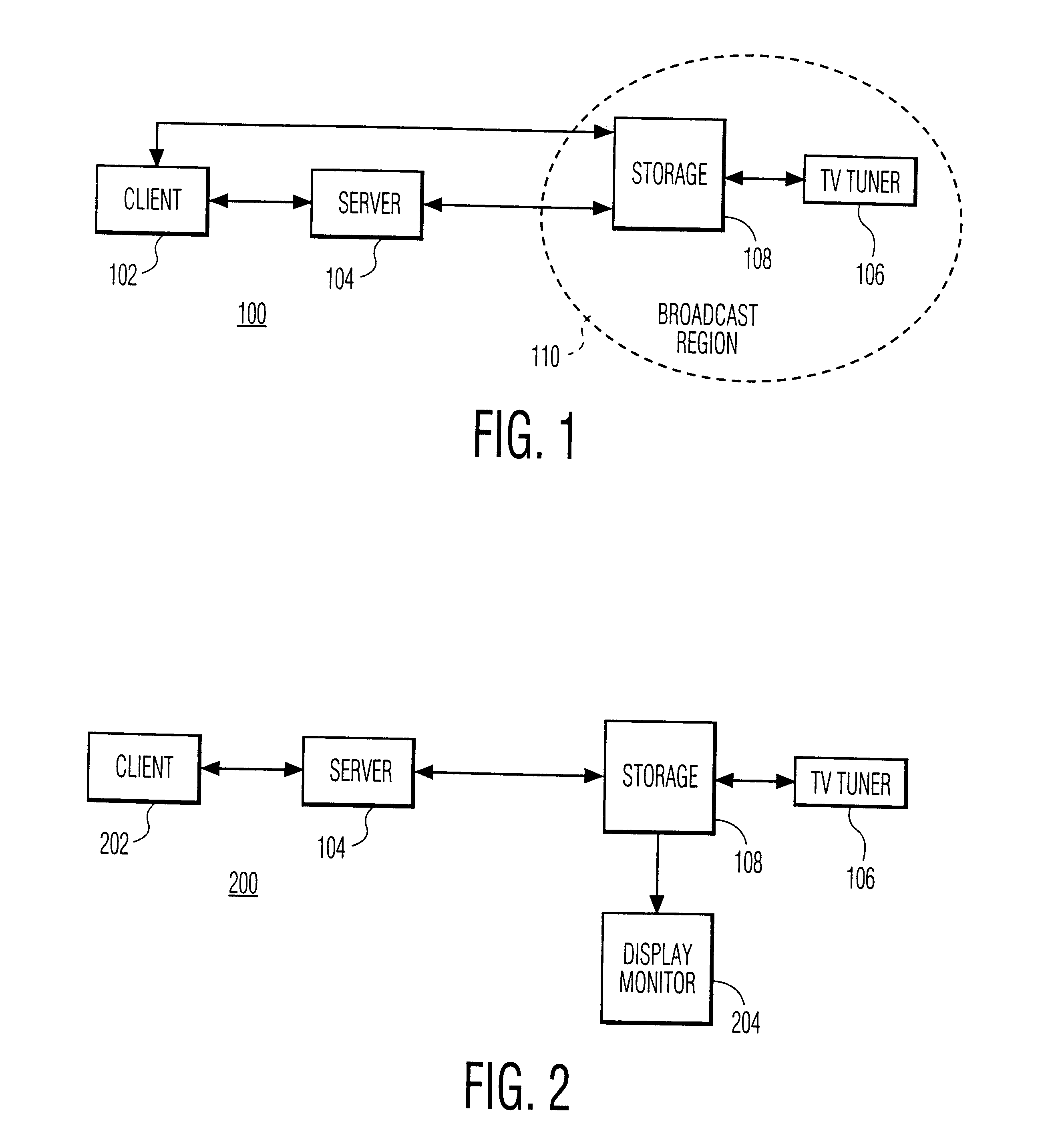
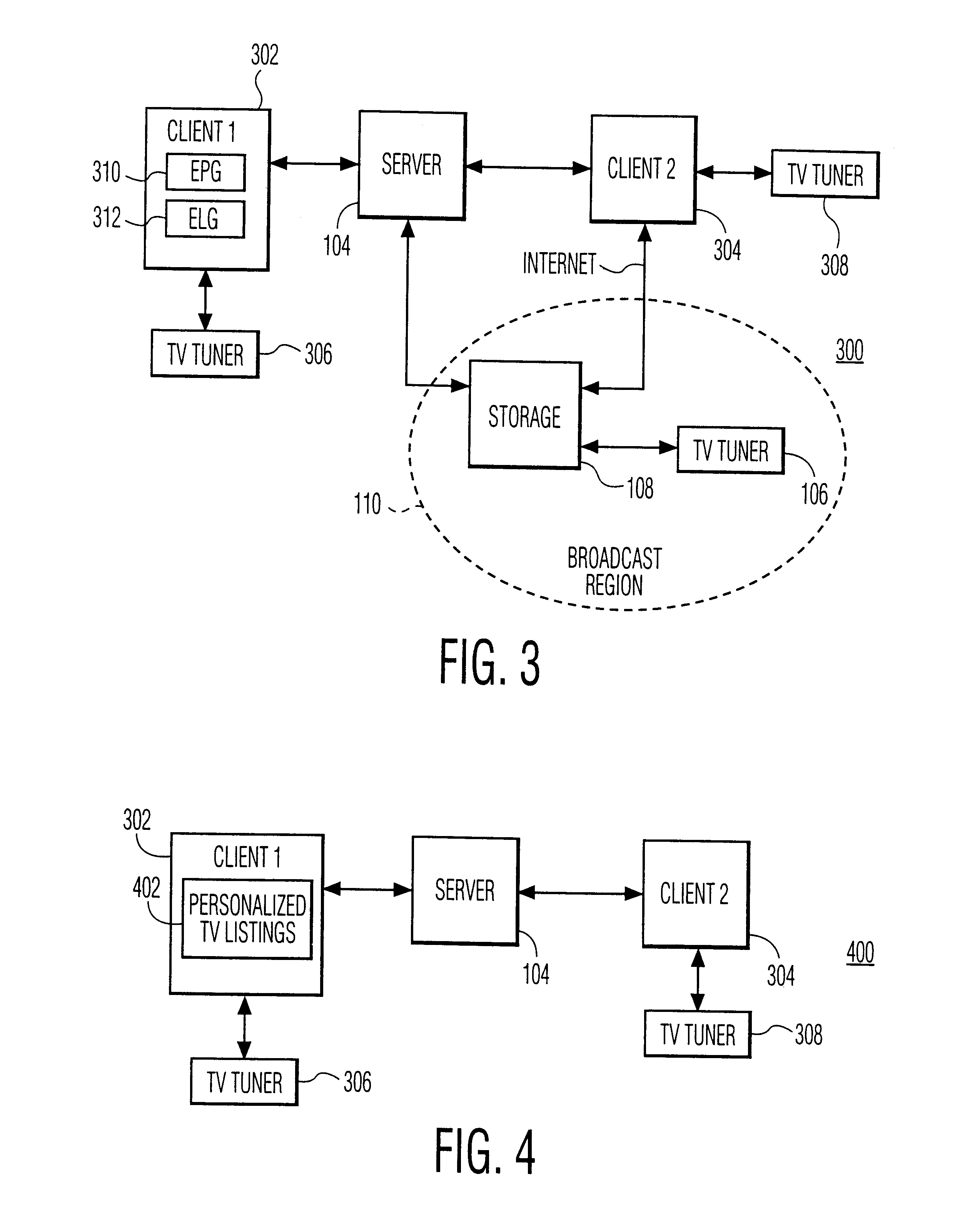
Time- and location-driven personalized TV
InactiveUS6611654B1Improve mobilityIncrease demandTelevision system detailsTelevision conference systemsPersonalizationTime frame
A server system enables a subscriber to select a specific broadcast program for recording and a specific location and time frame for play-out of the recorded program.
Owner:PHILIPE ELECTRONICS NORTH AMERICA
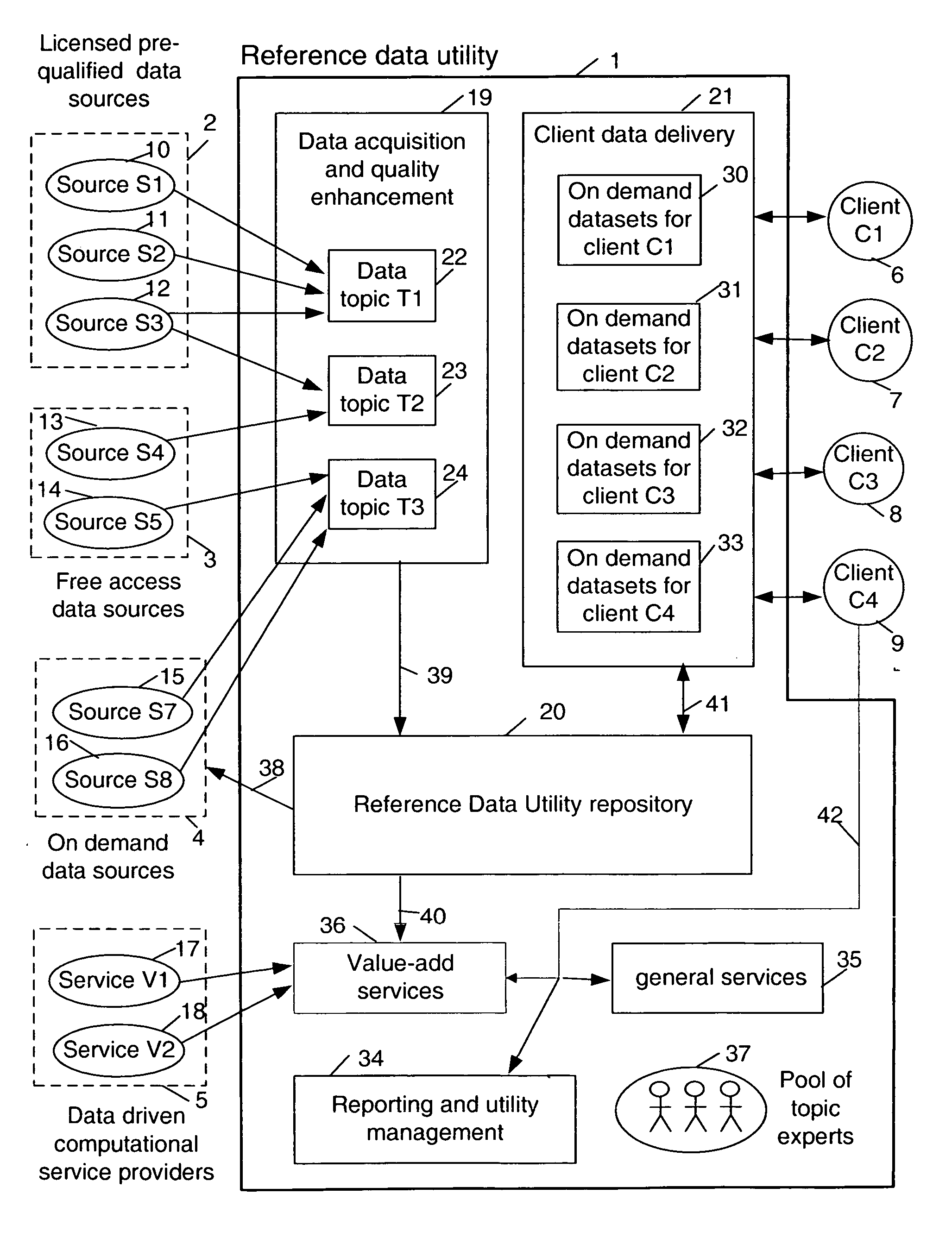
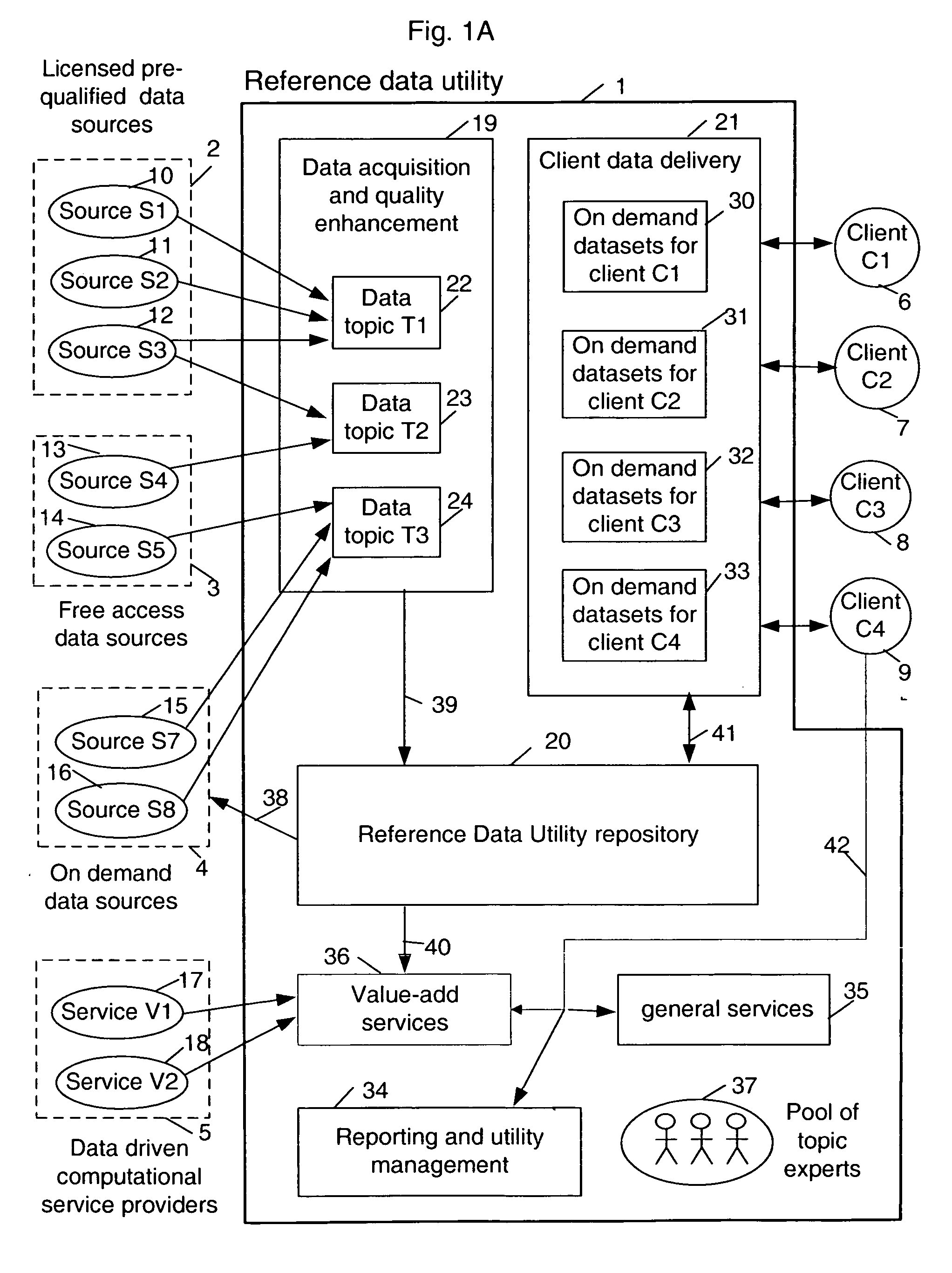
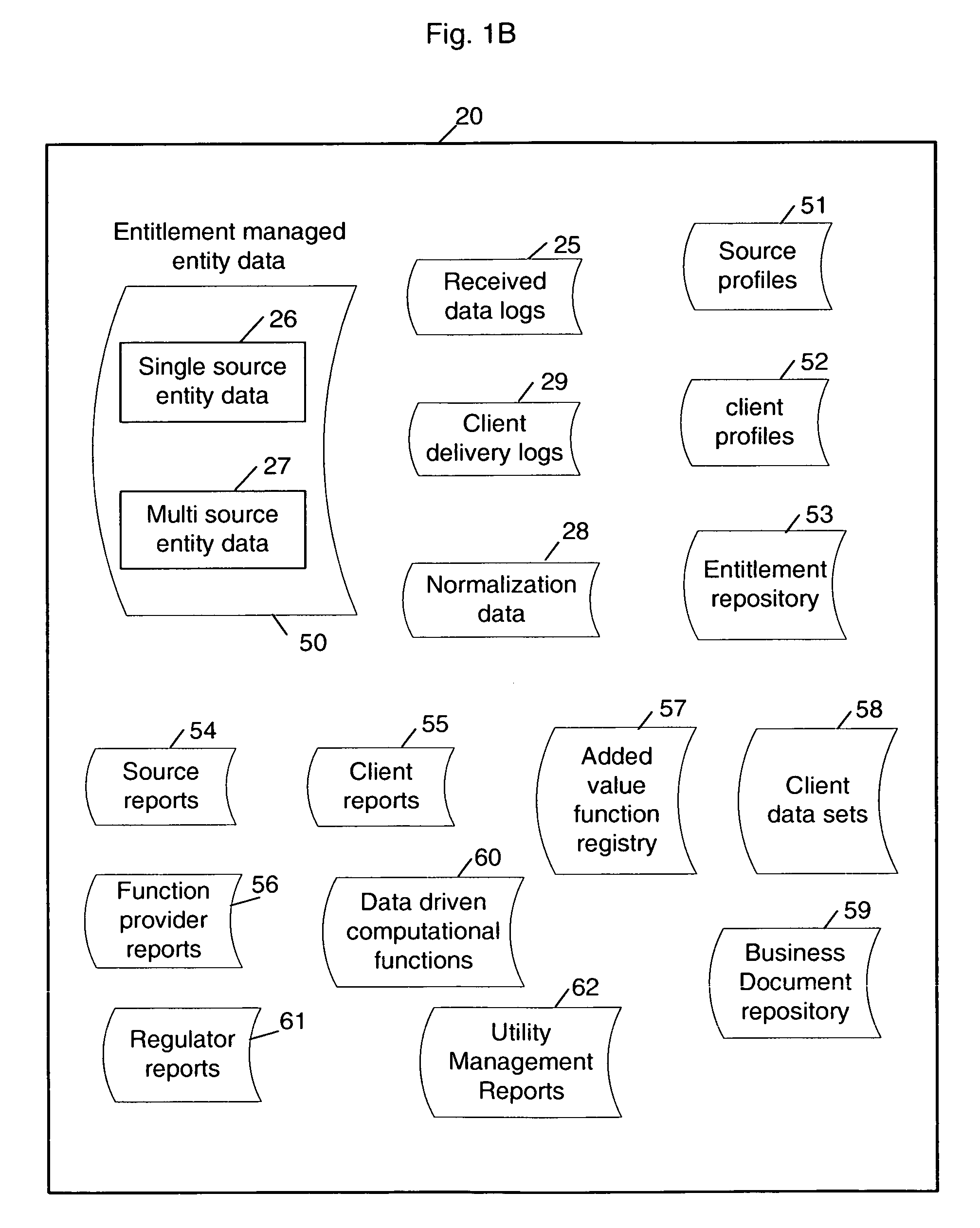
Multi-source multi-tenant entitlement enforcing data repository and method of operation
InactiveUS20060235831A1Easy to optimizeLow costFinanceSpecial data processing applicationsData qualityData store
Forming and maintaining a multi-source multi-tenant data repository on behalf of multiple tenants. Information in the multi-source multi-tenant data repository is received from multiple sources. Different sources and different data quality enhancement processes may yield different values for attributes of the same referred entity. Information in the multi-source multi-tenant data repository is tagged with annotations documenting the sources of the information, and any data quality processing actions applied to it. Tenants of the multi-source multi-tenant data repository have entitlement to values from some sources and to the results of some quality enhancement processes. Aspects of the method maintain this entitlement information; employ evolutionarily tracked source data tags; receive requests for information, locate the requested information, apply any sourcing preference, enforce entitlements and return entitled values to the requester. An outsourced reference data utility is one context where such a multi-source multi-tenant data repository is useful.
