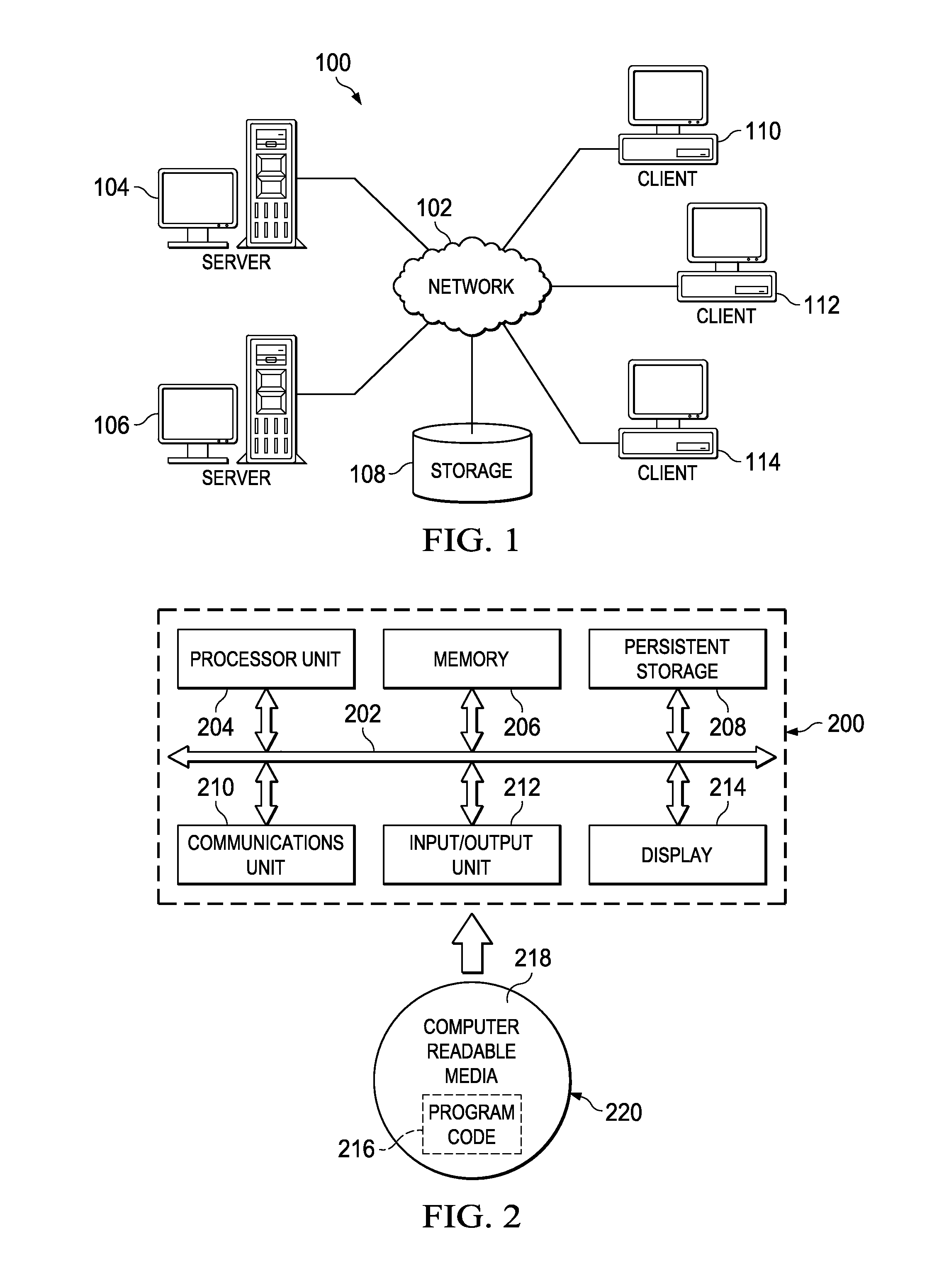
Patents
Literature
59 results about "Infrastructure security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Infrastructure security is the security provided to protect infrastructure, especially critical infrastructure, such as airports, highways rail transport, hospitals, bridges, transport hubs, network communications, media, the electricity grid, dams, power plants, seaports, oil refineries, and water systems. Infrastructure security seeks to limit vulnerability of these structures and systems to sabotage, terrorism, and contamination.
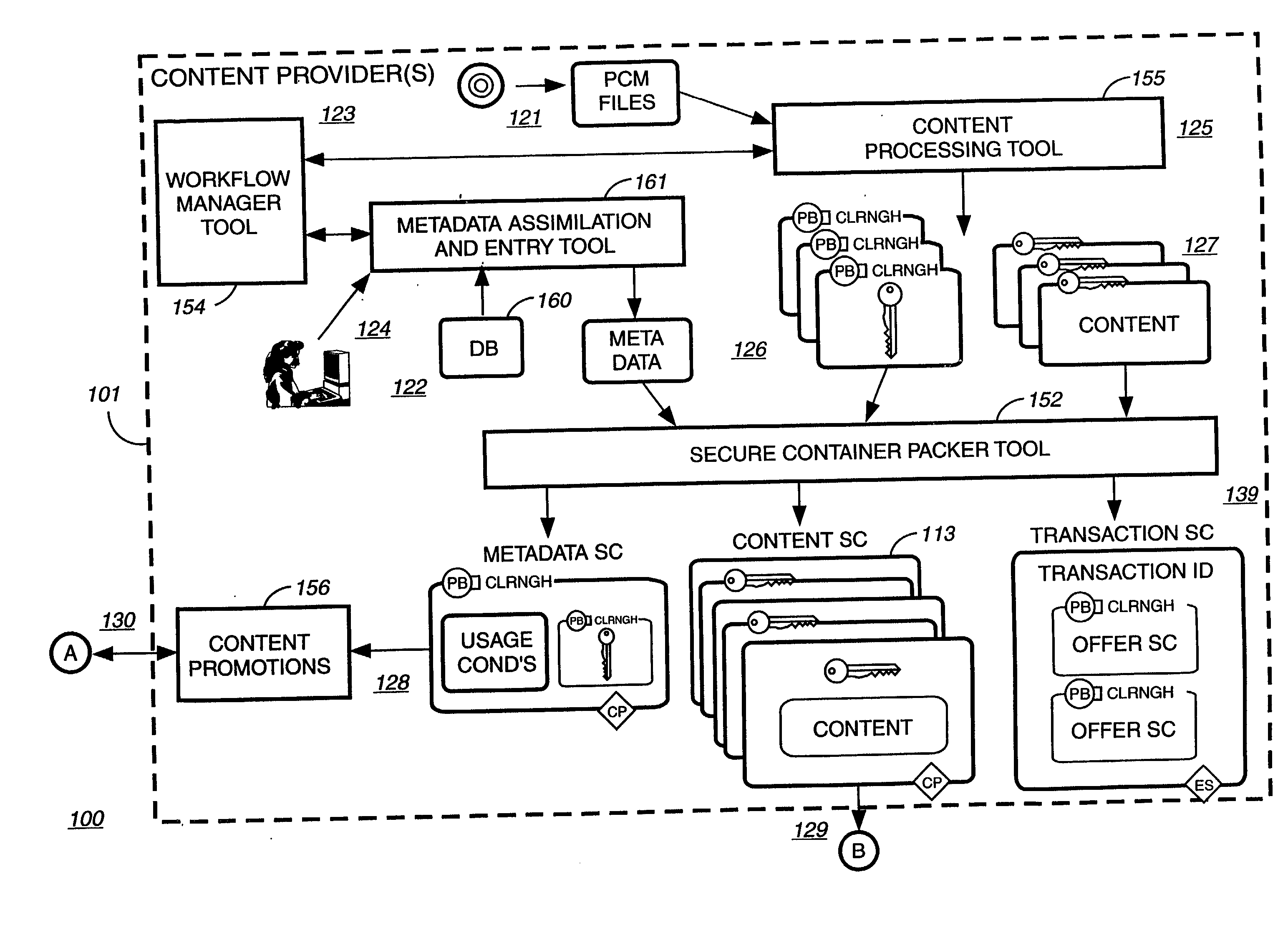
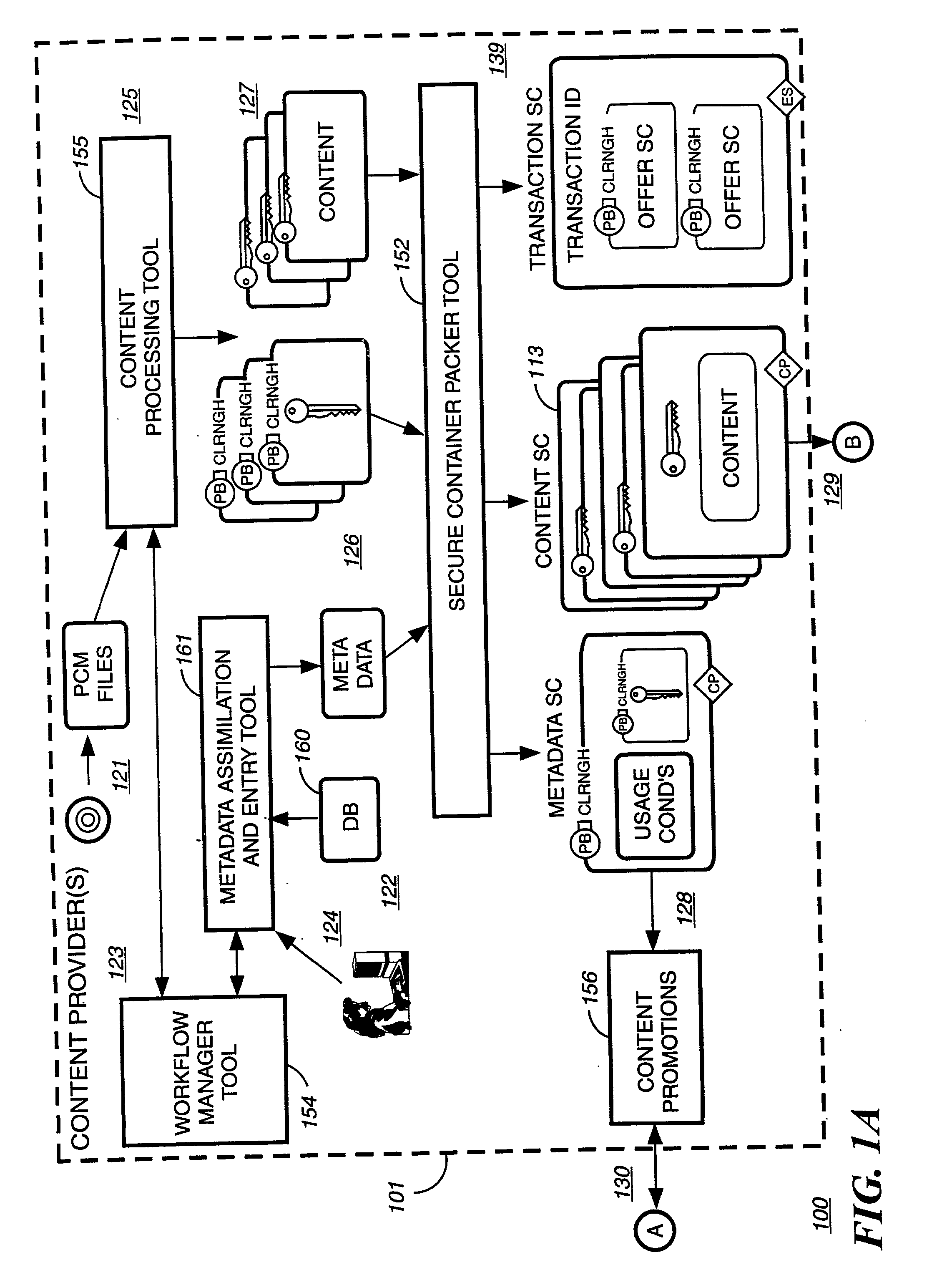
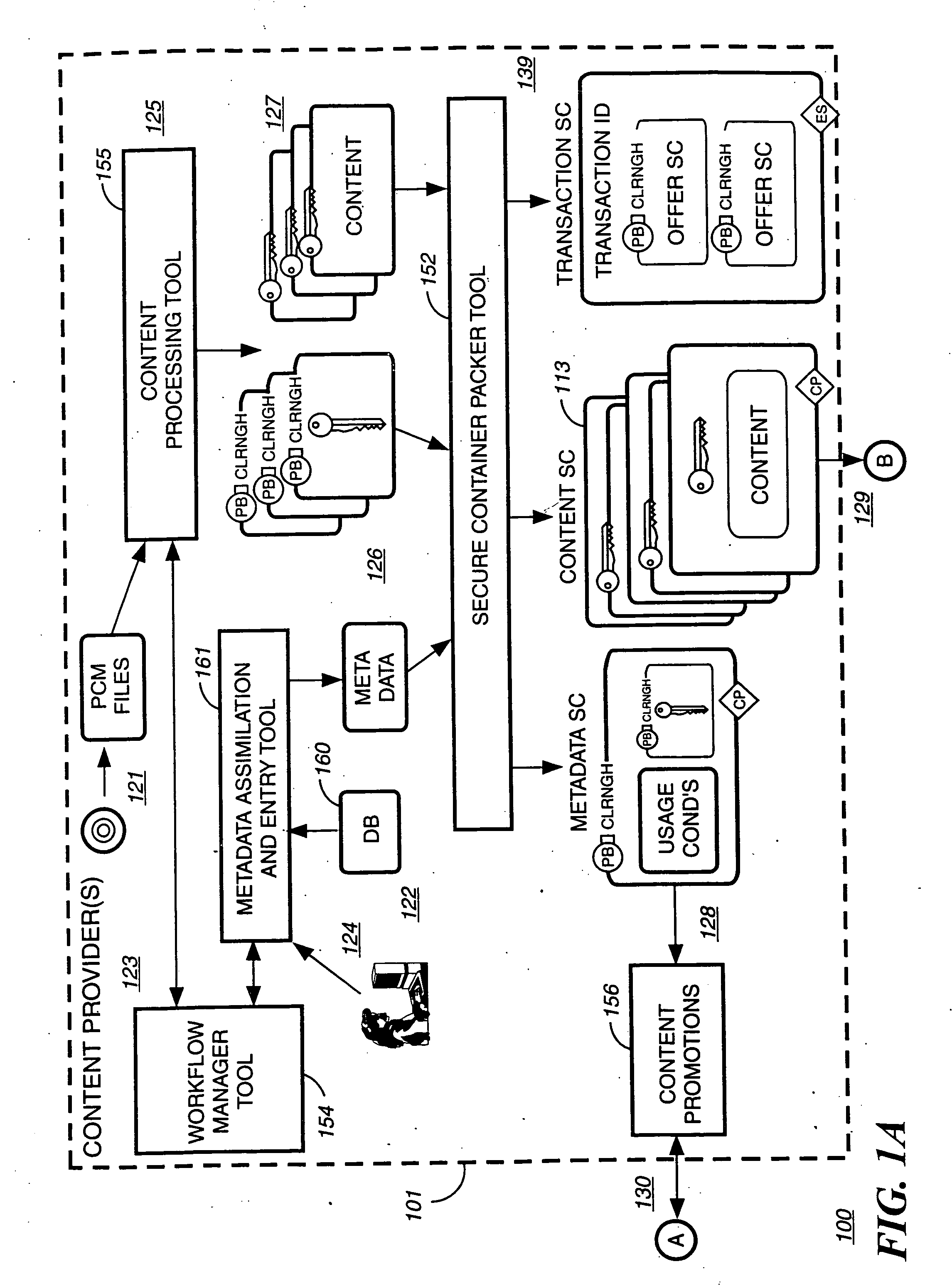
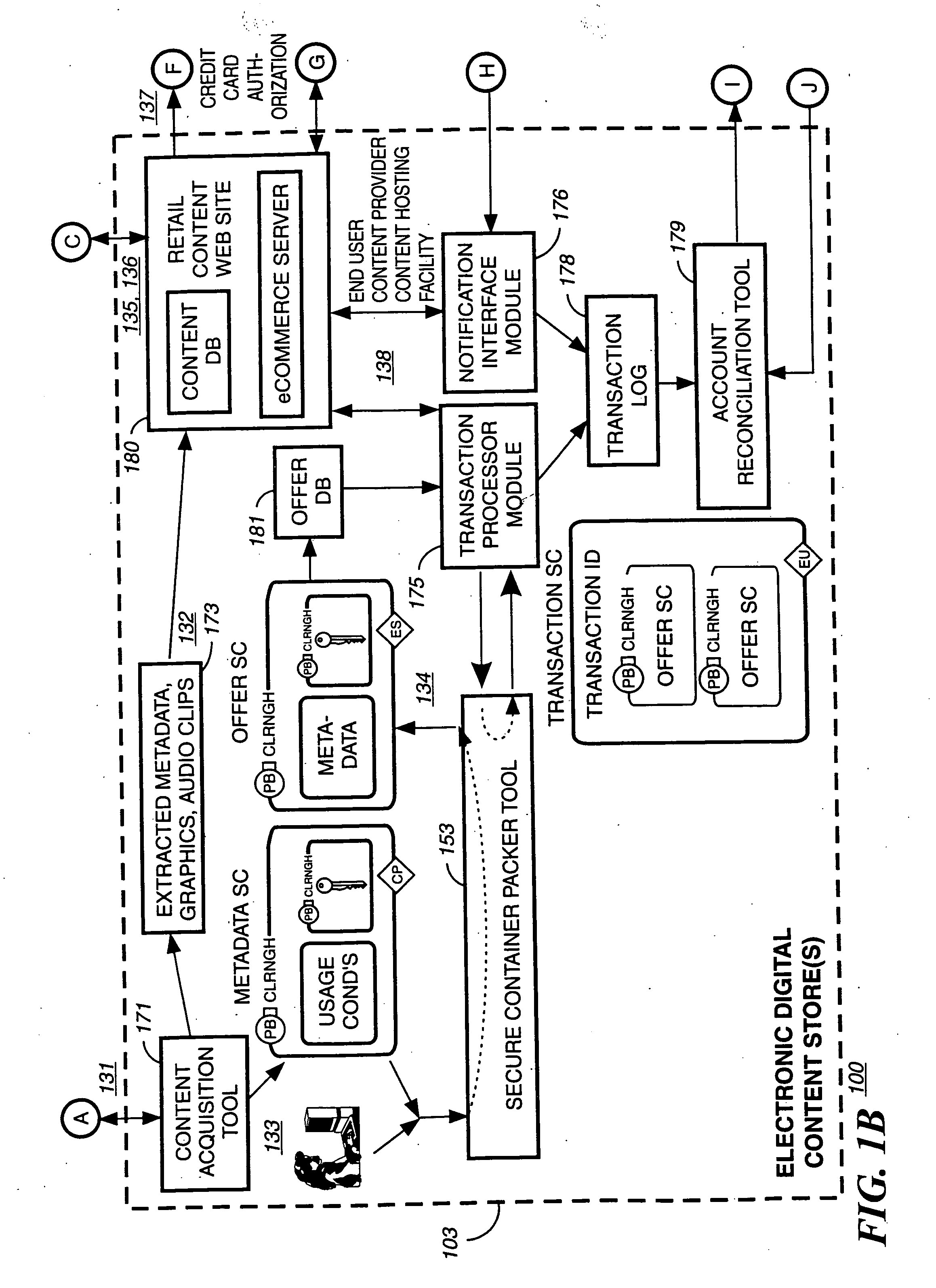
Digital content distribution using web broadcasting services
InactiveUS20030135464A1Website content managementElectronic credentialsBroadcast channelsDigital content
A method of securely receiving data on a user's system from a web broadcast infrastructure with a plurality of channels. The method comprising the steps of: receiving promotional metadata from a first web broadcast channel, the promotional metadata related to data available for reception; assembling at least part of the promotional metadata into a promotional offering for review by a user; selecting by a user, data to be received related to the promotional metadata; receiving data from a second web broadcast channel, the data selected from the promotional metadata, and wherein the data has been previously encrypted using a first encrypting key; and receiving the first decrypting key via a computer readable medium, the first decrypting key for decrypting at least some of the data received via the second web broadcast channel. In another embodiment, a method and system to transmit data securely from a web broadcast center is disclosed.
Owner:IBM CORP
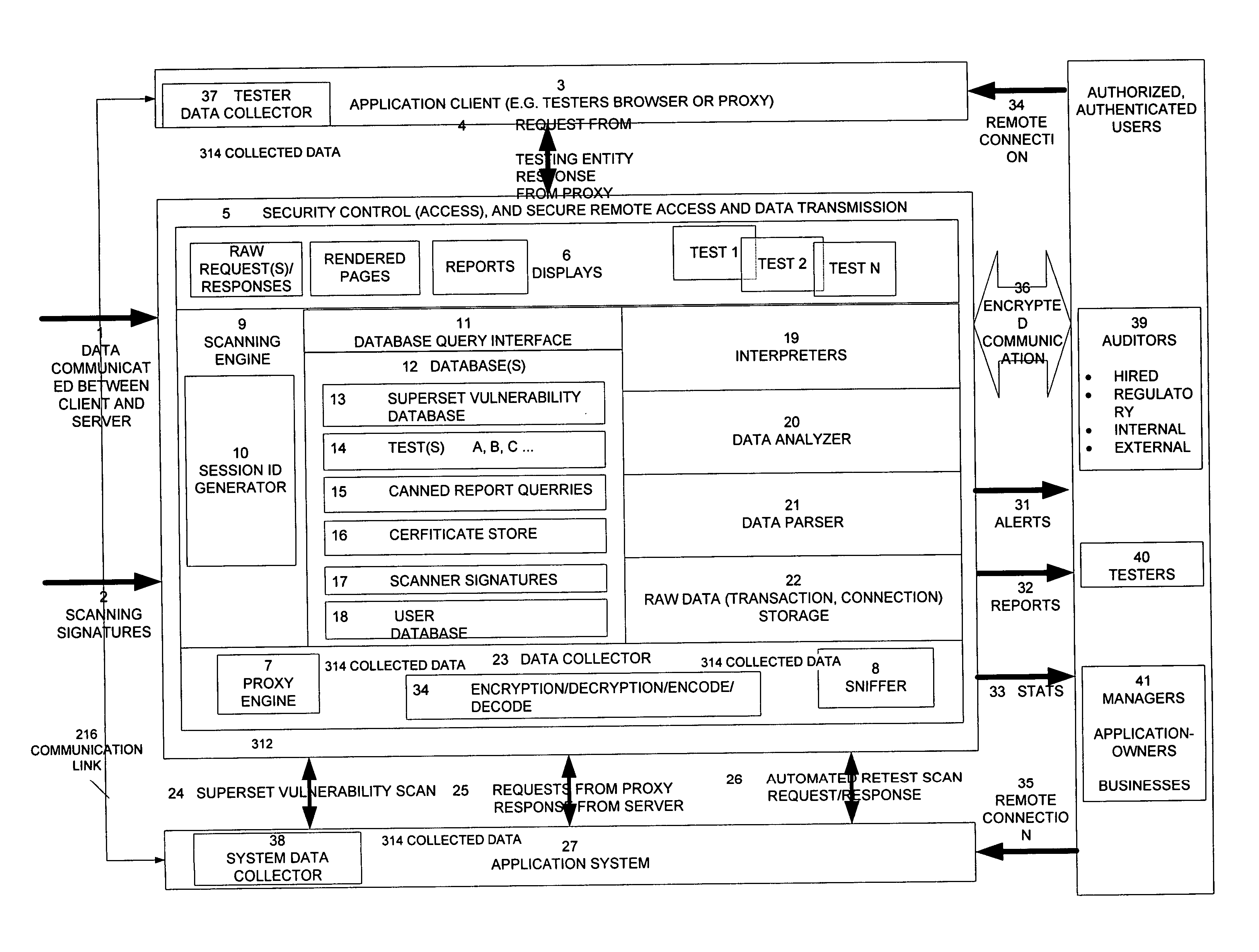
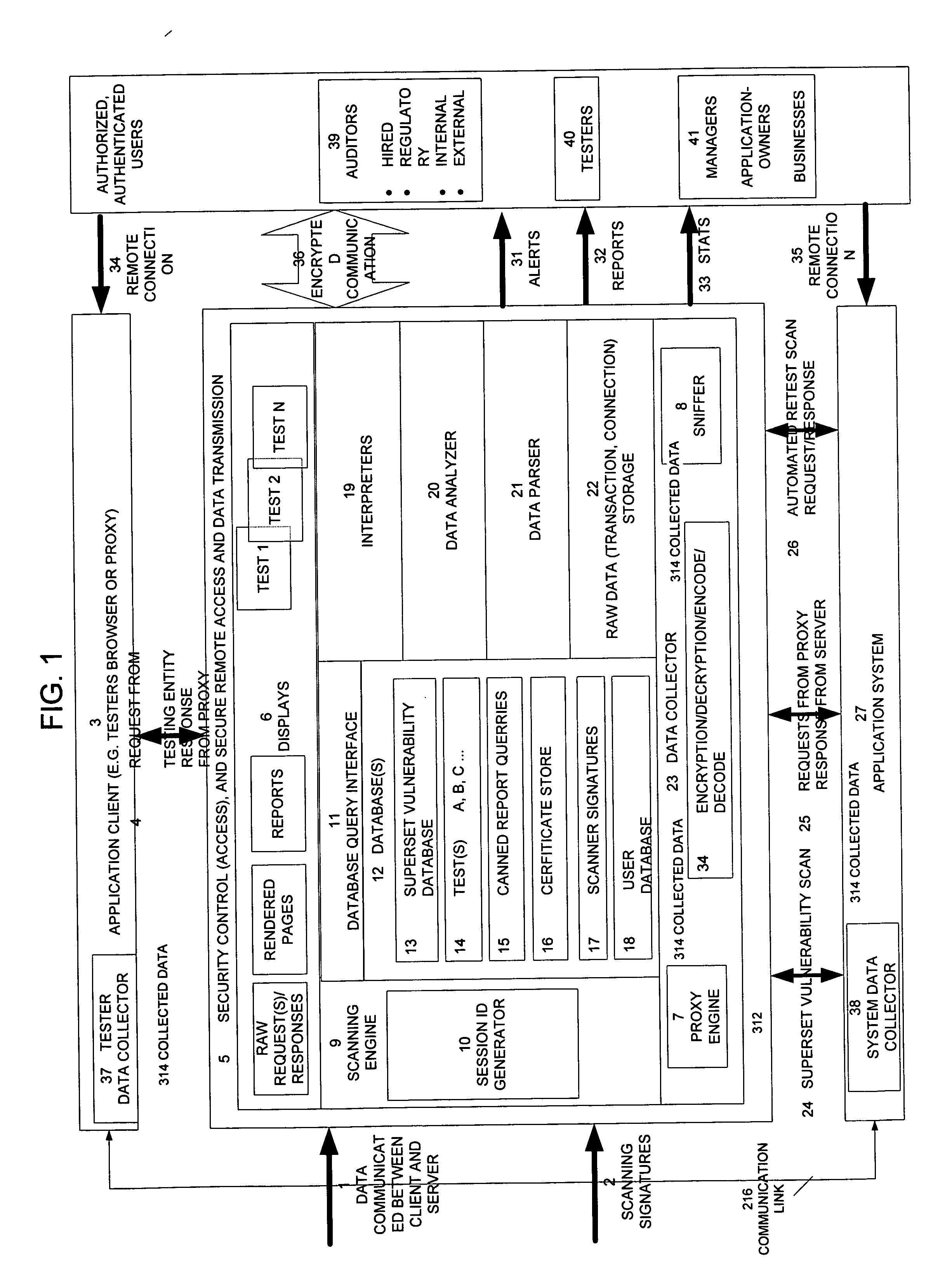
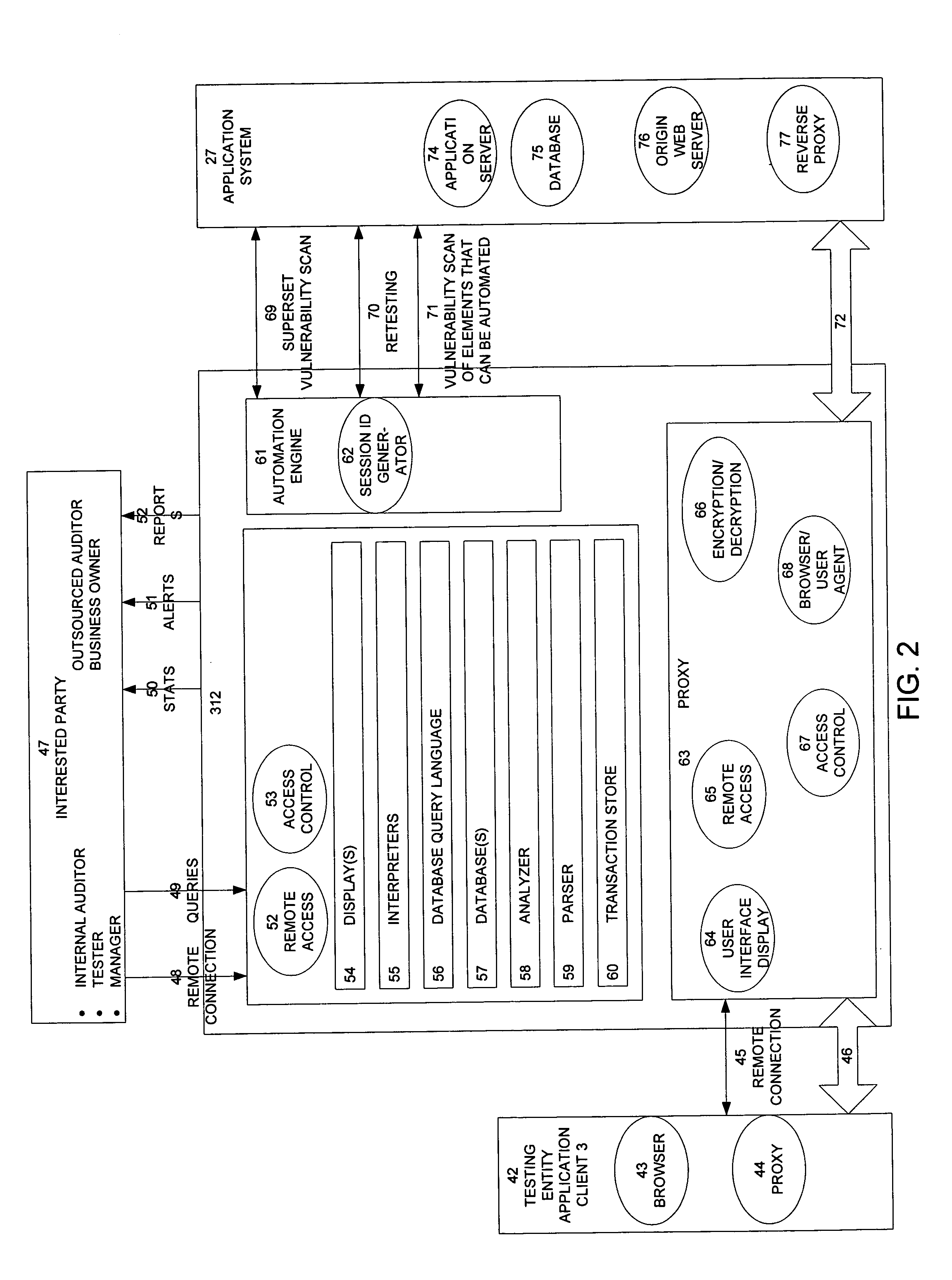
Method, system, and apparatus for managing, monitoring, auditing, cataloging, scoring, and improving vulnerability assessment tests, as well as automating retesting efforts and elements of tests
InactiveUS20050138426A1Streamline and improve test effortImprove consistencyDigital data processing detailsHardware monitoringAnalysis dataWeb application
A scalable method, system, and apparatus for non-intrusively auditing and improving security assessments includes capturing, storing, presenting, displaying, inspecting, monitoring, and analyzing data flow in client-server security assessments and / or network / infrastructure security assessments. The invention provides interested parties with a mechanism to non-intrusively audit in real-time the vulnerability test effort, as well as review, replay, and analyze all aspects of the security assessment during and after the test. For web application assessments, the data capture includes one of the following or some combination: an intermediary with all data passing through the intermediary; a sniffer that can passively extract all data being communicated between the application and tester; and a plurality of computing modules (e.g., software, appliances, etc.) installed in the tester environment or within the application system environment (e.g., software installed on the tester's computer, or on the computer where the intermediary is running, or software installed on the application systems proxy or web server, or an appliance in either environment) for storing, processing, analyzing, reporting, and displaying the data.
Owner:STYSLINGER BRIAN
Digital content distribution using web broadcasting services
InactiveUS20060053077A1Website content managementElectronic credentialsBroadcast channelsDigital content
Owner:INT BUSINESS MASCH CORP
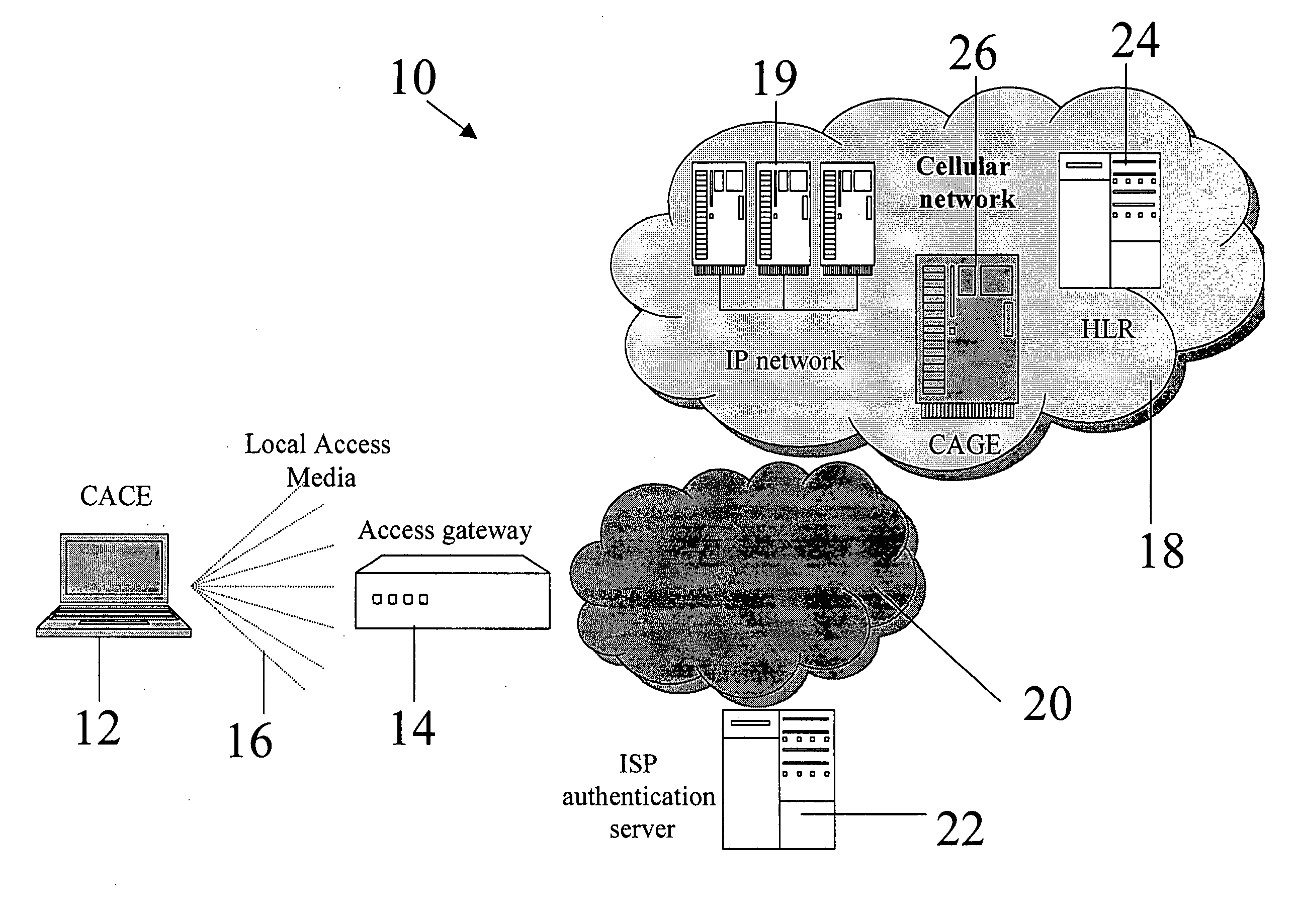
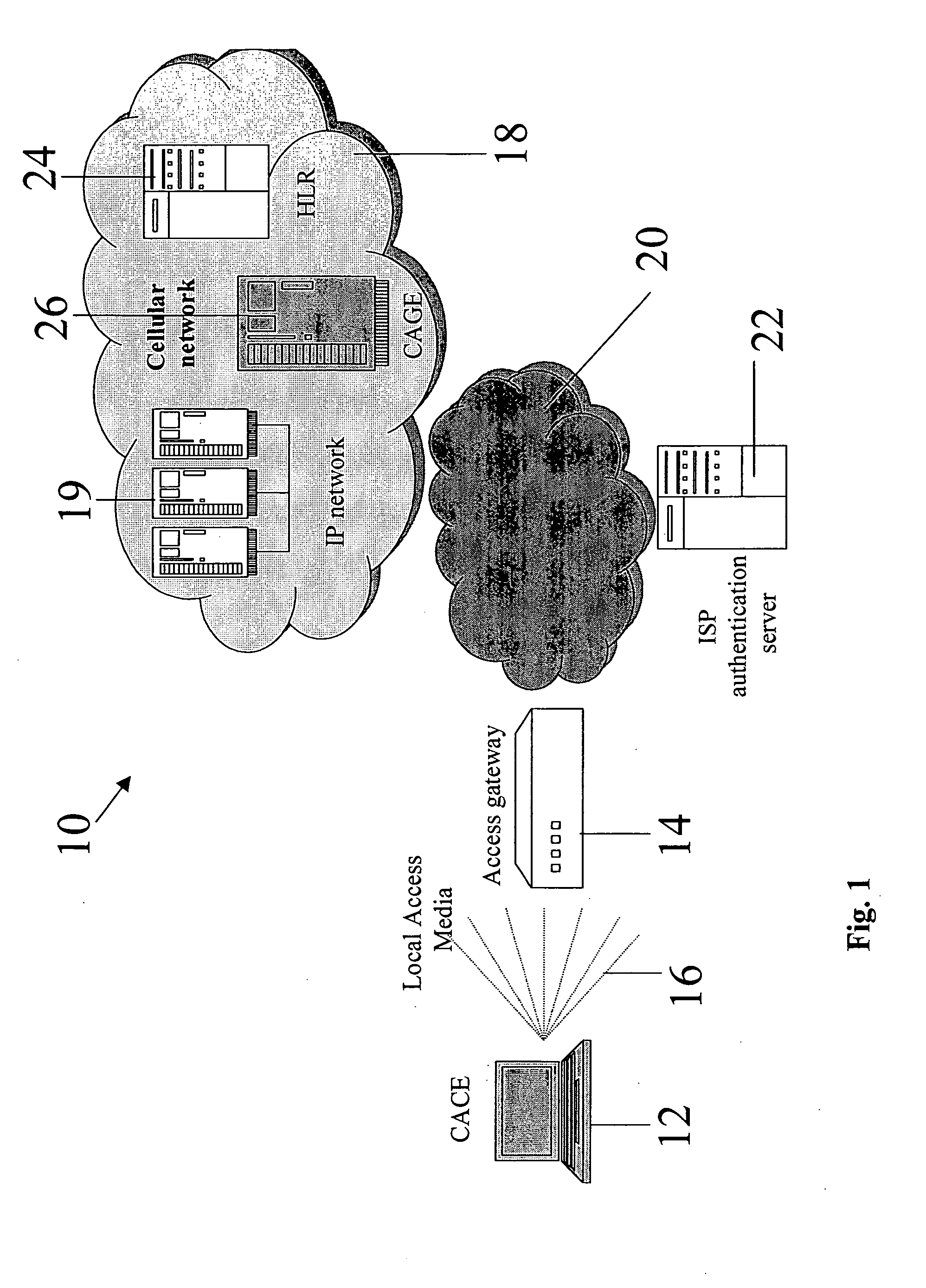
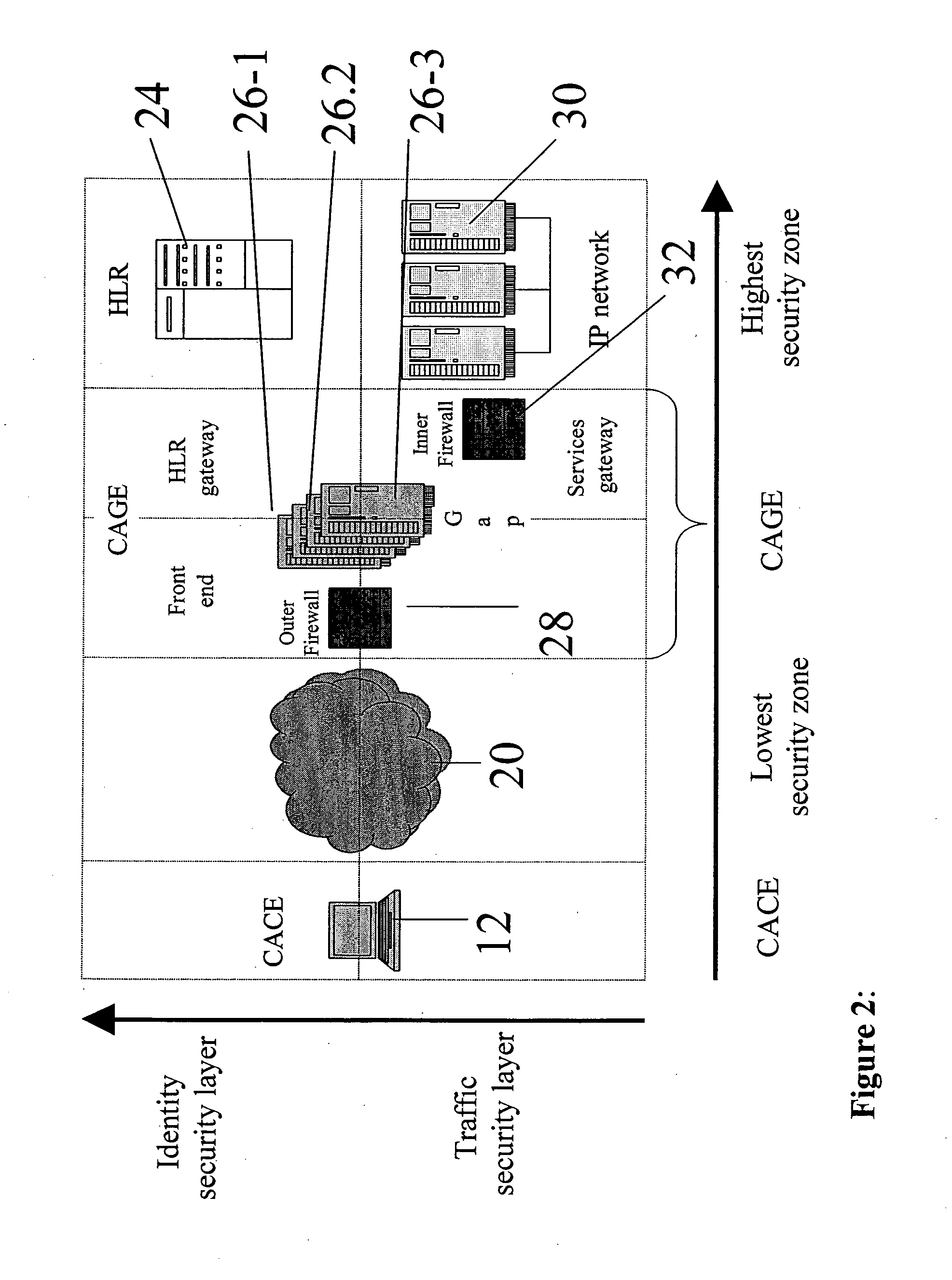
Accessing cellular networks from non-native local networks
InactiveUS20050124288A1Broadcast transmission systemsData switching by path configurationThe InternetWireless lan
A multiple entity gateway for supporting cellular authentication from a non-cellular network, the gateway comprising a plurality of entities each located at a different one of a plurality of secure zones and having at least one gap between said entities across said secure zones, said gateway being configured to predefine communication signals allowed across said gap between said entities, thereby to filter out non-allowed signals, and provide secure cellular authentication for a communication originating from said non-cellular network. The gateway allows cellular users to connect to a cellular network via a wireless local area network such as a hotspot, use the services of the cellular network, the Internet and the hotspot at will, and be securely authenticated and charged through the cellular infrastructure.