Owner:ADINOLFI RONALD EMMETT +9
Assessment of best fit cloud deployment infrastructures
InactiveUS20140279201A1Enhancing cloud serviceEfficient and effectiveFinanceBuying/selling/leasing transactionsApplication softwareInformation processor
A system configured to facilitate selling hybrid cloud services comprises a plurality of user interface structures each coupled to an information processor. A first user interface structure is configured to request information characterizing deployment of an application within a current operational infrastructure. A second user interface structure is configured to display a recommended deployment infrastructure supporting migration of the application thereto. A third user interface structure is configured to display information characterizing migration of the application to the recommended deployment infrastructure. The information processor is configured to receive the current application deployment characterizing information from the first user interface structure, to determine the recommended deployment infrastructure using at least a portion of the current application deployment characterizing information, and to determine the information characterizing migration of the application to the recommended deployment infrastructure using at least a portion of the current application deployment.
Owner:HCL TECH LTD
System and method for qualifying requests in a network
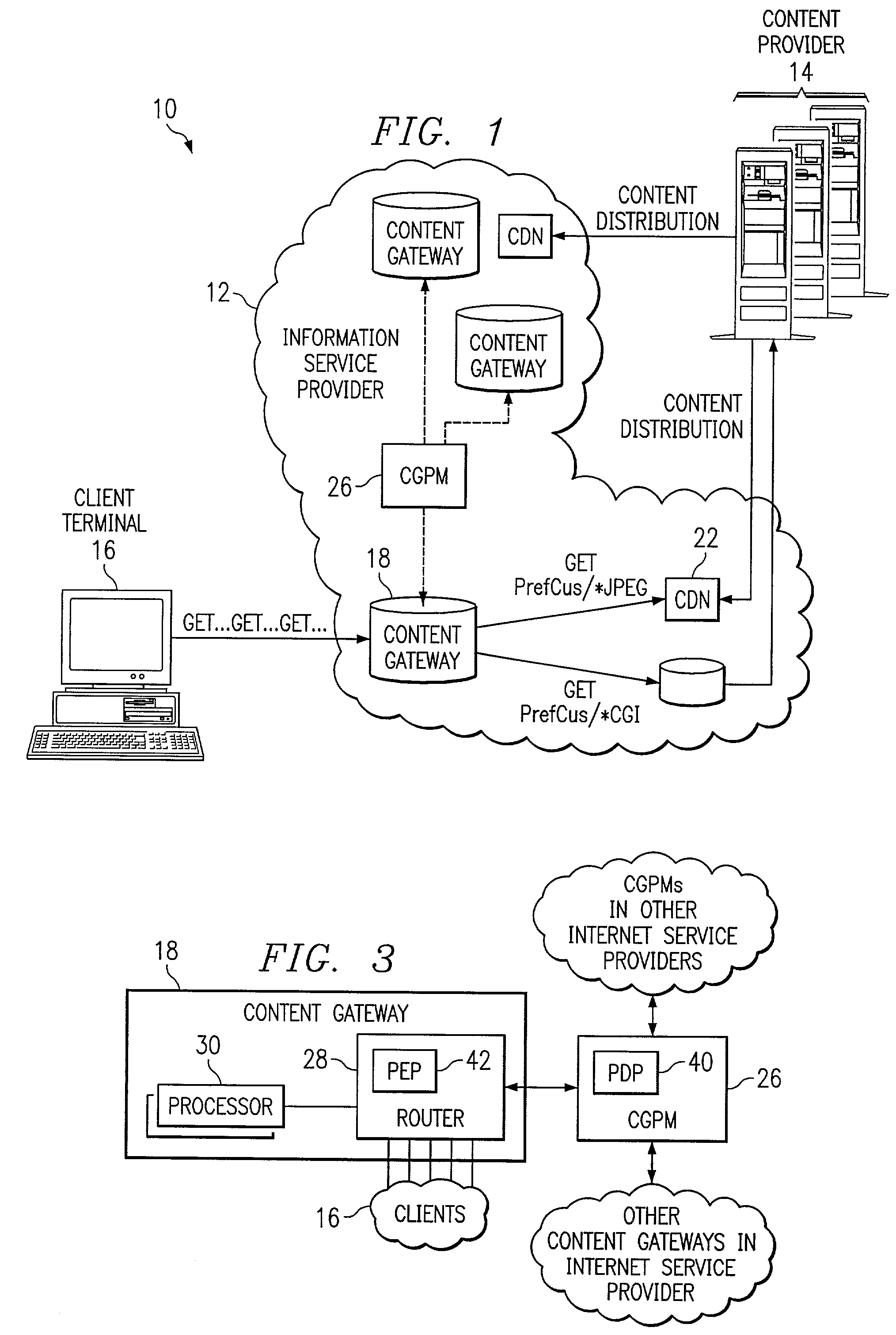
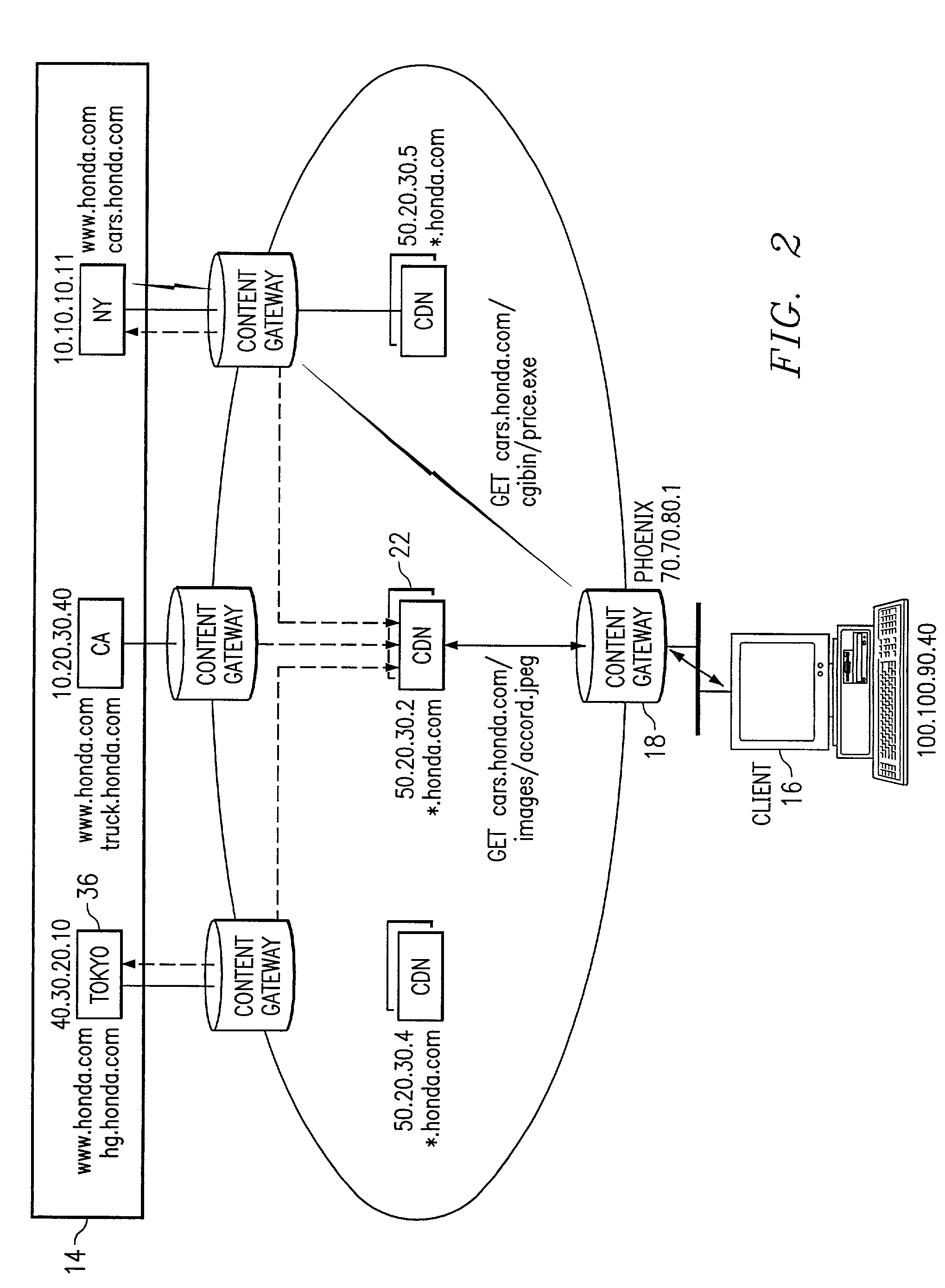
ActiveUS6968389B1Good serviceEliminate and greatly reduce disadvantageMultiple digital computer combinationsData switching networksDomain nameName server
An information service provider network includes a content gateway to process requests for information from a client terminal. The content gateway includes a router for receiving a domain name server query from an originator associated with a request for information. The router including a database defining a relationship between domain names and addresses associated with accelerated servicing of requests. The router determines whether the domain name of the domain name server query is indexed in the database. The domain name is qualified in response to the domain name being in the database. If qualified, the router sends an address to the originator of the query corresponding in the database to the domain name. The address is to a processor associated with the router that performs accelerated services on the request.
Owner:CISCO TECH INC
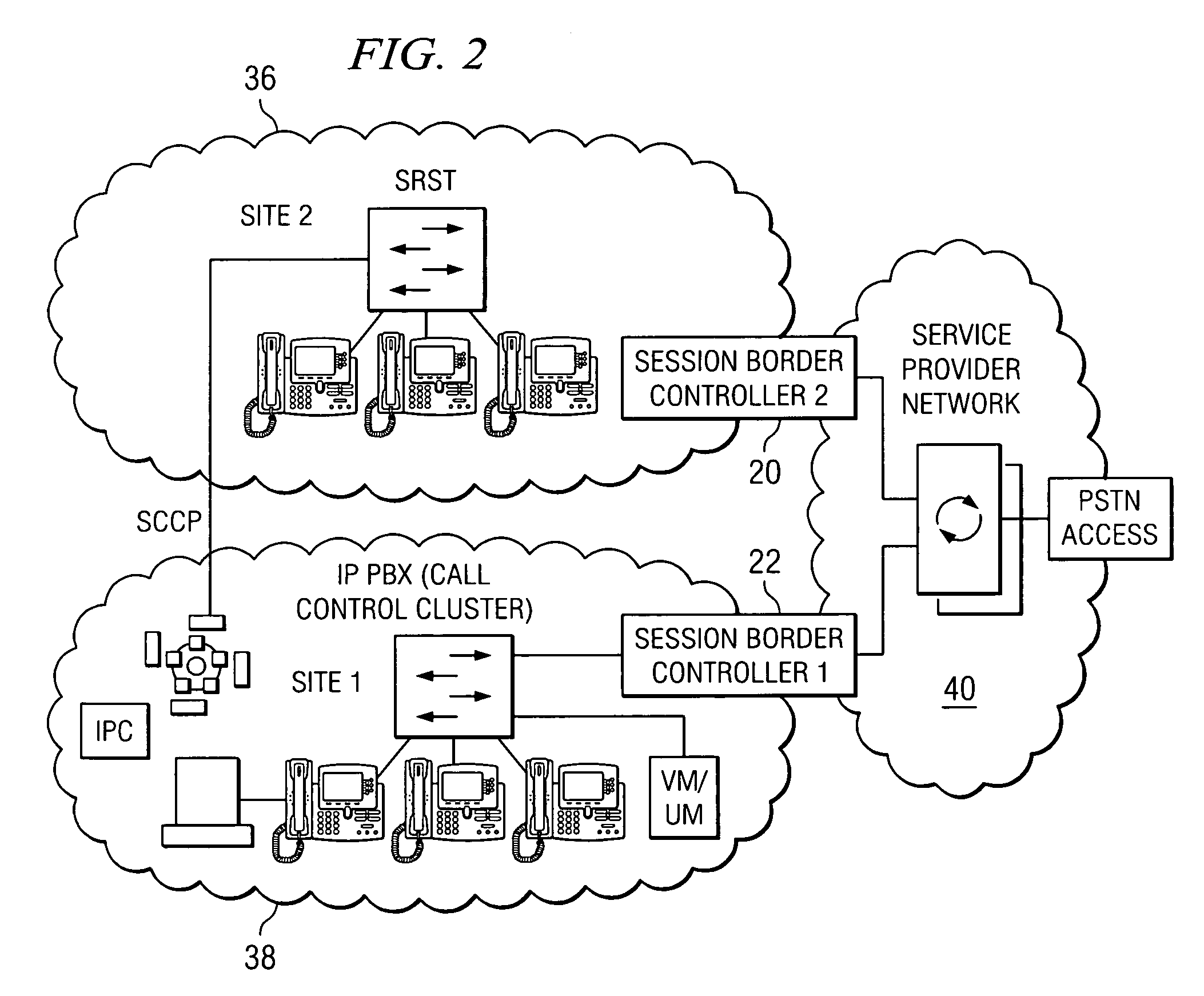
System and method for optimizing communications between session border controllers and enpoints in a network environment
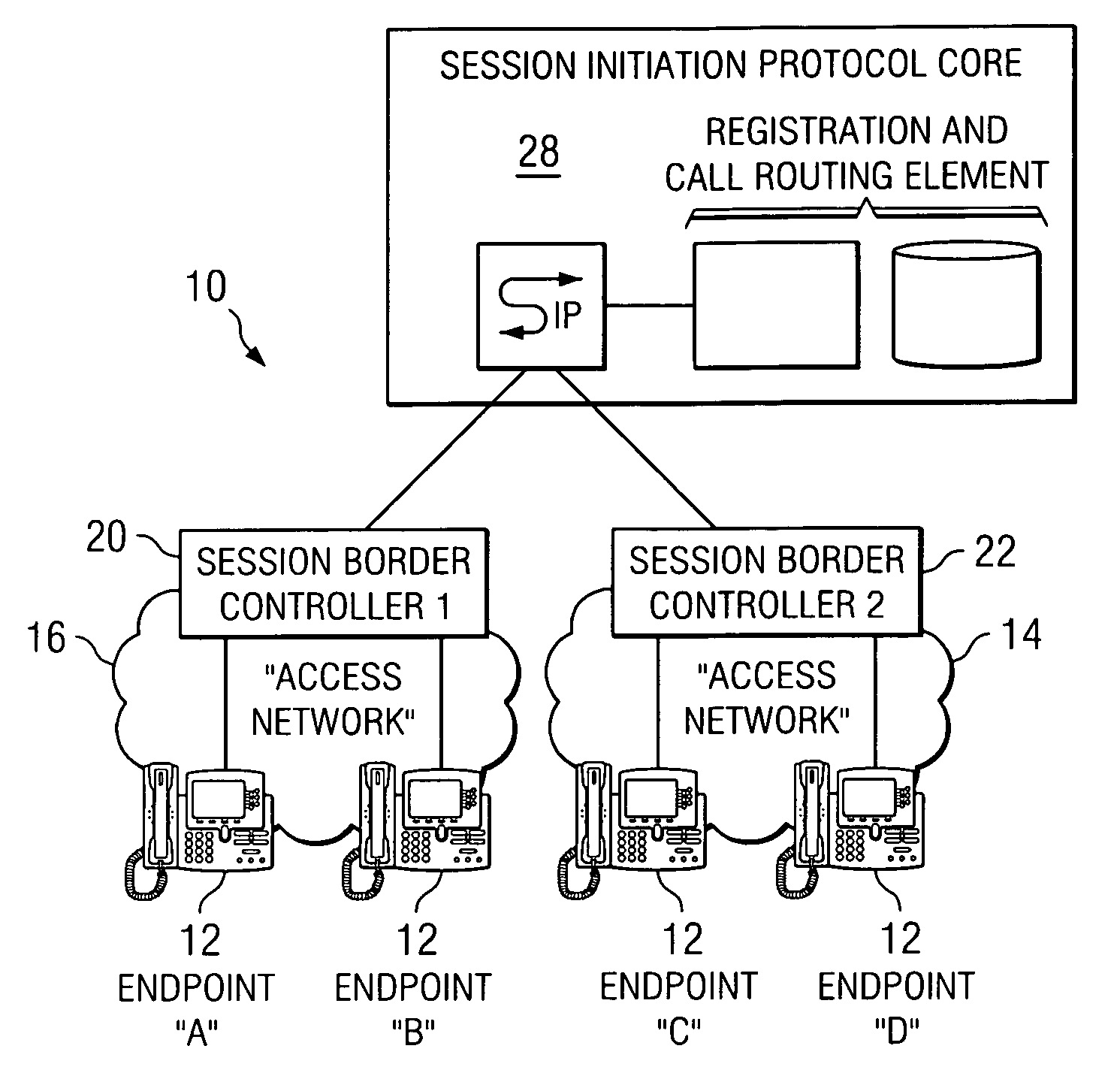
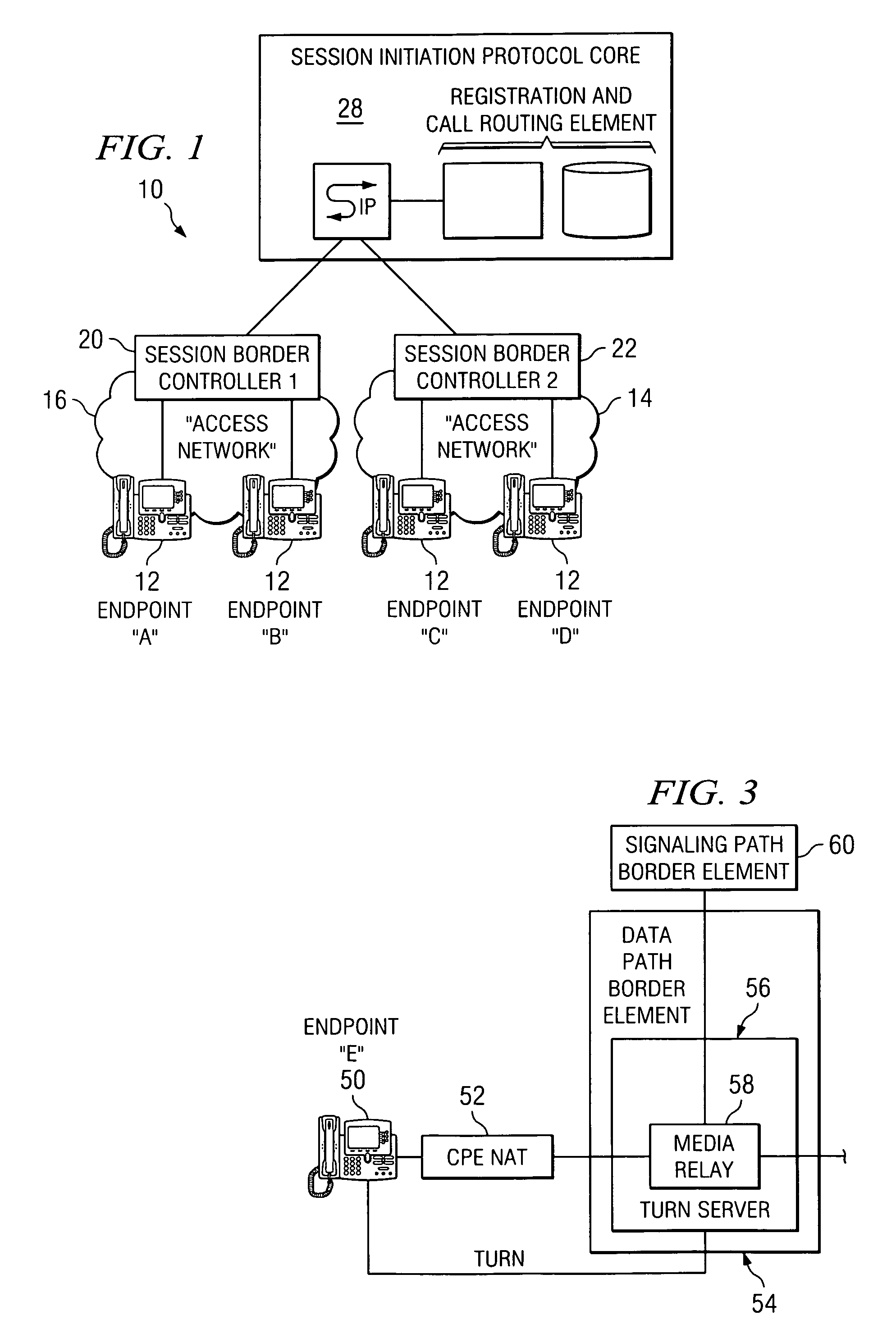
ActiveUS20070019619A1Reduce disadvantagesReduce problemsMultiplex system selection arrangementsSpecial service provision for substationDatapathSession border controller
An apparatus for optimizing communications between session border controllers in a network environment is provided that includes a session border controller (SBC) operable to communicate with a first endpoint and a second endpoint. The SBC is also operable to communicate with a data path border element (DBE) and a signaling path border element (SBE). The DBE is operable to provide a media relay for a communication session involving the endpoints, the media relay being invoked by either of the endpoints using a traversal using relay network address translation (TURN) protocol, which allows the SBC to operate in either of two modes depending on protocol support present in the endpoints.