Owner:FLASH NETWORKS
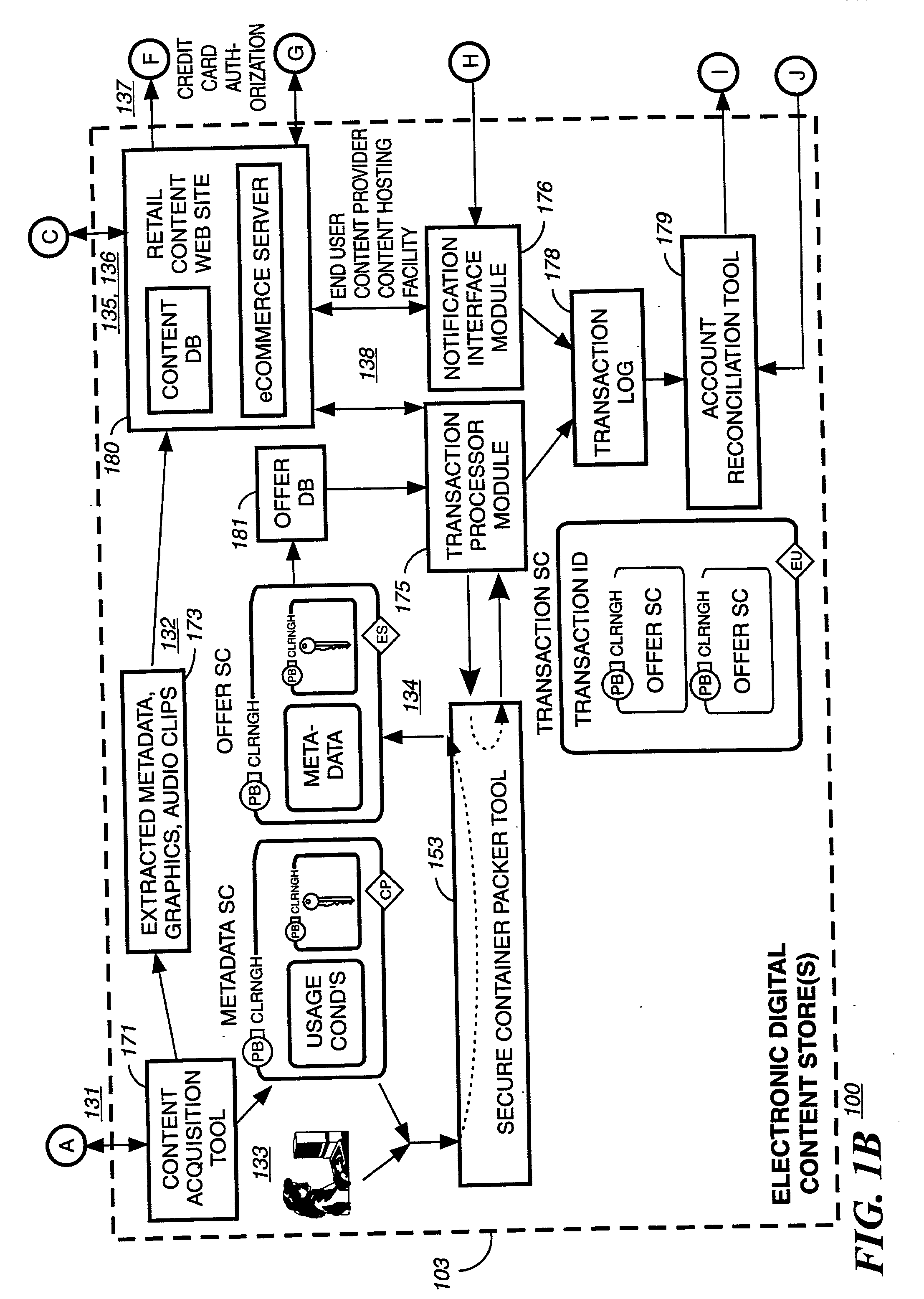
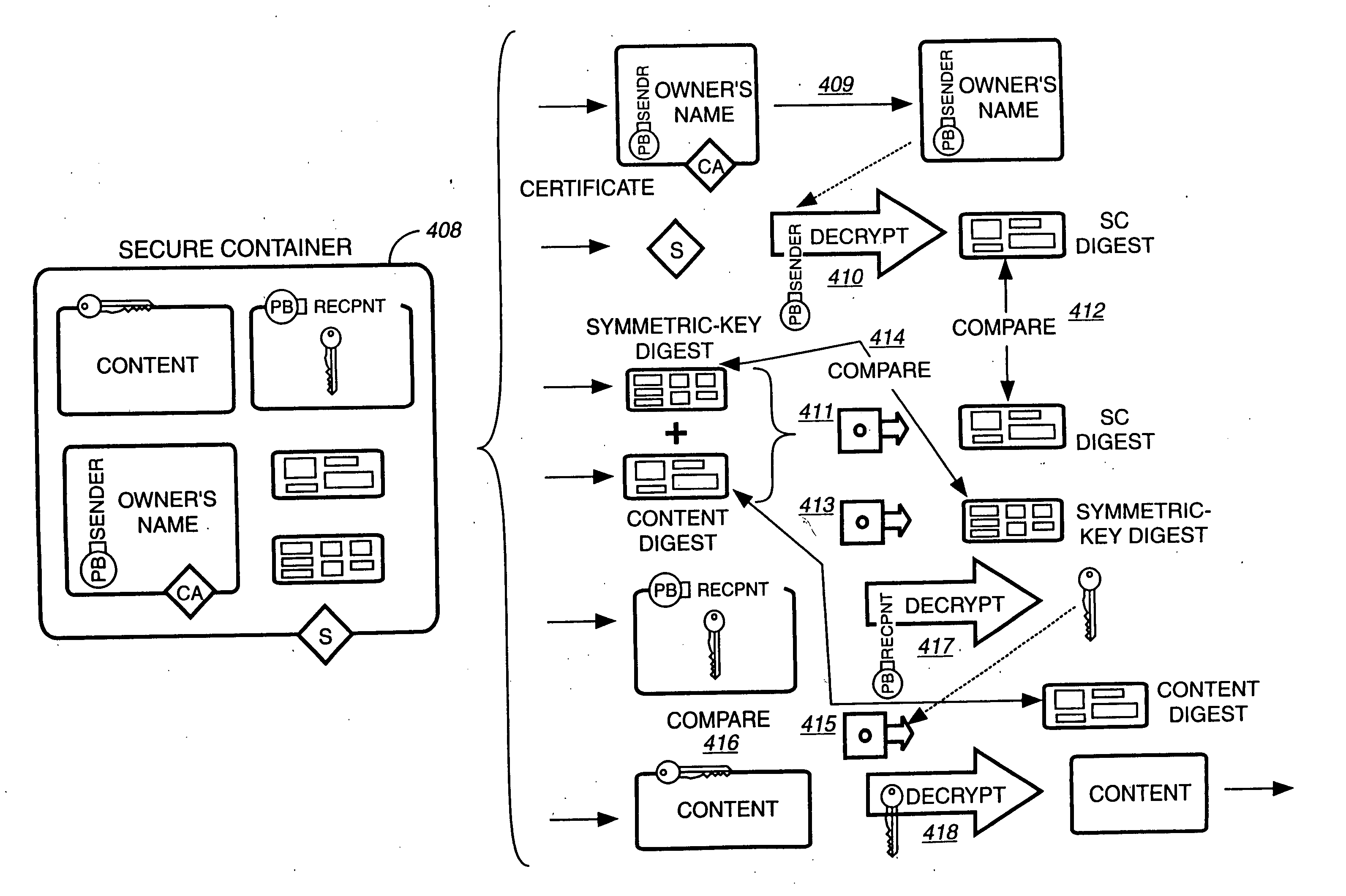
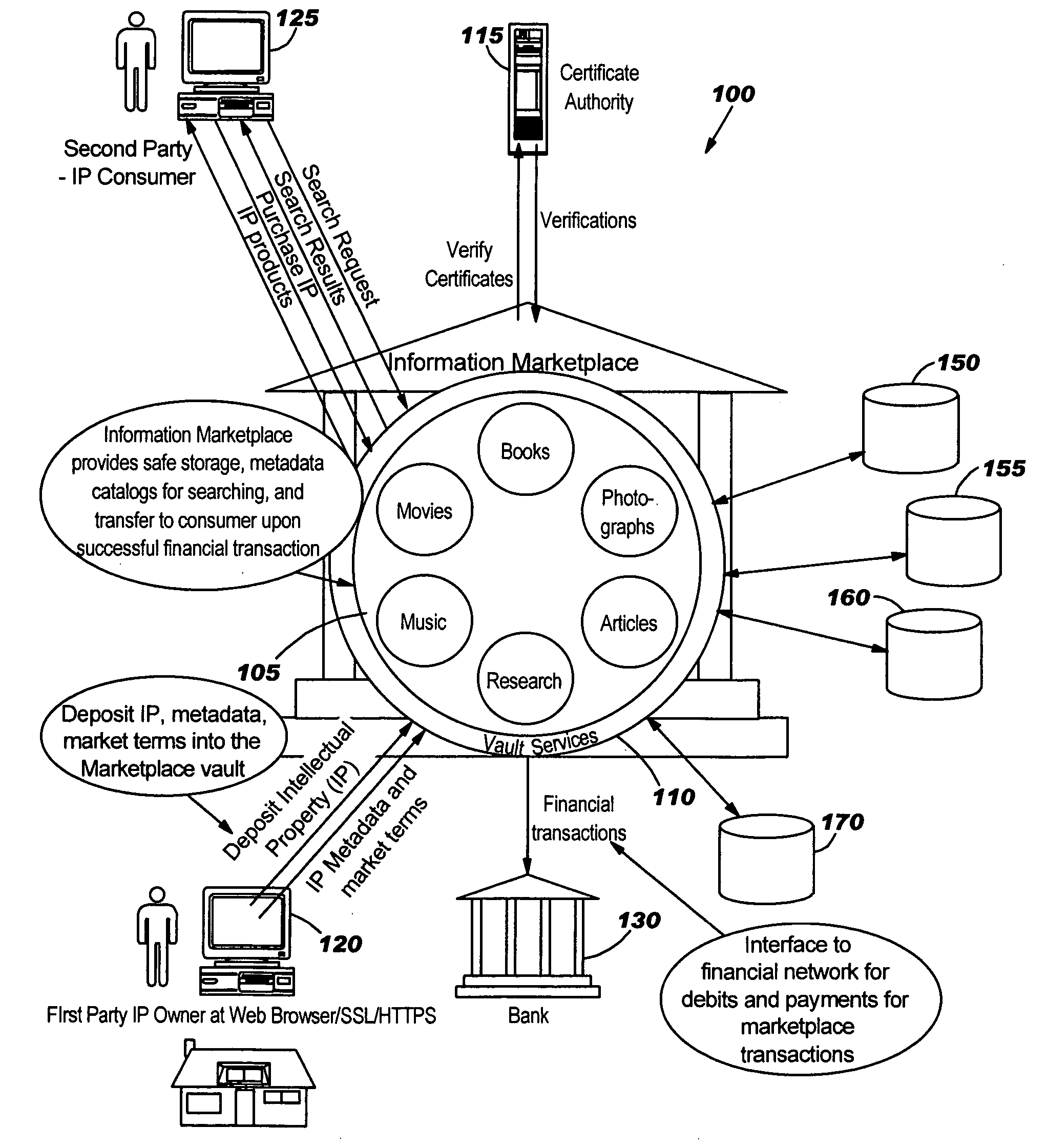
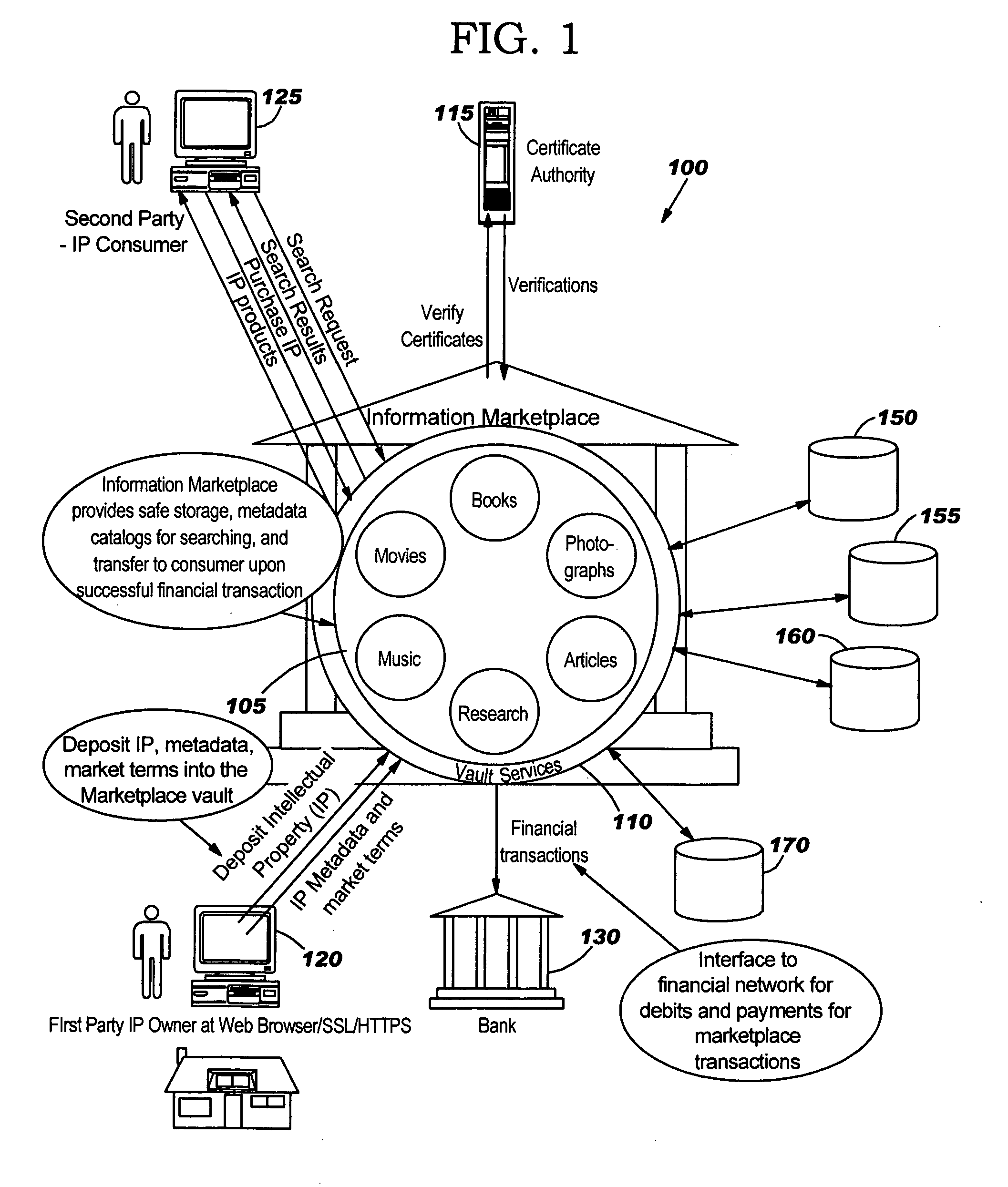
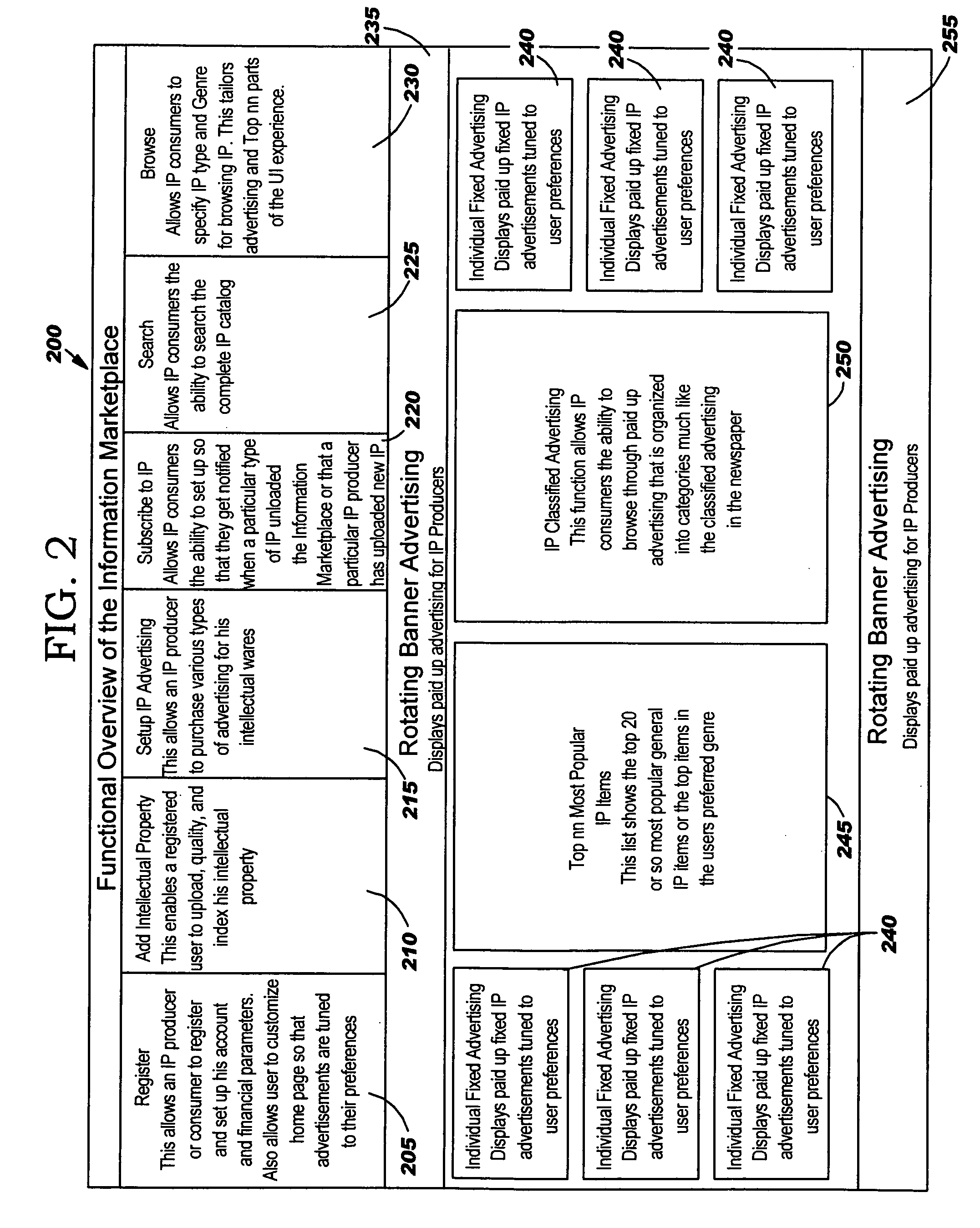
System and method for providing a secure intellectual property marketplace
ActiveUS20060085360A1FinanceComputer security arrangementsInformation repositoryIntellectual property
A system and method for providing an intellectual property marketplace (IM) using a secured information vault so that individual owners of intellectual property (IP) may control and manage the access and dissemination of the IP. Producers of the IP may also receive compensation for transactions in the marketplace. Multiple services for adding IP such as books, movies, video, papers, research, music, inventions, or the like, to the IM include controlling authorized access to the IP and generation of advertising based on types of IP in order to solicit potential consumers. Transactions may be securely transacted using public keying infrastructure (PKI). Consumers subscribing to the IM may also be automatically notified when IP is added to the IM based on predetermined preferences established by the consumer.
Owner:GOOGLE LLC
Wide-area, real-time monitoring and visualization system
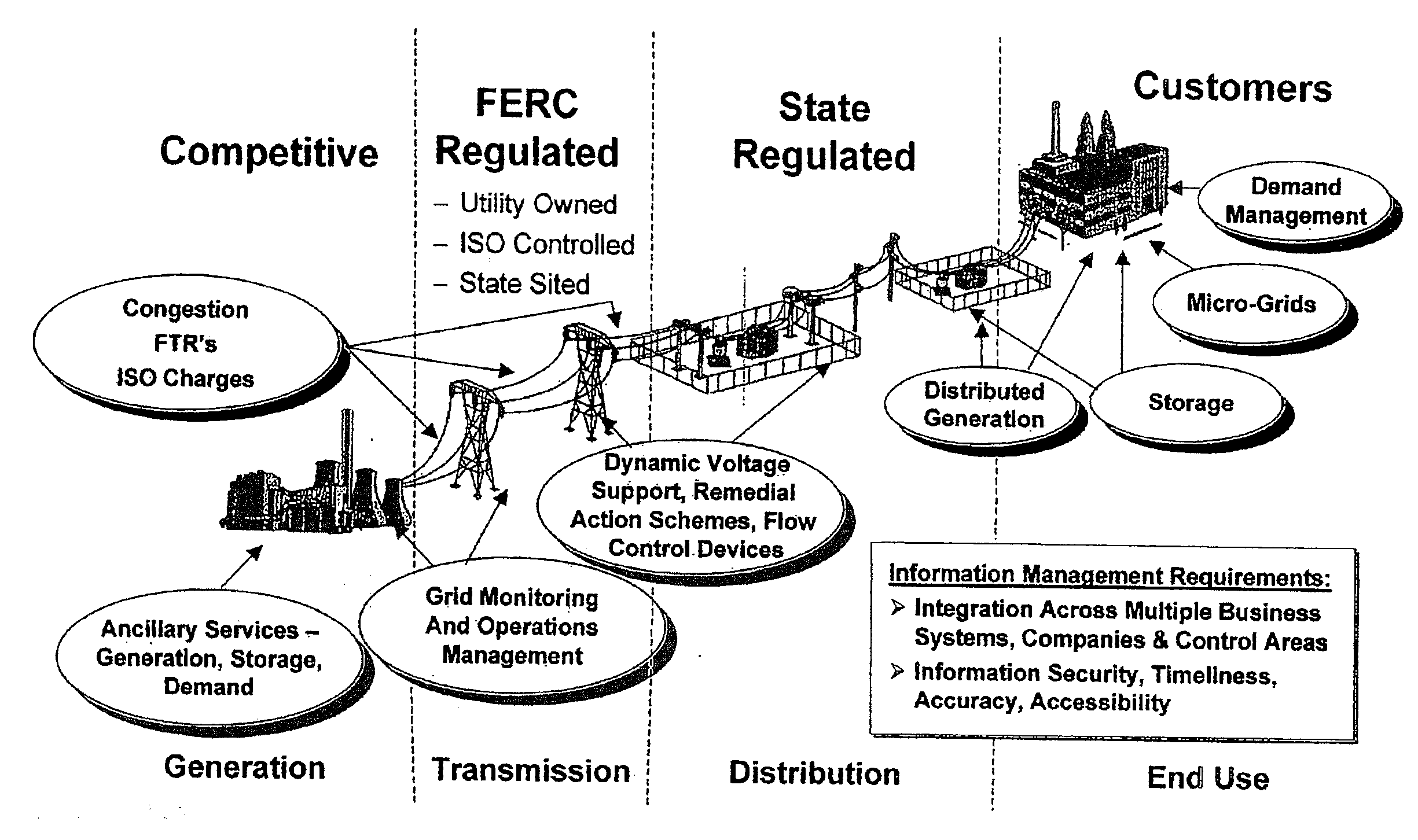
A real-time performance monitoring system for monitoring an electric power grid. The electric power grid has a plurality of grid portions, each grid portion corresponding to one of a plurality of control areas. The real-time performance monitoring system includes a monitor computer for monitoring at least one of reliability metrics, generation metrics, transmission metrics, suppliers metrics, grid infrastructure security metrics, and markets metrics for the electric power grid. The data for metrics being monitored by the monitor computer are stored in a data base, and a visualization of the metrics is displayed on at least one display computer having a monitor. The at least one display computer in one said control area enables an operator to monitor the grid portion corresponding to a different said control area.
Owner:ELECTRIC POWER GROUP
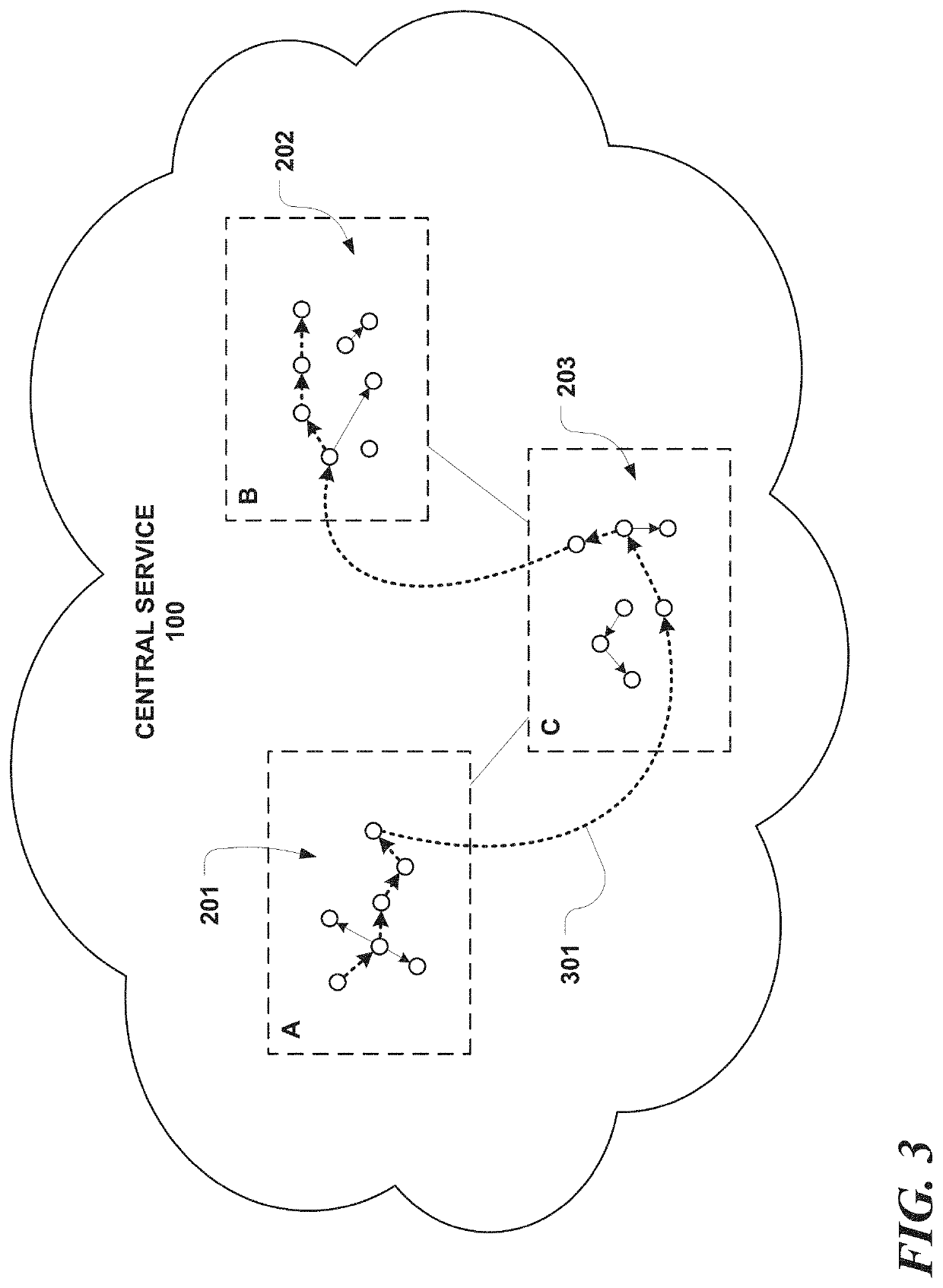
Extending infrastructure security to services in a cloud computing environment
InactiveUS20140317716A1SSO is facilitatedDigital data processing detailsMultiple digital computer combinationsTrust relationshipBase exchange
A cloud deployment appliance (or other platform-as-a-service (IPAS) infrastructure software) includes a mechanism to deploy a product as a “shared service” to the cloud, as well as to enable the product to establish a trust relationship between itself and the appliance or IPAS. The mechanism further enables multiple products deployed to the cloud to form trust relationships with each other (despite the fact that each deployment and each product typically, by the nature of the cloud deployment, are intended to be isolated from one another). In addition, once deployed and provisioned into the cloud, a shared service can become part of a single sign-on (SSO) domain automatically. SSO is facilitated using a token-based exchange. Once a product registers with a token service, it can participate in SSO. This approach enables enforcement of consistent access control policy across product boundaries, and without requiring a user to perform any configuration.