Owner:CISCO TECH INC
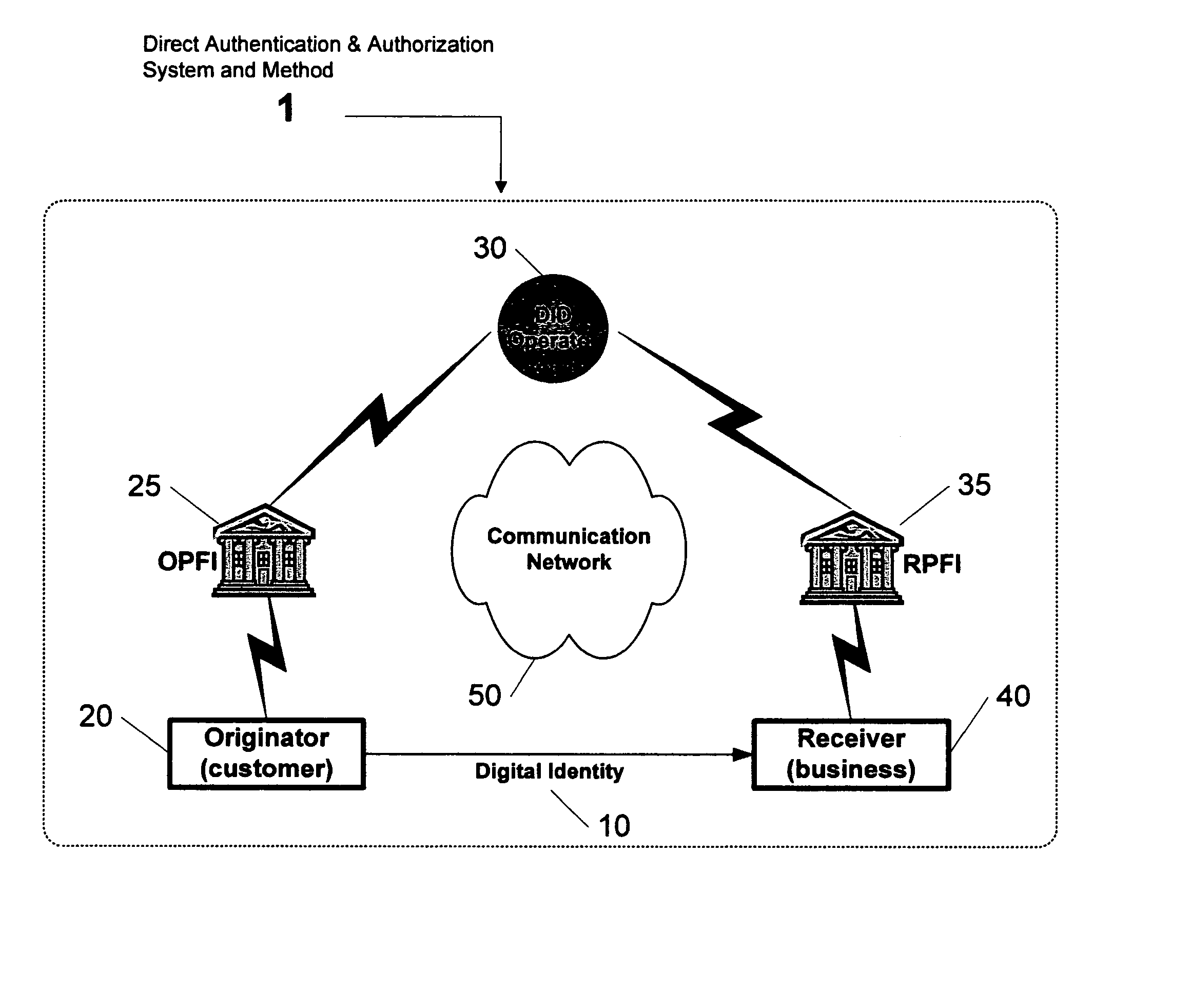
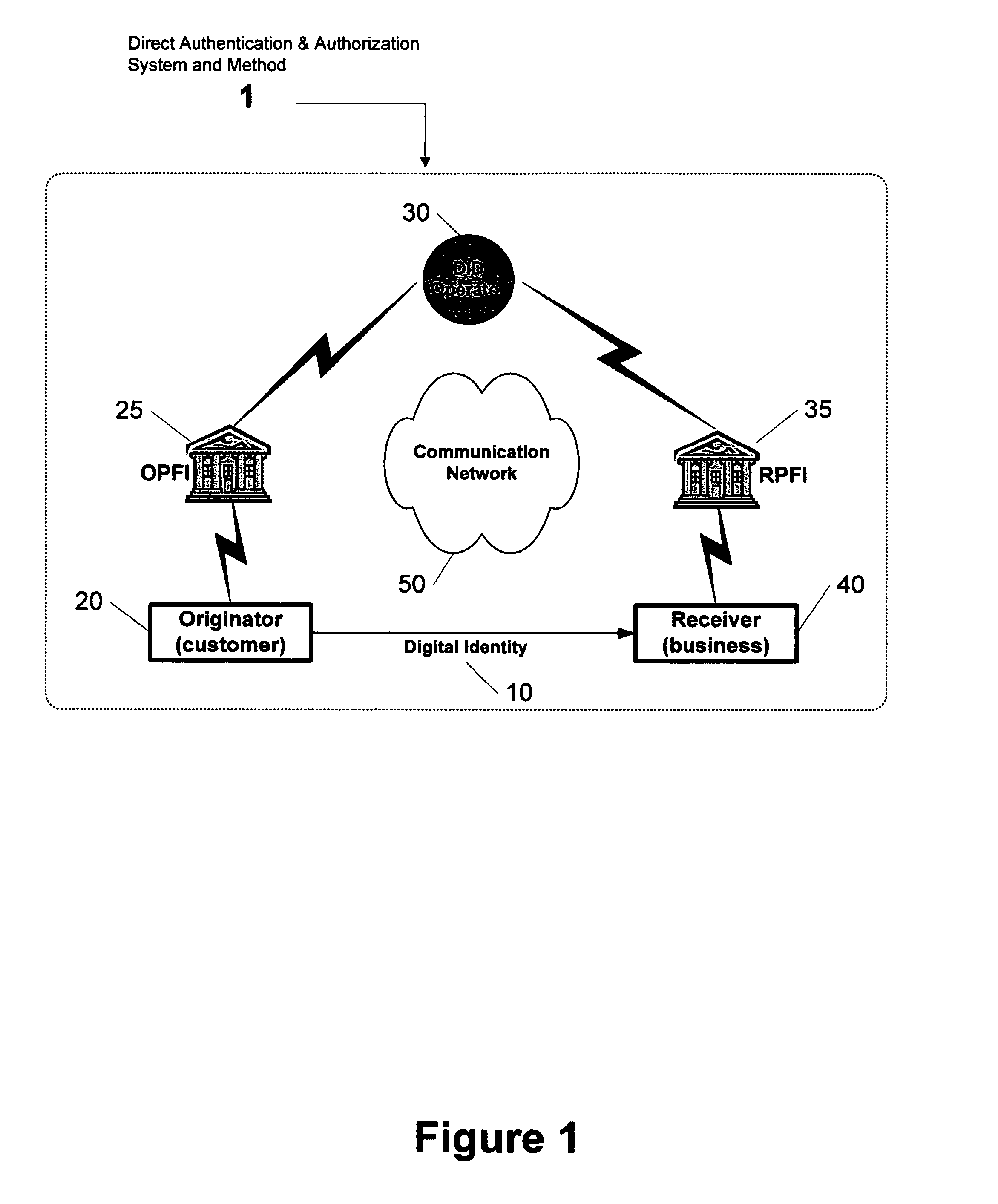
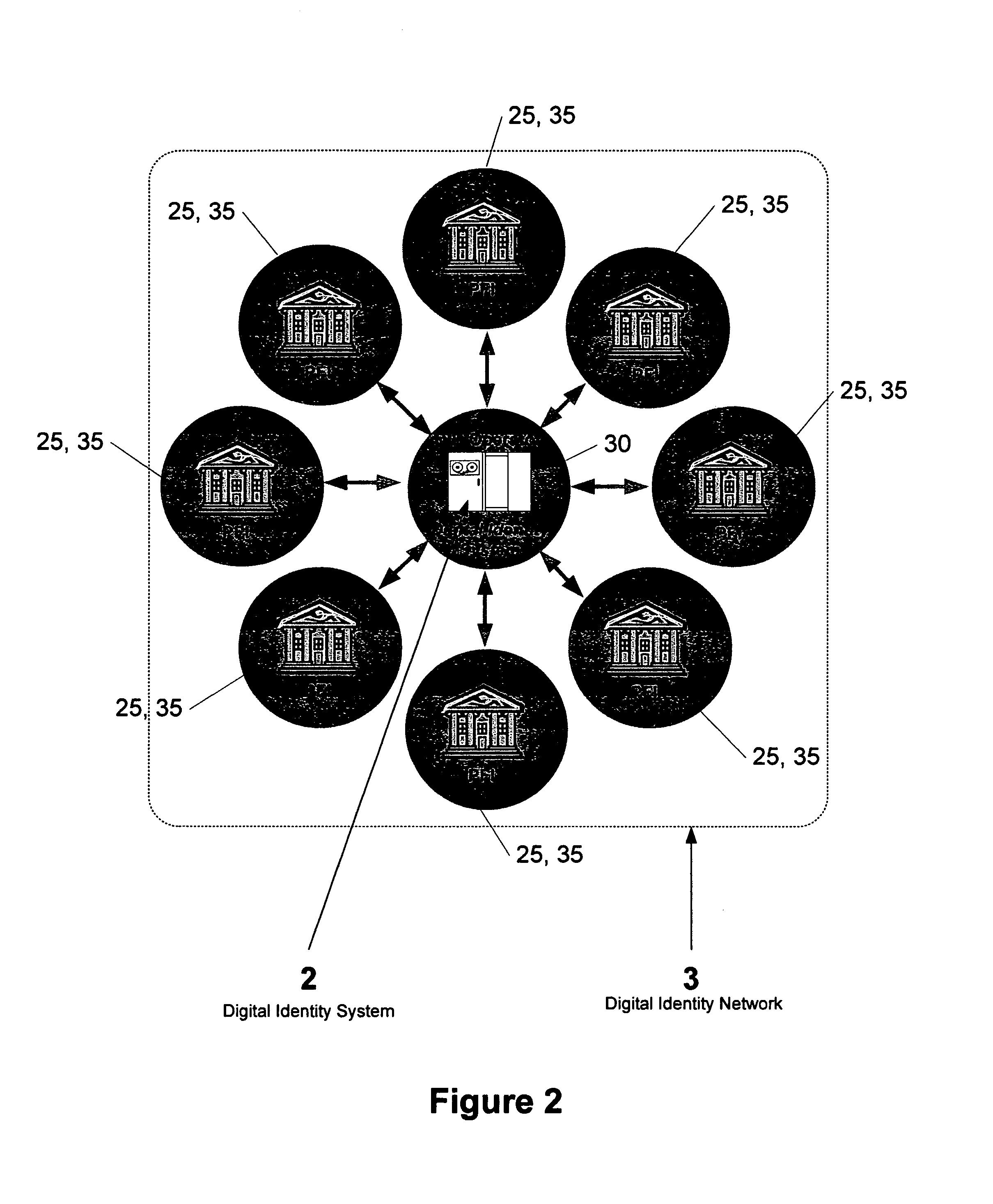
Direct authentication and authorization system and method for trusted network of financial institutions
A system and method for direct authentication and / or authorization of transactions. The system includes a trusted Digital Identity (DID) Network connecting an Originating Participating Financial Institution (OPFI) and a Receiving Participating Financial Institution (RPFI) through a DID Operator. The DID Operator may further be coupled to a DID System that calculates digital identities for Originators. According to the method, direct authentication of the Originator and / or authorization of the transaction is initiated upon the Originator communicating its digital identity to the Receiver. The Receiver subsequently provides the digital identity to the RPFI. The RPFI is then able to communicate with the OPFI for authentication of the Originator and / or authorization of the transaction through the DID Operator based on Originator's digital identity. The transaction between the Originator and Receiver can be financial or non-financial and may include, for example, account-to-account transfers, identity authentication or express agreements. In another embodiment, authentication and / or authorization may be performed in real time.
Owner:ASGHARI KAMRANI NADER +1
Rendering content-targeted ads with e-mail
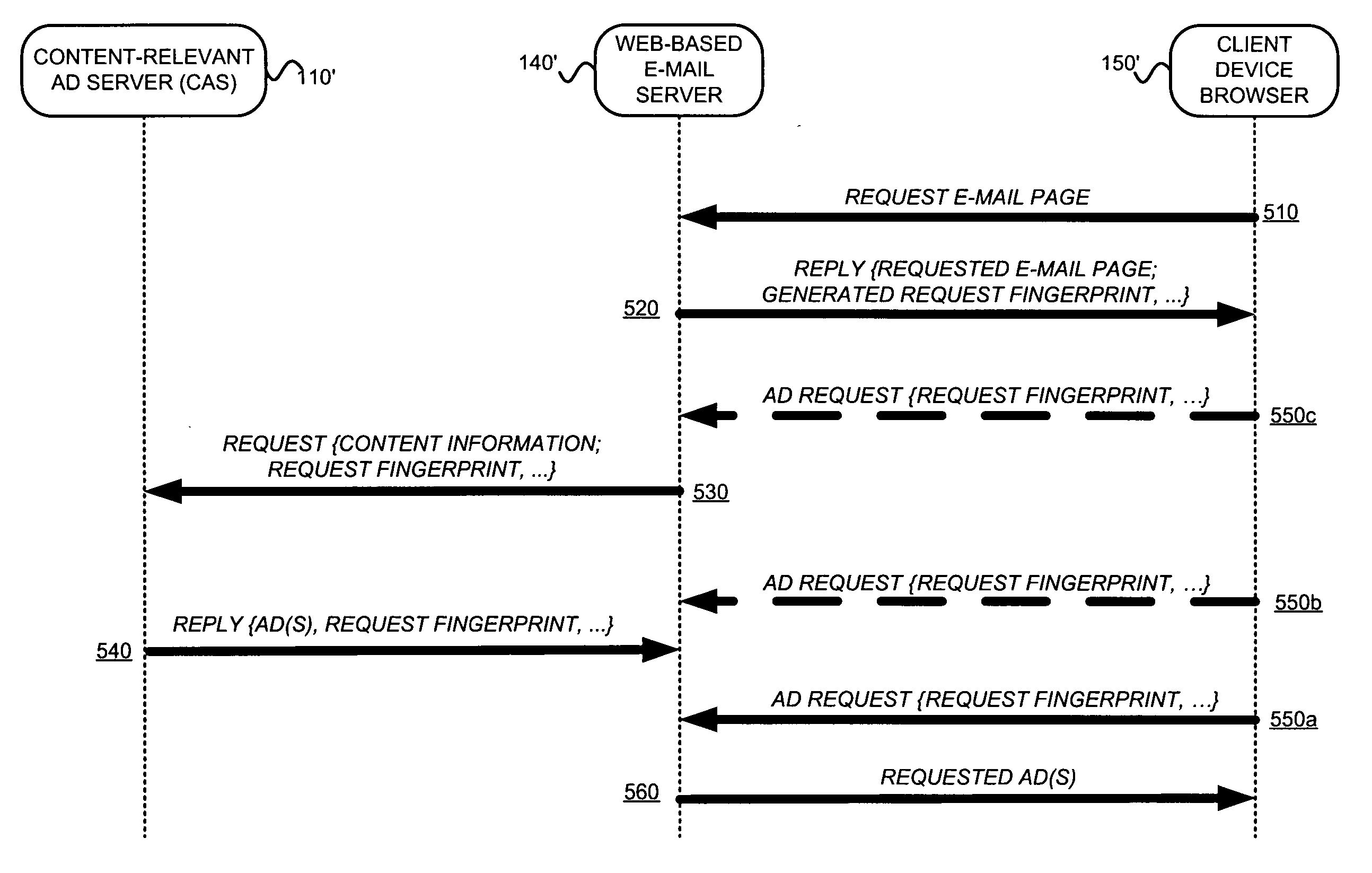
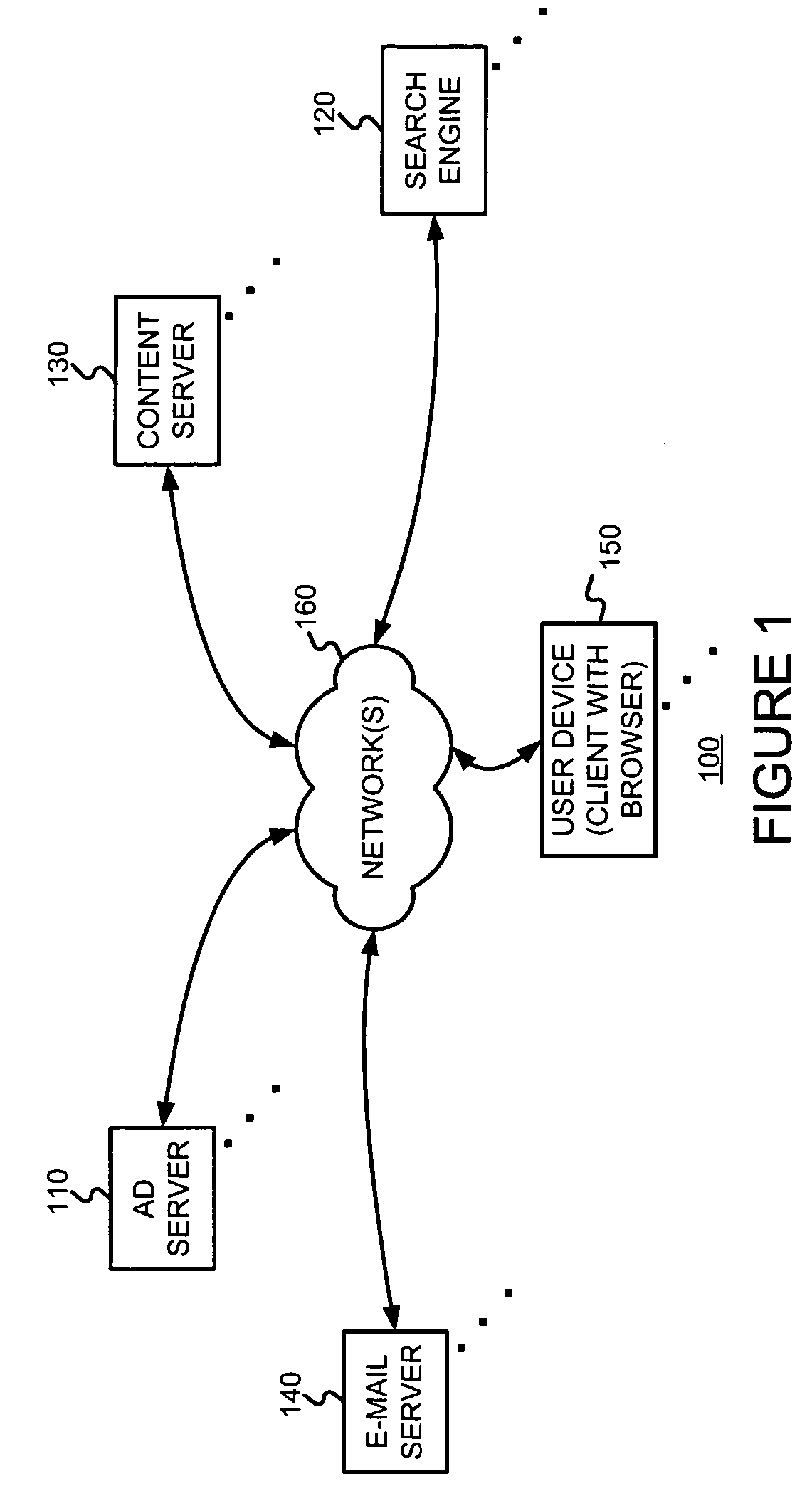
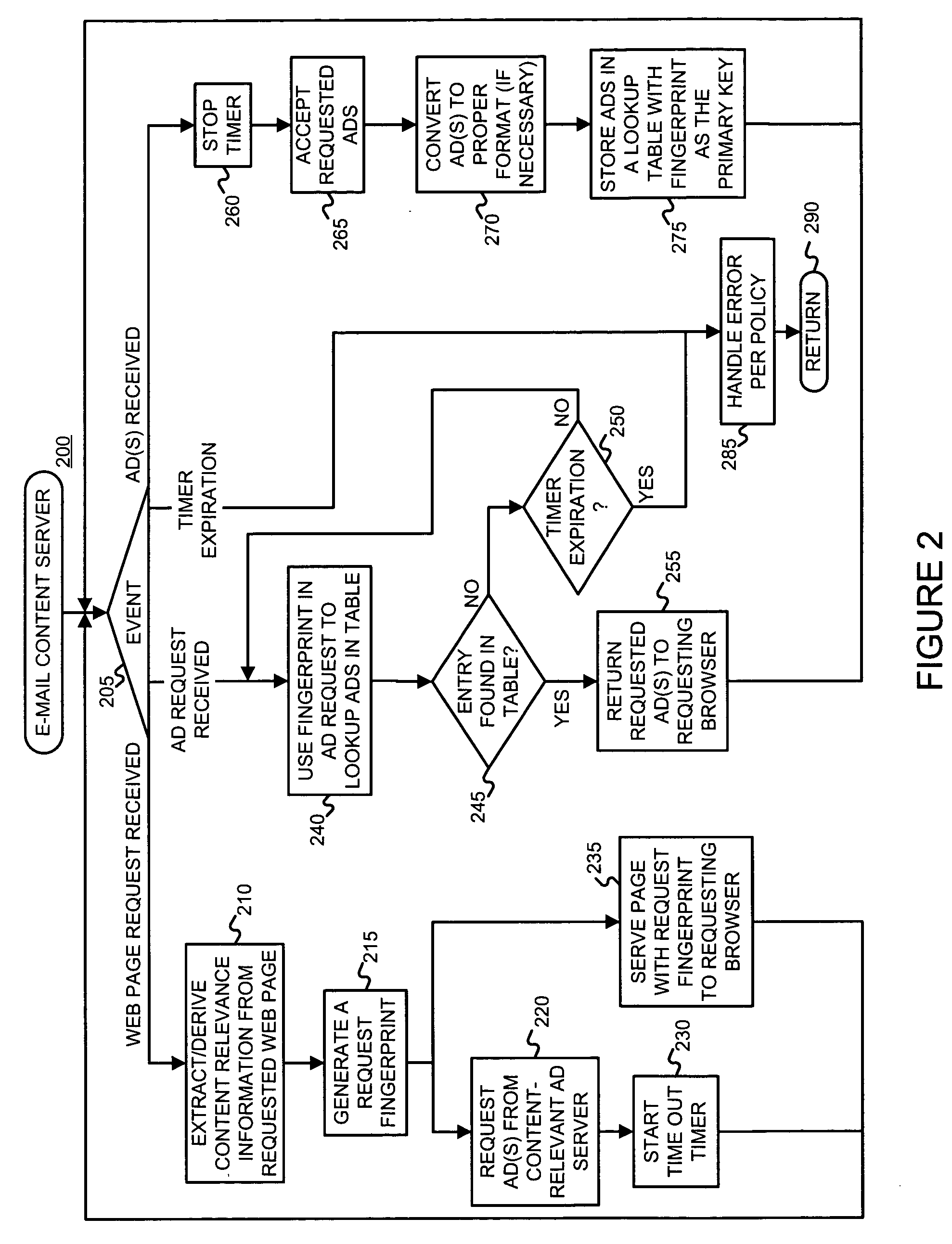
InactiveUS20050222903A1Good serviceMarketingSpecial data processing applicationsPaper documentDocument preparation
An asynchronous and opportunistically available scheme under which a user's e-mail (or a document including e-mail content) is rendered immediately, and later updated with appropriate advertisements if and when they became available, is described. This scheme ensures that the availability of advertisements will not adversely affect the rendering of the e-mail content. For example, a Web-based e-mail server may facilitate the serving of advertisements with e-mail by (a) accepting a request for a document including e-mail, (b) generating a request identifier, (c) serving the requested document in association with the request identifier, and (d) obtaining at least one ad relevant to content of the e-mail. The Web-based e-mail server may further (e) store the obtained ad(s), (f) accept an ad request, (g) read the stored ad(s) using information from the ad request, and (h) serve the ad(s).
Owner:GOOGLE LLC
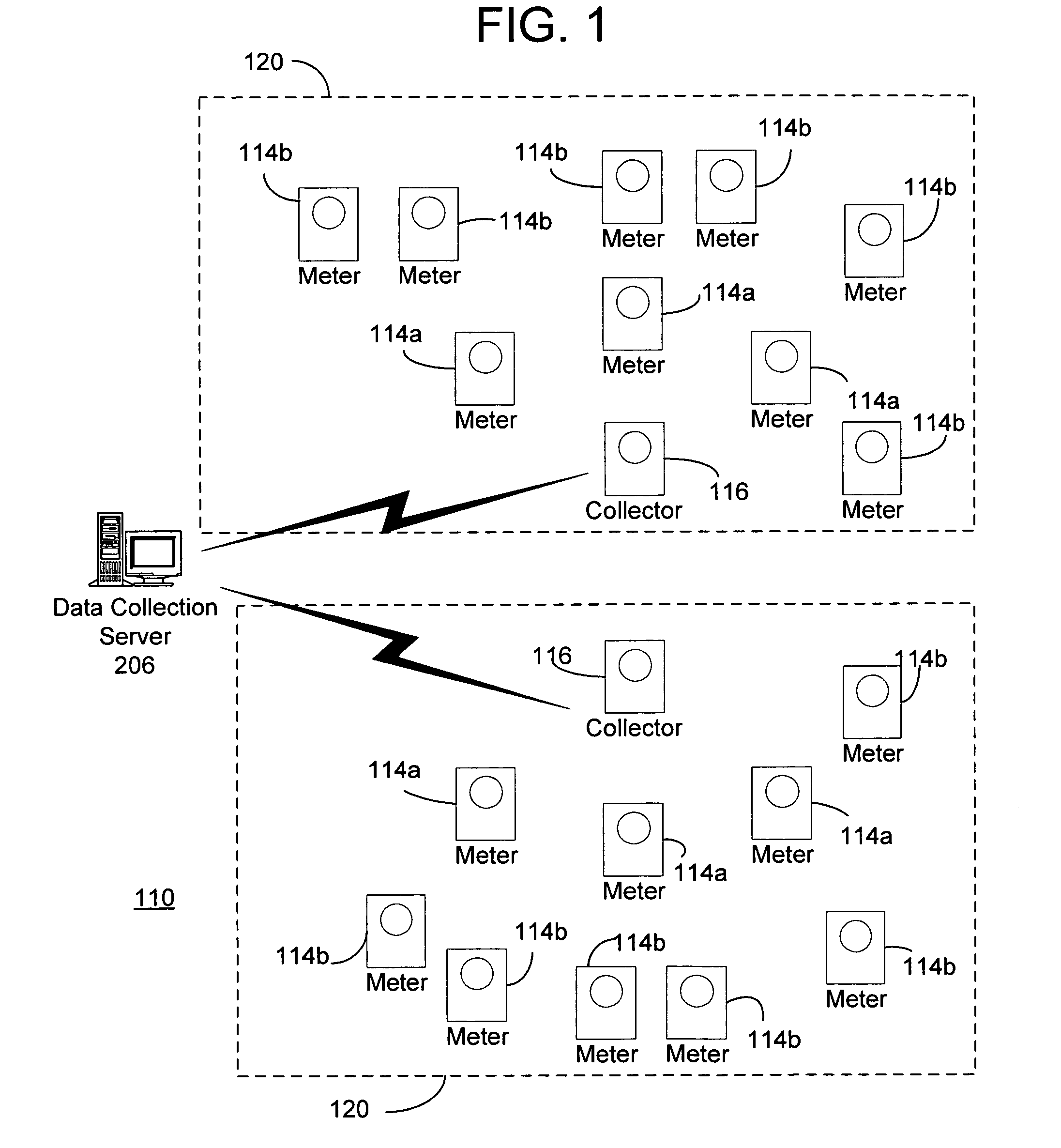
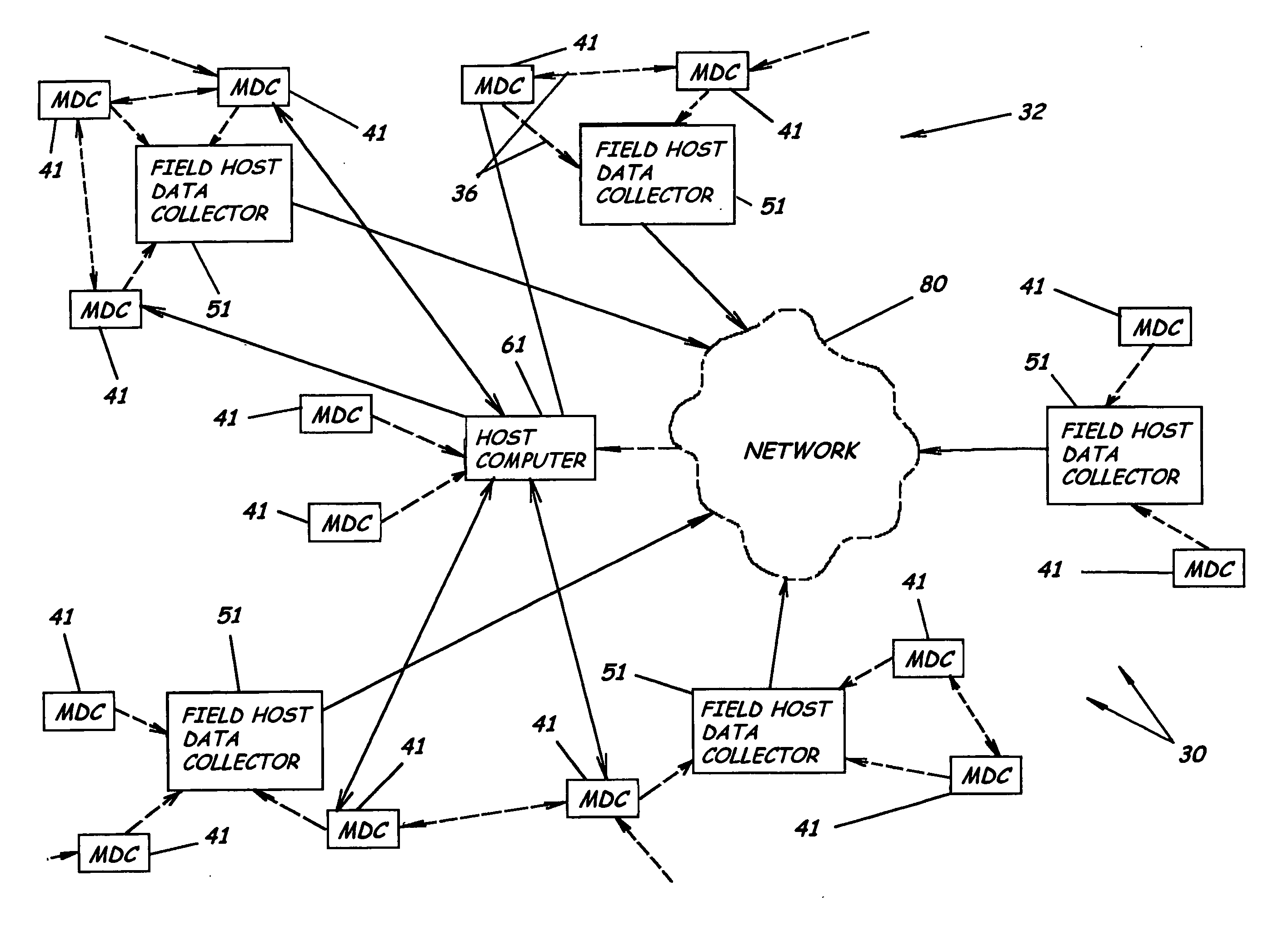
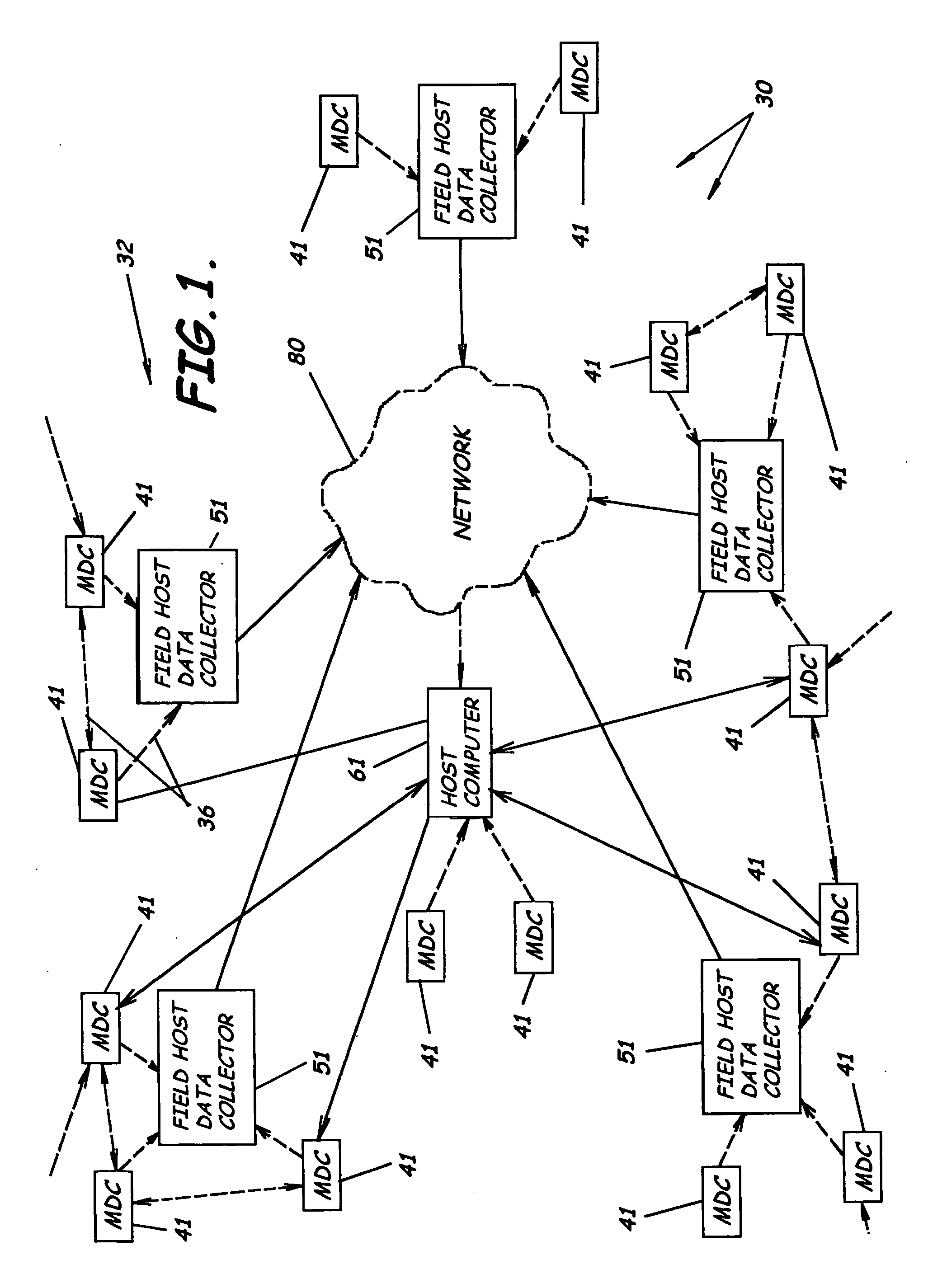
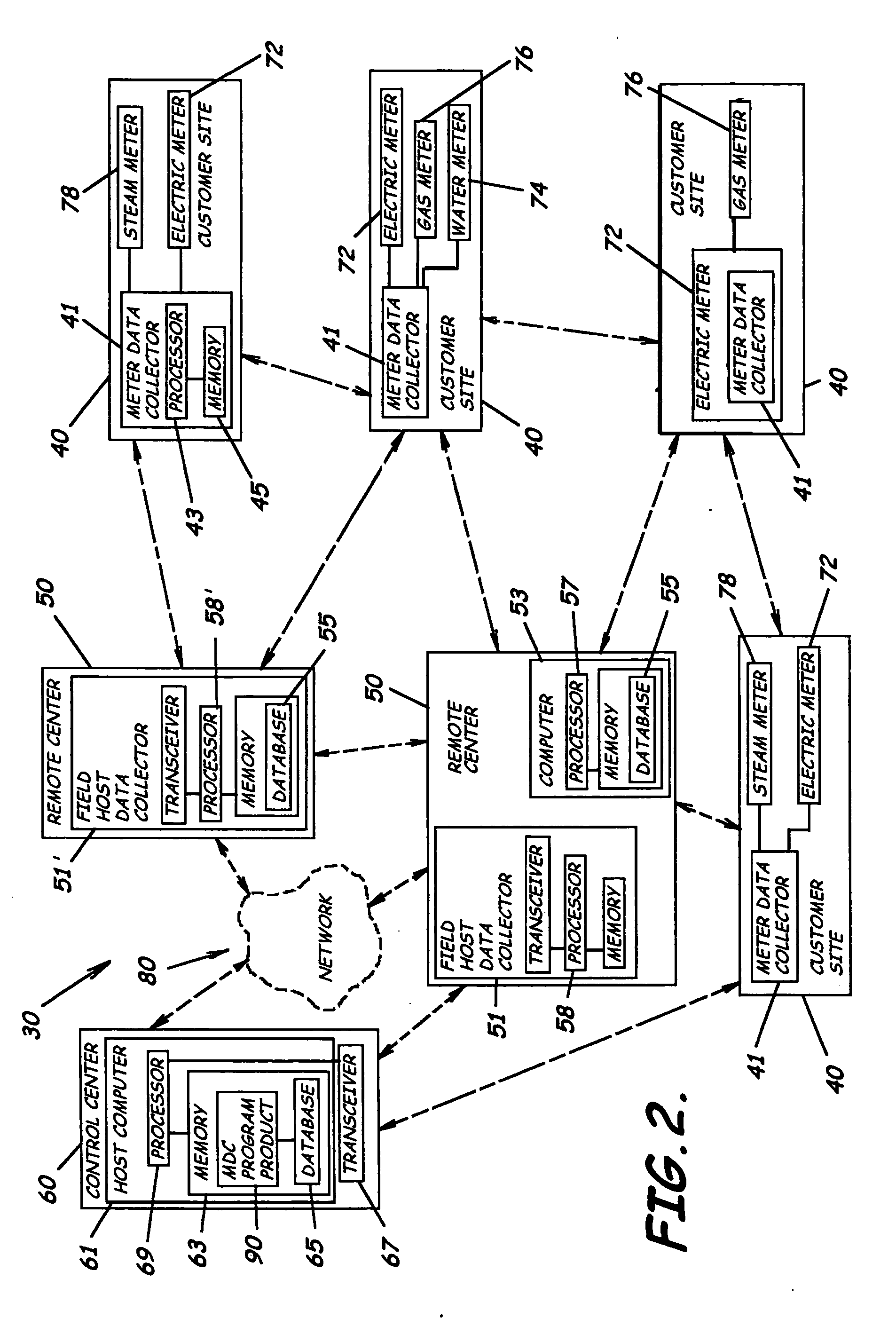
Automated meter reading system, communication and control network from automated meter reading, meter data collector, and associated methods
InactiveUS20070013547A1Easy to getReduce acquisition timeElectric signal transmission systemsTariff metering apparatusData acquisitionComputer science
An automated meter reading network system to collect utility usage data from multiple utility meters having utility meter sensors, program product, and associated methods are provided. The system includes multiple meter data collectors each in communication with one or more utility meters to collect utility usage data and forming a wireless communications network. The system also includes a host computer in communication with the meter data collectors either directly or through multiple field host data collectors which can be connected to the host computer through a wide area network. The system also includes a meter data collector program product at least partially stored in the memory of the host computer to manage the communication network. The meter data collector program product is adapted to analyze signal strength between nodes and to dynamically adjust the power level settings of the individual nodes to enhance network performance.