Owner:IBM CORP
Behavior detection system for detecting abnormal behavior
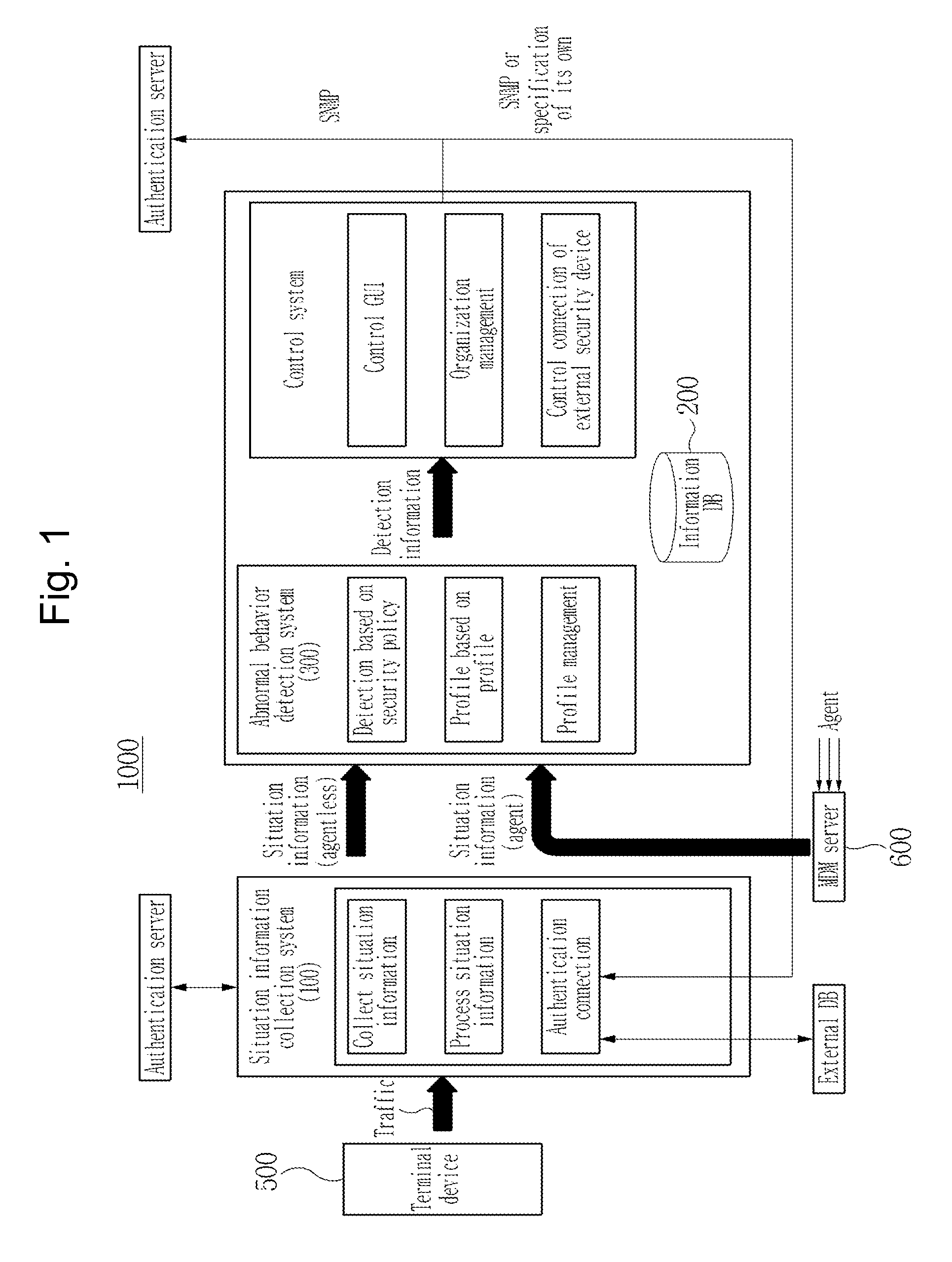
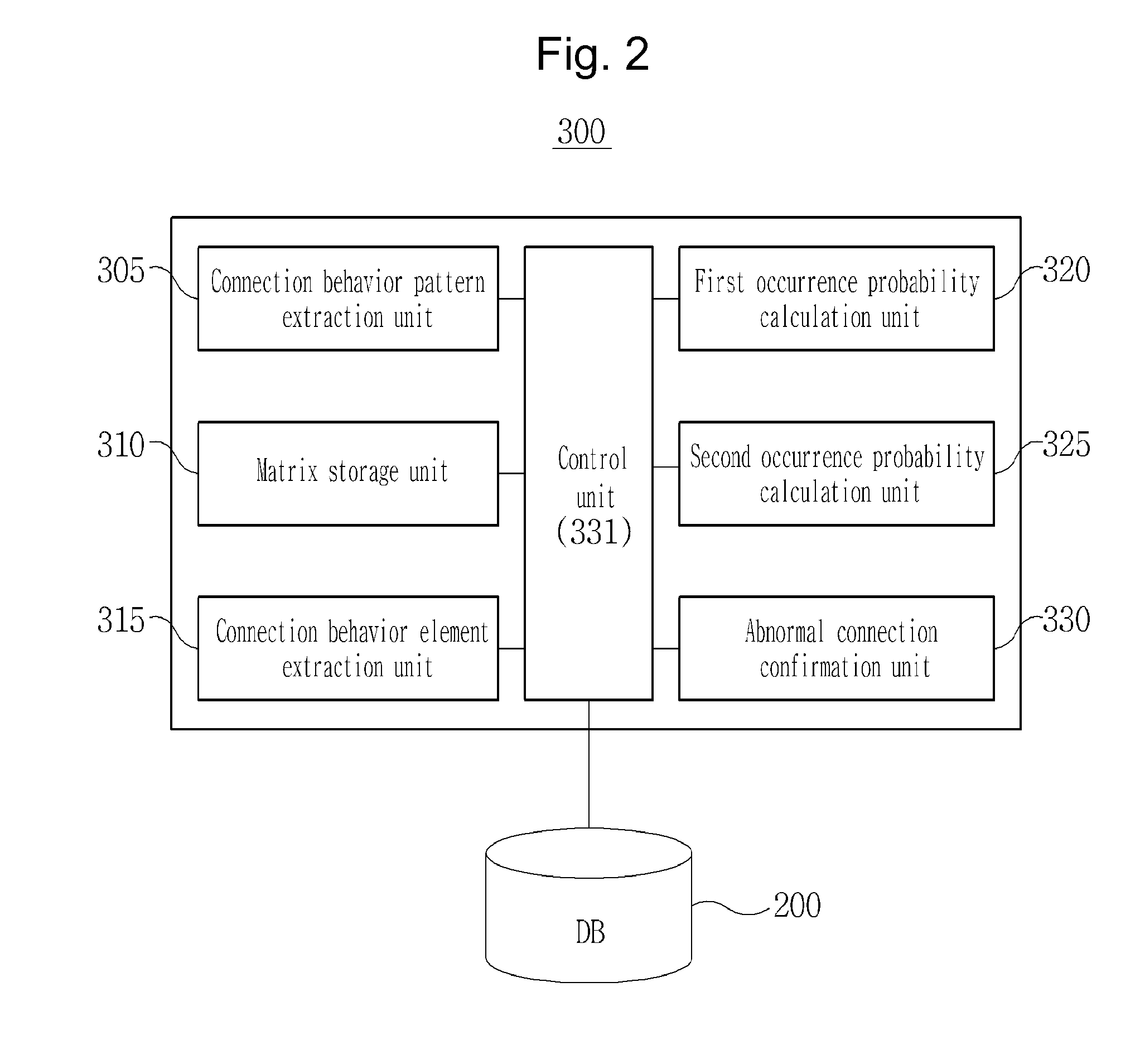
InactiveUS20150180893A1Memory loss protectionUnauthorized memory use protectionWorking environmentData mining
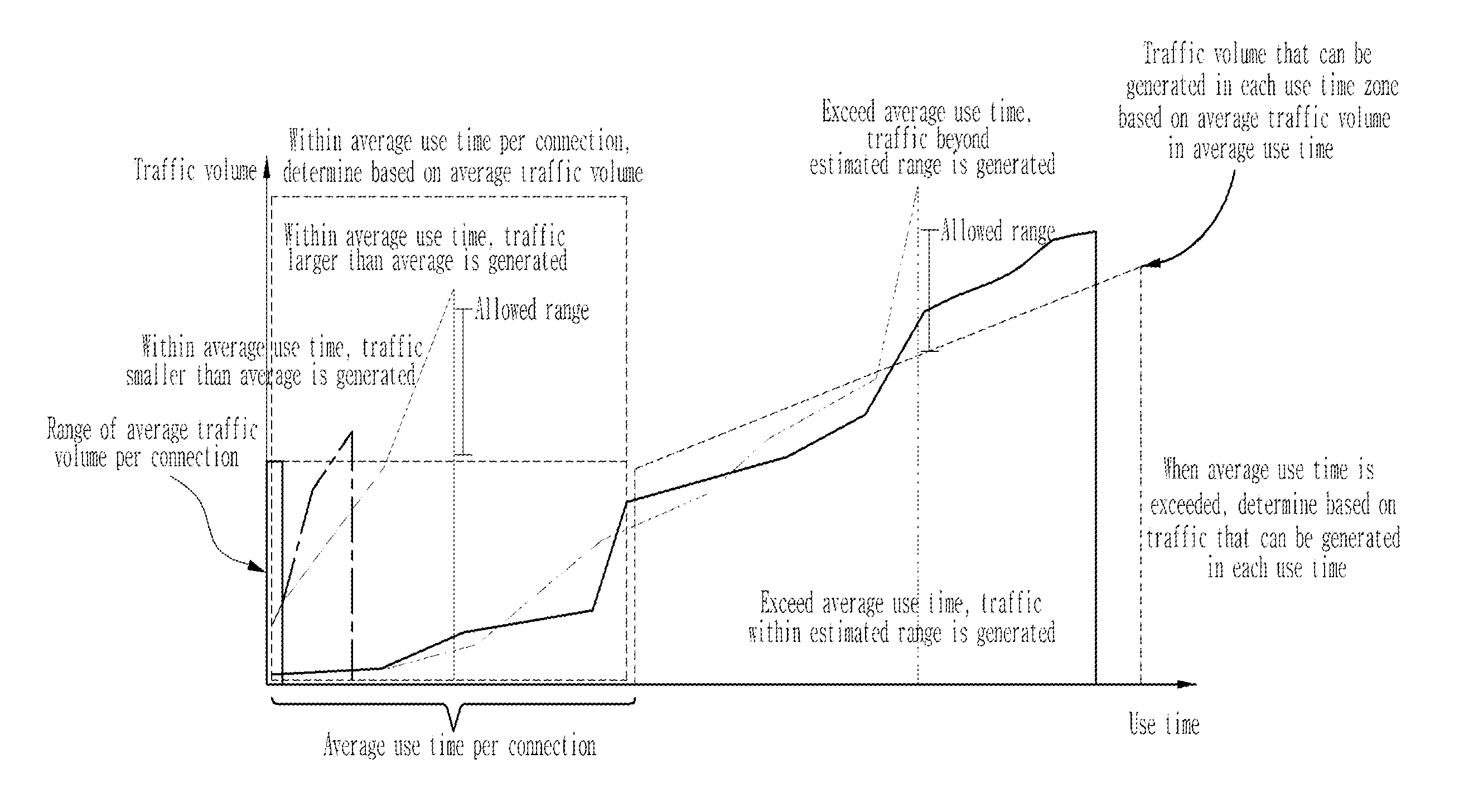
Disclosed is a behavior detection system for detecting an abnormal behavior, can perform dynamic control based on situation information and a profile of each user to cope with an element threatening security of an internal infrastructure of an enterprise, such as information leakage, in BYOD and smart work environment. The system calculates probabilities of behaviors occurring for respective connection behavior elements, calculates standard deviations of the probabilities based on weighting factors and determines whether or not the calculated behavior occurrence probabilities and behavior standard deviation correspond to a normal behavior, existence of an abnormal connection behavior in a BYOD and smart work environment is detected and an abnormal user is detected by examining whether or not an average traffic volume, an average use time and traffic volume with respect to a use time exceeds respective standard values.
Owner:KOREA INTERNET & SECURITY AGENCY
Electric power information system cloud safety guarantee system and implementation method thereof
InactiveCN105337971AReal-time intelligent monitoring fastReduce consumptionData processing applicationsTransmissionEffective actionStructure of Management Information
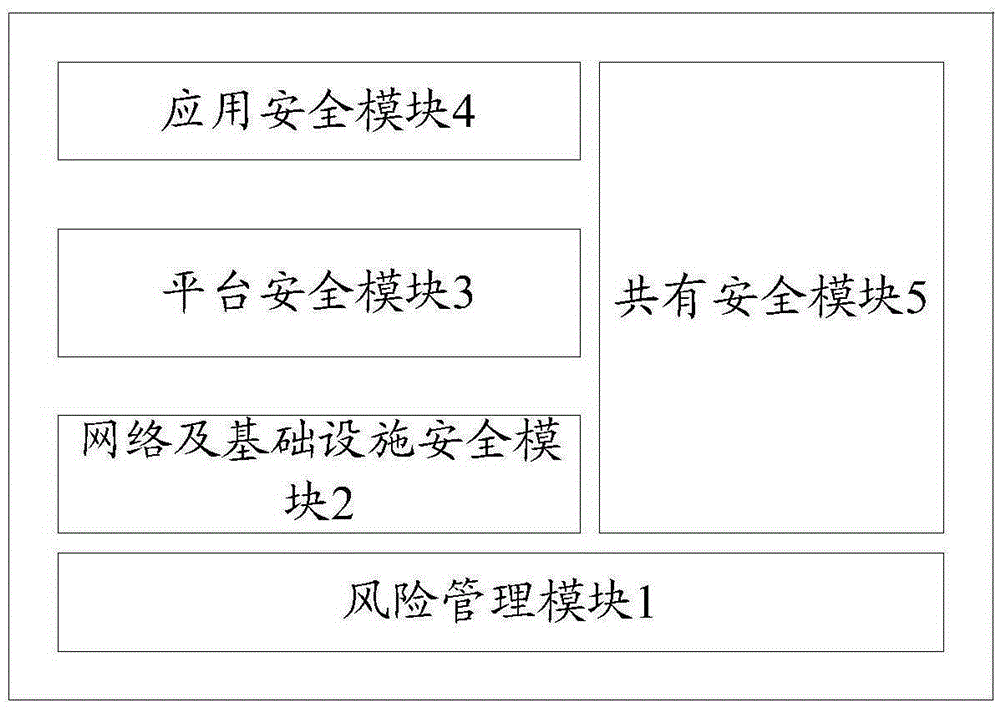
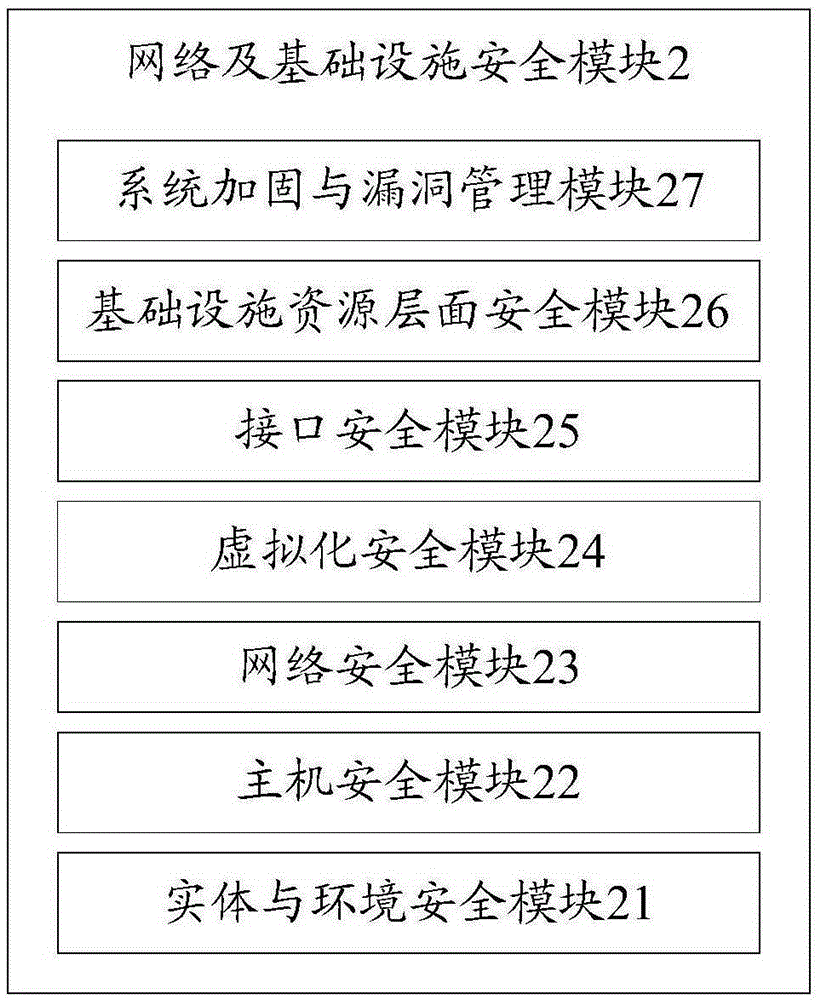
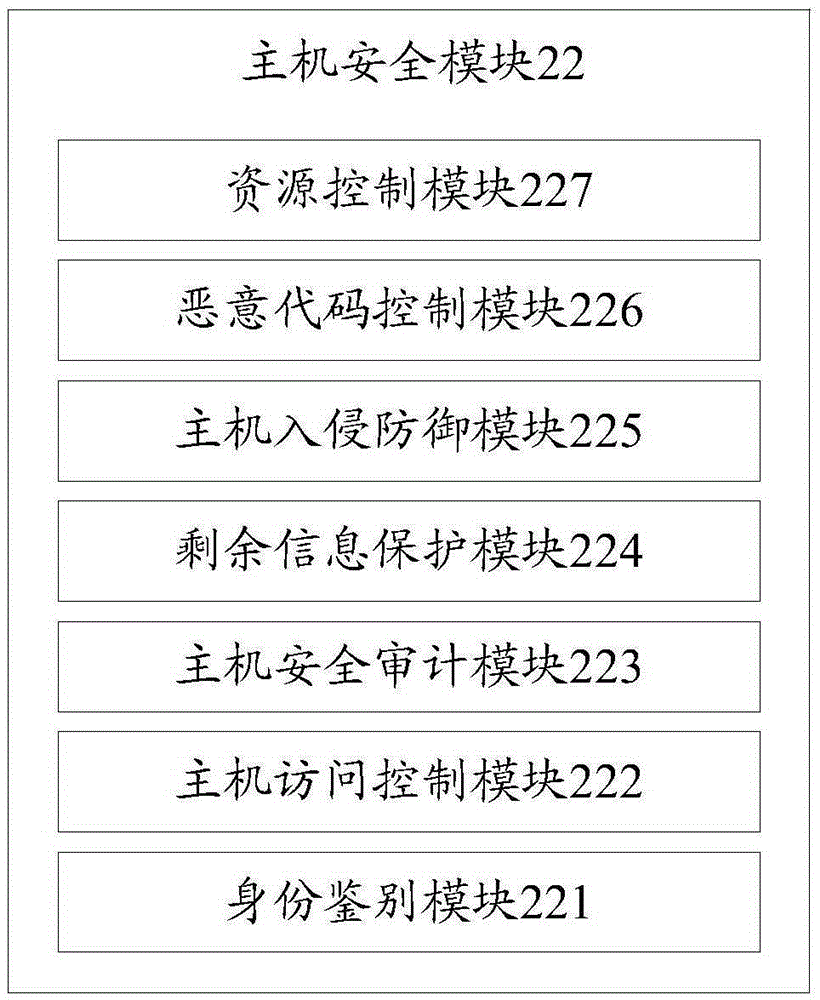
The invention discloses an electric power information system cloud safety guarantee system and an implementation method thereof. The electric power information system cloud safety guarantee system comprises a risk management module, a network and infrastructure safety module, a platform safety module and an application safety module, and a shared safety module, wherein the risk management module, the network and infrastructure safety module, the platform safety module and the application safety module are arranged successively from top to bottom; and the shared safety module is arranged among the network and infrastructure safety module, the platform safety module and the application safety module. The electric power information system cloud safety guarantee system and the implementation method thereof utilize targeted effective actions for different hierarchical structures and needs for a cloud computing platform in an electric power information system, and are integratively in linkage with multi-layers, and interact and coordinate with each other, and are integrated with monitoring and detection of abnormal behavior events, virus searching and killing, interdicting defense and attack and multi-protection, and can realize real-time intelligent monitoring of virus and attack, integration of detection analysis and safety defense, and can quickly perform real-time intelligent protection and can clean the virus and useless files, and can reduce the consumption, and can perform stereo, deep and dynamically protective comprehensive monitoring and defense for the cloud computing platform in the electric power information system.
Owner:SHANGHAI DIANJI UNIV
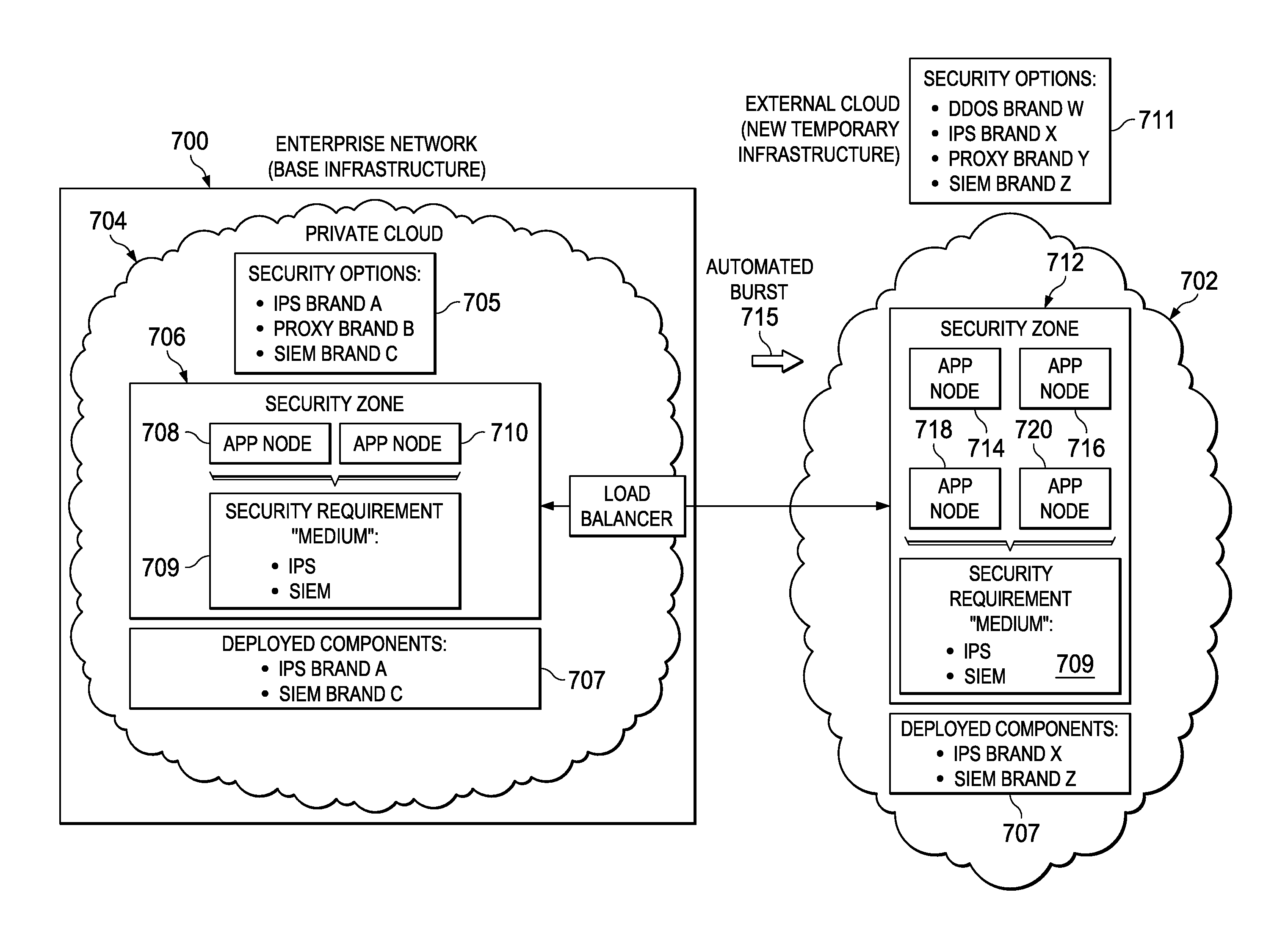
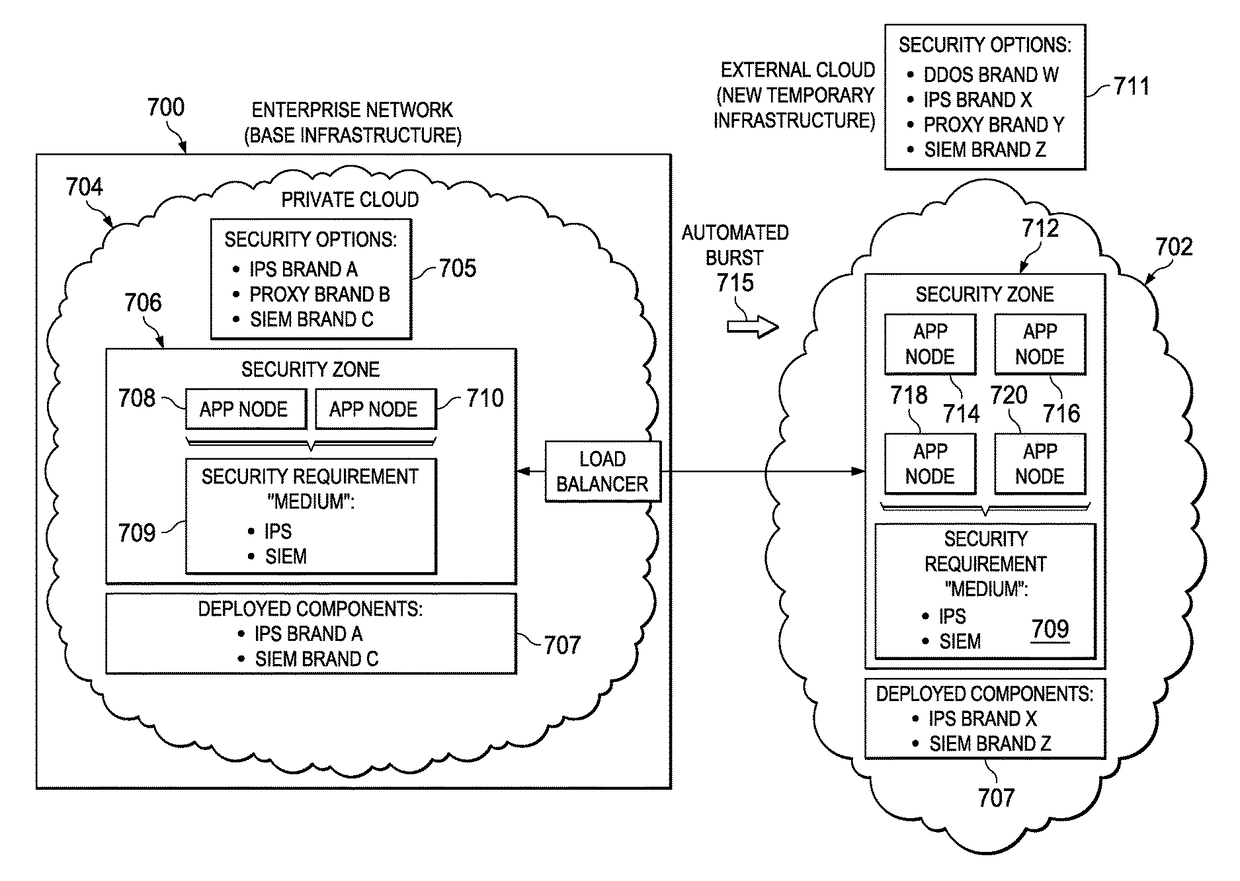
Secure application zones for cloud burst environments
A cloud infrastructure security assurance service is enhanced to facilitate bursting of cloud applications into other cloud infrastructures. The security assurance service provides a mechanism to enable creation and management of secure application zones within a cloud infrastructure. When the security assurance service receives an indication that a workload associated with a cloud application triggers a cloud burst, the service is extended into a new cloud infrastructure. Once the security assurance service is instantiated in the new cloud infrastructure, it identifies the broad security requirements of the application, as well as the security capabilities of the new environment. Using this information, the security assurance service computes a minimal security environment needed by the cloud application for the burst operation. The security assurance service then configures the necessary topology in the new cloud environment, and the burst operation is then completed by having the cloud application deployed in that topology.