Owner:ENERGY TECH GROUP
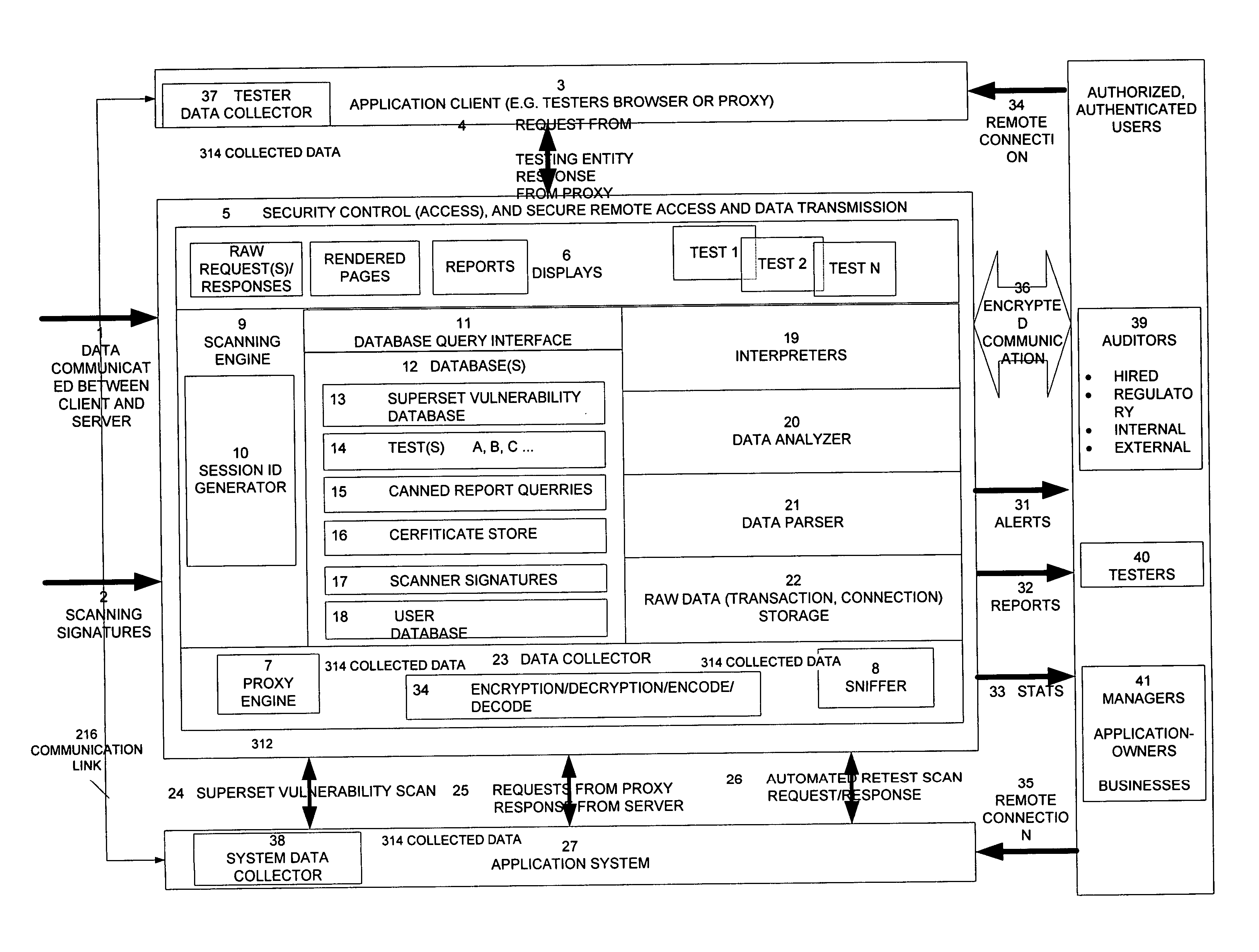
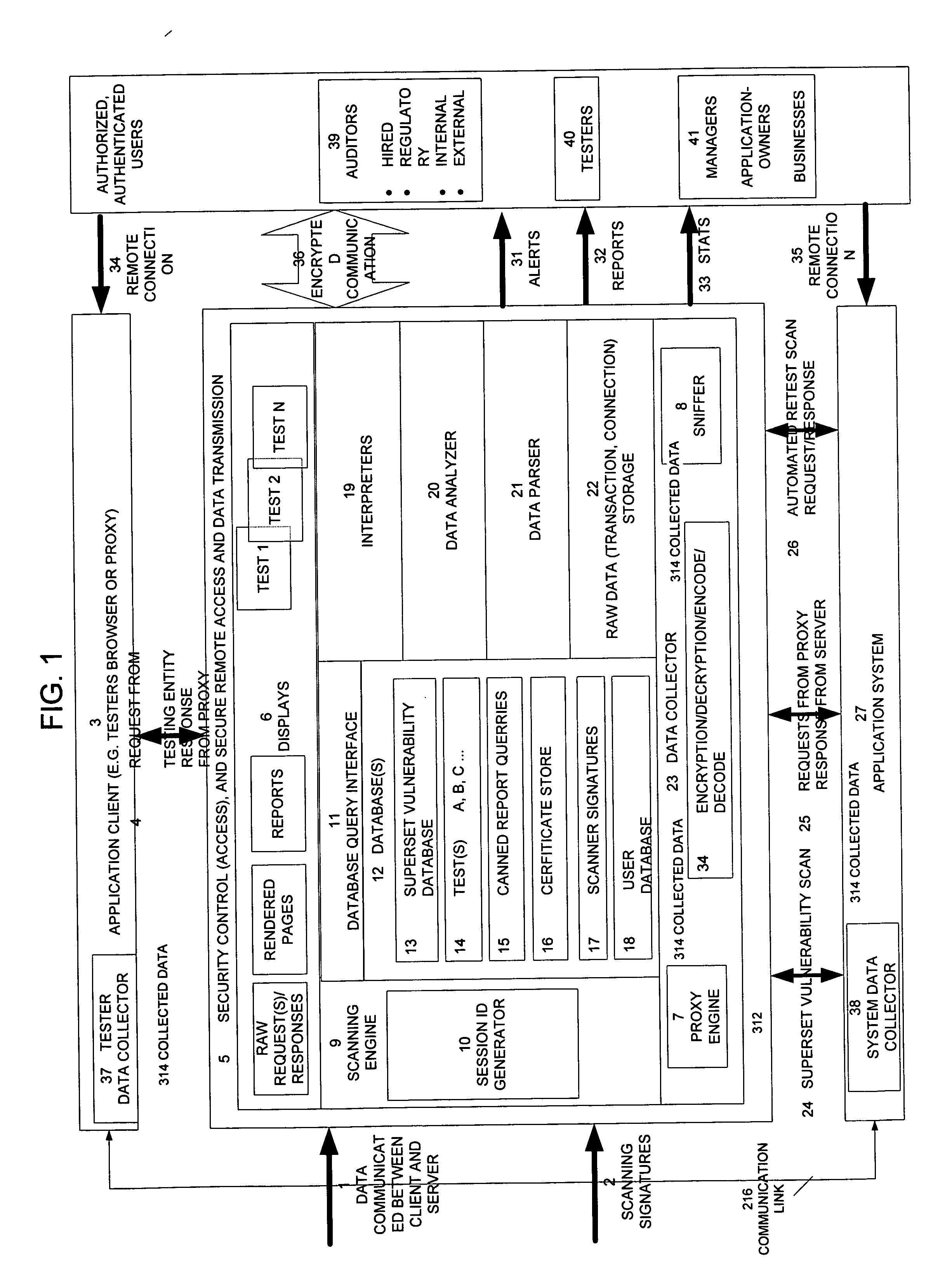
Method, system, and apparatus for managing, monitoring, auditing, cataloging, scoring, and improving vulnerability assessment tests, as well as automating retesting efforts and elements of tests
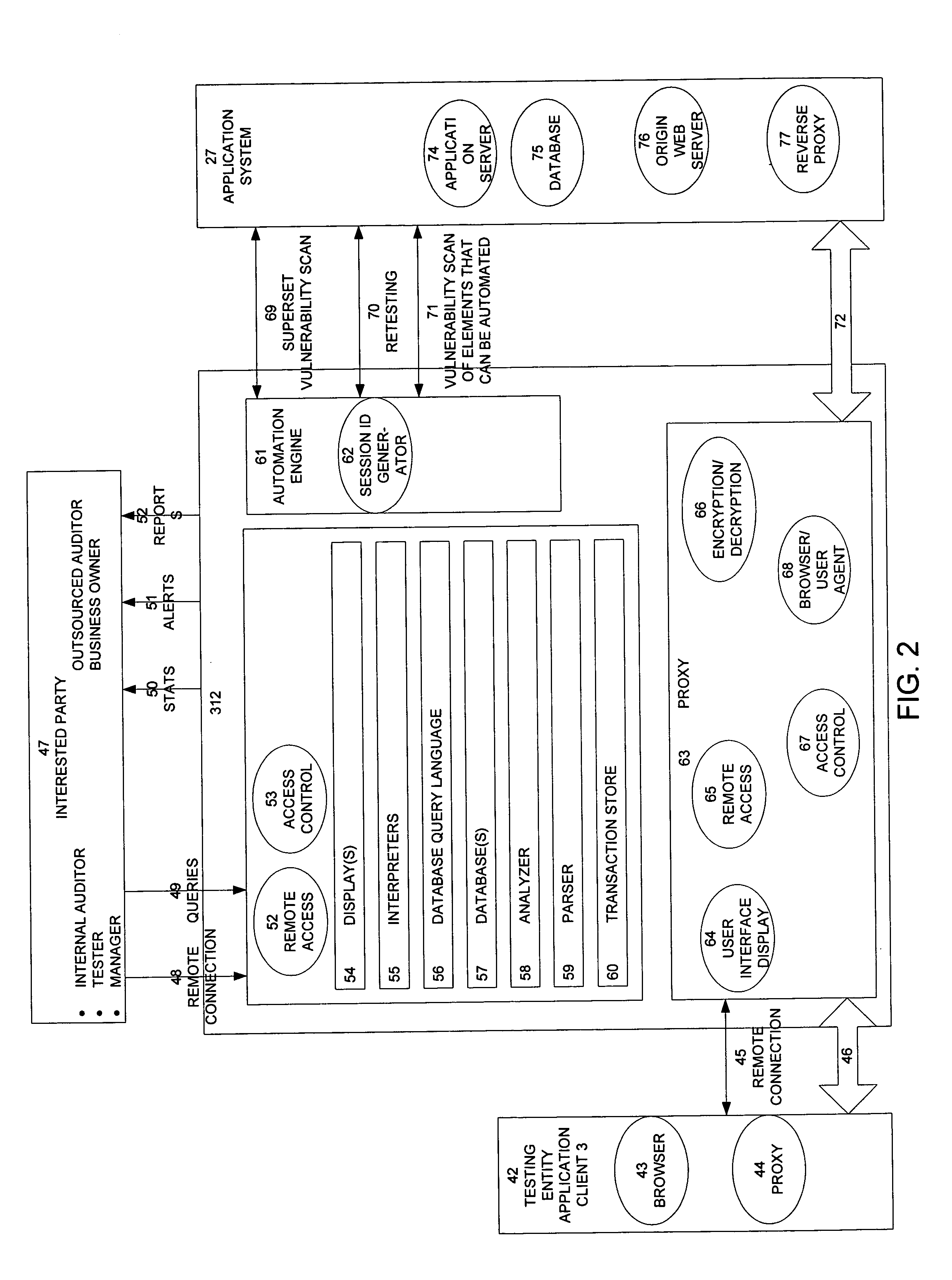
InactiveUS20050138426A1Streamline and improve test effortImprove consistencyDigital data processing detailsHardware monitoringAnalysis dataWeb application
A scalable method, system, and apparatus for non-intrusively auditing and improving security assessments includes capturing, storing, presenting, displaying, inspecting, monitoring, and analyzing data flow in client-server security assessments and / or network / infrastructure security assessments. The invention provides interested parties with a mechanism to non-intrusively audit in real-time the vulnerability test effort, as well as review, replay, and analyze all aspects of the security assessment during and after the test. For web application assessments, the data capture includes one of the following or some combination: an intermediary with all data passing through the intermediary; a sniffer that can passively extract all data being communicated between the application and tester; and a plurality of computing modules (e.g., software, appliances, etc.) installed in the tester environment or within the application system environment (e.g., software installed on the tester's computer, or on the computer where the intermediary is running, or software installed on the application systems proxy or web server, or an appliance in either environment) for storing, processing, analyzing, reporting, and displaying the data.
Owner:STYSLINGER BRIAN
Method and apparatus for the automated delivery of notifications to contacts based on predicted work prioritization
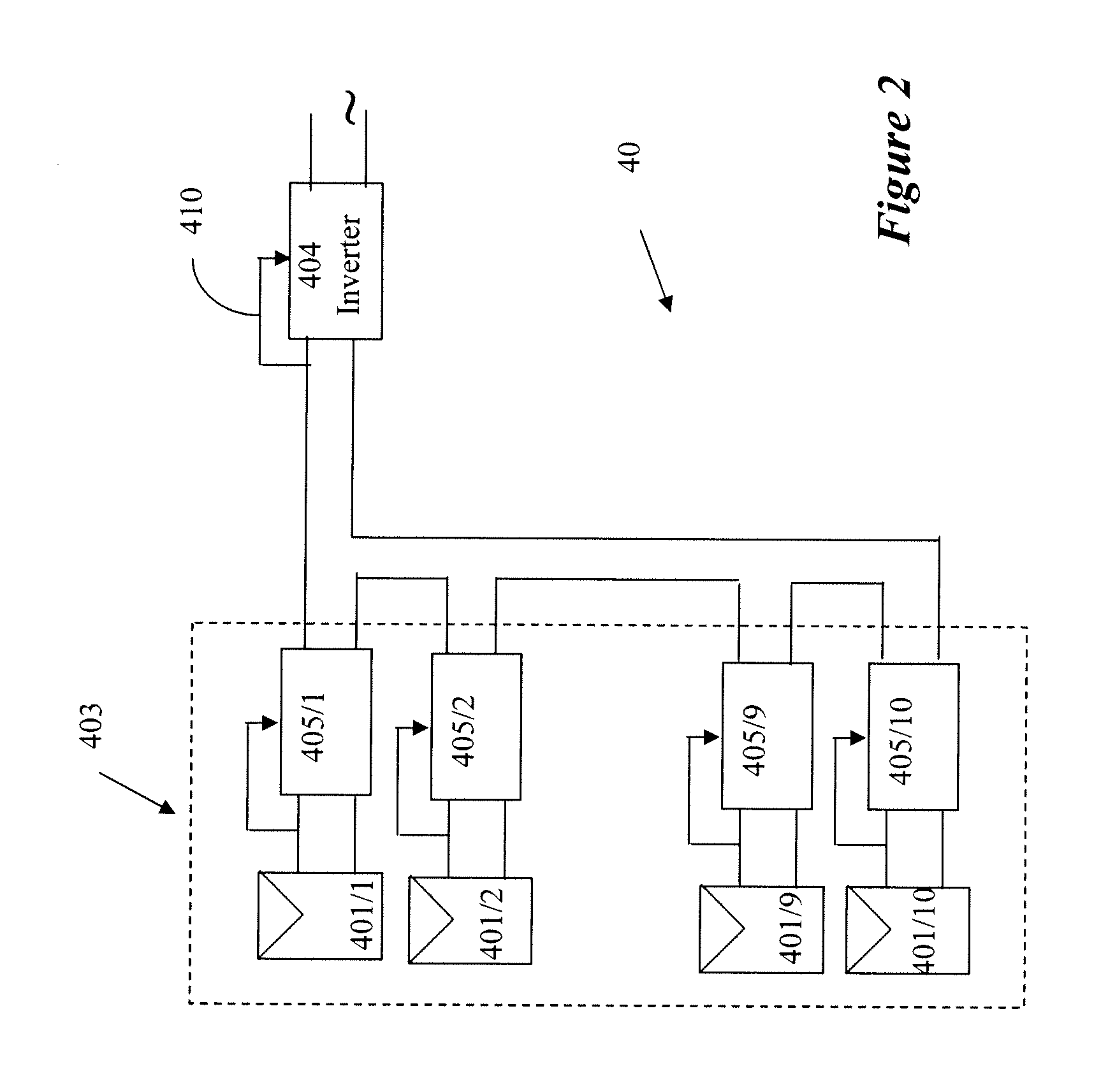
ActiveUS20070071222A1Improved customer serviceImproved contact center effectivenessSpecial service for subscribersManual exchangesContact centerComputer science
In one embodiment, a contact center is provided that includes: (a) a work item queue 208, 250 comprising an intra-enterprise contact associated with at least first and second internal endpoints of an enterprise; and (b) a selector operable to select and assign a work item to an agent. In selecting the work item, the selector considers both a customer contact and the intra-enterprise contact. The intra-enterprise contact, for example, can be a training notification.