Owner:IBM CORP
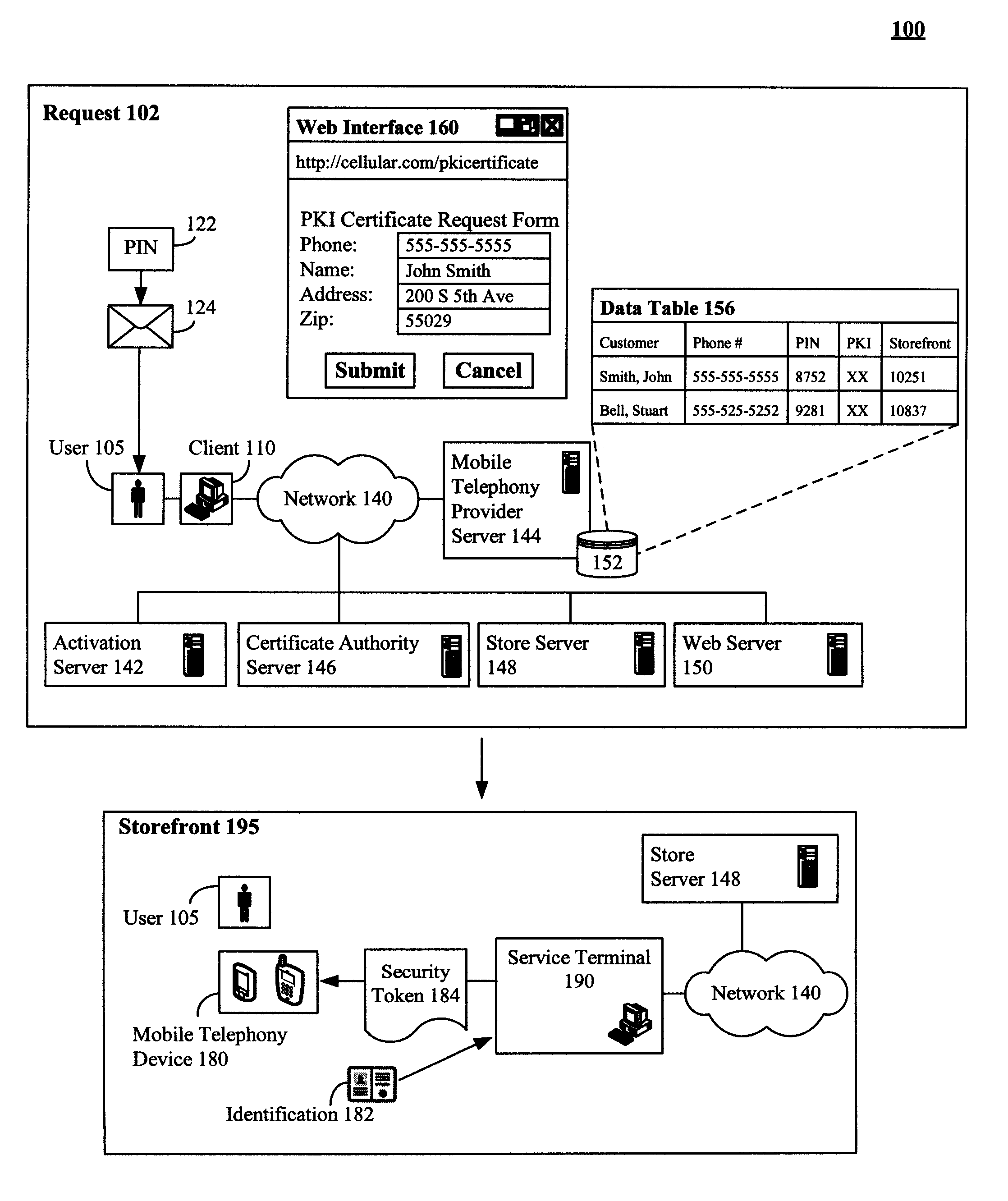
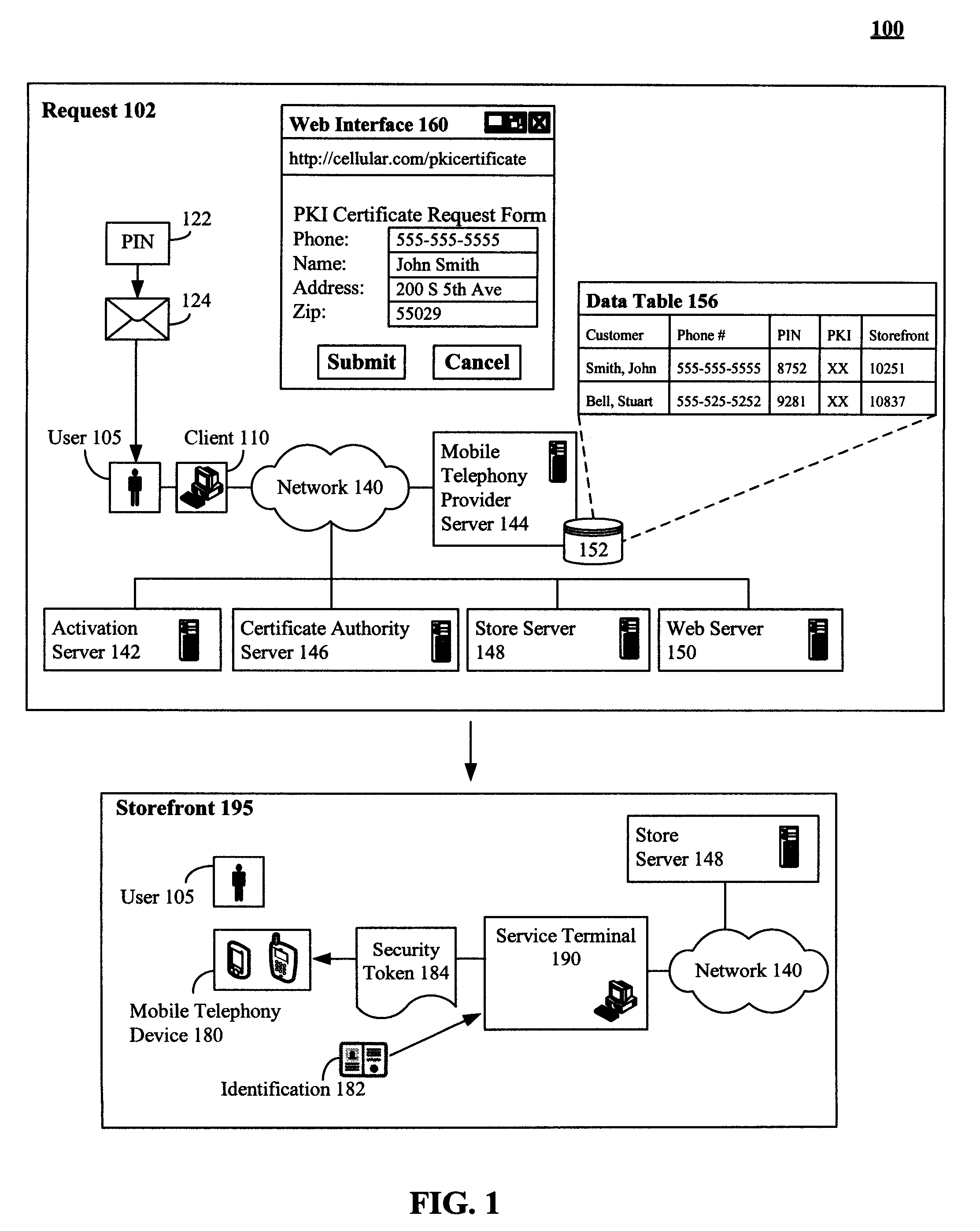
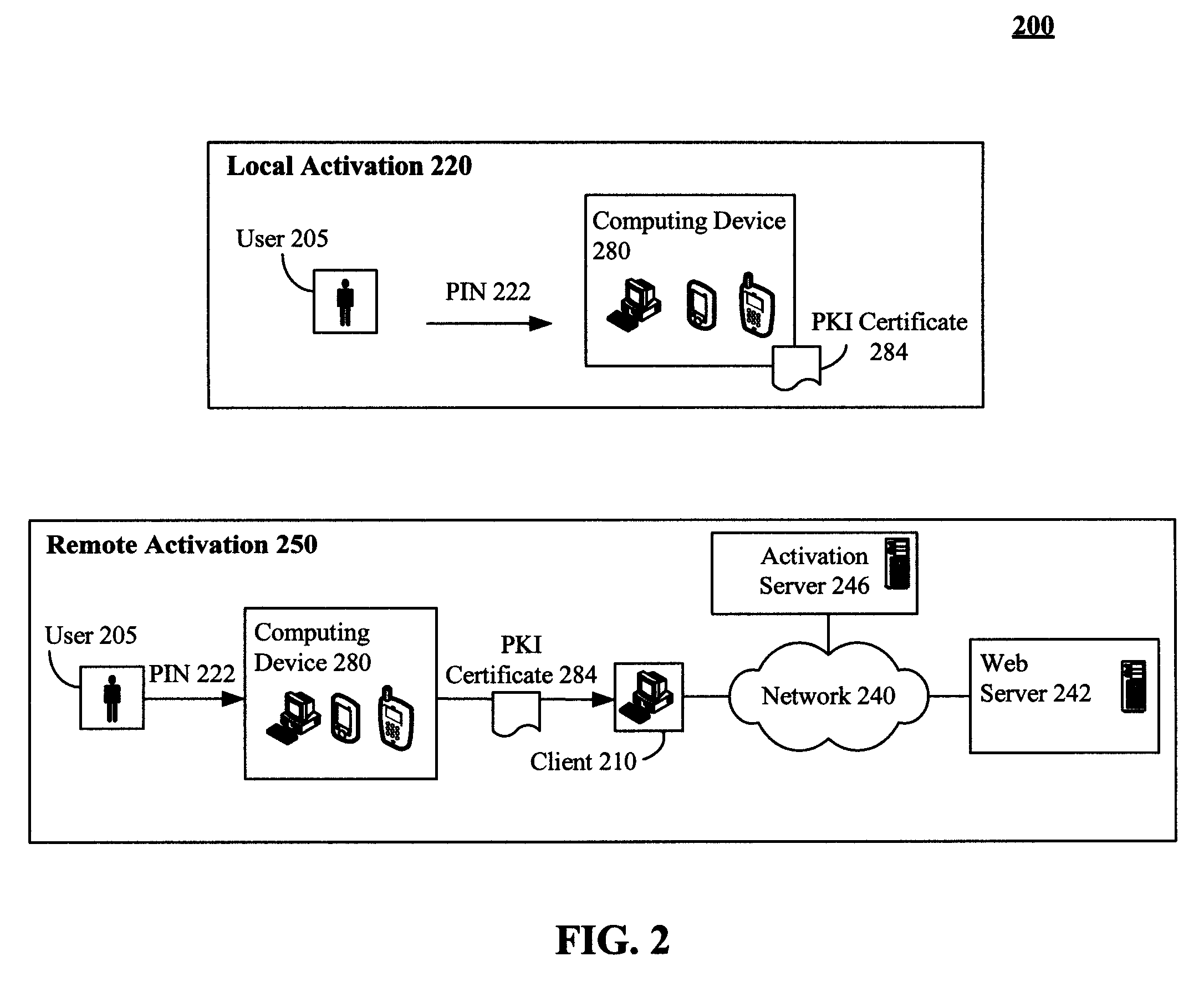
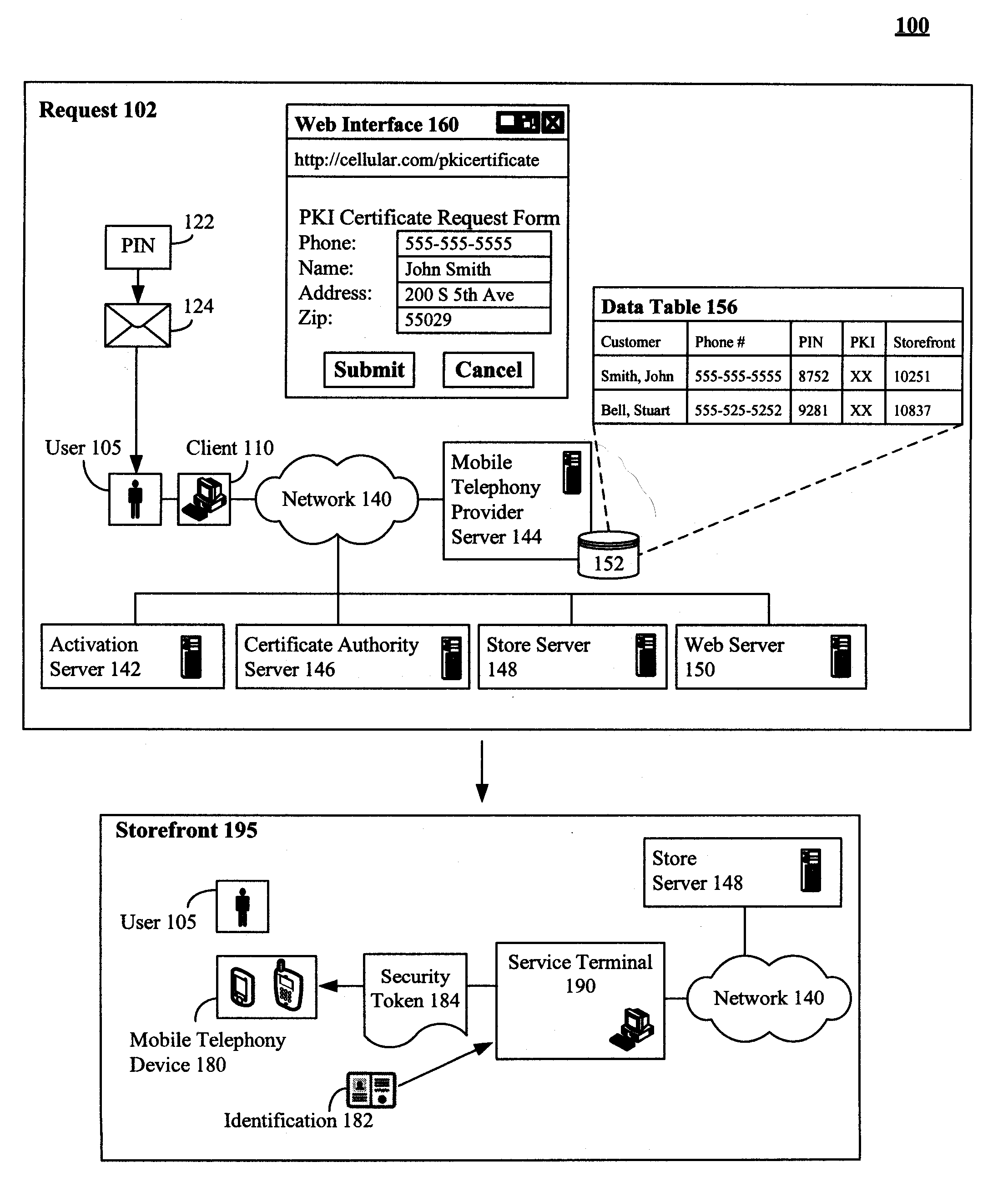
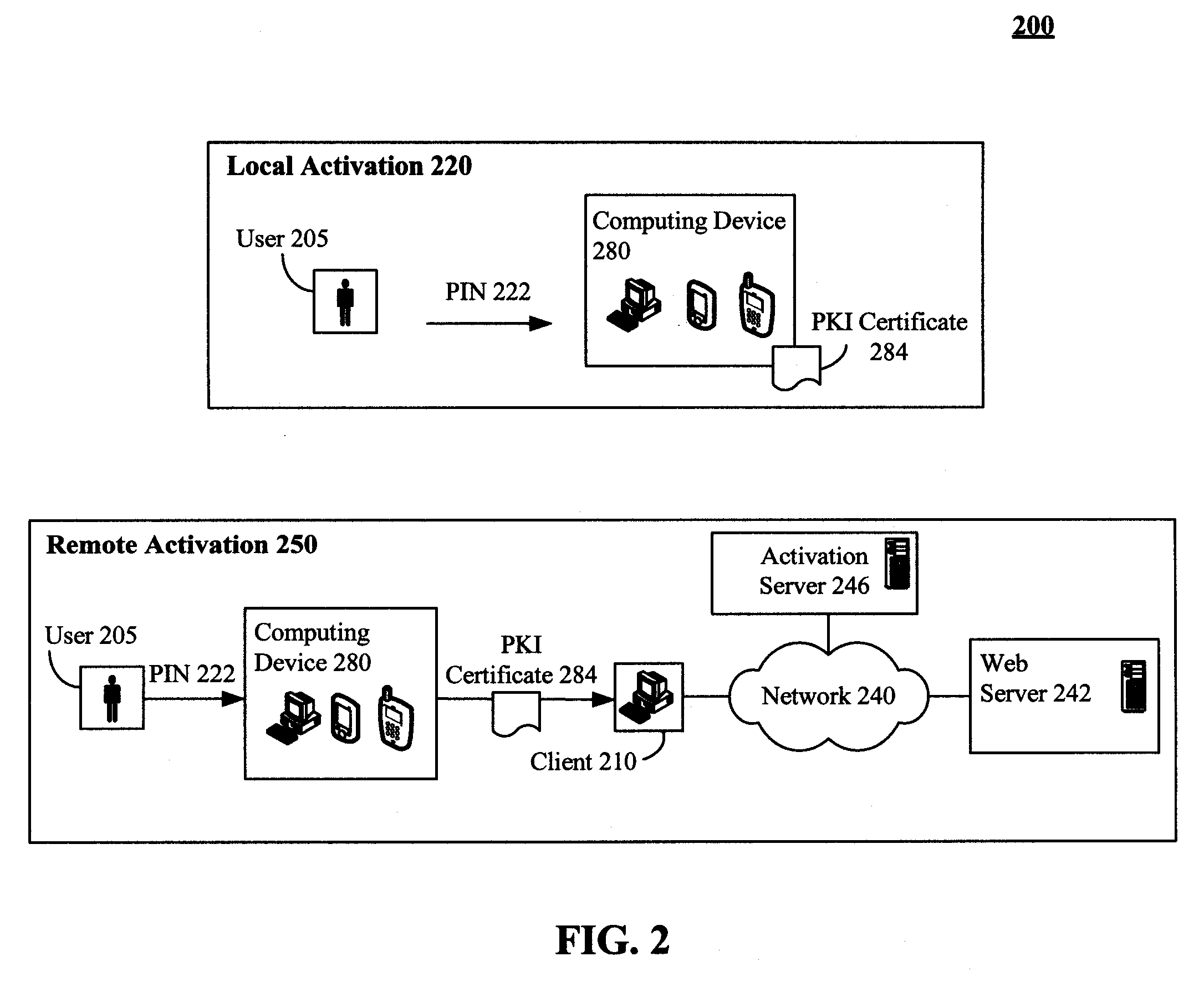
Secure physical distribution of a security token through a mobile telephony provider's infrastructure
ActiveUS7945959B2Secure deliveryDigital data processing detailsNetwork topologiesPhoto identificationBiological activation
The present invention discloses a system and method of leveraging mobile telephone provider assets and distribution network to securely deliver security tokens, such as PKI certificates. The invention is not limited to using a mobile telephony infrastructure and other pre-existing distributions can also be used. In the invention, a user requested security token can be delivered to a storefront associated with a mobile telephone provider. The storefront can be one proximate to a requesting user. An optional activation key can also be conveyed to the requesting user. The requesting user can be required to physically travel to the storefront to receive the security token. At the storefront, an identity of the requesting user can be verified, such as through photo identification. The security token can be provided when the requesting user has been successfully verified. Use of the security token can still require activation involving the activation key.
Owner:WRP IP MANAGEMENT LLC
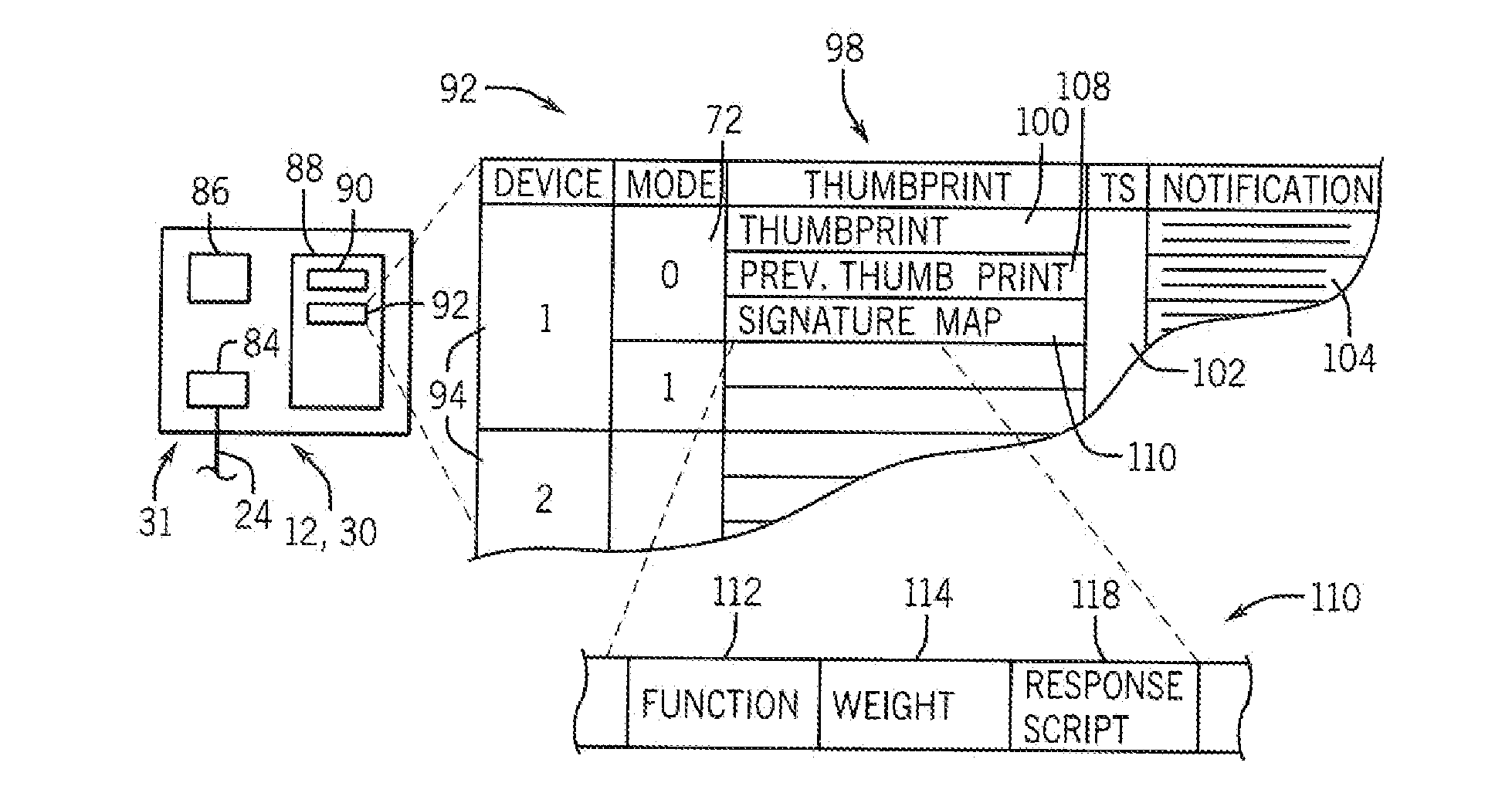
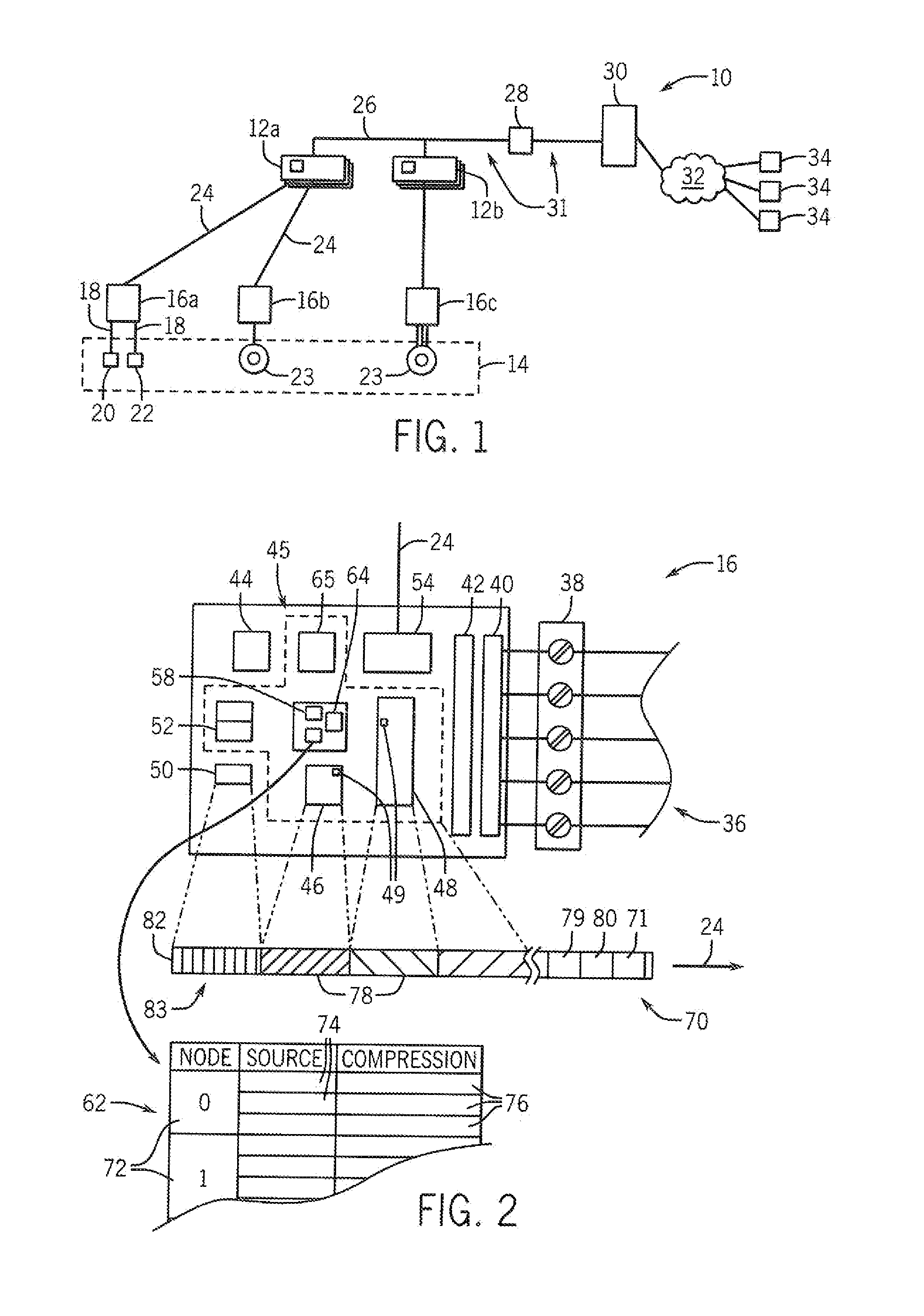
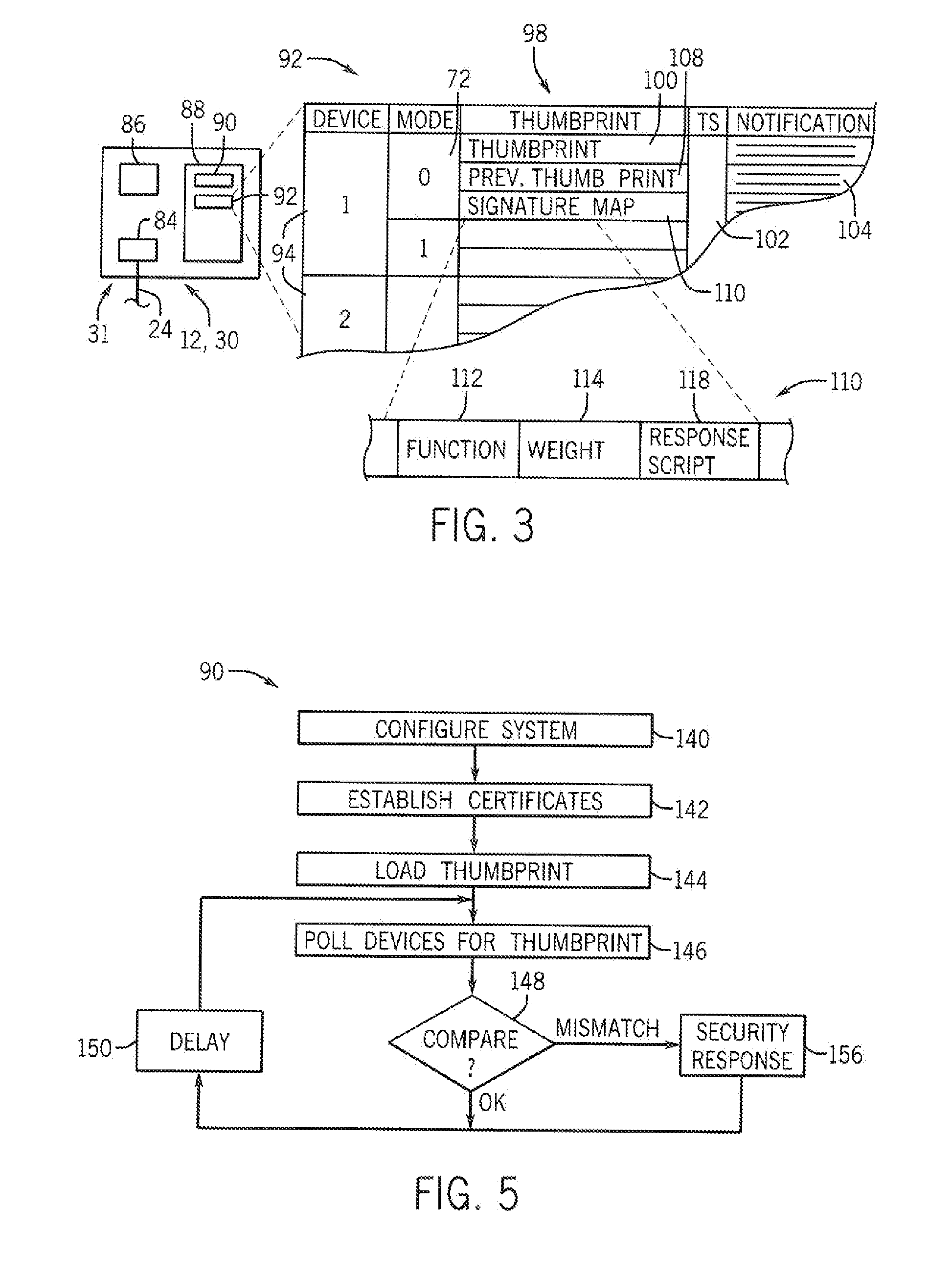
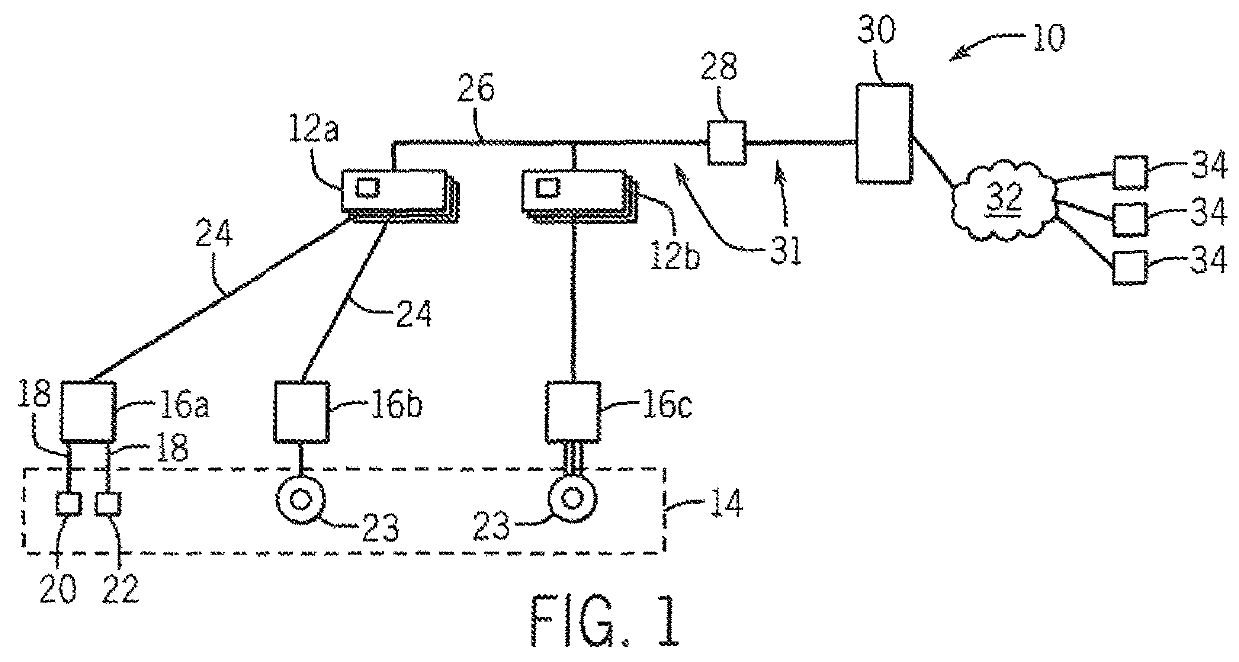
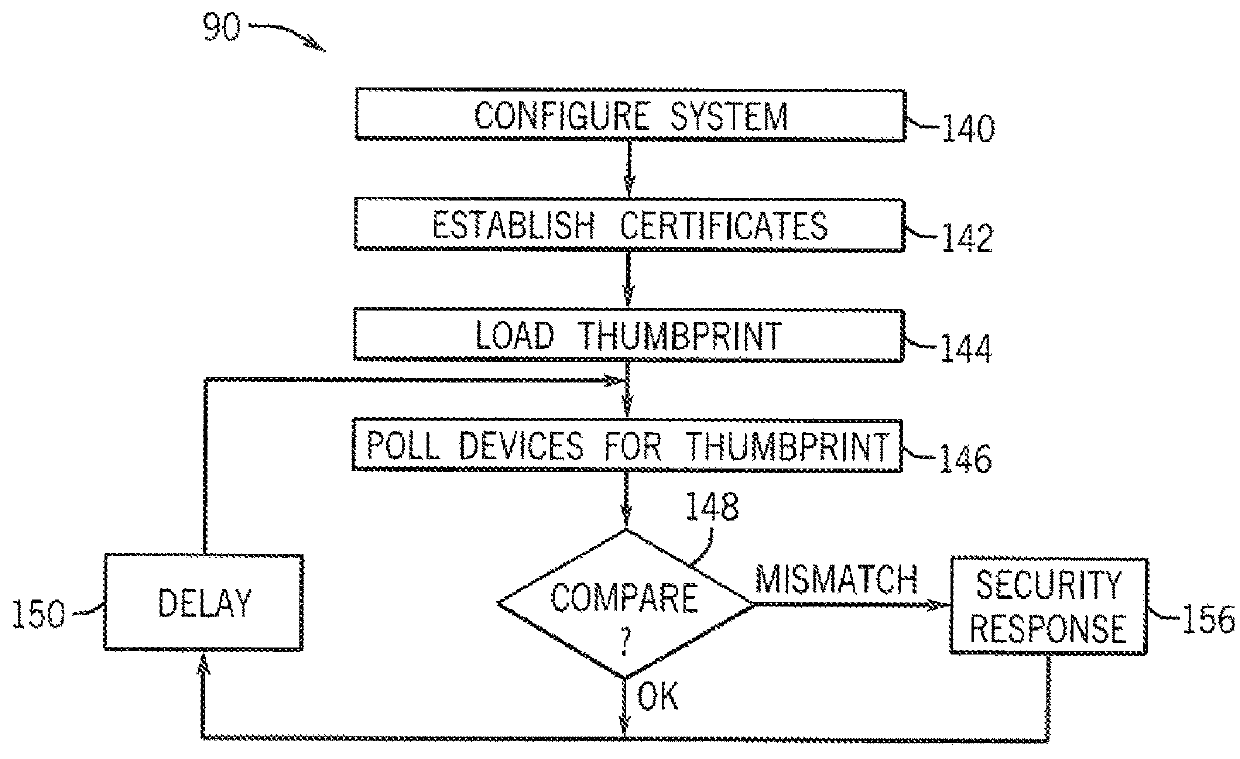
Security System for Industrial Control Infrastructure
ActiveUS20160357176A1Without consuming excess bandwidthMinimal impact capacityUser identity/authority verificationPlatform integrity maintainanceEngineeringInfrastructure security
An industrial control system providing security against tampering or modification generates periodic state thumbprints defining a state of control elements that may be forwarded to a security or safety appliance for comparison to a benchmark thumbprint indicating no tampering. The transmitted state thumbprint may capture not only programs but also configuration and environmental states of the control element.
Owner:ROCKWELL AUTOMATION TECH
Extending infrastructure security to services in a cloud computing environment
InactiveUS9426155B2SSO is facilitatedDigital data processing detailsTransmissionTrust relationshipBase exchange
A cloud deployment appliance (or other platform-as-a-service (IPAS) infrastructure software) includes a mechanism to deploy a product as a “shared service” to the cloud, as well as to enable the product to establish a trust relationship between itself and the appliance or IPAS. The mechanism further enables multiple products deployed to the cloud to form trust relationships with each other (despite the fact that each deployment and each product typically, by the nature of the cloud deployment, are intended to be isolated from one another). In addition, once deployed and provisioned into the cloud, a shared service can become part of a single sign-on (SSO) domain automatically. SSO is facilitated using a token-based exchange. Once a product registers with a token service, it can participate in SSO. This approach enables enforcement of consistent access control policy across product boundaries, and without requiring a user to perform any configuration.
Owner:INT BUSINESS MASCH CORP
Security system for industrial control infrastructure using dynamic signatures
ActiveUS10042354B2Improve securityReduce riskTechnology managementDigital data protectionActivity monitorControl data
An industrial control system hardened against malicious activity monitors highly dynamic control data to develop a dynamic thumbprint that can be evaluated to detect deviations from normal behavior of a type that suggest tampering or other attacks. Evaluation of the dynamic thumbprint may employ a set of ranges defining normal operation and reflecting known patterns of interrelationship between dynamic variables.
Owner:ROCKWELL AUTOMATION TECH
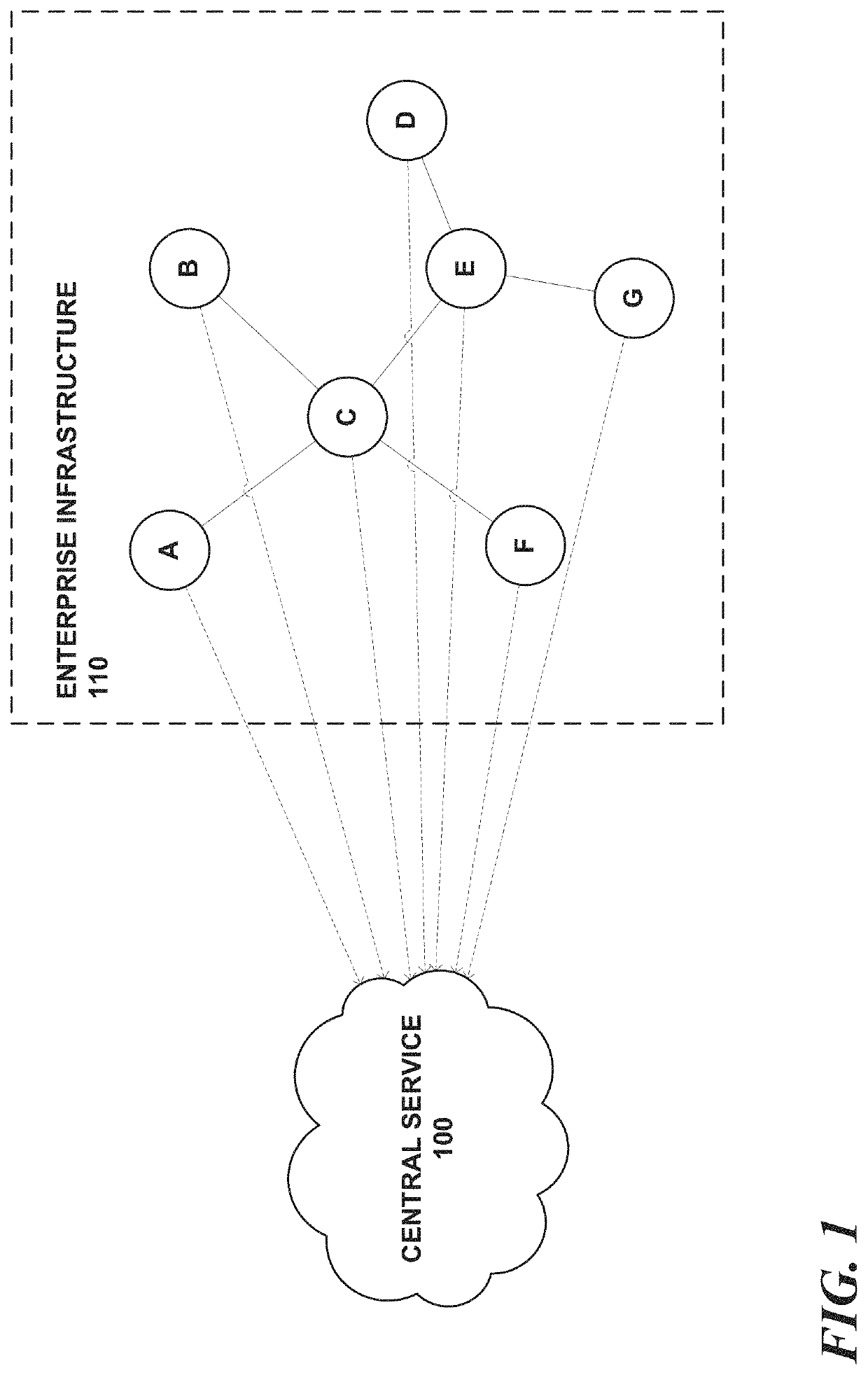
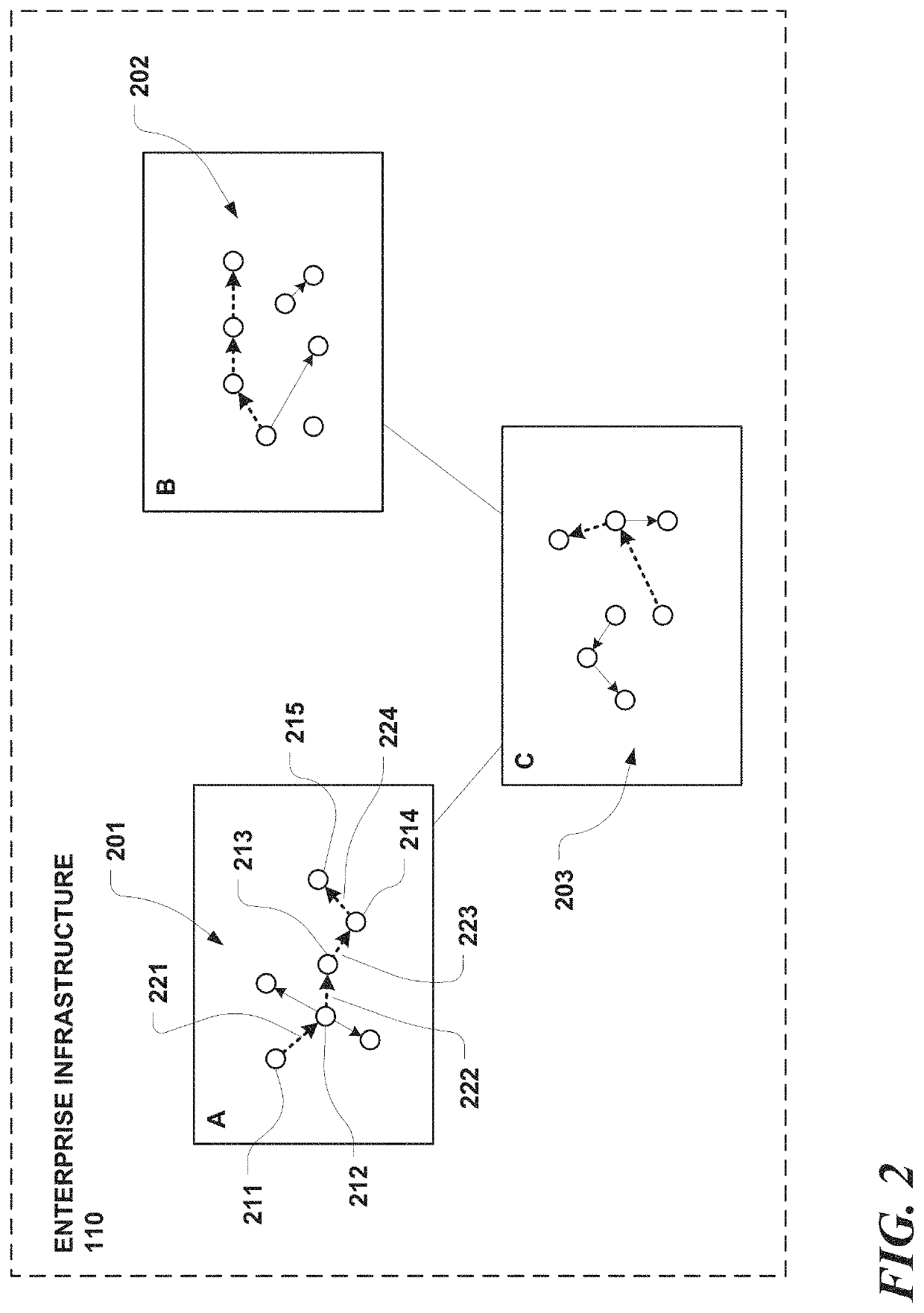
Methods and system for identifying relationships among infrastructure security-related events
A novel enterprise security solution allows for precise interception and surgical response to attack progression, in real time, as it occurs across a distributed infrastructure. The solution includes a data monitoring and management framework that continually models system level host and network activities as mutually exclusive infrastructure wide execution sequences and bucketizes them into unique execution trails. A multimodal intelligent security middleware detects indicators of compromise in real-time on top of subsets of each unique execution trail using rule based behavioral analytics, machine learning based anomaly detection, and other sources. Each detection result dynamically contributes to aggregated risk scores at execution trail level granularities. These scores can be used to prioritize and identify highest risk attack trails to end users, along with steps that such end users can perform to mitigate further damage and progression of an attack.
Owner:CONFLUERA INC
Railway safety monitoring system and monitoring method
ActiveCN106452567AAvoid causing accidentsHigh positioning accuracyElectromagnetic transmissionTransceiverEngineering
the invention provides a railway safety monitoring system and monitoring method. The system comprises one and more phase-sensitive optical time-domain reflectometers arranged along a railway, corresponding data processing units, coaxial cables, a first network photoelectric transceiver, a communication optical cable along the railway, a second network photoelectric transceiver, and a server. According to the system and method, the railway safety is monitored by employing the conventional communication optical cable, the cost is low, passive distributed detection is realized, electromagnetic interference resistance is achieved, the development of the field of the railway optical cable safety monitoring system is greatly promoted, and good guarantee is provided for monitoring of railway train operation, infrastructure safety, and illegal authorization construction.
Owner:NANJING PIONEER AWARENESS INFORMATION TECH CO LTD
Secure application zones for cloud burst environments
Owner:INT BUSINESS MASCH CORP
Sensing cable for leakage monitoring of long-distance tunnels/pipelines
InactiveCN105022131AResolve accuracyResolve in timeDetection of fluid at leakage pointFibre mechanical structuresTime domainEngineering physics
The present invention discloses a sensing cable for leakage monitoring of long-distance tunnels / pipelines, which allows leakage to be converted to optical loss of optical fibers through reasonable physical design and is used for monitoring optical loss distribution along the optical fibers by utilizing the technology of the optical time domain reflection (OTDR), thereby random leakage monitoring of long-distance structure is achieved. The sensing cable provided by the invention comprises leakage-deformation conversion materials, constraining materials and sensor fibers, wherein two types of sensor fibers are arranged in the sensing cable, thereby reducing optical loss caused by other factors except leakage and improving reliability of monitoring. The sensing cable provided by the invention has the advantages of simple structure, perfect technology of OTDR, low cost, long monitoring distance and strong market competitiveness, and on-line monitoring with low cost and high precision for leakage of long-distance tunnels / pipelines is achieved, thereby national infrastructure security is guaranteed and national resources are protected.
Owner:SUZHOU UNIV
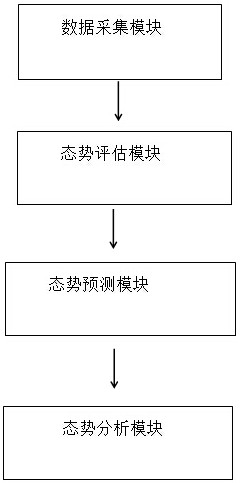
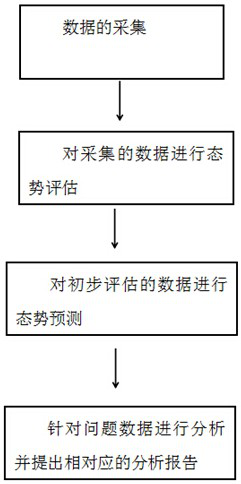
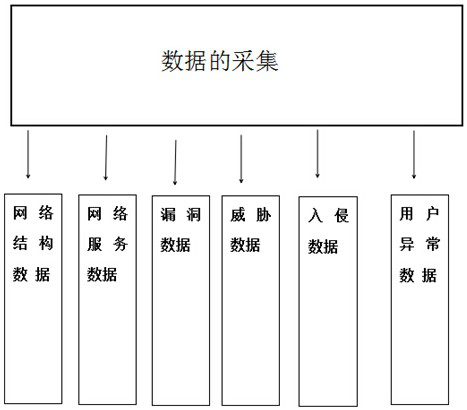
Network security situation awareness system and method
The invention relates to a network security situation awareness system and a network security situation awareness method. The network security situation awareness method comprises the steps of 1, acquiring data, and widely acquiring network security data; 2, carrying out situation assessment on the collected data, establishing assessment of multiple levels and multiple angles during situation assessment, assessing service security, data security, infrastructure security and overall security conditions of the network, and selecting different assessment methods for different application backgrounds and different network scales; 3, carrying out situation prediction on the preliminarily evaluated data to prevent large-scale security events; and 4, analyzing the problem data and proposing a corresponding analysis report. The method is high in pertinence and wide in data acquisition range, and can perform comprehensive acquisition and subsequent perception on network structure data, networkservice data, vulnerability data, threat data, intrusion data and user abnormal data.