Owner:AVAYA INC
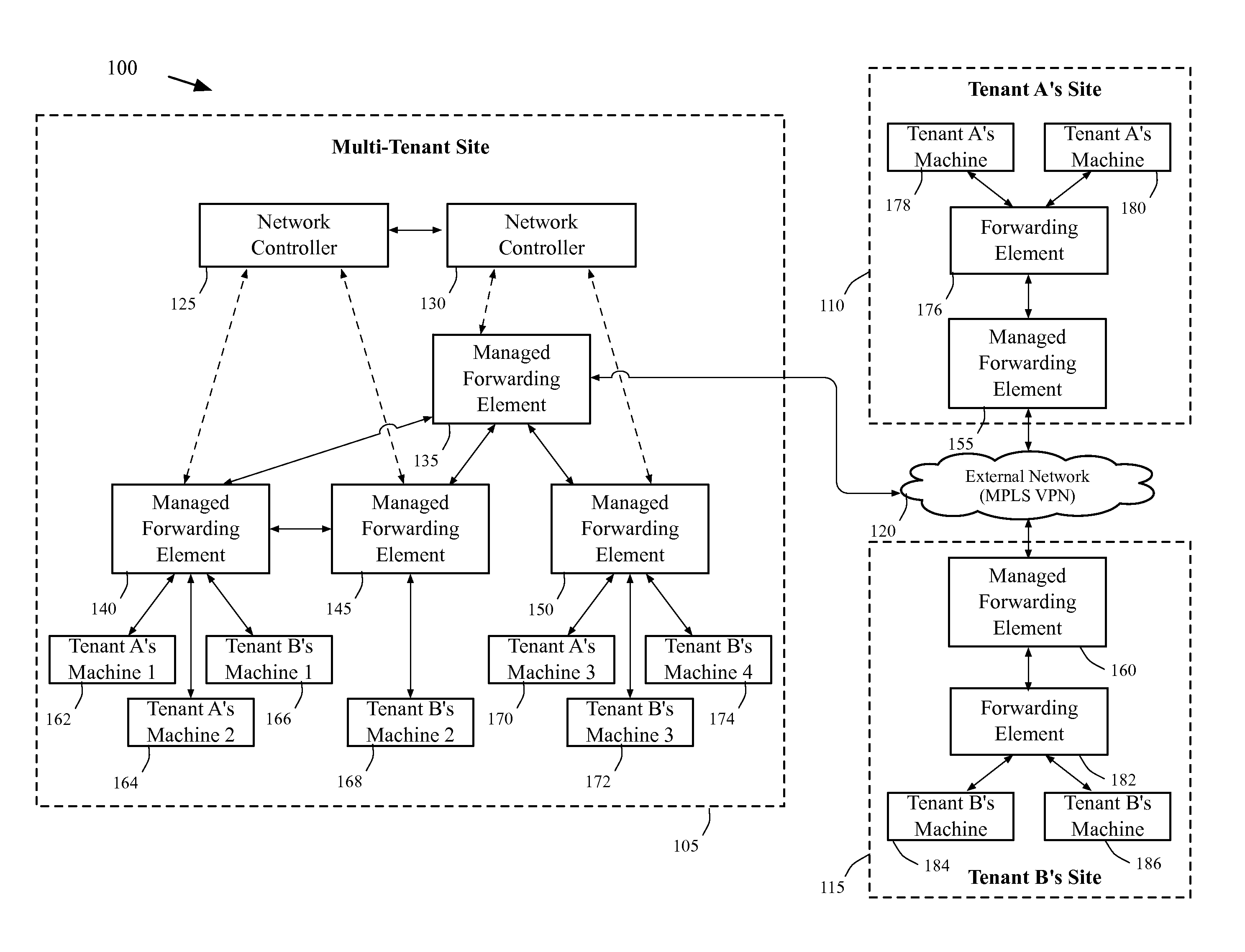
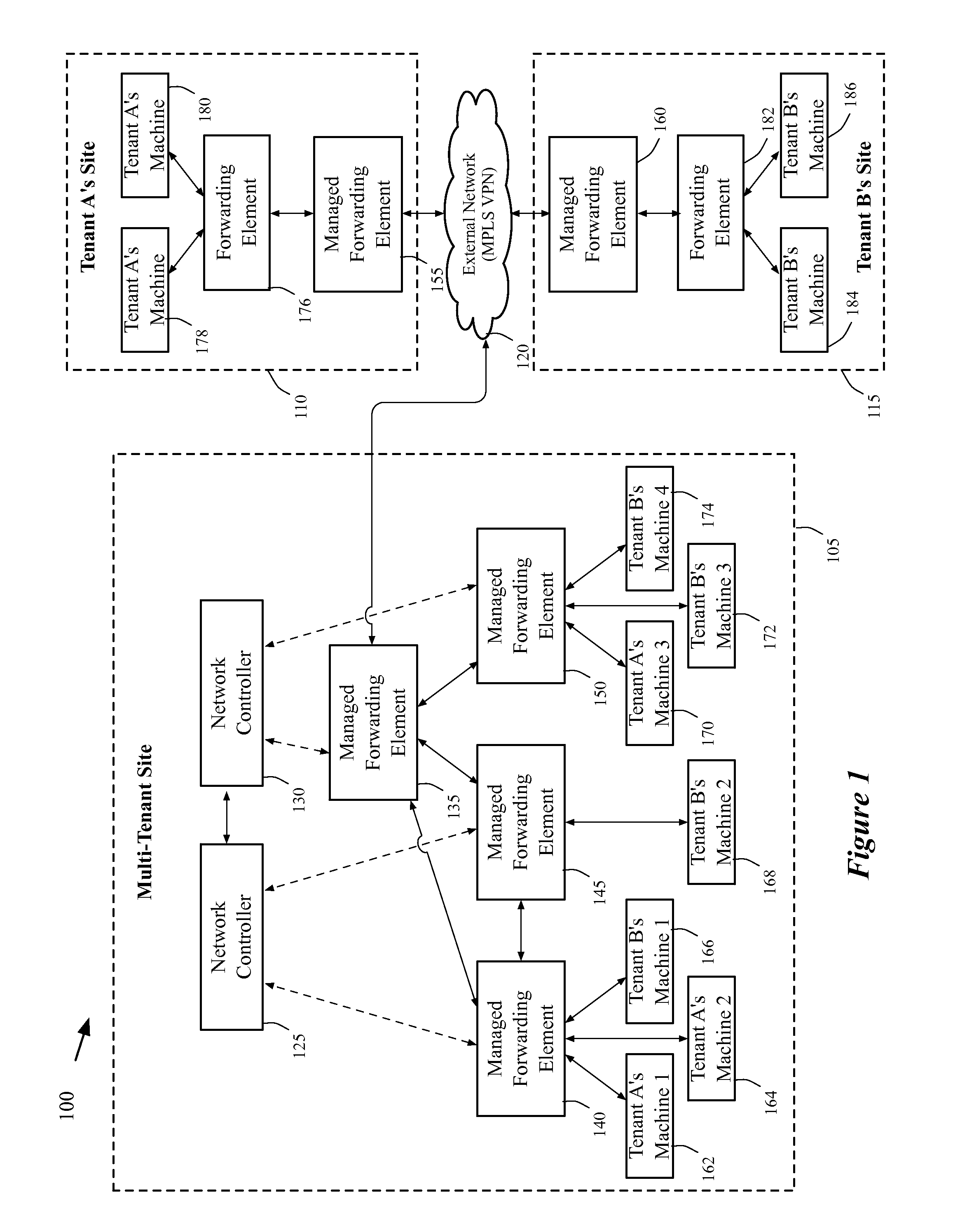
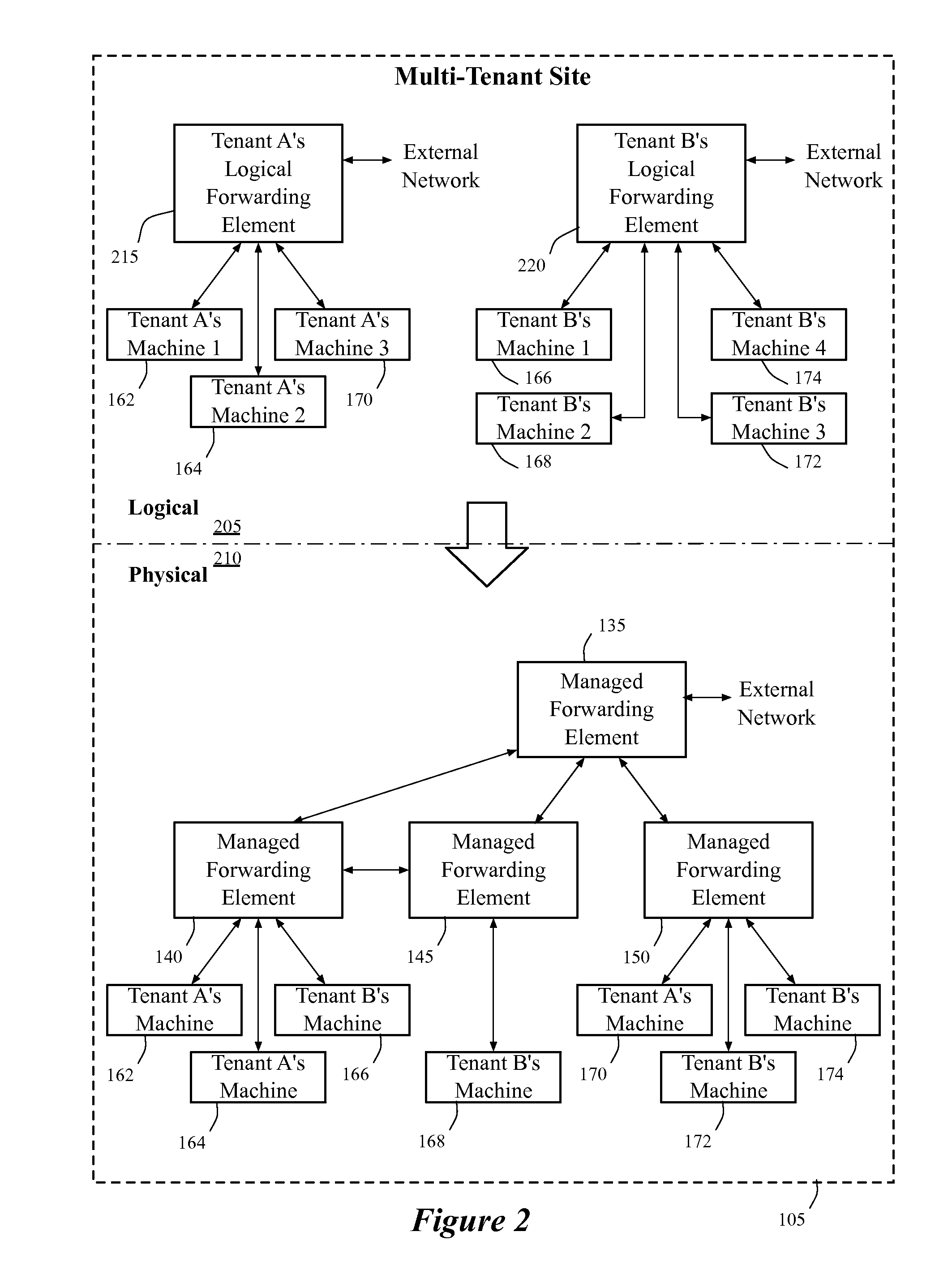
Extension of logical networks across layer 3 virtual private networks
ActiveUS20130287026A1Increase heightGood serviceData switching by path configurationPrivate networkLogical network
A method of manages a set of managed forwarding elements that forward data between machines. The method configures (1) a first managed forwarding element to operate in a first network that uses first and second address spaces that at least partially overlap with each other, (2) a second managed forwarding element to operate in a second network that uses the first address space, and (3) a third managed forwarding element to operate in a third network that uses the second address space. A machine in the second network and a machine in the third network have an identical address that belongs to both the first and second address spaces. The method directs the first managed forwarding element to connect to the second and third managed forwarding elements in a manner that enables