Owner:黑龙江省网络空间研究中心 +1
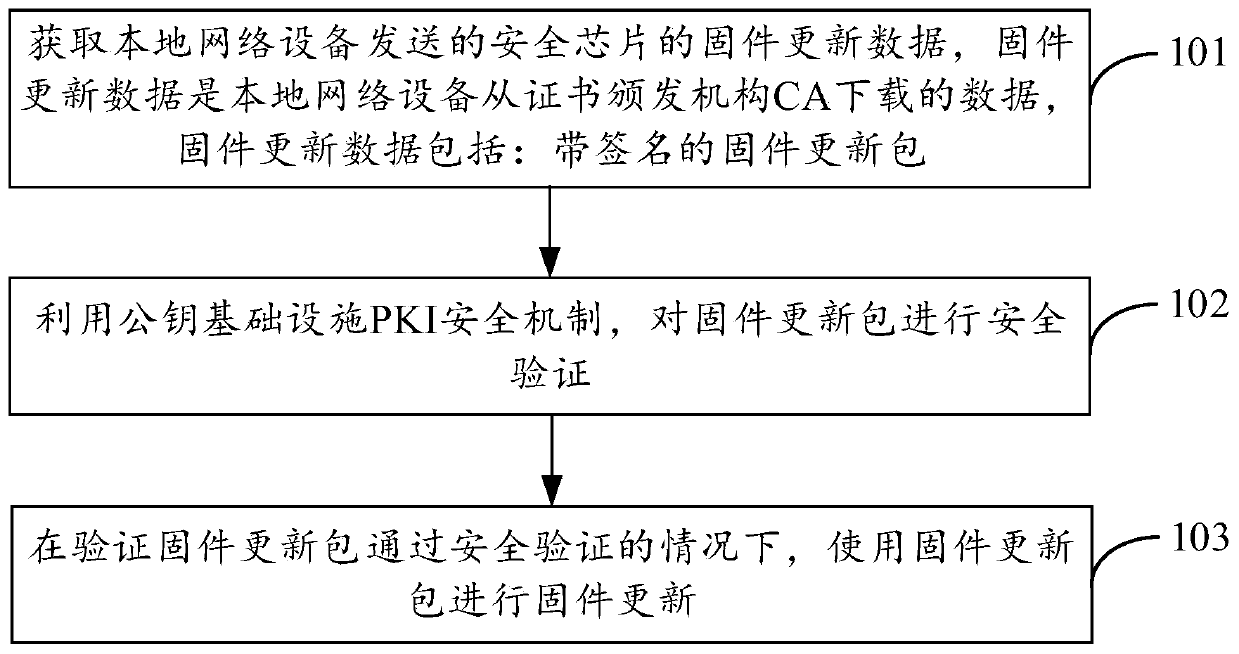
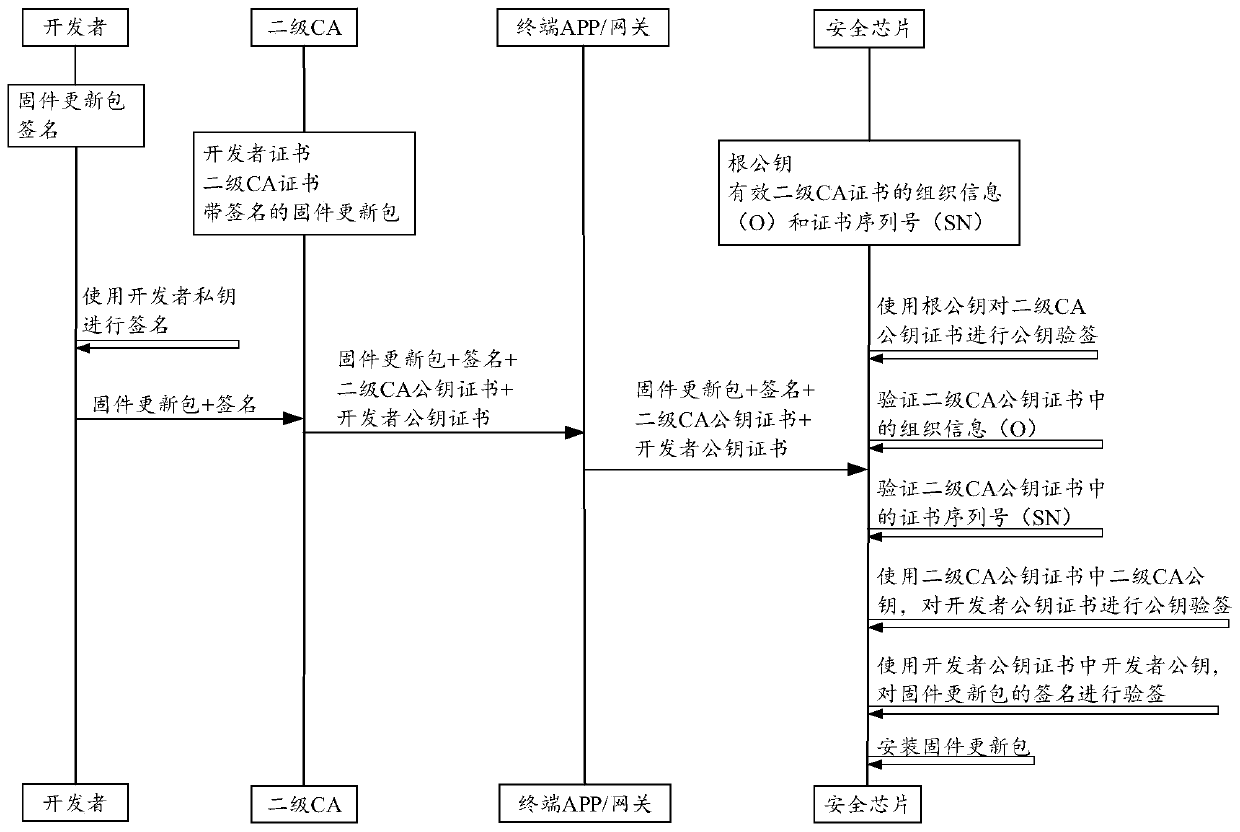
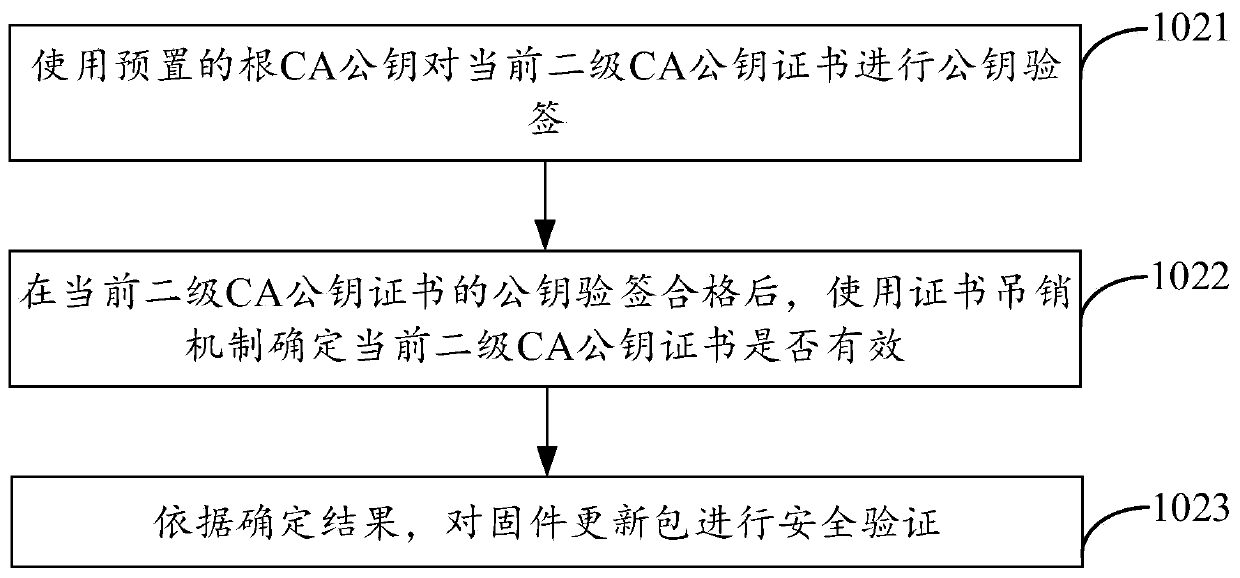
Security chip firmware updating method and device
ActiveCN110688648AReduce firmware update timeReduce work costsComputer security arrangementsSoftware deploymentData packPassword
The invention provides a security chip firmware updating method and device. The method is applied to a security chip in a local device, and comprises the following steps: obtaining firmware update data of the security chip sent by the local network device, the firmware update data being data downloaded by the local network device from a certificate authority CA, and the firmware update data comprising a signed firmware update packet; performing security verification on the firmware update package by using a public key infrastructure (PKI) security mechanism; and under the condition that the firmware update package passes the security verification, performing firmware update by using the firmware update package. Based on setting of a PKI architecture, the security chip does not need to establish real-time network connection with the CA, namely the cloud, in the firmware updating process, the problem that in the background art, the working pressure of the cloud is increased based on multiple times of network connection and multiple times of password establishment is avoided, the stability of upgrading transmission is improved, and the firmware updating time of the security chip is shortened.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
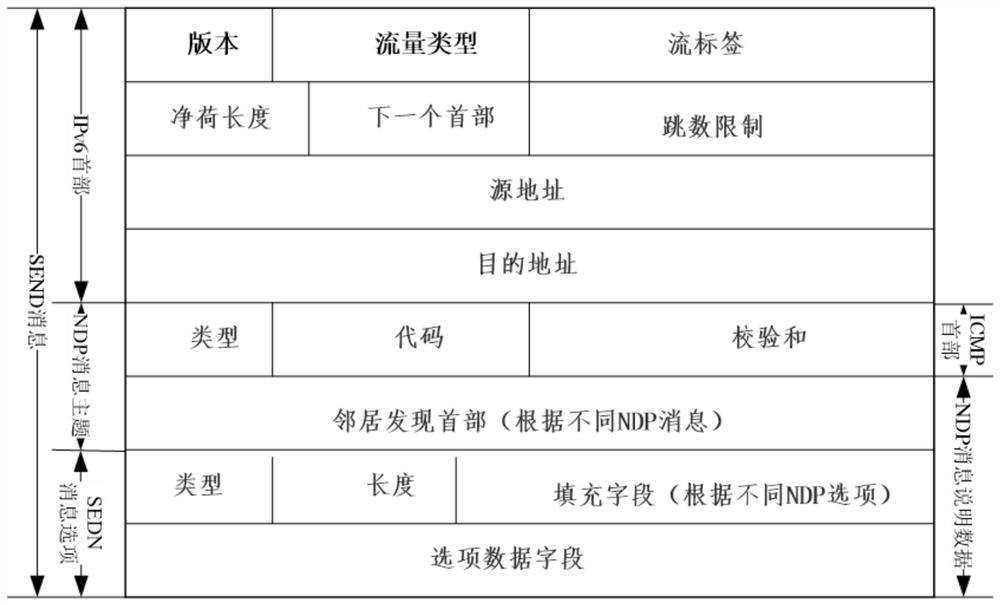
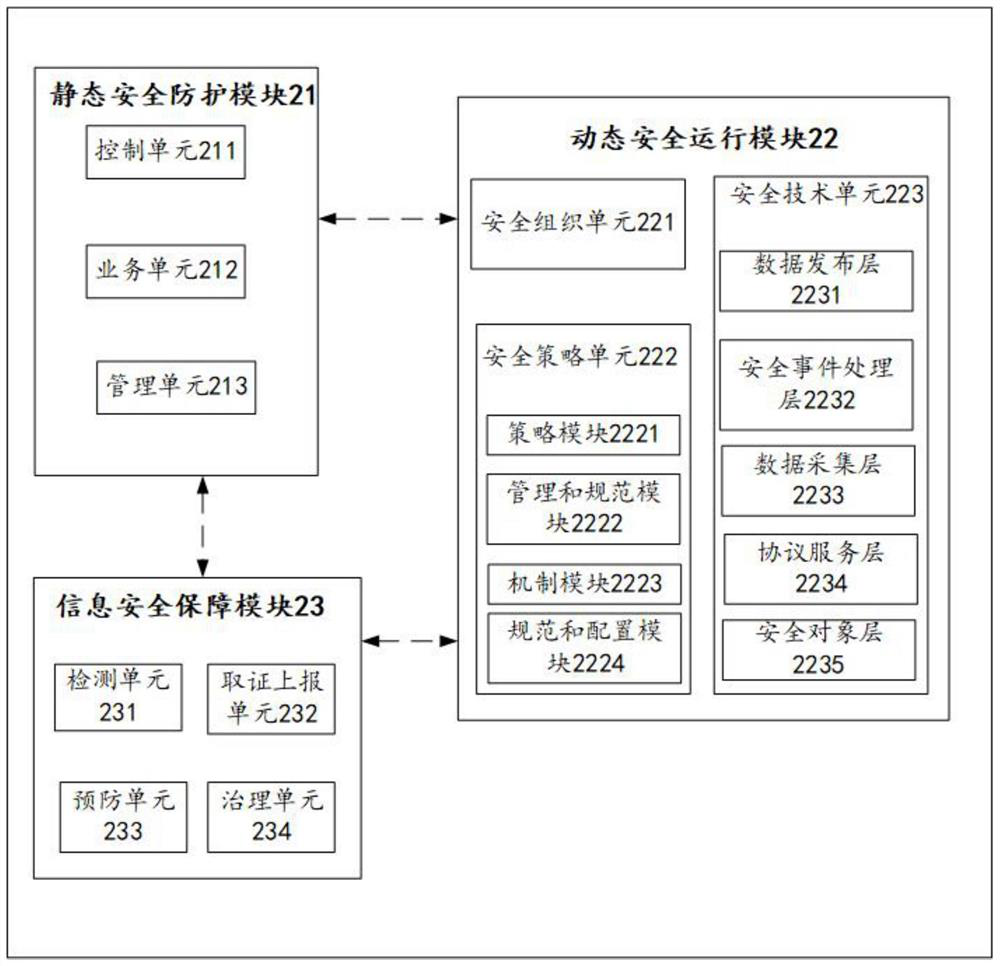
IPv6 network security protection system
ActiveCN111641639AAffects the control planeAffects the management planeUser identity/authority verificationInfrastructure securitySecurity information
The invention provides an IPv6 network security protection system, which comprises a static security protection module and a dynamic security operation module which are connected with each other through an IPv6 network, the static security protection module is used for carrying out isolation control on each unit or module through an IPv6 network, and adjusting corresponding security specificationsand control measures to monitor static security information of the IPv6 network; the dynamic safety operation module is used for discovering and managing network safety risks through safety detectionand matching of corresponding safety infrastructure, a safety organization unit, a safety strategy unit and a safety technology unit, and carrying out safety protection on a terminal network throughan IPv6 network. The isolation of three planes is logically realized; the intranet security of an enterprise is enhanced; the fault reporting transition period is safe; DNS security protection of fault reporting in an IPv4 network environment provides support for an IPv6 protocol, and network security risks and transition technology security risks are effectively controlled and prevented.
Owner:SHENZHEN POWER SUPPLY BUREAU
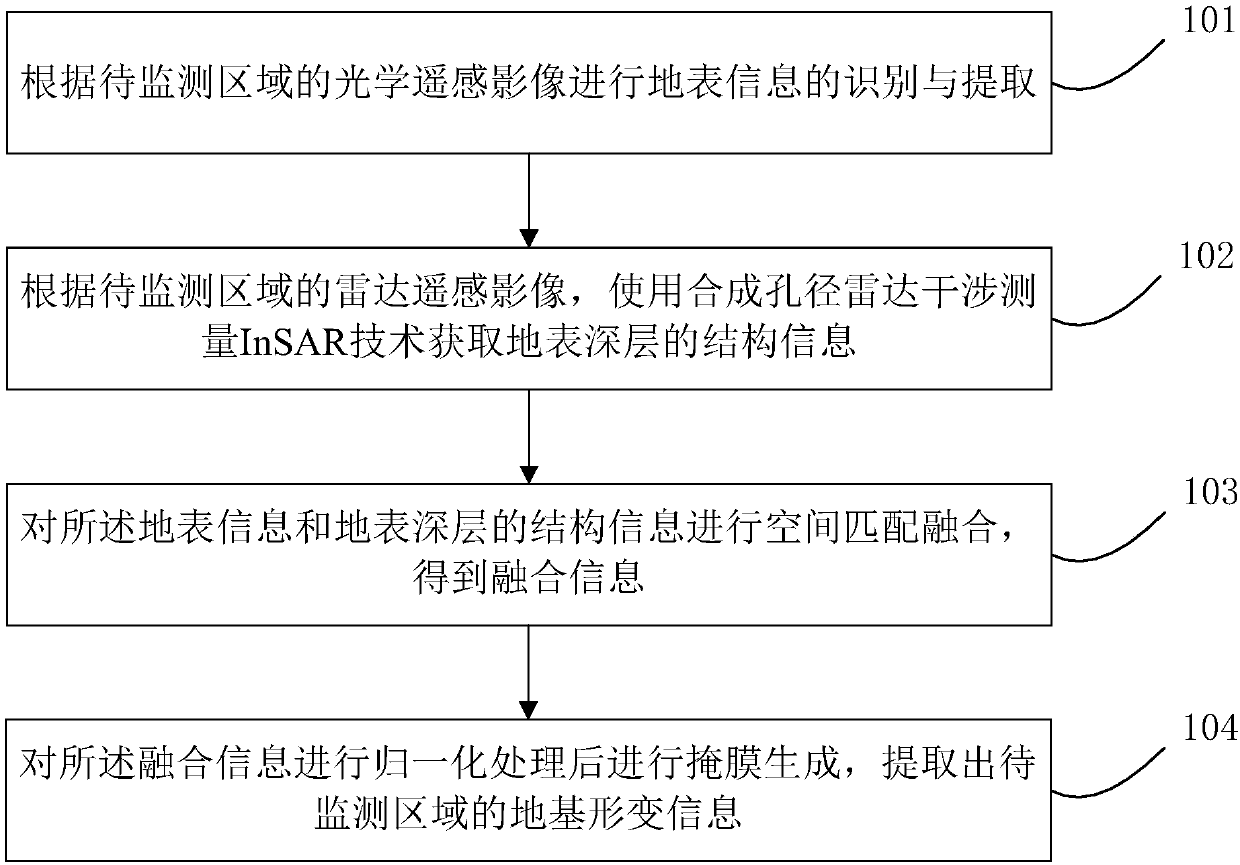
Safety monitoring method and system for traffic infrastructure
ActiveCN107944377AImprove traffic safetyRealize high-precision monitoringCharacter and pattern recognitionSynthetic aperture radarRadar
The invention discloses a safety monitoring method and system for traffic infrastructure. In the method, road extracting and monitoring technology combining high-resolution optical remote sensing technology and synthetic aperture radar interferometry technology is adopted; optical remote sensing images are used to carry out earth surface information identification and extraction, earth surface classification, road extraction and the like; based on the radar remote sensing images, InSAR technology is used to obtain deeper structural information, such as settlement, deformation and the like of transportation facilities. Through combination of optical remote sensing and radar remote sensing, recognition of road surface conditions and high-precision monitoring of earth surface deformation conditions of traffic facilities can be achieved in a coordinated manner, and effective support can be provided for improving road safety.
Owner:赤湾通信卫星应用技术(深圳)有限公司
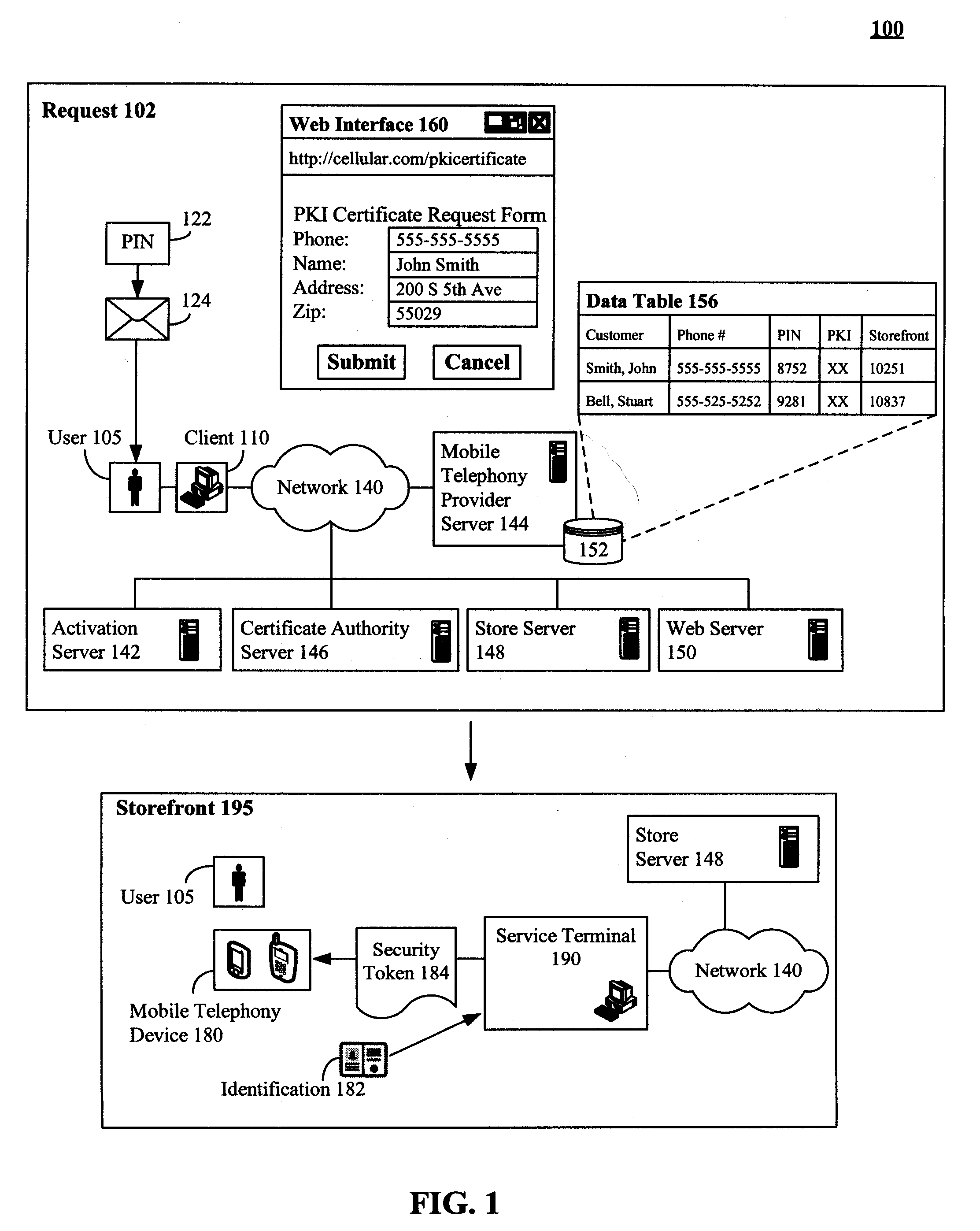
Secure physical distribution of a security token through a mobile telephony provider's infrastructure
ActiveUS20080313457A1Secure deliverySynchronising transmission/receiving encryption devicesDigital data processing detailsPhoto identificationInfrastructure security
The present invention discloses a system and method of leveraging mobile telephone provider assets and distribution network to securely deliver security tokens, such as PKI certificates. The invention is not limited to using a mobile telephony infrastructure and other pre-existing distributions can also be used. In the invention, a user requested security token can be delivered to a storefront associated with a mobile telephone provider. The storefront can be one proximate to a requesting user. An optional activation key can also be conveyed to the requesting user. The requesting user can be required to physically travel to the storefront to receive the security token. At the storefront, an identity of the requesting user can be verified, such as through photo identification. The security token can be provided when the requesting user has been successfully verified. Use of the security token can still require activation involving the activation key.
Owner:WRP IP MANAGEMENT LLC
Methods and system for tracking security risks over infrastructure
A novel enterprise security solution allows for precise interception and surgical response to attack progression, in real time, as it occurs across a distributed infrastructure. The solution includes a data monitoring and management framework that continually models system level host and network activities as mutually exclusive infrastructure wide execution sequences and bucketizes them into unique execution trails. A multimodal intelligent security middleware detects indicators of compromise in real-time on top of subsets of each unique execution trail using rule based behavioral analytics, machine learning based anomaly detection, and other sources. Each detection result dynamically contributes to aggregated risk scores at execution trail level granularities. These scores can be used to prioritize and identify highest risk attack trails to end users, along with steps that such end users can perform to mitigate further damage and progression of an attack.
Owner:CONFLUERA INC
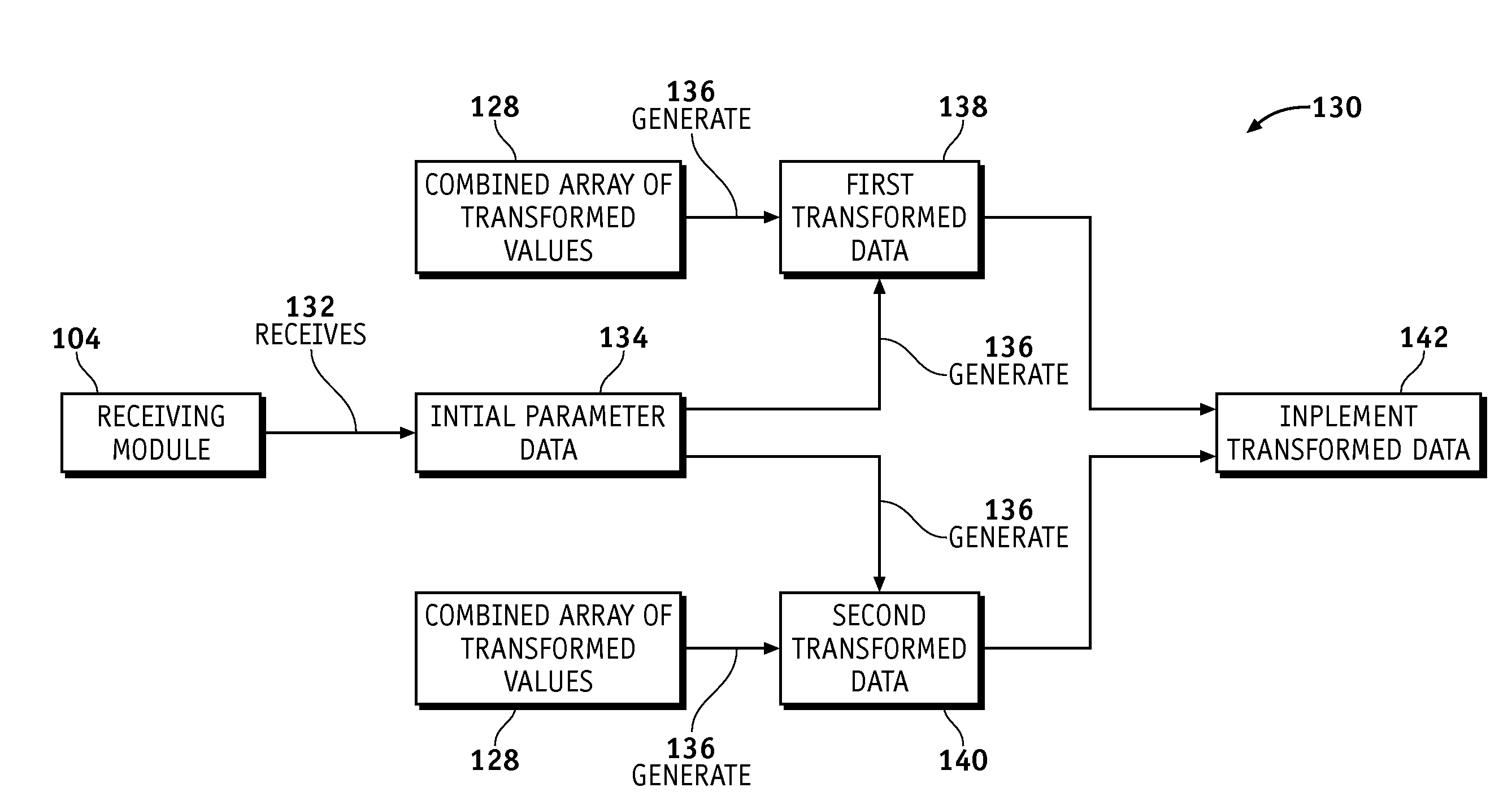
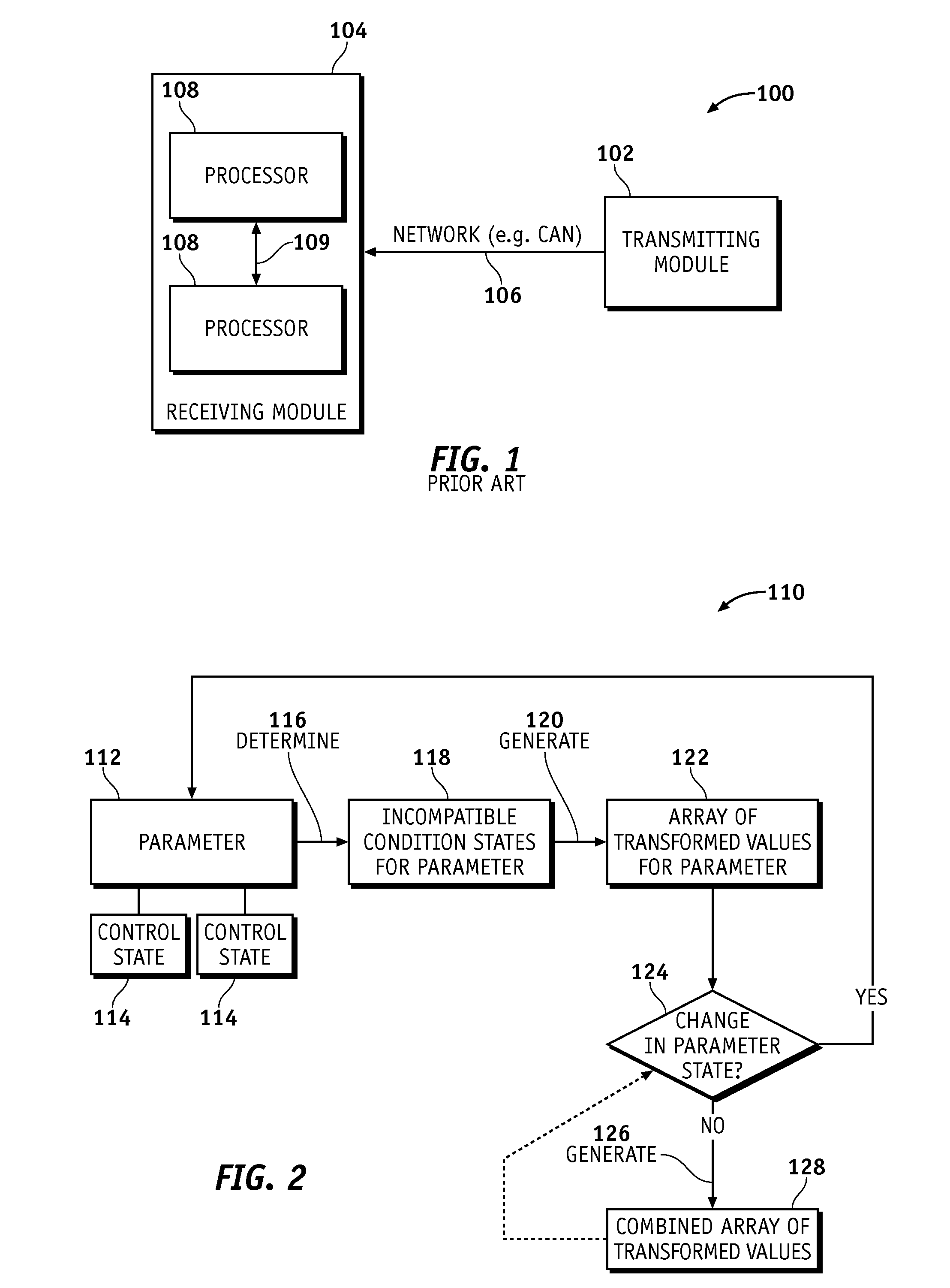
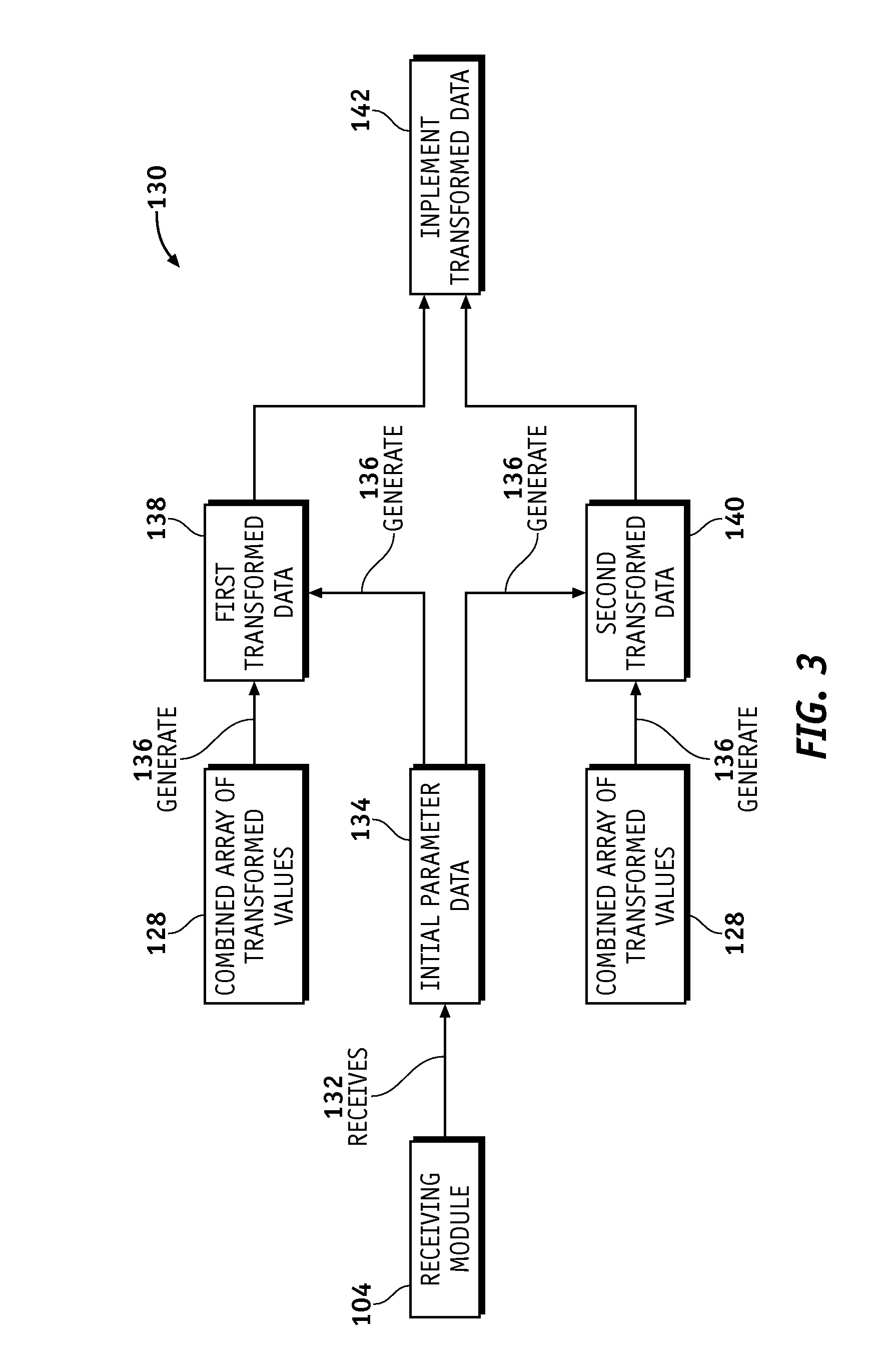
Vehicle Parameter Infrastructure Security Strategy
Owner:GM GLOBAL TECH OPERATIONS LLC
High-temperature-resistant flexible long-gauge strain sensor and manufacturing method and application thereof
PendingCN109579725AImprove applicabilityEffective engineering structureUsing optical meansGratingFiber Bragg grating
The invention discloses a high-temperature-resistant long-gauge flexible strain sensor capable of being used for strain monitoring of high-temperature facilities. Fiber bragg grating sensing is adopted as a sensing technology, and a high-temperature-resistant packaging process is utilized to realize strain monitoring under high temperature conditions. The high-temperature-resistant long-gauge flexible strain sensor comprises a fiber bragg grating and a packaging sheath, wherein the fiber bragg grating is fixed into the packaging sheath through anchoring areas at the two ends, and a grating area is positioned between the two anchoring areas. When the high-temperature-resistant long-gauge flexible strain sensors are arranged on the surfaces of the high-temperature facilities in a distributedmode, the strain monitored by the grating areas can reflect a certain range of strain of a structure. The high-temperature-resistant long-gauge flexible strain sensor is simple in sensing structure and low in cost and can be connected in series in a large number, the problem of high-temperature strain / stress monitoring of the high-temperature facilities (planes or curved surfaces) is solved, themarket competitiveness is high, and beneficial effects are generated on ensuring the safety of national infrastructures.
Owner:南京东智安全科技有限公司 +1
Optical fiber vibration real-time monitoring and alarming system for roadbed collapse
ActiveCN104374466ASolve the problem of delaySubsonic/sonic/ultrasonic wave measurementUsing wave/particle radiation meansInfrastructure securityGSM
The invention discloses an optical fiber vibration real-time monitoring and alarming system for roadbed collapse and belongs to the technical field of important infrastructure safety monitoring. The system is characterized in that a distributed type optical fiber vibration sensor is arranged in a roadbed in an S type, a distributed type optical fiber vibration system collects and positions vibration signals exerted on the distributed type optical fiber vibration sensor in real time, the vibration signals are processed through a roadbed collapse vibration signal recognizing system, the vibration signal which is generated by roadbed collapse is recognized, and recognized collapse disaster information is reported to a collapse disaster alarming final control center in real time through GSM / GPRS so that a collapse alarm can be given. The optical fiber vibration real-time monitoring and alarming system has the advantages that the distributed type optical fiber vibration testing system and the roadbed collapse vibration signal recognizing system are adopted for recognizing the vibration signal which is generated by the roadbed collapse in real time, the range of the collapse is determined according to the energy spectrum of the vibration signal and reported to the roadbed collapse disaster alarming final control center through the GSM / GPRS so that the alarm can be given for the collapse in real time, and the problem that an existing alarm for the roadbed collapse disaster is delayed is solved.
Owner:DALIAN UNIV OF TECH
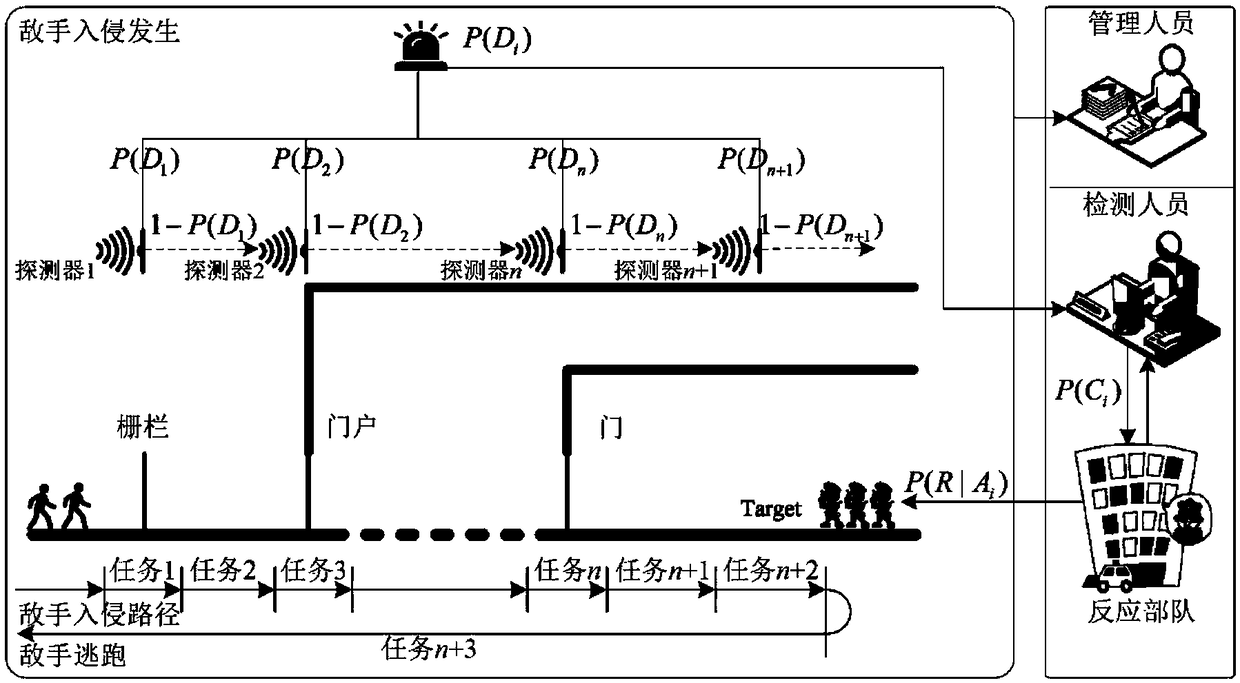
Risk monitoring method for a physical protection system of a key infrastructure
ActiveCN109190932AImplement emergency response plansImprove effectivenessResourcesModularityEngineering
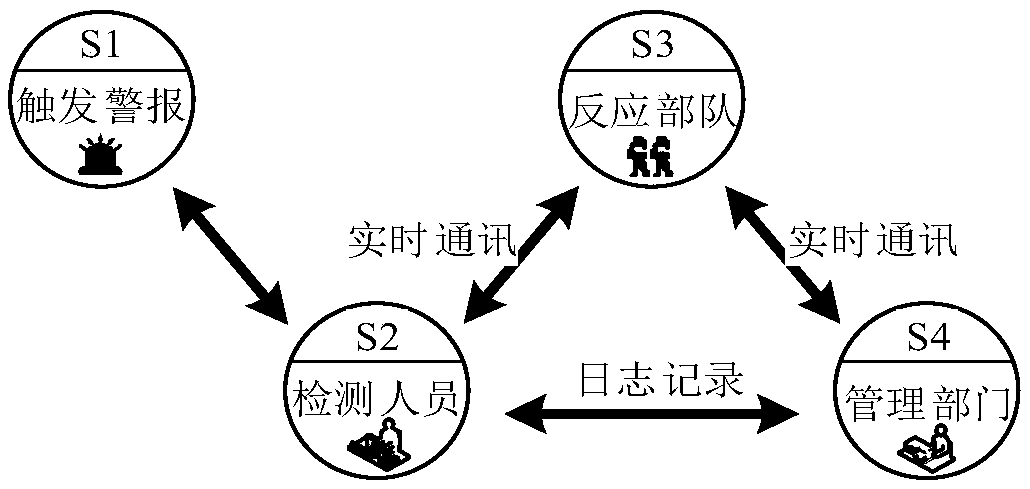
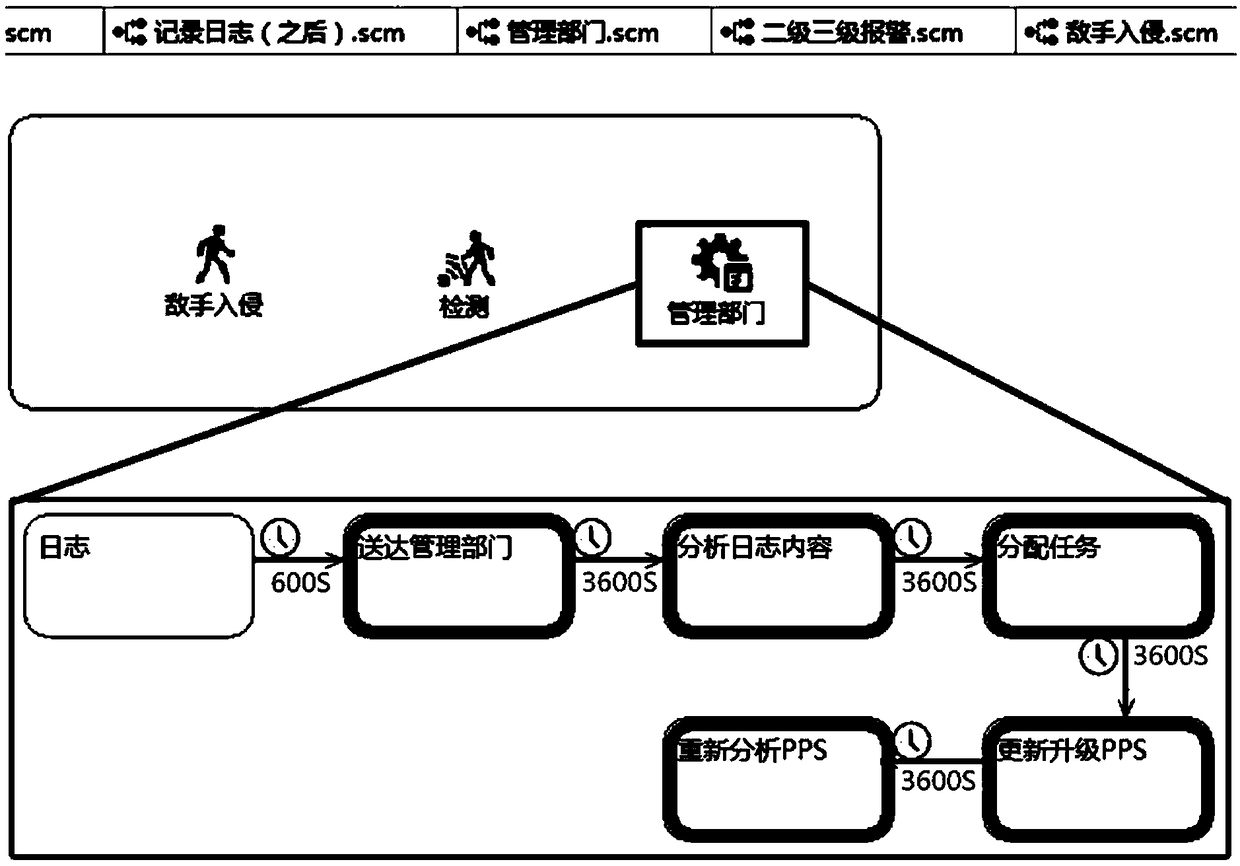
The invention discloses a risk monitoring method for a physical protection system of a key infrastructure, belonging to the field of key infrastructure security. The invention establishes a risk analysis model for a risk analysis method of a physical protection system and carries out risk monitoring, and the steps are as follows: modularization analysis of physical protection system rules, analysis of enemy intrusion information, analysis of intrusion detection rules, analysis of reaction force rules, analysis of management personnel rules, establishment of risk monitoring knowledge base, andestablishment of risk interactive simulator. The method can dynamically establish a physical protection system risk monitoring model (state, conversion and event) and an interaction modeling function(external event and internal event interaction) between physical protection system entities, thereby completing that risk monitoring of the key infrastructure. The risk monitoring method effectively integrates the physical protection system and its subsystems, and associates all the staff involved in the physical protection system for collaborative deduction, evaluates the weakness of the procedures, and improves the effectiveness of the drill procedures.
Owner:SOUTH CHINA UNIV OF TECH
Methods and system for characterizing infrastructure security-related events
A novel enterprise security solution allows for precise interception and surgical response to attack progression, in real time, as it occurs across a distributed infrastructure. The solution includes a data monitoring and management framework that continually models system level host and network activities as mutually exclusive infrastructure wide execution sequences and bucketizes them into unique execution trails. A multimodal intelligent security middleware detects indicators of compromise in real-time on top of subsets of each unique execution trail using rule based behavioral analytics, machine learning based anomaly detection, and other sources. Each detection result dynamically contributes to aggregated risk scores at execution trail level granularities. These scores can be used to prioritize and identify highest risk attack trails to end users, along with steps that such end users can perform to mitigate further damage and progression of an attack.
Owner:CONFLUERA INC
Track detection device based on inertial measurement
InactiveCN110626383AOperational impact is smallImprove efficiencyRailway auxillary equipmentRailway profile gaugesLaser rangingLaser scanning
The invention aims at providing a track detection device based on inertial measurement. The track detection device based on inertial measurement comprises an inertial measurement module; the inertialmeasurement module comprises a laser scanner, an adapter plate, a detection beam, laser range finders, connector interfaces, line boxes and an inertial navigation system, wherein the adapter plate isarranged on the detection beam; the laser scanner is arranged on the adapter plate; the laser range finders are arranged at the two ends of the detection beam; the inertial navigation system is arranged in the middle of the detection beam; the line boxes are arranged in the positions, on the detection beam, on the two sides of the inertial navigation system; and the connector interfaces are formedin the positions, on the detection beam, on the external sides of the line boxes. The track detection device based on inertial measurement has the advantages that the track detection device based oninertial measurement can be mounted on a running train and can also be mounted on a driving trolley to independently operate; and as a vehicle-mounted dynamic detection mode of the track detection device based on inertial measurement has small influences on normal operation, possesses high efficiency and high speed and really reflects the state of infrastructures under a train running condition, the vehicle-mounted dynamic detection mode of the track detection device based on inertial measurement can be used as one of main detection means of safety states of railway and urban rail transit infrastructures.
Owner:BEIJING AUTOMATION CONTROL EQUIP INST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com