the first managed forwarding element to forward data from a machine in the first network to the machine in the second network via the second managed forwarding element.
Owner:NICIRA
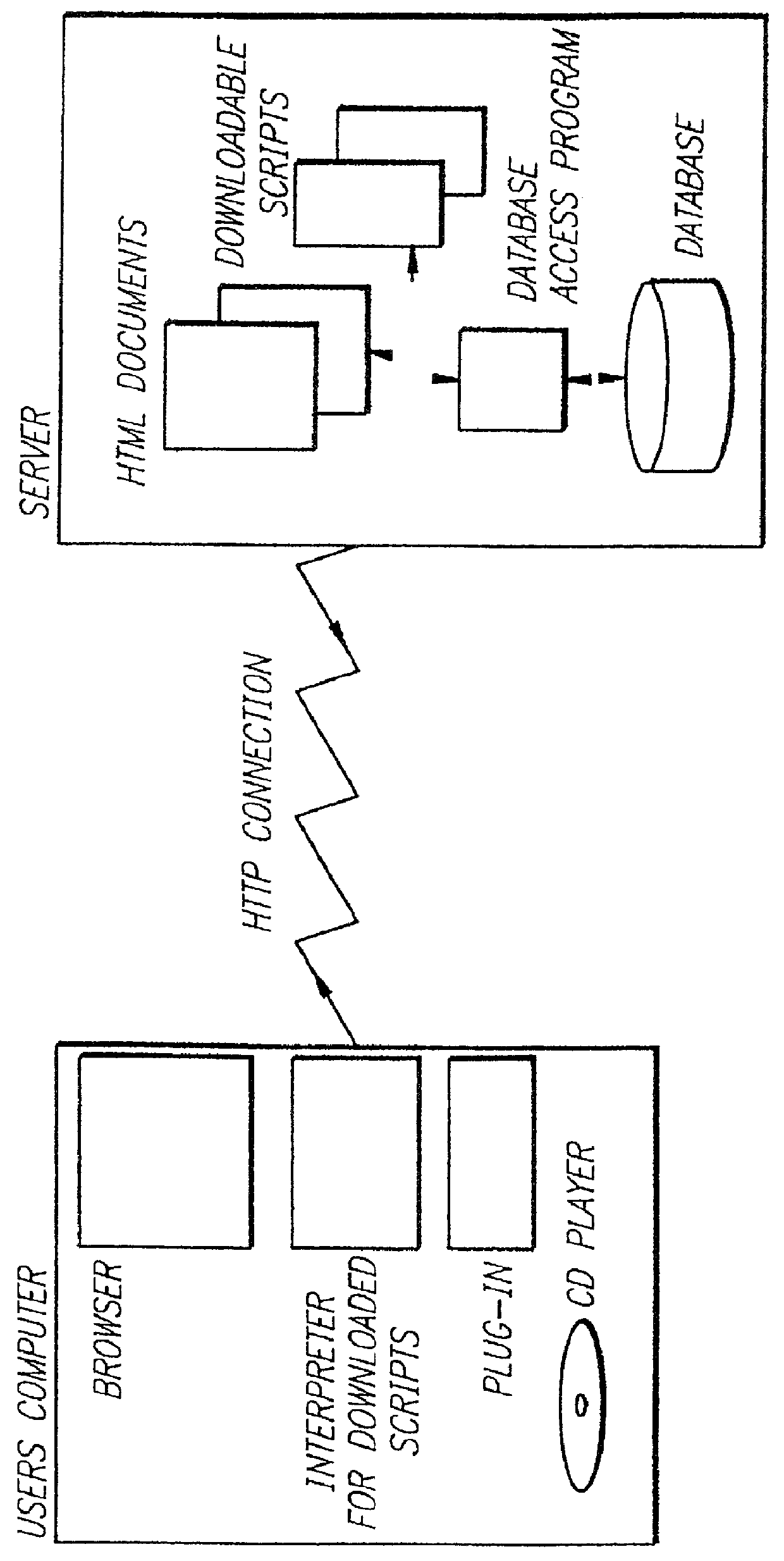
Method and system for finding approximate matches in database
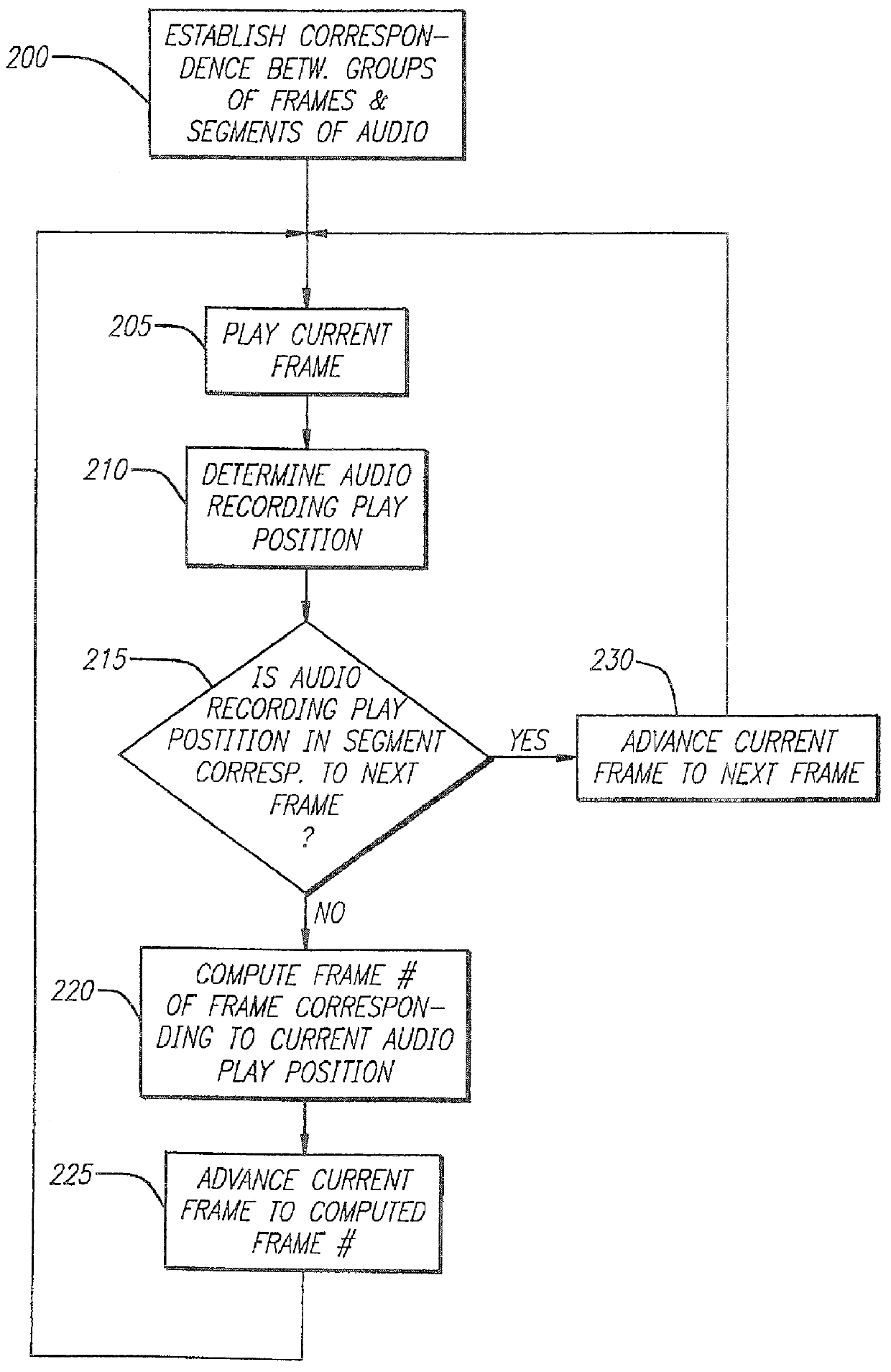
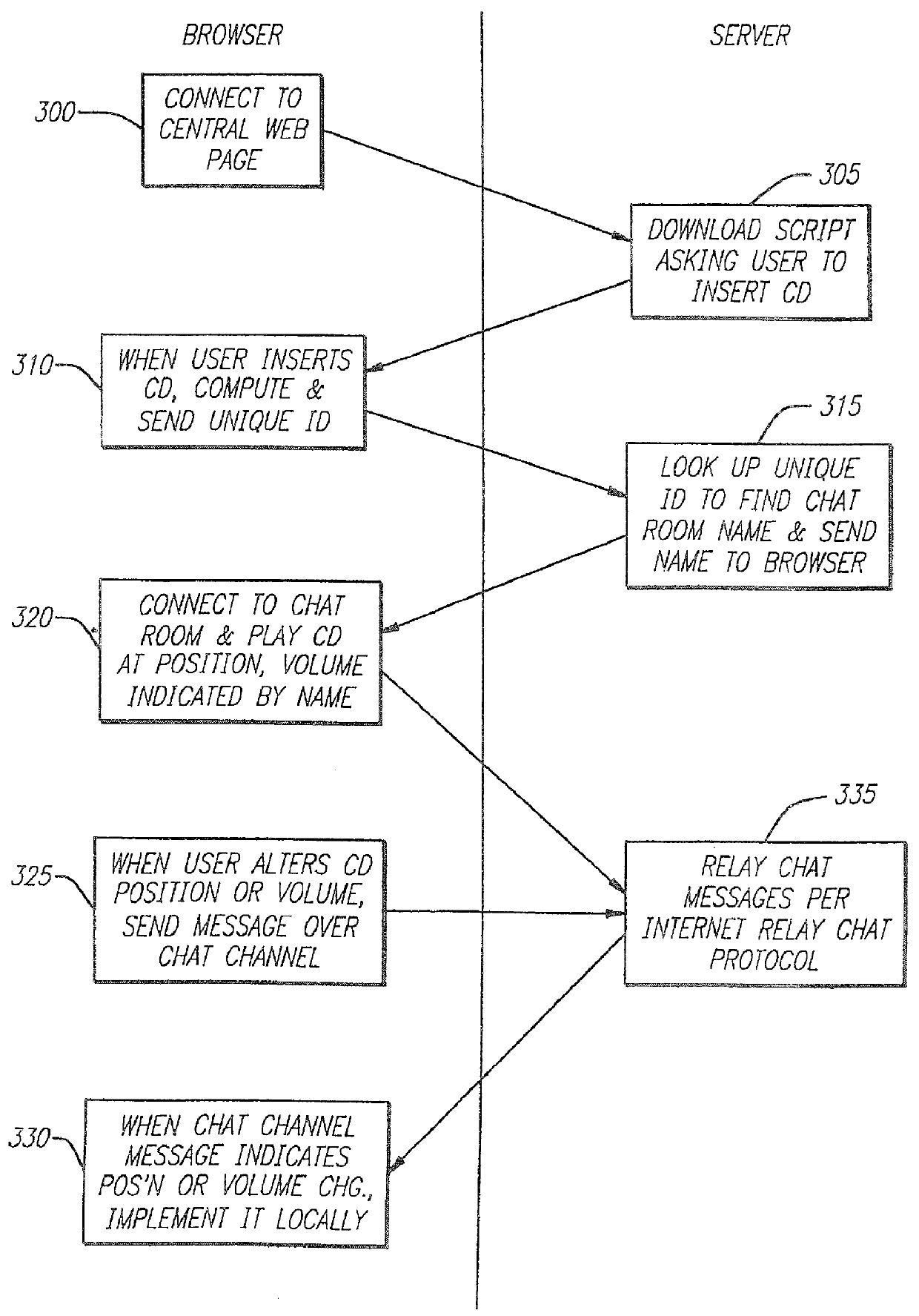
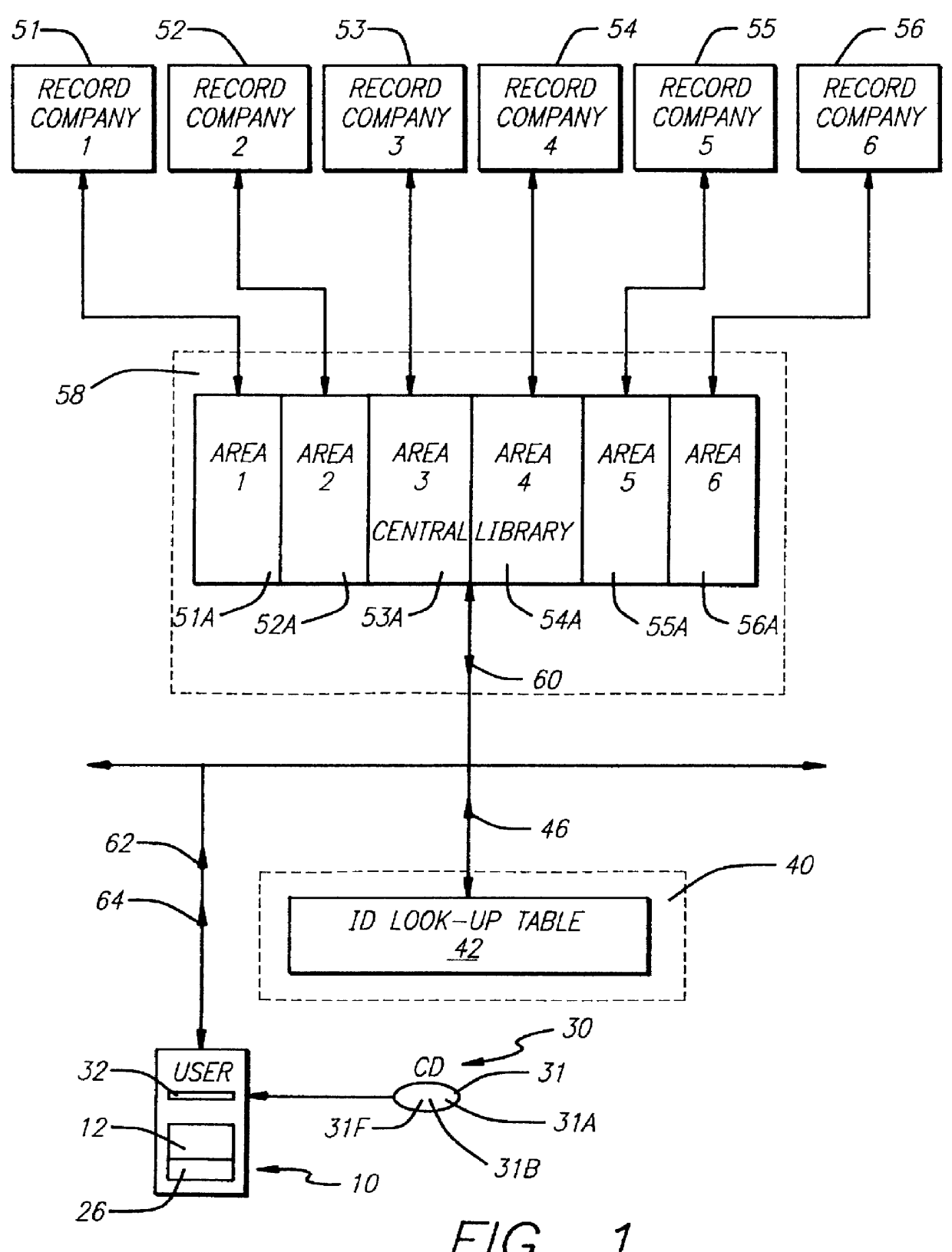
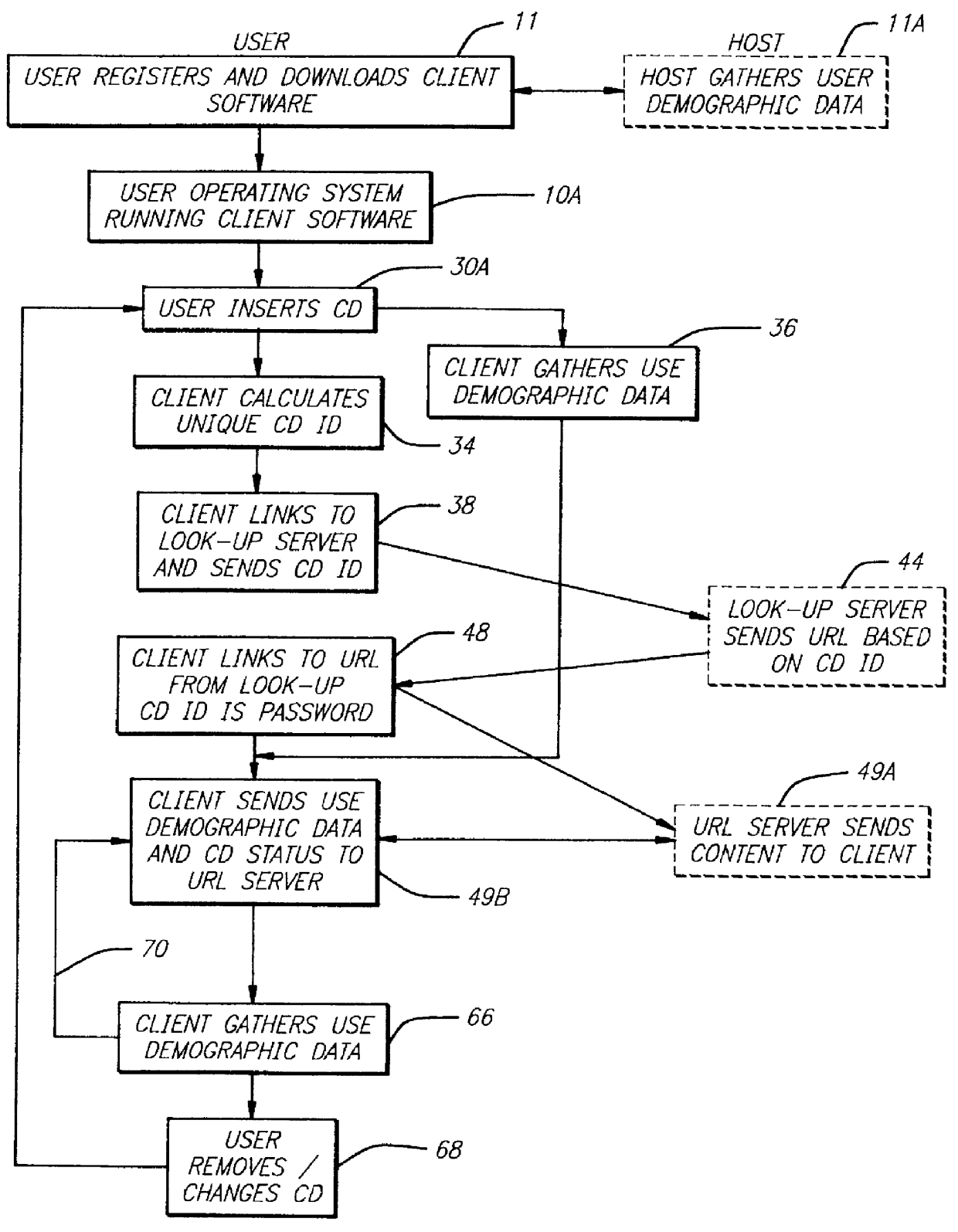
InactiveUS6061680A "chat roGood serviceDigital data processing detailsCoin-freed apparatusNetwork linkRemote computer
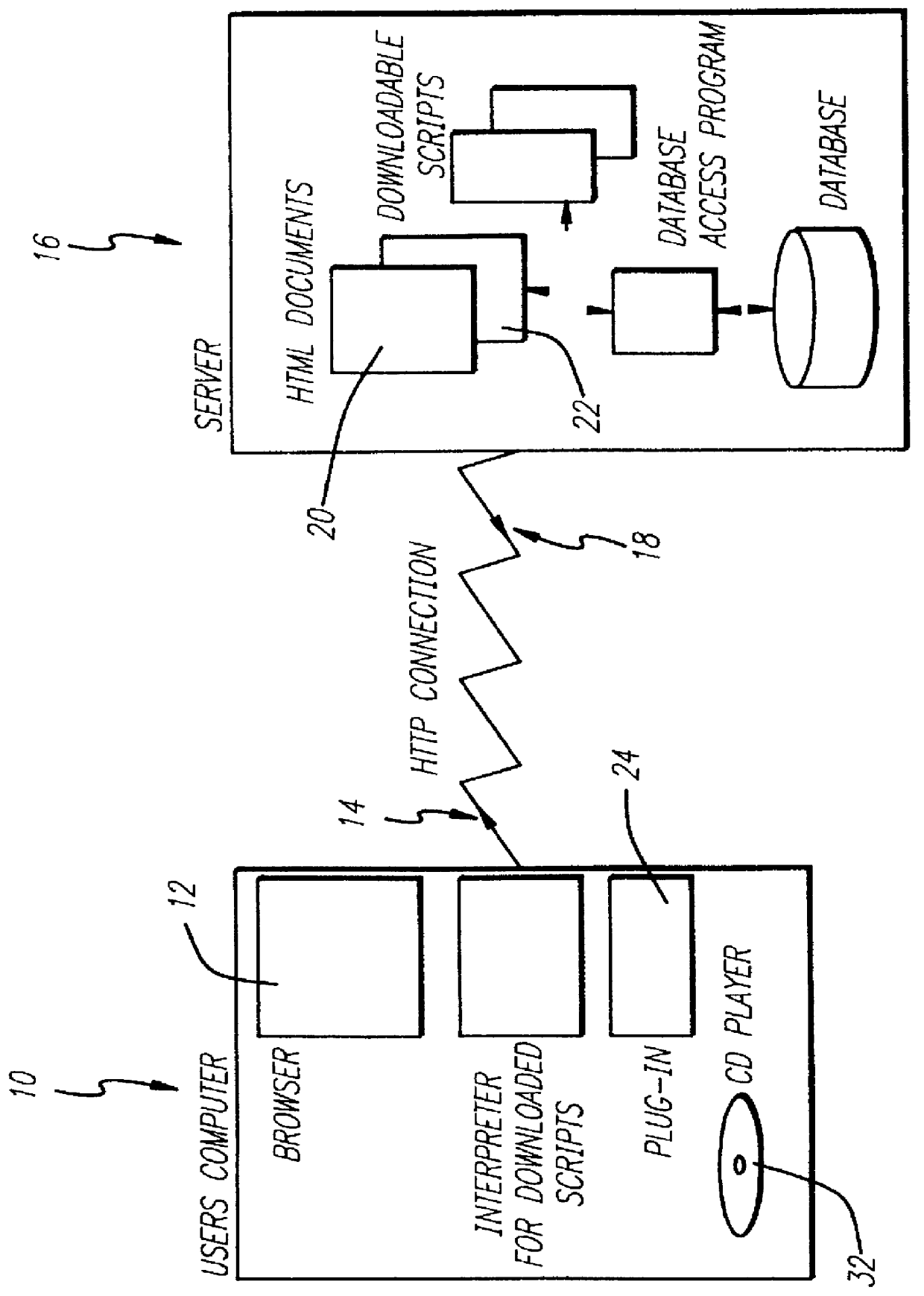
Entertainment content complementary to a musical recording is delivered to a user's computer by means of a computer network link. The user employs a browser to access the computer network. A plug-in for the browser is able to control an audio CD or other device for playing the musical recording. A script stored on the remote computer accessed over the network is downloaded. The script synchronizes the delivery of the complementary entertainment content with the play of the musical recording.
Owner:GRACENOTE
Network delivery of interactive entertainment complementing audio recordings
InactiveUS6154773A "chat roGood serviceCoin-freed apparatusBroadcast transmission systemsNetwork linkRemote computer
Owner:GRACENOTE
Advertising using extracted context sensitive information and data of interest from voice/audio transmissions and recordings
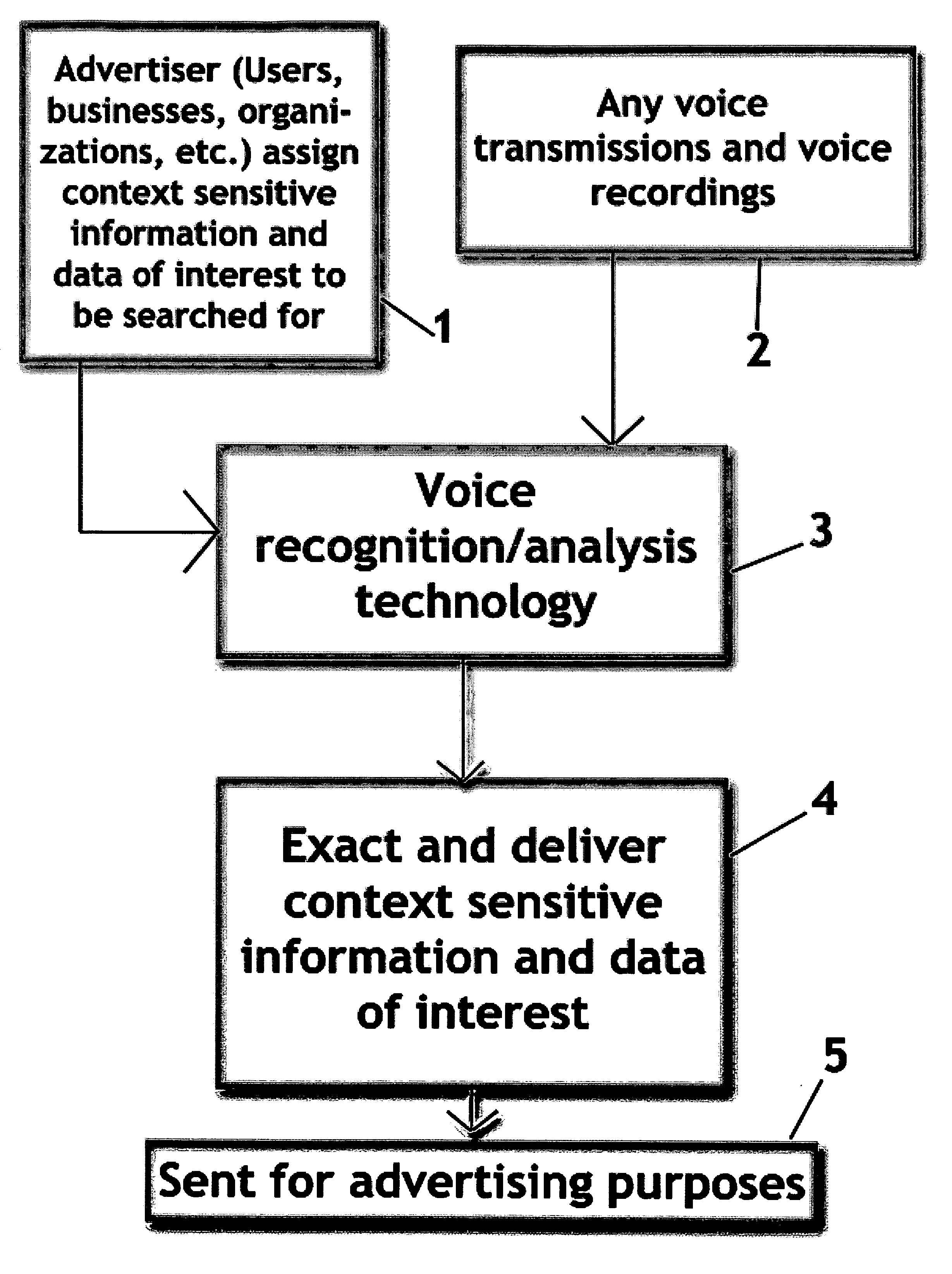
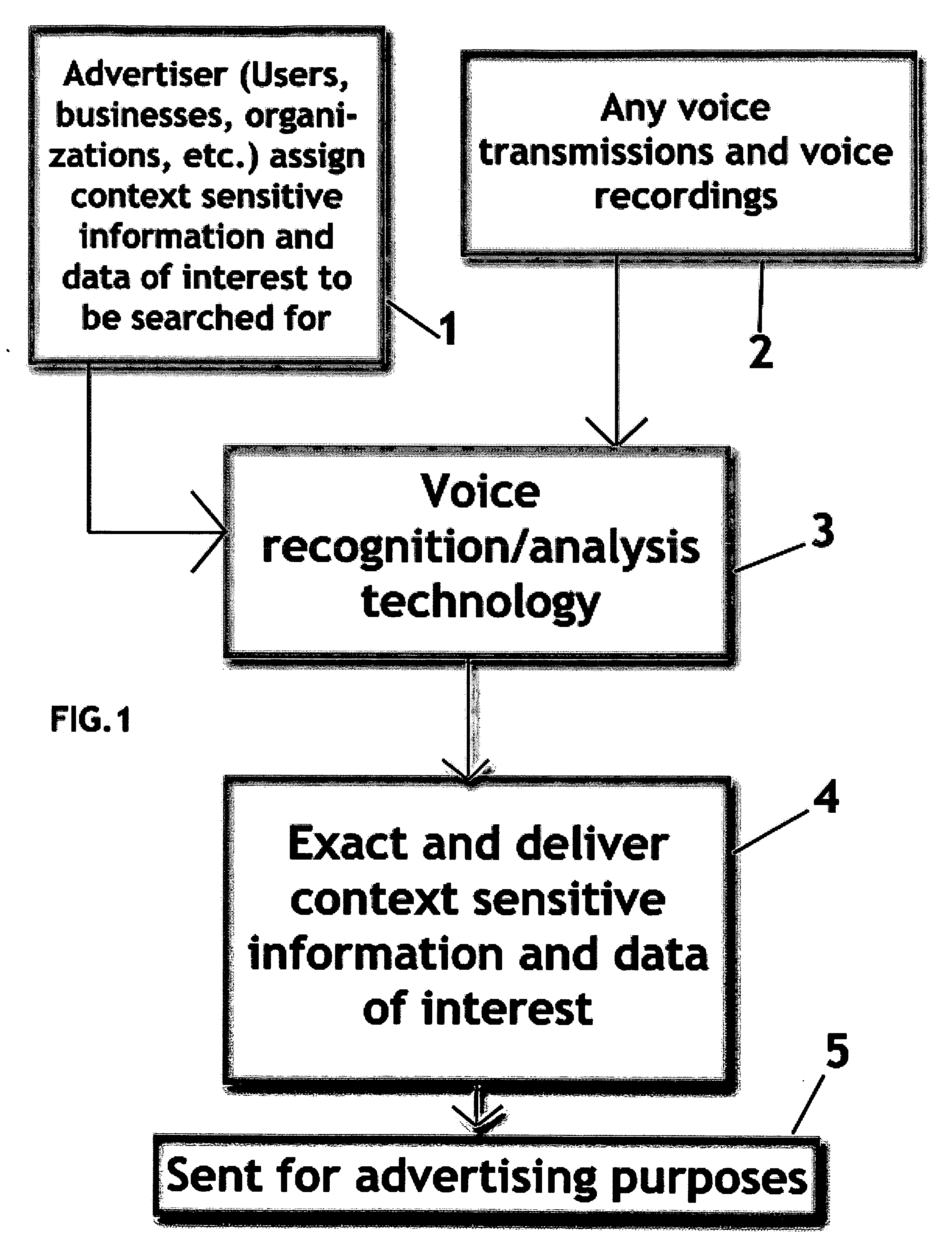
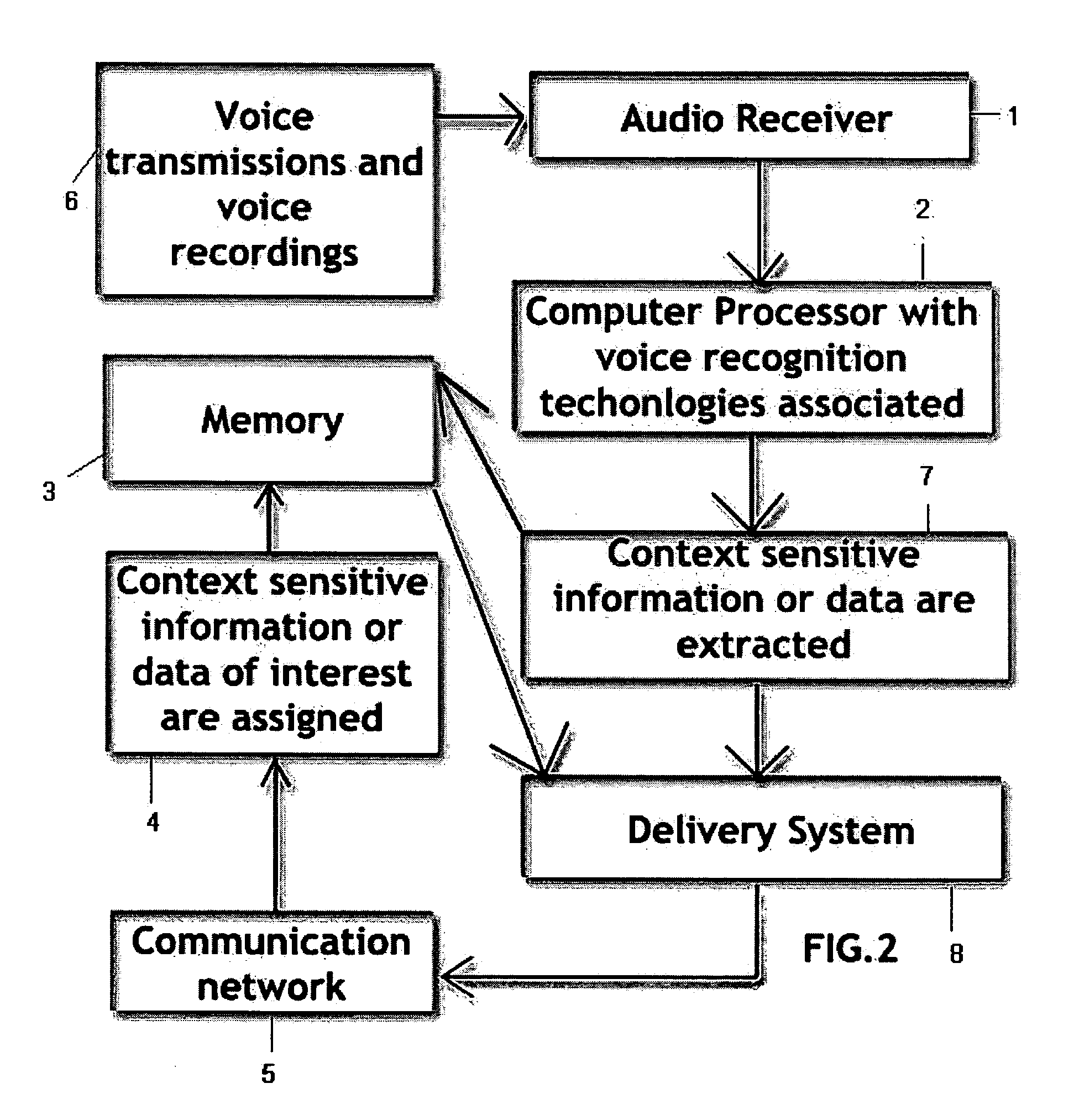
InactiveUS20080109222A1Without irritating consumersGood serviceSpeech recognitionMarketingPattern recognitionContext sensitivity
Method and apparatus that use voice / audio recognition and analysis technologies to deliver assigned context sensitive information and data of interest (keywords, phrases, mood, etc.). Context sensitive information and data of interest can be extracted from any voice / audio transmissions and voice / audio recordings (or any transmission or recording that includes voice / audio) for advertising purposes. This invention includes the said assigned context sensitive information and data of interest extraction method using voice / audio recognition and analysis technologies. Most importantly, this invention opens up new doors to advertising using extracted context sensitive information and data of interest from voice / audio transmissions and recordings (or any transmission that includes voice / audio).
Owner:LIU EDWARD
Information collection in multi-participant online communities
InactiveUS20080091692A1Improve functionalityImprove user experienceDigital data processing detailsWebsite content managementSynthetic dataComputer science
A database of personal information is built and controlled by the individual users creating it. This database can then be used to enhance the functionality and user experience associated with multi-participant online communities. By collecting information from users themselves, and by allowing users to maintain such data, the data can have significant added value both to the users and to any commercial services that wish to use it. Appropriate precautions are taken to ensure that users maintain control over the data they choose to share. Data is owned by the user that provided it, and any application or release of such data is only performed at user direction and under user control. The users are also given incentives to provide such data, in the form of promised rewards. These mechanisms improve the amount and quality of collected data, so that comprehensive databases describing users can be built more easily and effectively.
Owner:BRILIG
Removal component cartridge for increasing reliability in power harvesting systems
InactiveUS20080144294A1Simplifies diagnosisSimple repairPrinted circuit board receptaclesComponent plug-in assemblagesEngineeringElectric power
Owner:SOLAREDGE TECH LTD
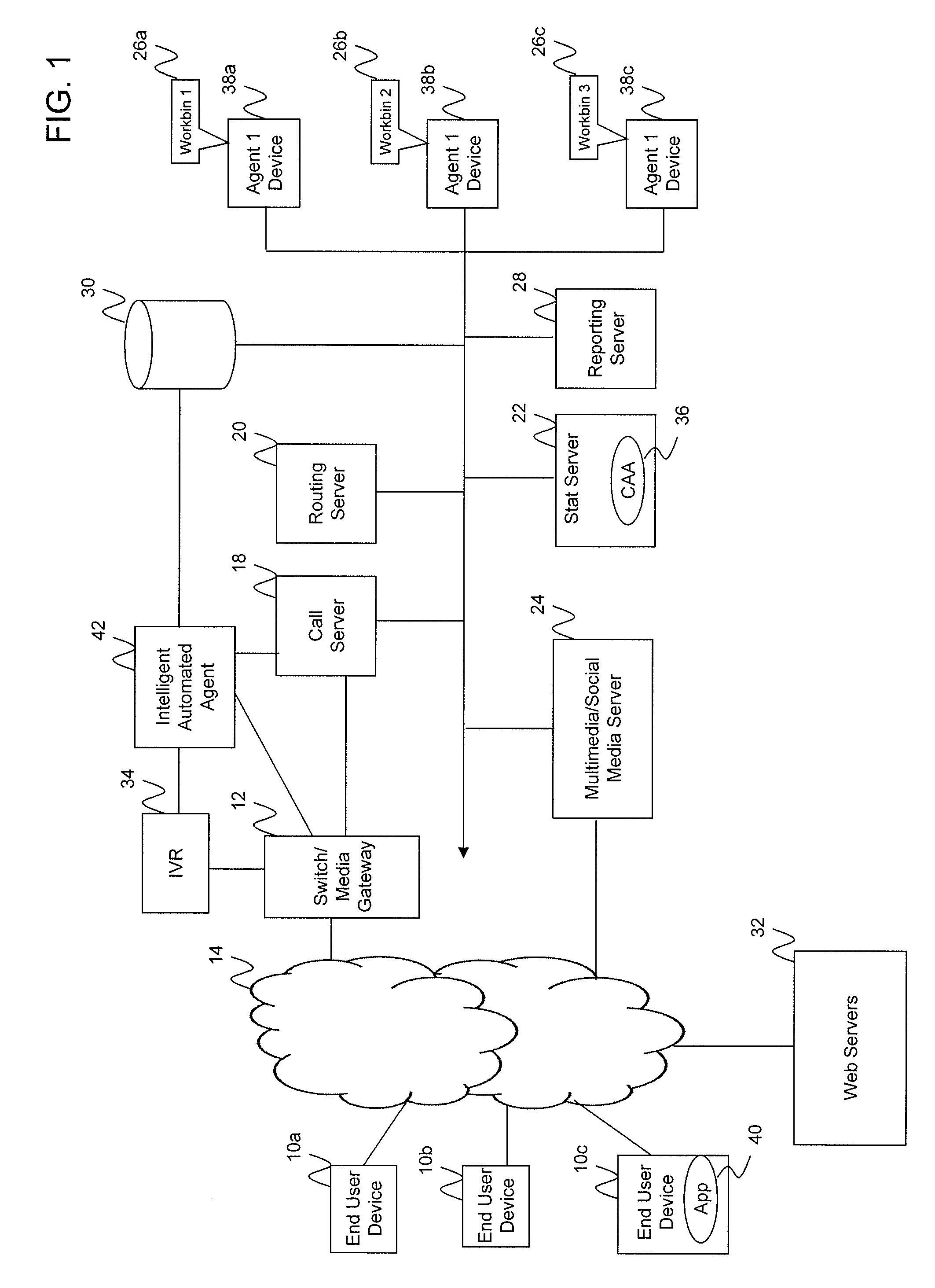
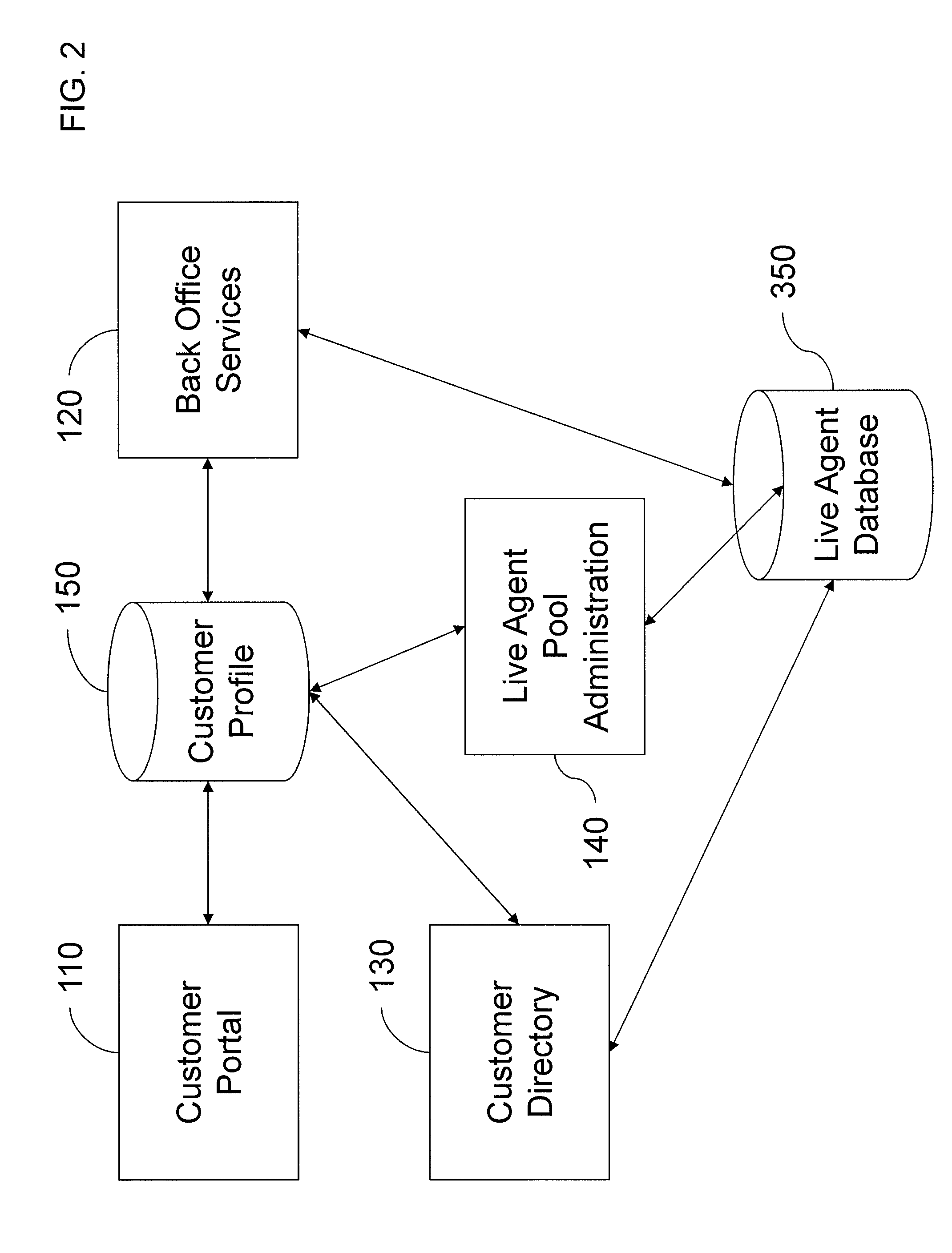
Intelligent automated agent for a contact center
InactiveUS20140314225A1Improve customer serviceGood and more personalized serviceCustomer relationshipSpecial service for subscribersContact centerData science
A system for handling customer interactions with a contact center for an enterprise includes an intelligent automated agent that includes a processor, a non-transitory storage device configured to store customer profile data, and a memory. The memory has instructions stored thereon that, when executed by the processor, causes the processor to: run an artificial intelligence engine configured to learn knowledge about a customer from past interactions between the contact center and the customer, and to apply the learned knowledge to future interactions; and maintain the customer profile data on the storage device. The maintaining of the customer profile data includes retrieving the customer profile data at a beginning of a new interaction, using the retrieved customer profile data to decide how to handle the new interaction, and updating the customer profile data after completion of the new interaction to reflect the new interaction as one of the past interactions.
Owner:GENESYS TELECOMMUNICATIONS LABORATORIES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com